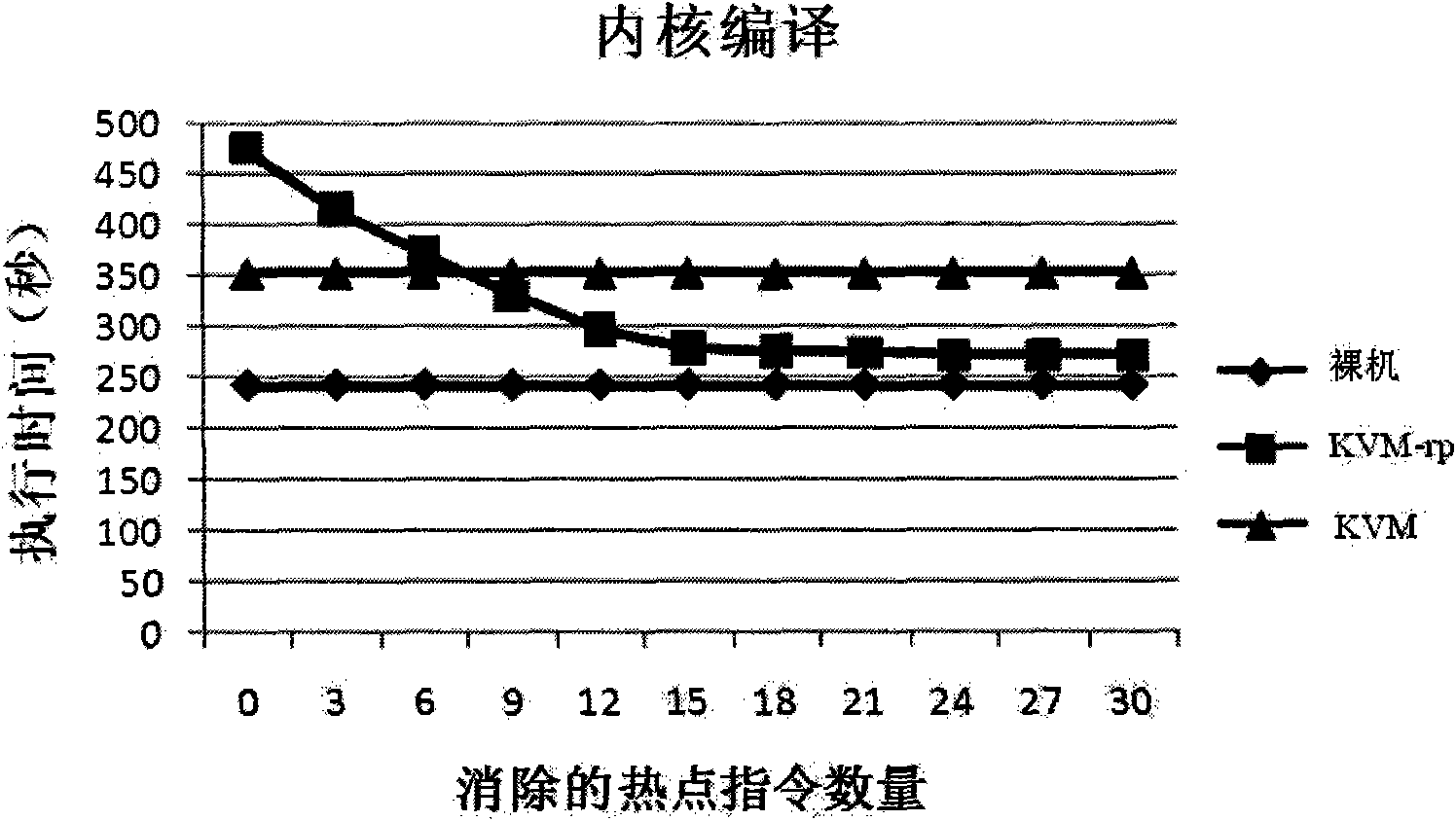
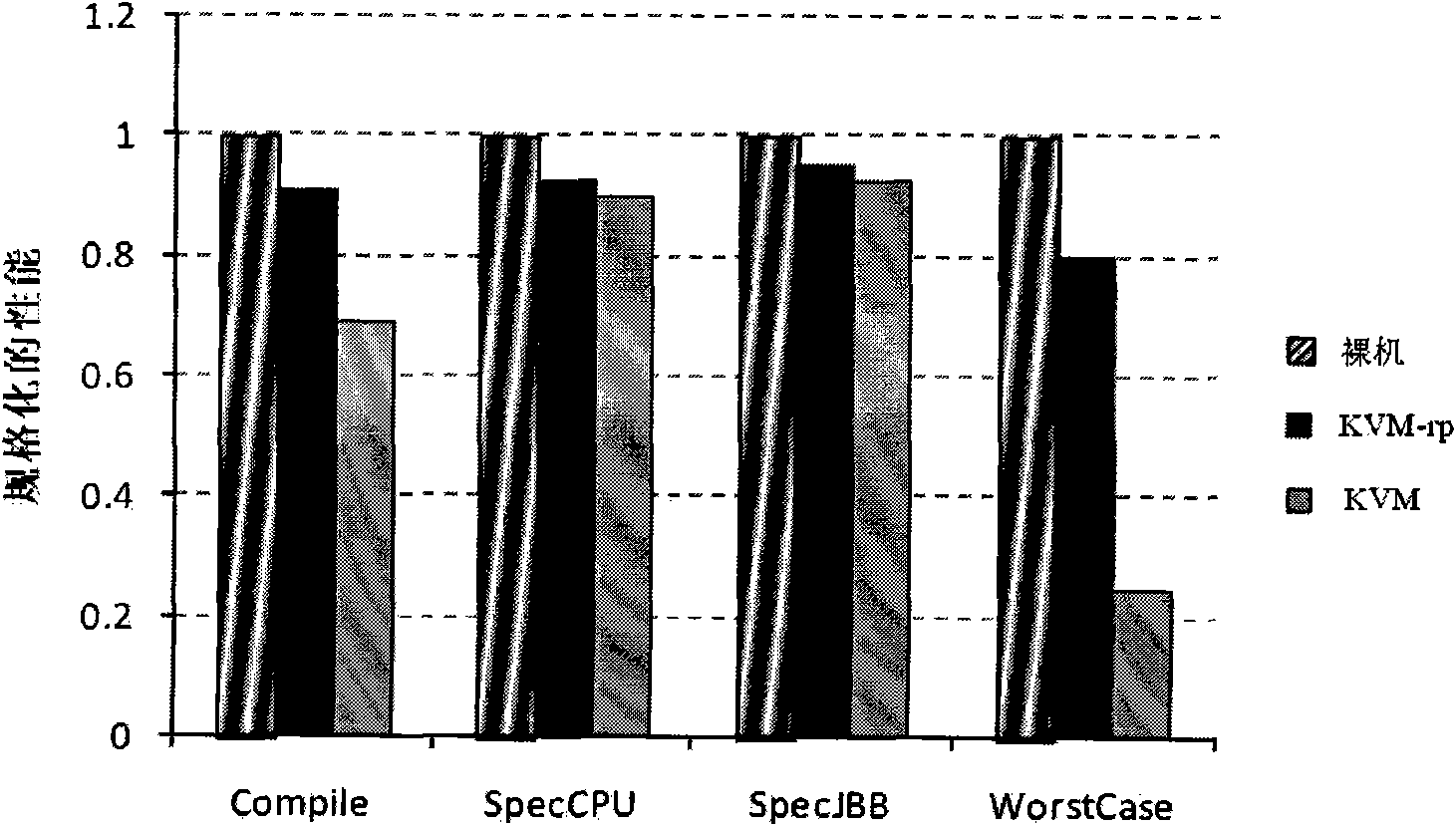
Patents
Literature
73 results about "Memory virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
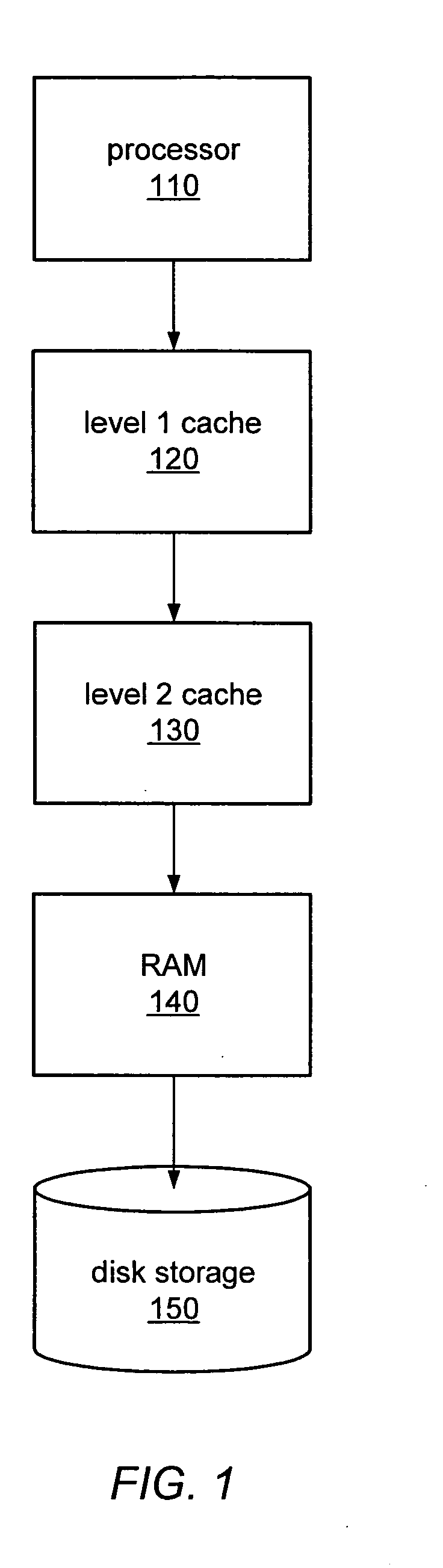
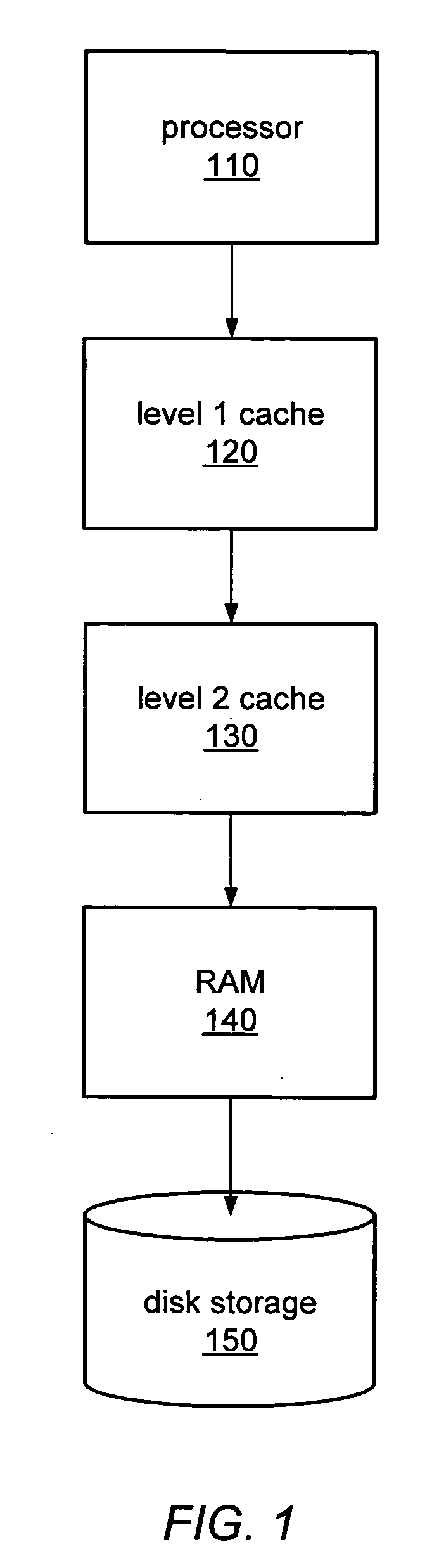
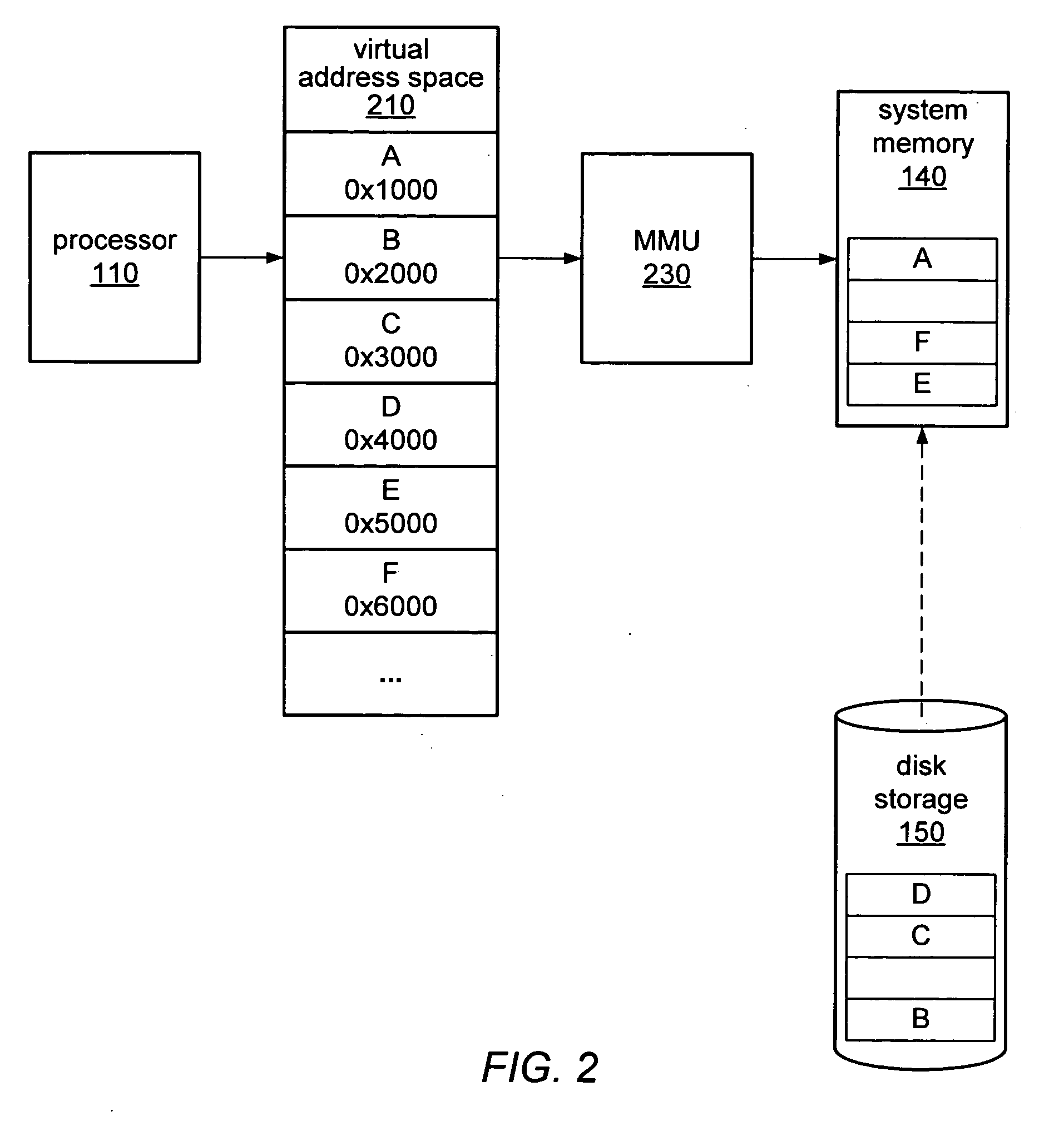
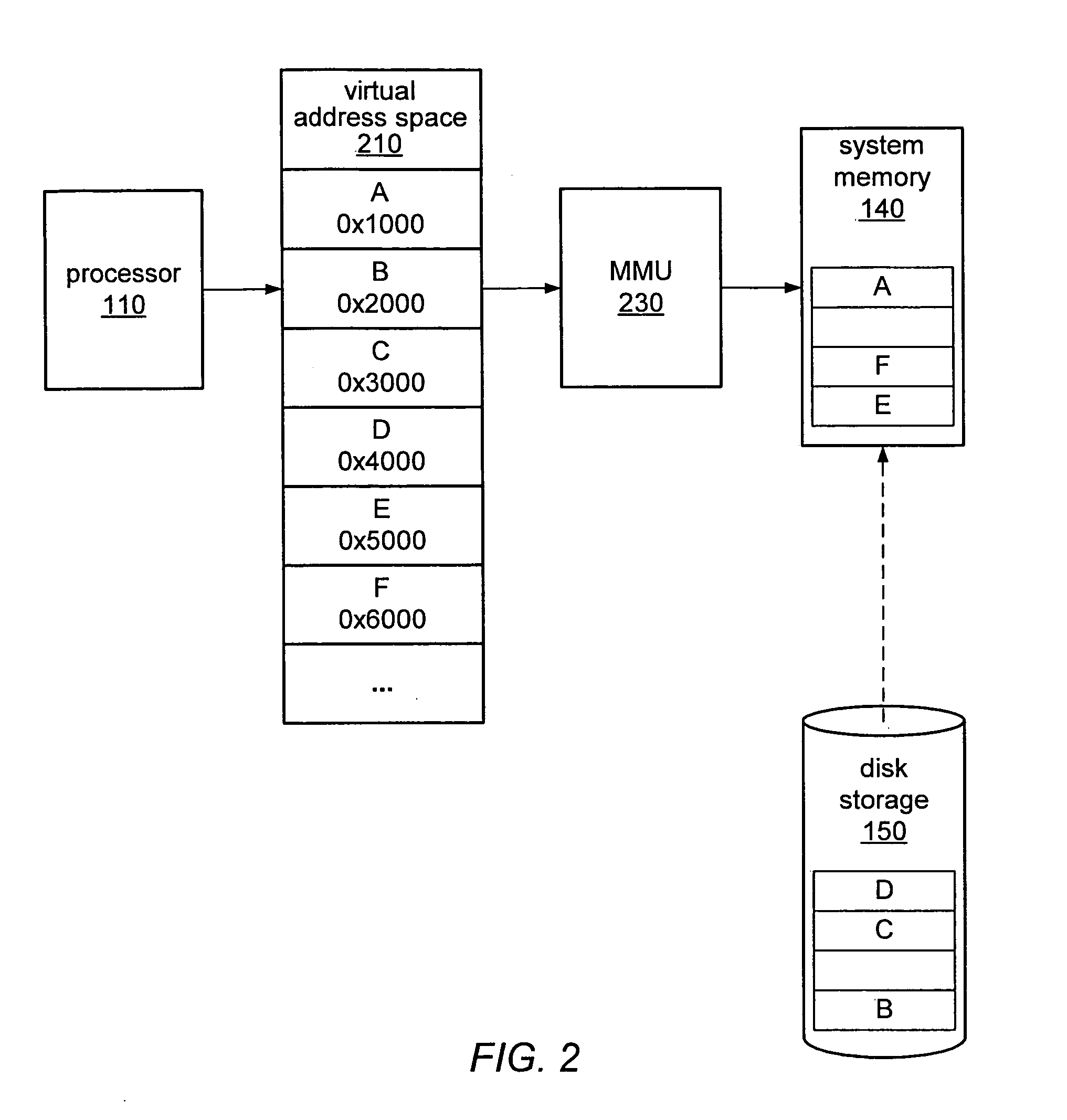
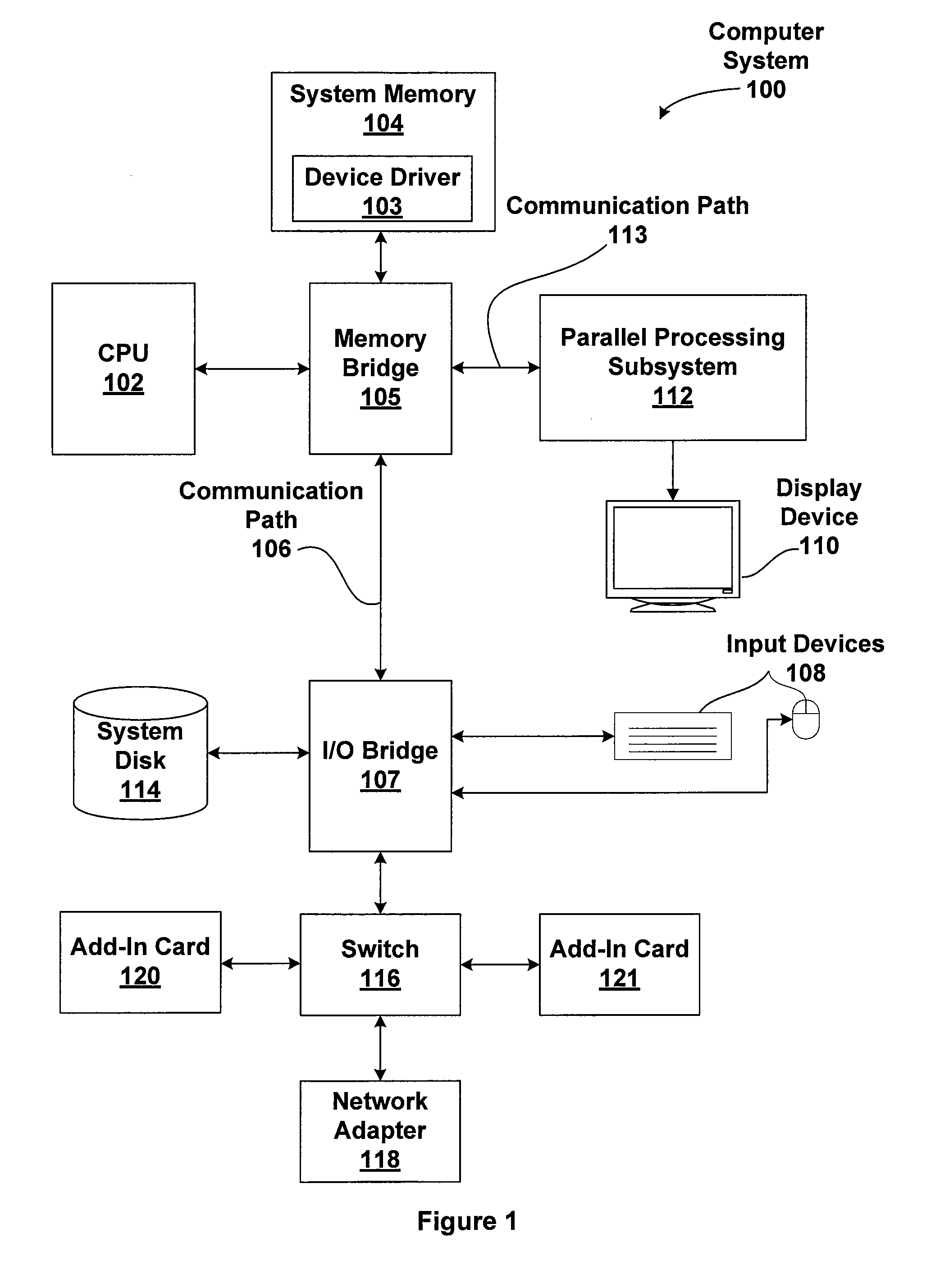
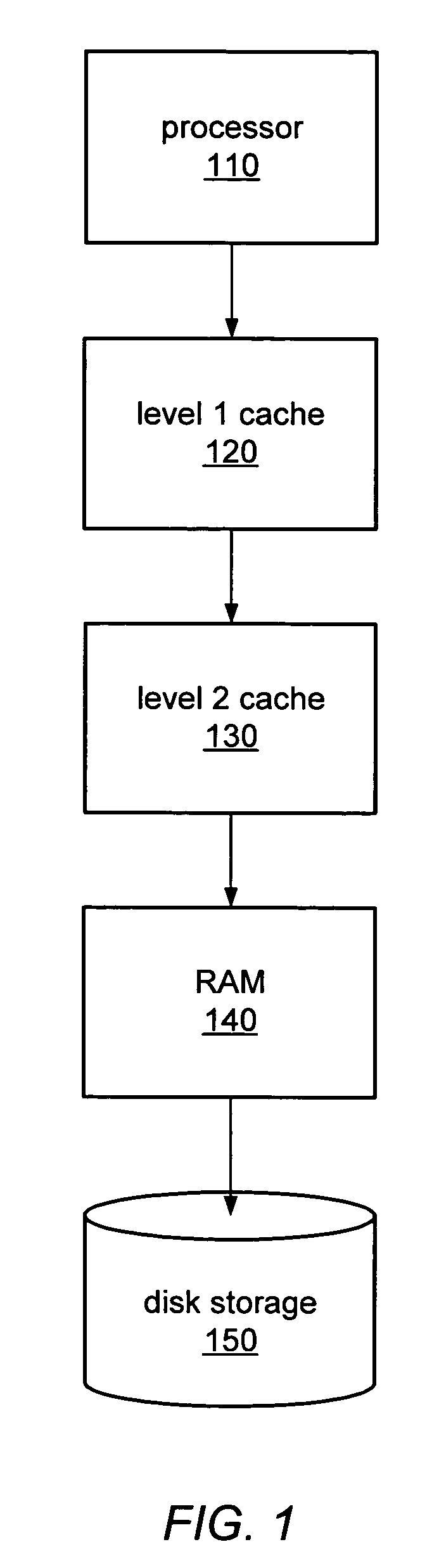
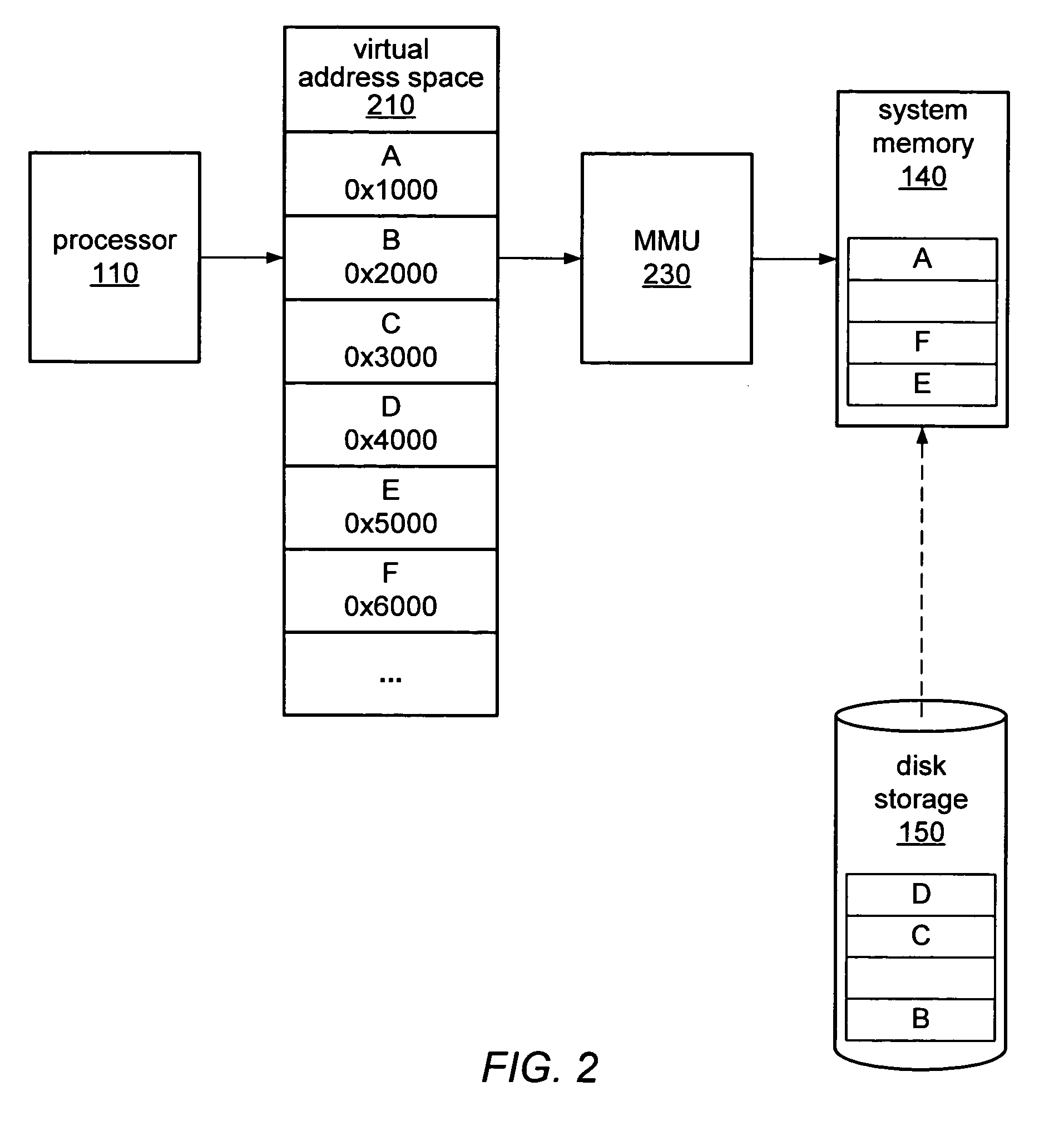
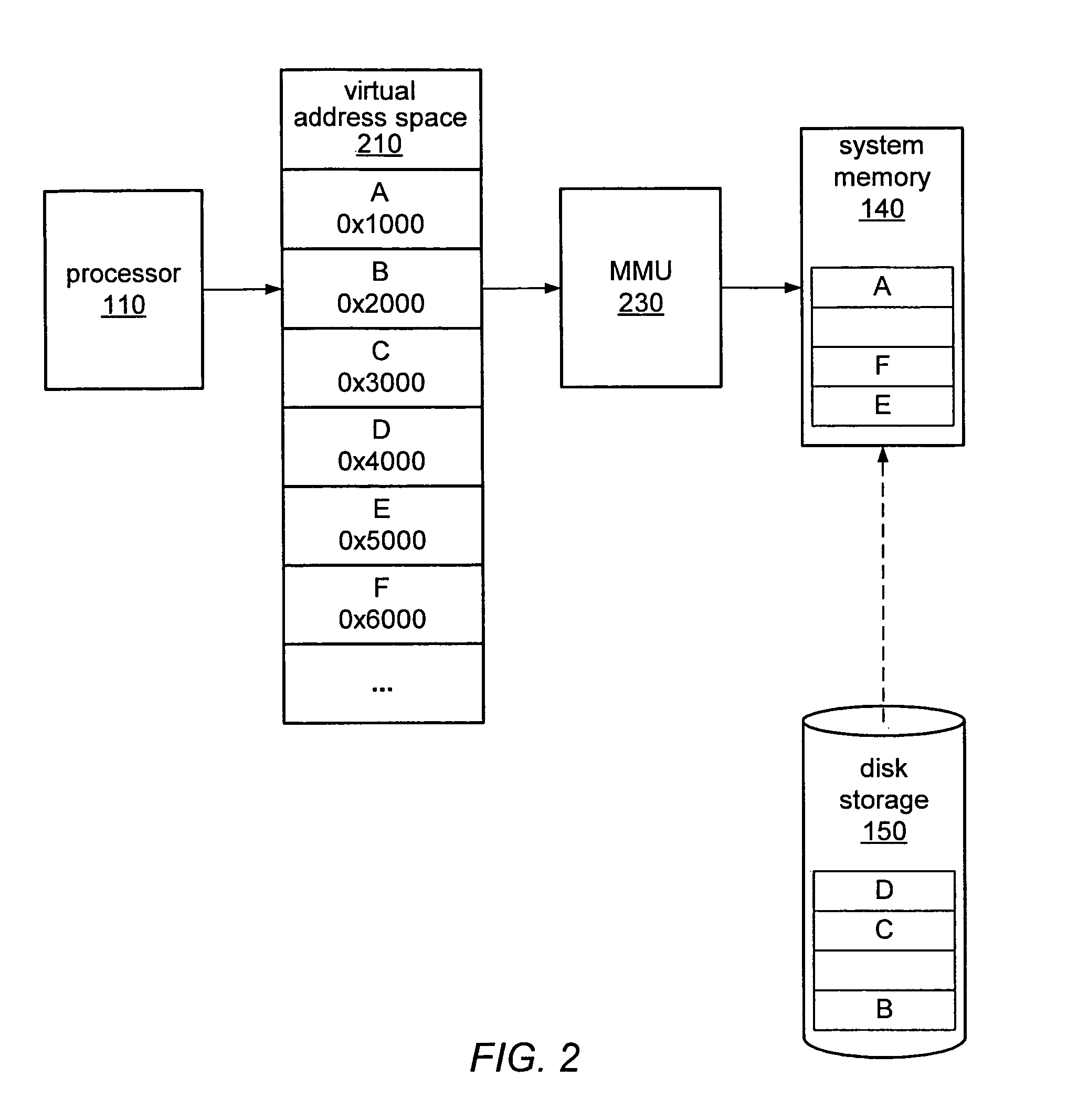
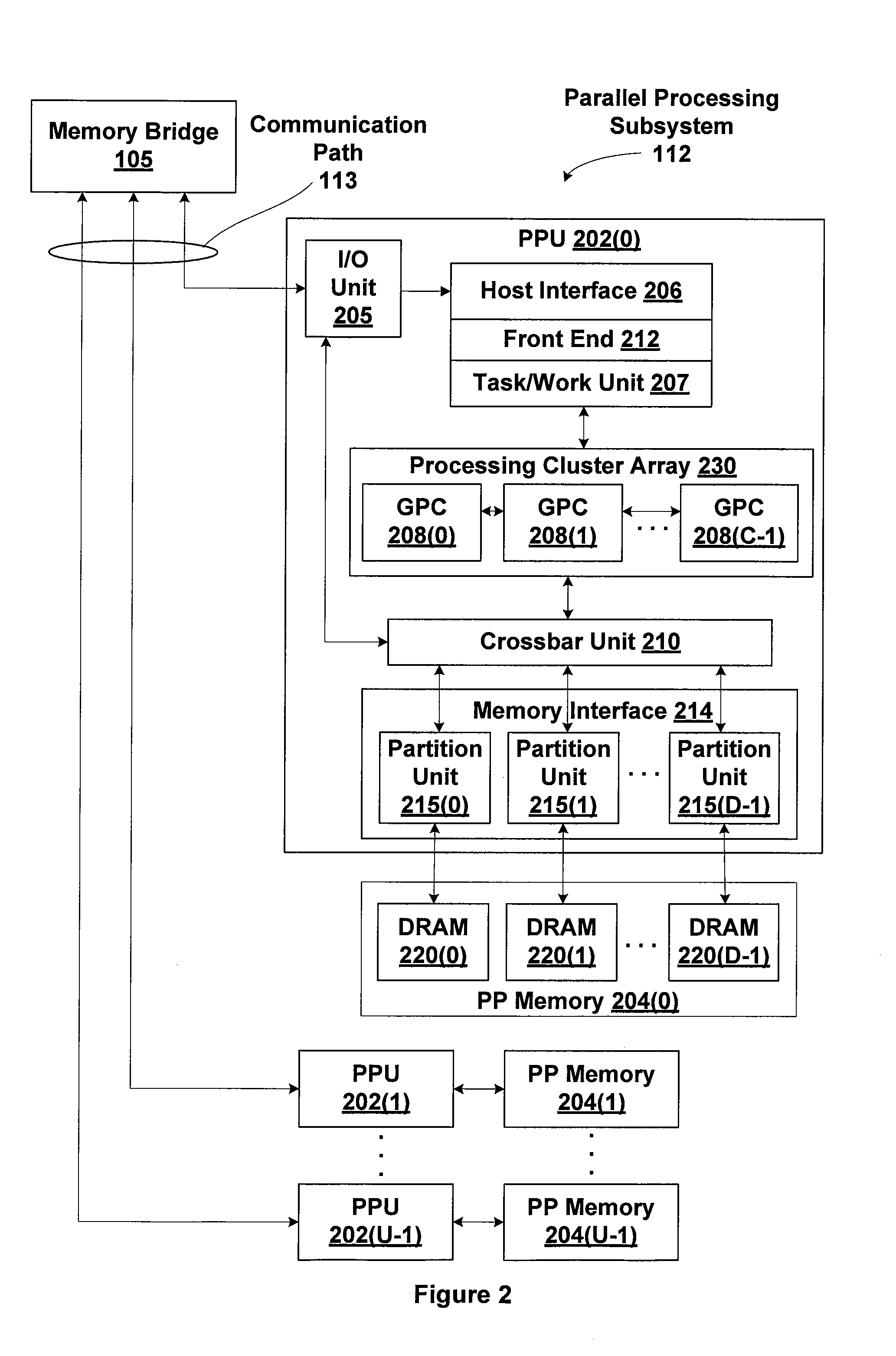
In computer science, memory virtualization decouples volatile random access memory (RAM) resources from individual systems in the data centre, and then aggregates those resources into a virtualized memory pool available to any computer in the cluster. The memory pool is accessed by the operating system or applications running on top of the operating system. The distributed memory pool can then be utilized as a high-speed cache, a messaging layer, or a large, shared memory resource for a CPU or a GPU application.
