Patents
Literature
126results about How to "Provide integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
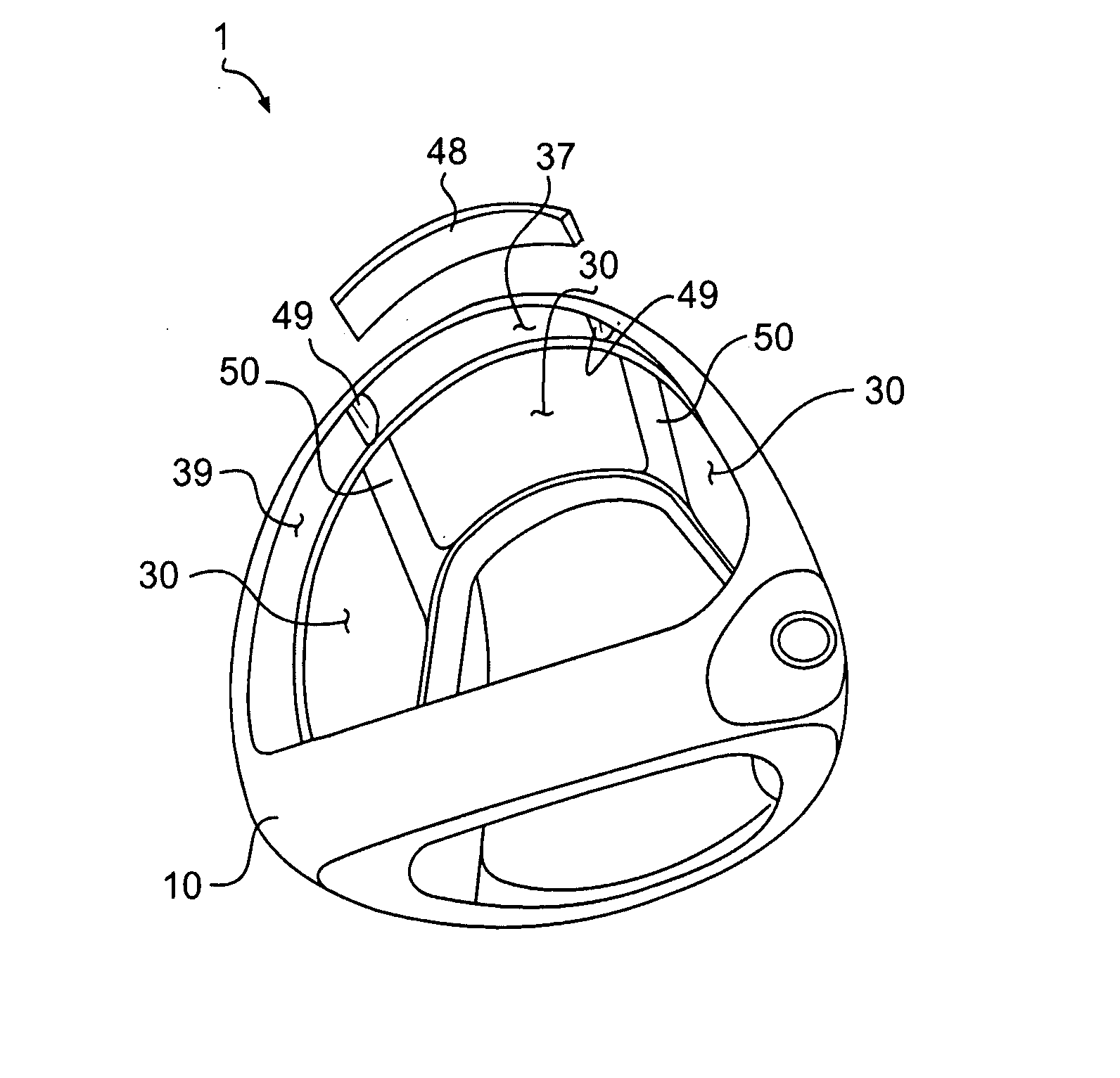
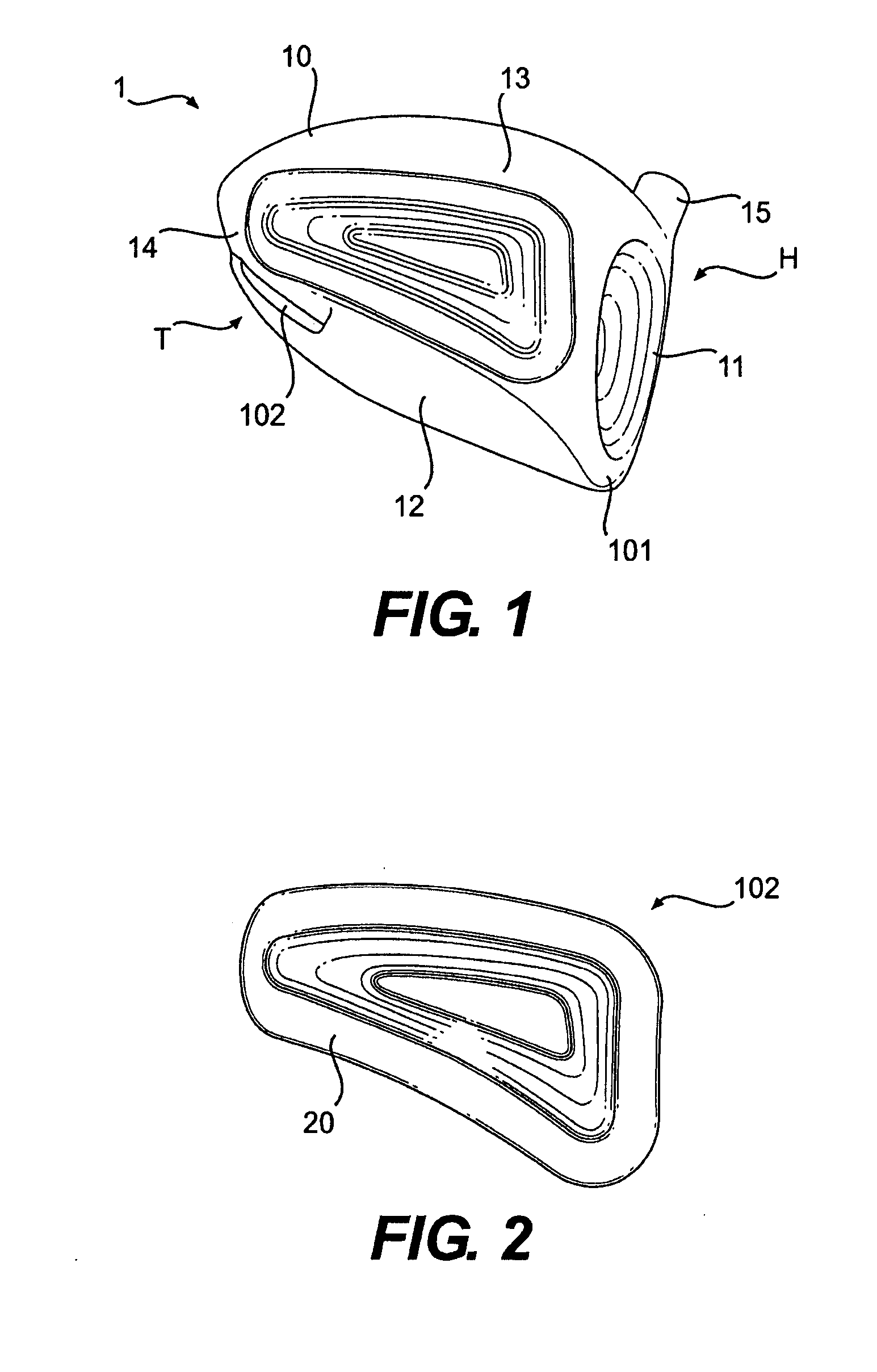
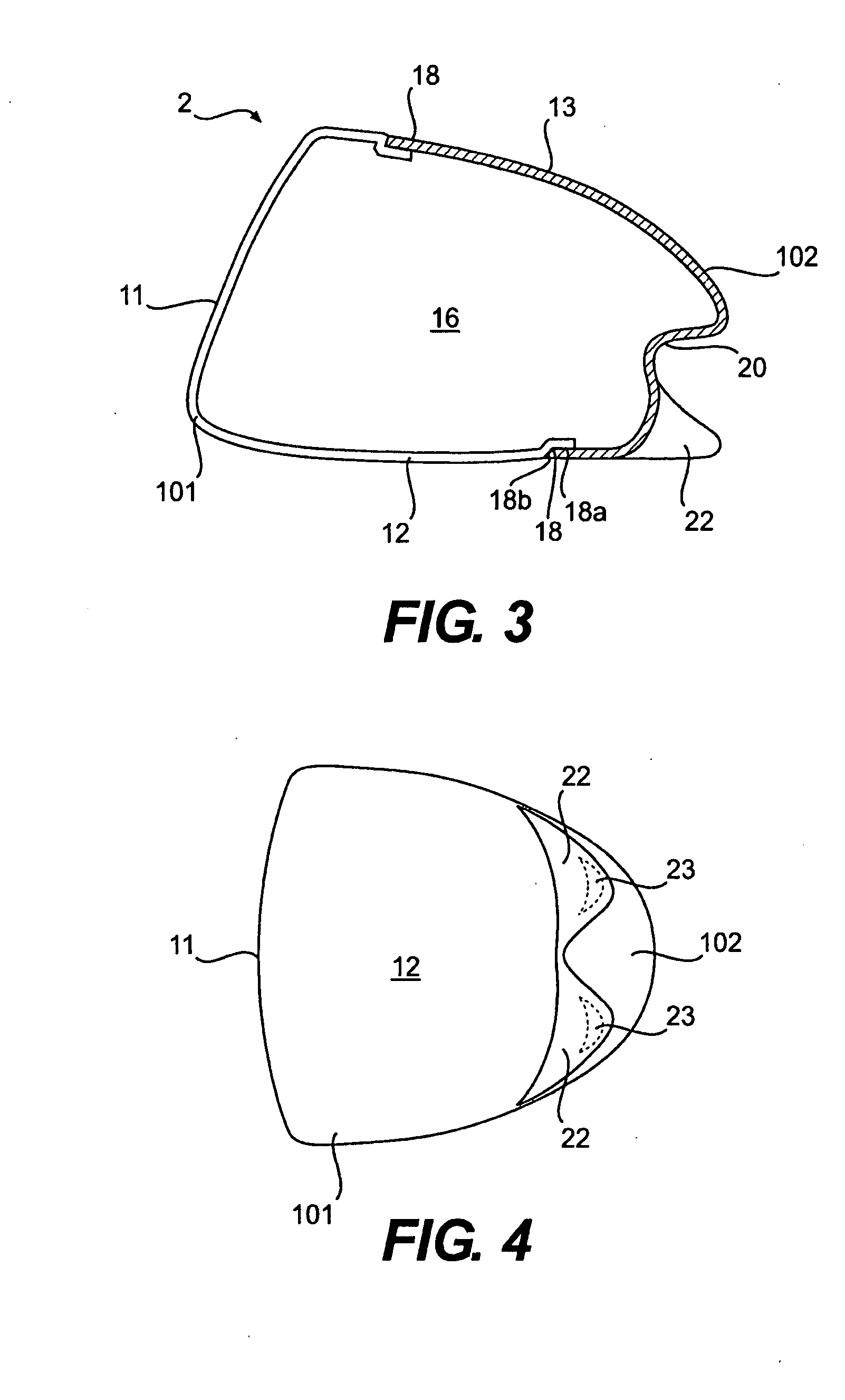
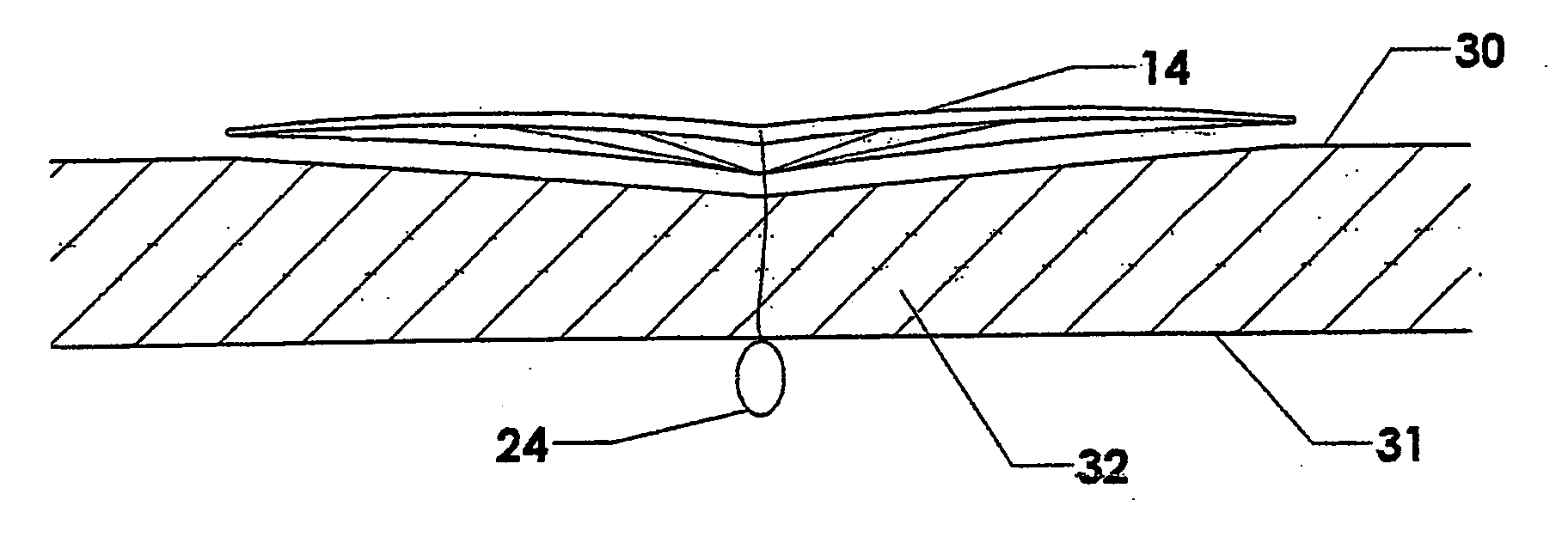
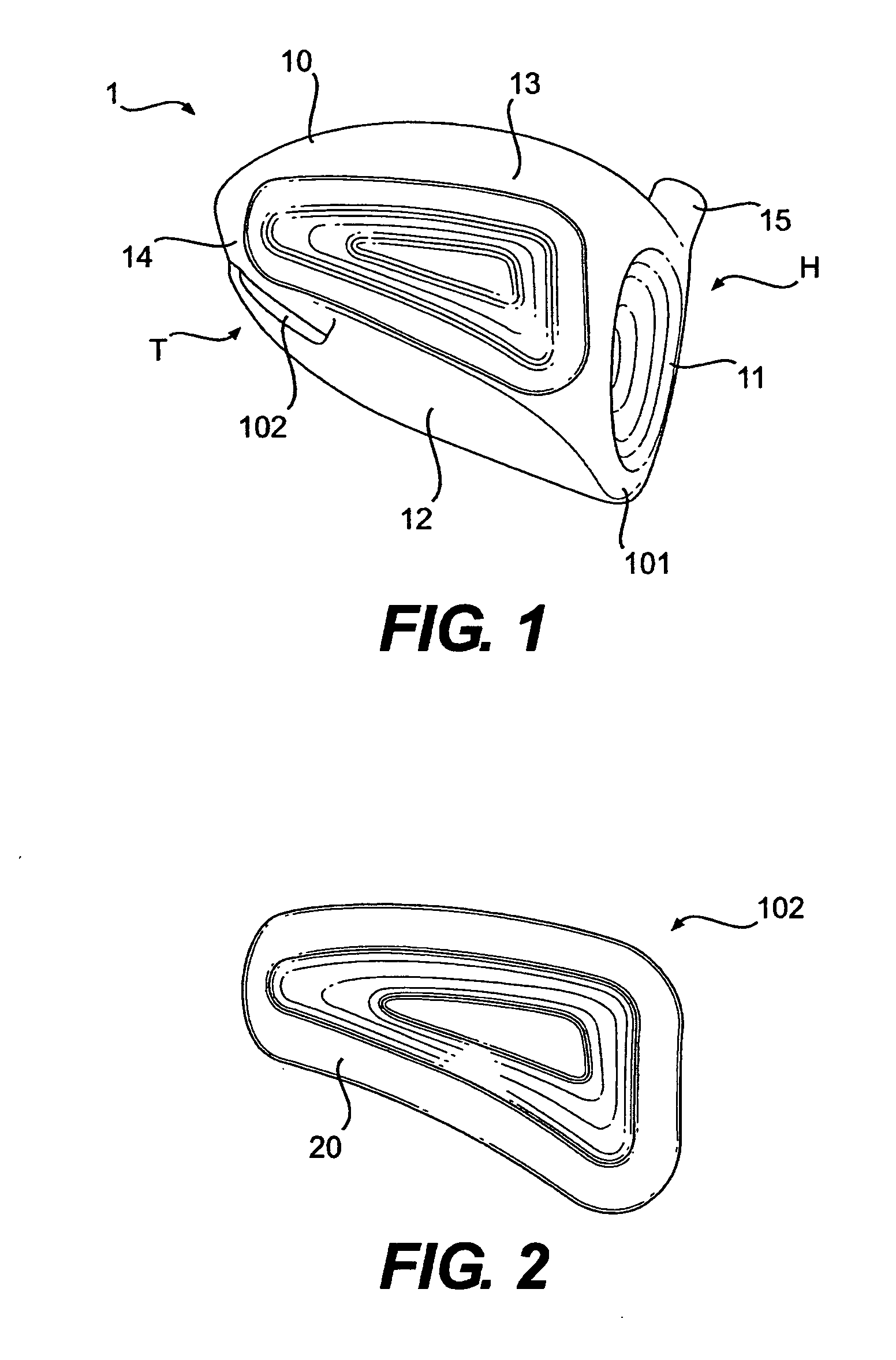
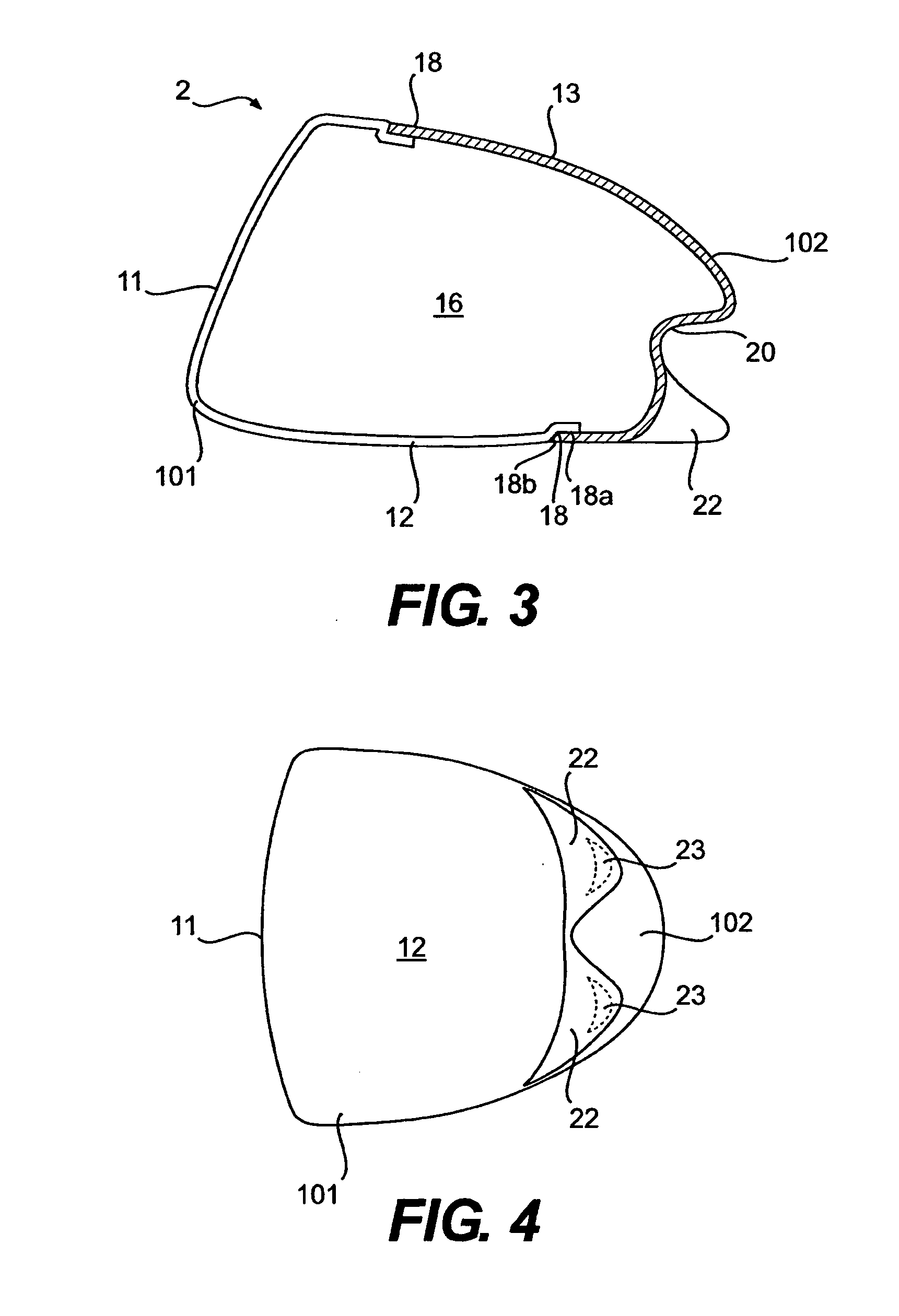
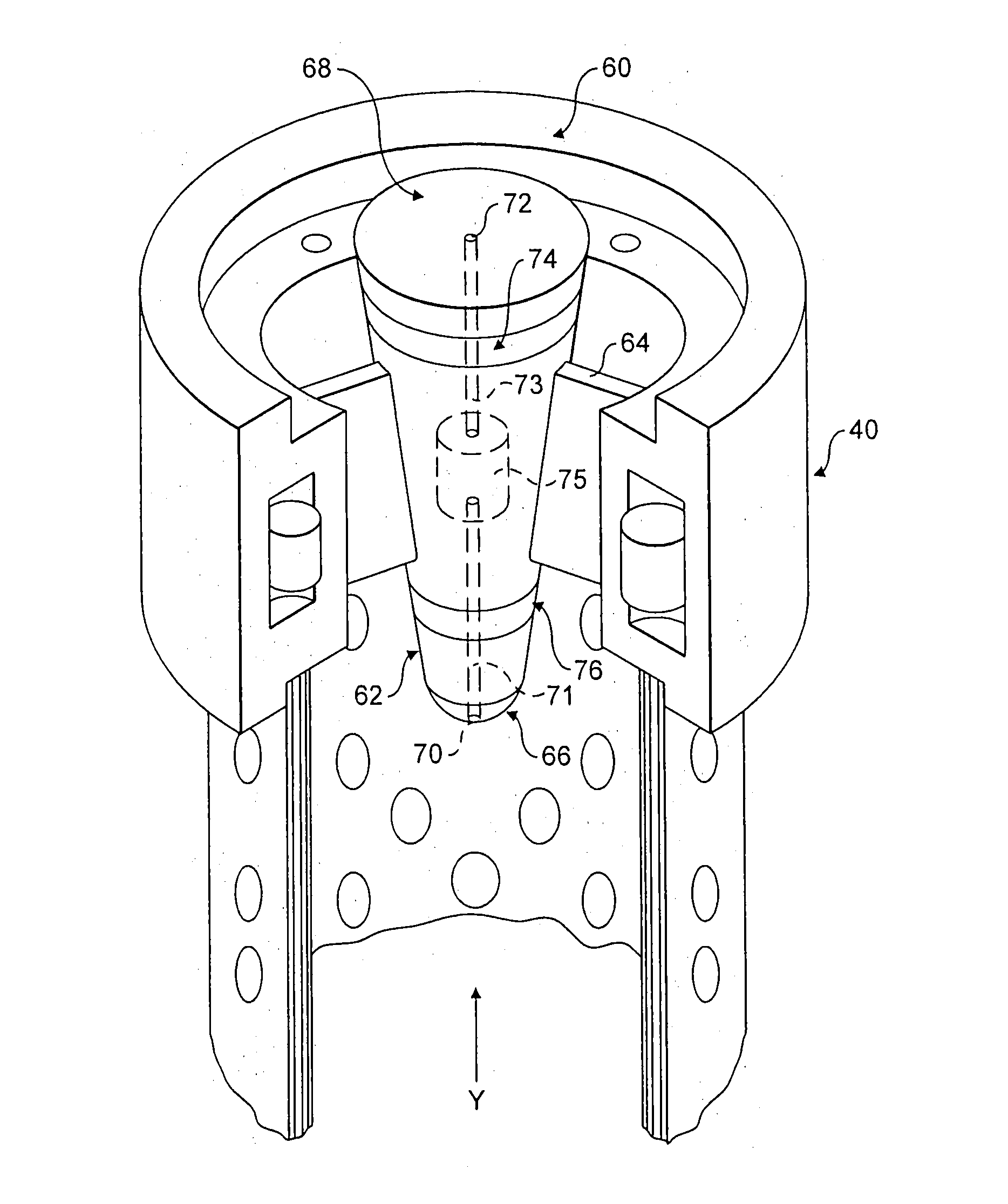
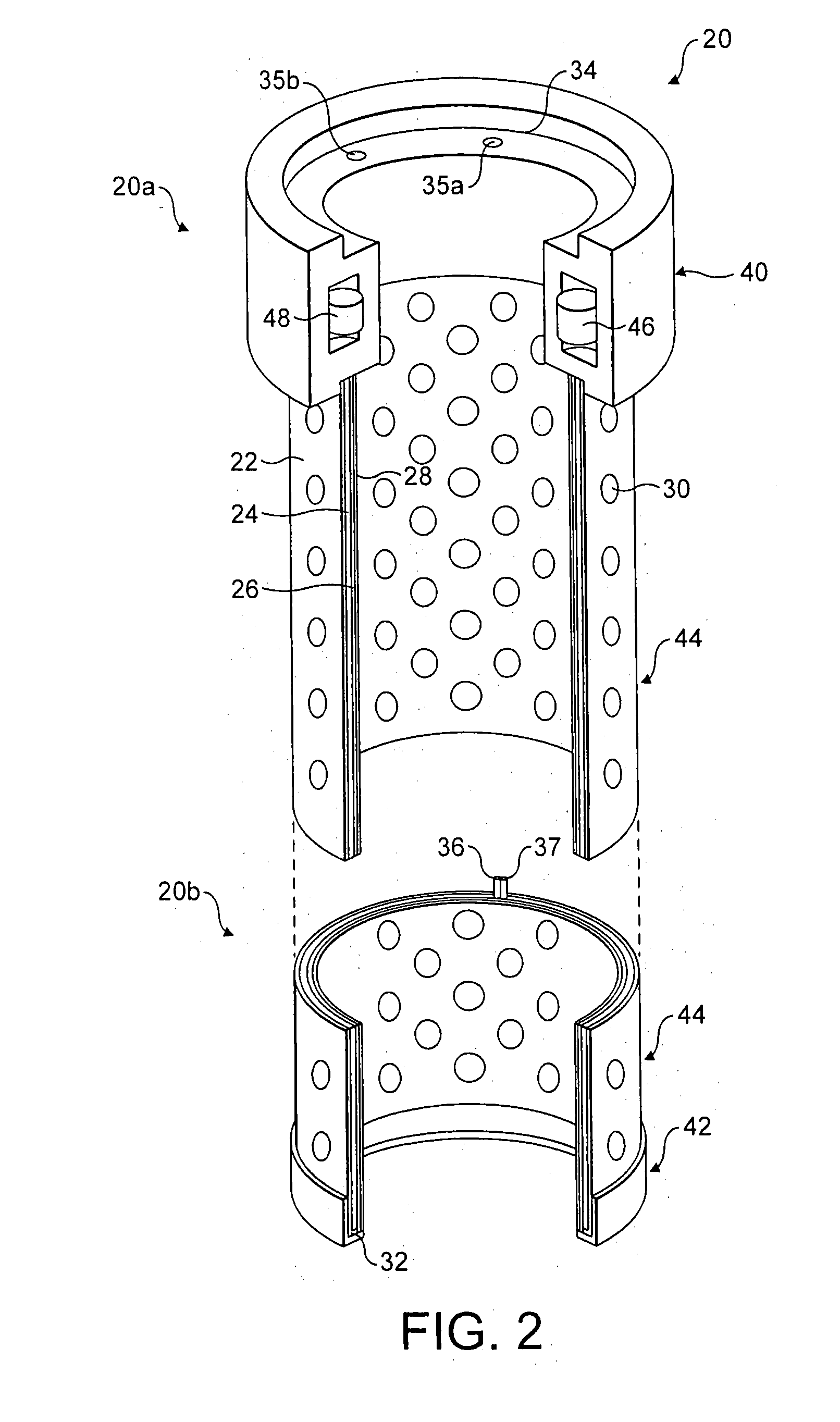
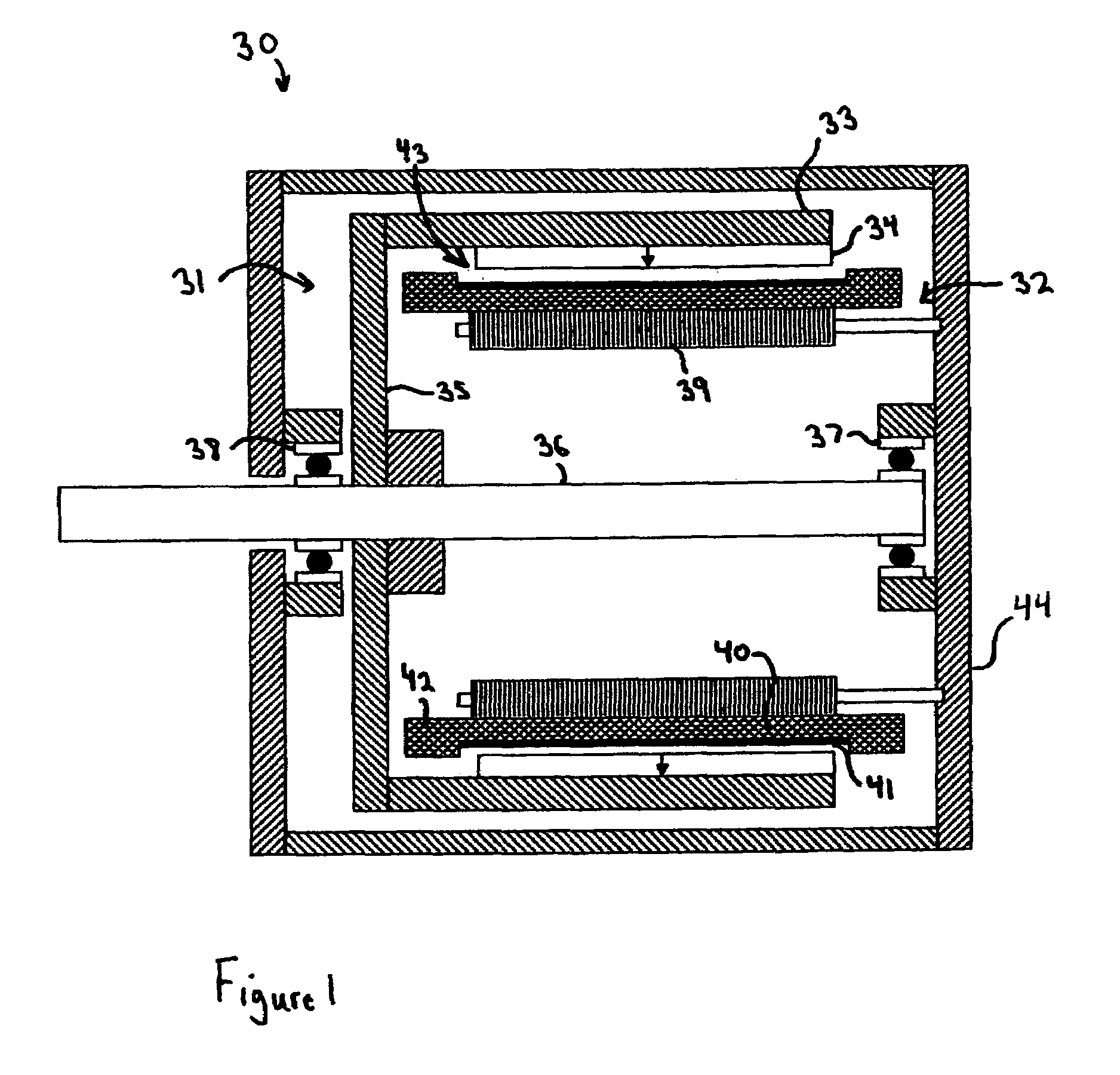
Golf club head
InactiveUS20080039228A1Improved playing characteristicProvide integrityGolf clubsRacket sportsAdhesiveEngineering
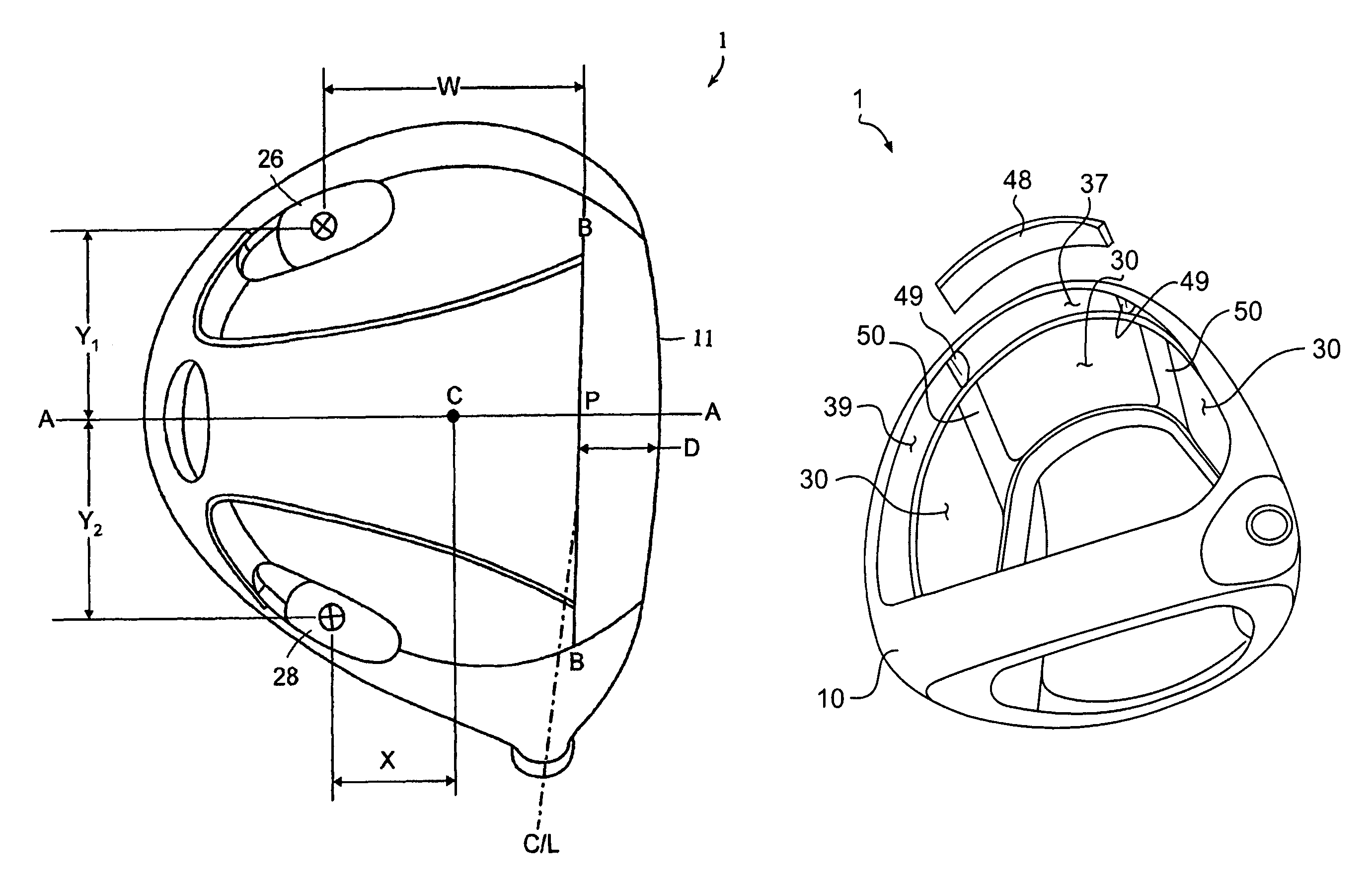
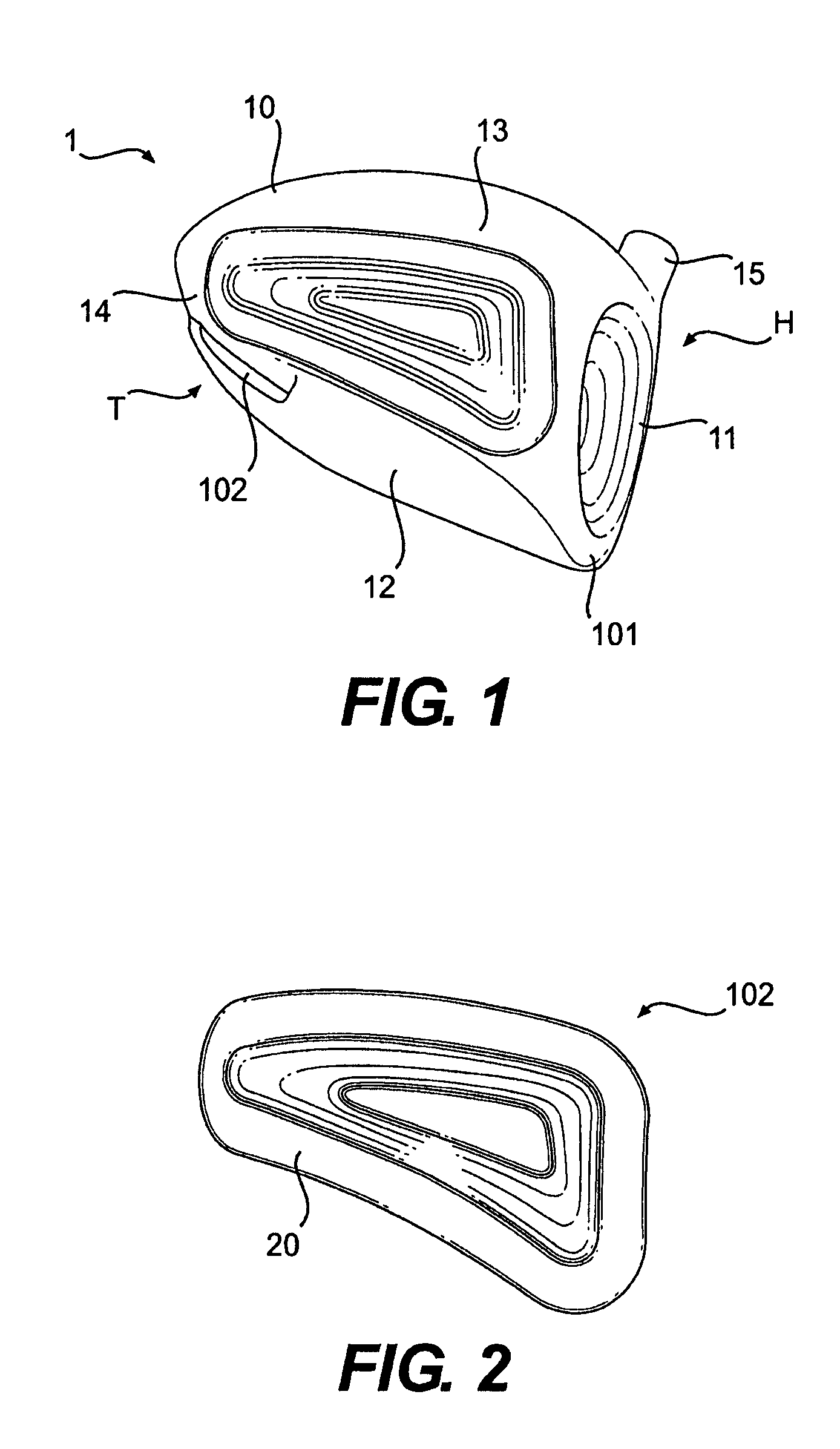
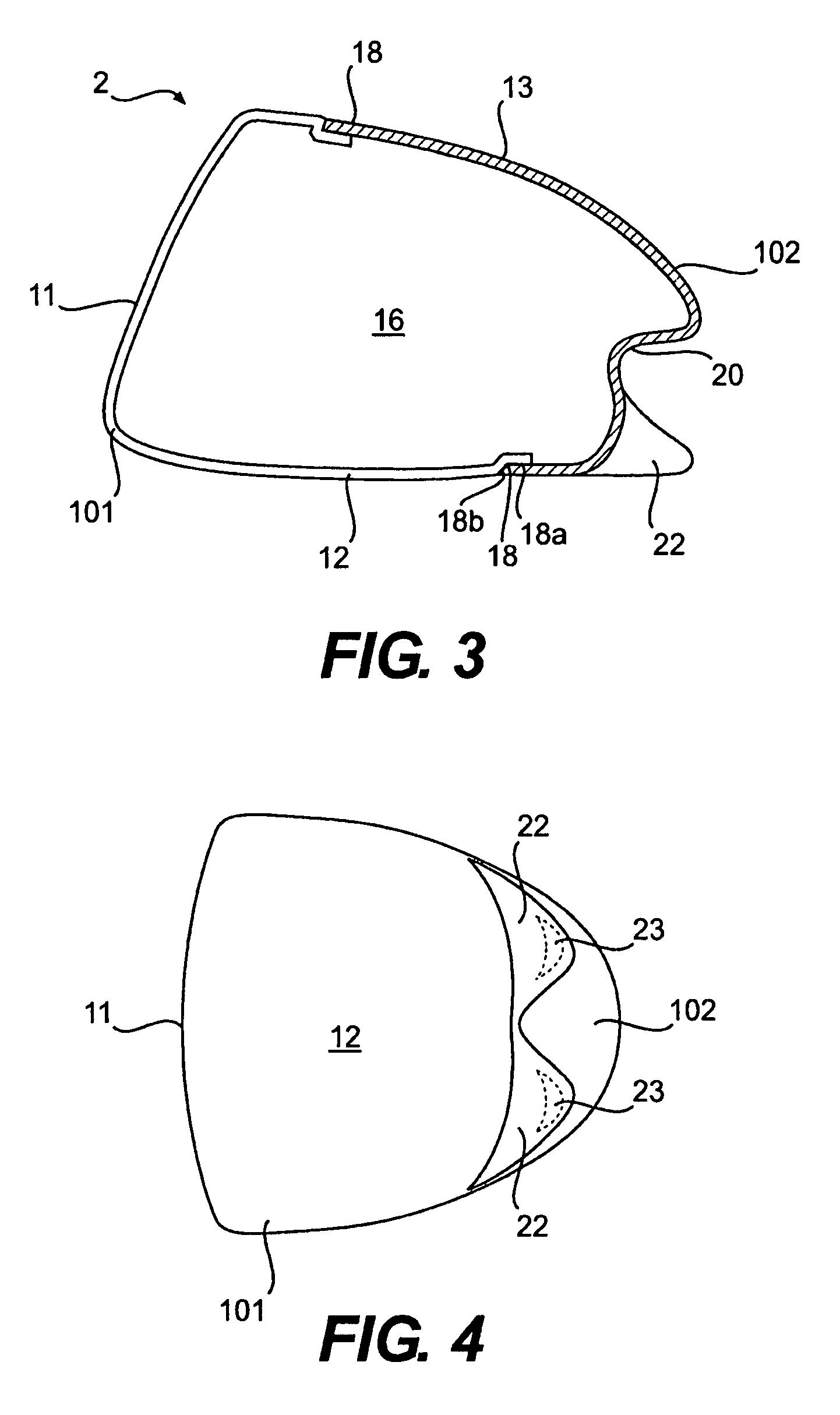
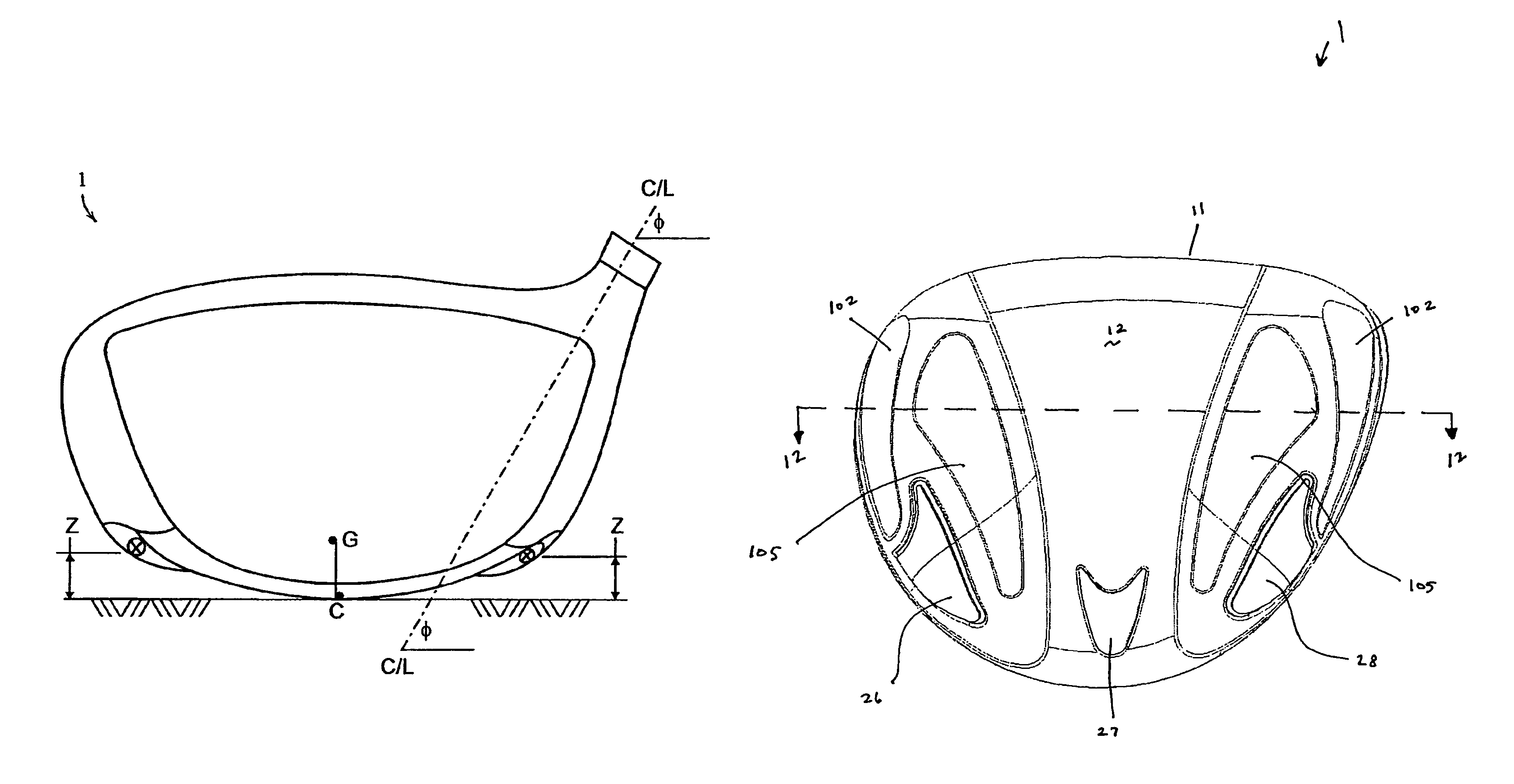
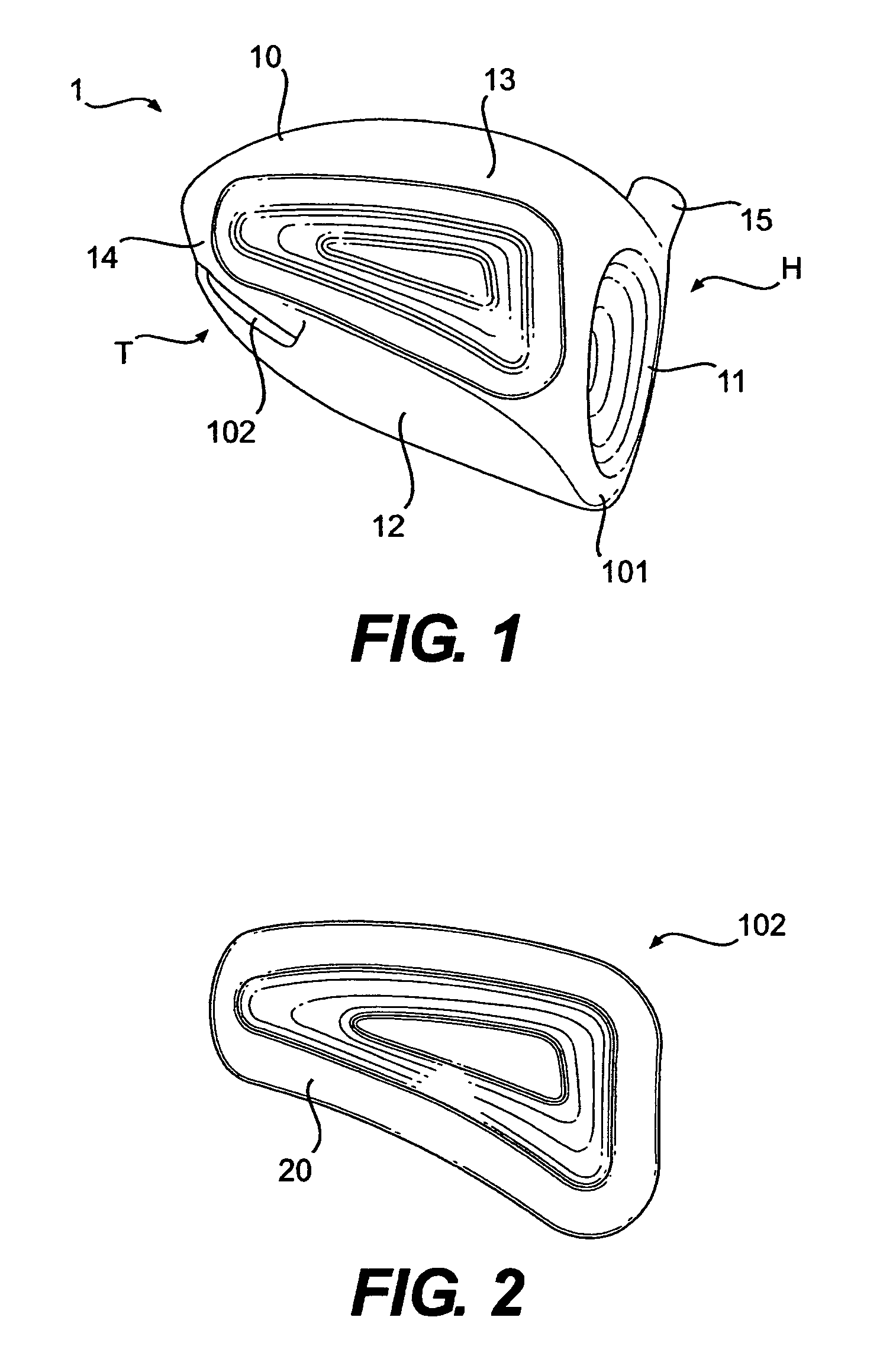
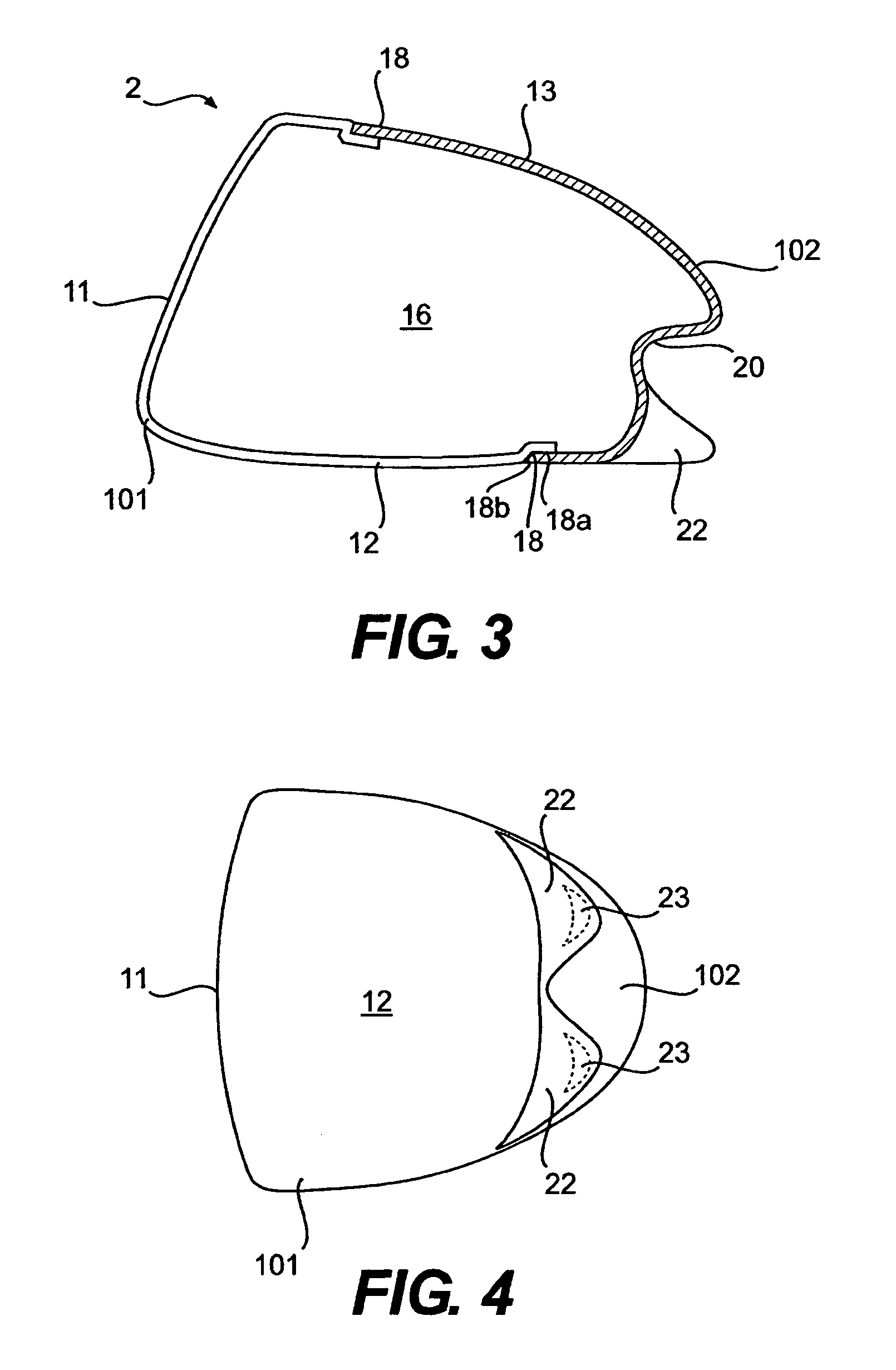
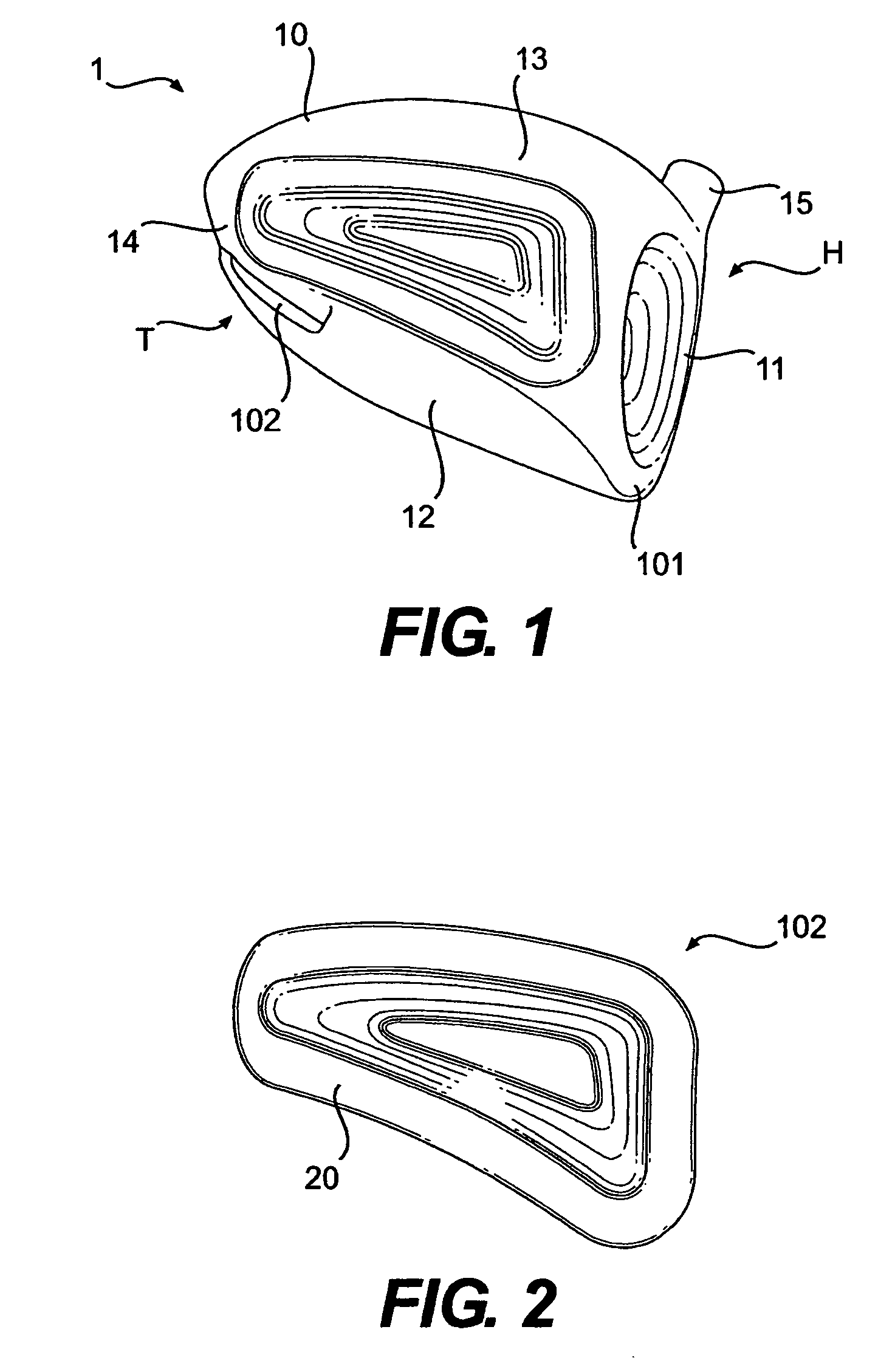
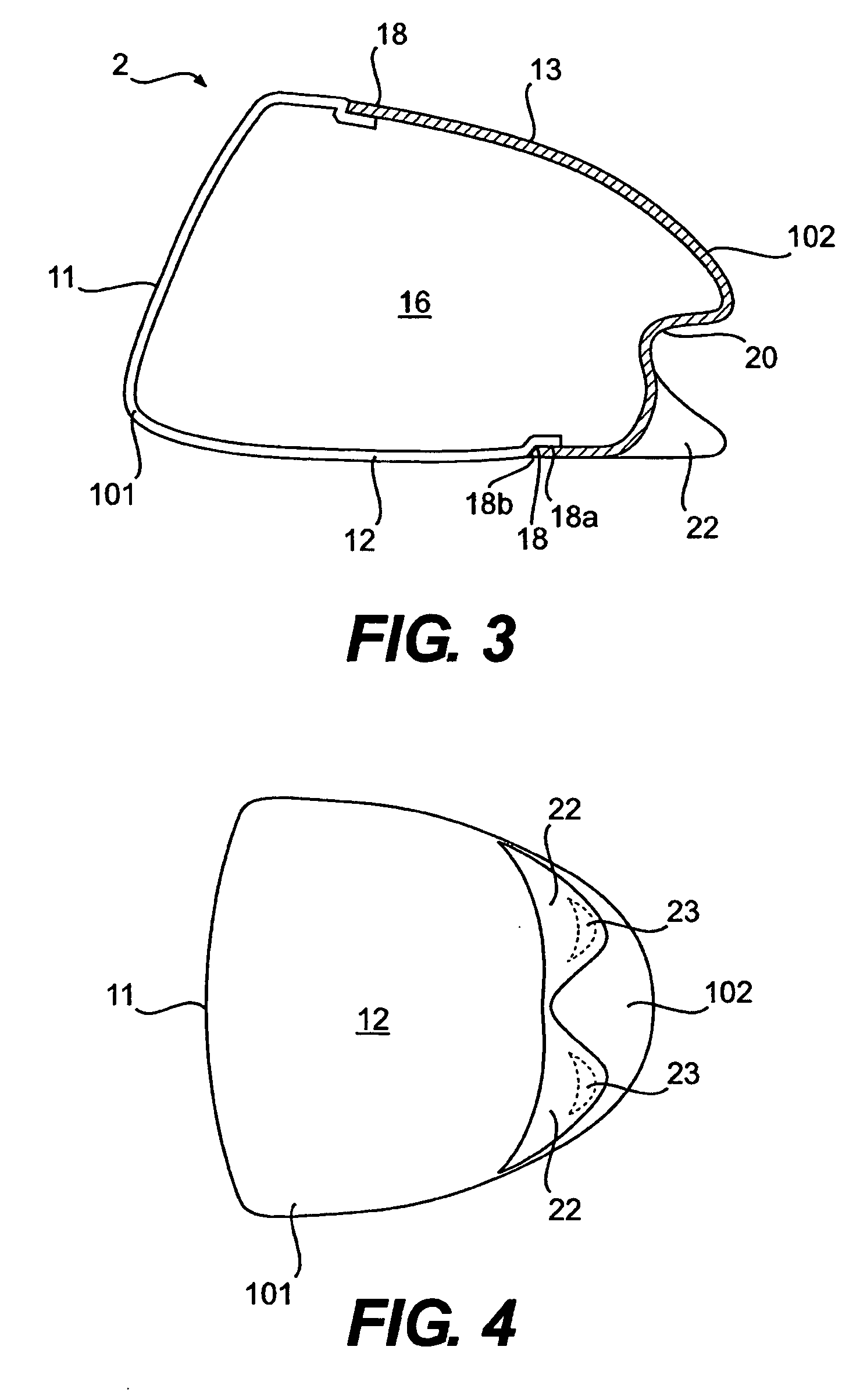
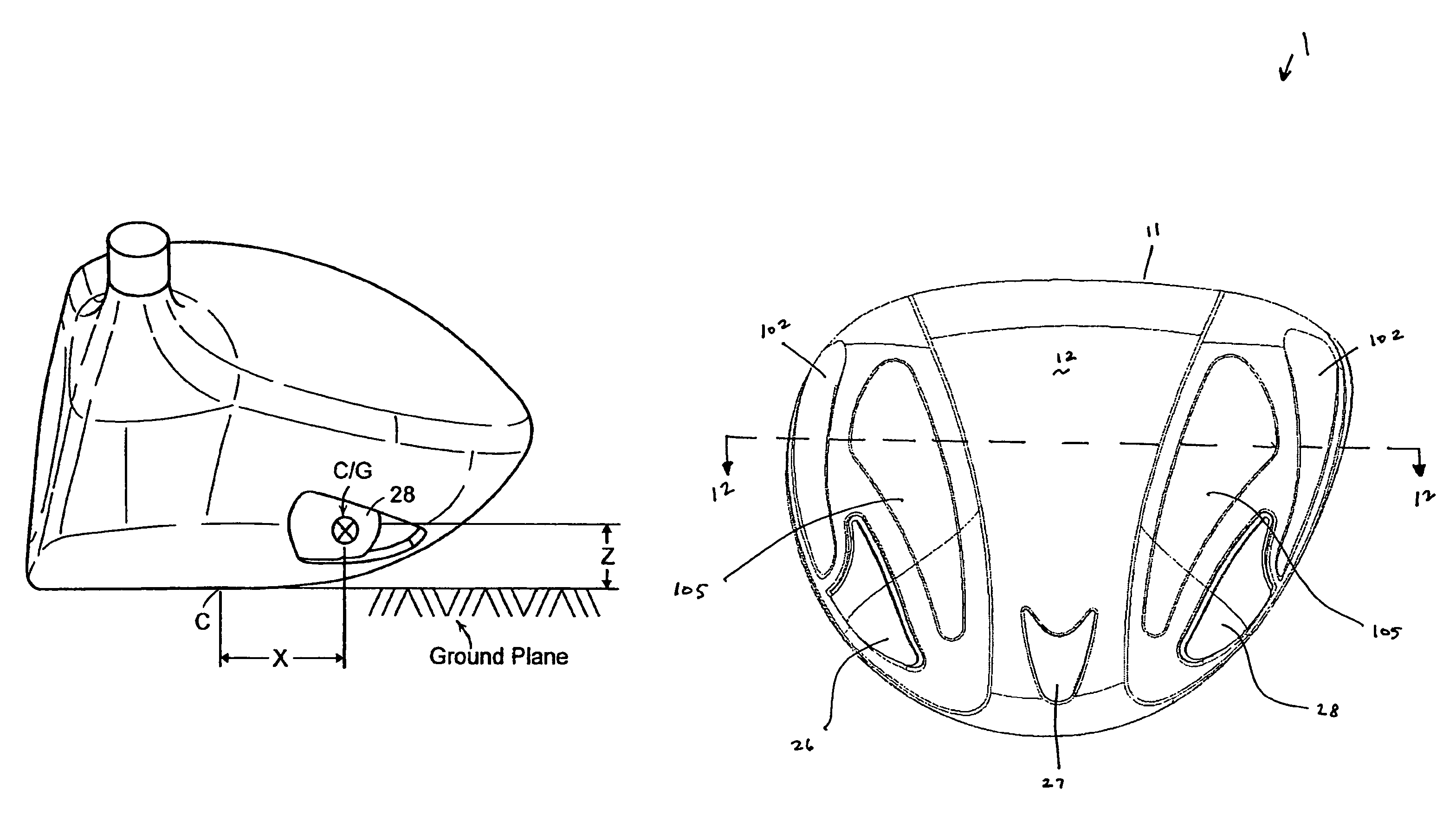
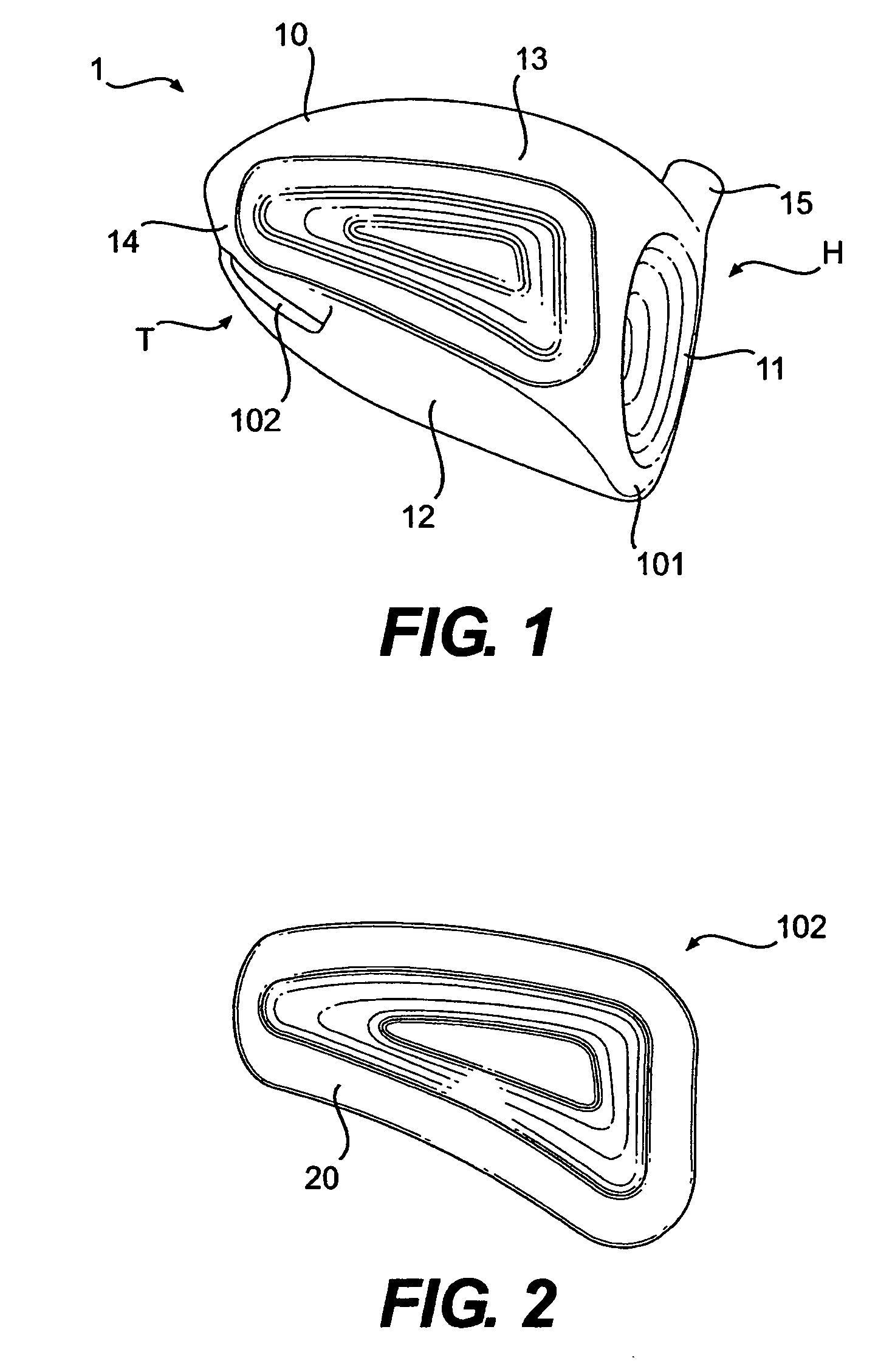
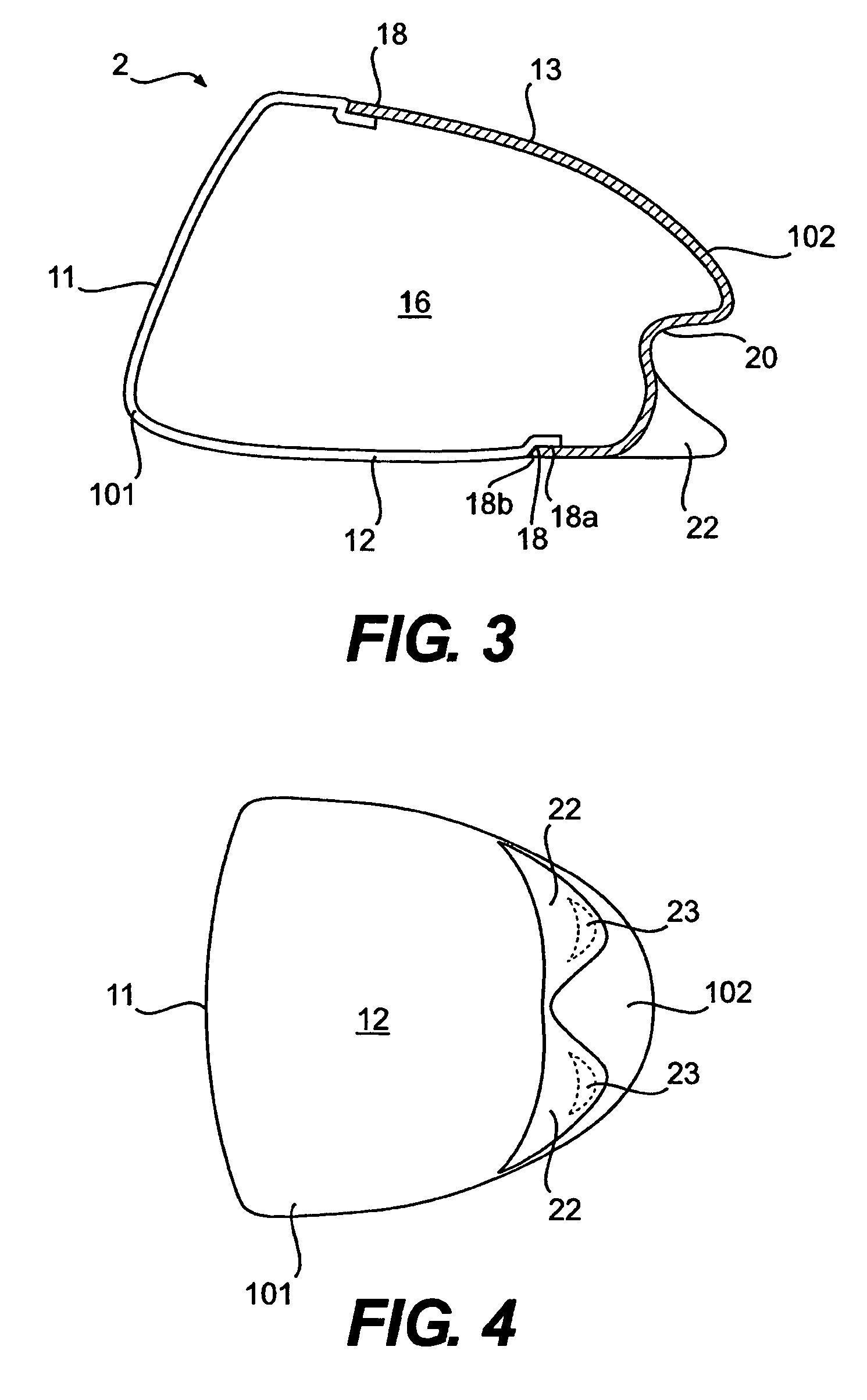
A hollow golf club head with a concave portion is disclosed and claimed. The club head includes a metallic portion and a light-weight portion, which may be formed of plastic, composite, or the like. The concave portion allows the club designer to make a club head having very thin portions while still maintaining the requisite structural integrity. Convex bulges may optionally be provided to house weight inserts to enhance the playing characteristics of the golf club. The metallic portion of the club head may take on the appearance of a frame, into which several light-weight inserts are positioned. These light-weight inserts may be positioned in the crown, skirt, and sole of the club head. The club head may be formed by co-molding, eliminating the need for welding or adhesives, freeing mass to be used in more beneficial ways. The club head may be large to increase playability and forgiveness. The club head may include one or more light-weight inserts to manipulate the playing characteristics of the resulting golf club. These inserts may have attachment surfaces that are relatively angled such that the inserts are subjected to compressive forces rather than shear forces upon impact with a golf ball during a golf swing.
