Patents
Literature
1504 results about "Binary tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
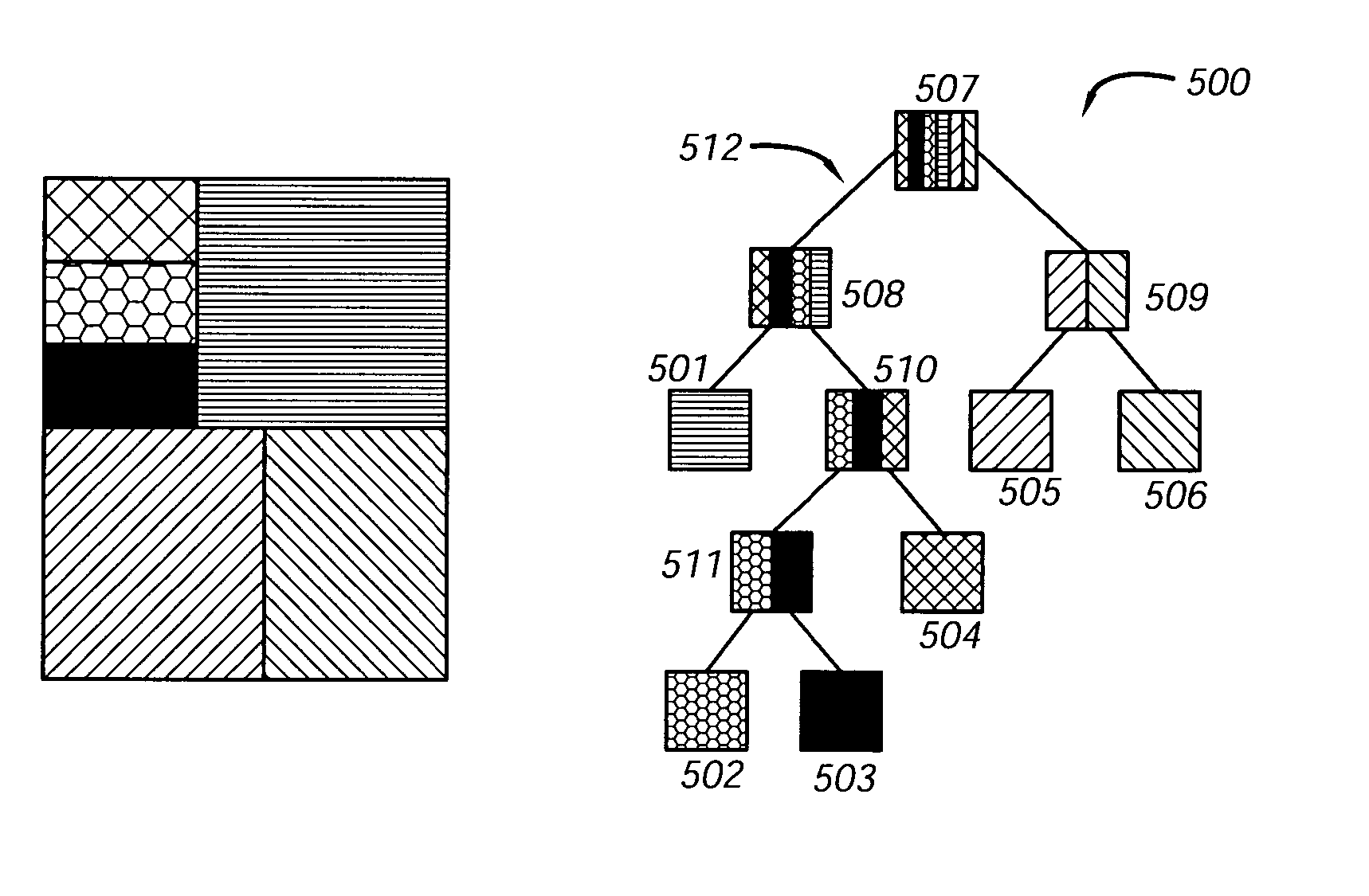
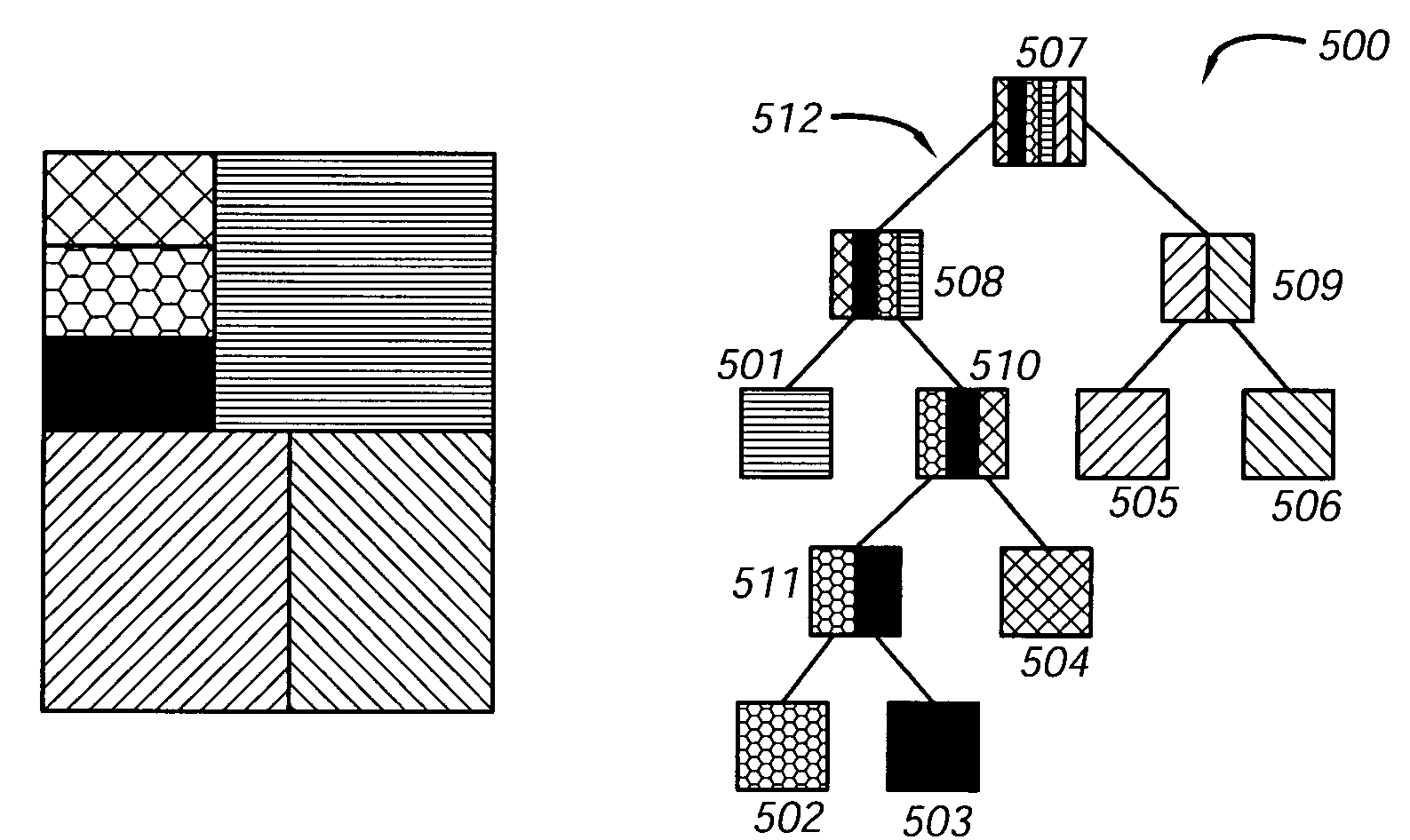
In computer science, a binary tree is a tree data structure in which each node has at most two children, which are referred to as the left child and the right child. A recursive definition using just set theory notions is that a (non-empty) binary tree is a tuple (L, S, R), where L and R are binary trees or the empty set and S is a singleton set. Some authors allow the binary tree to be the empty set as well.
Apparatus for speech recognition using multiple acoustic model and method thereof
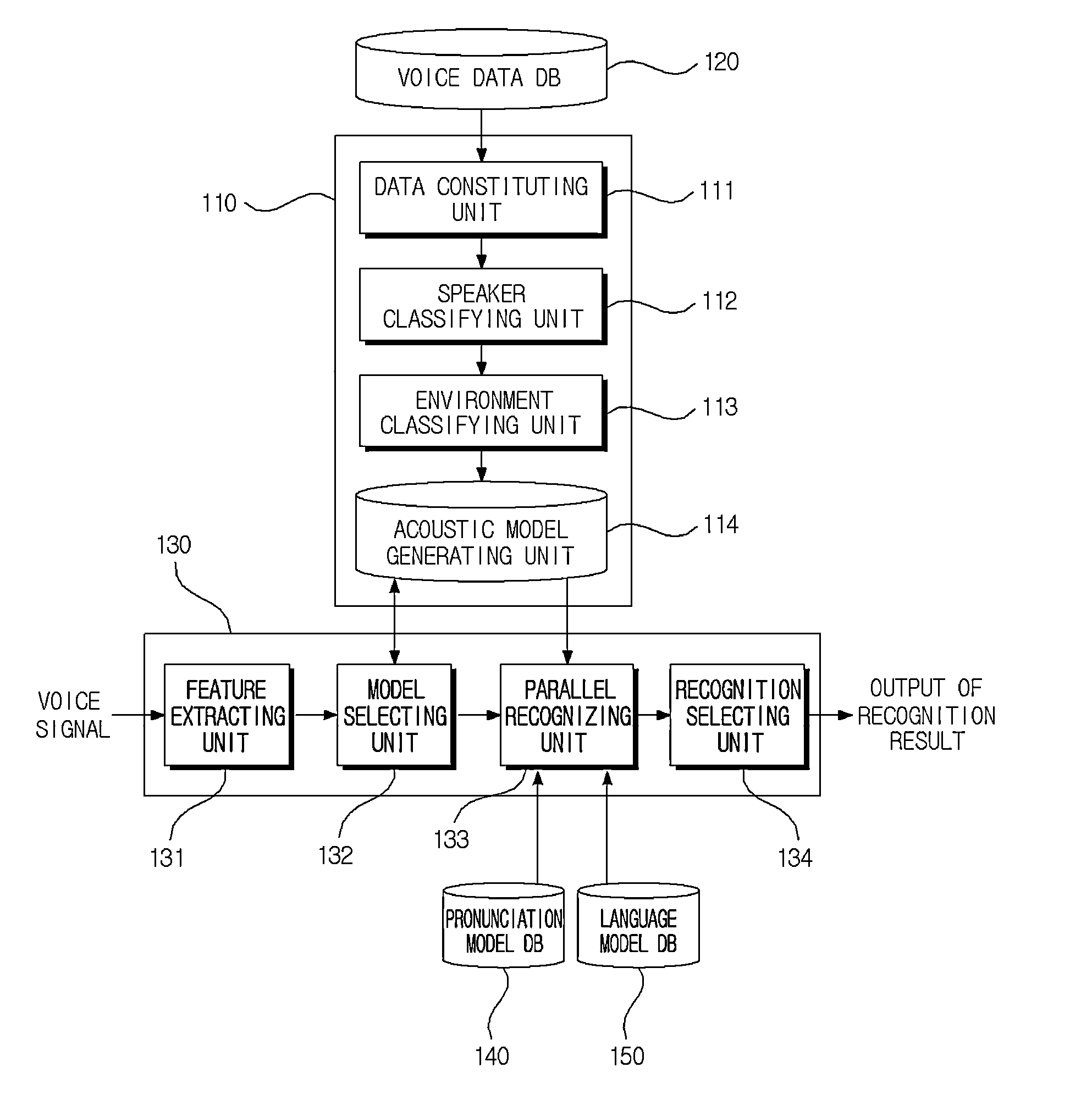
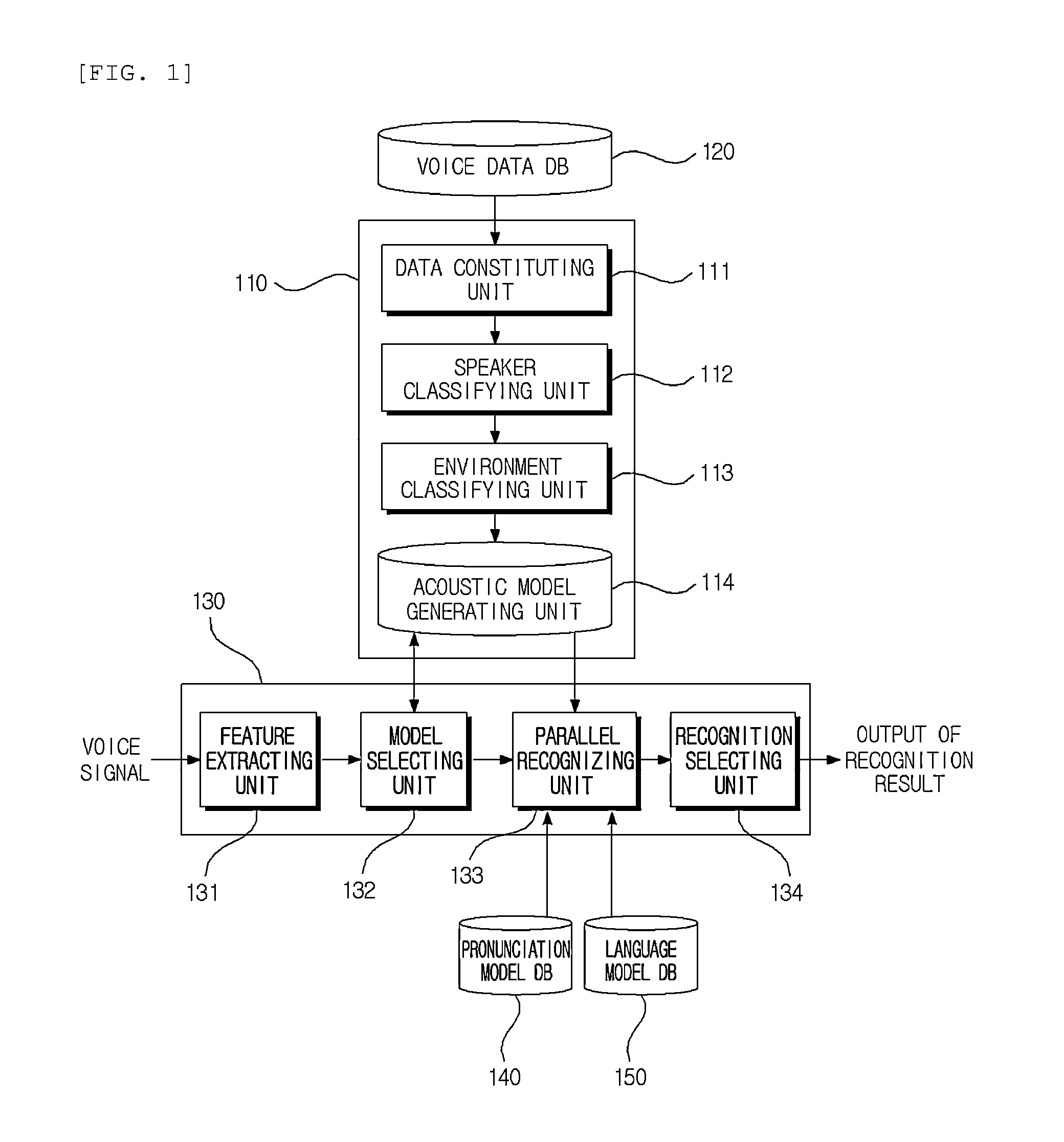
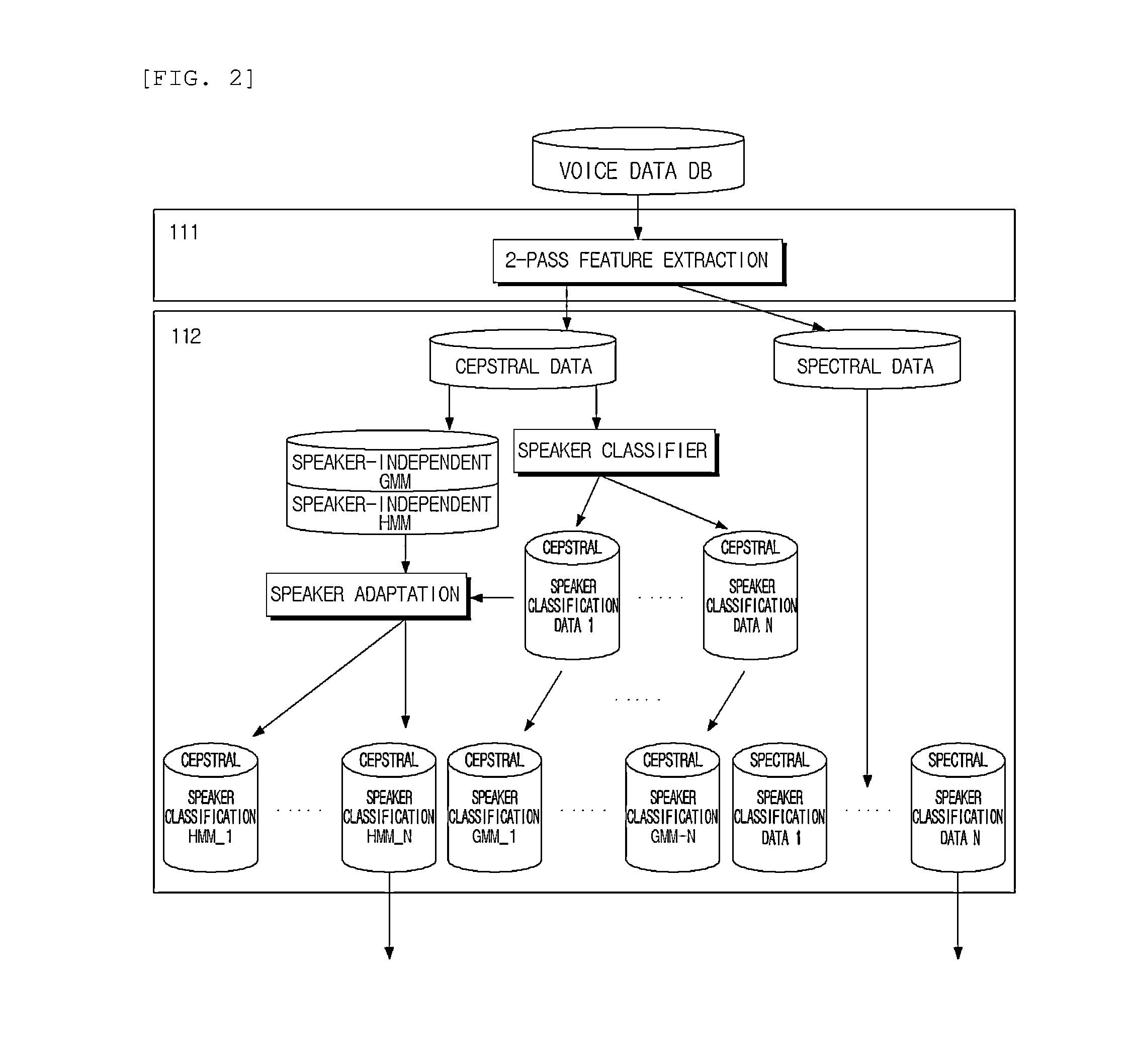
Disclosed are an apparatus for recognizing voice using multiple acoustic models according to the present invention and a method thereof. An apparatus for recognizing voice using multiple acoustic models includes a voice data database (DB) configured to store voice data collected in various noise environments; a model generating means configured to perform classification for each speaker and environment based on the collected voice data, and to generate an acoustic model of a binary tree structure as the classification result; and a voice recognizing means configured to extract feature data of voice data when the voice data is received from a user, to select multiple models from the generated acoustic model based on the extracted feature data, to parallel recognize the voice data based on the selected multiple models, and to output a word string corresponding to the voice data as the recognition result.
Owner:ELECTRONICS & TELECOMM RES INST
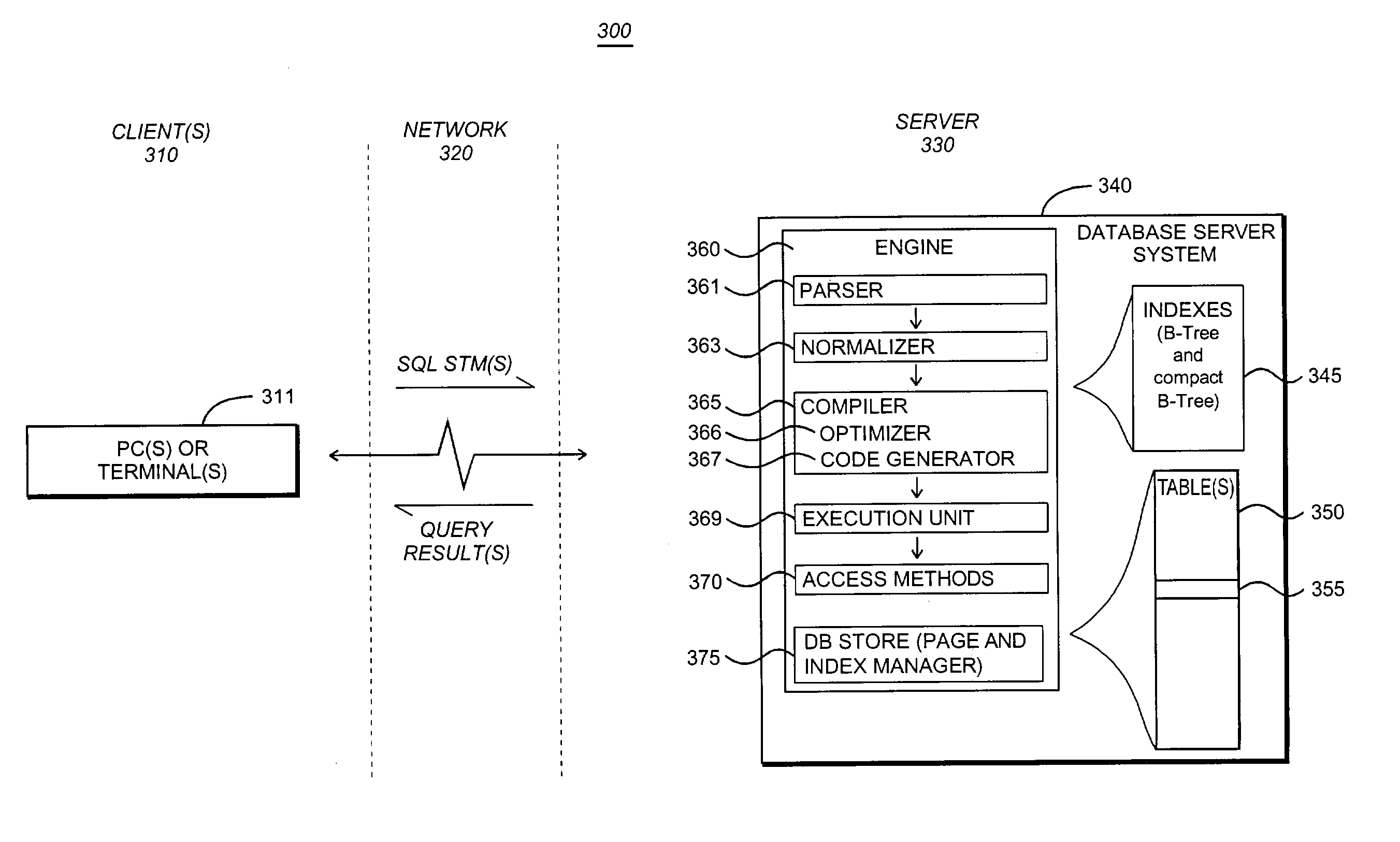
System and methodology for providing compact B-Tree
InactiveUS20030204513A1Data processing applicationsDigital data information retrievalTable (database)PathPing
An improved method for creating an index based on a path-compressed binary trie in a database system comprising database tables and indexes on those tables is described. For a given index to be created, a path-compressed binary trie for the given index is determined. The path-compressed binary trie comprises internal nodes and leaf nodes. Based on a traversal of the path-compressed binary trie, an index is created comprising a first array of internal nodes encountered during the traversal, and a second array of leaf nodes encountered during the traversal. The database system employs said first and second arrays for providing index-based access for a given key value.
Owner:IANYWHERE SOLUTIONS
Automatic photo album page layout
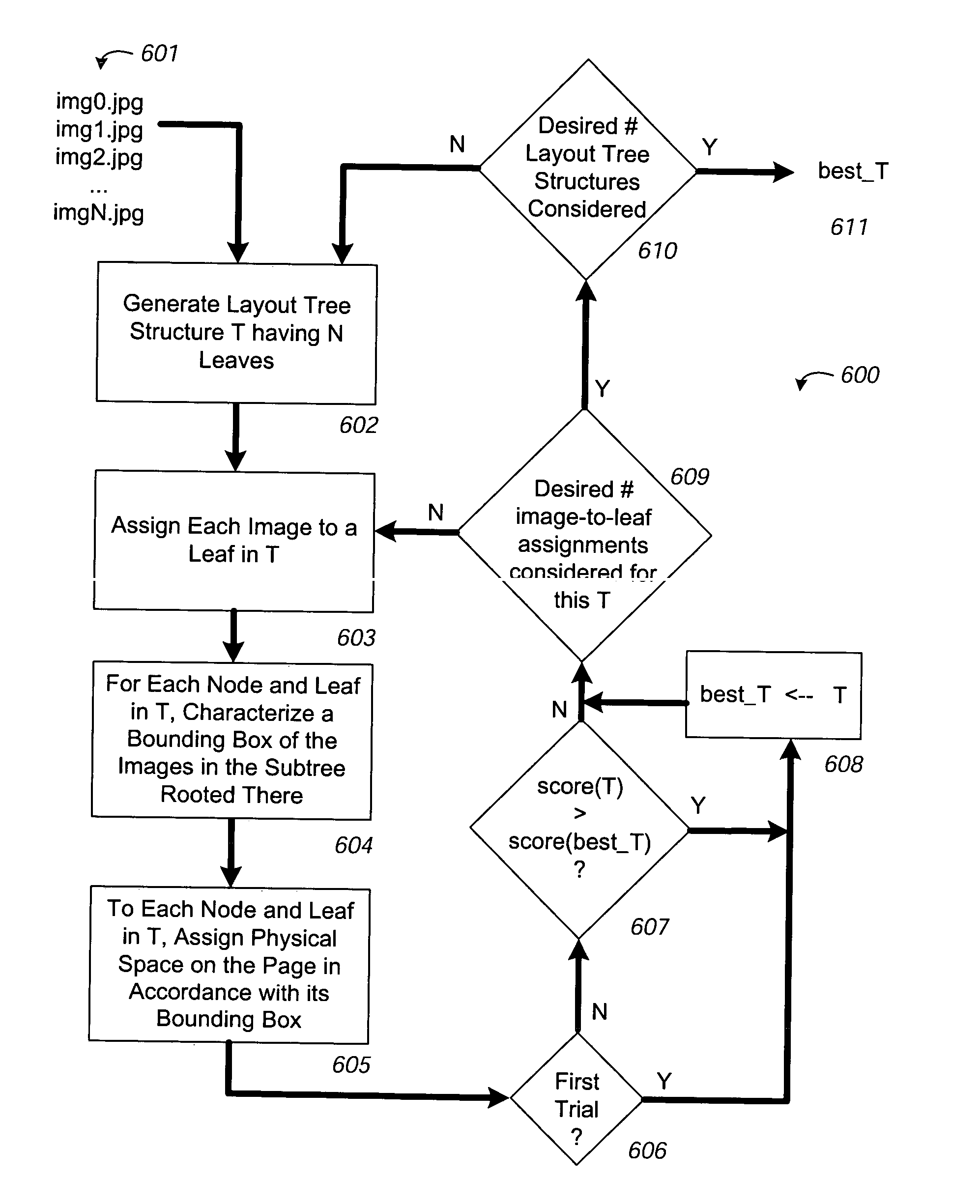
A method for locating objects, such as images having fixed aspect ratios, within a predefined space, such as a printed page, is provided. The method comprises generating a binary tree structure comprising at least one node and a plurality of leaves, each leaf corresponding to an image and being associated with one node. The method further comprises characterizing a bounding box for each node in the binary tree structure, the bounding box establishing a boundary for all leaves associated with the node. The method also comprises manipulating bounding boxes to fit within the predefined space. The method may be selectively repeated to reposition images within the binary tree structure or to reform the binary tree structure and characterize and manipulate using the reformed binary tree structure. The end result is at least one potential layout having all images located within the predefined space.