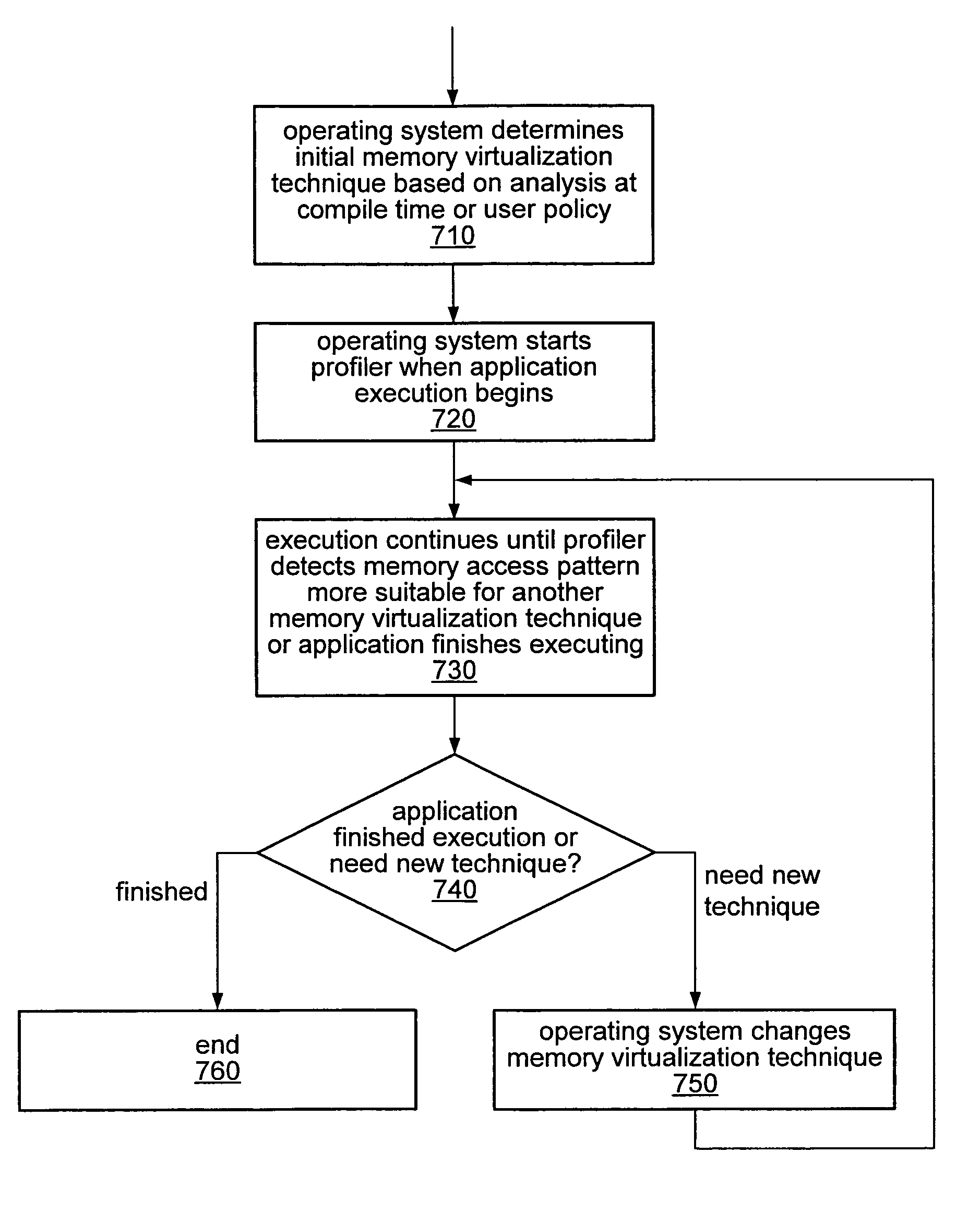
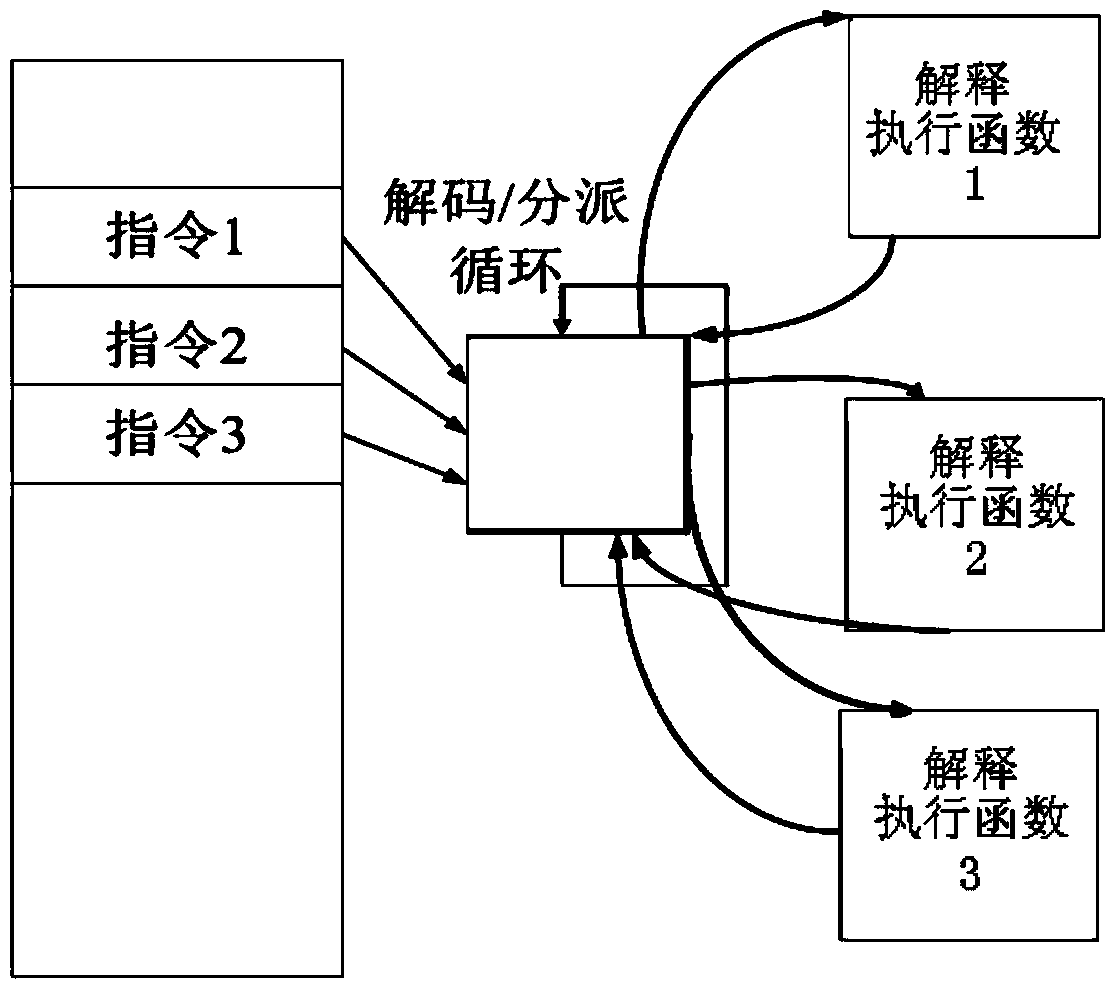
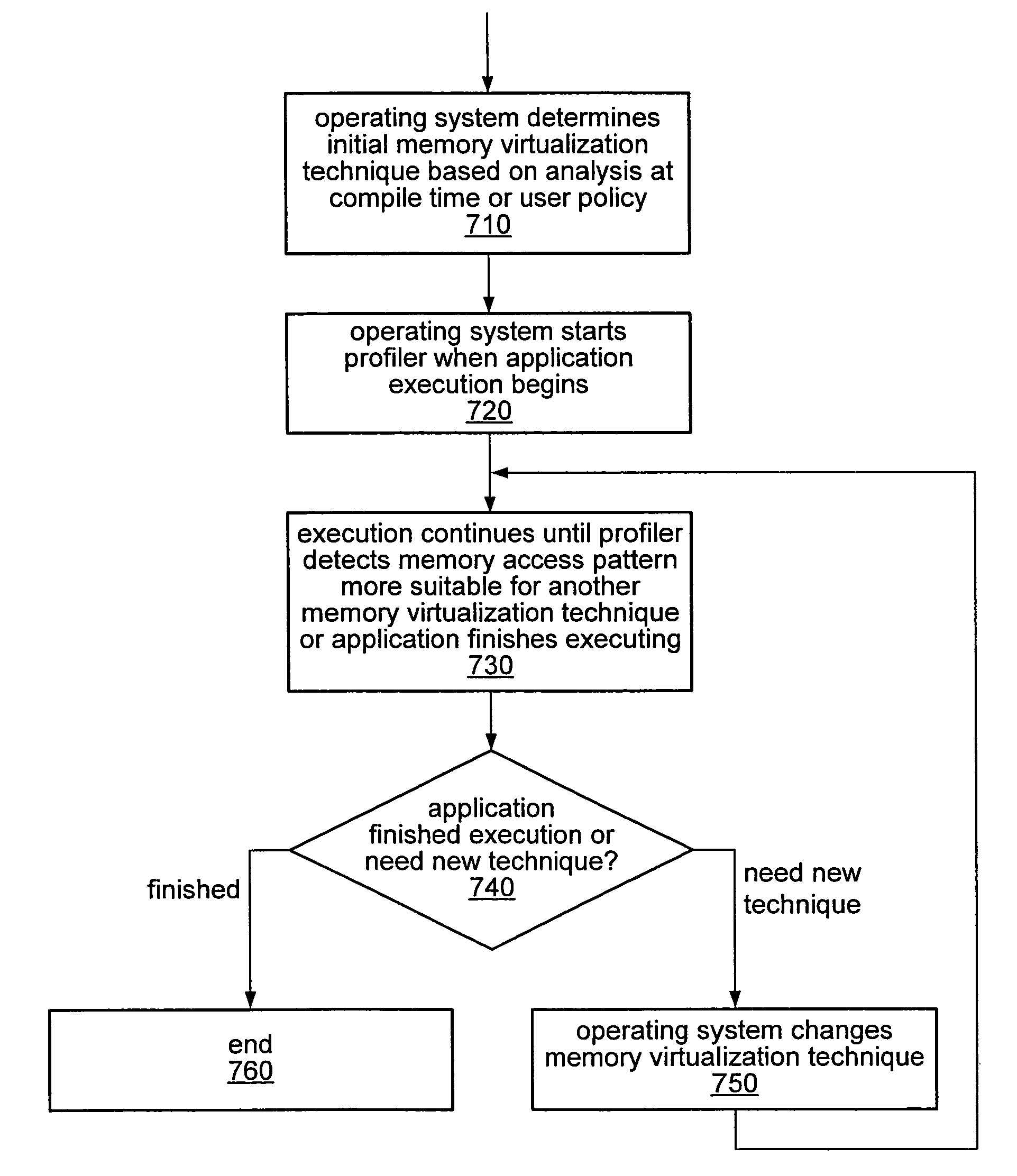
Dynamic selection of memory virtualization techniques
ActiveUS7752417B2Error detection/correctionMemory adressing/allocation/relocationVirtualizationComputerized system
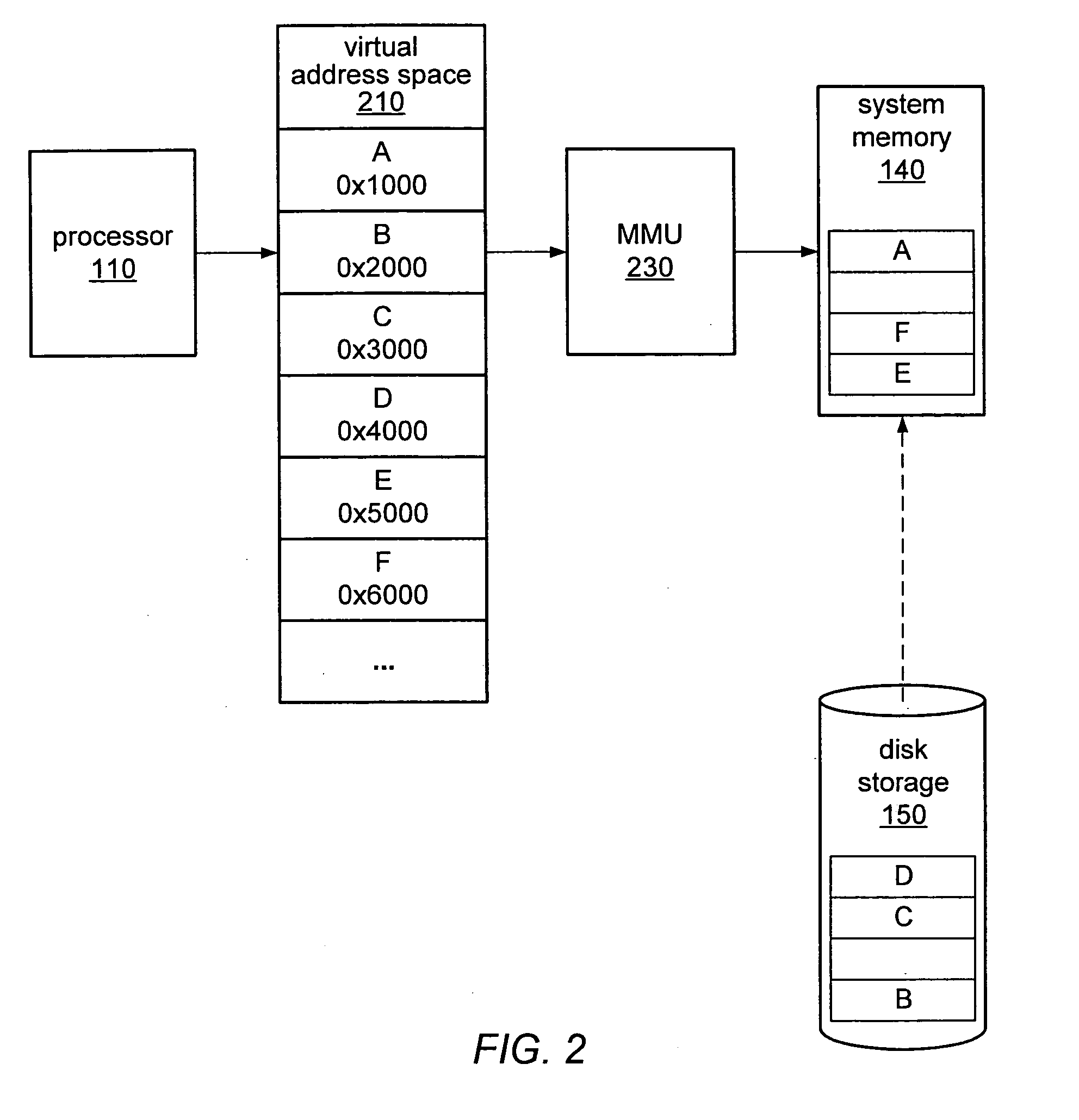
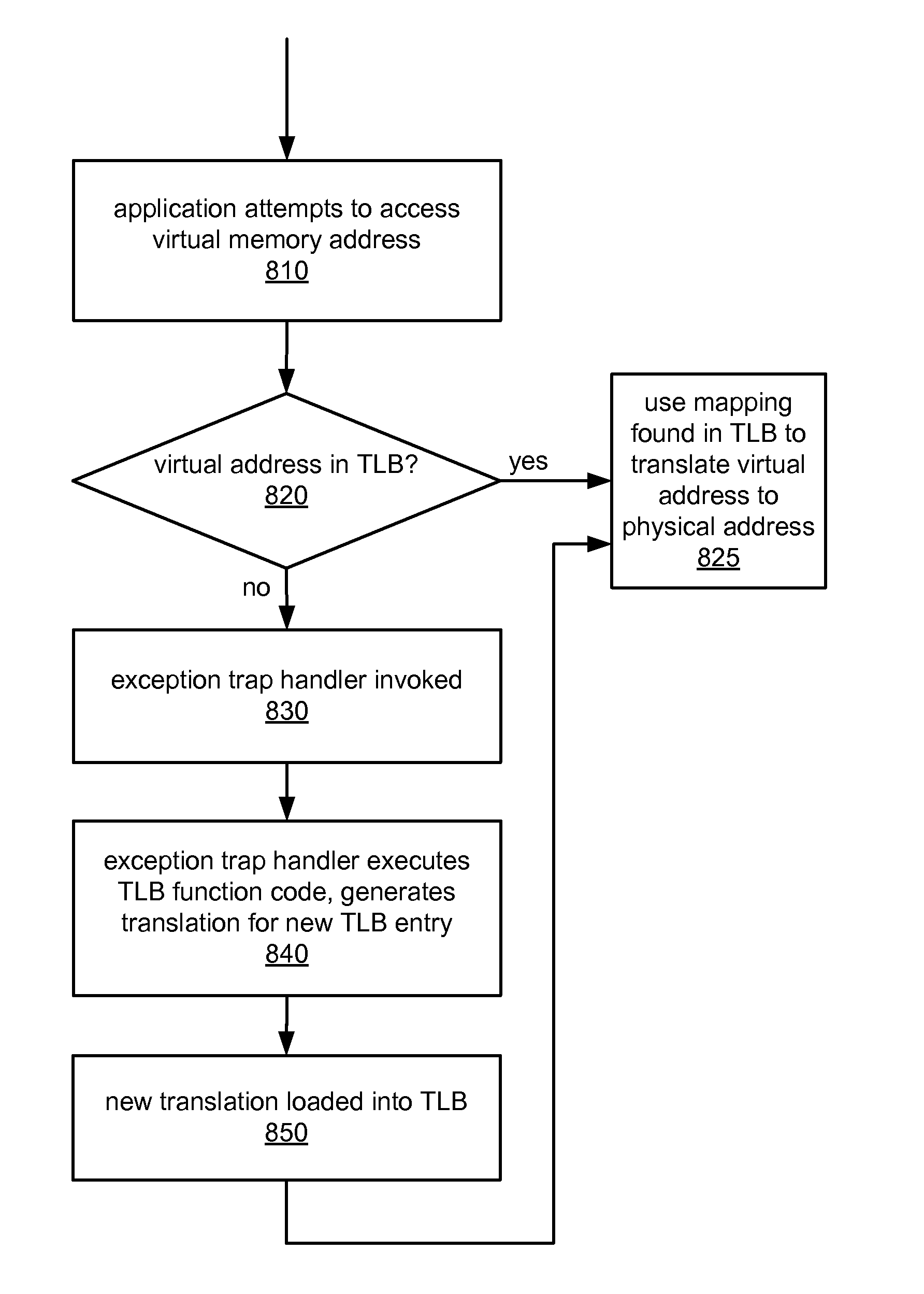
A computer system may be configured to dynamically select a memory virtualization and corresponding virtual-to-physical address translation technique during execution of an application and to dynamically employ the selected technique in place of a current technique without re-initializing the application. The computer system may be configured to determine that a current address translation technique incurs a high overhead for the application's current workload and may be configured to select a different technique dependent on various performance criteria and / or a user policy. Dynamically employing the selected technique may include reorganizing a memory, reorganizing a translation table, allocating a different block of memory to the application, changing a page or segment size, or moving to or from a page-based, segment-based, or function-based address translation technique. A selected translation technique may be dynamically employed for the application independent of a translation technique employed for a different application.
Owner:ORACLE INT CORP
Dynamic selection of memory virtualization techniques
ActiveUS20070283125A1Error detection/correctionMemory adressing/allocation/relocationVirtualizationComputerized system
A computer system may be configured to dynamically select a memory virtualization and corresponding virtual-to-physical address translation technique during execution of an application and to dynamically employ the selected technique in place of a current technique without re-initializing the application. The computer system may be configured to determine that a current address translation technique incurs a high overhead for the application's current workload and may be configured to select a different technique dependent on various performance criteria and / or a user policy. Dynamically employing the selected technique may include reorganizing a memory, reorganizing a translation table, allocating a different block of memory to the application, changing a page or segment size, or moving to or from a page-based, segment-based, or function-based address translation technique. A selected translation technique may be dynamically employed for the application independent of a translation technique employed for a different application.
