Dual encryption protocol for scalable secure group communication
a secure group communication and encryption protocol technology, applied in the field of multicasting, can solve the problems of multiple attacks, multicasting poses several problems, and the protocol cannot be easily extended to protect multicast data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
Introduction to the Dual Encryption Protocol
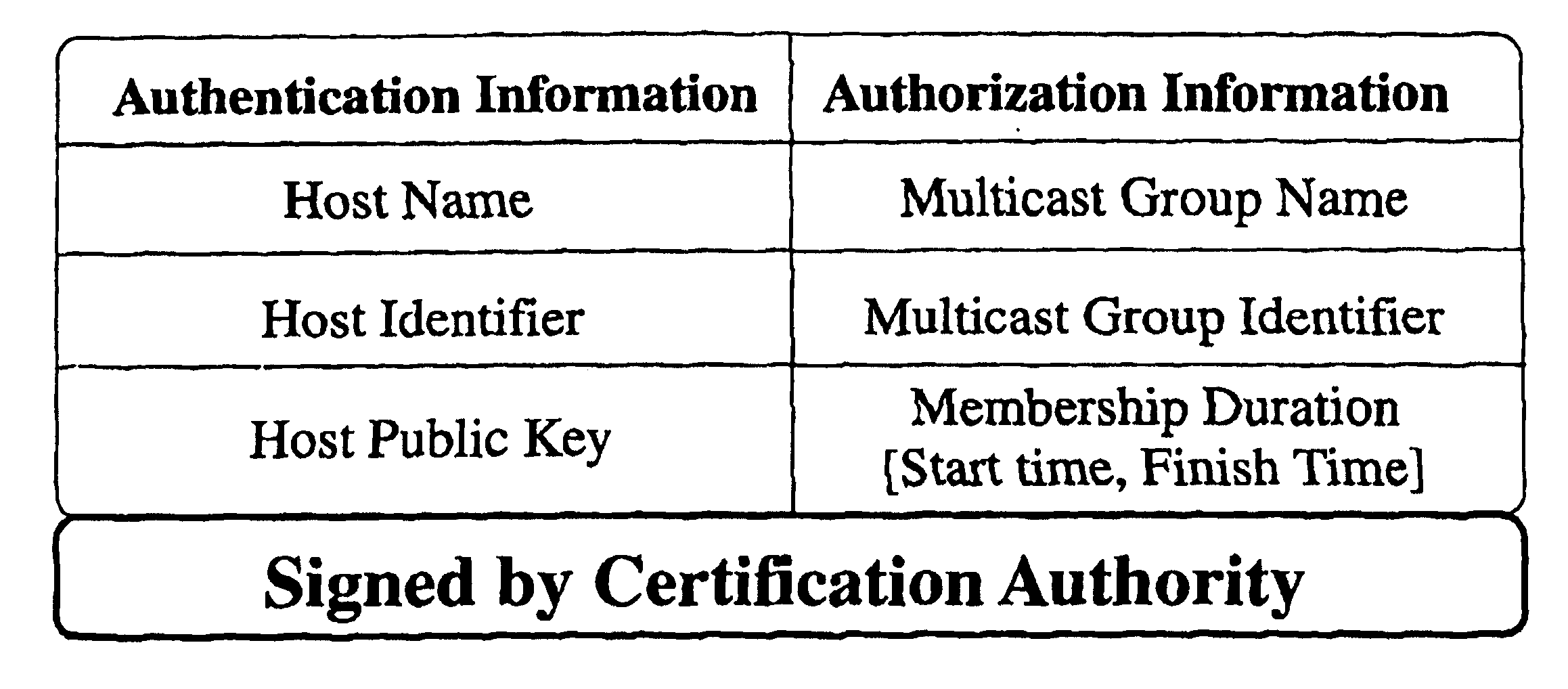
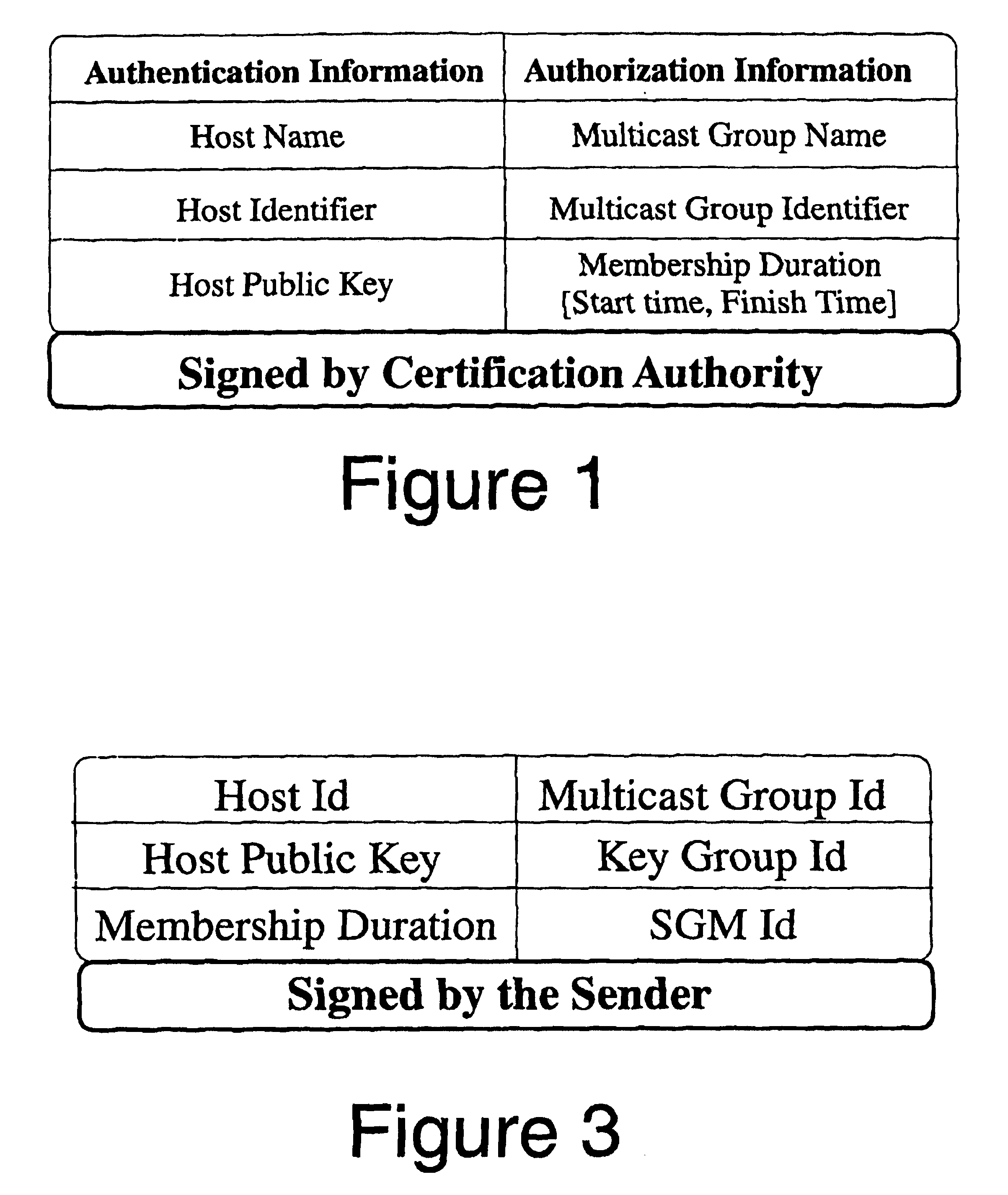
