Patents
Literature
116 results about "Logical tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
LOGICAL TREE: The Logical Tree is a tree structure that represents the hierarchy of controls and elements that constitute a piece of user interface in WPF, but without their inner parts. The logical tree is responsible for:
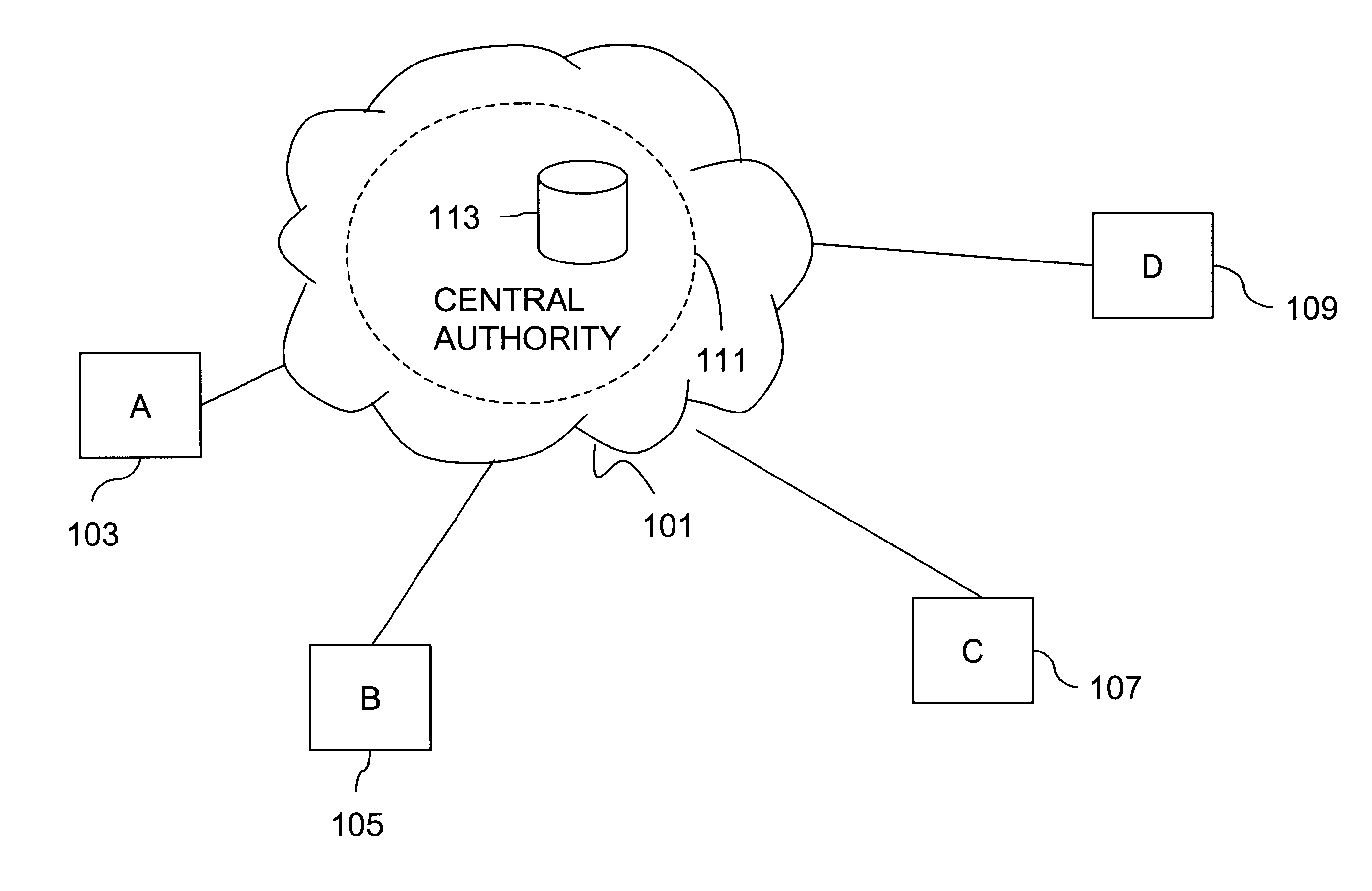
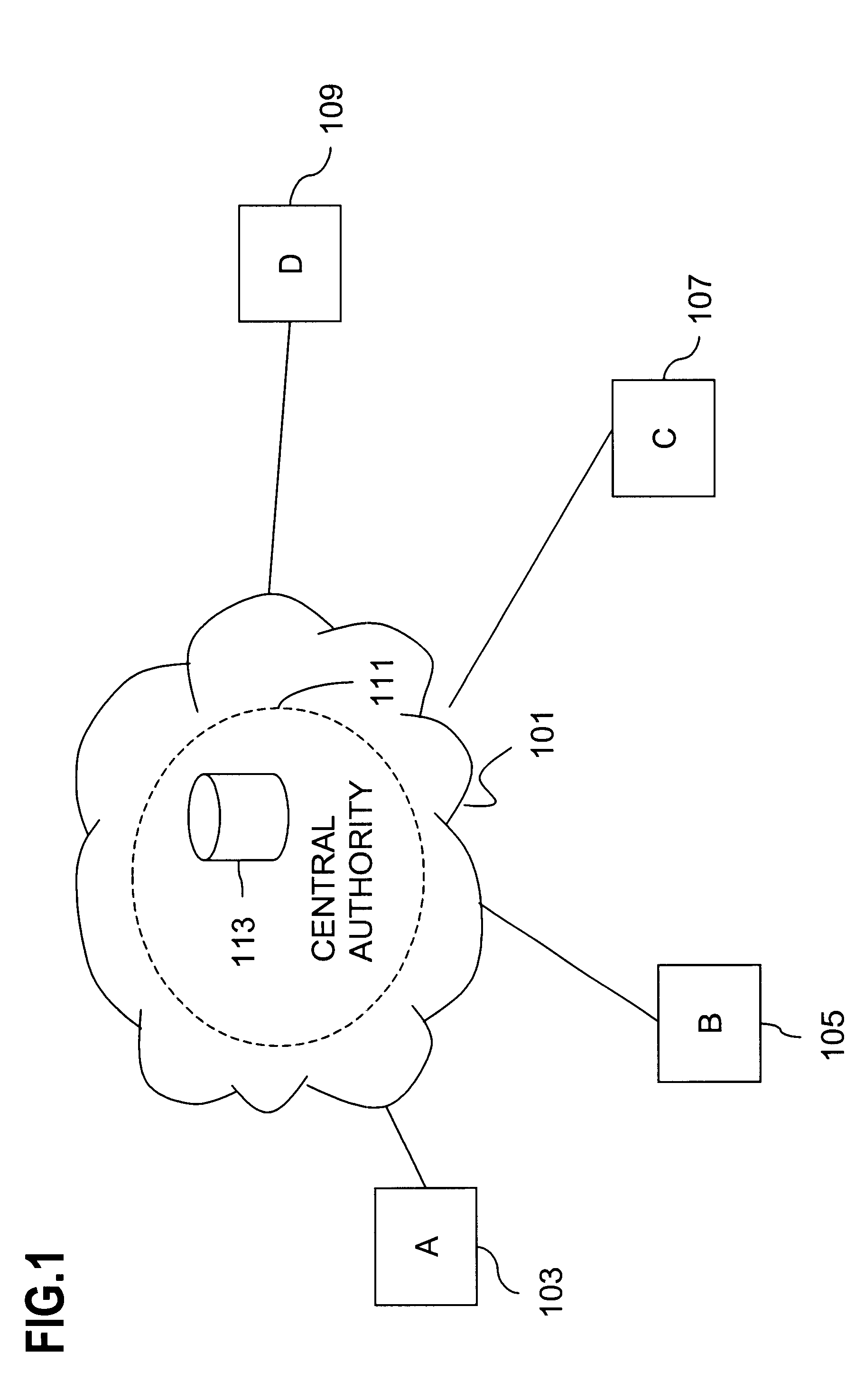
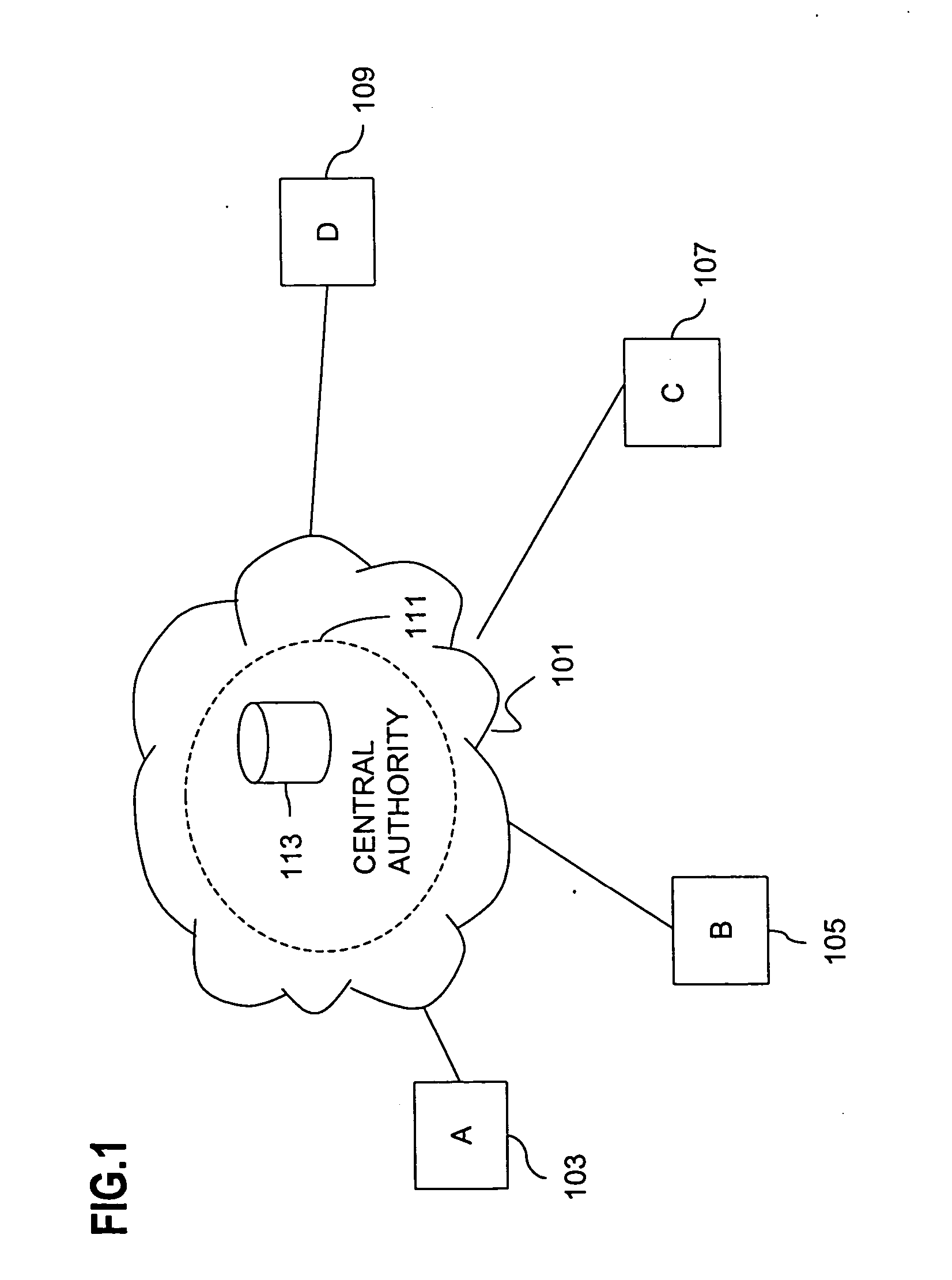
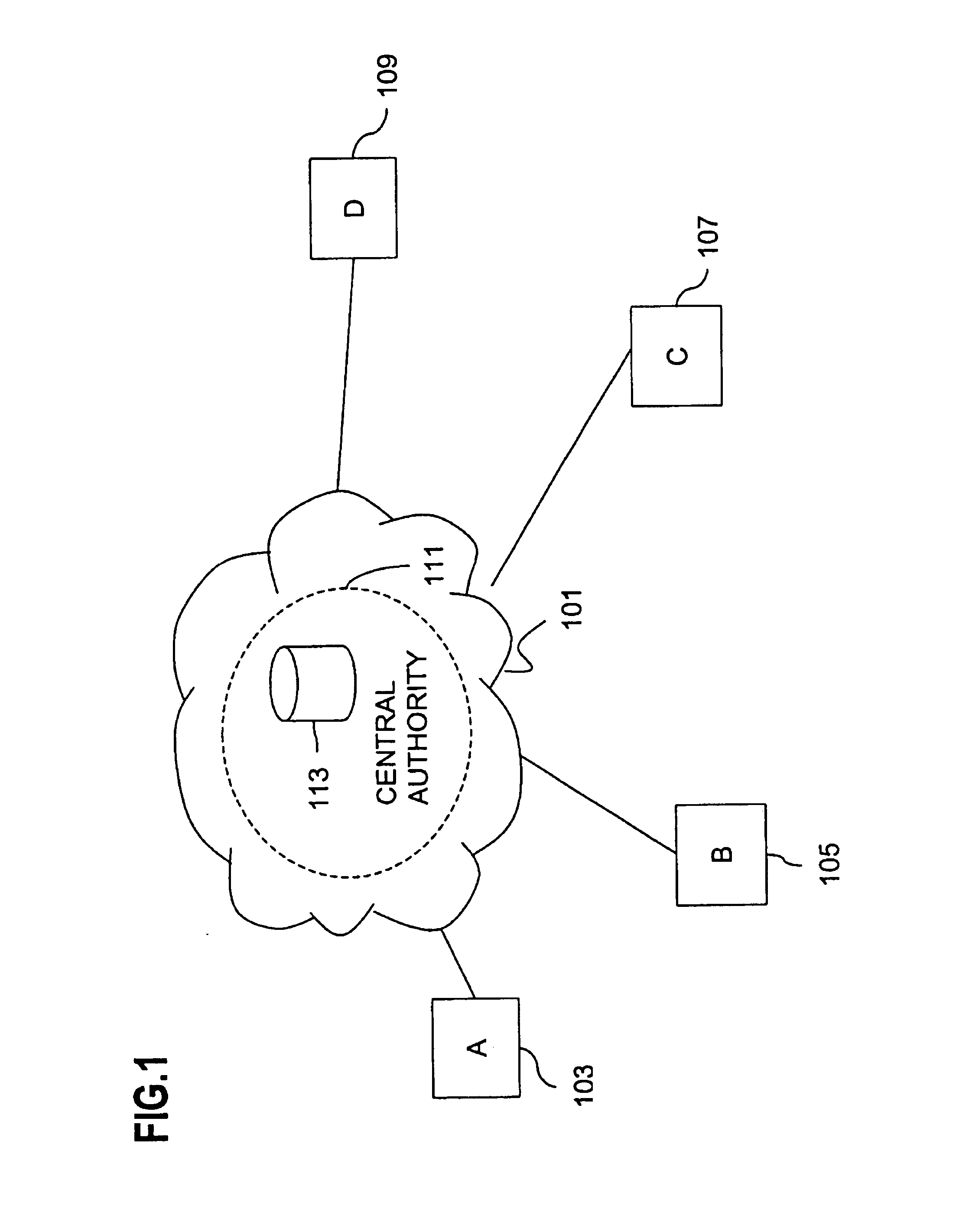
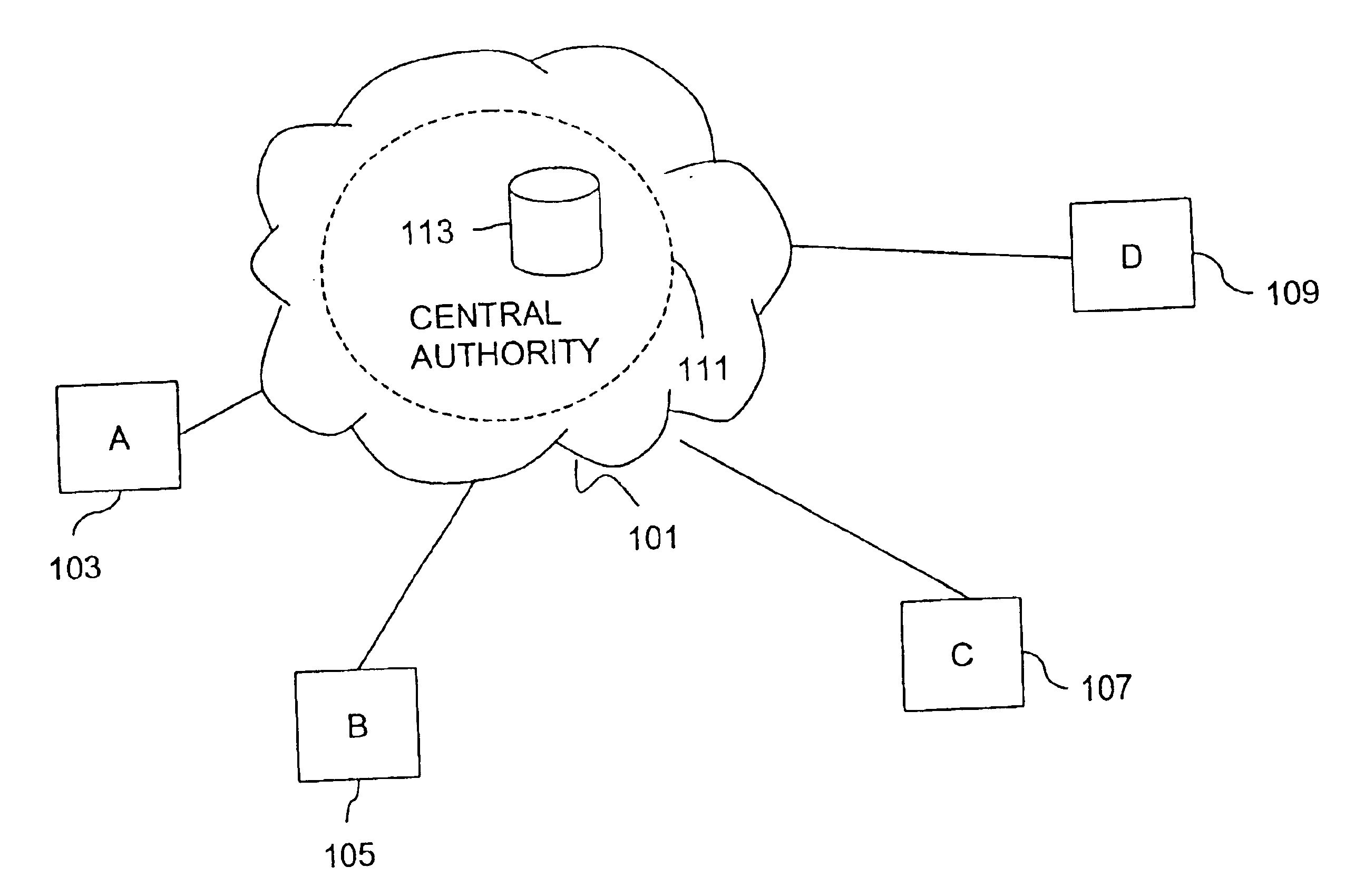
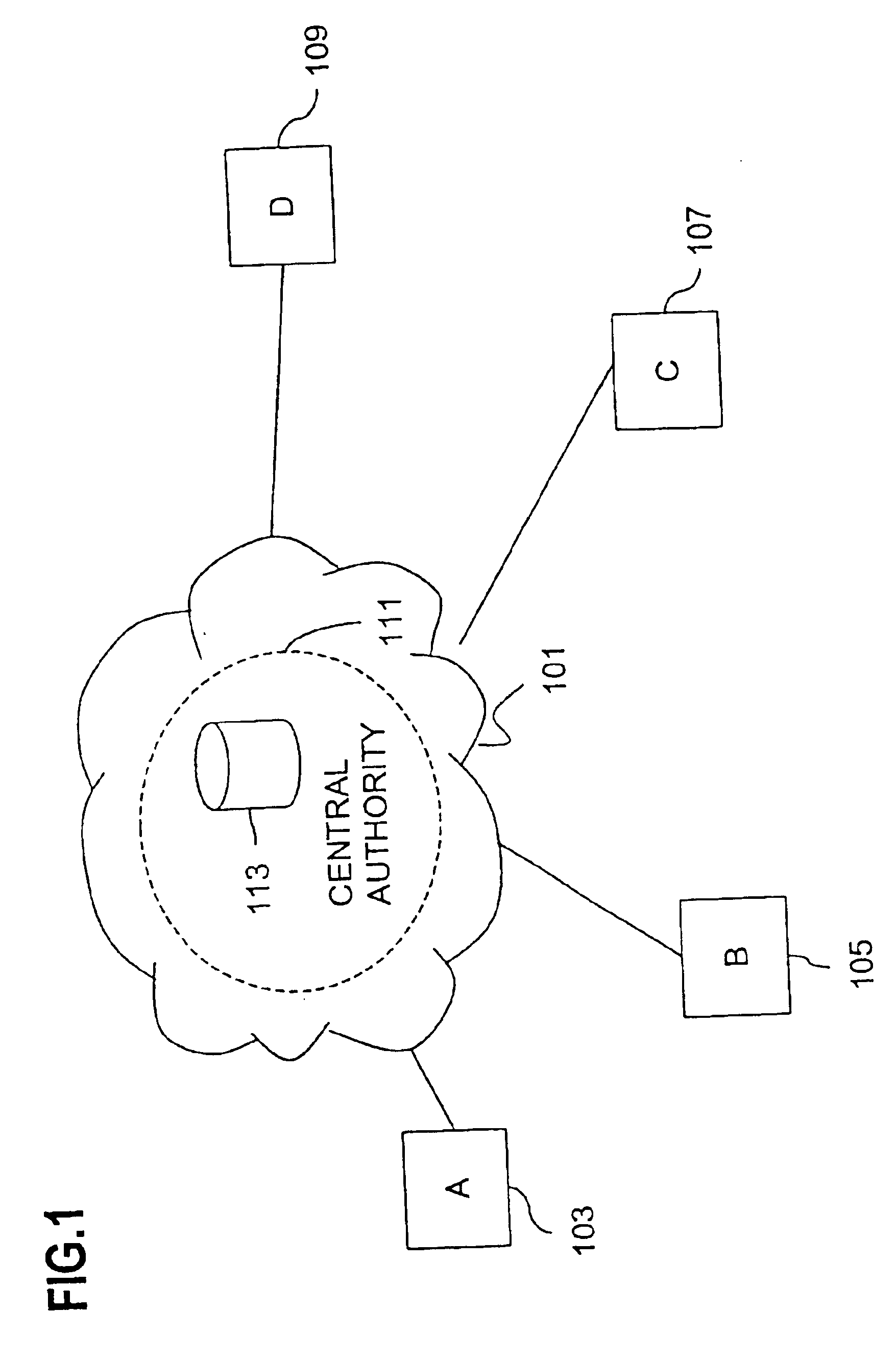
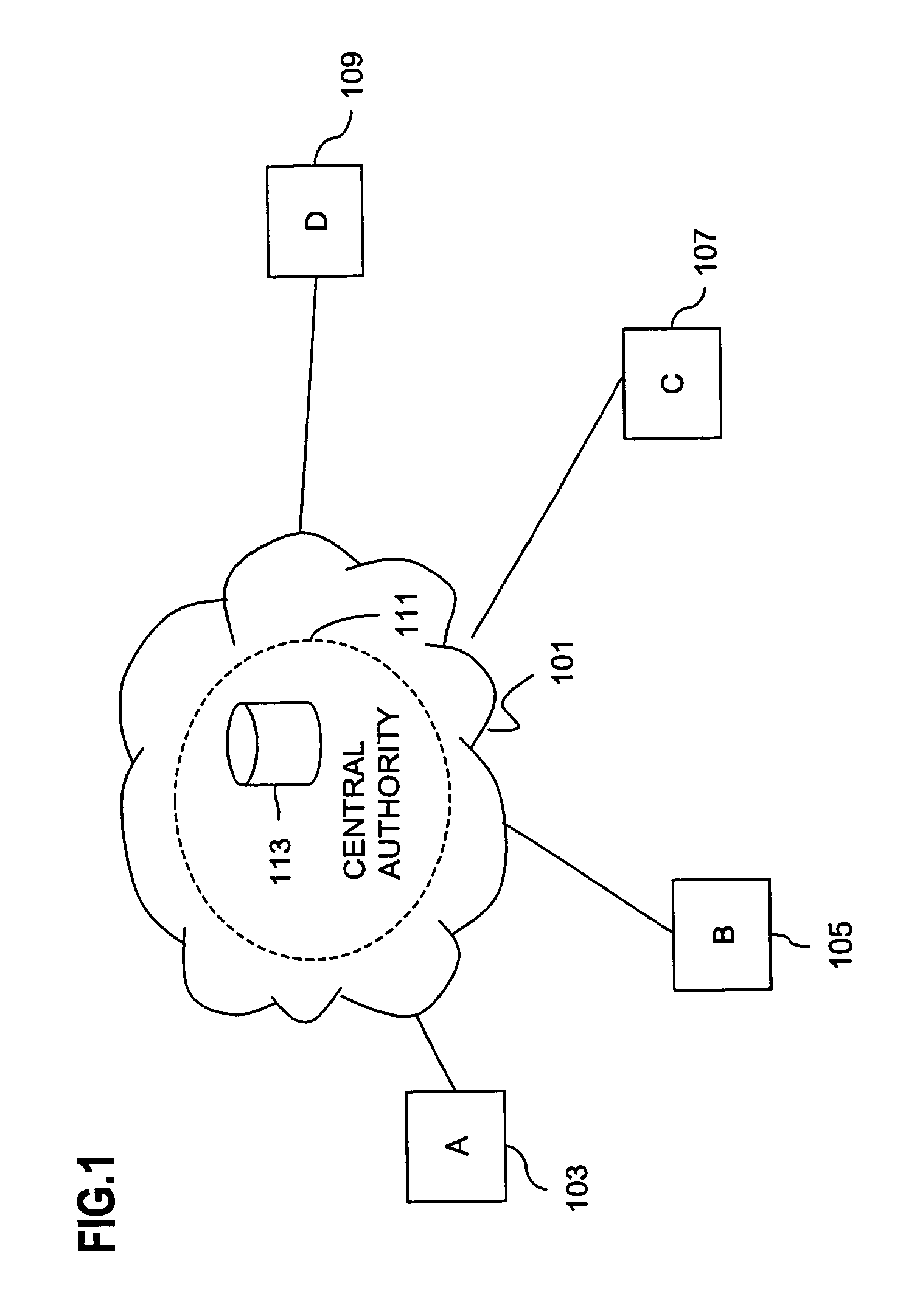
Method and apparatus for creating a secure communication channel among multiple event service nodes
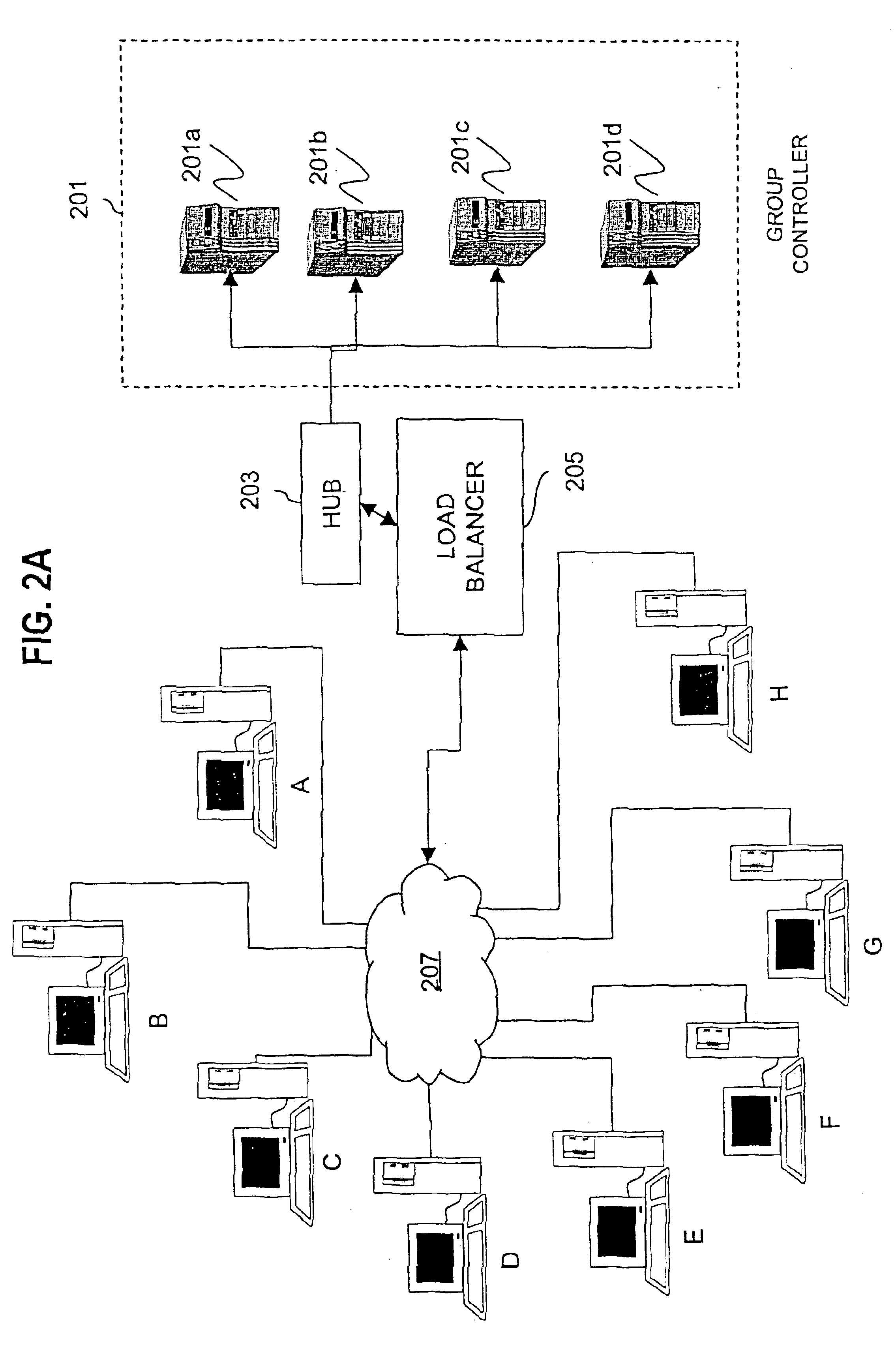
InactiveUS7013389B1Easy to scaleUser identity/authority verificationSecure communicationGroup session
An approach for establishing secure multicast communication among multiple event service nodes is disclosed. The event service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the event service nodes include the group session key and the private keys of the event service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the event service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can readily be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Event service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
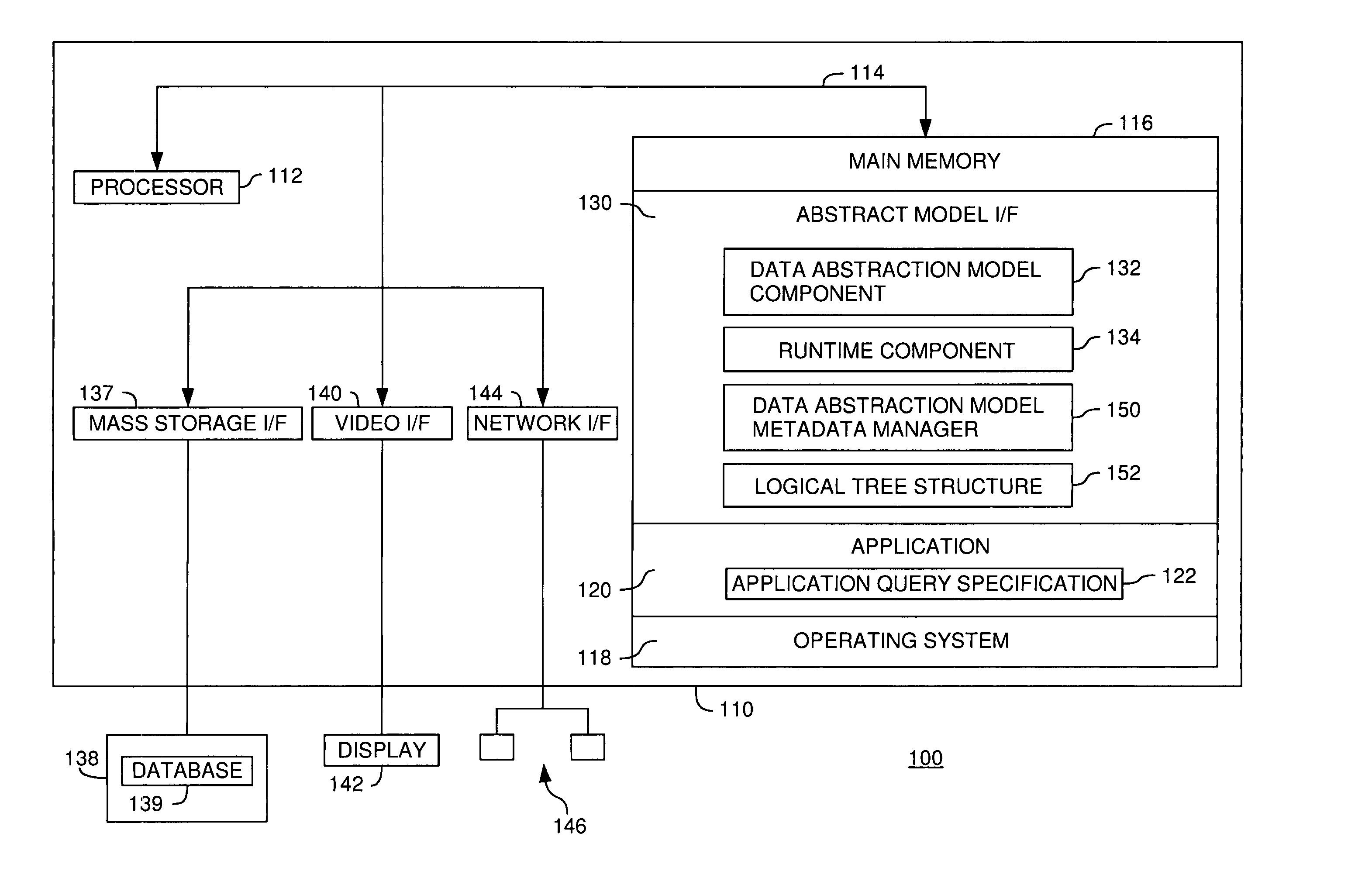
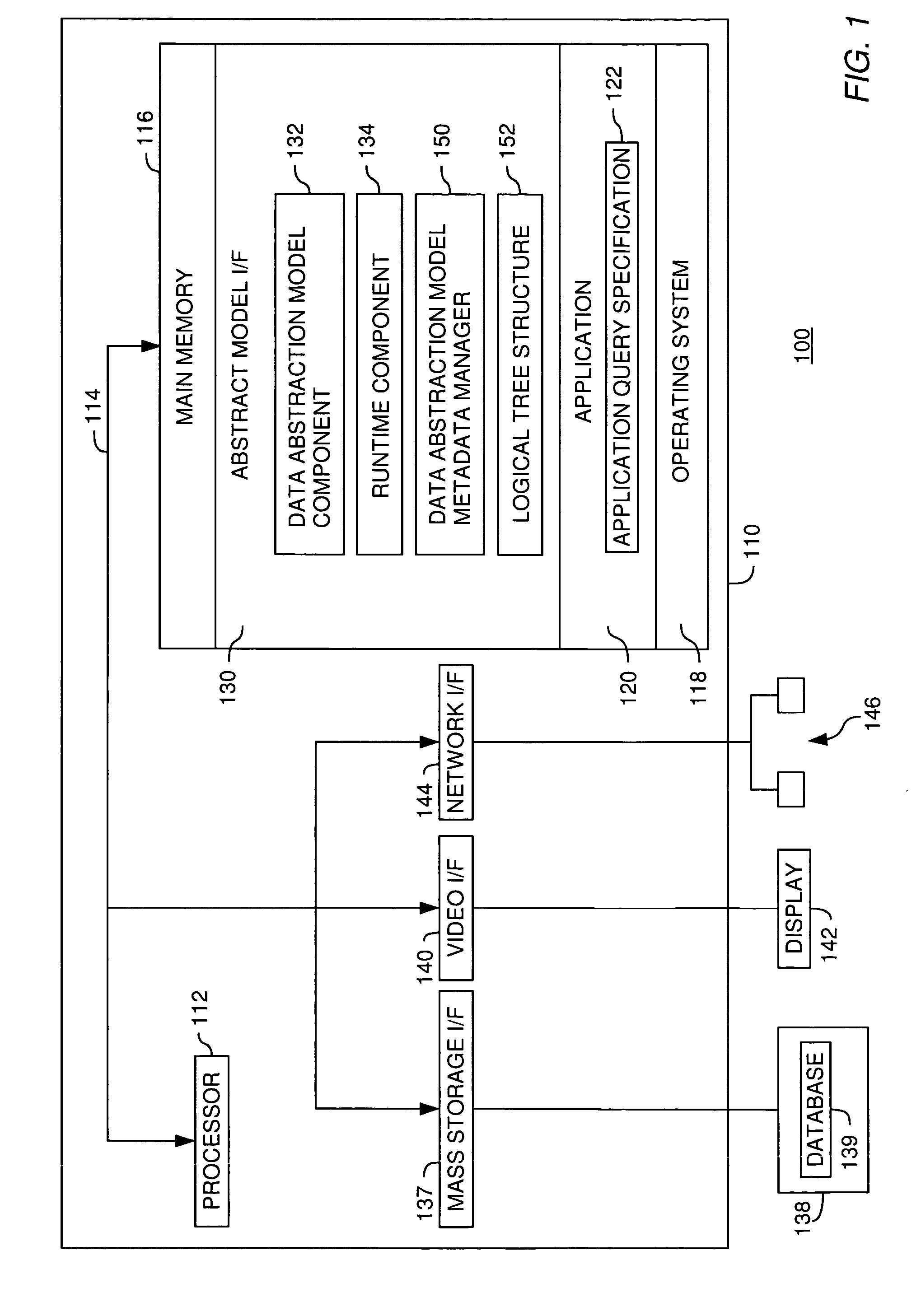
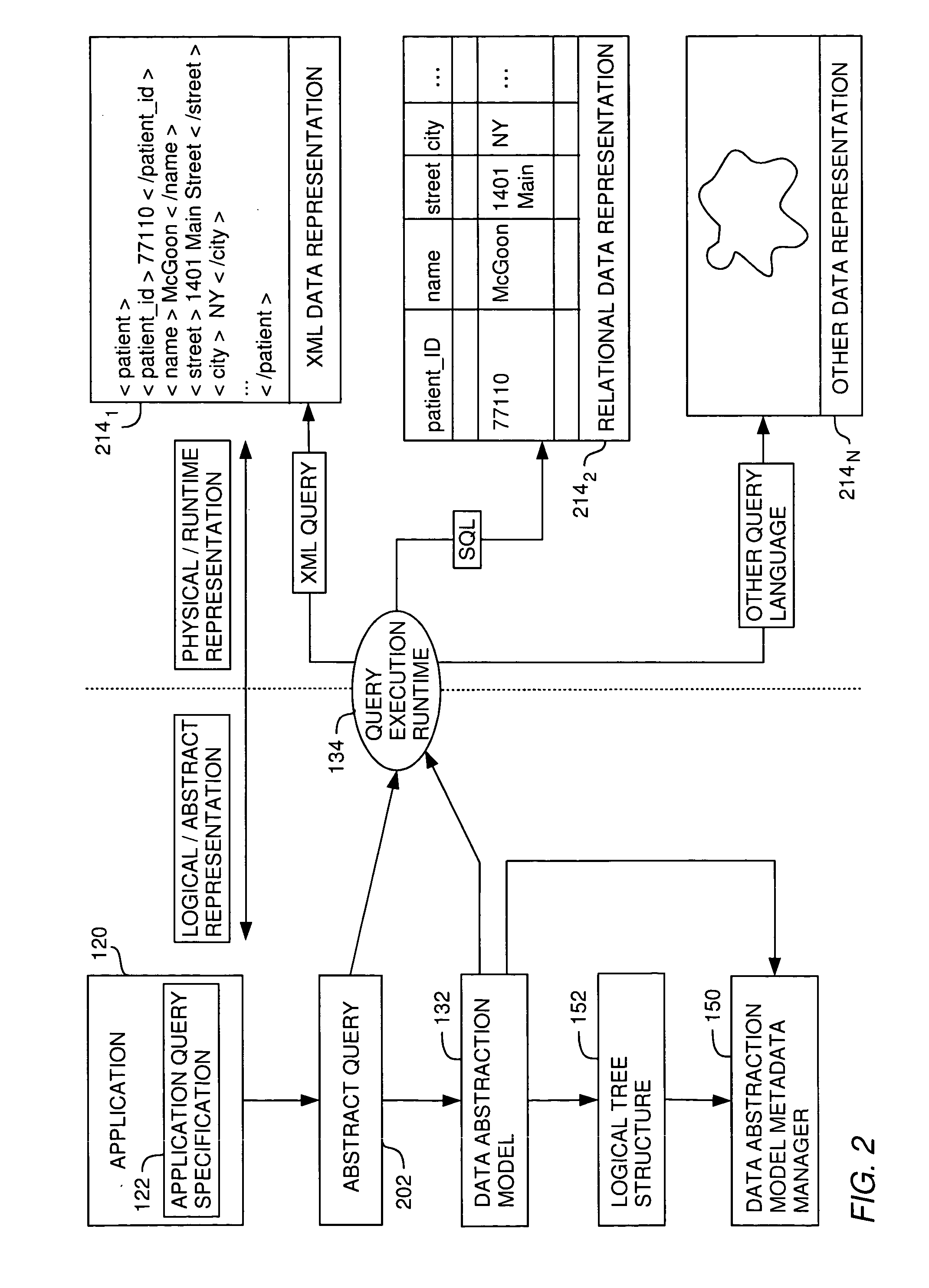
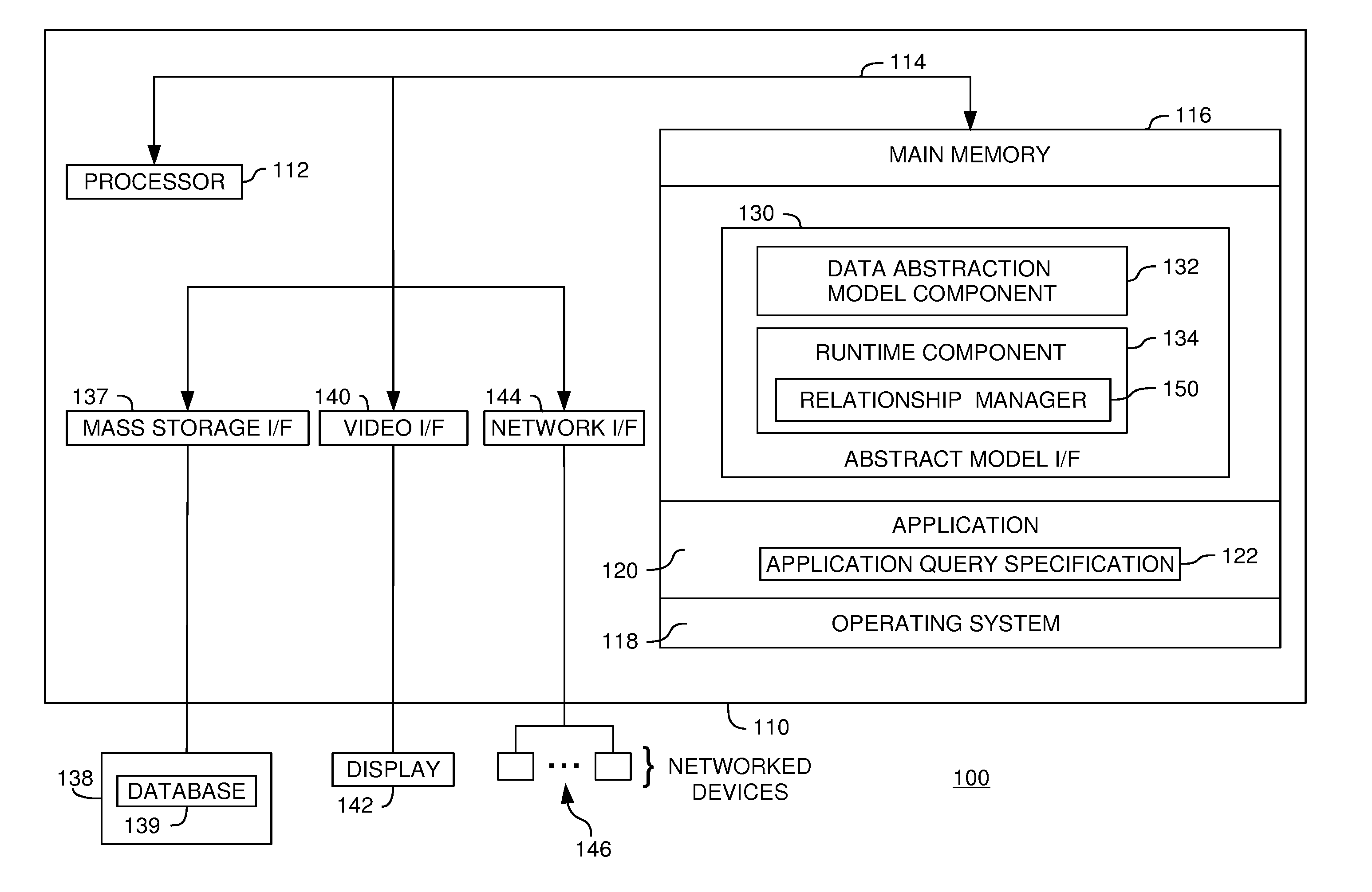
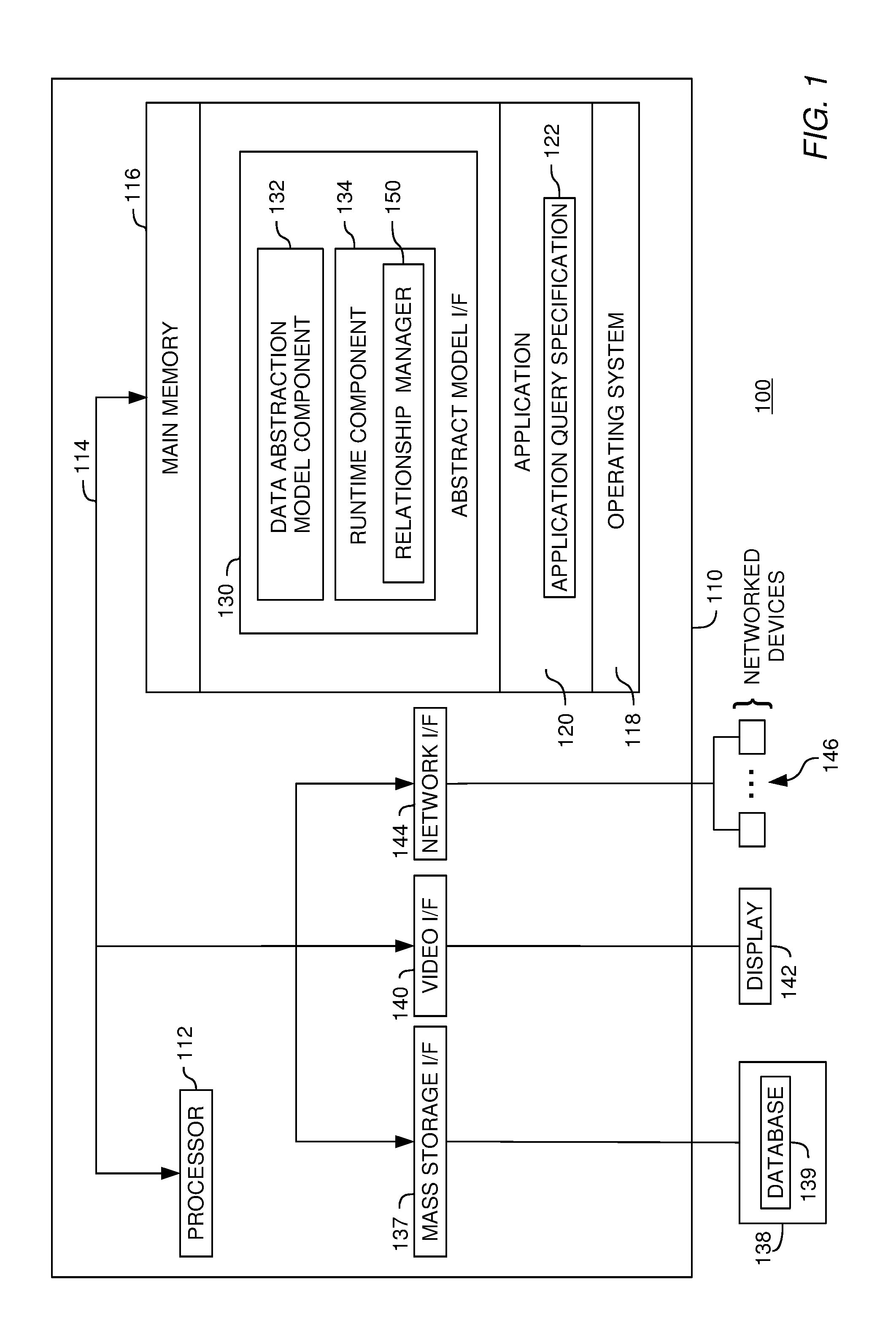
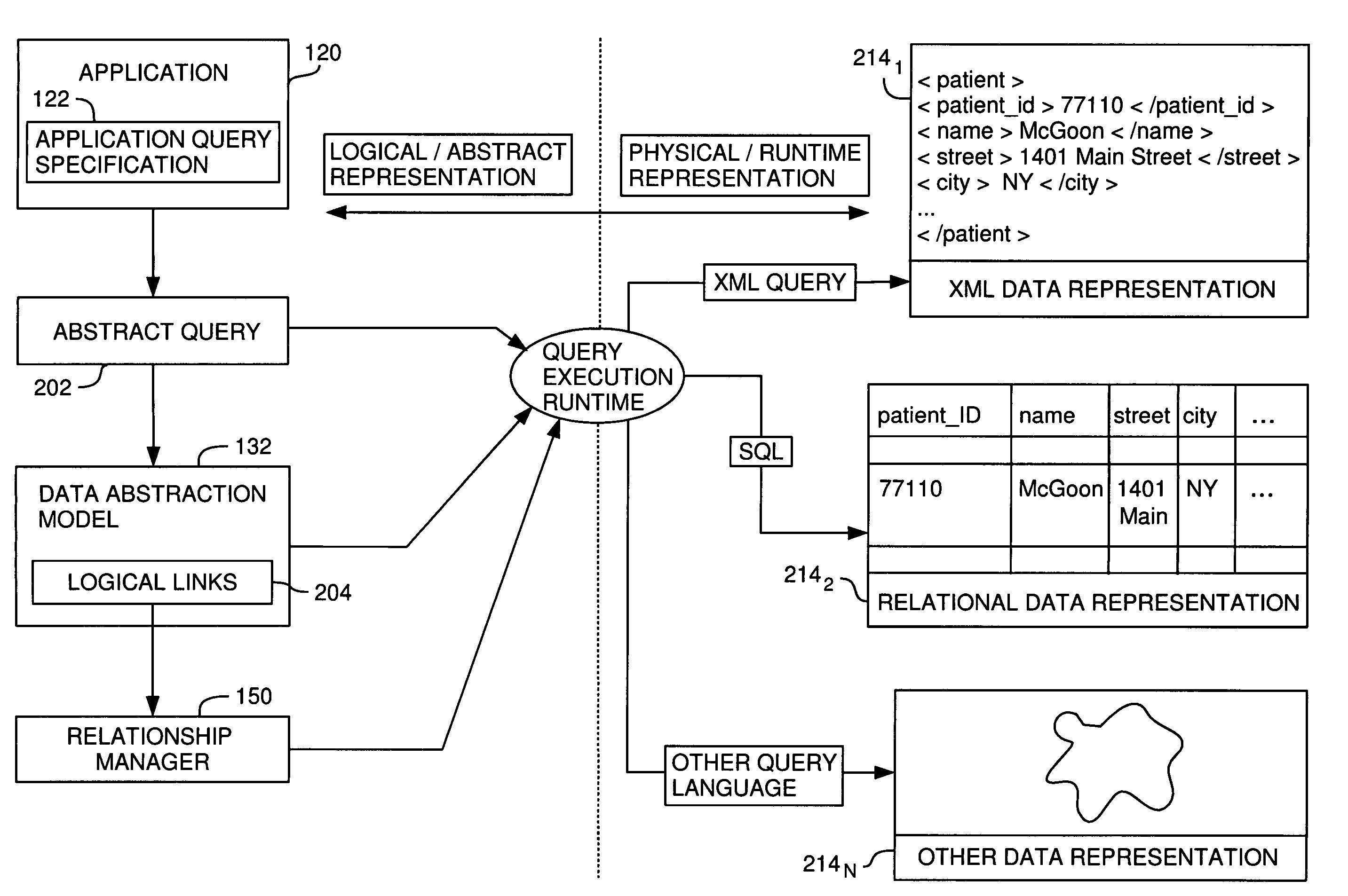
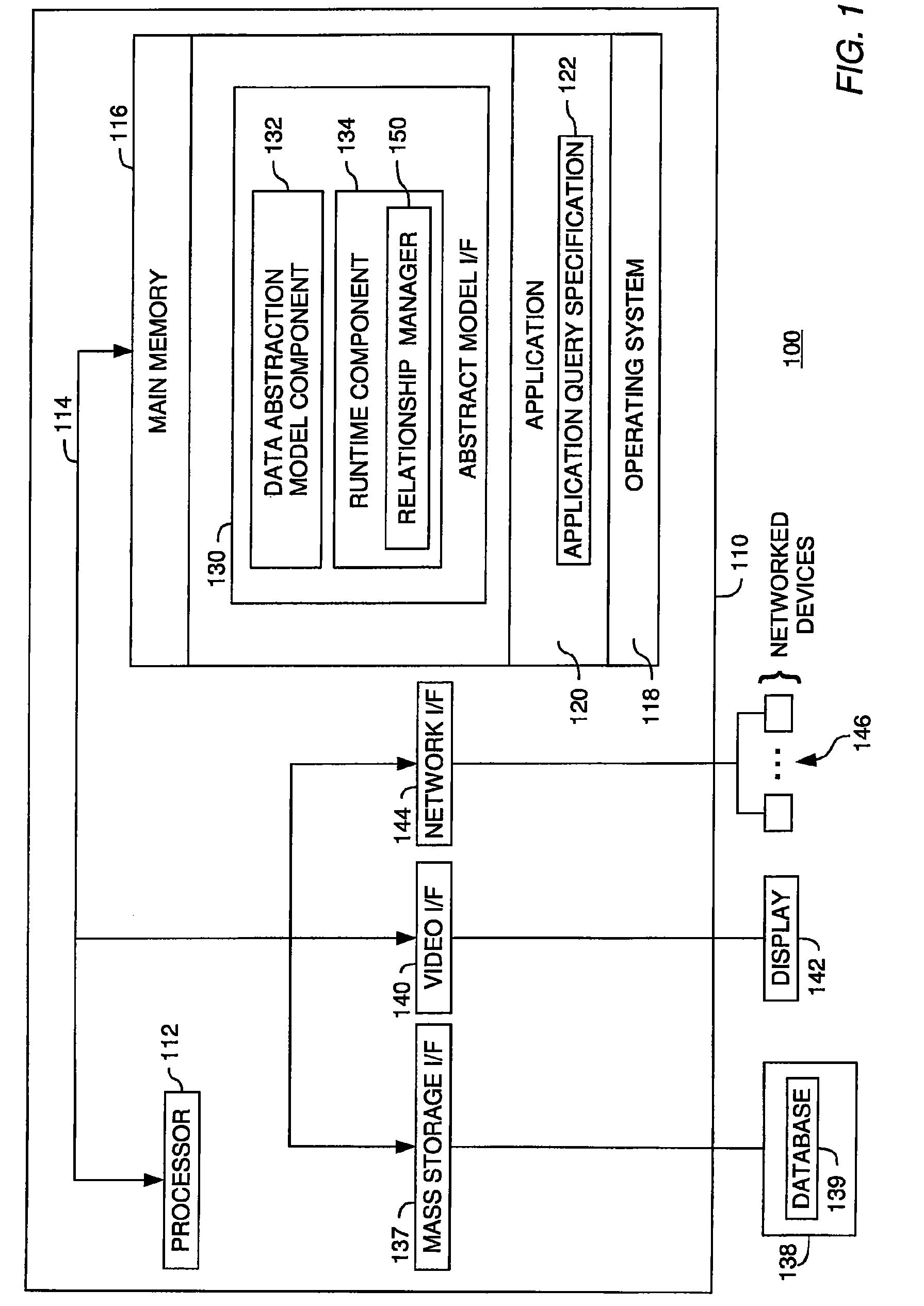
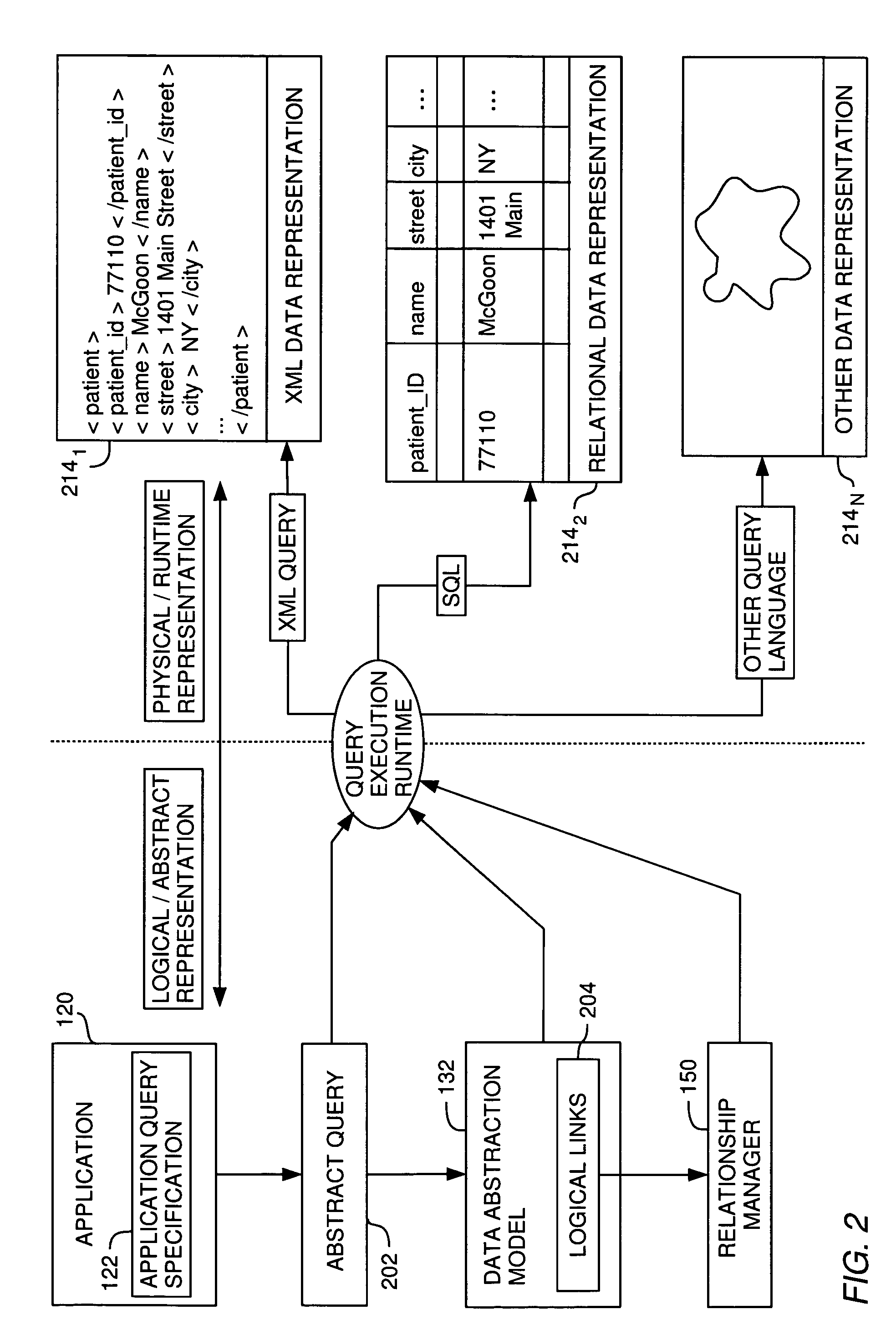
Metadata management for a data abstraction model
InactiveUS20060074953A1Data processing applicationsHospital data managementData abstractionMetadata management
A method, system and article of manufacture for managing metadata associated with a data abstraction model abstractly describing data in a database. One embodiment provides a method of managing metadata describing objects of a data abstraction model with logical fields that define abstract views of physical data in a database. The method