Patents
Literature
378 results about "Daemon" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In multitasking computer operating systems, a daemon (/ˈdiːmən/ or /ˈdeɪmən/) is a computer program that runs as a background process, rather than being under the direct control of an interactive user. Traditionally, the process names of a daemon end with the letter d, for clarification that the process is in fact a daemon, and for differentiation between a daemon and a normal computer program. For example, syslogd is the daemon that implements the system logging facility, and sshd is a daemon that serves incoming SSH connections.
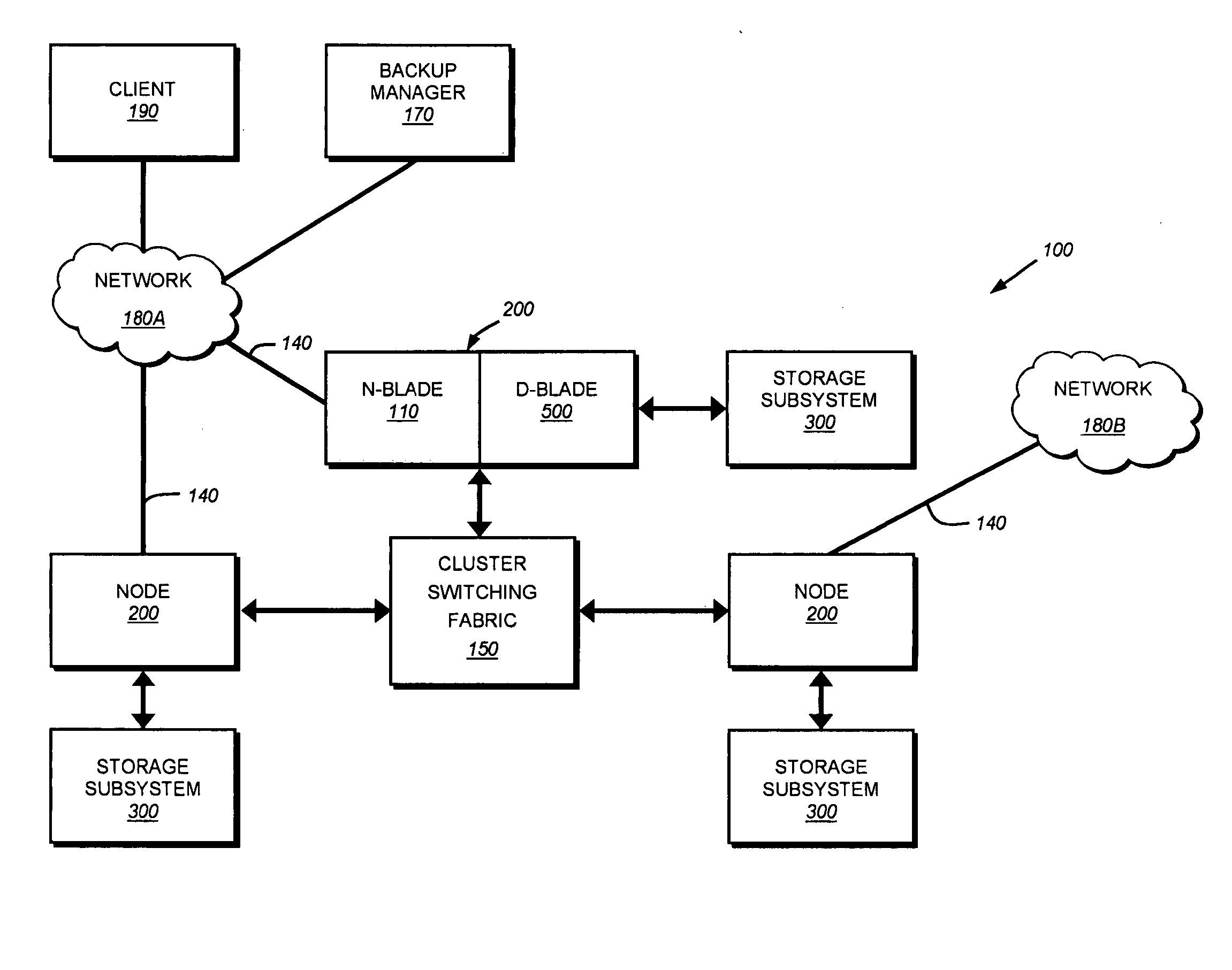
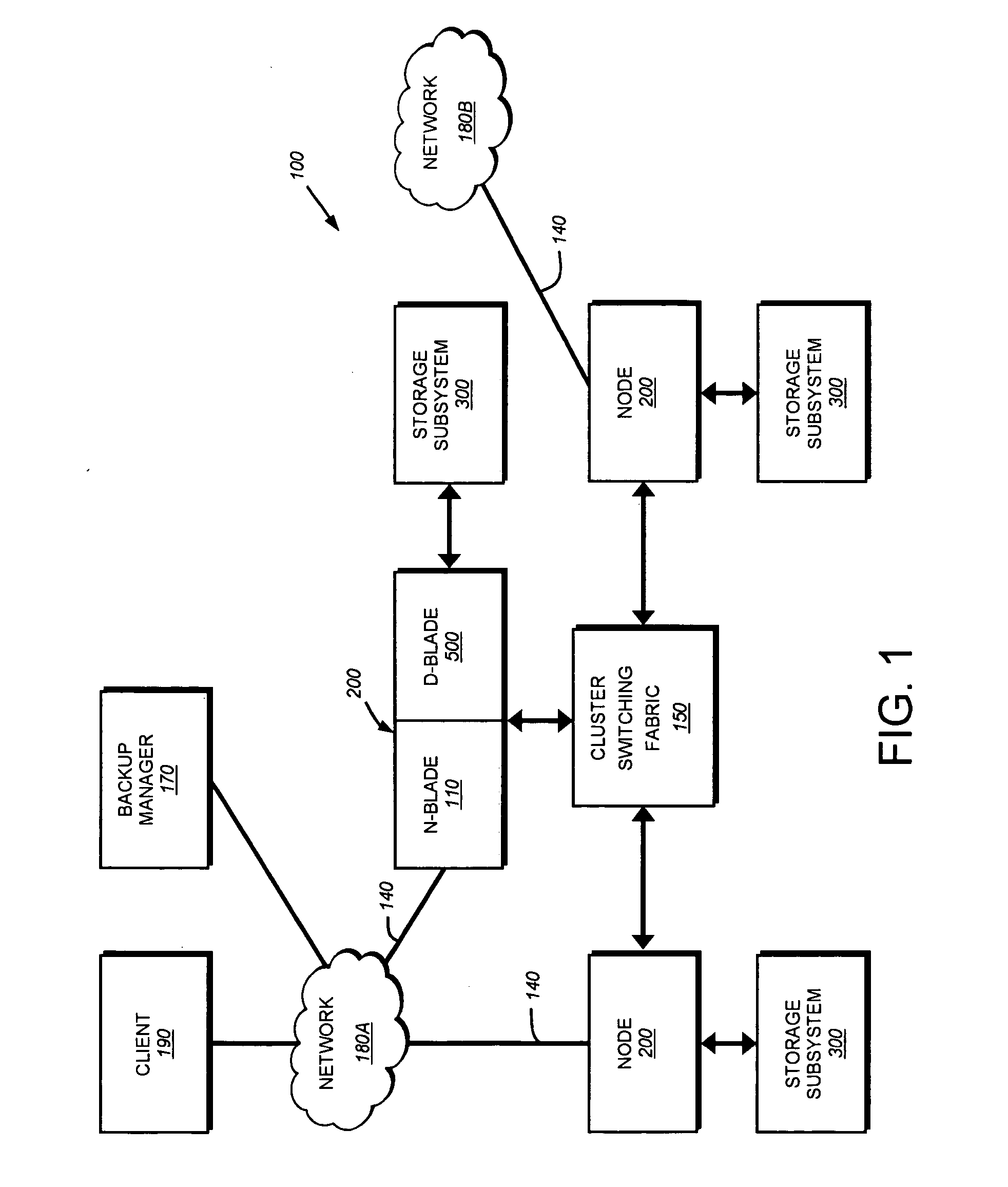
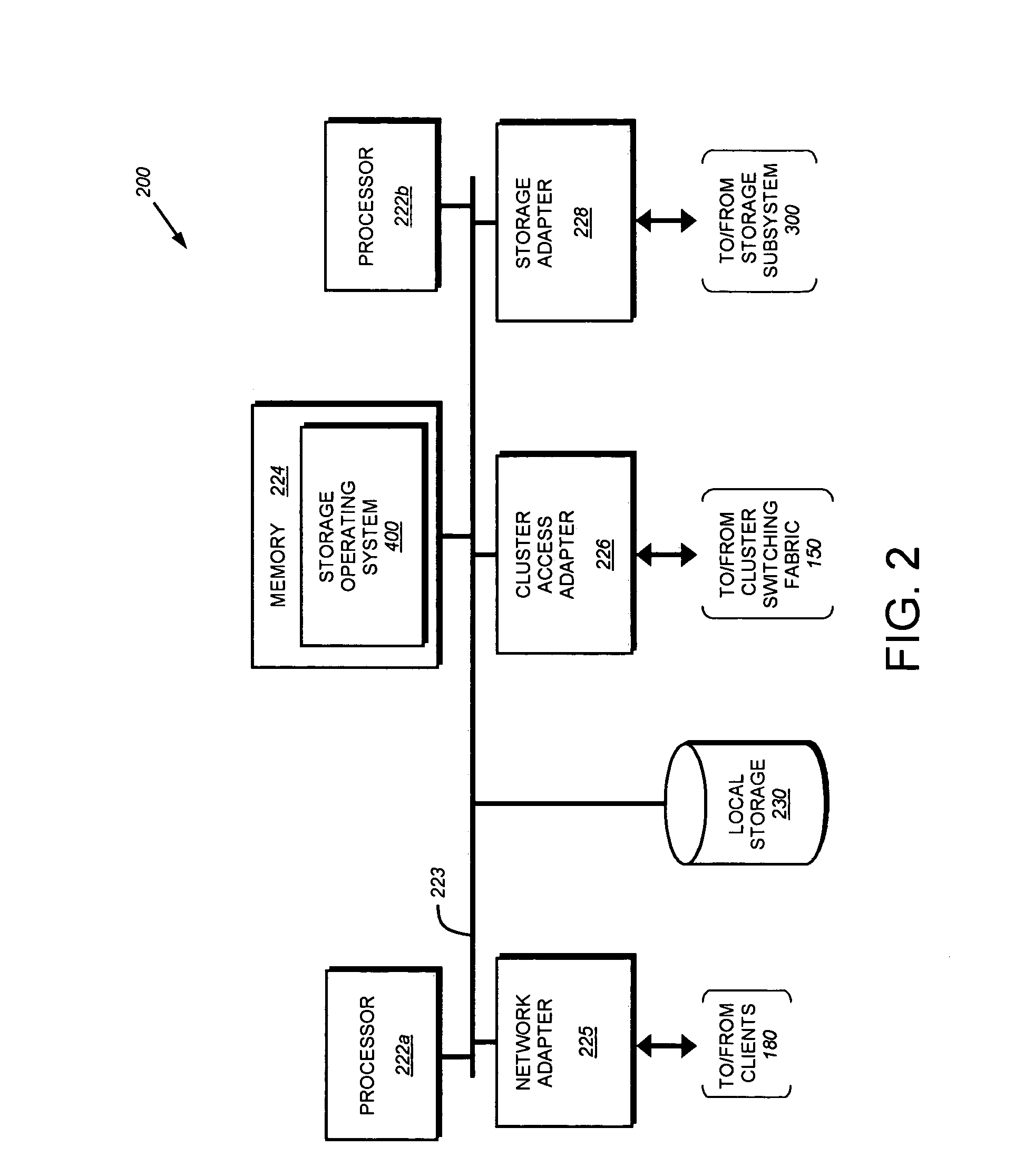
System and method for proxying network management protocol commands to enable cluster wide management of data backups
ActiveUS20060248294A1Overcome disadvantagesError detection/correctionTransmissionNetwork managementDistributed computing
A system and method enables cluster-wide management of backup operations issued by one or more backup managers to nodes of a cluster using a network management protocol, such as NDMP. An NDMP daemon executing on each node is extended to include a processing module and a backup module. The processing module interfaces with a backup manager to interpret the backup operation and, if necessary, forward (proxy) that operation to another NDMP daemon on another node of the cluster for processing in accordance with cluster's unified namespace.
Owner:NETWORK APPLIANCE INC
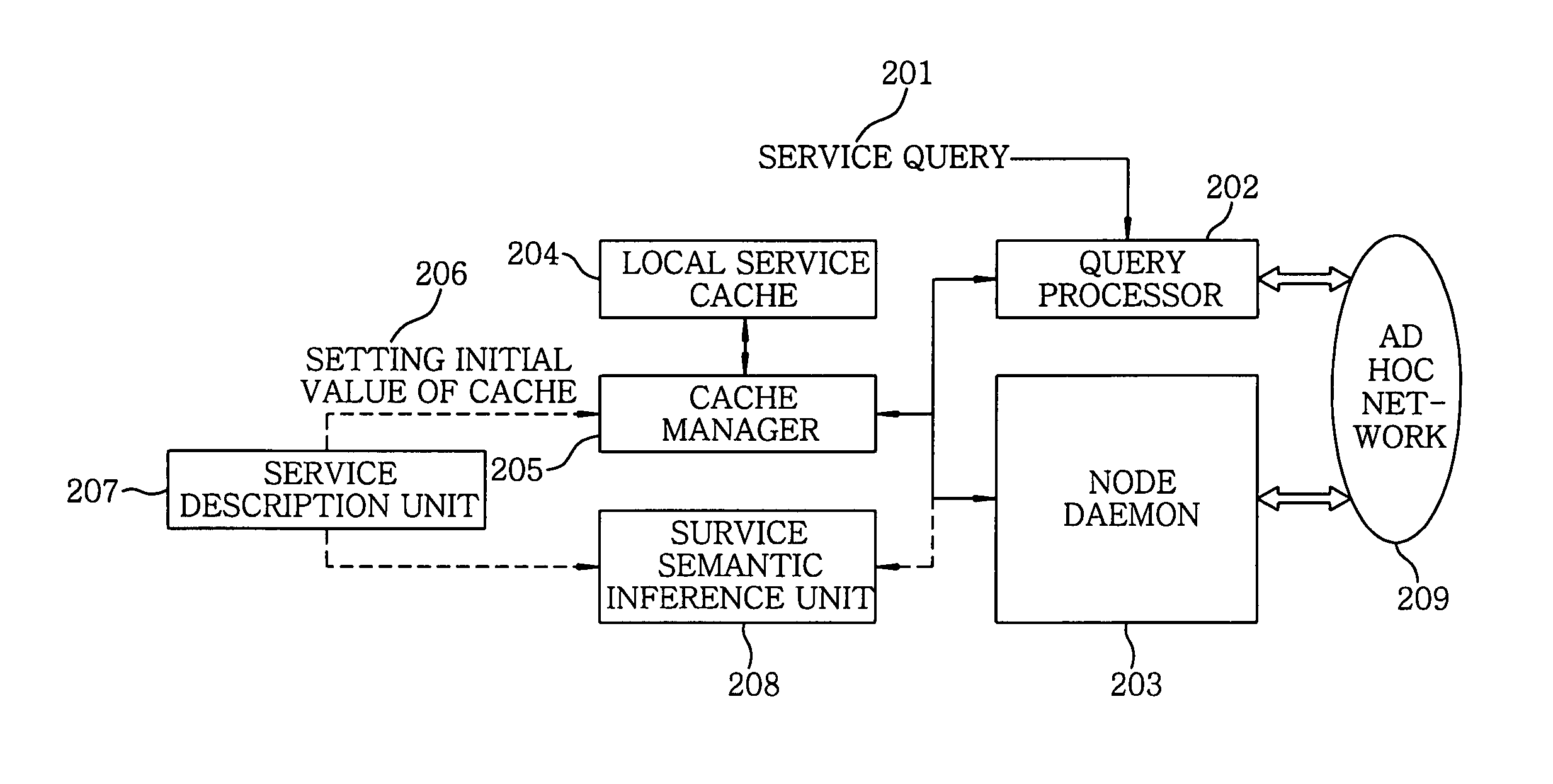
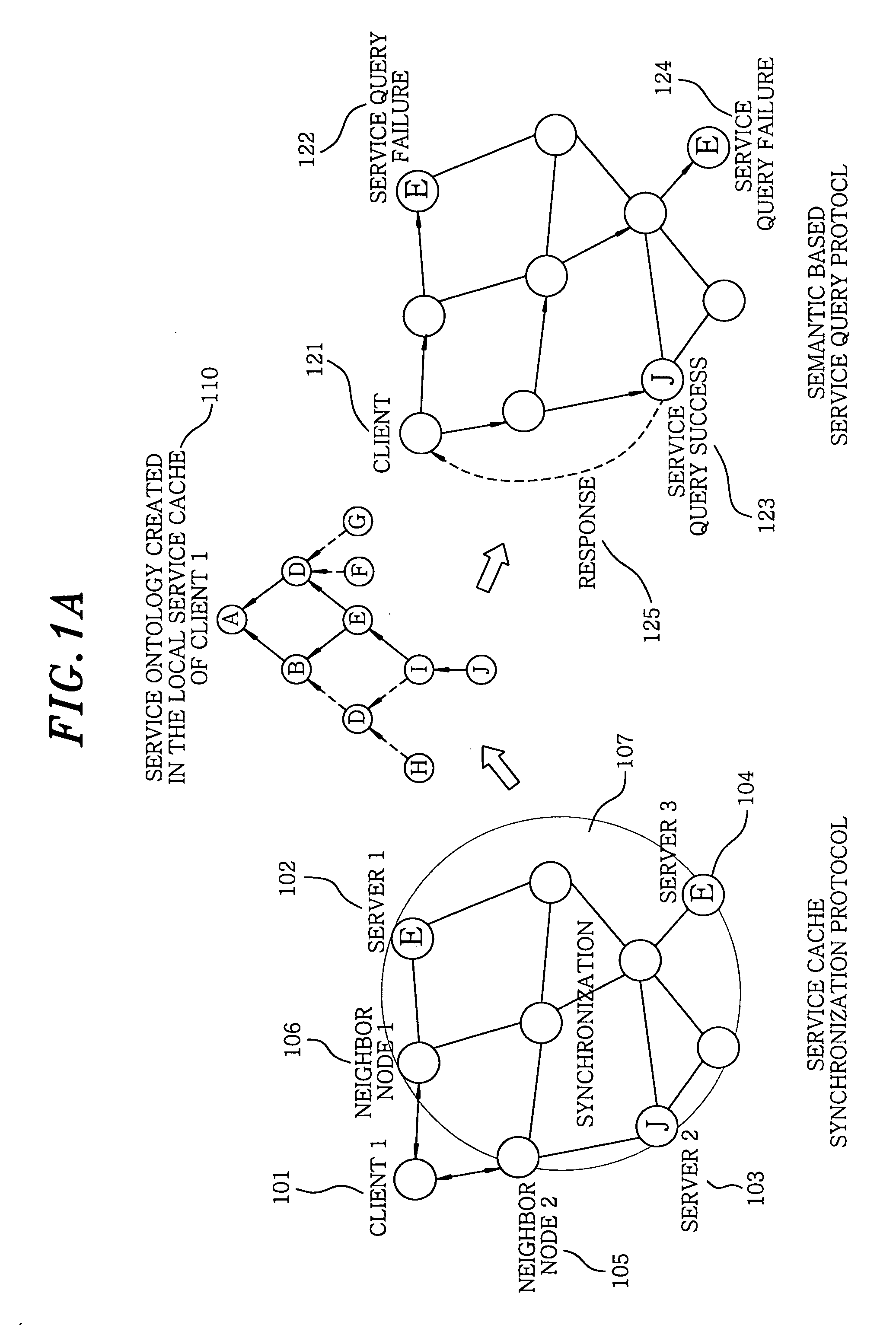
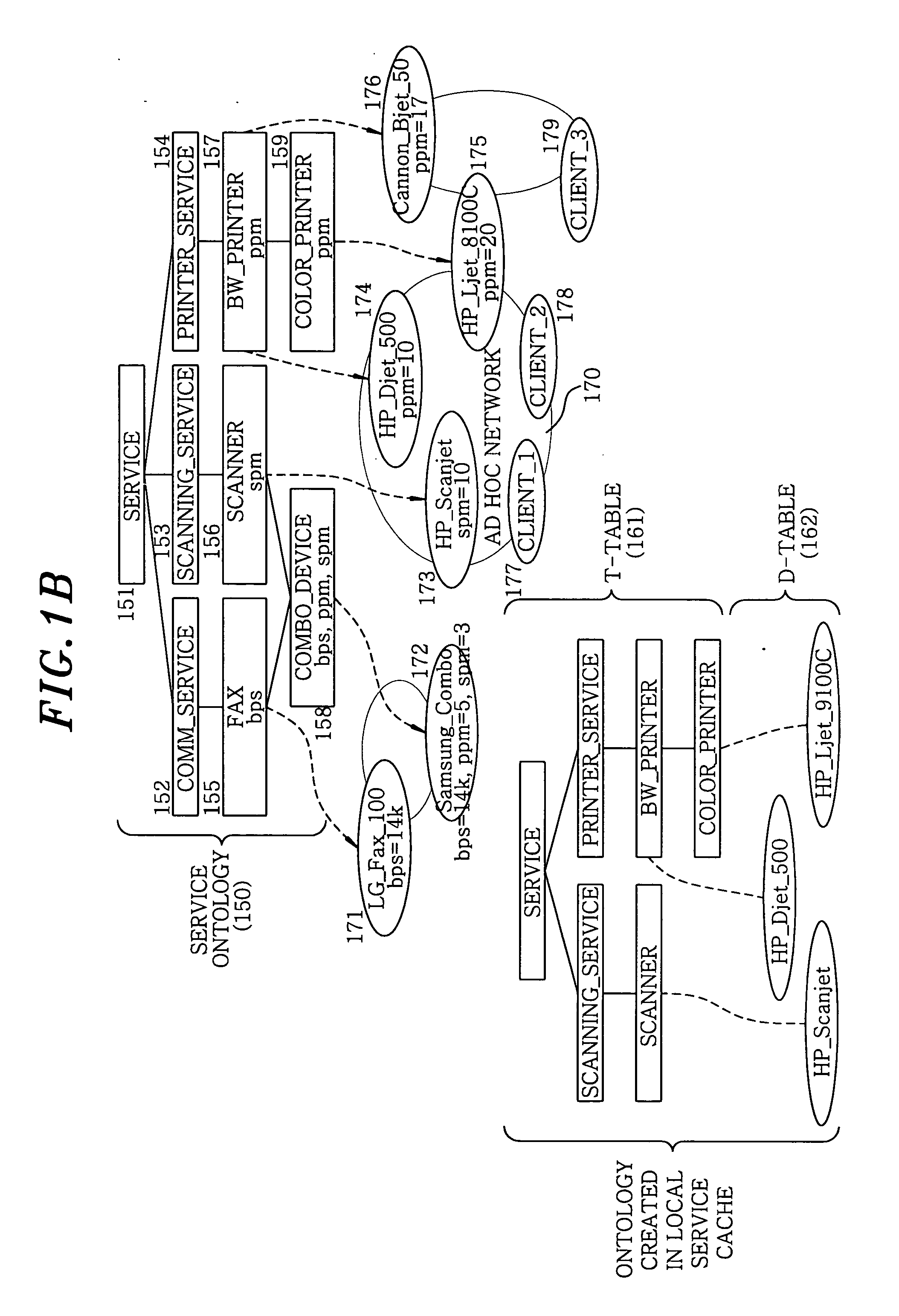
Ontology-based service discovery system and method for ad hoc networks
An ontology-based ad hoc service discovery system includes a local service cache, a cache manager, a service description unit, a query processor, a service semantic inference unit and a node daemon. The local service cache restores a service ontology by collecting class information of all services advertised on an ad hoc network and stores the service ontology. The cache manager manages the local service cache and performs various preset operations on the cache. The service description unit stores a description of a corresponding service for use in initializing the local service cache. The query processor starts performing a semantic based service query protocol by receiving a service query from a user or an application program. The service semantic inference unit inspects whether the service query transmitted from a client is coincident with the content of the service. The node daemon performs a service cache synchronization protocol with neighboring nodes.
