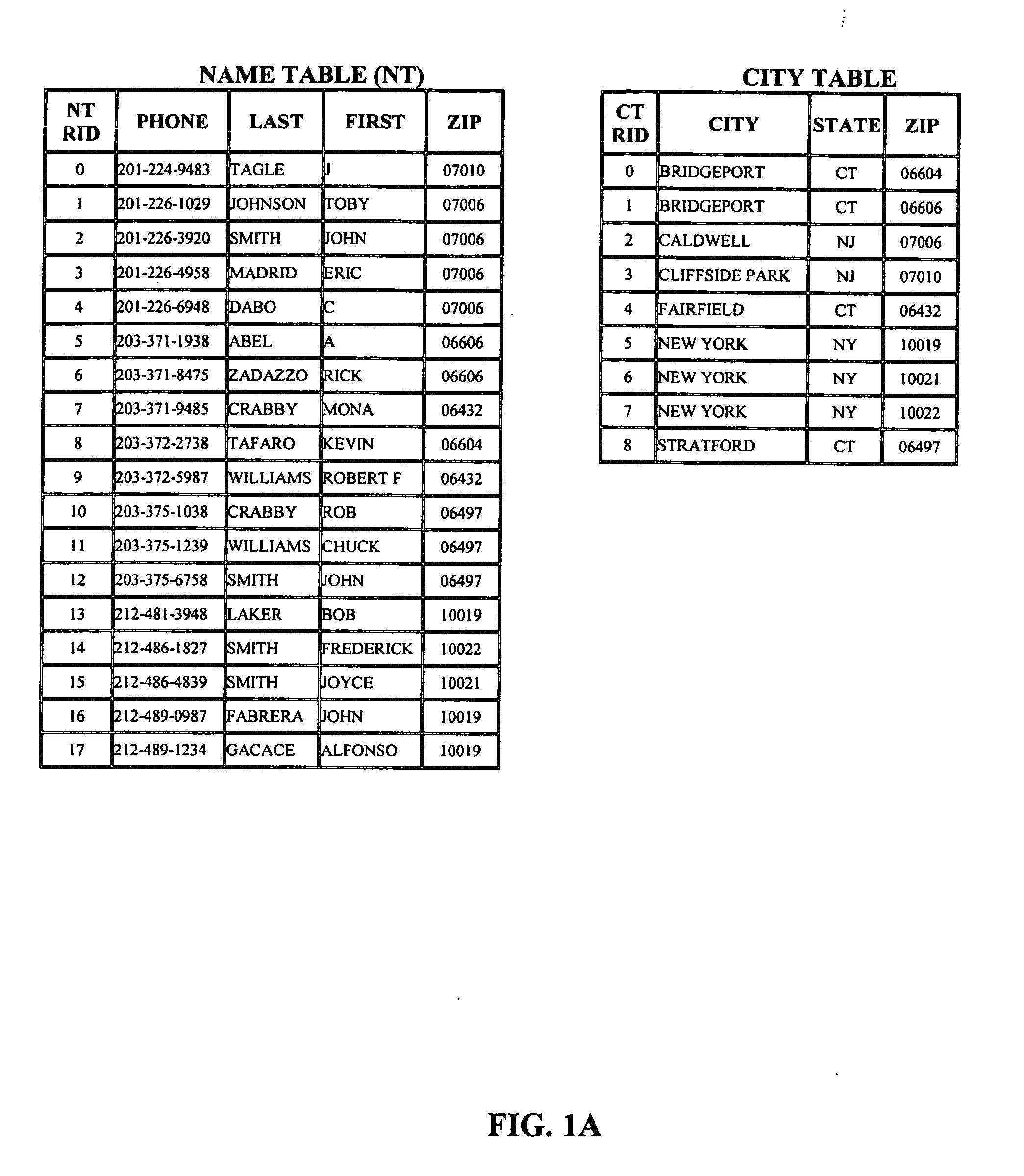
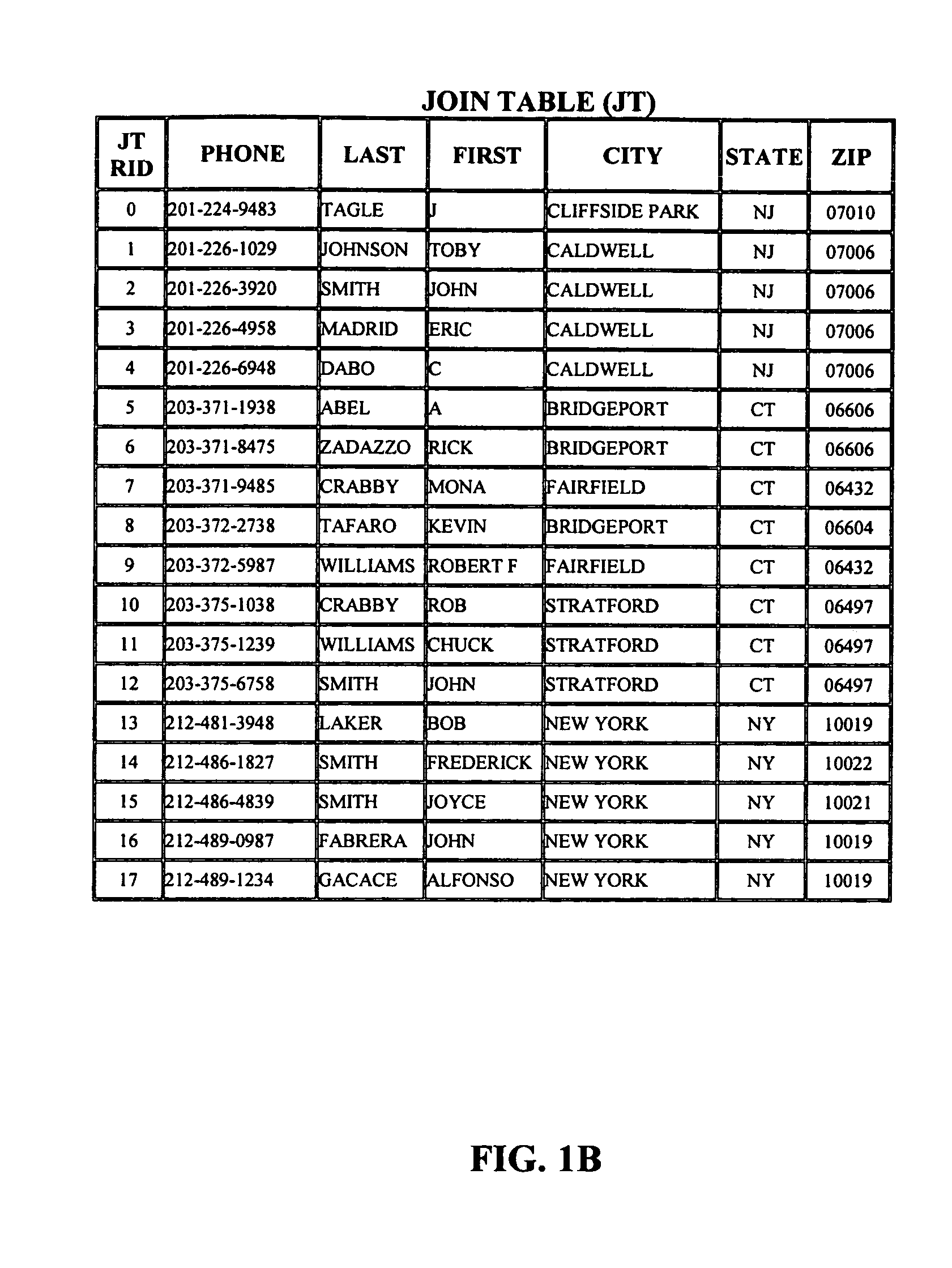
Patents
Literature
1003 results about "Disk space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
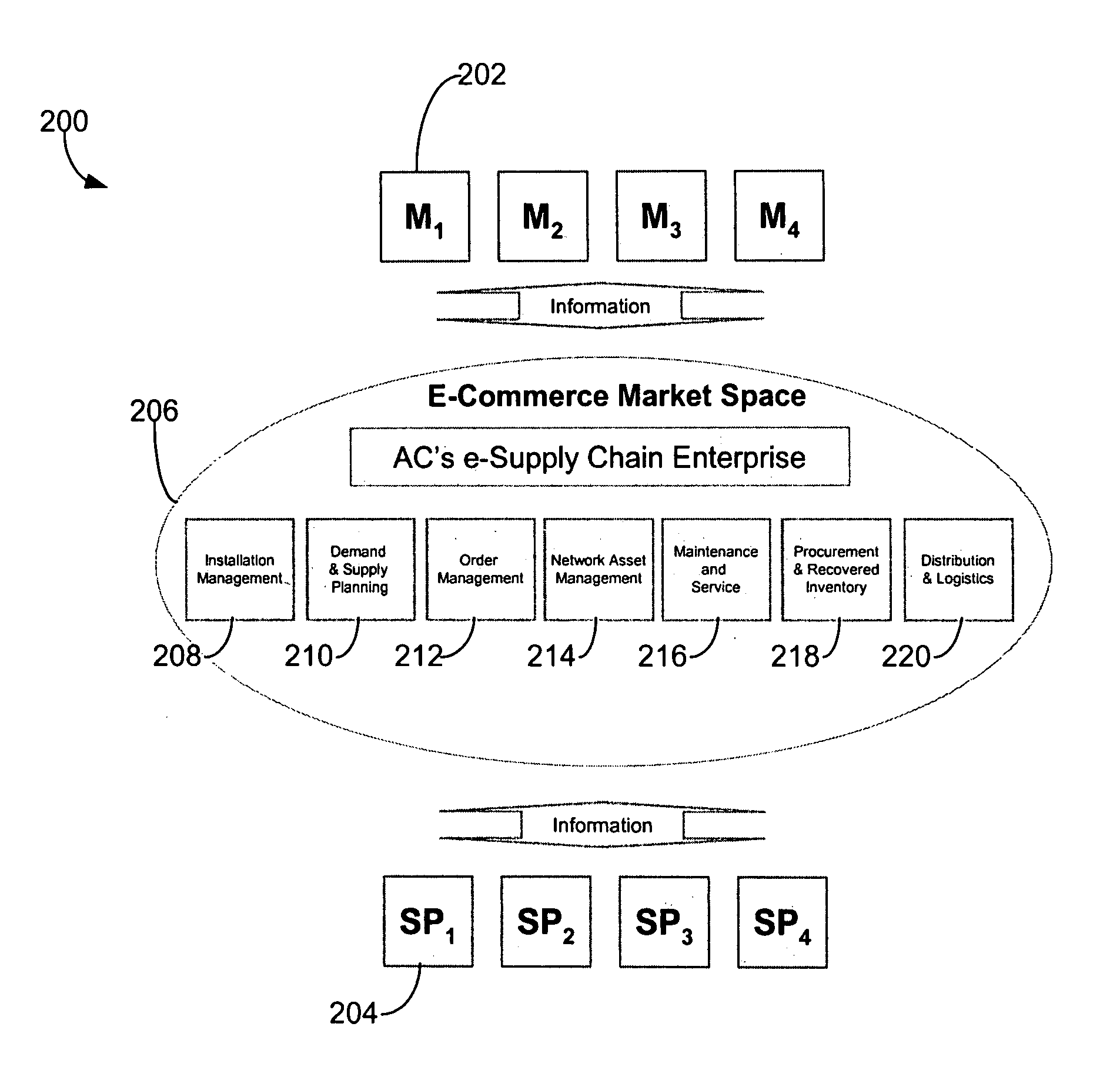
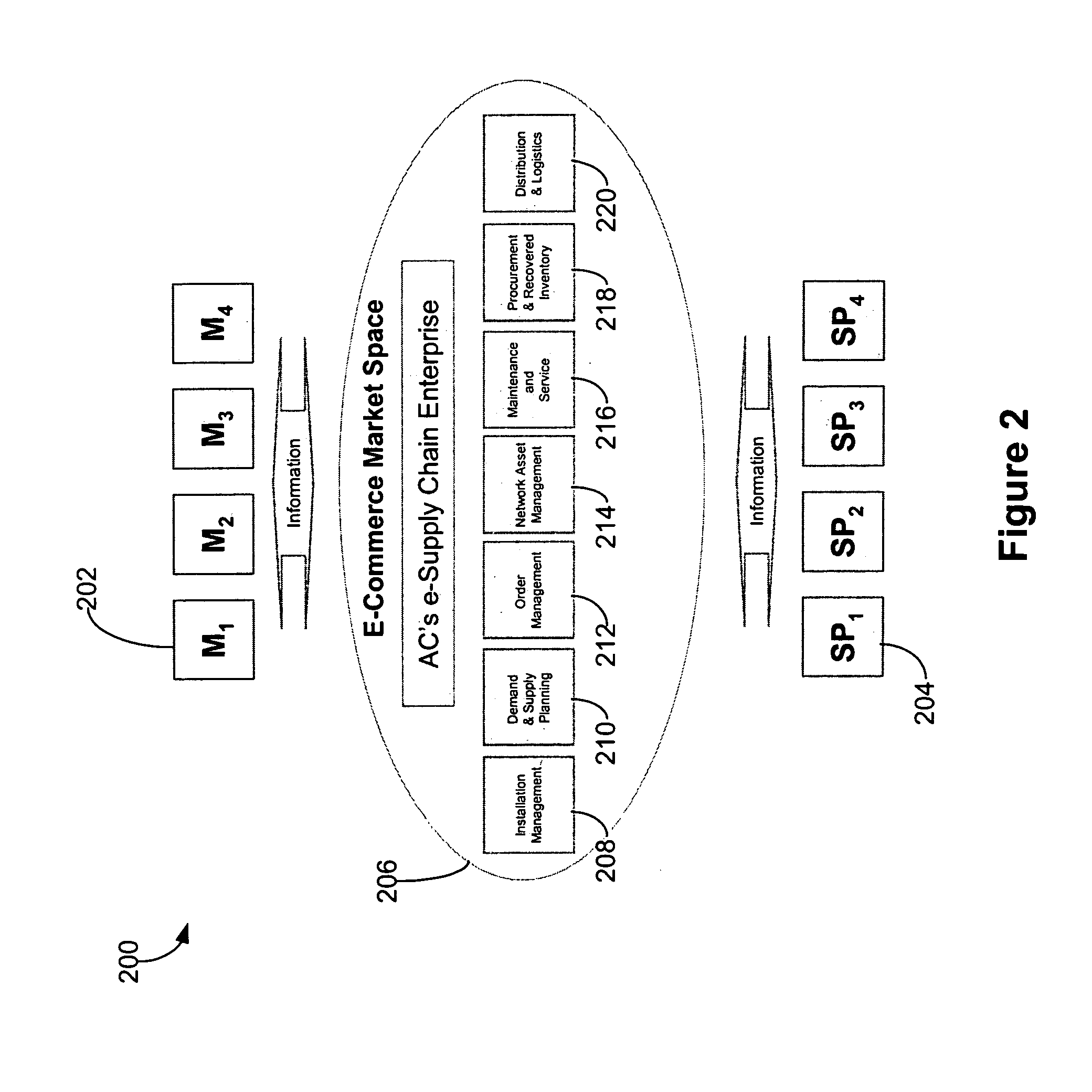
Scheduling and planning maintenance and service in a network-based supply chain environment
InactiveUS7716077B1Simple personalization processTechnology managementResourcesData synchronizationExternal data
A system, method and article of manufacture are provided for administrating a network-based supply chain on a network. Operation of entities is monitored. Entities include server processes, disk space, memory availability, CPU utilization, access time to a server, and / or a number of connections in a network-based supply chain. Items including merchandising content, currency exchange rates, tax rates, and / or pricing in the network-based supply chain are updated at predetermined intervals. In addition, external data stored separately from the network-based supply chain is synchronized with internal data stored on the network-based supply chain. Contact information received from users of the network-based supply chain is also managed. Users include service providers and manufacturer utilizing the network-based supply chain. The items are altered based on profiles of the users of the network-based supply chain.
Owner:ACCENTURE GLOBAL SERVICES LTD
Anatomical interbody implant and gripper for same
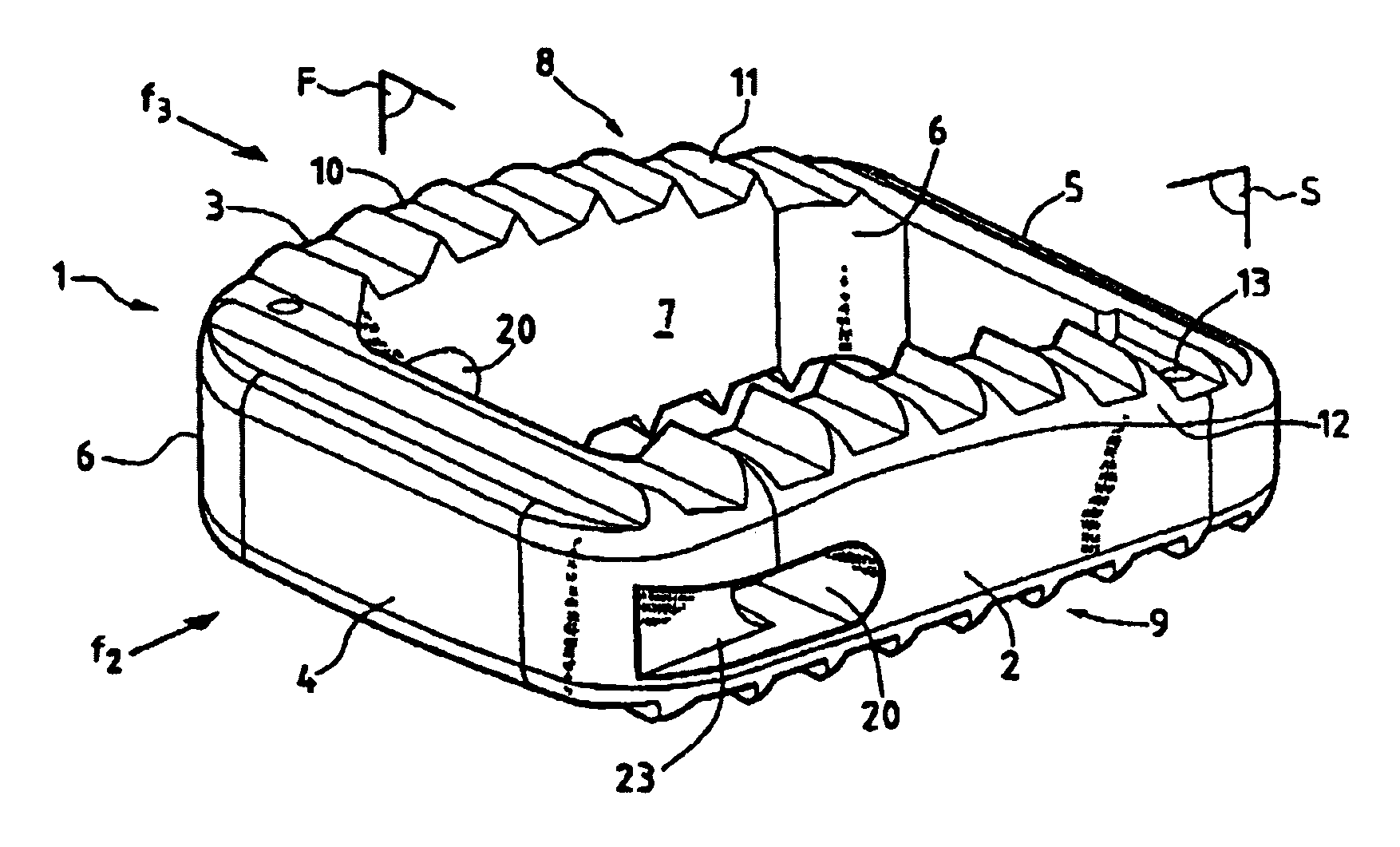
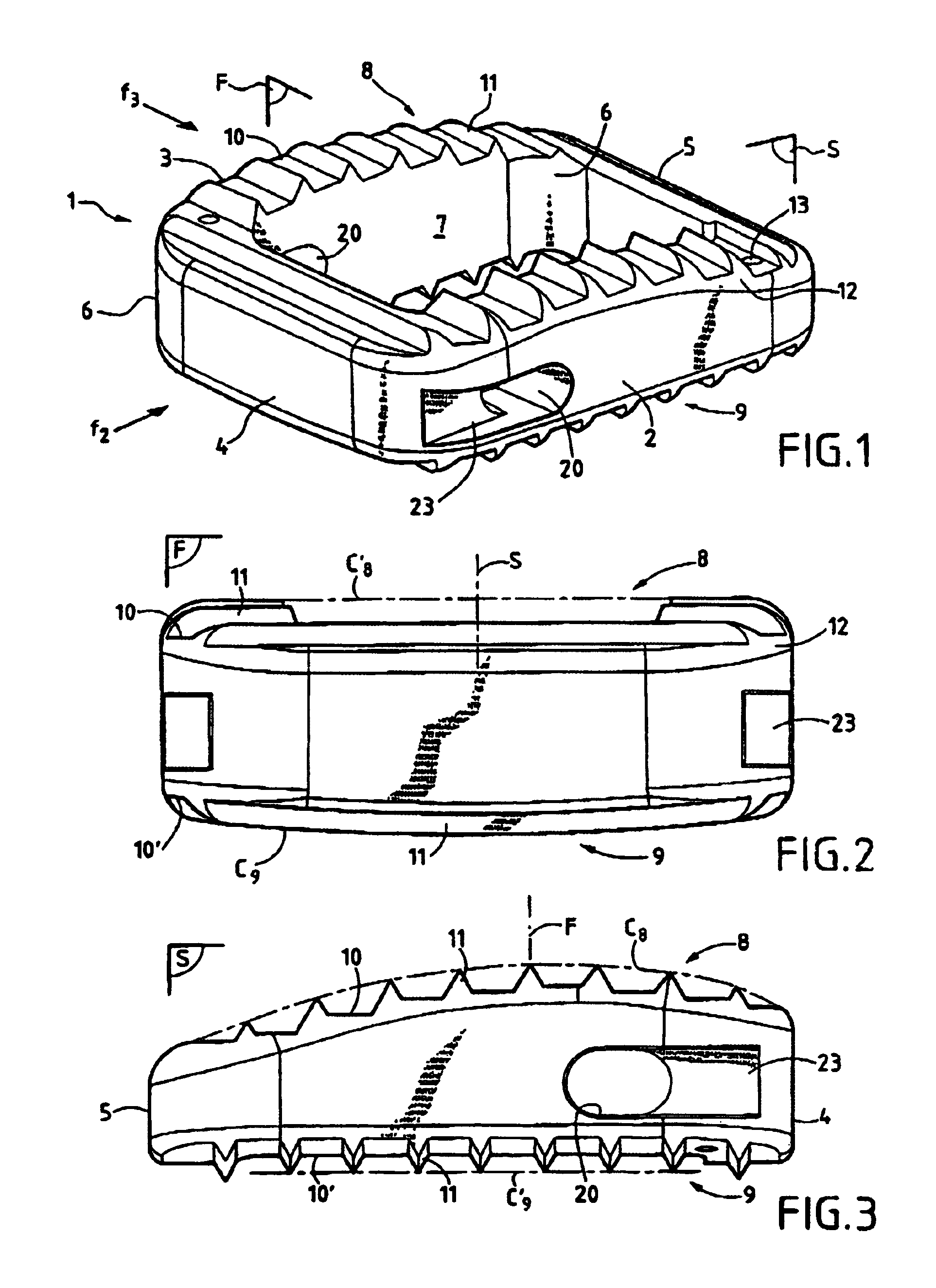
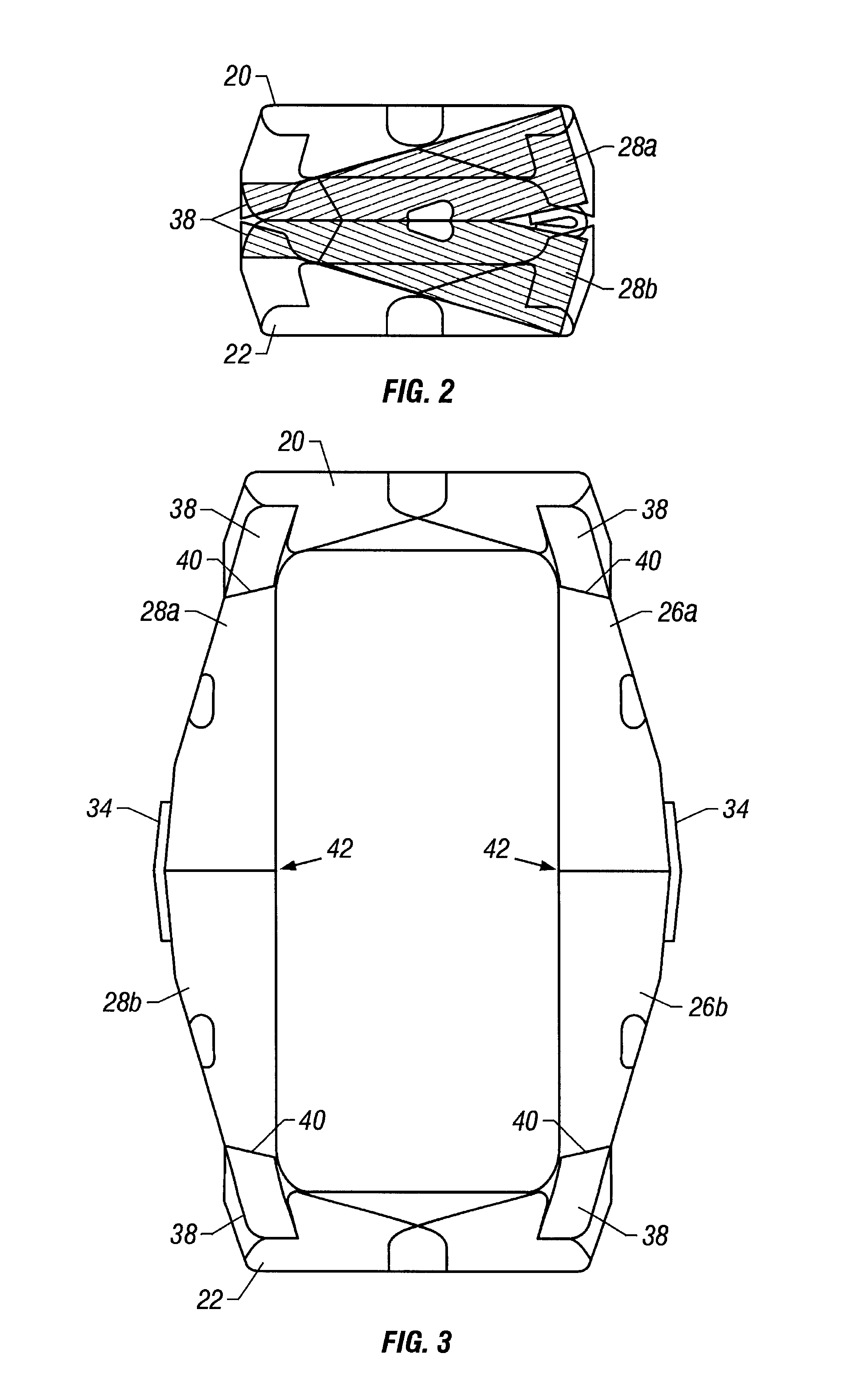
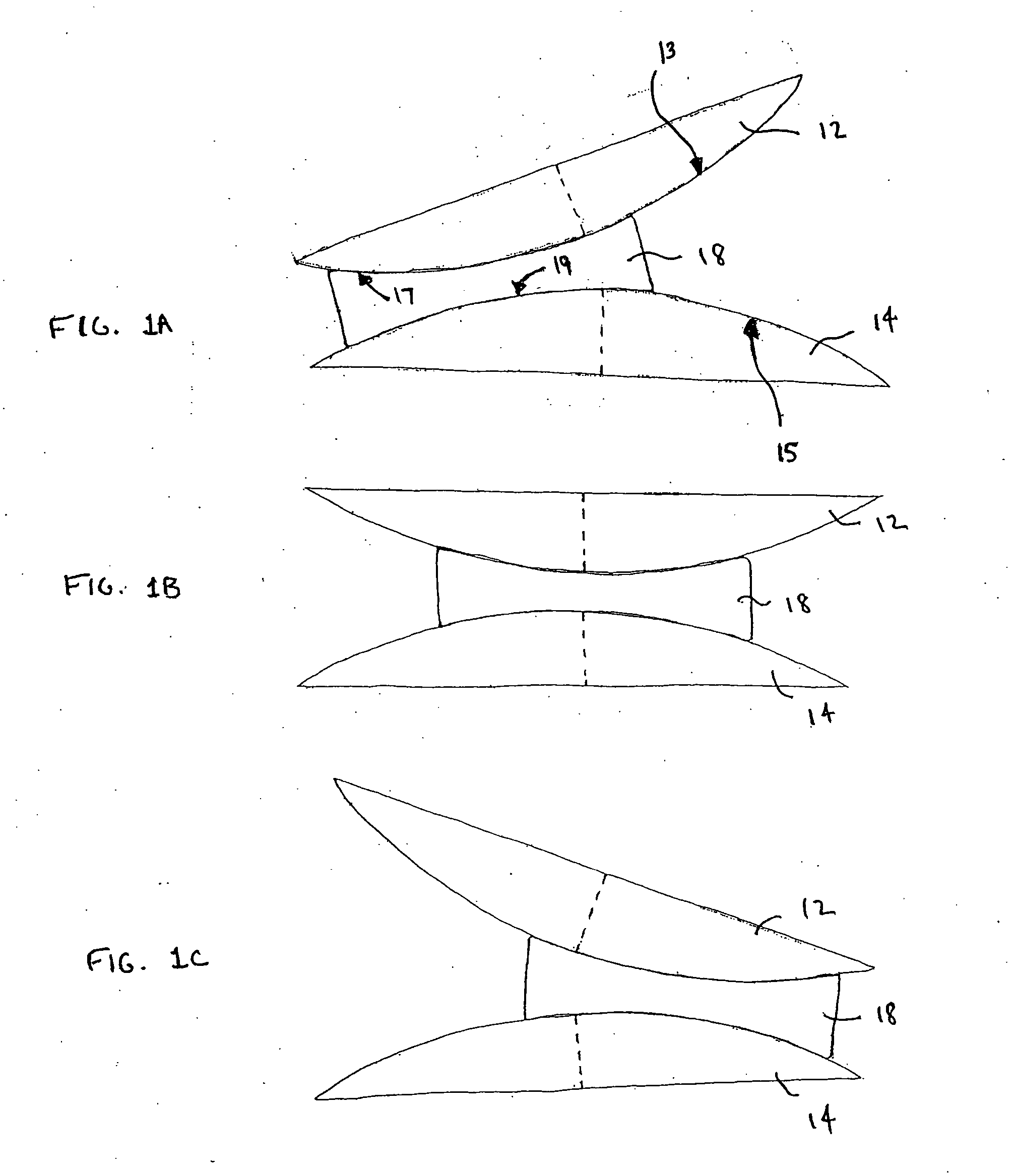
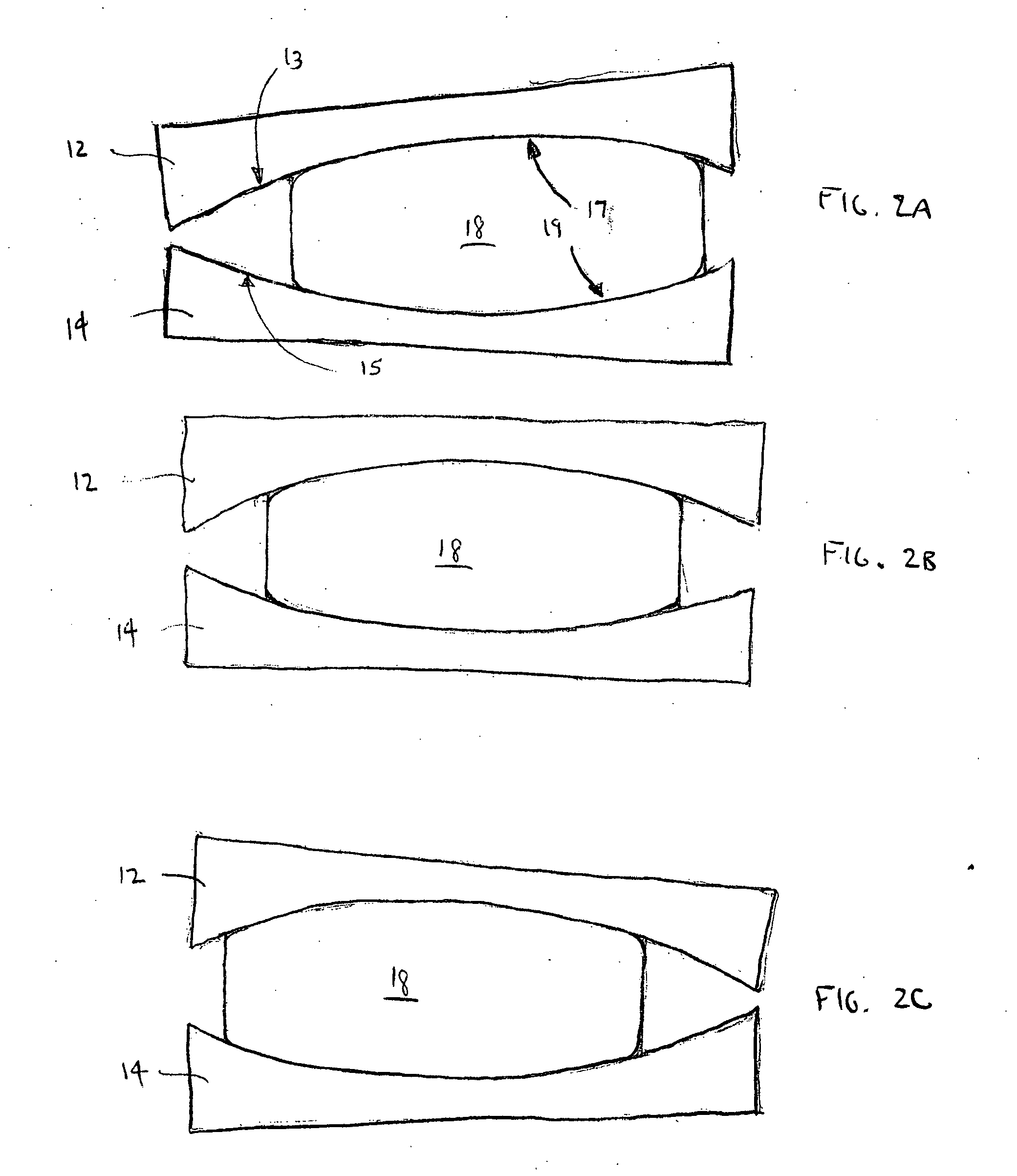
The invention relates to an intersomatic implant designed to be inserted in the disk space defined between two adjacent vertebrae, namely an overlying vertebra and an underlying vertebra, for the purpose of reestablishing the anatomic space between the vertebrae, the implant being in the form of a cage (1) that is generally in the shape of a rectangular block having at least two sagittal walls (2, 3) interconnected at least by an anterior transverse wall (4) and by a posterior transverse wall (5), the walls (2 to 5) presenting rims (10) extending on one surface to define a first transverse face (8) and on the other side to define a second transverse face (9).According to the invention, the implant comprises:a first transverse face (8) presenting in the sagittal plane a convex profile congruent with the sagittal anatomic profile of an overlying vertebra; anda second transverse face presenting in the frontal plane a convex profile congruent with the frontal anatomic profile of an overlying vertebra.
