Patents
Literature
109results about How to "Without complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
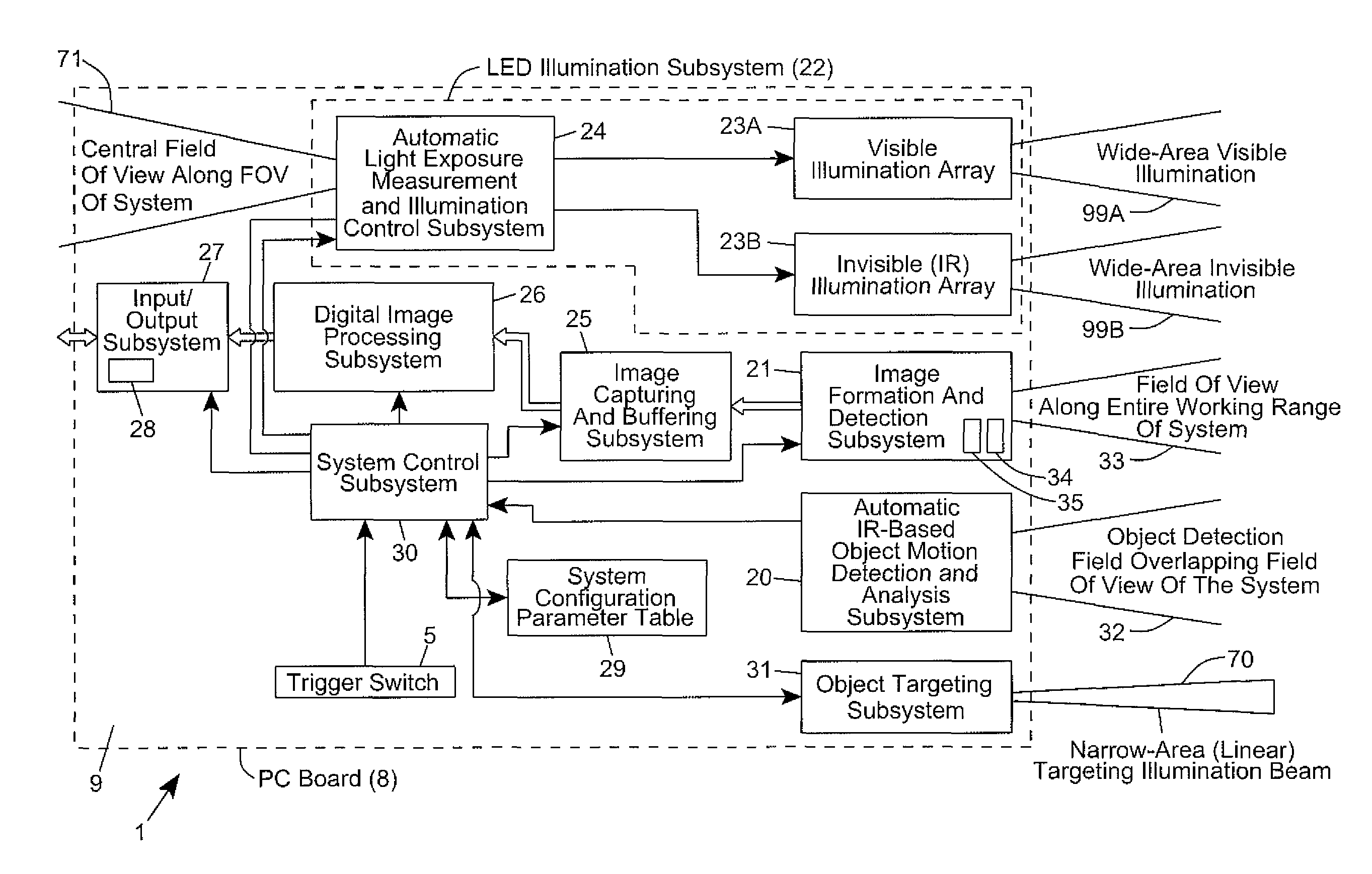
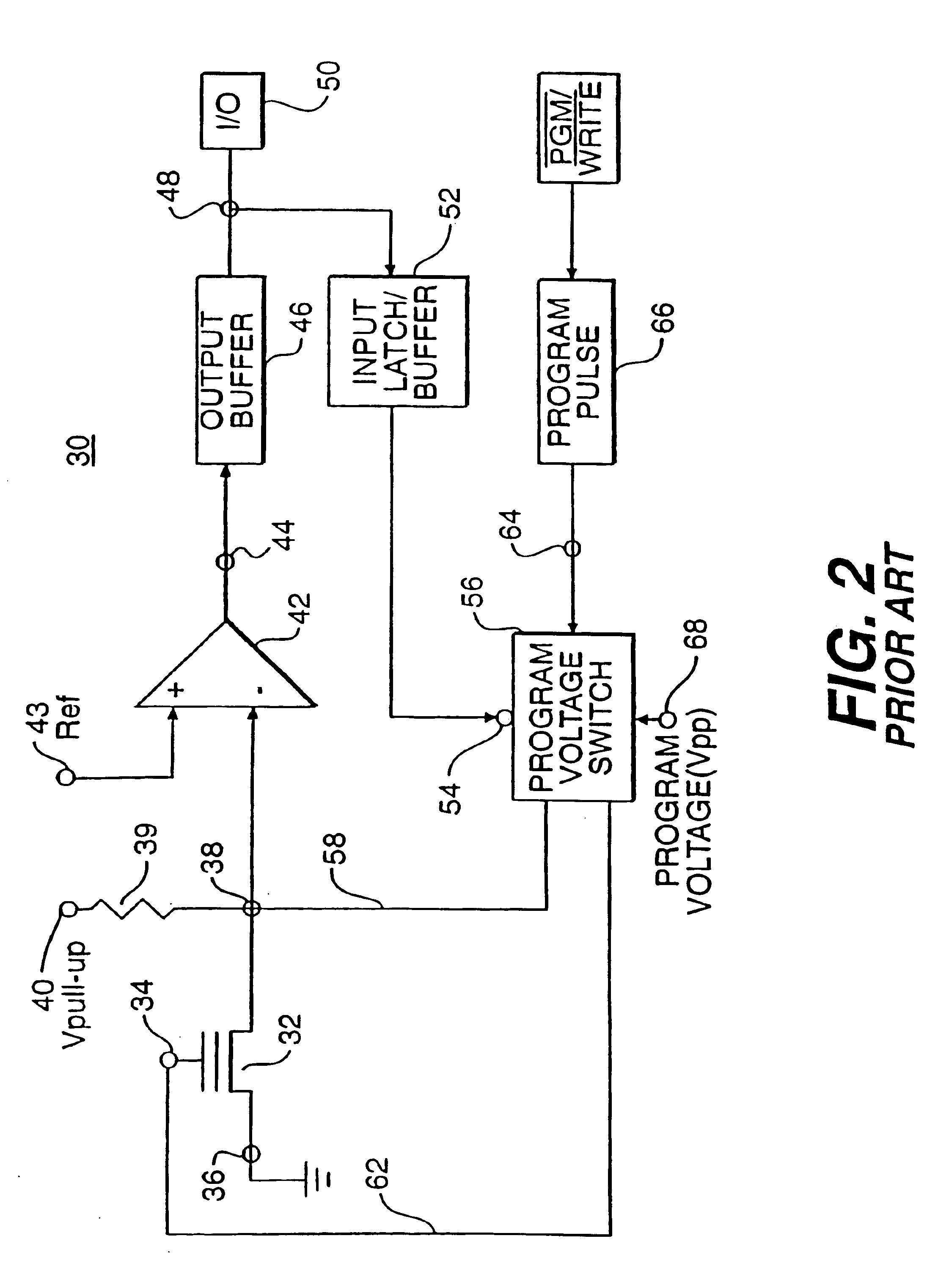
Method of and system for reading visible and/or invisible code symbols in a user-transparent manner using visible/invisible illumination source switching during data capture and processing operations
ActiveUS8408468B2Avoiding shortcoming and drawbackWithout complexityCharacter and pattern recognitionHybrid readersComputer scienceComputer graphics (images)
Method of and system for reading visible and / or invisible code symbols in a user-transparent manner using visible / invisible illumination switching during data capture and processing operations.
Owner:METROLOGIC INSTR
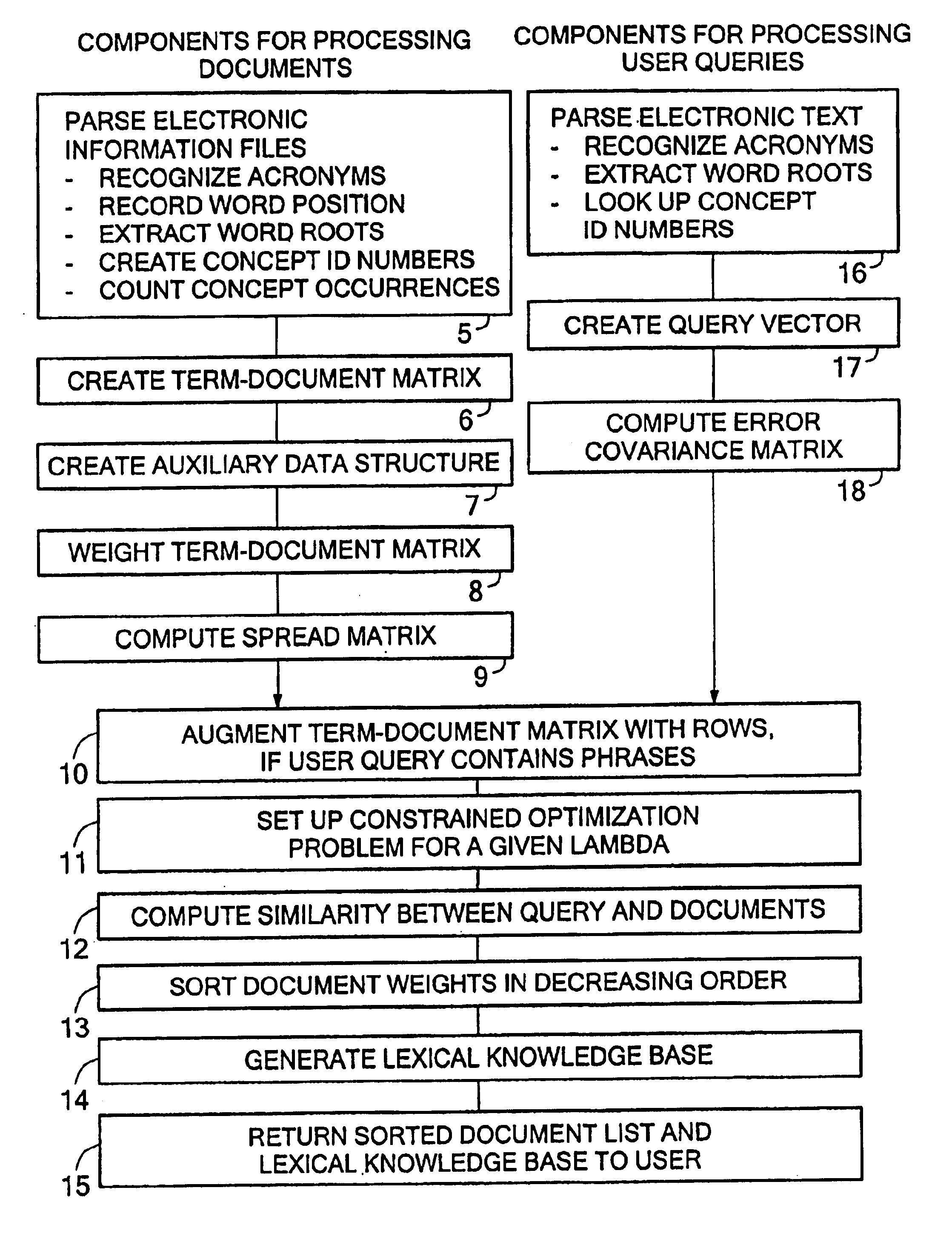
Internet navigation using soft hyperlinks
InactiveUS6862710B1High degree of correlationHigh degreeData processing applicationsWeb data indexingNavigation systemDocument preparation
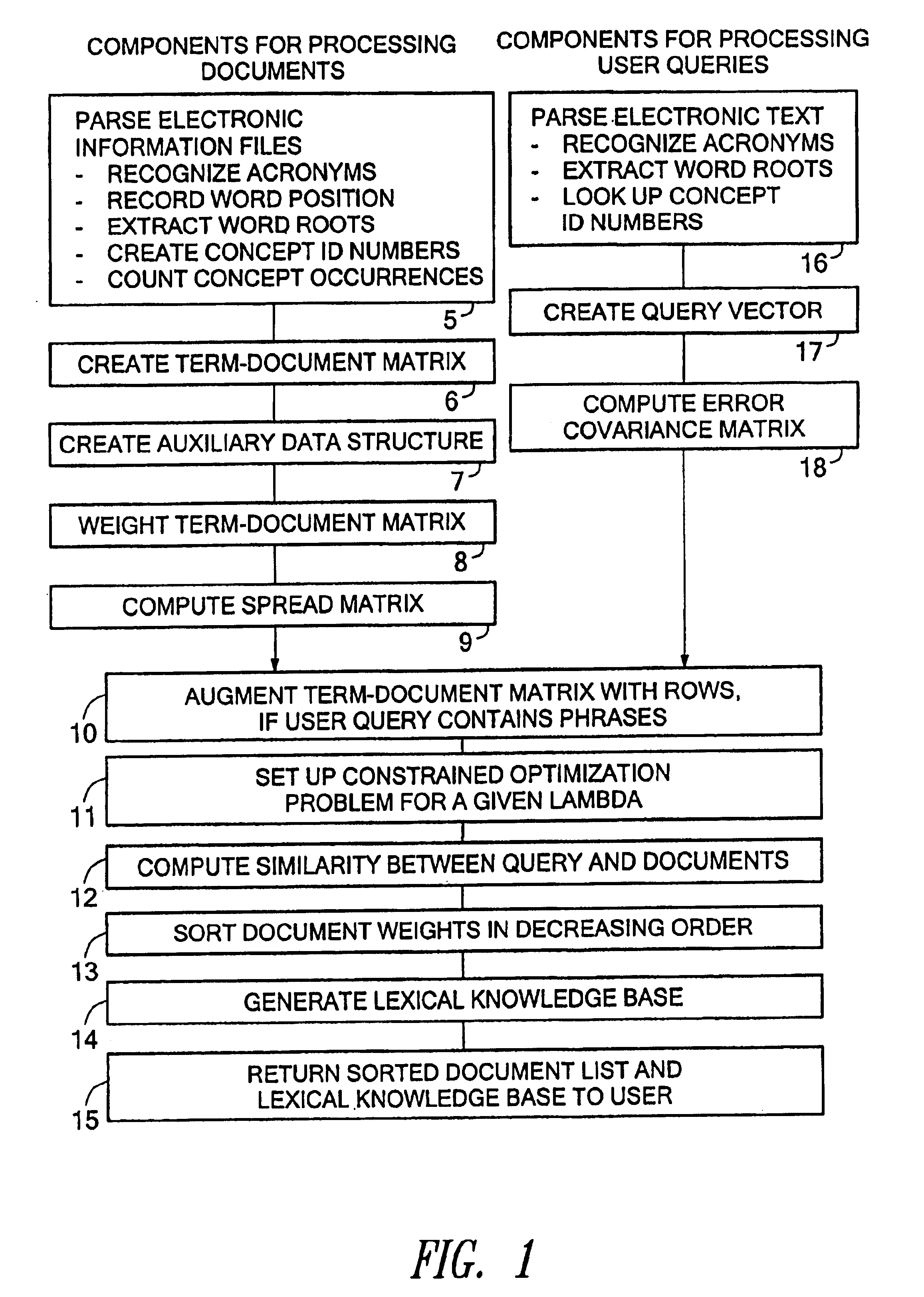
A system for internet navigation using soft hyperlinks is disclosed, in connection with an illustrative information retrieval system with which it may be used. The navigation tool provides freedom to move through a collection of electronic documents independent of any hyperlink which has been inserted within an HTML page. A user can click on any term in a document page, not only those that are hyperlinked. For example, when a user clicks on an initial word within the document, the disclosed system employs a search engine in the background to retrieve a list of related terms. In an illustrative embodiment, a compass-like display appears with pointers indicating the first four terms returned by the search engine. These returned terms have the highest degree of correlation with the initial search term in a lexical knowledge base that the search engine constructs automatically. The disclosed system allows the user to move from the current document to one of a number of document lists which cover different associations between the initial word clicked on by the user and other terms extracted from within the retrieved list of related terms. The disclosed system may further allow the user to move to a document that is considered most related to the initial word clicked on by the user, or to a list of documents that are relevant to a phrase or paragraph selection indicated by the user within the current page.
Owner:FIVER LLC
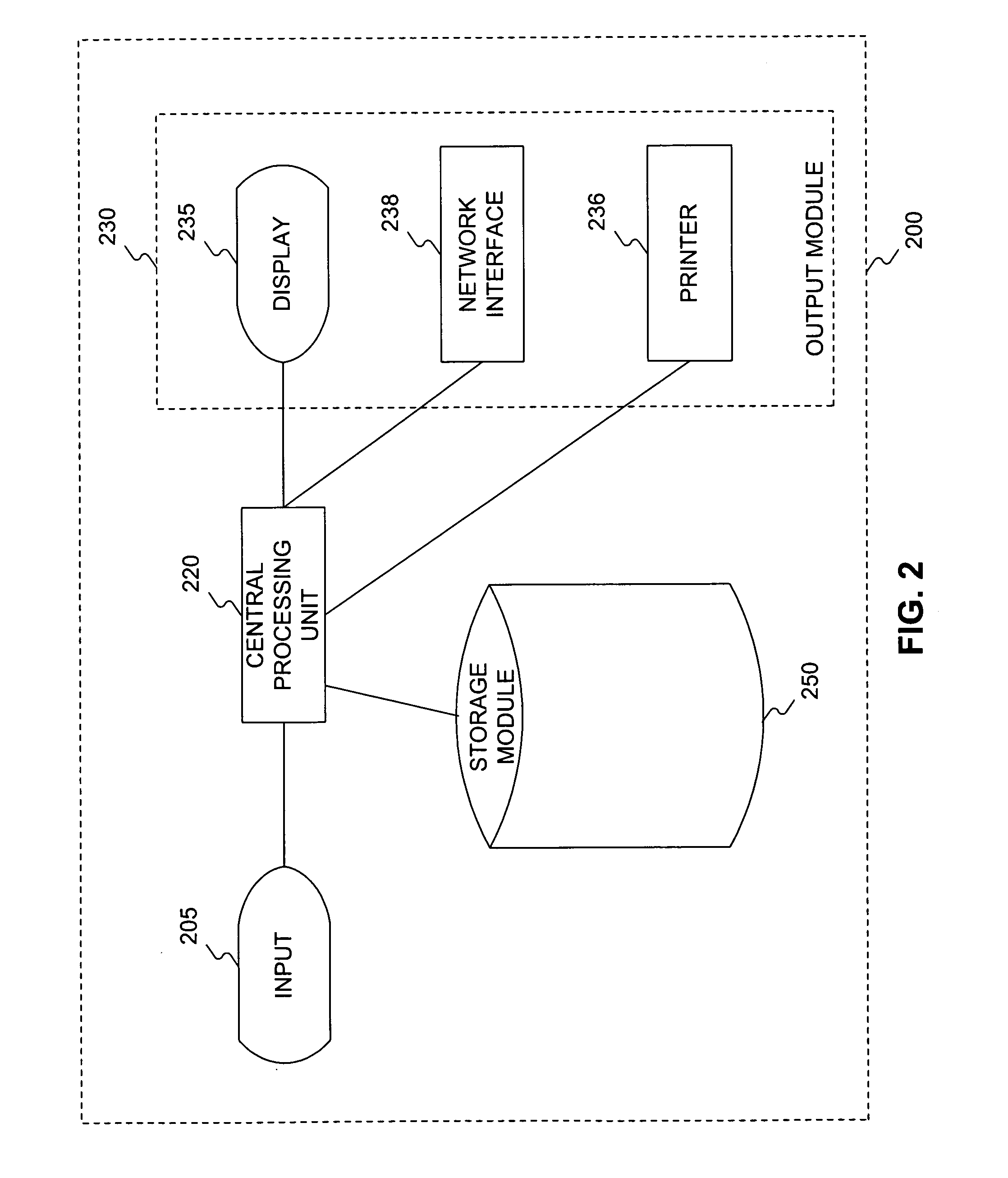
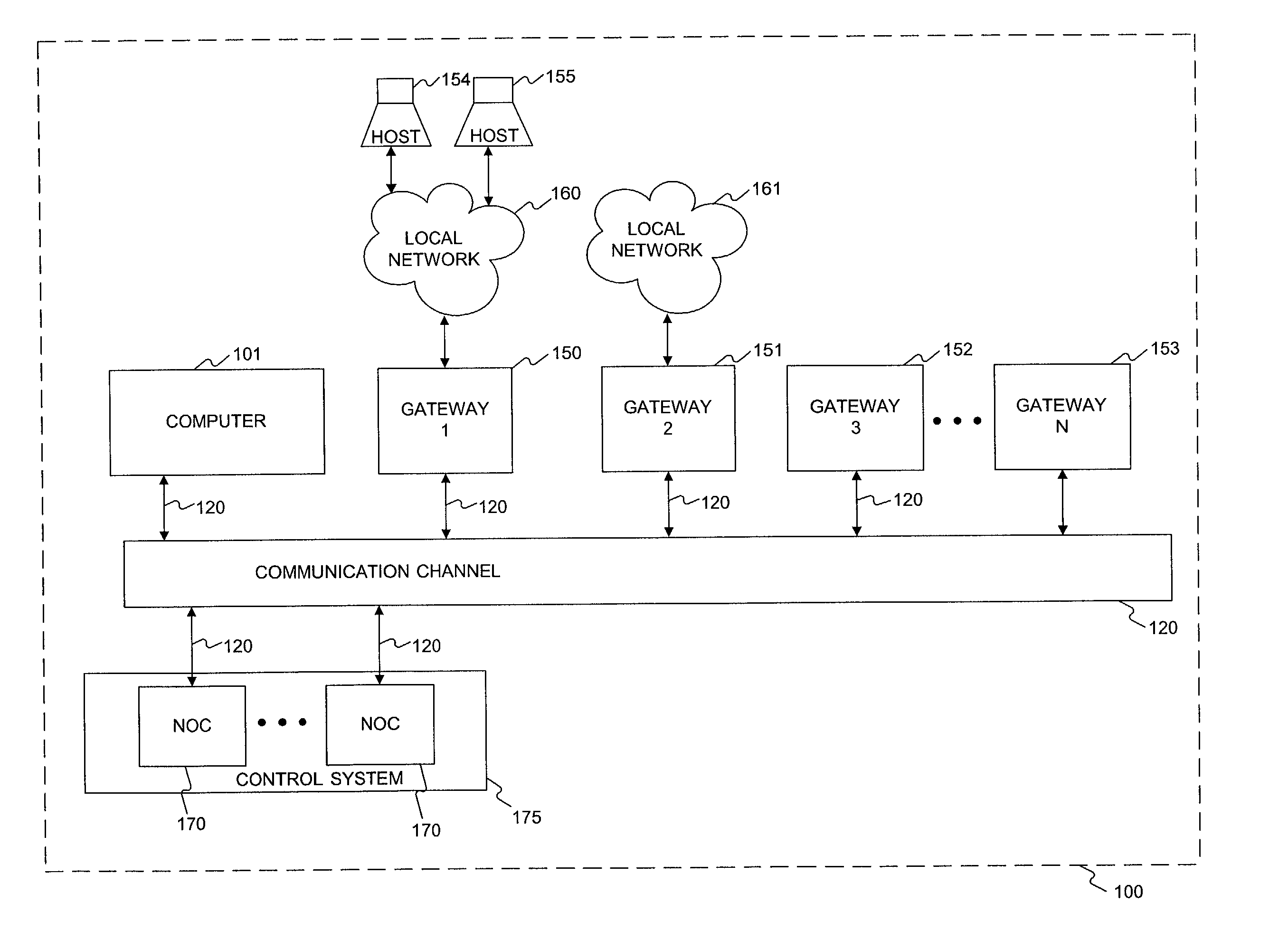
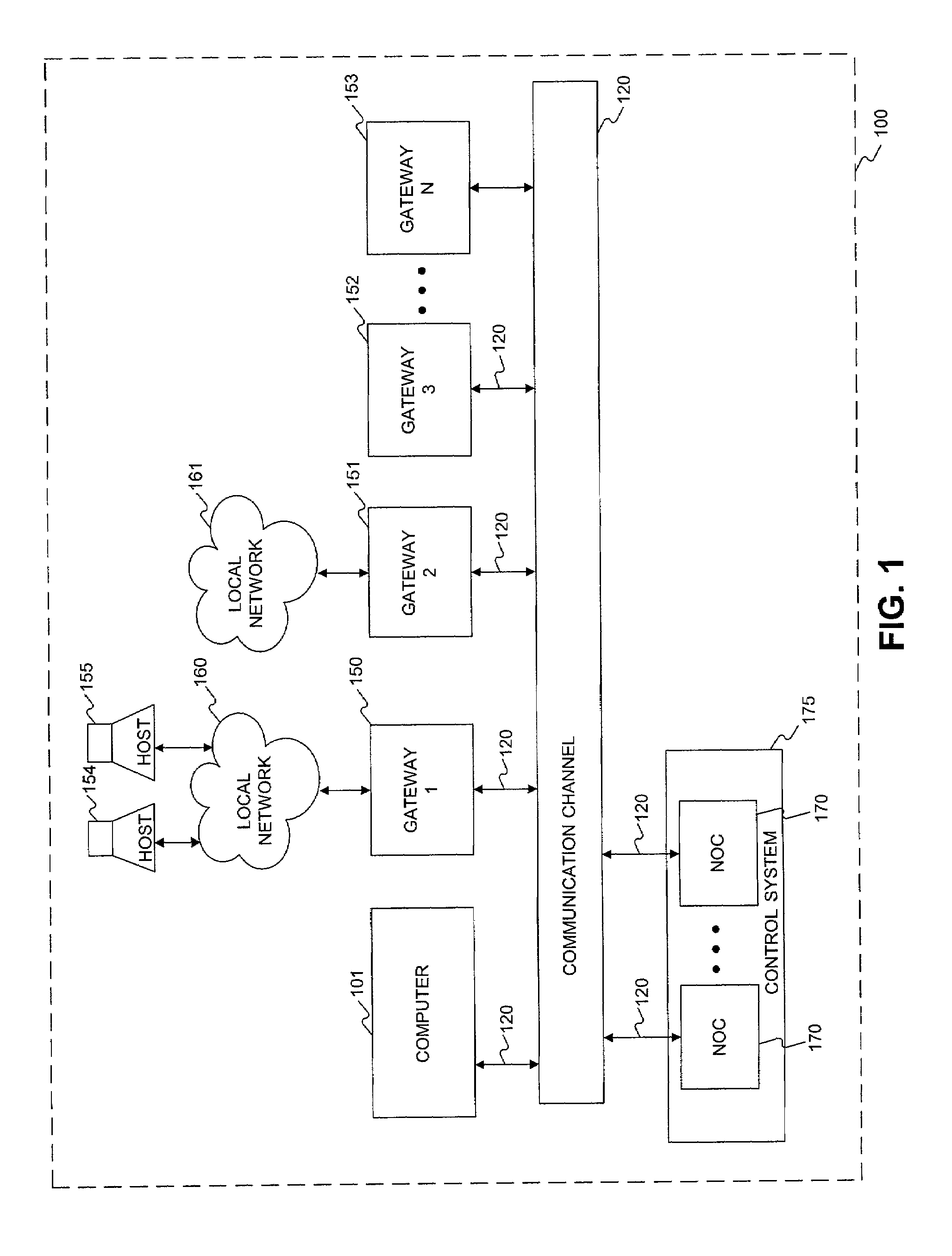
Methods and system for providing network services using at least one processor interfacing a base network
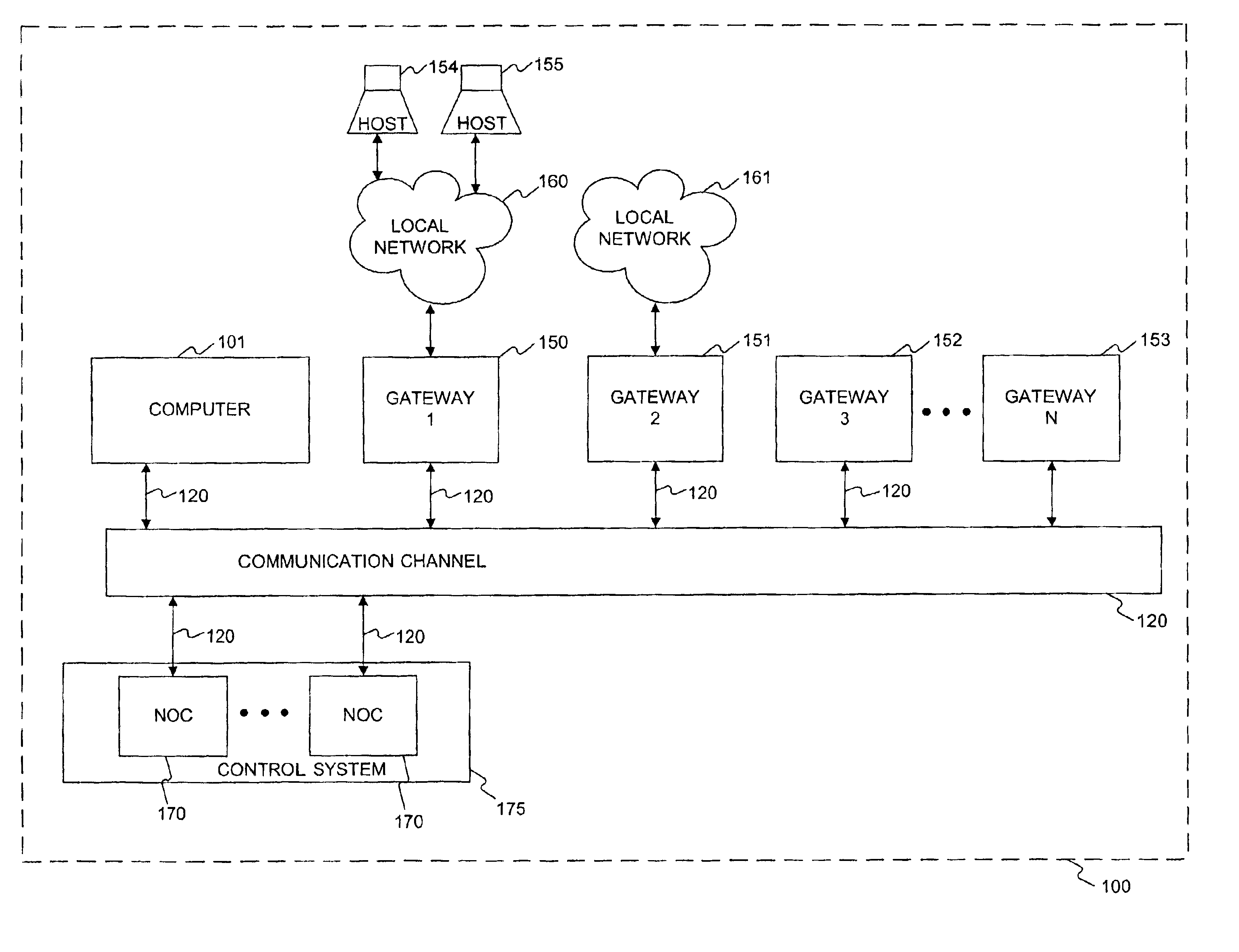
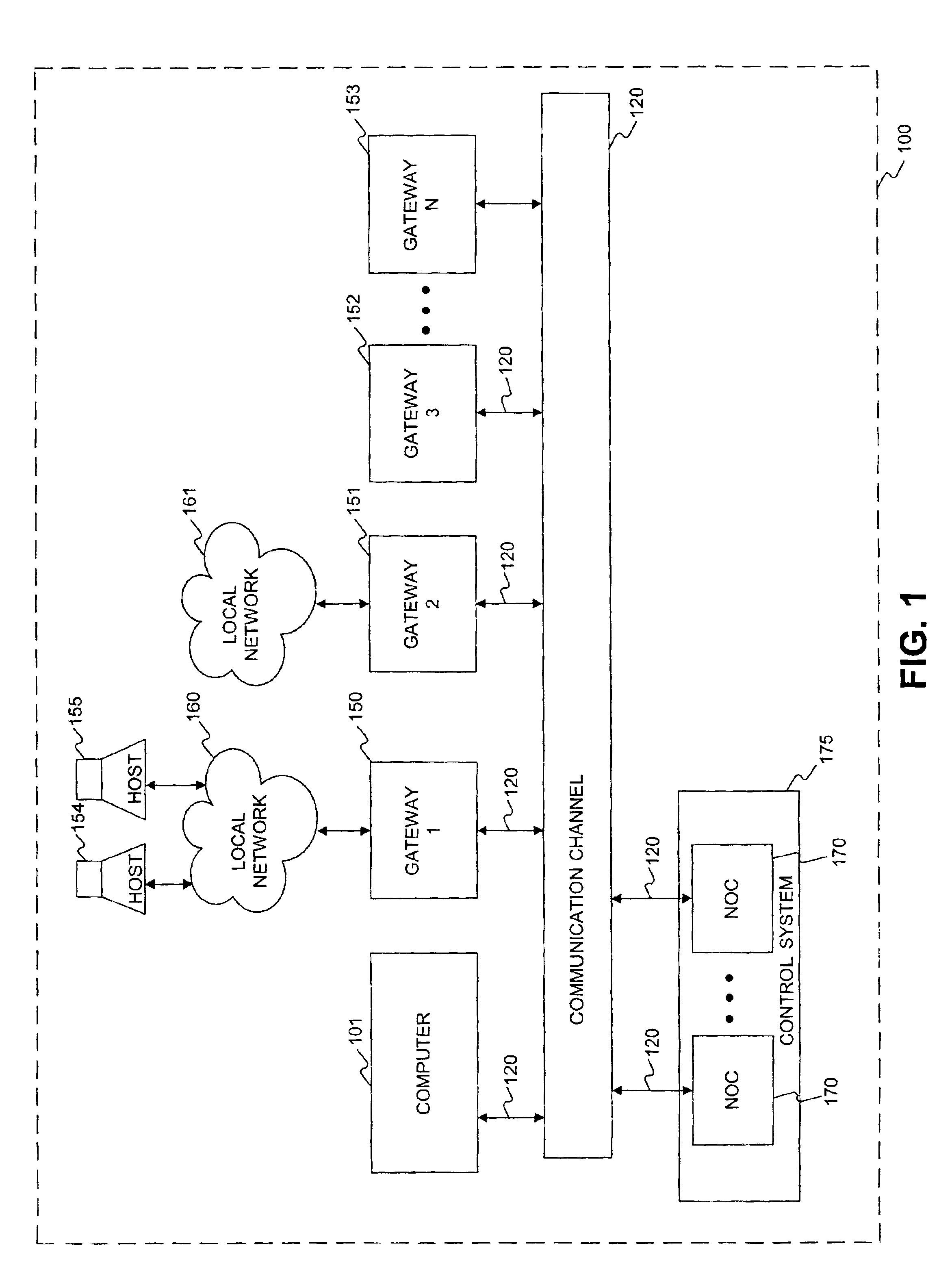
InactiveUS7181766B2Easily and effectively leverage powerWithout complexityDigital data processing detailsMultiple digital computer combinationsNetwork operations centerNetwork code
Methods and systems are provided for providing network services using at least one processor, such as a network operations center that interfaces a base network. The network operations center may receive information identifying a user authorized to administer a first processor, which may be separate from the network operations center, and a base address that is routable in the base network. The network operations center may provide through the base network code and information for self-configuring the first processor as a gateway that interfaces the base network at the base address. The first processor may execute the provided code to self-configure itself as the gateway based on the provided information. The network operations center may then provide through the base network to the first processor additional information enabling at least one tunnel through the base network to a second processor, which may also be separate from the network operations center, when the first and second processors each provide to the network operations center a consent for enabling the tunnel.
