Patents
Literature
1970results about "Data switching details" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
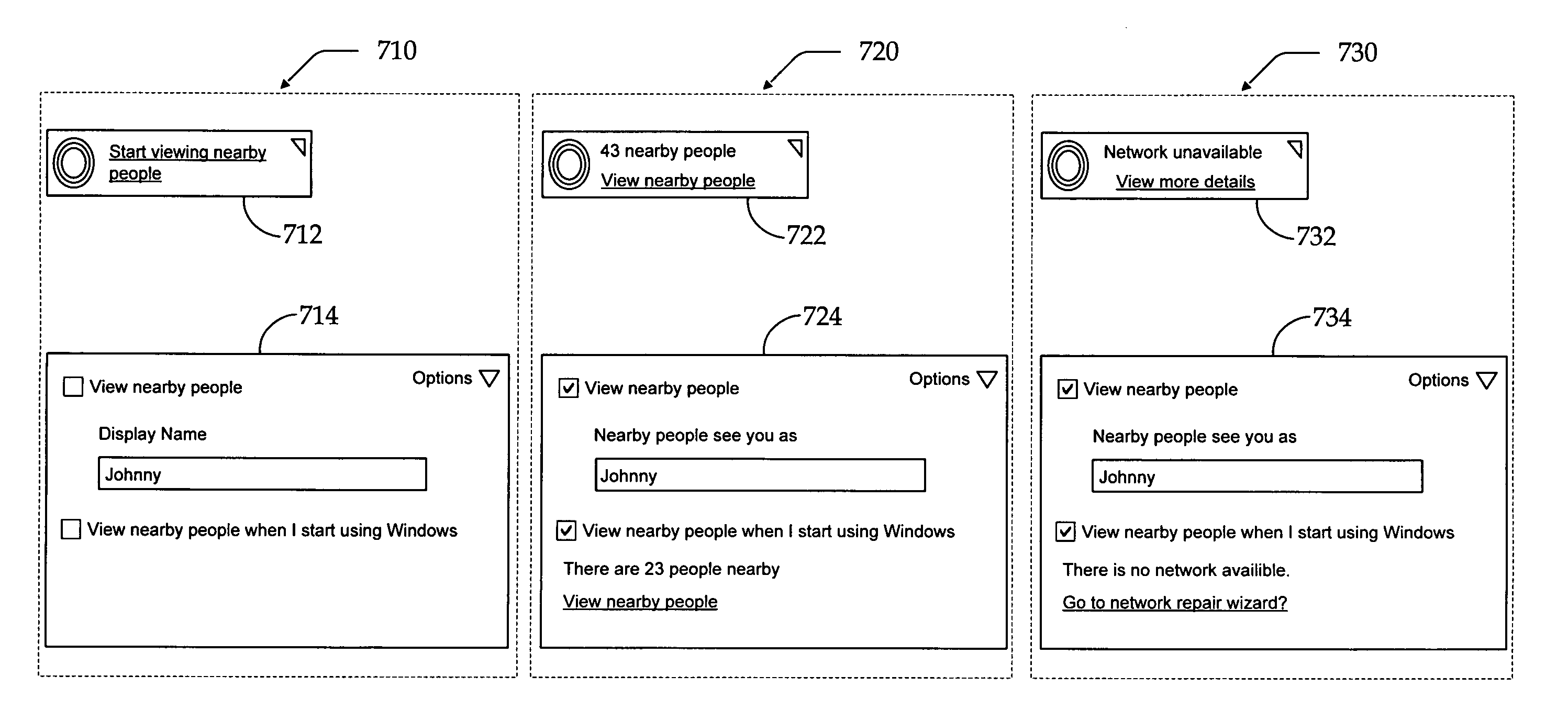
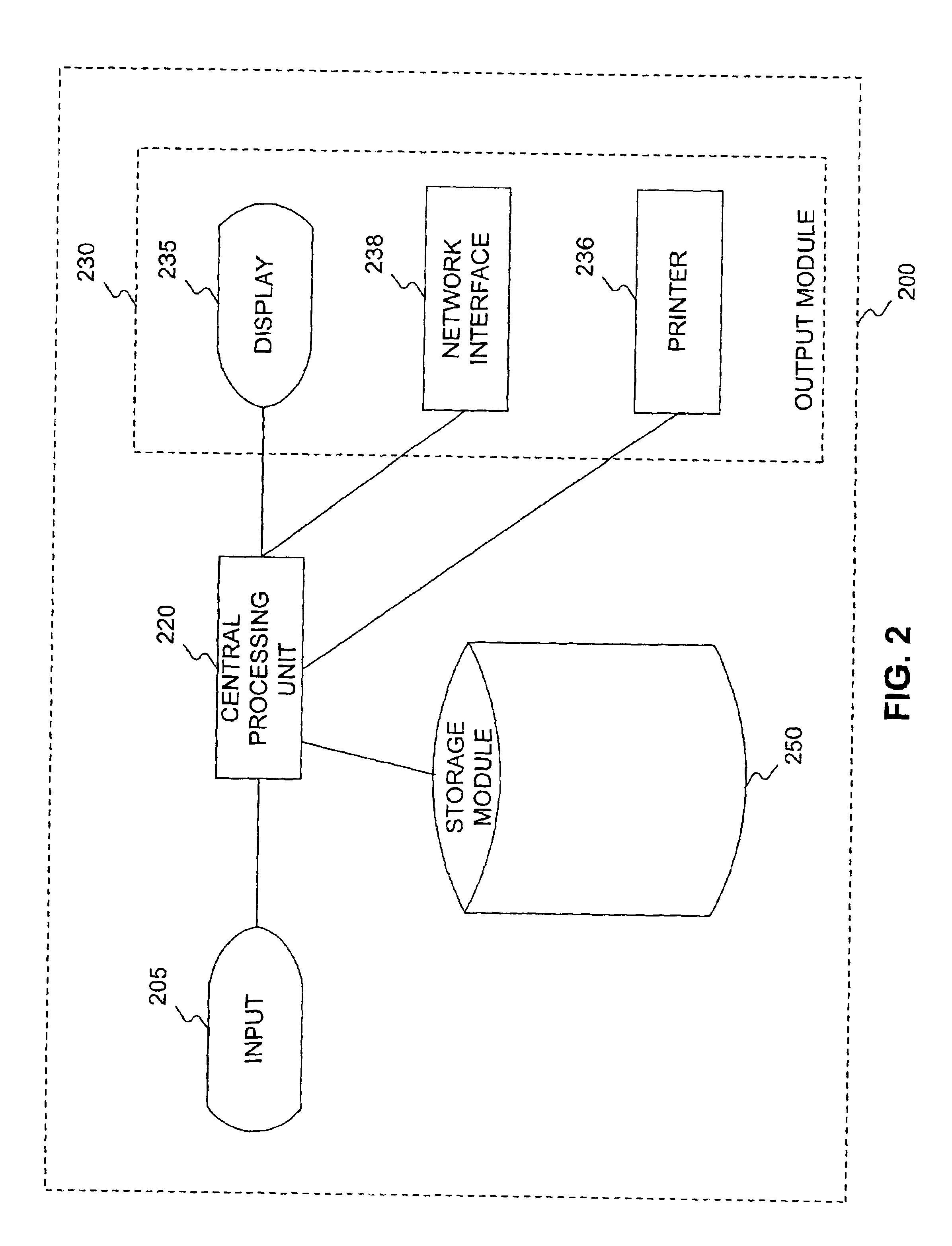
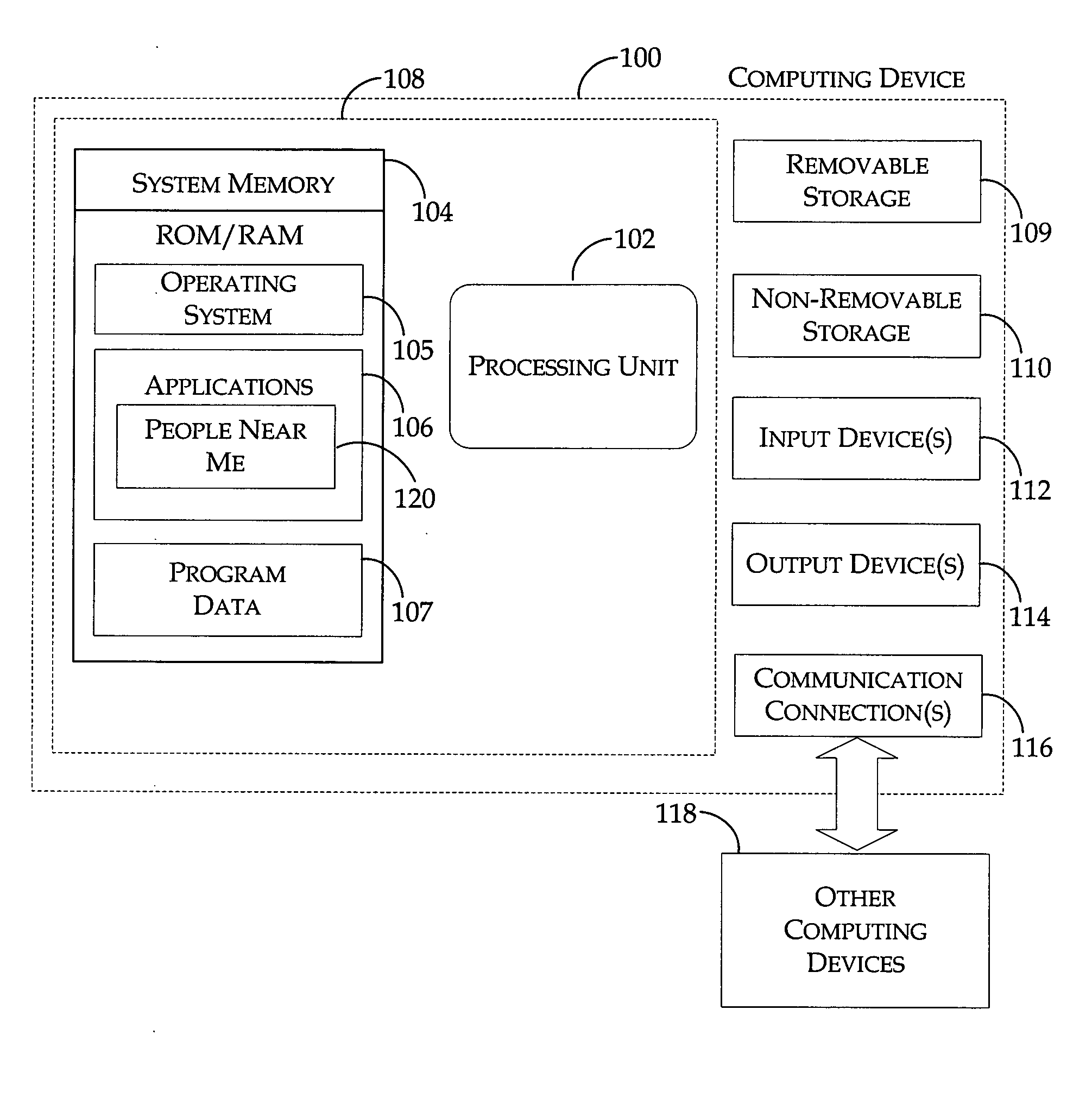
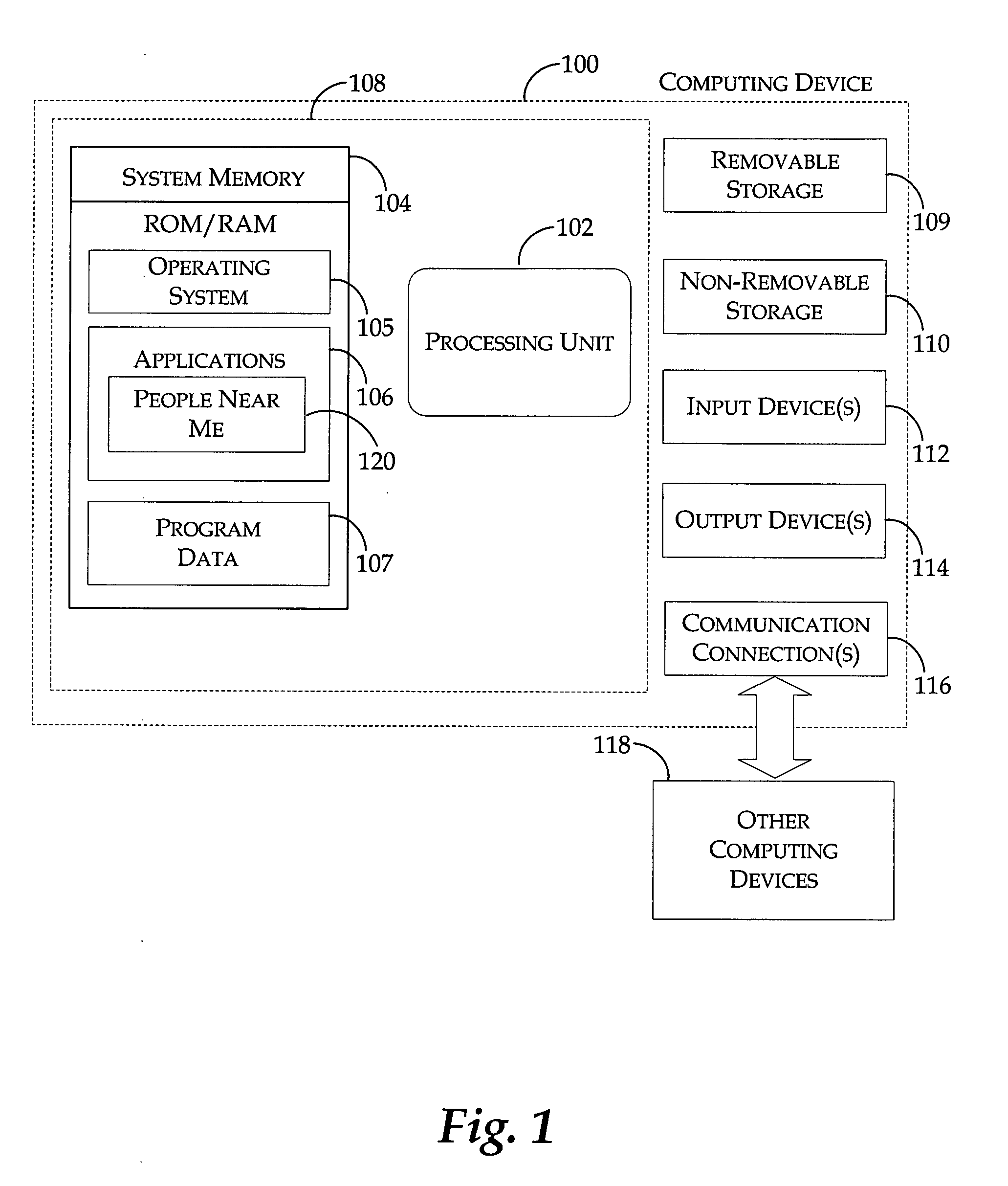
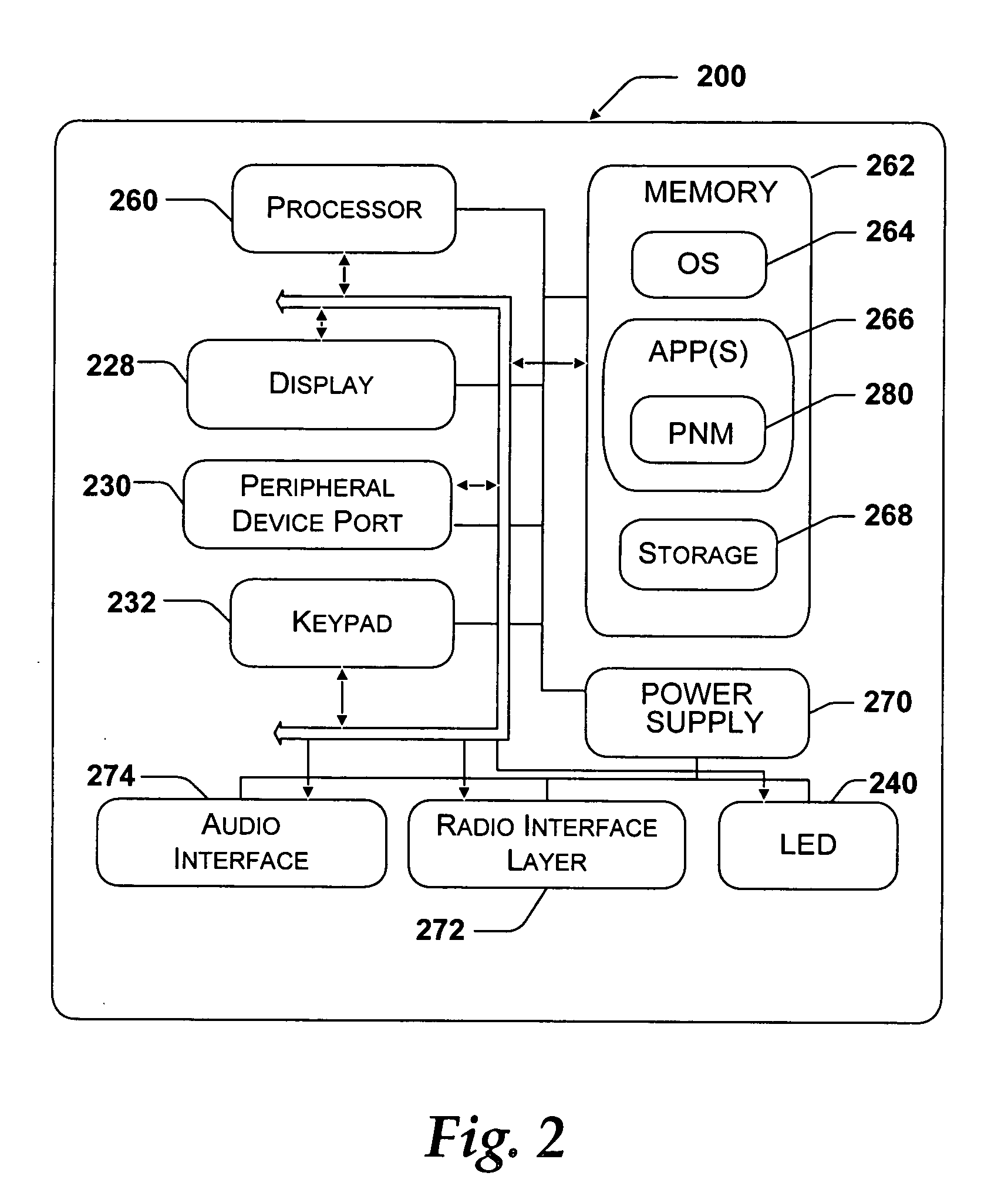
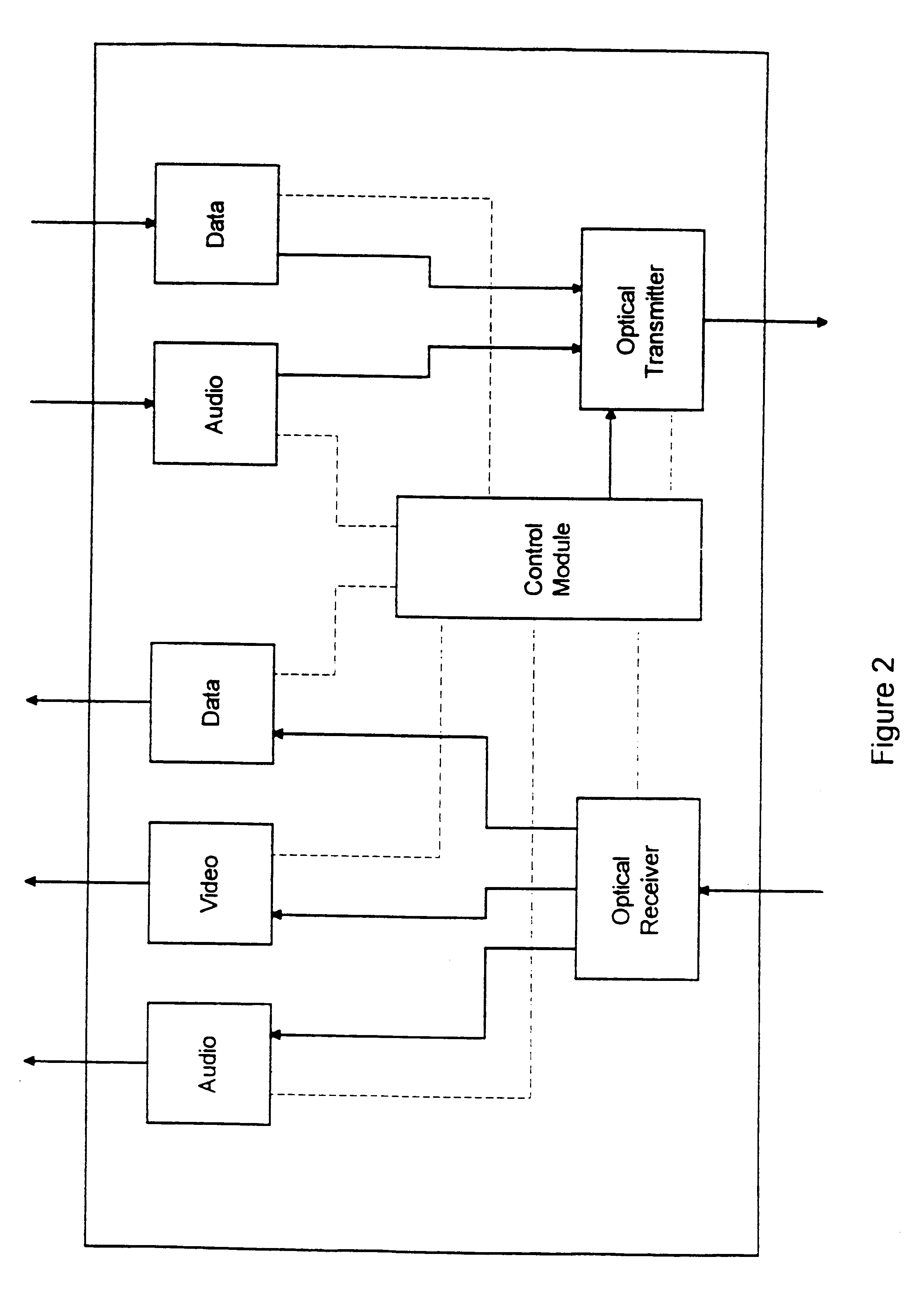
System and method for a user interface directed to discovering and publishing presence information on a network
A system and method is provided for a user interface directed to publication and discovery of the presence of users on a network. A sidebar tile is provided that peripherally and unobtrusively displays the presence information of nearby users on the network. The sidebar tile is also used to notify a local user that their information is also being published on the network. The sidebar tile provides options for selecting to change, enable, or disable the presence discovery service.
Owner:MICROSOFT TECH LICENSING LLC
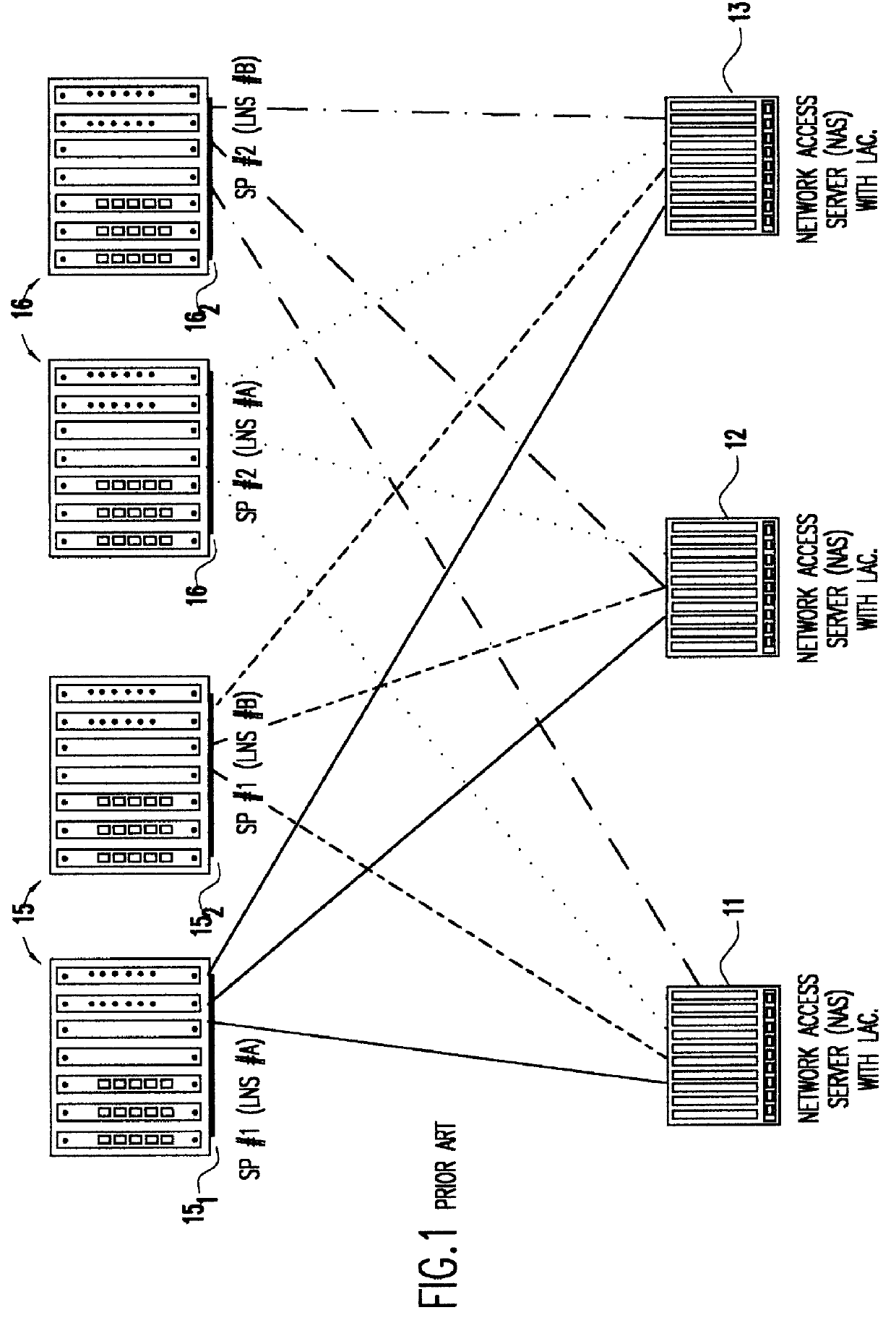
Layer two tunneling protocol (L2TP) merging and management
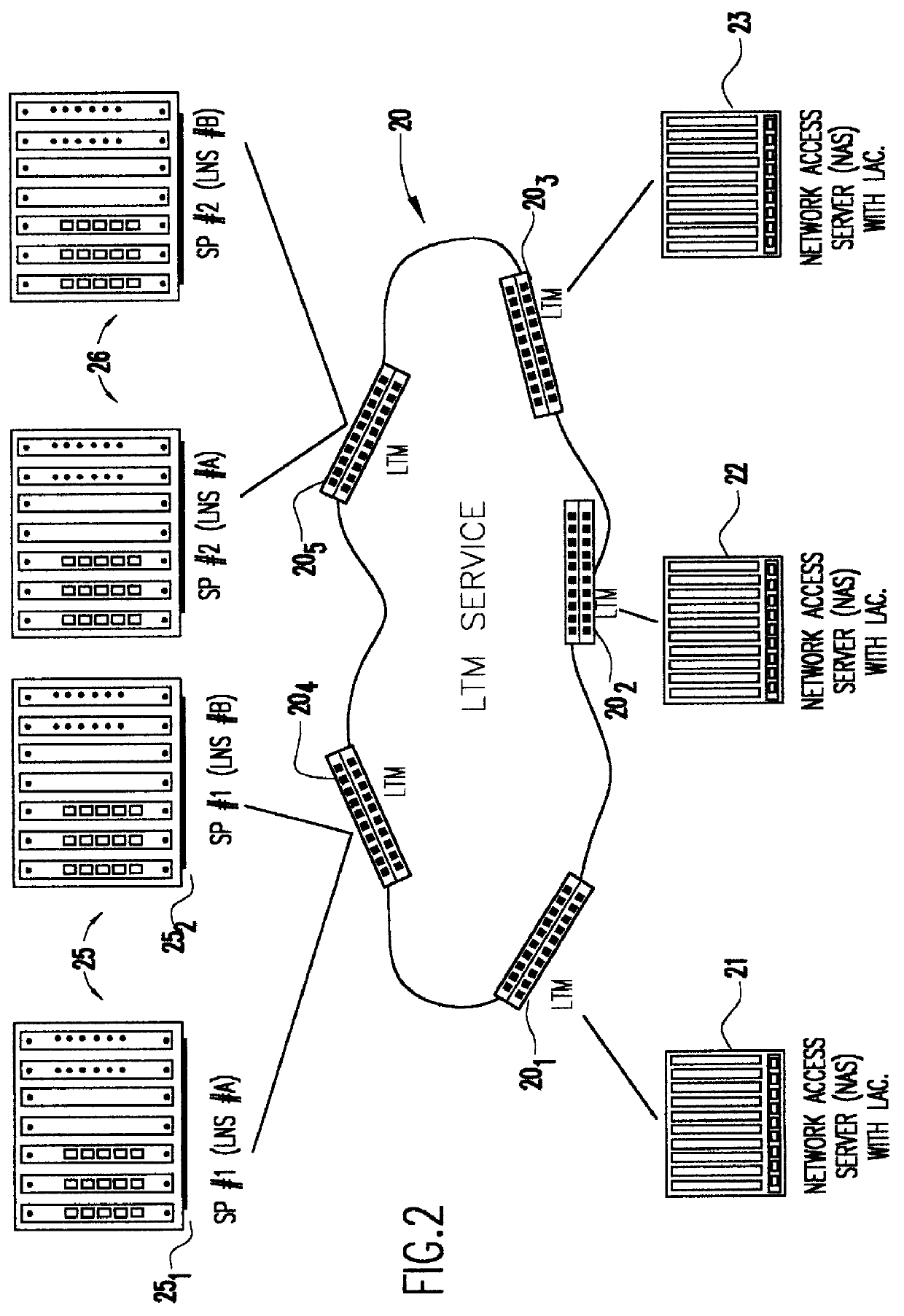
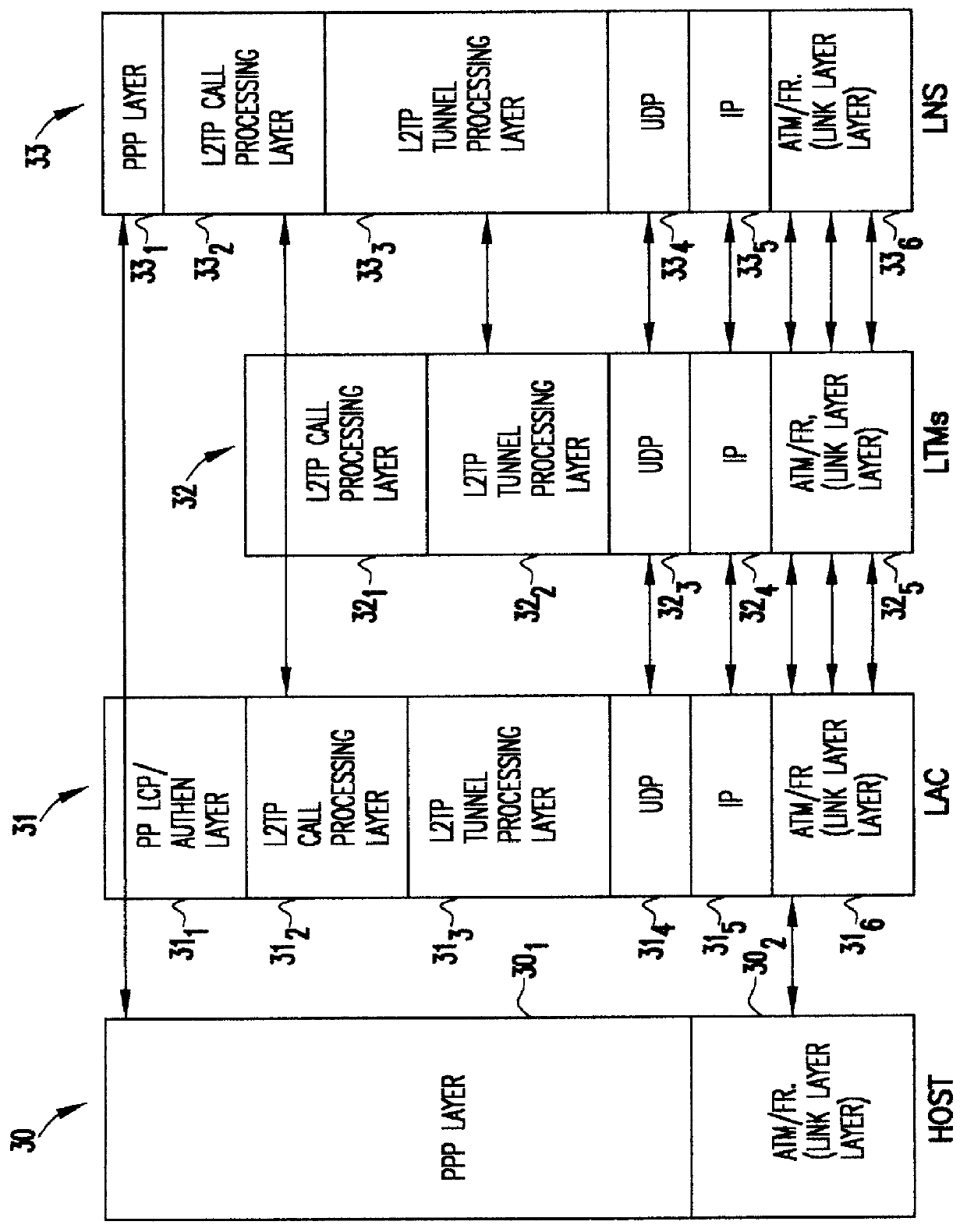
InactiveUS6094437AEasy to implementReduce complexityData switching detailsNetworks interconnectionDistributed computingEdge device
A system is provided for creating a tunneling service from the use of a traditional tunneling protocol, such as the layer two tunneling protocol (L2TP). In particular, the L2TP tunneling protocol, which is designed to go point-to-point between an L2TP Access Concentrator (LAC) and an L2TP Network Server (LNS), is abstracted so that L2TP becomes an access protocol to a tunneling service. A new L2TP tunnel merger and management (LTM) service is created which severs the tight configuration relationships between LAC and LNSs. Only a tight configuration between an LAC and its LTM edge device and between an LNS and its LTM edge device is required. An internal trunk protocol (INT protocol) carries needed information between LTM edge devices to establish ingress / egress L2TP access calls inside of separate L2TP access tunnels on opposite LTM edge devices. The addition of another LAC is accomplished by re-routing L2TP tunnels within the LTM service without reconfiguration of the LNSs, and the addition of another LNS is accomplished by re-routing L2TP tunnels within the LTM service without reconfiguration of the LACs. The LTM service determines the need for both additional trunk and access resources and establishes both new trunk / access tunnels to provide additional resources. The LTM service also determines excess resources on both trunk and access entities and releases trunk / access tunnels to provide the needed additional resources.