comprises traversing a logical tree structure representing the data abstraction model. The logical tree structure has a plurality of nodes, each representing a logical field or a category of logical fields of the data abstraction model. The method further comprises identifying metadata describing logical fields or categories represented by the plurality of nodes. The identified metadata is stored in a queryable database. A user is allowed to query the database to identify objects in the data abstraction model that may be used to construct an abstract query.
Owner:IBM CORP
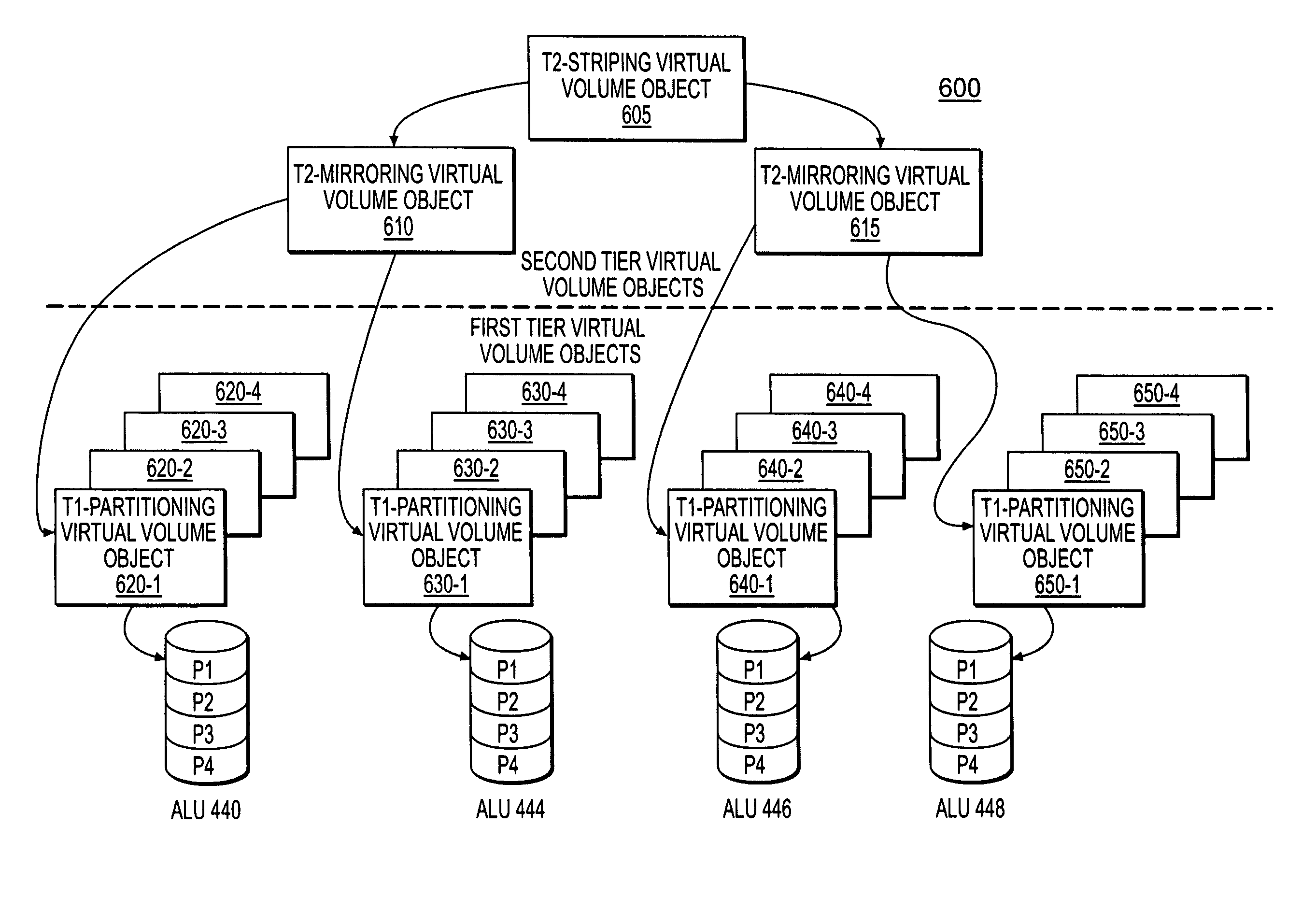
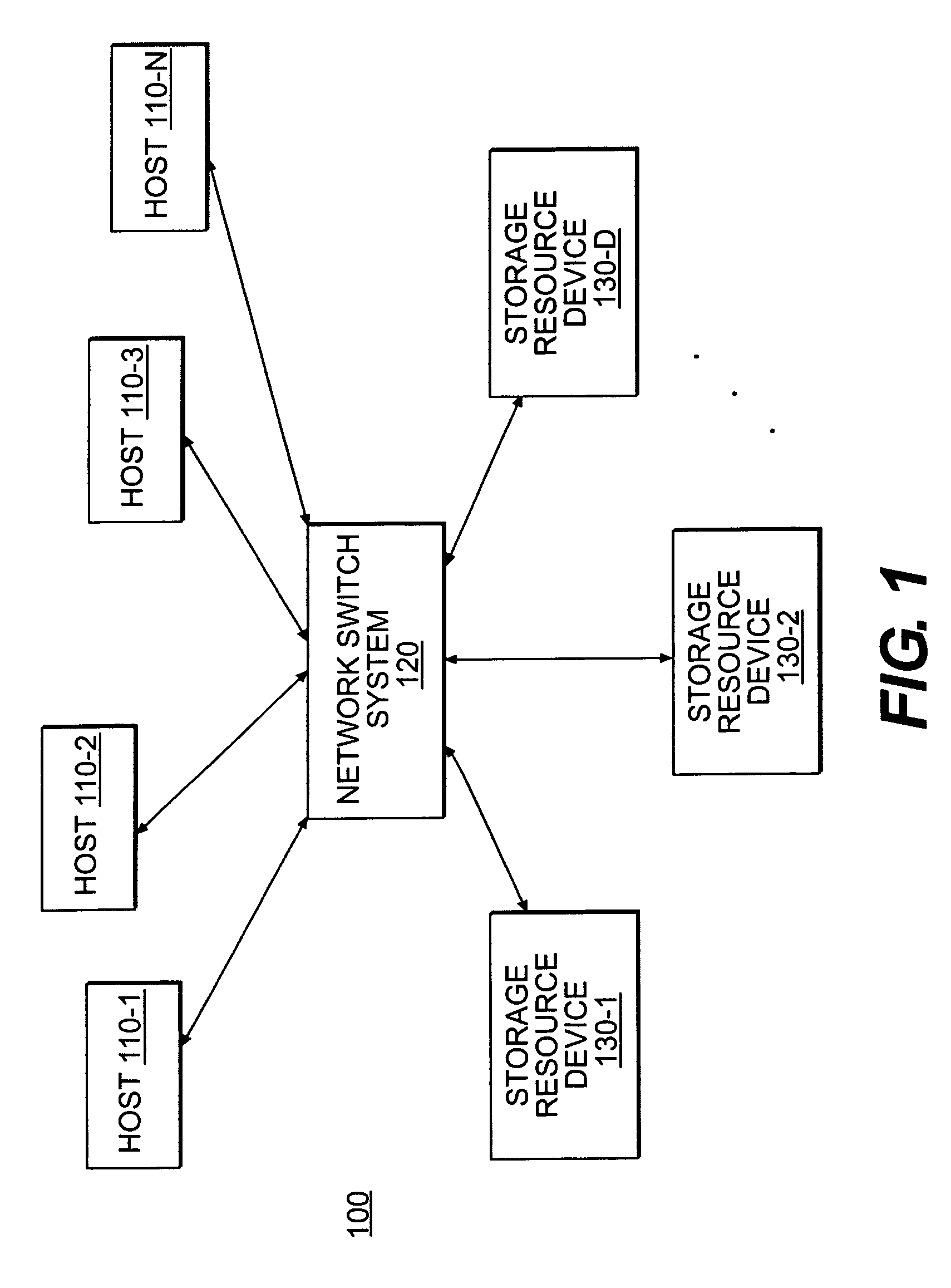
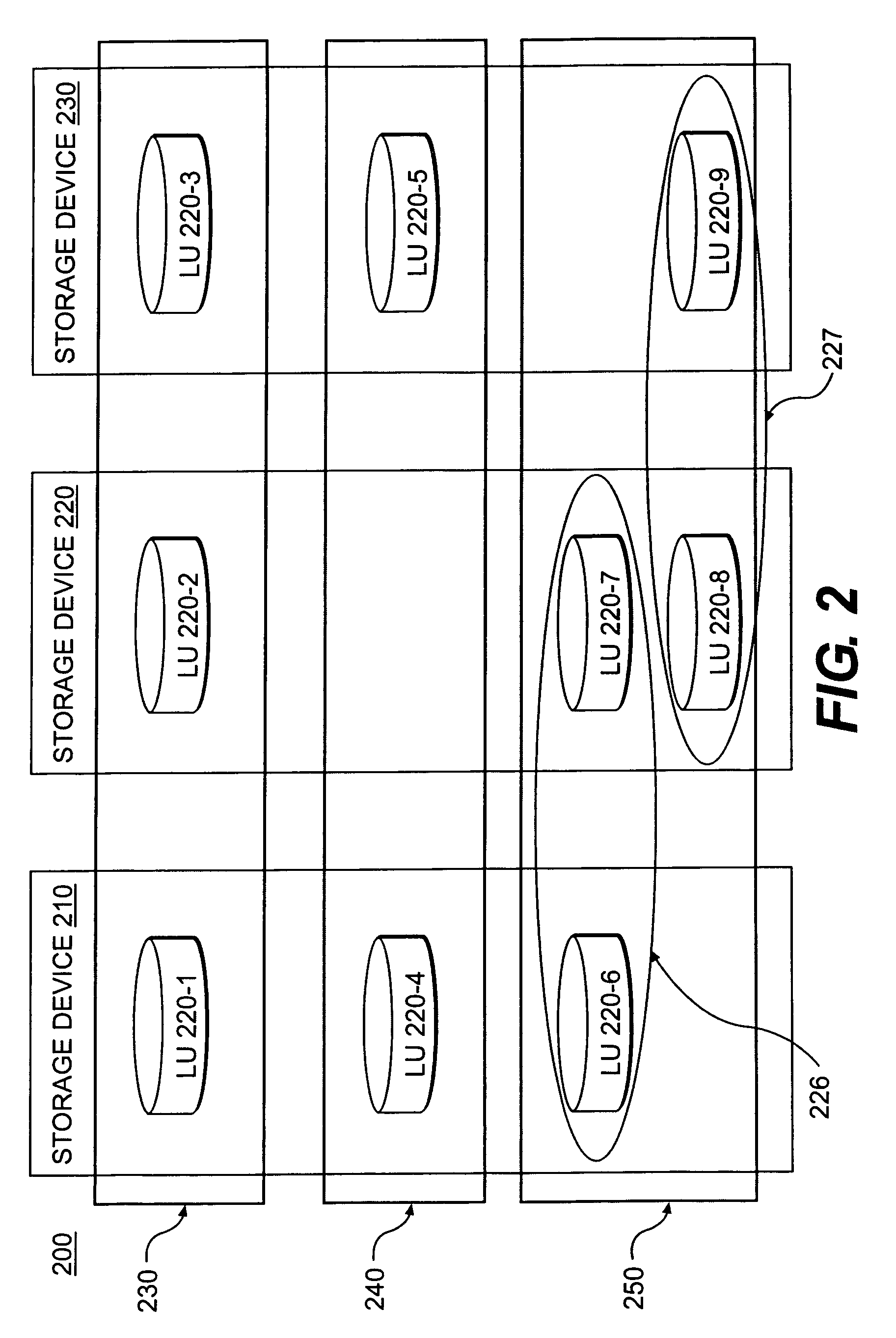
Systems and methods for configuring a storage virtualization environment
ActiveUS7383381B1Improve availabilityImprove scalabilityError detection/correctionTransmissionNetwork switchLogical tree
A storage virtualization environment is provided that includes a network switch system for initializing a virtual volume in a system including a host system, and storage devices. The network switch system includes storage processors including first and second tier storage processors and a Virtualization Coherency Manager (VCM) for receiving storage connectivity identifying which storage processors are connected to selected ones of the storage devices. Further, the network switch system includes a master storage processor for creating a logical tree based on the storage connectivity information, the logical tree reflecting a virtual volume of data distributed across the storage devices and includes (i) first tier objects representing partitions of the virtual volume data and (ii) second tier objects representing a logical configuration of the virtual volume. In one embodiment, the VCM assigns the first tier objects to selective ones of the first tier storage processors and assigns the second tier objects to selective ones of the second tier storage processors based on the logical tree. Further, each of the selective first and second tier storage processors initialize a local portion of the virtual volume to allow the host system to access the virtual volume through the network switch system.
