Patents
Literature
284results about How to "Efficient verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
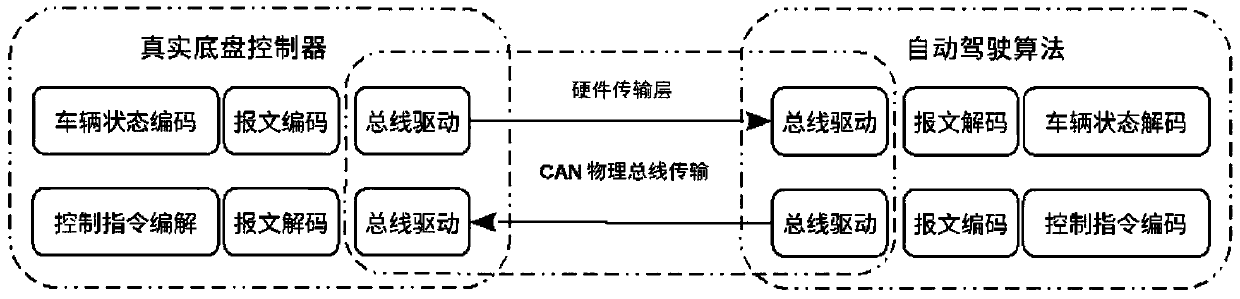
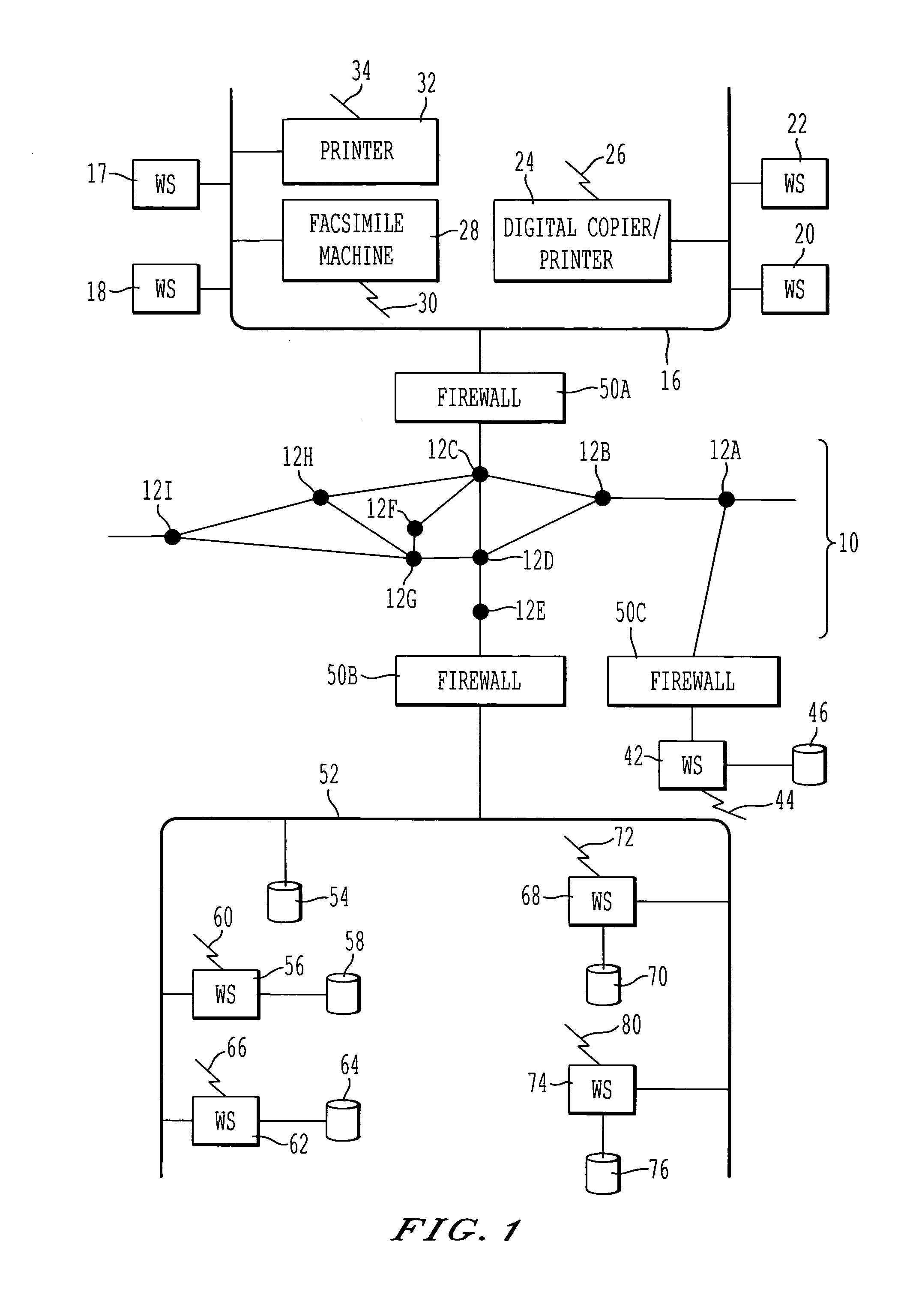
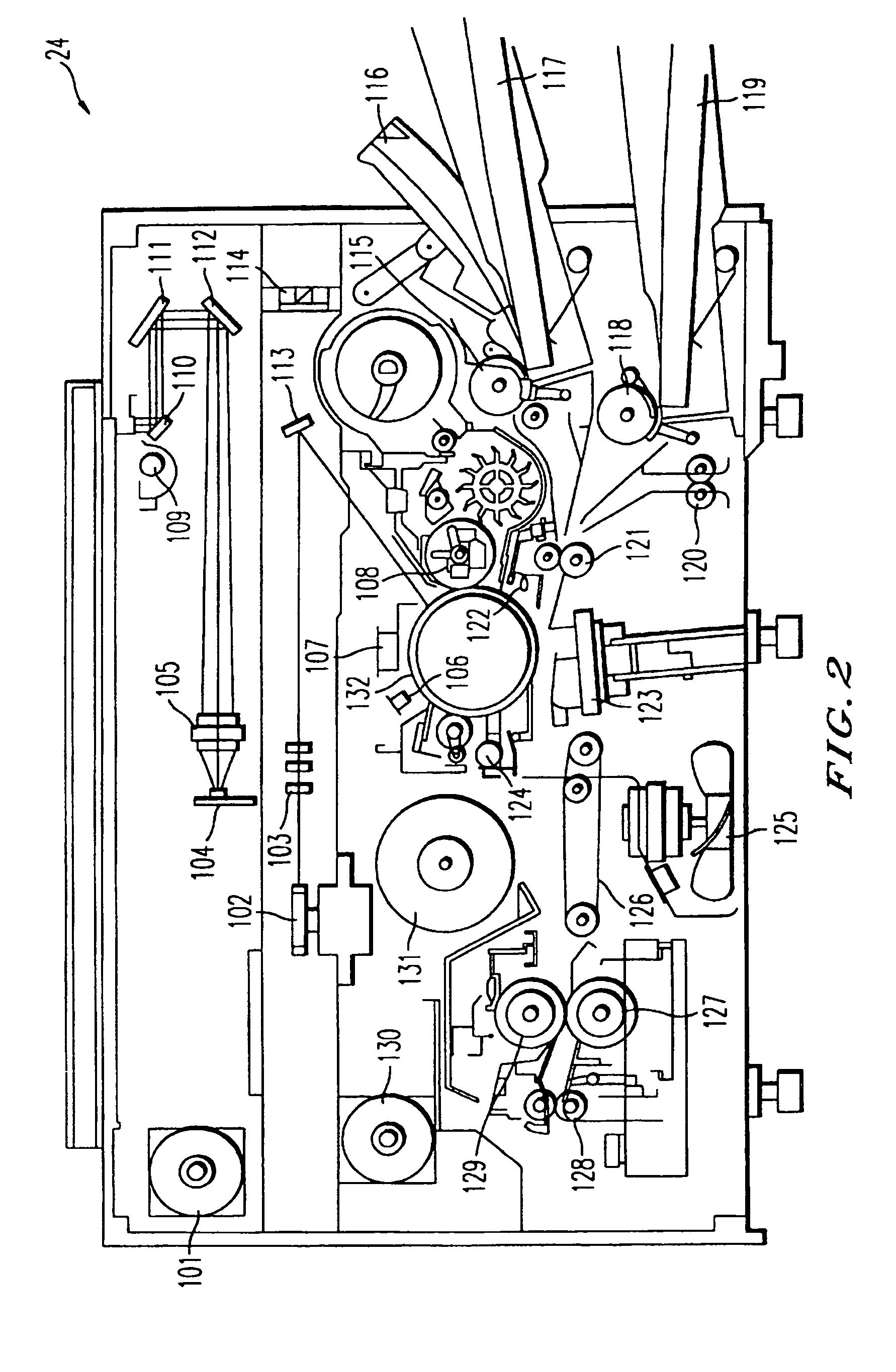
Data authentication system
InactiveUS20020169971A1Efficient verificationPossibility of leakageTelevision system detailsMultiple keys/algorithms usageKey storageMaster key
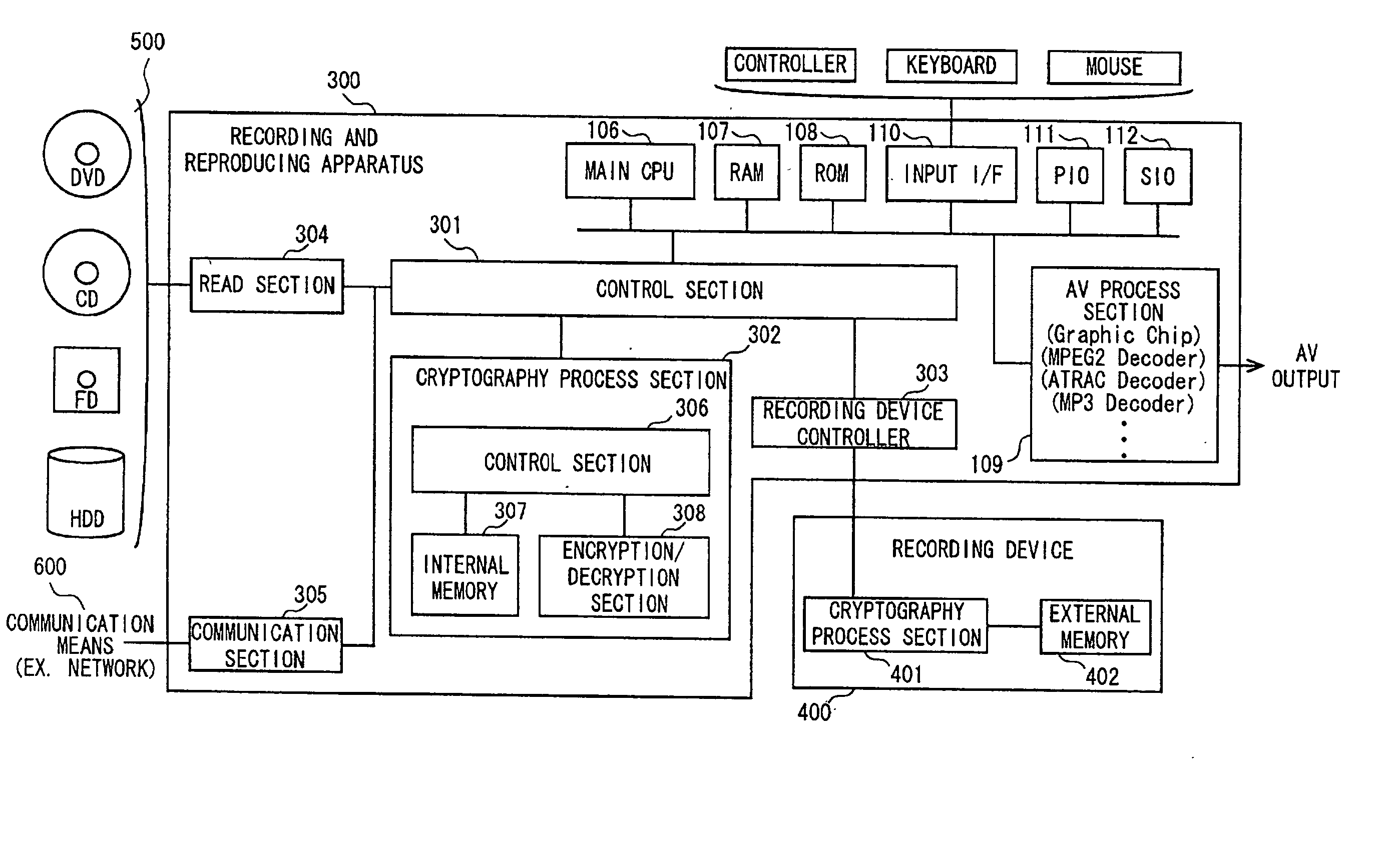
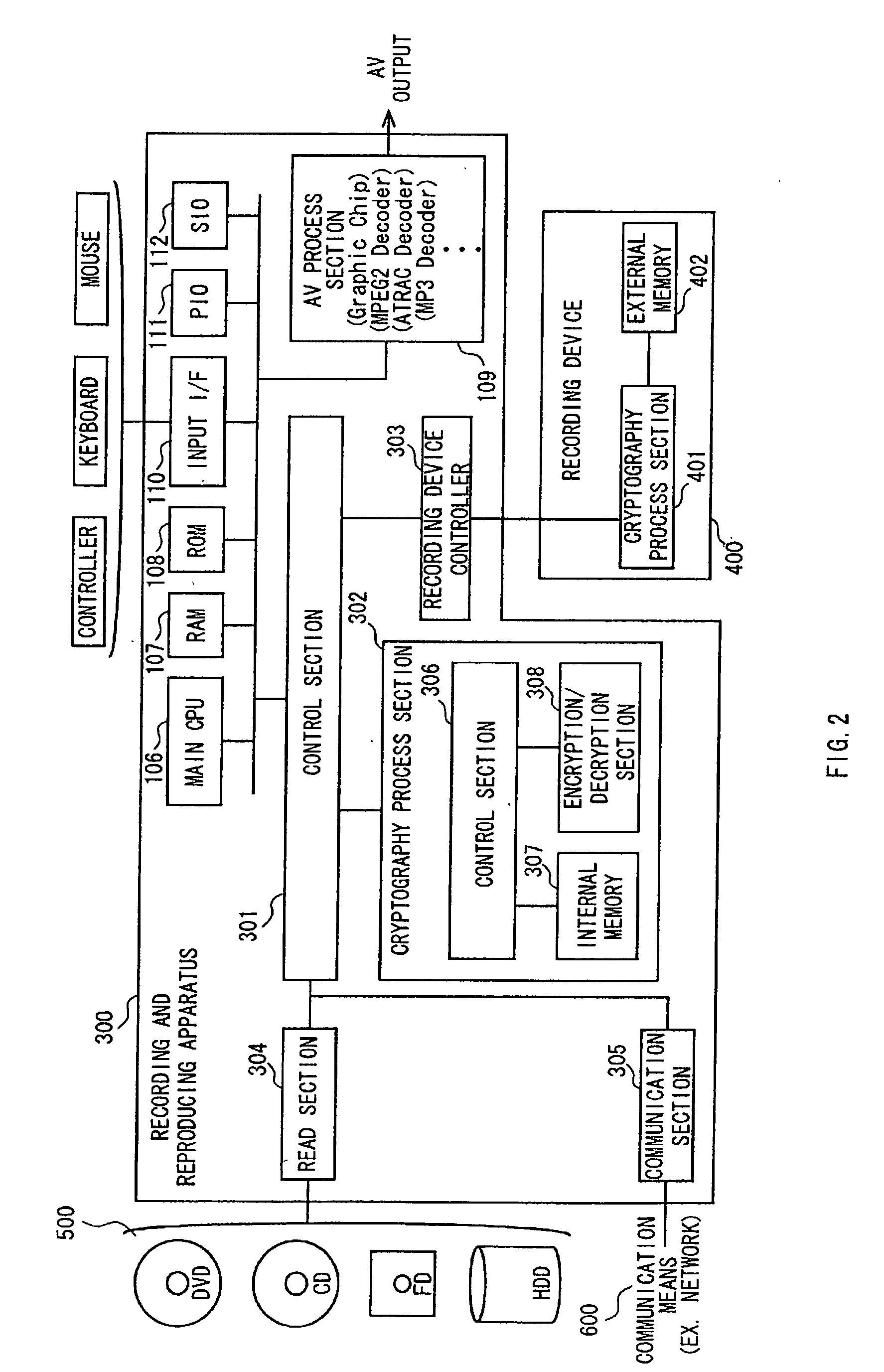
A data processing apparatus a data processing method efficiently ascertain that data are valid, prevent encryption processing key data from leaking, eliminate illegal use of contents data, restrict contents utilization, apply a different plurality of data formats to contents and efficiently execute reproduction processing of compressed data. The verification process of partial data is executed by collating the integrity partial data as check values for a combination of partial data of a content, and the verification process of the entirety of the combination of partial data is executed by collating partial-integrity-check-value-verifying integrity check values that verify the combination of the partial integrity check values. Master keys to generate individual keys necessary for a process of such as data encryption are stored in the storage section and keys are generated as required. An illegal device list is stored in the header information of a content and referred to when data is used. Keys specific to a data processing apparatus and common keys are stored and the keys are selectively used according to the content use restriction. Plural content blocks are coupled, and at least a part of the content blocks is applied to an encryption process by an encryption key Kcon, then encryption key data that is the encryption key Kcon encrypted by an encryption key Kdis is stored in the header section. A content data is made of compression data and an expansion processing program or a combination of types of compression programs and the reproducing apparatus can determine an expansion program applicable to a compressed content.
Owner:SONY CORP
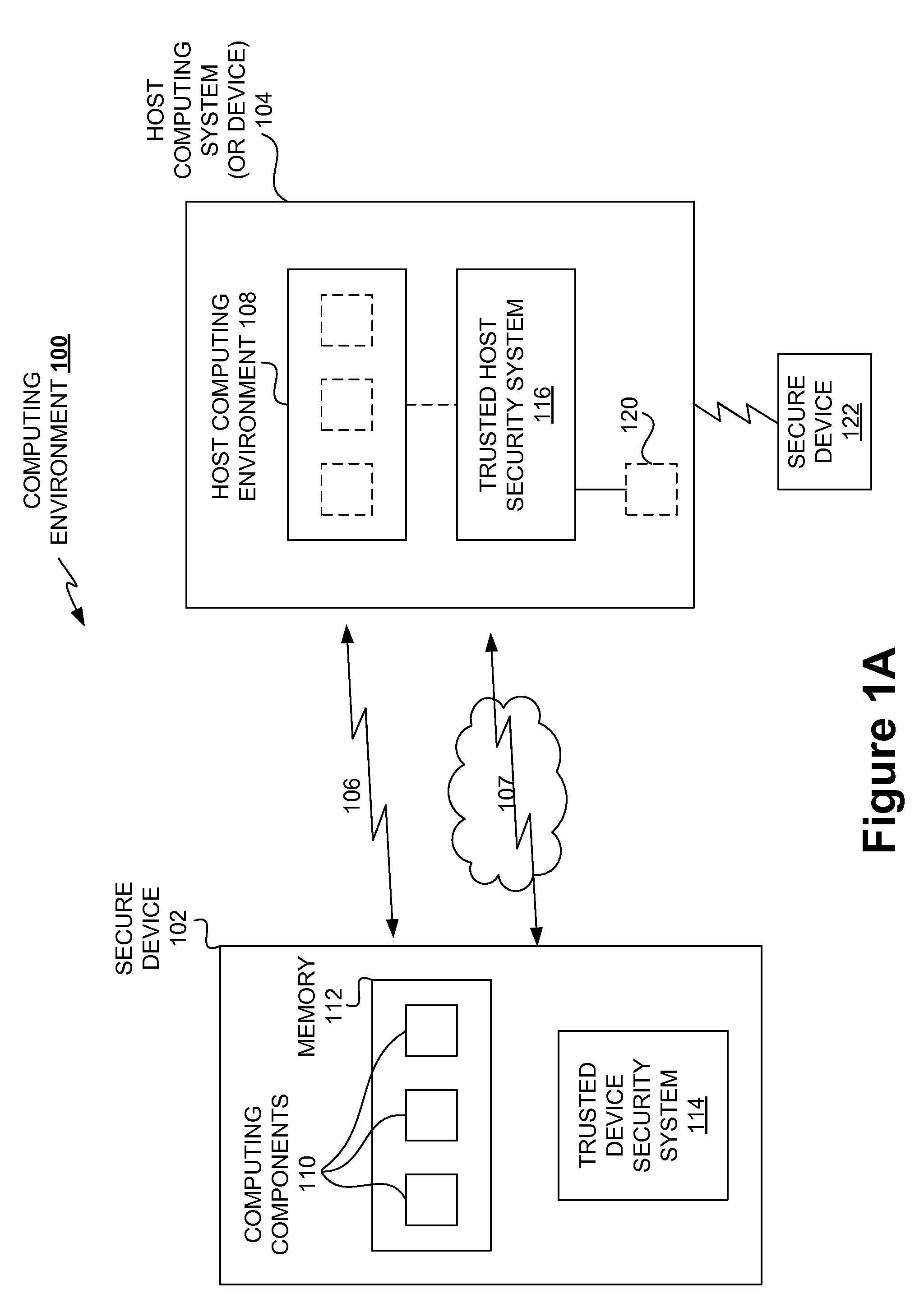
Securing stored content for trusted hosts and safe computing environments
InactiveUS20090049510A1Safe computing environmentEasy to usePublic key for secure communicationDigital data processing detailsHosting environmentComputer science
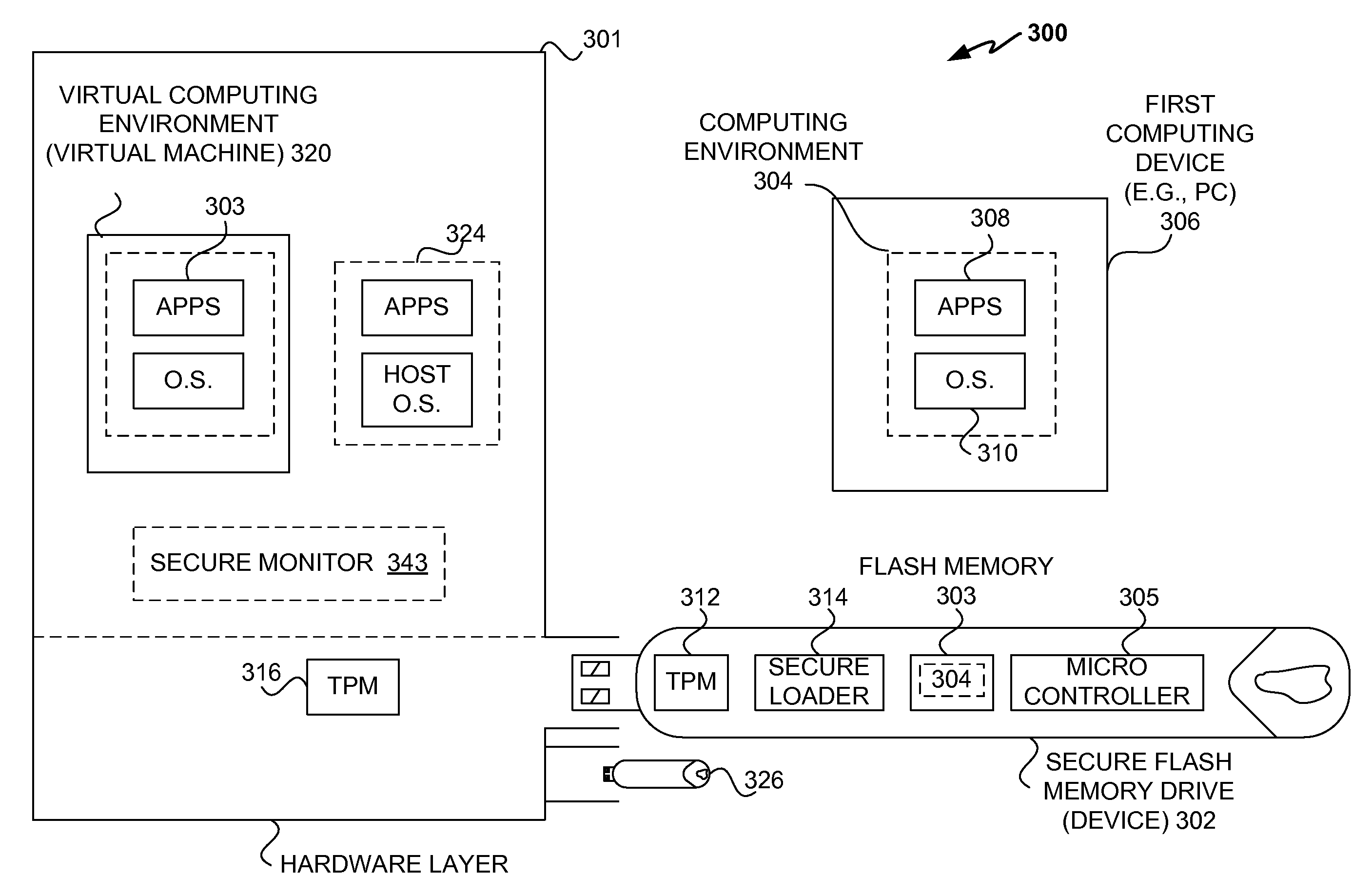
Techniques for protecting content to ensure its use in a trusted environment are disclosed. The stored content is protected against harmful and / or defective host (or hosted) environments. A trusted security component provided for a device can verify the internal integrity of the stored content and the host before it allows the content to come in contact with the host. As a counter part, a trusted security component provided for the host can verify and attest to the integrity of the host and / or specific host computing environment that can be provided for the content stored in the device. The trusted security component provided for a device effectively verify the host integrity based on the information attested to by the trusted security component provided for the host. If the trusted security component trusts the host, it allows the trusted host to provide a trusted host computing environment trusted to be safe for the content stored in the device. A trusted host can effectively provide a safe virtual environment that allows a content representing a copy (or image) of an original computing environment to operate on the host computing system to give a similar appearance as the original computing environment.