Owner:SCIENTX
Method and apparatus for providing an expandable spinal fusion cage
The spinal fusion cage of the invention comprises two opposing end plates, and three opposing collapsible legs. The two opposing end plates and three opposing collapsible legs are adapted to be configured into an expanded cage from a collapsed configuration. The expanded cage assumes a predetermined rigid shape and volume for disposition between two adjacent vertebrae. The collapsed configuration of the cage is adapted for posterior insertion into the disk space. The apparatus further comprises locking means for at least temporarily locking the legs and maintaining the cage in an expanded configuration. One of the legs is medially disposed on a first side of the cage and the other two are laterally disposed with respect to the end plates on a second side. The three legs have differing lengths so that the cage assumes a wedge-shaped envelope in the expanded configuration. The wedge-shaped envelope reestablishes a predetermined lordosis between fused vertebrae. The invention includes an inserter comprised of a tubular member and holding clamp disposed on the distal end of the tubular member. The holding clamp holds the cage in the collapsed configuration for insertion into a confined surgical theater. The cage is then reconfigured to the expanded configuration using the inserter. Further activation of the inserter causes the cage to be temporarily locked into the expanded configuration.
Owner:RGT UNIV OF CALIFORNIA
Efficient installation of software packages
InactiveUS20020188941A1Manual processProgram loading/initiatingMemory systemsResource utilizationSoftware engineering
Methods, systems, and computer program products for improving installation of software packages using an incremental conditional installation process (and optionally, caching of installation components). An object model is disclosed which enables specification of the conditional installation information as one or more elements of the model (and therefore of an object, document, etc., which is created according to the model). Conditional installation information may be defined at a suite level and / or at a component level. The identified checking process then executes to determine whether the corresponding suite or component should be installed. One or more components may be cached, if desired. Resource utilization is improved using the conditional installation and optional caching techniques, enabling reductions in disk space usage, CPU consumption, and / or networking bandwidth consumption.
Owner:IBM CORP
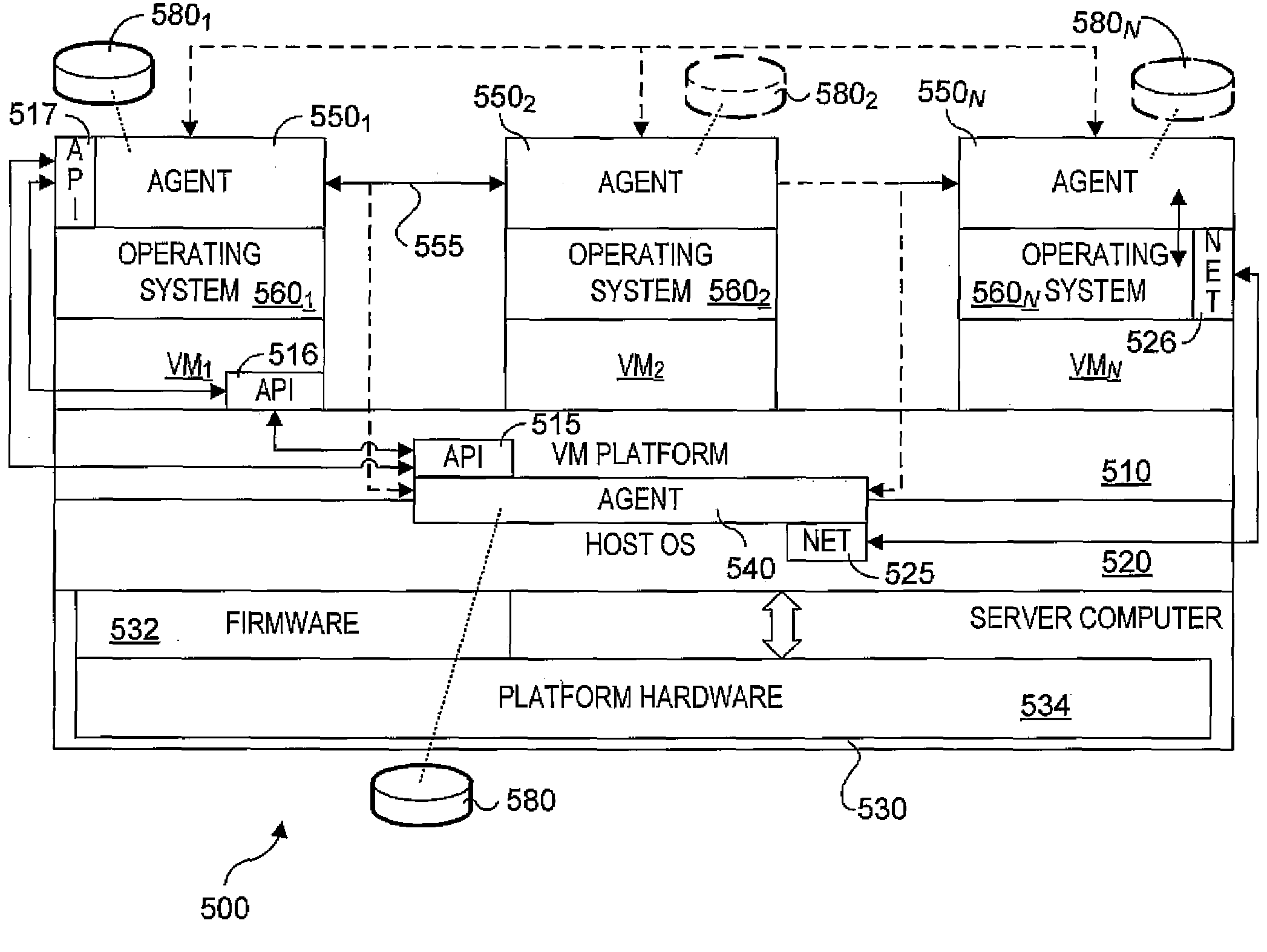
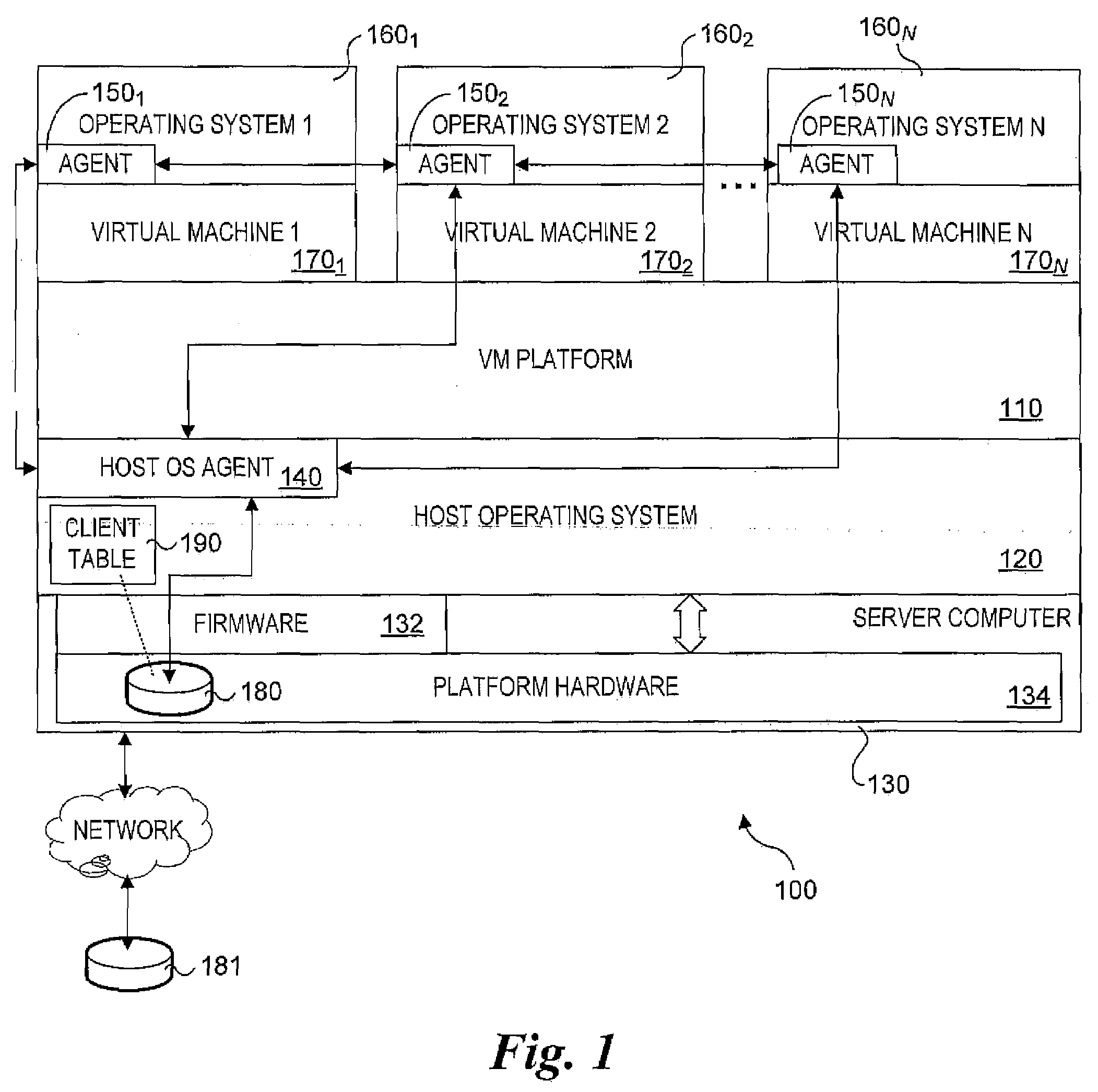
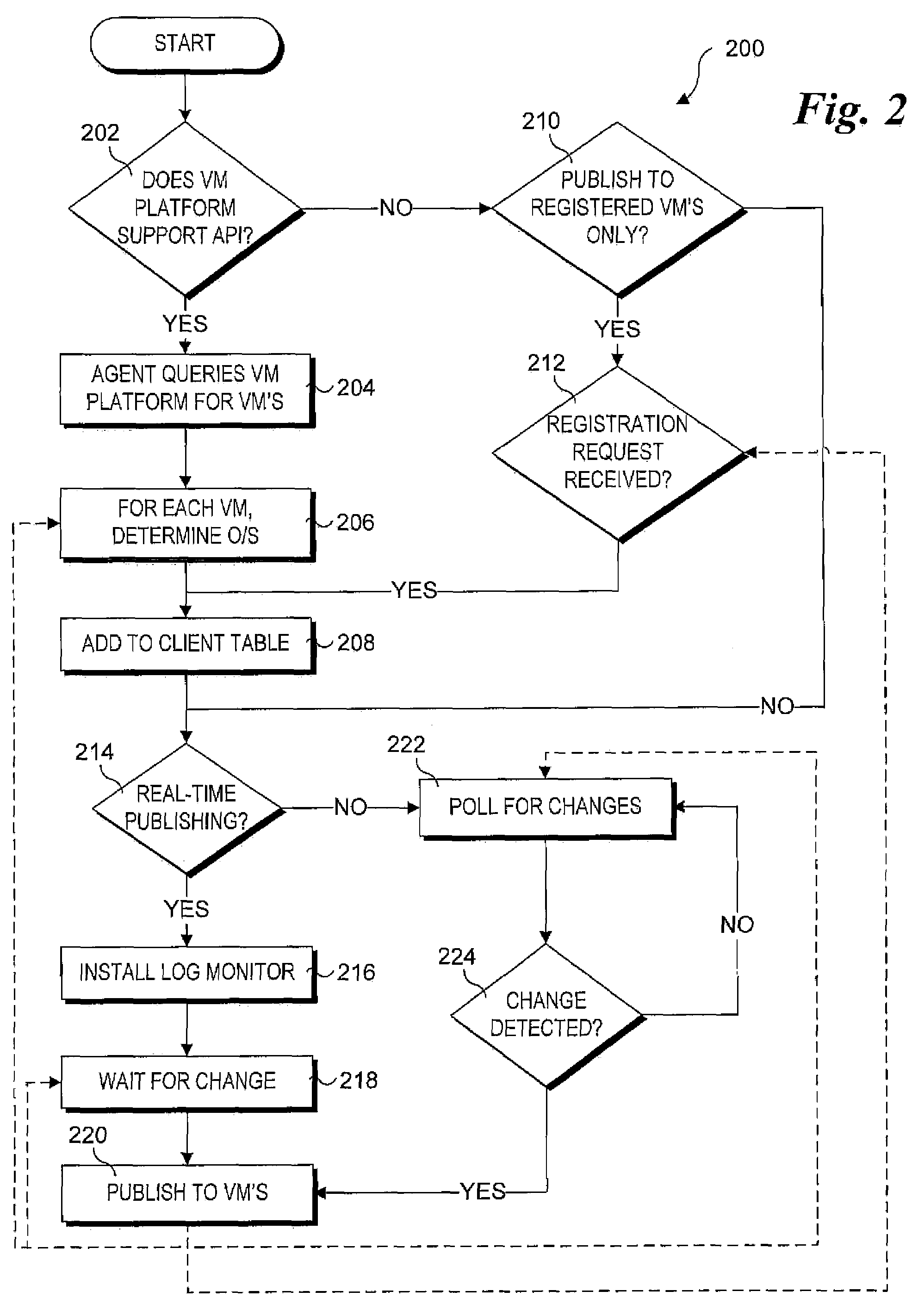
System and method for host and virtual machine administration
InactiveUS20080196043A1Reduce dependenceResource allocationError detection/correctionOperational systemEvent data
Methods, architectures, software / firmware and systems for enabling concurrent administration of host operating systems and virtual machine-hosted operating systems. Techniques are disclosed for monitoring and reporting various administrative data (e.g., performance data, event data, log data, etc.), as well as enabling allocation and reallocation of system resources, such as physical memory and disk space. The techniques support implementation of user-interfaces hosted by a virtual machine operating system or a host operating system that enable administrators and the like to manage operations of virtual machines and hosts via a unified interface. Moreover, the techniques support concurrent management of different operating system types.
Owner:FEINLEIB DAVID +2
Artificial spinal disk
InactiveUS20050107881A1Rotational shiftingInternal osteosythesisBone implantLateral bendingIntervertebral disk
An artificial spinal disk comprises a central capsule that is configured to slide laterally within the disk space with one or more of flexion, extension, and lateral bending of the spine so as to shift an instantaneous center of rotation of the artificial disk. In one embodiment, the invention comprises an artificial spinal disk comprising a first plate having an inwardly directed surface, a second plate having an inwardly directed surface facing generally toward the inwardly directed surface of the first plate, and a central capsule with outwardly directed opposed faces that slidably mate with the inwardly directed surfaces of the first and second plates.
Owner:SMART DISC
Digital servo control system for use in disk drives
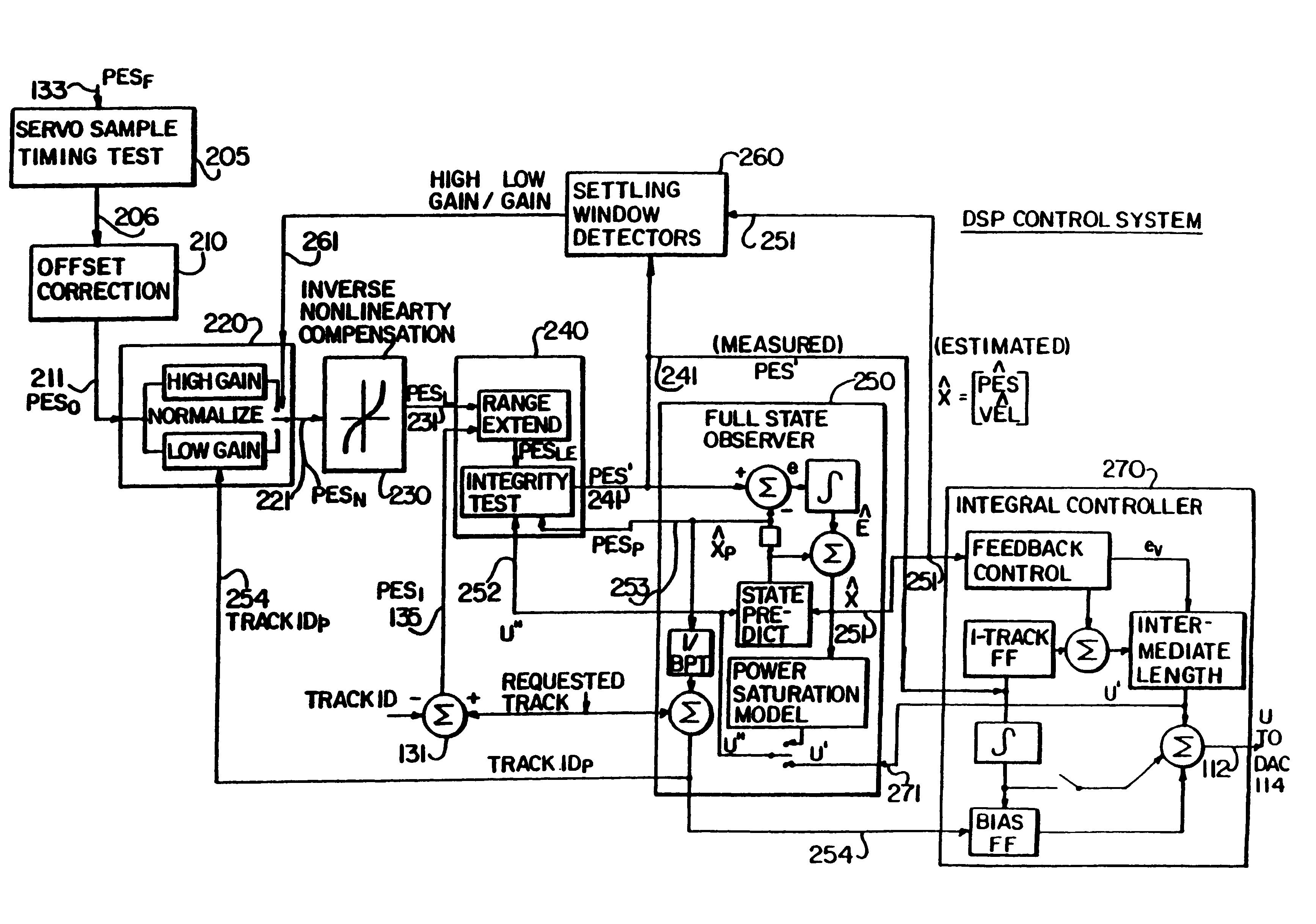
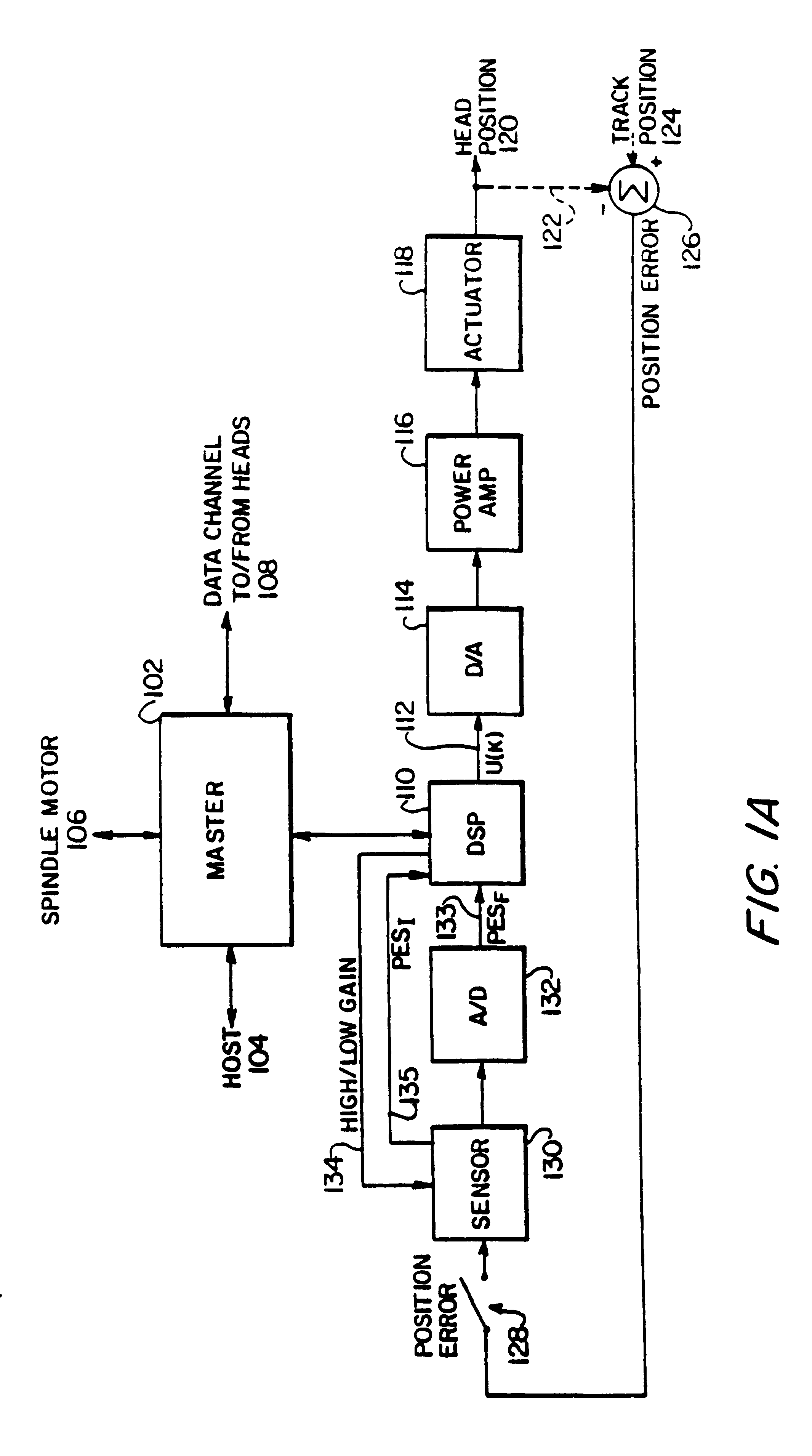
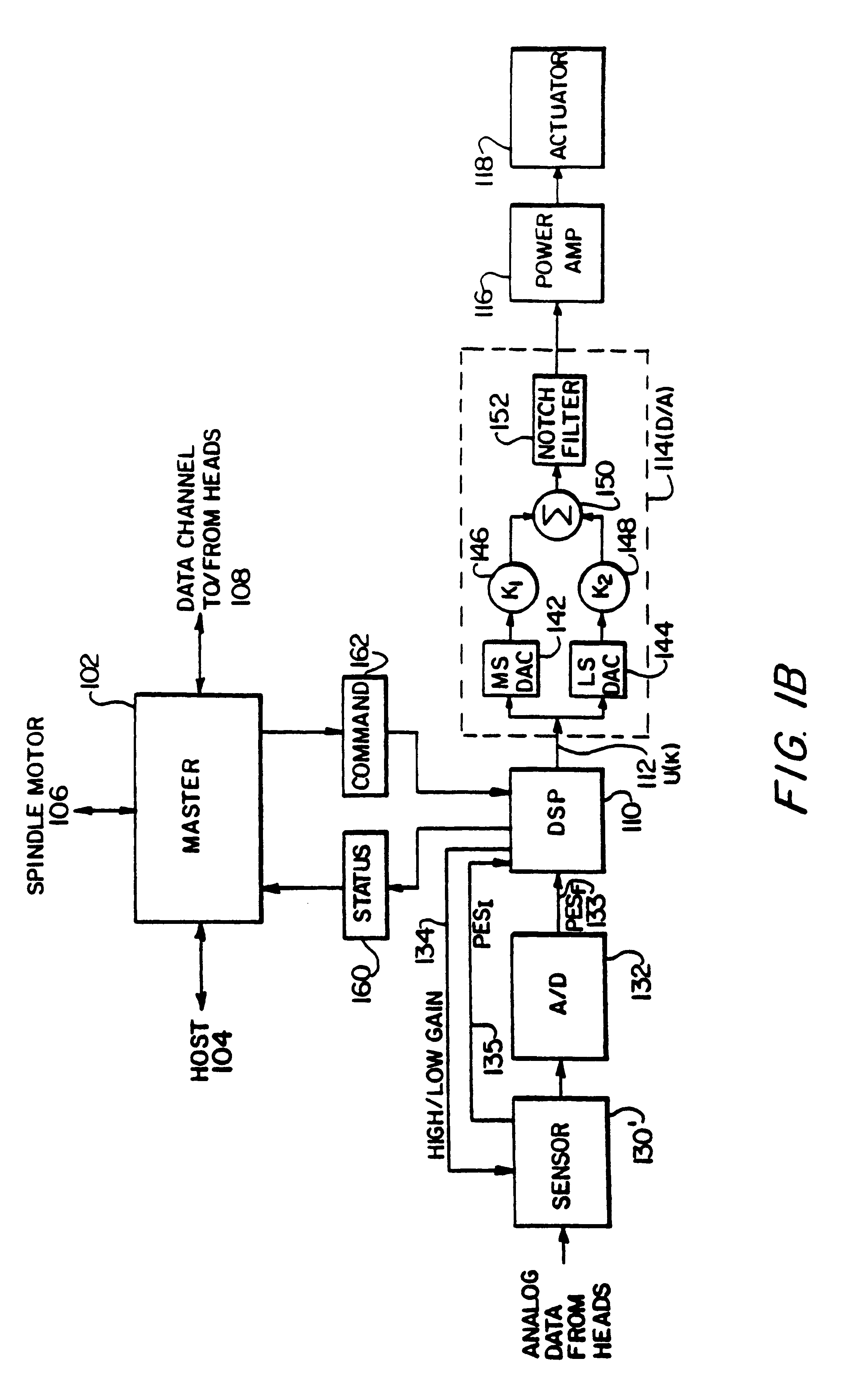
InactiveUS6347018B1Stable trackingSeek efficiencyTrack finding/aligningRecord information storagePretreatment methodControl theory
A digital servo control system for disk drives is an "embedded" system-one in which servo control information is embedded on the same disk surface as the user data. In contrast to known embedded-servo systems in which a space-consuming series of many dibit pairs is present, the present system provides only a single dibit pair in a fractional positional error (PESF) area. Thus, the disk drive's read head encounters only a single dibit pair per sample period (or per data sector), thus saving valuable disk space that may be used for user data. Various pre-processing methods may be provided so as to pre-process the measurement derived from the single dibit pair per sample period (or data sector), so as to compensate for non-ideal characteristics of the dibit measurement. The system thus provides an accurate and robust servo control system, while sacrificing a minimum amount of valuable disk space to the servo information field.