Owner:ORACLE SYST CORP
Methods and systems for partners in virtual networks
InactiveUS7028333B2Easily and effectively leverage powerWithout complexityDigital data processing detailsMultiple digital computer combinationsParallel computingVirtual address space
Owner:ORACLE SYST CORP
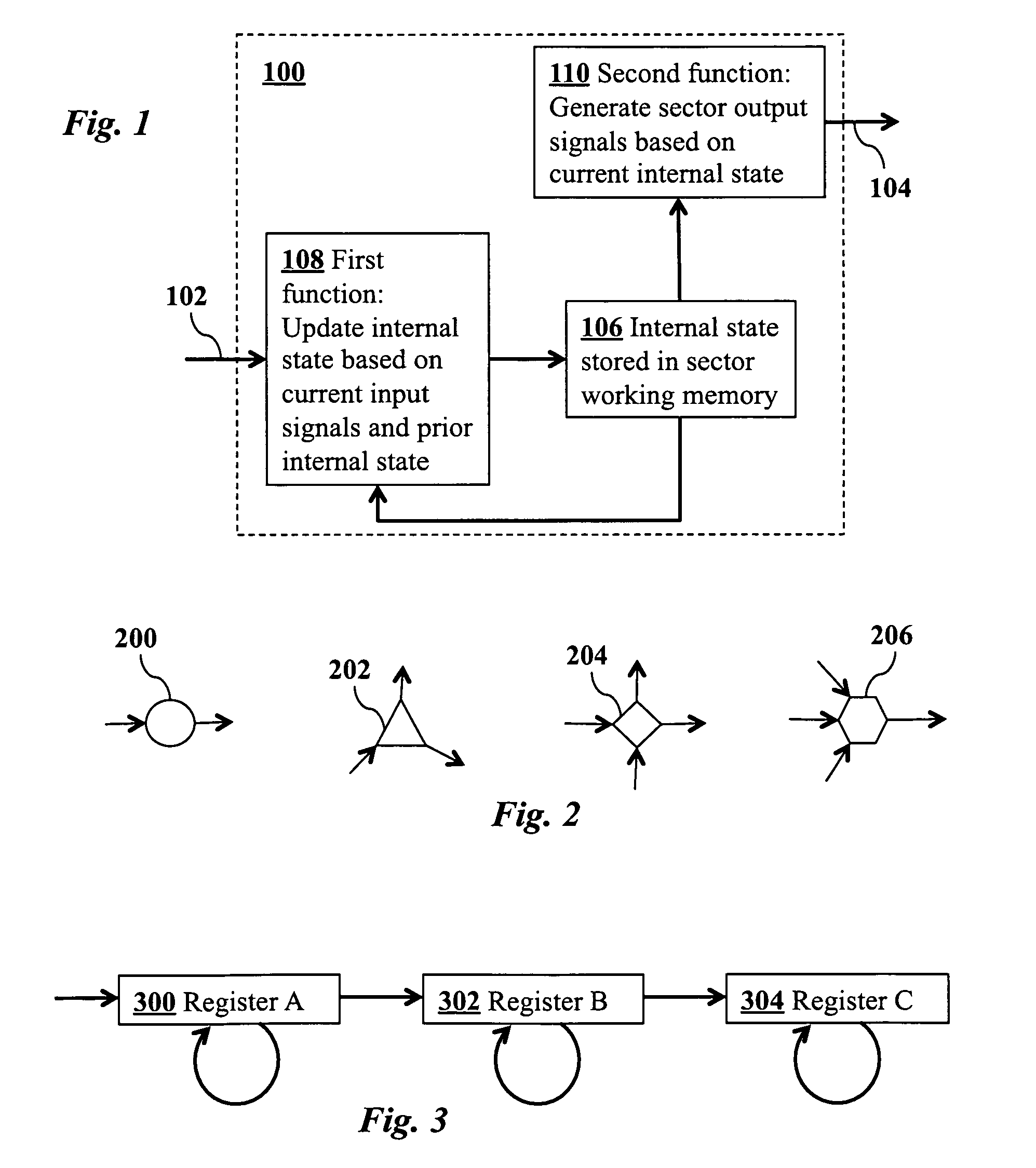
Method for efficiently simulating the information processing in cells and tissues of the nervous system with a temporal series compressed encoding neural network
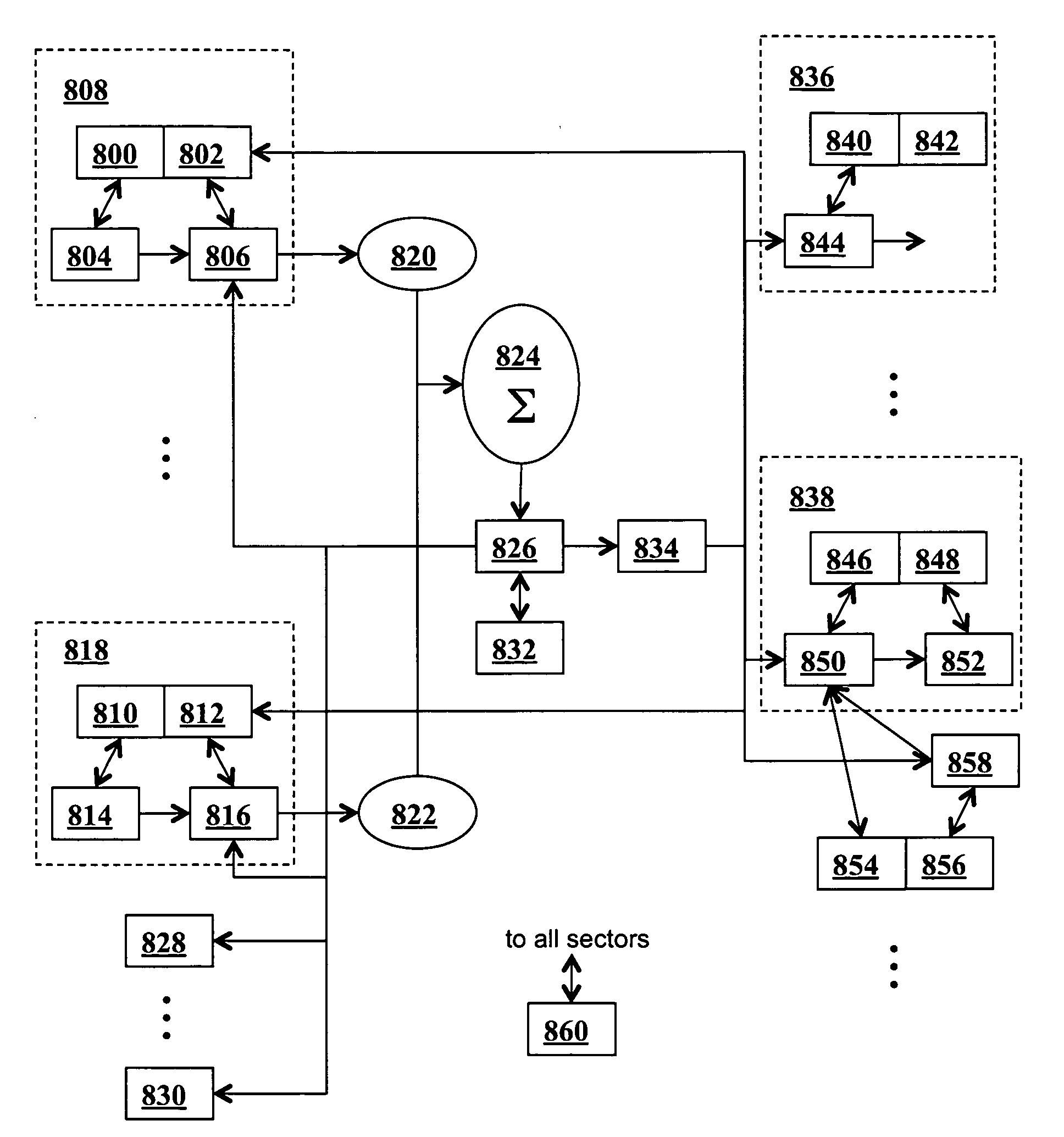
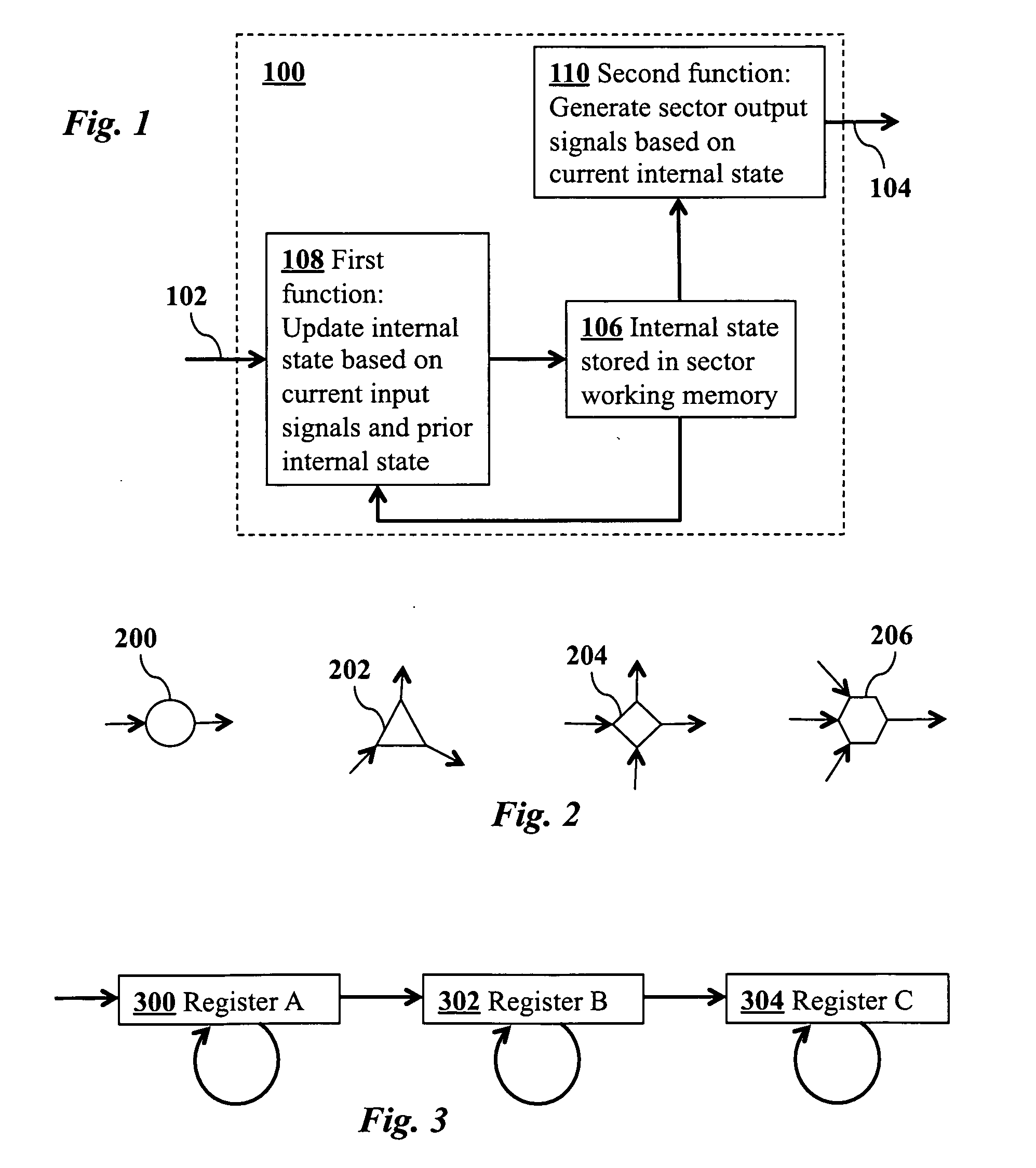
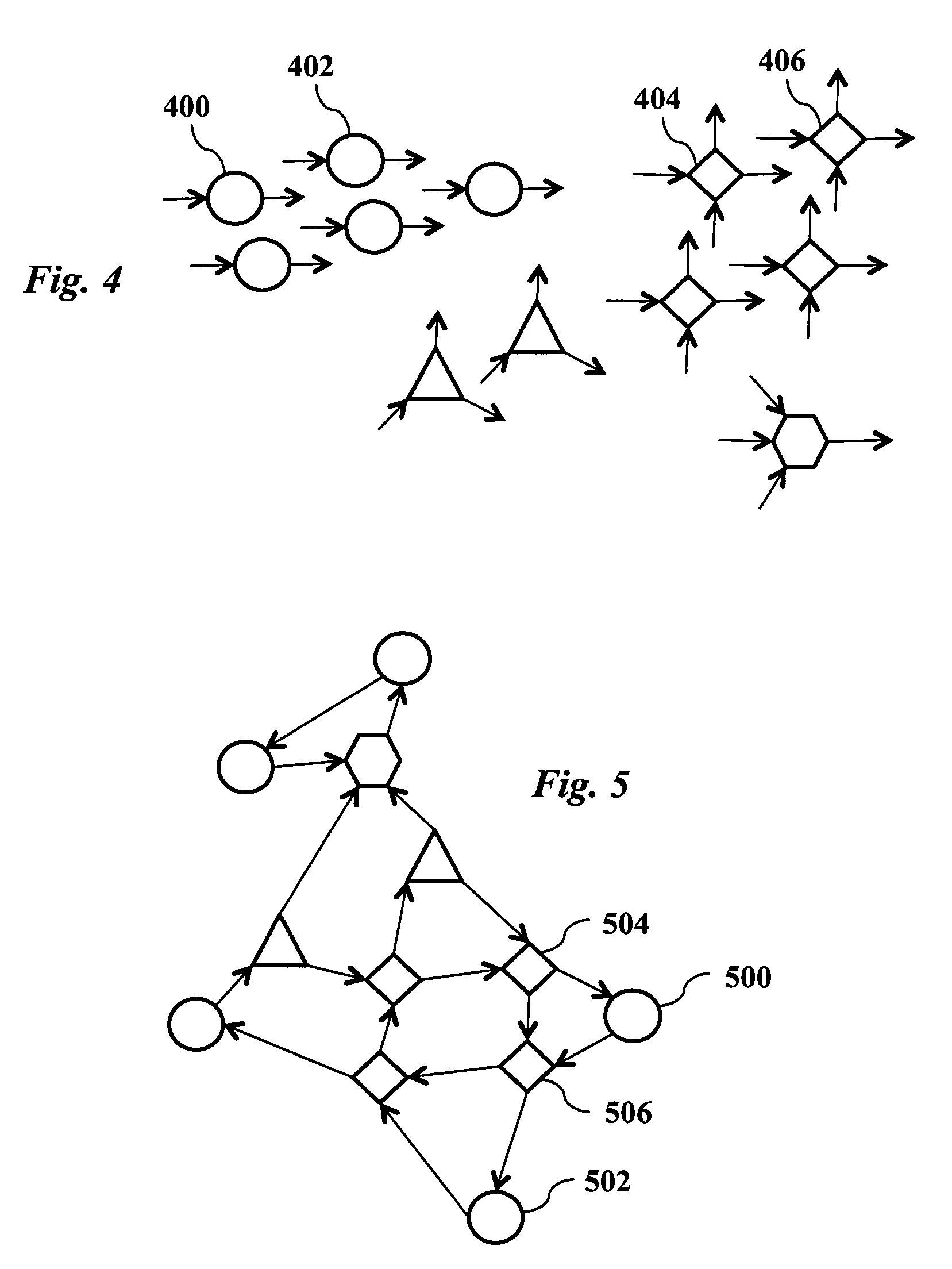
ActiveUS20110016071A1Effective simulationExact reproductionDigital computer detailsDigital dataInformation processingNervous system
A neural network simulation represents components of neurons by finite state machines, called sectors, implemented using look-up tables. Each sector has an internal state represented by a compressed history of data input to the sector and is factorized into distinct historical time intervals of the data input. The compressed history of data input to the sector may be computed by compressing the data input to the sector during a time interval, storing the compressed history of data input to the sector in memory, and computing from the stored compressed history of data input to the sector the data output from the sector.
Owner:CORTICAL DATABASE
Radio communication apparatus, ad-hoc system and communication system
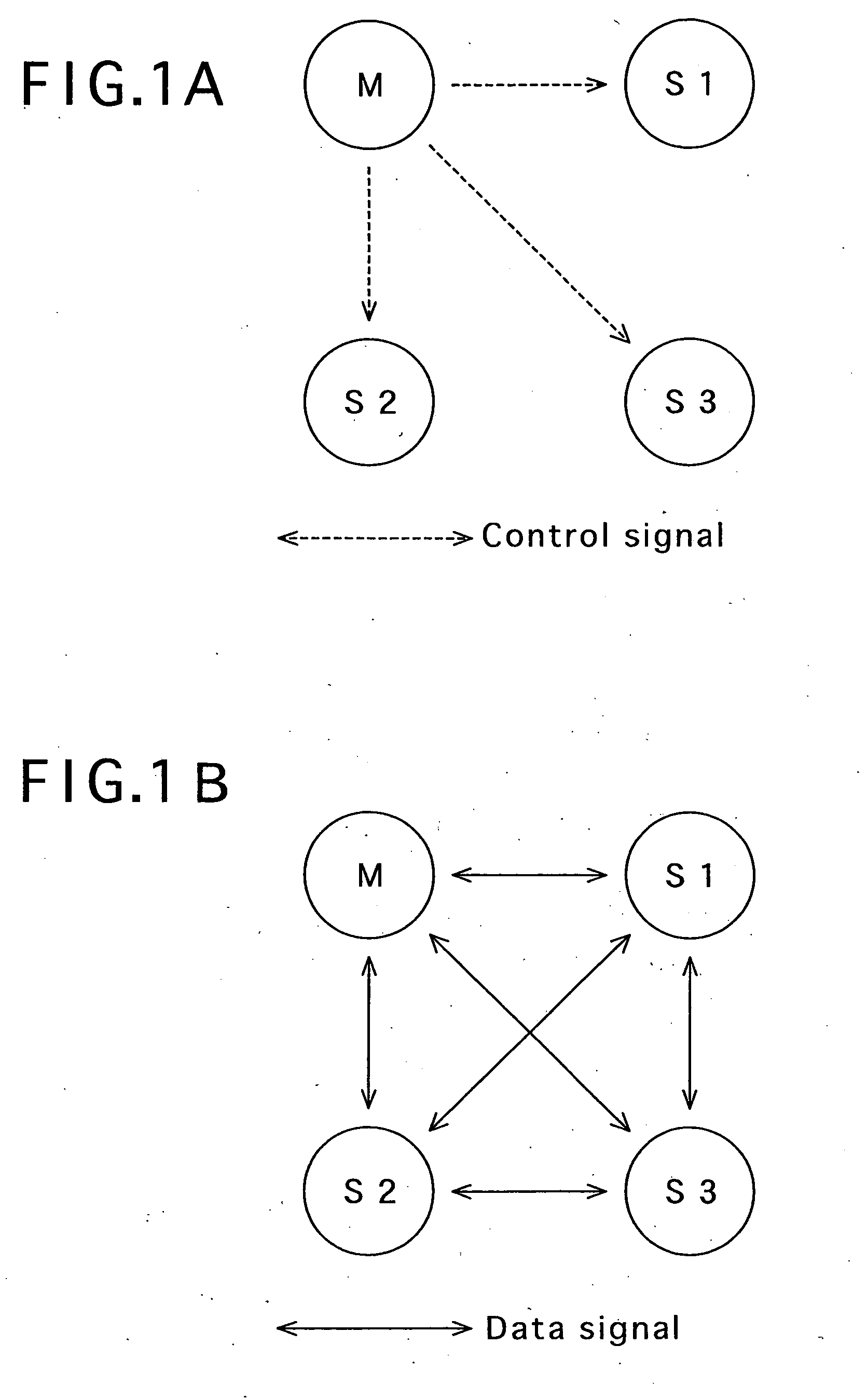
InactiveUS20070109989A1Increase costImprove economyNetwork topologiesRadio/inductive link selection arrangementsCommunications systemControl signal
An object of the present invention is to improve the network usage efficiency and economy. There is provided a radio communication apparatus (10) having ad-hoc communication means for building an ad-hoc network with other nearby radio communication apparatus and performing communication with the other radio communication apparatus by radio. The ad-hoc communication means comprises: node type setting means for searching the ad-hoc network for the master and setting the node type of the radio communication apparatus (10) to any of the master and slave on the basis of the search result; set-up information acquisition means for, when the node type of the radio communication apparatus (10) is set to the slave, transmitting and receiving control signals to and from the master to acquire set-up information required for communication with any of the master and slave in the ad-hoc network and storing the set-up information in storage means; and data signal transmission means for directly transmitting and receiving data signals to and from any of the master and slave in the ad-hoc network in accordance with the set-up information acquired from the master.
