Patents
Literature
10490 results about "Byte" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The byte is a unit of digital information that most commonly consists of eight bits. Historically, the byte was the number of bits used to encode a single character of text in a computer and for this reason it is the smallest addressable unit of memory in many computer architectures.
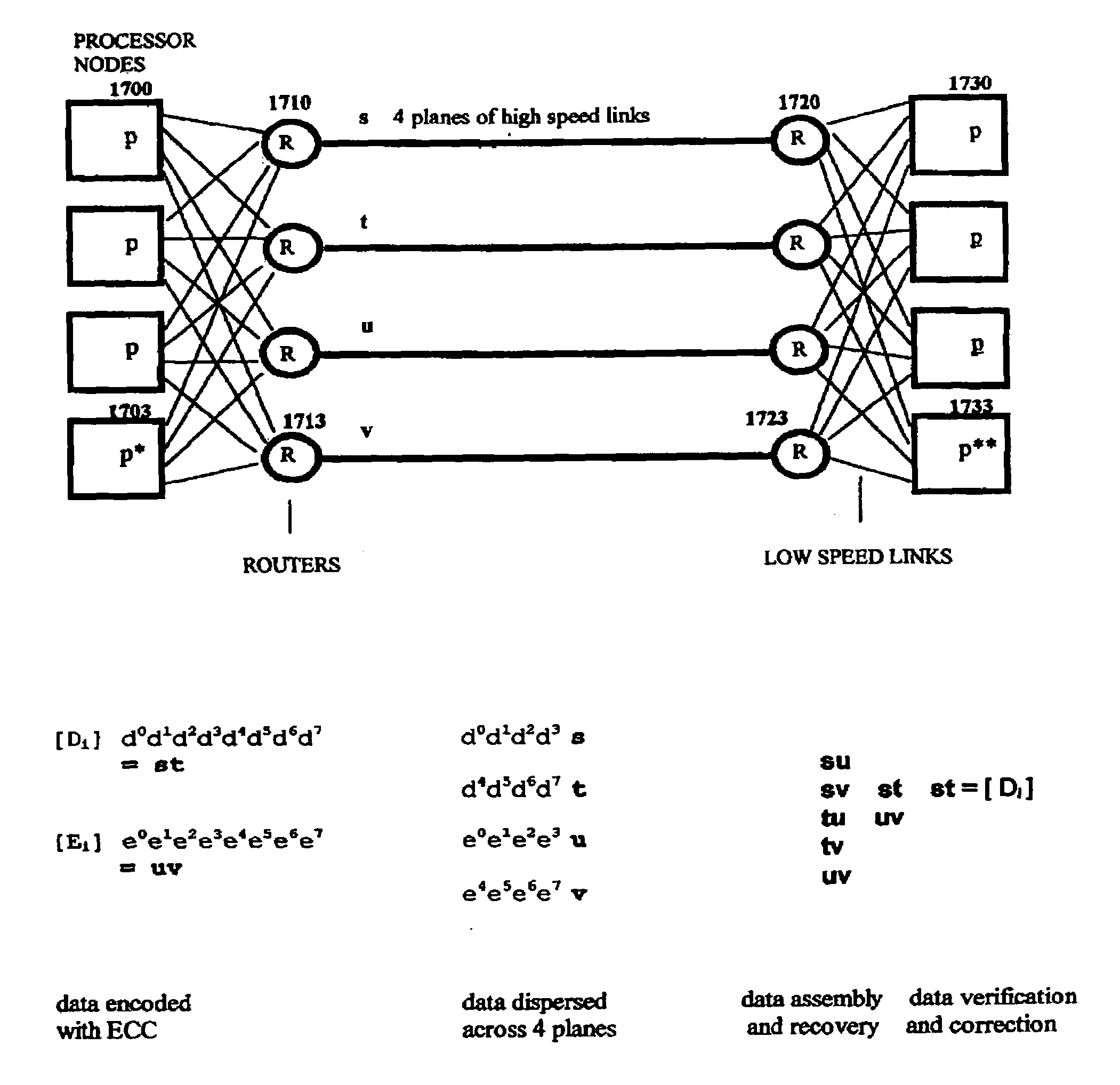
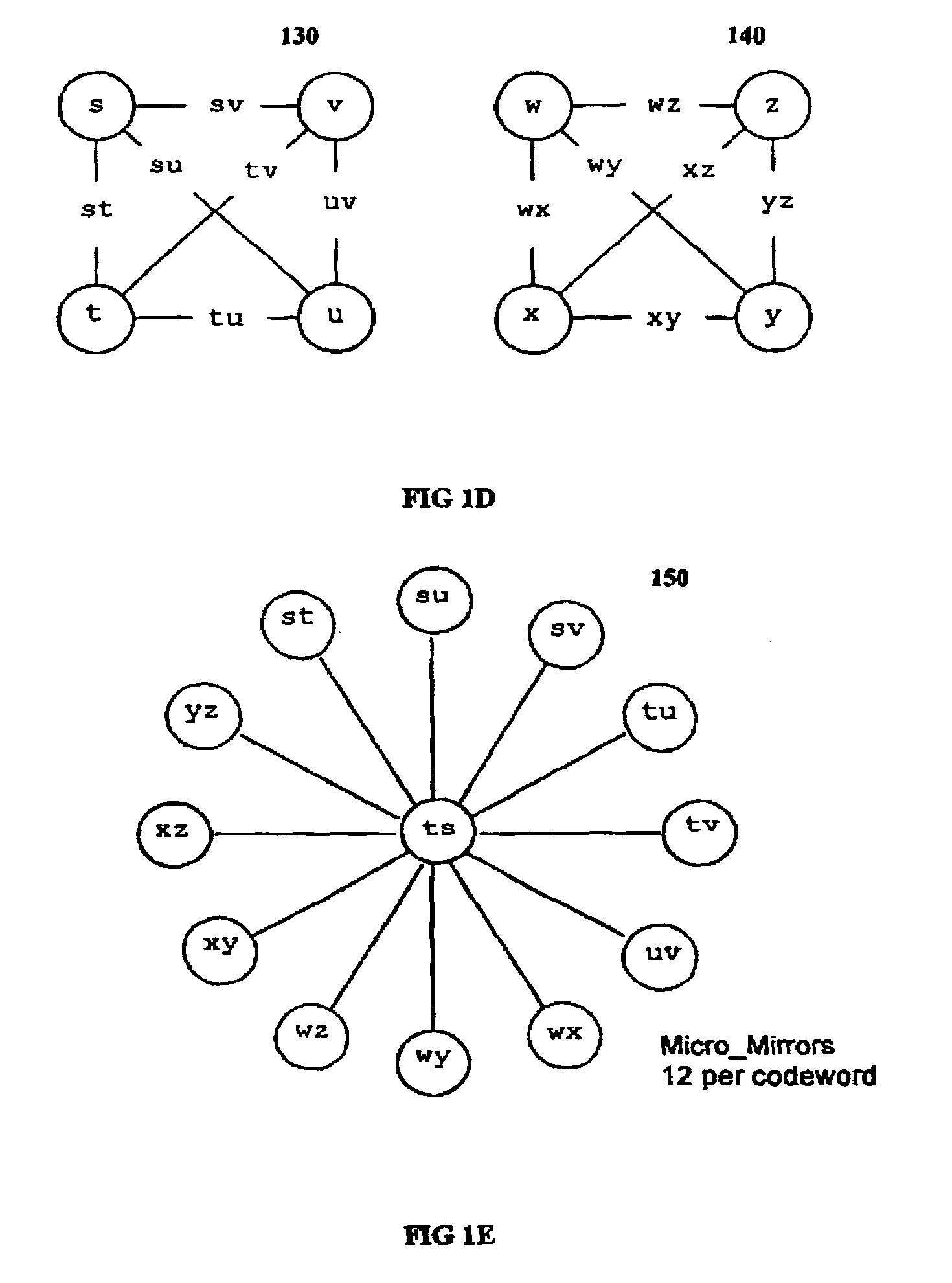
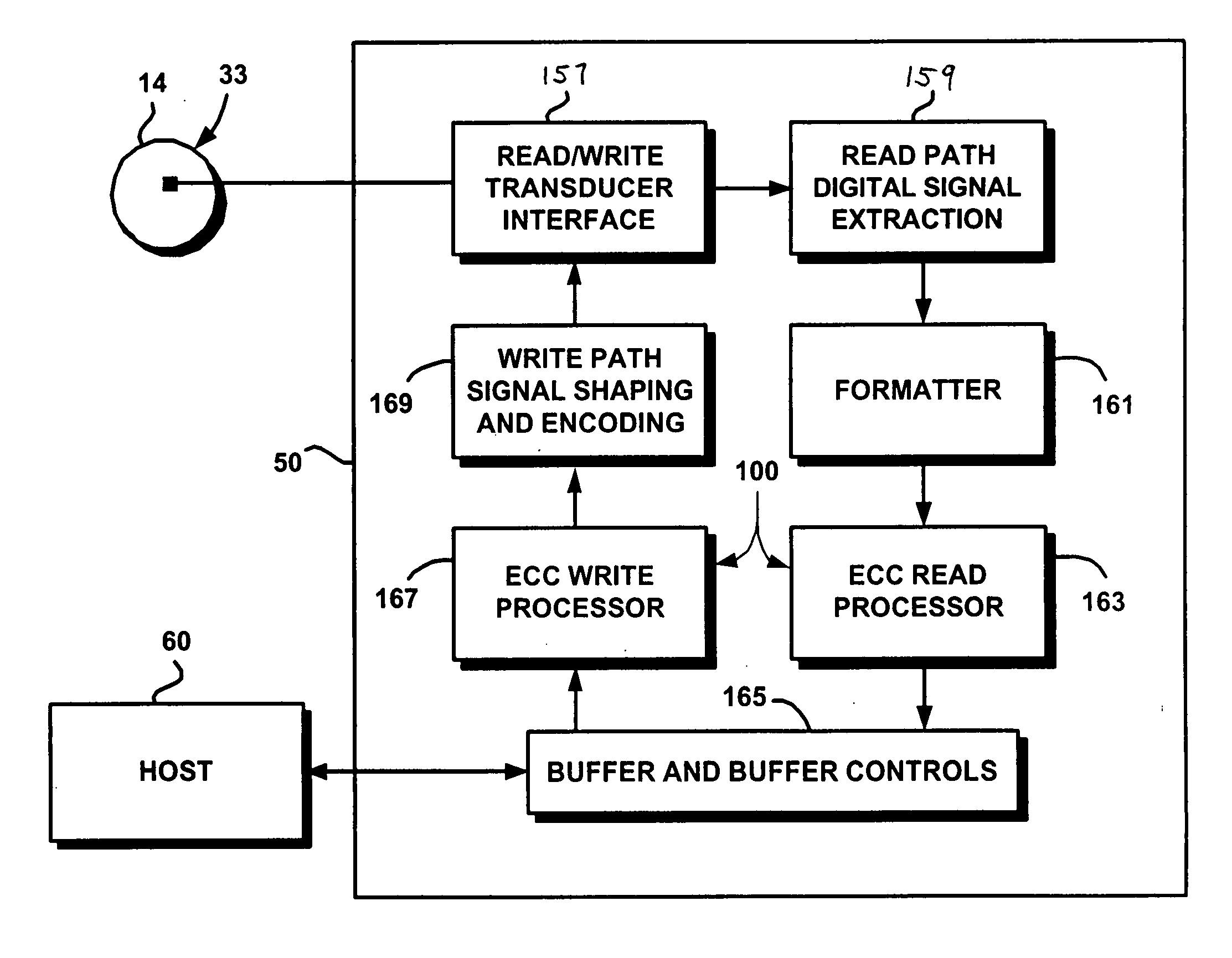
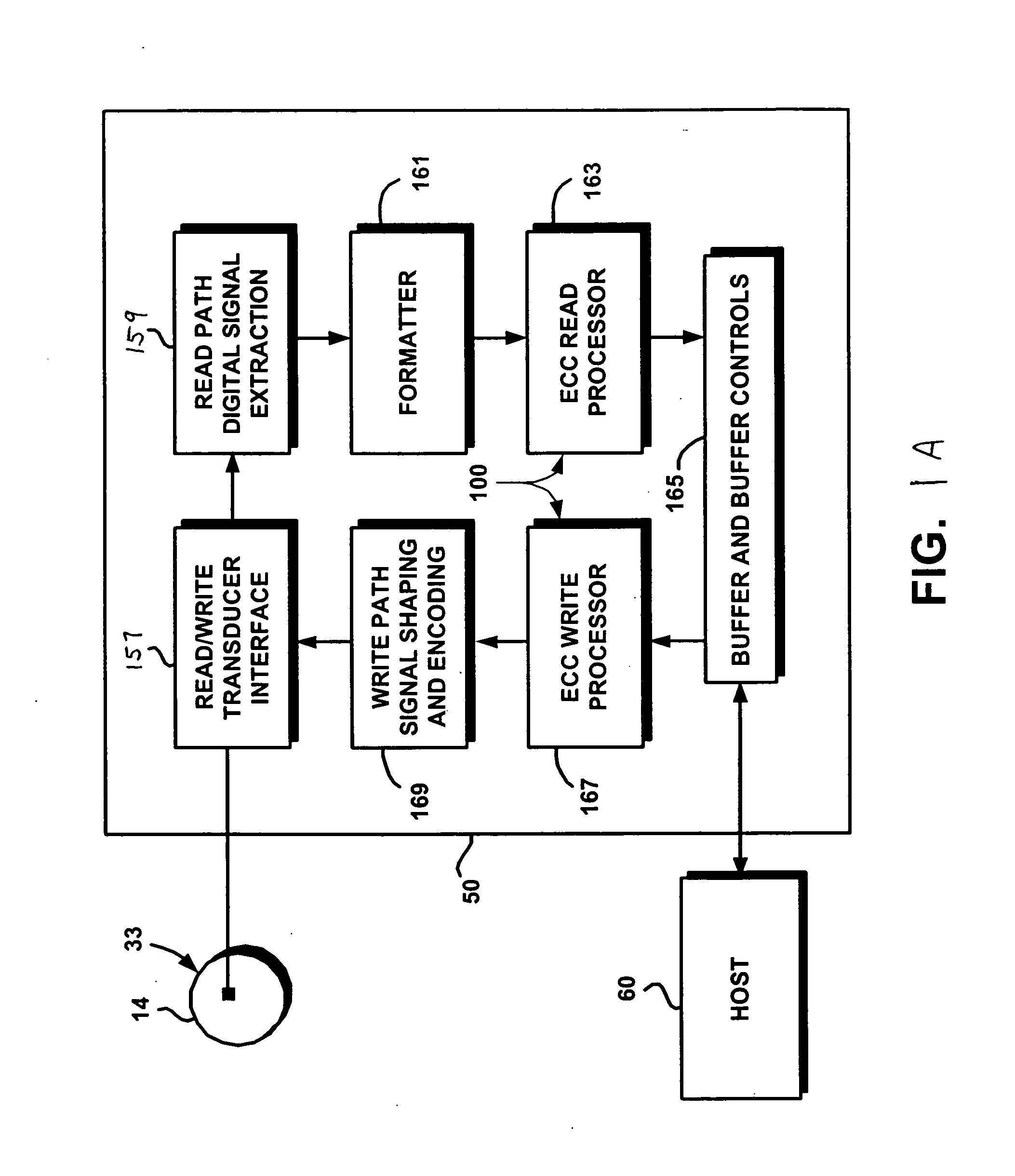
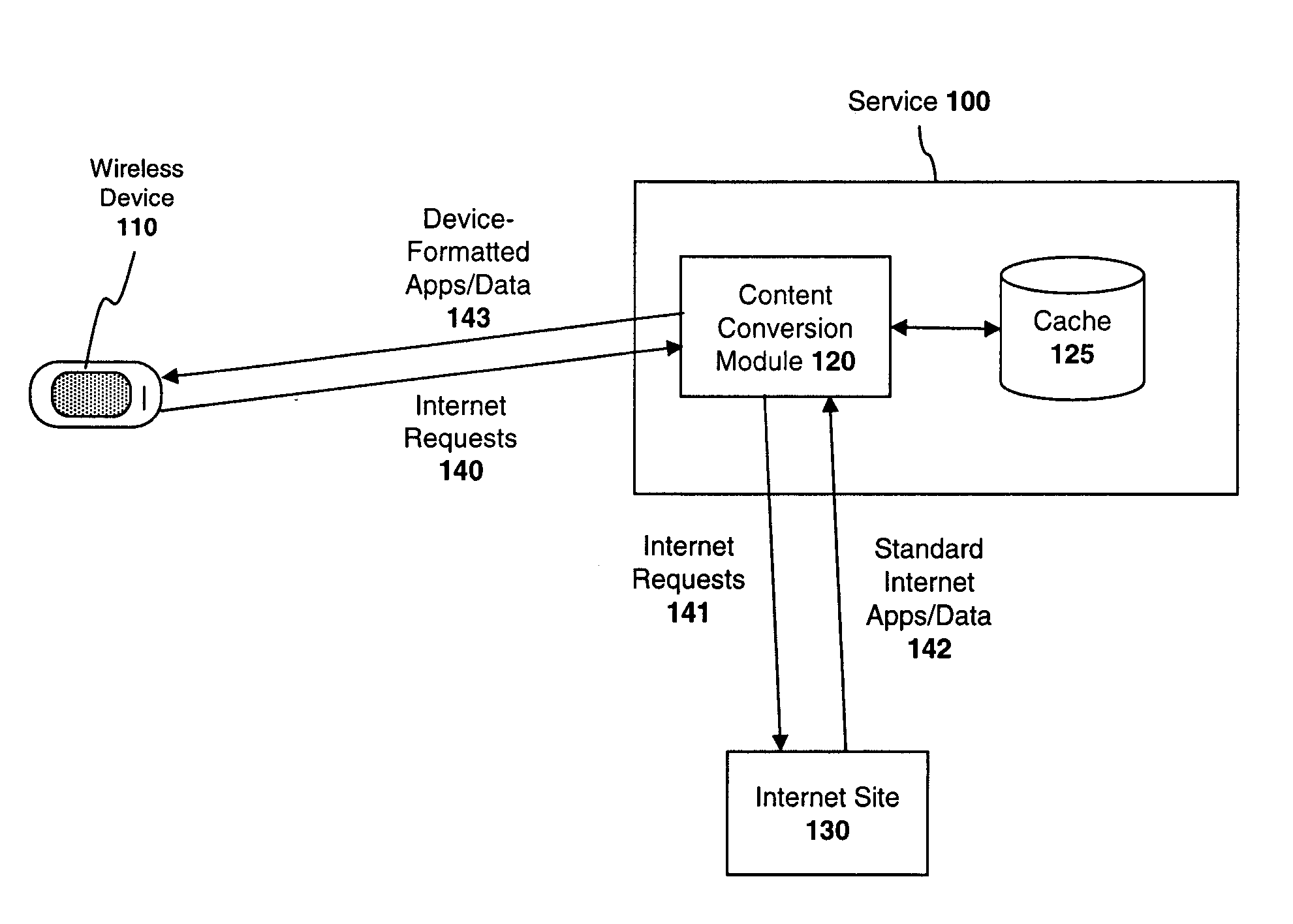
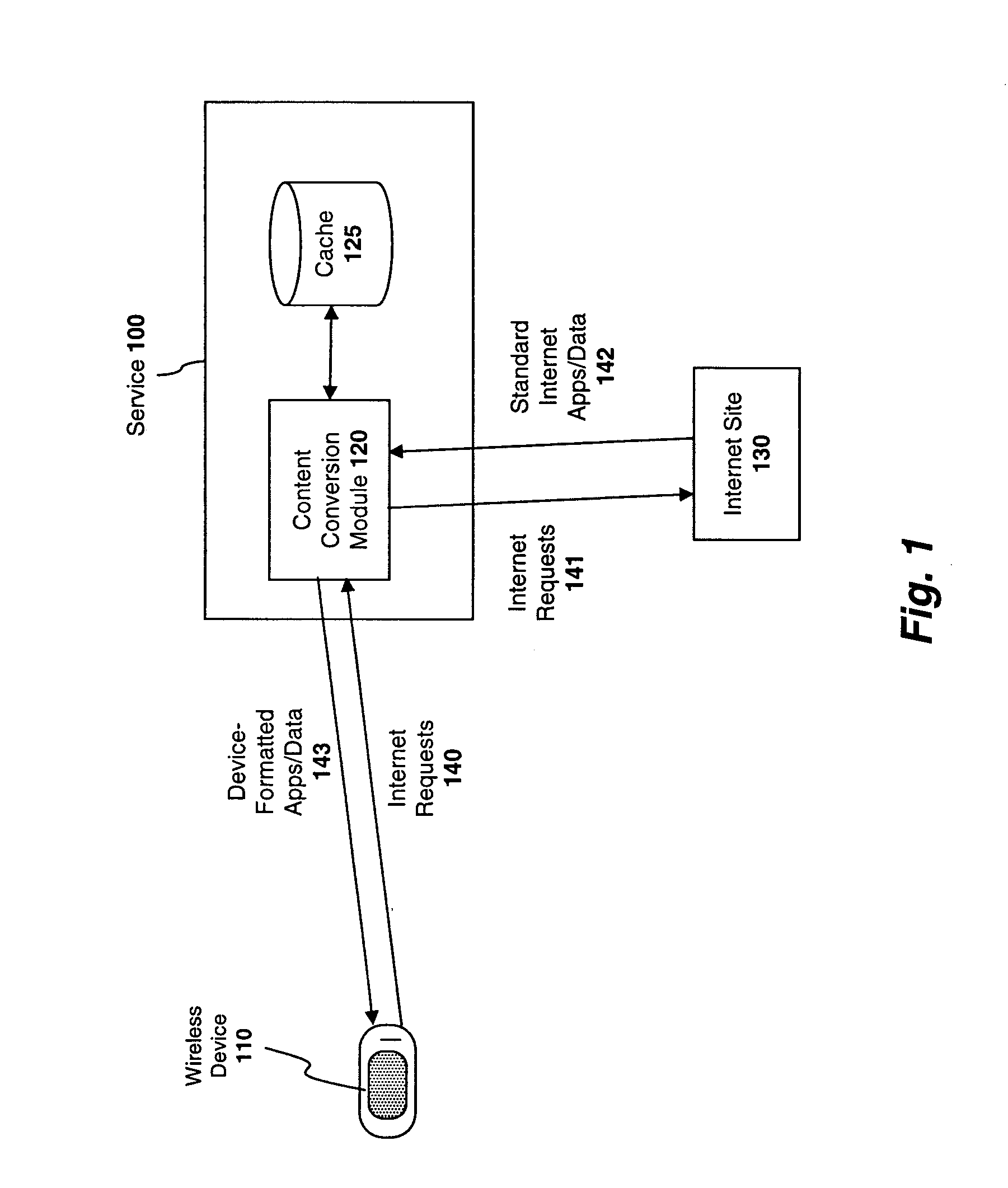
Multi-dimensional data protection and mirroring method for micro level data
ActiveUS7103824B2Detection errorLow common data sizeCode conversionCyclic codesData validationData integrity
The invention discloses a data validation, mirroring and error / erasure correction method for the dispersal and protection of one and two-dimensional data at the micro level for computer, communication and storage systems. Each of 256 possible 8-bit data bytes are mirrored with a unique 8-bit ECC byte. The ECC enables 8-bit burst and 4-bit random error detection plus 2-bit random error correction for each encoded data byte. With the data byte and ECC byte configured into a 4 bit×4 bit codeword array and dispersed in either row, column or both dimensions the method can perform dual 4-bit row and column erasure recovery. It is shown that for each codeword there are 12 possible combinations of row and column elements called couplets capable of mirroring the data byte. These byte level micro-mirrors outperform conventional mirroring in that each byte and its ECC mirror can self-detect and self-correct random errors and can recover all dual erasure combinations over four elements. Encoding at the byte quanta level maximizes application flexibility. Also disclosed are fast encode, decode and reconstruction methods via boolean logic, processor instructions and software table look-up with the intent to run at line and application speeds. The new error control method can augment ARQ algorithms and bring resiliency to system fabrics including routers and links previously limited to the recovery of transient errors. Image storage and storage over arrays of static devices can benefit from the two-dimensional capabilities. Applications with critical data integrity requirements can utilize the method for end-to-end protection and validation. An extra ECC byte per codeword extends both the resiliency and dimensionality.
Owner:HALFORD ROBERT
Techniques for detecting and correcting errors using multiple interleave erasure pointers
InactiveUS20050229069A1Correction capabilityTransmission systemsCode conversionBlock codeError location
Techniques for detecting and correcting burst errors in data bytes formed in a two-level block code structure. A second level decoder uses block level check bytes to detect columns in a two-level block code structure that contain error bytes. The second level decoder generates erasure pointers that identify columns in the two-level block structure effected by burst errors. A first level decoder then uses codeword check bytes to correct all of the bytes in the columns identified by the erasure pointers. The first level decoder is freed to use all of the codeword check bytes only for error byte value calculations. The first level decoder does not need to use any of the codeword check bytes for error location calculations, because the erasure pointers generated by the second level decoder provide all of the necessary error locations. This techniques doubles the error correction capability of the first level decoder.
Owner:HITACHI GLOBAL STORAGE TECH NETHERLANDS BV +1
Multiple network protocol encoder/decoder and data processor
InactiveUS6034963AReduce system costLow costTime-division multiplexData switching by path configurationRaw socketByte
A multiple network protocol encoder / decoder comprising a network protocol layer, data handler, O.S. State machine, and memory manager state machines implemented at a hardware gate level. Network packets are received from a physical transport level mechanism by the network protocol layer state machine which decodes network protocols such as TCP, IP, User Datagram Protocol (UDP), PPP, and Raw Socket concurrently as each byte is received. Each protocol handler parses and strips header information immediately from the packet, requiring no intermediate memory. The resulting data are passed to the data handler which consists of data state machines that decode data formats such as email, graphics, Hypertext Transfer Protocol (HTTP), Java, and Hypertext Markup Language (HTML). Each data state machine reacts accordingly to the pertinent data, and any data that are required by more than one data state machine is provided to each state machine concurrently, and any data required more than once by a specific data state machine, are placed in a specific memory location with a pointer designating such data (thereby ensuring minimal memory usage). Resulting display data are immediately passed to a display controller. Any outgoing network packets are created by the data state machines and passed through the network protocol state machine which adds header information and forwards the resulting network packet via a transport level mechanism.
Owner:NVIDIA CORP
Systems and Methods for Providing Dynamic Spillover of Virtual Servers Based on Bandwidth
The present solution provides a spillover management technique for virtual servers of an appliance based on bandwidth. A network administrator may configure a bandwidth threshold for one or more virtual servers, such as virtual servers providing acceleration or load balancing for one or more services. The bandwidth threshold may be specified as a number of bytes transferred via the virtual server. The bandwidth threshold may also be specified as a round trip time or derivative thereof. A user may specify the bandwidth threshold via a configuration interface. Otherwise, the appliance may establish the bandwidth threshold. The appliance monitors the bandwidth used by a first virtual server. In response to detecting the bandwidth reaching or exceeding the bandwidth threshold, the appliance dynamically directs client requests to a second virtual server.
Owner:CITRIX SYST INC
Method and system for recording and replaying the execution of distributed java programs
InactiveUS6832367B1Easy to copyGuaranteed orderError detection/correctionSpecific program execution arrangementsStream socketThread scheduling
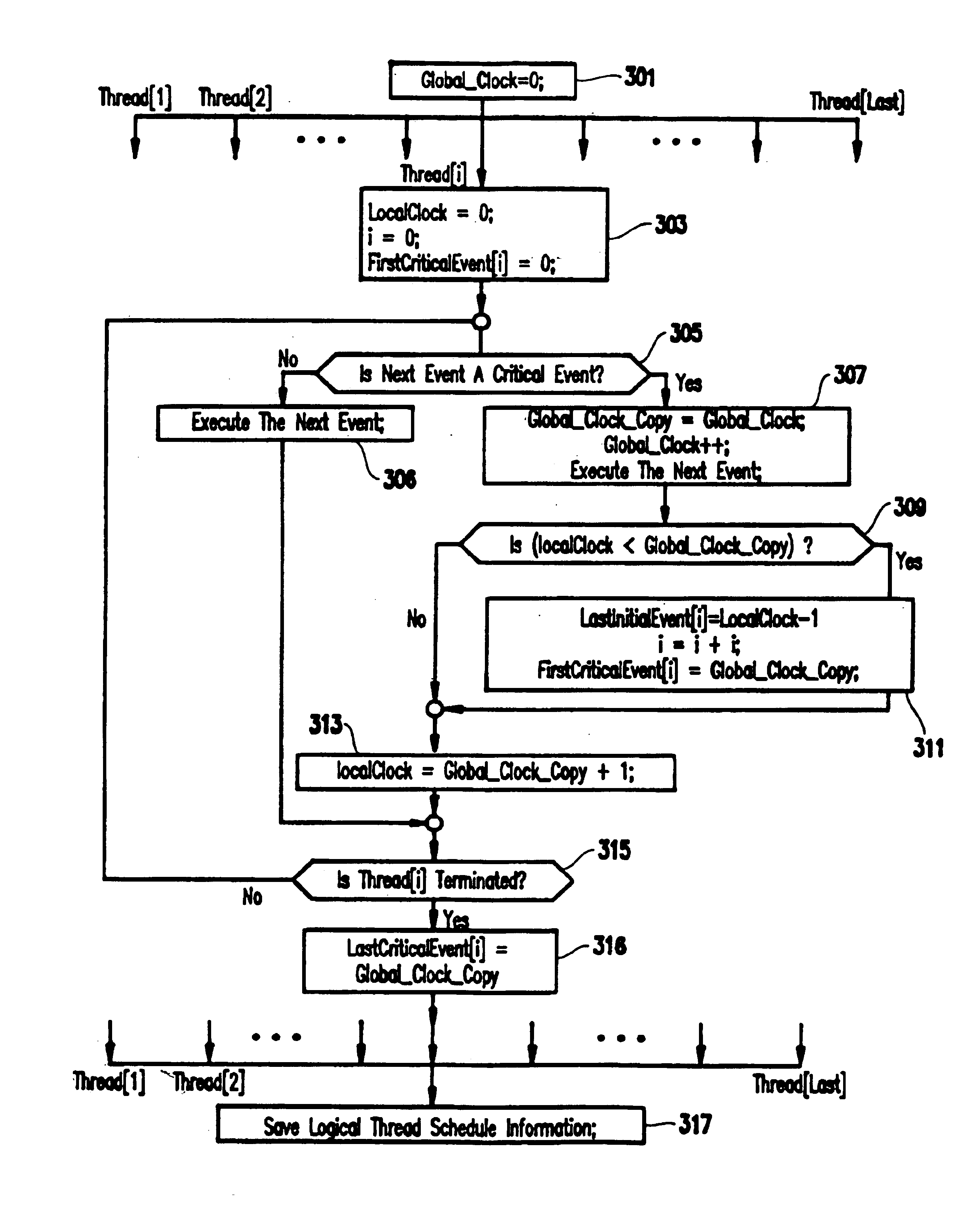
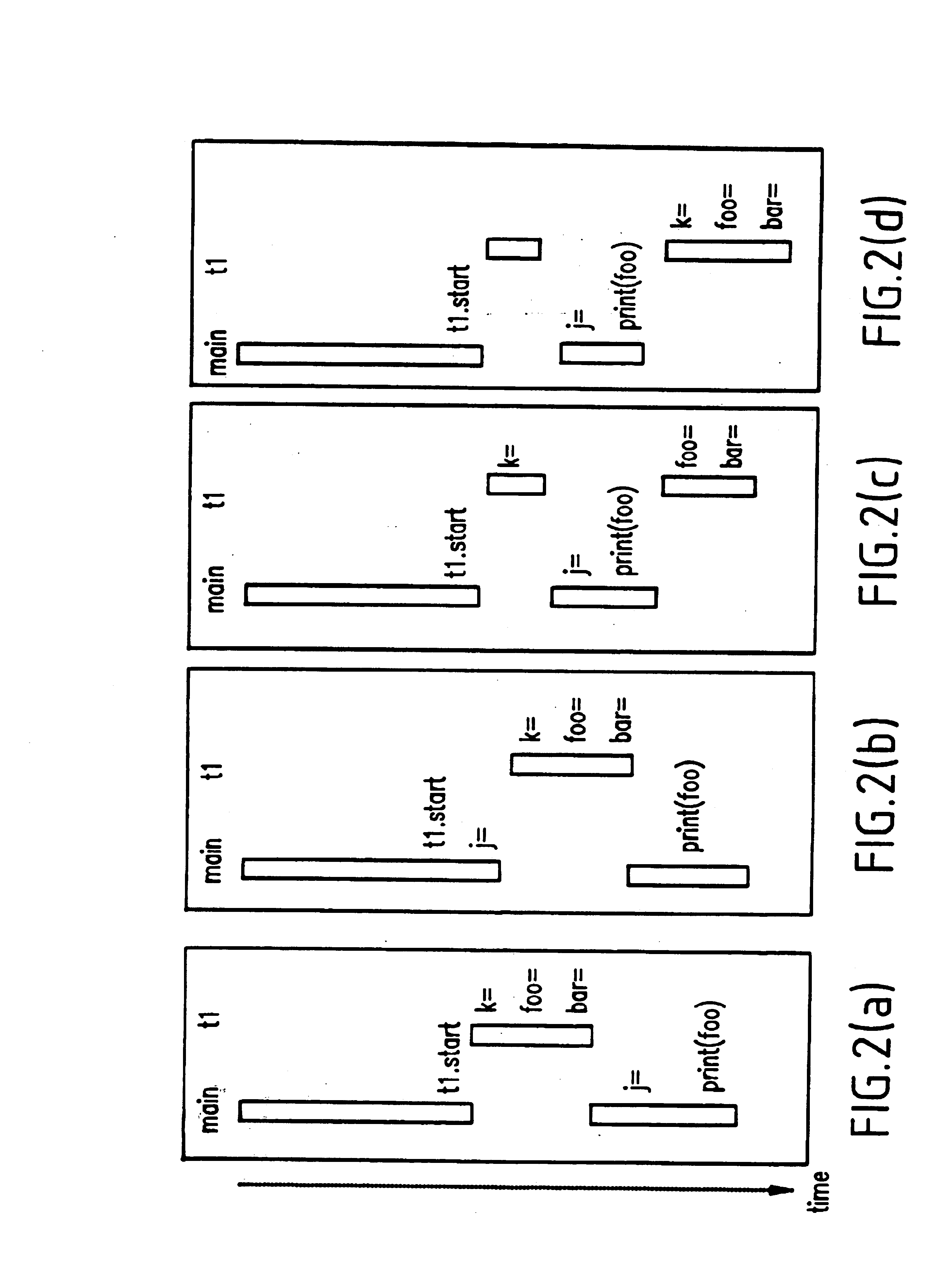
A method for recording and replaying execution of distributed programs on a computer system in a distributed environment, includes identifying an execution order of critical events of a program, generating groups of critical events of the program, wherein for each group, critical events belonging to the group belong to a common execution thread, and generating for each execution thread a logical thread schedule that identifies a sequence of the groups so as to allow deterministically replaying a non-deterministic arrival of stream socket connection requests, a non-deterministic number of bytes received during message reads, and a non-deterministic binding of stream sockets to local ports.