Owner:ELECTRONICS & TELECOMM RES INST
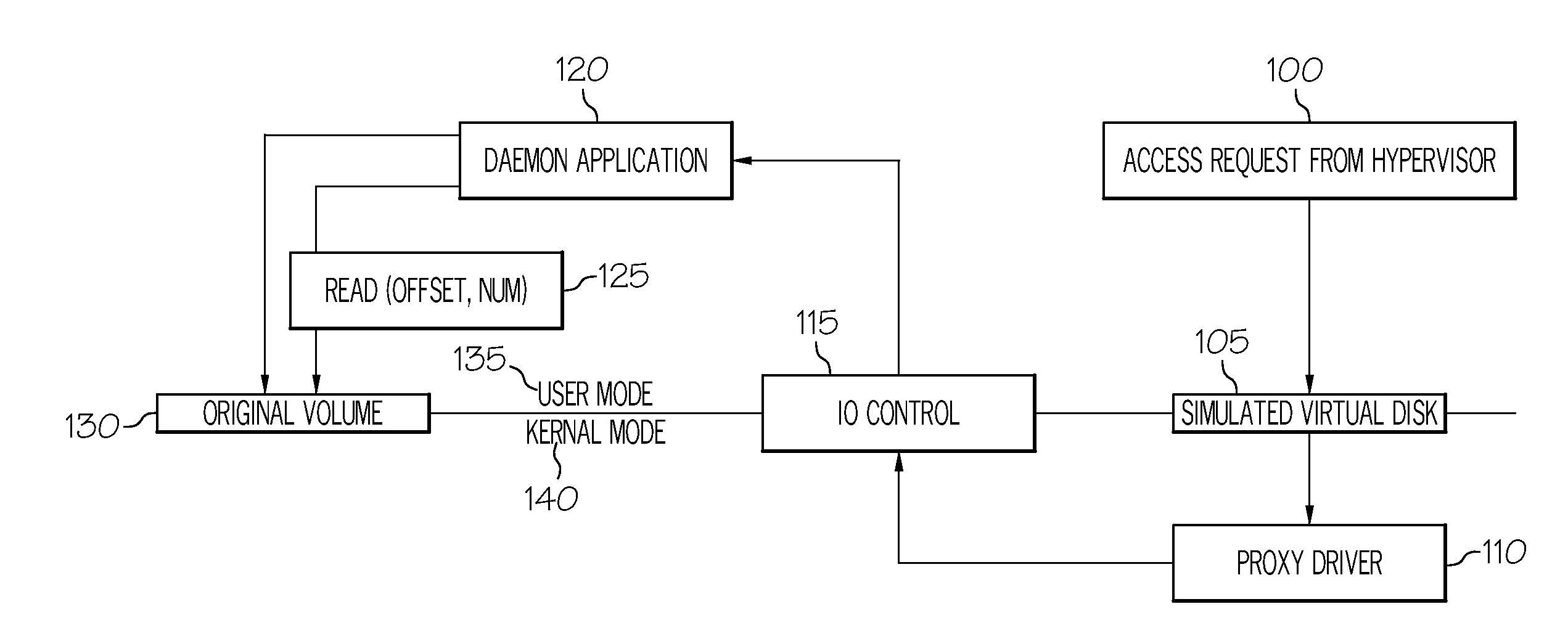
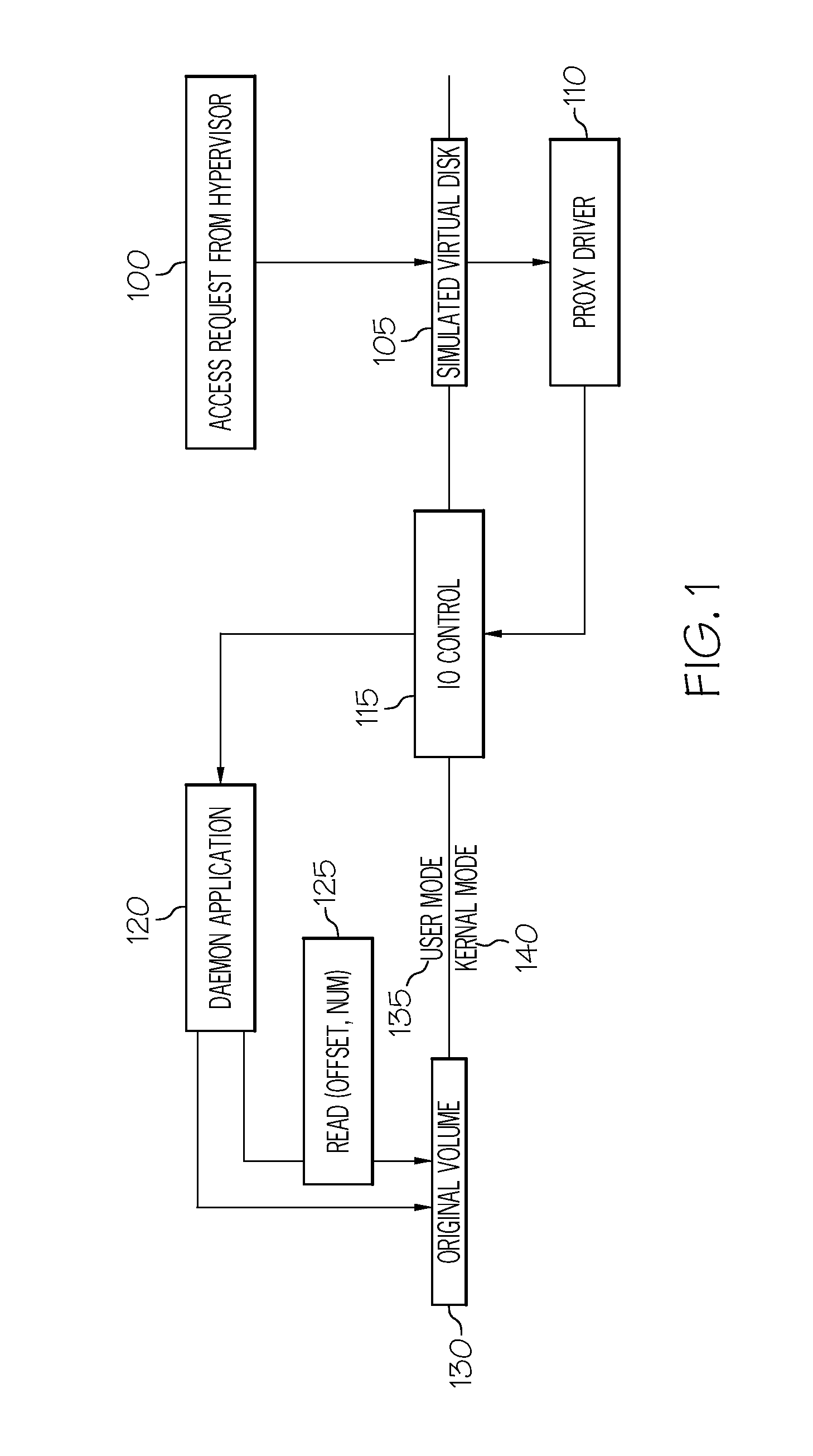
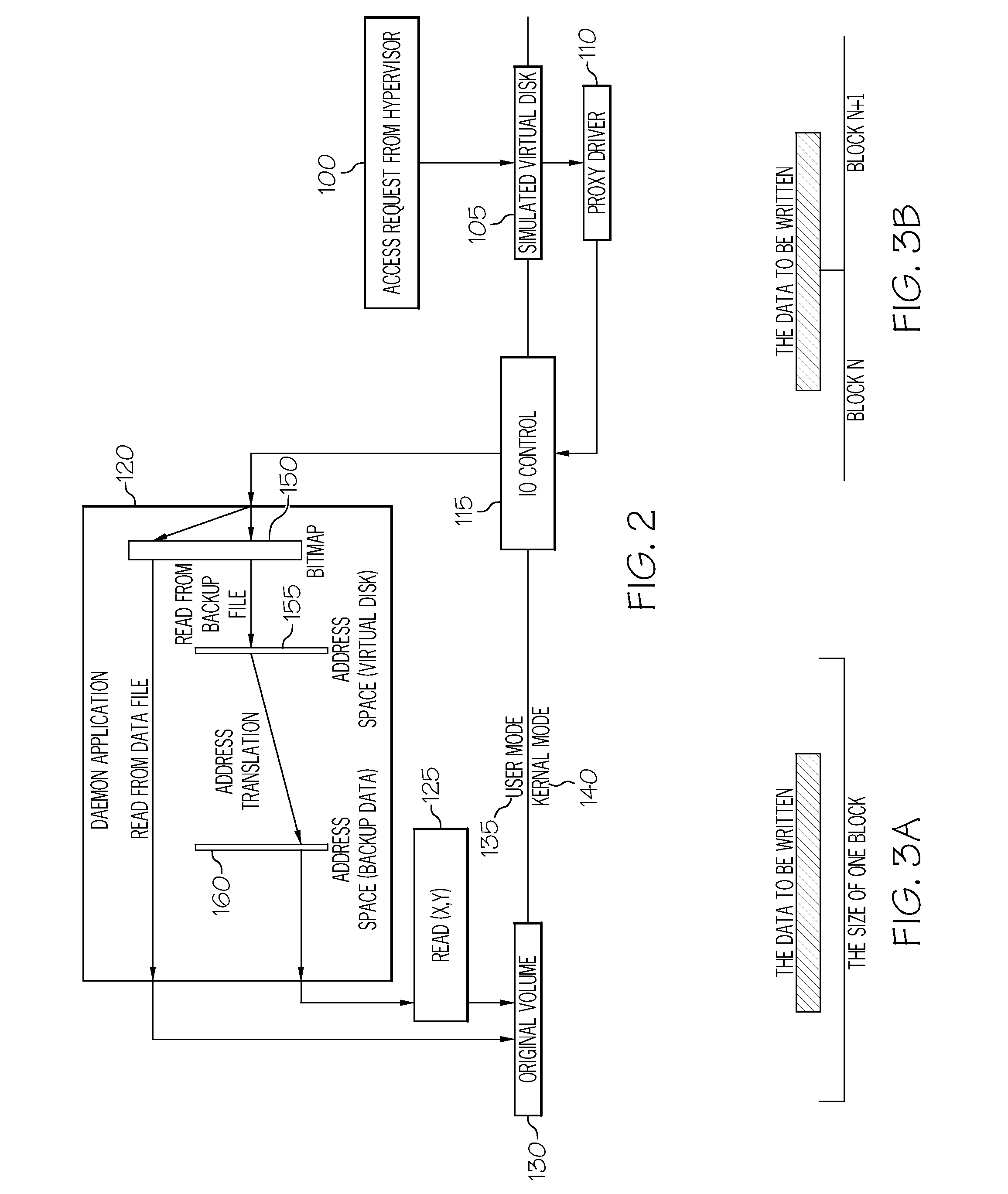
Data recovery using conversion of backup to virtual disk
A system includes a proxy processor configured to simulate a virtual disk, and a daemon processor in communication with the proxy processor and a backup repository. The proxy processor is configured to receive from an application a read request or a write request and to direct the read request or the write request to the daemon processor. The daemon processor is configured to receive the read request from the proxy processor and to access the backup repository or the simulated virtual disk, and to receive the write request from the proxy processor and to write data in the write request to the simulated virtual disk.
Owner:CA TECH INC
Parallel-aware, dedicated job co-scheduling method and system
InactiveUS20050131865A1Improve performanceImprove scalabilityProgram initiation/switchingSpecial data processing applicationsExtensibilityOperational system
In a parallel computing environment comprising a network of SMP nodes each having at least one processor, a parallel-aware co-scheduling method and system for improving the performance and scalability of a dedicated parallel job having synchronizing collective operations. The method and system uses a global co-scheduler and an operating system kernel dispatcher adapted to coordinate interfering system and daemon activities on a node and across nodes to promote intra-node and inter-node overlap of said interfering system and daemon activities as well as intra-node and inter-node overlap of said synchronizing collective operations. In this manner, the impact of random short-lived interruptions, such as timer-decrement processing and periodic daemon activity, on synchronizing collective operations is minimized on large processor-count SPMD bulk-synchronous programming styles.
Owner:LAWRENCE LIVERMORE NAT SECURITY LLC
Failure detection and fault tolerance method and failure detection and fault tolerance system for real-time cloud platform
ActiveCN103716182ANo loss of stateComprehensive detection effectData switching networksFault toleranceReal time services
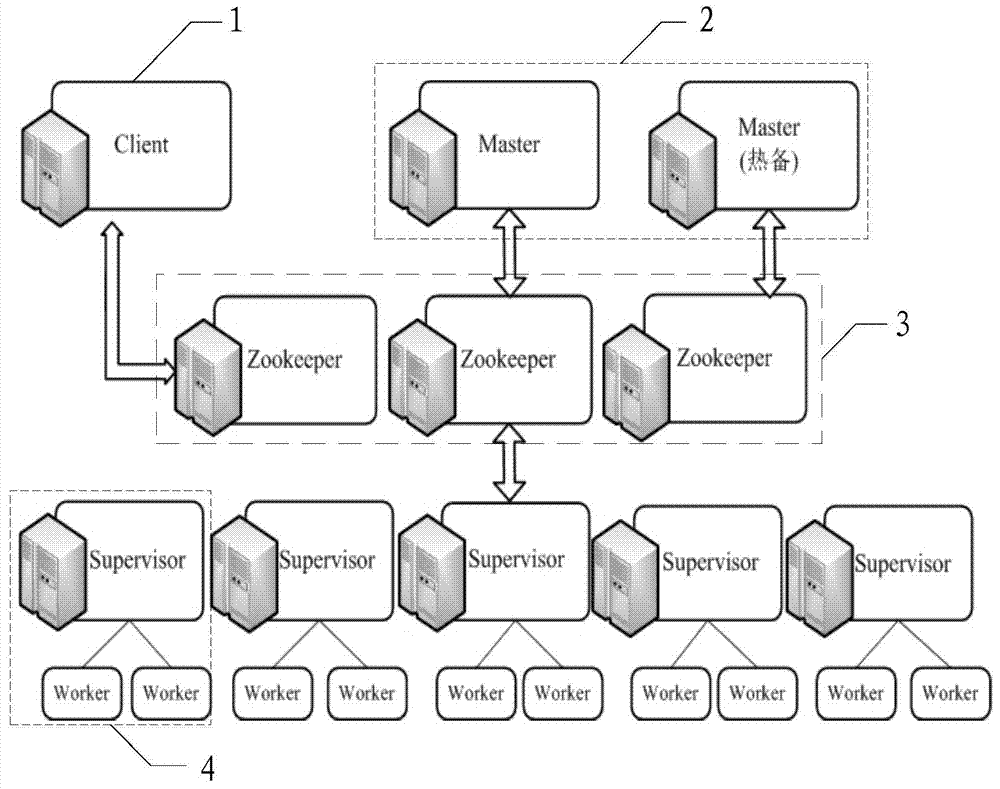
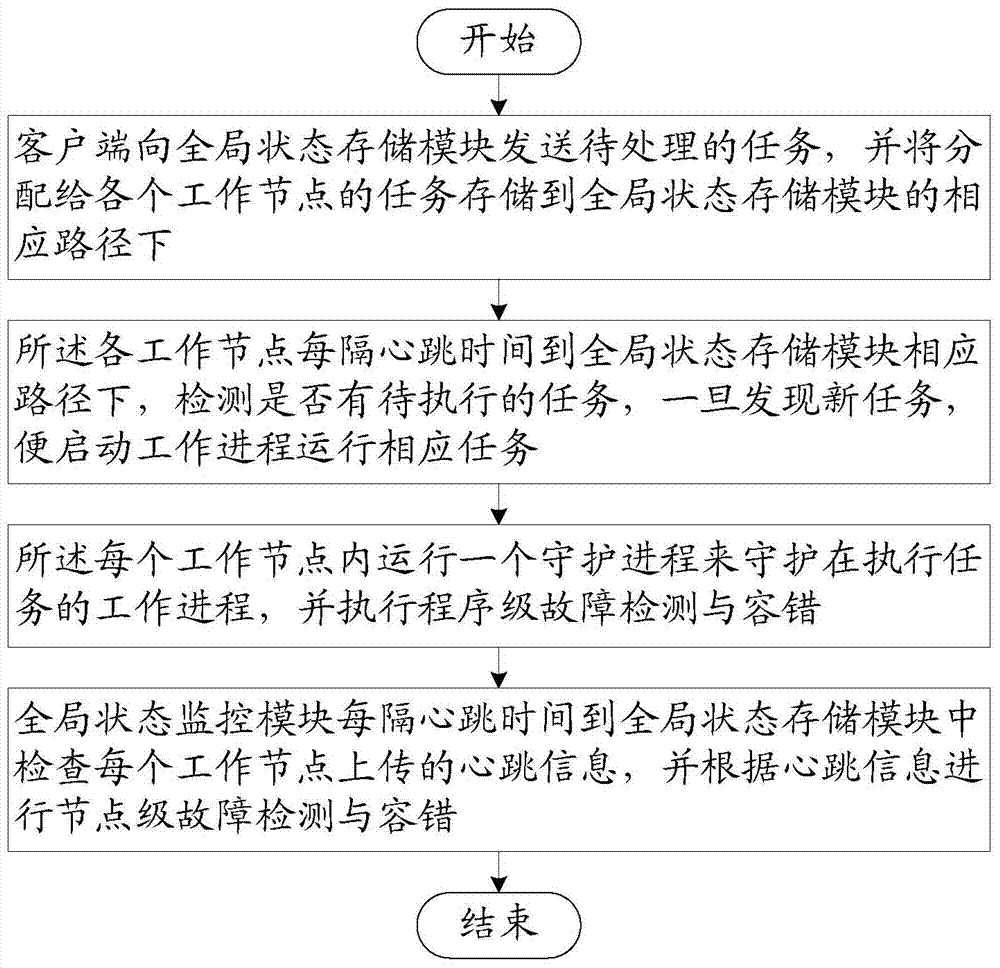
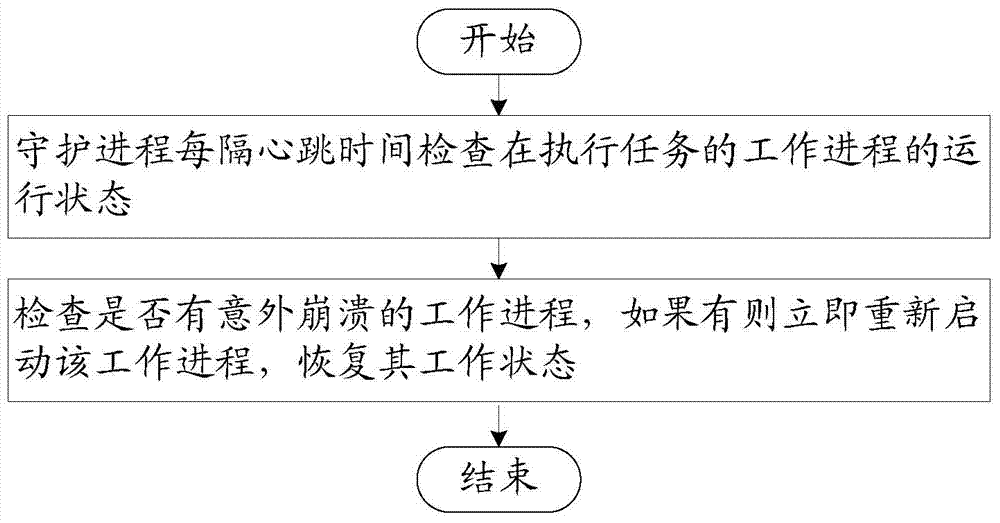
The invention relates to a failure detection and fault tolerance method and a failure detection and fault tolerance system for a real-time cloud platform. The system comprises a client used for sending a command, summiting a task and storing tasks assigned to working nodes in corresponding paths, a global state monitoring module used for monitoring the operation state of the working nodes, carrying out node-level failure detection and fault tolerance according to heartbeat information uploaded by the working nodes and performing migration of a task in a failure node, a global state storage module used for storing the working state and heartbeat information of the global state monitoring module and the working nodes, and working nodes used for performing a task, running a daemon process to guard a work process and performing program-level failure detection and fault tolerance. State information of a whole cluster is all stored in a Zookeeper system, a stateless architecture of the nodes is realized, a node failure does not cause state loss, the system has a perfect failure detection and fault tolerance mechanism, multilevel fault tolerance is realized, and uninterrupted operation of real-time services is guaranteed.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Computerized system and method for handling network traffic
ActiveUS20070168547A1Eliminate the problemMultiple digital computer combinationsTransmissionTraffic capacityComputerized system
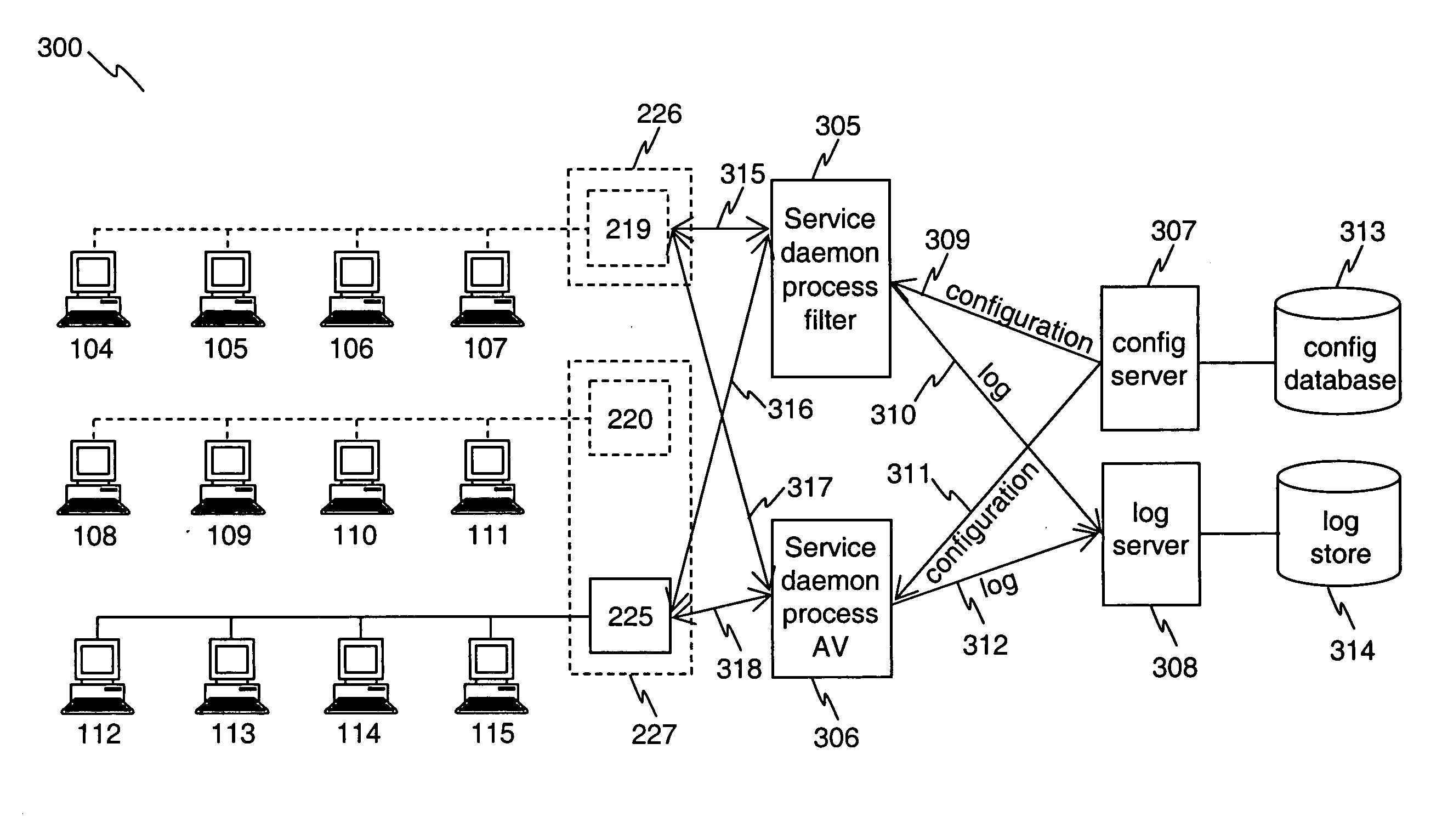
A computerized system and method for processing network content associated with multiple virtual domains. The processing may include anti-malware scanning and / or content filtering. The content associated with multiple domains may be processed in the same daemon process. In response to connection requests from virtual domains, the service process creates separate sockets to communicate with each virtual domain. A global configuration management module is used to provide configuration parameters for each session to the service process. A logging manager processes both the global logs and the logs from each virtual domain. Alternatively, the service process may initiate other service processes to handle incoming connections from one or more virtual domains, in order to better utilize resources in a multiple-CPU environment. Different service processes may be used to handle various aspects of content processes, for example one process may handle anti-malware scanning, while another process may handle content filtering.
Owner:FORTINET
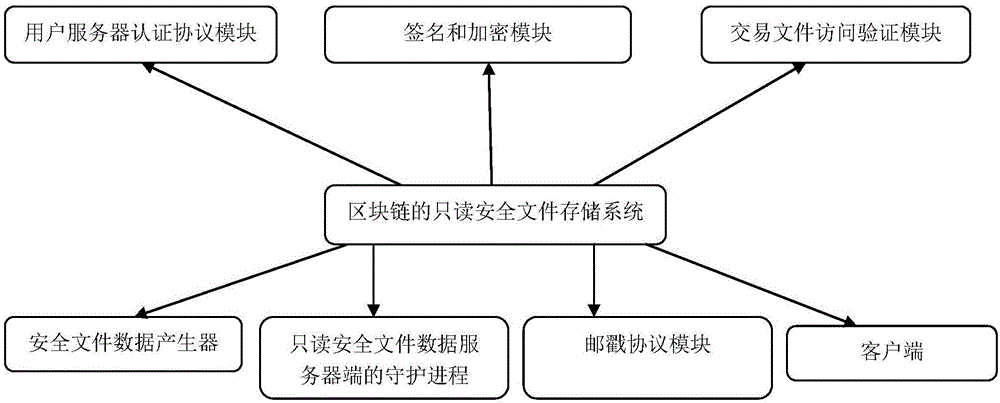
Read-only security file storage system for block chain and method thereof
InactiveCN106295401AFaster and more complete recoveryExtended storage timeInput/output to record carriersDigital data protectionData integrityCiphertext
The invention provides a read-only security file storage system for a block chain. The system comprises: (1) a user server authentication protocol module used for executing a mutual authentication protocol between a user and a server via a self-certified path name; (2) a signature and encryption module used for correctly encrypting a transaction file; (3) a transaction file access verification module used for verifying the trustworthiness of the user; (4) a security file data generator; (5) a daemon of a read-only security file data server; and (6) a client, wherein a traditional path is converted into data and digital signature is carried out in a client environment, then the data is distributed to an arbitrary number of running servers, and the daemon receives the request of the client and returns the data; and (7) a postmark protocol module used for detecting the integrity of transaction data. By adoption of the storage system and the method provided by the invention, the storage time of a large file system is shortened, and a creator can complete cryptographic operation, data creation and decryption according to ciphertext in an environment without a network.