Owner:ORACLE INT CORP
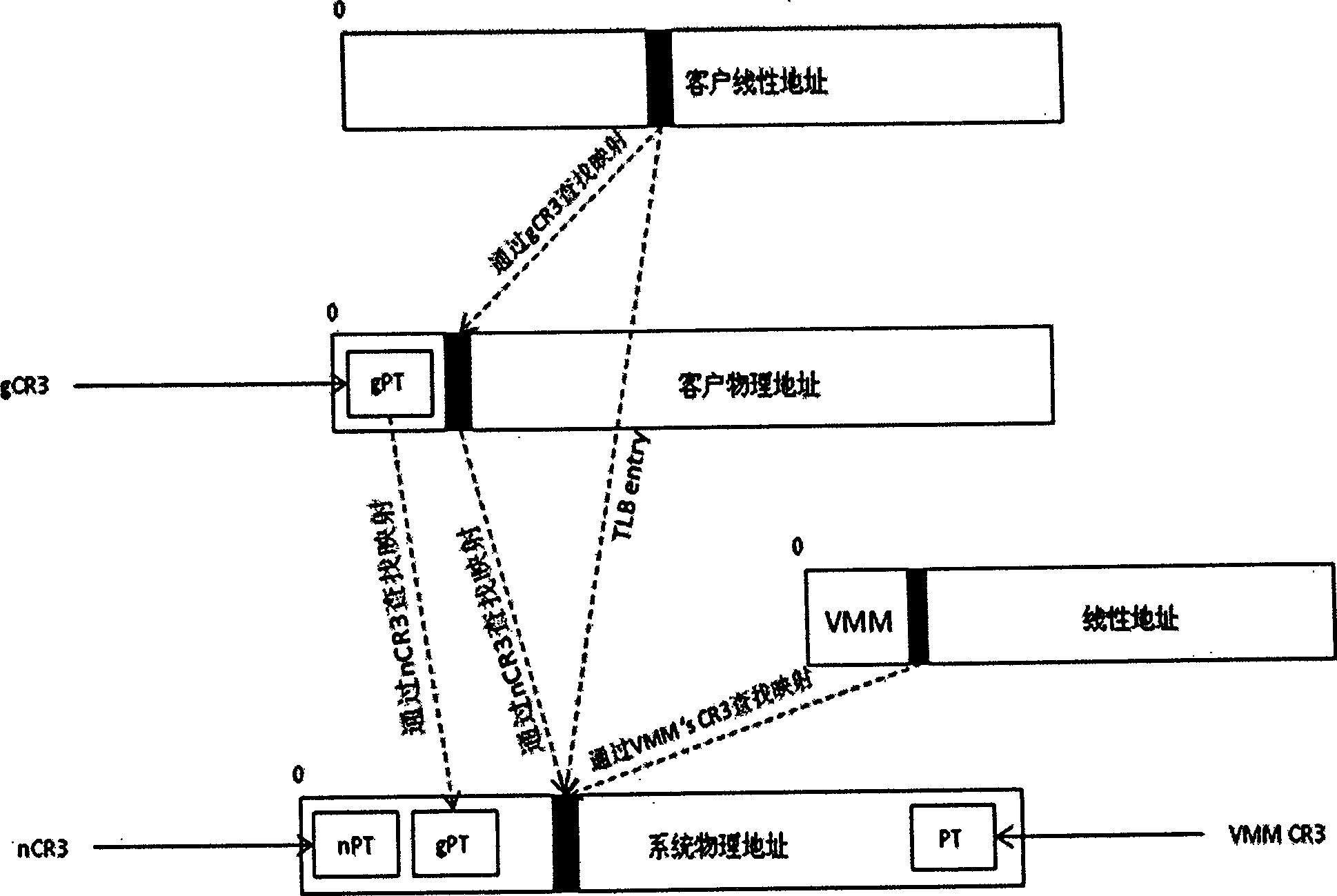
Function-based virtual-to-physical address translation
ActiveUS20070283123A1Simplify translation functionFunction increaseMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtualizationComputerized system
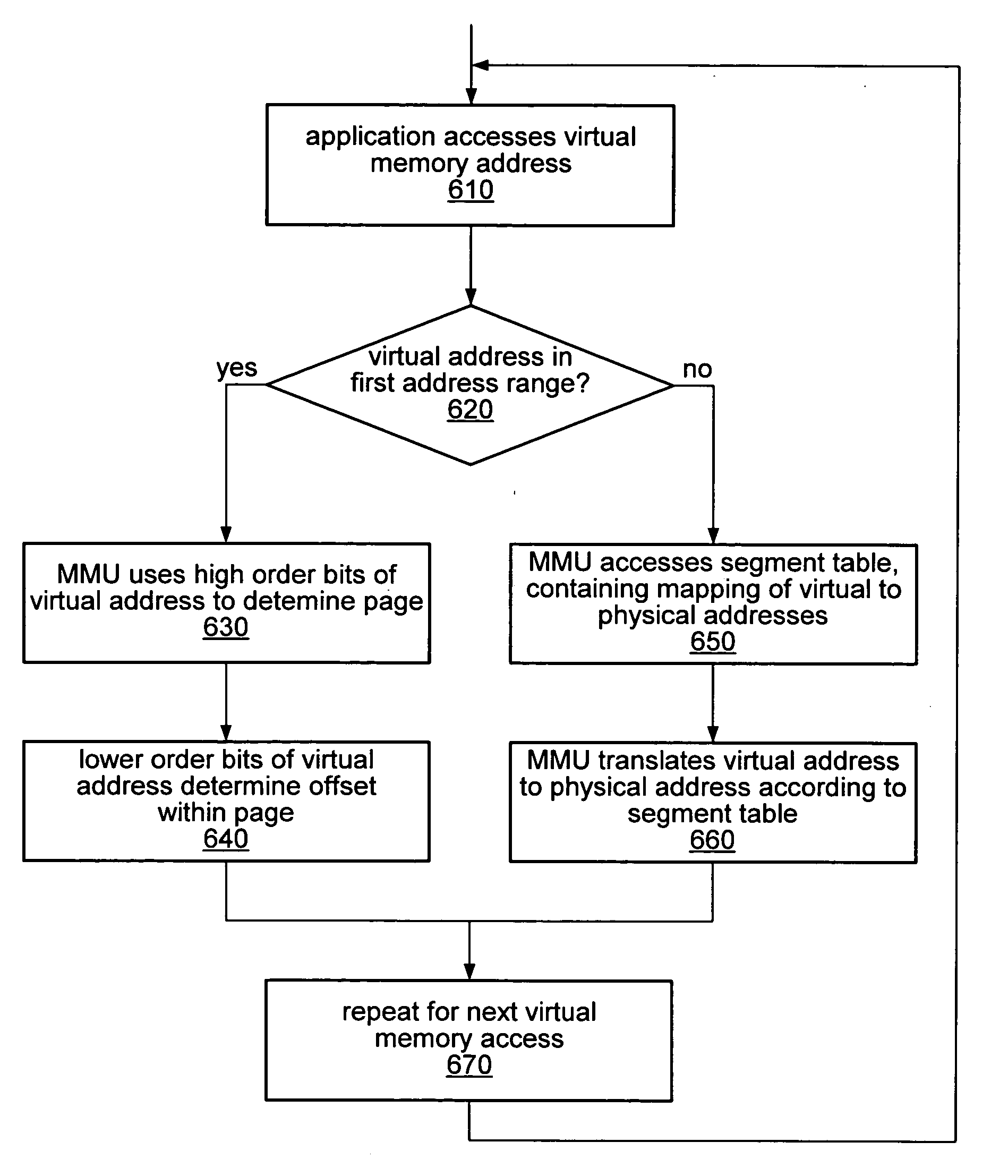
A computer system employing memory virtualization may employ a function-based technique for virtual-to-physical address translation. A function-based translation technique may involve replacing a generic trap handler and one or more translation table look-ups with a function to compute a corresponding physical address from a given virtual address. The computer system may be configured to determine a translation function dependent on mappings in one or more translation tables. The computer system may be configured to reorganize a memory, to reorganize one or more translation tables, or to allocate different blocks of memory to an application prior to determining a translation function. Different applications or threads executing on the computer system may employ different translation functions. Different regions of memory may be accessed using different translation functions. Some virtual addresses may be translated using a function while others may be translated using one or more translation table look-ups.
Owner:ORACLE INT CORP
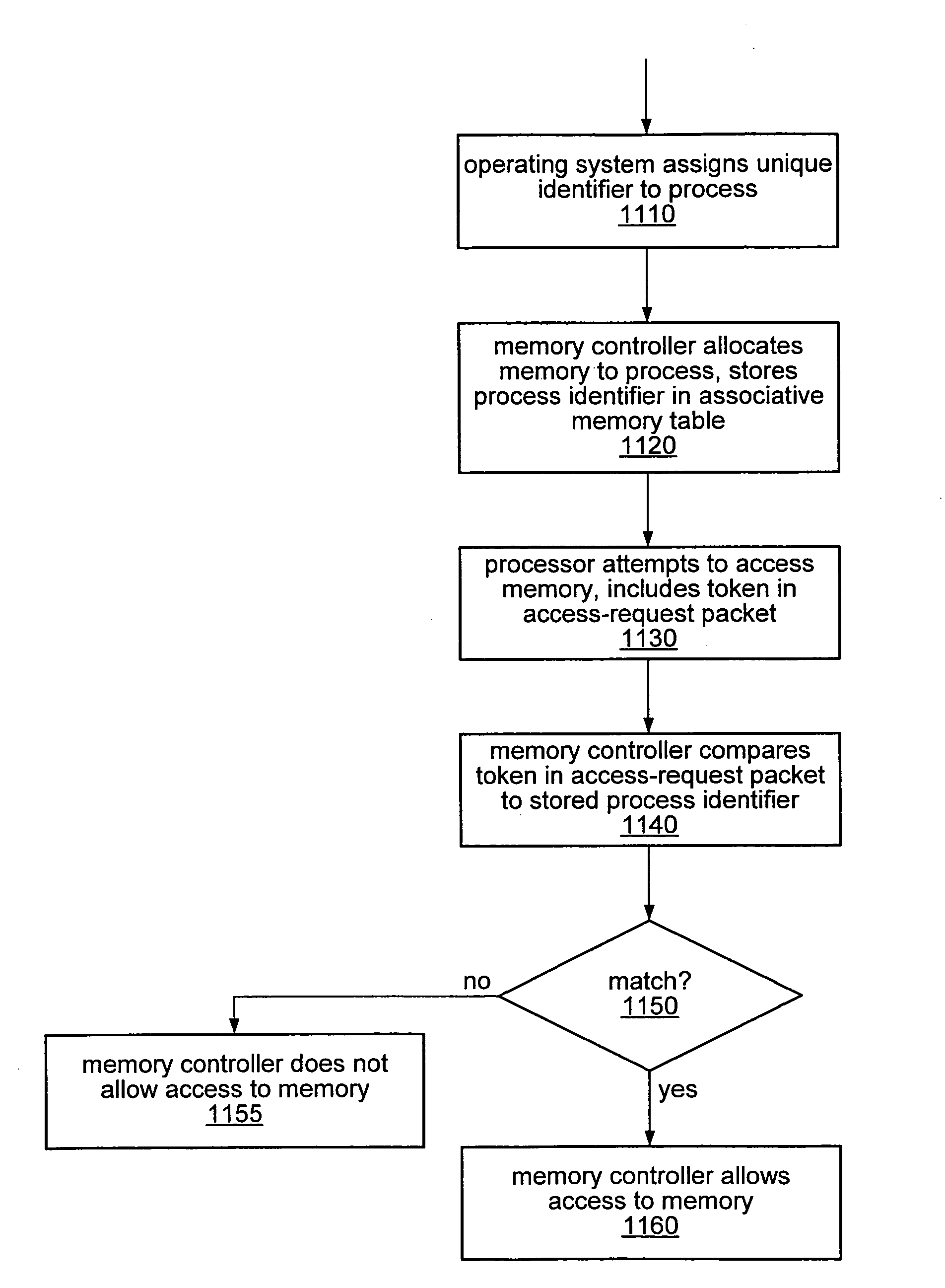
Memory protection in a computer system employing memory virtualization
ActiveUS20070283115A1Unauthorized memory use protectionComputer security arrangementsVirtualizationComputerized system
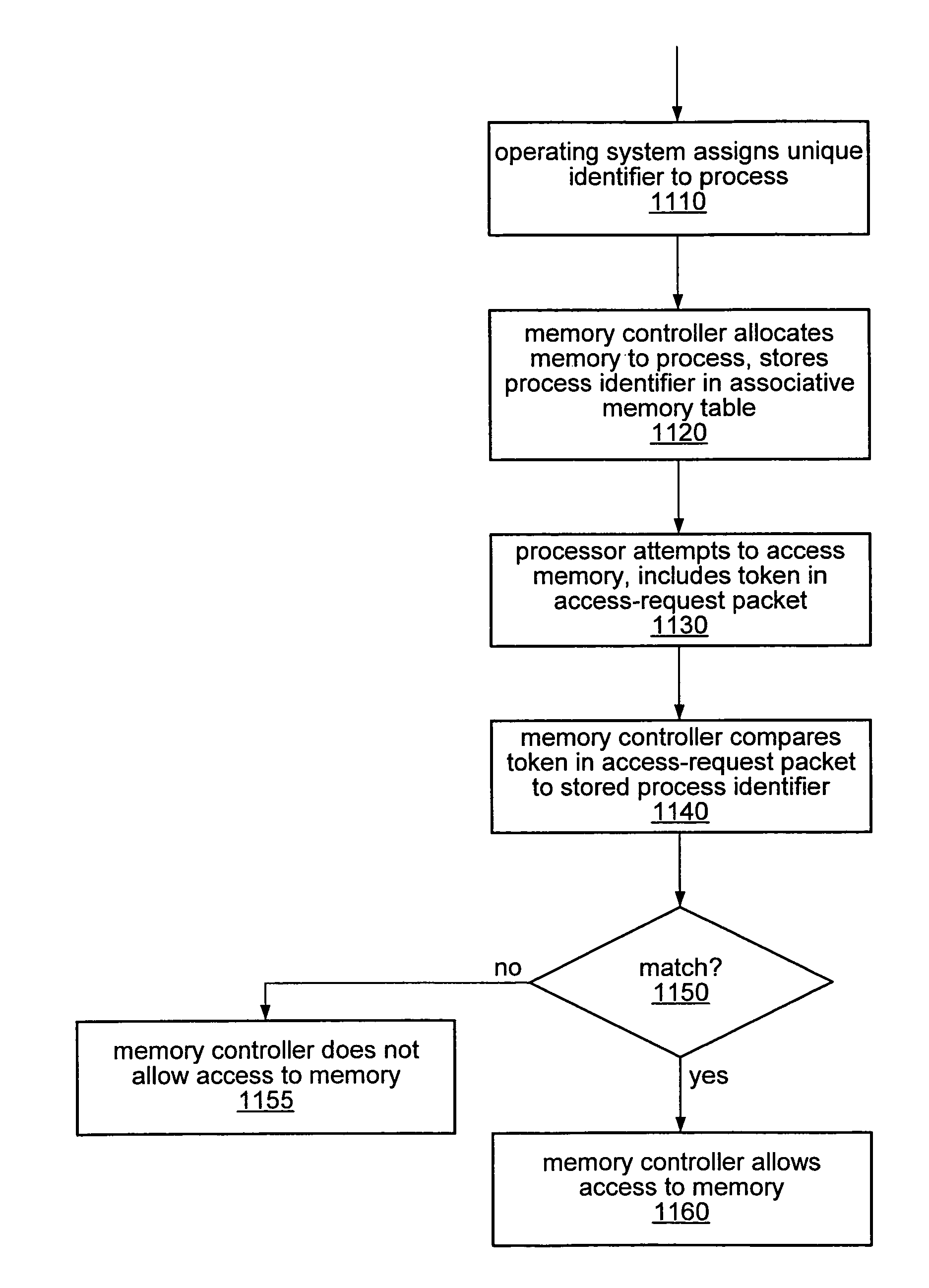
The use of a token-based memory protection technique may provide memory protection in a computer system employing memory virtualization. A token-based memory protection technique may include assigning a unique identifier to an application, process, or thread, and associating the identifier with a block of memory allocated to that application, process, or thread. Subsequent to assigning the identifier, a packet requesting access to that block of memory may include a token to be compared to the identifier. A memory controller may be configured to associate the identifier with the block of memory and to compare the token in the memory request packet to the identifier before granting access. If a second block of memory is subsequently allocated to the application, process, or thread, the identifier may be disassociated with the first block of memory and associated with the second block of memory.
Owner:ORACLE INT CORP
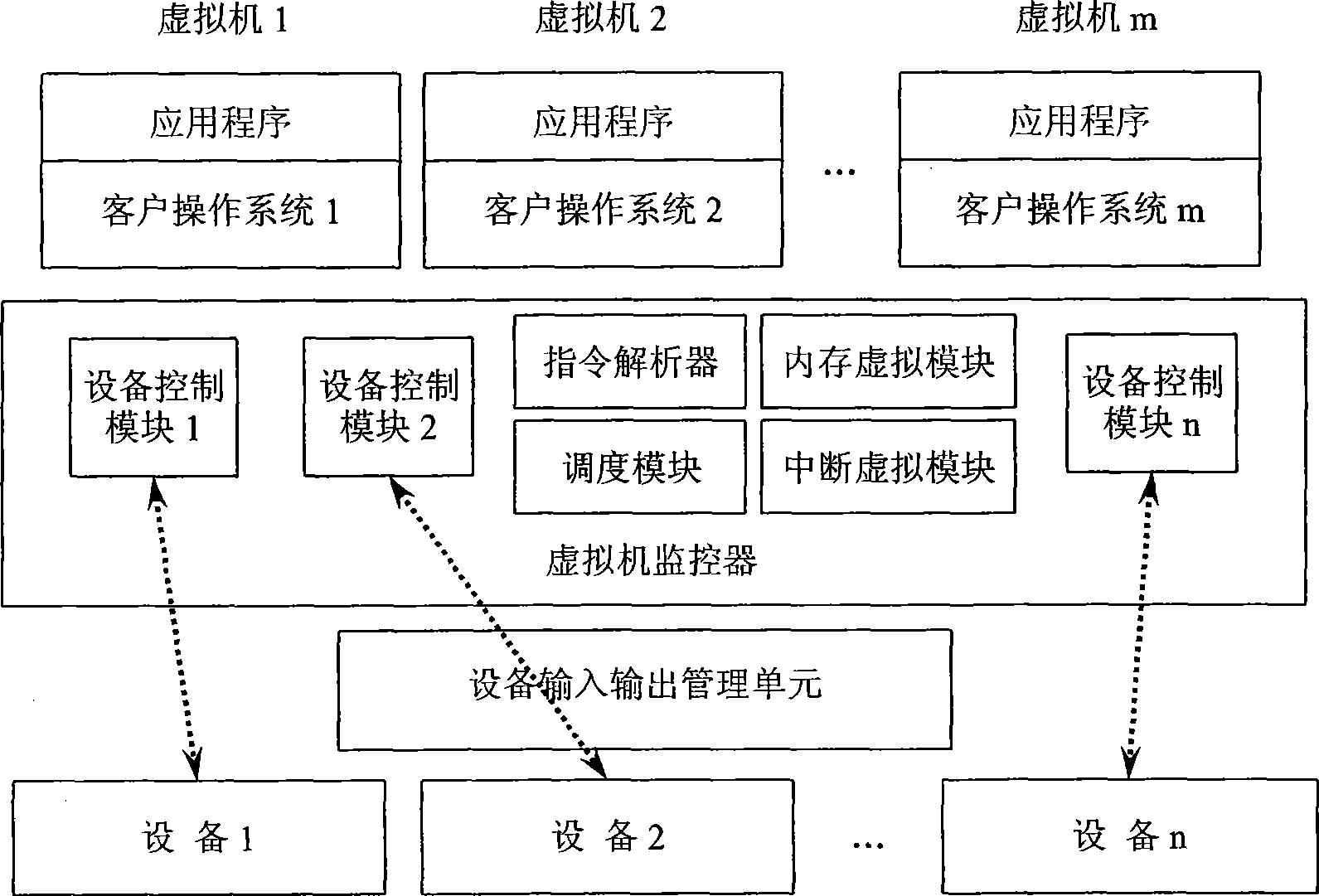
Virtual machine system based on the management technology of equipment access storage and equipment access control method thereof
InactiveCN101520738AReduce switching overheadImprove performanceSoftware simulation/interpretation/emulationOperational systemBottle neck
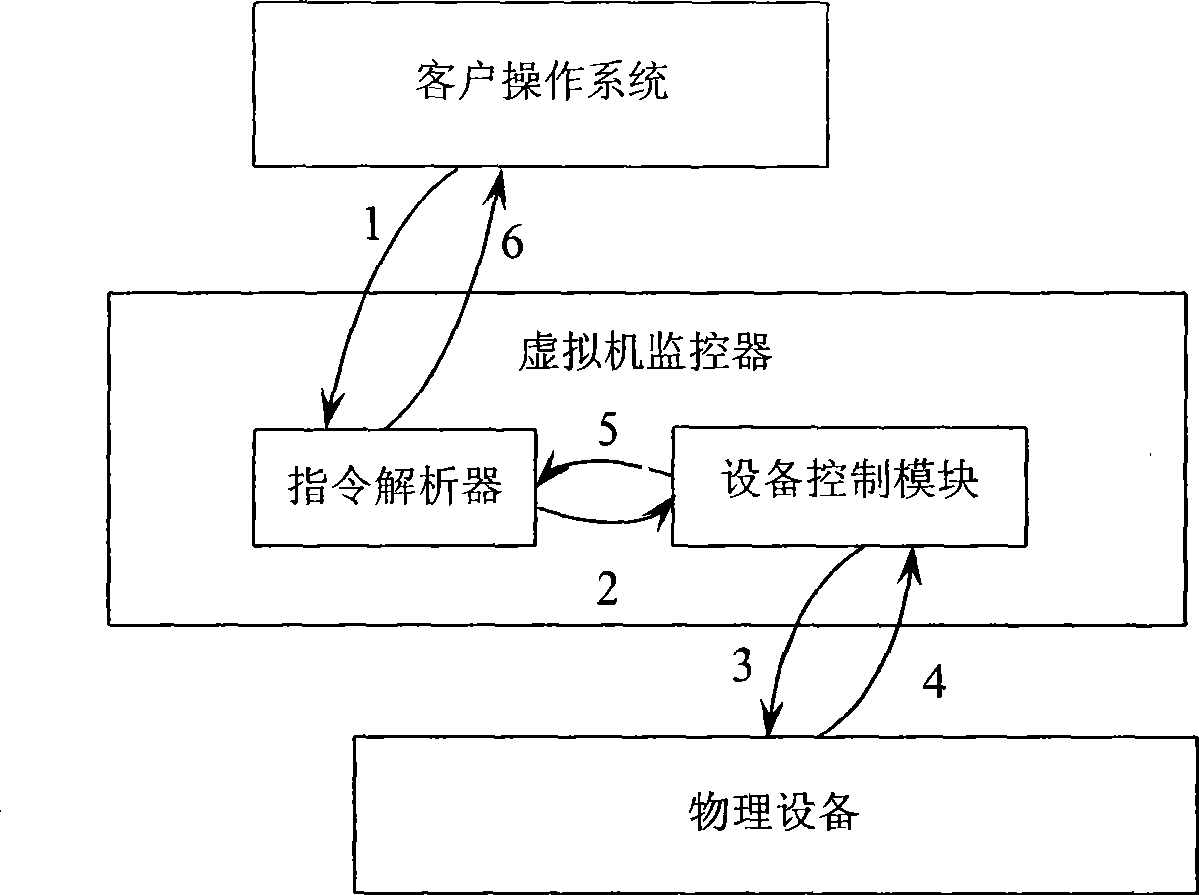
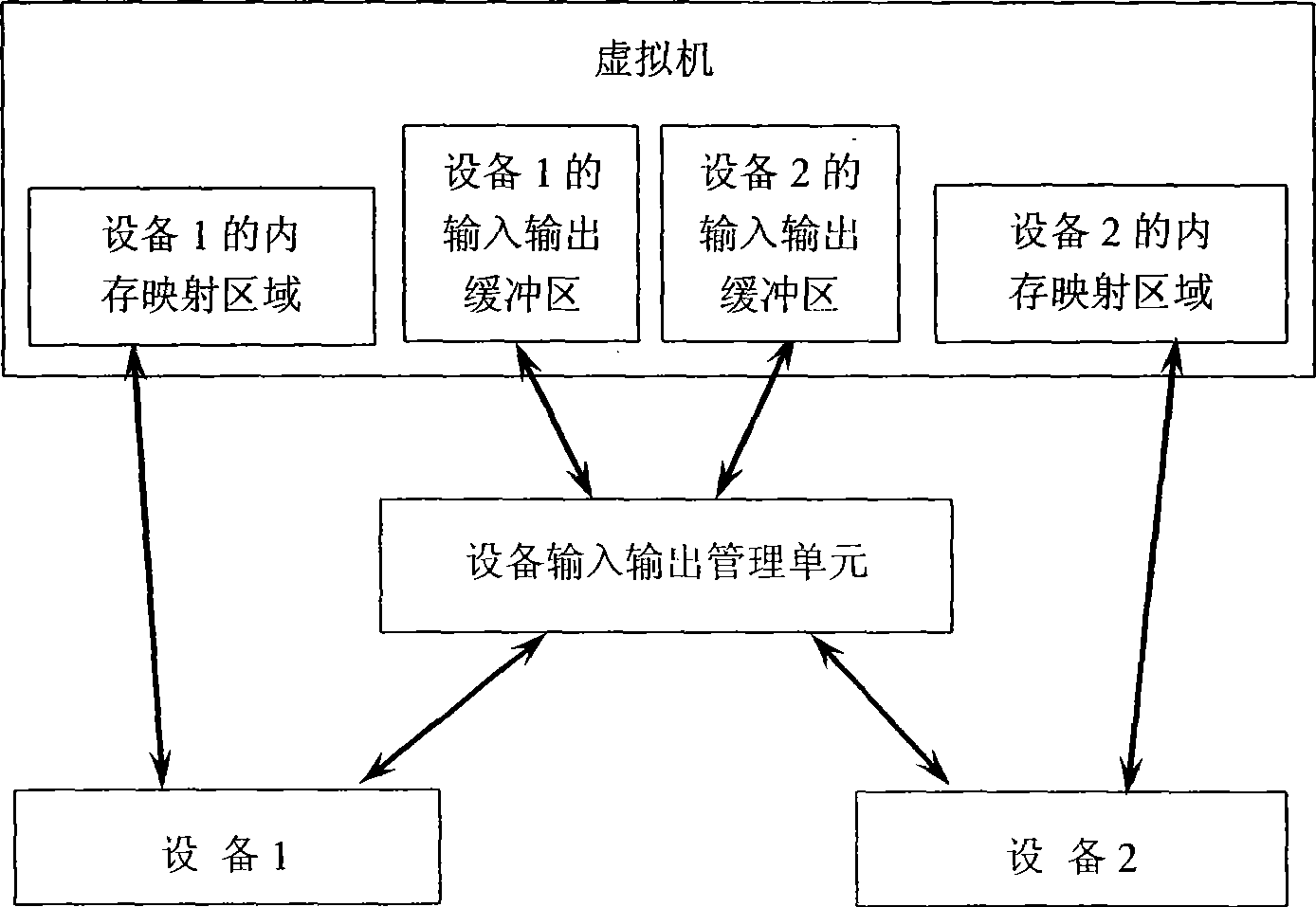
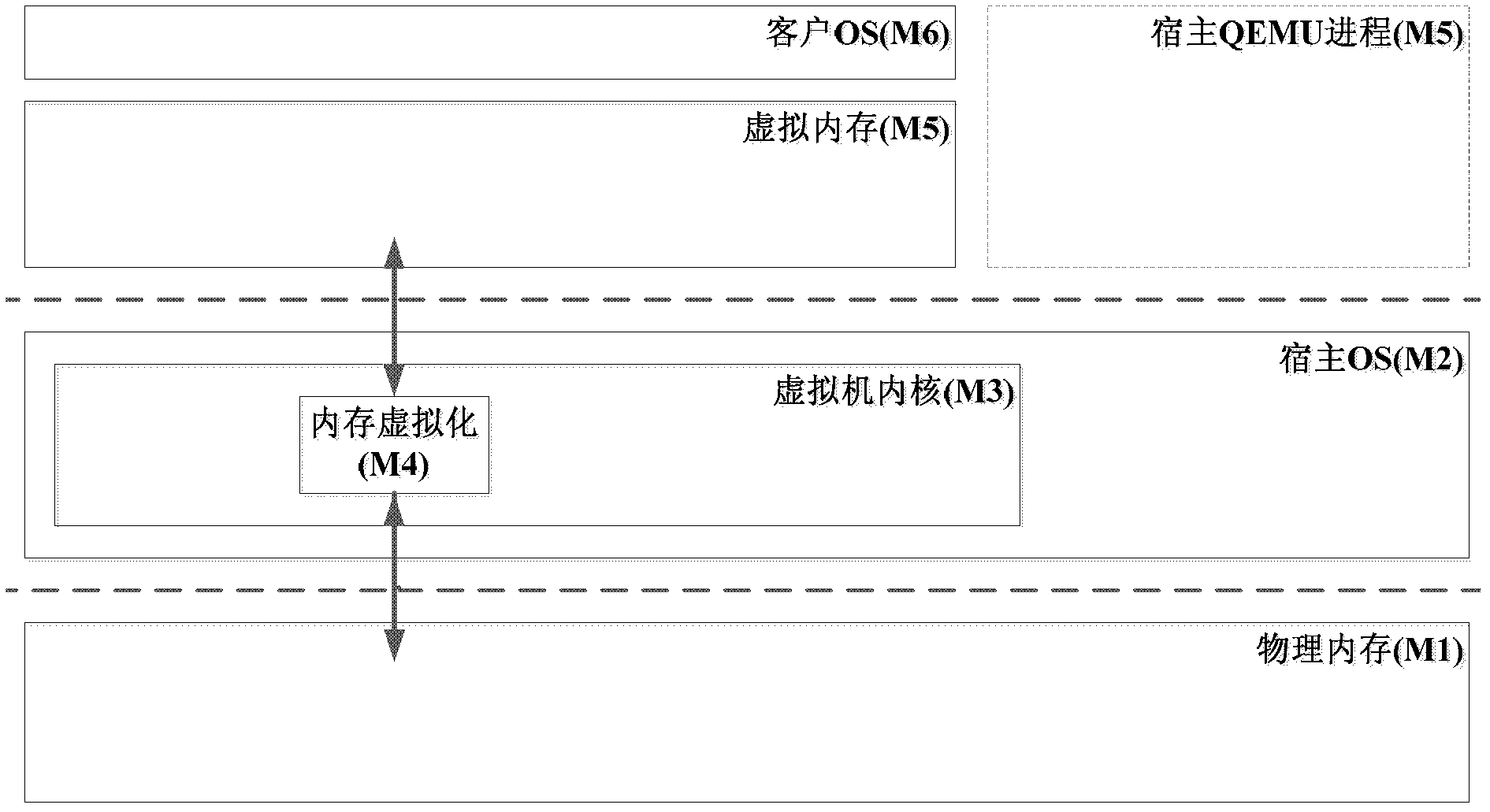
The invention provides a virtual machine system based on the management technology of equipment access storage and an equipment access control method thereof. The virtual machine system comprises a virtual machine monitor, an underlying hardware supporting the management technology of storage for equipment input and output, an equipment control module and a plurality of virtual machines; wherein the virtual machine monitor comprises a scheduling module which can schedule different virtual machines to run on a processor, a memory virtualization module used for completing memory management of the virtual system, an interrupt virtualization module, an instruction analyzer, a privilege calling interface used for providing services for privilege entity and a control module of a storage management unit of equipment input and output. In the virtual machine system, one equipment control module corresponds to physical equipment and is responsible for initiating privilege calling to the virtual machine monitor, receiving and executing an equipment port access instruction transmitted by the virtual machine monitor, detecting equipment state and hiding the virtualization equipment resources and the like. In the equipment access method provided by the invention, a client operating system in the virtual machine can access equipment data by a memory mapping mode; and the equipment utilizes the equipment access storage management technology to carry out direct storage access to virtual machine data. The virtual machine system and the equipment access control method lead the equipment performance to be improved greatly, relieve the system performance bottle-neck, and improve safety of equipment access control. The equipment access control method does not need to modify the client operating system, is easy to be realized and has wide application range.