Owner:ORACLE INT CORP
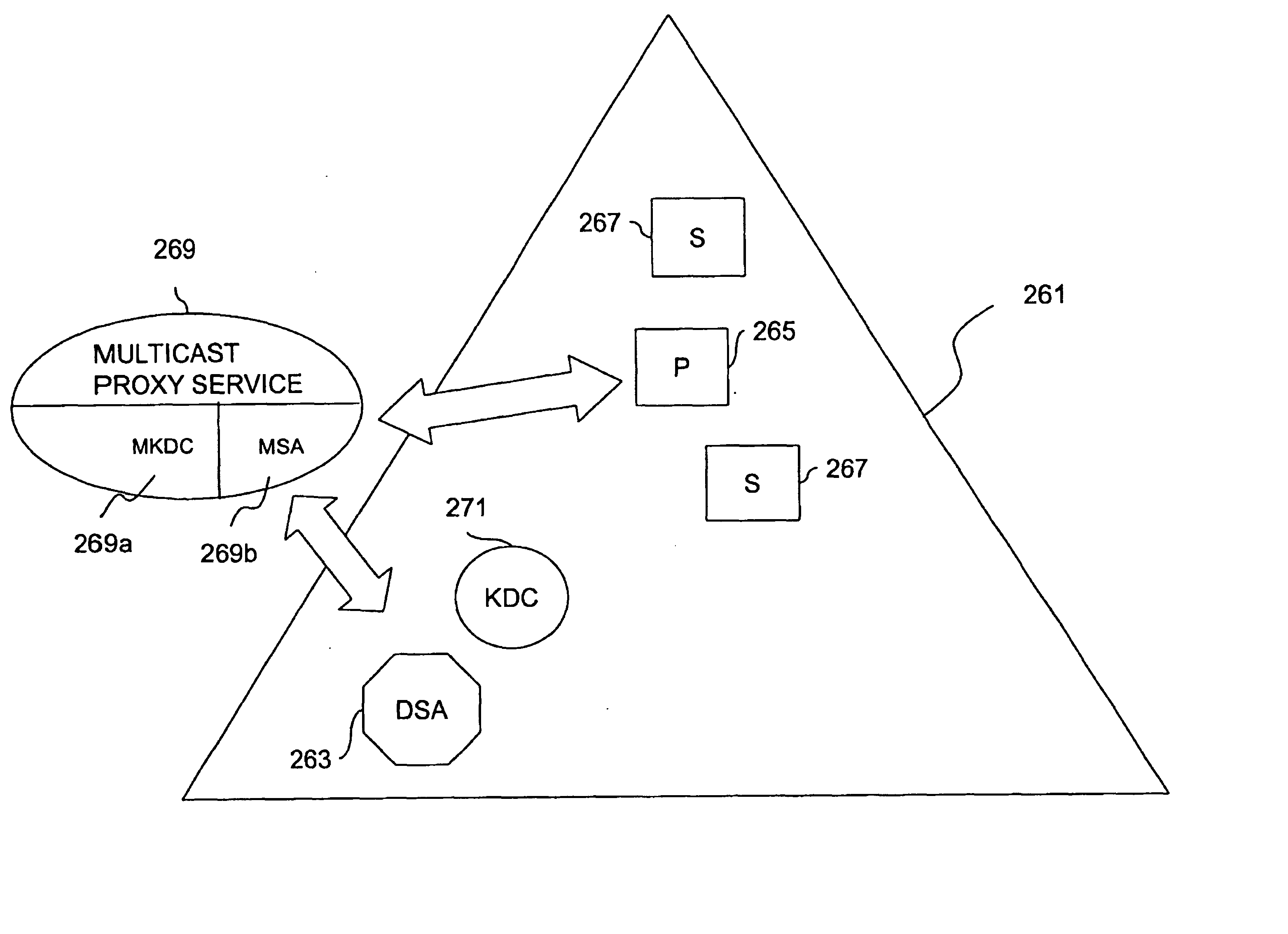
Method and apparatus for distributing and updating private keys of multicast group managers using directory replication
InactiveUS20050044356A1Optimize allocationKey distribution for secure communicationGroup sessionSecure multicast
An approach for establishing secure multicast communication among multiple multicast proxy service nodes is disclosed. The multicast proxy service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the multicast proxy service nodes include the group session keys that are members of the secure multicast or broadcast groups. Because keys as well as key version information are housed in the directory, multicast security can be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Multicast proxy service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
Method and apparatus for distributing and updating private keys of multicast group managers using directory replication
InactiveUS7103185B1Optimize allocationKey distribution for secure communicationSynchronising transmission/receiving encryption devicesGroup sessionSecure multicast
An approach for establishing secure multicast communication among multiple multicast proxy service nodes is disclosed. The multicast proxy service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the multicast proxy service nodes include the group session key and the private keys of the multicast proxy service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the multicast proxy service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Multicast proxy service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
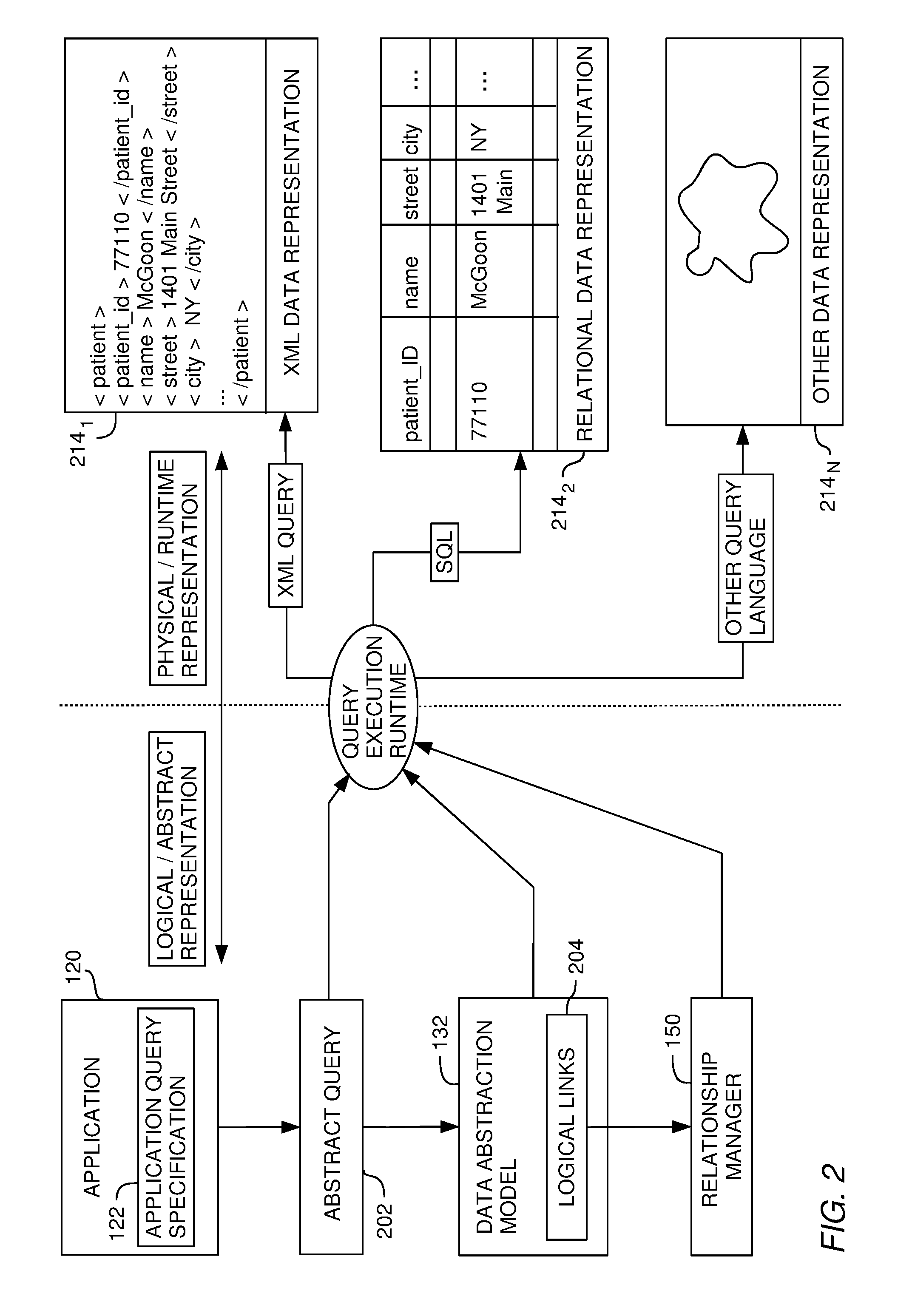
Relationship management in a data abstraction model
ActiveUS20100023498A1Data processing applicationsDigital data information retrievalCustomer relationship managementData abstraction
A method, system and article of manufacture for managing relationships in a data abstraction model abstractly describing data in a database. One embodiment provides a method of linking logical branches of data in a database based on the relationships. The method includes accessing a data abstraction model abstractly describing the data in the database. The data abstraction model defines a logical tree structure having a plurality of logical branches. Relationships between logical fields of different logical branches are identified and logical links abstractly describing the identified relationships are created.
Owner:INT BUSINESS MASCH CORP
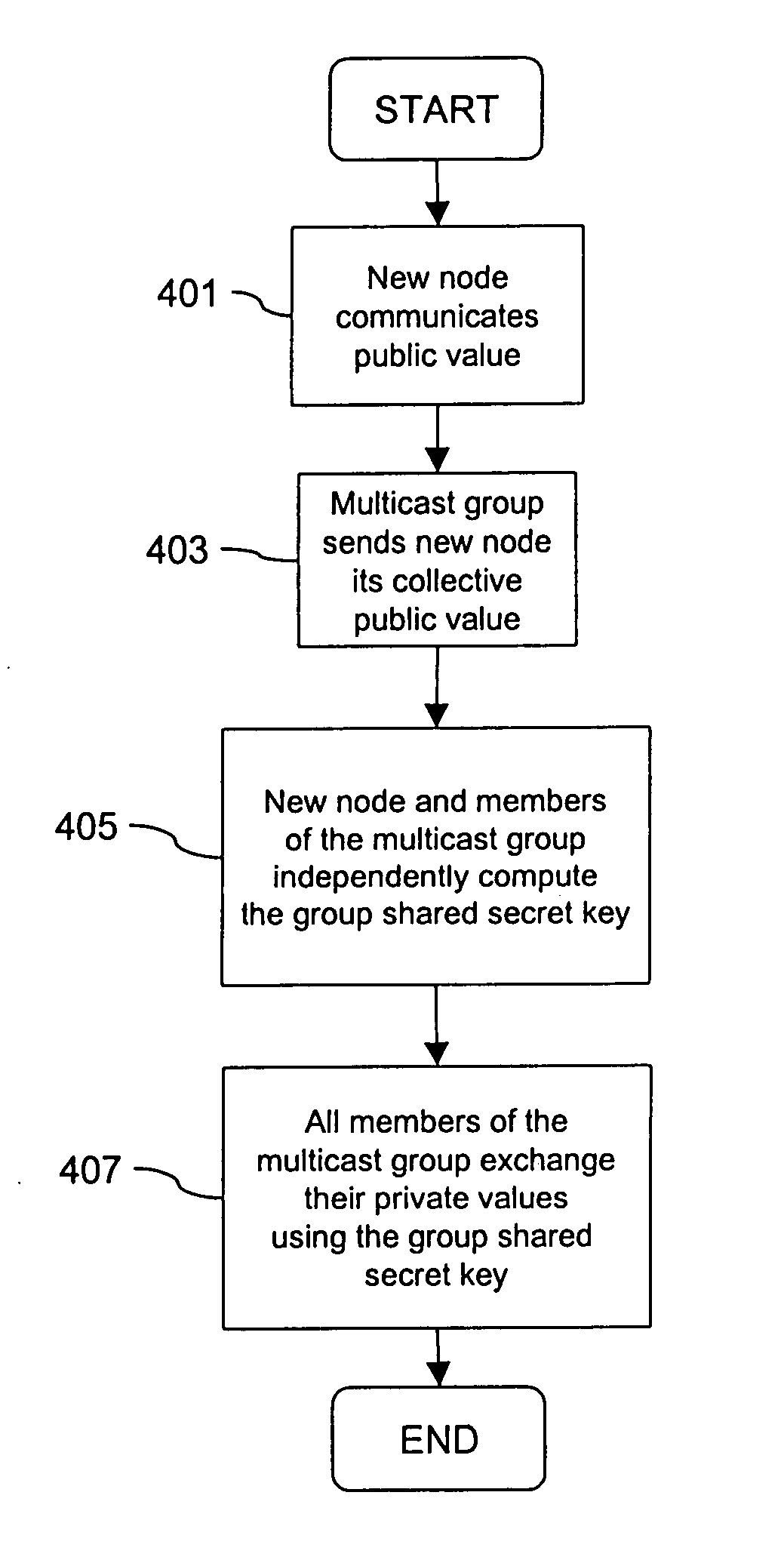
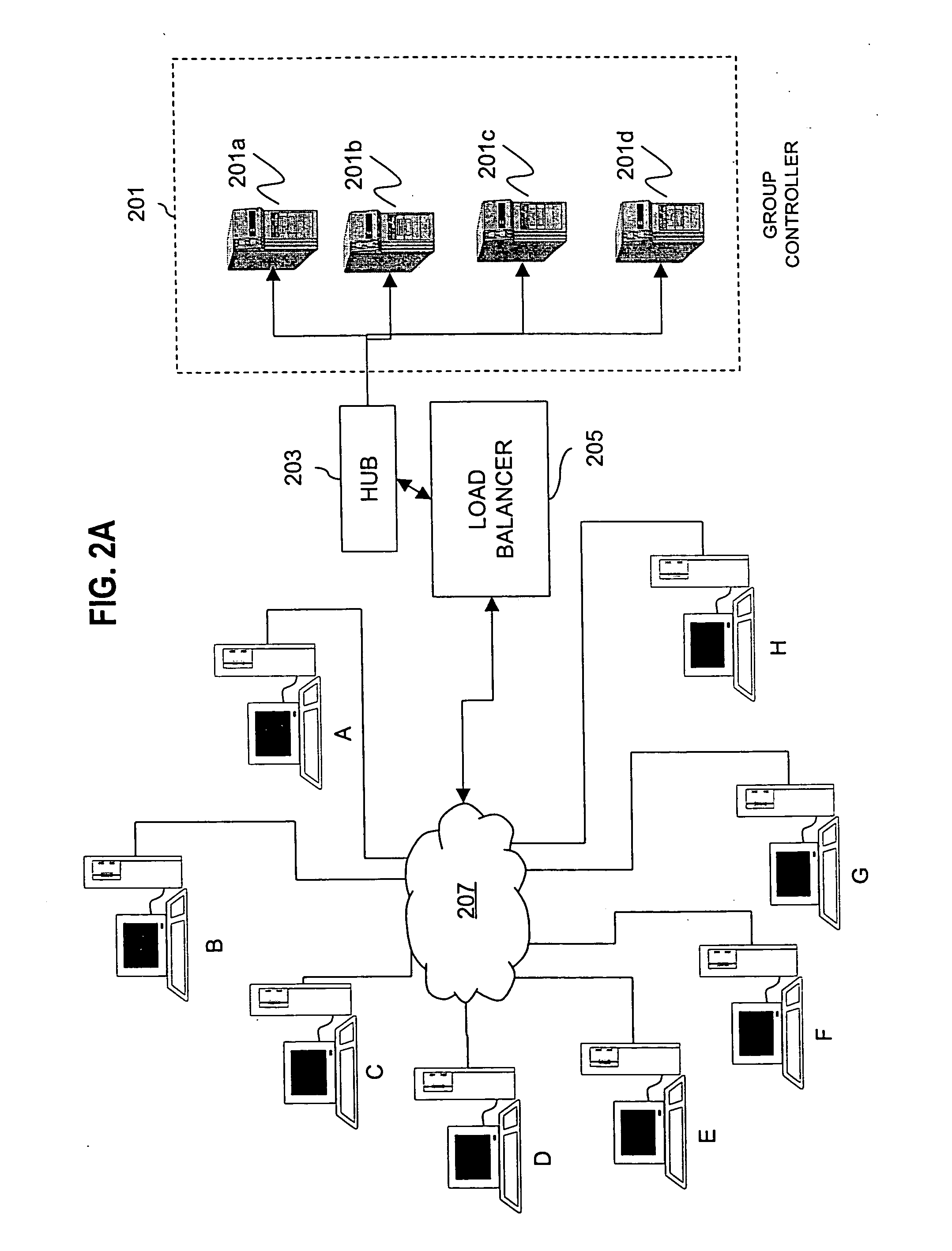
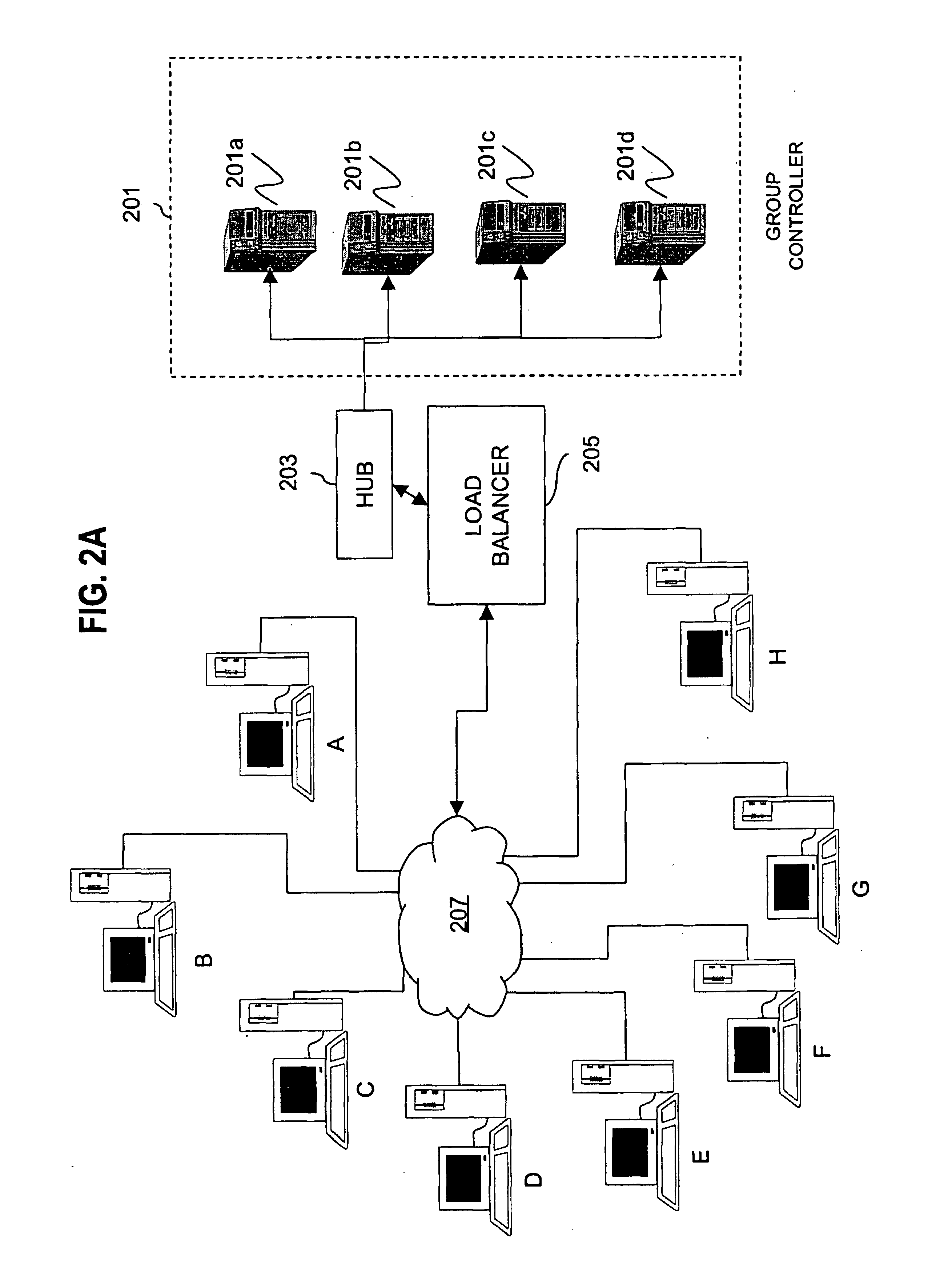
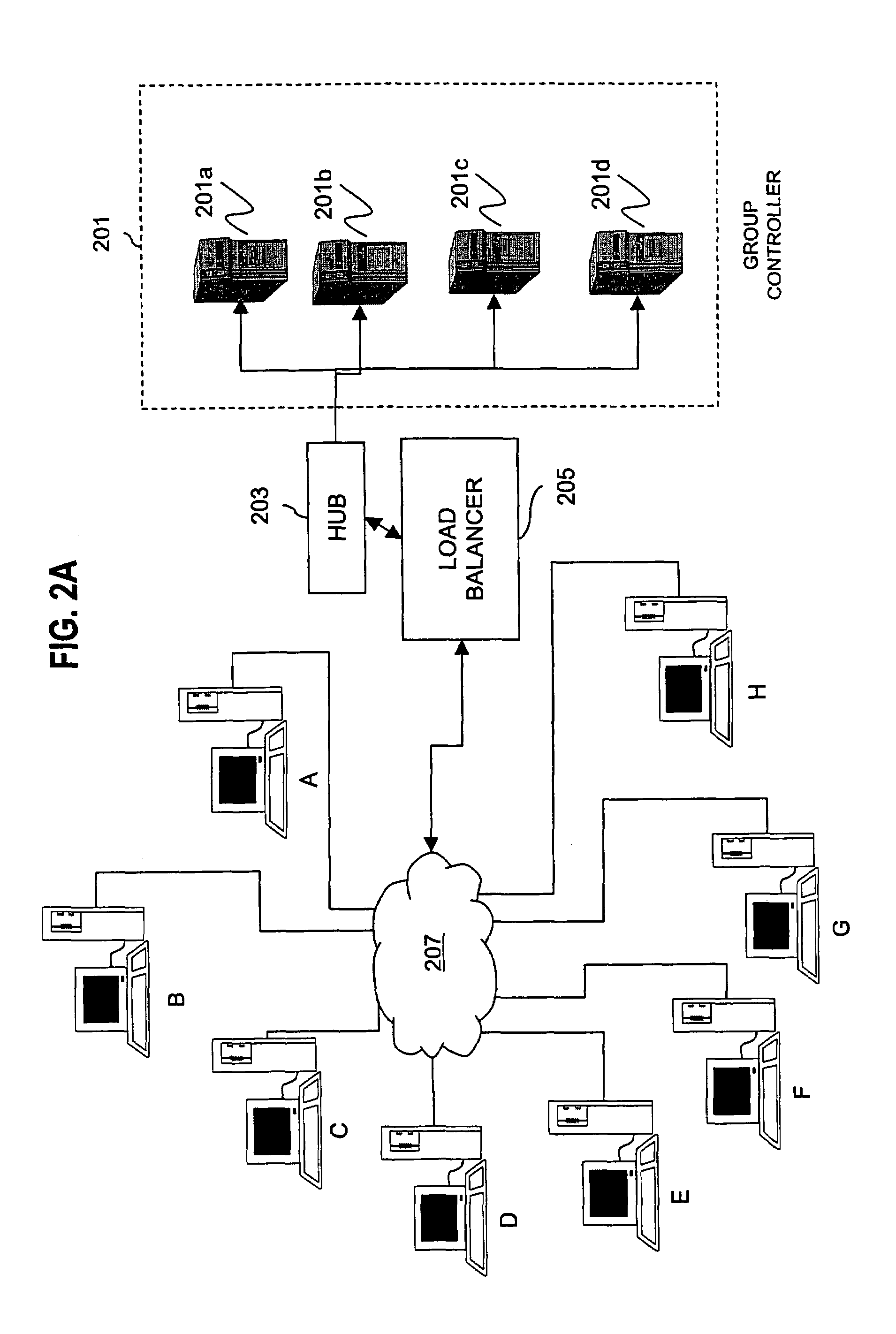
Method and apparatus for distributing and updating group controllers over a wide area network using a tree structure
InactiveUS6901510B1Reduces the workload on the group controllerSpecial service provision for substationKey distribution for secure communicationBinary treeWide area network
Apparatus and computer-readable media are disclosed for establishing secure multicast communication among multiple multicast proxy service nodes of domains of a replicated directory service that spans a wide area network. Domains are organized in a logical tree. Each domain has a logical tree that organizes the multicast proxy service nodes, a group manager at the root node, a multicast key distribution center, multicast service agent, directory service agent and key distribution center. Multicast proxy service nodes store a group session key and a private key. Replication of the directory performs key distribution. A multicast group member joins or leaves the group by publishing message. The local key distribution center and multicast service agent obtain the publisher's identity from a local directory service agent. Based on the identity, a secure channel is established with the directory service agent in the group member's domain. Keys of the binary tree branch that contains the joining or leaving node are updated, and an updated group session key and a new private key are received.
Owner:CISCO TECH INC
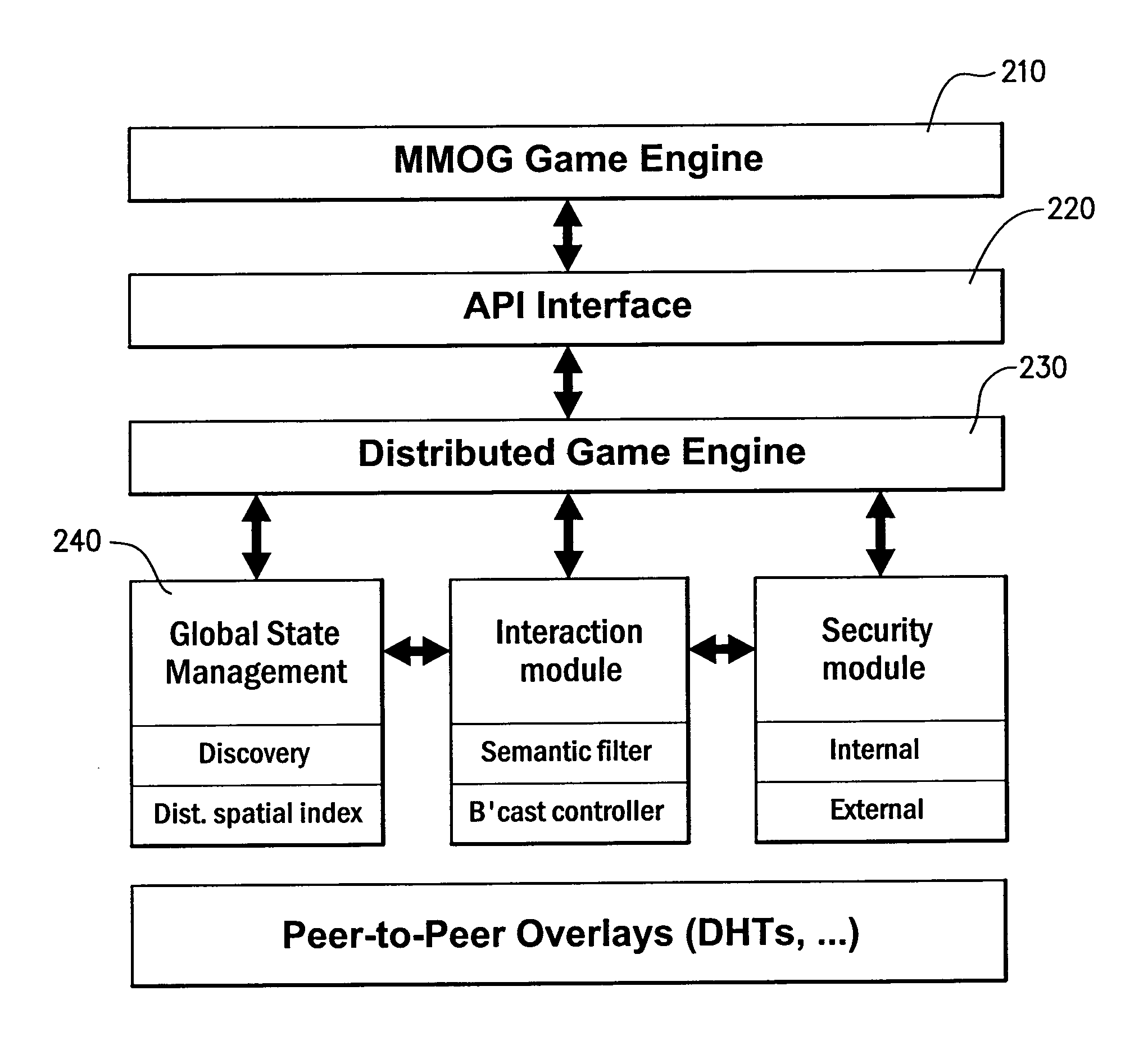
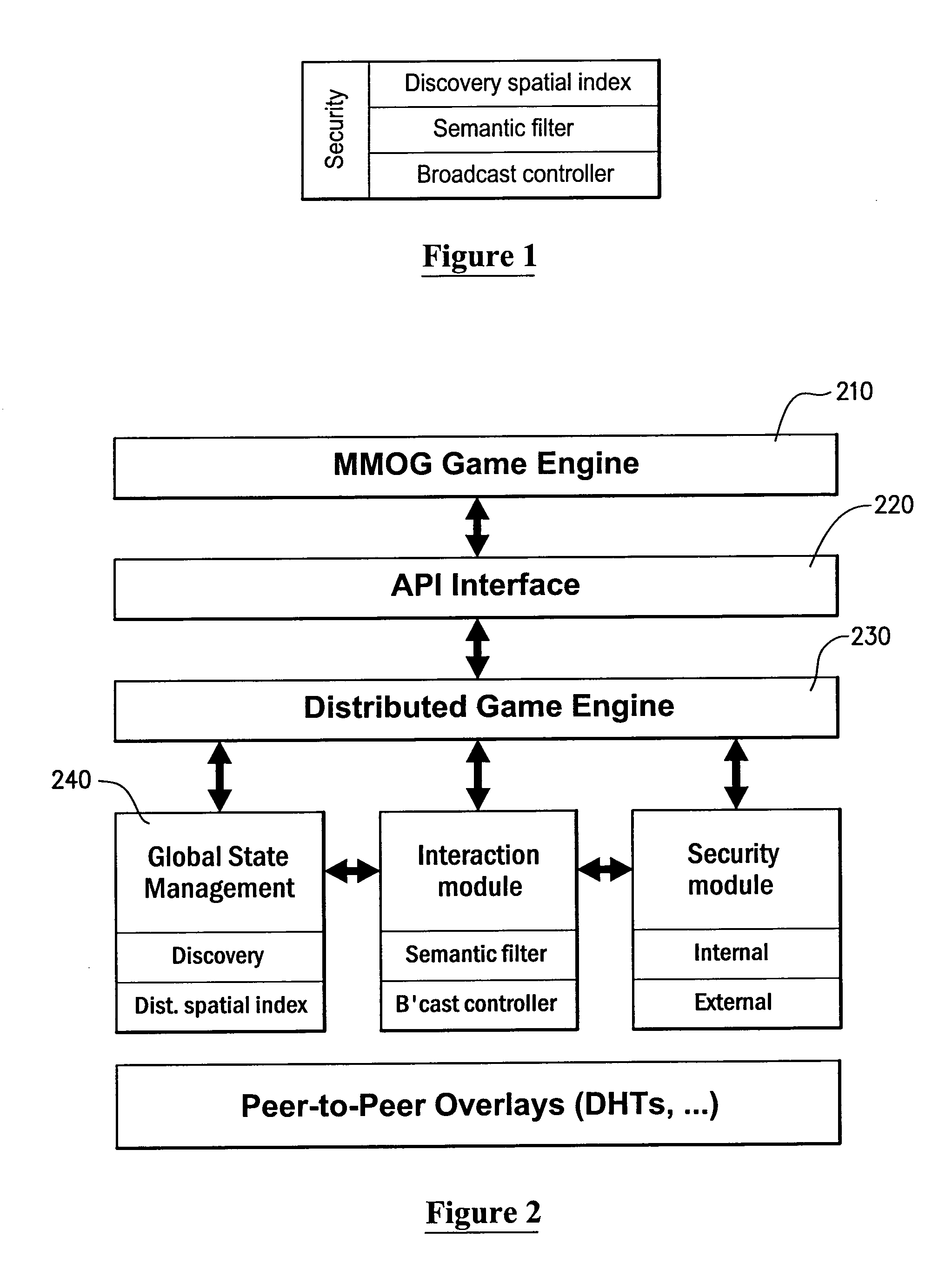
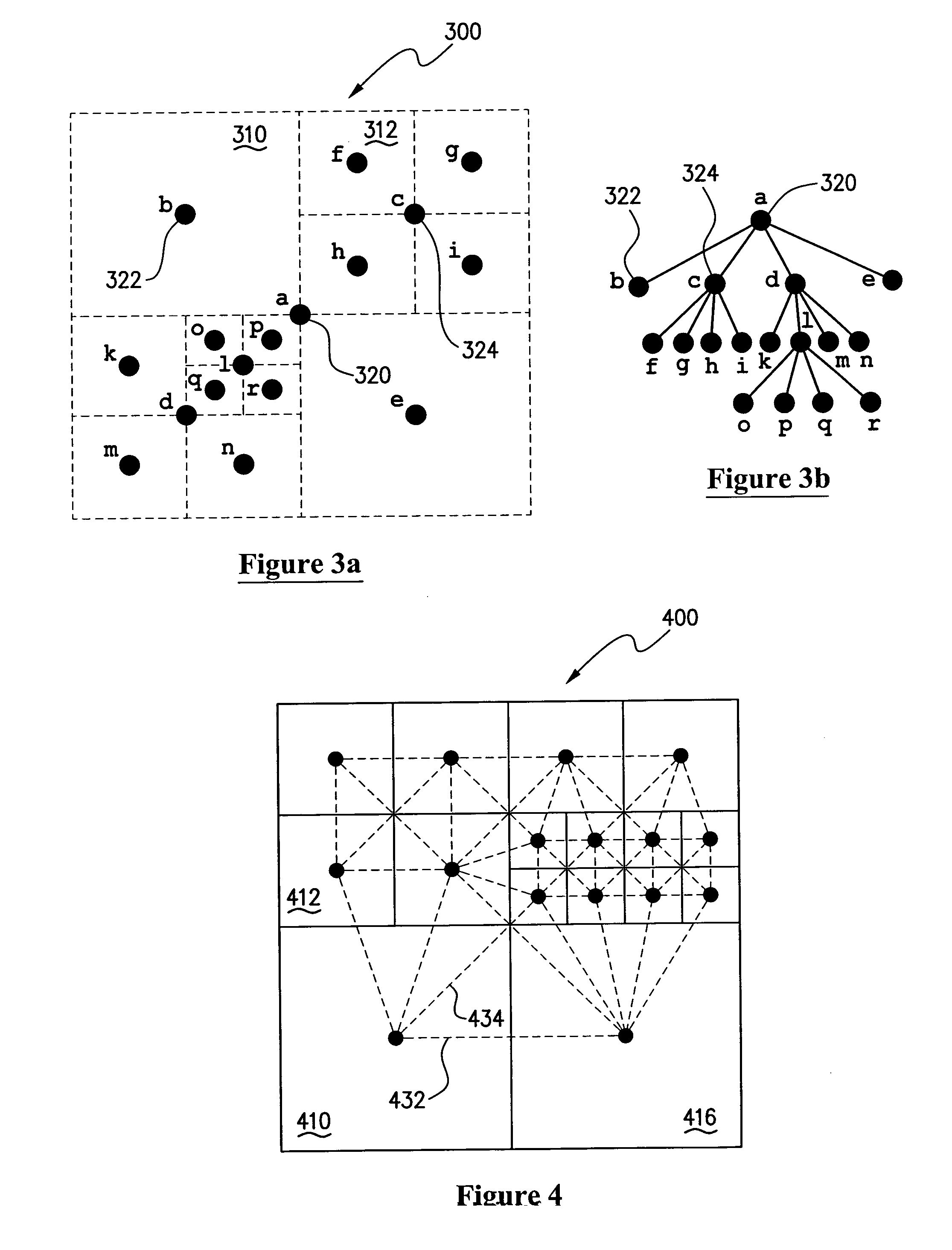
Decentralised multi-user online environment
InactiveUS20100146128A1Minimize the numberRaise the possibilityComputer security arrangementsMultiple digital computer combinationsSemantic filteringVirtual space
Protocols for facilitating a peer-to-peer real time network in which network state information and data processing is delegated to user nodes. A virtual space is recursively divided into a plurality of sub-regions represented by a logical tree, with responsibility for leaf nodes delegated to multiple user nodes. A distributed hash table can be used to store leaf node state and identity information. A discovery index protocol is provided for user nodes to effectively identify a user node responsible for a sub-region of interest. Further, a semantic filtering protocol limits communications primarily to other user nodes deemed relevant, so as to constrain bandwidth usage. A broadcast control protocol is provided to increase the number of simultaneous interactions for each user node. A security protocol is also provided to prevent any illegal activity by malicious nodes.