Owner:SHENZHEN FANXI ELECTRONICS CO LTD
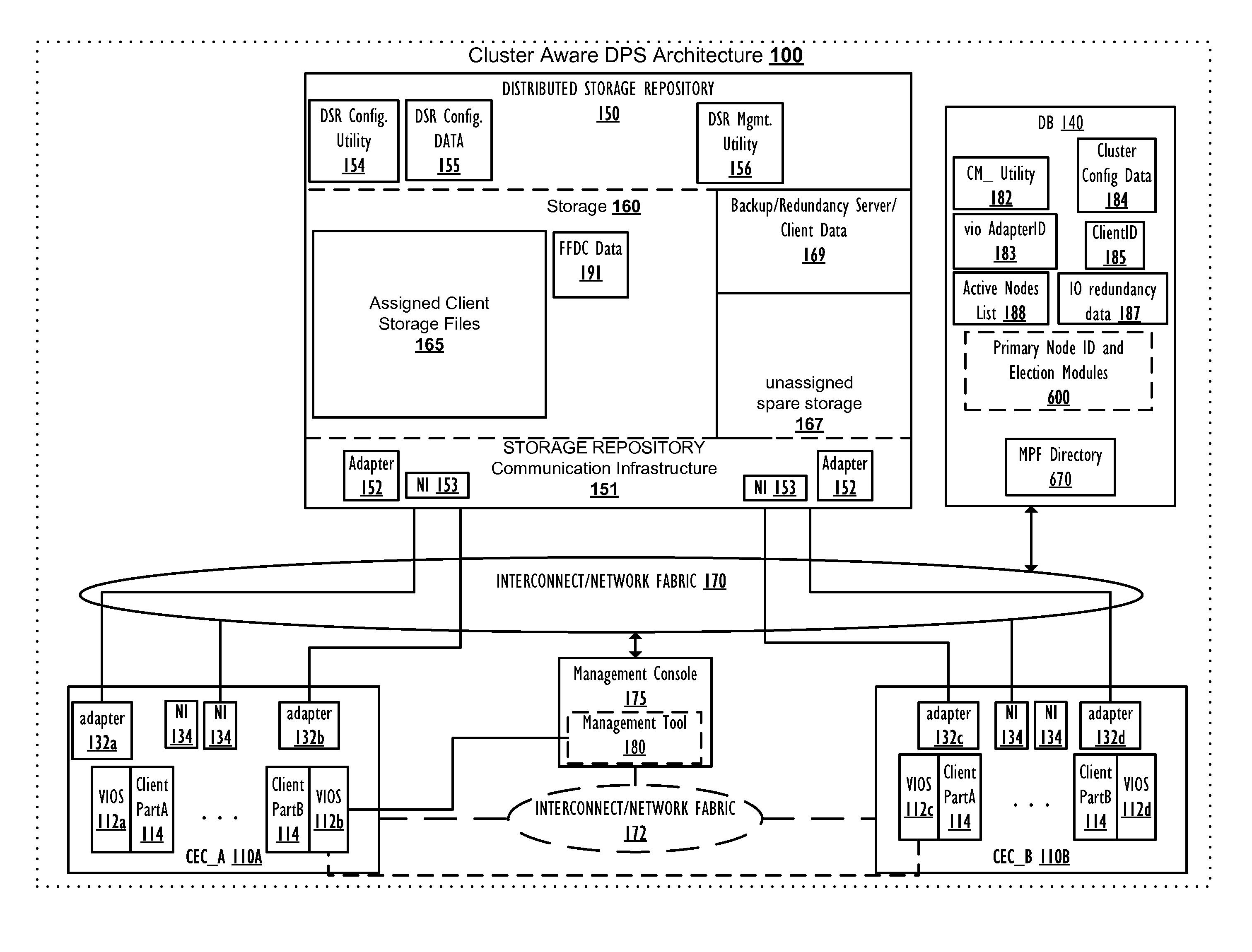
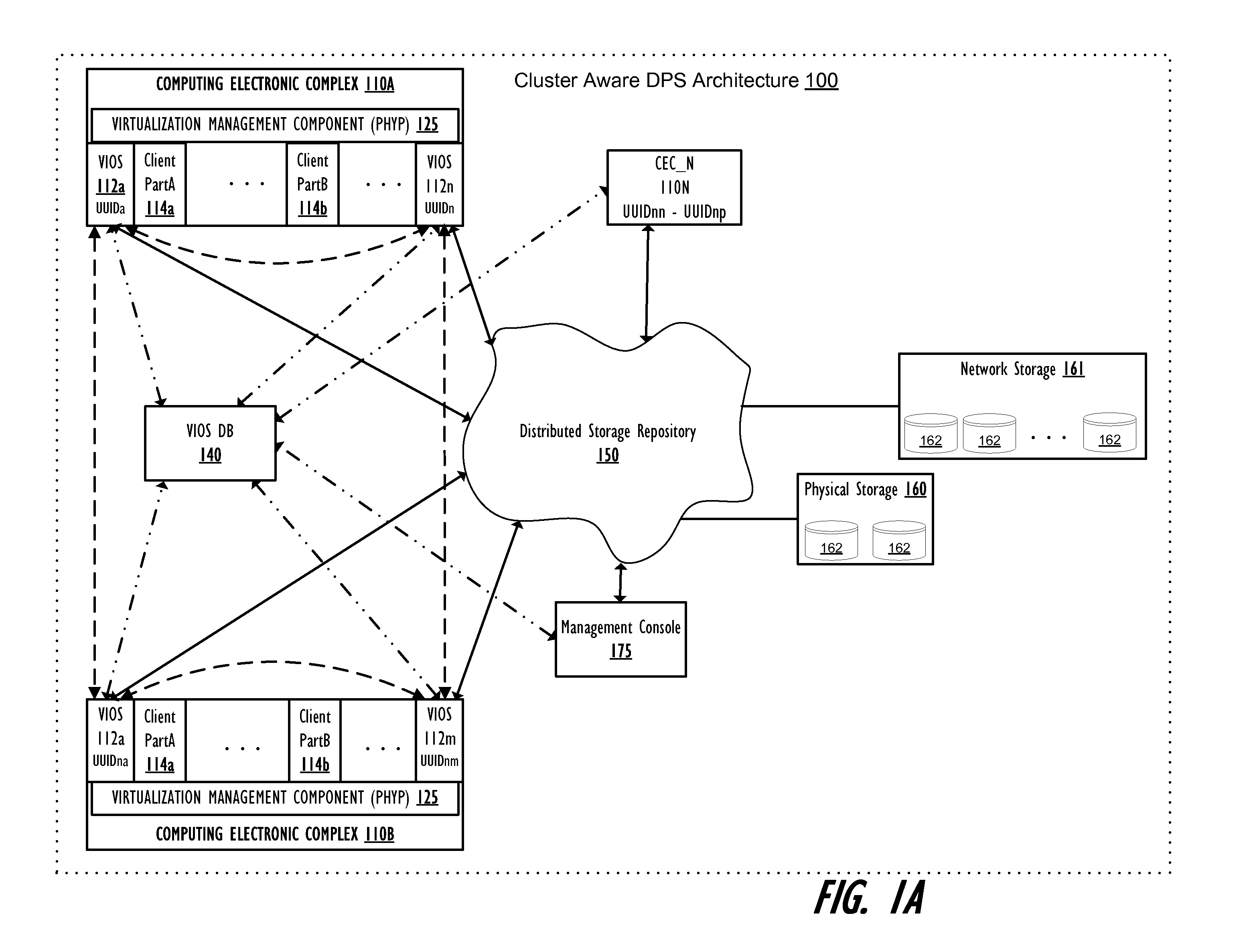
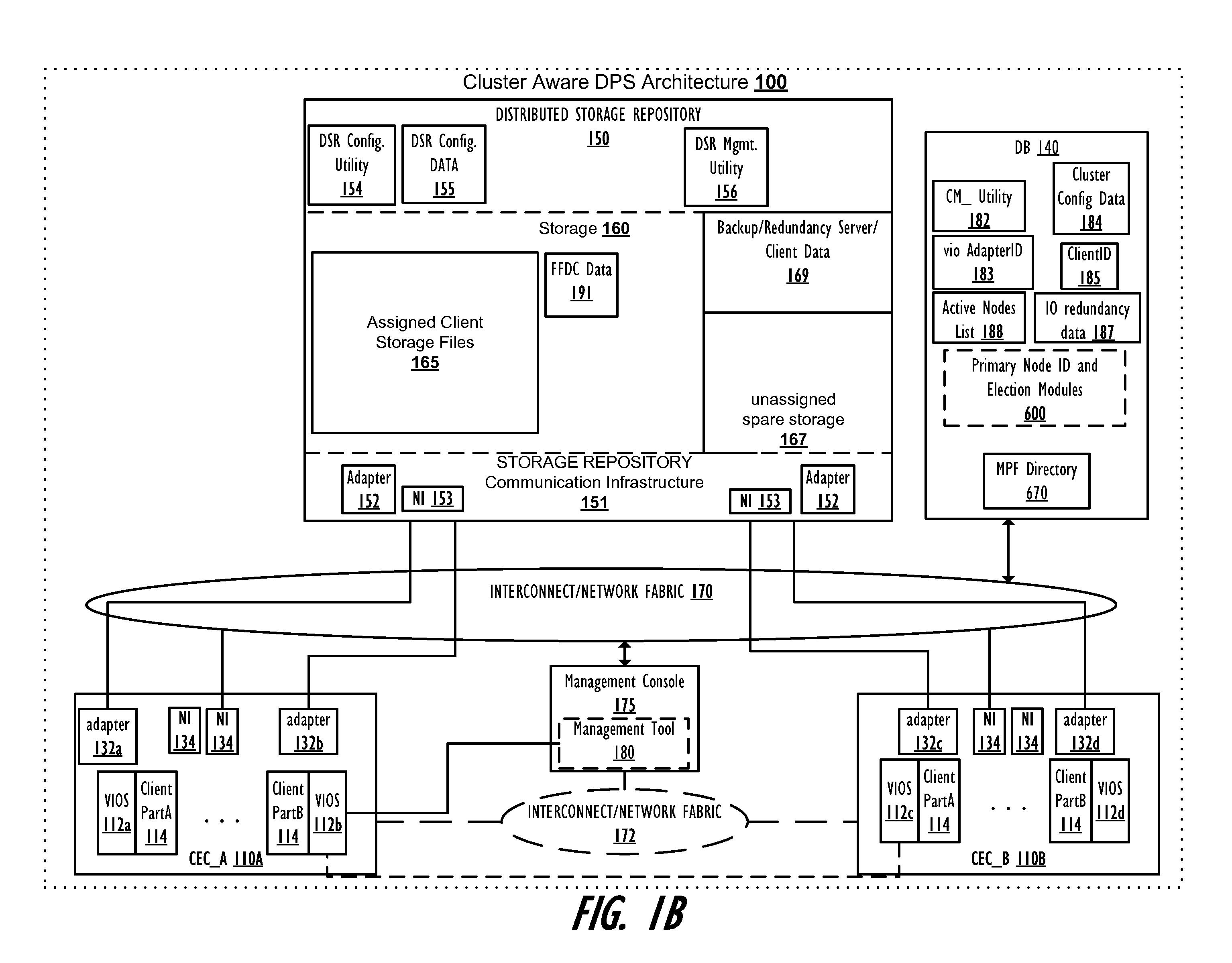
Single point, scalable data synchronization for management of a virtual input/output server cluster
InactiveUS20120180070A1Interprogram communicationTransmissionData synchronizationData processing system
A method, data processing system and computer program product provide scalable data synchronization for a virtual input / output server (VIOS) cluster and one or more registered callers. A first VIOS is commits as a primary node of the VIOS cluster and performs the functions of: registering one or more callers to receive notification from the first VIOS of specific events occurring within the cluster; receiving notification of an occurrence of one of the specific events; and in response to receiving notification of the specific events, a deamon of the first VIOS retrieving a message payload file from a message payload file directory within the shared VIOS DB and passing the message payload file to the API, which forwards / posts the relevant event notification information from the message payload file to the TCP socket of each registered caller.
Owner:IBM CORP
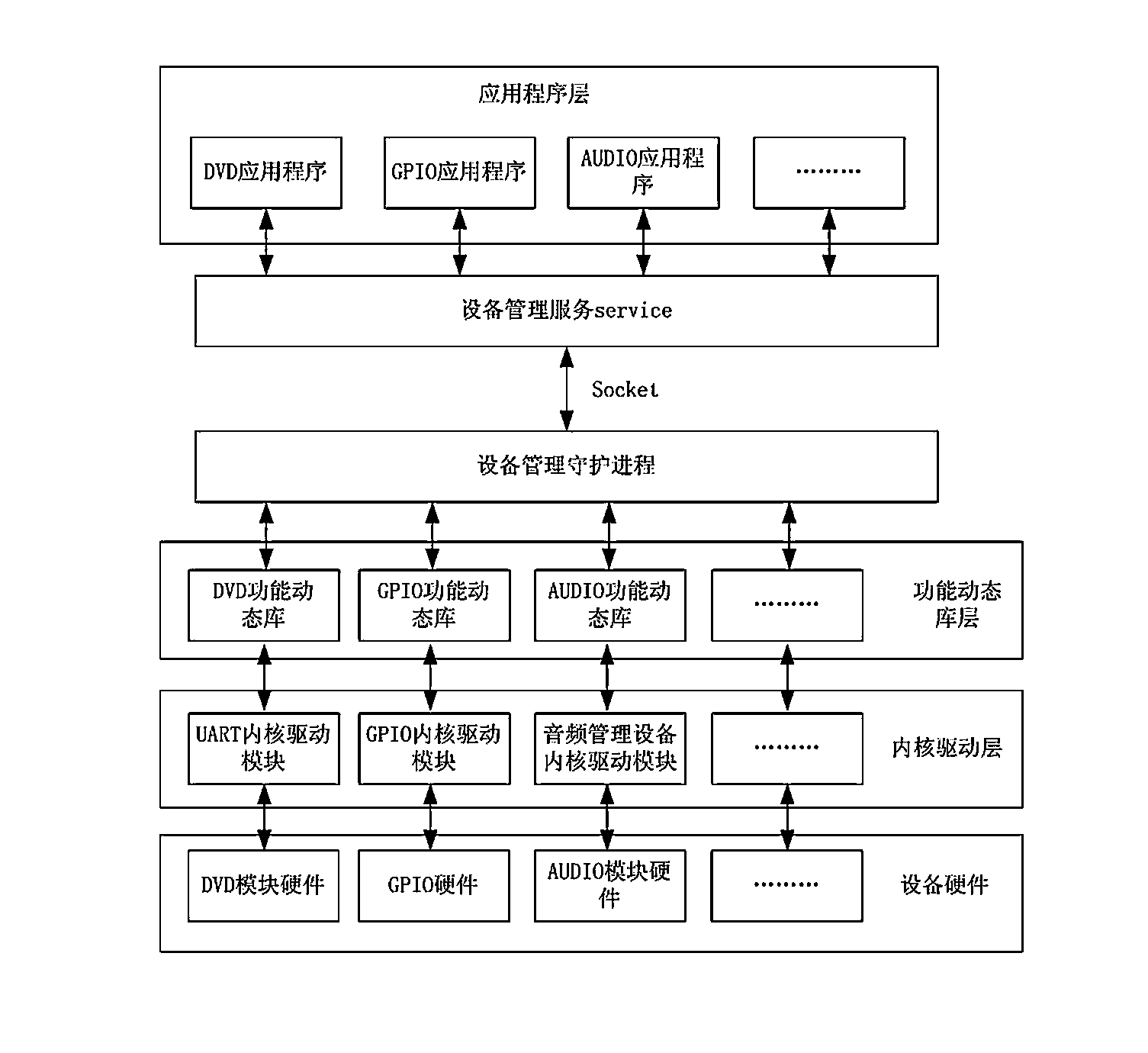
Device management framework based on android platform
InactiveCN103488478AEasy to controlEasy to manageSpecific program execution arrangementsApplication procedureFunctional interface
The invention discloses a device management framework based on an android platform. The device management framework comprises an application program layer, a management service module, a management daemon process module, a function dynamic depot layer and an inner core drive layer, wherein the application program layer is used for realizing calling an interface of the device management framework; the management service module is used for converting the function interface into a command call, and transmitting a command by using a Local Socket client end of a Socket in an Android; the management daemon process module receives the command by using a Local Socket service end of the Socket in the Android, analyzes the command, and calls the function dynamic depot layer according to the analysis result; the function dynamic depot layer is used for packaging an interface which is interactive with the inner core drive layer; the inner core drive layer is used for providing a standard operation interface of a Linux operating system to be called by the function dynamic depot layer, and operating each hardware device.
Owner:XIAMEN YAXON NETWORKS CO LTD
Method for fast recovery of I/O failure on a file system
InactiveUS20050066076A1Input/output to record carriersError detection/correctionFile systemFailure causes
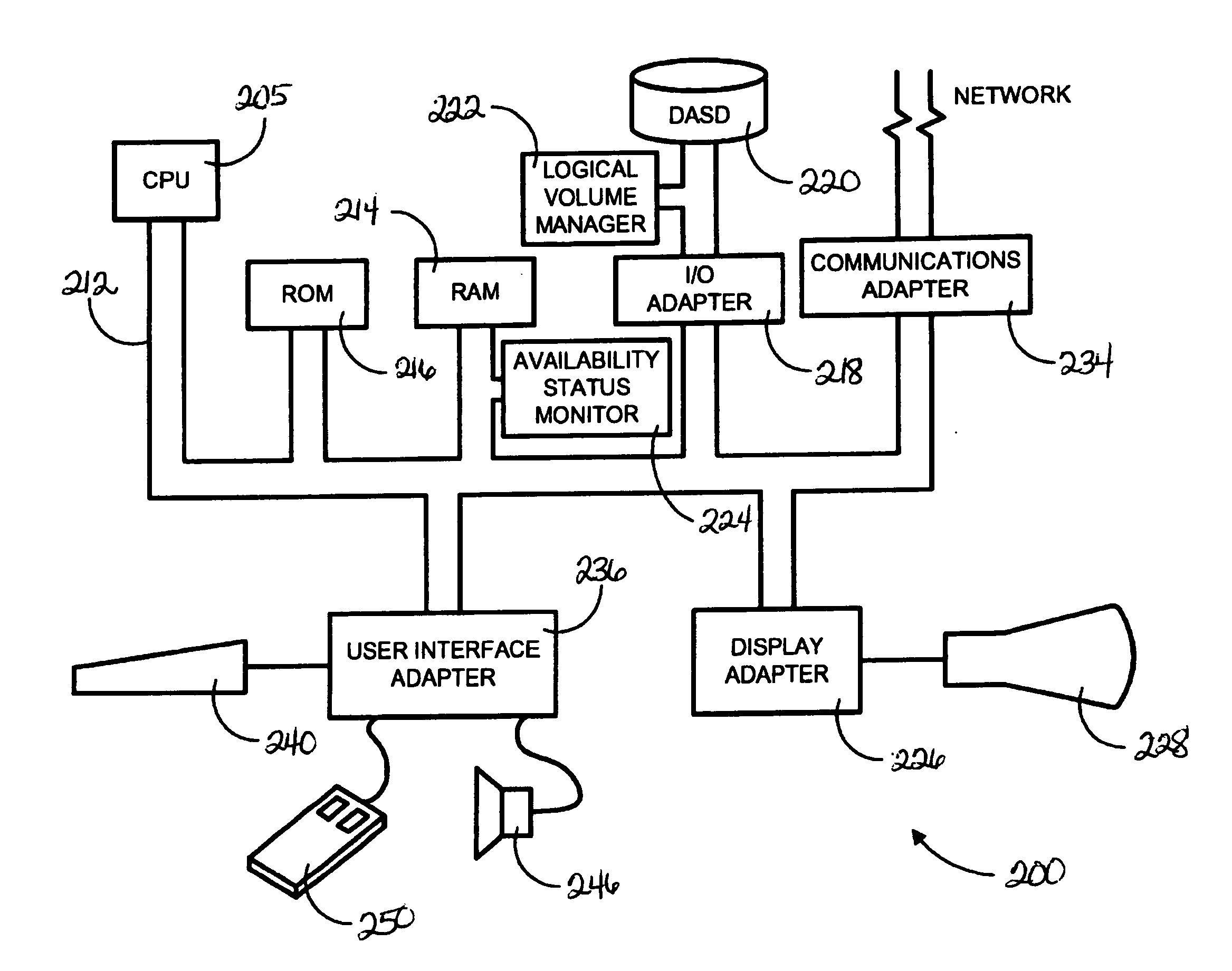
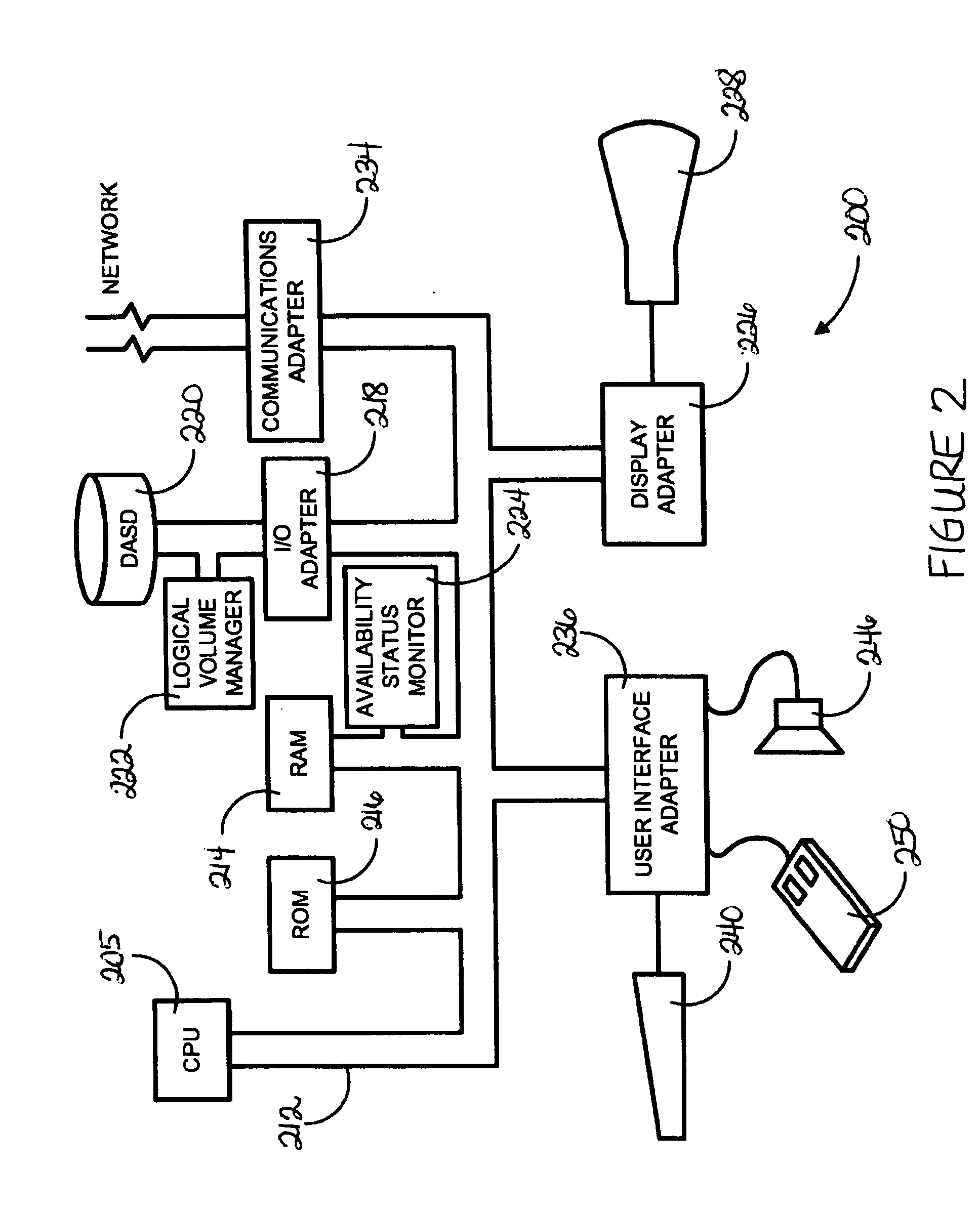
A method for enabling dynamic response to I / O failure caused by an out-of-space condition in a file system hosted on a logical volume. An I / O failure response (FR) daemon is implemented to bridge operations between the Logical Volume Manager (LVM) executing in user space and I / O control functions executing in the kernel space. When the file system does not have sufficient space to complete an I / O, the I / O controller signals the I / O FR daemon, which executes the following sequence of operations: (1) alert the LVM that the file system requires additional space; (2) provide a notification to the application level about the resizing; and (3) re-start the I / O operation once the resizing operation completes. The LVM receives the alert and initiates an automatic expansion of the file system to include additional storage space from reserve space on the volume group. The I / O is completed once the expansion operation completes.
Owner:IBM CORP
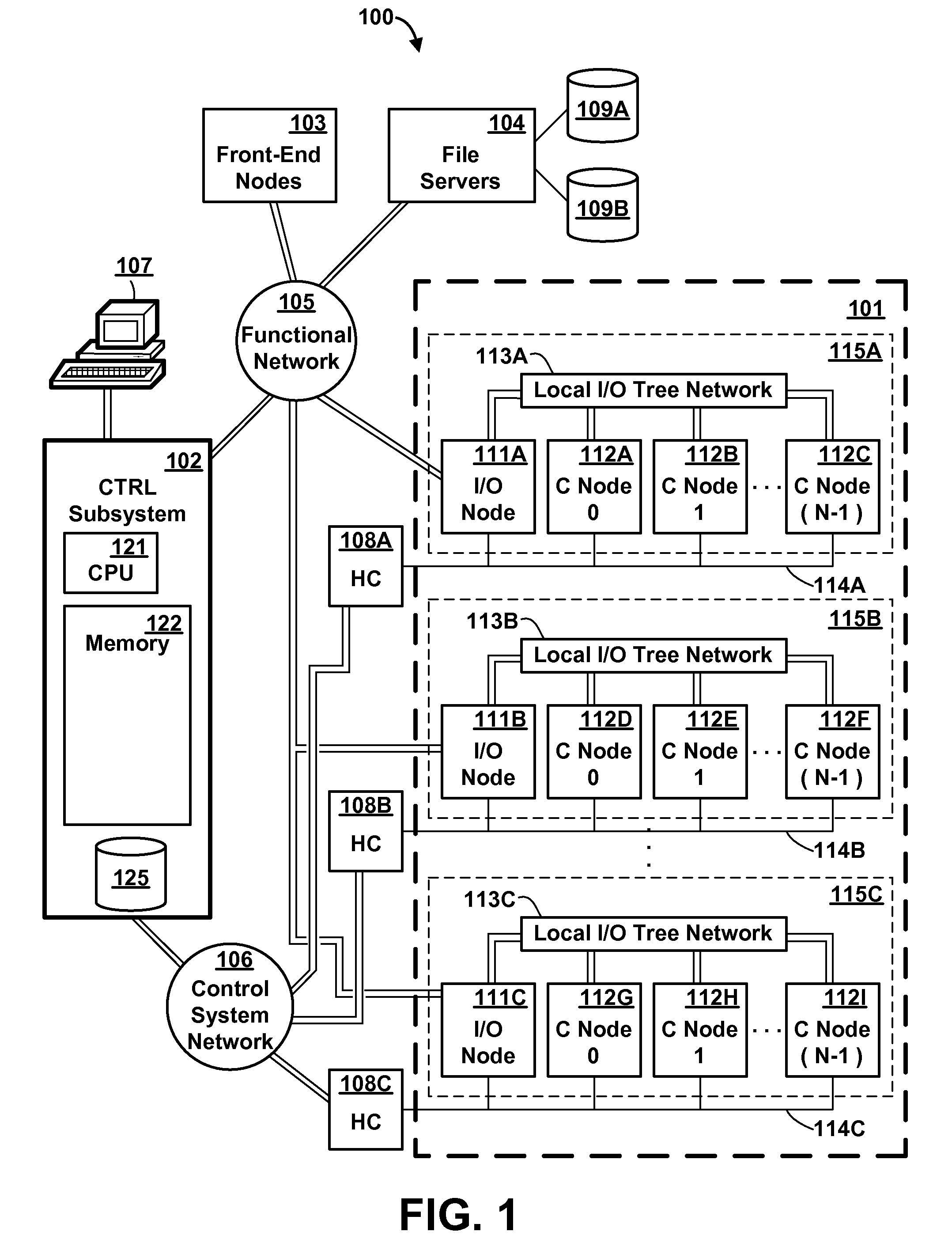
Memory Request/Grant Daemons in Virtual Nodes for Moving Subdivided Local Memory Space from VN to VN in Nodes of a Massively Parallel Computer System
InactiveUS20080270731A1Little overhead to implementEfficient use ofMemory adressing/allocation/relocationGeneral purpose stored program computerComputer architectureEngineering
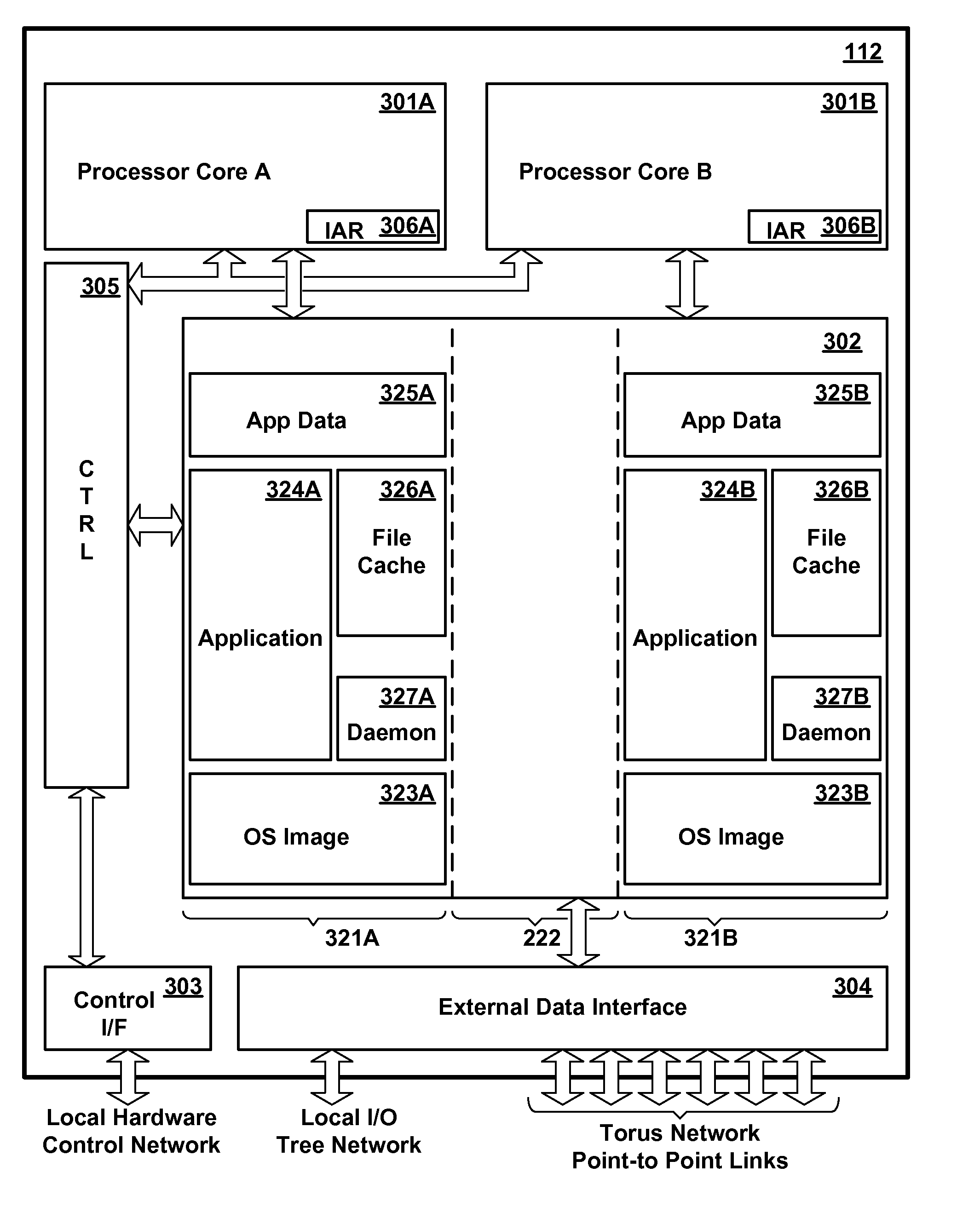
A memory management mechanism a nodal having multiple processors in a massively parallel computer system dynamically configures nodal memory on demand. A respective variable-sized subdivision of nodal memory is associated with each processor in the node. A processor may request additional memory, and the other processor(s) may grant or veto the request. If granted, the requested memory is added to the subdivision of the requesting processor. A processor can only access memory within its own subdivision. Preferably, each subdivision contains a daemon which monitors memory usage and generates requests for additional memory.