Owner:MAXTOR +1
Minimally invasive lateral intervertbral fixation system, device and method
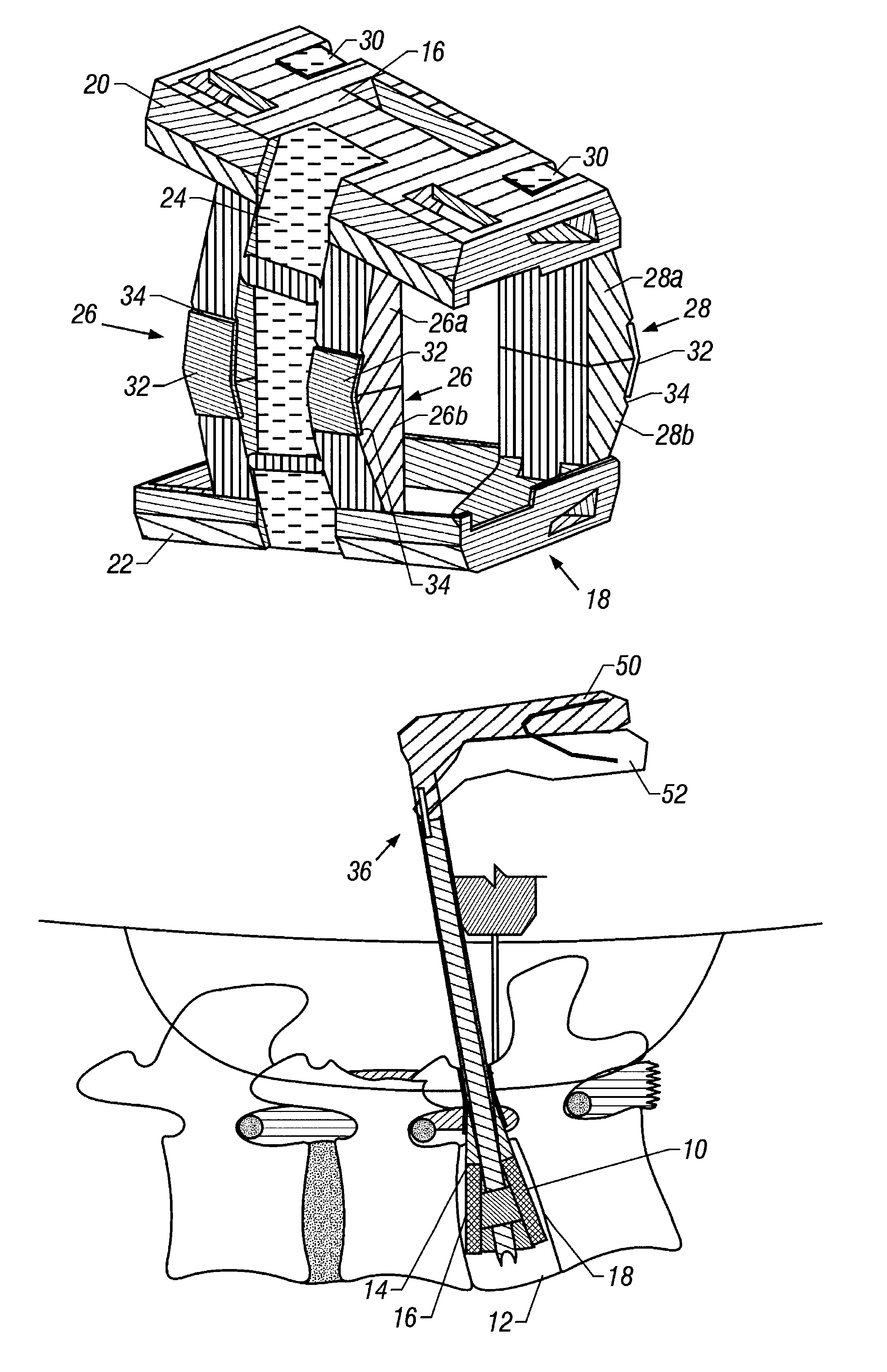
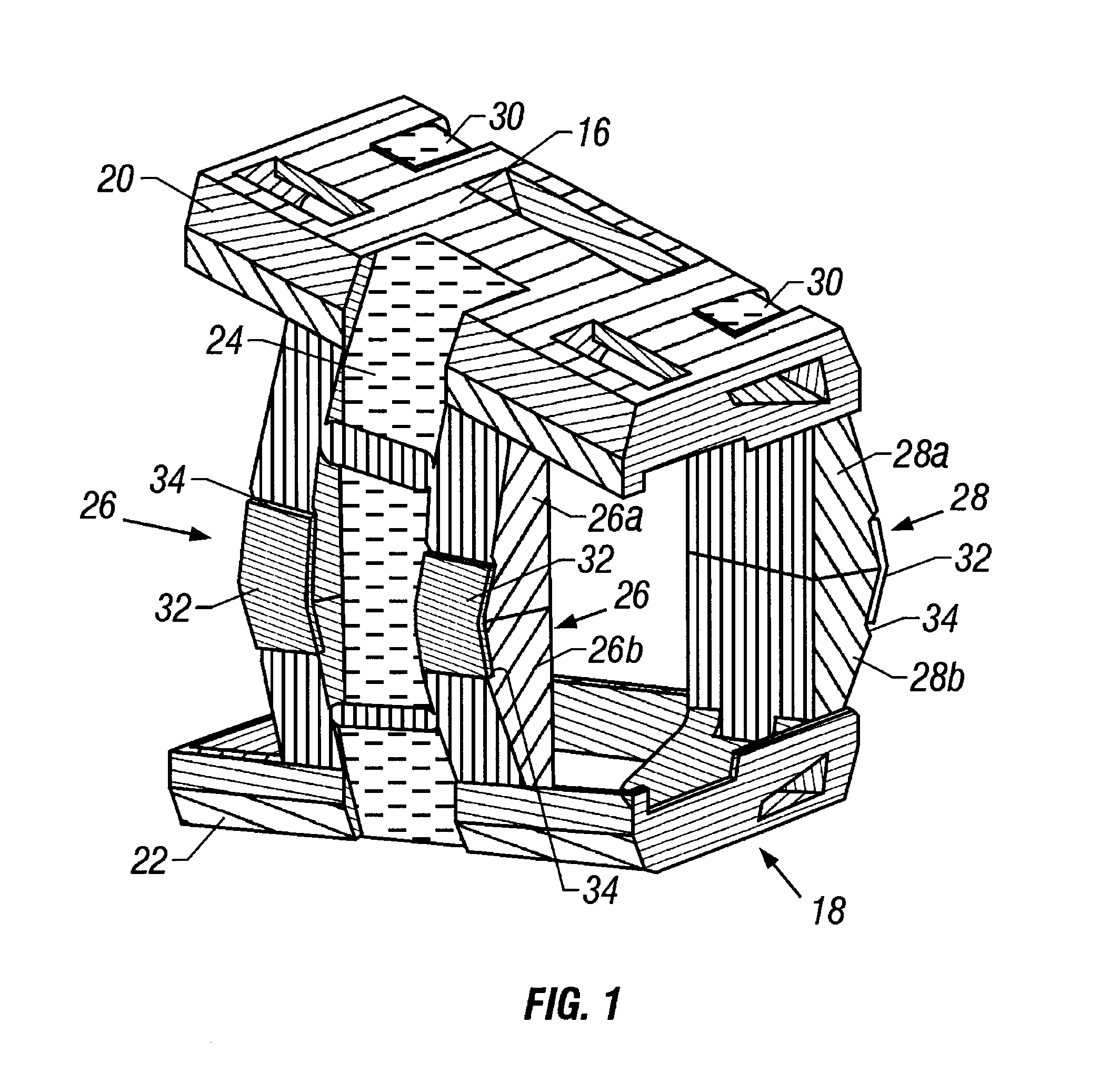
A system, device and method are disclosed for minimally invasive lateral intervertebral fixation. An intervertebral fixation device includes a weight-bearing shell configured to fit into a disk space between plural vertebrae, the weight-bearing shell including a keyway opening between and through plural sidewalls. A first plurality of anchors is rotatably disposed in a first orientation in relation to the weight-bearing shell. A second plurality of anchors is rotatably disposed in a second orientation in relation to the weight-bearing shell. A key is adapted to rotate the first plurality of anchors in divergent directions from the second plurality of anchors and to secure a first vertebra and a second vertebra, respectively. The key is further adapted to support the first plurality of anchors and the second plurality of anchors in divergent directions in relation to the weight-bearing shell, the first plurality of anchors and the second plurality of anchors secured to the first vertebra and the second vertebra.
Owner:INT SPINAL INNOVATIONS
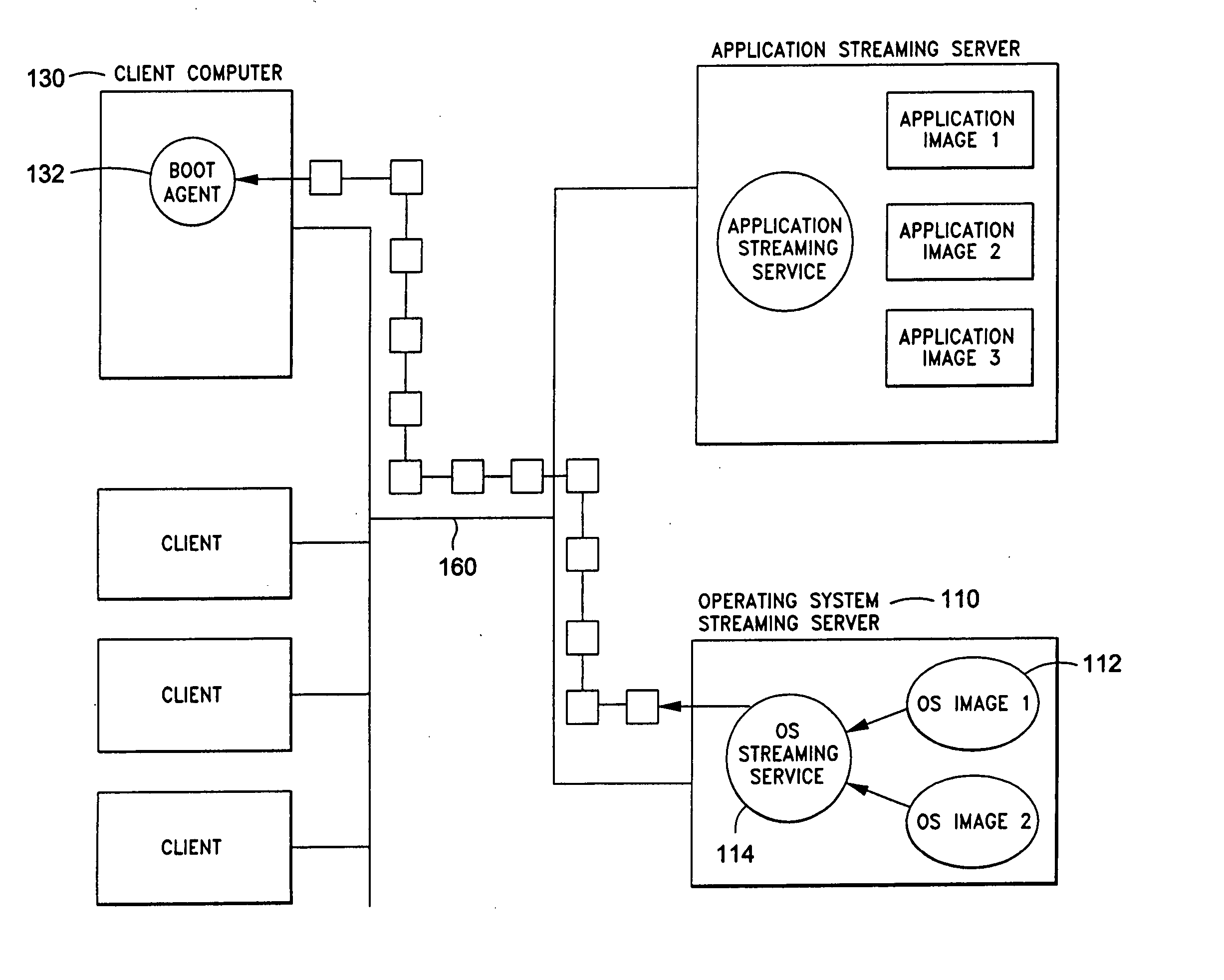
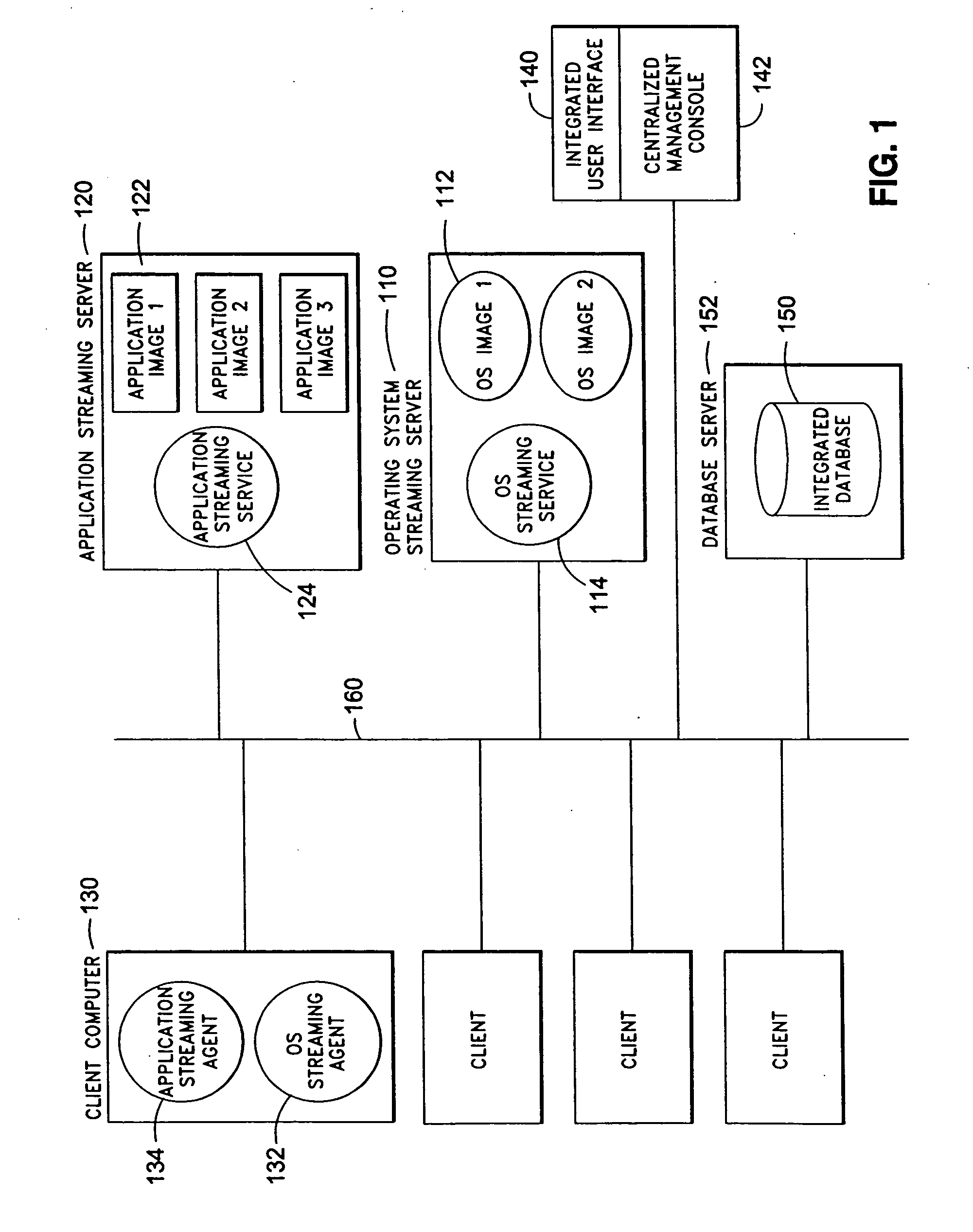
System and method for integrated on-demand delivery of operating system and applications
ActiveUS20060031547A1Accurate scaleMultiple digital computer combinationsProgram controlOperational systemSystems management
The present invention discloses a system and a method for integrated on-demand delivery of operating system and applications, where operating system images are separate and distinct from application images. Integration of operating system streaming and application streaming services makes streaming delivery possible to a wide range of client devices, including those without any local disk space such as thin-clients and diskless workstations. In addition, by integrating the centralized management of operating system delivery and application delivery, the present invention provides a complete solution to server-centric application management, thereby further reducing the total cost of ownership of network-based computing approach. Implementing the operating management functions at the client machine level of specificity and application management functions at the user level of specificity combined with providing separate and distinct operating system images and application images provides an inherently canonical architecture that allows proper scaling and affords appropriate security management functions. The result is a complete, scalable, robust, and reliable server-centric application and operating system management system with a lower total cost of ownership than existing products.
Owner:DELL MARKETING CORP
Systems, methods, and storage structures for cached databases
InactiveUS20080059492A1Improve read performanceSpace minimizationDigital data information retrievalDigital data processing detailsData miningDisk space
Systems and methods for clustered access to as many columns as possible given a particular ongoing query mix and a constrained amount of disk space is disclosed. A compressed database is split into group of columns, each column having duplicates removed and being sorted. Then certain groups are transferred to a fast memory depending on the record of previously received queries.
Owner:TARIN STEPHEN A
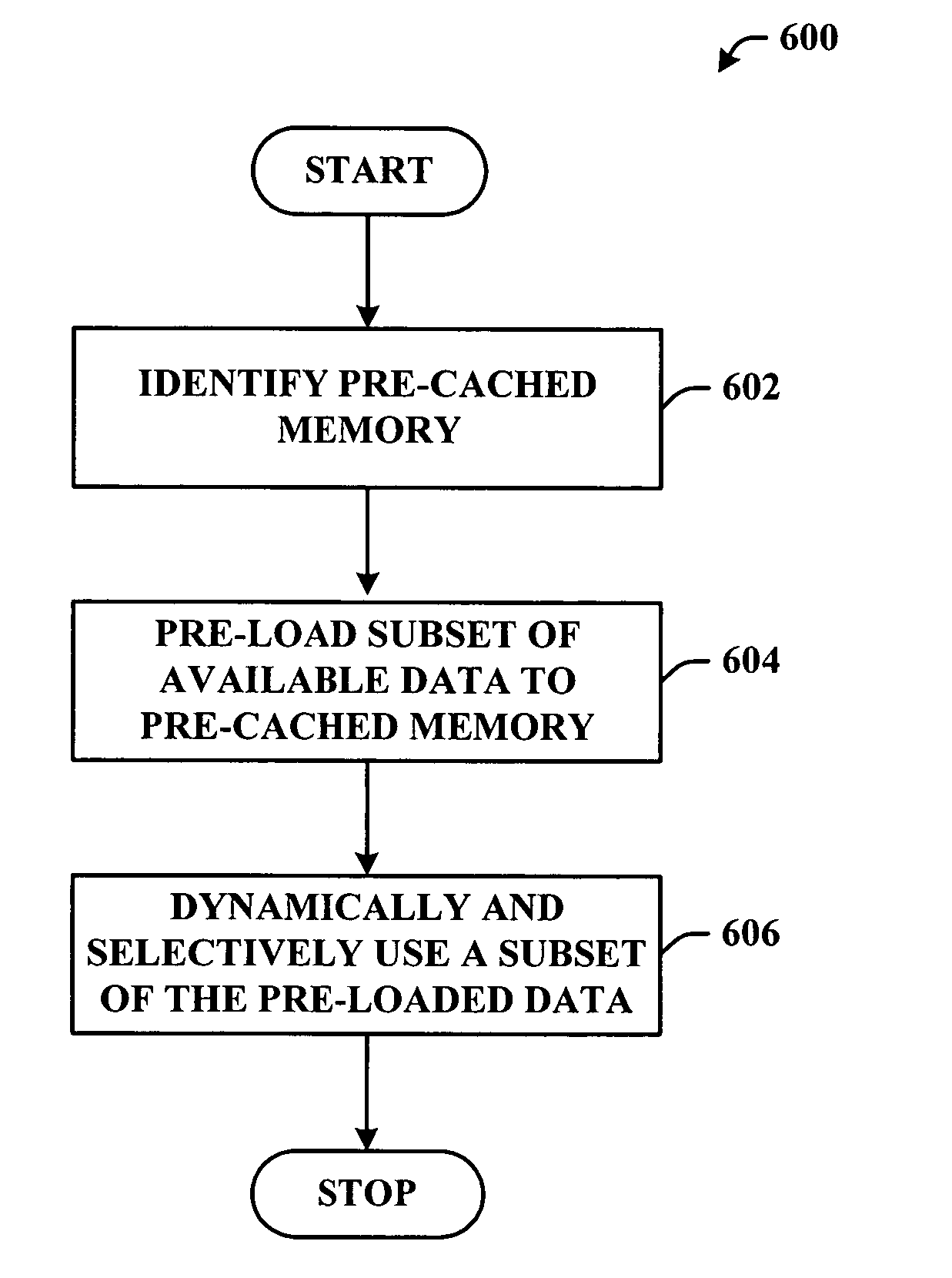
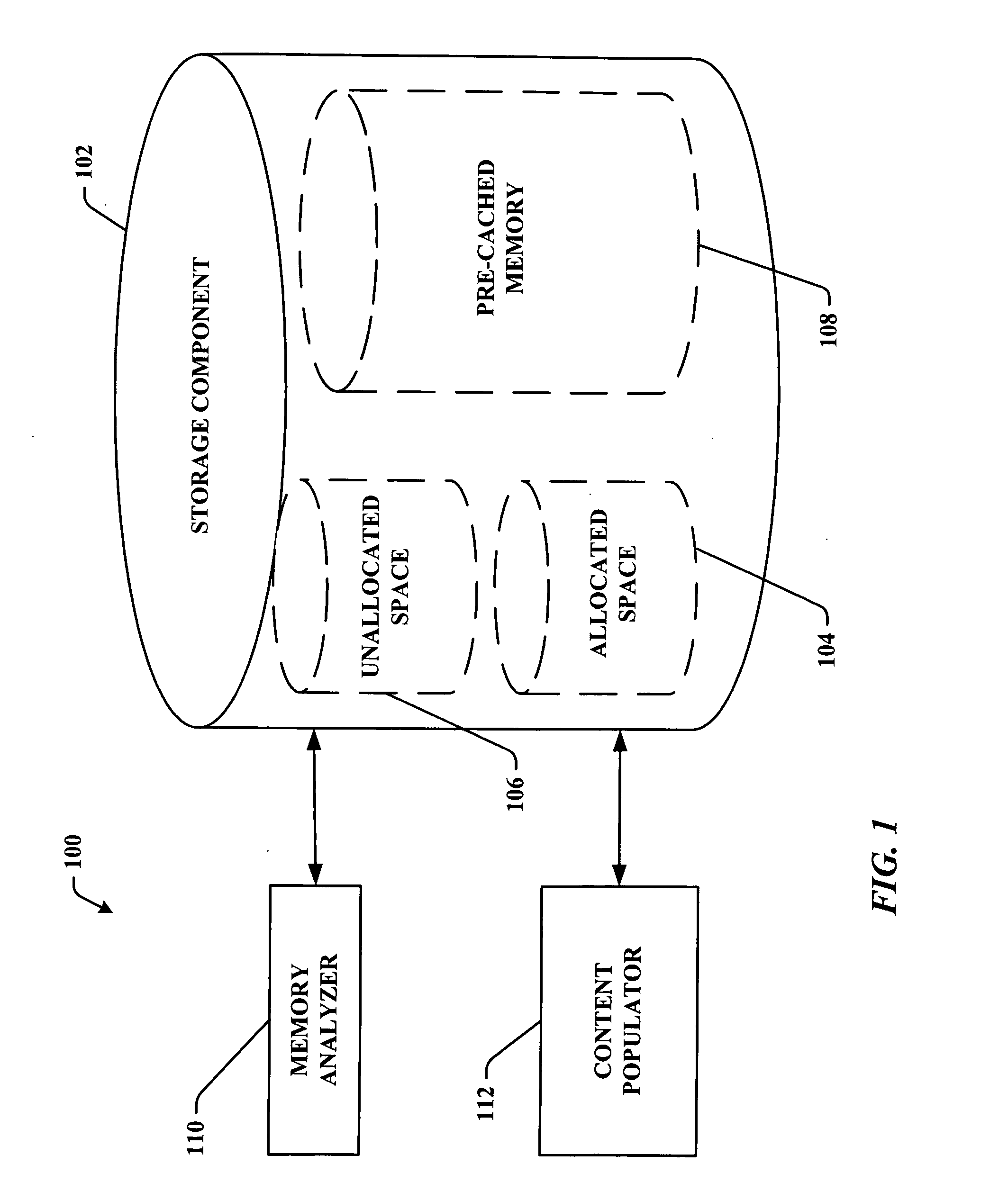
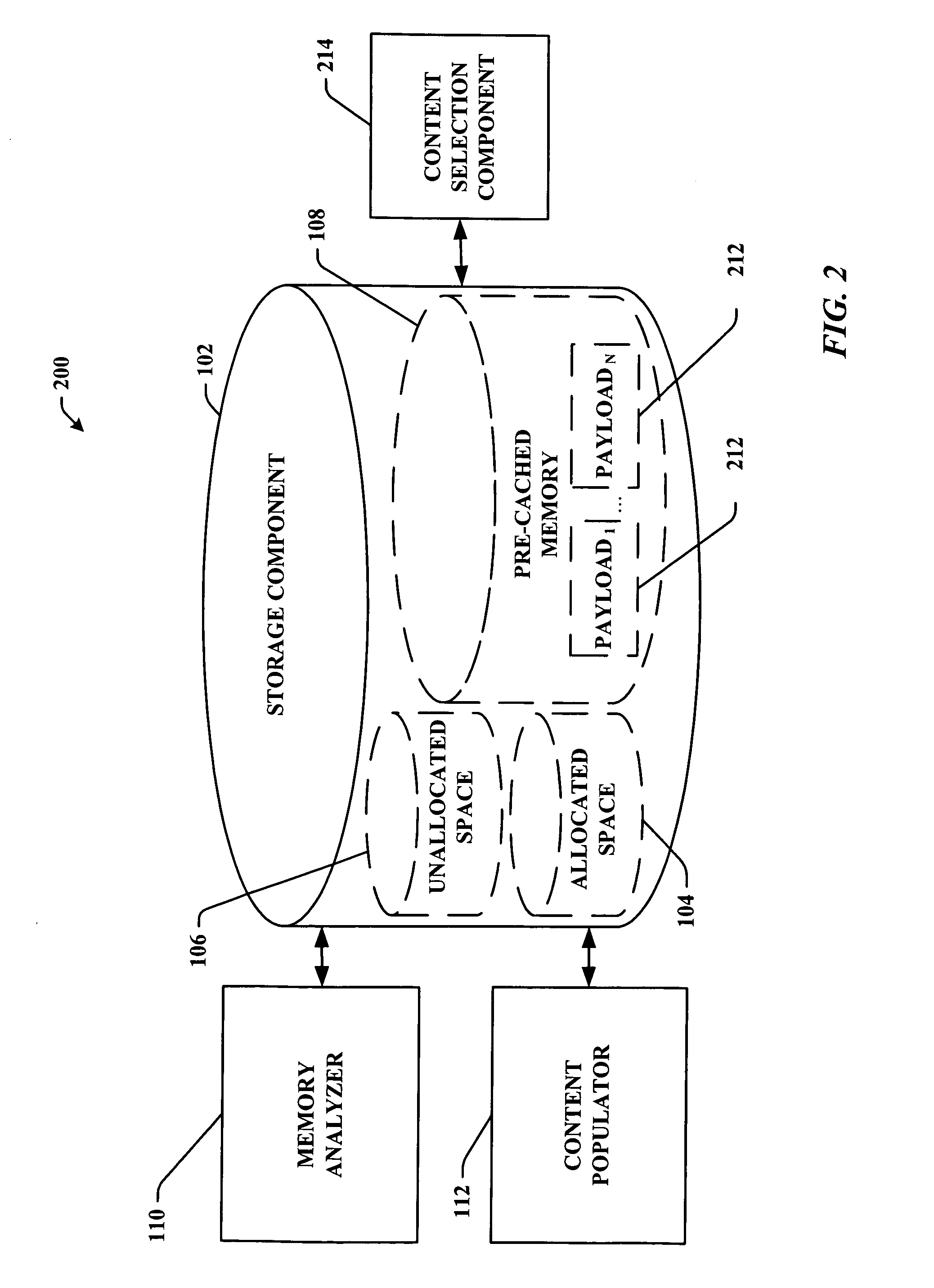
Pre-storage of data to pre-cached system memory
ActiveUS20070136533A1Improve utilizationImprove computing powerAdvertisementsTransmissionOperational systemData access
System(s) and method(s) that facilitate utilizing pre-cached disk space. Pre-cached memory space within a storage device is identified, and a subset of the pre-cached memory space is pre-populated with data so that the data can be selectively and dynamically accessed. During use of a computer (e.g., in a web-browsing session) a subset of the pre-stored data can be dynamically and selectively exposed to the user as a function of user and / or computer application state. Pre-storage of the data on pre-cached memory of the computer mitigates delayed data access (e.g., due to insufficient transmission bandwidth) thereby enhancing user computing experience. The user can utilize the device without having to distinguish between pre-cached and free memory. In other words, the operating system can present the cached memory to the user so that it appears as free memory without the user having to direct the system to do so.