Owner:NAT ICT AUSTRALIA
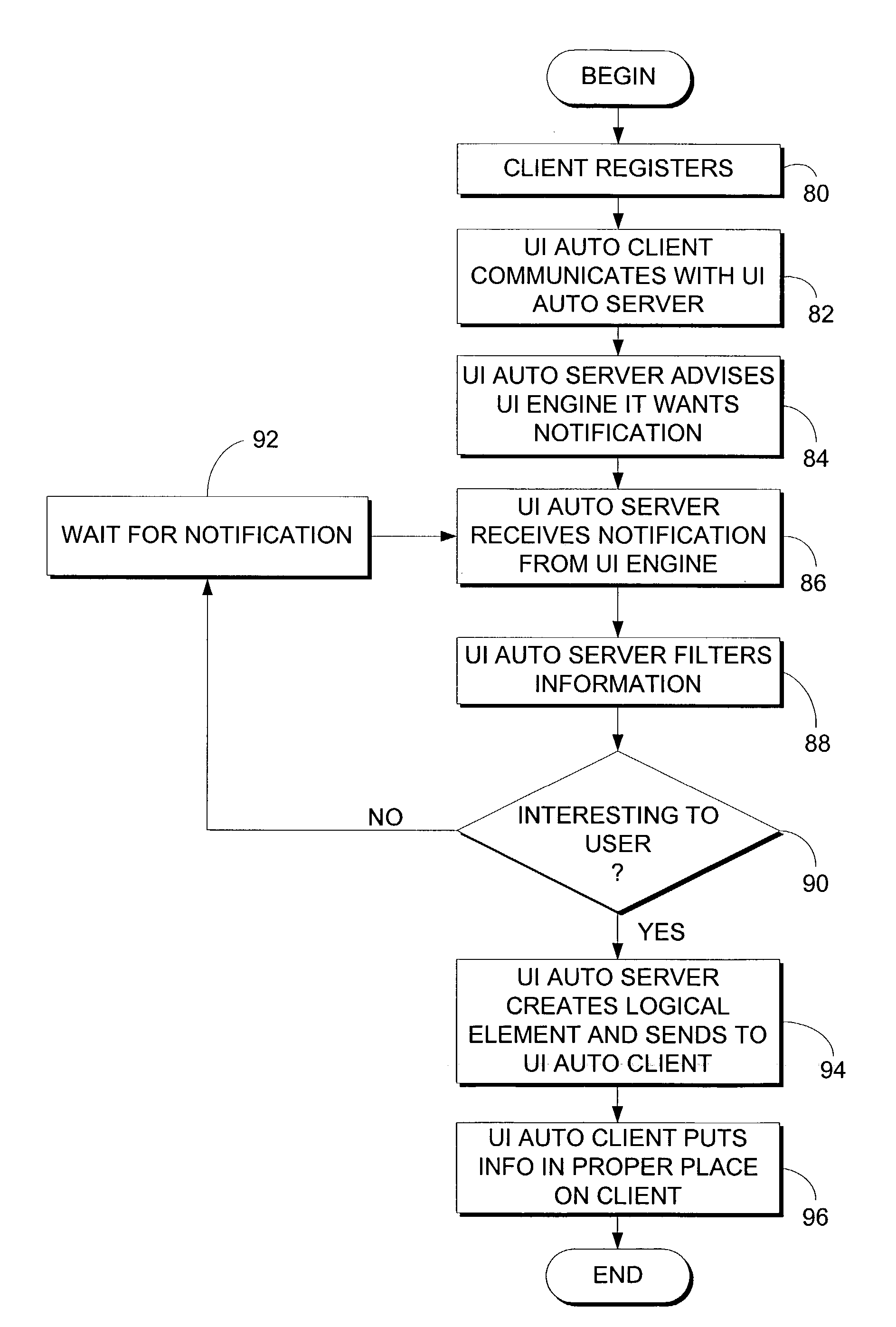
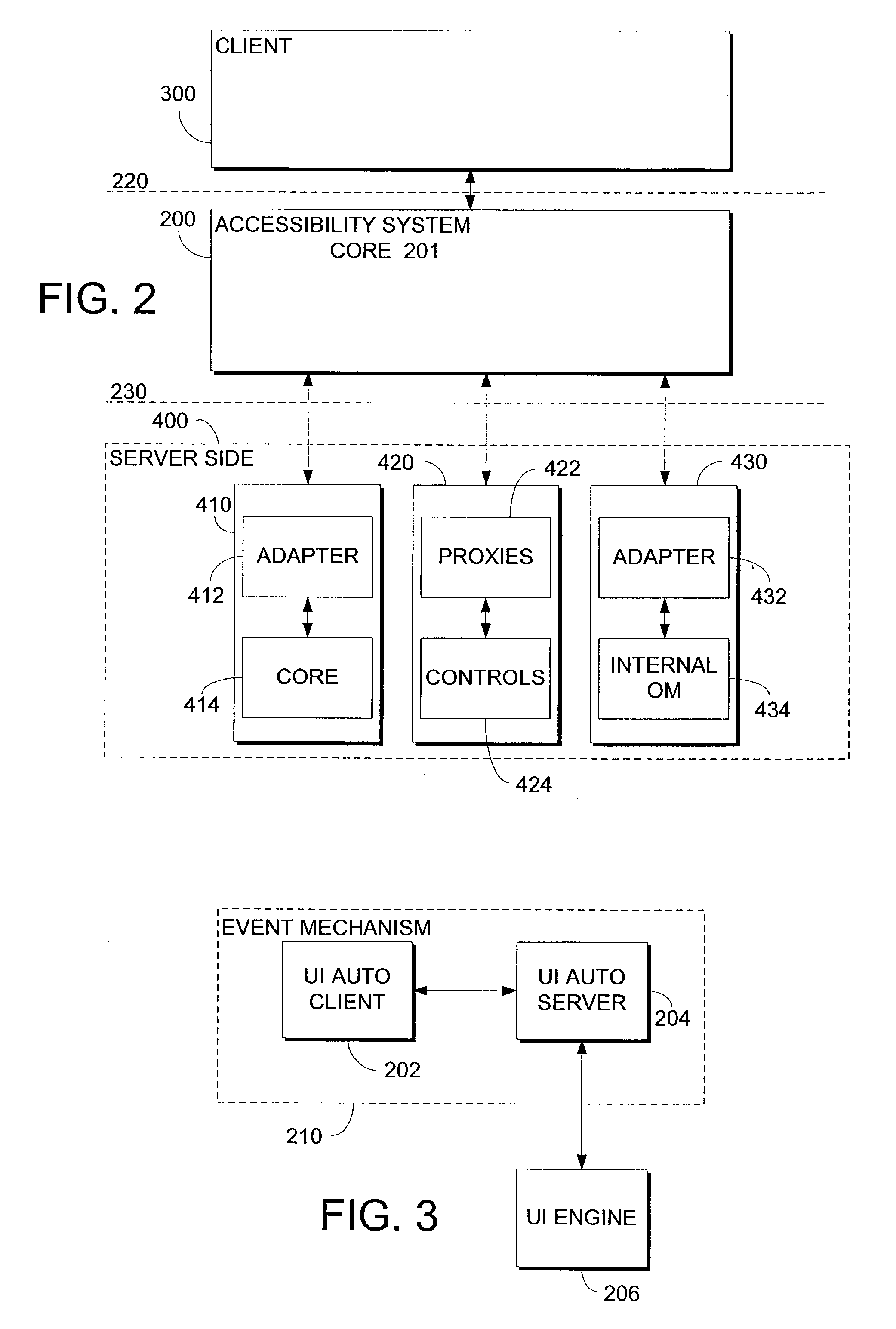
User interface automation framework classes and interfaces
InactiveUS7644367B2Television system detailsAnalogue secracy/subscription systemsLogical elementClient-side
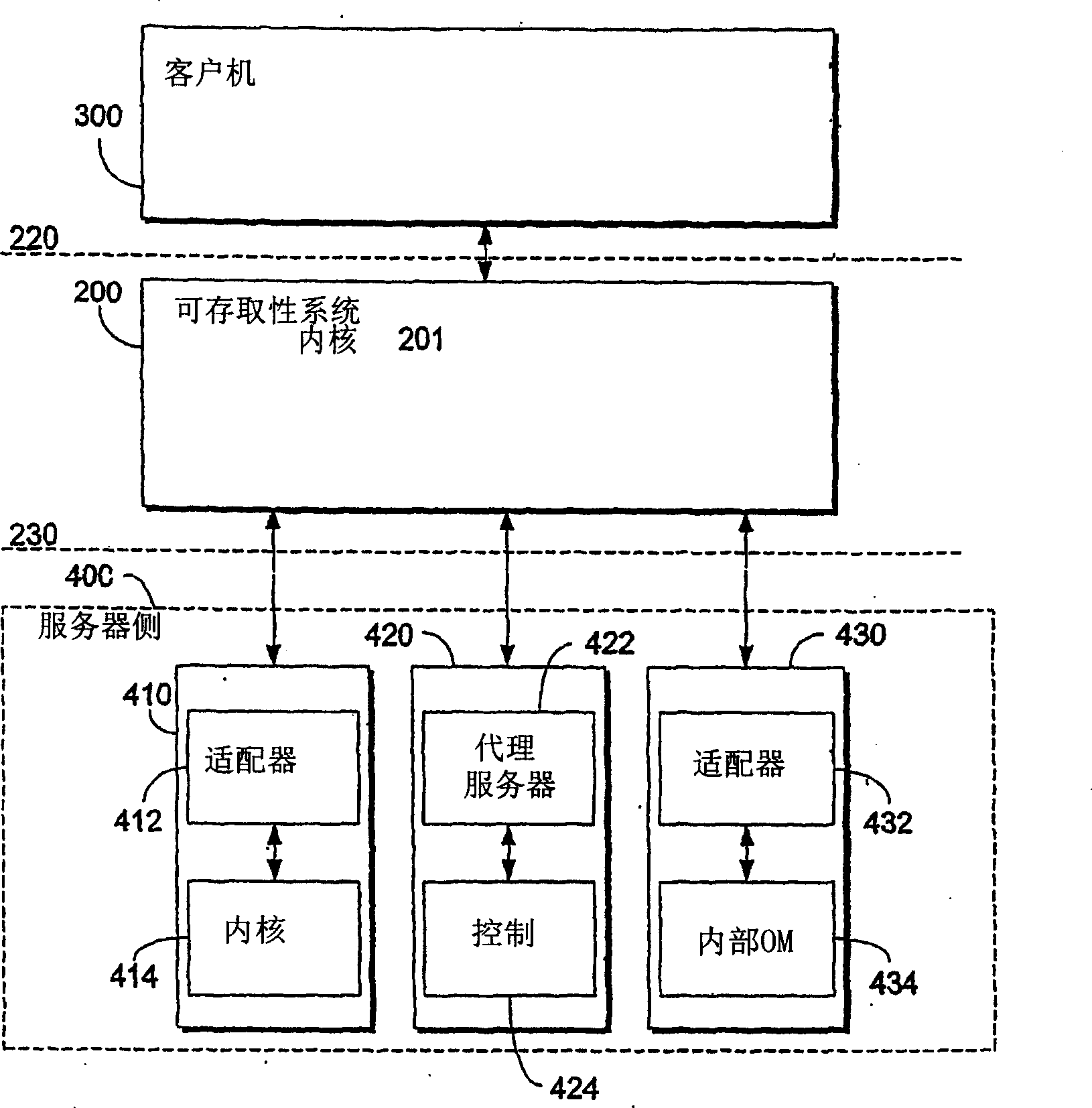
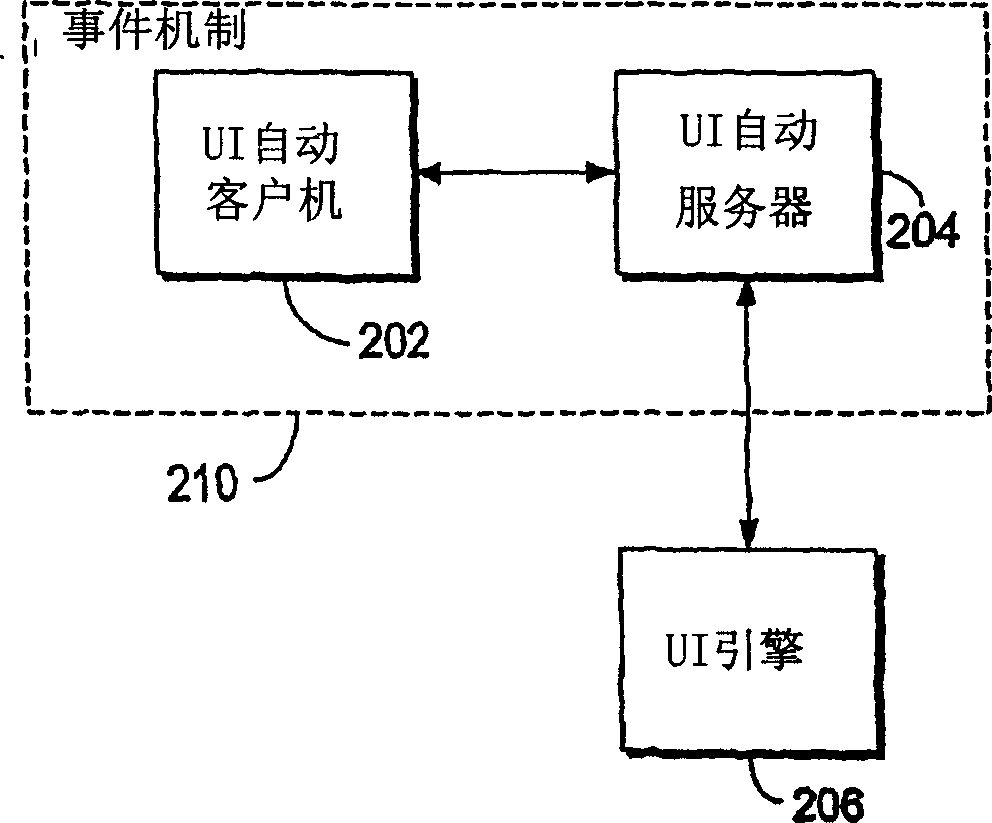
A method and system providing a client with user interface information are described. The method and system implement a set of application program interfaces for providing user interface information to a client through an accessibility system. The accessibility system includes a mechanism for transferring user interface information from a provider side to the client side and a logical tree for selectively revealing user interface information. The application program interface system includes client side application program interfaces for assisting the client in obtaining user interface information. The client side application program interfaces include an automation class, a logical element class, a raw element class, control pattern classes, and an input class. The provider side application program interfaces include a provider automation class, a provider automation interface, a raw element interface, and control pattern provider interfaces.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for creating a secure communication channel among multiple event service nodes
An approach for establishing secure multicast communication among multiple event service nodes is disclosed. The event service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the event service nodes include the group session key and the private keys of the event service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the event service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can readily be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service.
Owner:CISCO TECH INC
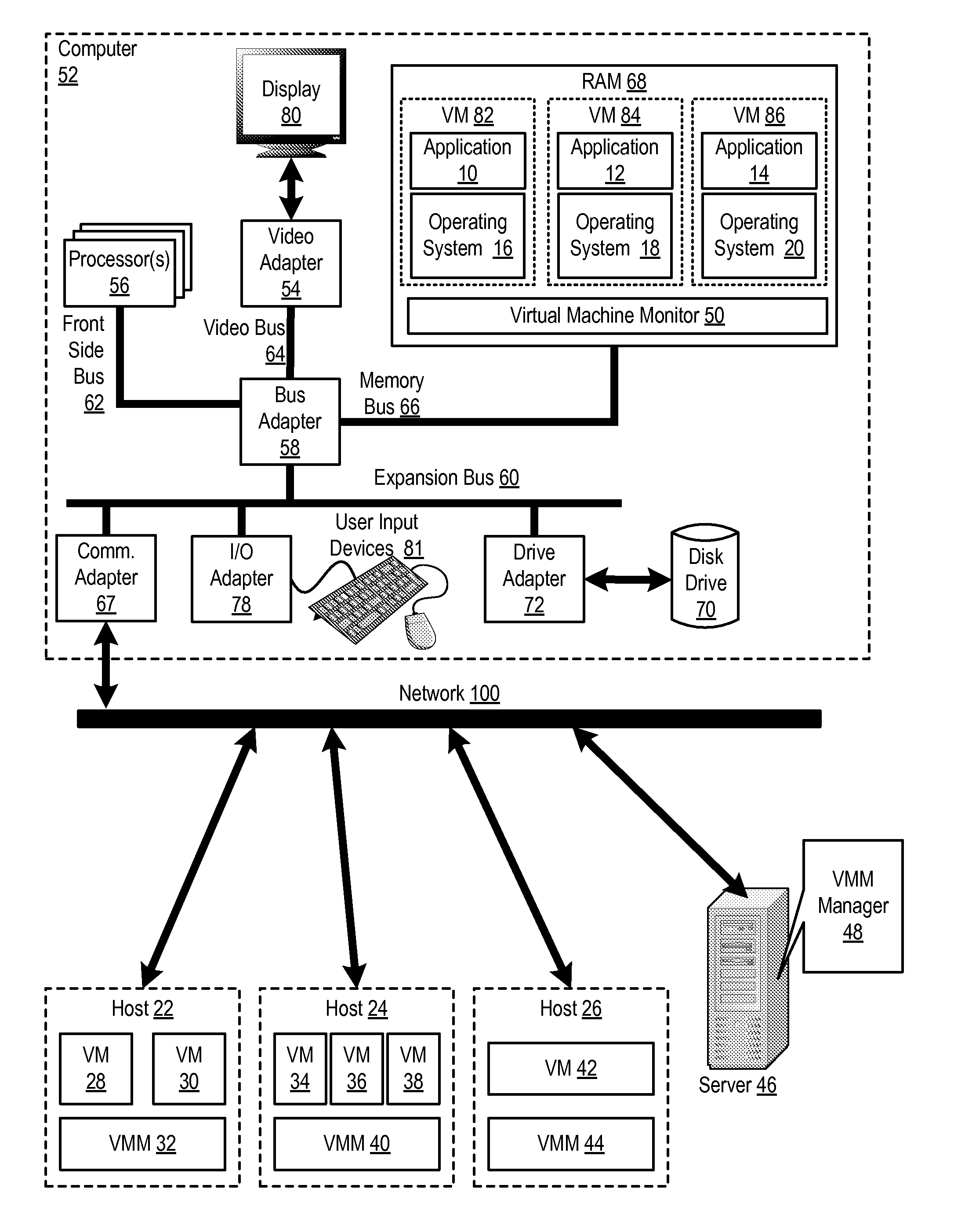
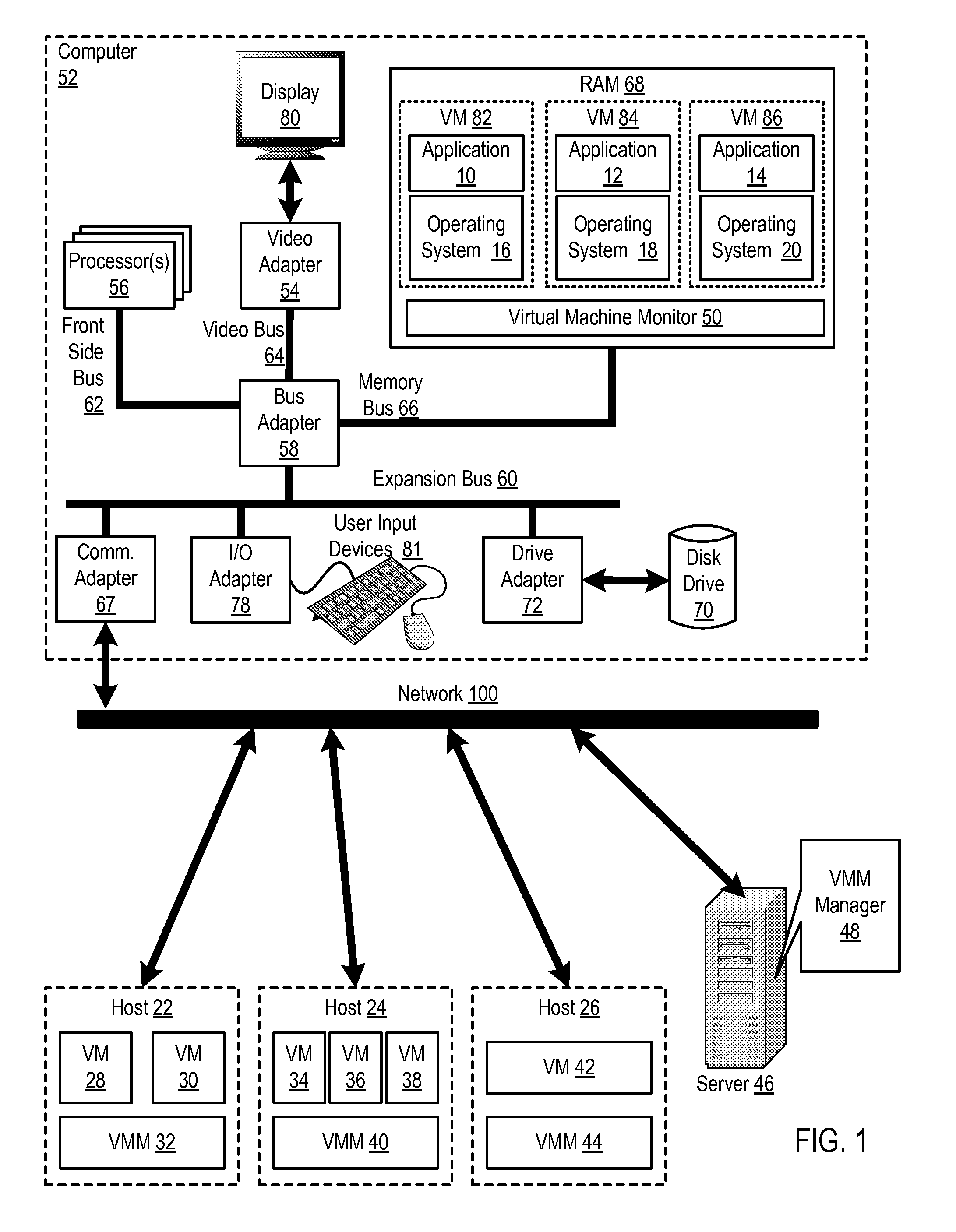
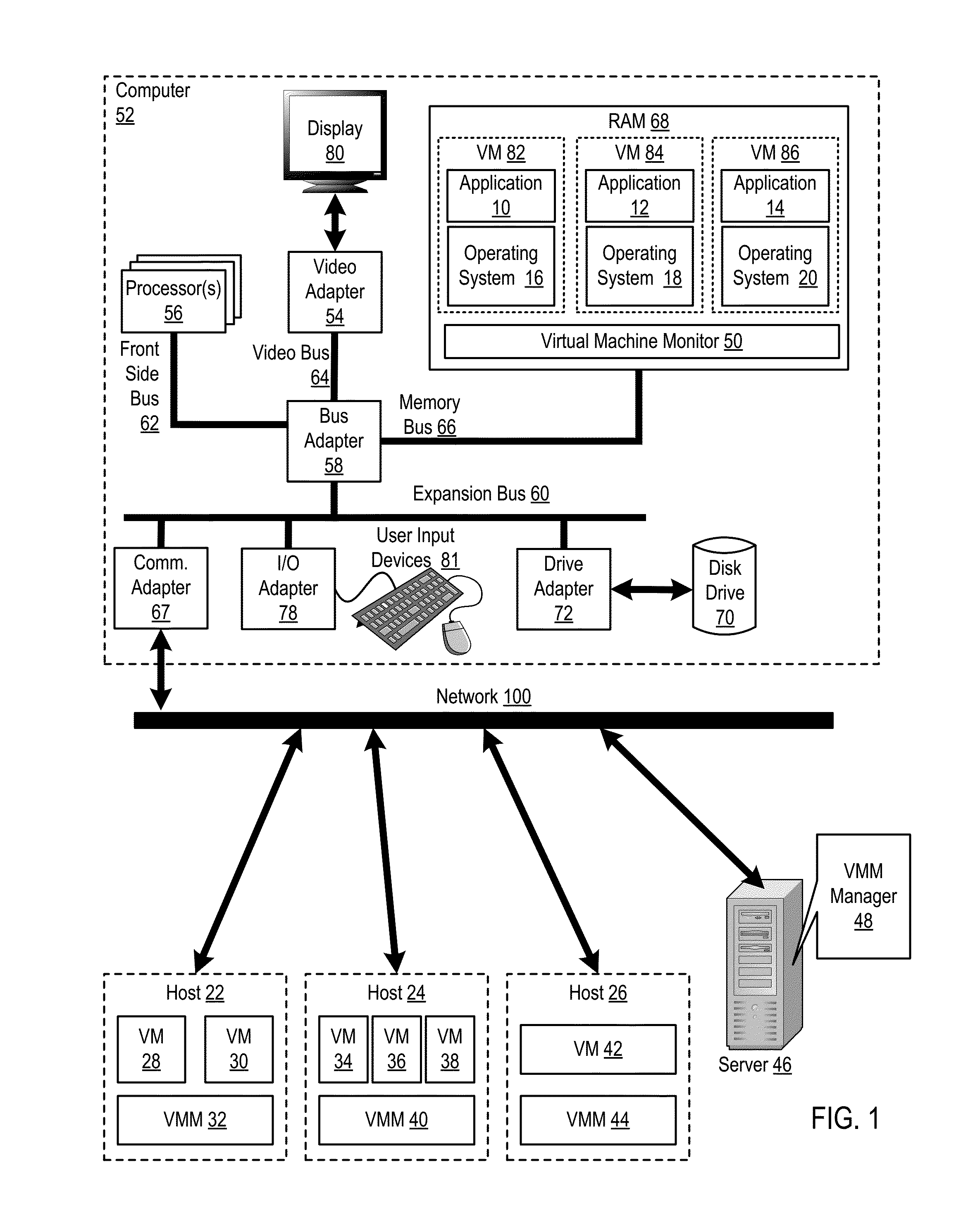
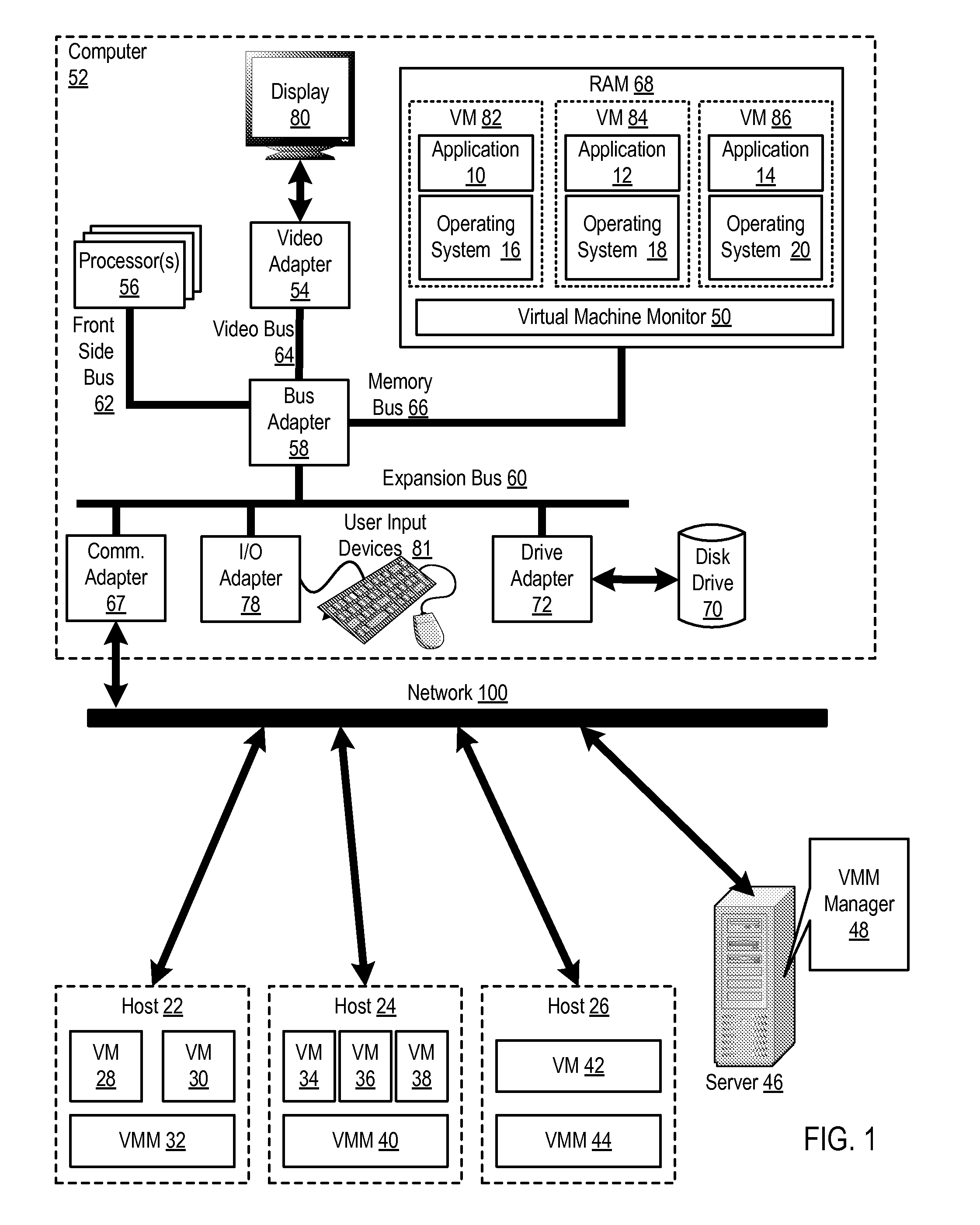
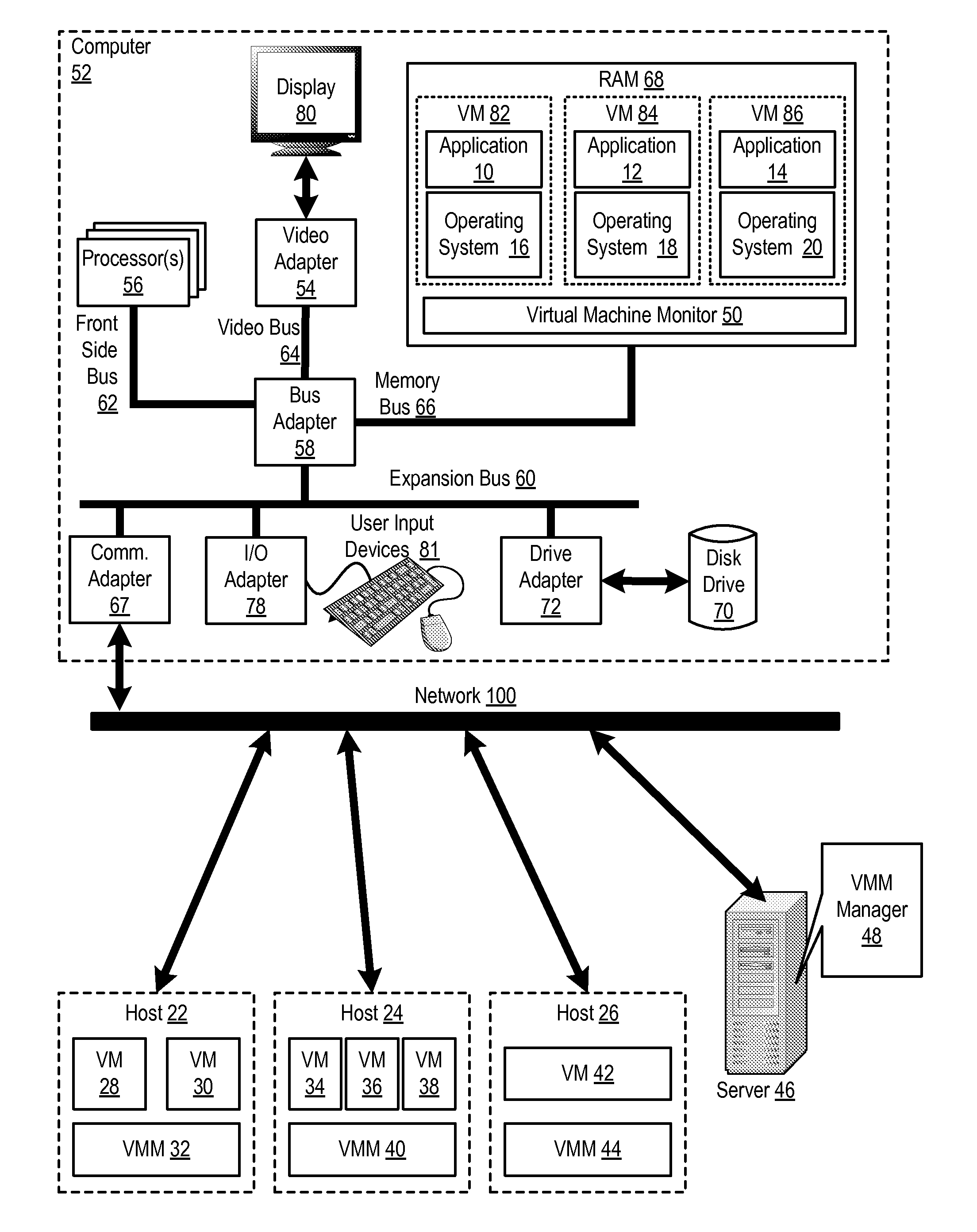
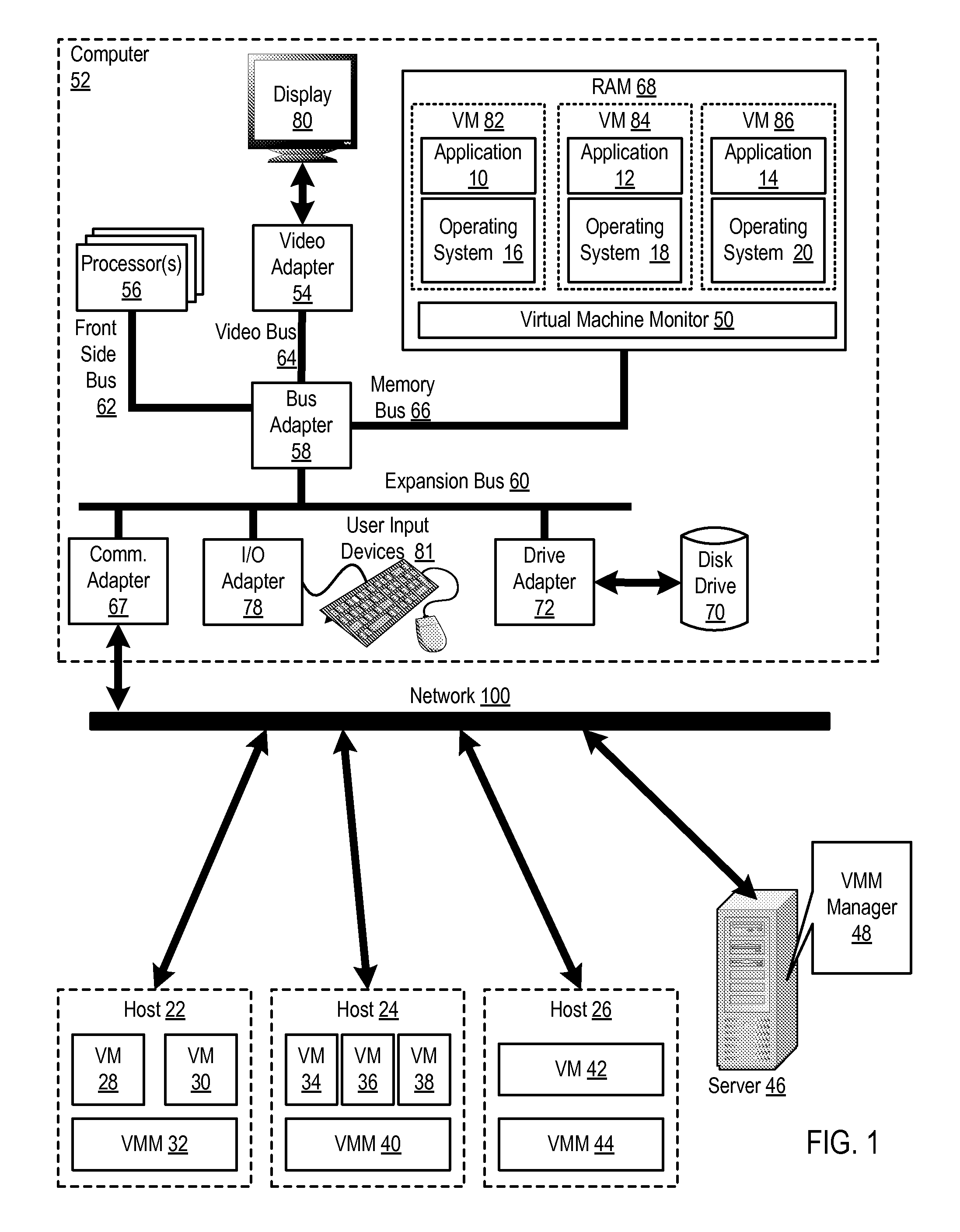
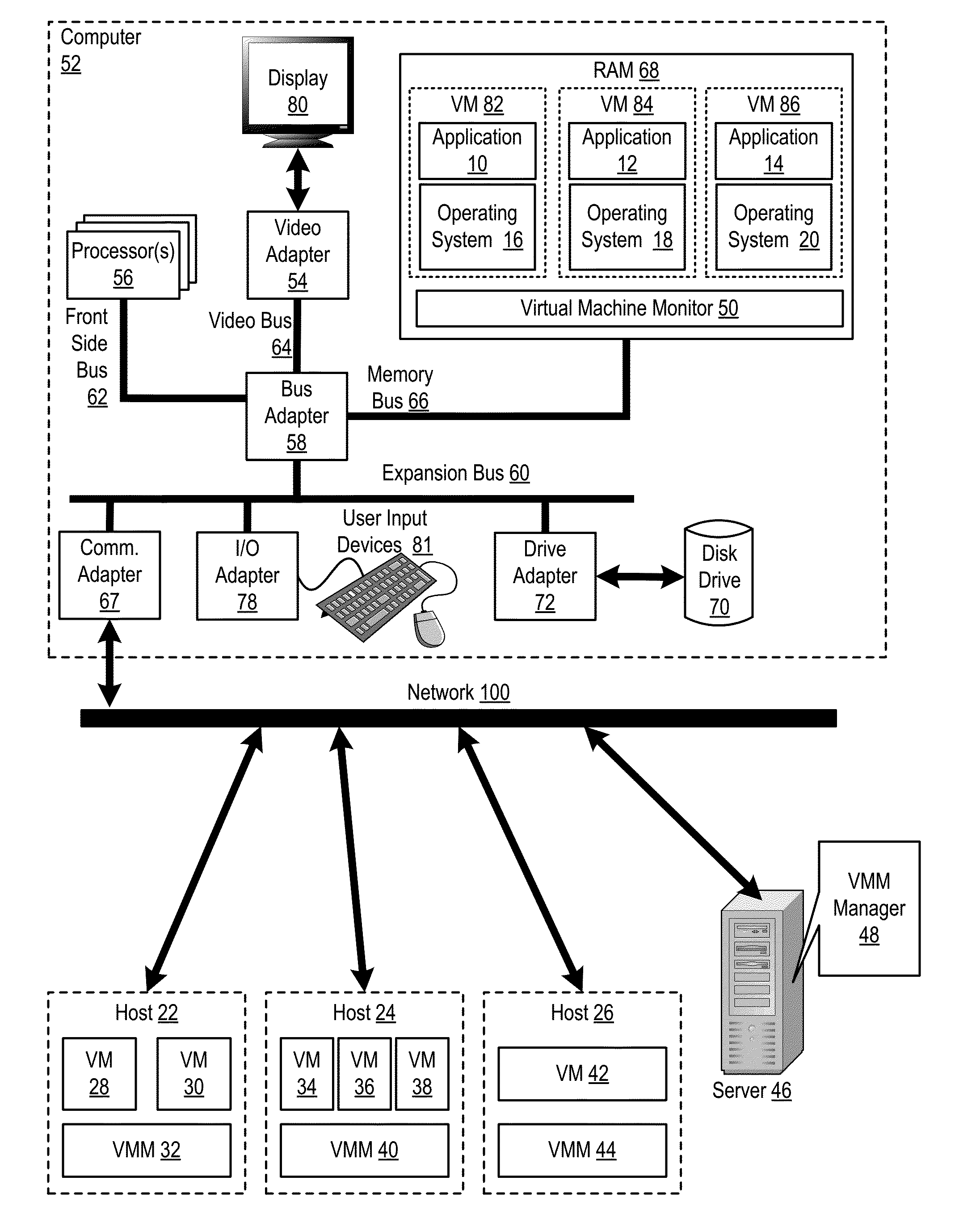
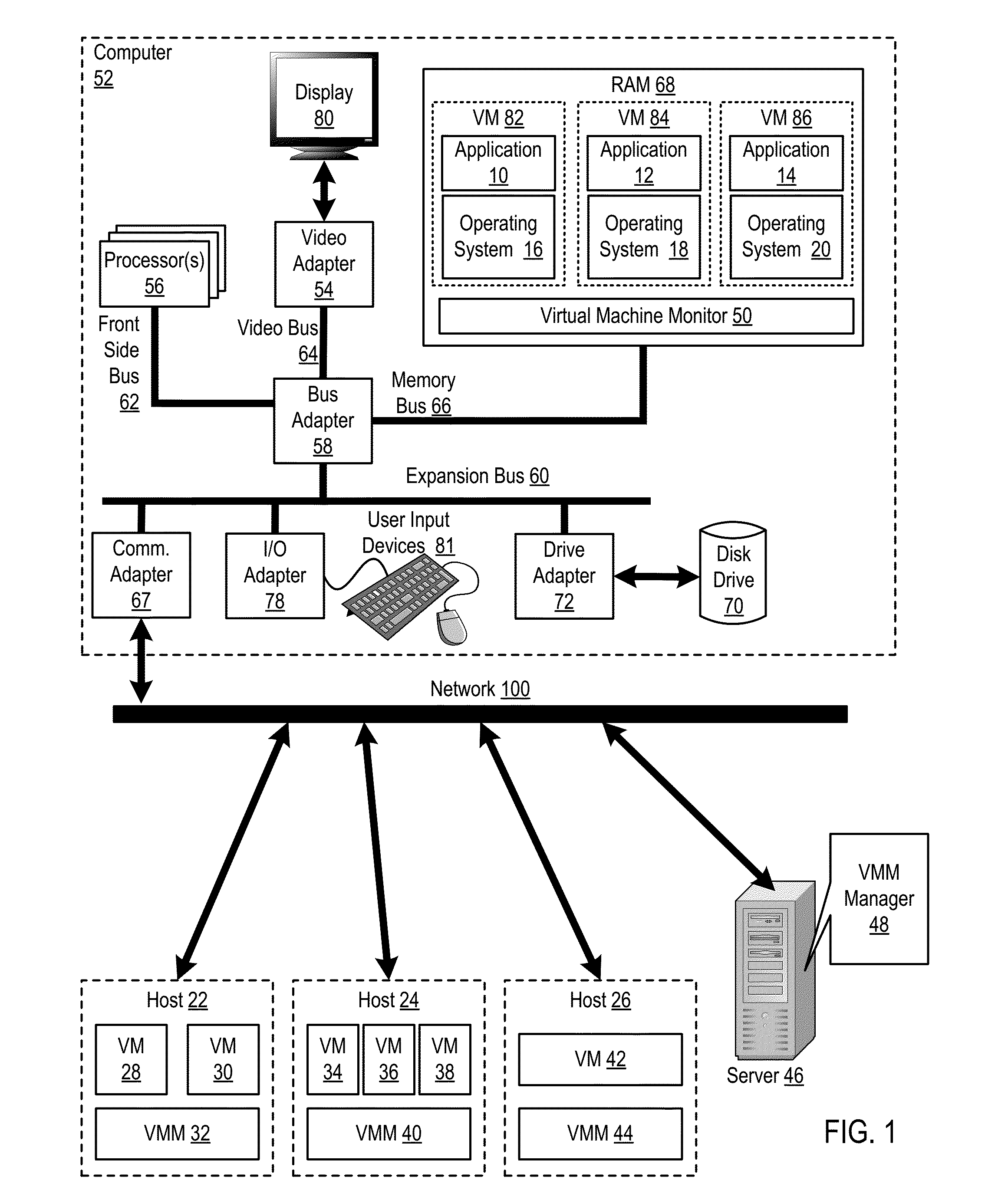
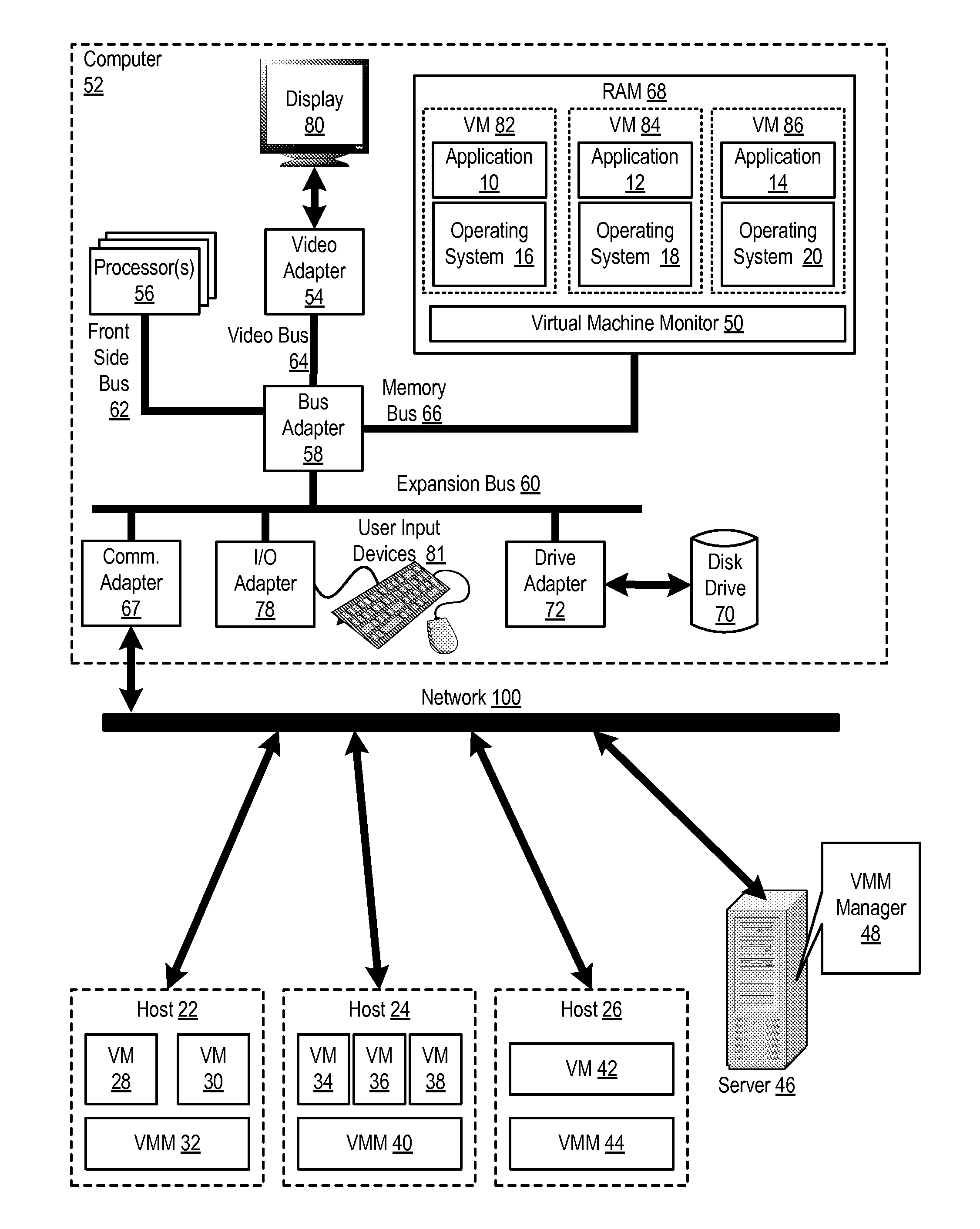
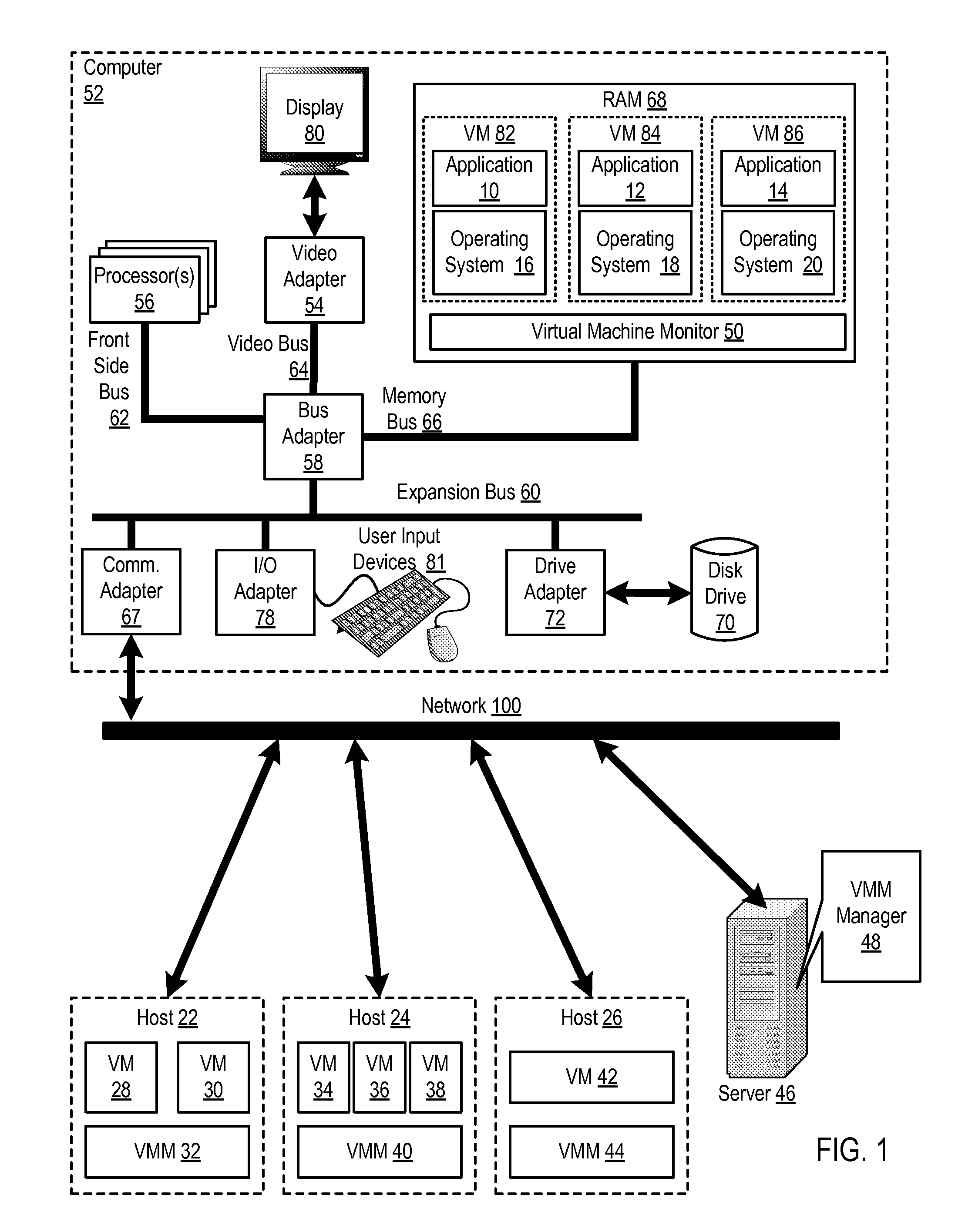
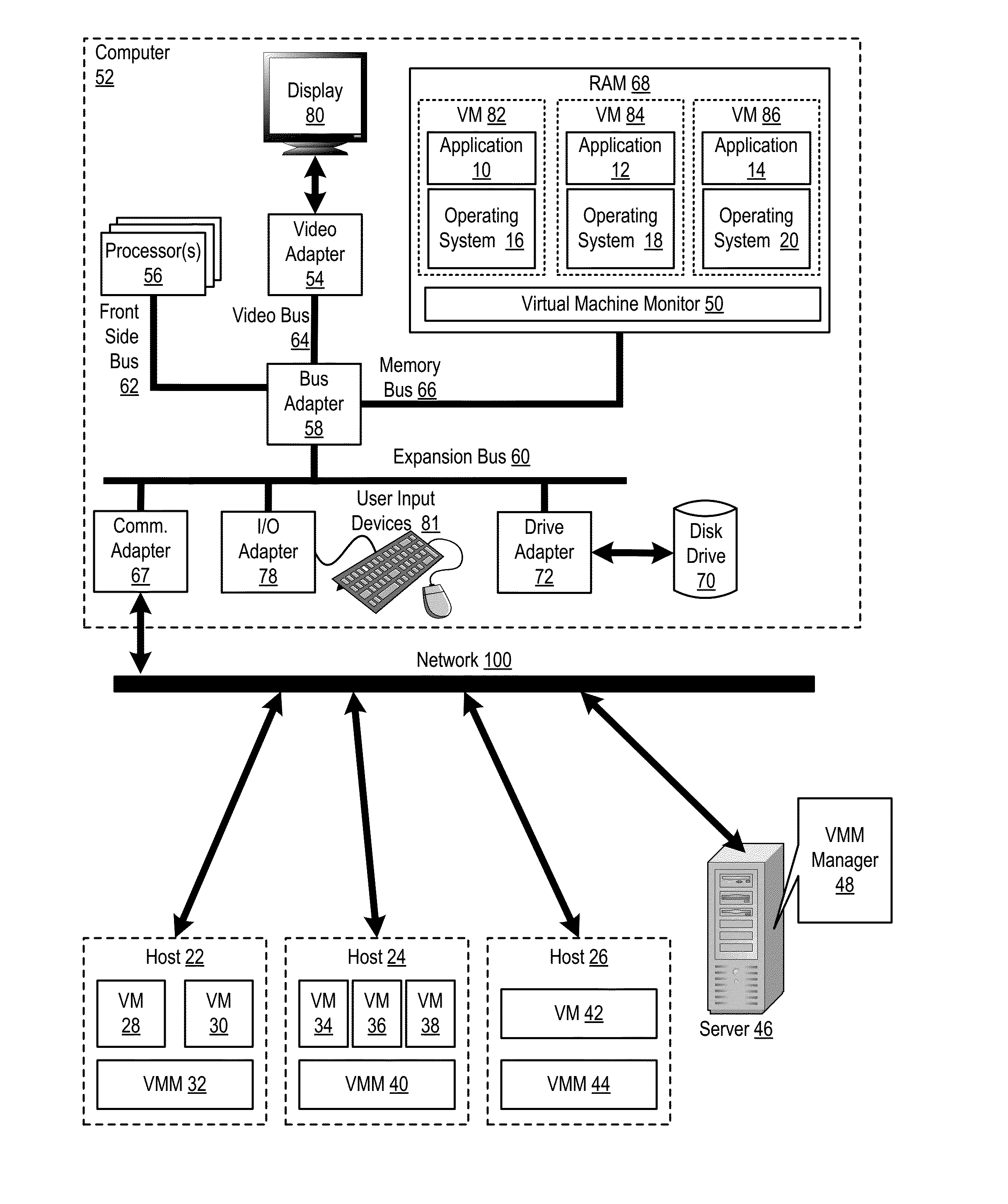
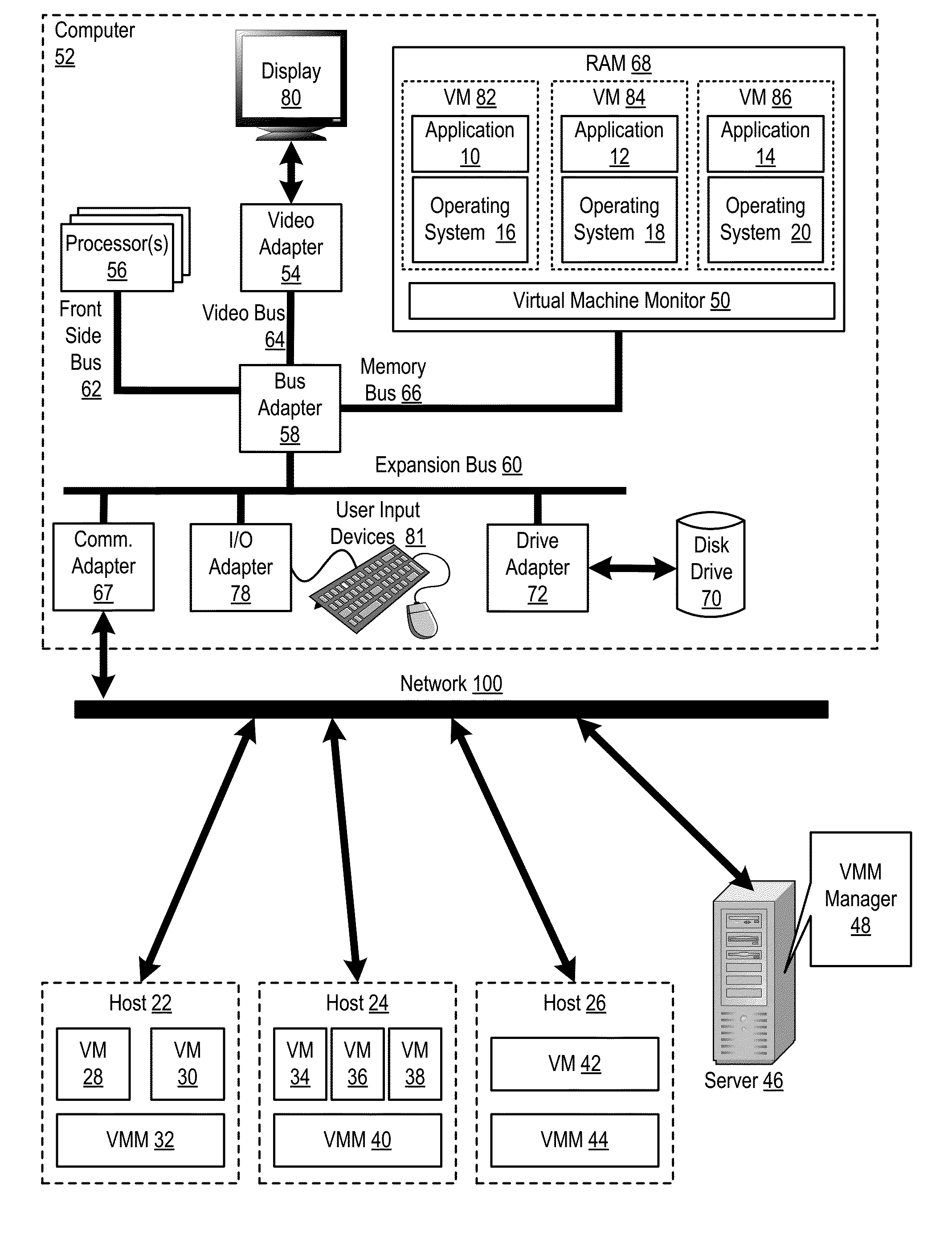
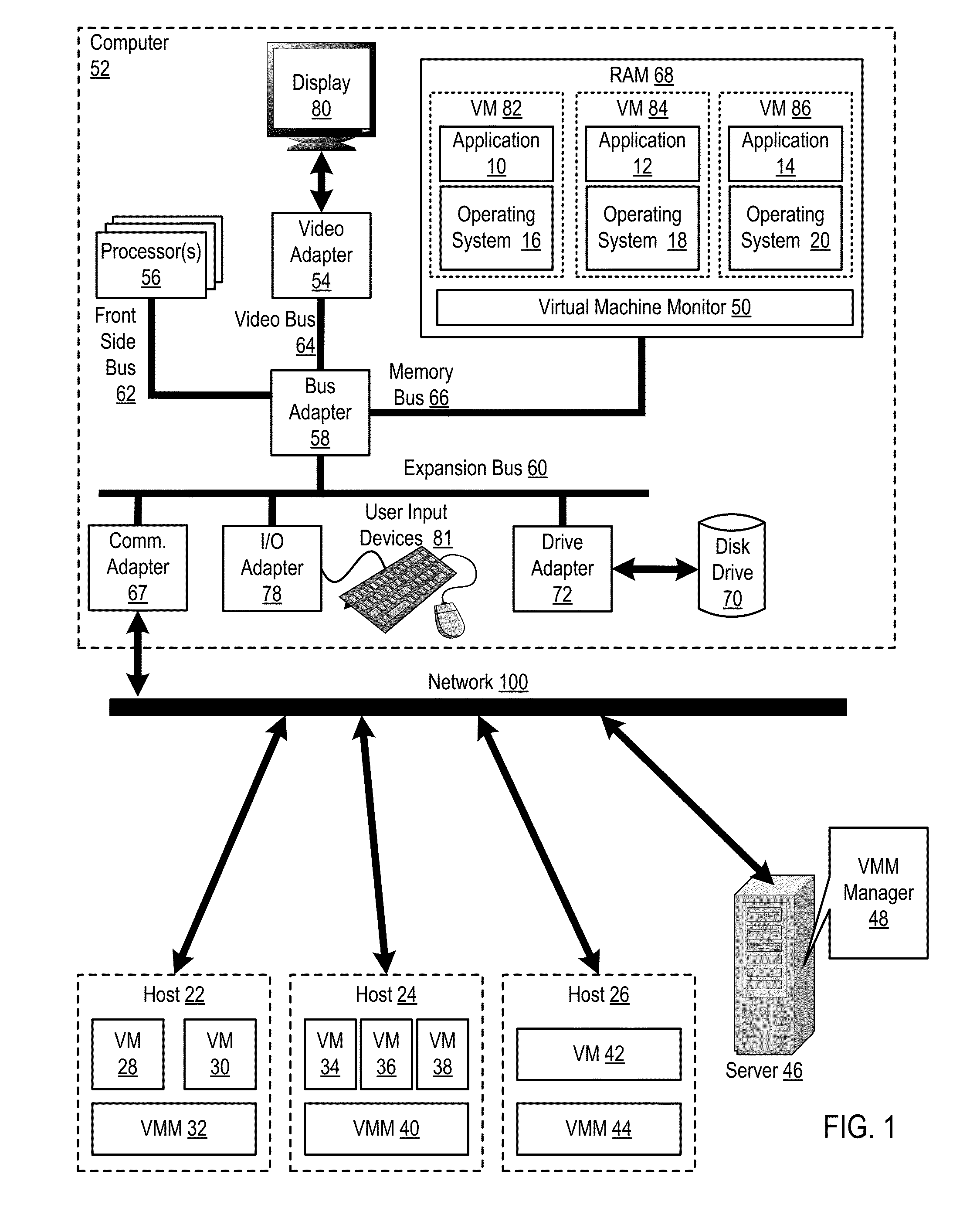
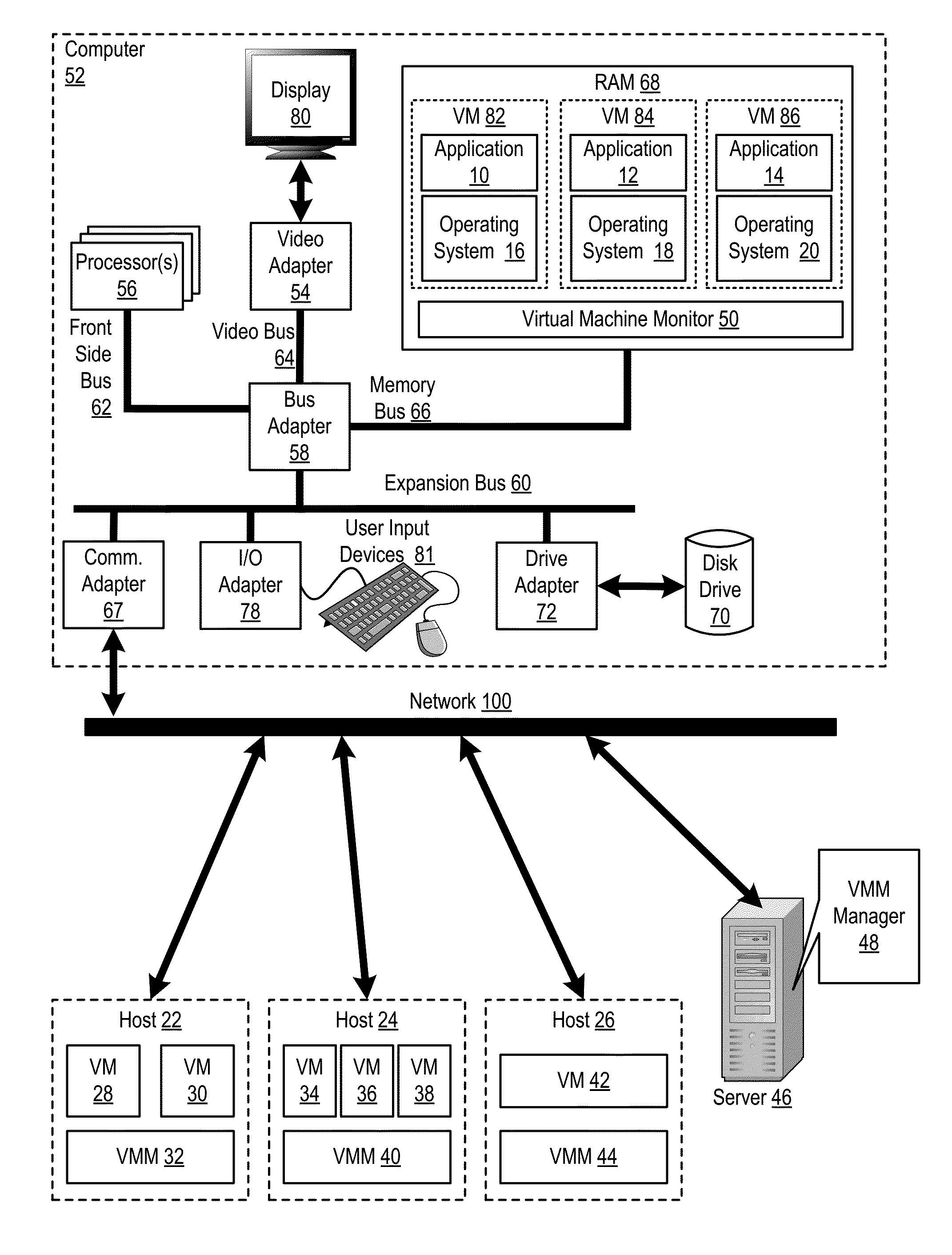
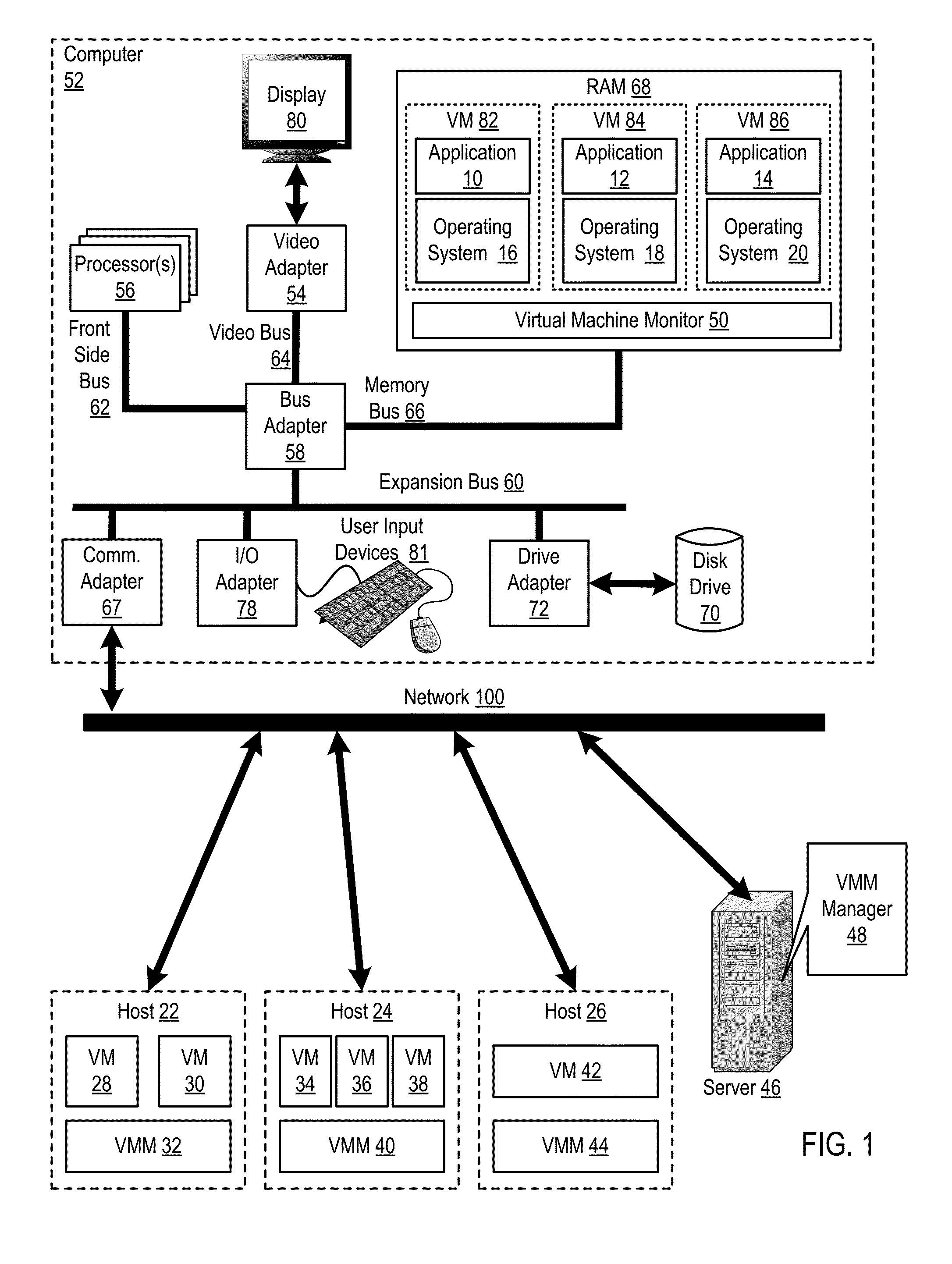
Administering virtual machines in a distributed computing environment
ActiveUS20150312326A1Digital computer detailsData switching networksDistributed Computing EnvironmentLogical tree
Owner:IBM CORP
Automatically deploying software packages used in computer systems
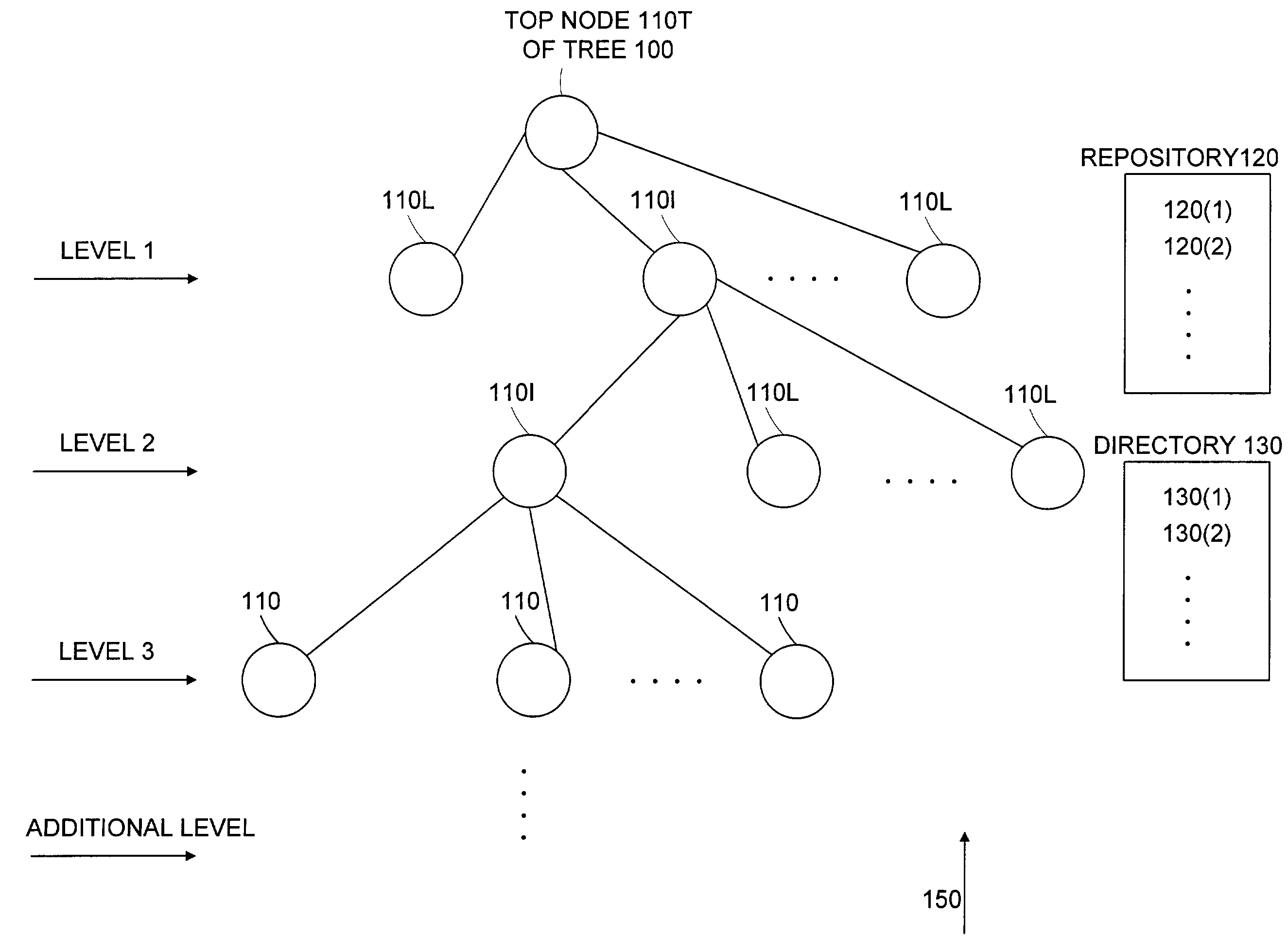
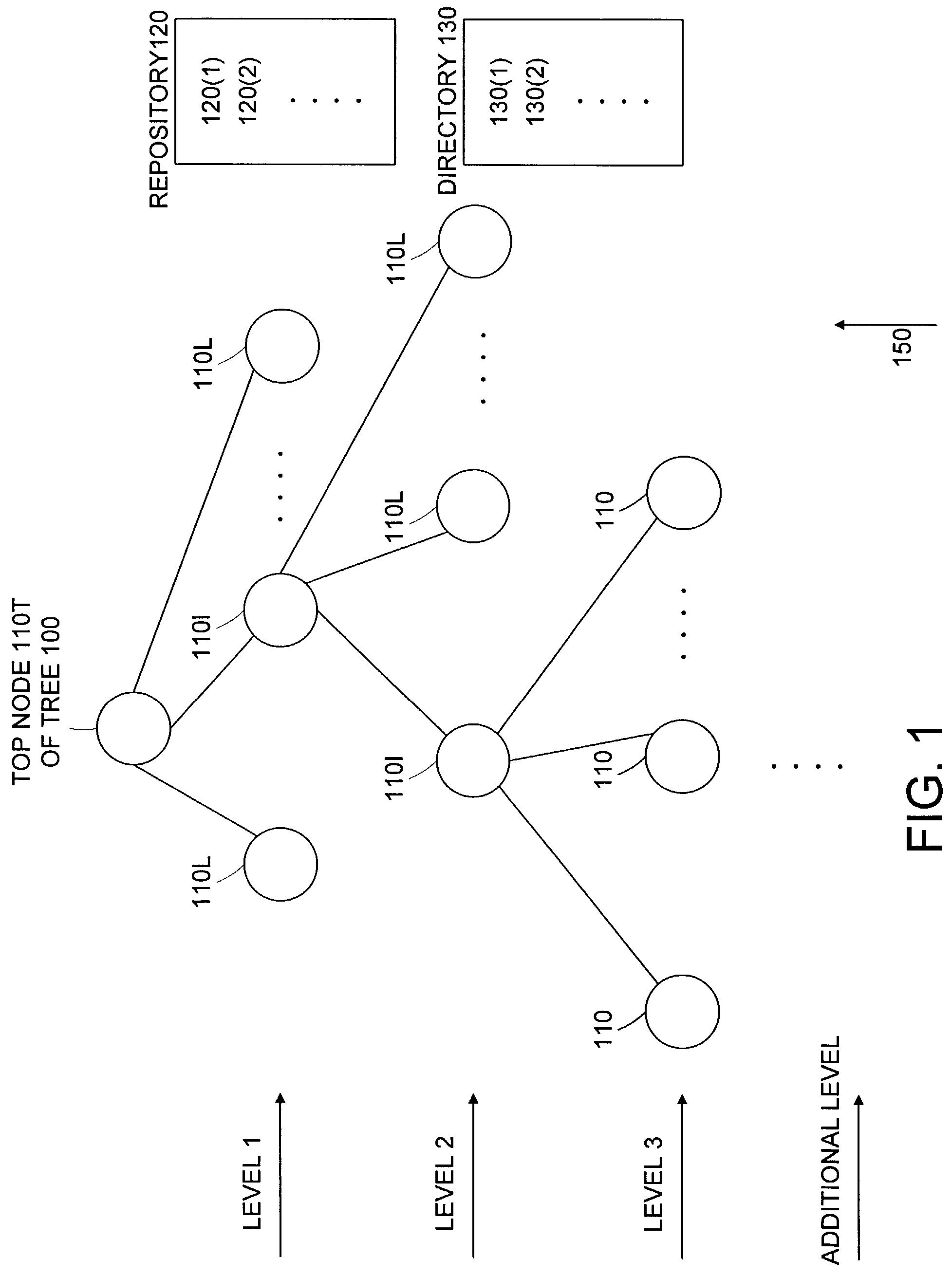