Owner:SAMSUNG ELECTRONICS CO LTD
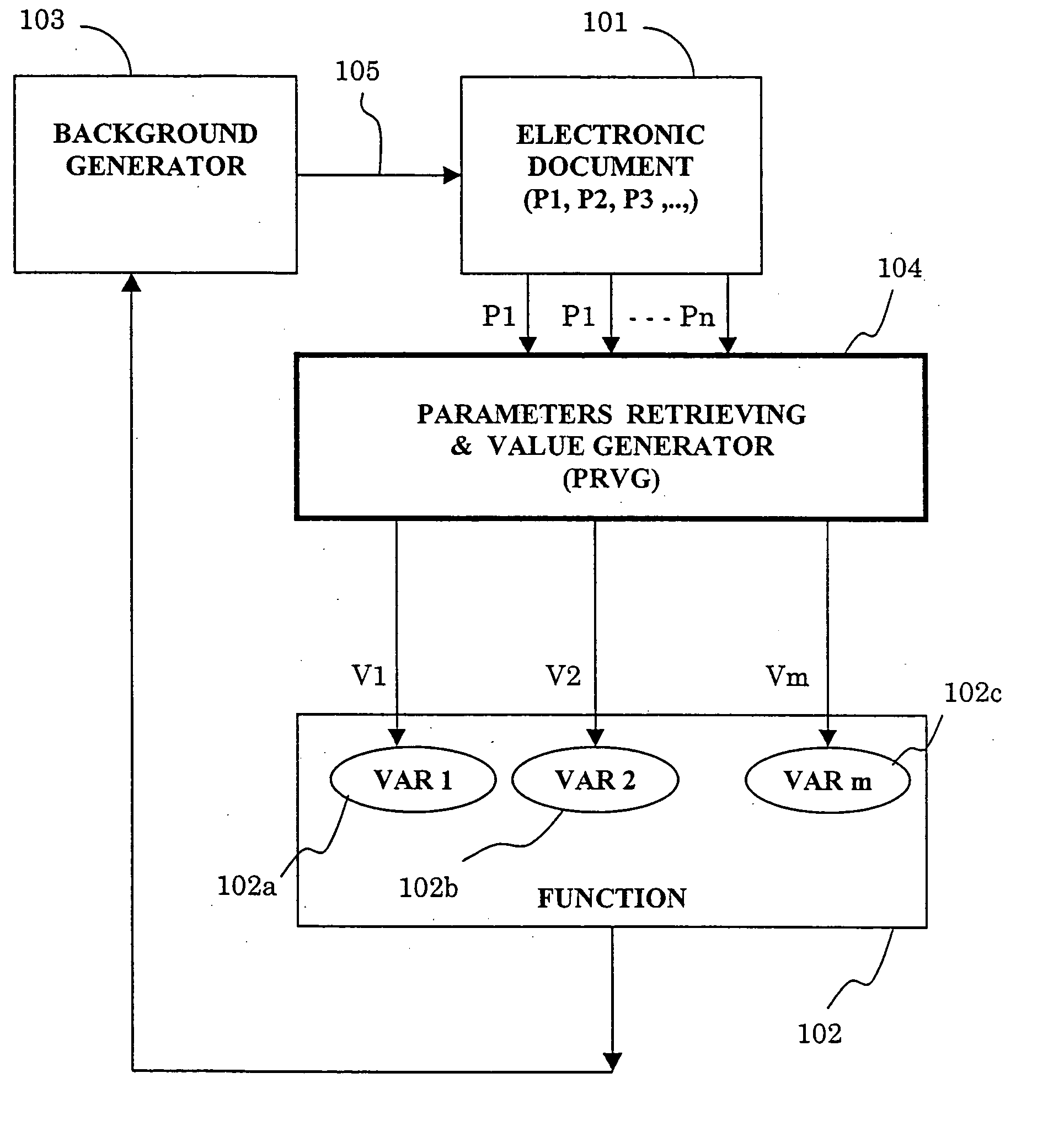
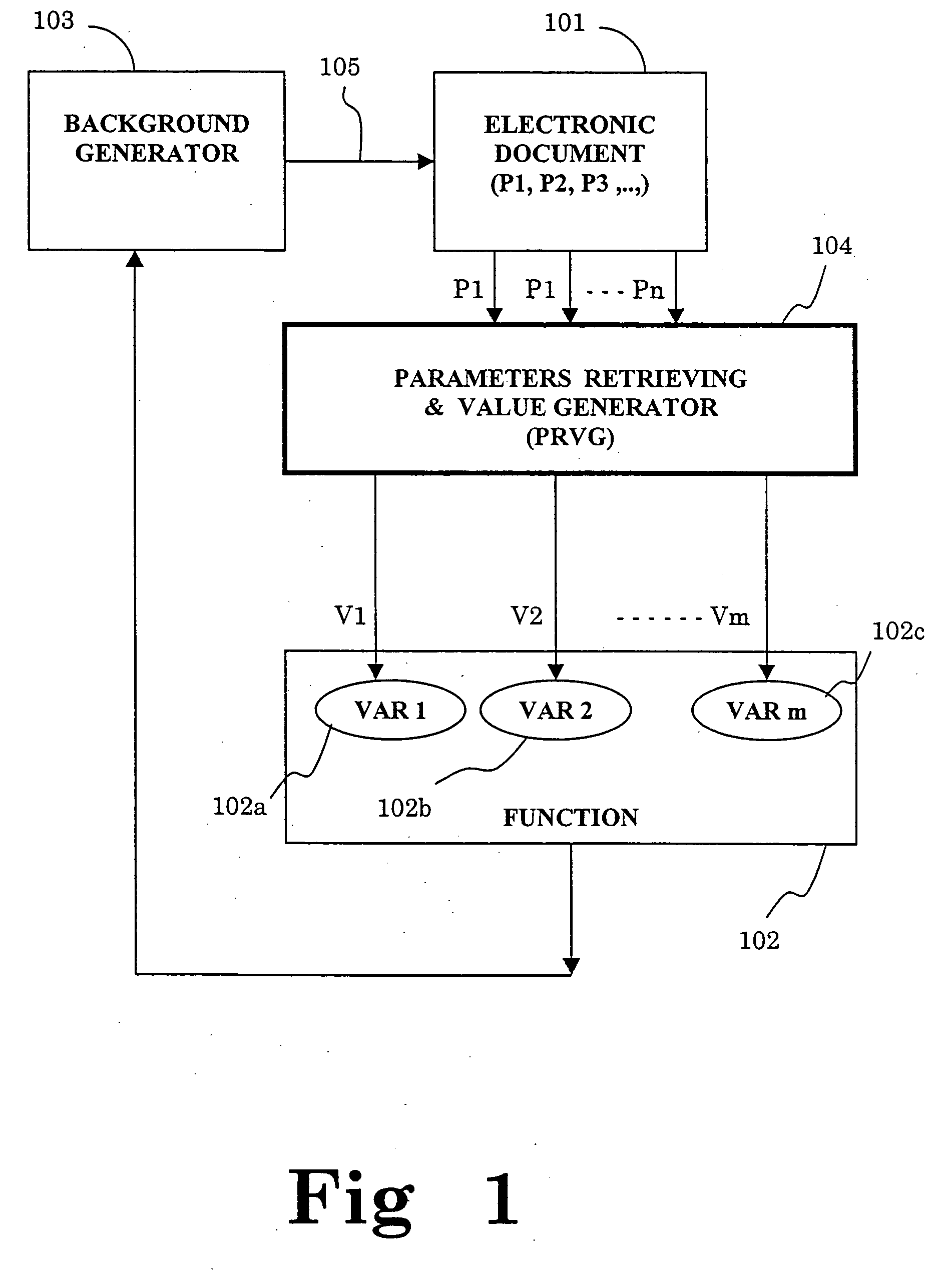
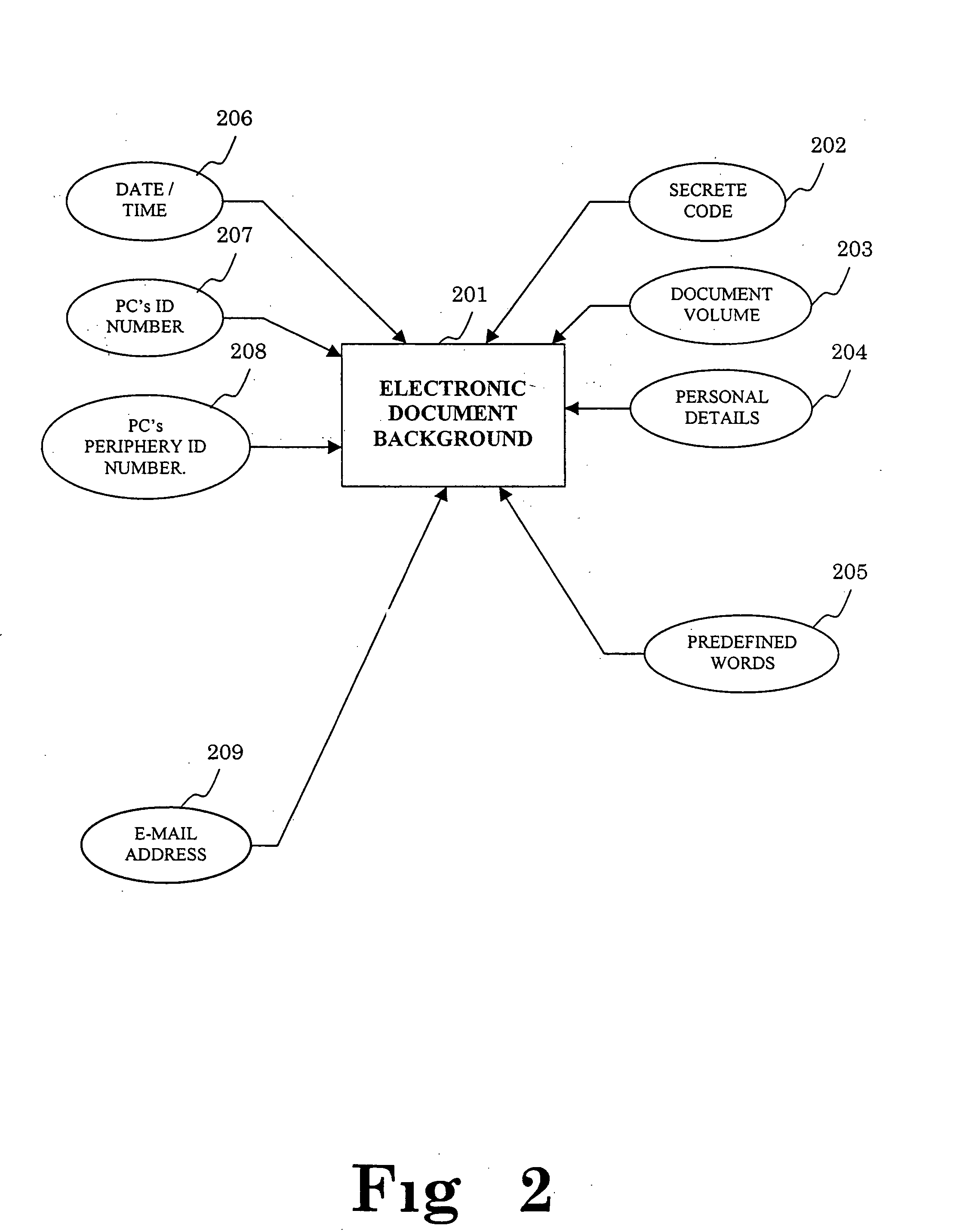
Method and system for assigning a background to a document and document having a background made according to the method and system
InactiveUS20050166144A1Efficient verificationEasy to identifyNatural language data processingSpecial data processing applicationsElectronic documentActivation function
This invention is concerned with a method and system for indicating selective parameters in a document, comprising: defining parameters for affecting the document; defining a function which includes the defined parameters as variables; providing a background generator receiving the function result as an input, for accordingly outputting a background relative to the input; and checking the document and substituting actual values reflecting the parameters to the function variables, and activating the function to obtain and provide results to the background generator, to produce and apply a specific background to the document, and the system produces a background to a document, and includes an electronic document with associated parameters; parameters retrieving and value generator for examining predefined parameters, and providing values to variables of a predefined function; a predefined function including variables, for producing an output result, which is provided to a background generator; and a background generator receiving the function output result, for accordingly applying to the document a specific background relative to the function result.
Owner:TELEFON AB LM ERICSSON (PUBL)
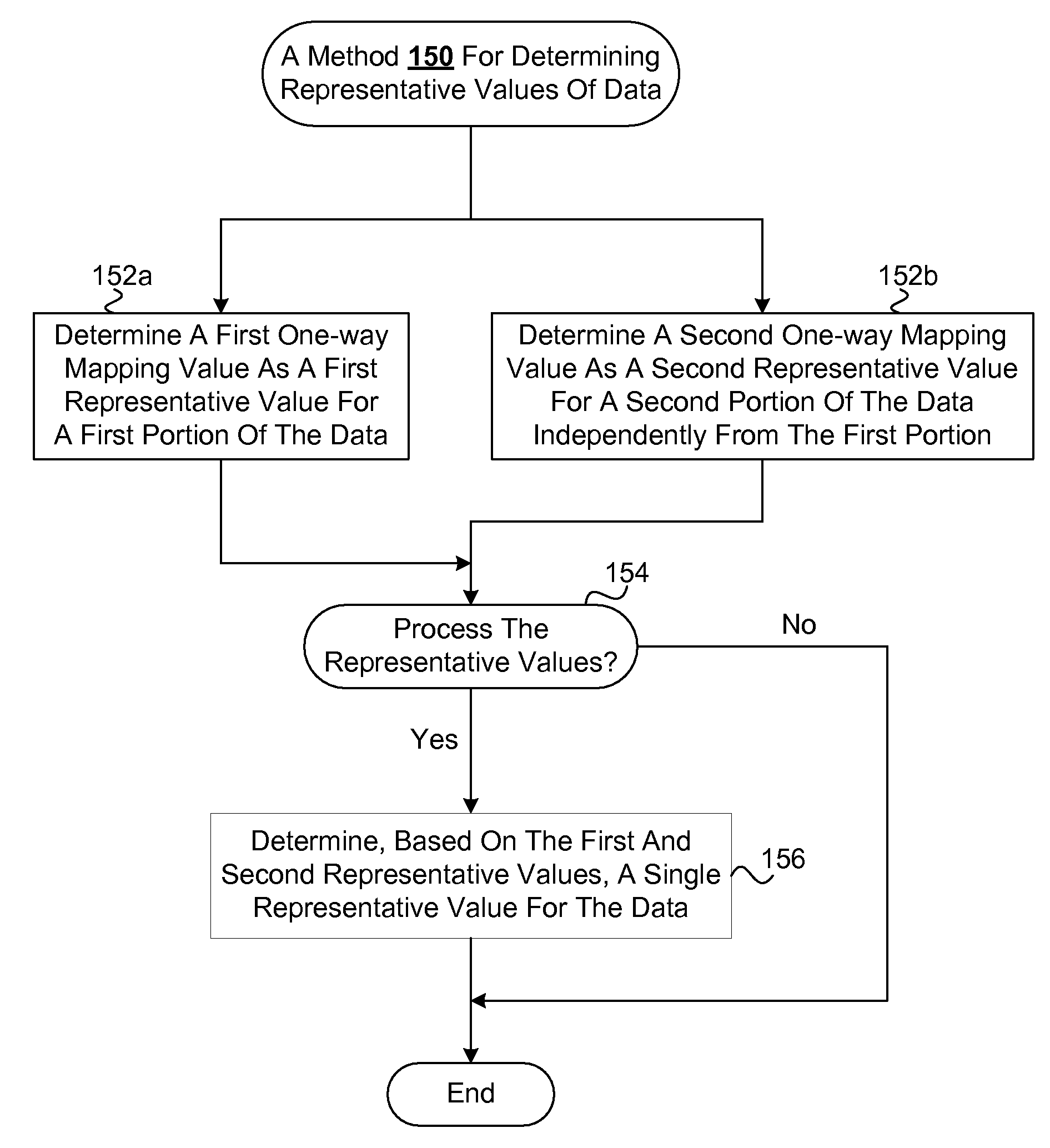
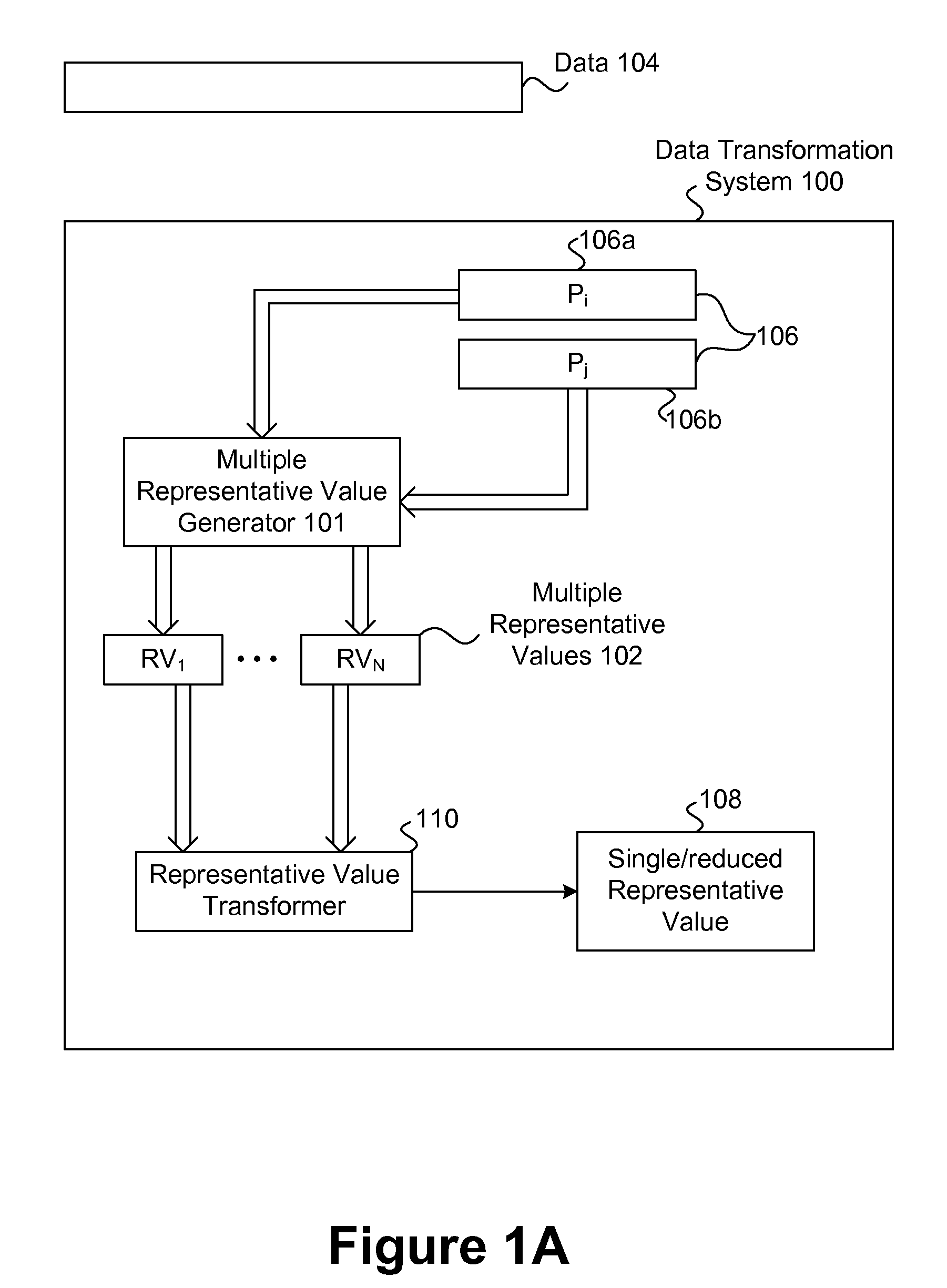
Representation and verification of data for safe computing environments and systems
InactiveUS20100106976A1Efficient verificationLess timeDigital data information retrievalUnauthorized memory use protectionDatasheetData integrity
Techniques for representation and verification of data are disclosed. The techniques are especially useful for representation and verification of the integrity of data (integrity verification) in safe computing environments and / or systems (e.g., Trusted Computing (TC) systems and / or environments). Multiple independent representative values can be determined independently and possibly in parallel for respective portions of the data. The independent representative values can, for example, be hash values determined at the same time for respective distinct portions of the data. The integrity of the data can be determined based on the multiple hash values by, for example, processing them to determine a single hash value that can serve as an integrity value. By effectively dividing the data into multiple portions in multiple processing streams and processing them in parallel to determine multiple hash values simultaneously, the time required for hashing the data can be reduced in comparison to conventional techniques that operate to determine a hash value for the data as a whole and in a single processing stream. As a result, the time required for integrity verification can be reduced, thereby allowing safe features to be extended to devices that may operate with relatively limited resources (e.g., mobile and / or embedded devices) as well as improving the general efficiency of device that are or will be using safety features (e.g., Trusted Computing (TC) device).