Owner:IBM CORP
Method for finding global extrema of a set of shorts distributed across an array of parallel processing elements
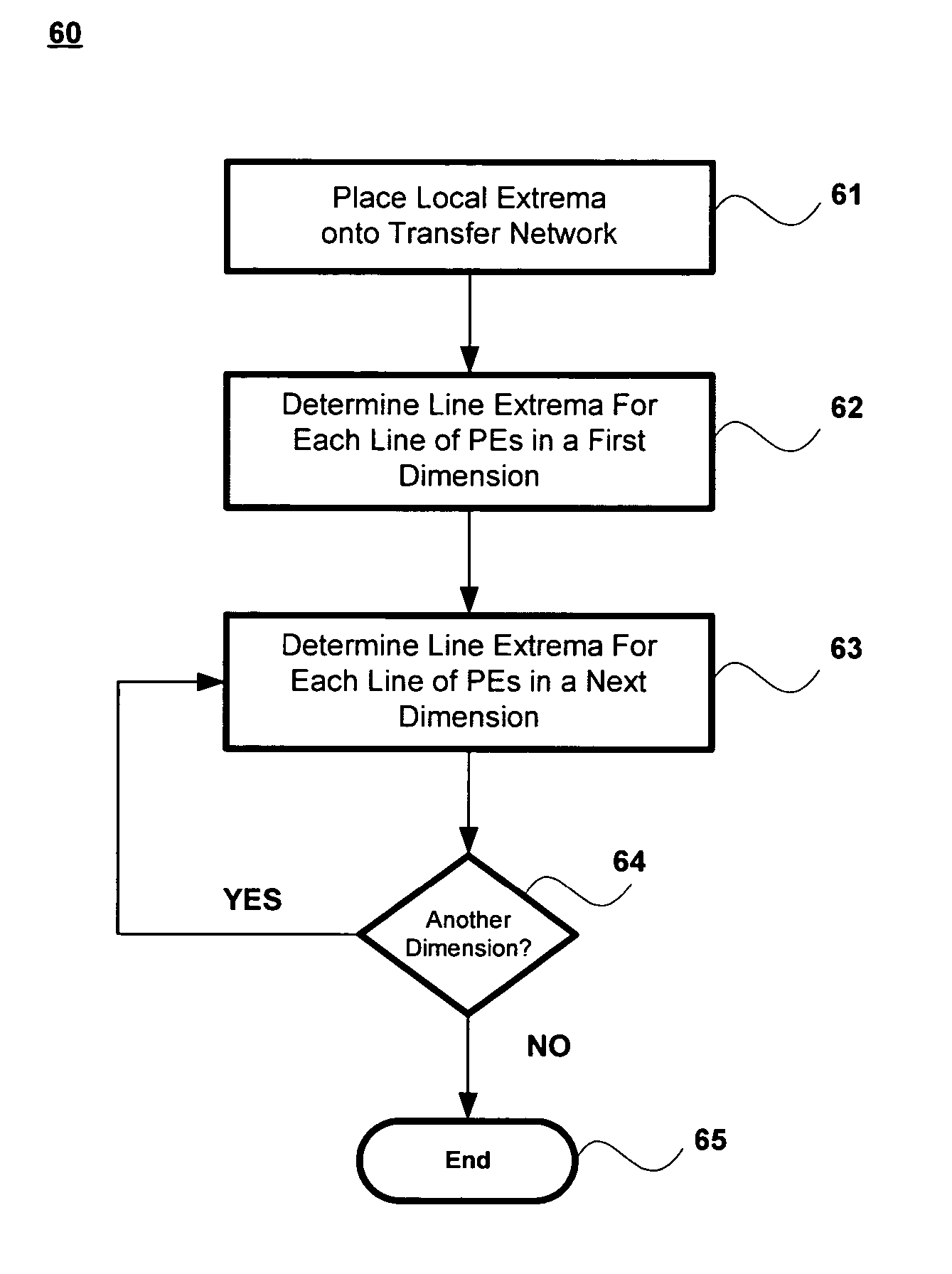
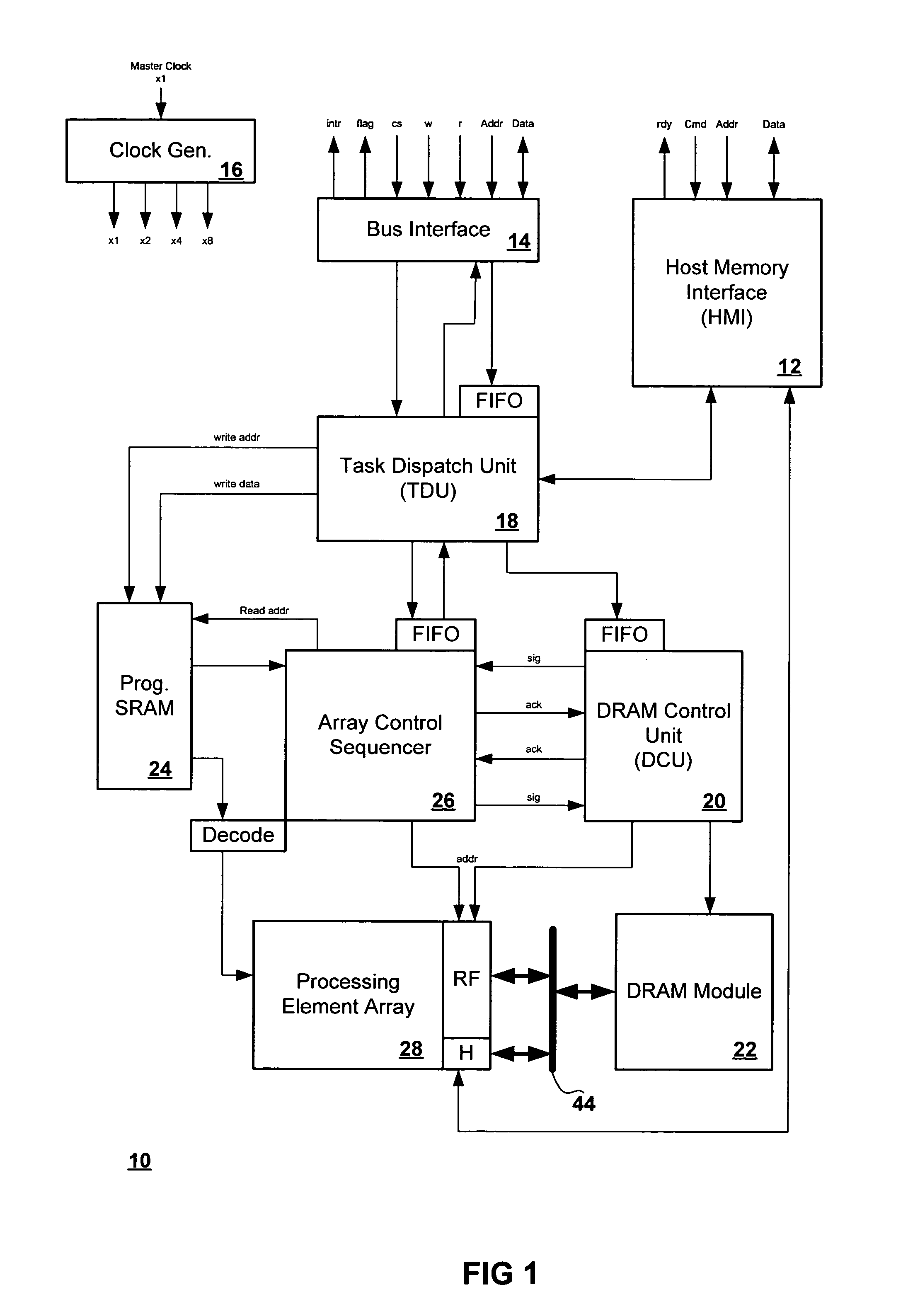
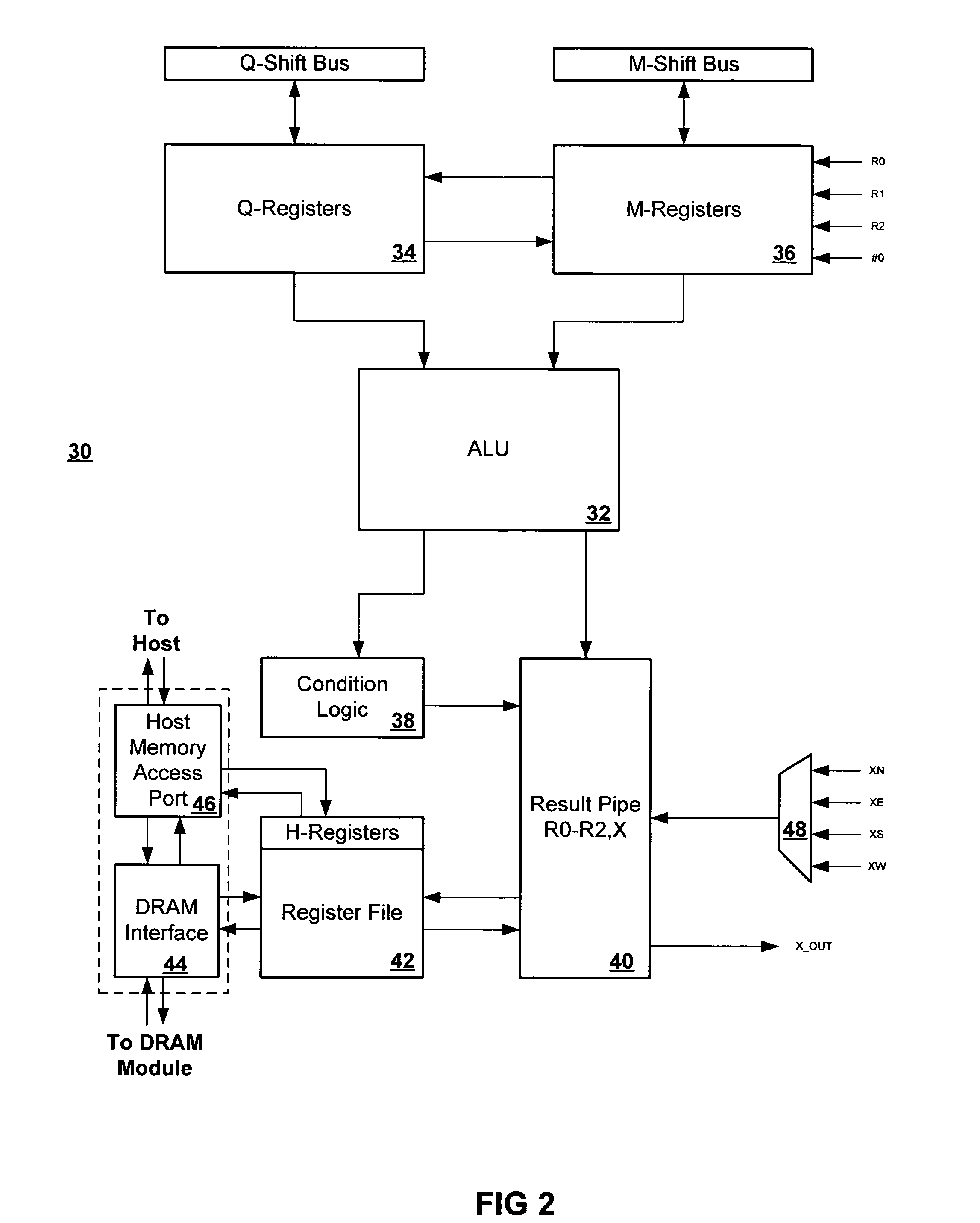
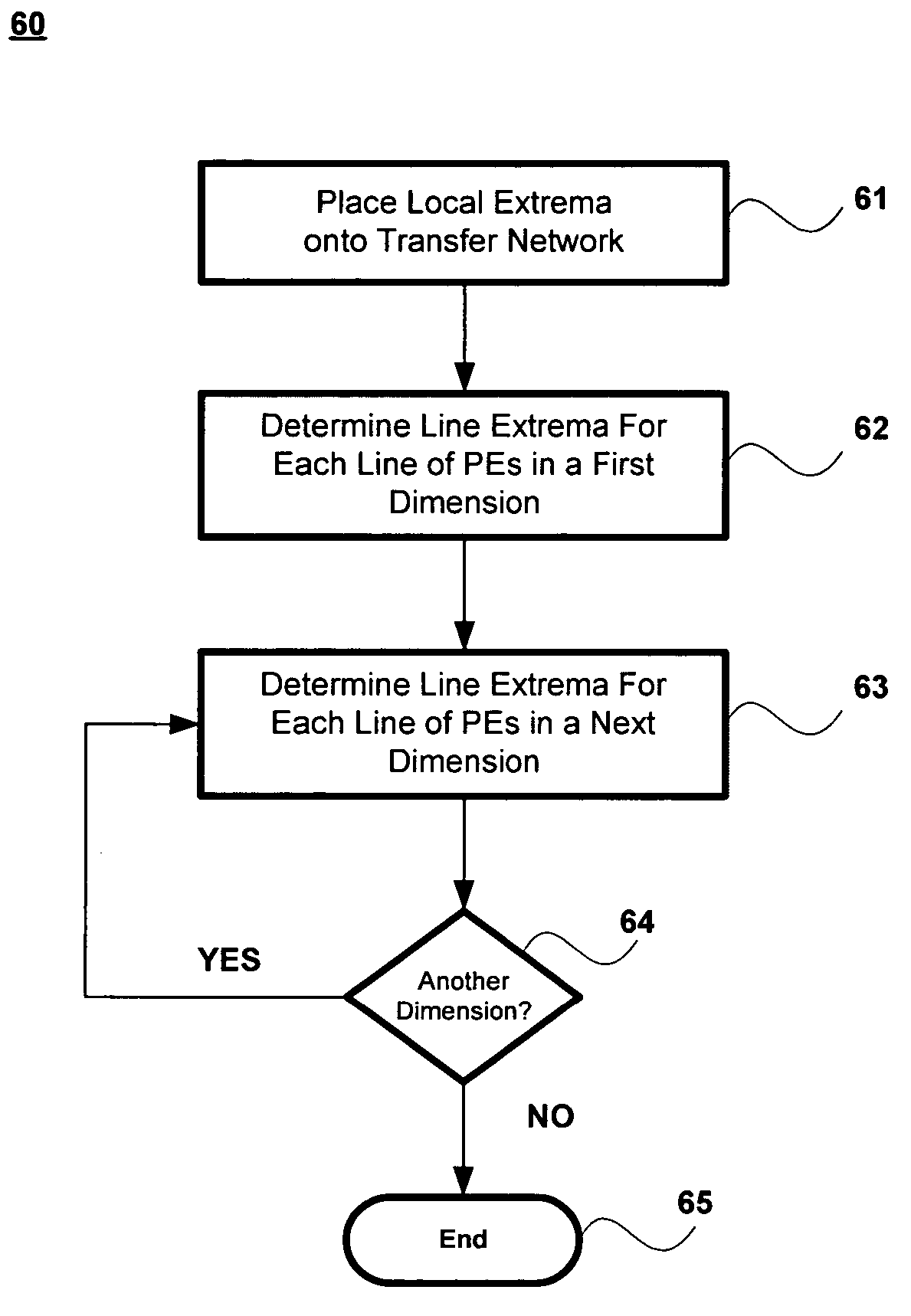
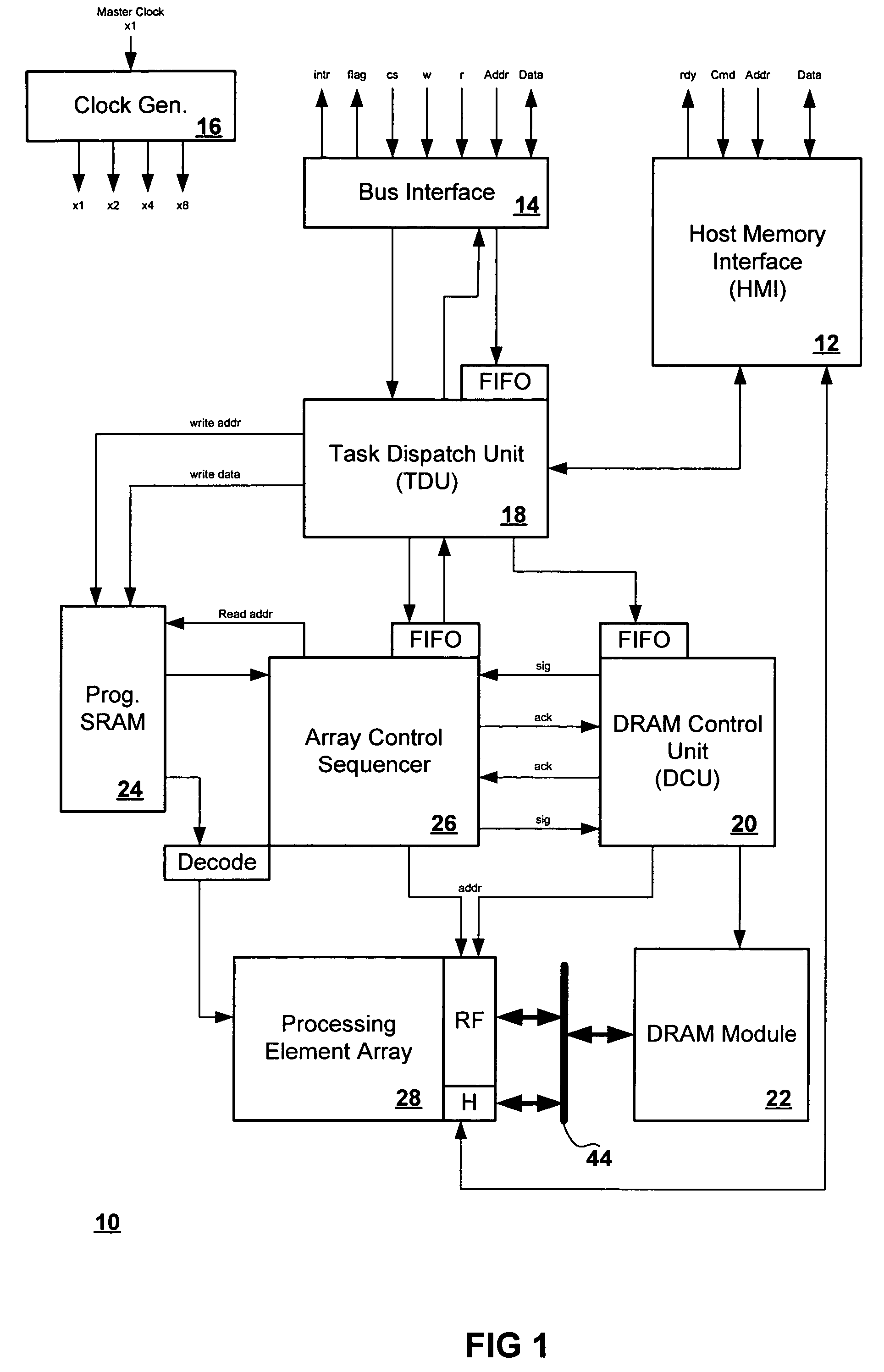
ActiveUS7574466B2Single instruction multiple data multiprocessorsDigital data processing detailsProcessing elementParallel processing
A method for finding an extrema for an n-dimensional array having a plurality of processing elements, the method includes determining within each processing element a first dimensional extrema for a first dimension, wherein the first dimensional extrema is related to the local extrema of the processing elements in the first dimension and wherein the first dimensional extrema has a most significant byte and a least significant byte, determining within each processing element a next dimensional extrema for a next dimension of the n-dimensional array, wherein the next dimensional extrema is related to the first dimensional extrema and wherein the next dimensional extrema has a most significant byte and a least significant byte; and repeating the determining within each processing element a next dimensional extrema for each of the n-dimensions, wherein each of the next dimensional extrema is related to a dimensional extrema from a previously selected dimension.
Owner:MICRON TECH INC
Method for finding global extrema of a set of bytes distributed across an array of parallel processing elements
ActiveUS7447720B2Digital data processing detailsDigital computer detailsProcessing elementParallel processing
A method for finding an extrema for an n-dimensional array having a plurality of processing elements, the method includes determining within each of the processing elements a dimensional extrema for a first dimension of the n-dimensional array, wherein the dimensional extrema is related to one or more local extrema of the processing elements in the first dimension, determining within each of the processing elements a next dimensional extrema for a next dimension of the n-dimensional array, wherein the next dimensional extrema is related to one or more of the first dimensional extrema, and repeating the determining within each of the processing elements a next dimensional extrema for each of the n-dimensions, wherein each of the next dimensional extrema is related to a dimensional extrema from a previously selected dimension.
Owner:MICRON TECH INC
Natural language interface for searching database
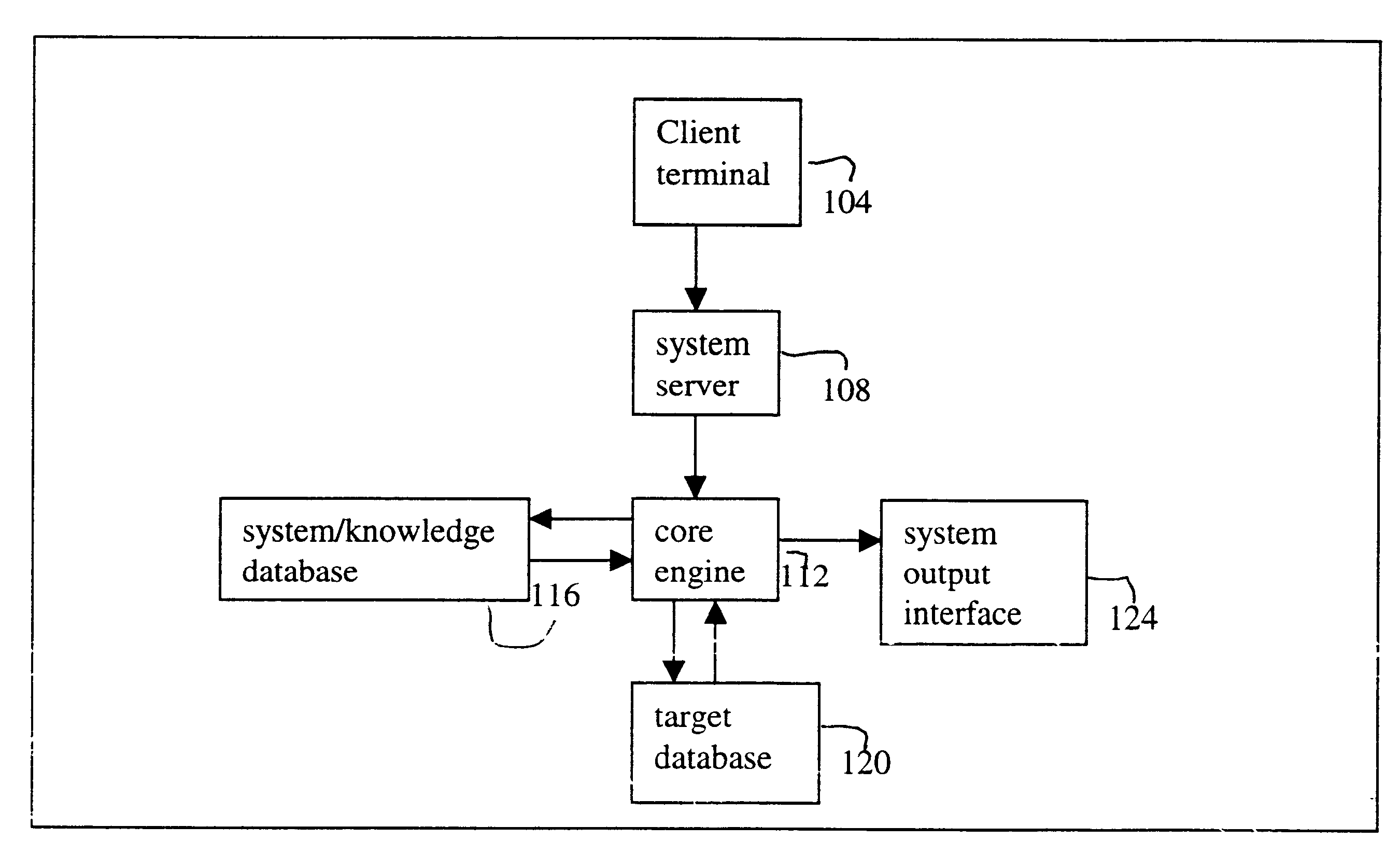
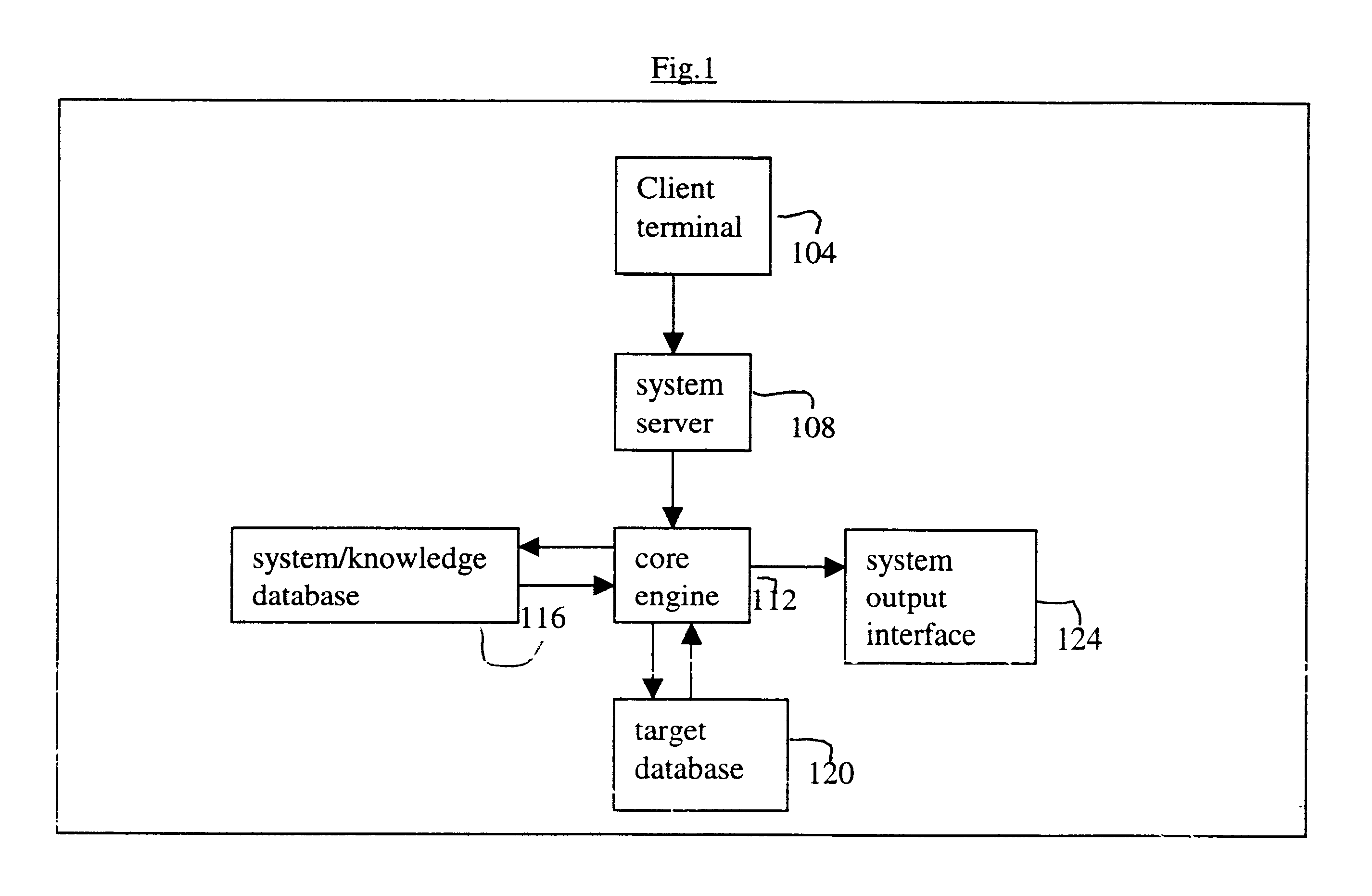
InactiveUS6598039B1Data processing applicationsDigital data information retrievalSearch wordsSystems analysis
A system and method for searching information from a database using a natural language. In one embodiment, the system analyzes a natural language search request and converts the search request into one or more search words. The search words are further converted into a string of bytes, and a subset of a target database, referred to as the datasoup, is searched. If there is a match between the bytes and raw data in the datasoup, the searched data is retrieved from the target database. The searched data is then formatted and provided to a user. Optionally, the searched data can be provided to the user unformatted. In another embodiment, the system includes a system server configured to receive a natural language search request, a core engine coupled to the system server and to the target database, and a system database coupled to the core engine, where the core engine accesses the system database to analyze the search request. The system database stores global rules, one or more preference files, and one or more dictionaries, and the preference file stores information about the user.