Techniques are provided for automatically deploying software packages. Management agents represent these packages, a logical tree represents the deployed structure, and a node of the tree represents a management agent. A node that does not have any child node is referred to as a leaf node. A recursive process associated with at least one repository generates the structure. The repositories include information for configuring the nodes and thus control the deployment process. During deployment, a non-leaf node, referred to as an initiator node, uses information received from a corresponding repository to generate its child nodes. A child node, if being an initiator node, recursively generates its child nodes until the recursive process stops as there is no additional child node to be generated. Further, node identifiers are automatically established and assigned to respective nodes. Those identifiers are used by software instances such as management agents represented by nodes to communicate with other software instances such as repositories or directories for registering information about nodes, looking up information about other nodes, etc.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
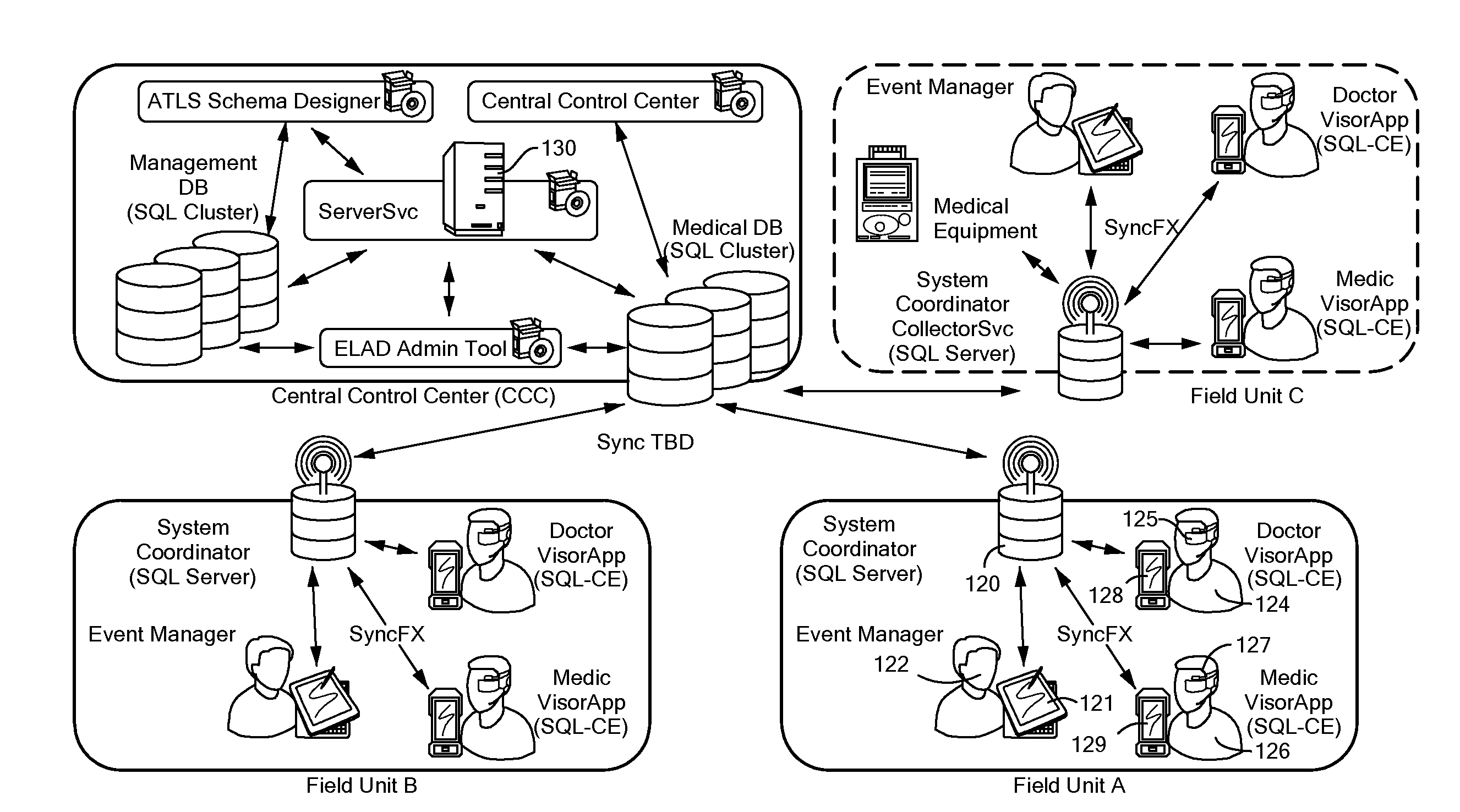
System and Method for Mobile Workflow Processing
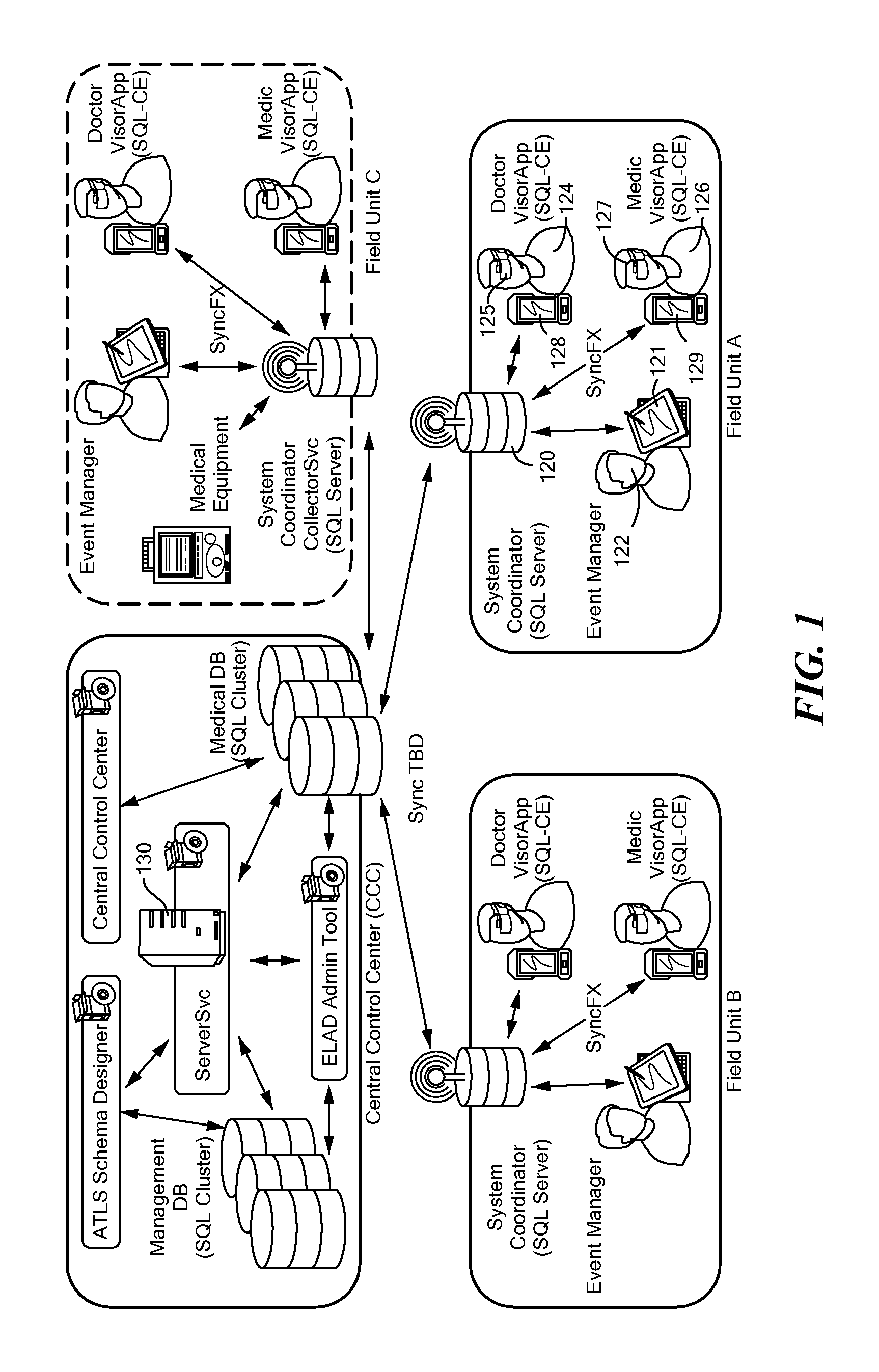
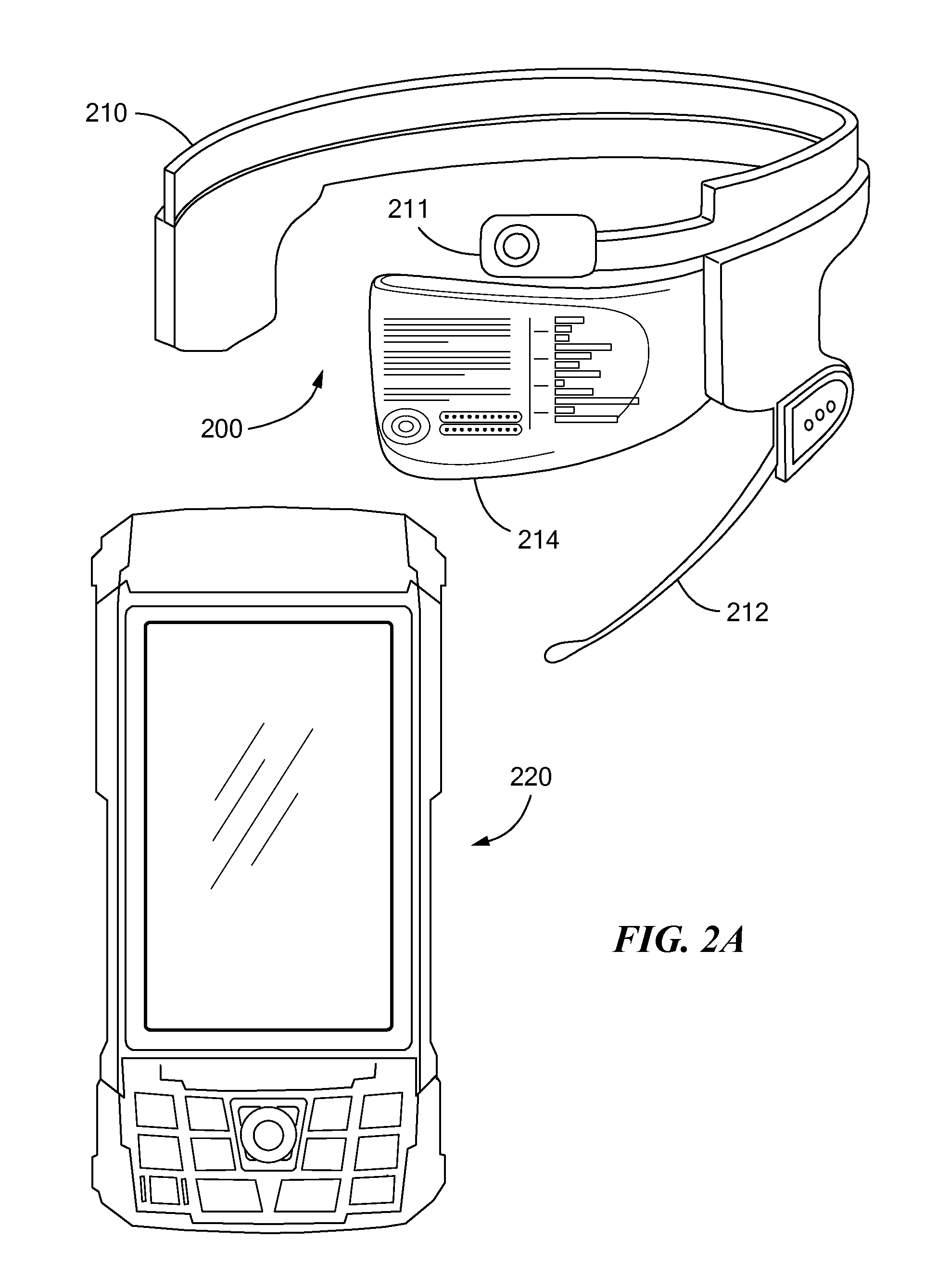
InactiveUS20120166203A1Speech recognition is facilitatedFacilitate two-way audio communicationMedical communicationData processing applicationsDisplay deviceWork flow
A system and method of wirelessly serving a work flow protocol to agents for use with respect to subjects. The agents wear headsets, each with a display and a microphone coupled to a portable controller. The work flow protocol causing presentation of queries through the headsets based on a logical tree structure. Data generated by speech of the agents is received and stored.
Owner:POPULATION RES
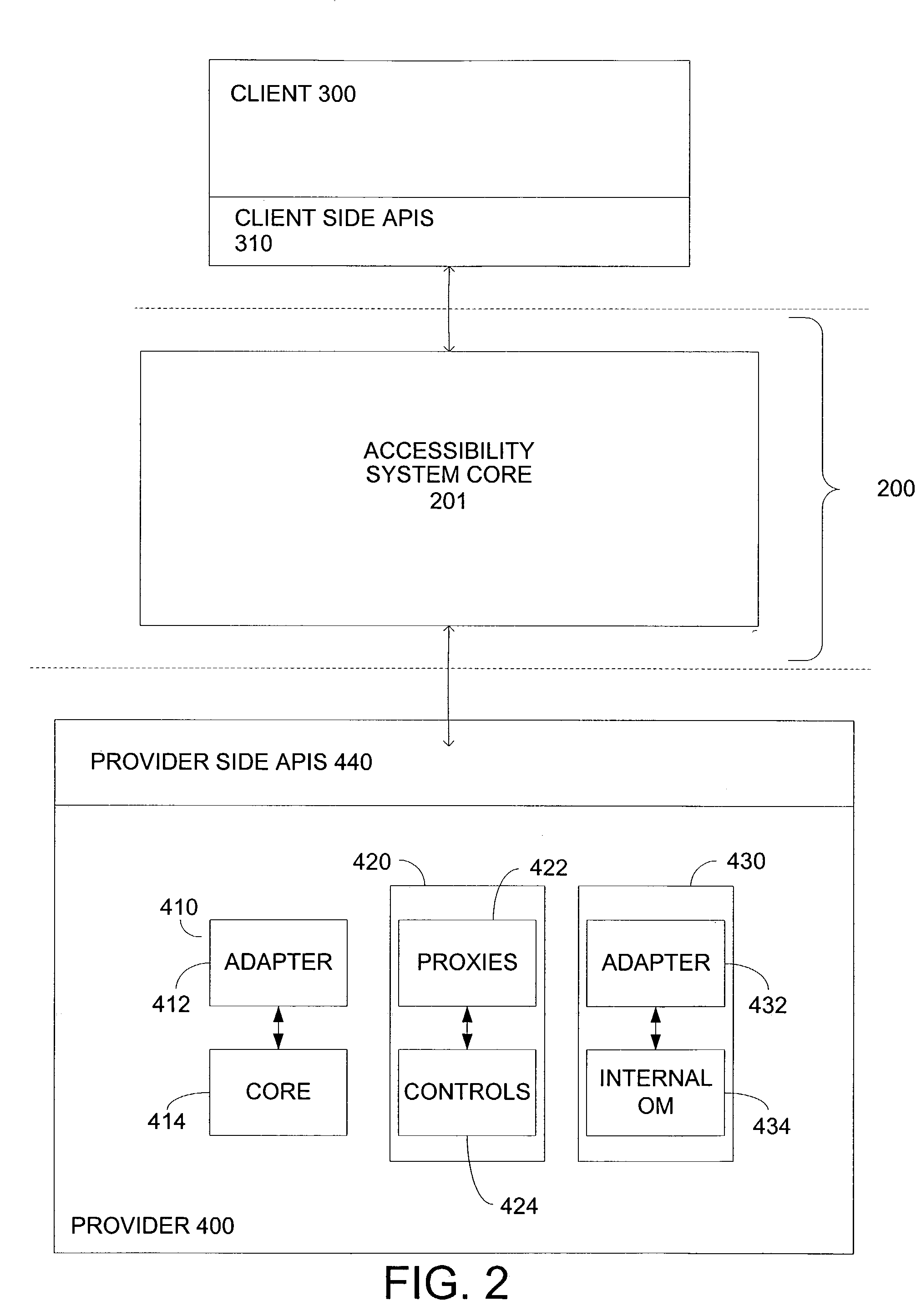
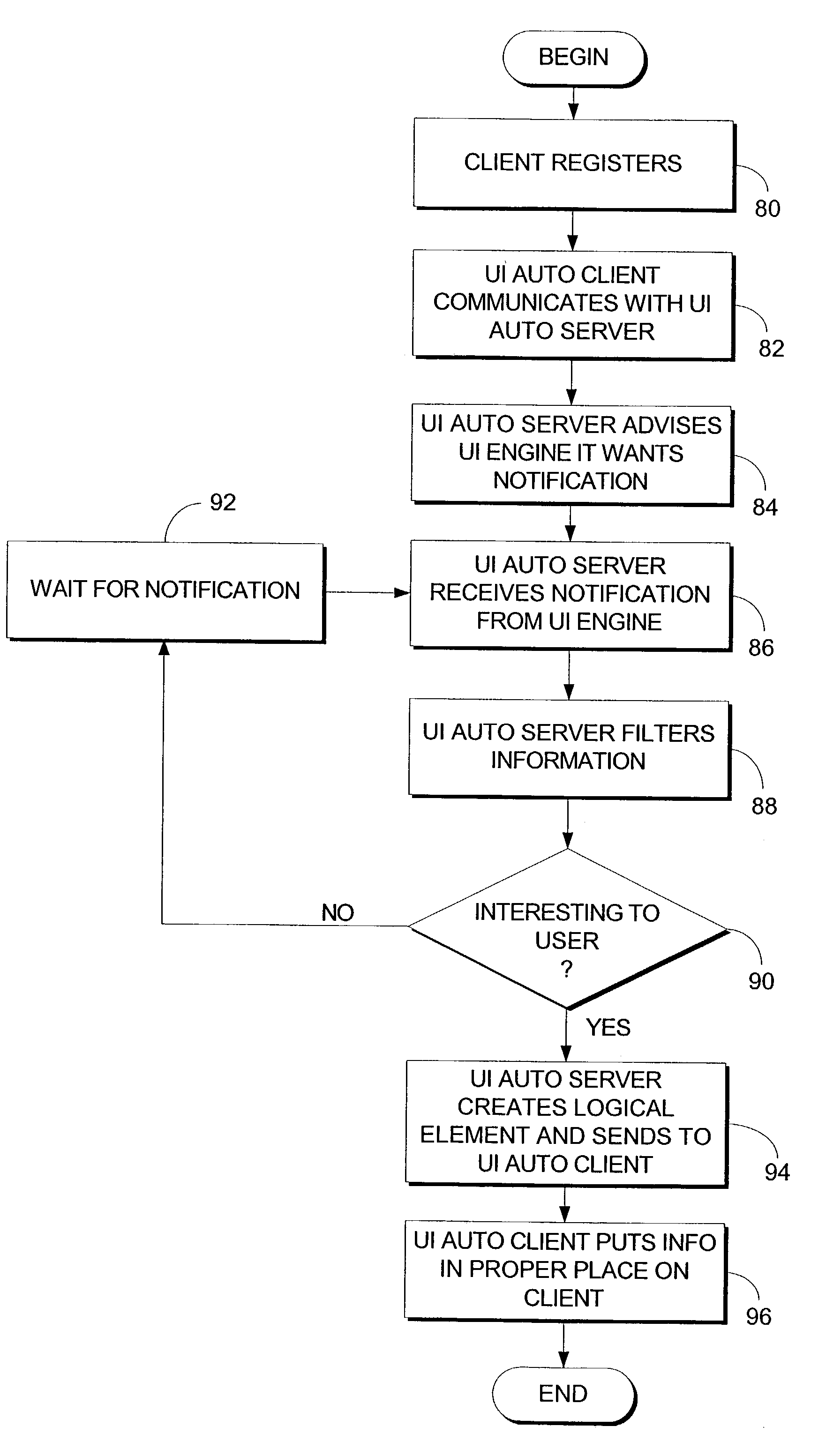
Accessibility system and method
A method and system providing a client with user interface information are described. An accessibility system for providing user interface information to a client. The accessibility system comprises an accessibility system core including user interface automation services and APIs. The user interface automation tools filter information based on whether the user interface information is interesting to the client. The accessibility system additionally comprises a client side interface including a logical tree for revealing user interface information that is interesting to the client and for hiding user interface information that is not interesting to the client. The accessibility system also comprises a server side interface for facilitating information transfer from a server side regardless of the server side technology.
Owner:MICROSOFT TECH LICENSING LLC
Administering virtual machines in a distributed computing environment
InactiveUS20150309817A1Digital computer detailsTransmissionDistributed Computing EnvironmentLogical tree