Owner:黄歆媚
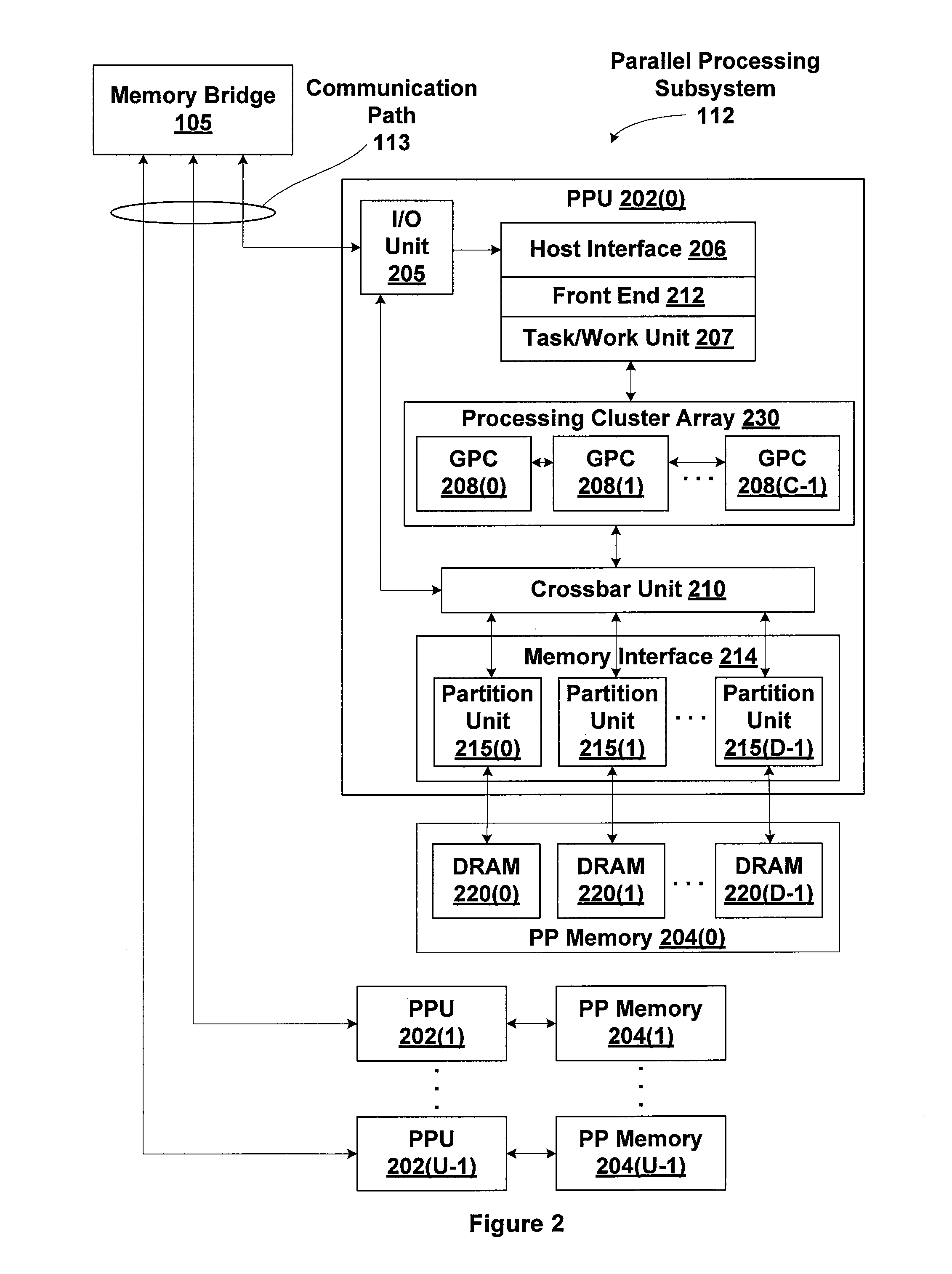
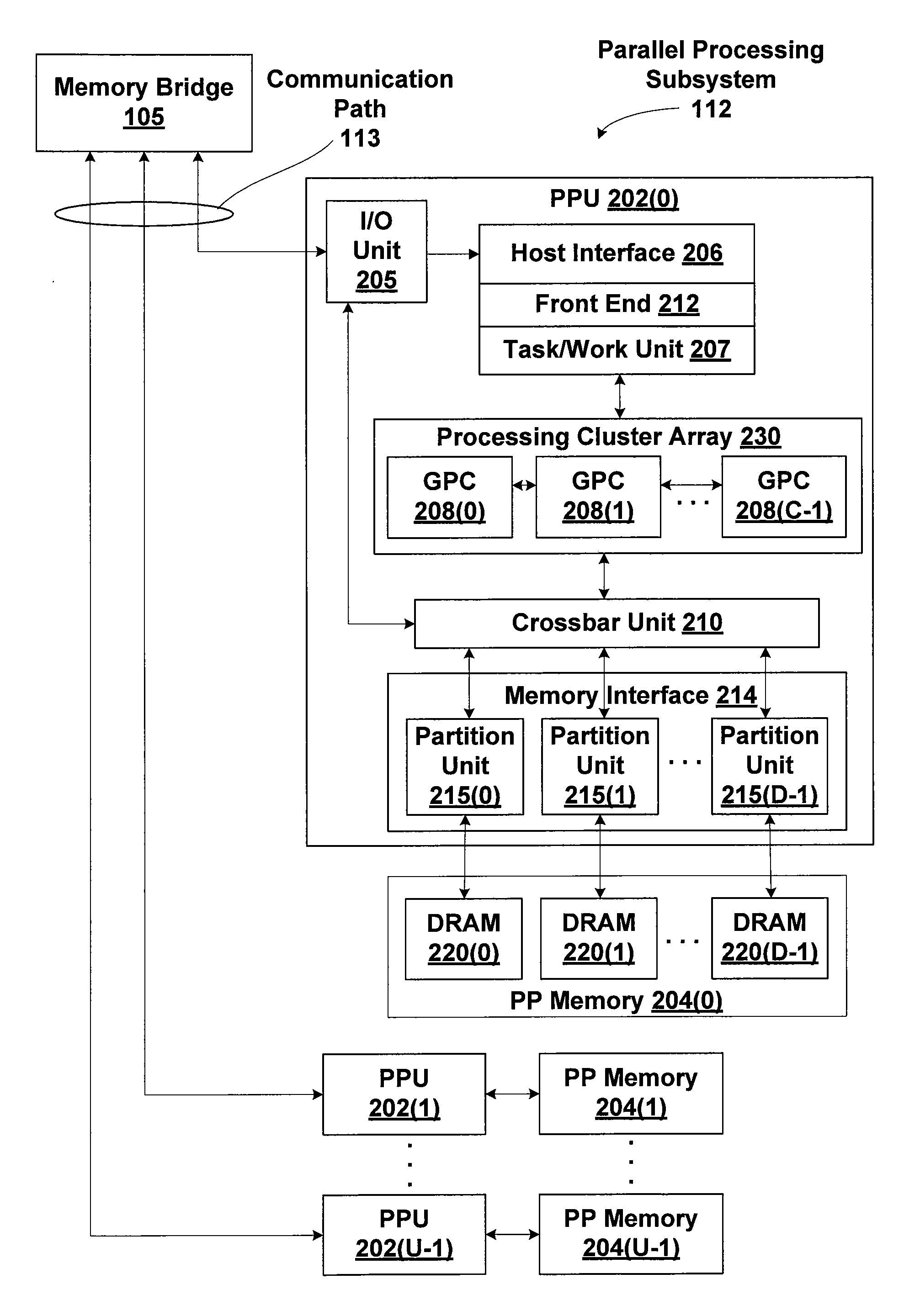
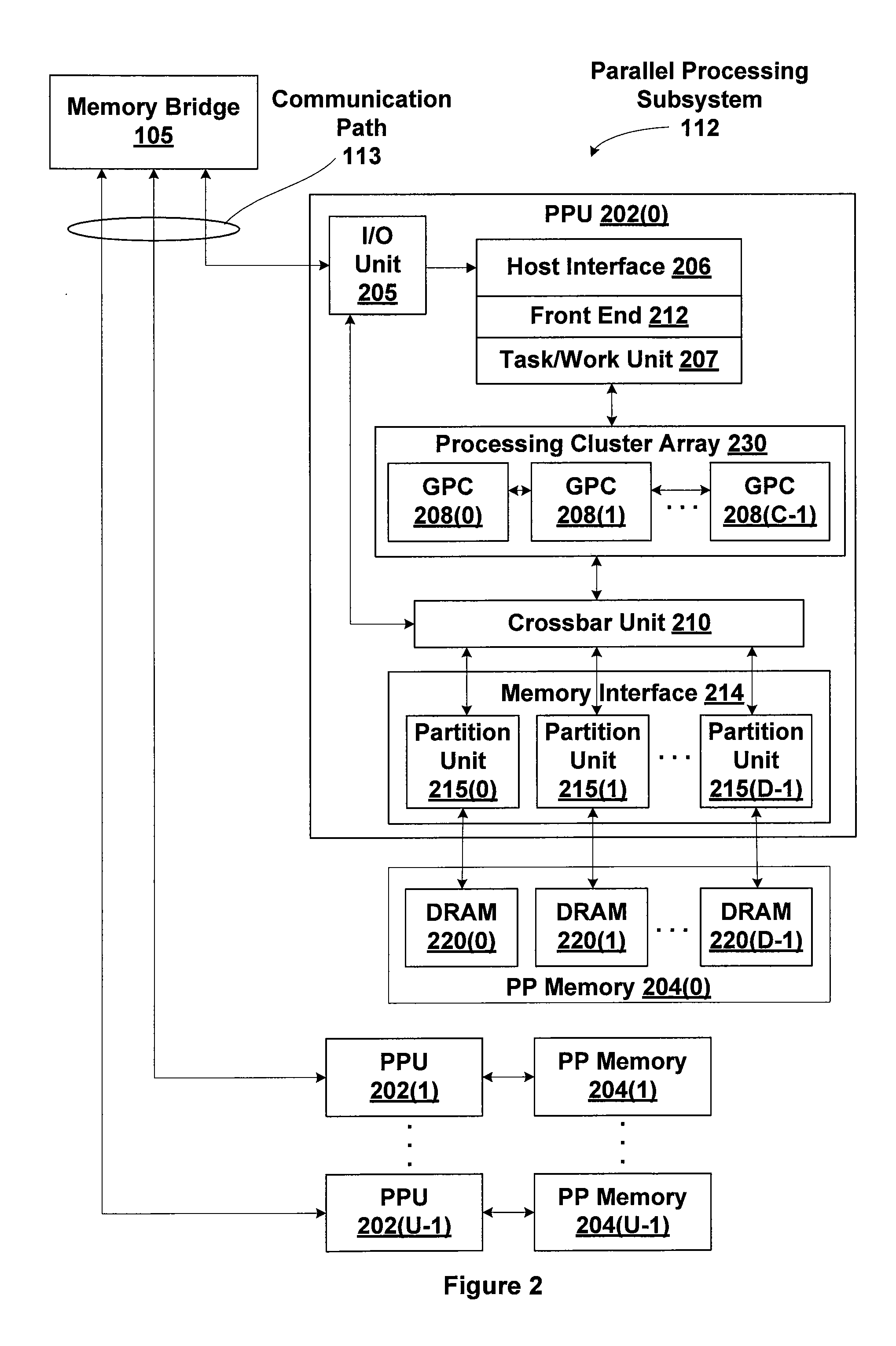
Efficient memory virtualization in multi-threaded processing units
ActiveUS20140123145A1Improve performanceLess development workMultiprogramming arrangementsMemory systemsVirtual memoryVirtualization
A technique for simultaneously executing multiple tasks, each having an independent virtual address space, involves assigning an address space identifier (ASID) to each task and constructing each virtual memory access request to include both a virtual address and the ASID. During virtual to physical address translation, the ASID selects a corresponding page table, which includes virtual to physical address mappings for the ASID and associated task. Entries for a translation look-aside buffer (TLB) include both the virtual address and ASID to complete each mapping to a physical address. Deep scheduling of tasks sharing a virtual address space may be implemented to improve cache affinity for both TLB and data caches.
Owner:NVIDIA CORP
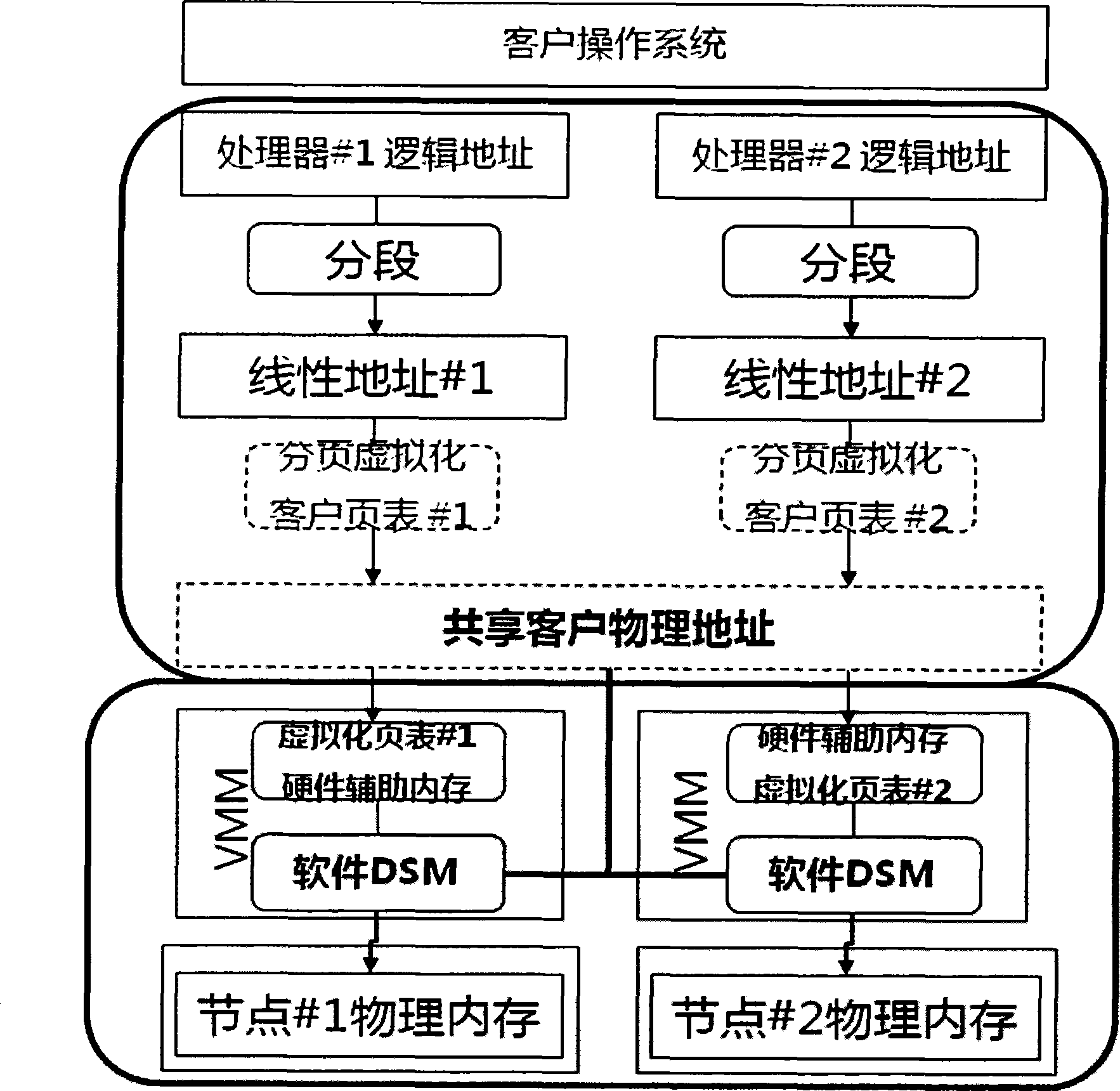
NUMA structure implementing method based on distributed internal memory virtualization
InactiveCN101477496AGuaranteed correctnessImprove manageabilityMemory adressing/allocation/relocationUnauthorized memory use protectionInternal memoryVirtualization
The invention discloses a realization method for NUMA (Non-Uniform Memory Access) structure based on distributed hardware-assisted memory virtualization. The method comprises the following four steps: step one, preparation stage; step two, normal work stage; step three, NUMA processing local request stage; and step four, NUMA processing remote request stage. The invention adopts the latest hardware-assisted memory virtualization technology and the distributed shared storage algorithm, provides a NUMA-structure shared single physical address space, and realizes the transparent and unified management to the multi-host memory resource by a guest operation system, so as to reduce the complexity of the application programming and increase the usability of system resource. Furthermore, the invention has the advantages of favorable use and development prospects.
Owner:HUAWEI TECH CO LTD
Hybrid techniques for memory virtualization in a computer system
ActiveUS20070283124A1Memory architecture accessing/allocationMemory systemsComputerized systemPhysical address
A computer system may employ a first memory virtualization and corresponding virtual-to-physical address translation technique for a first application executing on a processor and a second memory virtualization and corresponding virtual-to-physical address translation technique for a second application executing on the same processor transparent to the first application. Different virtualization and corresponding translation techniques may be employed on a per-thread basis, rather than a per-application basis. Different virtualization and corresponding translation techniques may be employed for accesses to different ranges of virtual or corresponding physical addresses. Different virtualization and corresponding translation techniques may employ different page sizes. A first or second virtualization and corresponding translation technique may include page-based, segment-based, or function-based virtual-to-physical address translation. The selection of a first or second memory virtualization and corresponding address translation technique may be dependent on a predicted workload and / or on a user policy.
Owner:ORACLE INT CORP
Function-based virtual-to-physical address translation
ActiveUS7822941B2Function increaseMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtualizationComputerized system
A computer system employing memory virtualization may employ a function-based technique for virtual-to-physical address translation. A function-based translation technique may involve replacing a generic trap handler and one or more translation table look-ups with a function to compute a corresponding physical address from a given virtual address. The computer system may be configured to determine a translation function dependent on mappings in one or more translation tables. The computer system may be configured to reorganize a memory, to reorganize one or more translation tables, or to allocate different blocks of memory to an application prior to determining a translation function. Different applications or threads executing on the computer system may employ different translation functions. Different regions of memory may be accessed using different translation functions. Some virtual addresses may be translated using a function while others may be translated using one or more translation table look-ups.
Owner:ORACLE INT CORP
MIPS platform-oriented memory virtualization method
ActiveCN102567217AMeet the needs of virtualization applicationsModerate difficultyMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationMemory virtualizationComputer science
The invention relates to a microprocessor without interlocked piped stages (MIPS) platform-oriented memory virtualization method. The method comprises an address forming method of MIPS platform-oriented memory virtualization, an address space forming method of MIPS platform-oriented memory virtualization, an address forming and address space mapping method of MIPS platform-oriented memory virtualization, an address forming and address space mapping maintenance mechanism of MIPS platform-oriented memory virtualization and an address mapping realization process of MIPS platform-oriented memory virtualization. The MIPS platform-oriented memory virtualization method has the following advantages that: (1) the technical problems, such as lack of hardware assist and support for a MIPS processor, three layers of address mapping of memory virtualization in the MIPS platform, isolation and security of access to a physical memory by multiple virtual machines, and the like, are all solved; (2) the system has the advantage of light weight; (3) the virtualization application requirement in the embedded field can be satisfied, and the virtualization application requirement in the server field also can be satisfied.
Owner:BEIHANG UNIV
Implementing method for distributed internal memory virtualization technology
InactiveCN101477495AImprove manageabilityImprove programmabilityMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationInternal memoryVirtualization
The invention provides a realization method for distributed memory virtualization technology. The method mainly adopts the latest virtualization technology of combing hardware and software together, conducts virtualization and integration to the memory resource distributed in a multi-host combining with distributed shared storage algorithm, provides a shared single physical address space for an upper grade guest operation system, and realizes the management and the use of the guest operation system to the distributed memory. The invention carried out innovation on the basis of the current mature technology, is simple to implement, and has excellent use and development prospects.
Owner:HUAWEI TECH CO LTD
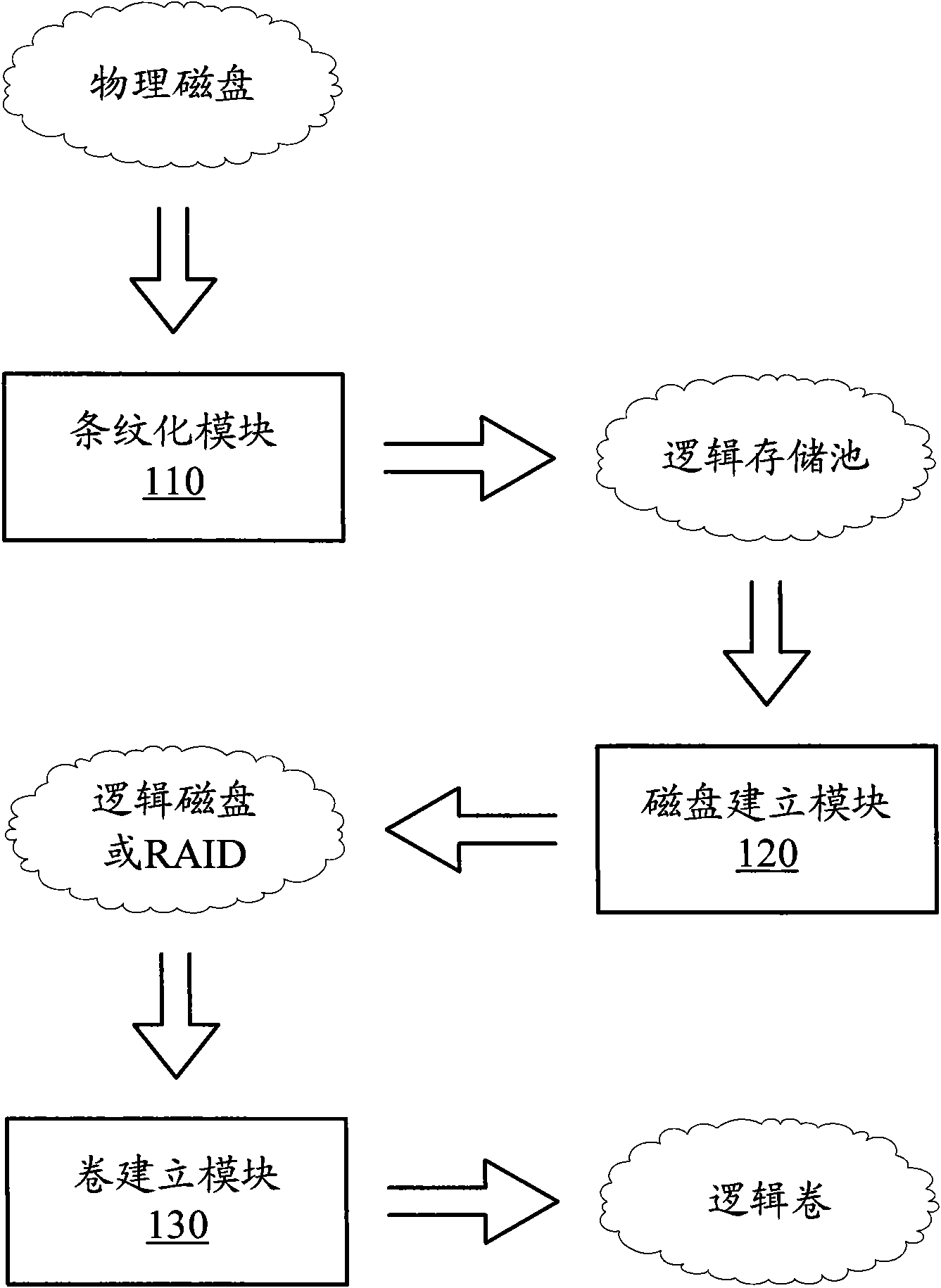
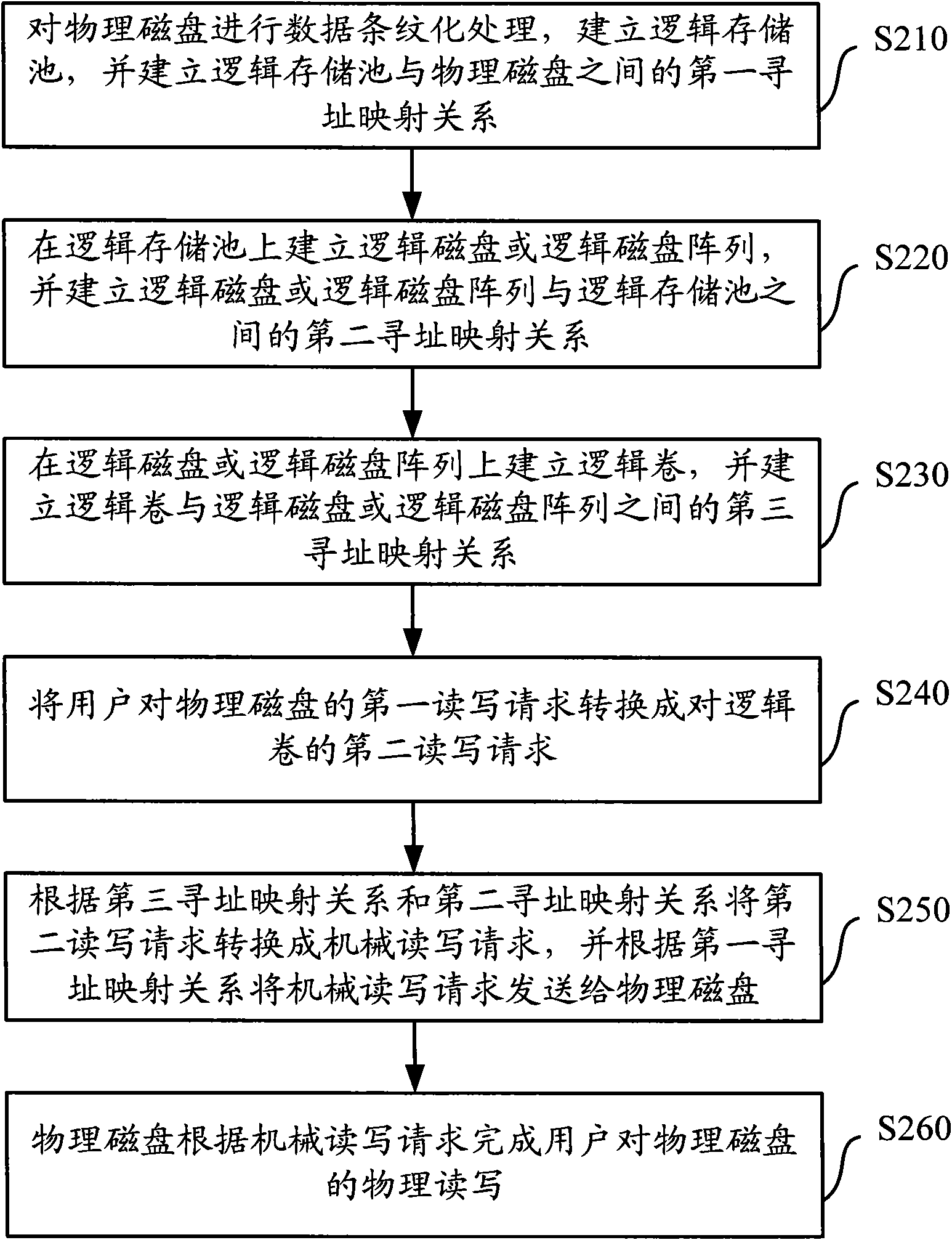
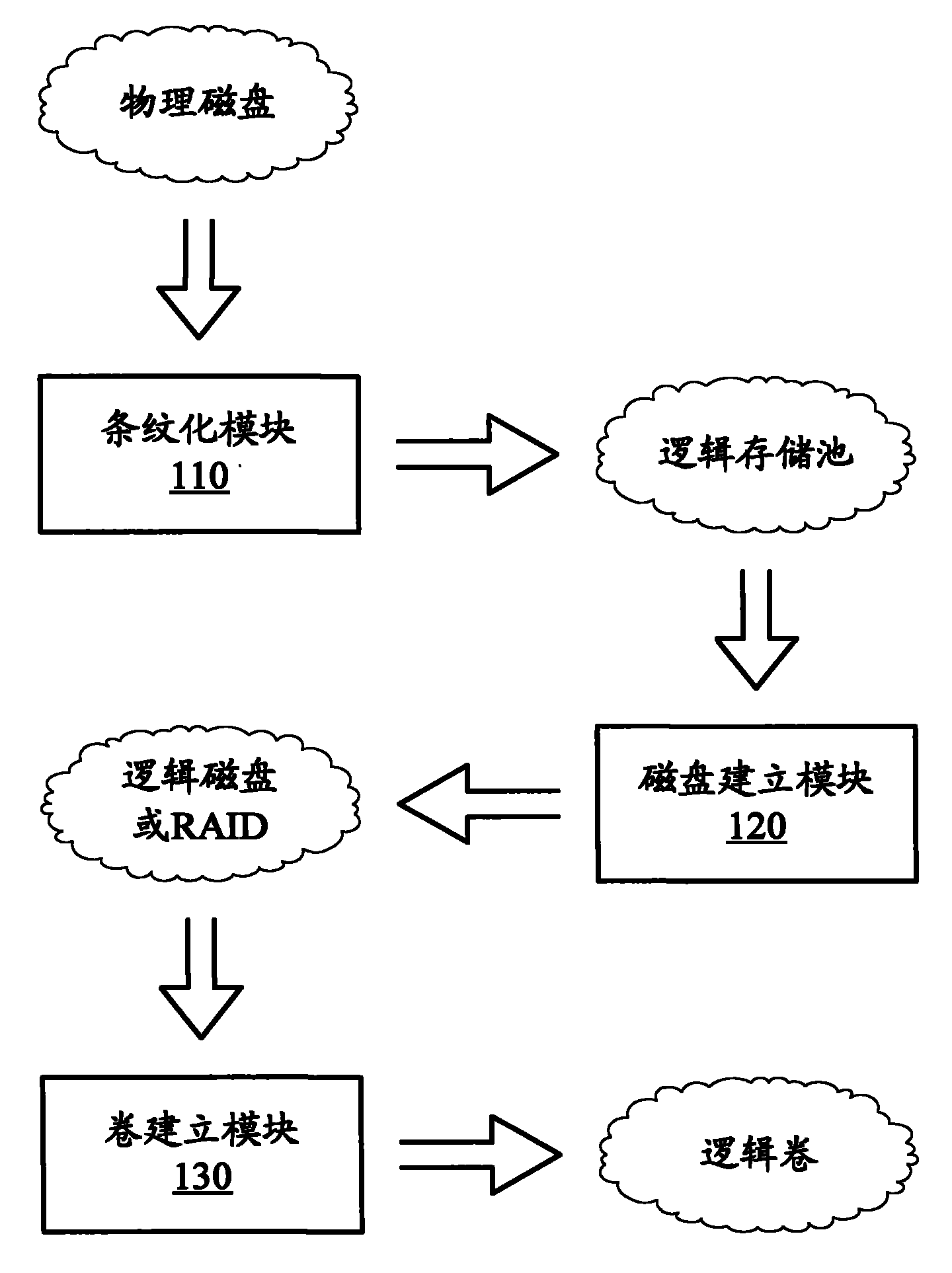
Memory virtualization system and method
ActiveCN101788889ABalance I/O loadAvoid overall overheatingInput/output to record carriersVirtualizationMemory virtualization
The invention discloses a memory virtualization system and a method to balance IO load of physical disks. In the system, a striping module processes the physical disks by means of striping data to build a logic pond; a disk-building module builds a logic disk or a logic disk array on a logic memory pond; and a volume-building module builds a logic volume on the logic disk or the logic disk array. With the three layers of virtualization process, a read and write request of a customer is performed by being dispersed to the plurality of physical disks, and compared with the prior art that the read and write request of the customer is performed by being concentrated on one physical disk, the invention balances the IO load of the physical disks, effectively prevents some date of the physical disks from over heating, and improves the security and the performance of the memory system.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Efficient memory virtualization in multi-threaded processing units
ActiveUS20140123146A1Improve performanceLess development workProgram initiation/switchingResource allocationVirtual memoryVirtualization
A technique for simultaneously executing multiple tasks, each having an independent virtual address space, involves assigning an address space identifier (ASID) to each task and constructing each virtual memory access request to include both a virtual address and the ASID. During virtual to physical address translation, the ASID selects a corresponding page table, which includes virtual to physical address mappings for the ASID and associated task. Entries for a translation look-aside buffer (TLB) include both the virtual address and ASID to complete each mapping to a physical address. Deep scheduling of tasks sharing a virtual address space may be implemented to improve cache affinity for both TLB and data caches.