Owner:TDC THE
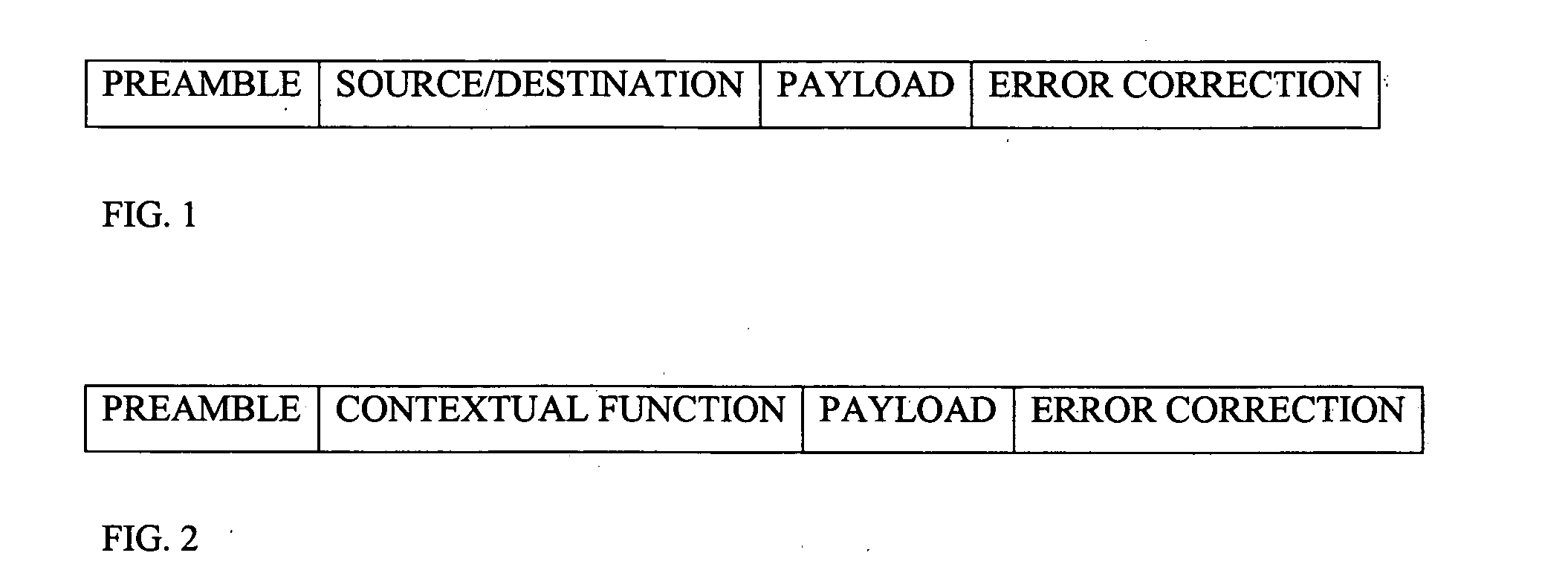
Communications system
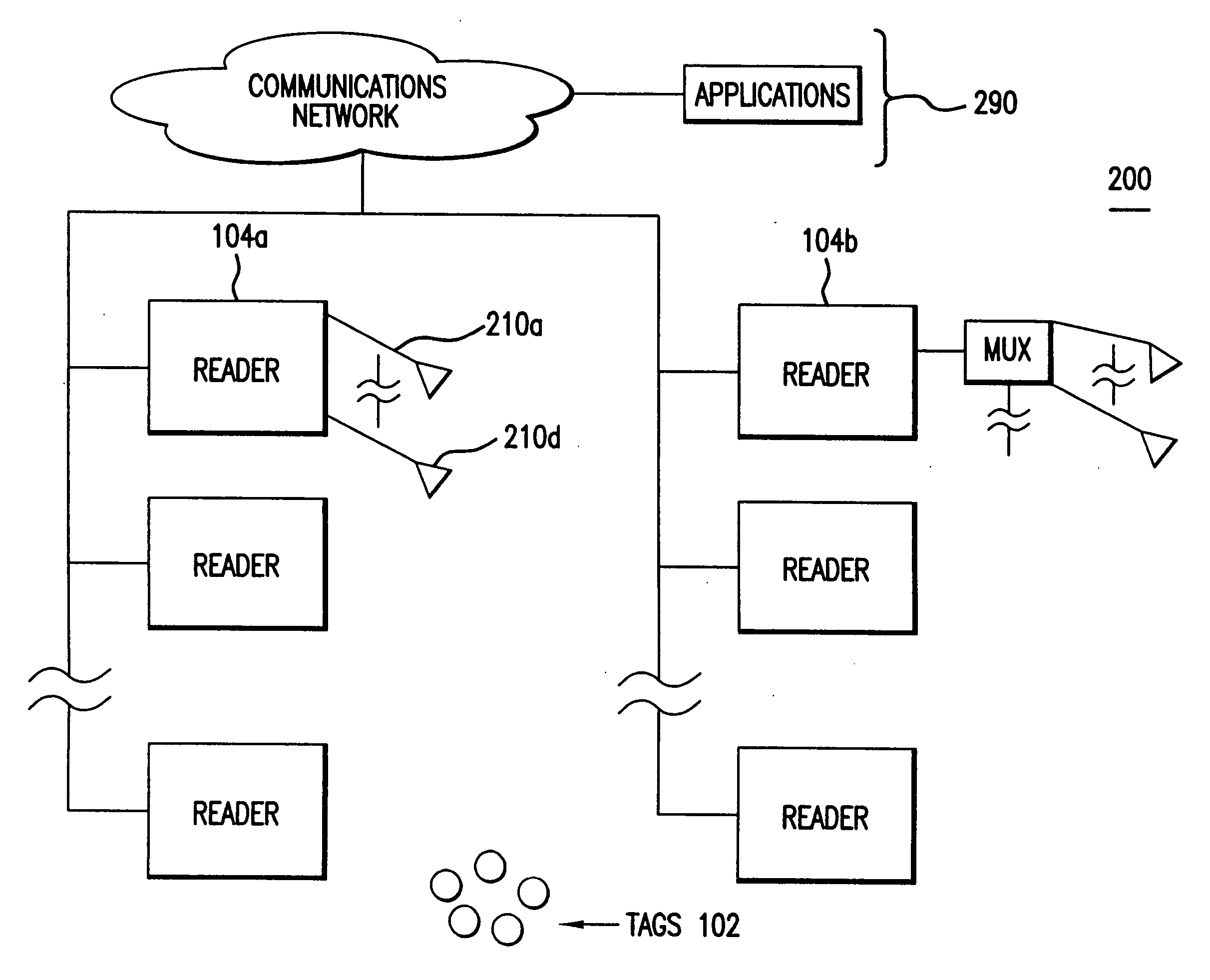
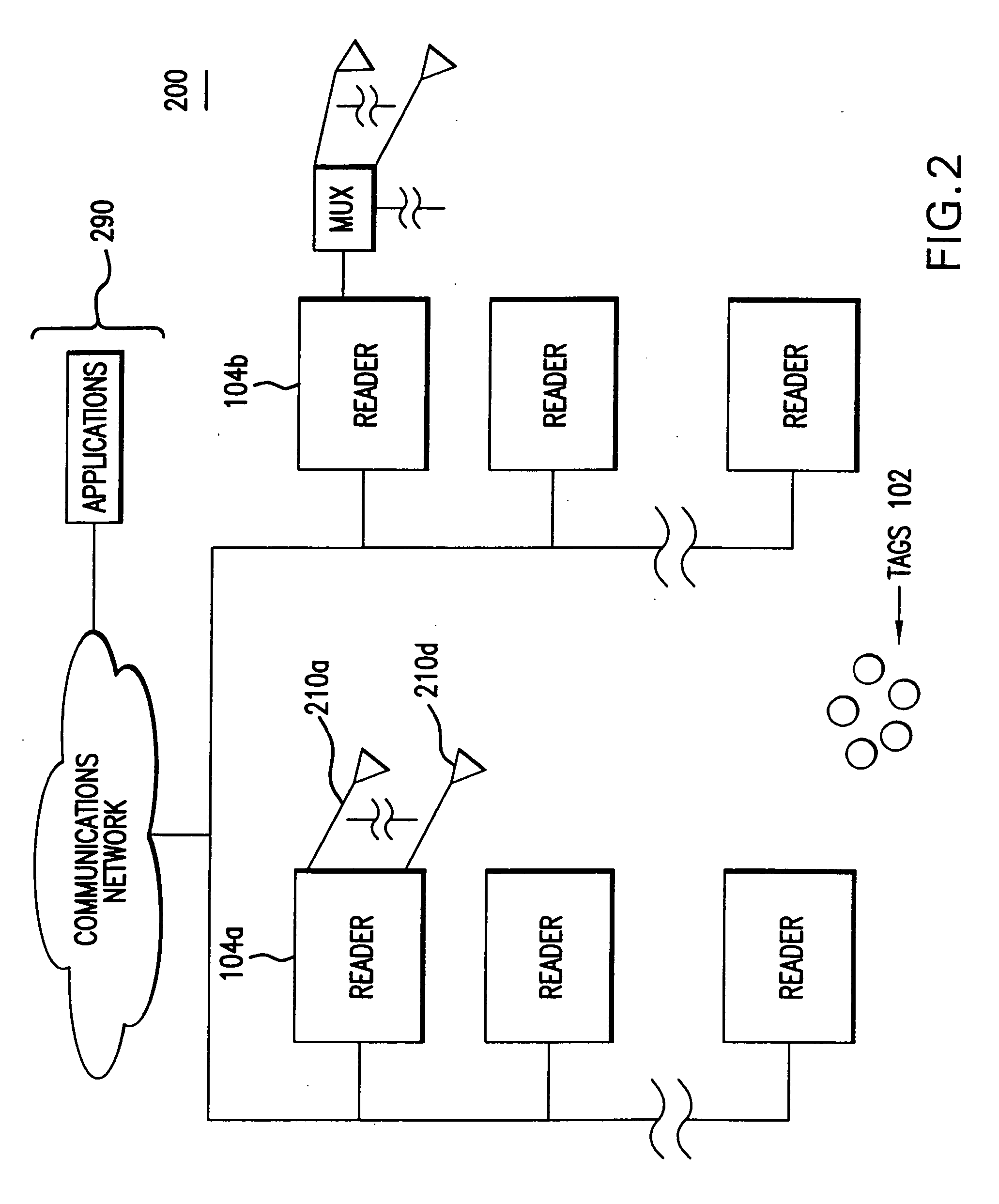
ActiveUS20050172024A1Data switching detailsMultiple digital computer combinationsCommunications systemPlug and play
A communications system for a network of stations, is provided where stations identify themselves upon being informed of the desires of an inquisitor station. Additionally, techniques for “plug and play”, self-healing and homogenizing the heterogeneous parts of a network, are provided.
Owner:TANTALUS SYST CORP
User interface for a remote control application
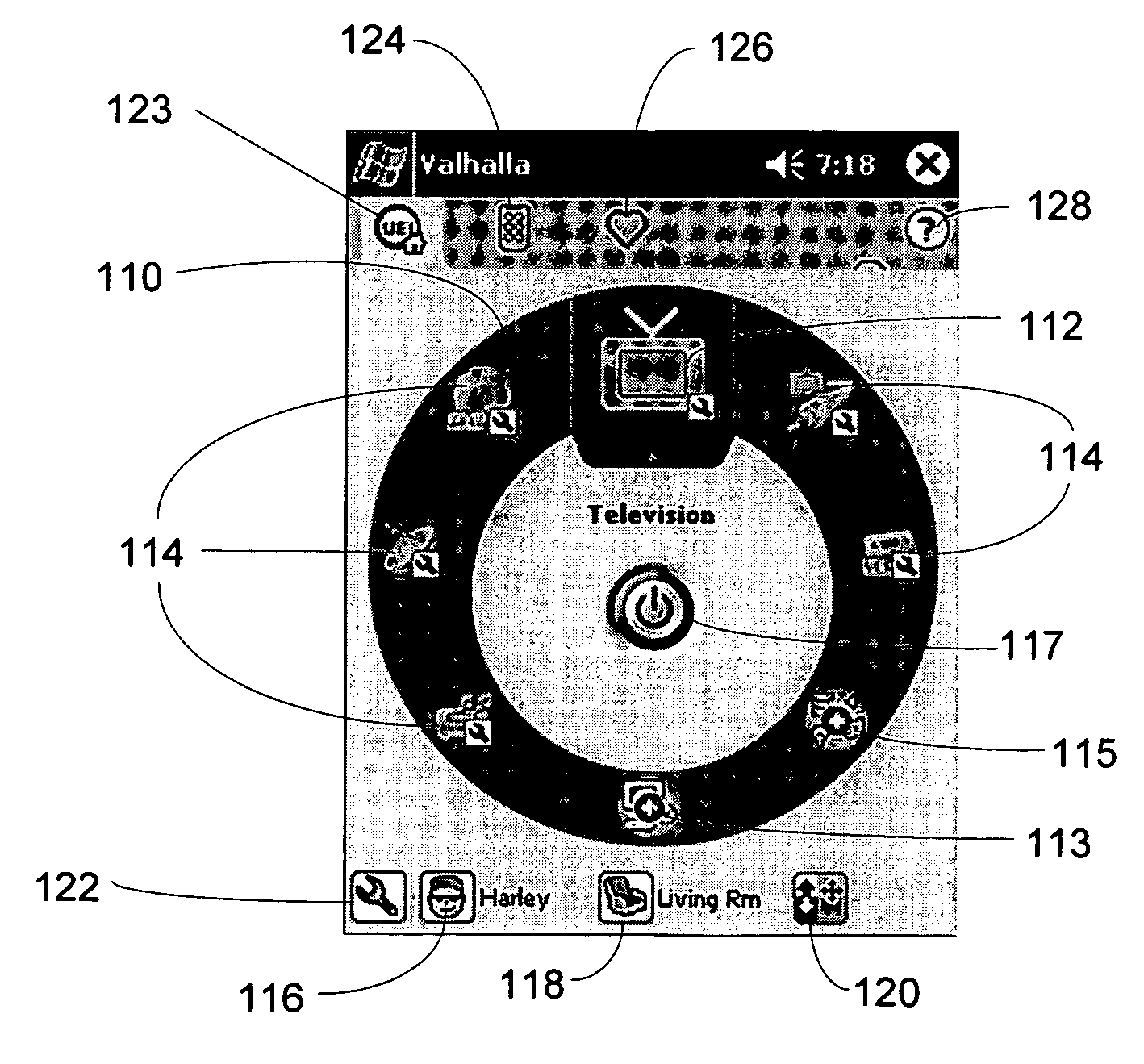
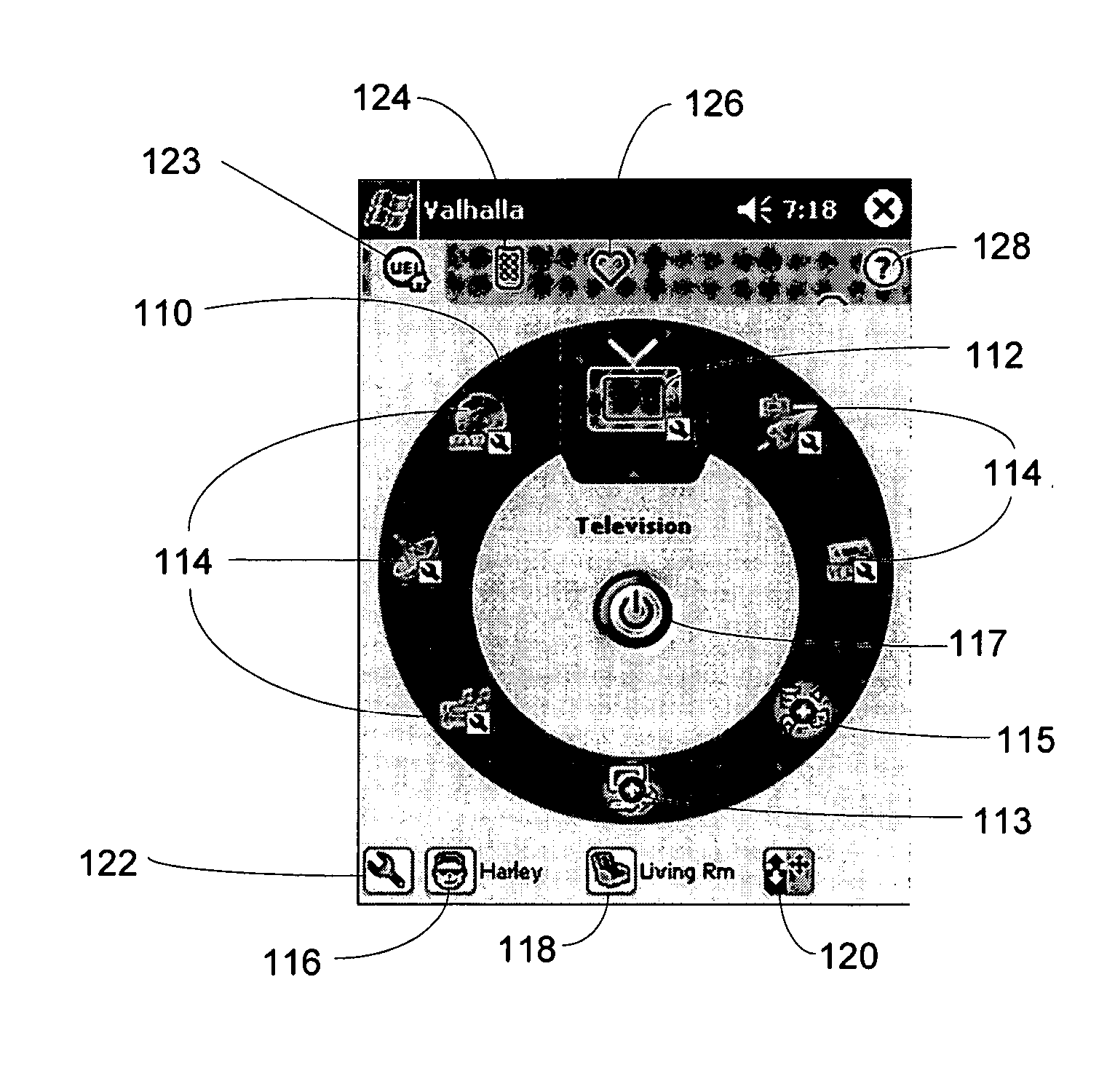
ActiveUS20060161865A1Television system detailsElectric signal transmission systemsGraphicsGraphical user interface
A hand-held electronic device having a remote control application user interface that functions to displays operational mode information to a user. The graphical user interface may be used, for example, to setup the remote control application to control appliances for one or more users in one or more rooms, to perform activities, and to access favorites. The remote control application is also adapted to be upgradeable. Furthermore, the remote control application provides for the sharing of operational mode information.