Owner:MICROSOFT TECH LICENSING LLC
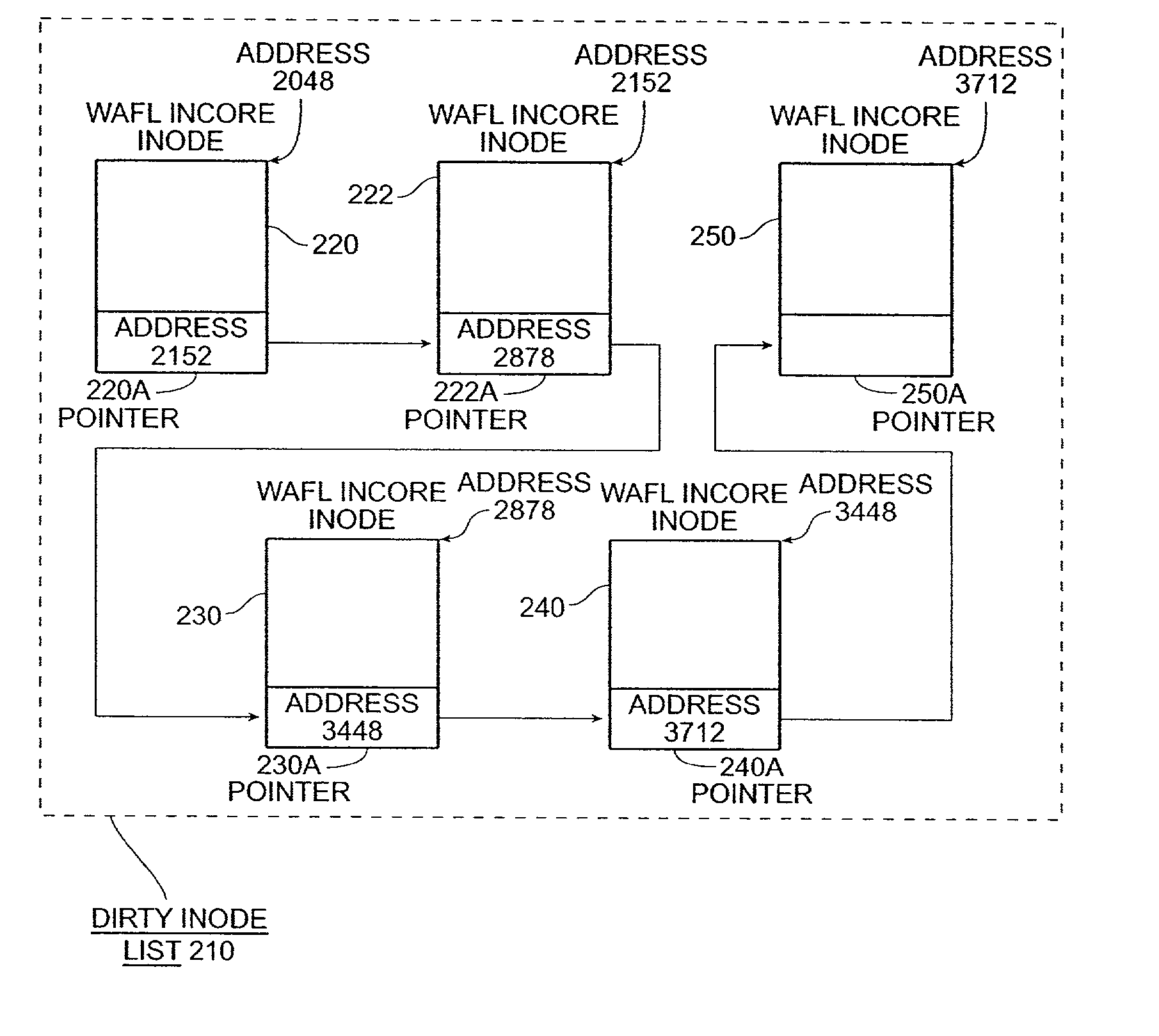
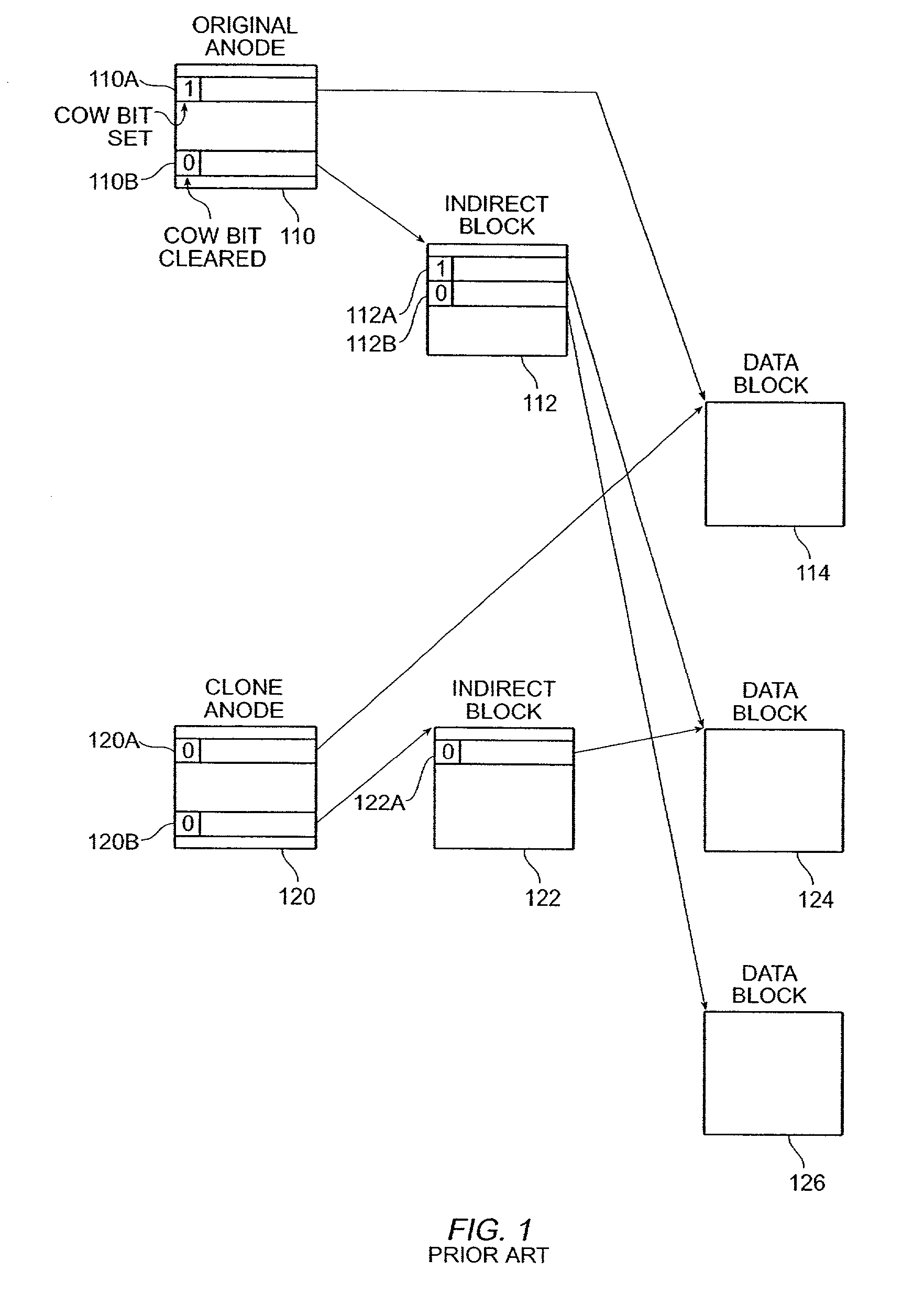
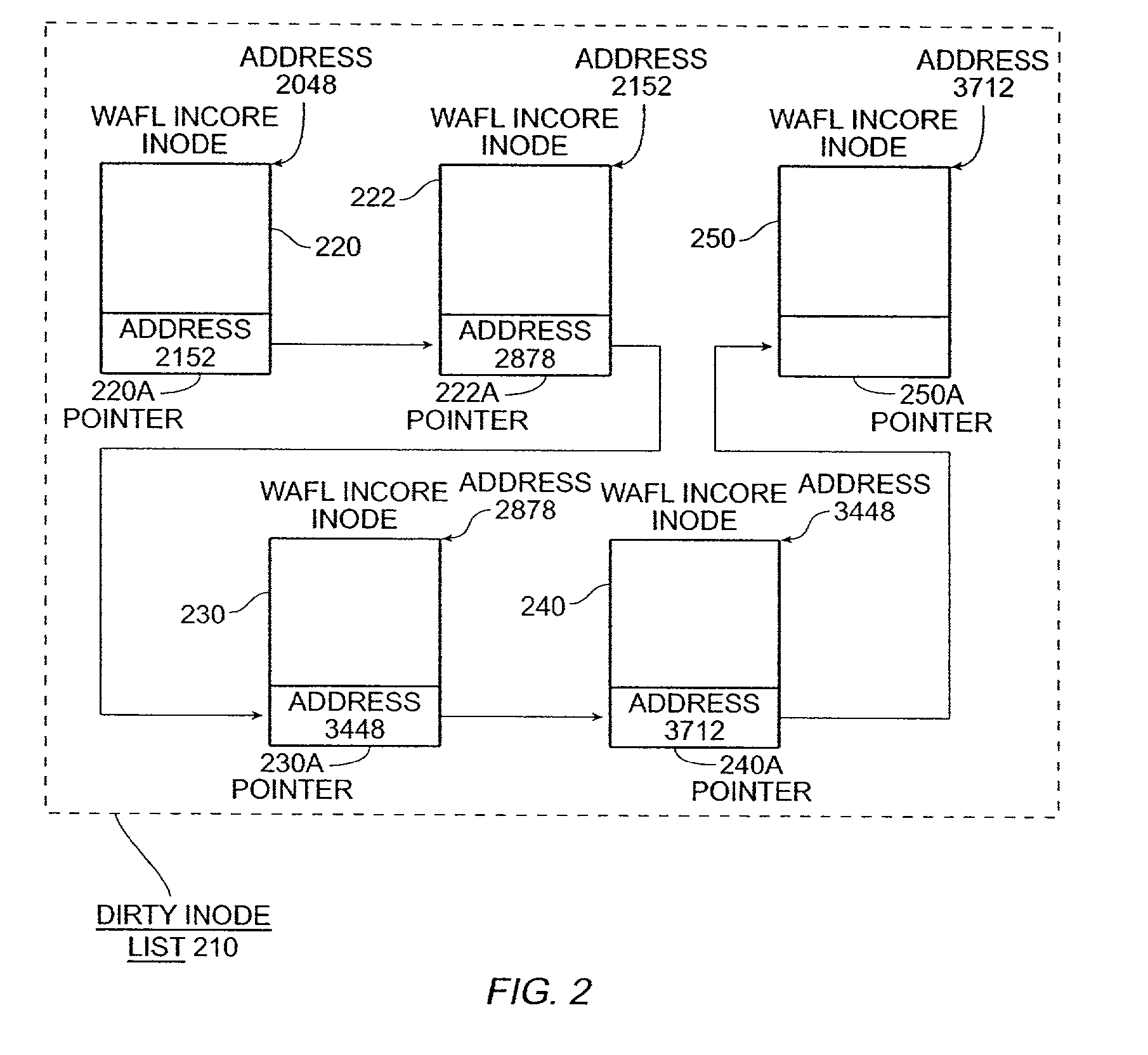
Write anywhere file-system layout
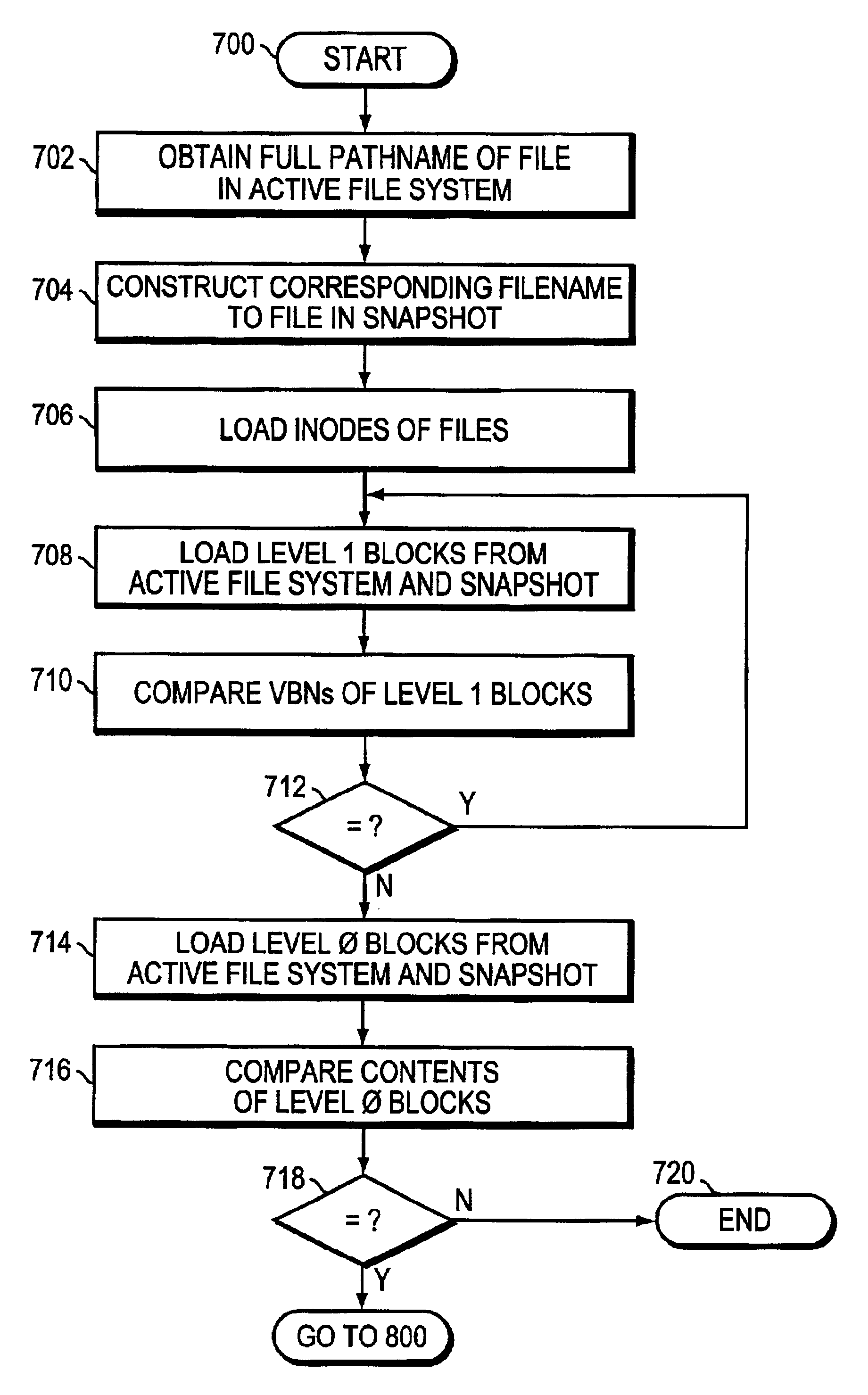
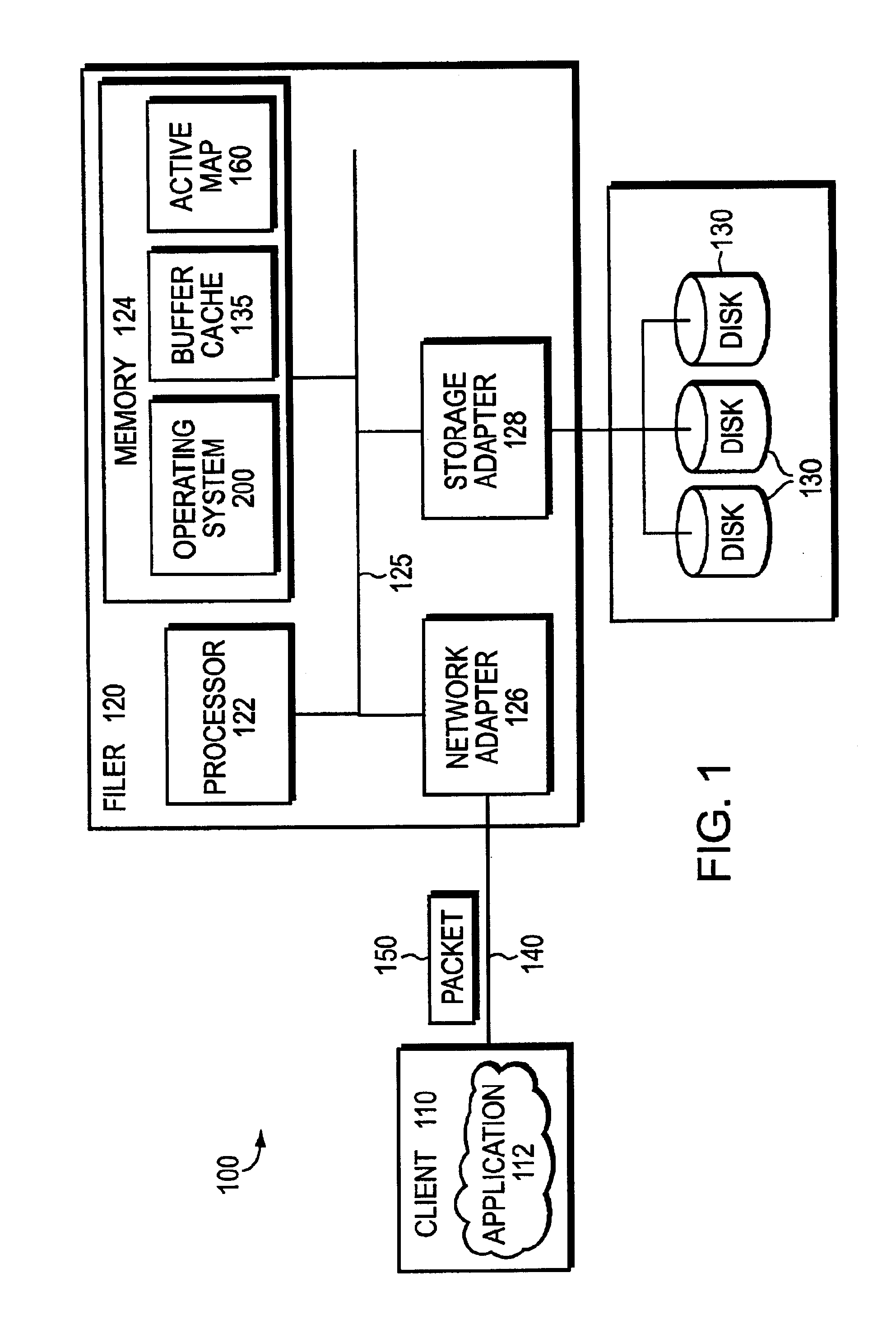
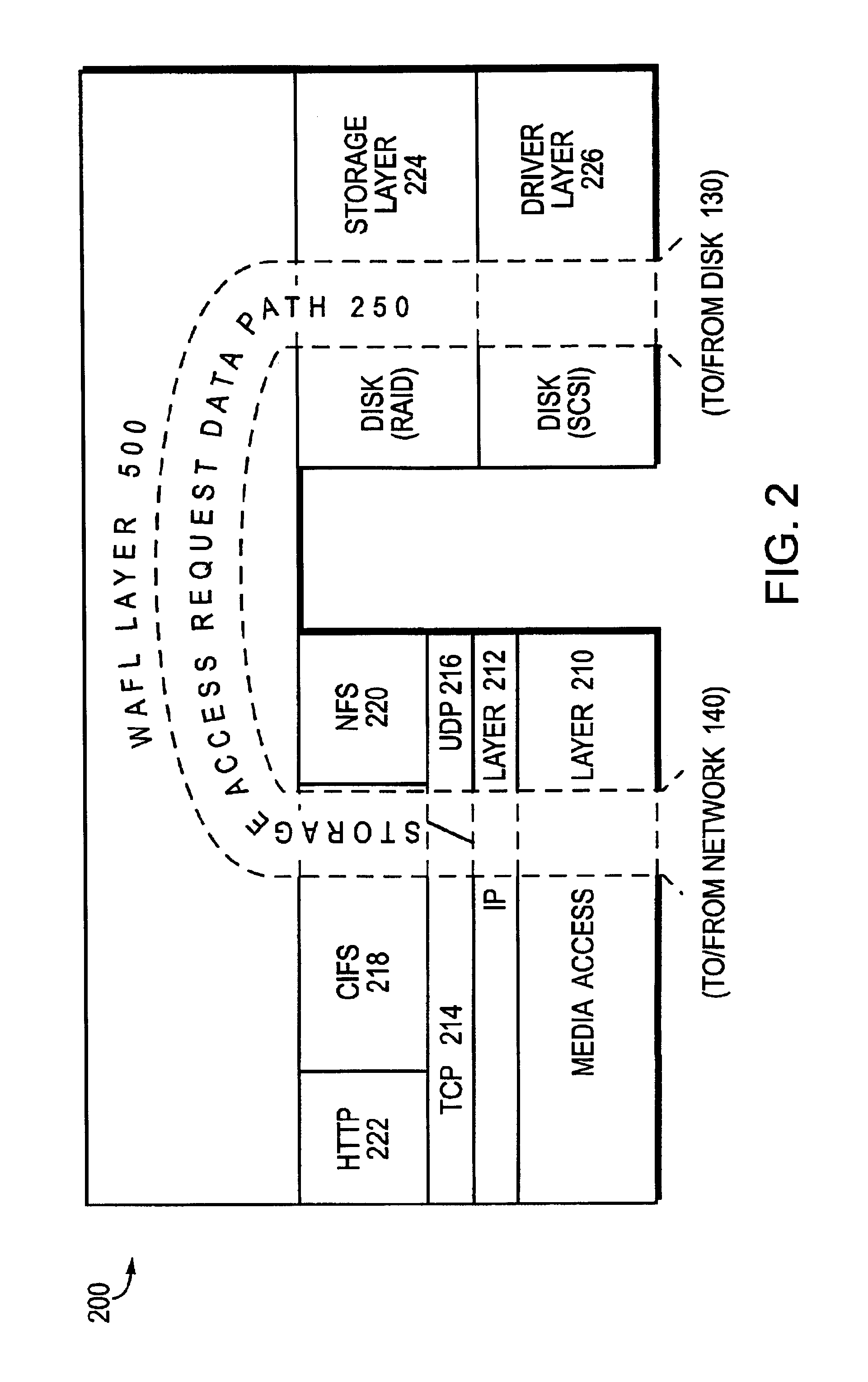
The present invention provides a method for keeping a file system in a consistent state and for creating read-only copies of a file system. Changes to the file system are tightly controlled. The file system progresses from one self-consistent state to another self-consistent state. The set of self-consistent blocks on disk that is rooted by the root inode is referred to as a consistency point. To implement consistency points, new data is written to unallocated blocks on disk. A new consistency point occurs when the fsinfo block is updated by writing a new root inode for the inode file into it. Thus, as long as the root inode is not updated, the state of the file system represented on disk does not change. The present invention also creates snapshots that are read-only copies of the file system. A snapshot uses no disk space when it is initially created. It is designed so that many different snapshots can be created for the same file system. Unlike prior art file systems that create a clone by duplicating the entire inode file and all of the indirect blocks, the present invention duplicates only the inode that describes the inode file. A multi-bit free-block map file is used to prevent data from being overwritten on disk.
Owner:NETWORK APPLIANCE INC
Adjusting Available Persistent Storage During Execution in a Virtual Computer System
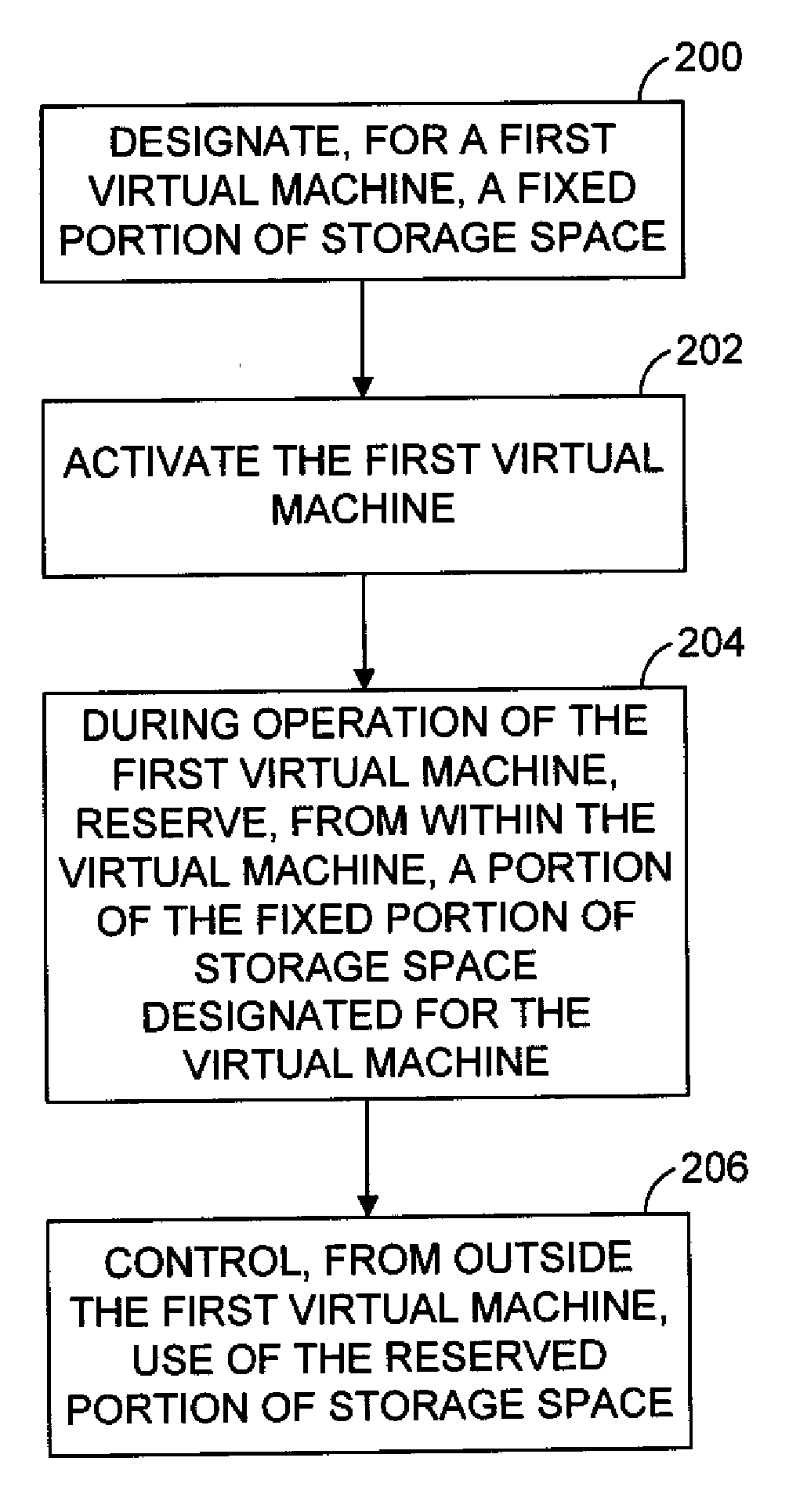
ActiveUS20080270674A1Memory adressing/allocation/relocationComputer security arrangementsVirtual computingRunning time
The amount of virtual disk space that is available for use by software executing within a virtual machine may be dynamically adjusted while the virtual machine is running in a virtual computer system. According to one aspect, a method for flexible run-time reservation of disk space from a virtual machine is provided. The method includes designating for use by a first virtual machine, a fixed portion of disk space accessible by a computing system. The first virtual machine is activated. During operation of the first virtual machine, a portion of the fixed portion of the disk space designated for use by the first virtual machine is reserved from within the first virtual machine. Use of the reserved portion is controlled from outside of the first virtual machine.