Owner:GO ALBERT FRANCE
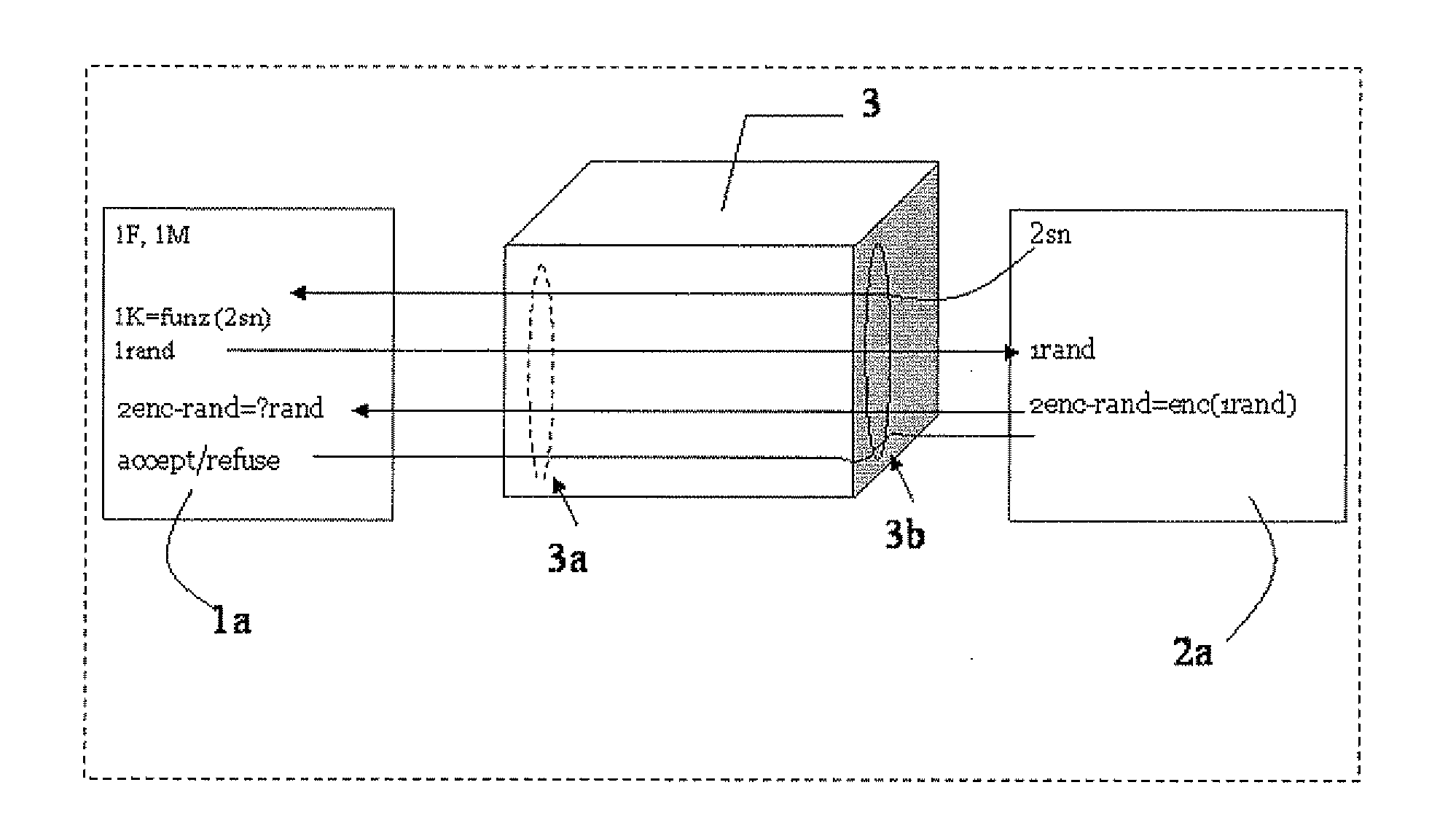
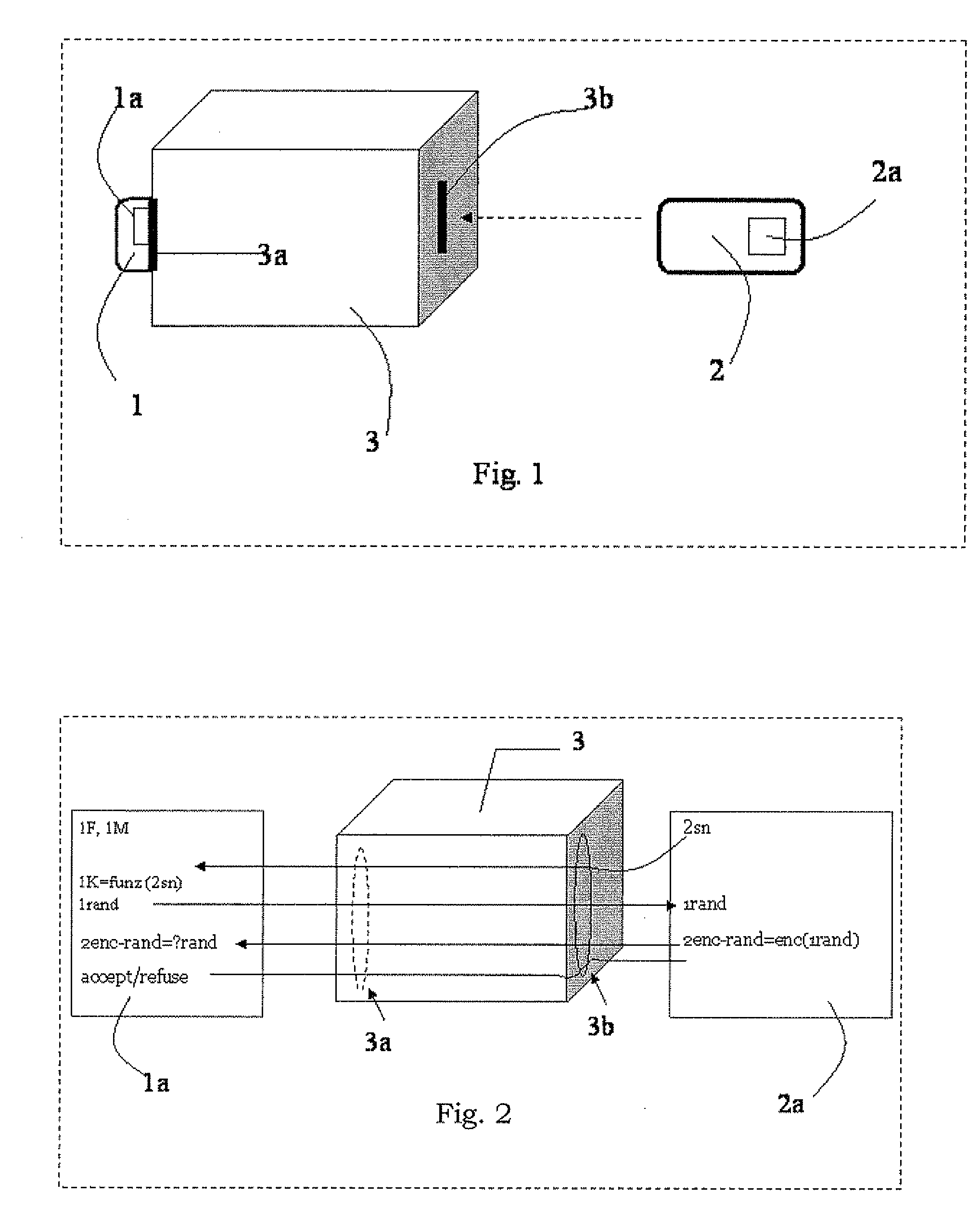
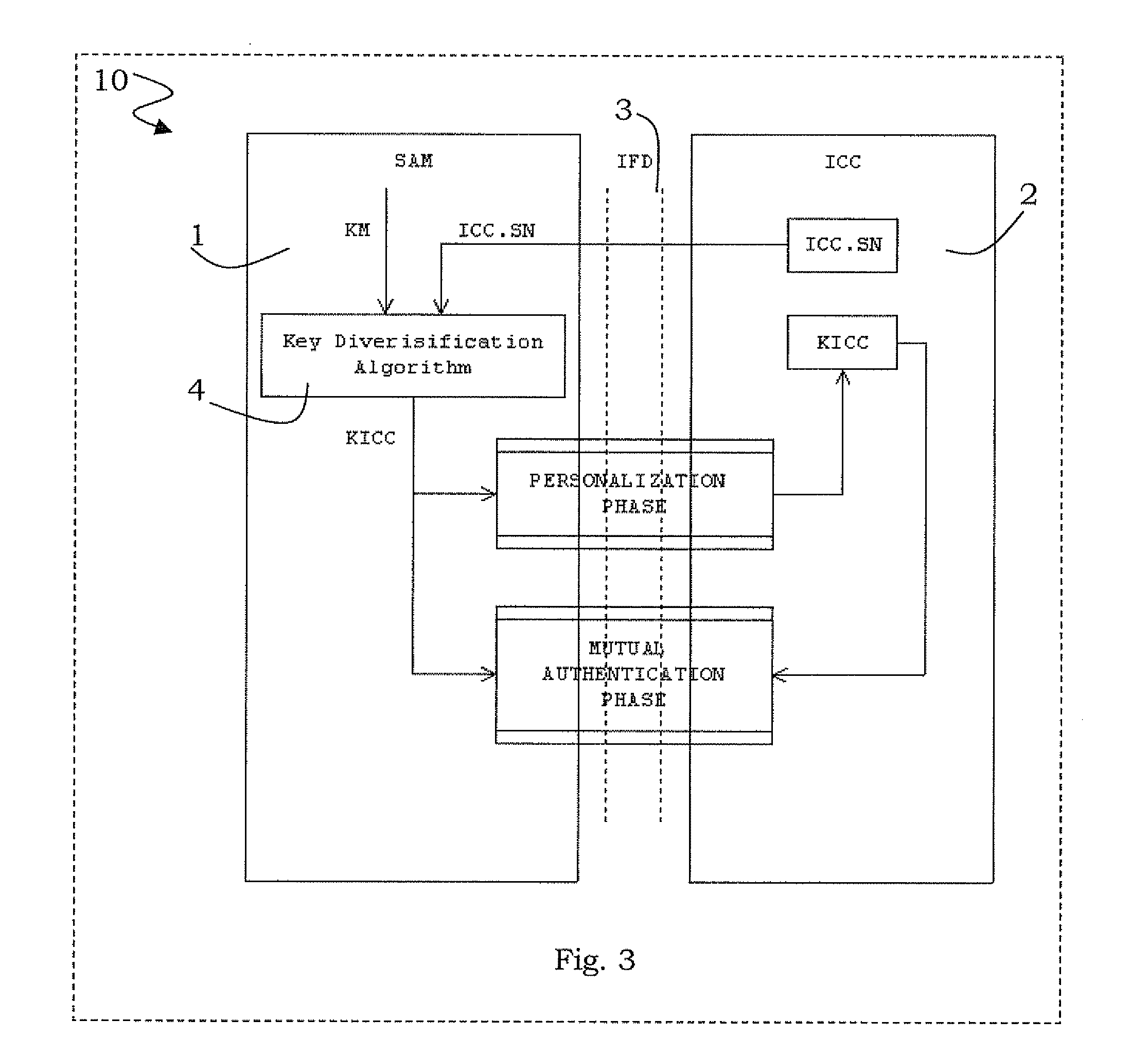
Method for key diversification on an IC card
InactiveUS20080008315A1Shorten the timeNon-time consuming and non-computational intensive operationsAcutation objectsUser identity/authority verificationCommunication interfaceMaster key
Key diversification is performed during a mutual authentication between a SAM integrated circuit (IC) card storing a master key, and a user IC card storing an identification number. The user IC card is connected to the SAM IC card through a communications interface. The key diversification includes deriving sub keys from the master key, and computing ciphered strings through corresponding cryptographic computations on a string obtained by an elaboration on the identification number with the sub keys. A diversification key is generated by linking together a combination of bytes of the ciphered strings.
Owner:STMICROELECTRONICS INT NV
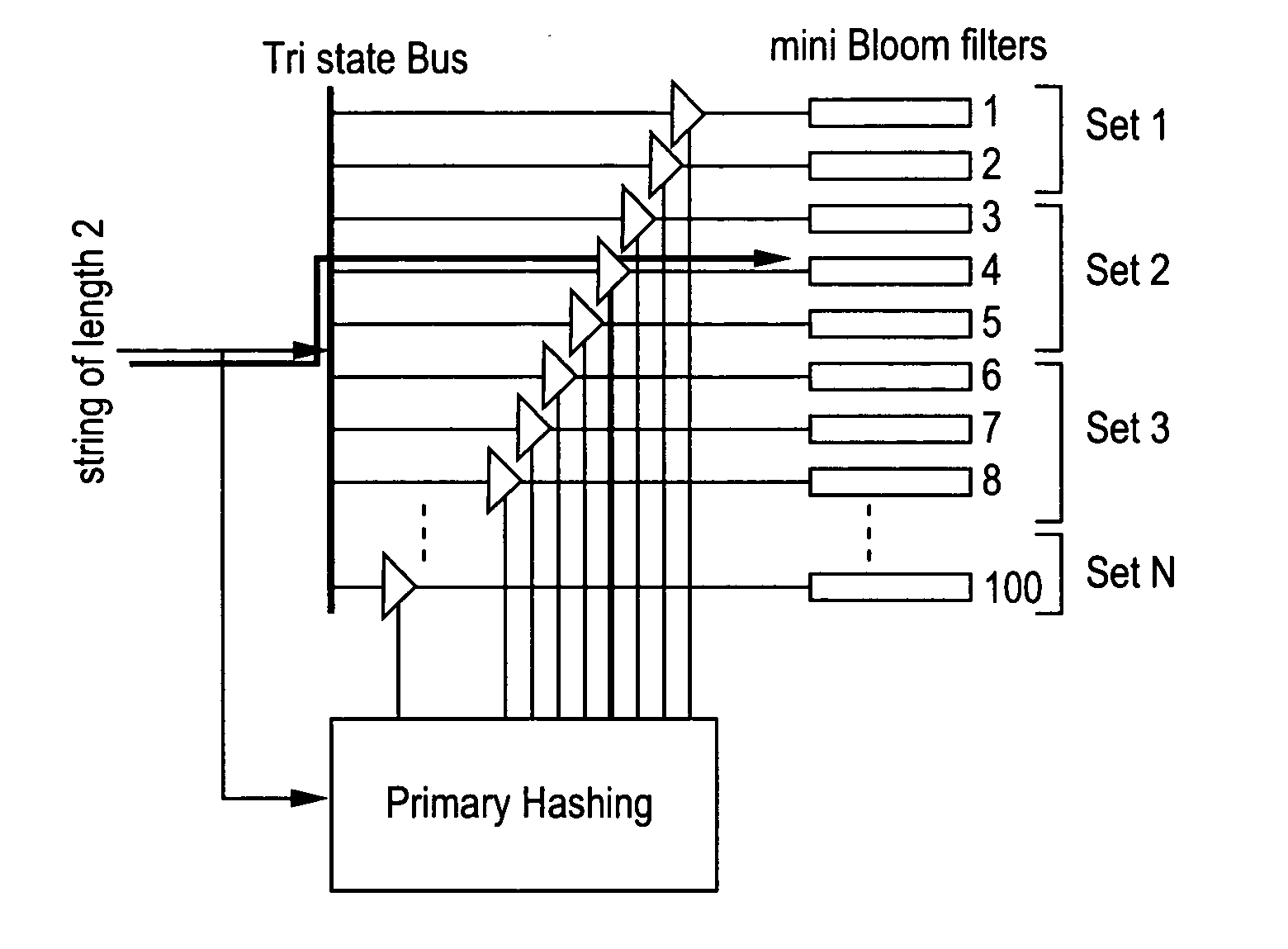
Method and apparatus for detecting predefined signatures in packet payload using bloom filters
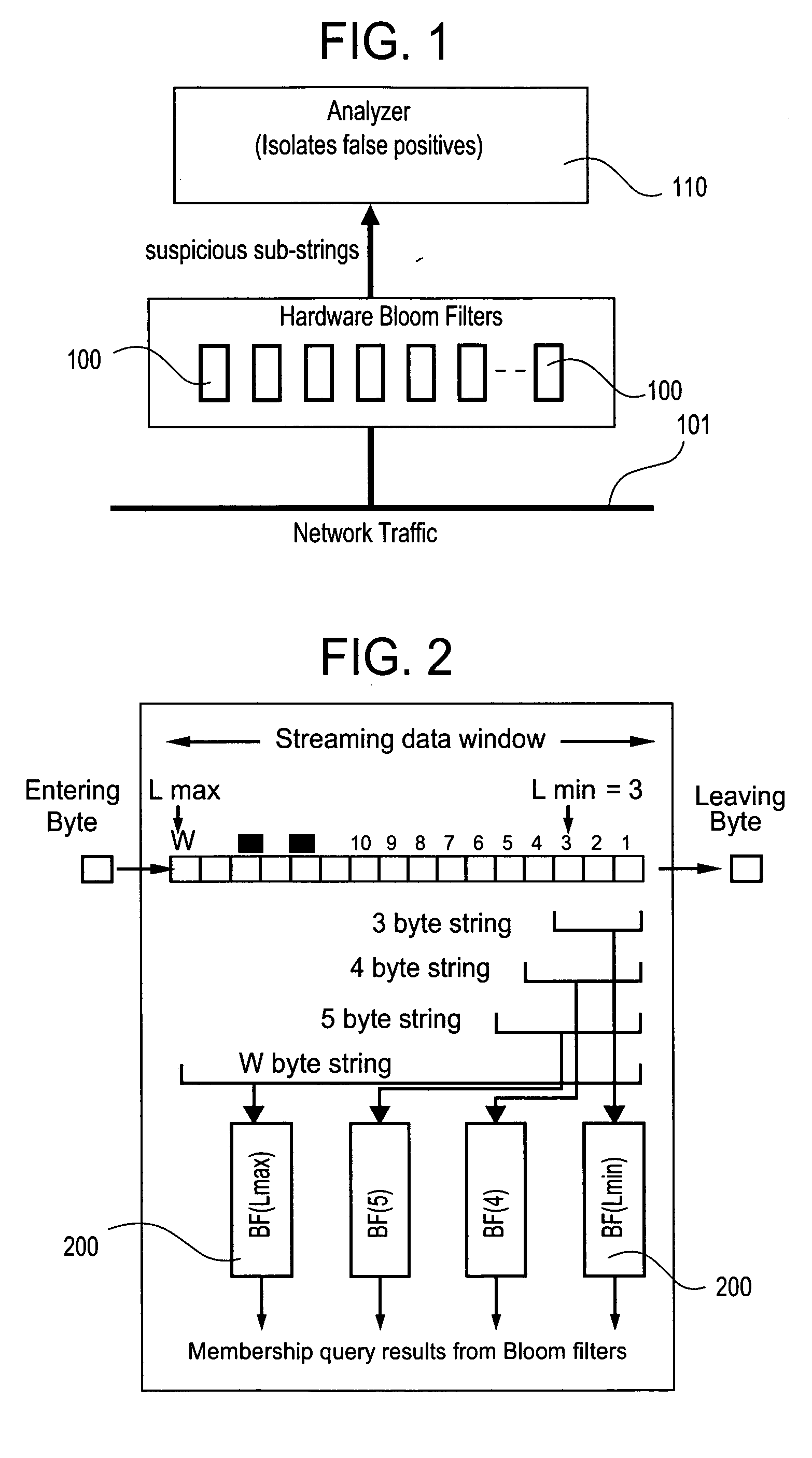
ActiveUS20050086520A1Digital data processing detailsUser identity/authority verificationBloom filterNetwork data
The present invention relates to a method and apparatus based on Bloom filters for detecting predefined signatures (a string of bytes) in a network packet payload. A Bloom filter is a data structure for representing a set of strings in order to support membership queries. Hardware Bloom filters isolate all packets that potentially contain predefined signatures. Another independent process eliminates false positives produced by the Bloom filters. The system is implemented on a FPGA platform, resulting in a set of 10,000 strings being scanned in the network data at the line speed of 2.4 Gbps.
Owner:WASHINGTON UNIV IN SAINT LOUIS
Systems and methods for backing up data files
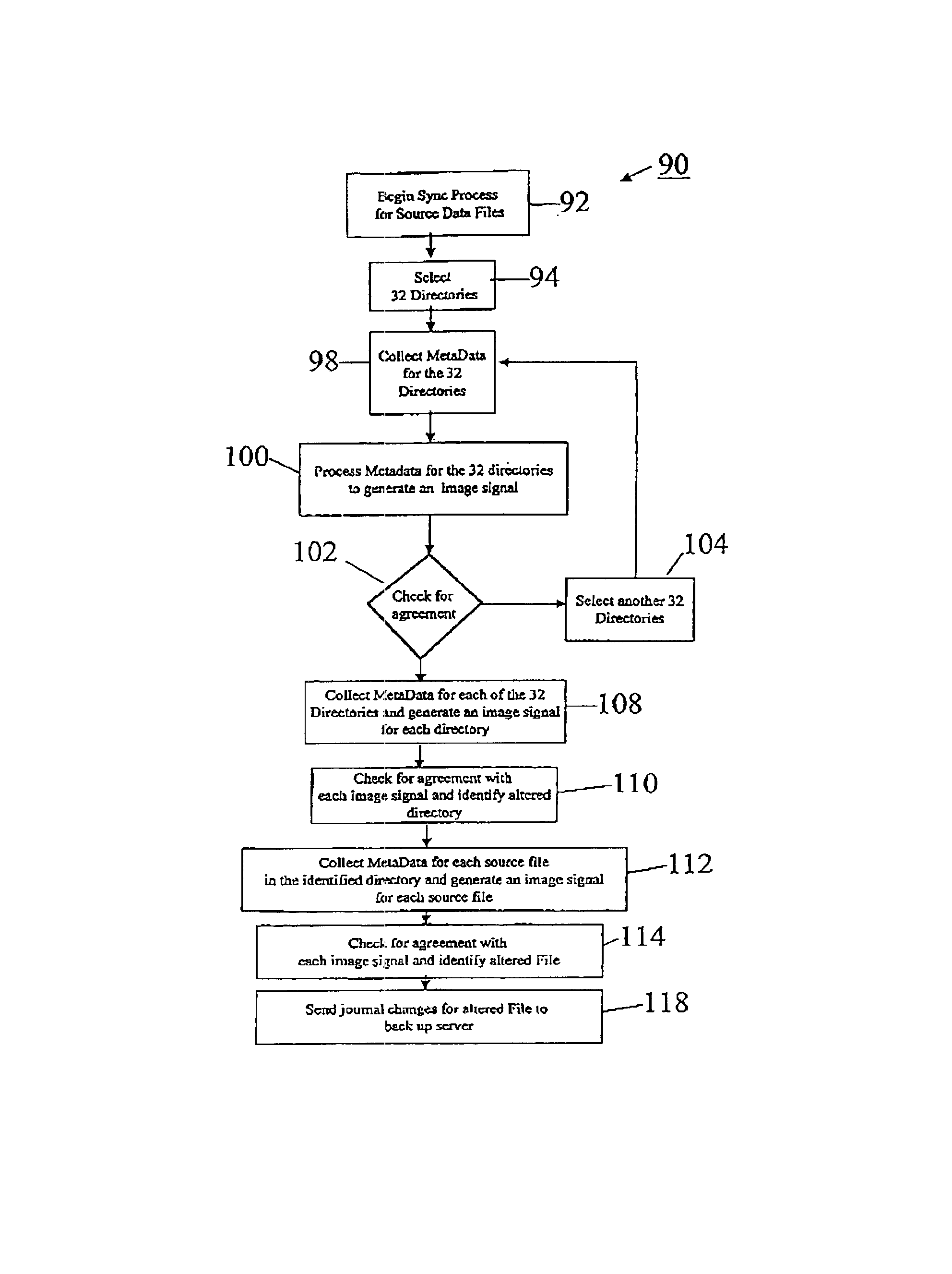
InactiveUS6847984B1Provide integrityReduce demandData processing applicationsError detection/correctionBaseline dataData file
The invention provides systems and methods for continuous back up of data stored on a computer network. To this end the systems of the invention include a synchronization process that replicates selected source data files data stored on the network and to create a corresponding set of replicated data files, called the target data files, that are stored on a back up server. This synchronization process builds a baseline data structure of target data files. In parallel to this synchronization process, the system includes a dynamic replication process that includes a plurality of agents, each of which monitors a portion of the source data files to detect and capture, at the byte-level, changes to the source data files. Each agent may record the changes to a respective journal file, and as the dynamic replication process detects that the journal files contain data, the journal files are transferred or copied to the back up server so that the captured changes can be written to the appropriate ones of the target data files.
Owner:KEEPITSAFE INC
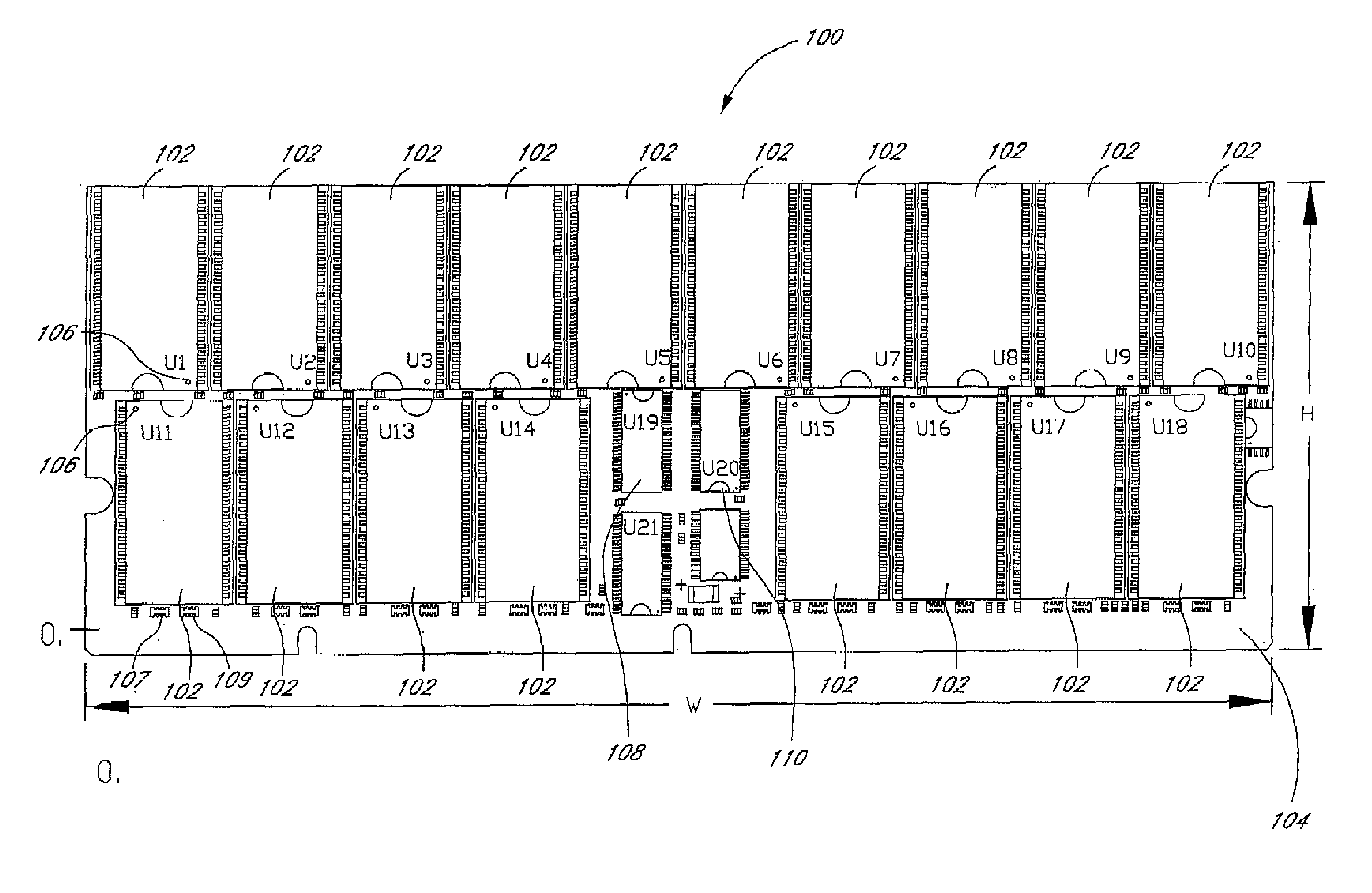
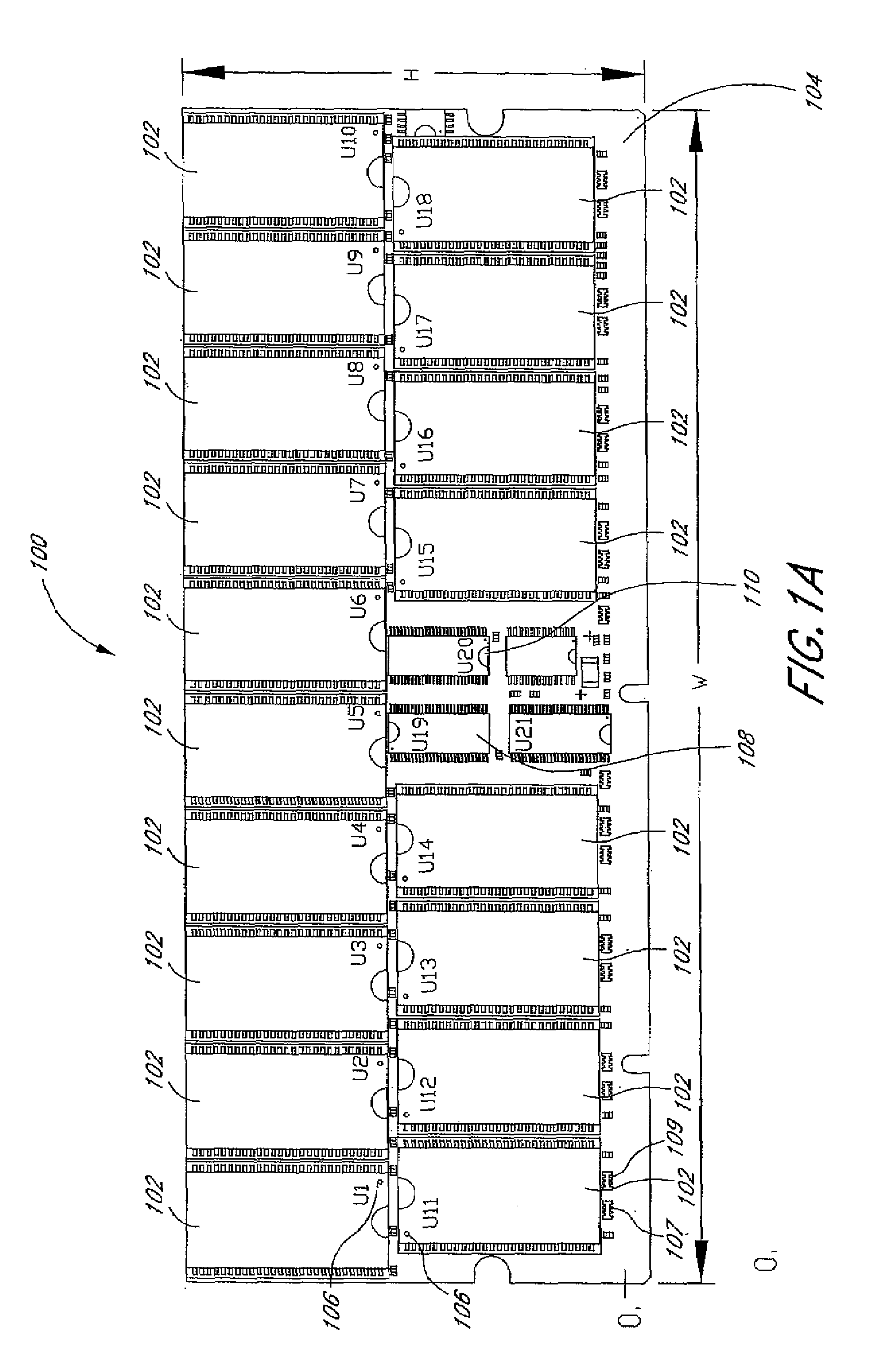
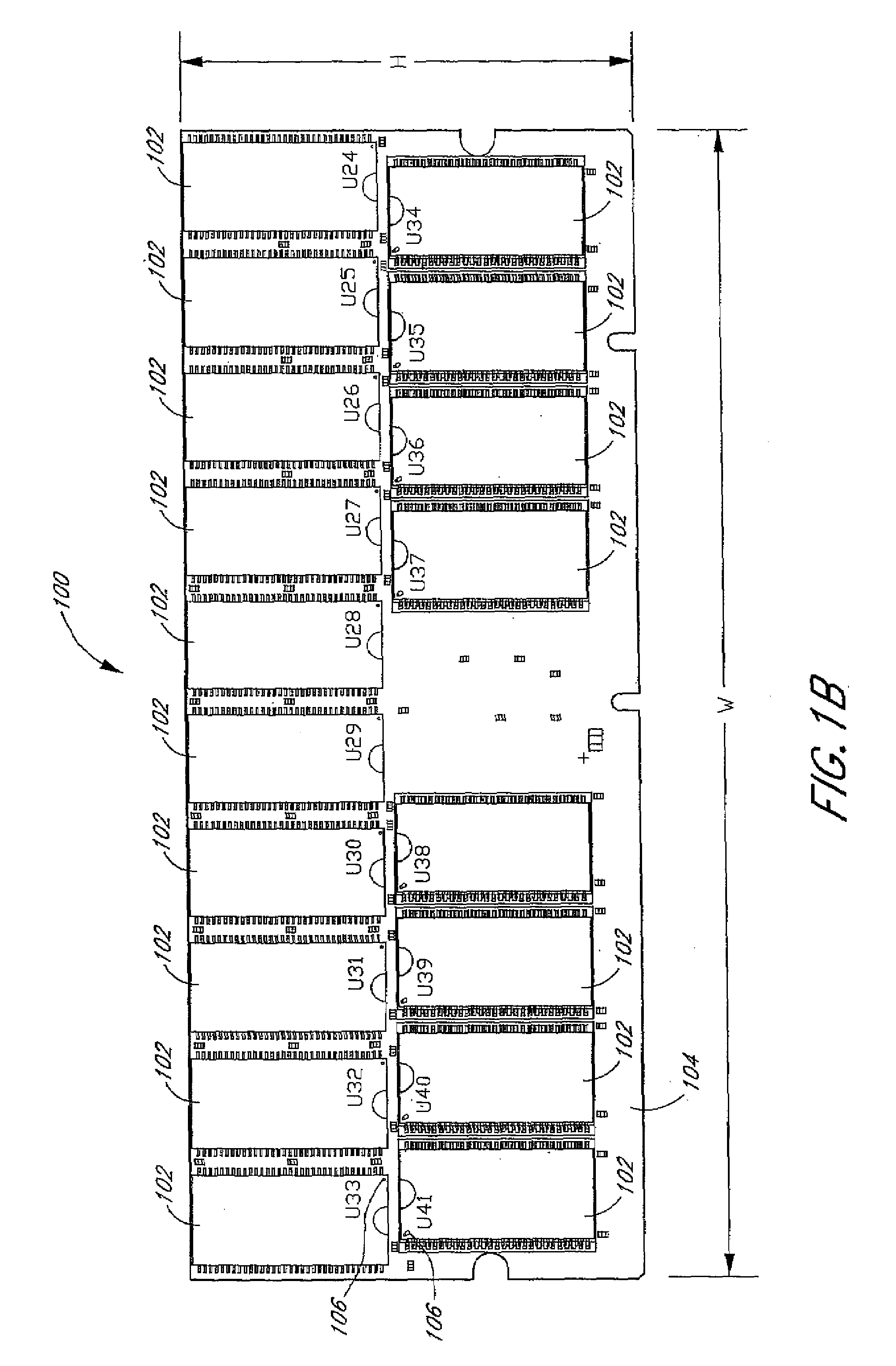
Arrangement of integrated circuits in a memory module
InactiveUS20050018495A1Final product manufactureCross-talk/noise/interference reductionGigabyteProcessor register
Abstract of the Disclosure Integrated circuits utilizing standard commercial packaging are arranged on a printed circuit board to allow the production of one-Gigabyte, two-Gigabyte, and four-Gigabyte capacity memory modules. A first row of integrated circuits is oriented in an opposite orientation to a second row of integrated circuits. The integrated circuits in the first row on a first lateral portion of the printed circuit board and in the second row on the first lateral portion are connected to a first addressing register with two register integrated circuits. The integrated circuits in the first row on the second lateral portion and in the second row on the second lateral portion are connected to a second addressing register with two register integrated circuits. Each addressing register processes a non-contiguous subset of the bits in each data word.