Owner:IPMOBILE INCORPD +1
Methods and systems for using names in virtual networks
InactiveUS7028334B2Easily and effectively leverage powerWithout complexityDigital data processing detailsUser identity/authority verificationParallel computingVirtual address space
Owner:ORACLE SYST CORP
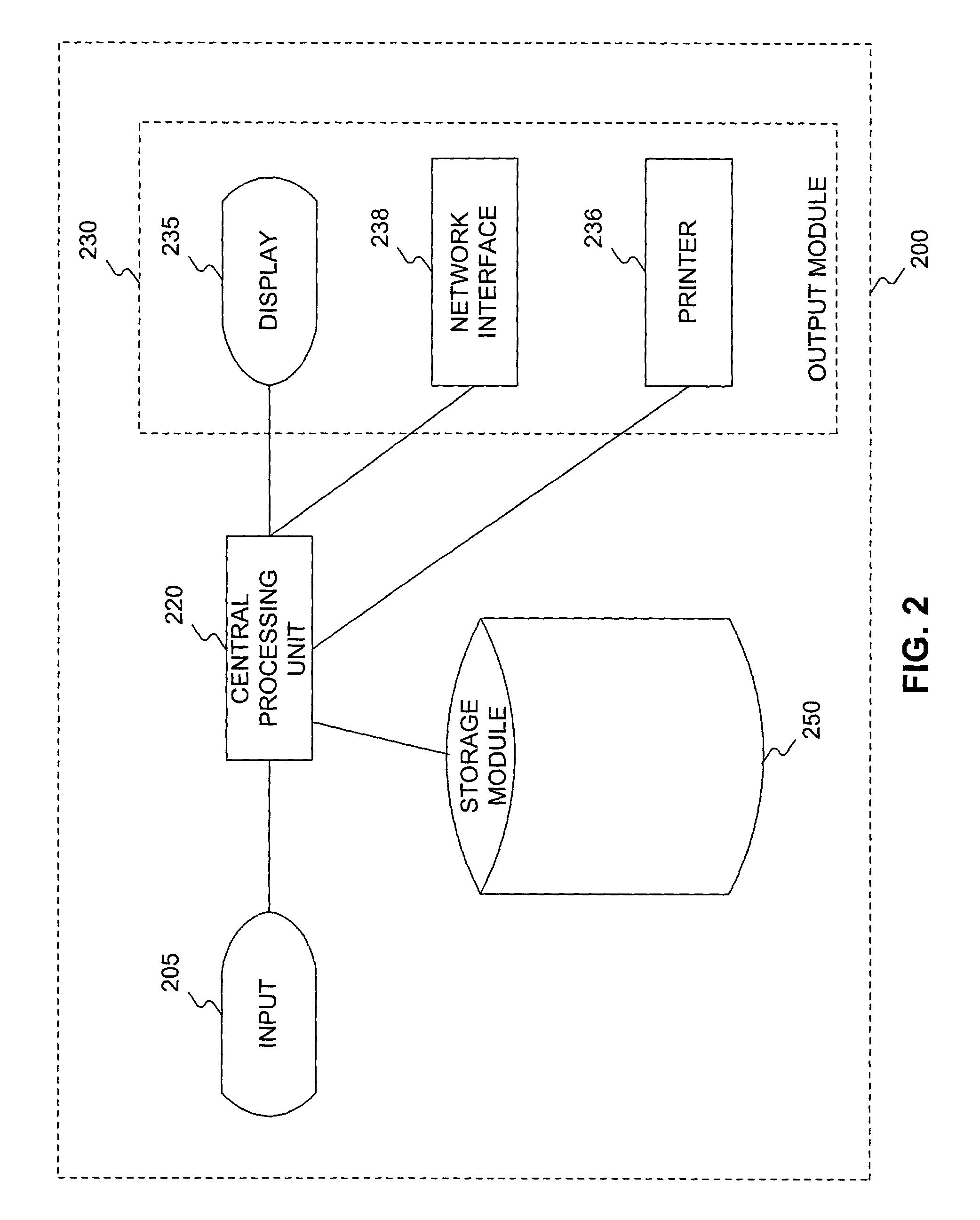
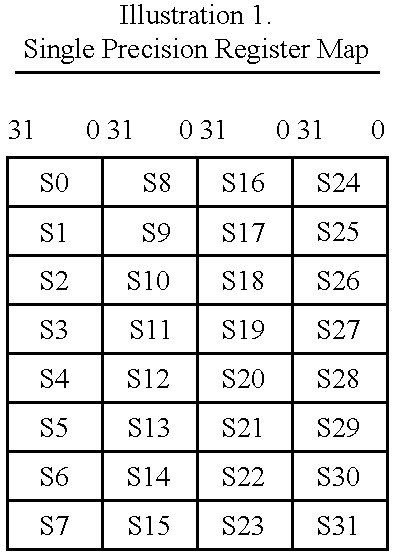
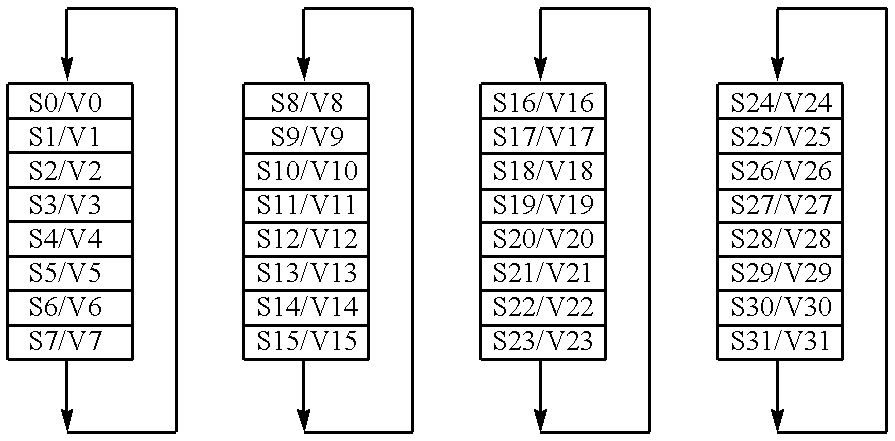
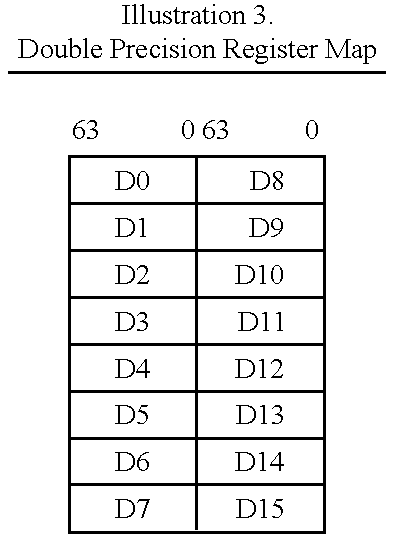
Vector register addressing
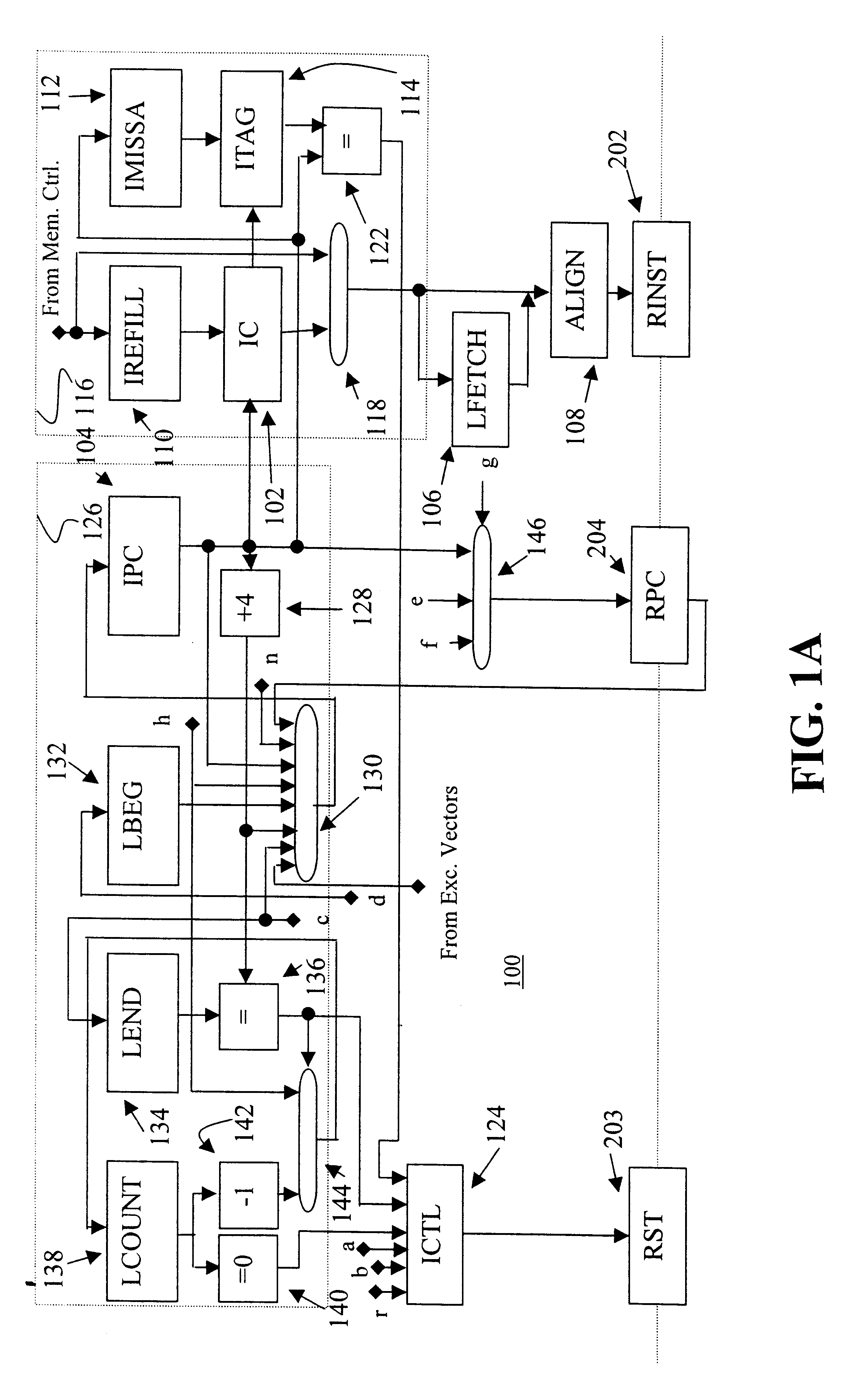
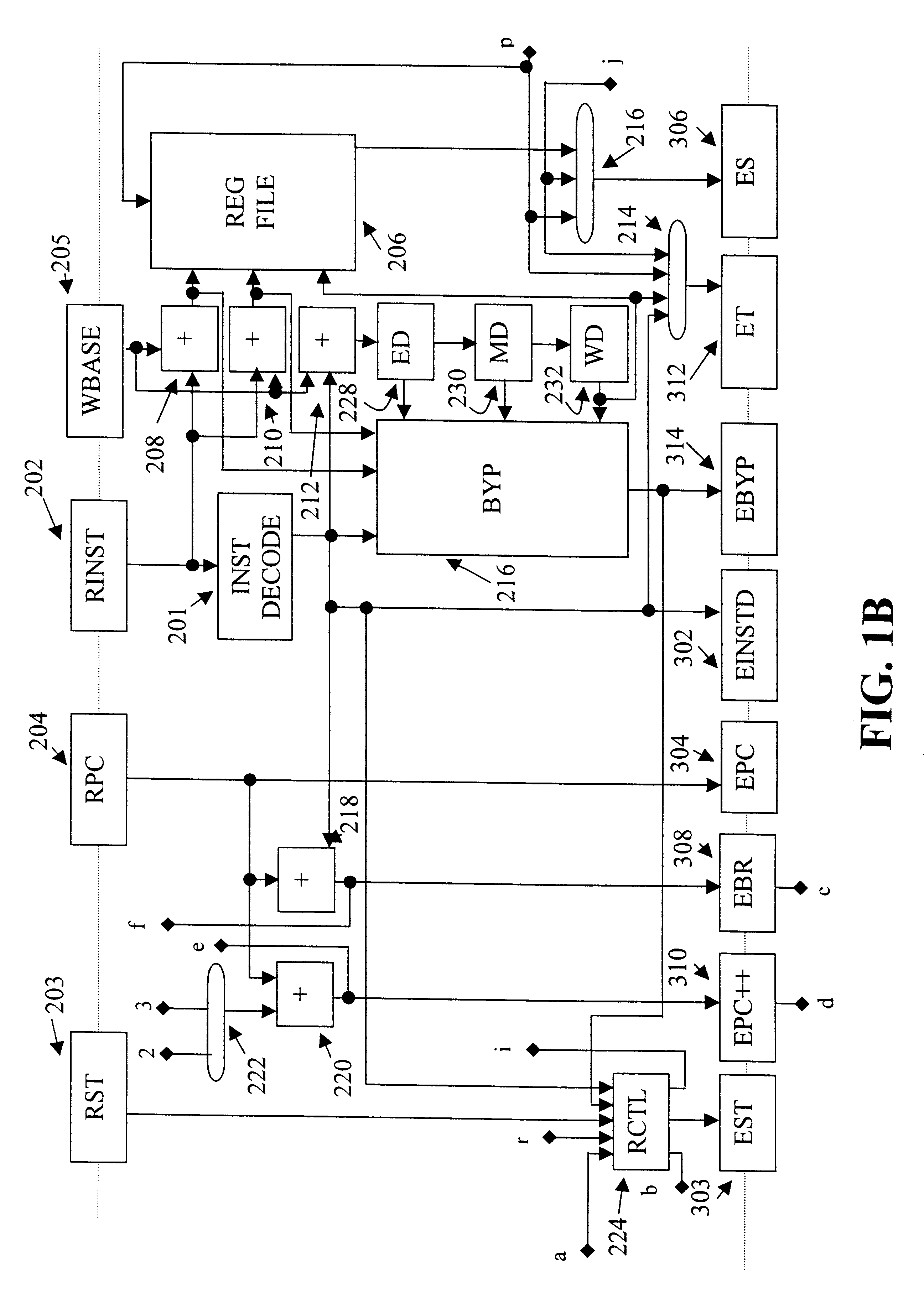
InactiveUS6332186B1Without complexityWithout costRegister arrangementsInstruction analysisMemory addressProcessing Instruction
A floating point unit 26 is provided with a register bank 38 comprising 32 registers that may be used as either vector registers V or scalar registers S. Data values are transferred between memory 30 and the registers within the register bank 38 using contiguous block memory access instructions. Vector processing instructions specify a sequence of processing operations to be performed upon data values within a sequence of registers. The register address is incremented between each operation by an amount controlled by a stride value. Accordingly, the register address can be incremented by values such as 0, 1, 2 or 4 between each iteration. This provides a mechanism for retaining block memory access instructions to contiguous memory addresses whilst supporting vector matrix and / or complex operations in which the data values needed for each iteration are not adjacent to one another in the memory 30.
Owner:ARM LTD
High data density RISC processor
InactiveUS6282633B1High densityIncrease in CPIInstruction analysisDigital computer detailsProgram instructionProcessor register
A RISC processor implements an instruction set which, in addition to optimizing a relationship between the number of instructions required for execution of a program, clock period and average number of clocks per instruction, also is designed to optimize the equation S=IS * BI, where S is the size of program instructions in bits, IS is the static number of instructions required to represent the program (not the number required by an execution) and BI is the average number of bits per instruction. Compared to conventional RISC architectures, this processor lowers both BI and IS with minimal increases in clock period and average number of clocks per instruction. The processor provides good code density in a fixed-length high-performance encoding based on RISC principles, including a general register with load / store architecture. Further, the processor implements a simple variable-length encoding that maintains high performance.
Owner:TENSILICA
Methods and systems for hairpins in virtual networks
InactiveUS7047424B2Easily and effectively leverage powerWithout complexityData switching detailsMemory loss protectionParallel computingVirtual network
Methods and systems are provided for enabling communication between a first processor and a second processor using at least one additional processor separate from the first and second processors, wherein one or more firewalls selectively restrict the communication. In one embodiment, the additional processor may determine whether the first and second processors mutually consent to enabling a hairpin between the first and second processors. The first processor may be provided with a first information identifying the hairpin and the second processor may be provided with a second information identifying the hairpin, when the additional processor may determine that the first and second processors mutually consent to the hairpin. Moreover, a first information flow may be established from the first processor to the hairpin based on the provided first information, and a second information flow may be established from the second processor to the hairpin based on the provided second information. The hairpin may forward the first information flow received from the first processor to the second processor such that the communication between the first and second processors is allowed by the firewalls.
Owner:ORACLE SYST CORP
Downhole filter
InactiveUS7188687B2Without complexityWithout expenseDrilling rodsConstructionsParticulatesEngineering
A downhole filter comprises a tubular member having a wall defining a plurality of openings. The openings have an outer width less than an inner width. The parts of the opening defining the smaller width are defined by radially outer parts of the openings, such that particulates or sand prevented from passing through the openings will tend to be retained to the outside of the tubular member. A method comprises providing a tubular string having a non-porous tubular portion and a porous tubular portion, and installing the tubular string within a wellbore such that the porous tubular portion is located adjacent a fluid-producing formation within the wellbore. In another embodiment, an apparatus comprises a drill string comprising a non-porous tubular portion and a porous tubular portion, and an earth removal member operatively connected to a lower end of the drill string.
