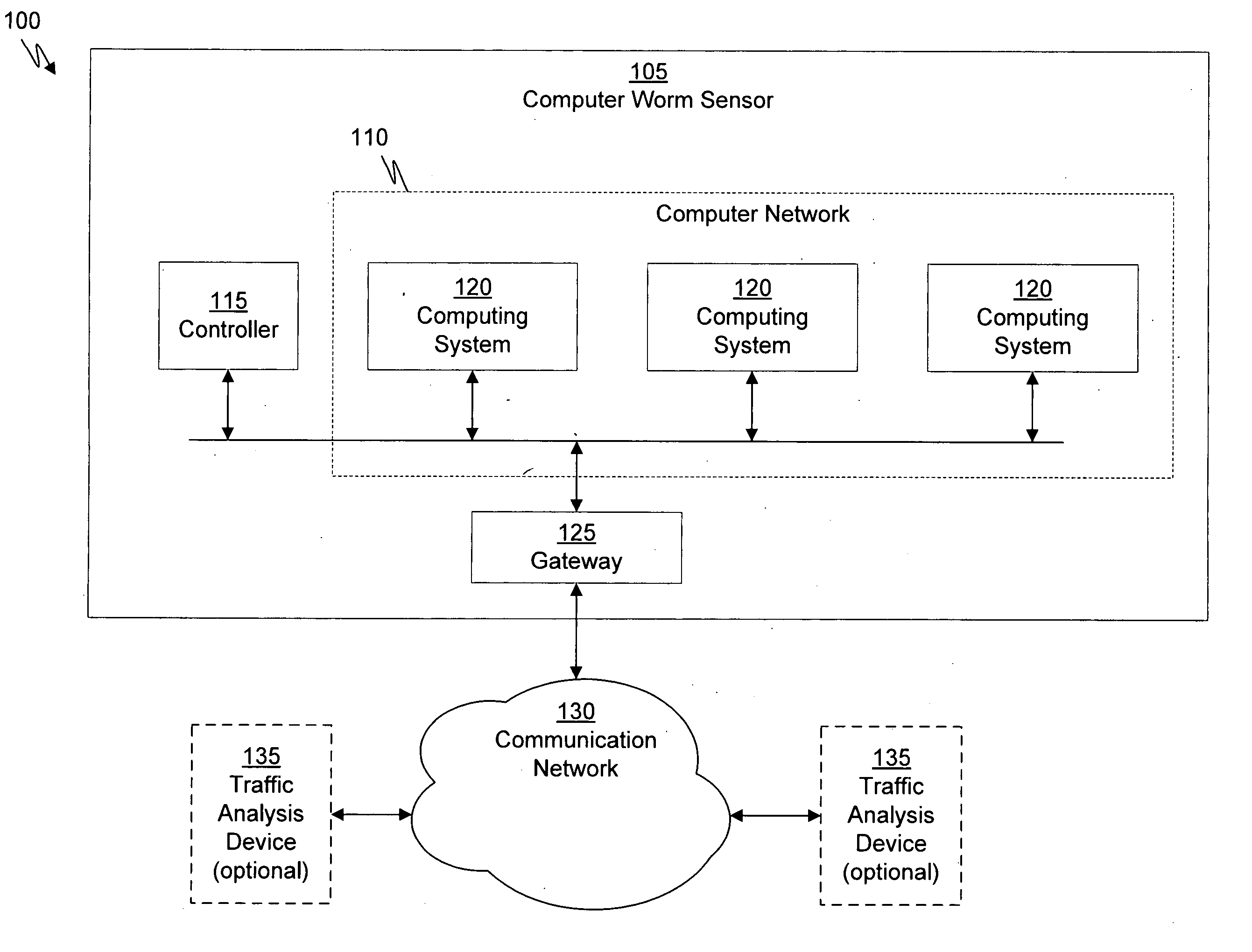
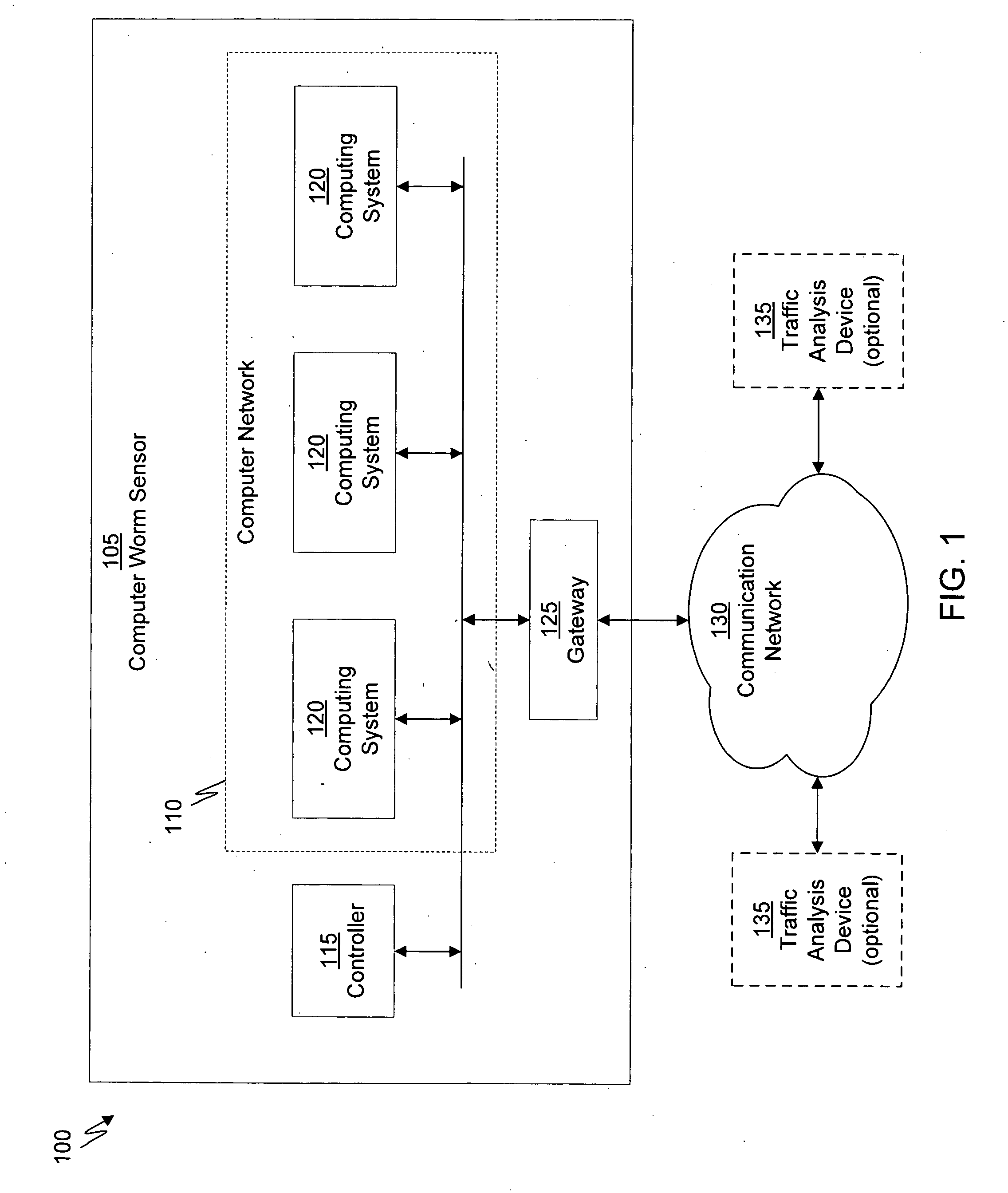
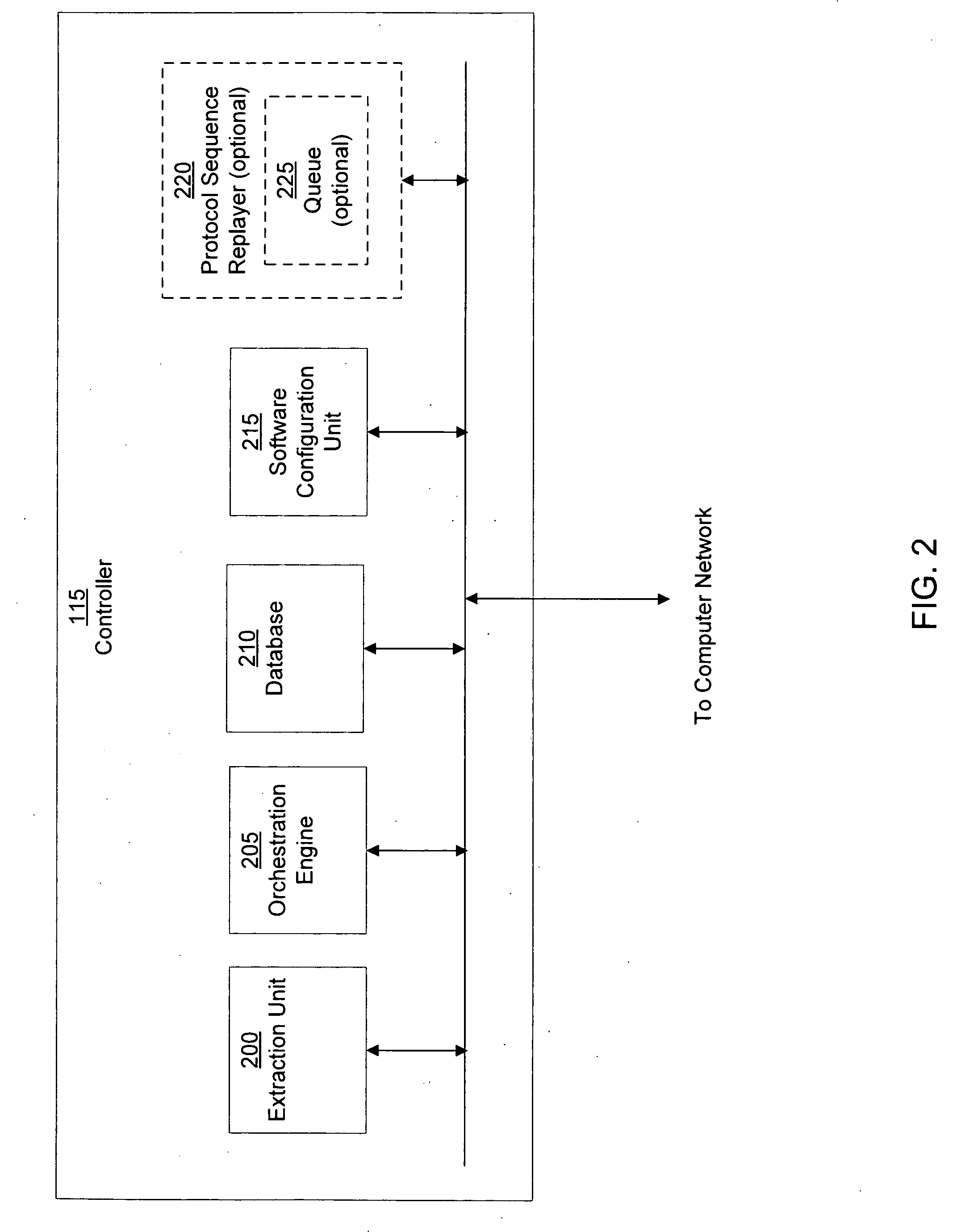
Patents
Literature
52903results about "Hardware monitoring" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
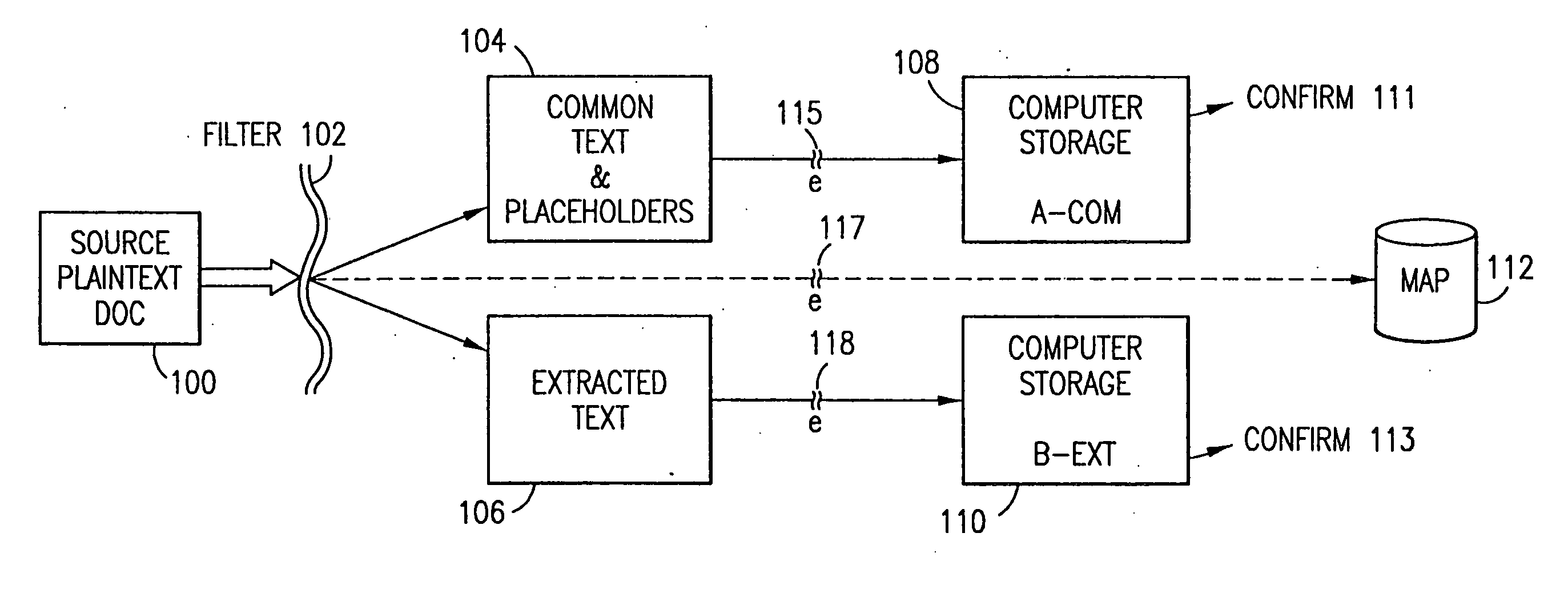
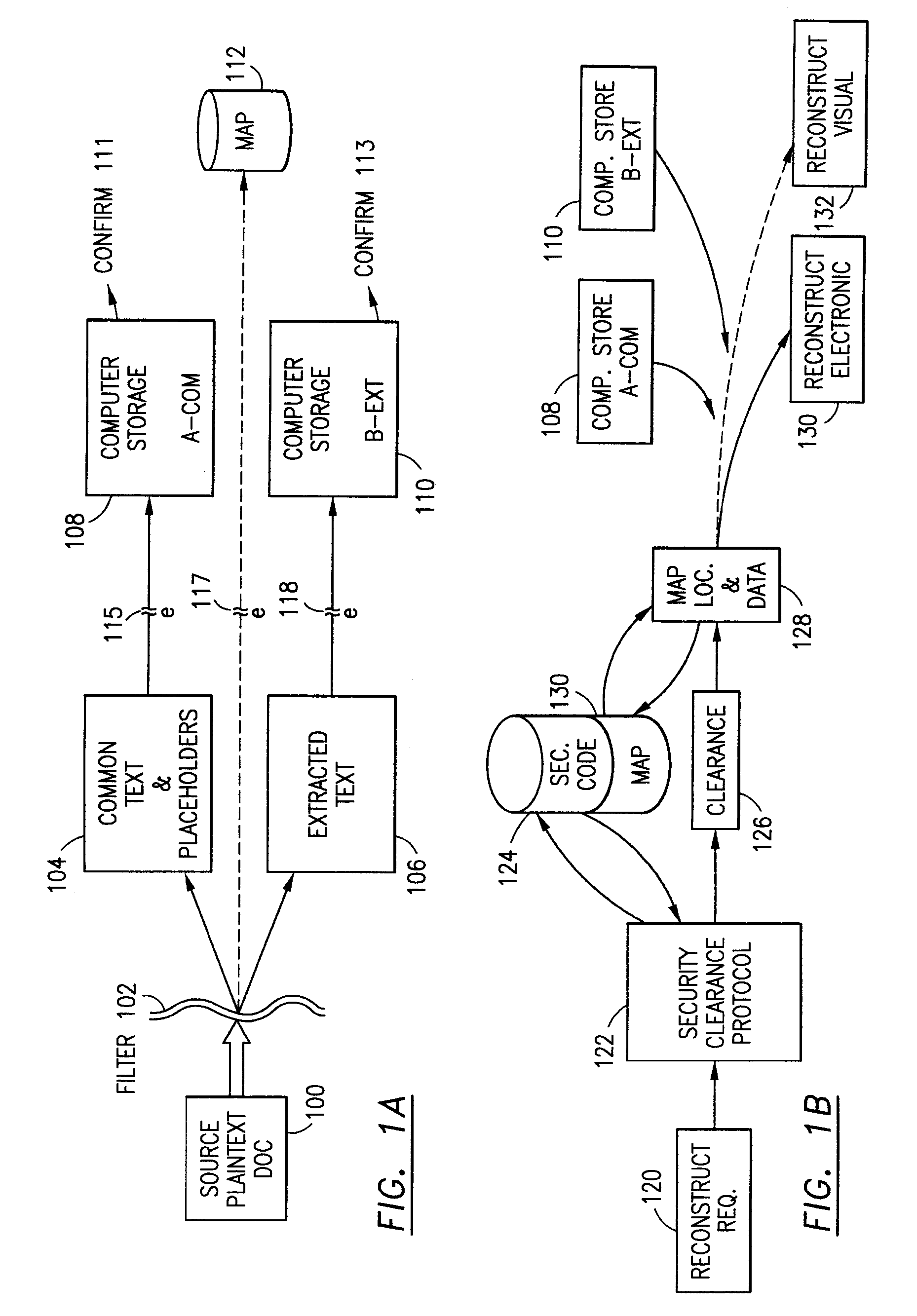
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
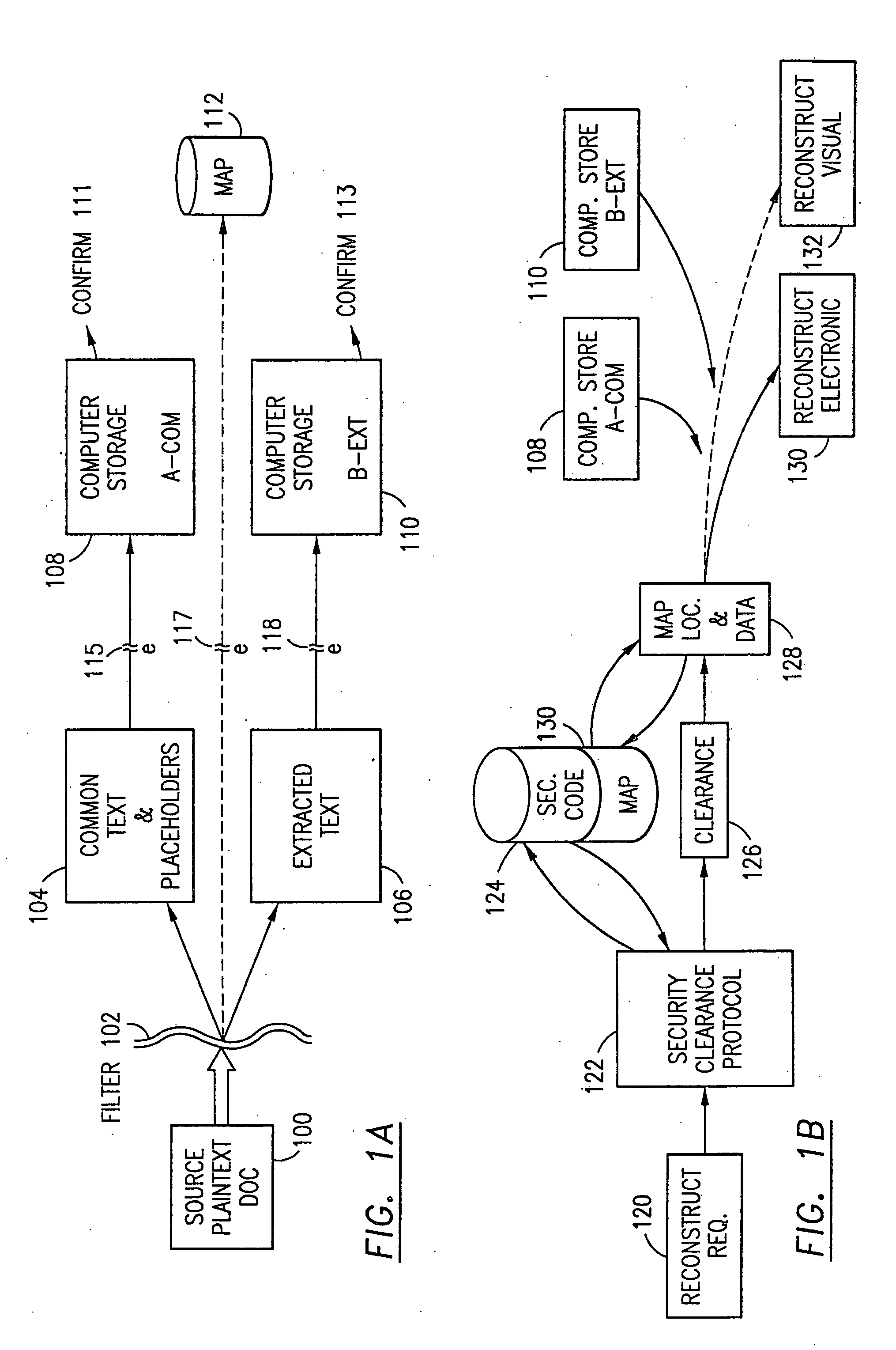
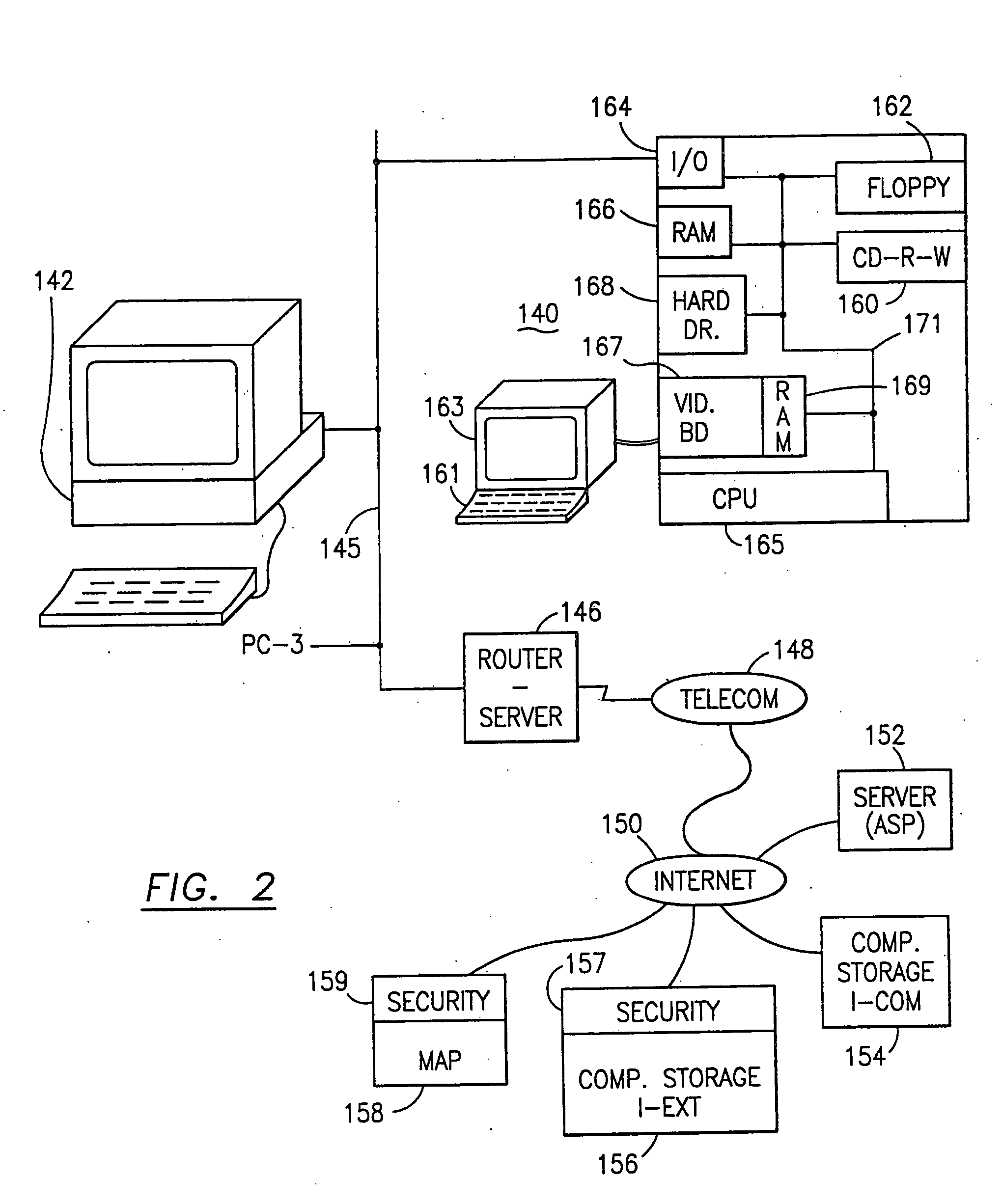
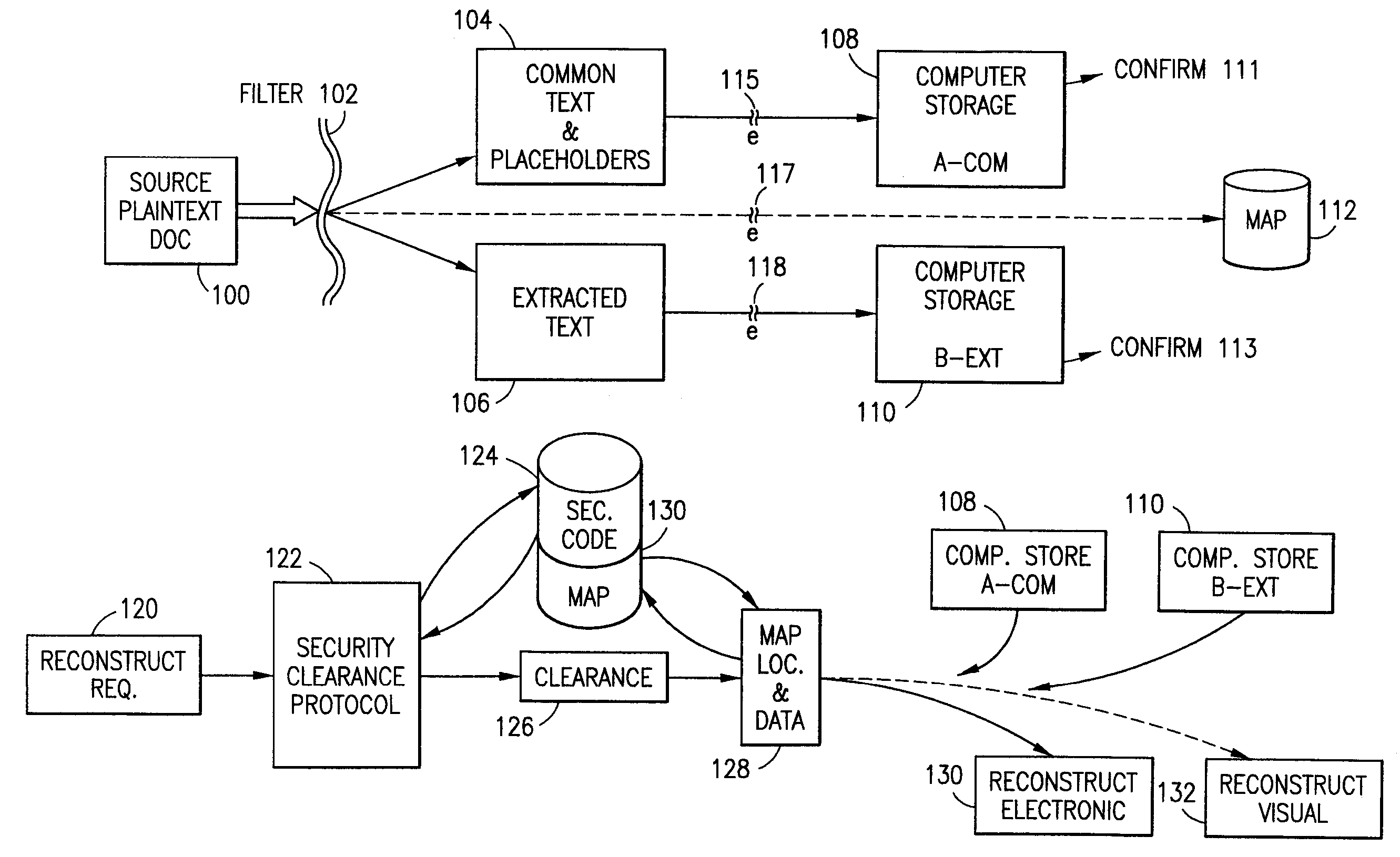
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
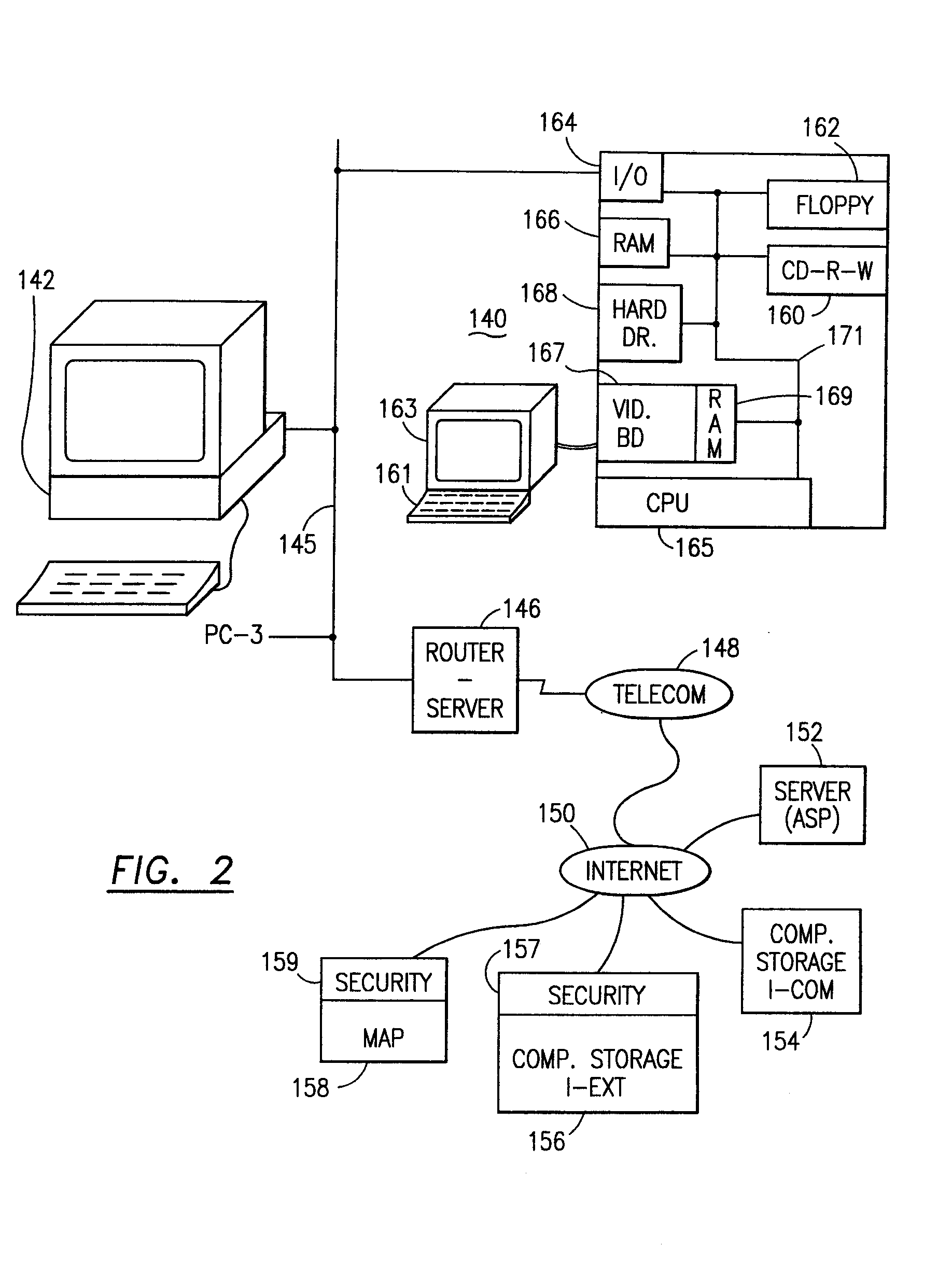
Data security system and method
ActiveUS7103915B2Memory loss protectionDigital data processing detailsPlaintextInformation processing
The method for securing data includes establishing a group of security sensitive items, filtering data and extracting and separating the security items from remainder data. The filtered data are separately stored (locally on a PC or on another computer in a LAN or WAN or on the Internet.) A map may be generated. The filter and / or map may be destroyed or stored. The data input, extracted data and remainder data may be deleted from the originating computer. Encryption may be utilized to enhance security (including transfers of data, filter and map). Reconstruction of the data is permitted only in the presence of a predetermined security clearance. A plurality of security clearances may be used to enable a corresponding plurality of partial, reconstructed views of the plaintext (omitting higher security words). A computer readable medium containing programming instructions and an information processing system is encompassed.