Owner:NETLIST INC
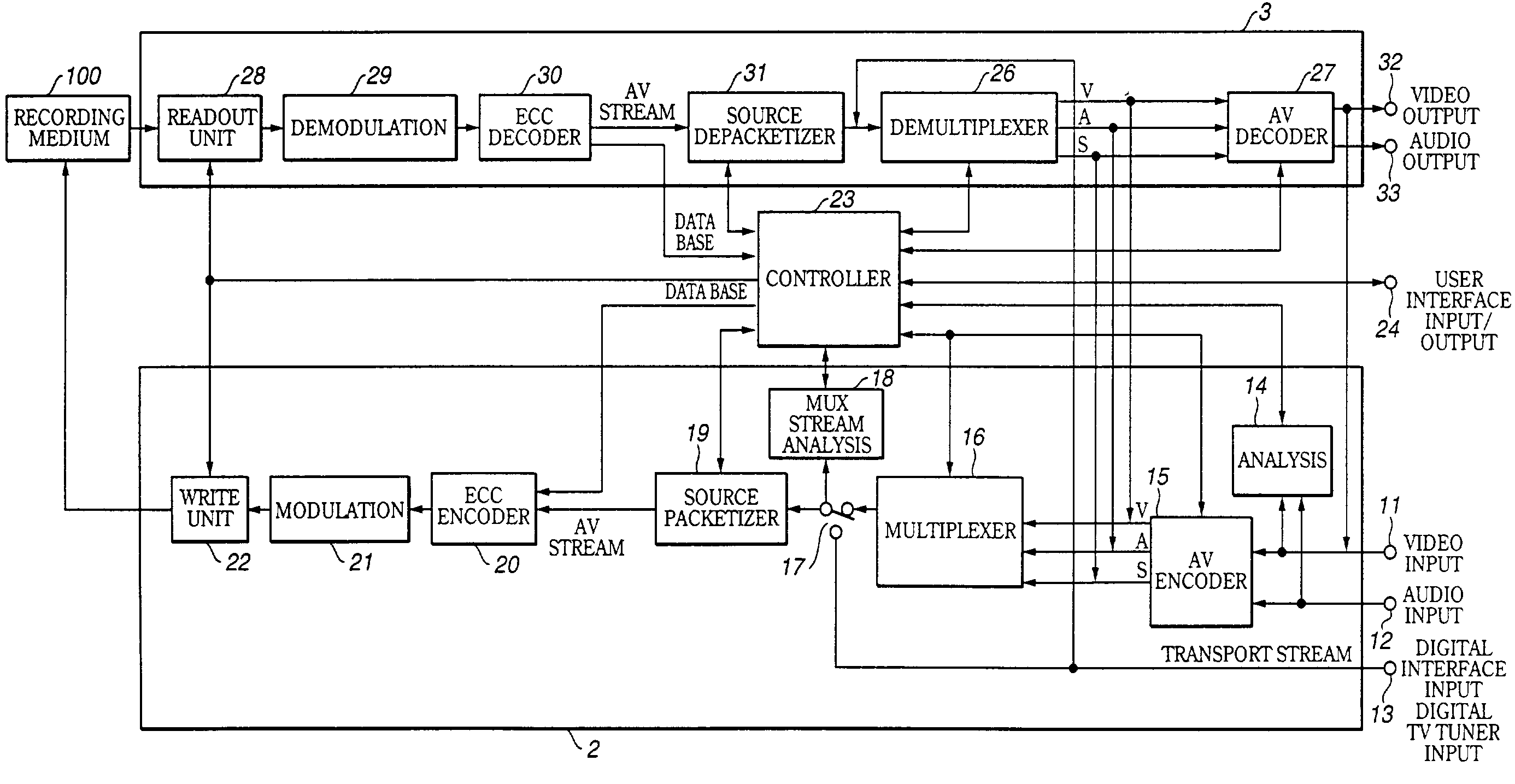
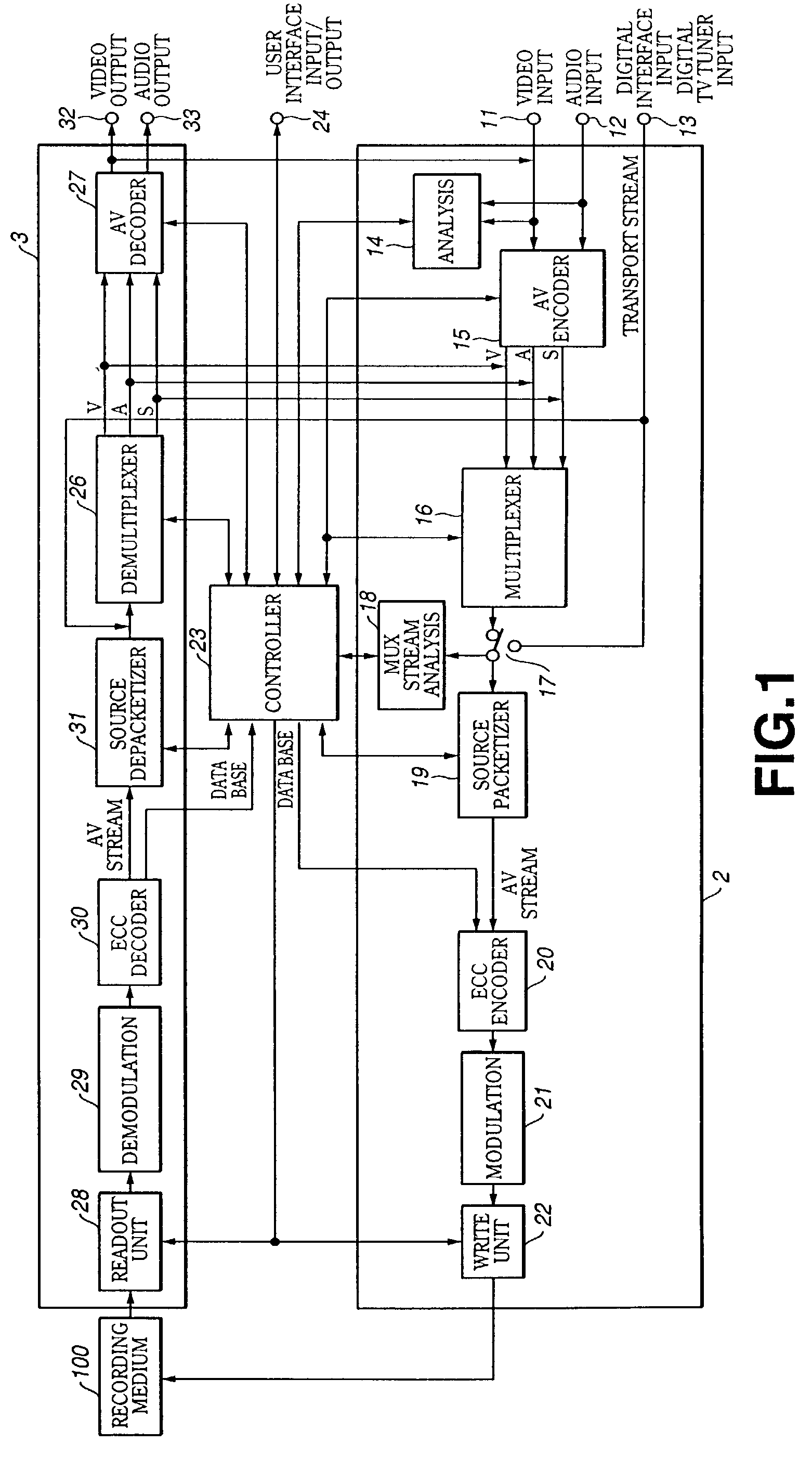
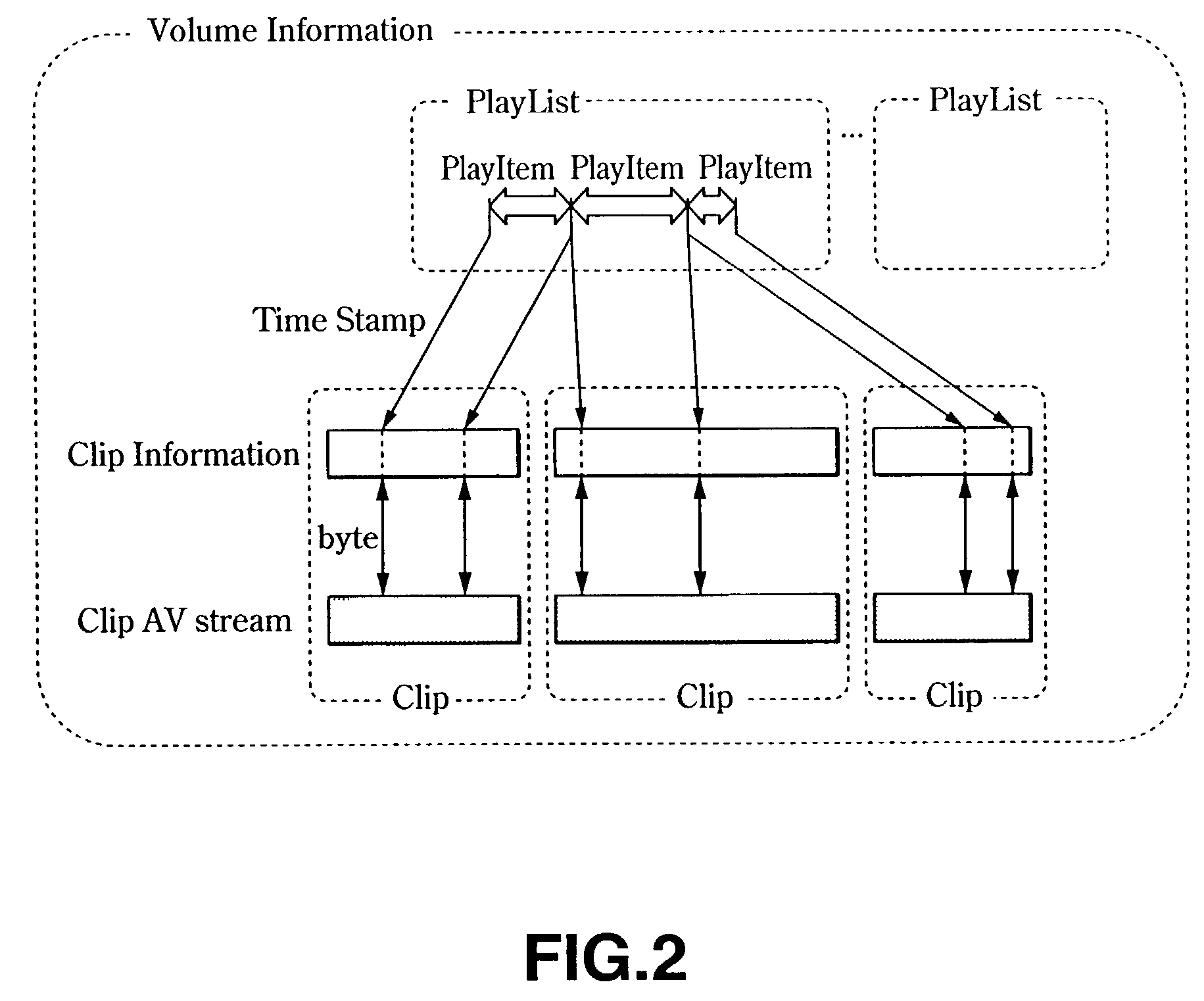
Information processing apparatus and method, program, and recording medium
InactiveUS7236687B2Precise managementTelevision system detailsElectronic editing digitised analogue information signalsInformation processingByte
If, in encoding and recording an AV stream, time_controlled_flag as the attribute information is set to 1, the relation between the time lapse of an AV stream and the amount of data bytes of the AV stream is linear within a preset error range. If the time_controlled_flag of the AV stream file is set to 1, and a certain time portion of the stream is erased by way of partial stream erasure, an unoccupied area corresponding to the erased time portion and which can be recorded at a bitrate indicated by TS_average_rate may be created on the disc.
Owner:SONY CORP
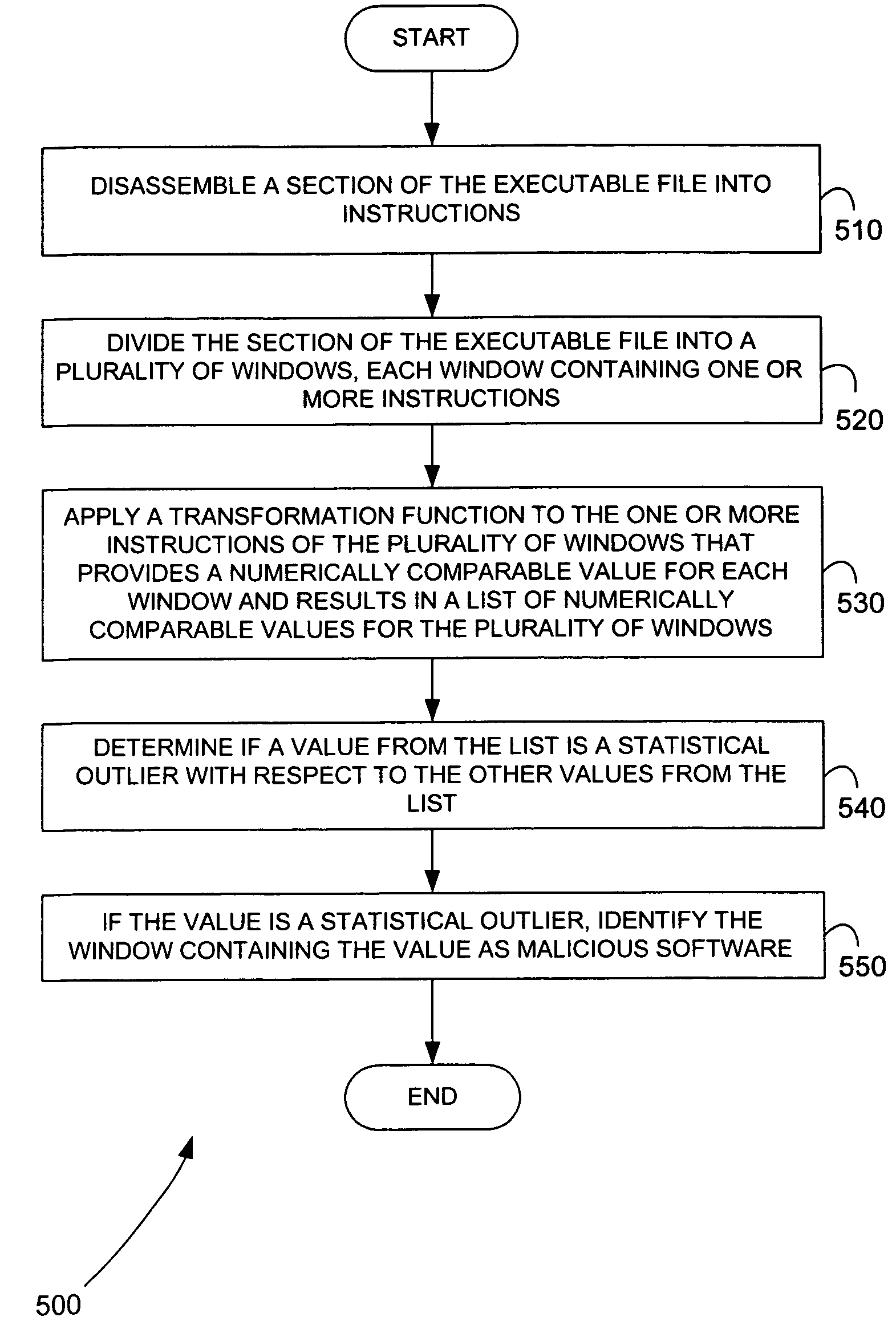
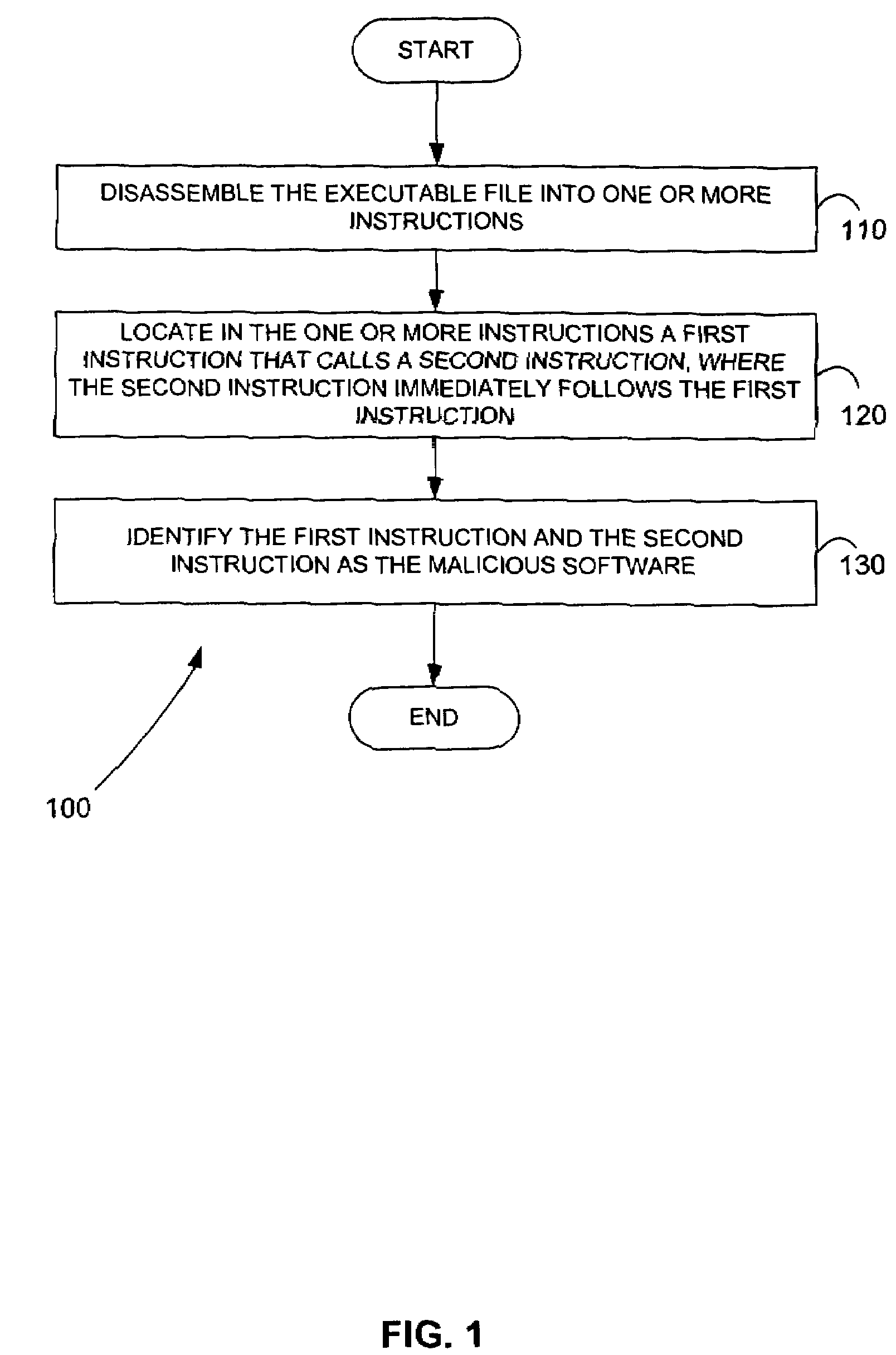
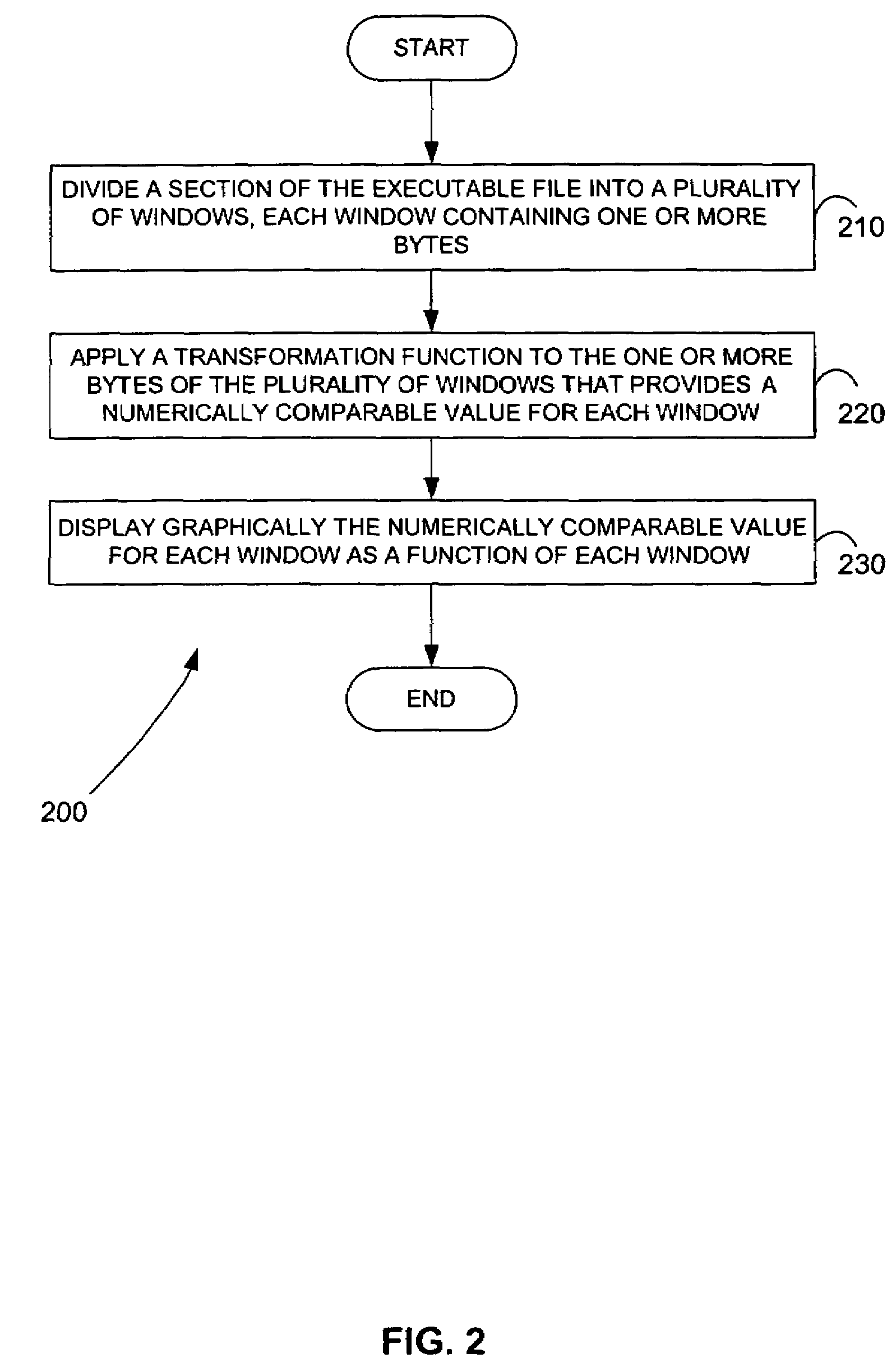
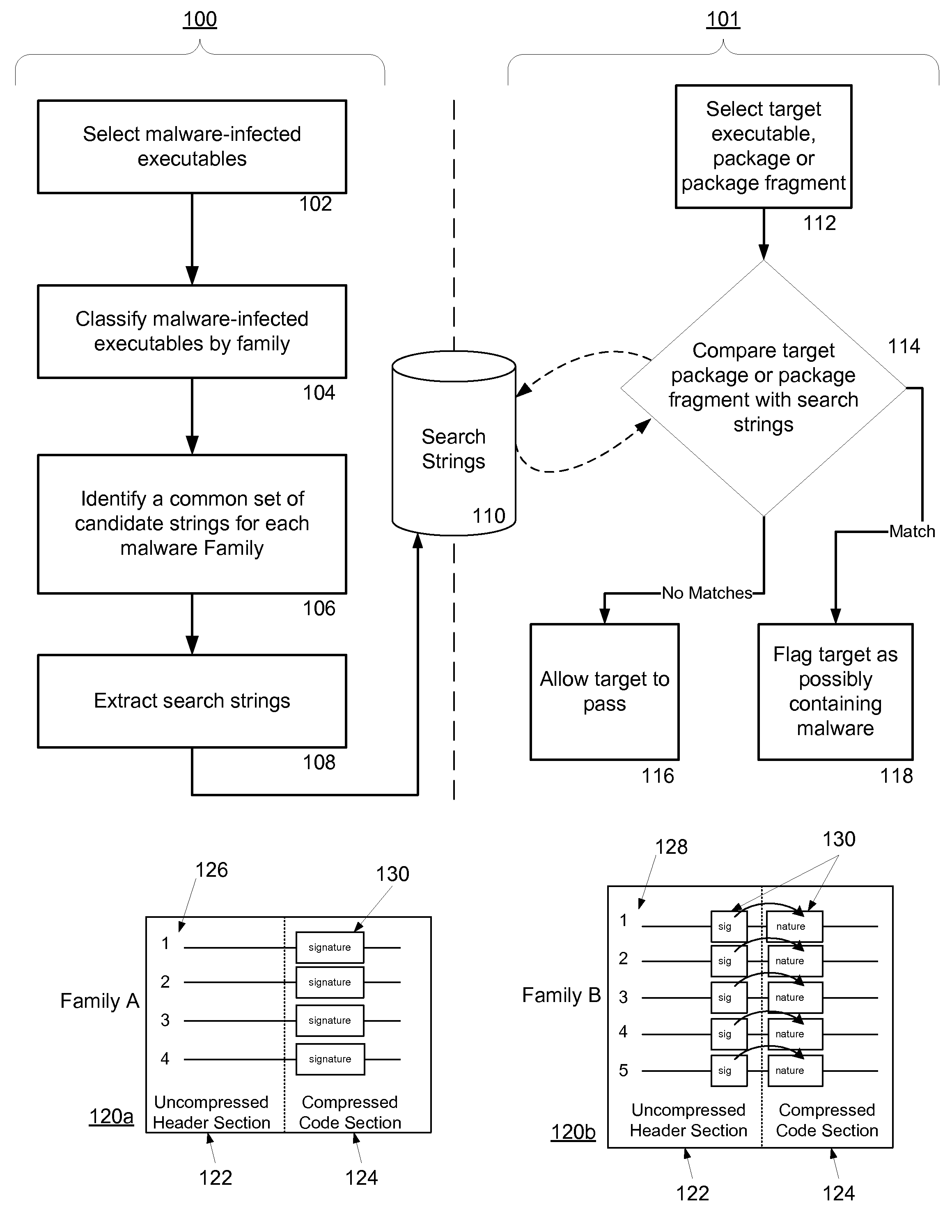
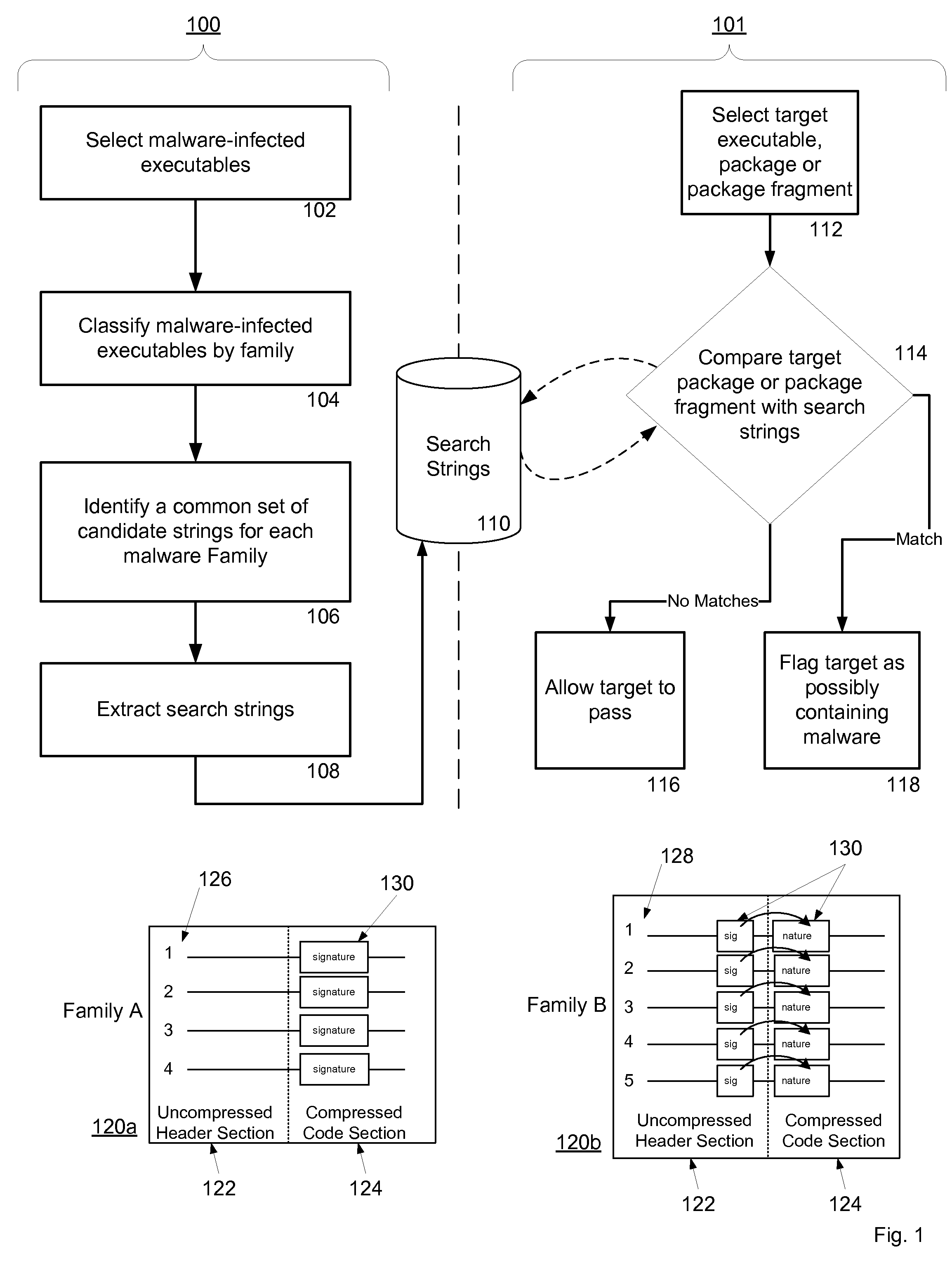
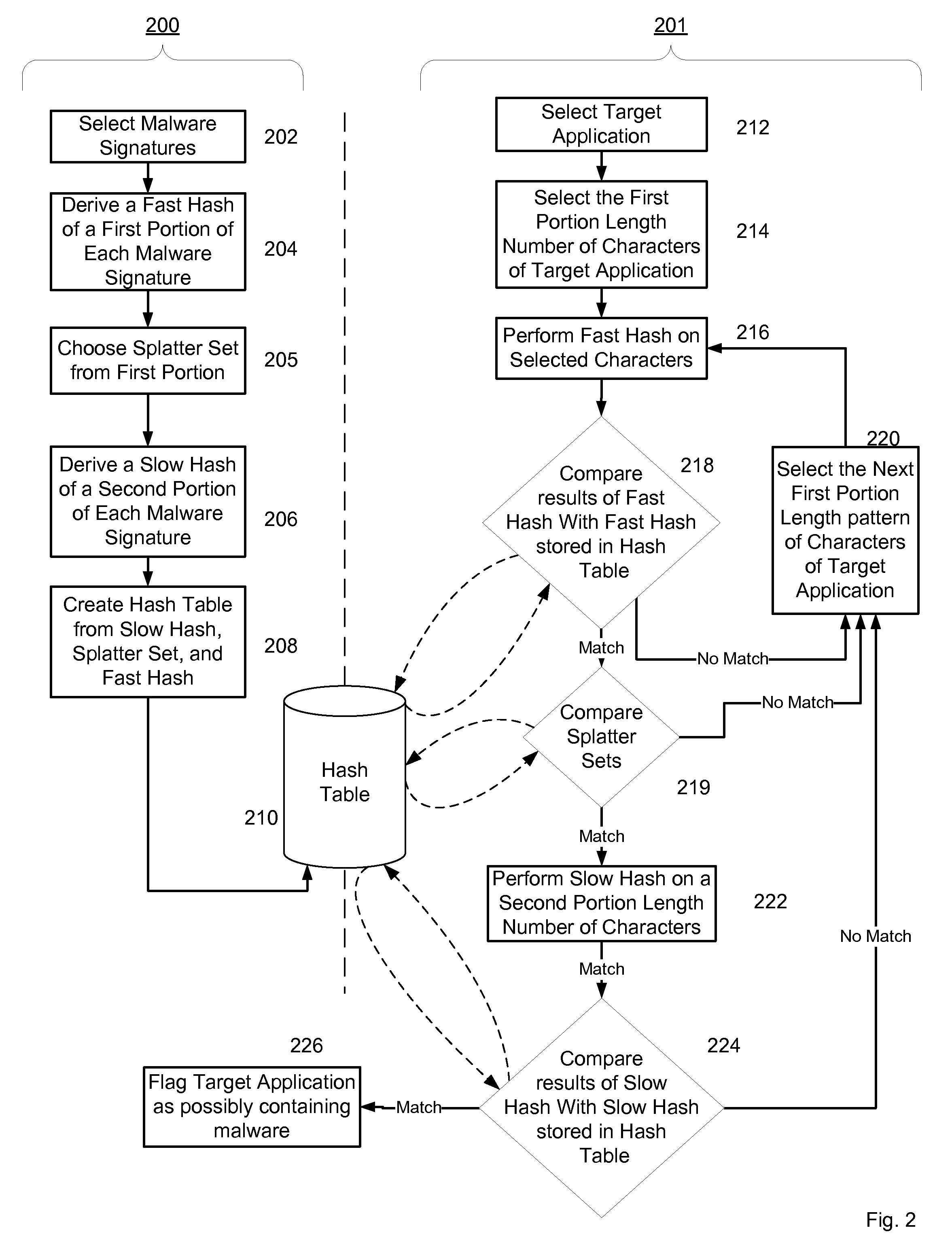
Methods for identifying malicious software
ActiveUS7644441B2Memory loss protectionEncryption apparatus with shift registers/memoriesGraphicsEncrypted function
Malicious software is identified in an executable file by identifying malicious structural features, decryption code, and cryptographic functions. A malicious structural feature is identified by comparing a known malicious structural feature to one or more instructions of the executable file. A malicious structural feature is also identified by graphically and statistically comparing windows of bytes or instructions in a section of the executable file. Cryptography is an indicator of malicious software. Decryption code is identified in an executable file by identifying a tight loop around a reversible instruction that writes to random access memory. Cryptographic functions are identified in an executable file be obtaining a known cryptographic function and performing a string comparison of the numeric constants of the known cryptographic function with the executable file.