Owner:VMWARE INC
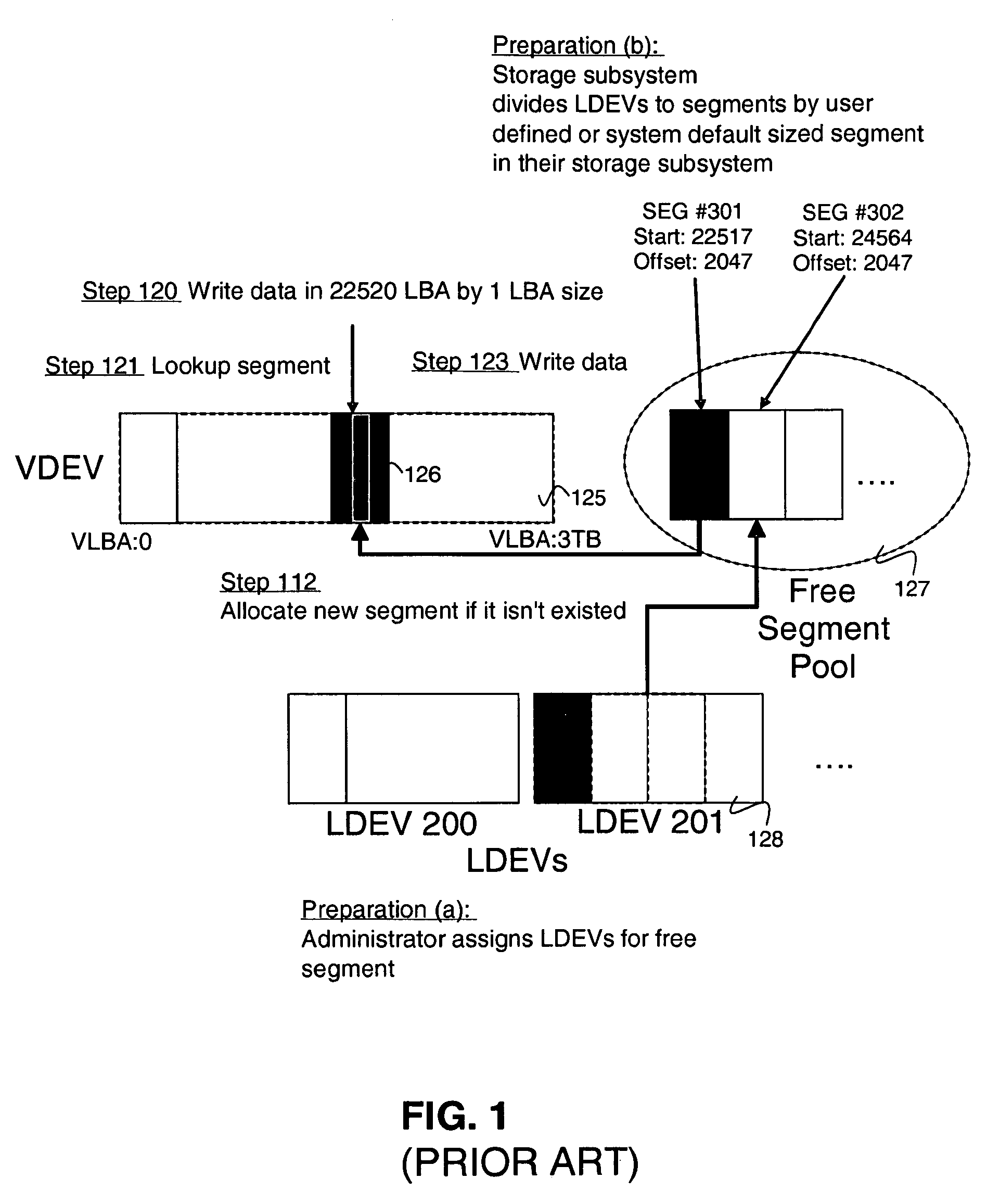
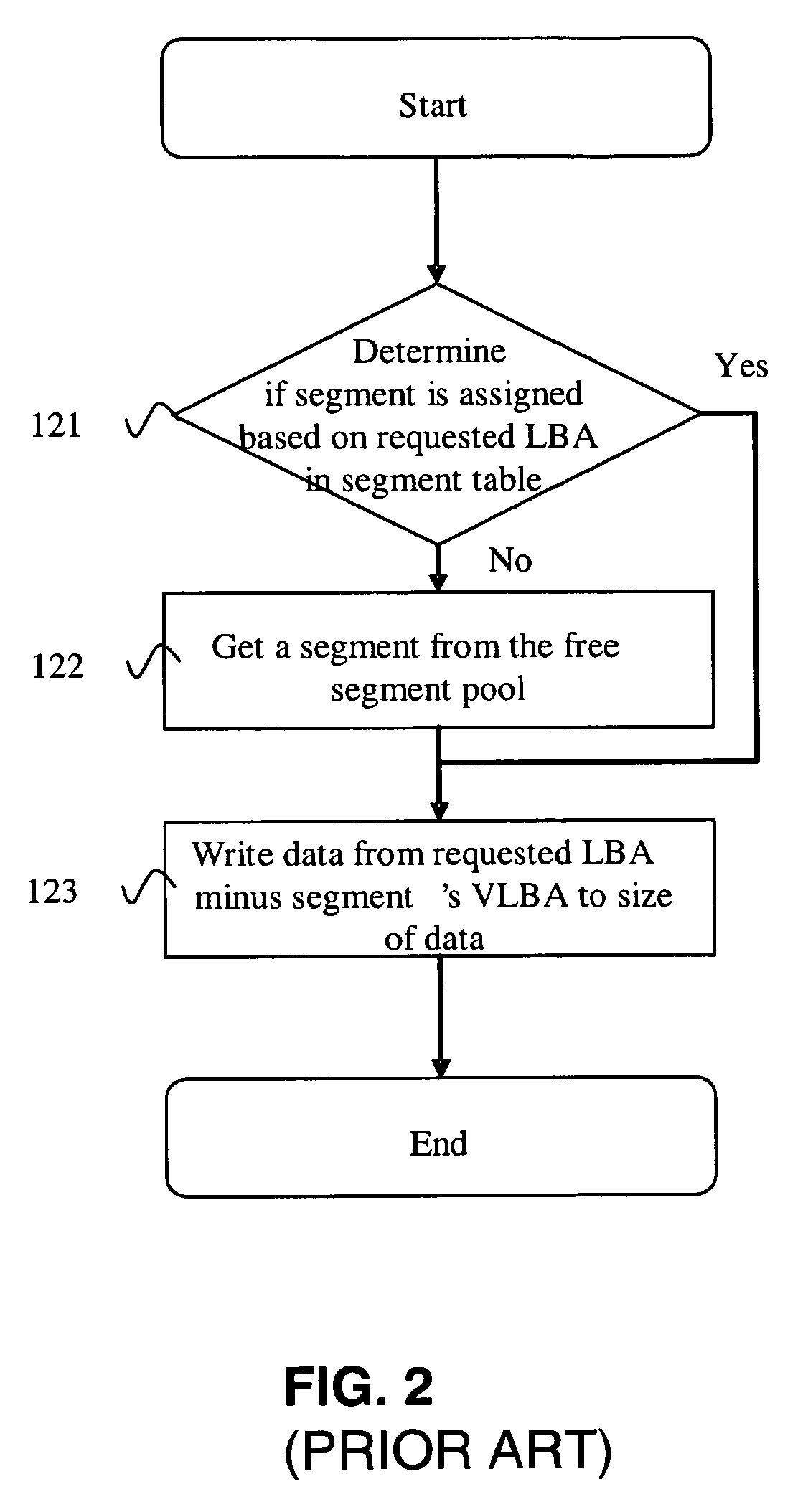
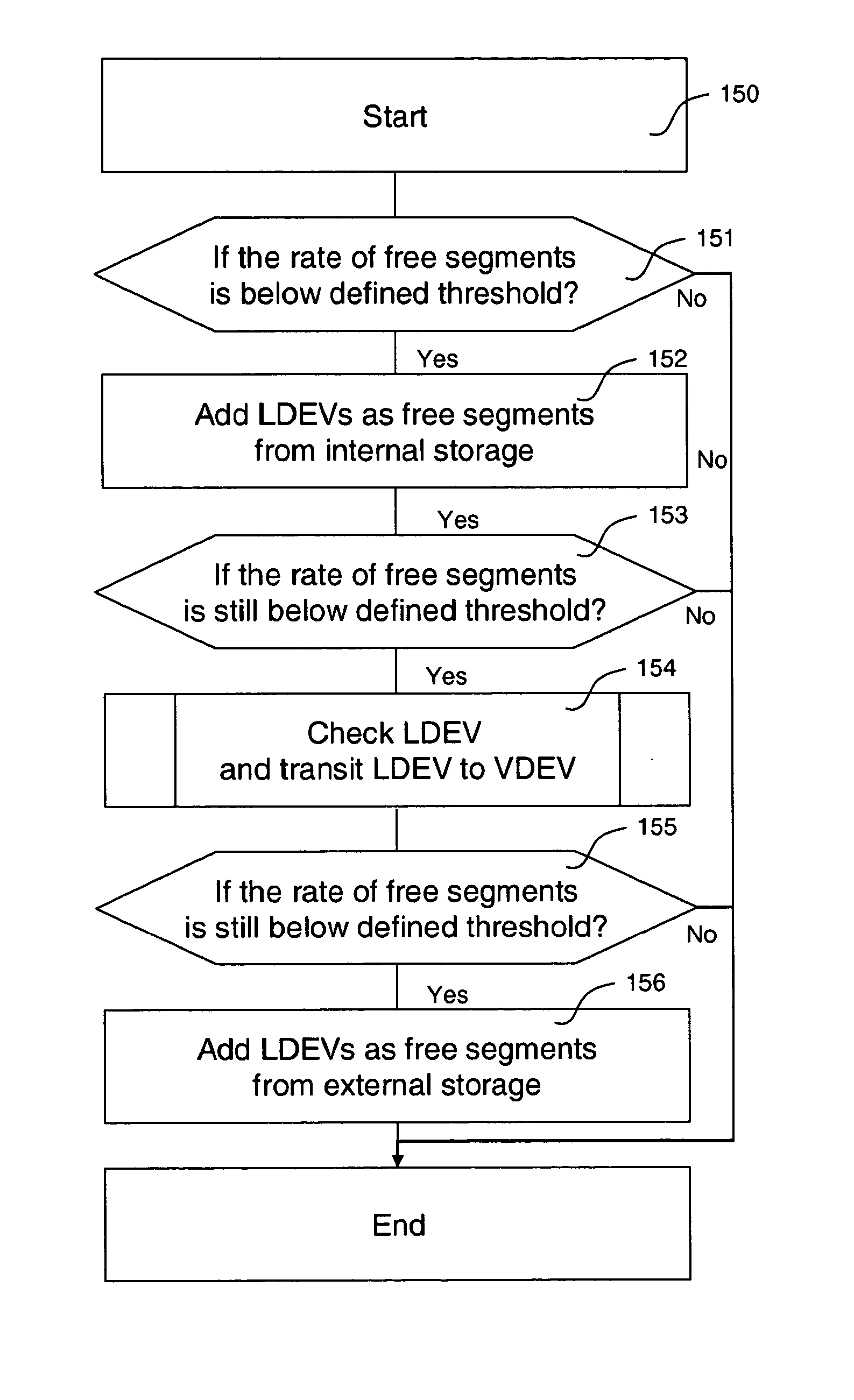
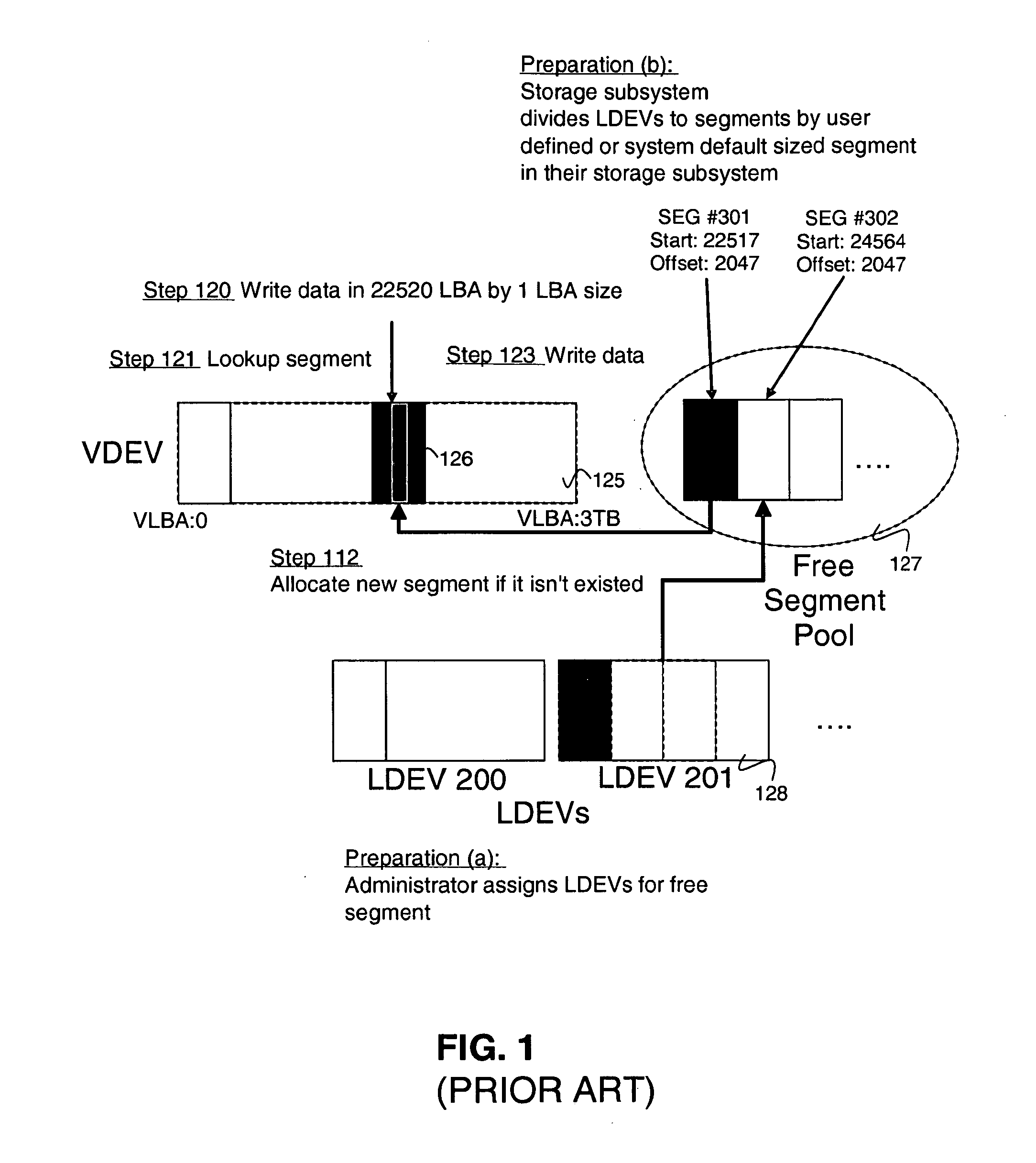
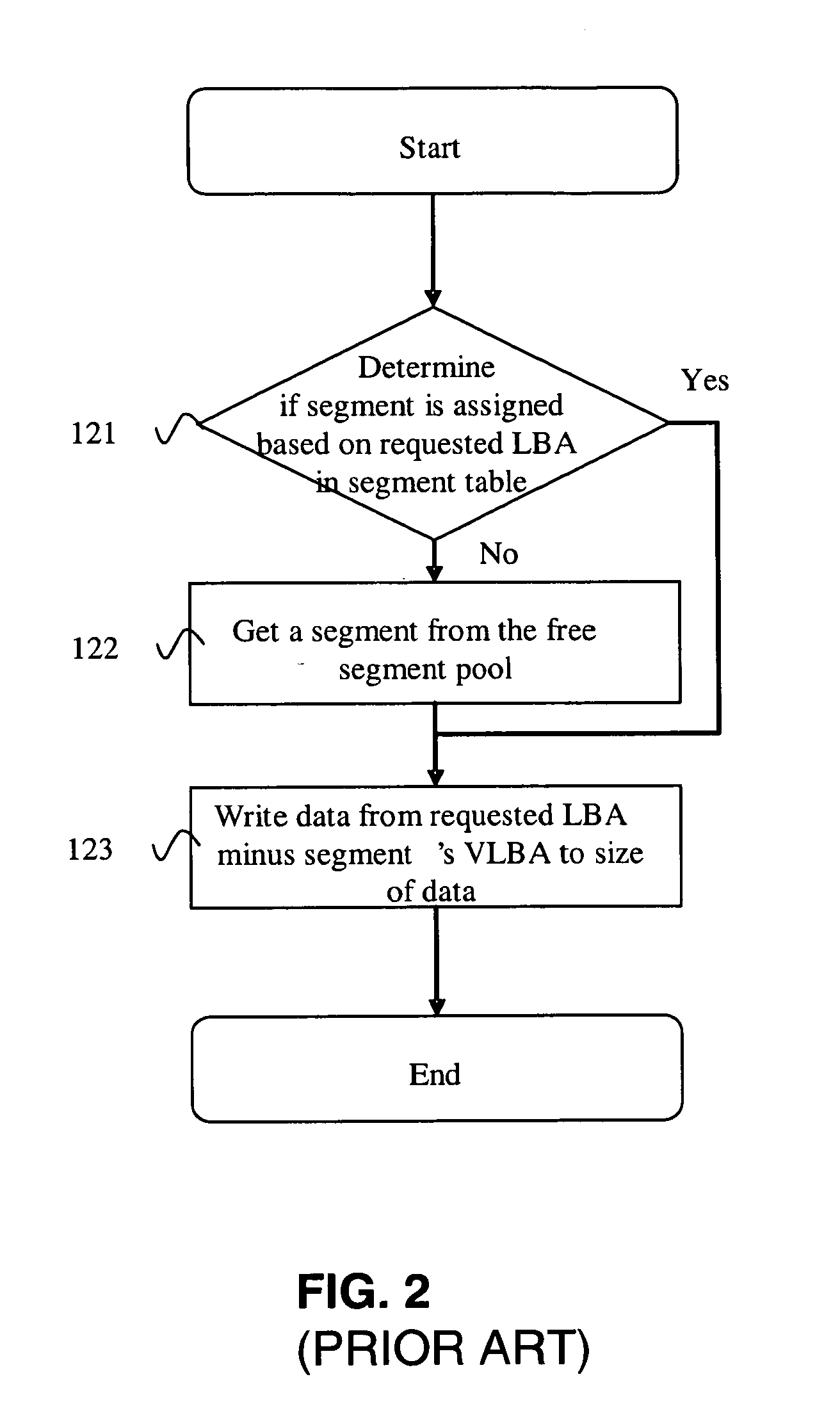
System and method for managing disk space in a thin-provisioned storage subsystem
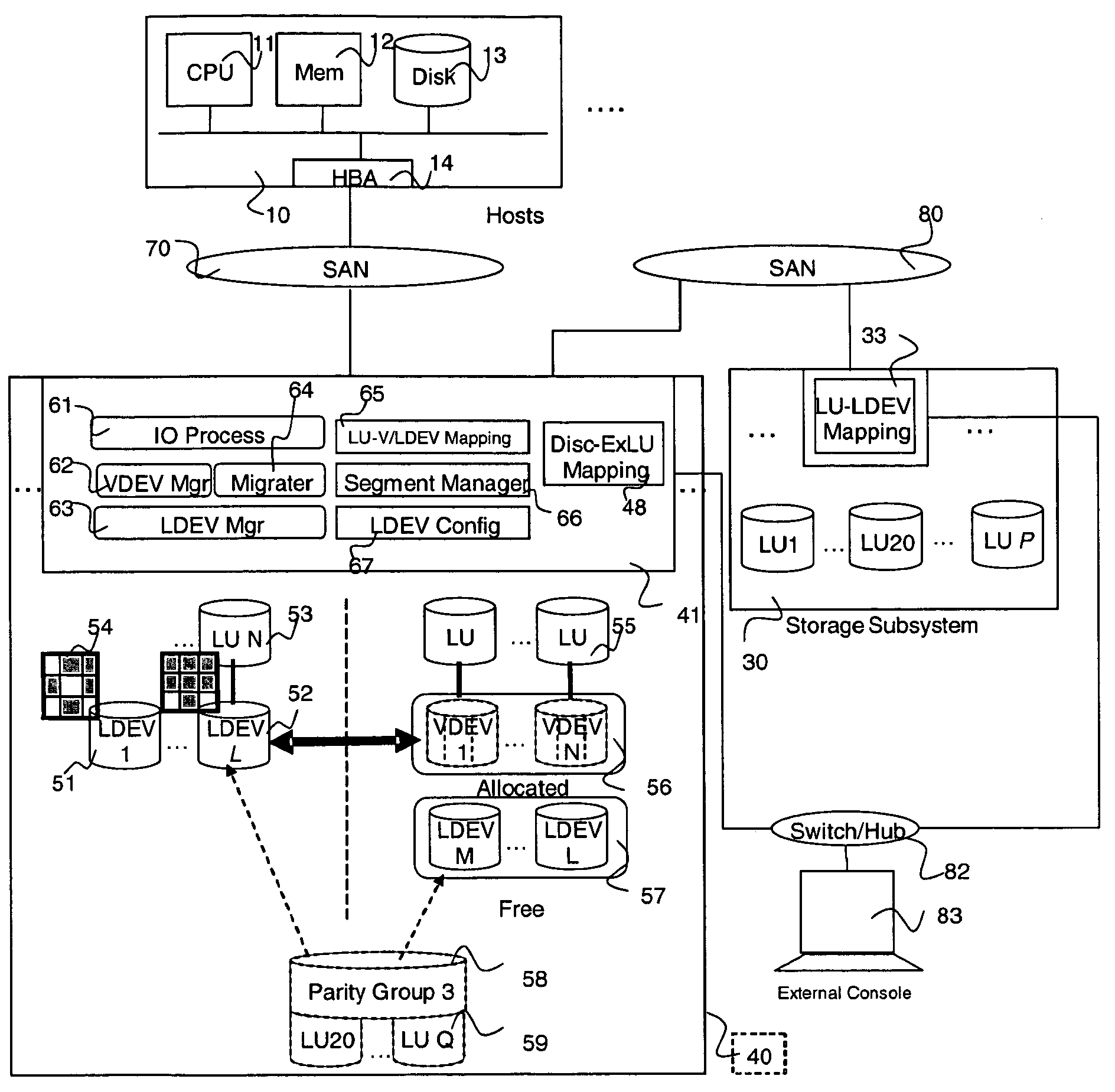
InactiveUS7130960B1Input/output to record carriersComputer security arrangementsExternal storageVirtual device
A system and method for managing disk space in a thin-provisioned storage subsystem. If a number of free segments in a free segment pool at a storage subsystem is detected as below a desired minimum, one or more of the following is performed: selecting and adding logical devices (LDEVs) from an internal storage as free segments to the free segment pool, transitioning LDEVs to a virtual device (VDEV), and / or selecting and adding LDEVs from an external storage as free segments to the free segment pool. The transitioning includes identifying partially used or completely used LDEVs and transitioning these to the VDEV. Data migration may also occur by: selecting a source segment at a VDEV for migration, reading data from the source segment, writing the data to a target segment, the target segment being a free segment from the free segment pool, and assigning the target segment to the VDEV.
Owner:HITACHI LTD
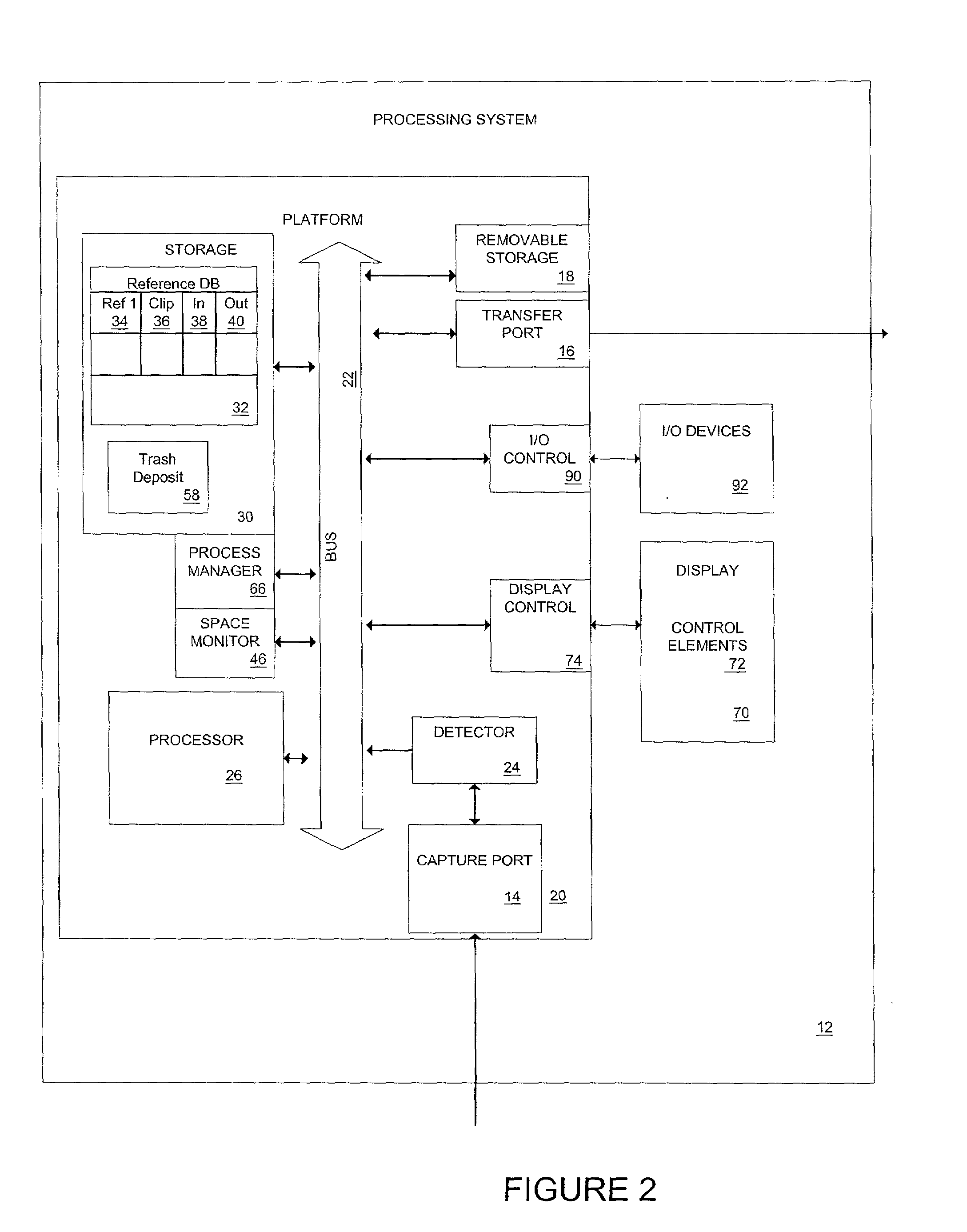
Disk space management and clip remainder during edit operations
InactiveUS7444593B1Save storage spaceElectronic editing digitised analogue information signalsAnalogue secracy/subscription systemsHandling systemWorld Wide Web
The method of storing a time based stream of information to generate a presentation is provided for in which a processing system is used. The methods provide for deleting a selected time based stream of information from the storage medium. In one embodiment, a process manager in the processing system deletes selected information in response to a user selection command. This process manager may further check for reference data to the information and only delete the information is no more than one reference to the selected information exists. A trash depository may be used as an intermediary holding area for the information prior to is deletion. Other aspect of the present invention relating to the processing system conserving storage for a time based stream of information for use in authoring a presentation are also described.
Owner:APPLE INC
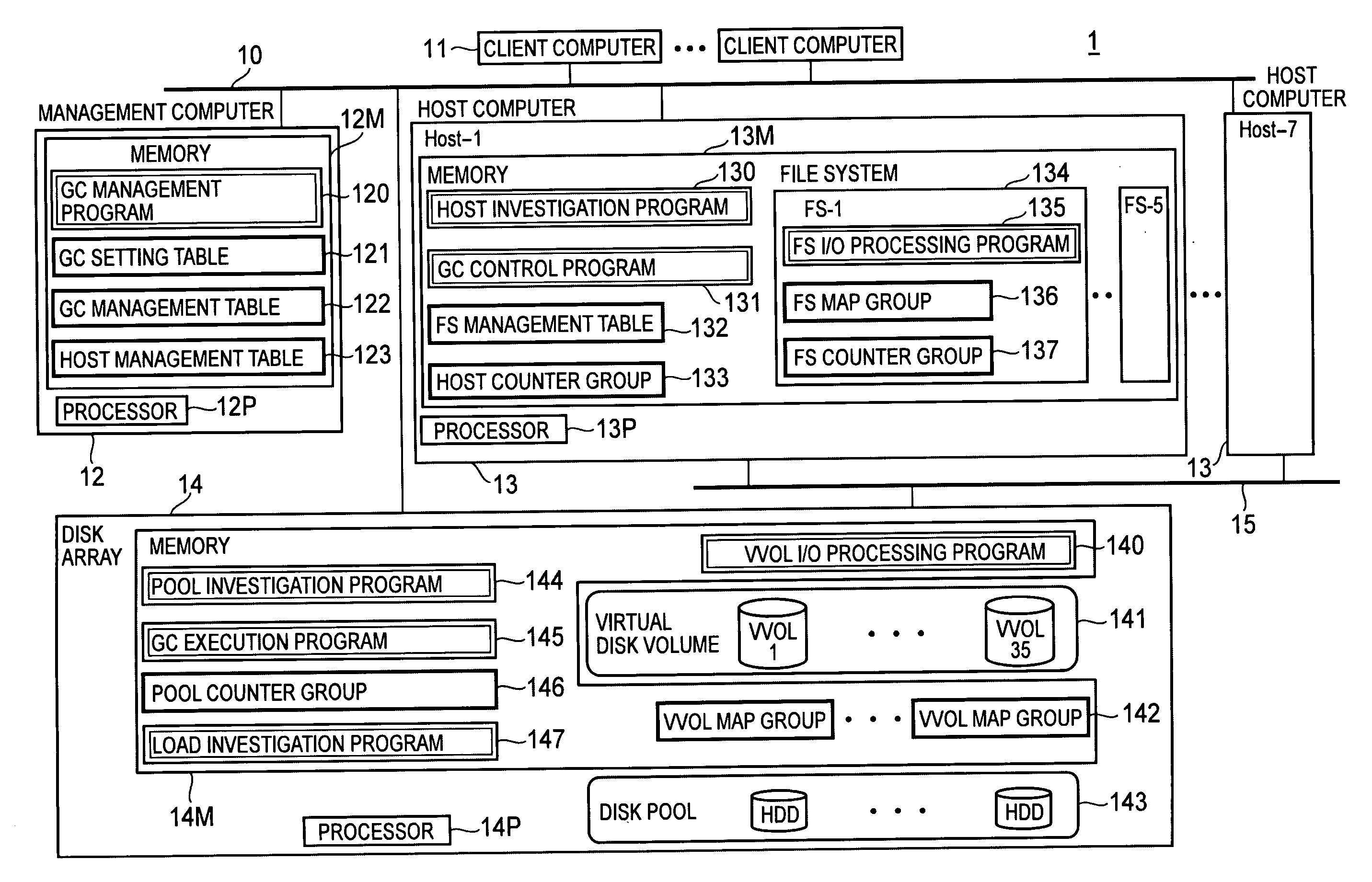
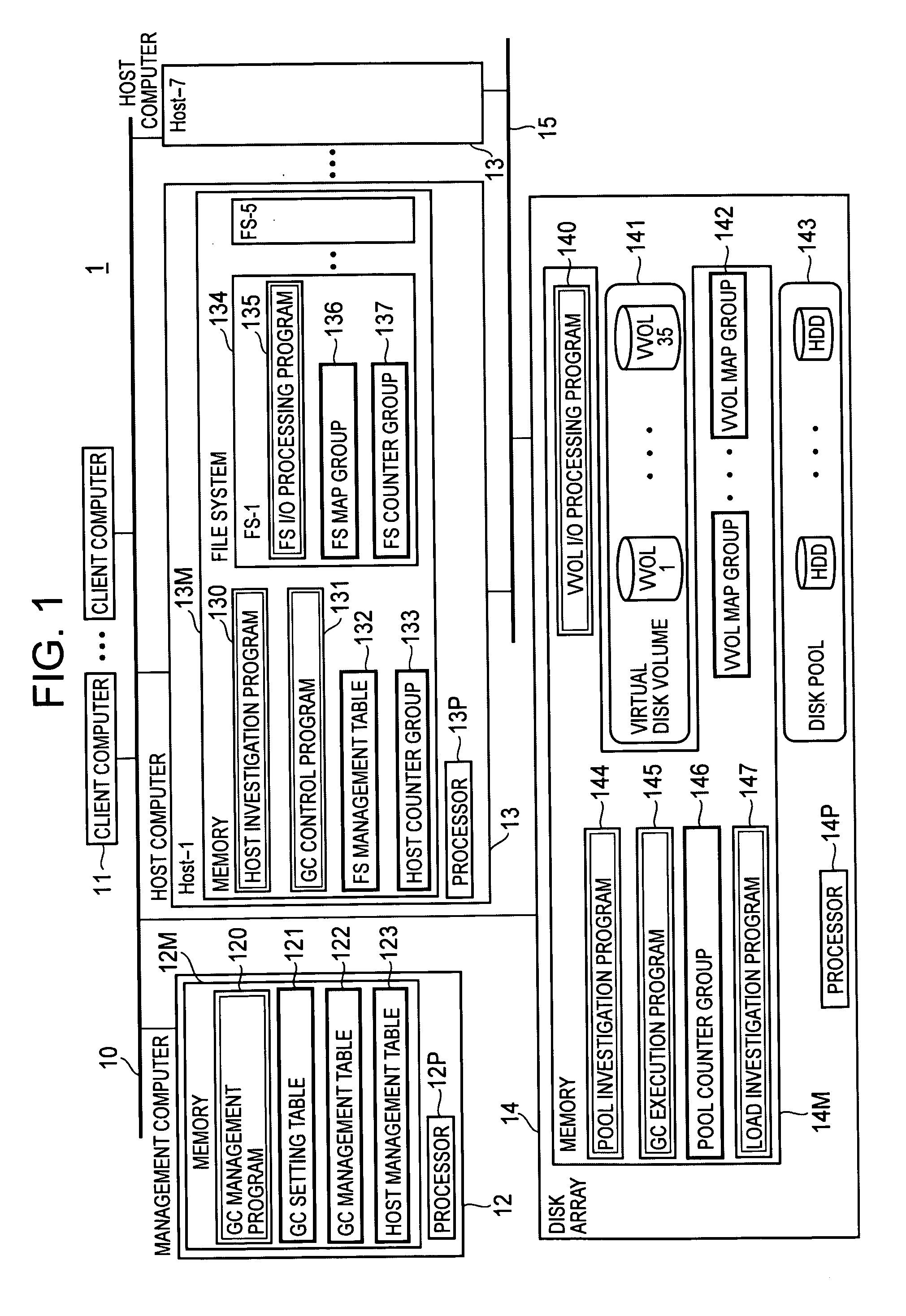
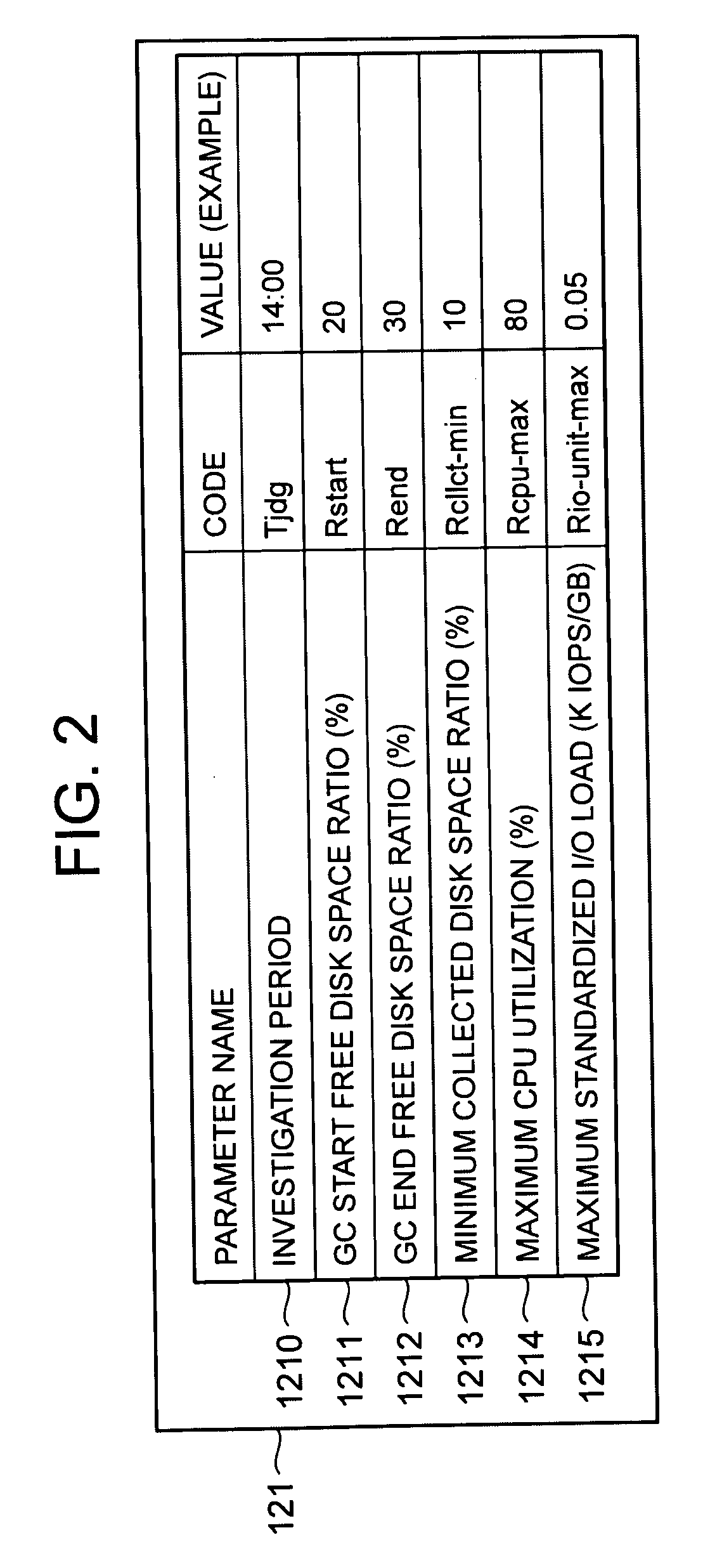
Computer system and garbage collection method of disk space
InactiveUS20090198946A1Avoid processing inefficienciesMemory systemsInput/output processes for data processingComputerized systemWaste collection
A processor of a management computer acquires the free disk space amount of a disk pool, acquires the invalid disk space amount from a plurality of host computers, determines a host computer to which the instruction for the physical disk space collection is issued on the basis of the invalid disk space amount, and judges that the free disk space amount is smaller than a predetermined threshold value before transmitting a GC control request to the determined host computer; another processor generates and transmits invalid disk space position information indicating the position of the invalid disk space in a virtual volume in cases where a host investigation request is received; and the other processor collects the physical disk space of a physical disk allocated to the storage disk space of the virtual volume in the disk pool.