Owner:WEATHERFORD TECH HLDG LLC
Position determination using carrier phase measurements of satellite signals
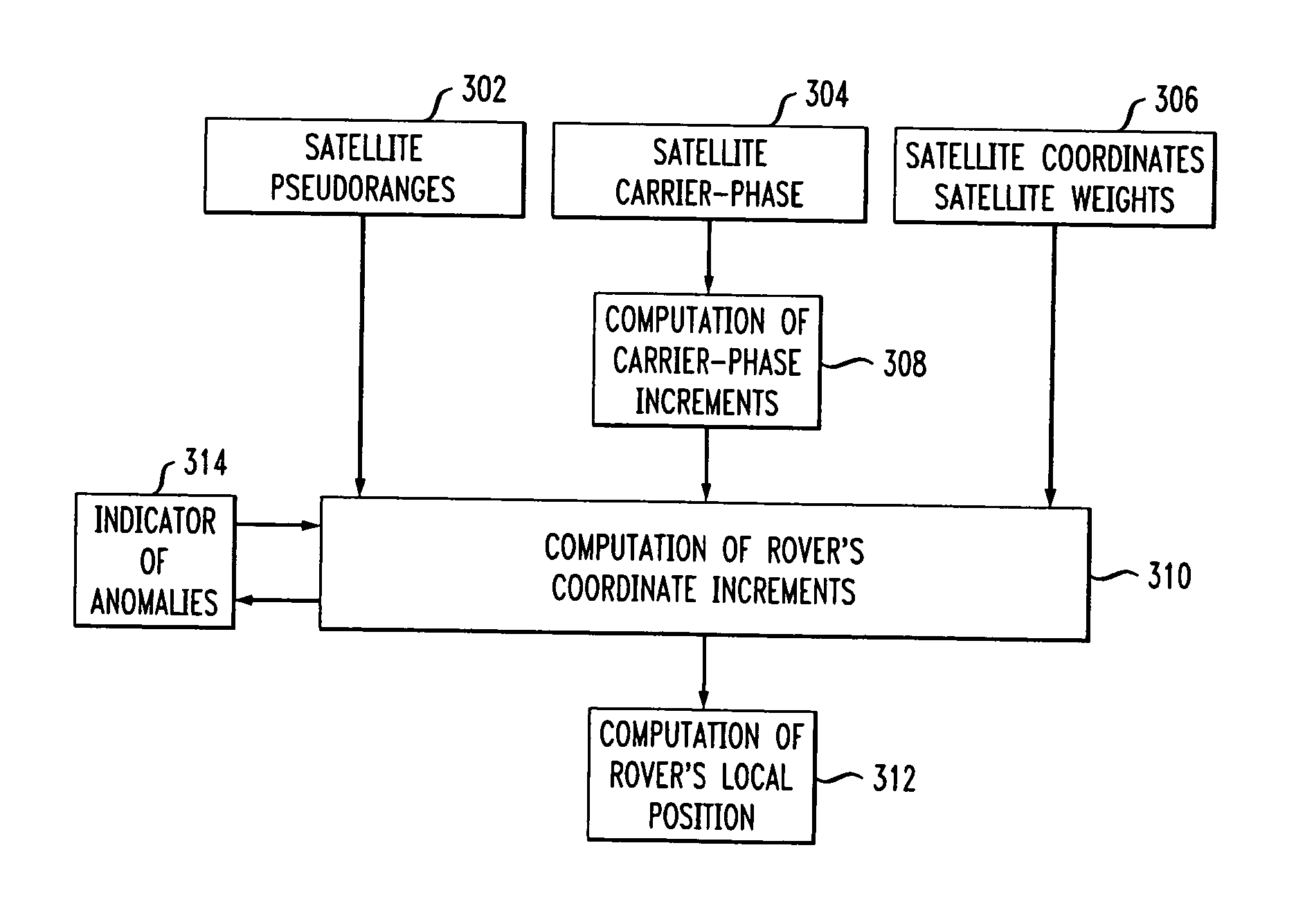
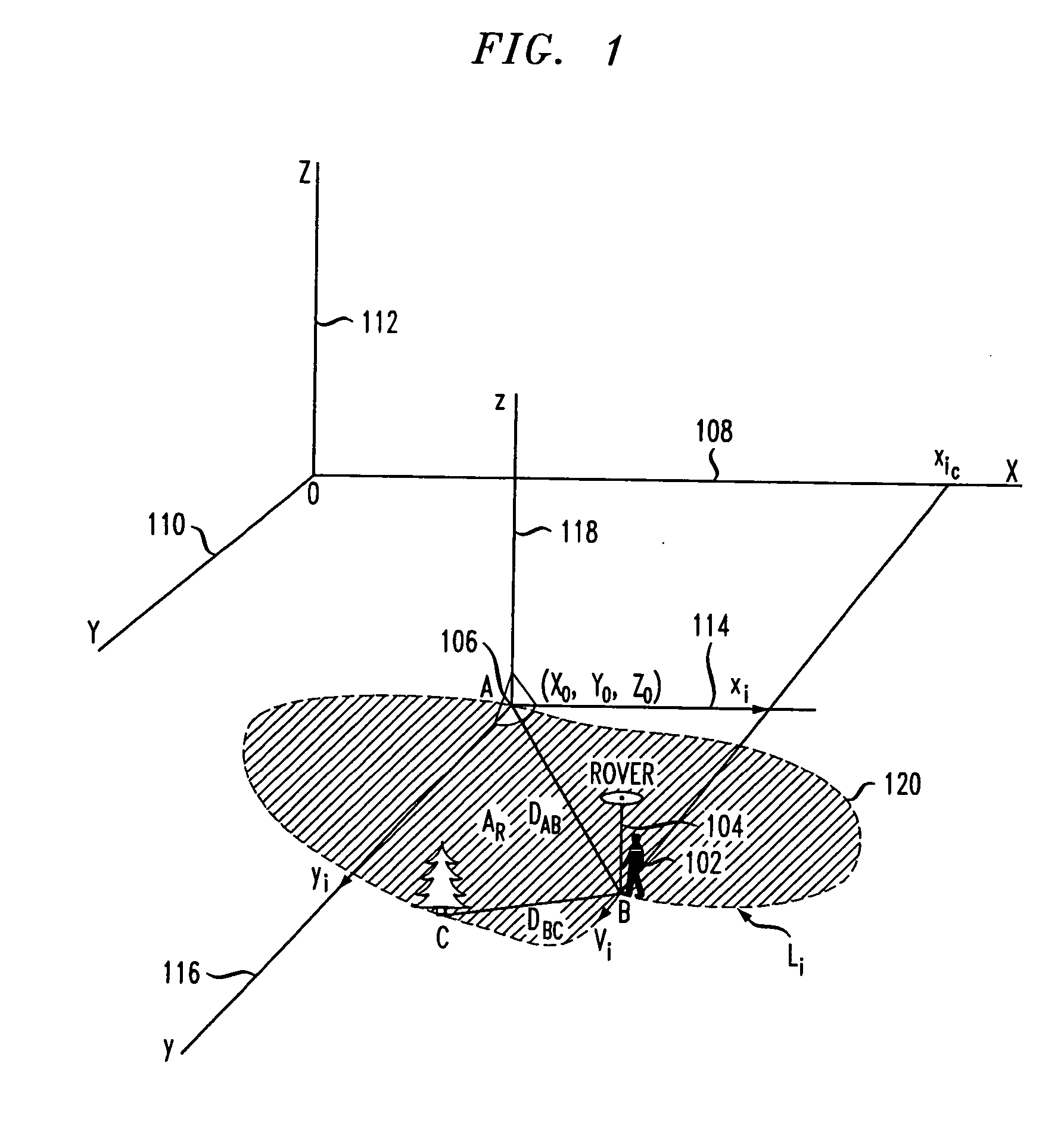
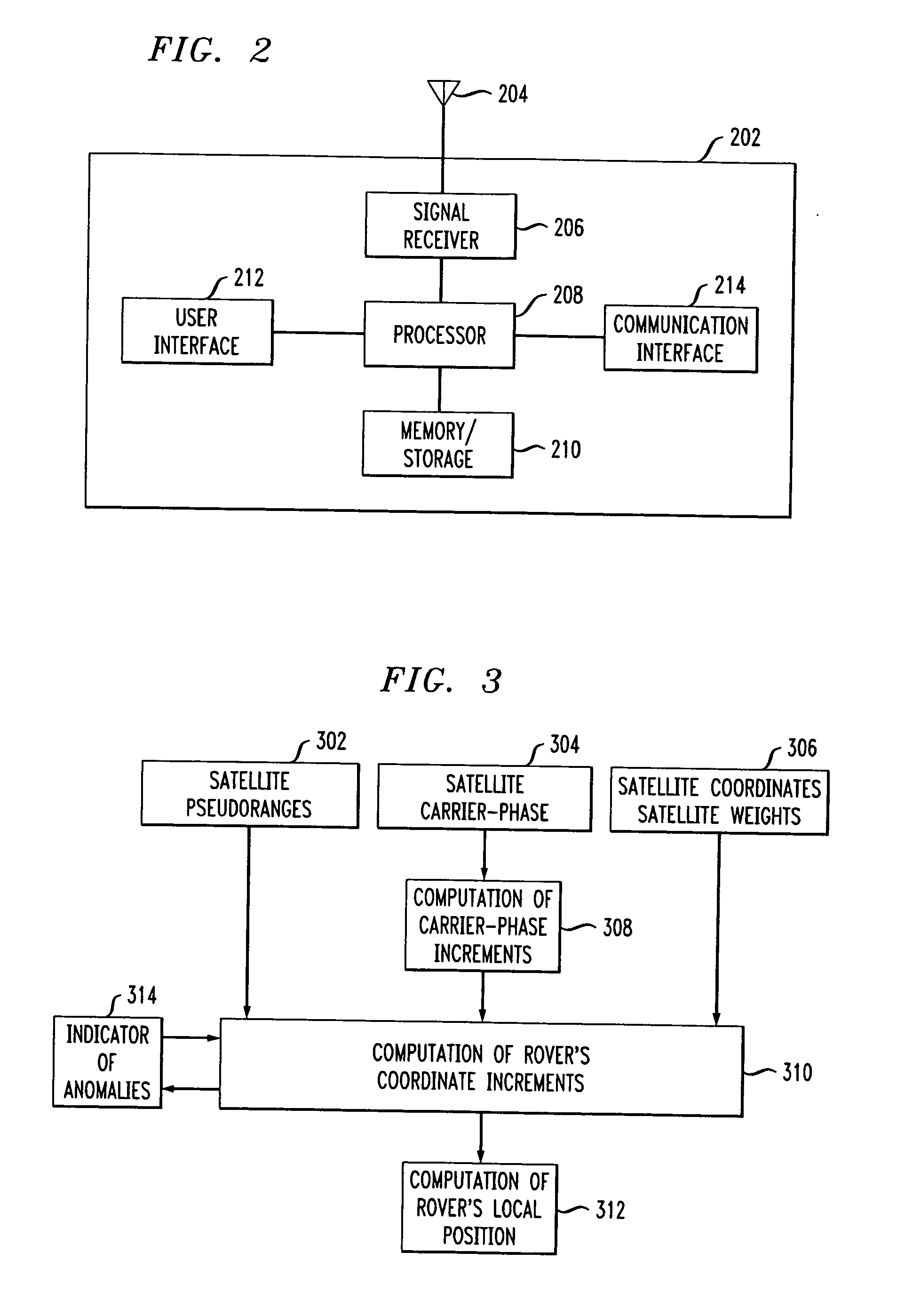
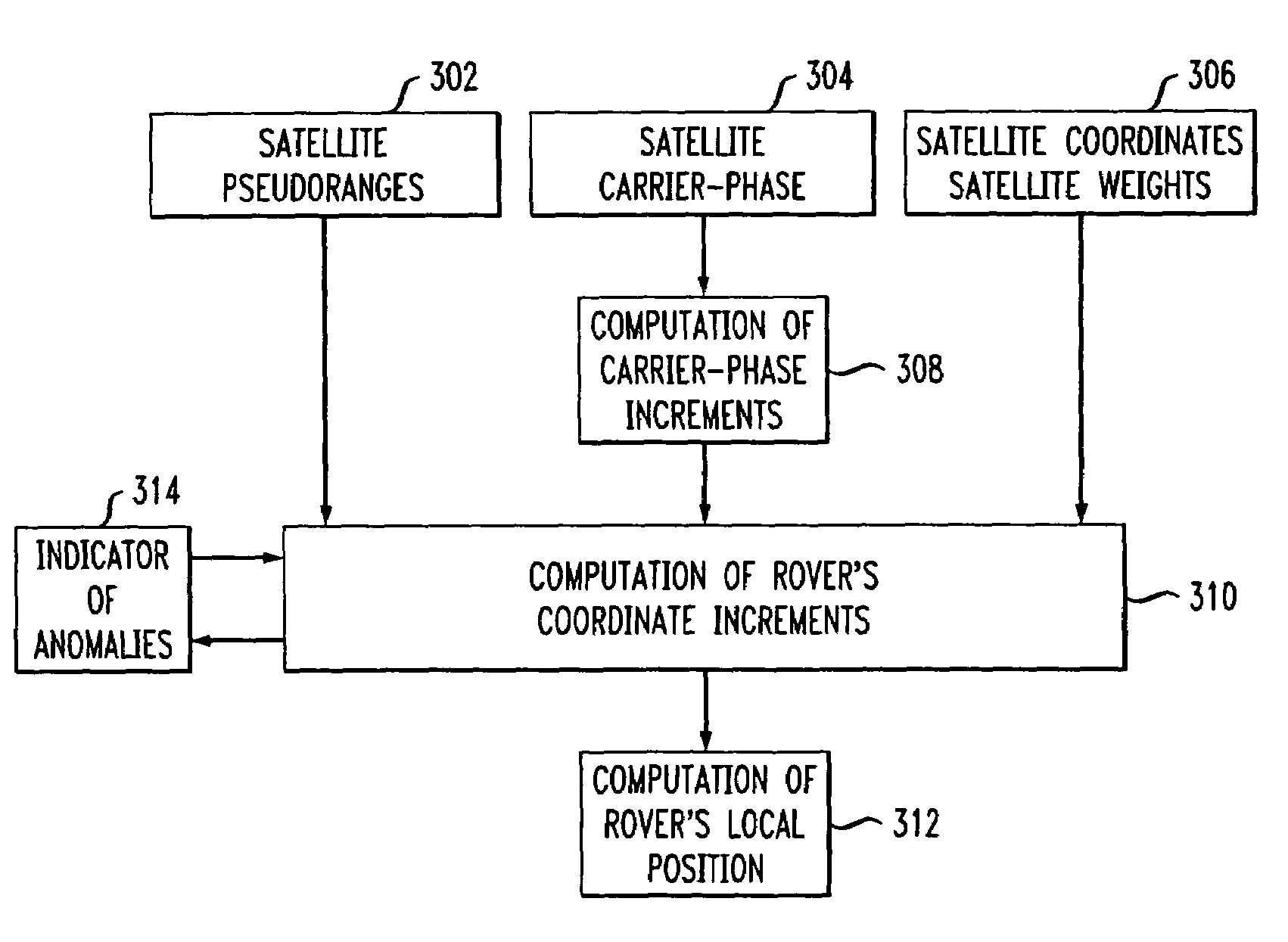
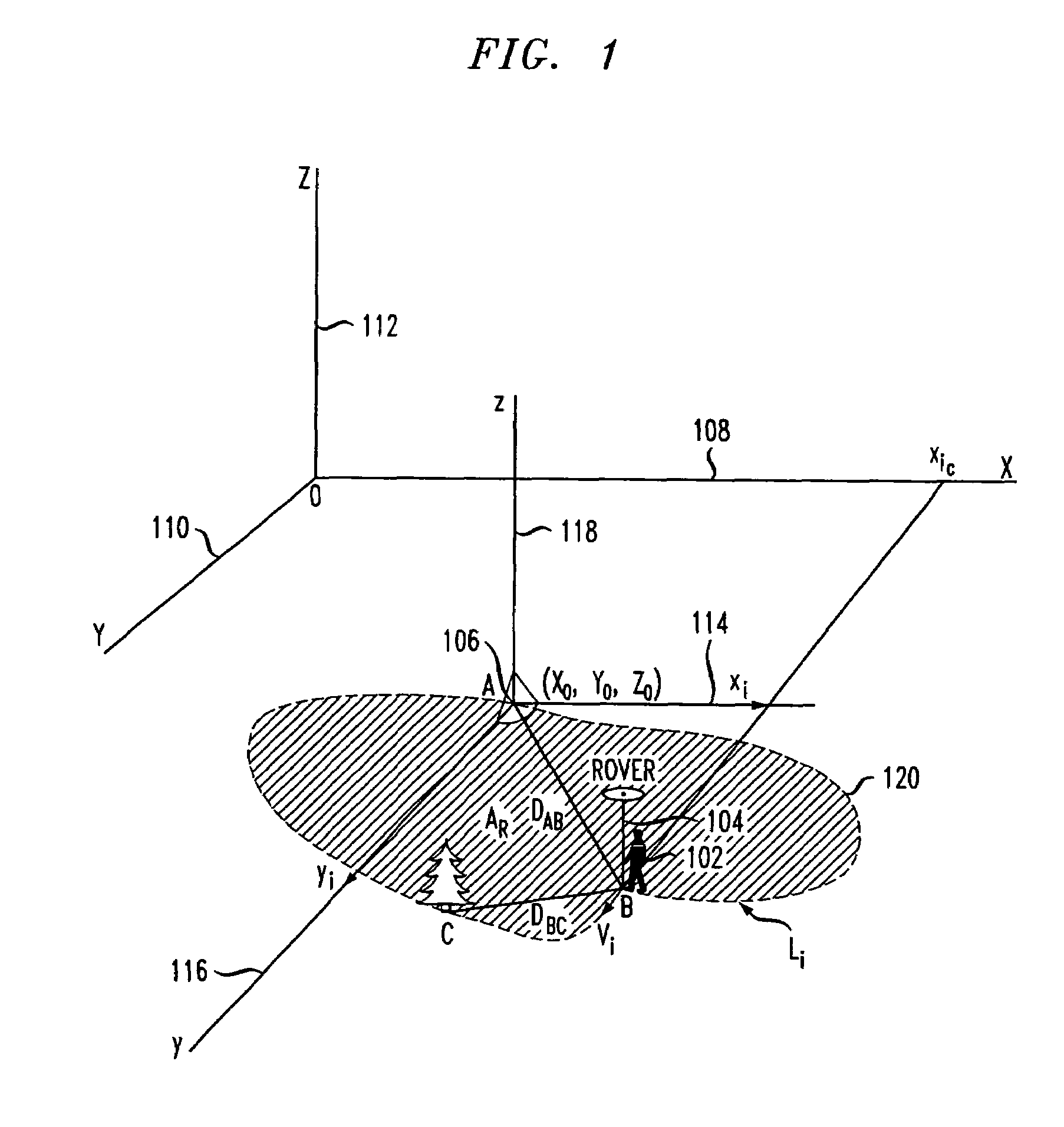
ActiveUS20070052583A1Improved relative position determination accuracyWithout cost and complexityPosition fixationNavigation instrumentsLeast squaresMarine navigation
Disclosed is a method and apparatus for determining the relative position of a mobile unit that moves from an initial location to a plurality of successive positions. The mobile unit receives signals from a plurality of navigation satellites and tracks the carrier phases of the signals during movement. For each of the received signals, carrier phase increments are calculated over a plurality of epochs. Anomalous carrier phase increments are determined and eliminated from further calculations. The non-eliminated carrier phase increments are then used to calculate coordinate increments for each of the time epochs. If, after elimination, the remaining number of carrier-phase increments is less than a threshold for a particular epoch, then coordinate increments for the particular epoch may be extrapolated using data from prior epochs. In various embodiments, least squares method and Kalman filtering may be used to calculate the coordinate increments. The coordinate increments may then be summed over a plurality of time epochs in order to determine a position of the mobile unit relative to its initial position.
Owner:TOPCON GPS
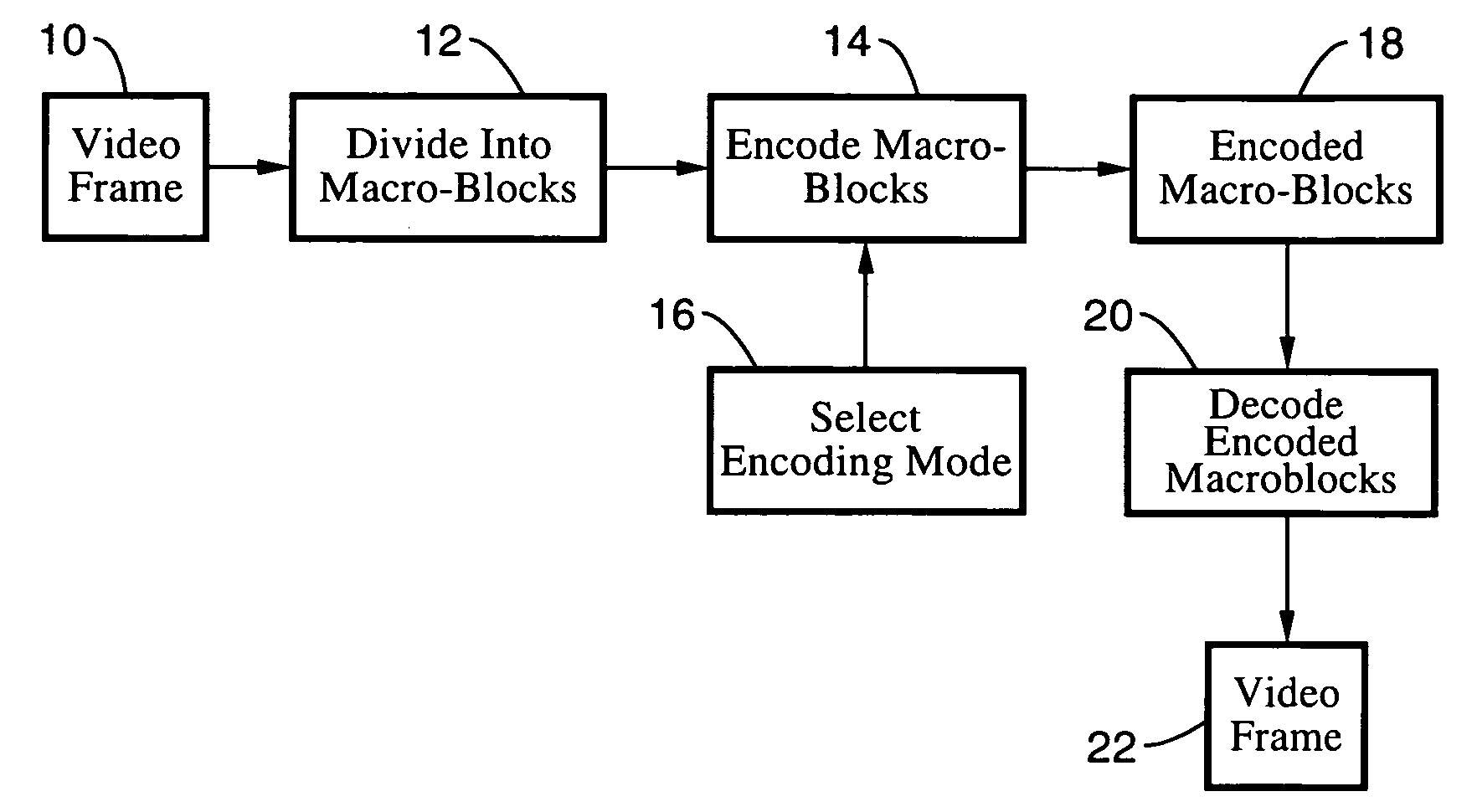
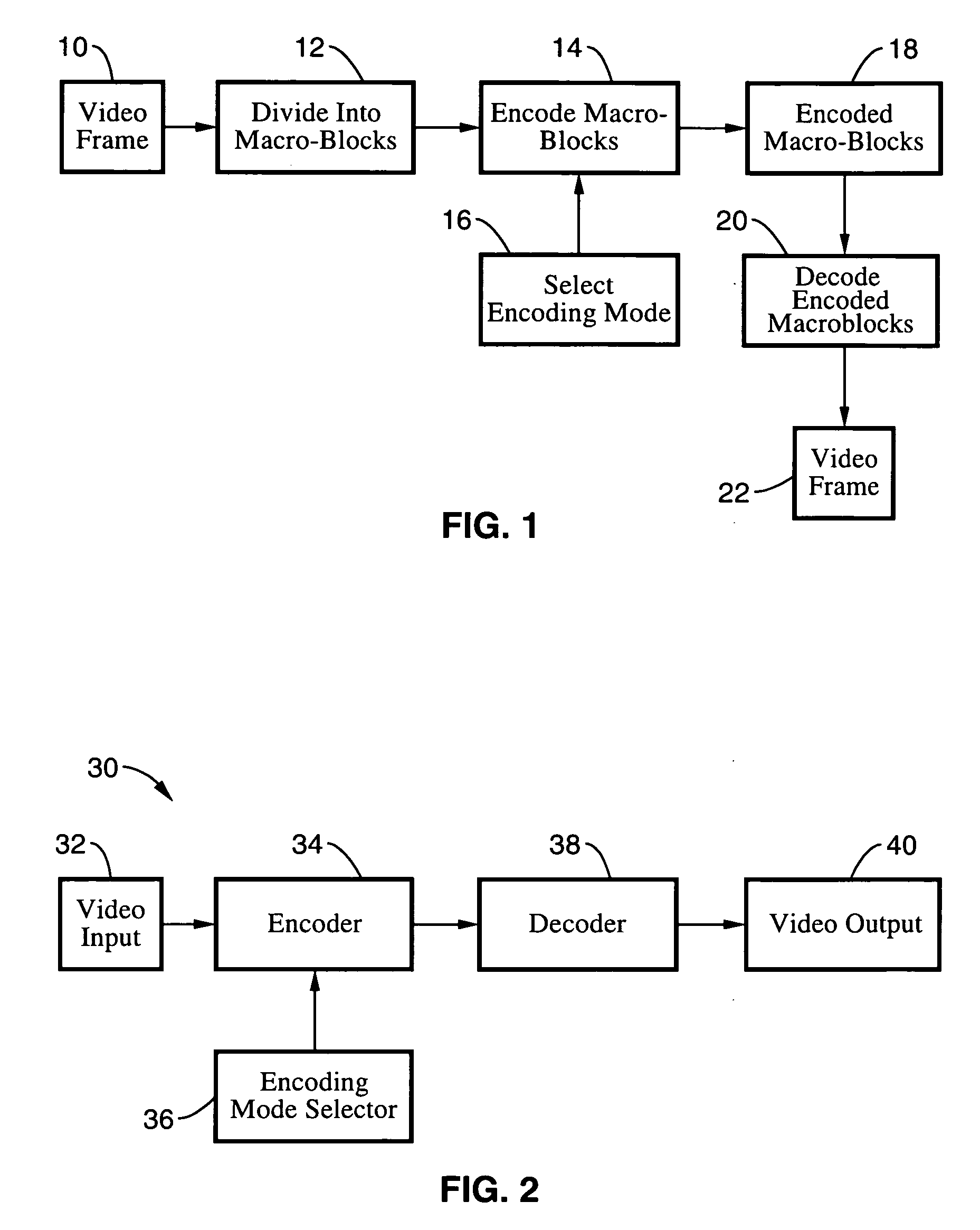
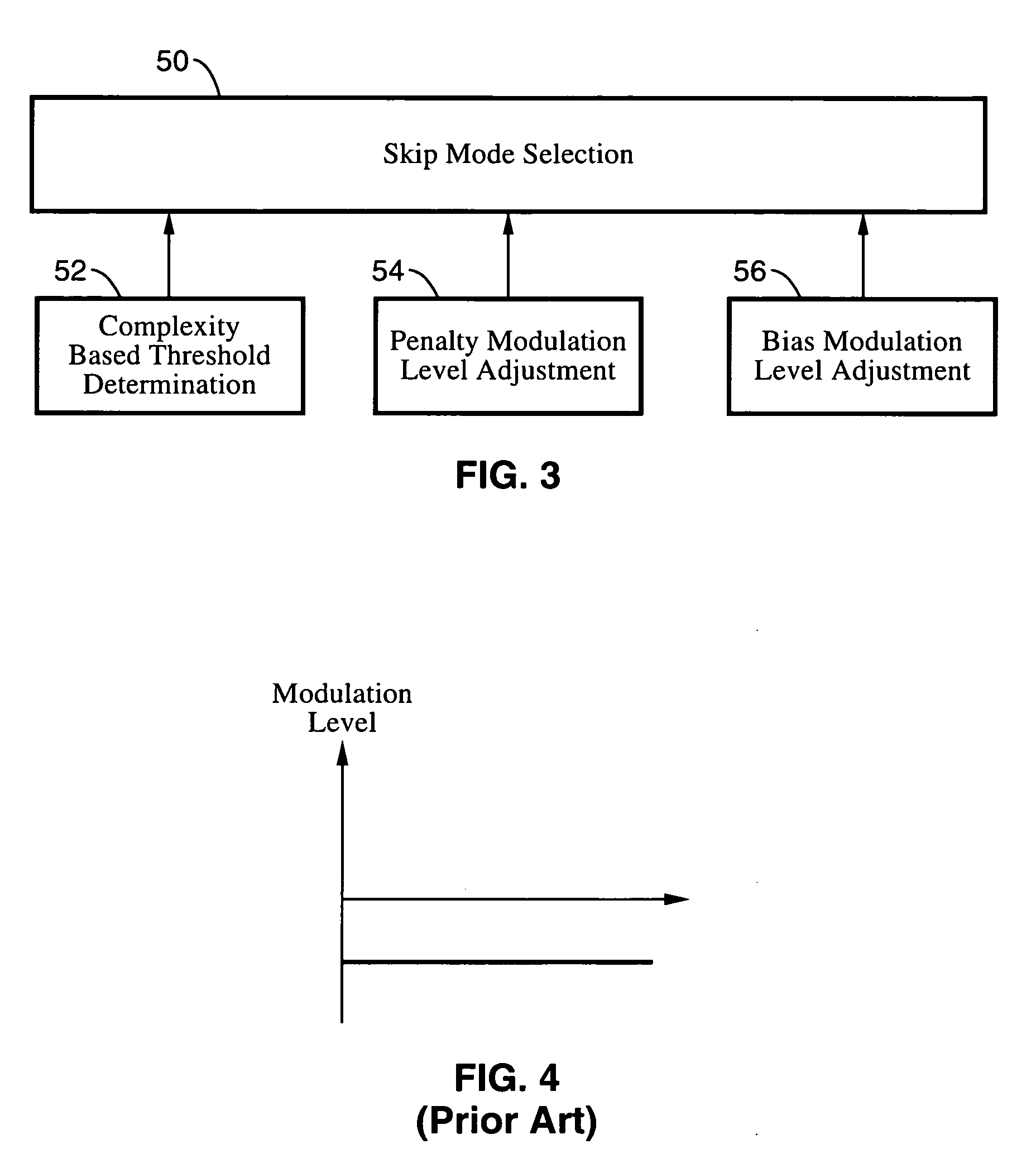
Complexity adaptive skip mode estimation for video encoding
InactiveUS20070274396A1Quality improvementCompressing bit rate obtainedColor television with pulse code modulationColor television with bandwidth reductionComputer architectureVideo encoding
In a system and method for coding moving pictures, the cost of skip mode is estimated to determine the best coding mode. Skip mode selection within the framework of the AVC standard is improved by complexity based threshold determination, penalty modulation level adjustment and bias modulation level adjustment for the encoding mode selection.
Owner:SONY CORP +1
Adjustable arc rotor-type sprinkler with selectable uni-directional full circle nozzle rotation
ActiveUS7287711B2Reduce wearPrevent frostbiteWatering devicesMovable spraying apparatusEngineeringNozzle
Owner:HUNTER INDUSTRIES
Low viscosity bilayer disrupted softening composition for tissue paper
InactiveUS6855229B2Good flexibilityAcceptable strengthNatural cellulose pulp/paperSpecial paperCelluloseAmmonium compounds
Disclosed is a composition for softening a wet laid cellulosic structure. A particularly preferred structure is an absorbent tissue. Further disclosed are tissue structures softened using the composition. The composition includes an effective amount of a softening active ingredient; a vehicle in which the softening active ingredient is dispersed; an electrolyte dissolved in the vehicle; and a bilayer disrupter. The electrolyte and the bilayer disrupter cooperate to cause the viscosity of the composition to be less than the viscosity of a dispersion of the softening active ingredient in the vehicle alone. Preferably, the softening active ingredient is a quaternary ammonium compound with the formula:(R1)4-m—N+—[(CH2)n—Y—R3]mX−the vehicle is water, the electrolyte is calcium chloride, and the bilayer disrupter is a nonionic surfactant. Also disclosed is a method of using the compound by adding it at a use concentration to the wet end of a papermaking process.
Owner:THE PROCTER & GAMBLE COMPANY
Method and apparatus for treating the body
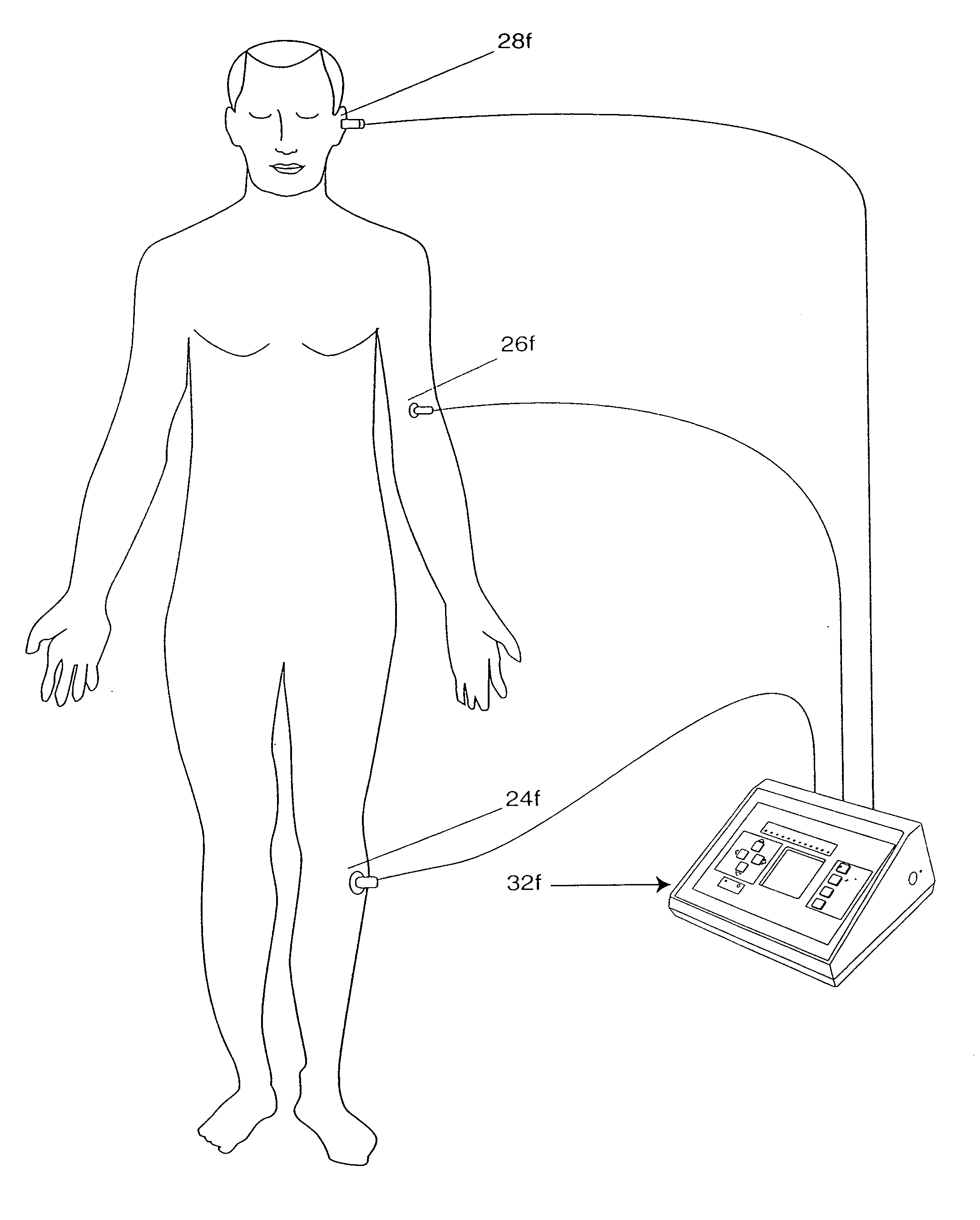
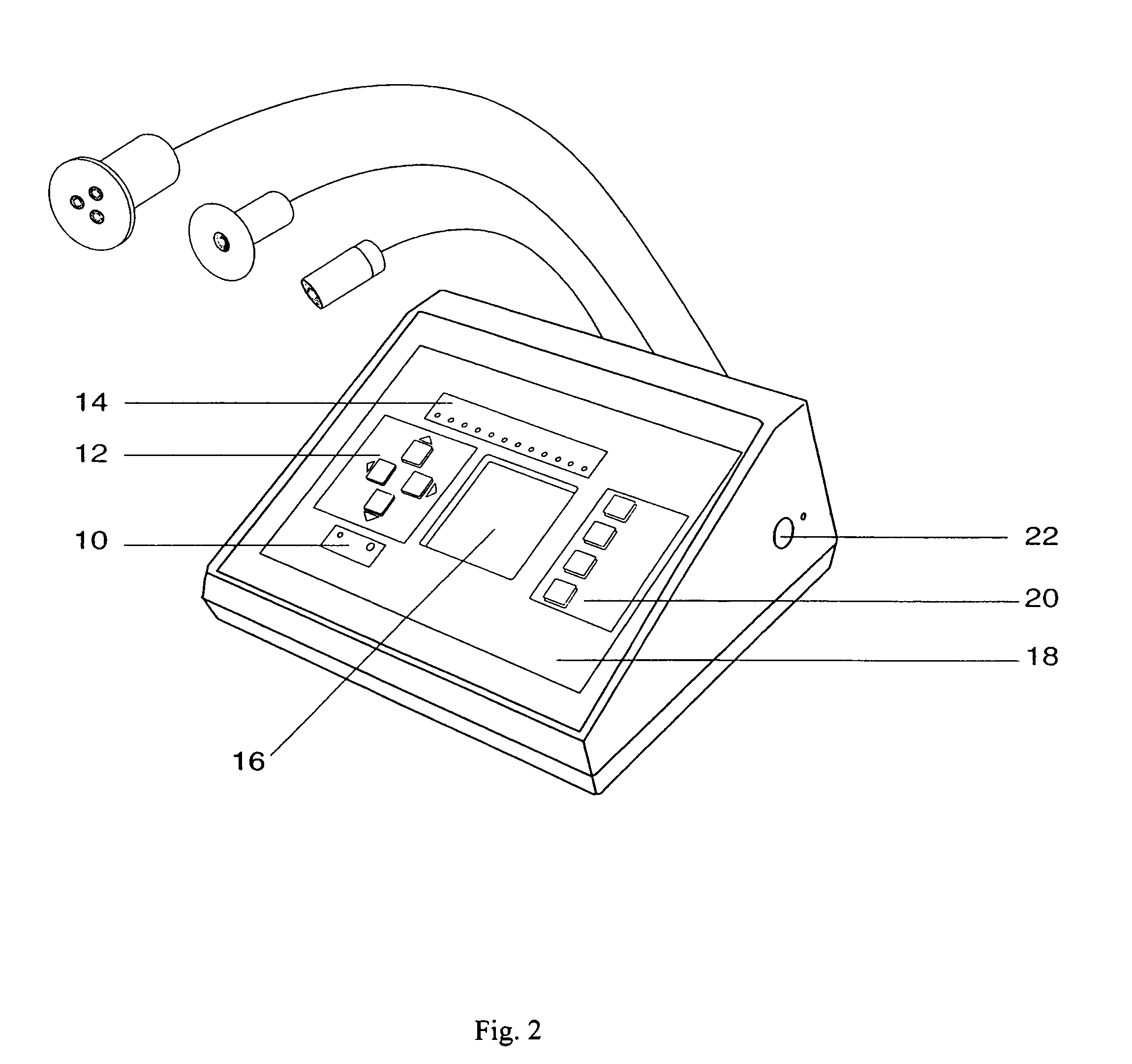
InactiveUS7993381B2Preventing plateau effectExtend your lifeSurgeryDiagnostic recording/measuringDiseaseThroat
A therapeutic method in which plural points on the body are stimulated by light of different wavelengths emitted from wands, probes or other applicators under the control of a central microprocessor. The microprocessor executes program instructions to produce light at each applicator whose intensity, frequency, duration and pulsation accord with protocols which are automatically selected depending on the portion of the body being treated. The protocols can be manually overridden by the therapist, in which case the changed parameters are stored in memory. The apparatus is particularly useful in performing traditional therapeutic methods to treat internal disorders, substance abuse, pediatric and podiatric problems and disorders of the ear, nose, throat, as well as musculoskeletal, neurological or dermatological disorders.
