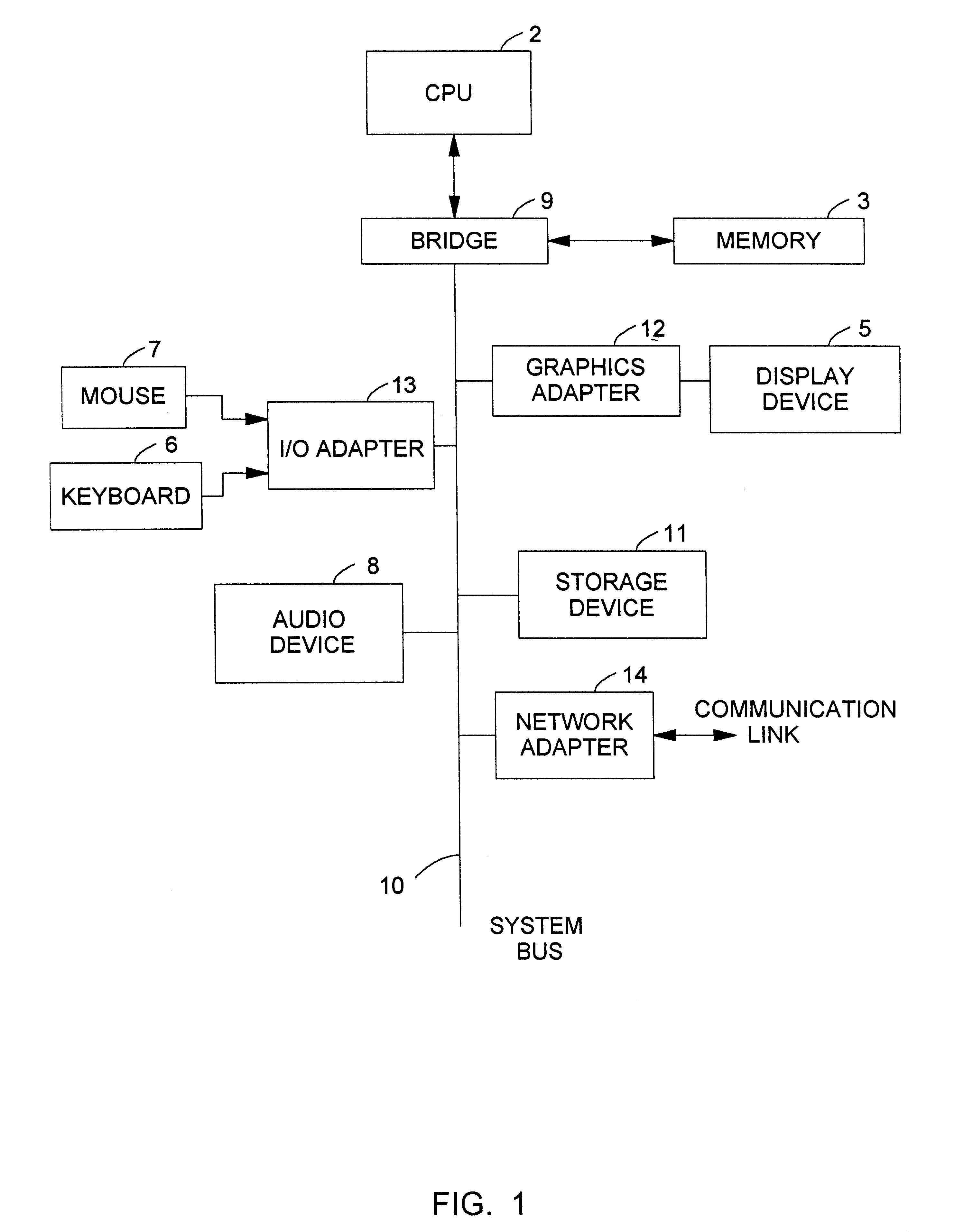
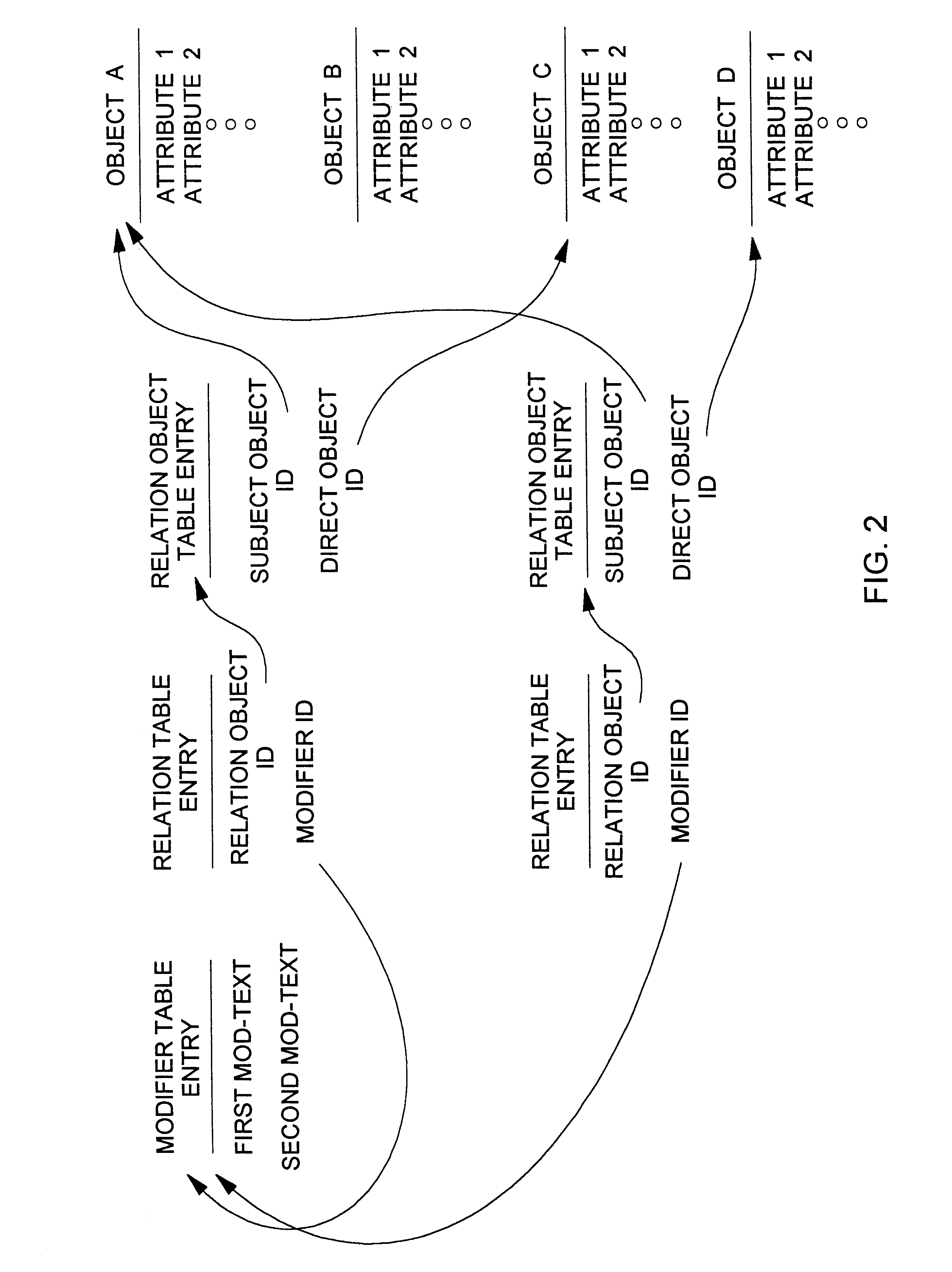
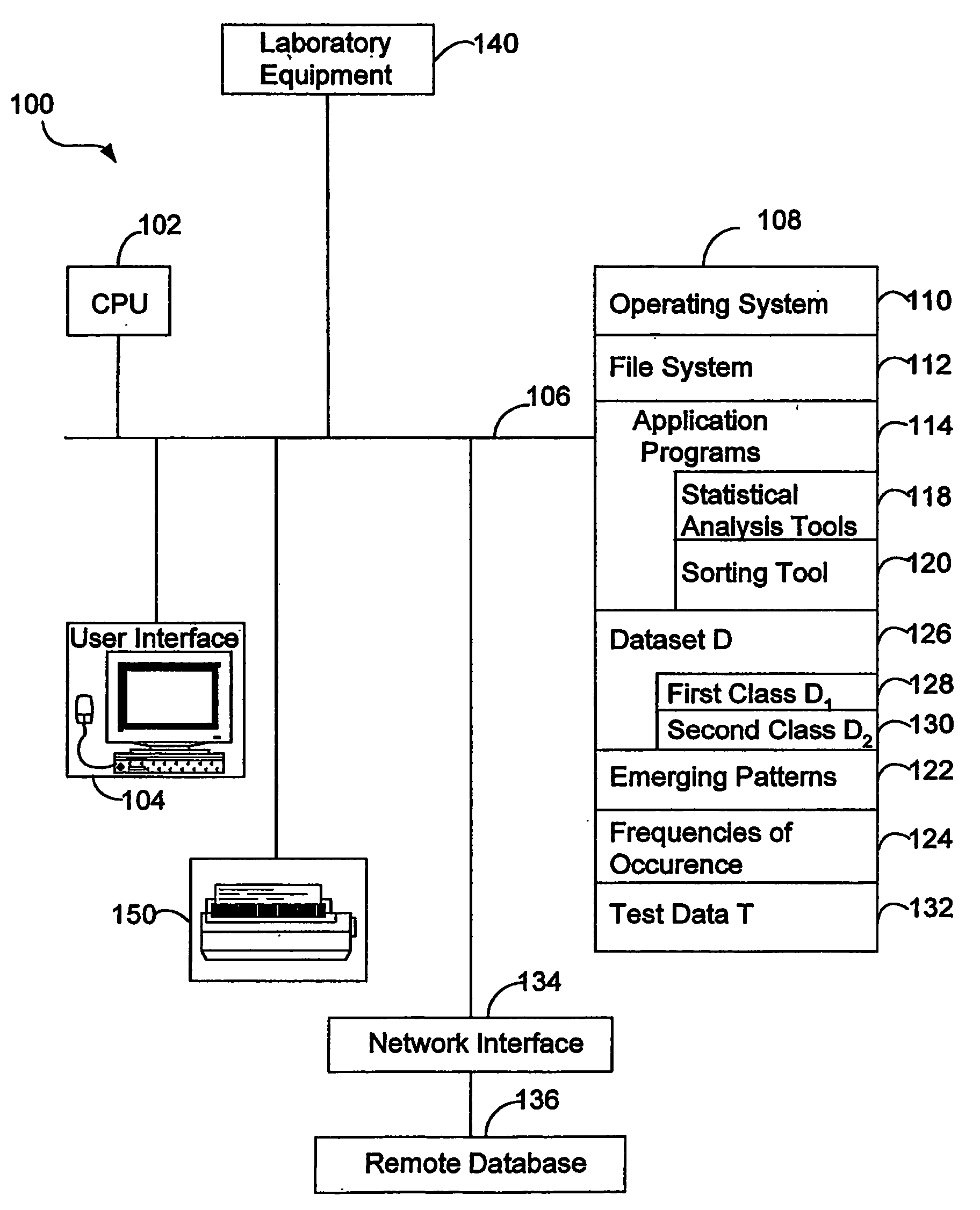
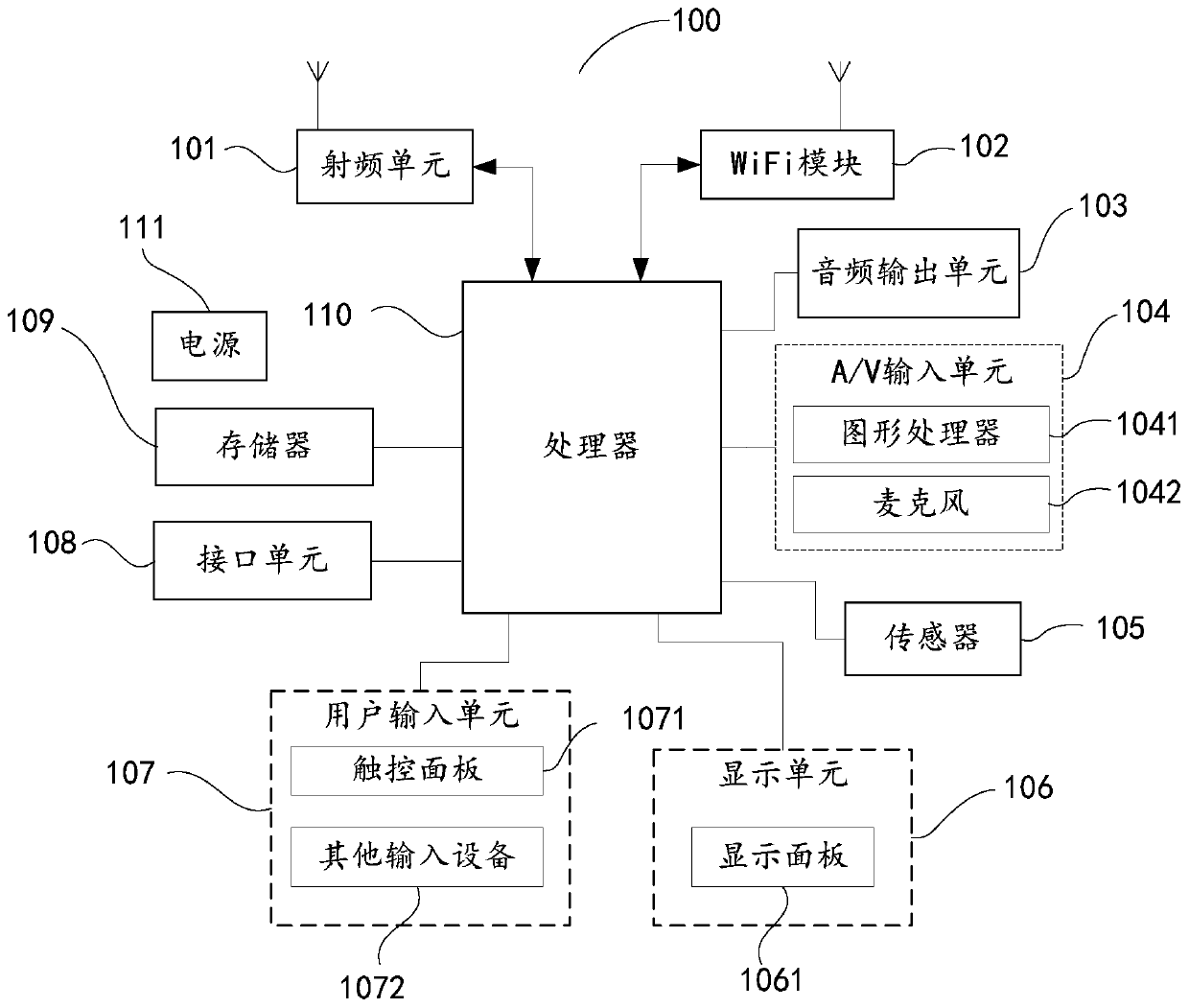
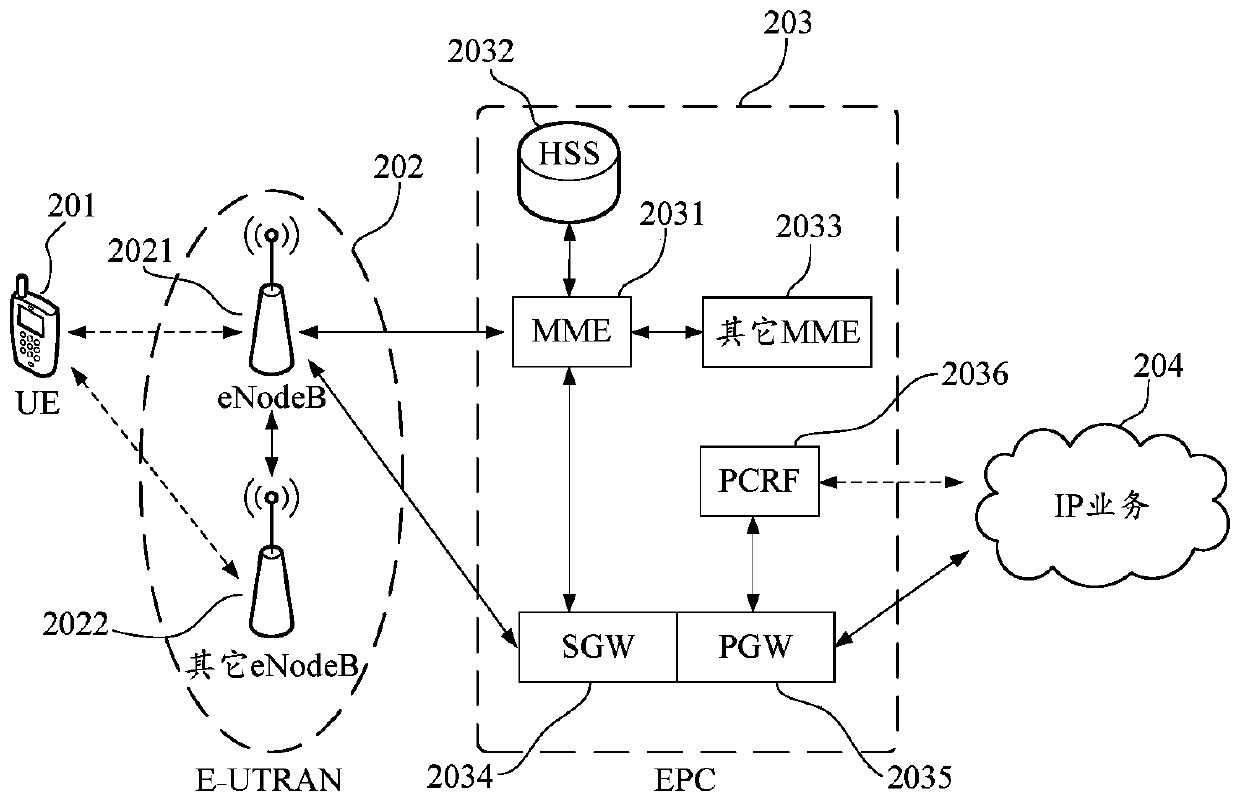
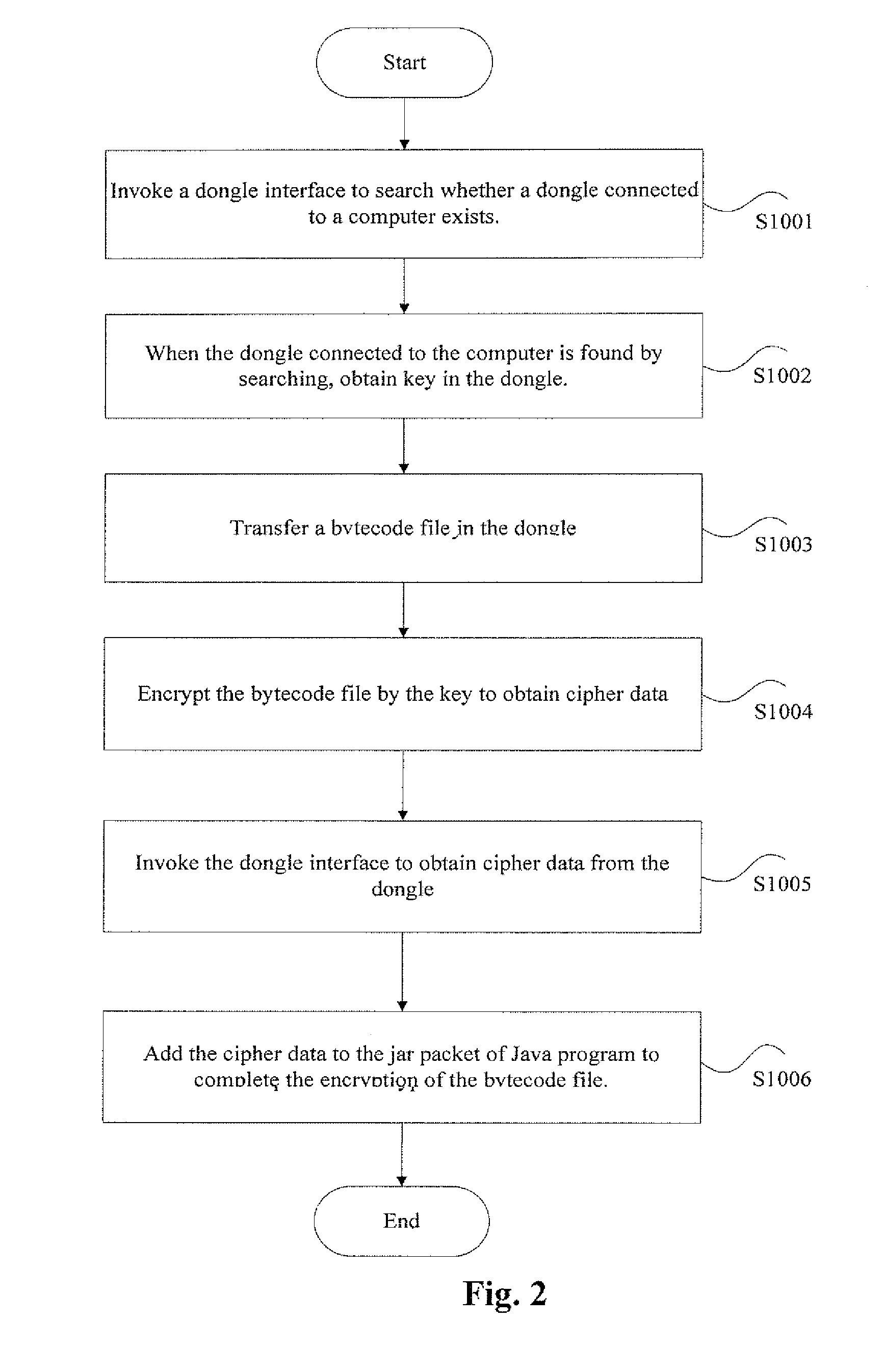
Patents
Literature
673 results about "First class" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In database modeling, a first class item is one that has an identity independent of any other item. The identity allows the item to persist when its attributes change, and allows other items to claim relationships with the item.
System and method for mapping a design model to a common repository with context preservation
InactiveUS6343265B1Improved GUIEasy to understandData processing applicationsSoftware designModeling languageData structure
Disclosed is a system for mapping objects defined in a design model, such as an object oriented design model defined using a design language such as the Universal Modeling Language (UML), to a data model accessible to an application development tool. A design model is provided that includes at least two models. A first model includes a first class and a second model includes a second class. The first class and second class have the same name, and the first class and second class have at least one different attribute and method. The first model, the first class, and attributes and methods therein are mapped to a first data structure that indicates that the first class is included with the first model. The second model, the second class, and attributes and methods therein are mapped to a second data structure that indicates that the second class is included with the second model. In this way, the first class and the second class are distinguished according to their model in the data structures.
Owner:IBM CORP
Database query handler supporting querying of textual annotations of relations between data objects
InactiveUS6618732B1EffectivelySave storage spaceData processing applicationsDigital data processing detailsDatabase queryCustomer relationship management
An improved command handler (and database system utilizing the improved command handler) interfaces to a datastore storing item data for a plurality of items and bi-directional modifier data, corresponding to a relation between at least one first item and at least one second item, that represents first text characterizing semantics of a relationship of the at least one first item to the at least one second item, and represents second text characterizing semantics of a relationship of the at least one second item to the at least one first item. The command handler operates, in response to receiving a first-type query command that specifies at least one given item, to access the datastore to identify i) at least one related item that is related to the given item, and identify ii) either the first text or the second text characterizing semantics of the relation between the given item and the at least one related item. The command hander returns i) data corresponding to the at least one related item; and ii) data corresponding to the identified first text and or second text characterizing semantics of the relation between the given item and the at least one related item. Preferably, the data returned in response to the first-type query command identifies the at least one related item. and identifies the first text or second text characterizing semantics of the relation between the given item and the at least one related item. In addition, the command handler preferably supports additional commands that retrieve from the datastore information related to specified objects, object types, and relations.The command handler (and database system) of the present invention may be used in a wide assortment of software applications, including enterprise applications (such as e-business applications, supply chain management applications, customer relationship management applications, decision support applications), the file system in operating systems, web browsers, e-mail applications and personal information management applications. Importantly, the command handler (and database system) provides an efficient mechanism to query the organization of the data elements (and the relationships therebetween) stored and accessed in such software applications, in a manner that efficient and readily adaptable to client-server database systems or other distributed database systems.
Owner:REVELINK
Prediction by collective likelihood from emerging patterns
InactiveUS20060074824A1Low costCost efficientBiostatisticsCharacter and pattern recognitionTraining data setsTest sample
A system, method and computer program product for determining whether a test sample is in a first or a second class of data (for example: cancerous or normal), comprising: extracting a plurality of emerging patterns from a training data set, creating a first and second list containing respectively, a frequency of occurrence of each emerging pattern that has a non-zero occurrence in the first and in the second class of data; using a fixed number of emerging patterns, calculating a first and second score derived respectively from the frequencies of emerging patterns in the first list that also occur in the test data, and from the frequencies of emerging patterns in the second list that also occur in the test data; and deducing whether the test sample is categorized in the first or the second class of data by selecting the higher of the first and the second score.