Owner:HITACHI LTD
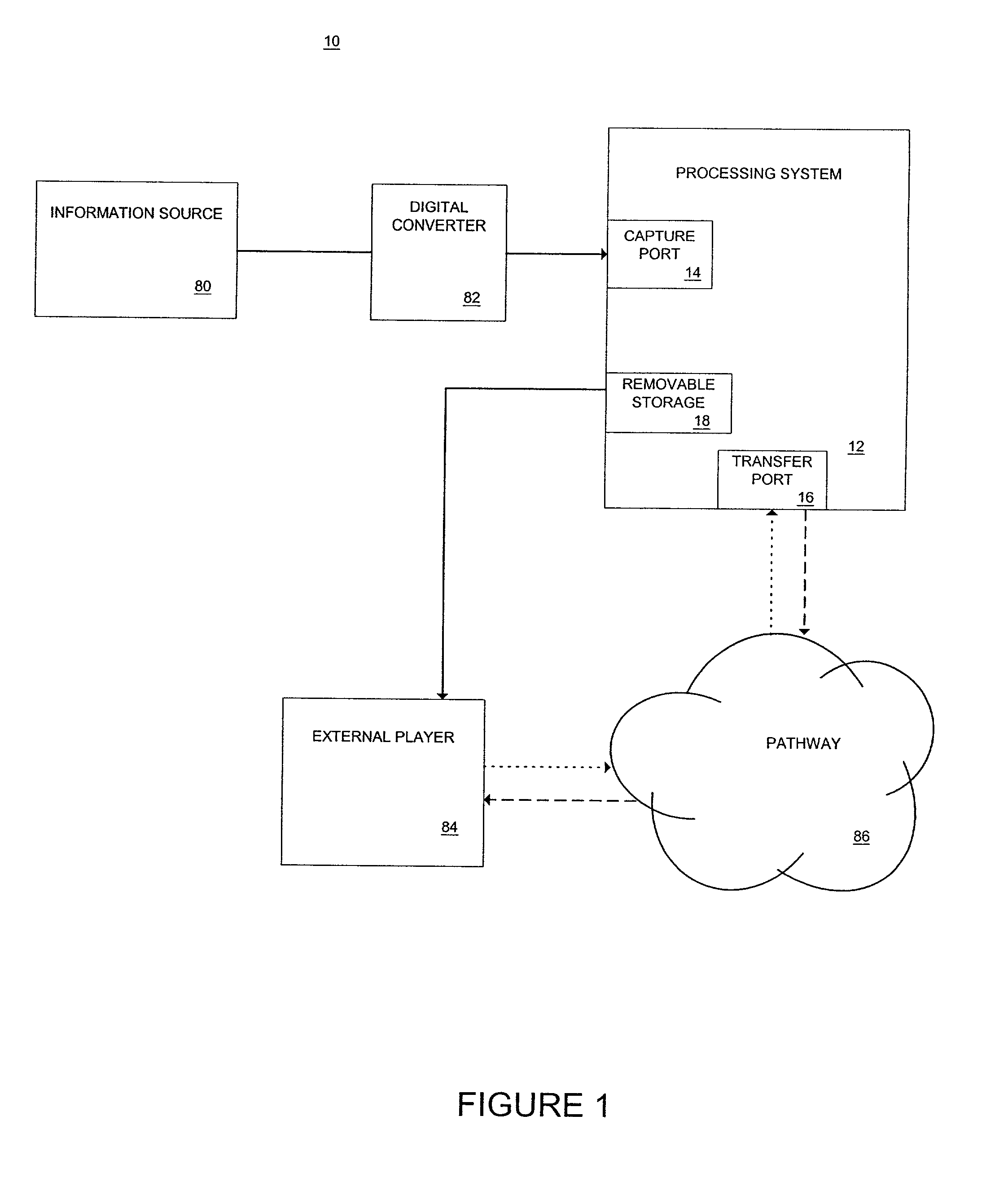
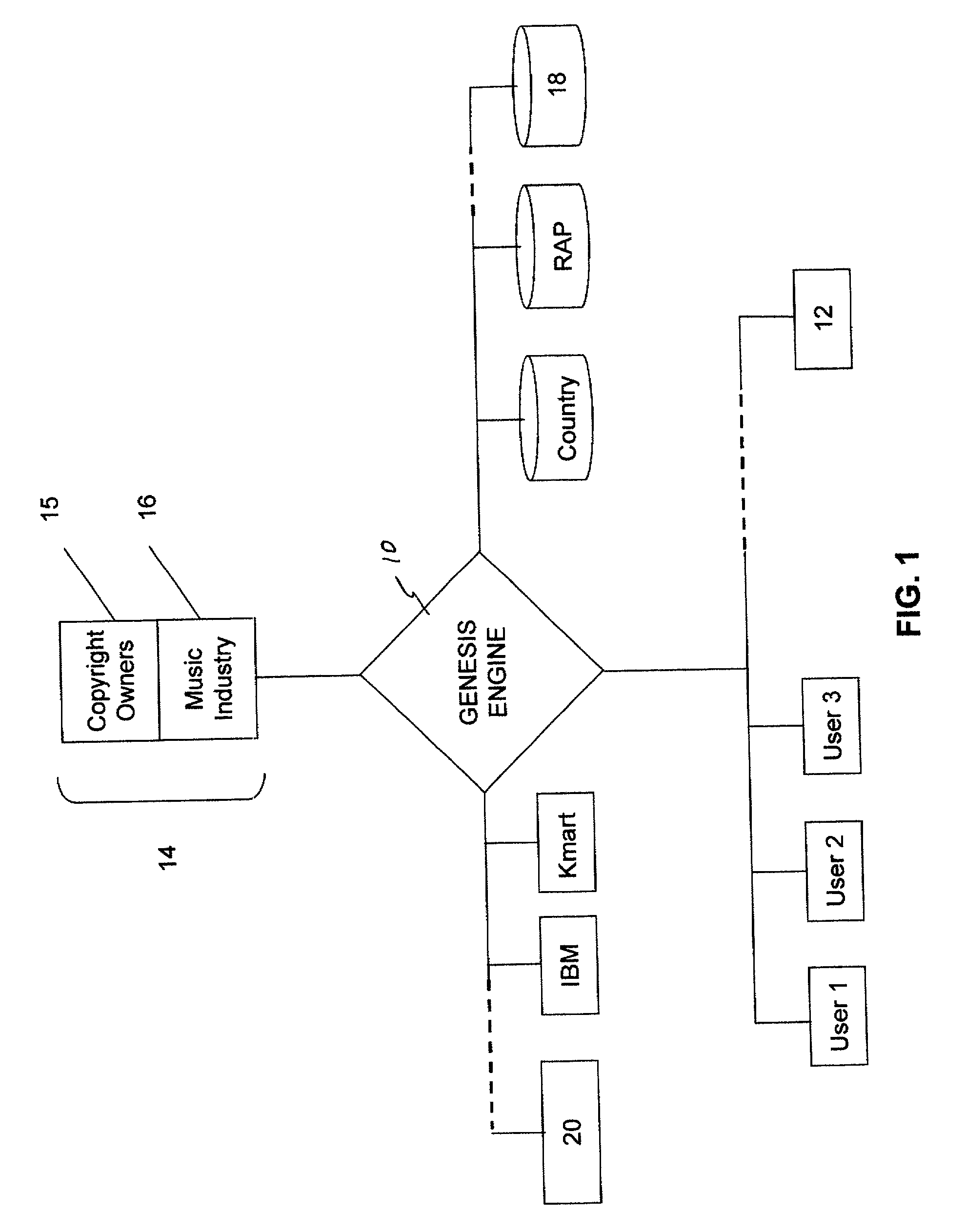
Method of and apparatus for delivery of proprietary audio and visual works to purchaser electronic devices
InactiveUS20010037304A1Computer security arrangementsBuying/selling/leasing transactionsSupercomputerData warehouse
A method of delivering audio and audio visual works to users of computer terminals includes the steps of: providing a data warehouse of digitized works; providing program means for end user computers to access, select and play at least one of the works; providing means for controlling end user access to the works and for collecting payment for playing at least one of the works; and diverting a portion of the payment for playing the at least one work to the holder of a copyright to the at least one work. The method preferably includes the additional steps of encrypting the works; and providing the end user with program means for deciphering the works. The method still further preferably includes additional the steps of delivering advertising matter to the end user with each work the end user selects and plays; keeping a record of the particular works each end user selects and plays; customizing advertising delivered to the end user to fit within any pattern of work selection by the particular end user. An apparatus for performing the method is also provided, including a computer hive made up of several inter-linked computers having specialized functions, the computers operating in unison to build a supercomputer that has shared disk space and memory, in which each node belongs to the collective and possesses its own business rules and membership to an organization managerial hierarchy.
Owner:PAIZ RICHARD S
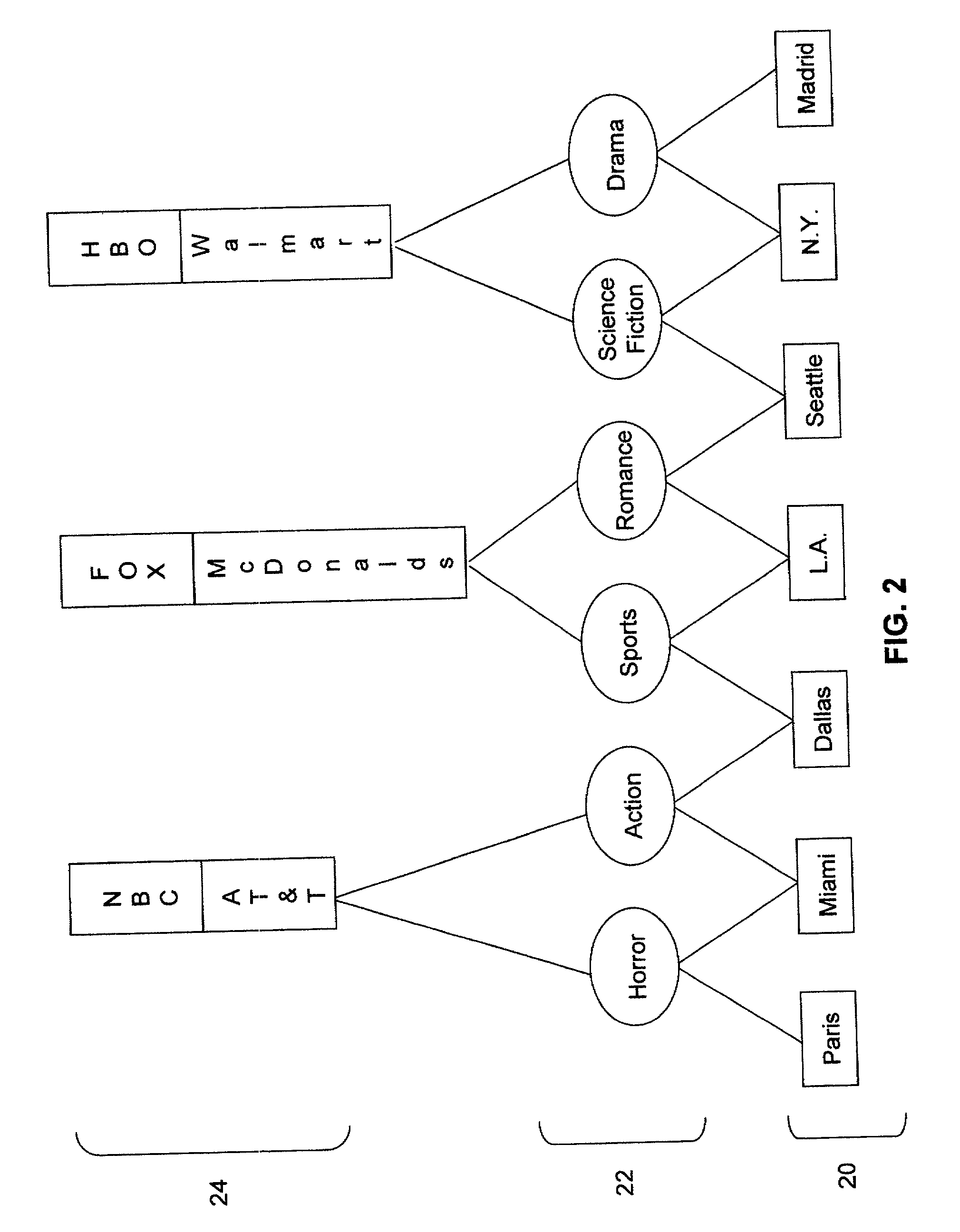
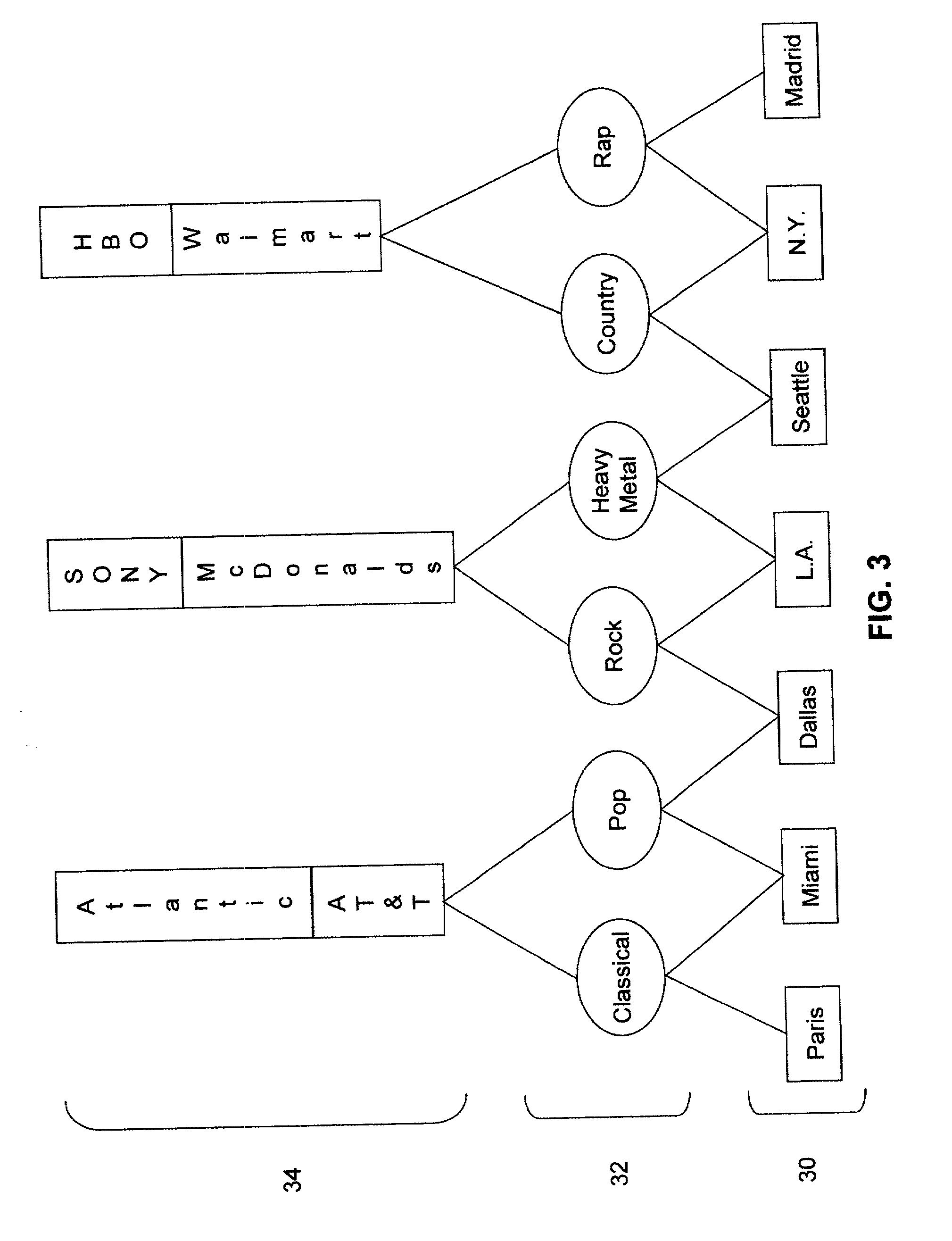
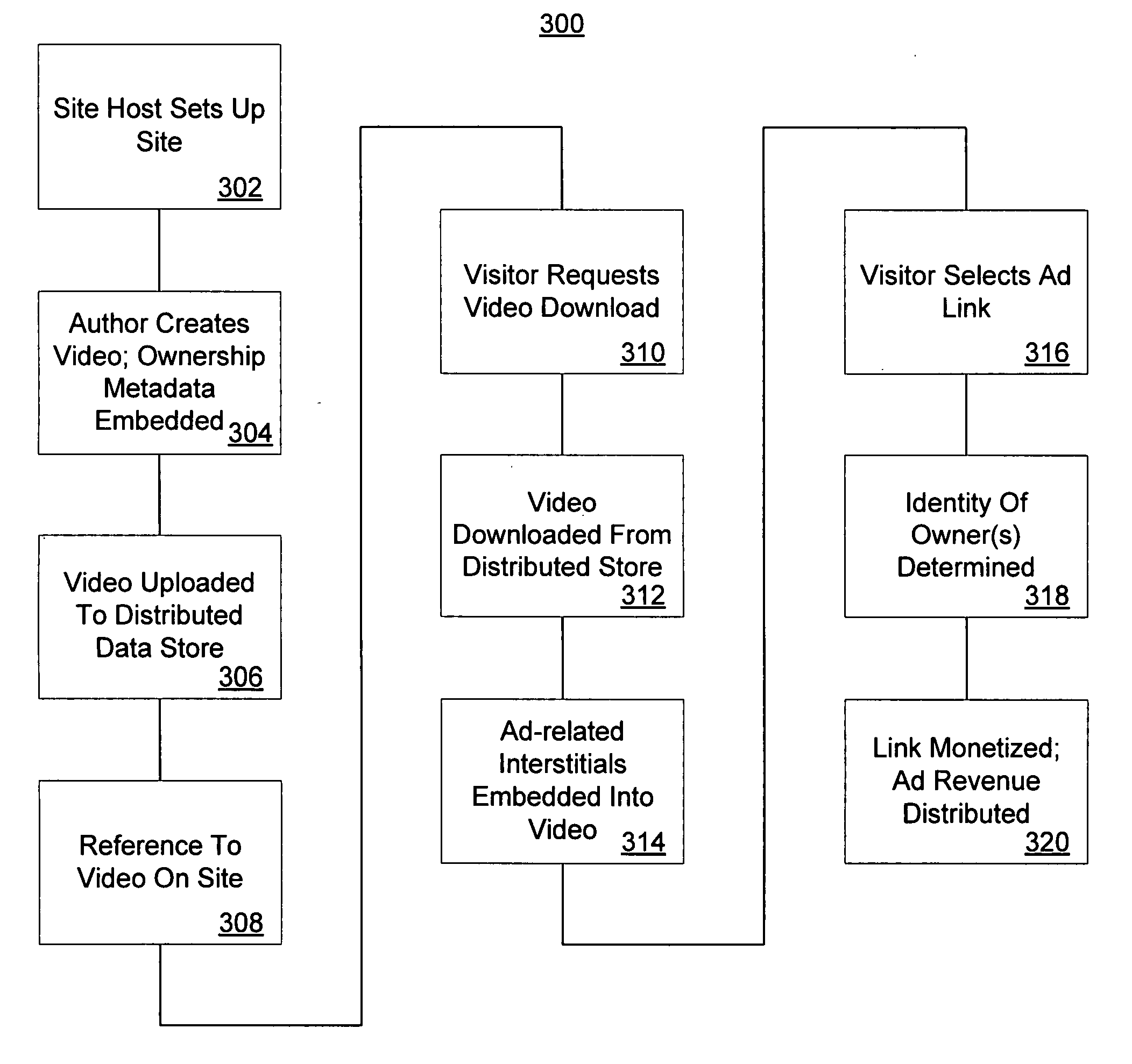
Collaborative video via distributed storage and blogging
InactiveUS20060294571A1Television system detailsAnalogue secracy/subscription systemsComposite mediaSubject matter
Systems and methods for sharing video or media content on a distributed network are disclosed. End users may be induced through a variety of ways to allocate some amount of unused disk space and otherwise idle bandwidth for storing media produced in a blogging or web-publishing context. For example, when a user creates a blog, the user may link certain video or media files to it. Such video may be kept in a distributed store across a variety of peer machines. If a visitor visits the blog, the visitor may see contextual ads based upon the subject matter associated with the blog, and the blog owner may receive a share of the advertising revenue generated. A visitor may download the video and combine it with new content. Thus, composite media files may be created from sections taken from any number of previously created video clips, each of which may be associated with a different owner. The composite media files may include pointers to any or all of the original owners, as well as the respective length of each included section. The composite video may then be added to a different blog. Anyone visiting the new blog may also see contextual ads, with pro-rated portions of the generated ad revenue flowing proportionally to each of the original media owners.
Owner:MICROSOFT TECH LICENSING LLC
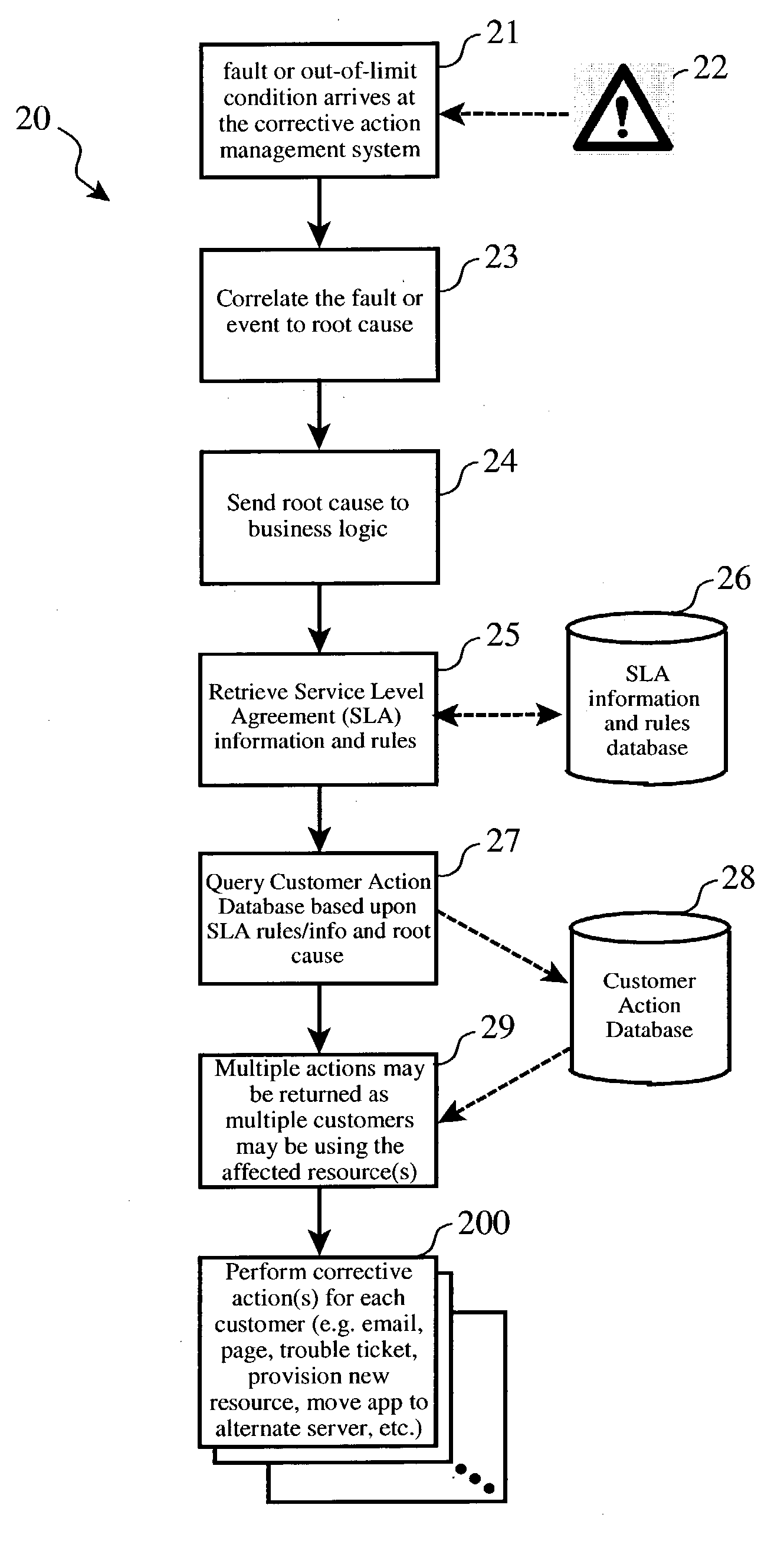
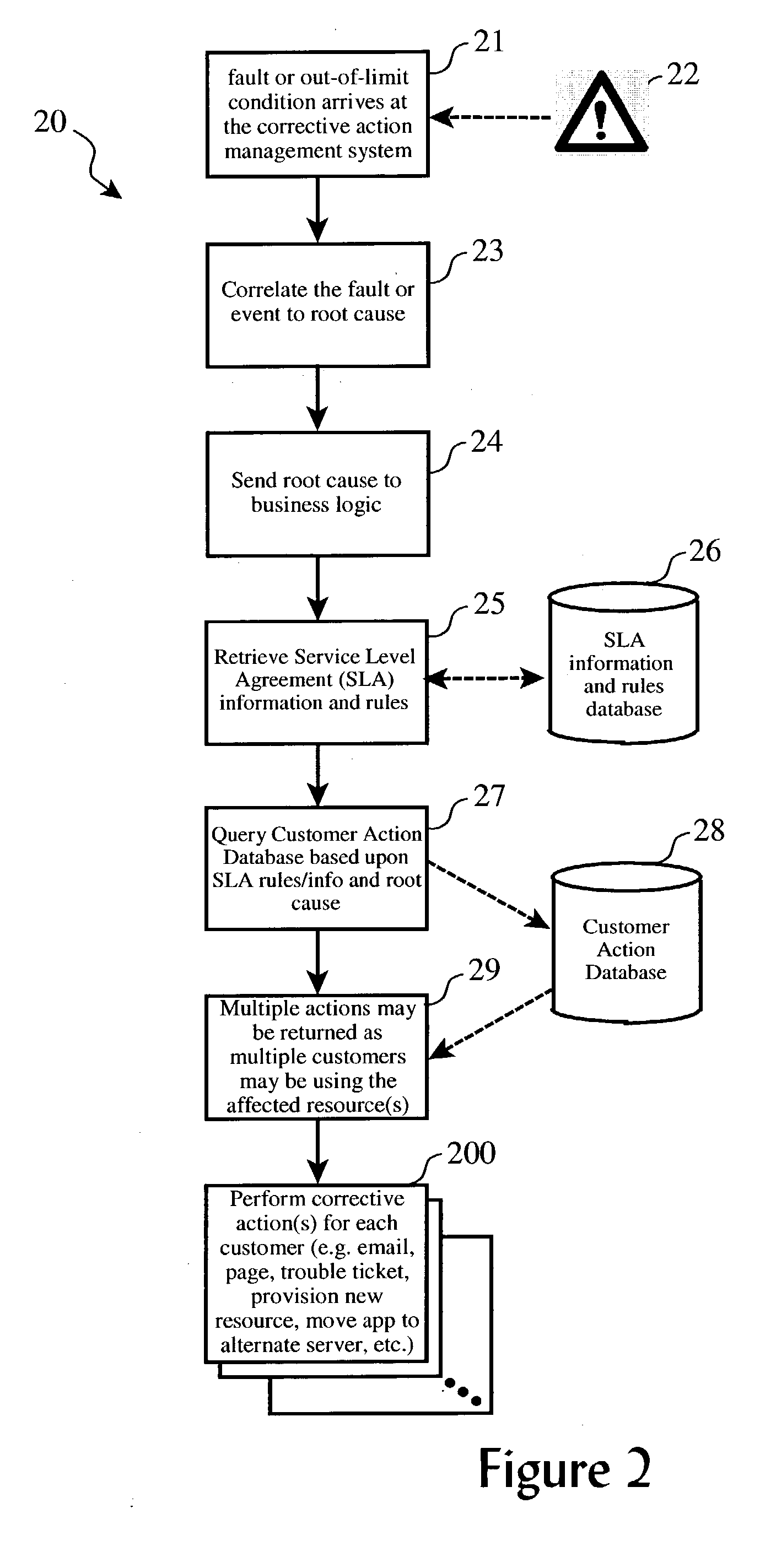
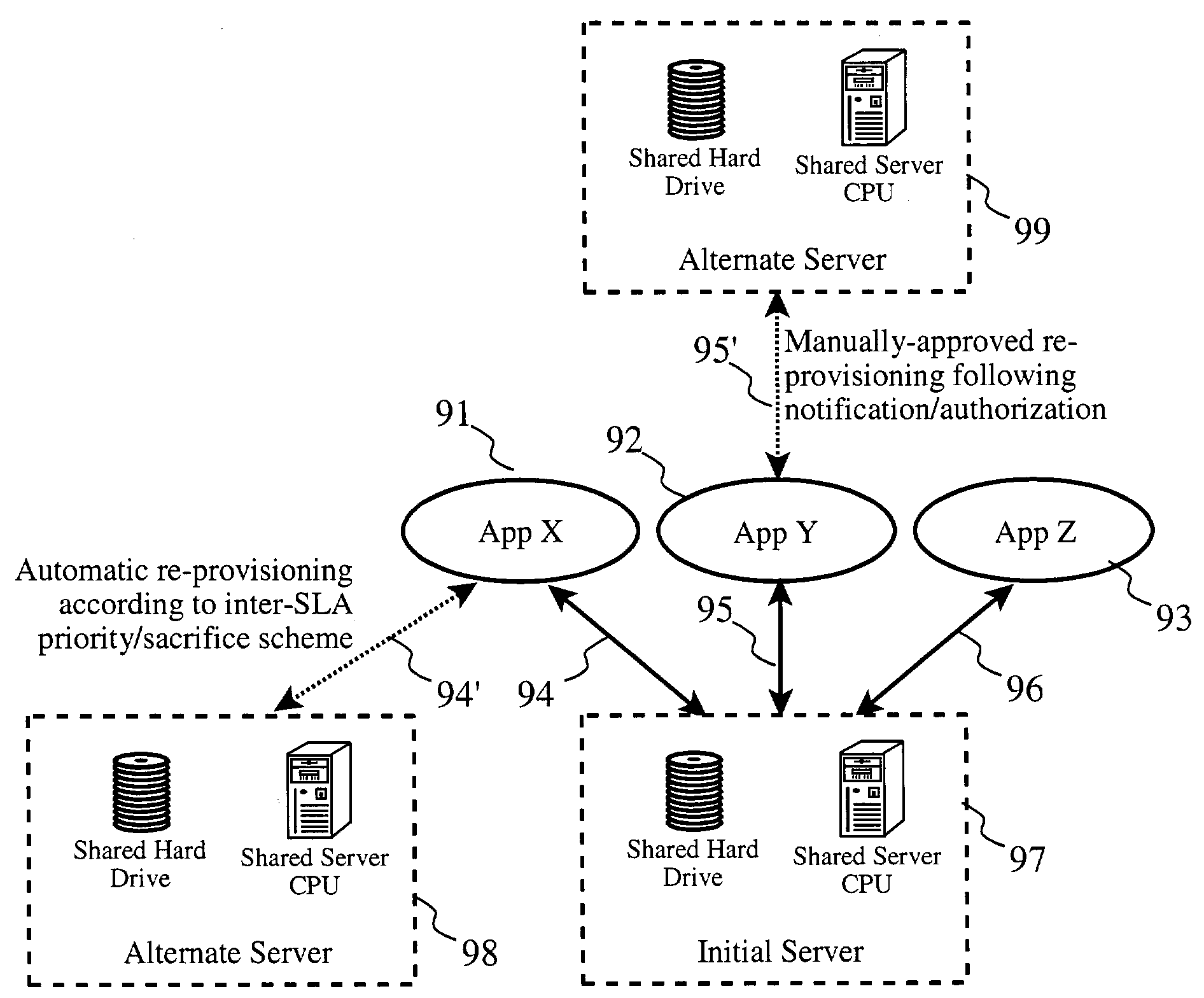
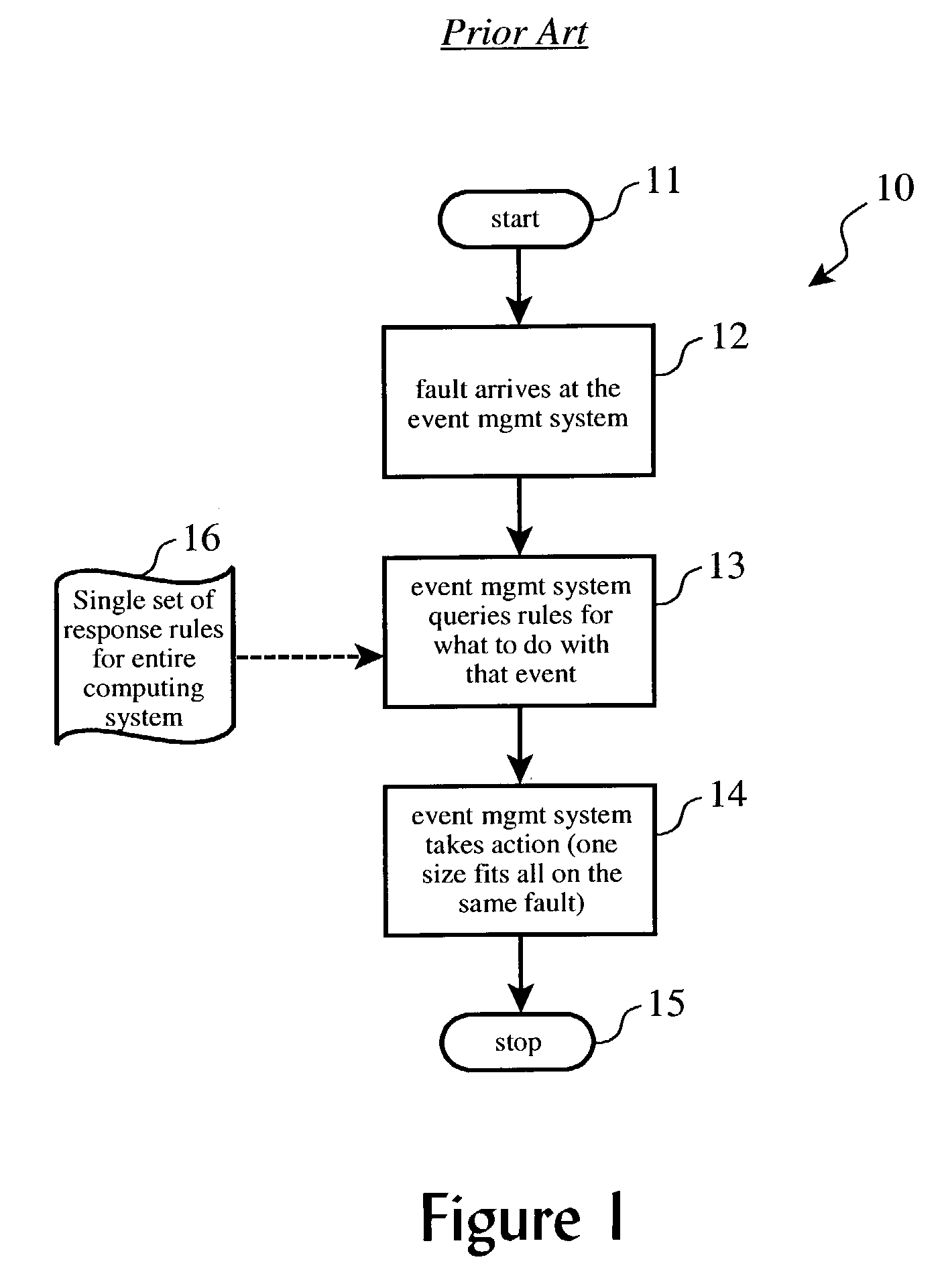
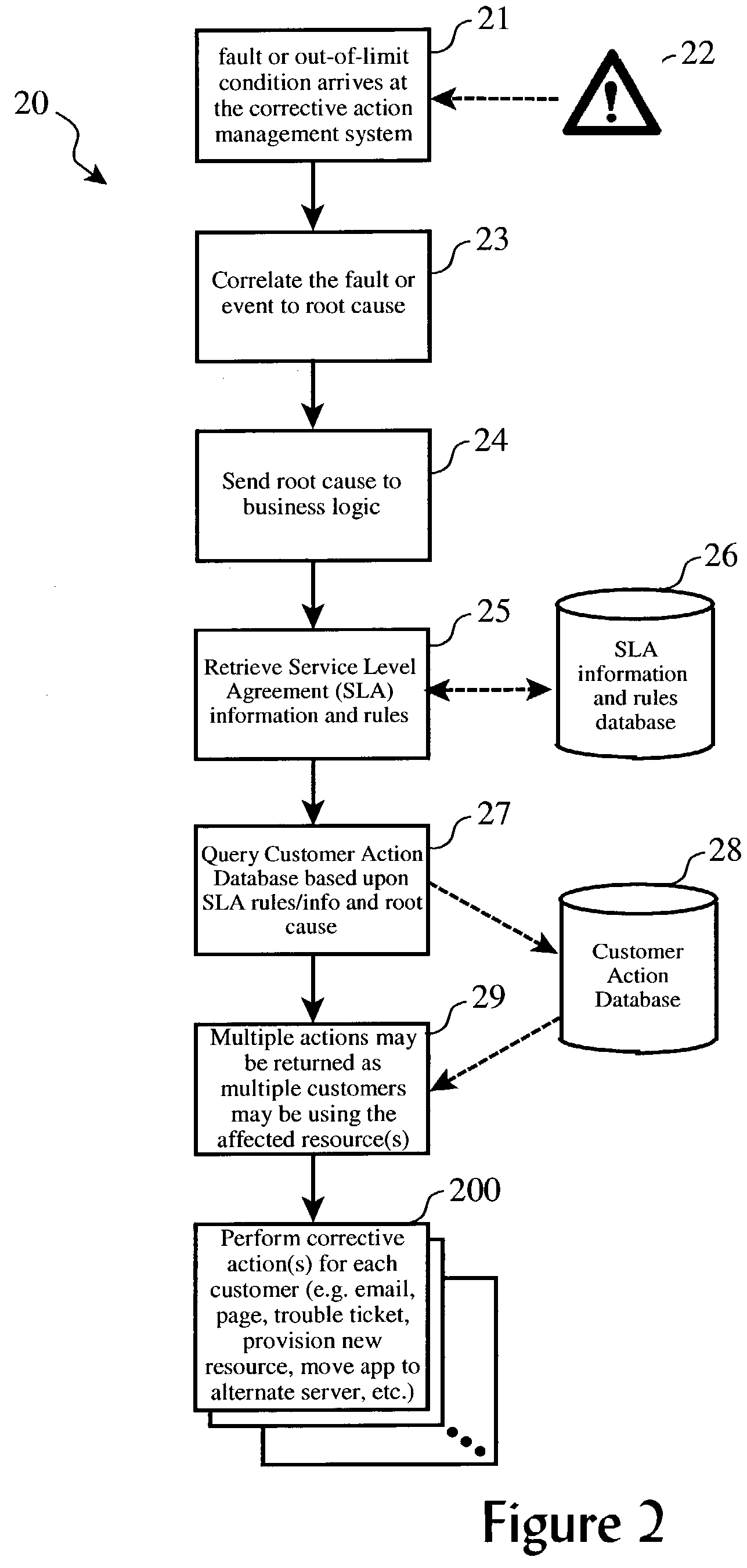
System management infrastructure for corrective actions to servers with shared resources
ActiveUS20040210889A1Hardware monitoringNon-redundant fault processingHard disc driveSystems management
A corrective action method or subsystem for providing corrective actions in a for a computing domain shared among multiple customers wherein different domain resources are shared by different customers, and each customer's corrective action preferences are accommodated differently according a repository of customer preferences. A database may be queried when a fault event or out-of-limits condition is detected for a given shared resource to determine which customers share the resource, determine each affected customer's response preferences, and to perform corrective actions according to those response preferences. For example, three customers may share a particular hard drive in a shared computing system. One customer may prefer to receive an email notice when the drive is nearly full, another may prefer to receive additional allocation of disk space elsewhere, and the third may prefer to receive a written report of space utilization.