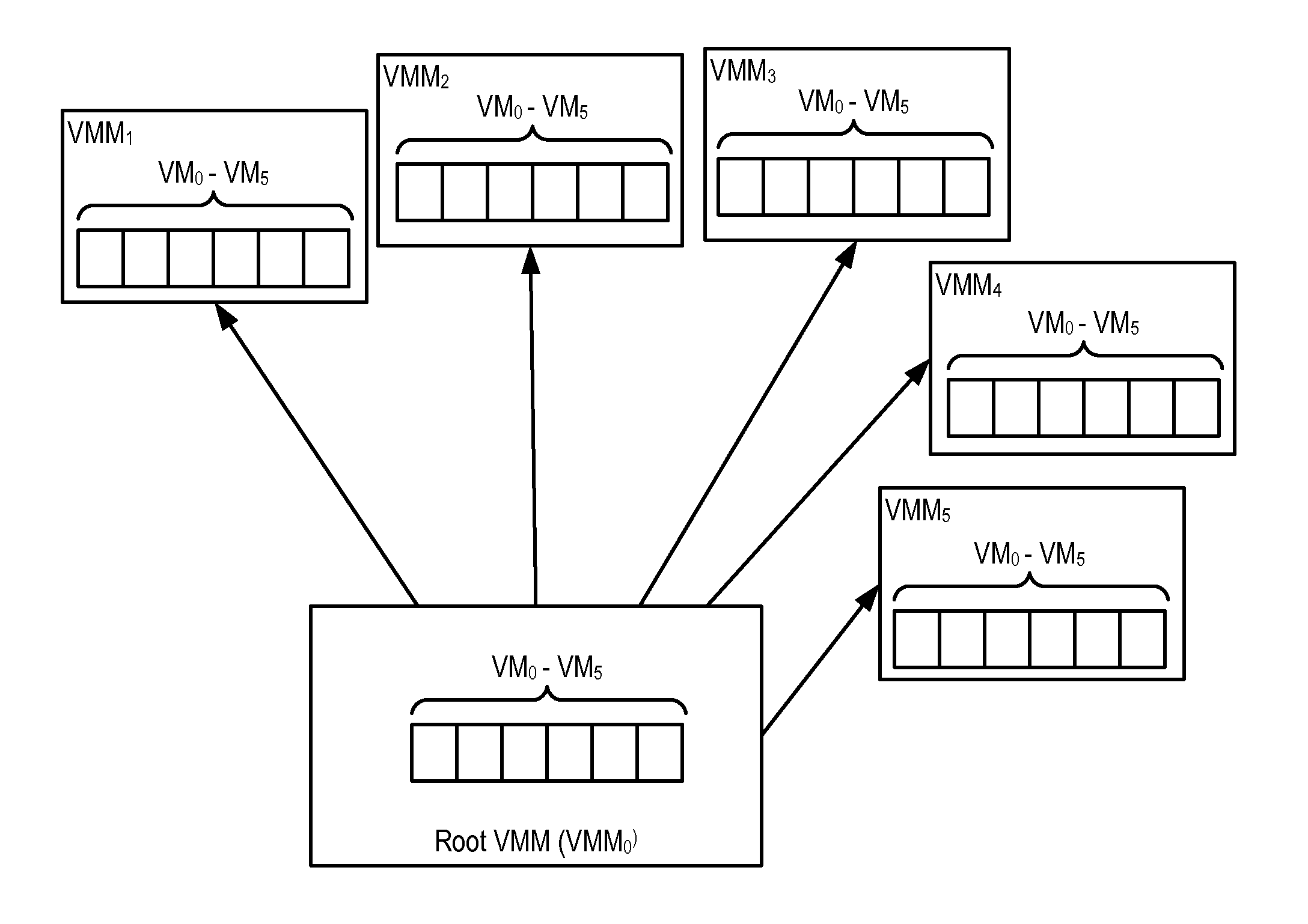
In a distributed computing environment that includes hosts that execute a VMM, where each VMM supports execution of one or more VMs, administering VMs may include: assigning, by a VMM manager, the VMMs of the distributed computing environment to a logical tree topology, including assigning one of the VMMs as a root VMM of the tree topology; and executing, amongst the VMMs of the tree topology, a broadcast operation, including: pausing, by the root VMM, execution of one or more VMs supported by the root VMM; sending, by the root VMM, to other VMMs in the tree topology, a message indicating a pending transfer of the paused VMs; and transferring the paused VMs from the root VMM to the other VMMs.
Owner:IBM CORP
Metadata hierarchy management method and system of storage virtualization system
InactiveCN1545047AReduce loadImprove search speedSpecial data processing applicationsData virtualizationDatabase
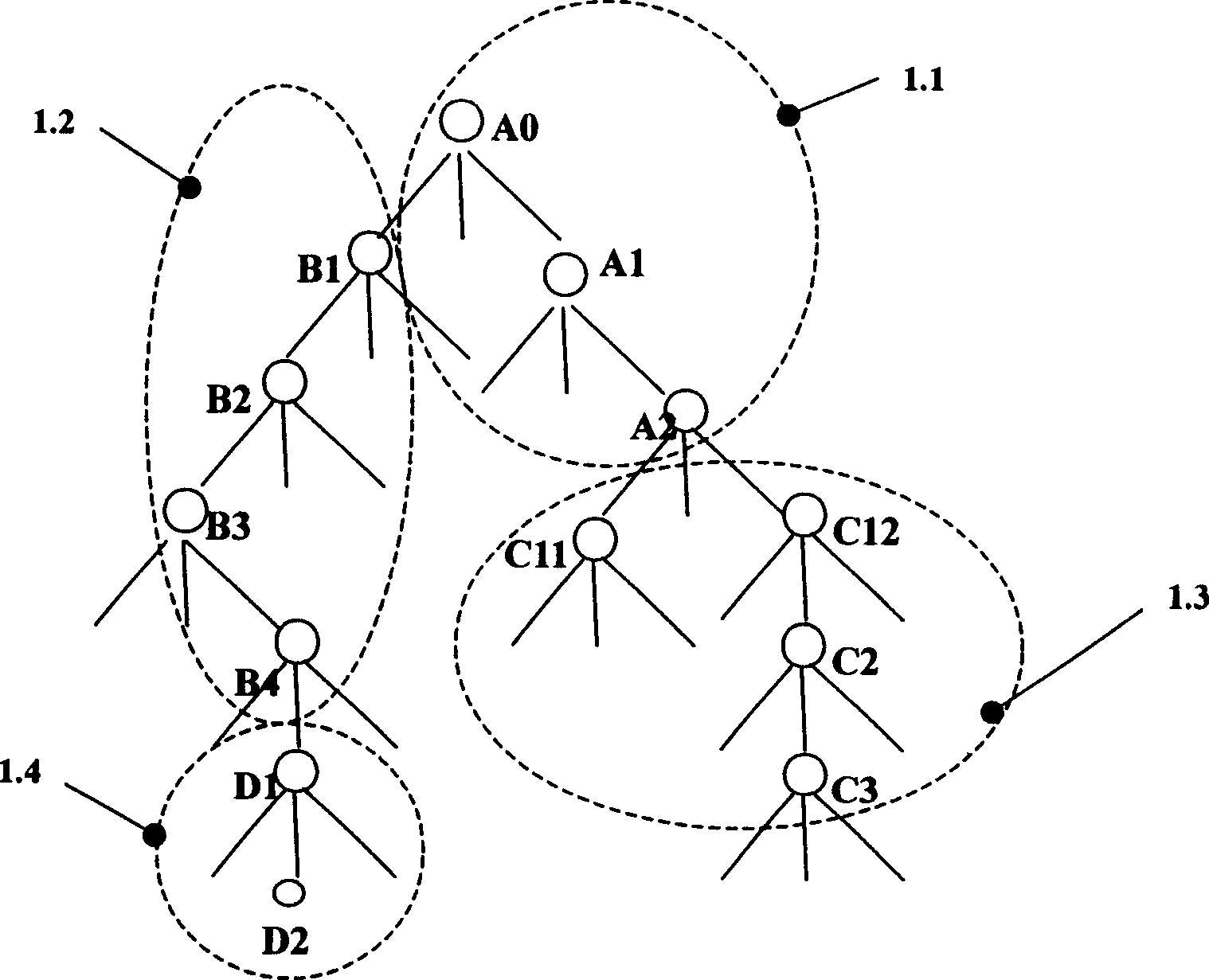
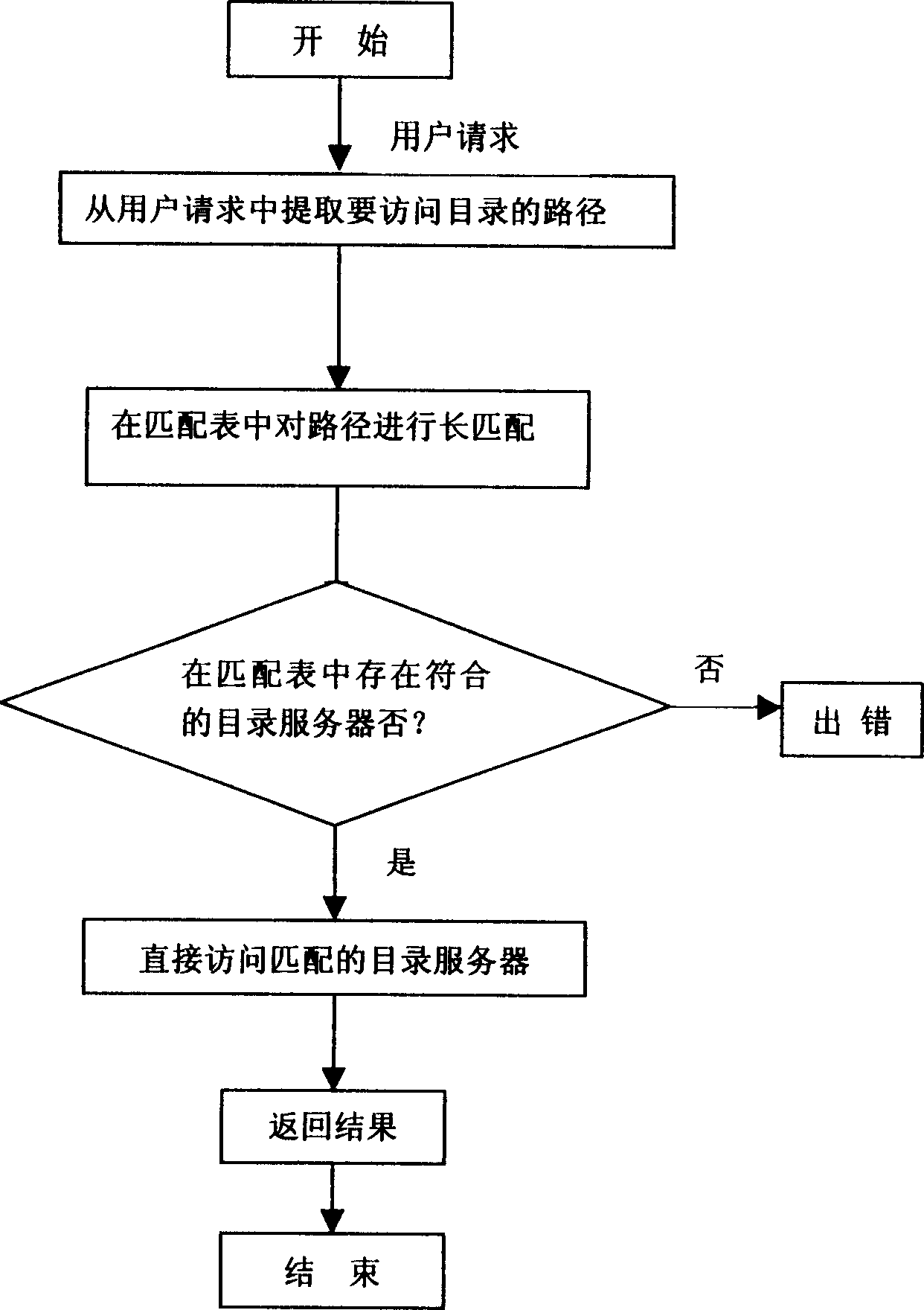
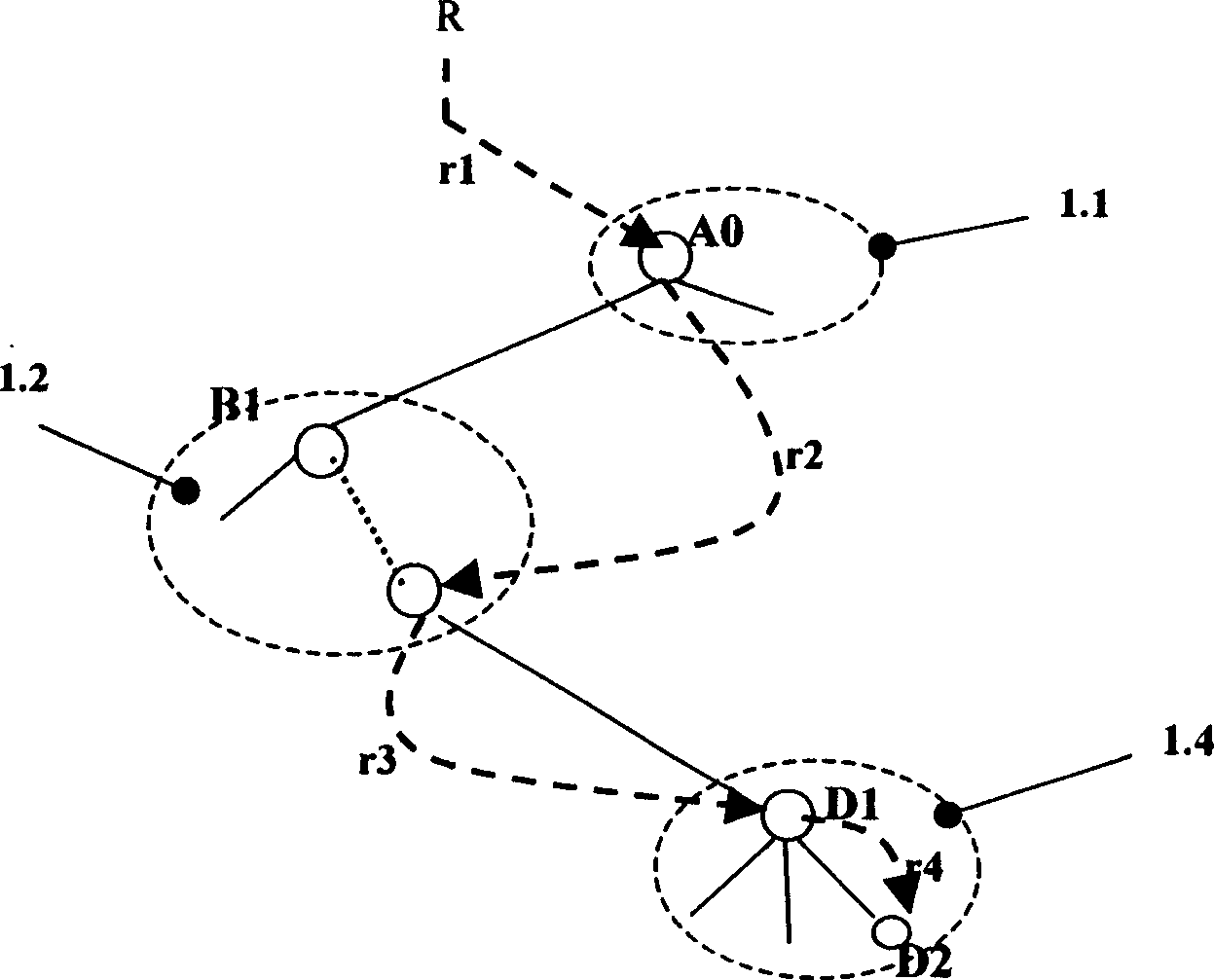
The invention discloses a cell data layer managing method and system of a virtual storage system. The method makes layer management on a cell logic tree, introduces a matching table to lighten the pressure on the root directory server, able to not only rapidly and accurately orient to the directory to be accessed by the user but also achieve better extendable property of the system. The matching table is resident in the memory, and occupies extremely small space because of only recording the root entry address of each directory server, convenient to manage. It also has very high matching efficiency. The system includes the matching table, and the cell data servers and directory servers of the matching table management module; the matching table at least includes the names of the directory servers and the root directories of the cell data logic sub-trees stored in the directory servers. It has characters of high efficiency, good extendable property and easy management.
Owner:HUAZHONG UNIV OF SCI & TECH
System and method for providing access to user interface information
A method and system providing a client with user interface information are described. An accessibility system for providing user interface information to a client. The accessibility system comprises an accessibility system core including user interface automation services and APIs. The user interface automation tools filter information based on whether the user interface information is interesting to the client. The accessibility system additionally comprises a client side interface including a logical tree for revealing user interface information that is interesting to the client and for hiding user interface information that is not interesting to the client. The accessibility system also comprises a server side interface for facilitating information transfer from a server side regardless of the server side technology.