Owner:HEWLETT PACKARD DEV CO LP
Transaction-based storage system and method that uses variable sized objects to store data
ActiveUS20050257083A1Increase write speedImprove reading speedMemory loss protectionError detection/correctionExtendible hashingBinary tree
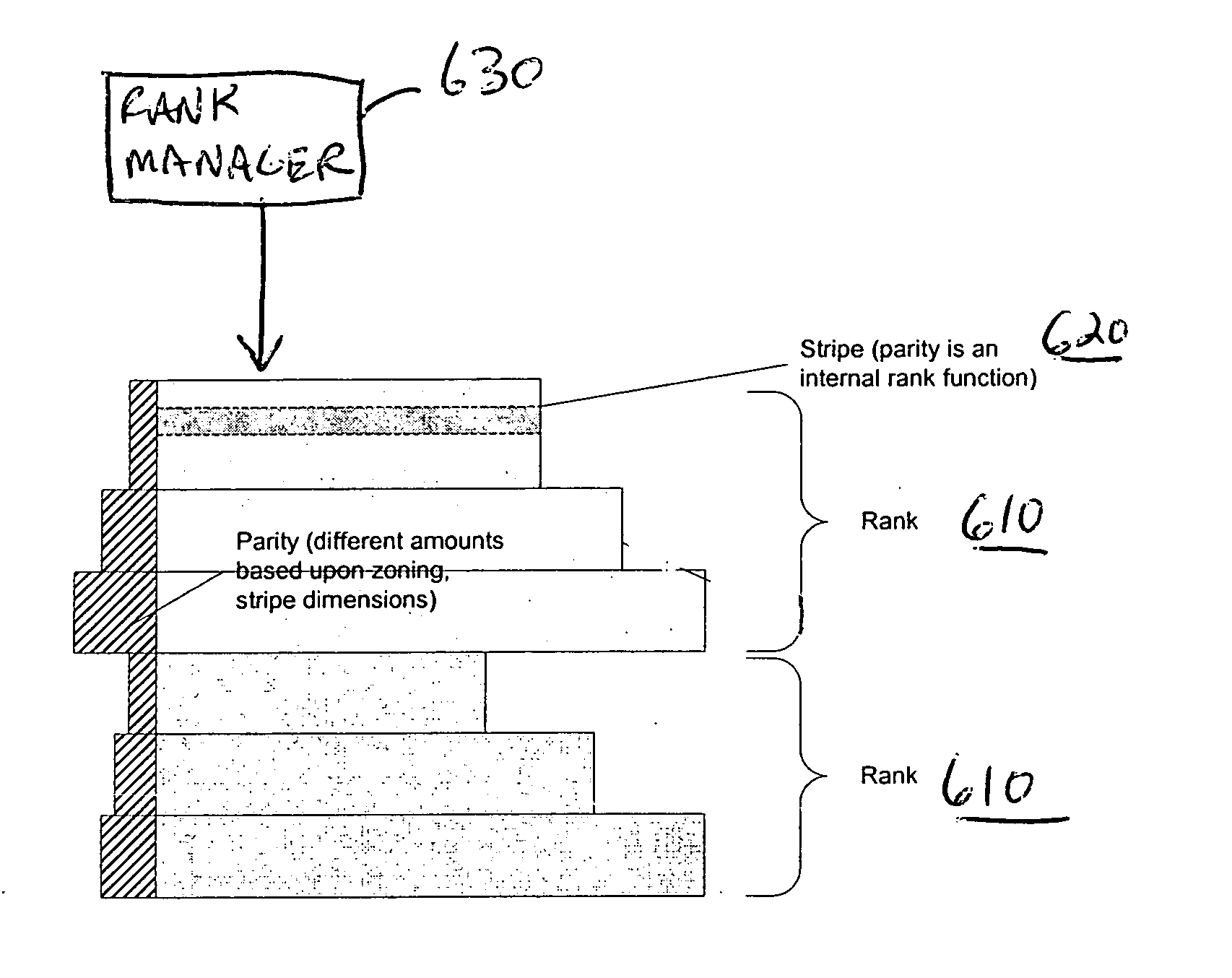
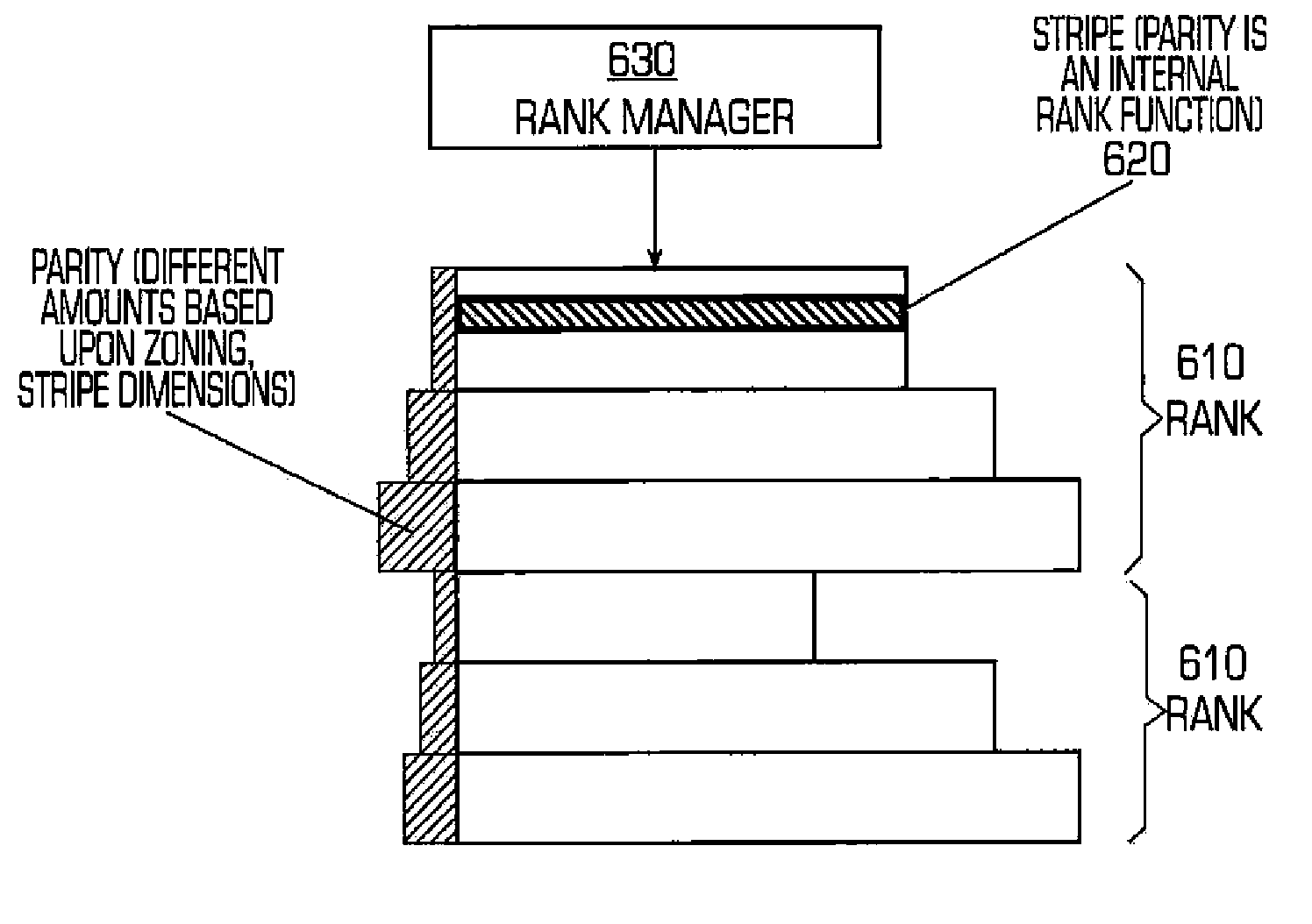
The present invention provides a storage system for storing variable sized objects. The storage system is preferably a transaction-based system that uses variable sized objects to store data. The storage system is preferably implemented using arrays disks that are arranged in ranks. Each rank includes multiple stripes. Each stripe may be read and written as a convenient unit for maximum performance. A rank manager is able to dynamically configure the ranks to adjust for failed and added disks by selectively shortening and lengthening the stripes. The storage system may include a stripe space table that contains entries describing the amount of space used in each stripe. An object map provides entries for each object in the storage system describing the location (e.g., rank, stripe and offset values), the length and version of the object. A volume index translates regions of logical storage into object identifiers. The storage system may implement various types of formats such as I-node, binary tree and extendible hashing formats.
Owner:COUSINS ROBERT E
Transaction-based storage system and method that uses variable sized objects to store data
The present invention provides a storage system for storing variable sized objects. The storage system is preferably a transaction-based system that uses variable sized objects to store data. The storage system is preferably implemented using arrays disks that are arranged in ranks. Each rank includes multiple stripes. Each stripe may be read and written as a convenient unit for maximum performance. A rank manager is able to dynamically configure the ranks to adjust for failed and added disks by selectively shortening and lengthening the stripes. The storage system may include a stripe space table that contains entries describing the amount of space used in each stripe. An object map provides entries for each object in the storage system describing the location (e.g., rank, stripe and offset values), the length and version of the object. A volume index translates regions of logical storage into object identifiers. The storage system may implement various types of formats such as I-node, binary tree and extendible hashing formats.
Owner:COUSINS ROBERT E
Single pass automatic photo album page layout
A method for quickly and efficiently locating objects, such as images having fixed aspect ratios, within a predefined space, such as a printed page, is provided. The method comprises generating a binary tree containing a first image. The system generates a second tree, where the second tree modifies the first tree by inserting a second image at a location or position on the first tree. This iterative process of inserting images one at a time continues until the system generates a final tree including all images. In each iteration, the position in the binary tree where the system inserts each subsequent image can be either a leaf or a node. The system generates a series of candidate trees, one for each subsequent image inserted into each and every location in the preceding tree, and the candidate tree having a highest score indicates the selected location for the subsequent image and the new baseline, preferred binary tree.
Owner:HEWLETT PACKARD DEV CO LP
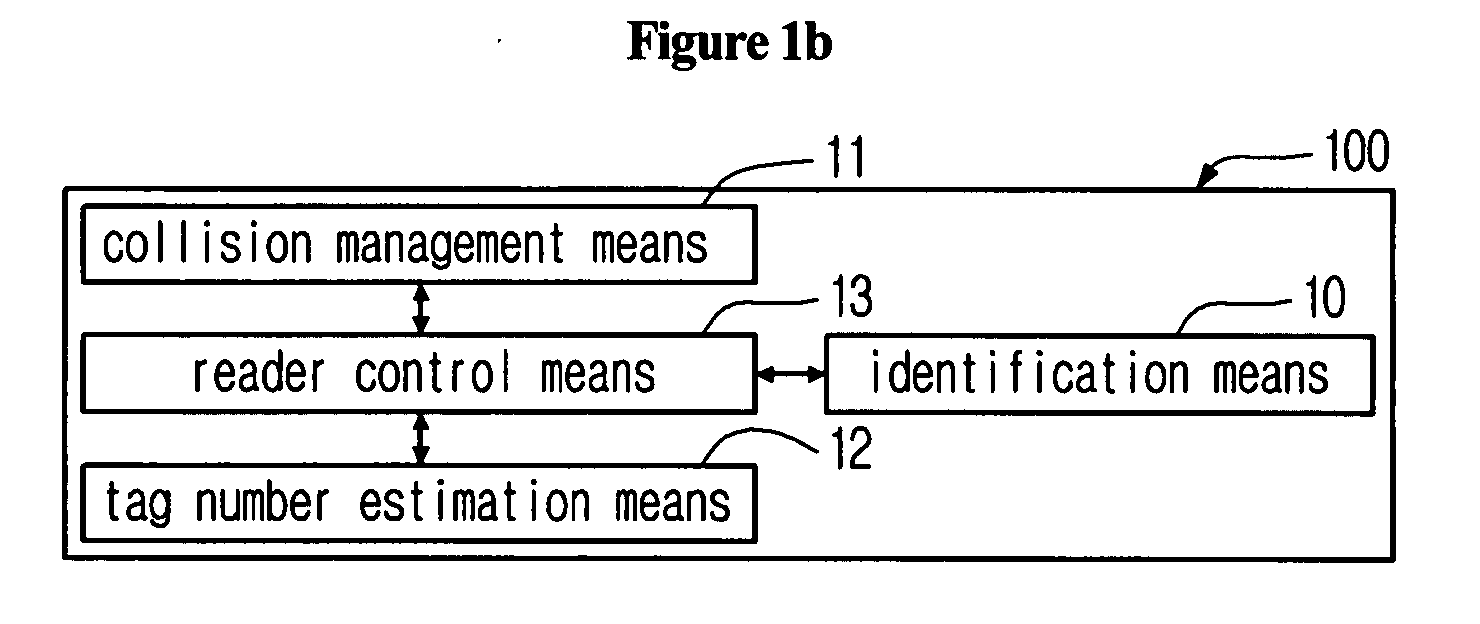
System for tag estimation and anti-collision and method thereof
ActiveUS20080150674A1Overcomes shortcomingQuick identificationNetwork traffic/resource managementElectric testing/monitoringIdle timeIdentification device
The present application discloses a system and a method for tag estimation and anti-collision in an RFID system, which can estimate an exact number of tags within an RF area and can rapidly identify tags by using the estimated number of tags in an RFID system. The system includes an RFID reader and RFID tags. The RFID reader includes an identification means, a collision management means, a tag number estimation means, and a reader control means. The RFID tag includes a tag communication means, a message reading means, a counter management means, an information storage means, and a tag control means. The disclosed system and method can prevent occurrence of too many idle times slots in the DFSA and too many initial collisions in the binary tree scheme, and thus can identify a large number of tags at a high speed with a small number of time slots.
Owner:INTELLECTUAL DISCOVERY CO LTD
Automated taxonomy generation
InactiveUS20060004747A1Maximize likelihoodData processing applicationsDigital data information retrievalPaper documentDocument preparation
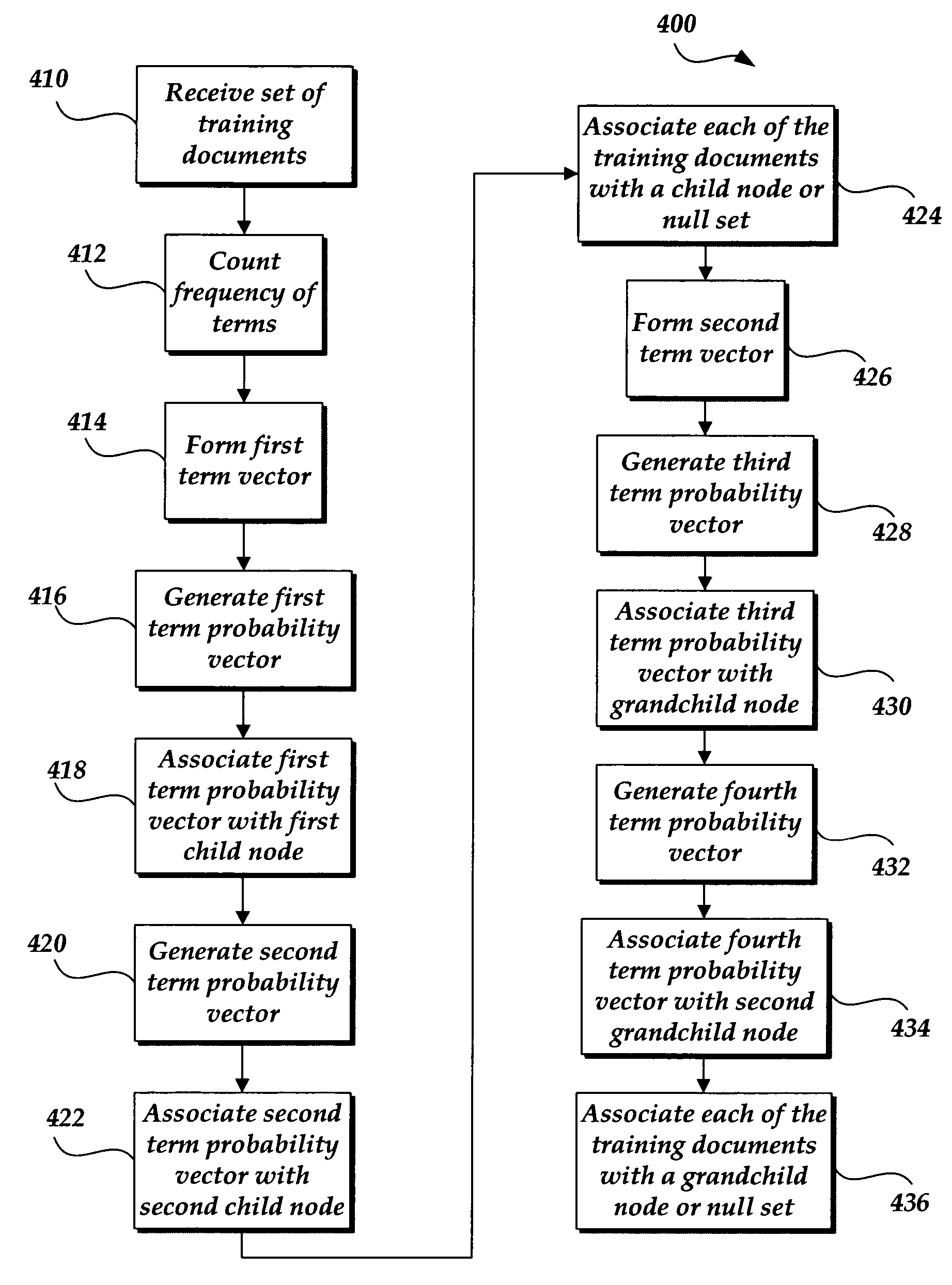
In a hierarchical taxonomy of document, the categories of information may be structured as a binary tree with the nodes of the binary tree containing information relevant to the search. The binary tree may be ‘trained’ or formed by examining a training set of documents and separating those documents into two child nodes. Each of those sets of documents may then be further split into two nodes to create the binary tree data structure. The nodes may be generated to maximize the likelihood that all of the training documents are in either or both of the two child nodes. In one example, each node of the binary tree may be associated with a list of terms and each term in each list of terms is associated with a probability of that term appearing in a document given that node. New documents may be categorized by the nodes of the tree. For example, the new documents may be assigned to a particular node based upon the statistical similarity between that document and the associated node.
Owner:SERVICENOW INC
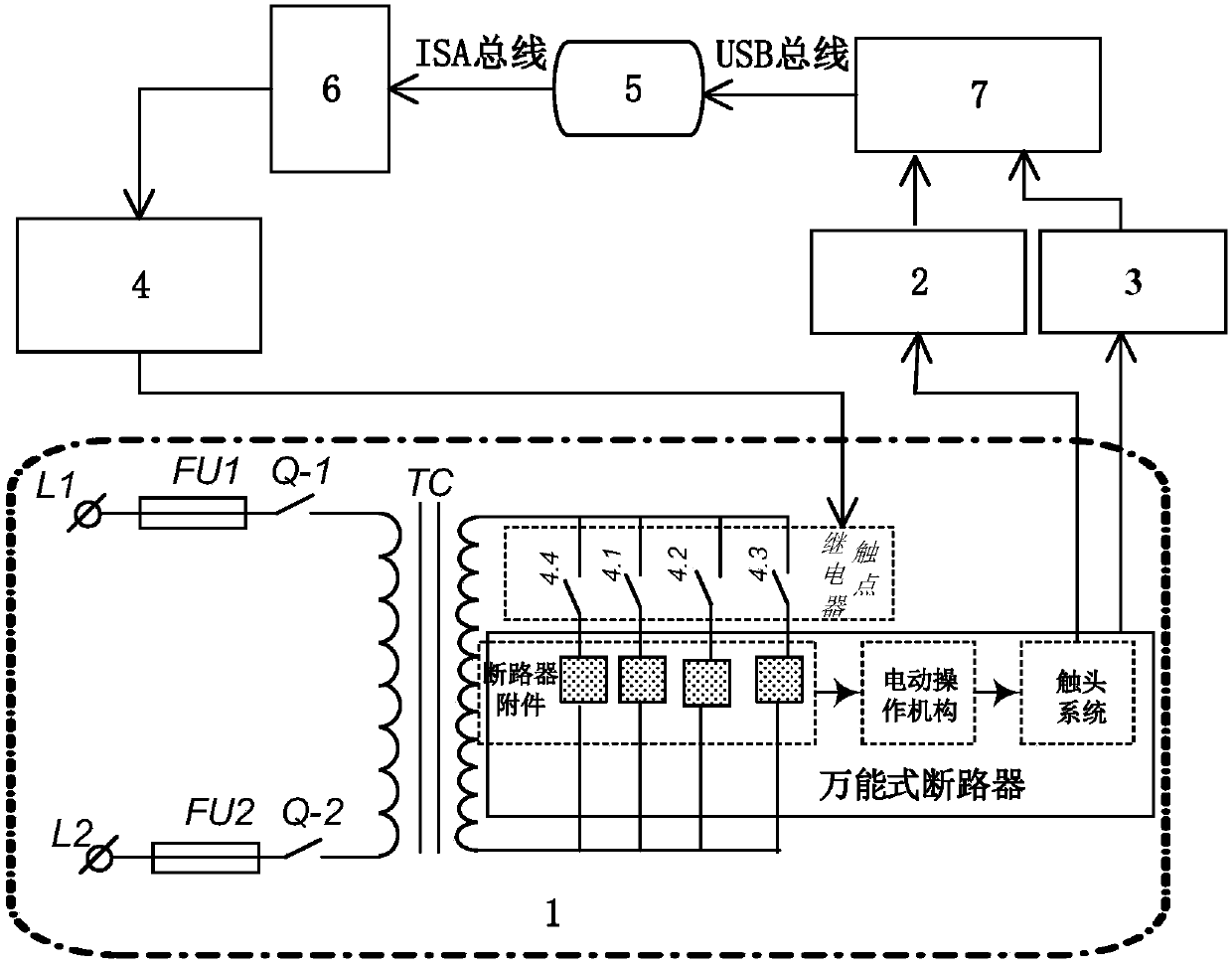
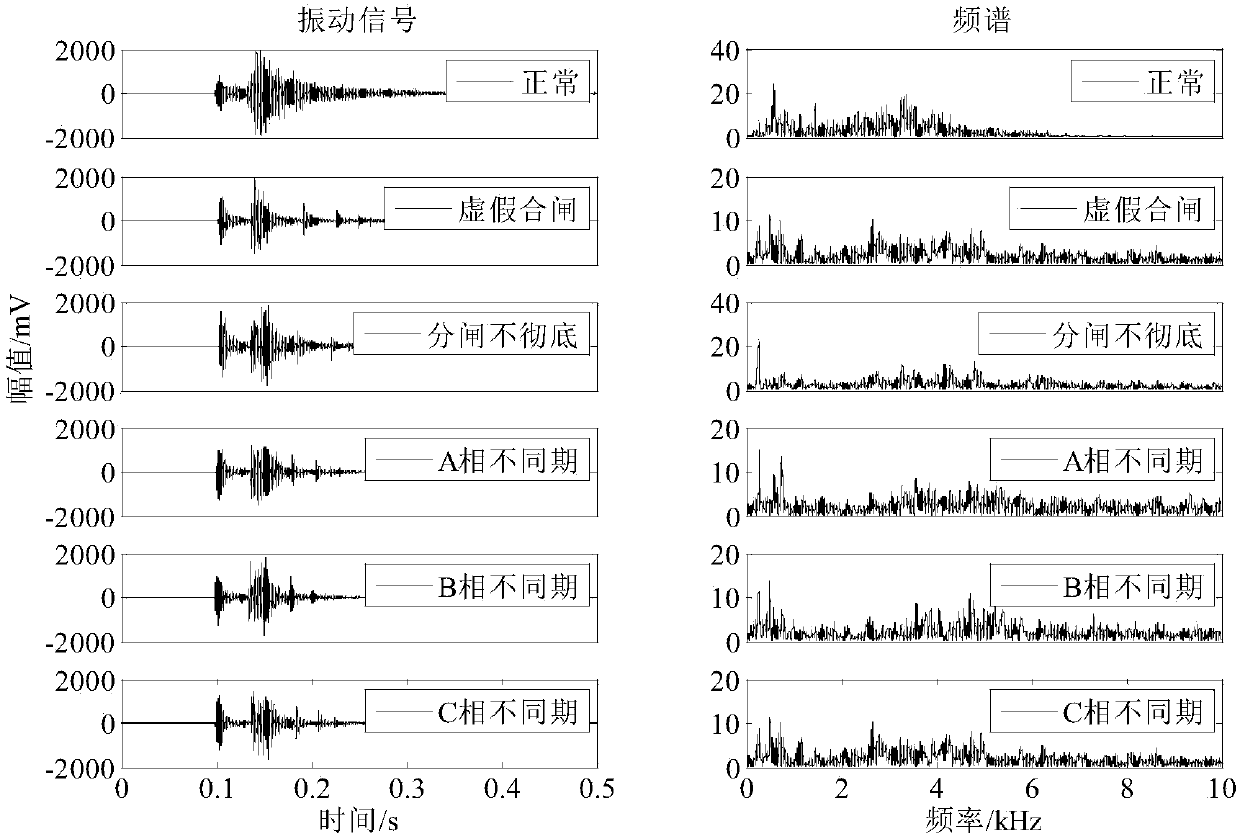
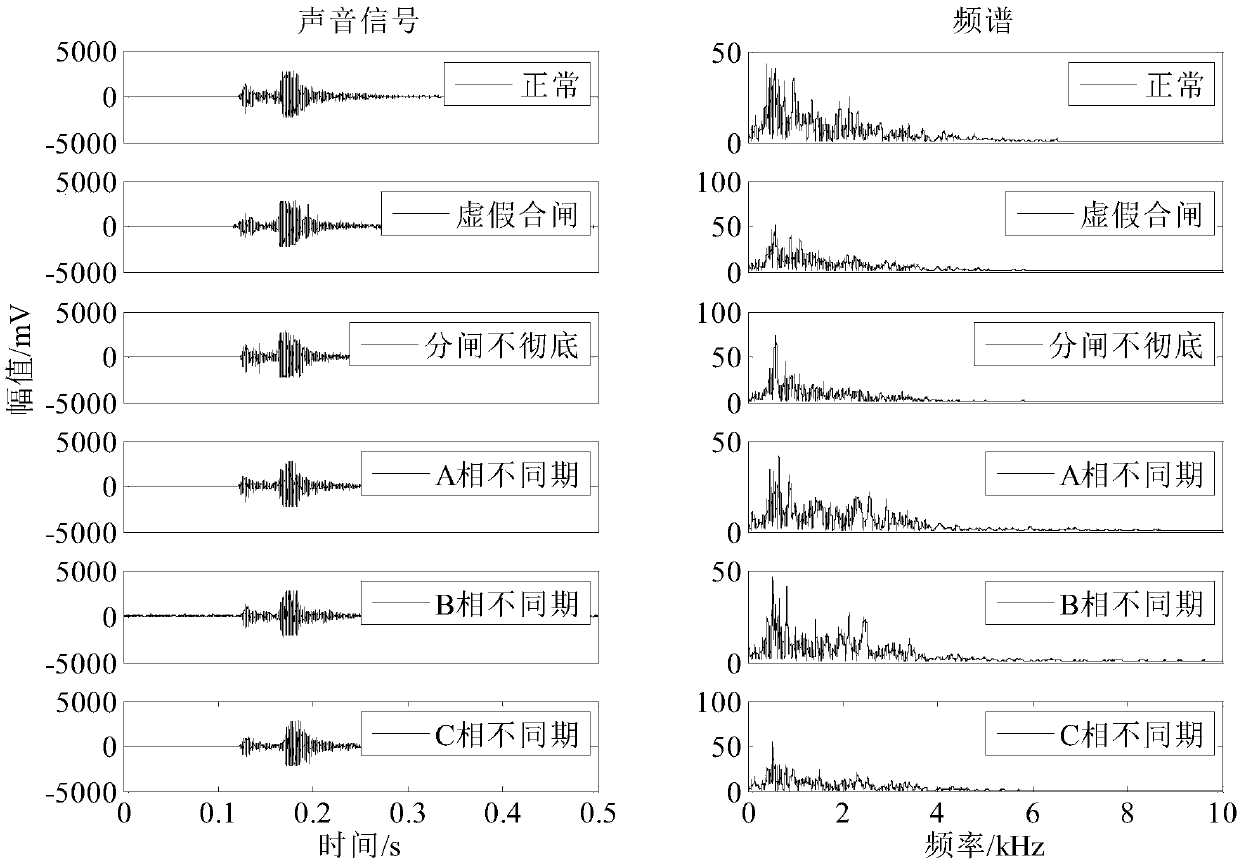
Universal circuit breaker mechanical fault diagnosis method based on feature fusion of vibration and sound signals
InactiveCN106017879AImprove reliabilityThe detection method is simpleMachine part testingCircuit interrupters testingDiagnostic Radiology ModalityMachining vibrations
The invention provides a universal circuit breaker mechanical fault diagnosis method based on feature fusion of vibration and sound signals. The method includes steps of 1, collecting machine vibration signals and machine sound signals during an engaging and disengaging process of a universal circuit breaker; 2, adopting an improved wavelet packet threshold value denoising algorithm for denoising; 3, adopting a complementary total average empirical mode decomposition algorithm for extracting a plurality of solid mode function components reflecting state information of engagement and disengagement actions of the circuit breaker from the denoising signals; 4, determining the number Z of the solid mode function components; 5, calculating the energy ratio, the sample ratio and the power spectrum entropy as three types of features; 6, adopting a combination core principal component analysis method for performing dimension reduction on a feature sample with unified three types of features of the vibration and the sound signals and obtaining M principle components; 7, establishing a related vector machine based sequence binary tree multiple classifier model.
Owner:HEBEI UNIV OF TECH
Automatic photo album page layout
A method for locating objects, such as images having fixed aspect ratios, within a predefined space, such as a printed page, is provided. The method comprises generating a binary tree structure comprising at least one node and a plurality of leaves, each leaf corresponding to an image and being associated with one node. The method further comprises characterizing a bounding box for each node in the binary tree structure, the bounding box establishing a boundary for all leaves associated with the node. The method also comprises manipulating bounding boxes to fit within the predefined space. The method may be selectively repeated to reposition images within the binary tree structure or to reform the binary tree structure and characterize and manipulate using the reformed binary tree structure. The end result is at least one potential layout having all images located within the predefined space.