Owner:SYNOPSYS INC
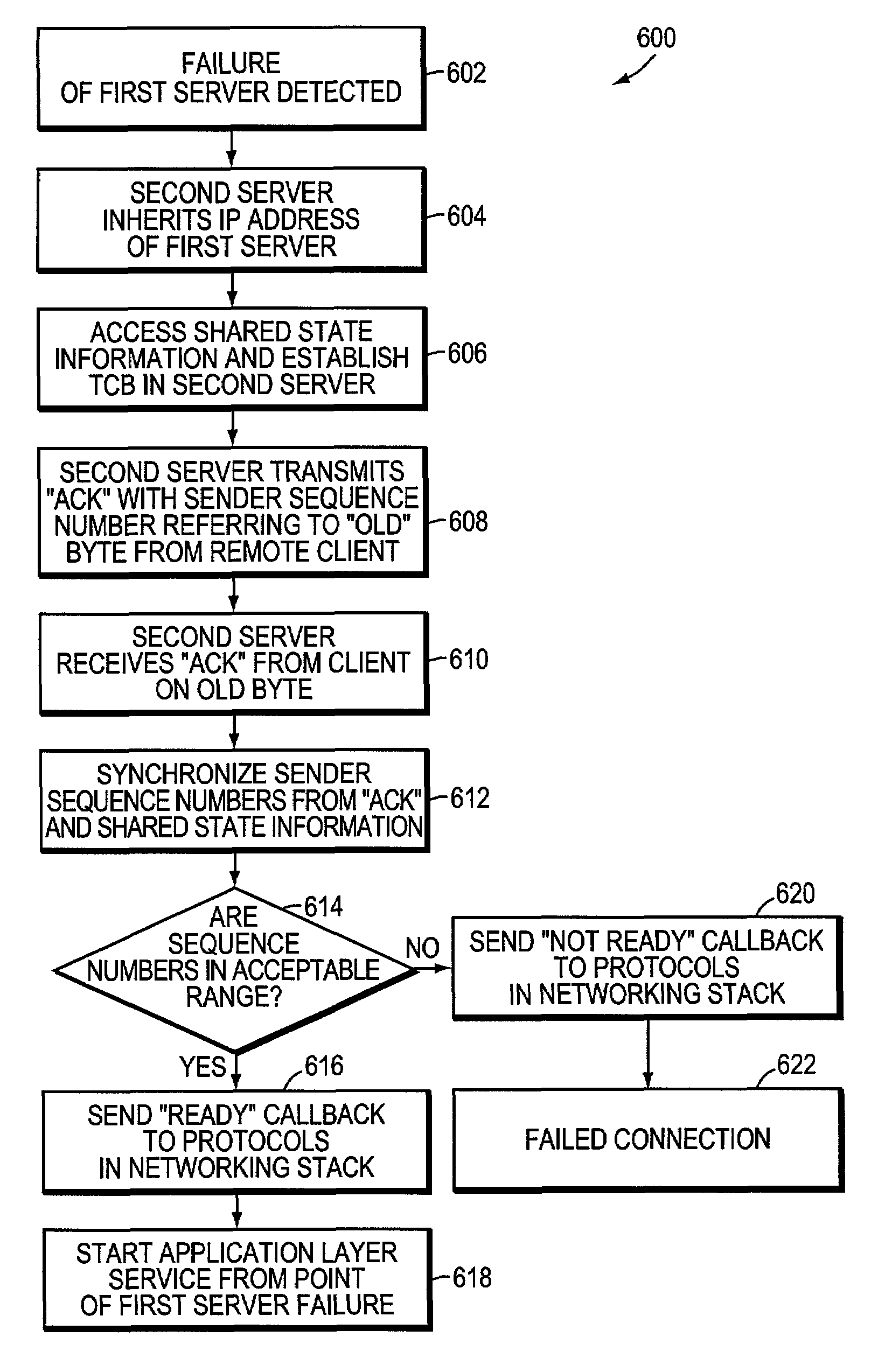
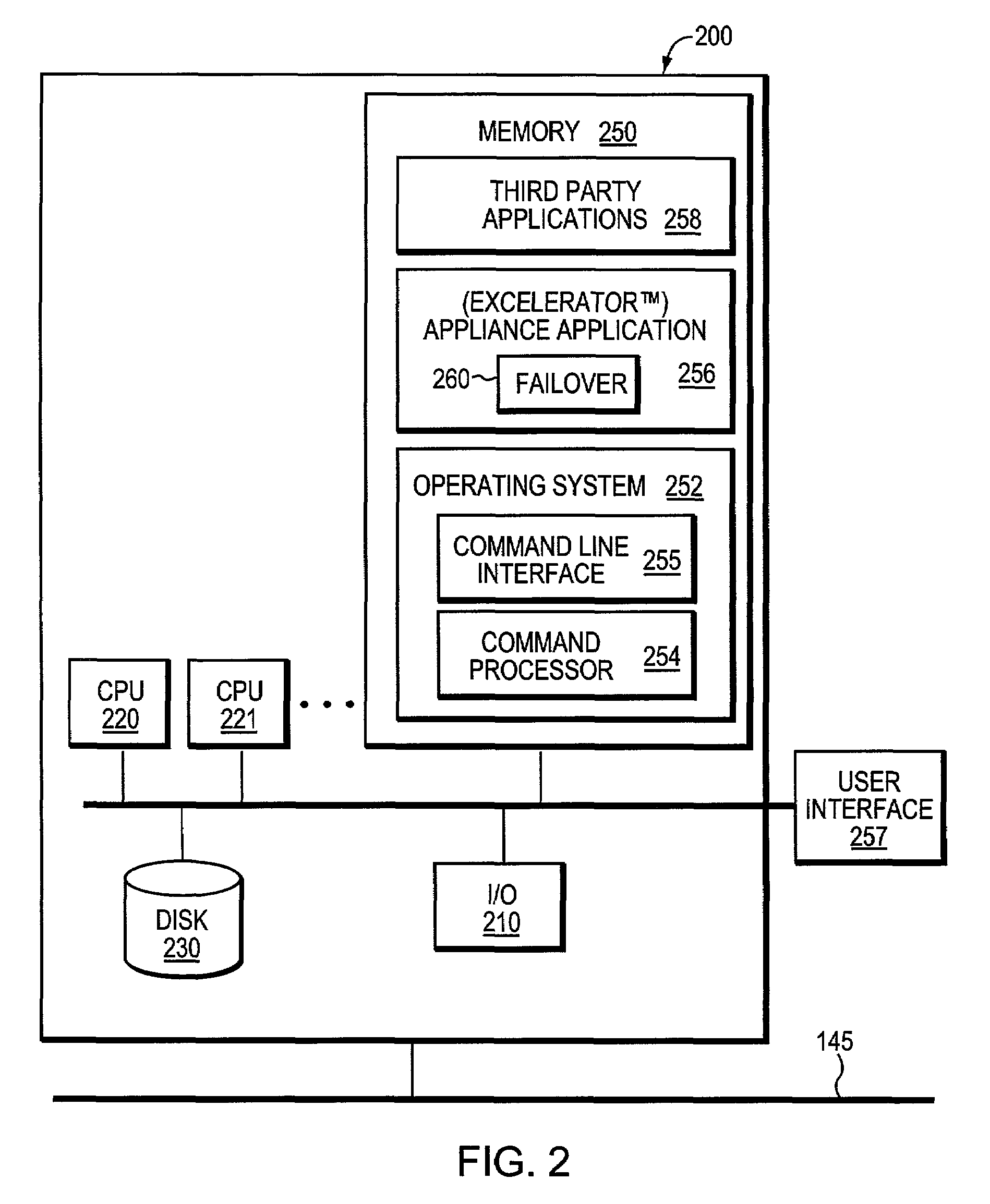
System and method for transparent takeover of TCP connections between servers
A system and a method for transparent takeover (or failover) of a remote client TCP connection from a first server in a cluster of interconnected servers to a second server provides the storing of shared state information relative to the connection on each involved server and using of the shared state information to reestablish the connection on the second server. A message using a sequence number to refer to a previously transmitted data element (such as a byte) is sent by the second server and a received client acknowledgement (ACK) of that sequence number, or a higher one, is used to synchronize the server's data packet transmission sequence number with the ACK-transmitted sequence number. If synchronization is successful, then the connection is restarted on the second server from the point of termination / failure on the first server.
Owner:MICRO FOCUS SOFTWARE INC
Integrity verifying and correcting software
InactiveUS6023586AEfficiently provideData processing applicationsDigital computer detailsSelf-healingApplication software
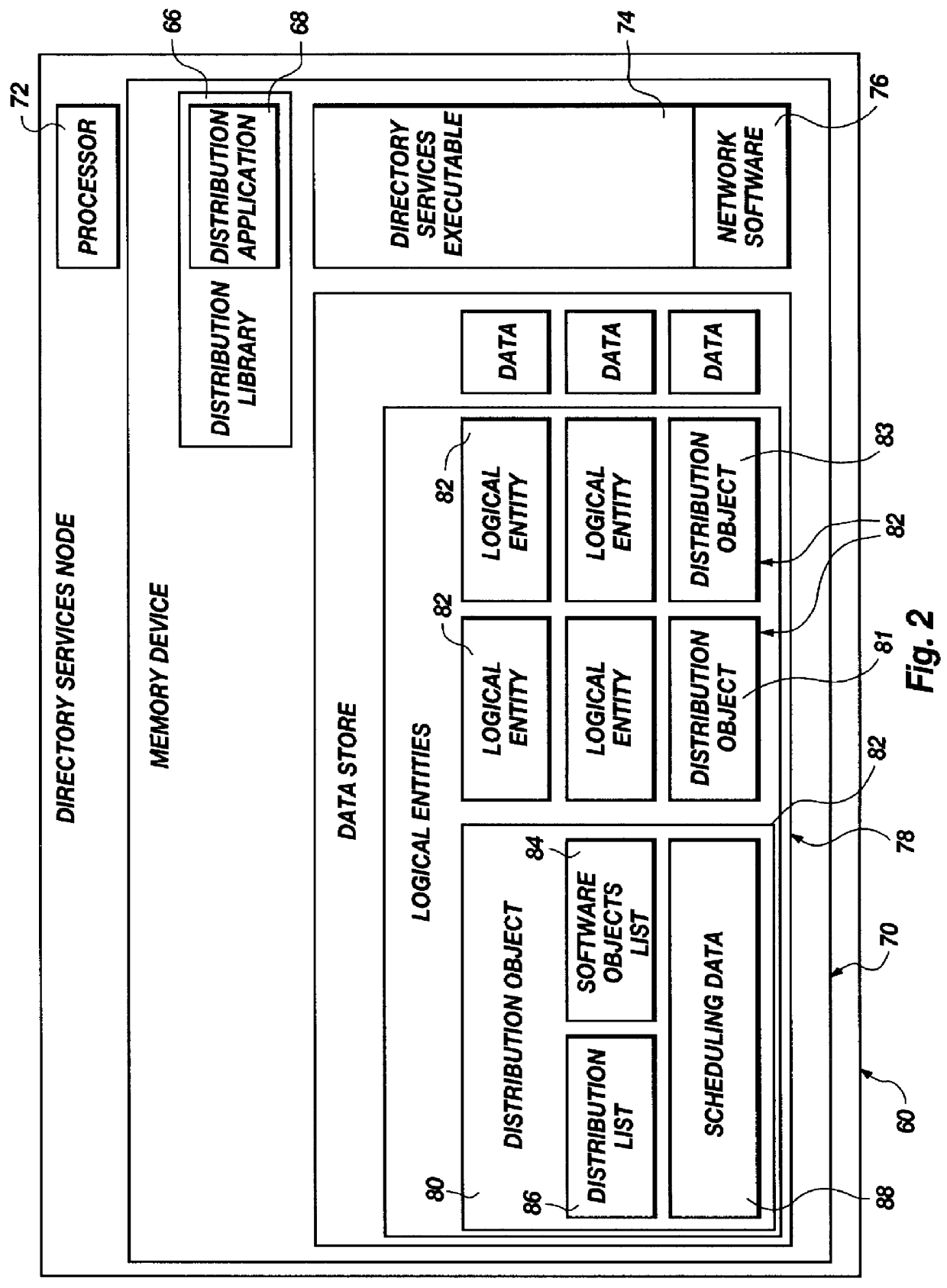
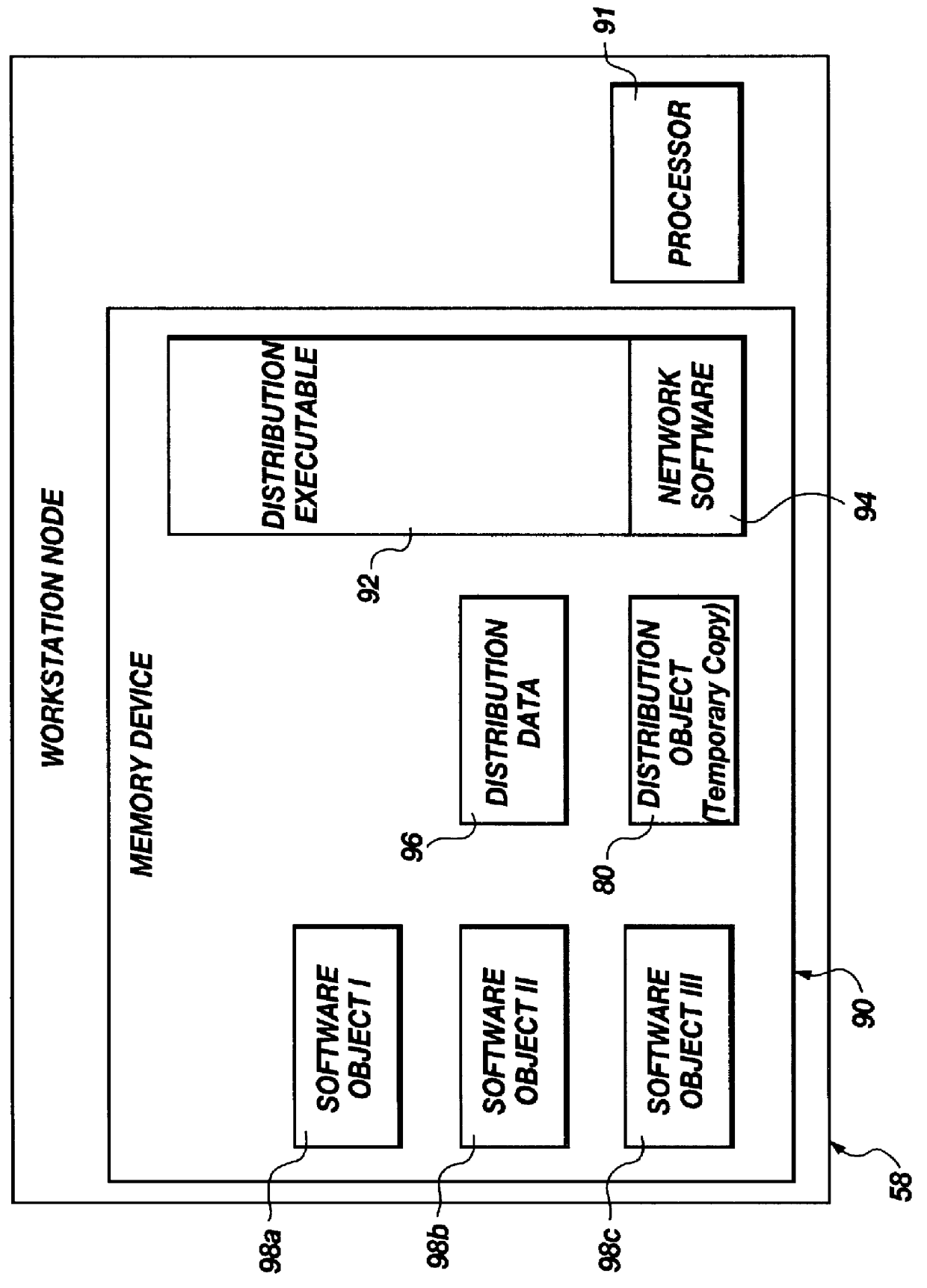
An apparatus and method for self-healing of software may rely on a distribution object in a directory services of a network to provide data for controlling distribution of software and installation of files associated therewith. A software object may represent a software product, system, data structure, application, or the like, from a single byte, to a complex program. A directory services system is responsible for maintaining a data store of inter-related logical entities (directory services objects), including software objects and a distribution object containing all distribution information associated with certain distribution processes. Maintenance methods may be programmed into a directory services object or some other executable to verify the existence of files required for particular software. Verification may be completed in association with a launch request, by explicit request, or in an ongoing maintenance procedure. Maintenance may include executables and data to control, complete, and record integrity of distributed files as a distinct activity or as an ongoing, routine, periodic process of verification and appropriate re-installation of files, operating transparently to a user.
Owner:RPX CORP
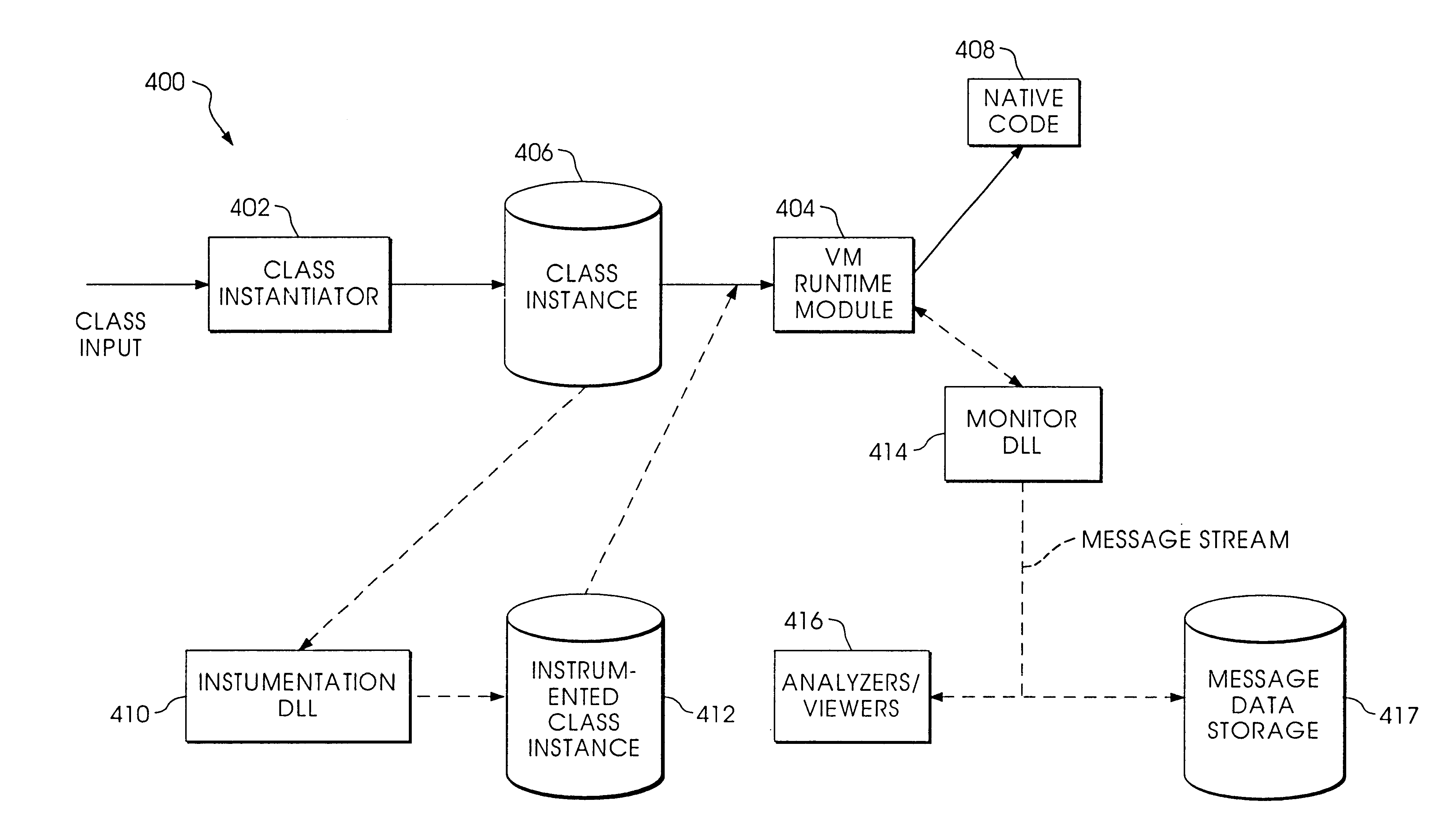
Byte code instrumentation
InactiveUS6314558B1Software testing/debuggingSpecific program execution arrangementsMessage flowTime function
Instrumenting a computer program to provide instrumented byte code includes examining the byte code, selecting portions of the byte code for instrumentation, and instrumenting the portions to provide instrumented byte code. Selecting the portions may include choosing portions of the byte code corresponding to method entry, method exit, a throw, a method call, or a new line number. Instrumenting a portion of the byte code corresponding to a method call may include instrumenting a local line number of source code corresponding to the byte code being instrumented. Instrumenting the portions may include adding calls to instrumentation runtime functions that pass parameters indicative of the portions being instrumented. At least one of the parameters that is passed may include a line number of the source code corresponding to the portion being instrumented or a object pointer for the method corresponding to the portion being instrumented. Data from instrumentation may be passed via a message stream that is viewed as the data is being generated and / or stored.
Owner:BORLAND
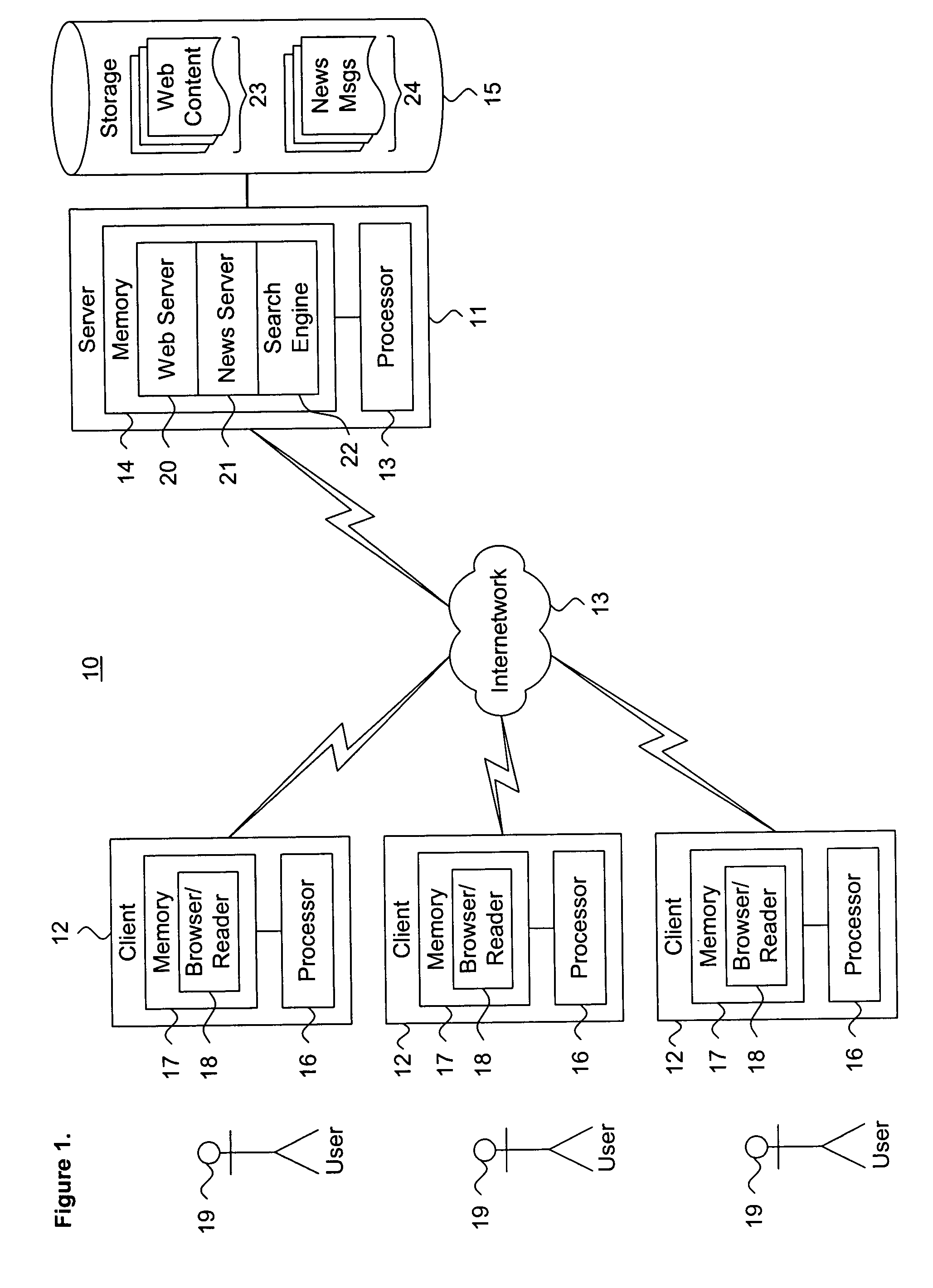
Identifying language attributes through probabilistic analysis
ActiveUS7386438B1Natural language data processingSpeech recognitionNatural language processingDocument preparation
A system and method for identifying language attributes through probabilistic analysis is described. A set of language classes and a plurality of training documents are defined, Each language class identifies a language and a character set encoding. Occurrences of one or more document properties within each training document are evaluated. For each language class, a probability for the document properties set conditioned on the occurrence of the language class is calculated. Byte occurrences within each training document are evaluated. For each language class, a probability for the byte occurrences conditioned on the occurrence of the language class is calculated.