Owner:AGENCY FOR SCI TECH & RES
Text categorization toolkit
InactiveUS6212532B1Data processing applicationsDigital data information retrievalFeature extractionText categorization
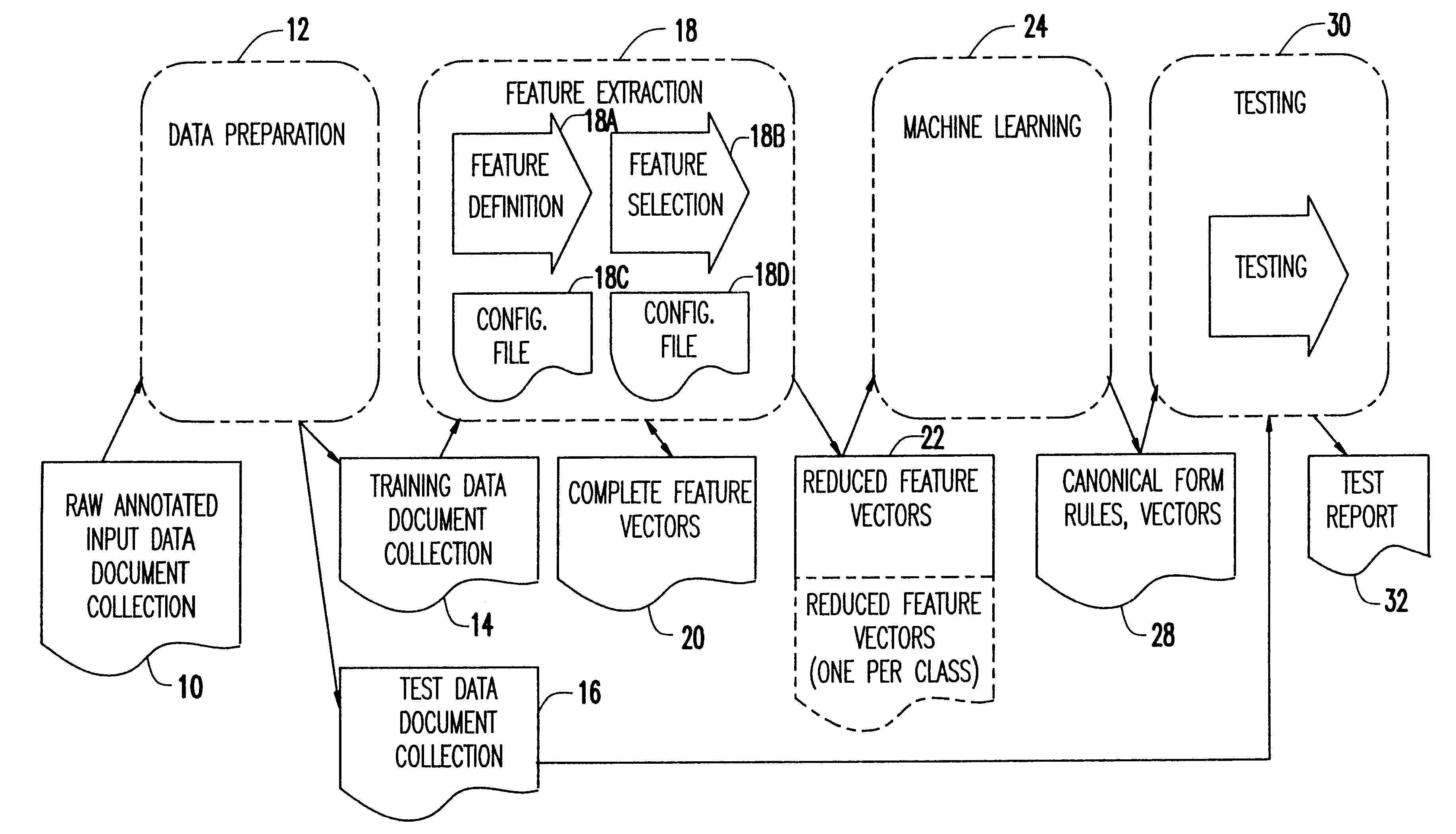
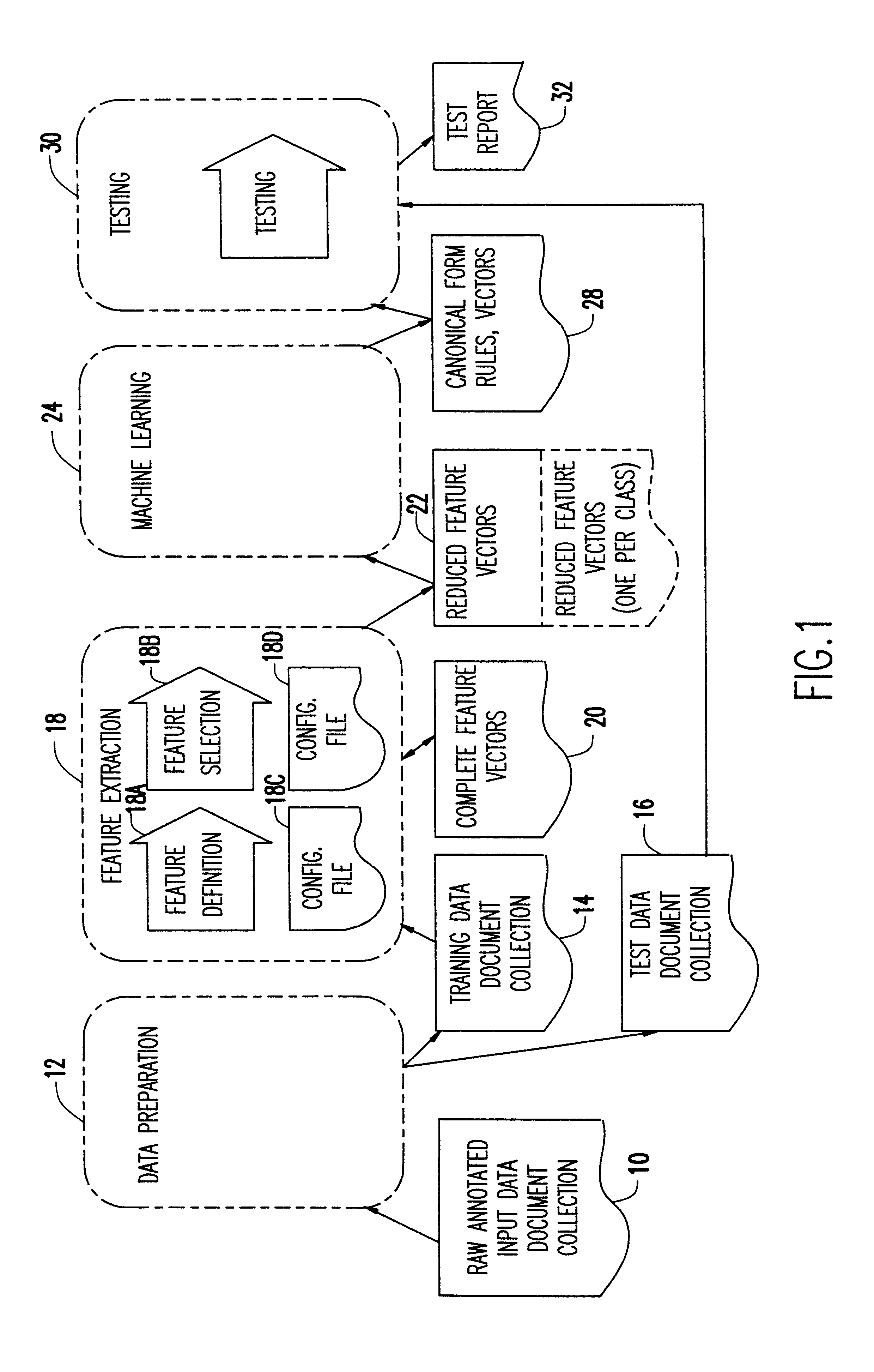
A module information extraction system capable of extracting information from natural language documents. The system includes a plurality of interchangeable modules including a data preparation module for preparing a first set of raw data having class labels to be tested, the data preparation module being selected from a first type of the interchangeable modules. The system further includes a feature extraction module for extracting features from the raw data received from the data preparation module and storing the features in a vector format, the feature extraction module being selected from a second type of the interchangeable modules. A core classification module is also provided for applying a learning algorithm to the stored vector format and producing therefrom a resulting classifier, the core classification module being selected from a third type of the interchangeable modules. A testing module compares the resulting classifier to a set of preassigned classes, where the testing module is selected from a fourth type of the interchangeable modules, where the testing module tests a second set of raw data having class labels received by the data preparation module to determine the degree to which the class labels of the second set of raw data approximately corresponds to the resulting classifier.
Owner:IBM CORP
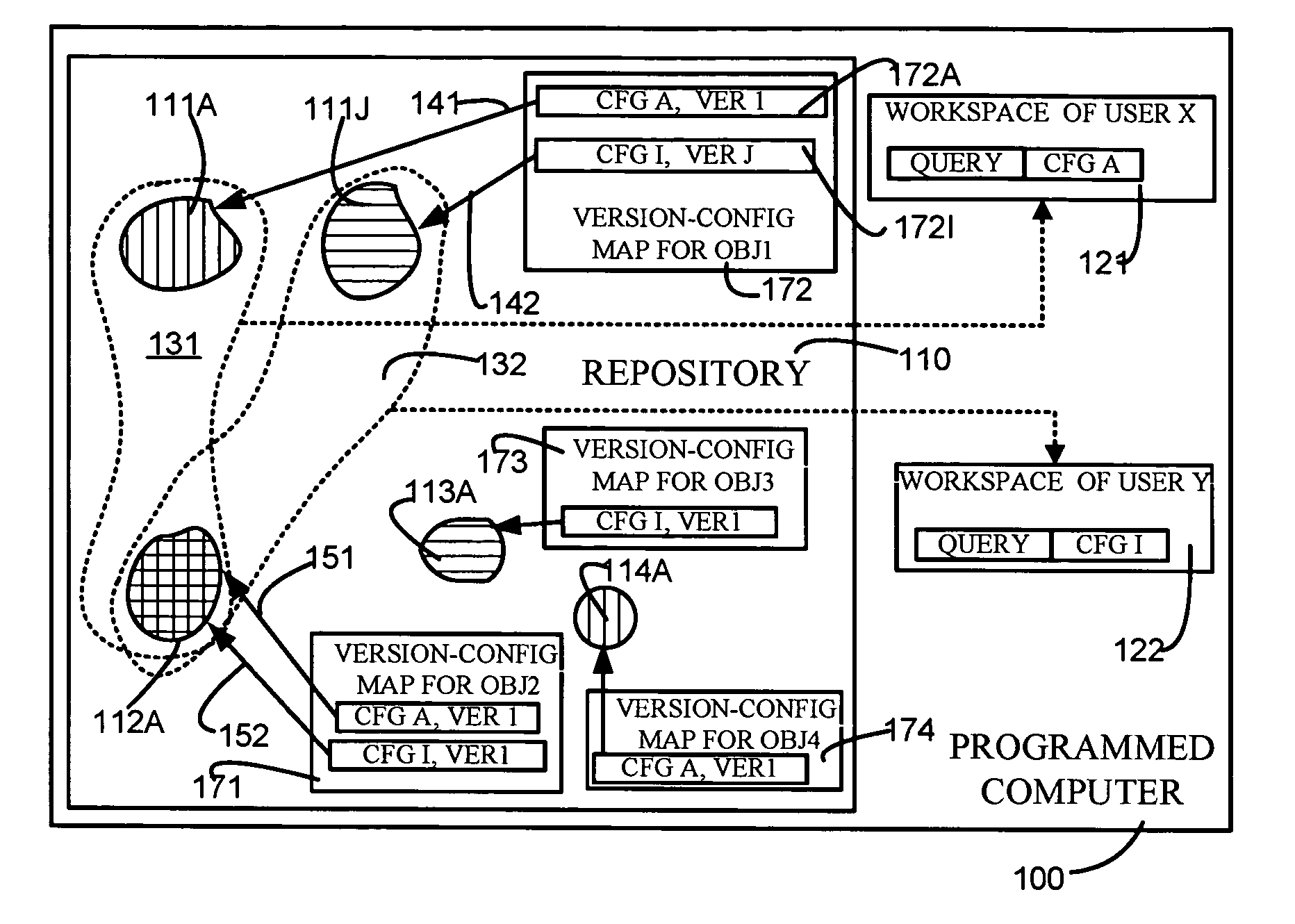
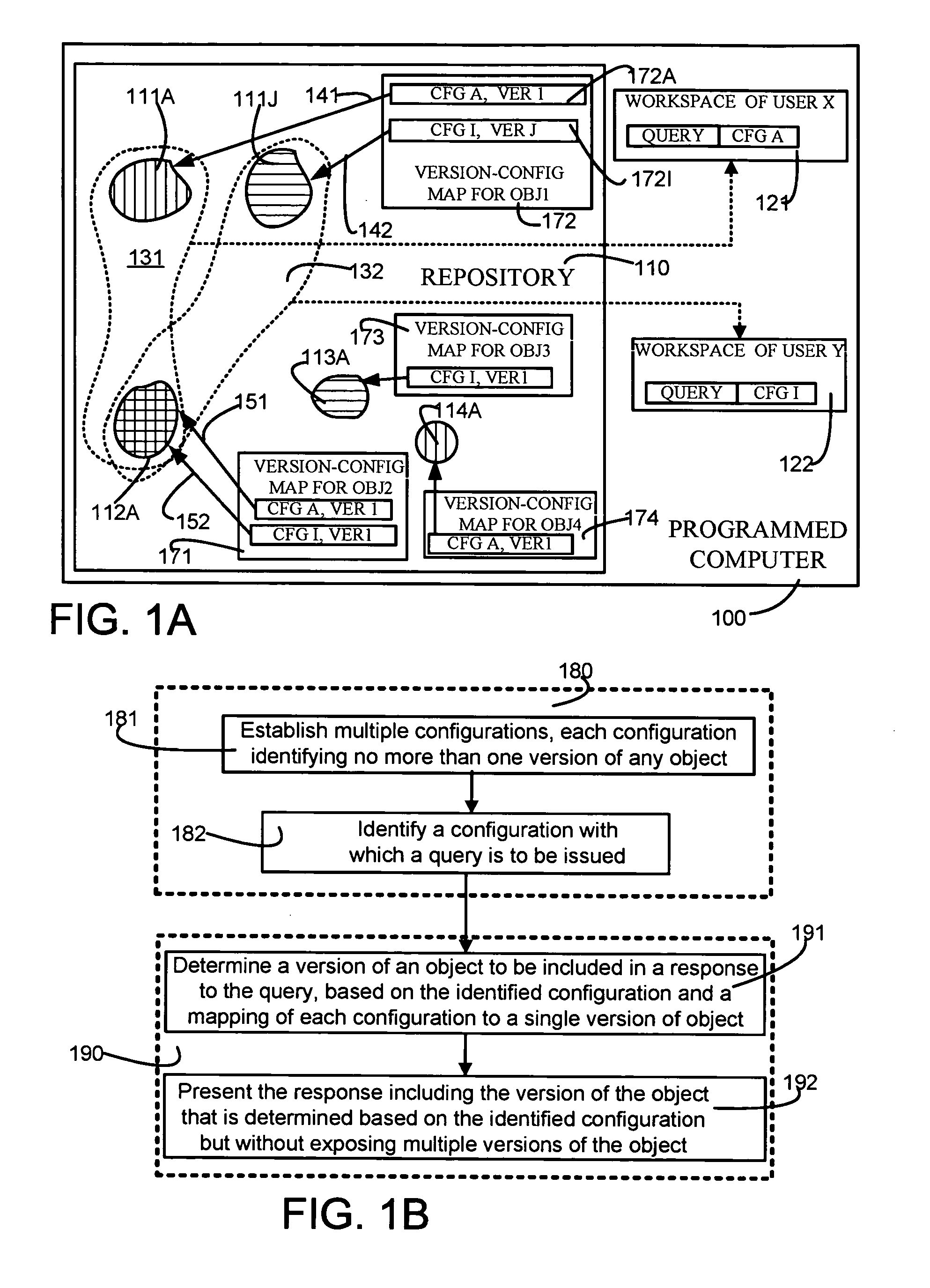
Object versioning
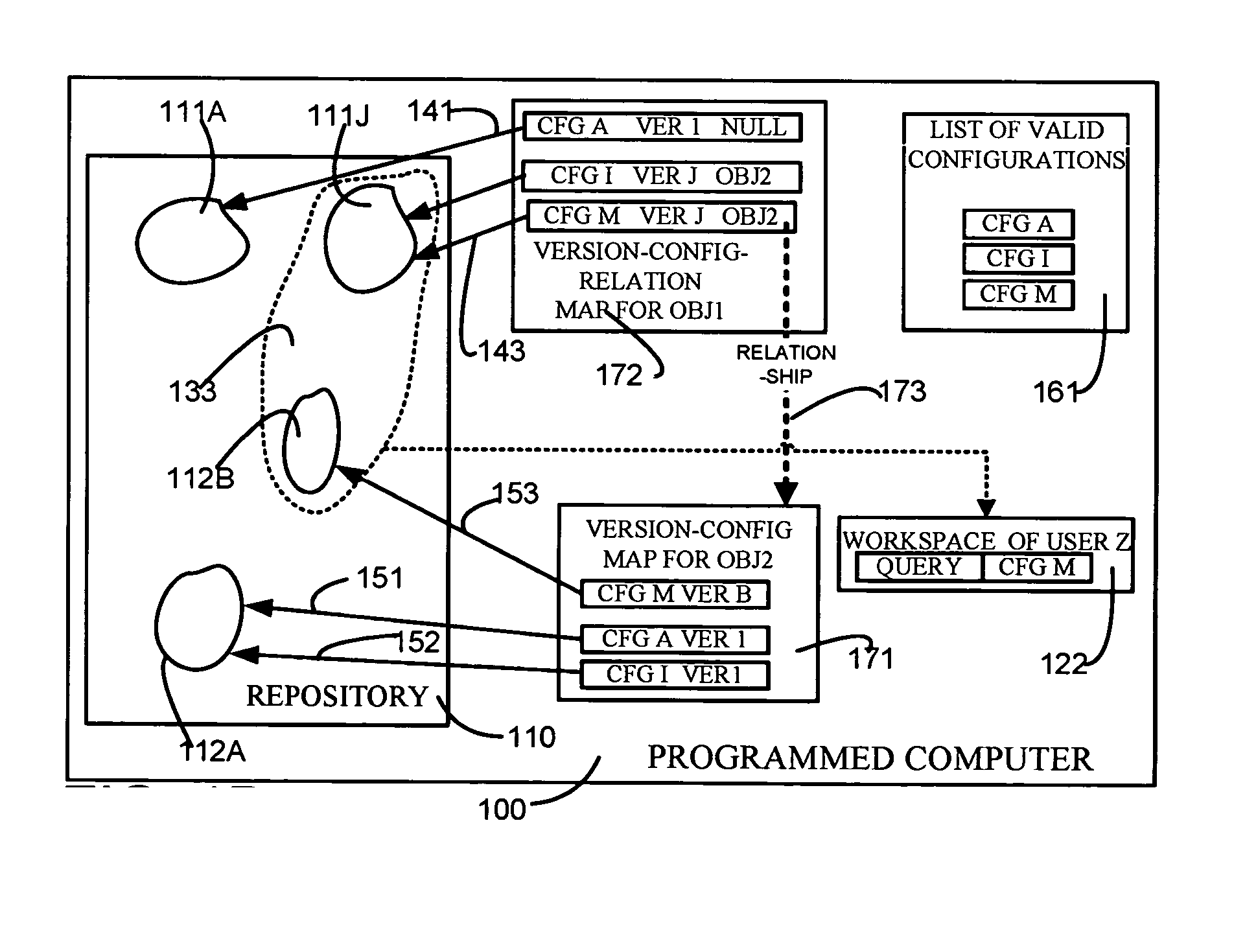
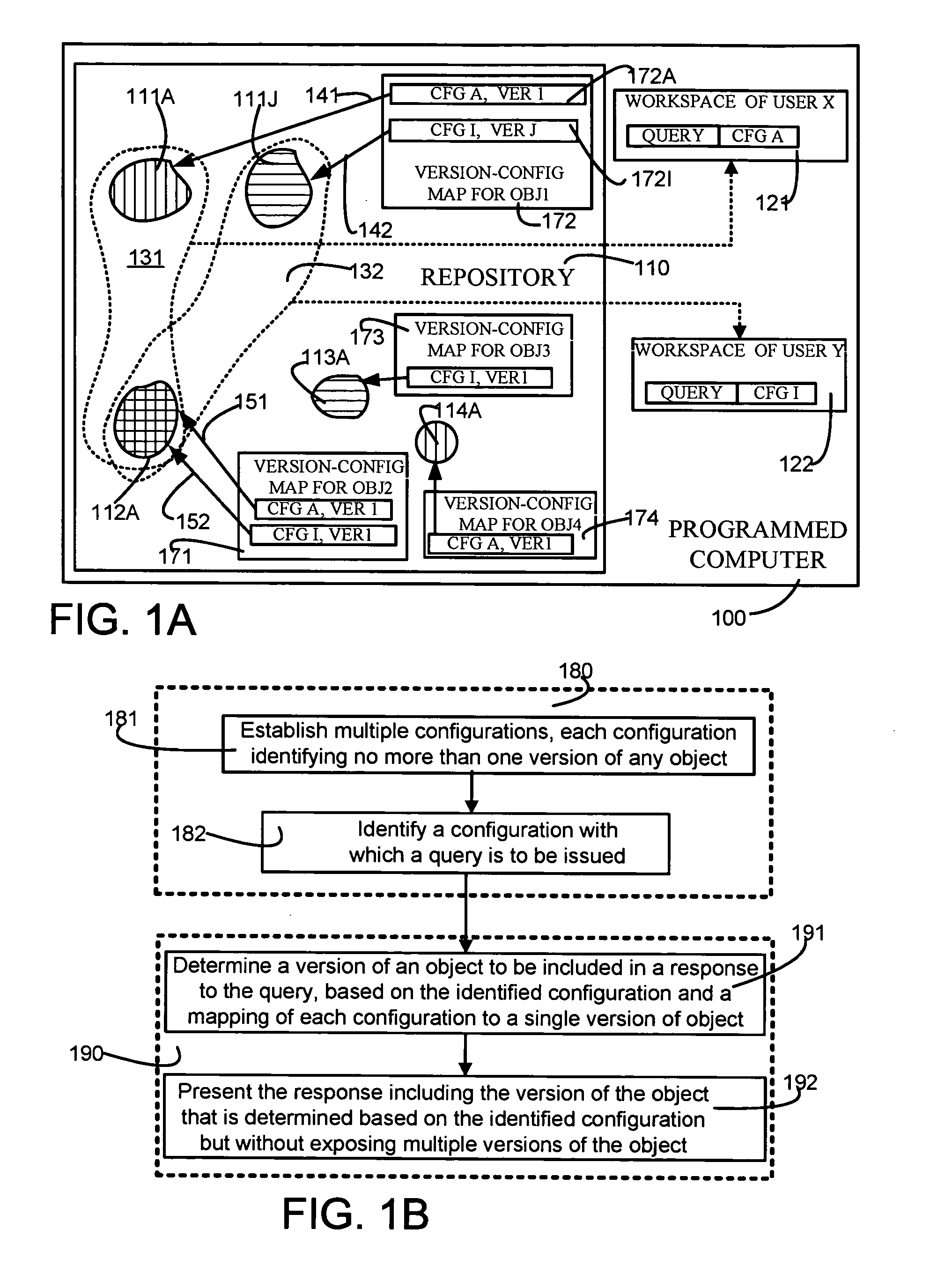
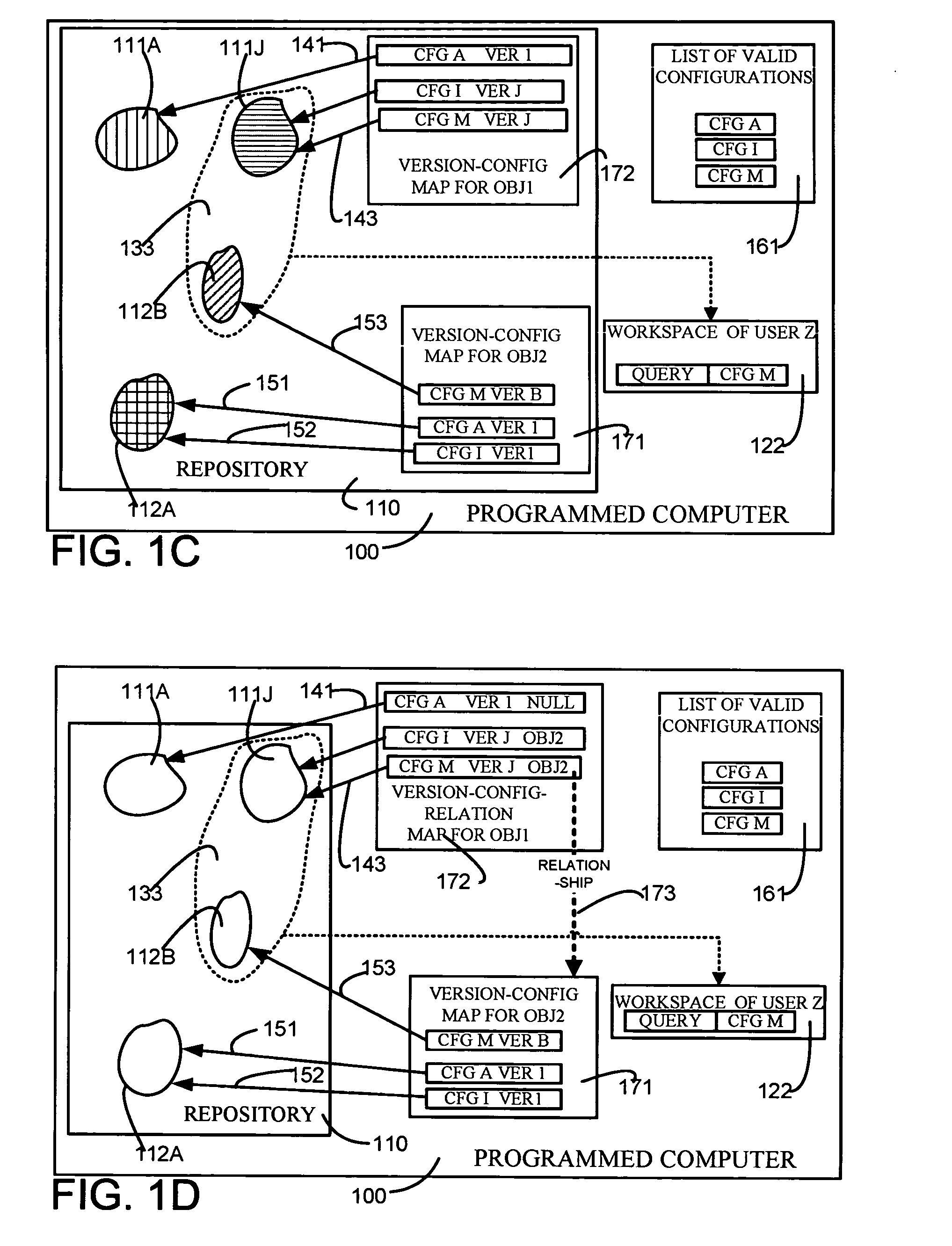
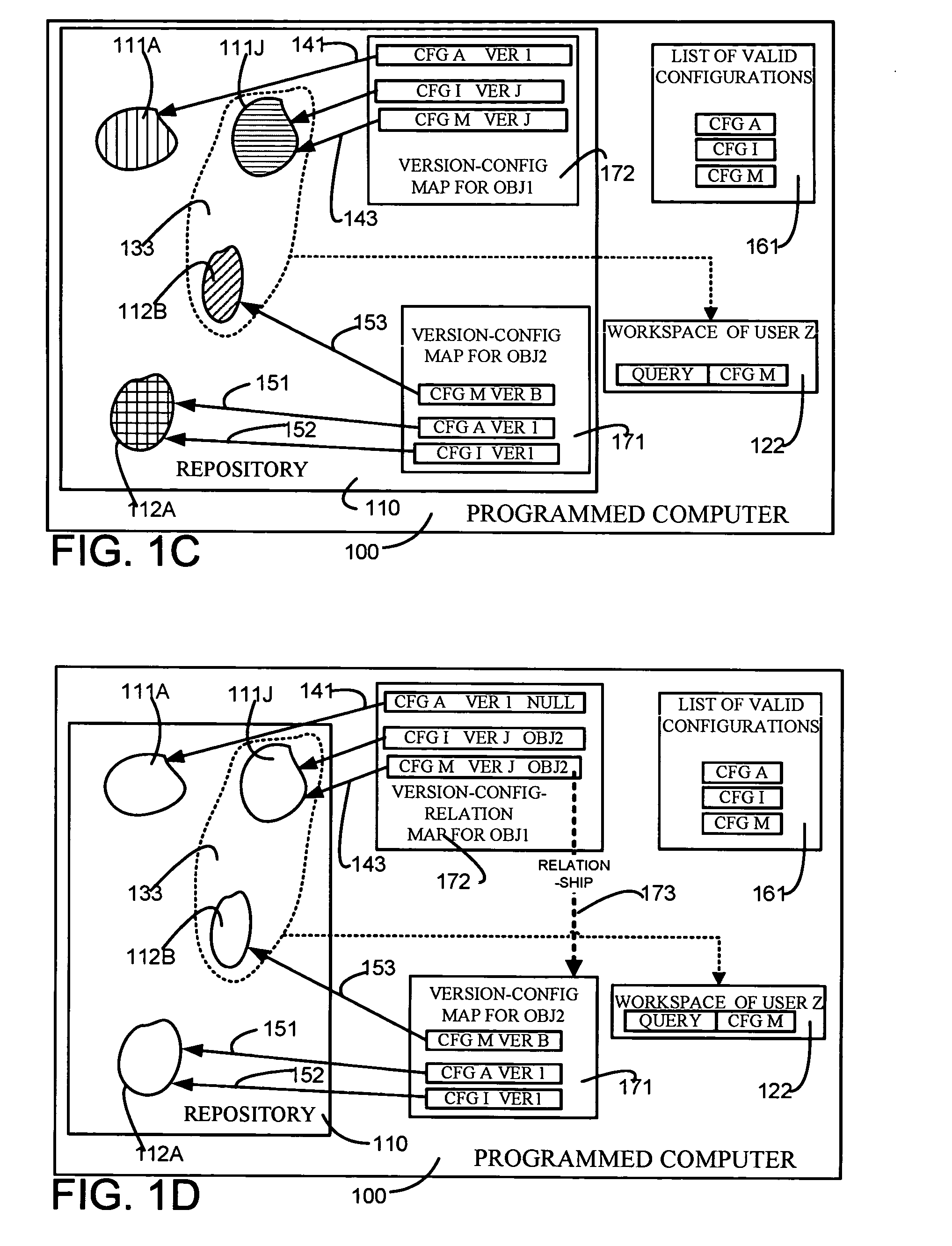
ActiveUS20050131964A1Eliminate needData processing applicationsDigital data information retrievalRevision controlUnique identifier
A repository contains multiple versions of an object, and any version of the object can be modified by a user, as and when necessary. A table for one object (“first object”) that is contained in another object (“second object”) has at least two columns, namely one column for a minimum version of the second object and another column for a maximum version of the second object. If a number of versions of the first object are responsive to a query, then one version of the first object is selected if a version of the second object that is responsive to the query happens to be in the range defined by the just-described minimum version number and the maximum version number. Depending on the embodiment, the second object can be an immediate parent of the first object, or can be an ancestor (also called “first class object”) of the first object that is not contained in any other object. In some embodiments, one or more attributes of the first object are stored in a first table along with a unique identifier and a version number. In addition, information on relations of the first object to other objects as well as an identity of a configuration (to which the current version of the first object belongs) are stored in a second table. Therefore, a pair of tables are used for each object, so as to decouple information that defines an object from information on relationships of the object. If a change happens in just the relationship of an object then no change is made to the table containing the definition of the object. Similarly, if a change happens in just the definition of the object, then no change is made to the table containing the relations of the object. Moreover, when a change happens to an object, if the object has a number of ancestors and decendants only an immediate parent of the object is updated, thereby to eliminate a versioning chain reaction (i.e. other objects are not affected).