Owner:UNIVERSAL ELECTRONICS INC
User interface for a remote control application
InactiveUS20060150120A1Television system detailsElectric signal transmission systemsGraphicsGraphical user interface
Owner:UNIVERSAL ELECTRONICS INC
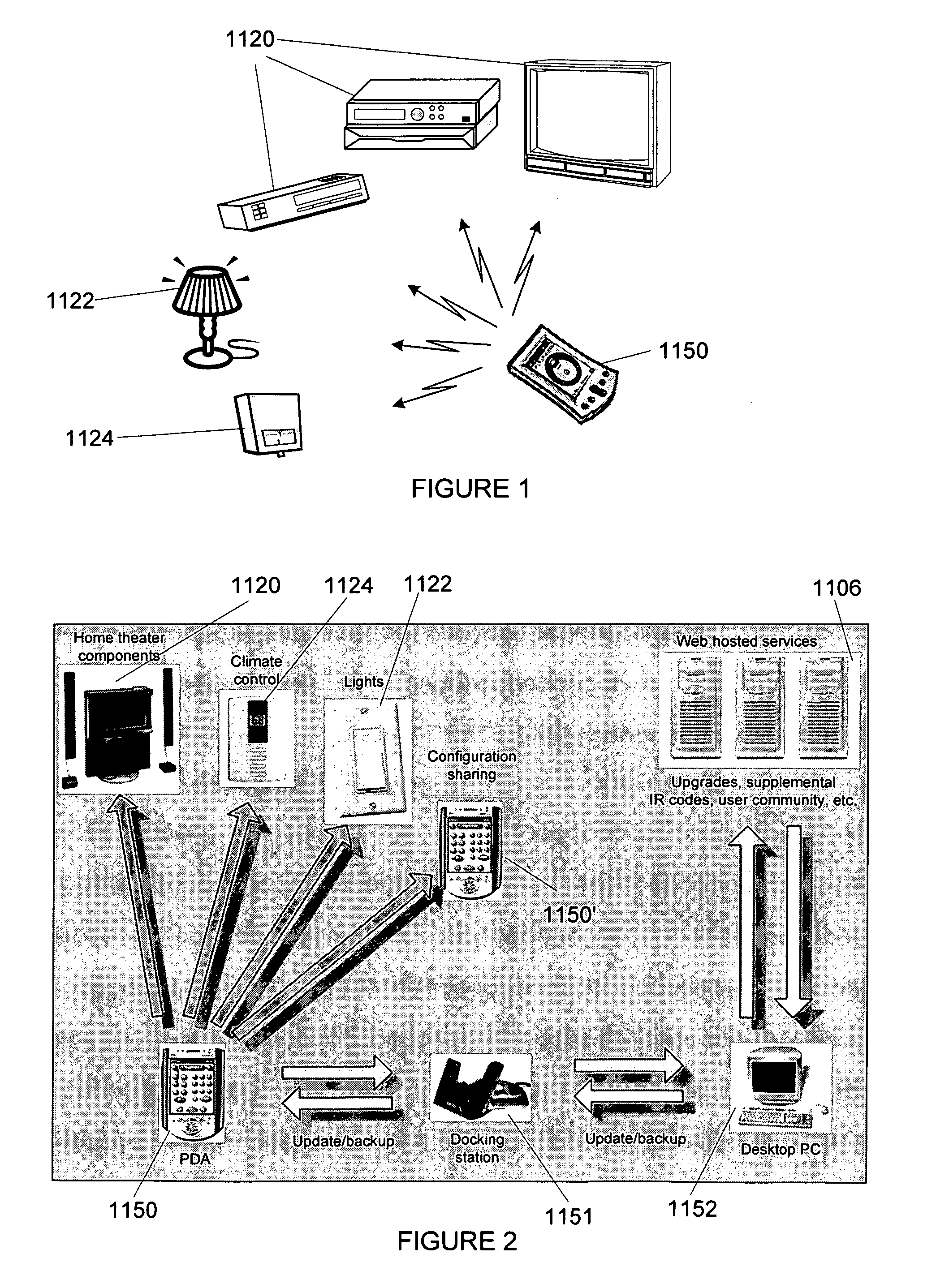
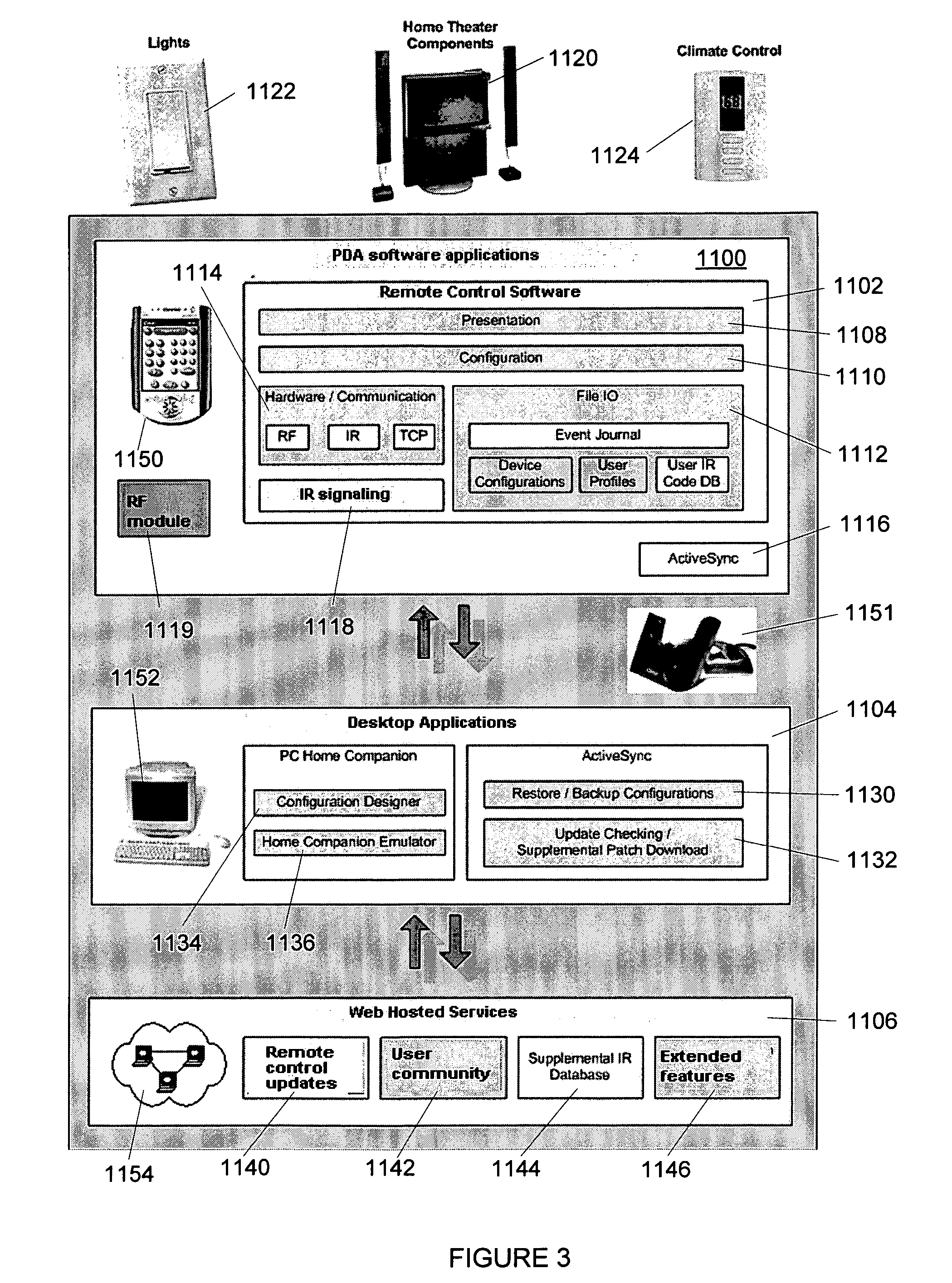
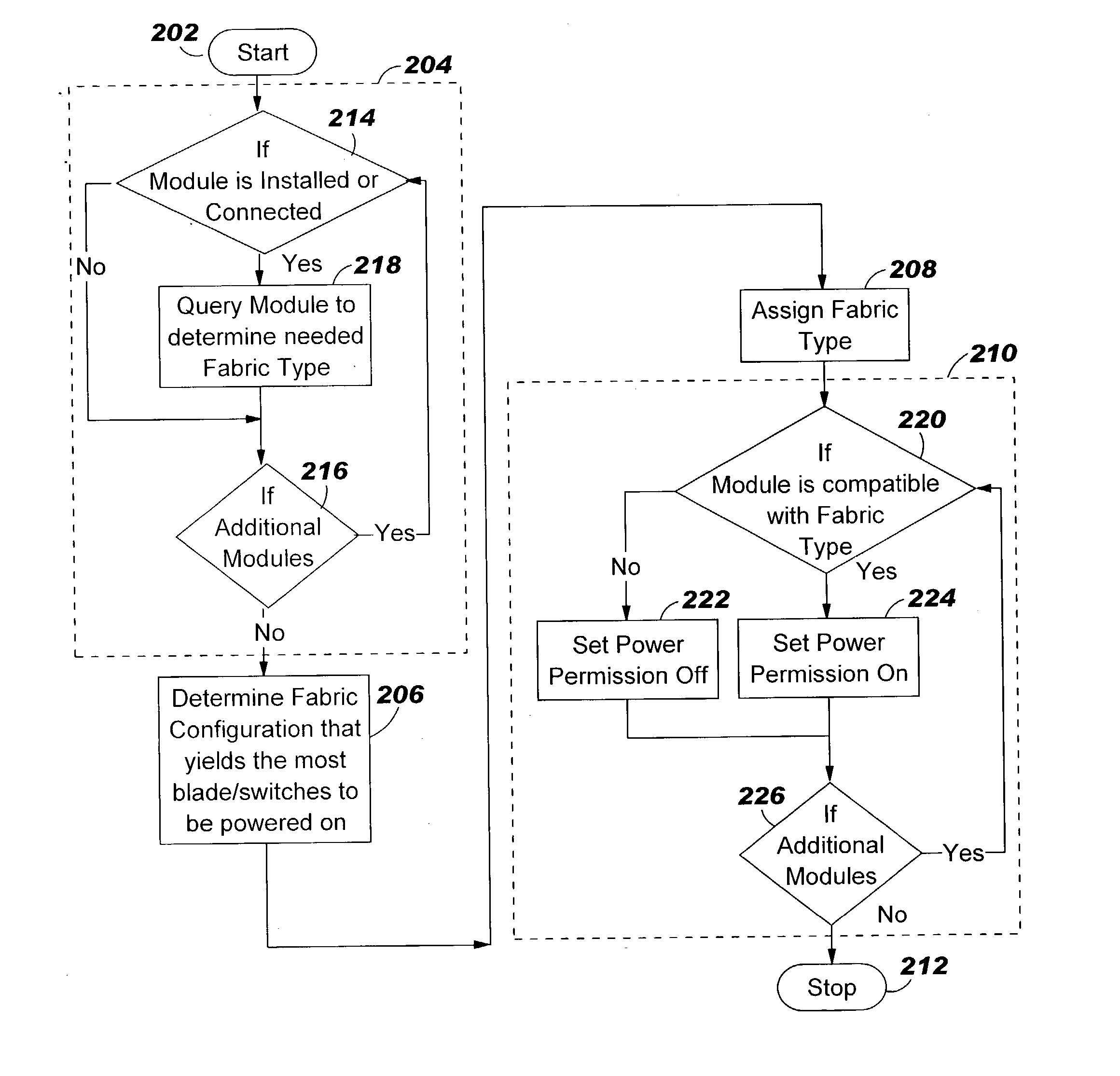
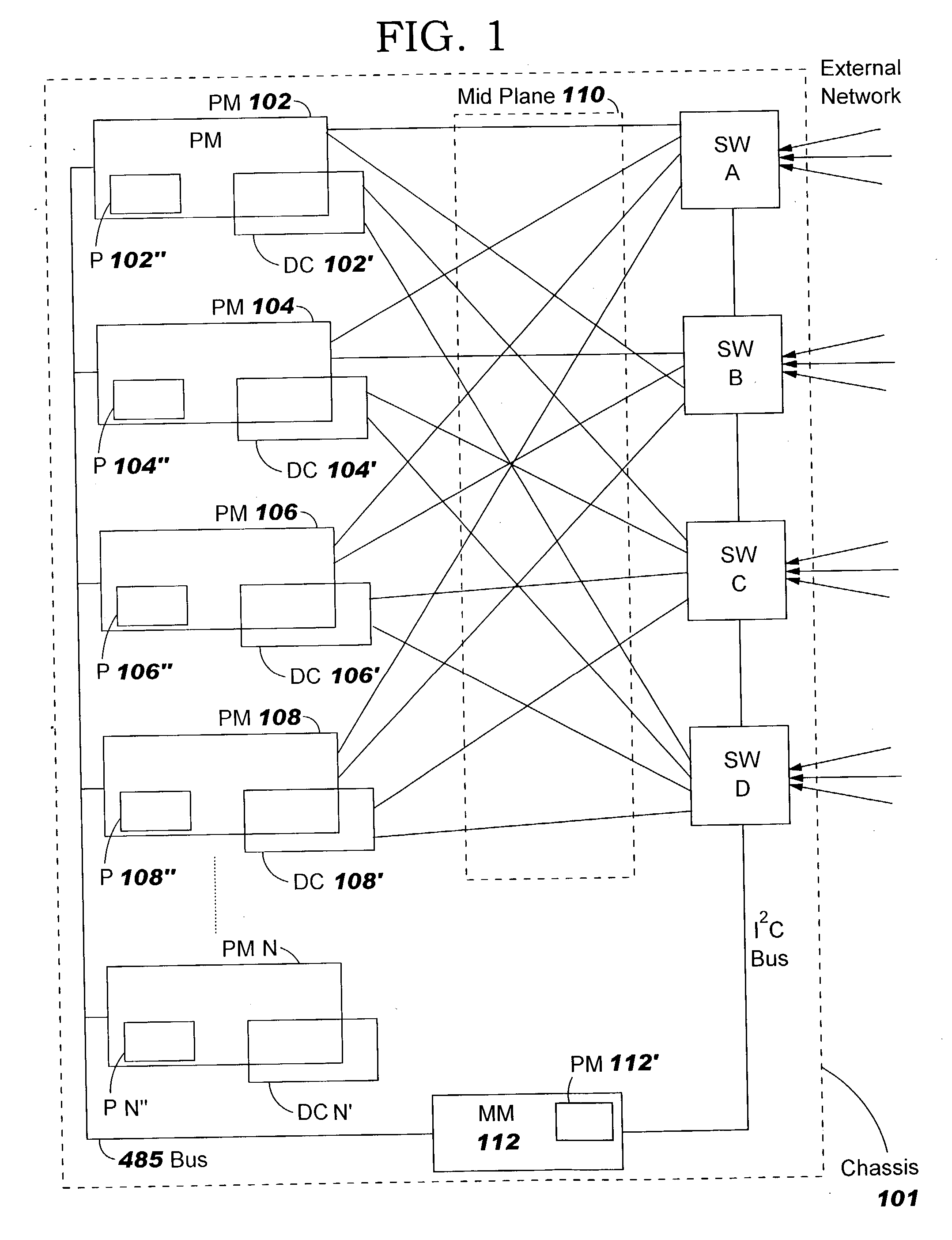
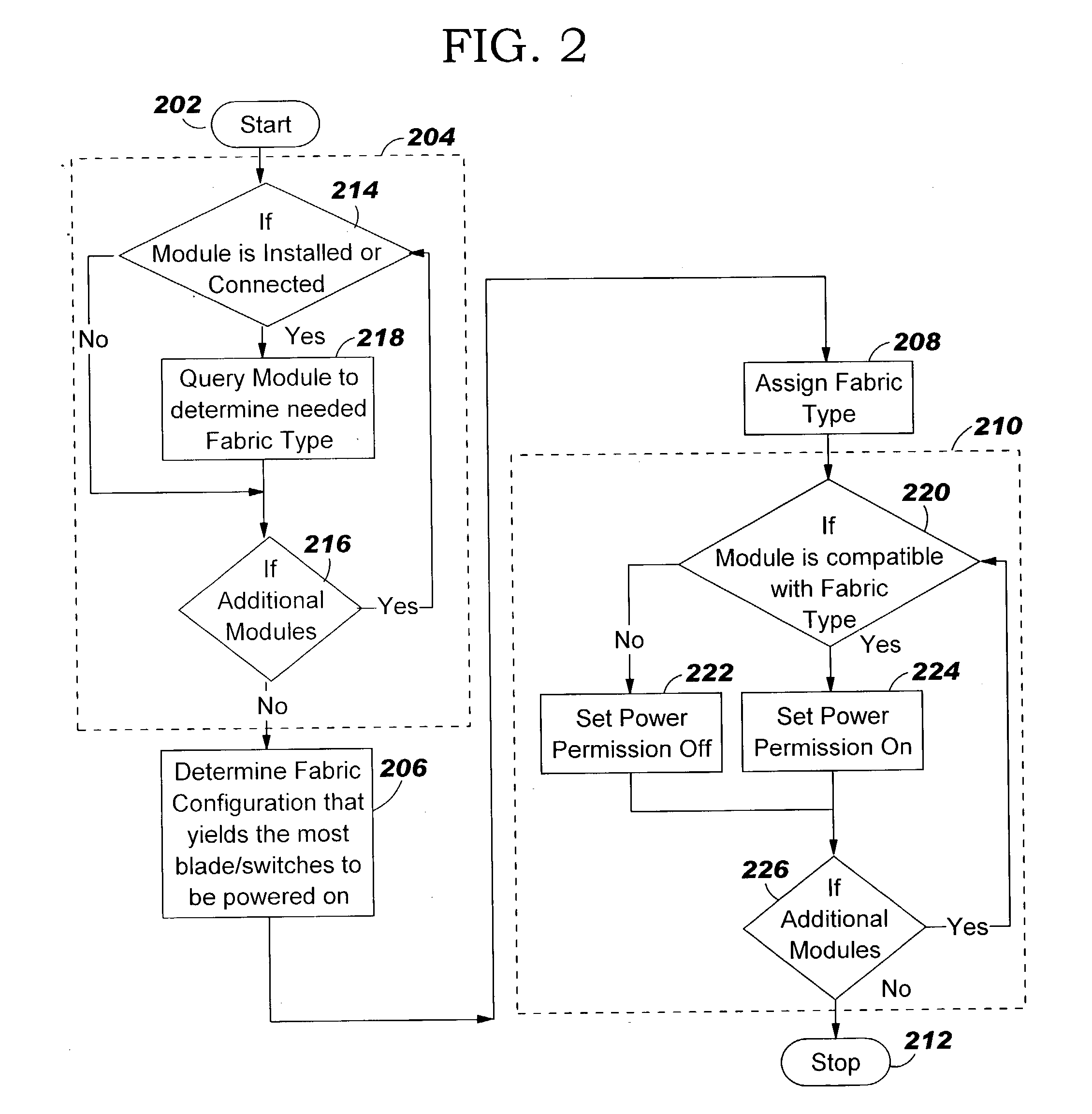
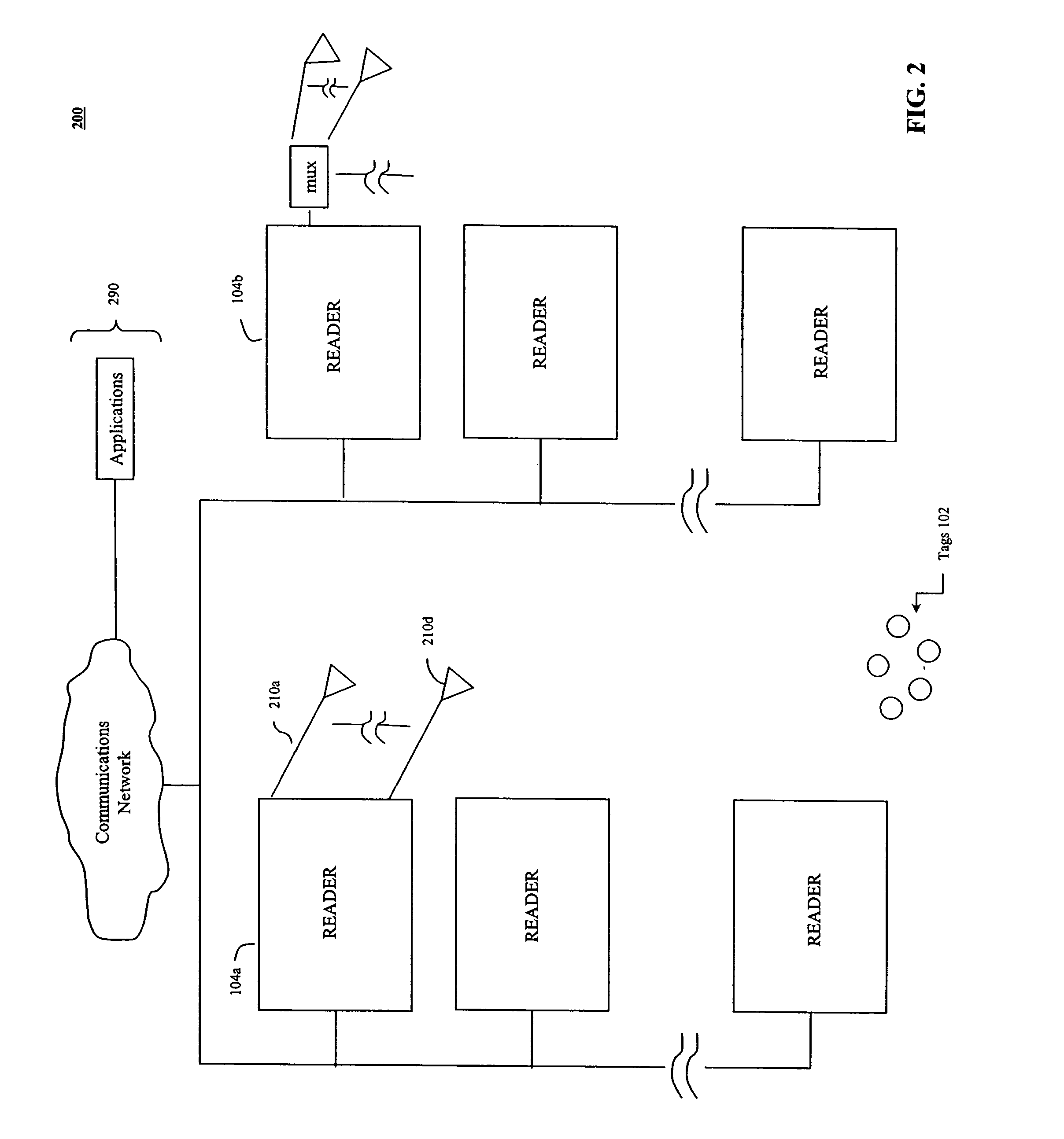
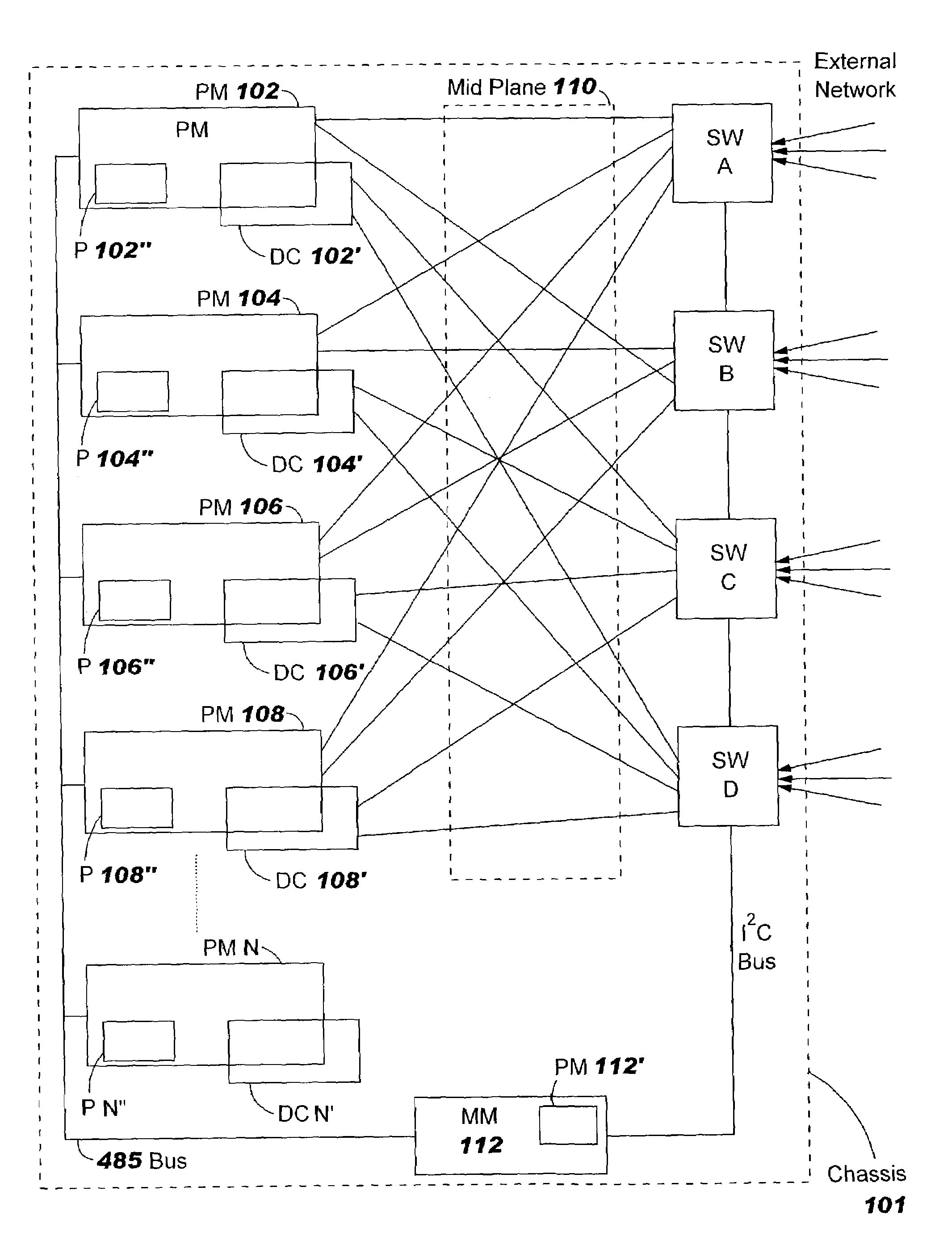
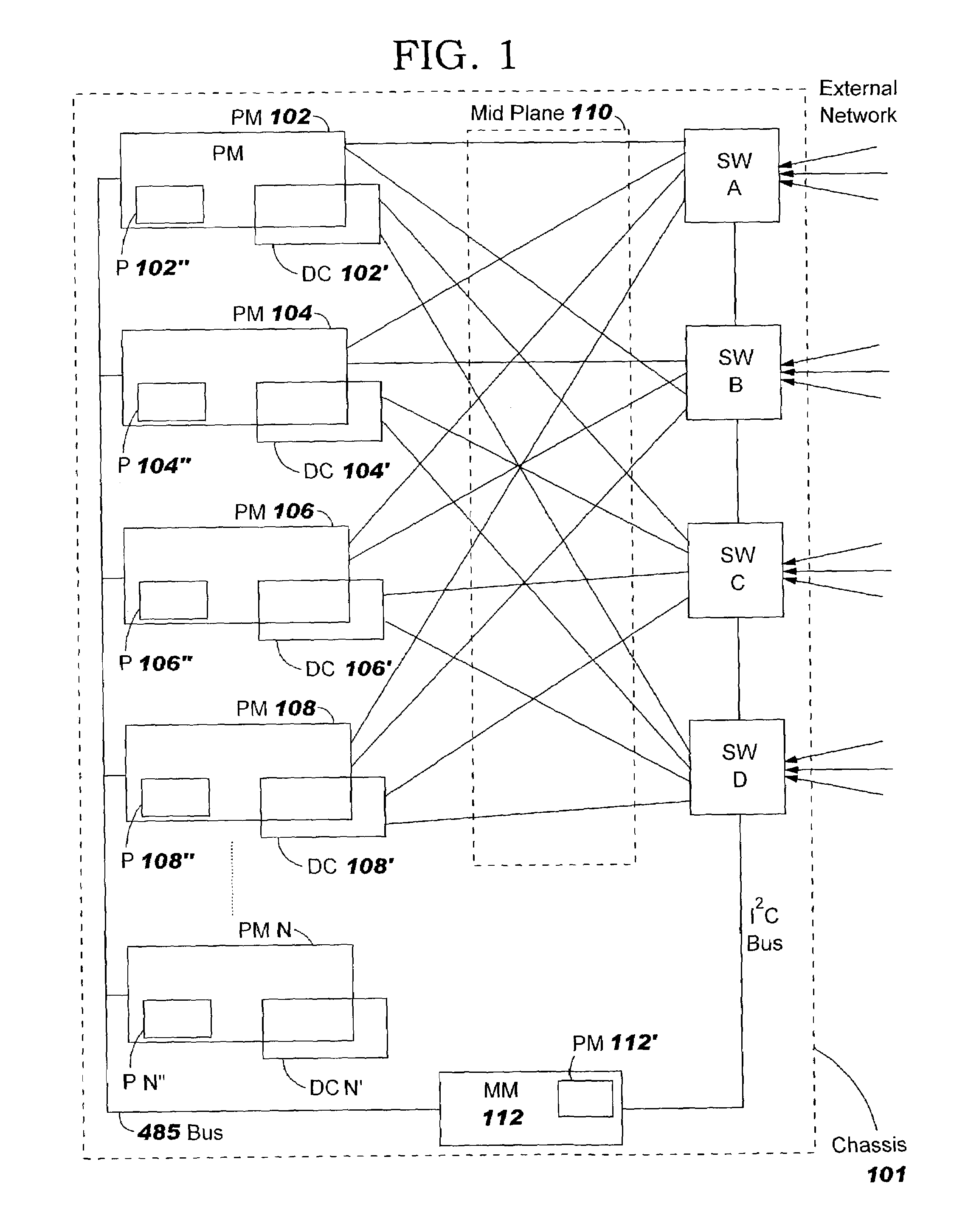
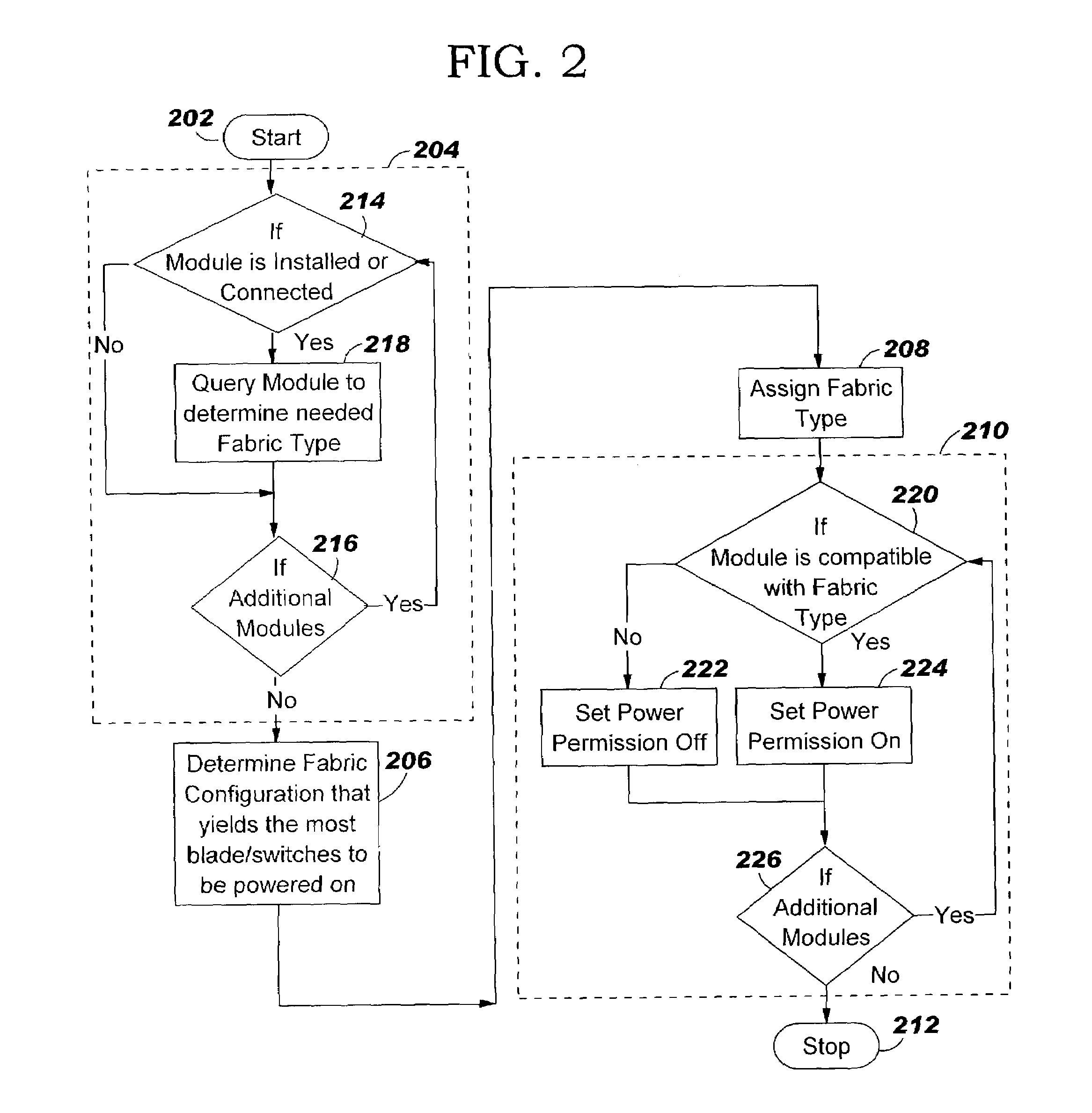
Apparatus, method and program product for automatically distributing power to modules inserted in live chassis
InactiveUS20040117536A1Error has likelihoodCost of operationData switching detailsVolume/mass flow measurementComputer moduleField service
When a blade and / or interconnect device is inserted into the chassis of a powered or live server the procedure is known as hot-plugging. Before power is applied to the hot-plugged blade and / or interconnect device the fabric type of already installed blades and / or interconnect devices is correlated with fabric types of newly hot-plugged blade and / or interconnect device. Depending upon results of the correlation, power to the hot-plugged blade and / or interconnect device is allowed or denied.
Owner:IBM CORP
Methods and systems for hairpins in virtual networks
InactiveUS7047424B2Easily and effectively leverage powerWithout complexityData switching detailsMemory loss protectionParallel computingVirtual network
Methods and systems are provided for enabling communication between a first processor and a second processor using at least one additional processor separate from the first and second processors, wherein one or more firewalls selectively restrict the communication. In one embodiment, the additional processor may determine whether the first and second processors mutually consent to enabling a hairpin between the first and second processors. The first processor may be provided with a first information identifying the hairpin and the second processor may be provided with a second information identifying the hairpin, when the additional processor may determine that the first and second processors mutually consent to the hairpin. Moreover, a first information flow may be established from the first processor to the hairpin based on the provided first information, and a second information flow may be established from the second processor to the hairpin based on the provided second information. The hairpin may forward the first information flow received from the first processor to the second processor such that the communication between the first and second processors is allowed by the firewalls.
Owner:ORACLE SYST CORP
System and method for a user interface directed to discovering and publishing presence information on a network
A system and method is provided for a user interface directed to publication and discovery of the presence of users on a network. A sidebar tile is provided that peripherally and unobtrusively displays the presence information of nearby users on the network. The sidebar tile is also used to notify a local user that their information is also being published on the network. The sidebar tile provides options for selecting to change, enable, or disable the presence discovery service.