Owner:INT BUSINESS MASCH CORP
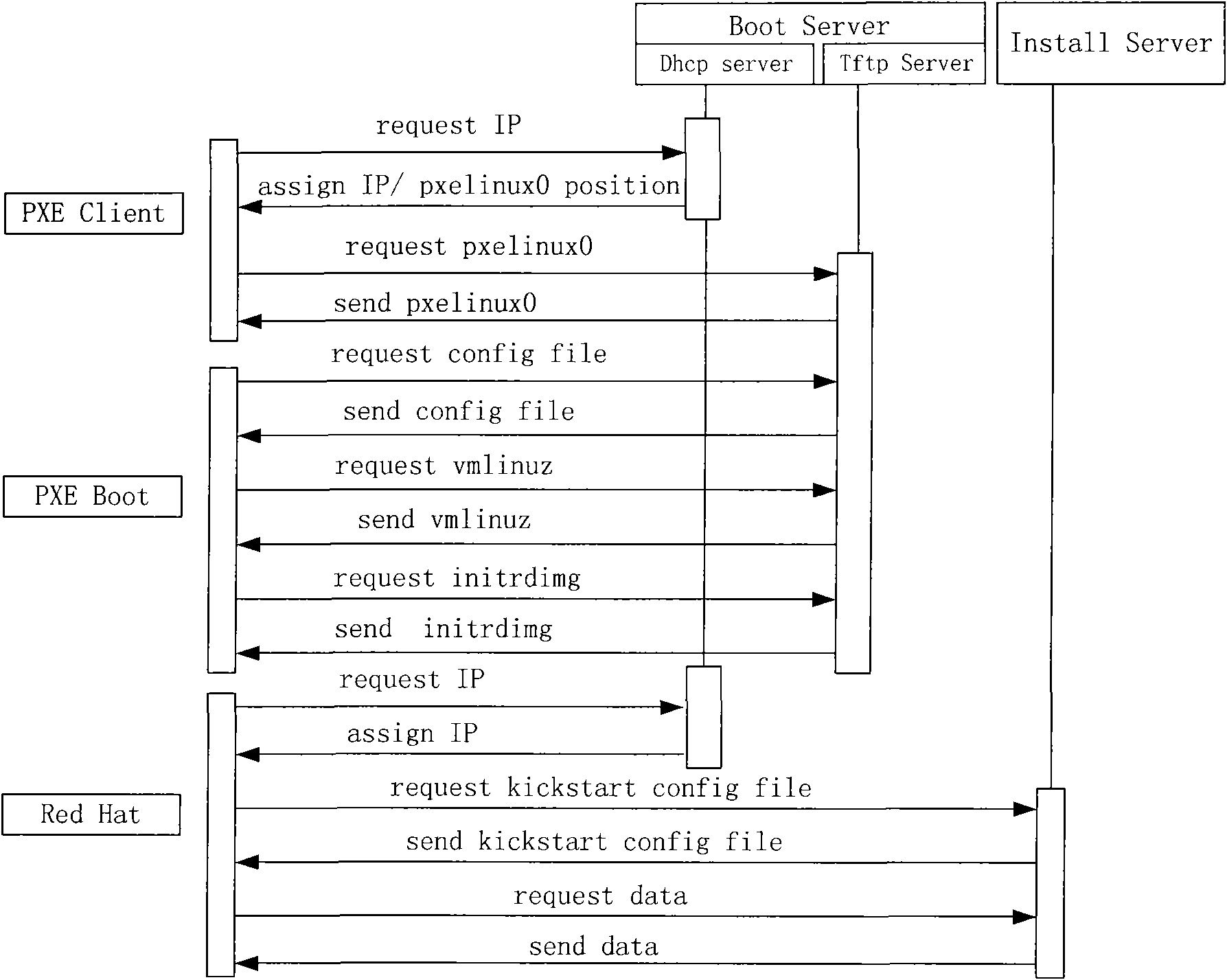
Method for rapidly deploying extensible cluster
InactiveCN101820387AFunction increaseSpeed up deploymentData switching networksIp addressCentralized management
The invention relates to a method for rapidly deploying an extensible cluster. The method is implemented by using a modified DHCP server, a command line tool and a node daemon, wherein the modified DHCP server is responsible for distributing IP addresses and assigning TFTP server addresses for nodes to be deployed, intensively managing all nodes which are being deployed and are deployed successfully and preferentially selecting a node with the lightest load from the successfully deployed nodes while selecting a TFTP server; the command line tool can dynamically modify configuration information read in when the DHCP server starts so as to make use of hardware resources of the deployed nodes in a better way and perform a deploying process stably; the node daemon is downloaded from a main deployment server after the installation of a script in kickstart is completed, runs automatically and is responsible for reporting the state of the node daemon to the main deployment server, downloading a necessary file, starting TFTP and NFS services and the like. The method can adapt to the extension of cluster scale, achieves deployment effect which becomes more remarkable along with the extension of the cluster scale, has a flexible operation and controls an entire deployment process by configuring files or command lines.
Owner:SHANGHAI JUNESH INFORMATION TECH CO LTD
Process-to-process communication method of application software and system
InactiveCN102833080AReduce development costsReduce maintenance costsSpecial service provision for substationInterprogram communicationOperational systemSoftware engineering
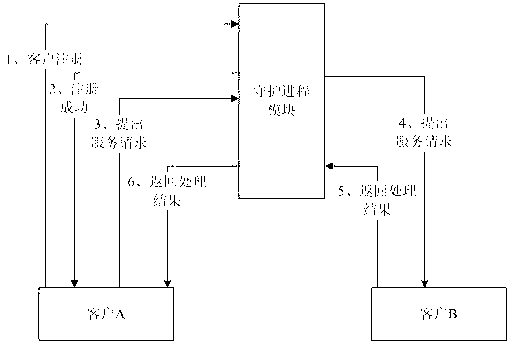
The invention relates to a process-to-process communication method of application software and a system. The method comprises receiving registration information of a client through a daemon module; and monitoring, forwarding and responding to service request information of the client, and comprises the specific steps of a client A sending a service request to the daemon module to request the daemon module to return one or more services provided by a client B; the daemon module forwarding the service request of the client A to the client B after receiving the service request sent by the client A; the client B processing the service request of the client A, and returning the processing result to the daemon module; and the daemon module returning the processing result of the client B to the client A. The process-to-process communication method provided by the invention is independent of the operation system, and the same software can be operated on different operation systems, thereby facilitating quick software project development by technicians, and reducing the software development and maintenance cost.
Owner:KONKA GROUP
Application server and remote control method thereof
ActiveCN101227428AImprove scalabilityGood automatic upgradeSubstation remote connection/disconnectionProcess mechanismExtensibility
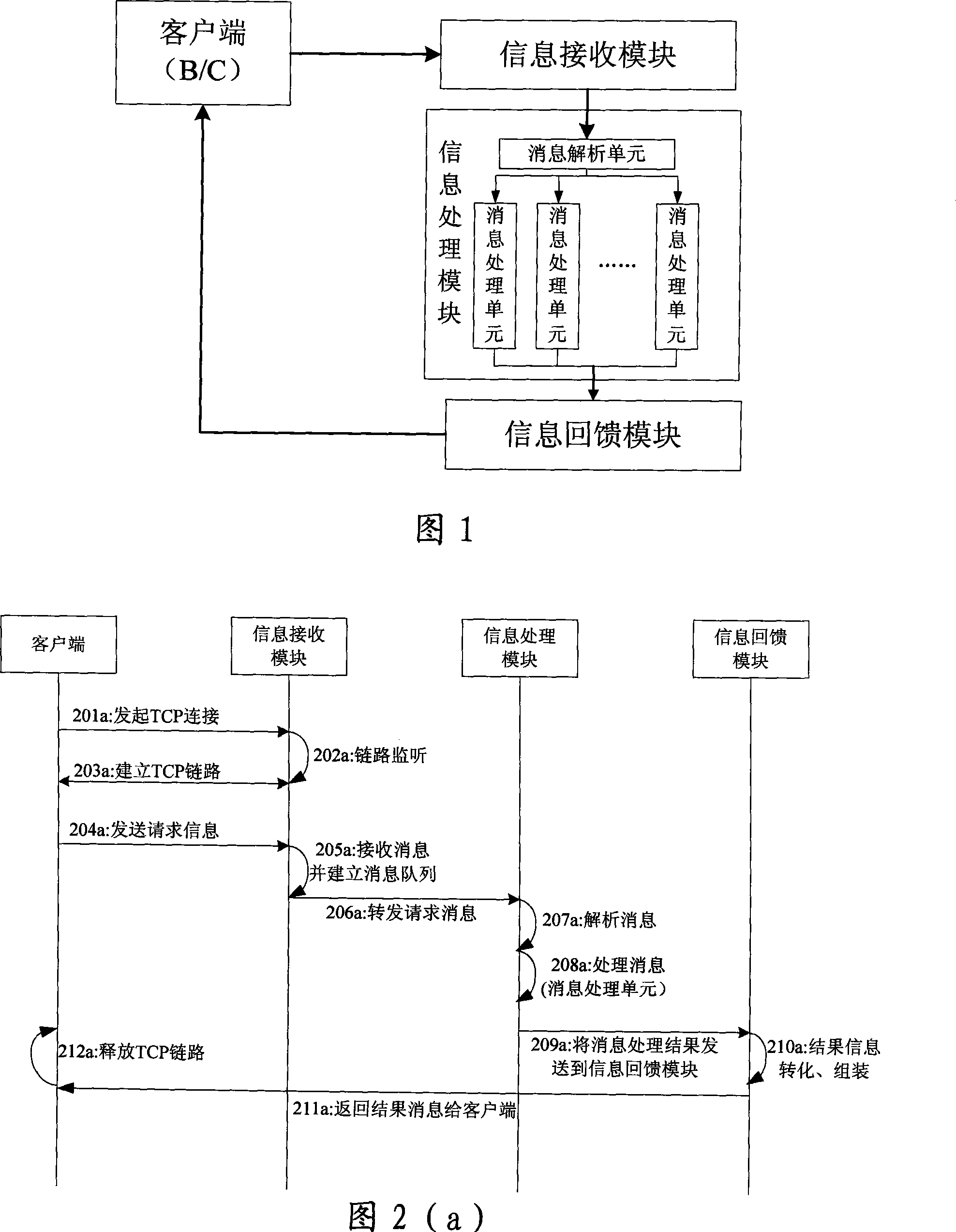
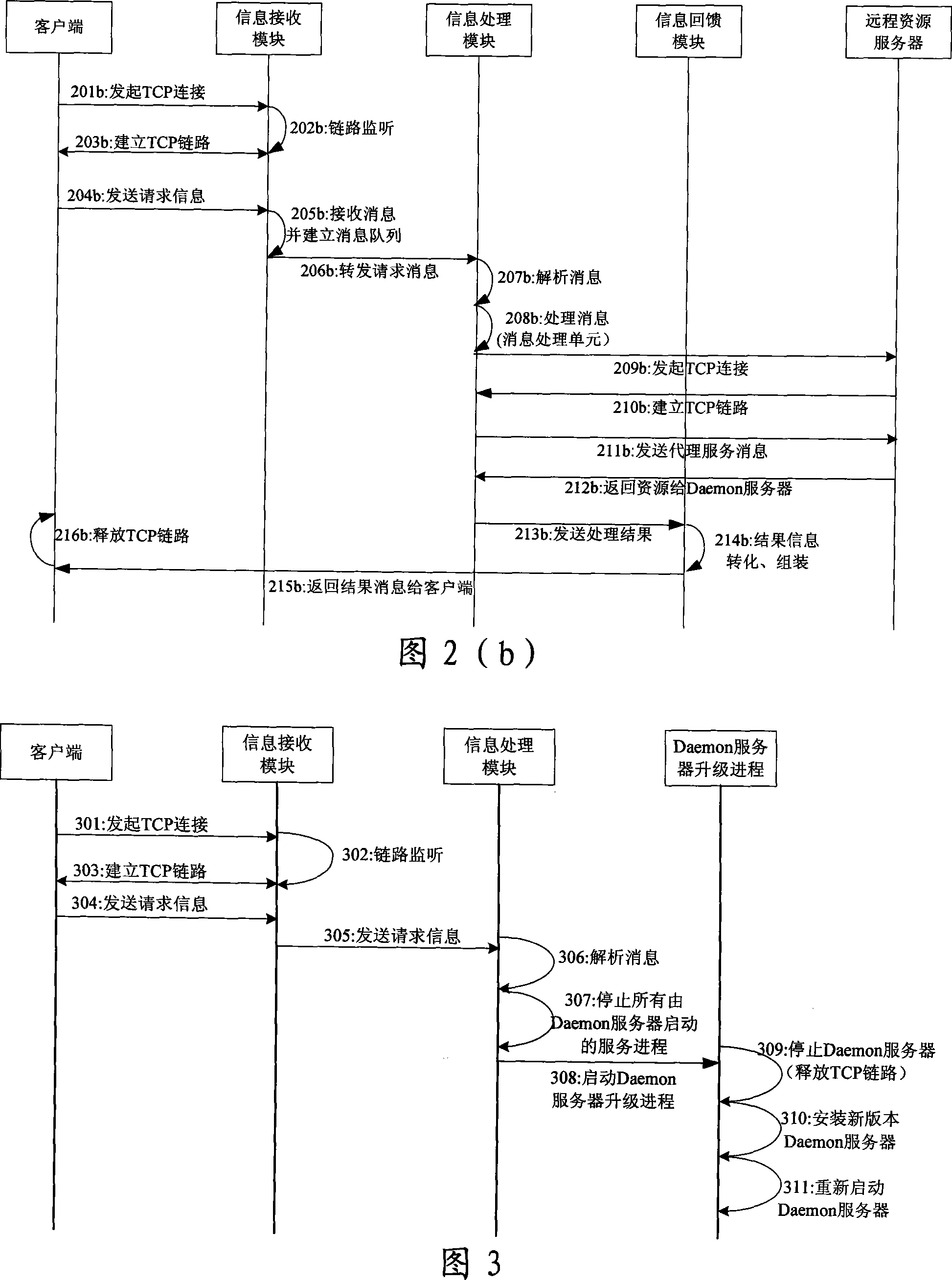
The invention discloses a Daemon applied server and a remote control method, which belongs to the remote control field of computers. The Daemon applied server of the invention comprises an information receiving module, an information processing module and an information feedback module which are connected in turn, wherein the information receiving module is used to receive various request information in concurrency type from user ends, and various request information is sent to the information processing module according to the receiving sequence or priority level sequence, the information processing module is applied in utilizing system function to process mechanism response and process various request information of user ends, the information feedback module is used to return the request information processing results to client ends. The invention achieves type independence between client end requests and applied server operation systems, and meanwhile, the applied server which is provided by the invention has very excellent expandable property, automatic upgrading function, service agent mechanism and easy construction.
Owner:SICHUAN YUECHENG ENVIRONMENTAL PROTECTION & ENERGY SAVING TECH CO LTD
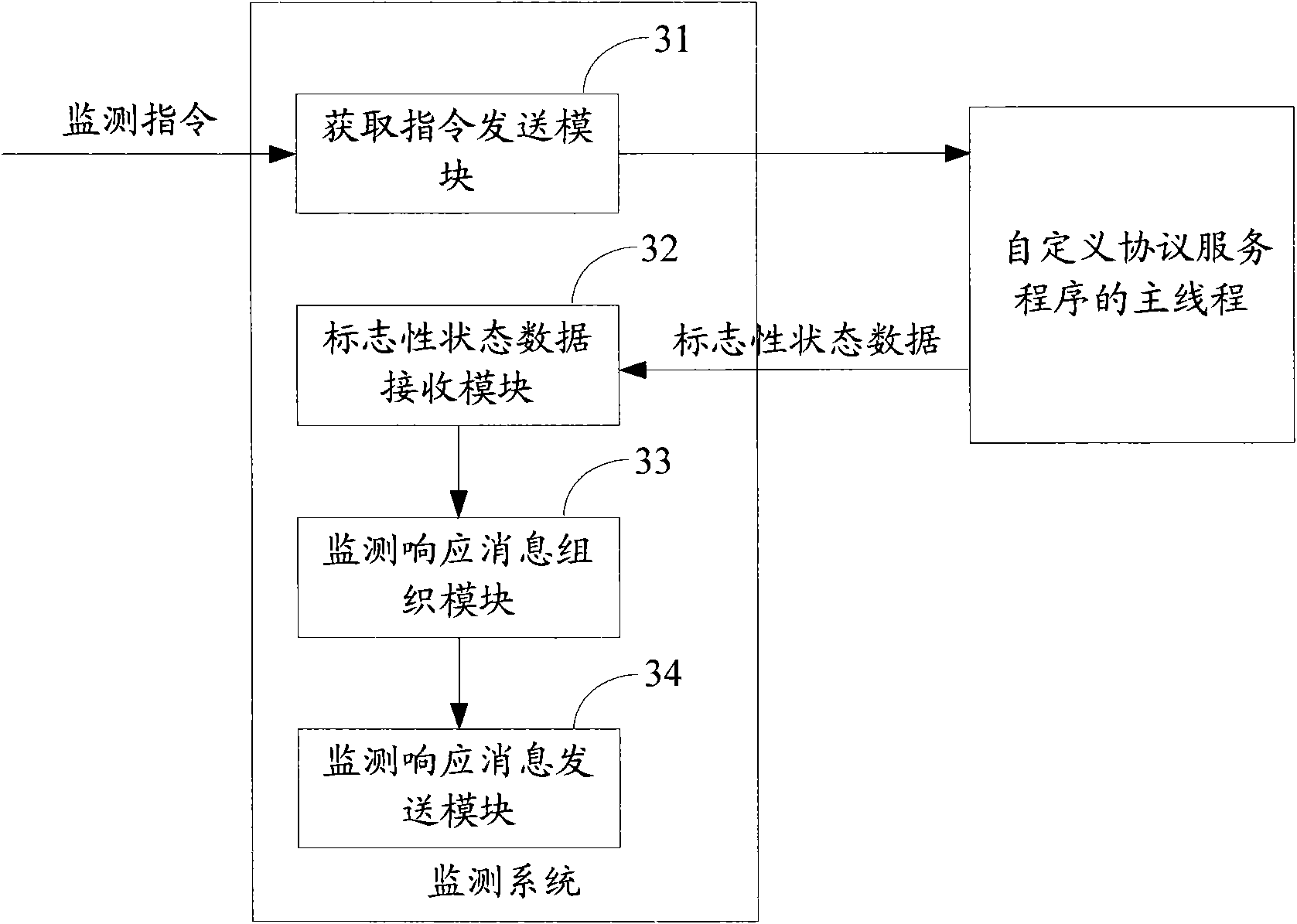
Monitoring method and monitoring system of self-defined protocol service program
InactiveCN101561774AInterprogram communicationDetecting faulty computer hardwareMonitoring systemMonitoring methods
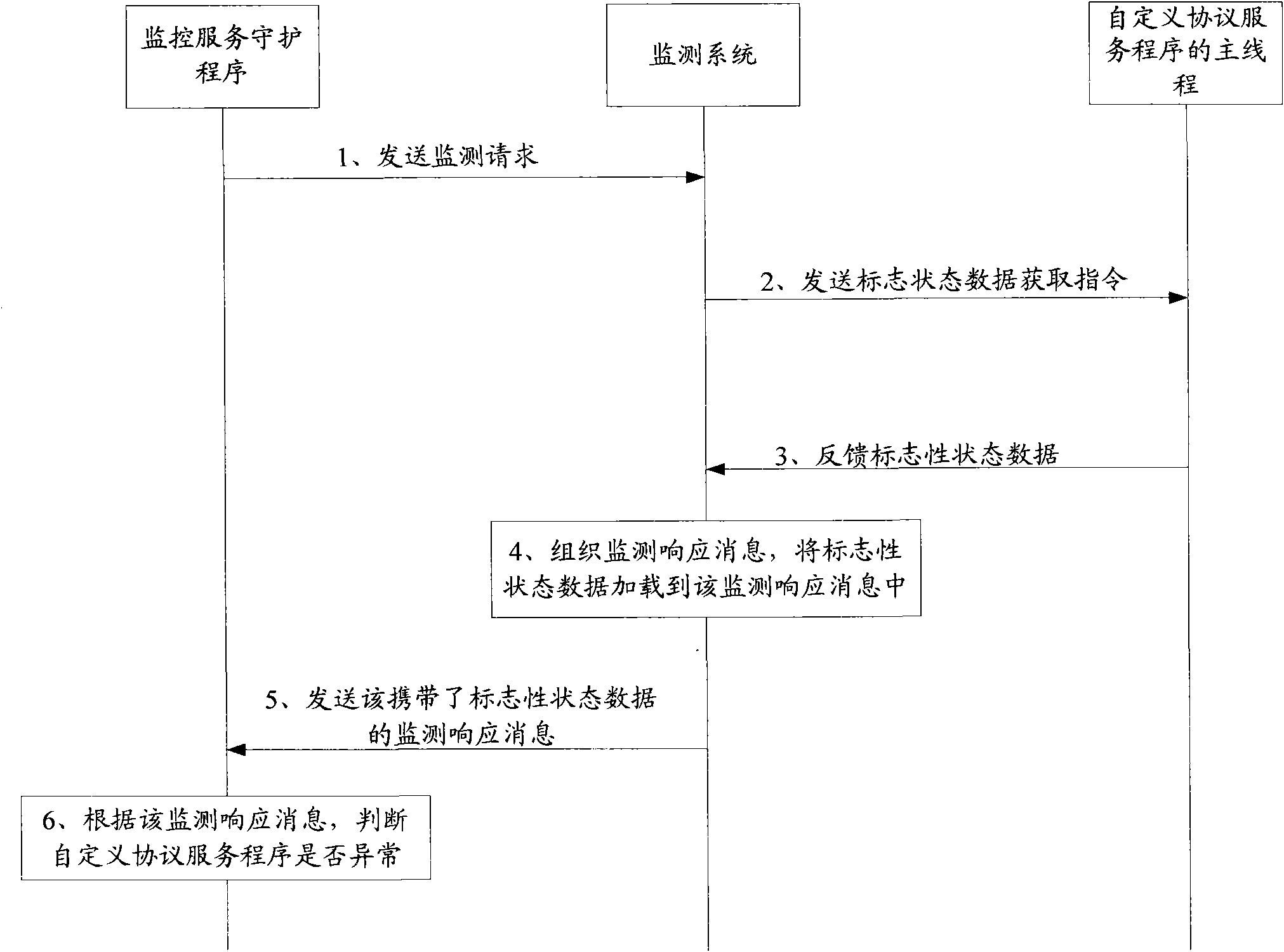