Owner:ORACLE INT CORP
Document generation
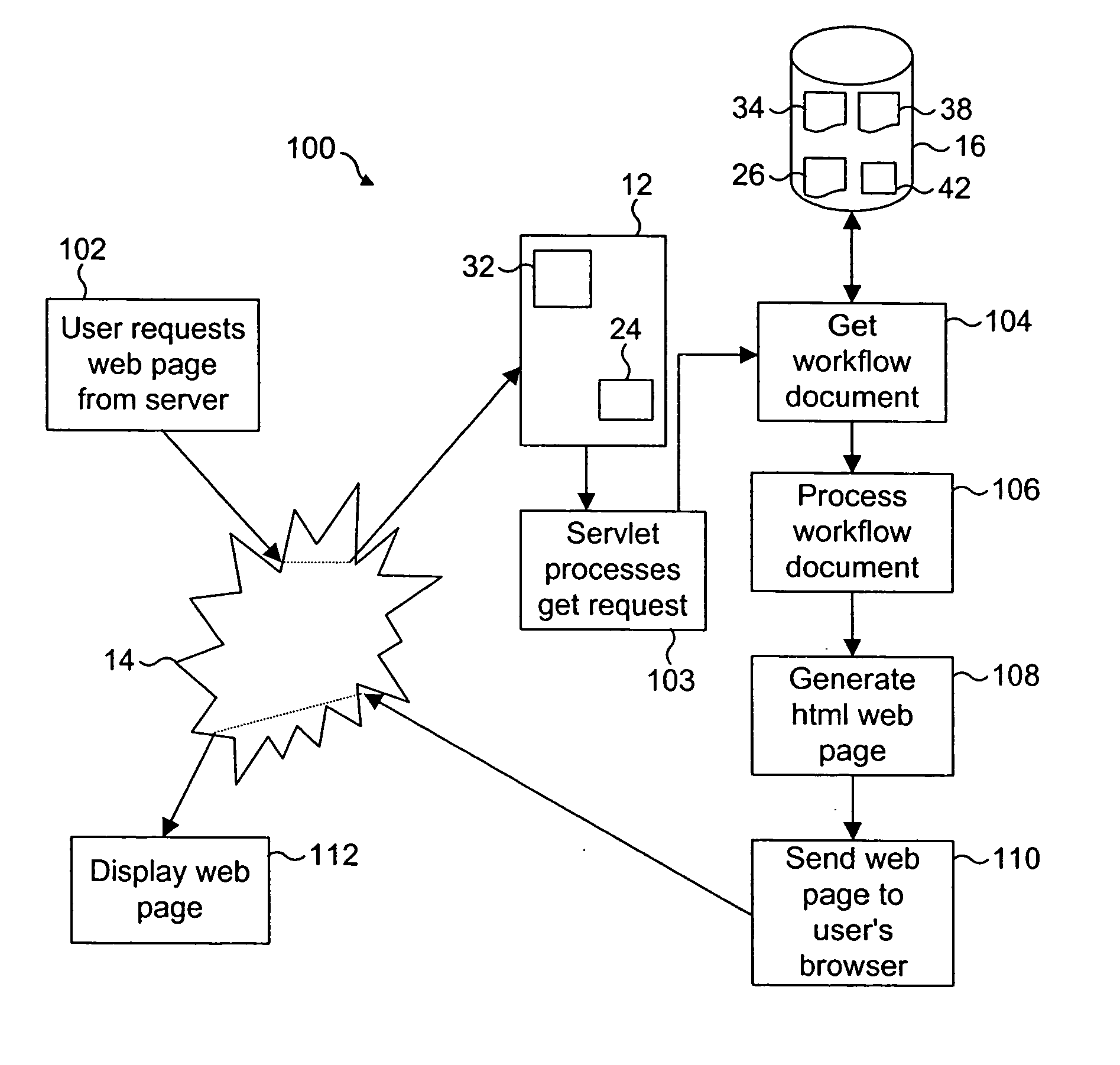
InactiveUS20040261017A1Add supportShorten the timeWebsite content managementSpecial data processing applicationsDocument preparationDocumentation
A method of dynamically generating a response document (such as an XML, document) from a workflow document which comprises a plurality of a first type of workflow instructions for retrieving data, and a plurality of a second type of corresponding workflow instructions for converting the retrieved data into a plurality of markup language fragments, is described. The method comprises: processing a selected task of a workflow document using the first type of instruction of that selected task; converting the results of the precessing step into a markup language fragment using the second type of instruction of that selected task; storing the markup language fragment in a response document; and reporting the processing, converting and storing steps to create a completed response document comprising a plurality of markup language fragments.
Owner:HEWLETT PACKARD CO
Methods and systems for managing data
InactiveUS20050289127A1Increase speedAvoid accessDigital data processing detailsFile metadata searchingInformation typeData system
Systems and methods for managing data, such as metadata. In one exemplary method, a search is performed based on a search query of at least metadata of a first plurality of files and a set of a permissions is determined for a first user, wherein the set of permissions defines at least a right to view information. Results of the search are displayed based upon the set of permissions. In the metadata database, there is metadata from a number of files of different types. The type of information in metadata for a first type of file differs from a type of information in metadata for a second type of file.
Owner:APPLE INC
Method for constructing semantic map on line by utilizing fusion of laser radar and visual sensor
PendingCN111928862AEasy to driveImprove reuse efficiencyInstruments for road network navigationElectromagnetic wave reradiationEngineeringVision sensor
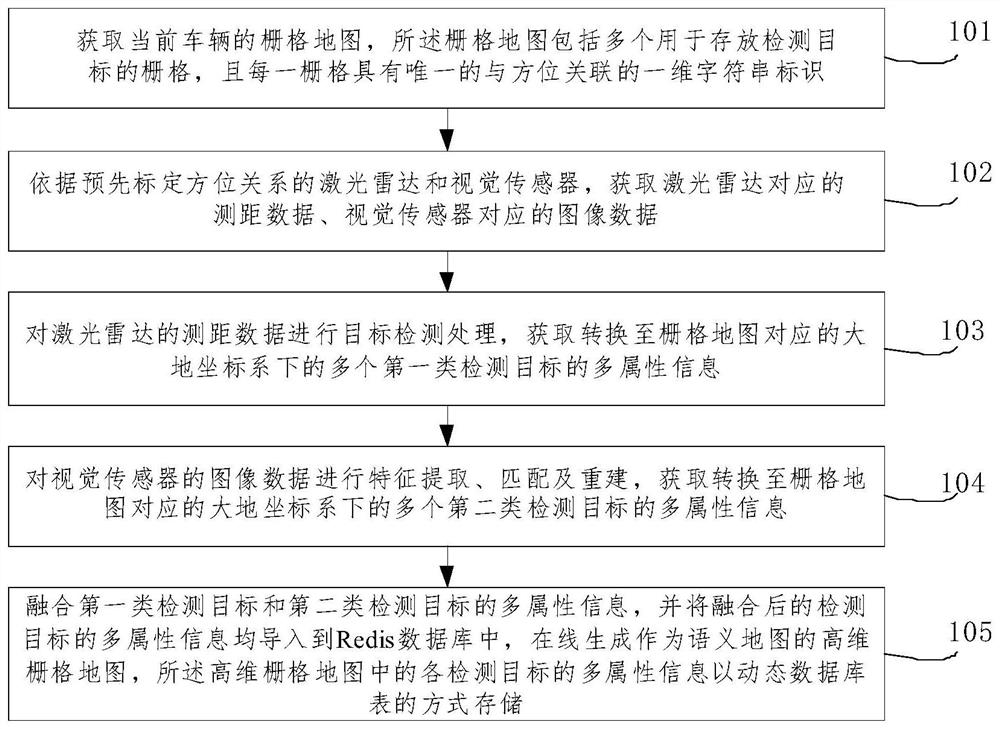
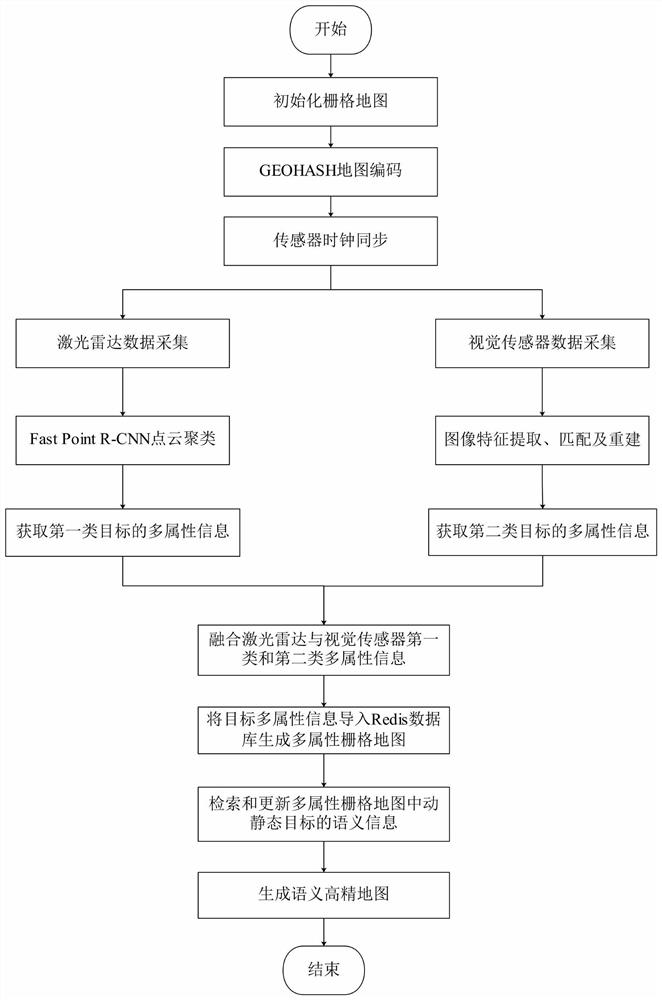
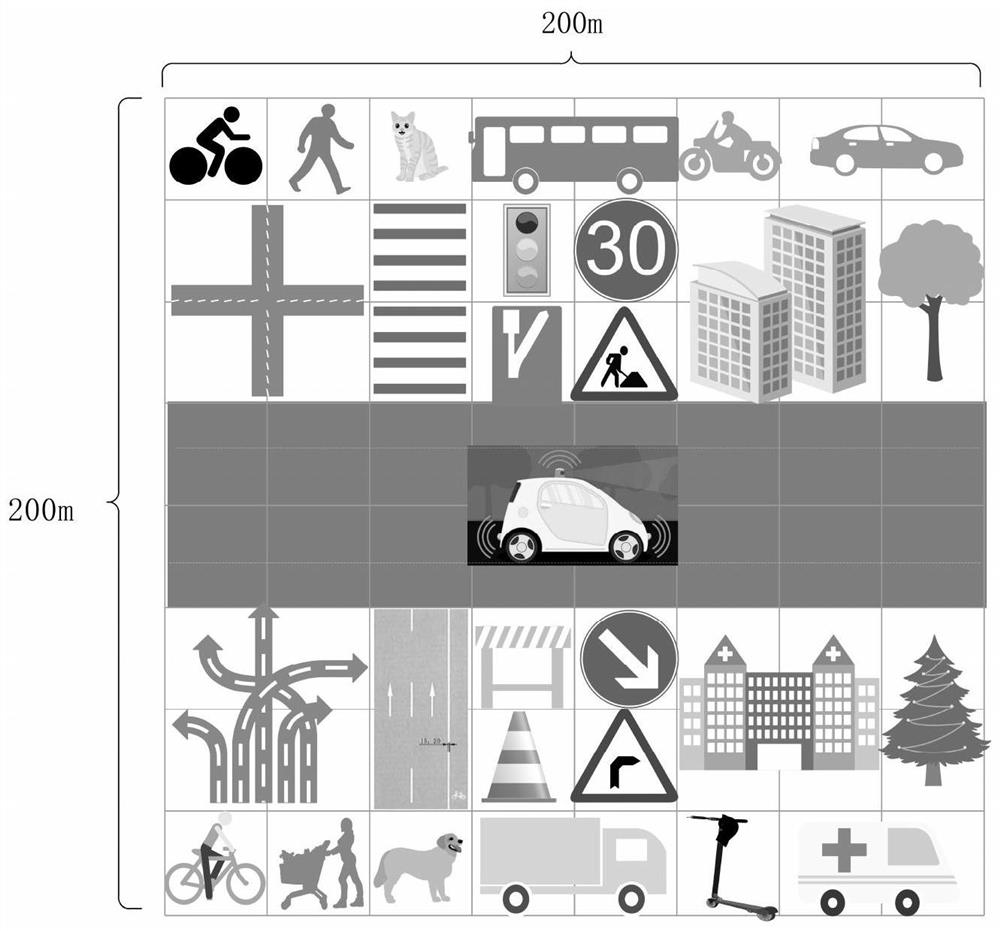
The invention relates to a method for constructing a semantic map on line by utilizing fusion of a laser radar and a visual sensor. The method comprises the following steps: acquiring an initialized grid map of a current vehicle, and acquiring distance measurement data corresponding to the laser radar and image data corresponding to the visual sensor; performing target detection processing on theranging data of the laser radar to obtain multi-attribute information of a plurality of first-class detection targets; performing feature extraction and matching on the image data of the visual sensorto obtain multi-attribute information of a plurality of second-class detection targets; fusing the multi-attribute information of the first type of detection targets and the second type of detectiontargets, importing the fused multi-attribute information of the detection targets into a Redis database, generating a high-dimensional grid map serving as a semantic map, and storing the multi-attribute information of each detection target in the high-dimensional grid map in a dynamic database table mode. According to the method, the multi-dimensional semantic information of the dynamic and staticenvironments around the vehicle can be represented online in real time.
Owner:廊坊和易生活网络科技股份有限公司
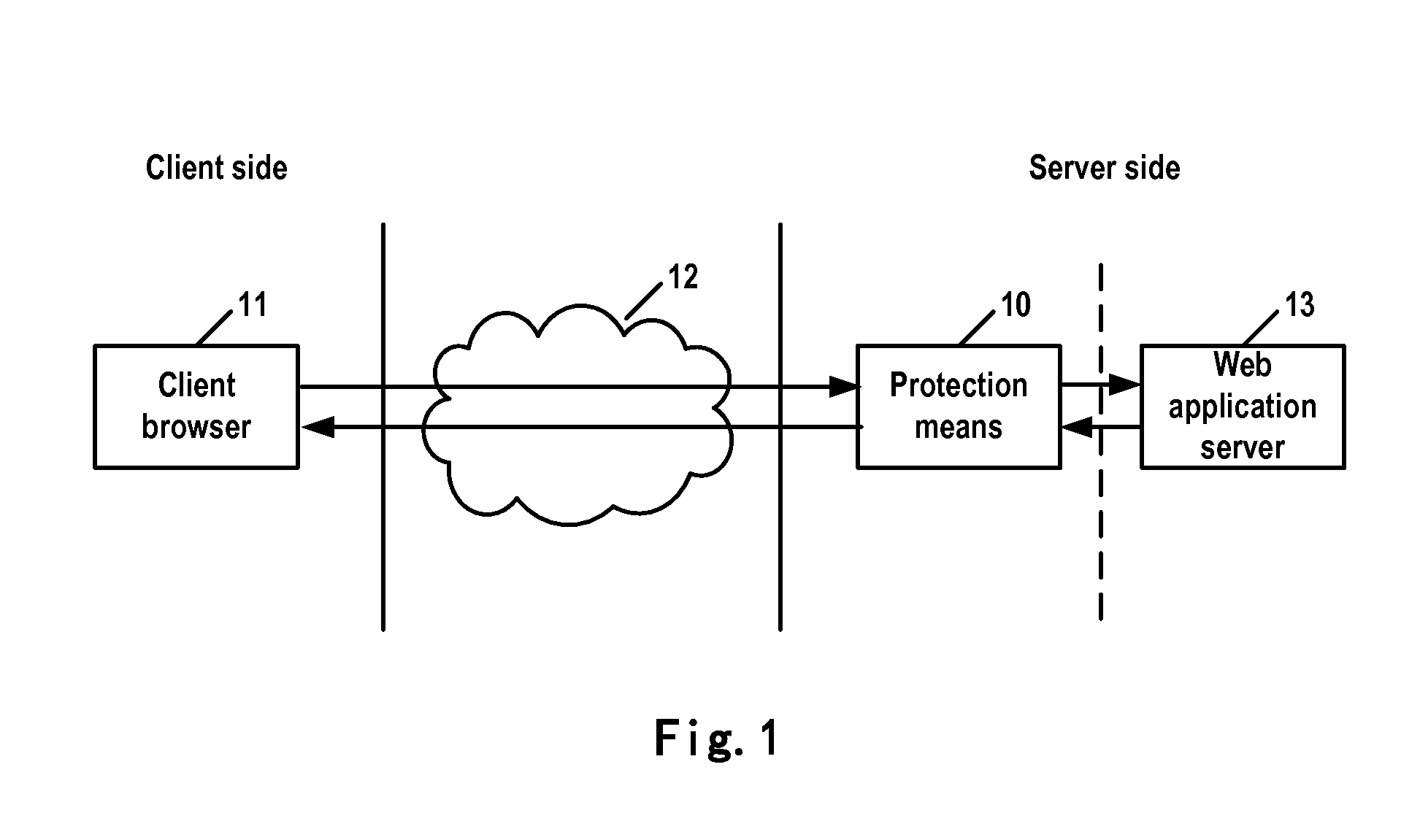
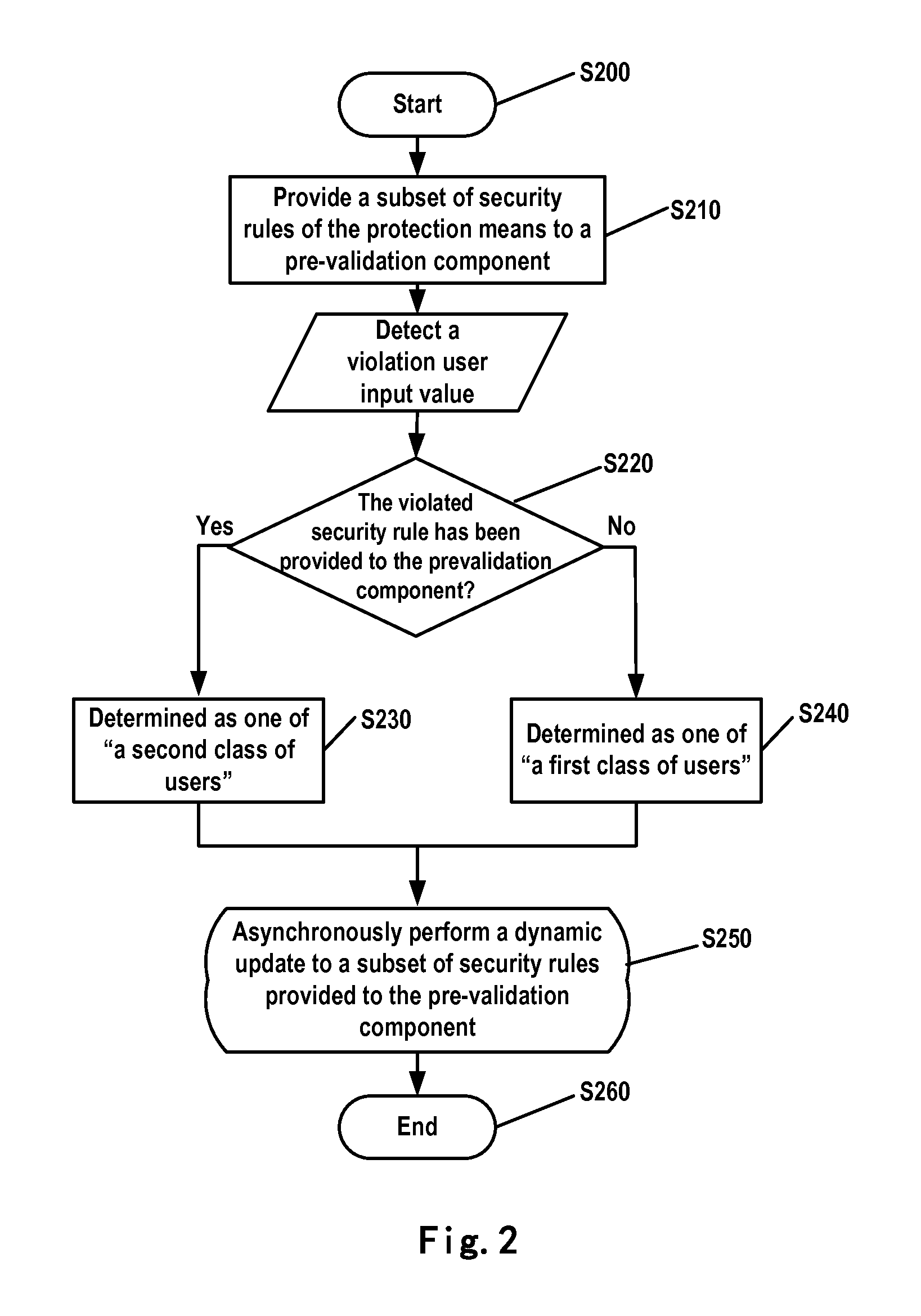
Method and apparatus for security validation
ActiveUS20120304249A1Increase experienceEffectively lead to differentiationDigital data authenticationPlatform integrity maintainancePre validationUser input
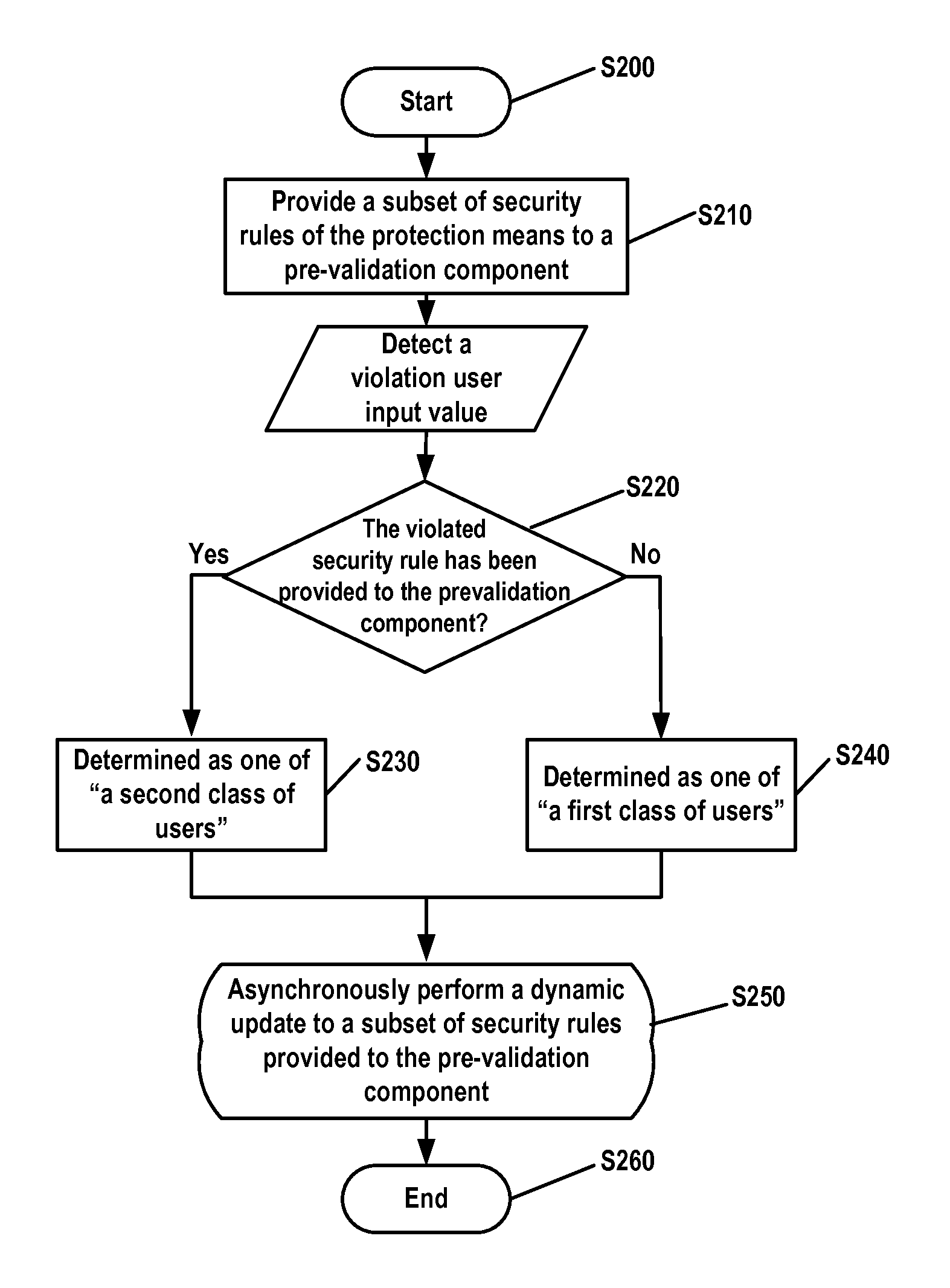
A computer-implemented method, apparatus, and article of manufacture for security validation of a user input in a computer network application. The method includes: providing a subset of security rules of a server-side protection means to a pre-validation component deployed at a client side, so as to enable security validation of a user input on the client side by the pre-validation component; validating the user input based on at least one of the security rules; determining, in response to detecting a user input violation and that a violated security rule has not been provided to the pre-validation component, the user as a first class of users; determining, in response to detecting the user input violation and that the violated security rule has been provided to the pre-validation component, the user as a second class of users; and performing different security protection actions to the first and second class of users.