Owner:MICROSOFT TECH LICENSING LLC
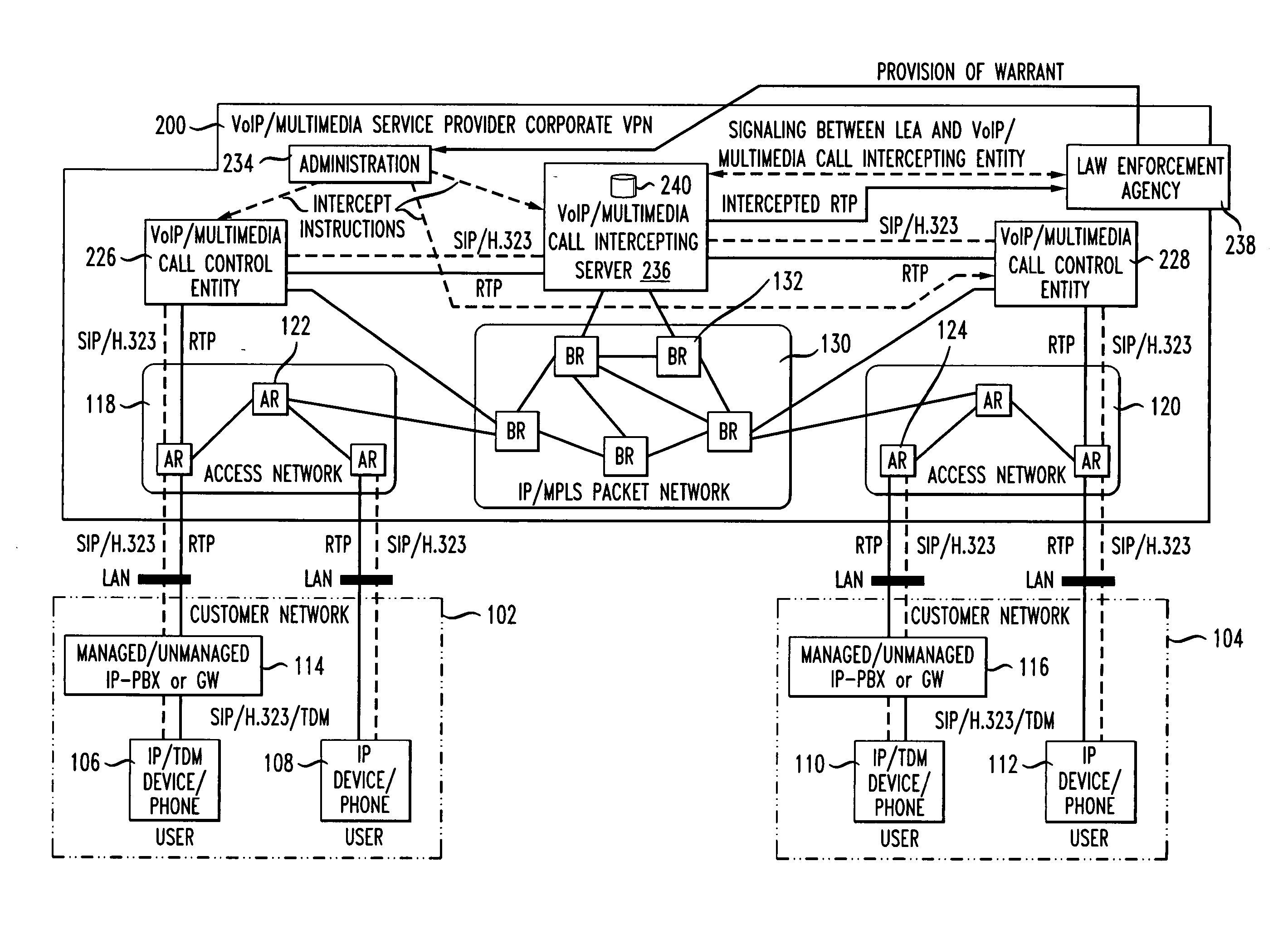
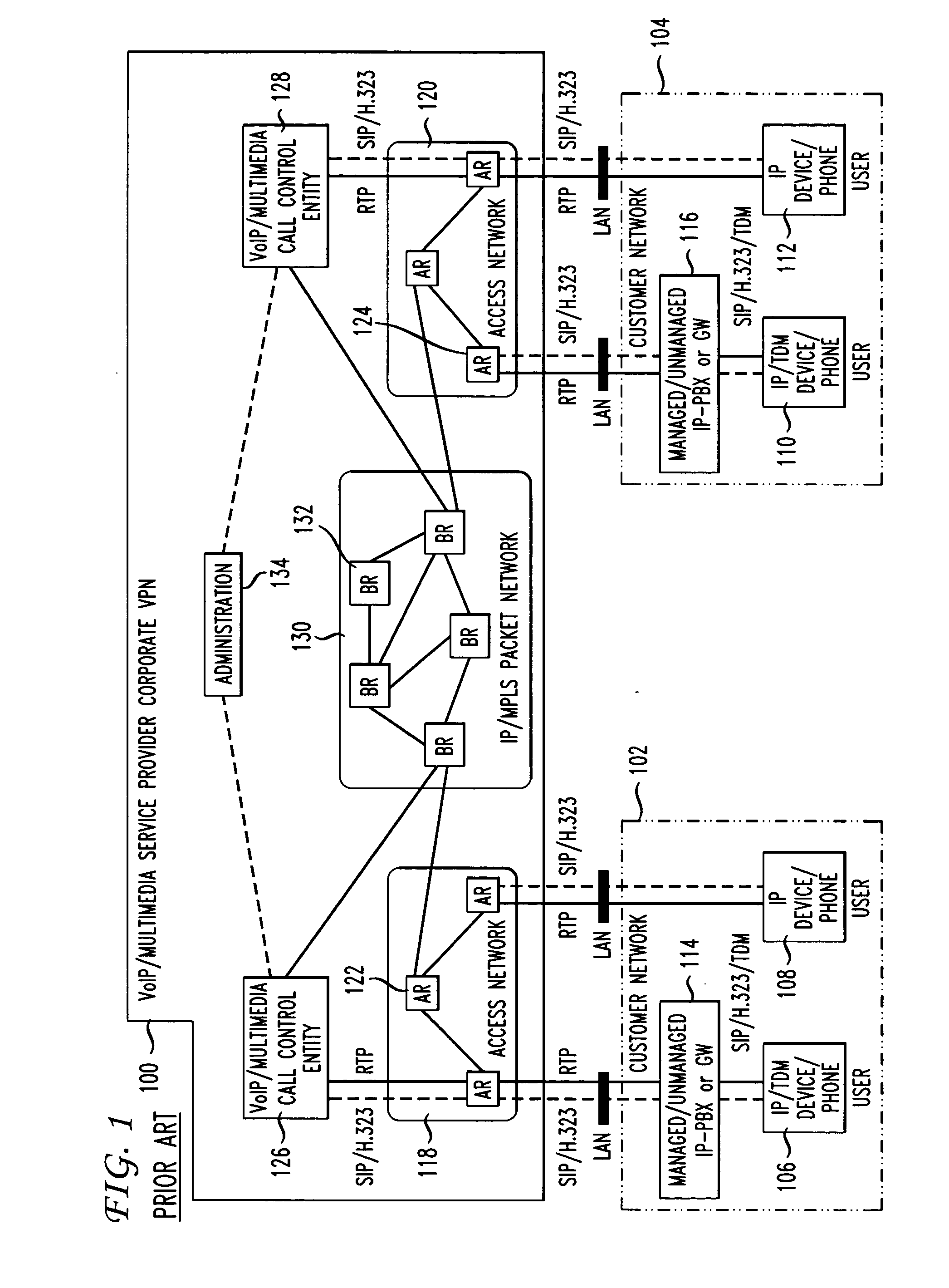
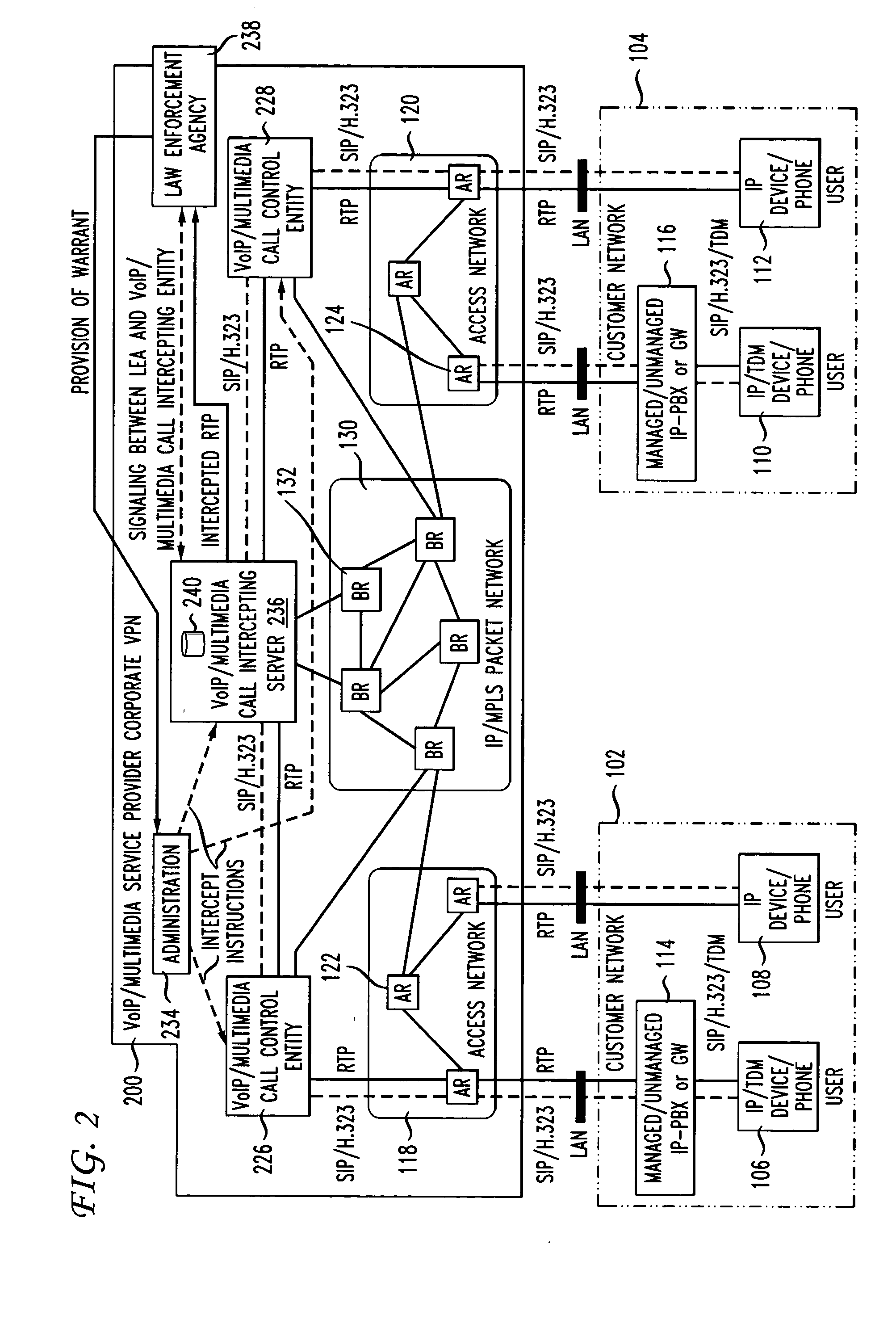
Calea in a VPN environment (formerly called restricted anti-calea
InactiveUS20050175156A1Data switching detailsSupervisory/monitoring/testing arrangementsTelecommunicationsUniform resource locator
Method and system are disclosed for intercepting voice / multimedia calls in a VPN environment. The calls are diverted to a voice / multimedia call intercepting server where the intercept subject is identified. The identification may be based on an image / picture as well as identifying information about the intercept subject provided to the VPN administrator. The identifying information may be, for example, a telephone number, URL, name, and the like, for the intercept subject. The combination of image / picture and identifying information is especially useful to confirm telephone numbers, URLs, names, and the like that can be used by someone other than real intercept subject. Once the identity of the intercept subject is confirmed, the call content is duplicated, encapsulated, and / or transported to the law enforcement agency. The method and system of the invention then re originates the call to prevent the intercept subject from detecting the intercept.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
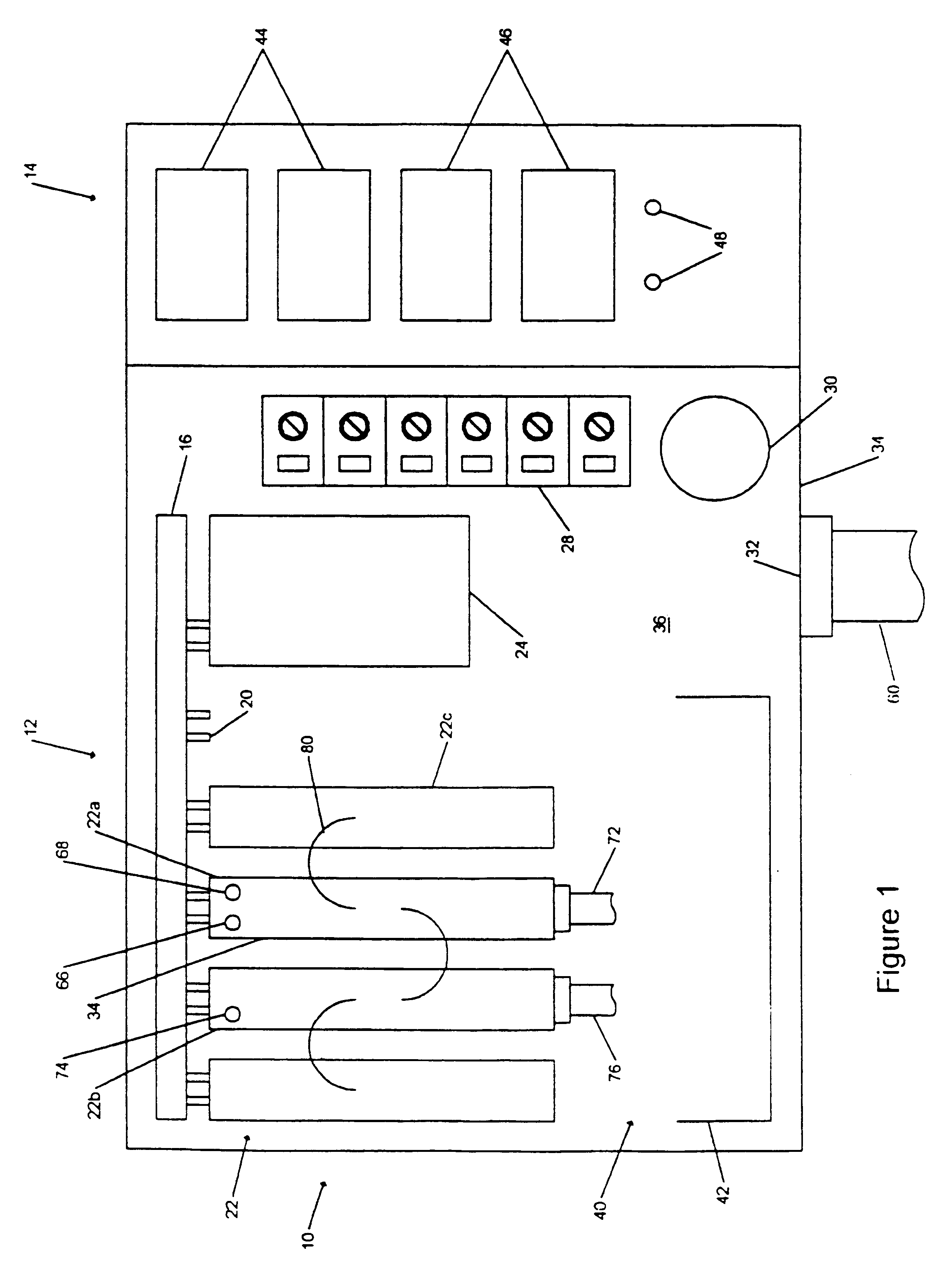
Universal demarcation point
A universal demarcation point for managing the delivery of communications services to a subscriber that provides an interface between a utility distribution network and subscriber owned equipment. The universal demarcation point includes a utility accessible portion and a subscriber accessible portion. The utility accessible portion has an input port, an output port, a plurality of modular connectors, a power supply, and a plurality of service modules. The input port provides access to the universal demarcation point for delivery of communications service from the utility distribution network. The communications services are delivered through a hybrid cable. The hybrid cable has a plurality of fiber optic cables and a plurality of copper cables. The fiber optic cables are capable of transmitting light signals and the copper cables are capable of transmitting electric power. The output port provides access for delivering the communications services from the universal demarcation point into the subscriber's dwelling. The plurality of connectors are fixedly mounted to the universal demarcation point. The power supply is removably mounted to the universal demarcation point. The power supply converts the electric power into a voltage for powering the operation of the universal demarcation point. The service modules are capable of plugging into the modular connectors and convert the light signals that are transmitted on the fiber optic cables onto cables that are suitable for use in the subscriber's dwelling. The subscriber accessible portion is adjacent to the utility accessible portion and has ports that enable the subscriber to test the integrity of the communications services delivered from the utility distribution network.
Owner:WHITE OAK GLOBAL ADVISORS
Optimization of a binary tree traversal with secure communications
InactiveUS20040134984A1Improve securityData switching detailsMemory record carrier reading problemsSecure communicationTree traversal
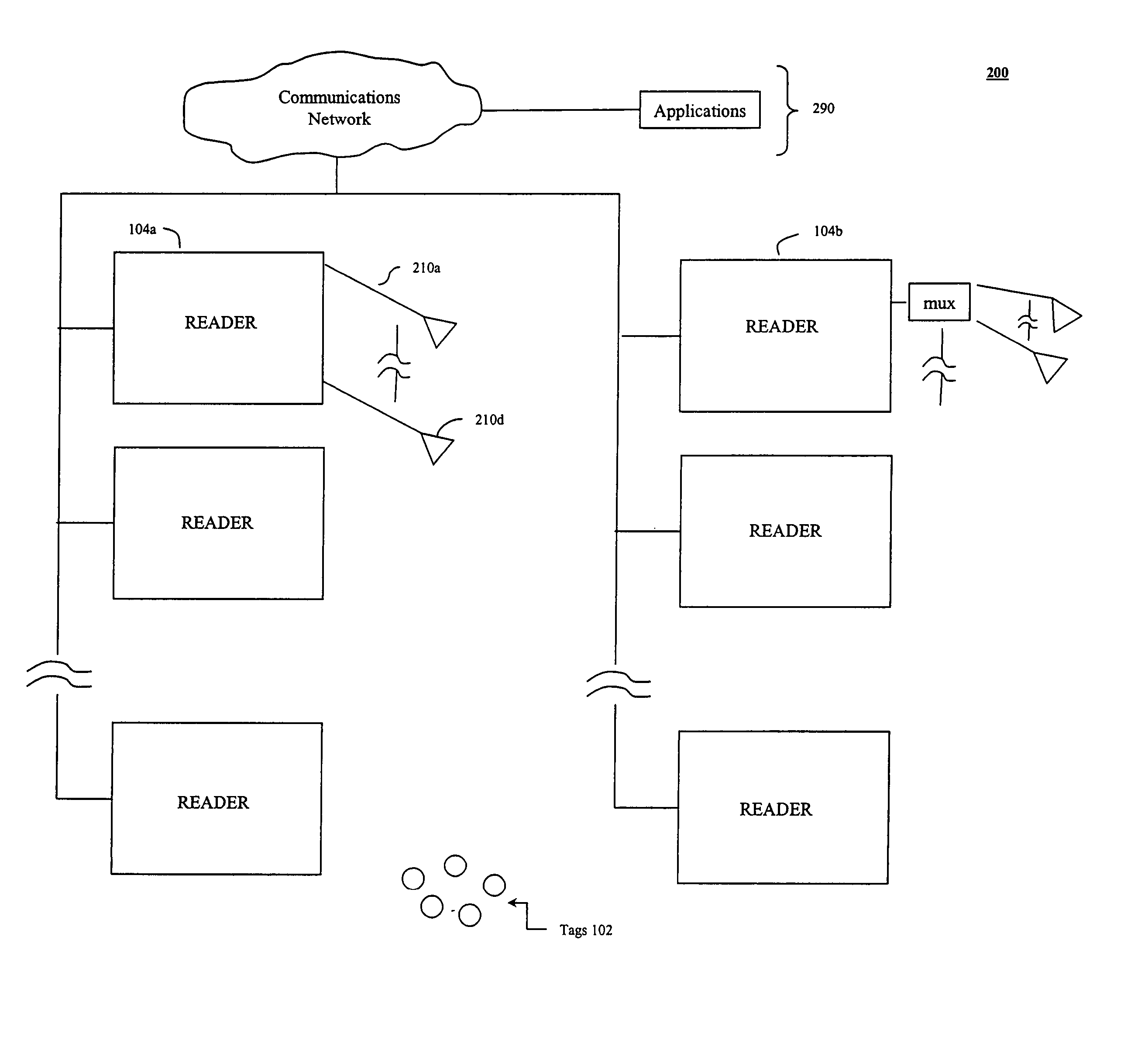
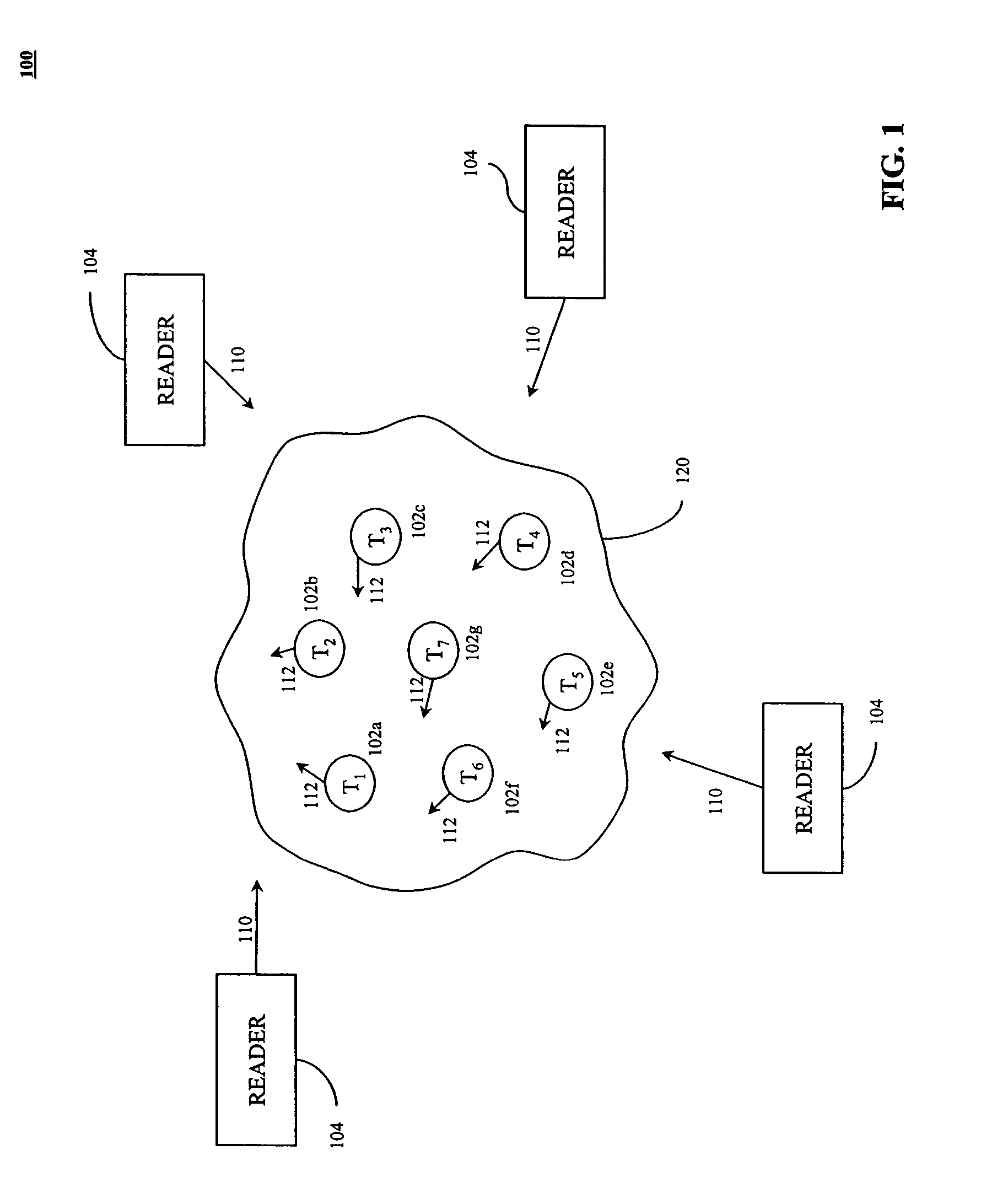
Methods and systems for the negotiation of a population of RFID tags with improved security is provided. In one aspect, a binary traversal is performed to singulate tags without using information that directly identifies the tags in the tag population. A key is generated to identify each RFID tag of the population of RFID tags. The generated key does not include bits identifying an item with which the particular RFID tag is associated. A binary tree algorithm is operated to identify one or more tags in the population of RFIDs tags using the generated keys. In another aspect, frequency hopping and / or spread spectrum techniques are used to provide improved security while negotiating tags. In another aspect, the reader causes the tags to scroll series of bits back to the reader for each bit sent to the tags to provide improved security.
Owner:SYMBOL TECH INC
Apparatus, method and program product for automatically distributing power to modules inserted in live chassis
InactiveUS6976112B2Likelihood of equipment damage dueCost of operationData switching detailsVolume/mass flow measurementDistributed powerEmbedded system
When a blade and / or interconnect device is inserted into the chassis of a powered or live server the procedure is known as hot-plugging. Before power is applied to the hot-plugged blade and / or interconnect device the fabric type of already installed blades and / or interconnect devices is correlated with fabric types of newly hot-plugged blade and / or interconnect device. Depending upon results of the correlation, power to the hot-plugged blade and / or interconnect device is allowed or denied.
Owner:INT BUSINESS MASCH CORP
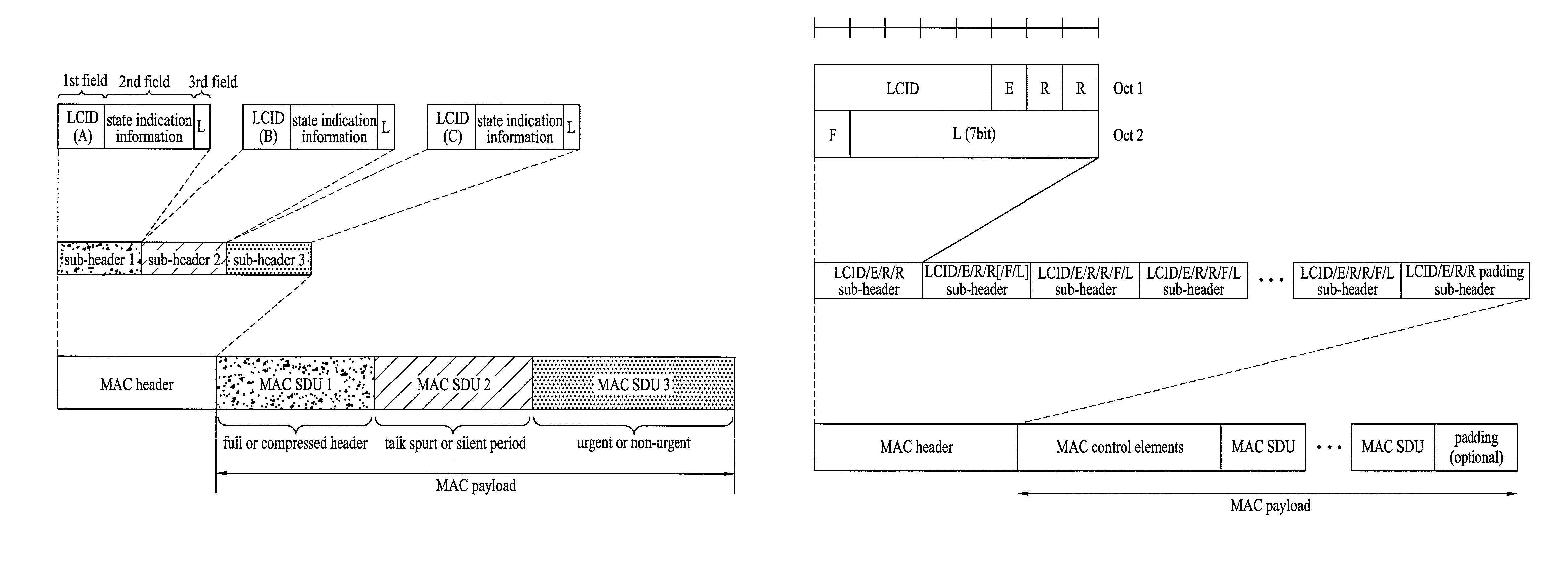
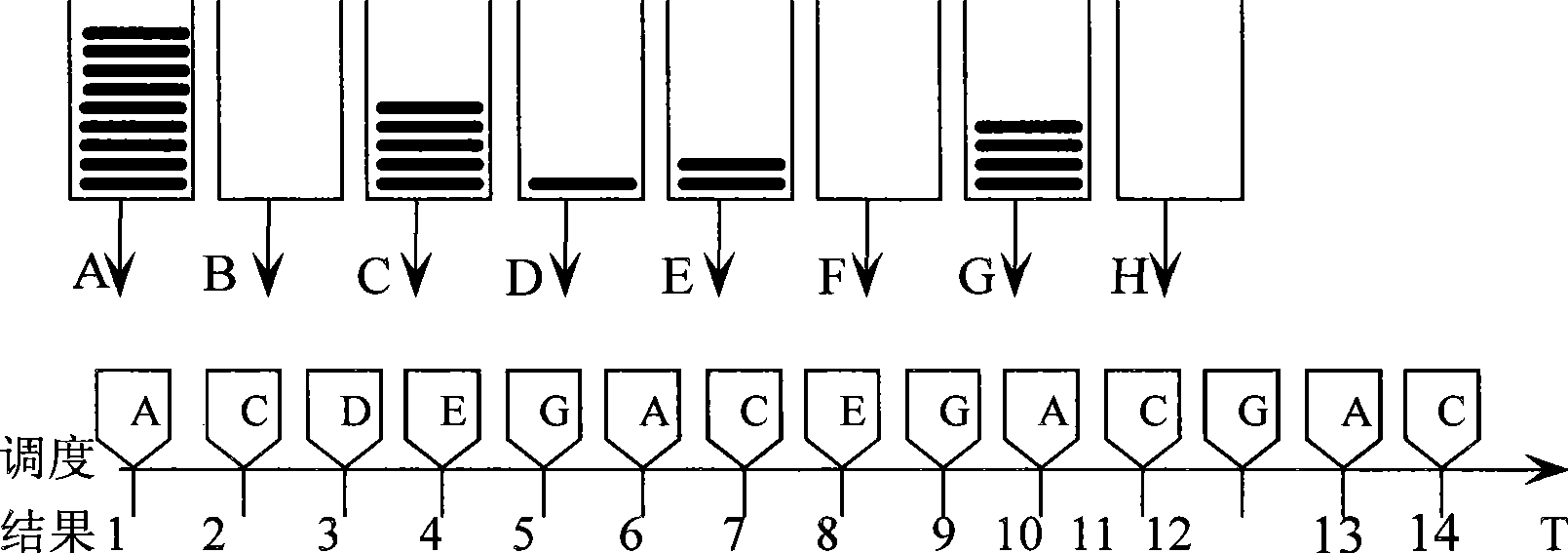
Methods of transmitting data blocks in wireless communication system
ActiveUS8081662B2Improve system efficiencyEfficient managementData switching detailsNetwork traffic/resource managementCommunications systemData science
Disclosed is a method for generating a data block to be transmitted from a specific layer in a transmitting side to a receiving side in a wireless communication system. The method includes receiving an upper layer datei block from an upper layer and generating a lower layer data block including at least part of the upper layer data block and state indication information indicating a state of the upper layer data block, the state indication information being selected variably according to a logical channel through which the upper layer data block is received. This method optimizes overhead of a header of each upper layer data block according to contents of the upper layer data block and event situations associated with the upper layer data block, thereby increasing system efficiency.
Owner:LG ELECTRONICS INC
Purchase request approving apparatus, method, and storage medium storing same
InactiveUS6910018B1Efficiently inputting approvalEfficiently rejectionData switching detailsBuying/selling/leasing transactionsClient-sideDatabase
In a client-server environment in which a plurality of clients are connected on a network, a manager of a company displays an approval request list window (07-01-00) in which a list of purchase-requested articles is displayed, on a client by a predetermined operation, selects a desired article from the articles displayed in the window, and clicks a software button “approval select” or “rejection select” in accordance with approval or rejection of the selected article. At this time, the article for which approval is selected can be formally ordered.