Owner:DIGITAL DOORS
Techniques for detecting and correcting errors using multiple interleave erasure pointers
InactiveUS20050229069A1Correction capabilityTransmission systemsCode conversionBlock codeError location
Techniques for detecting and correcting burst errors in data bytes formed in a two-level block code structure. A second level decoder uses block level check bytes to detect columns in a two-level block code structure that contain error bytes. The second level decoder generates erasure pointers that identify columns in the two-level block structure effected by burst errors. A first level decoder then uses codeword check bytes to correct all of the bytes in the columns identified by the erasure pointers. The first level decoder is freed to use all of the codeword check bytes only for error byte value calculations. The first level decoder does not need to use any of the codeword check bytes for error location calculations, because the erasure pointers generated by the second level decoder provide all of the necessary error locations. This techniques doubles the error correction capability of the first level decoder.
Owner:HITACHI GLOBAL STORAGE TECH NETHERLANDS BV +1
Methods and systems for monitoring user, application or device activity
InactiveUS20050183143A1Improve securityMemory loss protectionUnauthorized memory use protectionWorking environmentComputer usage
Methods and systems are provided for capturing usage data from a user computer, processing a subset of such data to form output, and offering access to selective views of such output, such as to assist a company's management in monitoring computer usage in a work environment. The output may be processed and viewed according to software application, device, or specified user. The output, or a report generated therefrom, may be accessible in differing degrees to individuals having appropriate levels of permission.
Owner:SERGEANT LAB
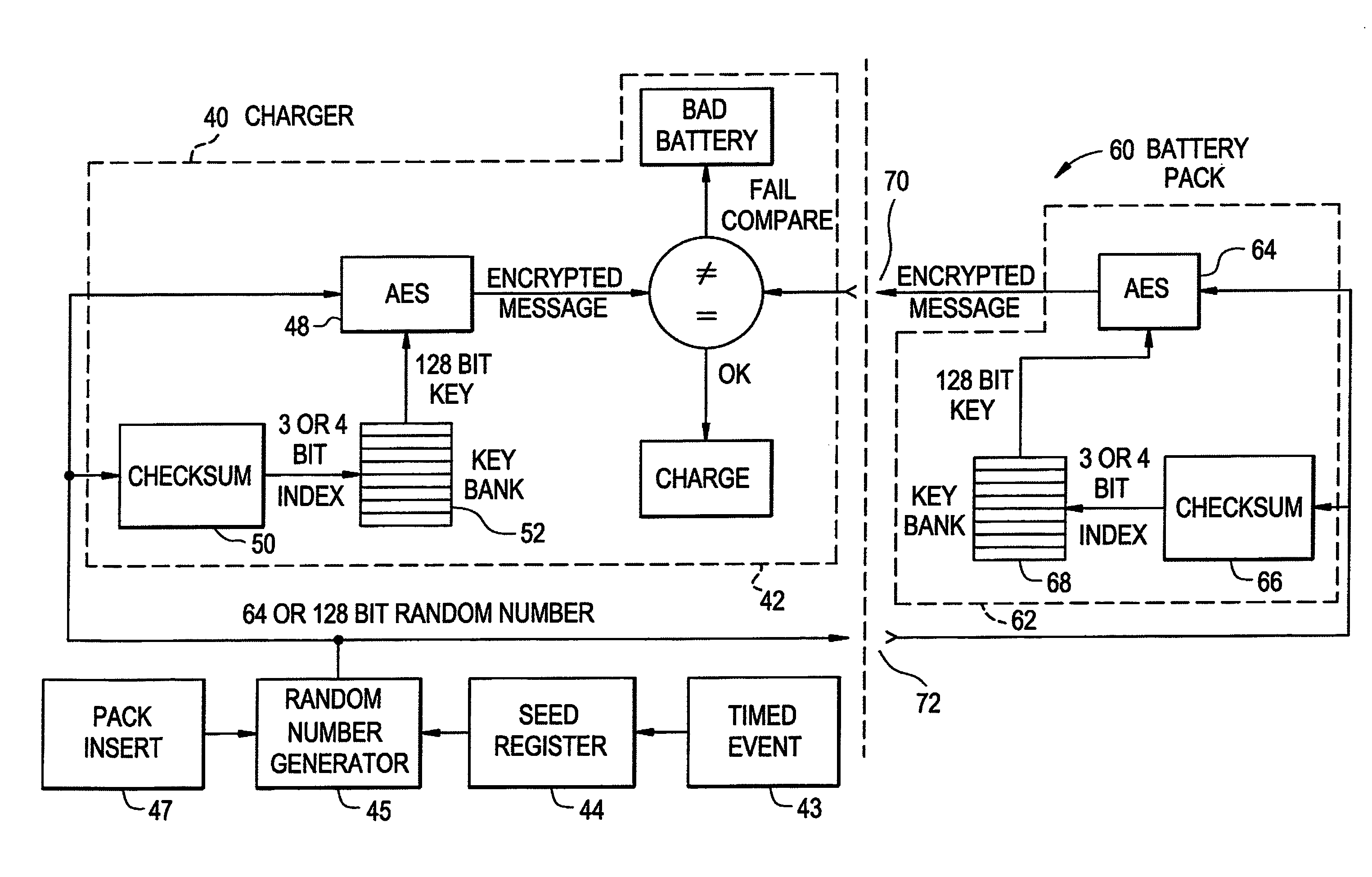
Rechargeable battery pack and operating system
InactiveUS7941865B2Data stream serial/continuous modificationVolume/mass flow measurementOperational systemData stream
A method and system for authenticating a smart battery having a smart battery and an electronic device. Both the device and the smart battery generate encrypted random strings using key material based by A / D noise bits as a seed value. A pseudo random number is generated from the A / D noise that is transmitted to both the electronic device and the smart battery. The pseudo random number is used by both devices as a key index to select one of a plurality of keys stored in separate key libraries. The keys, or key material, is used to execute an encryption algorithm. The two encryption data streams are then compared to authenticate the smart battery.
Owner:BLACK & DECKER INC
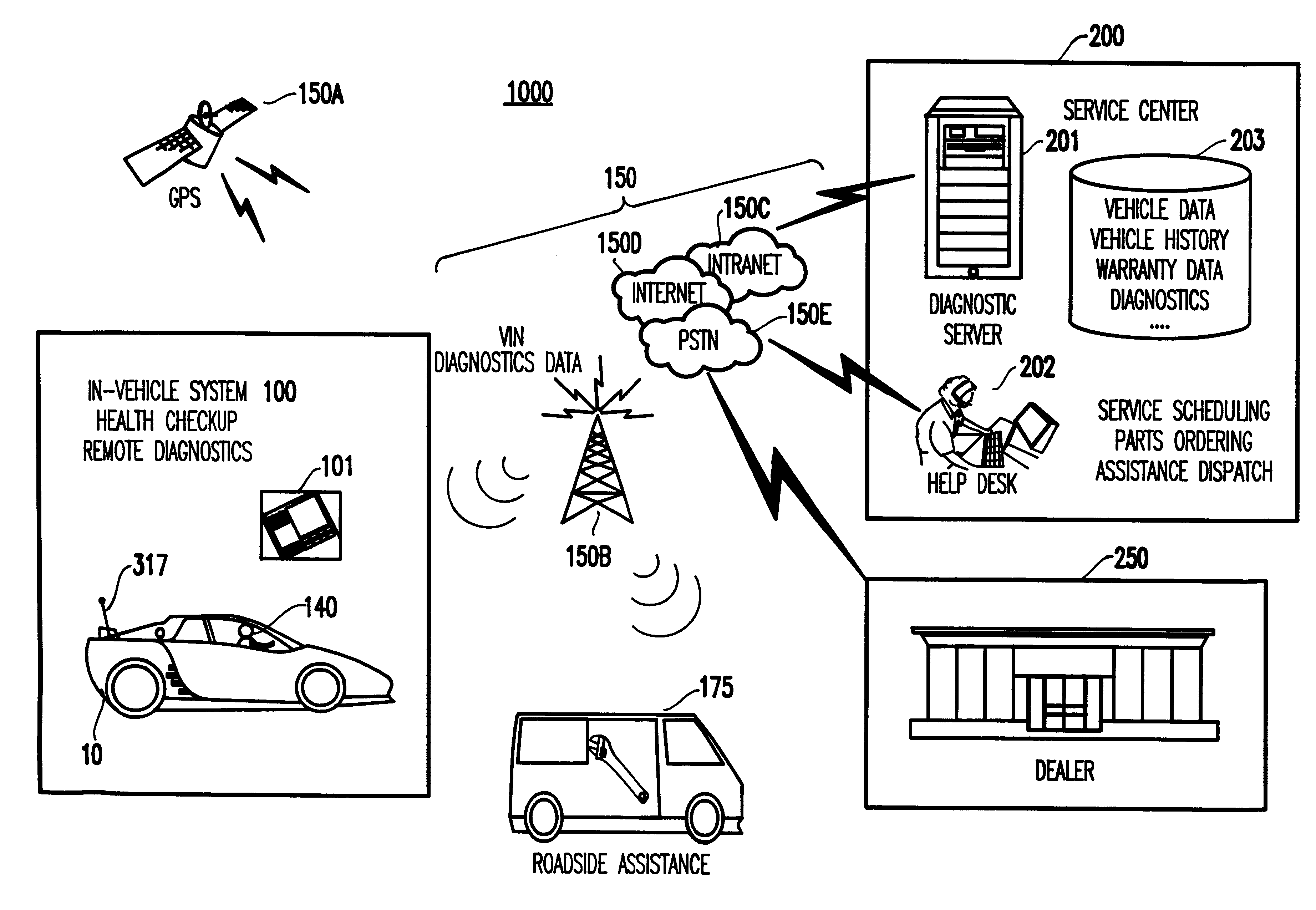
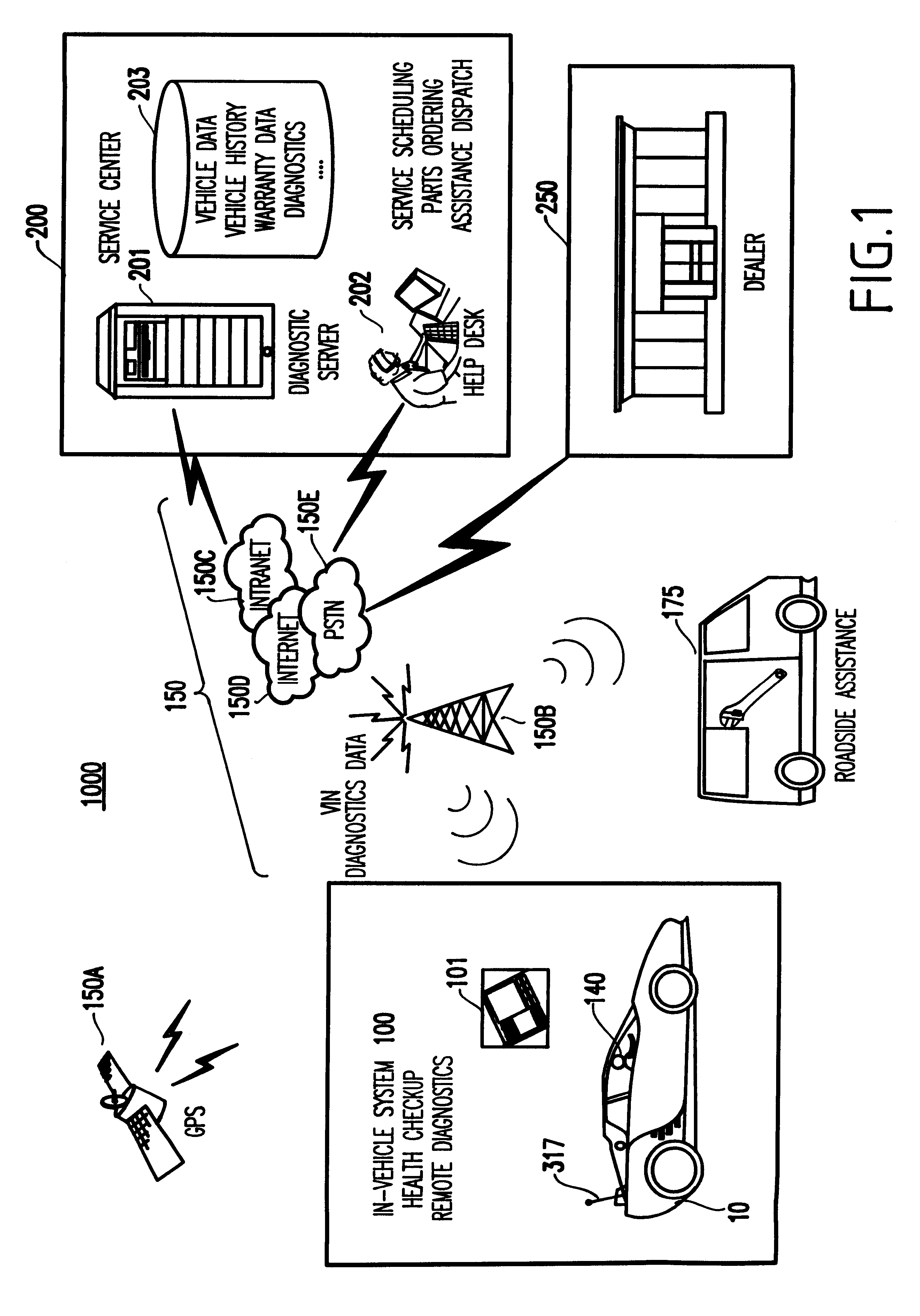
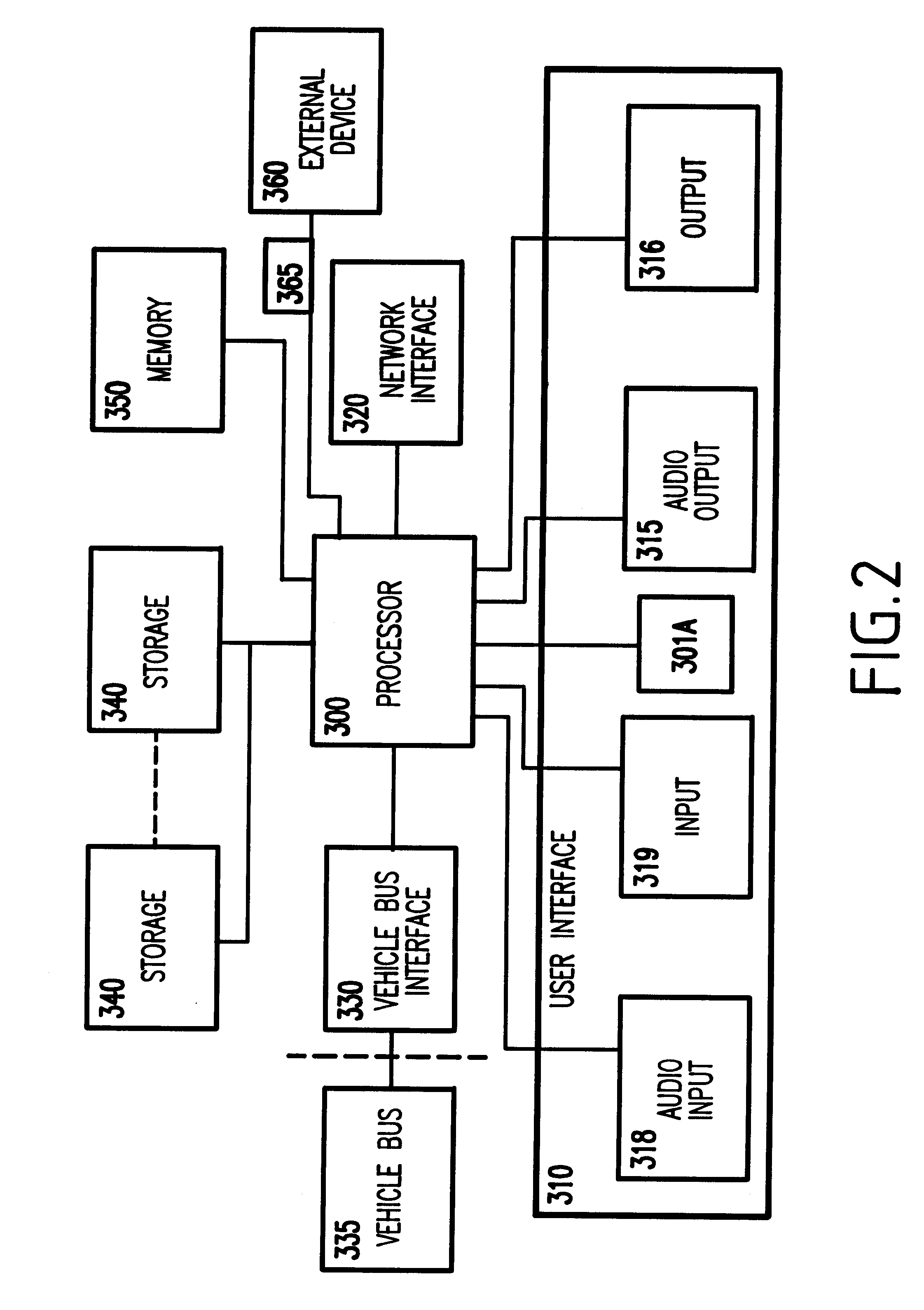
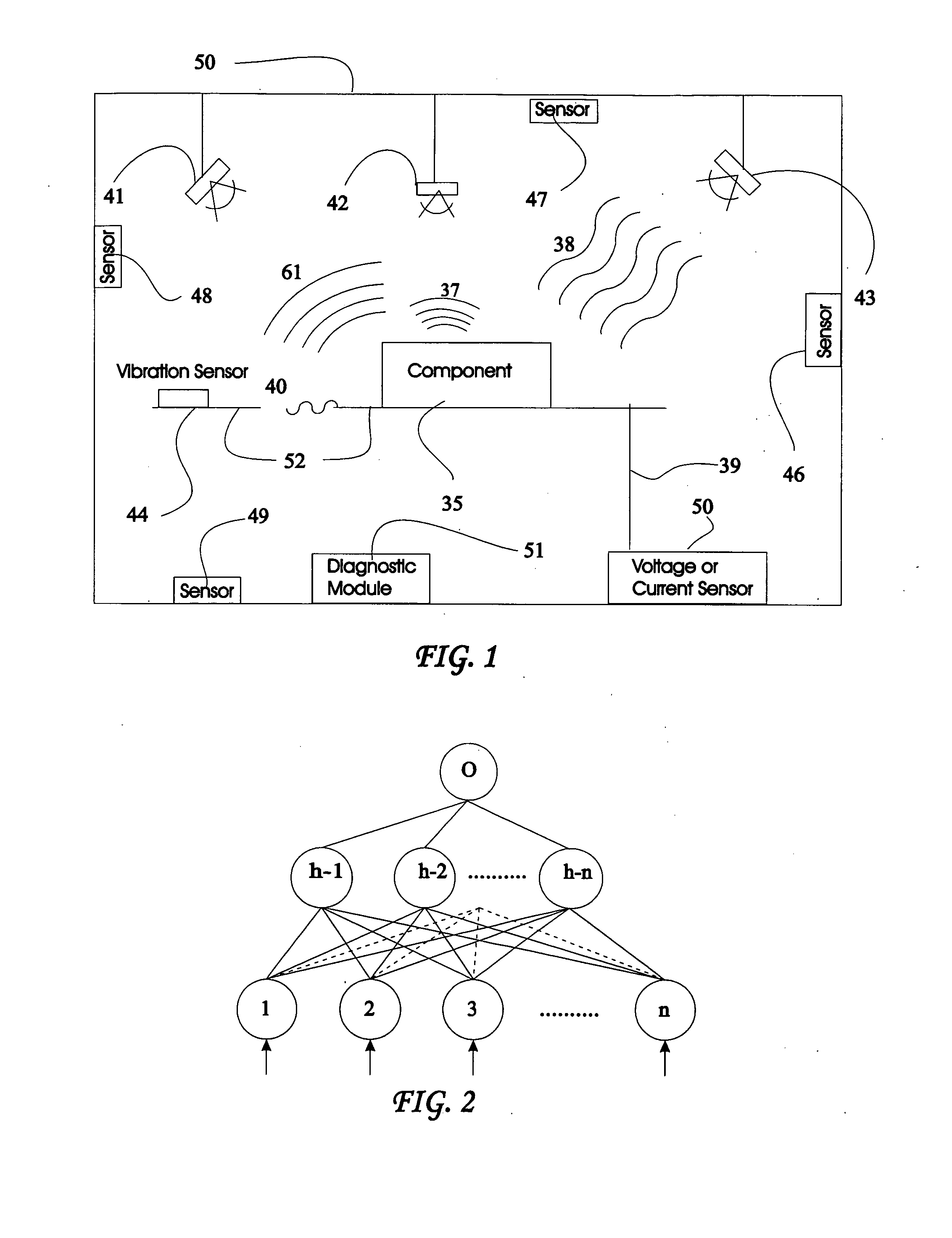
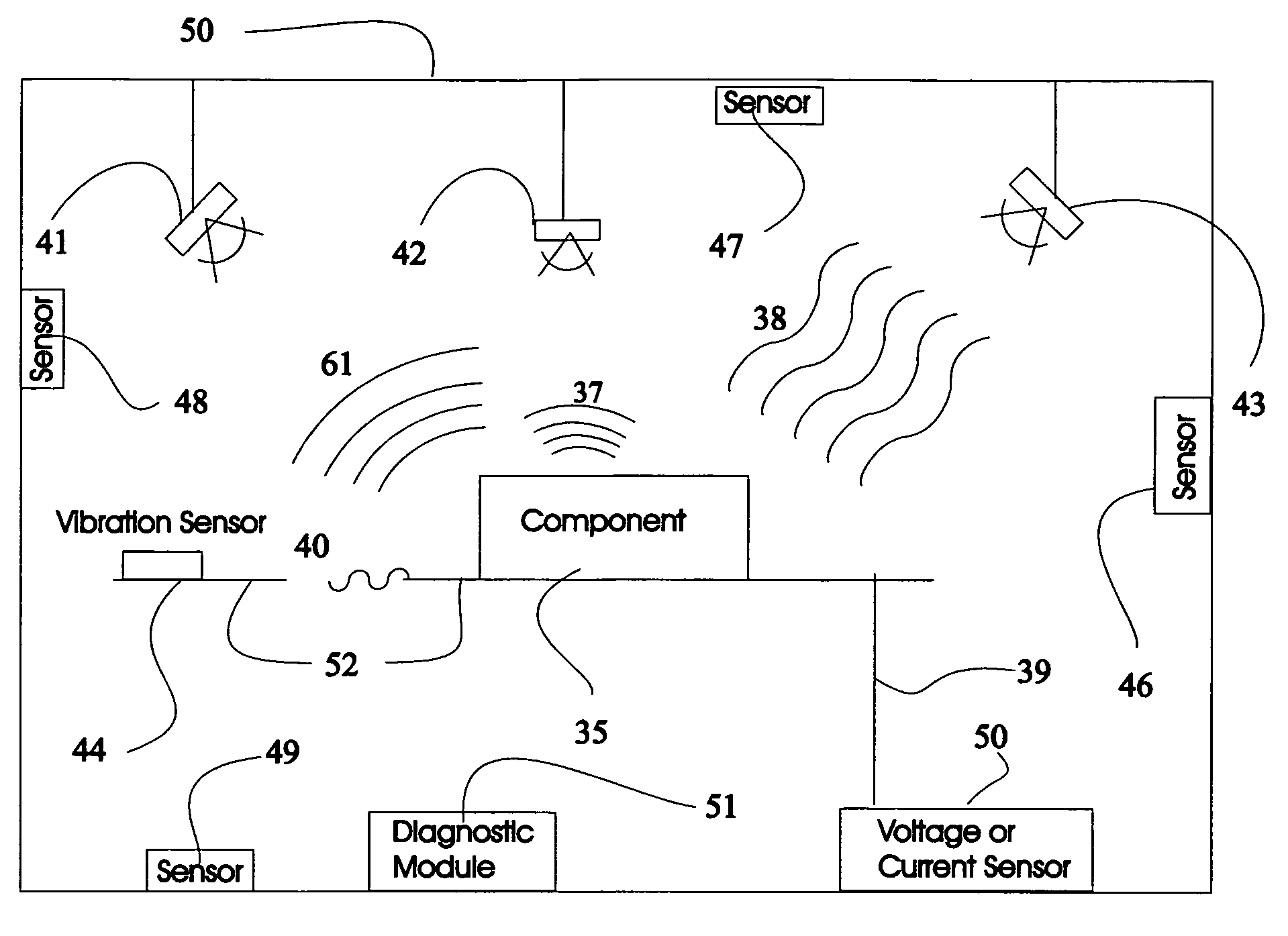
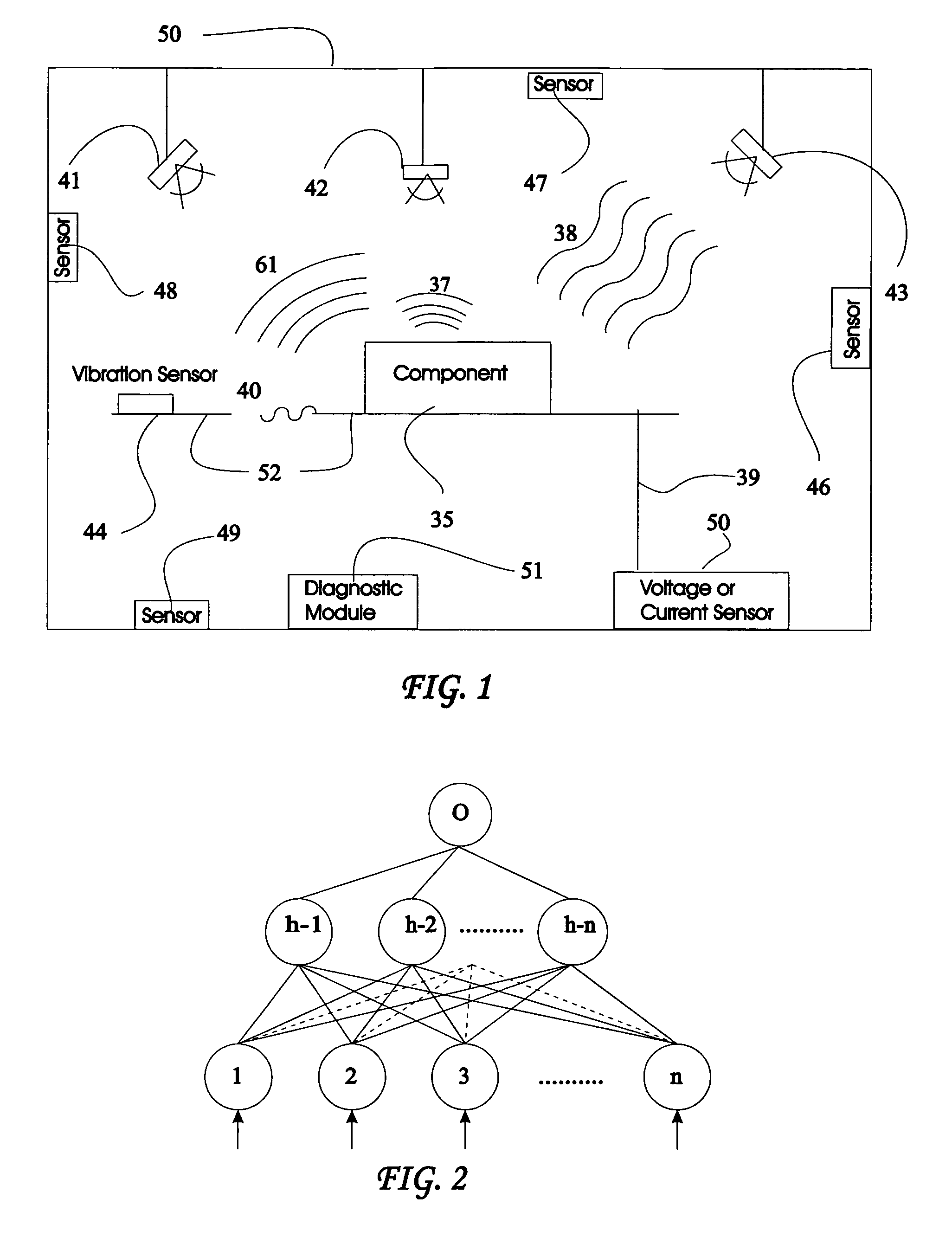
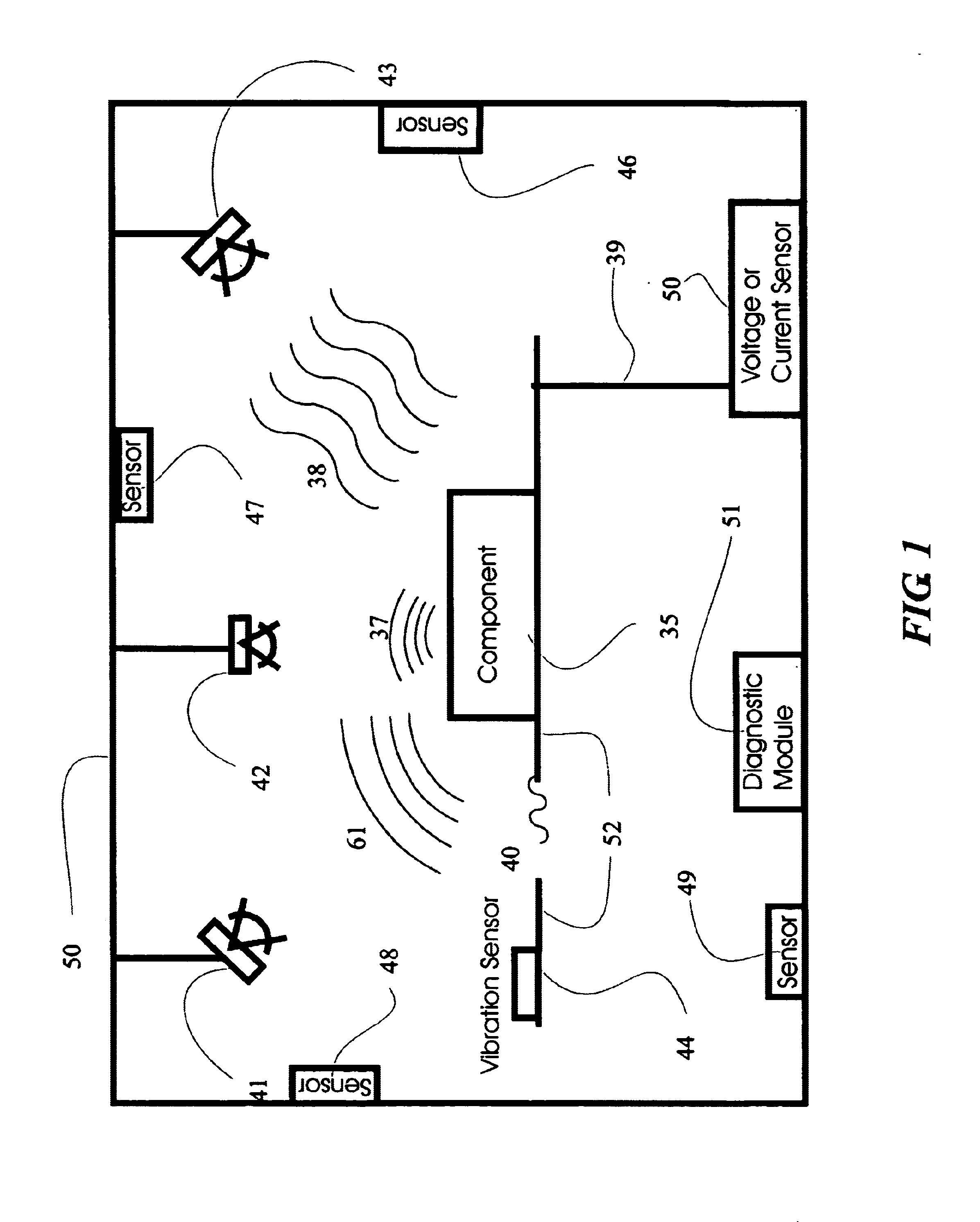
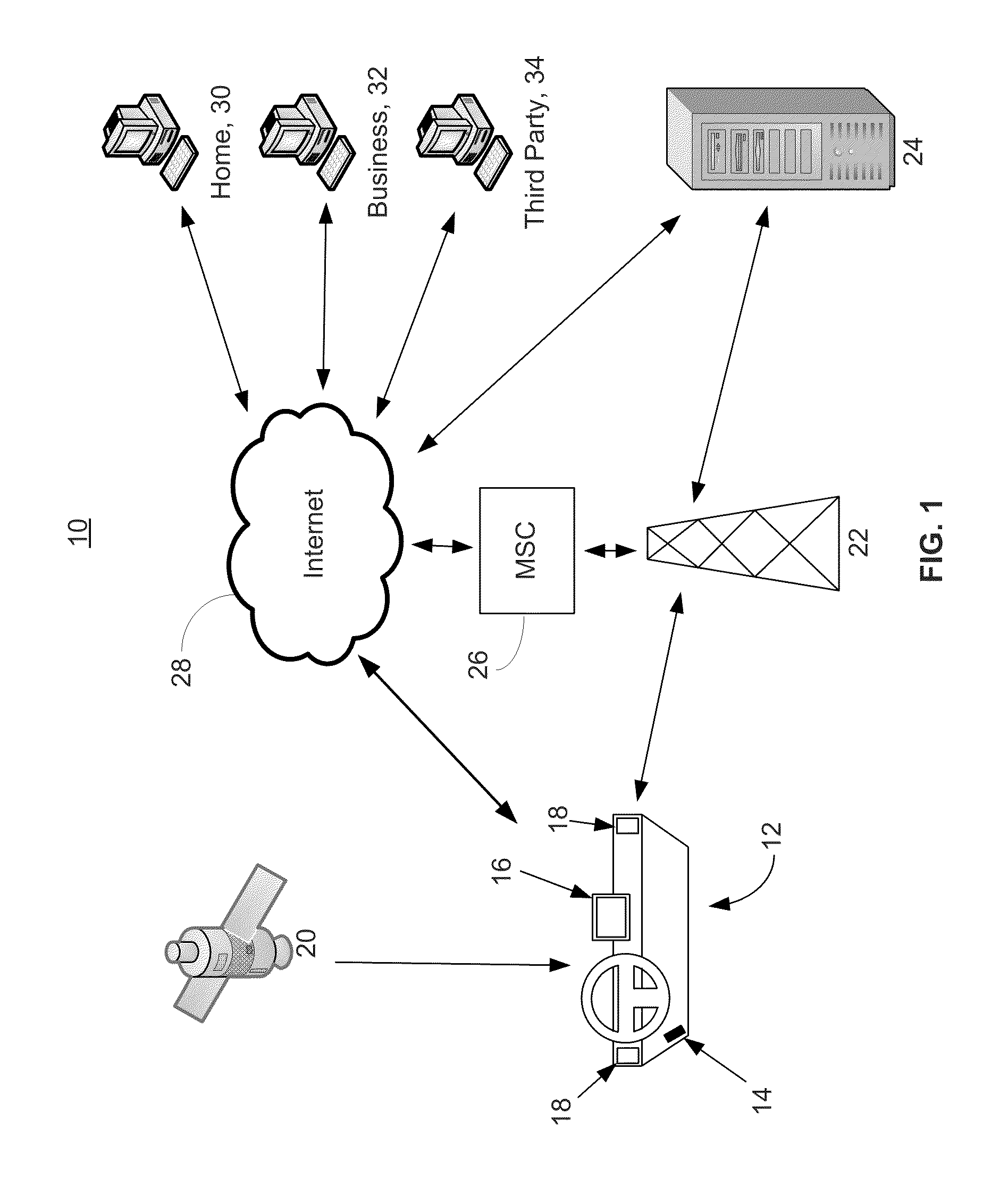
System and method for vehicle diagnostics and health monitoring
InactiveUS6330499B1Vehicle testingRegistering/indicating working of vehiclesSession managementCommunications system
A system and method for vehicle diagnostic and health monitoring includes a client computer device within the vehicle, coupled to the vehicle's monitoring systems, for data management, remote session management and user interaction, a communication system, coupled to the client computer device, for providing remote communication of data including data derived from internal monitoring systems of the vehicle, and a remote service center including a vehicle data store, a server computer, a diagnostic engine, and a communicator for communicating the results of analysis of vehicle information to the client computer device via the communication system.