Owner:IBM CORP
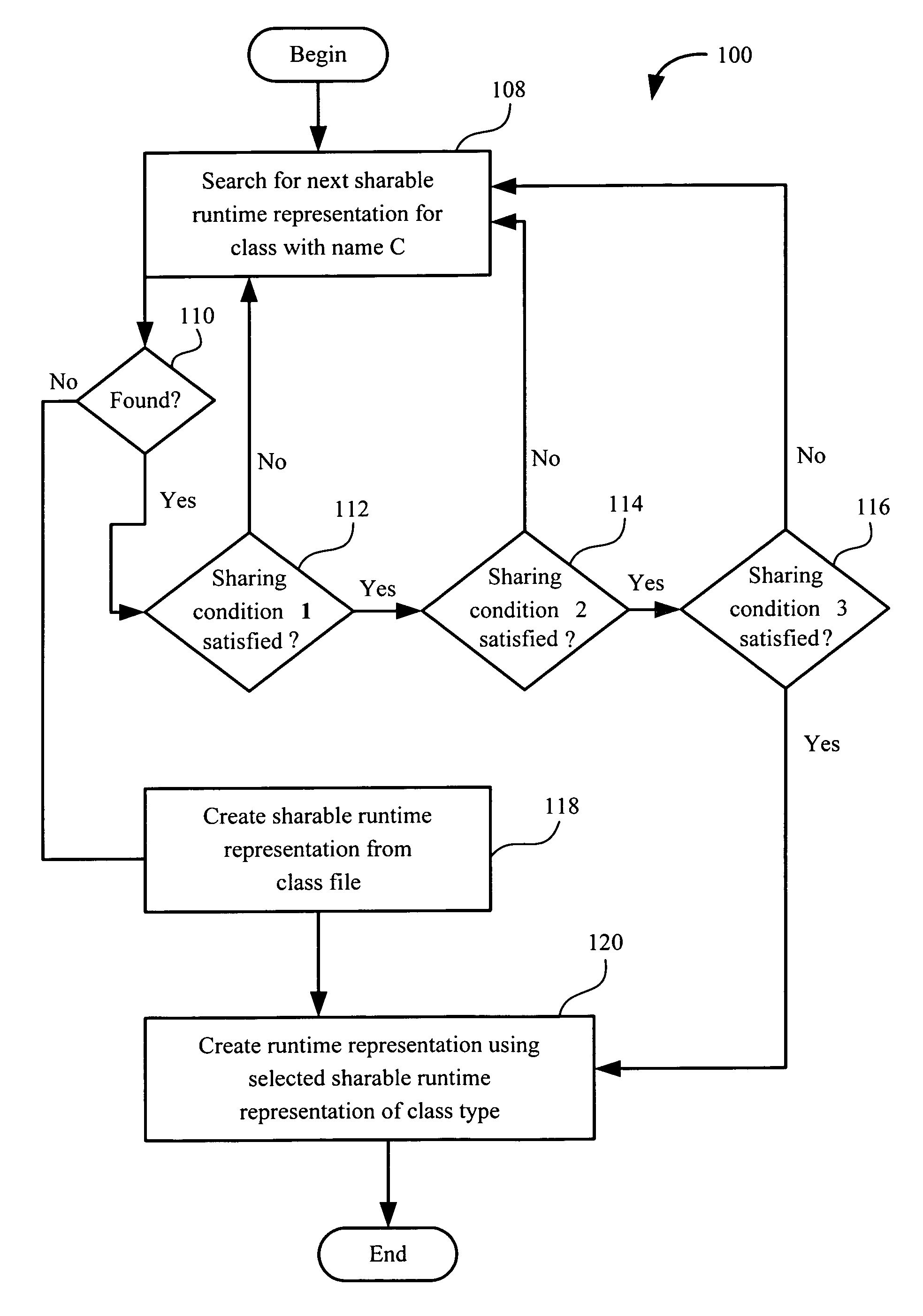
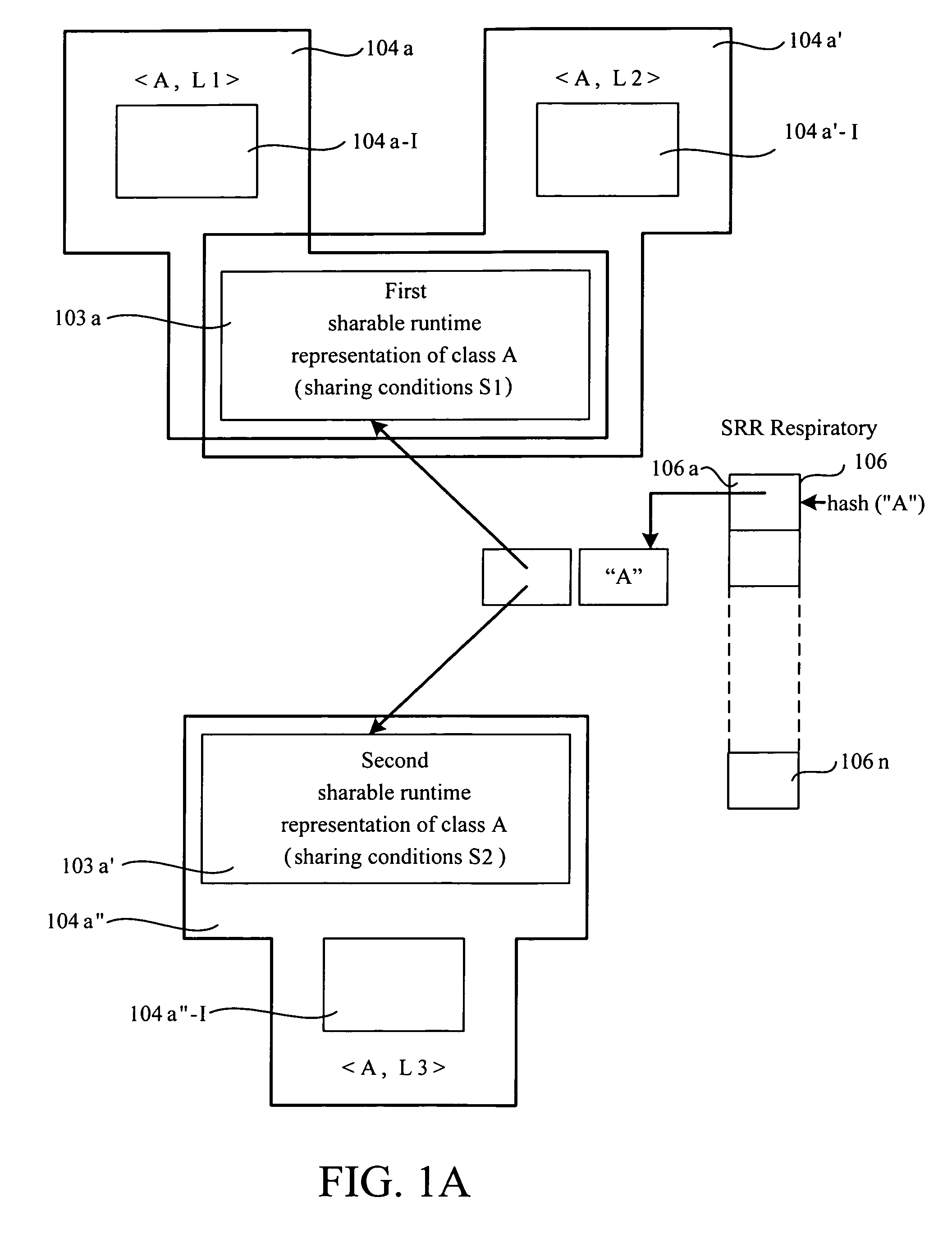
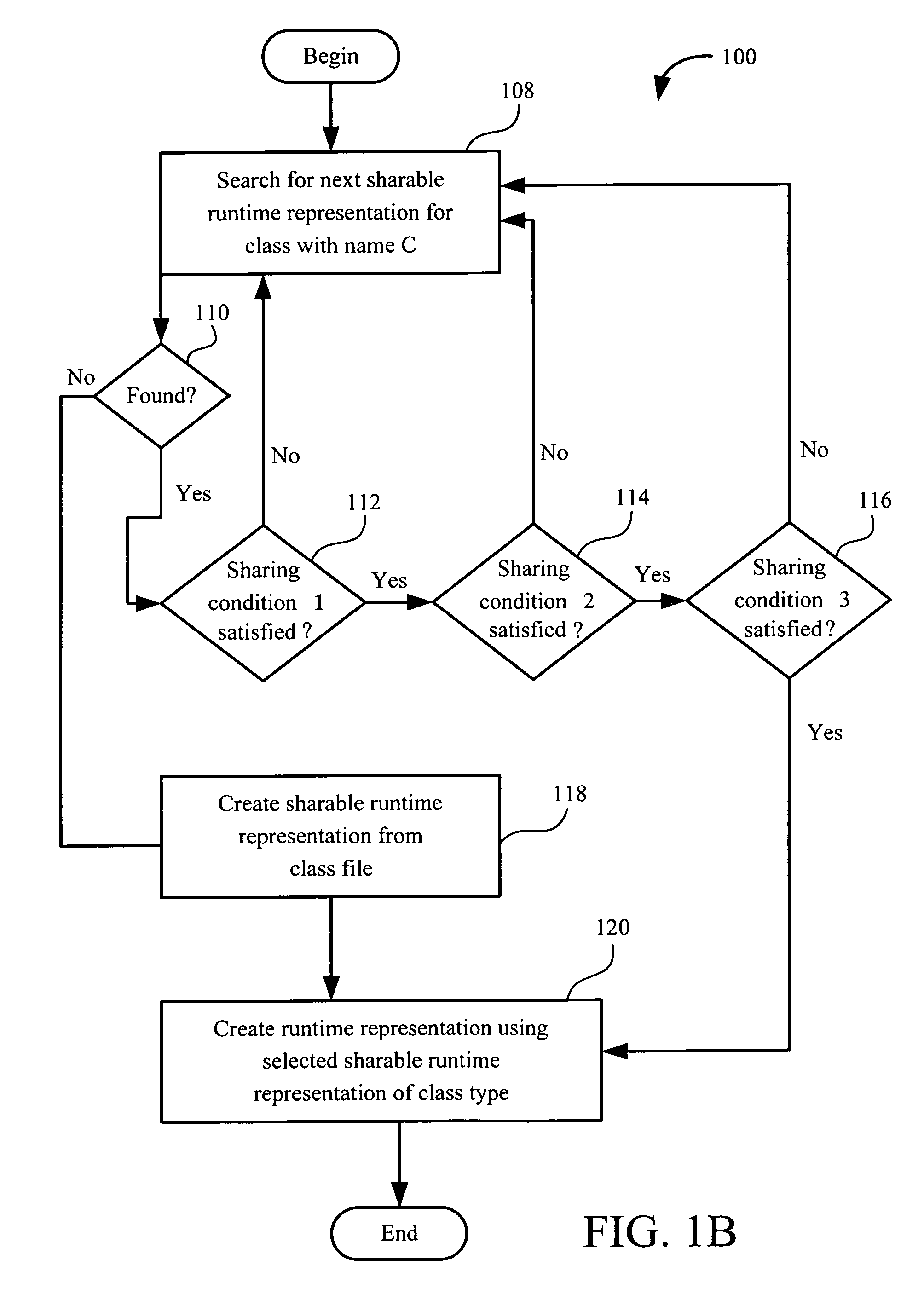
Sharing runtime representation of software component methods across component loaders
ActiveUS7406687B1Increasing main memory conservationLow running costSoftware engineeringSpecific program execution arrangementsByteClass type
A computer implemented process for making a bytecode of a method sharable by a first class loader and a second class loader is provided. The first class loader and the second class loader are capable of dynamically loading a class having a class file, and translating the class file into first and second class types, respectively. The process includes dividing a runtime representation of the first class type into first loader independent and first loader dependent parts and determining whether a runtime representation of the second class type can use the first loader independent part. If the first loader independent part can be used by the runtime representation of the second class type, the process includes generating a second loader dependent part using the first loader independent part. Further included is performing a loader re-entrant interpretation of a bytecode of the method if the method is invoked.
Owner:ORACLE INT CORP
Categorizing data to perform access control
InactiveUS20120166442A1Digital data information retrievalDigital data processing detailsControl setData pack
Systems and methods categorize data to perform access control. A system receives first data, where the first data comprises at least a portion of data to be categorized. The system analyzes the first data to determine Whether the first data belongs to a first category. If the first data belongs to a first category, the system applies a first access control set to actions on the data to be categorized. Further, if one or more of the actions on the data to be categorized has an access control status of pending after applying the first access control set, the system receives second data, where the second data comprises at least a portion of data to be categorized. The system analyzes the second data to determine whether the second data belongs to a second category. If the second data belongs to a second category, the system applies a second access control set to at least one of the actions having the access control status of pending.
Owner:IBM CORP
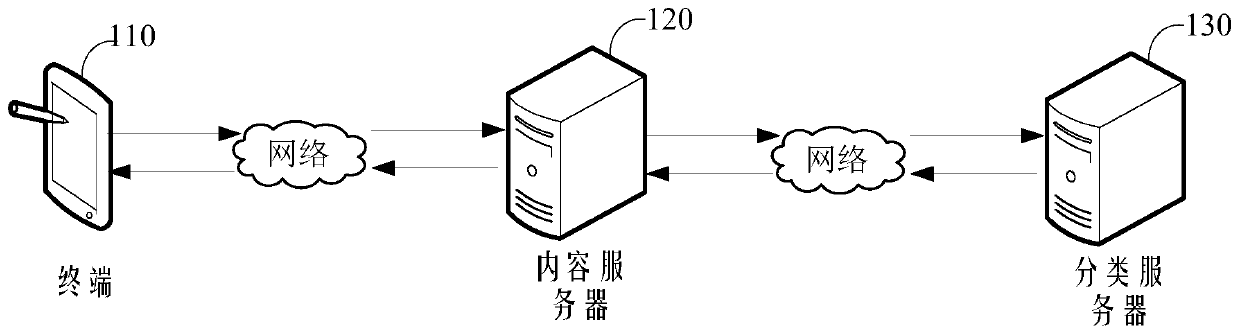
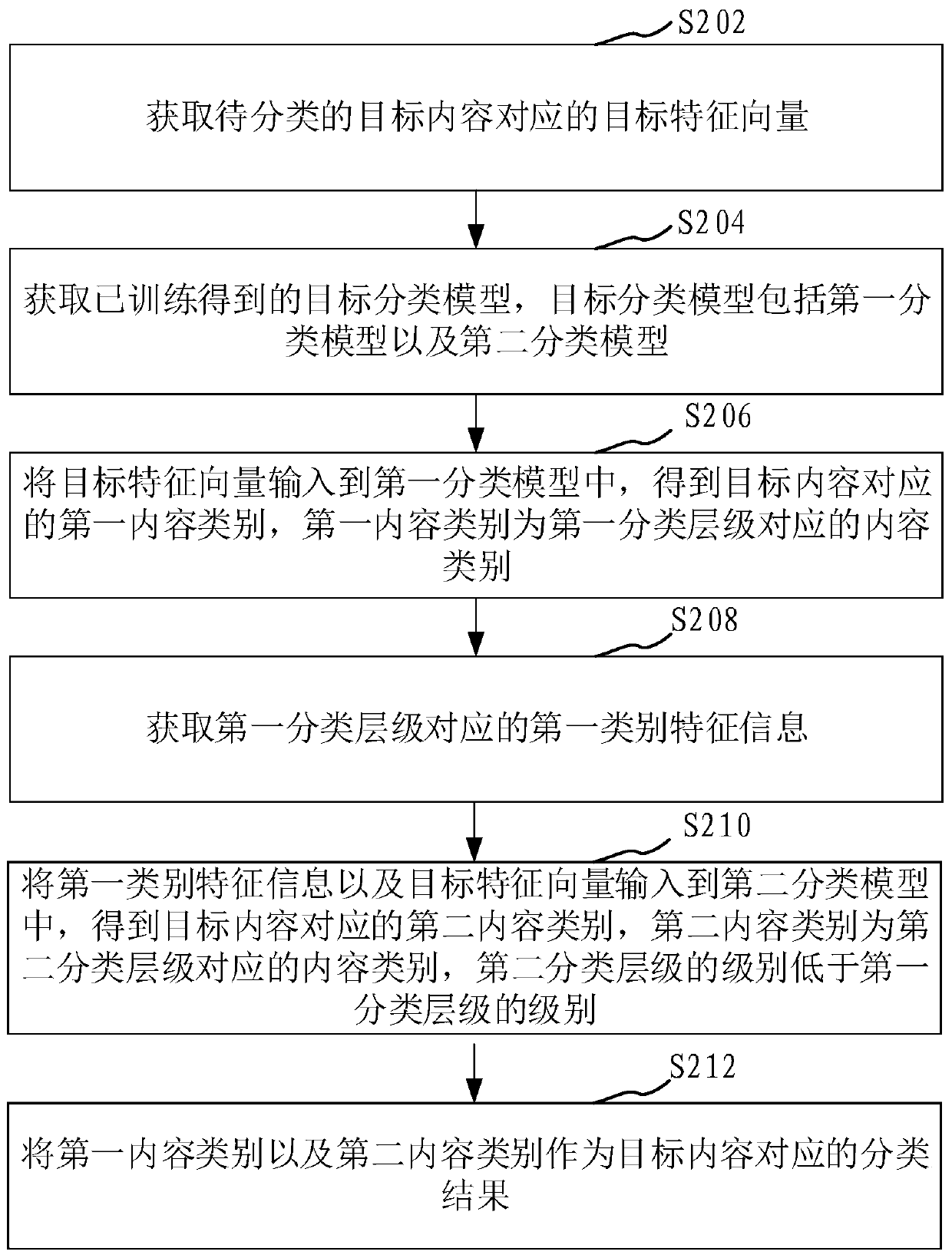
Content classification method and device, computer equipment and storage medium
PendingCN110737801AImprove accuracyVideo data clustering/classificationCharacter and pattern recognitionFeature vectorClassification methods
The invention relates to a content classification method and a device, a computer device and a storage medium. The method comprises the steps of obtaining a target feature vector corresponding to to-be-classified target content; obtaining a target classification model obtained by training, wherein the target classification model comprises a first classification model and a second classification model; inputting the target feature vector into a first classification model to obtain a first content category corresponding to the target content, the first content category being a content category corresponding to the first classification hierarchy; obtaining first category feature information corresponding to the first classification hierarchy; inputting the first category feature information and the target feature vector into a second classification model to obtain a second content category corresponding to the target content, the second content category being a content category corresponding to a second classification level, and the level of the second classification level being lower than the level of the first classification level; and taking the first content category and the second content category as classification results corresponding to the target content. The method can improve the content classification accuracy.
Owner:TENCENT TECH (SHENZHEN) CO LTD
System, Apparatus, and Method for Internet Content Detection
A method of detecting content communicated via a network is provided consisting of the steps of: classifying the content into a first category and a second category by means of a classification process; detecting one or more behaviour parameters of a user accessing the content, where the behaviour patterns are associated with the content either consisting of first category content or second category content; and further classifying the content into first category content and second category content based on the behaviour parameters detected for the user. The first category content generally consists of restricted or illegal content, and the second category content generally consists of unrestricted or legal content. The classification process consists of a pattern recognition technique that includes a training phase and a testing phase. The training phase provides statistical properties of a plurality of data objects which are labelled prior to testing as either restricted or unrestricted. The testing phase determines whether one or more data objects of content communicated via the network constitute restricted content or unrestricted content. A related system, network apparatus and computer program is provided.
Owner:VARGAS MARTIN MIGUEL
Object versioning
ActiveUS7209933B2Eliminate needData processing applicationsDigital data information retrievalUnique identifierFirst-class citizen
A repository contains multiple versions of an object, and any version of the object can be modified by a user, as and when necessary. A table for one object (“first object”) that is contained in another object (“second object”) has at least two columns, namely one column for a minimum version of the second object and another column for a maximum version of the second object. If a number of versions of the first object are responsive to a query, then one version of the first object is selected if a version of the second object that is responsive to the query happens to be in the range defined by the just-described minimum version number and the maximum version number. Depending on the embodiment, the second object can be an immediate parent of the first object, or can be an ancestor (also called “first class object”) of the first object that is not contained in any other object. In some embodiments, one or more attributes of the first object are stored in a first table along with a unique identifier and a version number. In addition, information on relations of the first object to other objects as well as an identity of a configuration (to which the current version of the first object belongs) are stored in a second table. Therefore, a pair of tables are used for each object, so as to decouple information that defines an object from information on relationships of the object. If a change happens in just the relationship of an object then no change is made to the table containing the definition of the object. Similarly, if a change happens in just the definition of the object, then no change is made to the table containing the relations of the object. Moreover, when a change happens to an object, if the object has a number of ancestors and decendants only an immediate parent of the object is updated, thereby to eliminate a versioning chain reaction (i.e. other objects are not affected).
Owner:ORACLE INT CORP
Product Lifecycle Management Method and Apparatus
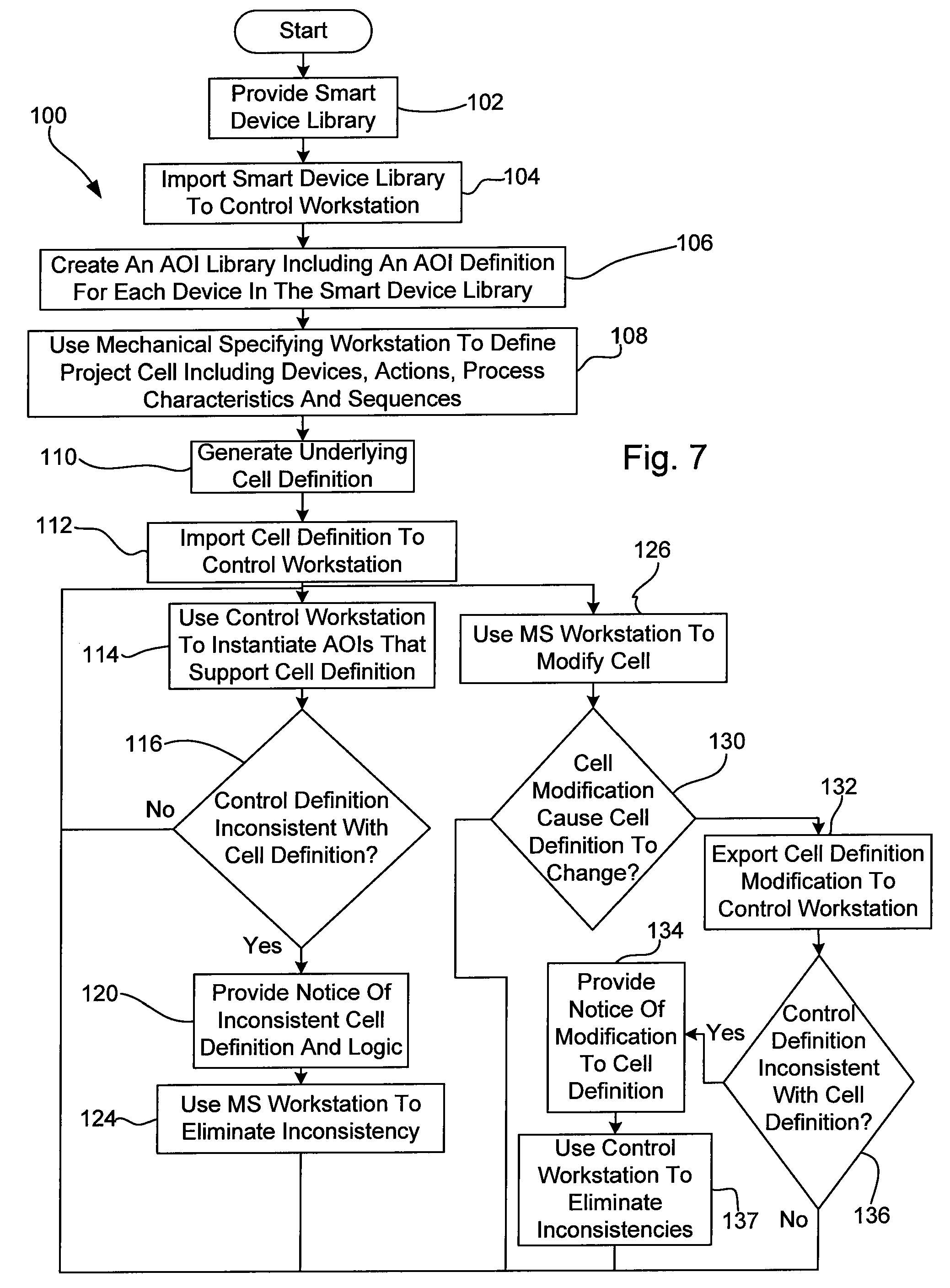
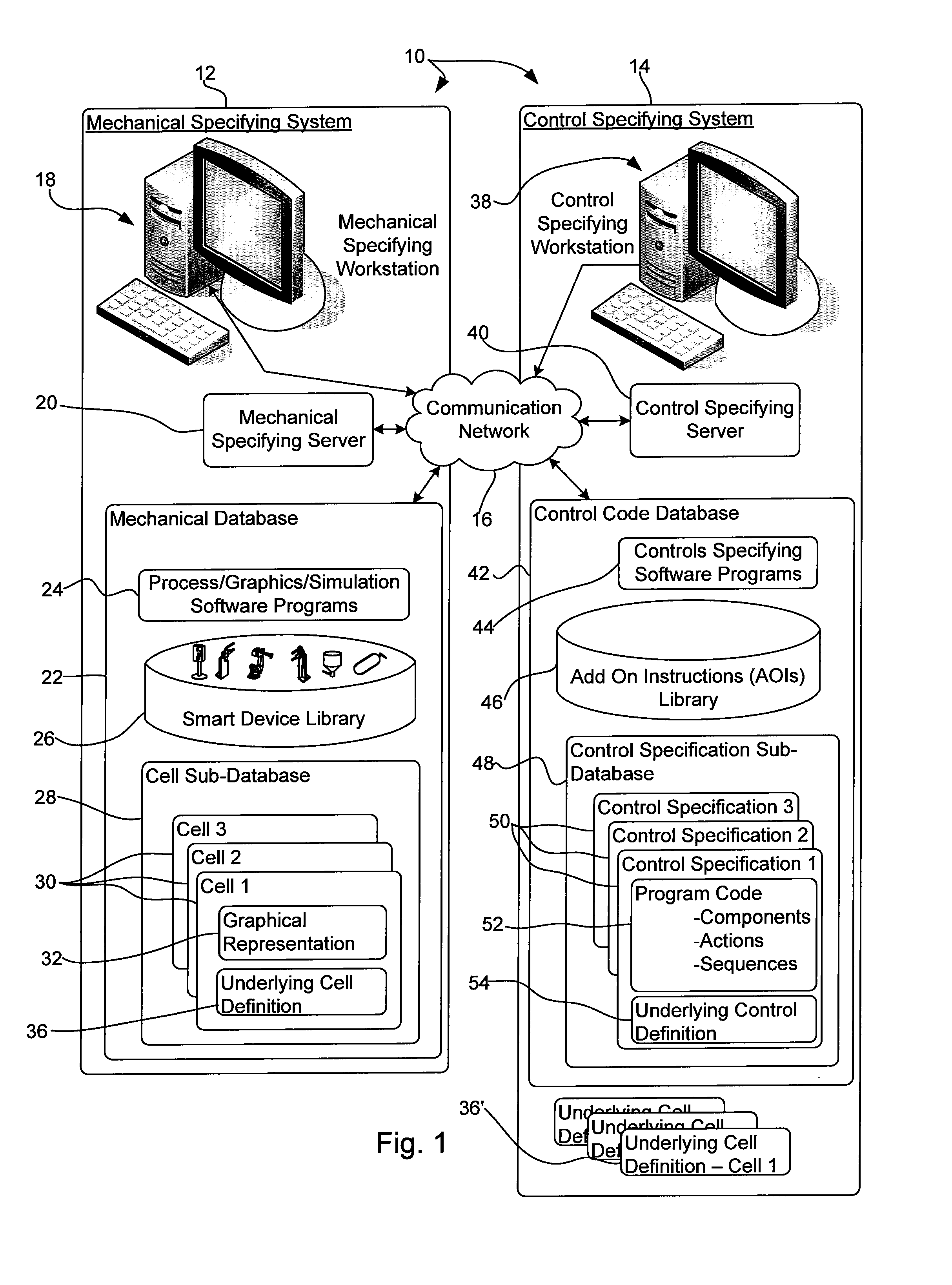
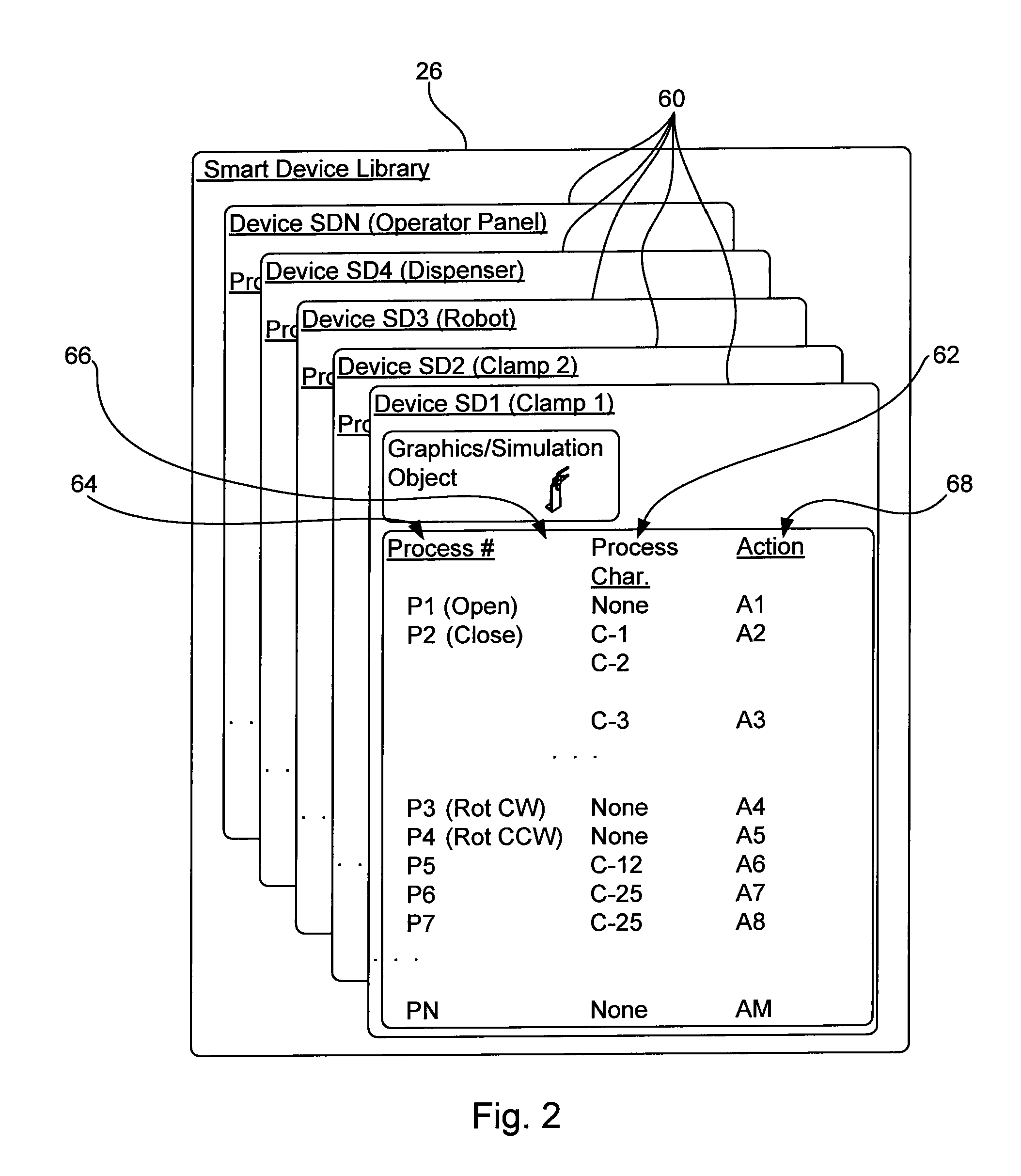
InactiveUS20090192857A1Easy to processInconsistency can be eliminatedProgramme controlComputer controlInformation typePERQ
A method for synchronizing activities during design of an industrial automated system wherein the automated system includes a plurality of different features and the design of the automated system requires at least first and second different information types, the method comprising the steps of using a first software program to specify a first type system definition including a set of first information type instances corresponding to the automated system, after the first type system definition has been specified, using a second software program to specify a second type system definition including a set of second information type instances corresponding to the automated system, after the second type system definition has been specified, comparing the first and second system definitions to identify system features supported by only one of the first and second type system definitions and where only one of the first and second type system definitions supports a system feature, the second software program providing notice to the first software program indicating that the first and second type system definitions are imperfectly correlated.