Owner:NVIDIA CORP
Platform virtualization system
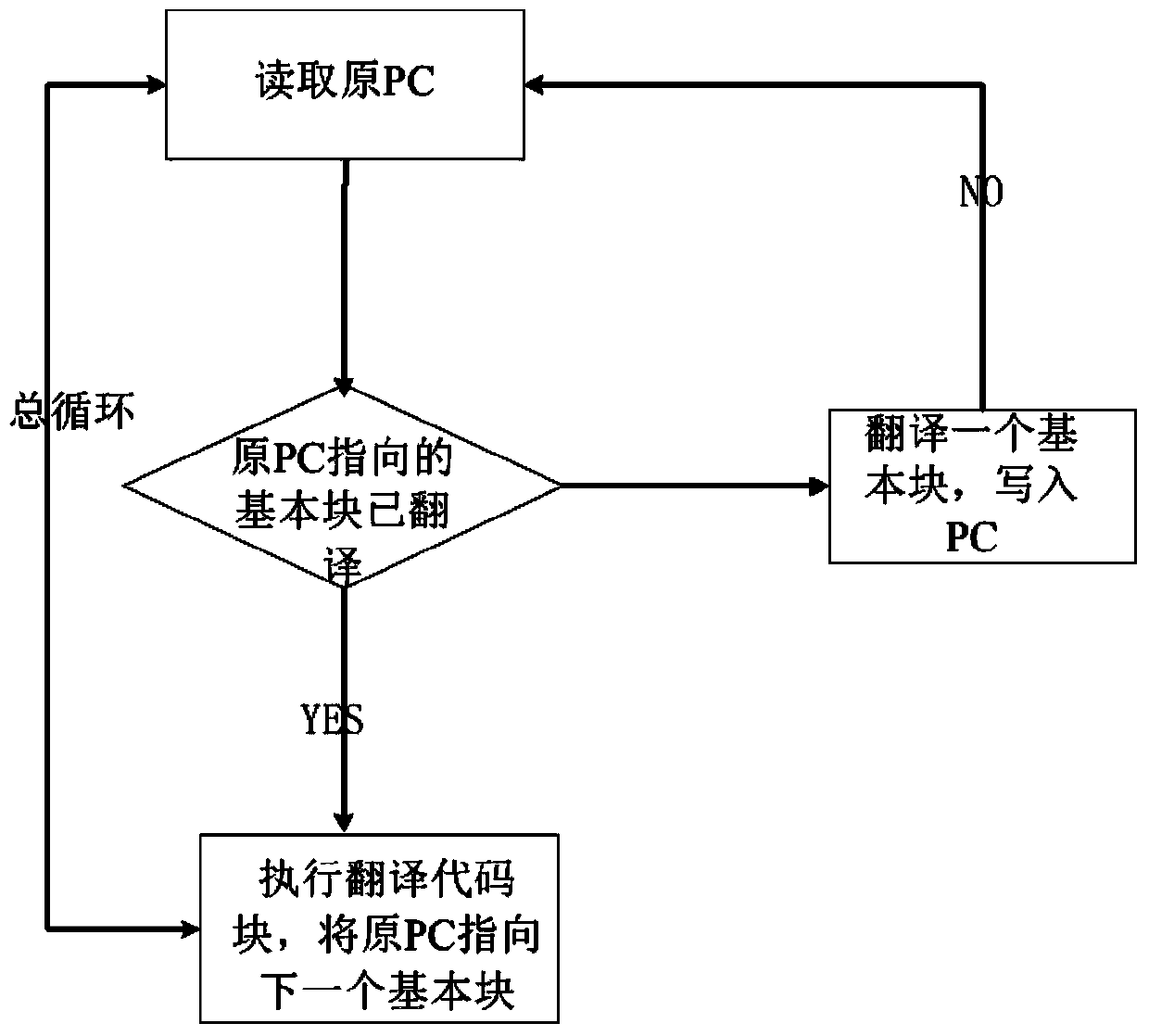
InactiveCN103793260AEase system deploymentRelieve pressureSoftware simulation/interpretation/emulationCode TranslationMemory virtualization
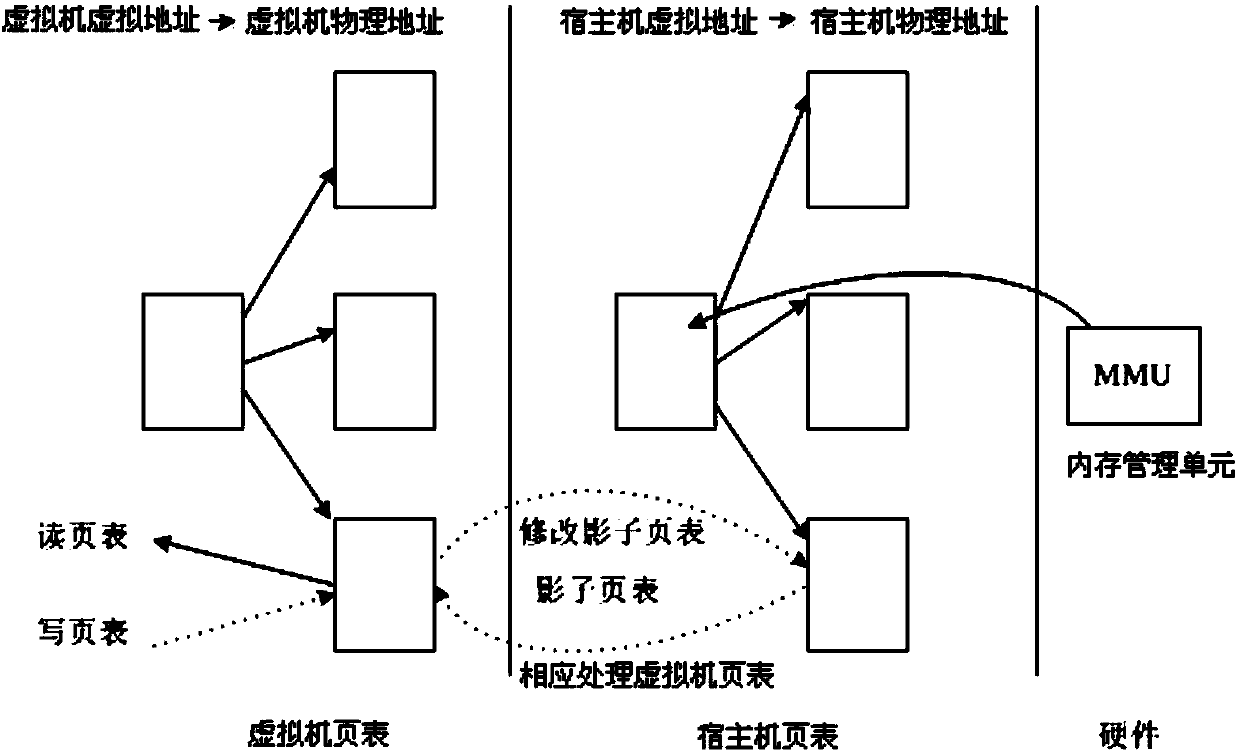
The invention relates to a platform virtualization system comprising a CPU simulator, a memory virtualization module, and an external virtualization module. The CPU simulator reads an X86 architecture code instruction and judges whether an instruction basic block is translated or not; a binary translator is used for translation and comprises a translation engine and an execution engine; the translation engine translates an X86 architecture code into a Loongson platform code; the execution engine prepares the operational context of the Loongson platform code, locates the Loongson platform code corresponding to the X86 architecture code from a Loongson platform code cache and executes the code. The memory virtualization module uses a shadow page-table method. The external virtualization module establishes a corresponding device model for each external device. An X86 architecture virtual machine interacts with the external devices through the device models, thereby discovering and accessing the devices. The platform virtualization system allows information systems not matching with the domestic Loongson hardware platform yet to run in the domestic software-hardware environments in a virtualized manner, and contributions are made for the smooth transition between new and old technical systems in the automatic upgrading process of the information systems.
Owner:INST OF CHINA ELECTRONICS SYST ENG CO +1
Hybrid techniques for memory virtualization in a computer system
ActiveUS7827381B2Memory architecture accessing/allocationMemory systemsComputerized systemPhysical address
A computer system may employ a first memory virtualization and corresponding virtual-to-physical address translation technique for a first application executing on a processor and a second memory virtualization and corresponding virtual-to-physical address translation technique for a second application executing on the same processor transparent to the first application. Different virtualization and corresponding translation techniques may be employed on a per-thread basis, rather than a per-application basis. Different virtualization and corresponding translation techniques may be employed for accesses to different ranges of virtual or corresponding physical addresses. Different virtualization and corresponding translation techniques may employ different page sizes. A first or second virtualization and corresponding translation technique may include page-based, segment-based, or function-based virtual-to-physical address translation. The selection of a first or second memory virtualization and corresponding address translation technique may be dependent on a predicted workload and / or on a user policy.
Owner:ORACLE INT CORP
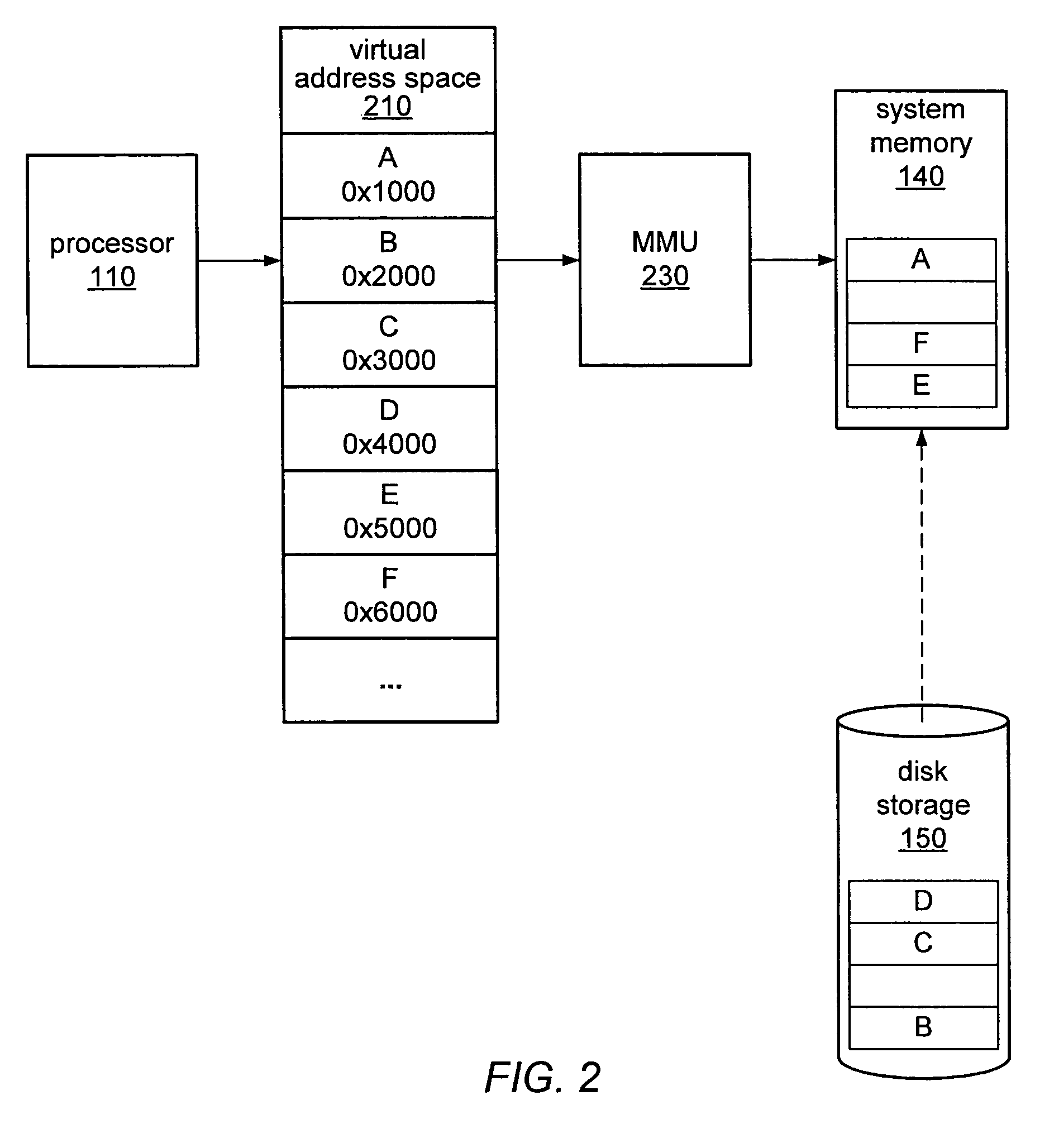
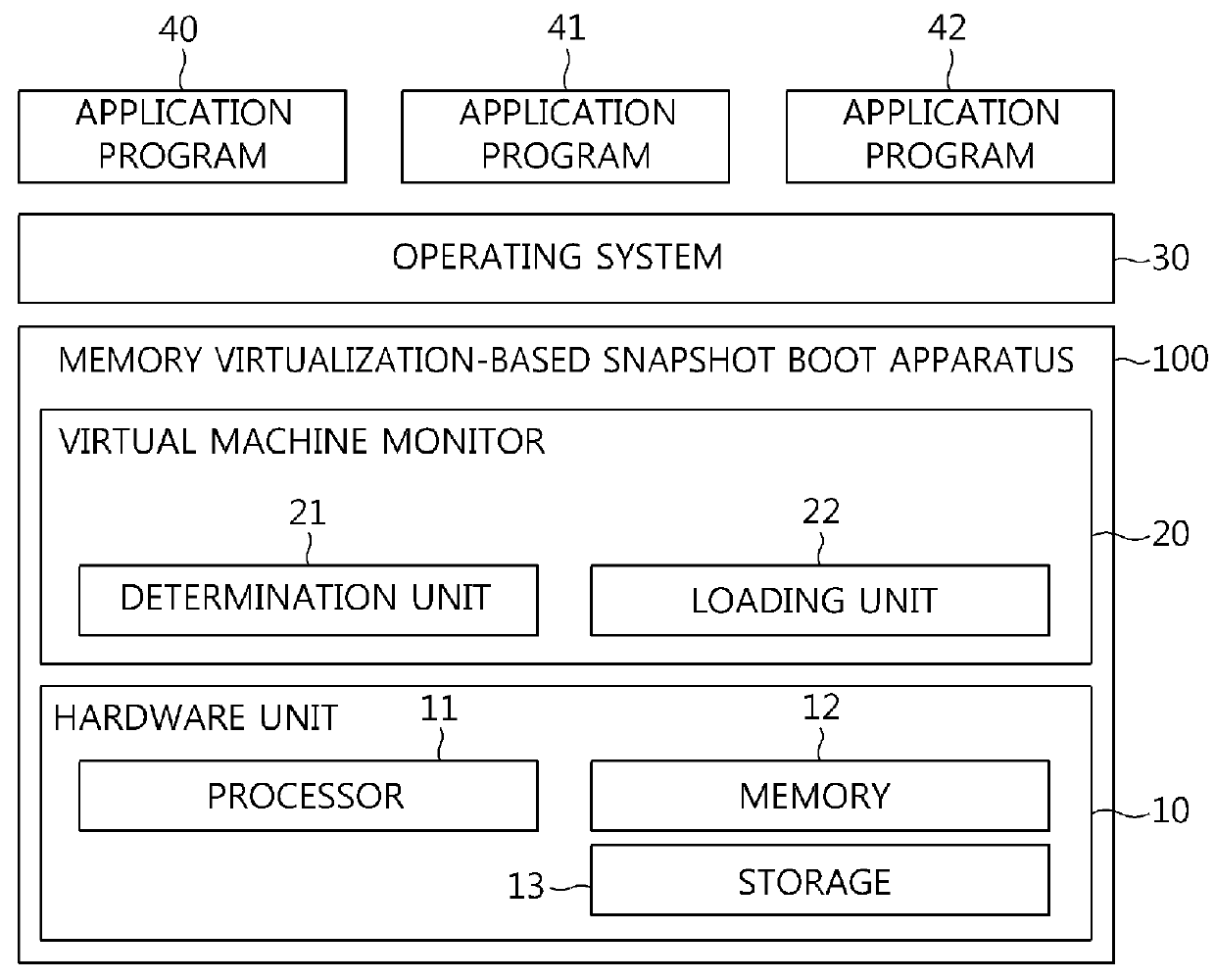
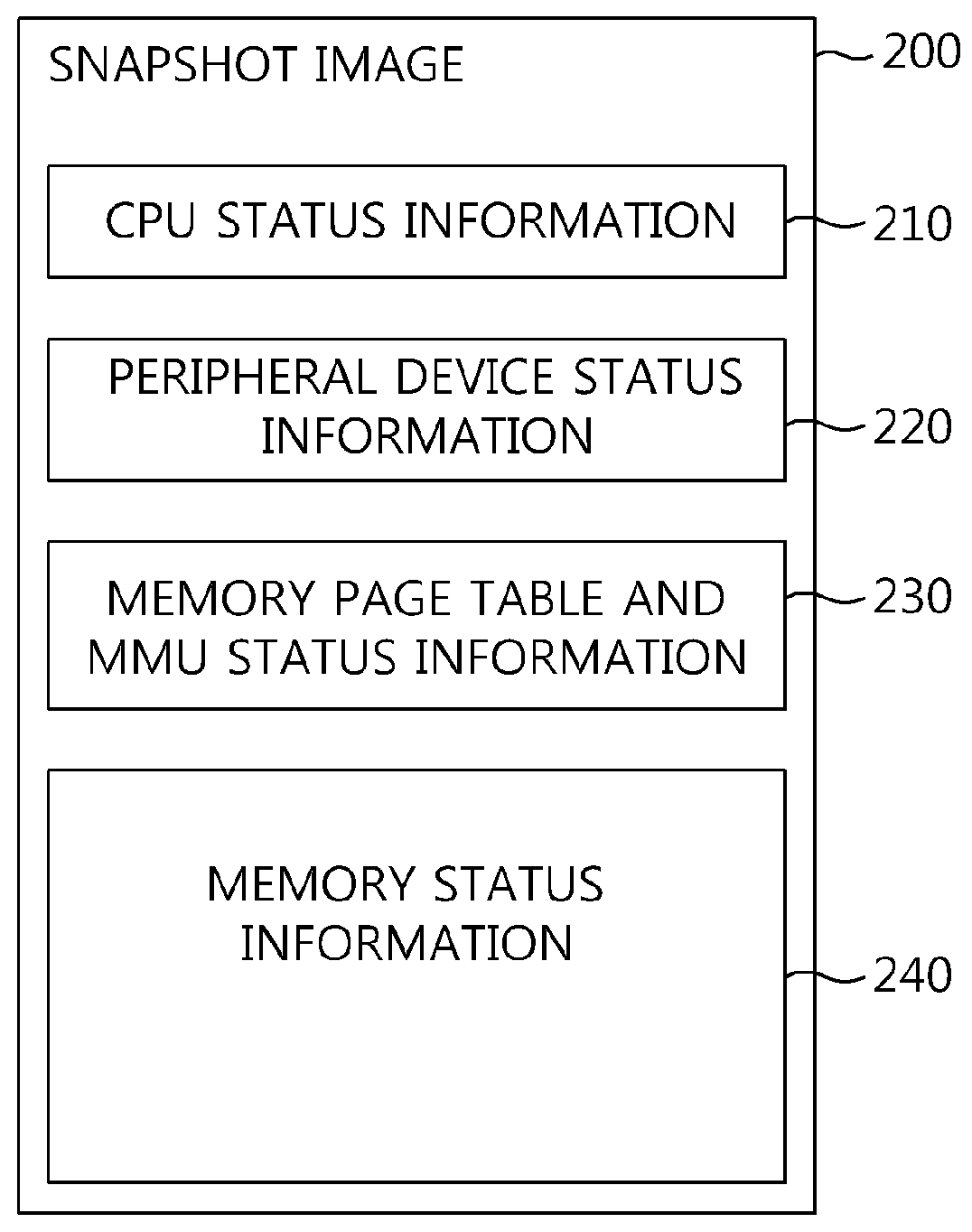
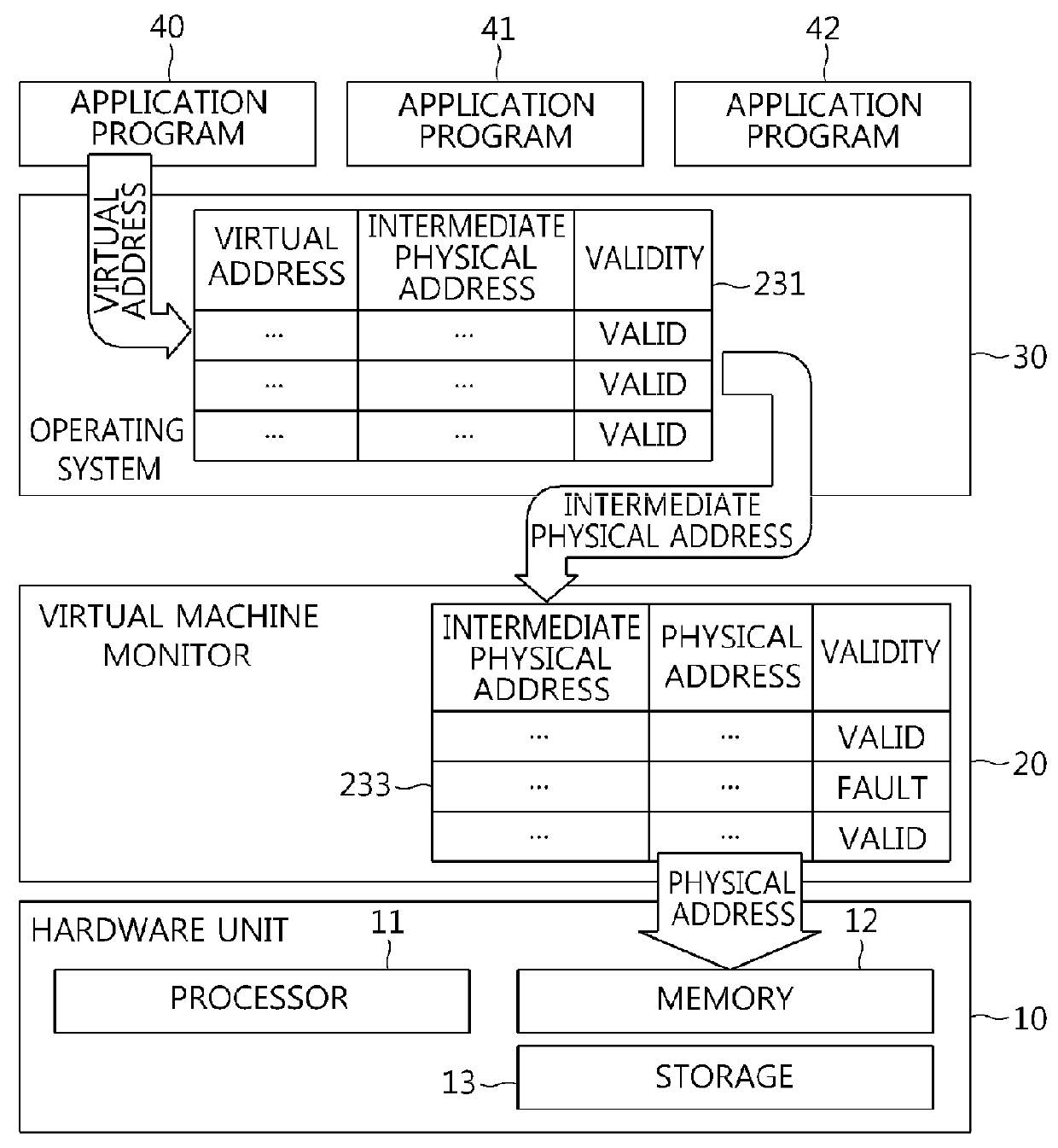
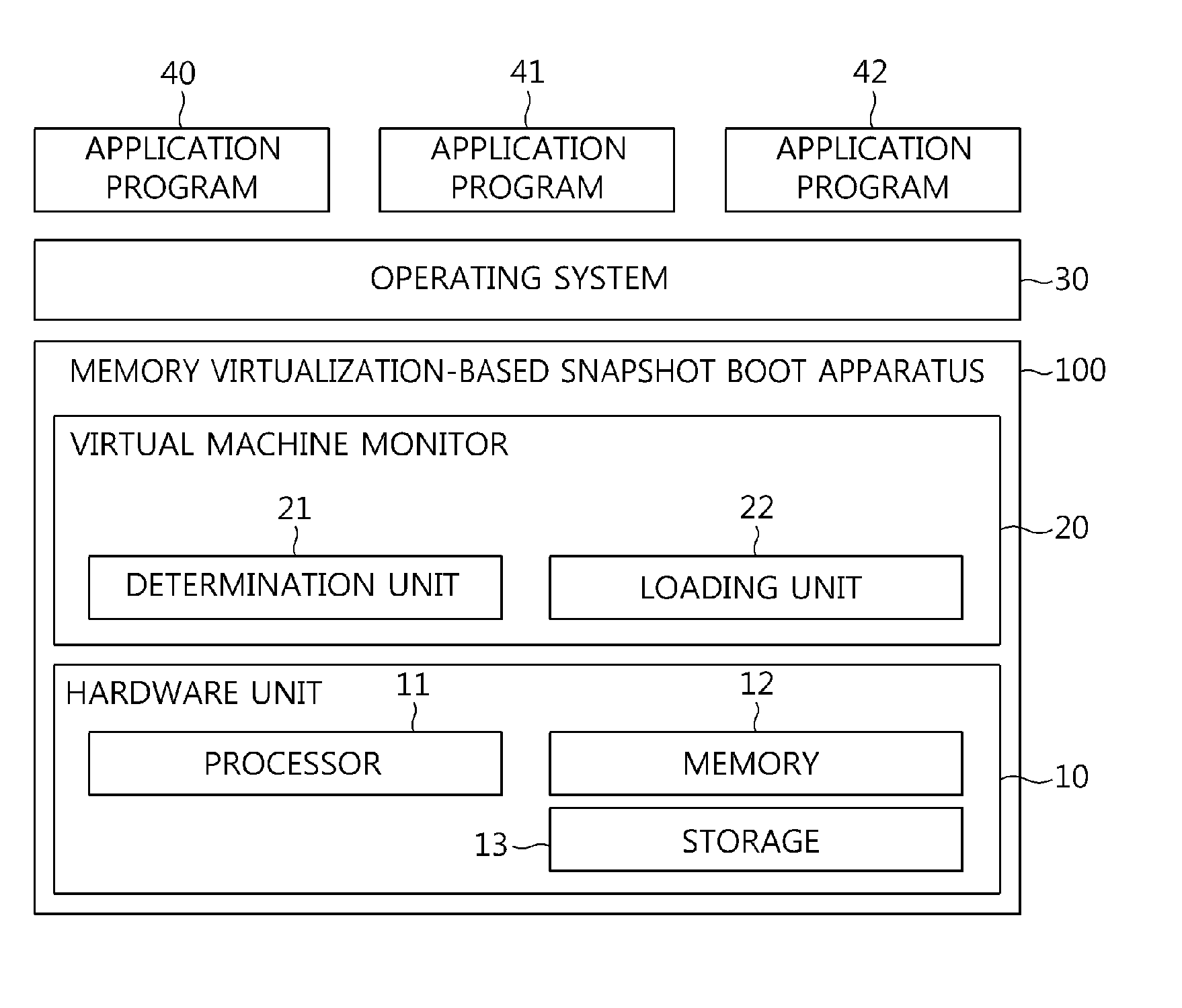
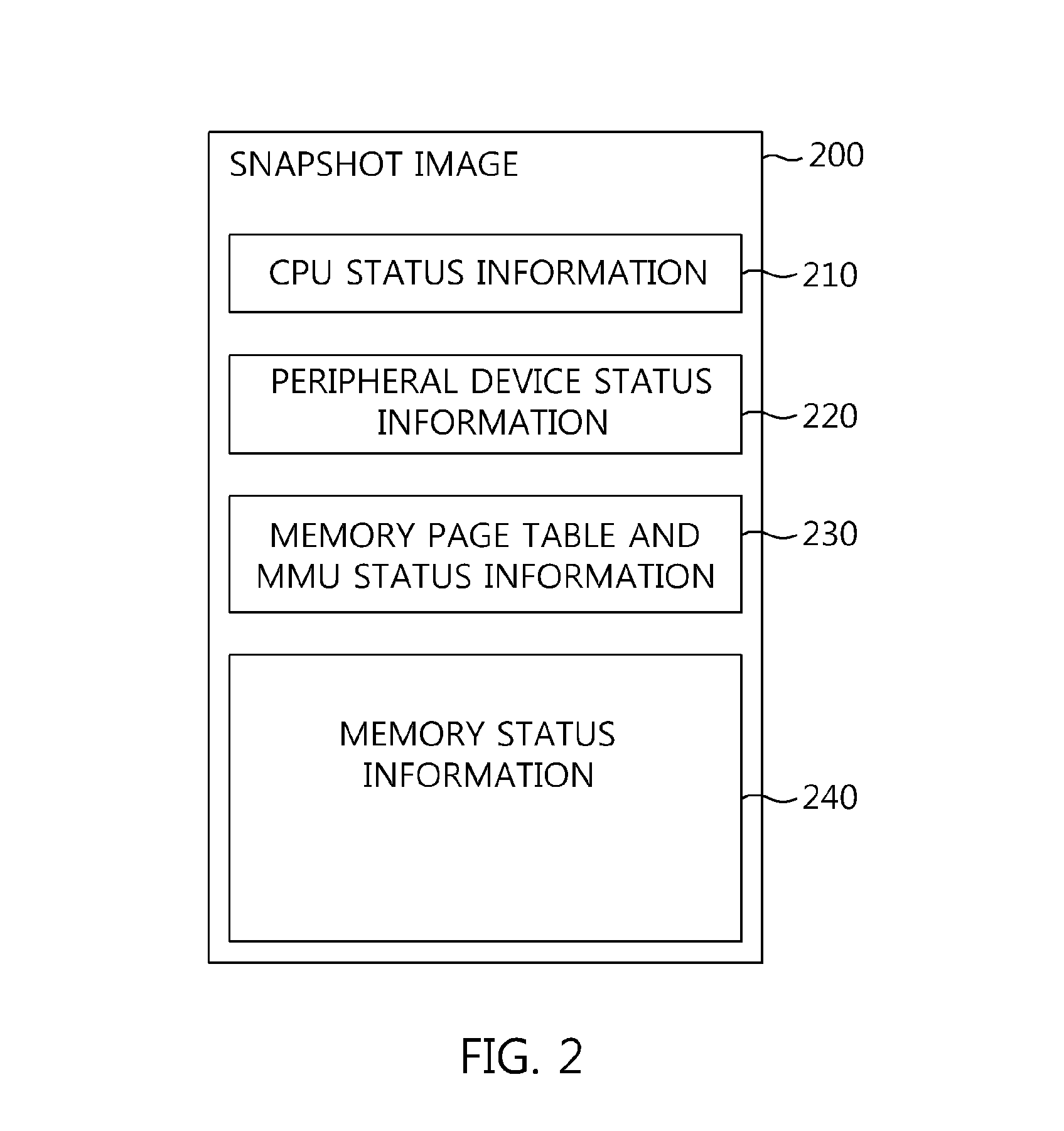
Memory virtualization-based snapshot boot apparatus and method
InactiveUS9384007B2Easy to operateBootstrappingSoftware simulation/interpretation/emulationVirtualizationOperational system