Owner:COBRA GOLF
Methods and devices for anchoring to soft tissue
InactiveUS20060259074A1Promote cell ingrowthFacilitate attachmentSuture equipmentsSurgical needlesBiomedical engineeringStomach
Disclosed are methods and devices for placing anchors into soft tissue such as the walls of the stomach. The anchoring device includes a tissue interface that is introduced in a collapsed configuration and which expands radially outward. The tissue interface includes a framework capable of distributing a load applied to the linkage element across the surface area of the tissue interface.
Owner:BOSTON SCI SCIMED INC +1
Part solid, part fluid and flow electrochemical cells including metal-air and li-air battery systems
PendingUS20130189592A1Provide integrityAvoid shortingPrimary cell to battery groupingFuel and primary cellsLithium–air batteryEngineering
Owner:CALIFORNIA INST OF TECH
Golf club head
InactiveUS7803065B2Improved playing characteristicProvide integrityGolf clubsRacket sportsAdhesiveEngineering
A hollow golf club head with a concave portion is disclosed and claimed. The club head includes a metallic portion and a light-weight portion, which may be formed of plastic, composite, or the like. The concave portion allows the club designer to make a club head having very thin portions while still maintaining the requisite structural integrity. Convex bulges may optionally be provided to house weight inserts to enhance the playing characteristics of the golf club. The metallic portion of the club head may take on the appearance of a frame, into which several light-weight inserts are positioned. These light-weight inserts may be positioned in the crown, skirt, and sole of the club head. The club head may be formed by co-molding, eliminating the need for welding or adhesives, freeing mass to be used in more beneficial ways. The club head may be large to increase playability and forgiveness. The club head may include one or more light-weight inserts to manipulate the playing characteristics of the resulting golf club. These inserts may have attachment surfaces that are relatively angled such that the inserts are subjected to compressive forces rather than shear forces upon impact with a golf ball during a golf swing.