Owner:KYNDRYL INC
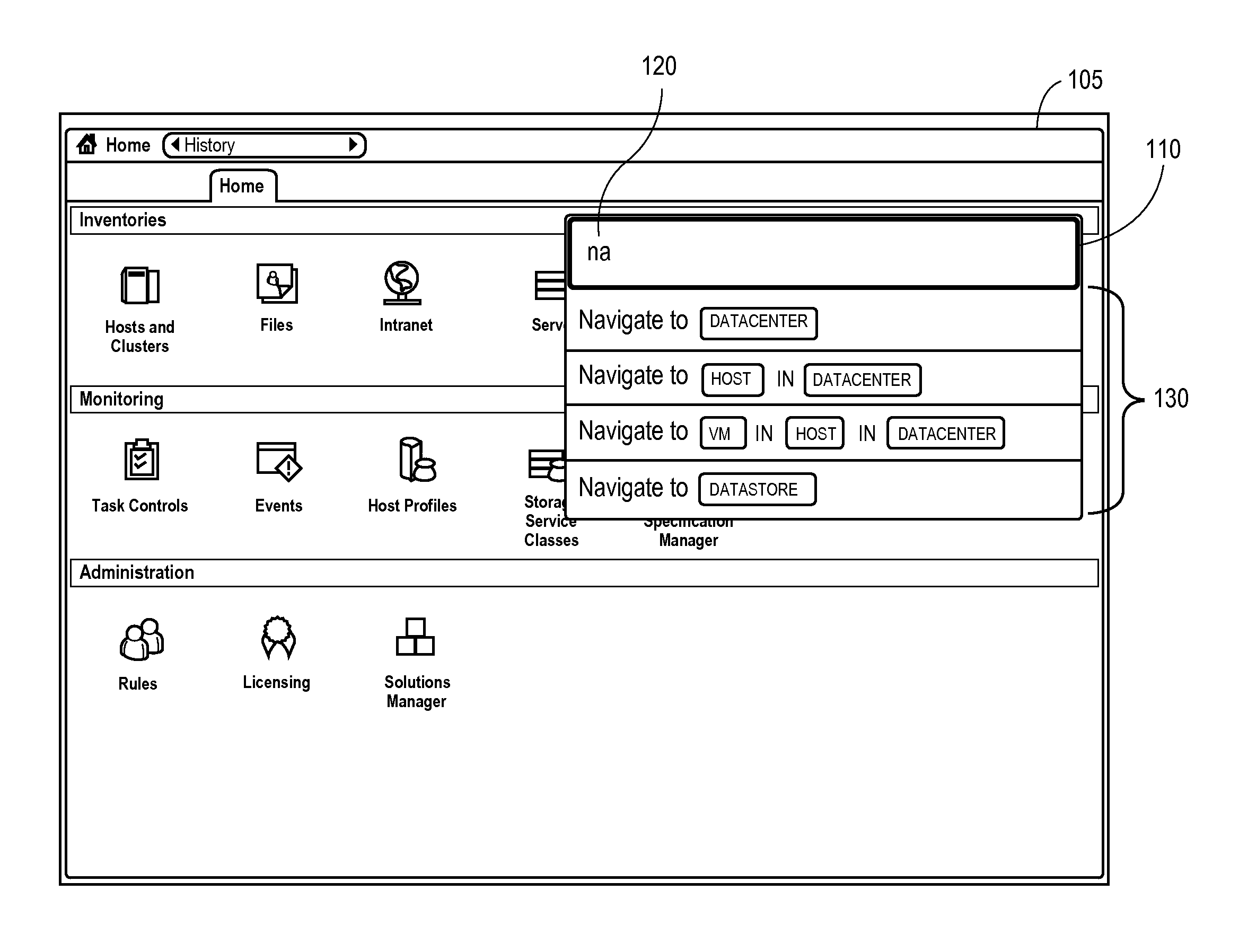
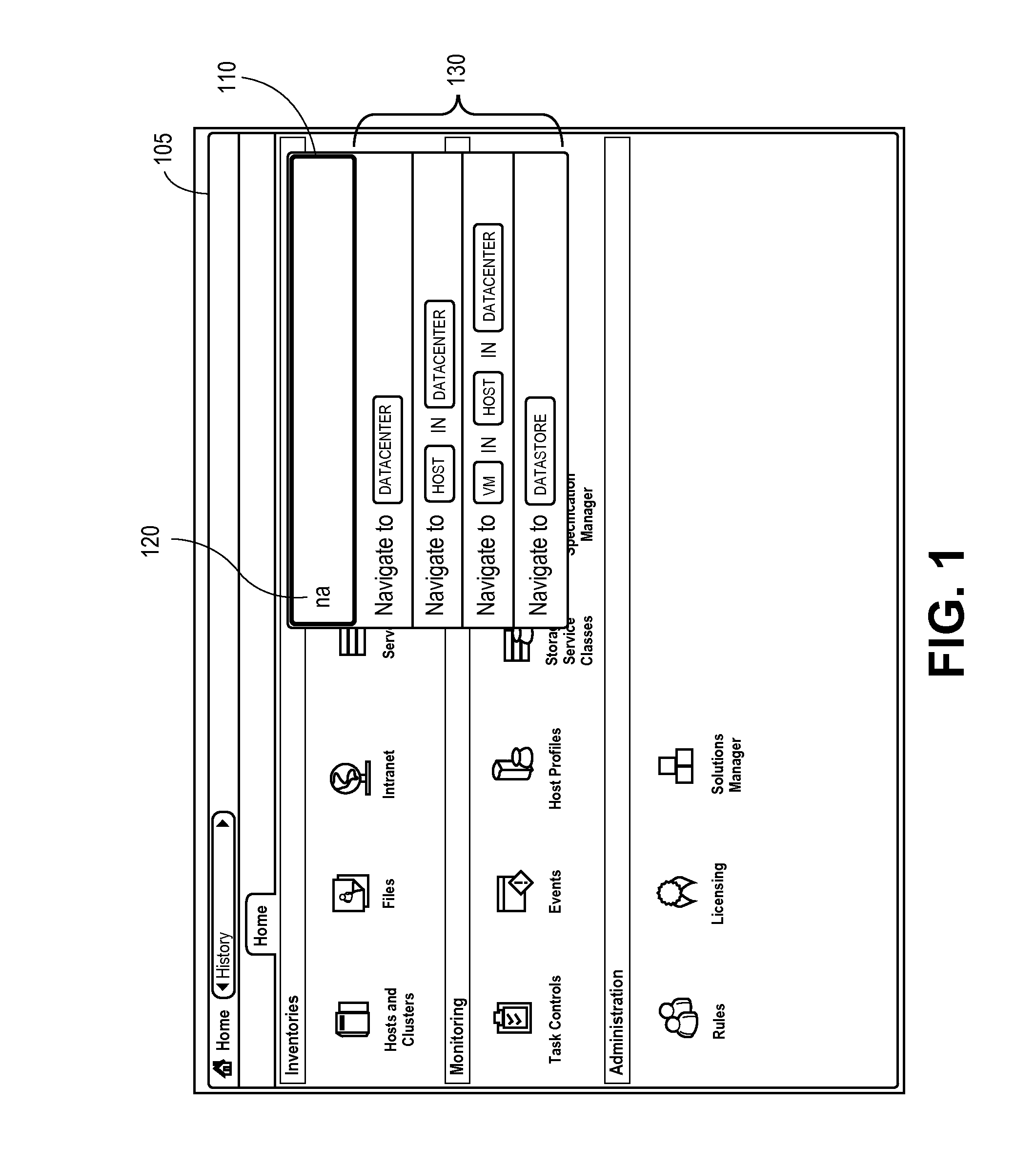
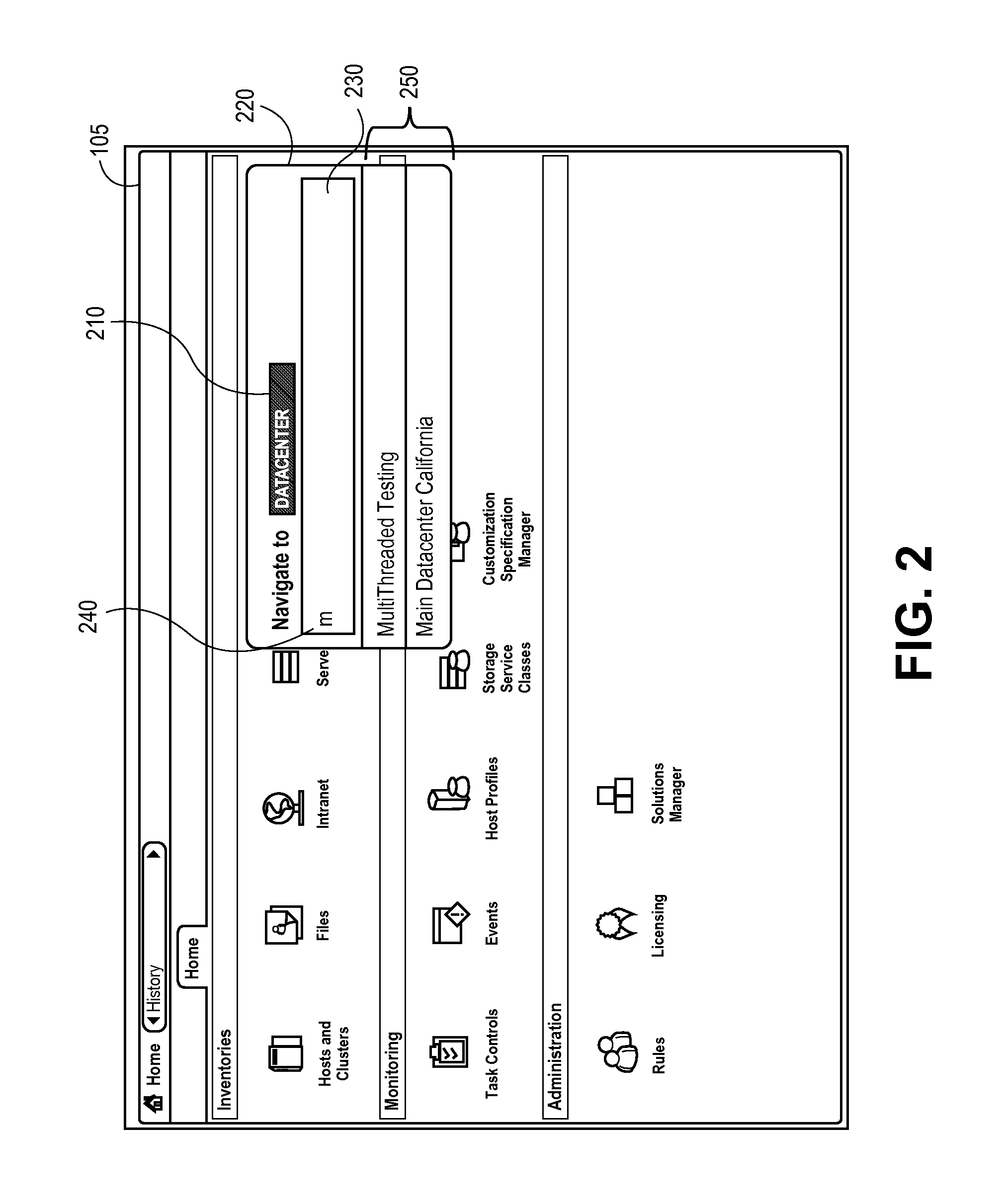
Efficient command processing
ActiveUS20150082218A1Execution for user interfacesInput/output processes for data processingData centerGeolocation
Exemplary methods, apparatuses, and systems receive input command requests and present suggestions for command actions or command objects. An action request is received within a datacenter management user interface and a first command suggestion is provided. The first command suggestion includes one or more placeholder object categories. A first suggested object is identified according to a received object property and the action request. The object property can be CPU utilization, disk space, memory, uptime, version, software type, geographic location, keyword, or name. In response to receiving the action request, the first suggested object is determined to be compatible with the action request, in response to identifying the first suggested object is compatible with the received object property and the action request, a second command suggestion is provided. The second command suggestion includes the first suggested object.
Owner:VMWARE INC
File folding technique
InactiveUS7072910B2Reduce in quantityReduce space consumptionData processing applicationsDigital data information retrievalFile systemFile server
A file folding technique reduces the number of duplicate data blocks of a file consumed on a storage device of a file server configured to generate a persistent image of its active file system at a point in time. According to the file folding technique, if “old” data blocks of the file are over-written with “new” data and that new data is identical to the data of the persistent file image, the old data blocks are “freed” and the file is directed to refer to the persistent image for its data. The invention reduces disk space consumption in a file server configured to generate persistent images of its active file system and, in particular, reduces overall persistent image disk usage.
Owner:NETWORK APPLIANCE INC
System and method of using pre-enrolled speech sub-units for efficient speech synthesis
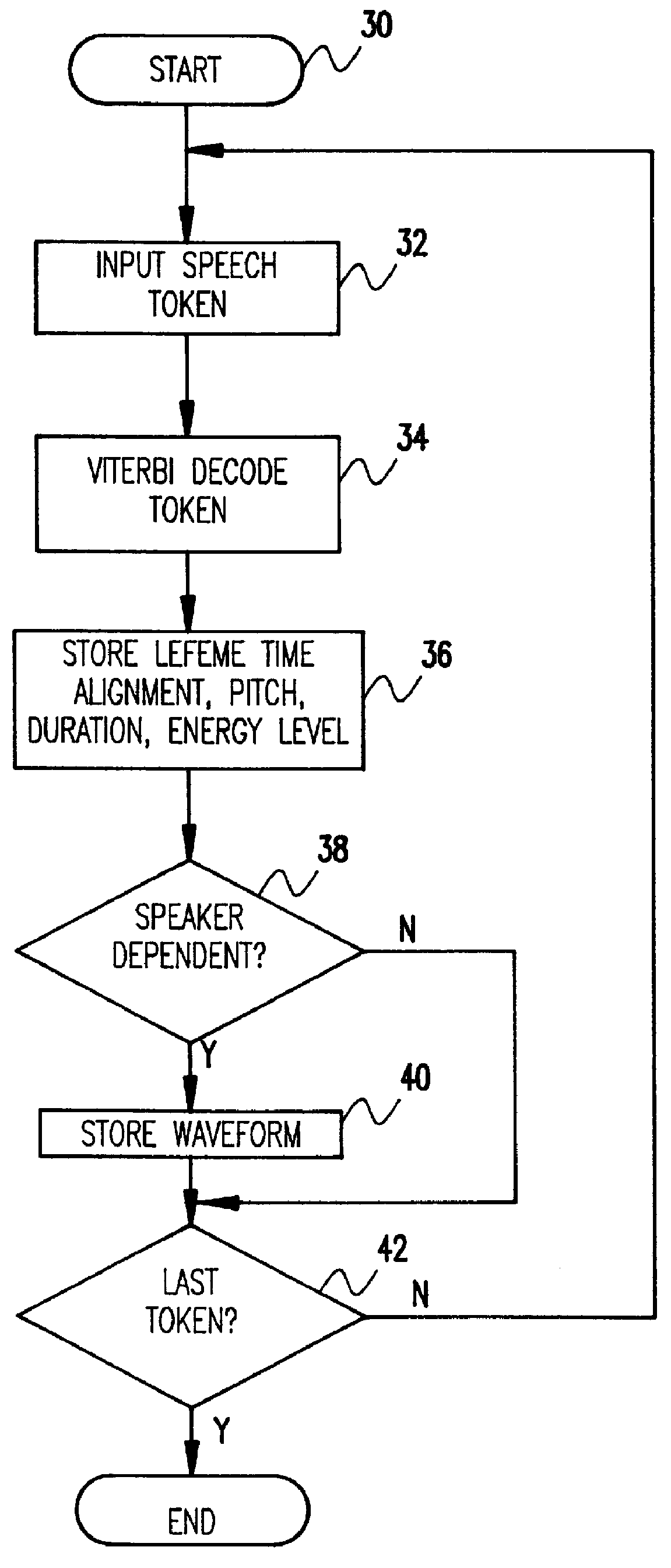
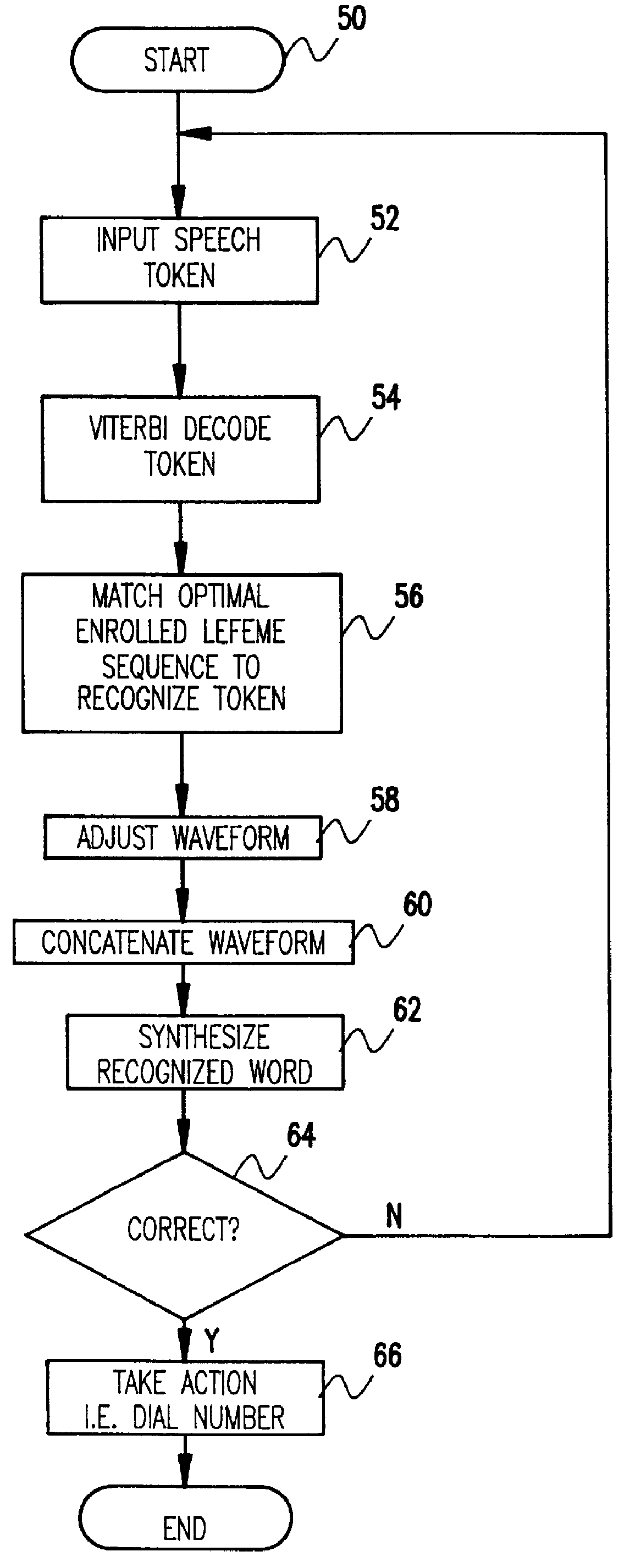
InactiveUS6041300AReduce the amount requiredAbility to provideAutomatic call-answering/message-recording/conversation-recordingSubscriber signalling identity devicesSpoken languageHands free
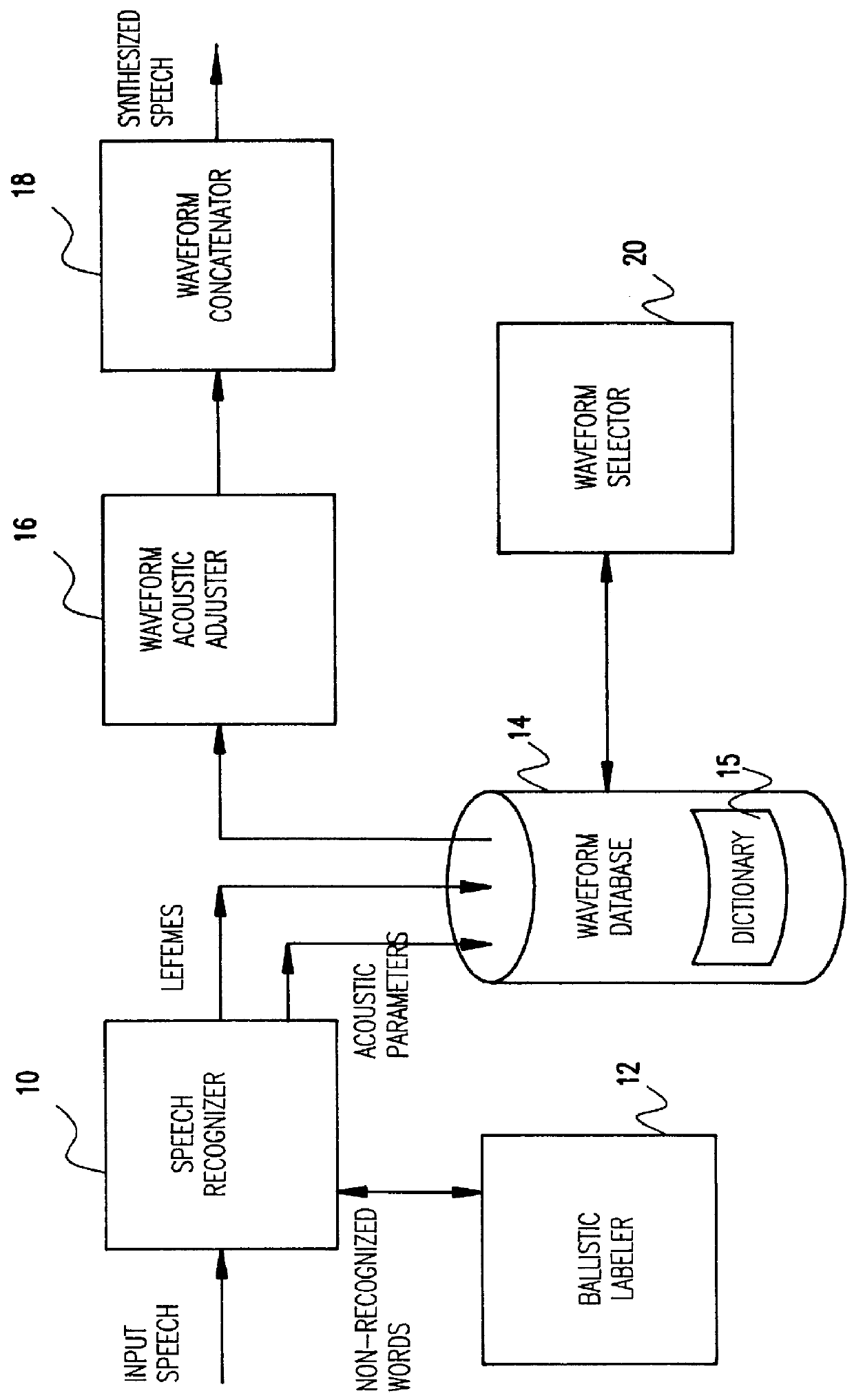
A speech recognition system is disclosed useful in, for example, hands-free voice telephone dialing applications. The system will match a spoken word (token) to one previously enrolled in the system. The system will thereafter synthesize or replay the recognized word so that the speaker can confirm that the recognized word is indeed the correct word before further action is taken. In the case of voice activated dialing, this avoids wrong numbers. The token itself is not explicitly recorded; rather, only the lefemes may be recorded from which the token can be reconstructed for playback. This greatly reduces the amount of disk space that is needed for the database as well as provides the ability to reconstruction data in real time for synthesis use by a local name recognition machine.