Owner:MAC BEAM
Method for efficiently simulating the information processing in cells and tissues of the nervous system with a temporal series compressed encoding neural network
ActiveUS8200593B2Effective simulationExact reproductionDigital computer detailsDigital dataInformation processingNervous system
A neural network simulation represents components of neurons by finite state machines, called sectors, implemented using look-up tables. Each sector has an internal state represented by a compressed history of data input to the sector and is factorized into distinct historical time intervals of the data input. The compressed history of data input to the sector may be computed by compressing the data input to the sector during a time interval, storing the compressed history of data input to the sector in memory, and computing from the stored compressed history of data input to the sector the data output from the sector.
Owner:CORTICAL DATABASE
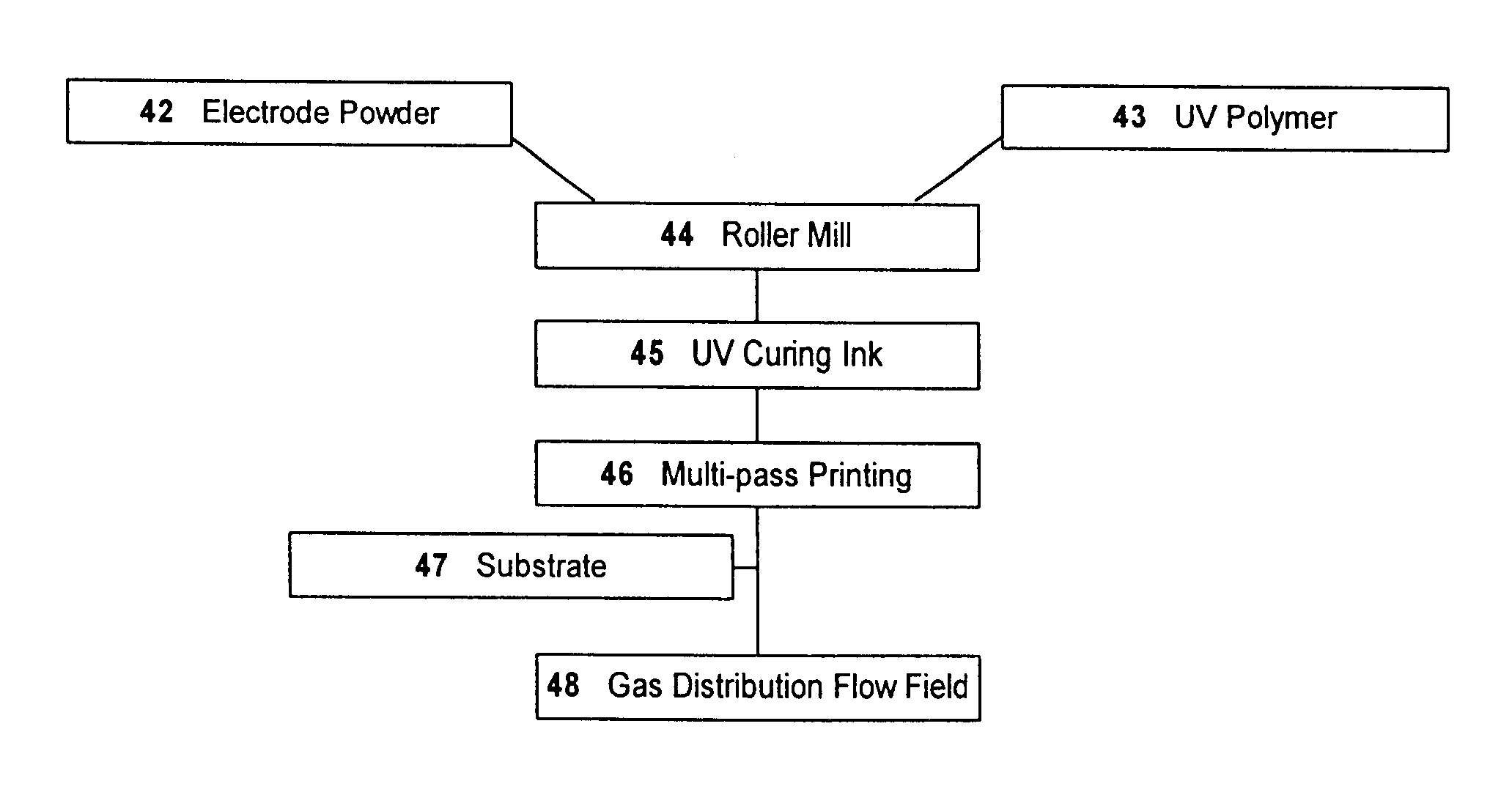
Technique for rapid cured electrochemical apparatus component fabrication
InactiveUS6399233B1Minimal wasteSimplifies current production processAdditive manufacturing apparatusElectrode manufacturing processesManufacturing technologyFuel cells
A process for the fabrication of a component or component feature for an electrochemical apparatus including providing a printing medium comprising a rapid curable polymer containing carrier and a powder of a component material precursor, printing one of a uniform layer or a pattern of such printing medium on a substrate, and rapidly curing the curable polymer to form a cured part; and the parts made by this process. A process for the fabrication or a multi-layer cell of an SOFC including providing a printing medium comprising a radiation curable polymer containing carrier and a powder of a component material precursor, printing one of a uniform layer or a pattern of such printing medium on a substrate, and radiation curing the curable polymer to form a cured part; and the parts made by this process. The process can use an ultraviolet light curable polymer binder and electrode material powder in an industrial printer to form a solid fuel cell electrode component.
Owner:TECH MANAGEMENT
Analog-to-digital converter
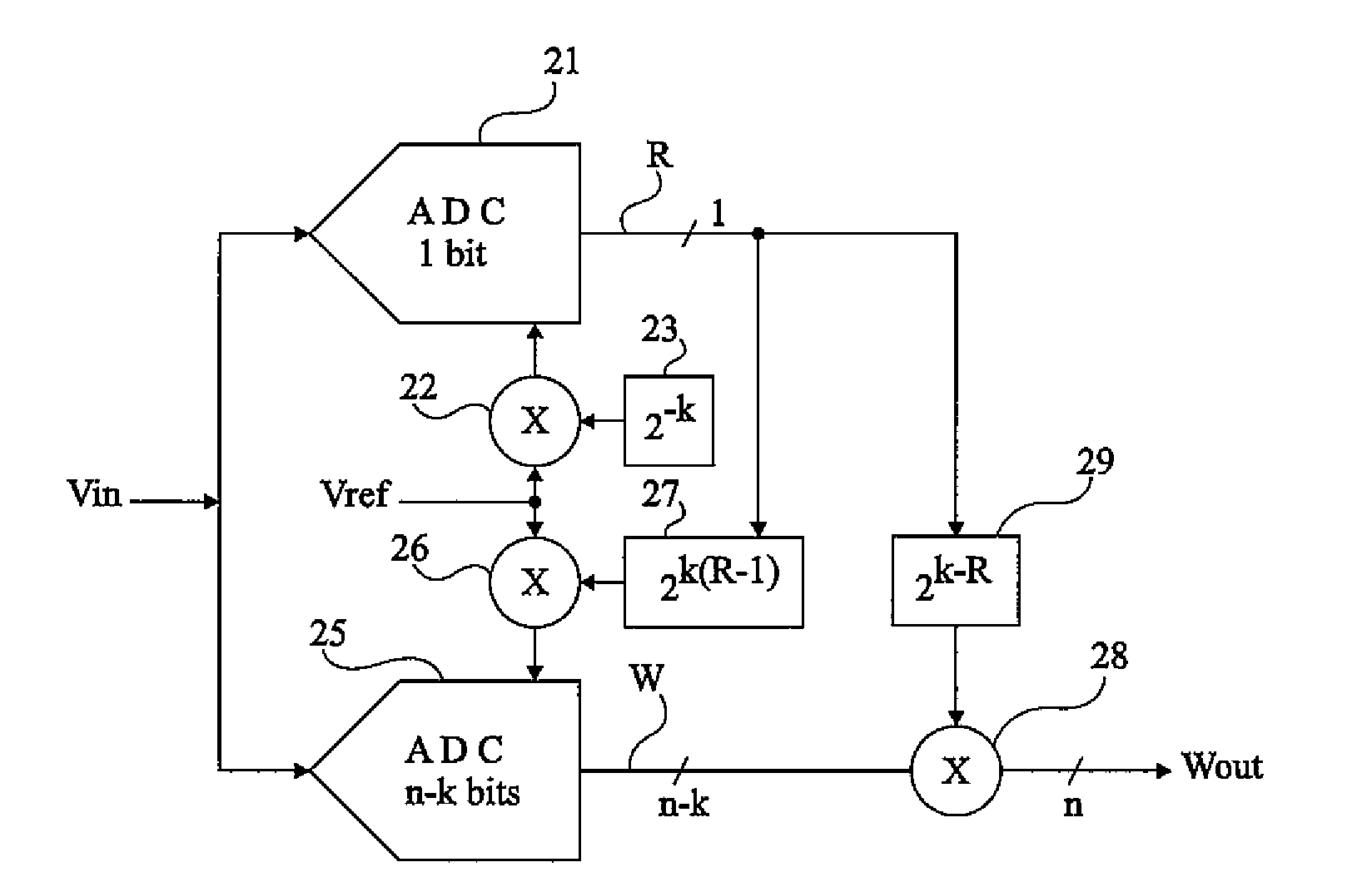
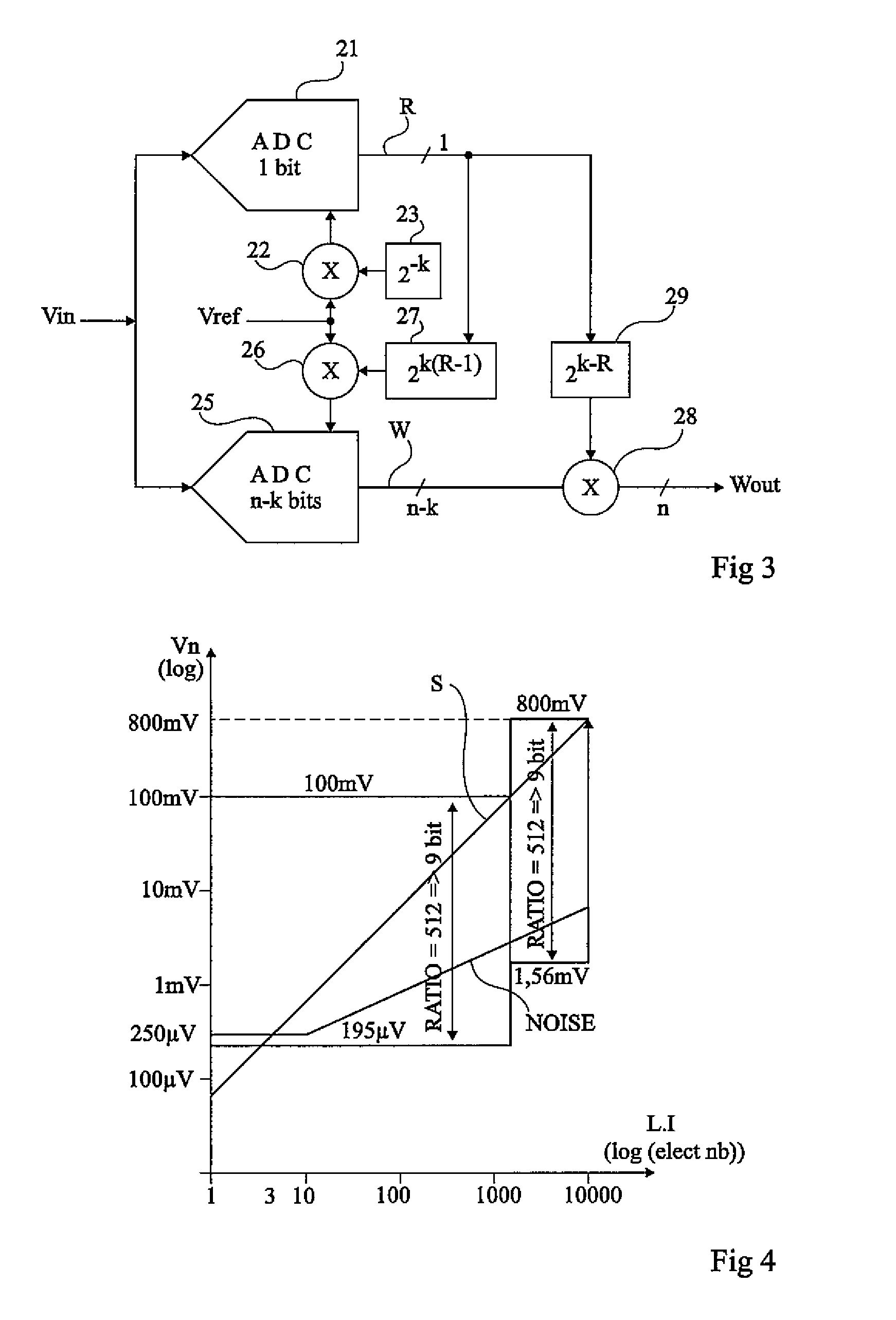
ActiveUS20100039306A1Increase the number of digitsWithout complexityElectric signal transmission systemsAnalogue-digital convertersLeast significant bitA d converter
A method of analog-to-digital conversion over n bits of an analog signal, including the steps of: comparing the amplitude of the analog signal with a threshold representing the amplitude of the full-scale analog signal divided by 2k, where k is an integer smaller than n; performing an analog-to-digital conversion of the analog signal over n-k bits to obtain the n-k most significant bits of a binary word over n bits if the result of the comparison step indicates that the amplitude of the input signal is greater than the threshold, and the n-k least significant bits of this binary word otherwise. An analog-to-digital converter and its application to image sensors.
Owner:STMICROELECTRONICS SRL
Methods for Administering Aripiprazole
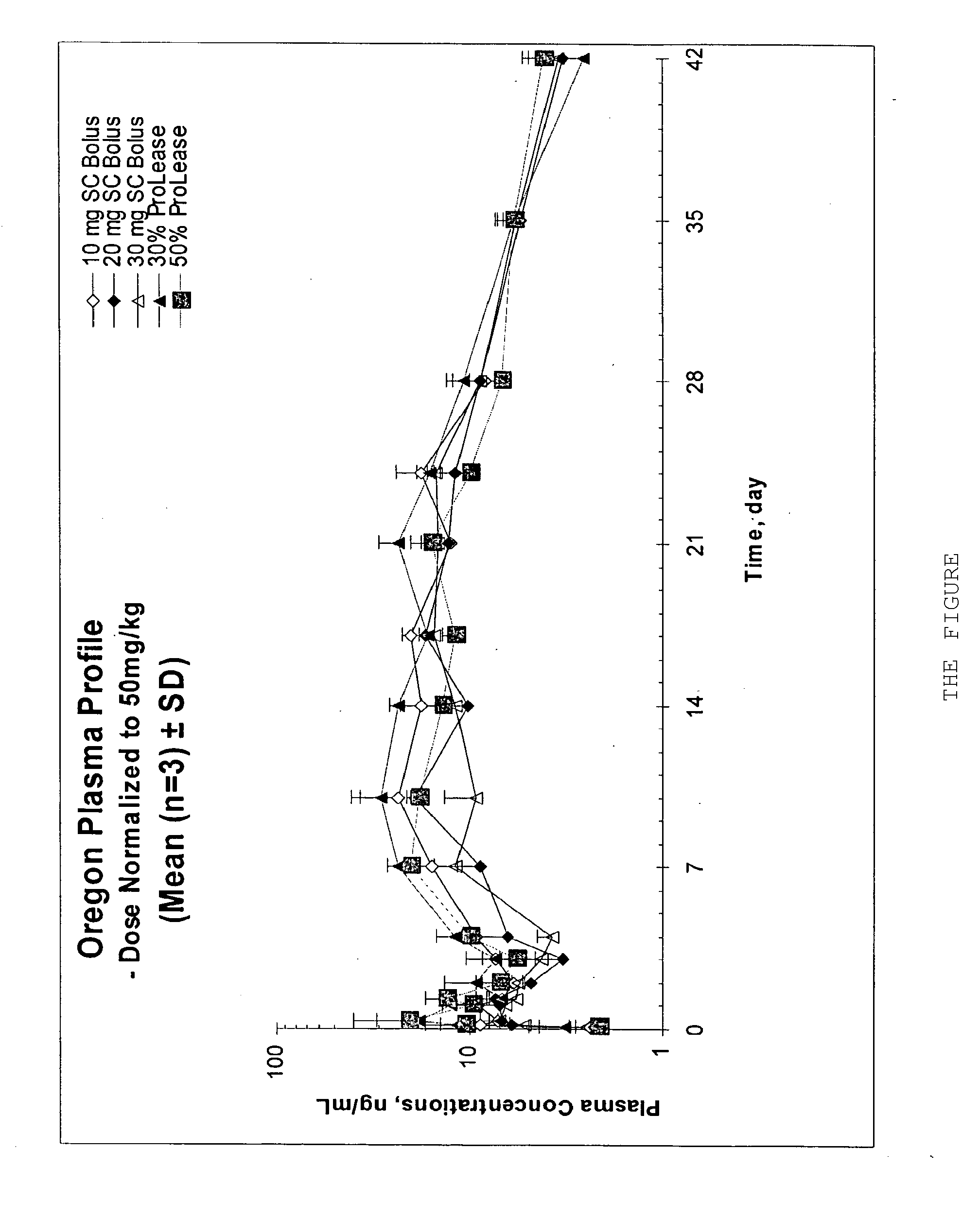
ActiveUS20090143403A1Without complexityWithout expenseOrganic active ingredientsNervous disorderActive agentMicrosphere
The present invention relates, in part, to the discovery that a pharmaceutical composition comprising aripiprazole and a carrier administered in a bolus injection resulted in an extended release profile similar to that obtained by the injection of a poly lactide-co-glycolide microsphere formulation containing the active agent. This surprising result suggests that pharmacologically beneficial extended release formulations without the complexities and expense associated with the manufacture microspheres.