Owner:COBRA GOLF
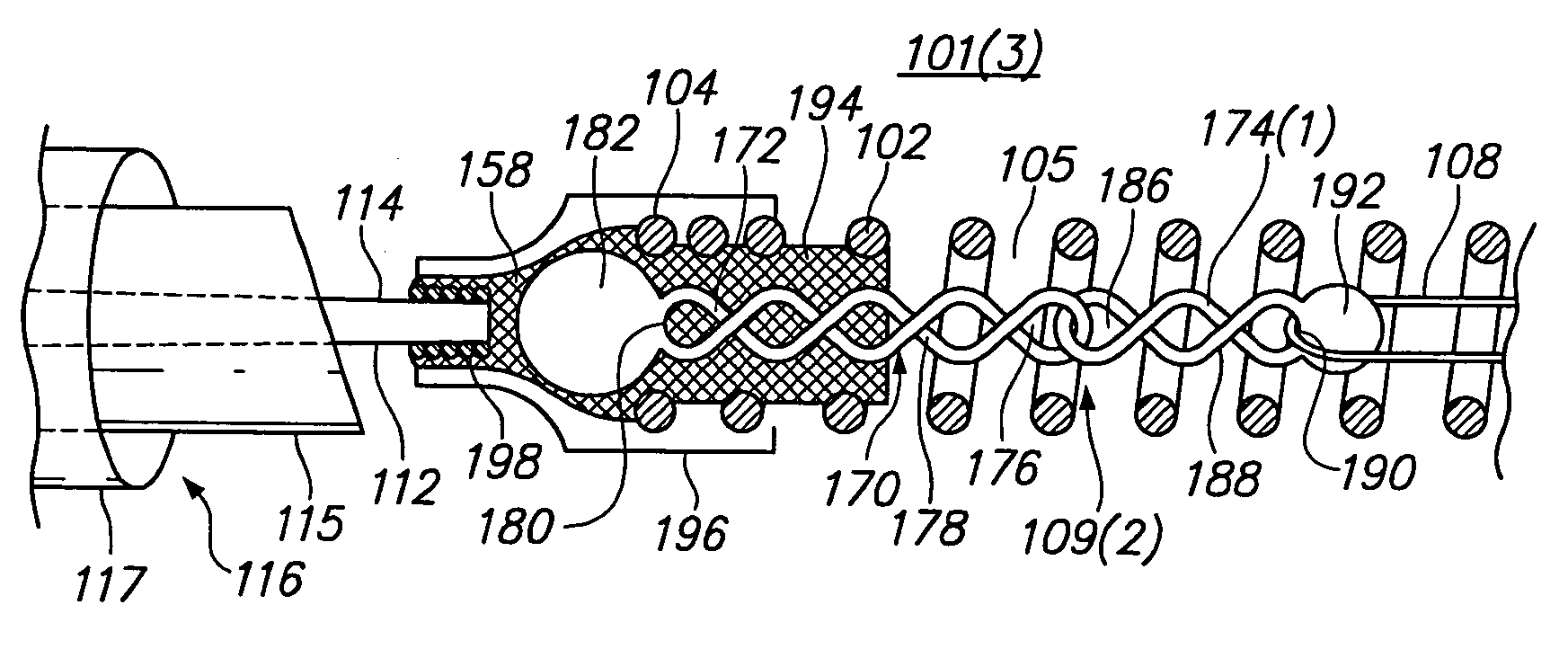
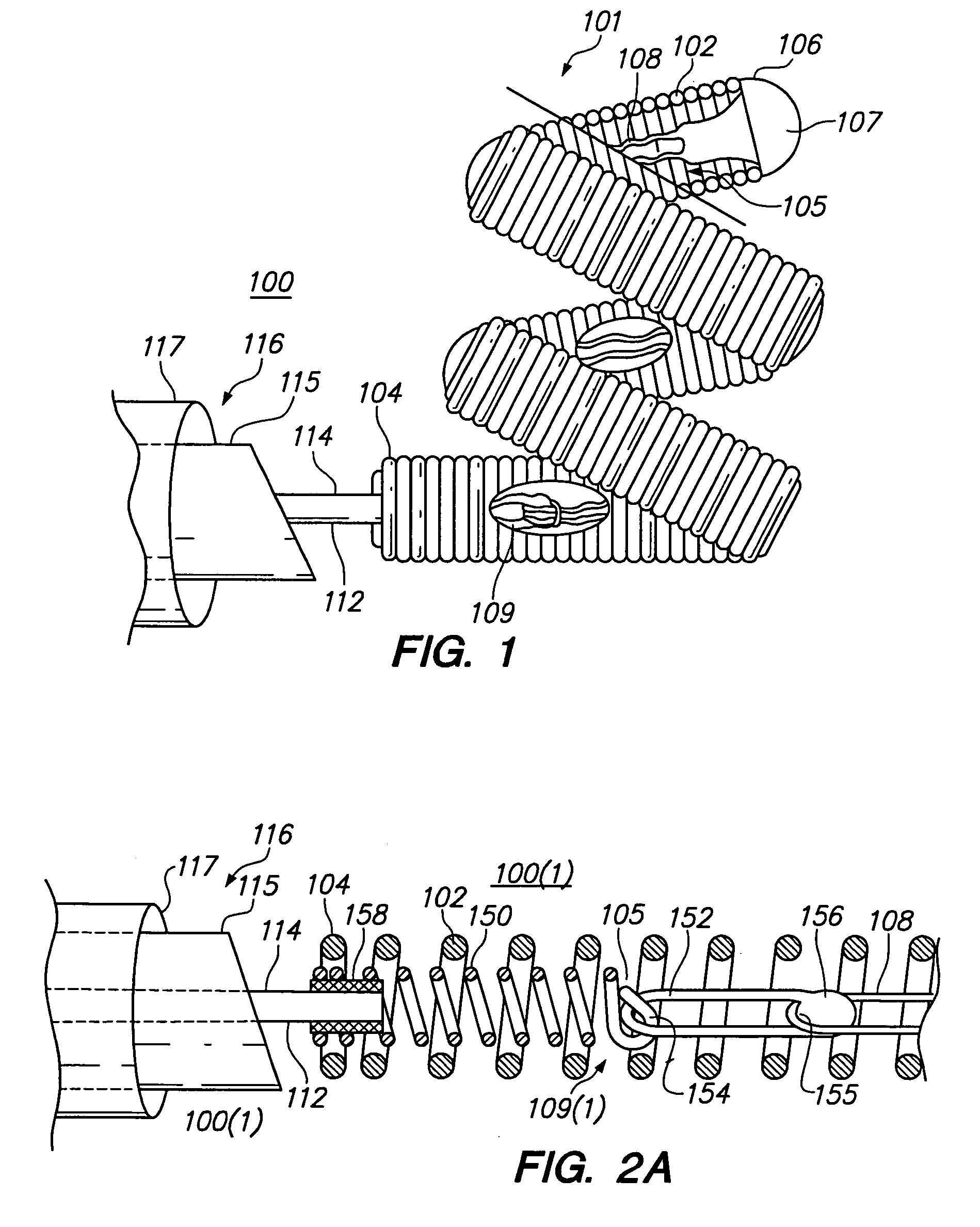
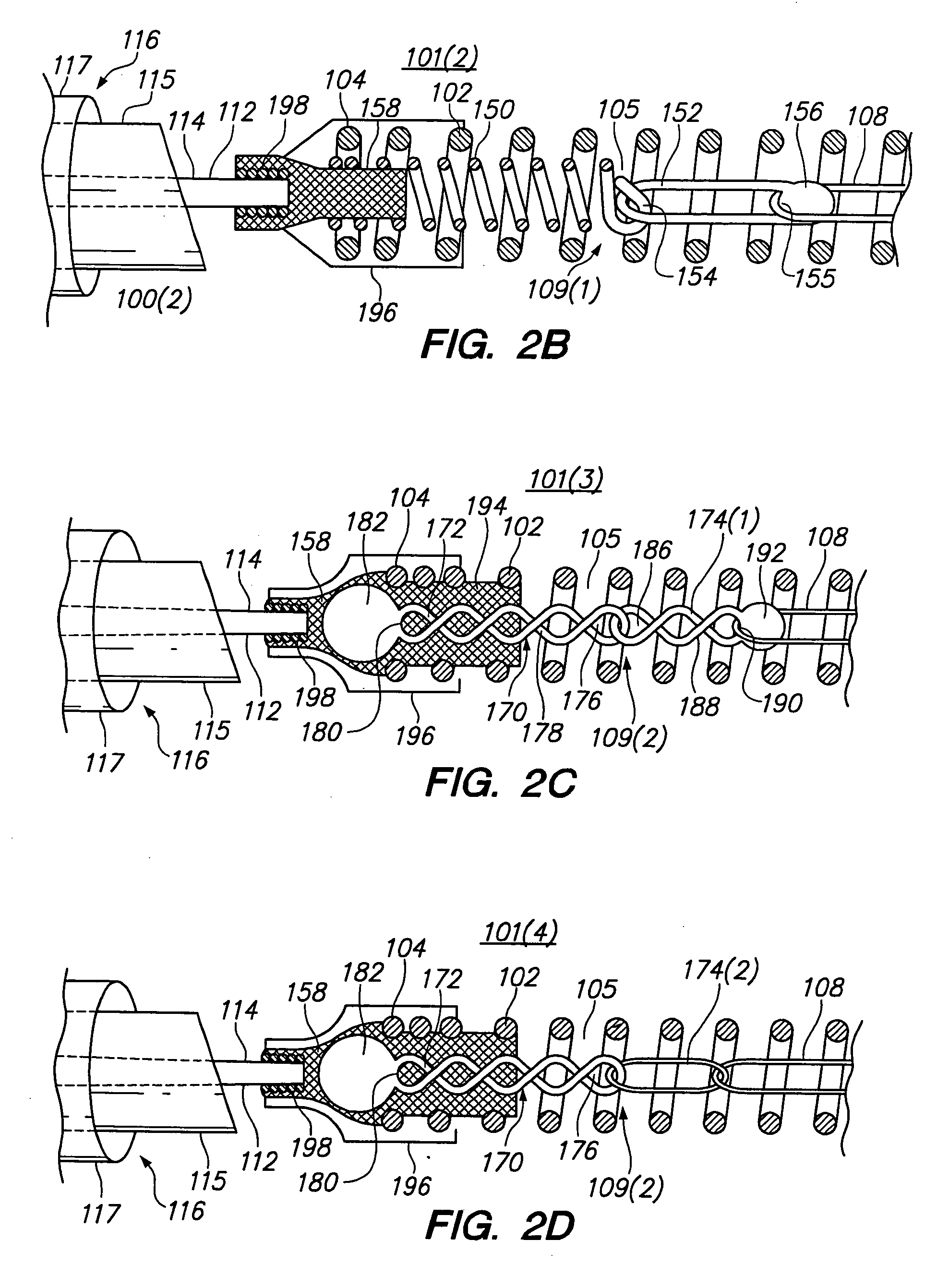
Anchor assemblies in stretch-resistant vaso-occlusive coils
Vaso-occlusive devices are provided for occluding an aneurysm within the human vasculature. The vaso-occlusive device also includes a stretch-resisting member that extends through at least a portion of a lumen of the primary coil and is directly or indirectly attached to the primary coil at two locations axially separated from each other to prevent or minimize axial stretching of the primary coil. At one location, the stretch-resisting member is coupled to the primary coil via a flexible anchor assembly disposed within the lumen. In one embodiment, the anchor assembly may comprise an anchor coil and a link directly or indirectly coupled between the anchor coil and the stretch-resisting member. Alternatively, the anchor assembly may comprise a chain of twisted links.
Owner:STRYKER EURO OPERATIONS HLDG LLC +1
Golf club head
ActiveUS20070054751A1Improved playing characteristicProvide integrityGolf clubsRacket sportsAdhesiveEngineering
A hollow golf club head with a concave portion is disclosed and claimed. The club head includes a metallic portion and a light-weight portion, which may be formed of plastic, composite, or the like. The concave portion allows the club designer to make a club head having very thin portions while still maintaining the requisite structural integrity. Convex bulges may optionally be provided to house weight inserts to enhance the playing characteristics of the golf club. The metallic portion of the club head may take on the appearance of a frame, into which several light-weight inserts are positioned. These light-weight inserts may be positioned in the crown, skirt, and sole of the club head. The club head may be formed by co-molding, eliminating the need for welding or adhesives, freeing mass to be used in more beneficial ways. The club head may be large to increase playability and forgiveness.