The invention provides a monitoring method and a monitoring system of a self-defined protocol service program, which is applicable to the software field. The method comprises the following steps: when the self-defined protocol service program receives a monitoring request transmitted by a monitoring service daemon, landmark state data is transmitted to the main thread of the self-defined protocol service program to obtain a command; the landmark state data fedback through the main thread is received; monitoring response message is organized, and the landmark state data is loaded to the monitoring response message; and the monitoring response message is transmitted to the monitoring service daemon. As the monitoring system is embedded in the self-defined protocol service program, the monitoring service daemon of an LVS load balancing server can monitor the running states of real servers, and the LVS load balancing server enables the real server in failure to stop service, thus leading the real servers with recovered service to be capable of being accessed again.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
System and method for controlling co-scheduling of processes of parallel program
InactiveUS7424712B1More processedEffective controlProgram synchronisationMemory systemsComputer scienceCo scheduling
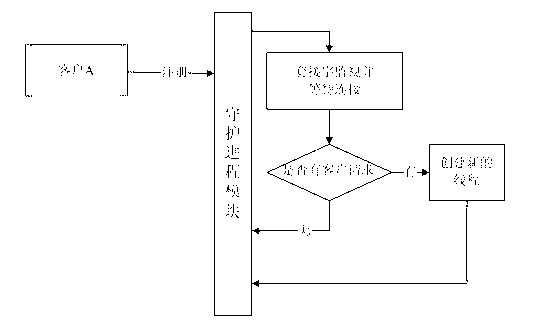
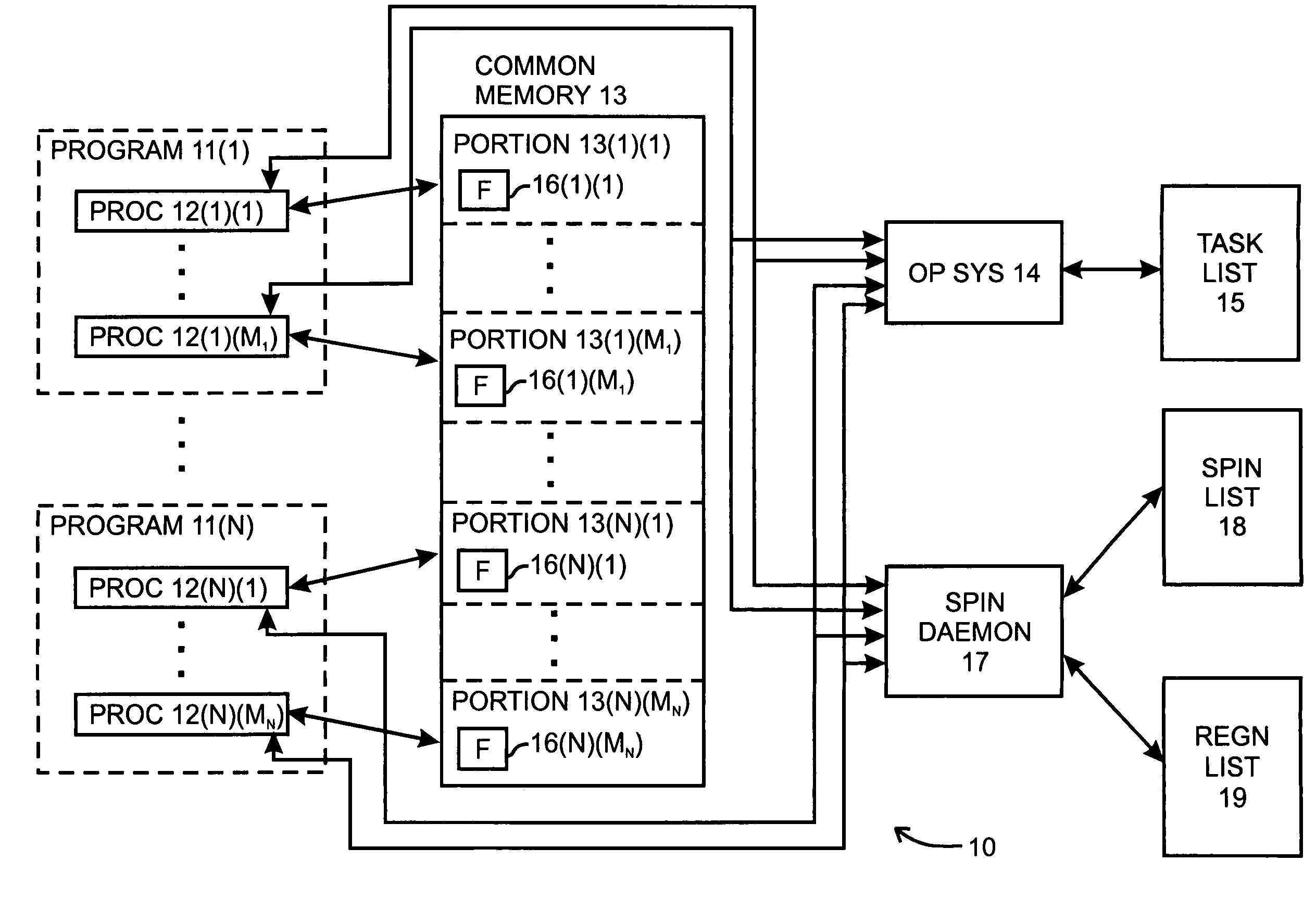
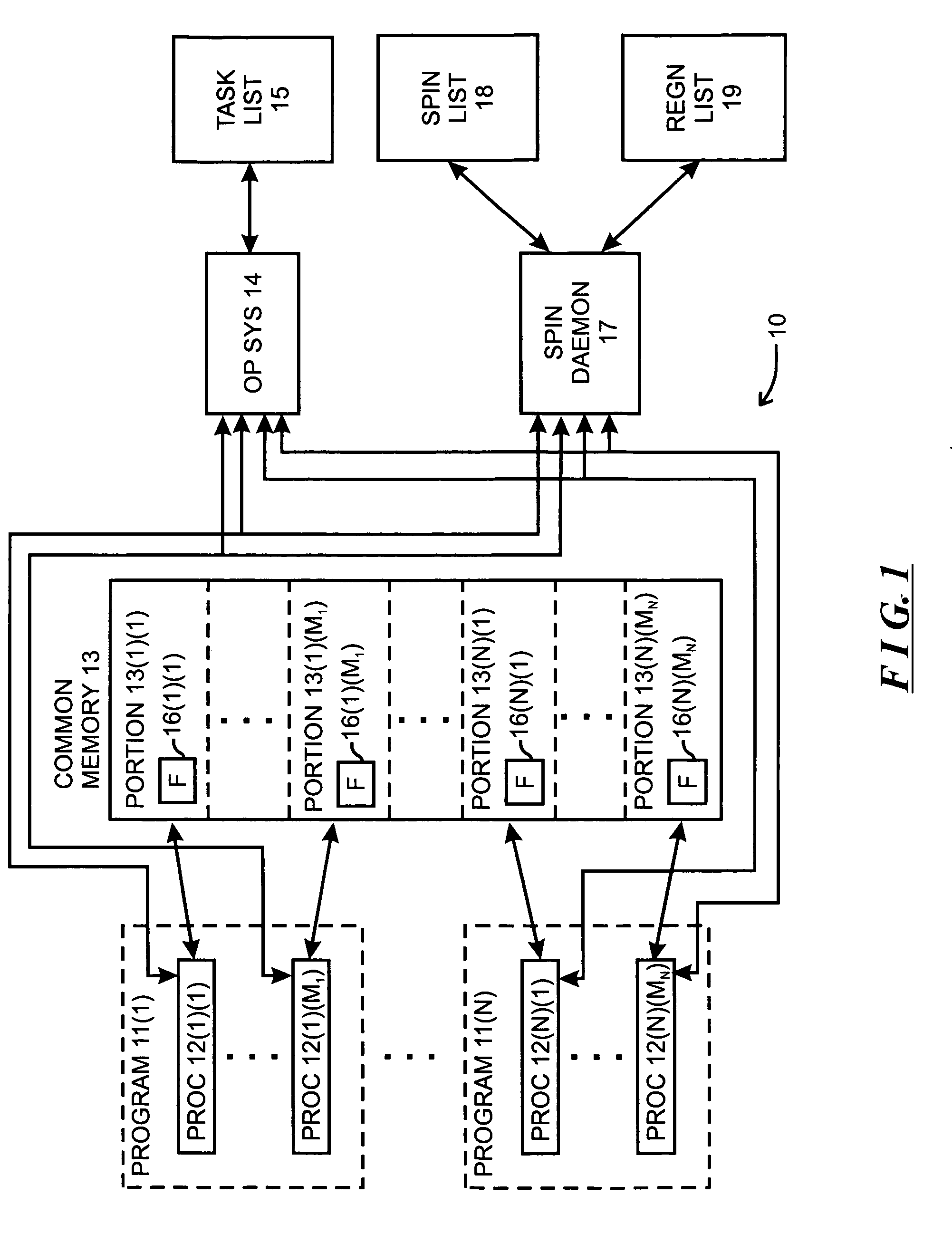
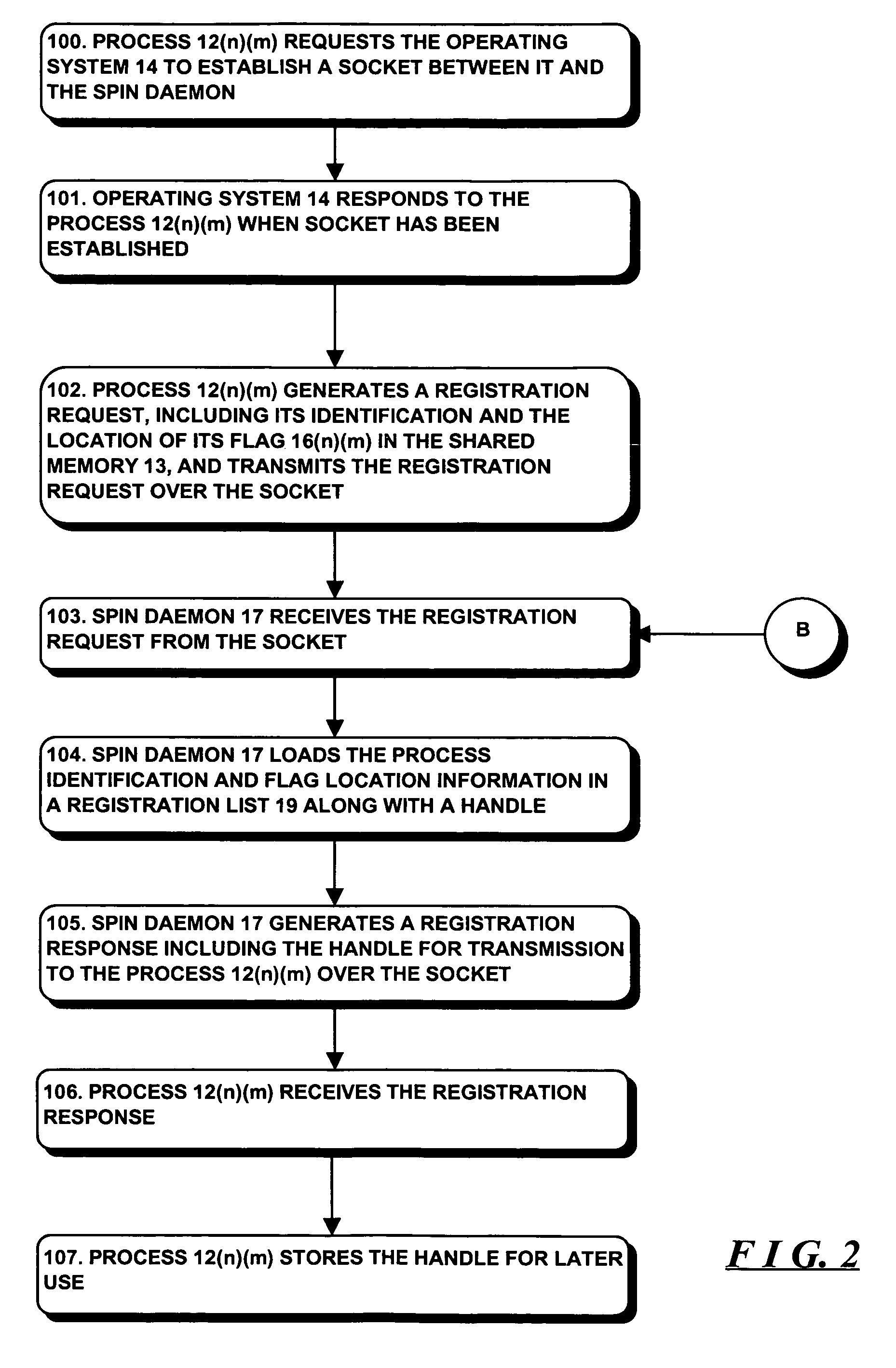
A system is described for controlling co-scheduling of processes in a computer comprising at least one process and a spin daemon. The process, when it is waiting for a flag to change condition, transmits a flag monitor request to the spin daemon and enables itself to be de-scheduled. The spin daemon, after receiving a flag monitor request, monitors the flag and, after the flag changes condition, enables the process to be re-scheduled for execution by the computer. Since the spin daemon can monitor flags for a number of processes, the ones of the processes that are waiting will not need to be executed, allowing other processes that are not just waiting to be processed more often.
Owner:ORACLE INT CORP
Hardware counter virtualization-based performance analysis method for multiple virtual machines
InactiveCN102073535AImplement virtualizationEasy to analyzeSoftware testing/debuggingSoftware simulation/interpretation/emulationVirtualizationMessage passing
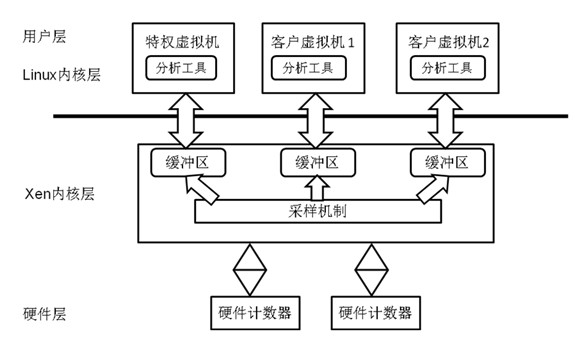
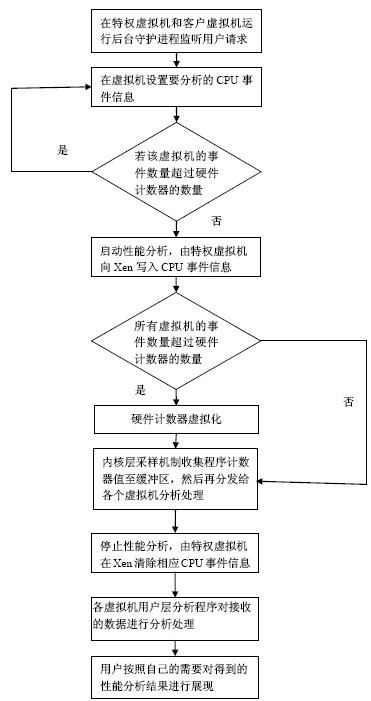
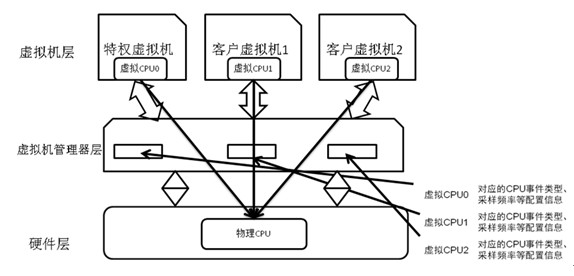
The invention discloses a hardware counter virtualization-based performance analysis method for multiple virtual machines. The method comprises the following steps of: when performance analysis is performed on multiple virtual machines at the same time and the multiple virtual machines need to occupy hardware counters, if the total number of central processing unit (CPU) events analyzed by multiple virtual machines surpasses the number of the hardware counters, virtualizing the hardware counters so as to meet requirements, otherwise, not virtualizing the hardware counters; and acquiring sampling information on the manager layer of an Xen virtual machine through a sampling mechanism, distributing the information to buffer zones which correspond to the virtual machines and analyzing and processing the information by using user layer programs of the virtual machines so as to obtain corresponding analysis result and detailed performance information. A request, which is used for starting or stopping performance analysis, of each virtual machine is monitored by a background daemon, Xenstore is taken as a message sending mechanism among the virtual machines, virtualization of the hardware counters is realized by time-sharing multiplexing technology, convenience is brought to program performance analysis in a virtual environment, and analysis accuracy is ensured well.
Owner:HUAZHONG UNIV OF SCI & TECH
Software setup system
Owner:MULLIGAN J SCOTT +1
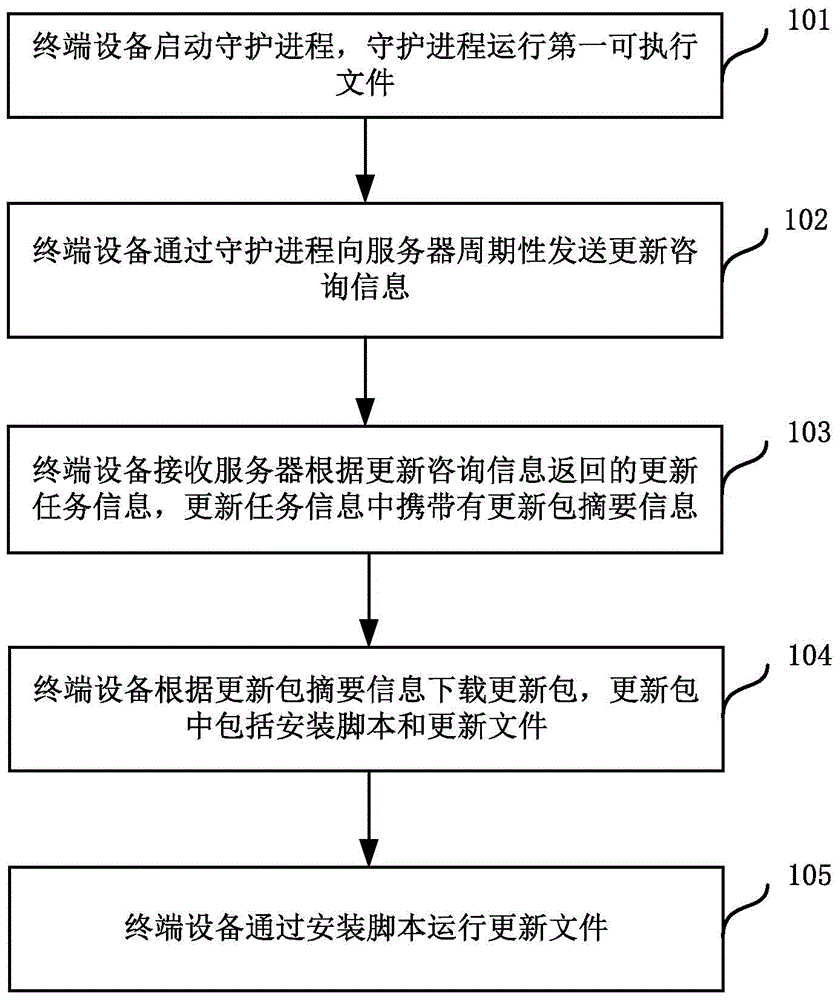
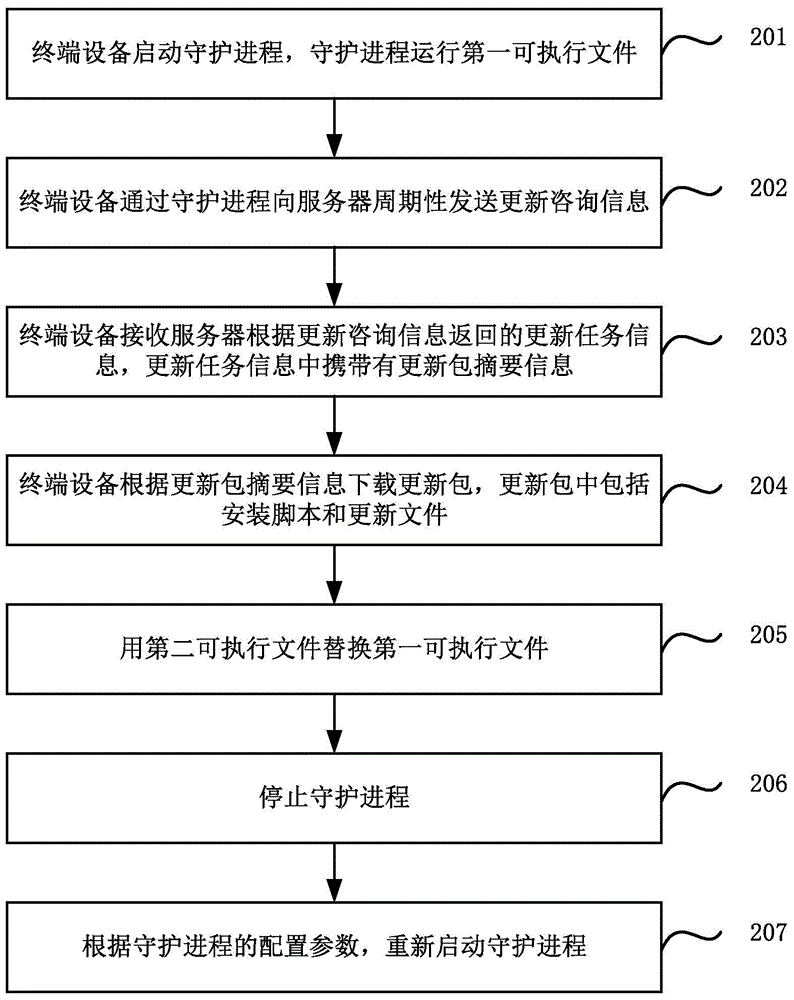
Updating method, device and system
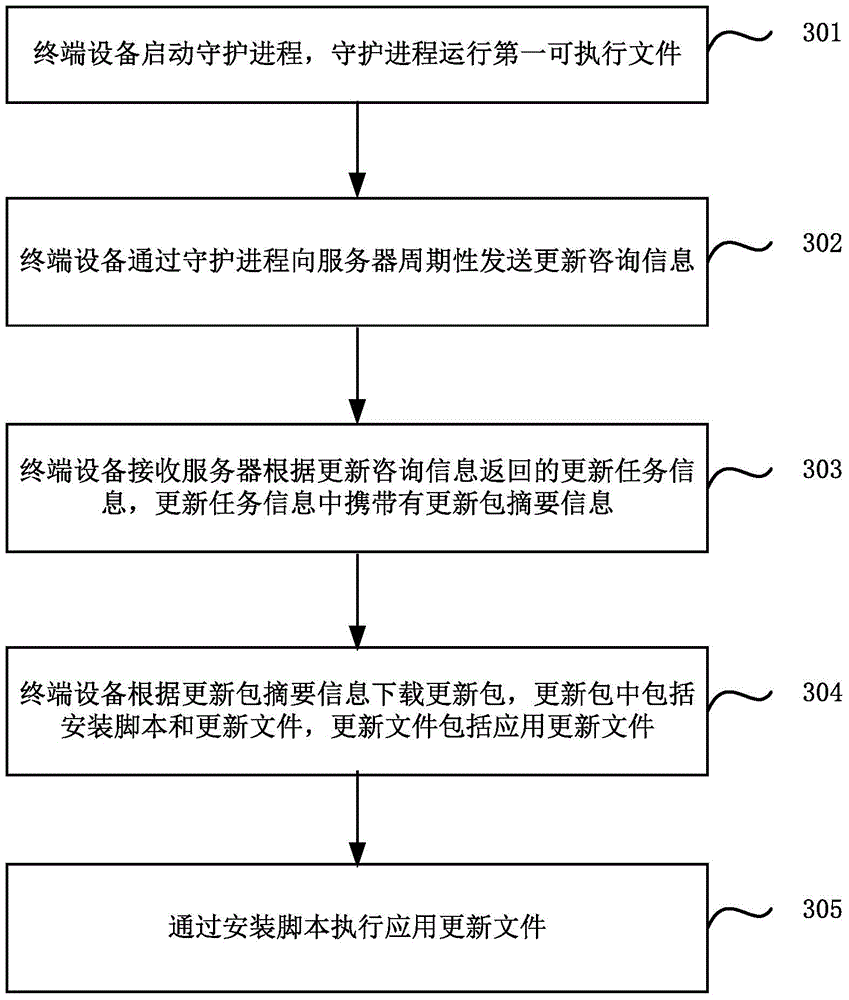
Embodiments of the present application relate to an updating method, device and system. The method comprises: a terminal device starting a daemon process, and the daemon process running a first executable file; periodically sending updated advisory information to a server by using the daemon process, and receiving updated task information returned by the server according to the updated advisory information, wherein the updated task information carries update package summary information; the terminal device downloading an update package according to the update package summary information, wherein the update package comprises an installation script and an update file; and running the update file by using the installation script. Thus, the automatic updating can be implemented, a manual operation of a user is not required, and the automatic updating of an application plug-in without a UI can also be implemented.
