Patents
Literature
1439 results about "Virtual address space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
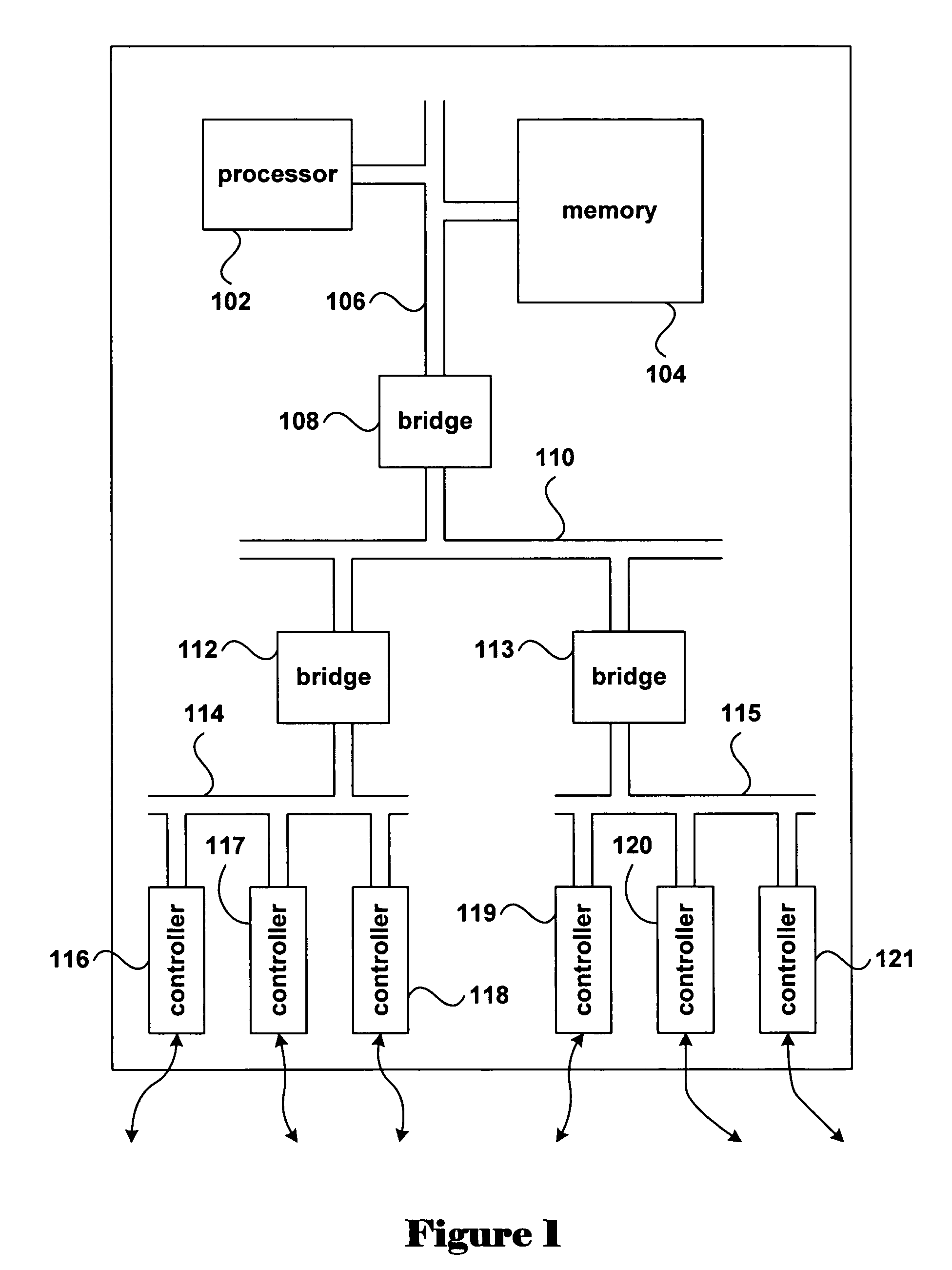
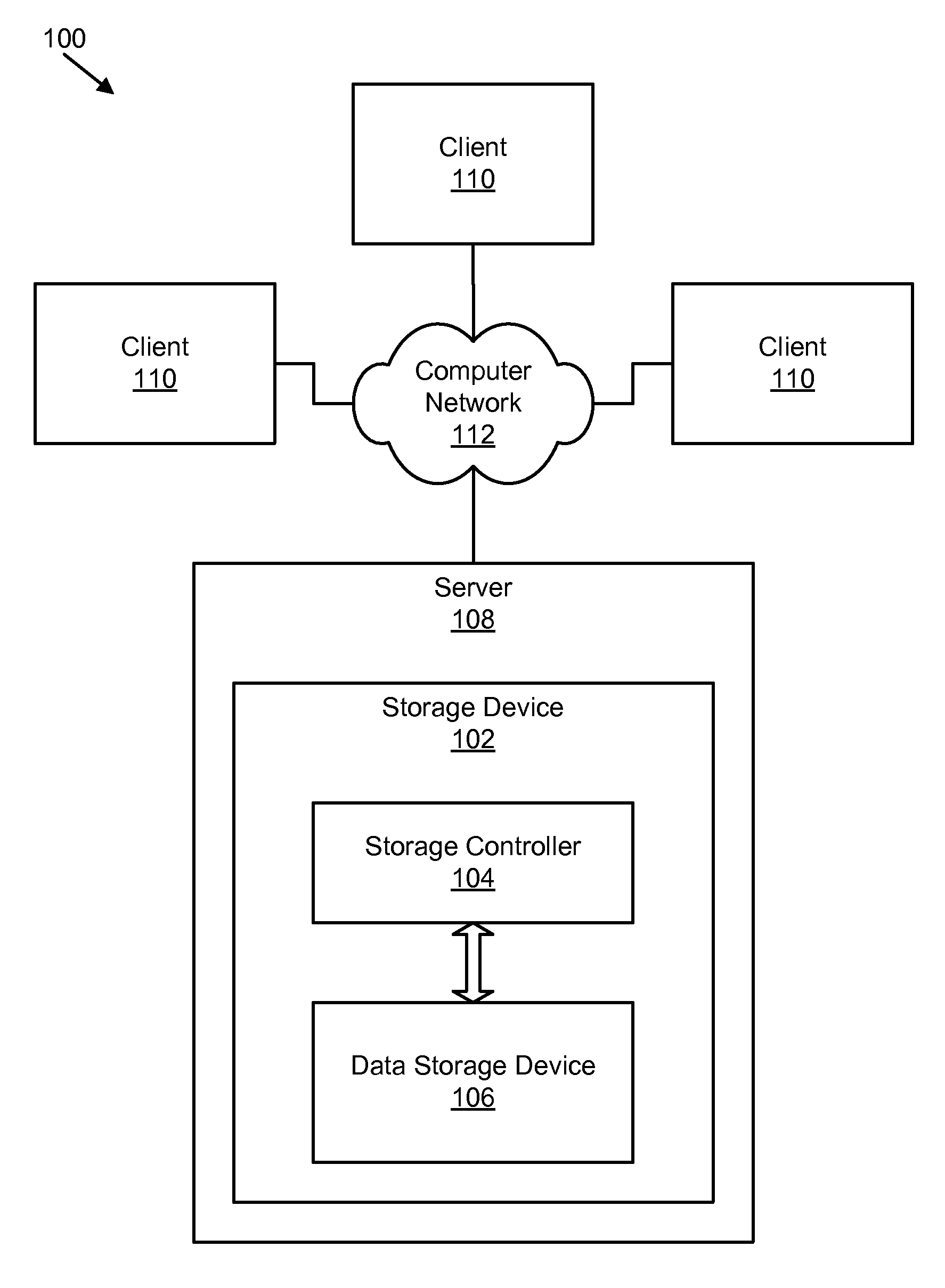
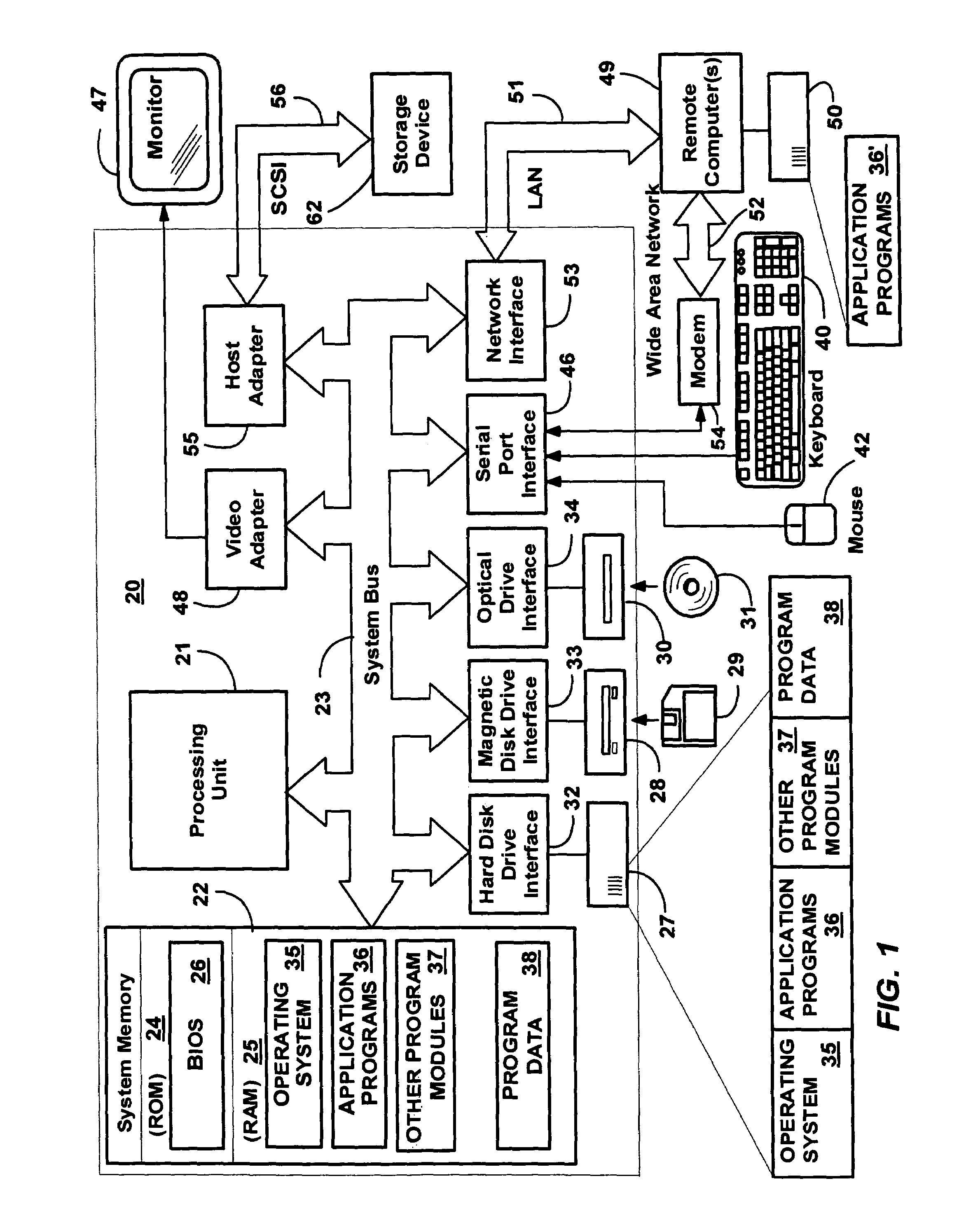
In computing, a virtual address space (VAS) or address space is the set of ranges of virtual addresses that an operating system makes available to a process. The range of virtual addresses usually starts at a low address and can extend to the highest address allowed by the computer's instruction set architecture and supported by the operating system's pointer size implementation, which can be 4 bytes for 32-bit or 8 bytes for 64-bit OS versions. This provides several benefits, one of which is security through process isolation assuming each process is given a separate address space.
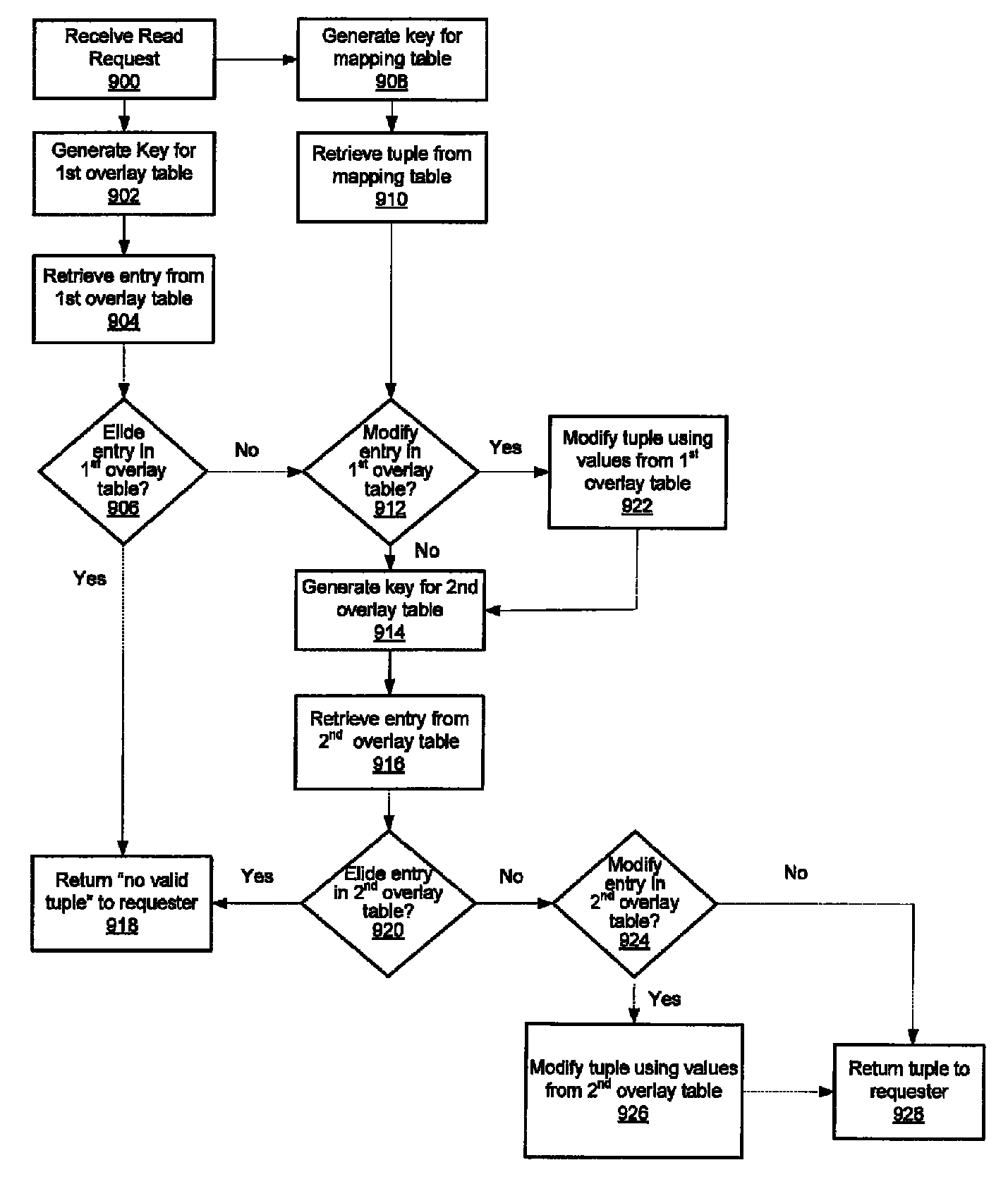
Garbage collection in a storage system
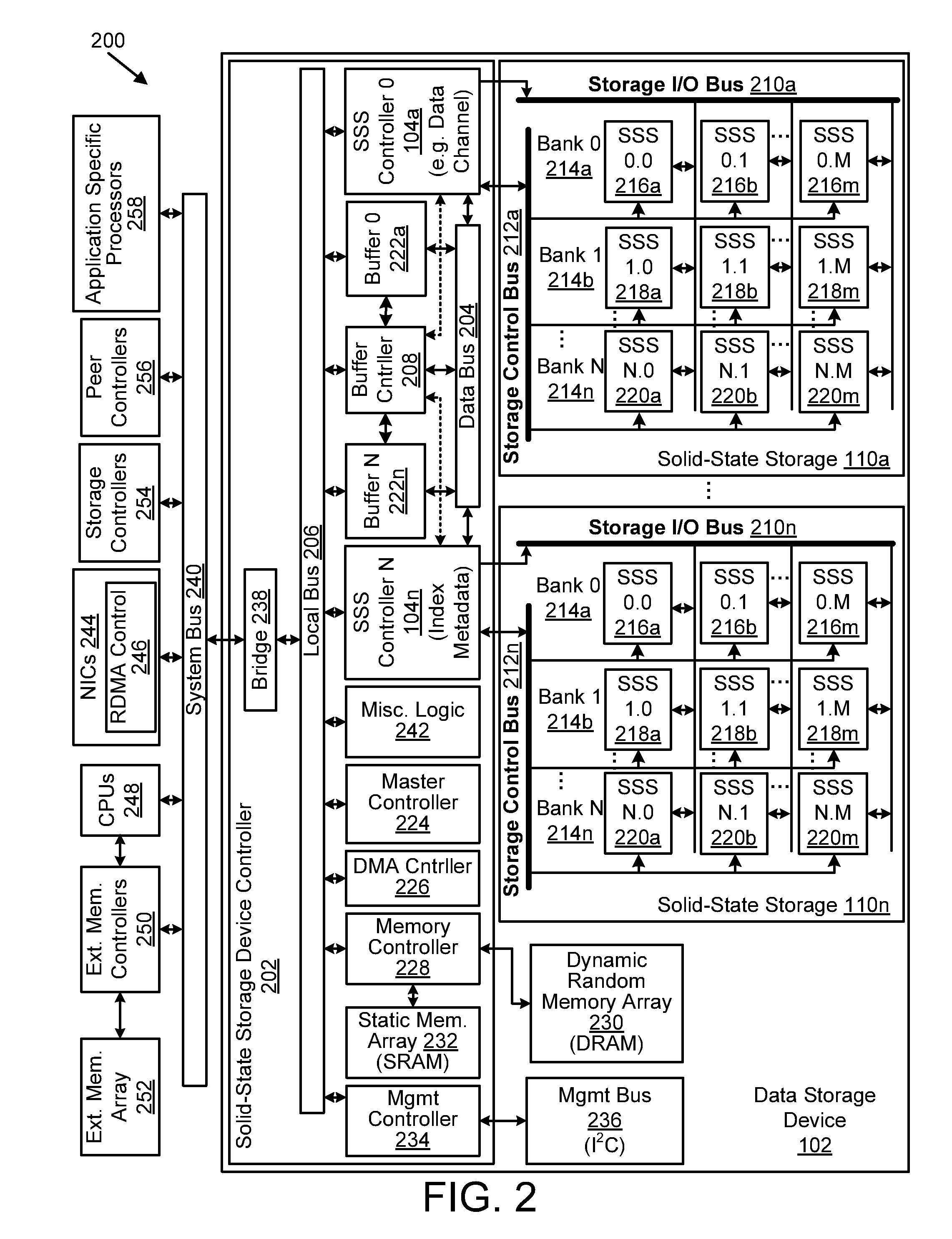
ActiveUS8527544B1Memory architecture accessing/allocationDigital data information retrievalRefuse collectionControl store
A system and method for performing garbage collection. A system includes a storage medium, a first table including entries which map a virtual address to locations in the storage medium, and a second table with entries which include a reverse mapping of a physical address in a data storage medium to one or more virtual addresses. A storage controller is configured to perform garbage collection. During garbage collection, the controller is configured to identify one or more entries in the second table which correspond to a segment to be garbage collected. In response to determining the first table includes a valid mapping for a virtual address included in an entry of the one of the one or more entries, the controller is configured to copy data from a first location identified in the entry to a second location in the data storage medium, and reclaim the first storage location.