Owner:HEWLETT PACKARD DEV CO LP
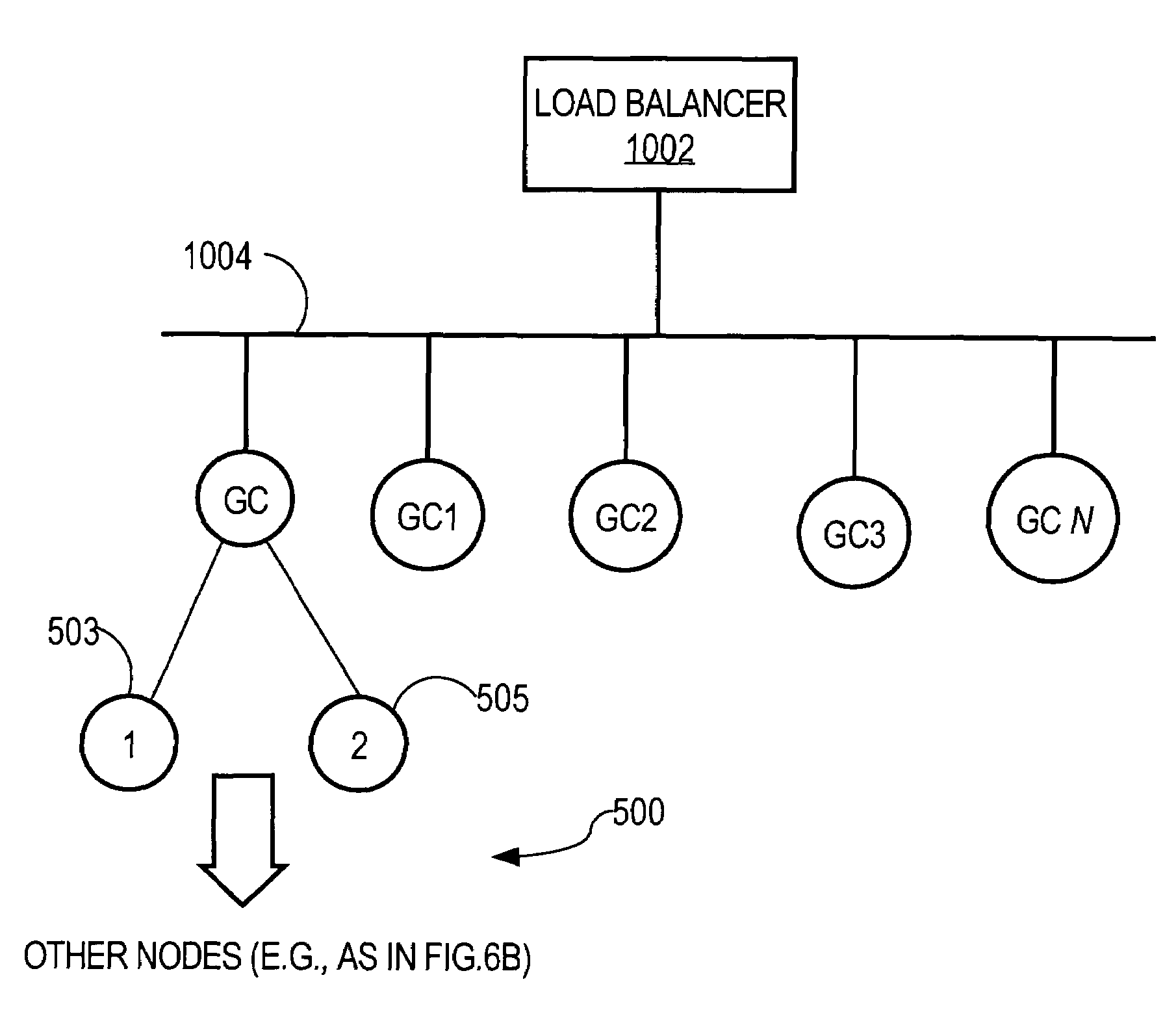
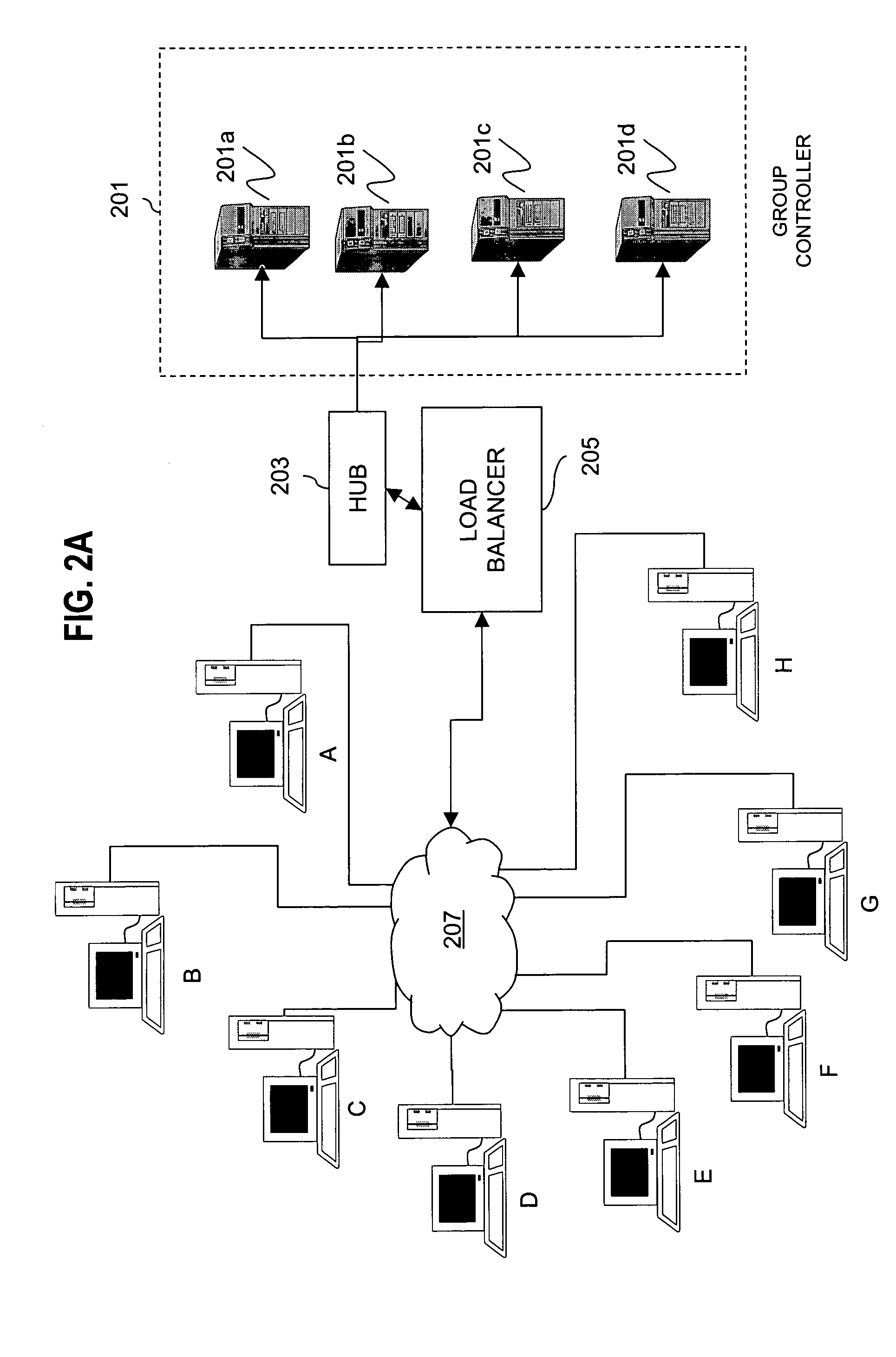
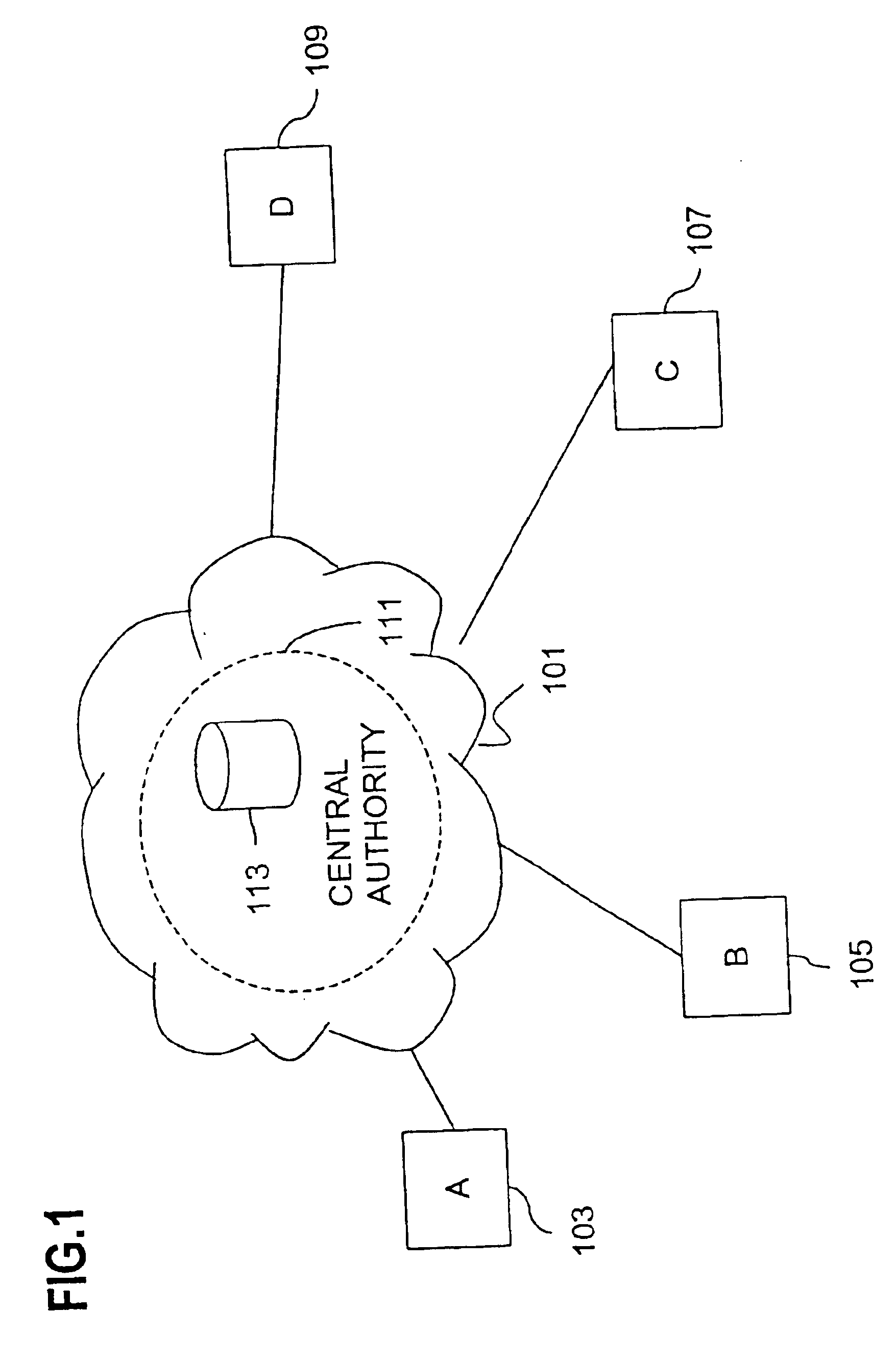
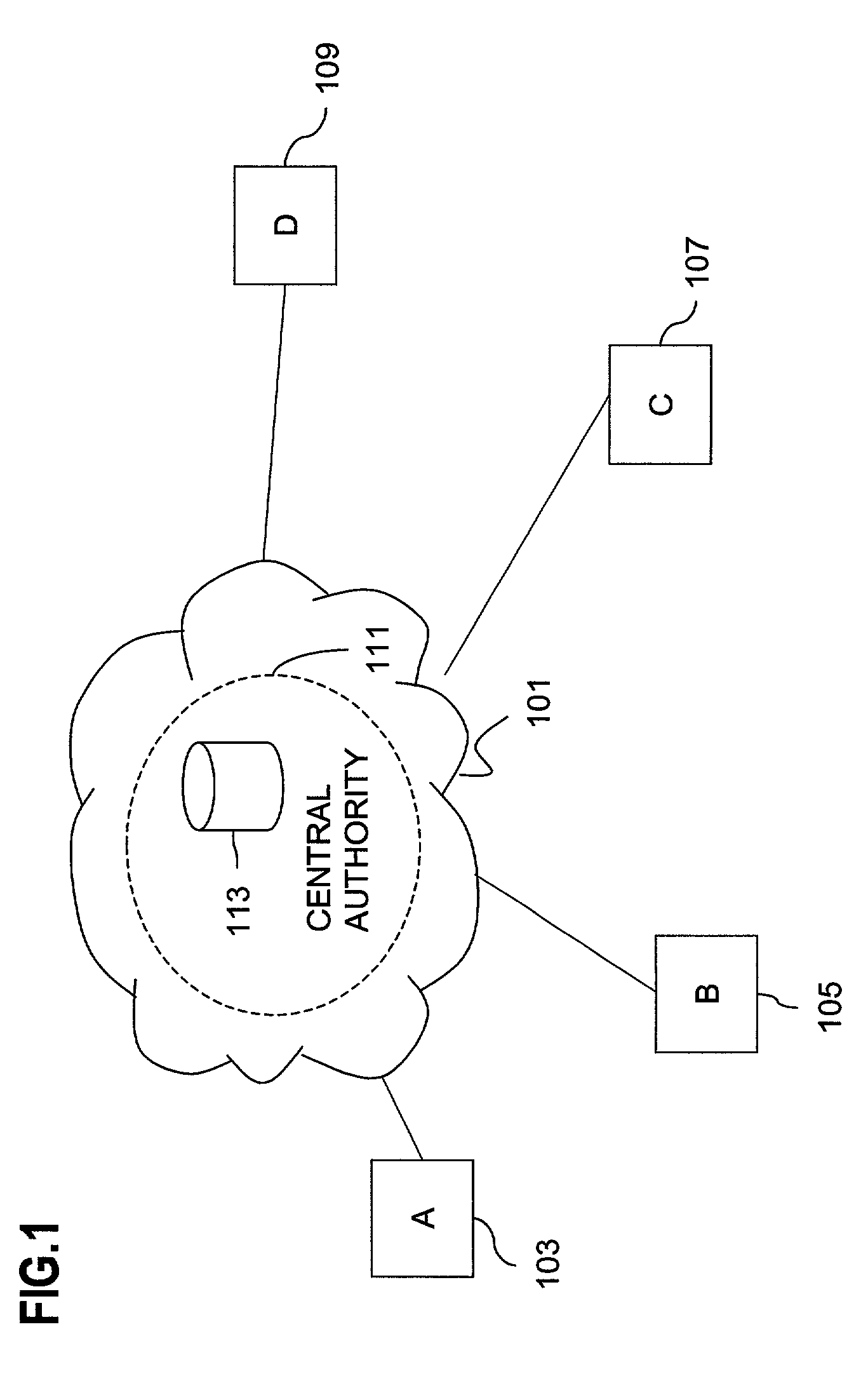
Method for overcoming the single point of failure of the central group controller in a binary tree group key exchange approach
InactiveUS7260716B1Improve scalabilityLess attentionKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer networkStructure of Management Information
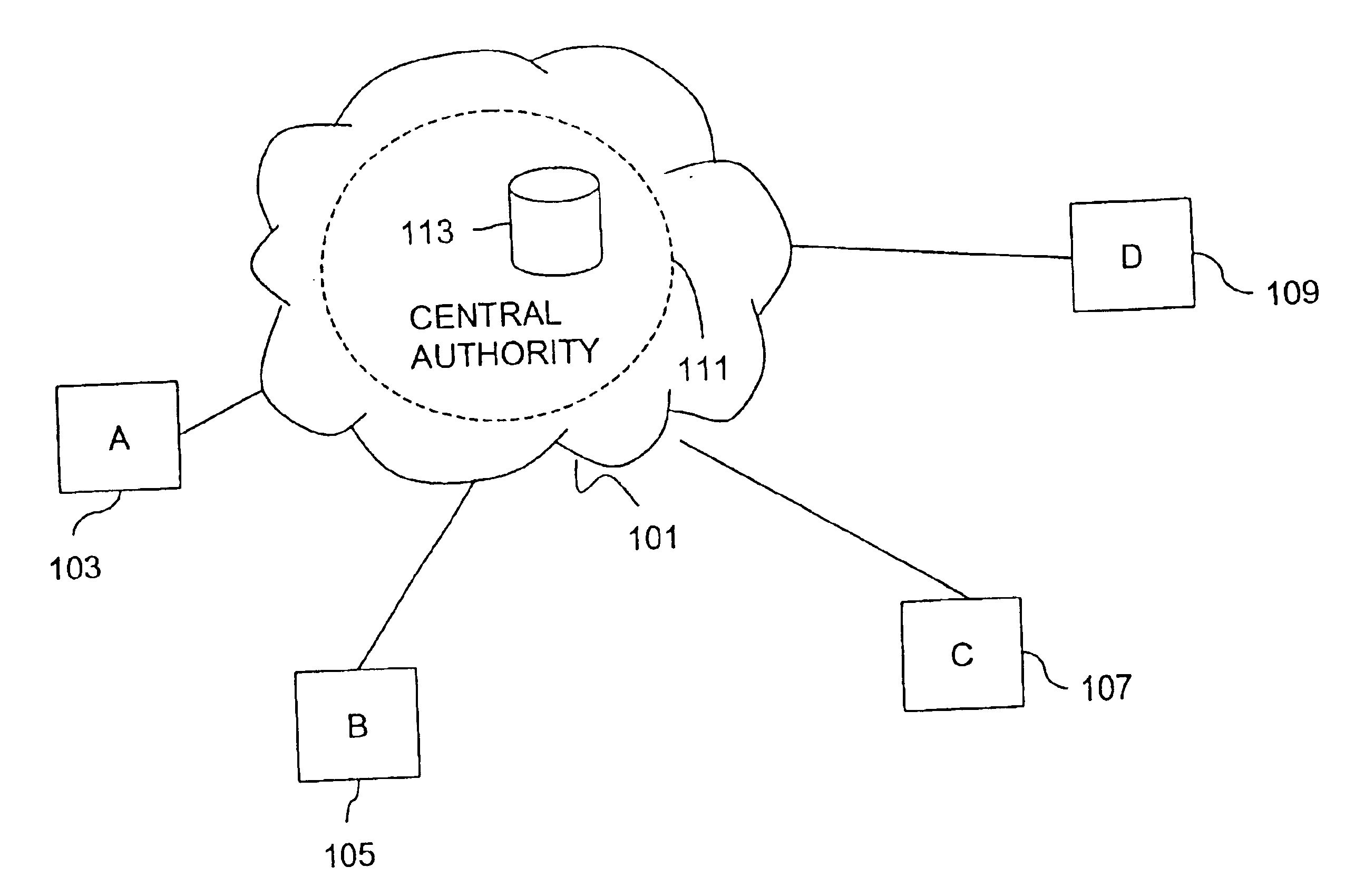
An approach for managing addition or deletion of nodes in a multicast or broadcast group, which avoids introducing a single point of failure at a group controller, certificate authority, or key distribution center, is disclosed. A central group controller utilizes a binary tree structure to generate and distribute session keys for the establishment of a secure multicast group among multiple user nodes. The central group controller is replicated in a plurality of other group controllers, interconnected in a network having a secure communication channel and connected to a load balancer. The secure communication channel is established using a public key exchange protocol. The load balancer distributes incoming join / leave requests to a master group controller. The master group controller processes the join or leave, generates a new group session key, and distributes the new group session key to all other group controller replicas. Each group controller is successively designated as master group controller in real time when a former master group controller crashes or relinquishes its master authority.
Owner:CISCO TECH INC
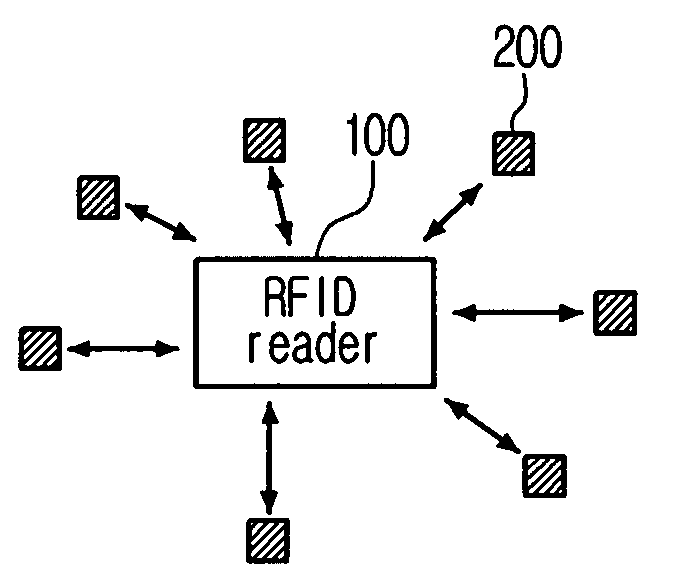
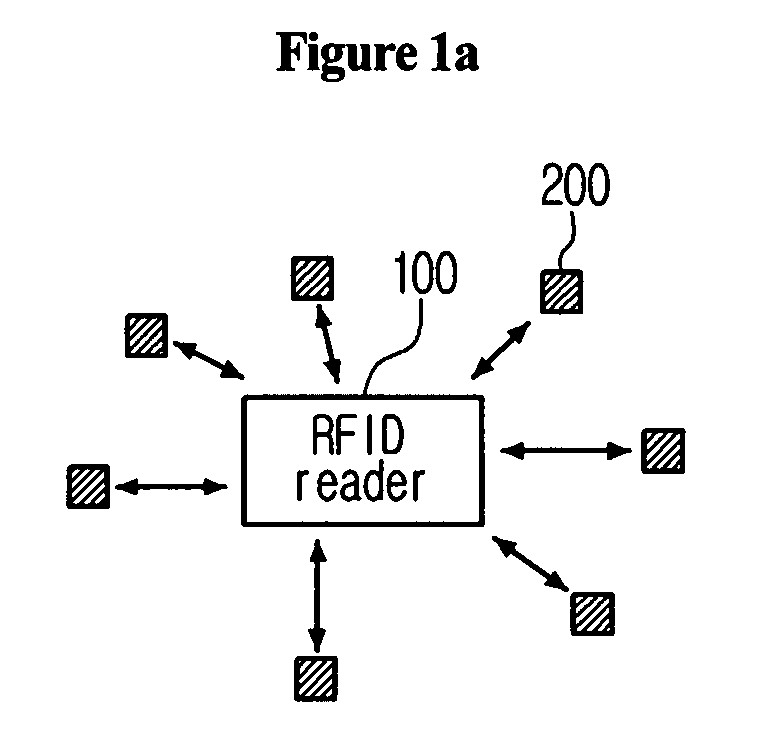
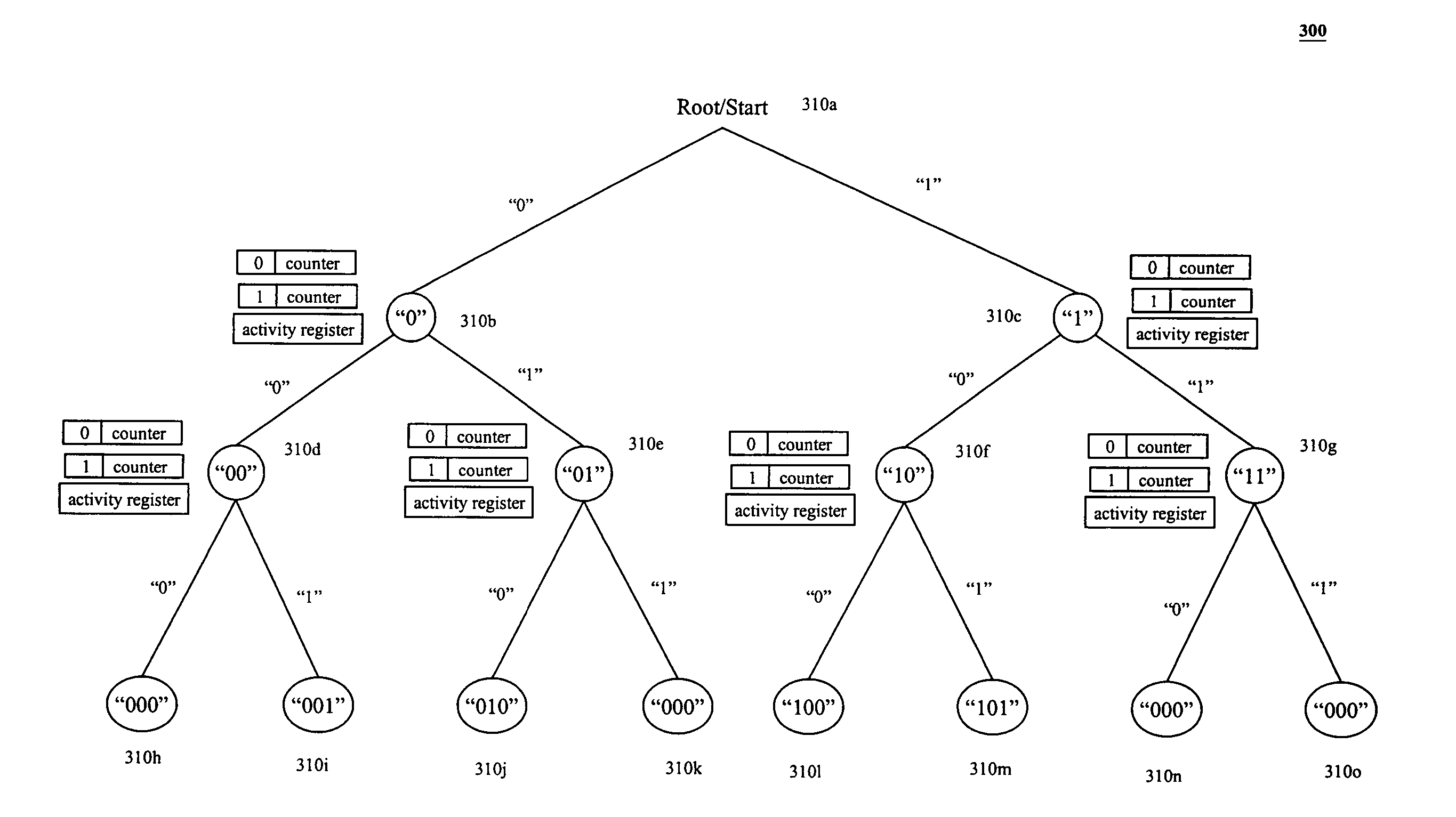
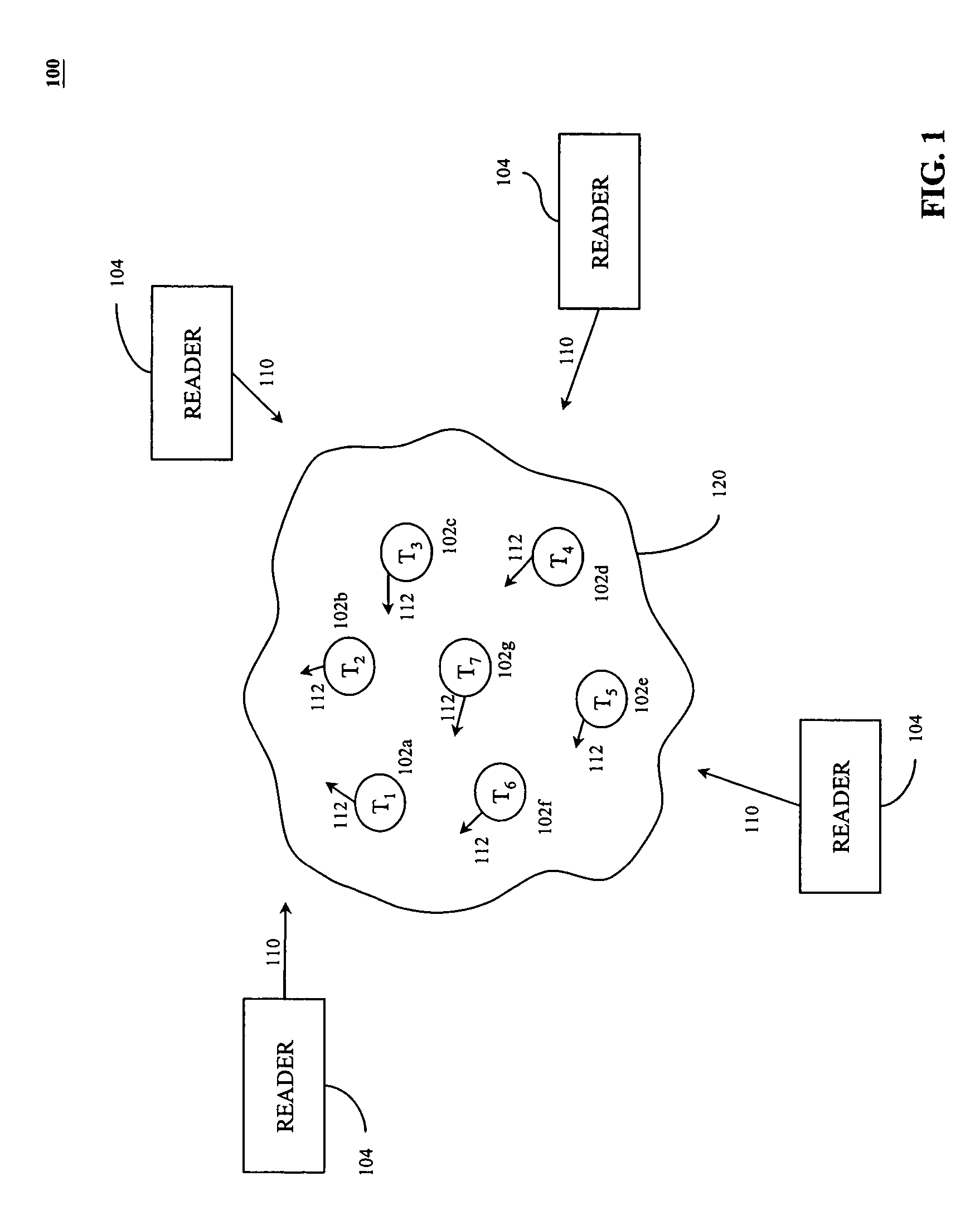
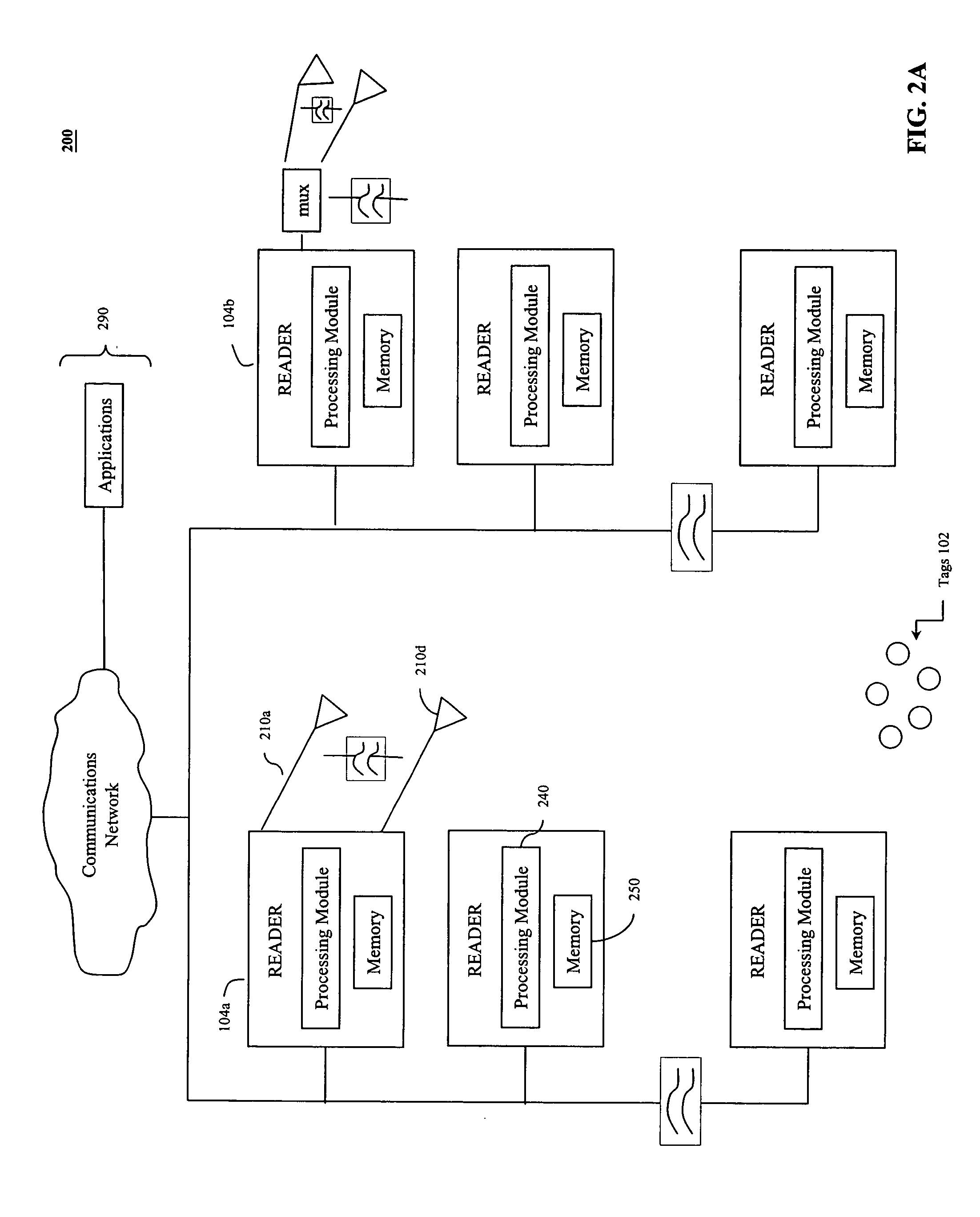
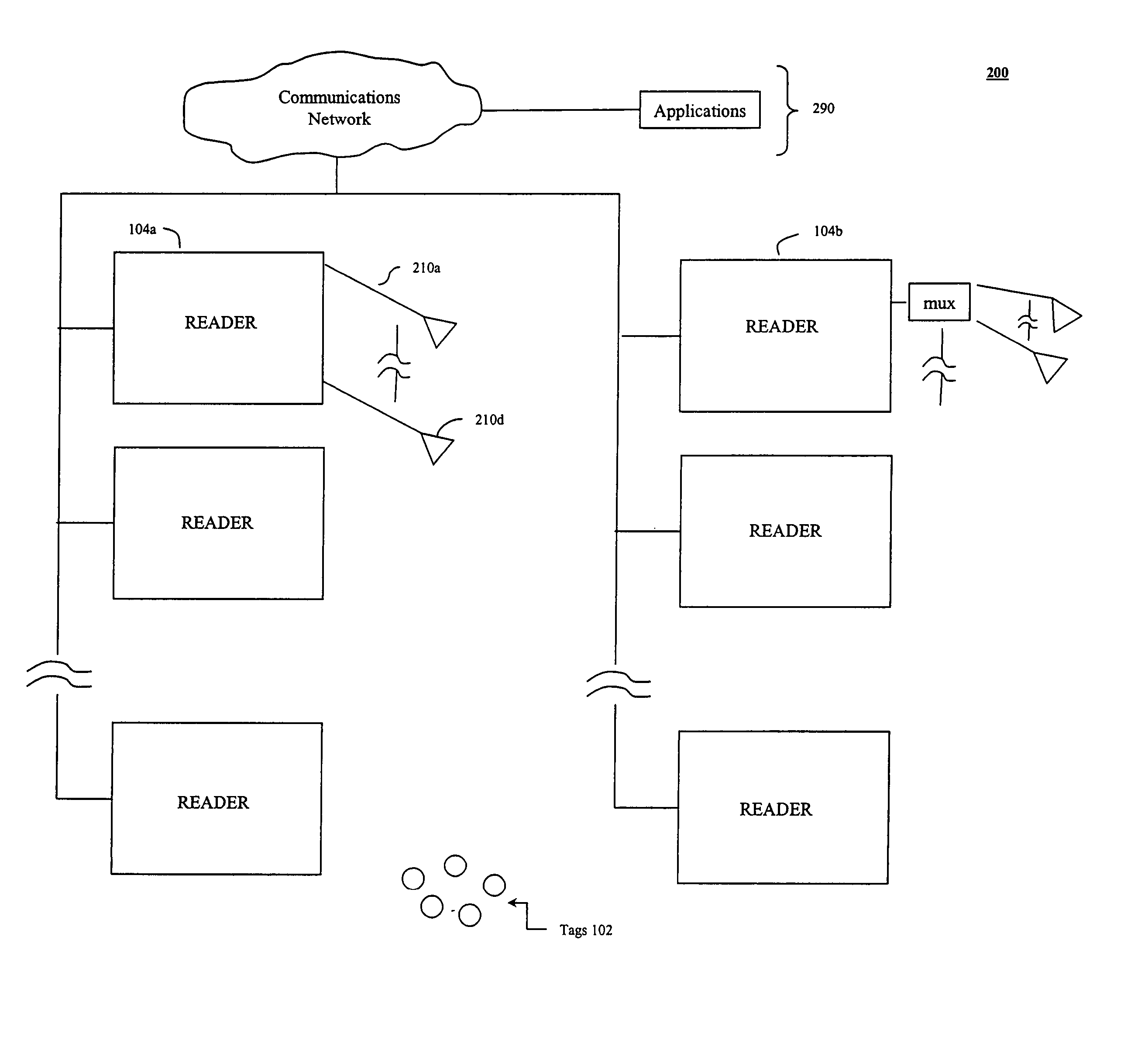
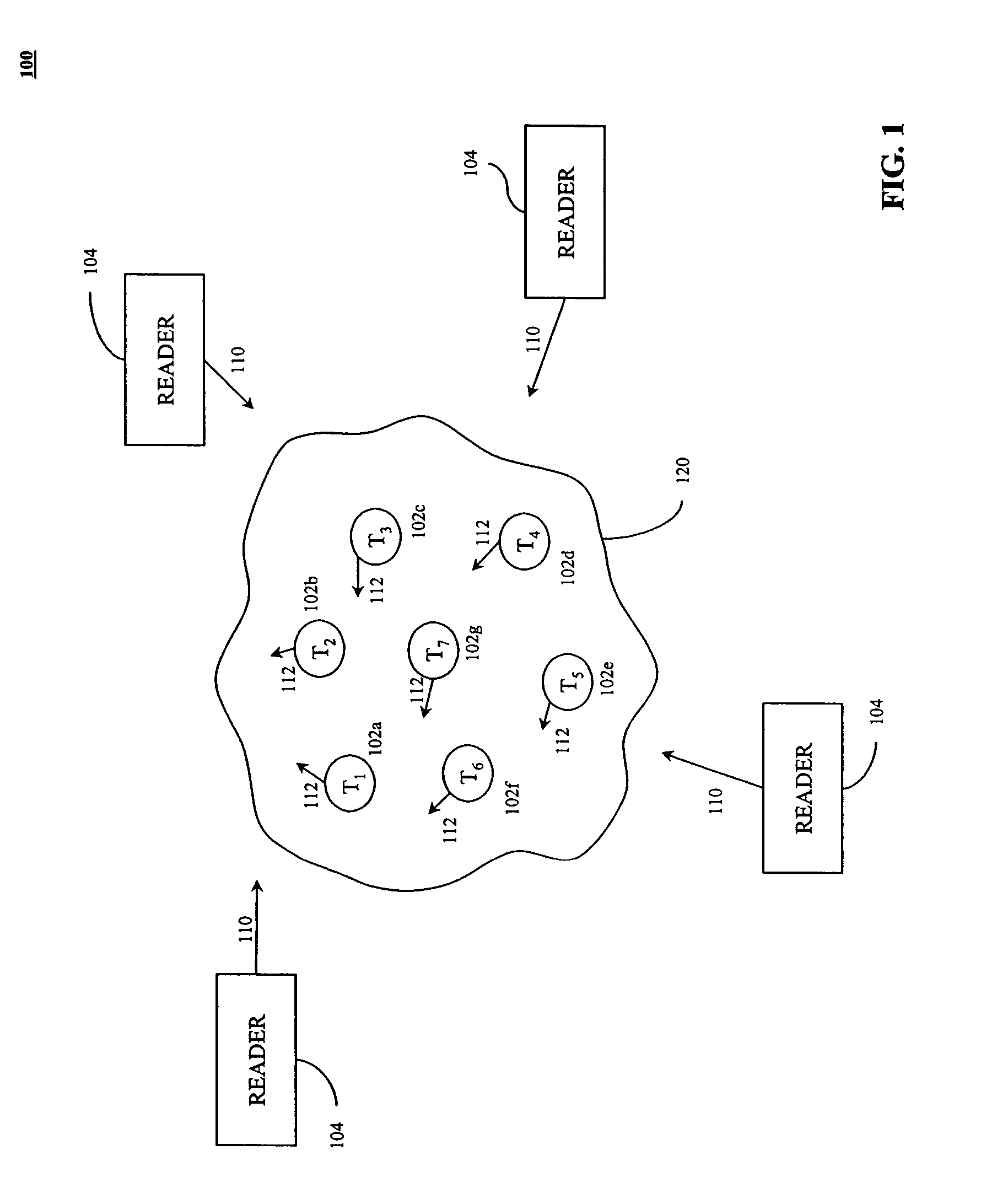
Method for the efficient reading of a population of radio frequency identification tags with unique identification numbers over a noisy air channel
ActiveUS7068148B2Improve efficiencyEfficiently read a binary treeNear-field transmissionMemory record carrier reading problemsTheoretical computer scienceBinary tree
A method for reading and tracking radio frequency identification (RFID) tags in the presence of a noisy air channel is provided. In accordance with the method, a binary tree data structure is used to characterize a plurality of RFID tags, each of which is associated with a unique identification (ID) number. During communication between a tag reader and one or more RFID tags, the tag reader traverses the binary tree, eliminating tags from communication until one tag with a unique ID number is isolated and verified. As the binary tree is traversed, counters associated with each node in the tree are incremented based on tag matches, such that, over time, counters associated with nodes in tag-populated branches will tend to have a high value and counters associated with nodes in unpopulated tree branches will tend to have low values. Where the read process is subject to noise and the tag reader is forced make a decision at a branching node, the tag reader makes a branch prediction based on the current value of the node counters associated with each of the possible alternative branches.