Owner:ROCKWELL AUTOMATION TECH
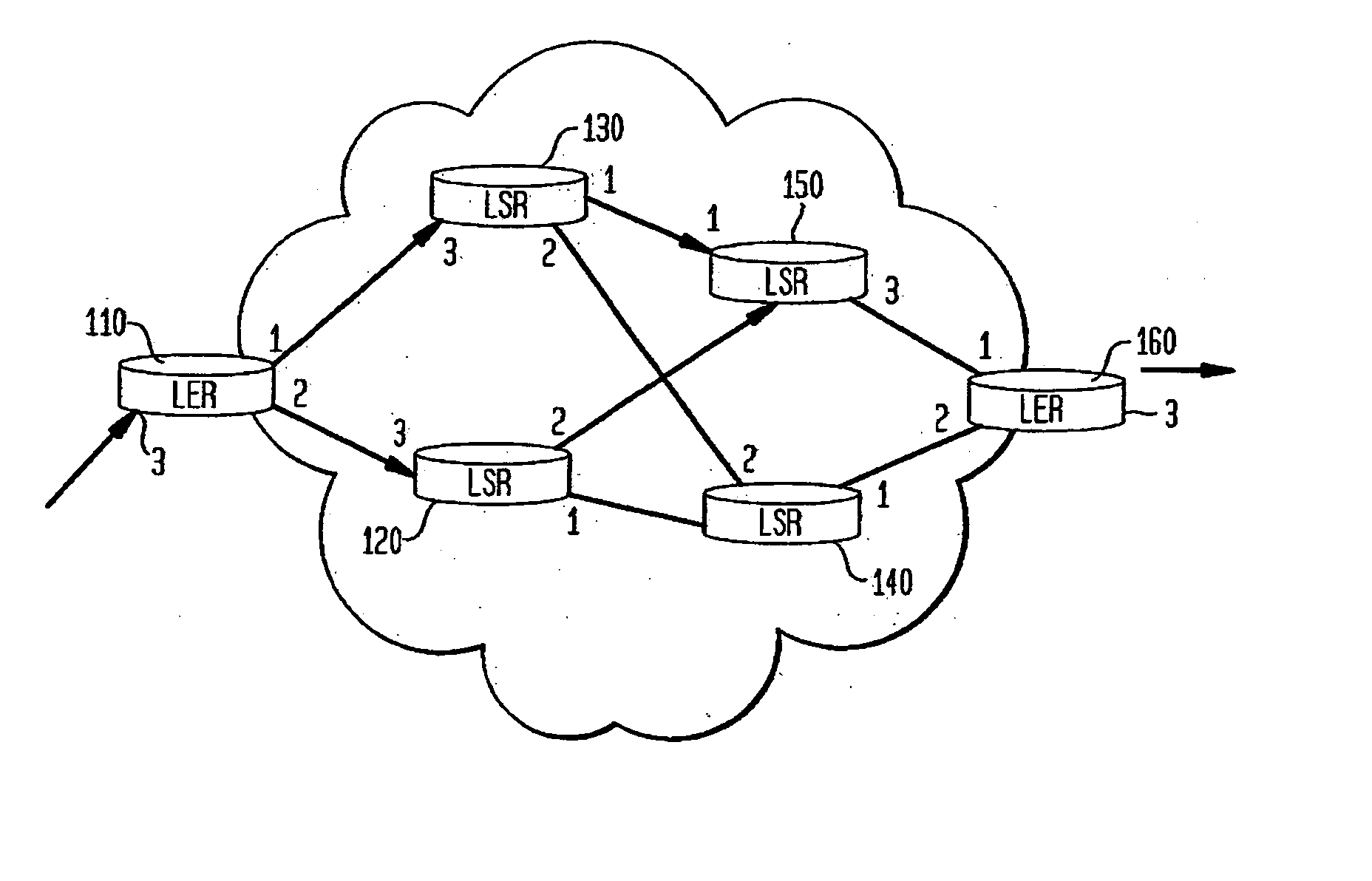
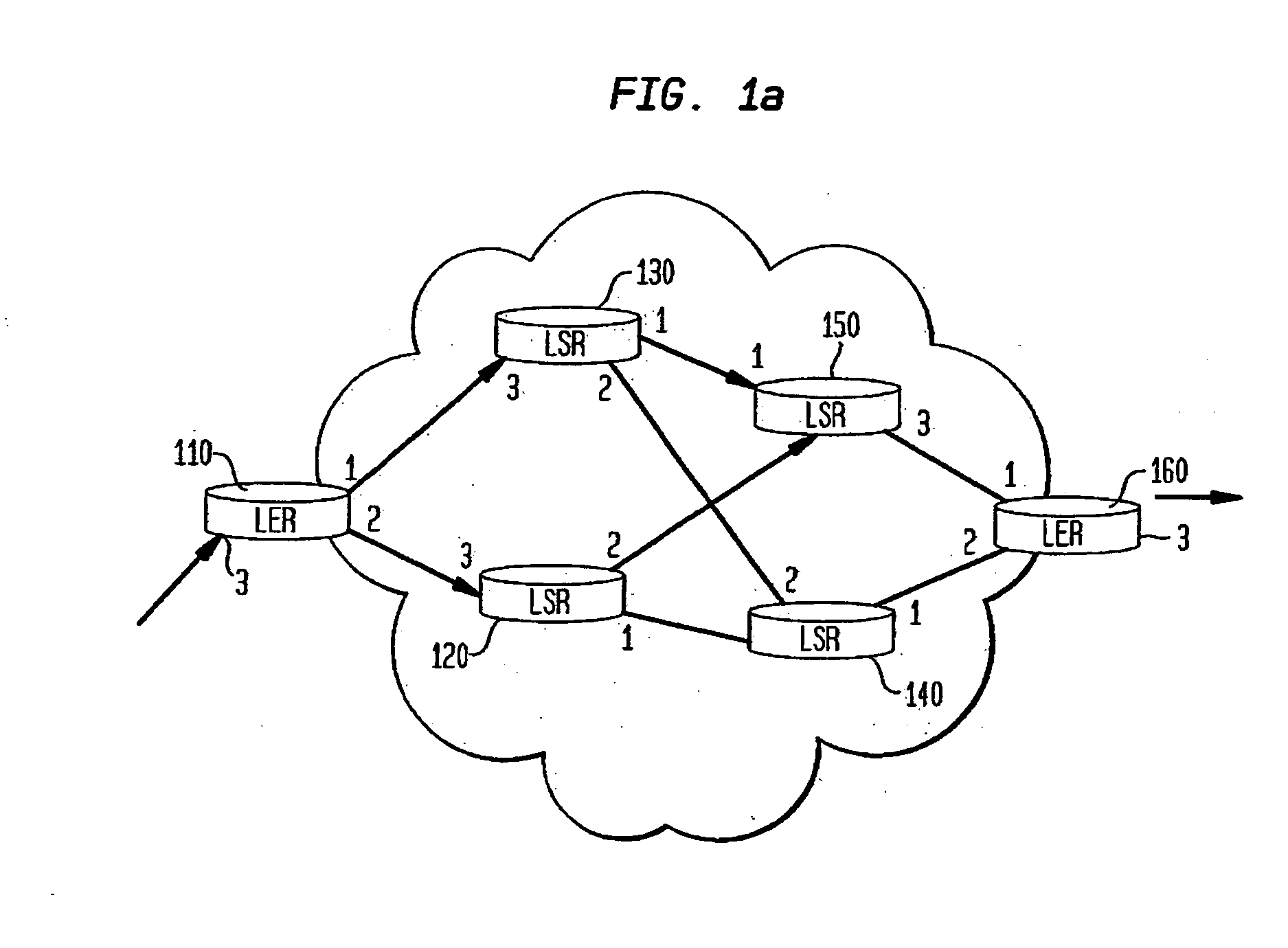
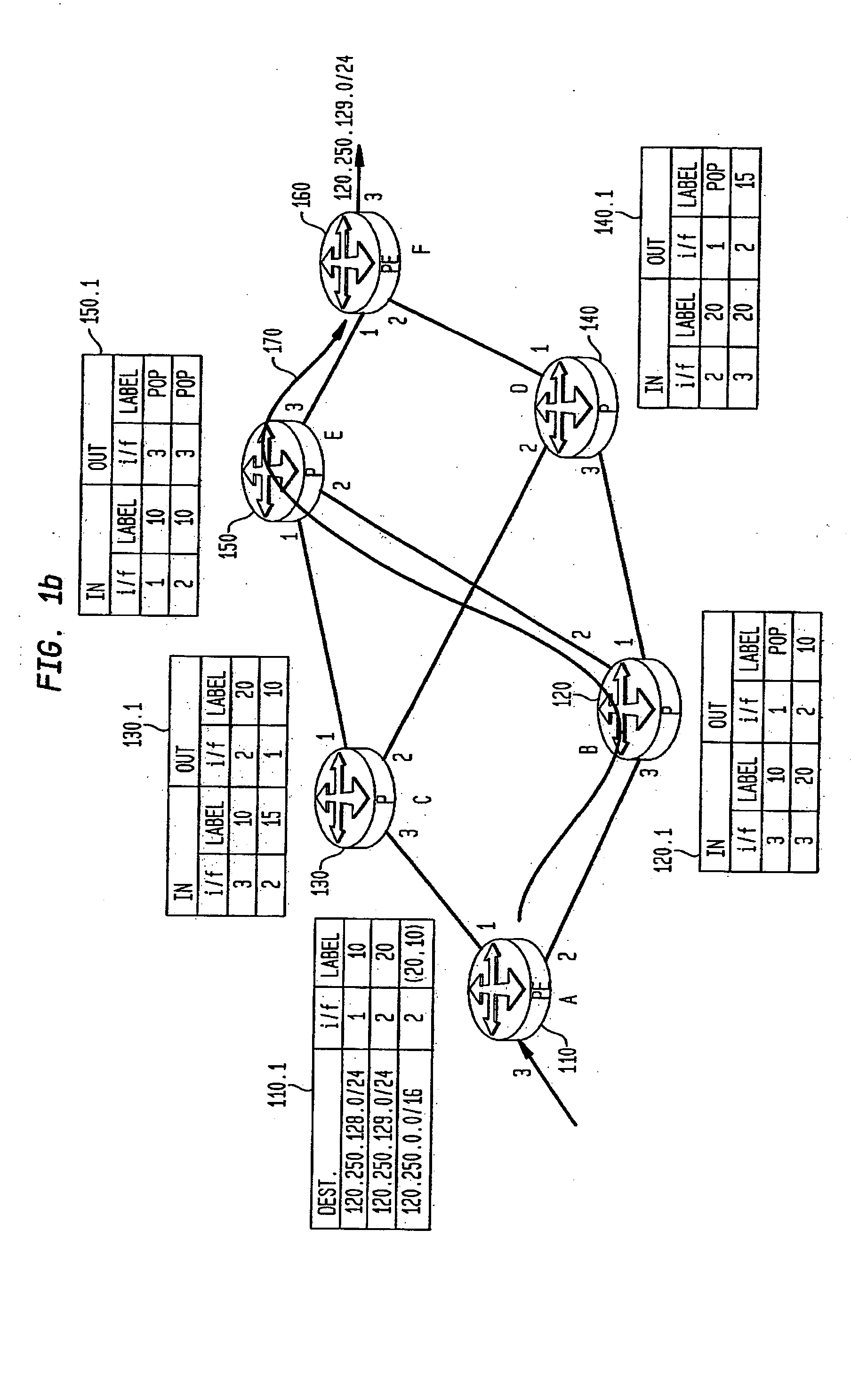
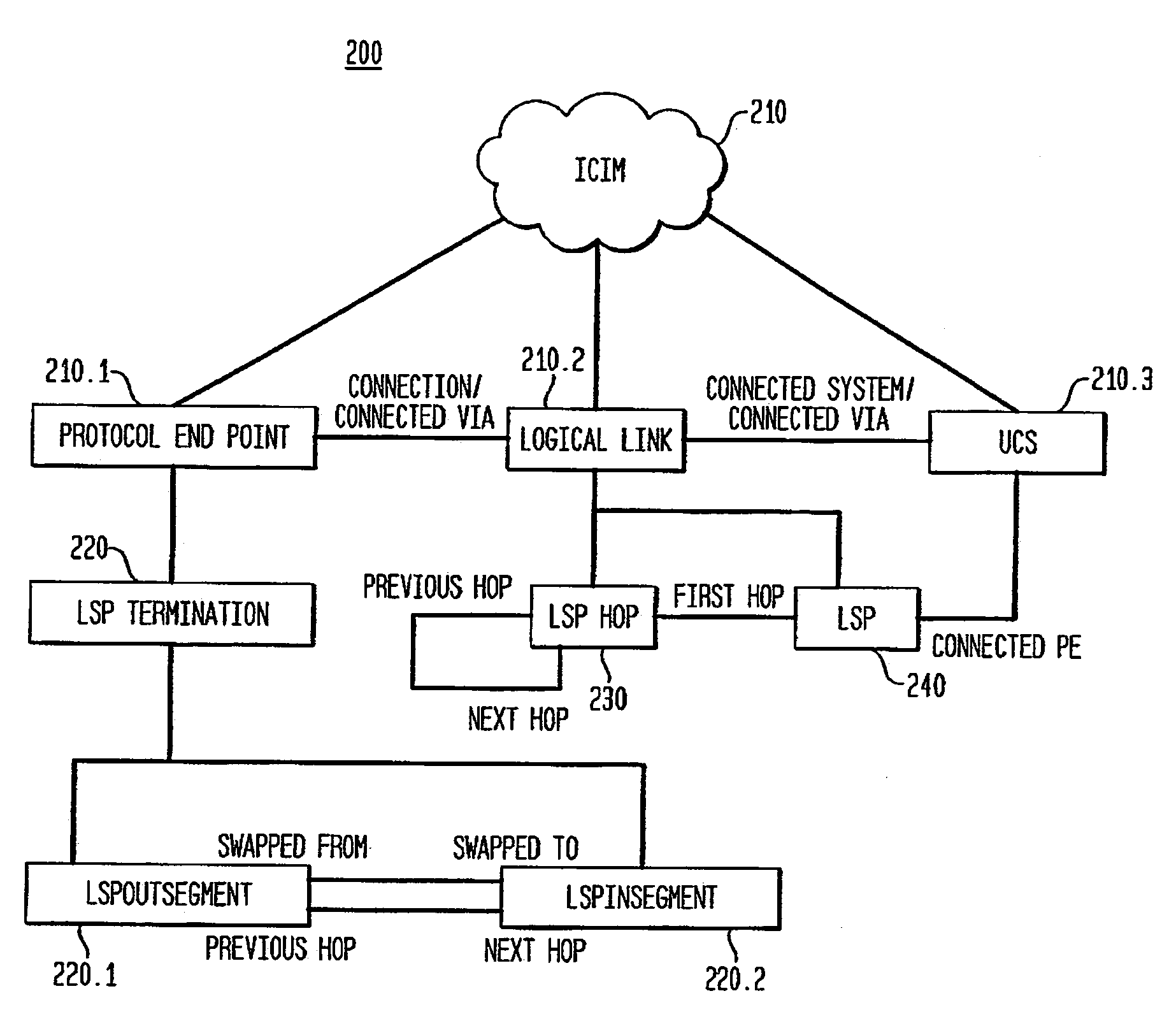
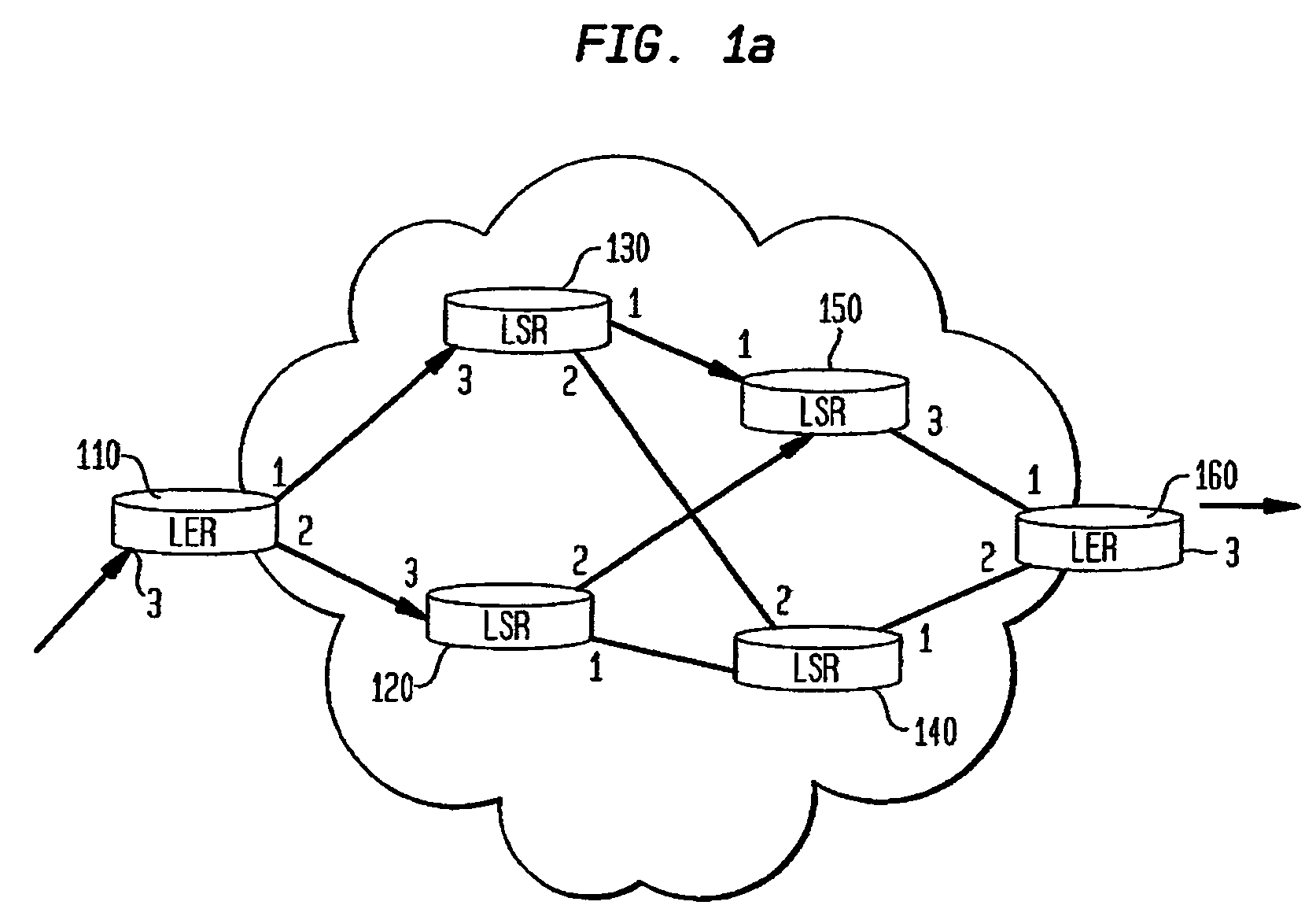
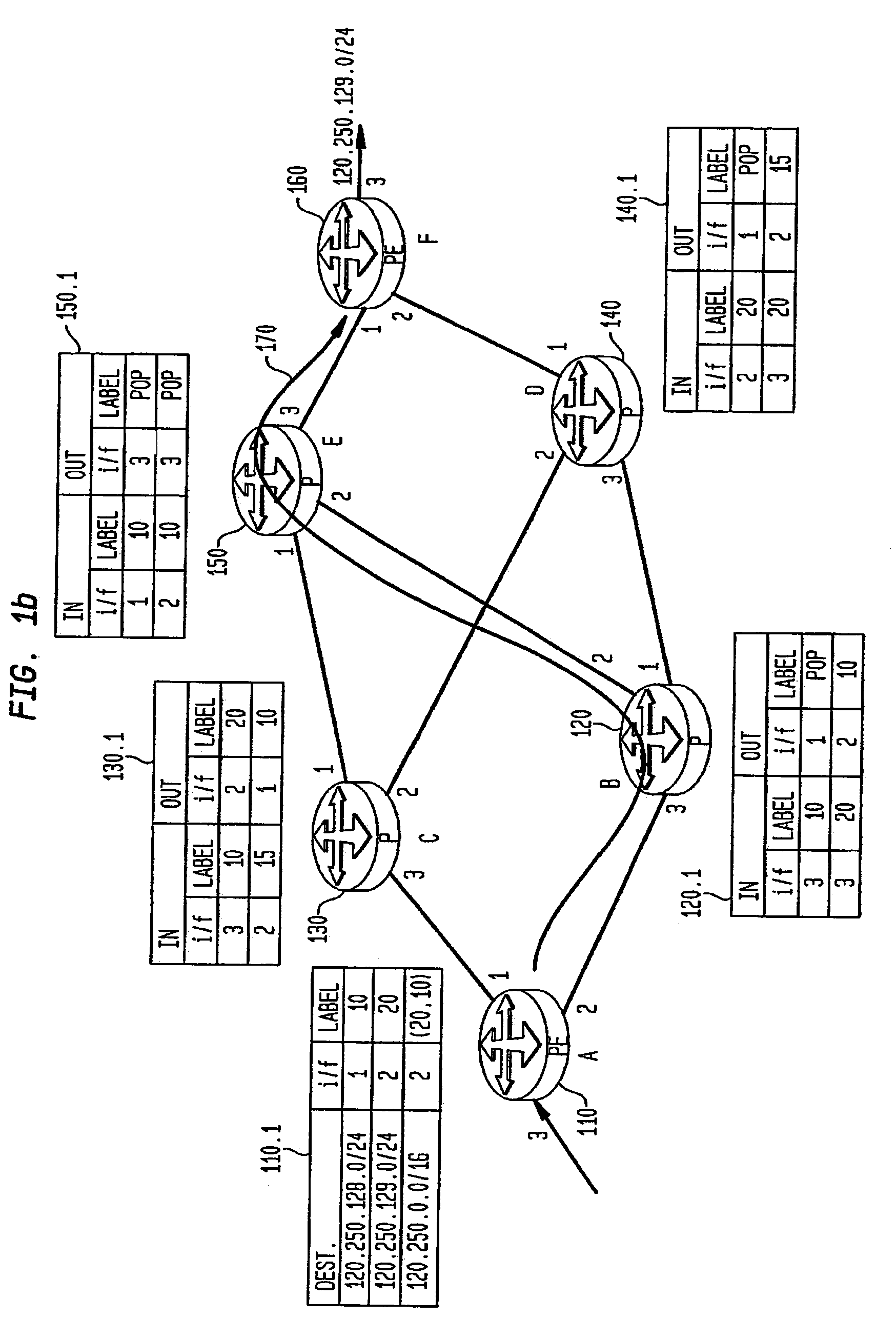
Model-based method and apparatus for determining MPLS network properties
Embodiments of the present invention are directed to a method and apparatus for the identification or discovery for properties of MPLS networks through a modeling technique. Aspects of the present invention provide for discovering or identifying the Label Switched Paths in MPLS networks. The method comprises the steps of representing a network by a model comprising a plurality of configuration non-specific first object classes that are representations of types of components associated with the network components, and a plurality of configuration non-specific second object classes that are representations of relationships among the representation of types of component, identifying instances of a first one and a second one of the types of components object class, and identifying the label switch path by traversing the instances of the first and second types of components object classes through select ones of the relationship object classes associated with the first and second type of components object classes.