Owner:COBRA GOLF
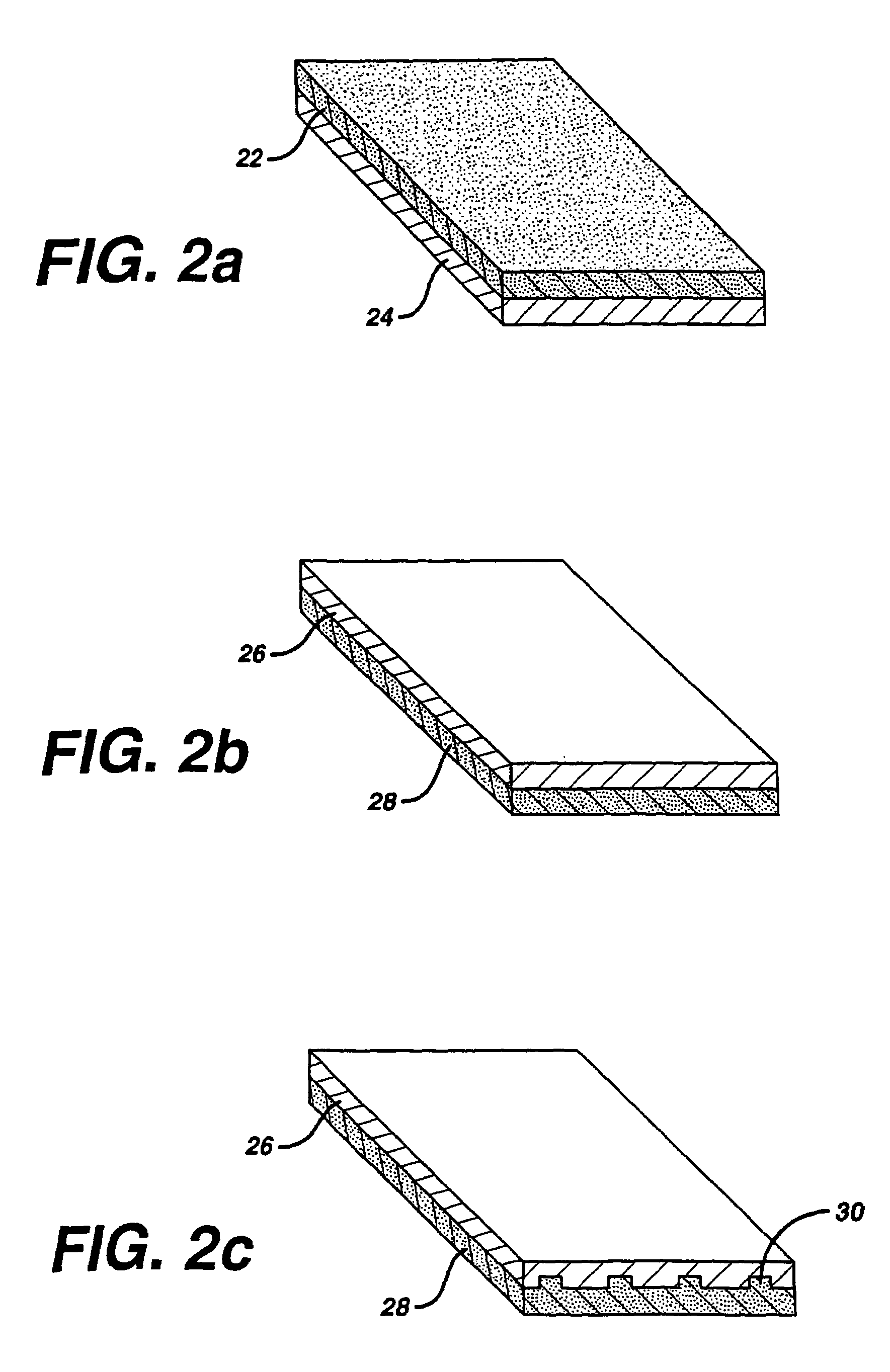
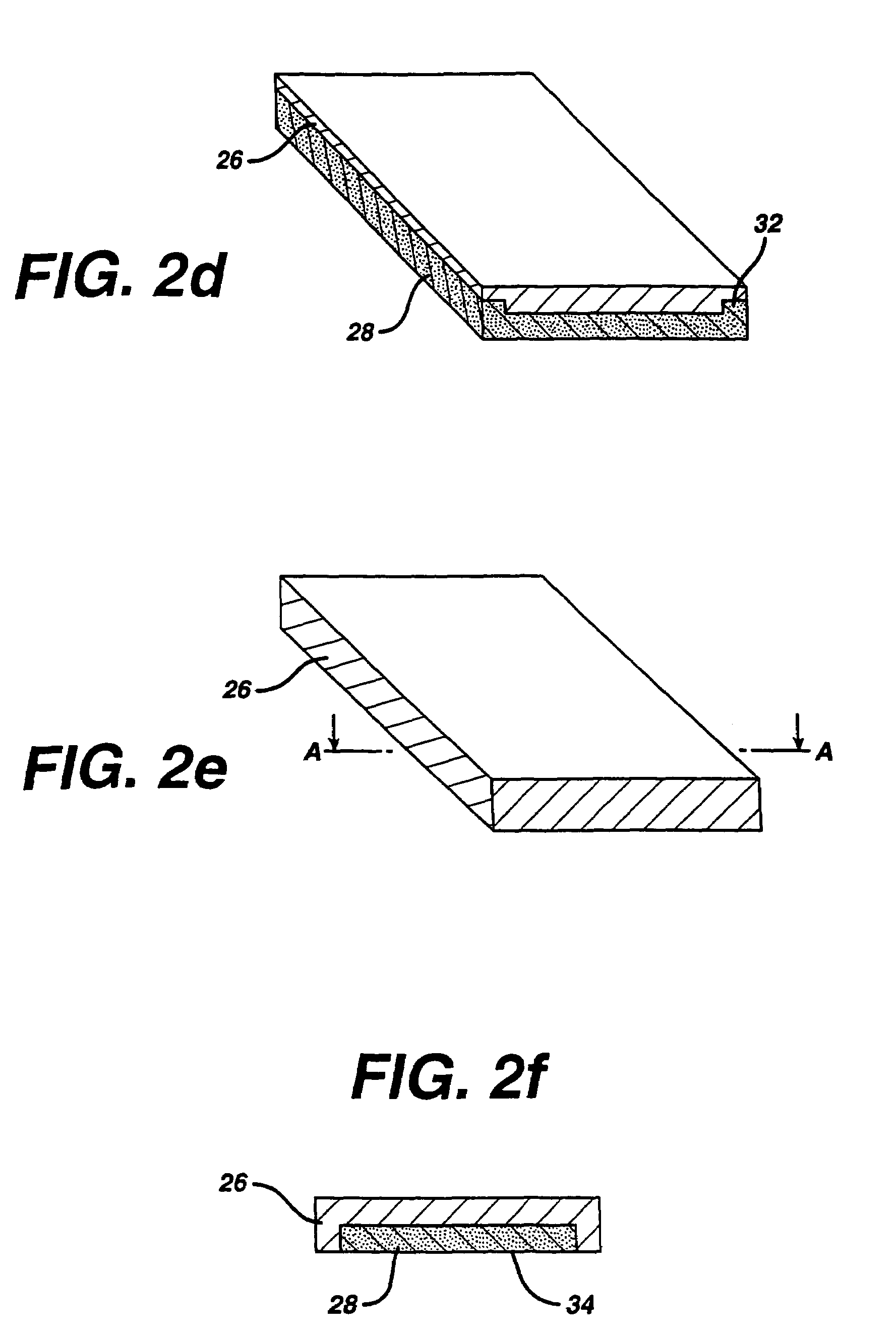
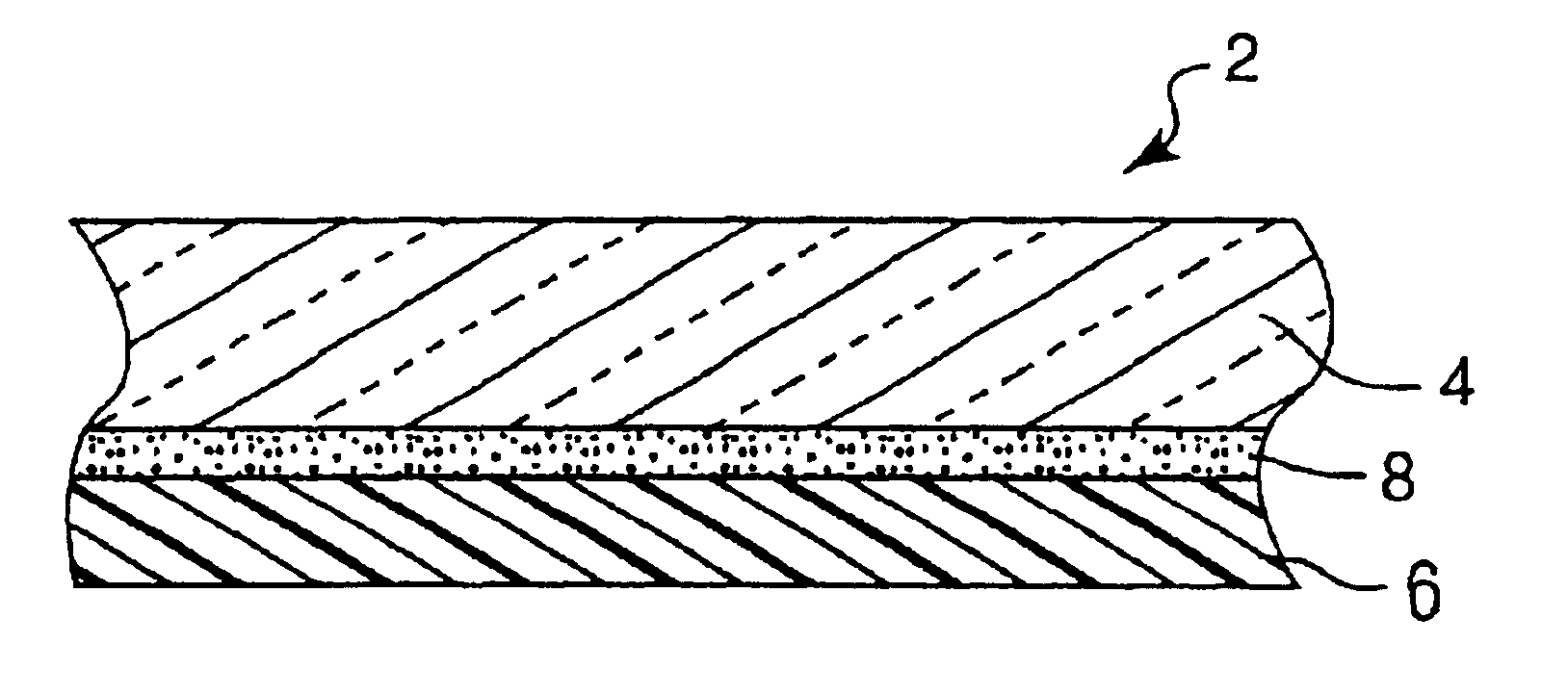
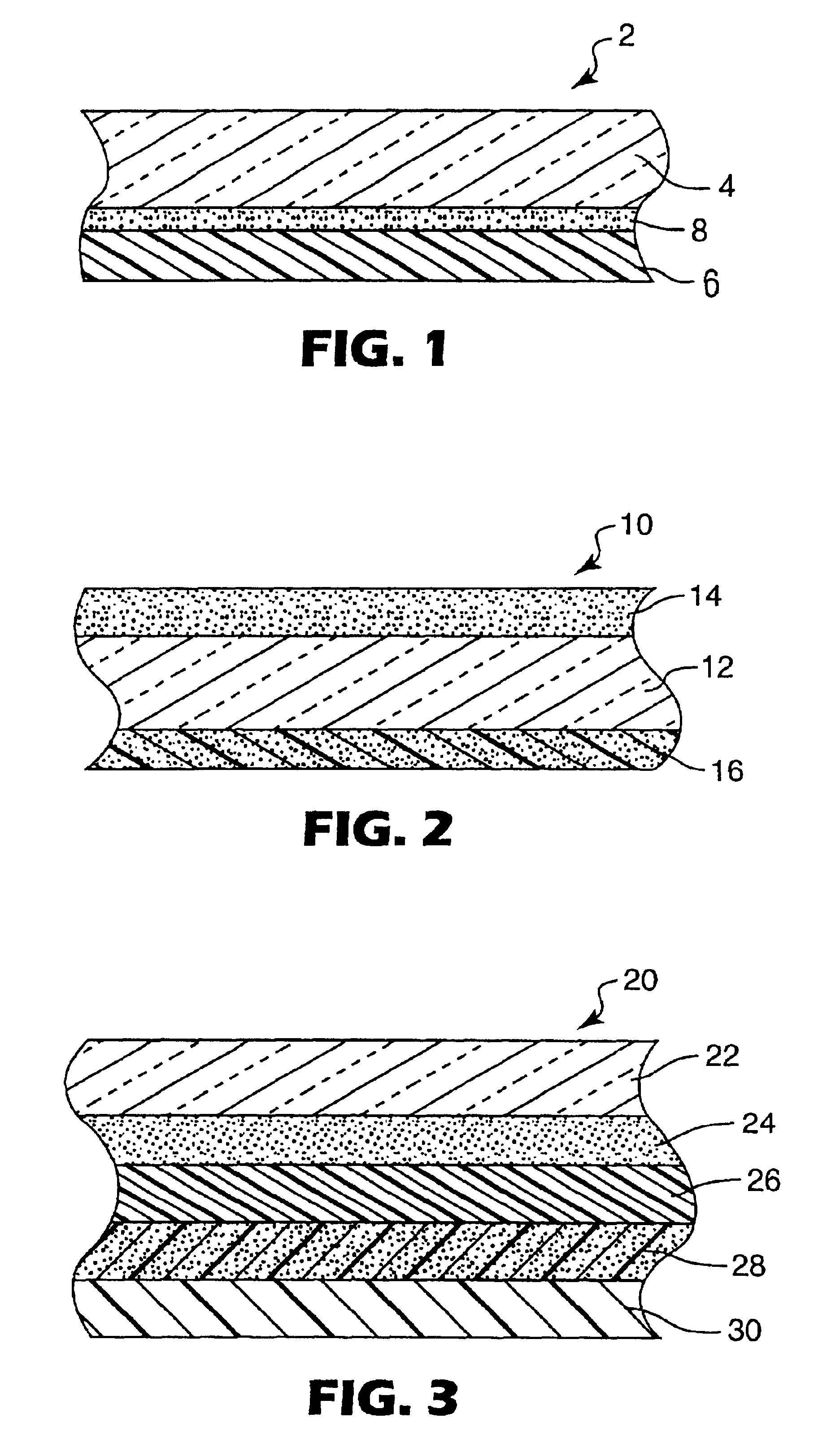
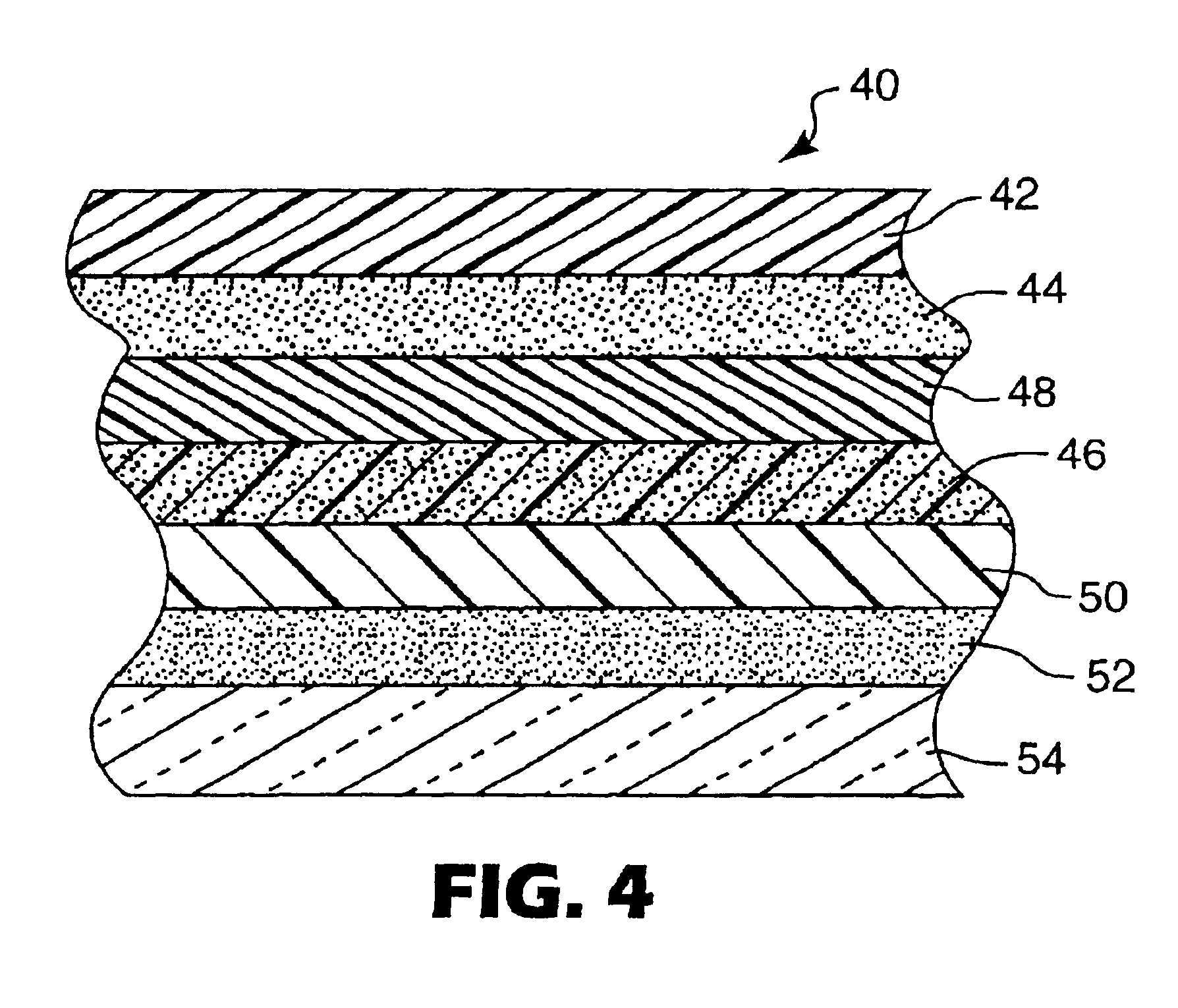
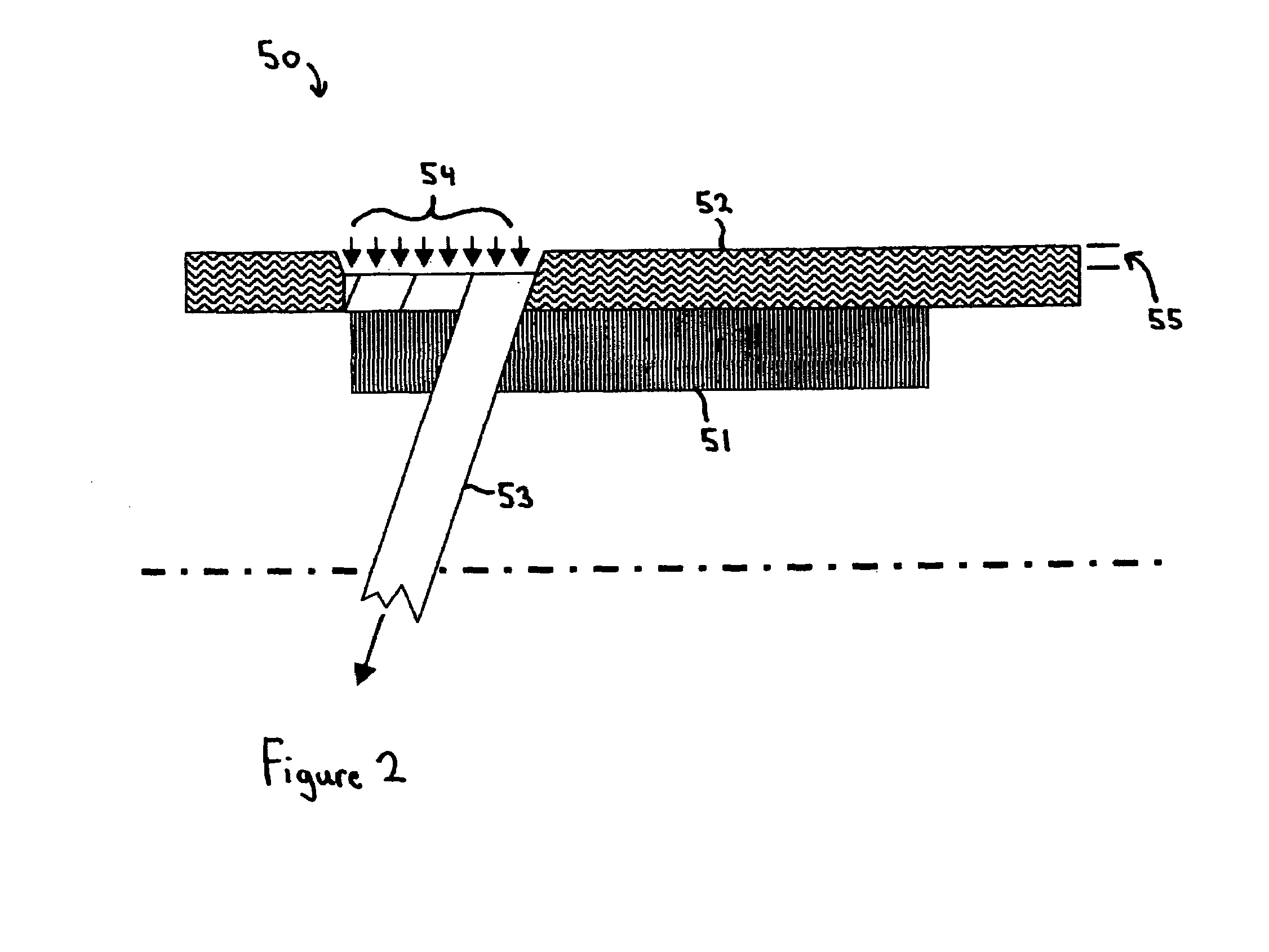
Multi-layer absorbent wound dressing
InactiveUS6903243B1Improve water absorptionIncreased durabilitySynthetic resin layered productsAdhesive dressingsBiomedical engineeringBody fluid
A multi-layer wound dressing comprising at least two absorbent layers, and materials for forming absorbent layers are provided. The absorbent layers have different absorbencies, with the layer closest to the wound having a lower absorbency than the layer furthest from the wound. The wound dressing typically contains additional non-absorbing layers, such as a backing film and wound-facing film. The dressing provides absorbency of wound exudates while preventing the absorbent material from entering the wound. In specific implementations the dressing is substantially transparent prior to application to a wound, as well as after application to the wound when body fluids have been absorbed.
Owner:3M INNOVATIVE PROPERTIES CO
Golf club head
ActiveUS8523705B2Improved playing characteristicProvide integrityGolf clubsRacket sportsAdhesiveGolf Ball
Owner:COBRA GOLF
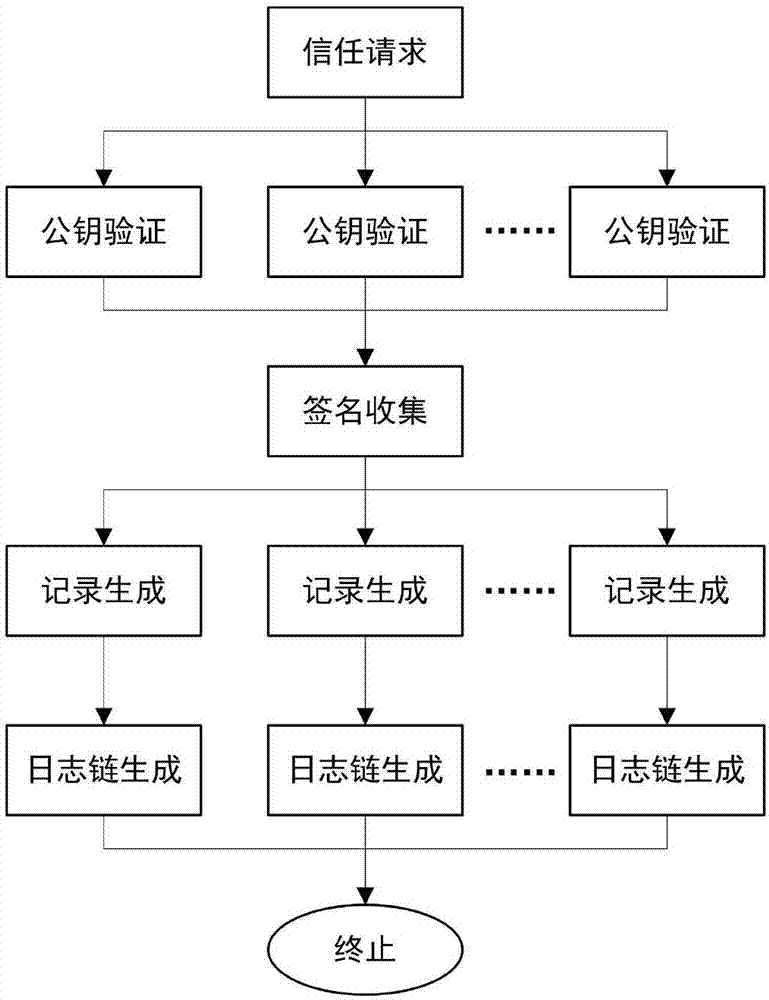
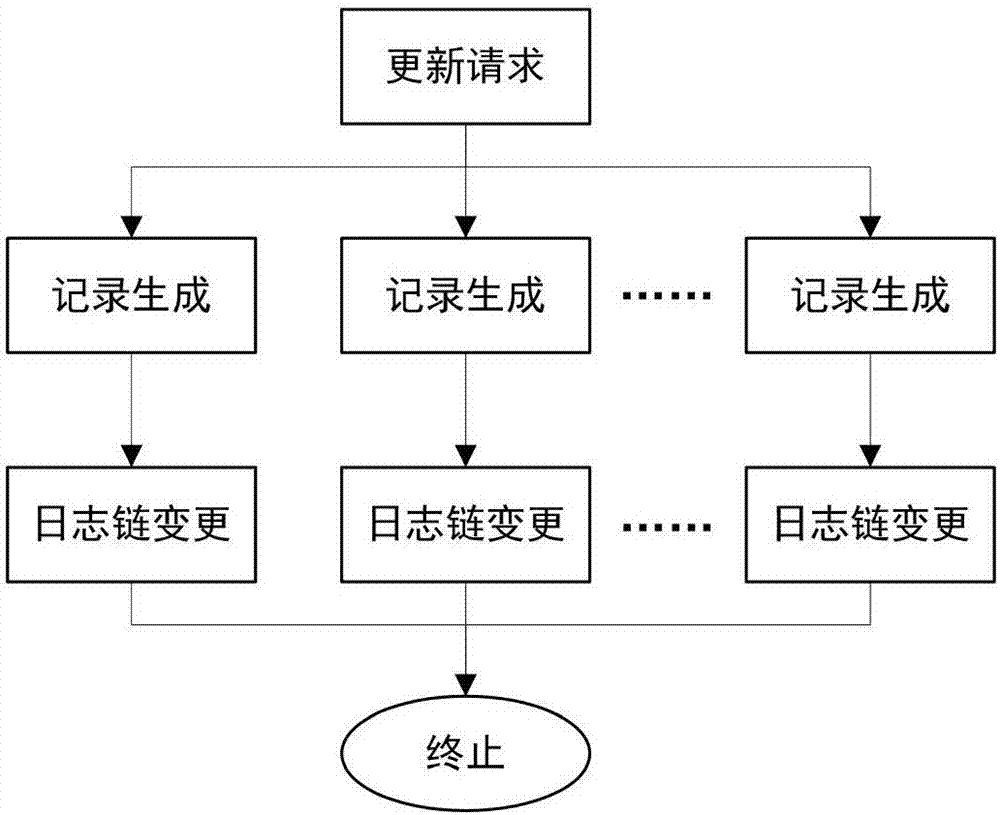
Decentralized public key management method and system based on trusted network
ActiveCN107070644AEfficient verificationEfficient queryKey distribution for secure communicationStructure of Management InformationUser identifier
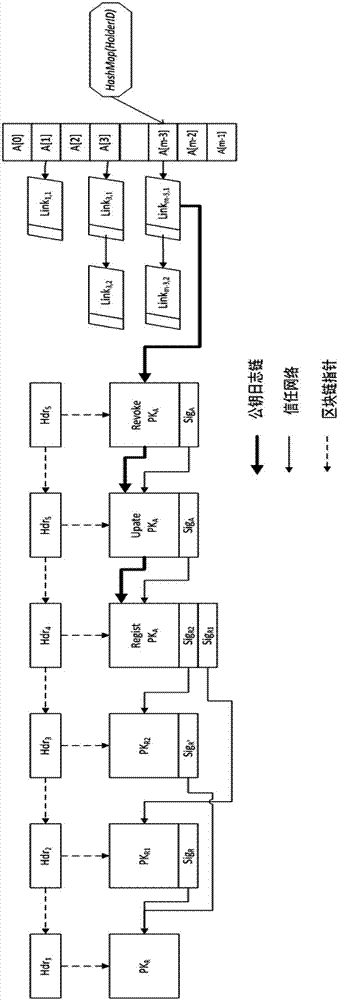
The invention mainly belongs to the technical field of information security, and specifically relates to a novel decentralized public key management method and a trusted model. The method is constructed on distributed data network platforms such as a block chain and P2P (Peer to Peer) in order to ensure that all nodes in the platforms can participate in maintenance of whole-life-cycle management of public keys of users, and the changes of the public keys of the users in various states in a life cycle are recorded in a bill form. Through the method, public keys passing verification can be recorded and added into a consistent public key storage structure of a platform to be saved; a public key log chain is generated for all public key records of the same user according to a time sequence, and an authentication chain and a trusted network are formed on the basis of a referrer signature; and efficient search of the public keys can be realized on the basis of user identifiers. Through adoption of the method, the public keys of the users can be issued and acquired conveniently and accurately, and the effectiveness, correctness, consistency and non-fraudulence of acquired public keys are ensured. The method can be taken as an infrastructure supporting authentication, encryption, integrity and accountability services.
Owner:UNIV OF SCI & TECH BEIJING
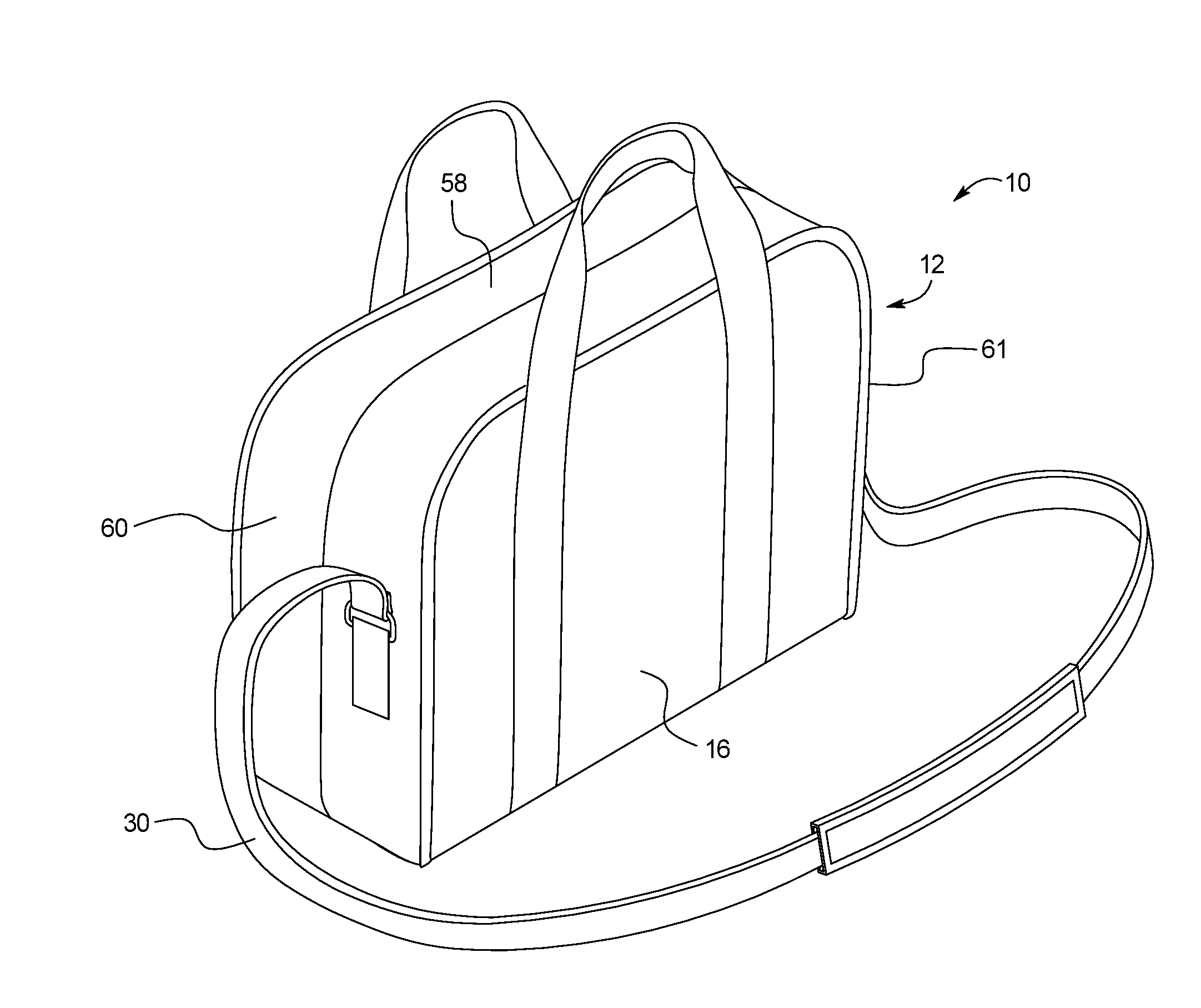
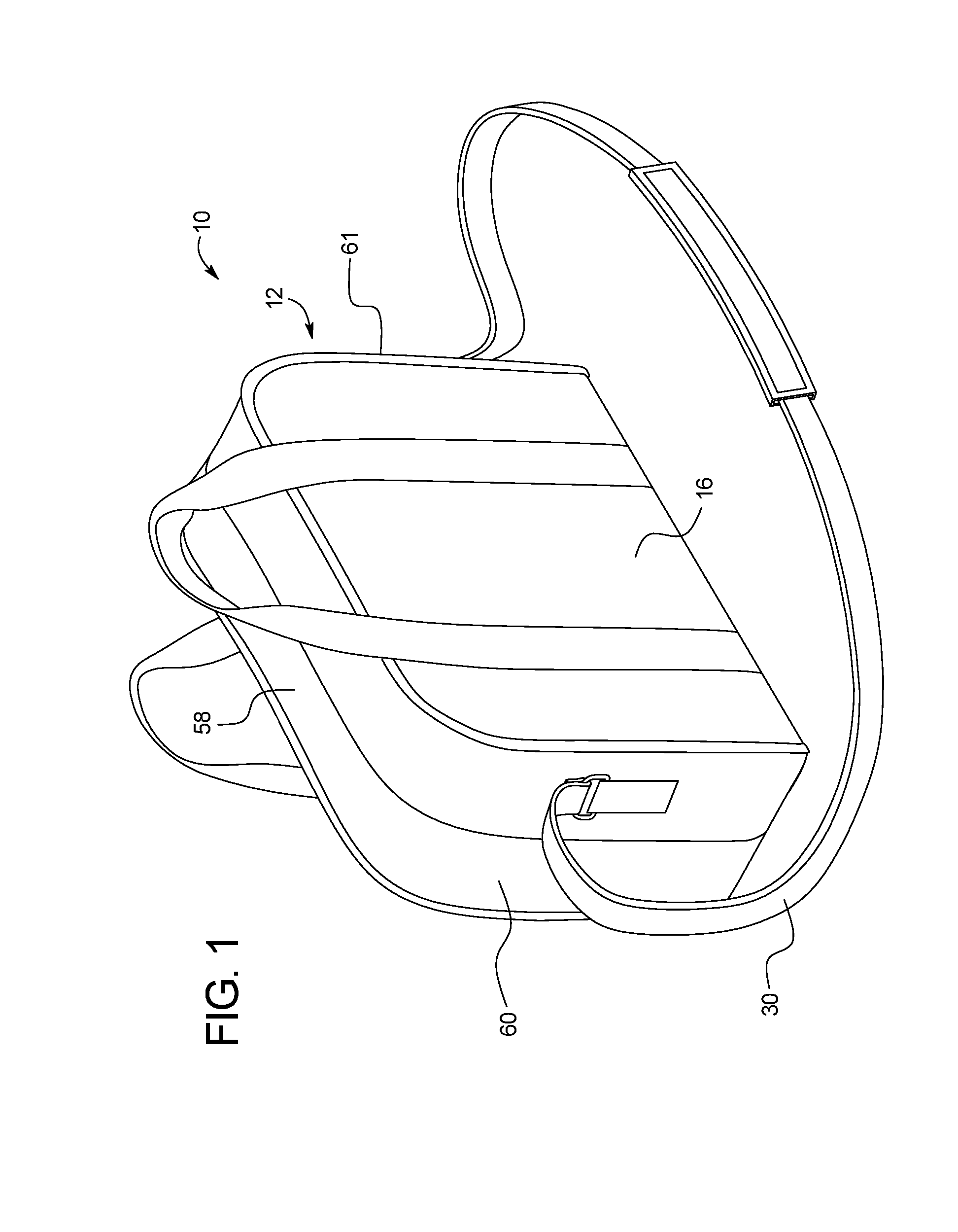
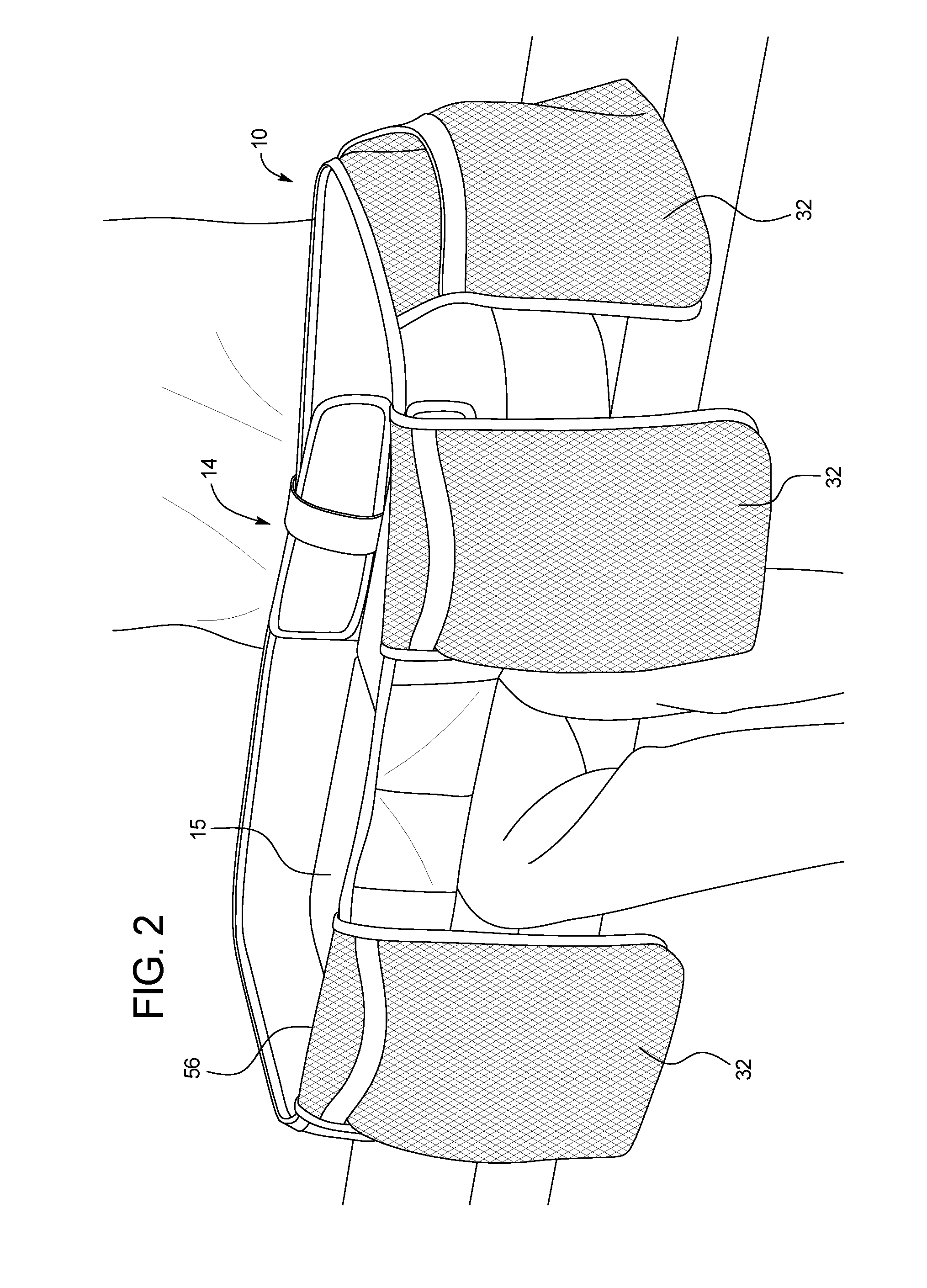
Method of Using a Convertible Diaper Changing Bag
A method of using a convertible includes providing a convertible bag that includes a changing surface including a first tray panel and a second tray panel; first and second panel side walls extending perpendicular from the first and second tray panels, respectively; a shoulder strap including a first strap end and a second strap end, wherein each of the first and second strap ends is removably attached to the bag; and a plurality of connection points for removably attaching the first and second strap ends to the bag. The convertible bag moves between a closed position and an open position. In the closed position, the first panel and the second panel are parallel. In the open position, the first and second tray panels are within a plane.