Owner:PURE STORAGE
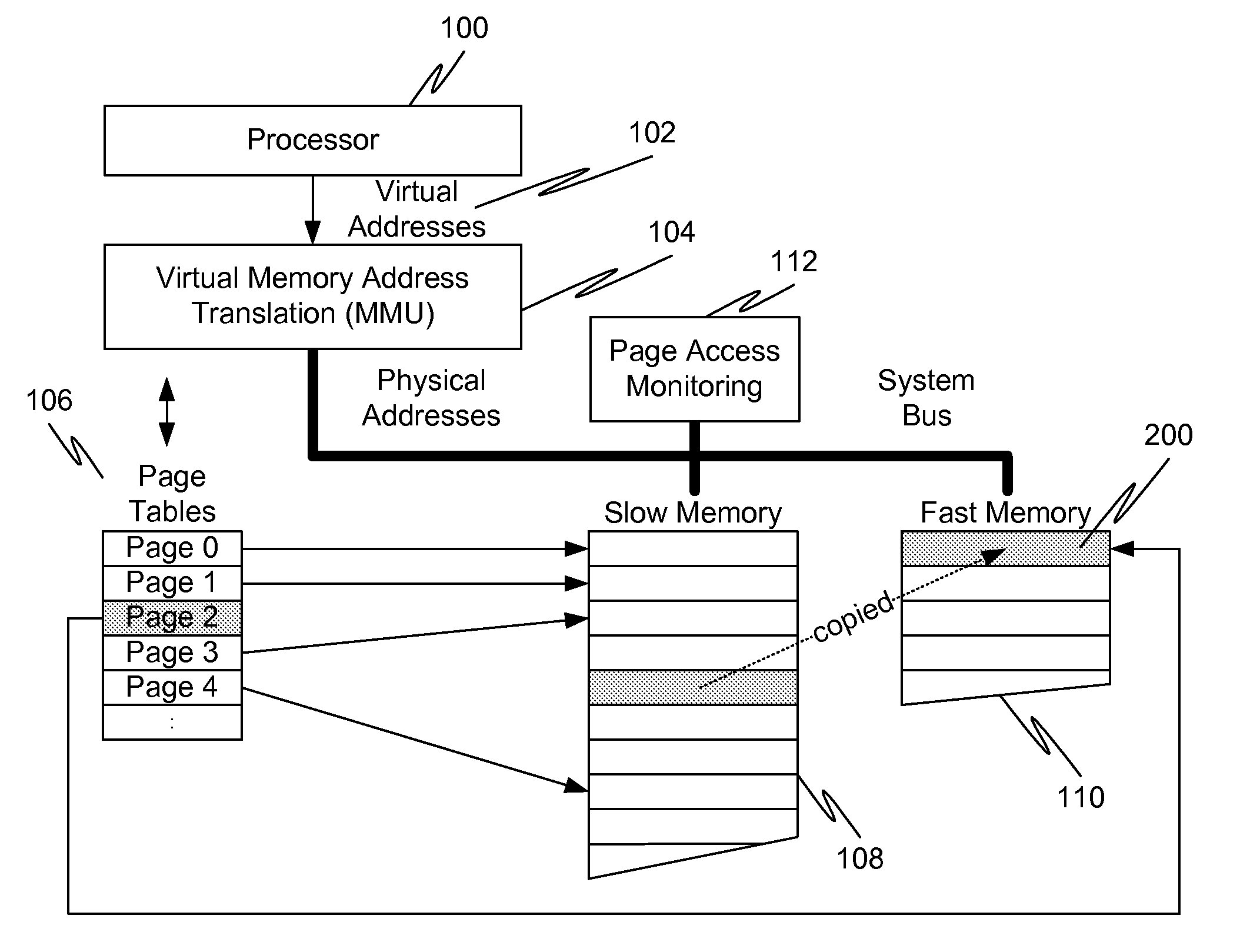
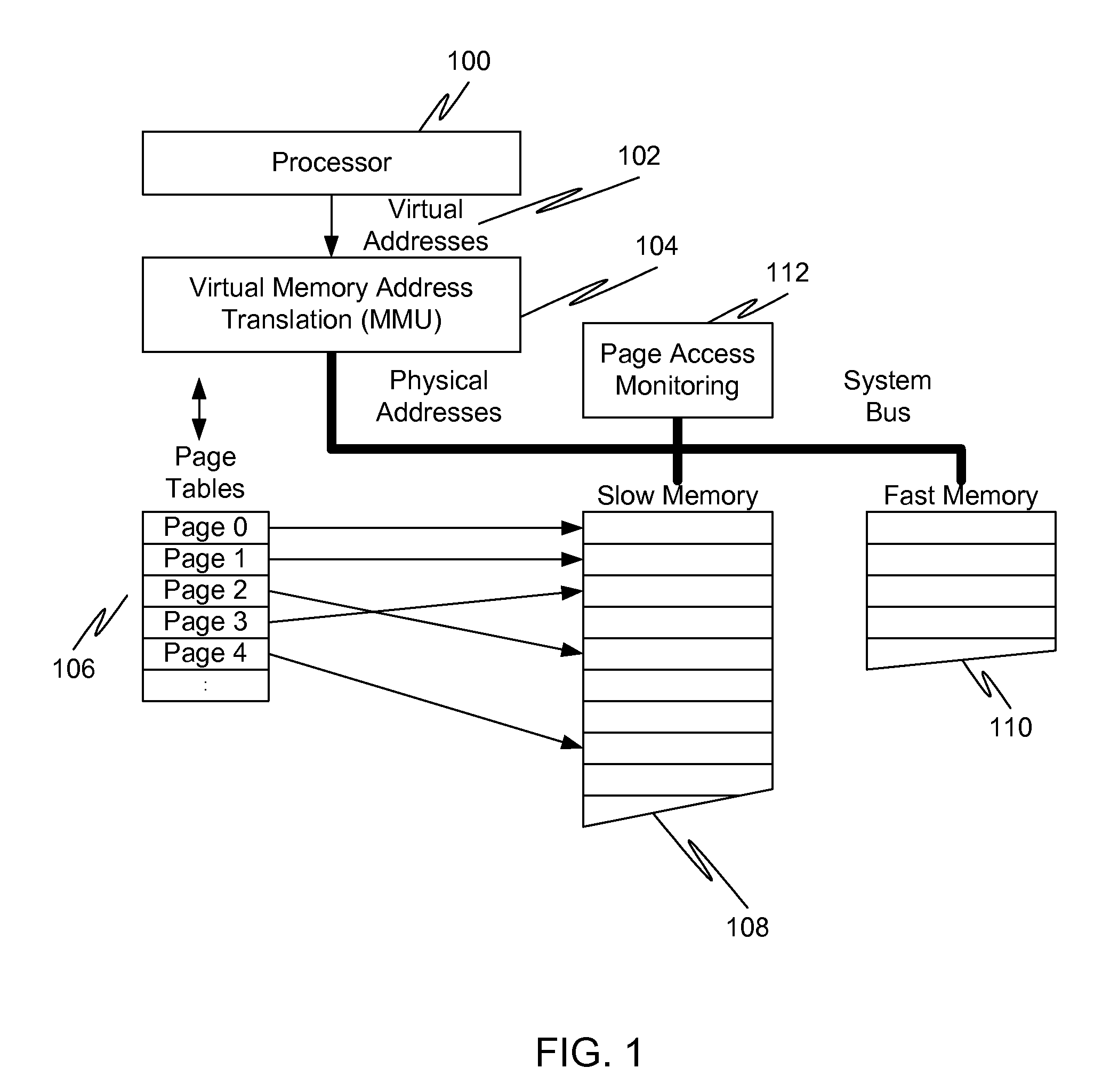
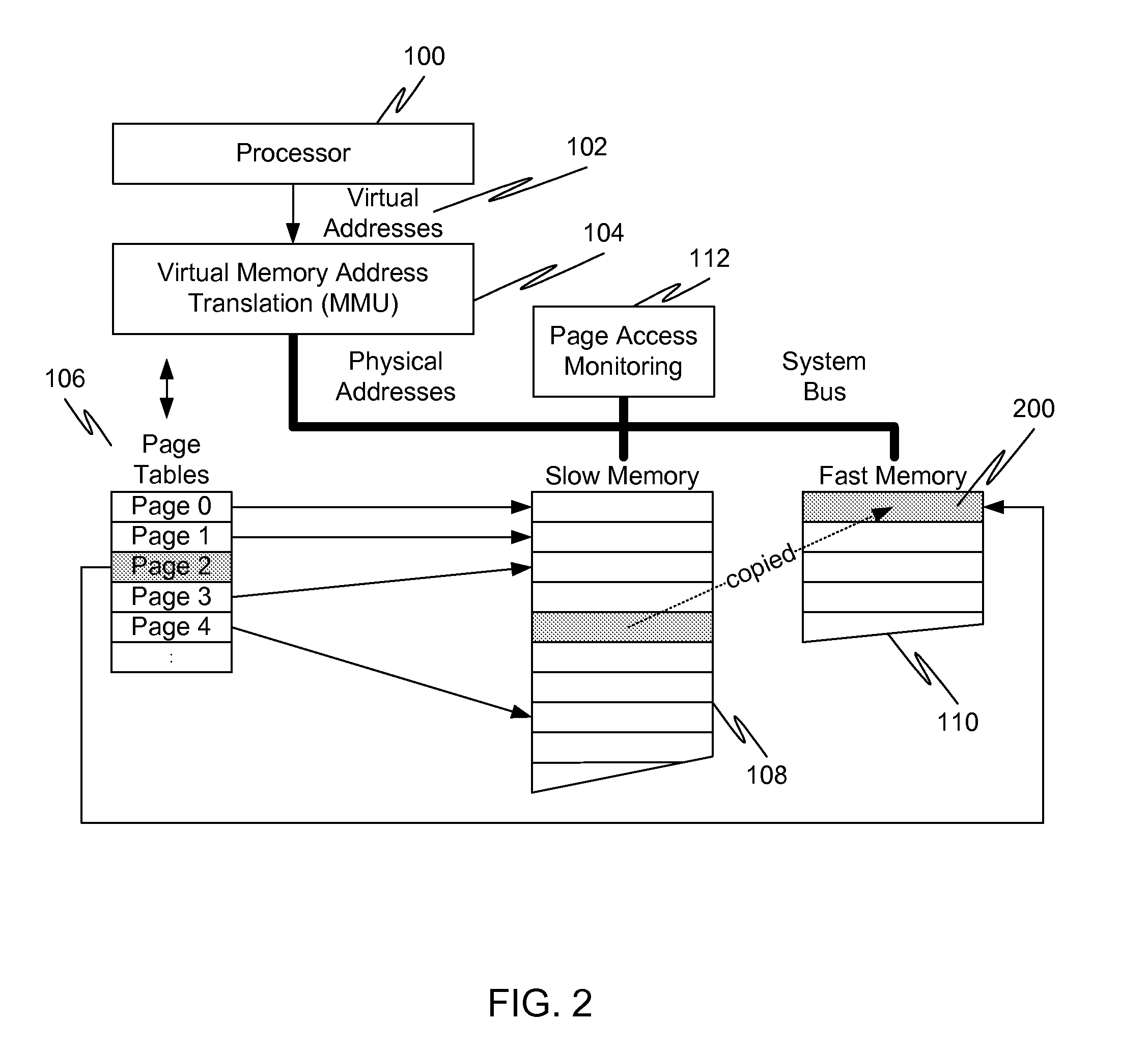
Caching using virtual memory
InactiveUS20120017039A1Memory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryPage table
In a first embodiment of the present invention, a method for caching in a processor system having virtual memory is provided, the method comprising: monitoring slow memory in the processor system to determine frequently accessed pages; for a frequently accessed page in slow memory: copy the frequently accessed page from slow memory to a location in fast memory; and update virtual address page tables to reflect the location of the frequently accessed page in fast memory.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
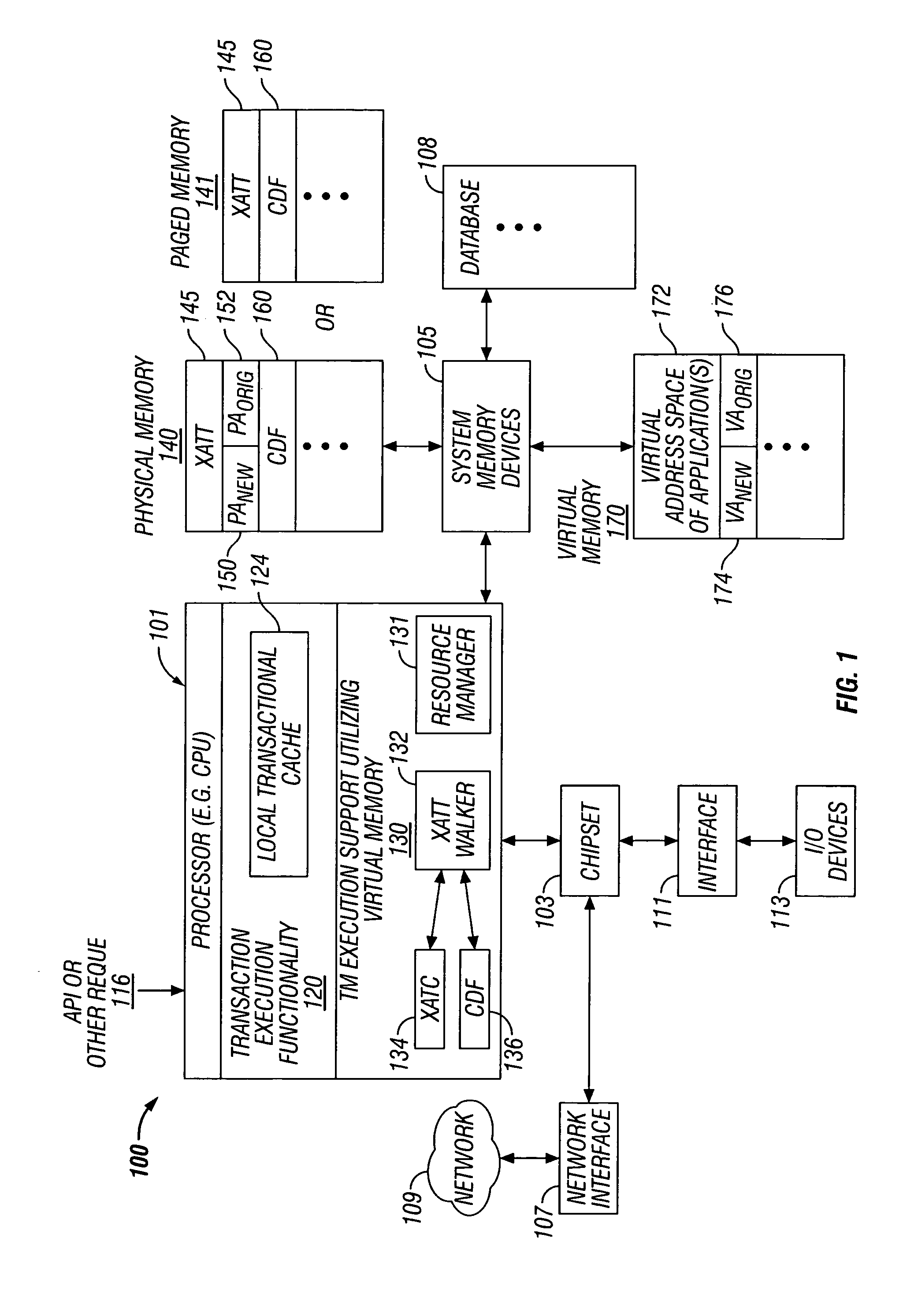
Transactional memory execution utilizing virtual memory
ActiveUS7685365B2Memory adressing/allocation/relocationTransaction processingVirtual memoryTransactional memory
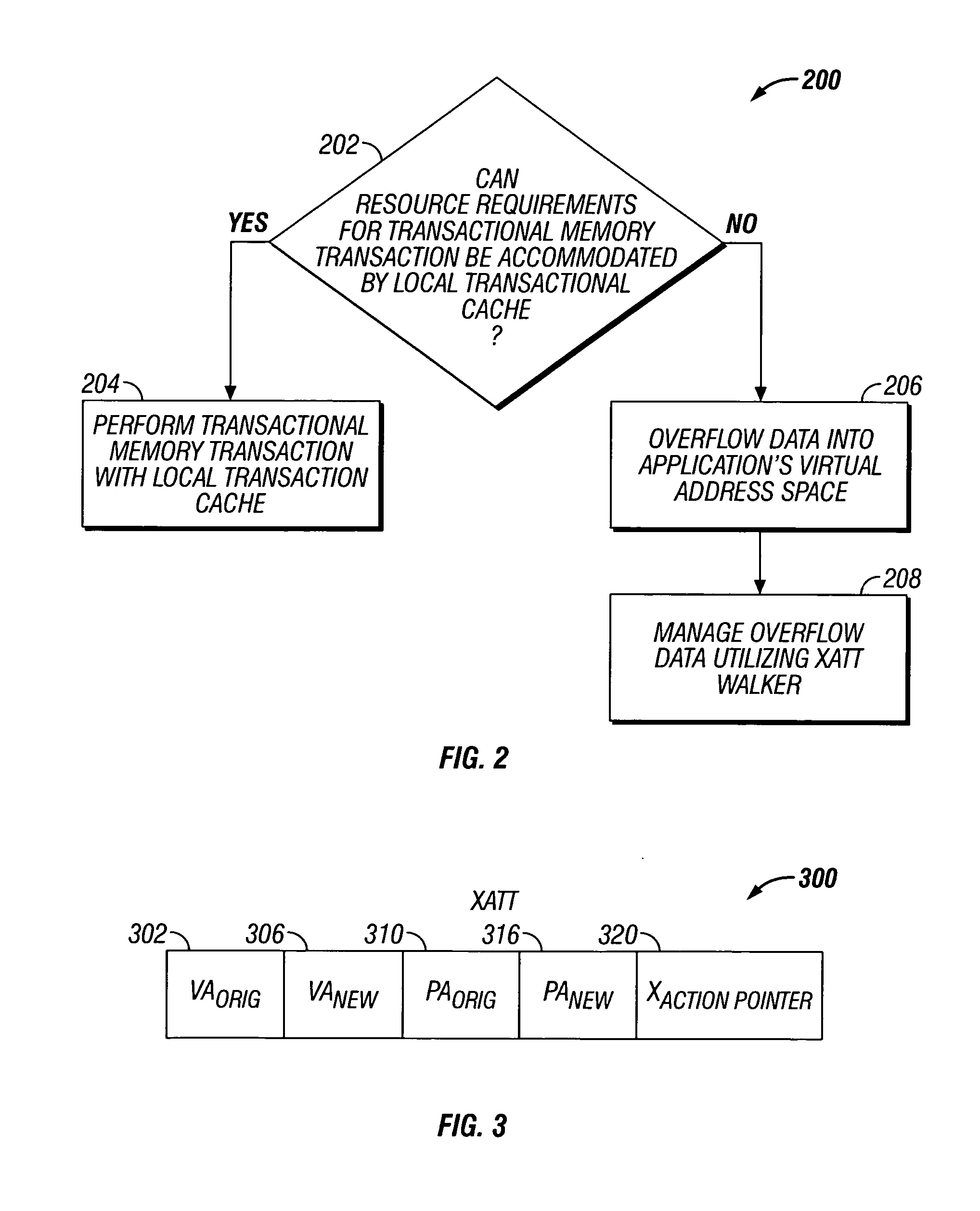
Embodiments of the invention relate to transactional memory execution utilizing virtual memory. A processor includes a local transactional cache and a resource manager. The resource manager responsive to a transactional memory transaction request from a requesting thread determines whether the local transactional cache is capable of accommodating the transactional memory transaction request and, if so, the local transactional caches performs the transactional memory transaction. However, if the local transactional cache is not capable of accommodating the transactional memory transaction request, data for the transactional memory transaction request is overflowed into an application's virtual address space associated with the requesting thread.
Owner:INTEL CORP
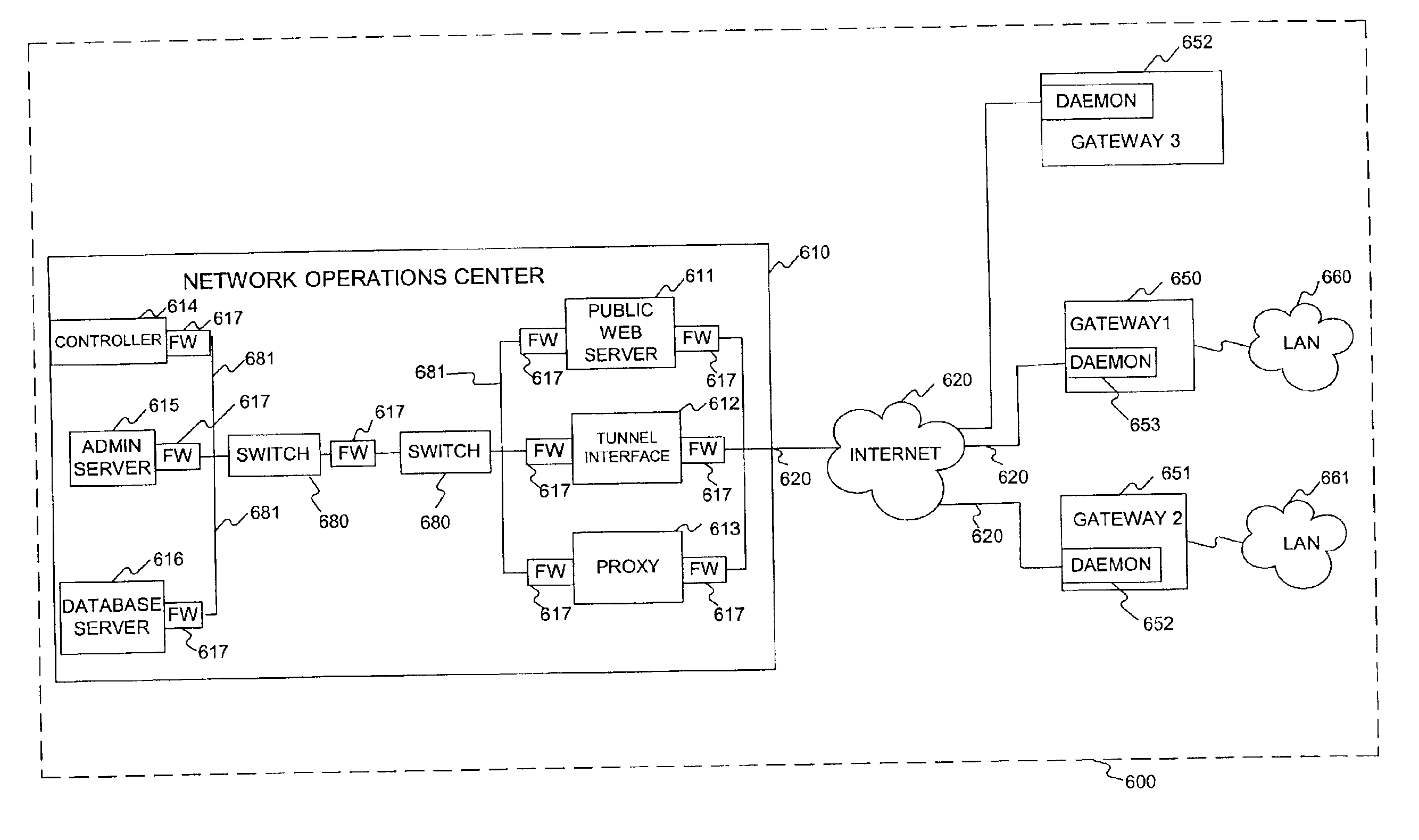
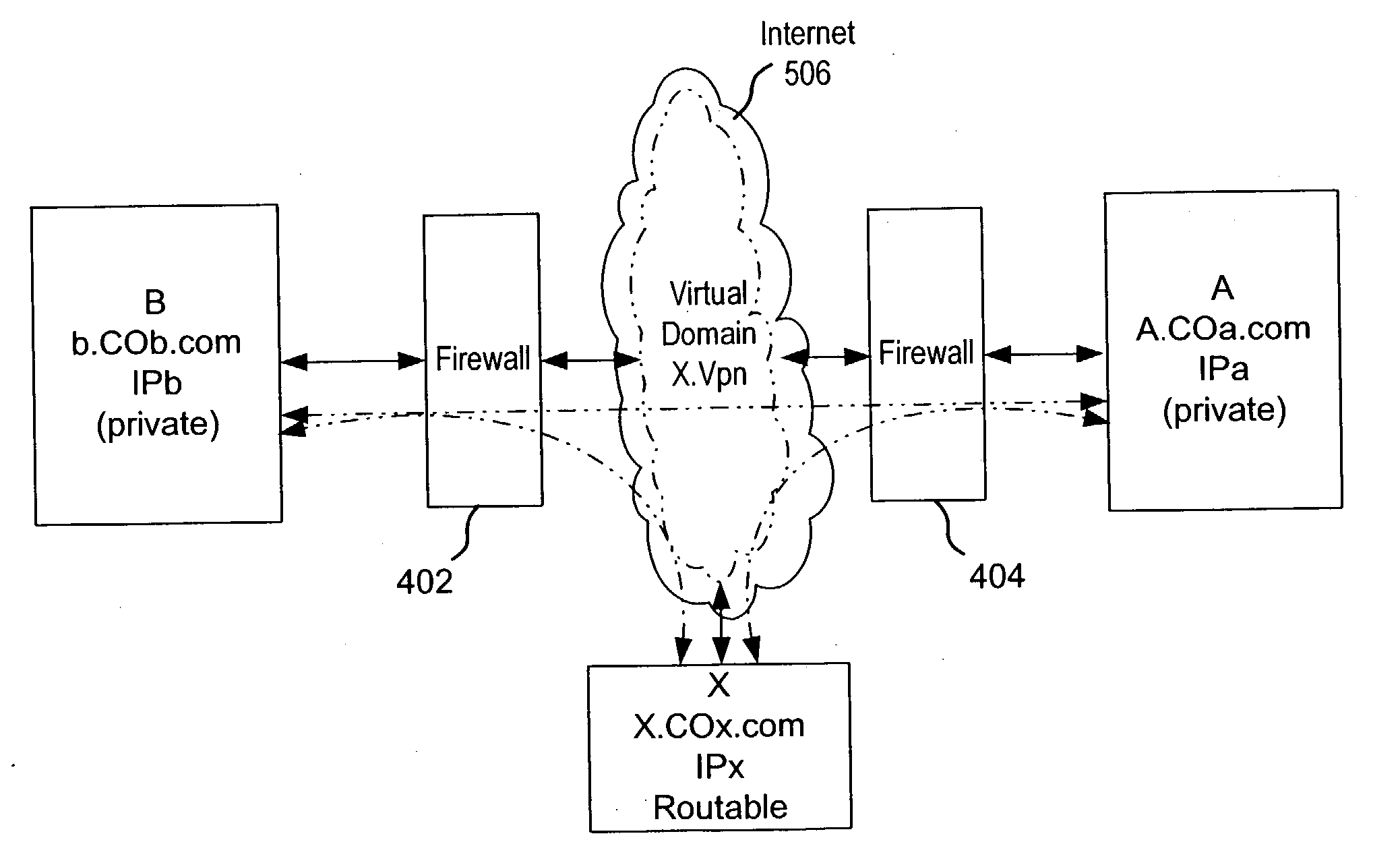
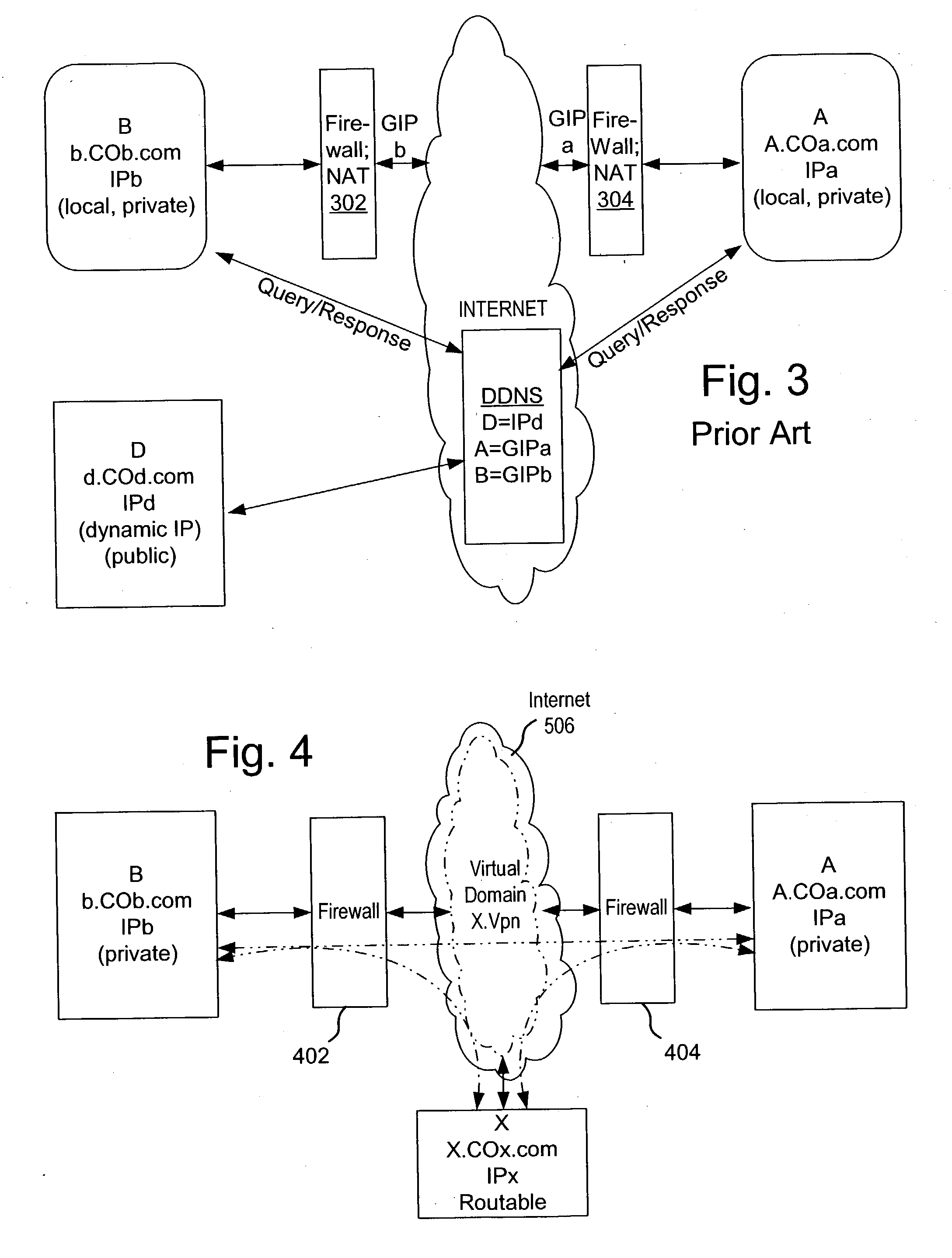
Secure virtual community network system
ActiveUS20040249911A1Convenient introductionMultiple digital computer combinationsOffice automationPrivate networkPublic network
A private virtual dynamic network is provided for computing devices coupled to public networks or private networks. This enables computing devices anywhere in the world to join into private enterprise intranets and communicate with each other. In one embodiment, the present invention provides a separate private virtual address realm, seen to each user as a private network, while seamlessly crossing public and private network boundaries. One implementation of the present invention uses an agent to enable an entity to participate in the network without requiring the member to add new hardware or software.