Owner:SAMSUNG ELECTRONICS CO LTD
Decentralized public key management method and system based on trusted network
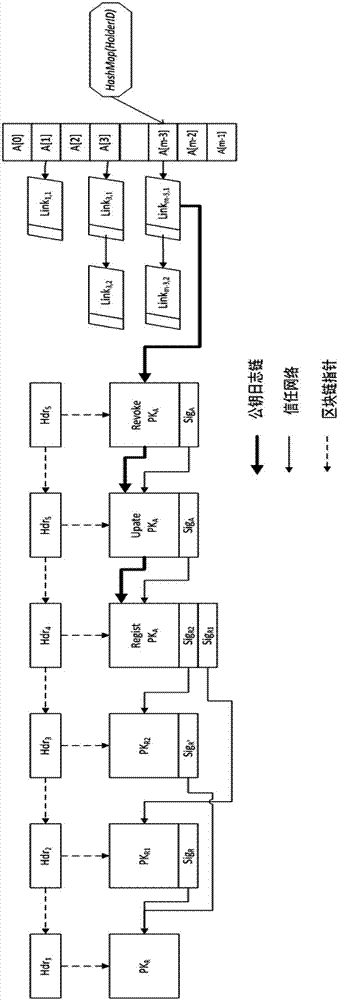
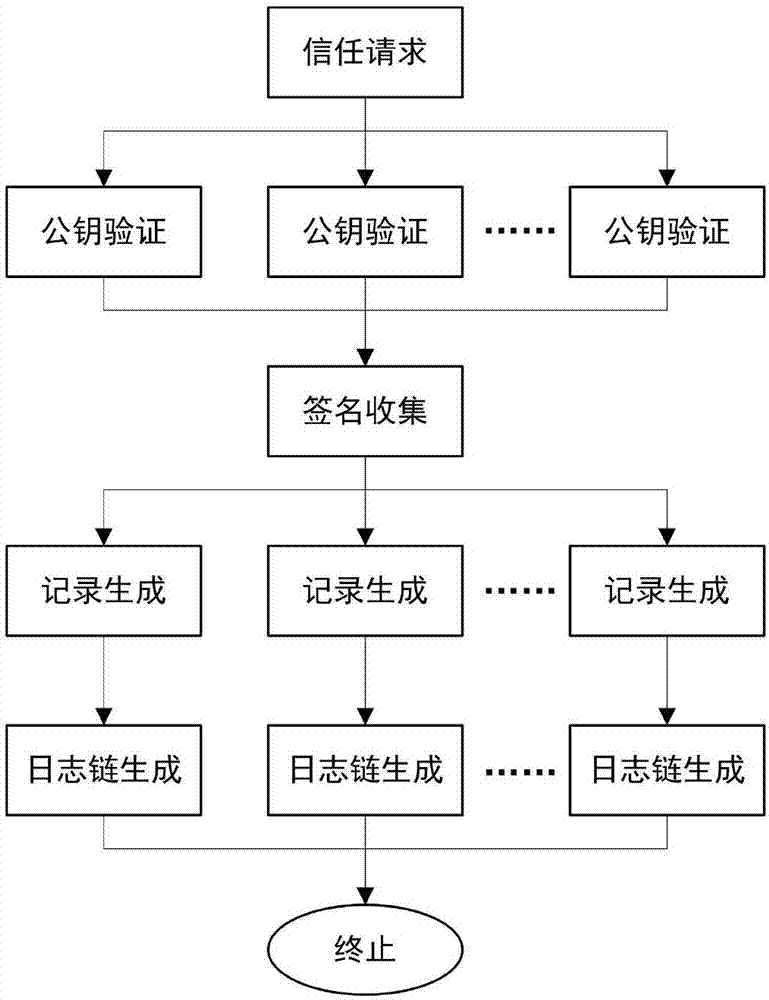
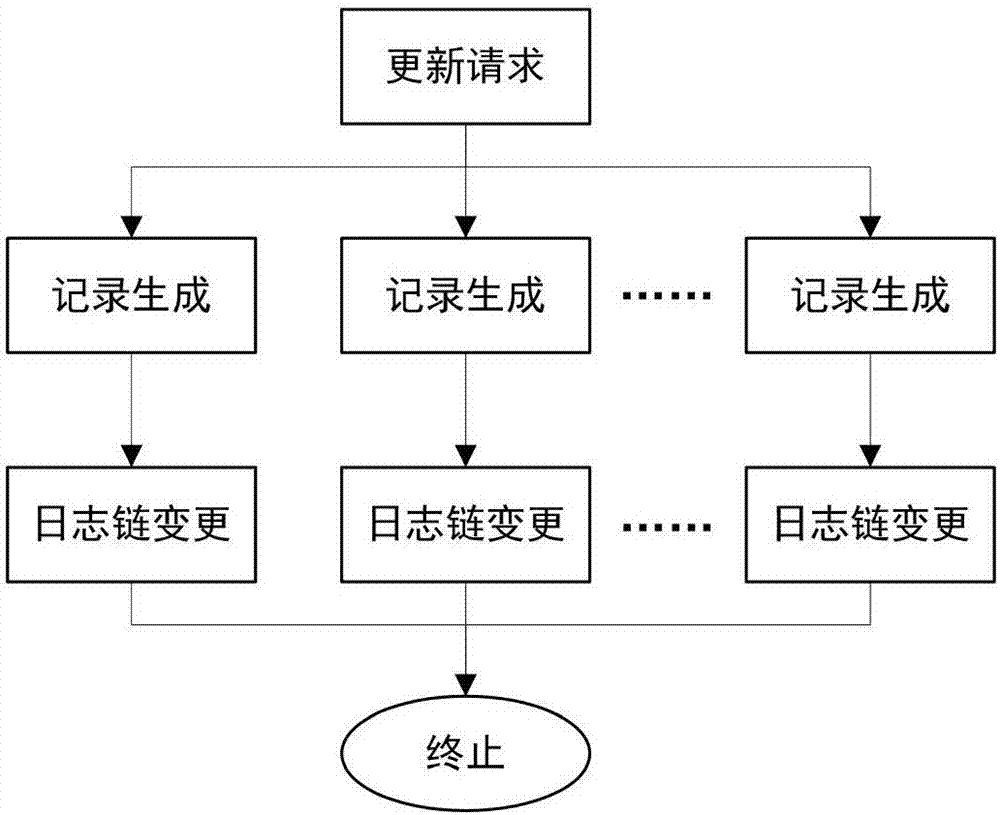
ActiveCN107070644AEfficient verificationEfficient queryKey distribution for secure communicationStructure of Management InformationUser identifier
The invention mainly belongs to the technical field of information security, and specifically relates to a novel decentralized public key management method and a trusted model. The method is constructed on distributed data network platforms such as a block chain and P2P (Peer to Peer) in order to ensure that all nodes in the platforms can participate in maintenance of whole-life-cycle management of public keys of users, and the changes of the public keys of the users in various states in a life cycle are recorded in a bill form. Through the method, public keys passing verification can be recorded and added into a consistent public key storage structure of a platform to be saved; a public key log chain is generated for all public key records of the same user according to a time sequence, and an authentication chain and a trusted network are formed on the basis of a referrer signature; and efficient search of the public keys can be realized on the basis of user identifiers. Through adoption of the method, the public keys of the users can be issued and acquired conveniently and accurately, and the effectiveness, correctness, consistency and non-fraudulence of acquired public keys are ensured. The method can be taken as an infrastructure supporting authentication, encryption, integrity and accountability services.
Owner:UNIV OF SCI & TECH BEIJING
Portion-level in-memory module authentication
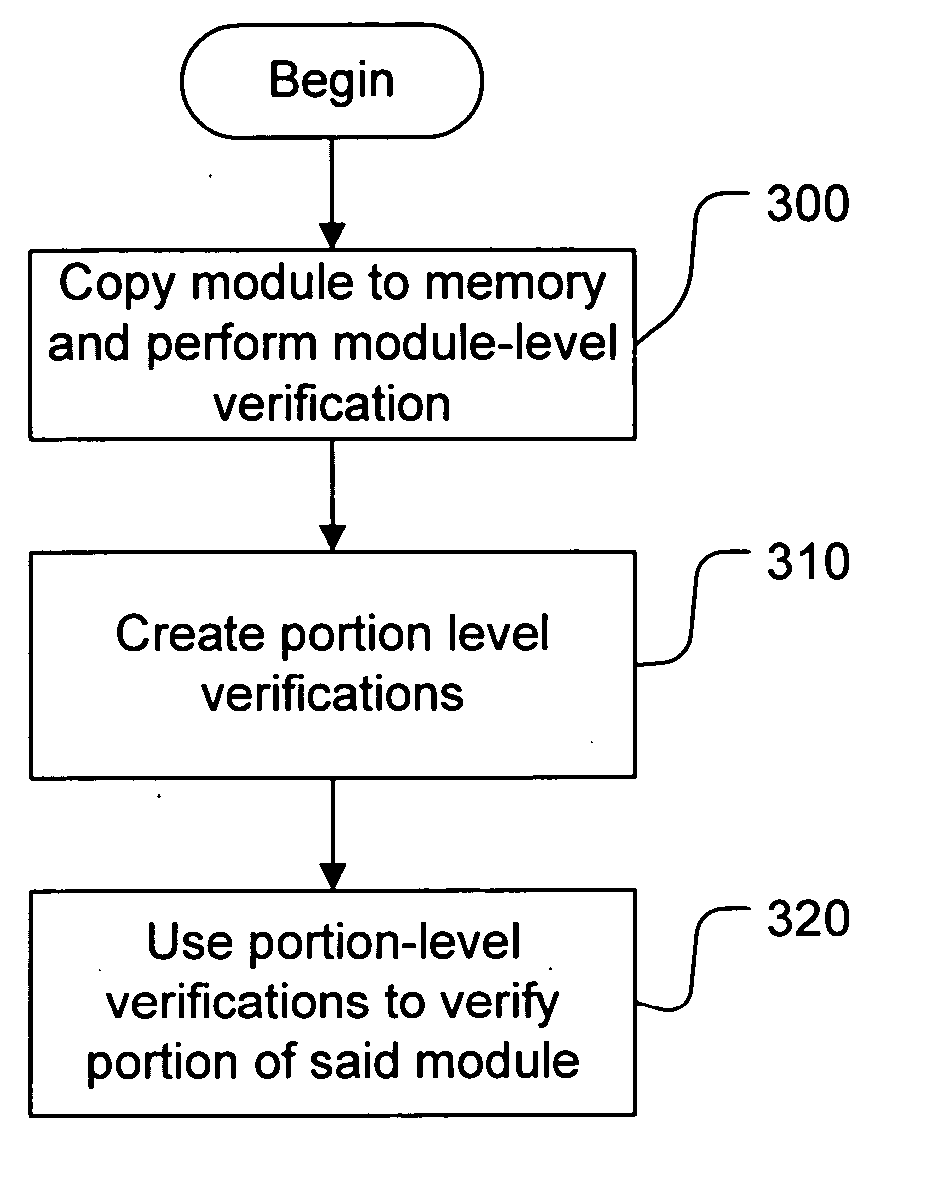
InactiveUS20050198051A1Efficient verificationEfficient methodMemory loss protectionDigital data processing detailsMemory moduleSoftware modules
Dynamic run-time verification of a module which is loaded in memory (in whole or in part) for execution is enabled by storing hashes of smaller portions of the module (e.g. page-level hashes) as they should look when loaded into memory for execution. After an initial authentication is completed, hashes of smaller portions of the module are stored. These hashes consist of the portion of memory as modified by changes which would be made by the operating system loader operating normally. Thus, the hashes can be used to verify that the portion as loaded into memory for execution is 1) a correct copy of the portion of the software module, 2) correctly modified for execution by the processor, and 3) not tampered with since loading. Additionally, during execution of the module, new portions / pages of the module which are loaded can be verified to ensure that they have not been changed, and a list of hot pages of the module can be made, including pages to be continually re-verified, in order to ensure that no changes have been made in the module.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic-based verification apparatus for verification from electronic system level to gate level, and verification method using the same
InactiveUS20110184713A1Reduce verification timeImprove verification efficiencyAnalogue computers for electric apparatusCAD circuit designElectronic systemsComputer architecture
The simulation consists of a front-end simulation and a back-end simulation. The front-end simulation can use an equivalent model at different abstraction level, or a simulation model for the back-end simulation. The back-end simulation uses the simulation result of front-end simulation so that it can run one or more simulation runs sequentially or in parallel. Alternatively, models at lower level of abstraction are simulated together with a model at higher level of abstraction in parallel using two or more simulators.
Owner:YANG SEI YANG
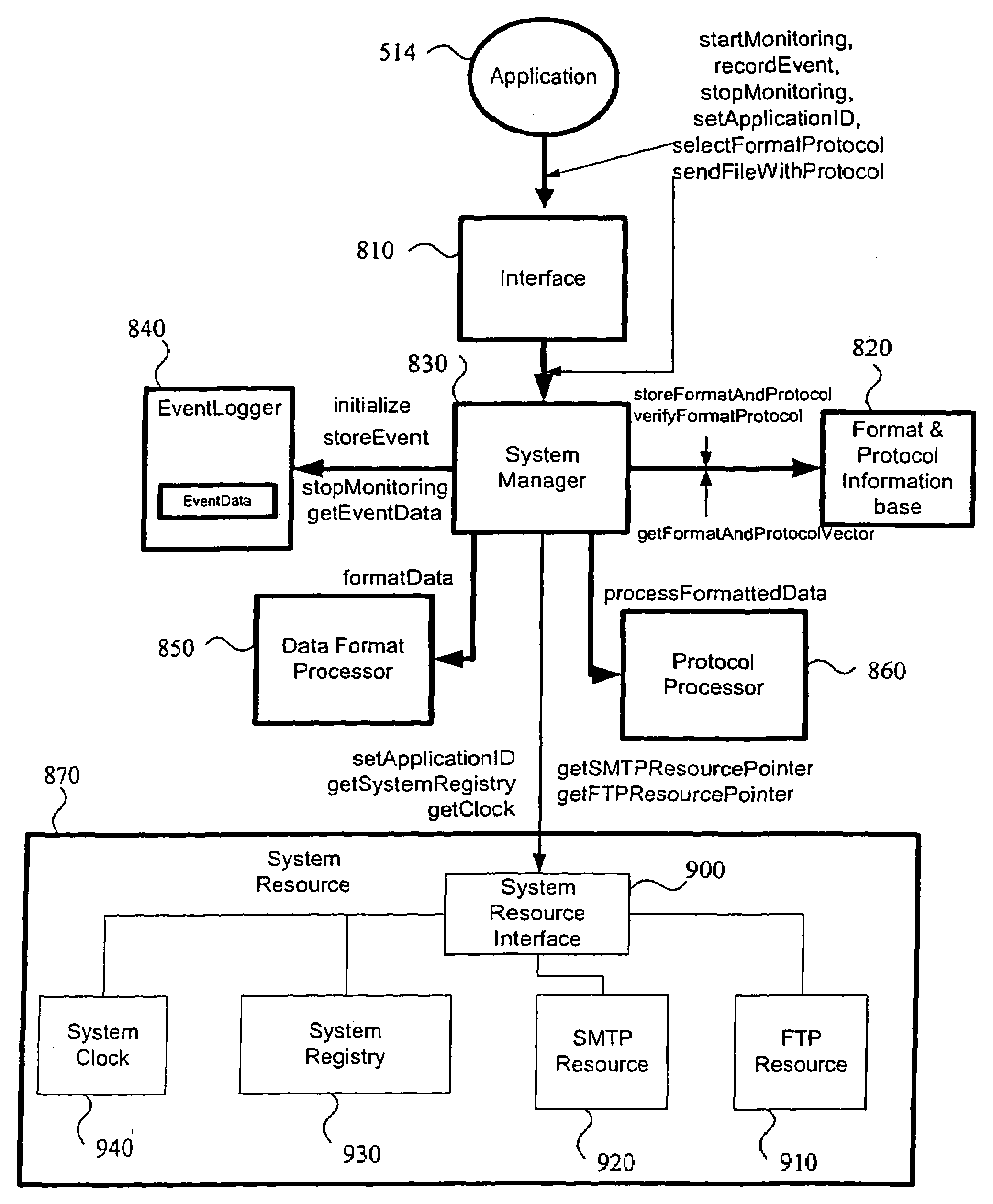
Method and system of remote diagnostic, control and information collection using a dynamic linked library of multiple formats and multiple protocols with restriction on protocol
InactiveUS6988141B1Facilitate configuration and received data analysisReduce analysisMultiple digital computer combinationsTransmissionApplication softwareRemote diagnostics
A method, system and computer program product for (1) collecting information from a remote application unit and / or (2) diagnosing or controlling the remote application unit. By utilizing a shareable computer code device (e.g., a dynamic linked library), a new application can utilize tested, proven code without having to reproduce existing functionality. Moreover, by supporting multiple data formats and / or multiple communication protocols, a computer code device increases the likelihood that a supported format and / or protocol will be either receivable or understandable by a receiver.
Owner:RICOH KK
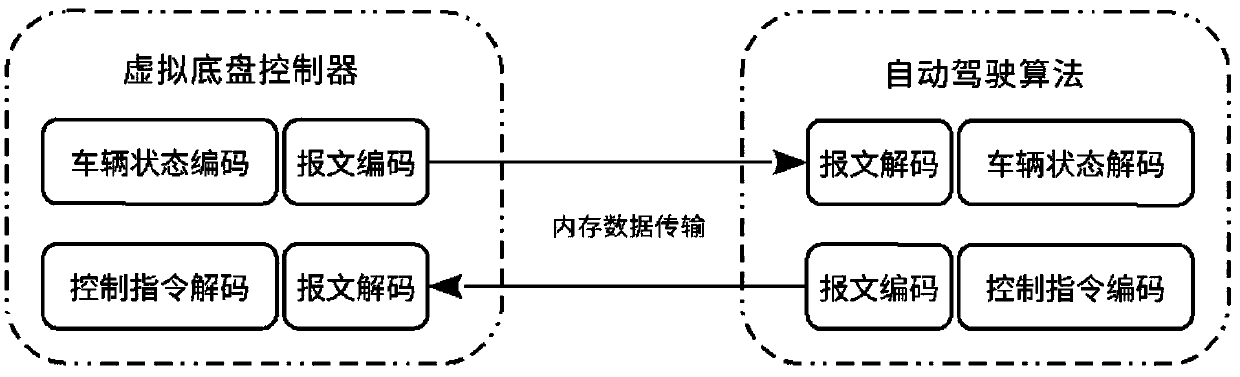
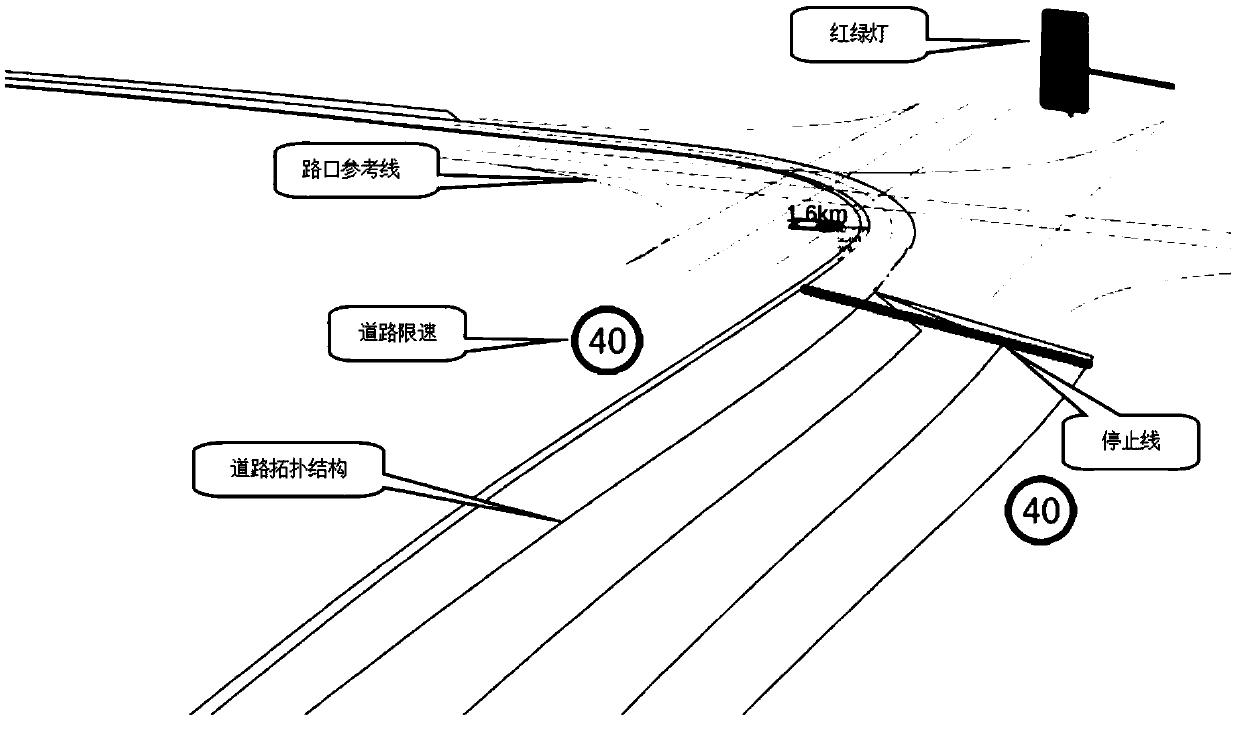
Multifunctional simulation system for automatic driving
ActiveCN108803607AImprove portabilityEfficient verificationPosition/course control in two dimensionsVehiclesVirtual vehicleData interface
The invention provides a multifunctional simulation system for automatic driving. The multifunctional simulation system comprises a virtual vehicle module, a virtual chassis control module, a virtualroad module, a virtual traffic module, a time control unit module and a visualized interactive interface module, the virtual road module provides cartographic information for an automatic driving algorithm and the virtual traffic module, the virtual traffic module provides road conditions including vehicles, pedestrian, traffic lights and the like for the automatic driving algorithm, the automaticdriving algorithm communicates with the virtual vehicle module through a virtual chassis so as to obtain vehicle information and send vehicle control instructions, a visualized interactive interfacesends human-computer interaction information to the simulation system and displays system information in a visualized three-dimensional effect, and finally, the time control unit module controls intervals of simulation time of the simulation system comprising the automatic driving algorithm. Data interfaces of the virtual modules are kept consistent with those of a real system, so that multifunctional modes, including hardware-in-loop simulation, of the simulation system can be realized.