Owner:OTSUKA PHARM CO LTD
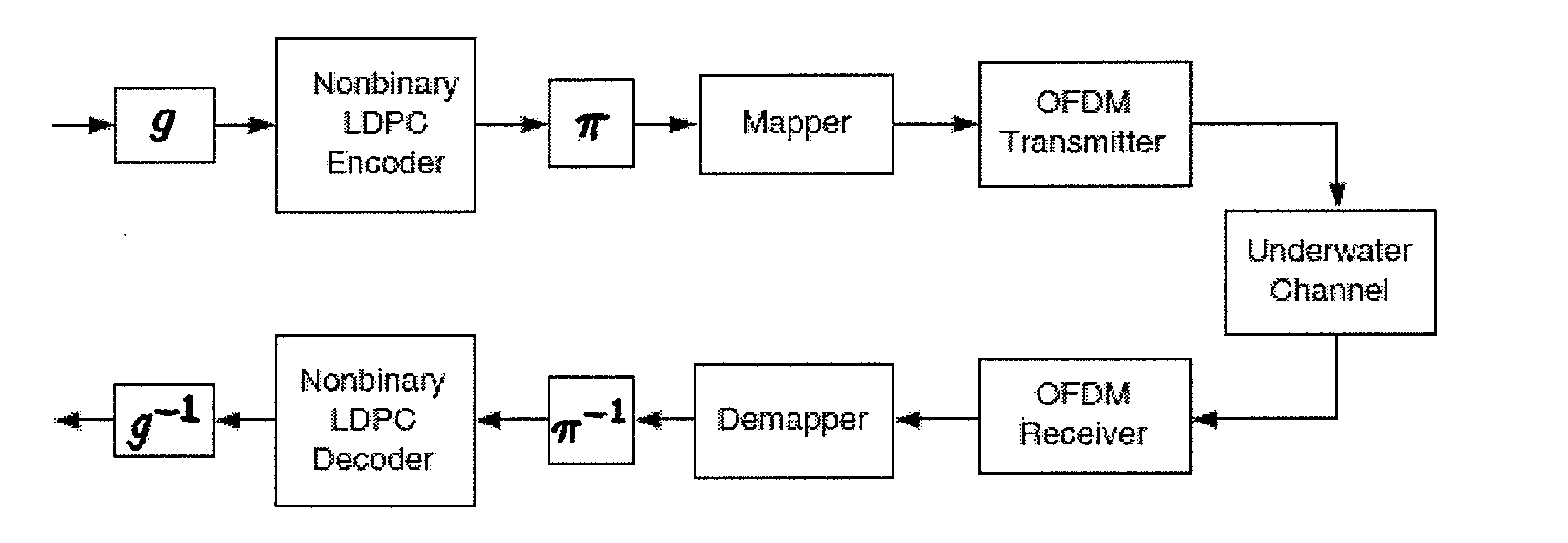
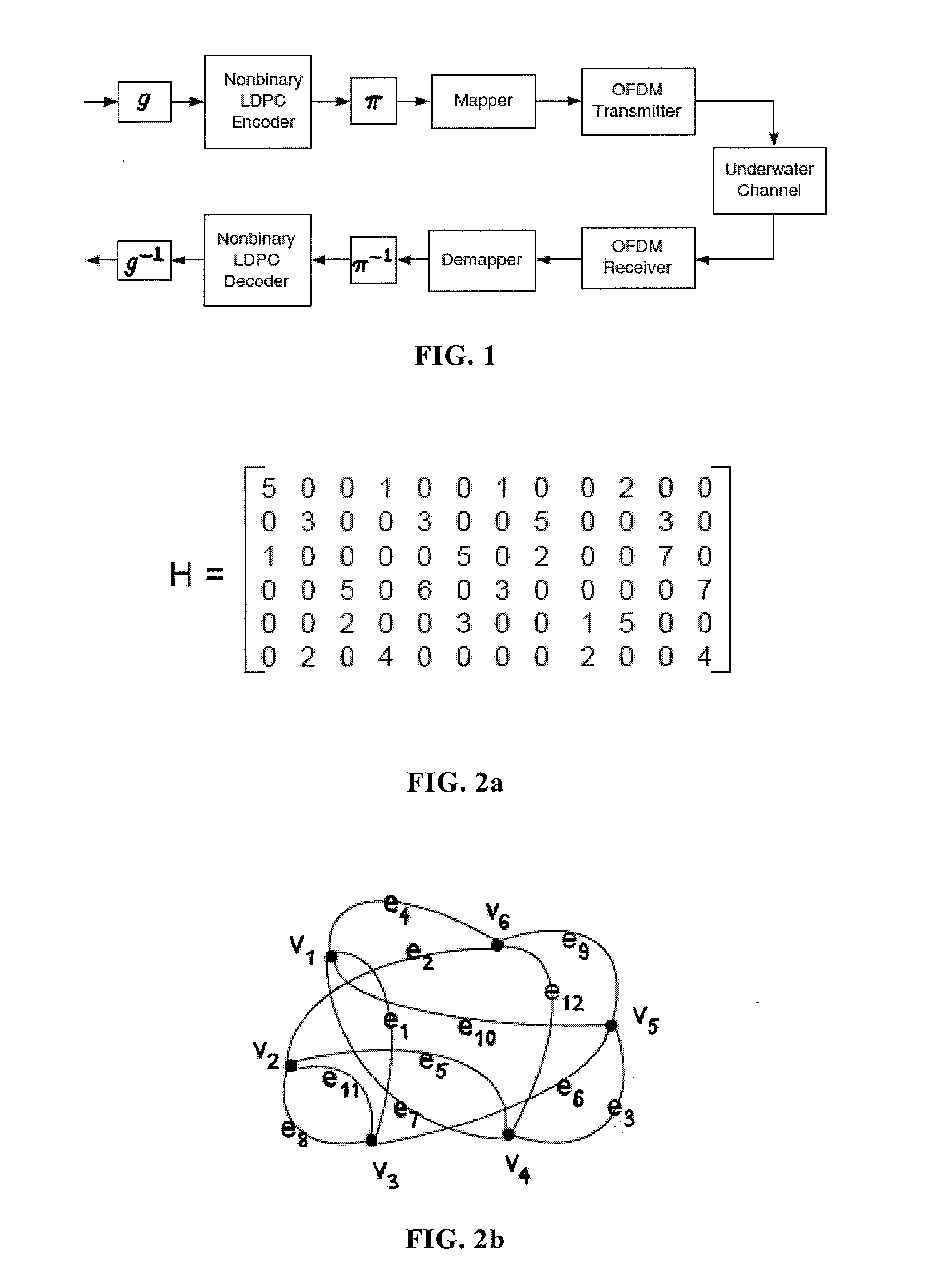
Apparatus, Systems and Methods Including Nonbinary Low Density Parity Check Coding For Enhanced Multicarrier Underwater Acoustic Communications
ActiveUS20110029845A1Improve throughputConsiderable resource reductionSonic/ultrasonic/infrasonic transmissionError correction/detection using LDPC codesTheoretical computer sciencePeak value
Owner:UNIV OF CONNECTICUT
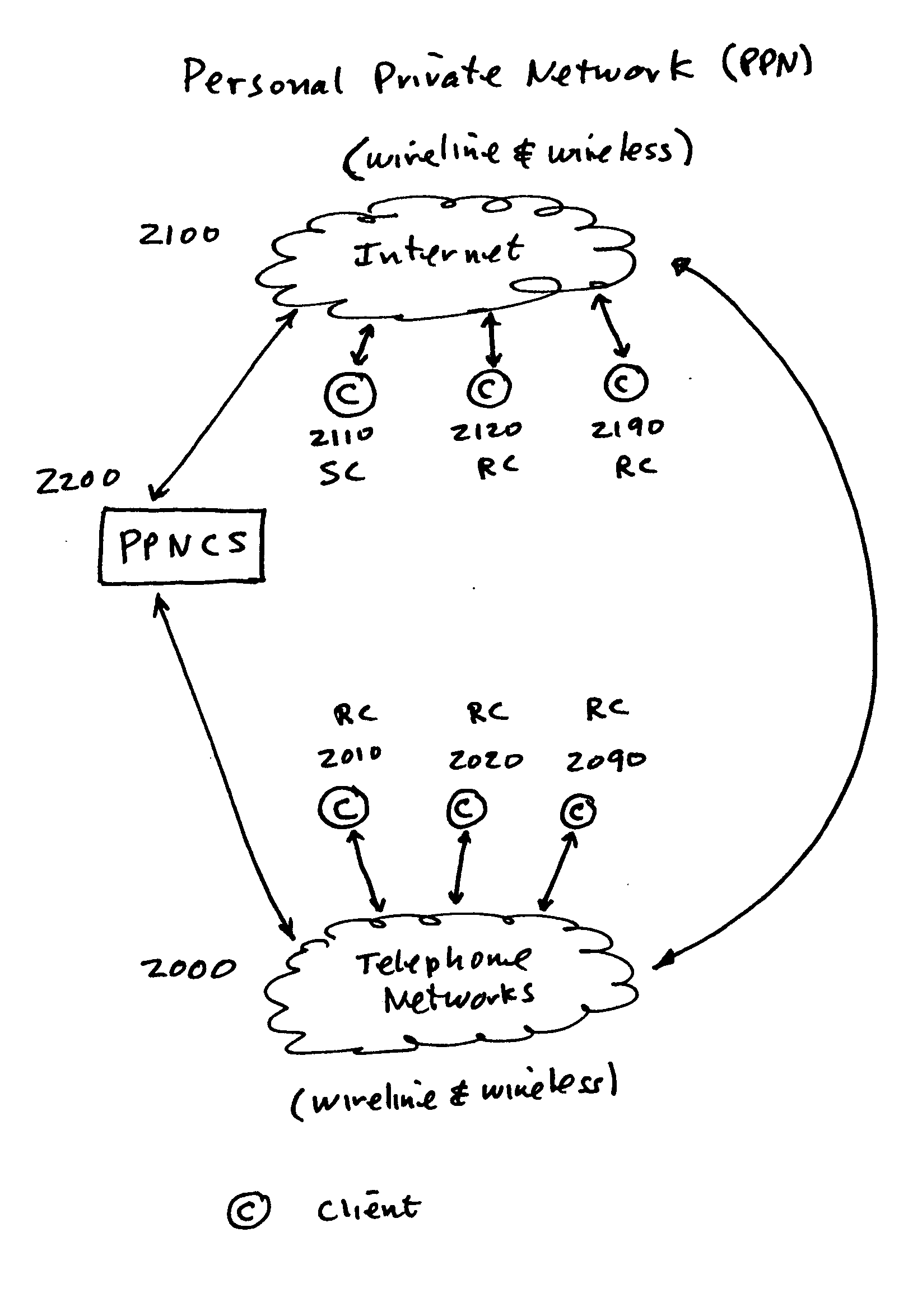
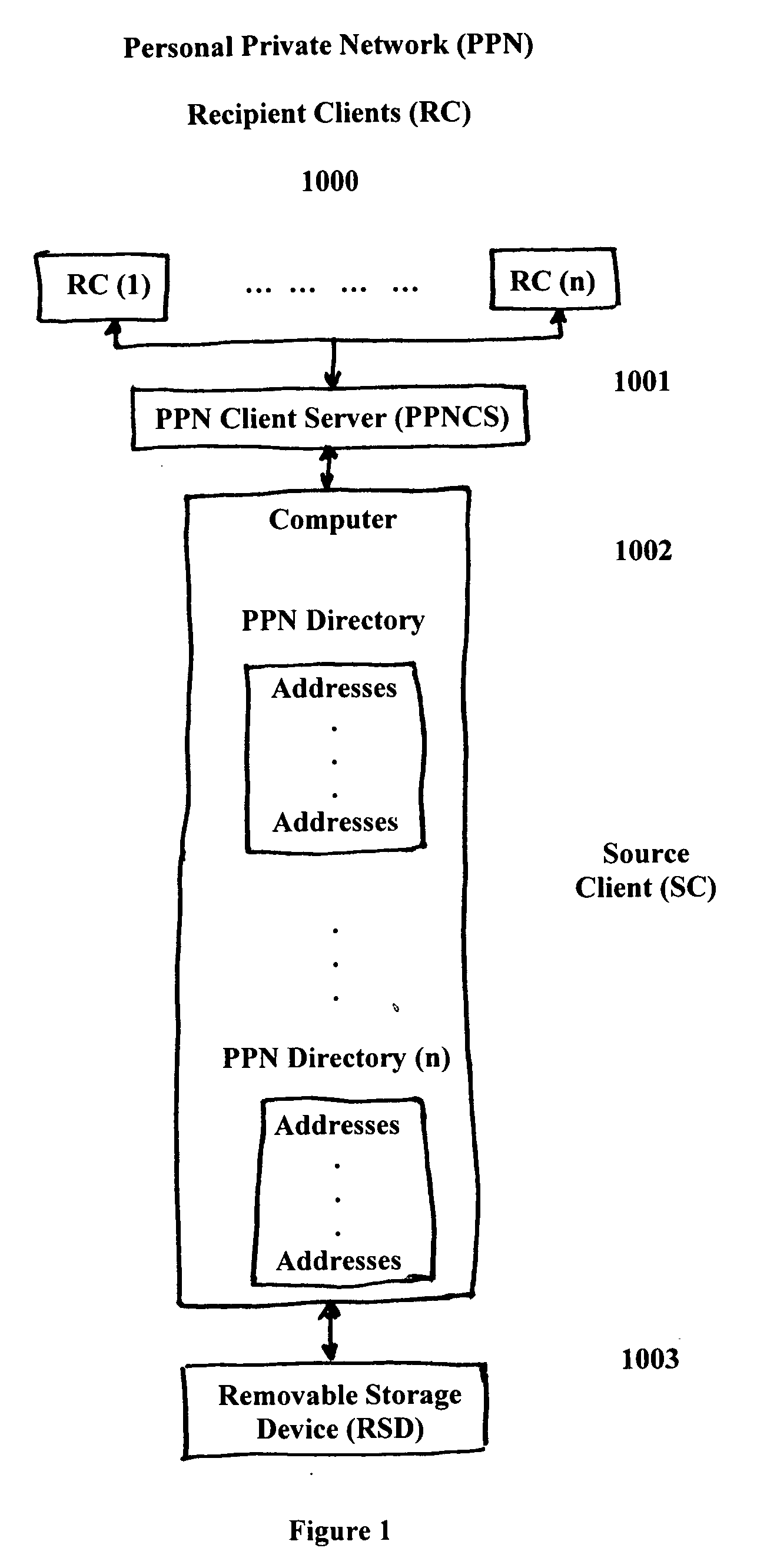
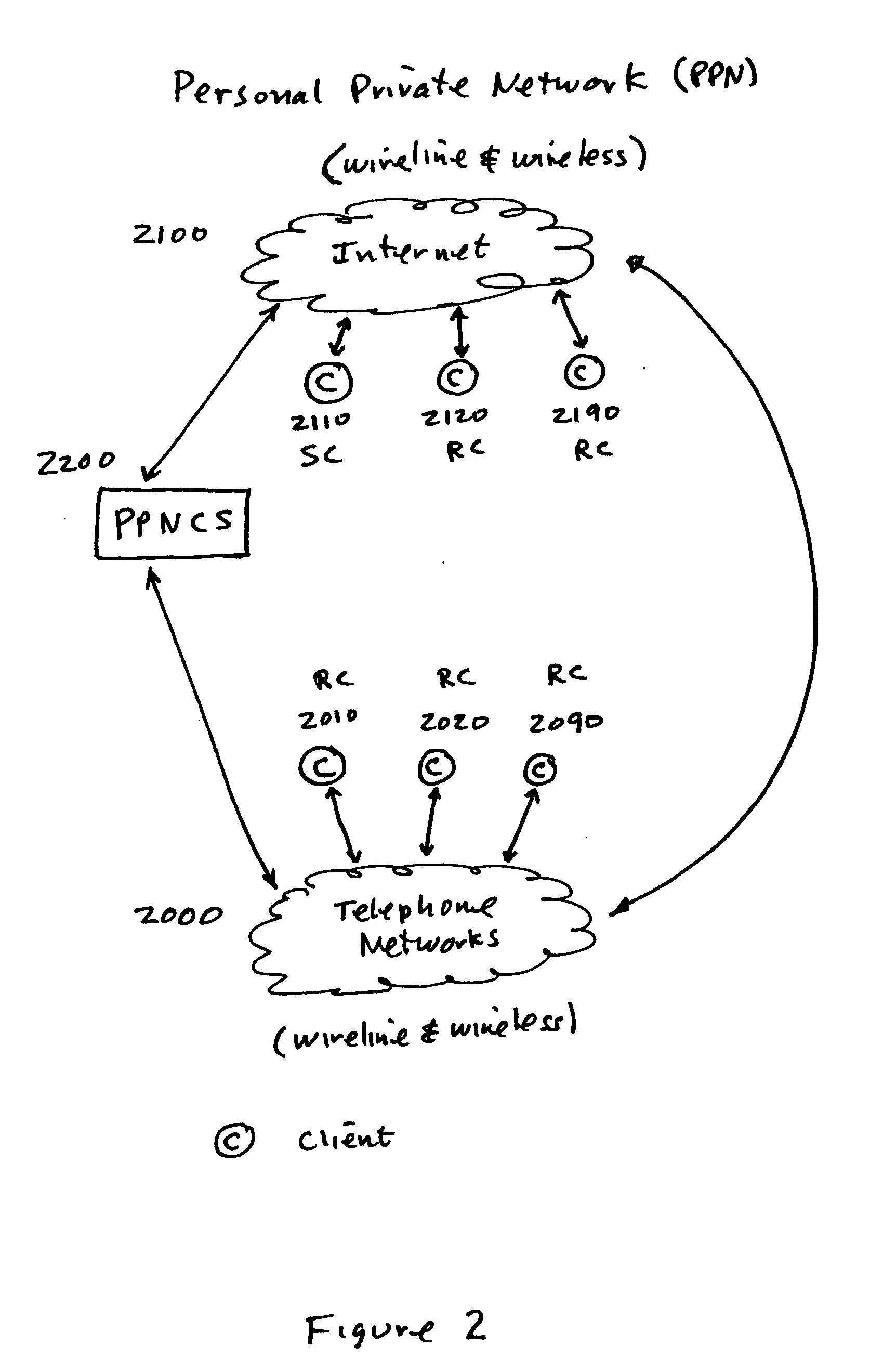
Method and system for user created personal private network (PPN) with secure communications and data transfer
InactiveUS20050132183A1Easily and effectively leverageWithout complexitySecuring communicationDigital dataSecure communication
Methods and systems are provided for any individual with access to a network to create, operate and thereafter dismantle a personal private network (PPN) which is secure across all forms of media which facilitate digital data transfer, including but not limited to, both wireless and wireline based networks. In one embodiment, utilizing browser-based management objects and a PPN client server the present invention provides for any individual with access to the Internet or other types of networks to create, control and utilize his own PPN with any one or a plurality of authorized participants. This invention facilities this capability with the creation of secure pipelines between each authorized participant of the PPN, where, if necessary, to establish these secure pipelines, a tunnel under, around or through border servers and / or firewalls is created. Each PPN provides the authorized participants with complete freedom to communicate, to review information and to transfer data between participants with full and complete encryption security. The creation, operation and the dismantlement of a PPN is totally within the capabilities and control of the originating party, the source client, and requires no actions from any network or system administrators. Additionally, all of the PPN secure pipeline creation and infrastructure mapping for the enablement of the PPN, plus access controls and codes for authorizing participation and initiating participation and disconnection can be encased in a PPN secure access key.
Owner:GEARHART GLENN
Position determination using carrier phase measurements of satellite signals
ActiveUS7522099B2High measurement accuracyWithout complexityNavigation instrumentsBeacon systemsEngineeringLeast squares
Disclosed is a method and apparatus for determining the relative position of a mobile unit that moves from an initial location to a plurality of successive positions. The mobile unit receives signals from a plurality of navigation satellites and tracks the carrier phases of the signals during movement. For each of the received signals, carrier phase increments are calculated over a plurality of epochs. Anomalous carrier phase increments are determined and eliminated from further calculations. The non-eliminated carrier phase increments are then used to calculate coordinate increments for each of the time epochs. If, after elimination, the remaining number of carrier-phase increments is less than a threshold for a particular epoch, then coordinate increments for the particular epoch may be extrapolated using data from prior epochs. In various embodiments, least squares method and Kalman filtering may be used to calculate the coordinate increments. The coordinate increments may then be summed over a plurality of time epochs in order to determine a position of the mobile unit relative to its initial position.