Owner:SYMBOL TECH LLC
Method for producing 3D perspective view avionics terrain displays
InactiveUS6862501B2Reduce computationReduce data loadData processing applicationsAnalogue computers for trafficTerrainAviation
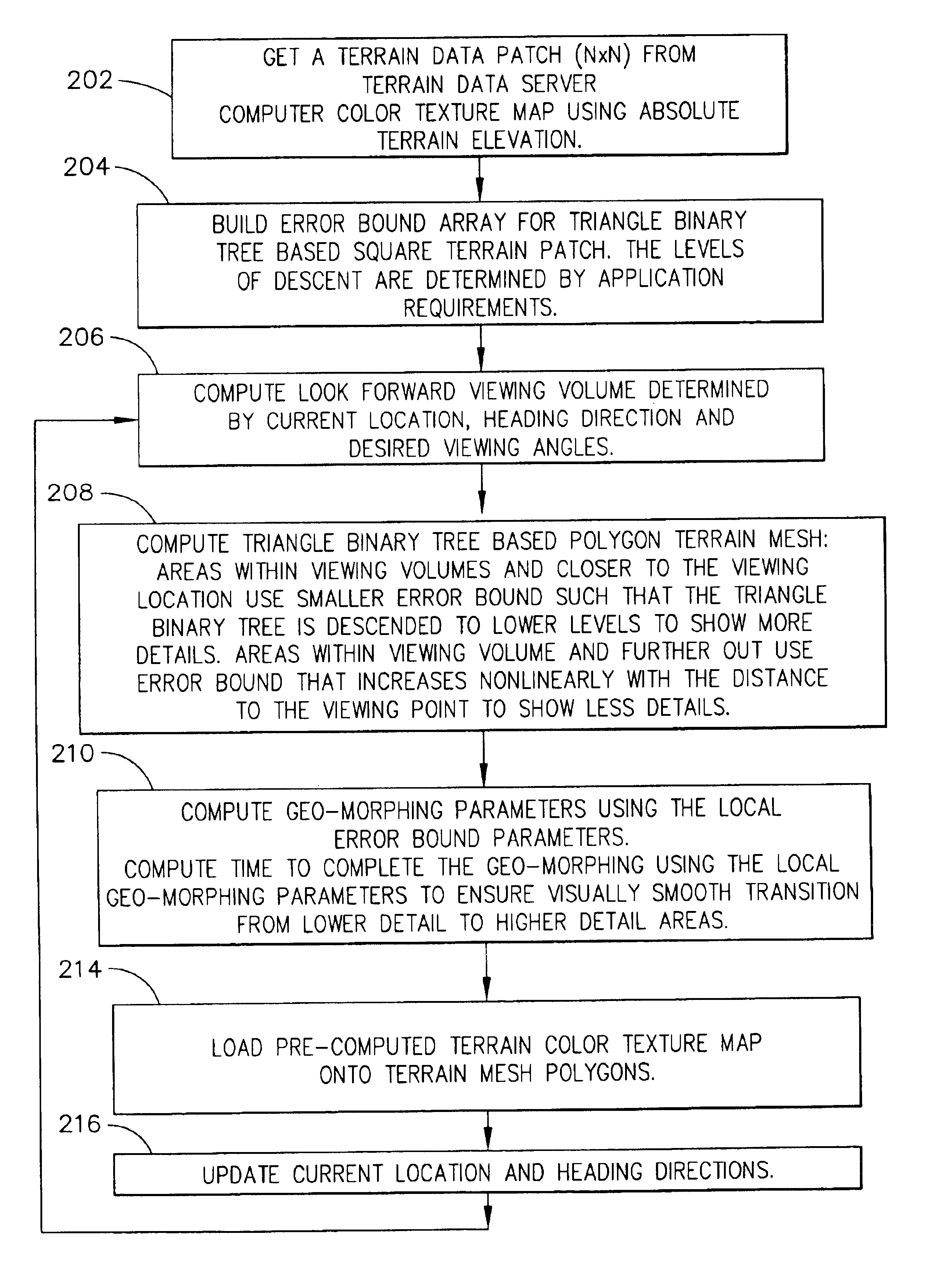
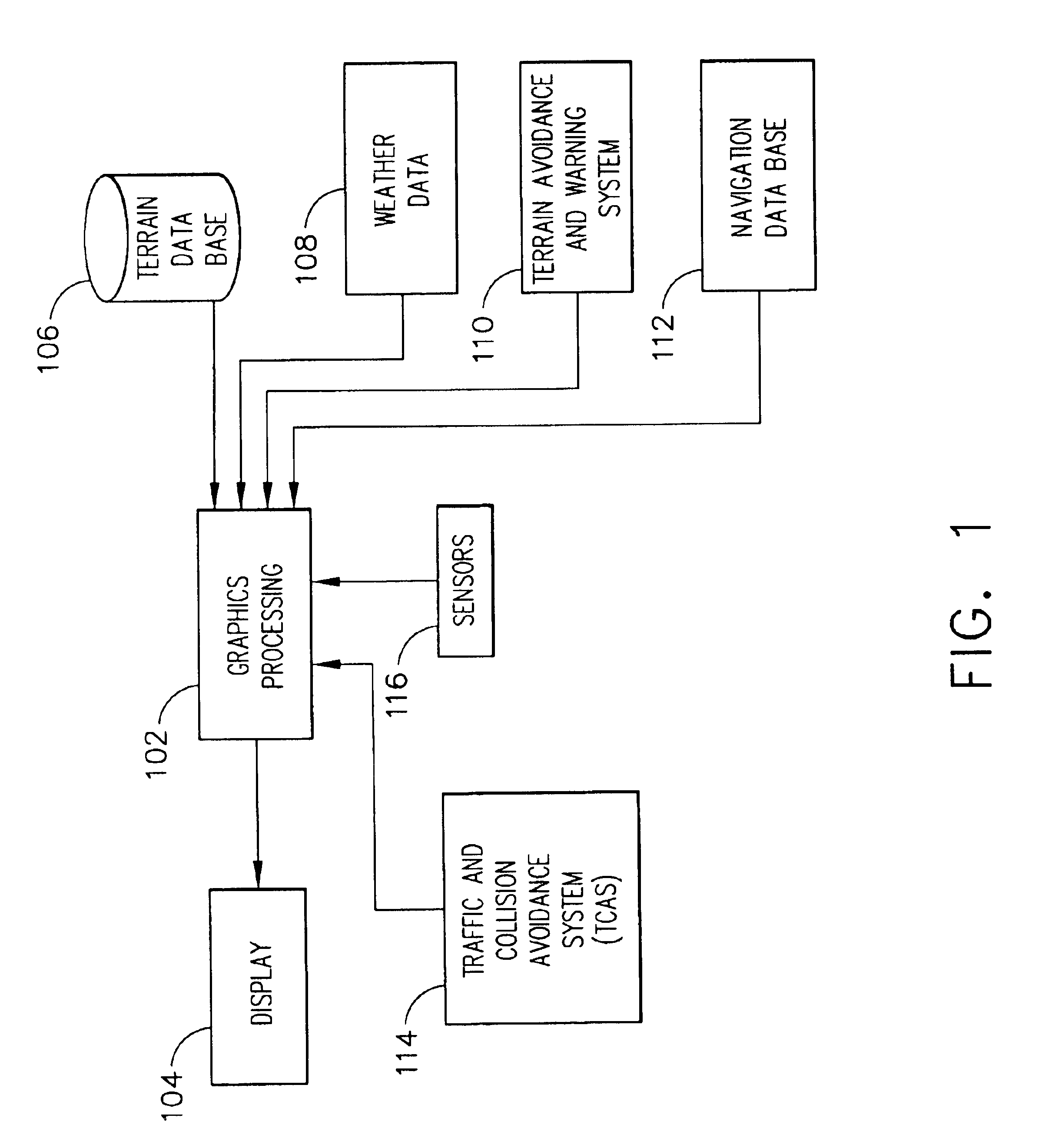
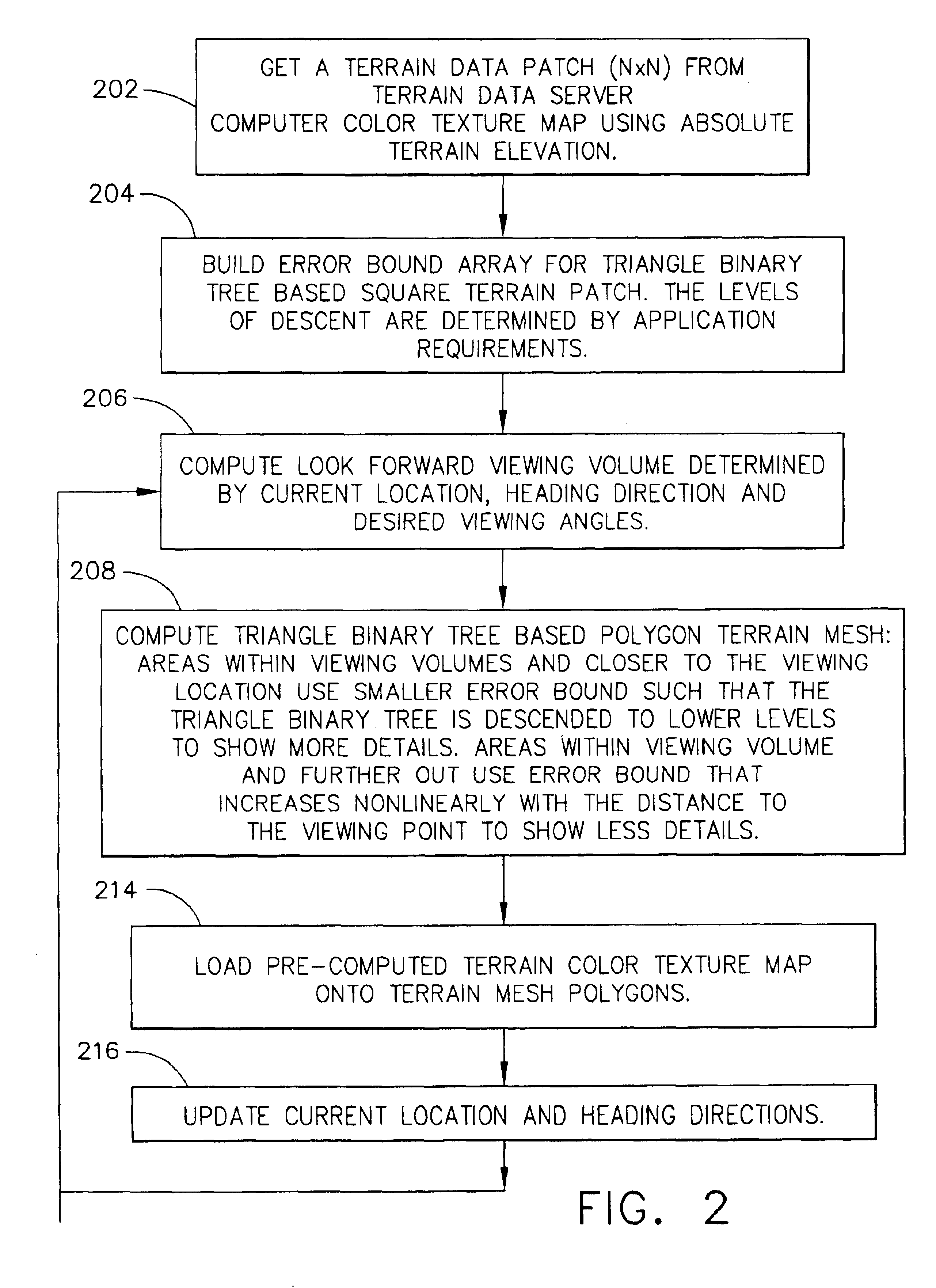
Methods for generating information for displaying terrain on an aircraft display system that significantly reduces the computation and data load for producing the terrain display. This is accomplished through the use of intelligent level of detail control that computes and displays terrain and dynamic on-terrain perspective projection lines and distance rings aligned with the aircraft heading for depth perception and relative altitude awareness. The terrain details are processed and displayed in a manner that shows all significant terrain features, e.g., peaks, towers, and the like, but through the use of nonlinear error bound geometric morphing, coupled with triangle binary tree based terrain mesh generation, the polygon count, and thus the computational load, are significantly reduced, while visual fidelity is maintained.
Owner:HONEYWELL INT INC
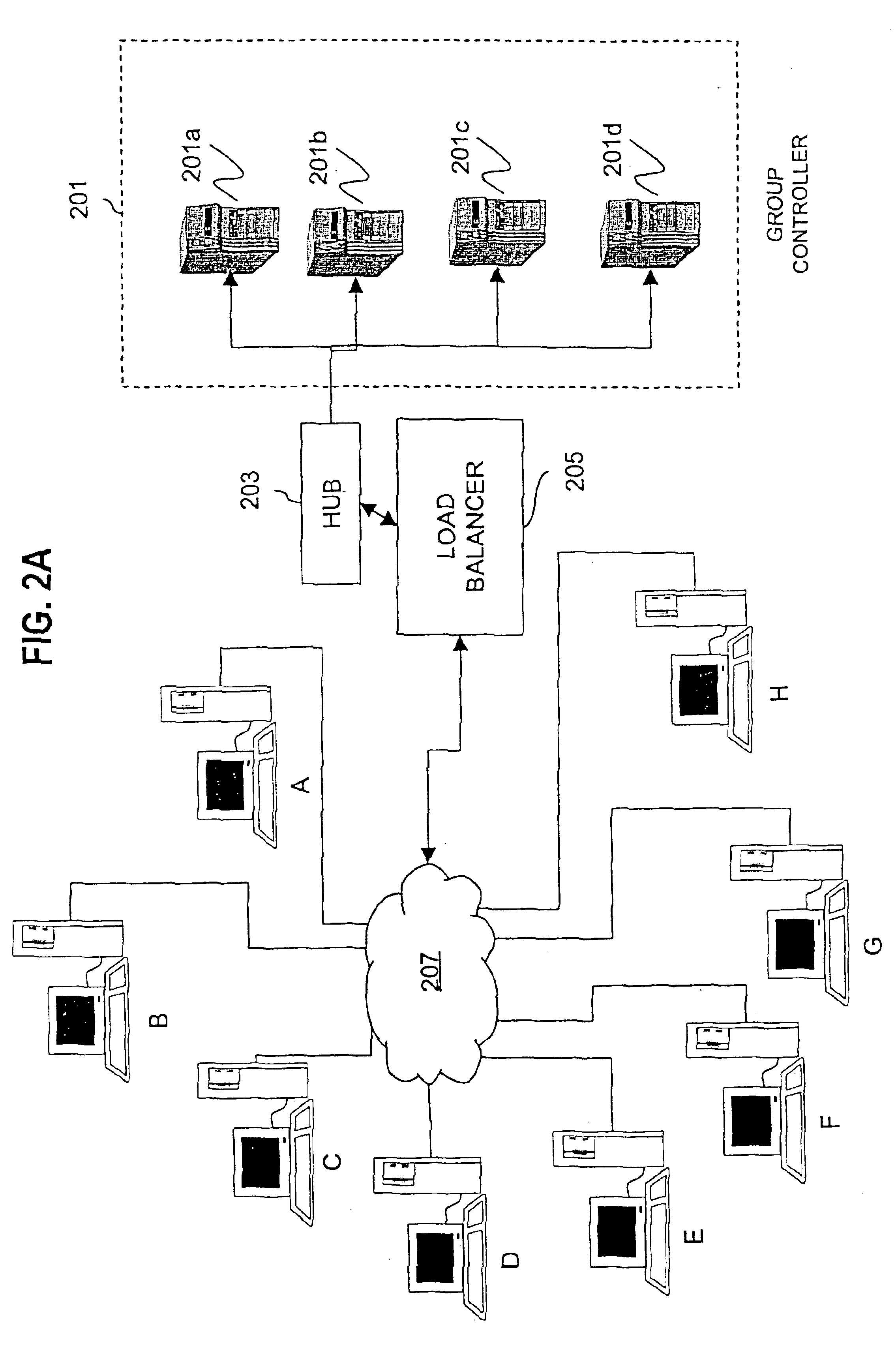
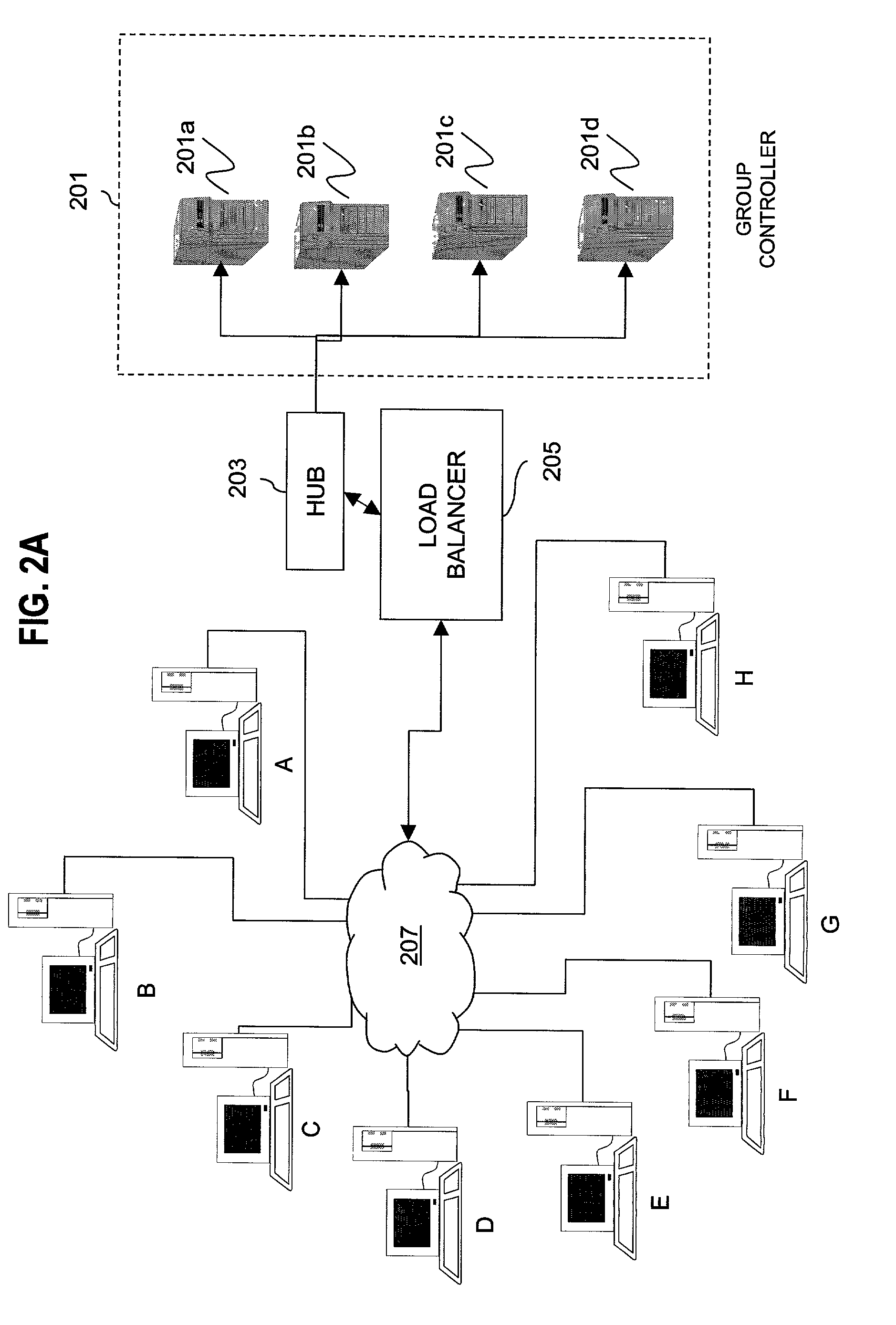
Method and apparatus for distributing and updating group controllers over a wide area network using a tree structure
InactiveUS6901510B1Reduces the workload on the group controllerSpecial service provision for substationKey distribution for secure communicationBinary treeWide area network
Apparatus and computer-readable media are disclosed for establishing secure multicast communication among multiple multicast proxy service nodes of domains of a replicated directory service that spans a wide area network. Domains are organized in a logical tree. Each domain has a logical tree that organizes the multicast proxy service nodes, a group manager at the root node, a multicast key distribution center, multicast service agent, directory service agent and key distribution center. Multicast proxy service nodes store a group session key and a private key. Replication of the directory performs key distribution. A multicast group member joins or leaves the group by publishing message. The local key distribution center and multicast service agent obtain the publisher's identity from a local directory service agent. Based on the identity, a secure channel is established with the directory service agent in the group member's domain. Keys of the binary tree branch that contains the joining or leaving node are updated, and an updated group session key and a new private key are received.
Owner:CISCO TECH INC
Optimization of a binary tree traversal with secure communications
InactiveUS20040134984A1Improve securityData switching detailsMemory record carrier reading problemsSecure communicationTree traversal
Methods and systems for the negotiation of a population of RFID tags with improved security is provided. In one aspect, a binary traversal is performed to singulate tags without using information that directly identifies the tags in the tag population. A key is generated to identify each RFID tag of the population of RFID tags. The generated key does not include bits identifying an item with which the particular RFID tag is associated. A binary tree algorithm is operated to identify one or more tags in the population of RFIDs tags using the generated keys. In another aspect, frequency hopping and / or spread spectrum techniques are used to provide improved security while negotiating tags. In another aspect, the reader causes the tags to scroll series of bits back to the reader for each bit sent to the tags to provide improved security.