Owner:北京领骏科技有限公司
Method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols with delegating protocol processor
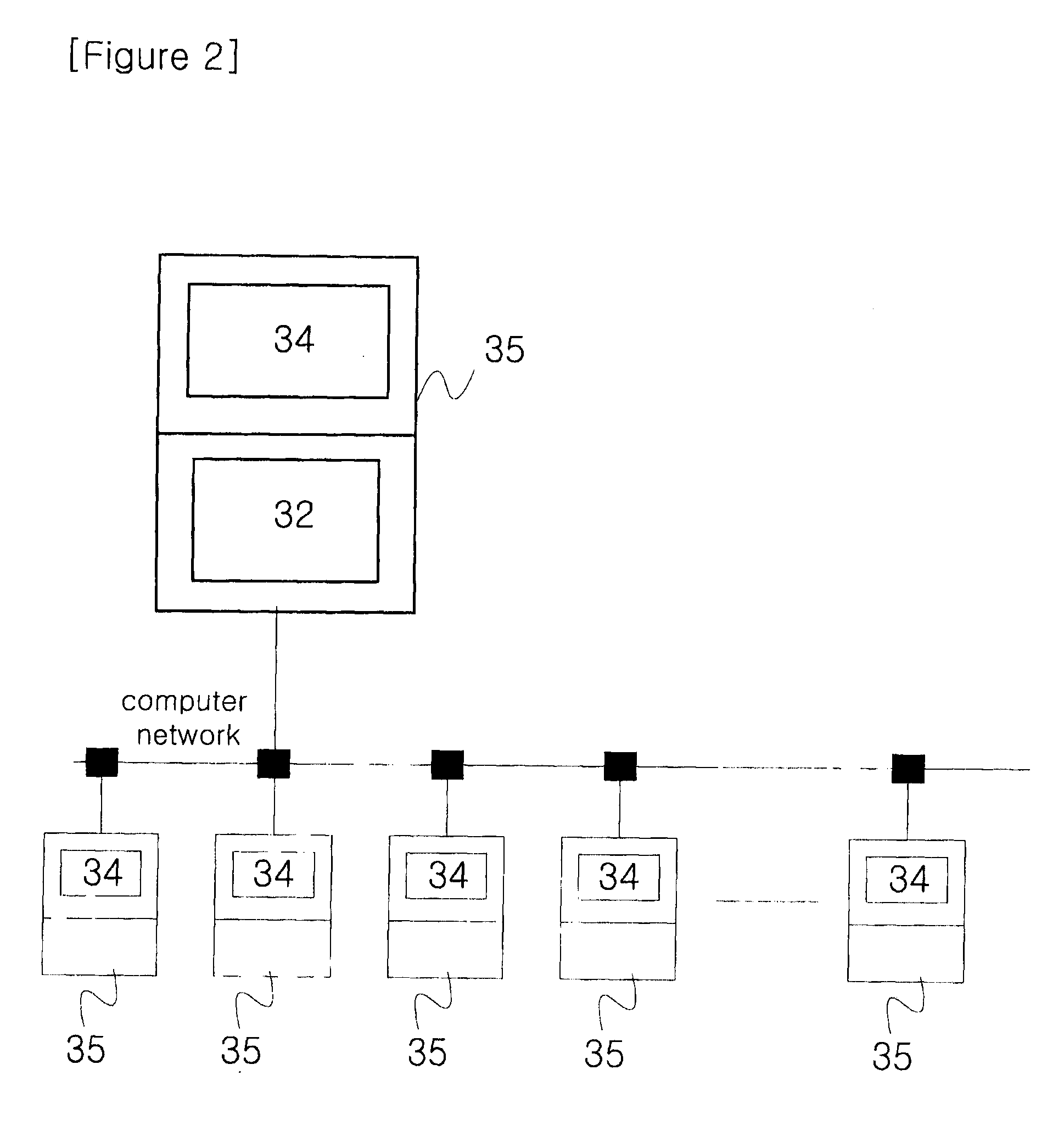
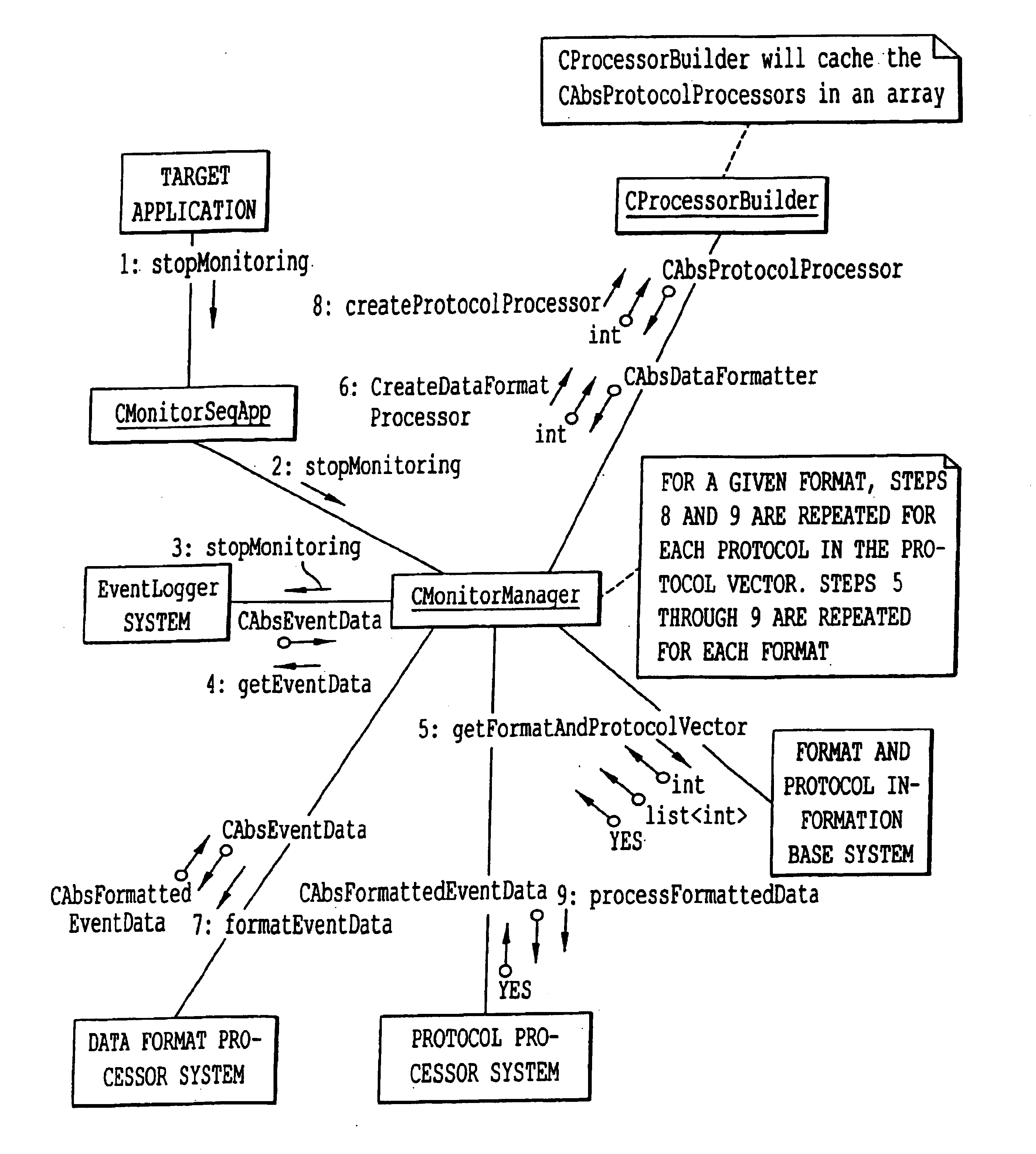
InactiveUS7047293B2Easy to analyzeEasy to configureInput/output to record carriersError detection/correctionProtocol processingNetwork Communication Protocols
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. The event information for a particular target application is formatted and transmitted according to a combination of a data format and communication protocol requested by the target application. The transmission of data representing the event information is handled in at least two levels of software classes, with at least one abstract software class having a declared virtual function and two or more software classes derived from the at least one abstract class and having definitions of the function for communicating the event information through specified communication protocols. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
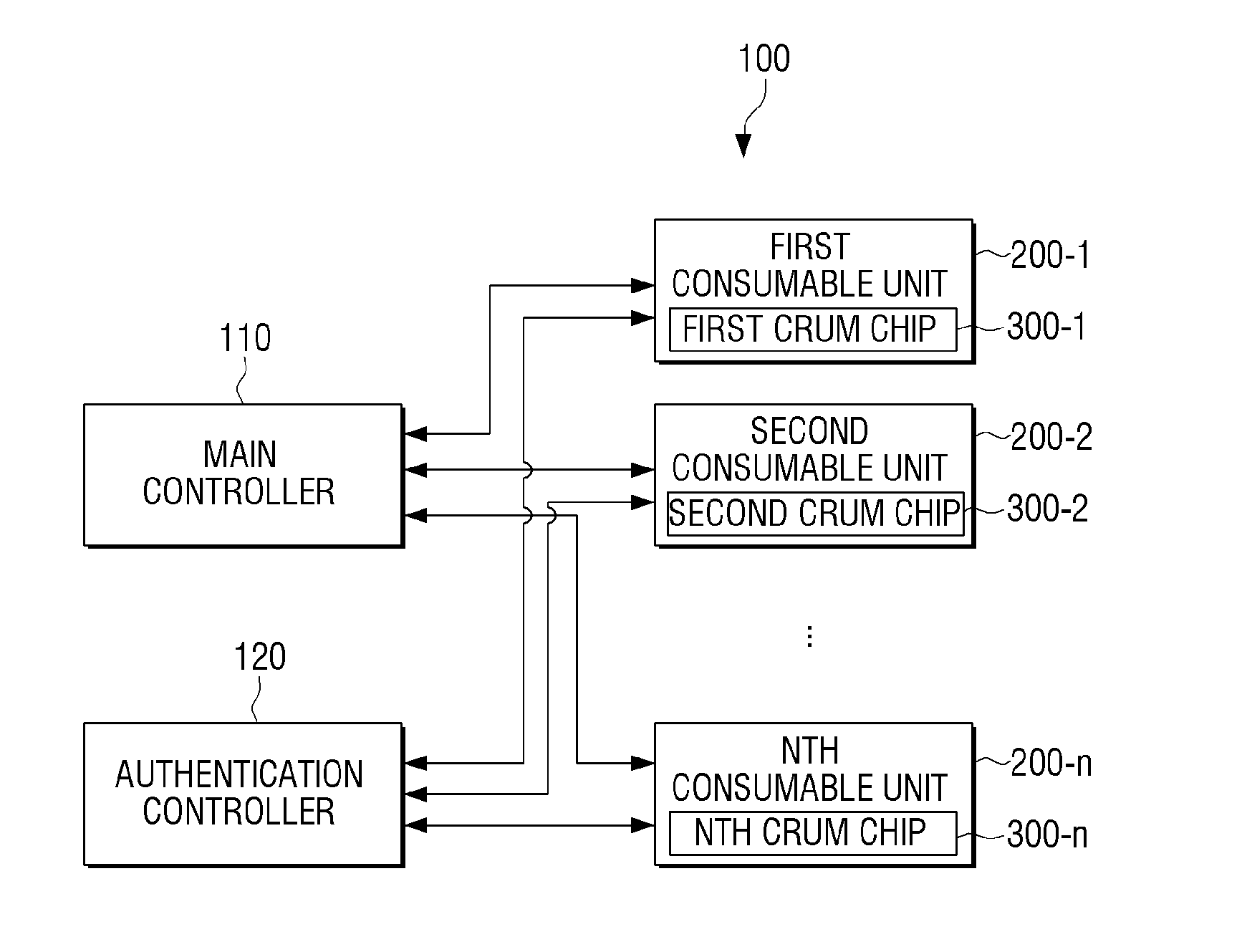
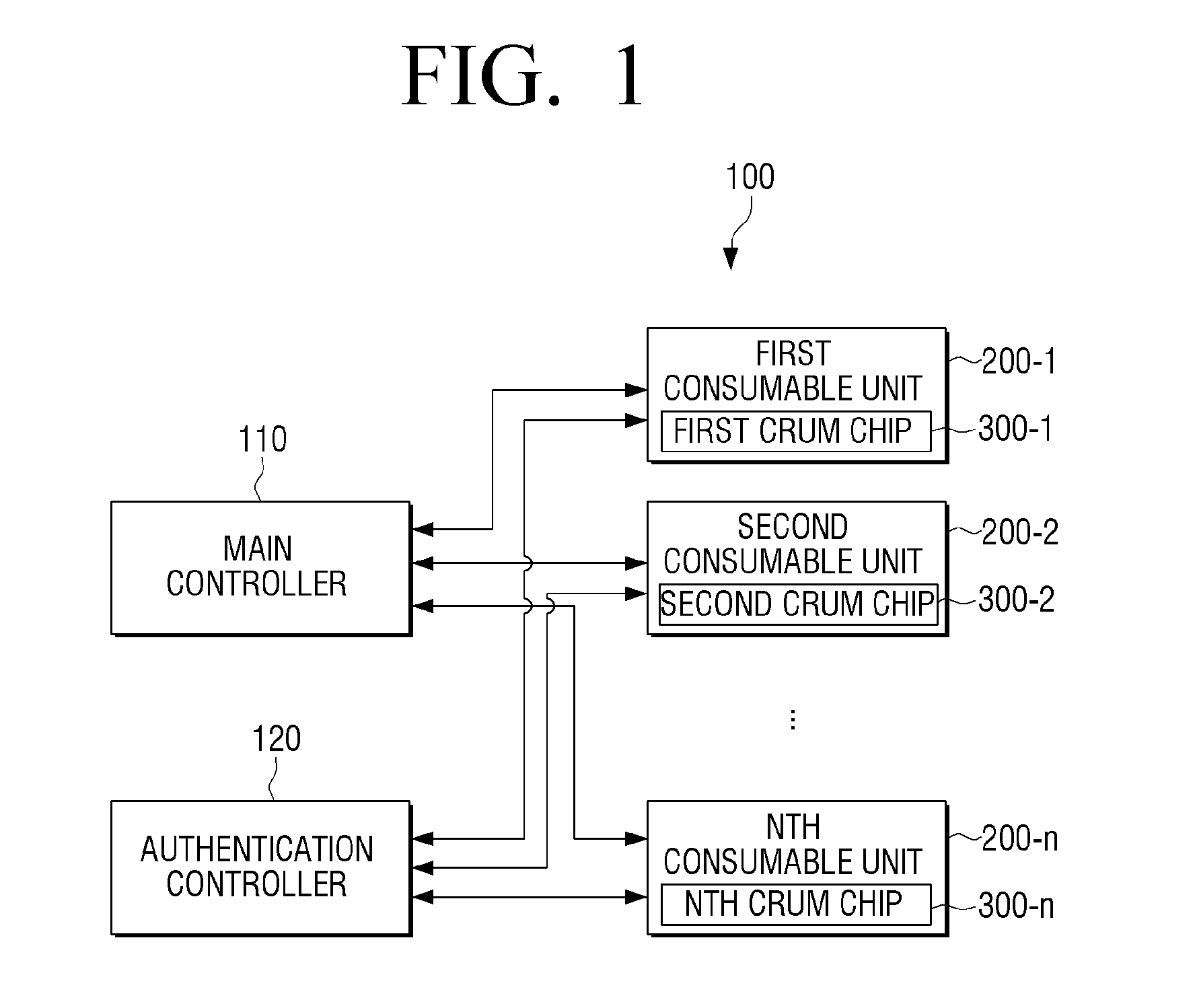
Crum chip mountable in comsumable unit, image forming apparatus for authentificating the crum chip, and method thereof
ActiveUS20150089630A1Efficient verificationImprove securityDigital data processing detailsUnauthorized memory use protectionApplication-specific integrated circuitIntegrated circuit
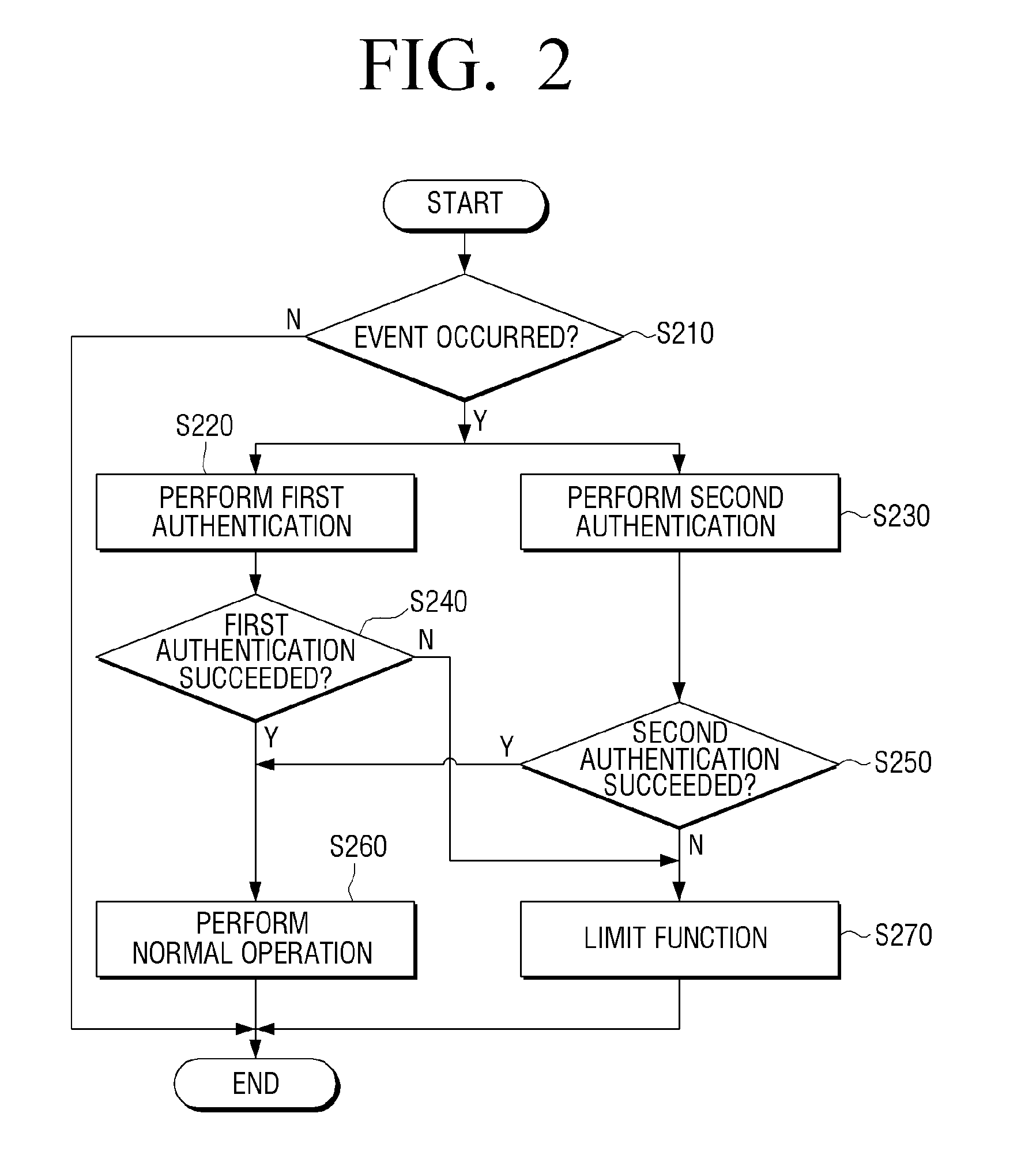
Provided herein is an image forming apparatus, comprising: a consumable unit where a CRUM (Customer Replaceable Unit Monitoring) chip is mounted; and a main body configured to perform at least one of a first authentication and a second authentication of the consumable unit, when the consumable unit is mounted, wherein the main body comprises: a main controller for performing the first authentication according to firmware stored in the image forming apparatus; and an authentication controller for using at least one ASIC (Application Specific Integrated Circuit) to perform the second authentication of the consumable unit. Accordingly, it is possible to effectively authenticate a consumable unit even when the image forming apparatus is hacked.