Owner:TOPCON GPS
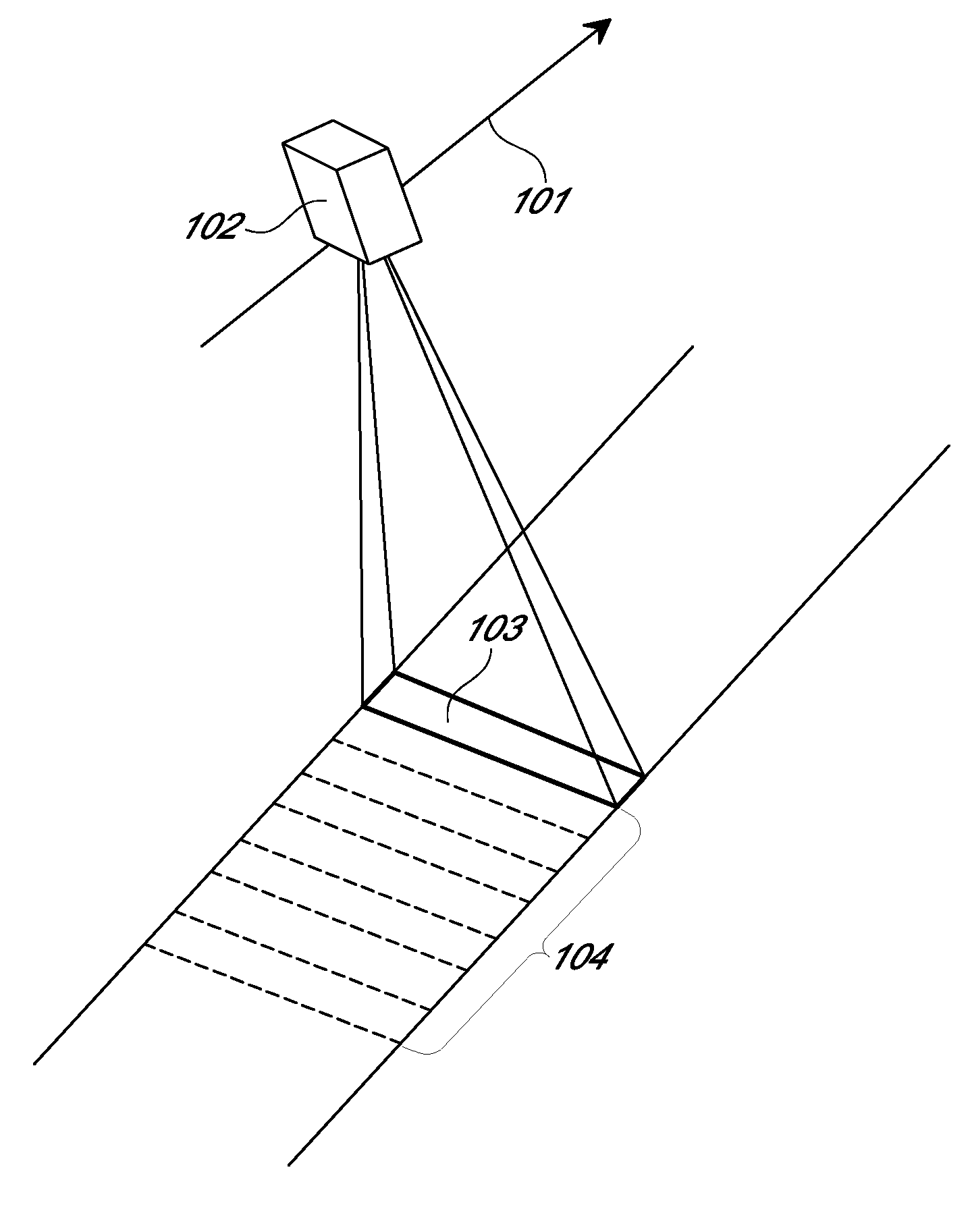
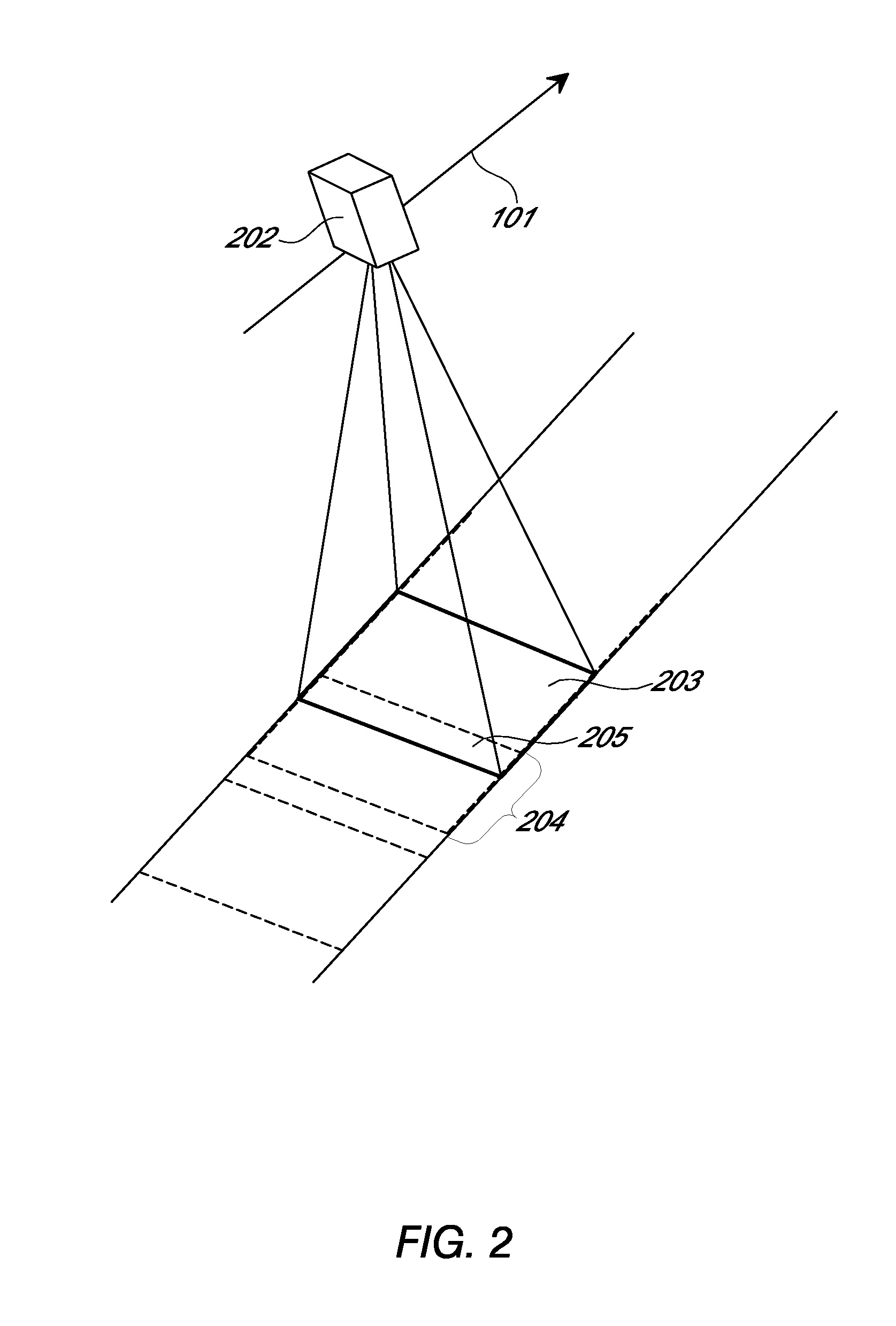
Systems and methods for overhead imaging and video
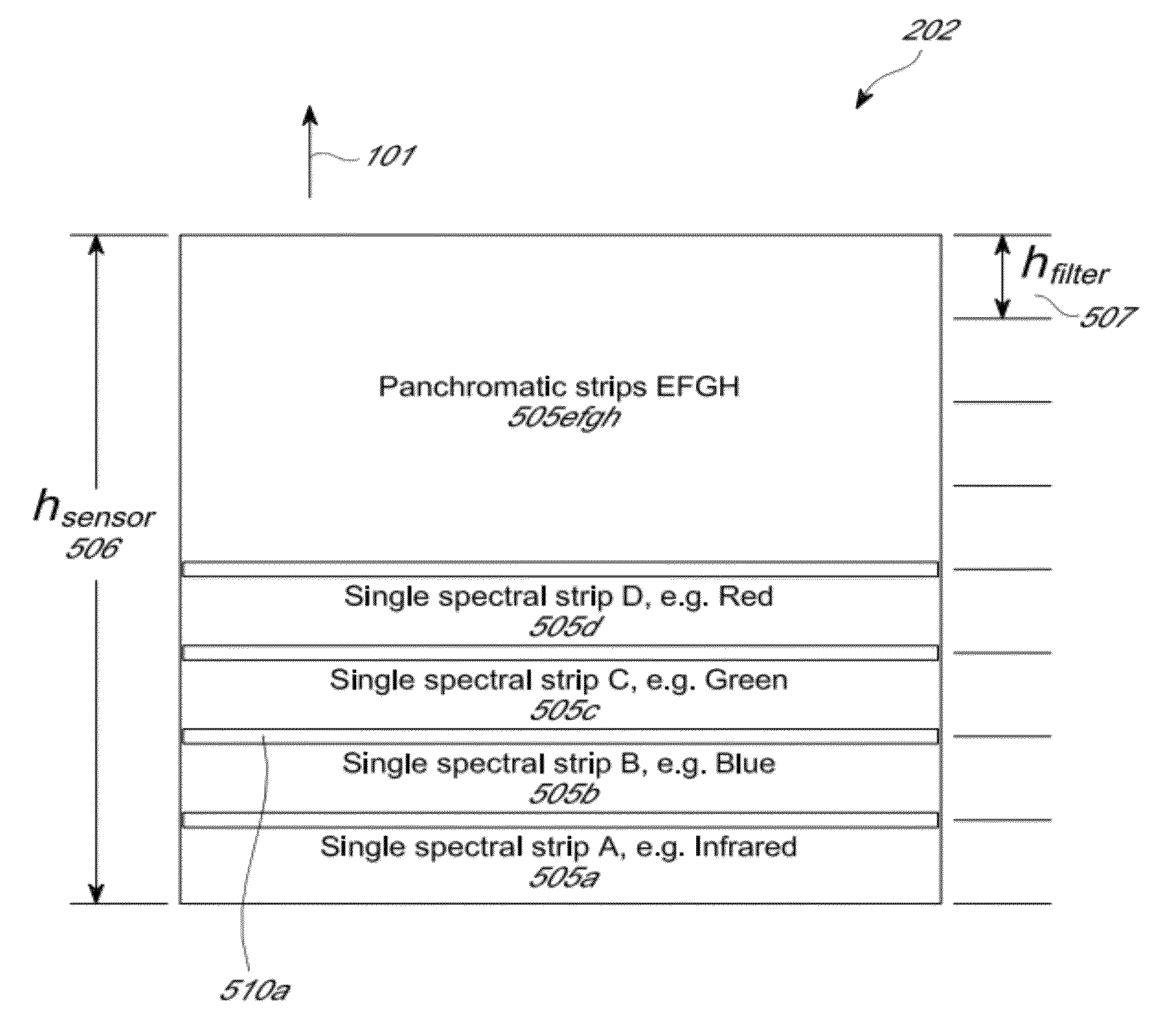
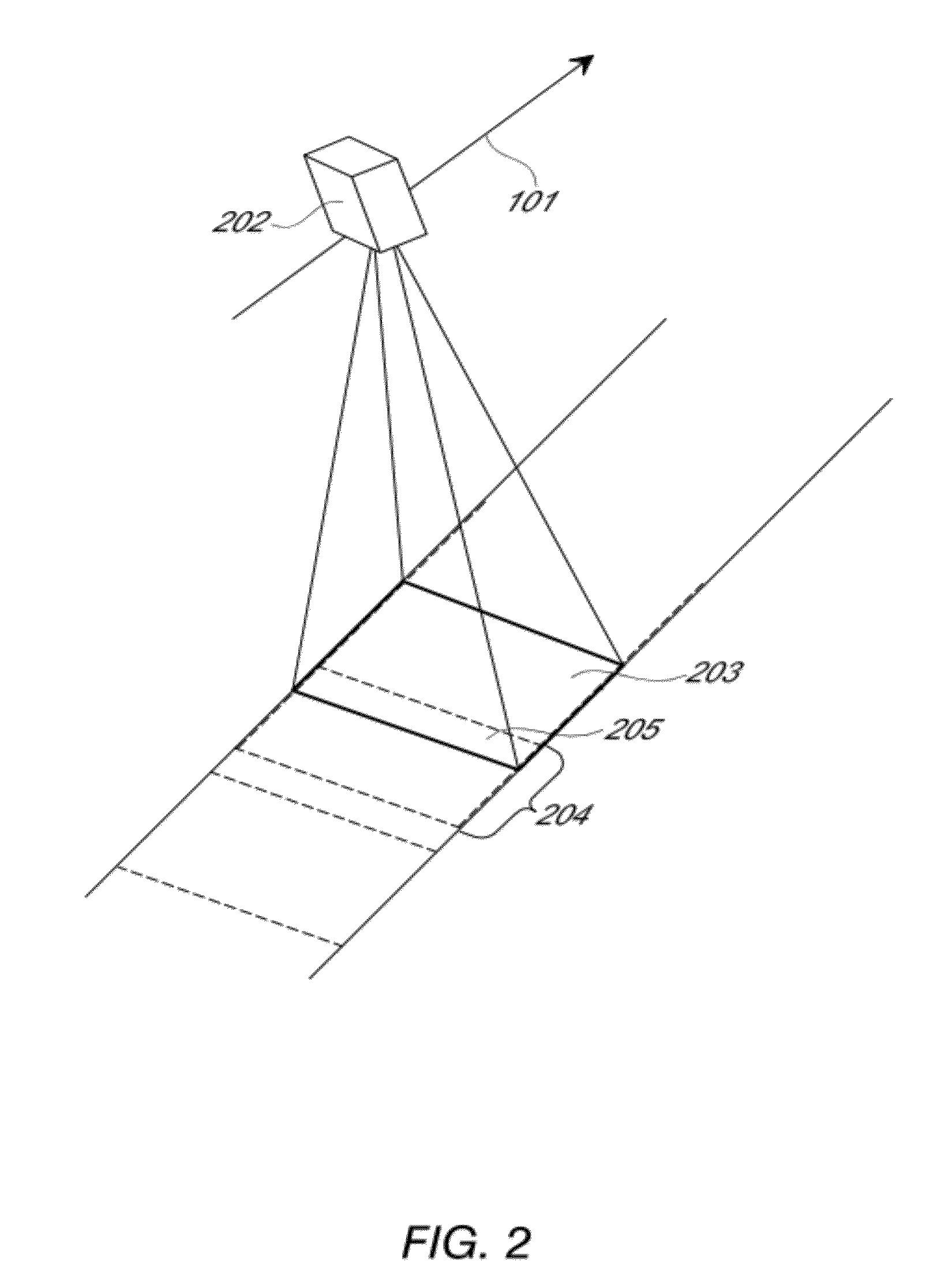
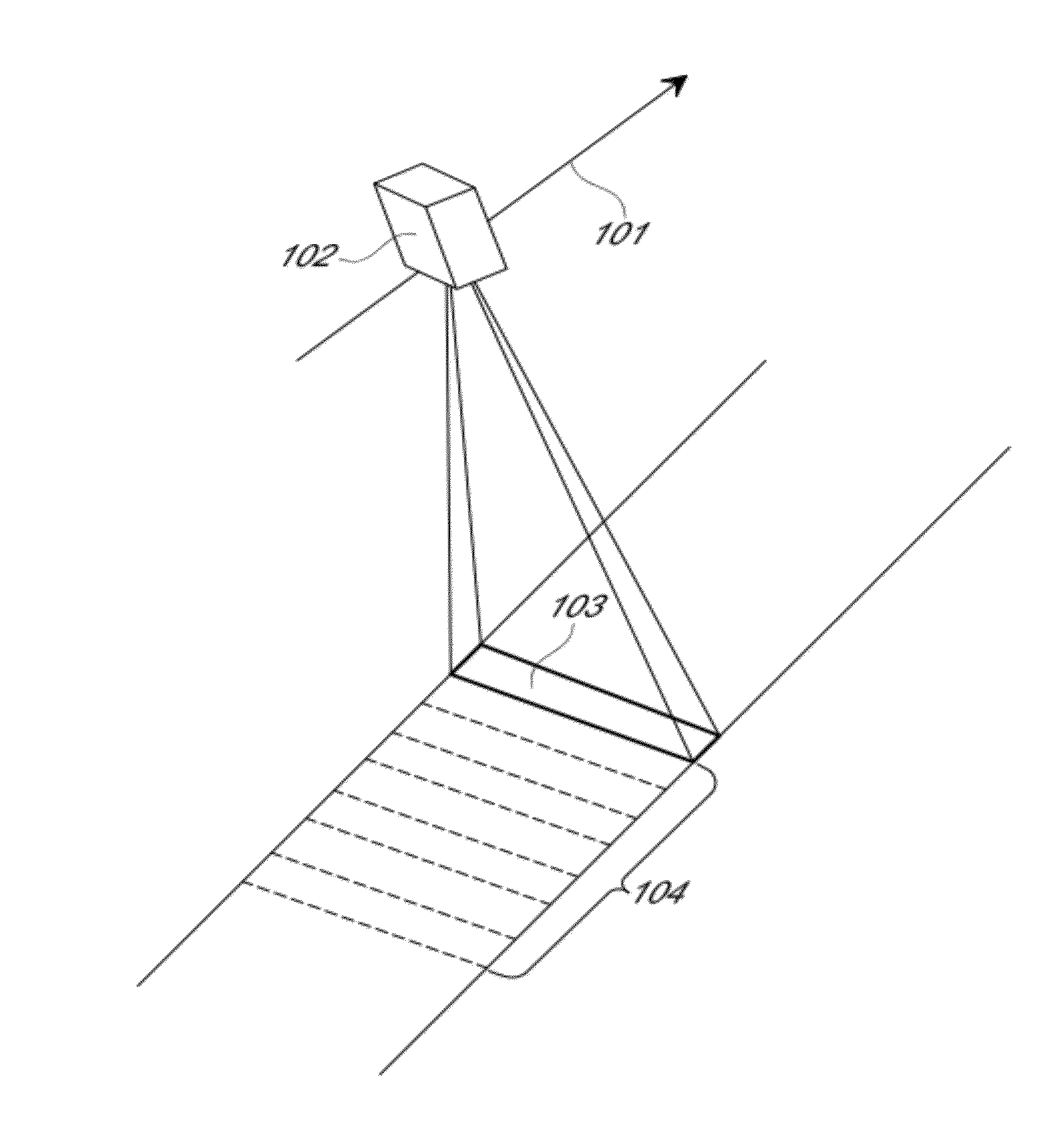
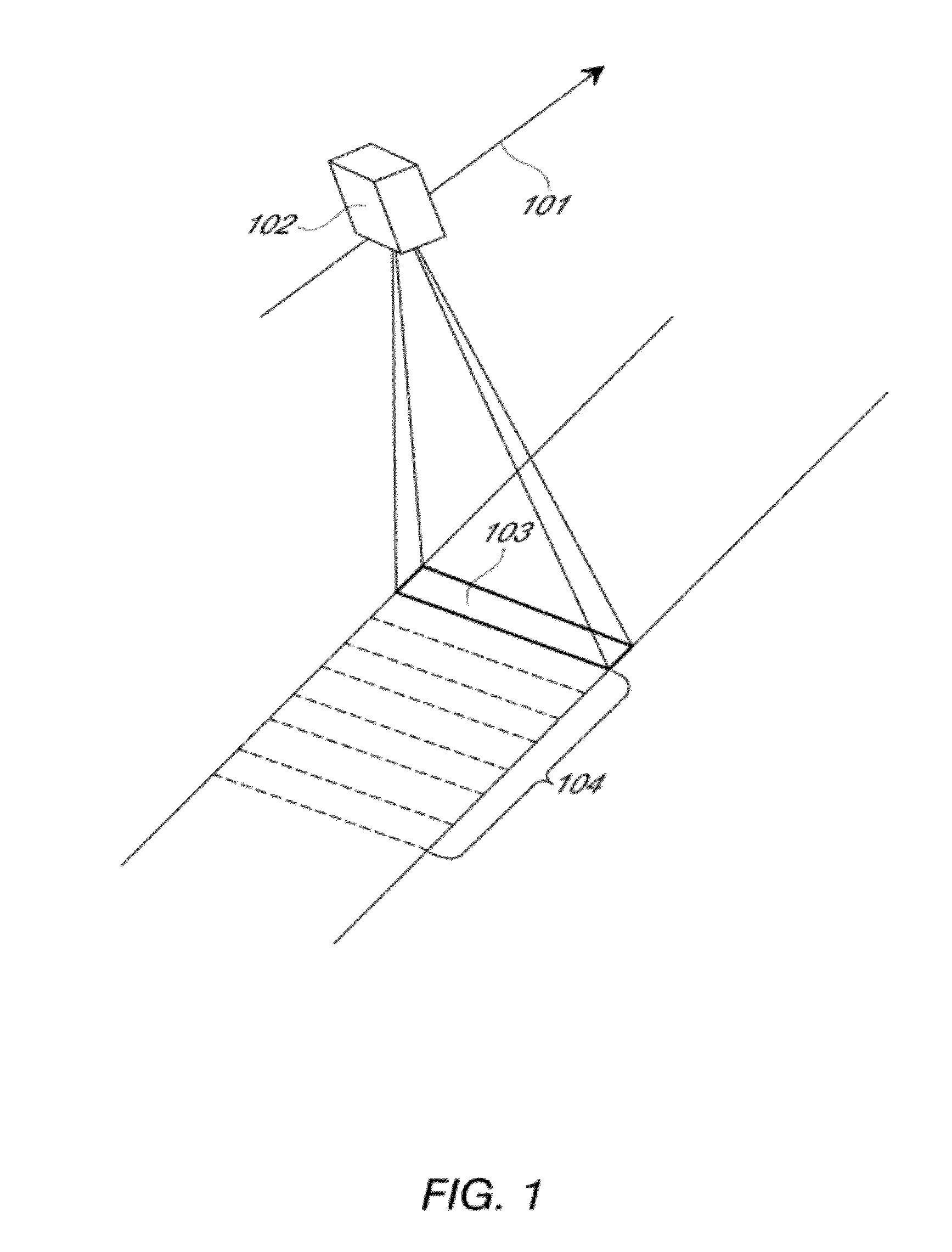
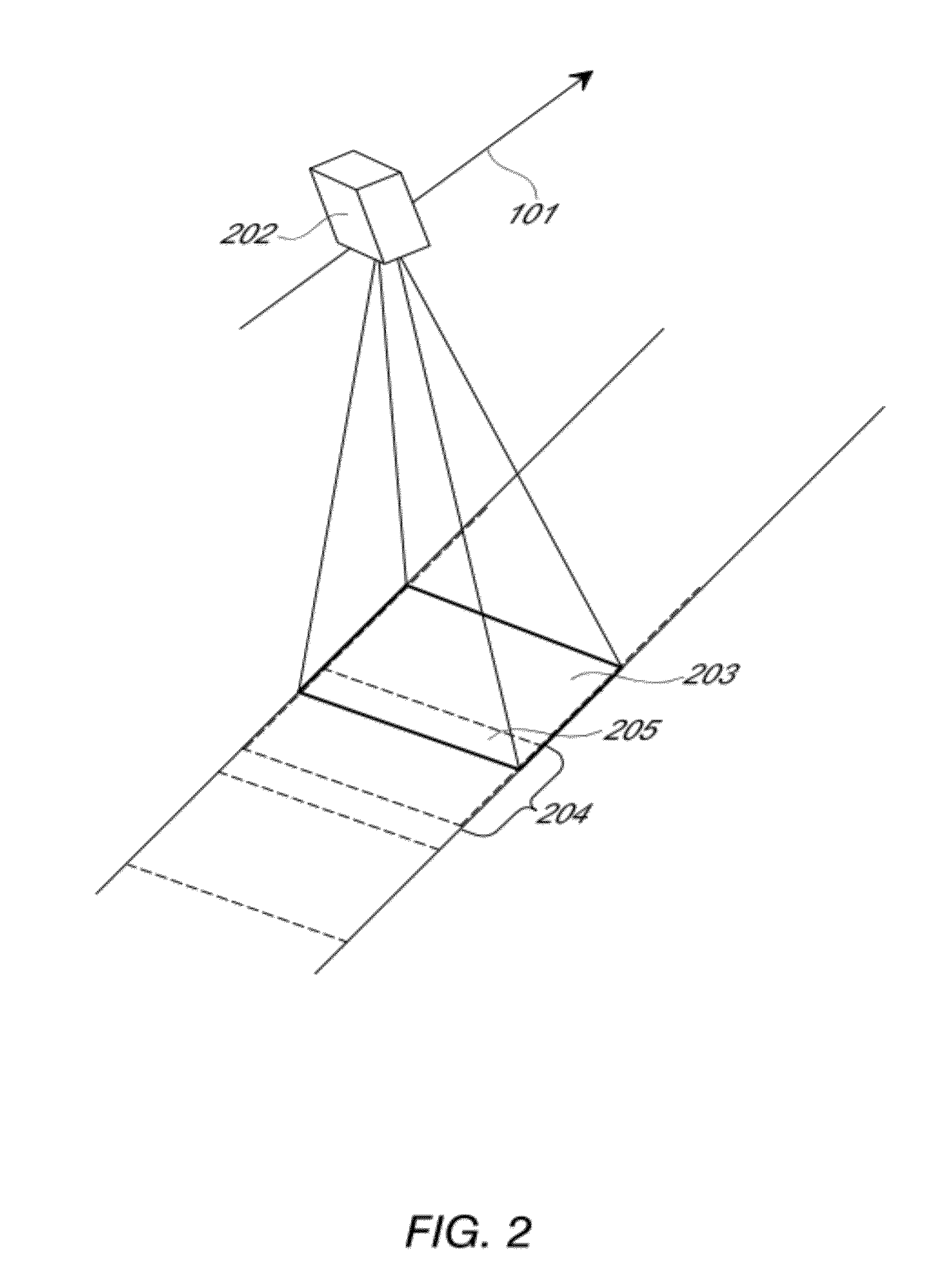
ActiveUS8487996B2Efficient acquisition and processingWithout complexityTelevision system detailsSpectrum investigationColor imageStaring
Examples of an imaging sensor include a two-dimensional staring sensor with spectral filter strips for multispectral overhead imaging. The sensor may also include a panchromatic sensor with block or strip filters. The sensor may be used to collect multispectral color image data at a sampling resolution from overhead imaging platforms such as airplanes or satellites. The sensor can be used to provide video images. If a panchromatic sensor is included, the sensor may be used to collect panchromatic image data. Examples of methods for processing the image date include using the panchromatic image data to perform multi-frame enhancement or panchromatic sharpening on spectral images to improve their quality and resolution.
Owner:PLANET LABS PBC
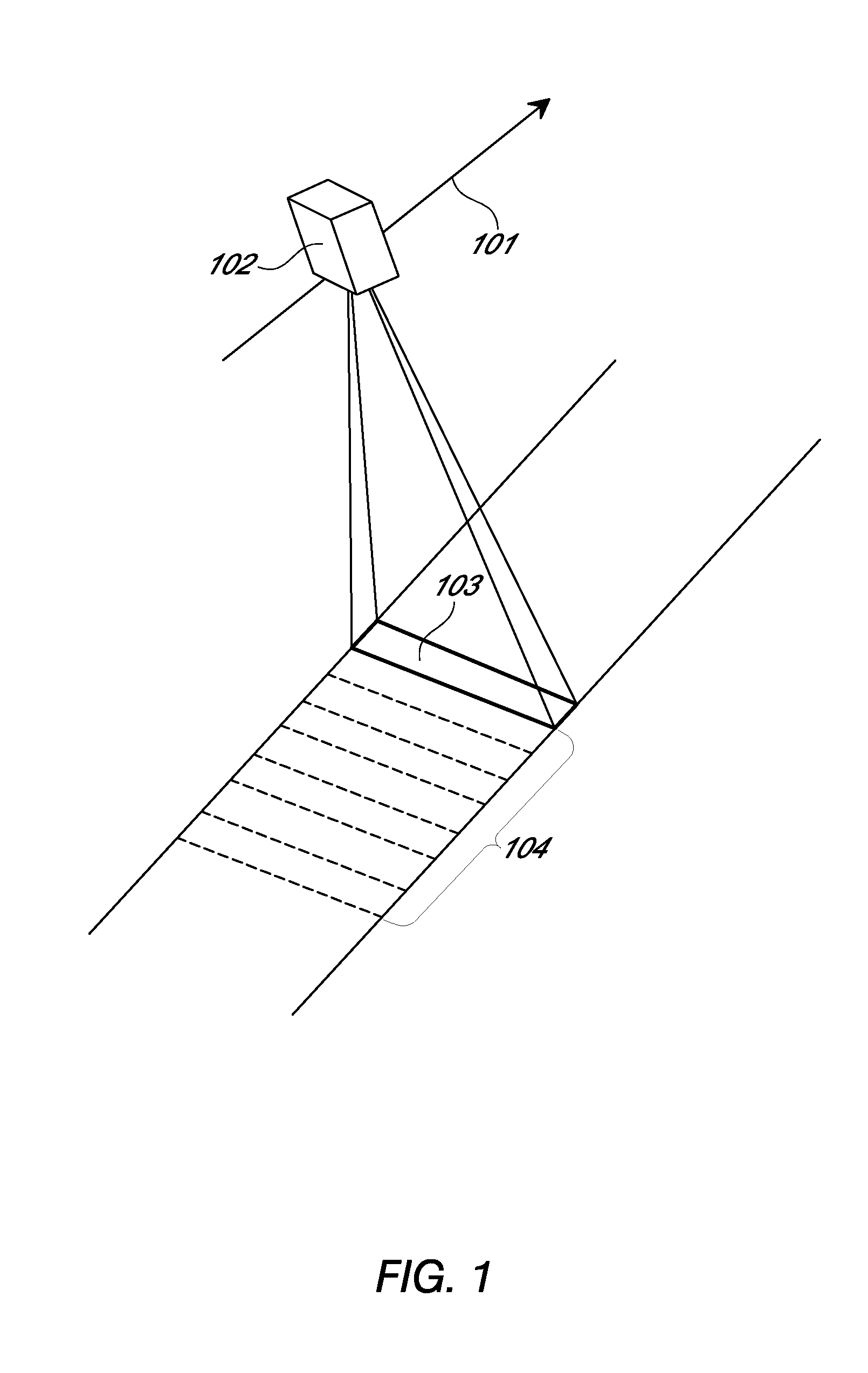
Systems and methods for overhead imaging and video
ActiveUS20120293669A1Efficient acquisition and processingWithout complexityTelevision system detailsSpectrum investigationColor imageVideo image
Examples of an imaging sensor include a two-dimensional staring sensor with spectral filter strips for multispectral overhead imaging. The sensor may also include a panchromatic sensor with block or strip filters. The sensor may be used to collect multispectral color image data at a sampling resolution from overhead imaging platforms such as airplanes or satellites. The sensor can be used to provide video images. If a panchromatic sensor is included, the sensor may be used to collect panchromatic image data. Examples of methods for processing the image date include using the panchromatic image data to perform multi-frame enhancement or panchromatic sharpening on spectral images to improve their quality and resolution.
Owner:PLANET LABS PBC
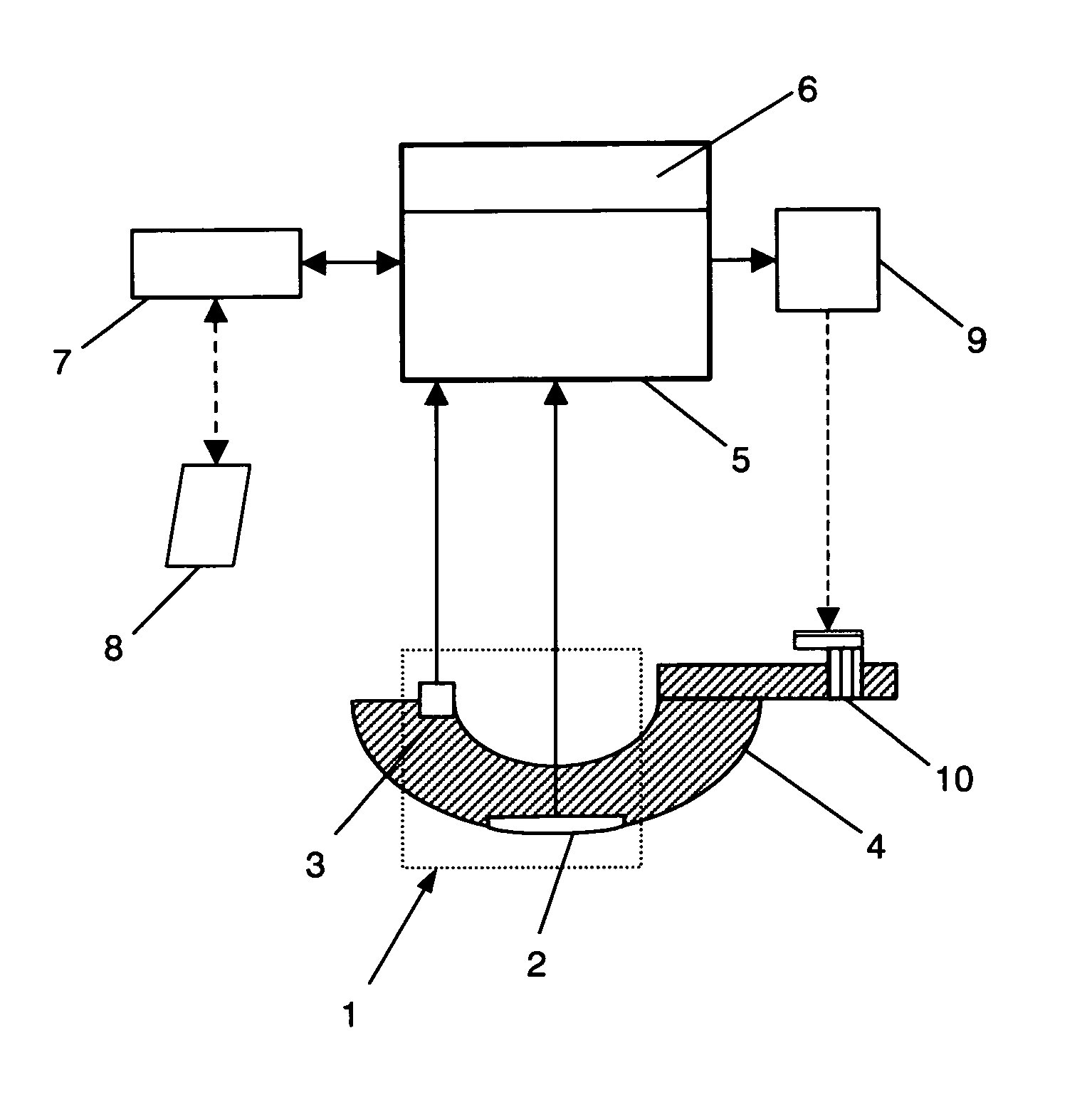
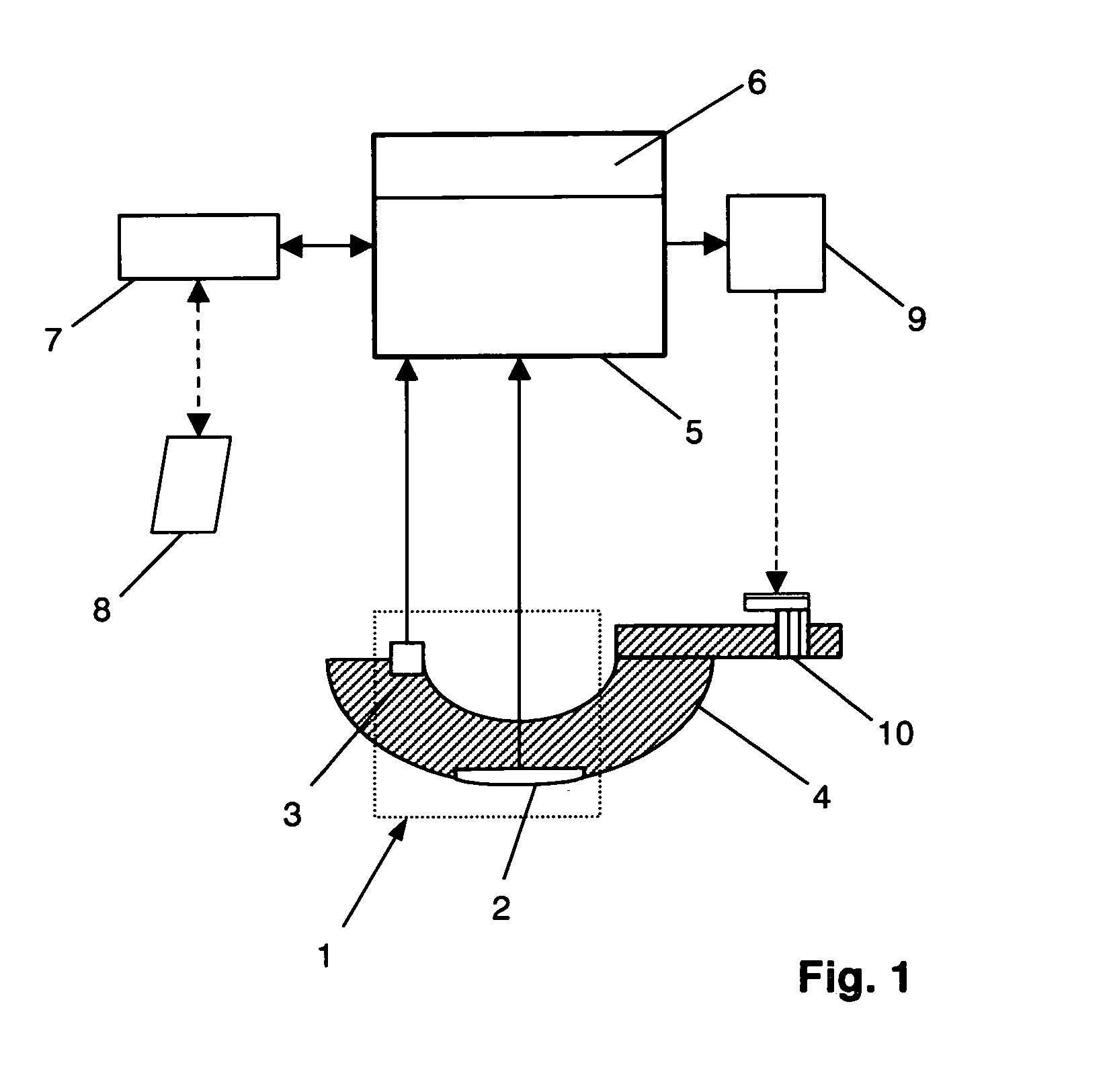
Ultrasonic diagnostic apparatus
InactiveUS20090012399A1Without complexityImprove computing powerUltrasonic/sonic/infrasonic diagnosticsInfrasonic diagnosticsUltrasonic beamLight beam
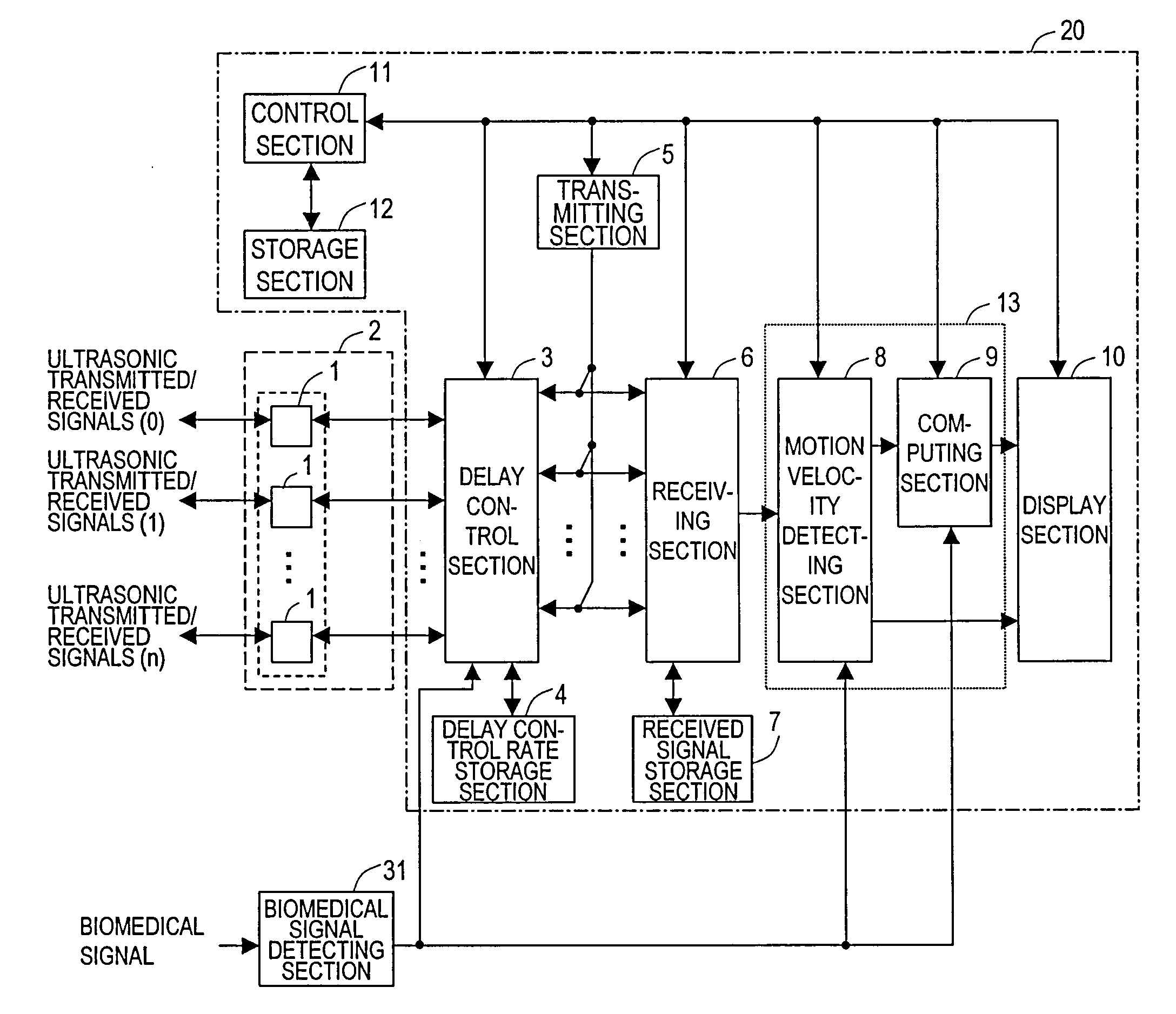
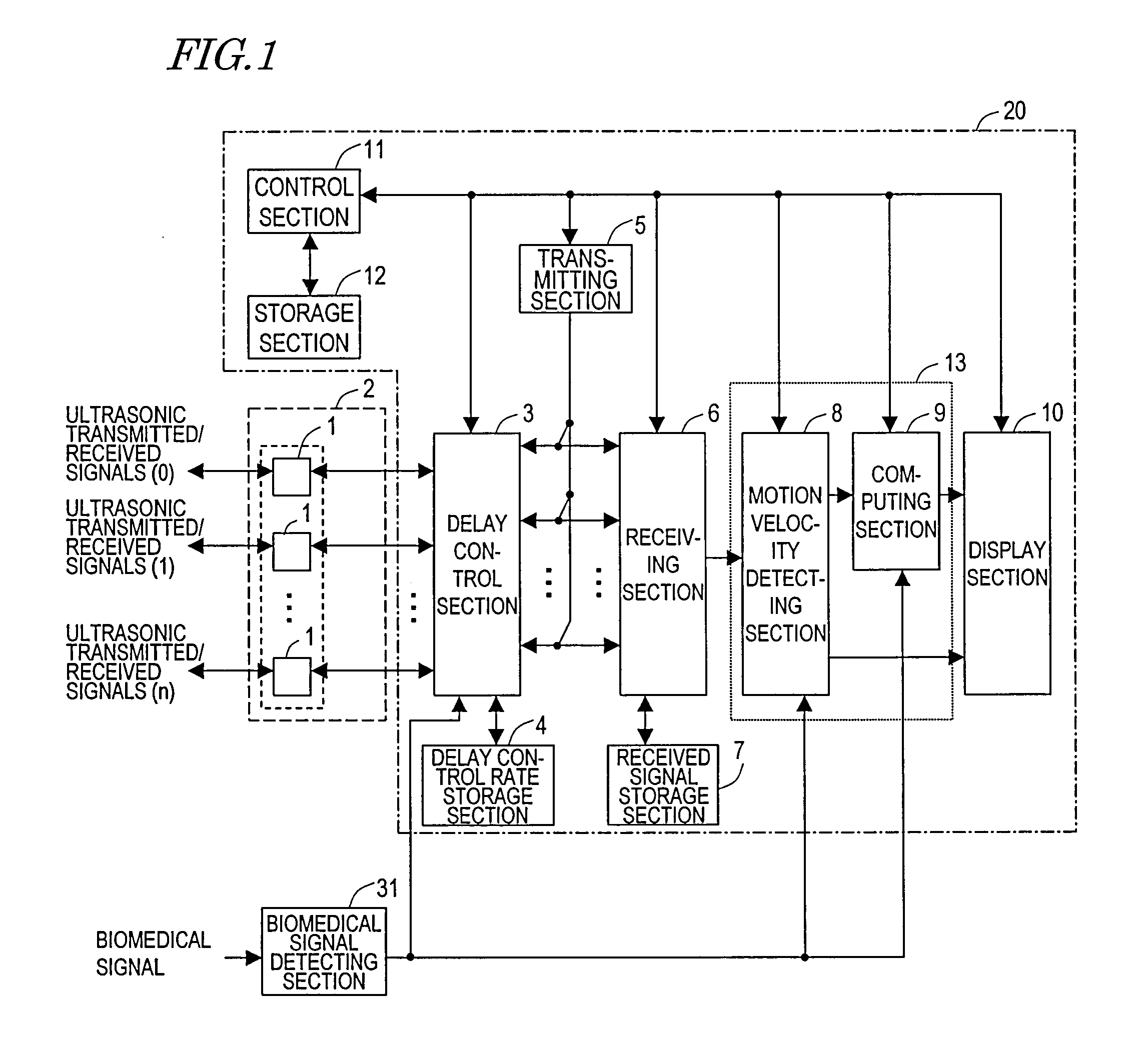
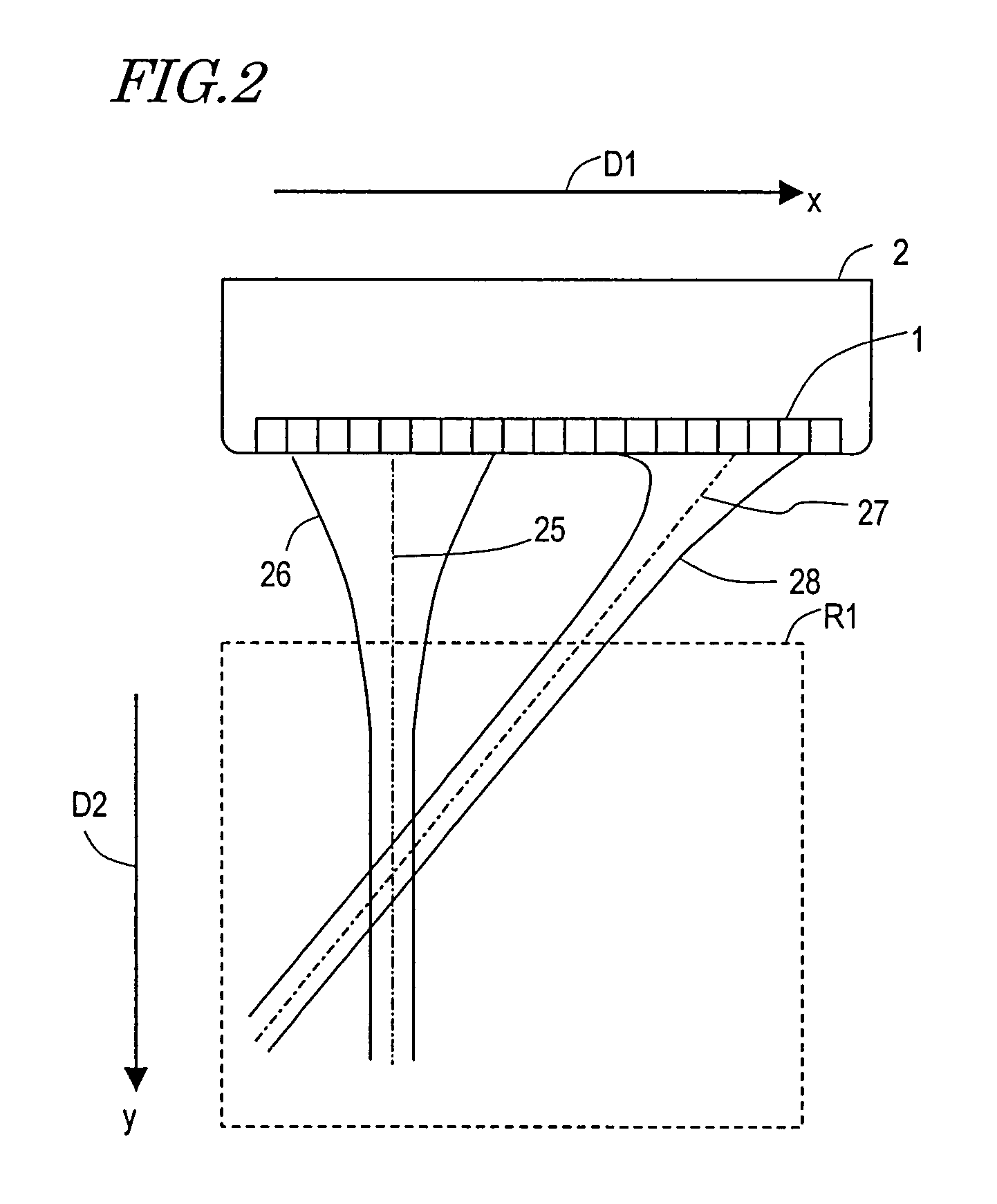
The ultrasonic diagnostic apparatus of the invention evaluates a shape or qualitative property of an organism's arterial wall tissue and includes: a delay control section 3 for controlling delays for ultrasonic vibrators 1 in an ultrasonic probe 2; a transmitting section 5 for driving the probe under the control of the control section 3 such that the probe 2 transmits a first ultrasonic beam toward different locations within a scan region, defined along the axis of the artery, every predetermined frame period; a receiving section 6 for receiving ultrasonic echoes, generated by getting the first beam reflected by the wall, at the probe every set of frame periods, thereby outputting a first group of ultrasonic echo signals; and a signal processing section 13 for calculating a thickness variation, or elasticity, of the tissue between measuring points on the tissue in response to the first group of echo signals. The section 13 selects one of the echo signals of the first group every frame period according to an axial velocity of the tissue to make calculations at each measuring point.