Owner:F POSZAT HU
Locking technique for control and synchronization
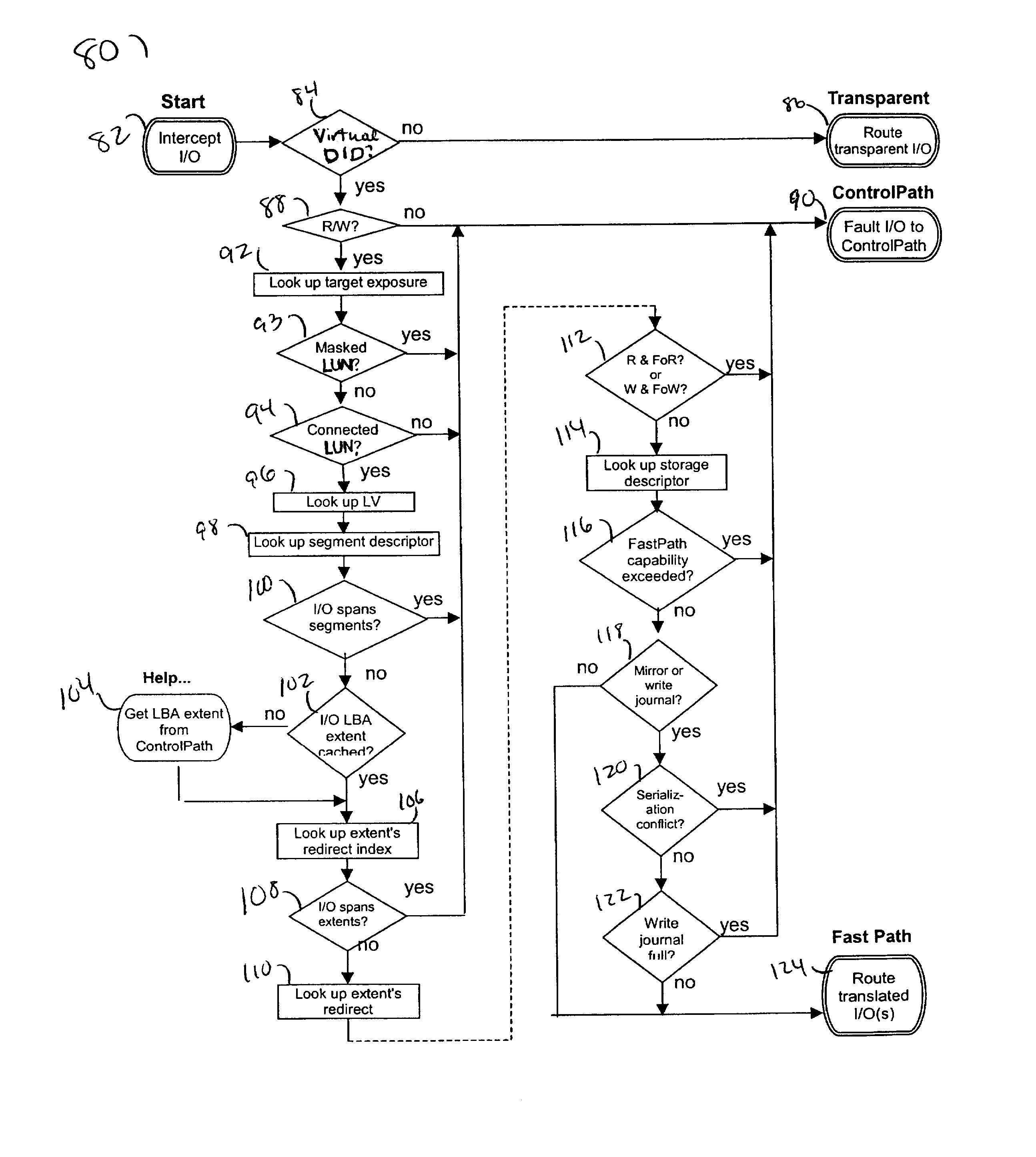
InactiveUS6973549B1Digital data information retrievalMultiprogramming arrangementsFast pathLocking mechanism
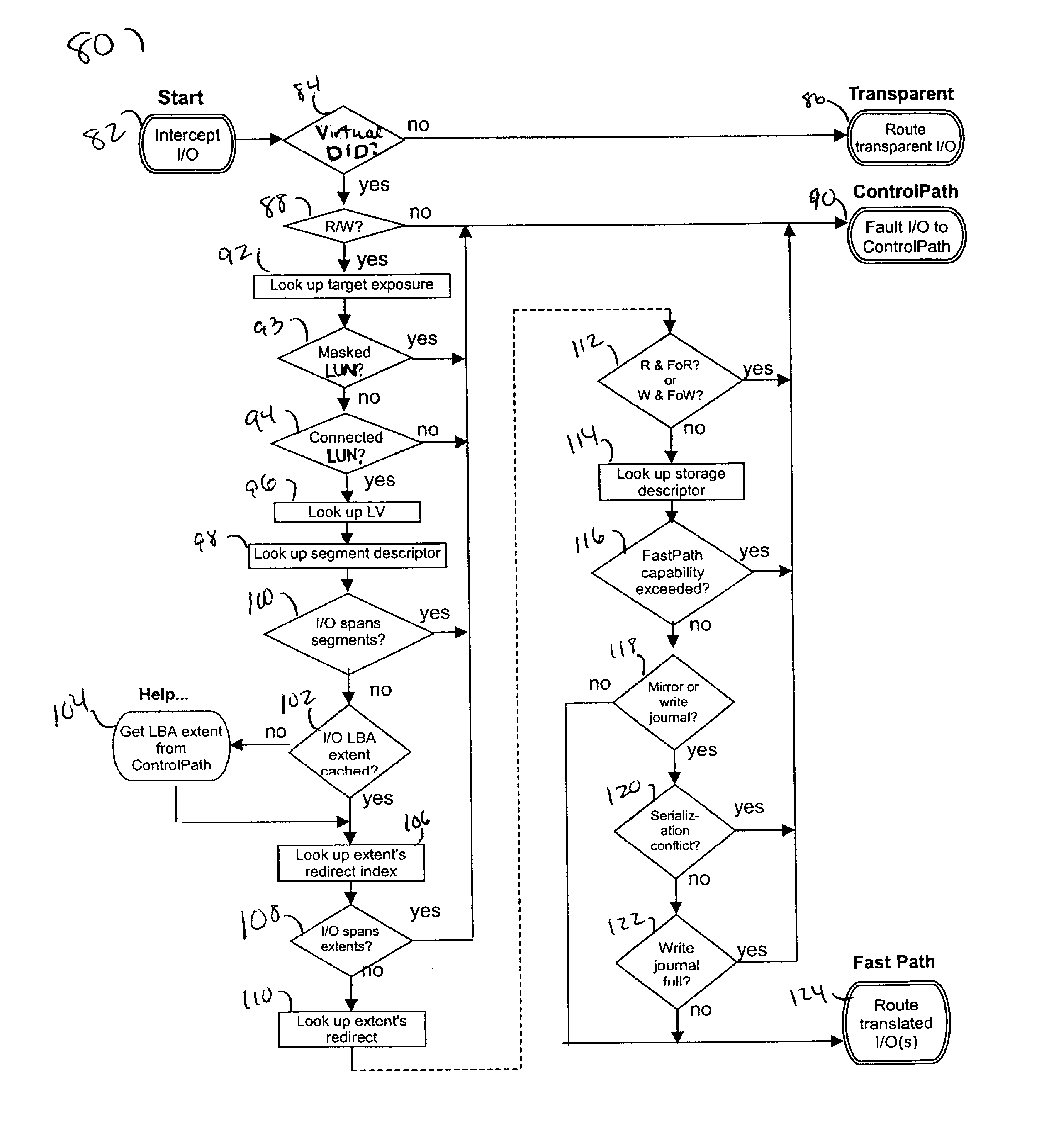
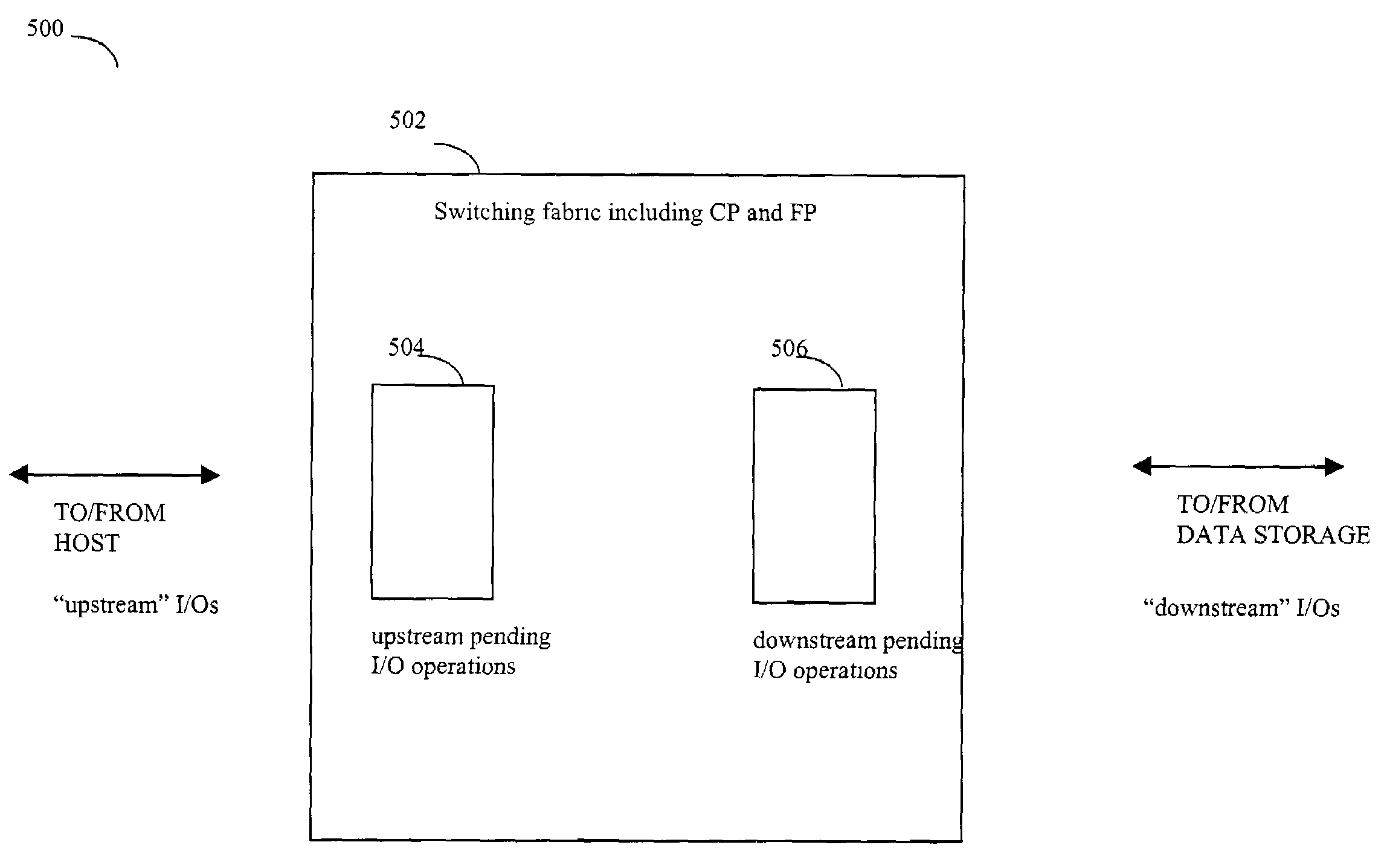
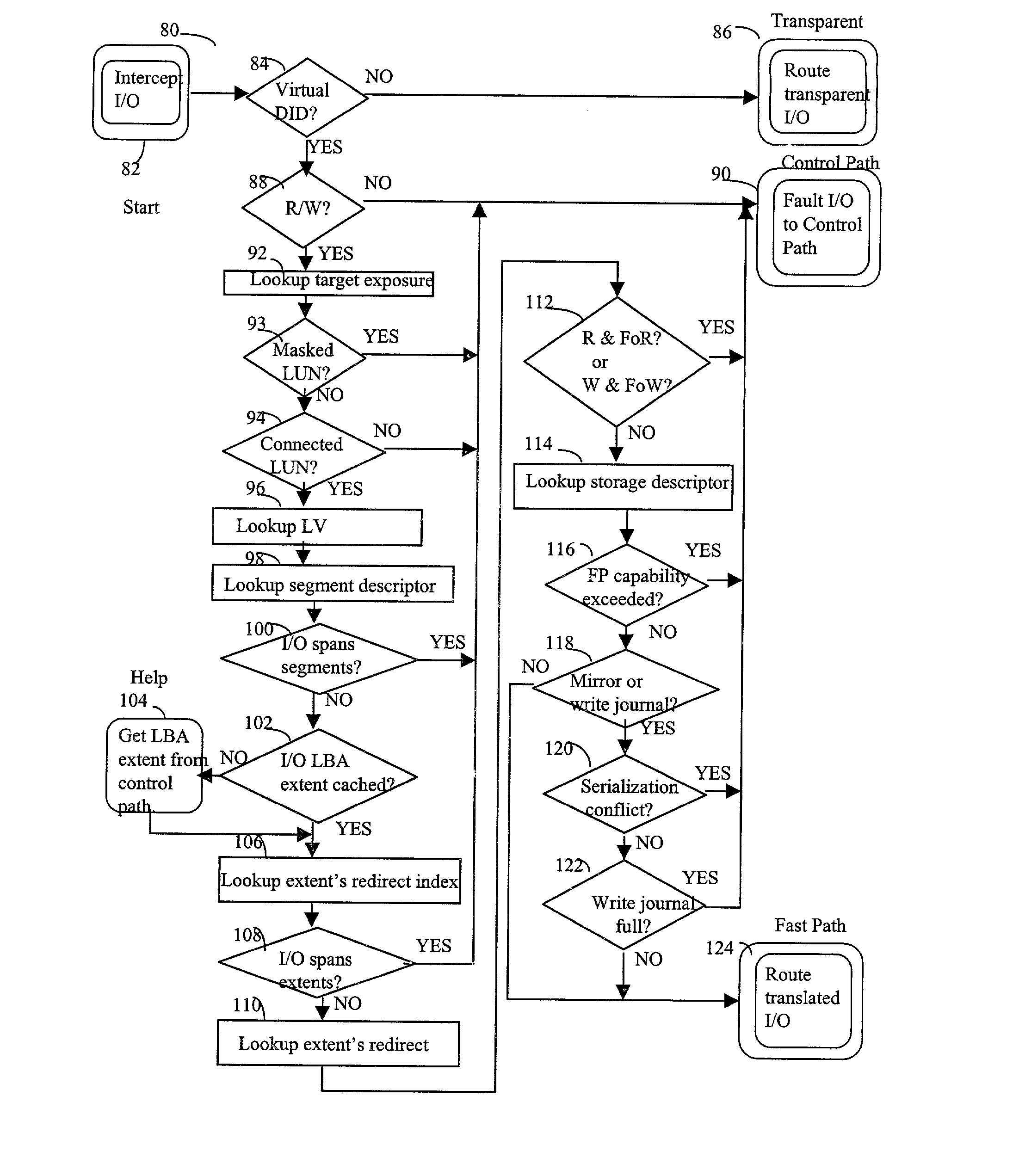
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
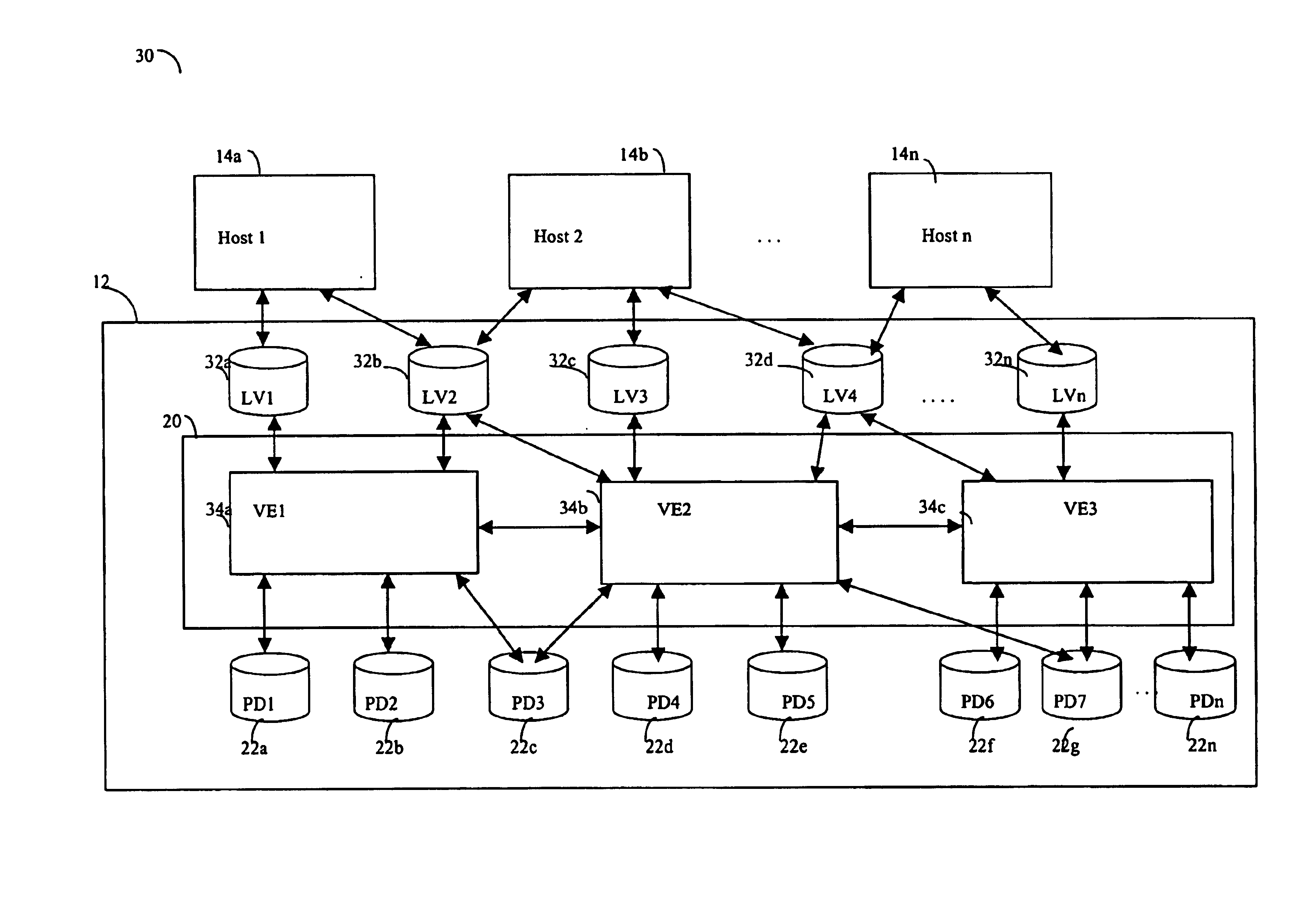
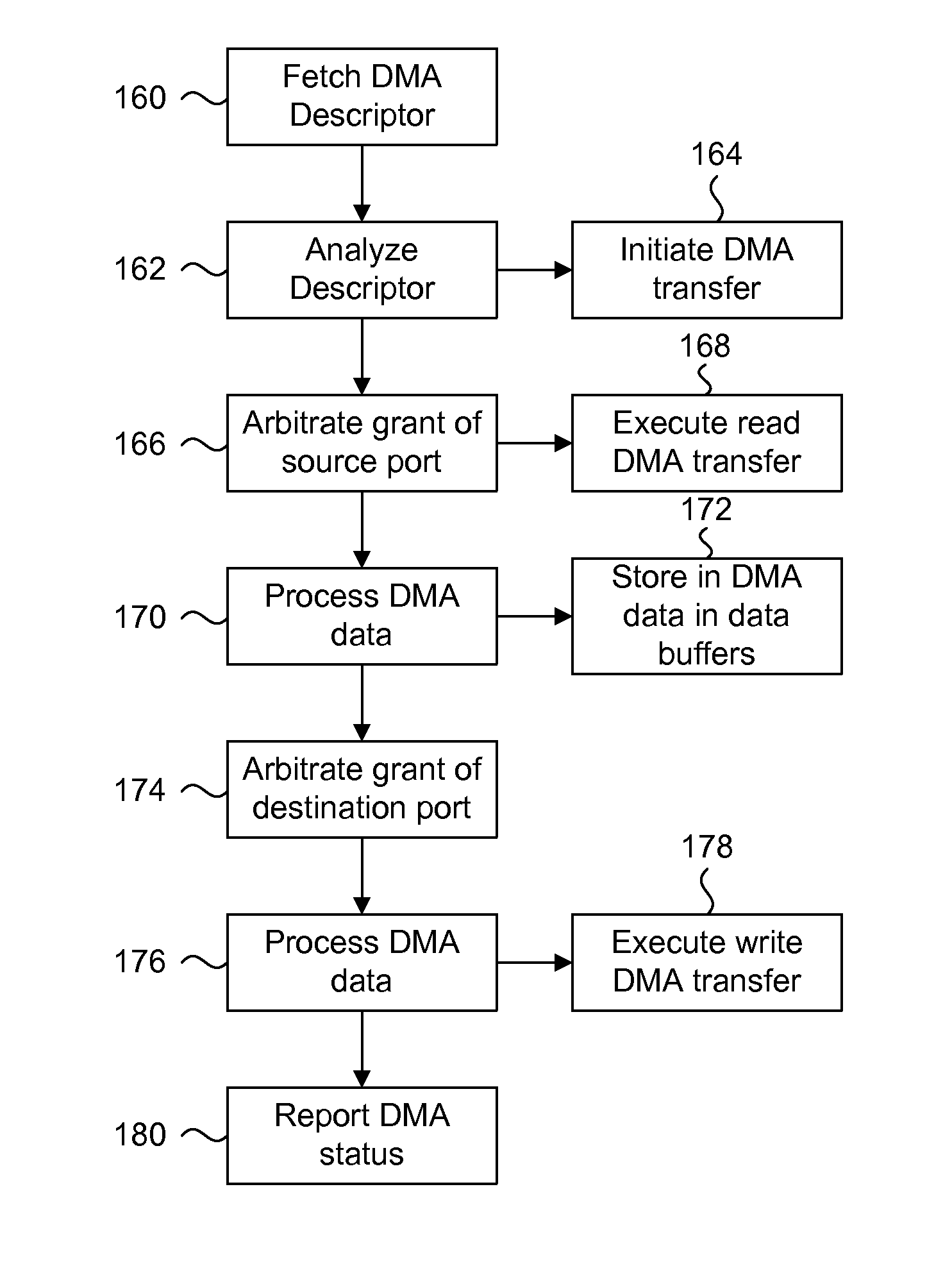
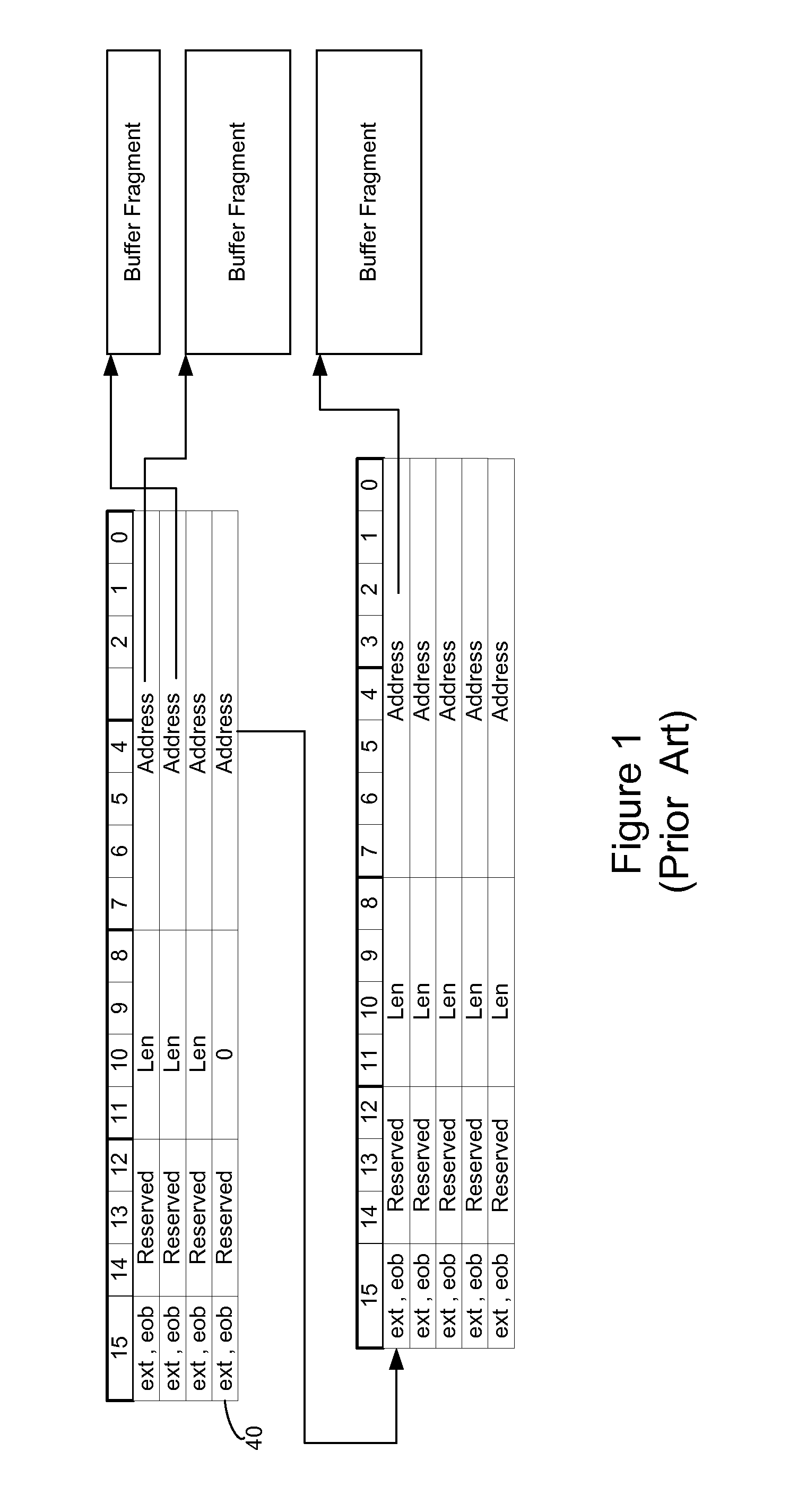
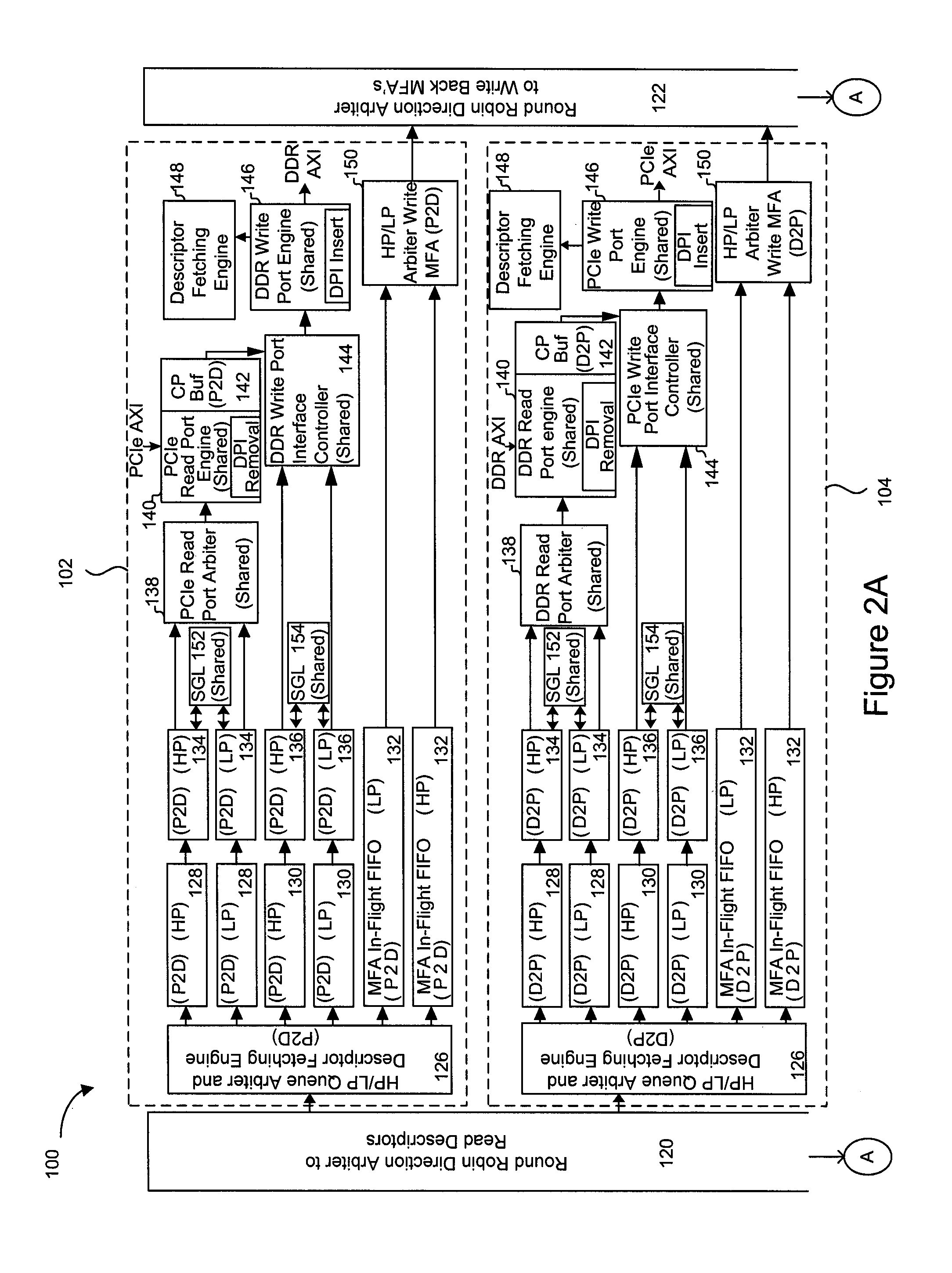
Logical address direct memory access with multiple concurrent physical ports and internal switching
A DMA engine is provided that is suitable for higher performance System On a Chip (SOC) devices that have multiple concurrent on-chip / off-chip memory spaces. The DMA engine operates either on logical addressing method or physical addressing method and provides random and sequential mapping function from logical address to physical address while supporting frequent context switching among a large number of logical address spaces. Embodiments of the present invention utilize per direction (source-destination) queuing and an internal switch to support non-blocking concurrent transfer of data on multiple directions. A caching technique can be incorporated to reduce the overhead of address translation.