Owner:HEWLETT PACKARD DEV CO LP
System and method for verifying digital signatures on certificates
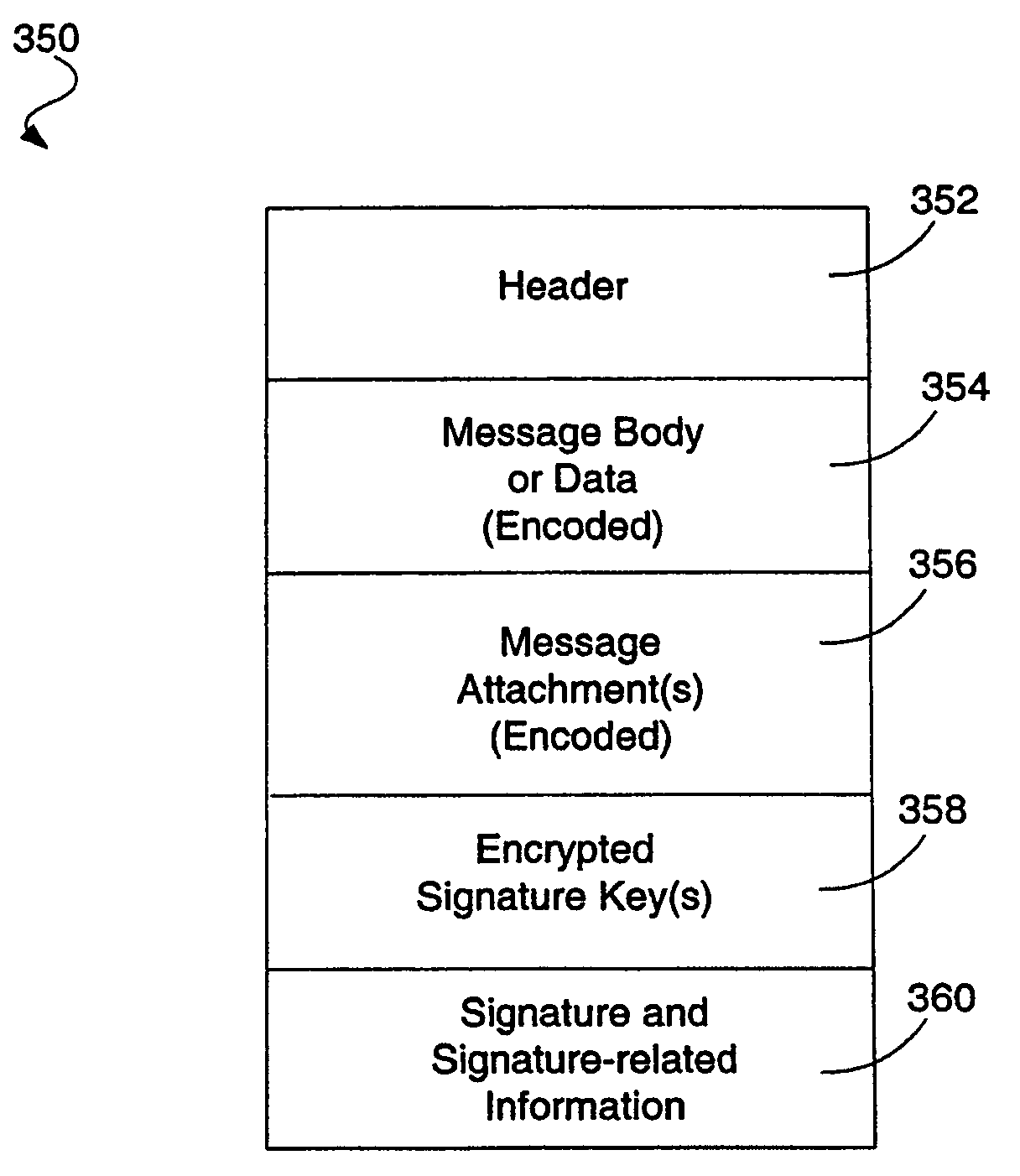
ActiveUS20060095388A1Efficient verificationCostly and time-consumeUser identity/authority verificationElectronic credentialsDigital signatureDigital signature forgery
A system and method for verifying a digital signature on a certificate, which may be used in the processing of encoded messages. In one embodiment, when a digital signature is successfully verified in a signature verification operation, the public key used to verify that digital signature is cached. When a subsequent attempt to verify the digital signature is made, the public key to be used to verify the digital signature is compared to the cached key. If the keys match, the digital signature can be successfully verified without requiring that a signature verification operation in which some data is decoded using the public key be performed.
Owner:MALIKIE INNOVATIONS LTD
Object-oriented method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols
ActiveUS7533333B2Low costEasy to analyzeData processing applicationsData switching networksThree levelInformation Harvesting
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. The event information for a particular target application is formatted and transmitted according to a combination of a data format and communication protocol requested by the target application. The formatting of data representing the event information is handled in at least three levels of software classes, with two levels of abstract classes and one concrete software class. The formatting of information to be transmitted through the requested communication protocol is handled in at least three levels of software classes, with one abstract class and two levels of concrete classes. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
Method and system of remote diagnostic, control and information collection using a dynamic linked library of multiple formats and multiple protocols with intelligent formatter
InactiveUS7287085B1Facilitate configuration and received data analysisReduce analysisMultiple digital computer combinationsTransmissionSoftware engineeringRemote diagnostics
A method, system and computer program product for (1) collecting information from a remote application unit and / or (2) diagnosing or controlling the remote application unit. By utilizing a shareable computer code device (e.g., a dynamic linked library), a new application can utilize tested, proven code without having to reproduce existing functionality. Moreover, by supporting multiple data formats and / or multiple communication protocols, a computer code device increases the likelihood that a supported format and / or protocol will be either receivable or understandable by a receiver.
Owner:RICOH KK
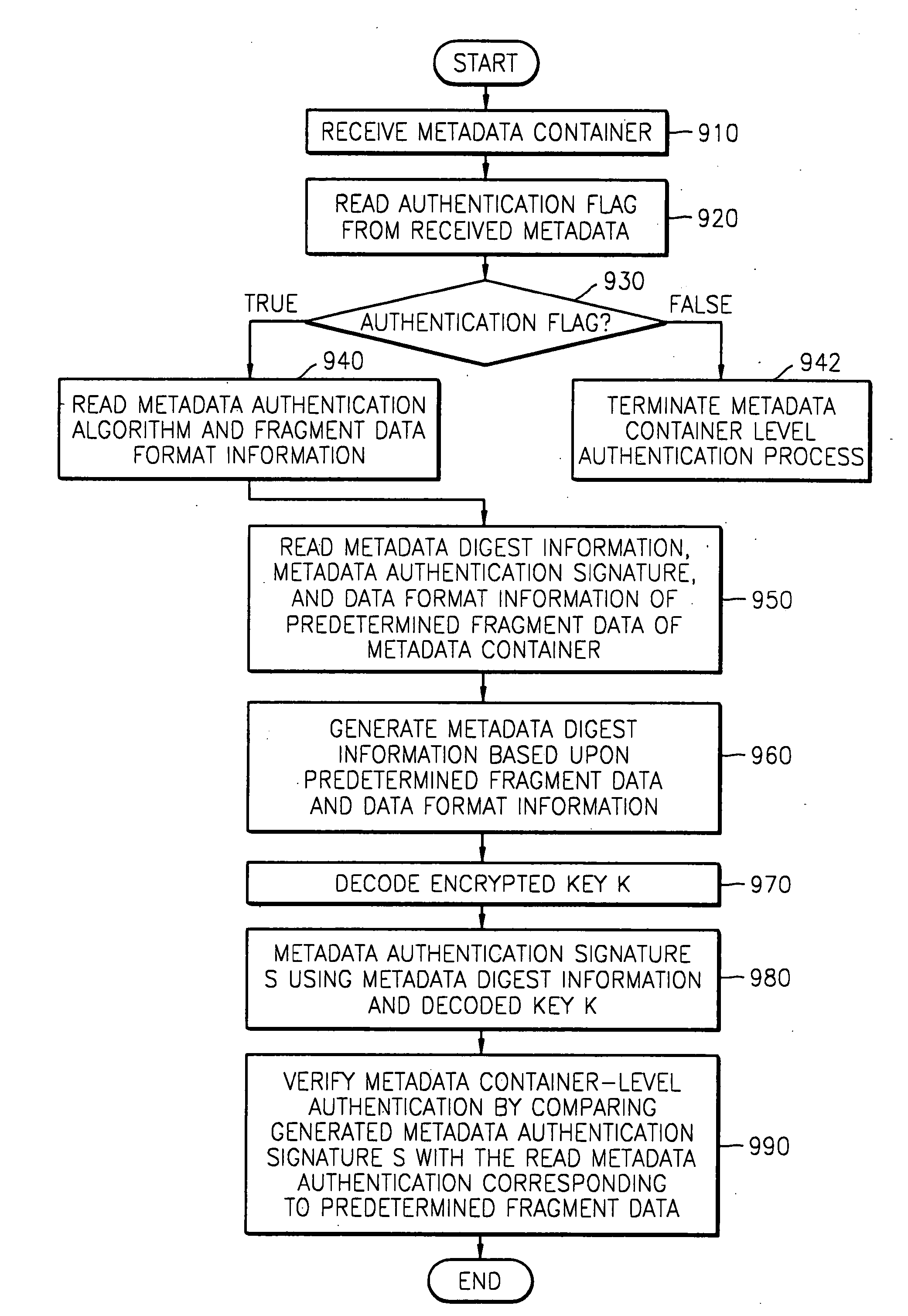
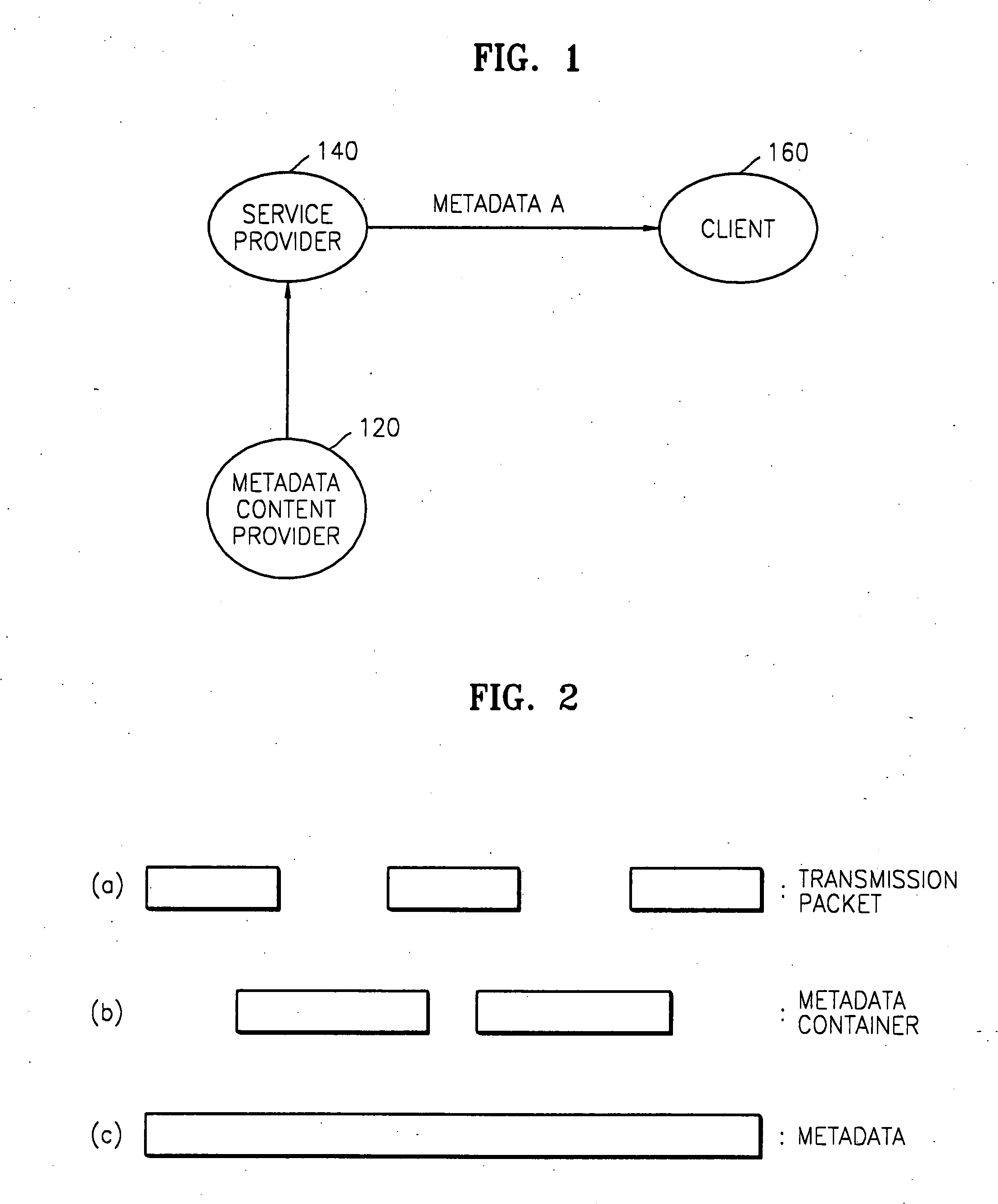
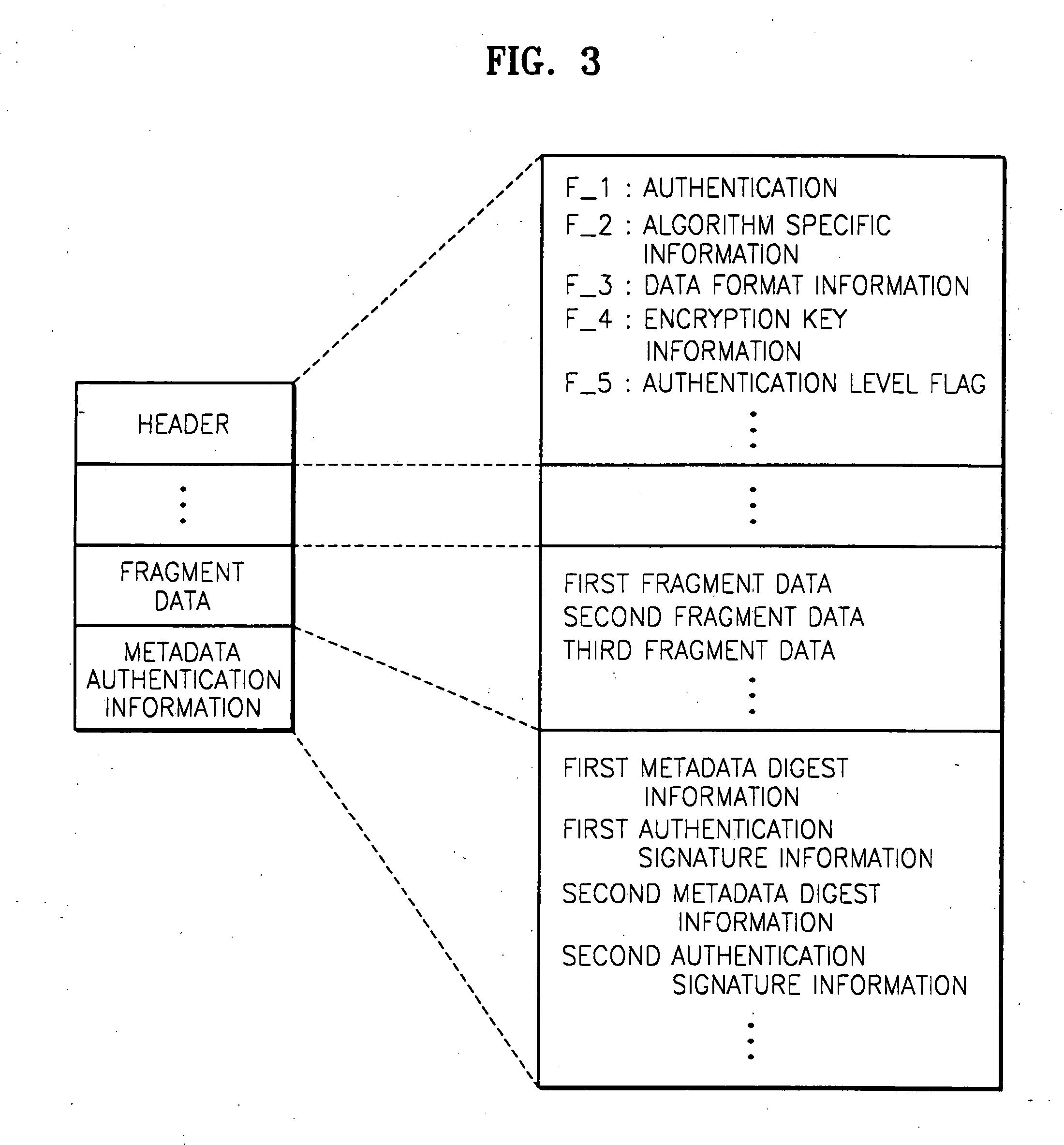
Method of managing metadata
InactiveUS20080072054A1Efficient verificationMultiple keys/algorithms usageDigital data processing detailsMetadata managementClient-side
Managing metadata in a metadata transmission server by generating a plurality of metadata fragment data by partitioning metadata to be transmitted based upon predetermined segment units, selecting predetermined metadata fragment data from among the plurality of the metadata fragment data, generating metadata-related authentication information using the selected metadata fragment data, and transmitting the selected metadata fragment data and the metadata-related authentication information including data format information indicating type of the selected metadata fragment data. A metadata receiving client uses the transmitted metadata fragment data, the metadata-related authentication information and the metadata format type information to authenticate the received metadata.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols with delegating protocol processor
ActiveUS20060164683A1Easy to analyzeEasy to configureDigitally marking record carriersError detection/correctionProtocol processingSystems approaches
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. The event information for a particular target application is formatted and transmitted according to a combination of a data format and communication protocol requested by the target application. The transmission of data representing the event information is handled in at least two levels of software classes, with at least one abstract software class having a declared virtual function and two or more software classes derived from the at least one abstract class and having definitions of the function for communicating the event information through specified communication protocols. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
Method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols with verification of formats and protocols
InactiveUS7171670B2Low costEasy to analyzeHardware monitoringMultiprogramming arrangementsReliable transmissionNetwork Communication Protocols
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. A combination of a data format and communication protocol requested by a target application is verified for validity. If the requested combination is invalid, a valid combination is substituted for more reliable transmission. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
Nonvolatile memory device and method of operating the same
ActiveUS20150270010A1Easy to operateReduce overheadRead-only memoriesDigital storageNon-volatile memoryData entry
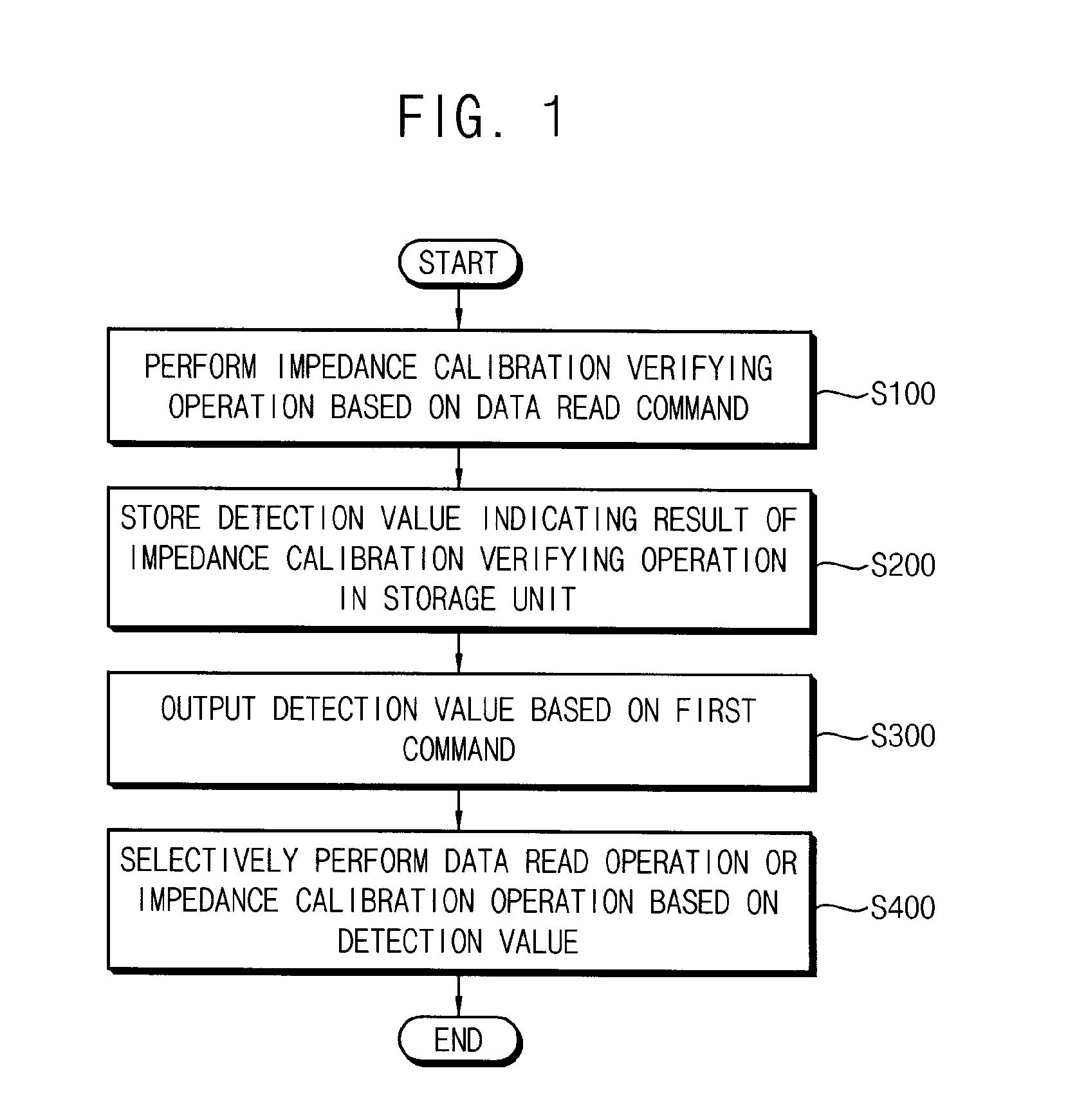
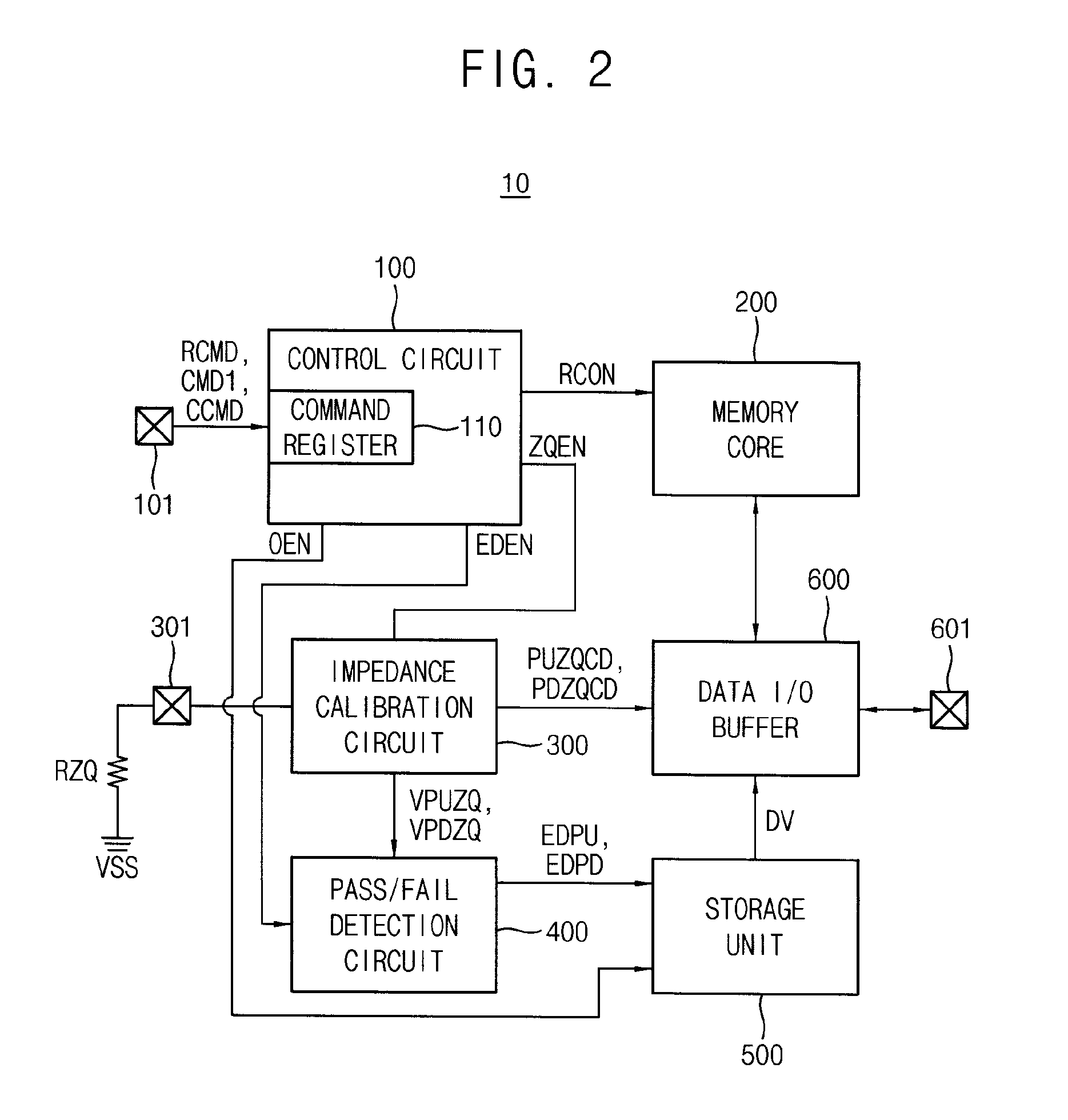
In a method of operating a nonvolatile memory device, an impedance calibration verifying operation is performed based on a data read command. The impedance calibration verifying operation ascertains whether an impedance calibration operation is normally performed for a data input / output (I / O) terminal of the nonvolatile memory device. A detection value is stored in a storage unit. The detection value indicates a result of the impedance calibration verifying operation. The detection value is output based on a first command received after the nonvolatile memory device receives the data read command. A data read operation or the impedance calibration operation is selectively performed based on the detection value.