Owner:GOOGLE LLC
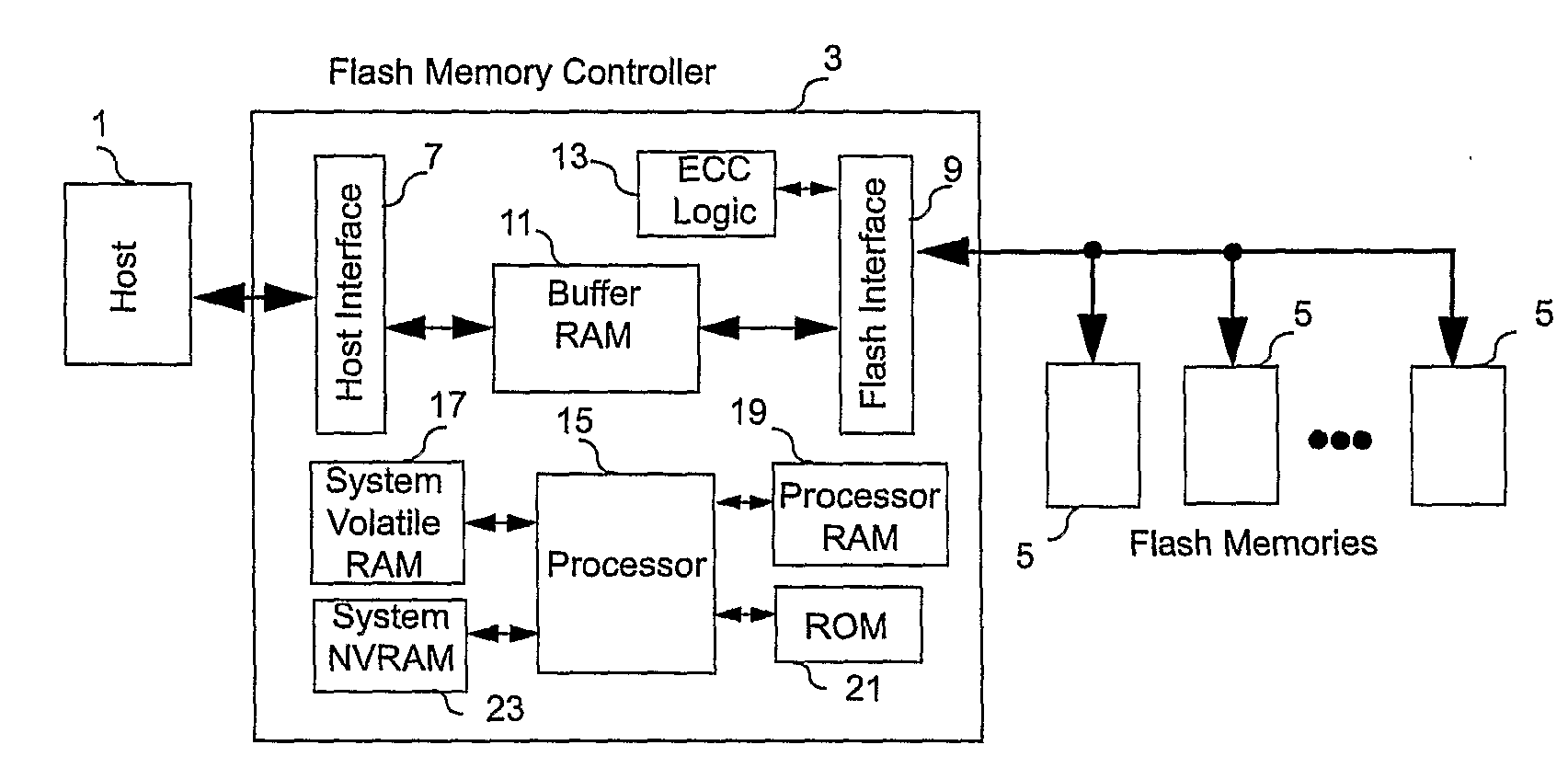
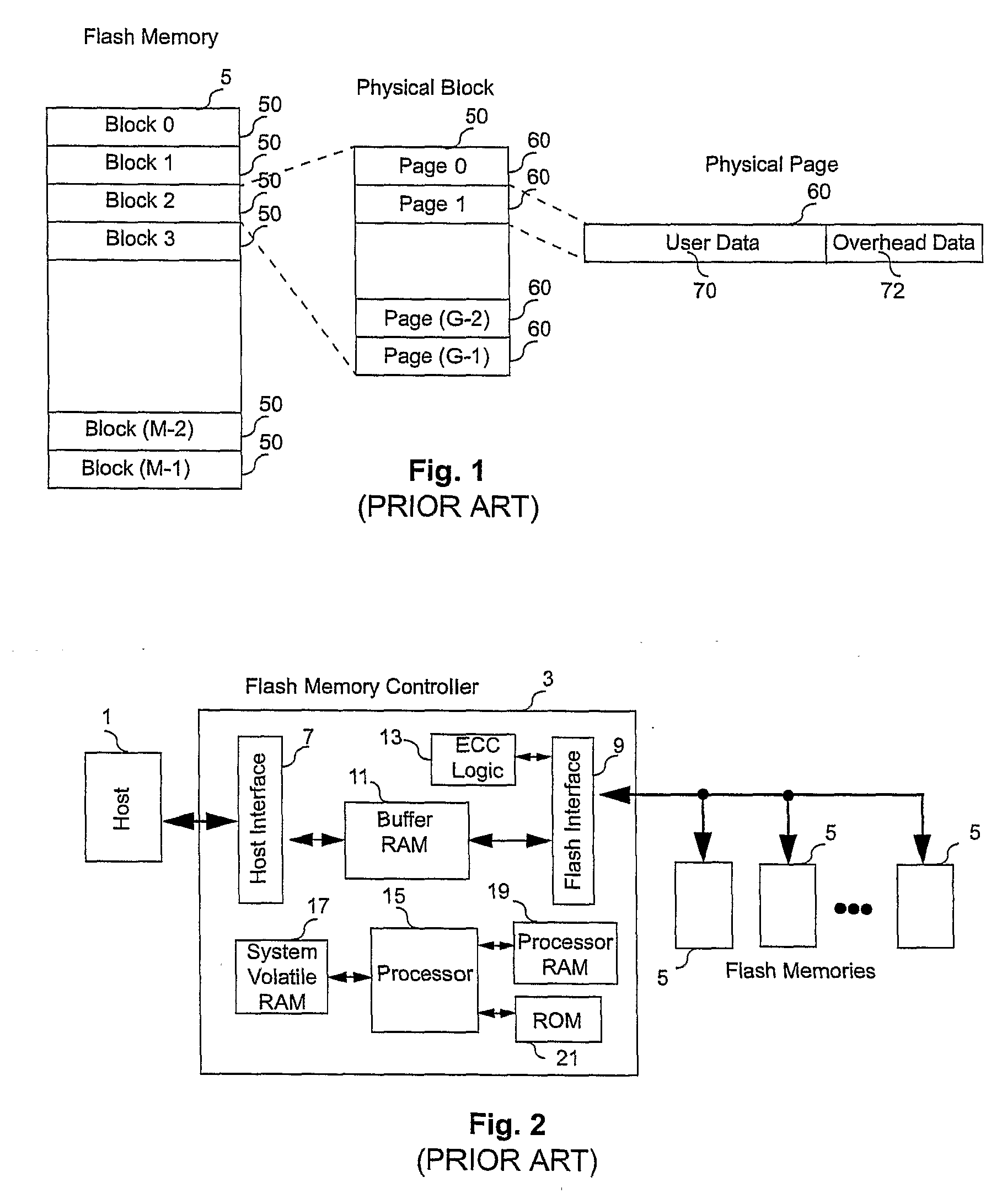
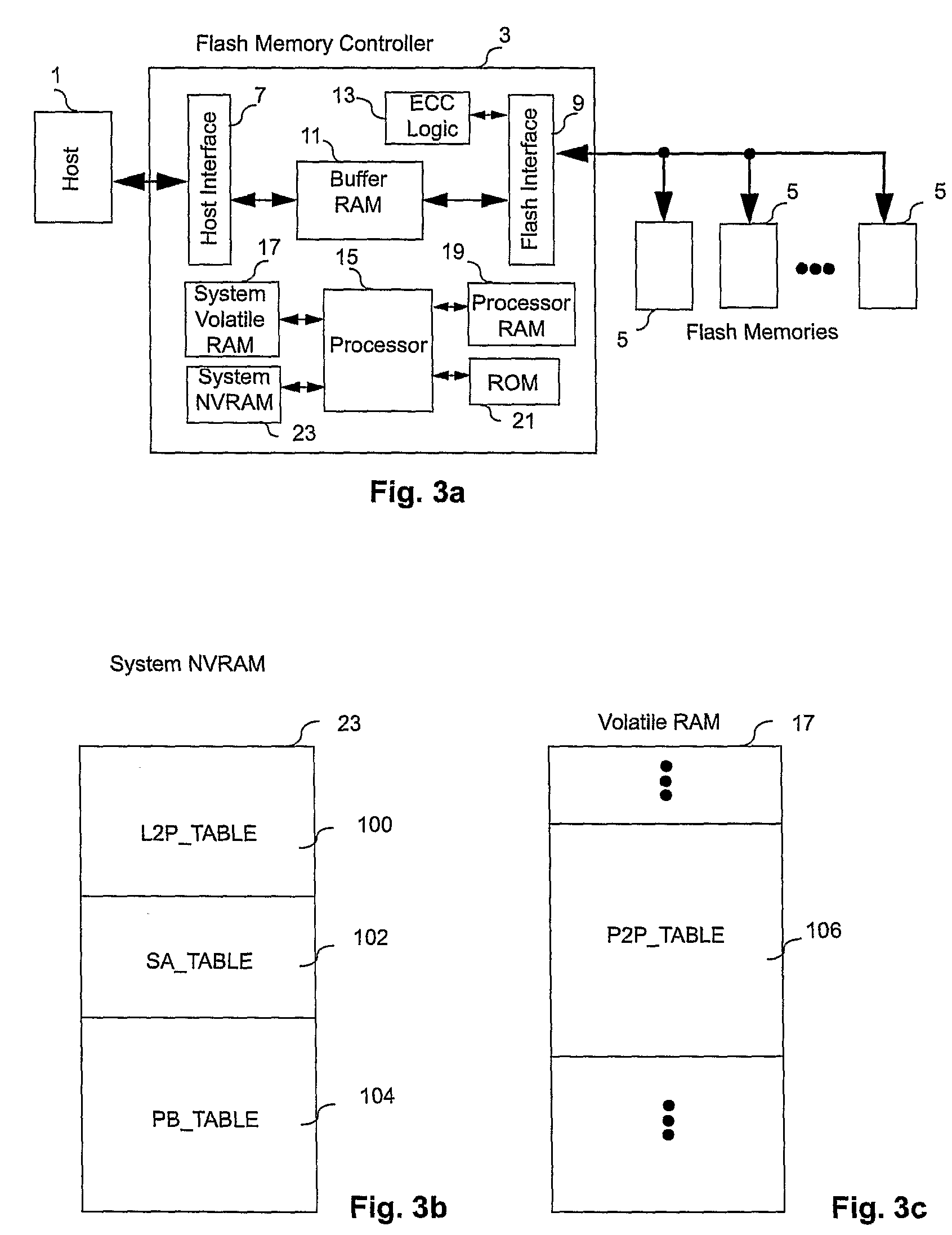
Controller for Non-Volatile Memories and Methods of Operating the Memory Controller
ActiveUS20080270680A1Improve system performanceReduce stepsMemory adressing/allocation/relocationRead-only memoriesMemory controllerByte
A non-volatile memory system (3) is proposed consisting of a first non-volatile flash memory (5) having a plurality of blocks, each block having a plurality of pages, each block being erasable and each page being programmable, and a second non-volatile random access memory (23) having a plurality of randomly accessible bytes. The second non-volatile memory (23) stores data for mapping logical blocks to physical blocks and status information of logical blocks. Each logical block has an associated physical page pointer stored in the second non-volatile memory (23) that identifies the next free physical page of the mapped physical block to be written. The page pointer is incremented after every page write to the physical block, allowing all physical pages to be fully utilized for page writes. Furthermore, a method of writing and reading data is disclosed whereby the most recently written physical page associated with a logical address is identifiable by the memory system without programming flags into superseded pages, or recording time stamp values in any physical page or block of the first non-volatile memory (5). Furthermore, a method is provided for a logical block to be mapped to two physical blocks instead of one to provide additional space for page writes, resulting in reduction in page copy operations, thereby increasing the performance of the system.
Owner:CHANG CHEE KENG
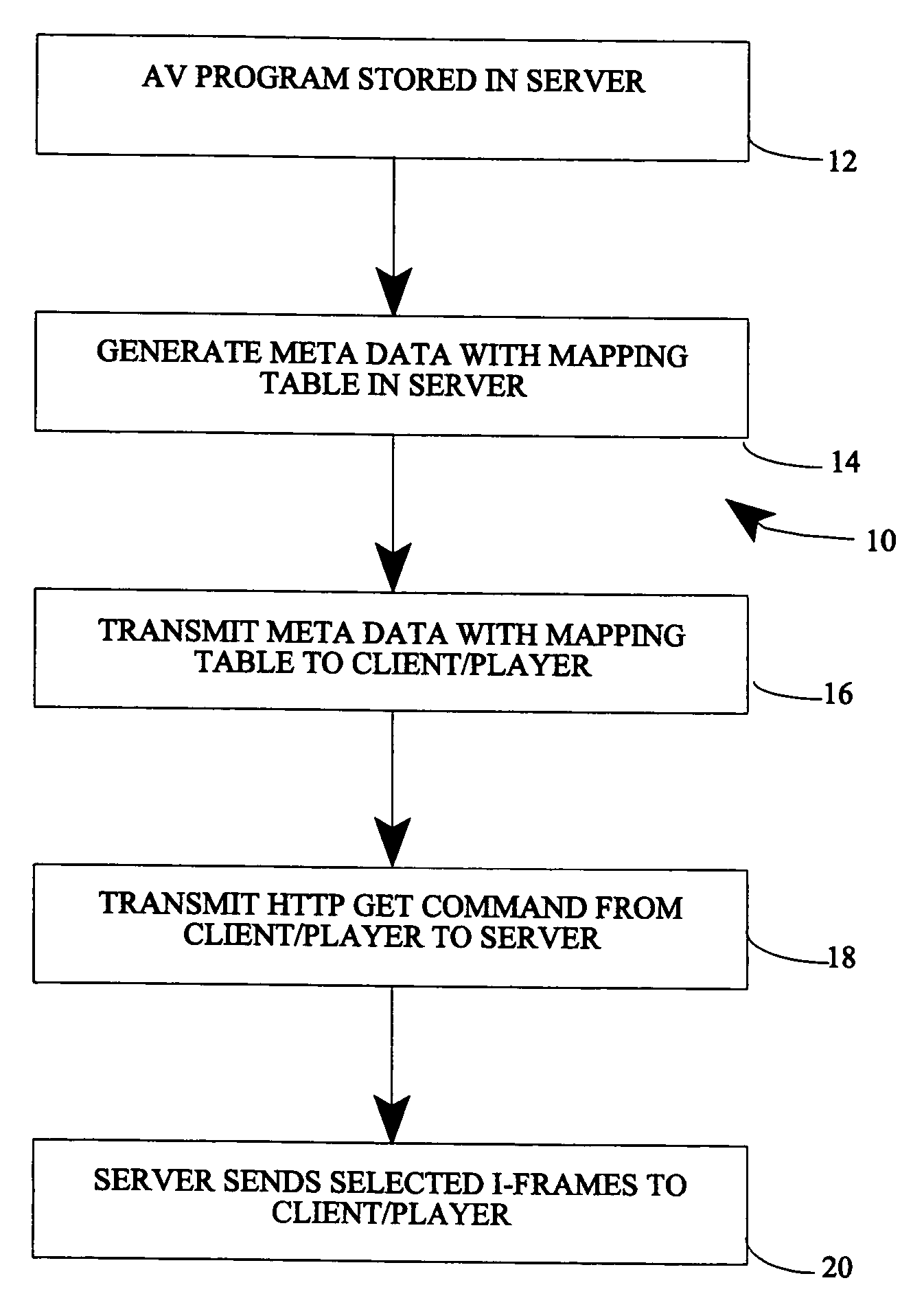
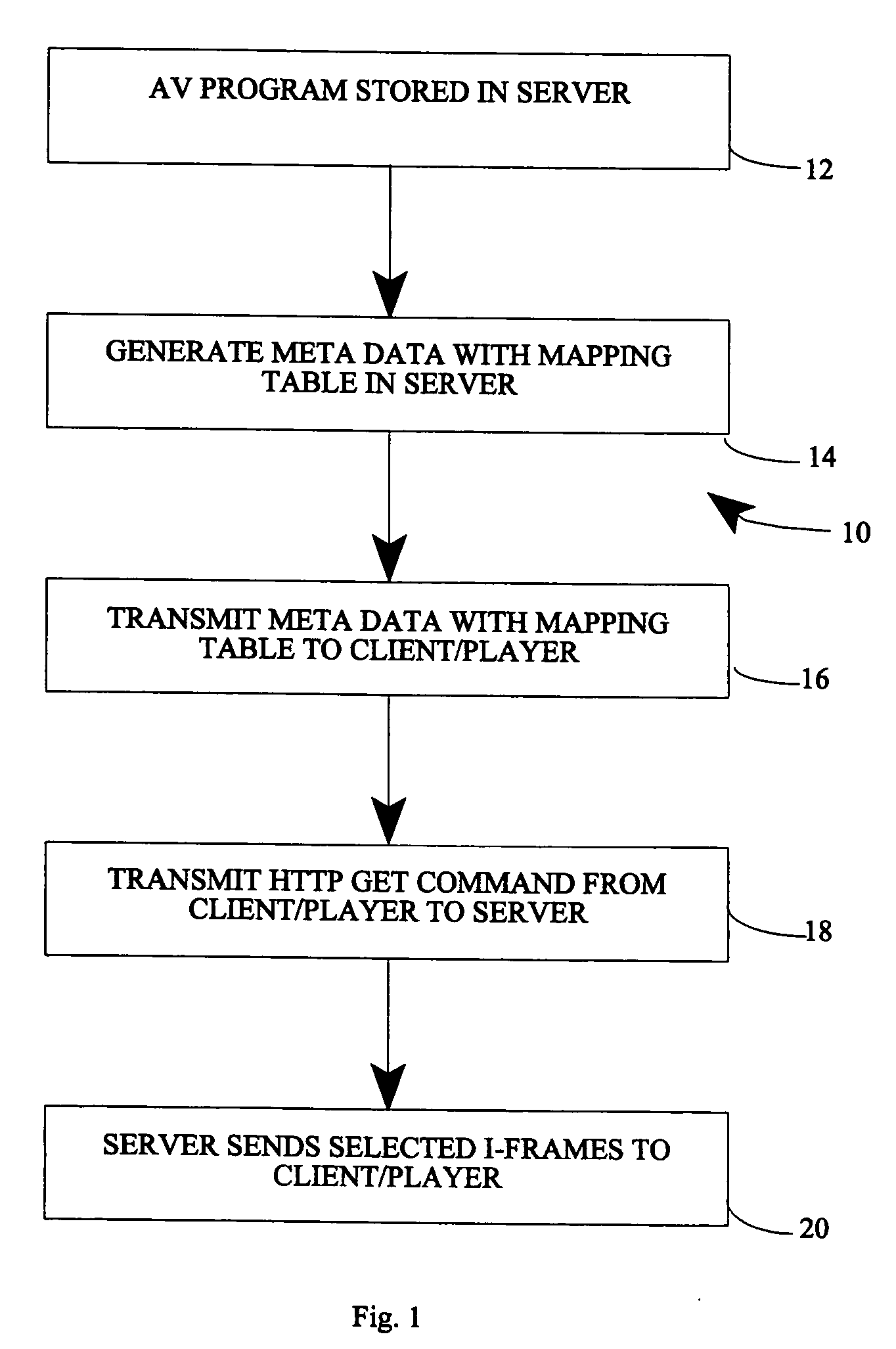
Method and system of enabling trick play modes using HTTP GET
A method of providing operational commands to a AV program transmitted using HTTP protocol includes storing an AV program in a server; generating meta data in the server, wherein the meta data includes a mapping table associating time ranges for the AV program to byte ranges for the AV program; transmitting the meta data and mapping table to a client / player associated with the server; generating and transmitting a HTTP GET command from the client / player to the server as a function of a desired operational command; and selecting appropriate I-frames in the server and transmitting the I-frames to the client / player in response to the HTTP GET command.
Owner:SHARP LAB OF AMERICA INC
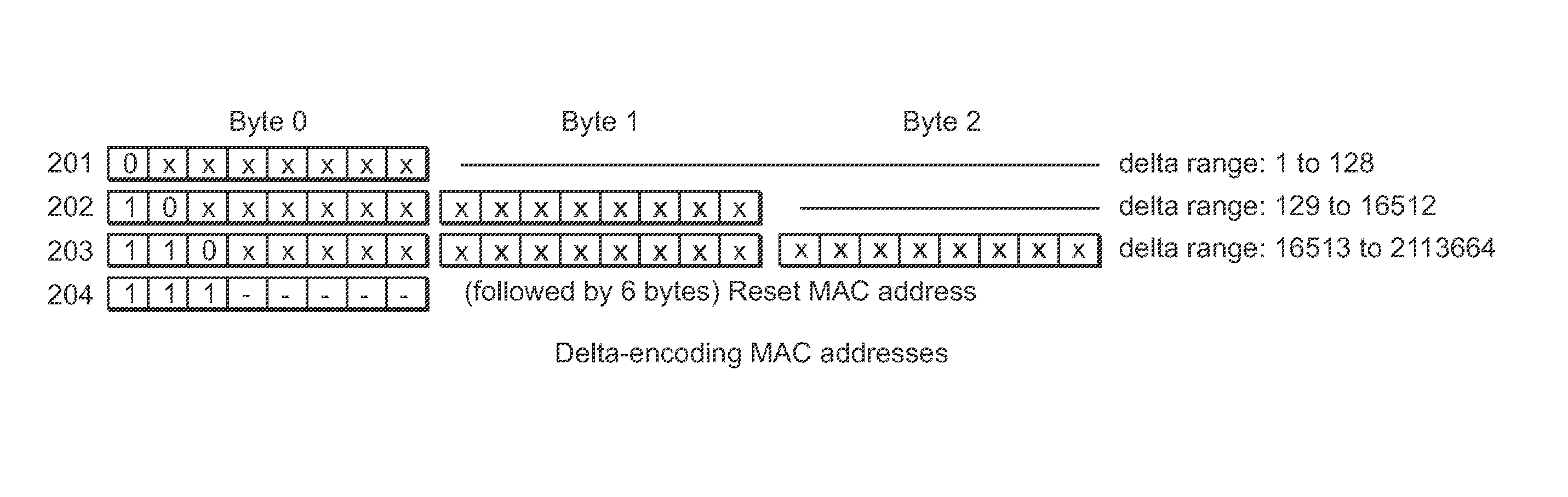
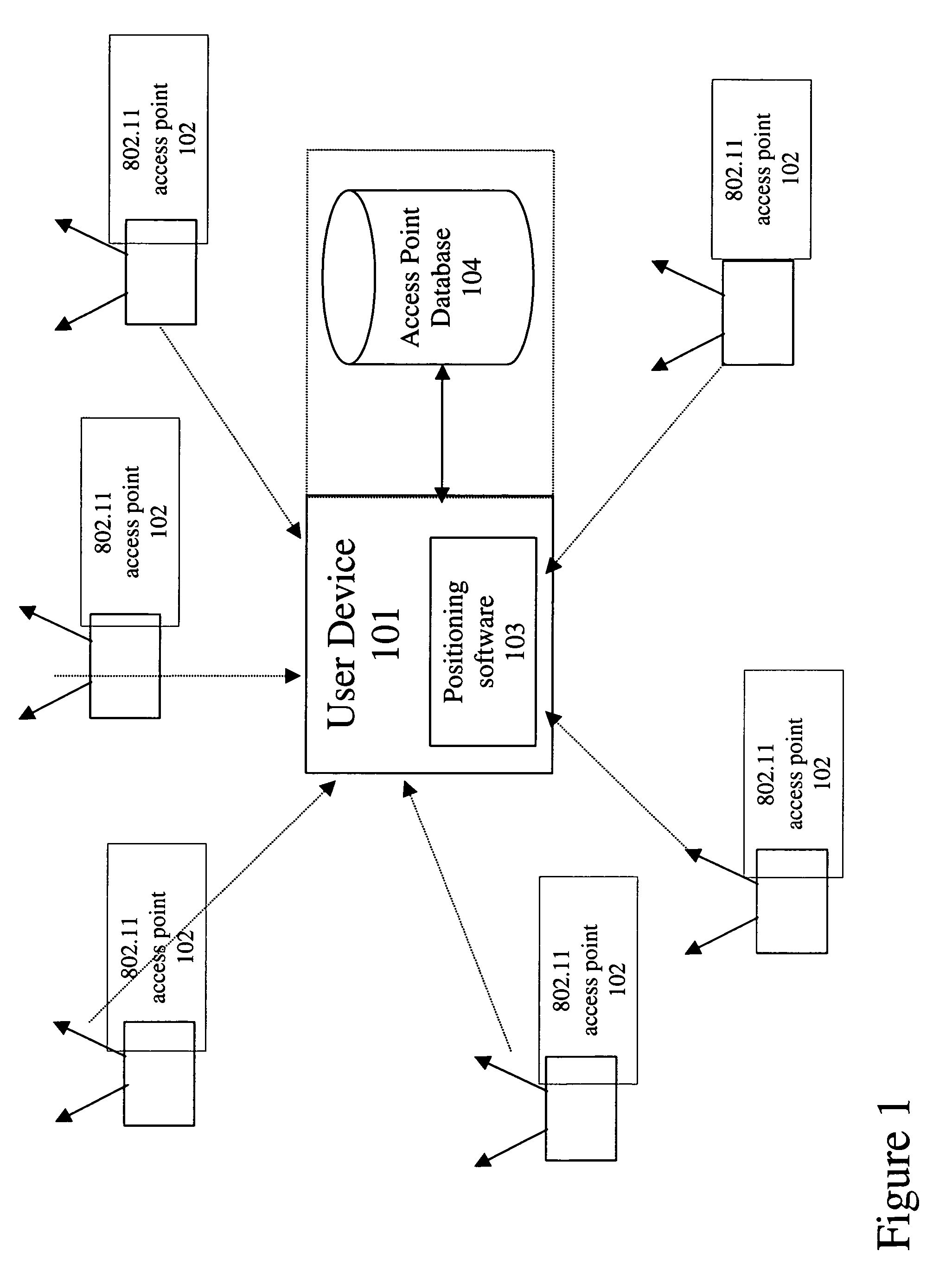
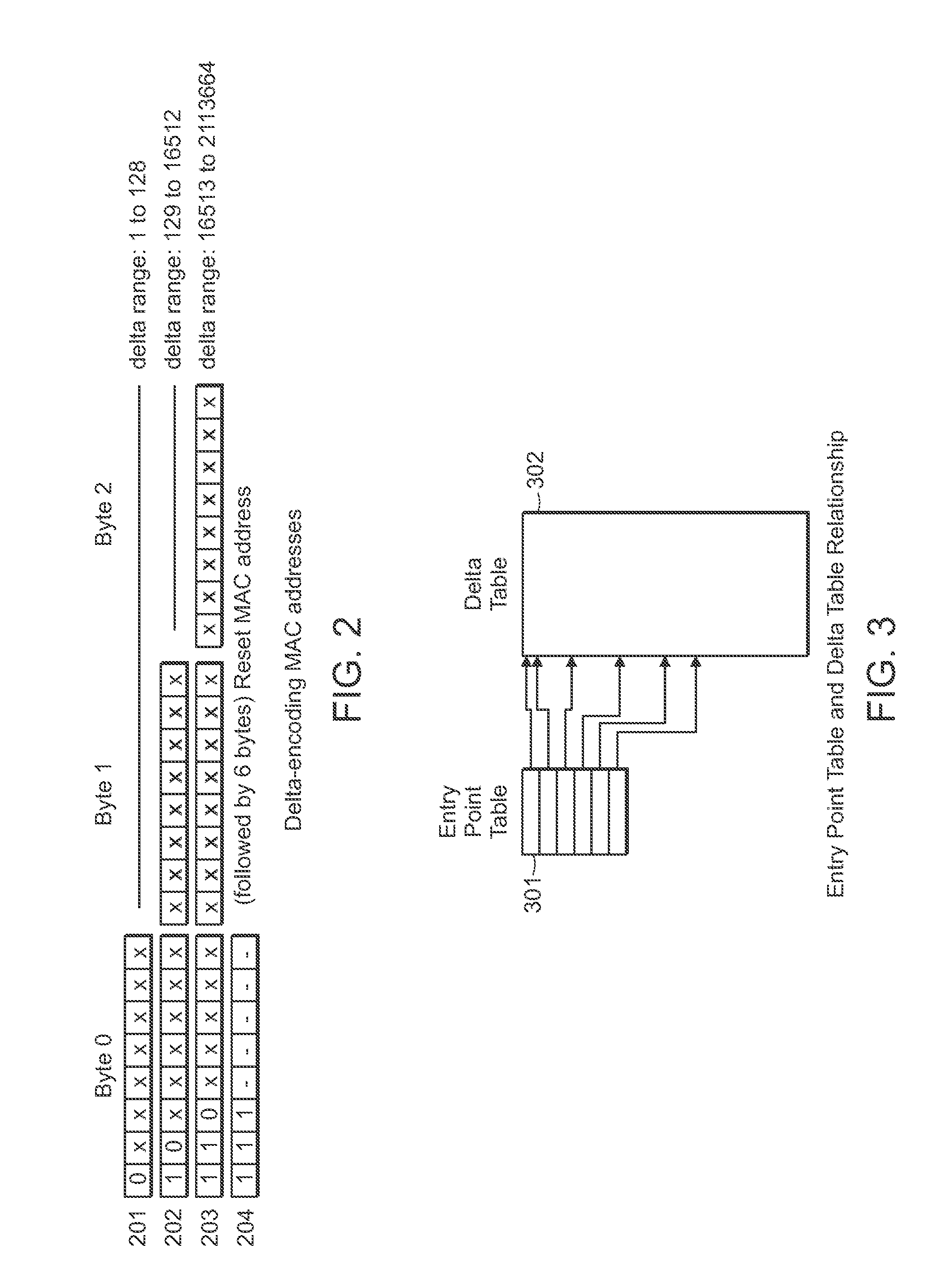
Encoding and compression of a location beacon database
A method of delta-encoding and compressing a table containing 6-byte MAC addresses is provided. The MAC addresses are sorted, a first MAC address is stored, and only the binary differences between succeeding MAC addresses are stored. A method of reading a delta-encoded and compressed MAC address table is provided. A first unencoded MAC address is read. The remaining MAC addresses are generated by successively adding stored binary differences to the result of the previous addition. A method of encoding and compressing a location table is provided. A reference latitude and longitude is selected and stored. The offsets from the reference latitude and longitude are stored for the remaining locations. A method of reading an encoded location table is provided. A stored reference latitude and longitude is read. Stored offsets are read and applied to the reference latitude and longitude to generate a set of latitude and longitude locations.
Owner:SKYHOOK WIRELESS
System and method for inserting sync bytes into transport packets
ActiveUS20090007190A1Satellite broadcast receivingBroadcast specific applicationsByteComputer science
The disclosed embodiments relate to a system and method for inserting sync bytes into a video transport stream. More specifically, there is provided a method comprising determining a parsing procedure supported by a first set top box, appending a first transport packet to comply with the parsing procedure of the first set top box, and transmitting the first transport packet to the first set top box.