Owner:CARRUM TECH LLC
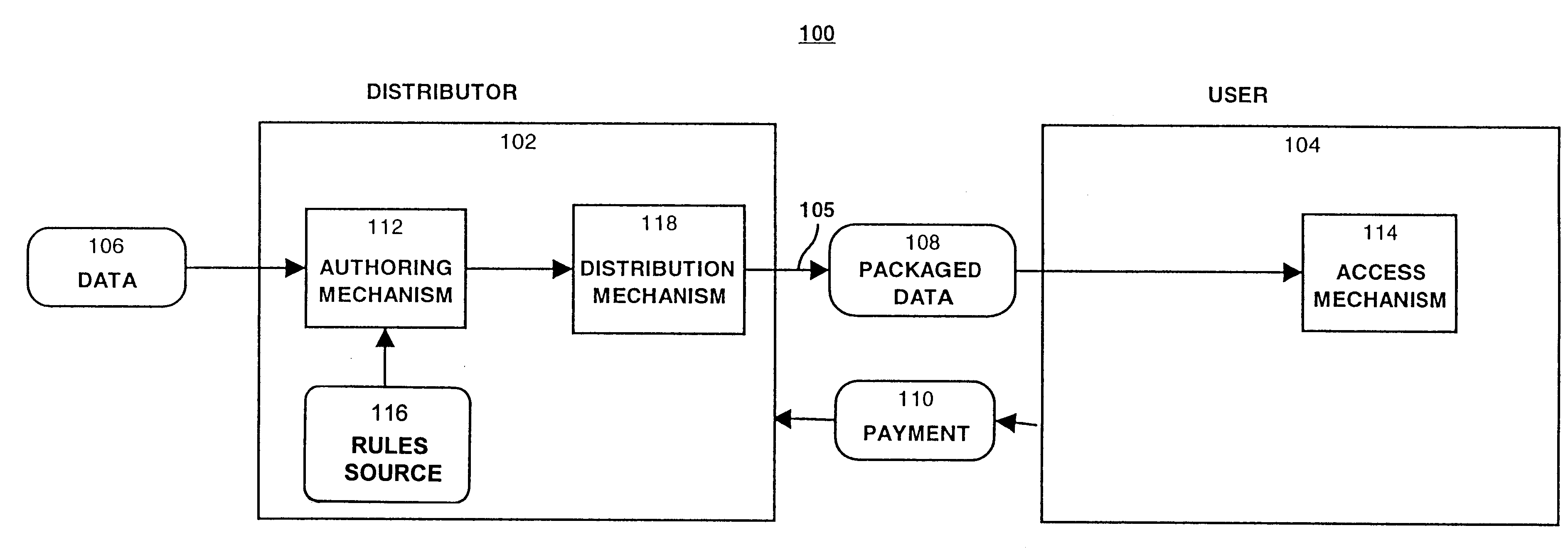
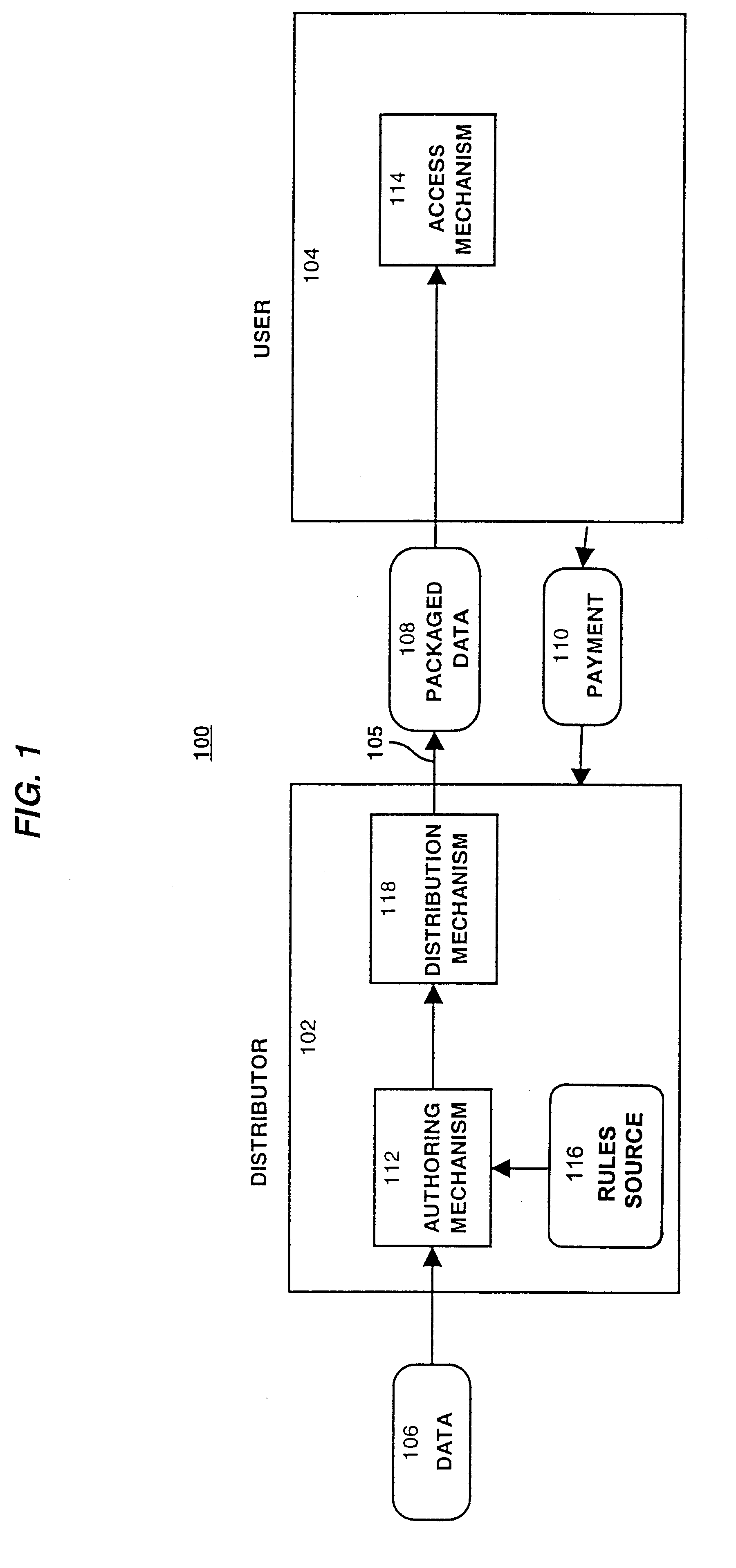
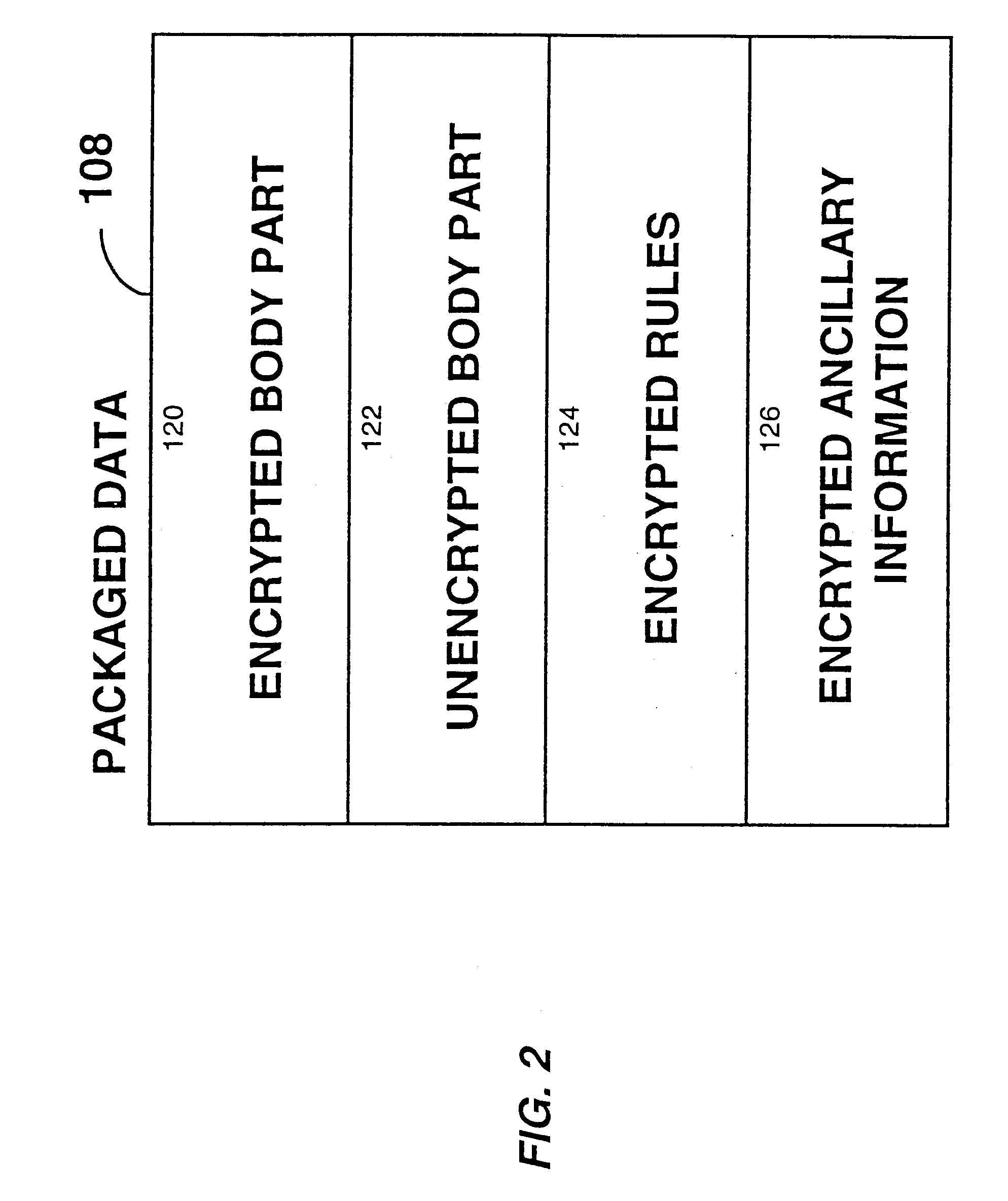
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
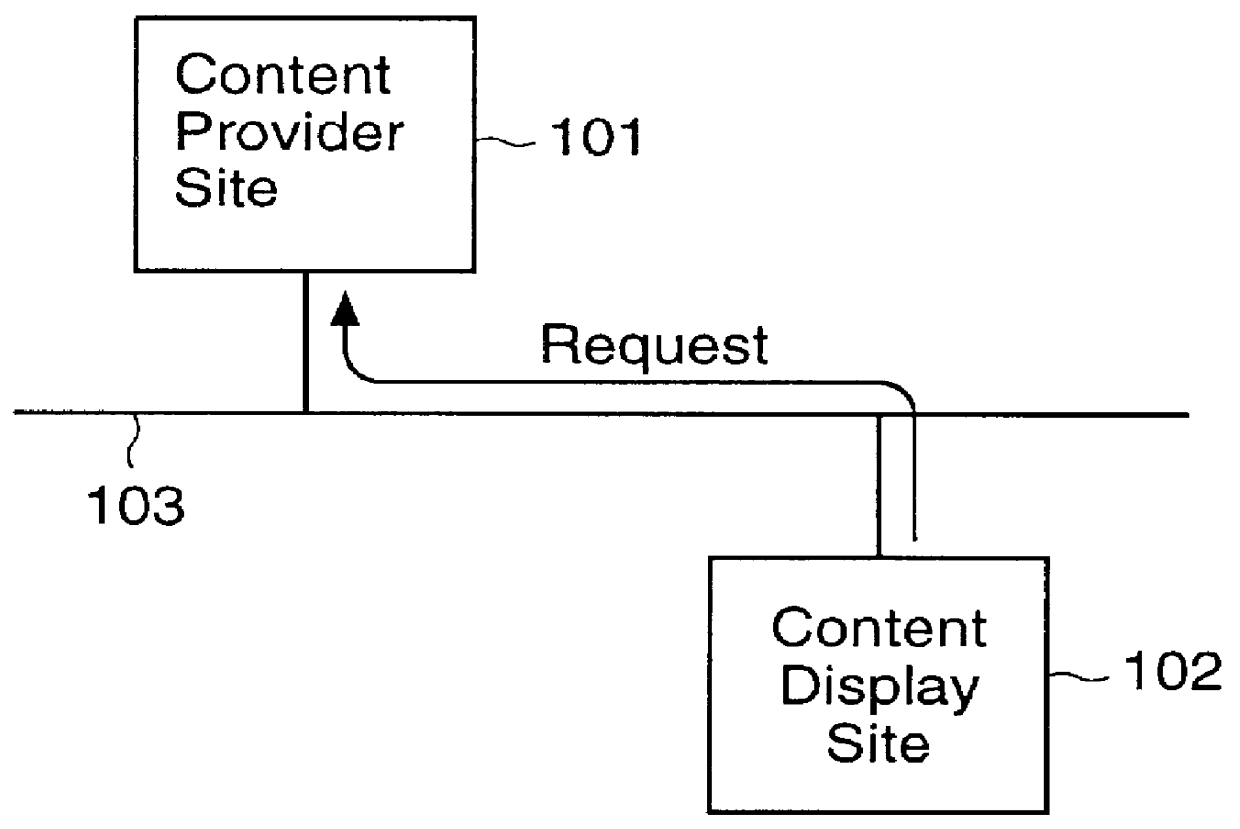
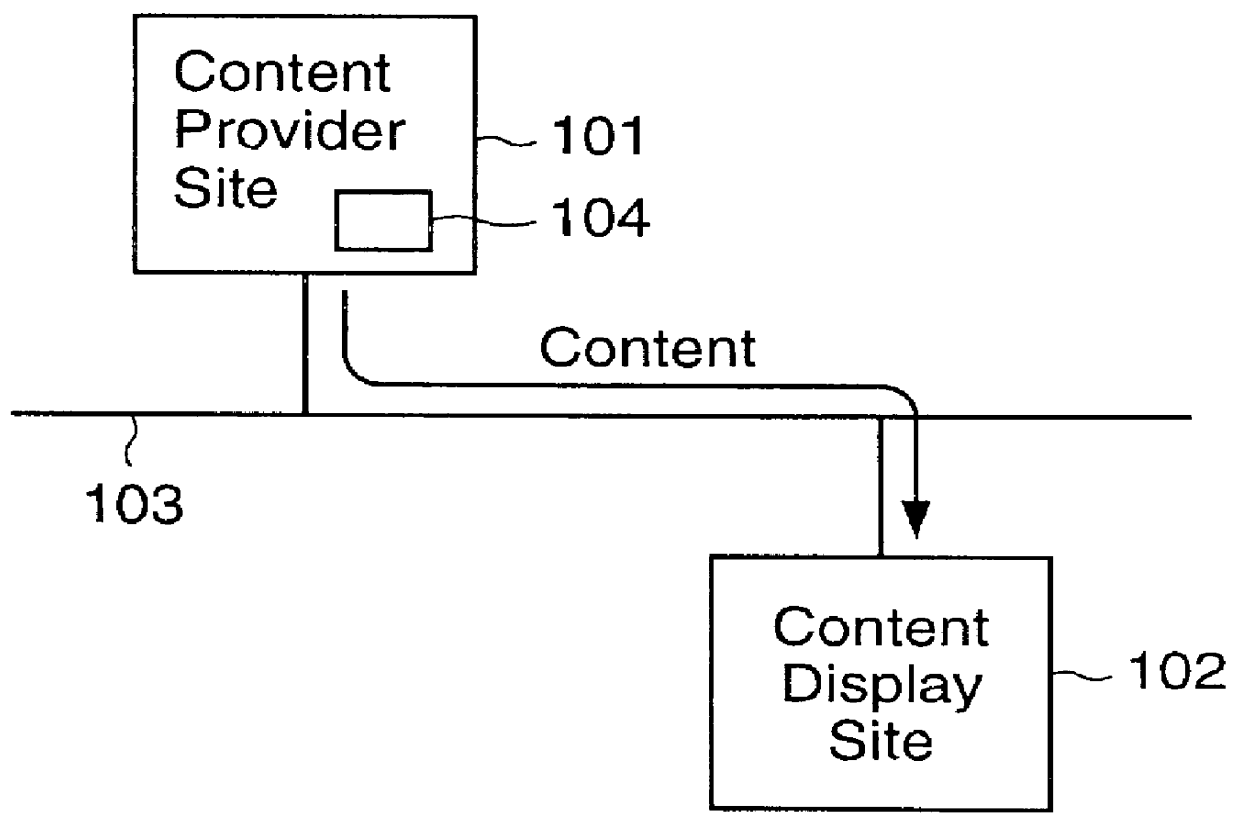
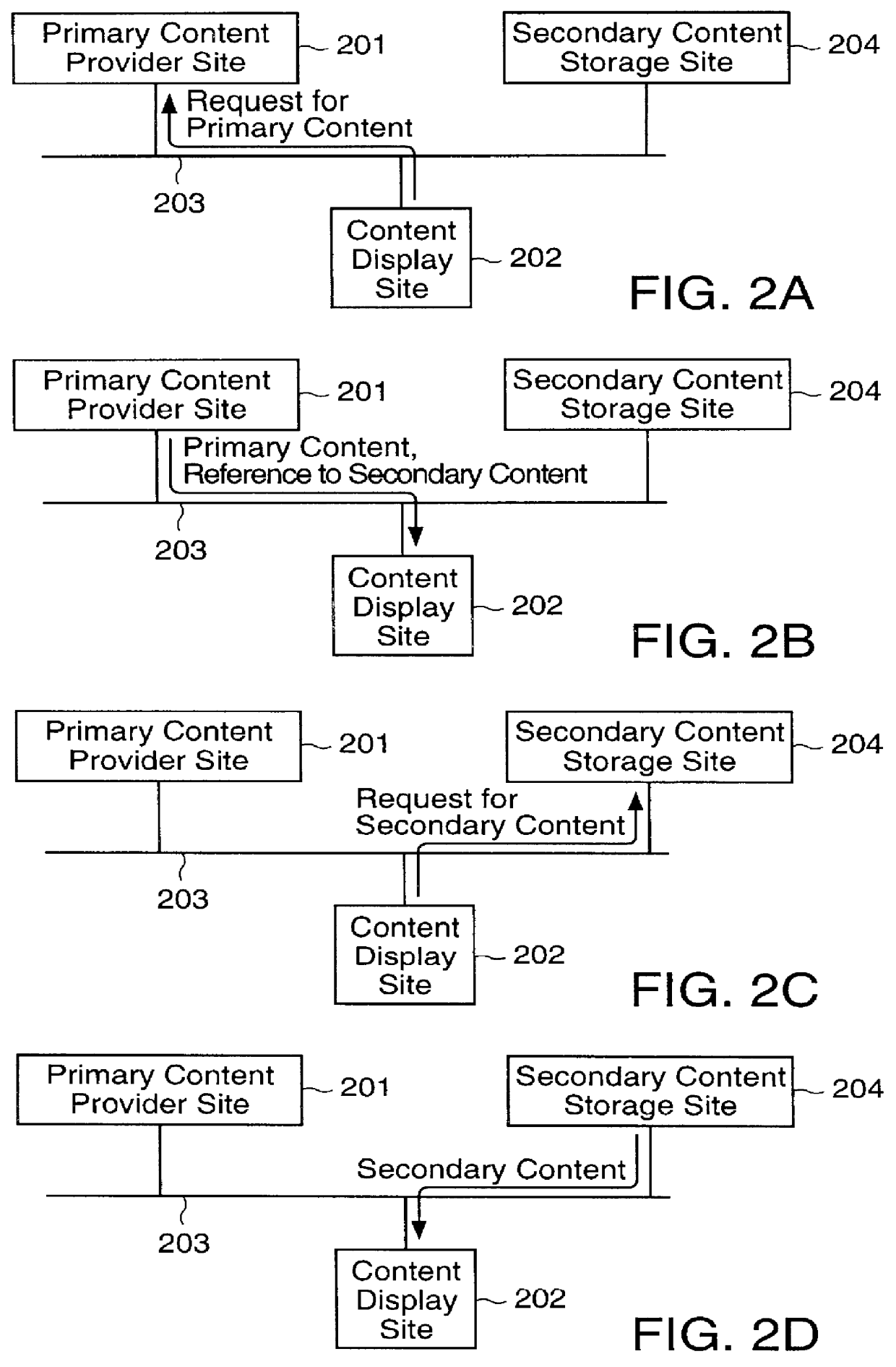
Content display monitor
InactiveUS6108637AComplete banking machinesDigital data information retrievalWeb siteComputerized system
The invention can enable monitoring of the display of content by a computer system. Moreover, the invention can enable monitoring of the displayed content to produce monitoring information from which conclusions may be deduced regarding the observation of the displayed content by an observer. The invention can also enable monitoring of the display at a content display site of content that is provided by a content provider site over a network to the content display site. Additionally, the invention can enable the expeditious provision of updated and / or tailored content over a network from a content provider site to a content display site so that the content provider's current and appropriately tailored content is always displayed at the content display site. Aspects of the invention related to transfer of content over a network are generally applicable to any type of network. However, it is contemplated that the invention can be particularly useful with a computer network, including private computer networks (e.g., America Online TM ) and public computer networks (e.g., the Internet). In particular, the invention can be advantageously used with computer networks or portions of computer networks over which video and / or audio content are transferred from one network site to another network site for observation, such as the World Wide Web portion of the Internet.
Owner:NIELSEN COMPANY US LLC THE A DELAWARE LIMITED LIABILITY
Sensor assemblies
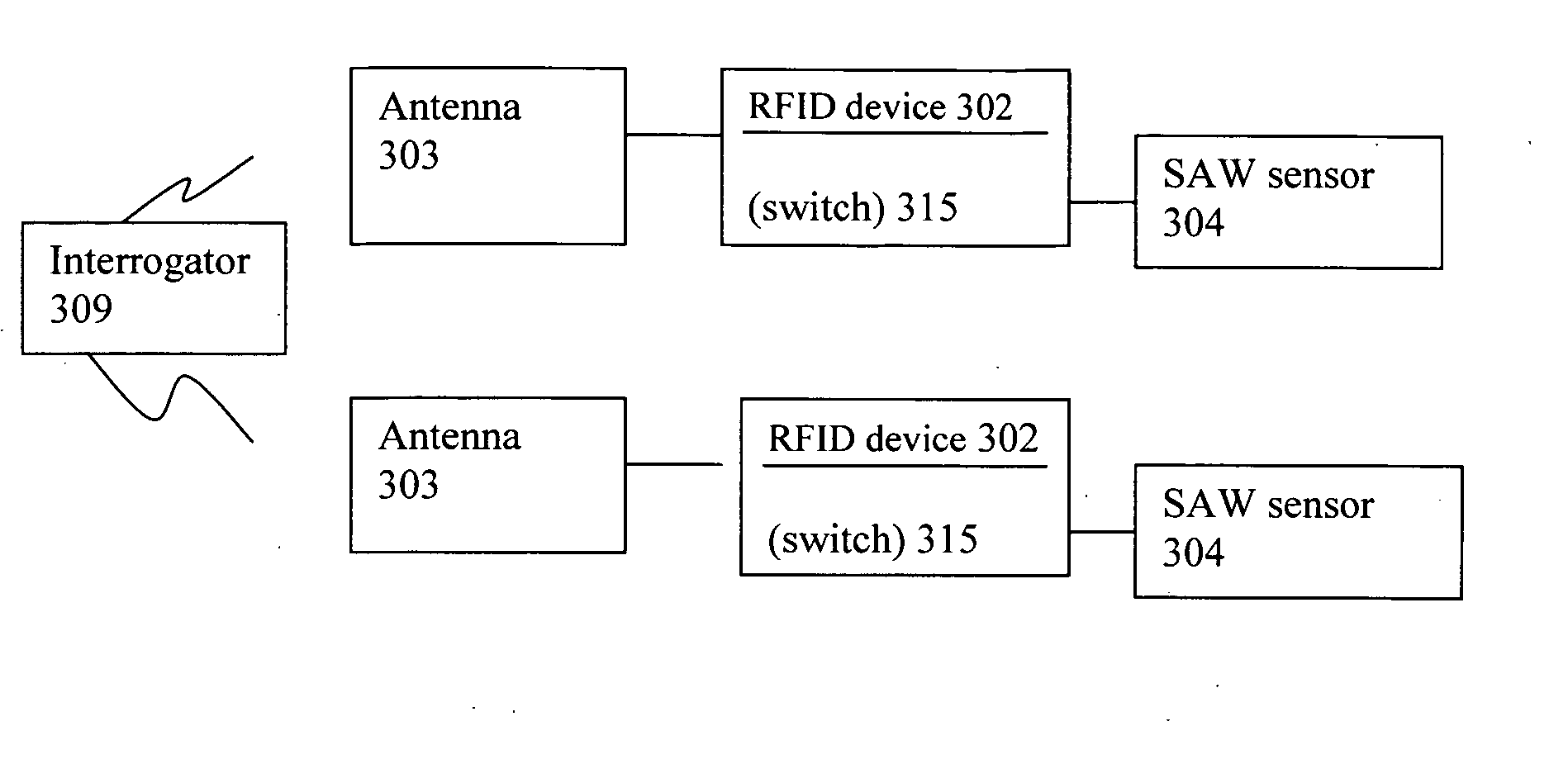
InactiveUS20060025897A1Low costPrecise positioningVehicle testingRegistering/indicating working of vehiclesRadio frequency signalPhysical quantity
Sensor assembly capable of obtaining and providing a measurement of a physical quantity, e.g., measurement of temperature and / or pressure of a vehicular tire, includes an antenna capable of receiving a radio frequency signal, a radio frequency identification (RFID) device coupled to the antenna, a sensor coupled to the RFID device arranged to generate a measurement of the physical quantity or quantities, and a switch coupled to the RFID device and arranged to connect or disconnect the sensor from a circuit with the antenna dependent on whether the antenna receives a particular signal associated with the RFID device. When the antenna receives the particular signal associated with the RFID device, the RFID device causes the switch to close and connect the sensor in the circuit with the antenna to enable the measurement generated by the sensor to be directed to and transmitted by the antenna.
Owner:AMERICAN VEHICULAR SCI
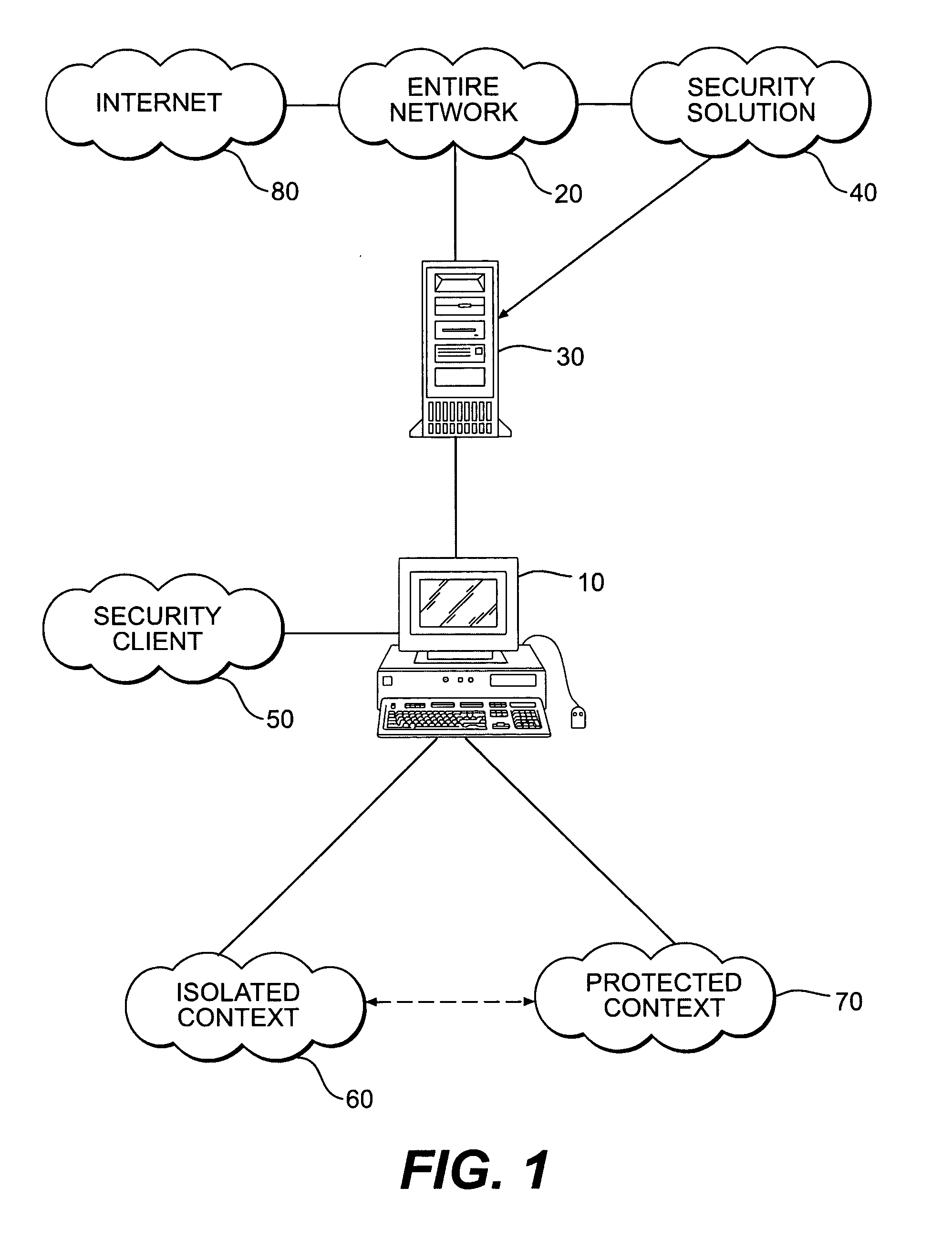
Systems and methods for secure client applications
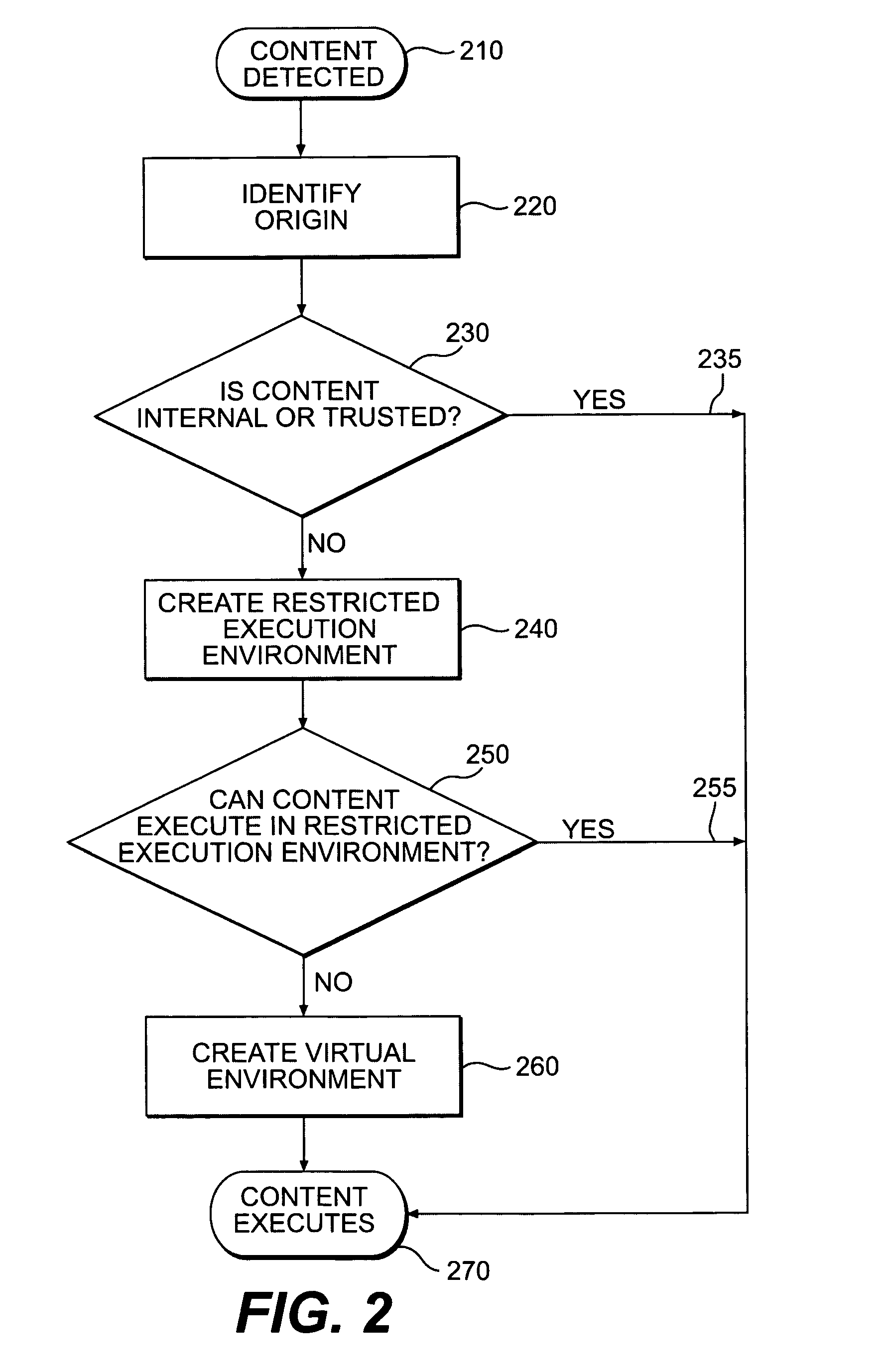
ActiveUS20050149726A1Avoid attackMinimize impactDigital data processing detailsHardware monitoringVirtualizationClient-side
An innovative security solution which separates a client into a Protected Context, which is the real files and resources of the client, and an Isolated Context, which is a restricted execution environment which makes use of virtualized resources to execute applications and modify content in the Isolated Context, without allowing explicit access to the resources in the Protected Context. The solution further consolidates user interfaces to allow users to seamlessly work with content in both contexts, and provide a visual indication of which display windows are rendered from content executed in the Isolated Context.