Owner:MICROSEMI SOLUTIONS (US) INC
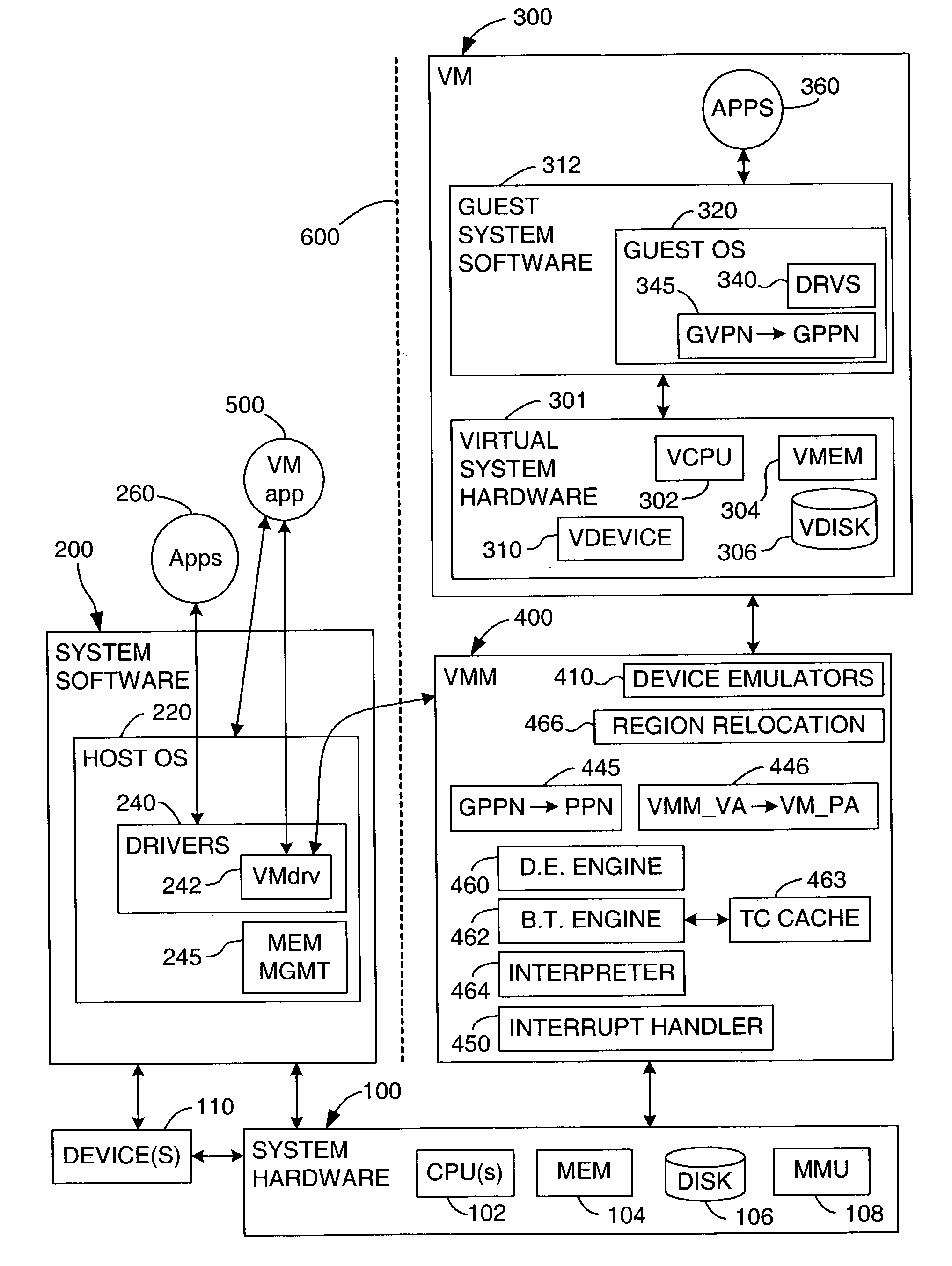
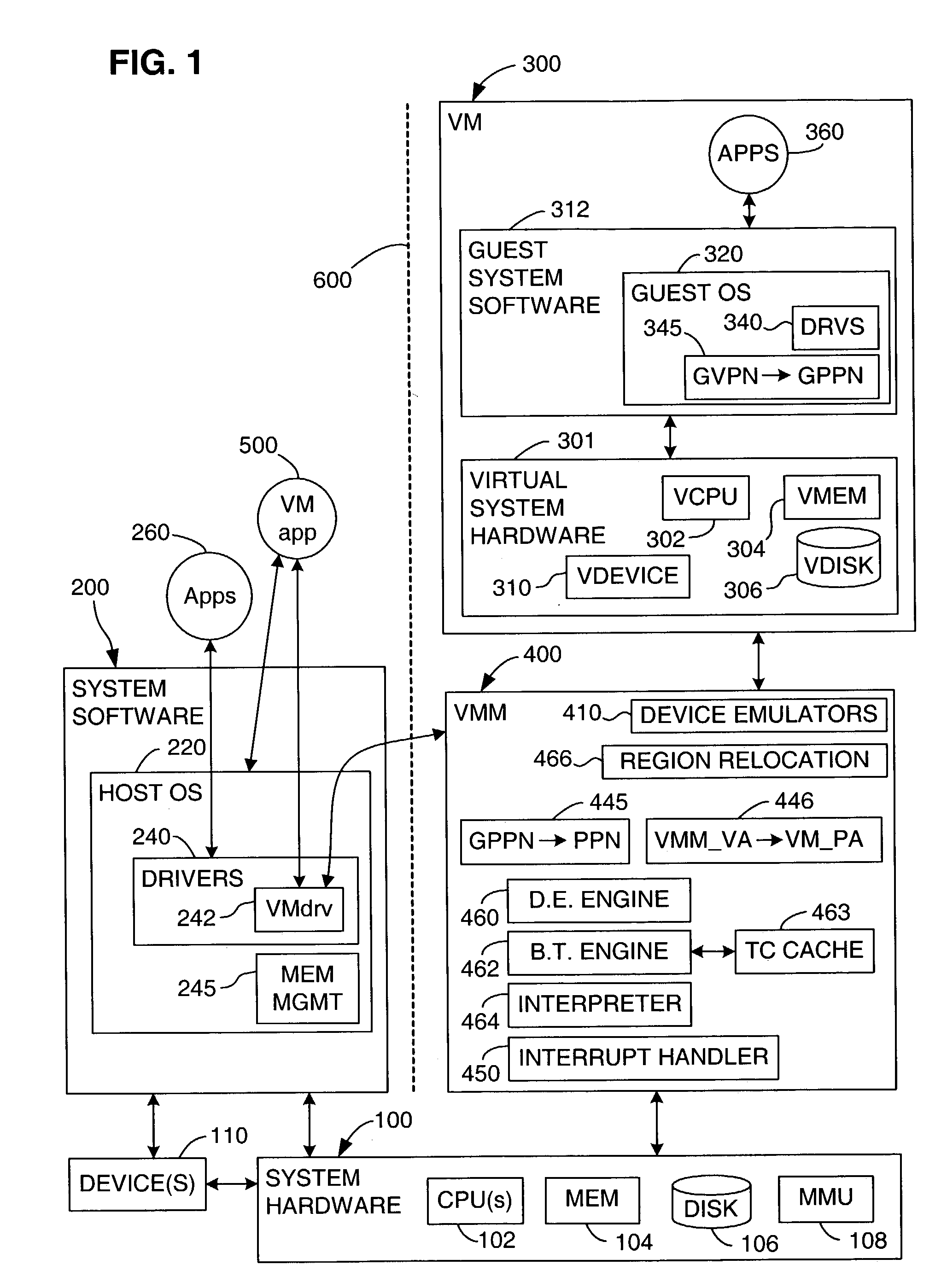
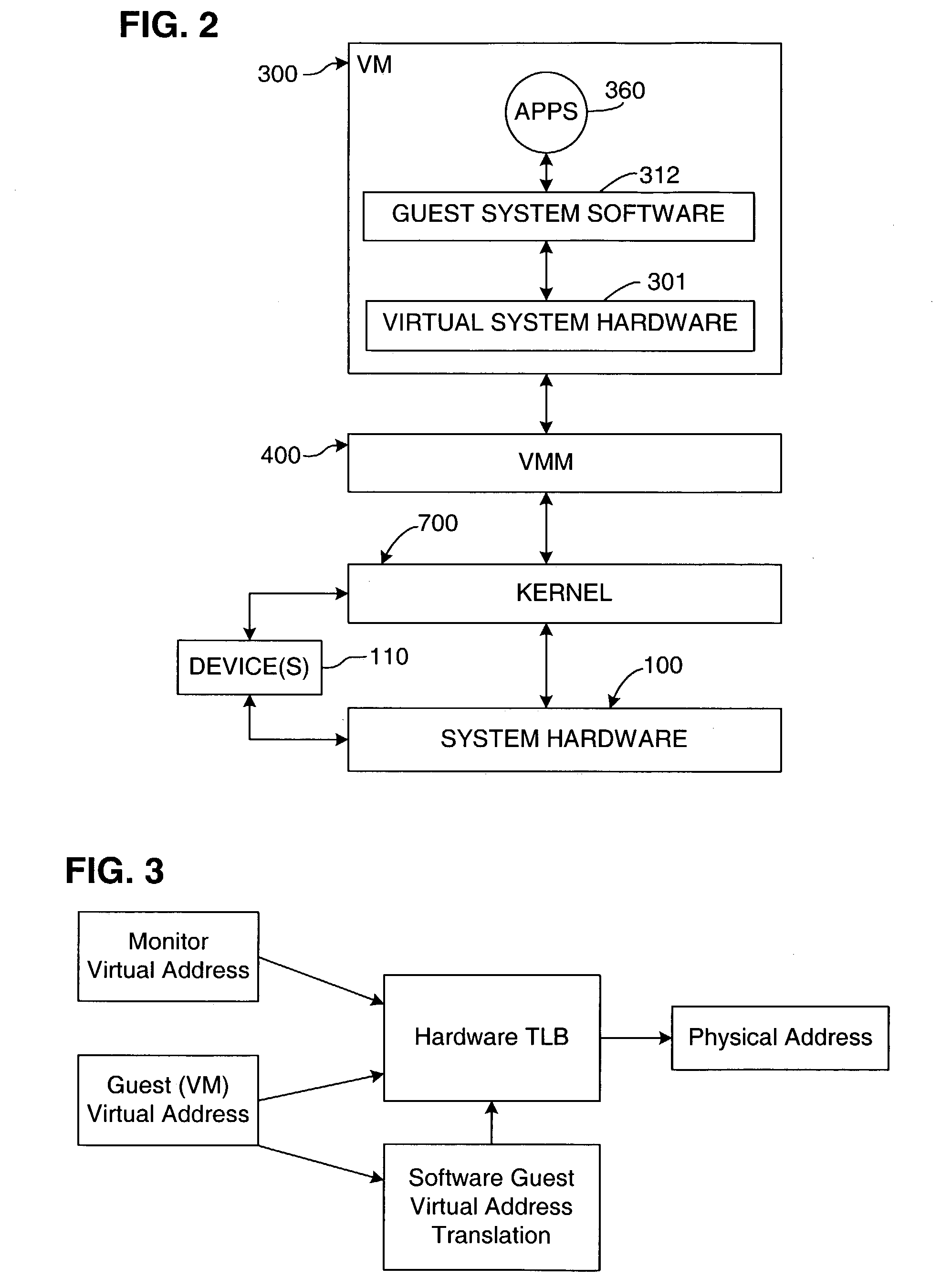
Processor-architecture for facilitating a virtual machine monitor
InactiveUS20050091652A1Easy to operateGeneral purpose stored program computerMultiprogramming arrangementsVirtualizationVirtual address space
Virtual-machine-monitor operation and implementation is facilitated by number of easily implemented features and extensions added to the features of a processor architecture. These features, one or more of which are used in various embodiments of the present invention, include a vmsw instruction that provides a means for transitioning between virtualization mode and non-virtualization mode without an interruption, a virtualization fault that faults on an attempt by a priority-0 routine in virtualization mode attempting to execute a privileged instruction, and a flexible highest-implemented-address mechanism to partition virtual address space into a virtualization address space and a non-virtualization address space.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
TLB miss fault handler and method for accessing multiple page tables
ActiveUS7111145B1Memory adressing/allocation/relocationComputer security arrangementsVirtual memoryError processing
A virtual memory system implementing the invention provides concurrent access to translations for virtual addresses from multiple address spaces. One embodiment of the invention is implemented in a virtual computer system, in which a virtual machine monitor supports a virtual machine. In this embodiment, the invention provides concurrent access to translations for virtual addresses from the respective address spaces of both the virtual machine monitor and the virtual machine. Multiple page tables contain the translations for the multiple address spaces. Information about an operating state of the computer system, as well as an address space identifier, are used to determine whether, and under what circumstances, an attempted memory access is permissible. If the attempted memory access is permissible, the address space identifier is also used to determine which of the multiple page tables contains the translation for the attempted memory access.
Owner:VMWARE INC
Web Service System and Method
ActiveUS20100299437A1Quick identificationEasy to implementDigital computer detailsTransmissionWeb serviceMicroservices
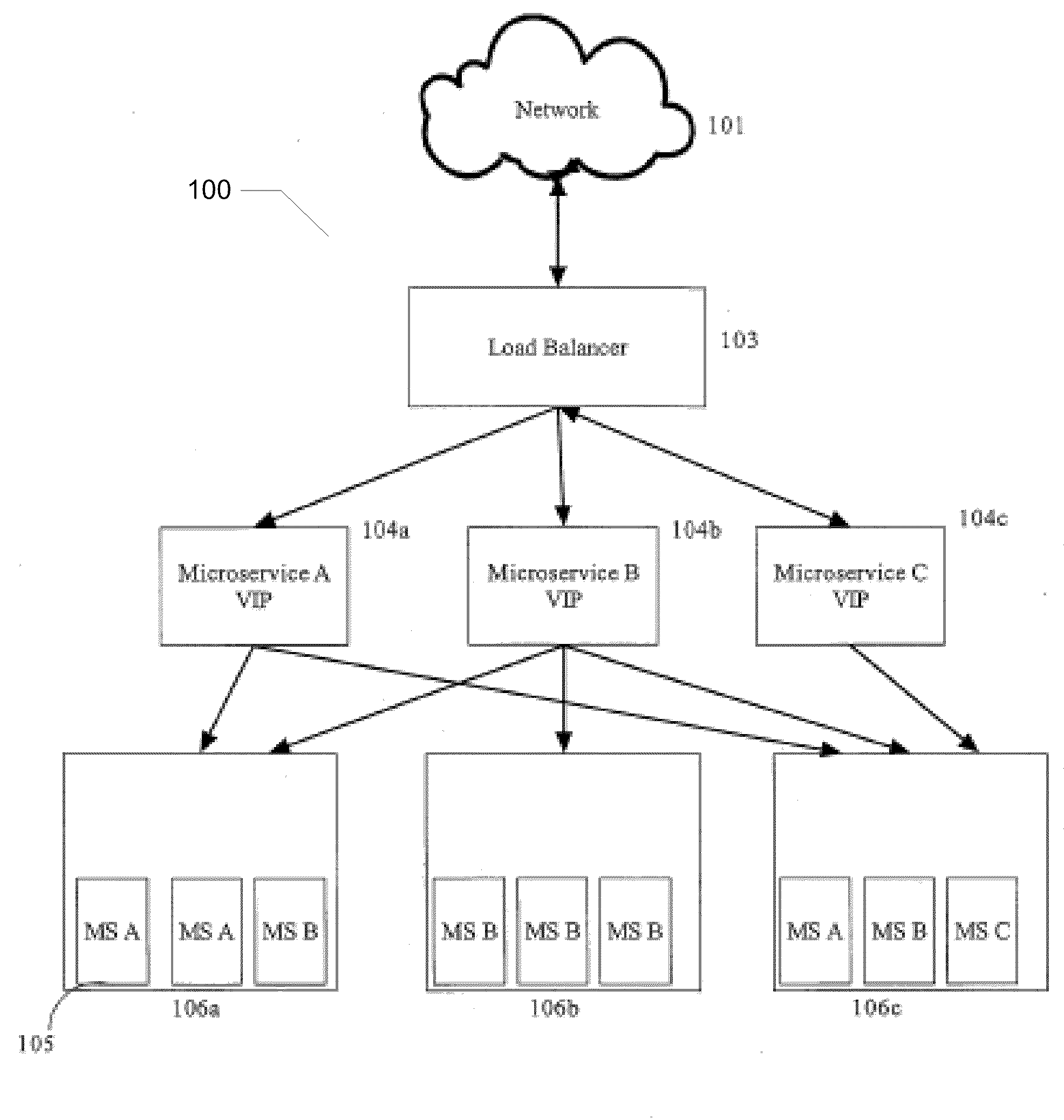
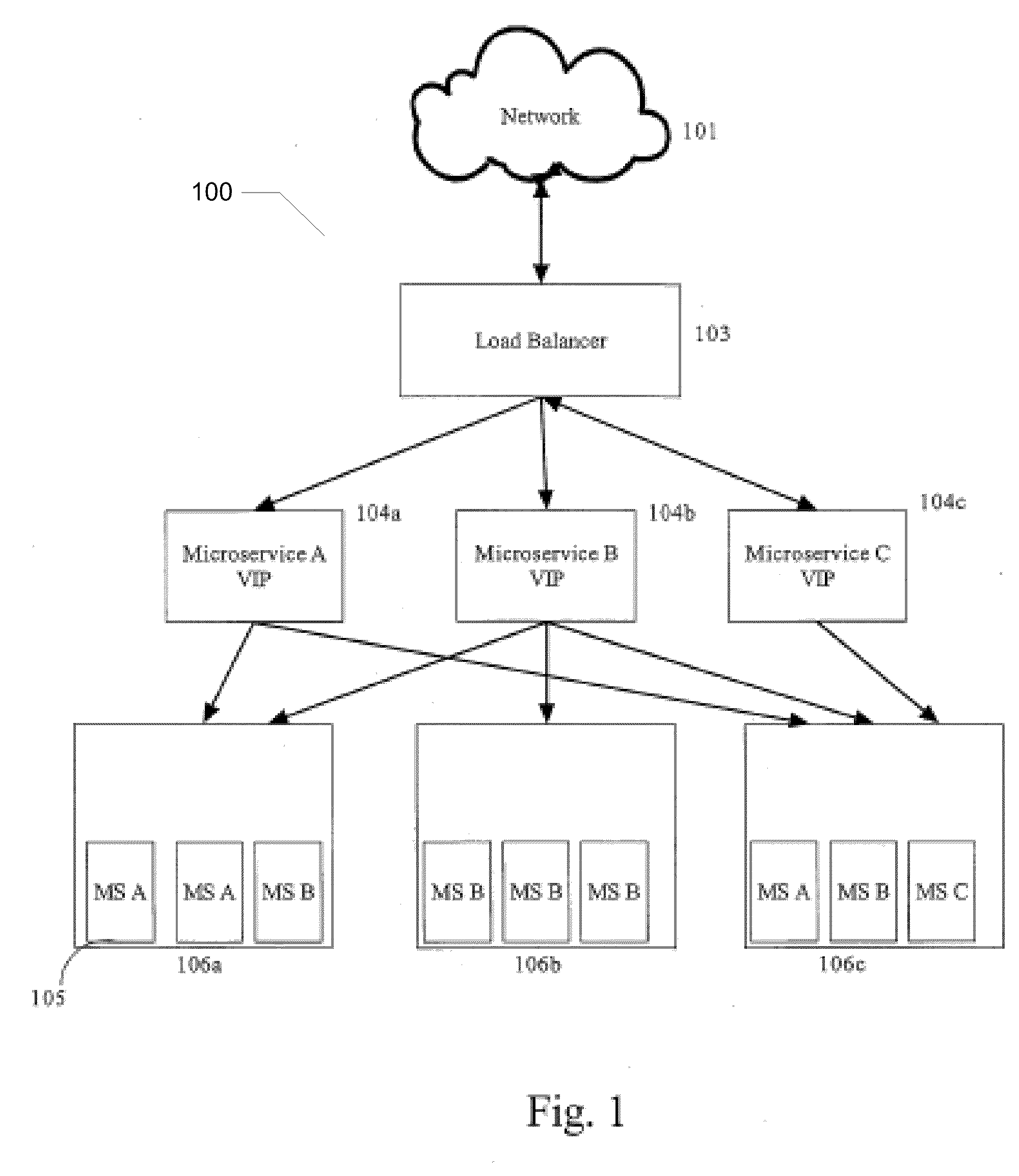
A system for providing a web service on a network of addressable nodes, said web service comprising a plurality of discrete, individually-addressable microservices, said system comprising: (a) at least one load balancer configured for routing a request from a node for a microservice to one of a plurality of virtual addresses, each virtual address corresponding to a unique microservice, and (b) one or more physical nodes associated with each virtual address, each physical node comprising one or more microservices, each microservice comprising a microservice-specific module for executing a particular function, said microservice-specific module linked to an interface for communicating over said network, each microservice being one of a plurality of individually-addressable microservices constituting a web service.
Owner:COMCAST INTERACTIVE MEDIA
Fast path caching
InactiveUS20030140209A1Input/output to record carriersMemory adressing/allocation/relocationFast pathData operations
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
Apparatus, system, and method for application direct virtual memory management
ActiveUS20120210095A1Memory adressing/allocation/relocationMicro-instruction address formationPosition dependentVirtual memory management
An apparatus, system, and method for application direct virtual memory management. The method includes detecting a system memory access to a virtual memory address within a monitored page of data not loaded in main memory of a computing system. The method includes determining a first swap address for a loaded page of data in the main memory. The first swap address is defined in a sparse virtual address space exposed by a persistent storage device. The first swap address is associated in an index with a first deterministic storage location. The index is managed by the persistent storage device. The method includes storing the loaded page on a persistent storage device at the first deterministic storage location. The method includes moving the monitored page from a second deterministic storage location to the main memory. The second deterministic storage location is associated with a second swap address in the index.
Owner:SANDISK TECH LLC
Method for removing duplicate data from a storage array
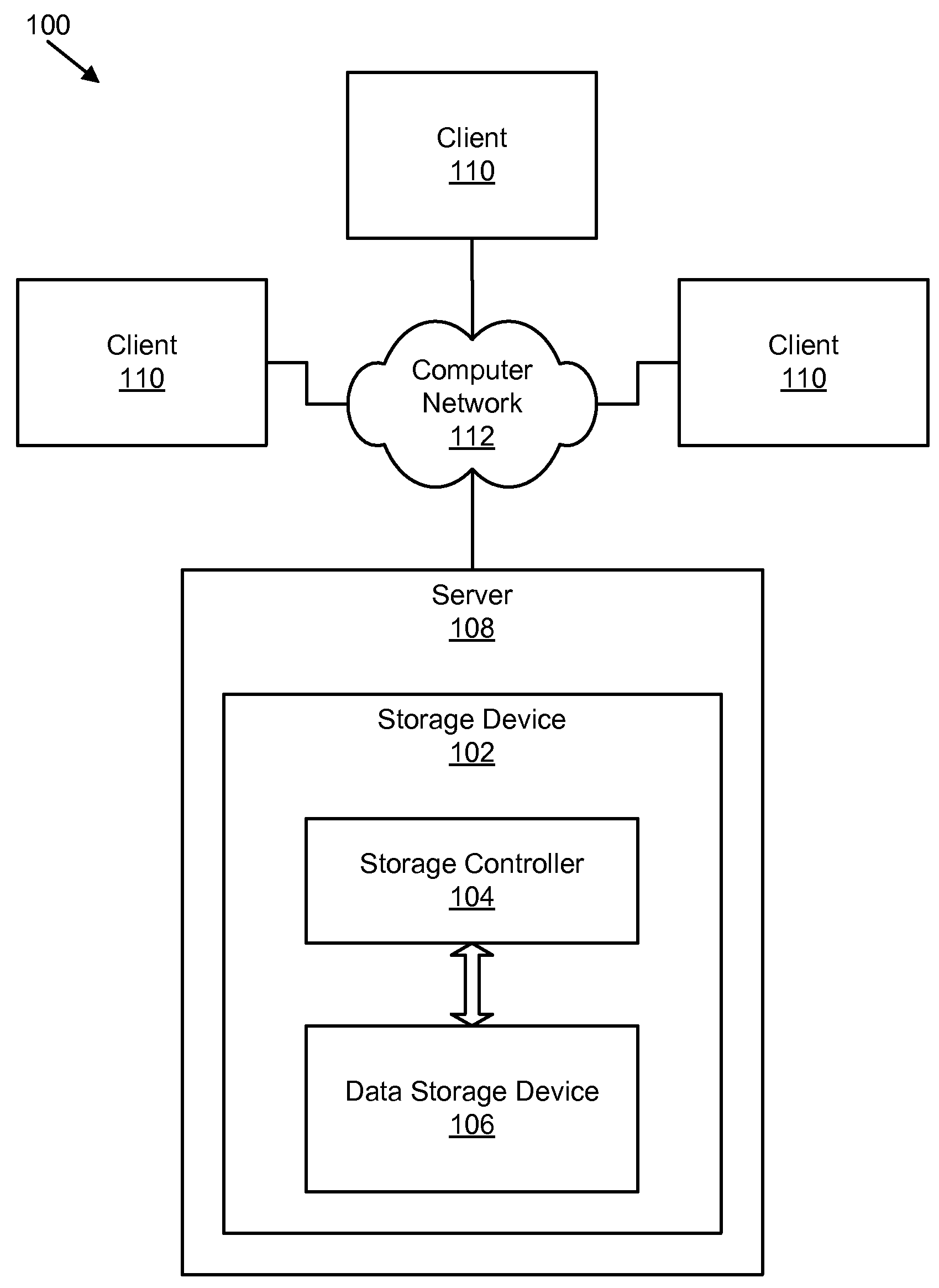
ActiveUS20130086006A1Digital data processing detailsSpecial data processing applicationsGranularityComputer science
A system and method for efficiently removing duplicate data blocks at a fine-granularity from a storage array. A data storage subsystem supports multiple deduplication tables. Table entries in one deduplication table have the highest associated probability of being deduplicated. Table entries may move from one deduplication table to another as the probabilities change. Additionally, a table entry may be evicted from all deduplication tables if a corresponding estimated probability falls below a given threshold. The probabilities are based on attributes associated with a data component and attributes associated with a virtual address corresponding to a received storage access request. A strategy for searches of the multiple deduplication tables may also be determined by the attributes associated with a given storage access request.