Owner:EMC IP HLDG CO LLC
Efficient memory usage for unified document object model implementation for Java
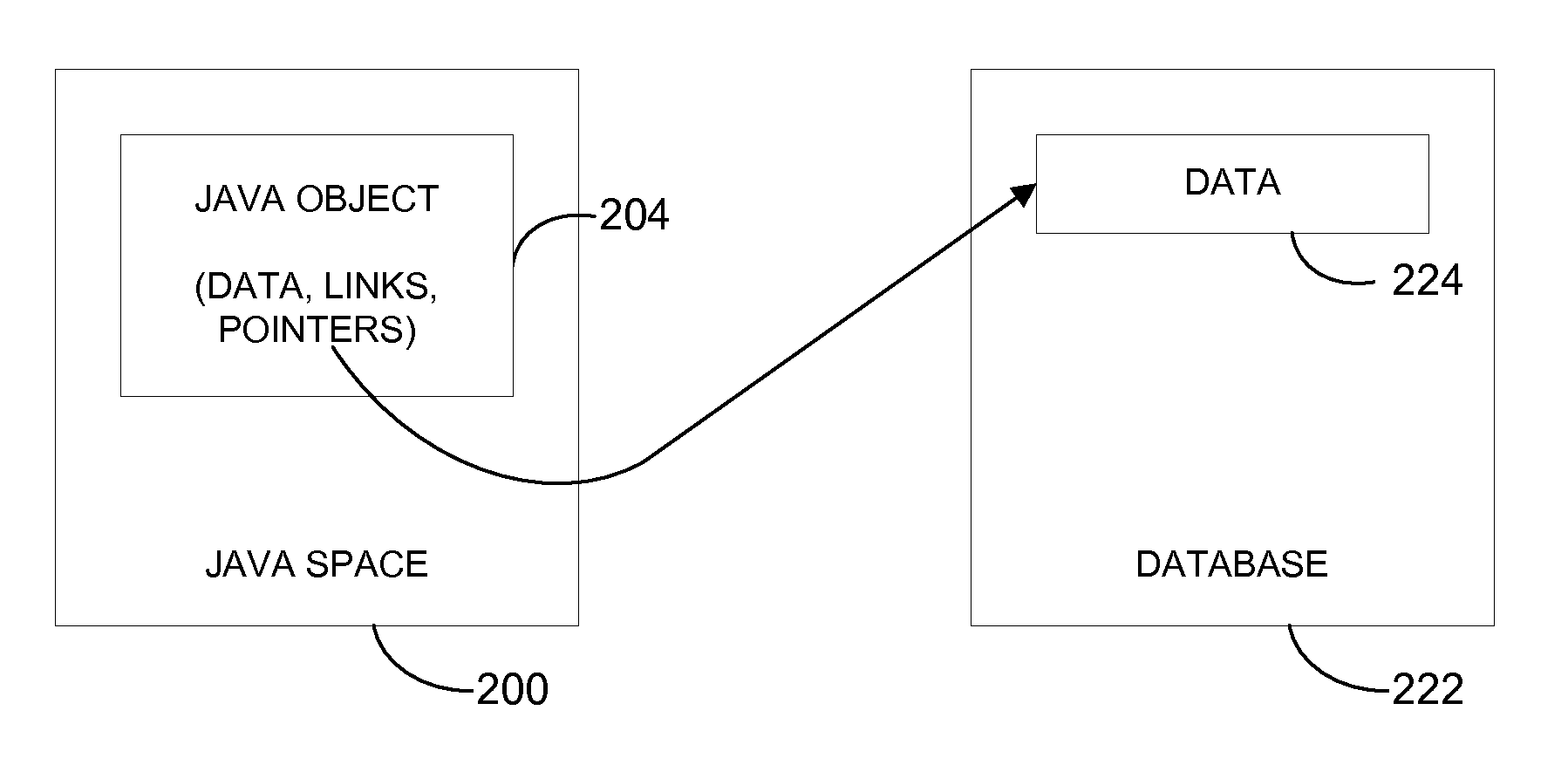
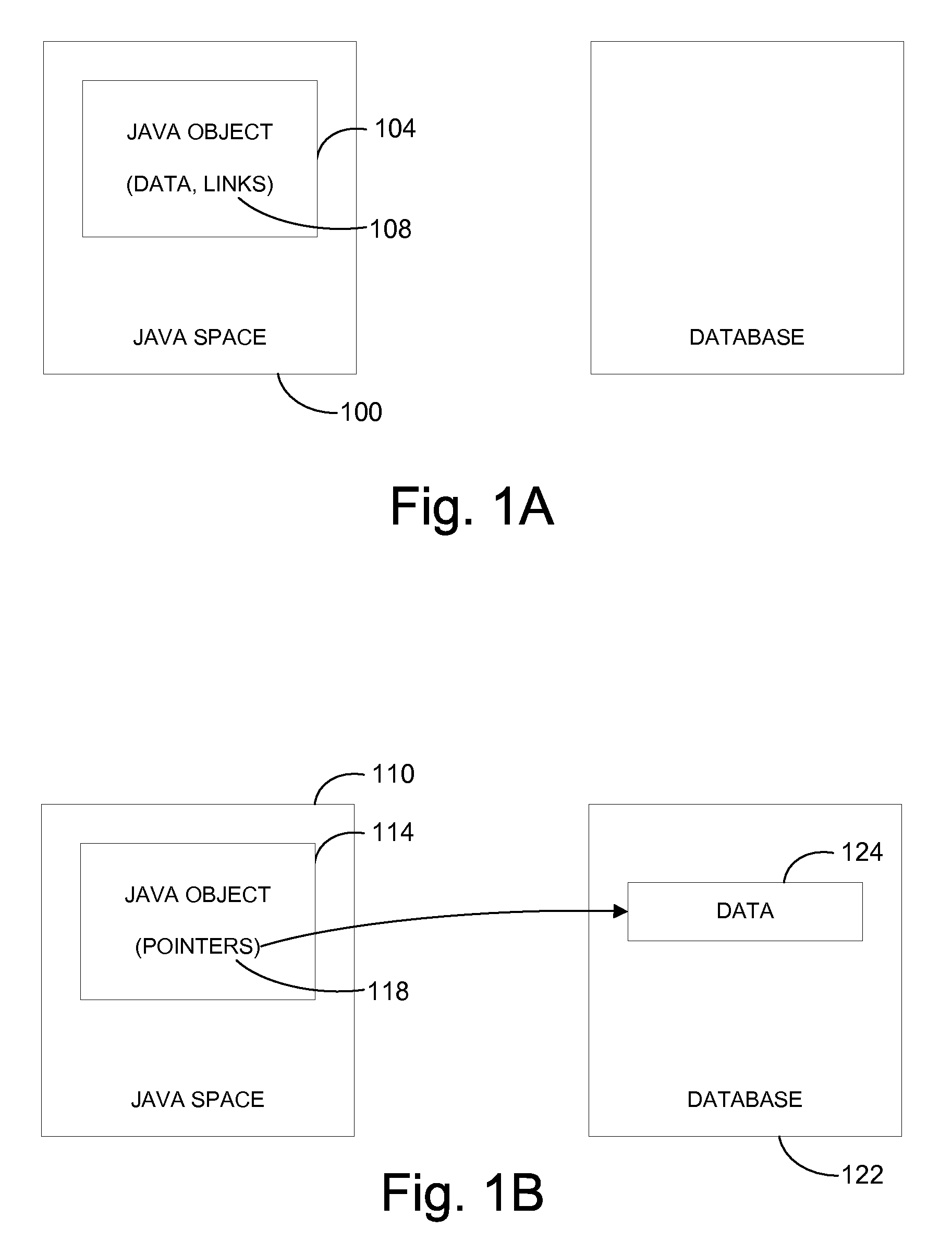
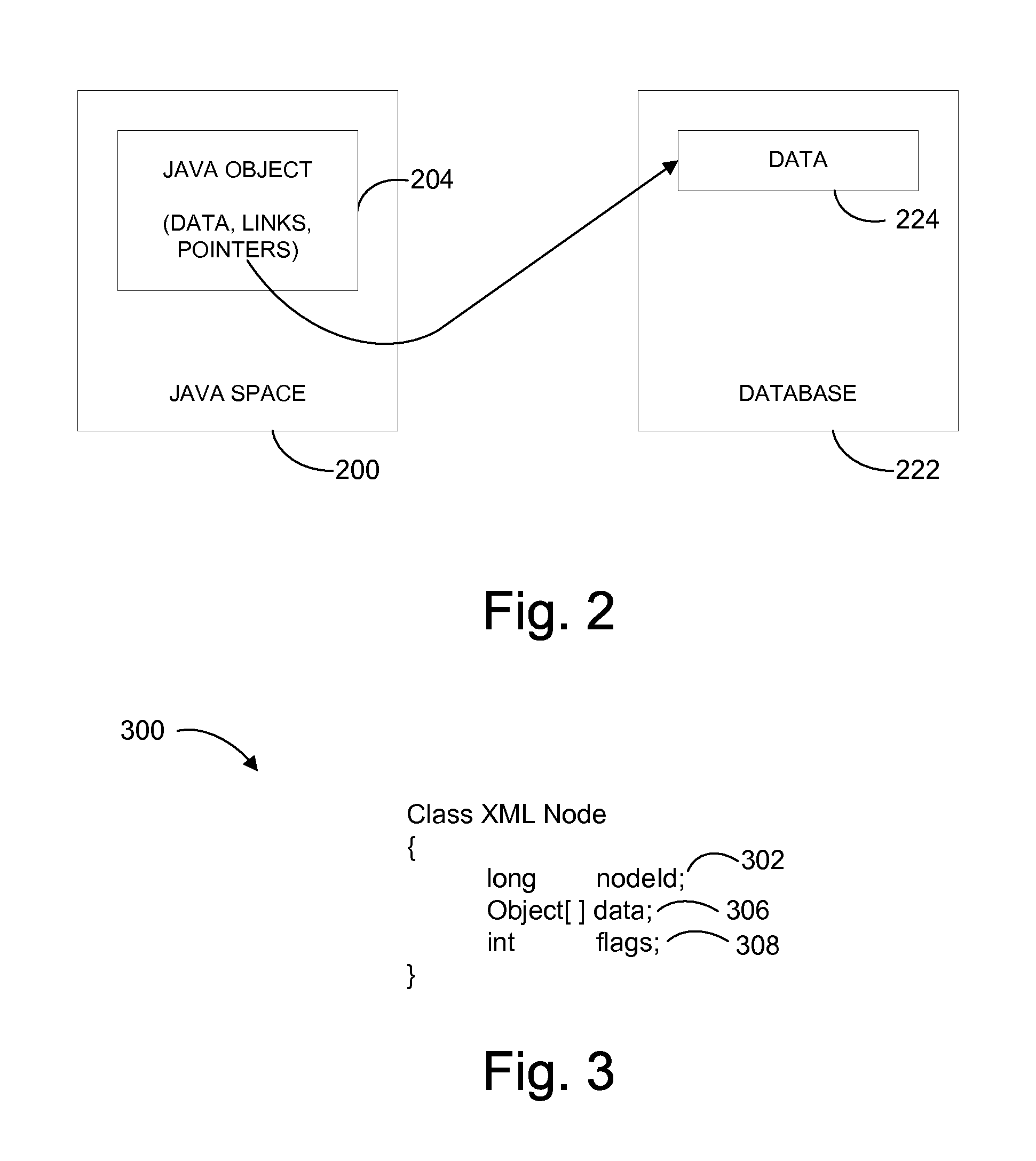
ActiveUS7870112B2Digital data processing detailsProgram controlJavaApplication programming interface
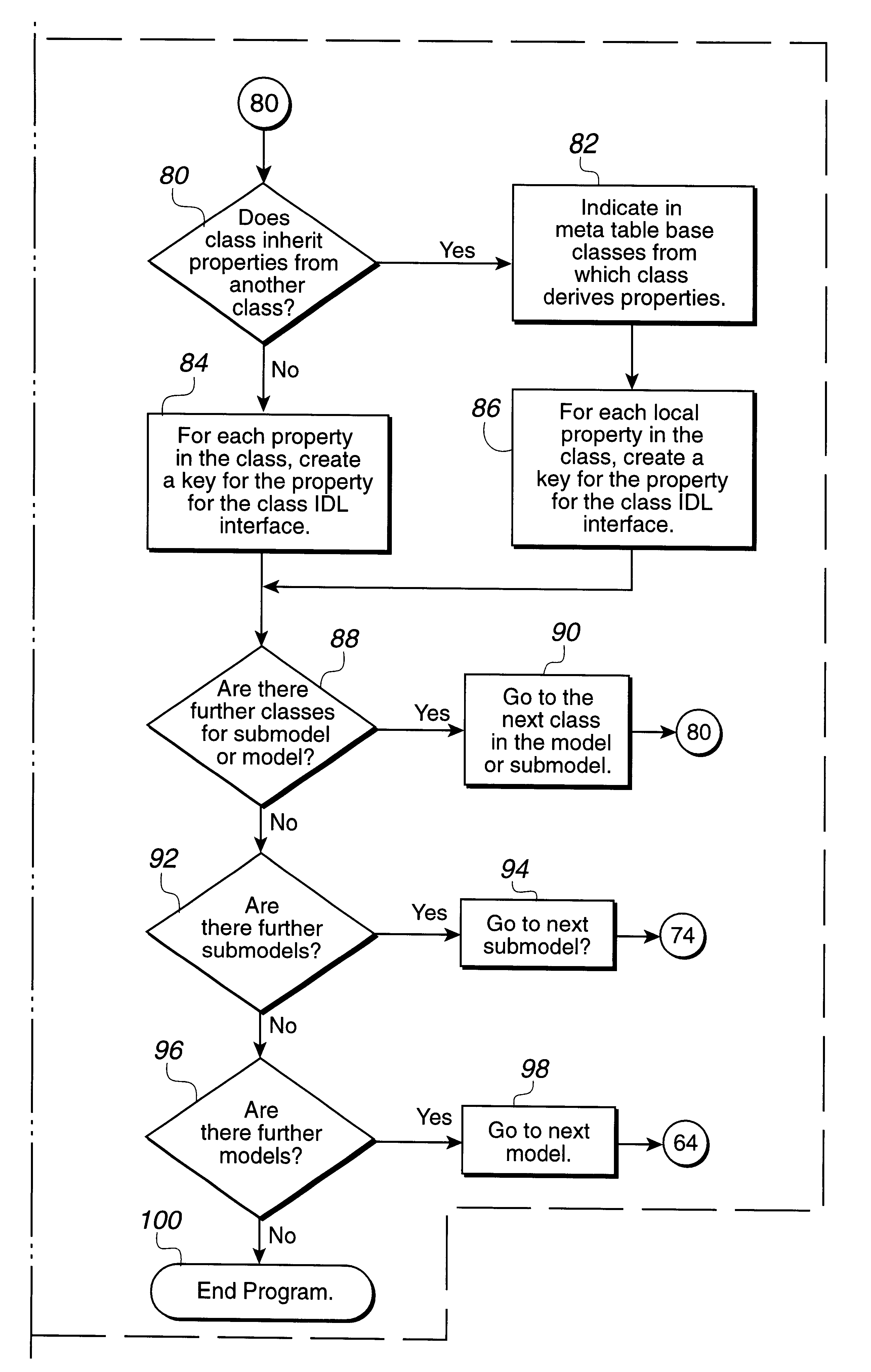
Methods and apparatus for enabling an object associated with an XML node class to be used for both a document object model (DOM) application programming interface (API) that supports an in-memory representation of XML nodes and a DOM API that supports a database-backed representation of XML nodes are disclosed. According to one aspect of the present invention, a method for creating an object that represents an XML node in a Java space includes determining whether the object is to represent a pure node. An object of a first class is created to represent a database-backed node when the object is not determined to represent the pure node, and the object of the first class is created to represent a pure node when the object is determined to represent the pure node. The object includes the same set of fields whether the object represents a pure node or a database-backed node.
Owner:ORACLE INT CORP
Model-based method and apparatus for determining MPLS network properties
InactiveUS7720003B2Error preventionFrequency-division multiplex detailsObject ClassTheoretical computer science
Embodiments of the present invention are directed to a method and apparatus for the identification or discovery for properties of MPLS networks through a modeling technique. Aspects of the present invention provide for discovering or identifying the Label Switched Paths in MPLS networks. The method comprises the steps of representing a network by a model comprising a plurality of configuration non-specific first object classes that are representations of types of components associated with the network components, and a plurality of configuration non-specific second object classes that are representations of relationships among the representation of types of component, identifying instances of a first one and a second one of the types of components object class, and identifying the label switch path by traversing the instances of the first and second types of components object classes through select ones of the relationship object classes associated with the first and second type of components object classes.
Owner:EMC IP HLDG CO LLC
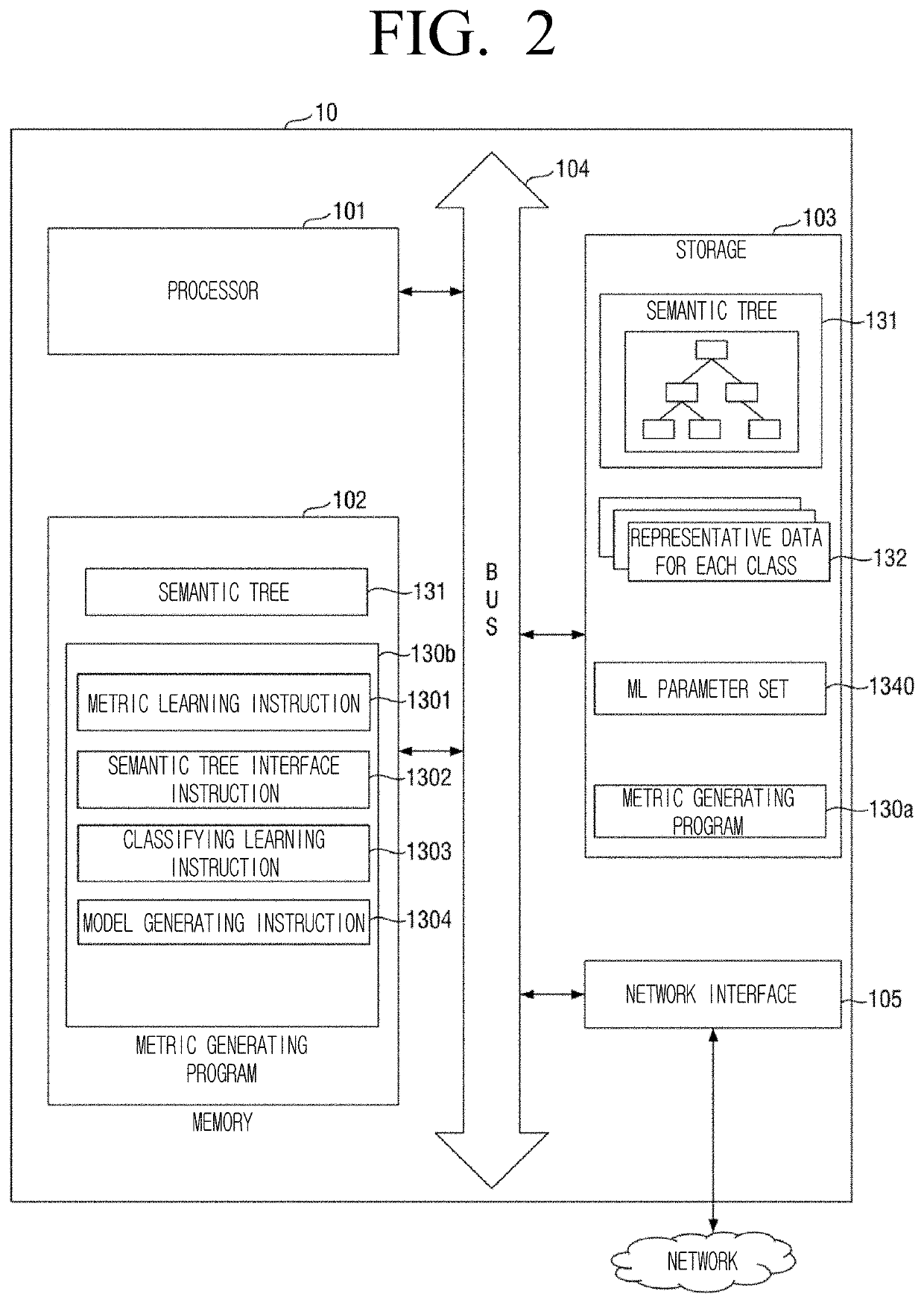
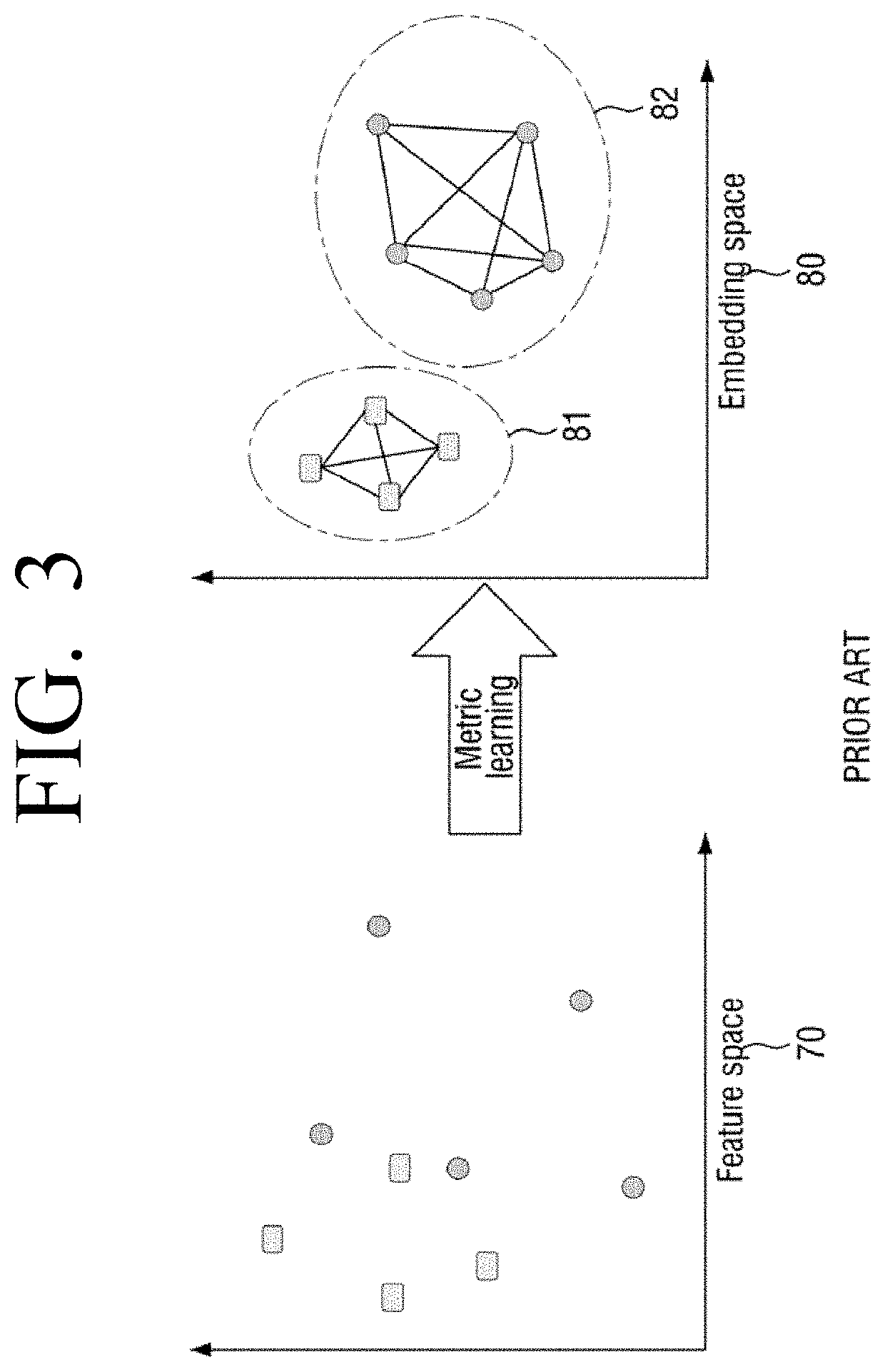
Apparatus related to metric-learning-based data classification and method thereof
ActiveUS20200257975A1Reduce lossesAccelerate the lossSemantic analysisCharacter and pattern recognitionEngineeringFeature data
The present invention provides artificial intelligence technology which has machine-learning-based information understanding capability, including metric learning providing improved classification performance, classification of an object considering a semantic relationship, understanding of the meaning of a scene based on the metric learning and the classification, and the like. An electronic device according to one embodiment of the present invention comprises a memory in which at least one instruction is stored, and a processor for executing the stored instruction. Here, the processor extracts feature data from training data of a first class, obtains a feature point by mapping the extracted feature data to an embedding space, and makes an artificial neural network learn in a direction for reducing a distance between the obtained feature point and an anchor point.
Owner:SAMSUNG ELECTRONICS CO LTD
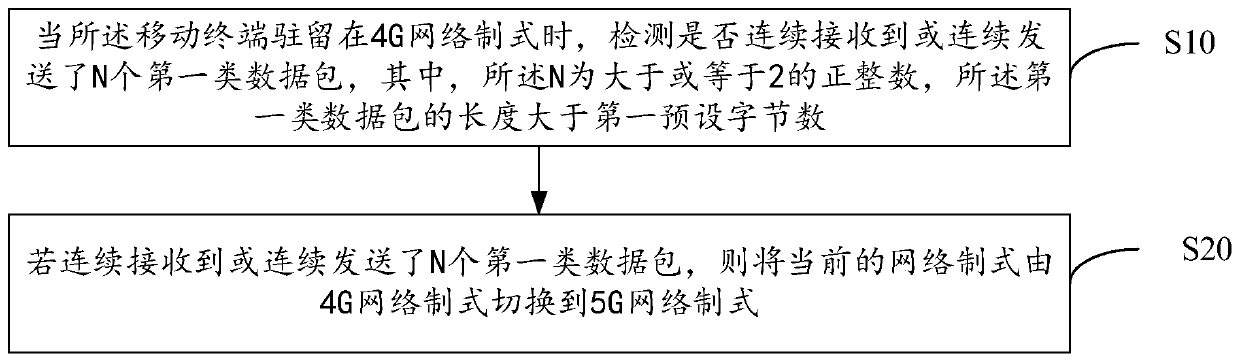
Network switching method, mobile terminal and computer readable storage medium
ActiveCN110784898AHigh energy consumptionImprove transmission efficiencyPower managementHigh level techniquesData packEngineering
The invention discloses a network switching method, a mobile terminal and a computer readable storage medium. The network switching method comprises the steps that when the mobile terminal resides ina 4G network system, whether N first-class data packets are continuously received or continuously sent or not is detected, wherein N is a positive integer larger than or equal to 2, and the length ofthe first-class data packets is larger than a first preset byte number; and if the N first type data packets are continuously received or continuously sent, the current network type is switched from the 4G network type to the 5G network type. According to the invention, the network type is switched from the 4G network type to the 5G network type only when a large amount of data needs to be transmitted, so that the data transmission efficiency is improved, and unnecessary terminal energy consumption is prevented from being increased.
Owner:深圳市威创力合科技有限公司
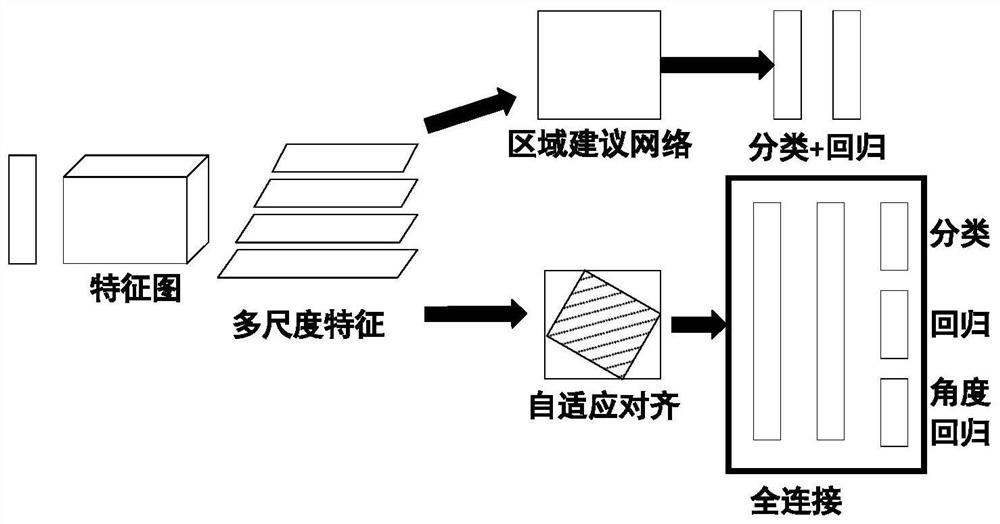
Multi-scale rotating ship target detection algorithm
ActiveCN111881918AEfficient integrationReduce the impactCharacter and pattern recognitionNeural architecturesPattern recognitionAlgorithm
The invention provides a multi-scale rotating ship target detection algorithm. The algorithm comprises the following steps: acquiring a multi-scale feature map of an input image, wherein the multi-scale feature map comprises a first-class scale feature map, a second-class scale feature map and a third-class scale feature map of which the scales are sequentially increased; performing feature fusionon the multi-scale feature map by adopting a feature pyramid network, wherein the feature pyramid network adopts a ResNet residual network as a basic framework; inputting the feature map output by the feature pyramid network into a region suggestion network through a 3 * 3 convolution layer, classifying each anchor frame by adopting the region suggestion network according to a set classificationjudgment condition, endowing each anchor frame with parameter coordinates, and obtaining a rotating boundary frame based on parameter coordinate regression; performing adaptive region-of-interest alignment on a rotation bounding box generated by the region suggestion network to obtain a high-quality feature map; and screening the candidate boxes of the high-quality feature map according to a set rotation non-maximum suppression constraint condition to obtain a detection target.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Protecting method and system of JAVA source code
ActiveUS20140195824A1Easily decompiledUnauthorized memory use protectionHardware monitoringCiphertextSoftware engineering
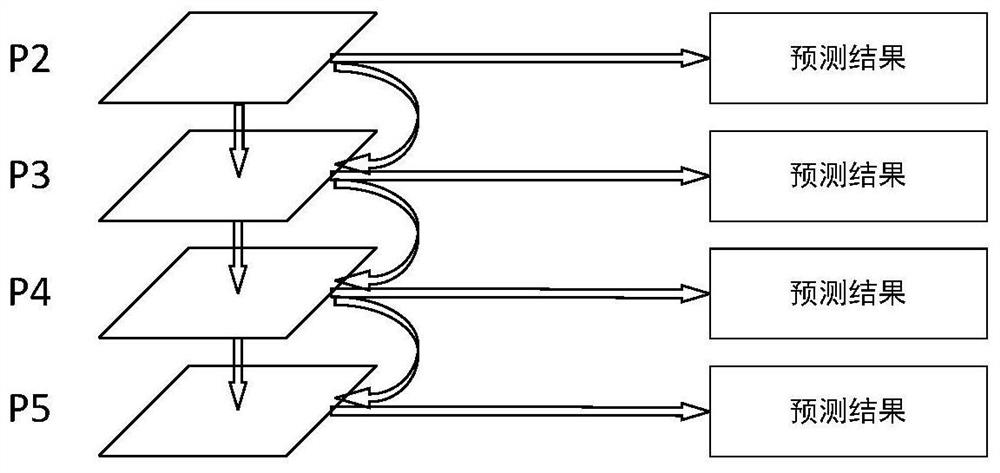
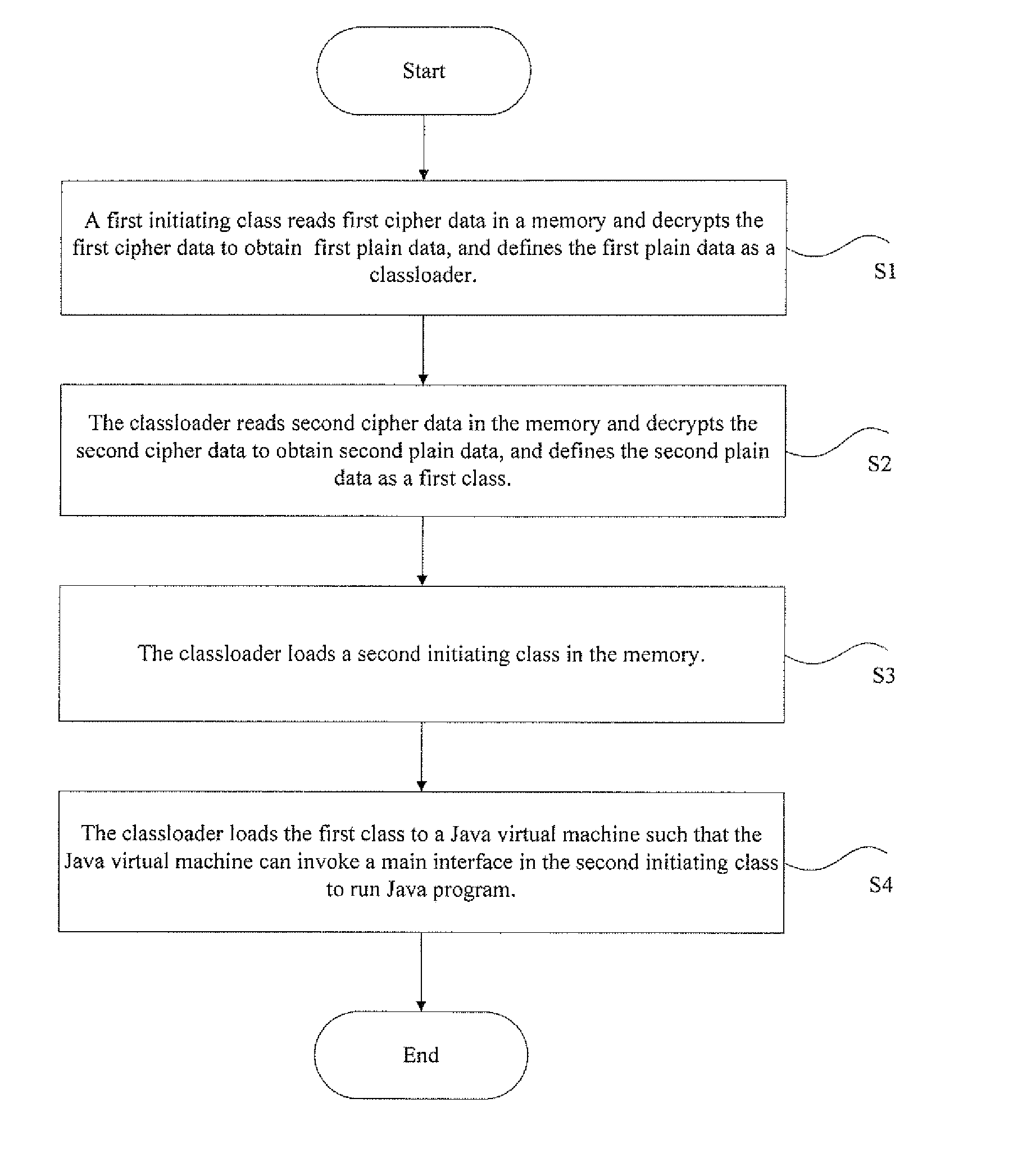
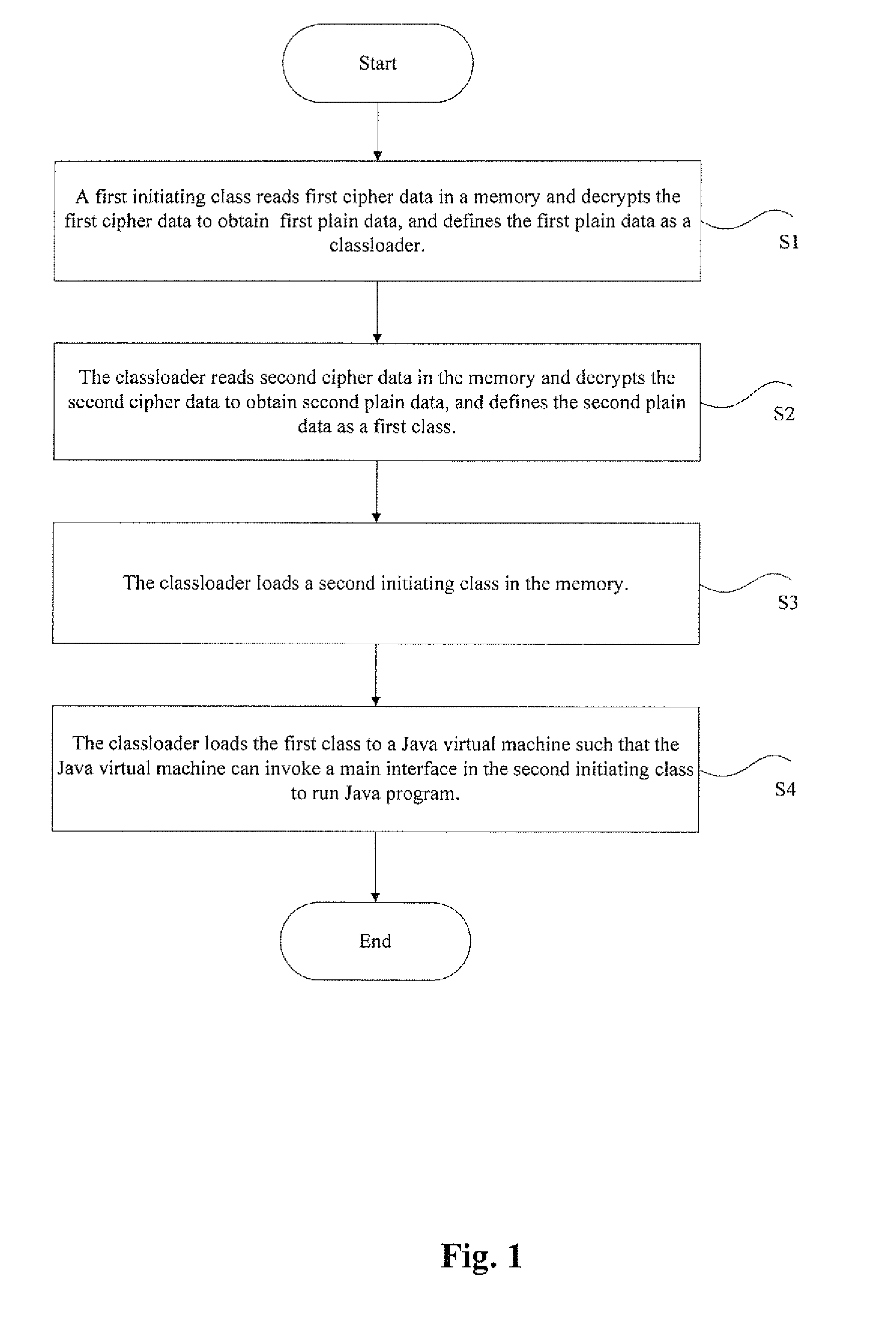
The present disclosure discloses a protecting method and system of Java source code. When a first initiating class is invoked, the method comprises following steps, wherein the first initiating class is an initiating class of Java program: the first initiating class decrypts first cipher data to obtain a class loader; the class loader reads second cipher data to the memory and decrypts the second cipher data to obtain a first class, wherein the first class is a class run by a Java virtual machine, and the suffix of the first class is .class; the class loader loads a second initiating class to the memory; wherein the second initiating class is an original class in jar packet of the Java program; and the class loader loads the first class to the Java virtual machine so that the Java virtual machine can invoke a main interface in the second initiating class to run the Java program. The present disclosure can protect Java source code and make it difficult to decompile the Java source code.