Owner:GOOGLE LLC
Obfuscation techniques for enhancing software security
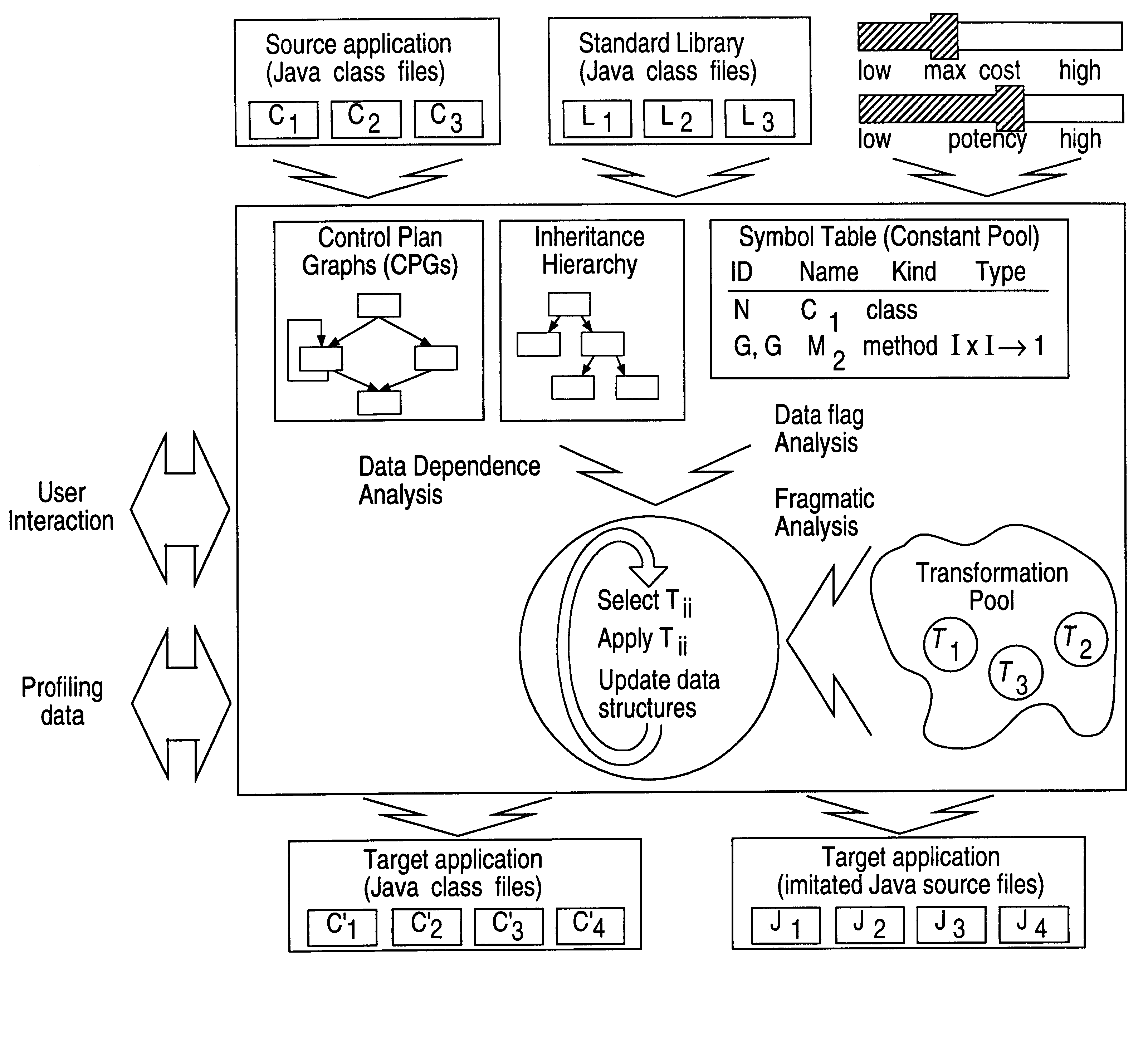
InactiveUS6668325B1Guaranteed maximum utilizationDigital data processing detailsUnauthorized memory use protectionObfuscationTheoretical computer science
The present invention provides obfuscation techniques for enhancing software security. In one embodiment, a method for obfuscation techniques for enhancing software security includes selecting a subset of code (e.g., compiled source code of an application) to obfuscate, and obfuscating the selected subset of the code. The obfuscating includes applying an obfuscating transformation to the selected subset of the code. The transformed code can be weakly equivalent to the untransformed code. The applied transformation can be selected based on a desired level of security (e.g., resistance to reverse engineering). The applied transformation can include a control transformation that can be creating using opaque constructs, which can be constructed using aliasing and concurrency techniques. Accordingly, the code can be obfuscated for enhanced software security based on a desired level of obfuscation (e.g., based on a desired potency, resilience, and cost).
Owner:INTERTRUST TECH CORP
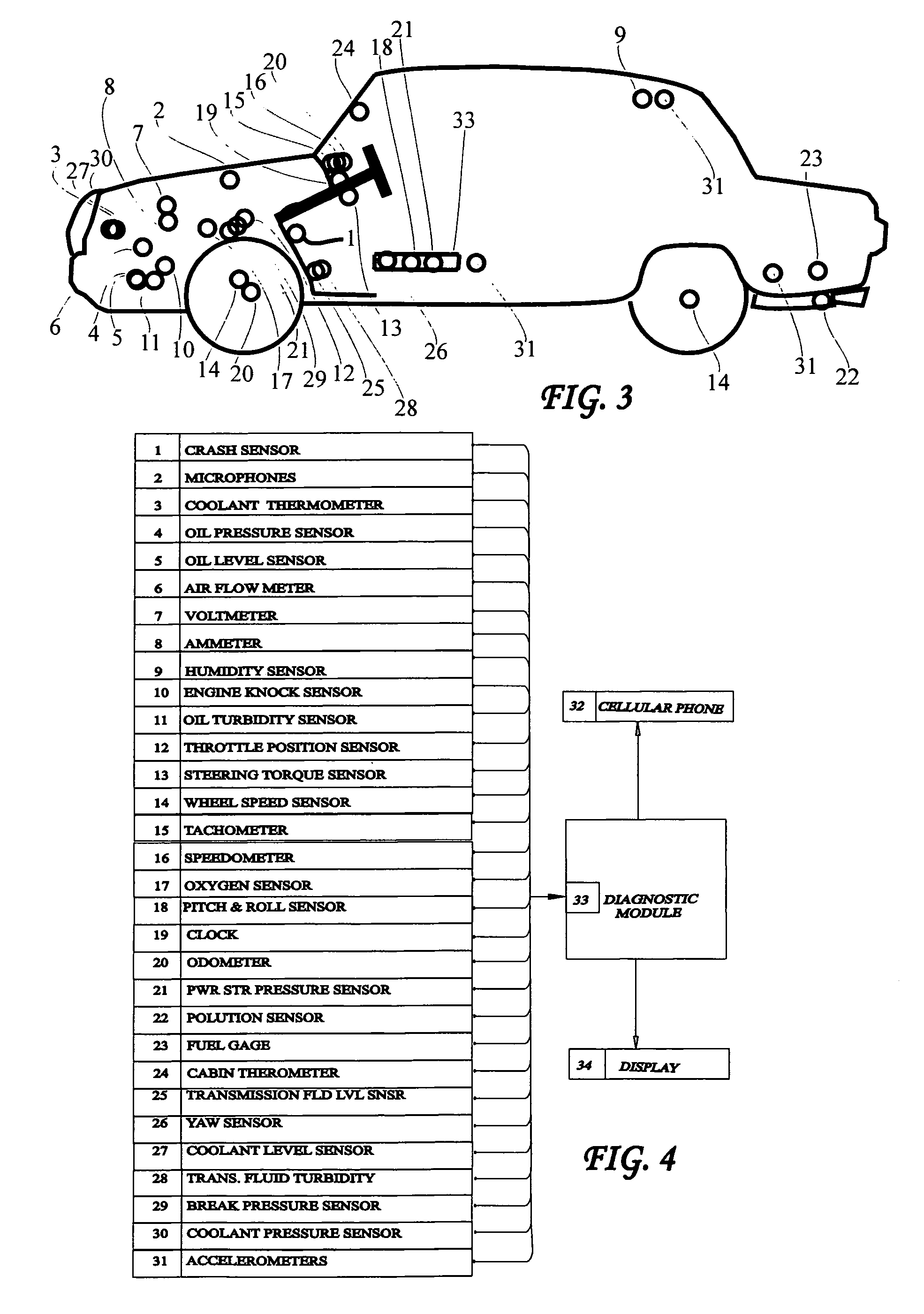
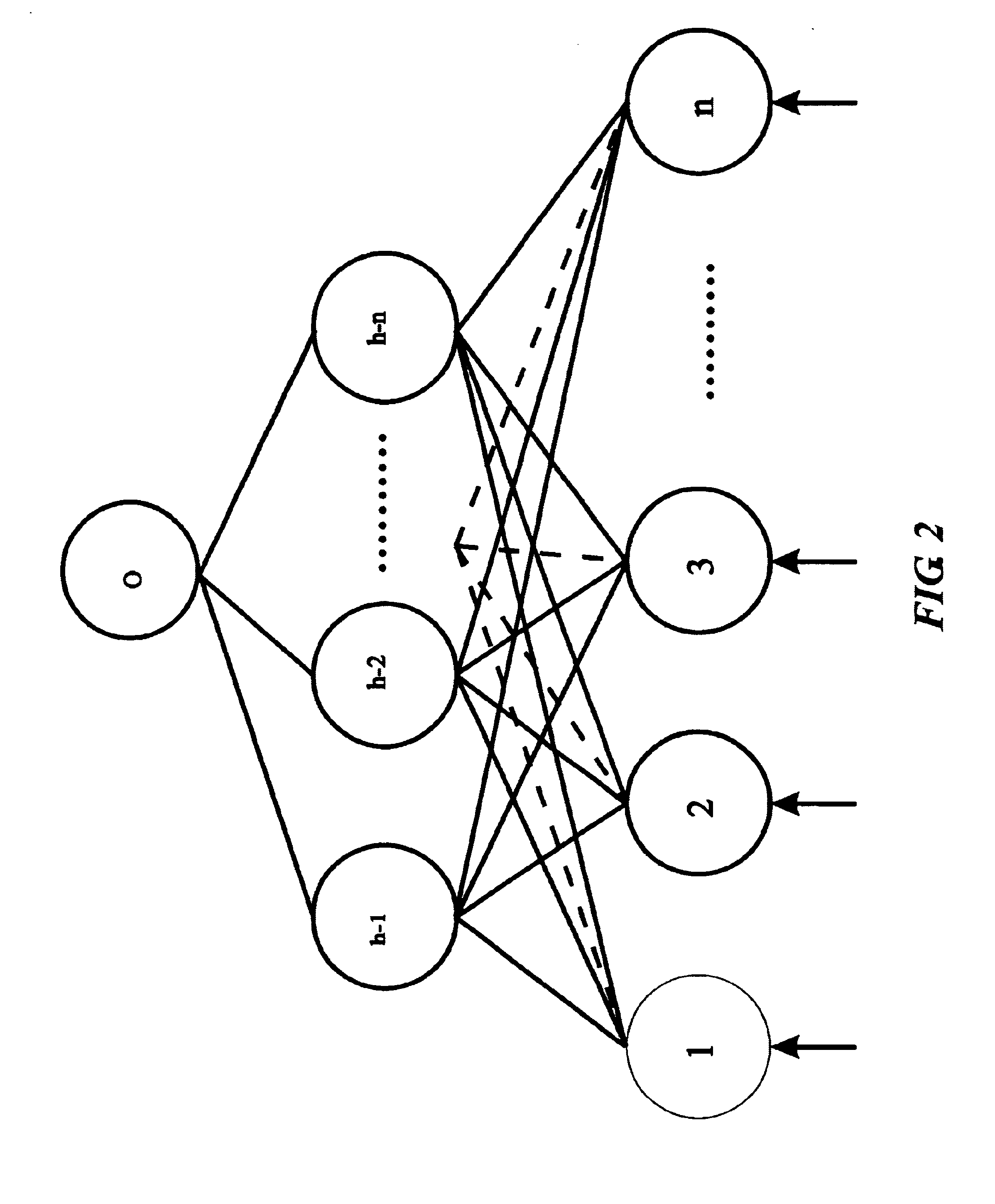
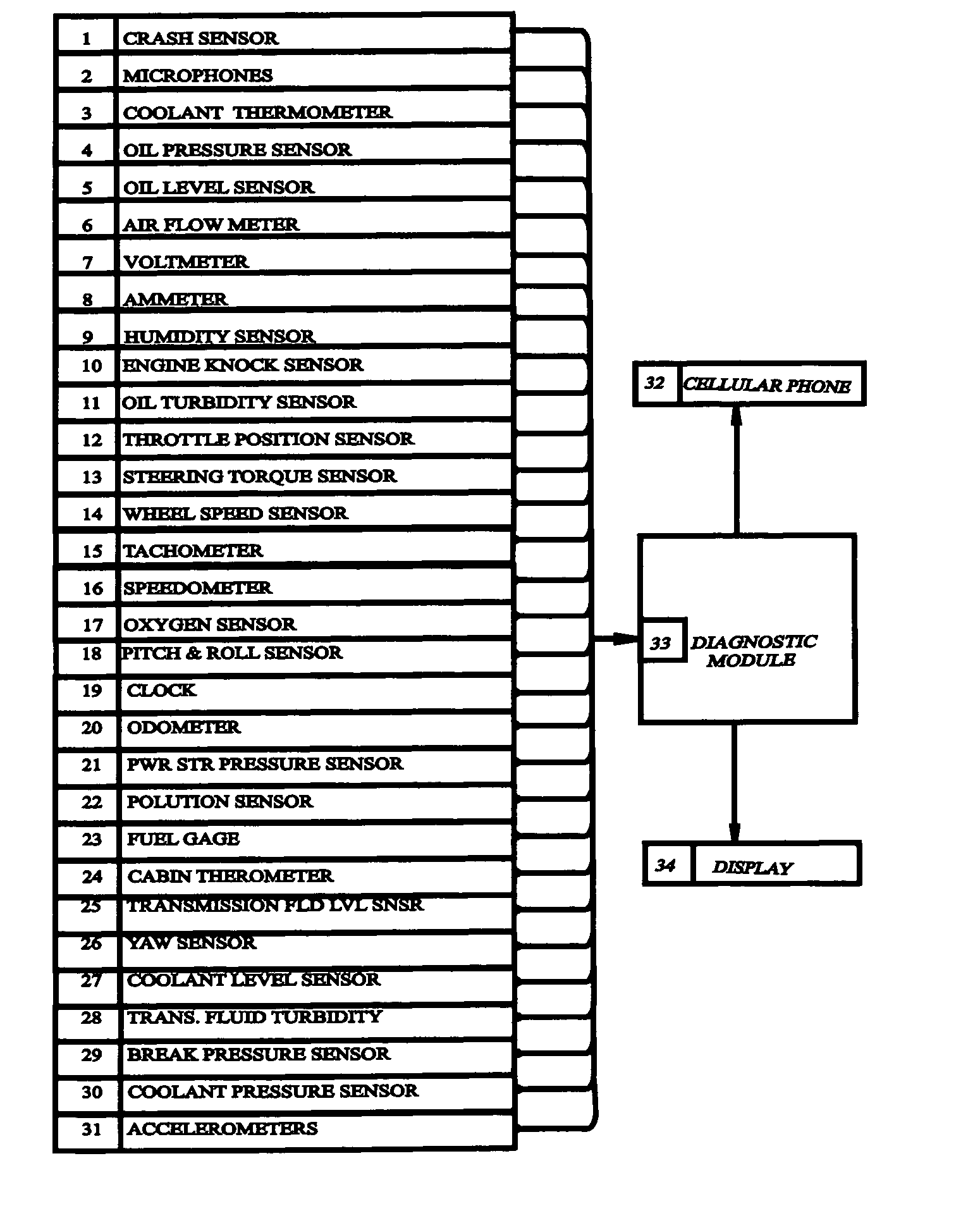
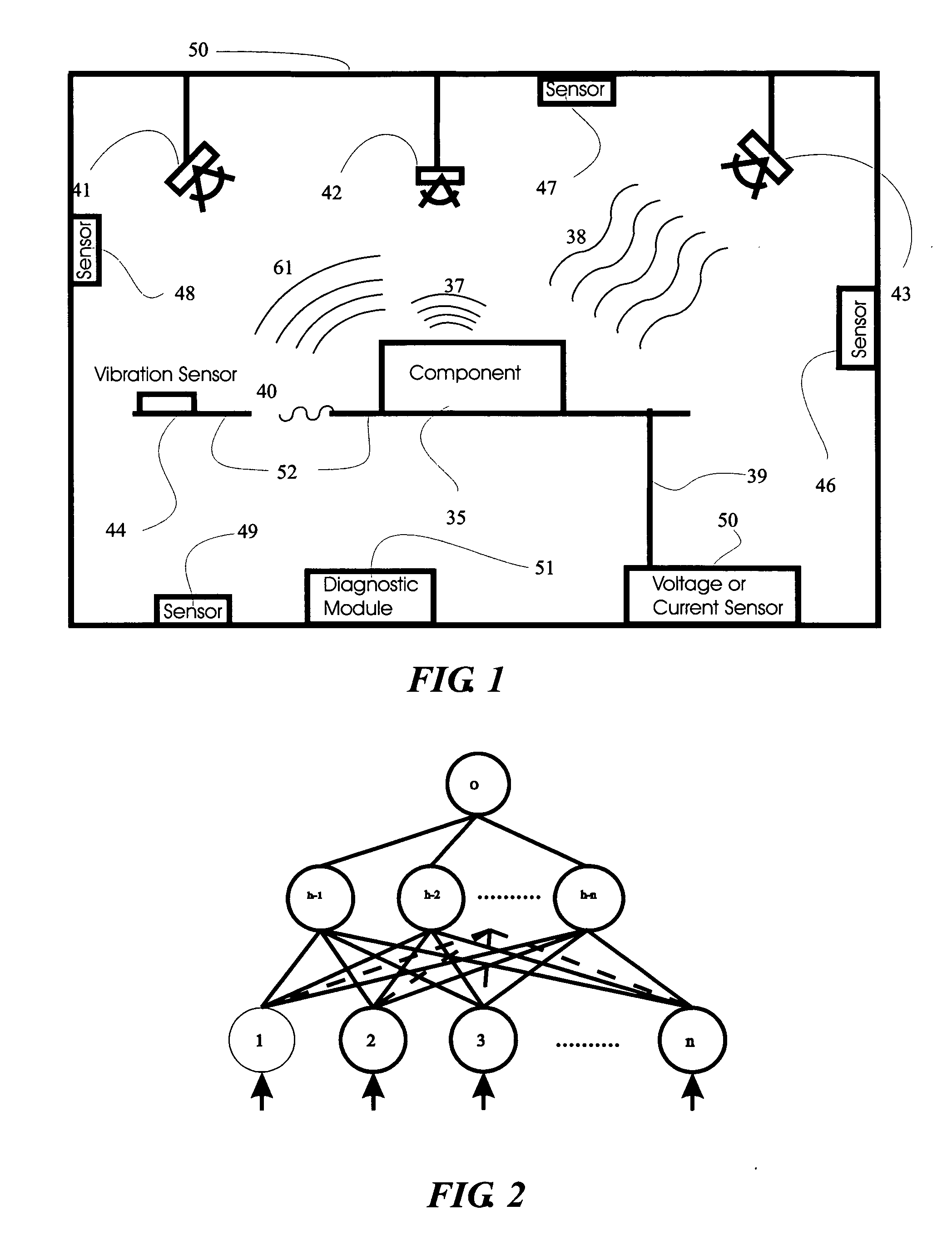
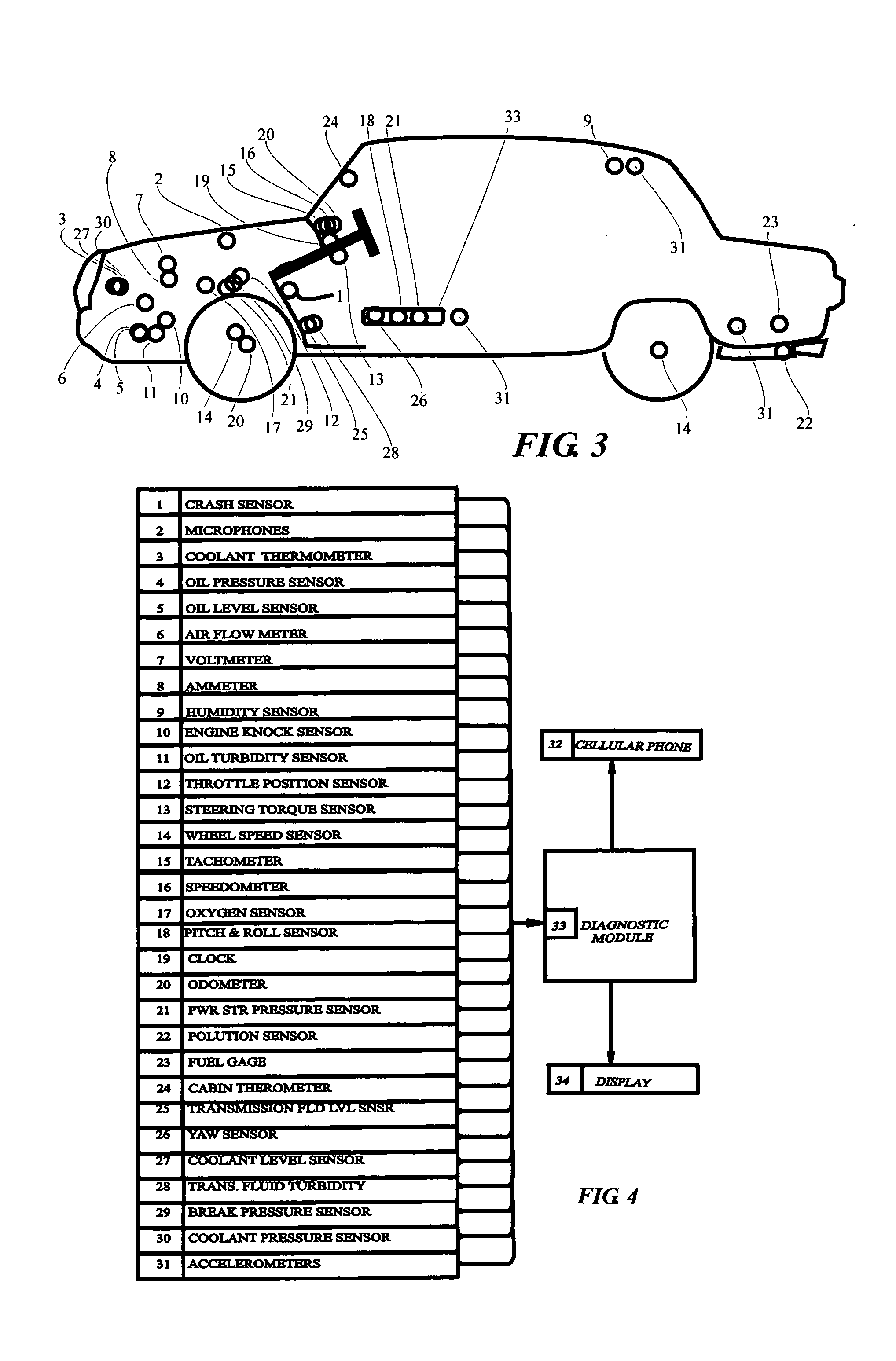
System and method for vehicle diagnostics
InactiveUS7103460B1Low costPrecise positioningVehicle testingRegistering/indicating working of vehiclesReliability engineeringDiagnostic methods
Method and system for diagnosing whether vehicular components are operating abnormally based on data obtained from sensors arranged on a vehicle. In a training stage, output from the sensors during normal operation of the components is obtained, each component is adjusted to induce abnormal operation thereof and output from the sensors is obtained during the induced abnormal operation. A determination is made as to which sensors provide data about abnormal operation of each component based on analysis of the output from the sensors during normal operation and during induced abnormal operation of the components. During operation of the vehicle, the output from the sensors is obtained and analyzed, e.g., by inputting it into a pattern recognition algorithm or neural network generated during the training stage, in order to output an indication of abnormal operation of any components being diagnosed.