Owner:PURE STORAGE
Apparatus, system, and method for validating that a correct data segment is read from a data storage device
ActiveUS20100031000A1Digital data information retrievalMemory adressing/allocation/relocationData segmentNetwork packet
An apparatus, system, and method are disclosed for validating that correct data is read from a storage device. A read request receiver module receives a read storage request to read a data segment of a file or object stored on a data storage device. The storage request includes one or more source parameters for the data segment. The source parameters include one or more virtual addresses that identify the data segment. A hash generation module generates one or more hash values from the virtual addresses. A read data module reads the requested data segment and returns one or more data packets and corresponding stored hash values stored with the data packets. The stored hash values were generated from a data segment written to the data storage device that contains data of the data packets. A hash check module verifies that the generated hash values match the respective stored hash values.
Owner:UNIFICATION TECH LLC
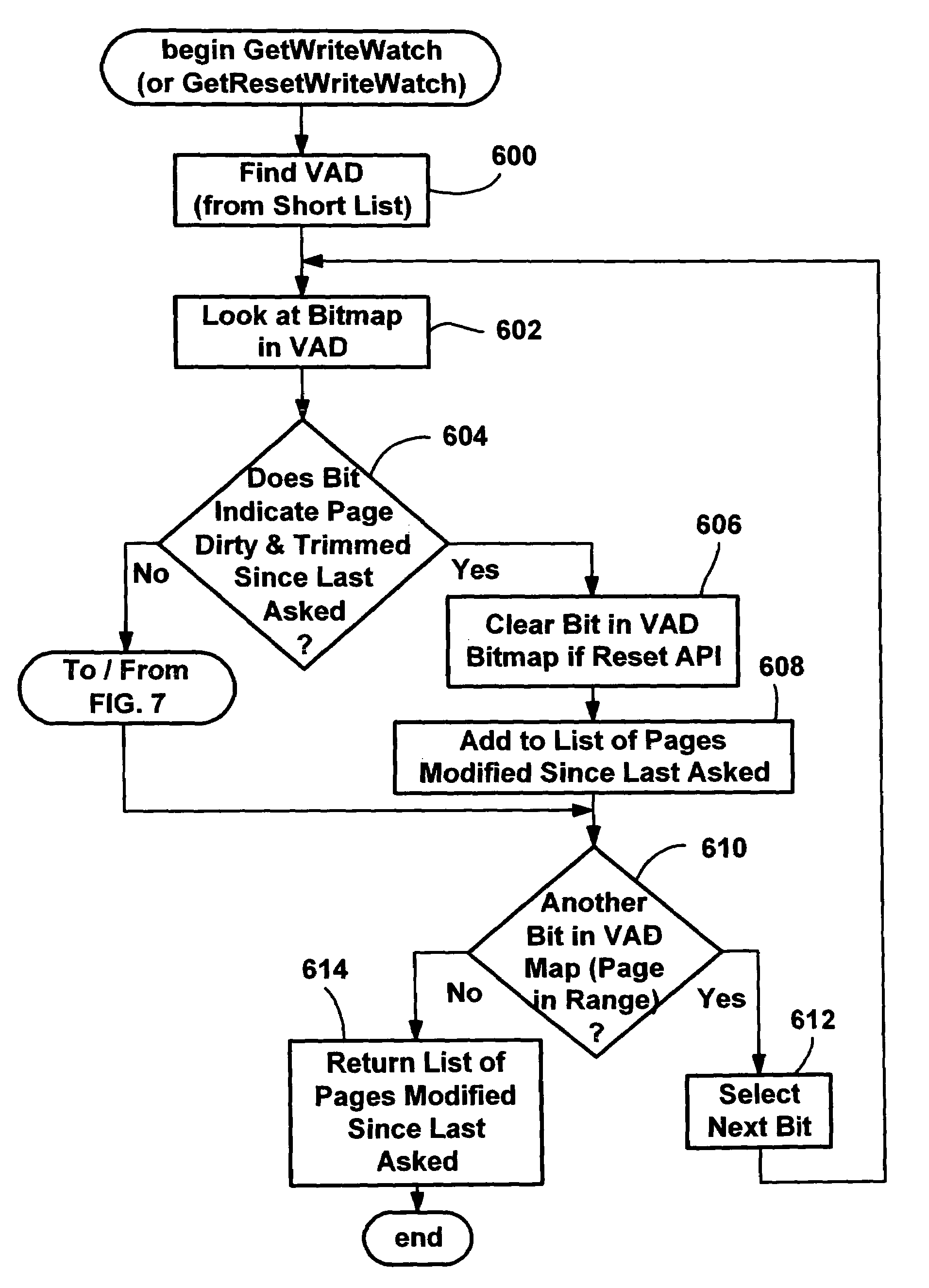
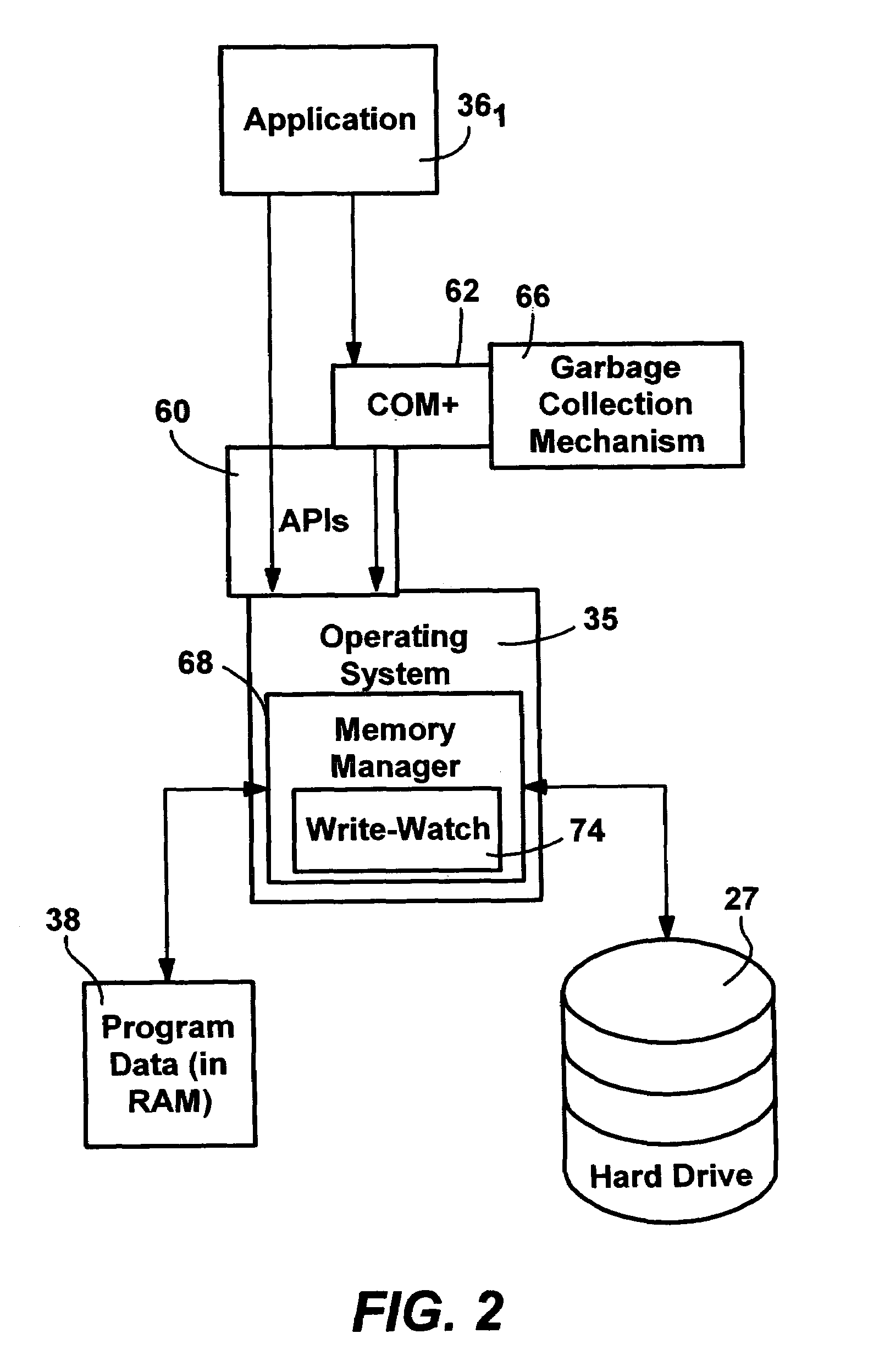
Efficient write-watch mechanism useful for garbage collection in a computer system
InactiveUS7065617B2Efficient write-watchReduce performanceData processing applicationsMemory adressing/allocation/relocationComputerized systemWaste collection
An efficient write-watch mechanism and process. A bitmap is associated with the virtual address descriptor (VAD) for a process, one bit for each virtual page address allocated to a process having write-watch enabled. As part of the write-watch mechanism, if a virtual address is trimmed to disk and that virtual address page is marked as modified, then the corresponding bit in the VAD is set for that virtual address page. In response to an API call (e.g., from a garbage collection mechanism) seeking to know which virtual addresses in a process have been modified since last checked, the memory manager walks the bitmap in the relevant VAD for the specified virtual address range for the requested process. If a bit is set, then the page corresponding to that bit is known to have been modified since last asked. If specified by the API, the bit is cleared in the VAD bitmap so that it will reflect the state since this time of asking. If the bit is not set, to determine if the page was modified, the page table entry (PTE) is checked for that page, and if the PTE indicates the page was modified, the page is known to be modified, otherwise that page is known to be unmodified since the last call. One enhancement uses page directory tables to locate a series of trimmed pages, sometimes avoiding the need to access the PTE.
Owner:MICROSOFT TECH LICENSING LLC
Methods and systems for partners in virtual networks
InactiveUS7028333B2Easily and effectively leverage powerWithout complexityDigital data processing detailsMultiple digital computer combinationsParallel computingVirtual address space
Owner:ORACLE SYST CORP
Method, system, and program for managing memory for data transmission through a network
InactiveUS20050080928A1Memory adressing/allocation/relocationMultiple digital computer combinationsVirtual memoryData transmission
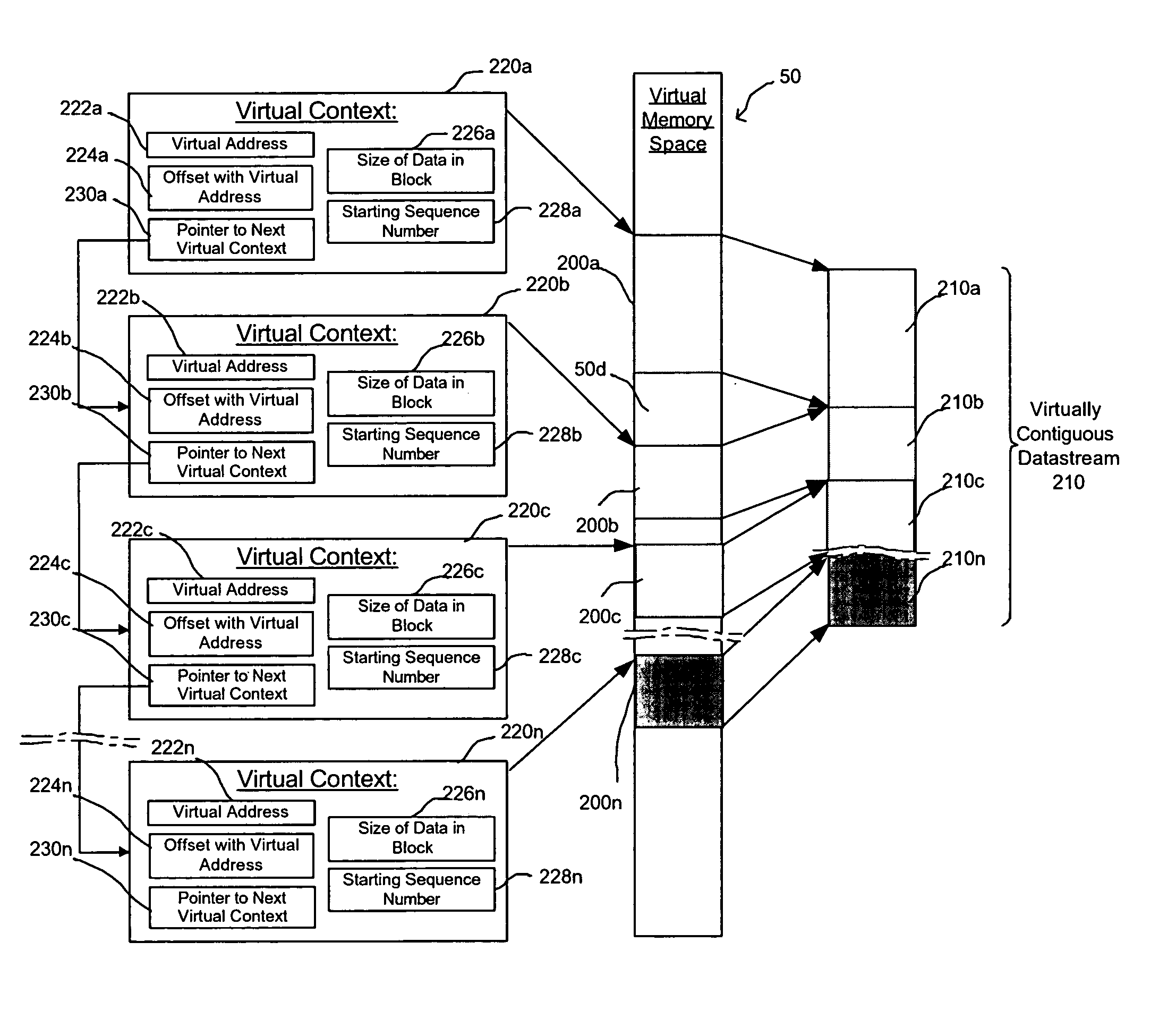
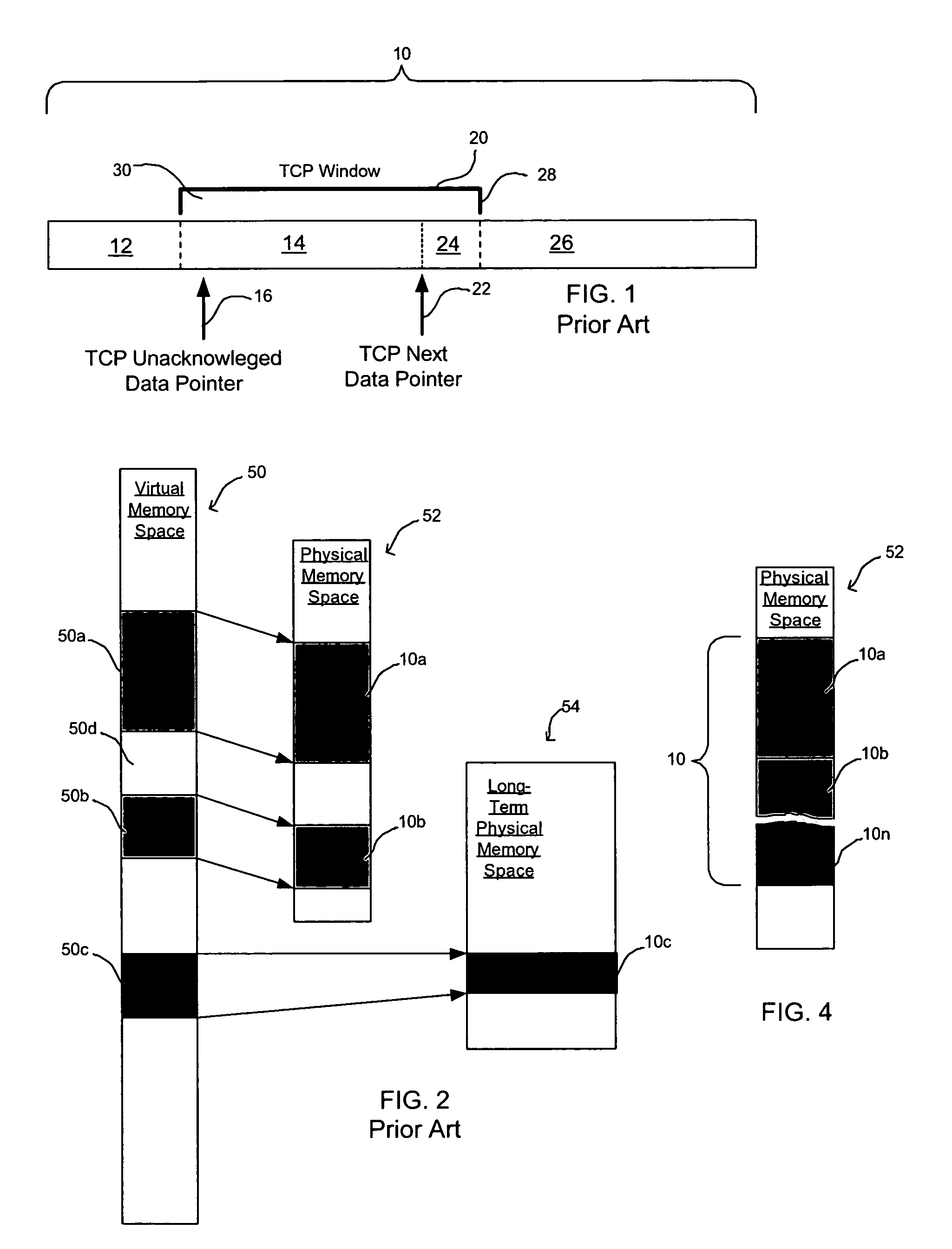
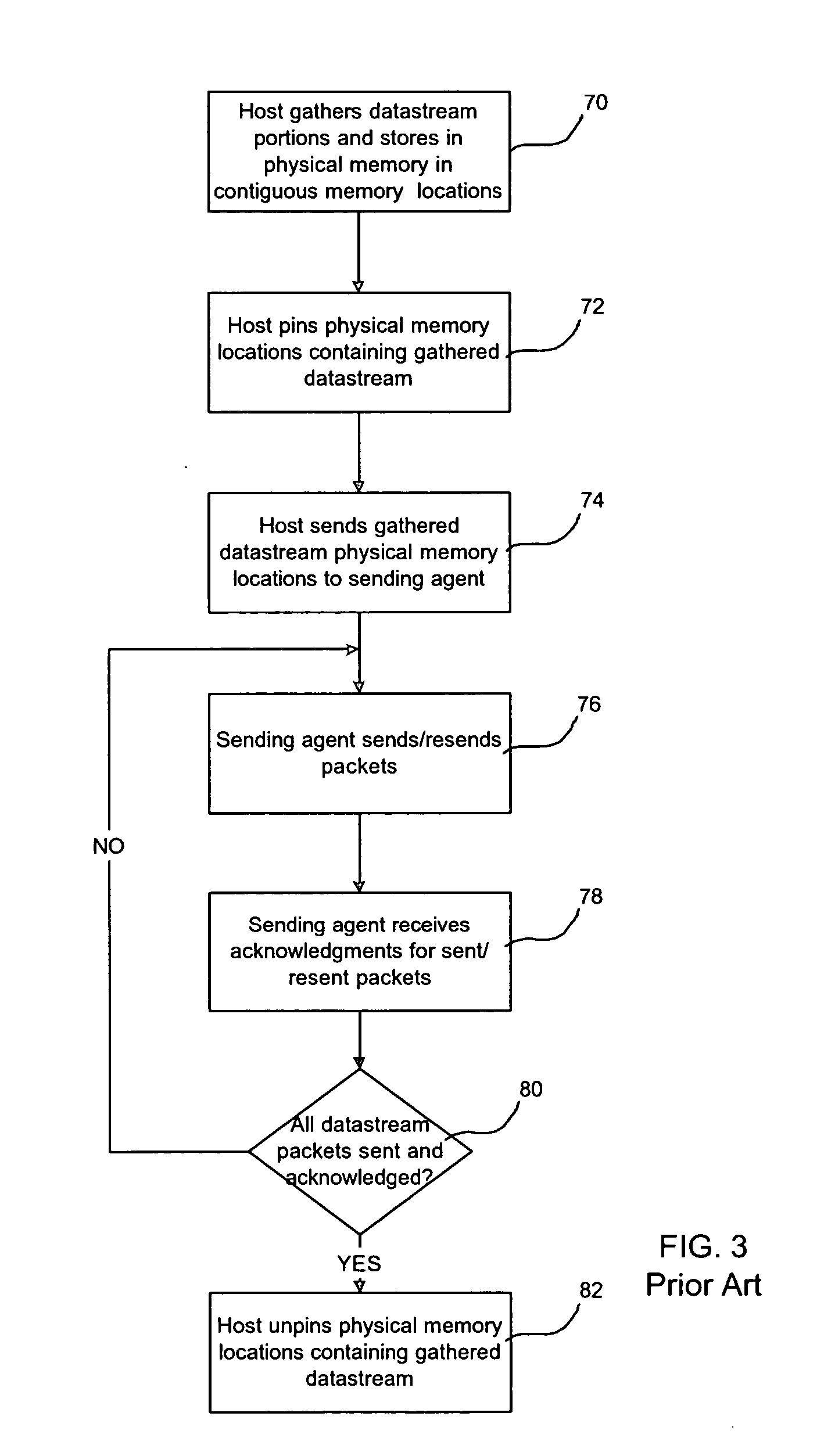
Provided are a method, system, and program for managing memory for data transmission through a network. Virtual memory addresses of the data to be sent are provided to a sending agent. The sending agent provides to a host the virtual addresses of requested data. In response, the requested data addressed by the virtual addresses or the physical memory locations of the requested data are provided to the sending agent for sending to a destination.
Owner:INTEL CORP
Methods and systems for managing virtual addresses for virtual networks
ActiveUS6996628B2Easily and effectively leverage powerWithout complexityDigital data processing detailsMultiple digital computer combinationsComputer scienceVirtual address space
Methods and systems are provided for enabling a virtual network between a first processor and a second processor using at least one additional processor separate from the first processor and the second processor. In one embodiment, the at the at least one additional processor may determine a first virtual address and a first base address for the first processor such that the first virtual address is routable through the virtual network and the first base address is routable through a base network and determine a second virtual address and a second base address for the second processor such that the second virtual address is routable through the virtual network and the second base address is routable through the base network. The at least one additional processor may provide the first virtual address and the first base address to the first processor and the second virtual address and the second base address to the second processor. Moreover, the virtual network may be enabled over the base network based on the first virtual address, the first base address, the second virtual address, and the second base address.