Owner:MICROSOFT TECH LICENSING LLC
Administering virtual machines in a distributed computing environment
InactiveUS20150312330A1Resource allocationDigital computer detailsDistributed Computing EnvironmentLogical tree
In a distributed computing environment that includes hosts that execute a VMM, where each VMM supports execution of one or more VMs, administering VMs may include: assigning, by a VMM manager, the VMMs of the distributed computing environment to a logical tree topology, including assigning one of the VMMs as a root VMM of the tree topology; and executing, amongst the VMMs of the tree topology, a broadcast operation, including: pausing, by the root VMM, execution of one or more VMs supported by the root VMM; sending, by the root VMM, to other VMMs in the tree topology, a message indicating a pending transfer of the paused VMs; and transferring the paused VMs from the root VMM to the other VMMs.
Owner:IBM CORP
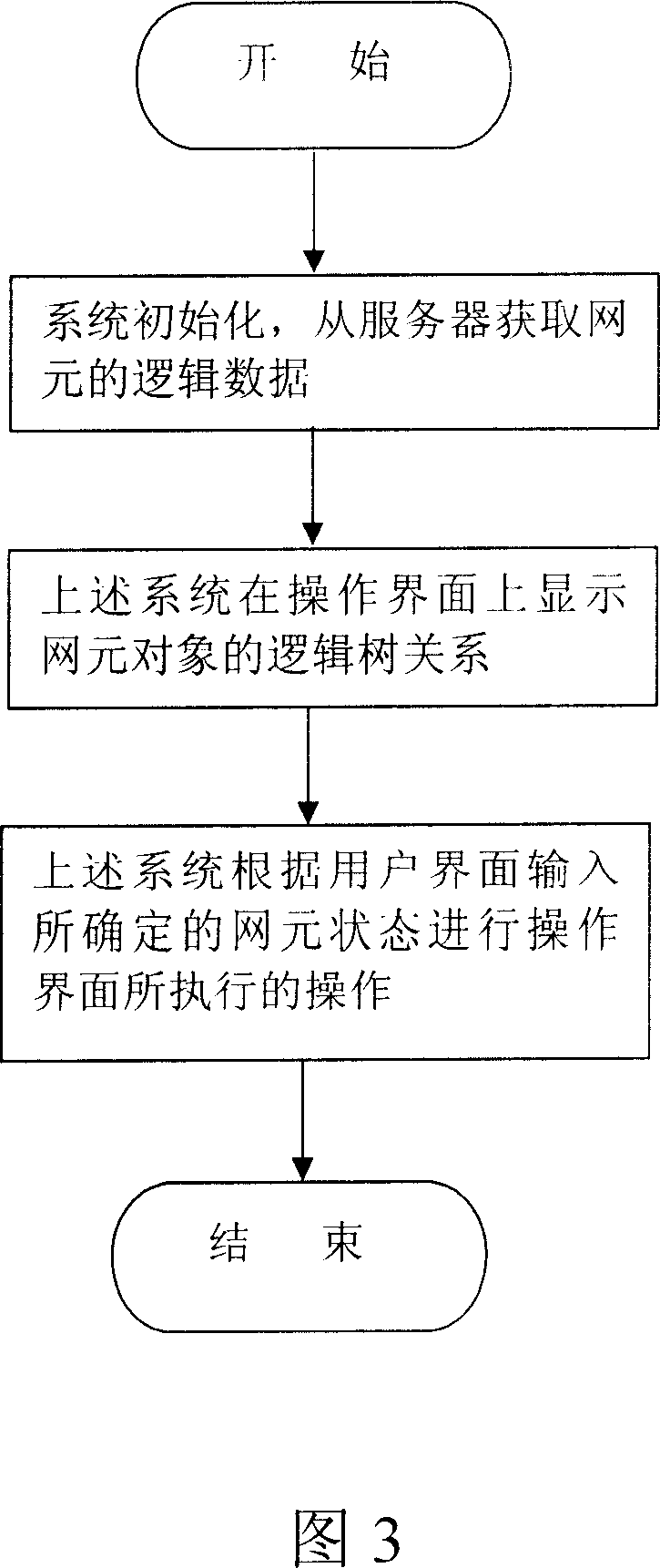
Tri-state tree representing and location method of network element object in network optimization system
InactiveCN1929393AClear structureIntuitive stateData switching networksSpecial data processing applicationsTheoretical computer scienceUser interface
This invention provides one network optimization network subject three tree appearing and positioning method, which comprises steps of system initiating, getting network logic data, displaying element logic tree relationship and inputting network by user interface for above operation interface wherein, the above three trees refer to one tree structure each point including select, semi-sleet and non select status.
Owner:ZTE CORP
Dual encryption protocol for scalable secure group communication
InactiveUSRE40708E1Key distribution for secure communicationMultiple keys/algorithms usageExtensibilityCryptography protocols
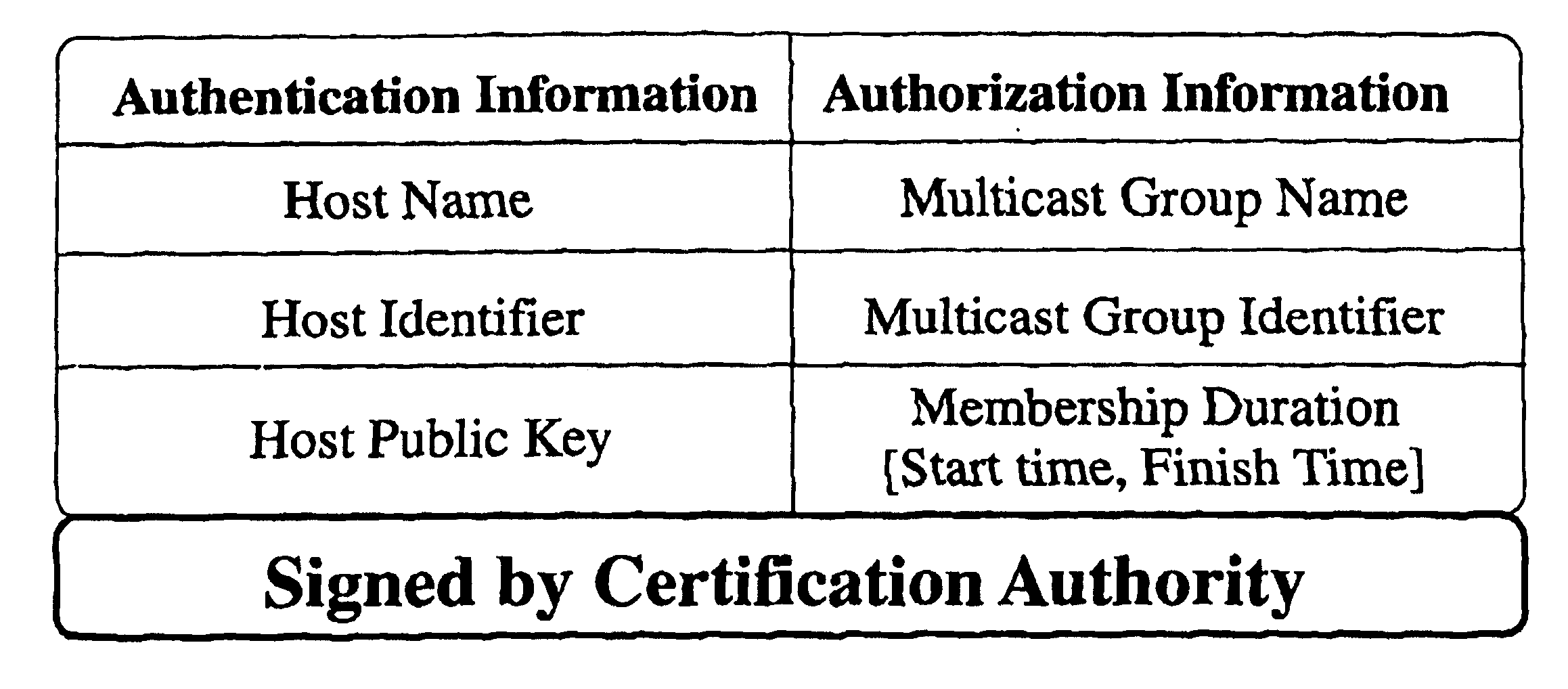
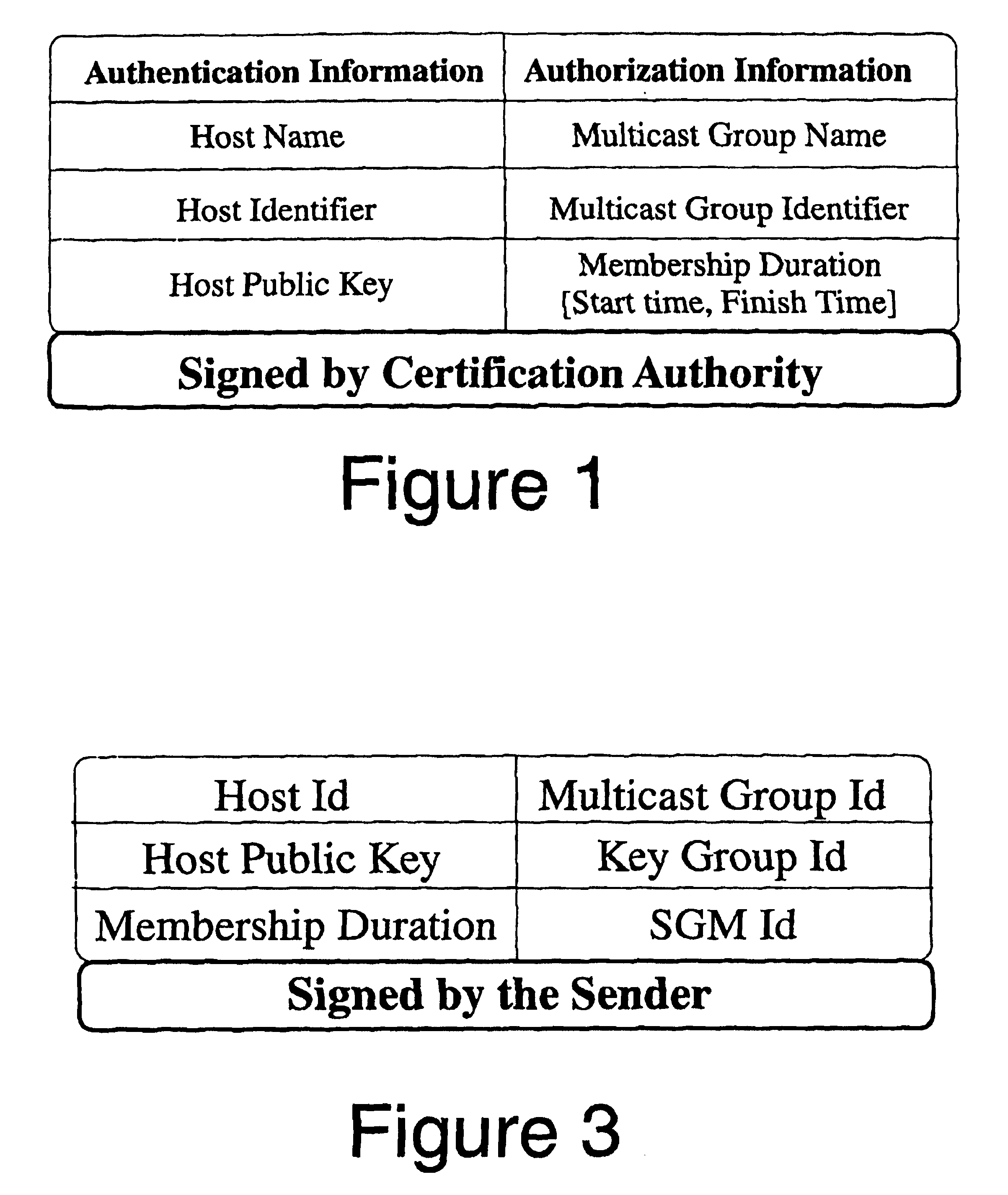
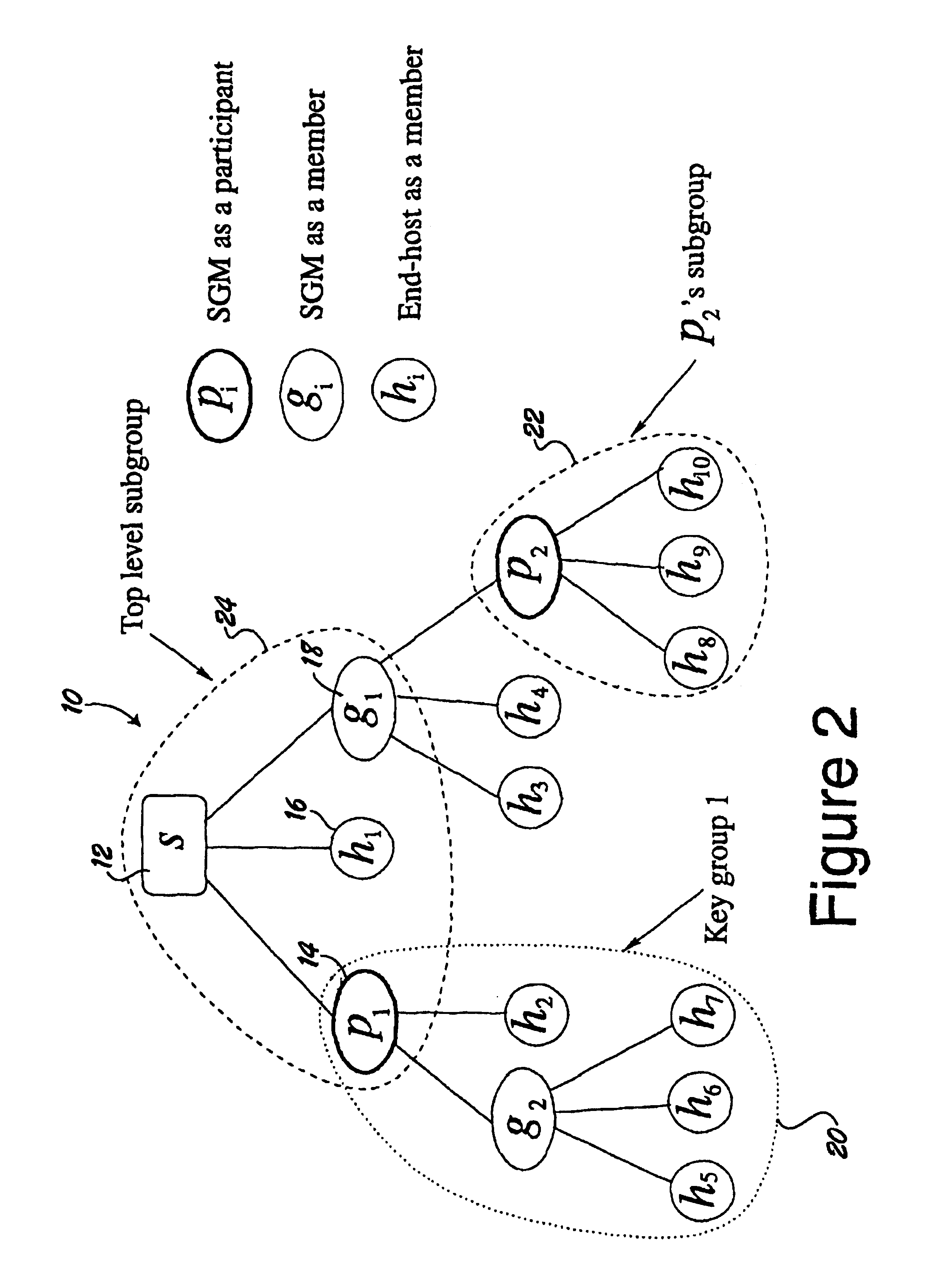
A logical tree structure and method for managing membership in a multicast group provides scalability and security from internal attacks. The structure defines key groups and subgroups, with each subgroup having a subgroup manager. Dual encryption allows the sender of the multicast data to manage distribution of a first set of encryption keys whereas the individual subgroup managers manage the distribution of a second set of encryption keys. The two key sets allow the sender to delegate much of the group management responsibilities without compromising security because a key from each set is required to access the multicast data. Security is further maintained via a method in which subgroup managers can be either member subgroup managers or participant subgroup managers. Access to both keys is provided to member subgroup managers whereas access to only one key is provided to participant subgroup managers. Nodes can be added without the need to generate a new encryption key at the top level which provides improved scalability.
Owner:PANASONIC CORP
Administering virtual machines in a distributed computing environment
InactiveUS20150312109A1Digital computer detailsData switching networksDistributed Computing EnvironmentLogical tree
In a distributed computing environment that includes hosts that execute a VMM, with each VMM supporting execution of one or more VMs, administering VMs may include: assigning, by a VMM manager, the VMMs of the distributed computing environment to a logical tree topology, including assigning one of the VMMs as a root VMM of the tree topology; and executing, amongst the VMMs of the tree topology, a scatter operation, including: pausing, by the root VMM one or more executing VMs; storing, by the root VMM in a buffer, a plurality of VMs to scatter amongst the other VMMs of the tree topology; and sending, by the root VMM, to each of the other VMMs of the tree topology a different one of the VMs stored in the buffer.
Owner:IBM CORP
Administering virtual machines in a distributed computing environment
InactiveUS20150309816A1TransmissionSoftware simulation/interpretation/emulationDistributed Computing EnvironmentLogical tree
In a distributed computing environment that includes hosts which each execute a VMM, with each VMM supporting execution of one or more VMs, administering a the VMs may include: assigning, by a VMM manager, the VMMs of the distributed computing environment to a logical tree topology, including assigning one of the VMMs as a root VMM of the tree topology; and executing, amongst the VMMs of the tree topology, an allgather operation, including: sending, by the root VMM, to other VMMs in the tree topology, a request to retrieve VMs supported by the other VMMs; pausing, by each of the other VMMs, a VM supported by the VMM; providing, by each of the other VMMs as a response to the root VMM's request, the paused VM; and broadcasting, by the root VM to the other VMMs as a set of VMs, the received VMs.
Owner:IBM CORP
Administering virtual machines in a distributed computing environment
InactiveUS20150312108A1Digital computer detailsData switching networksDistributed Computing EnvironmentLogical tree
Administering VMs in a distributed computing environment that includes hosts that execute a VMM, with each VMM supporting execution of one or more VMs, includes: assigning the VMMs to a logical tree topology with one as a root; and executing, by the VMMs of the tree topology, a reduce operation, including: sending, by the root VMM to each of other VMMs of the tree topology, a request for an instance of a particular VM; pausing, by each of the other VMMs, the requested instance of the particular VM; providing, by each of the other VMMs to the root VMM in response to the root VMM's request, the requested instance of the particular VM; and identifying, by the root VMM, differences among the requested instances of the particular VM including, performing a bitwise XOR operation amongst the instances of the particular VM.
Owner:IBM CORP
Administering virtual machines in a distributed computing environment
In a distributed computing environment that includes hosts that execute a VMM, with each VMM supporting execution of one or more VMs, administering VMs may include: assigning, by a VMM manager, the VMMs of the distributed computing environment to a logical tree topology, including assigning one of the VMMs as a root VMM of the tree topology; and executing, amongst the VMMs of the tree topology, a scatter operation, including: pausing, by the root VMM one or more executing VMs; storing, by the root VMM in a buffer, a plurality of VMs to scatter amongst the other VMMs of the tree topology; and sending, by the root VMM, to each of the other VMMs of the tree topology a different one of the VMs stored in the buffer.