Owner:IBM CORP
Minimally invasive lateral intervertbral fixation system, device and method
A system, device and method are disclosed for minimally invasive lateral intervertebral fixation. An intervertebral fixation device includes a weight-bearing shell configured to fit into a disk space between plural vertebrae, the weight-bearing shell including a keyway opening between and through plural sidewalls. A first plurality of anchors is rotatably disposed in a first orientation in relation to the weight-bearing shell. A second plurality of anchors is rotatably disposed in a second orientation in relation to the weight-bearing shell. A key is adapted to rotate the first plurality of anchors in divergent directions from the second plurality of anchors and to secure a first vertebra and a second vertebra, respectively. The key is further adapted to support the first plurality of anchors and the second plurality of anchors in divergent directions in relation to the weight-bearing shell, the first plurality of anchors and the second plurality of anchors secured to the first vertebra and the second vertebra.
Owner:INT SPINAL INNOVATIONS
Pivotal lateral cage and method of insertion
A process for inserting a pivotable interbody spacer including an insertion instrument configured to manipulate a pivotable interbody spacer during insertion, wherein the insertion instrument includes means for coupling the interbody spacer and a means for fixing the angular position of the interbody spacer. According to one method for inserting an interbody spacer in a spinal disk space, the interbody spacer is grasped by the insertion instrument and fixed at a first angular position. The interbody spacer is next inserted into a surgical site. Next, the interbody spacer is released from a first angular position. Then, the insertion instrument is pivoted about a coupling of the interbody spacer such that the interbody spacer is in a second angular position. The angular position of the interbody spacer is then fixed in the second angular position. This insertion process continues until the interbody spacer is positioned in the desired location.
Owner:BEACON BIOMEDICAL
System and method for managing disk space in a thin-provisioned storage subsystem
InactiveUS20060242378A1Input/output to record carriersComputer security arrangementsExternal storageVirtual device
A system and method for managing disk space in a thin-provisioned storage subsystem. If a number of free segments in a free segment pool at a storage subsystem is detected as below a desired minimum, one or more of the following is performed: selecting and adding logical devices (LDEVs) from an internal storage as free segments to the free segment pool, transitioning LDEVs to a virtual device (VDEV), and / or selecting and adding LDEVs from an external storage as free segments to the free segment pool. The transitioning includes identifying partially used or completely used LDEVs and transitioning these to the VDEV. Data migration may also occur by: selecting a source segment at a VDEV for migration, reading data from the source segment, writing the data to a target segment, the target segment being a free segment from the free segment pool, and assigning the target segment to the VDEV.
Owner:HITACHI LTD
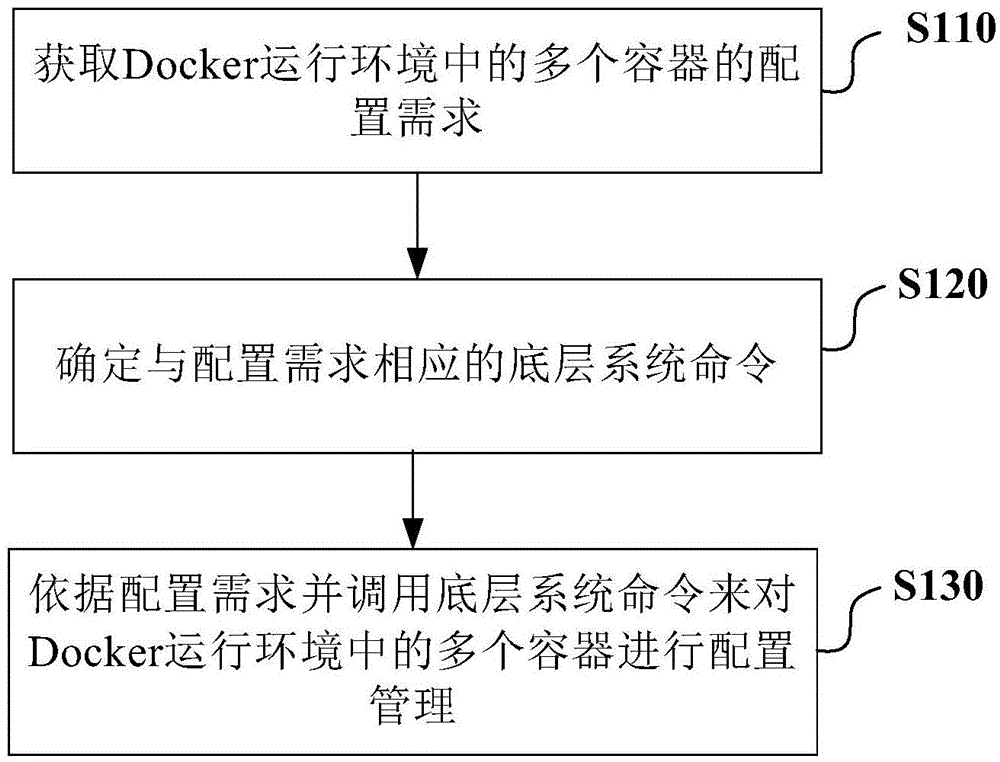
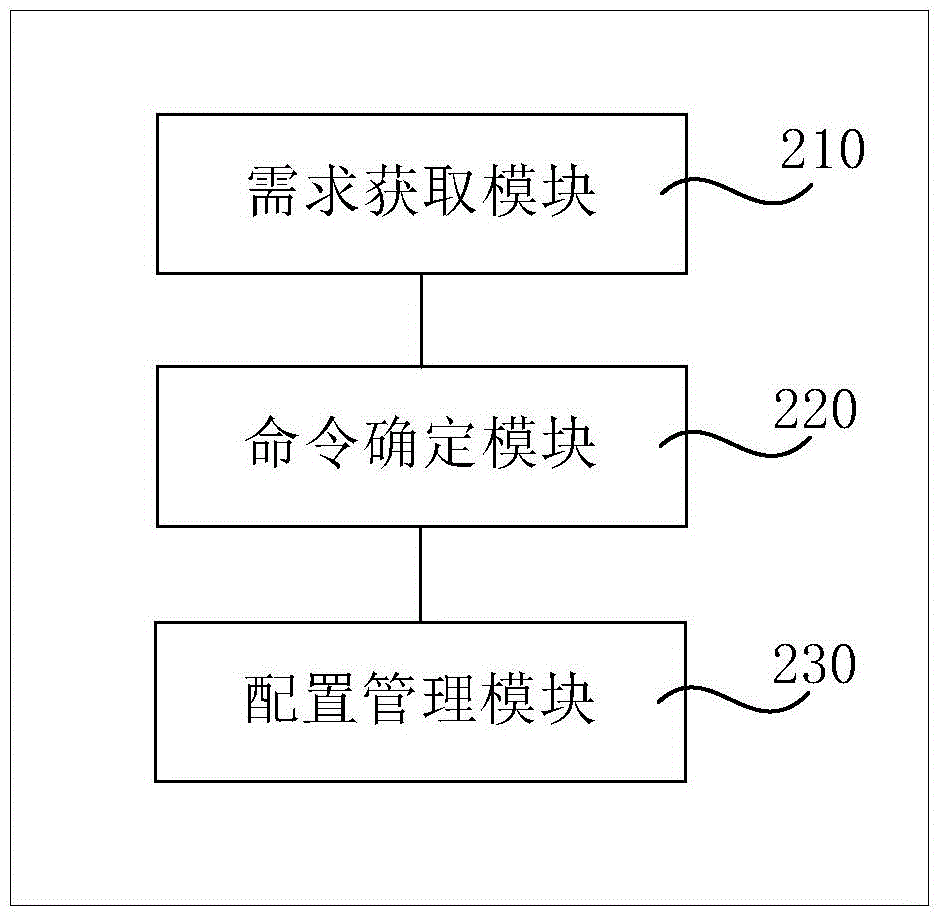
Configuration management mode and device based on Docker
InactiveCN104951360AQuick configurationQuick and easy configurationResource allocationVirtualizationIp address
The invention provides a configuration management mode based on a Docker. The configuration management mode is applied in a Docker operating environment which comprises multiple containers. The configuration management mode comprises the steps that configuration requirements of the containers in the Docker operating environment are acquired; underlying system commands corresponding to the configuration requirements are determined; the containers in the Docker operating environment are configured and managed according to the configuration requirements and by calling the underlying system commands. According to the embodiment of the configuration management mode, the problem that an original configuration management mode of the Docker on the virtualized containers in the Docker is incomplete is solved; by executing the underlying system commands, the multiple containers can be rapidly configured to meet the requirements of an actual generating environment; for example, the CPU usage rate of each container can be reasonably limited, IP addresses of the containers in the network configuration can be flexibly limited, usable independent disk space can be configured and distributed for each container, and therefore various actual configuration requirements of an administrator on the multiple containers in the Docker operating environment can be met.
Owner:BEIJING QIHOO TECH CO LTD +1
System management infrastructure for corrective actions to servers with shared resources
A corrective action method or subsystem for providing corrective actions in a for a computing domain shared among multiple customers wherein different domain resources are shared by different customers, and each customer's corrective action preferences are accommodated differently according a repository of customer preferences. A database may be queried when a fault event or out-of-limits condition is detected for a given shared resource to determine which customers share the resource, determine each affected customer's response preferences, and to perform corrective actions according to those response preferences. For example, three customers may share a particular hard drive in a shared computing system. One customer may prefer to receive an email notice when the drive is nearly full, another may prefer to receive additional allocation of disk space elsewhere, and the third may prefer to receive a written report of space utilization.
Owner:KYNDRYL INC
Total quotas for data storage system
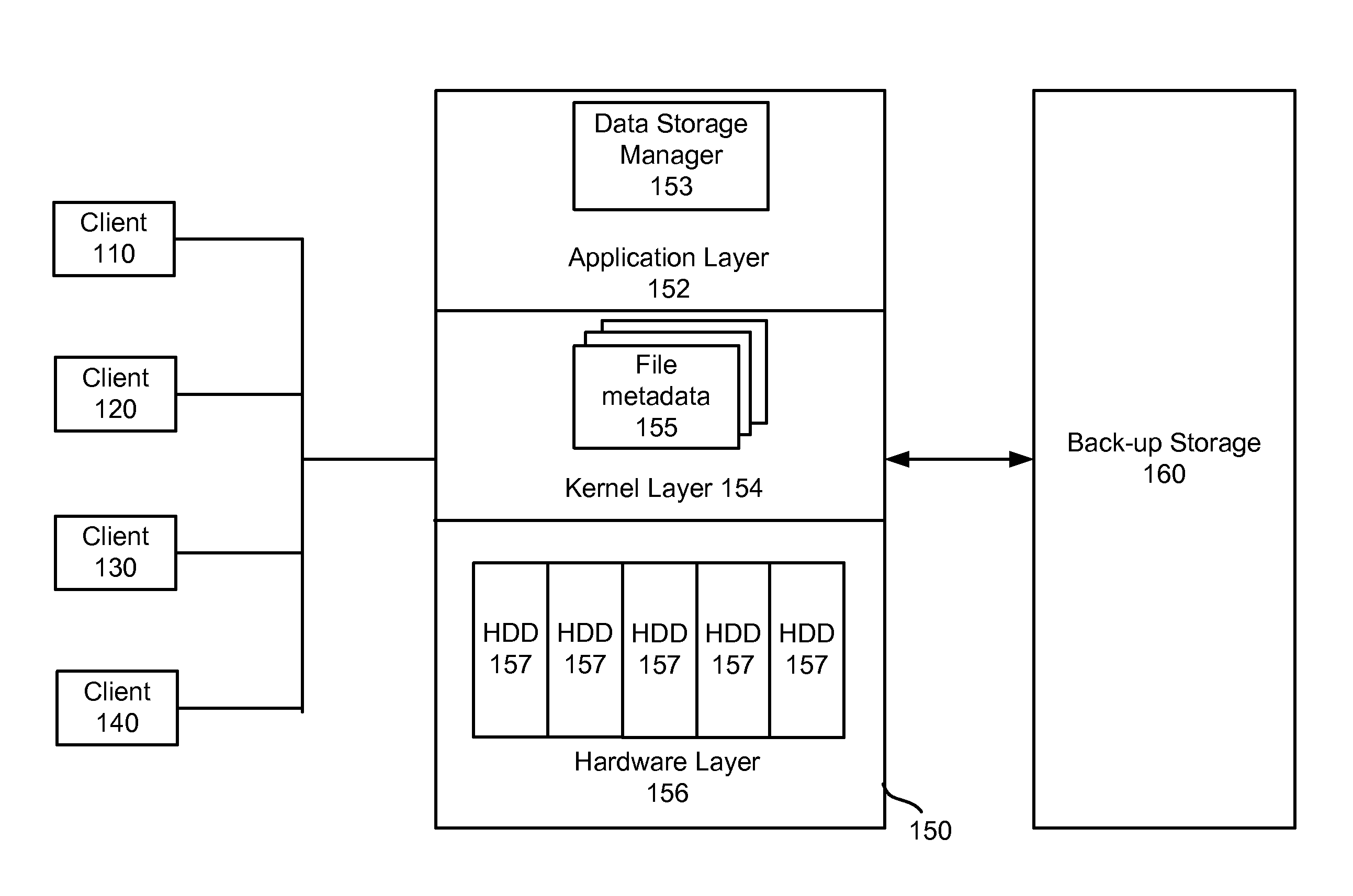
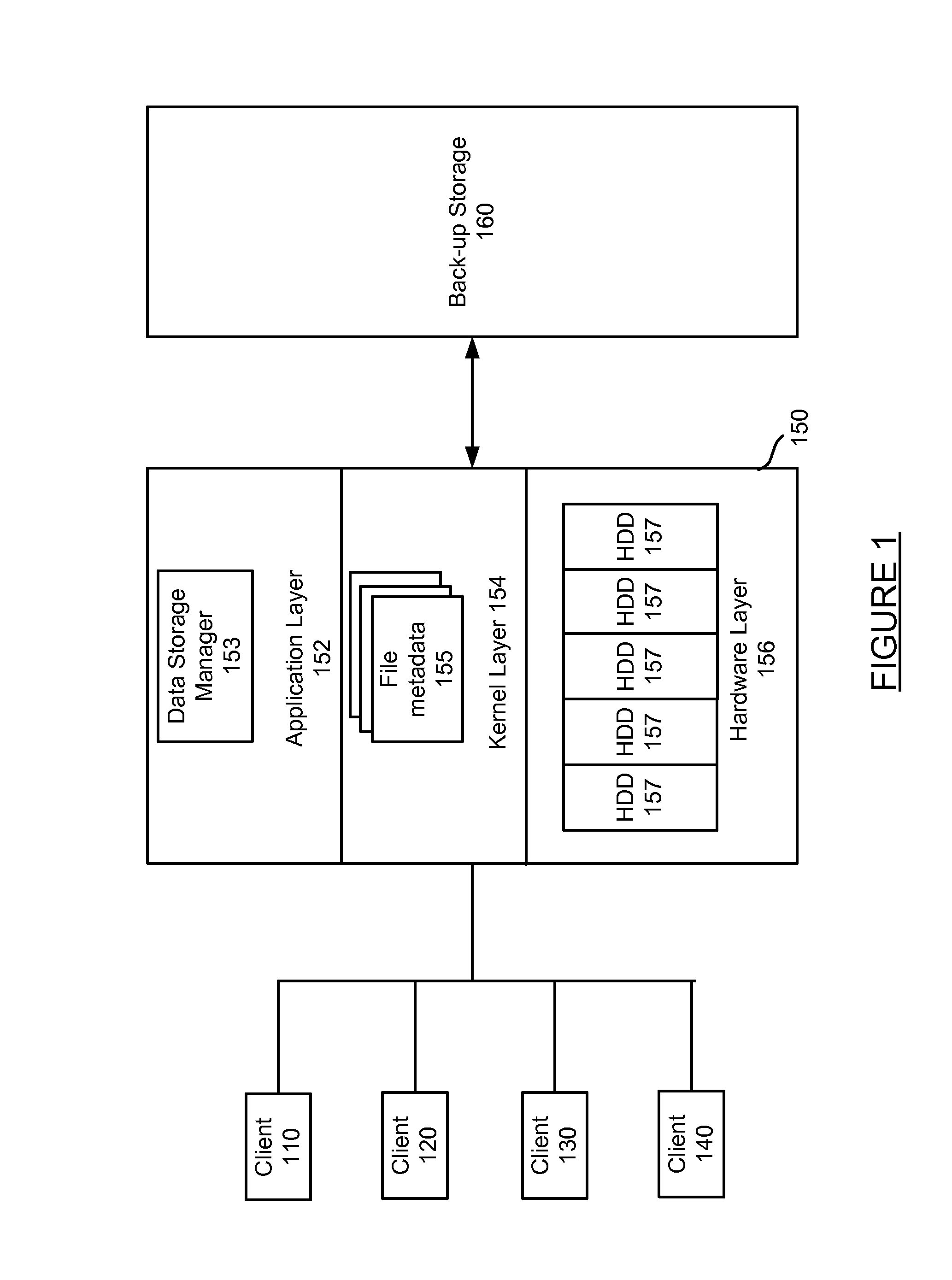
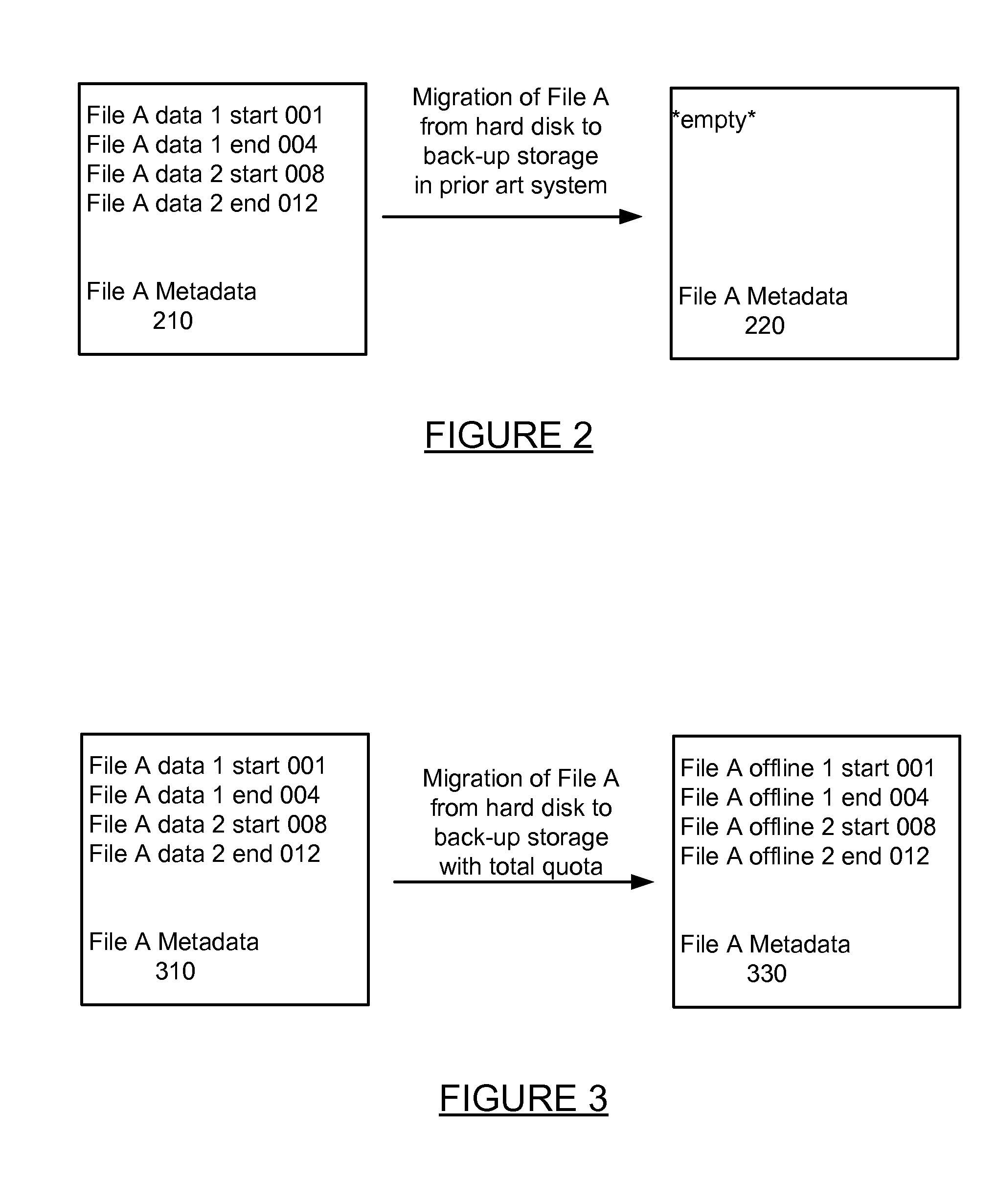
InactiveUS20140281214A1Input/output to record carriersError detection/correctionHard disc driveData type
Quotas are tracked for user usage of hard disk drive space and offline backup storage space. The quota is enforced against the total space utilized by a user, not just high tier hard drive space usage. When data is migrated from hard disk drive space to backup storage space, data metadata is updated to reflect data kept offline for the user. As such, when users request to store new data, the data usage of hard disk space and backup storage space is determined from the metadata that reflects both data types, and the total storage spaced for the user is used to grant or reject the user's request to store more data in the system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and device for processing metadata
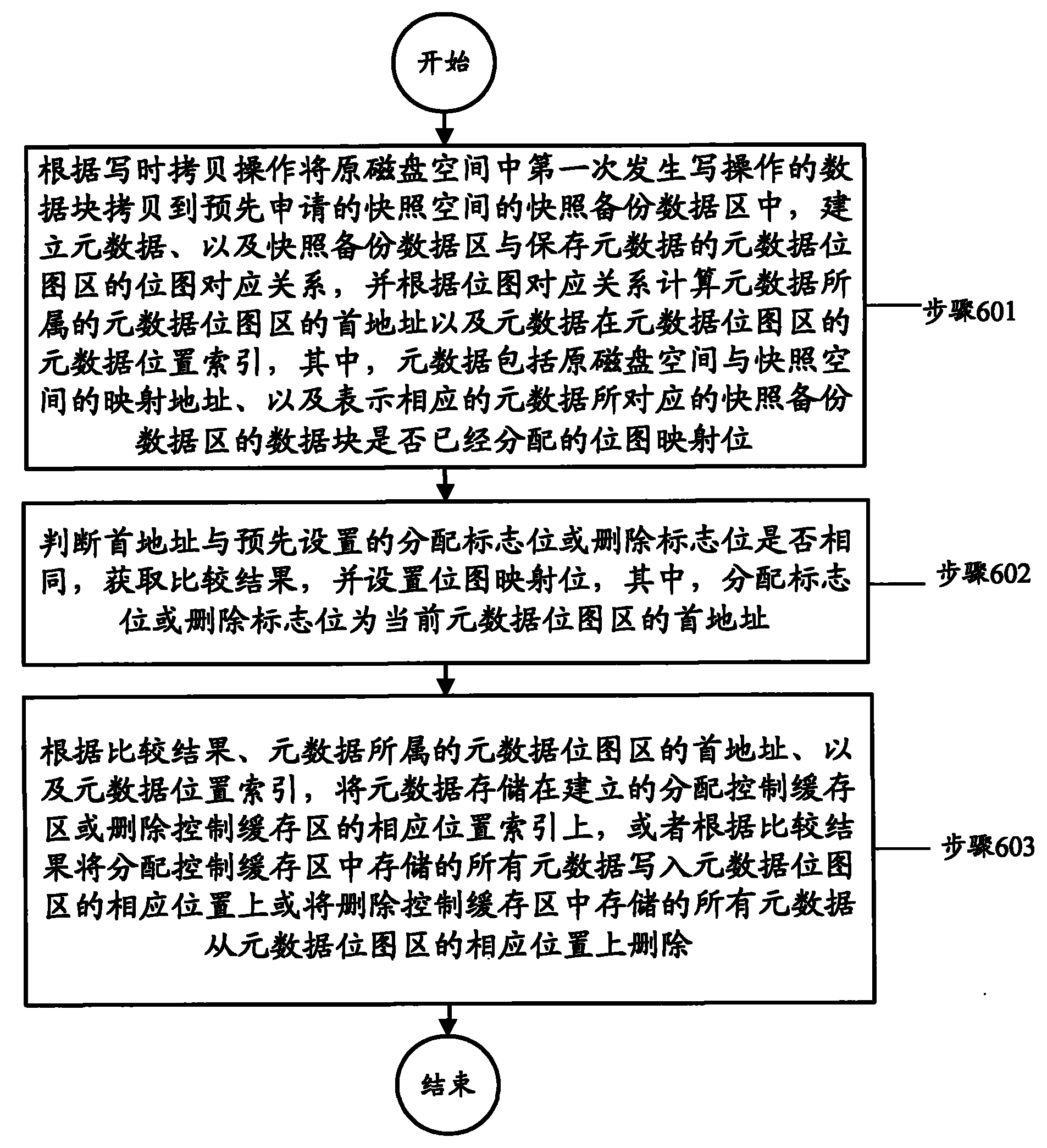
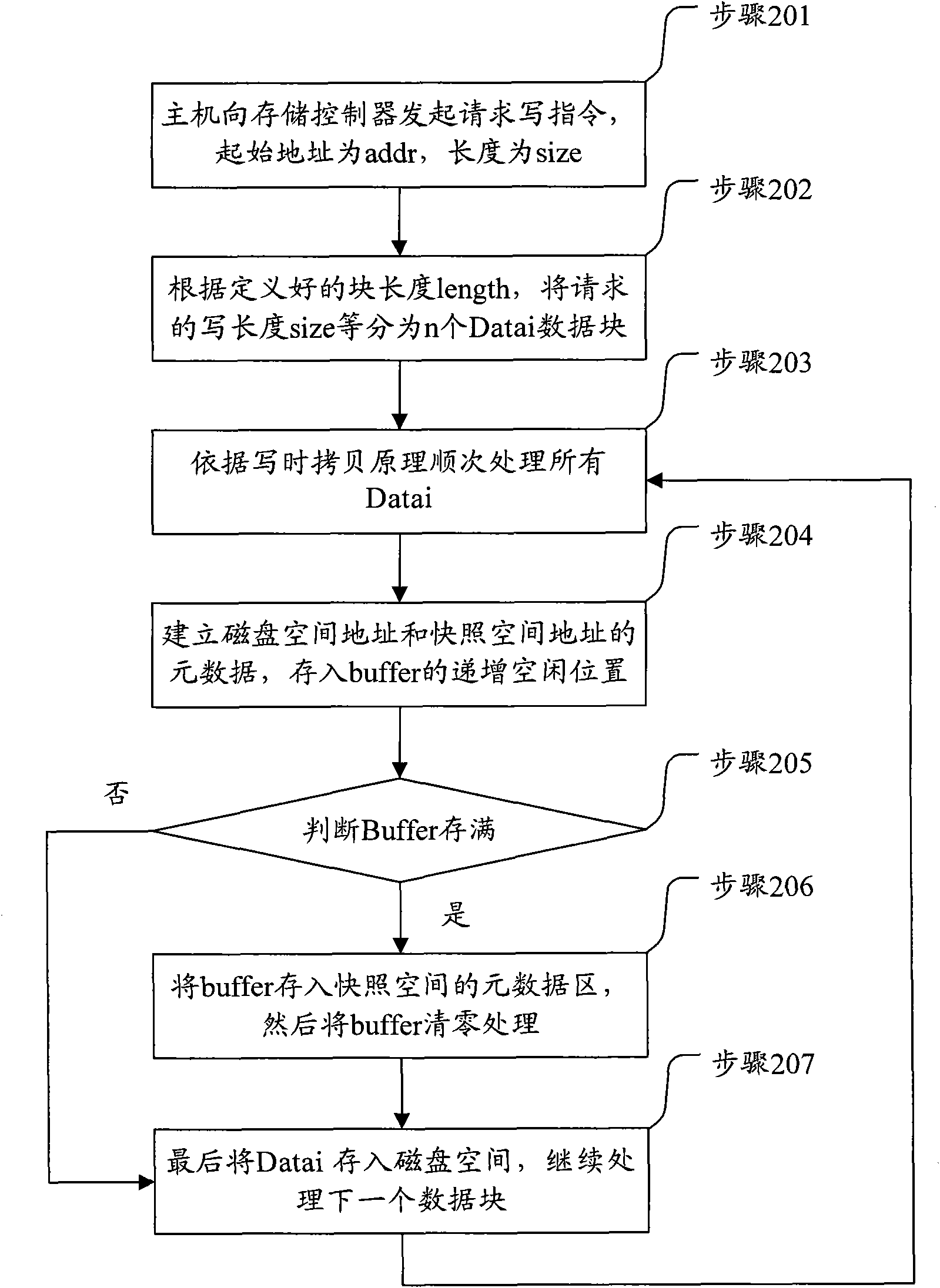
ActiveCN101814044AImprove processing efficiencyReduce the number of timesMemory adressing/allocation/relocationRedundant operation error correctionBitmapMetadata
The invention discloses a method and a device for processing metadata. The method comprises the following steps of: copying data written for the first time in an original disk space into a snapshot backup data area according to copy-on-write operation, establishing metadata and bitmap corresponding relationships and calculating a first address of a metadata bitmap area where the metadata belongs and metadata position indexes of the metadata in the metadata bitmap area according to the bitmap corresponding relationships; judging whether the first address is the same as a preset allocation marker bit or a deletion marker bit or not to obtain a comparison result and setting bitmap mapping bits; and according to the comparison result, the first address of the metadata bitmap area where the metadata belongs, and the metadata position indexes, storing the metadata into corresponding position indexes of an allocation control buffer area or a deletion control buffer area, or writing all the metadata in the allocation control buffer area into corresponding positions of the metadata bitmap area or deleting all the metadata in the deletion control buffer area from the corresponding positionsof the metadata bitmap area.
Owner:ZTE CORP
Software packaging and publishing management method
The invention discloses a software packaging and publishing management method. According to the method, after iterative content of a version is confirmed, a corresponding version number is selected during packaging, only a needed script is generated, the content needing to be published is precisely controlled, and codes which are not tested are prevented from being deployed into a formal environment; when script packaging is executed, components with source codes not updated are not recompiled, therefore, only changed parts are compiled, compiling time is shortened, and incremental compiling is realized; based on version tracing of historical version logs, a log directory is generated every time packaging is performed; and when a user needs to generate a historical version of a certain time, logs of the needed historical version are selected, a packaging script is selected from the logs, and a script command is executed to generate a needed package. In this way, it is not needed to back up generated packages every time packaging is performed, only the package generated this time is stored, therefore, storage space is reduced, and maintenance of the historical version is realized with little hard-disk space.
Owner:XIAMEN YUEXUN INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com