Owner:AMERICAN VEHICULAR SCI
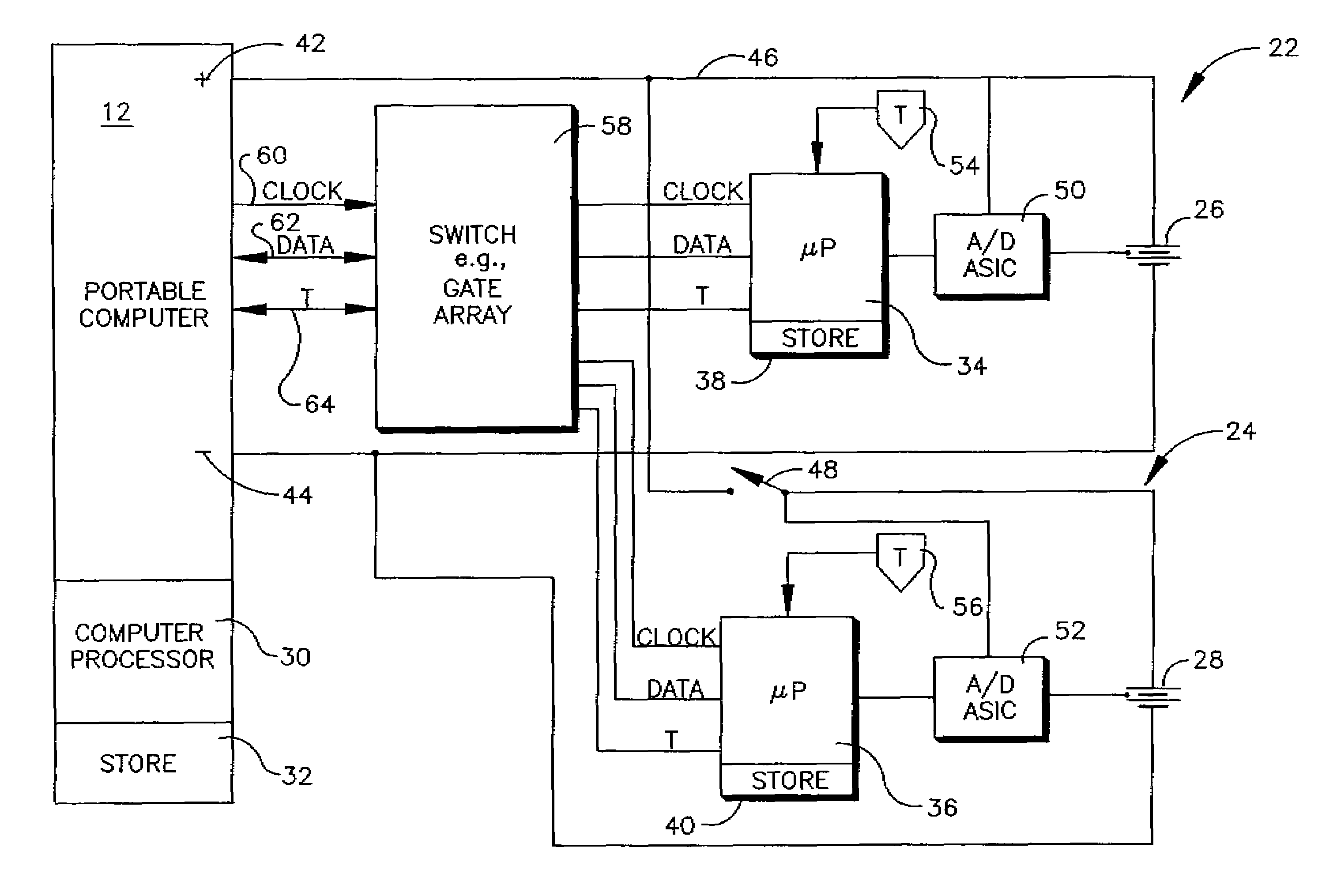
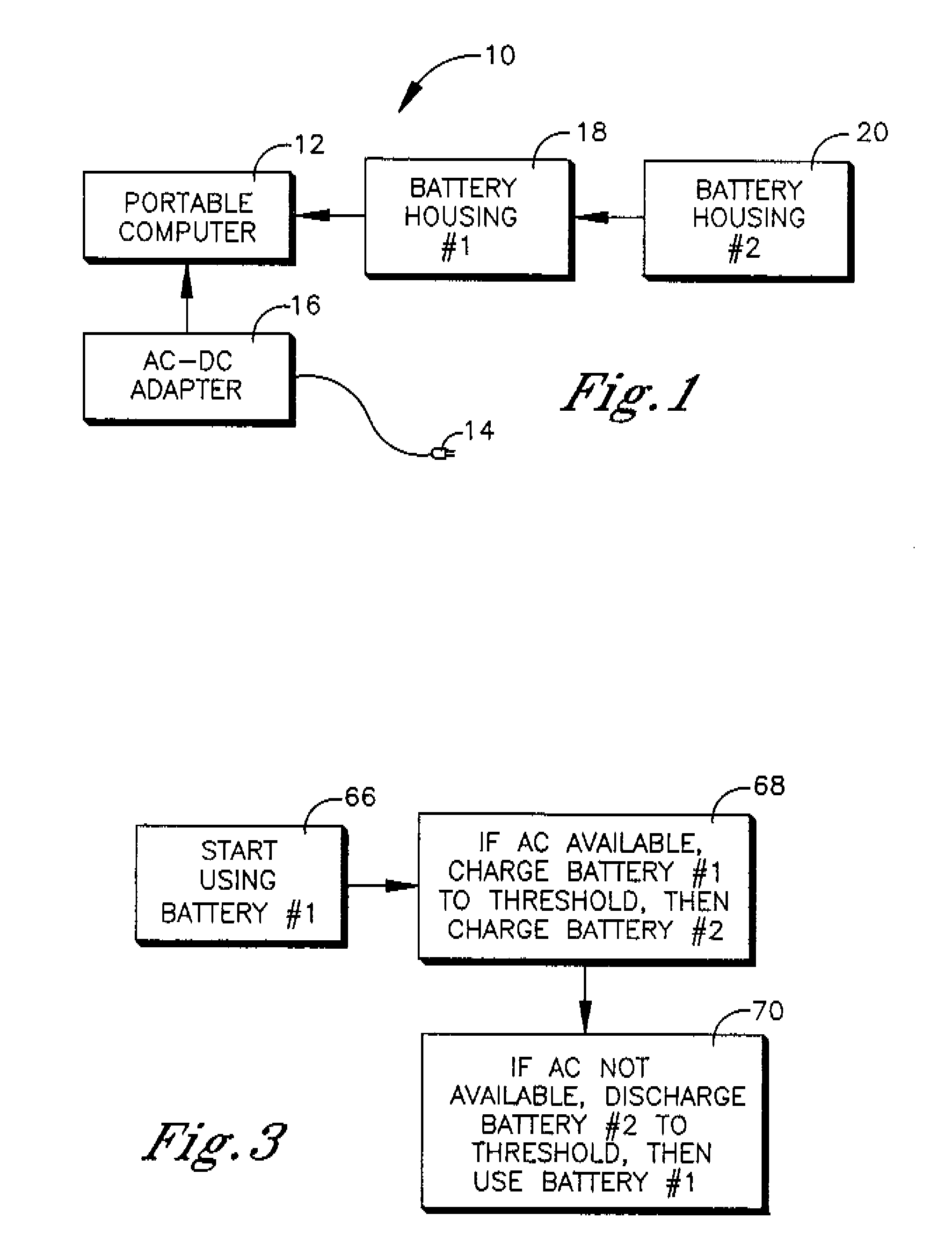
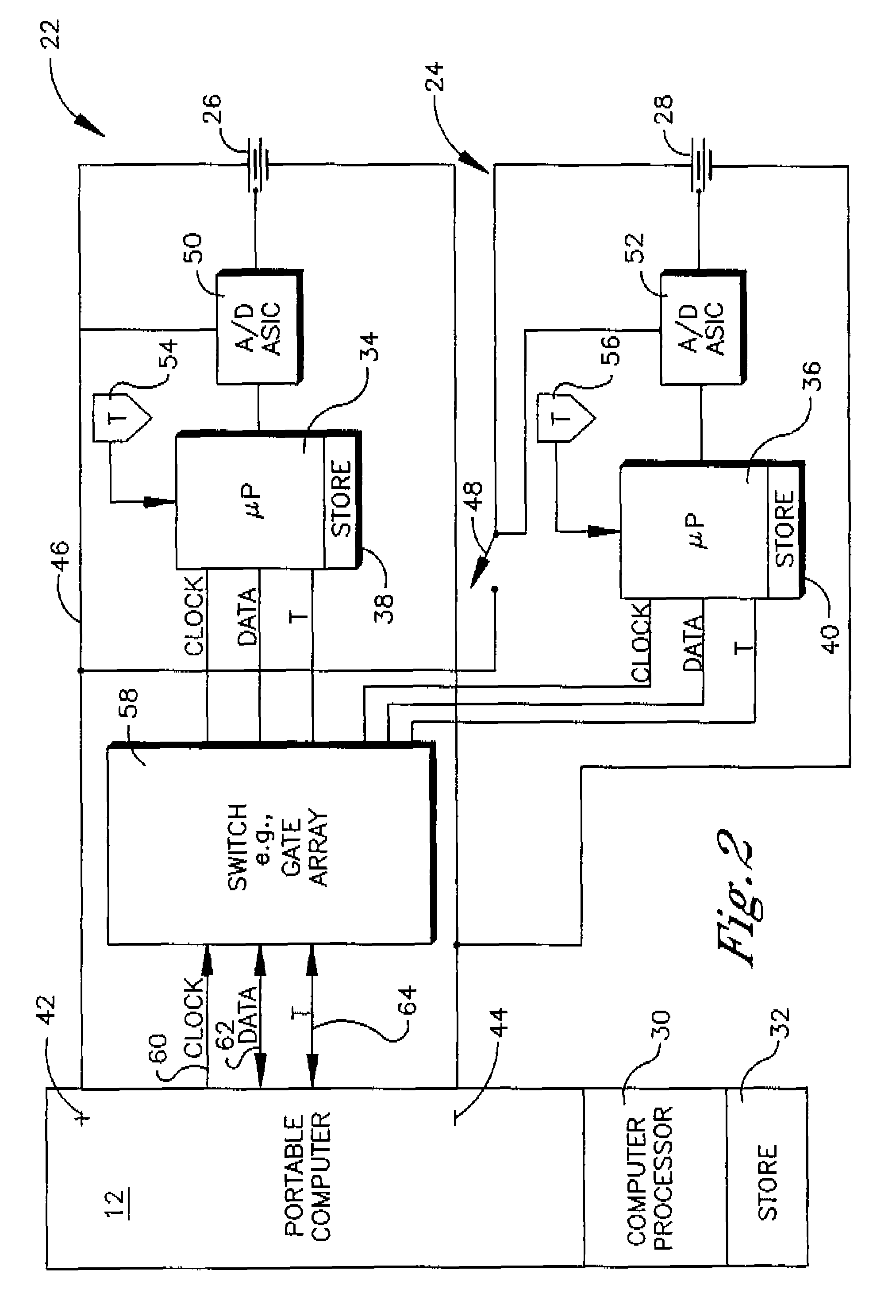
Battery pack for portable computer
A first battery assembly is in a first battery housing that is mechanically engageable with a portable computer, and a second battery assembly is in a second battery housing that is mechanically couplable to the first battery housing. A switch has a first configuration in which communication is established between the portable computer and the first battery assembly and a second configuration in which communication is established between the portable computer and the second battery assembly.
Owner:LENOVO PC INT
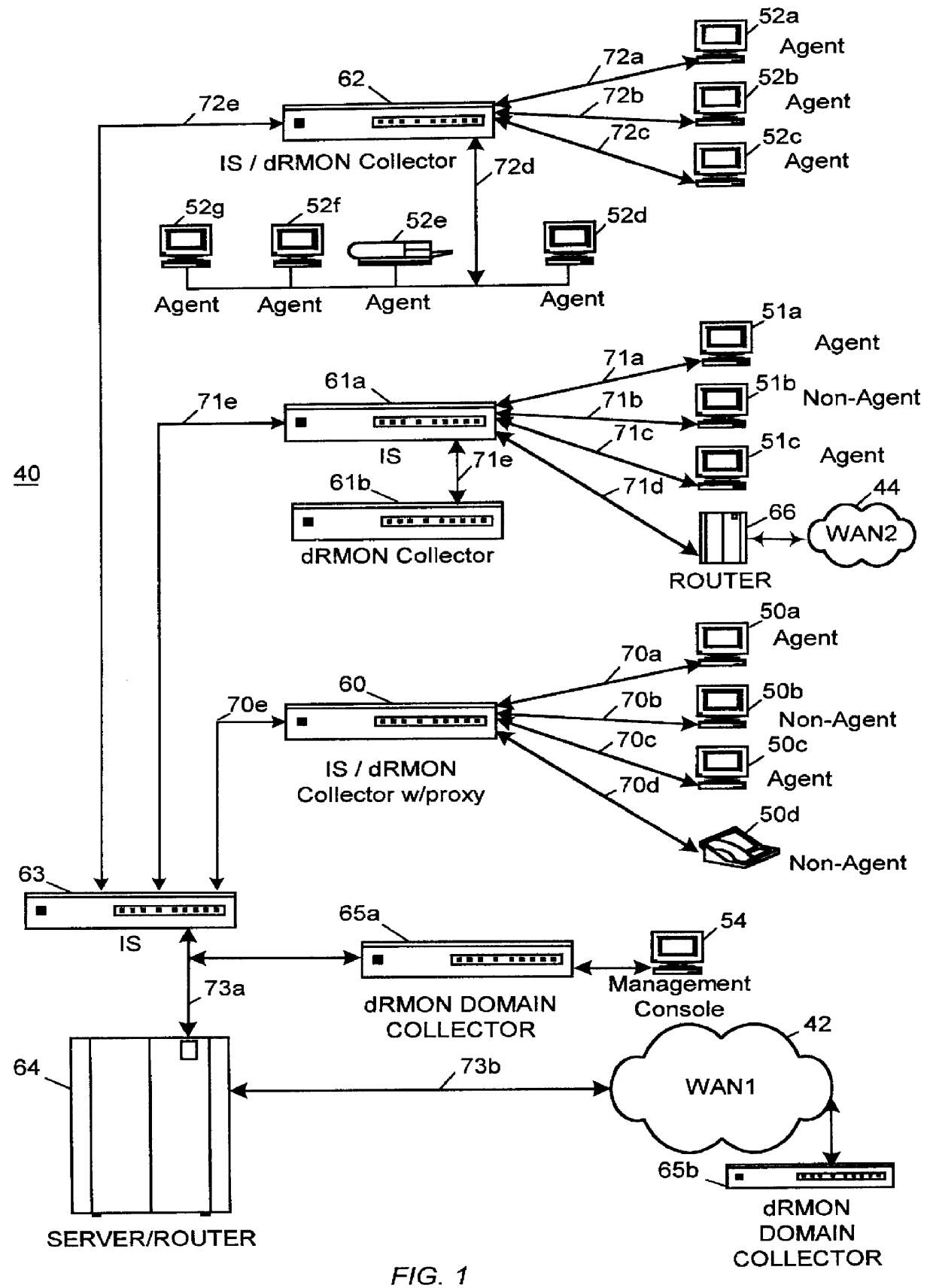
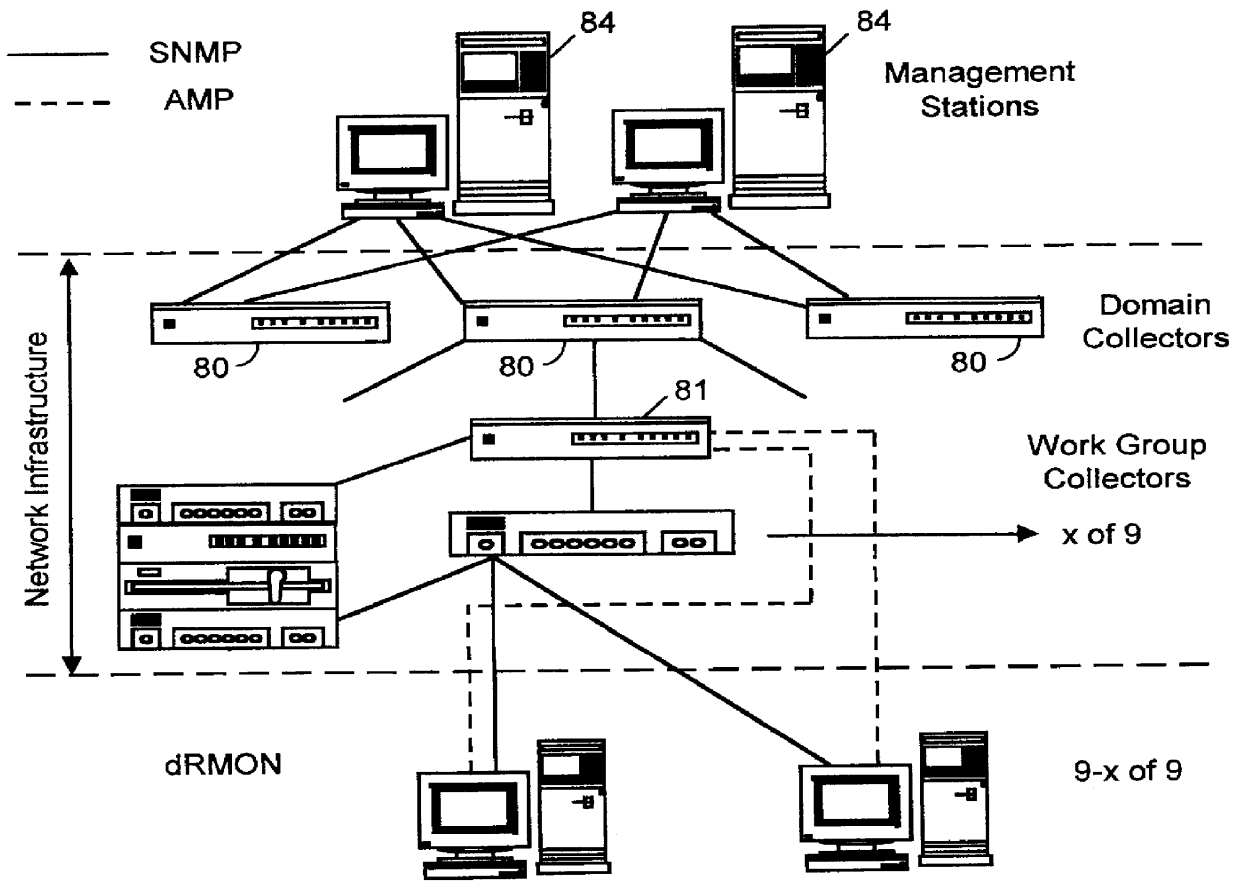
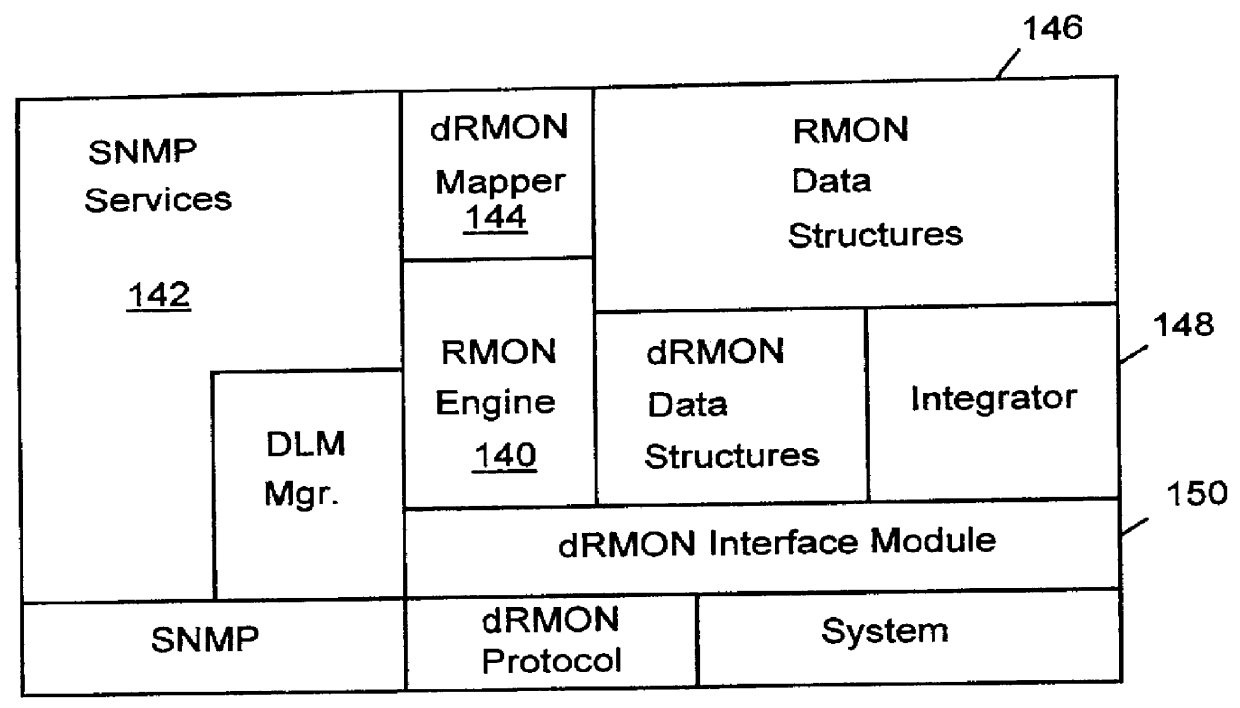
Distributed remote monitoring (dRMON) for networks
InactiveUS6108782AError preventionFrequency-division multiplex detailsNetwork operating systemOperational system
Distributed remote monitoring (dRMON) of network traffic and performance uses distributed nodes to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create combined views of network performance. A collector may mimic a prior art, non-distributed, network probe and may interact with network management software as though it were a stand alone network probe thereby simplifying a user's interaction with the distributed system. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments. The invention has applications in a variety of communication system environments including local area networks, cable television distribution systems, ATM systems, and advanced telephony systems. A specific embodiment of the invention solves is particularly optimized to work in LAN environments with end systems running under Windows-compatible network operating systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Wireless and powerless sensor and interrogator
InactiveUS6988026B2Low costPrecise positioningVehicle testingRegistering/indicating working of vehiclesCapacitanceRadio frequency energy
Arrangement and method for monitoring a tire mounted to the vehicle in which a thermal radiation detecting device detects the temperature of the tire at different circumferential locations along the circumference of the tire. The detected temperatures of the tire are analyzed to determine, for example, whether a difference in thermal radiation is present between the circumferential locations of the tire, and if so, an action is effected in response to the analysis. The thermal radiation detecting devices are preferably supplied with power wirelessly, e.g., through an inductive system, a capacitive system or a radio frequency energy transfer system.
Owner:AMERICAN VEHICULAR SCI
Mobile systems and methods for responding to natural language speech utterance
ActiveUS20100145700A1Promotes feeling of naturalOvercome deficienciesVehicle testingInstruments for road network navigationInformation processingRemote system
Owner:DIALECT LLC
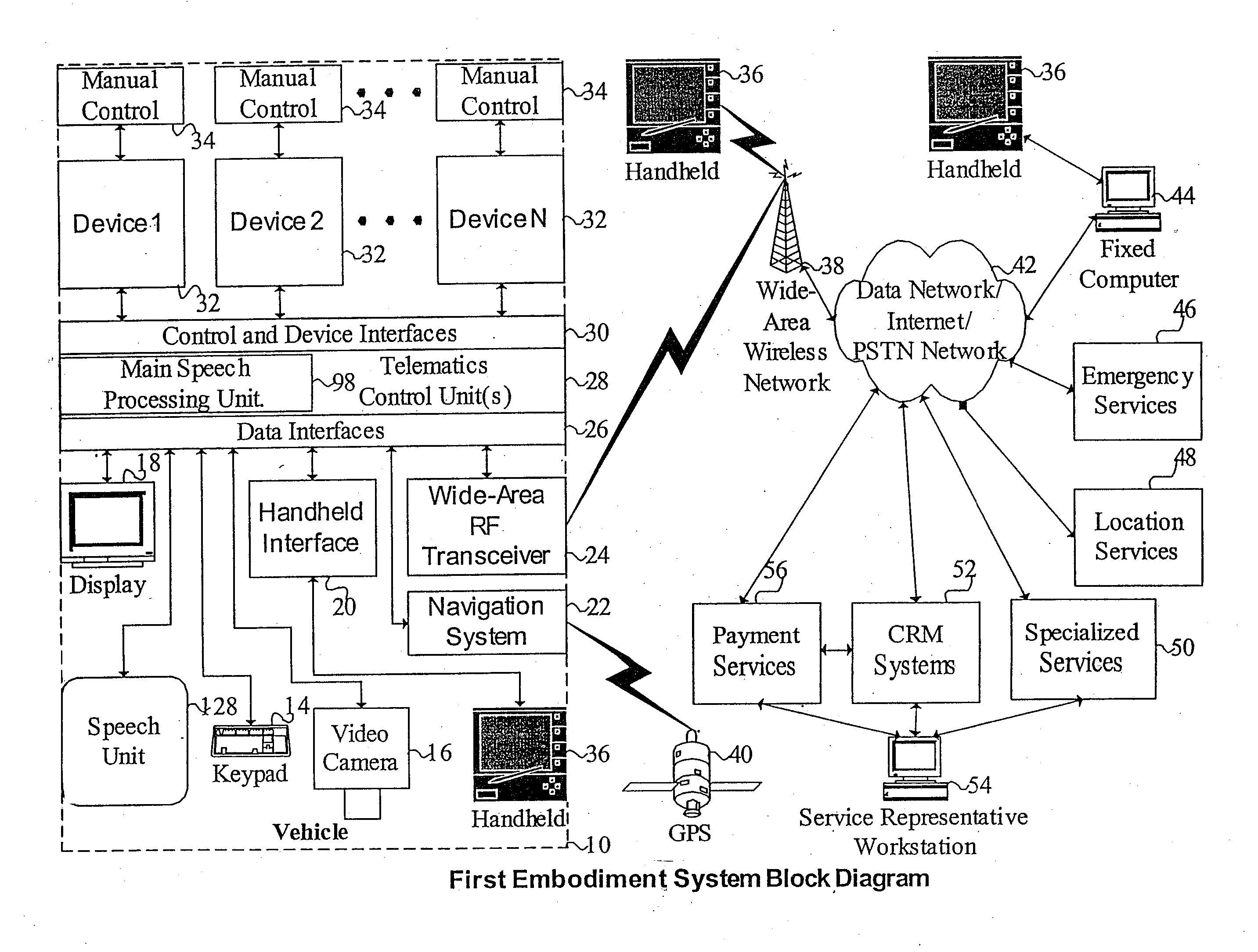
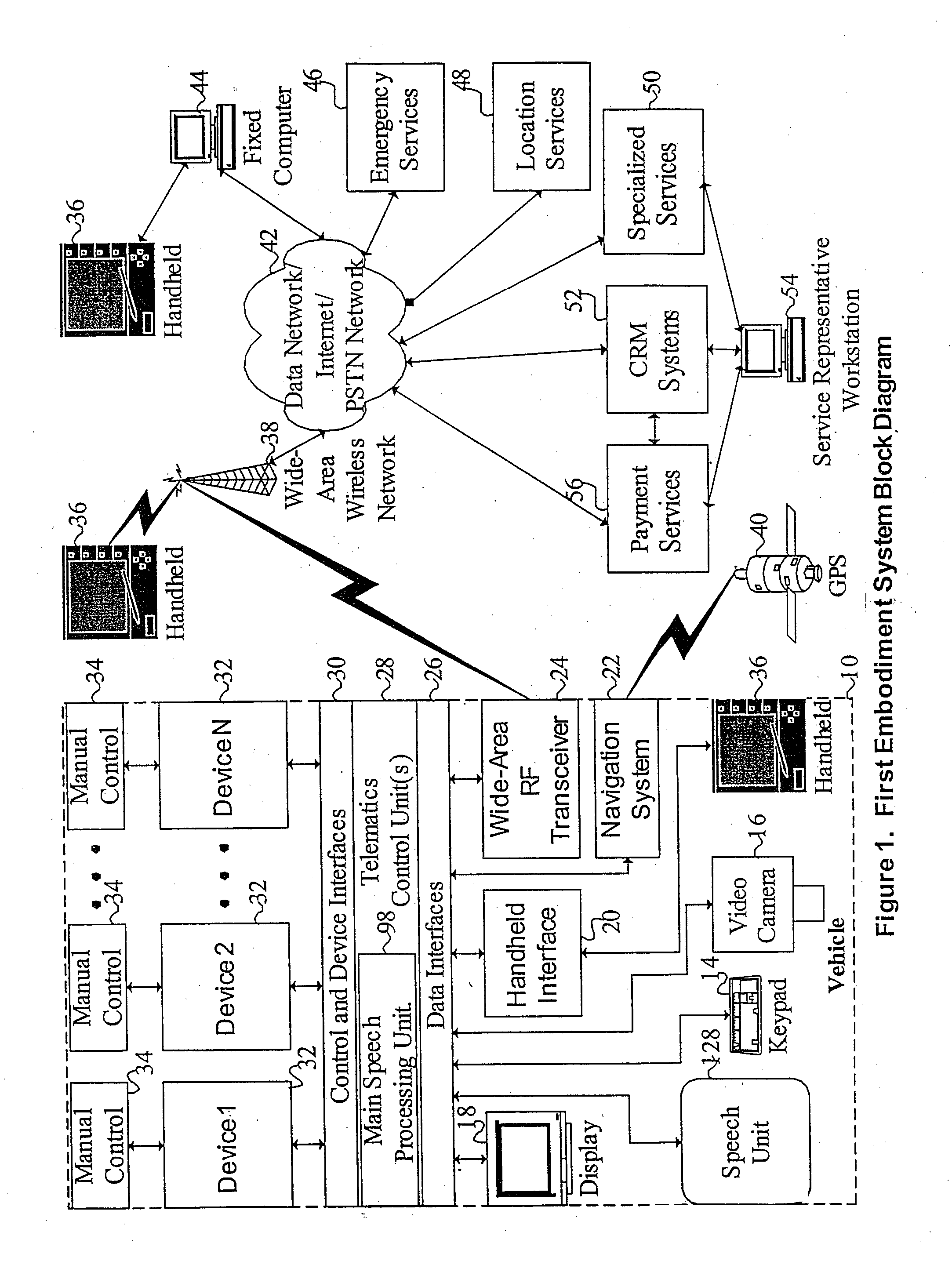
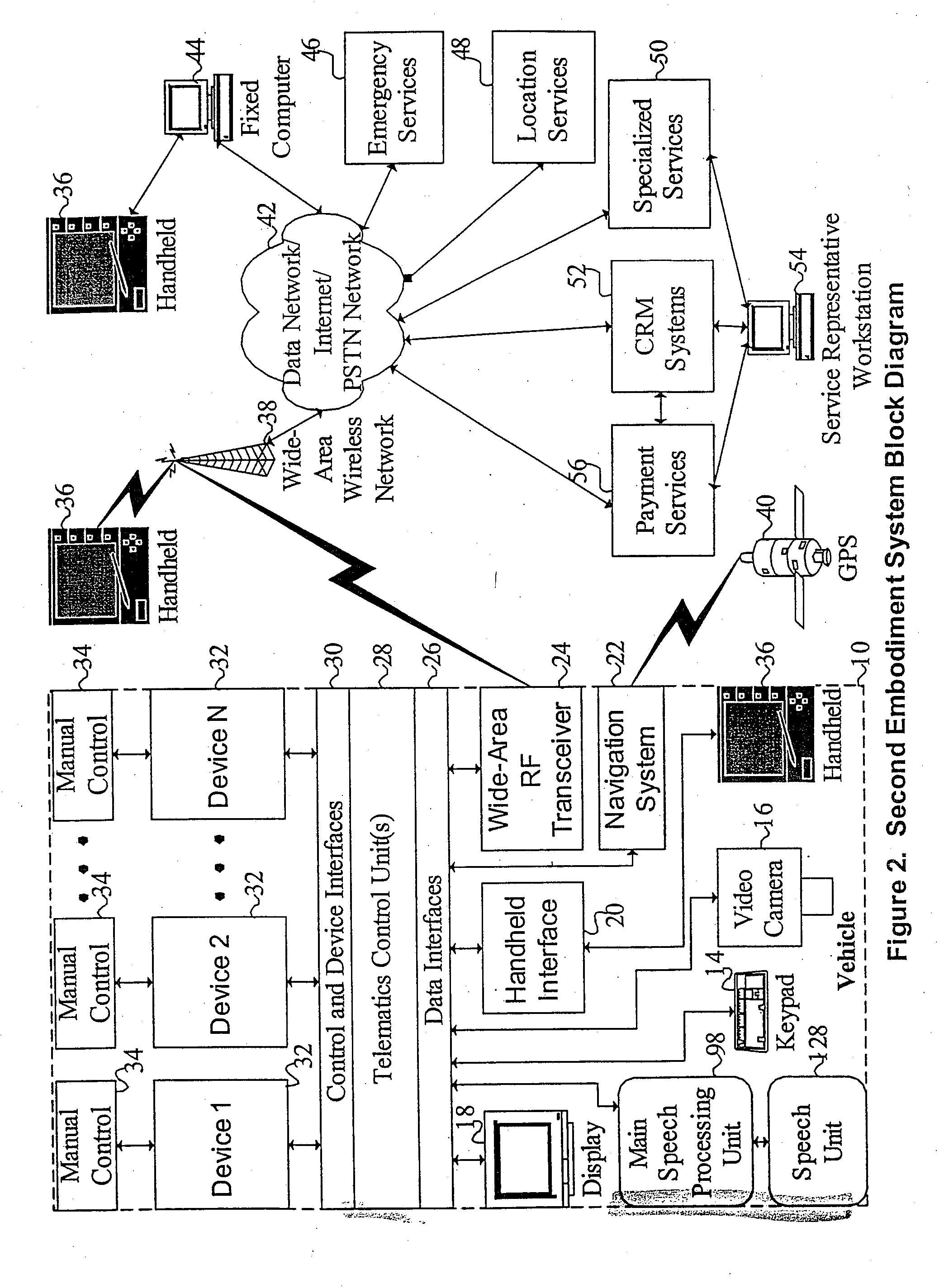
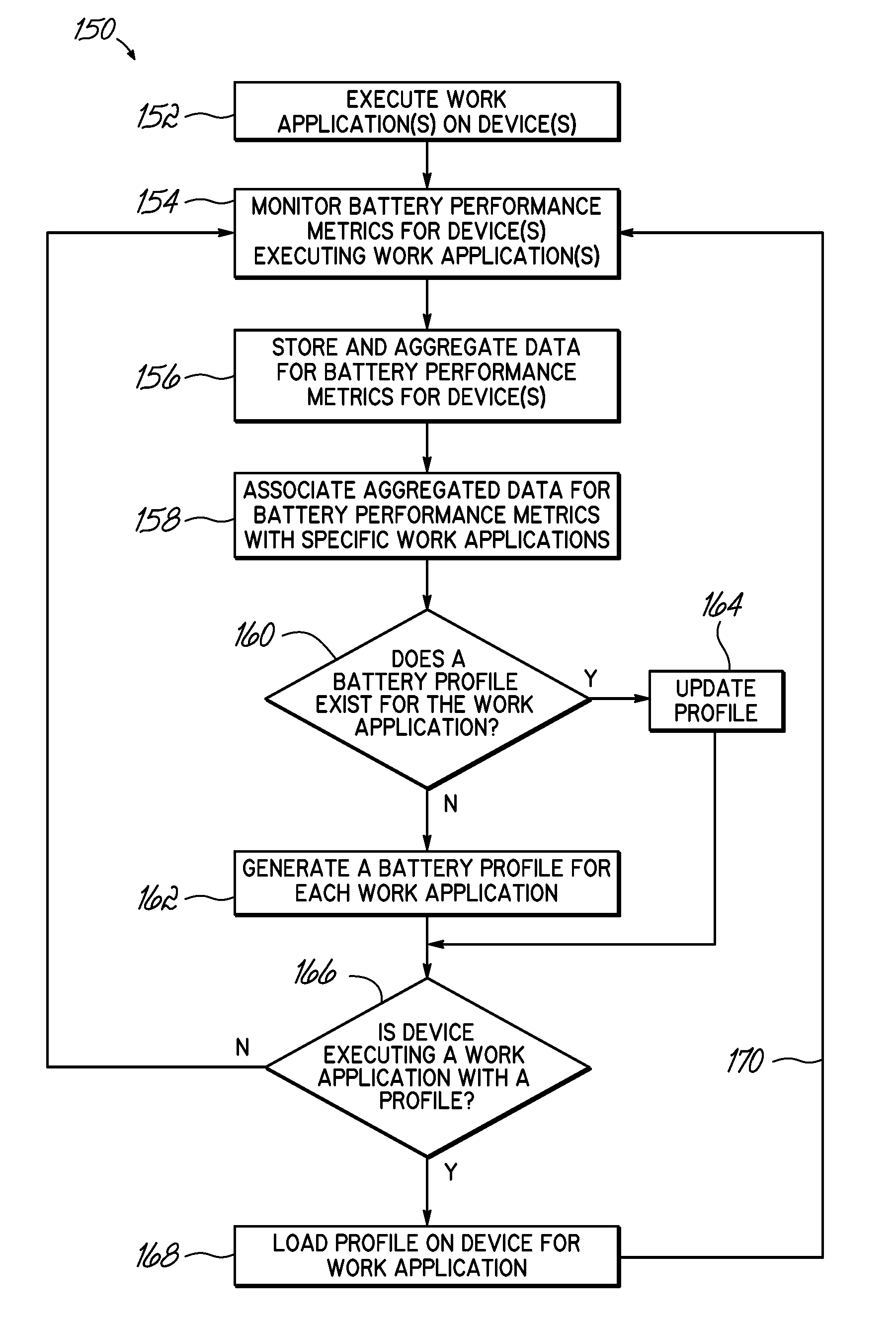
Receiving application specific individual battery adjusted battery use profile data upon loading of work application for managing remaining power of a mobile device
A method and system of managing power usage of devices including selectively executing a program application on a plurality of battery powered devices. Battery usage data is generated for a battery in one or more of the devices during execution of the work application. The battery usage data includes the run-time of the battery for the work application being executed. The data is aggregated and stored for the plurality of devices in memory. An application specific battery profile is generated using the stored battery usage data. The application specific battery profile is associated with the work application being run by the client devices.