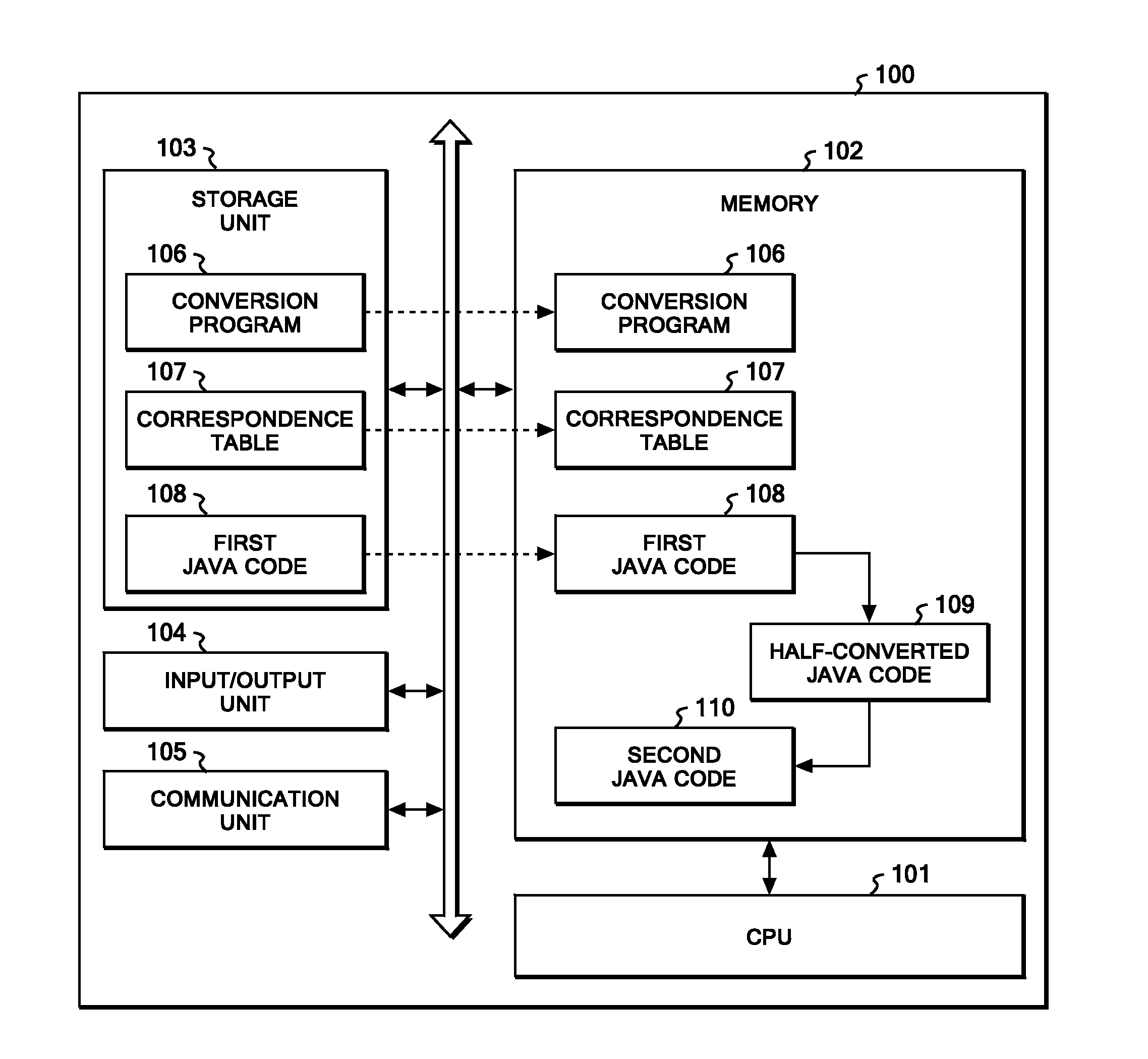
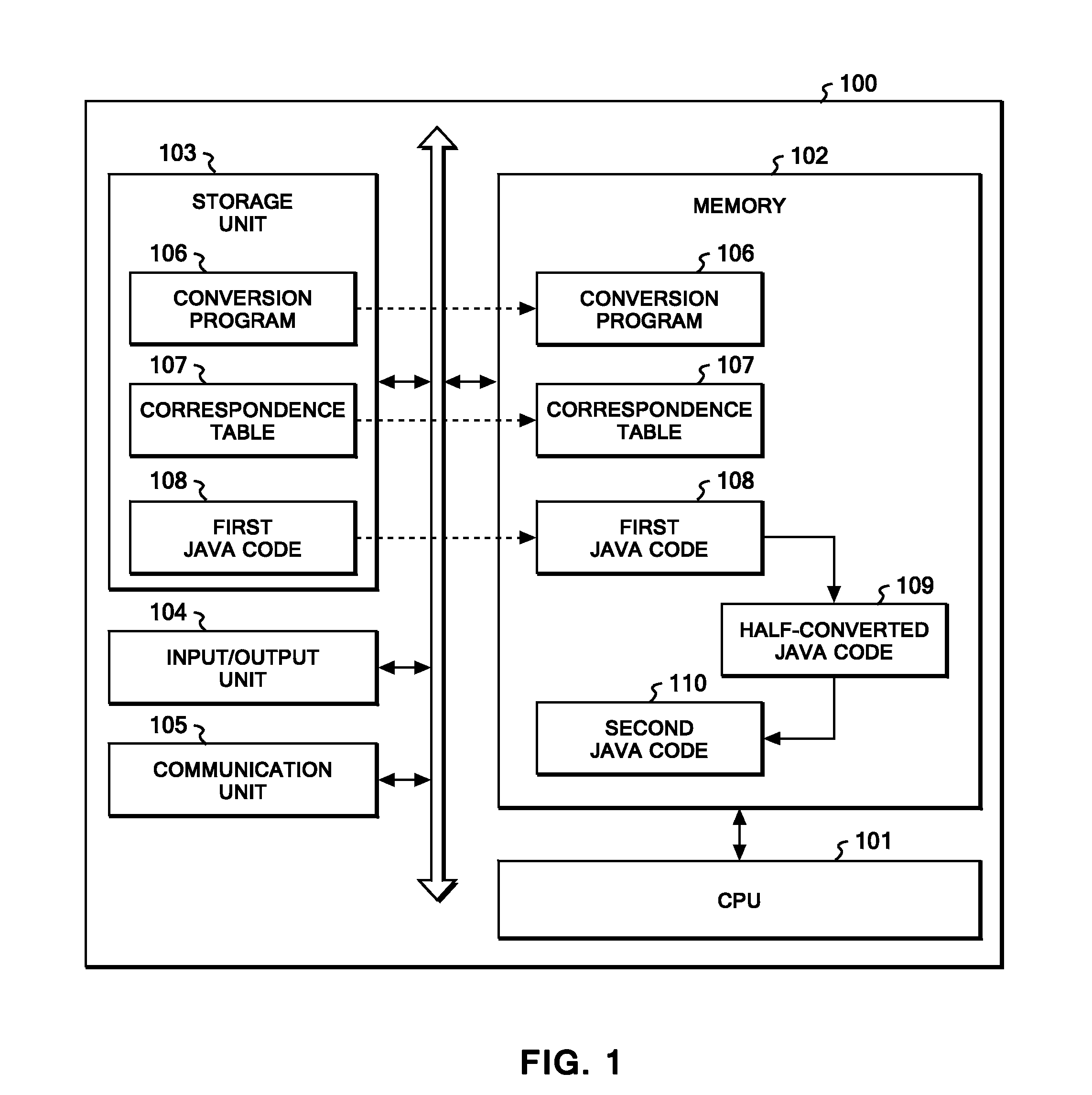
Owner:FEITIAN TECHNOLOGIES
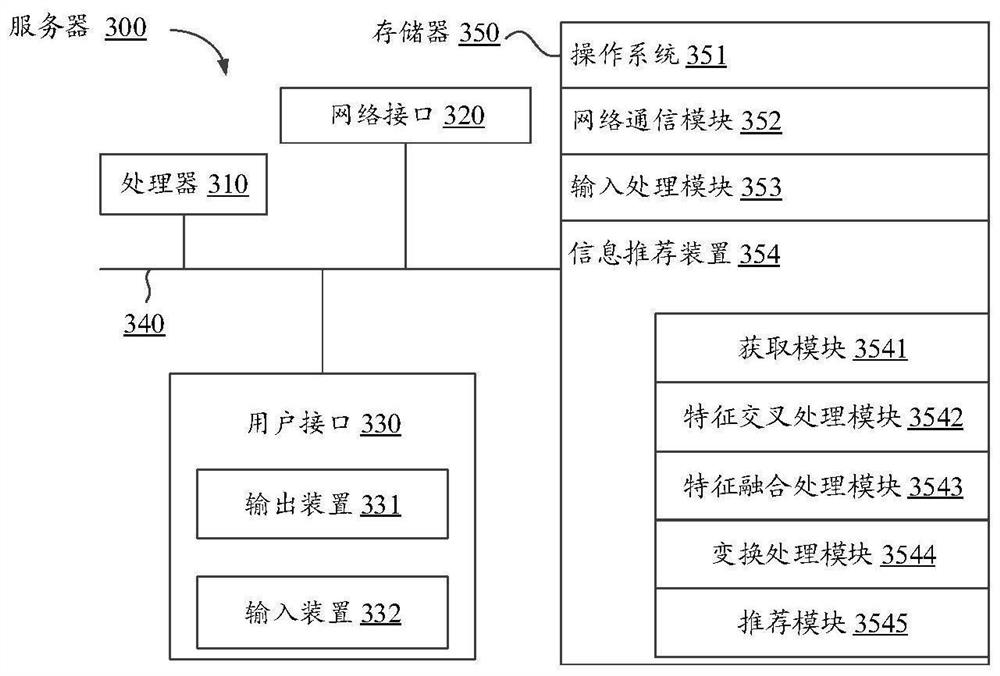
Information recommendation method, device and equipment and computer readable storage medium
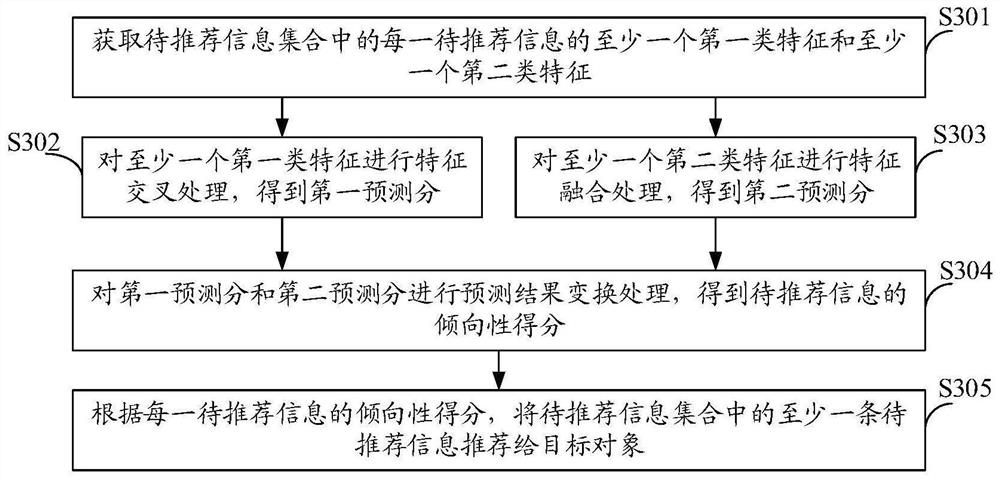
PendingCN112163165ACharacterize popularityImprove recommendation effectDigital data information retrievalSpecial data processing applicationsEngineeringPrediction score
The embodiment of the invention provides an information recommendation method, device and equipment and a computer readable storage medium, and relates to the technical field of artificial intelligence. The method comprises the steps of obtaining at least one first type of feature and at least one second type of feature of each piece of to-be-recommended information in a to-be-recommended information set, and performing feature cross processing on the at least one first type of feature to obtain a first prediction score; performing feature fusion processing on the at least one second type of features to obtain a second prediction score; performing prediction result transformation processing on the first prediction score and the second prediction score to obtain a tendency score of the to-be-recommended information; and recommending at least one piece of to-be-recommended information in the to-be-recommended information set to a target object according to the tendency score of each piece of to-be-recommended information. Through the embodiment of the invention, the popularity degree of the to-be-recommended information on the specific crowd can be described more accurately, and theinformation recommendation effect on the specific crowd is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Converting program code of a multi-threaded program into program code causing less lock contentions
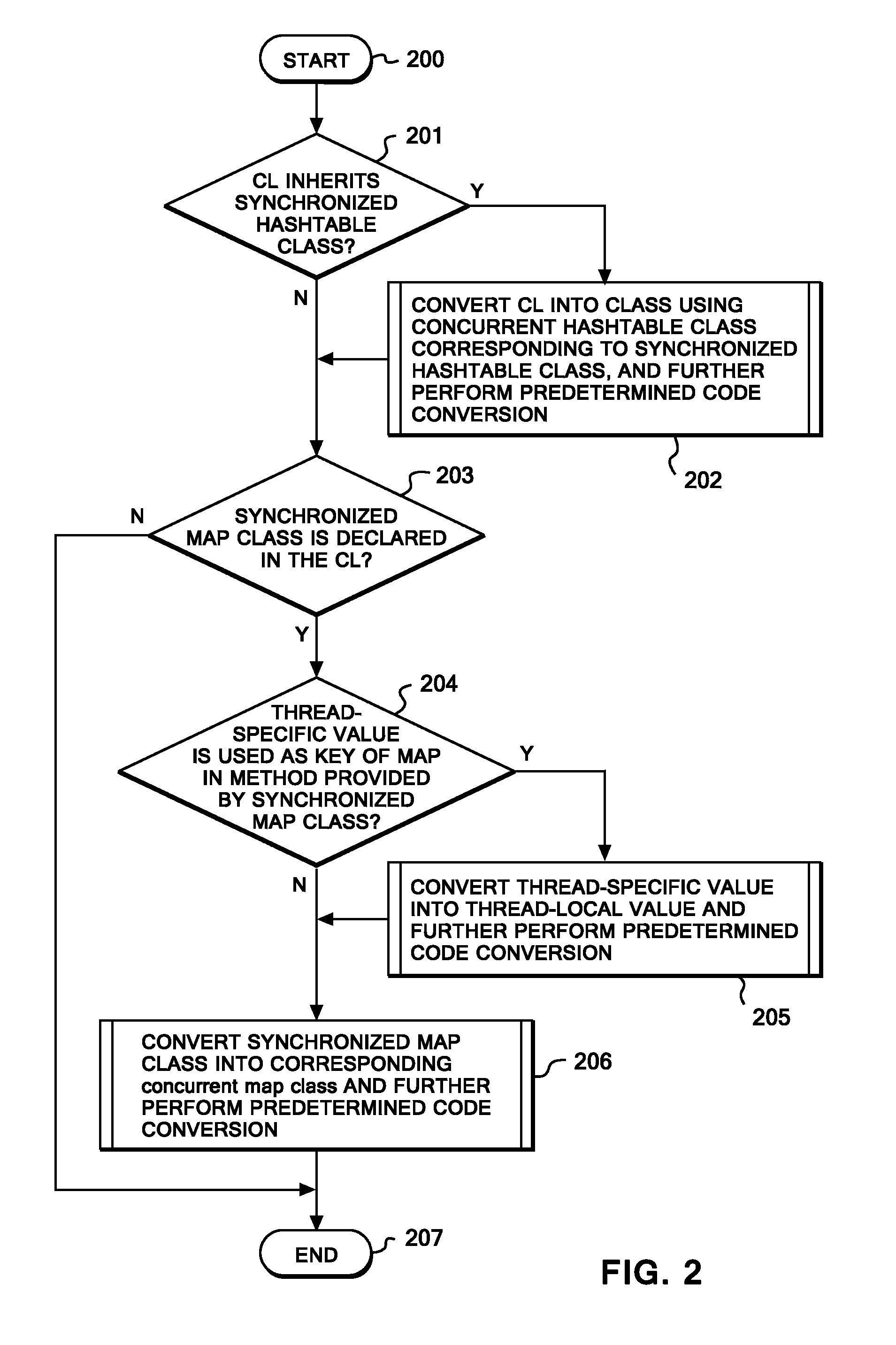
InactiveUS20100229160A1Less lock contentionShorter lock holding sectionSoftware engineeringProgram controlProgramming languageComputerized system
A method, computer system, and computer readable article of manufacture for converting a first program code in a multi-threaded program into a second program code which causes less lock contention. A processing unit determines whether the first program code includes either a first class having a method call to a third class that operates while taking synchronization by locking, or a second class inheriting a parent class that operates while taking synchronization by locking. If the first class, then it is converted into a class with a method call to a concurrent operation executable class that is functionally equivalent and a shorter lock holding section. If the second class, then it is converted into a class with a method call to a concurrent operation executable class that is functionally equivalent to that of the parent class, and a shorter lock holding section.
Owner:IBM CORP
Technique for transaction reconcilliation
InactiveUS20030204456A1Facilitate manual reconciliationEasy to implementComplete banking machinesFinanceDatabaseTransaction Type
A computerized accounting technique is provided. A record of a first type of transaction is identified based upon a record of a second type of transaction. The first type of transaction is a different type of transaction than the second type of transaction. Data is added to the record of the second type transaction based upon the identity of the first type transaction. Based upon this added data, the record of the second type transaction is reconciled with another record representing the second type transaction.
Owner:CHECKFREE SERVICES CORP
Compressed-file recovery method of APFS file system and storage medium
ActiveCN108108394AAchieve recoveryFile access structuresFile/folder operationsRestoration methodData mining
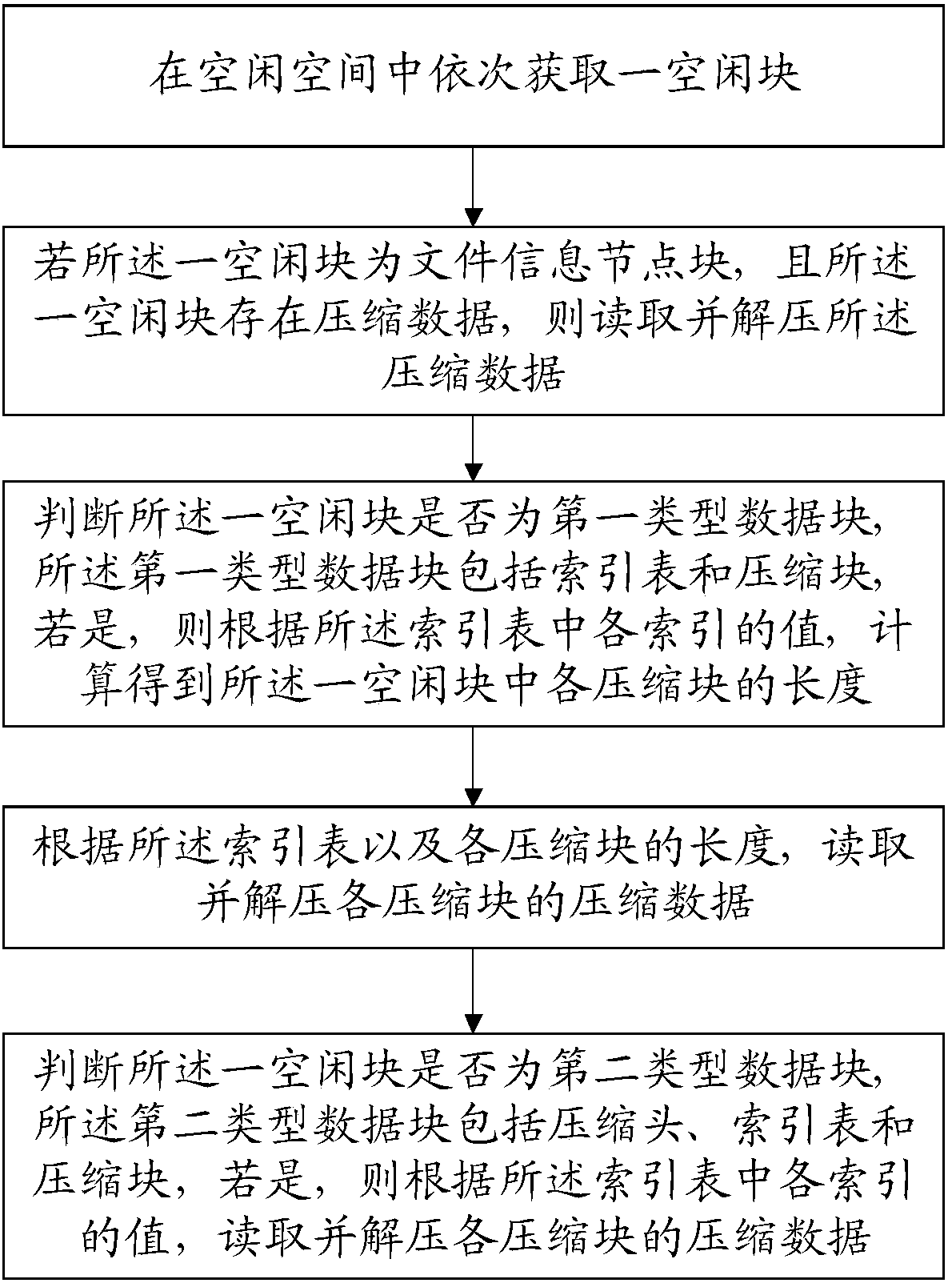
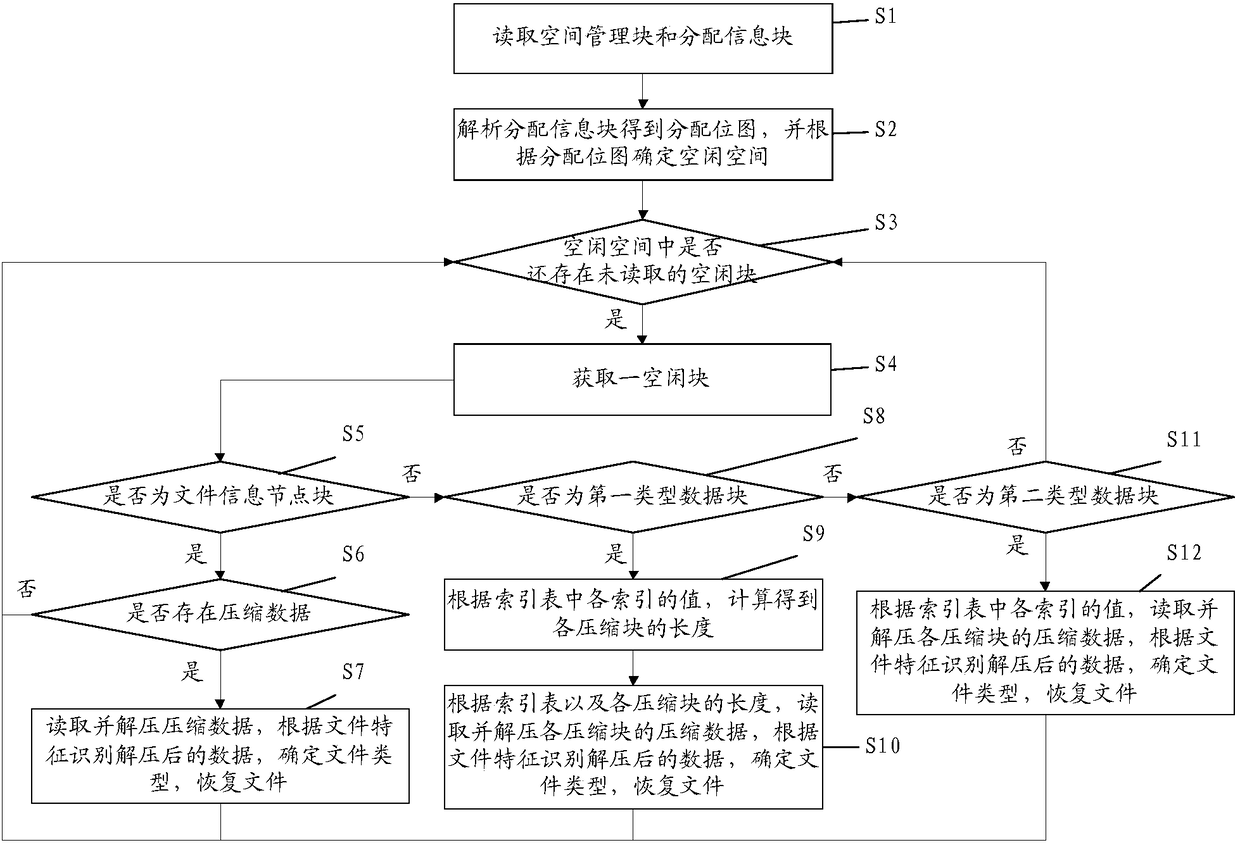
The invention discloses a compressed-file recovery method of an APFS file system and a storage medium. The method includes: sequentially acquiring an idle block in idle space; reading and decompressing compressed data if the idle block is a file information node block and the compressed data exist; judging whether the idle block is a first-type data block, and if yes, calculating and obtaining length of each compressed block according to a value of each index in an index table, wherein the first-type data block includes the index table and the compressed blocks; reading and decompressing compressed data of each compressed block according to the index table and the length of each compressed block; and judging whether the idle block is a second-type data block, and if yes, reading and decompressing compressed data of each compressed block according to a value of each index in an index table, wherein the second-type data block includes a compression header, the index table and the compressed blocks. The method can completely recover deleted compressed data in a case where the compressed data are not overwritten.