Owner:SYMBOL TECH INC
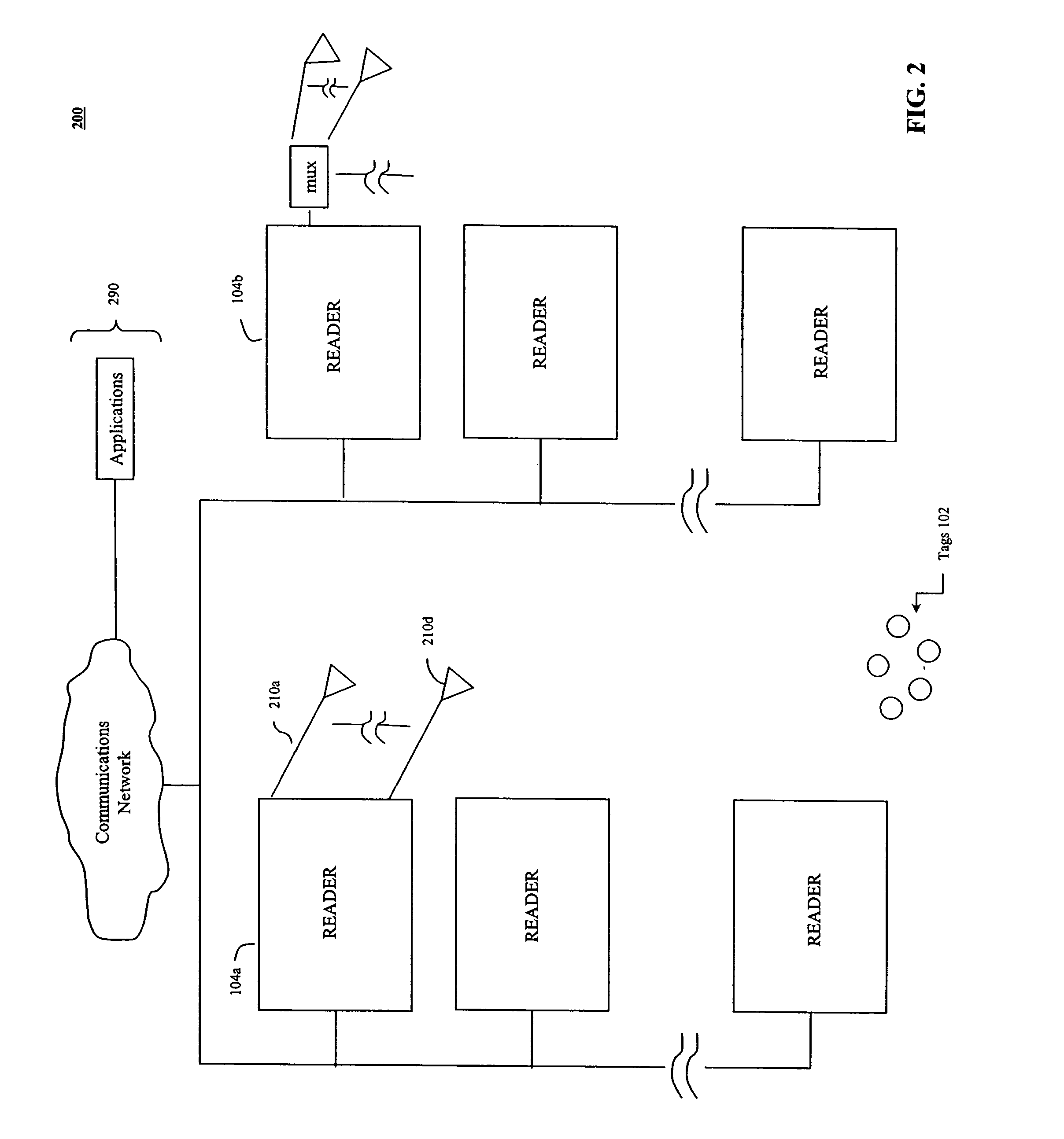
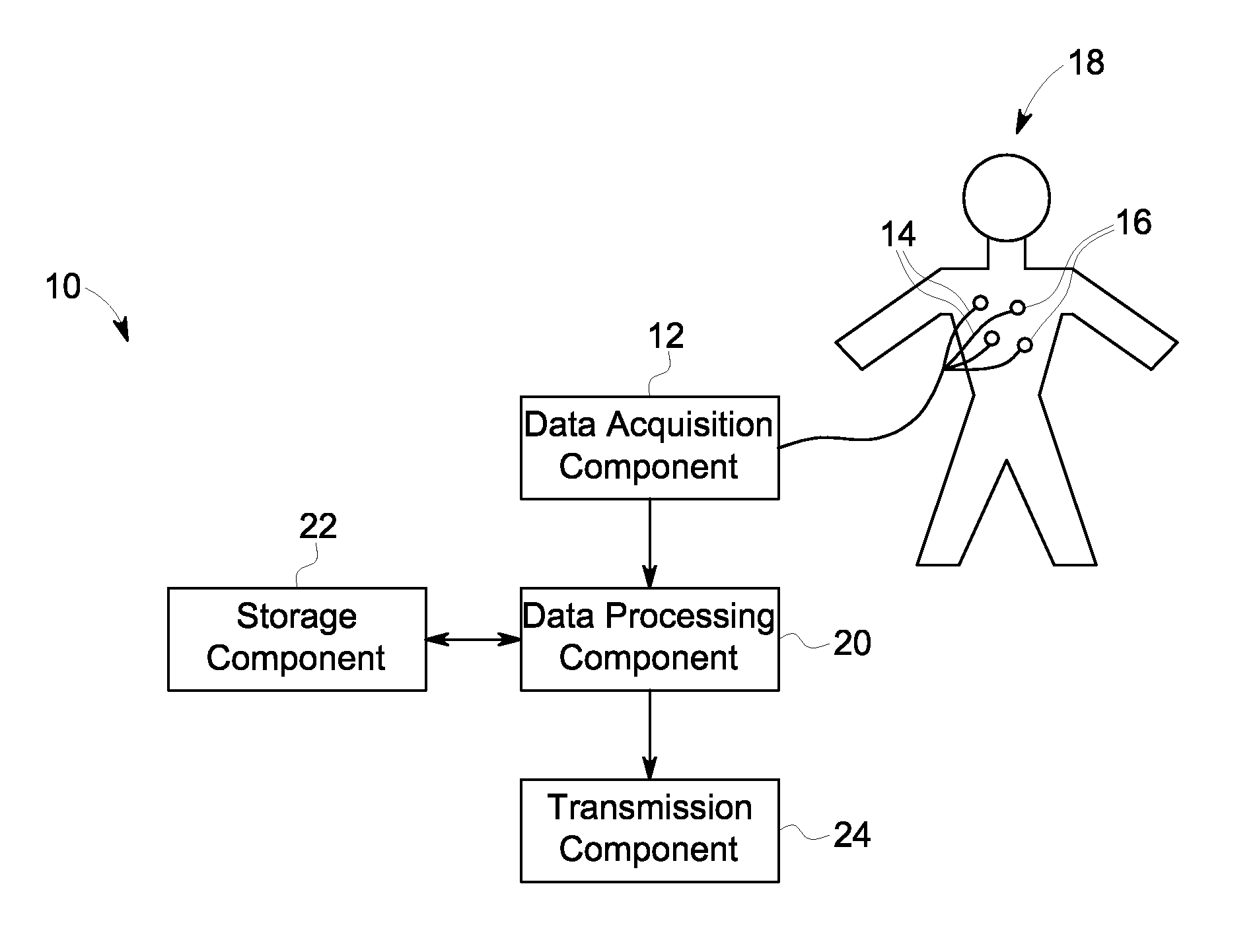
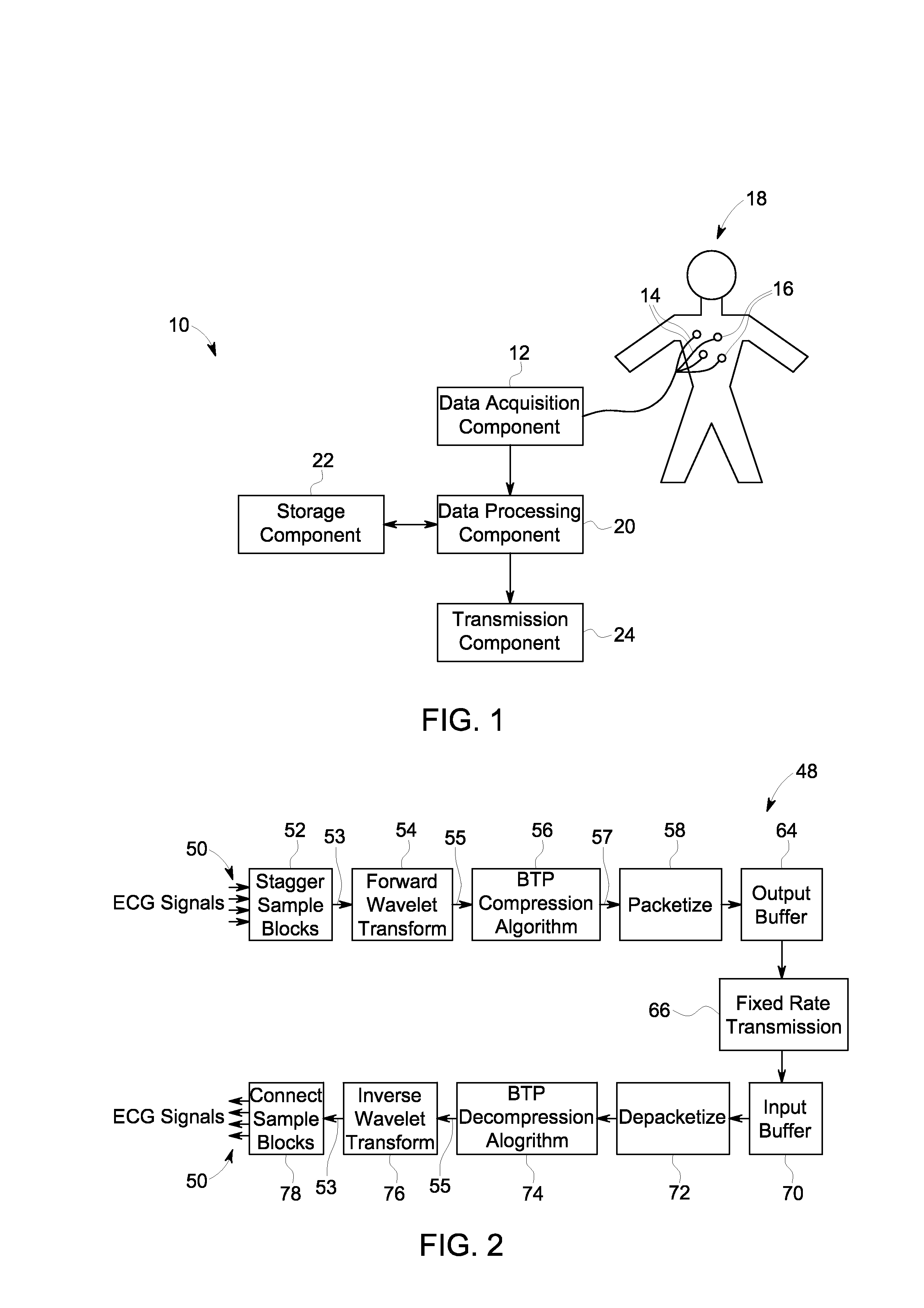
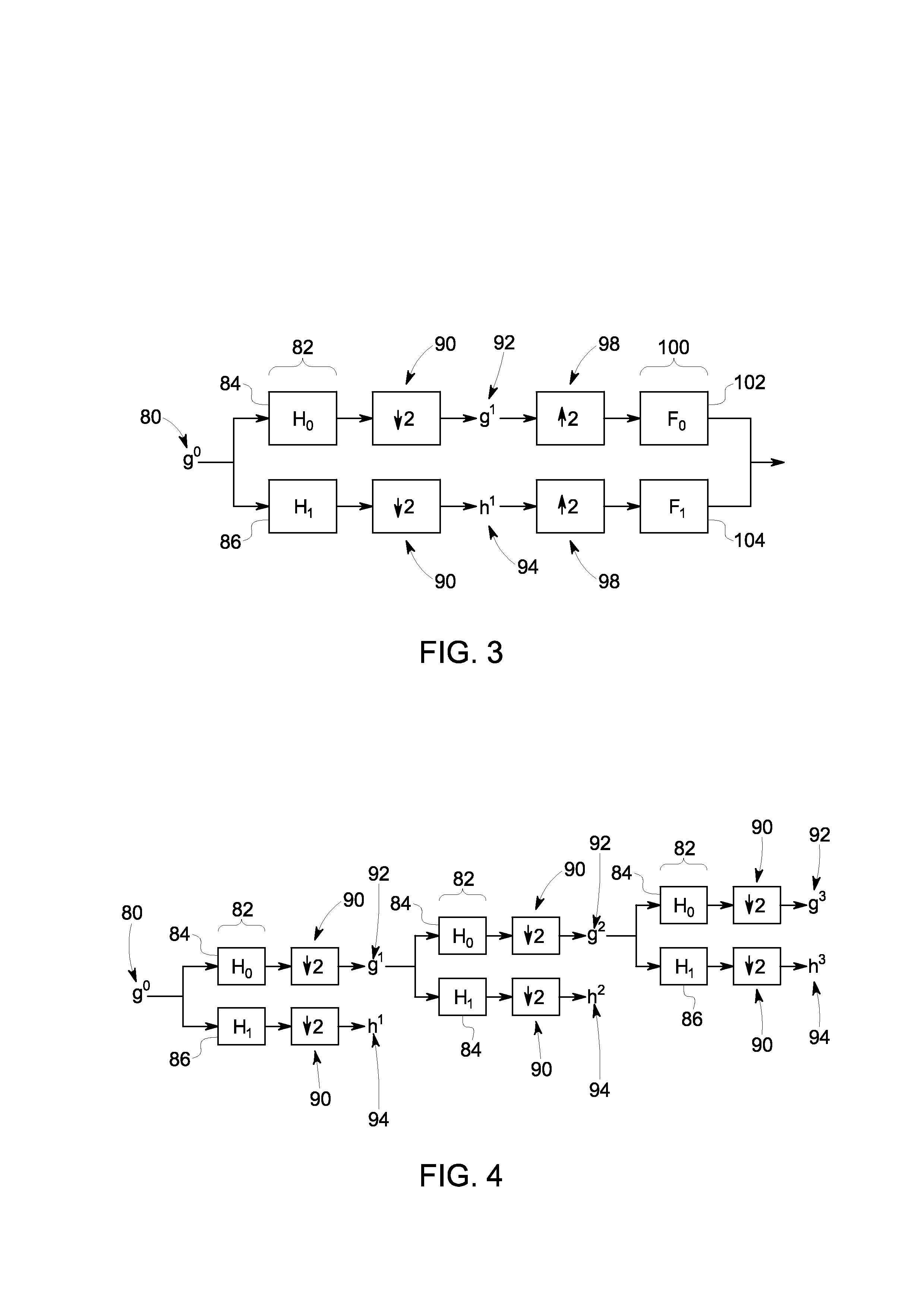
Compression of electrocardiograph signals
A generally lossless compression system suitable for compression of data in a real-time, remote monitoring application is disclosed. In one embodiment, the real-time monitoring application is subject to a fixed-delay transmission constraint. In one implementation, a specific set partitioning method (e.g., binary tree partitioning) is employed on blocks of data that are wavelet transformed in a reversible manner so that encoded blocks may be transmitted losslessly or truncated and transmitted with some loss.
Owner:GENERAL ELECTRIC CO
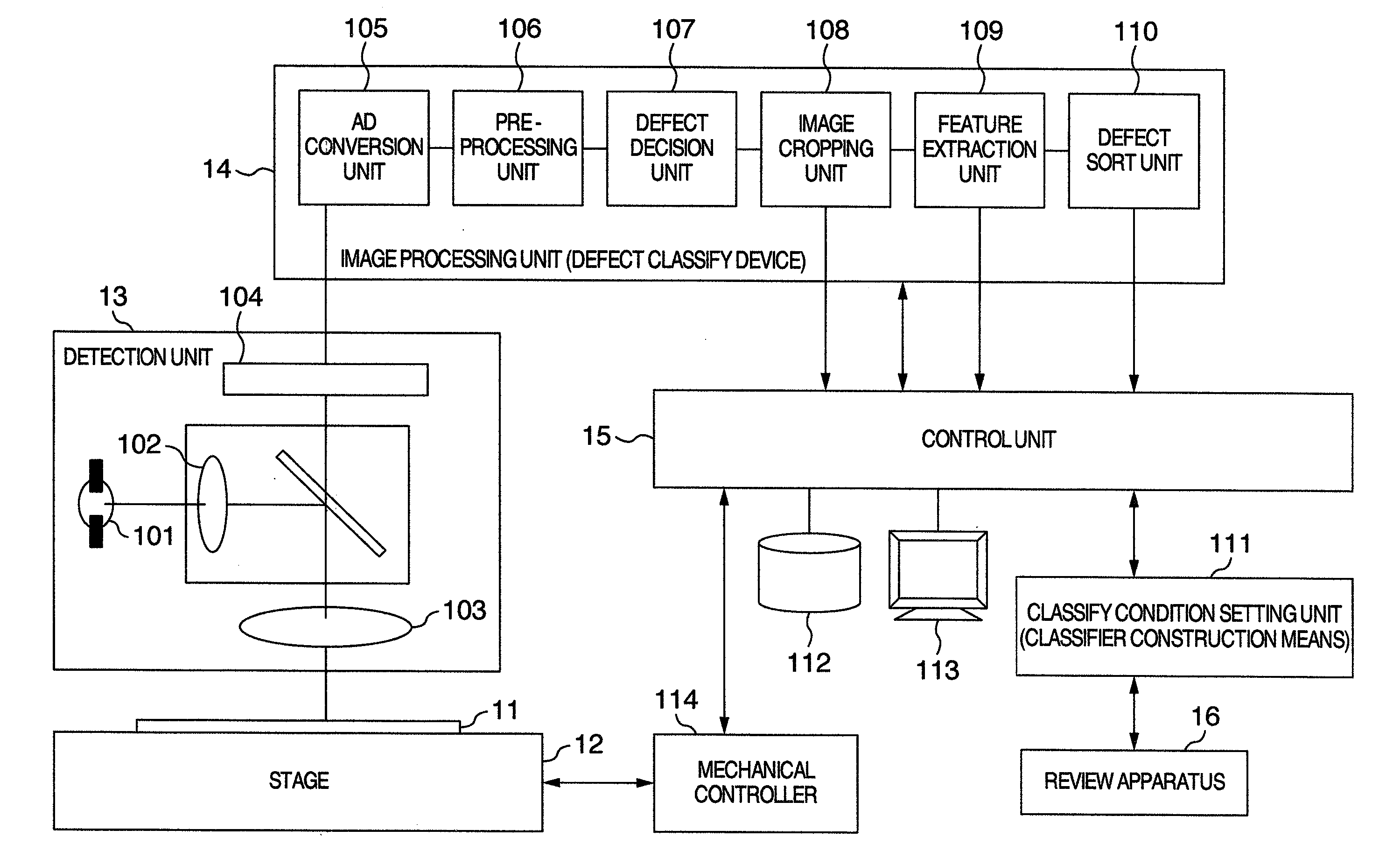
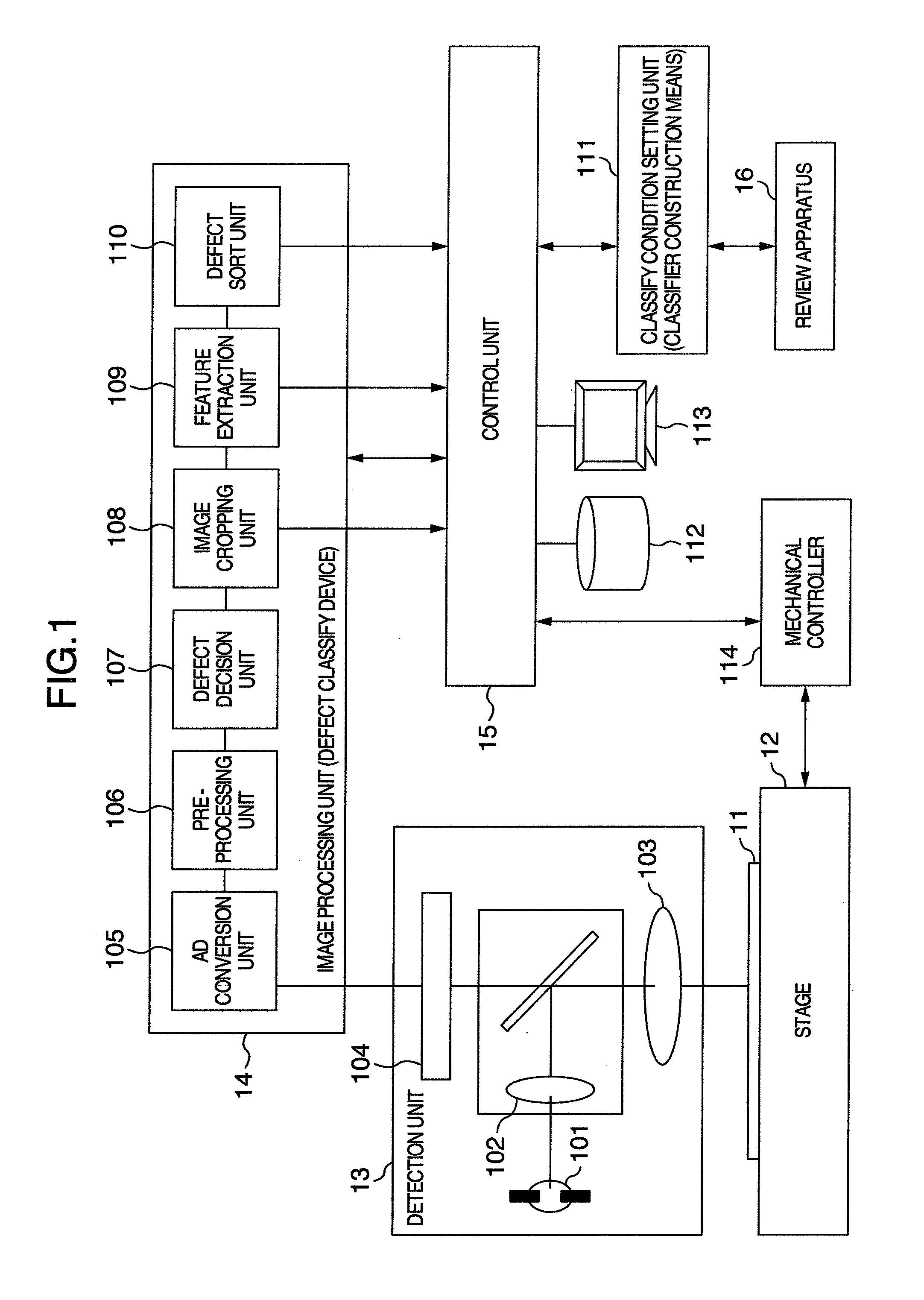
Defect classification method and apparatus, and defect inspection apparatus
InactiveUS20080075352A1Easy to understandEasy to set upImage enhancementImage analysisClassification methodsFeature data
A defect classification method to classify defects by using a classifier having a binary tree structure based on features of defects extracted from detected signals acquired from a defect inspection apparatus includes a classifier construction process for constructing the classifier by setting a branch condition including defect classes respectively belonging to groups located on both sides of the branch point, a feature to be used for branching, and a discriminant reference, for each branch point in the structure based on instruction of defect classes and feature data respectively associated therewith beforehand. The process includes a priority order specification process for previously specifying target classification performance of purity and accuracy for each defect class, whole and in worst case, with priority order, and an evaluation process for evaluating whether the specified target classification performance under the branching condition is satisfied and displaying a result of evaluation, every item.
Owner:HITACHI HIGH-TECH CORP
Method and apparatus providing secure multicast group communication
InactiveUS7434046B1Eliminating single point of failureReduce in quantityKey distribution for secure communicationMultiple keys/algorithms usageComputer networkGroup session
An approach for establishing secure multicast communication among multiple members that participate in a multicast group is disclosed. In one feature, multiple multicast proxy service nodes (MPSNs) are defined and control when members join or leave the multicast group. The MPSNs are logically represented by a first binary tree in which each node of the first binary tree is associated with a domain of a directory service and one or more of the MPSNs. A second binary tree is created that has leaf nodes representing each member. The second binary tree is stored in a domain of the directory service with a root node that represents one or more of the MPSNs. The members can each establish multicast communication and serve as a key distribution center. When a member joins the multicast group, a new group session key is determined by replicating a branch of the second binary tree.
Owner:CISCO TECH INC
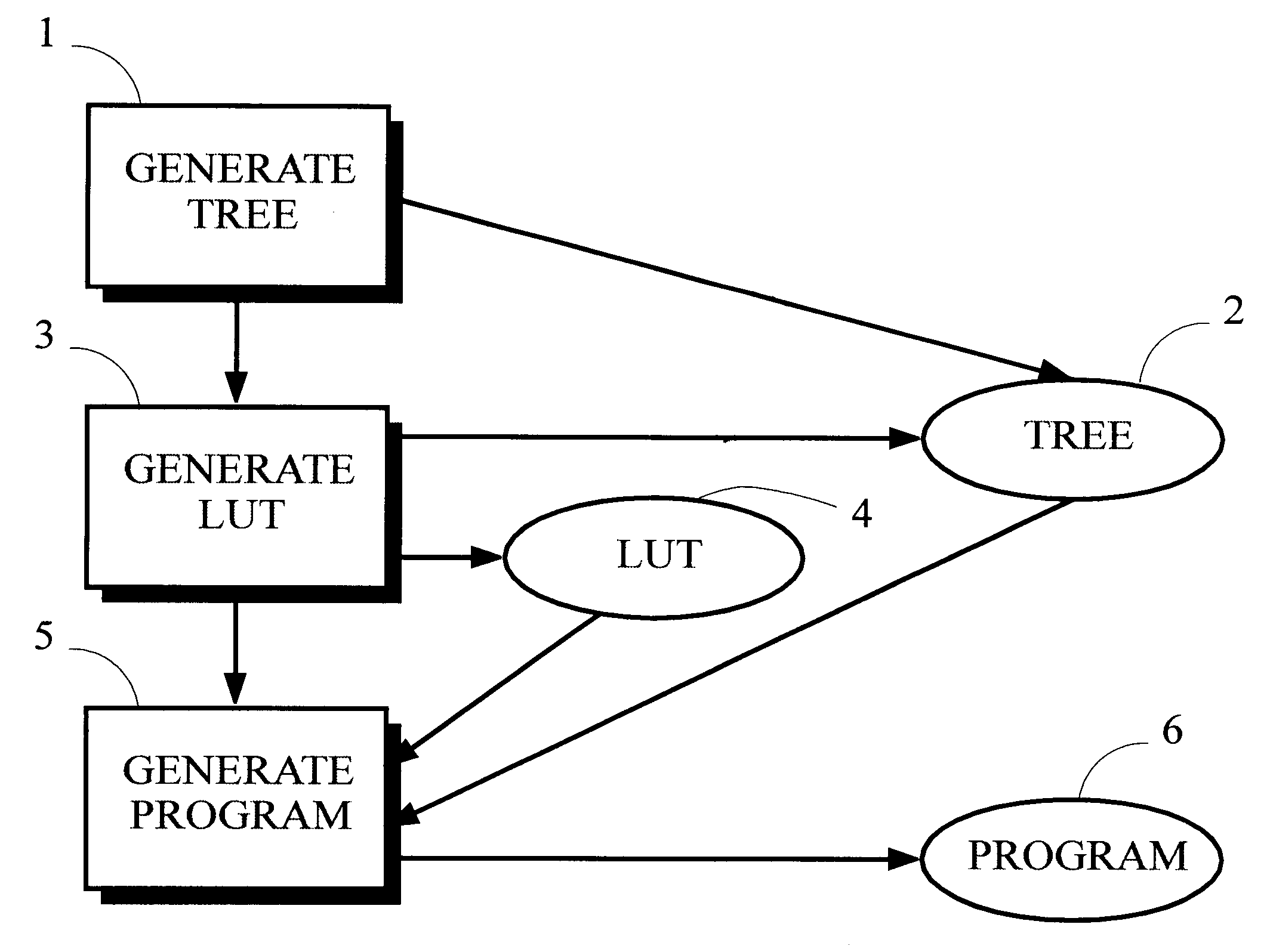
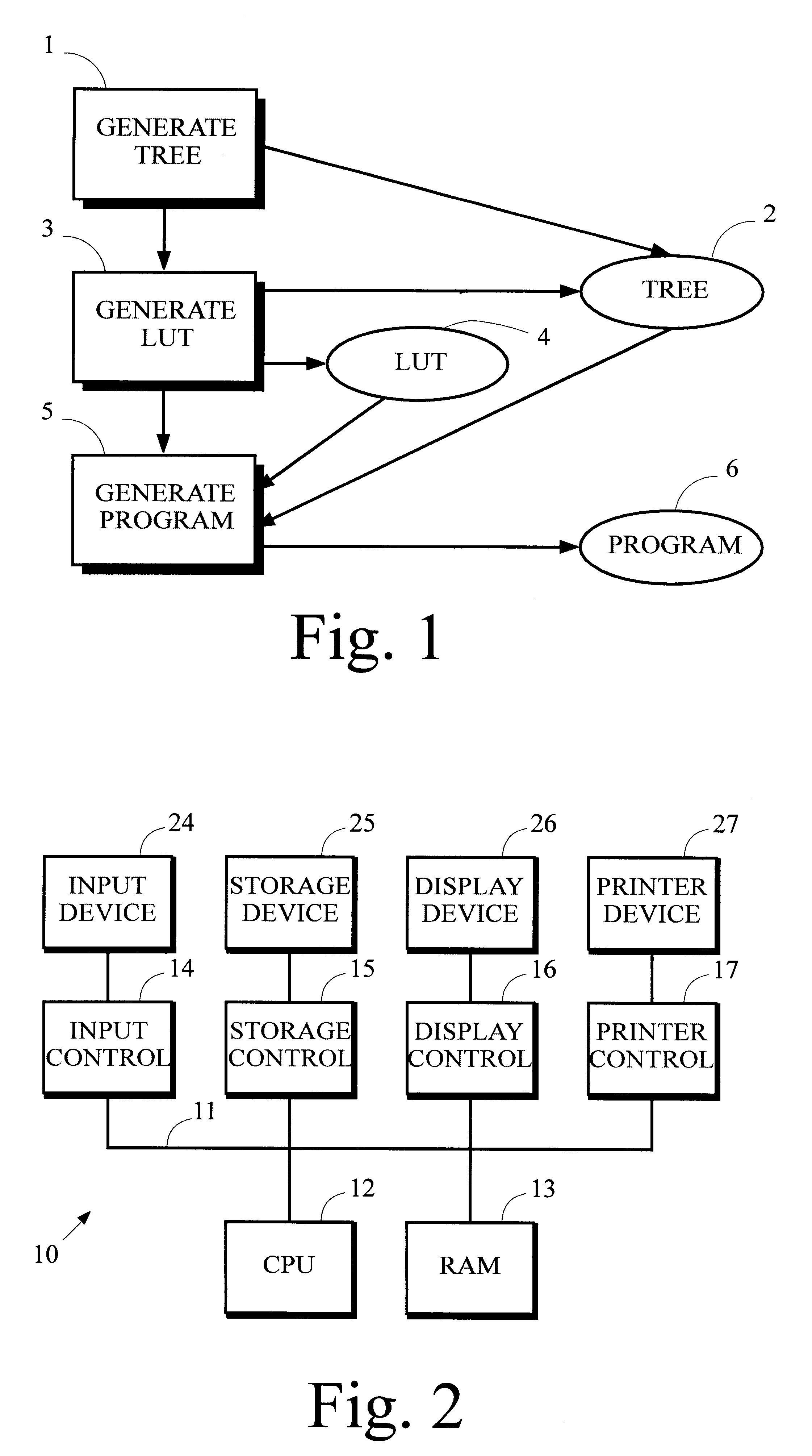
Automatic generation of program logic to decode variable-length codes
A program for decoding variable-length codes like Huffman codes is generated by receiving information describing a particular coding scheme that defines an association between source symbols and the variable-length codes, generating a binary tree that represents the coding scheme, generating a lookup table from the binary tree that can be used to decode variable-length codes having a length less than or equal to a threshold length, and processing the binary tree and the lookup table to generate the decode program.