Owner:ANNA & EVE
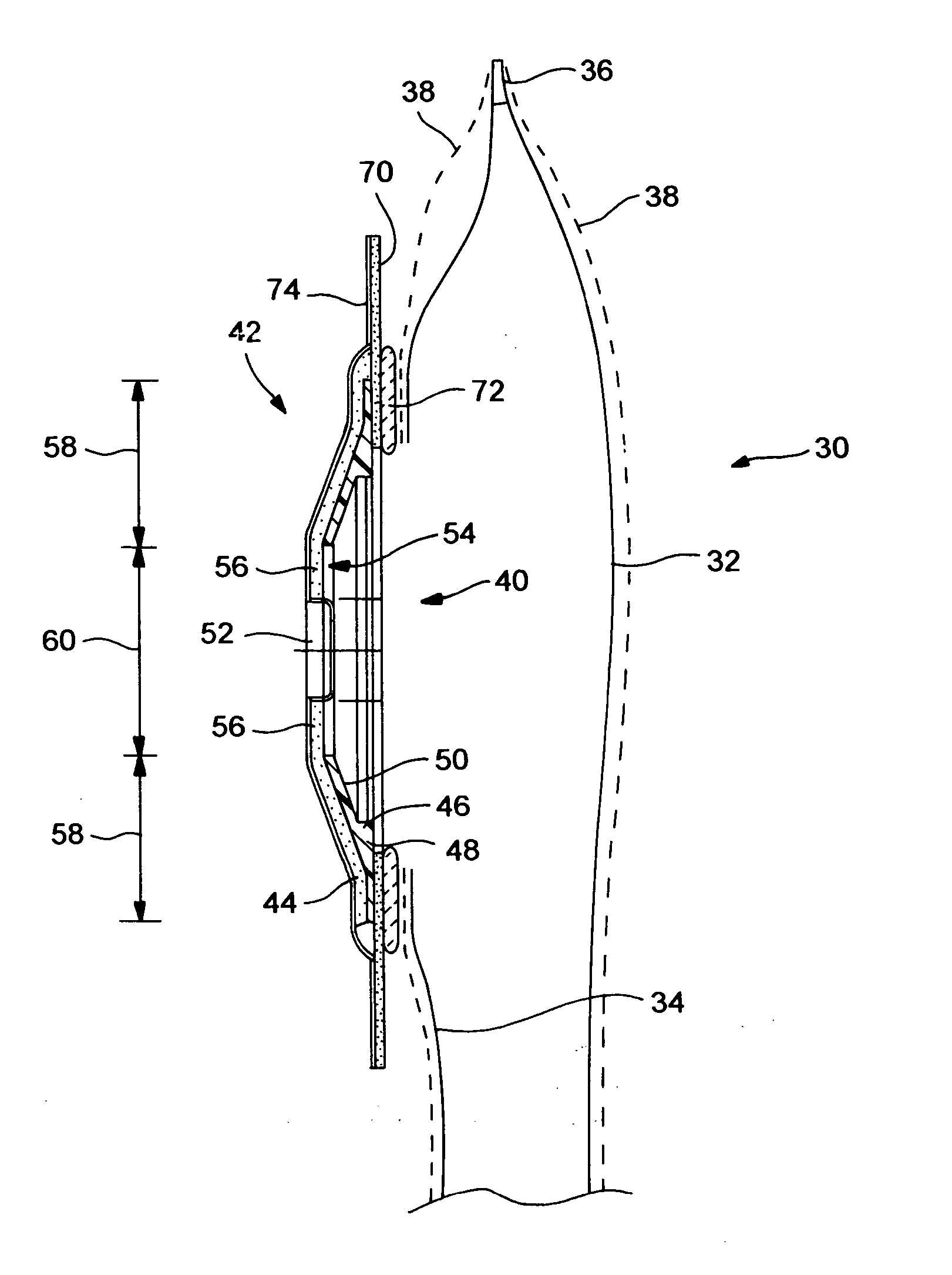
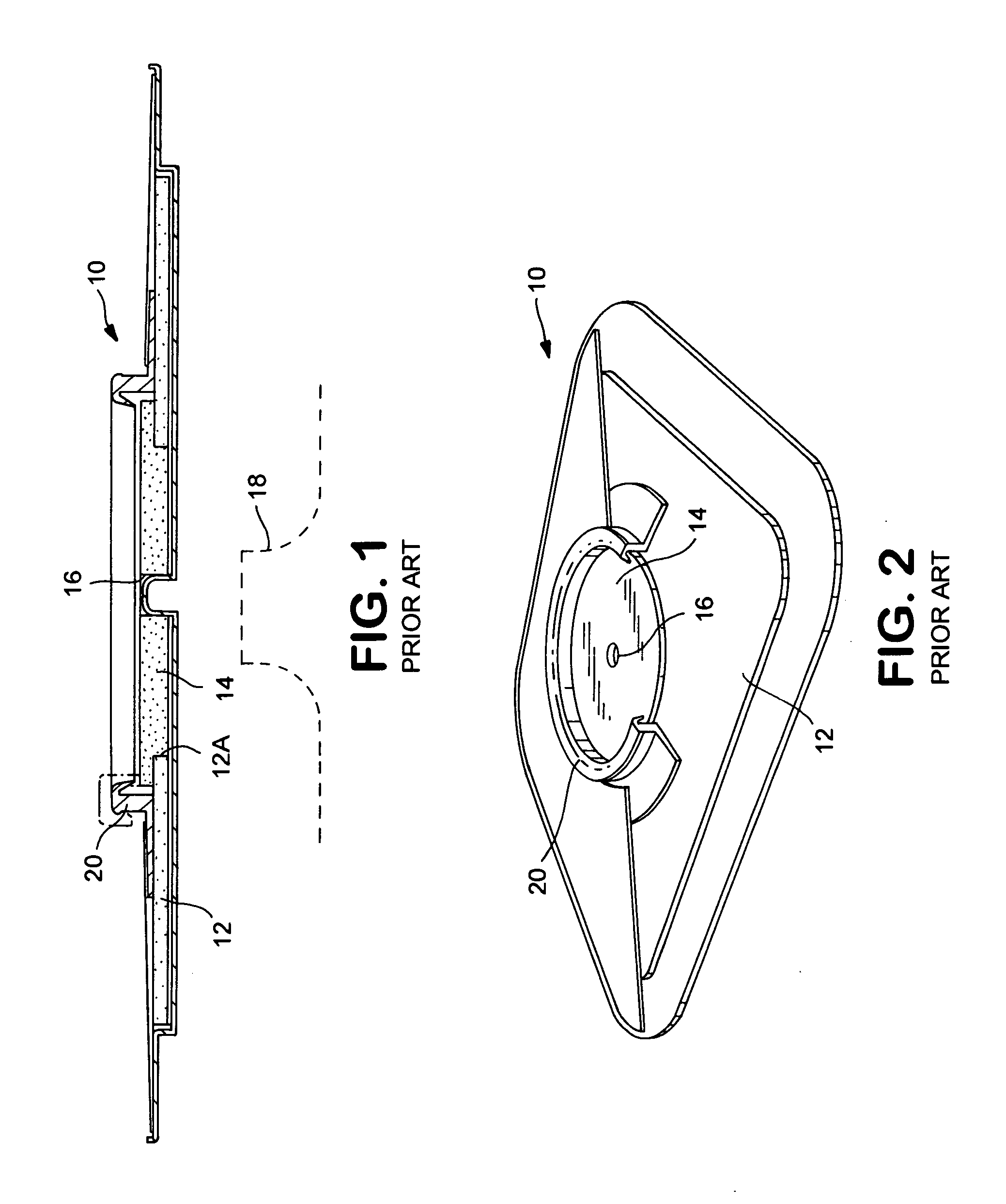
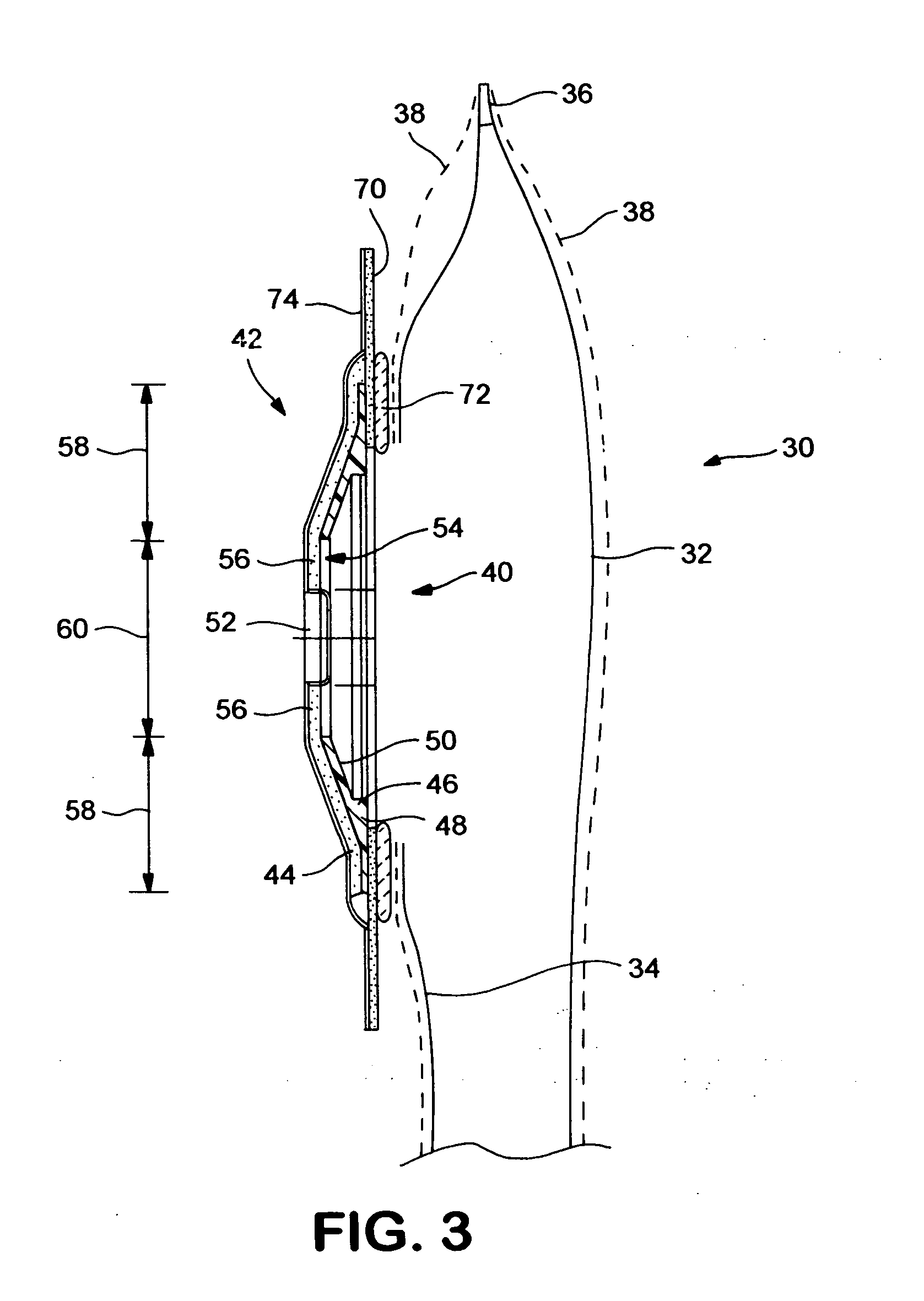
Ostomy appliance
InactiveUS20050054997A1Facilitate and aid shapingProvide integrityNon-surgical orthopedic devicesColostomyEngineeringFlange
An ostomy body fitment for attaching an ostomy pouch to a person's body comprises a shapeable adhesive pad, and a shape defining member. In a first annular fixed shape zone, the shapeable pad is supported and shaped by the shape defining member. In a second central reshapeable zone, a portion of the adhesive pad is unsupported by the shape defining member, and can be molded to fit an individual's stoma. A flexible flange for removable adhesive attachment to an ostomy pouch has an attachment zone outside the periphery of the shape defining member, to reduce direct application of external forces.
Owner:CONVATEC TECH INC
Systems for monitoring and applying electrical currents in an organ perfusion system
ActiveUS20080234768A1Reliable electrical connectionDifferent shapesDead animal preservationExternal electrodesOxygenRight atrium
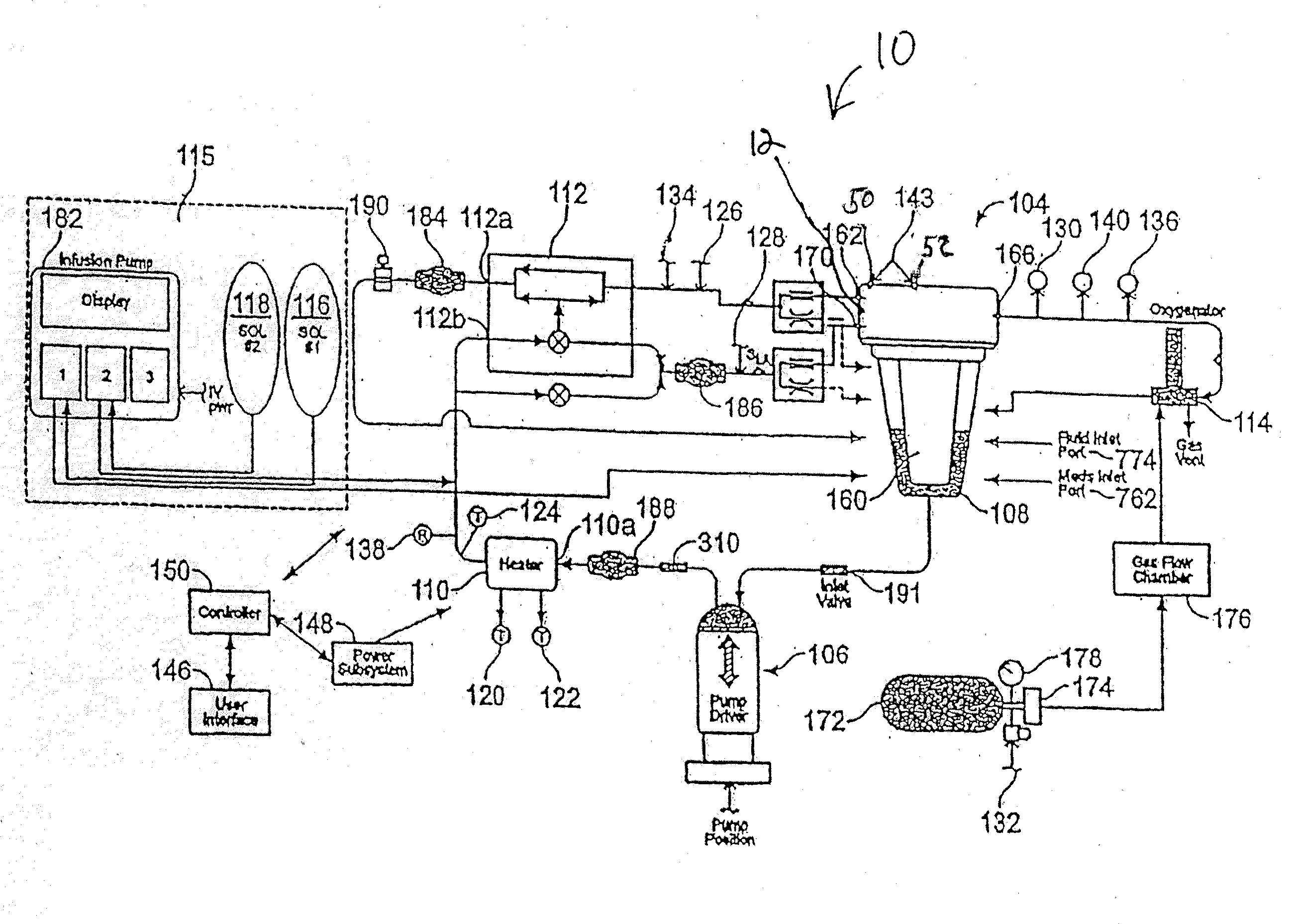
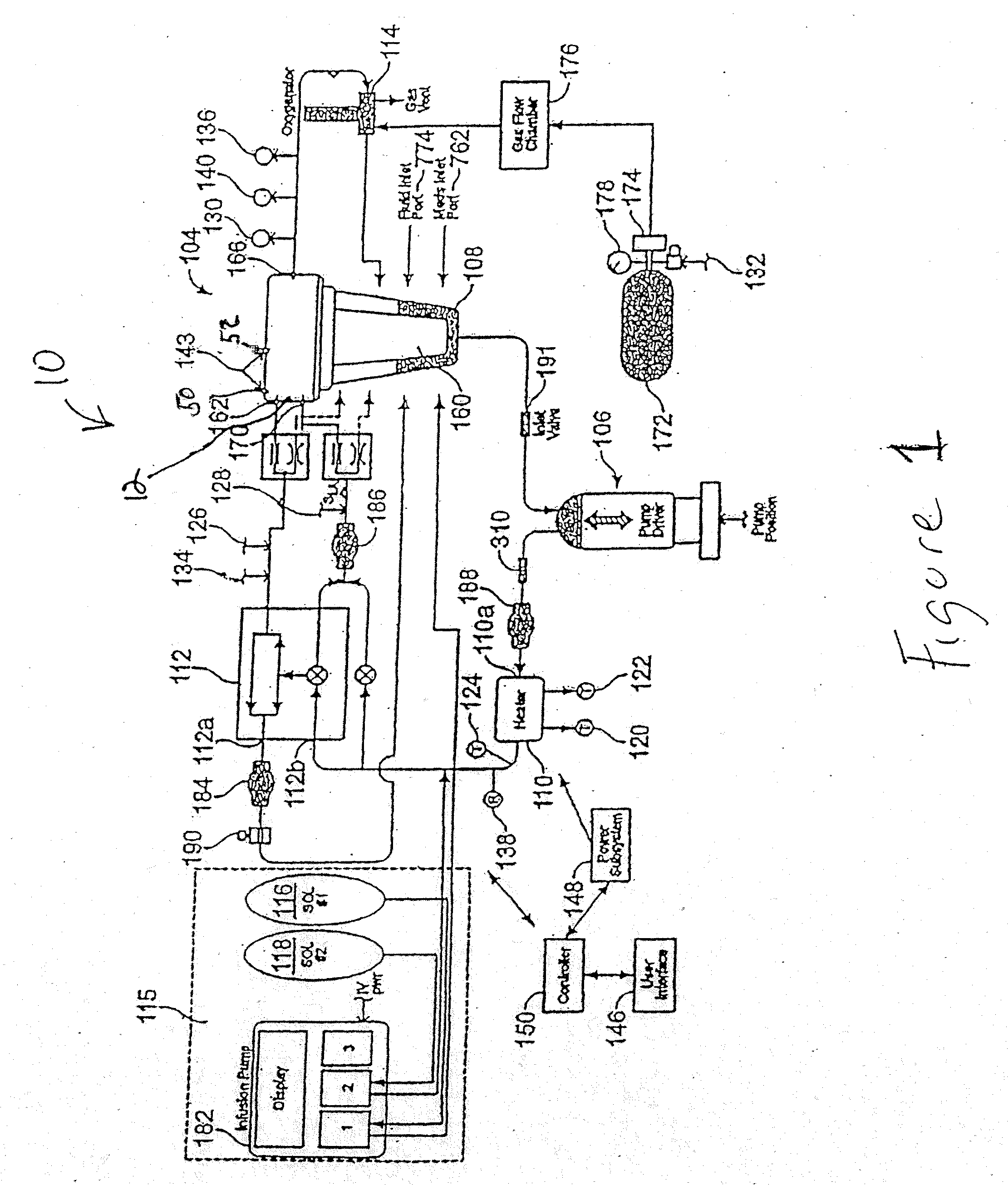
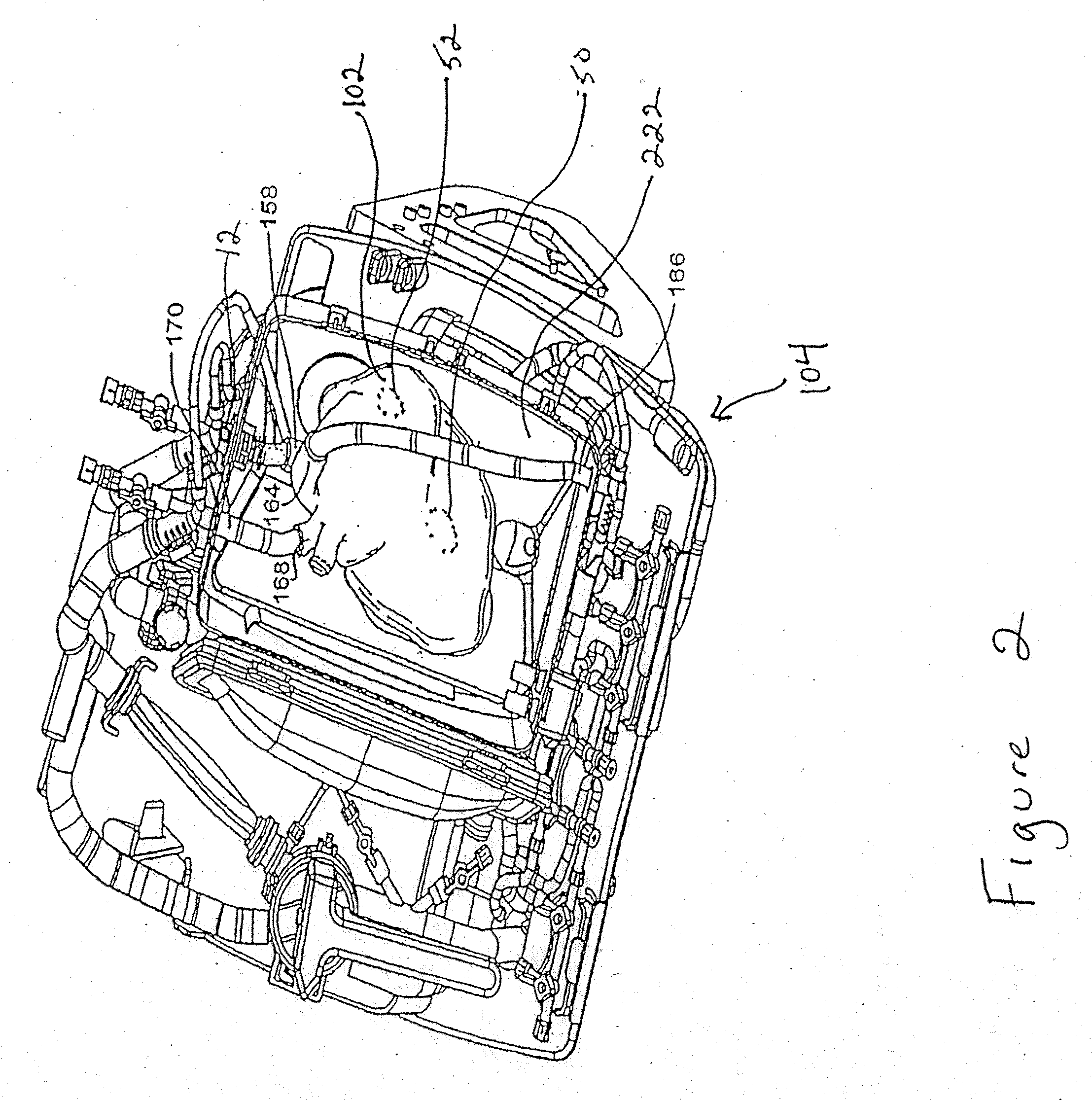
Electrode systems have been developed for use in perfusion systems to measure the electrical activity of an explanted heart and to provide defibrillation energy as necessary. The perfusion systems maintain the heart in a beating state at, or near, normal physiological conditions; circulating oxygenated, nutrient enriched perfusion fluid to the heart at or near physiological temperature, pressure and flow rate. These systems include a pair of electrodes that are placed epicardially on the right atrium and left ventricle of the explanted heart, as well as an electrode placed in the aortic blood path.
Owner:TRANSMEDICS
Color changing matrix as wear indicator
InactiveUS7338664B2Easy to combineProvide integrityPowder deliveryCosmetic preparationsWater insolubleMedicine
A sustained-release matrix for dental application includes either an anti-microbial agent or a colorant that is released from the matrix when the matrix contacts water. The preferred matrices include a water-soluble polymer and a water-insoluble support resin.
Owner:THE GILLETTE CO
Hybrid adhesives, articles, and methods
InactiveUS6949297B2Useful optical transmissivityImprove stabilityDecorative surface effectsSynthetic resin layered productsAdhesive
Described are curable adhesives containing a polyacrylate component and an epoxy component, and that are preferably optically clear, as well as methods of using such adhesives and optical components and optical elements prepared from the adhesives.
Owner:3M INNOVATIVE PROPERTIES CO
Monitoring downhole production flow in an oil or gas well
InactiveUS20100326654A1Potential failureProvide economySurveyFluid removalElectrical resistance and conductanceProcess engineering
An apparatus monitors a production flow from a gravel pack into a tubular sand screen disposed concentrically around downhole production tubing in an oil or gas well. A tubular sample layer is disposed concentrically around the sand screen to be exposed to the radial production flow in use. The sample layer is electrically insulated from the production tubing in use. An erosion sensor provides a signal which varies in dependence upon an electrical resistance of the sample layer, which is related to the erosion of the sample layer. An apparatus also monitors a substantially longitudinal production flow through downhole production tubing in an oil or gas well. A method and apparatus are used to monitor the condition of a gravel pack within an oil or gas well. Other methods monitor temperature or pressure conditions within an oil or gas well.