Owner:SAMSUNG ELECTRONICS CO LTD
Multi-stage system for verification of container contents
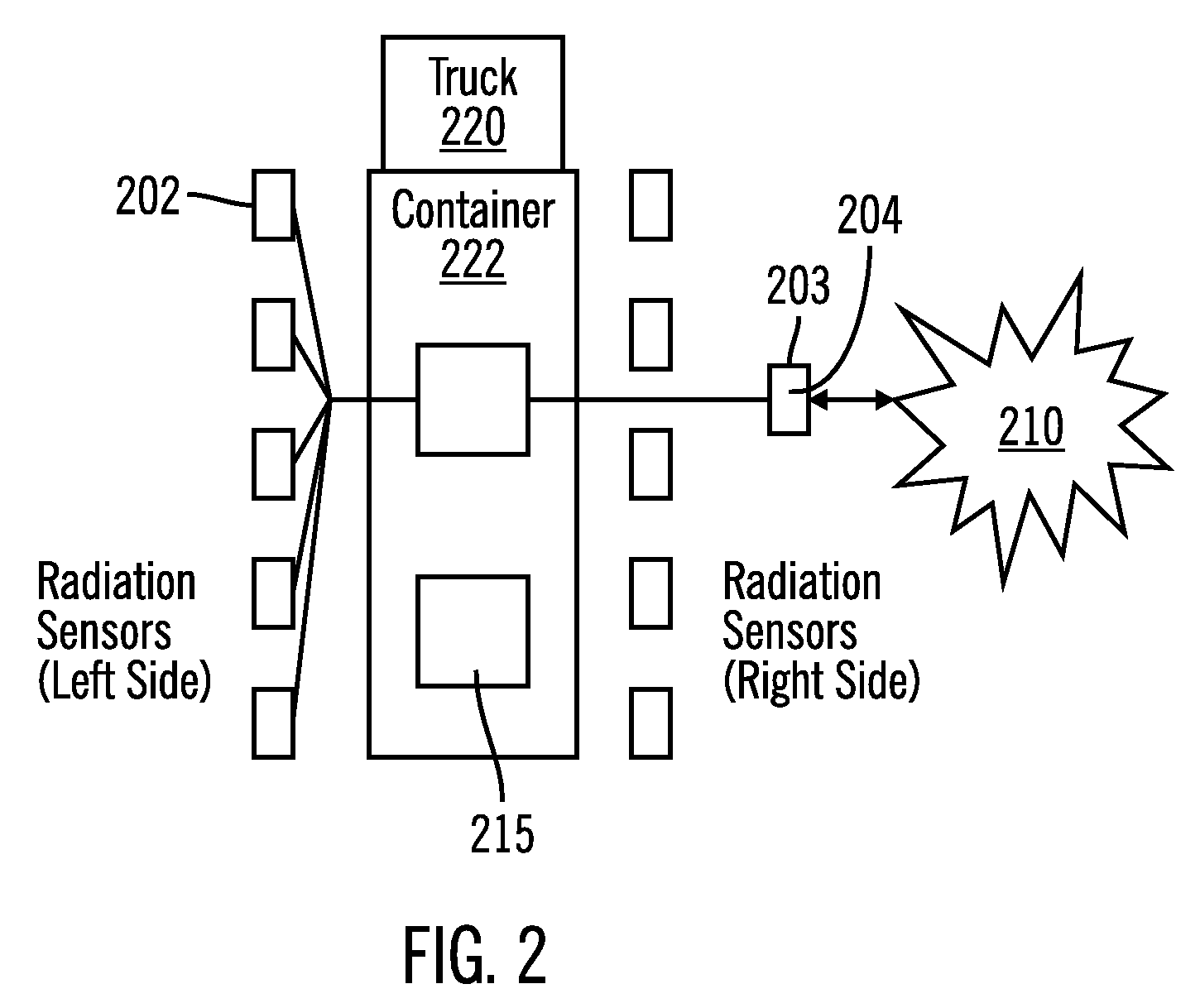
InactiveUS7760103B2Further analysisWithout negative impact to the flow of commerceMeasurement with semiconductor devicesMaterial analysis by optical meansNeutron pulseIsotope
A multi-stage process utilizing one or more radiation sensors on a distributed network for the detection and identification of radiation, explosives, and special materials within a shipping container. The sensors are configured as nodes on the network. The system collects radiation data from one or more nodes and compares the collected data to one or more stored spectral images representing one or more isotopes to identify one or more isotopes present. The identified one or more isotopes present are corresponded to possible materials or goods that they represent. The possible materials or goods are compared with the manifest relating to the container to confirm the identity of materials or goods contained in the container or to detect and / or identify unauthorized materials or goods in the container. For shielded materials, explosives and other types of material detection, a neutron pulse device could be incorporated into the system.
Owner:S2 PHOTONICS LLC +1
Method and system of remote diagnostic, control and information collection using a dynamic linked library of multiple formats and multiple protocols with restriction on protocol
InactiveUS20060031538A1Facilitate configuration and received data analysisReduce analysisMultiple digital computer combinationsTransmissionData formatRemote diagnostics
A method, system and computer program product for (1) collecting information from a remote application unit and / or (2) diagnosing or controlling the remote application unit. By utilizing a shareable computer code device (e.g., a dynamic linked library), a new application can utilize tested, proven code without having to reproduce existing functionality. Moreover, by supporting multiple data formats and / or multiple communication protocols, a computer code device increases the likelihood that a supported format and / or protocol will be either receivable or understandable by a receiver.
Owner:RICOH KK
Real-time local and global SAR estimation for patient safety and improved scanning performance
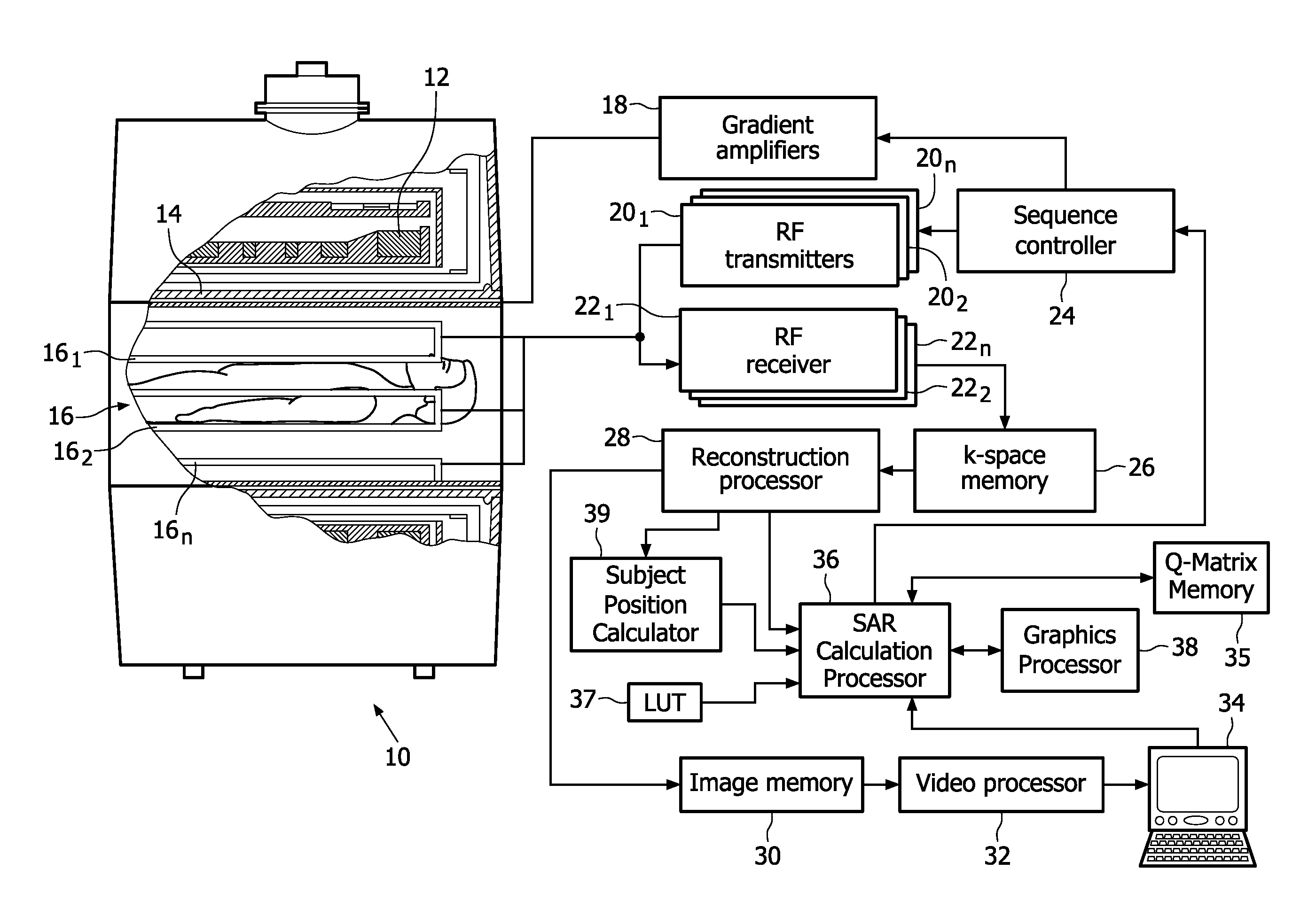
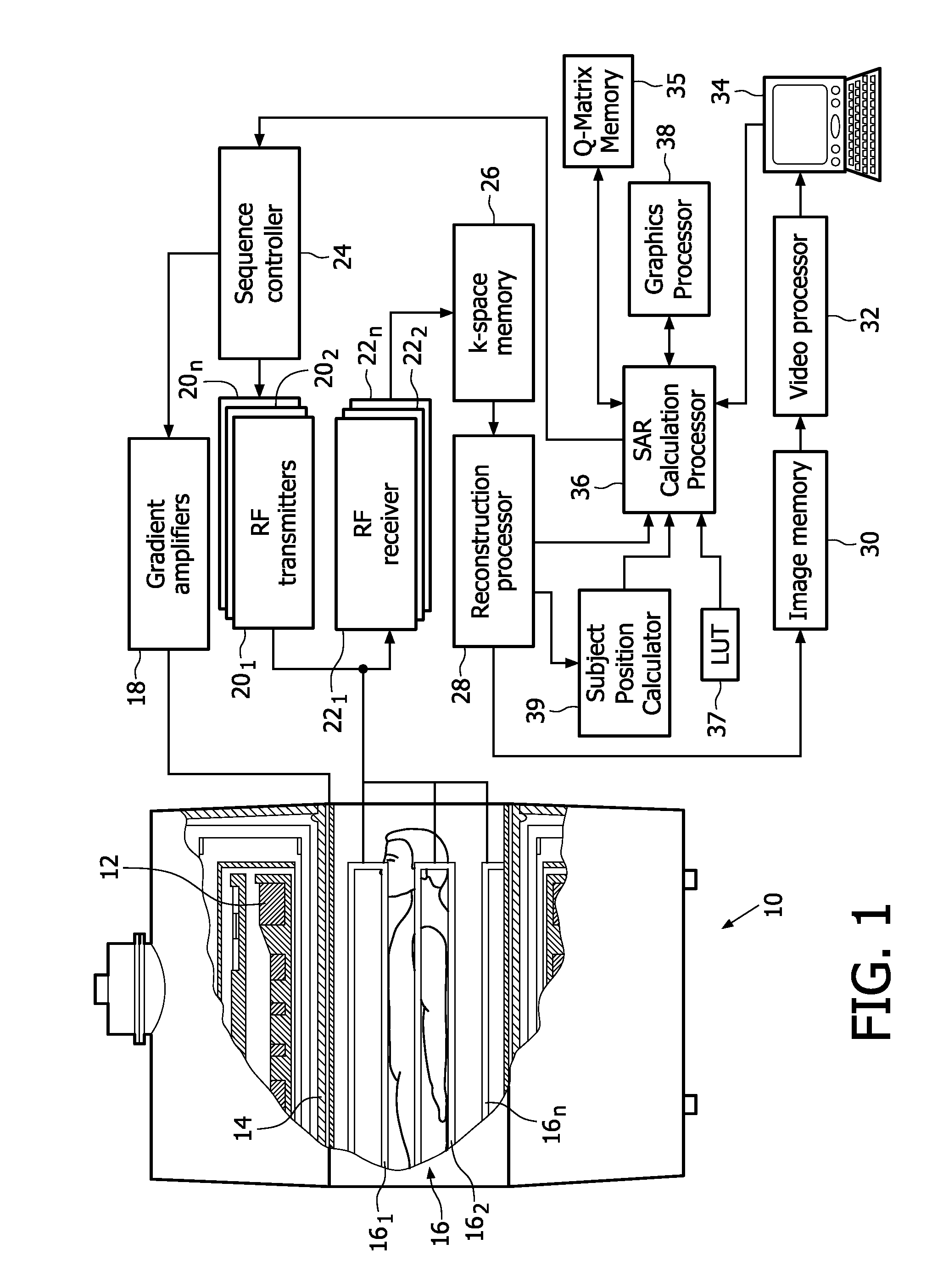
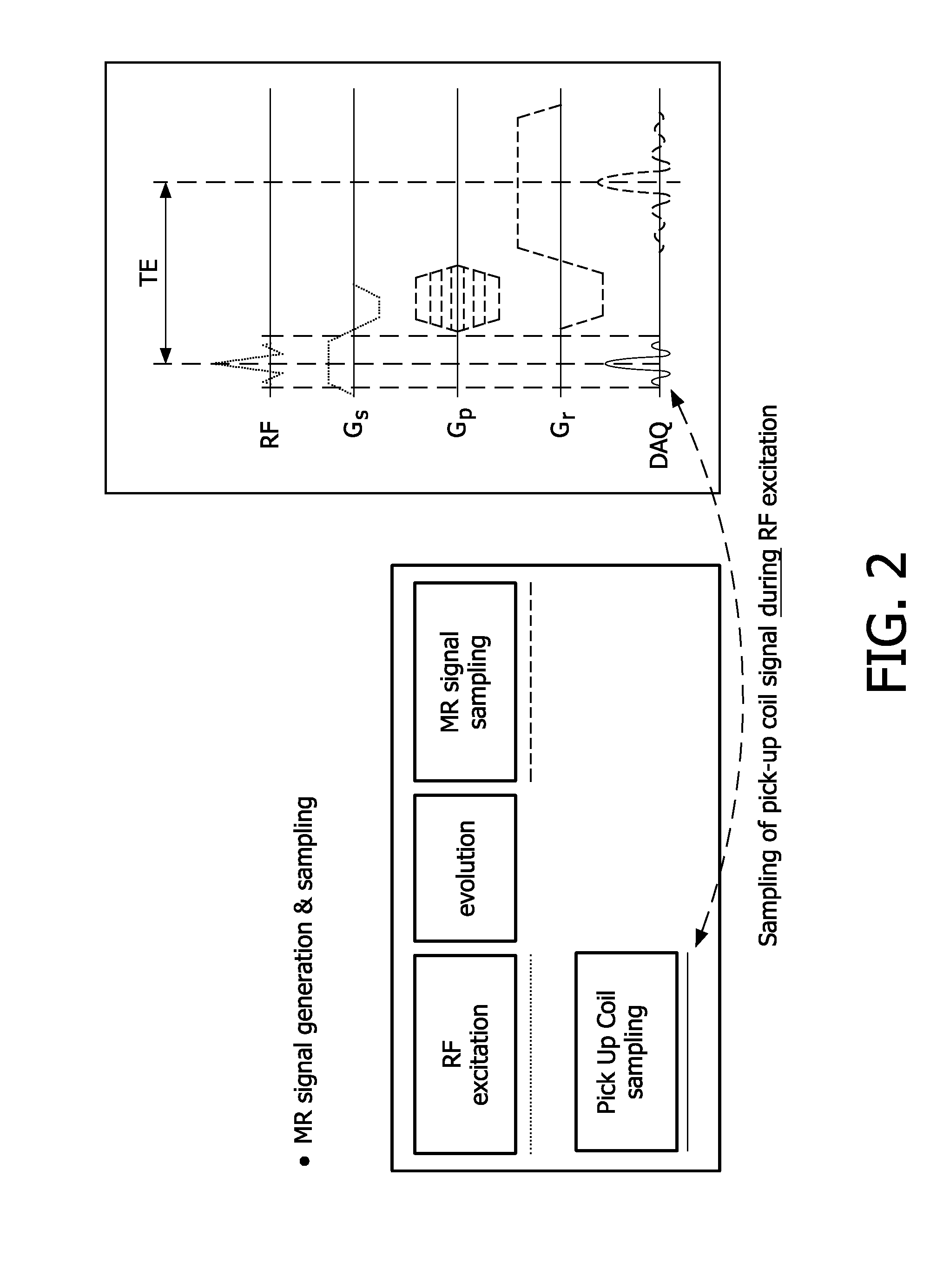
ActiveUS20110043205A1Efficient verificationCalculation speed be increaseElectric/magnetic detectionMeasurements using NMRElectric fieldPatient specific
In a method and apparatus to enable increased RF duty cycle in high field MR scans, a specific energy absorption rate (SAR) calculation processor (36) calculates the local and global SAR or even a spatial SAR map. The efficient implementation by using pre-averaged data (based on E-fields) makes a fast and accurate SAR estimation possible. By incorporating additional information as e.g. patient position the SAR calculation accuracy can be increased as well as by using more patient specific precalculated information (e.g. based on different bio meshes), the so called Q-matrices. Optionally, a sequence controller (24) creates a global SAR optimal RF pulse. After the optimal RF pulse is applied, the SAR and its spatial distribution are determined. SAR hotspots are also determined. Q-matrices within an appropriate radius around the hotspots are averaged and added to a global Q-matrix in a weighted fashion. After the global Q-matrix is updated, a new optimal RF pulse is created. One or more of the steps can be repeated to converge the SAR to a minimum.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Secure processing of an authorization verification request
ActiveUS20190199535A1Favorably carry-outEfficient executionKey distribution for secure communicationDigital data information retrievalAuthorizationData structure
Provided is a method for secure processing of an authorization verification request front a unit requesting authorization verification, the authorization verification request being included in a transaction of a block chain, wherein a registration entity performs a check on a block chain data structure and on the transaction protected by the block chain and, in the event of a successful check, forwards the authorization verification request to a certification entity. The authorization verification request is included in a transaction and the registration entity performs a check on a block chain data structure and on the transaction. The transaction and the authorization verification request are protected by the block chain. In particular, the authorization verification request can no longer be altered retrospectively and information that has been transmitted to the registration entity within the context of the authorization verification request is stored in the block chain and protected against manipulation.
Owner:SIEMENS AG
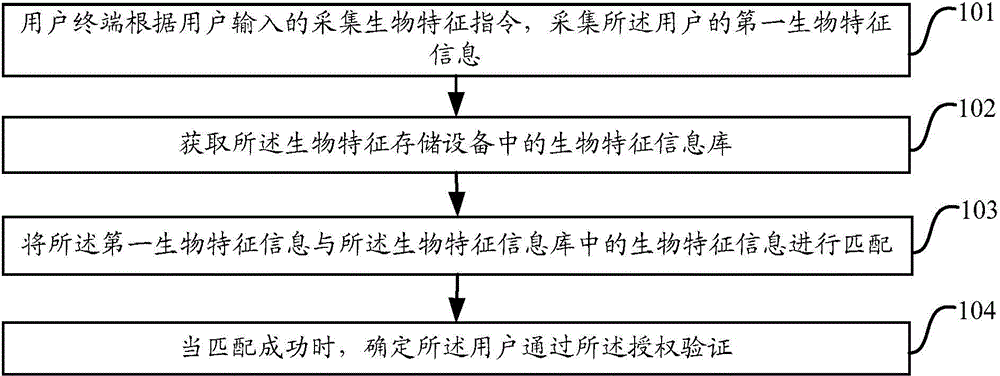
Method for verifying authorization on basis of biological recognition
InactiveCN104462922AEfficient verificationDigital data authenticationInformation repositoryUser input
The invention provides a method for verifying authorization on the basis of biological recognition. The method includes acquiring first biological characteristic information of users according to biological characteristic acquisition instructions inputted by the users; acquiring biological characteristic information bases in biological characteristic storage equipment; matching the first biological characteristic information with biological characteristic information in the biological characteristic information bases; determining that the users pass authorization verification if the first biological characteristic information is successfully matched with the biological characteristic information in the biological characteristic information bases. At least one piece of biological characteristic information is preliminarily stored in each biological characteristic information base. The method has the advantages that characteristic images of biological information of the users are stored in the biological characteristic storage equipment by the aid of biological recognition, and accordingly the users and documents can be efficiently verified, can be verified in an offline manner and can be automatically verified.