Owner:SEIKO EPSON CORP
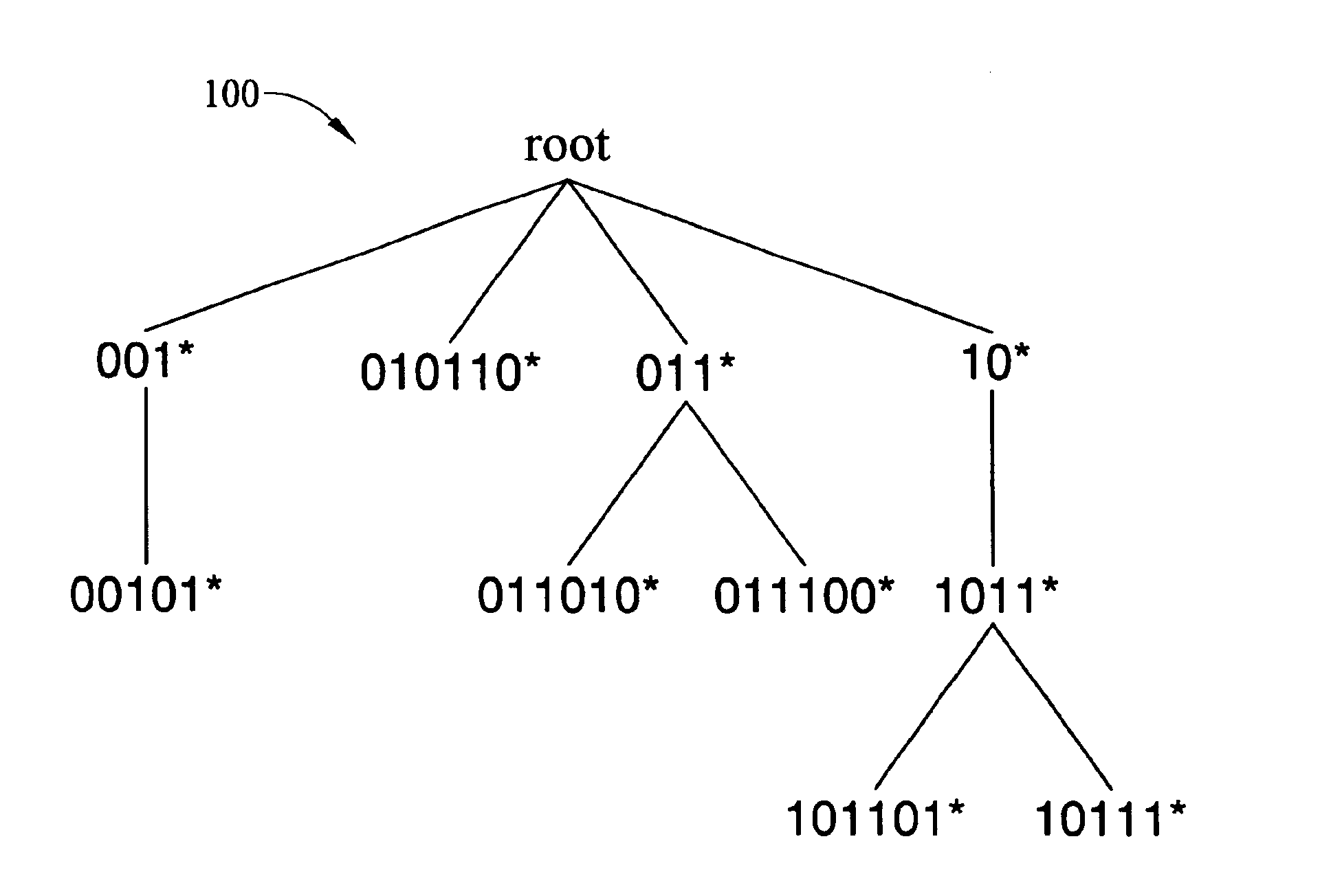
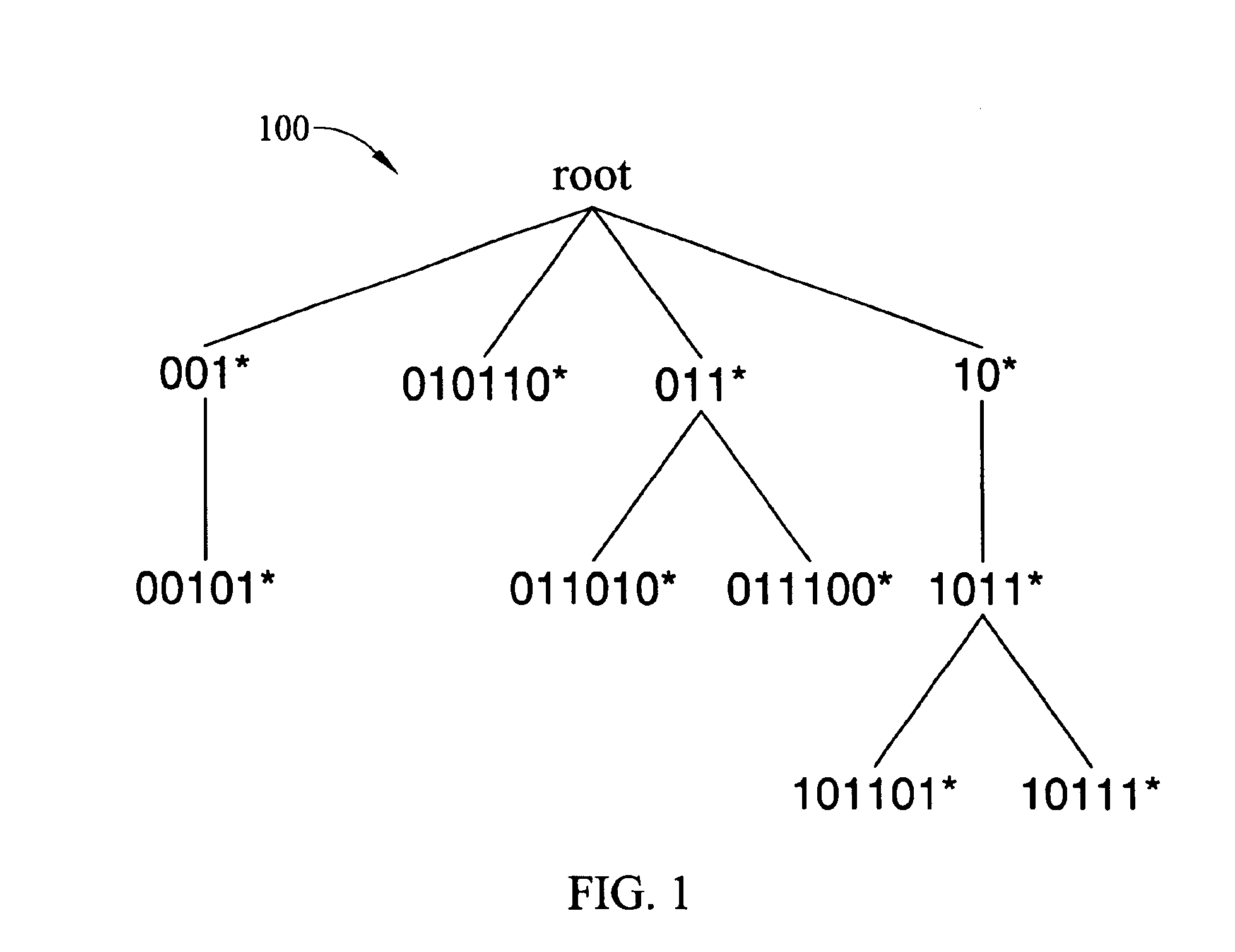
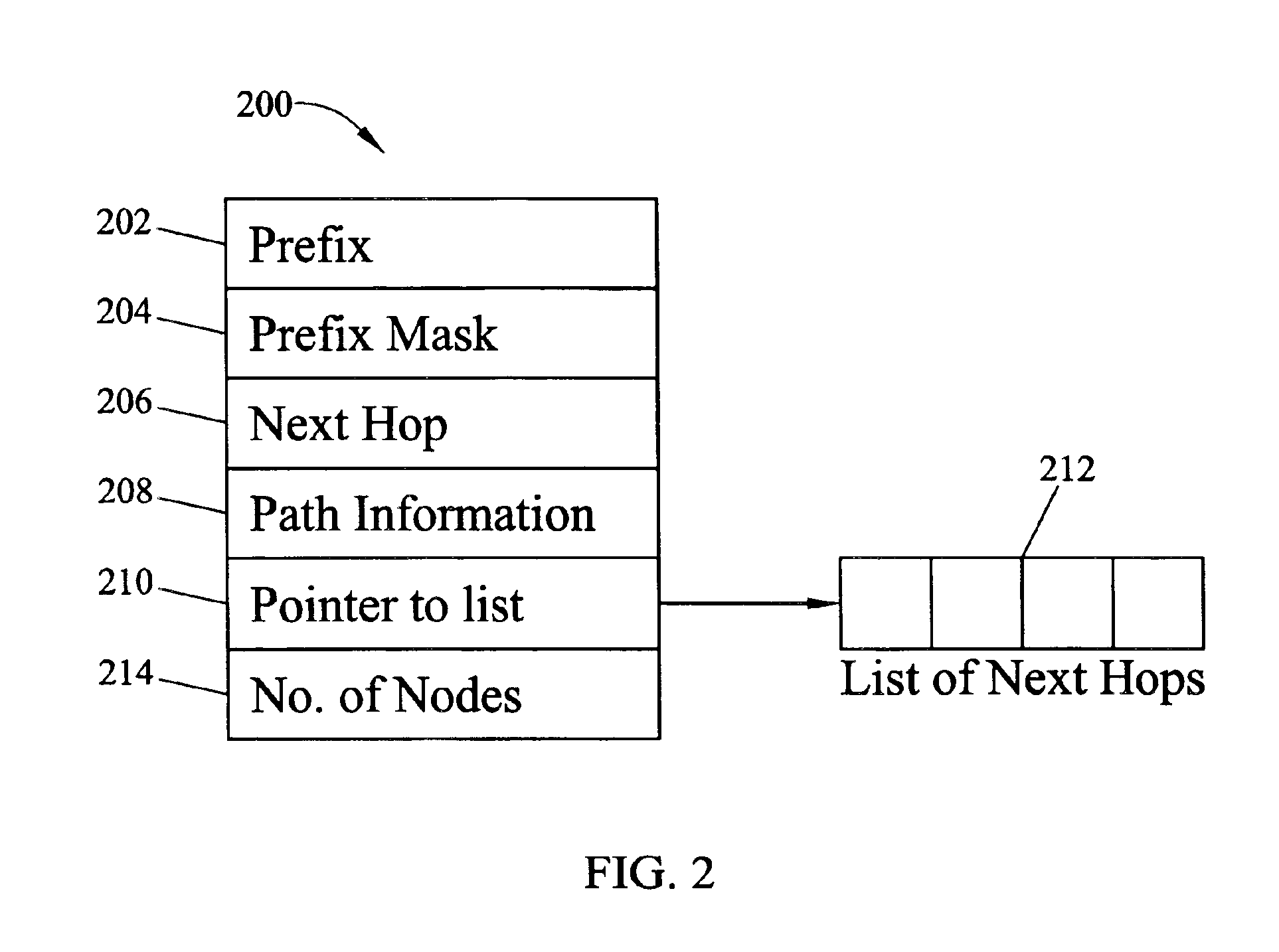
Methods and systems for fast binary network address lookups using parent node information stored in routing table entries
InactiveUS6934252B2Reduce in quantityReduce routingData processing applicationsError preventionRouting tableNetwork addressing
Methods and systems for using binary searches for variable length network address prefix lookups are disclosed. Variable length prefixes are stored in a network address forwarding table. Each prefix corresponds to an entry in the forwarding table. The entries correspond to nodes in a binary tree. Each entry in the forwarding table includes path information regarding parent nodes of each entry in the binary tree. When a lookup is performed in the routing table, bits in the path information are used to determine the longest parent node prefix that matches the address being searched. The longest parent node prefix corresponds to the longest matching prefix.
Owner:NORTH CAROLINA STATE UNIV
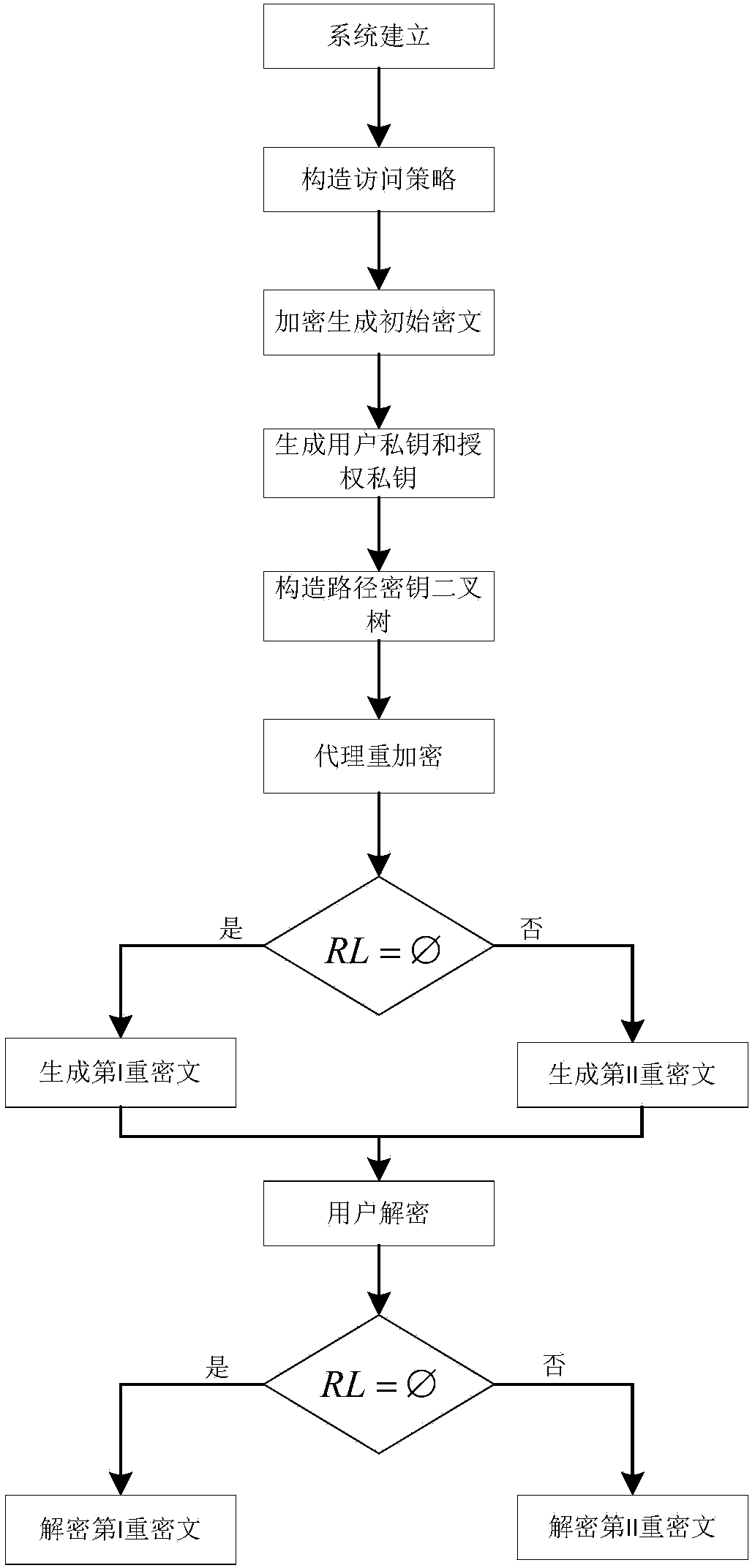
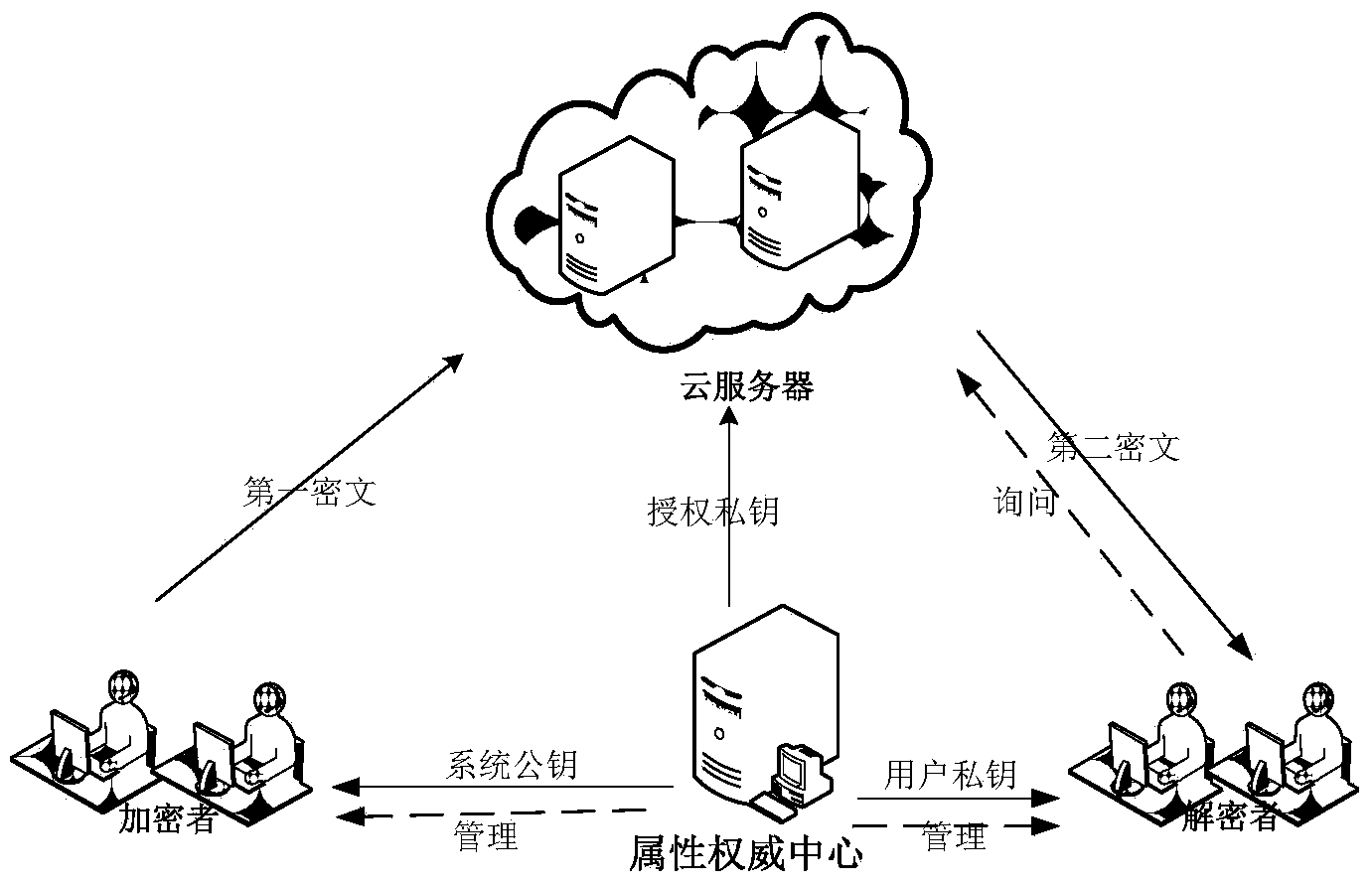
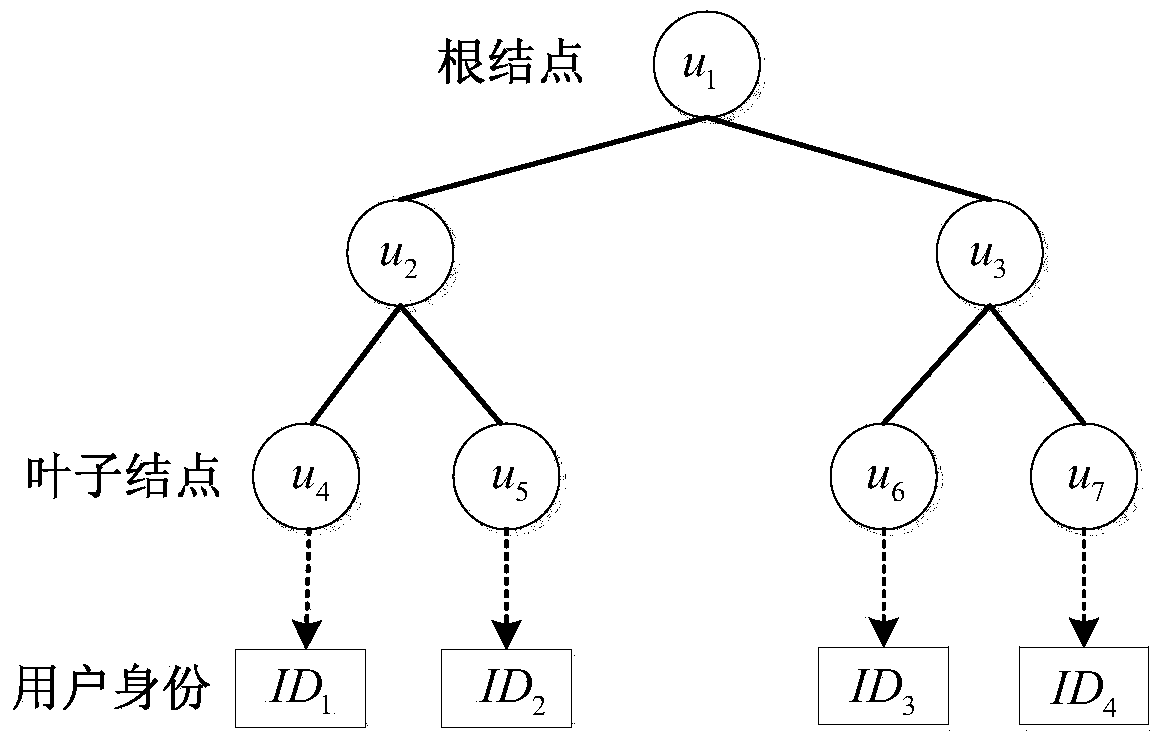
Method for realizing timely user attribute cancel based on ciphertext-policy attribute-based encryption
ActiveCN104113408AReduce workloadTroubleshoot update issuesKey distribution for secure communicationPlaintextBinary tree
Owner:XIDIAN UNIV
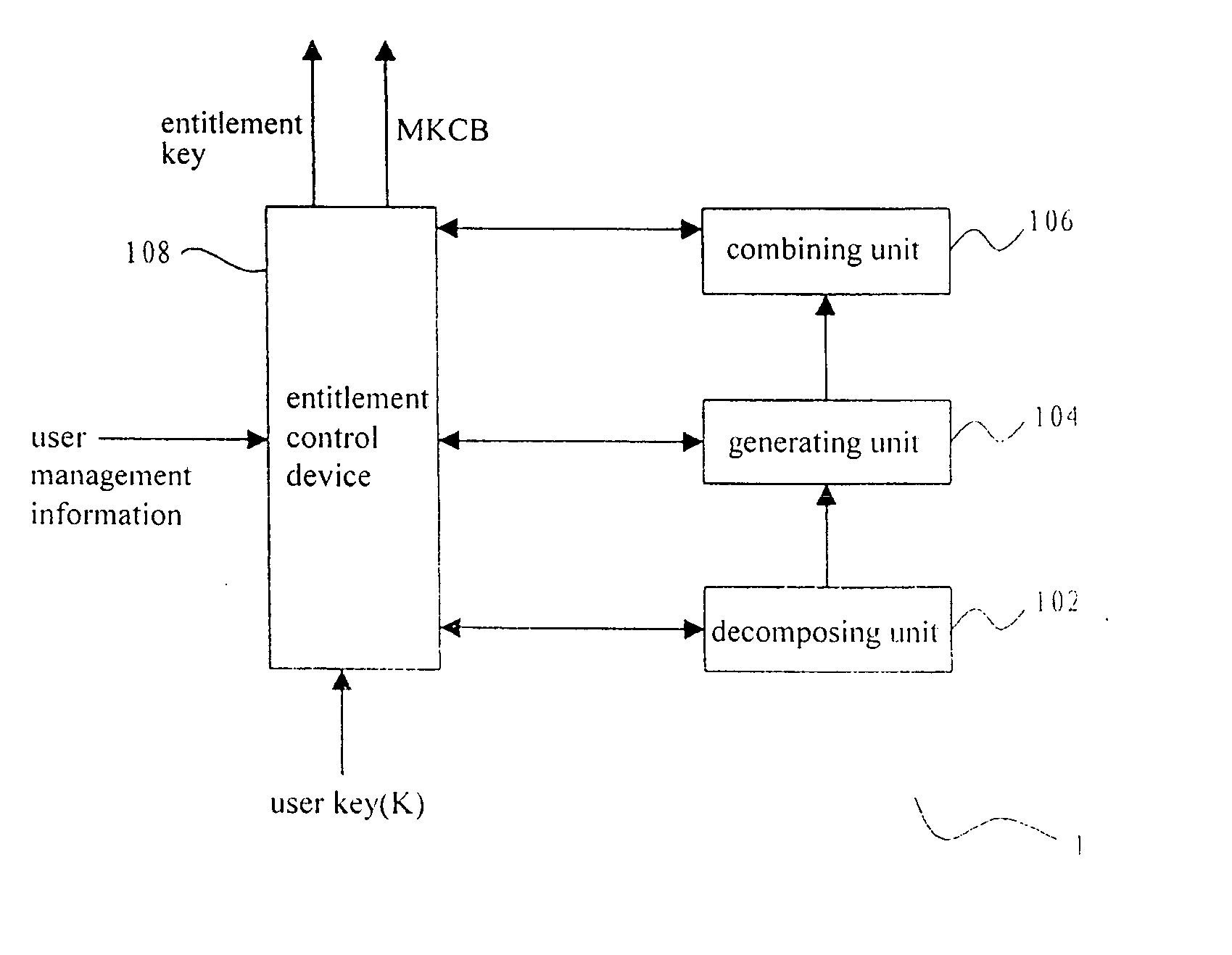
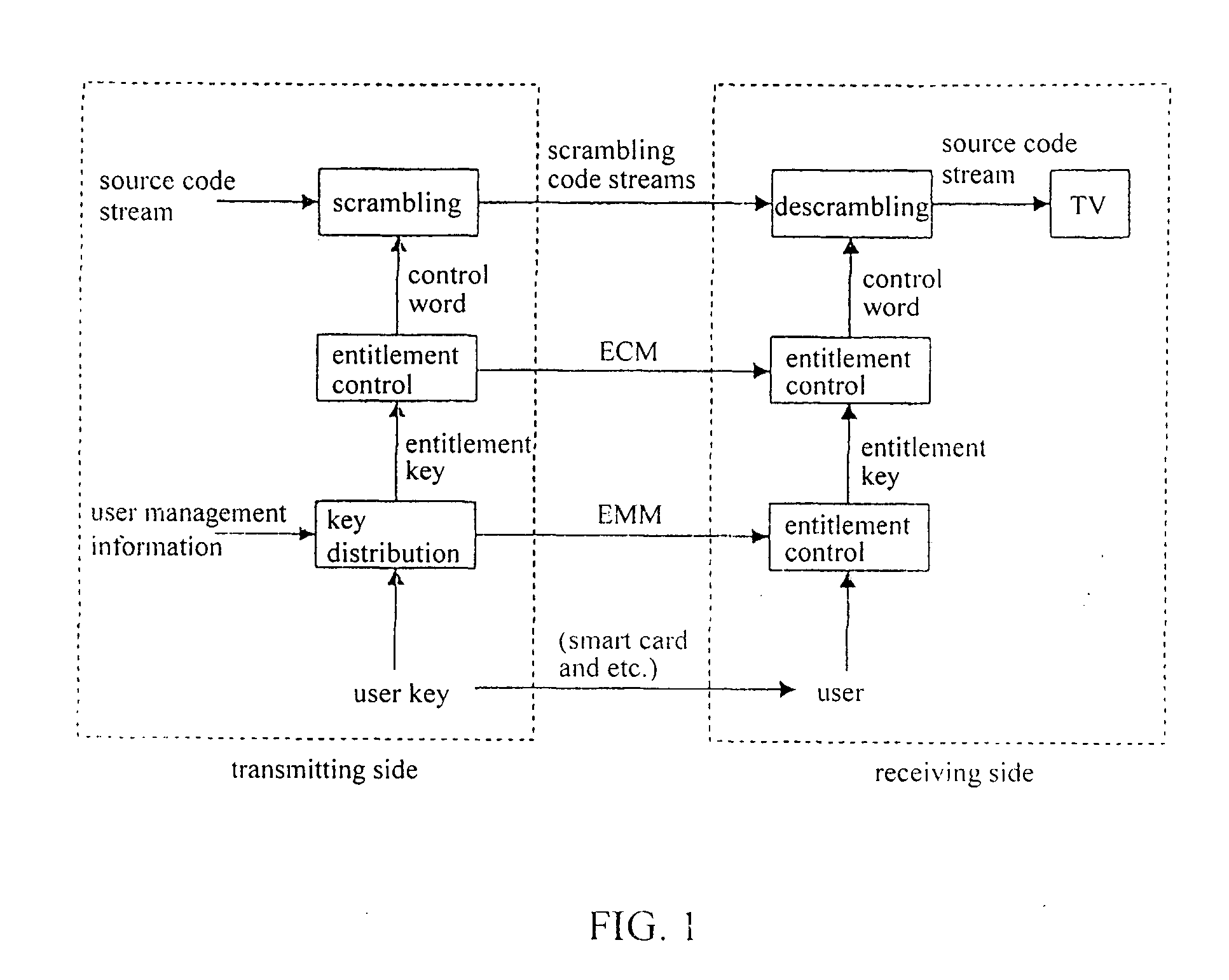
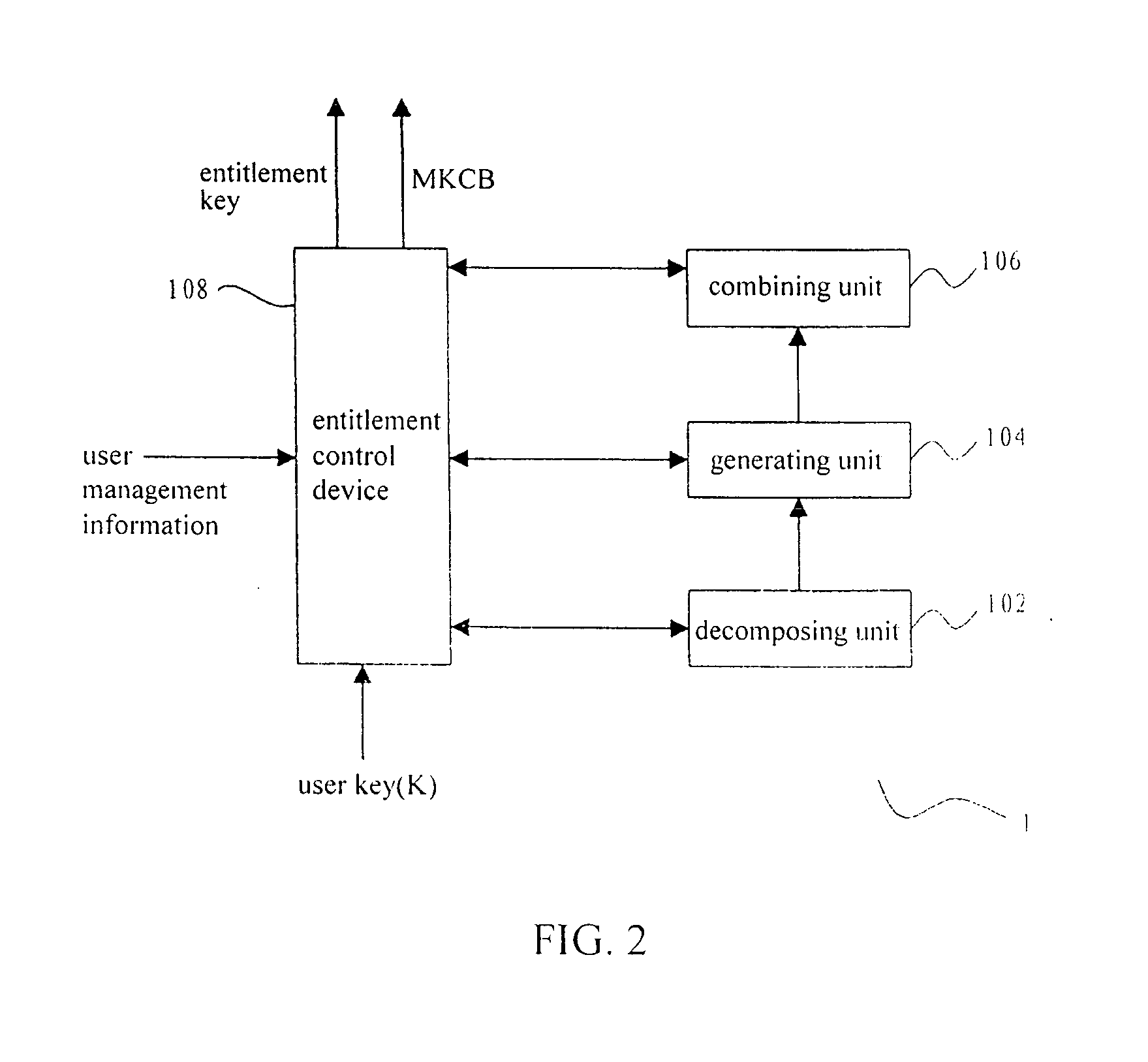
Key distribution in a conditional access system
InactiveUS20040120529A1Reducing amount of information (length)Save a lotKey distribution for secure communicationUser identity/authority verificationCiphertextConditional access systems
Methods and apparatus for key distribution in a conditional access system, assuming that the set of all user nodes which the system can accommodate is a complete set, and a subset is composed of all user nodes or part of user nodes. One method comprises: decomposing said subset into at least one secondary subset; assigning a different user key to each secondary subset, each said user key being transmitted to all users in a corresponding secondary subset; encrypting an entitlement key by using each said user key so as to generate a cipher text corresponding to each said secondary subset; and combining said cipher text to generate a media key control block and transmitting said media key control block to all users in said subset. Since a classification method of a binary tree and a multiple tree is used, the invention can save a lot of network resources.