Owner:TELEDYNE INSTR INC
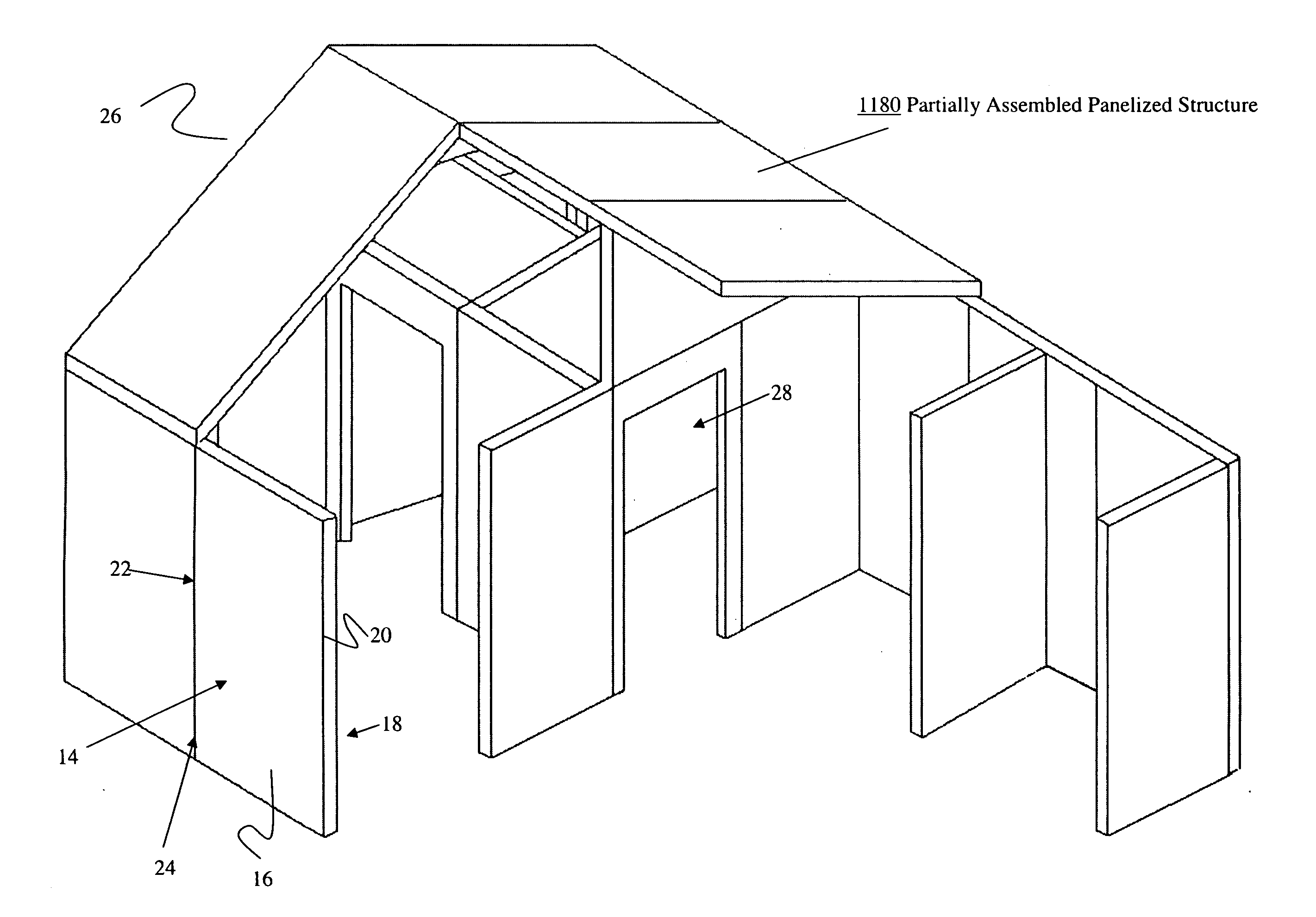
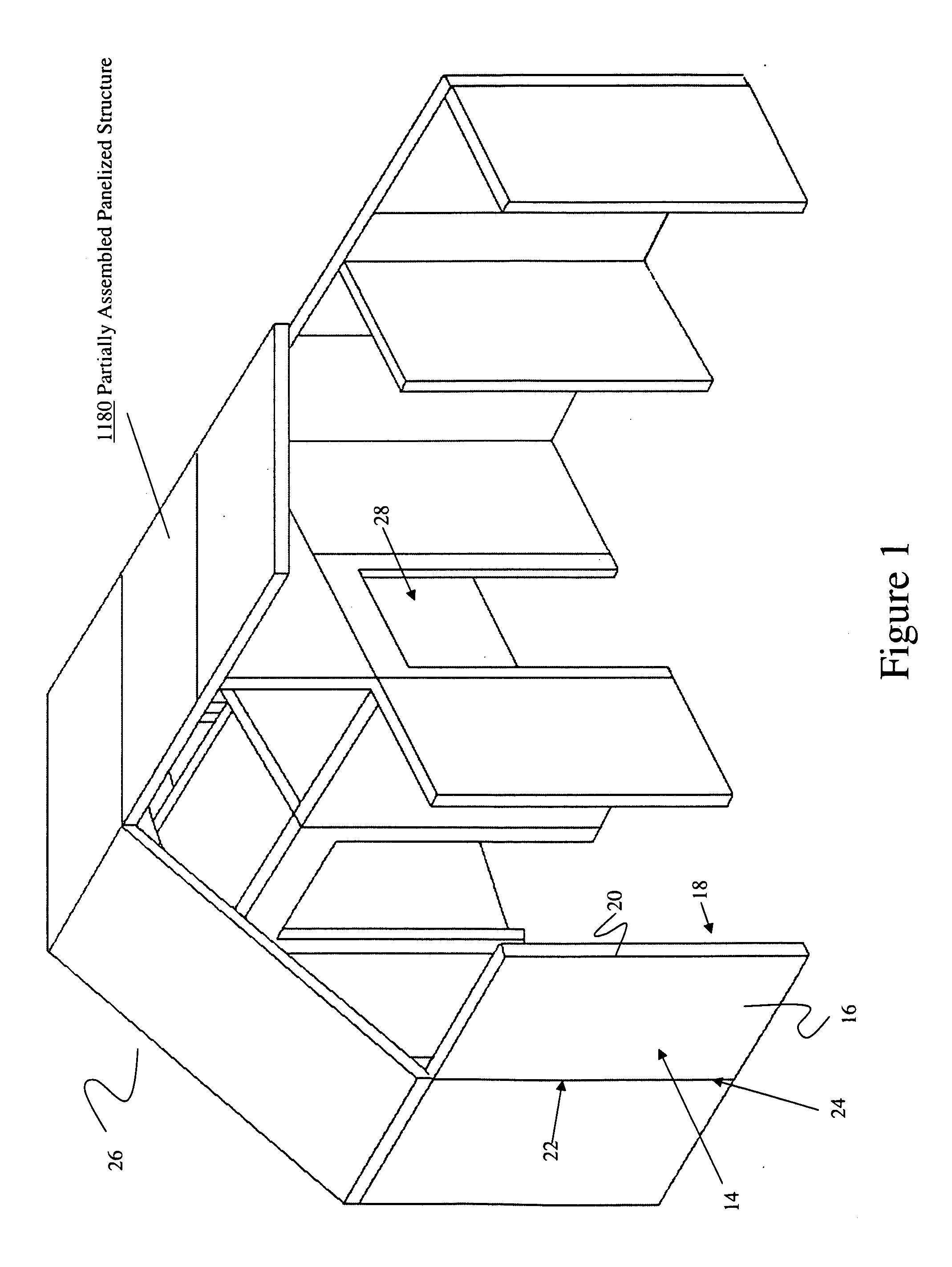
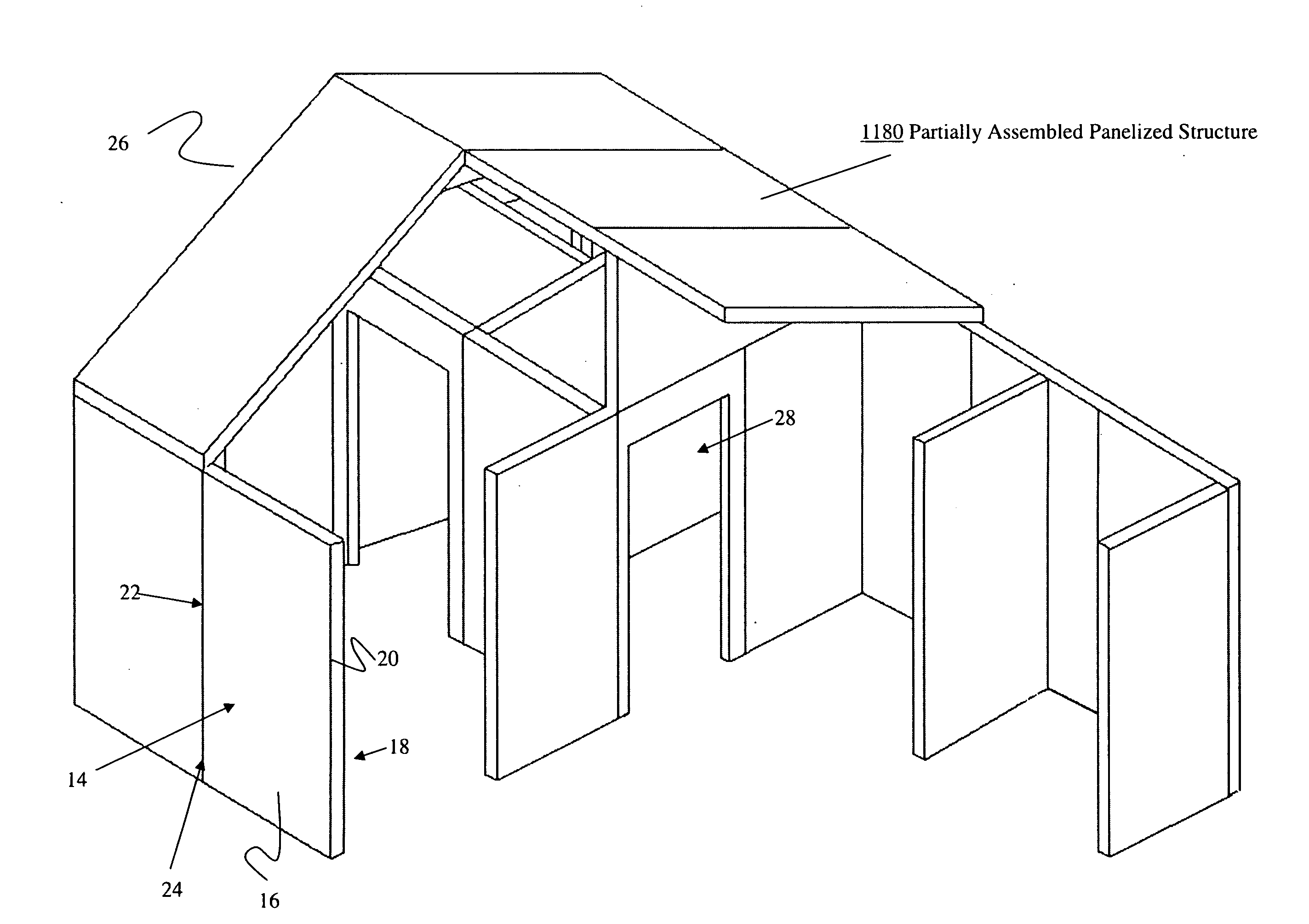
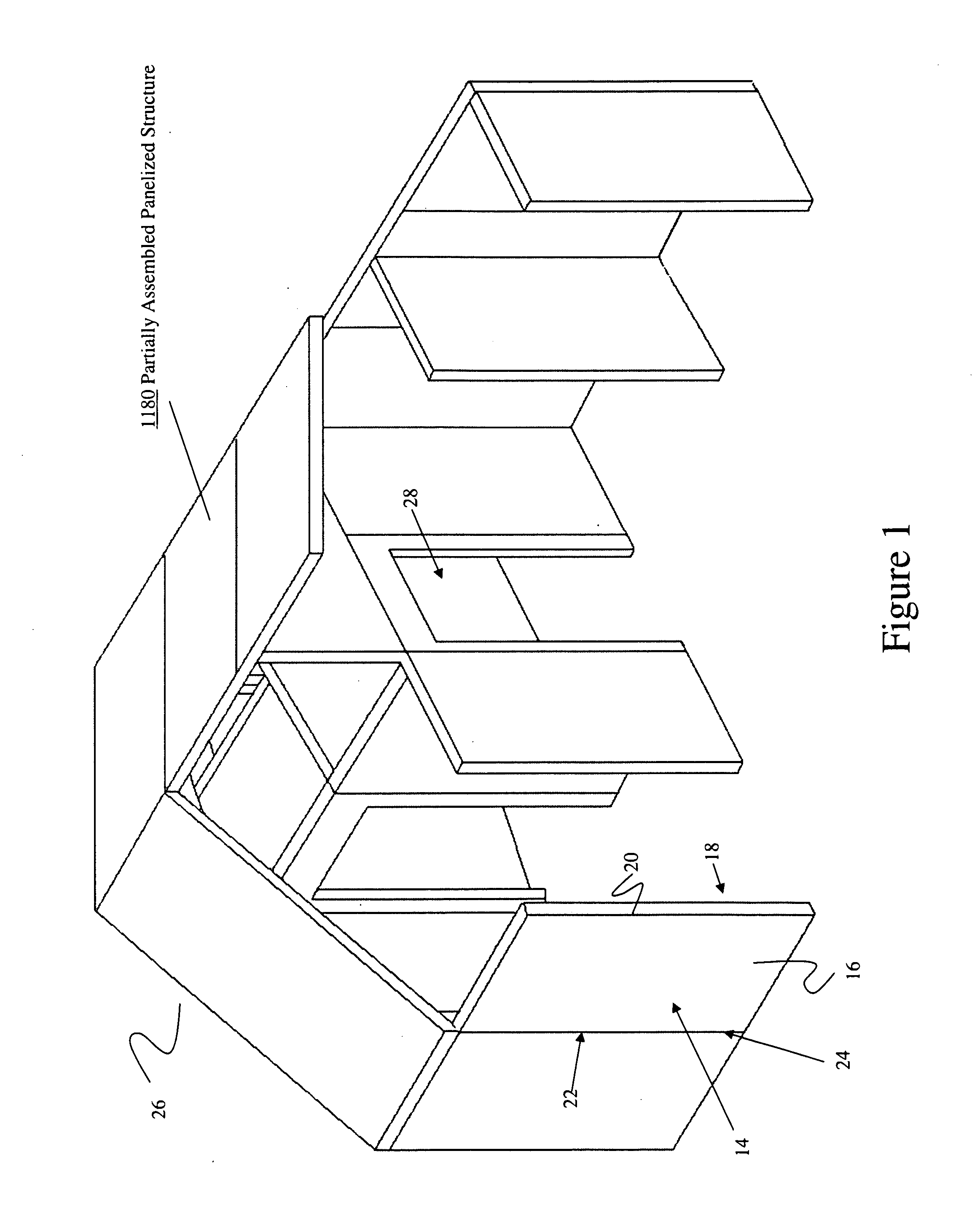
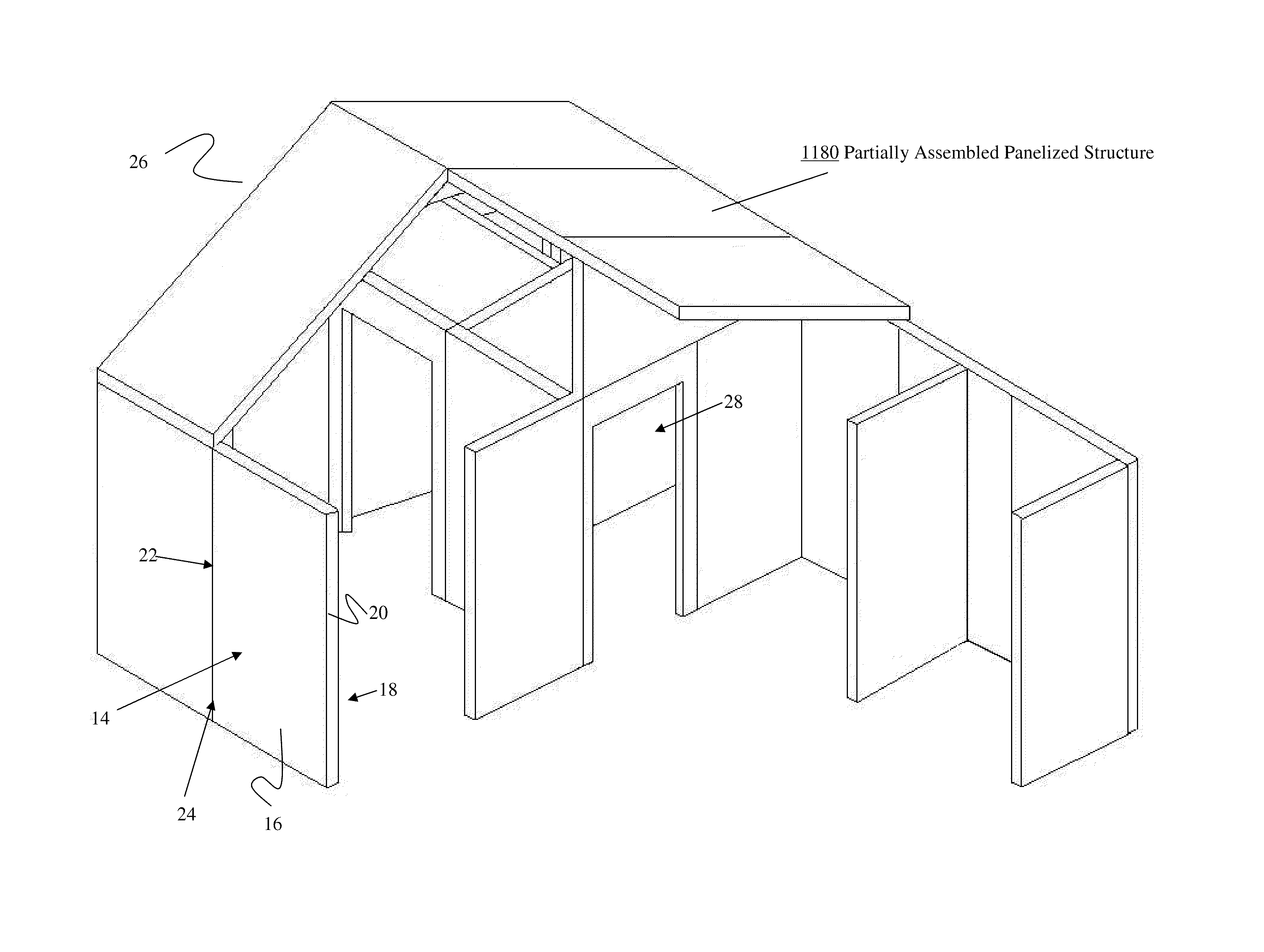
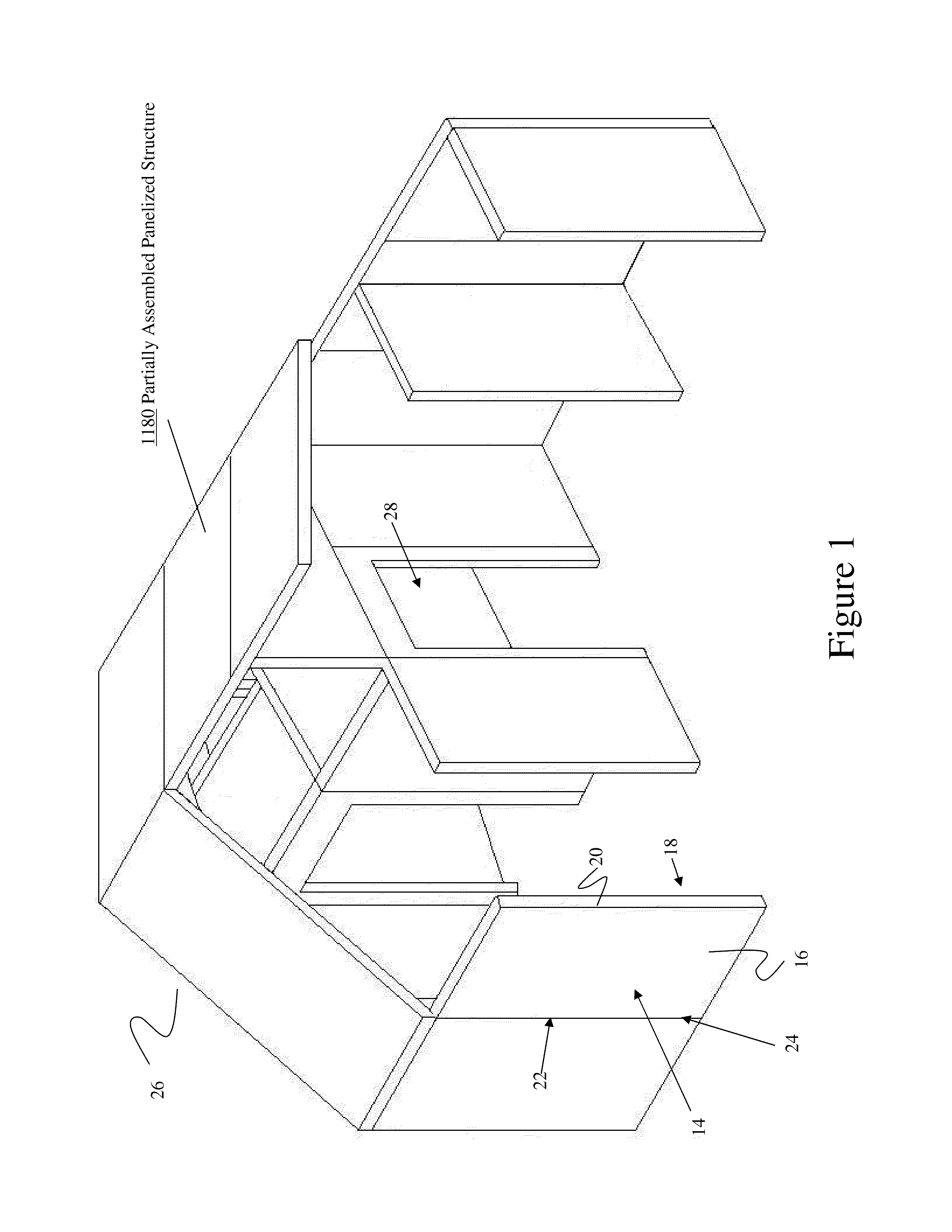
Structural Building Panels with Multi-Laminate Interlocking Seams
ActiveUS20100325989A1Energy efficiencyProvide integrityBuilding roofsSolar heating energyLocking mechanismModularity
Systems and methods providing a modular building having pre-fabricated panel wall components are easily assembled to form a predetermined structure that provides for mating alignment and securement of the modular panels with each other along their adjoining seams, without requiring additional locking mechanisms for stabilizing the panels.
Owner:LEAHY CHARLES H
Golf club head
InactiveUS20070060414A1Enhance playing characteristicEnhances playing characteristicGolf clubsRacket sportsAdhesiveGolf Ball
A hollow golf club head with a concave portion is disclosed and claimed. The club head includes a metallic portion and a light-weight portion, which may be formed of plastic, composite, or the like. The concave portion allows the club designer to make a club head having very thin portions while still maintaining the requisite structural integrity. Convex bulges may optionally be provided to house weight inserts to enhance the playing characteristics of the golf club. The metallic portion of the club head may take on the appearance of a frame, into which several light-weight inserts are positioned. These light-weight inserts may be positioned in the crown, skirt, and sole of the club head. The club head may be formed by co-molding, eliminating the need for welding or adhesives, freeing mass to be used in more beneficial ways. The club head may be large to increase playability and forgiveness.
Owner:COBRA GOLF
Method for fastening building materials together
InactiveUS20060059825A1The process is convenient and fastProvide structural integrityAdhesive processesCeilingsRoof tileAdhesive
Methods and structures involving the use of a double-sided adhesive membrane assembly having one adhesive surface with low initial tackiness to permit a substrate to be re-positionable even if pressed into contact against the adhesive. The method allows wood deck components, flooring planks, roofing tiles, and other building material components to be fastened together conveniently while securing a waterproofing and / or sound-deadening effect.