Owner:ADVANCED NEW TECH CO LTD
Method for high availability of services in cloud computing systems
ActiveUS9106537B1Improve usabilityEliminate disadvantagesProgram controlData switching networksCloud baseHigh availability
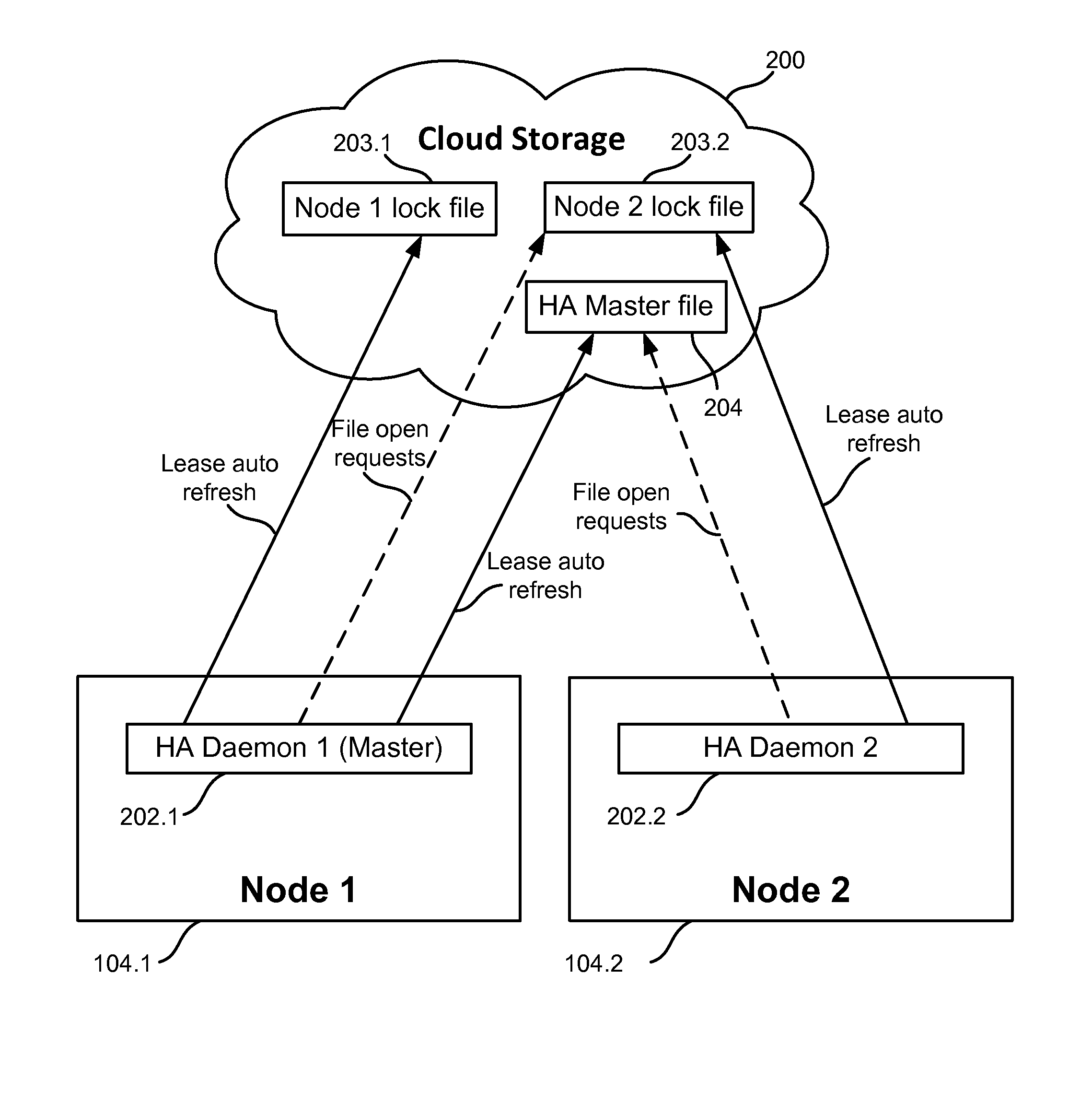
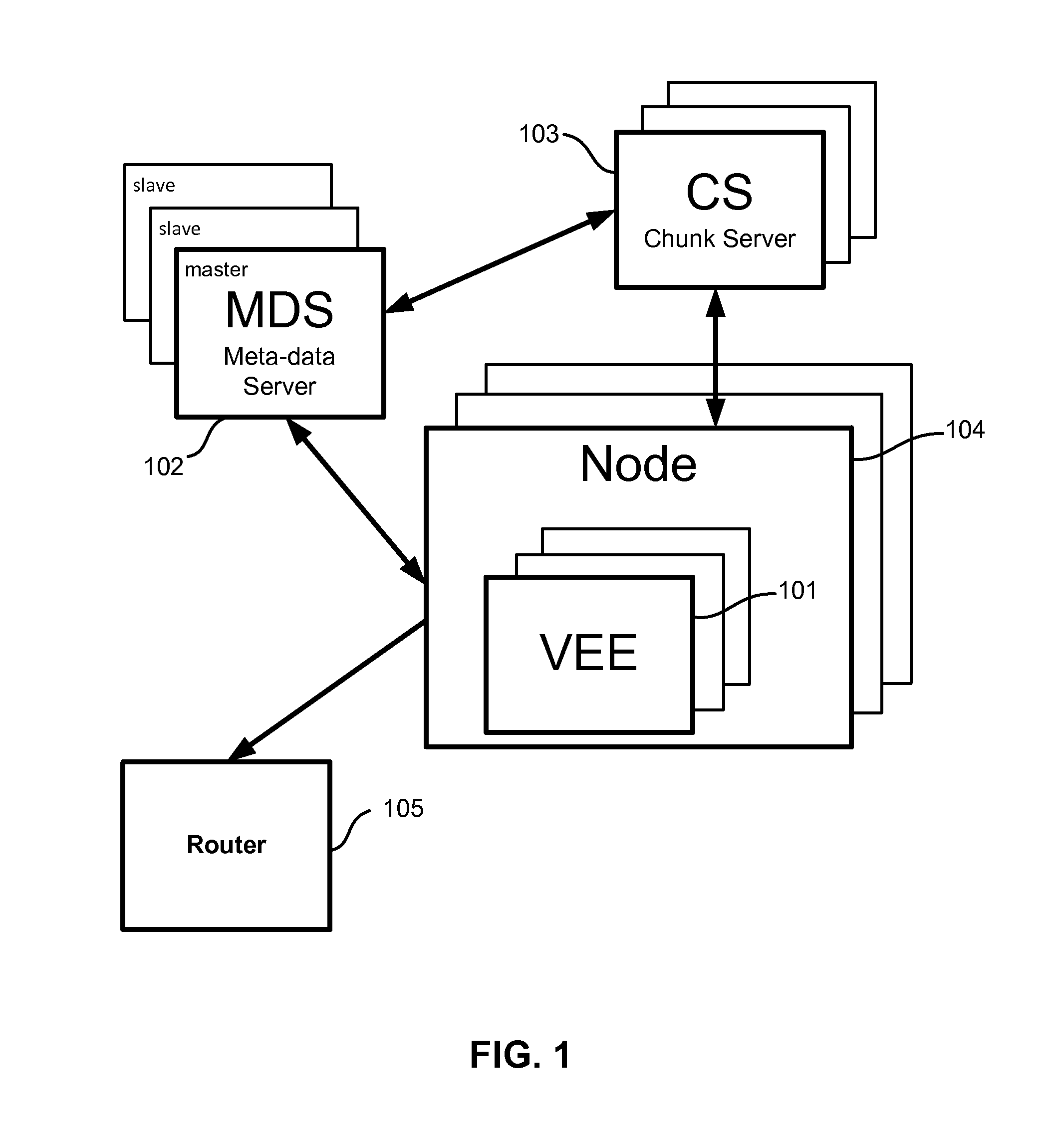
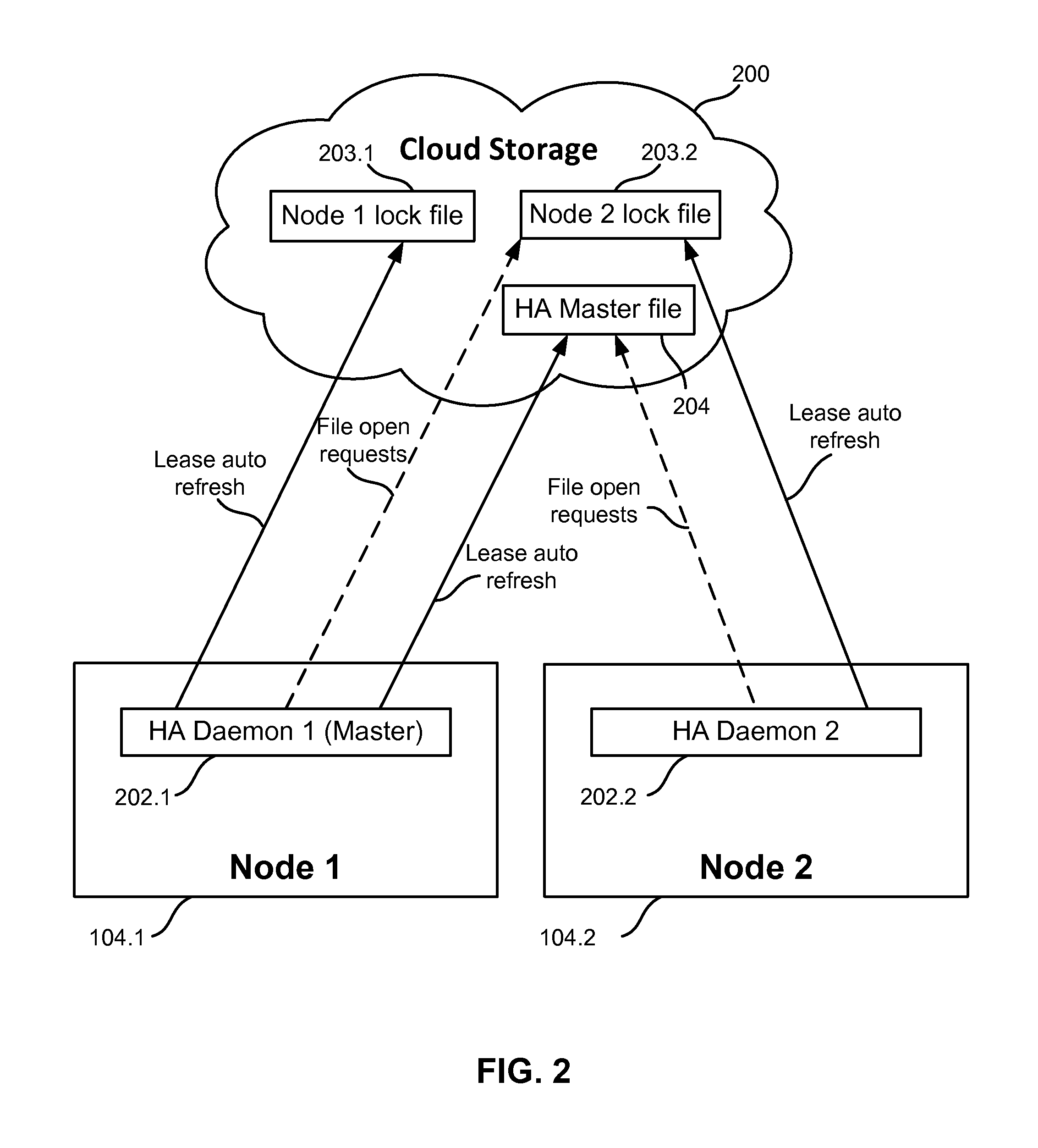
A method and computer program product for providing High Availability (HA) of services in a cloud-based system. The services are the applications used by the end users of the cloud system. The system uses shared cloud distributed storage. The cloud data is distributed over several nodes and is duplicated in an on-line mode. Each user launches and runs his own Virtual Execution Environment VEE (VM or Container) used as a cloud service. If one of the hardware nodes becomes unavailable, the HA system restores all of the VEEs of the failed node on a functional hardware node. Each node has a daemon, which monitors the situation and, if one of the nodes crashes, a master daemon provides for the restoration of the services of this node on other available nodes of the cloud.
Owner:VIRTUOZZO INT GMBH
Method and apparatus for browsing a management information base
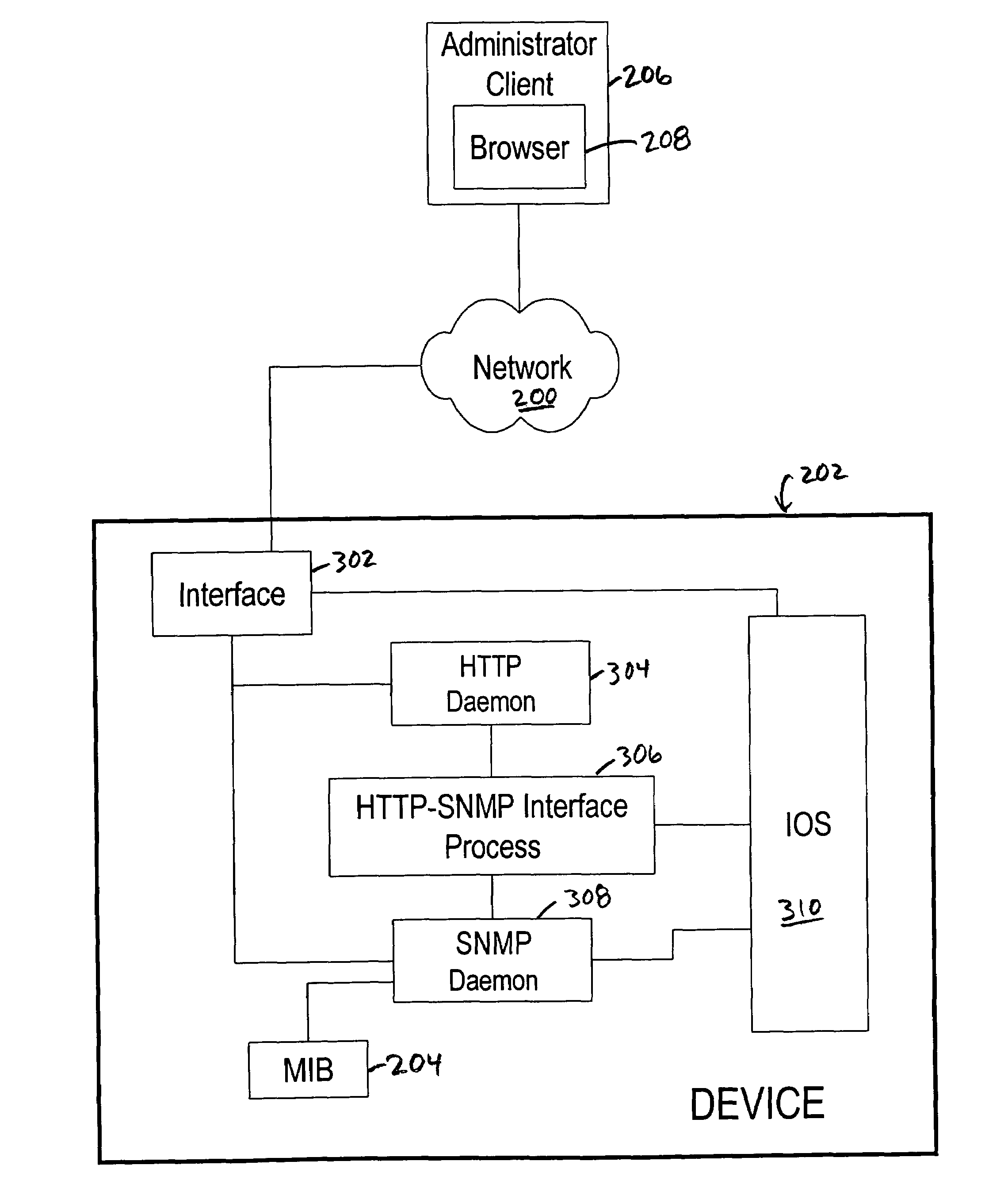
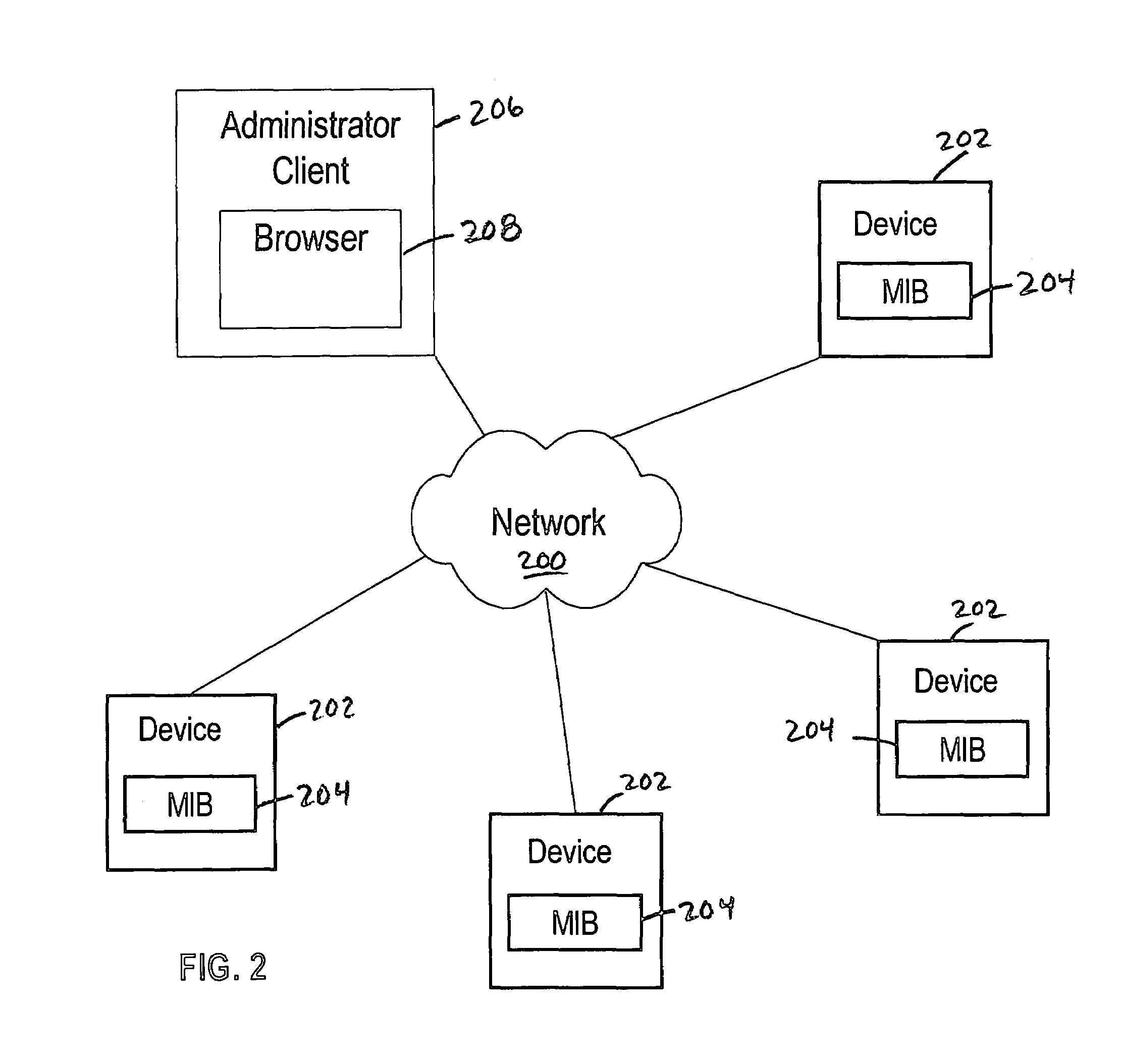
InactiveUS7739362B1Convenient and efficient techniqueValuable memory savingError preventionTransmission systemsManagement information baseHypertext Transfer Protocol
A method and apparatus are disclosed for browsing one or more Management Information Base (MIB) objects that are stored in a network device, such as a router or switch. In one embodiment, the network device receives a connection of a Web browser at an HTTP daemon and further receives a request from the Web browser to obtain the current value of the MIB variable. The request may be sent in a Hypertext Transfer Protocol (HTTP). The HTTP daemon passes the request to an HTTP-SNMP interface. The HTTP-SNMP interface creates an SNMP query for the current value of the MIB variable and sends the query to an SNMP daemon of the network device. The SNMP daemon obtains the current value of the variable from a MIB of the network device. The network device then returns the current value of the MIB variable to the Web browser which can display it.
Owner:CISCO TECH INC
Inter-process communication method based on application layer of android and basic application communication system
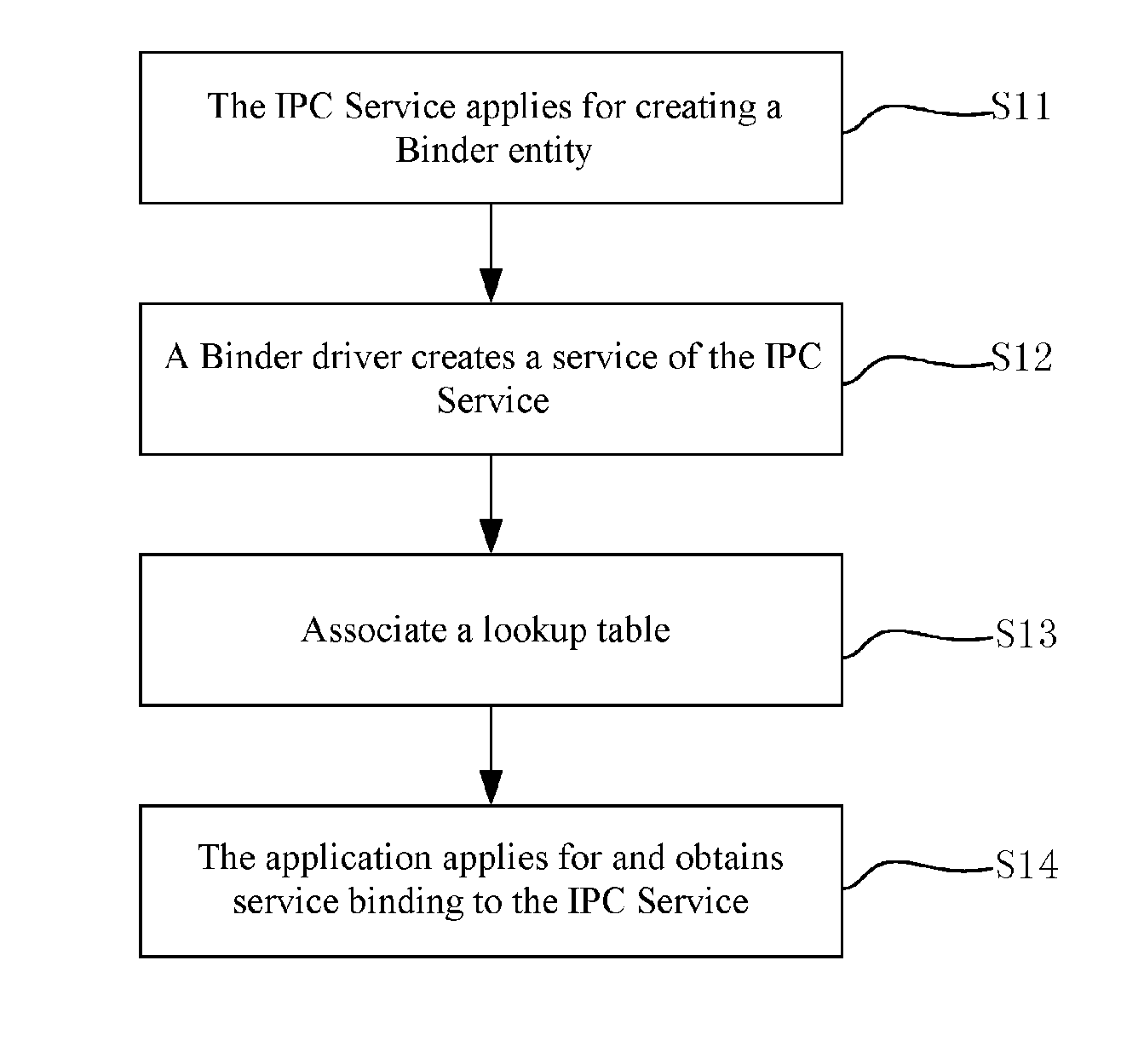
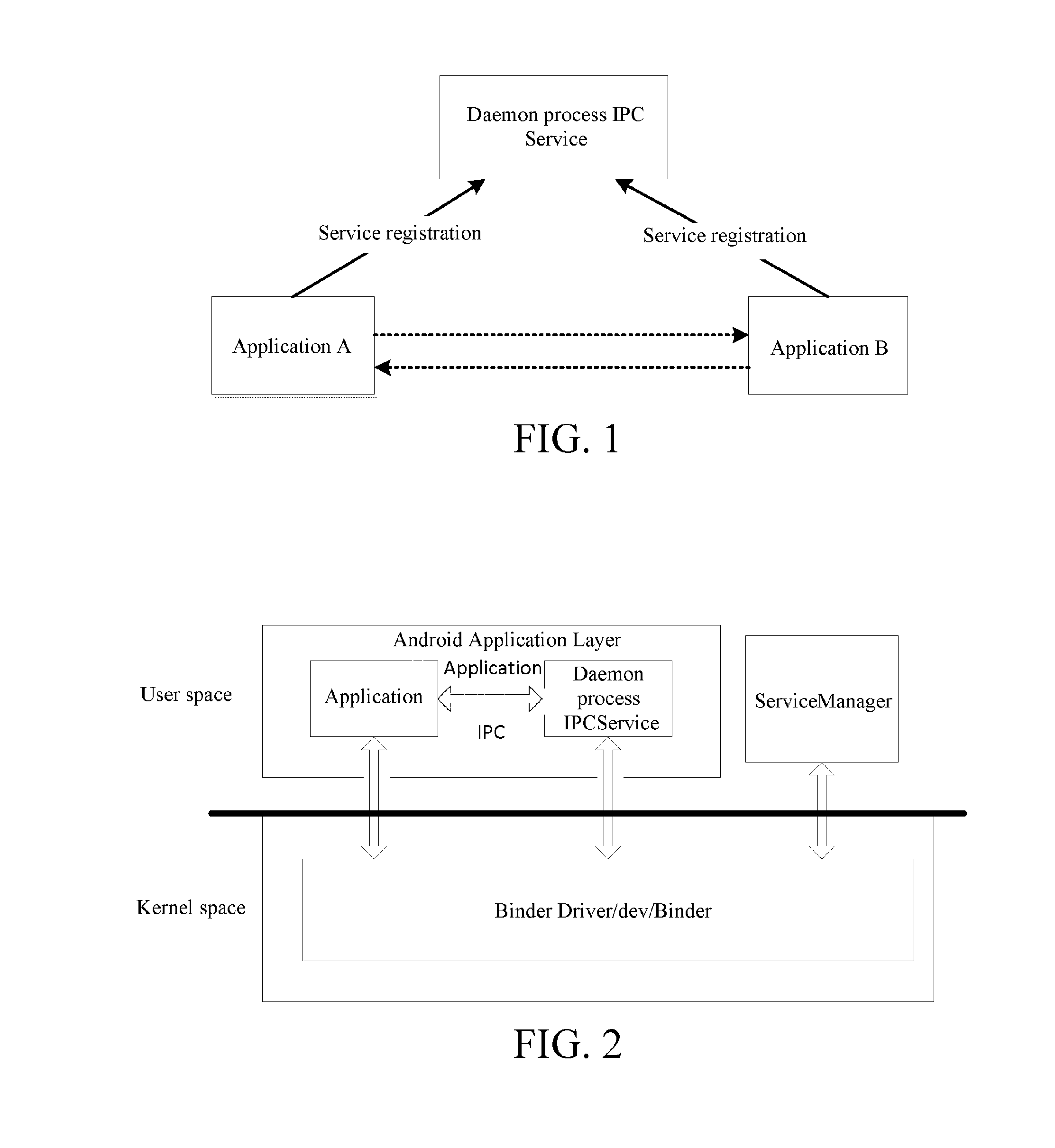
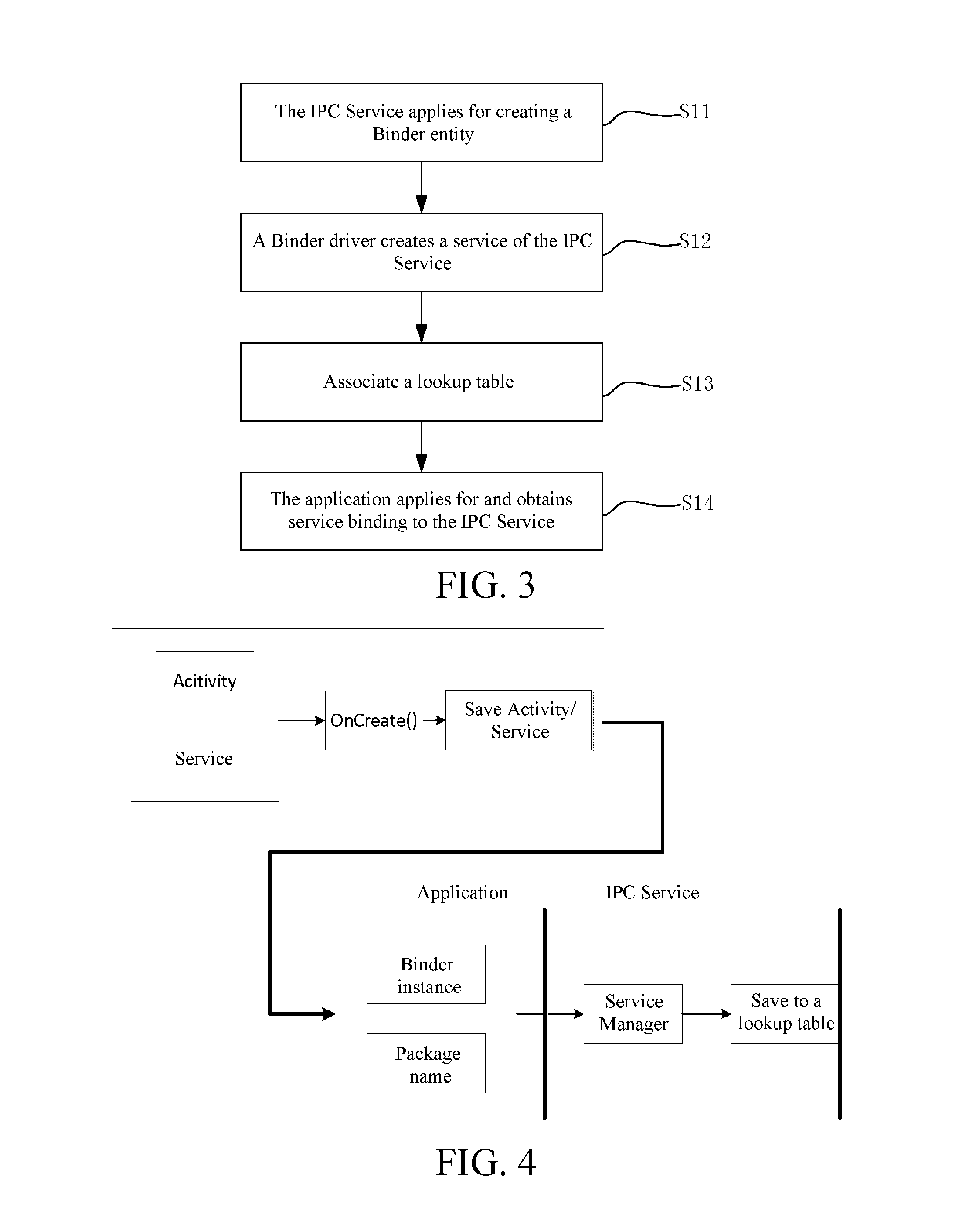
ActiveUS20160344846A1Rapidly and safely builtMore convenienceService provisioningInterprogram communicationVirtualizationCommunications system
Disclosed in the present invention are an inter-process communication method based on an application layer of Android and a basic application communication system. In accordance with a client / server communication mode, frame encapsulation applications for the mutual communication between system-level applications and user applications are created and virtualized as a client side; a daemon process IPC Service is created and virtualized as a server side; registration and binding of the IPC Service are completed through the applications, so as to achieve mutual communication among every application. Through the adoption of the technical solution of the present invention, a special communication mechanism can be rapidly and safely built during the inter-process communication of every application.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
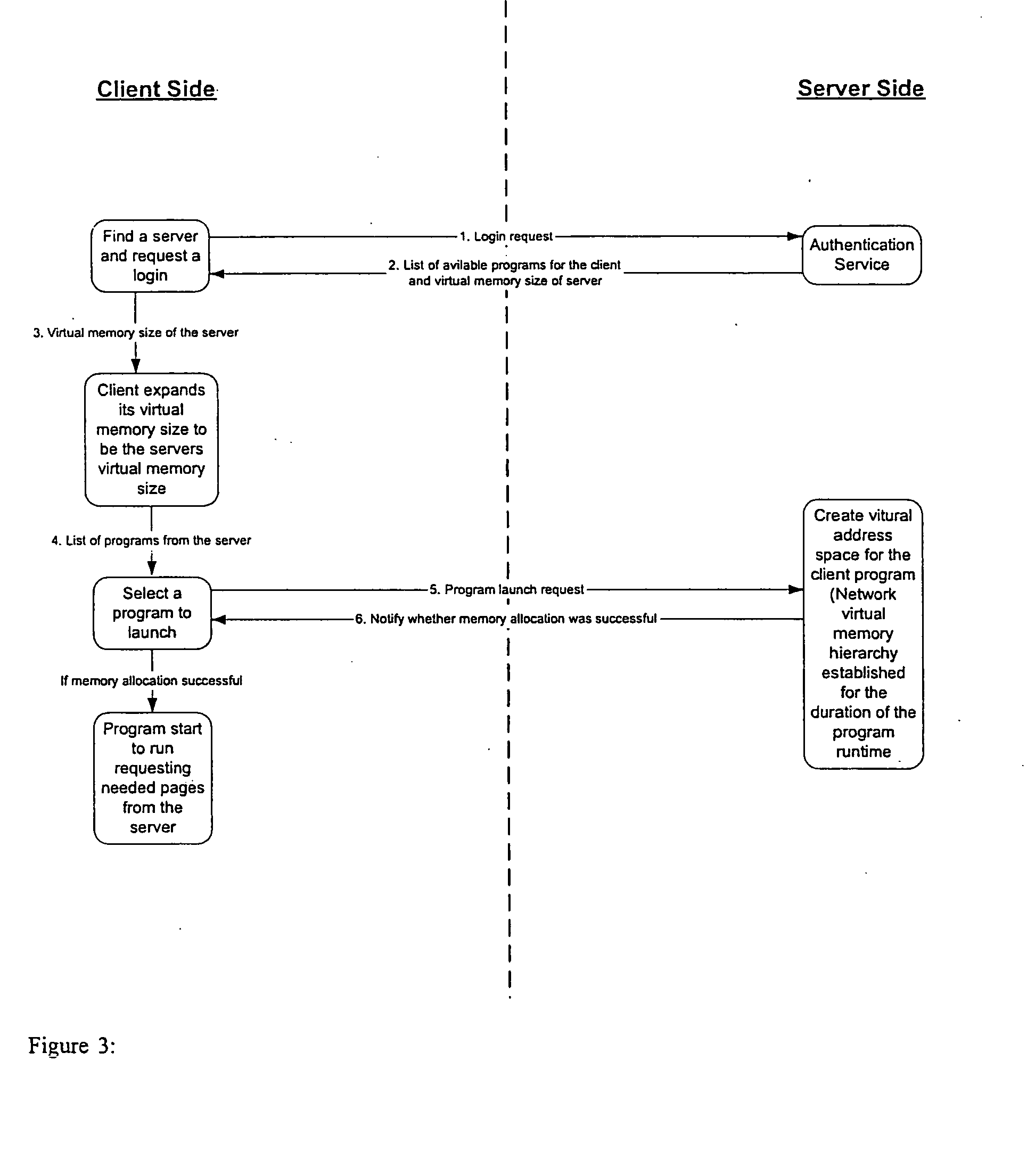
Method and apparatus for platform independent network virtual memory (PINVM) hierarchy
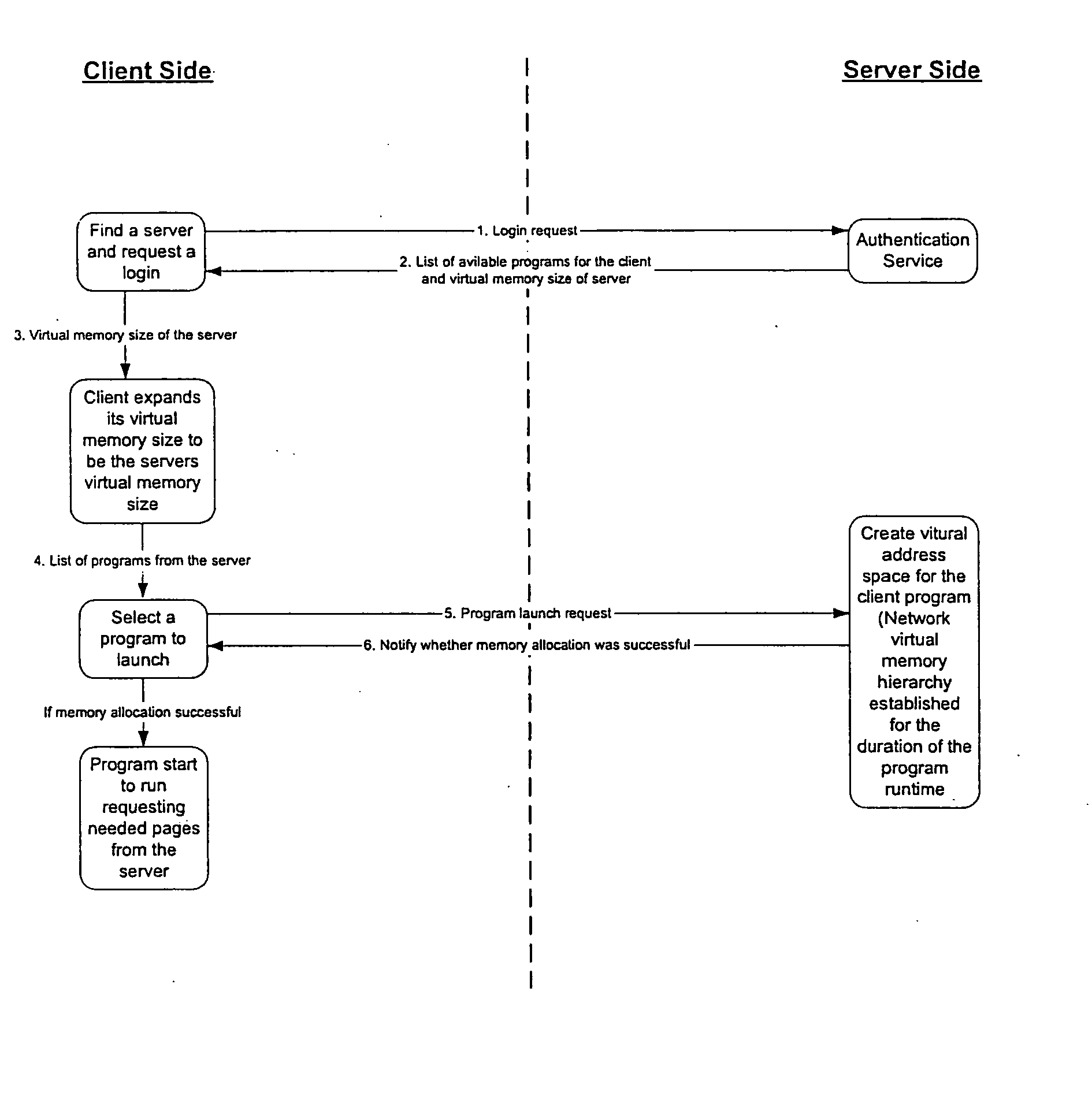
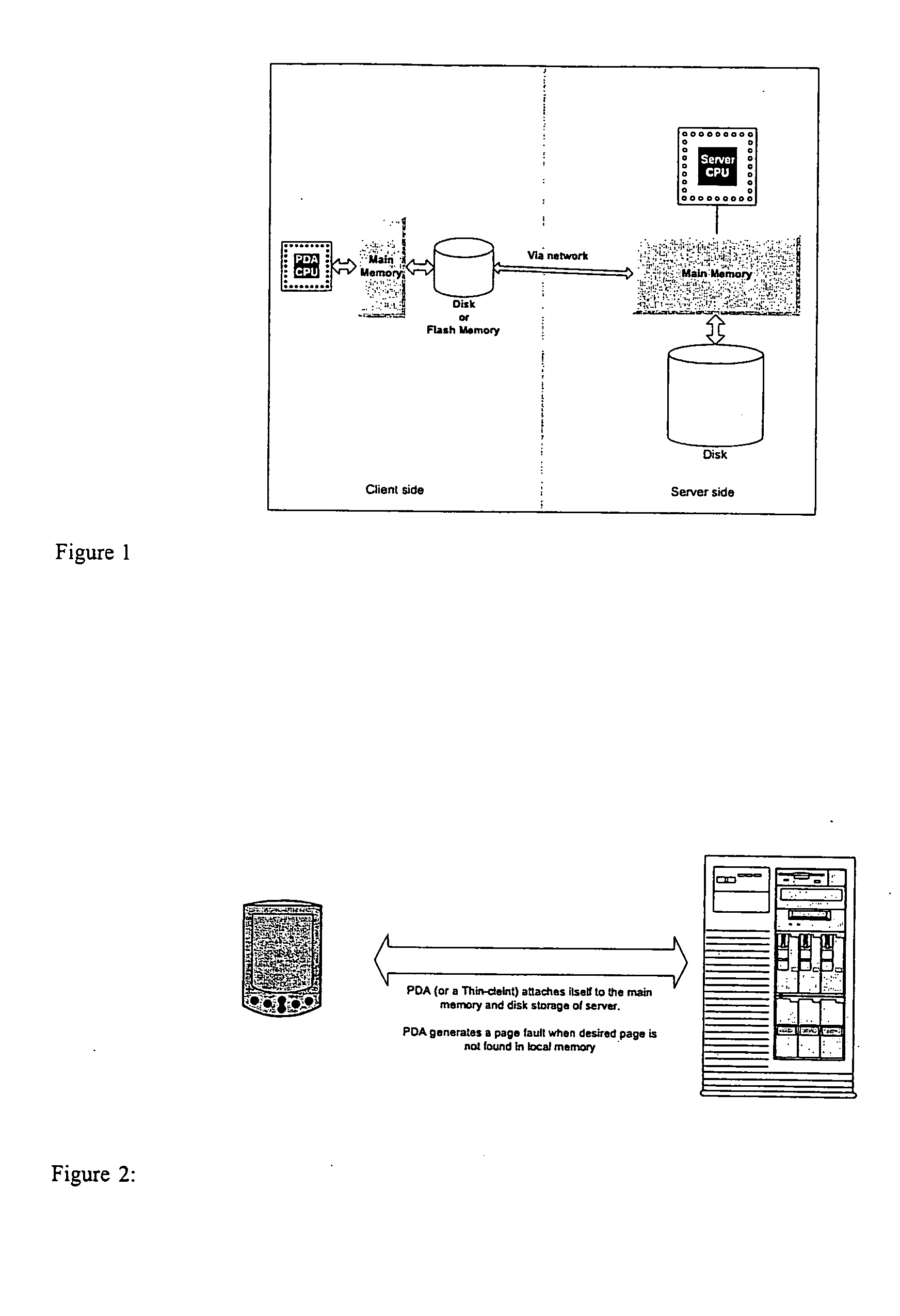
InactiveUS20050055419A1Digital computer detailsElectric digital data processingClient-sideVirtual memory
A thin-client / server session is established using platform independent network virtual memory (PINVM). The server contains a collection of programs that are compiled for the client architecture. The client finds a server for PINVM. The server provides the client with the list of programs as well as the size of virtual memory space that will be allowed for the client to use. The client-side daemon process adjusts the available memory size so that the client OS thinks the memory size available is as large as the virtual memory size provided by the server during the session. The network virtual memory hierarchy is established, with the server's memory and hard disk attached to the client's physical memory hierarchy. After the client selects a program to launch, the server creates a virtual address space for the client program using the network memory hierarchy established. The program can now run on the client.