The present invention relates to a memory virtualization-based snapshot boot apparatus and method. The memory virtualization-based snapshot boot apparatus includes hardware unit including a processor, memory, and storage, the storage storing status information corresponding to an operating system, and a Virtual Machine Monitor (VMM) operated by the processor and configured to operate the operating system by loading the status information into the memory. In accordance with the present invention, technology for loading only a part of a snapshot image and booting a system is implemented using virtualization technology, thus shortening the booting time of the system.
Owner:ELECTRONICS & TELECOMM RES INST
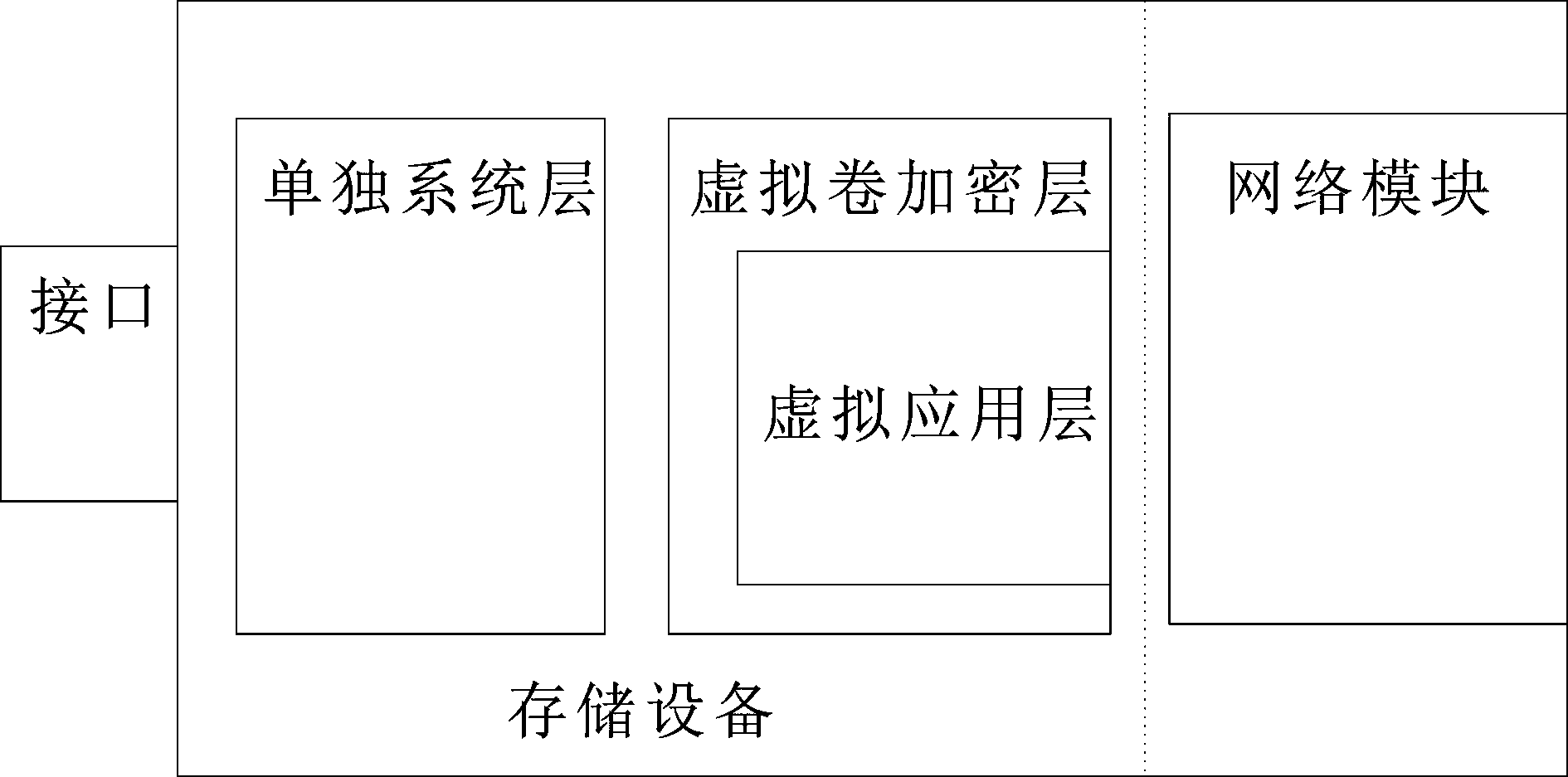
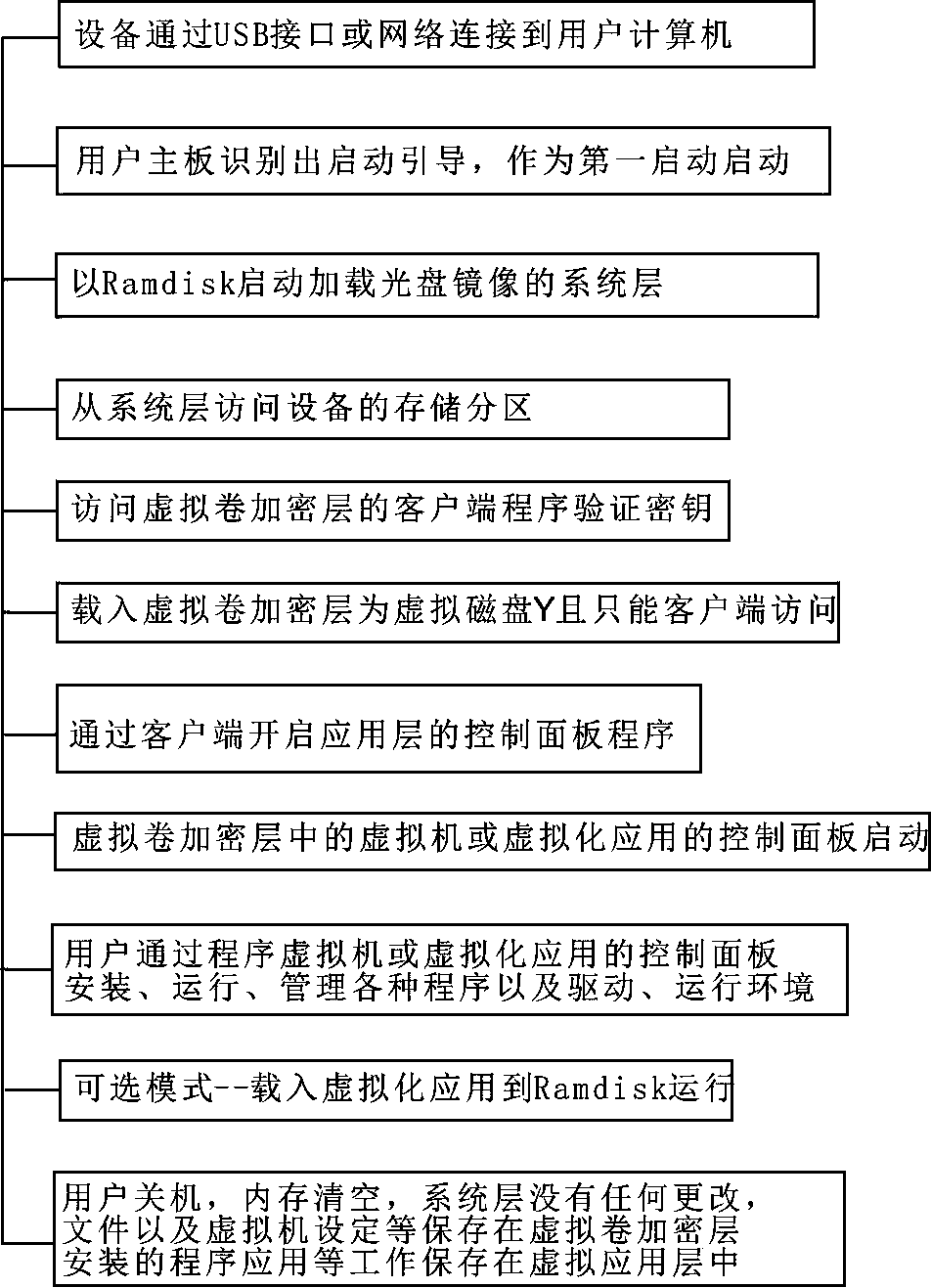
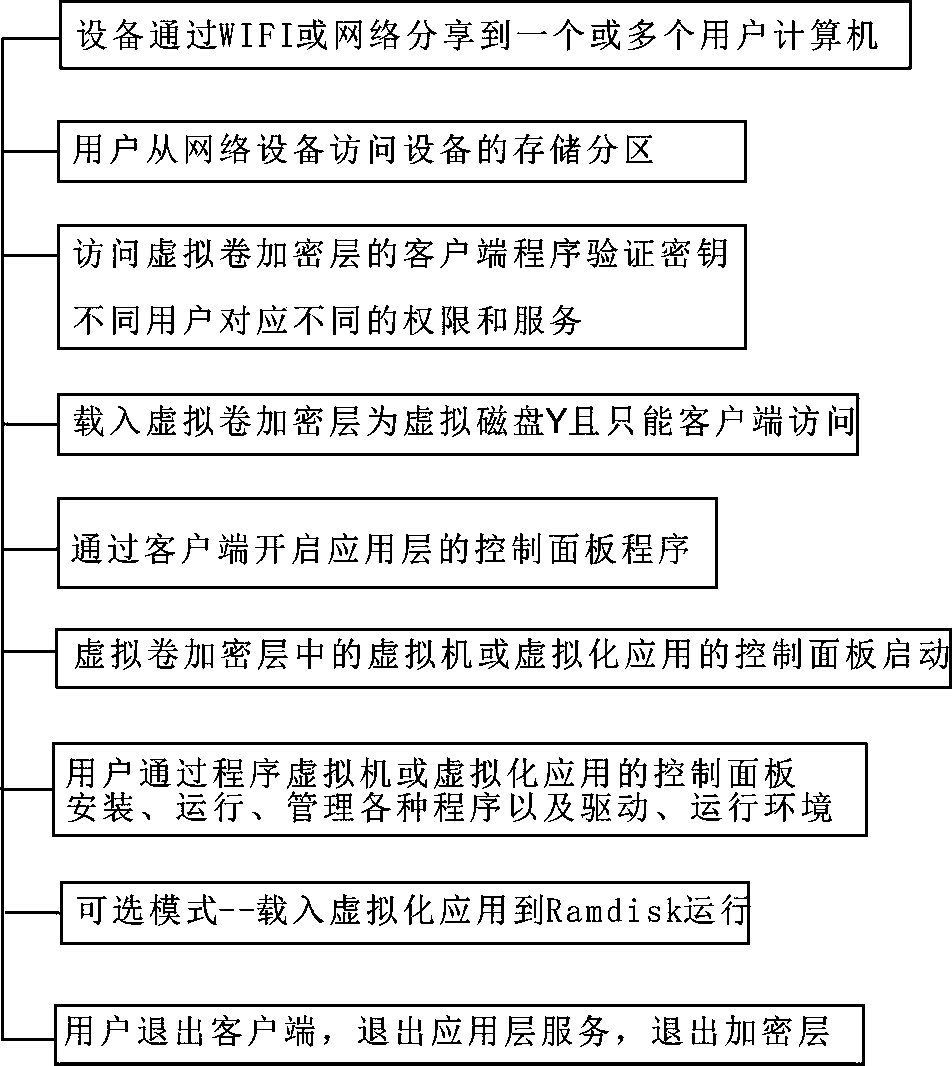
Layered computing virtualization implementing method and device
InactiveCN104298472ALow costLower the thresholdInput/output to record carriersUnauthorized memory use protectionComputer hardwareVirtualization
Disclosed are a layered computing virtualization implementing method and a corresponding device. The method comprises virtualizing three independent virtualization layers including a mobile system layer, a virtual volume encryption layer and a virtual application layer to achieve cross-device mobile computing and network-based virtualized working space. The mobile system layer is implemented through a read only mirror system and can be loaded into Ramdisk for running; the virtual volume encryption layer is implemented by establishing a virtual volume, verifying keys, loading the virtual volume as a virtual disk and controlling access of the virtual volume; the application layer is implemented through a virtual machine and a virtual application environment and by extracting Library and a registries required by applications. The virtual application layer is arranged inside the virtual volume encryption layer, and the virtual volume encryption layer and the mobile system layer directly exist in a storage device and are stored separately without mutual containing. The applications inside the virtual application layer can obtain higher speed by taking disks virtualized from memory or a part of the memory as buffer memory.
Owner:张维加
Memory virtualization method based on guest operatiion system kernel code replacement
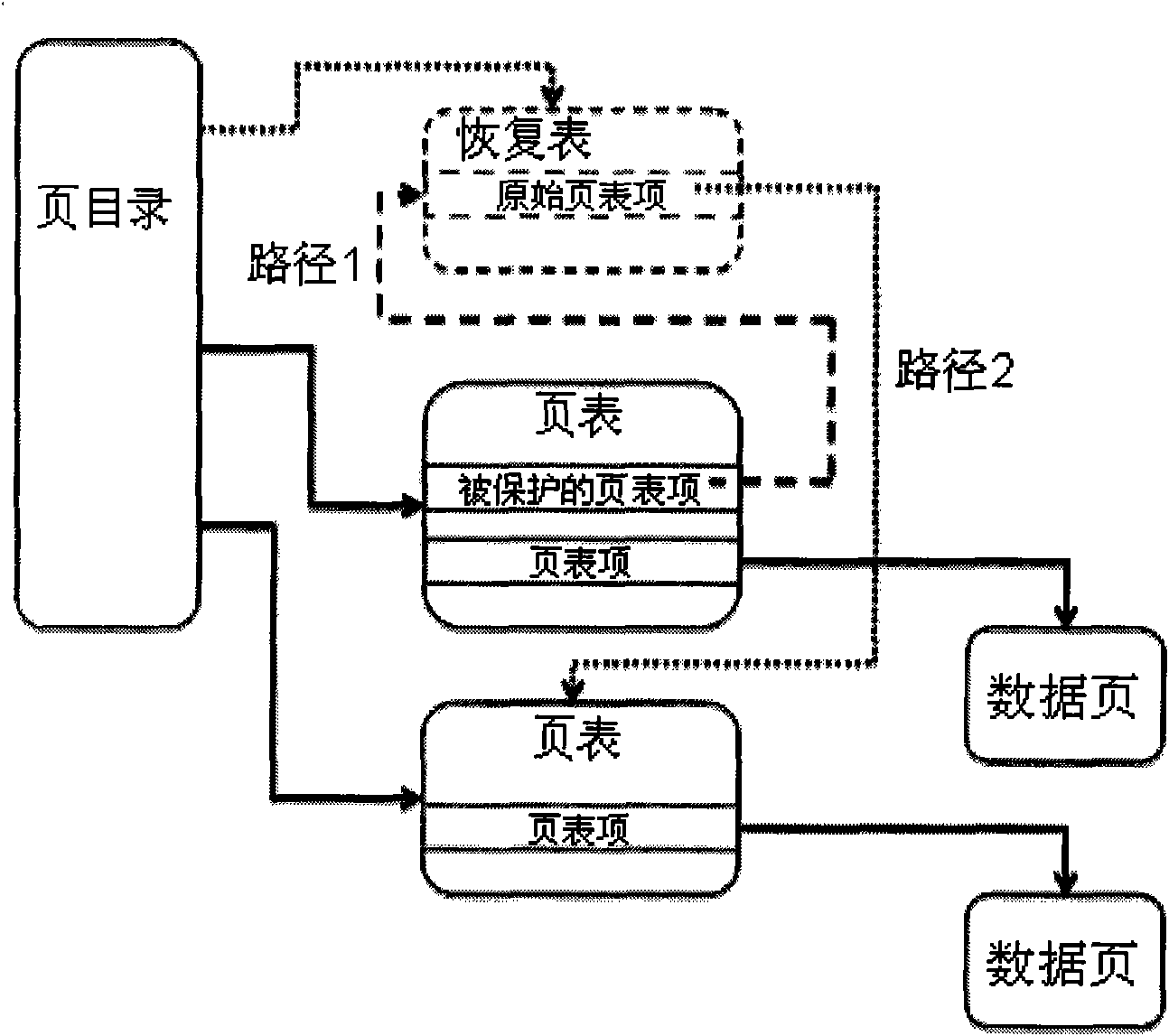
InactiveCN101882113AOvercome limitationsImprove performanceMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationMemory addressOperational system
The invention discloses a memory virtualization method based on guest operatiion system kernel code replacement, which belongs to the technical field of computer software. The method comprises the following steps: (1) converting all page table entries PTE pointing page table pages or page directory pages into protected page table entries P-PTE; simultaneously, maintaining a recovery table for each process; (2) establishing a memory page number mapping table G2H from a guest to a host and a memory page number mapping table H2G from the host to the guest in a VMM (Virtual Machine Manager) to complete bidirectional memory address conversion; and (3) reading the page directory pages PDE and common page table entries PTE and P-PTE and writing in the PDE and the PTE according to the mapping tables G2H and H2G. Compared with the prior art, the invention has small expenses and high performance of memory virtualization on the premise of not modifying a guest operatiion system kernel source code, and thereby, the problem of poorer memory virtualization performance in the traditional full-Virtualization system is solved.