Owner:HIERSTAR SUZHOU
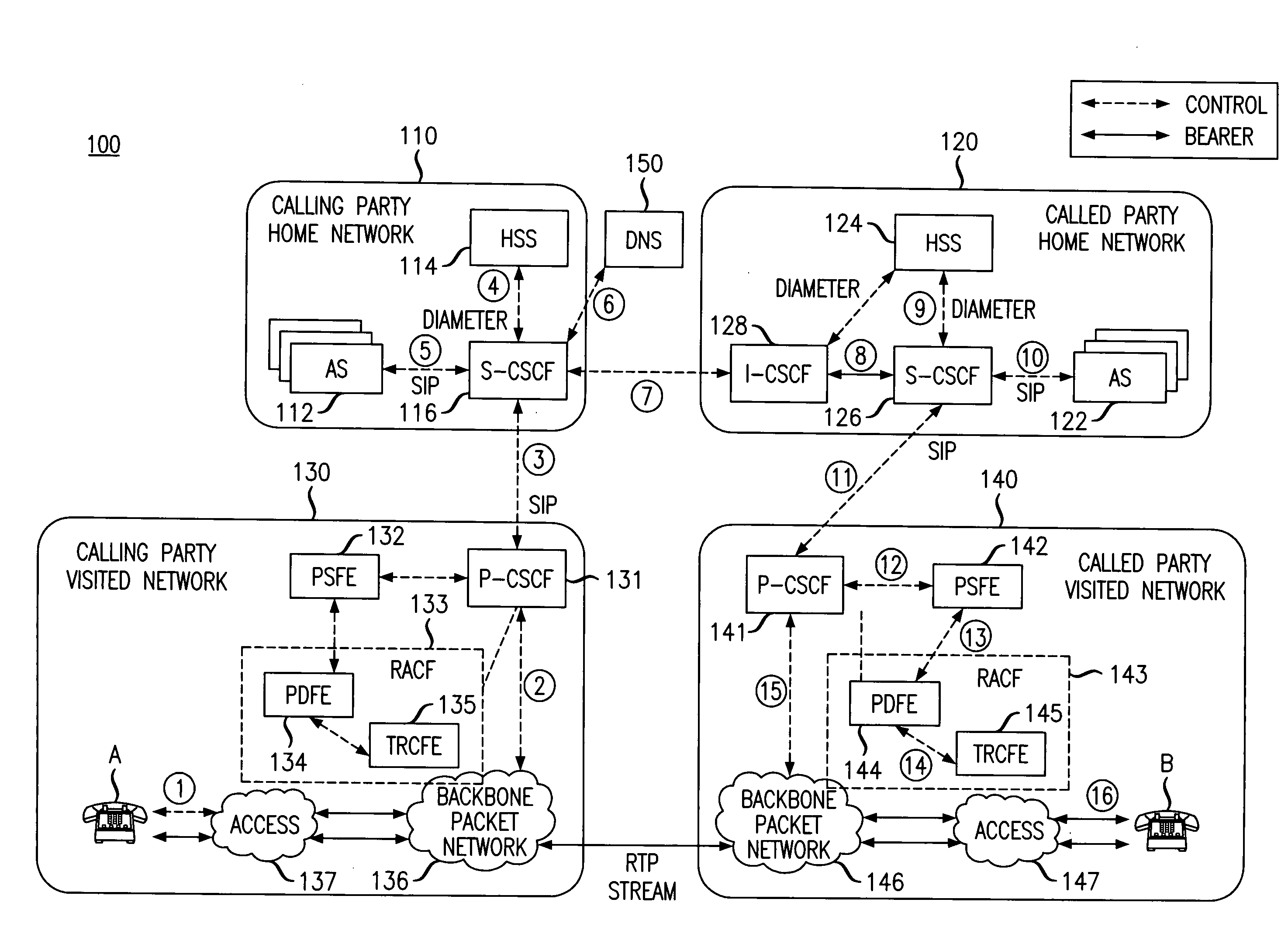
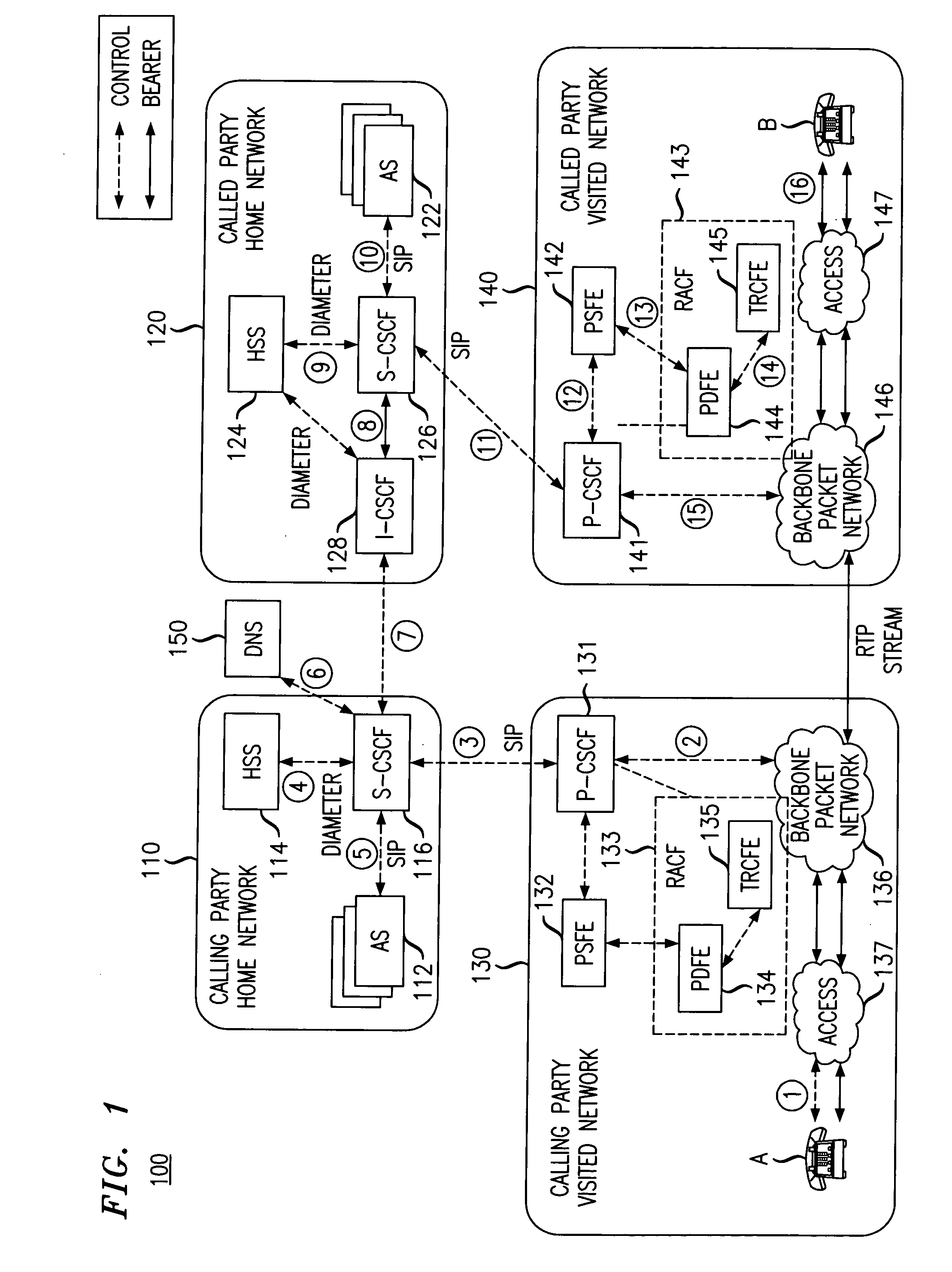
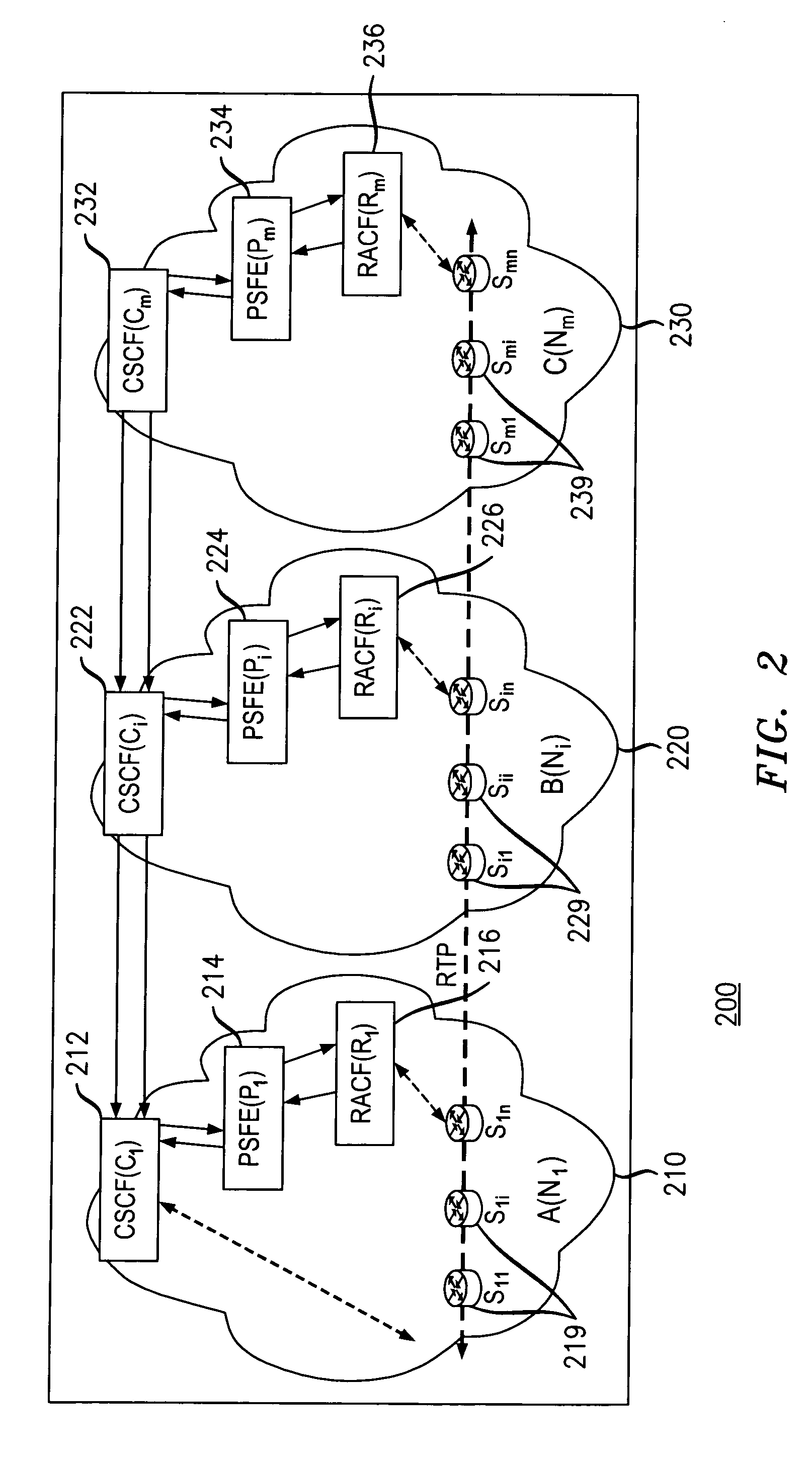
Network call back to add conference participants and/or media capabilities
ActiveUS20100034367A1Efficiently establishedEfficient allocationSpecial service for subscribersData switching networksStreaming dataComputer science
An exemplary method includes receiving at a calling party network a notice of an intended communication between a calling endpoint and a plurality of called endpoints located in a plurality of called party networks, wherein the intended communication requires a resource in each of the calling party network and the called party networks for supporting a streaming data protocol. The notice is forwarded toward the plurality of called party networks and in parallel with said forwarding, a determination of resource availability for the calling party network is initiated for the intended communication. The method further includes determining for the intended communication the determination of resource availability for the calling party network, wherein the determination is for a first resource for the first network; and verifying resource availability for the intended communication based on the determination for the calling party network and a resource availability indicator for each called party network.
Owner:PROVENANCE ASSET GRP LLC
Electronic device and method for verifying correct program execution
ActiveUS20110041013A1Fine granularityConsume additional data processing timeFunctional testingReal errorProgram code
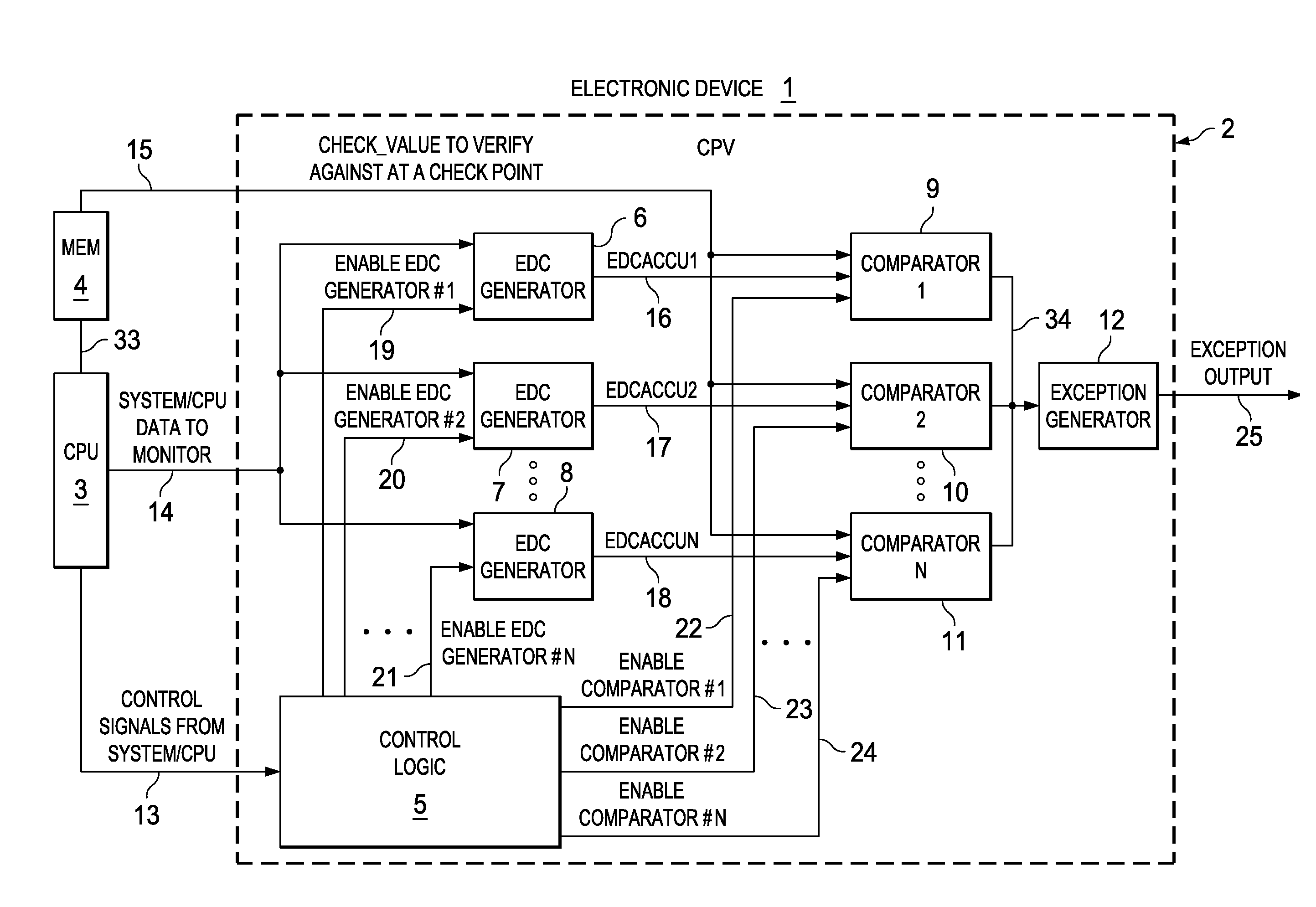
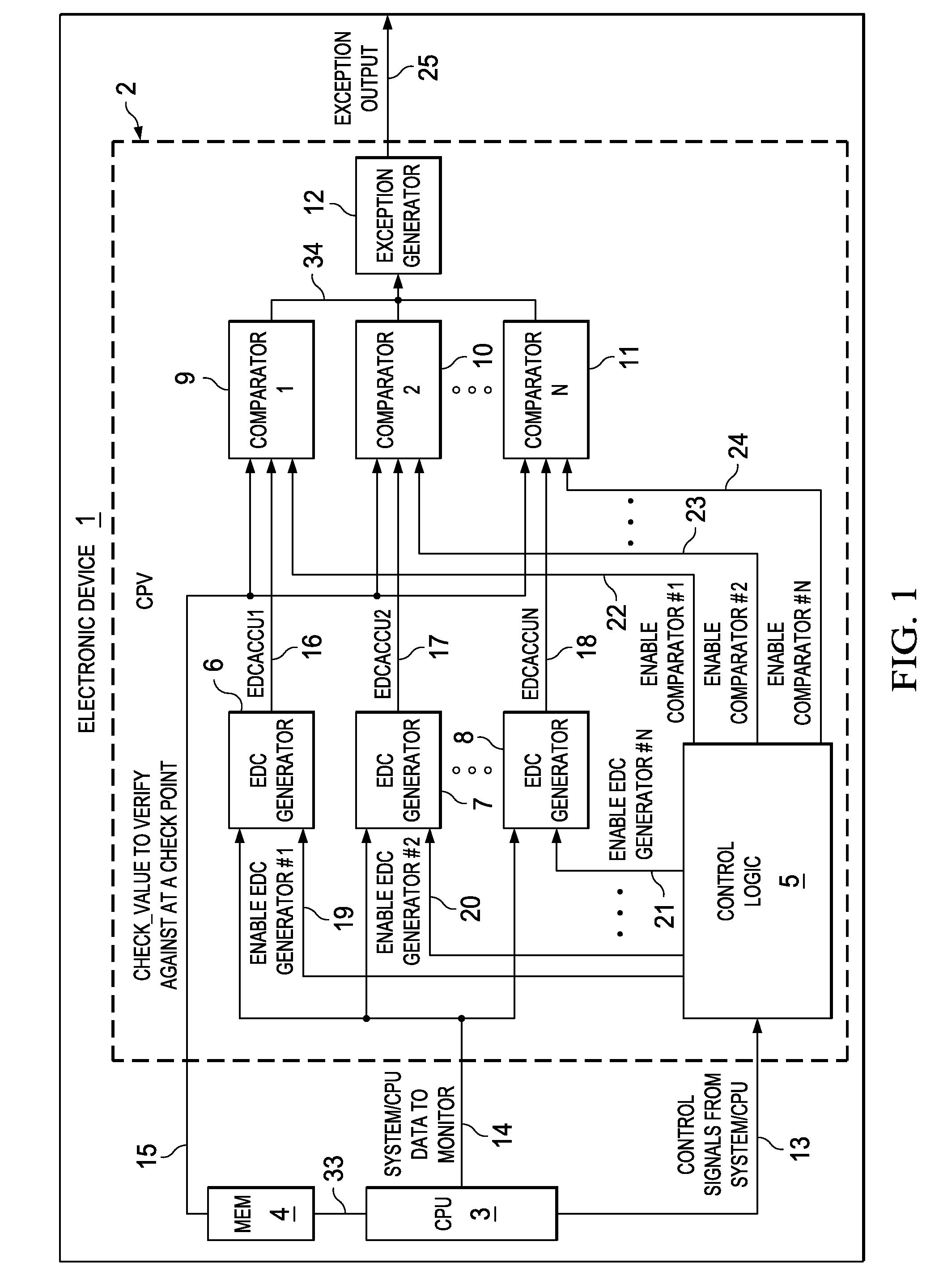
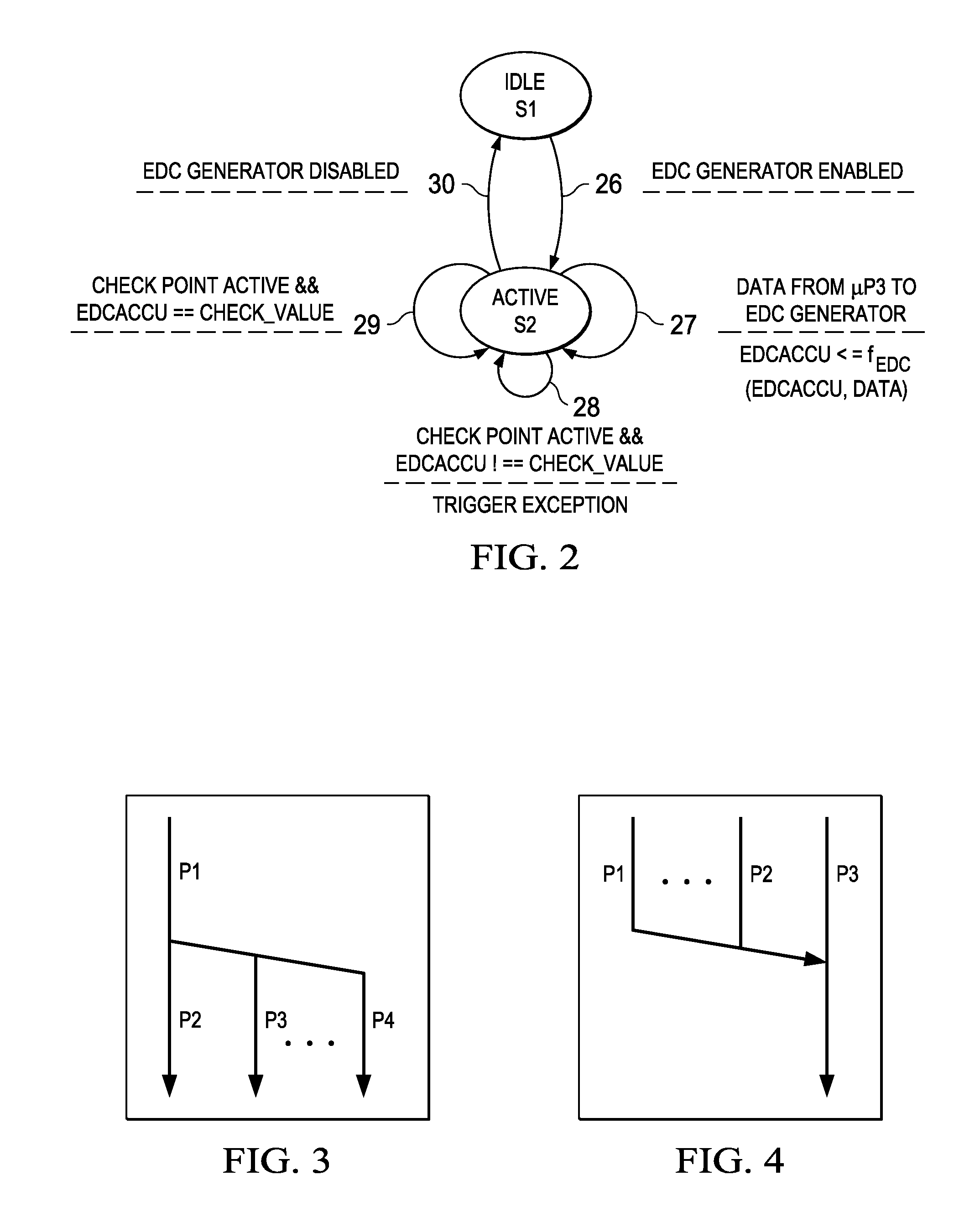
An electronic device is provided which comprises a microprocessor for executing a program code and a first hardware code path verifying (CPV) stage coupled to the microprocessor. The hardware CPV stage comprises a first error detection code (EDC) generator configured to continuously determine an error detection code on a continuous sequence of code relating to an actually executed portion of the program code and to compare the actual error detection code with a predetermined error code so as to verify correct execution of the program code and to indicate an error.