Owner:SYRACUSE UNIVERSITY
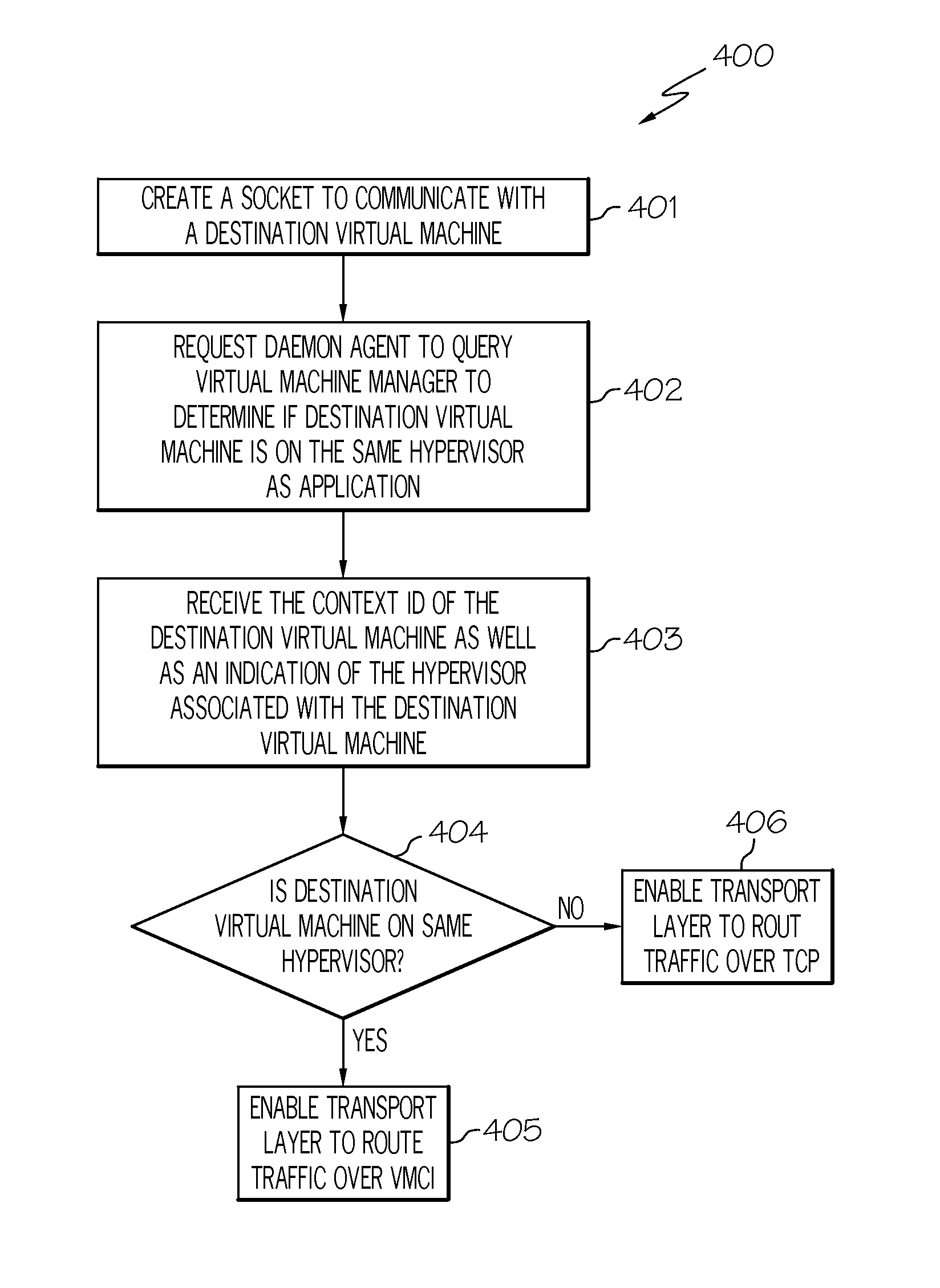
Automatically selecting optimal transport protocol in a cloud computing environment
ActiveUS20130191826A1Software simulation/interpretation/emulationMemory systemsTransmission protocolTransport layer
A method, system and computer program product for selecting an optimal transport protocol in a cloud computing environment. An application creates a socket to communicate with a destination Virtual Machine (VM). The application requests a daemon agent to query a virtual machine manager to determine if the destination VM is on the same hypervisor as the application. The daemon agent receives a VMCI address (“context ID”) and an indication of the hypervisor associated with the destination VM from the virtual machine manager. The daemon agent enables the transport layer to route traffic over the VMCI protocol to the destination VM using its context ID in response to the destination VM being on the same hypervisor as the application. In this manner, the application is able to route traffic using an optimal transport protocol, including VMCI, depending on peer hypervisor association without requiring any code modifications to the application.
Owner:IBM CORP
Platform for uniting north direction interfaces and starting method thereof
InactiveCN101304331AVersatileSimplify the installation processData switching detailsProgram loading/initiatingProcess moduleSoftware engineering
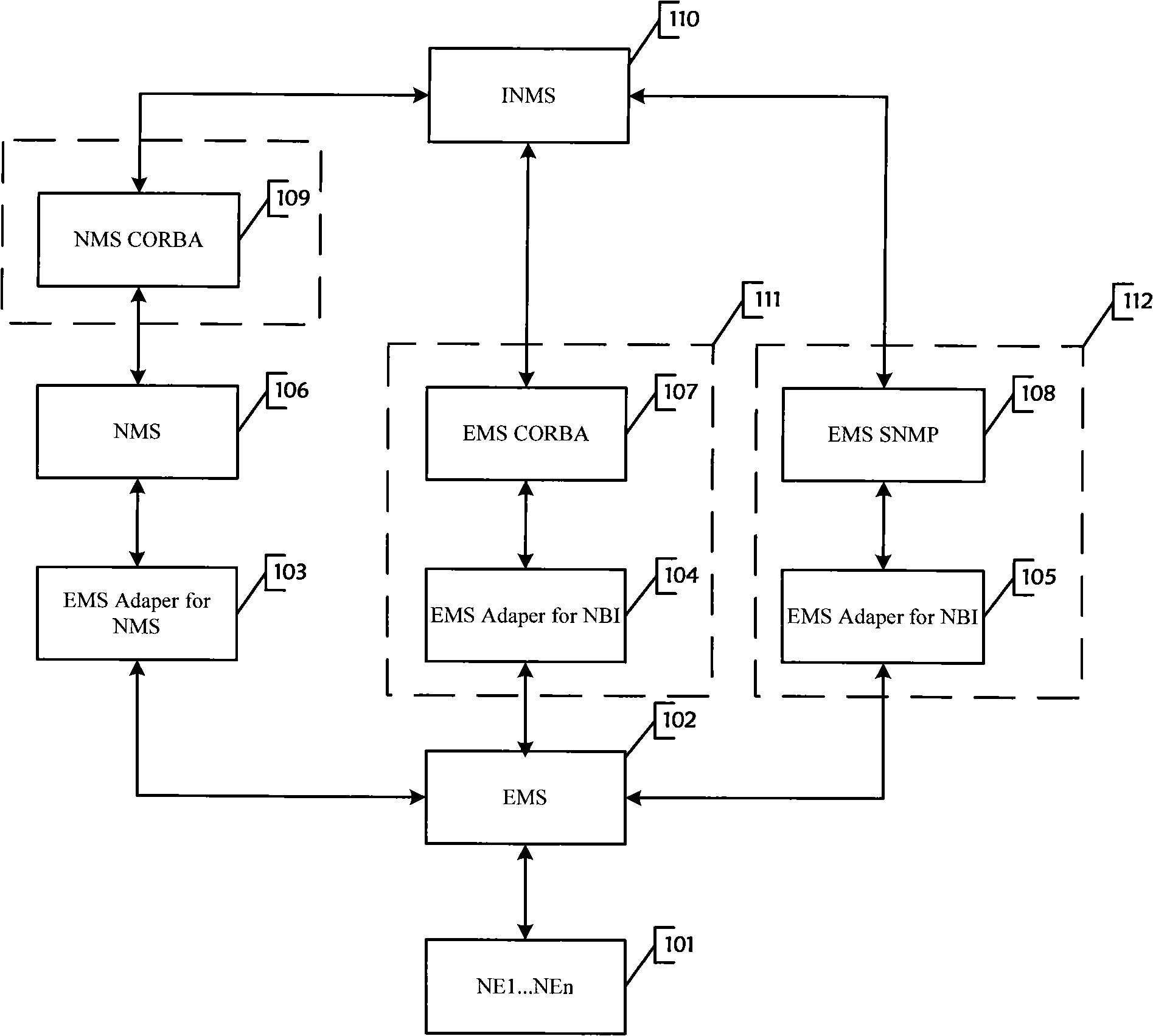
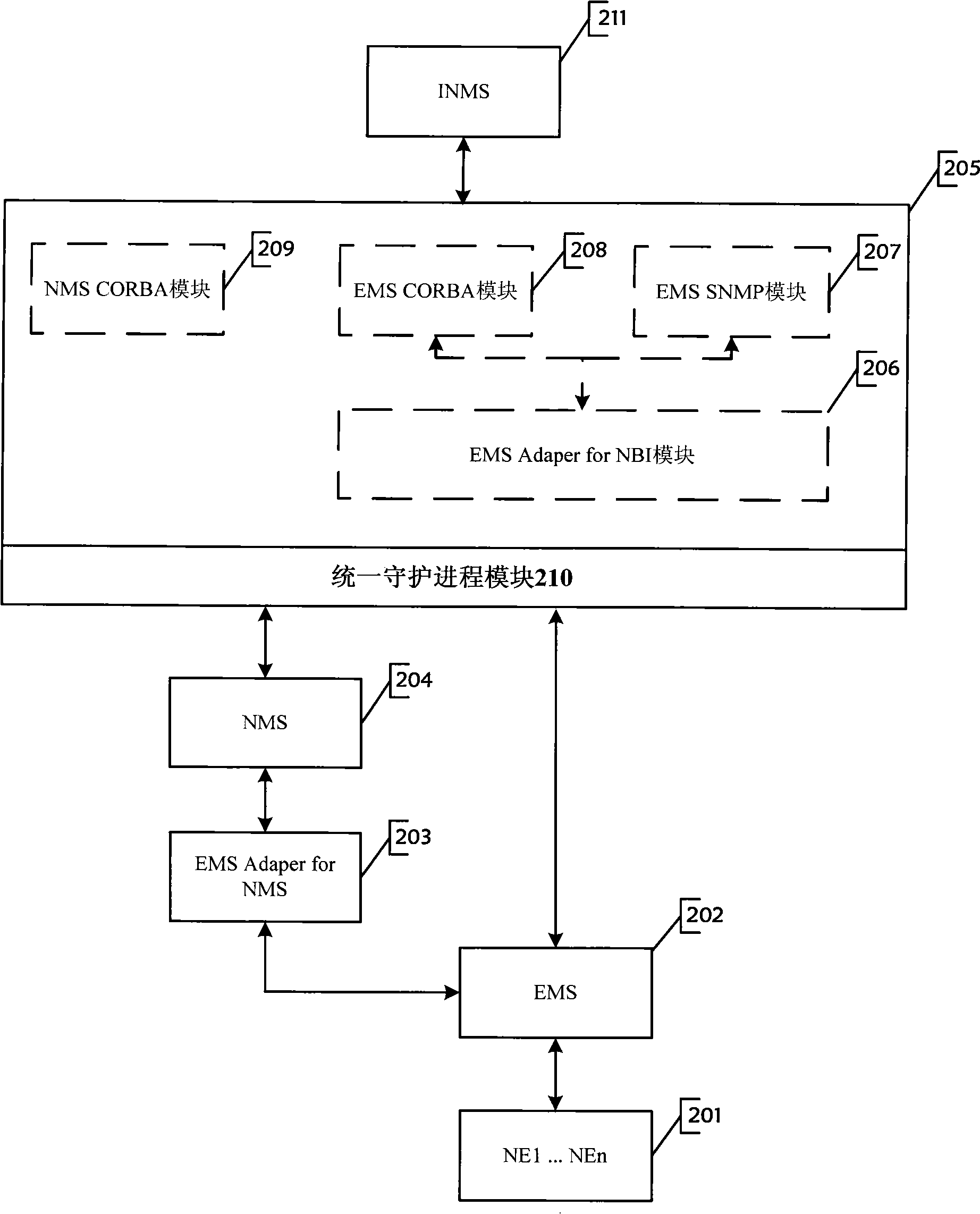
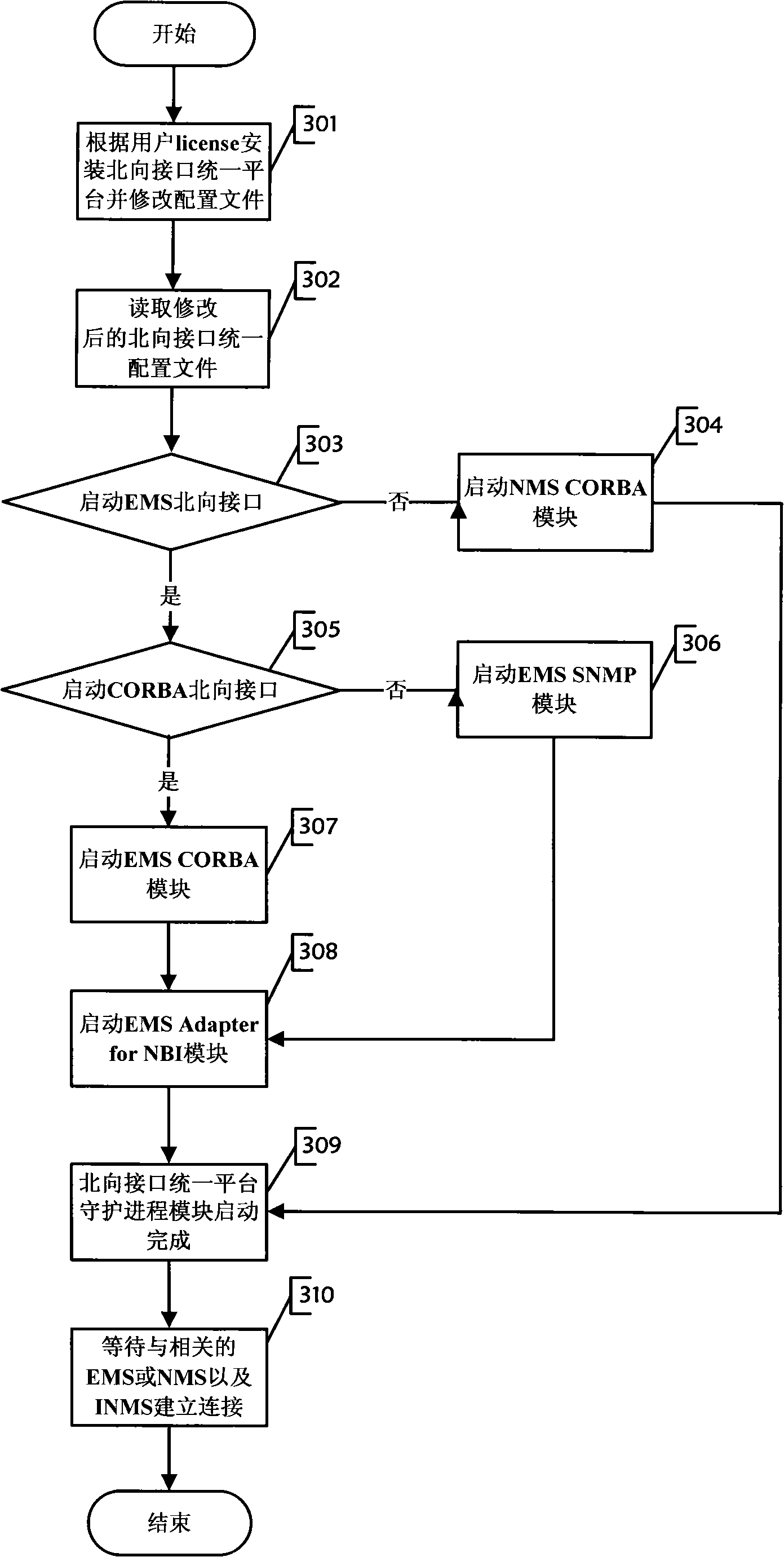
The invention discloses a unified platform with a northbound interface, which comprises a NMS CORBA module, an EMS CORBA module, an EMS SNMP module, an EMS Adaper for NBI module and a unified daemon process module; wherein, the unified daemon process module is used for starting, guarding and closing the EMS Adaper for NBI module, the EMS SNMP module, the EMS CORBA module and the NMS CORBA module. The starting method of the unified platform is choosing an installation module according to the permission information obtained by the user, and then modifying the unified allocation file of the northbound interface after the successful installation to cause the unified platform with a northbound interface to start normally. The unified platform with a northbound interface of the invention provides a CORBA supported by the EMS and the NMS northbound interface function and a SNMP supported by the EMS and the NMS northbound interface function. The platform is simple in installation process which can be installed in one trial. Meanwhile, the starting parameter only depends on one unified allocation file, which decreases the complexity and error probability, reduces the cost and simplifies the configuration.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
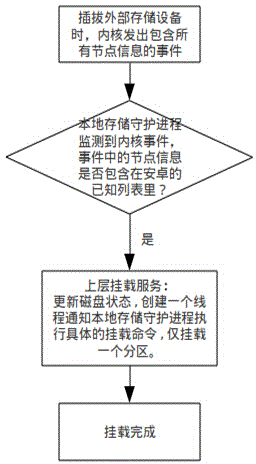
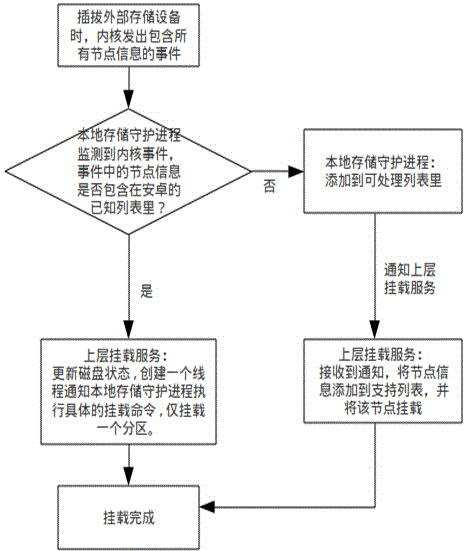
Method for mounting multi-partition storage device in Android system
InactiveCN104391657ABreak the limitEasy to manageInput/output to record carriersProgram controlExternal storageSoftware engineering
The invention relates to a method for mounting a storage device in the Android system, and in particular relates to a method for mounting a multi-partition storage device in the Android system. The method comprises the steps of 1, sending an event containing all node information through an inner core when inserting and drawing an external storage device; 2, determining that the local storage daemon process monitors the event from the inner core and whether the node information in the event is included into a known lift of the Android; if so, enabling upper mounting to be performed, namely, updating the disk state, creating a thread to inform the local storage daemon process of implementing a specific mounting command, and mounting a partition only; if not so, enabling the local storage daemon process to work, adding to a list that can be processed, informing of performing the upper mounting, namely, receiving the information, adding the node information to a support list, and mounting the node; 3, finishing the mounting. With the adoption of the method, each partition can be successfully mounted for a user to use, and therefore, the waste of the disk space can be avoided.