Owner:IBM CORP
Binning predictors using per-predictor trees and MDL pruning
ActiveUS20070185896A1Reduce information lossReduces the introduction of false information artifactsDigital data processing detailsCharacter and pattern recognitionMemory footprintData selection
Binning of predictor values used for generating a data mining model provides useful reduction in memory footprint and computation during the computationally dominant decision tree build phase, but reduces the information loss of the model and reduces the introduction of false information artifacts. A method of binning data in a database for data mining modeling in a database system, the data stored in a database table in the database system, the data mining modeling having selected at least one predictor and one target for the data, the data including a plurality of values of the predictor and a plurality of values of the target, the method comprises constructing a binary tree for the predictor that splits the values of the predictor into a plurality of portions, pruning the binary tree, and defining as bins of the predictor leaves of the tree that remain after pruning, each leaf of the tree representing a portion of the values of the predictor.
Owner:ORACLE INT CORP
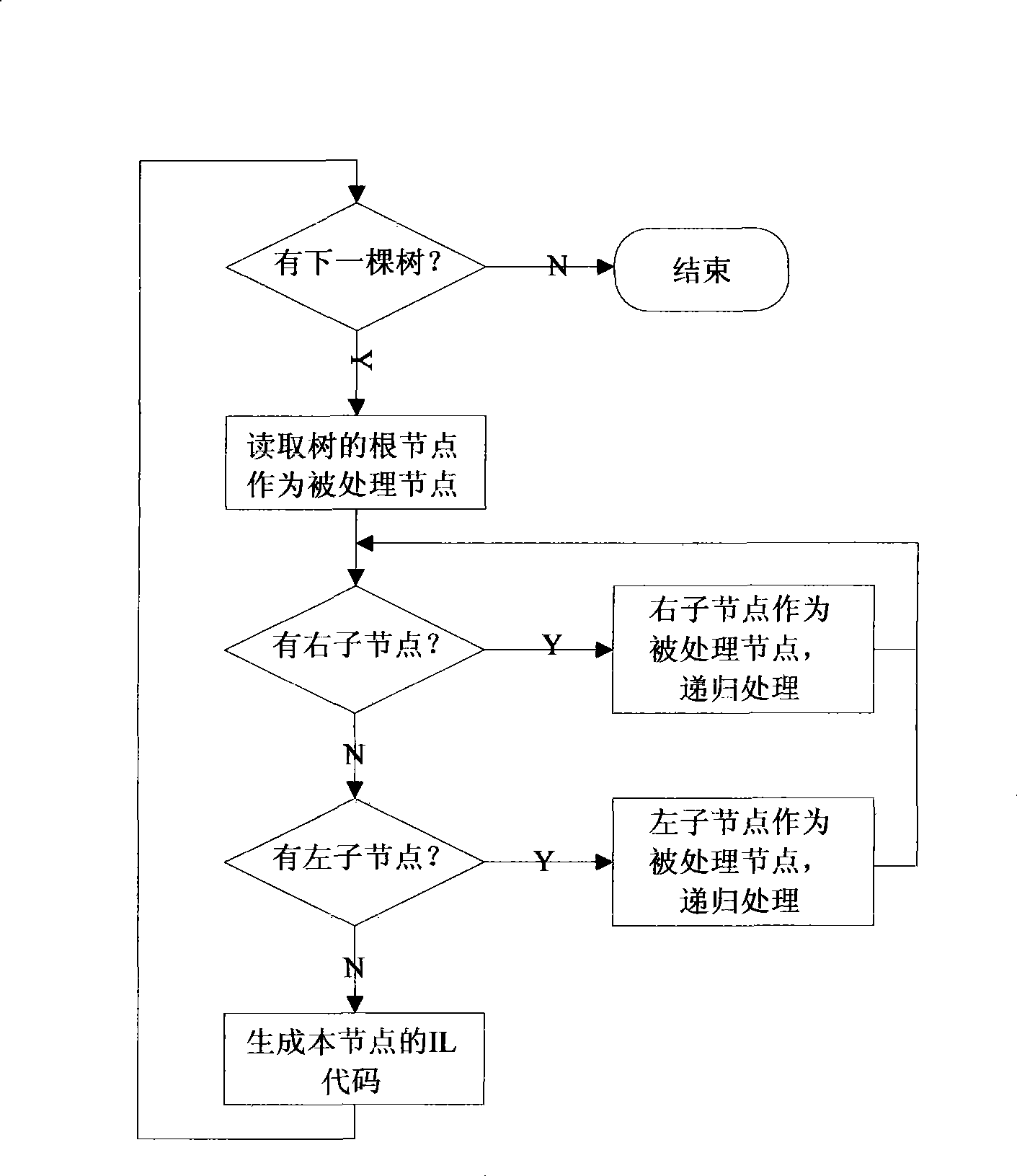
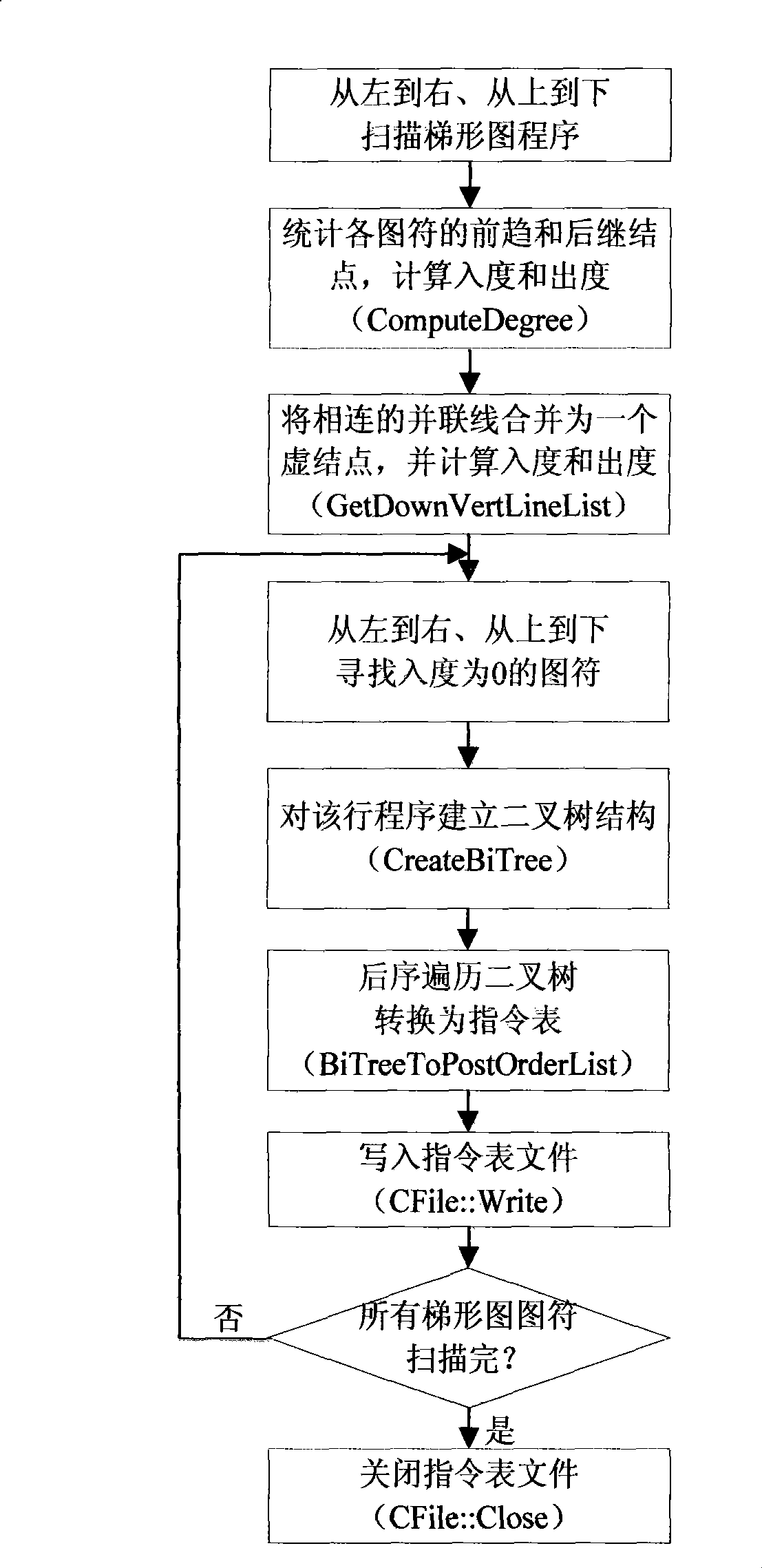
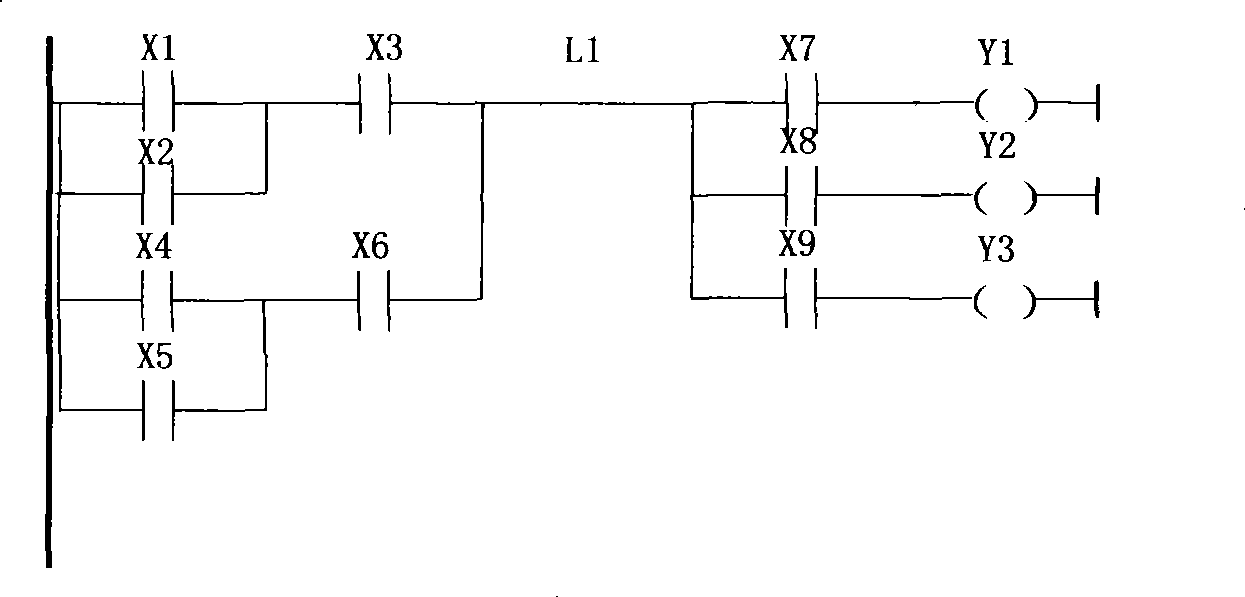
Method and system for conversing trapezoidal pattern to be instruction catalogue program, and interpretation execution method and system
InactiveCN101364098AImprove the efficiency of explain executionAchieve conversionProgramme control in sequence/logic controllersParallel computingMaster controller
The invention discloses a method and a system for converting a ladder diagram into an instruction list and carrying out the interpretive execution of an instruction list. The ladder diagram conversion method comprises the following steps: mapping the ladder diagram to an AOV diagram, establishing a binary tree representative of the logical relationship between the instructions based on the AOV diagram, and converting the ladder diagram to the instruction list by the postorder traversal of the binary tree. The method and the system perform the conversion between various complex ladder diagrams and instruction lists, particularly the conversion of the multi-output ladder diagram to the instruction list. Additionally, the converted instruction list exists in the form of postorder expression, which is conducive to increasing the efficiency of interpretive execution of the PLC master controller.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
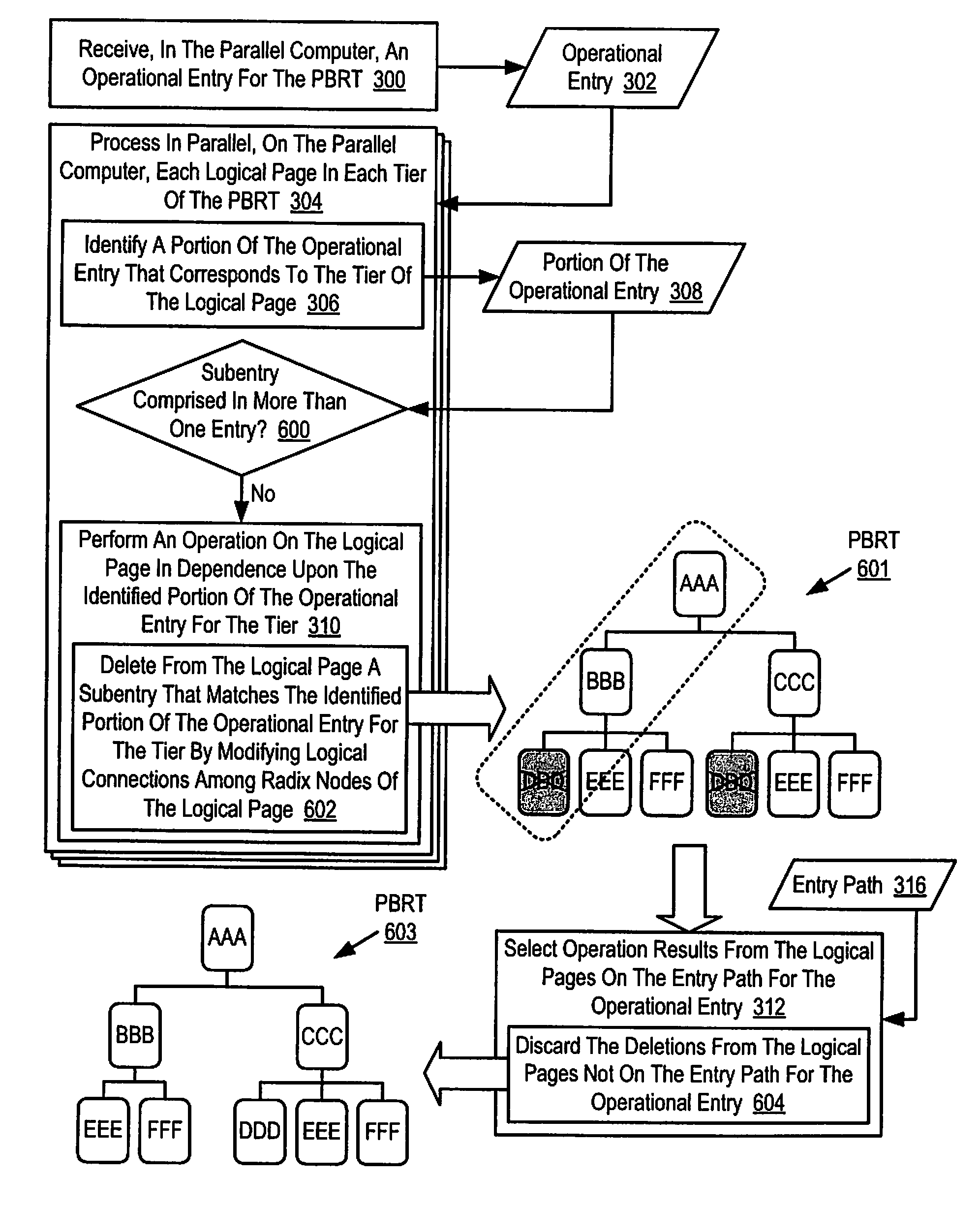
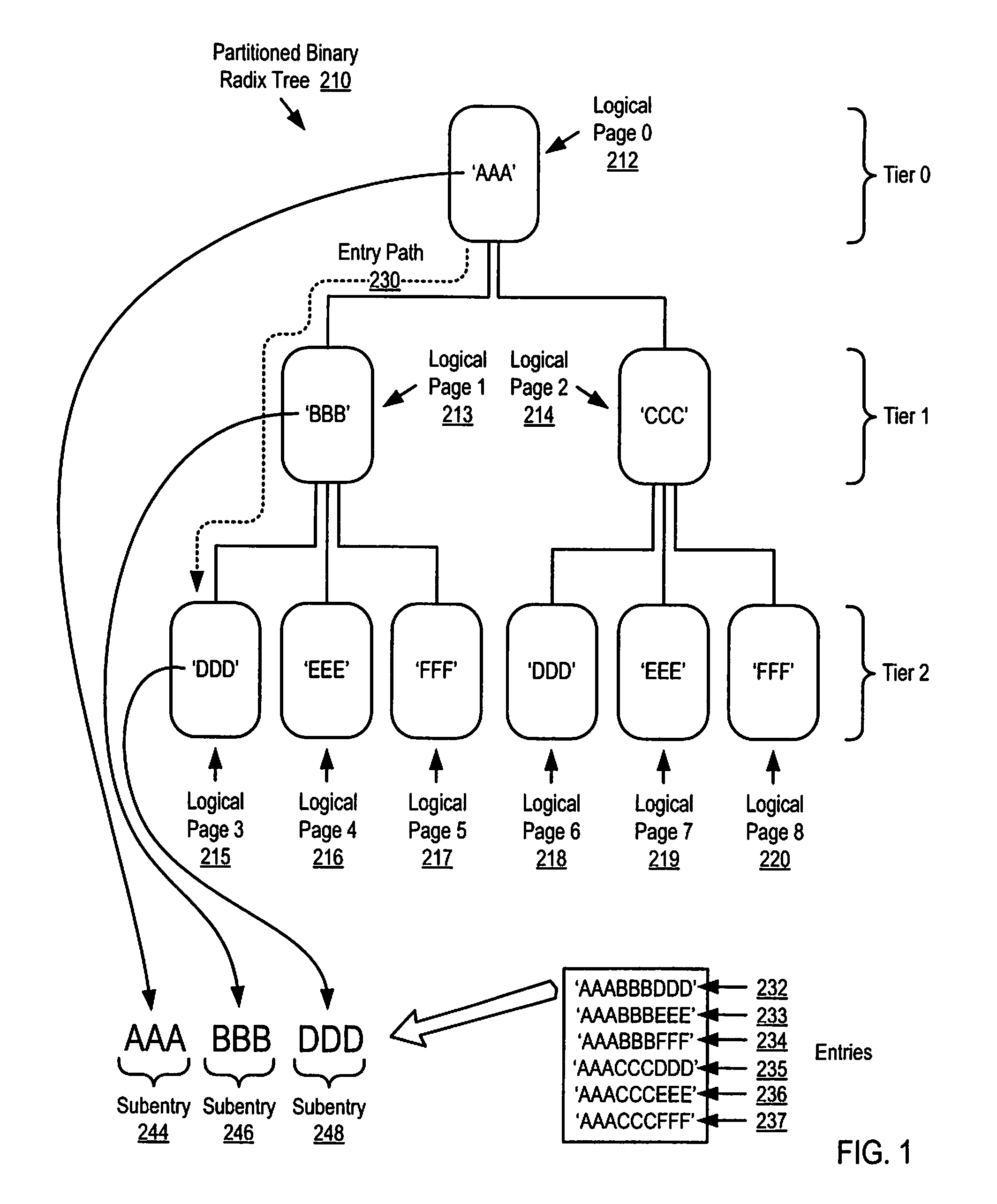
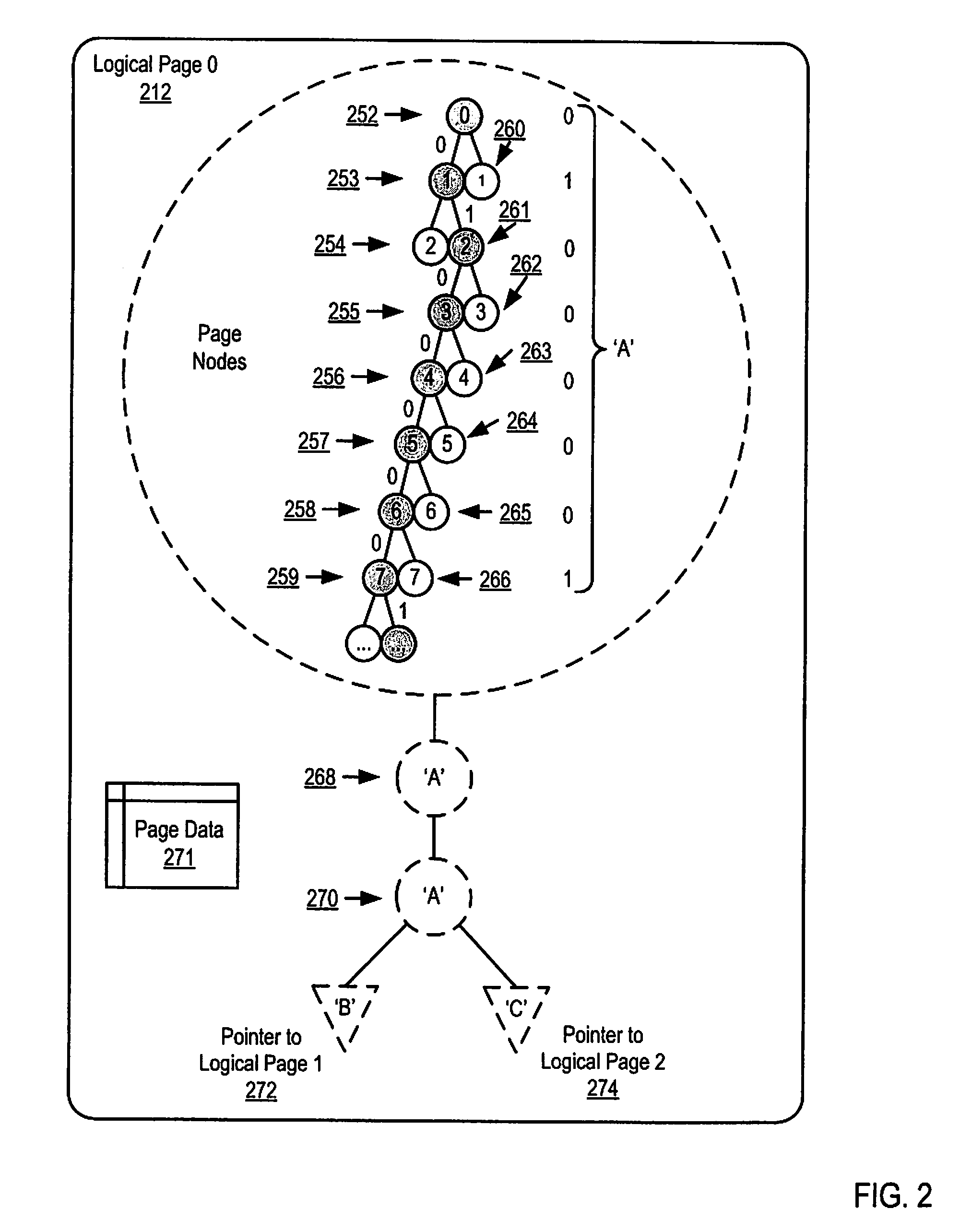
Parallel Execution of Operations for a Partitioned Binary Radix Tree on a Parallel Computer
InactiveUS20080126739A1Digital data information retrievalDigital data processing detailsBinary treeParallel processing
Methods, apparatus, and products are disclosed for parallel execution of operations for a partitioned binary radix tree that include: receiving, in a parallel computer, an operational entry for the PBRT, the PBRT comprising a plurality of logical pages that contain a plurality of entries, each logical page included in a tier and containing one or more subentries corresponding to the tier of the logical page containing the subentry, each entry is composed of a subentry from each logical page on an entry path; processing in parallel, on the parallel computer, each logical page in each tier, including: identifying a portion of the operational entry that corresponds to the tier of the logical page, and performing an operation on the logical page in dependence upon the identified portion of the operational entry for the tier; and selecting operation results from the logical pages on the entry path for the operational entry.