Owner:ORACLE SYST CORP
User interface for a file system shell
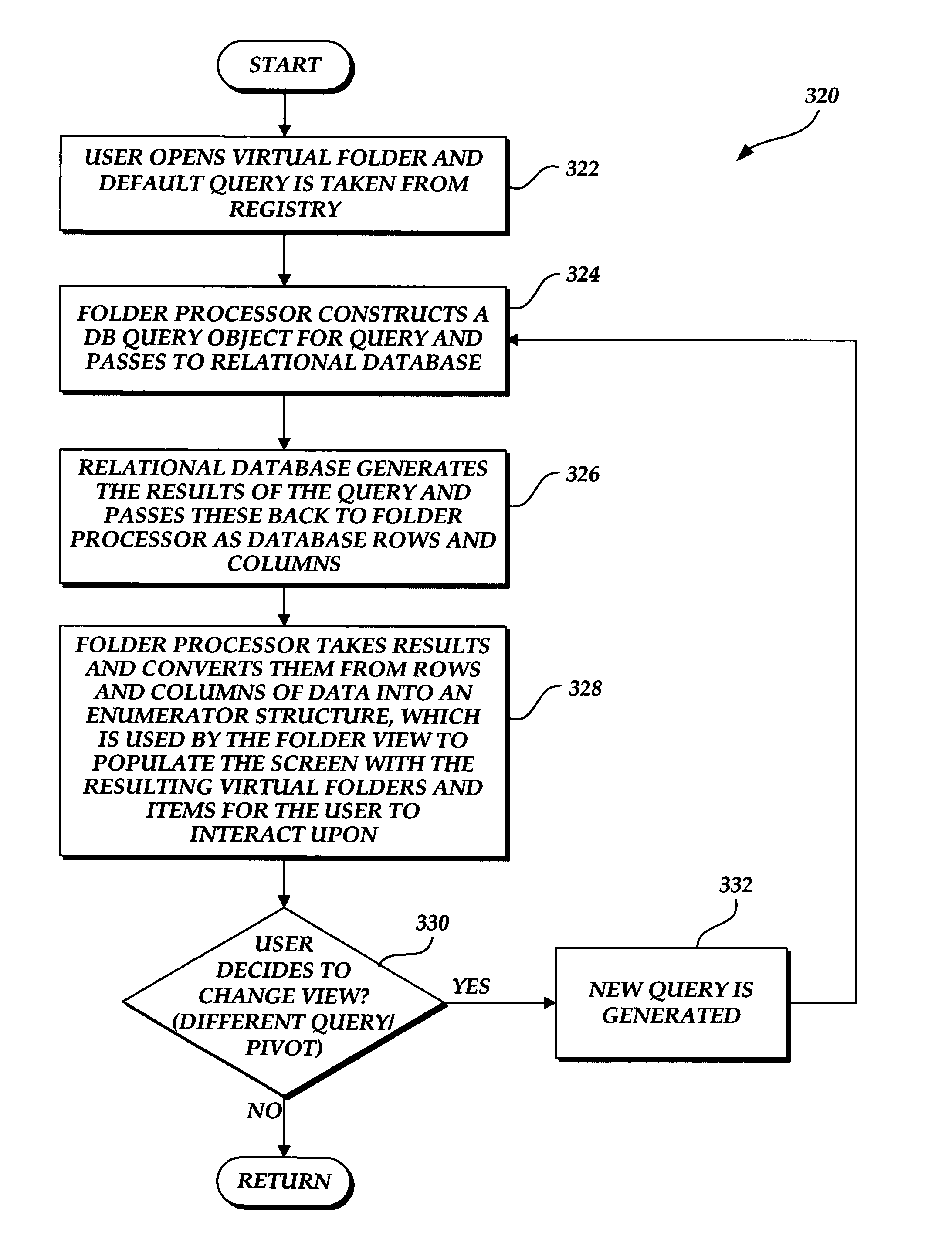
InactiveUS7769794B2Adapt quicklyDigital data information retrievalSpecial data processing applicationsView basedFile system
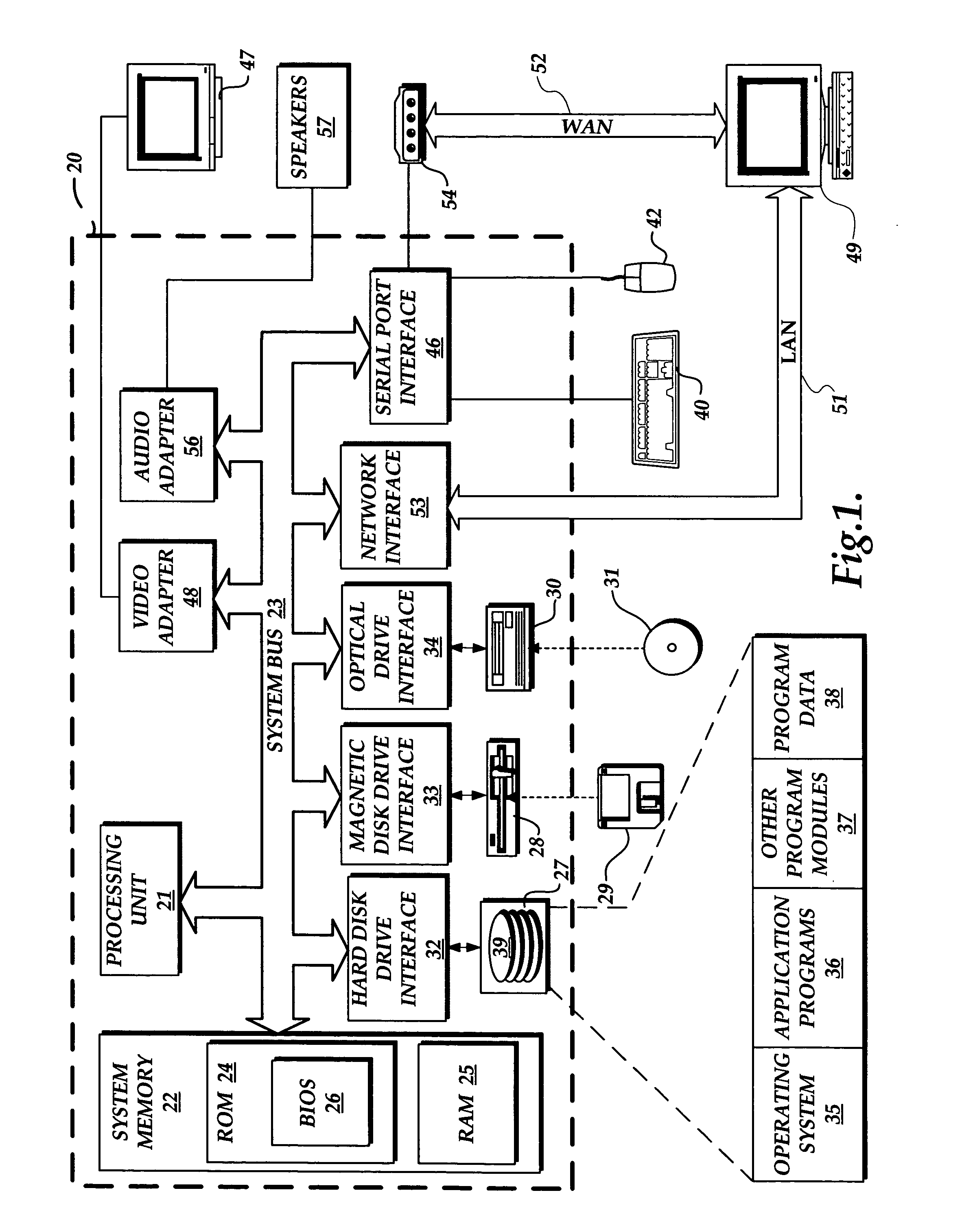
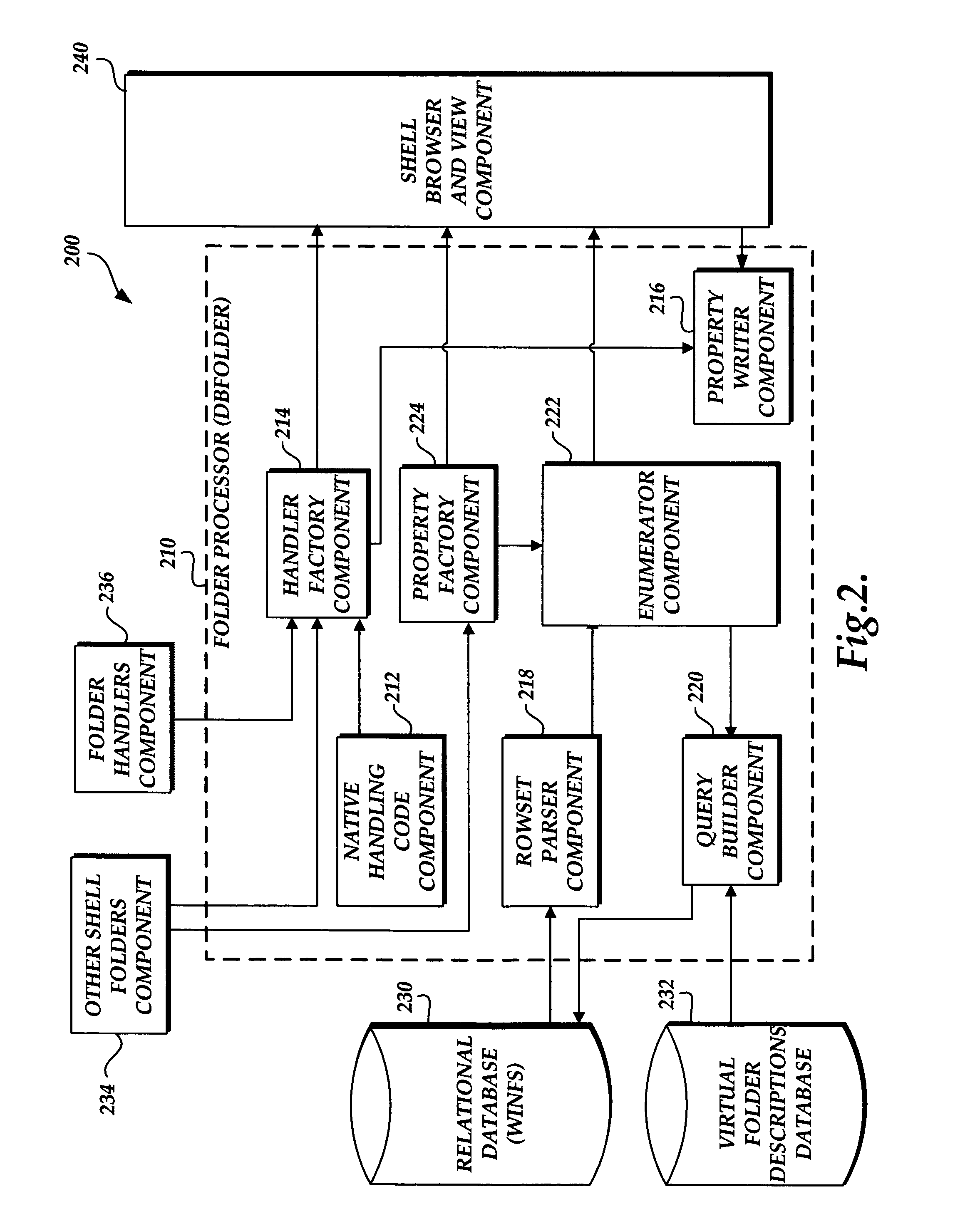
A file system shell is provided. One aspect of the shell provides virtual folders which expose regular files and folders to users in different views based on their metadata instead of the actual physical underlying file system structure on the disk. Users are able to work with the virtual folders through direct manipulation (e.g., clicking and dragging, copying, pasting, etc.). Filters are provided for narrowing down sets of items. Quick links are provided which can be clicked on to generate useful views of the sets of items. Libraries are provided which consist of large groups of usable types of items that can be associated together, along with functions and tools related to the items. A virtual address bar is provided which comprises a plurality of segments, each segment corresponding to a filter for selecting content. A shell browser is provided with which users can readily identify an item based on the metadata associated with that item. An object previewer in a shell browser is provided which is configured to display a plurality of items representing multiple item types.
Owner:MICROSOFT TECH LICENSING LLC
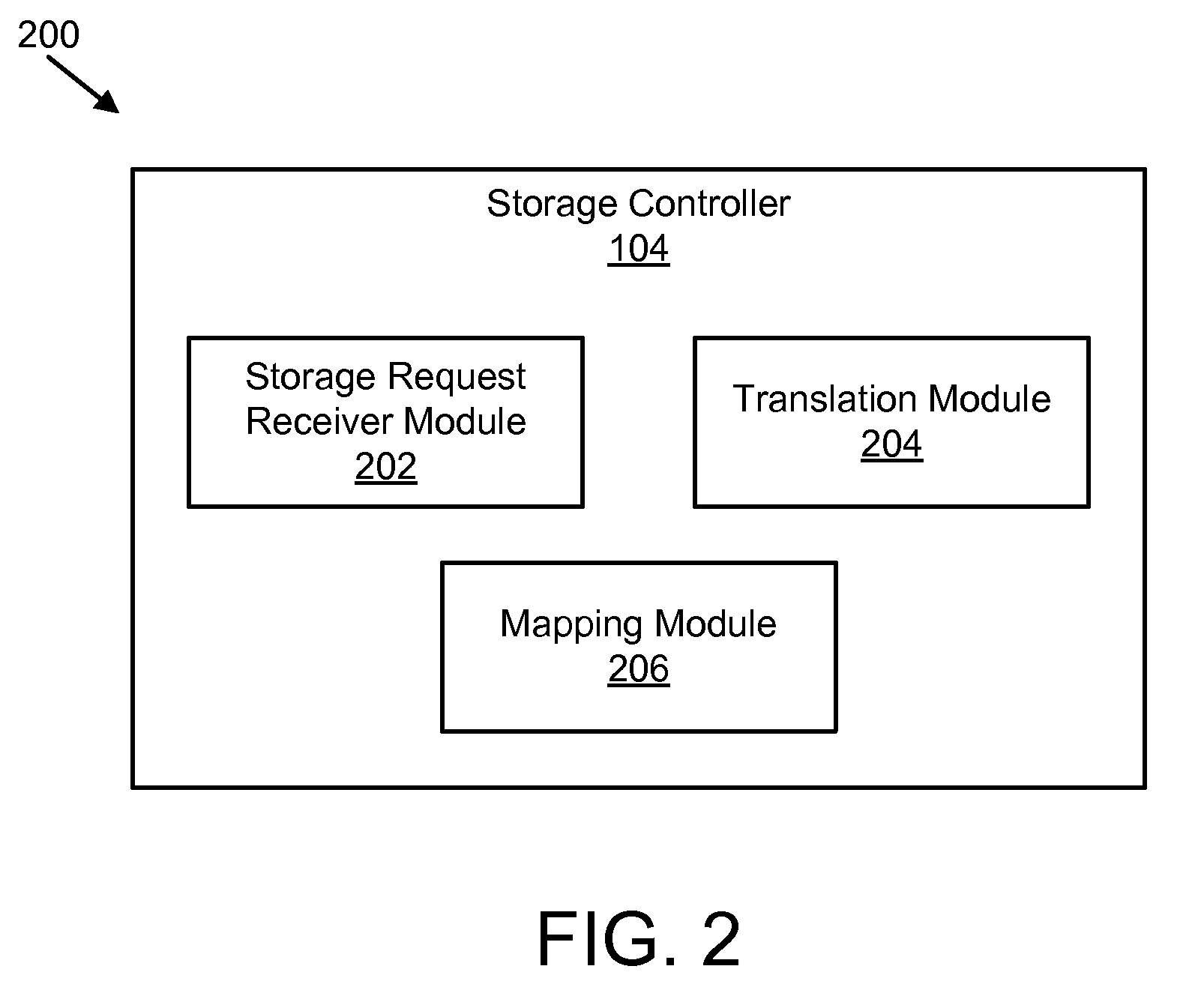
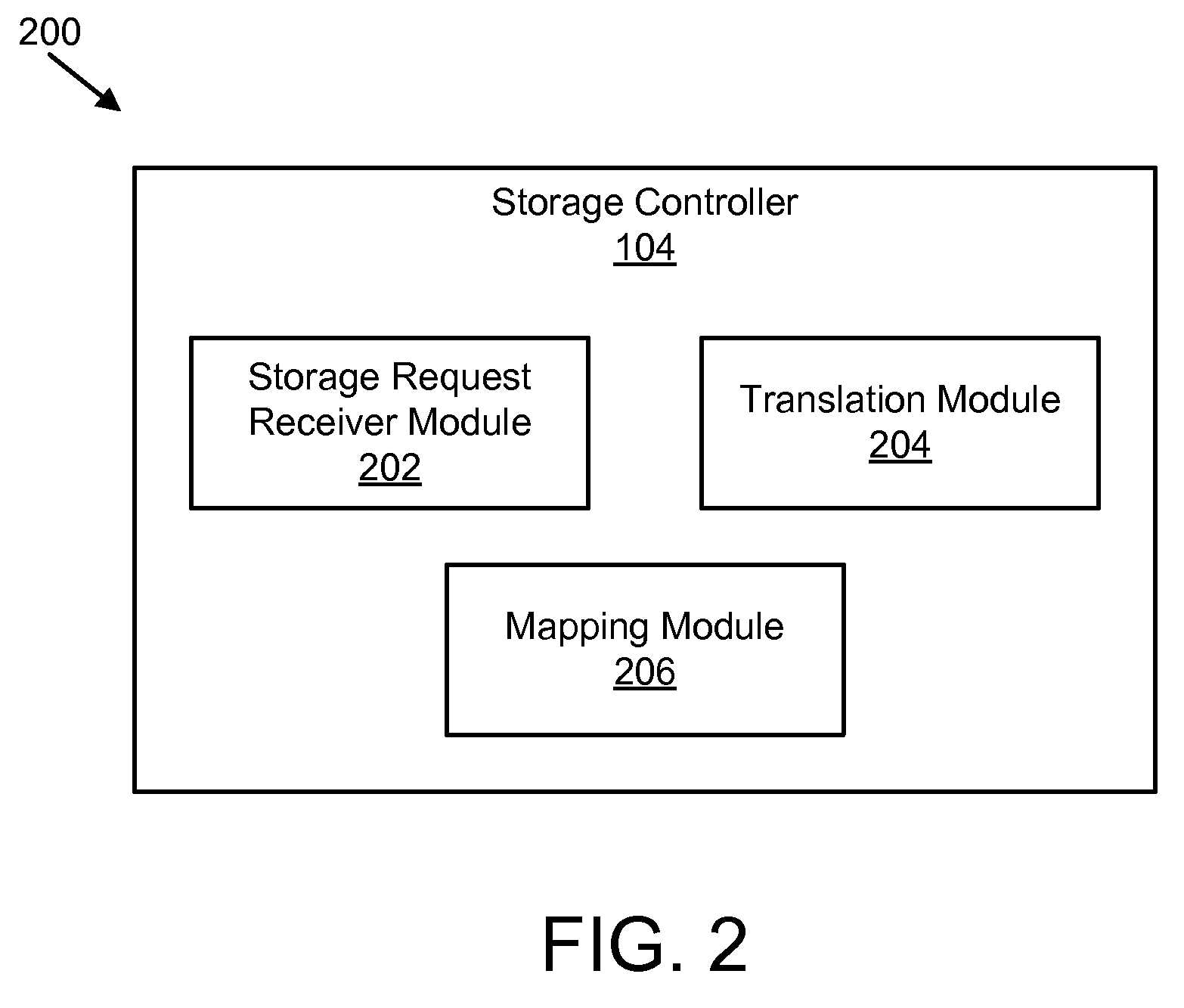
Apparatus, system, and method for converting a storage request into an append data storage command
ActiveUS20090150605A1Shorten write timeImprove efficiencyMemory architecture accessing/allocationProgram synchronisationData segmentNetwork packet
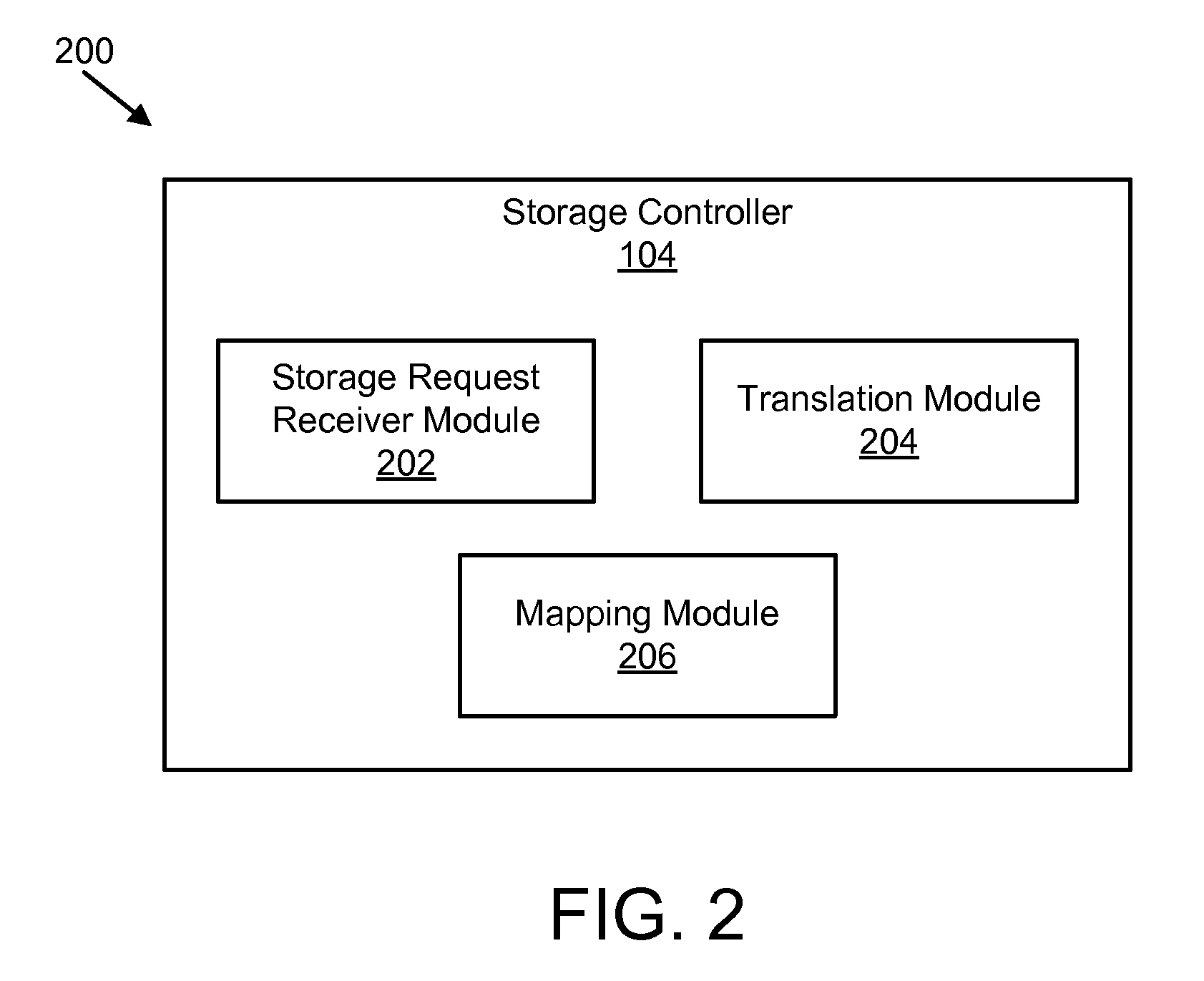
An apparatus, system, and method are disclosed for converting a storage request to an append data storage command. A storage request receiver module receives a storage request from a requesting device. The storage request is to store a data segment onto a data storage device. The storage request includes source parameters for the data segment. The source parameters include a virtual address. A translation module translates the storage request to storage commands. At least one storage command includes an append data storage command that directs the data storage device to store data of the data segment and the one or more source parameters with the data, including a virtual address, at one or more append points. A mapping module maps source parameters of the data segment to locations where the data storage device appended the data packets of the data segment and source parameters.
Owner:UNIFICATION TECH LLC
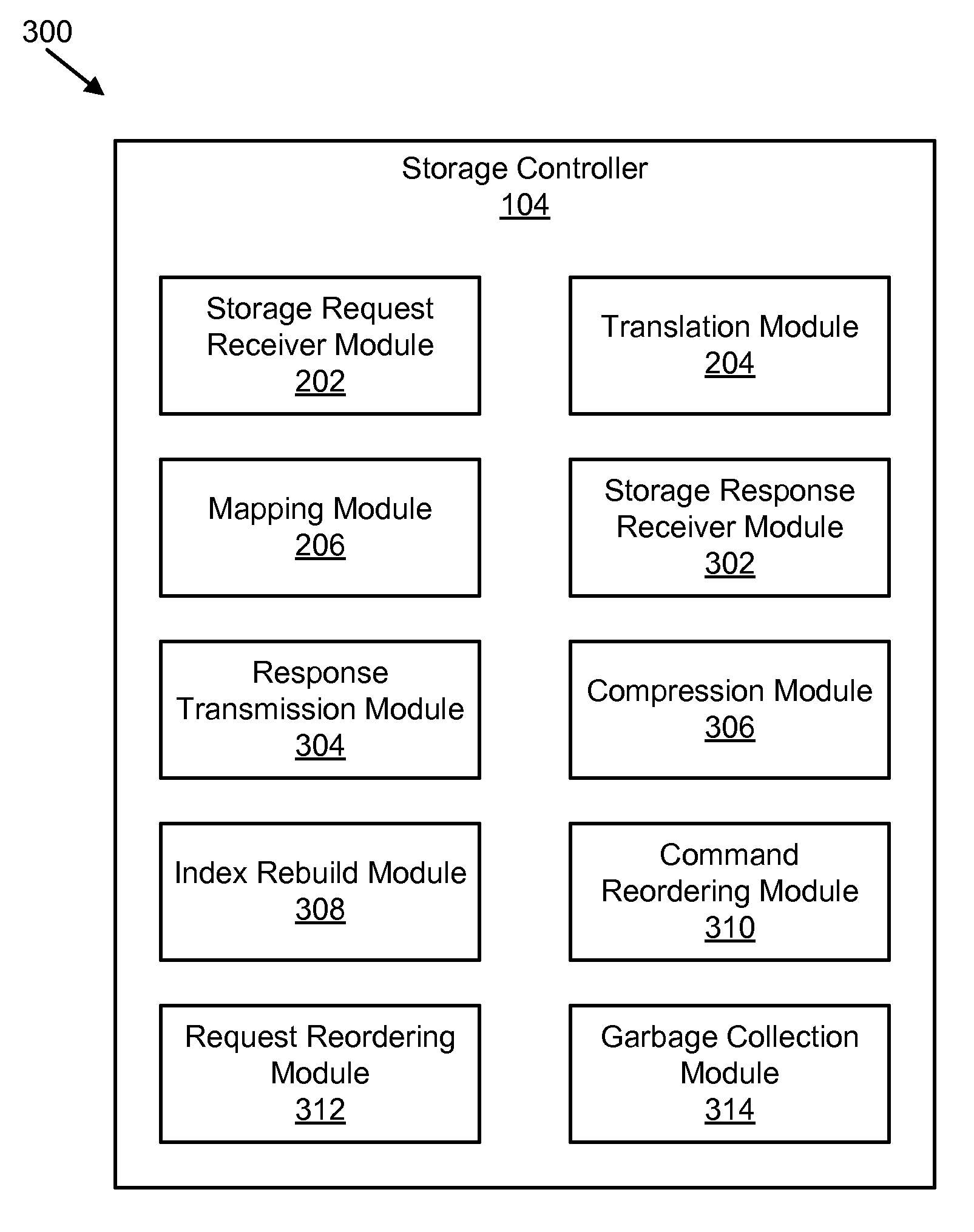
Apparatus, system, and method for efficient mapping of virtual and physical addresses
ActiveUS20090150641A1Efficient mappingEfficient identificationMemory architecture accessing/allocationProgram synchronisationData segmentData store
An apparatus, system, and method are disclosed for efficiently mapping virtual and physical addresses. A forward mapping module uses a forward map to identify physical addresses of data of a data segment from a virtual address. The data segment is identified in a storage request. The virtual addresses include discrete addresses within a virtual address space where the virtual addresses sparsely populate the virtual address space. A reverse mapping module uses a reverse map to determine a virtual address of a data segment from a physical address. The reverse map maps the data storage device into erase regions such that a portion of the reverse map spans an erase region of the data storage device erased together during a storage space recovery operation. A storage space recovery module uses the reverse map to identify valid data in an erase region prior to an operation to recover the erase region.