Owner:SHANGHAI INFOTM MICROELECTRONICS
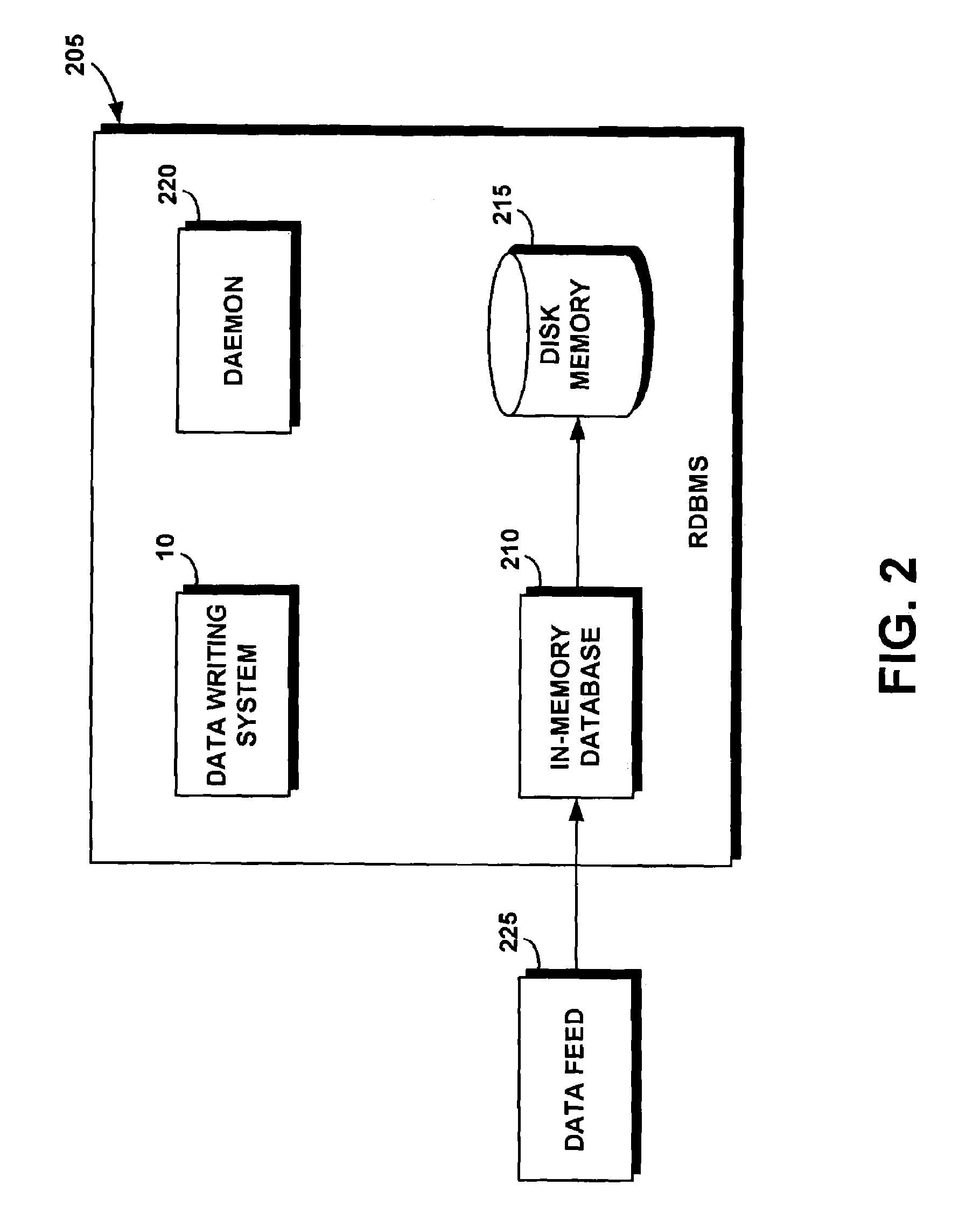
System and method for efficiently writing data from an in-memory database to a disk database
InactiveUS7113953B2Reduce lag timeWrite efficientlyData processing applicationsDatabase management systemsIn-memory databaseParallel computing
A system and associated method write data from an in-memory database to a disk database in an efficient manner and with a relatively short lag time. The integration of data from in-memory to disk is achieved by limiting the operations of the in-memory database to insert only. The system shortens lag time by reducing the number of transactions required to transfer data from in-memory database to disk memory. The system compiles into an RDBMS, knowledge about the structure of the in-memory database, and then uses the end of the transaction callbacks from the RDBMS to keep the in-memory database and the disk memory in synch. The RDBMS includes a daemon that runs periodically to find records in the in-memory database that have not yet been written to the RDBMS, and then writes the found records to the RDBMS as part of a single transaction. If the transaction completes successfully, the in-memory database is updated to reflect which records have been “flushed” to the RDBMS. If the transaction fails, no action is taken. The present system synchronizes the in-memory database with the RDBMS.
Owner:IBM CORP
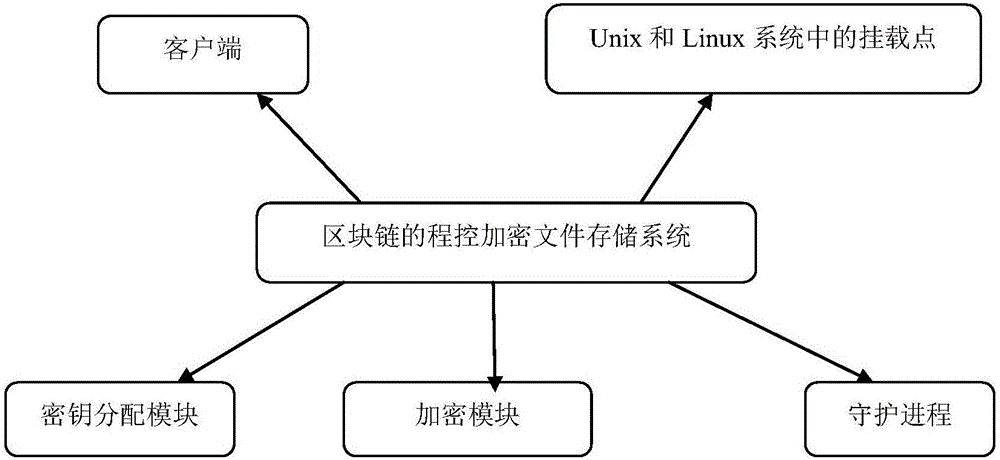
Program-controlled encrypted file storage system for block chain and method thereof
ActiveCN106326752AInput/output to record carriersUser identity/authority verificationUnixFile system
The invention provides a program-controlled encrypted file storage system for a block chain. The program-controlled encrypted file storage system comprises: (1) a client, in which all files are added after being encrypted; (2) mounting points in Unix and Linix systems, which are used for covering up concrete operation details of transaction files; (3) a secret key distribution module for enabling a single user to distribute a secret key to each physical address of each transaction file; (4) an encryption module which is used for the program-controlled encrypted file storage system to mount one virtual transaction file system onto one standard Unix and Linix file systems; (5) a daemon process which is loaded to the client and used for converting a standard program-controlled encrypted file storage system call into a special program-controlled encrypted file storage system call. According to the program-controlled encrypted file storage system for the block chain and a method thereof, processing speeds when big files are read and written and small files are created are higher than those of a common encryption file storage system by over multiple times.
Owner:SHENZHEN QIANHAI HUANRONG LIANYI INFORMATION TECH SERVICES CO LTD
Method and Apparatus for Subdividing Local Memory in Nodes of a Massively Parallel Computer System
InactiveUS20080040561A1Little overhead to implementEfficient use ofGeneral purpose stored program computerProgram controlLocal memoriesOn demand
A memory management mechanism a nodal having multiple processors in a massively parallel computer system dynamically configures nodal memory on demand. A respective variable-sized subdivision of nodal memory is associated with each processor in the node. A processor may request additional memory, and the other processor(s) may grant or veto the request. If granted, the requested memory is added to the subdivision of the requesting processor. A processor can only access memory within its own subdivision. Preferably, each subdivision contains a daemon which monitors memory usage and generates requests for additional memory.
Owner:IBM CORP
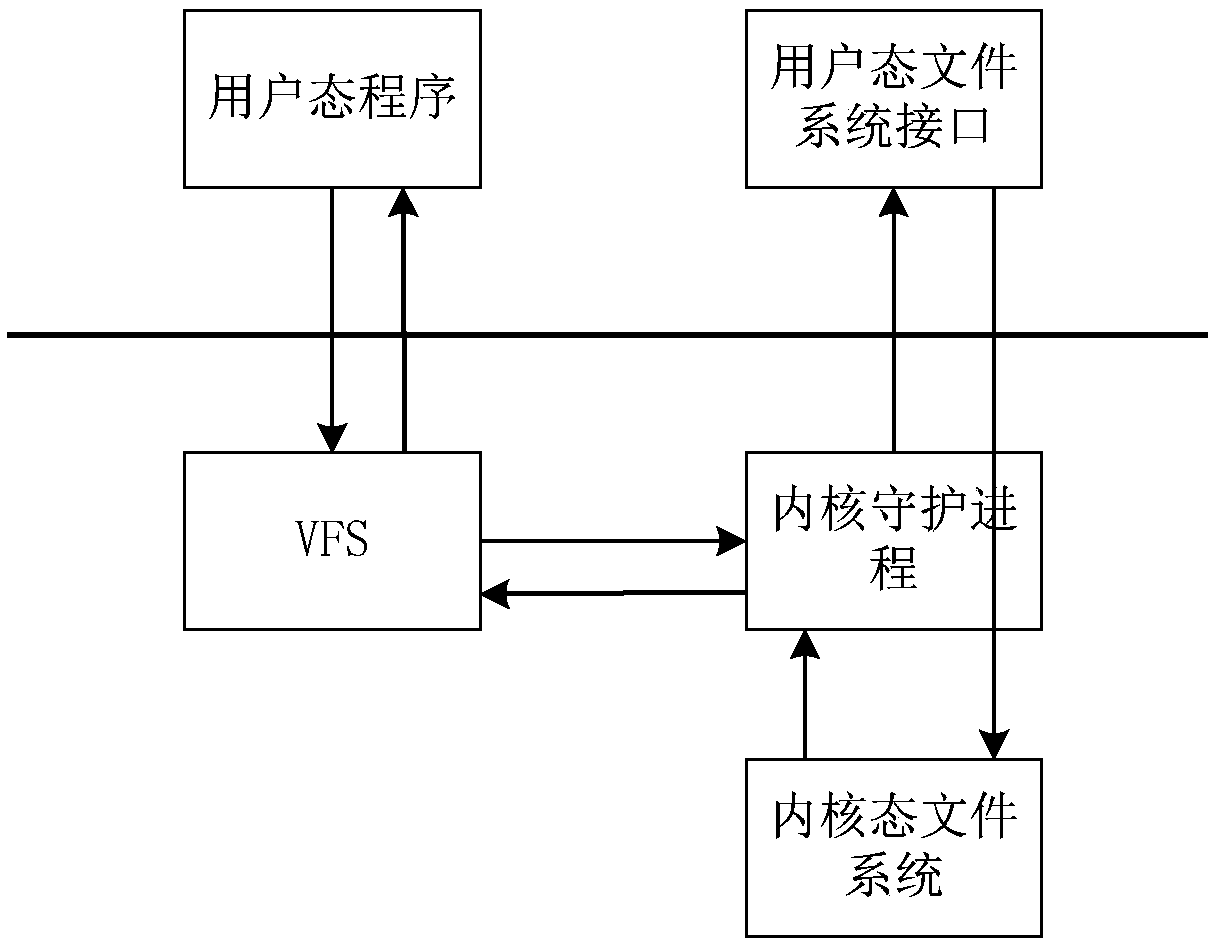
A user-mode file system processing method
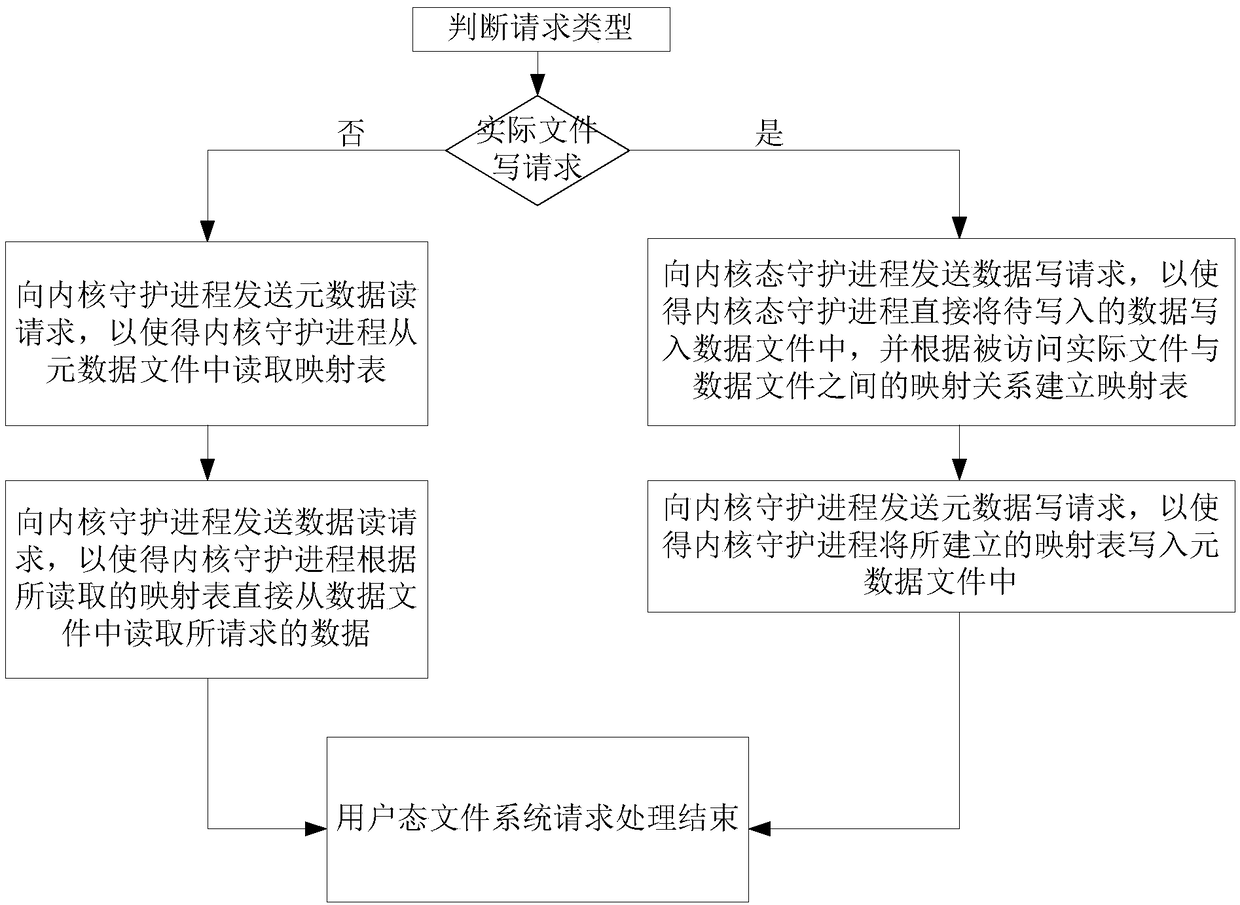
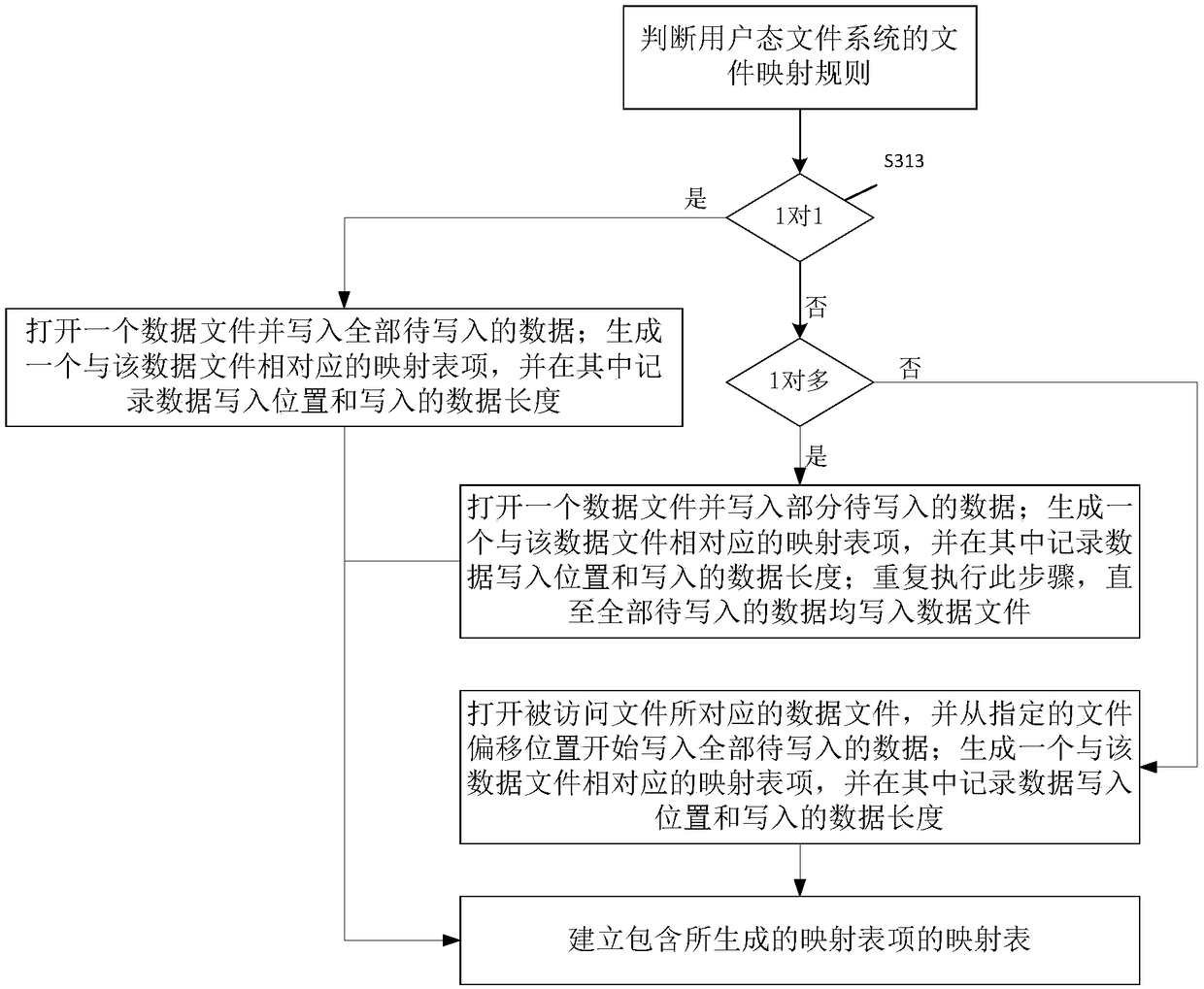
ActiveCN109445685AImprove I/O bandwidthImprove access speedInput/output to record carriersFile access structuresFile systemData file
The invention discloses a user-mode file system reqeust processing method, including sending data write request to kernel daemon to make kernel daemon directly write data to be written into data file,and establishing mapping table according to mapping relation between accessed actual file and data file, sending data write request to kernel daemon to make kernel daemon directly write data to be written into data file, and sending data write request to kernel daemon; then using the kernel daemon to send a metadata write request to the kernel daemon so that the kernel daemon writes the established mapping table into the metadata file; if the request is an actual file read request, using the kernel daemon to send a metadata read request to the kernel daemon so that the kernel daemon reads themapping table from the metadata file; sending a data read request to the kernel daemon to cause the kernel daemon to read the requested data directly from the data file according to the read mappingtable. The invention can reduce the switching times between the user state and the kernel state in the process of reading / writing the data file, and improve the data transmission performance.
Owner:HUAZHONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com