Owner:TEXAS INSTR INC
Method and system of remote diagnostic, control and information collection using a dynamic linked library of multiple formats and multiple protocols with intelligent protocol processor
InactiveUS7120674B1Facilitate configuration and received data analysisReduce analysisMultiple digital computer combinationsData switching networksProtocol processingApplication software
A method, system and computer program product for (1) collecting information from a remote application unit and / or (2) diagnosing or controlling the remote application unit. By supporting dynamic generation of multiple data formats and / or multiple communication protocols, a computer code device increases the likelihood that a supported format and / or protocol will be either receivable or understandable by a receiver without having to pre-generate the protocol or format processor. By utilizing a shareable computer code device (e.g., a dynamic linked library), a new application can utilize tested, proven code without having to reproduce existing functionality.
Owner:RICOH KK
Ethernet passive optical network ring and its method of authorization and collision detection
InactiveUS20050088964A1Reduce collisionCollision detectionLaser detailsError preventionFiberCollision detection
An Ethernet passive optical network (EPON) ring for providing protection against fiber failures. The optical network unit (ONU) is coupled to the ring fiber by a three-port passive optical splitting module that has three two-way optical passages. By the three two-way optical passages, the OUN receives / transmits data from / to the two ends of the optical line termination (OLT) to provide protection while the fiber failure. Moreover, it provides better authorization of users and simpler collision detection by the two-way transmission of the three-port passive optical splitting module to prevent hackers from invading and to reduce collisions.
Owner:IND TECH RES INST
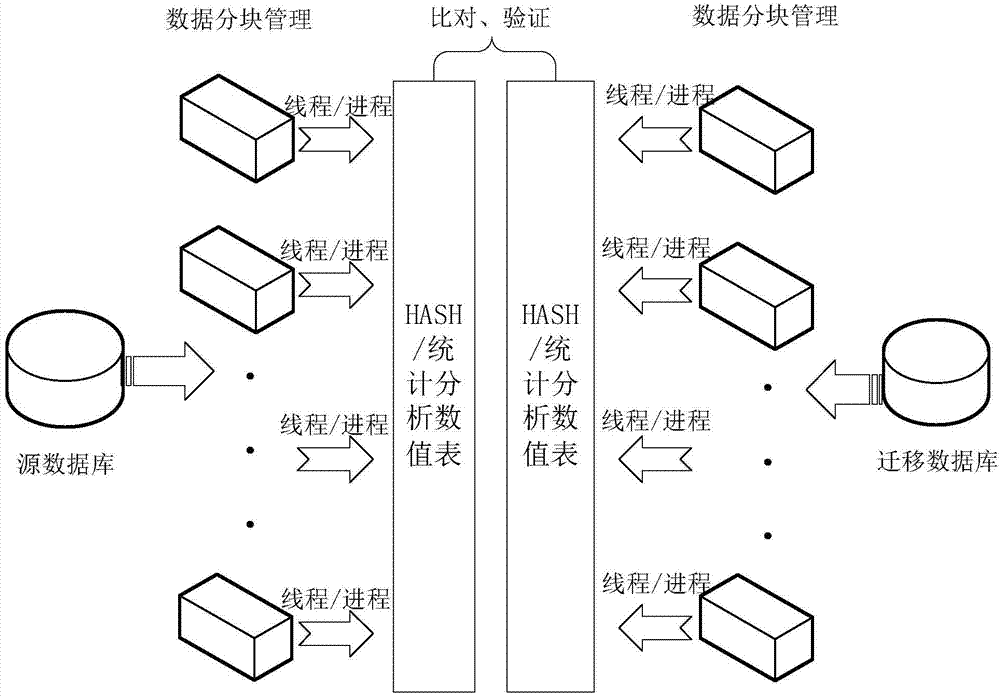
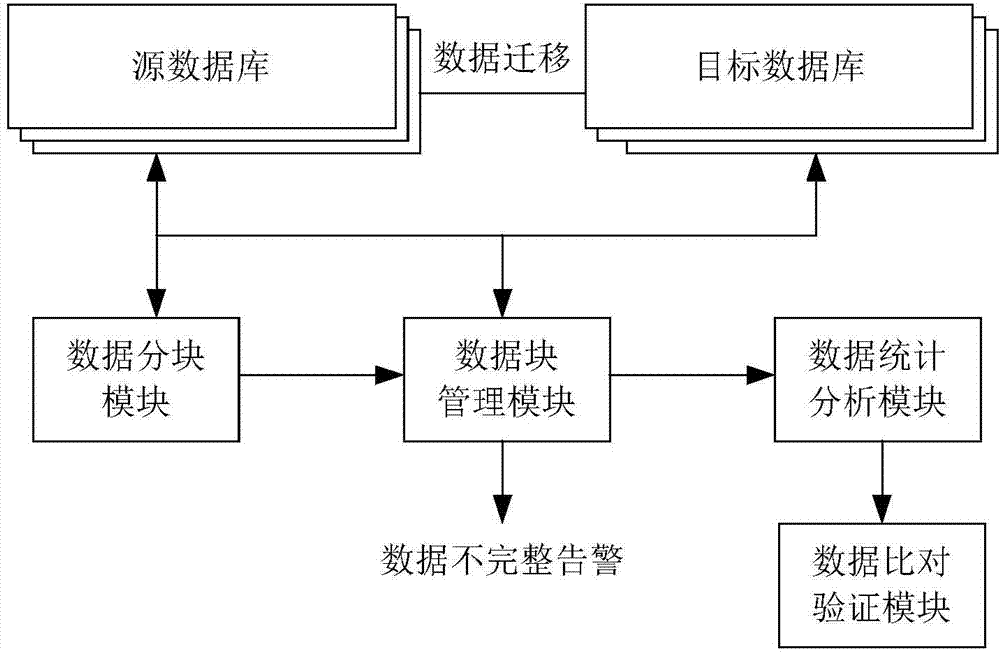
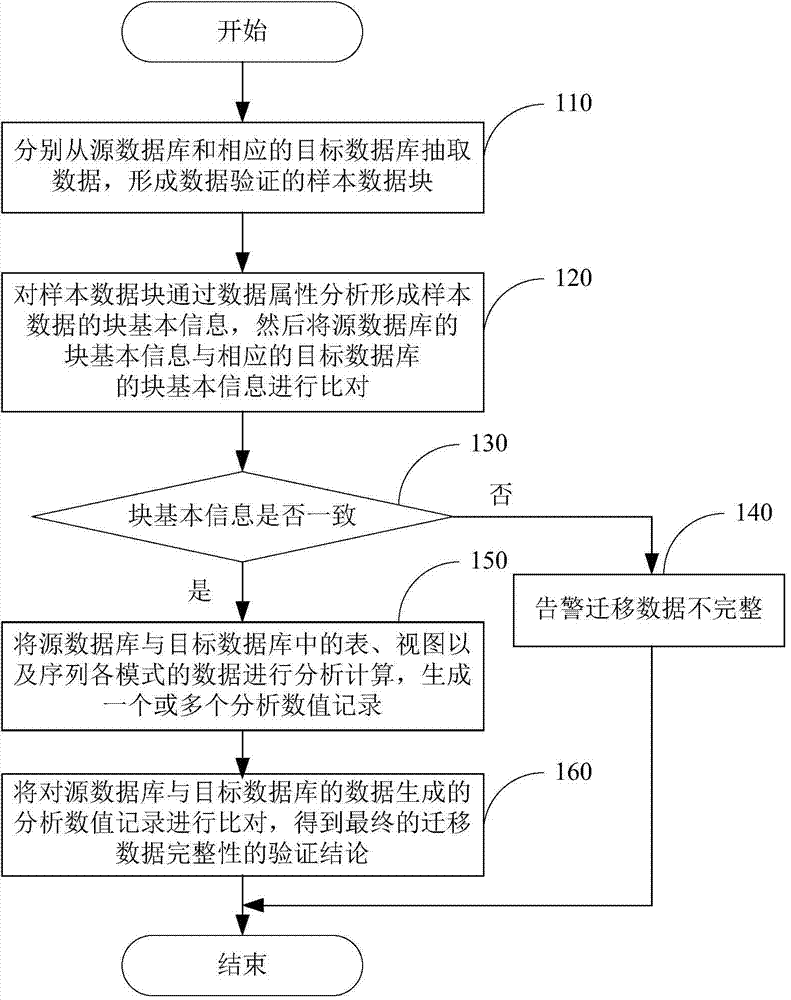
Database migration data verification method and system
ActiveCN104504122AReduce loadEfficient verificationSpecial data processing applicationsData integritySource Data Verification
The invention discloses a database migration data verification method and system. The system comprises various source databases and target databases. The method comprises that a data segmentation module extracts data from the source databases and the corresponding target databases to form sample data blocks of data verification. A data block management module performs data attributive analysis on the sample data blocks to form sample data block basic information and compares the block basic information of the source databases with corresponding target database basic information to obtain the conclusion of the integrity of migration data. By means of the method and the system, the block basic information obtained through sample extraction by the source databases and the target databases is compared to verify the database migration data, and accordingly, the loads of former comparison of a large number of data are reduced greatly.
Method and system of remote diagnostic control and information collection using a dynamic linked library of multiple formats and multiple protocols
InactiveUS20060168103A1Facilitate configuration and received data analysisReduce analysisTelemetry/telecontrol selection arrangementsTelephonic communicationData formatRemote diagnostics
A method, system and computer program product for (1) collecting information from a remote application unit and / or (2) diagnosing or controlling the remote application unit. By utilizing a shareable computer code device (e.g., a dynamic linked library), a new application can utilize tested, proven code without having to reproduce existing functionality. Moreover, by supporting multiple data formats and / or multiple communication protocols, a computer code device increases the likelihood that a supported format and / or protocol will be either receivable or understandable by a receiver.
Owner:RICOH KK
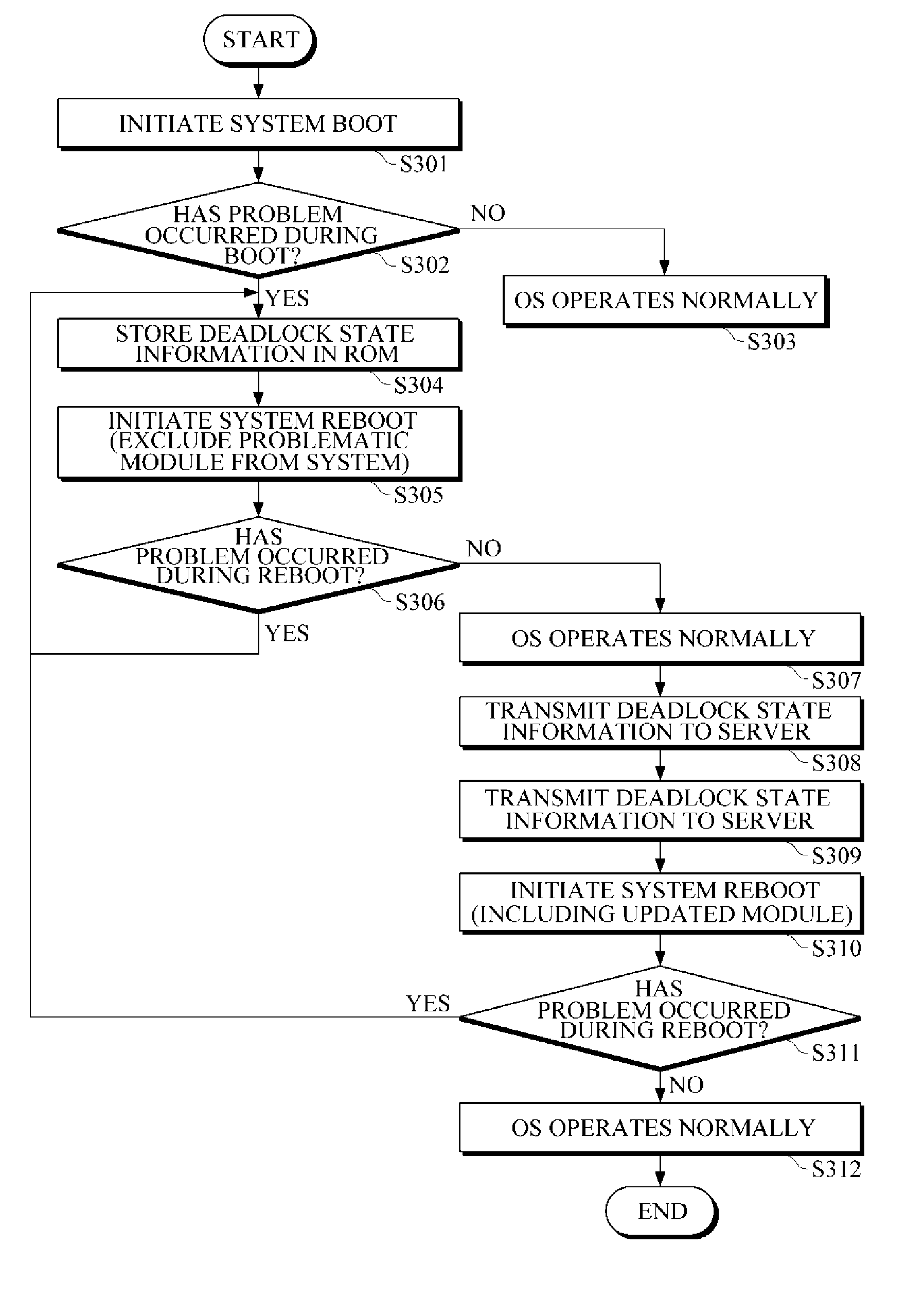
Apparatus and method for handling rebooting of mobile terminal
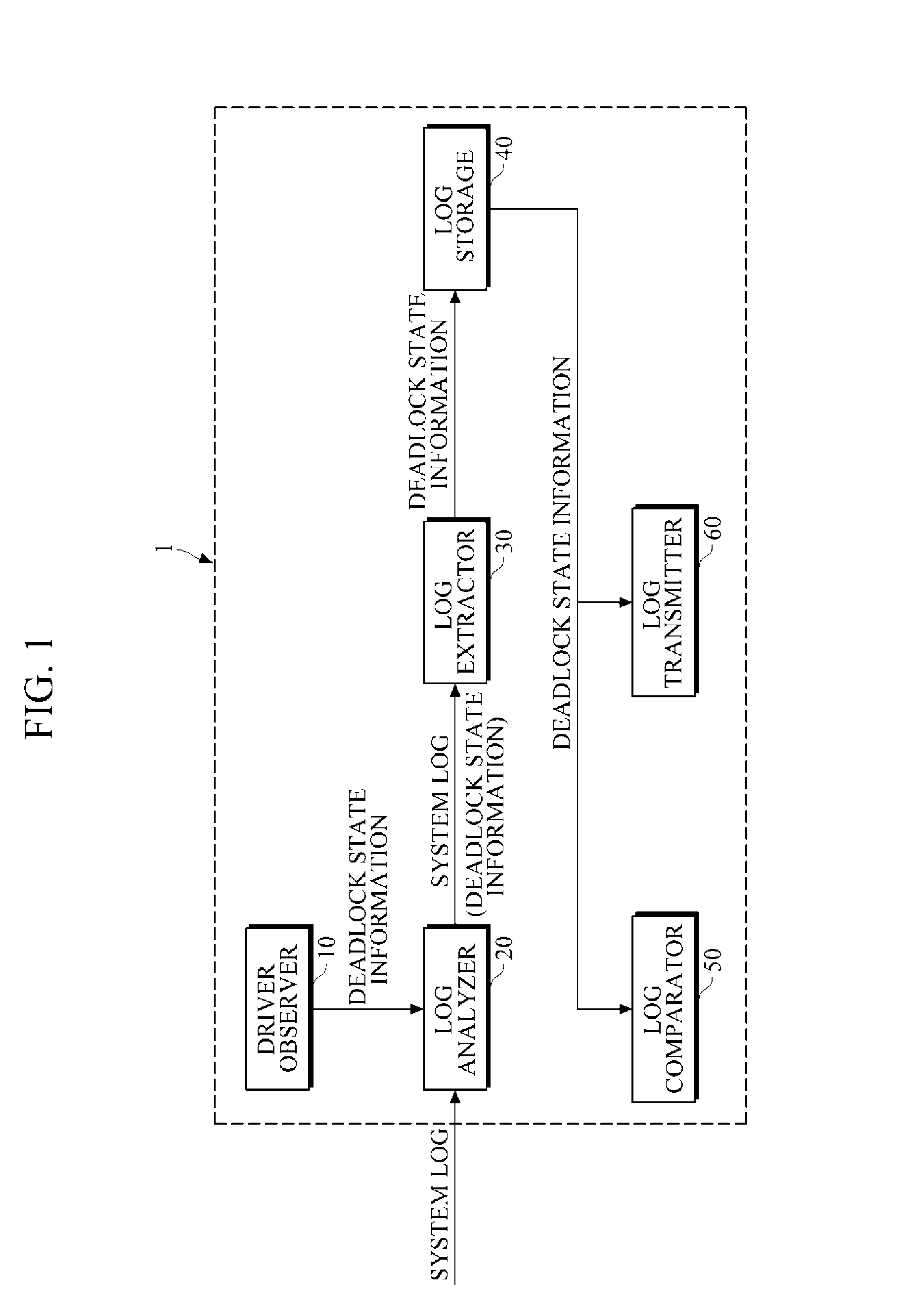
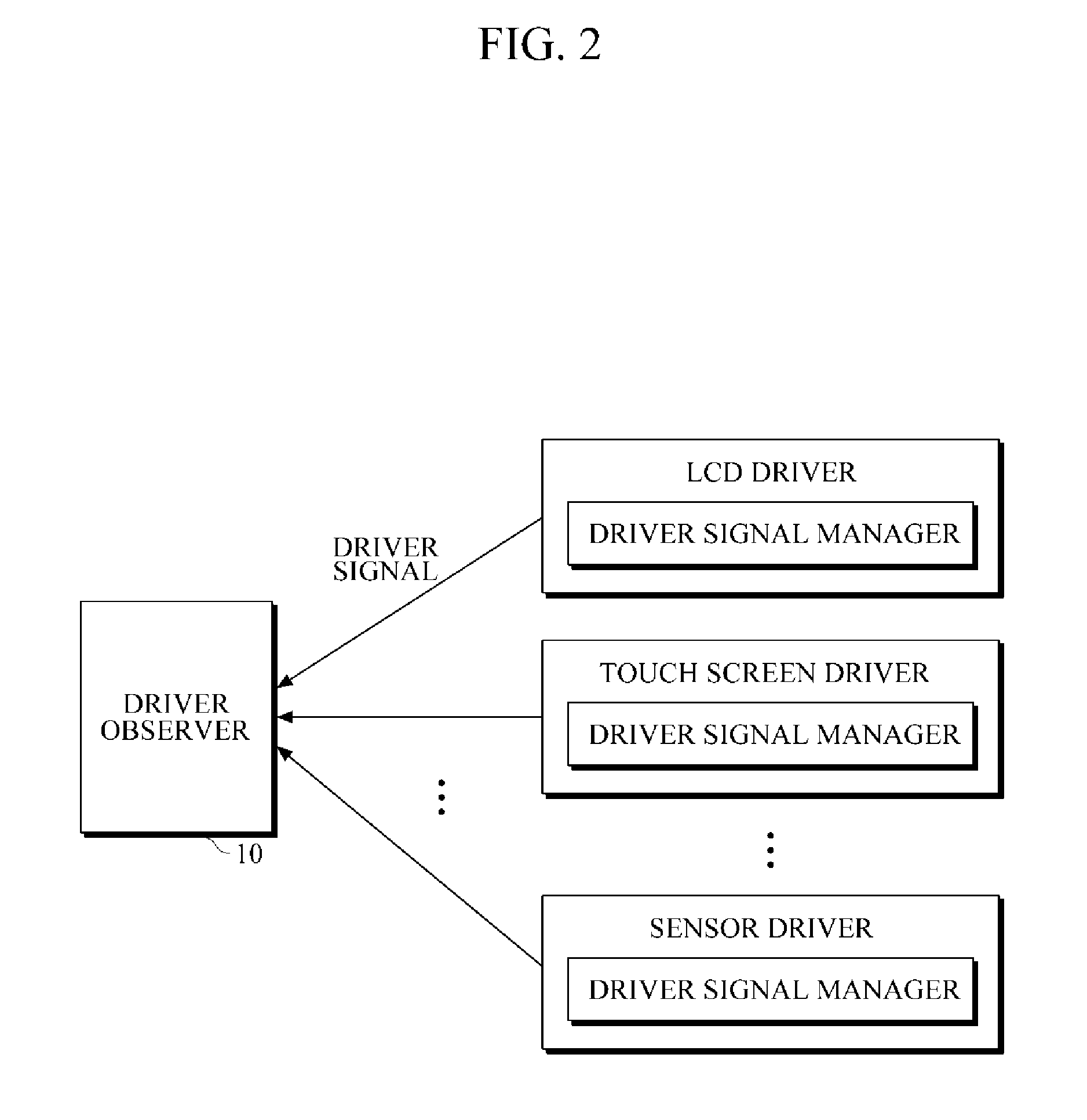
InactiveUS20130227356A1Process stabilityEfficient verificationMultiple digital computer combinationsBootstrappingComputer terminalComputer science
A mobile terminal to handle a booting process includes a processor to process the booting process, a log storage to store error information of a module extracted from a system log, and a log comparator, during the booting process, to extract the error information of the module from the log storage, and to exclude an initialization of the module based on the error information of the module stored in the log storage. A method that uses a processor to handle a booting process includes loading error information of a module from a system log to a log storage, processing, using the processor, the booting process by initializing multiple modules, and determining whether to initialize the module based on the loaded error information of the module.
Owner:PANTECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com