Owner:INTERDIGITAL CE PATENT HLDG
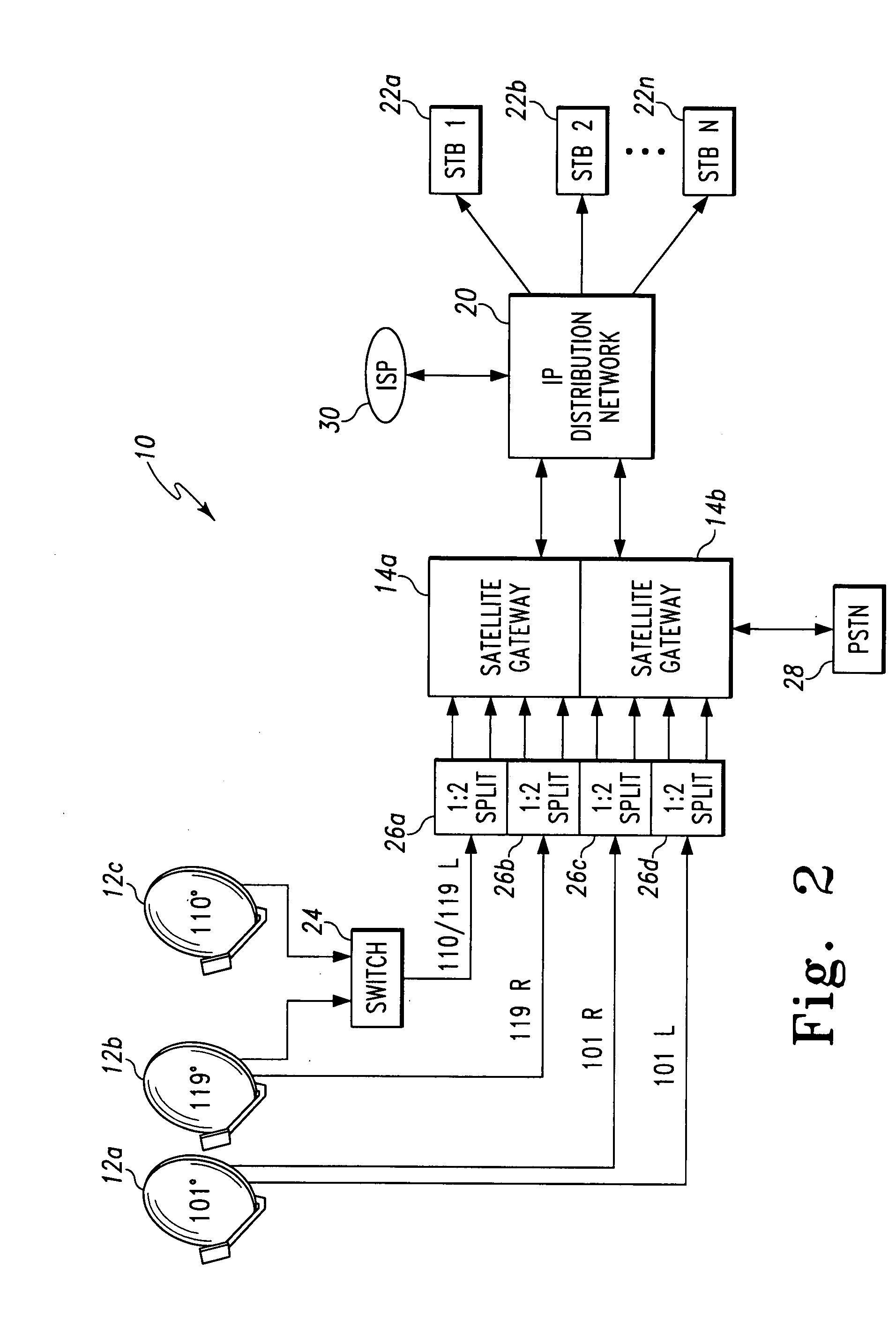
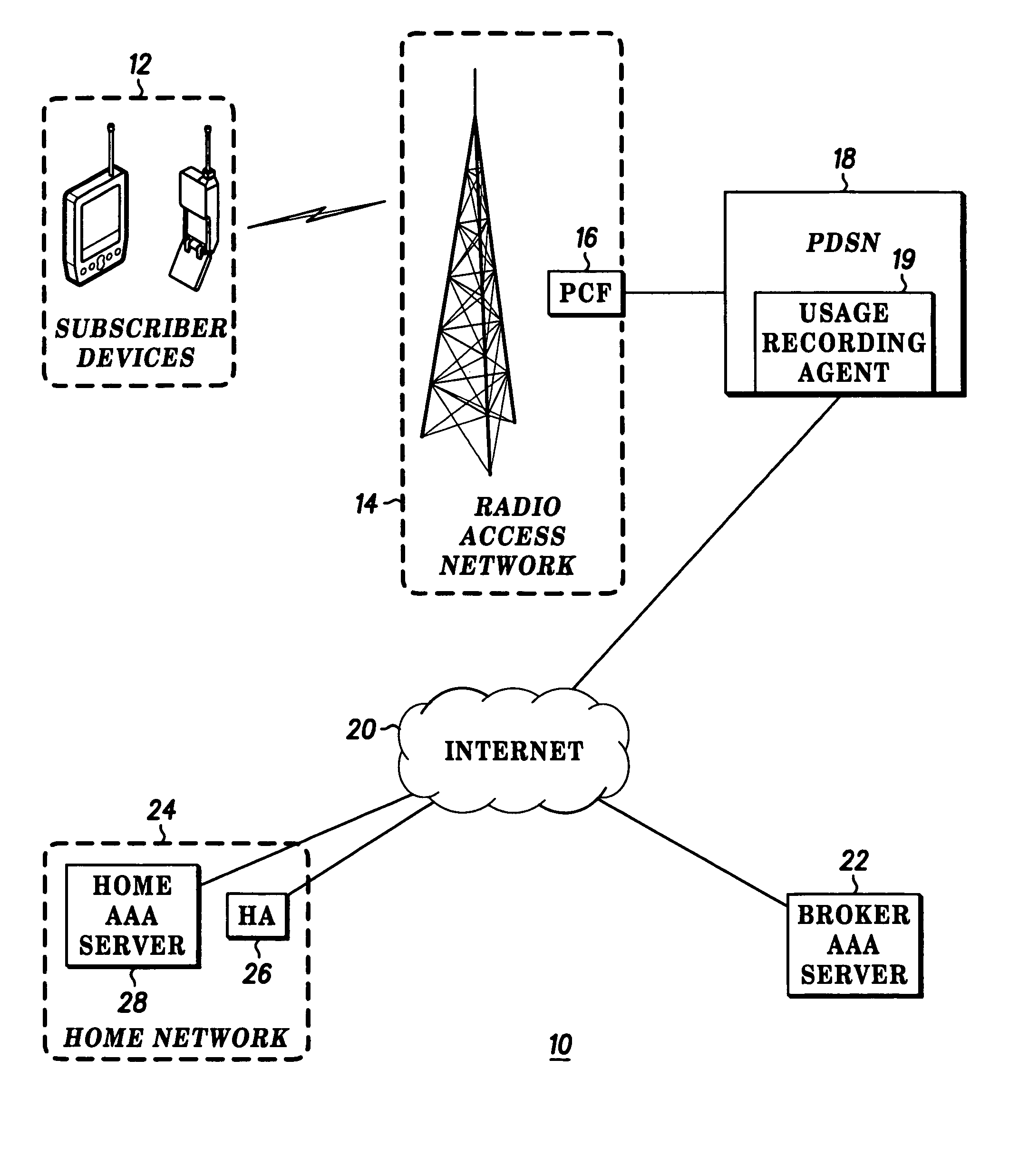
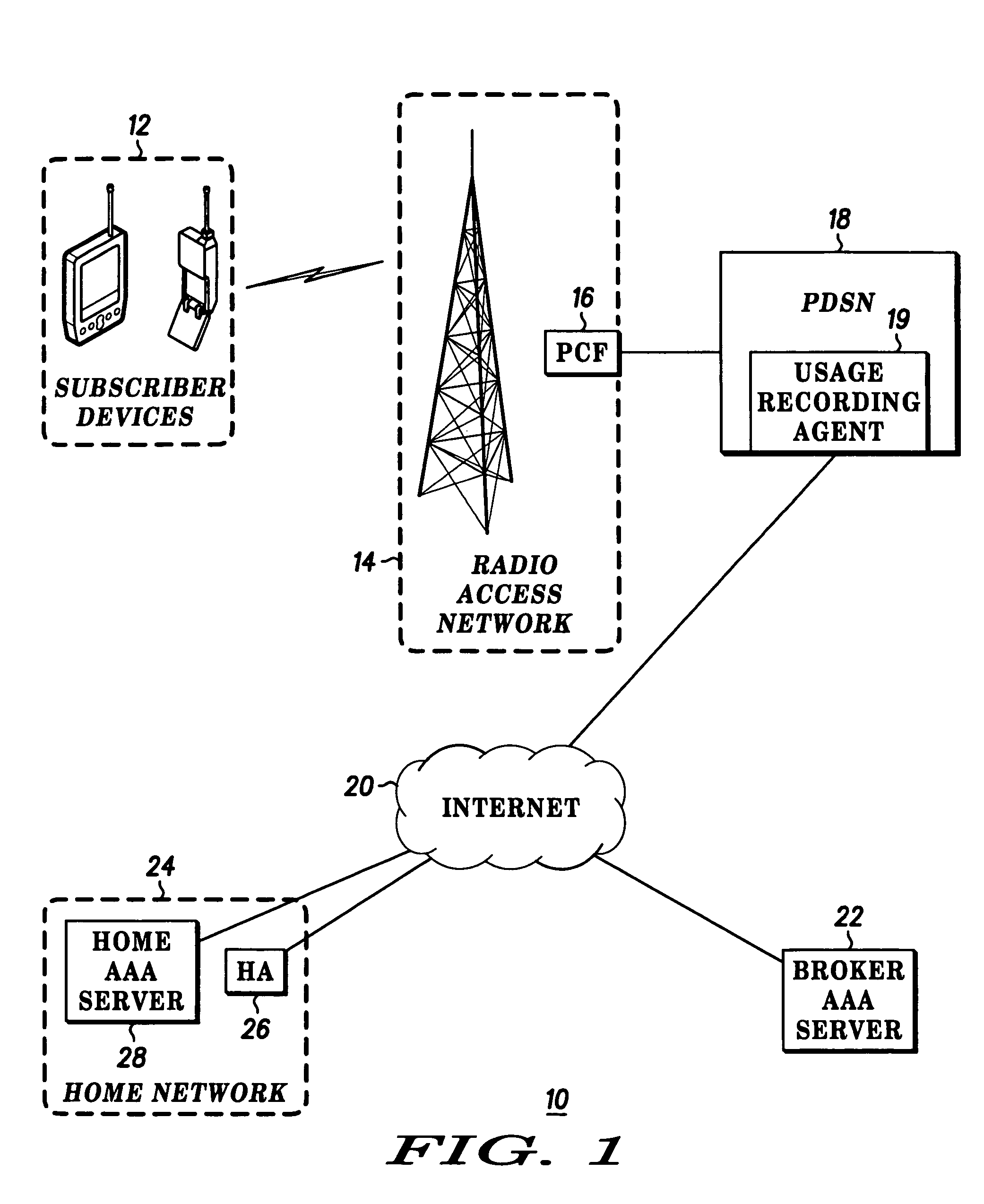
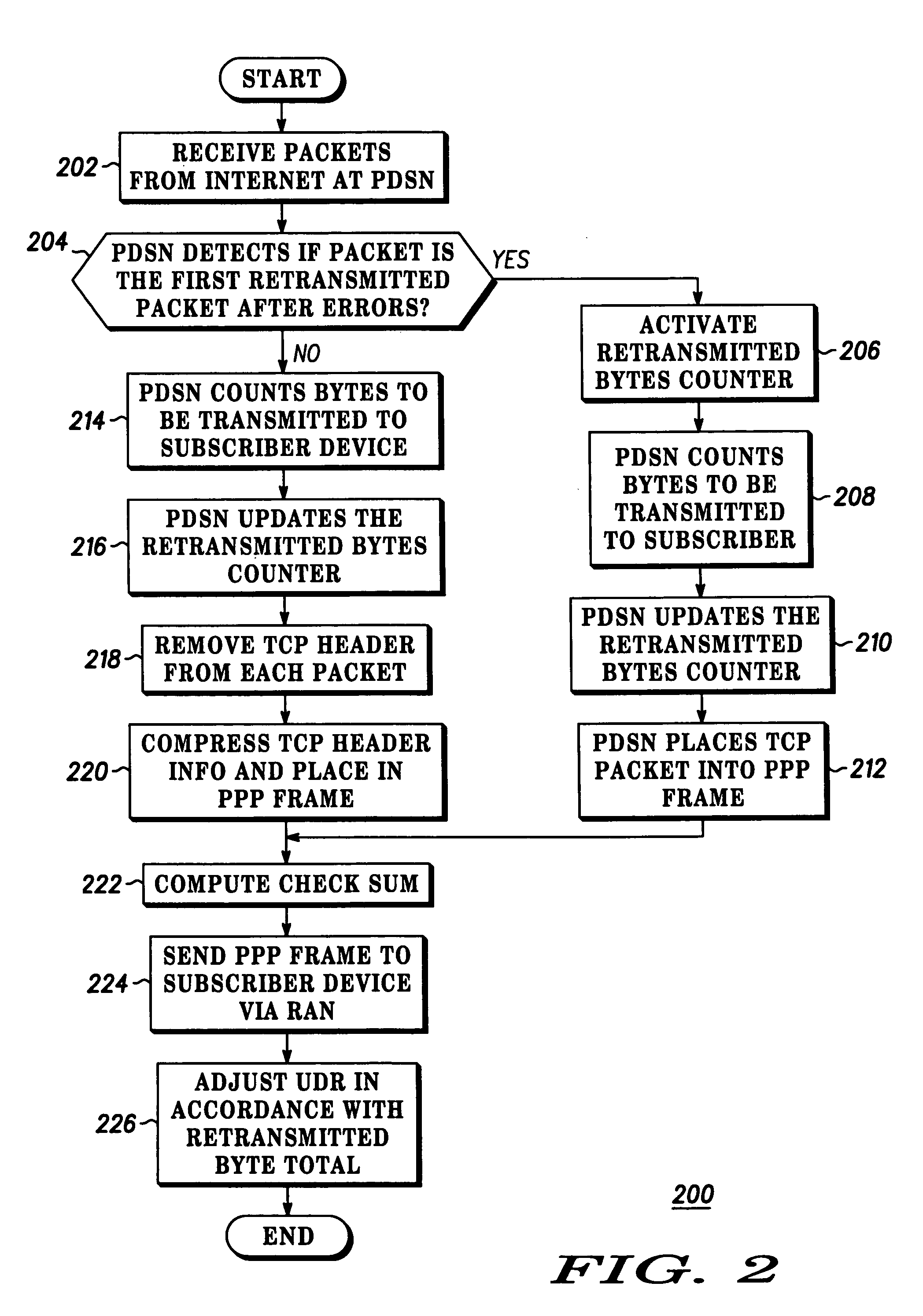
Method and device for providing more accurate subscriber billing
InactiveUS7113997B2Accurate billingError prevention/detection by using return channelMetering/charging/biilling arrangementsByte
A PDSN (18) includes a usage recording agent (19) for distinguishing between nonbillable and billable activity of a subscriber device 12. The usage recording agent (19) creates a record of a total number of bytes transmitted from the PDSN (18) to the RAN (14), counts bytes that are retransmitted from the PDSN (18) for providing a retransmitted byte total, and forwards the retransmitted byte total and the record to an AAA (28) so that the record can be adjusted in accordance with the retransmitted byte total.
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
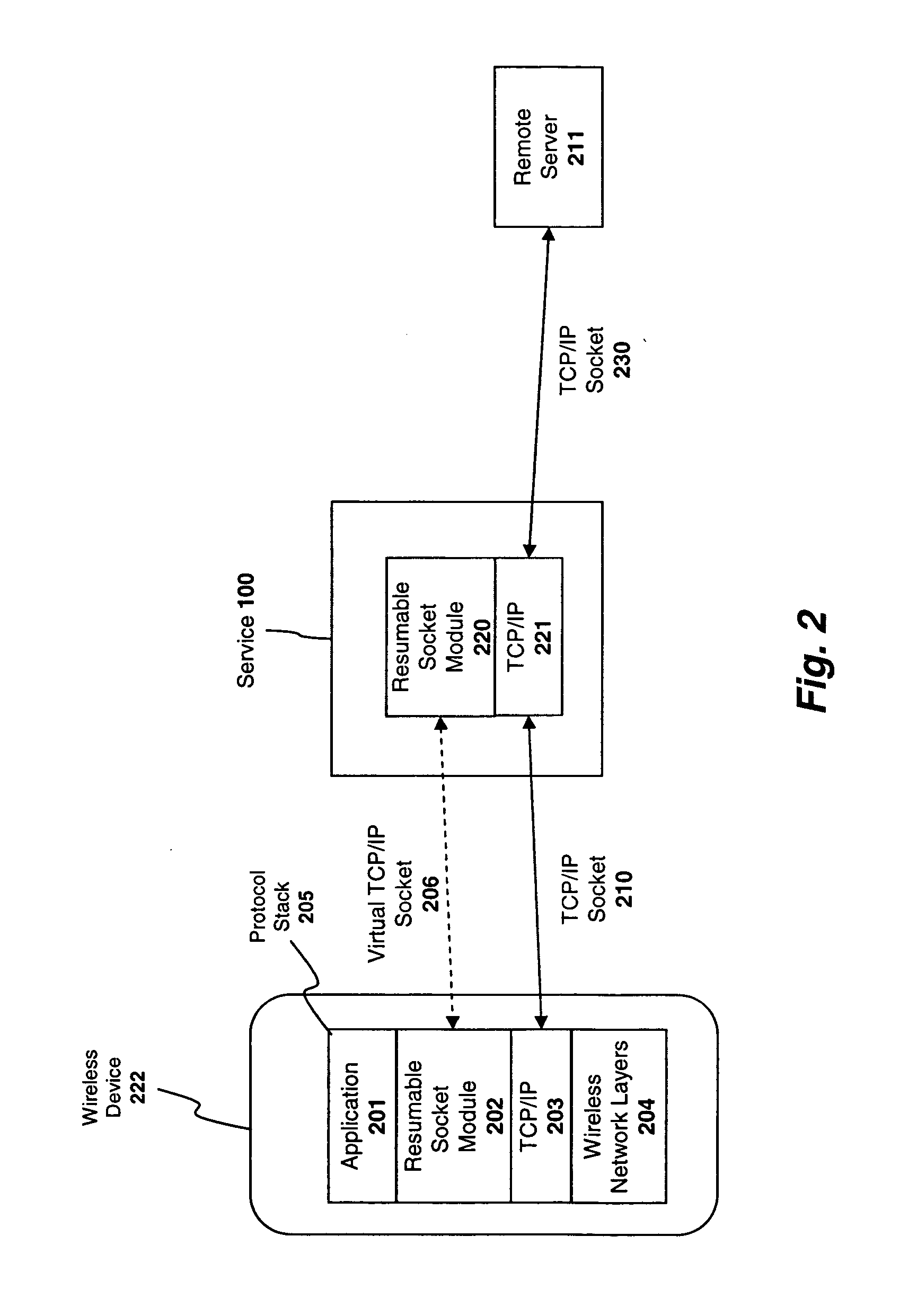
System and method for preserving socket connections over a wireless network
InactiveUS20090103515A1Time-division multiplexWireless commuication servicesNetworking protocolService provision
A system, apparatus, and method for maintaining a socket connection over a wireless network. For example, one embodiment of the invention is a wireless data processing device for emulating a socket connection comprising: a wireless radio for establishing a wireless communication channel with a wireless service provider over a wireless network; a network protocol stack including at least one layer configured to establish a socket connection with a remote server over the wireless network, the network protocol stack further including an application layer for executing applications capable of transmitting and receiving data over the socket connection; and a resumable socket module configured to emulate an open socket connection transparently to applications within the application layer, even when the wireless communication channel is temporarily lost, the resumable socket module counting a number of bytes transmitted or to be transmitted to the remote server and maintaining a buffer containing the bytes transmitted or to be transmitted.
Owner:MICROSOFT TECH LICENSING LLC
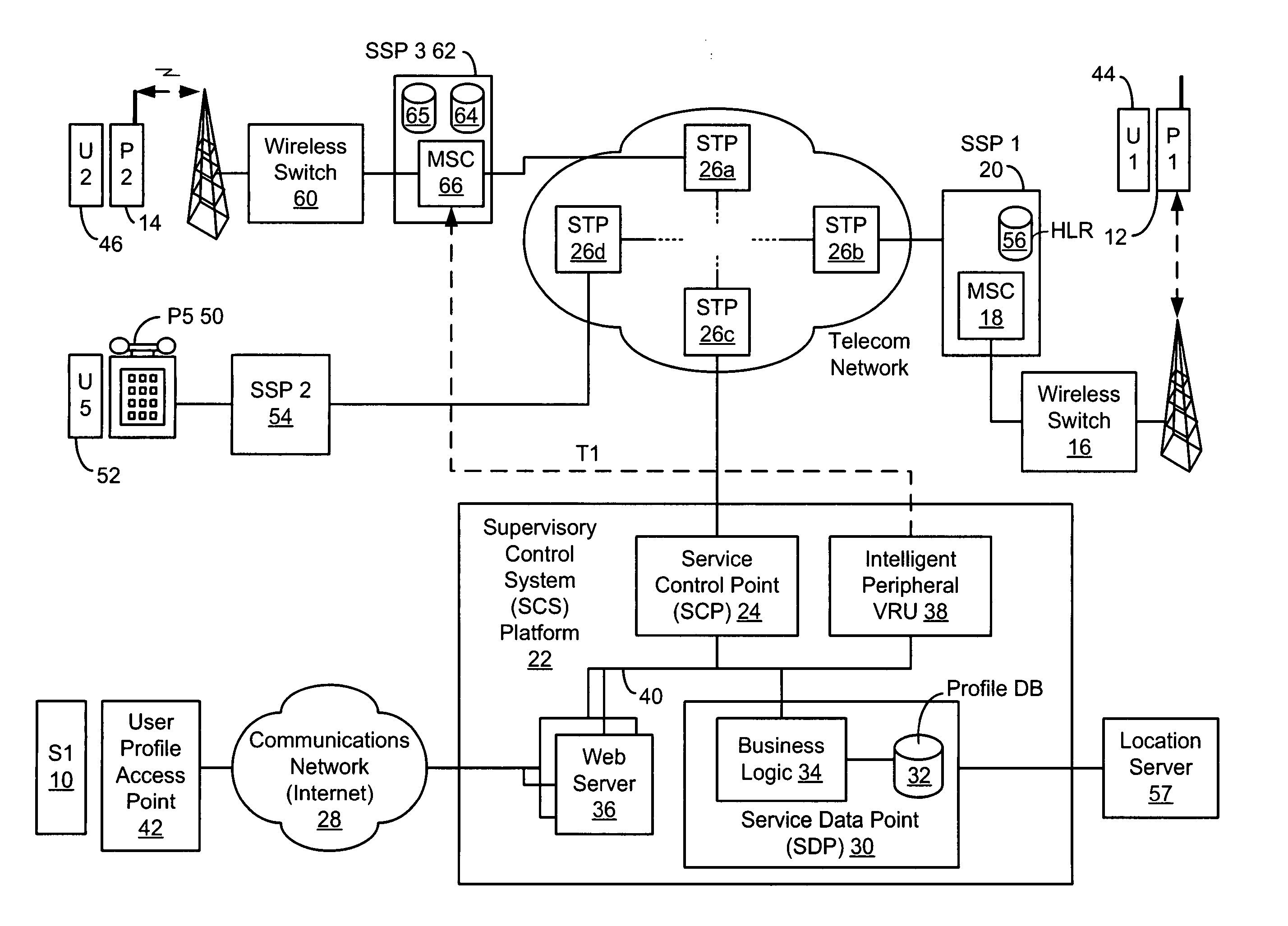
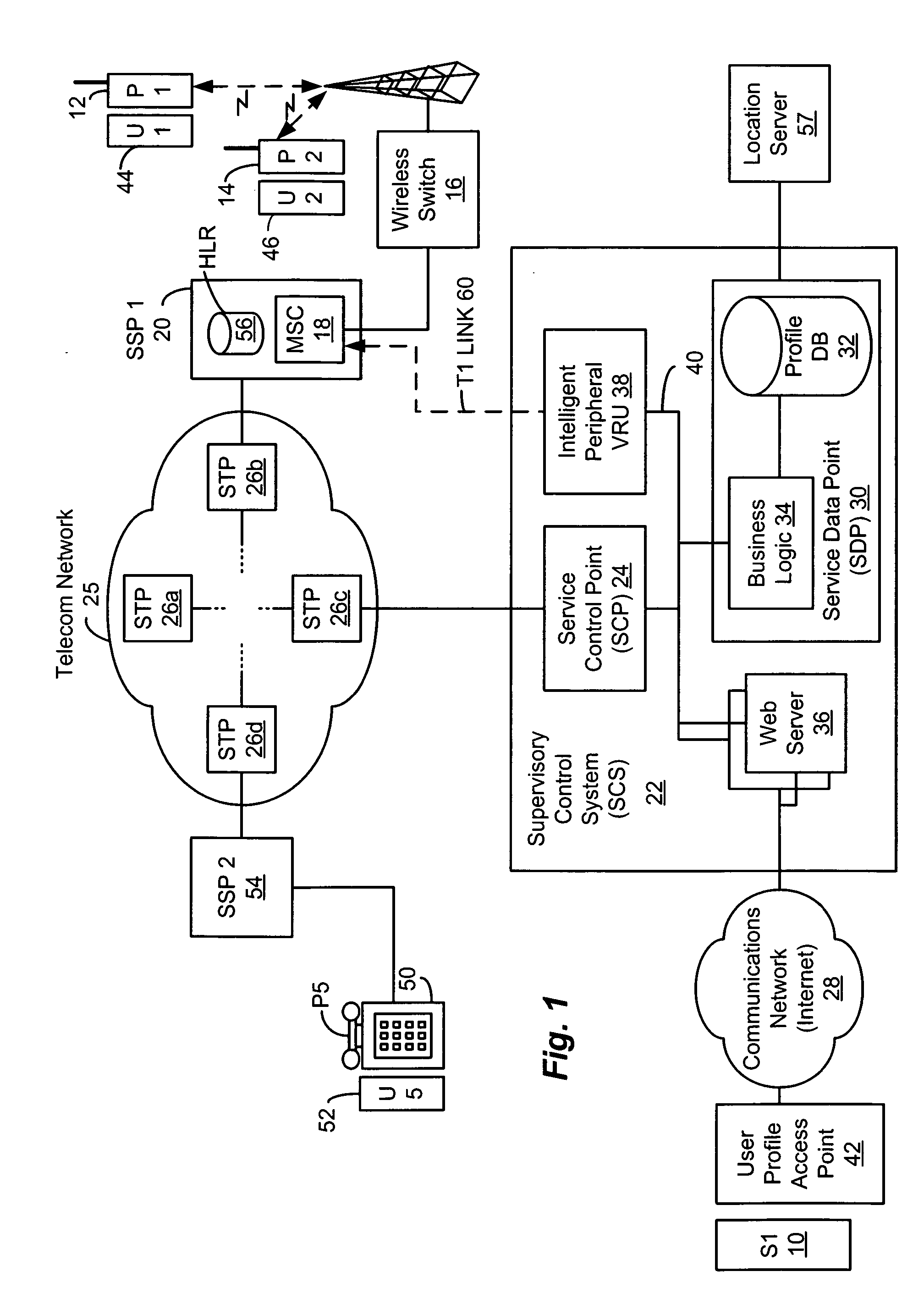
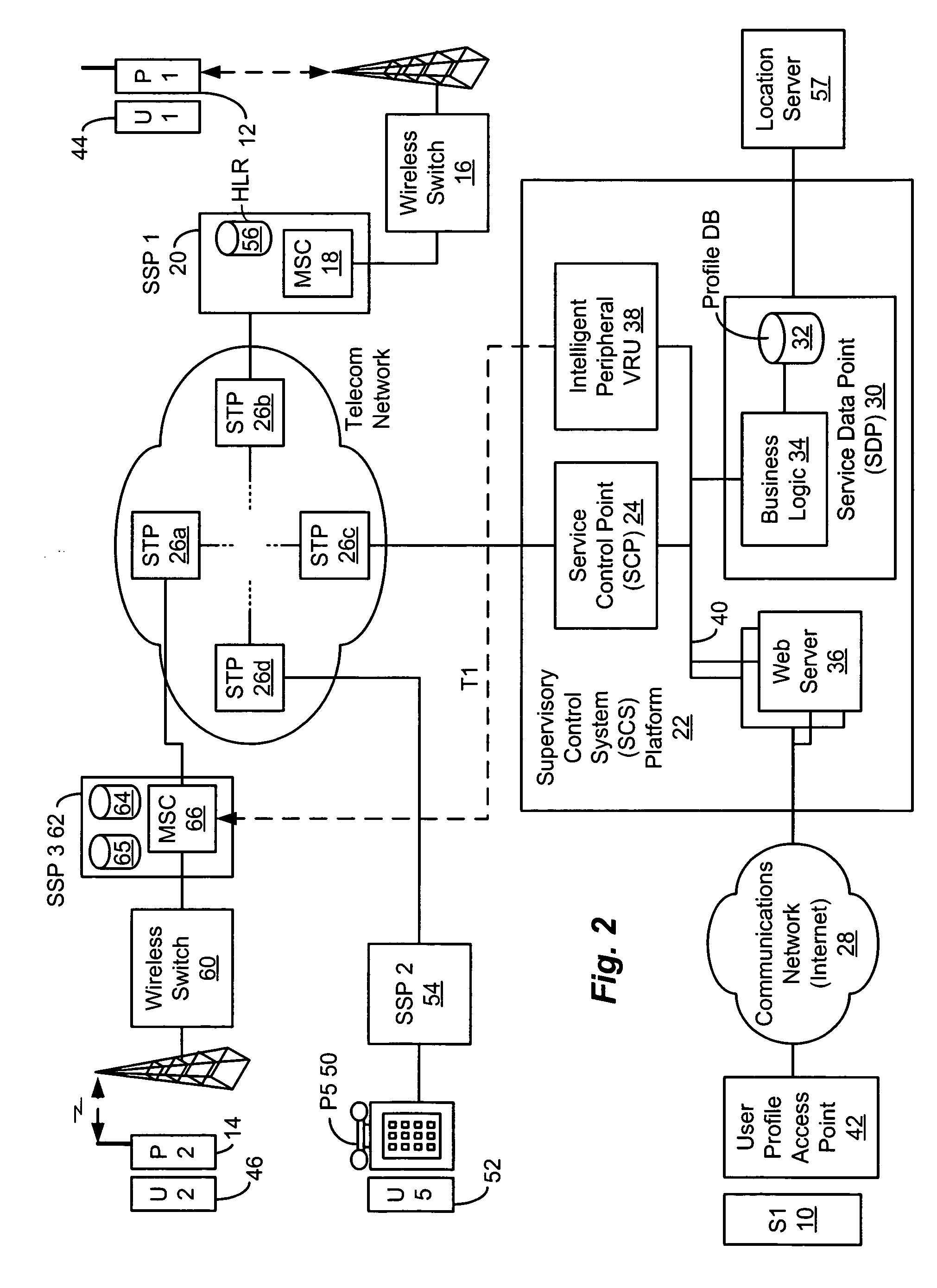
Method and system for providing supervisory control over wireless phone data usage
InactiveUS20050282559A1Reduce usageReduce in quantityAccounting/billing servicesSpecial service for subscribersByteUser profile
A system for controlling wireless phone usage enables a supervisor to establish user profiles for supervised users of wireless phones across a range of parameters, which are stored in a user profile database. Such parameters can include one or more locations, at which use of the wireless phone is restricted or permitted. In addition, restrictions on phone use, such as cumulative usage time, number of messages or number of bytes, can be provided based upon total phone usage within a specified control period, time periods, dates or days of the week during which phone use is restricted or permitted. One or more lists including numbers or other identifiers that are always-accessible can be provided, and one or more lists including numbers or other identifiers that are never-accessible can also be provided. In the event a call, message or browse does not satisfy predefined criteria, the communication attempt is blocked. Predetermined messages can be played or displayed to the called or calling party, as applicable, when a communication attempt is blocked. Boolean combinations of restrictions and permissive use criteria for the wireless phone can be specified to provide for flexibility when establishing use criteria for the wireless phone.