Owner:PEKING UNIV
Memory virtualization method and memory virtualization device
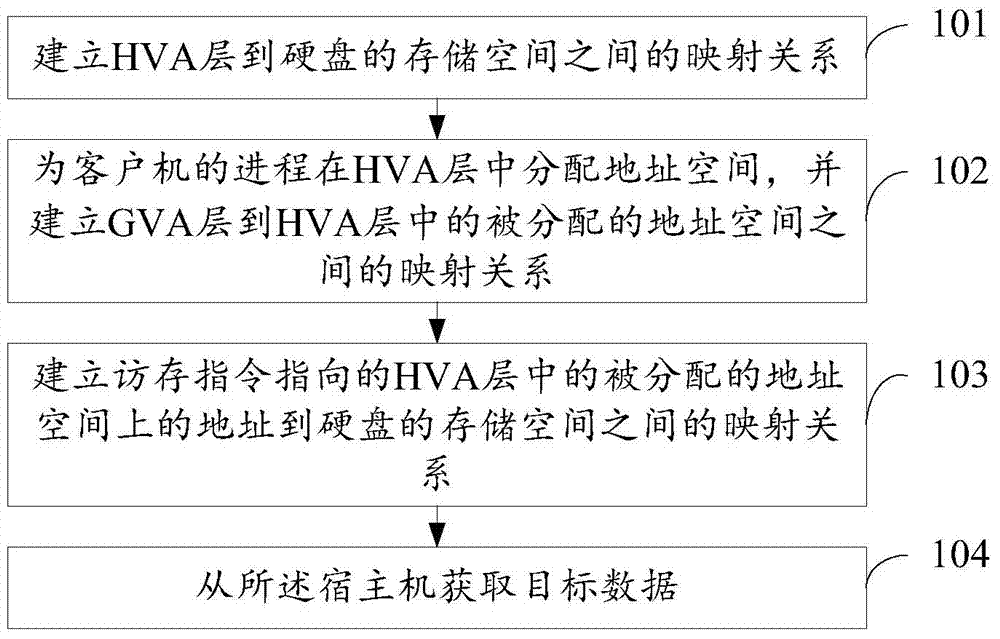
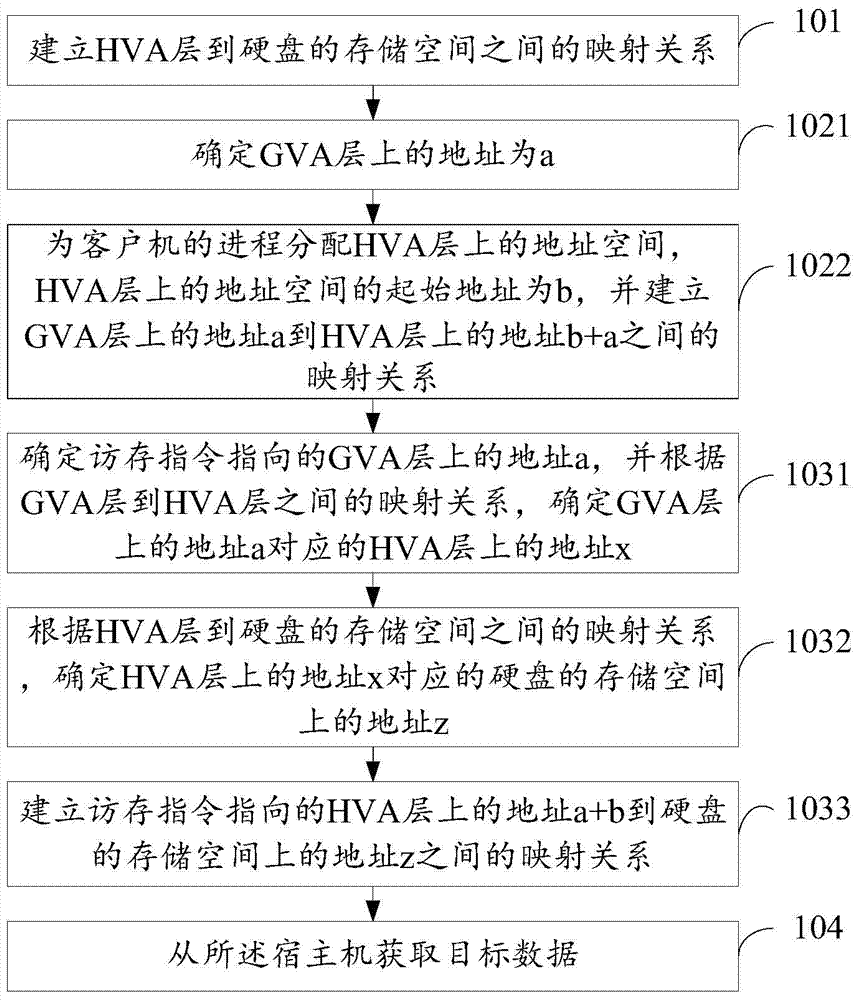
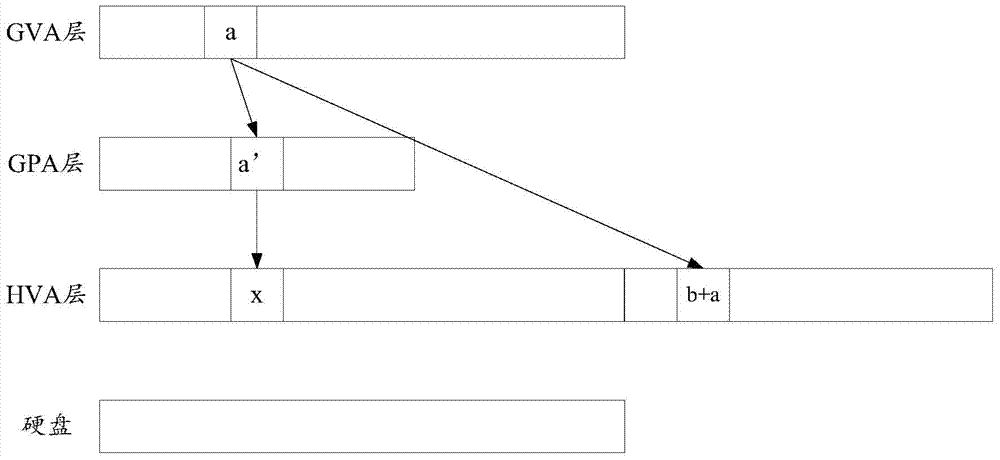
ActiveCN104750623AMapping avoidanceReduce stepsMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationMemory virtualizationElectronic information
An embodiment of the invention discloses a memory virtualization method and a memory virtualization device, and relates to the technical field of electronic information. Correction of mapping relationships by a core of a host machine can be avoided when the mapping relationships need to be corrected. The method includes establishing a mapping relationship between an HVA (host virtual address) layer and a storage space of a hard disk; distributing an address space for the progress of a client in the HVA layer, and establishing a mapping relationship between a GVA (guest virtual address) layer to the distributed address space in the HVA layer; establishing a mapping relationship between an address, pointed by an access command, on the distributed address space in the HVA layer and the storage space of the hard disk; acquiring target data from the host machine. The memory virtualization method and the memory virtualization device are applicable to memory virtualization of computing equipment.
Owner:HUAWEI TECH CO LTD +1
Memory protection in a computer system employing memory virtualization
The use of a token-based memory protection technique may provide memory protection in a computer system employing memory virtualization. A token-based memory protection technique may include assigning a unique identifier to an application, process, or thread, and associating the identifier with a block of memory allocated to that application, process, or thread. Subsequent to assigning the identifier, a packet requesting access to that block of memory may include a token to be compared to the identifier. A memory controller may be configured to associate the identifier with the block of memory and to compare the token in the memory request packet to the identifier before granting access. If a second block of memory is subsequently allocated to the application, process, or thread, the identifier may be disassociated with the first block of memory and associated with the second block of memory.
Owner:ORACLE INT CORP
Hardware to make remote storage access appear as local in a virtualized environment
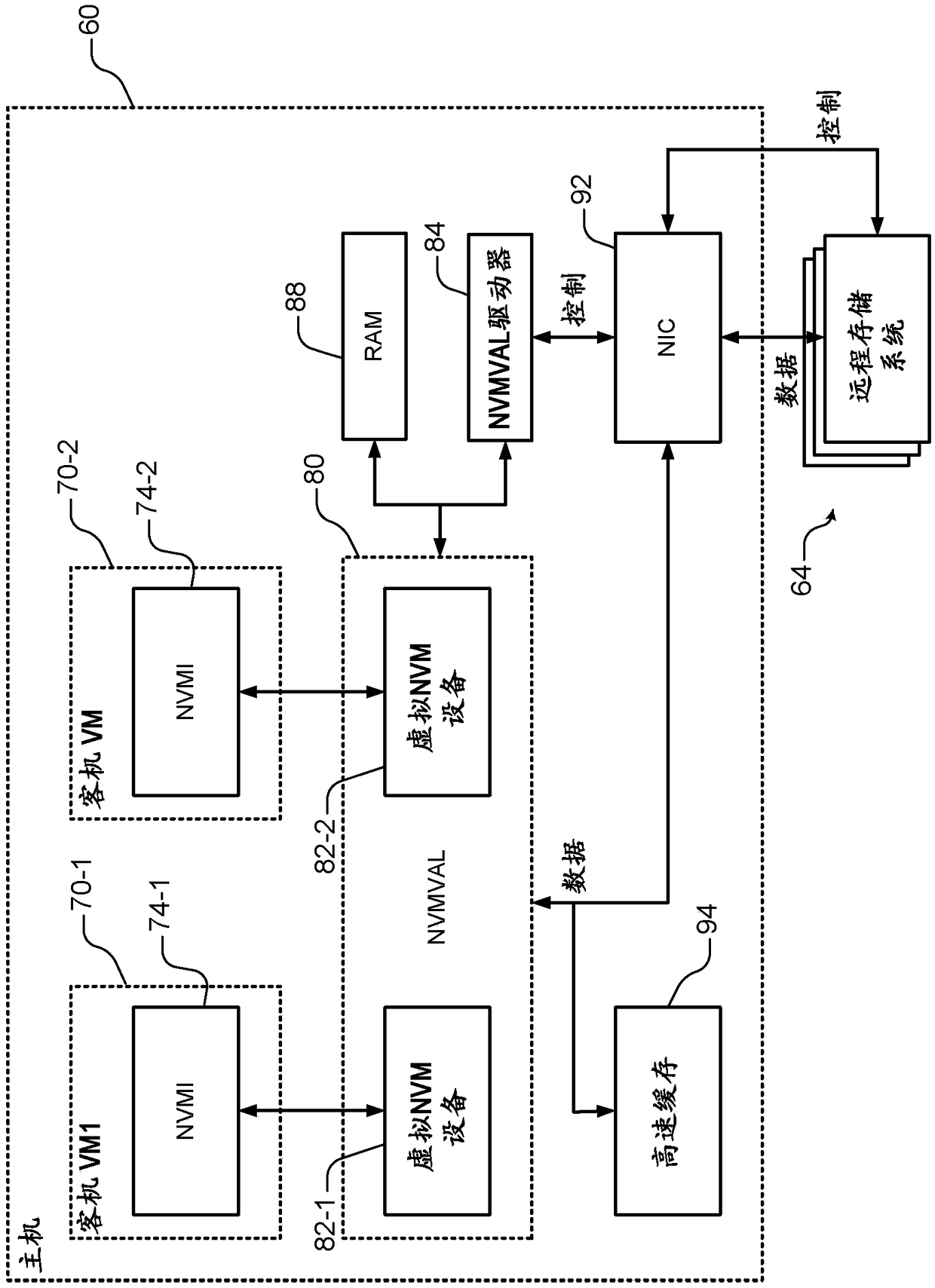
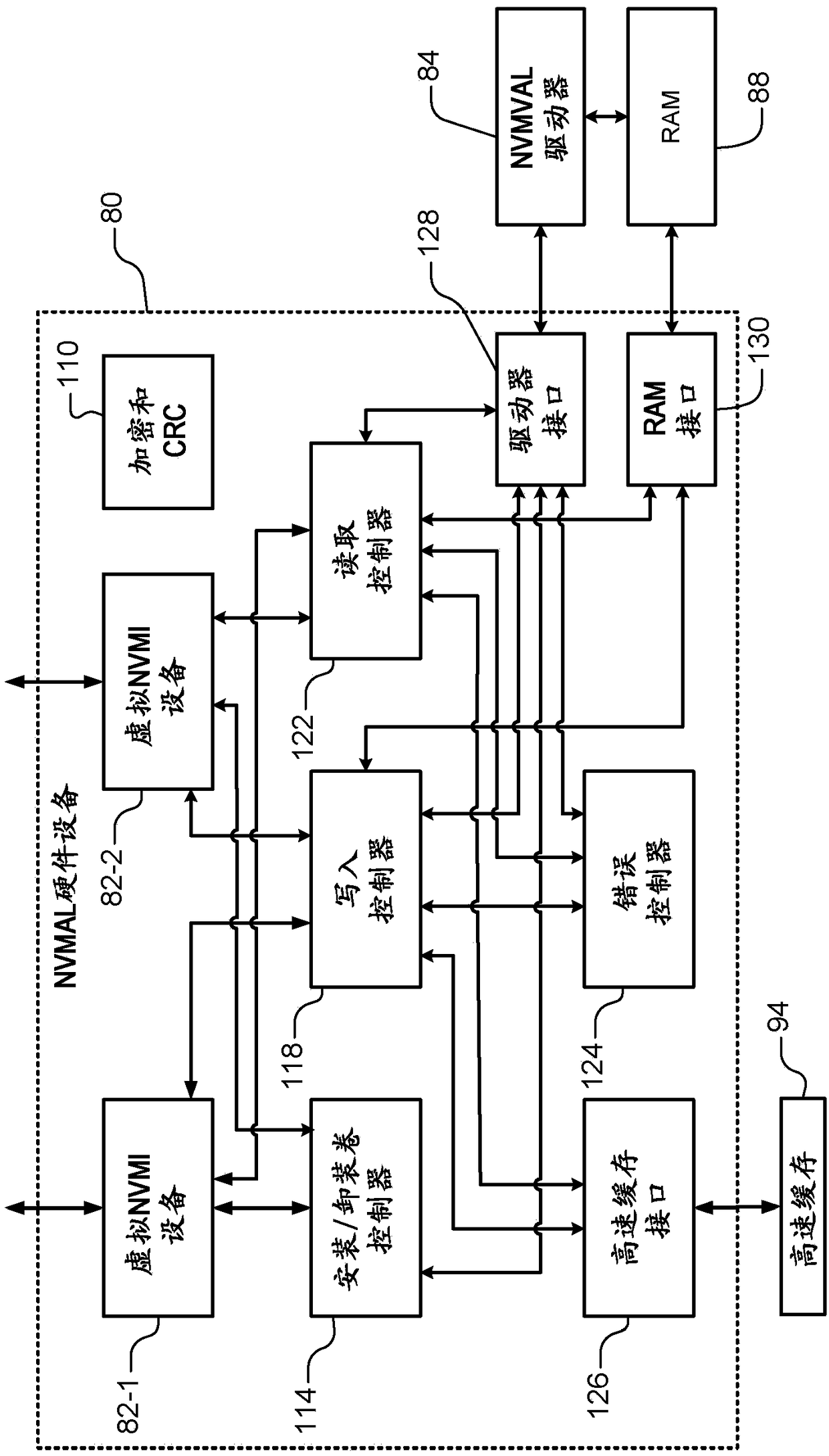
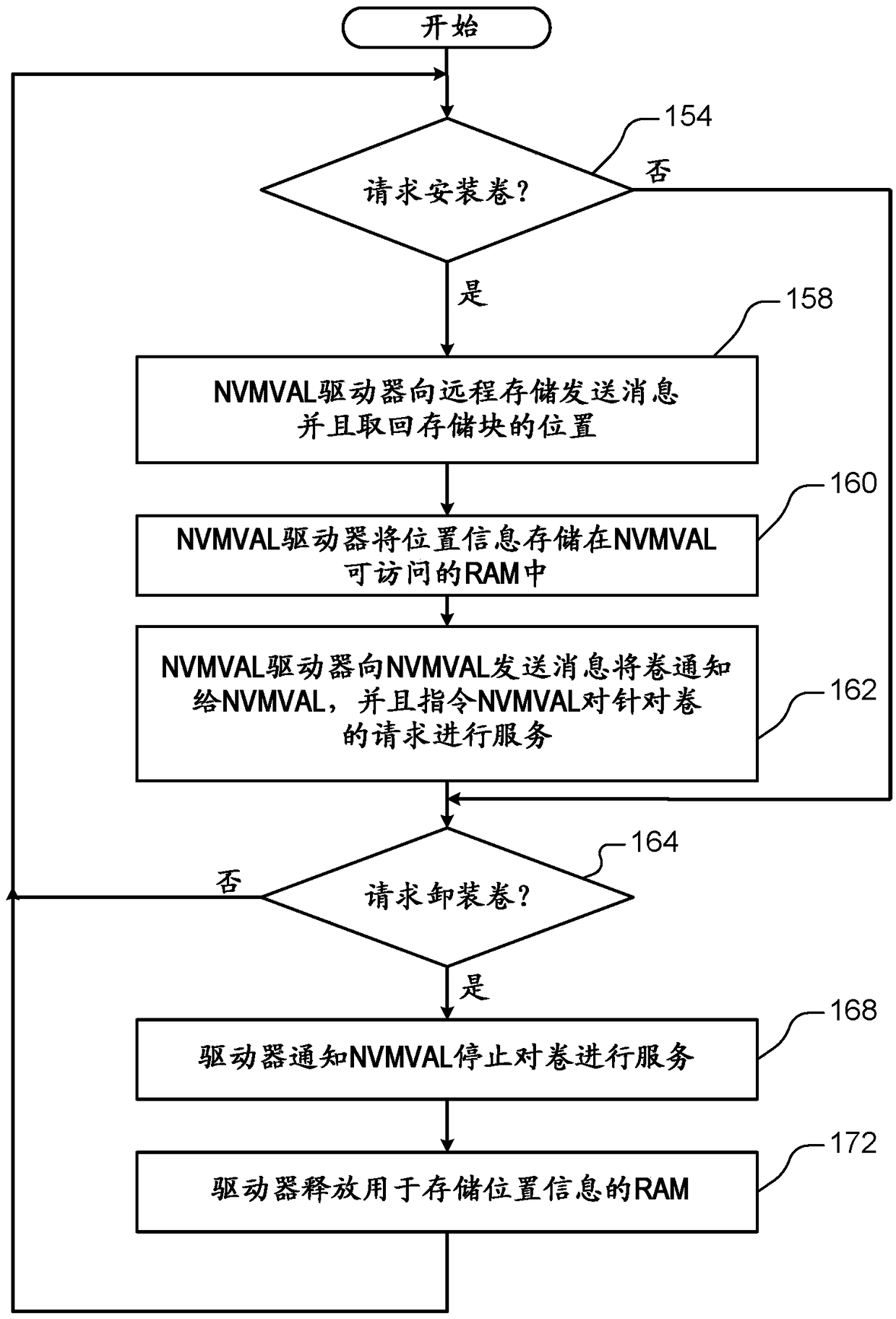
InactiveCN109496296AResource allocationInput/output processes for data processingVirtualizationAbstraction layer
A host computer includes a virtual machine including a device-specific nonvolatile memory interface (NVMI). A nonvolatile memory virtualization abstraction layer (NVMVAL) hardware device communicateswith the device-specific NVMI of the virtual machine. A NVMVAL driver is executed by the host computer and communicates with the NVMVAL hardware device. The NVMVAL hardware device advertises a local NVM device to the device-specific NVMI of the virtual machine. The NVMVAL hardware device and the NVMVAL driver are configured to virtualize access by the virtual machine to remote NVM that is remote from the virtual machine as if the remote NVM is local to the virtual machine.
Owner:MICROSOFT TECH LICENSING LLC
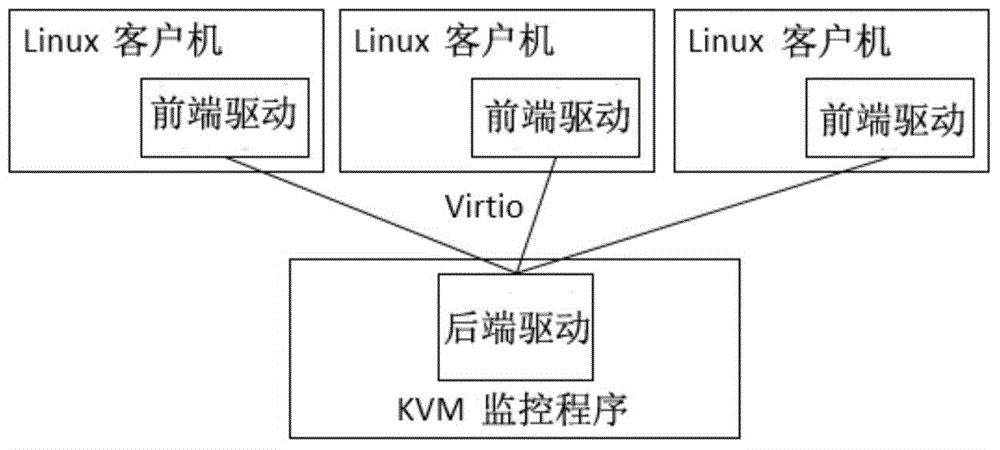
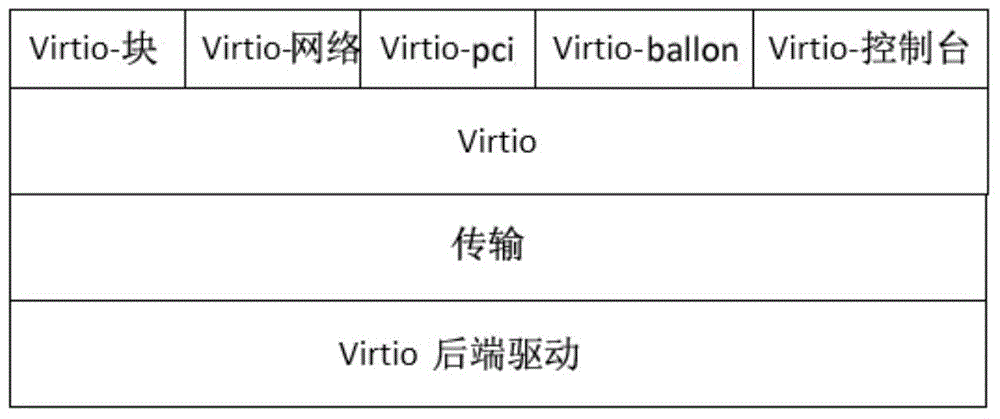
Embedded network virtualization environment VirtIO (virtual input and output) network virtualization working method
ActiveCN104618158AReduce the number of context switchesSave CPU resourcesData switching networksSoftware simulation/interpretation/emulationTime delaysNetwork virtualization
The invention provides an embedded network virtualization environment VirtIO virtualization working method. The embedded network virtualization environment VirtIO virtualization working method comprises, for a VirtIO front drive program, introducing a delay mechanism to a VirtIO network so that a client does not immediately transfer the control right to a host when performing network data I / O (input / output) but caching the data into a queue, and after a certain time, performs context switching to inform the host to obtain the data from the cache queue. The embedded network virtualization environment VirtIO virtualization working method can obviously reduce the number of times of context switching between the client and the host, save a large number of CPU (central processing unit) resources to process more network I / O. Experiments show that, within a set time delay, network throughput can be increased by more than three times.
Owner:SHANGHAI JIAO TONG UNIV
Efficient memory virtualization in multi-threaded processing units
ActiveUS20140122829A1Improve performanceLess development workMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryVirtualization
A technique for simultaneously executing multiple tasks, each having an independent virtual address space, involves assigning an address space identifier (ASID) to each task and constructing each virtual memory access request to include both a virtual address and the ASID. During virtual to physical address translation, the ASID selects a corresponding page table, which includes virtual to physical address mappings for the ASID and associated task. Entries for a translation look-aside buffer (TLB) include both the virtual address and ASID to complete each mapping to a physical address. Deep scheduling of tasks sharing a virtual address space may be implemented to improve cache affinity for both TLB and data caches.
Owner:NVIDIA CORP
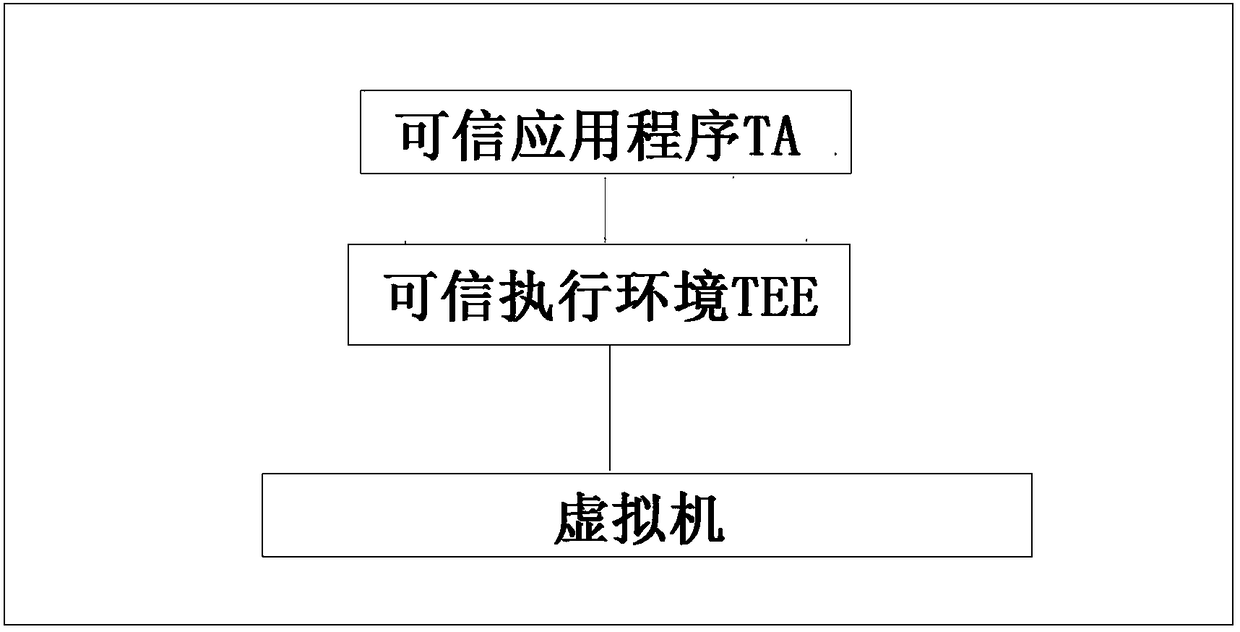
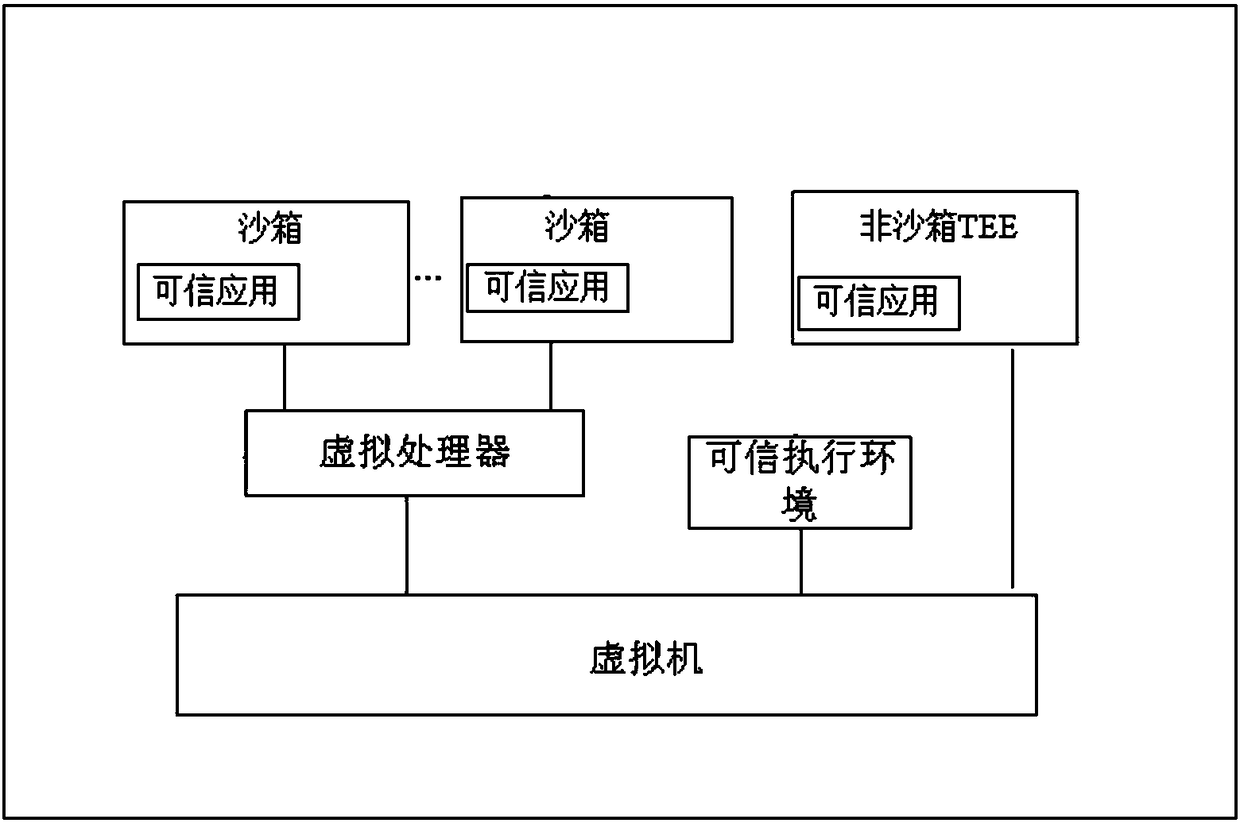
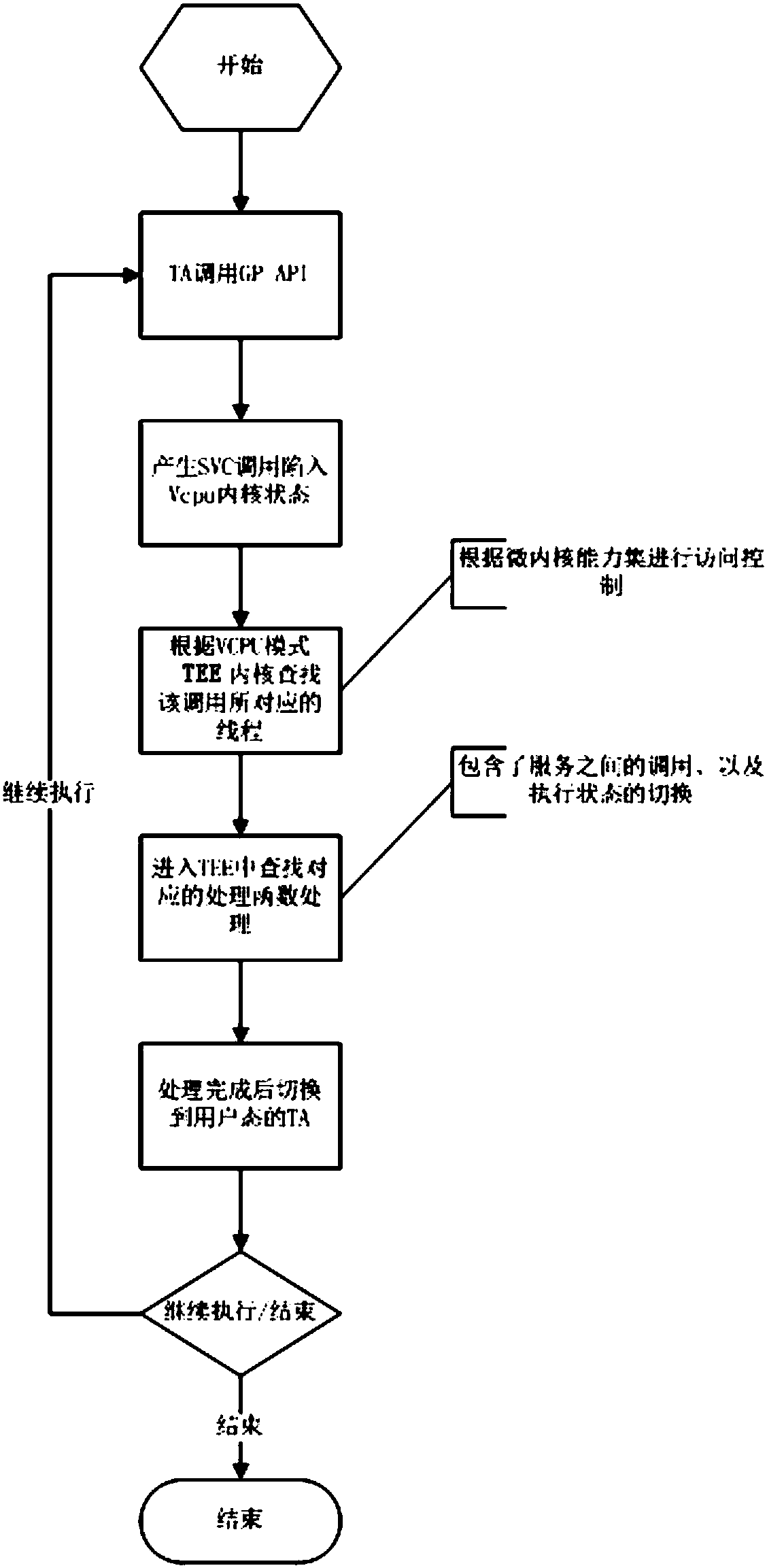
Secure virtualization system suitable for use in trusted execution environment (TEE)
ActiveCN108509251AAchieve isolationImprove securityInternal/peripheral component protectionPlatform integrity maintainanceMemory virtualizationApplication software
The invention discloses a secure virtualization system suitable for use in a trusted execution environment (TEE). The system includes at least one virtual machine, at least one trusted application (TA) and the at least one trusted execution environment. The virtual machine is built through Micro Hypervisor. The trusted execution environment is run on the virtual machine. The trusted application isrun in the trusted execution environment of the virtual machine. The trusted execution environment is configured to access the virtual machine in a first mode to realize calling of resources. Under the first mode, the virtual machine allows accessing of the trusted execution environment to the resources after it is determined that the trusted execution environment has access authority. The systemhas the advantages of: on the basis of trusted virtualization technology, building the virtual machine through the Micro Hypervisor, and running the GP (Global Platform) TEE and the corresponding TAon the virtual machine. Both the TEE and the TA are run on the respective virtual machine, thus complete isolation is realized, and security is greatly improved.