Owner:CANON KK
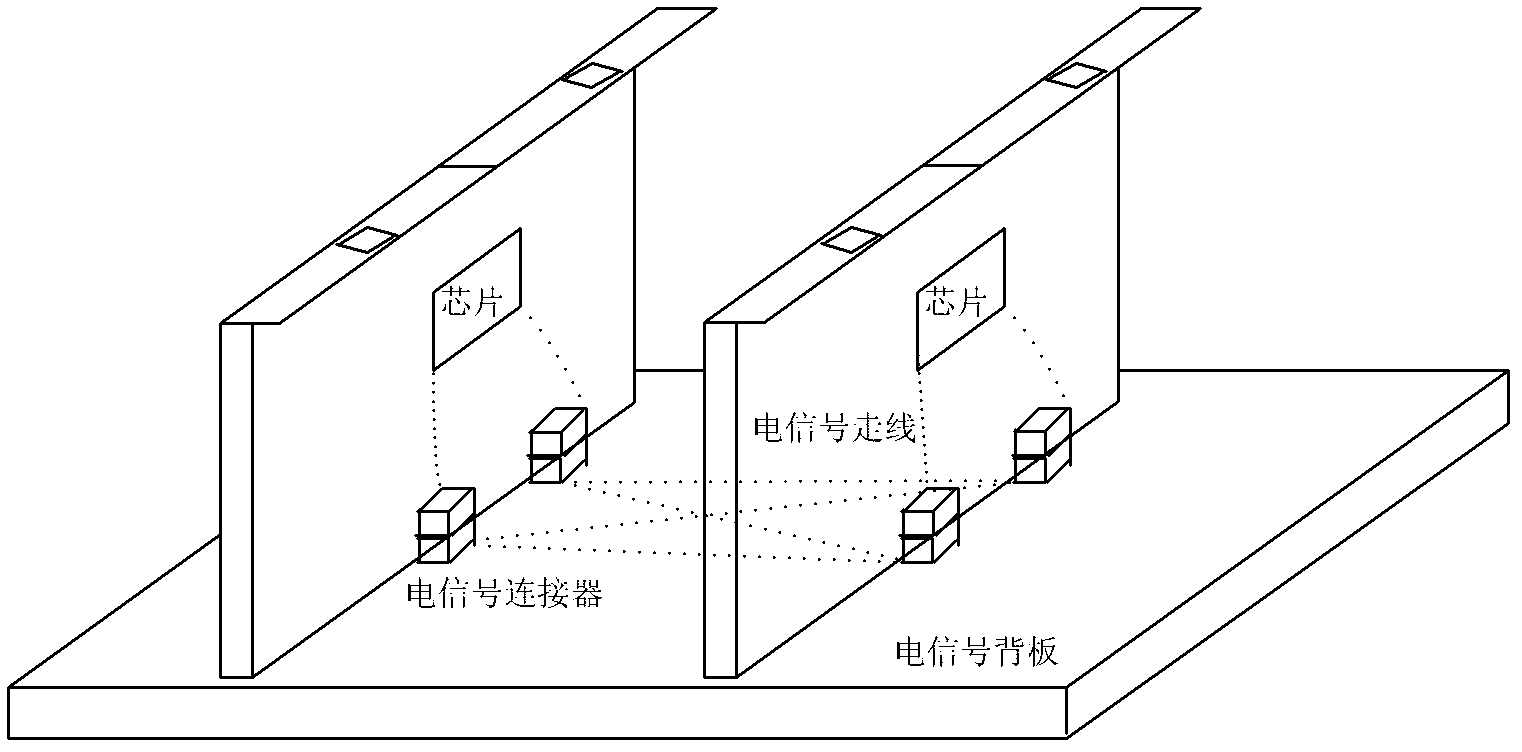
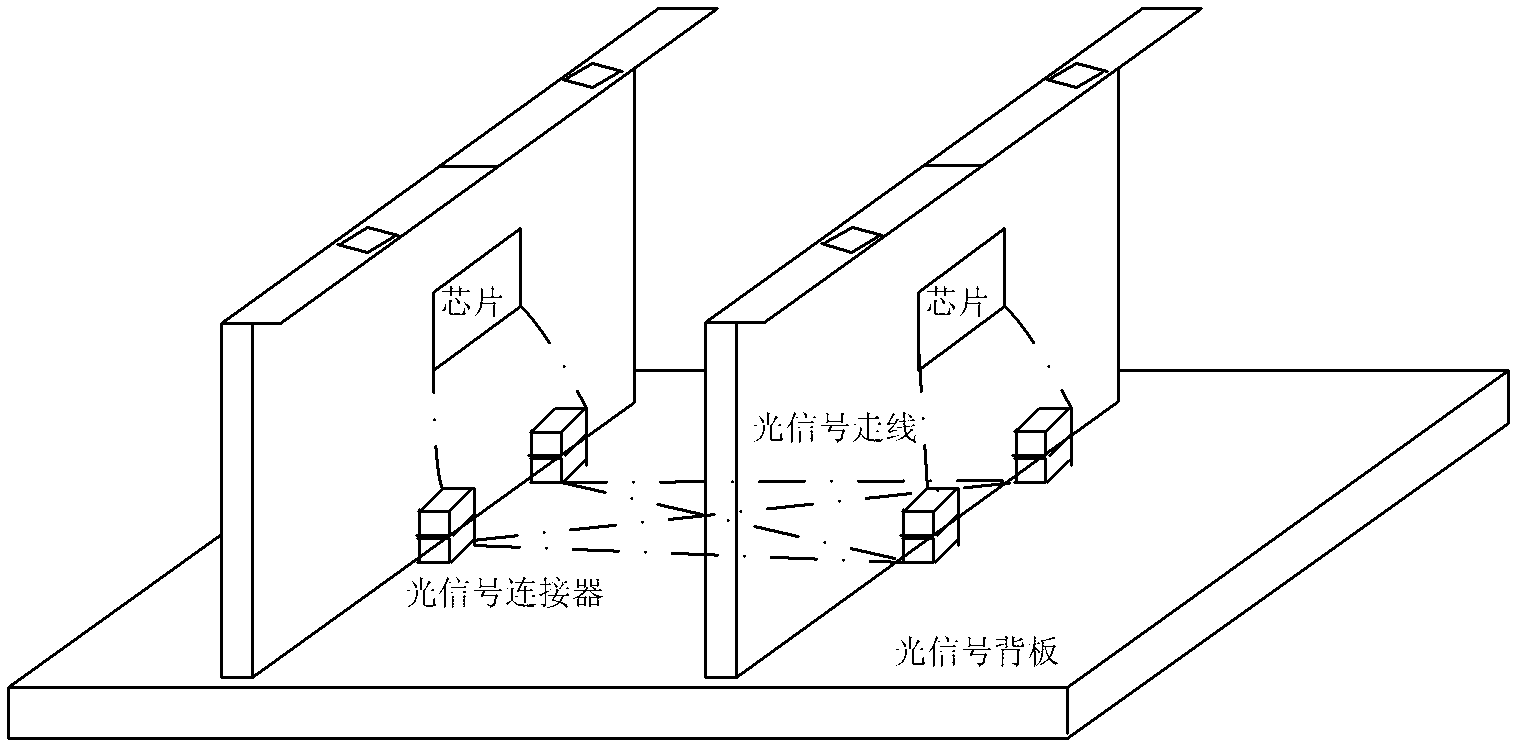
Back plate system
ActiveCN102307142AHigh bandwidthThe number of solutions is easily limitedData switching detailsElectricitySingle plate
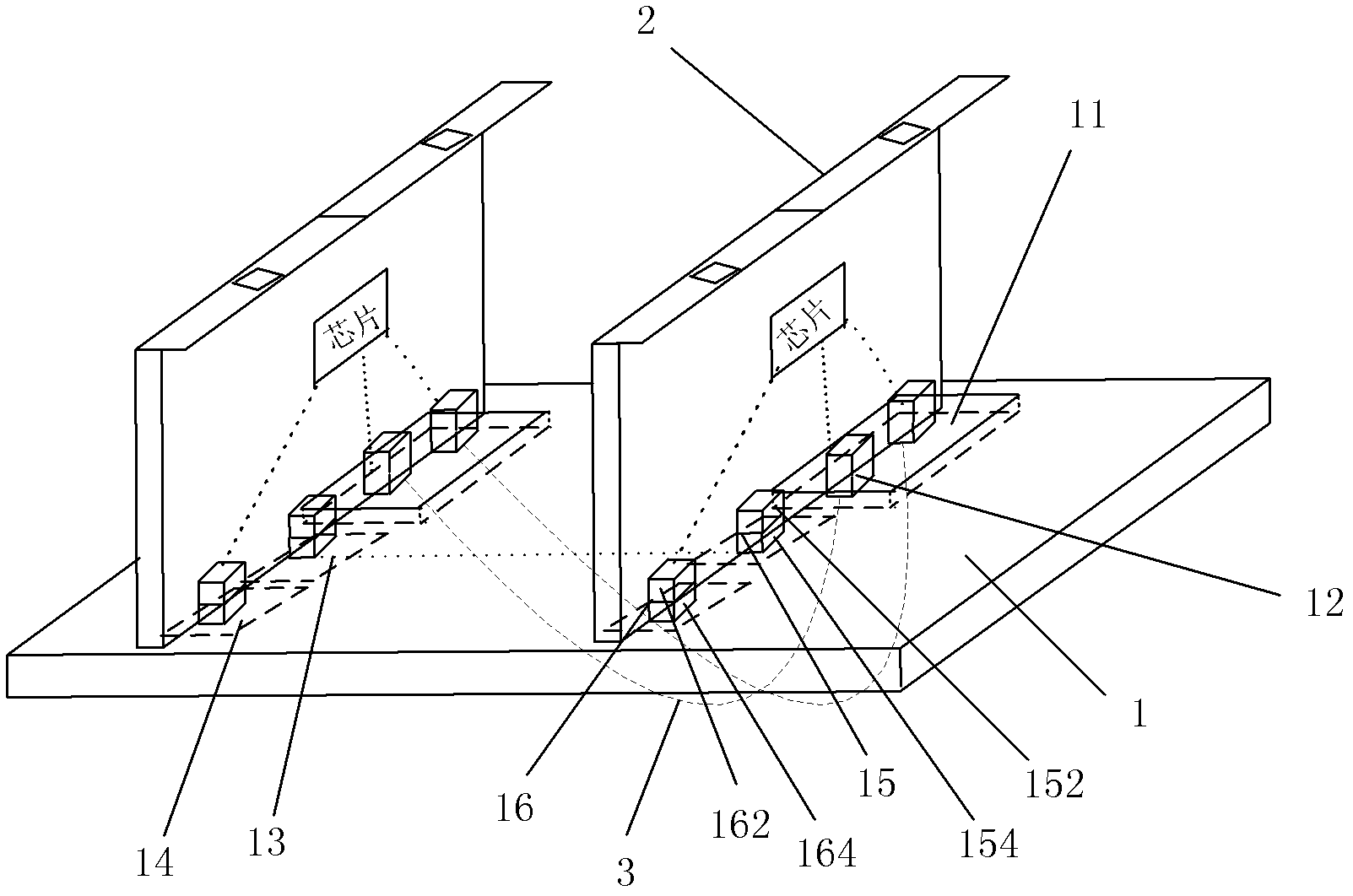
The invention discloses a back plate system which comprises an electrical back plate body, a plurality of single plates and active parallel optical cables, wherein each single plate is provided with one or more high speed electric connectors used for adapting the active parallel optical cables, the electrical back plate body comprises one or more high speed signal connection opening areas used for extension of the high speed electric connectors, and the high speed electric connectors on two adjacent single plates are connected through the active parallel optical cables. Through the back plate system, exchange bandwidth of a traditional back plate is increased.
Owner:ZTE CORP
Design method of intelligent WiFi wireless router
InactiveCN101729260AData switching detailsData switching by path configurationWireless routerComputer network
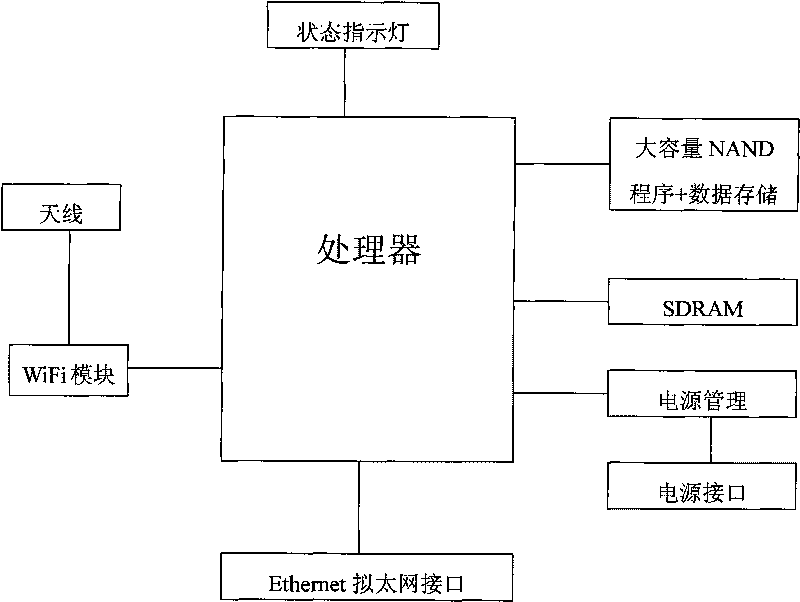
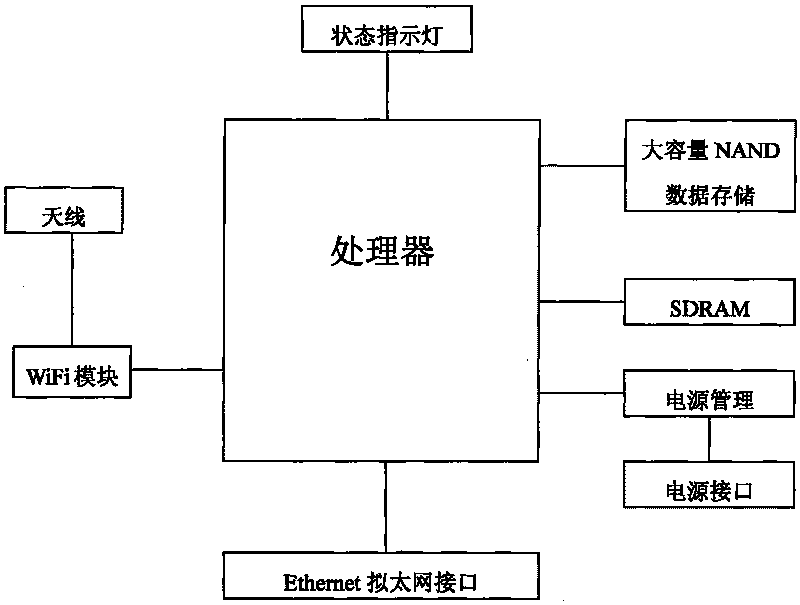
The invention provides a design method of an intelligent WiFi wireless router, in particular to the intelligent WiFi wireless router. The design method comprises the steps of: adding high-capacity Flash memory on the wireless router to be capable of realizing the subscription down load and the buffer memory of various internet contents; automatically downloading an information content which is pre-selected to be downloaded and comprises videos, music, pictures, news and emails, and the like, into the router according to an order which is sent by equipment with the WiFi such as mobile phones and computers, and the like; and fast sending the information content to the equipment with WiFi communication function such as the mobile phones and the computers, and the like, through a WiFi local network. Once the content is downloaded for once, a plurality of the WIFI equipment can share the content which has been memorized in the router, thereby reducing the wideband requirement of the external interface of the internet in occasions such as families, mini-type offices, internet bars and coffer bars, and the like, and improving the content downloading speed of the plurality of WIFI equipment. Furthermore, the intelligent WiFi wireless router also can be used as a mini-type server of the internet to support the BT automatic downloading and the date uploading.
Owner:SHANGHAI HYCTRON ELECTRONICS
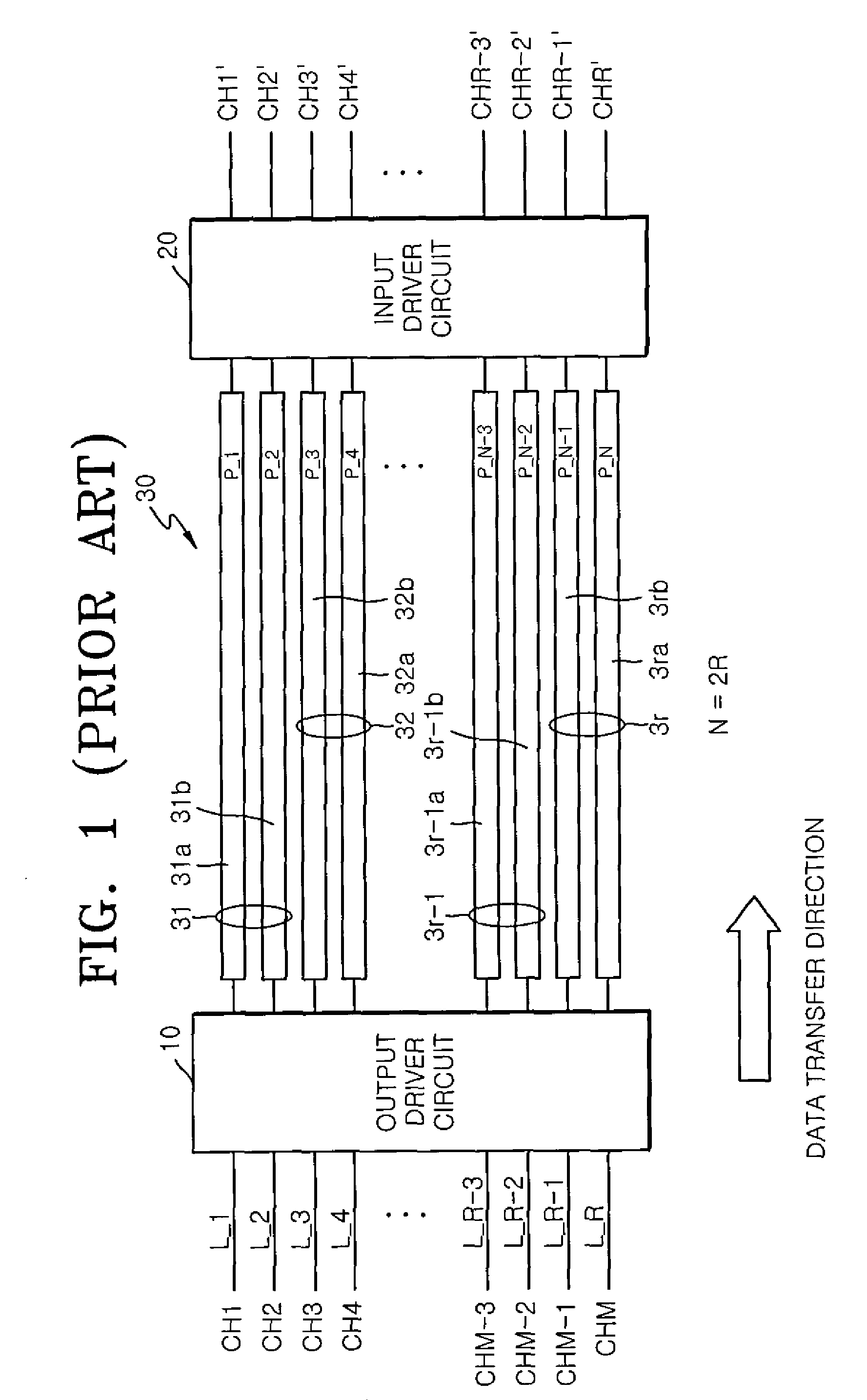
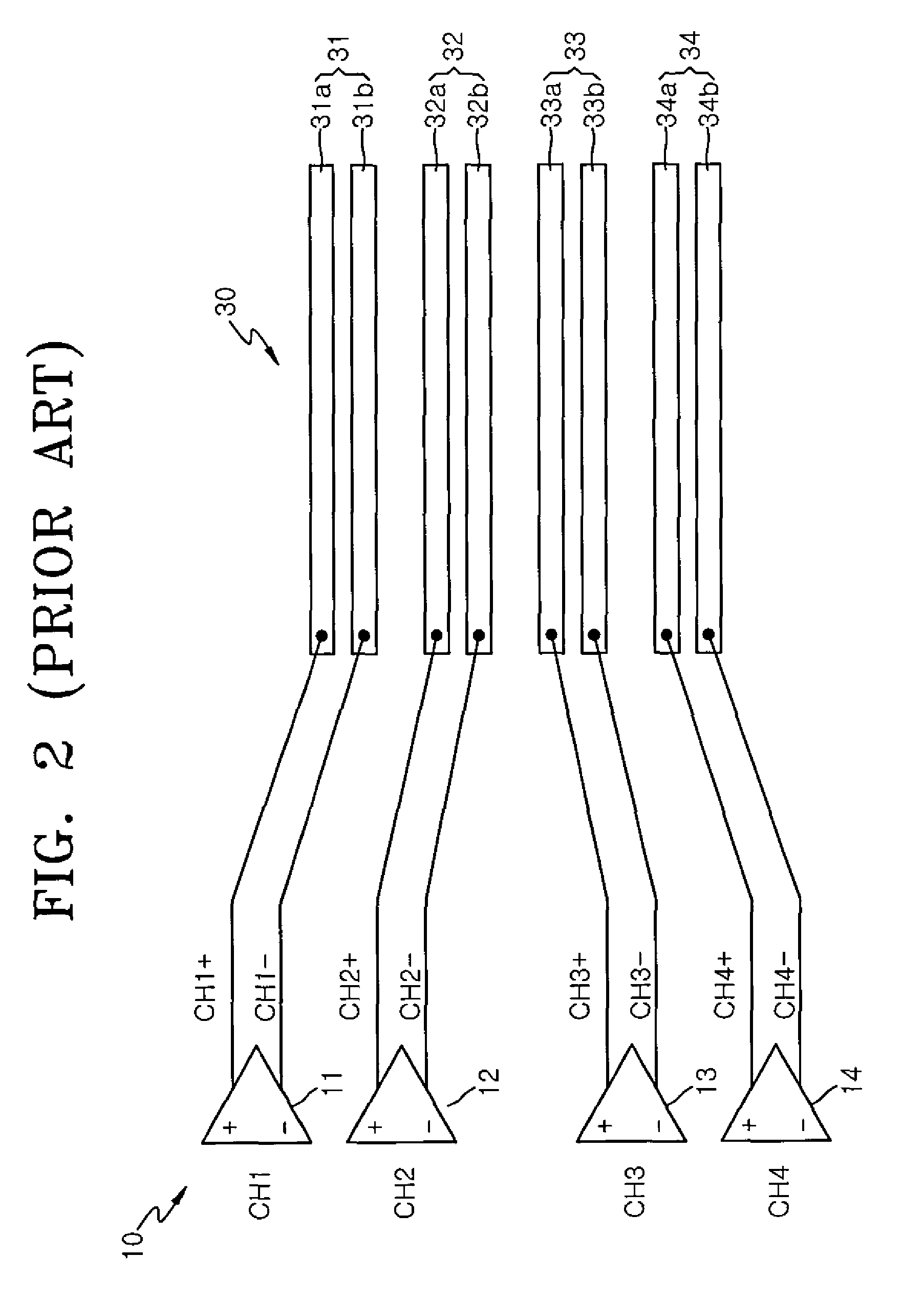
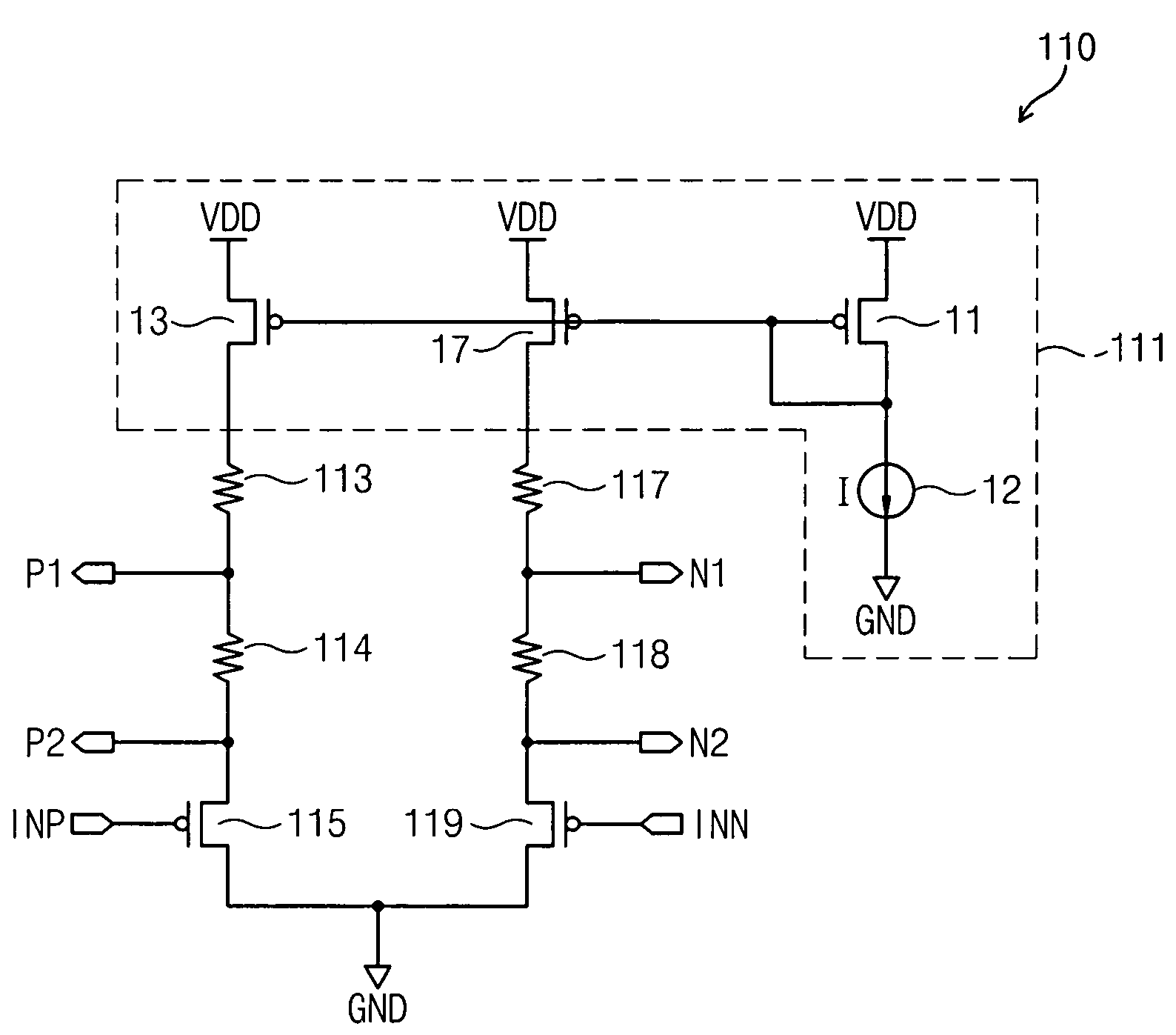
Input and output driver circuits for differential signal transfer, and differential signal transfer apparatus and methods
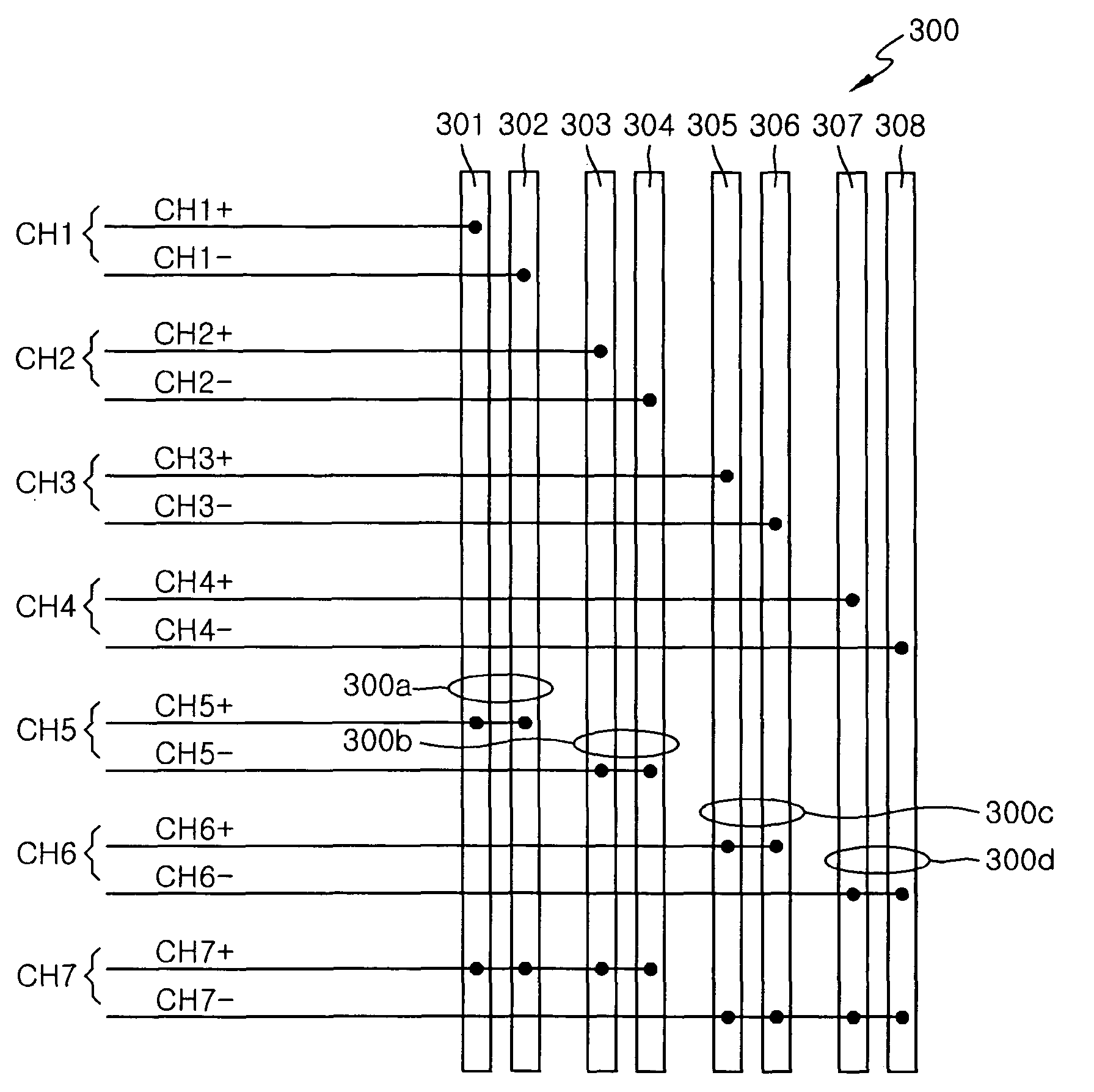
ActiveUS7826551B2Multiple input and output pulse circuitsData switching detailsDriver circuitDifferential signaling
In one aspect, a differential signal transfer method is provided which includes converting 2M−1 original signals into 2M−1 differential signal pairs, where M is an integer of 2 or more, and wherein each pair consists of a first differential signal and a second differential signal having opposite phases, and transferring the 2M−1 differential signal pairs to 2M signal lines such that each of the 2M signal lines includes overlapping differential signals among the first differential signals and the second differential signals of the 2M−1 differential signal pairs.
Owner:SAMSUNG ELECTRONICS CO LTD
Communications system of heterogeneous elements
ActiveUS7802015B2Data switching detailsMultiple digital computer combinationsTelecommunicationsCommunications system
A communications system for a network of stations, is provided where stations identify themselves upon being informed of the desires of an inquisitor station. Additionally, techniques for “plug and play”, self-healing and homogenizing the heterogeneous parts of a network, are provided.