Owner:VOCOLLECT
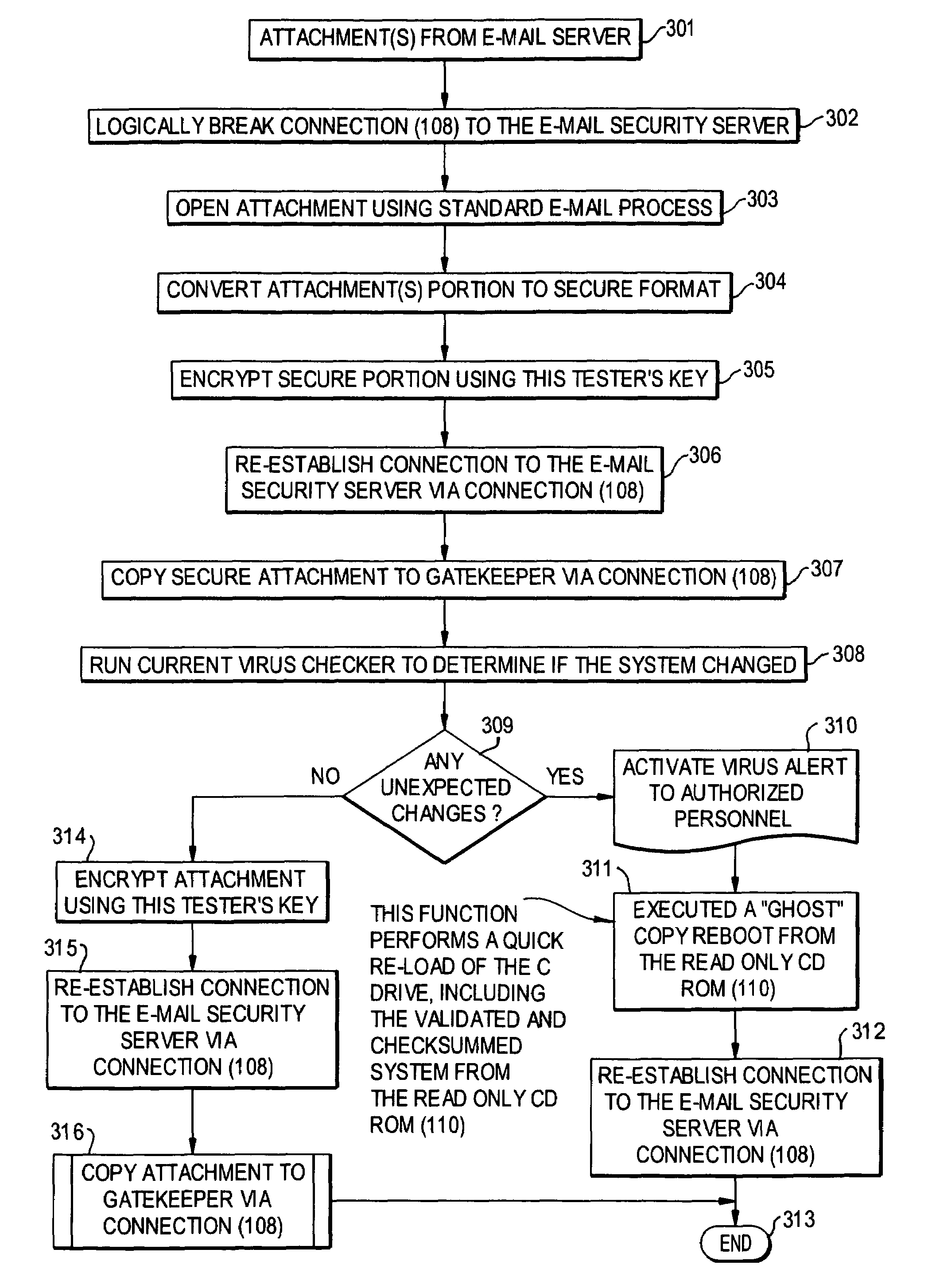
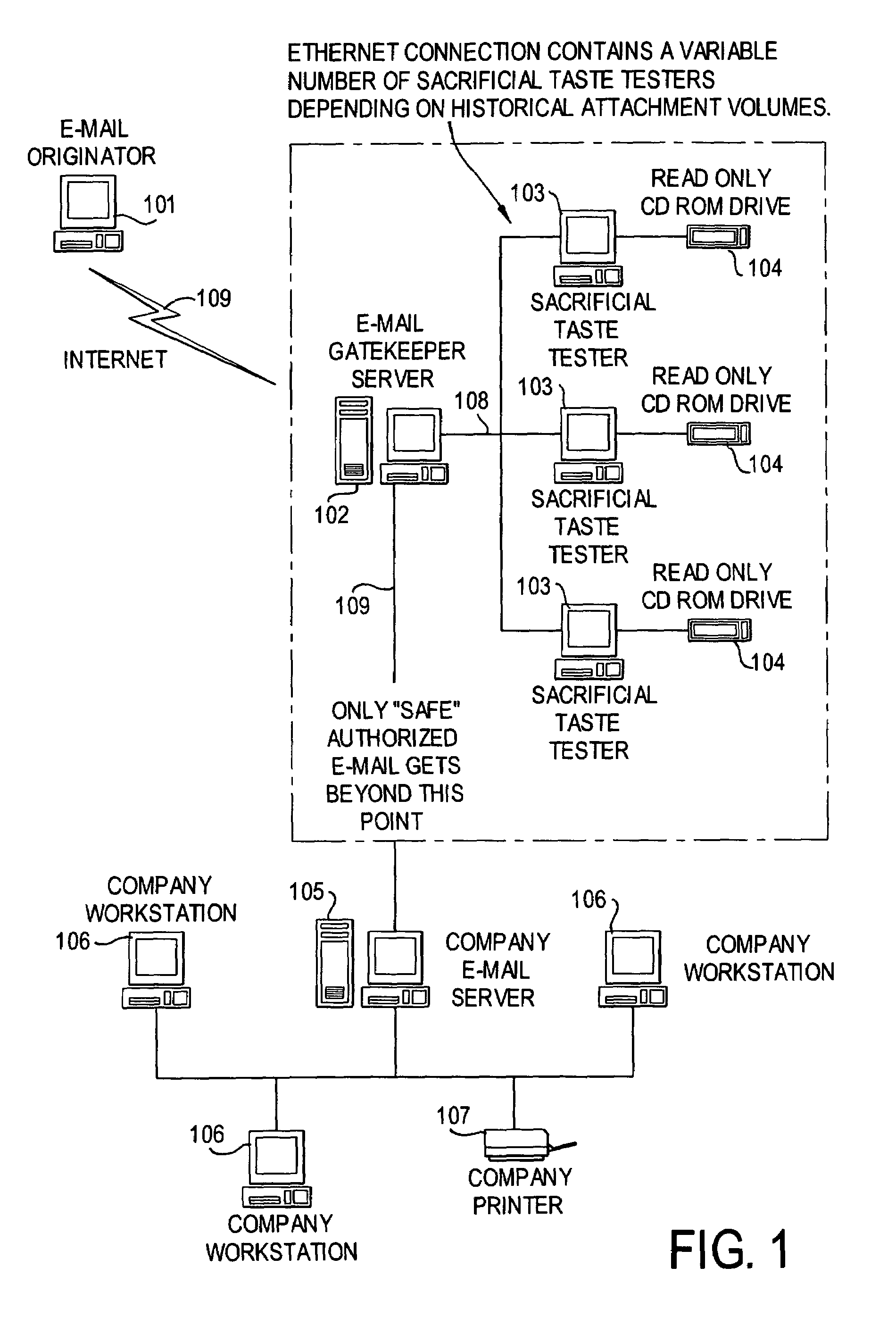
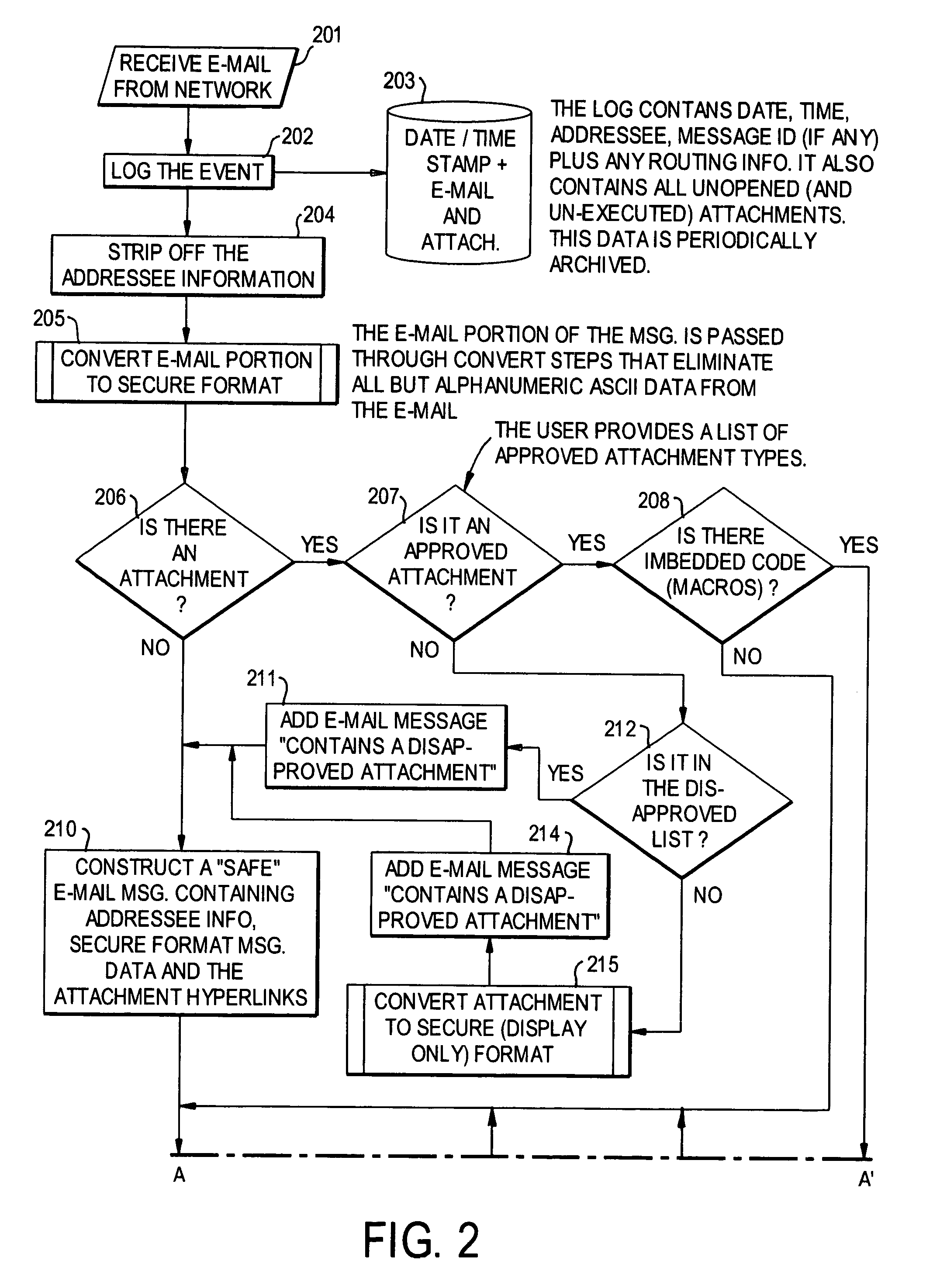
E-mail virus protection system and method
InactiveUS7506155B1Detection securityEnsuring Safe ExecutionHardware monitoringPlatform integrity maintainanceAdobeProtection system
A network is protected from e-mail viruses through the use of a sacrificial server. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
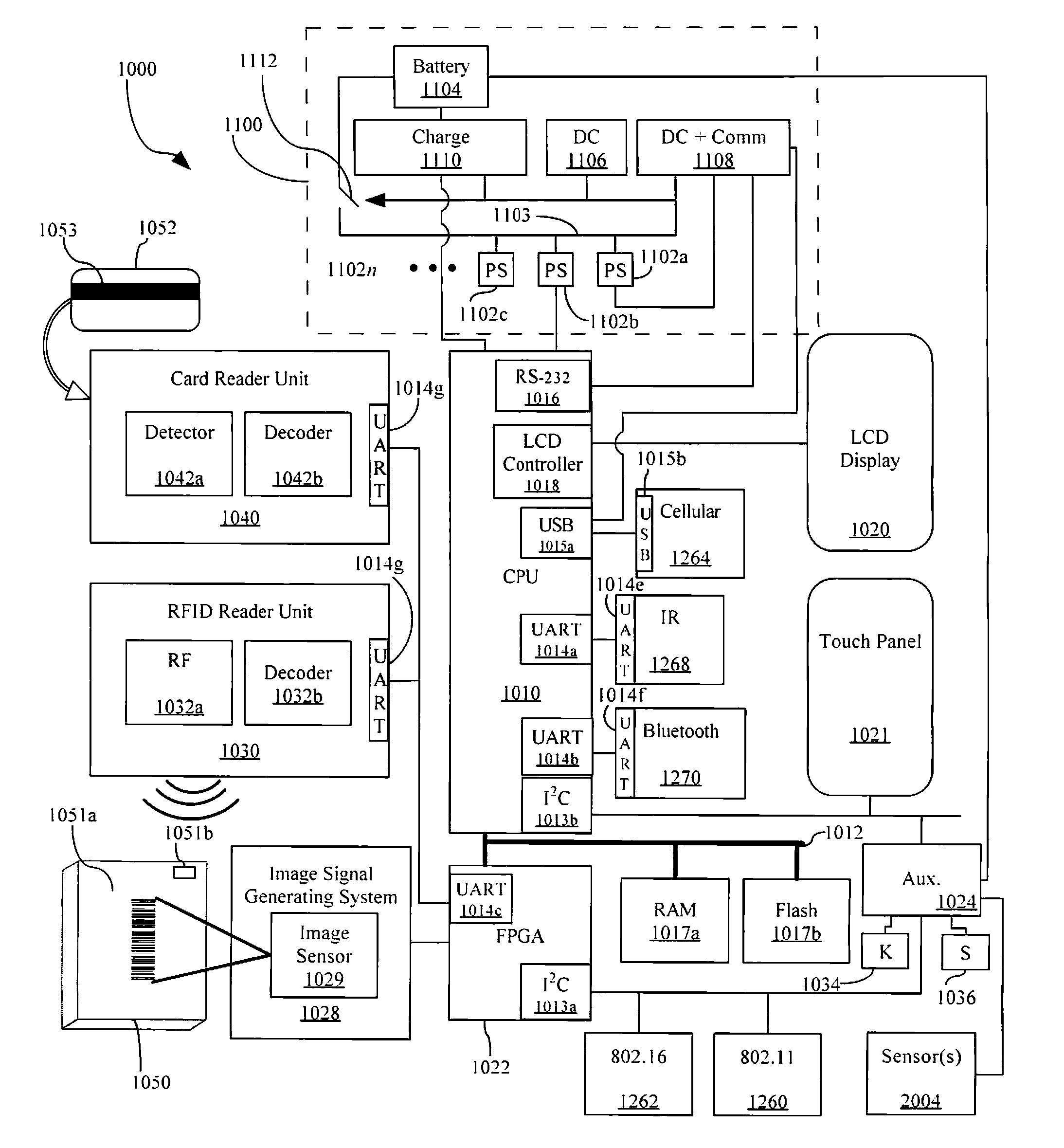
Apparatus and methods for monitoring one or more portable data terminals
Owner:HAND HELD PRODS
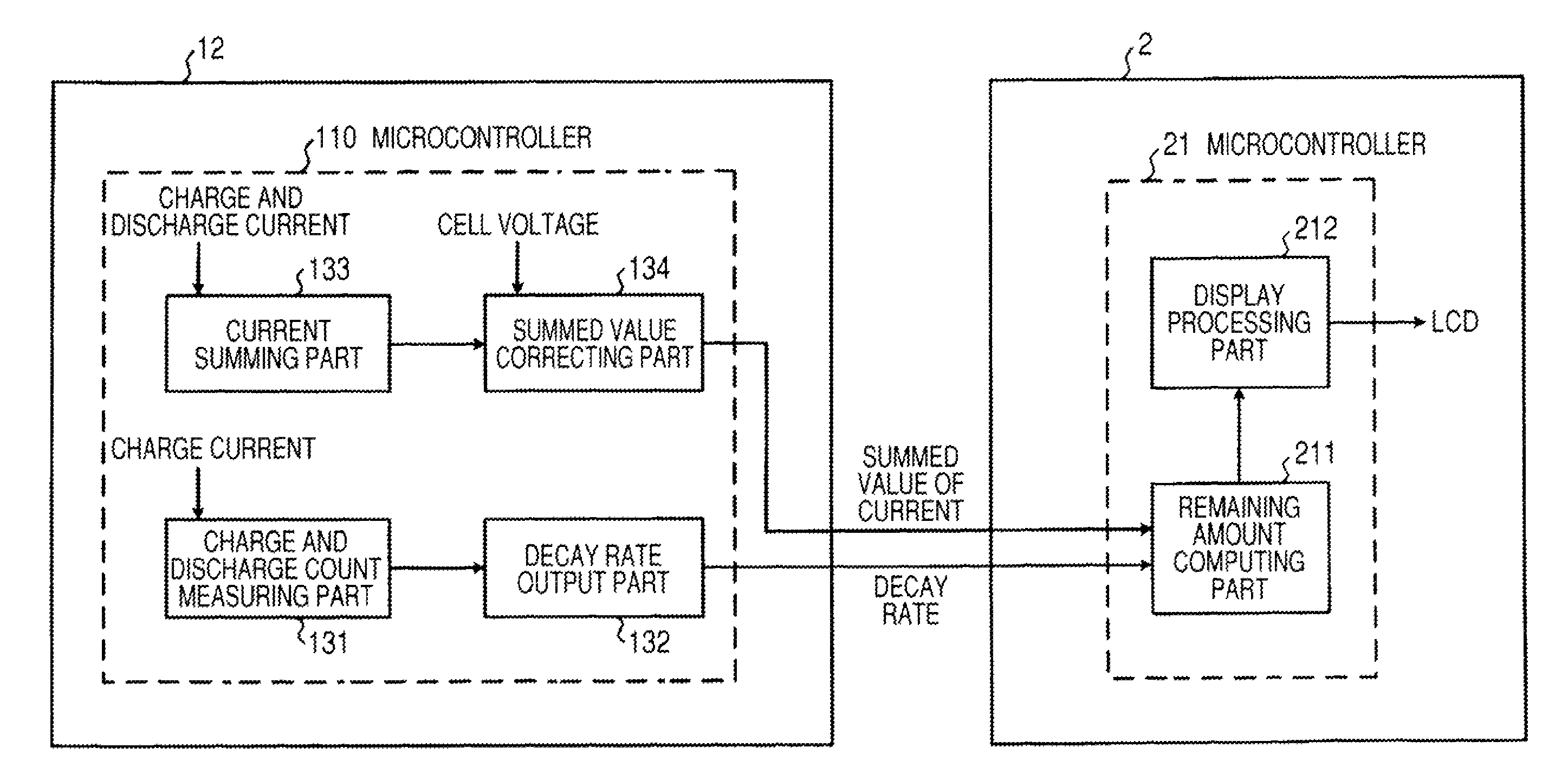
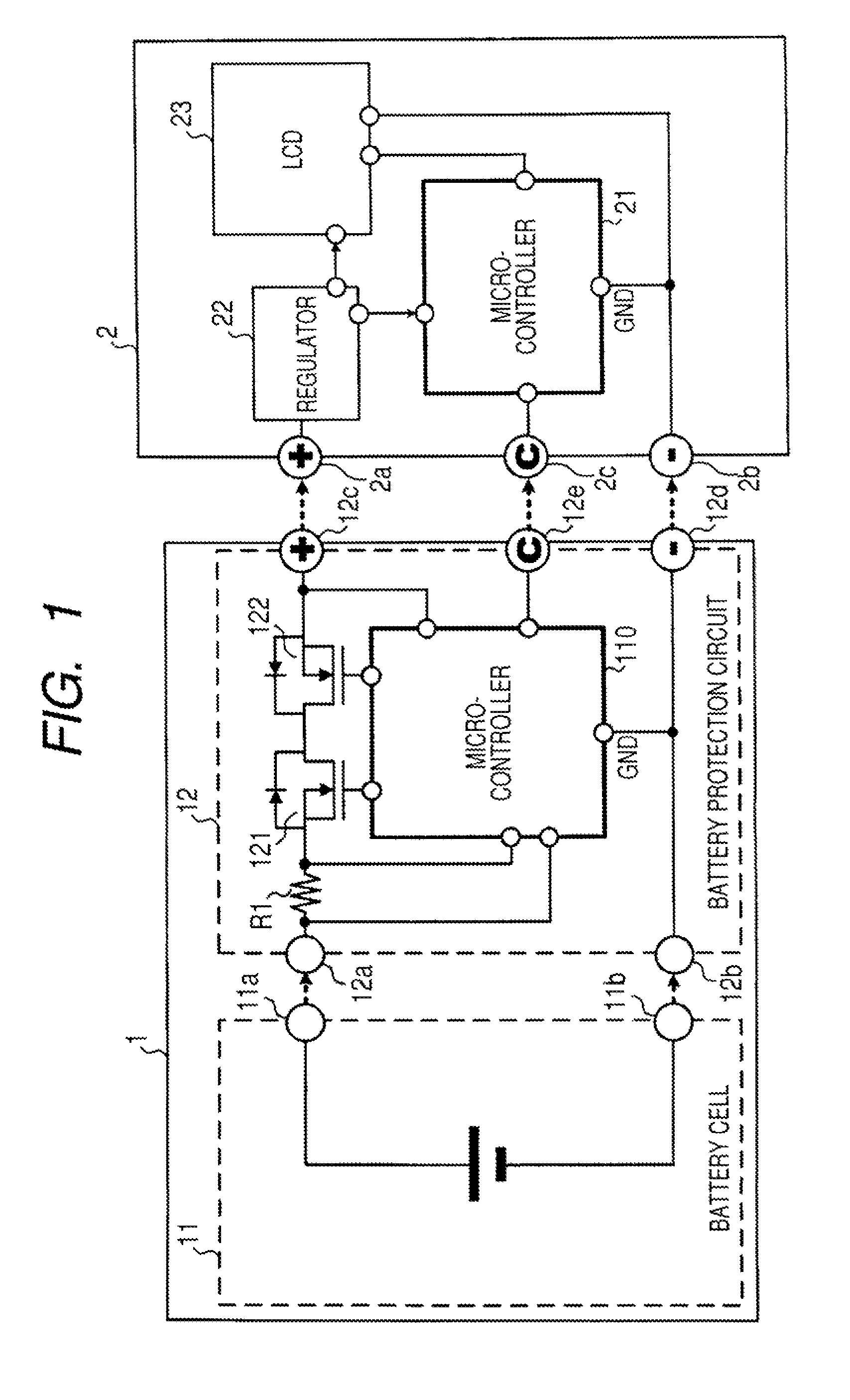
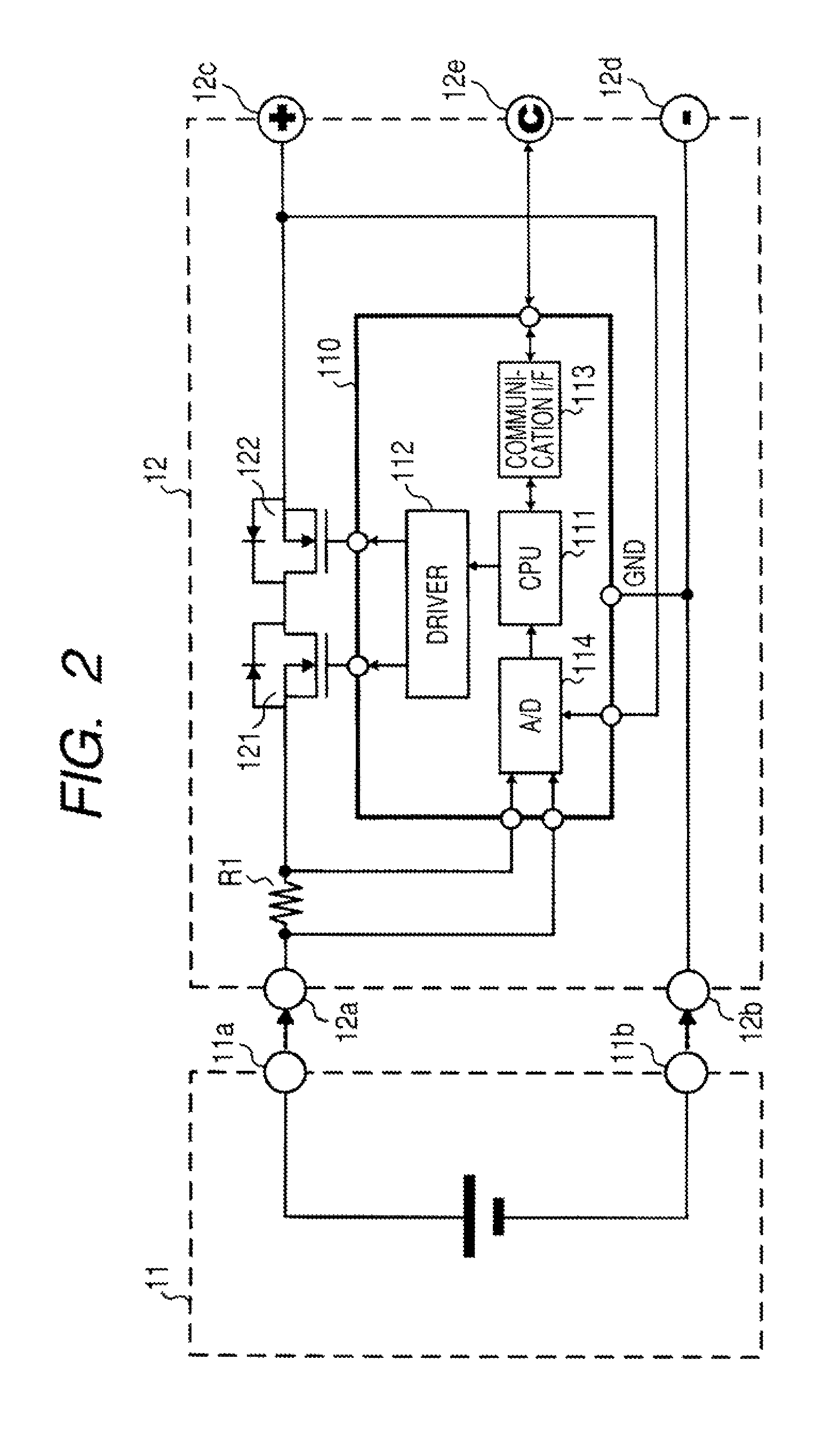
Battery pack, electronic appliance, and method of detecting remaining amount of battery
InactiveUS8359174B2Accurate detectionCircuit monitoring/indicationElectrical testingPower flowCharge current
A battery pack has a charge and discharge count measuring part (131) configured to measure the number of times of charges and discharges of a secondary battery based on the summed value of the charge current for the secondary battery, and a decay rate output part (132) configured to compute a decay rate that indicates a degree of decay of the secondary battery based on the number of times of charges and discharges measured by the charge and discharge count measuring part (131) and to output it to a device being a discharge load. For example, the charge and discharge count measuring part (131) repeatedly sums the detected values of the charge current to a predetermined threshold, and counts up the number of times of charges and discharges every time when the summed value reaches the threshold. Accordingly, even though charges and discharges are repeated at finer steps in a relatively narrow voltage range, the number of times of charges and discharges can be counted accurately, and the computing accuracy of the decay rate is improved. In the battery pack in which the secondary battery is accommodated, parameters for detecting the remaining amount of the battery are detected more accurately.
Owner:SONY CORP
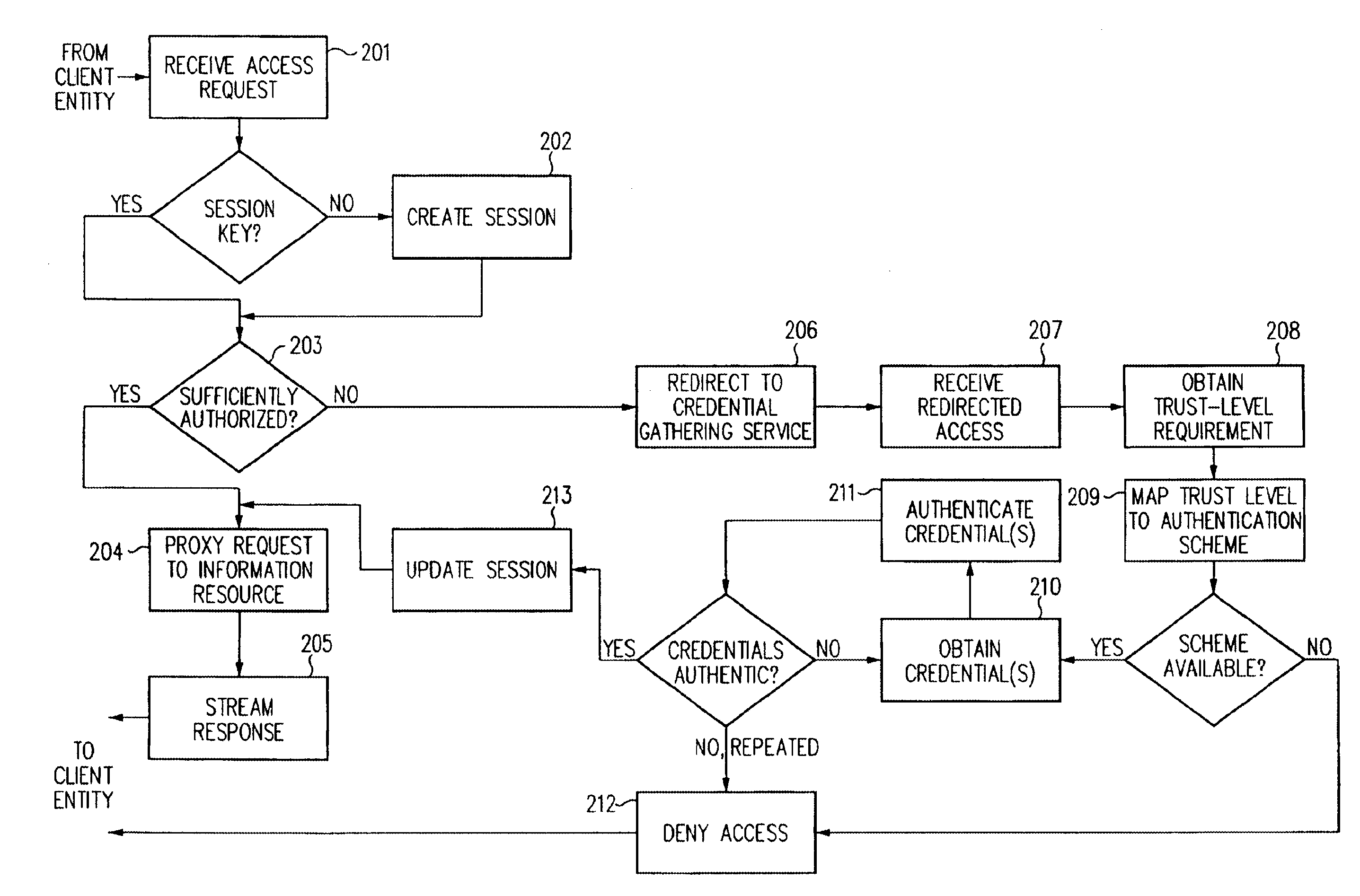
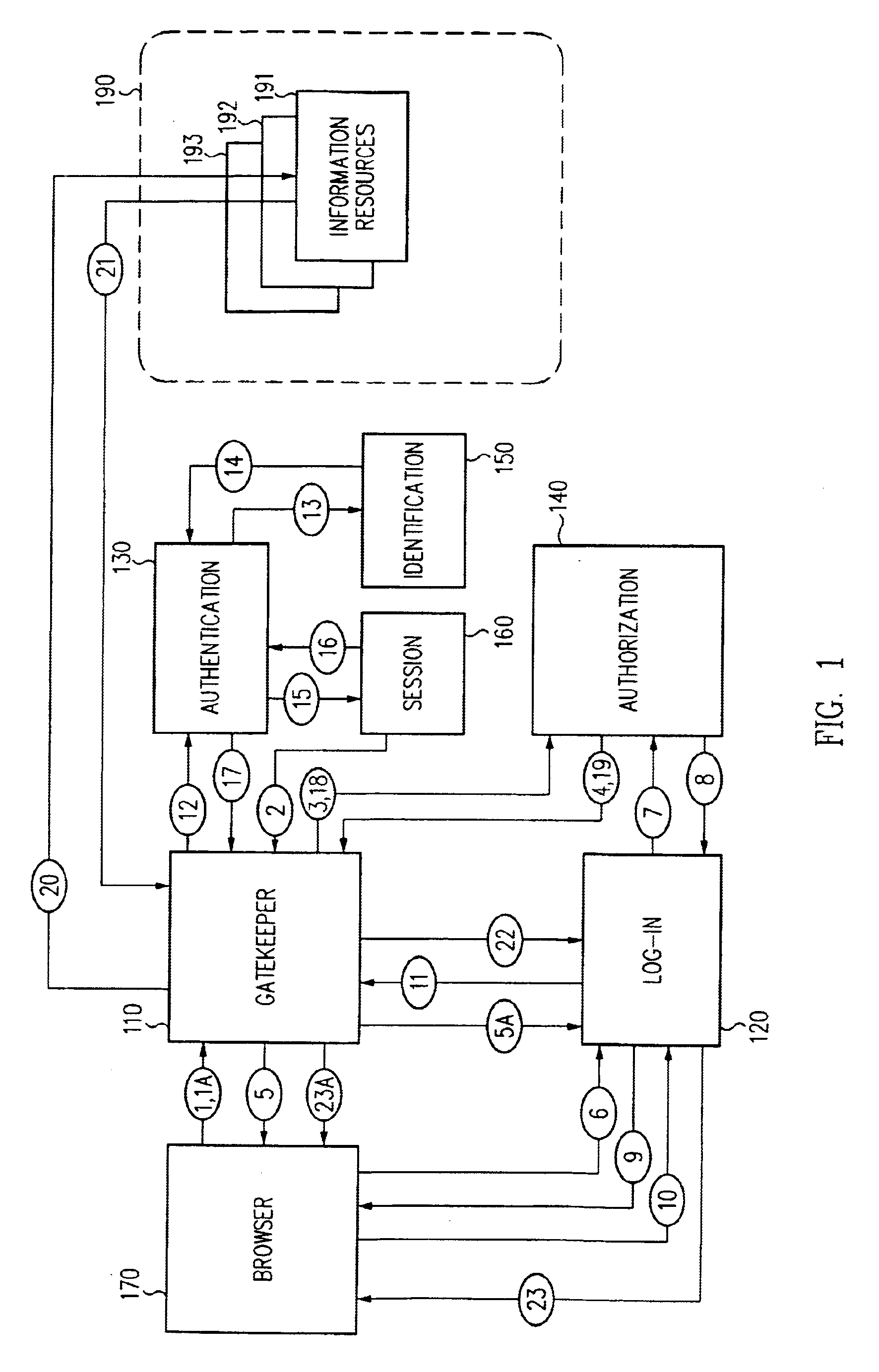
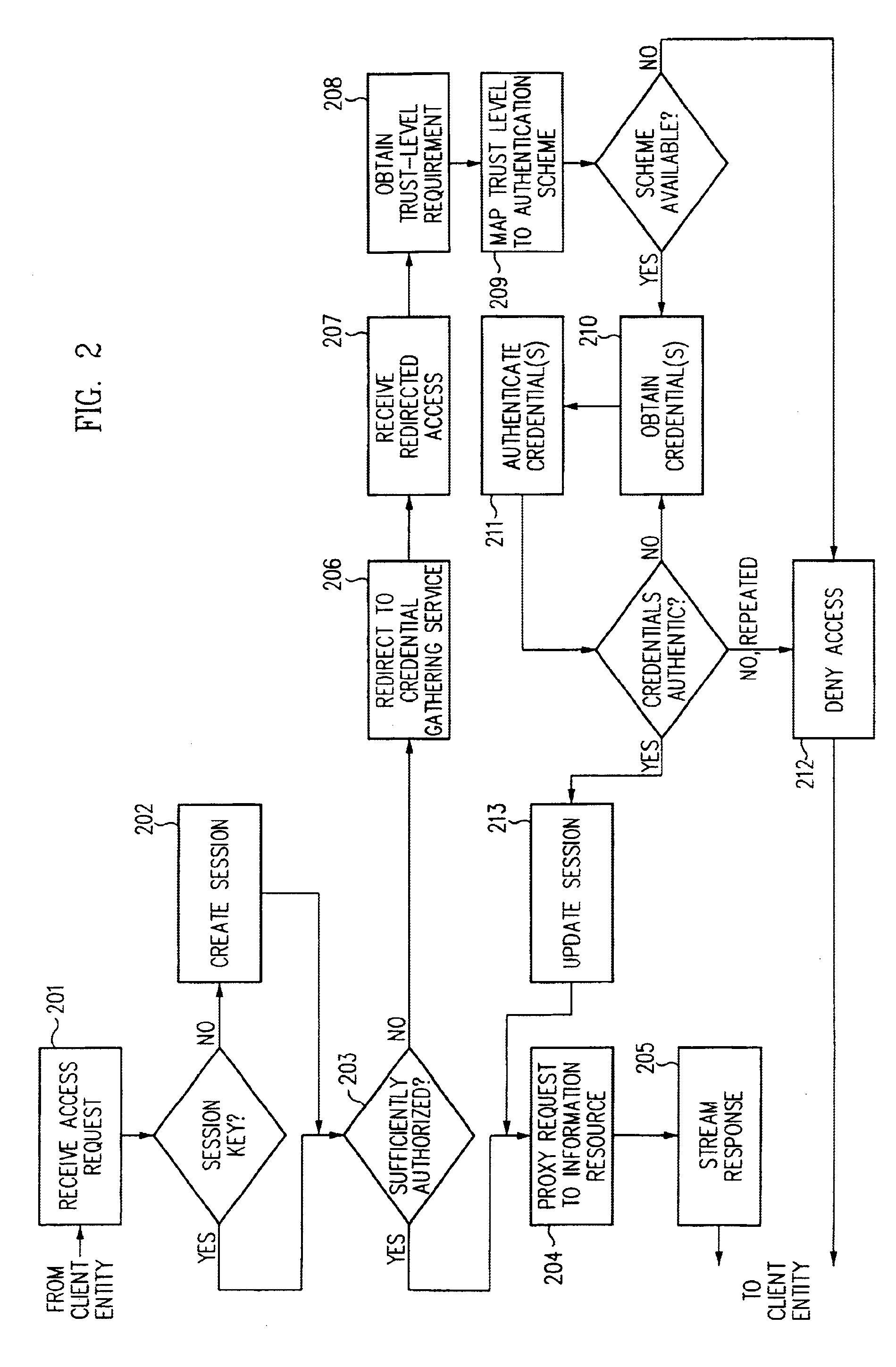
Single sign-on framework with trust-level mapping to authentication requirements
InactiveUS6892307B1Digital data processing detailsUser identity/authority verificationPasswordInformation resource
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels and a log-on service obtains credentials for an entity commensurate with the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:ORACLE INT CORP
System for obtaining vehicular information
InactiveUS20050273218A1Low costPrecise positioningVehicle testingVehicle seatsDirectional antennaRadio frequency
System for obtaining information about a vehicle or a component therein includes sensors arranged to generate and transmit a signal upon receipt and detection of a radio frequency (RF) signal and a multi-element, switchable directional antenna array. Each antenna element is directed toward a respective sensor and transmitter RF signals toward that sensor and receive return signals therefrom. A control mechanism controls transmission of the RF signals from the antenna elements, e.g., causes the antenna elements to be alternately switched on in order to sequentially transmit the RF signals and receive the return signals from the sensors or cause the antenna elements to transmit the RF signals simultaneously and space the return signals from the sensors via a delay line in circuitry from each antenna element such that each return signal is spaced in time in a known manner without requiring switching of the antenna elements.