Owner:PANASONIC CORP
Memory apparatus including programmable non-volatile multi-bit memory cell, and apparatus and method for demarcating memory states of the cell
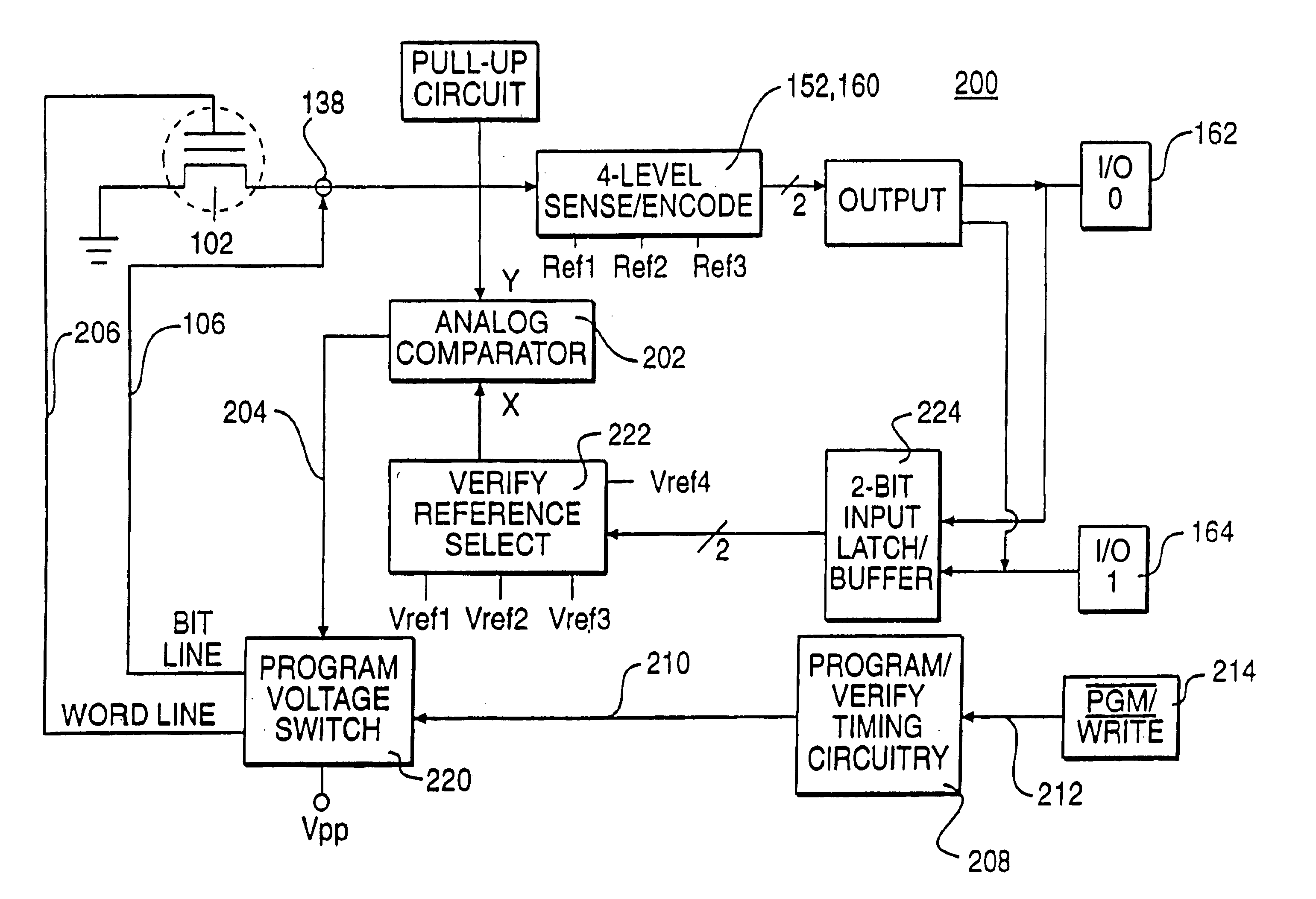
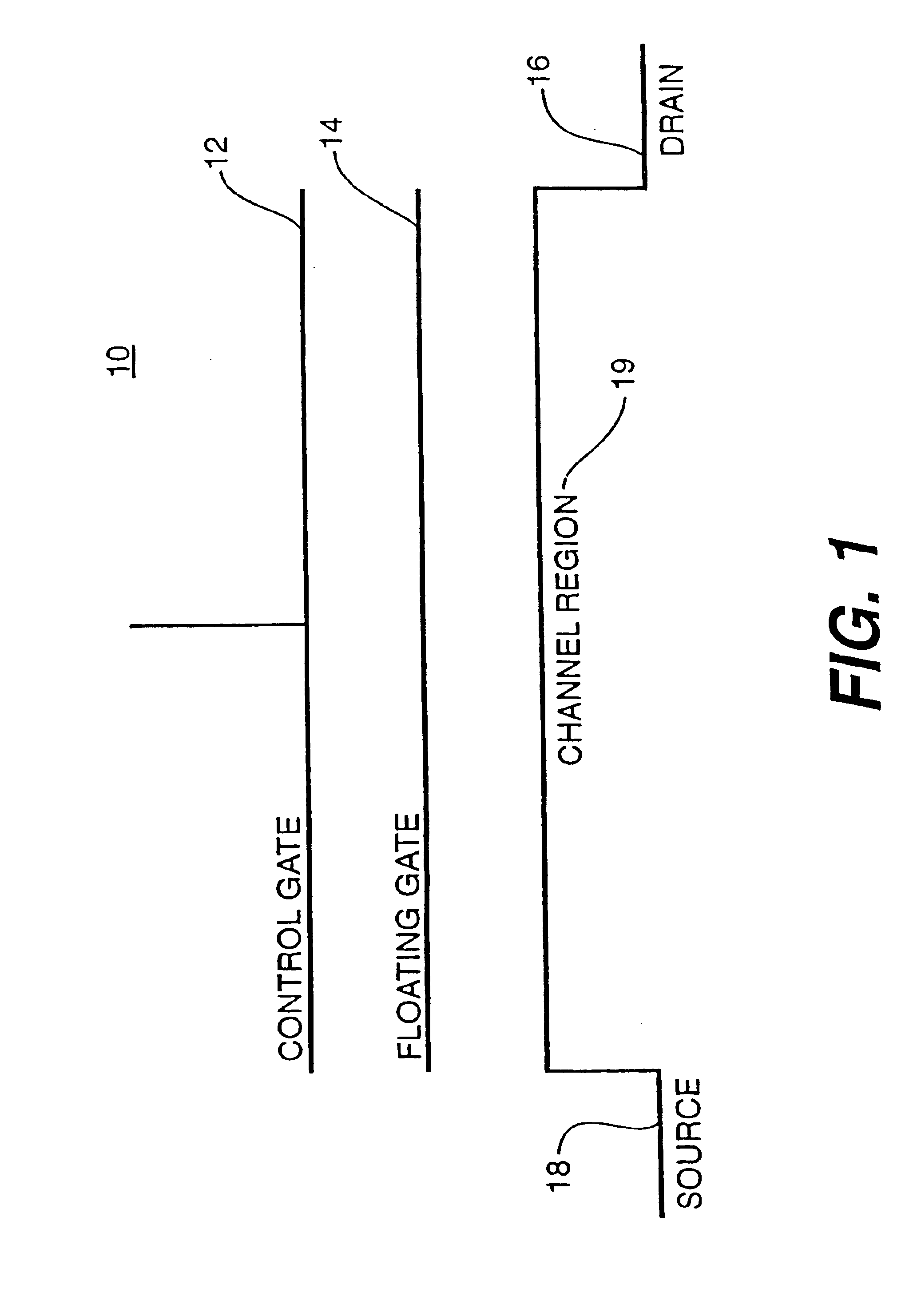
InactiveUS7006384B2Without complexityImprove accuracyRead-only memoriesDigital storageSignal onControl memory
Memory states of a multi-bit memory cell are demarcated by generating read reference signals having levels that constitute boundaries of the memory states. The read reference signals may be dependent upon the levels of programming reference signals used for controlling the programming of the memory cell. The memory cell can thus be programmed without reading out its memory state during the programming process, with programming margins being assured by the dependence of the read reference signals on the programming reference signals. Both sets of reference signals may be generated by reference cells which track variations in the operating characteristics of the memory cell with changes in conditions, such as temperature and system voltages, to enhance the reliability of memory programming and readout.
Owner:BTG INT LTD
Systems and methods for overhead imaging and video
ActiveUS20120300064A1Efficient acquisition and processingWithout complexityTelevision system detailsSpectrum investigationColor imageStaring
Examples of an imaging sensor include a two-dimensional staring sensor with spectral filter strips for multispectral overhead imaging. The sensor may also include a panchromatic sensor with block or strip filters. The sensor may be used to collect multispectral color image data at a sampling resolution from overhead imaging platforms such as airplanes or satellites. The sensor can be used to provide video images. If a panchromatic sensor is included, the sensor may be used to collect panchromatic image data. Examples of methods for processing the image date include using the panchromatic image data to perform multi-frame enhancement or panchromatic sharpening on spectral images to improve their quality and resolution.
Owner:PLANET LABS PBC
Locking system for a vehicle and method for operating thereof
InactiveUS20050219043A1Without complexityWithout expenseElectric signal transmission systemsDigital data processing detailsEnvironment effectBiological activation
Locking system for a vehicle, in which a locking / unlocking function can be initiated by the activation of at least one capacitate sensor located on an external handle of the vehicle entry, wherein the sensor includes at least a second control surface not accessible to the user or accessible only with difficulty, via which the impact of environmental influences on the sensor by can be distinguished from the activation of the sensor by the user through detection of control surface selective signal changes at the sensor. Method for operating a locking system for a vehicle, in which the vehicle is locked upon detection of an intention to lock or unlock by an activation of a first control surface by the hand of the user, and the authority to do so is confirmed using a data carrier, and that the vehicle is not locked or unlocked, when the control unit recognizes an environmental influenced activation of the sensor by the activation of the first as well as a second sensor, the second sensor not accessible to the hand of the user or accessible only with difficulty.
Owner:BAYERISCHE MOTOREN WERKE AG
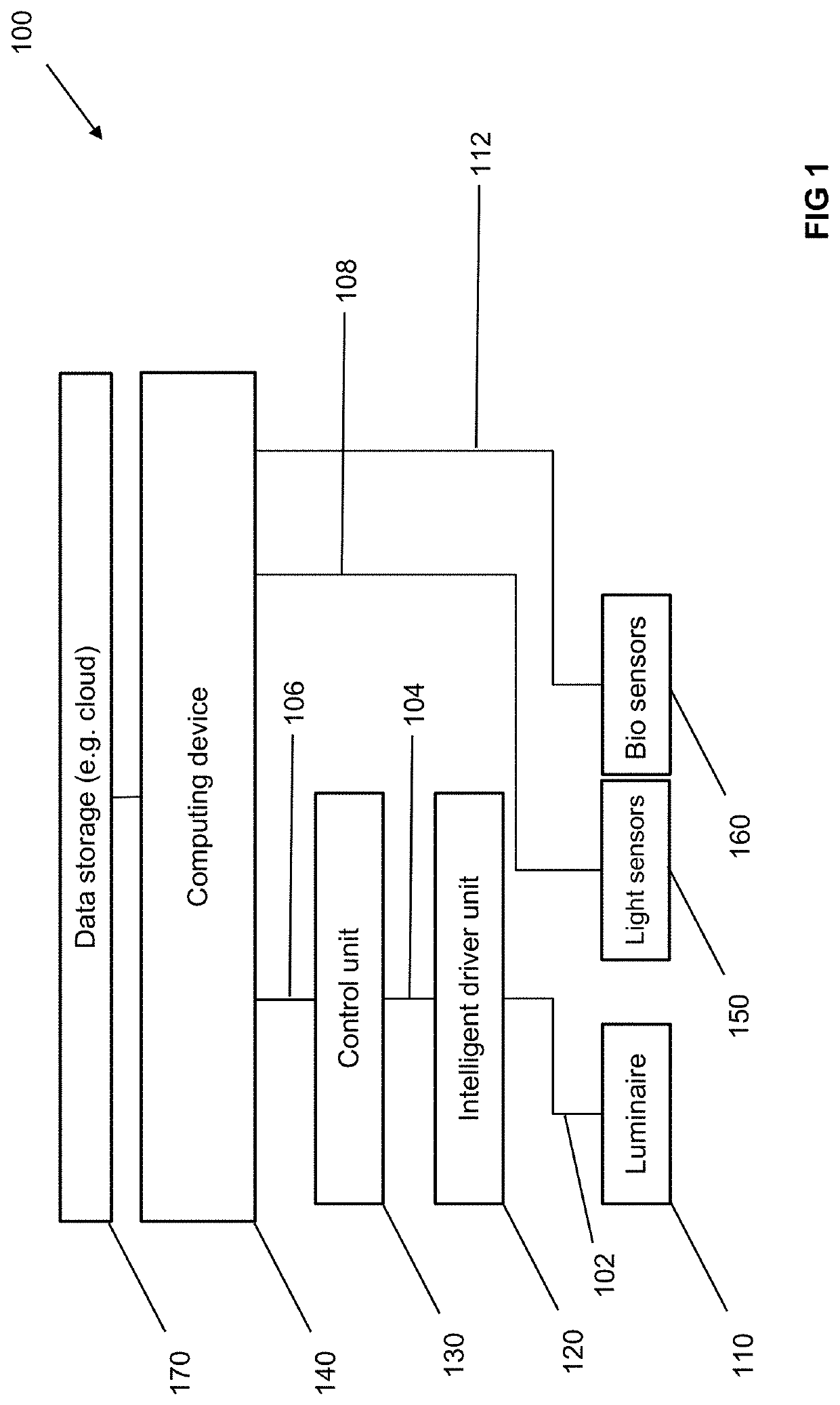
Controlled Agricultural Systems and Methods of Managing Agricultural Systems
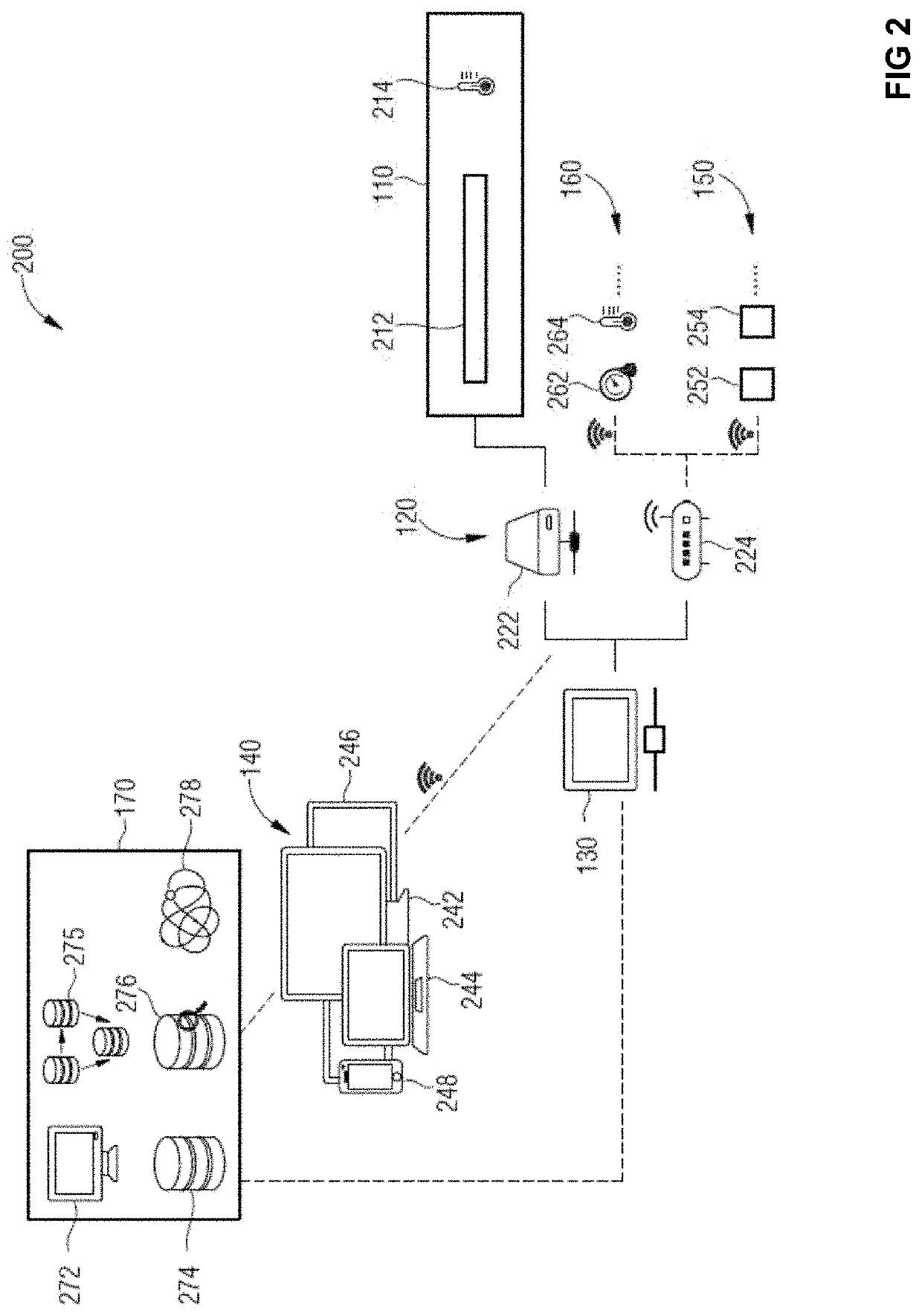
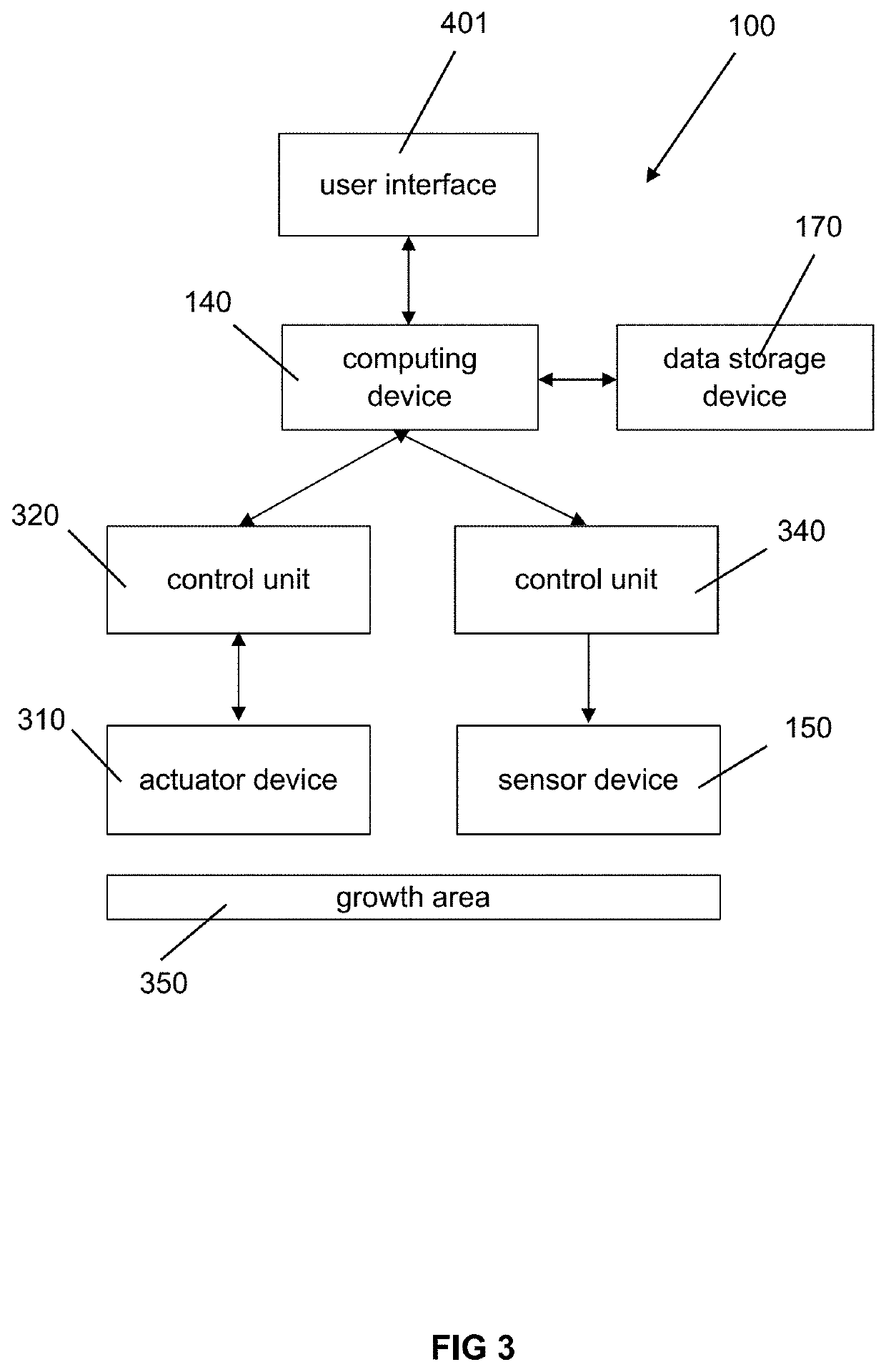
PendingUS20200134741A1High yieldQuality improvementData processing applicationsFertilising methodsAgricultural scienceActive agent
The present disclosure relates to different techniques of controlling an agricultural system, as for example a controlled agricultural system, an agricultural light fixture and a method for agricultural management.Furthermore, the disclosure relates to an agricultural system, which comprises a plurality of processing lines for growing plants of a given plant type, wherein a first processing line in the plurality of processing lines is configured to move a first plurality of plants through the agricultural system along a route; and apply a first growth condition to the first plurality of plants to satisfy a first active agent parameter for the first plurality of plants.
Owner:FLUENCE BIOENG INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com