Owner:TANTALUS SYST CORP
Network-on-chip digital router and its parallel data transmission method
InactiveCN101141261AAddressing increased competitionReduce data congestionData switching detailsData transmissionInteroperability Problem
The utility model relates to a network-on-chip digital router and a parallel data transmission method thereof, also known as the digital universal joint, pertaining to the field of the large scale integration. The network-on-chip parallel digital router is characterized in that a FIFO traveling wave shift buffer storage, a co-gradient matrices switch array, a route decision module and a parallel network port are gathered on the chips. Such method is different with the traditional network parallel data transmission. The utility model has the advantages that 1. The data transmission jam is not caused due to the increase of on-chip-bus with the processor. 2. The network parallel data transmission method improves the message transmission rate and reduces the time and resources needed for the conversion between parallel and serial data, so as to accelerate the data communication rate among the processors and increase the interoperability of a plurality of processors.
Owner:SHANDONG UNIV
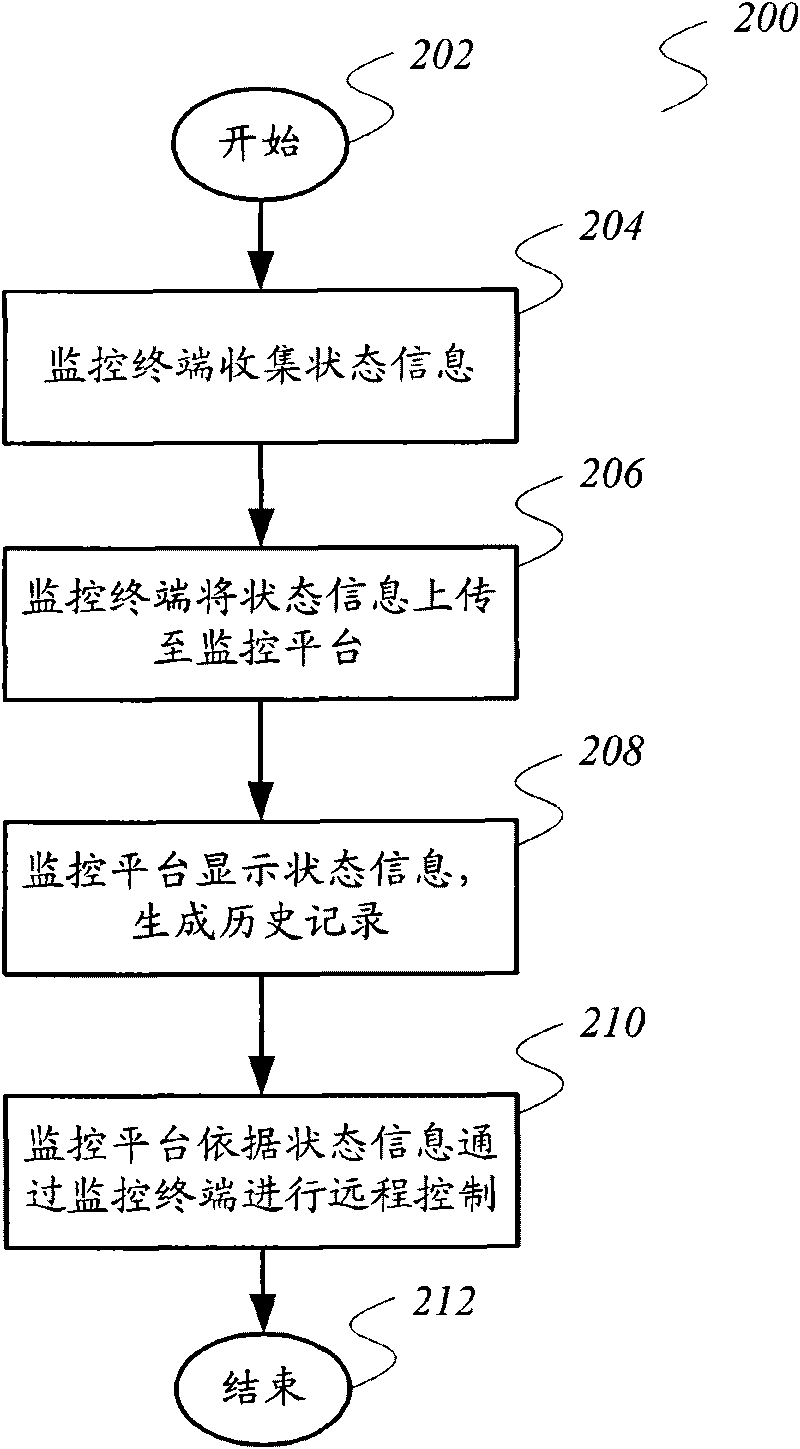
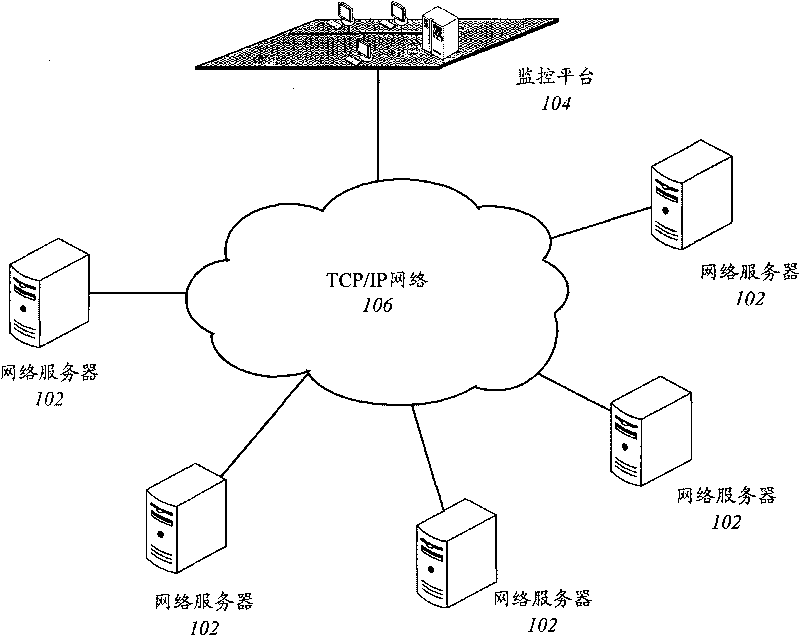
Network server centralized monitoring system and method
The invention relates to the remote control technology. The invention provides a network server centralized monitoring system and a method, which aim at the defect that a necessary network server automatic monitoring measure is lacked in the prior art, so the network service with the failure can not be restored in time. The network server centralized monitoring system comprises at least one monitoring terminal and a monitoring platform, wherein the monitoring terminal is arranged on the network server to be monitored, and is used for collecting and sending the state information of the monitored network server, and the monitoring platform is in communication connection with the monitoring terminal, is used for receiving the state information sent by the monitoring terminal, and sends control commands to the monitoring terminal according to the state information to realize the remote control on the network server. The invention also provides a network server centralized monitoring method. Through installing the monitoring terminal on the network server, the monitoring platform can master the current operation state of the network server in real time, and can realize the remote control on the network server through the monitoring terminal, and the safe operation of the network server can be ensured.
Owner:CHINA FANGDA GROUP CO LTD
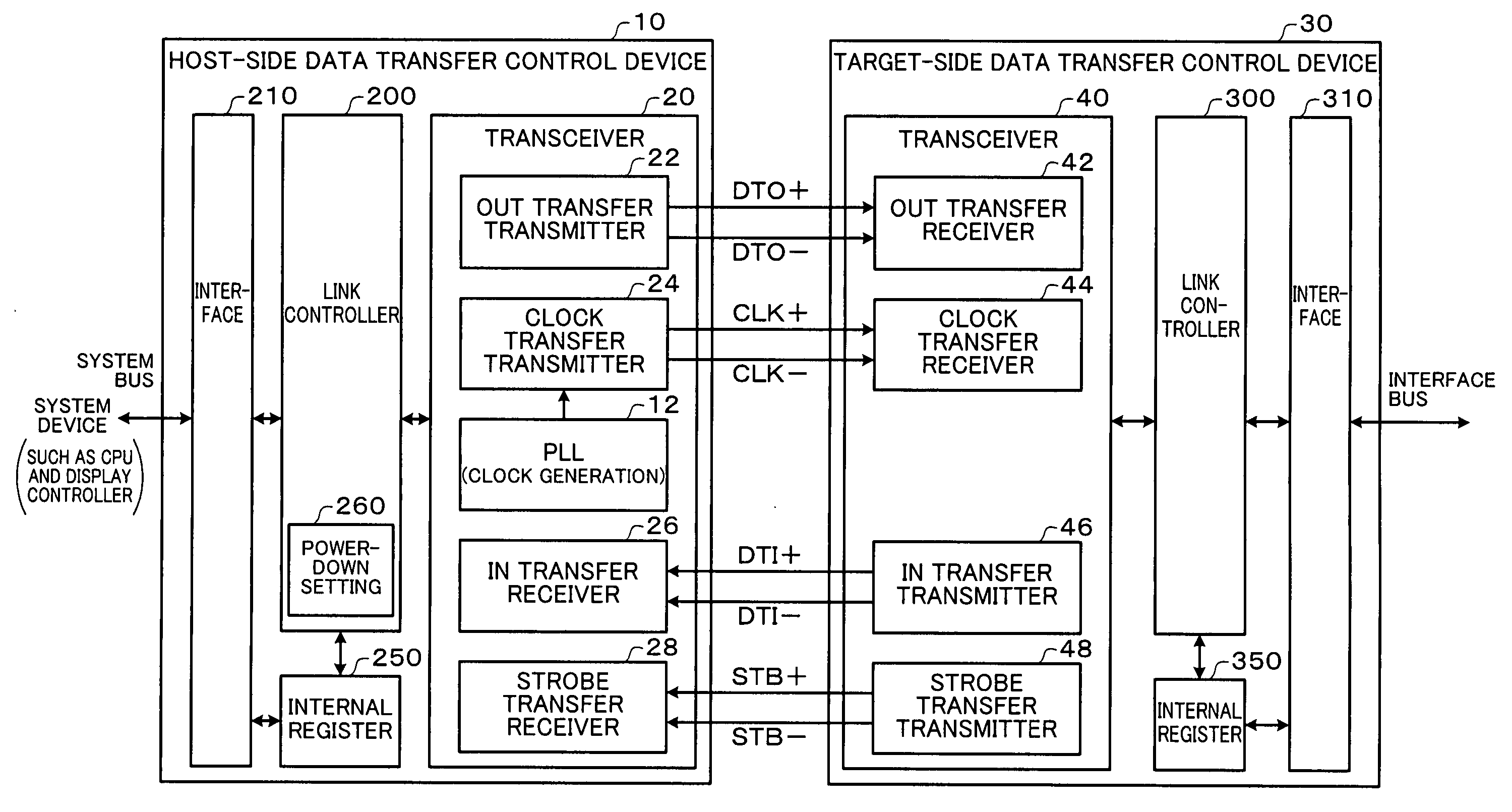
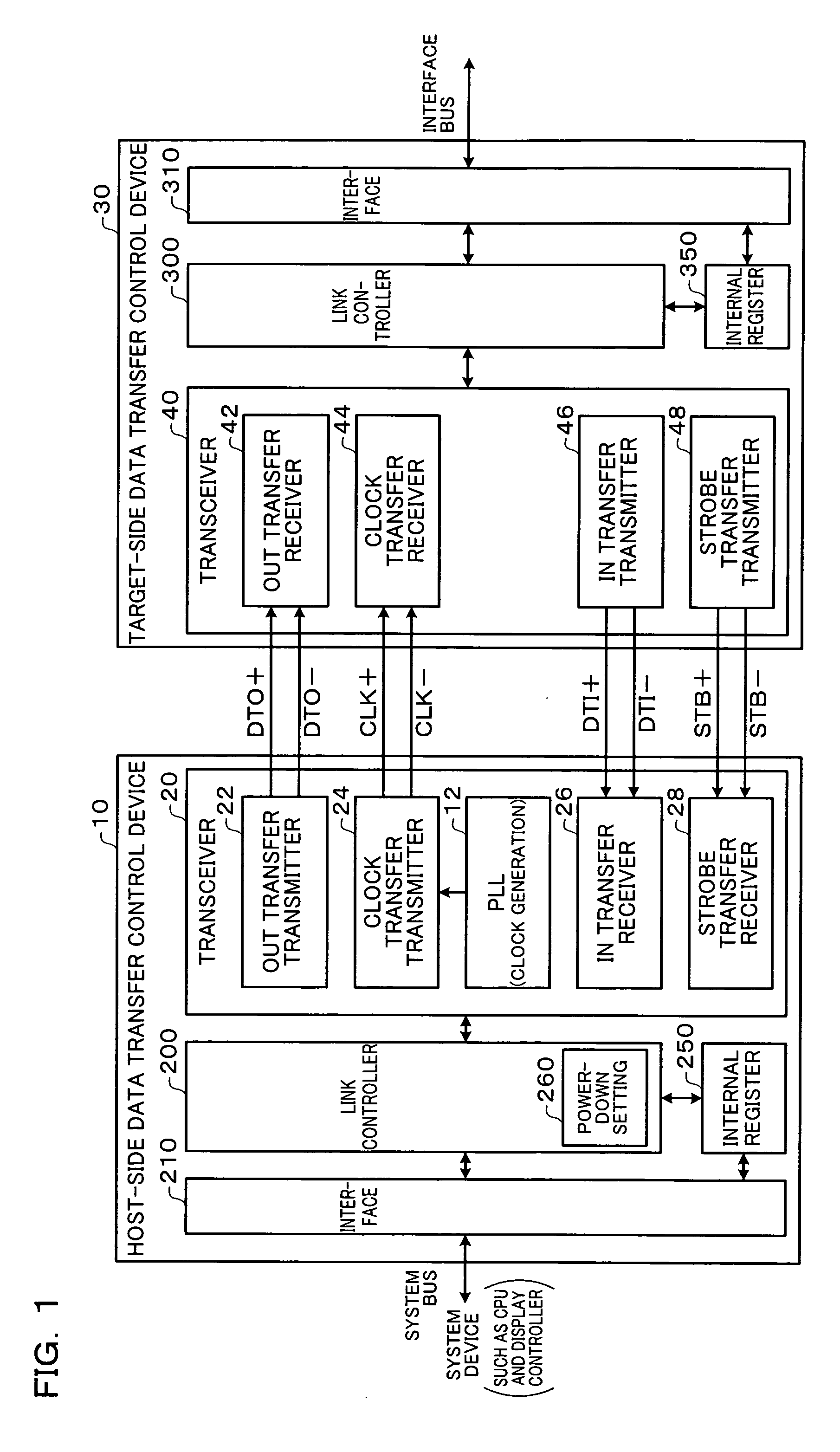
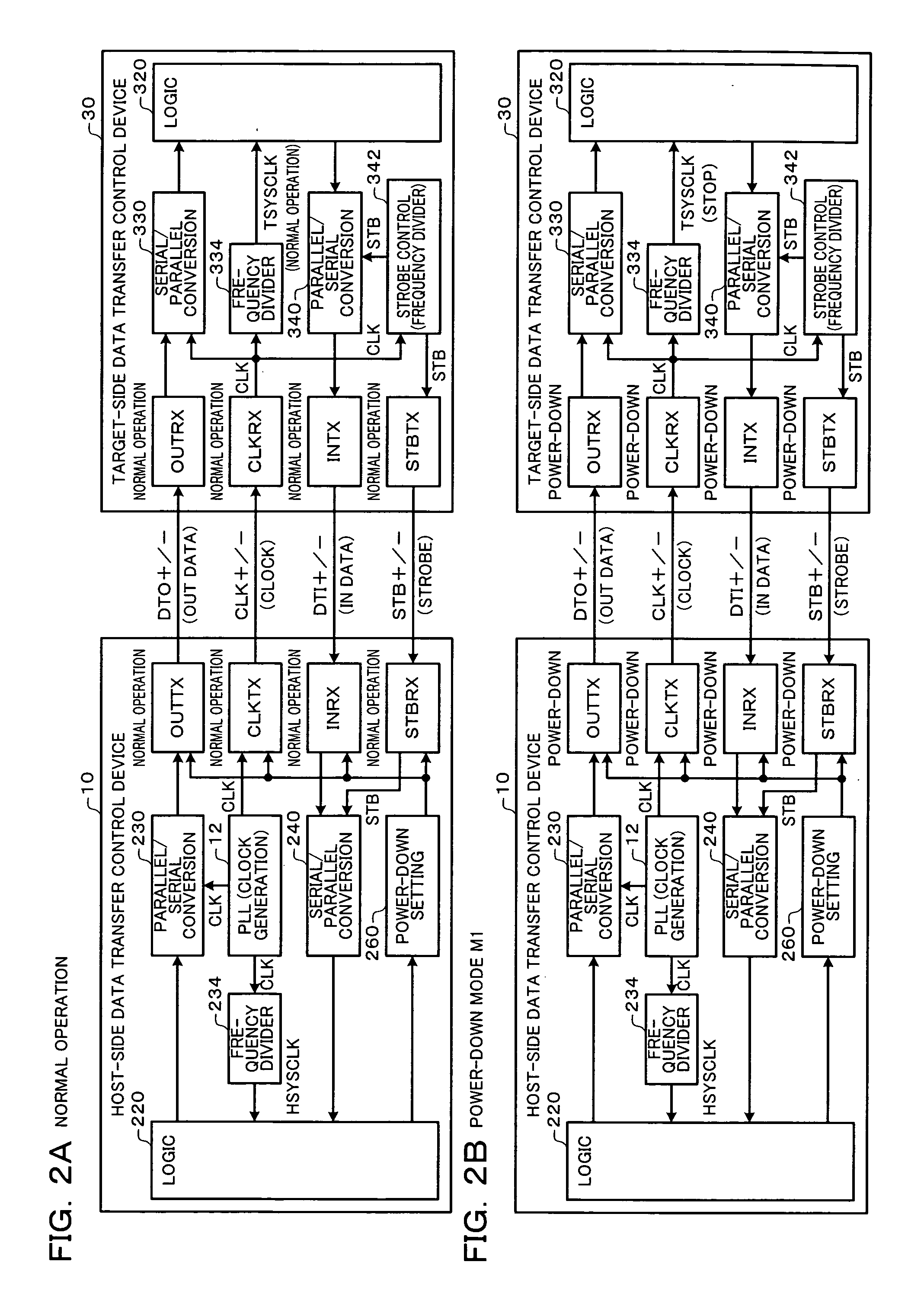
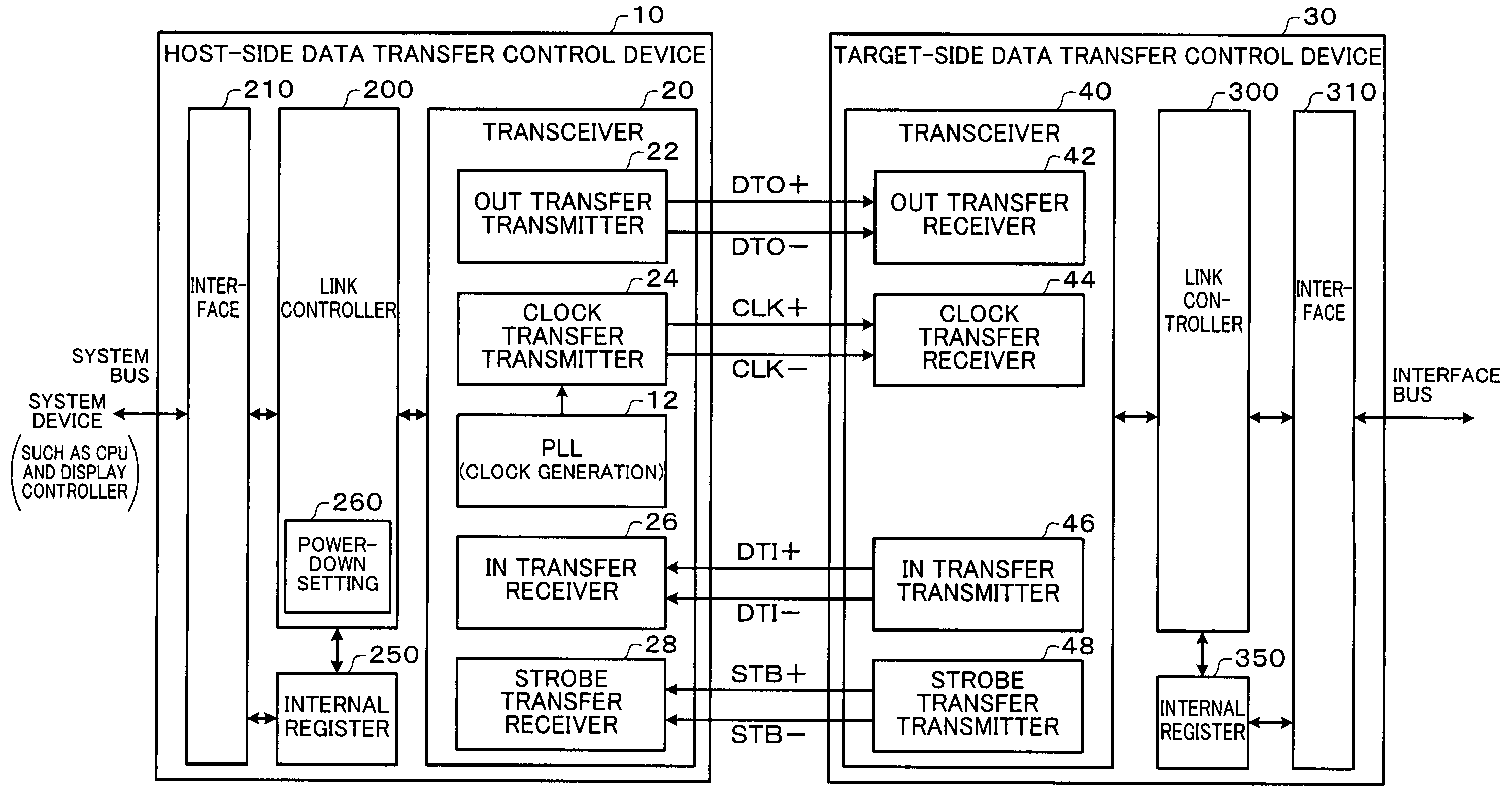
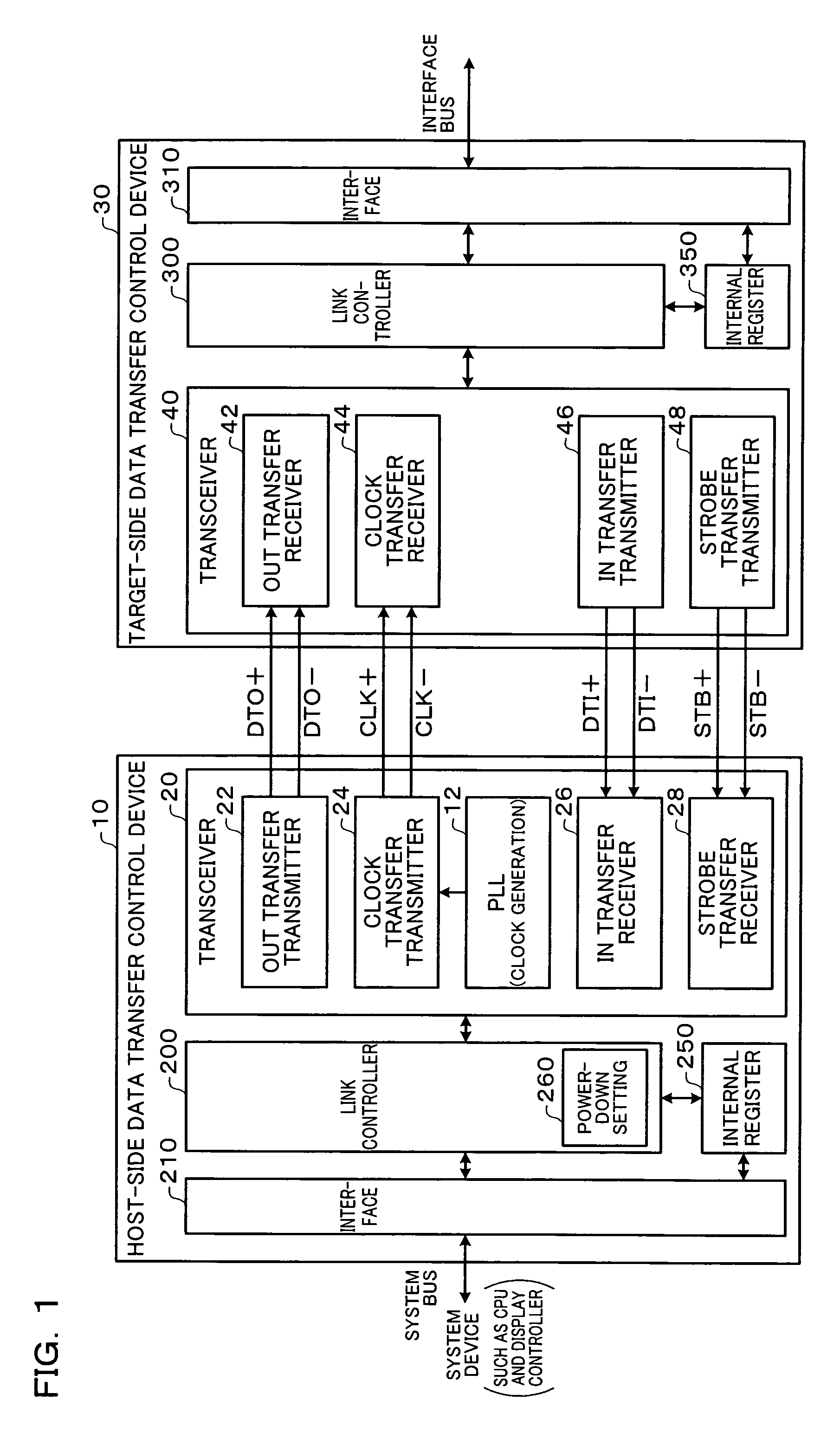
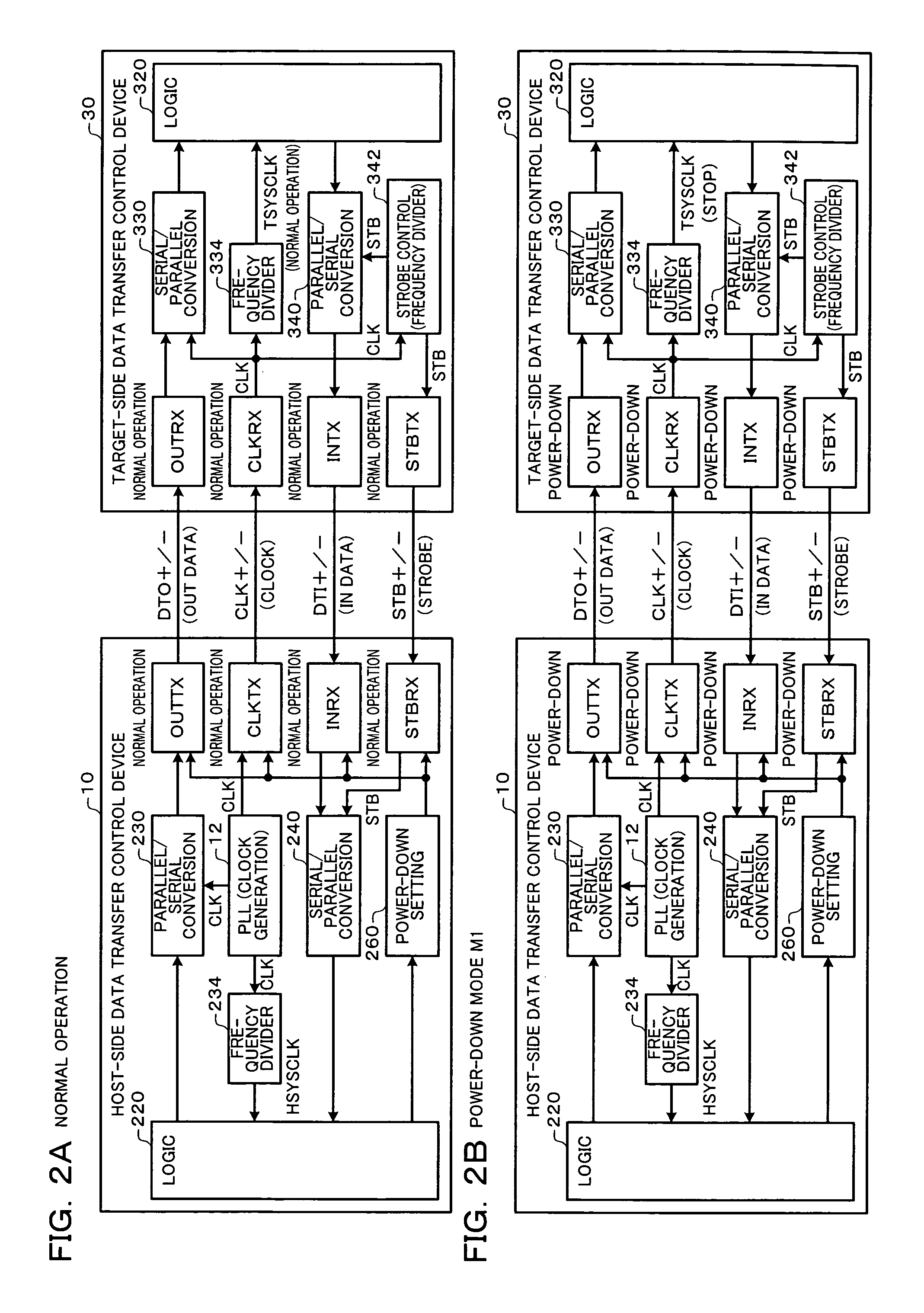
Data transfer control device and electronic instrument
A data transfer control device includes an OUT-transfer transmitter circuit which transmits OUT data by driving a serial signal line, a clock-transfer transmitter circuit which transmits a clock signal CLK by driving a serial signal line, a PLL circuit which generates the clock signal CLK, and a power-down setting circuit which sets a power-down mode. In a first power-down mode, the OUT-transfer transmitter circuit is set to the power-down mode, and the clock-transfer transmitter circuit is set to the power-down mode to stop a system clock signal of a target-side data transfer control device. In a second power-down mode, the OUT-transfer transmitter circuit is set to the power-down mode without setting the clock-transfer transmitter circuit to the power-down mode.