Owner:IBM CORP
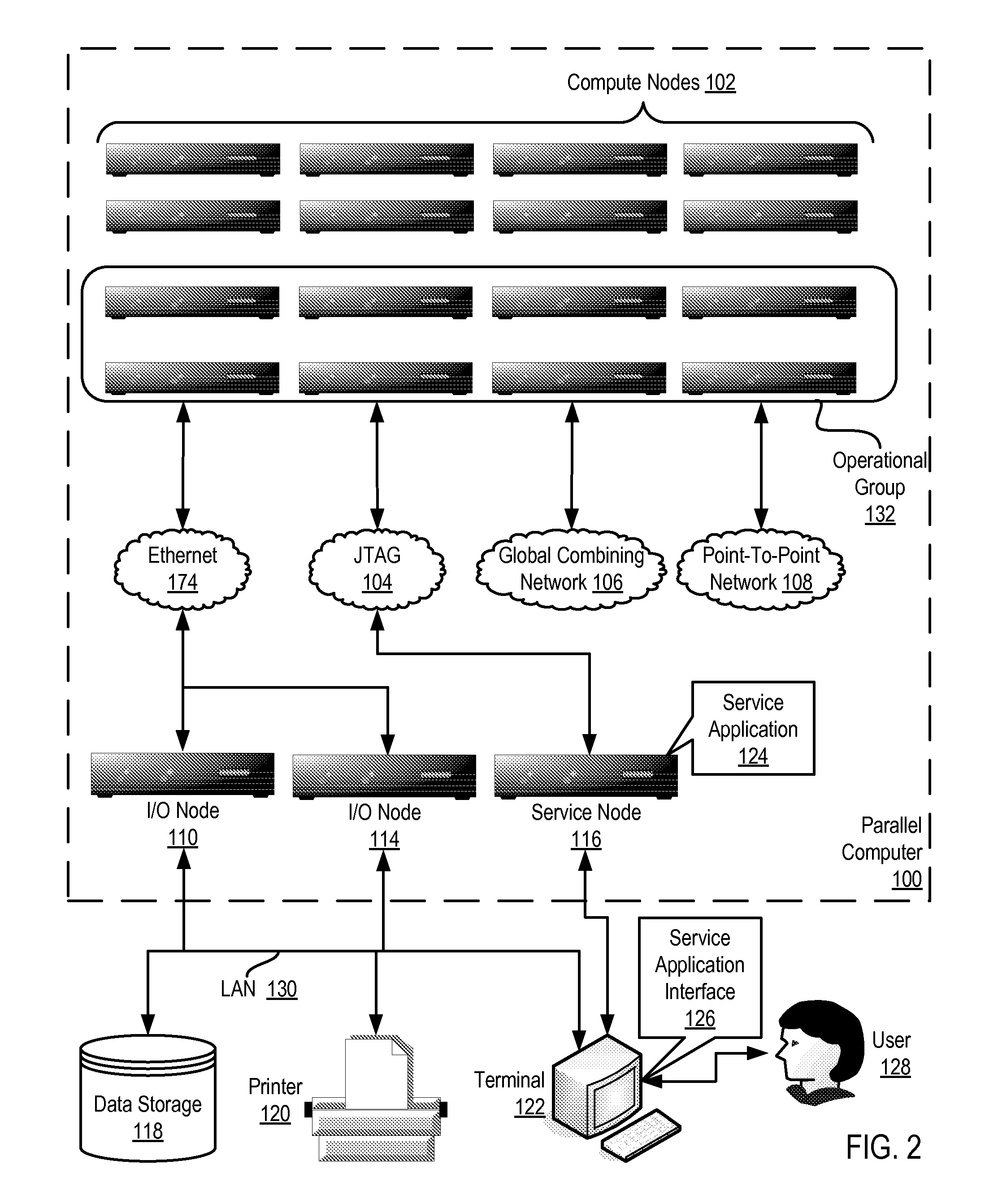
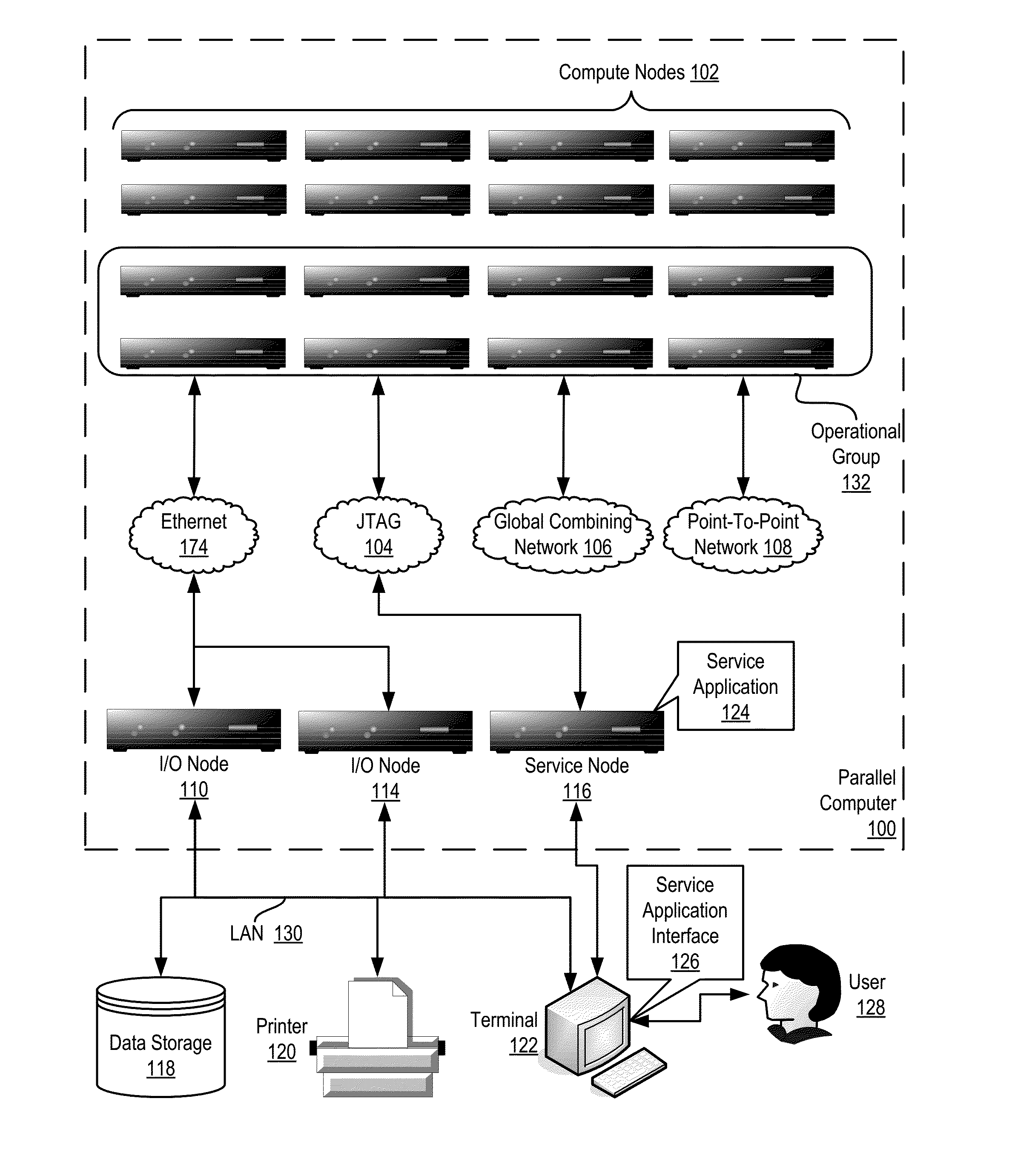
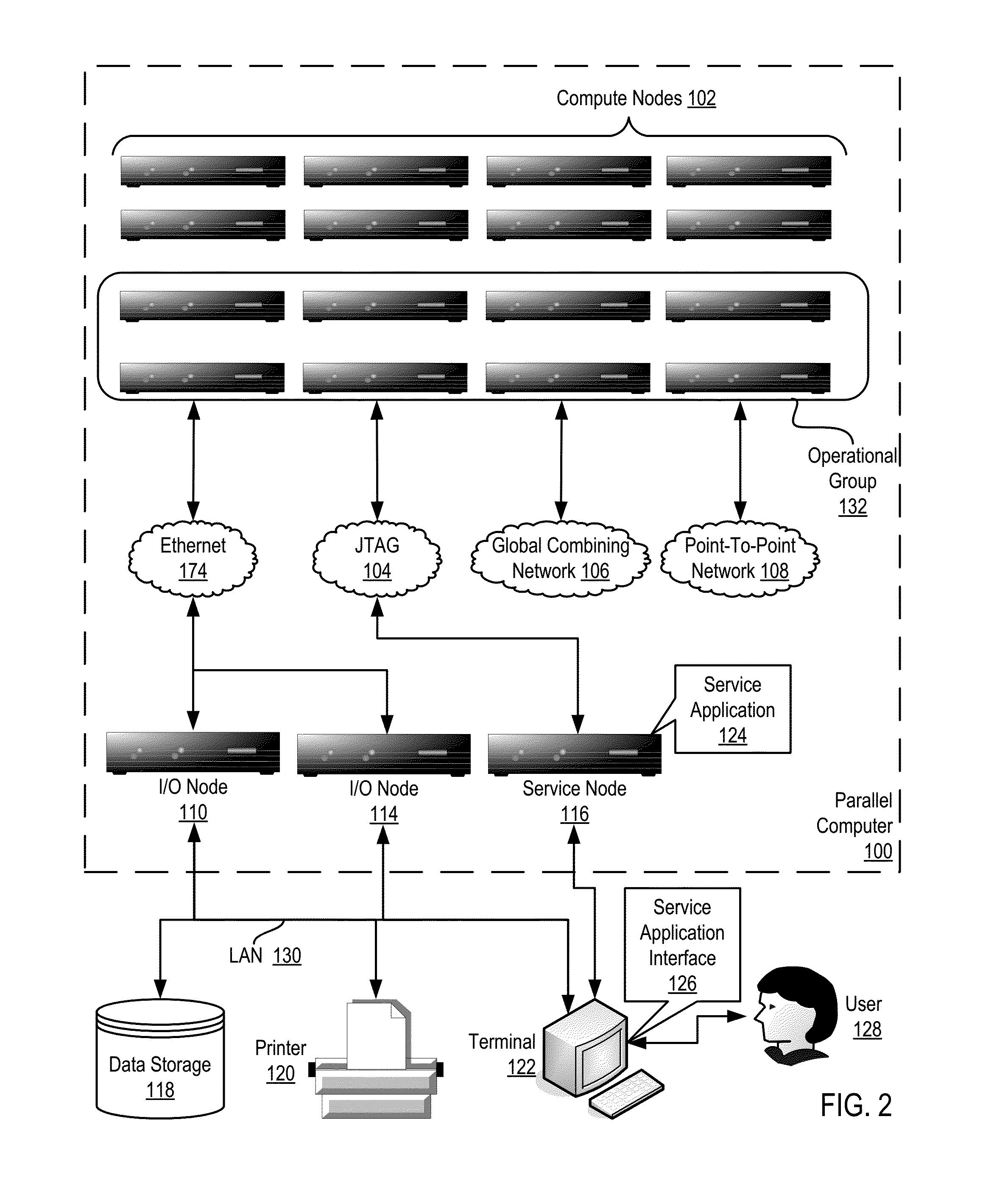
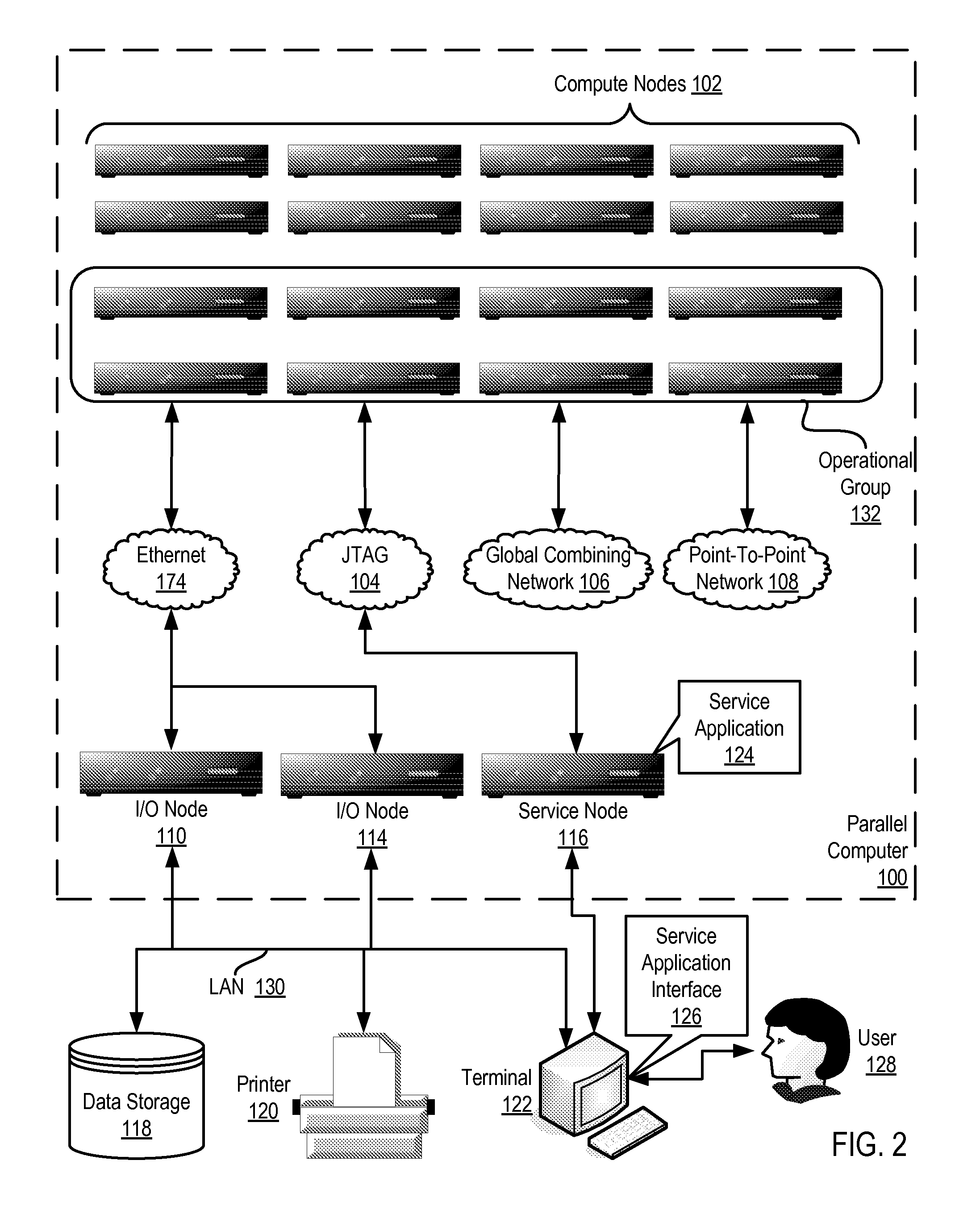
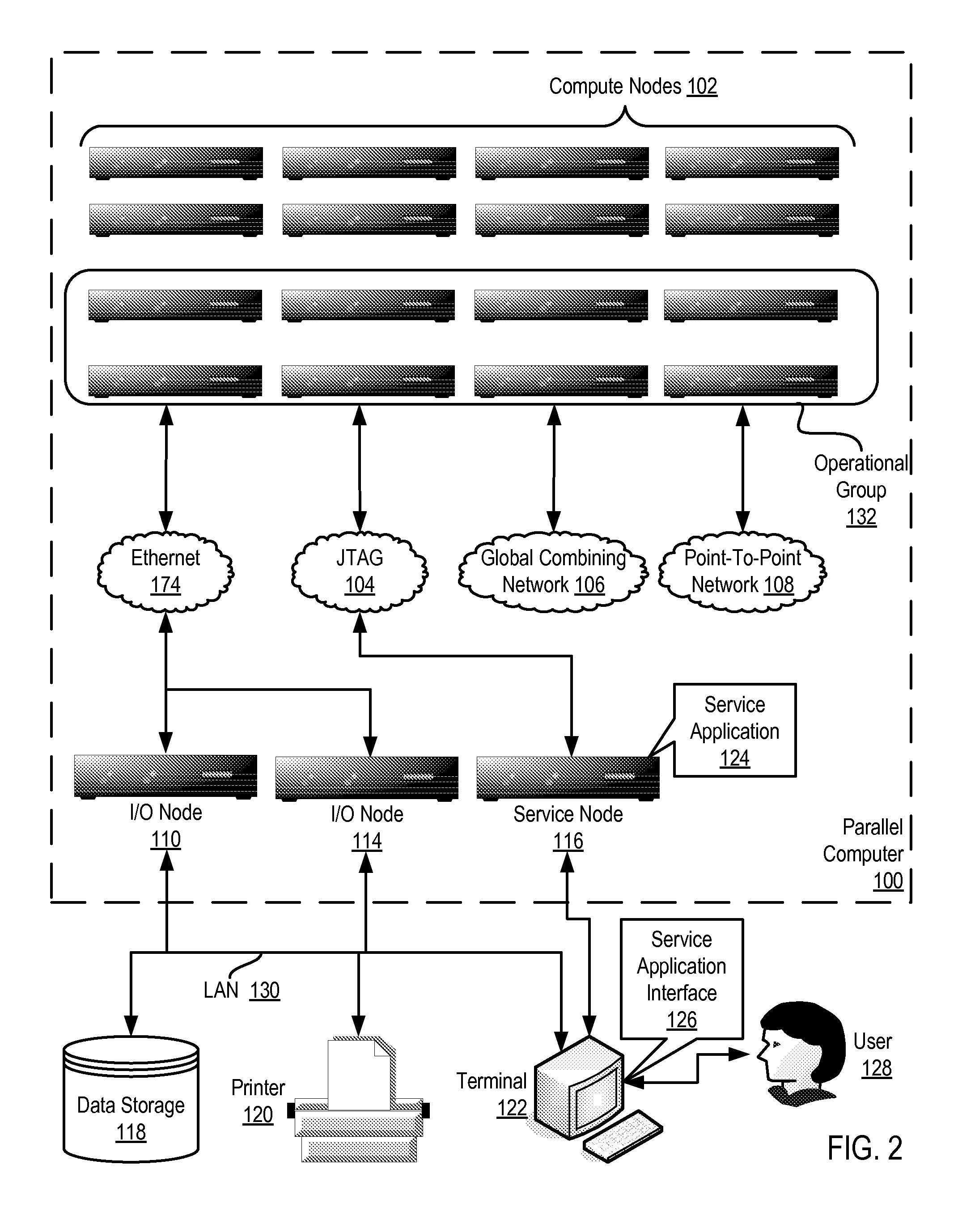
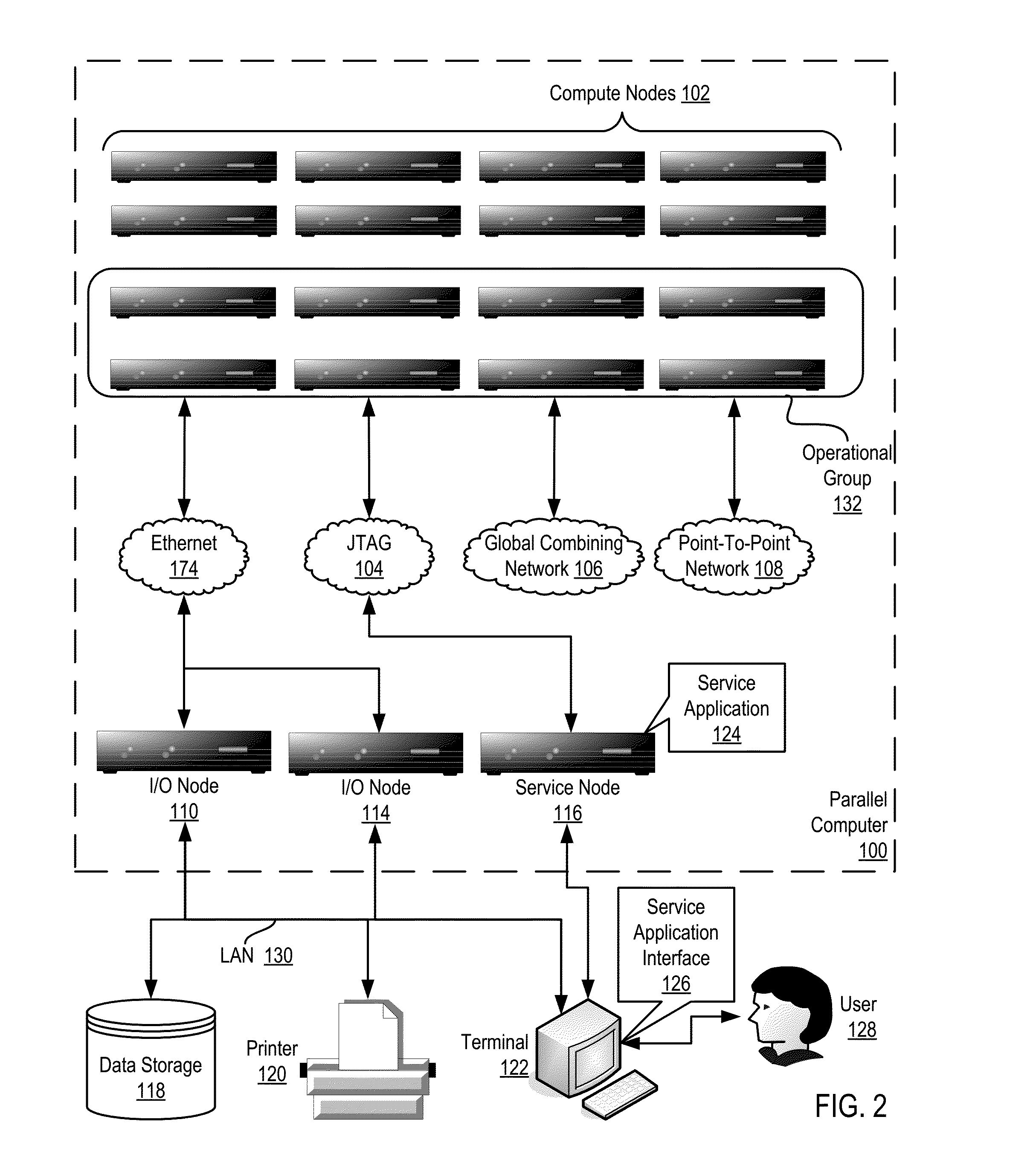
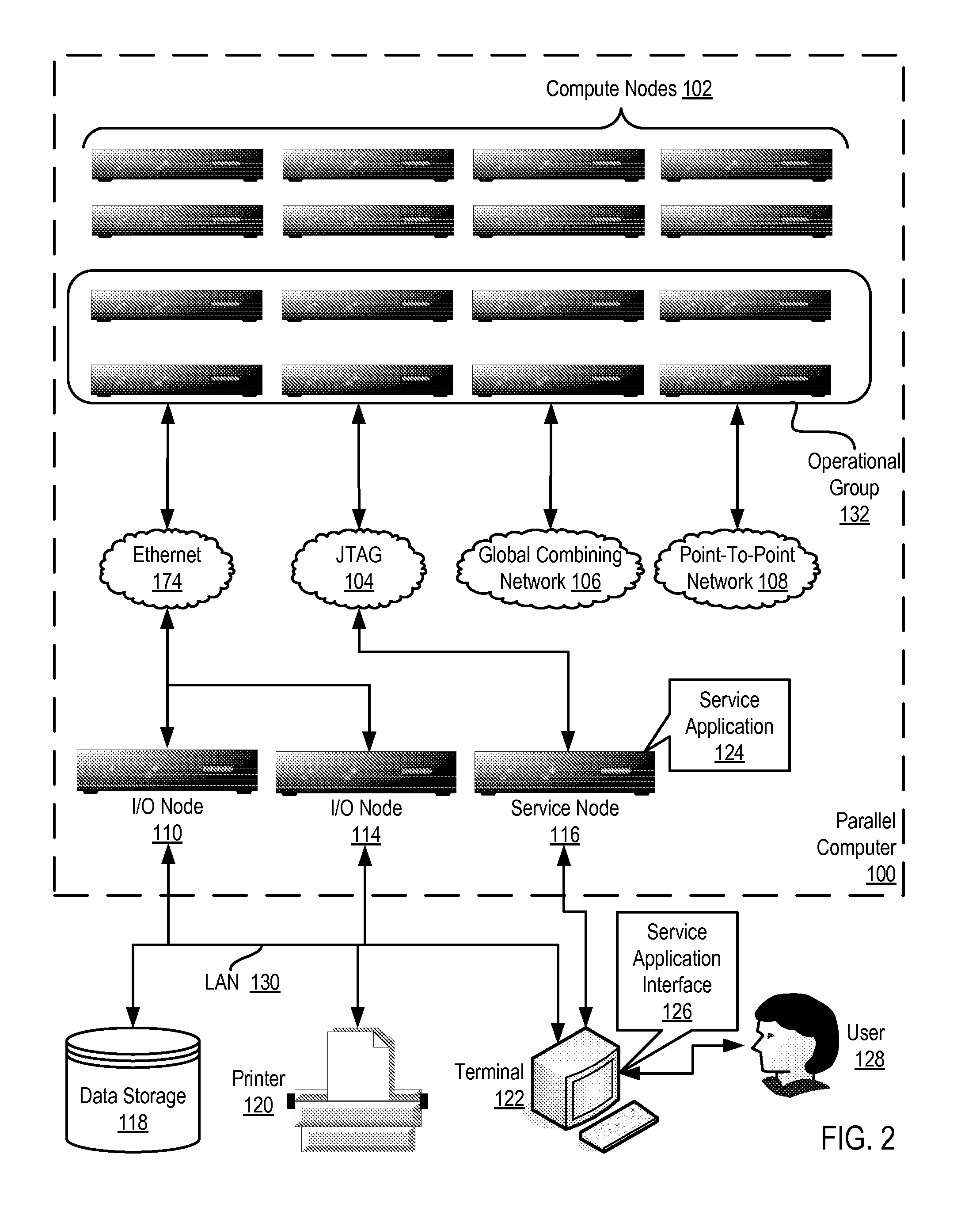
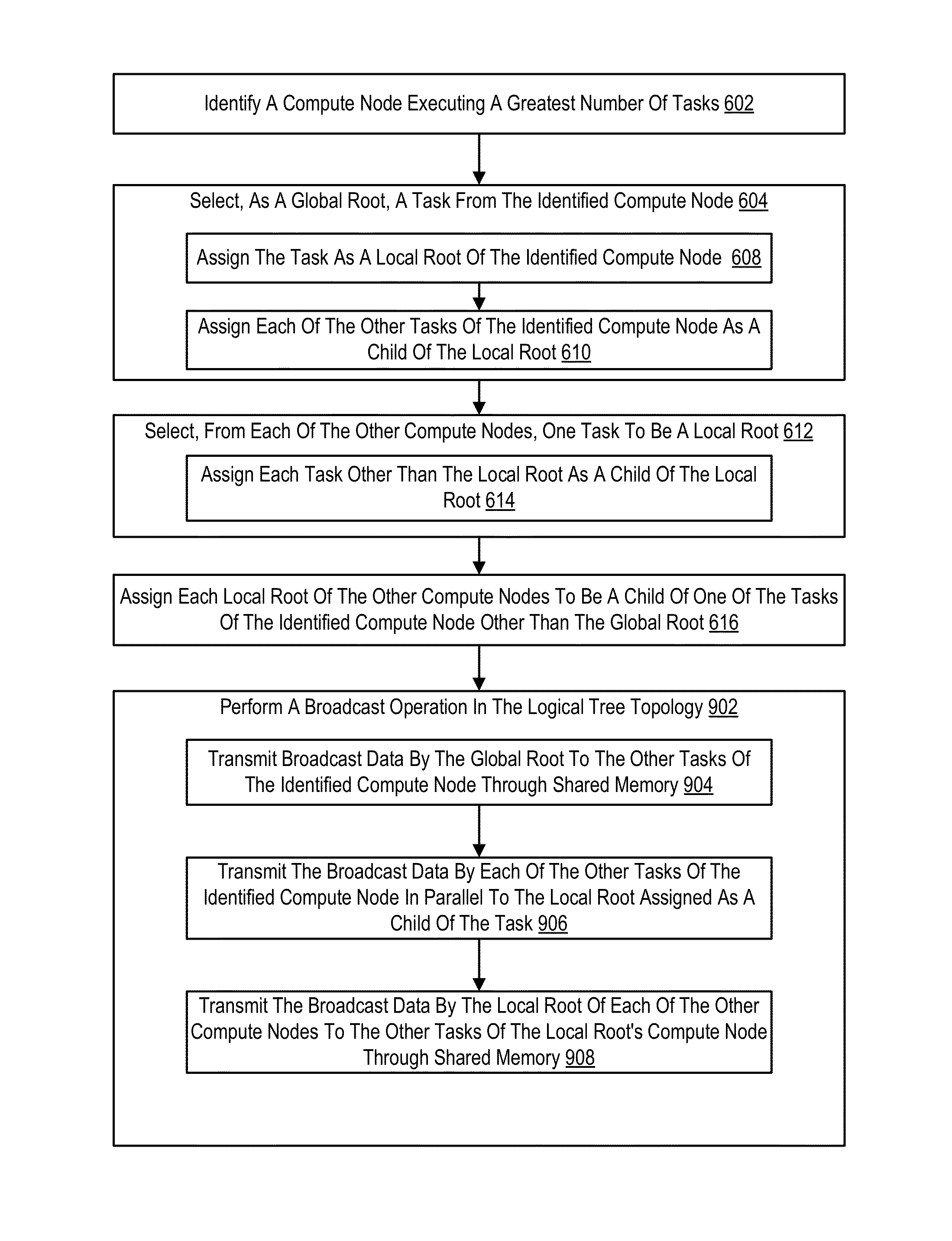
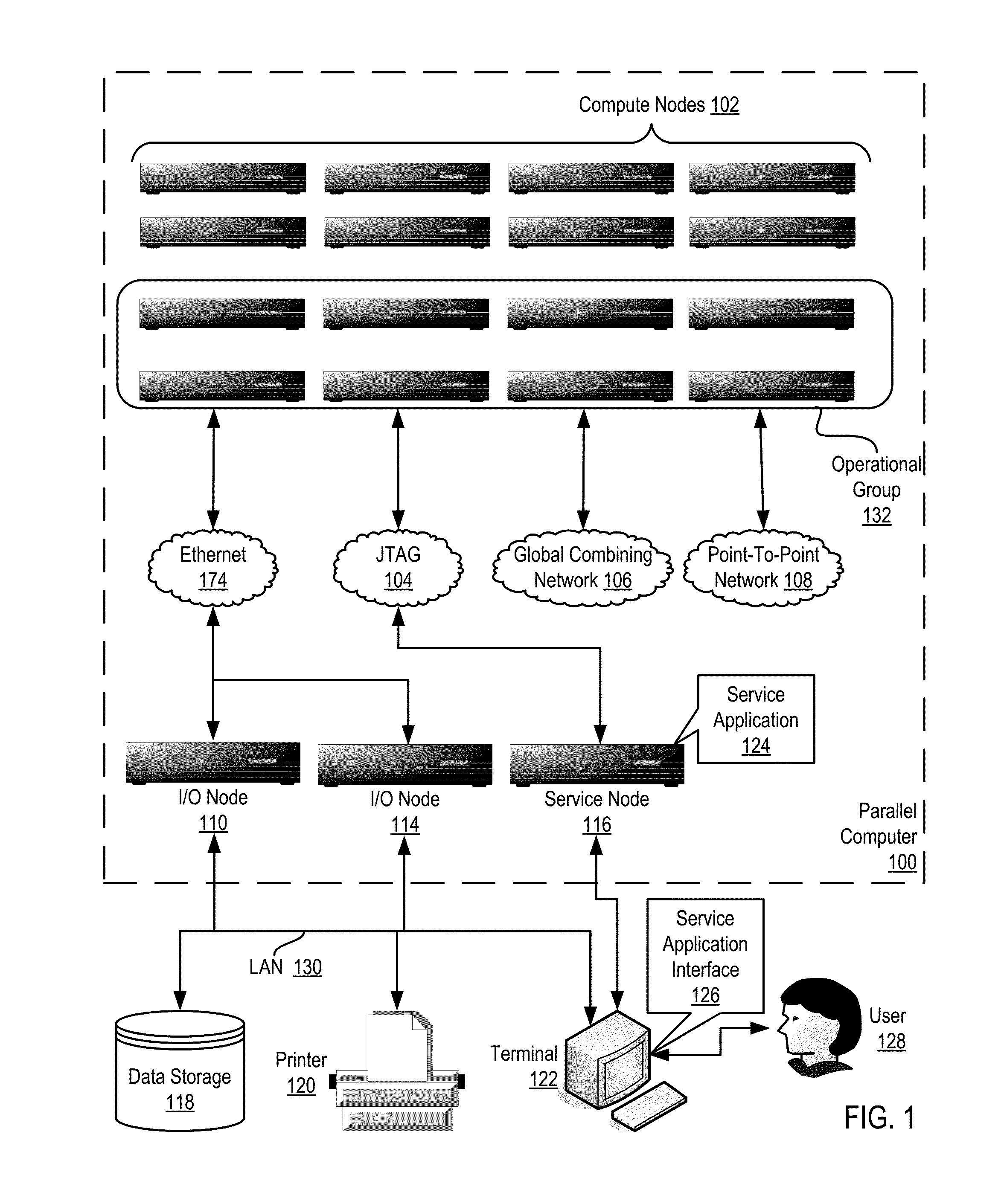
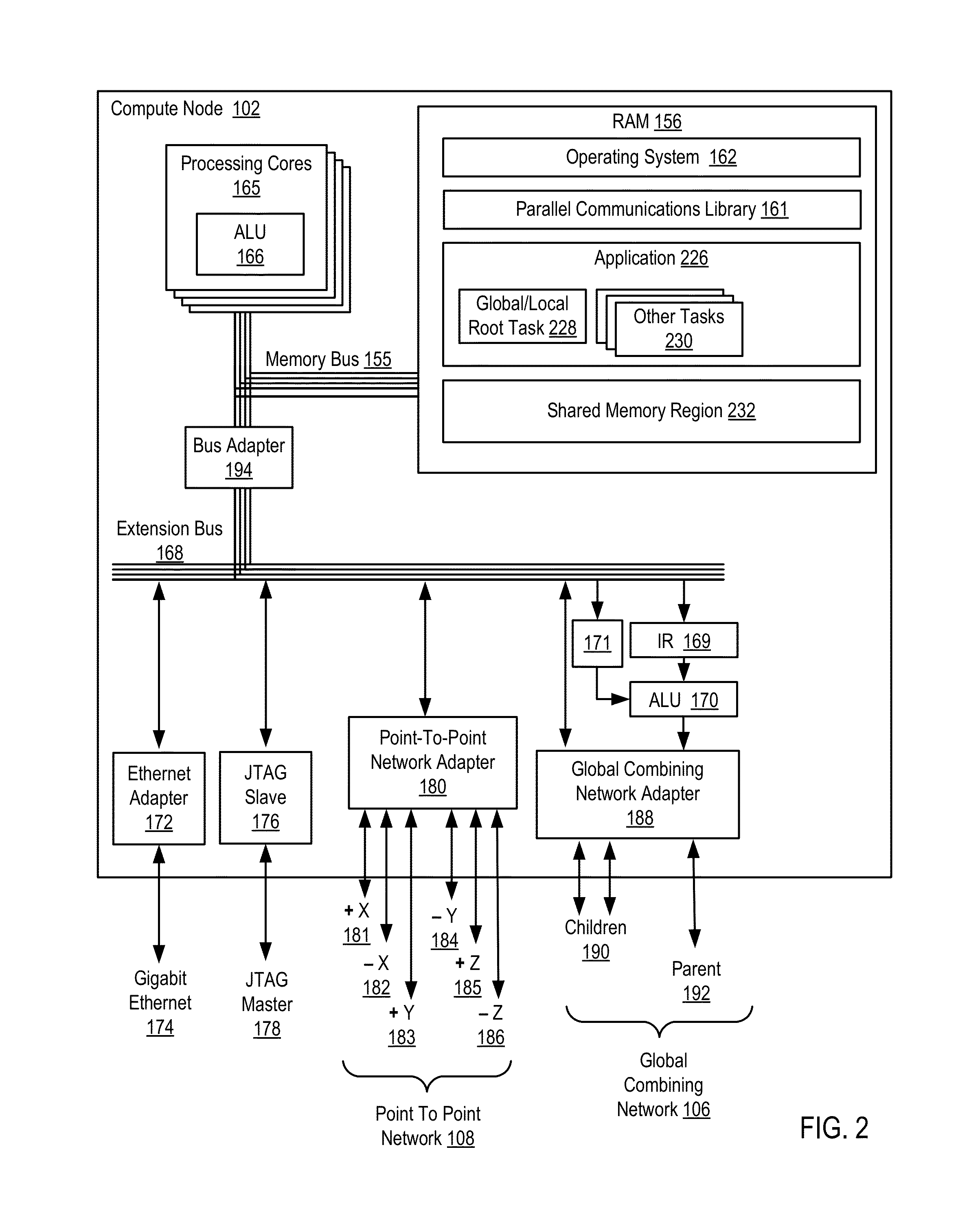
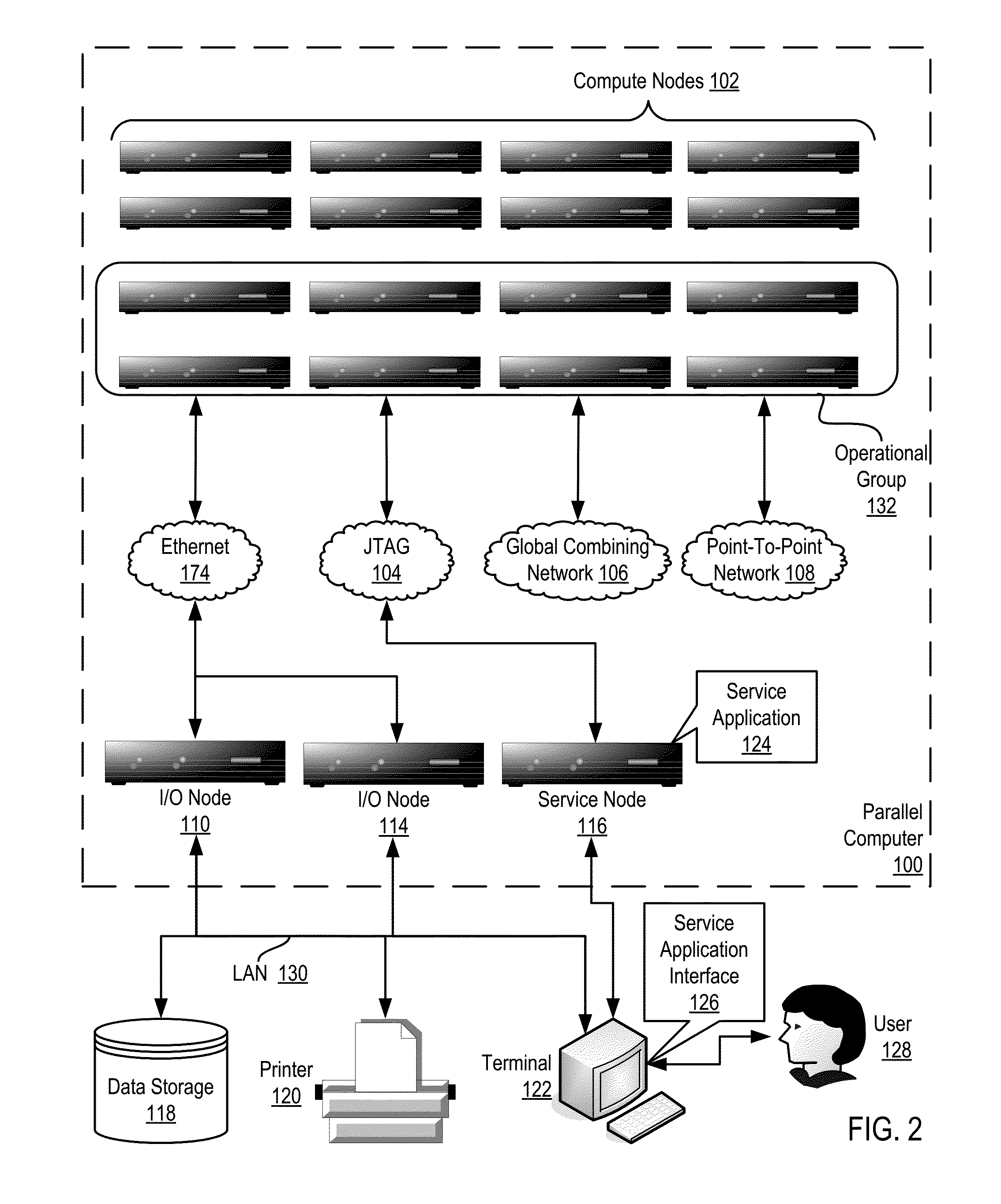
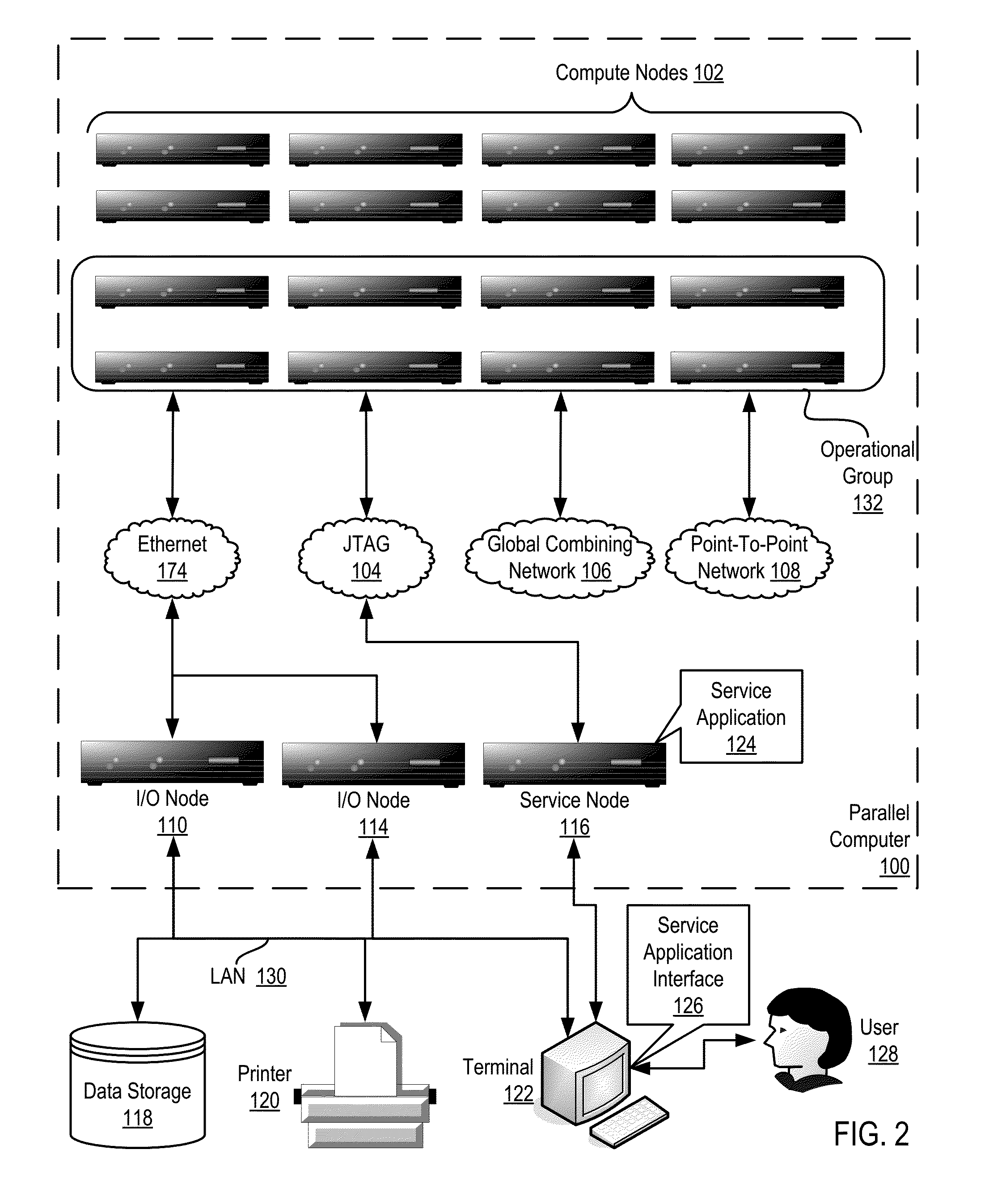
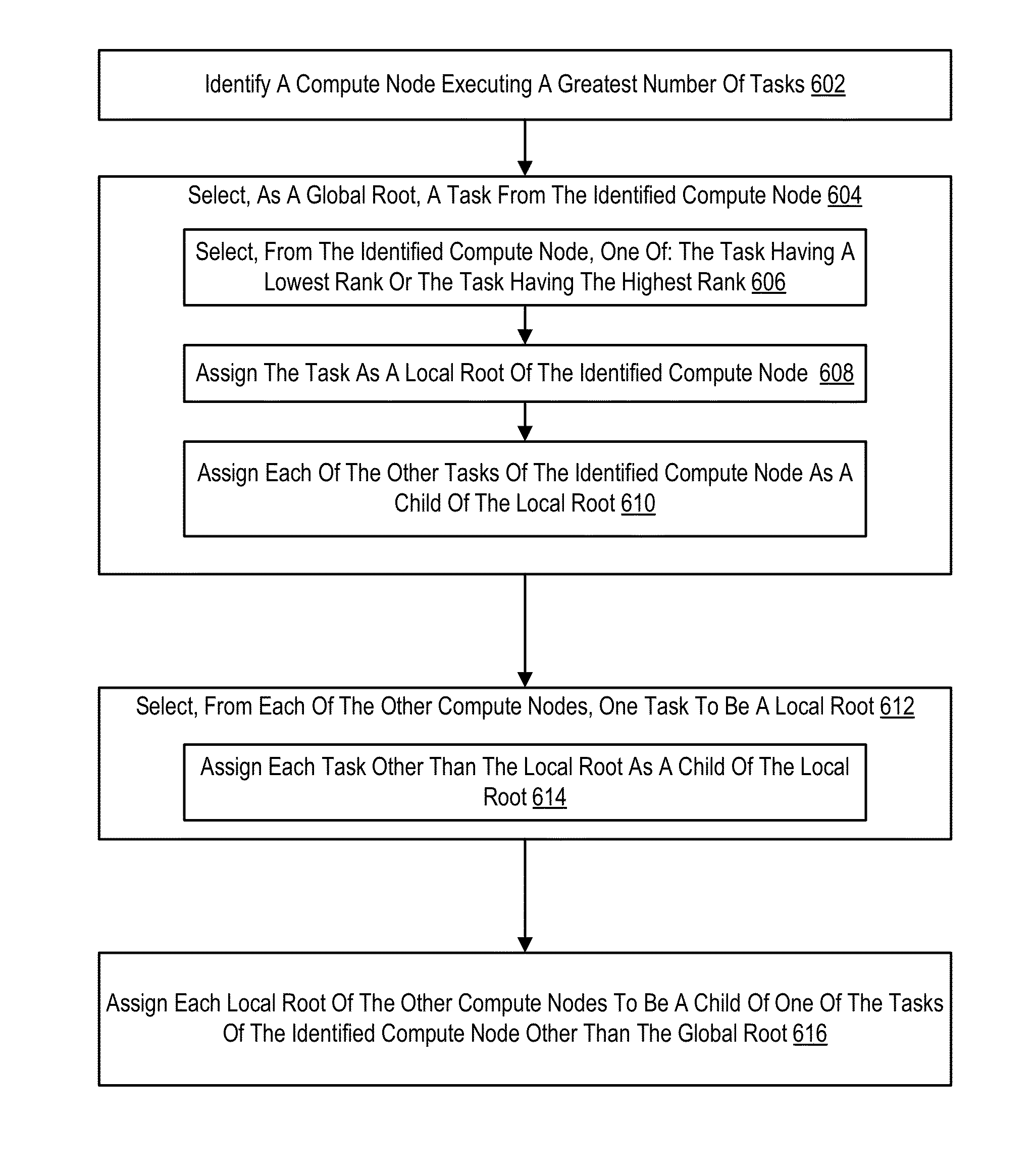
Constructing A Logical Tree Topology In A Parallel Computer
Constructing a logical tree topology in a parallel computer that includes compute nodes, where each node executes a number of tasks and at least one node executes a number of tasks different from another node includes: identifying a compute node executing a greatest number of tasks; selecting, as a global root, a task from the identified compute node, including assigning the task as a local root of the identified compute node and assigning each of the other tasks of the identified compute node as a child of the local root; selecting, from each of the other compute nodes, one task to be a local root, including assigning each task other than the local root as a child of the local root; and assigning each local root of the other compute nodes to be a child of one of the tasks of the identified compute node other than the global root.
Owner:IBM CORP
Administering virtual machines in a distributed computing environment
InactiveUS20150309821A1Resource allocationDigital computer detailsDistributed Computing EnvironmentLogical tree
In a distributed computing environment that includes which each execute a VMM, where each VMM supports execution of one or more VMs, administering the VMs may include: assigning, by a VMM manager, the VMMs of the distributed computing environment to a logical tree topology, including assigning one of the VMMs as a root VMM of the tree topology; and executing, amongst the VMMs of the tree topology, a gather operation, including: sending, by the root VMM, to other VMMs in the tree topology, a request to retrieve one or more VMs supported by the other VMMs; pausing, by the other VMMs, each VM requested to be retrieved; and providing, by the other VMMs to the root VMM, the VMs requested to be retrieved.
Owner:IBM CORP
Administering virtual machines in a distributed computing environment
InactiveUS20150309822A1Resource allocationDigital computer detailsDistributed Computing EnvironmentLogical tree
Administering VMs in a distributed computing environment that includes hosts that execute a VMM, with each VMM supporting execution of one or more VMs, includes: assigning the VMMs to a logical tree topology with one as a root; and executing, by the VMMs of the tree topology, a reduce operation, including: sending, by the root VMM to each of other VMMs of the tree topology, a request for an instance of a particular VM; pausing, by each of the other VMMs, the requested instance of the particular VM; providing, by each of the other VMMs to the root VMM in response to the root VMM's request, the requested instance of the particular VM; and identifying, by the root VMM, differences among the requested instances of the particular VM including, performing a bitwise XOR operation amongst the instances of the particular VM.
Owner:IBM CORP
Constructing a logical tree topology in a parallel computer
Constructing a logical tree topology in a parallel computer that includes compute nodes, where each node executes a number of tasks and at least one node executes a number of tasks different from another node includes: identifying a compute node executing a greatest number of tasks; selecting, as a global root, a task from the identified compute node, including assigning the task as a local root of the identified compute node and assigning each of the other tasks of the identified compute node as a child of the local root; selecting, from each of the other compute nodes, one task to be a local root, including assigning each task other than the local root as a child of the local root; and assigning each local root of the other compute nodes to be a child of one of the tasks of the identified compute node other than the global root.
Owner:IBM CORP
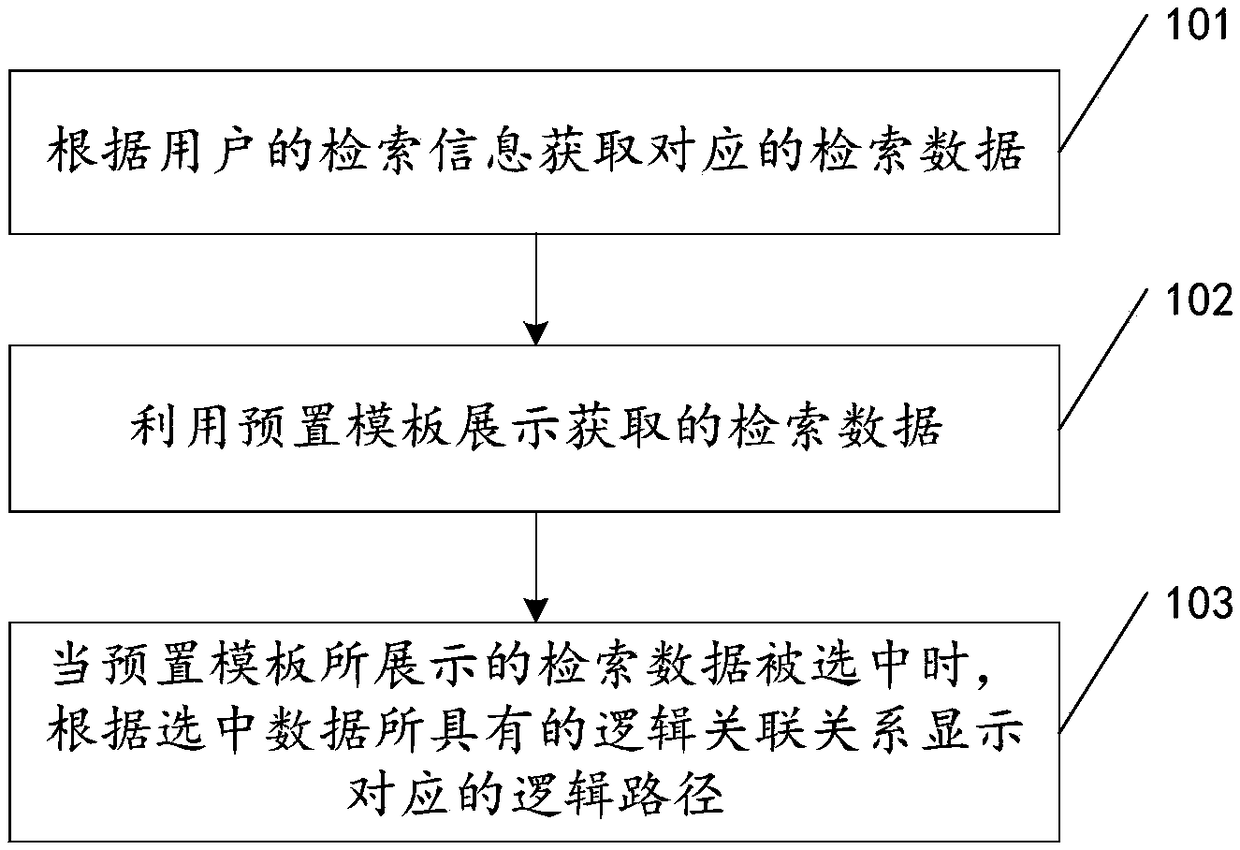
Method and apparatus for displaying associated data
InactiveCN109117424AComprehensive search resultsOptimize data query interaction experienceKnowledge representationSpecial data processing applicationsData informationData mining
The invention discloses a method and a device for displaying associated data, in accordance with the present invention, Used to enhance the user's retrieval experience, the main technical scheme of the invention is as follows: the retrieval information includes the keyword information in the retrieval knowledge points. The retrieval data is the data information with multiple logical associations.The logical association relationship is the association relationship between the retrieval knowledge points and other knowledge points under multiple logical tree structures. A preset template is usedto display the retrieval data, and the preset template is used to sort the retrieval data according to the preset dimension. When the retrieval data presented by the preset template is selected, Thelogical path is the hierarchical path of the retrieval knowledge points corresponding to the selected data under various logical tree structures, which is used to display the data information of otherknowledge points associated with the retrieval knowledge points of the selected data in different logical tree structures.
Owner:BEIJING GRIDSUM TECH CO LTD
Relationship management in a data abstraction model
InactiveUS7599924B2Digital data information retrievalData processing applicationsCustomer relationship managementData abstraction
A method, system and article of manufacture for managing relationships in a data abstraction model abstractly describing data in a database. One embodiment provides a method of linking logical branches of data in a database based on the relationships. The method includes accessing a data abstraction model abstractly describing the data in the database. The data abstraction model defines a logical tree structure having a plurality of logical branches. Relationships between logical fields of different logical branches are identified and logical links abstractly describing the identified relationships are created.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com