Owner:XIAMEN MEIYA PICO INFORMATION
Feature processing method and device for user classification model
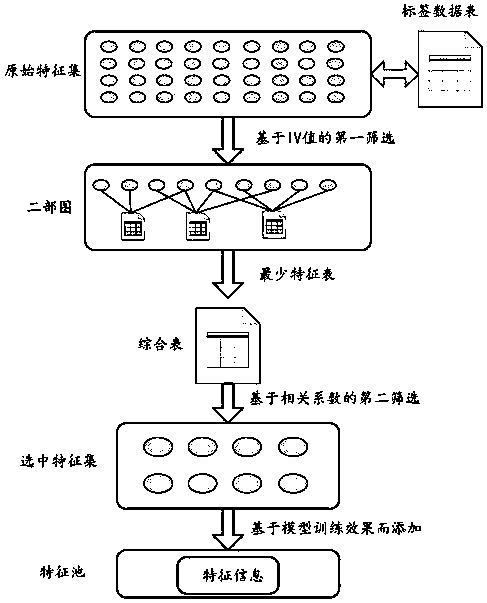
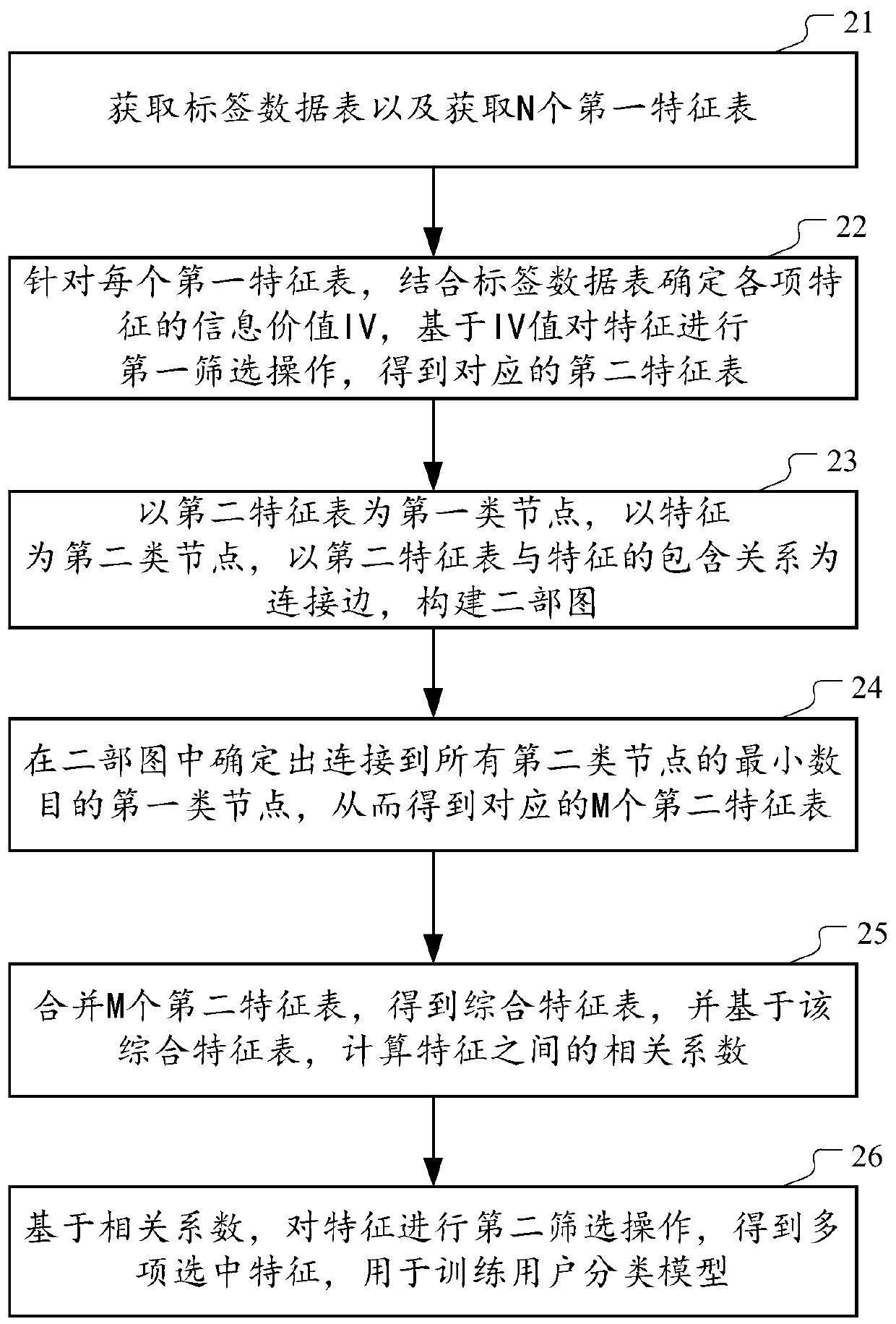
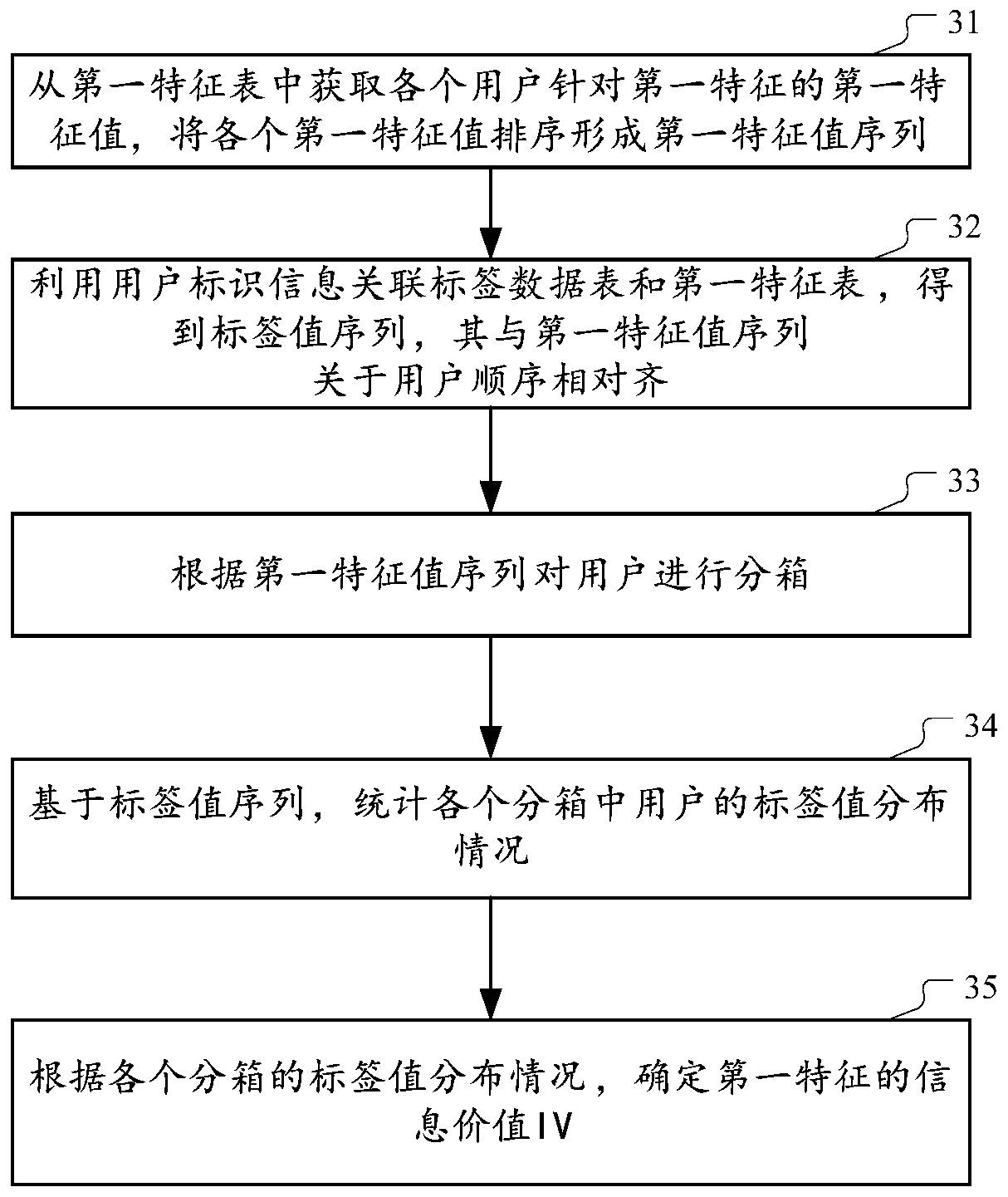
ActiveCN111291816ARapid modelingSpeed up the calculation processFinanceCharacter and pattern recognitionCorrelation coefficientLabeled data
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
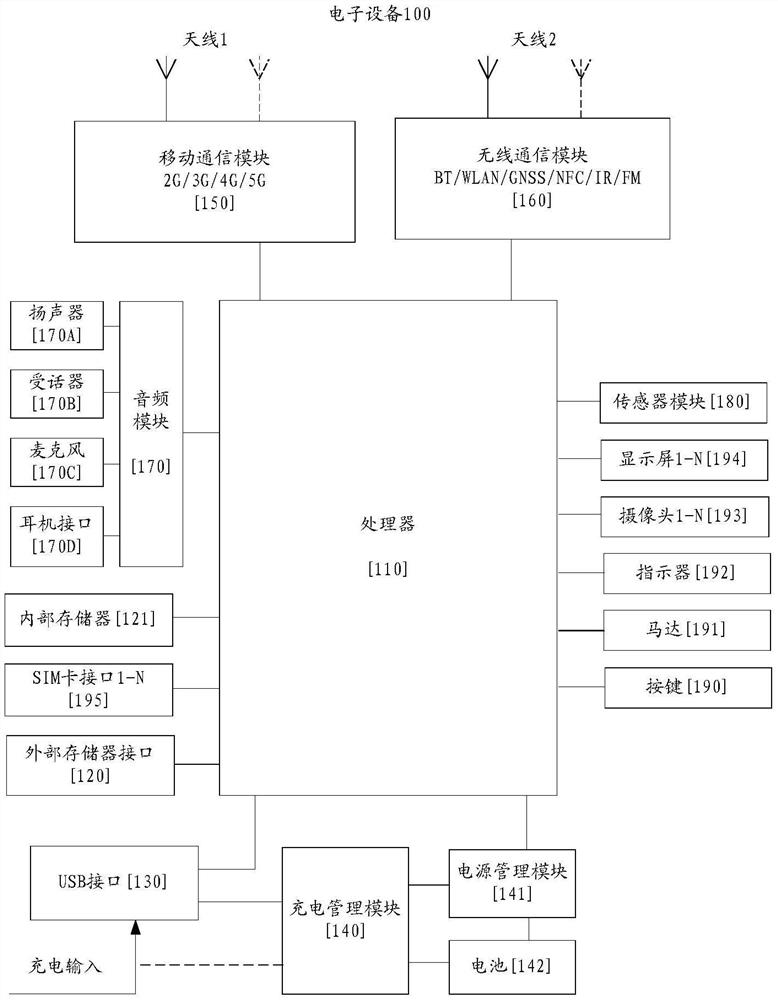
Application starting method and electronic equipment
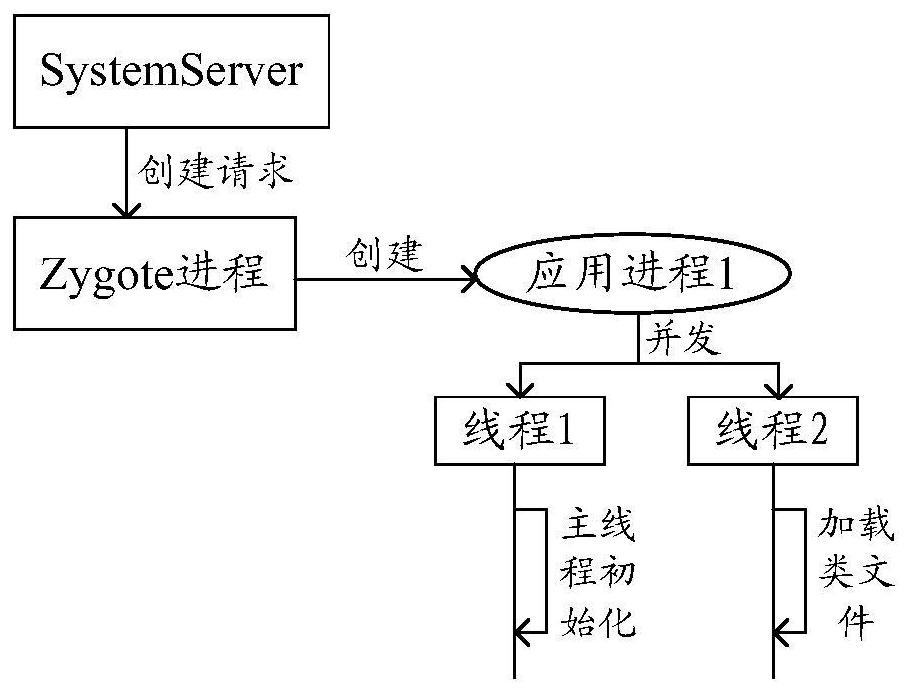
ActiveCN112527403AImprove user experienceReduce startup timeBootstrappingProgram loading/initiatingStart timeSoftware engineering
The invention provides an application starting method and electronic equipment, relates to the technical field of terminals, and aims to shorten the starting time consumed by cold starting of an application and improve the use experience of a user when the application is opened. The method comprises the steps that a system service process in the electronic equipment obtains a starting message of afirst application; in response to the starting message, the system service process sends a creation request of an application process to a daemon process, and the creation request comprises application information of the first application; in response to the creation request, the daemon process creates an application process for the first application, and the application process comprises a firstthread and a second thread; wherein the application process executes the first thread and the second thread in parallel, the first thread executes initialization of a main thread of the first application, and the second thread creates a first class loader according to the application information to load a class file of the first application; and the application process starts to run the code of the first application.
Owner:HONOR DEVICE CO LTD
Method and apparatus for classifying data using R-functions
ActiveUS7660775B2Digital computer detailsCharacter and pattern recognitionData setSystem combination
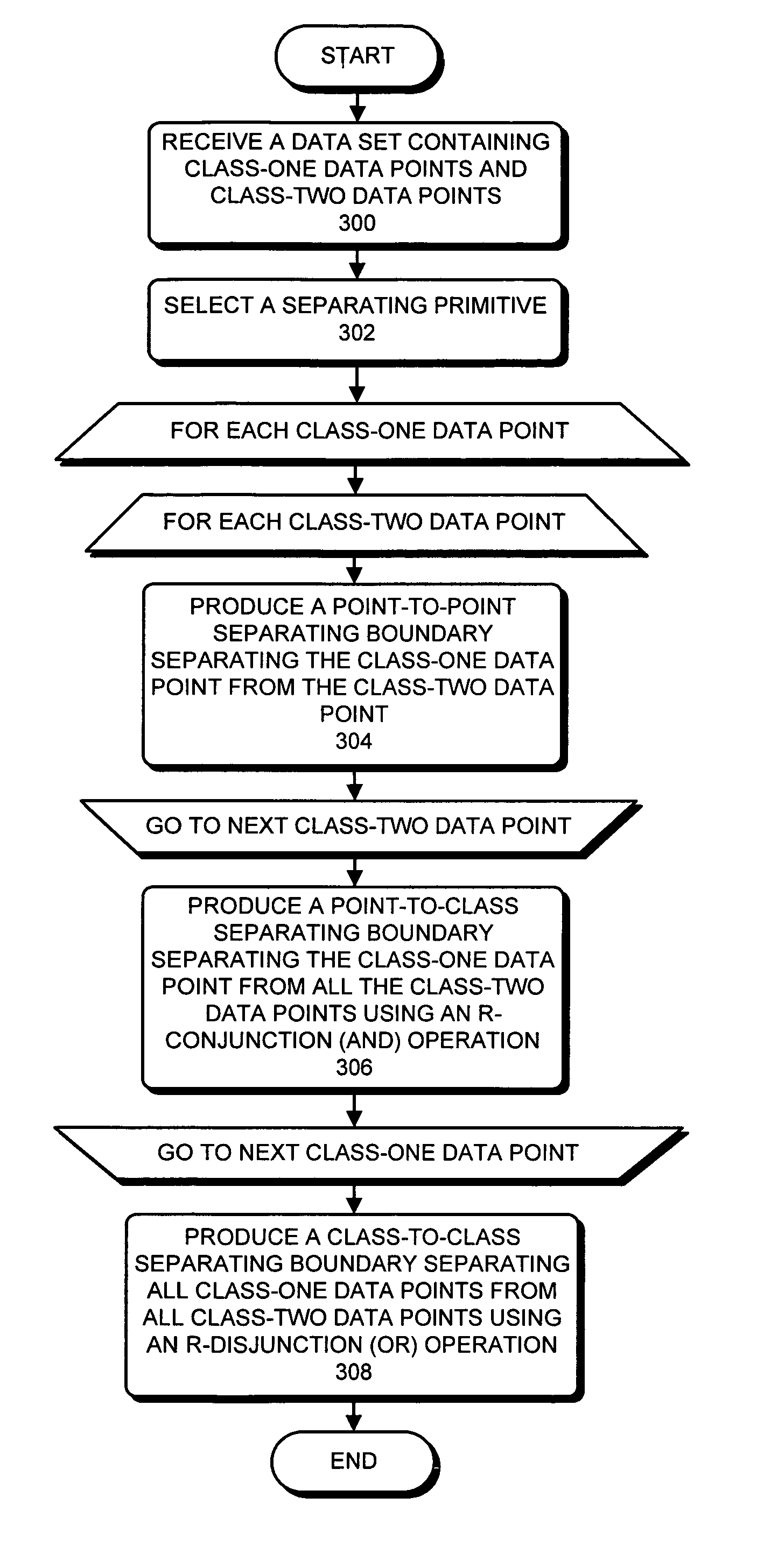
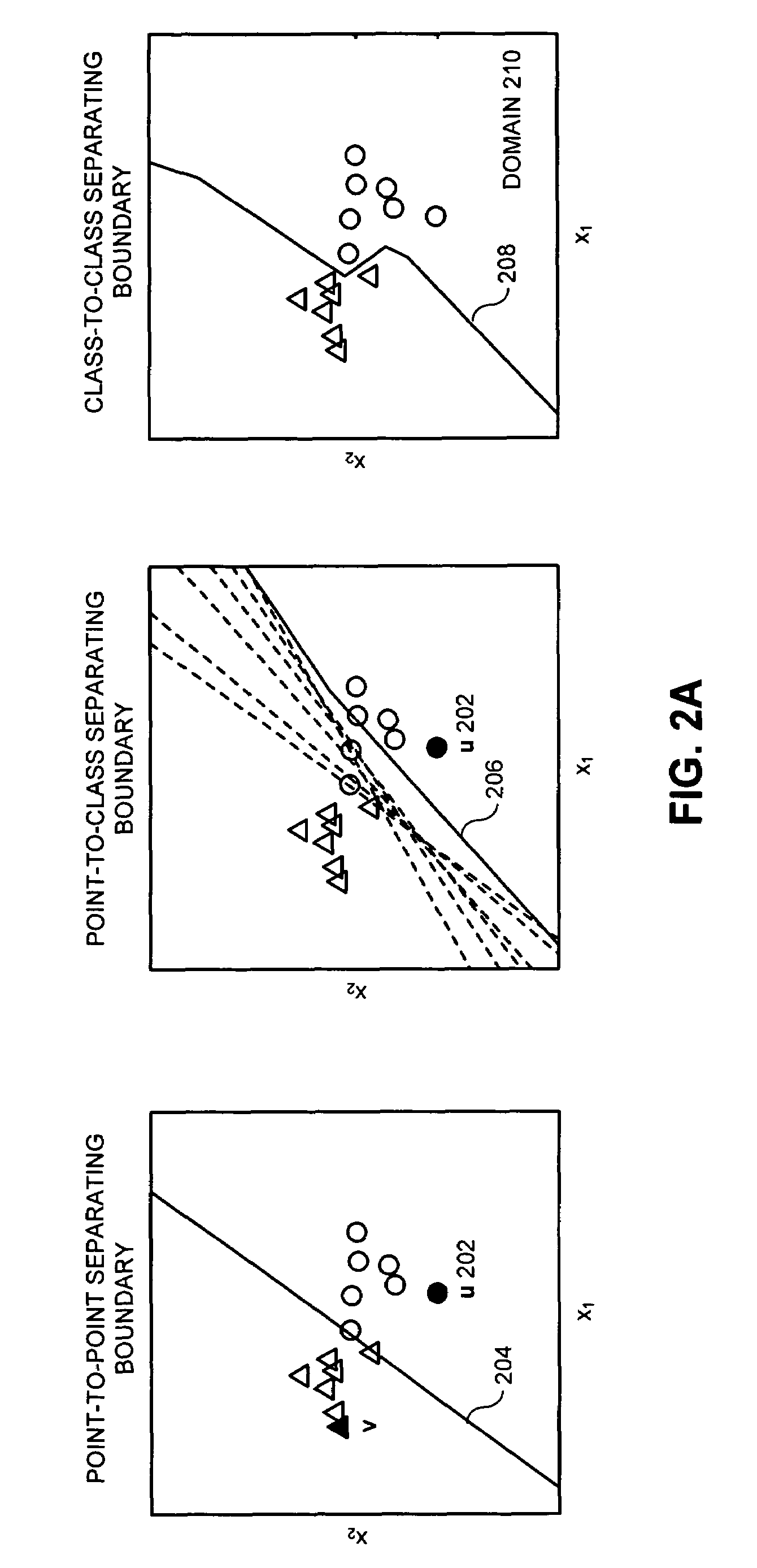
One embodiment of the present invention provides a system that constructs a classifier that distinguishes between different classes of data points. During operation, the system first receives a data set, which includes class-one data points and class-two data points. For each class-one data point in the data set, the system uses a separating primitive to produce a set of point-to-point separating boundaries, wherein each point-to-point separating boundary separates the class-one data point from a different class-two data point. Next, the system combines separating boundaries in the set of separating boundaries to produce a point-to-class separating boundary that separates the class-one data point from all of the class-two data points in the data set. Finally, the system combines the point-to-class separating boundaries for each of the class-one data points to produce a class-to-class separating boundary for the classifier that separates all of the class-one data points from all of the class-two data points in the data set.
Owner:ORACLE INT CORP
File system establishing method and device
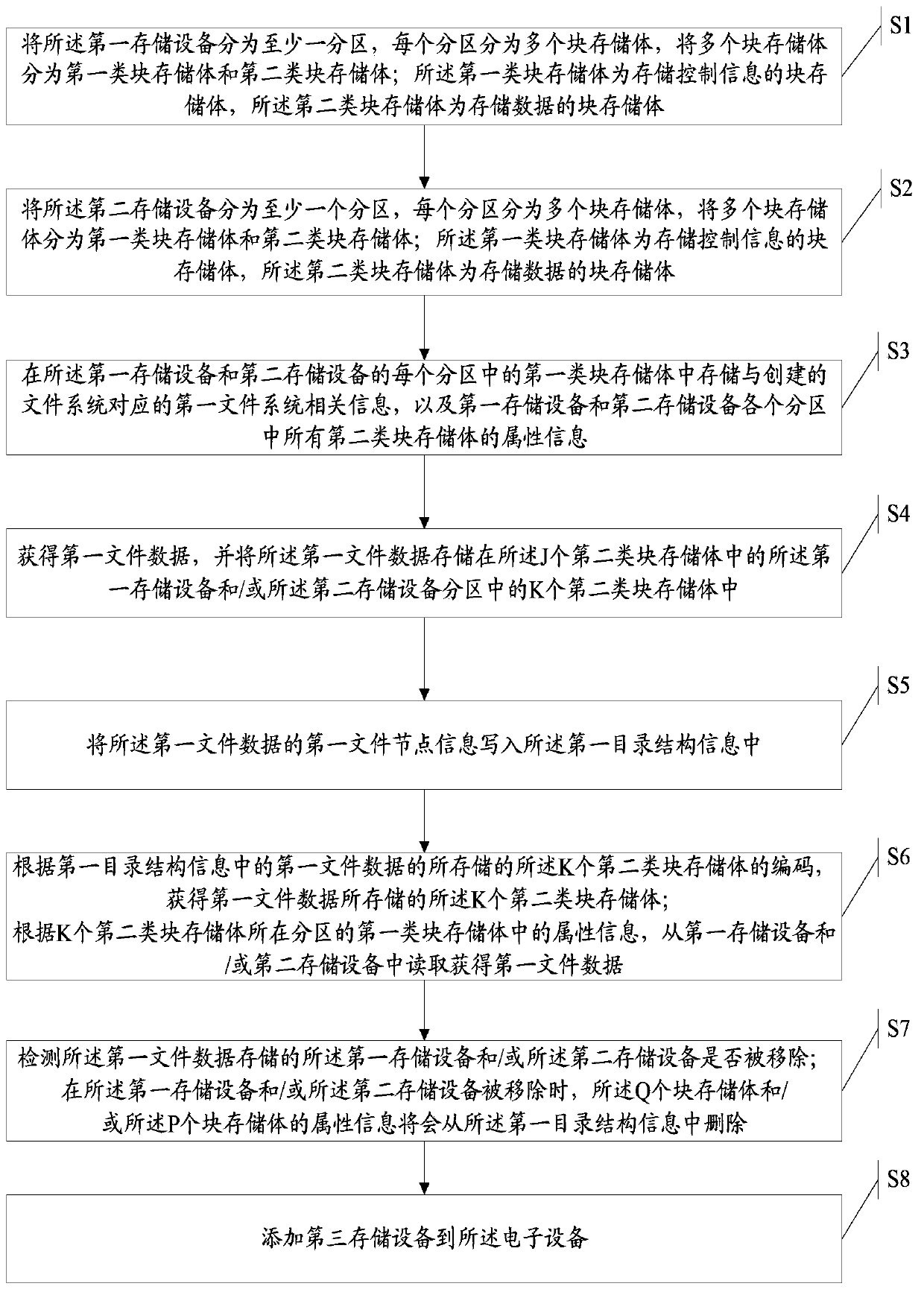
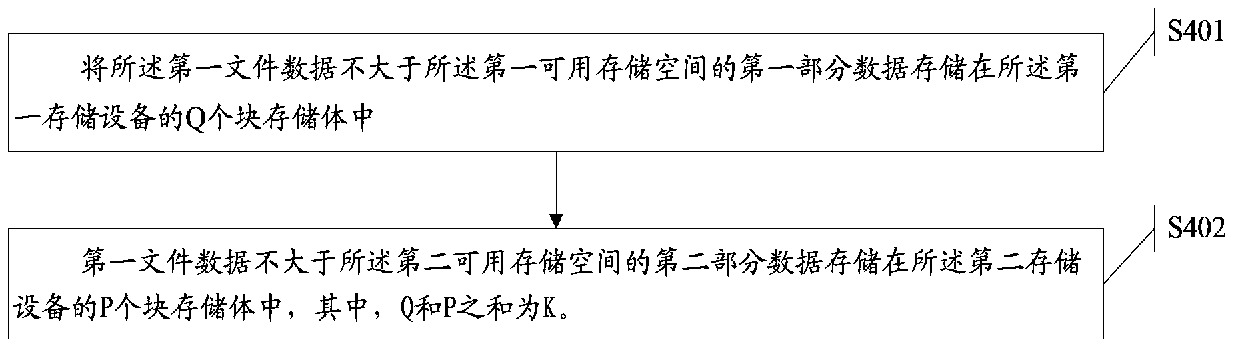
ActiveCN103678428ASolve the technical problem of not being able to create a file system on multiple storage devicesSolve the technical problem that the block storage bodies of multiple storage devices cannot be managed togetherSpecial data processing applicationsFile system functionsComputer hardwareFile system
The invention discloses a file system establishing method and device which are used for solving the technical problem that one file system can not be established on a plurality of storage devices and are applied to an electronic device. The electronic device at least comprises a first storage device and a second storage device; the first storage device and the second storage device are respectively provided with at least one subarea, and each subarea is provided with a plurality of storage blocks which are divided into first-class storage blocks and second-class storage blocks; the first-class storage blocks are used for storing control information, and the second-class storage blocks are used for storing data; information relevant to a first file system of established file systems, attribute information of all the second-class storage blocks in the first storage device and attribute information of all the second-class storage blocks in the second storage device are stored in the first-class storage blocks in each subarea of the first storage device and the first-class storage blocks in each subarea of the second storage device.
Owner:LENOVO (BEIJING) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com