Owner:SEIKO EPSON CORP
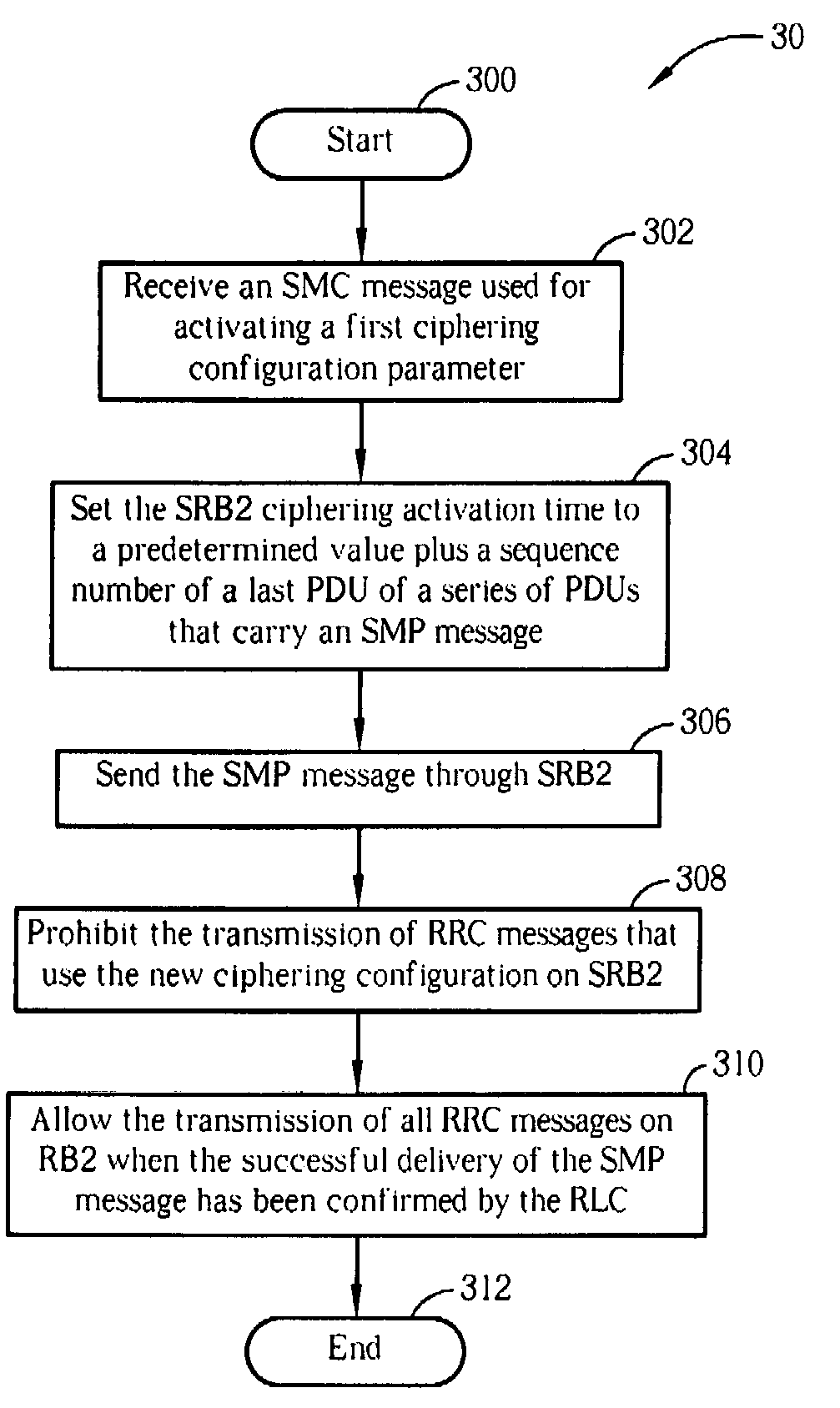
Method and apparatus for setting ciphering activation time in a wireless communications system
InactiveUS20070265875A1Accurate settingData switching detailsSubstation equipmentComputer hardwareCommunications system
A method for setting ciphering activation time in a user equipment of a wireless communications system includes receiving a first RRC (radio resource control) message for activating a first ciphering key, setting an activation time of a first SRB (signaling radio bearer) as a predefined number plus a first SN (sequence number) of a last PDU (protocol data unit) of a sequence of PDUs that carry a second RRC message utilized for indicating completion of activating the first ciphering key, transmitting the second RRC message on the first SRB, prohibiting the transmission of RRC messages using the first ciphering key on the first SRB, and allowing the transmission of RRC messages on the first SRB when the successful delivery of the second RRC message has been confirmed.
Owner:INNOVATIVE SONIC
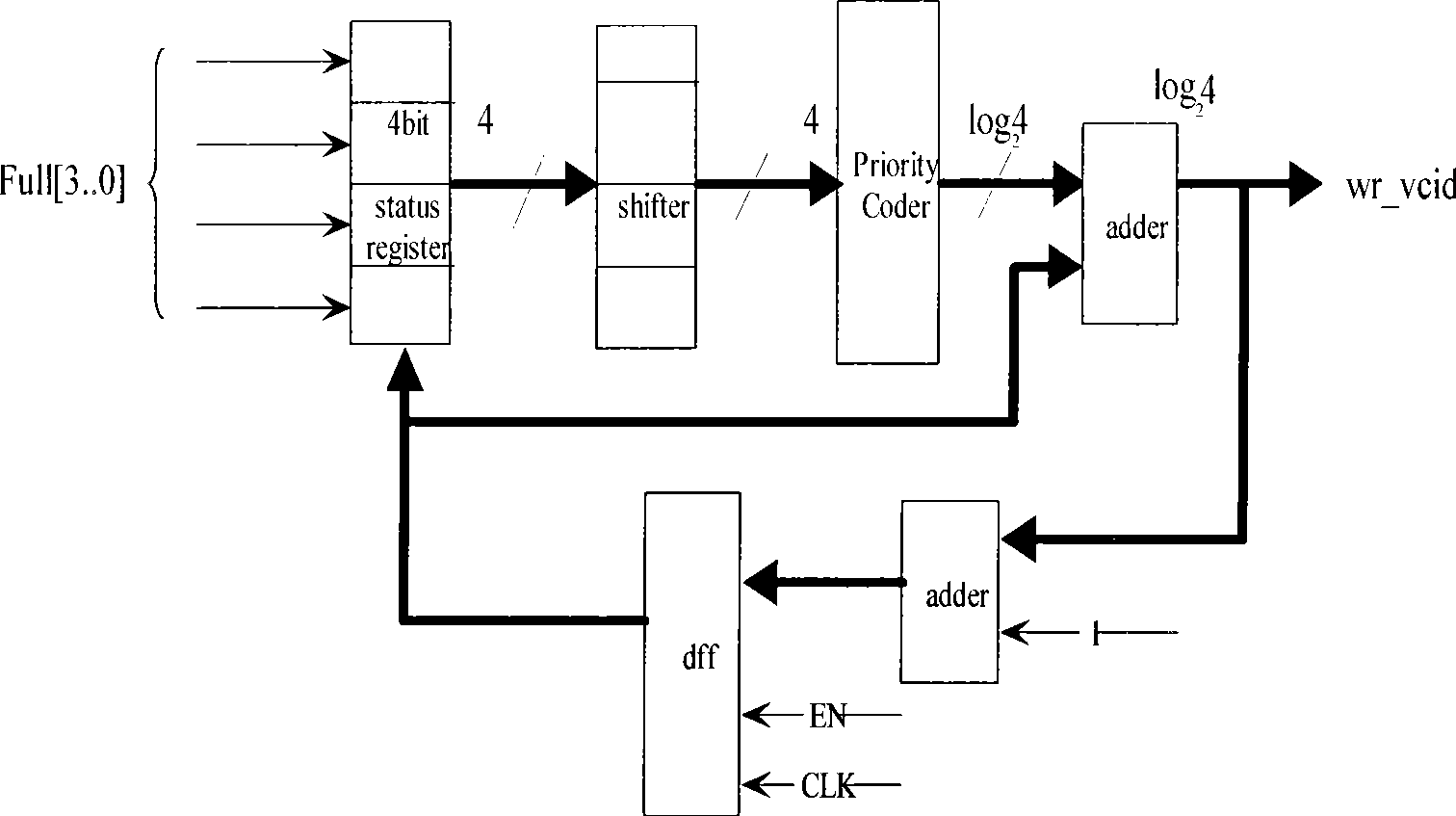
Distributed Ethernet switch and internal MAC address maintaining method thereof
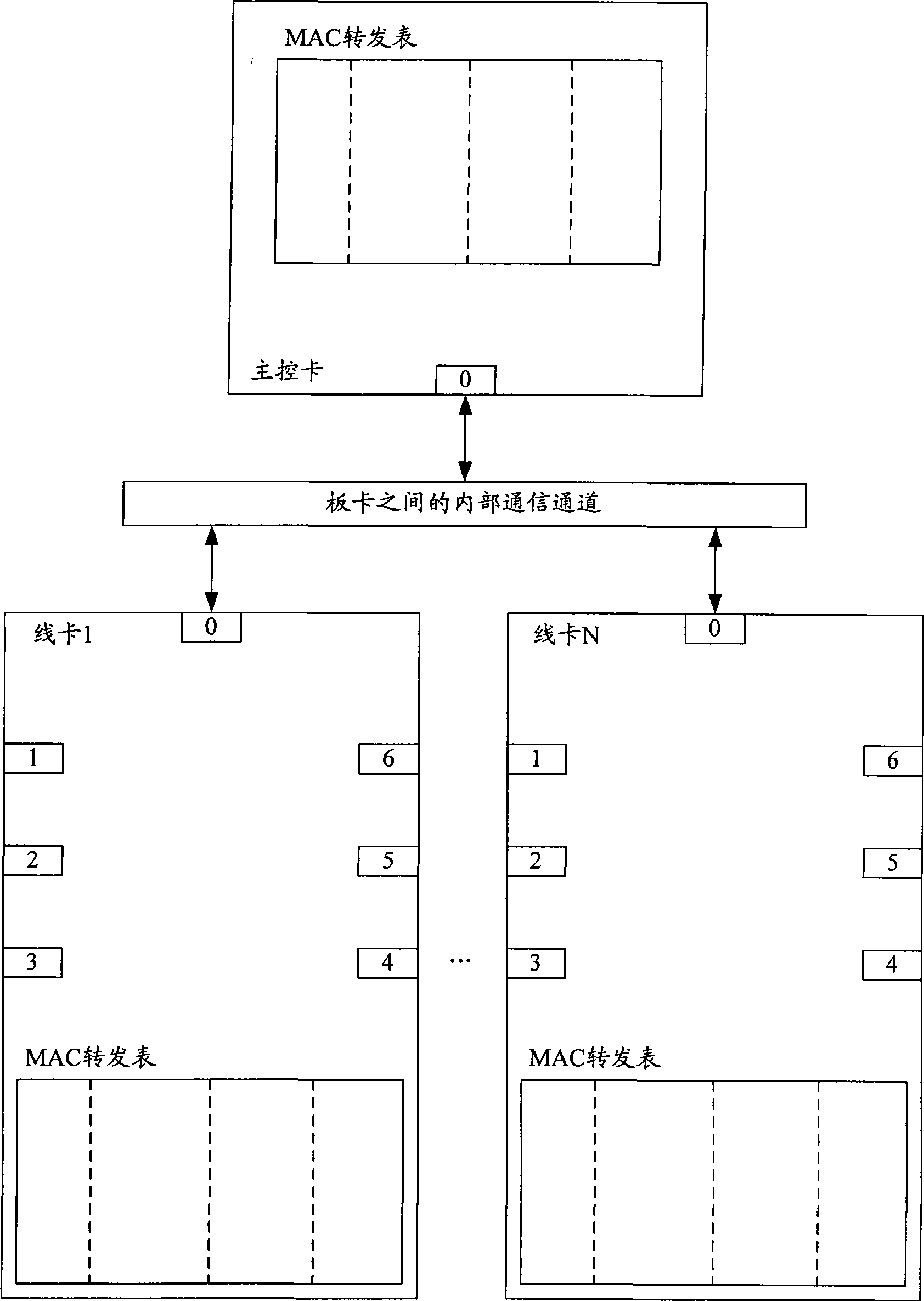
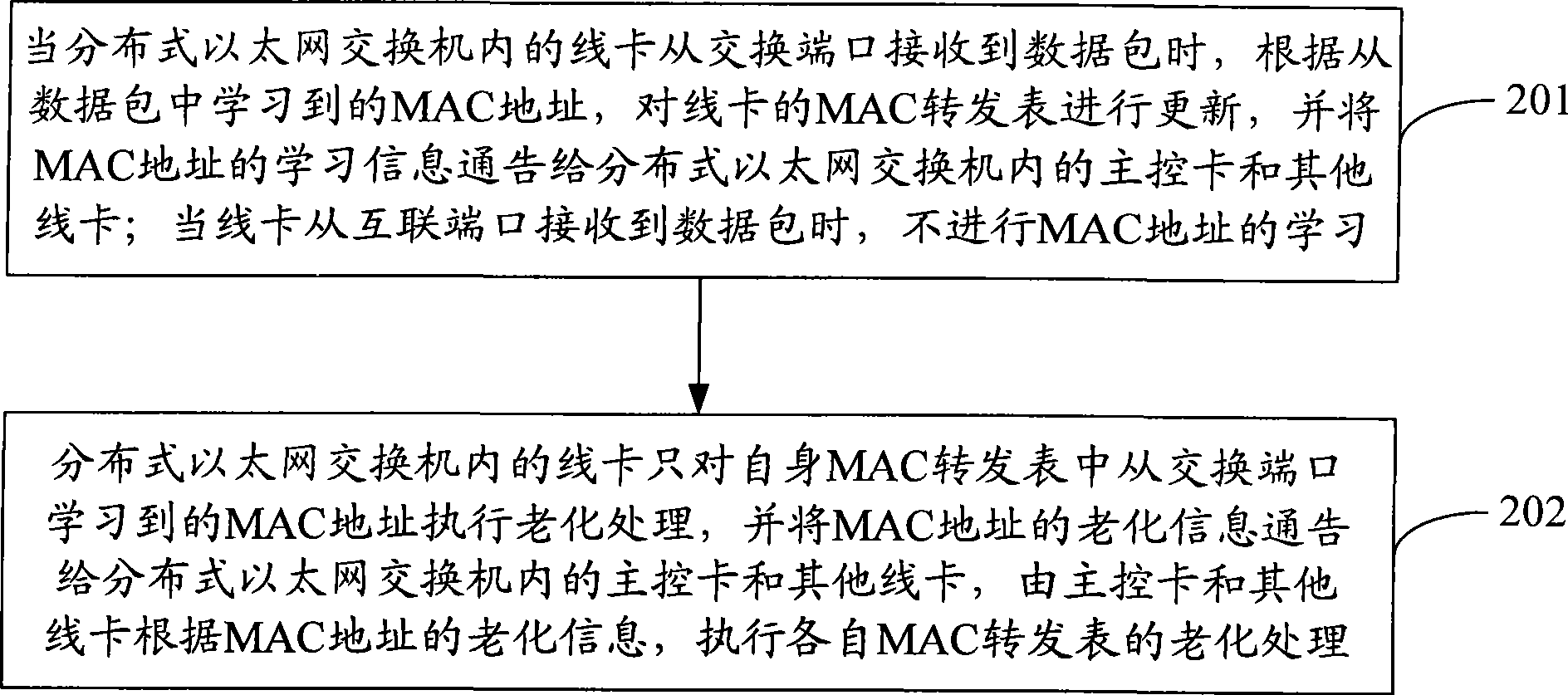
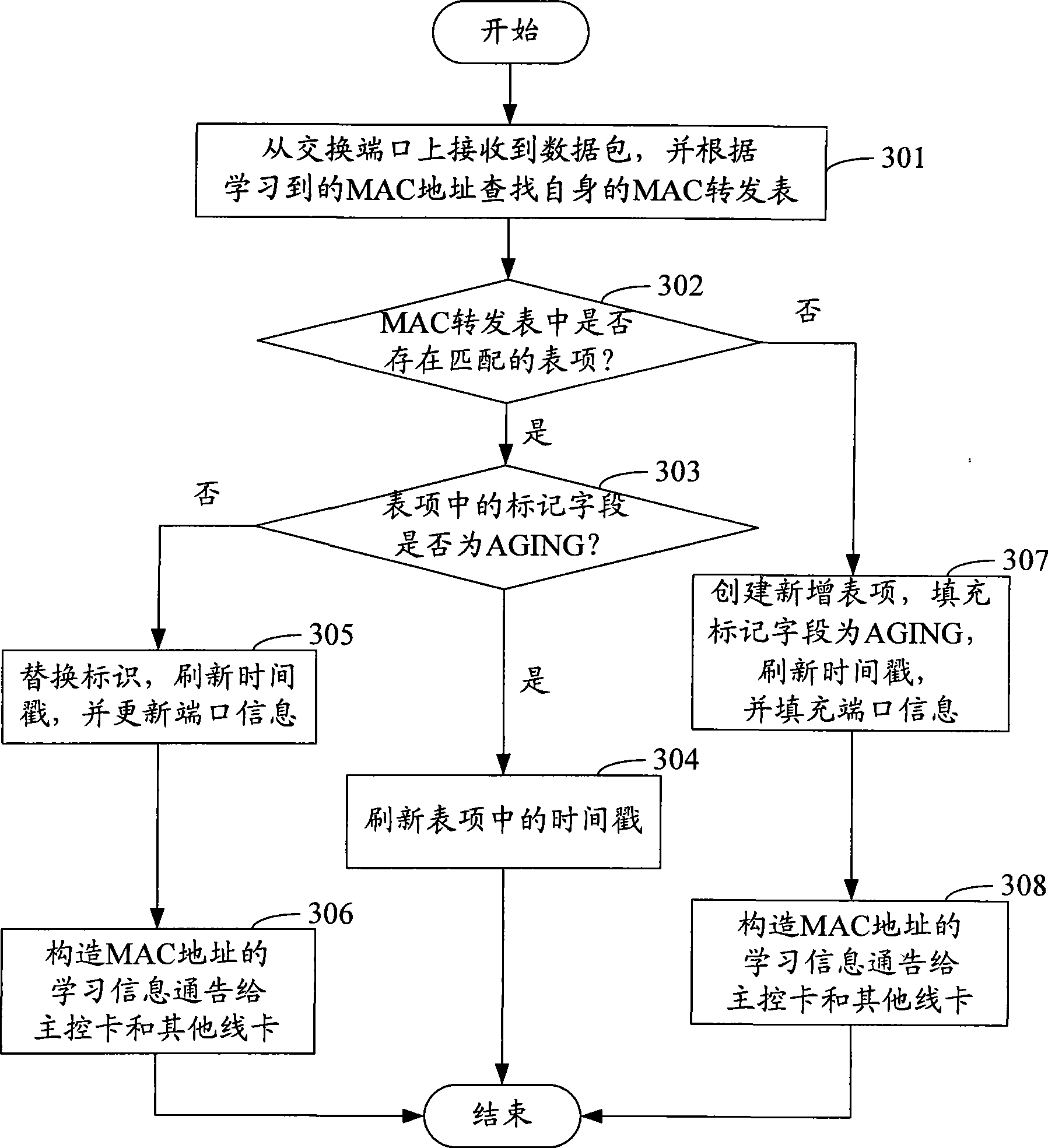
ActiveCN101488862AEasy maintenanceReduce the burden of inter-board communicationData switching detailsNetwork packetLine card
The invention discloses a distributed type medium access control (MAC) address maintenance method inside of Ethernet switch, the method comprises following steps: when a certain line card receives a data packet from an switching port, according to the MAC address learned from the data packet, the MAC forwarding list of the line card is updated according to the MAC address learned from the data packet, and the learning information of the MAC address is notified to the main control card and other line cards; when the line card receives the data packet from the interconnecting port, the learning of the MAC address can not performed; the line card performs aging process for the MAC address learned from the switching port in the oneself MAC forwarding list, and notifies the aging information of the MAC address to the main control card and other line cards, the aging process of each MAC forwarding list can be performed according to the aging information of the MAC address. The invention also discloses a distributed Ethernet switch capable of conveniently implementing the MAC address maintenance inside of the distributed Ethernet switch, the communication between boards can be reduced, and the processing logic can be simplified.
Owner:ZTE CORP
Routing node microstructure for on-chip network
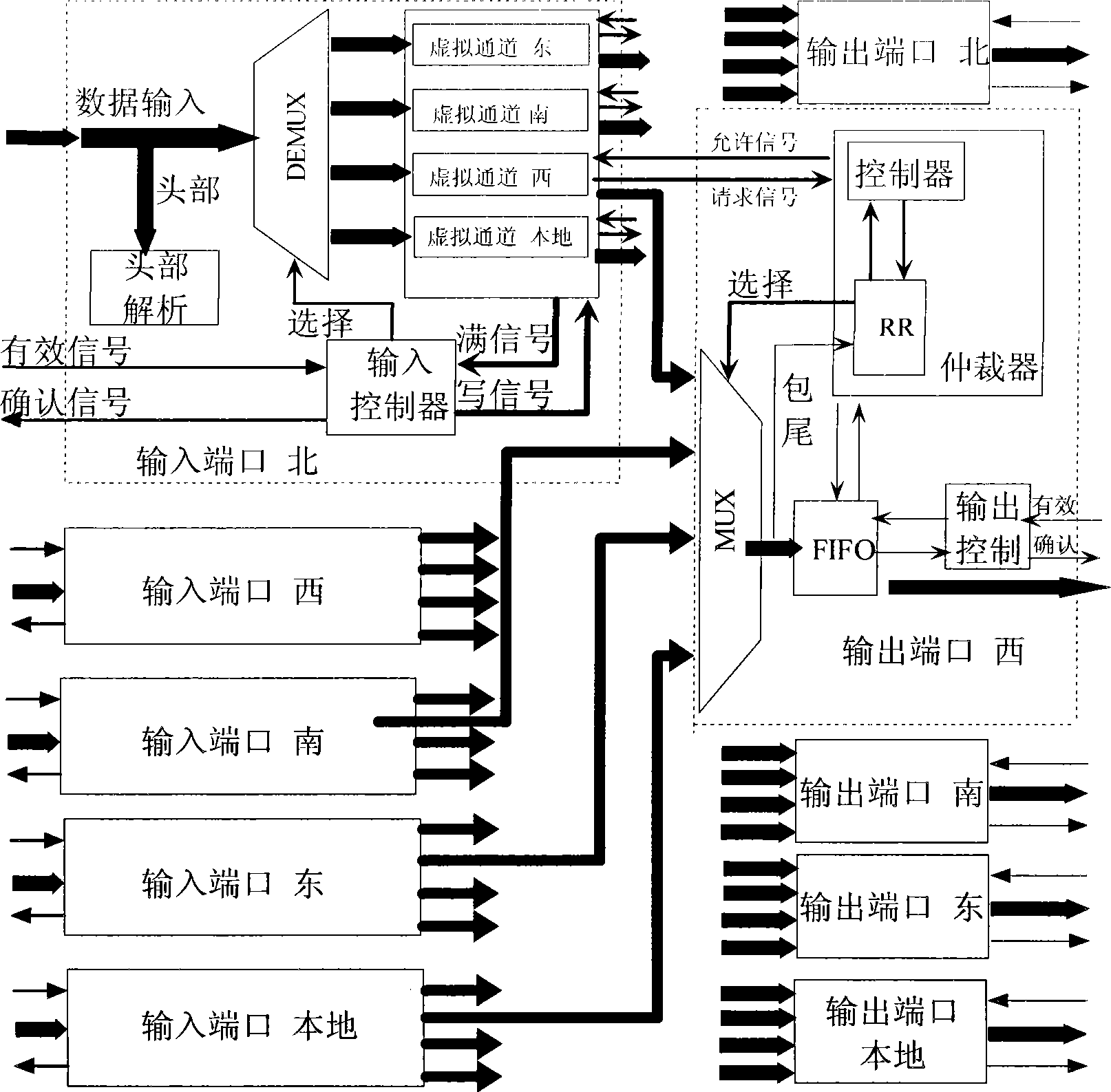
InactiveCN101383712AGuaranteed communication qualitySolve communication bottlenecksData switching detailsInput controlNetworks on chip
The invention discloses a route node microstructure of a network on chip, which comprises a head decode module, an input buffer module, an input control module, an output arbitration module, an output buffer module and an output control module. The head decode module performs the head analysis to data entering the route node from the upper route node, and inputs the data to the input buffer module; the input buffer module is used for the temporary storage of the data, and outputs the data to the output arbitration module under the action of the input control module. After the data enters the output arbitration module, the output arbitration module determines whether outputting the data to the output buffer module according to the state of the input control module, and the output arbitration module controls the whole output link so as to realize that the data is transmitted to the next route node. Through the route node microstructure of the invention, the data transmission among the route nodes of the network on chip can be realized, and the transmission efficiency can be greatly improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
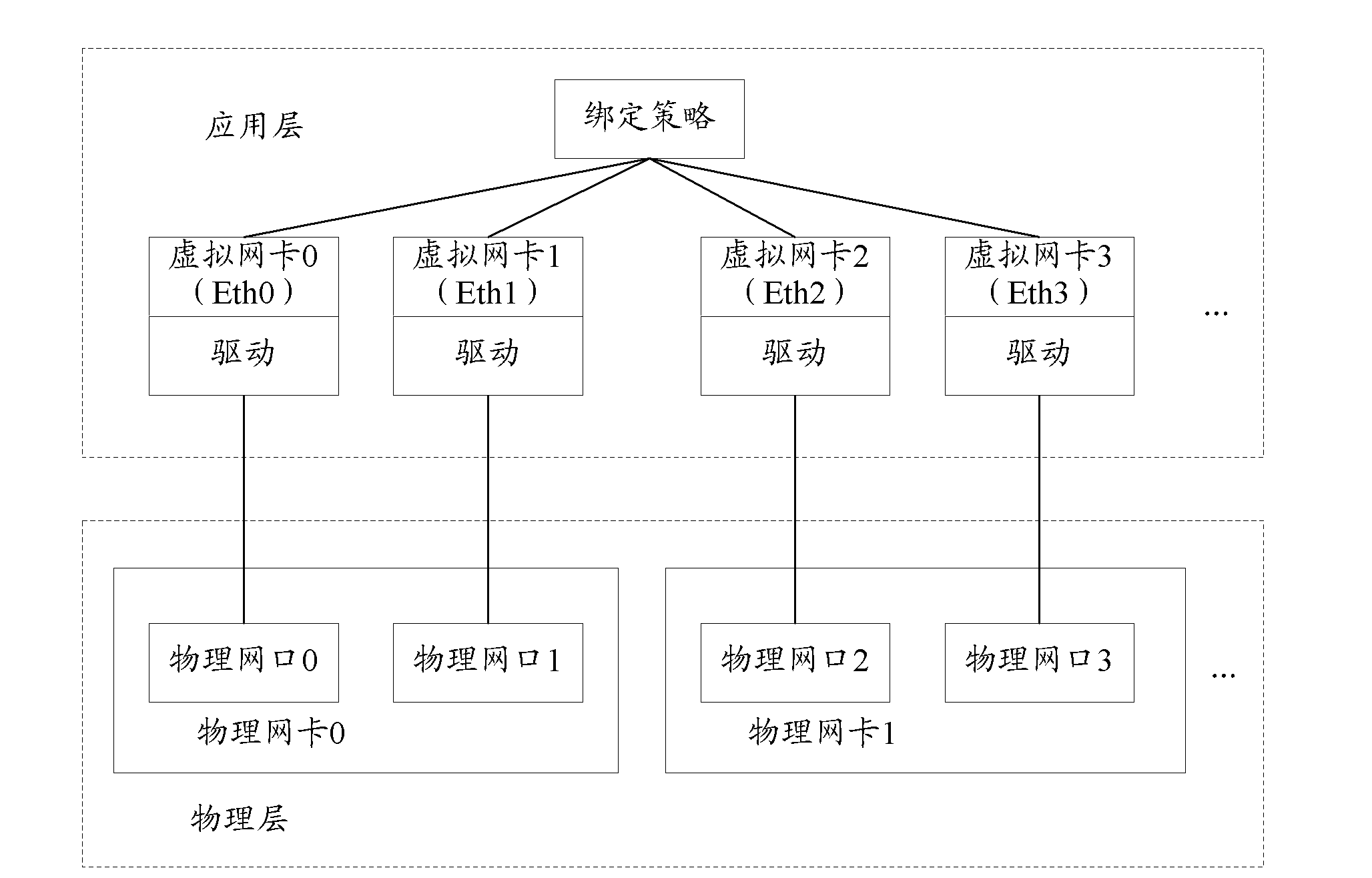
Method, network card and communication system for binding physical internet ports
ActiveCN102137169ARequirements for realizing secondary bindingMeet business needsData switching detailsCommunications systemProtocol Application
The invention discloses a method, a network card and a communication system for binding physical internet ports. The method comprises the steps of building a virtual port which corresponds to a virtual network card in an application layer, and binding the virtual port with other ports established in the application layer by application layer software; adding the multiple physical network ports needing to be bound to the established virtual ports; obtaining available physical ports which are determined to be normal in communication when the physical network ports in the visual ports are normal; and choosing one or multiple physical network ports from the available physical ports to receive and send messages according to an allocation mode when the messages need to be received and sent. According to the embodiment of the invention, the secondary binding of the physical network ports can be realized, thereby meeting business requirements better.