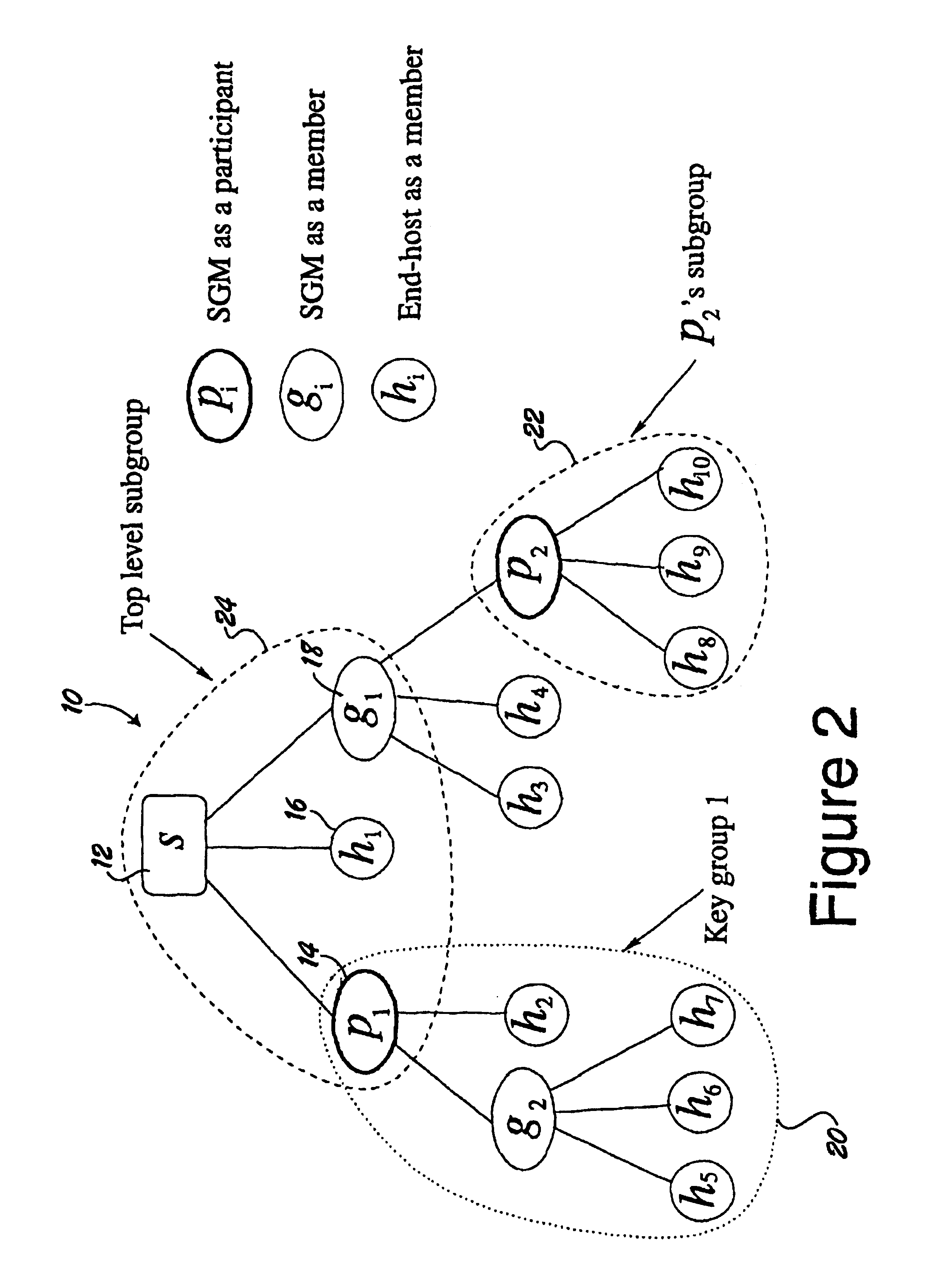
[0017]The dual encryption protocol is well suited for scalable secure multicasting. The protocol supports secure one-to-many groups communication, dynamic group membership and is scalable. The protocol uses hierarchical subgrouping of multicast members to address scalability. Each subgroup is managed by a subgroup manager (SGM). SGMs are either routers or hosts in the network that can handle the workload of managing a subgroup of the multicast group. The assumption is that the SGMs conform to the secure multicast protocol and do not actively participate in disrupting it. There is a distinction between participants and members of the group. Members of the group are end-hosts or SGMs that are entitled to the multicast data. On the other hand, participants of the group are SGMs that assist in enforcing the secure multicast protocol without having any access to the multicast data. With this distinction, it is possible to have SGMs assist in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com