Owner:WIERCINSKI ROBERT A +2
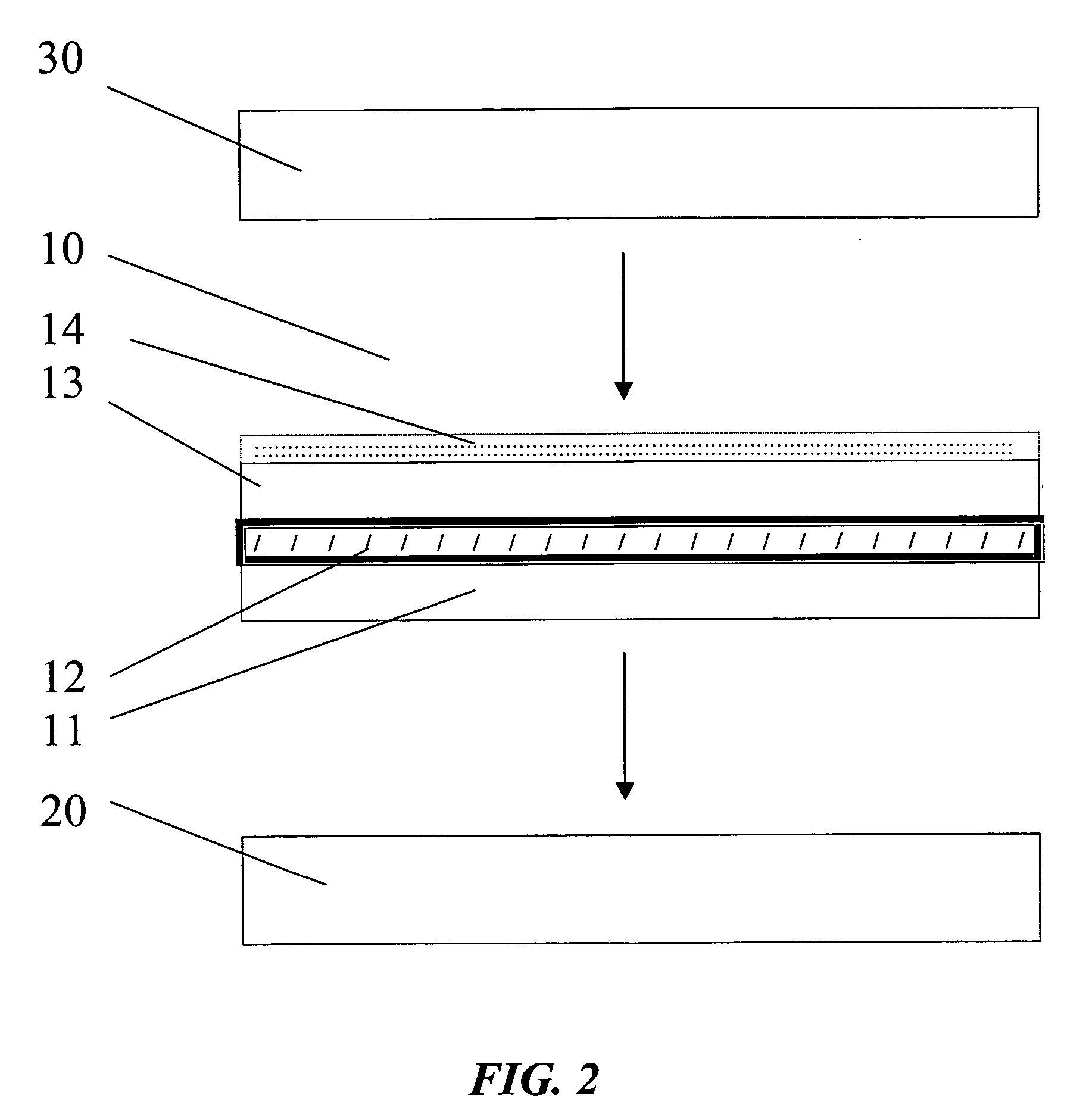
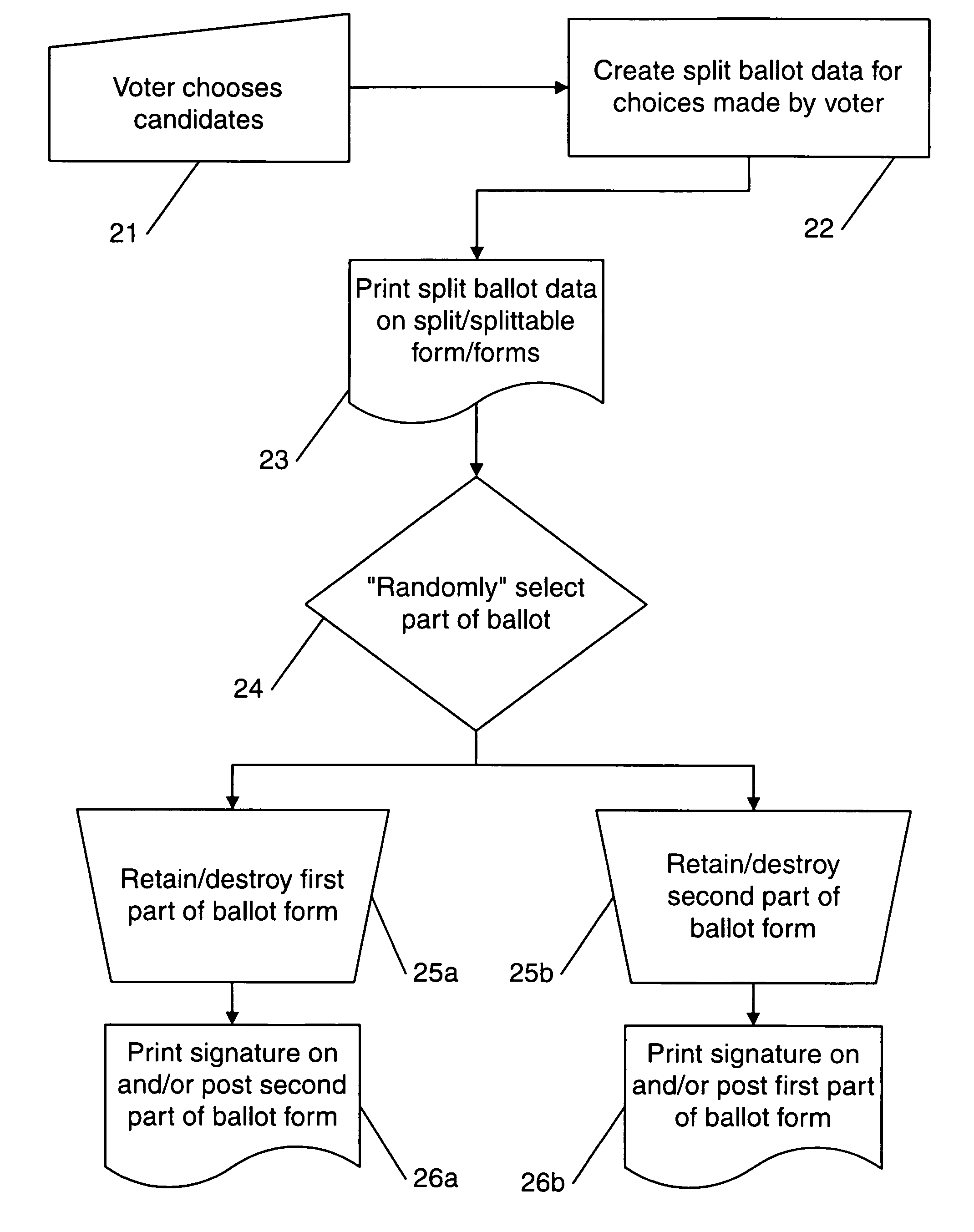
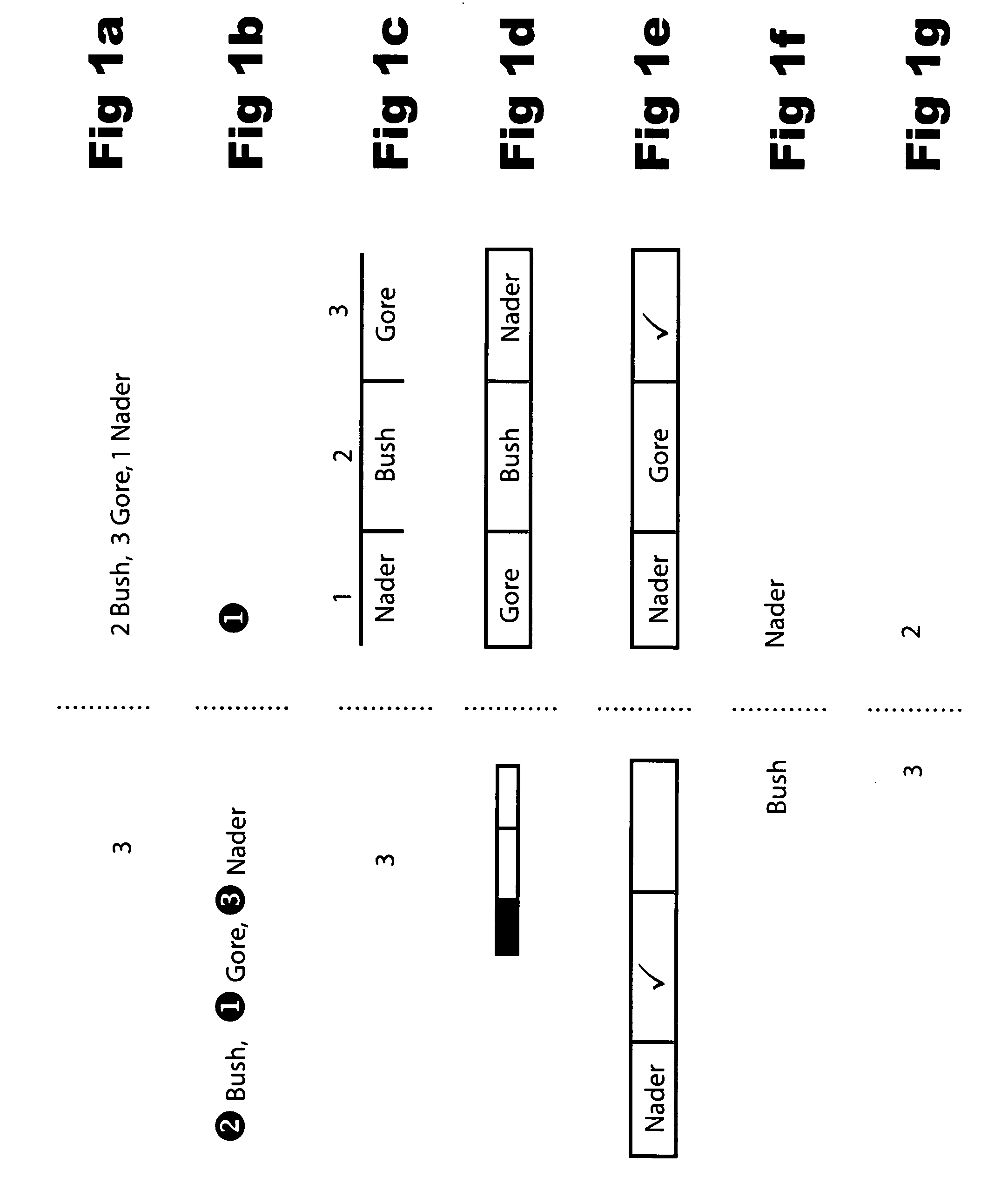
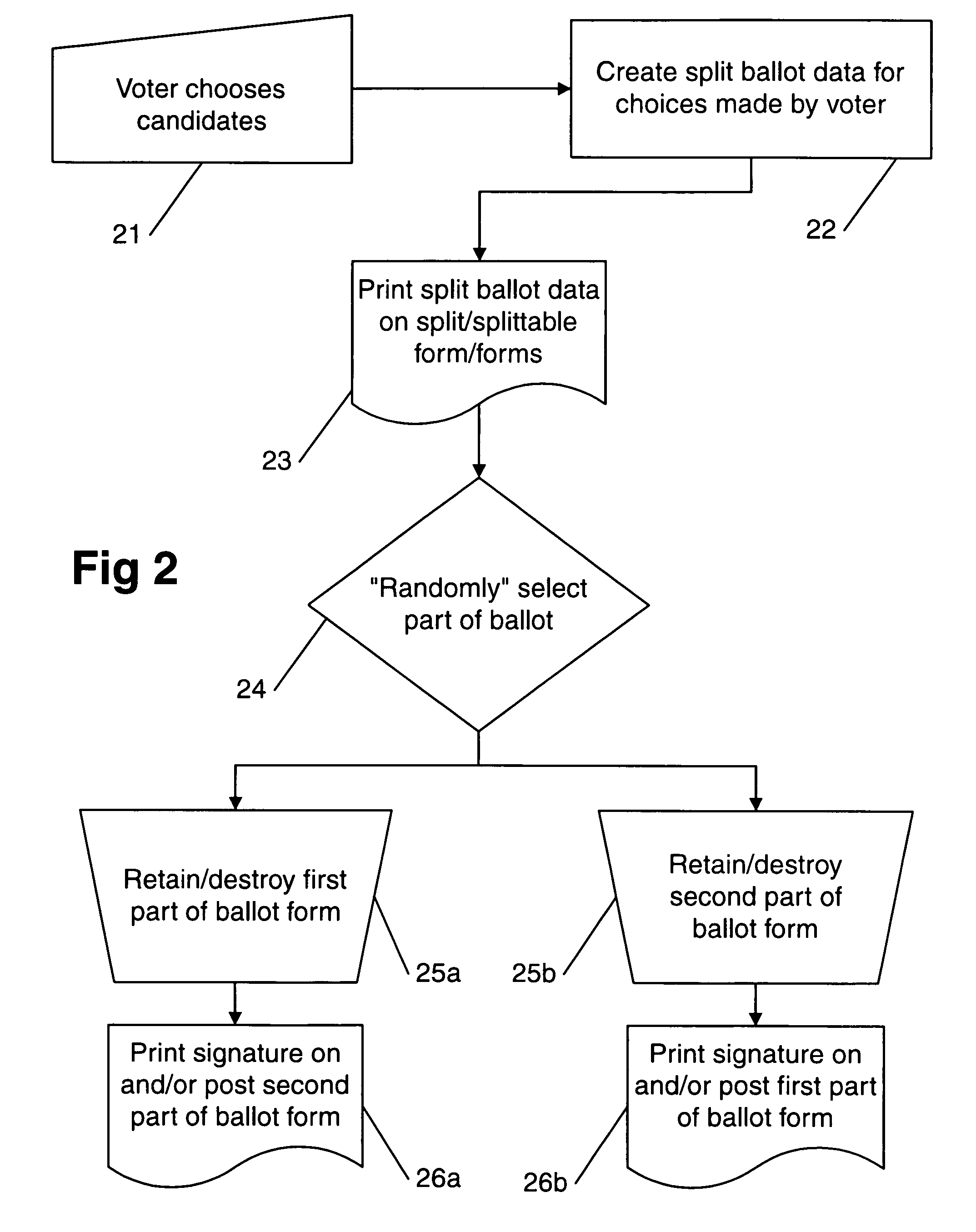
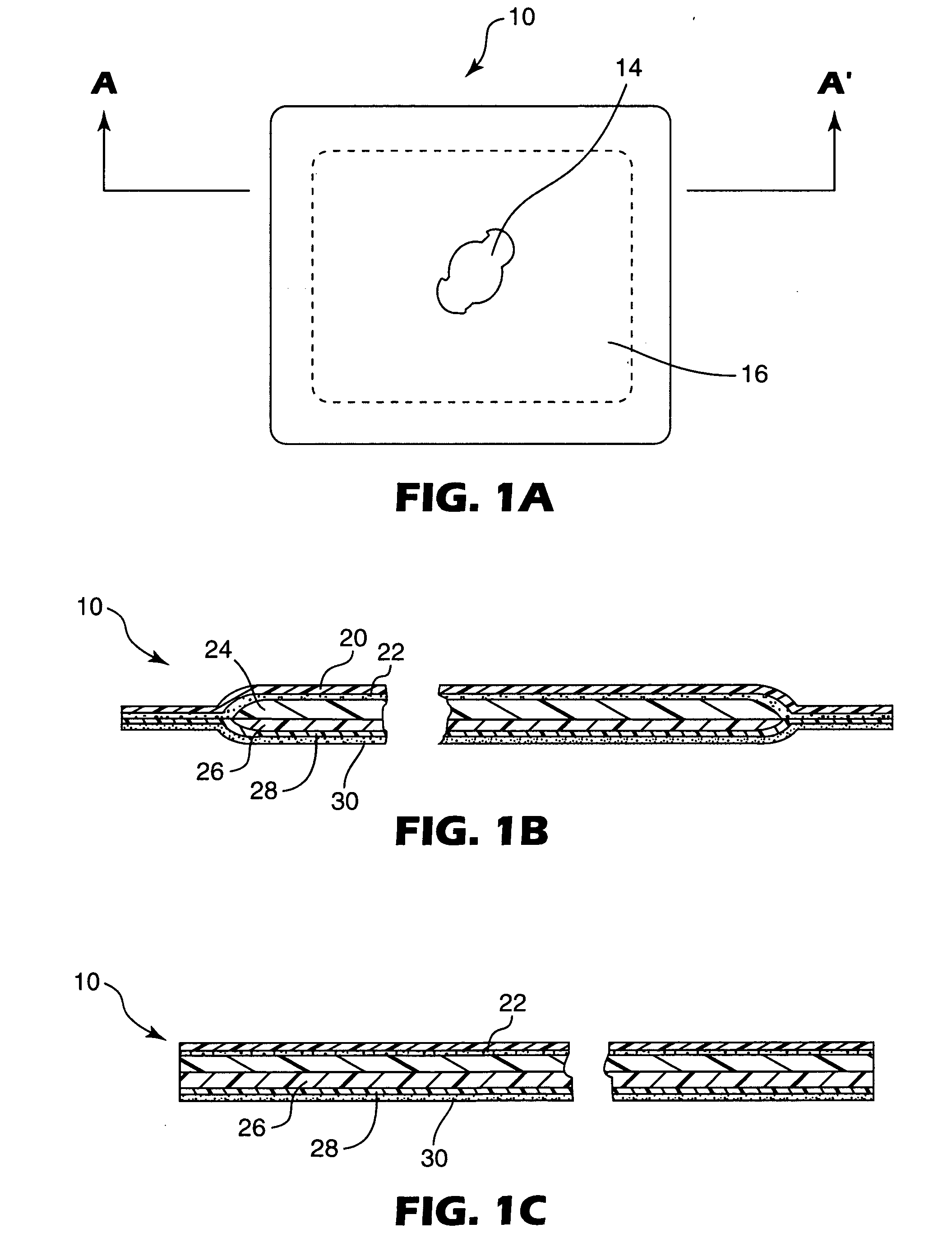
Ballot integrity systems
InactiveUS7516891B2Provide integrityEliminate background speckleVoting apparatusError detection/correctionComputer scienceSelf adhesive
Disclosed are voting systems based on paper ballots that provide integrity of the election outcome through the novel use of encrypted votes and other techniques. In some example embodiments, holes through layers allow voters to see and mark symbols on lower layers, carbonless coatings allow voters to obtain substantially identical marks on facing surfaces, self-adhesive stickers are removed from one position and placed by voters hiding vote-revealing indicia on a second position, and scratch-off layers bearing vote-revealing indicia are destroyed while being removed to expose coded information. Simplified cryptography for realizing these systems is also presented. Related systems allow those with various disabilities to develop and check voted ballot forms that are substantially indistinguishable from those voted by other voters. Inclusion of write-in votes is provided for. Also provided are inclusion of provisional ballots and spoilt ballots and integration with registration sign-in.
Owner:DIGITAL COMMUNITY LLC
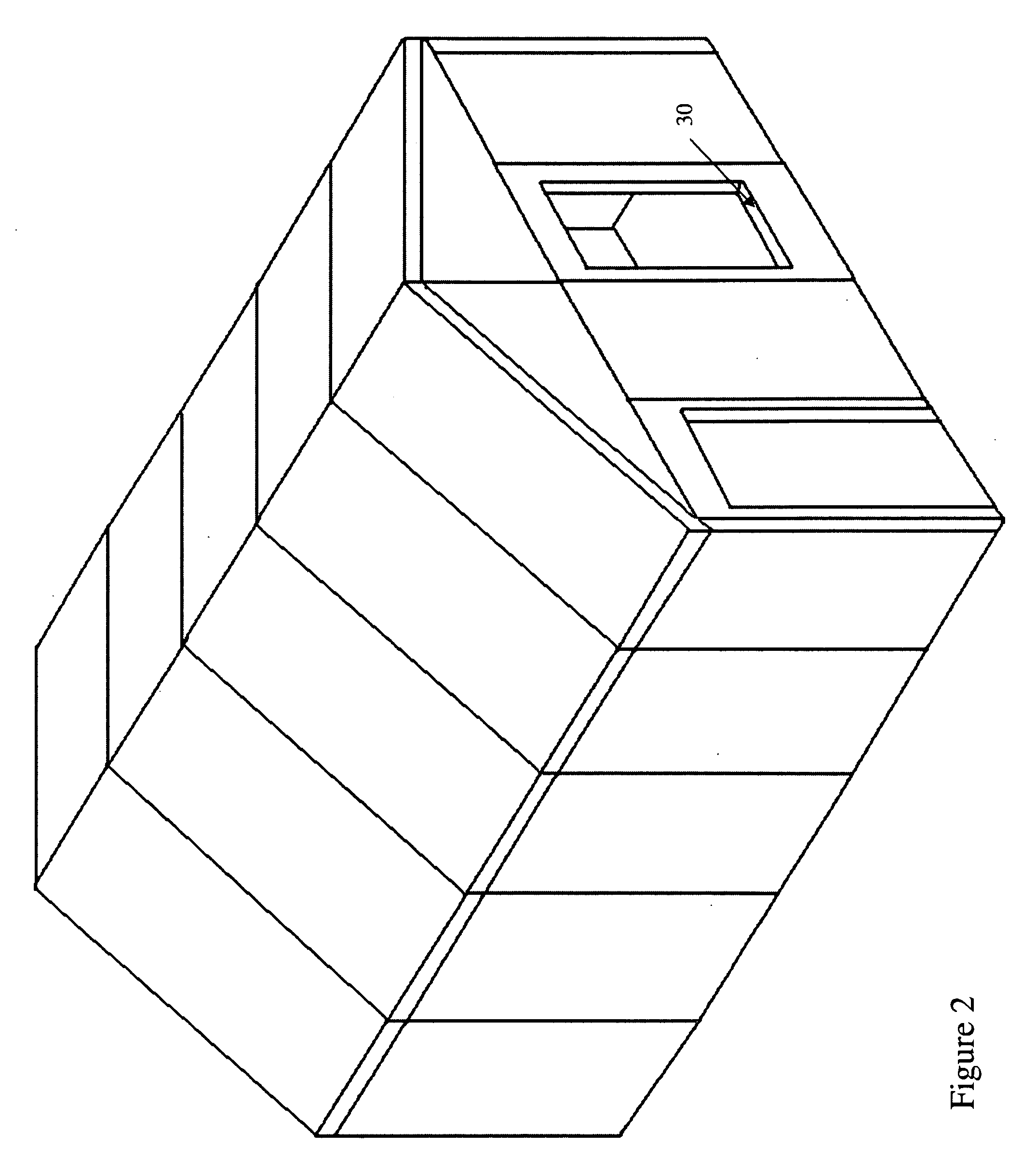
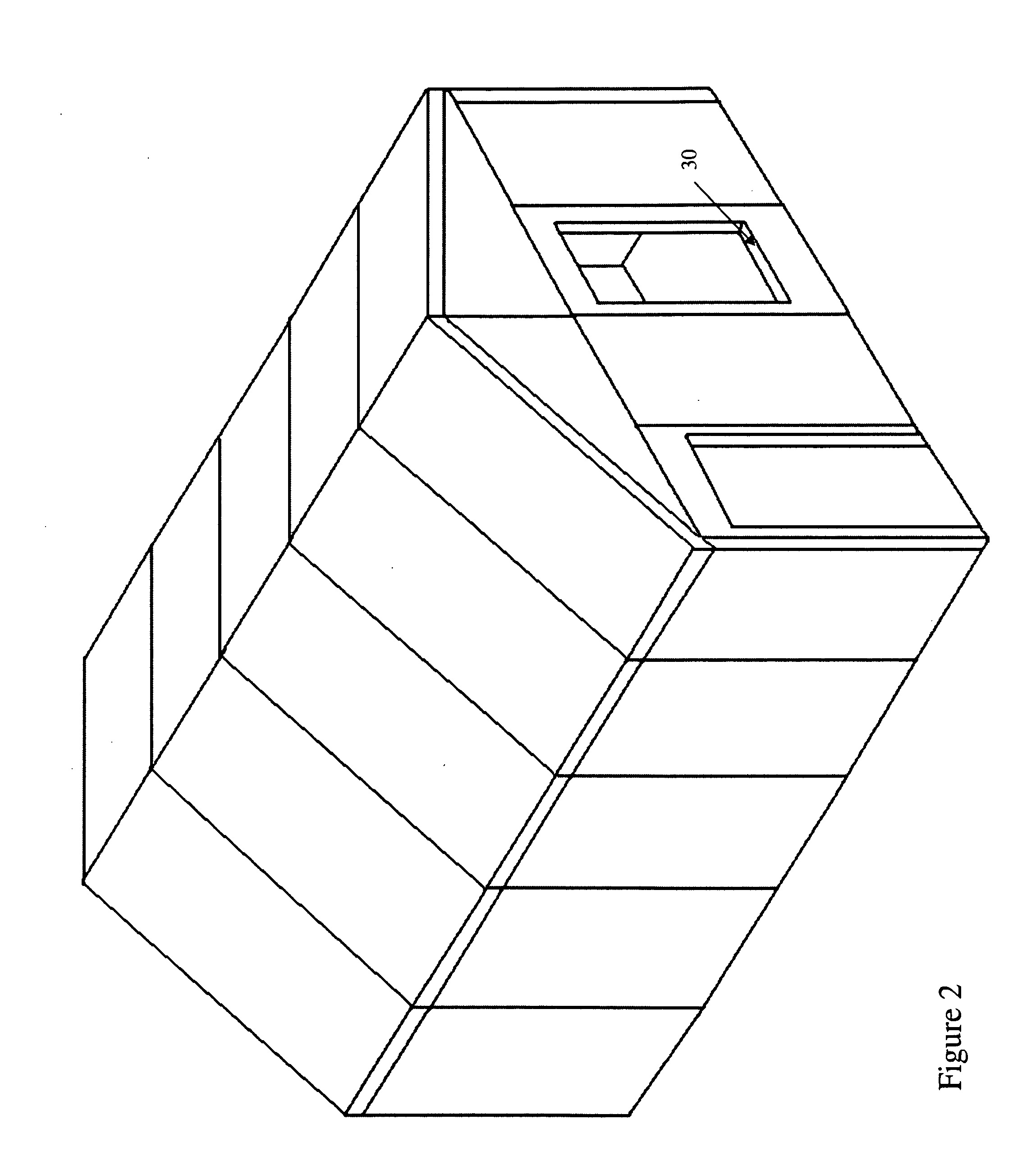
Structural Building Panels with Seamless Corners
ActiveUS20100325971A1Energy efficiencyProvide integrityStrutsClimate change adaptationModularityEngineering
Owner:LEAHY CHARLES H
Multi-layer absorbent wound dressing
InactiveUS20050226917A1Improve water absorptionIncreased durabilitySynthetic resin layered productsAdhesive dressingsWound dressingAbsorbent material
A multi-layer wound dressing comprising at least two absorbent layers, and materials for forming absorbent layers are provided. The absorbent layers have different absorbencies, with the layer closest to the wound having a lower absorbency than the layer furthest from the wound. The wound dressing typically contains additional non-absorbing layers, such as a backing film and wound-facing film. The dressing provides absorbency of wound exudates while preventing the absorbent material from entering the wound. In specific implementations the dressing is substantially transparent prior to application to a wound, as well as after application to the wound when body fluids have been absorbed.
Owner:3M INNOVATIVE PROPERTIES CO
Golf club head
InactiveUS7938740B2Improved playing characteristicProvide integrityGolf clubsRacket sportsAdhesiveEngineering
A hollow golf club head with a concave portion is disclosed and claimed. The club head includes a metallic portion and a light-weight portion, which may be formed of plastic, composite, or the like. The concave portion allows the club designer to make a club head having very thin portions while still maintaining the requisite structural integrity. Convex bulges may optionally be provided to house weight inserts to enhance the playing characteristics of the golf club. The metallic portion of the club head may take on the appearance of a frame, into which several light-weight inserts are positioned. These light-weight inserts may be positioned in the crown, skirt, and sole of the club head. The club head may be formed by co-molding, eliminating the need for welding or adhesives, freeing mass to be used in more beneficial ways. The club head may be large to increase playability and forgiveness.
Owner:COBRA GOLF
Various stress free sensor packages using wafer level supporting die and air gap technique
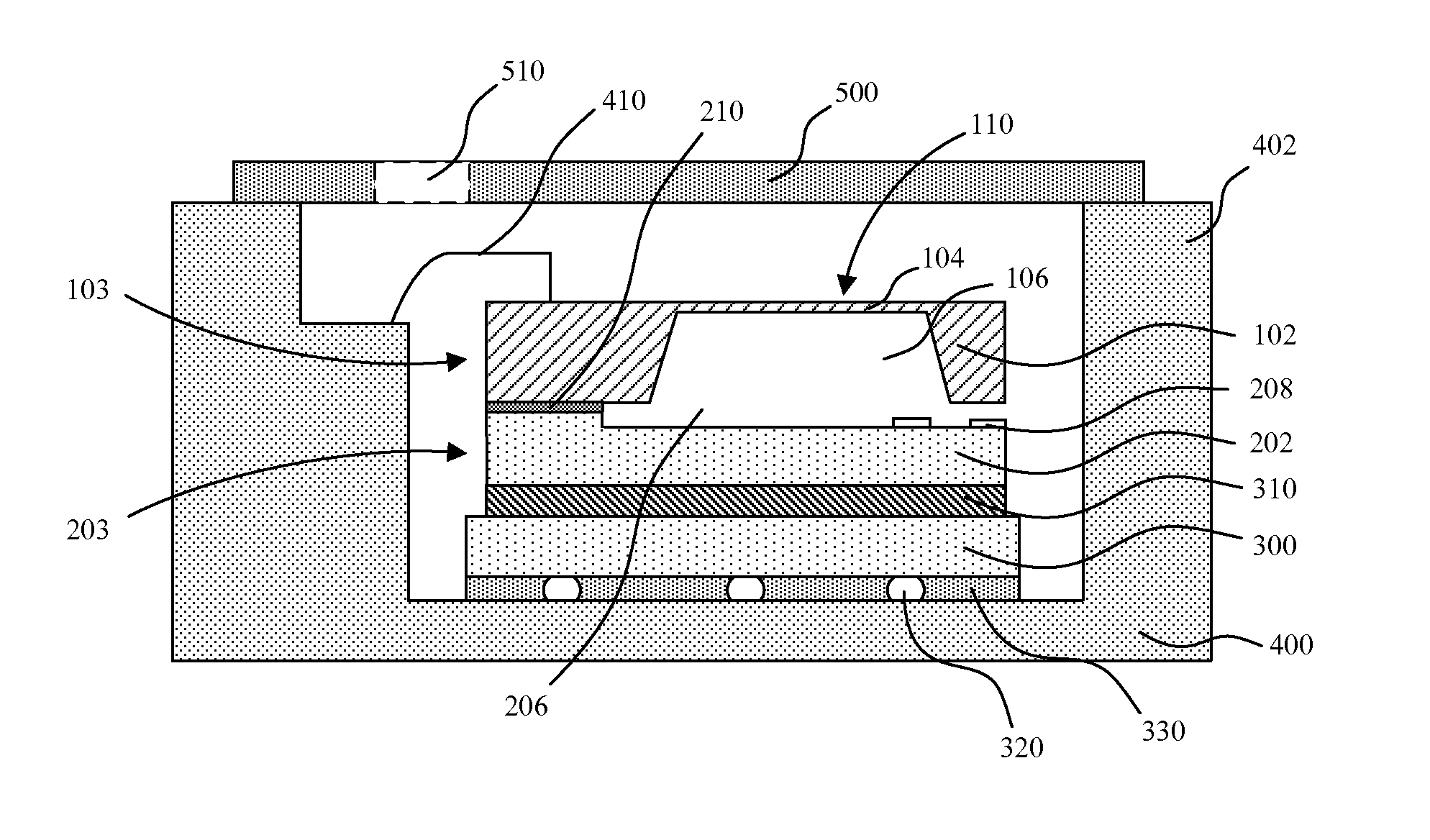
ActiveUS20160061677A1Provide integrityFluid pressure measurement using elastically-deformable gaugesFluid pressure measurement by electric/magnetic elementsEngineeringForce sensor
Sensor packages and manners of formation are described. In an embodiment, a sensor package includes a supporting die characterized by a recess area and a support anchor protruding above the recess area. A sensor die is bonded to the support anchor such that an air gap exists between the sensor die and the recess area. The sensor die includes a sensor positioned directly above the air gap.
Owner:APPLE INC
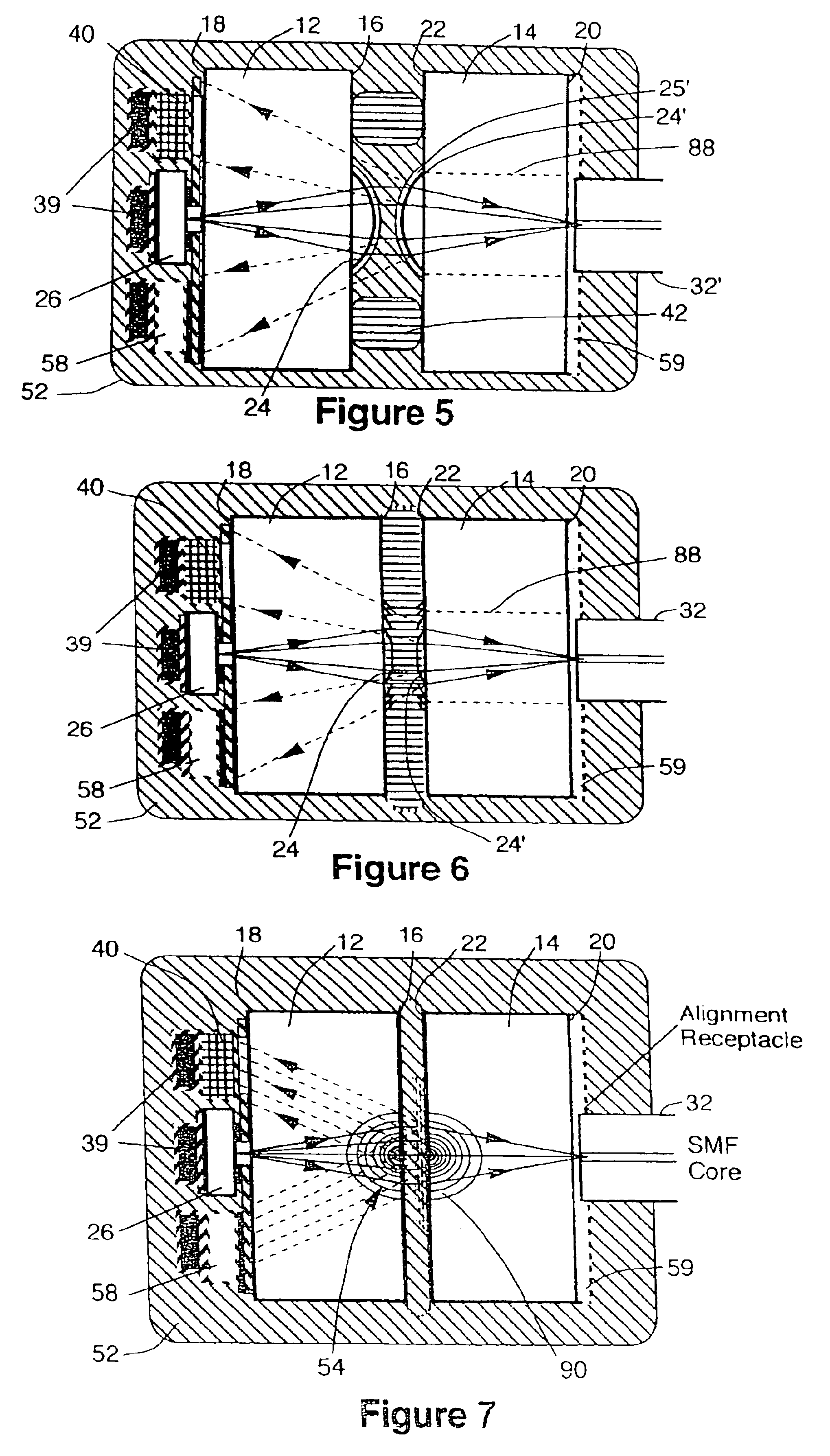
Opto-mechanical assembly
InactiveUS6931181B2Maximum efficiencyIncreased assembly process controlCoupling light guidesMountingsOpto electronicLight wave
A novel electro-opto-mechanical assembly is provided. The electro-opto-mechanical assembly comprising: a first wafer, the wafer having a top and bottom surface; at least one optical element disposed on one surface of the first wafer; at least one discrete opto-electronic transducer element disposed on the bottom surface of the first wafer and in optical communication with the optical element; and an optical waveguide; wherein the first wafer and the optical element form an optical relay which relays light between the discrete opto-electronic transducer and the optical waveguide and thereby forms an efficient optical coupling between the discrete opto-electronic transducer and the optical waveguide.