Owner:HUAWEI TECH CO LTD
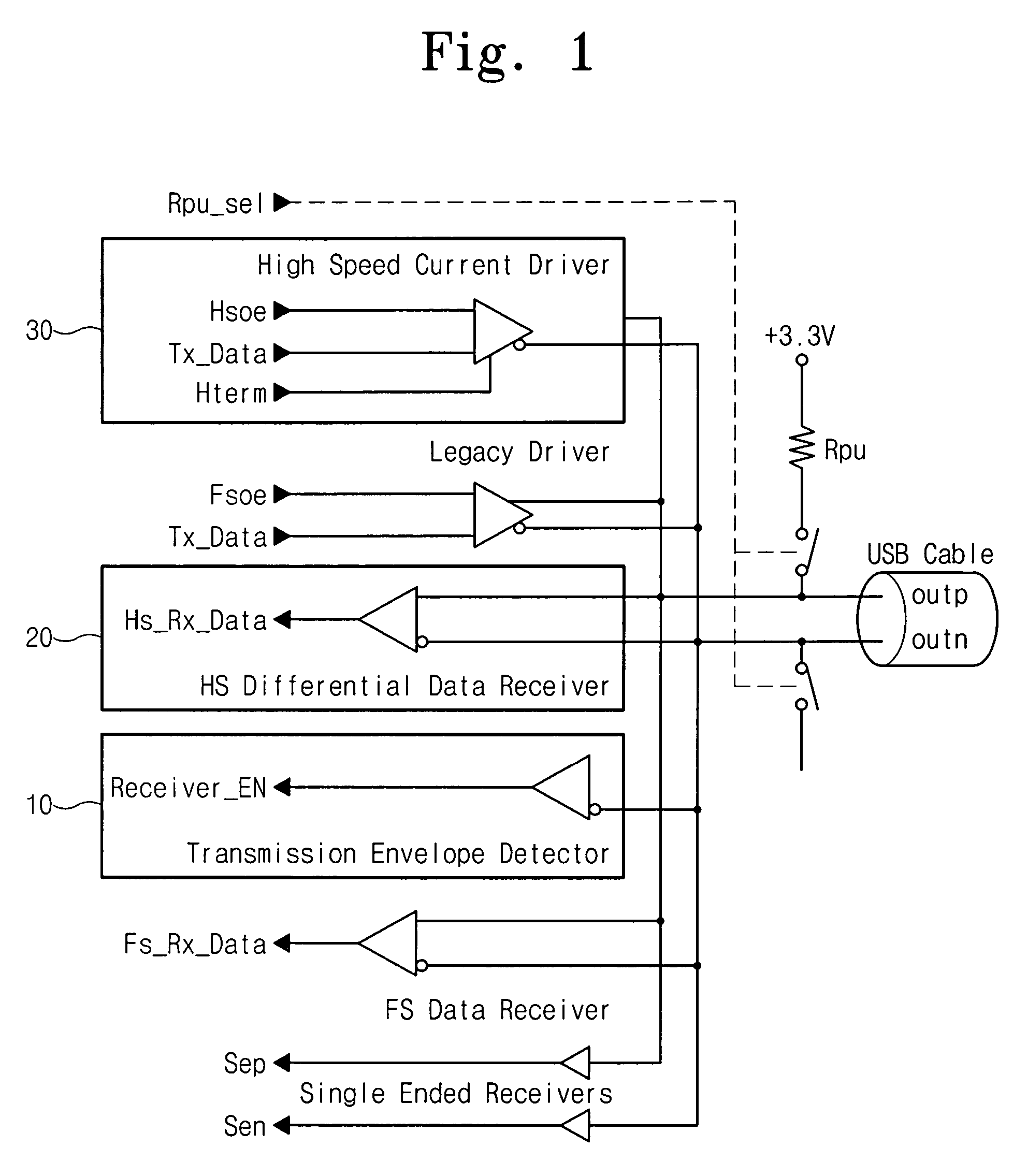
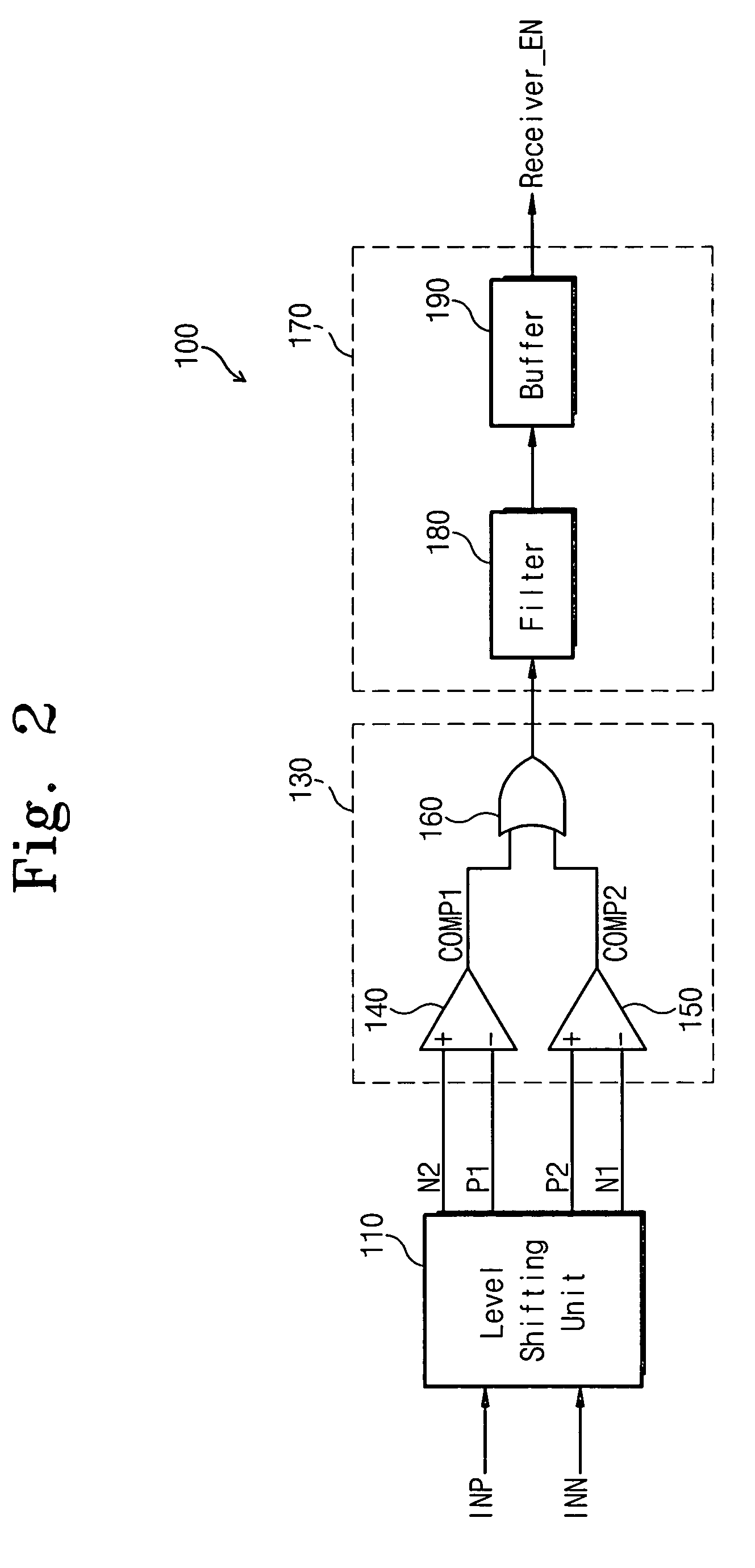
High speed analog envelope detector
ActiveUS7557633B2Simplifies the circuit architectureMultiple input and output pulse circuitsData switching detailsVoltage referenceData detection
A high speed analog transmission envelope (data-validity) detector for detecting the validity or invalidity of received data by generating (and comparing) first through fourth level-shifted signals based on a pair of differential input signals that are externally applied (received). Each of the first through fourth level-shifted signals has voltage levels different from (e.g., higher than) the differential input signals. After comparing the first through fourth level-shifted signals with each other, the comparison results are used in determining the validity of the differential input signals (data). The analog transmission envelope (data) detector flexibly adapts to variations in common mode voltage, and simplifies the circuit architecture because it does not require an additional reference voltage for determining the validity of received data.
Owner:SAMSUNG ELECTRONICS CO LTD
Data transfer control device and electronic instrument
A data transfer control device includes an OUT-transfer transmitter circuit which transmits OUT data by driving a serial signal line, a clock-transfer transmitter circuit which transmits a clock signal CLK by driving a serial signal line, a PLL circuit which generates the clock signal CLK, and a power-down setting circuit which sets a power-down mode. In a first power-down mode, the OUT-transfer transmitter circuit is set to the power-down mode, and the clock-transfer transmitter circuit is set to the power-down mode to stop a system clock signal of a target-side data transfer control device. In a second power-down mode, the OUT-transfer transmitter circuit is set to the power-down mode without setting the clock-transfer transmitter circuit to the power-down mode.
Owner:SEIKO EPSON CORP
Methods and systems for the negotiation of a population of RFID tags with improved security
InactiveUS20060065731A1Improve securityData switching detailsMemory record carrier reading problemsSpread spectrumComputer security
Methods and systems for the negotiation of a population of RFID tags with improved security is provided. In one aspect, tags are singulated without using information that directly identifies the tags in the tag population. A key is generated to identify each RFID tag of the population of RFID tags. The generated key does not include bits identifying an item with which the particular RFID tag is associated. An algorithm is operated to identify one or more tags in the population of RFIDs tags using the generated keys. In another aspect, frequency hopping and / or spread spectrum techniques are used to provide improved security while negotiating tags. In another aspect, the reader causes the tags to scroll series of bits back to the reader for each bit sent to the tags to provide improved security.
Owner:SYMBOL TECH INC
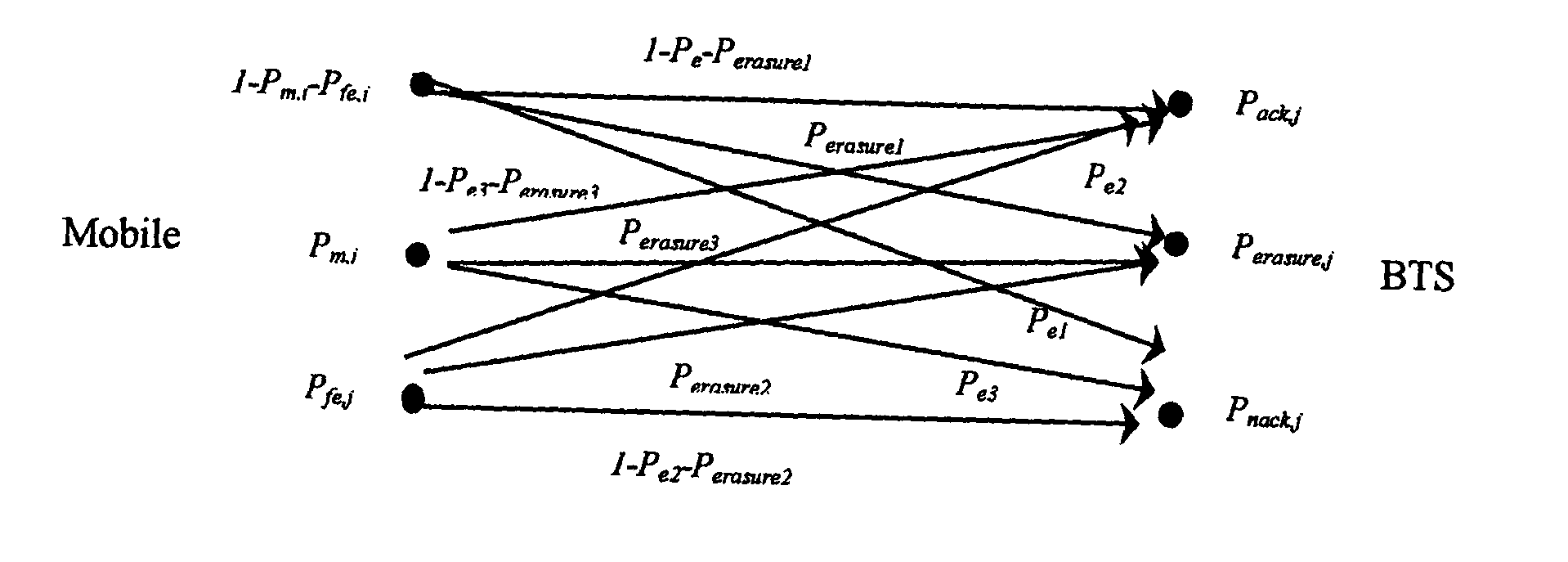
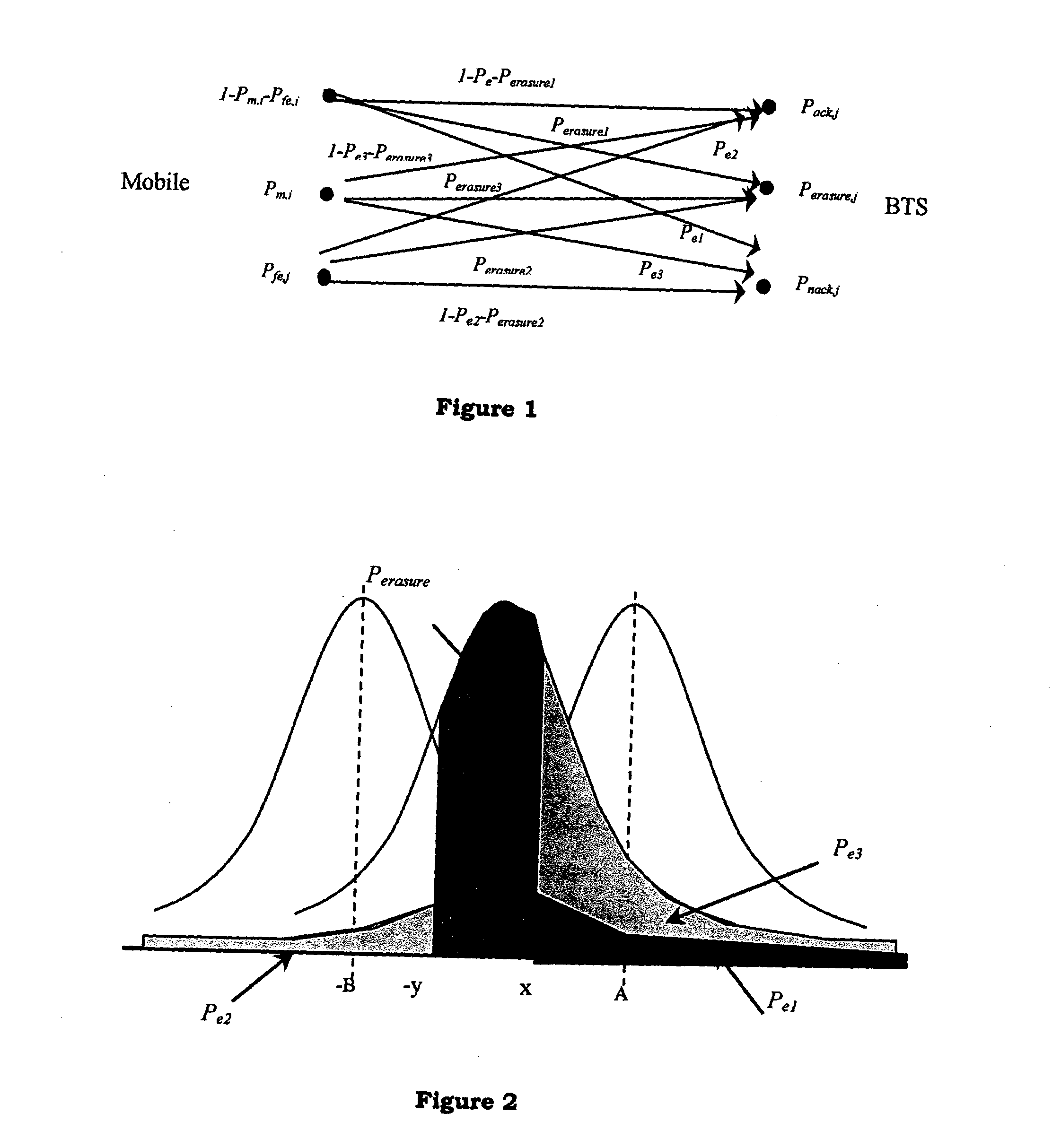
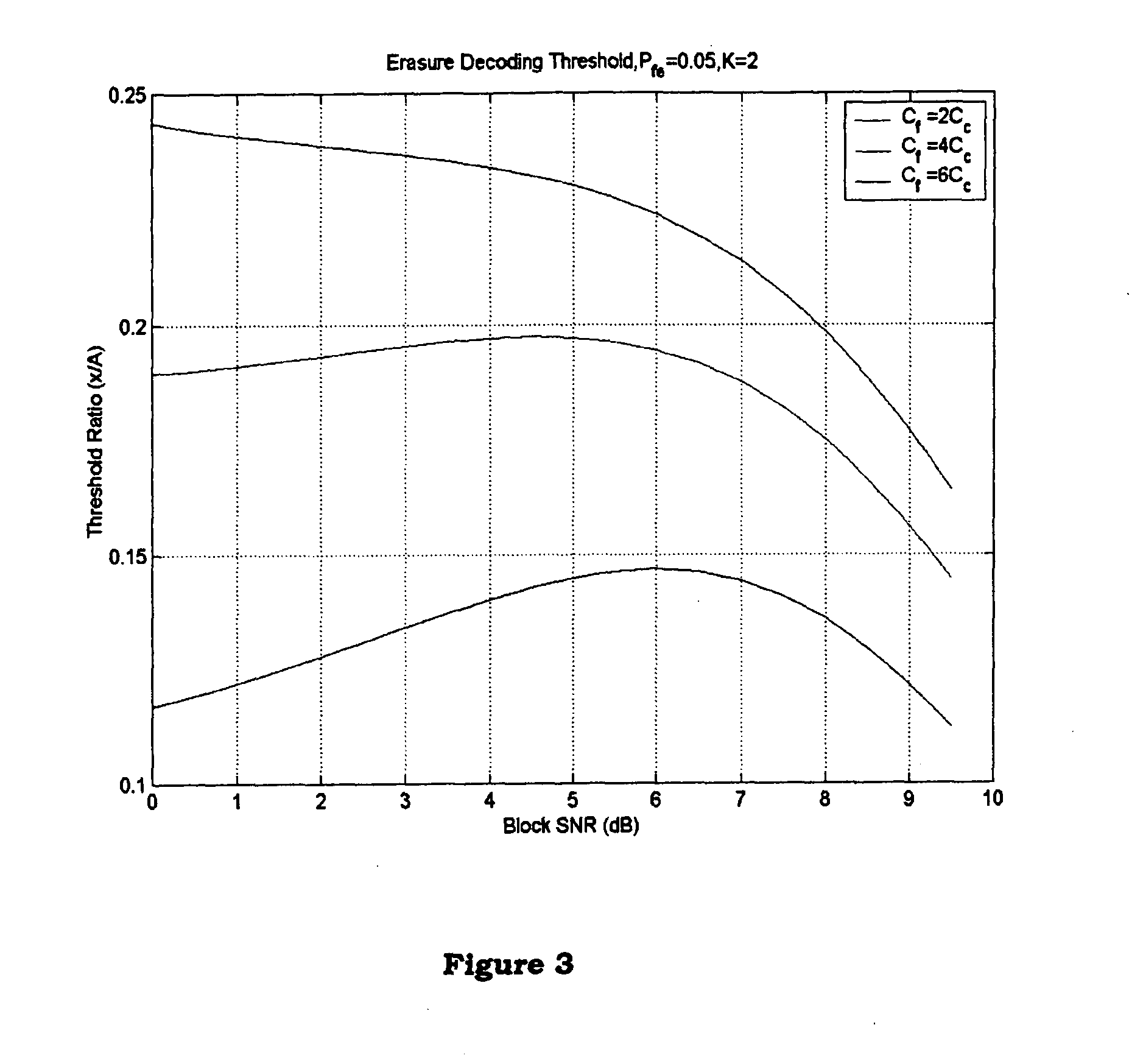
Erasure decoding optimization of acknowledgment/negative acknowledgement information in a wireless communication system
InactiveUS20050042985A1Improve throughput performanceError prevention/detection by using return channelData switching detailsCommunications systemComputer science
In the method of erasure decoding of acknowledgement (ACK) / negative acknowledgement (NACK) feedback information, a state of received ACK / NACK feedback information for associated sent data is detected based on at least one threshold derived using an objective function. The objective function includes at least a first term representing an affect on data throughput for at least one possible type of error in detecting a state of the received ACK / NACK feedback information.
Owner:WSOU INVESTMENTS LLC +1
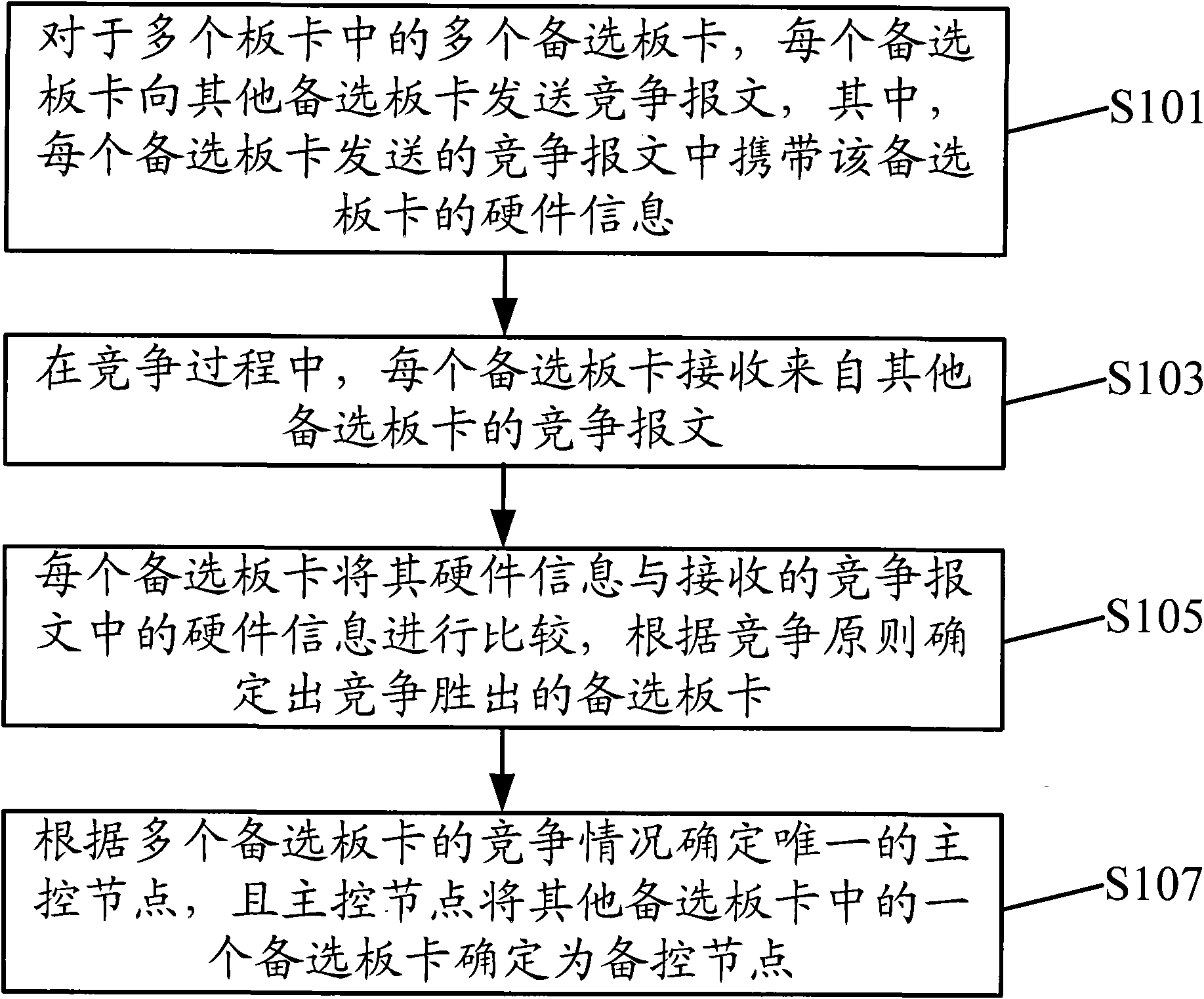
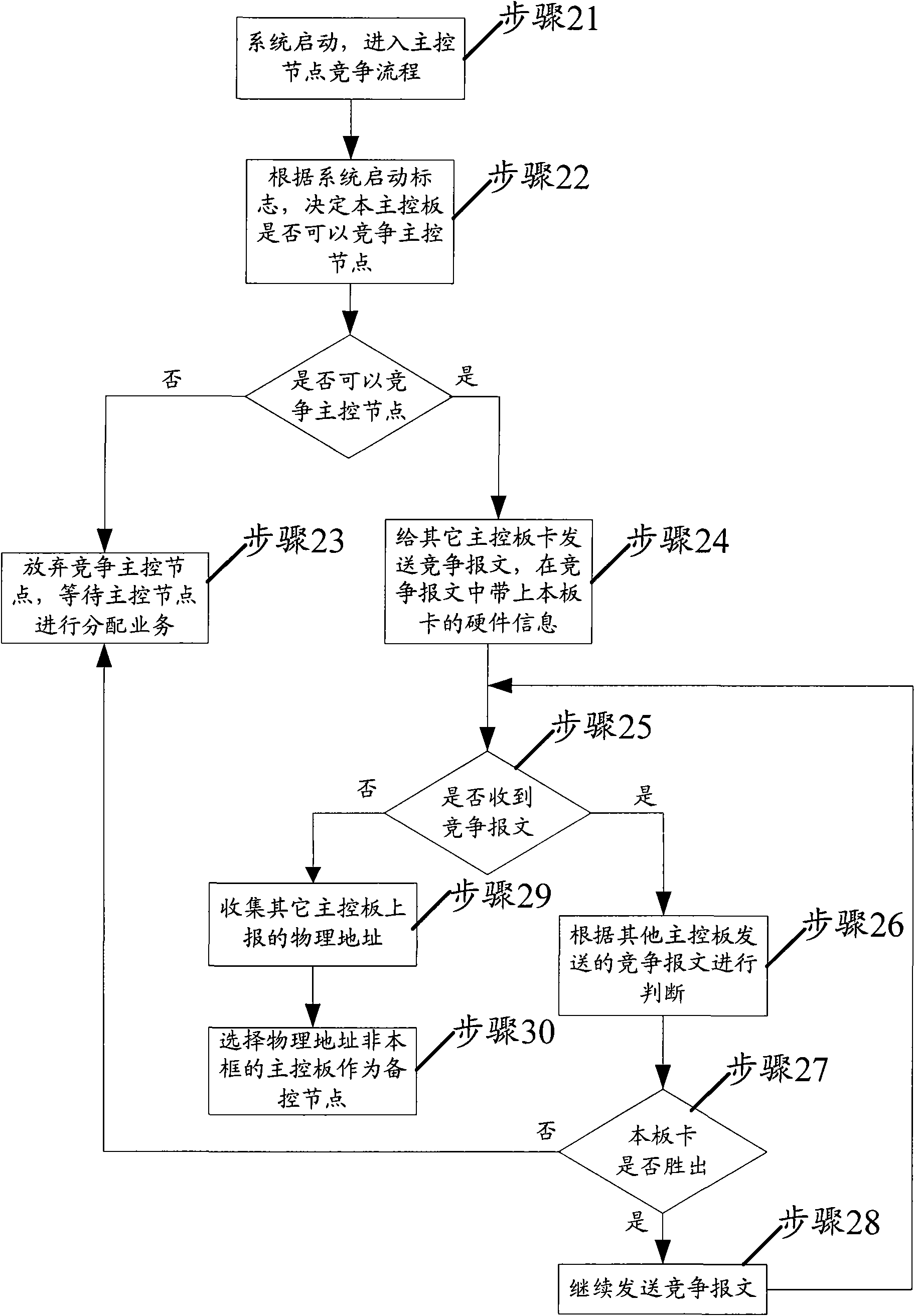
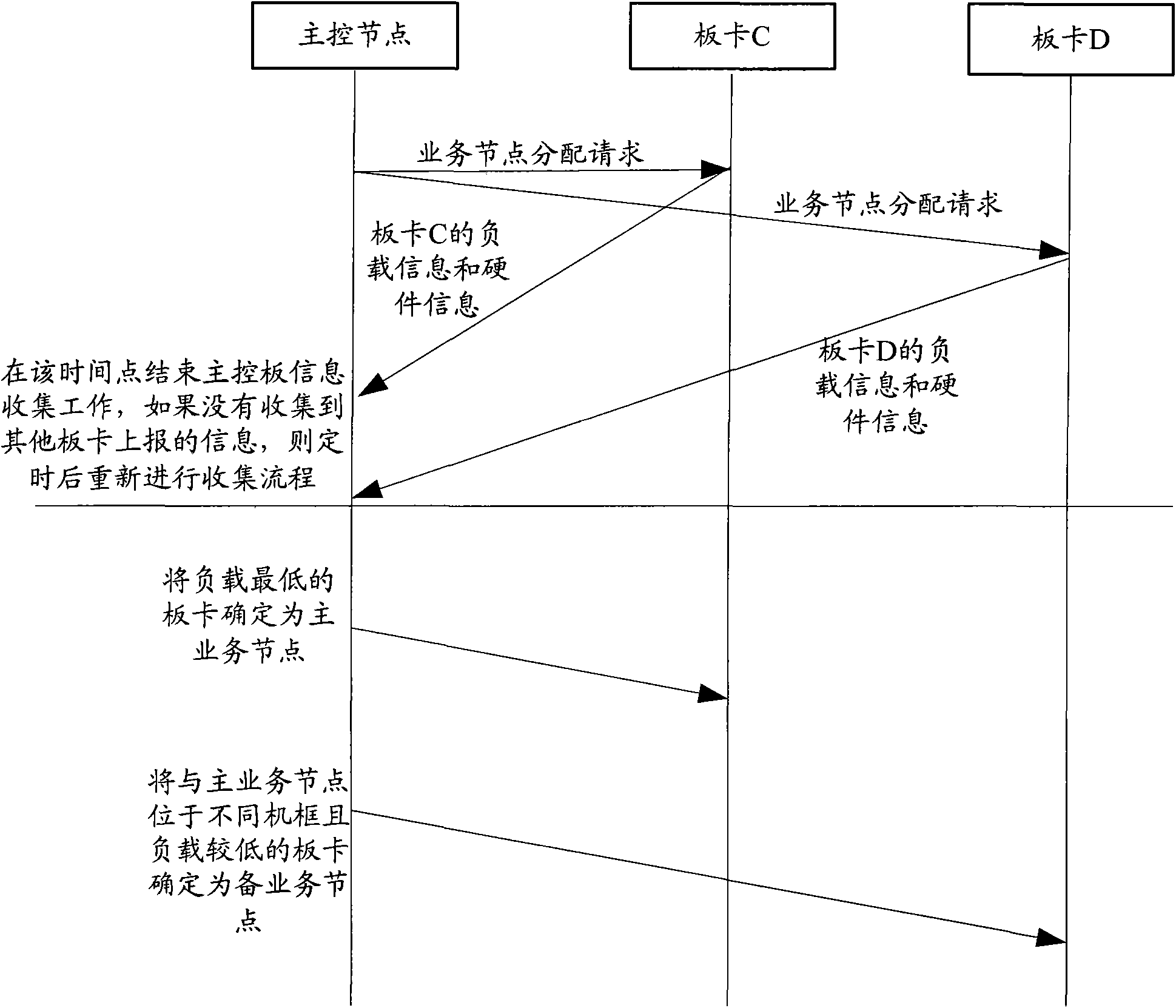
Method for realizing configuration of main and auxiliary board cards as well as board cards
InactiveCN101938417AGuaranteed performanceAvoid reliabilityData switching detailsComputer hardwareFixed frame
The invention discloses a method for realizing configuration of main and auxiliary board cards as well as board cards. The method comprises the following steps of: for a plurality of alternative board cards in a plurality of board cards, transmitting a competition message to other alternative board cards by each alternative board card, wherein the competition message transmitted by each alternative board card carries the hardware information of each alternative board card; in a competition process, receiving the competition message coming from other alternative board cards by each alternative board card; comparing the hardware information of each alternative board card with the hardware information in the received competition message by each alternative board card, and determining the alternative board cards winning in the competition according to a competition principle, wherein the competition principle is used for determining the alternative board cards as main control nodes according to the comparison result of the hardware information; and determining a unique main control node according to the competition conditions of the plurality of alternative board cards, and determining one alternative board card in other alternative board cards as an auxiliary control node by the main control node. In the invention, the determining range of the main control node is not limited in one fixed frame, and the performance of the finally determined main control node can be ensured.
Owner:ZTE CORP
Popular searches
Office automation Special data processing applications Digital output to display device Network connections Generating/distributing signals Transmission path multiple use Synchronising arrangement Information technology support system Non-electrical signal transmission systems Resonant circuit details
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com