Owner:BOSTON COMM GROUP
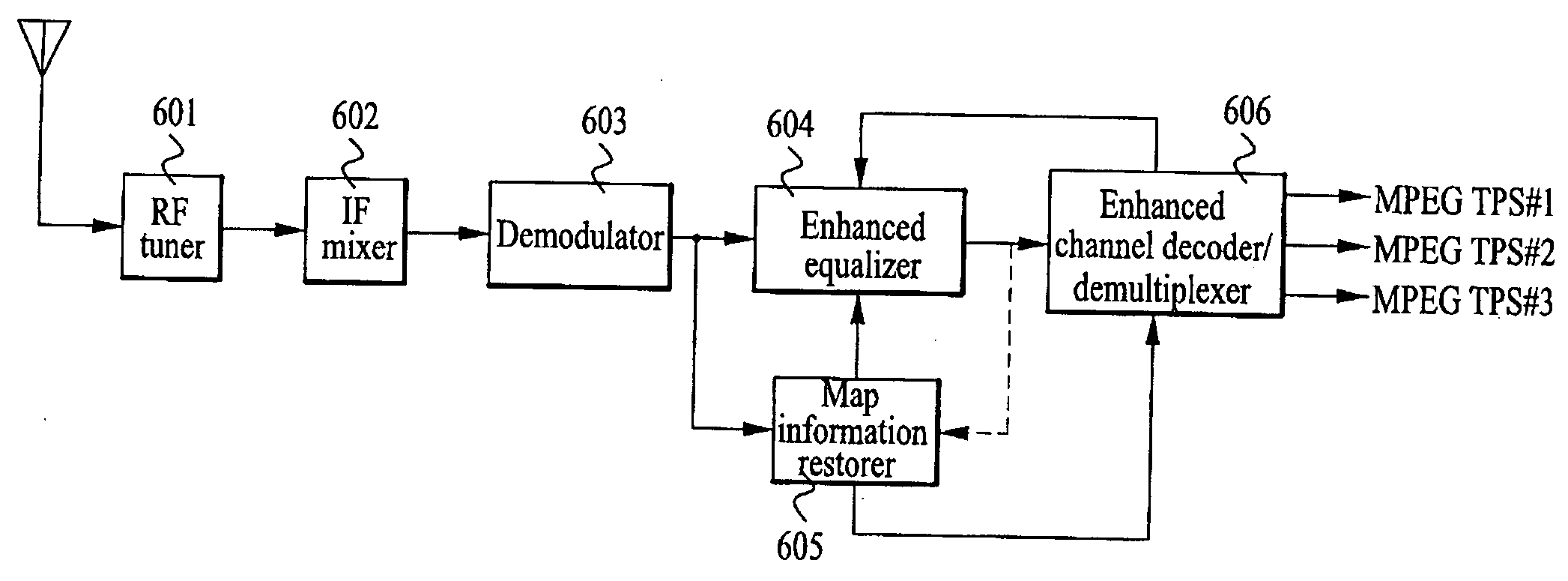
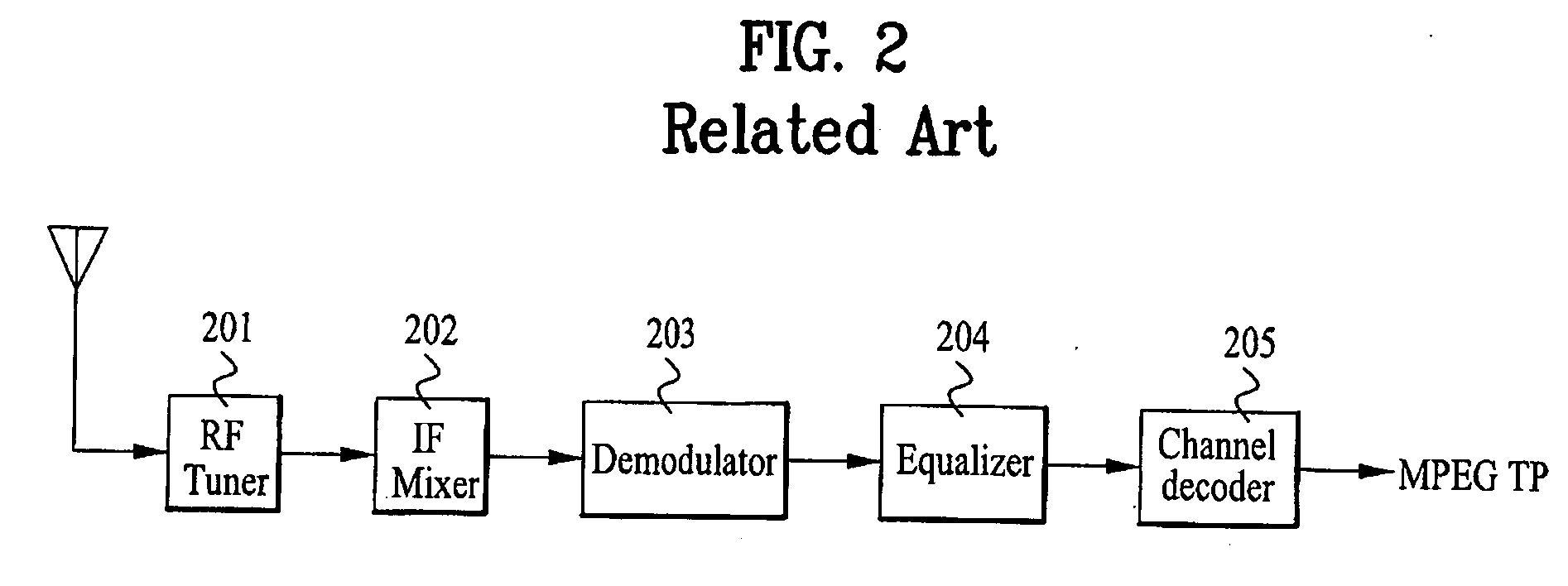
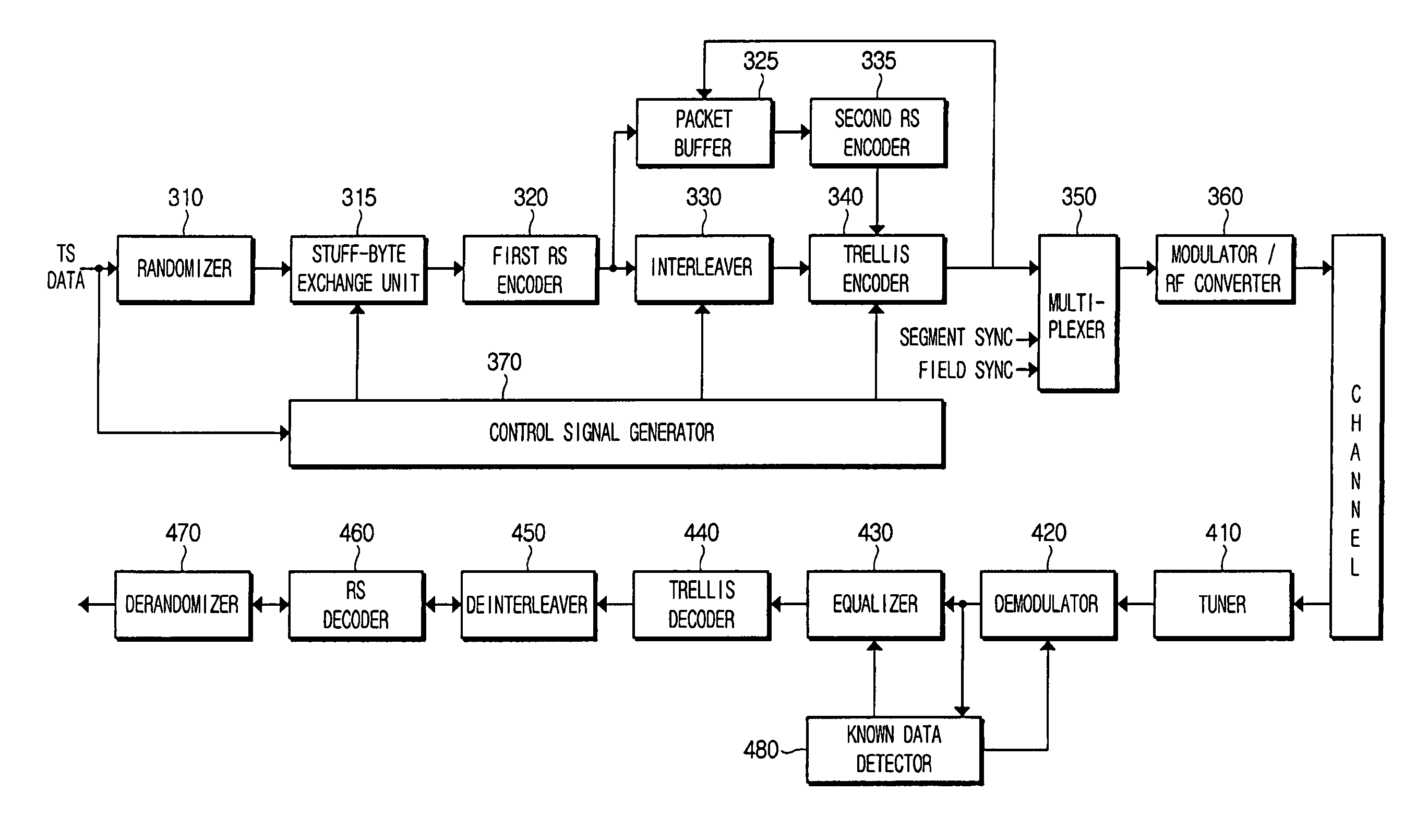
Digital E8-VSB reception system and E8-VSB data demultiplexing method
InactiveUS20050111586A1Enhanced signalStable receptionTelevision system detailsPulse modulation television signal transmissionMultiplexingChannel decoder
An enhanced 8-VSB reception system and E8-VSB data demultiplexing method, by which an E8-VSB signal can be stably received as well as a previous ATSC 8VSB signal, is disclosed. Herein, the enhanced data are coded at ½ code rate and ¼ code rate in the new E8-VSB transmission system compatible with the conventional ATSC 8VSB system, respectively. The ½ and ¼ enhanced data are multiplexed by 164-byte packet unit according to the previously determined multiplexing format and further pre-processed to output as the format of the MPEG transport packet. And, the pre-processed enhanced data and the main data are multiplexed again by 188-byte packet unit according to the previously determined multiplexing format. The E8-VSB map information, which was inserted in the field sync section in the E8-VSB transmission system to be transmitted, is extracted to generate the information indicating the attributes of the respective E8-VSB data. The normal data, ½ enhanced data, and ½ enhanced data are separated from each other to be decoded in the channel decoder.
Owner:LG ELECTRONICS INC
Non-Signature Malware Detection System and Method for Mobile Platforms
ActiveUS20070240221A1Suitable for useReliable detectionMemory loss protectionError detection/correctionEntry pointChecksum
A system and method for detecting malware on a mobile platform in a mobile network. The system and method verifies that an executable is malware-free by computing the checksum of the executable and comparing that checksum with a checksum obtained from a malware-free copy of the executable. The checksum is a sum of all 32-bit values in a code section and an import section of said executable, a byte sequence at an entry point in said executable, a size descriptor of an import table, a size descriptor of said import section, a cyclic redundancy check of said executable, or a combination thereof.
Owner:PULSE SECURE
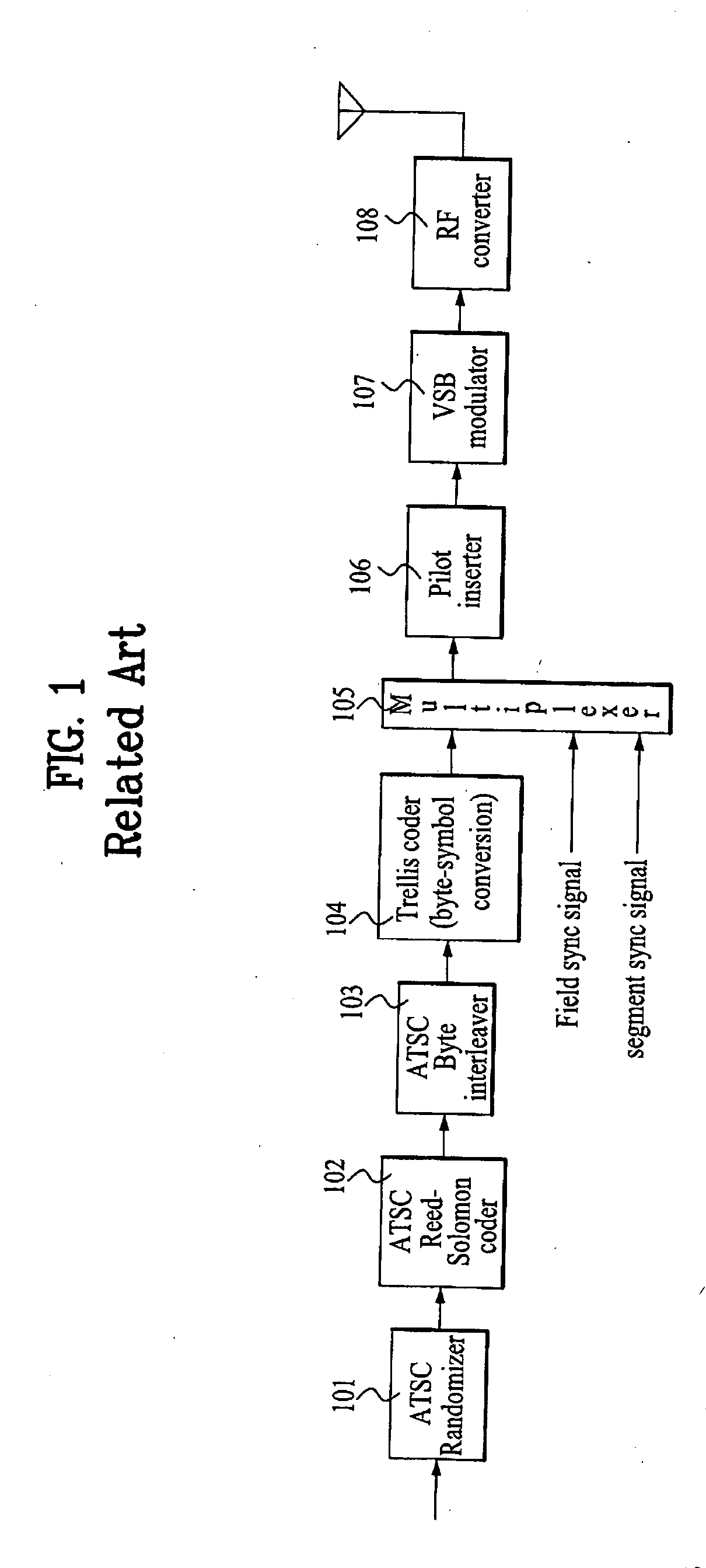
Digital broadcast transmitting and receiving system having an improved receiving performance and signal processing method thereof
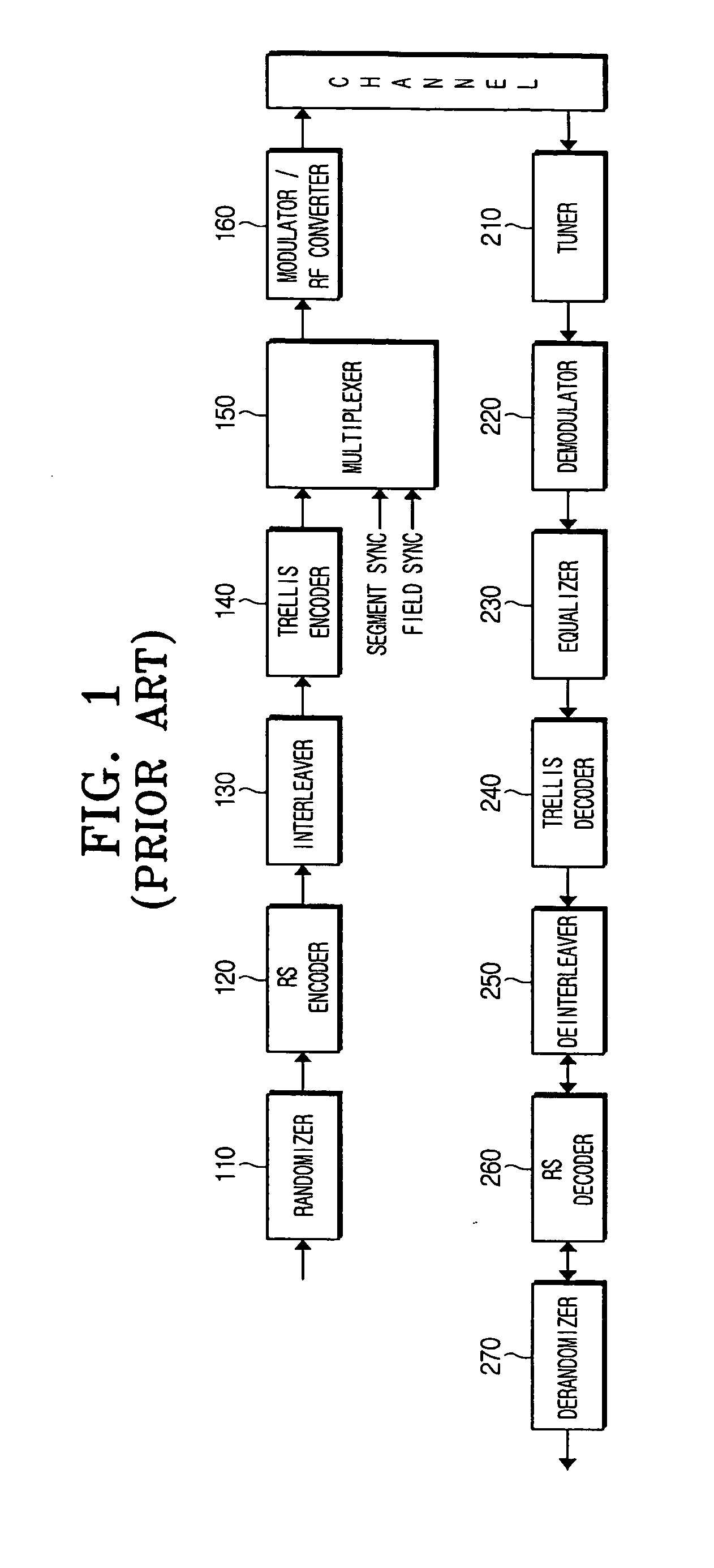
ActiveUS20050249301A1Improve reception performanceModulation with suppressed carrierCode conversionData streamEqualization
A digital broadcast transmitting and receiving system and a signal processing method thereof that improves the receiving performance of the system. A digital broadcast transmitter can include a randomizer to receive and randomize a data stream into a specified position of which stuff bytes are inserted, a stuff-byte exchange unit to generate known data having a predefined pattern and insert the known data into the specified position of the data stream into which the stuff bytes are inserted, an encoder to encode the data stream output from the stuff-byte exchange unit for an error correction, and a modulator and RF converter to modulate the encoded data stream, RF-convert the modulated data stream and transmit the RF-converted data. The digital broadcast receiving performance can be improved even in an inferior multi-path channel by detecting the known data from the received transmission and using the known data for synchronization and equalization in a digital broadcast receiver.
Owner:SAMSUNG ELECTRONICS CO LTD
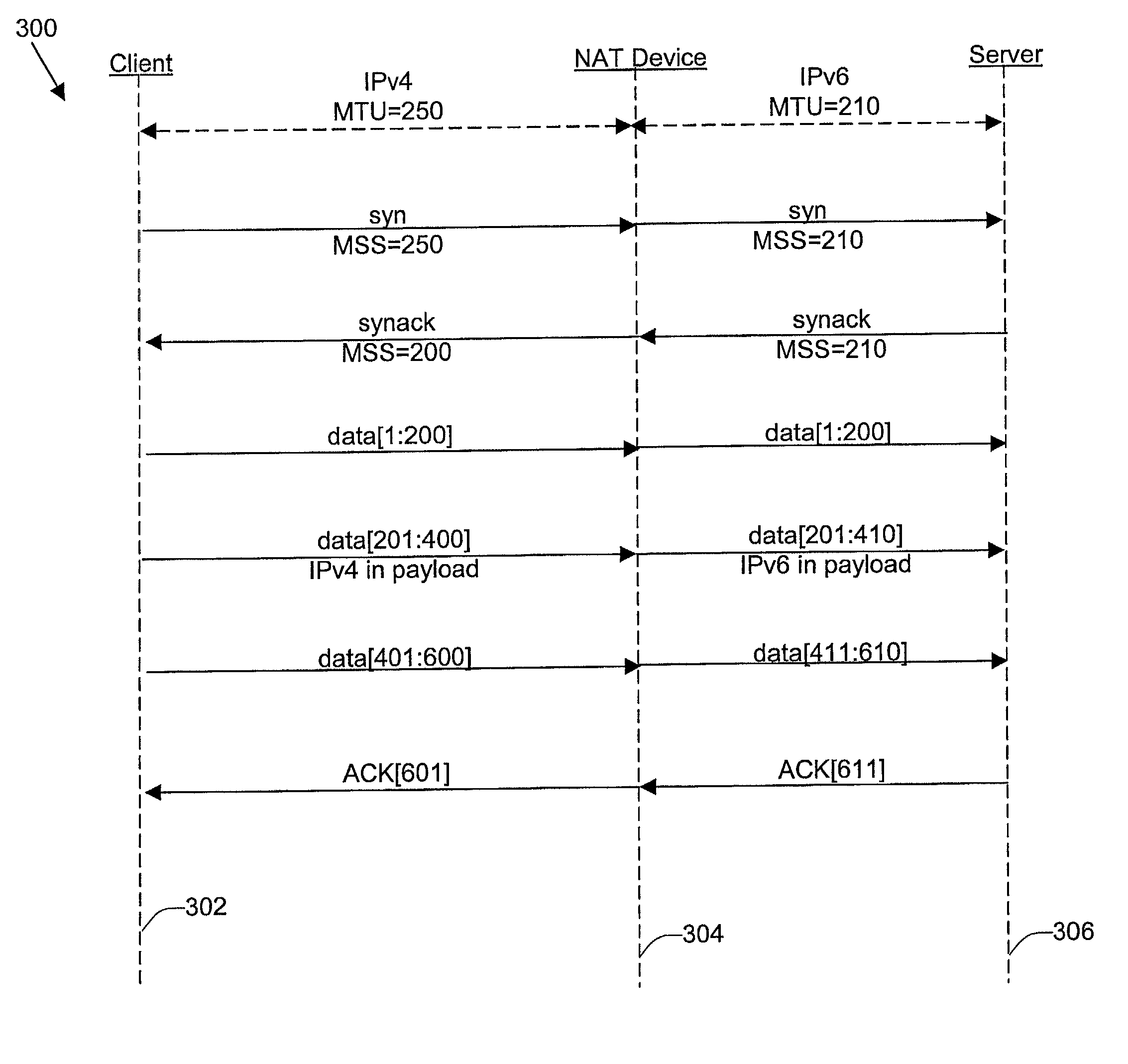
Mechanisms for avoiding problems associated with network address protocol translation
ActiveUS7006526B1Avoid problemsReduce morbidityError preventionTransmission systemsSize differenceSize increase
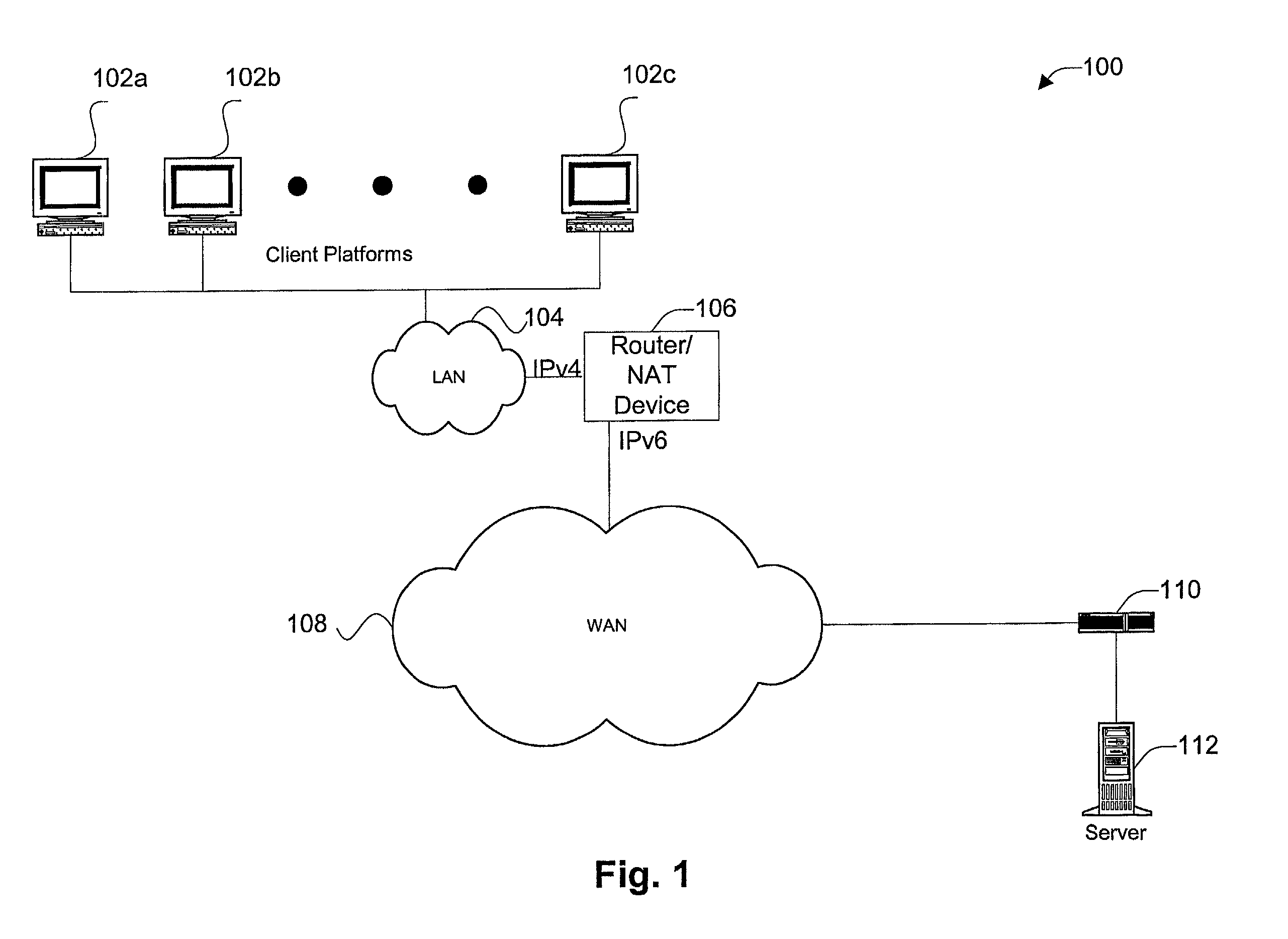
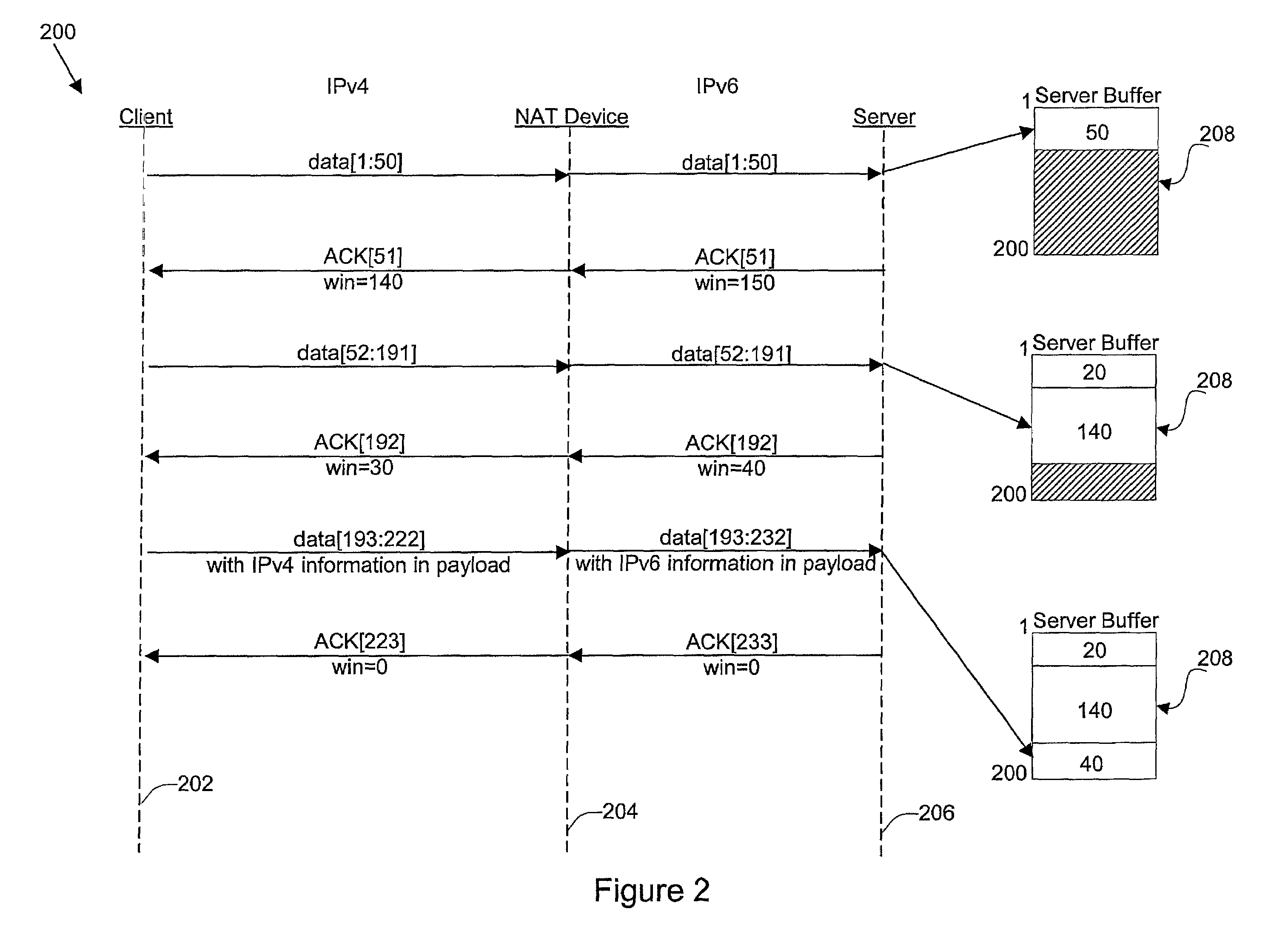
Disclosed are methods and apparatus for avoiding problems caused by converting between two different protocols, such as IPv4 and IPv6. These problems may include, but are not limited to, fragmentation of packets, dropping of packets, and retransmission of packets. Avoiding these problems will reduce the incidence of transmission delays, bandwidth degradation, and additional processing in the packet's transmission path due to such problems. In general terms, the present invention provides mechanisms for modifying a protocol parameter, such as a TCP or UDP parameter, to avoid problems associated with protocol translation, such as fragmentation. In one implementation, the protocol parameter limits the size of a particular portion of the a packet transmitted by a sending computer node or device. For example, a packet size indicator is communicated to the sending computer node so that the sending computer node sends packets limited by the packet size indicator to thereby avoid associated with the size of such packets. In specific TCP embodiments, the size indicator specifies a window size and / or a maximum segment size. For example, if packets transmitted by a sending node to a receiving node are converted from IPv4 to IPv6 and the window size indicated to the sending node (e.g., by the receiving node) is 512 bytes, the window size is adjusted to 500 bytes before reaching the sending node. The adjustment amount may be based on an estimated size increase resulting from converting from IPv4 to IPv6. In this example, the window size is decreased by 12 bytes since a conversion from IPv4 to IPv6 where one 4 byte IPv4 address is changed to a 16 byte Ipv6 address has an associated size difference of 12 bytes. In a specific embodiment, actual changes in packet size may tracked and the adjusted size indicator may be dynamically based on such tracked changes. In other embodiments, the changes in packet size are predicted, and the adjusted size is preemptively changed as needed.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com