Owner:IBM CORP
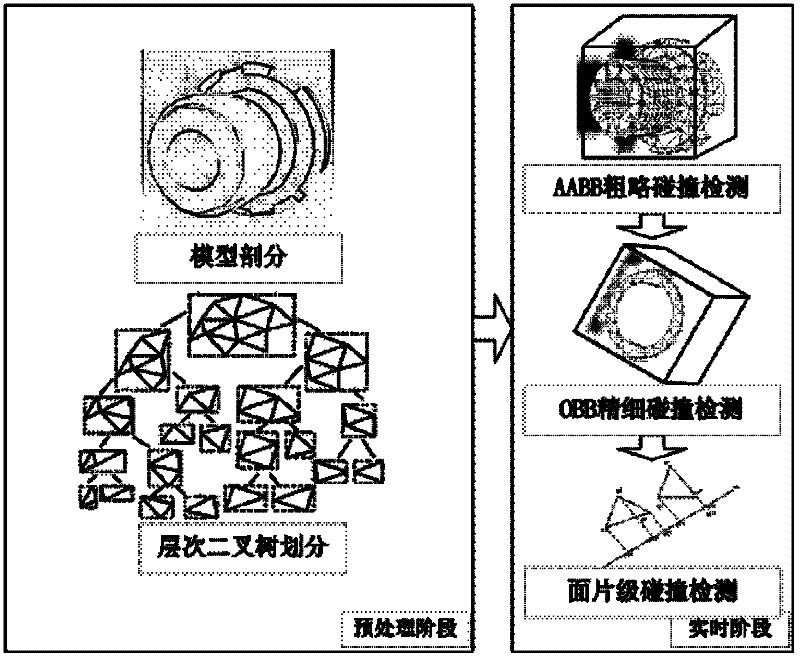
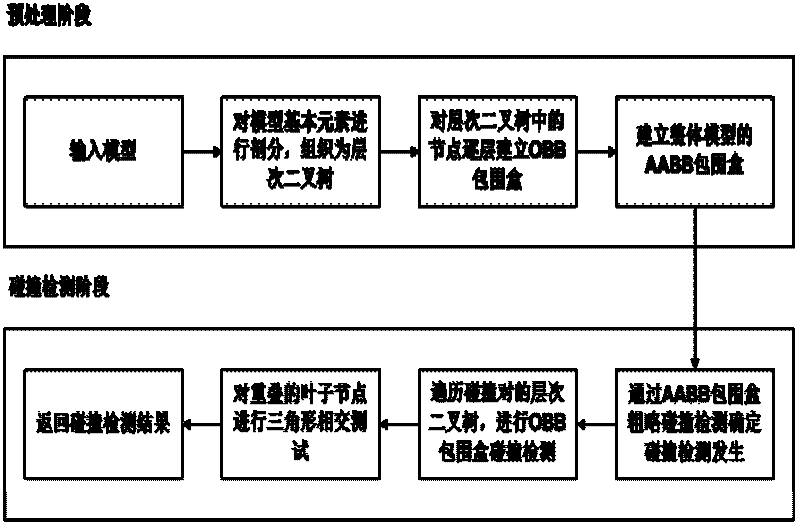
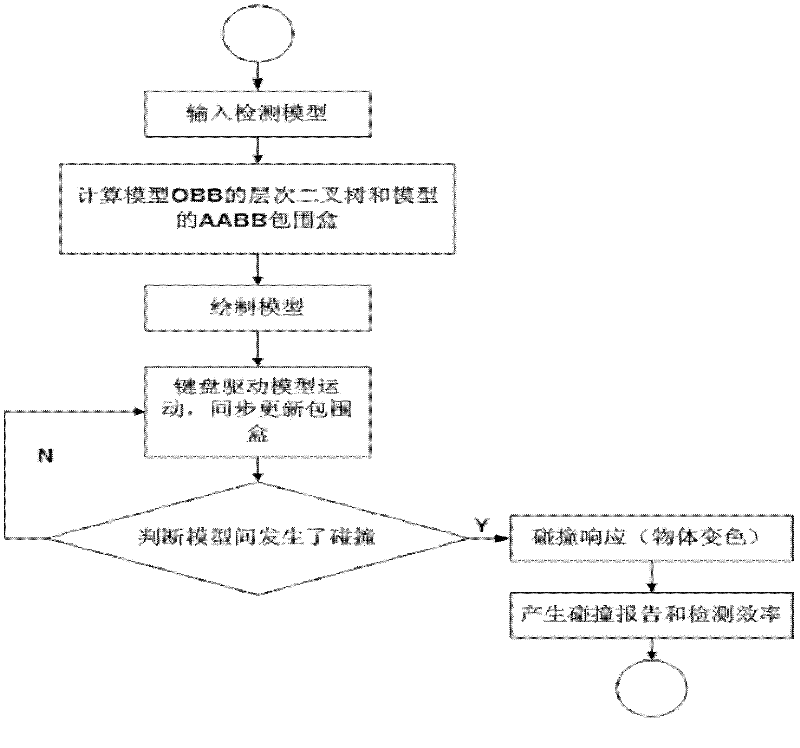
Virtual assembly-oriented collision detection method based on AABB (Axis Aligned Bounding Box)-OBB (Oriented Bounding Box) mixed bounding box
The invention provides a virtual assembly-oriented collision detection method based on an AABB (Axis Aligned Bounding Box)-OBB (Oriented Bounding Box) mixed bounding box. A pre-processing stage comprises the following steps of: splitting a model of a deformable object, establishing an OBB layered binary tree layer by layer, and establishing an AABB of the entire model. A real-time stage comprises the following steps of: maintaining the AABB at the peak of the binary tree, and carrying out rough collision detection on the entire model; maintaining an OBB at the other nodes, and carrying out accurate collision detection by using the OBB; and finally, carrying out patch-level collision detection. The method comprises the following steps of: loading a three-dimensional model; splitting the model, and establishing a layered binary tree; carrying out collision detection by using the AABB in the rough collision detection stage; carrying out collision detection by using the OBB in the accurate collision detection stage; and finally, carrying out patch-level collision detection. The method provided by the invention can ensure that in an aircraft engine assembling process, a spherical nut wrench is used for disassembling and assembling spherical nuts, and an internal hexagonal wrench is used for disassembling and assembling plug screws.
Owner:BEIHANG UNIV
System for scheduling multiple time dependent events
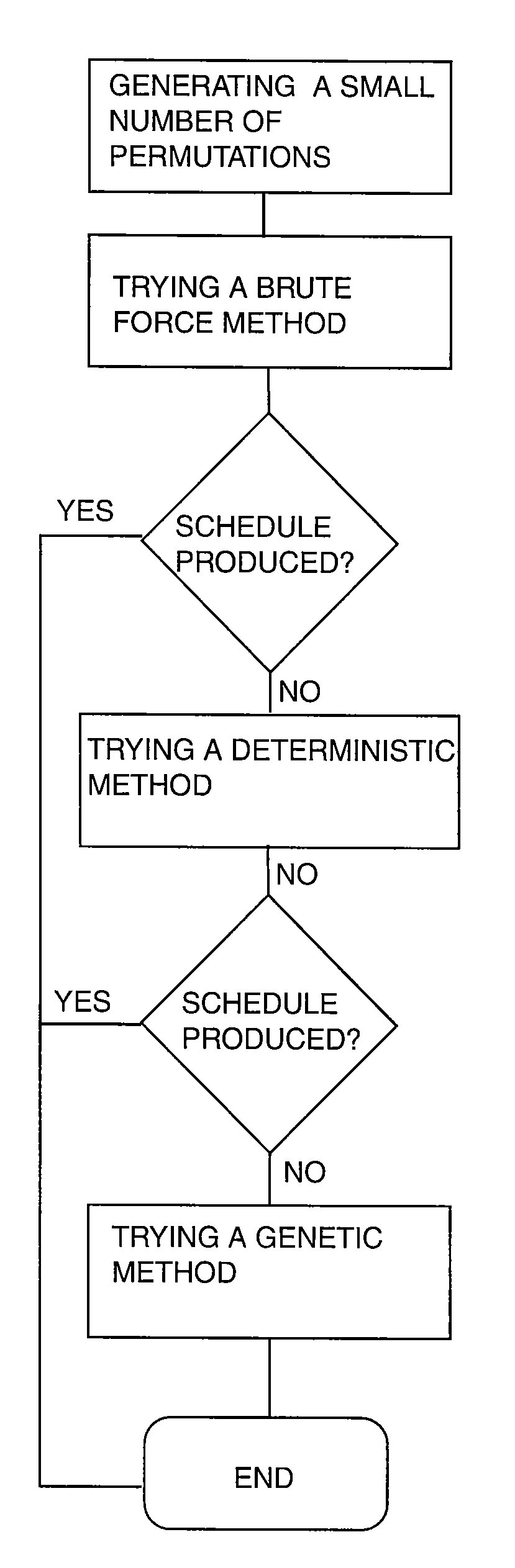
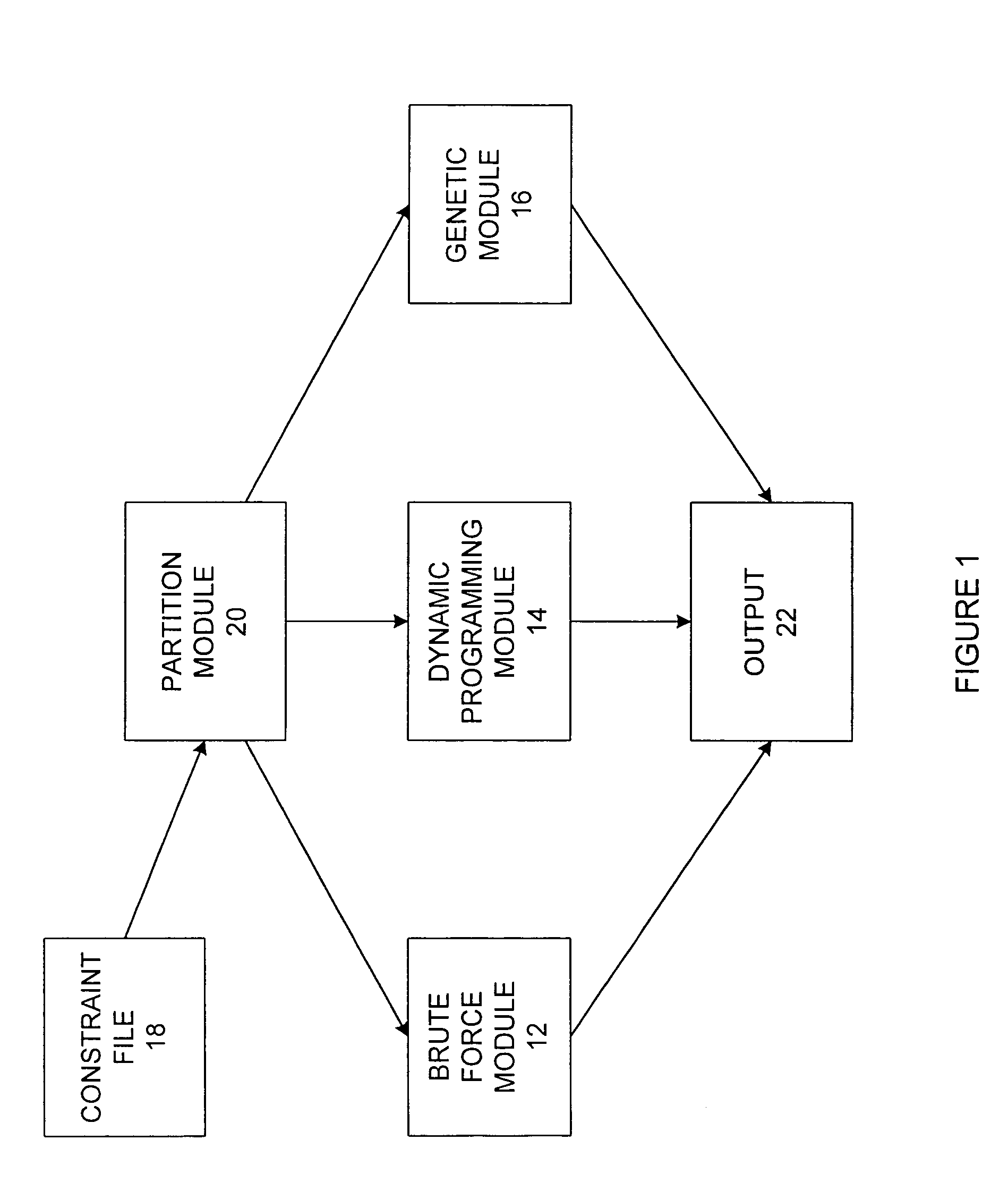
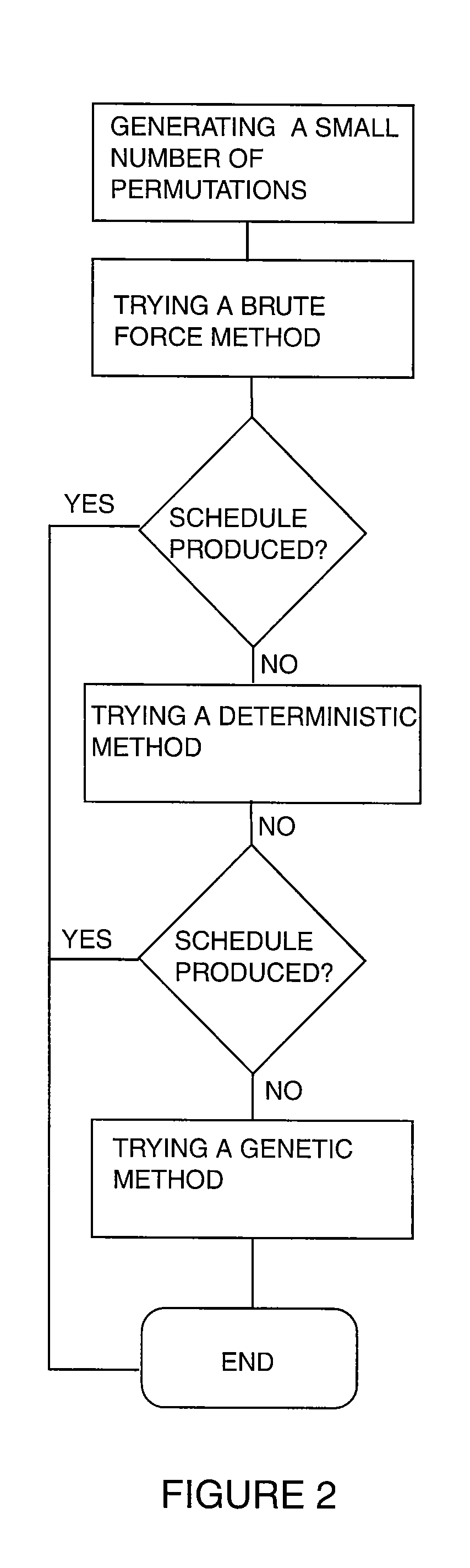
InactiveUS7246075B1Reduce the amount requiredSignificant memory savingResourcesSpecial data processing applicationsTime scheduleBrute force
A scheduling system for choosing the most appropriate heuristic for solving time-dependant scheduling problems. The invention includes a means for selecting the most appropriate heuristic method for generating a schedule from an enumerative (“brute force”) method, a dynamic programming method, and a genetic method. The invention further includes a hashing function that is capable of detecting duplicate solutions generated by the dynamic programming module and a height-balanced binary tree for providing search insertion and deletion operations.
Owner:MAGNOLIA CONSULTING INC
Target detection system and method based on covariance and binary-tree support vector machine
InactiveCN101794515AReduce feature dimensionEasy to handleRoad vehicles traffic controlCharacter and pattern recognitionVideo monitoringCovariance
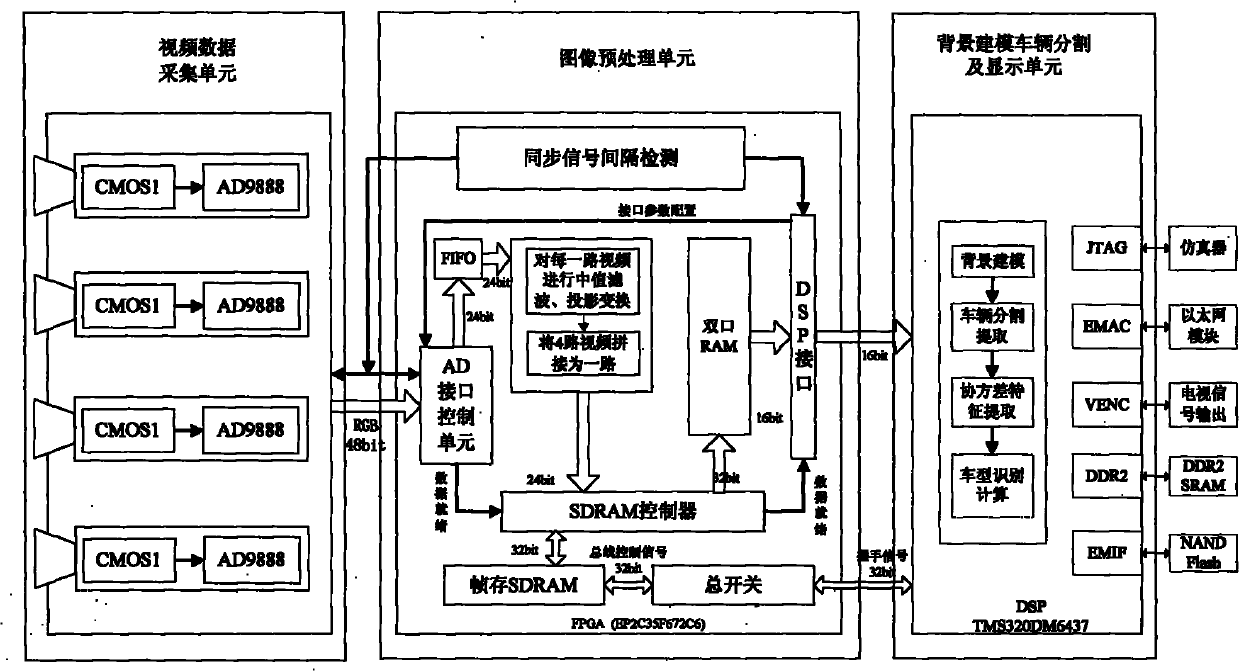
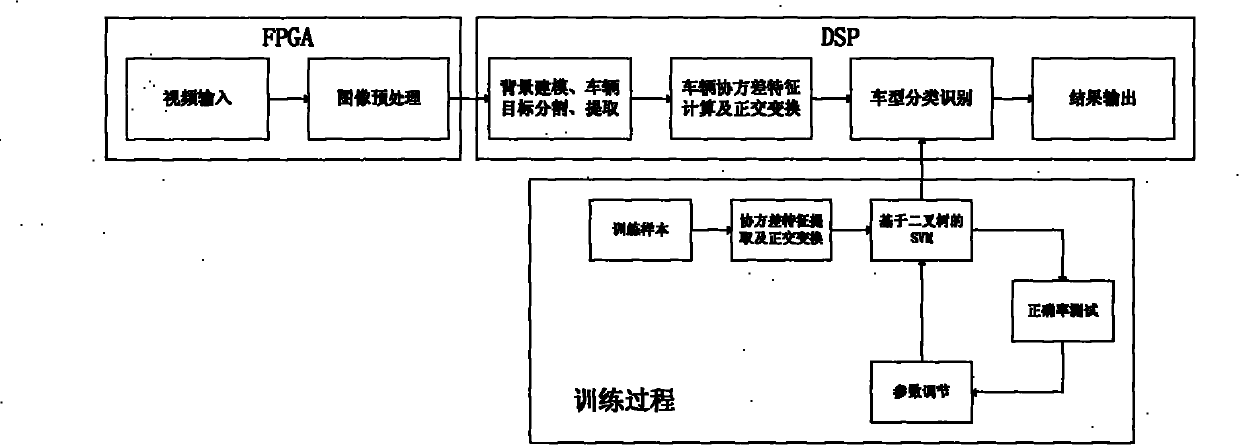
The invention discloses target detection system and method based on covariance and a binary-tree support vector machine. The system comprises a video data collecting unit, an image preprocessing unit and a background modeling vehicle partitioning and displaying unit. The video data collecting unit is used for acquiring information in real time and carrying out digitization and system conversion on analog videos. The image preprocessing unit comprises an FPGA (Field Programmable Gate Array) and a DSP (Digital Signal Processor), wherein the FPGA is used as a coprocessor; and the DSP is used as a main processor to accomplish the background modeling of video images, the partitioning and the extraction of vehicle targets and the realization of a model identification algorithm. Utilizing the combination of the FPGA and the DSP, the invention can realize multi-video real-time model identification through combining with the model identification algorithm based on the covariance features of the images and the support vector machine. The invention can be widely used for a plurality of fields of intelligent traffic management, intelligent video monitoring and the like.
Owner:HOHAI UNIV
Automated taxonomy generation
InactiveUS7266548B2Maximize likelihoodData processing applicationsDigital data information retrievalBinary treeDocument preparation
Owner:SERVICENOW INC
Scalable retrieval of data entries using an array index or a secondary key
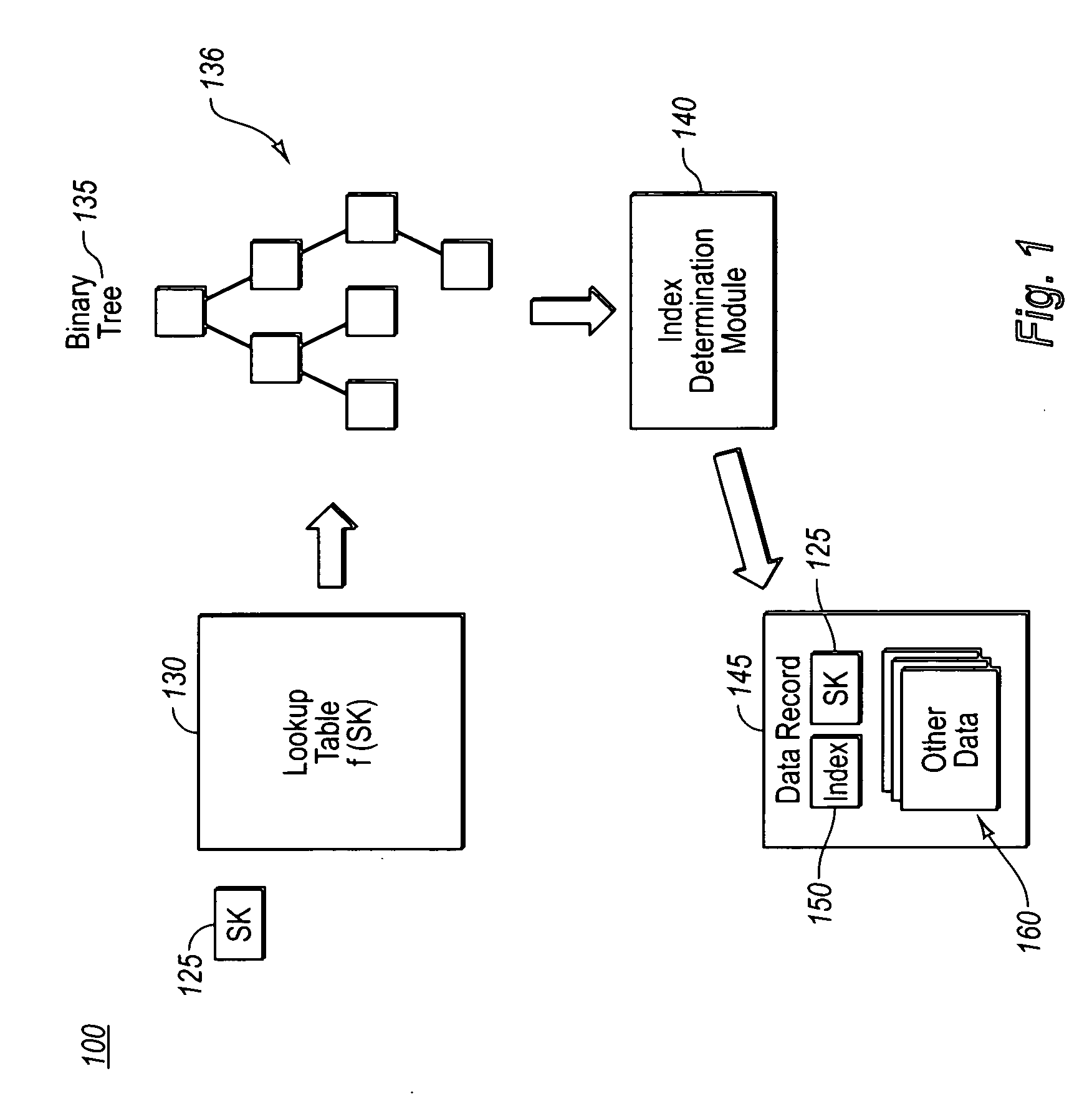
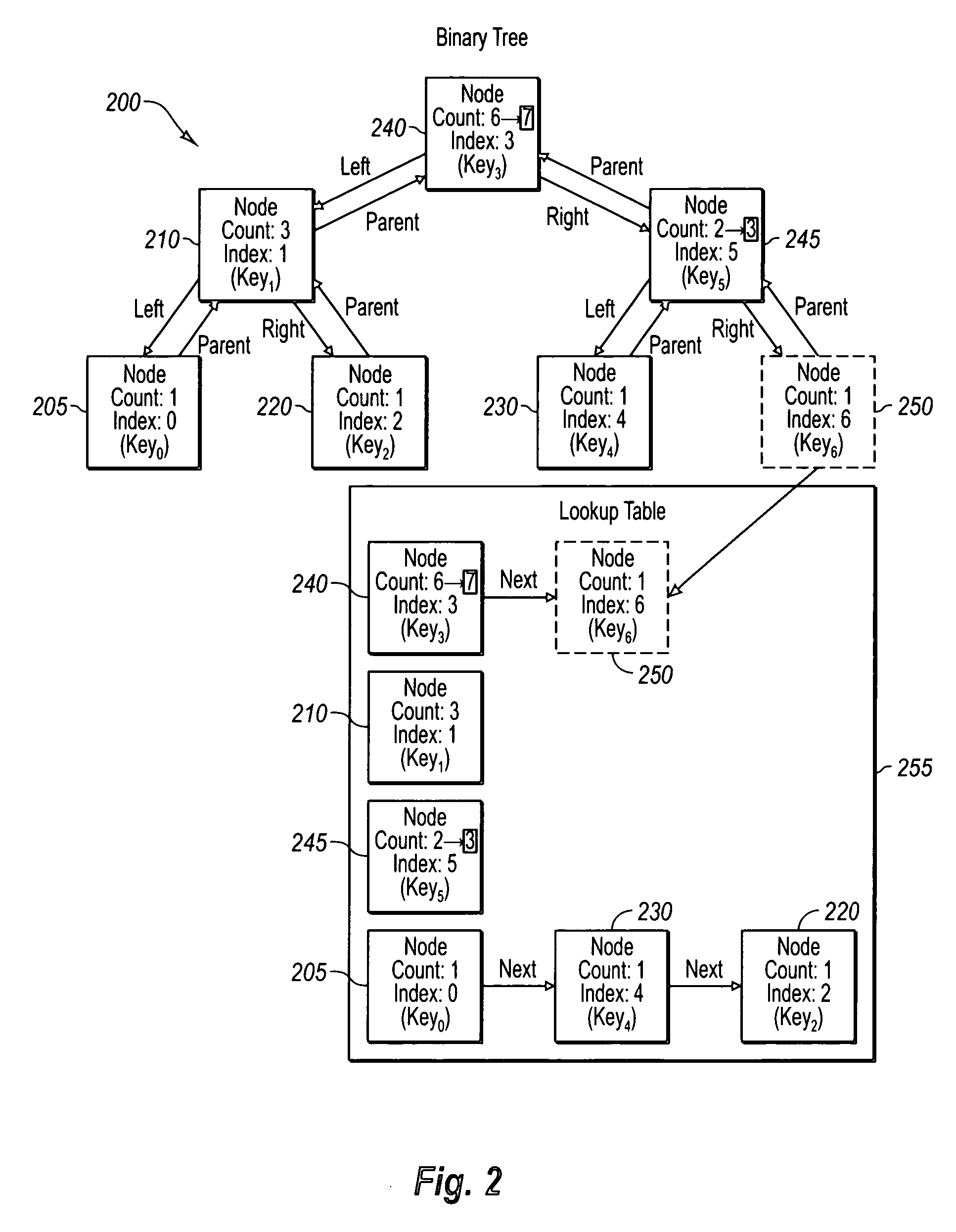
InactiveUS20070112795A1Efficiently determinedMinimize the numberData processing applicationsDigital data information retrievalArray data structureBinary tree
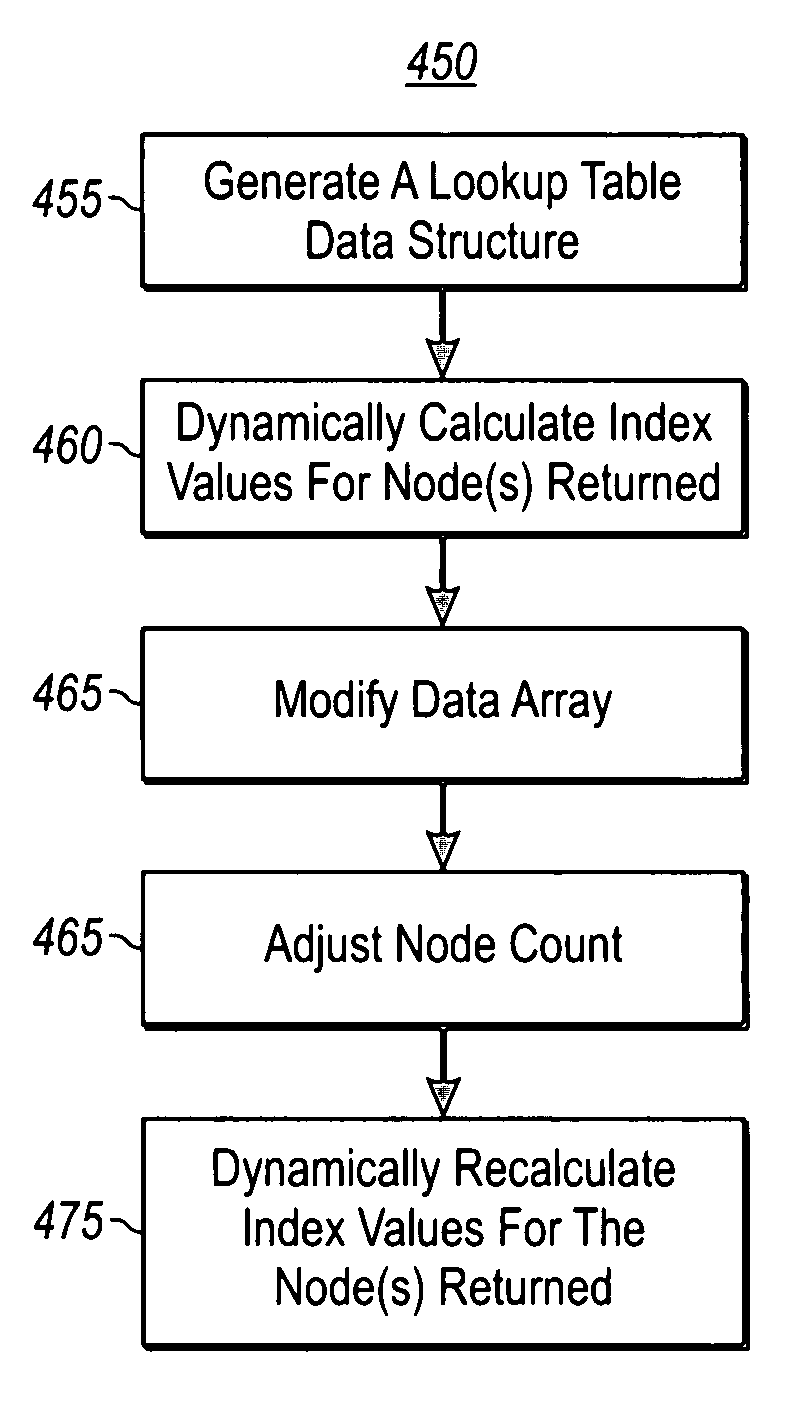
Example embodiments improve the lookup times and modification costs of indexing on a dynamically sorted list by using a combination of data structures to determine index values for secondary keys and vice versa. More specifically, exemplary embodiments provide a combination of a binary tree (e.g., a balanced binary tree) with a lookup table (e.g., linear dynamic hash table) to provide scalable retrieval of entries by either an array index or a secondary key. For example, given a key, a hash thereof returns a node placement within a balanced binary tree. This positioning can then be used at runtime to determine an index value for a data record, resulting in a near real-time lookup cost. Also note that modifications, such as reordering, insertions, and deletions, become a function of the nodes depth in the binary tree, rather than a linear function of number of records within the data array.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com