Owner:沈阳微可信科技有限公司
Memory virtualization method and system under Shenwei architecture
ActiveCN112363824AEliminate processing overheadEliminate page fault handling overheadResource allocationSoftware simulation/interpretation/emulationVirtualizationComputer architecture
The invention relates to a memory virtualization method and system under a Shenwei architecture. The method comprises the following steps: a buffer area for storing a shadow page table base address isbuilt; when the CPU queries that the TLB misses, the CPU accesses the buffer area to obtain a shadow page table base address of the current process, loads the shadow page table base address into a memory management unit, and starts page table query; when mapping missing occurs in the page table query, the CPU switches the client context to the host context to perform page missing interrupt processing; the corresponding TLB directly fills the virtual-real address conversion mapping obtained after page missing interrupt processing to realize TLB prefetching; and the CPU inquires the TLB again to finish the address conversion from the virtual address of the client to the physical address of the host. Based on the TLB characteristic of Shenwei architecture software management, the shadow pagetable and the TLB are refreshed at the same time, and therefore synchronization of the shadow page table and the client process page table is achieved.
Owner:PEKING UNIV +1
Network and system for network virtualization
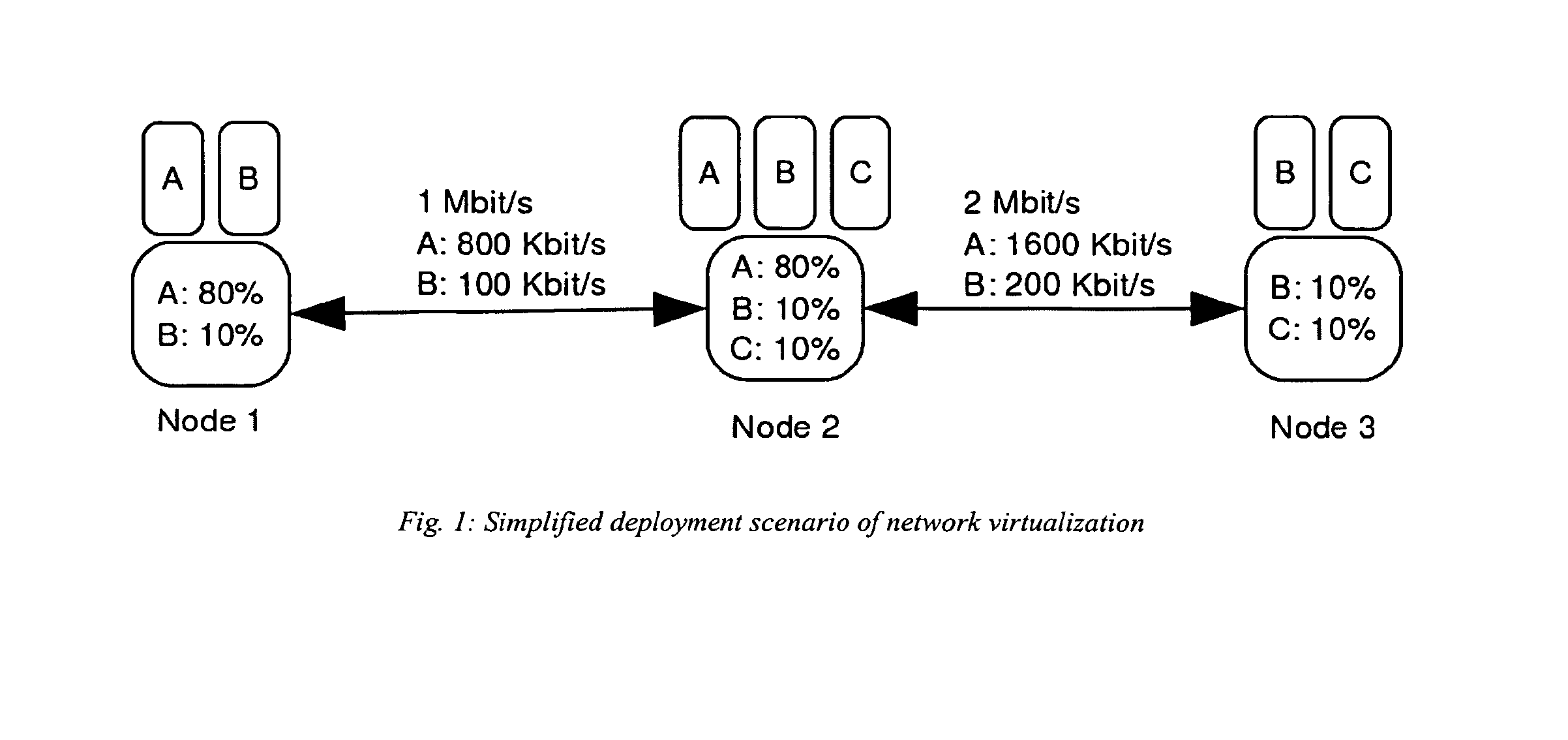
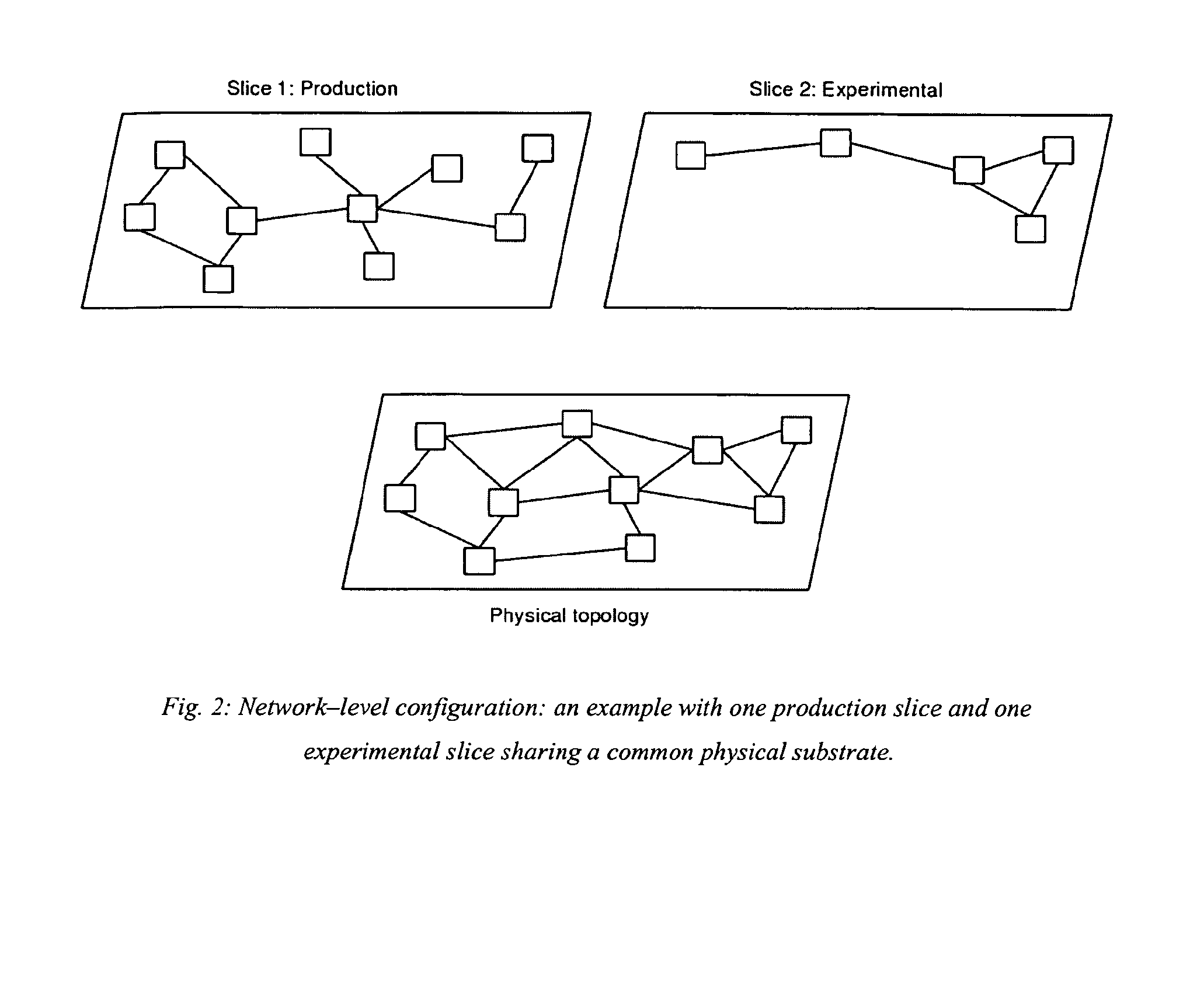
InactiveUS20130272216A1Level of flexibilityGuaranteed resourcesNetwork traffic/resource managementWireless commuication servicesNetwork virtualizationNested virtualization
Currently available network virtualization solutions are either specifically tailored for wired networks composed of nodes with very large processing power and storage space. The present invention relates to a novel virtualization framework specifically tailored to wireless networks. Such framework provides Wireless Internet Service Providers (WISP) with an effective virtualization solution, allowing production traffic to share part of the available network resources with a variable number of network slices where novel solutions, such as new routing protocols, services or network operation tools, can be experimentally tested in a severely controlled yet realistic environment.
Owner:ASSOCIAZIONE CREATE NET
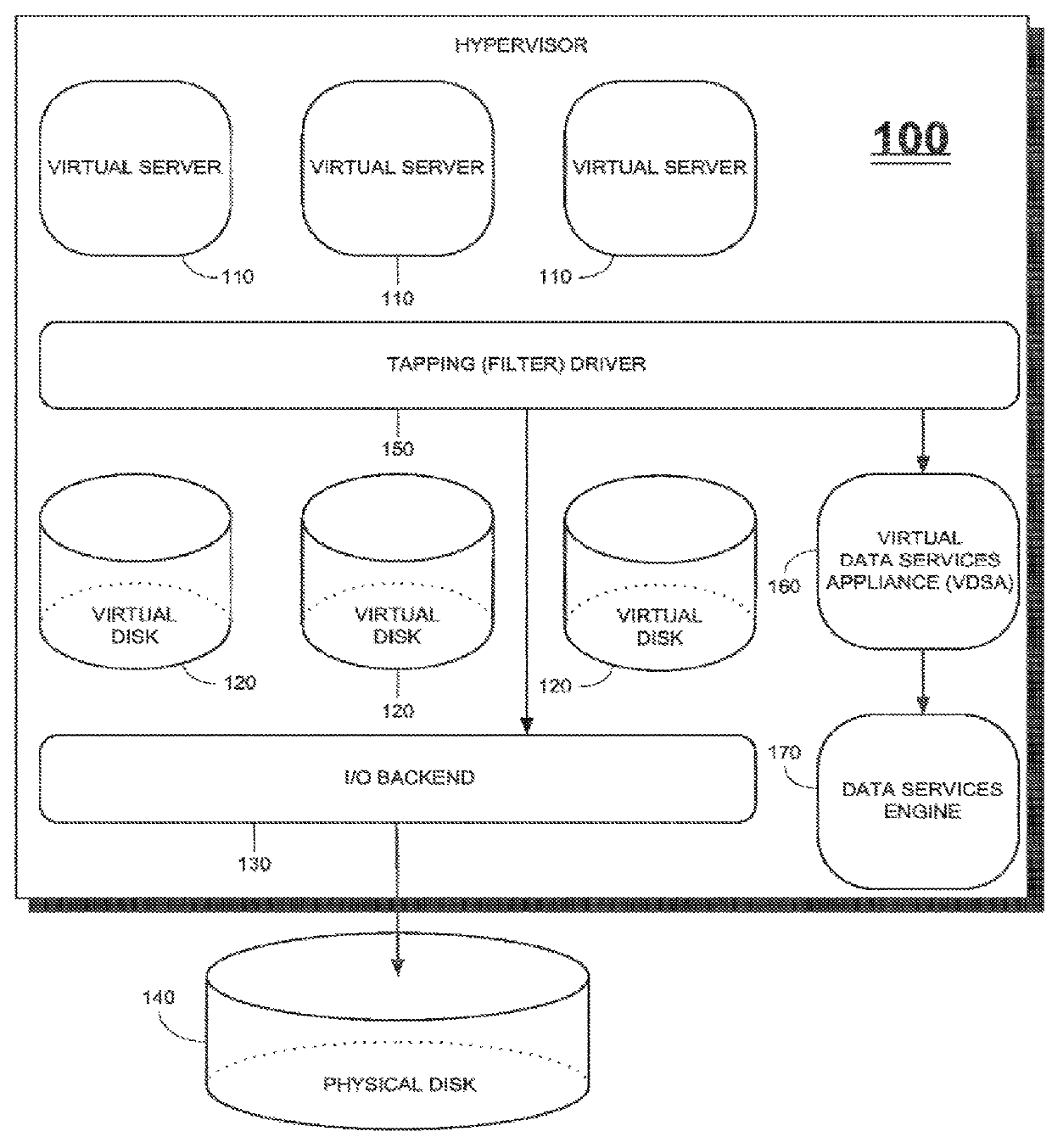
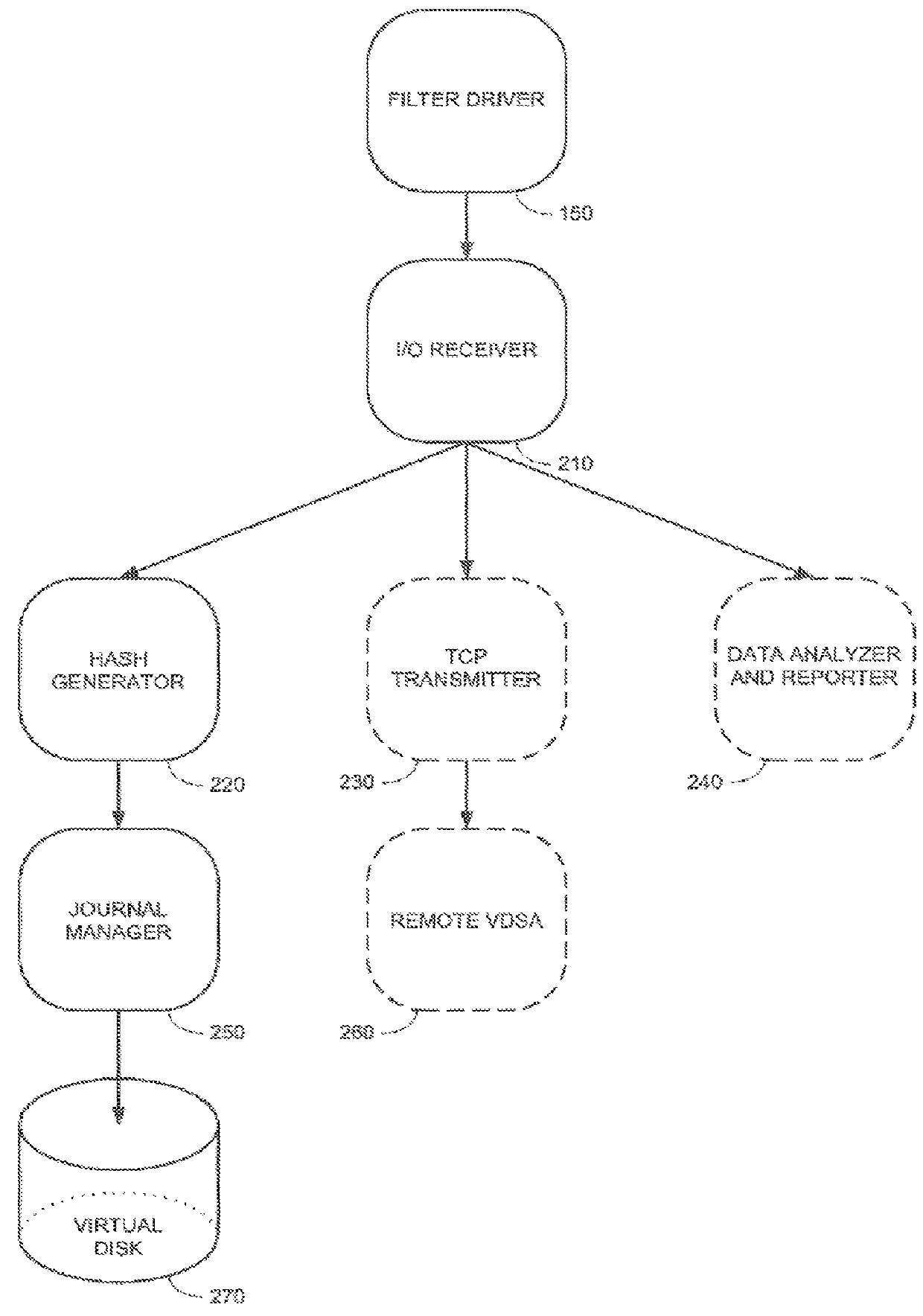
Methods and apparatus for providing hypervisor level data services for server virtualization
ActiveUS20160034296A1Data switching networksSoftware simulation/interpretation/emulationMemory virtualizationLevel data
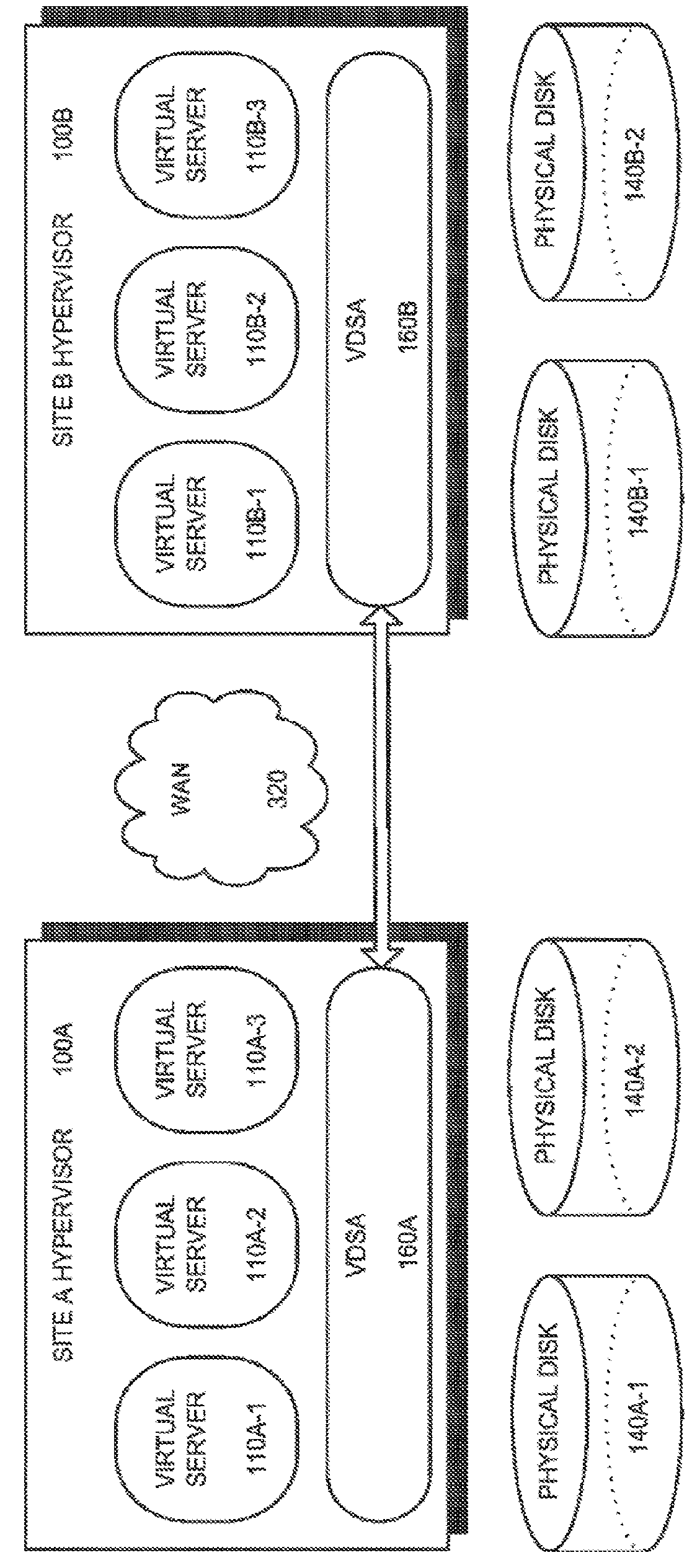
A system for cloud-based data services for multiple enterprises, including a plurality of cloud hypervisors that cooperatively provide cloud-based services to multiple enterprises, each hypervisor including a plurality of cloud virtual servers, each cloud virtual server being associated with an enterprise, at least one cloud virtual disk that is read from and written to by the at least one virtual server, each cloud virtual disk being associated with an enterprise, and a virtual data services appliance, which provides cloud-based data services, and multiple data services managers, one data services manager per respective enterprise, each of which coordinates the respective virtual data services appliances for those cloud hypervisors that service its corresponding enterprise.
Owner:ZERTO
A method and a device for realizing dual-live disaster recovery for a server virtualization system
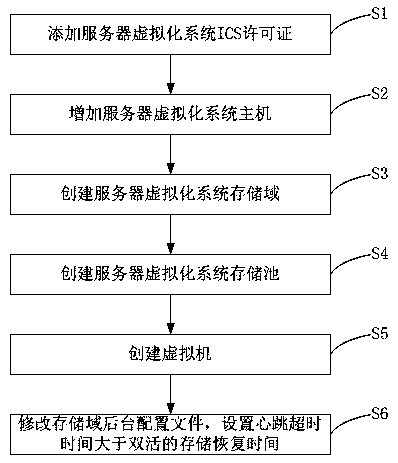
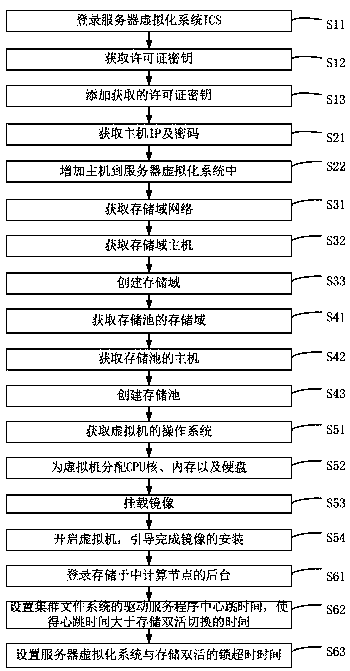
ActiveCN109240855AImprove securityAdapt to needsSoftware simulation/interpretation/emulationRedundant operation error correctionData accessComputer module
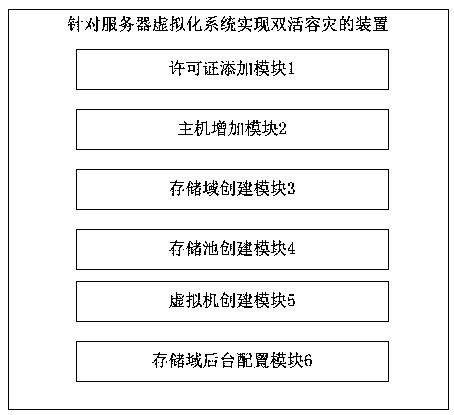
The invention provides a method and a device for realizing dual-live disaster recovery for a server virtualization system. The method includes: configuring a server virtualization system ICS, and creating a CFS storage domain and a shared storage pool; Modifying the storage domain profile to set the heartbeat timeout to be greater than the dual live storage recovery time. The device comprises a license adding module, which is used for adding an ICS license of a server virtualization system; A host adding module, configured to add a server virtualization system host; A storage domain creation module for creating a server virtualized system storage domain; A storage pool creation module for creating a server virtualization system storage pool; A virtual machine creation module for creating avirtual machine; The storage domain background configuration module used for modifying the storage domain background configuration file and setting the heartbeat timeout time to be greater than the dual-live storage recovery time. The invention enhances the safety of data access, more adapts to the needs of enterprise-level customers, and promotes the perfection of the functions of the company'svirtualized products.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
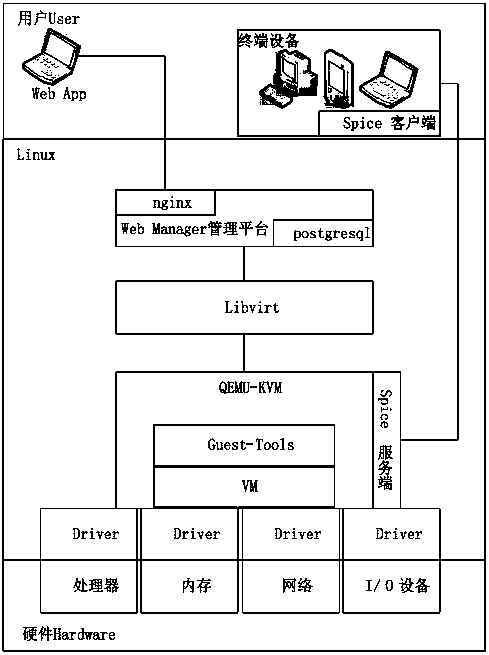
Setup method for mobile cloud desktop platform based on cloud architecture
InactiveCN107682445AReduce maintenance costsImprove service efficiencyTransmissionTest performanceMobile cloud
The invention relates to a setup method for a mobile cloud desktop platform based on cloud architecture. A KVM virtualization technology is responsible for CPU virtualization and memory virtualization. An IO device interface and a user state control interface of a virtual machine are simulated through adoption of a Qemu. A Web Manager management platform calls a Qemu-KVM to operate the virtual machine through a Libvirt API. A Spice server provides remote connection service. A URL and a port are input into a terminal device through a Spice client, and the terminal device is remotely connected with the virtual machine. According to the setup method for the mobile cloud desktop platform based on the cloud architecture, the reasonable cloud architecture is designed and a remote desktop protocol tool with high test performance is employed, so a user can access a cloud desktop for work whenever and wherever possible, and moreover, a professional office application is provided, user application and background management are effectively isolated, and a user is help to create a relatively simple and secure IT office system with relatively low maintenance cost and relatively high service efficiency.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Memory virtualization-based snapshot boot apparatus and method
InactiveUS20140297998A1Easy to operateDigital computer detailsBootstrappingMemory virtualizationNetwork virtualization
The present invention relates to a memory virtualization-based snapshot boot apparatus and method. The memory virtualization-based snapshot boot apparatus includes hardware unit including a processor, memory, and storage, the storage storing status information corresponding to an operating system, and a Virtual Machine Monitor (VMM) operated by the processor and configured to operate the operating system by loading the status information into the memory. In accordance with the present invention, technology for loading only a part of a snapshot image and booting a system is implemented using virtualization technology, thus shortening the booting time of the system.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com