Owner:UNIFICATION TECH LLC
I/O primitives
InactiveUS7013379B1Error detection/correctionMemory adressing/allocation/relocationFast pathLocking mechanism
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
Dynamic and variable length extents
InactiveUS20030140210A1Input/output to record carriersMemory adressing/allocation/relocationVariable-length codeFast path
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
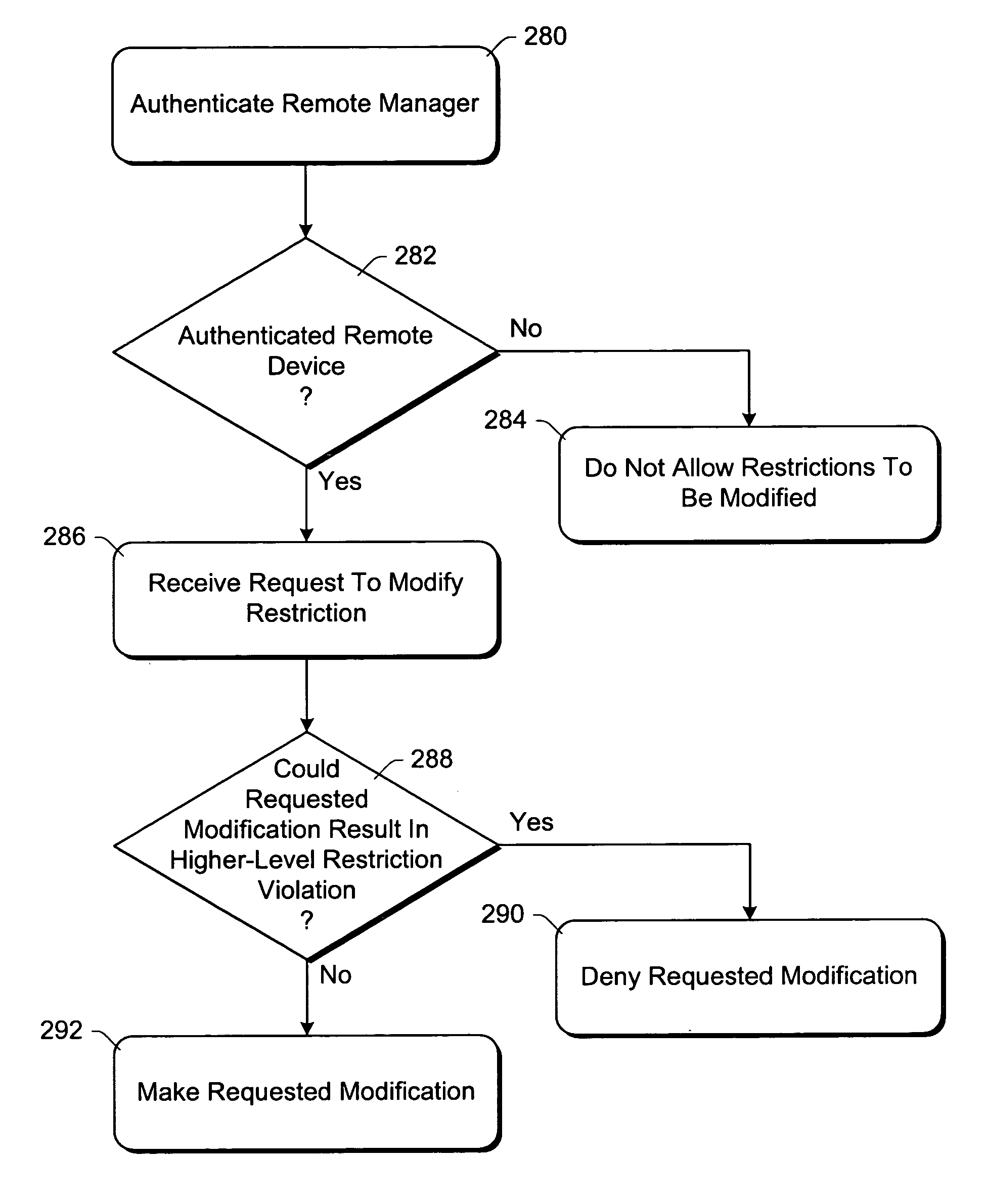
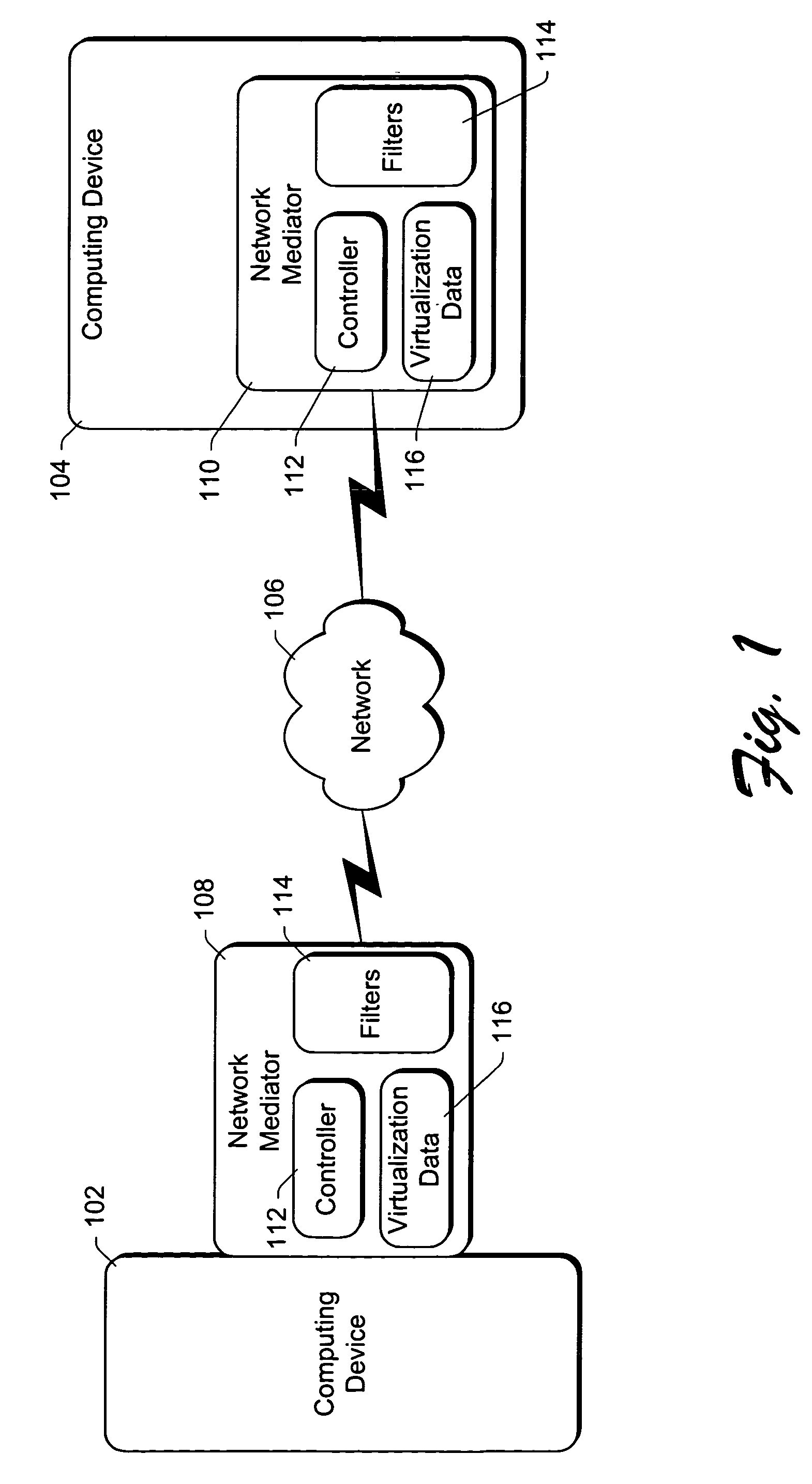
Using packet filters and network virtualization to restrict network communications
InactiveUS7093288B1Communication be restrictRandom number generatorsCharacter and pattern recognitionNetwork packetNetwork addressing
A network mediator corresponding to a computing device uses packet filters to restrict network communications. The network mediator includes a set of one or more filters, each filter having parameters that are compared to corresponding parameters of a data packet to be passed through the network mediator. The network mediator determines whether to allow the data packet through based on whether the data packet parameters match any filter parameters. The set of filters can be modified by a remote device, but cannot be modified by the computing device whose communications are being restricted. When a data packet is sent from the computing device, the data packet will include the virtual address which is changed to the network address by the network mediator prior to forwarding the packet on the network, and vice versa. By virtualizing the addresses, the computing device is restricted in accessing other devices over the network.
Owner:MICROSOFT TECH LICENSING LLC
Providing global translations with address space numbers
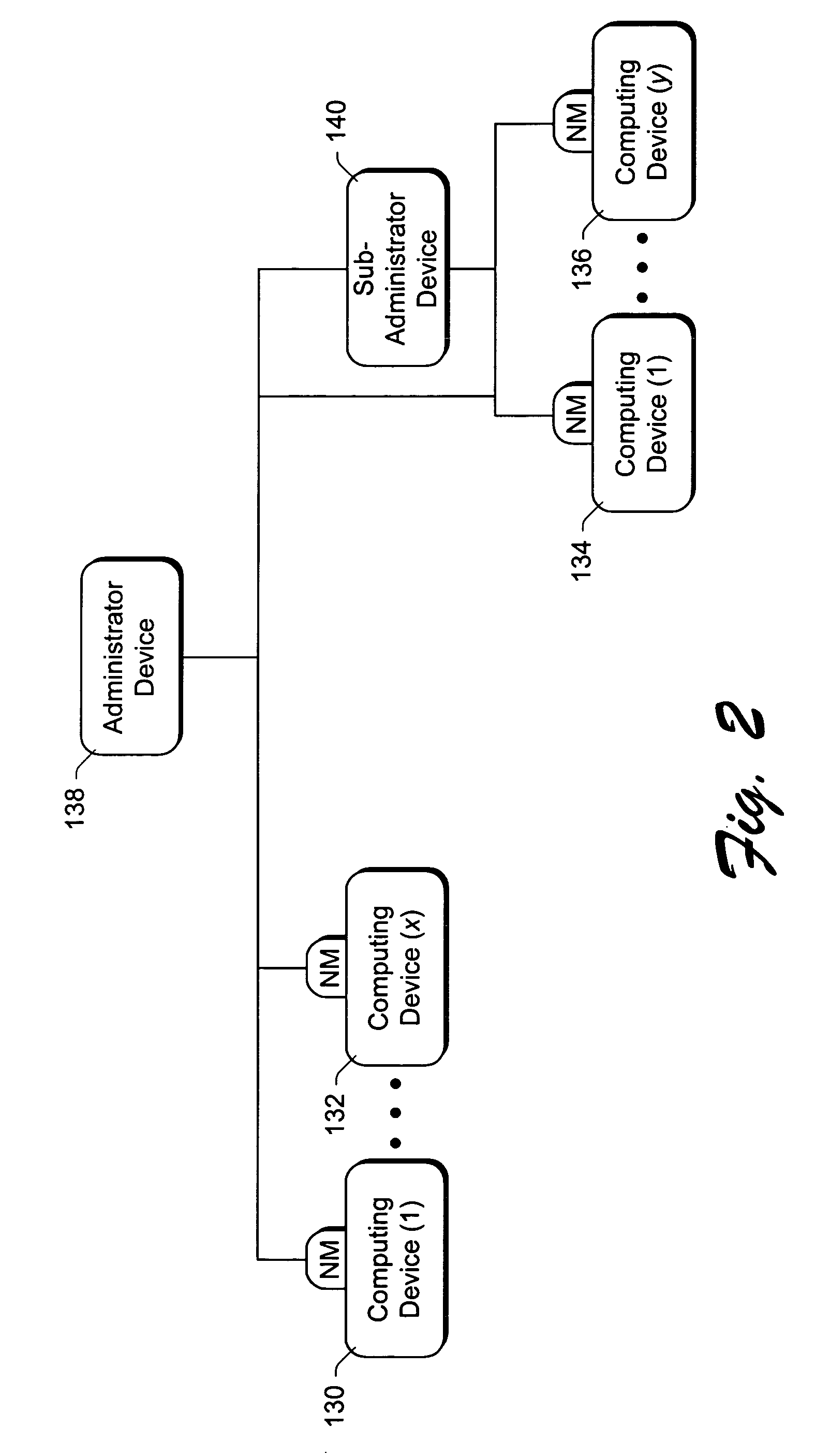
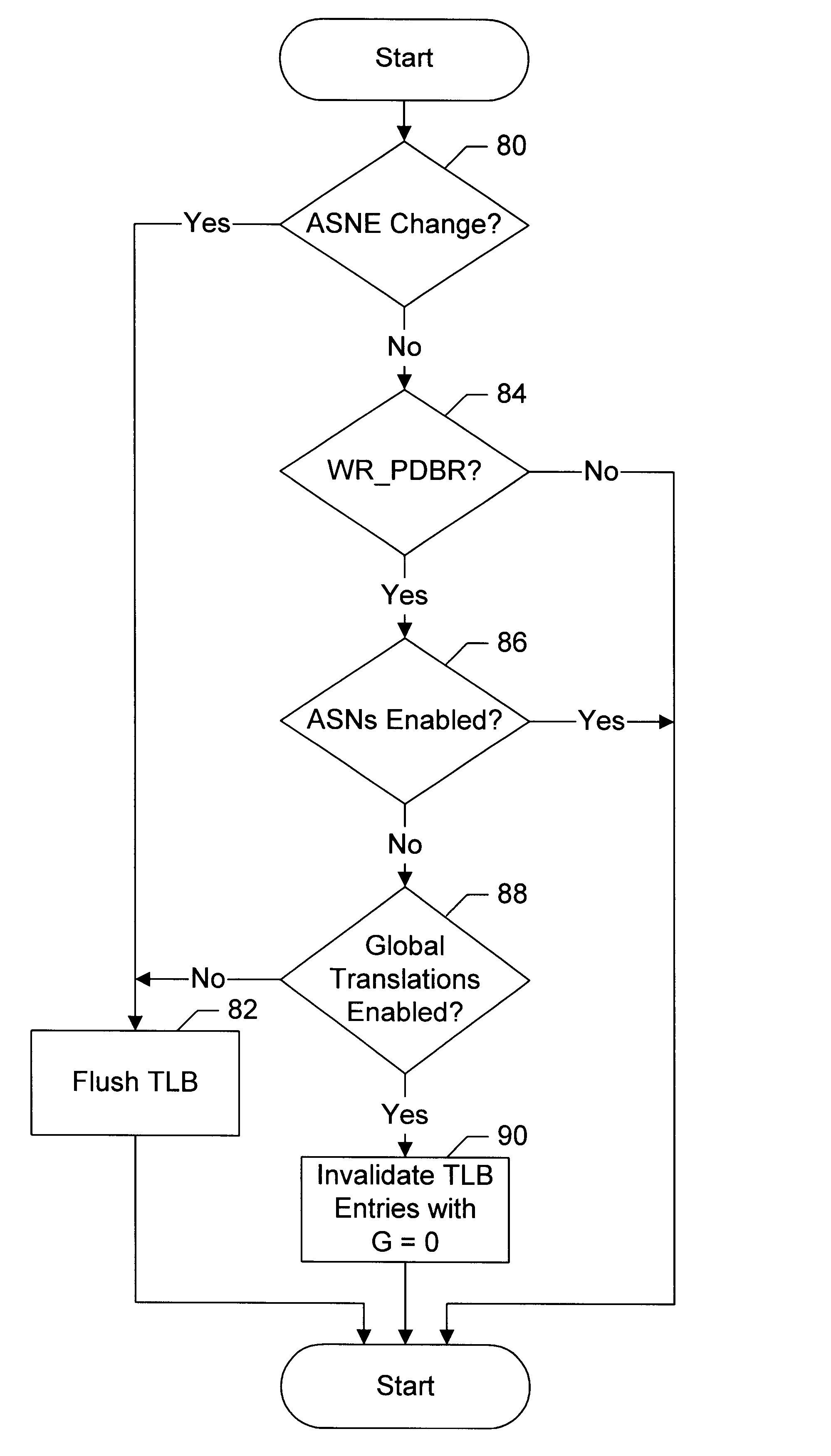
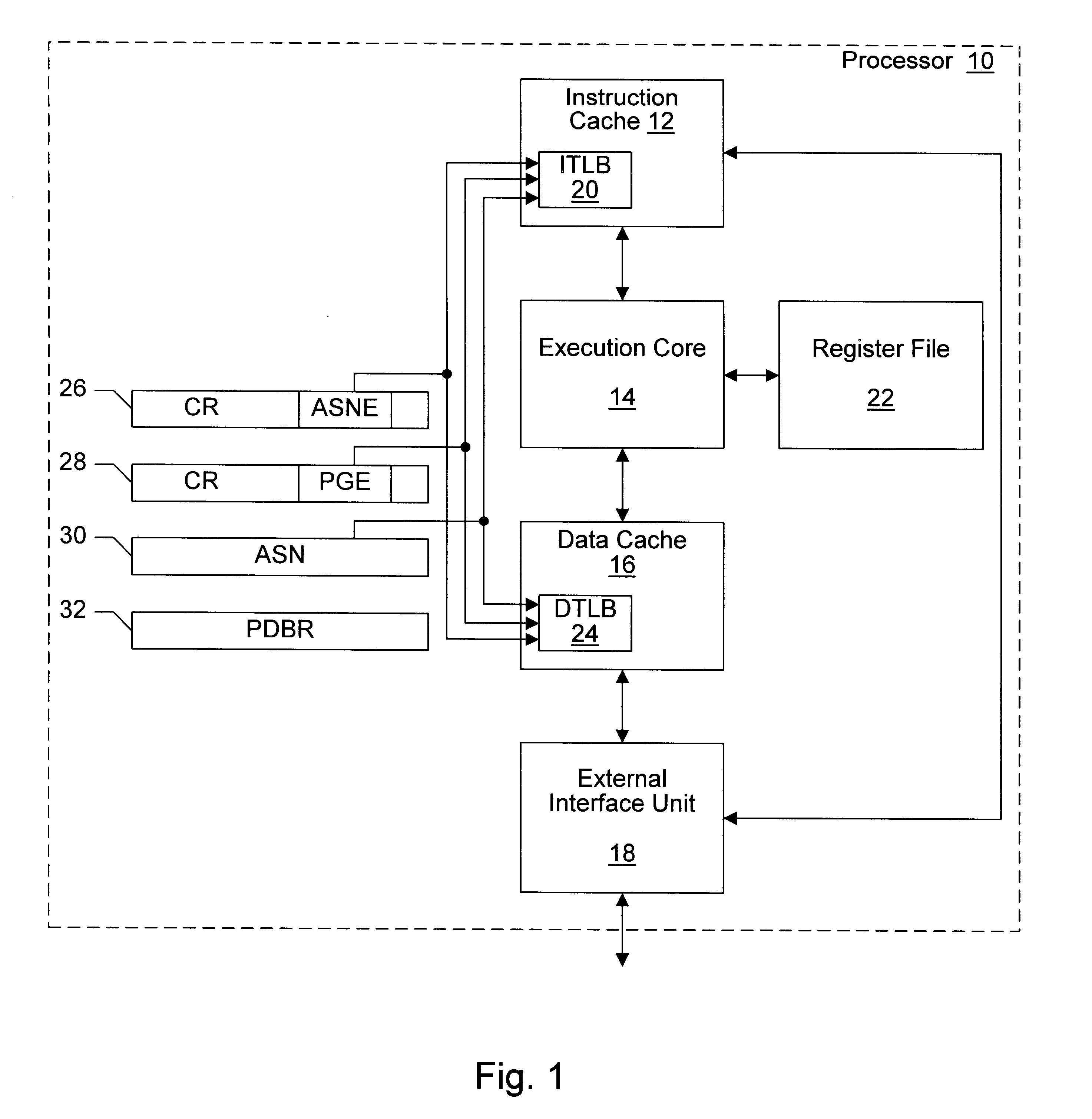
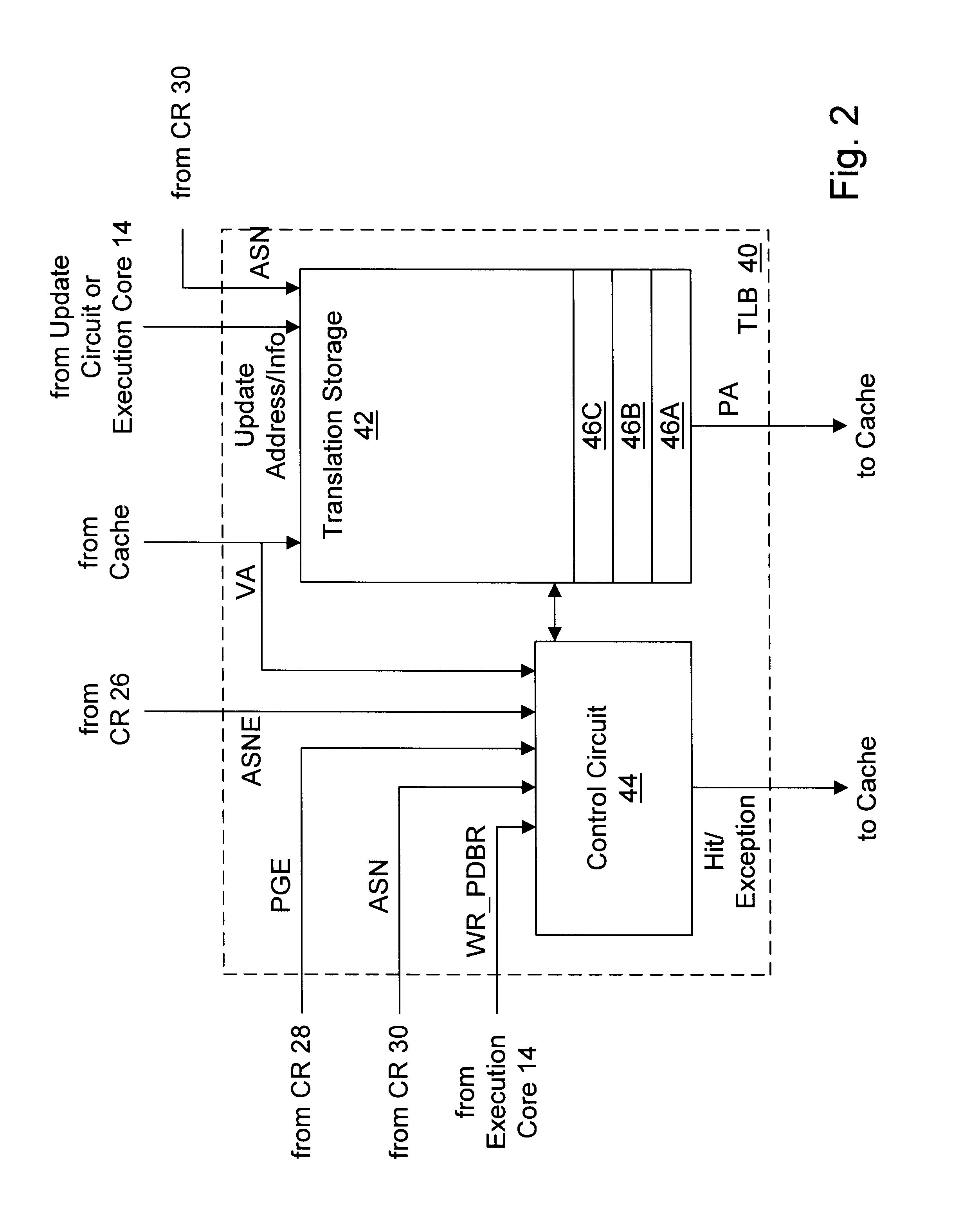
InactiveUS6604187B1Easy to useMemory architecture accessing/allocationMemory adressing/allocation/relocationOperational systemProcessor register
A processor provides a register for storing an address space number (ASN). Operating system software may assign different ASNs to different processes. The processor may include a TLB to cache translations, and the TLB may record the ASN from the ASN register in a TLB entry being loaded. Thus, translations may be associated with processes through the ASNs. Generally, a TLB hit will be detected in an entry if the virtual address to be translated matches the virtual address tag and the ASN matches the ASN stored in the register. Additionally, the processor may use an indication from the translation table entries to indicate whether or not a translation is global. If a translation is global, then the ASN comparison is not included in detecting a hit in the TLB. Thus, translations which are used by more than one process may not occupy multiple TLB entries. Instead, a hit may be detected on the TLB entry storing the global translation even though the recorded ASN may not match the current ASN. In one embodiment, if ASNs are disabled, the TLB may be flushed on context switches. However, the indication from the translation table entries used to indicate that the translation is global may be used (when ASNs are disabled) by the TLB to selectively invalidate non-global translations on a context switch while not invalidating global translations.
Owner:GLOBALFOUNDRIES US INC
Secure virtual address realm
InactiveUS20040249974A1Convenient introductionMultiple digital computer combinationsTransmissionPrivate networkPublic network
A private virtual dynamic network is provided for computing devices coupled to public networks or private networks. This enables computing devices anywhere in the world to join into private enterprise intranets and communicate with each other. In one embodiment, the present invention provides a separate private virtual address realm, seen to each user as a private network, while seamlessly crossing public and private network boundaries. One implementation of the present invention uses an agent to enable an entity to participate in the network without requiring the member to add new hardware or software.