Owner:JDS UNIPHASE CORP
Structural building panels with seamless corners
ActiveUS8539732B2Provide integrityProvide strengthStrutsClimate change adaptationUltimate tensile strengthStructure building
Owner:LEAHY CHARLES H
Pressure relief system for gun fired cannon cartridges
InactiveUS8925463B1Avoid disintegrationProvide integrityAmmunition projectilesSafety arrangementShape-memory alloyHigh velocity
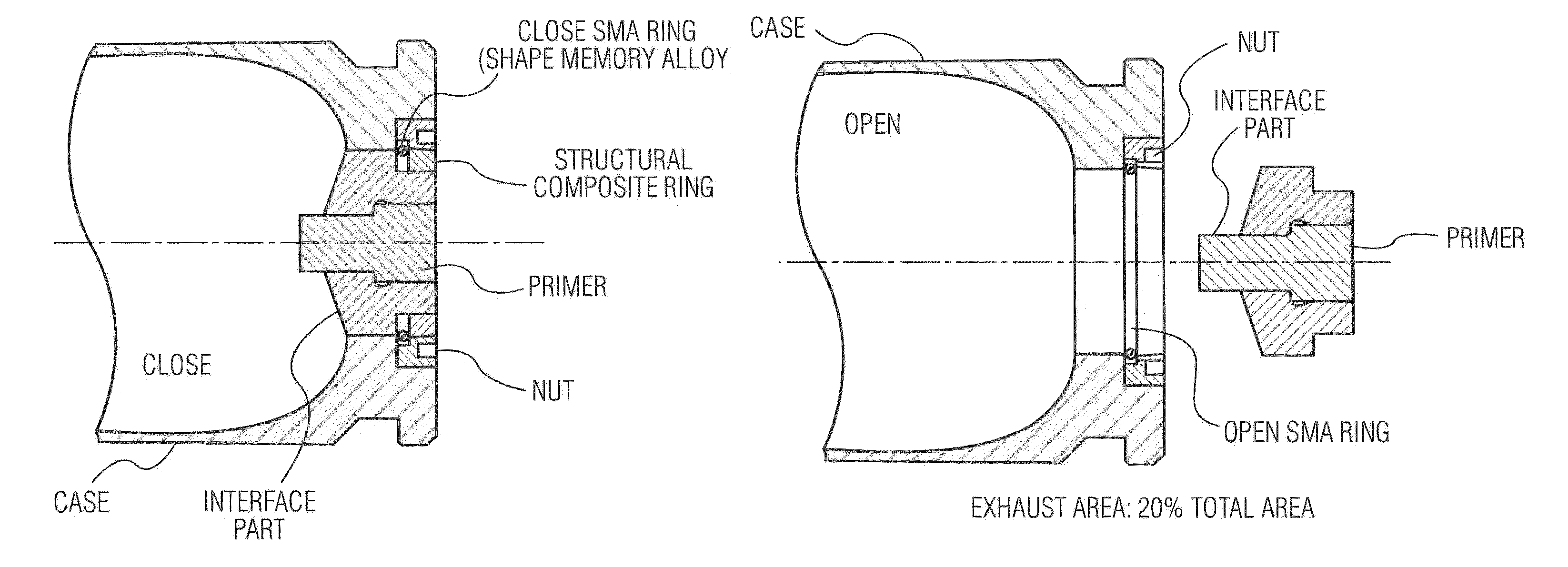
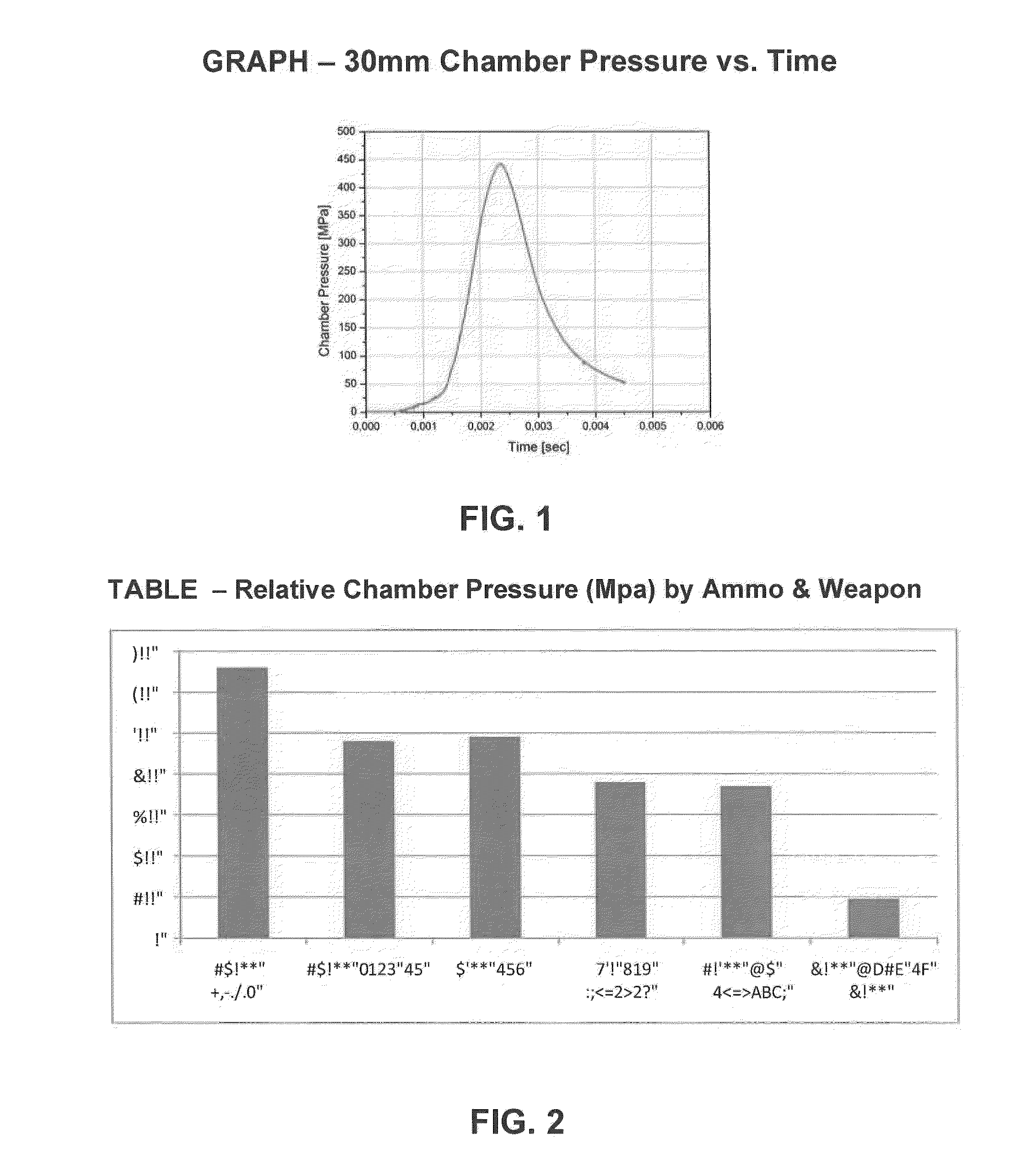
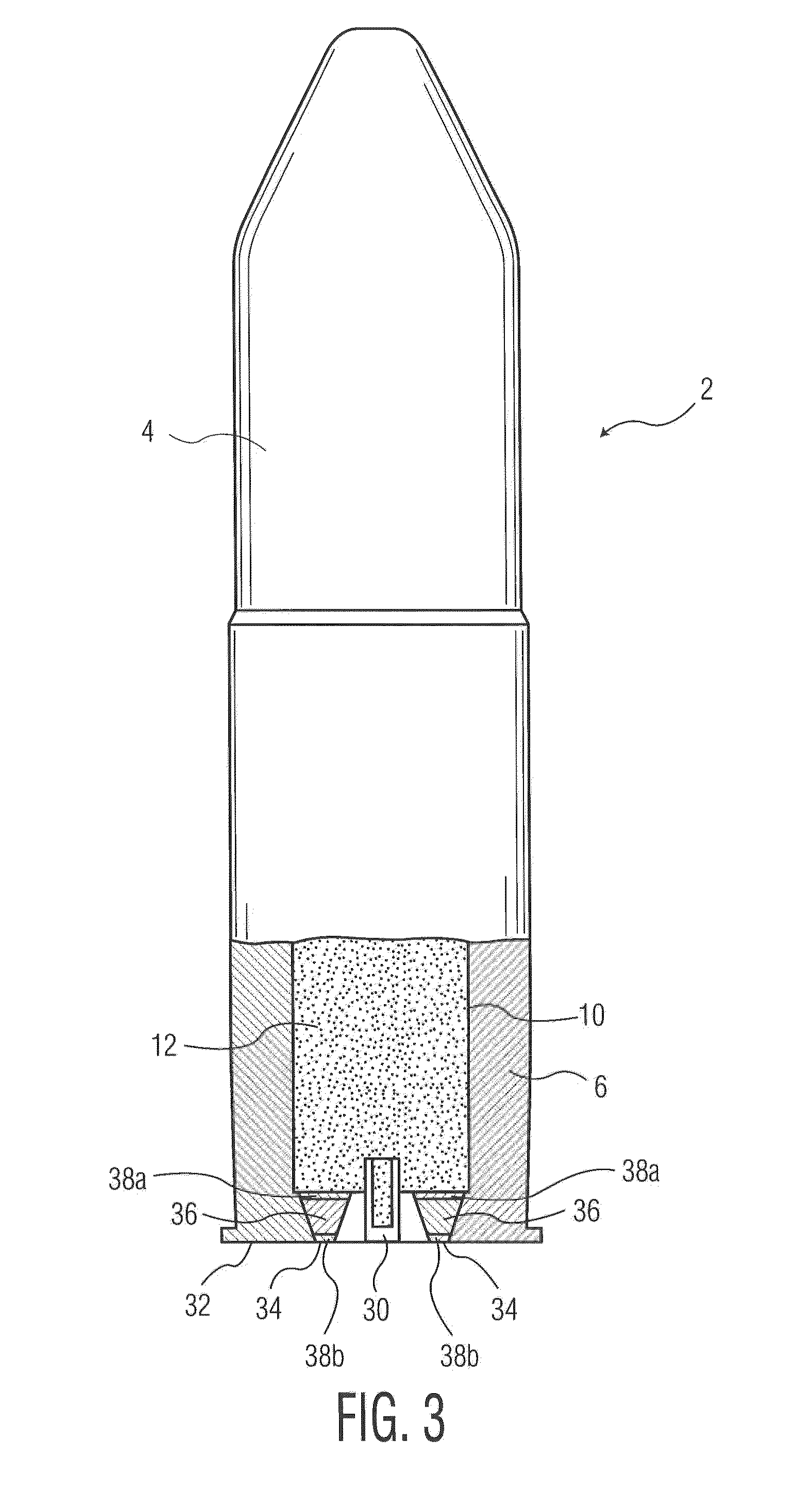
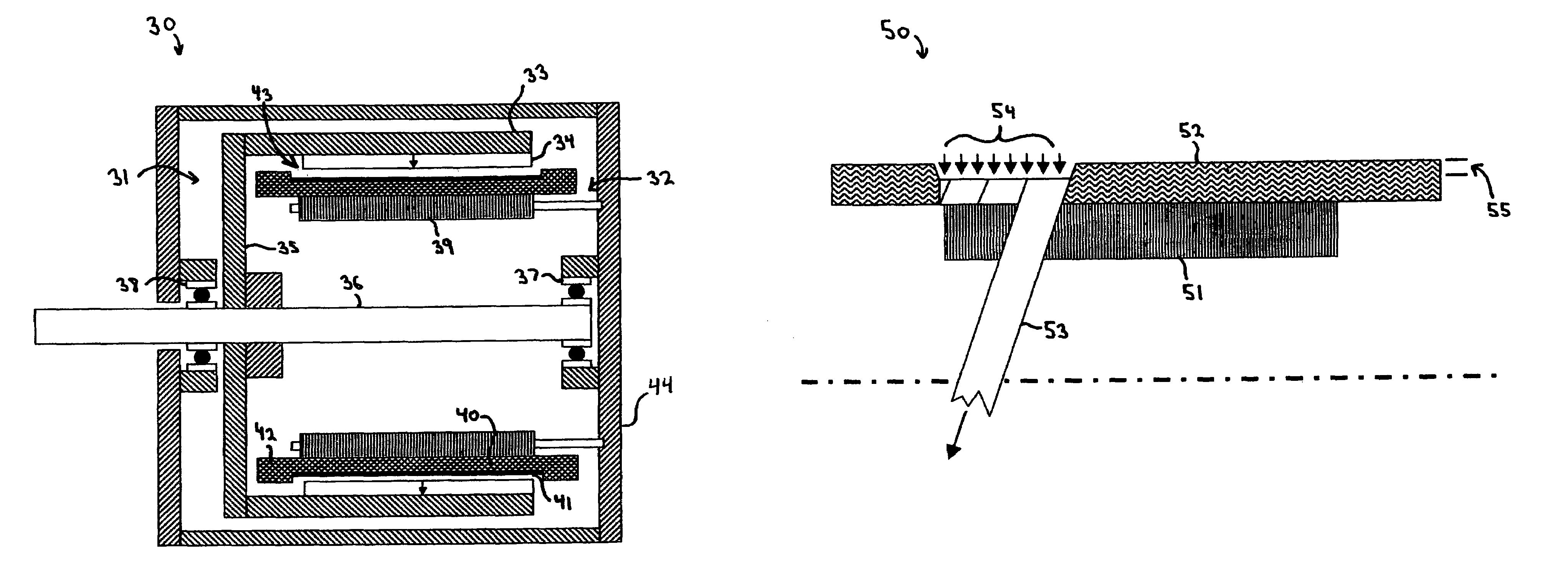
A high velocity munition comprises a projectile, mounted on a cartridge case, that can be fired from an automatic cannon or weapon. During storage or transport an IM venting device included in the cartridge case prevents the propellant charge from firing the projectile, leaving the cartridge damaged, but intact upon premature ignition. The IM vent exhaust channel is filled with a solid fusible material that melts at a lower temperature than the ignition temperatures of the igniter (or primer) and the propellant charge of the projectile. At least one non-fusible, ruptureable member is included in the IM vent channel and positioned to provide structural integrity to the fusible material in the channel. Alternatively or in addition to the fusible material, a shape memory alloy ring surrounds the igniter (or primer) and separates from the cartridge when the cartridge reaches a temperature that causes auto-ignition.
Owner:NOSTROMO HLDG LLC
Air core motor-generator
InactiveUS7525230B1Improve efficiencyLong reliable operating lifeWindingsMagnetic circuit rotating partsBrushless motorsMagnetic tension force
A brushless motor-generator includes a rotor having a ferromagnetic tube with radially polarized, alternating polarity permanent magnet poles, and an air core armature that magnetically exerts torque upon the rotor. The magnetic poles drive magnetic flux across a radial magnetic air gap inside of the tube and through windings of the armature that are located in the air gap. The windings utilize wire that is comprised of multiple individually insulated strands that are bundled together and sheathed in an outer electrically insulating serve that separates adjacent windings and provides a higher dielectric breakdown strength than the insulation on the individually insulated strands. A thin circumferentially tensioned band is wrapped around the outer diameter of the axially traversing portions of the windings where located inside the magnetic air gap, imparting radial compression and structural integrity to the windings and increasing the circumferential structural strength of the air core armature for torque production.
Owner:REVOLUTION ELECTRIC MOTOR
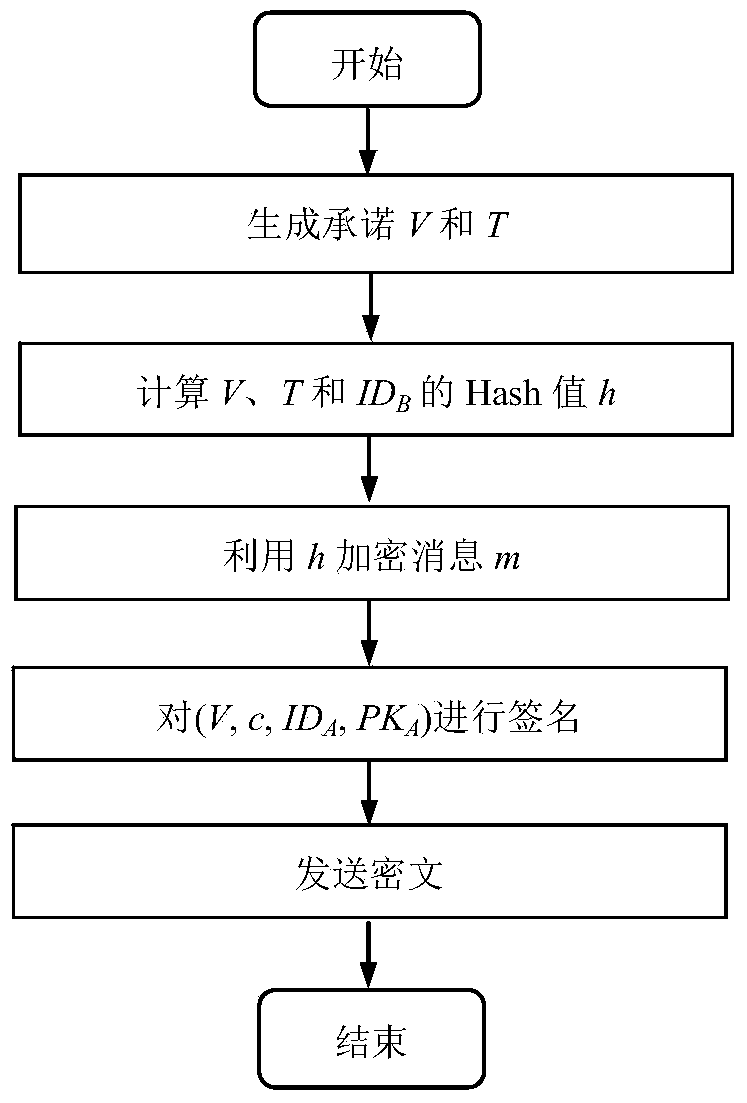
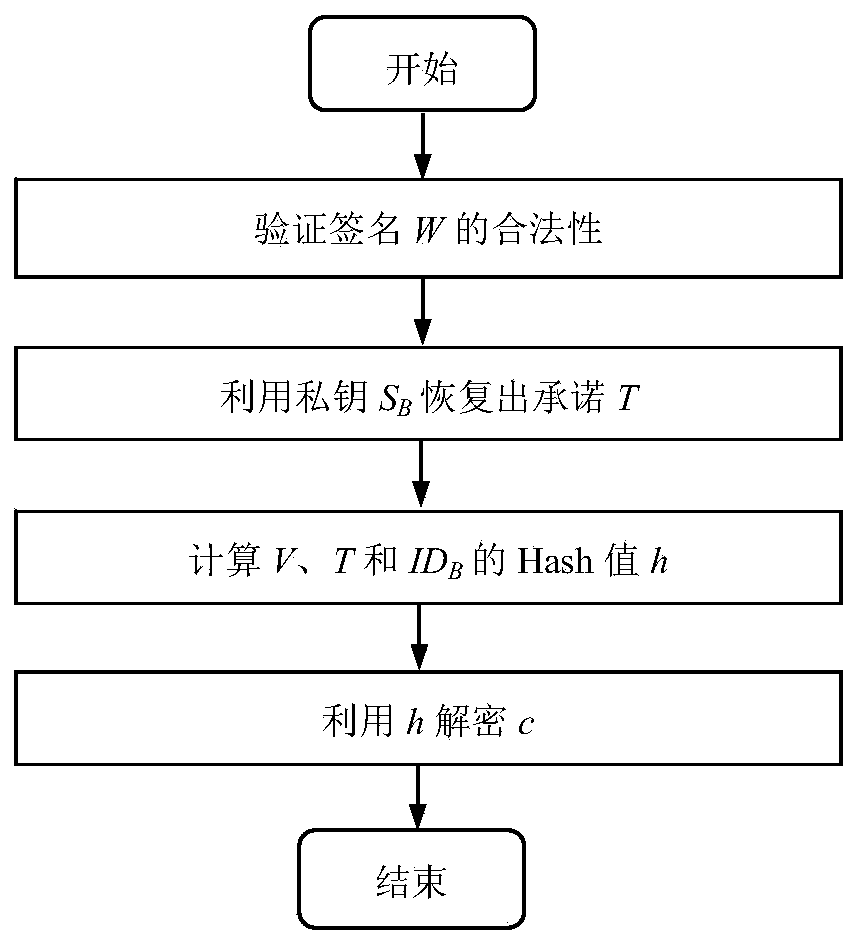
Signcryption method from certificateless environment to identity environment
InactiveCN104270249AProvide confidentialityProvide integrityUser identity/authority verificationSecure communicationCiphertext
The invention discloses a signcryption method from a certificateless environment to an identity environment and belongs to the field of secure communication. In order to enable a sending end based on the certificateless environment to send messages to a receiving end based on the identity environment through the signcryption method, the signcryption method includes the steps that after system parameters are initialized, a key generation center generates a part private key DA and sends the part private key DA to the sending end, and the sending end generates a secrete value randomly based on the system parameters, and a complete private key SA and a public key PKA are arranged with the part private key DA; a private key generation center generates a private key SB and sends the private key SB to the receiving end; the sending end generates a signcryption ciphertext according to the system parameters, the identity of the sending end, the complete private key SA, the public key PKA, the identity of the receiving end and the messages m, and the ciphertext, the identity of the sending end and the public key PKA are sent to the receiving end to conduct signcryption treatment. The signcryption method is used for signcryption communication of a heterogeneous network, and end-to-end secrete, complete, certificated and undeniable services are provided for users in the certificateless environment and users based on the identity environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Two piece air duct section
InactiveUS20050109415A1Minimizing air leaksProvide integrityDucting arrangementsLighting and heating apparatusEngineeringMechanical engineering
An air duct section is formed from at least two longitudinal duct portions that snap together to form a hollow duct having a longitudinal direction. The duct section has a pair of ends that are adjustable between male and female configurations. The interlocking device used to connect the duct portions allows continuous adjustability between the first end and the second end of the duct section while minimizing air leaks and providing structural integrity to the duct section.
Owner:SNYDER NAT CORP
Simplified three-stage fuel processor
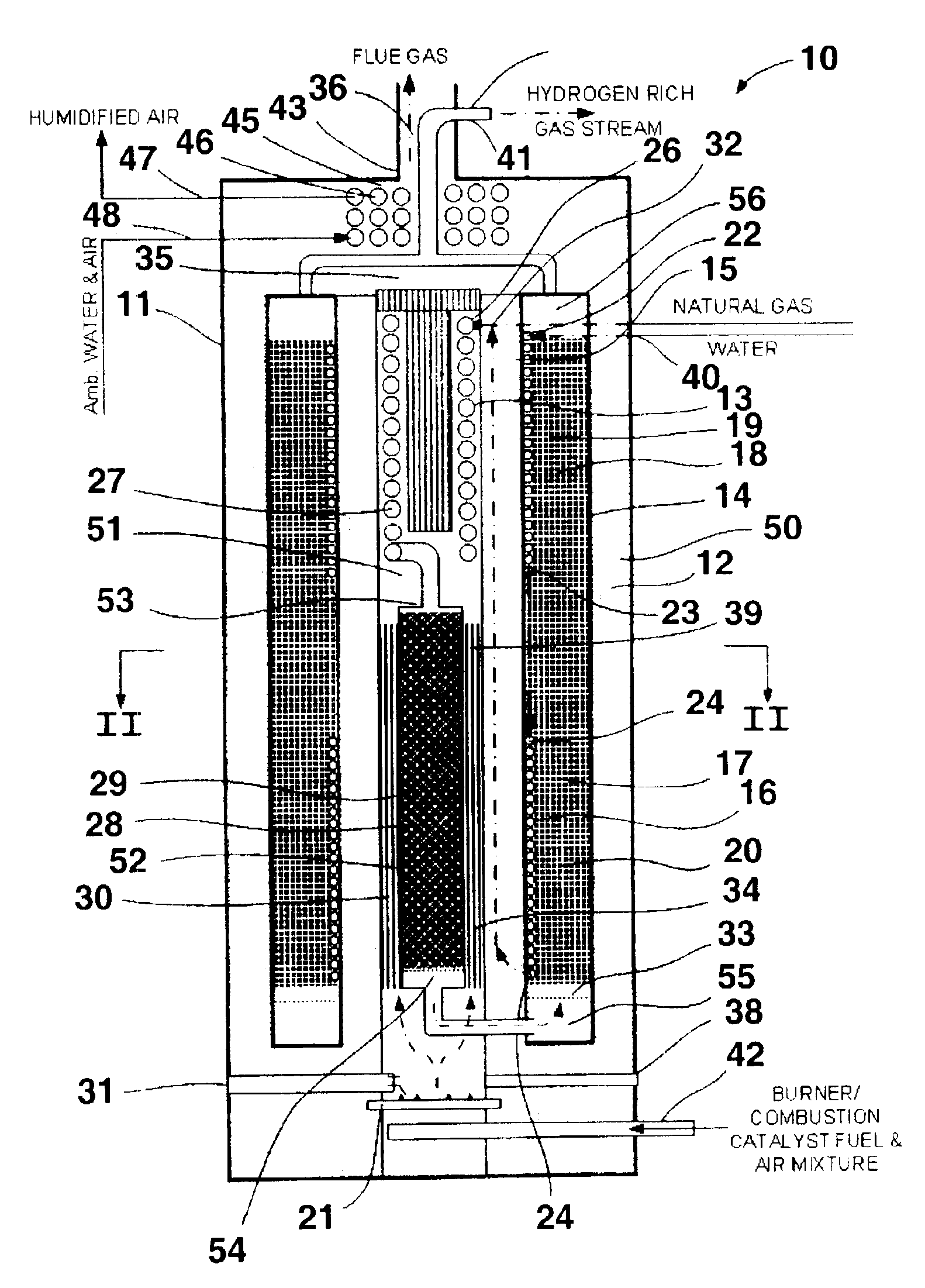
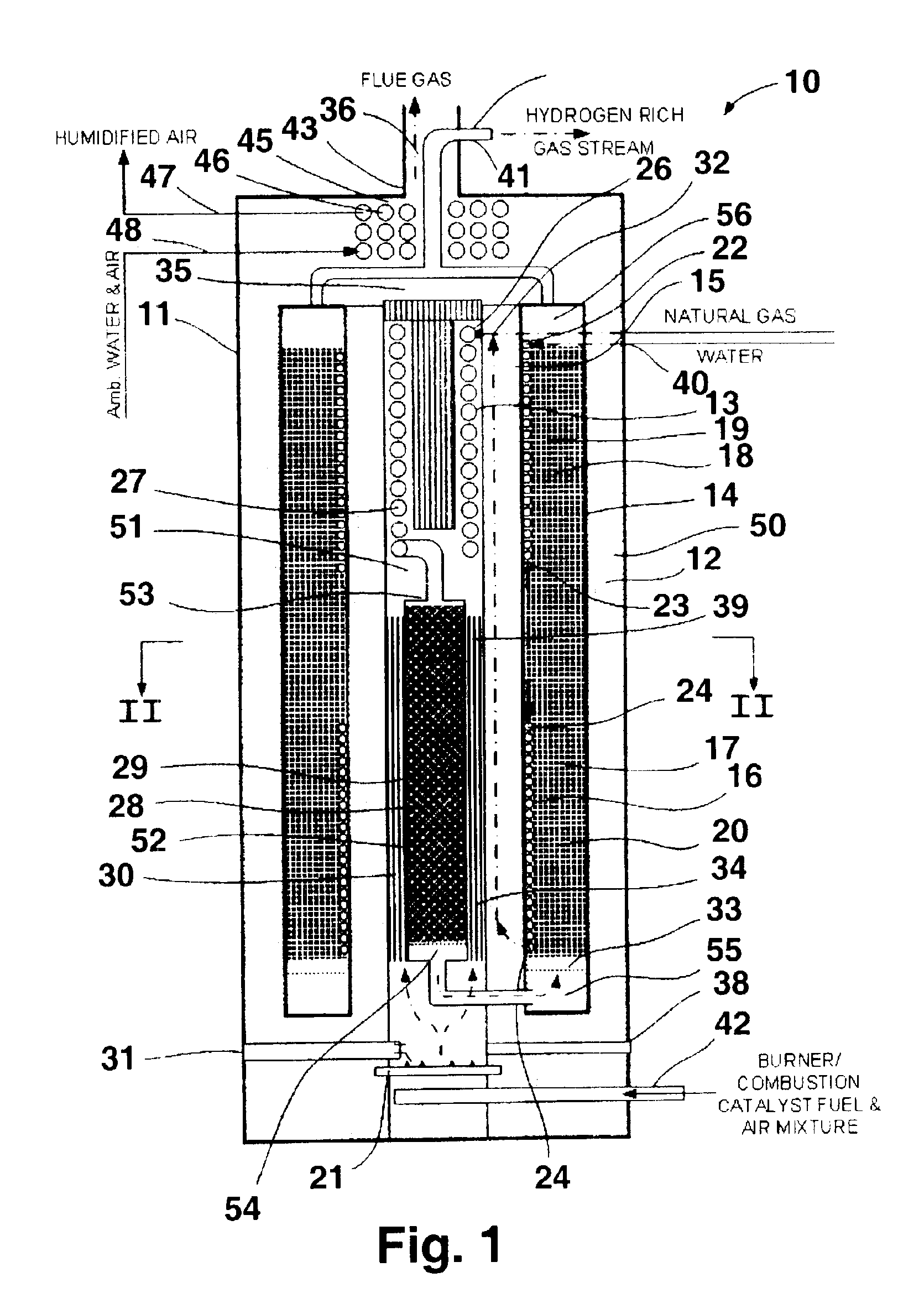
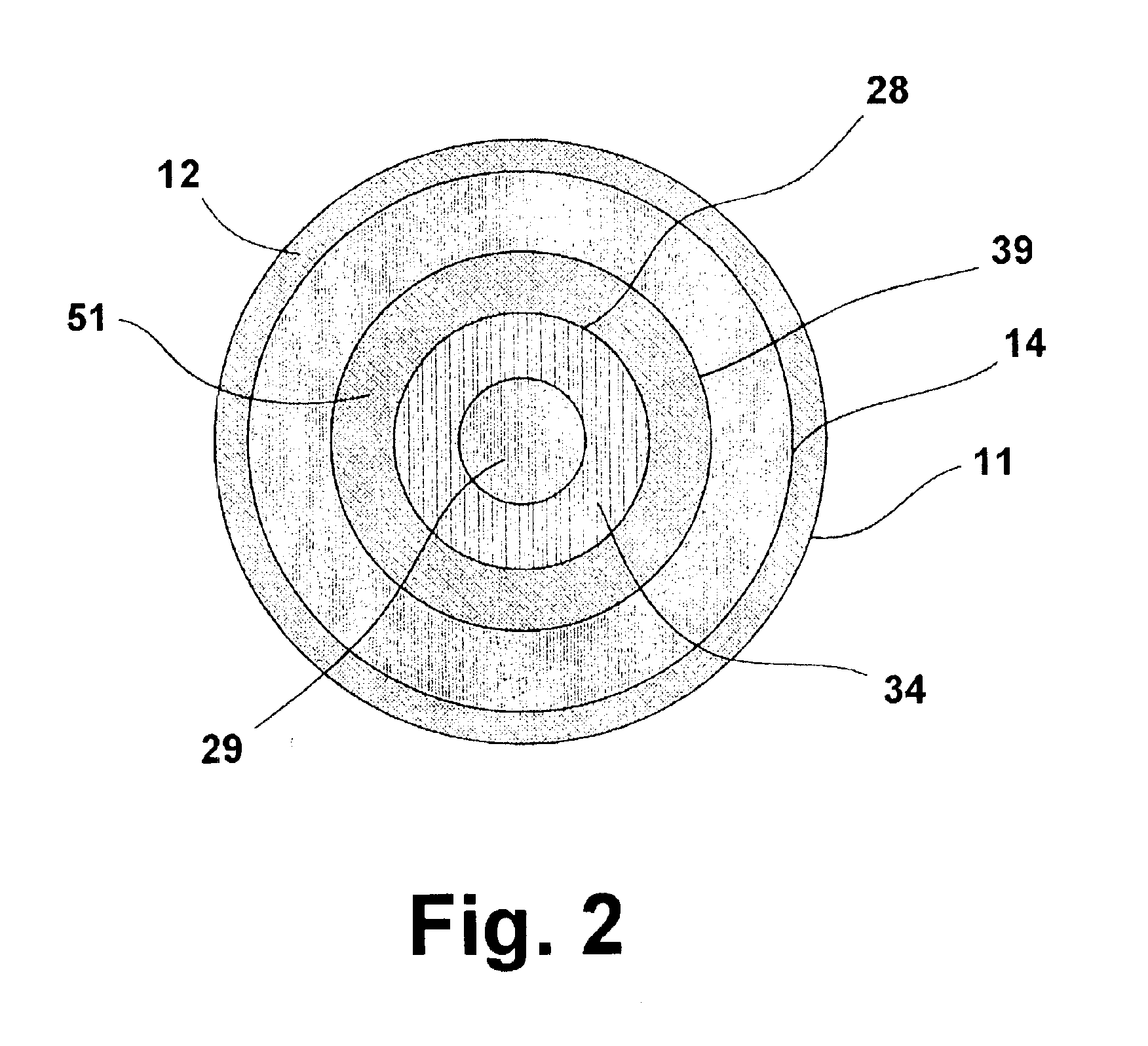
ActiveUS6932958B2Maximize fuel conversionImprove efficiencyThermal non-catalytic crackingMuffle furnacesInterior spaceCombustion chamber
A fuel processor for producing a hydrogen-rich product gas suitable for direct use in fuel cell applications includes a housing, an annular shift / methanator reactor vessel at least one reactor vessel wall disposed within the housing and forming an outer annular space between the at least one reactor vessel wall and the housing. A combustion chamber having at least one combustion chamber wall and forming a first inner annular space between the at least one combustion chamber wall and the at least one reactor vessel wall is disposed in the interior space formed by the annular shift / methanator reactor vessel, and a reformer reactor vessel having at least one reformer vessel wall and forming a second inner annular space between the at least one reformer vessel wall and the at least one combustion chamber wall is disposed within the combustion chamber.
Owner:GAS TECH INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com