Owner:AMERICAN VEHICULAR SCI
Virtual machine with dynamic data flow analysis
ActiveUS20070250930A1Memory loss protectionUnauthorized memory use protectionDynamic data flow analysisNetwork data
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, and concurrently simulate transmission of the network data to a plurality of destination devices.
Owner:FIREEYE SECURITY HLDG US LLC
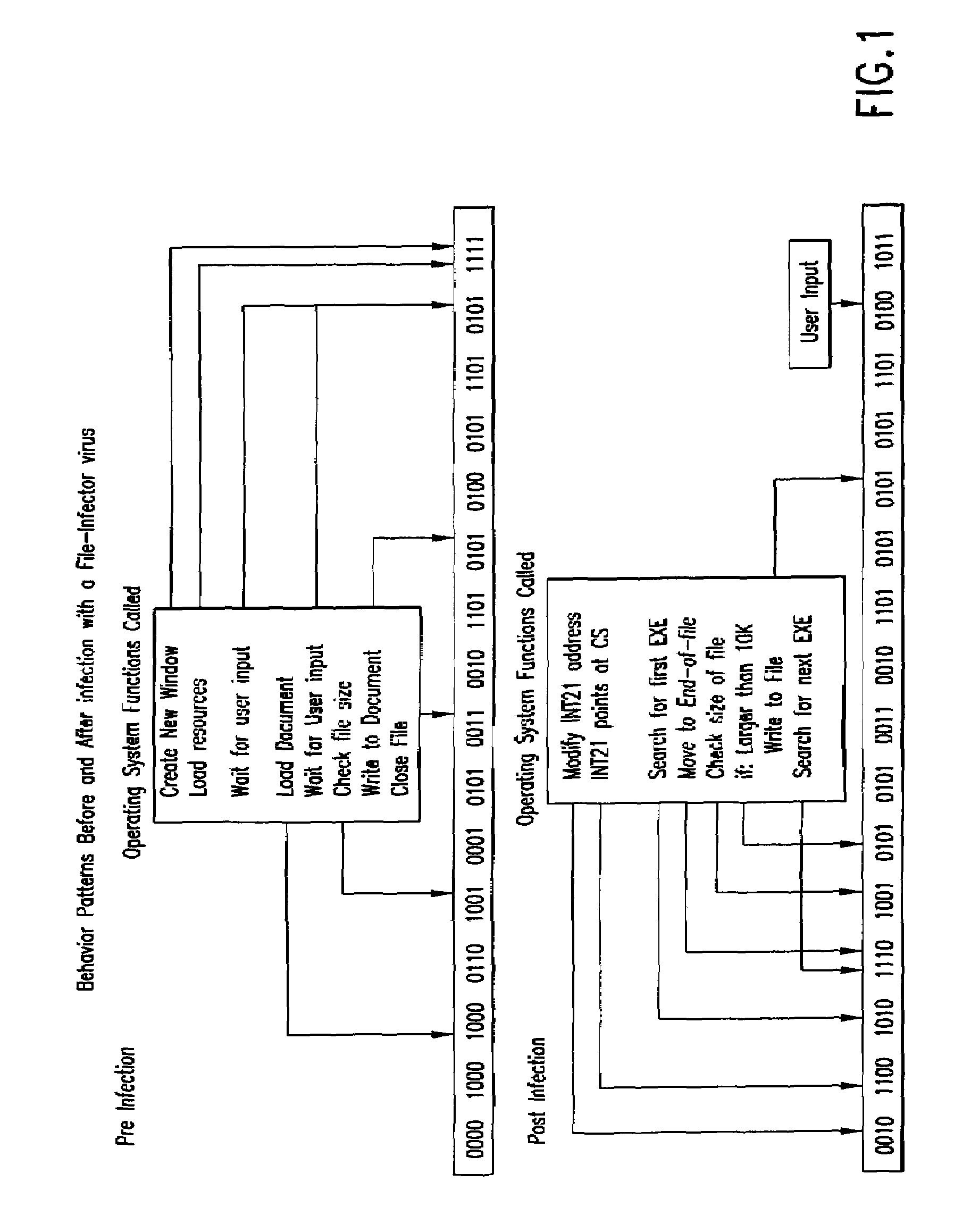
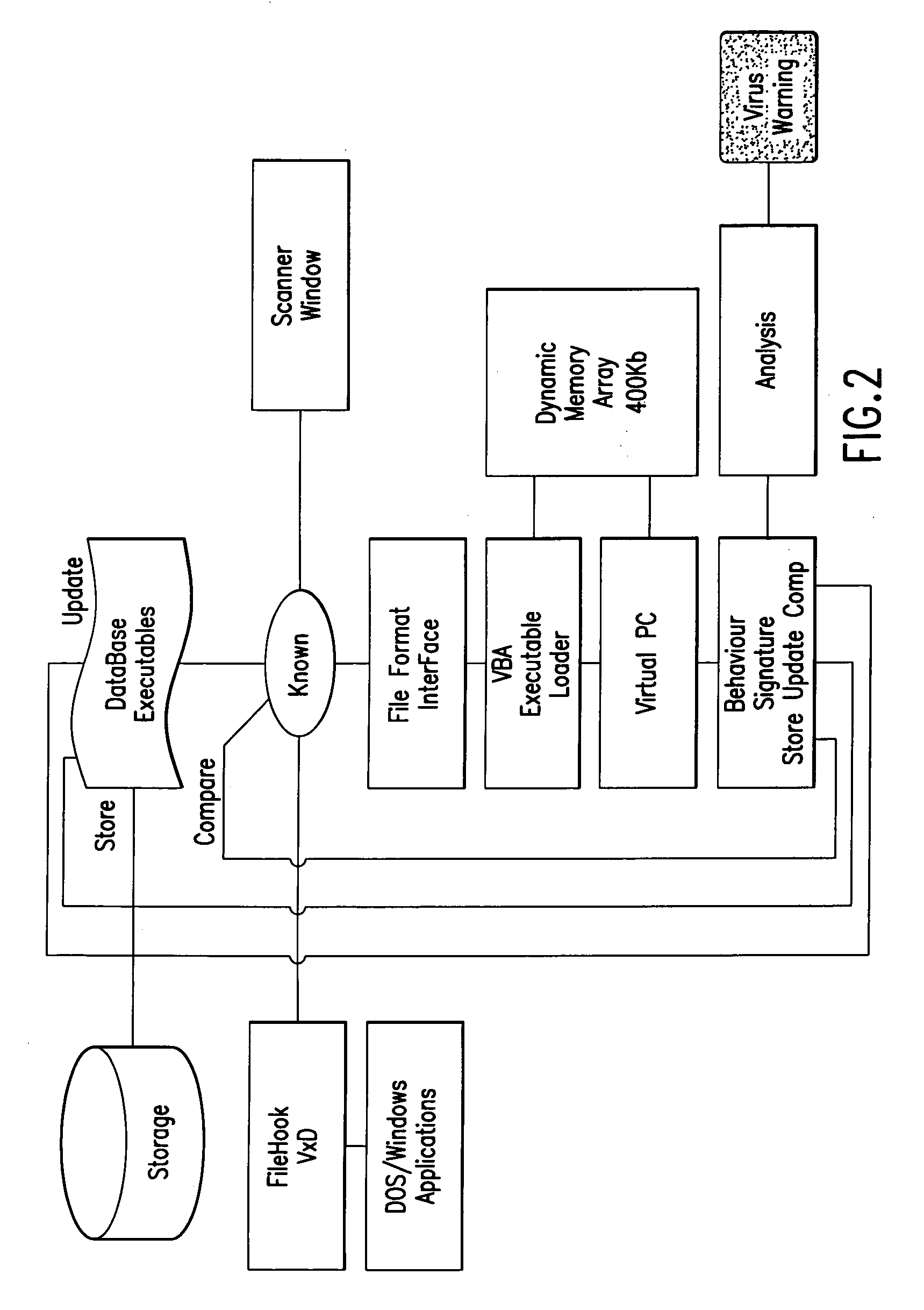
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS7093239B1Memory loss protectionDigital data processing detailsTheoretical computer scienceComputerized system
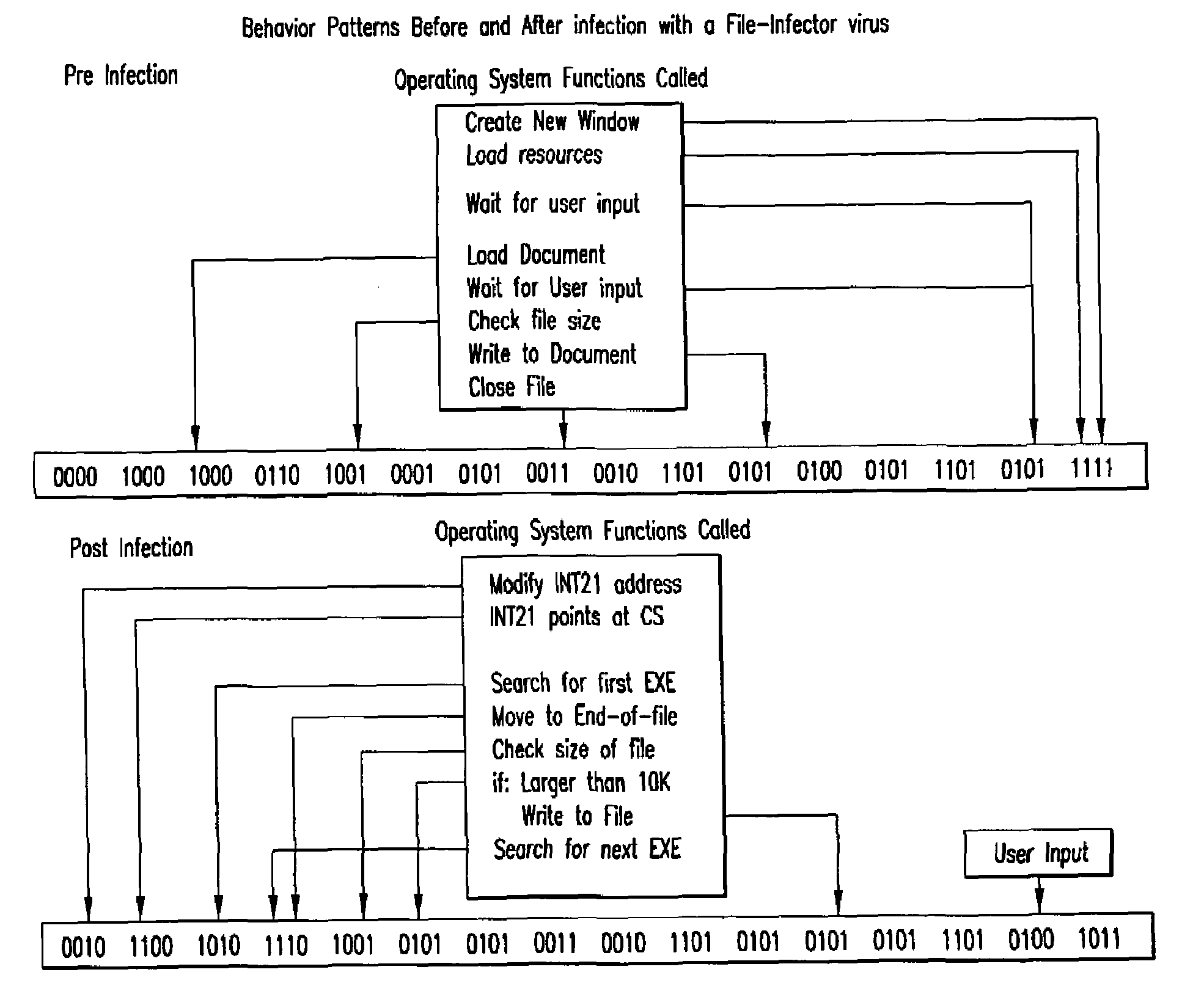
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
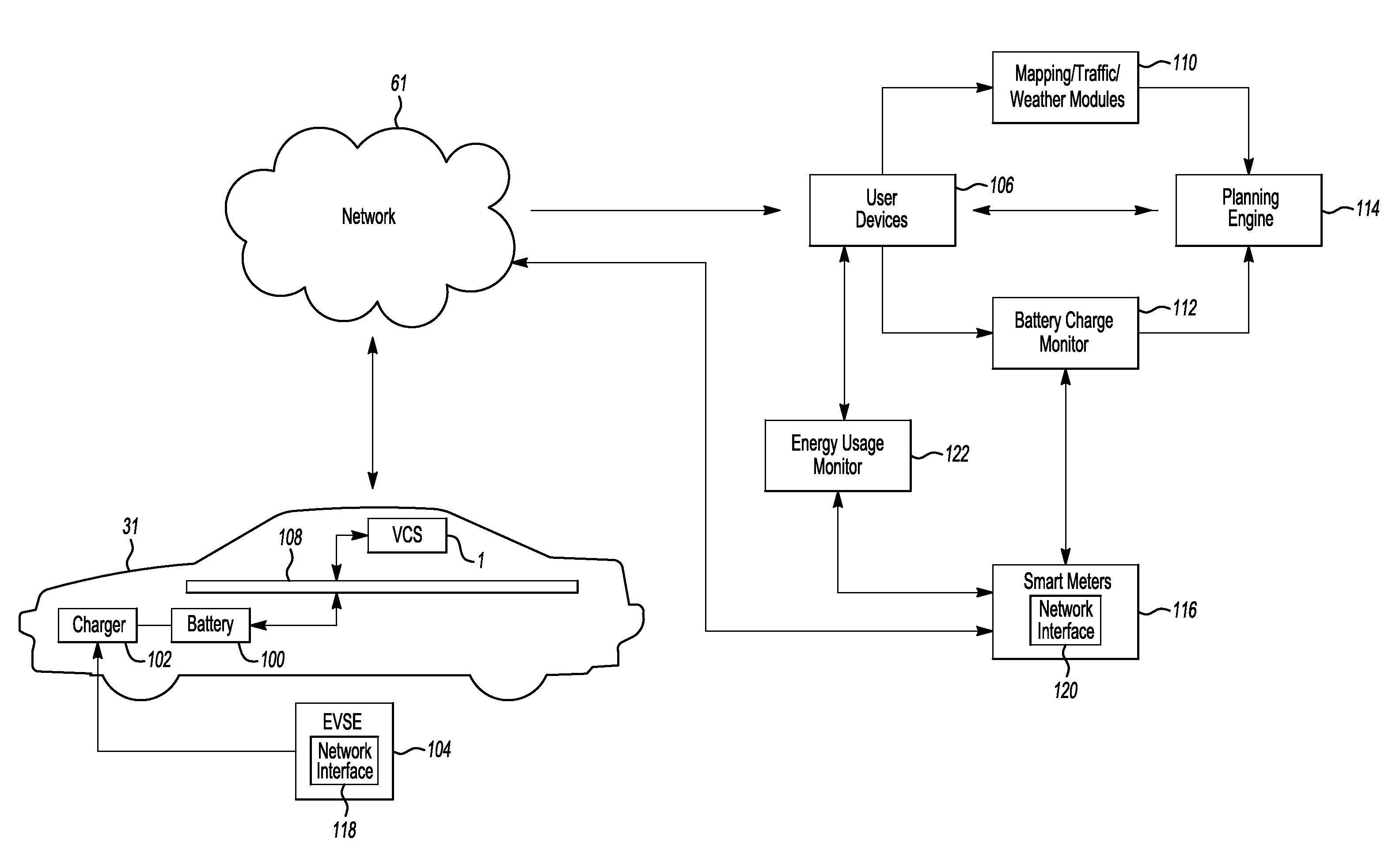
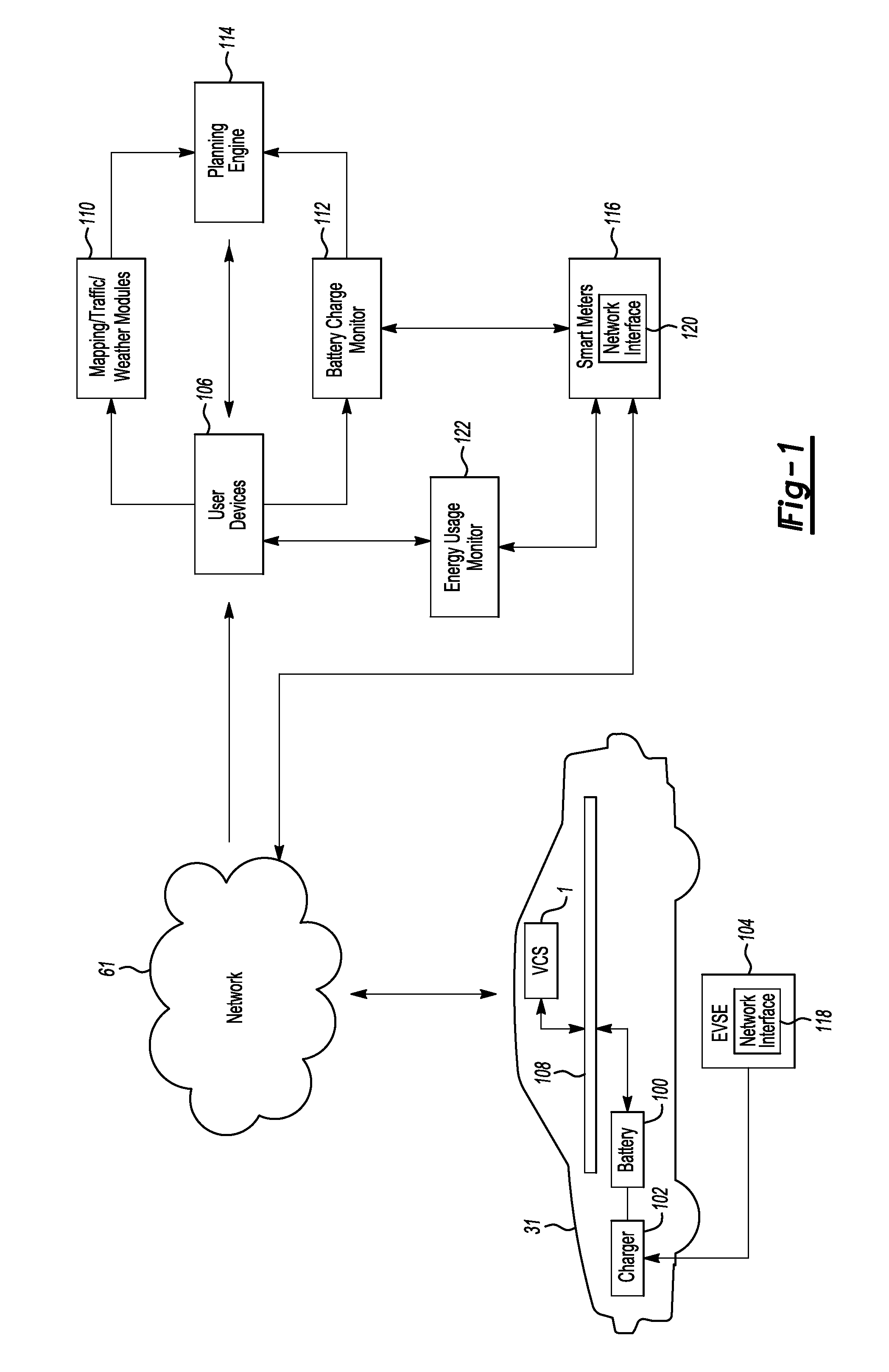
Method and system for monitoring an energy storage system for a vehicle for trip planning
One or more embodiments may include a trip planning system for planning a trip based on the charge of an electric vehicle battery. The trip planning system may include one or more computers located remotely from an electric vehicle which may have one or more battery packs for powering the electric vehicle. The computer(s) may be configured to receive geographic parameters defining a trip and a battery charge status of the one or more electric vehicle battery packs. The computer(s) may be further configured to determine that the trip cannot be completed based on the battery charge status. The computer(s) may additionally be configured to present a battery charge requirement for completing the trip.