Owner:INPRO NETWORK FACILITY LLC
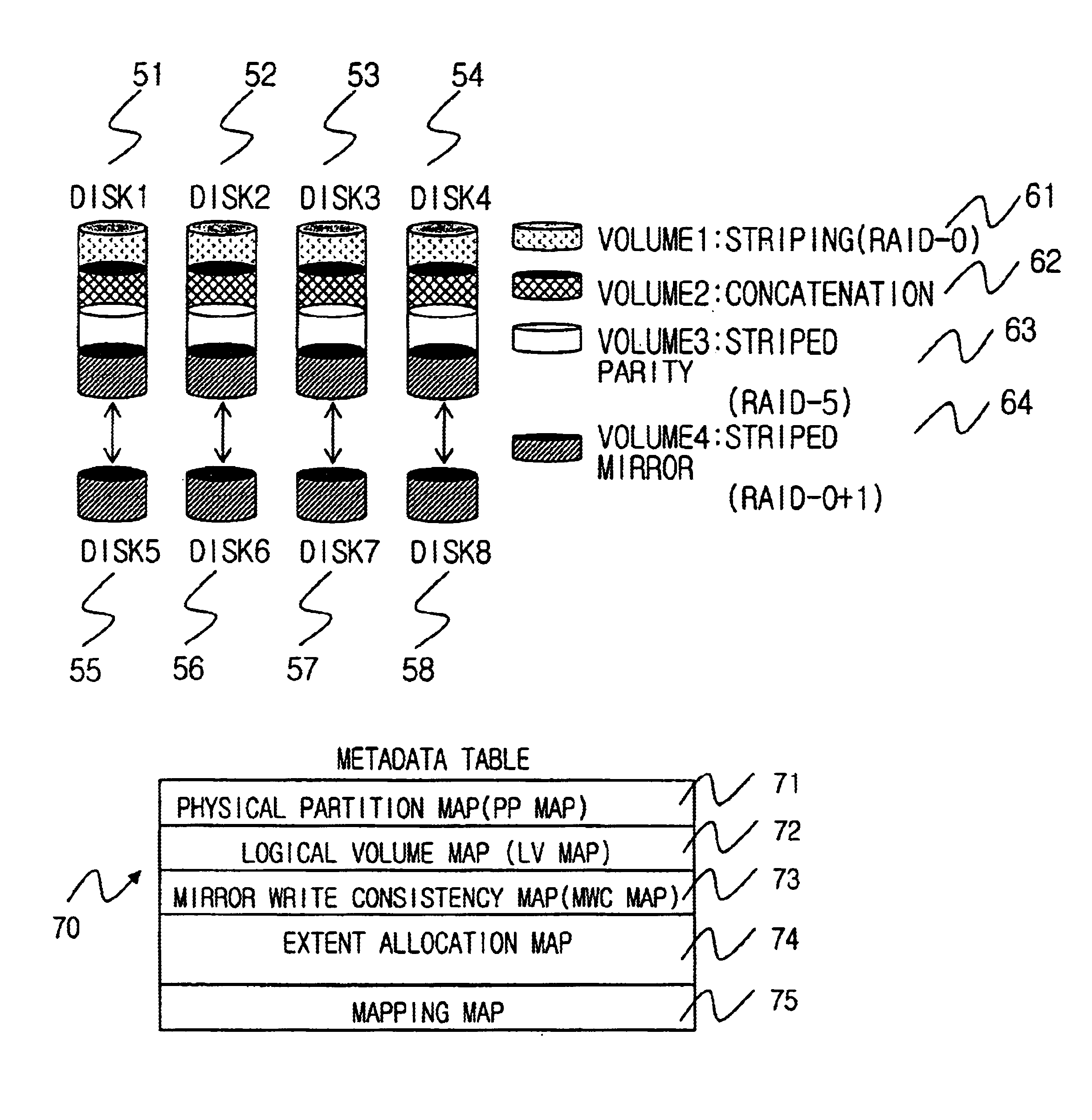
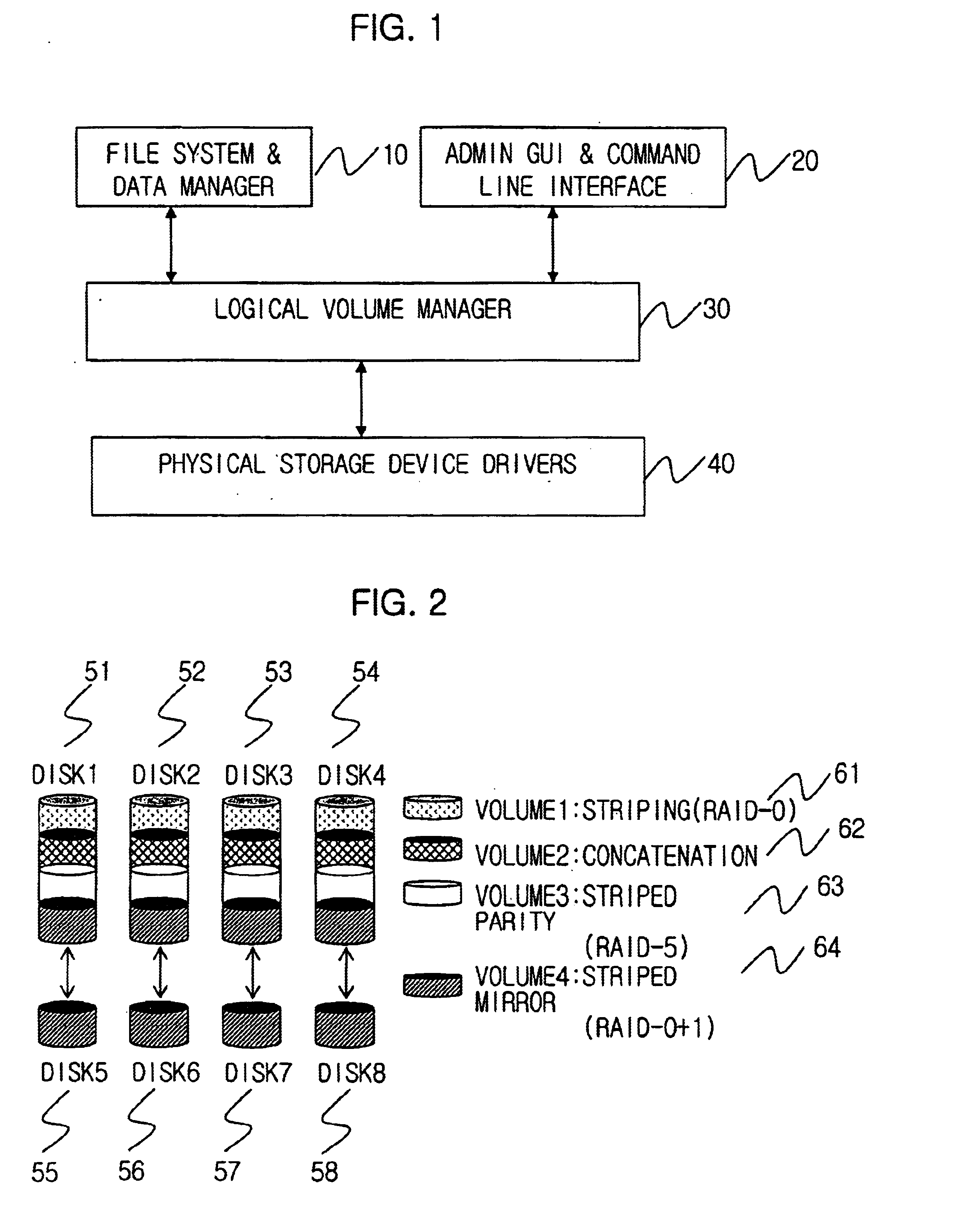
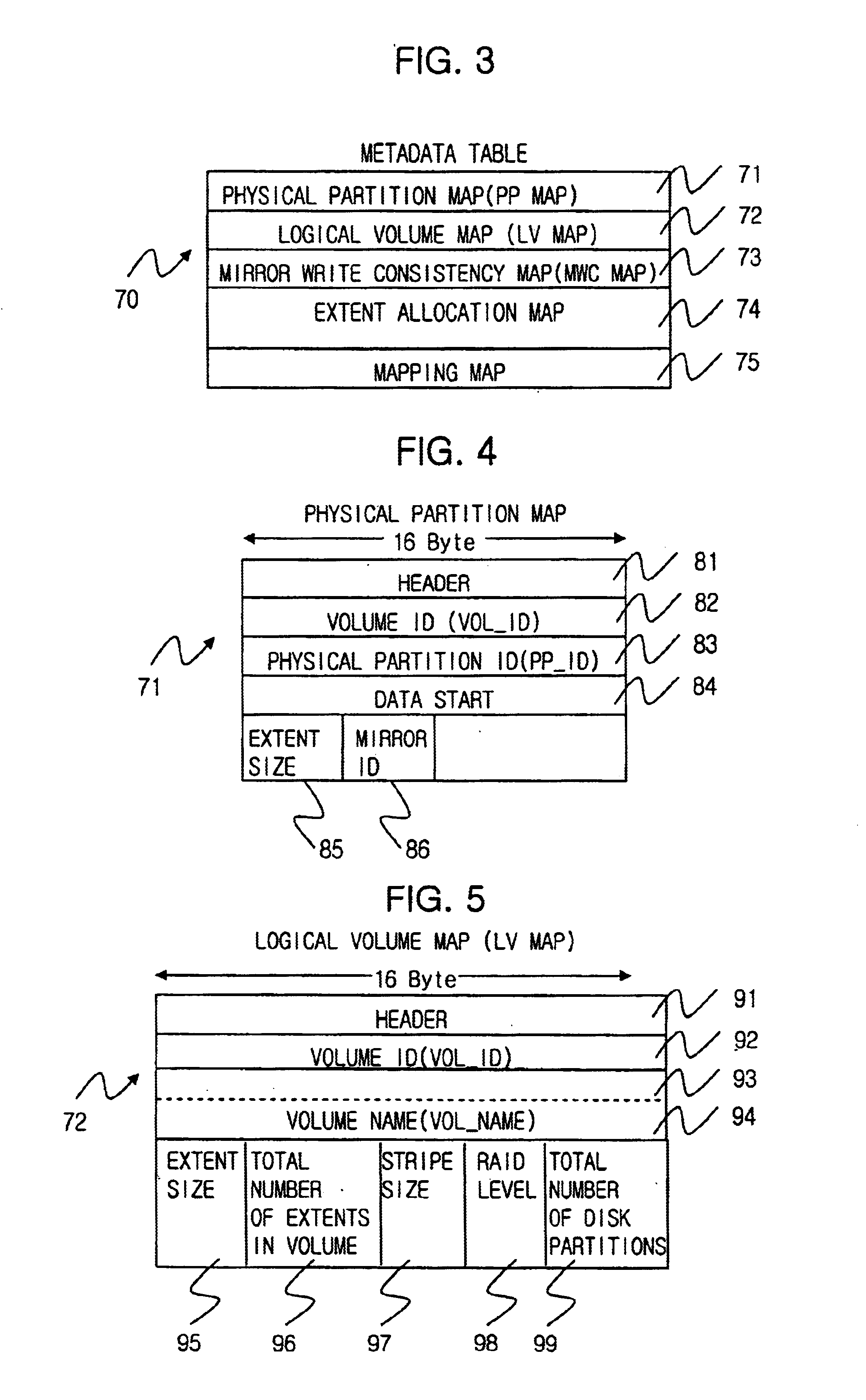
Method for managing logical volume in order to support dynamic online resizing and software raid and to minimize metadata and computer readable medium storing the same
InactiveUS6718436B2Increase or decrease sizeIncrease spaceInput/output to record carriersMemory adressing/allocation/relocationRAIDVolume table
A method for managing a logical volume for minimizing a size of metadata and supporting dynamic online resizing and software redundant array of independent disks (RAID), and a computer-readable recording medium storing instructions for embodying the method, are disclosed. The method includes the metadata having a disk partition table containing information of a disk partition in which the metadata is stored; a logical volume table for maintaining the information of the logical volume by storing duplicated information of the logical volume onto all disk partitions of the logical volume; an extent allocation table for indicating whether each extent in the disk partitions is used or not; and a mapping table for maintaining a mapping information for a physical address space corresponding to a logical address space which is a continuous address space equal in size of storage space of whole logical volume.
Owner:ELECTRONICS & TELECOMM RES INST
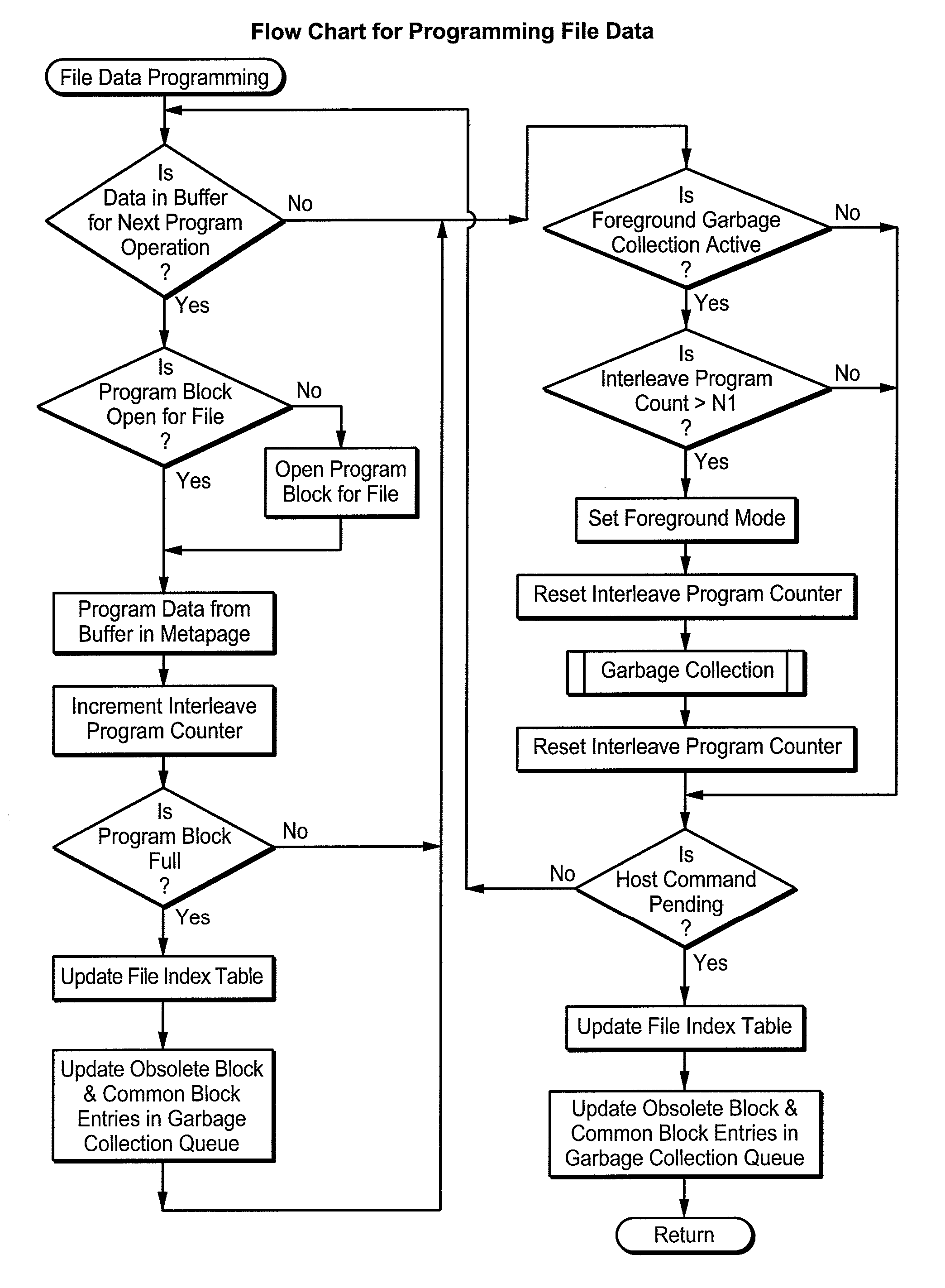
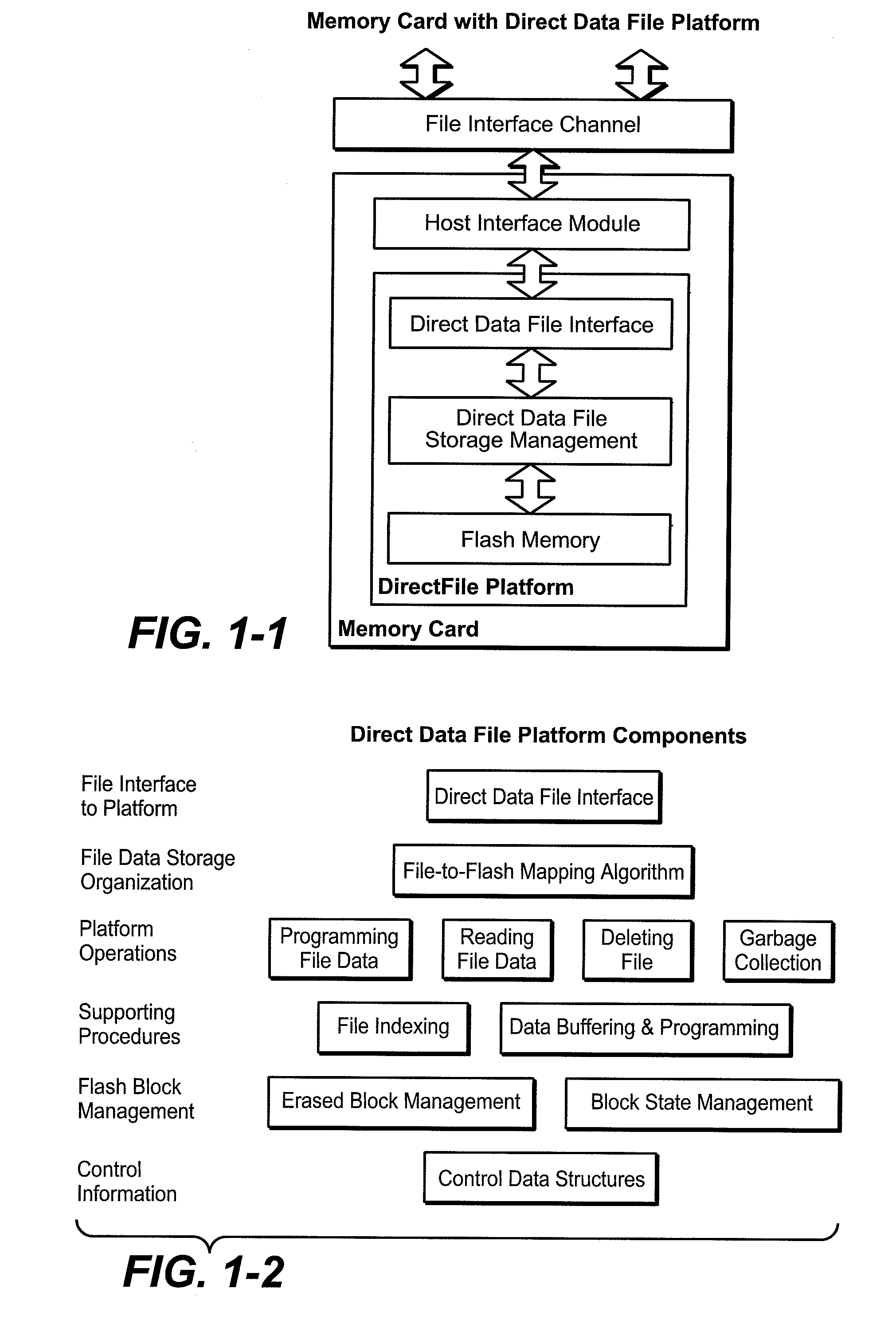
Data Consolidation and Garbage Collection in Direct Data File Storage Memories
ActiveUS20070033376A1Prevent ConsolidationImprove memory performanceMemory architecture accessing/allocationDigital data information retrievalData fileTerm memory
Host system data files are written directly to a large erase block flash memory system with a unique identification of each file and offsets of data within the file but without the use of any intermediate logical addresses or a virtual address space for the memory. Directory information of where the files are stored in the memory is maintained within the memory system by its controller, rather than by the host.
Owner:SANDISK TECH LLC
Virtualization system for computers with a region-based memory architecture
ActiveUS7089377B1Efficient sharingSoftware simulation/interpretation/emulationMemory systemsVirtualizationProcessor register
In a computer system with a non-segmented, region-based memory architecture, such as Intel IA-64 systems, two or more sub-systems share a resource, such as a virtual-to-physical address mapping and need to have overlapping regions of the virtual address space for accessing different physical addresses. Virtual addresses include a portion that is used to identify which region the issuing sub-system wants to access. For example, the region-identifying portion of virtual addresses may select a region register whose contents point to a virtual-to-physical address mapping for the corresponding region. To protect a second sub-system S2 from a first S1, whenever the S1 issues an address in a region occupied by S2, the region for the S2 is changed. This allows S1 to issue its addresses without change. In a preferred embodiment of the invention, S2 is a virtual machine monitor (VMM) and S1 is a virtual machine running on the VMM.
Owner:VMWARE INC
Fast path caching
InactiveUS6986015B2Input/output to record carriersMemory adressing/allocation/relocationFast pathData operations
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:INT BUSINESS MASCH CORP
Garbage collector for a virtual heap
InactiveUS6865657B1Memory architecture accessing/allocationData processing applicationsObject copyingRefuse collection
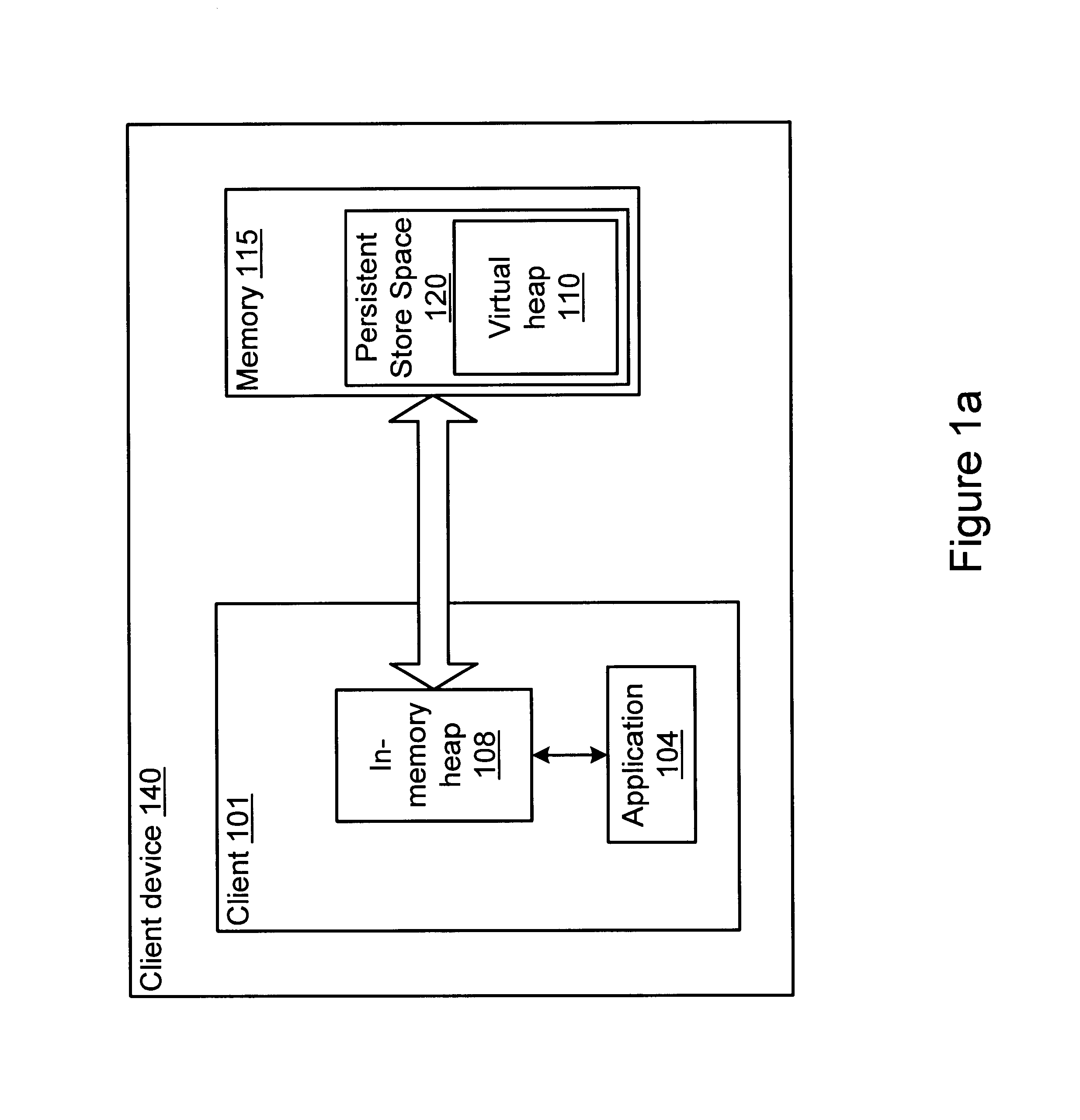
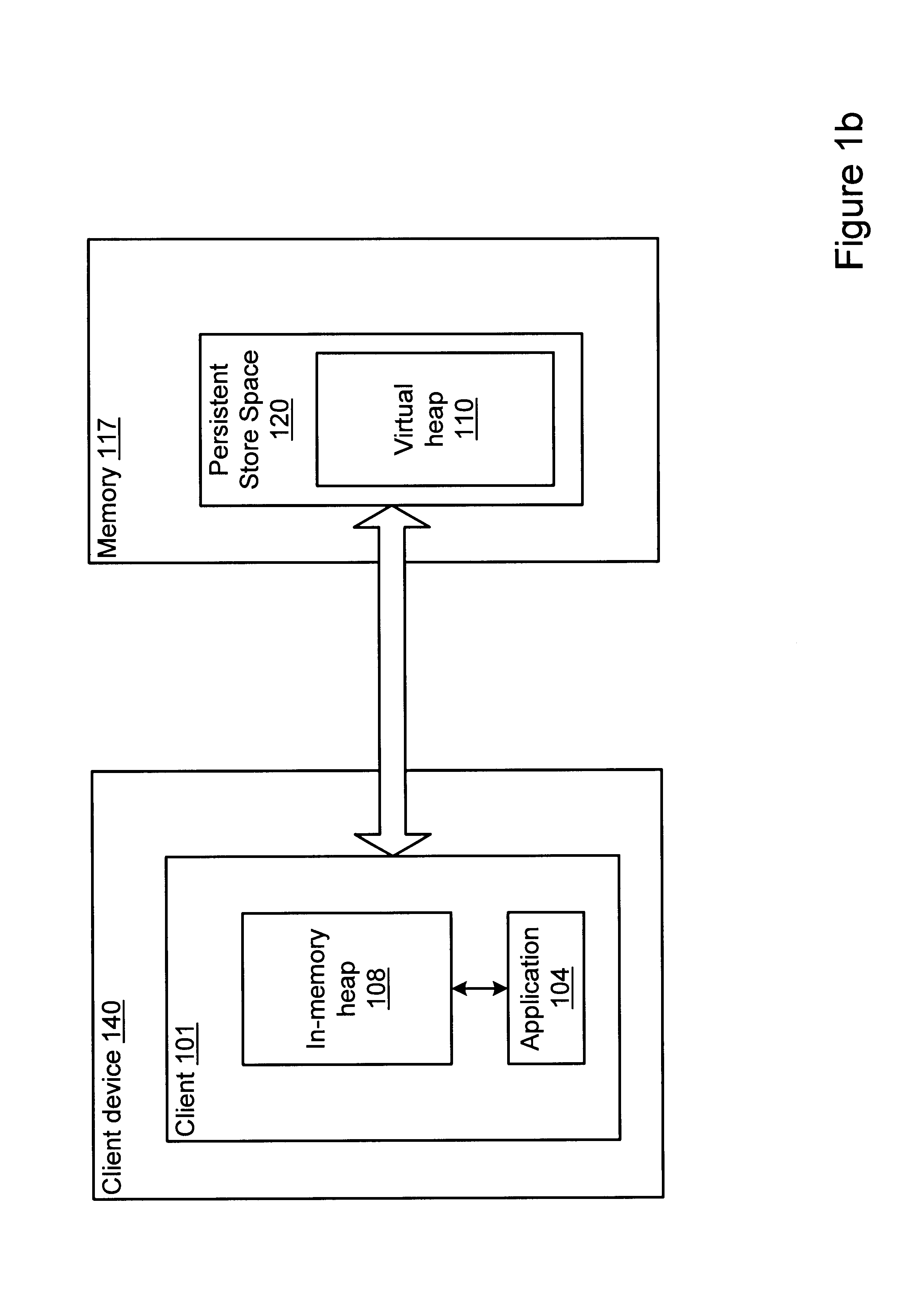
A method and system for performing generational garbage collection on a virtual heap in a virtual machine is provided. The garbage collection method is suited for use with small consumer and appliance devices that have a small amount of memory and may be using flash devices as persistent storage. The garbage collection method may provide good performance where only a portion of the virtual heap may be cached in the physical heap. The virtual heap may use a single address space for both objects in the store and the in-memory heap. In one embodiment, a single garbage collector is run on the virtual heap address space. The garbage collection method may remove non-referenced objects from the virtual heap. The garbage collection method may also include a compaction phase to reduce or eliminate fragmentation, and to improve locality of objects within the virtual heap. In one embodiment, the garbage collector for the virtual heap may be implemented as a generational garbage collector using working sets in the virtual heap, where each generation is confined to a working set of the heap. The generational garbage collector may allow the flushing of changes after each garbage collection cycle for each working set region. Heap regions with different flushing policies may be used. An object nursery region without flushing where objects are initially created may be used. When a garbage collection cycle is run, objects truly referenced in the object nursery may be copied back into heap regions to be flushed, while short-lived objects no longer referenced may be deleted without flushing.
Owner:ORACLE INT CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com