Owner:FORD GLOBAL TECH LLC
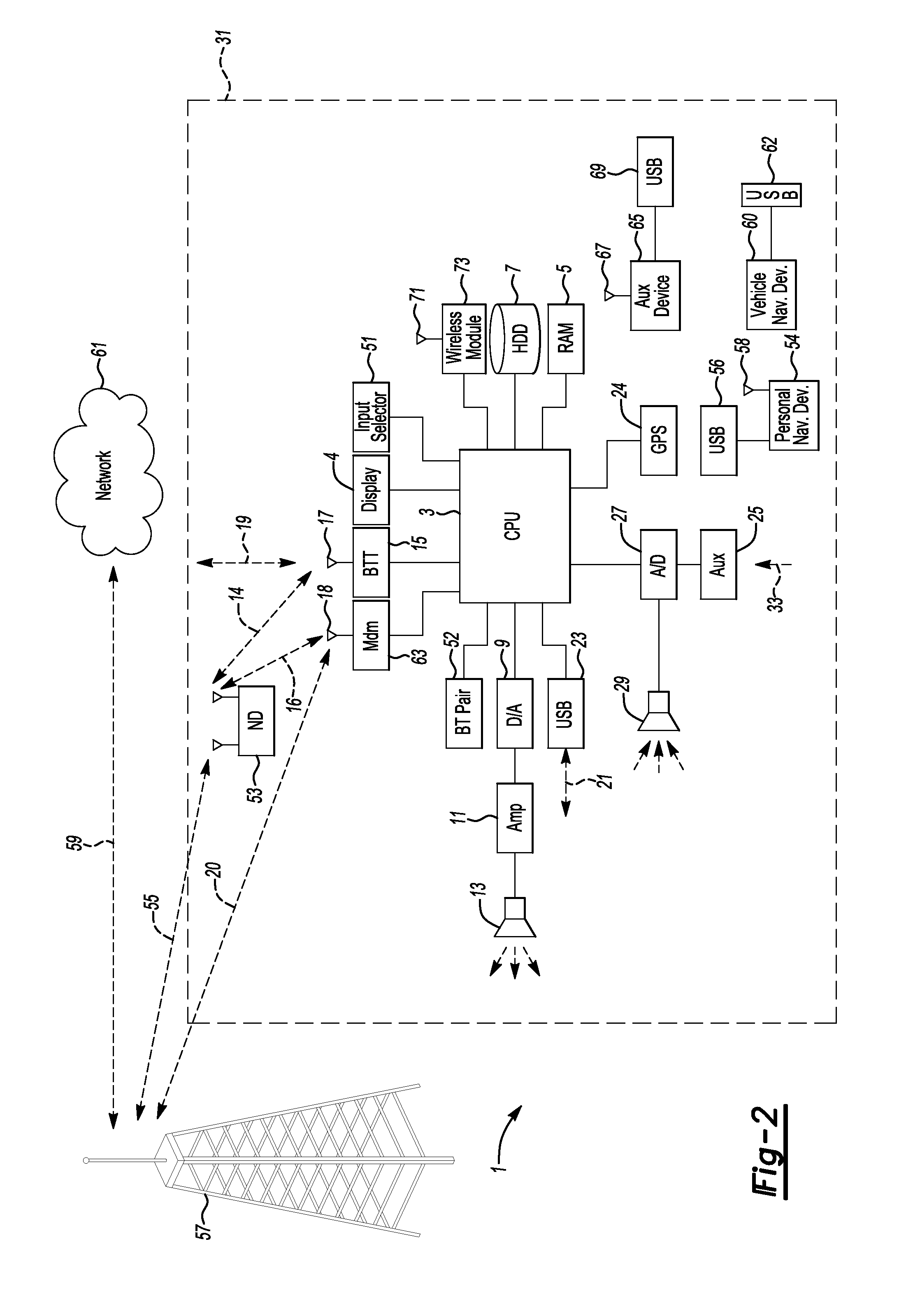
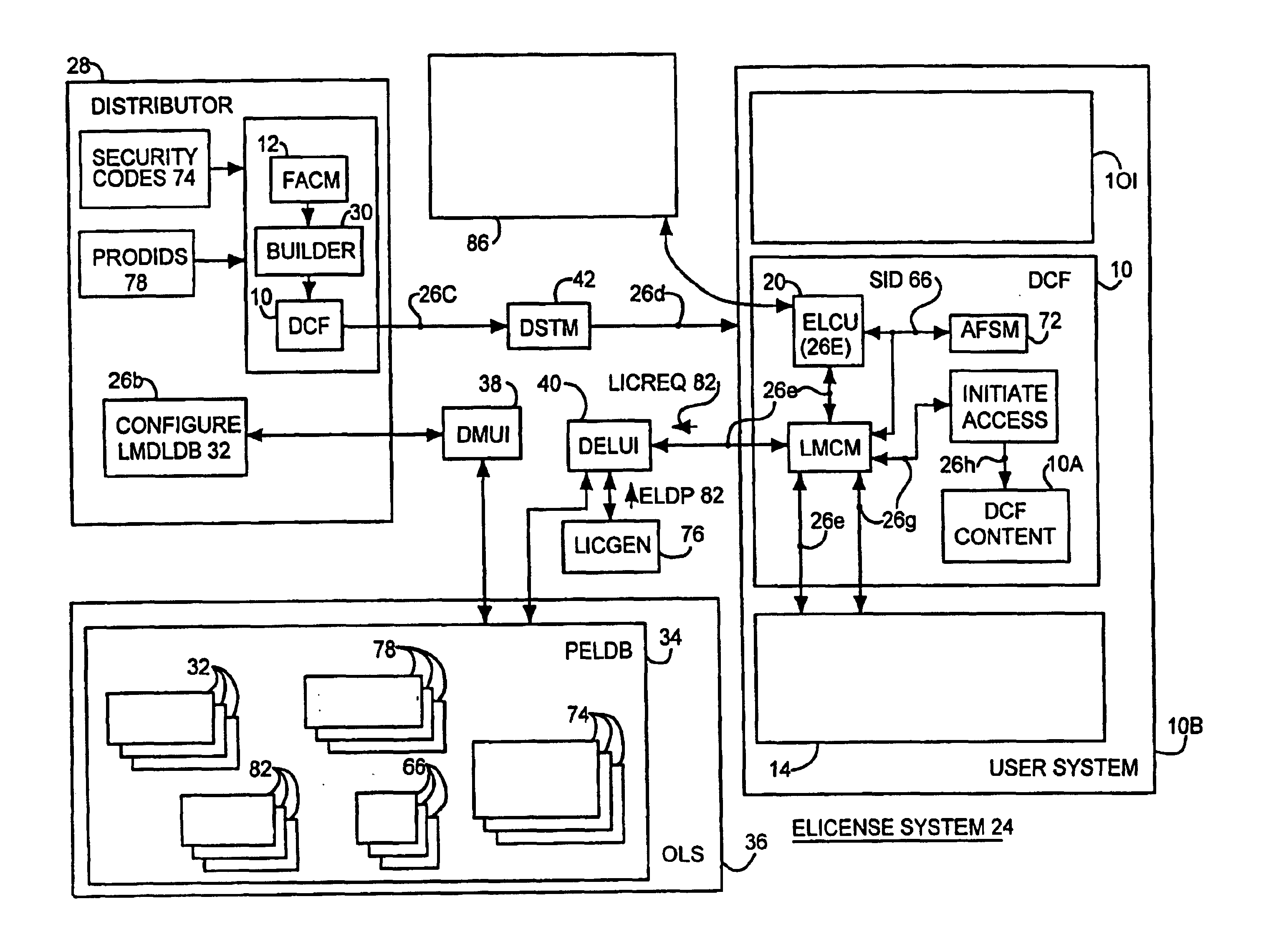
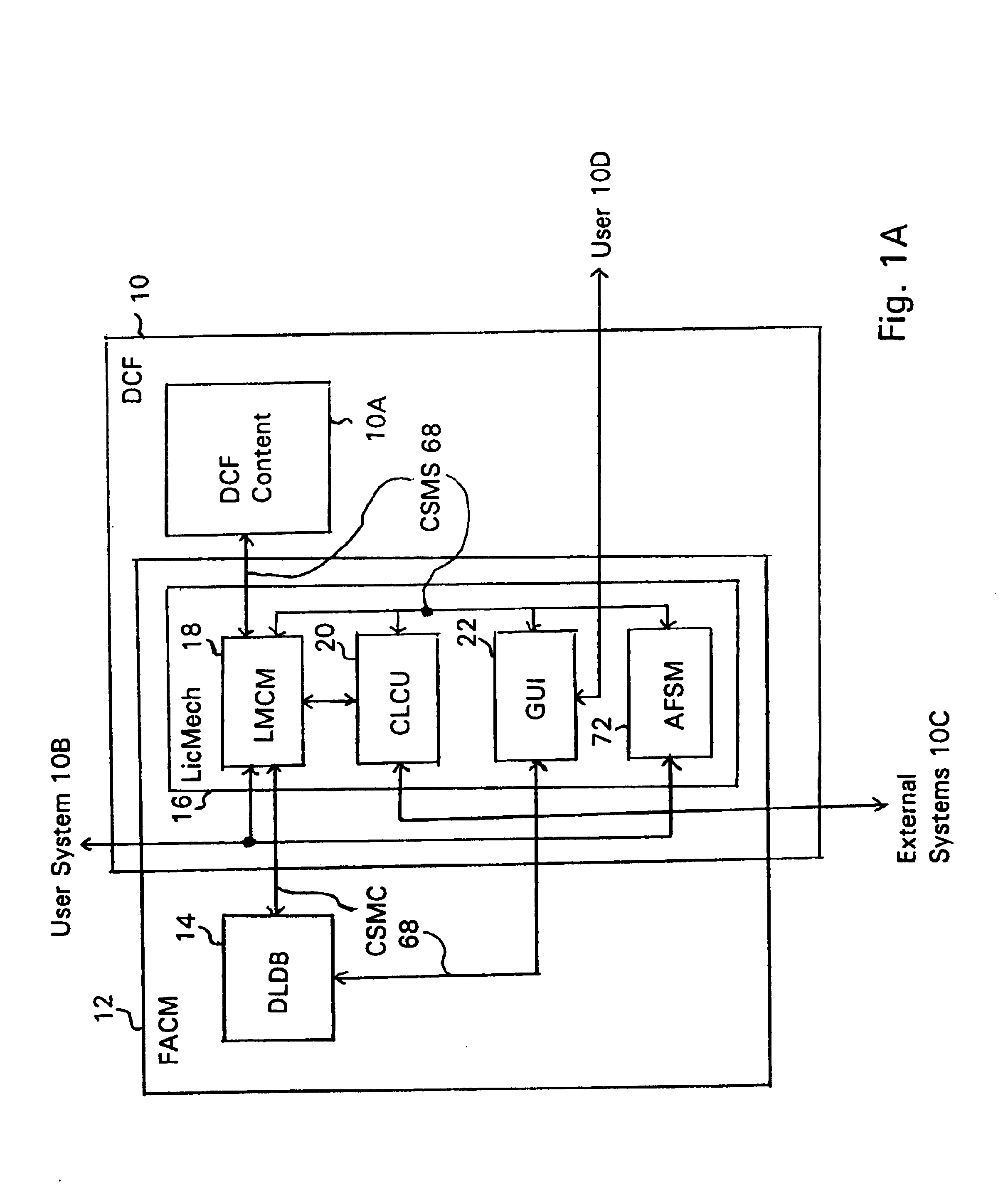
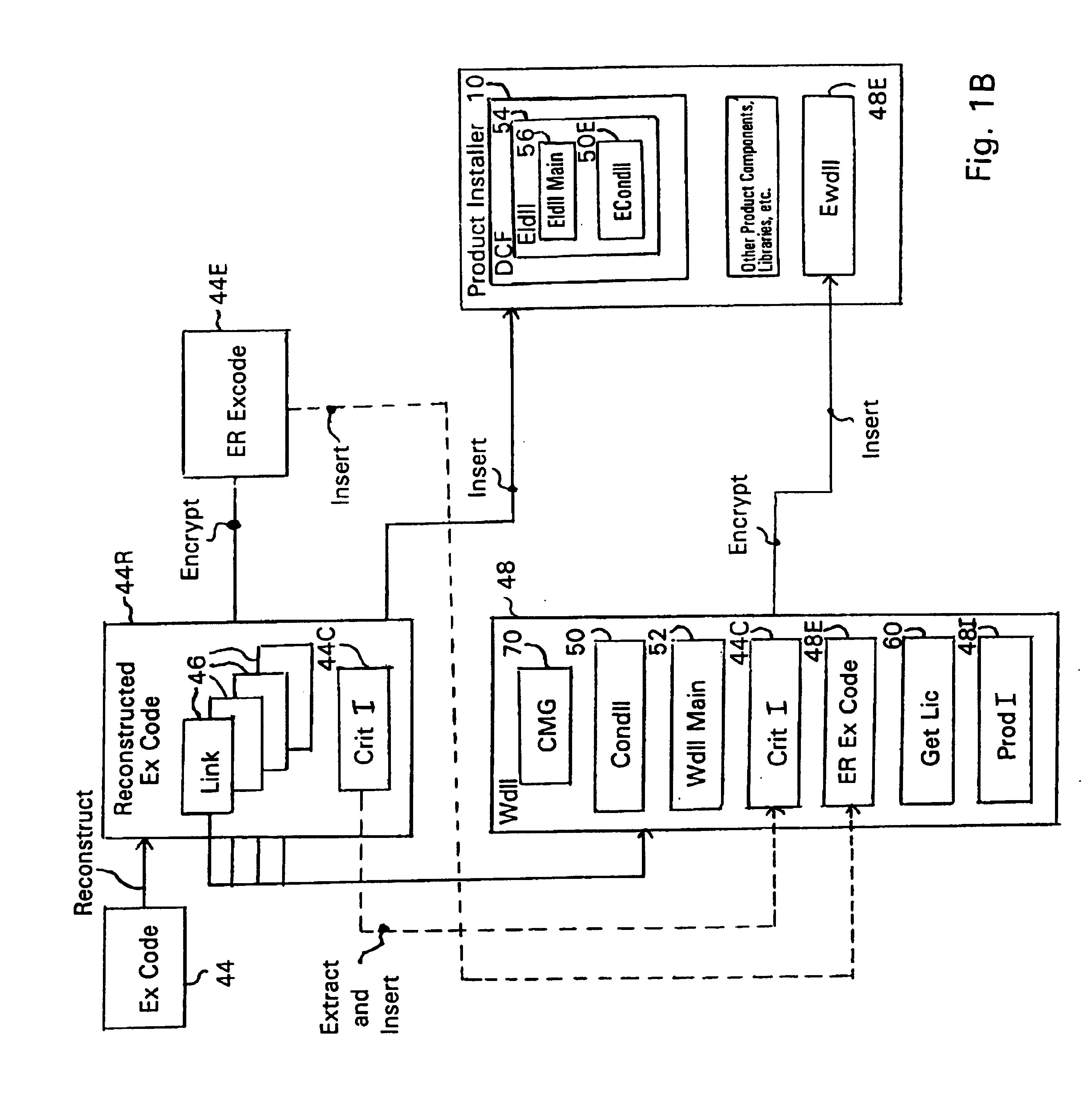
System and embedded license control mechanism for the creation and distribution of digital content files and enforcement of licensed use of the digital content files
A digital content file including a license control mechanism controlling the licensed use of digital content and a system and method for distributing licensable digital content files and licenses. A digital content file includes a digital content, which may be executable code or data, an embedded file access control mechanism and a dynamic license database associated with the file access mechanism for storing license information used by the file access control mechanism in controlling use of the digital content. The file access control mechanism includes a license monitor and control mechanism communicating with the dynamic license database and controlling use of the digital content and a license control utility providing communications between a user system and an external system to communicate license definition information and includes a graphical user interface. License information may be stored initially in the dynamic license database or provided from an external system. The system allows the distribution of digital content files and the acquisition of licenses with seamless transaction processing through an order processing system generating an order identification and authorization for a license and a product configuration and order database containing license management databases associated with the digital content files and containing license information to be transmitted to a user system upon receipt of an order identifier. The product configuration and order database also generates a license record for each transaction.
Owner:VIATECH TECH
Rental/car-share vehicle access and management system and method
ActiveUS20130317693A1Reduce the time required for installationImprove reliabilityVehicle testingTicket-issuing apparatusMobile appsTablet computer
A rental / car-share (RCS) vehicle access and management system and method, in some embodiments, utilizes barcodes, QR codes (or NFC / RFID), GPS, and a mobile app coupled with a wireless network to enable customers to bypass the reservation desk and pickup and drop off reserved RCS vehicles using a mobile phone, tablet or laptop. The QR code, RFID, or NFC communication with the mobile application allows for identification of the vehicle by a mobile application, which, if authorized, can access the vehicle via a temporary access code issued by remote servers. The remote servers and / or mobile application communicates with a control module that plugs into the on-board diagnostics module of the rental / car-share (RCS) vehicle and includes a host processing unit with a processor, an accelerometer, data storage, a GPS with internal GPS antenna; a wireless modem with internal antenna, and CAN bus transceivers connected with the processor, and a USB programmable interface.
Owner:ENTERPRISE HOLDINGS
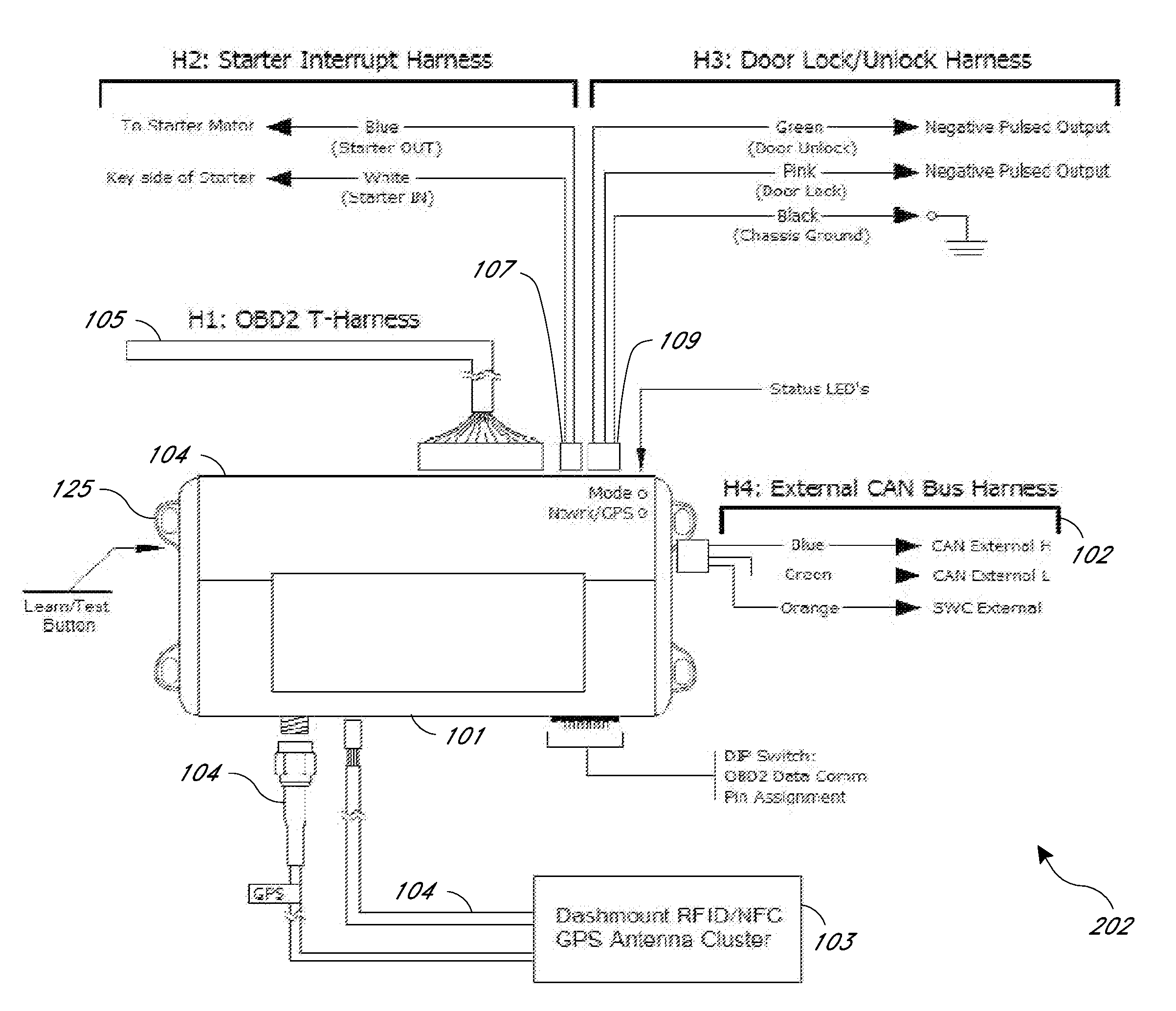
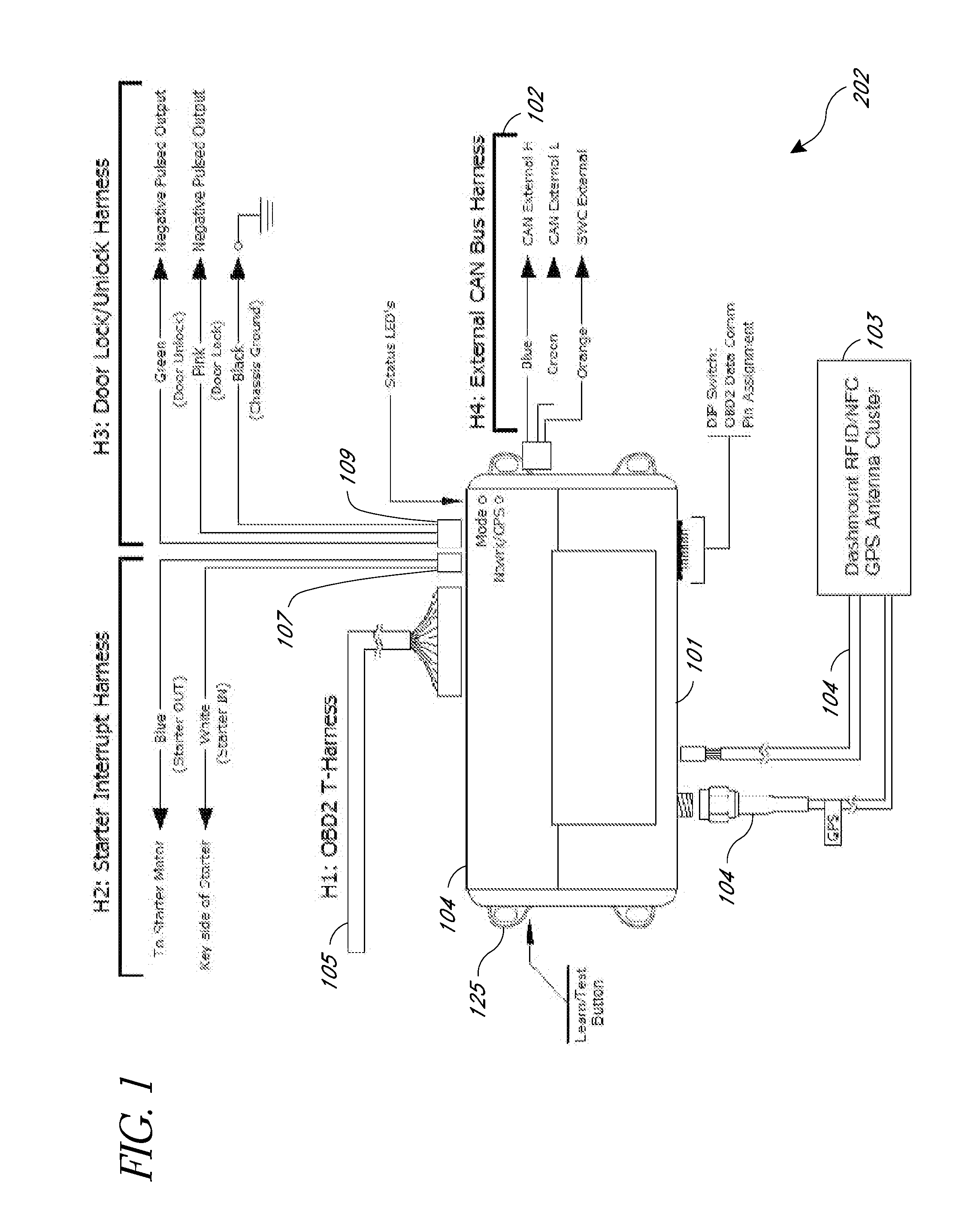
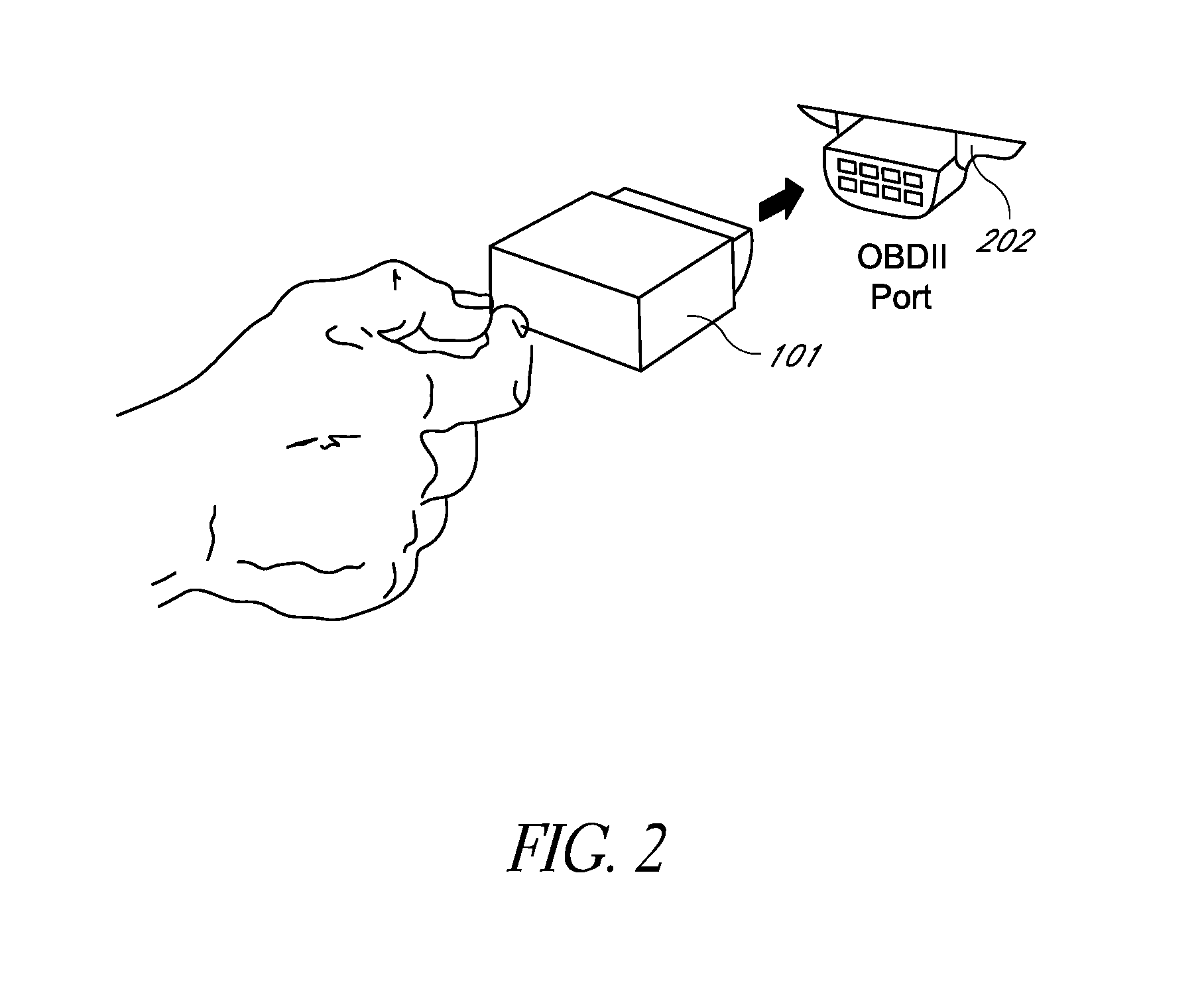
Systems and methods for linking vehicles to telematics-enabled portable devices
InactiveUS20110153367A1Prevent removalVehicle speed is limitedVehicle testingFinanceAccelerometer dataData port
Systems and methods are disclosed herein for transmitting telematics data from a vehicle. The systems include a smartphone holder that provides a communications link between a smartphone and a vehicle computer, through the smartphone dataport and the vehicle onboard diagnostics (OBD) port. The smartphone holder is configured to keep the smartphone in a stable, known position and orientation with respect to the vehicle, such that data from an accelerometer in the smartphone can be calibrated. The smartphone accelerometer data and telematics data from vehicle telematics sensors is then transmitted via the smartphone or stored locally.
Owner:HARTFORD FIRE INSURANCE
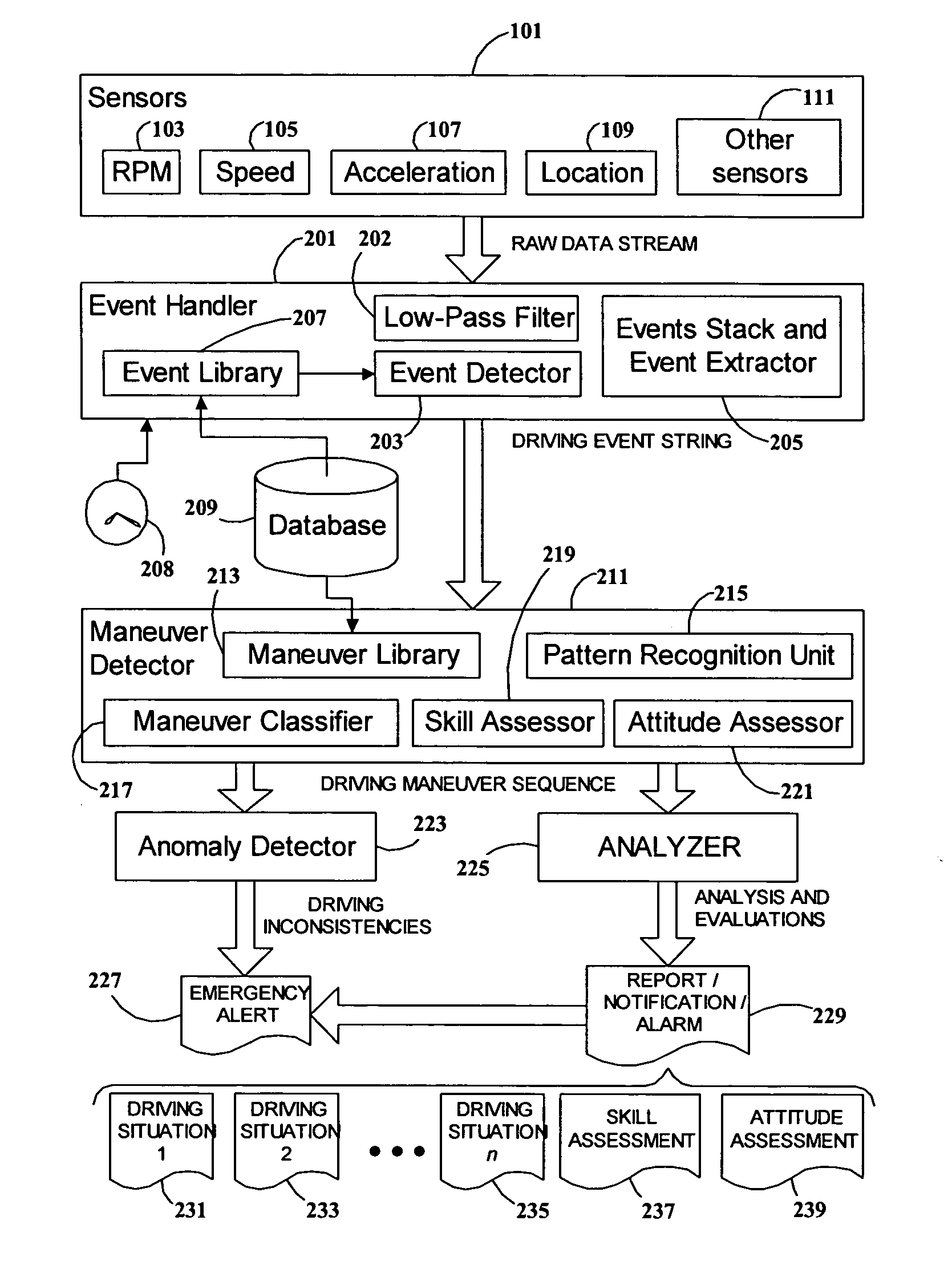
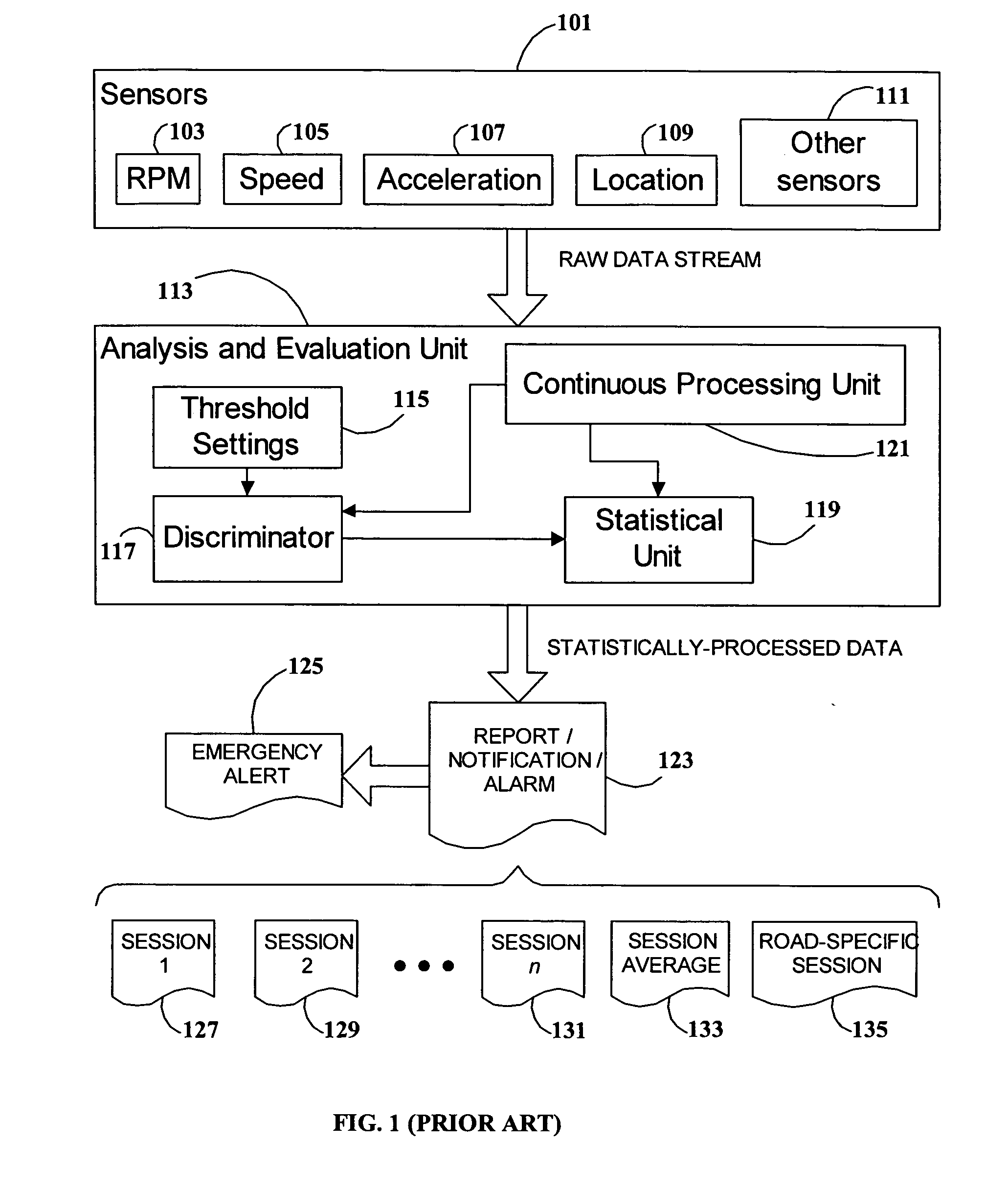
System and method for vehicle driver behavior analysis and evaluation
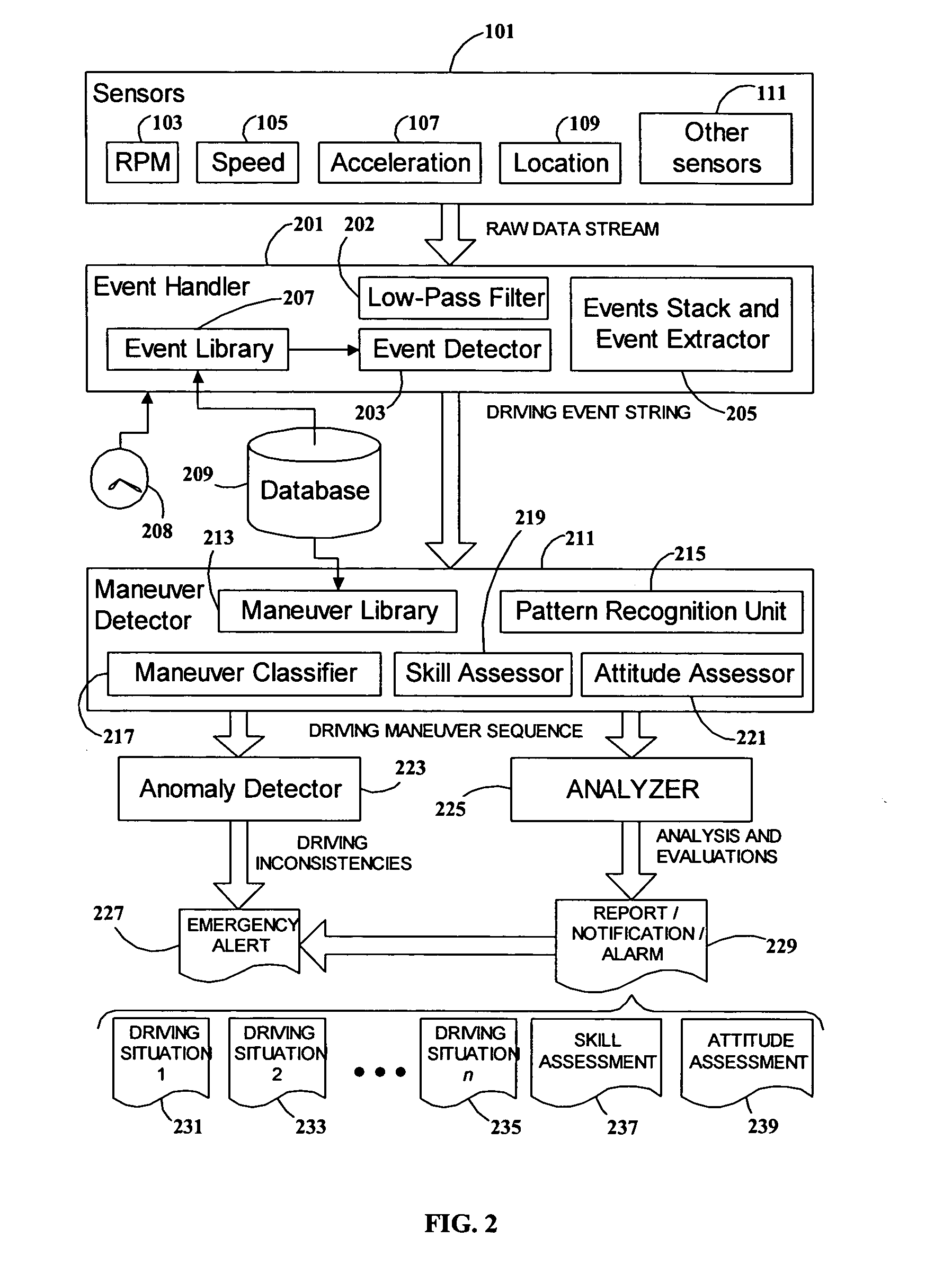
ActiveUS20050131597A1More informationEasy to useVehicle testingRegistering/indicating working of vehiclesData streamDriver/operator
A system and method for analyzing and evaluating the performance and attitude of a motor vehicle driver. A raw data stream from a set of vehicle sensors is filtered to eliminate extraneous noise, and then parsed to convert the stream into a string of driving event primitives. The string of driving events is then processed by a pattern-recognition system to derive a sequence of higher-level driving maneuvers. Driving maneuvers include such familiar procedures as lane changing, passing, and turn and brake. Driving events and maneuvers are quantified by parameters developed from the sensor data. The parameters and timing of the maneuvers can be analyzed to determine skill and attitude factors for evaluating the driver's abilities and safety ratings. The rendering of the data into common driving-related concepts allows more accurate and meaningful analysis and evaluation than is possible with ordinary statistical threshold-based analysis.
Owner:GREENROAD DRIVING TECH LTD
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com