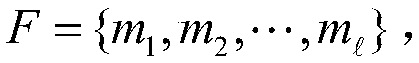Patents
Literature
42 results about "Digital signature forgery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
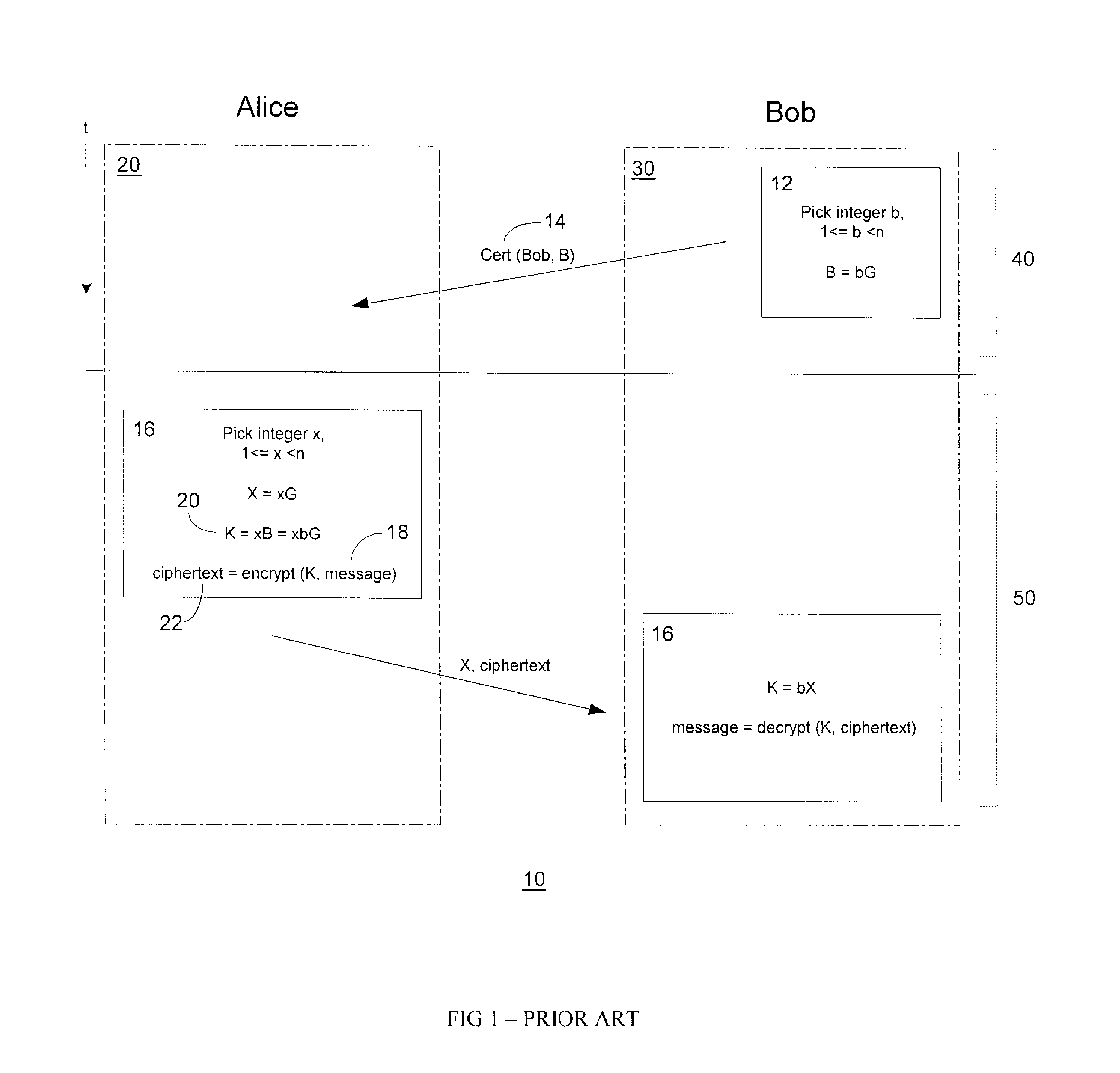
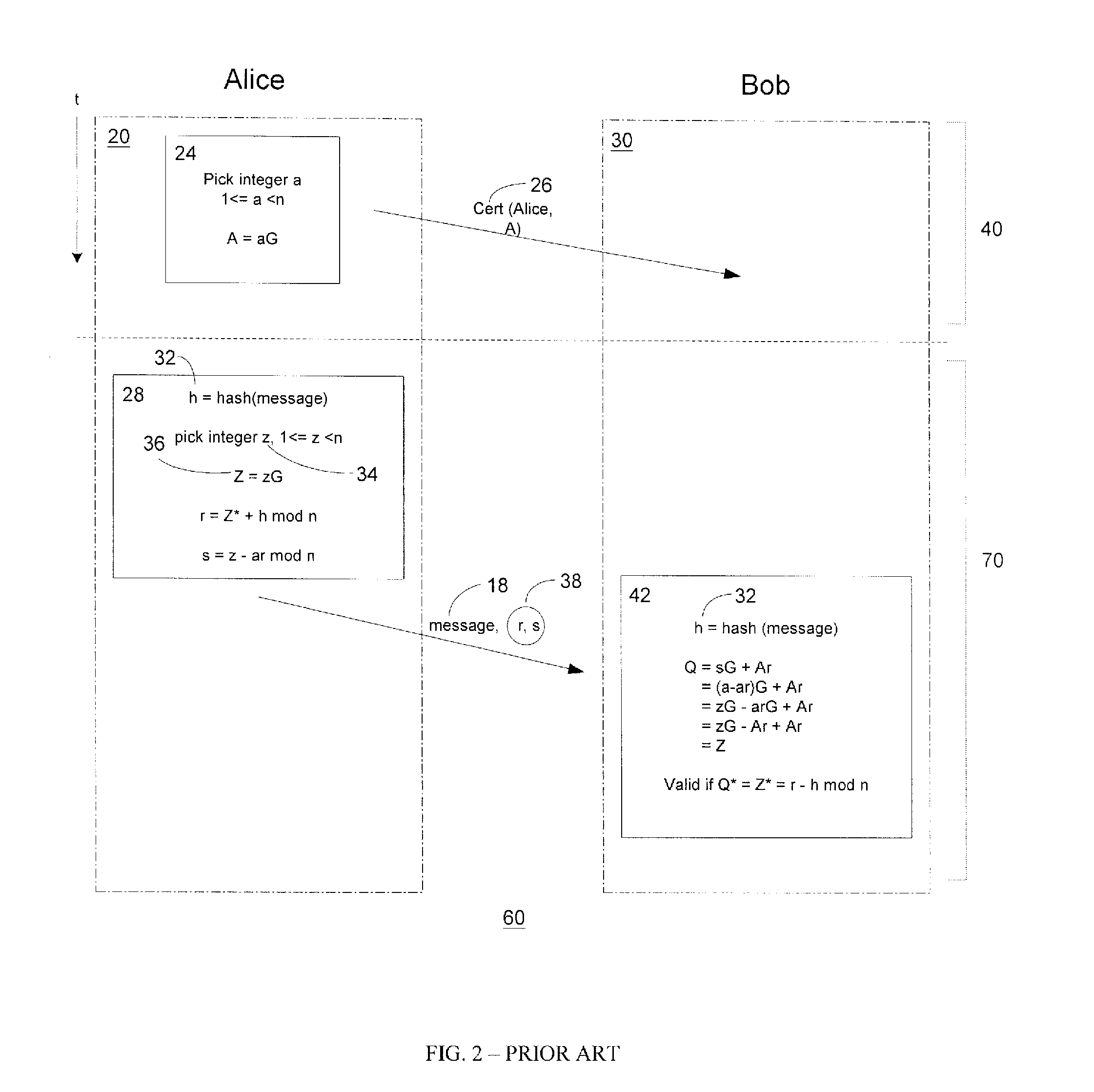
In a cryptographic digital signature or MAC system, digital signature forgery is the ability to create a pair consisting of a message, m, and a signature (or MAC), σ, that is valid for m, where m has not been signed in the past by the legitimate signer. There are three types of forgery: existential, selective, and universal.
Self-authentication of value documents using digital signatures
ActiveUS7051206B1Low costImprove reliabilityKey distribution for secure communicationPaper-money testing devicesCredit cardPublic key certificate
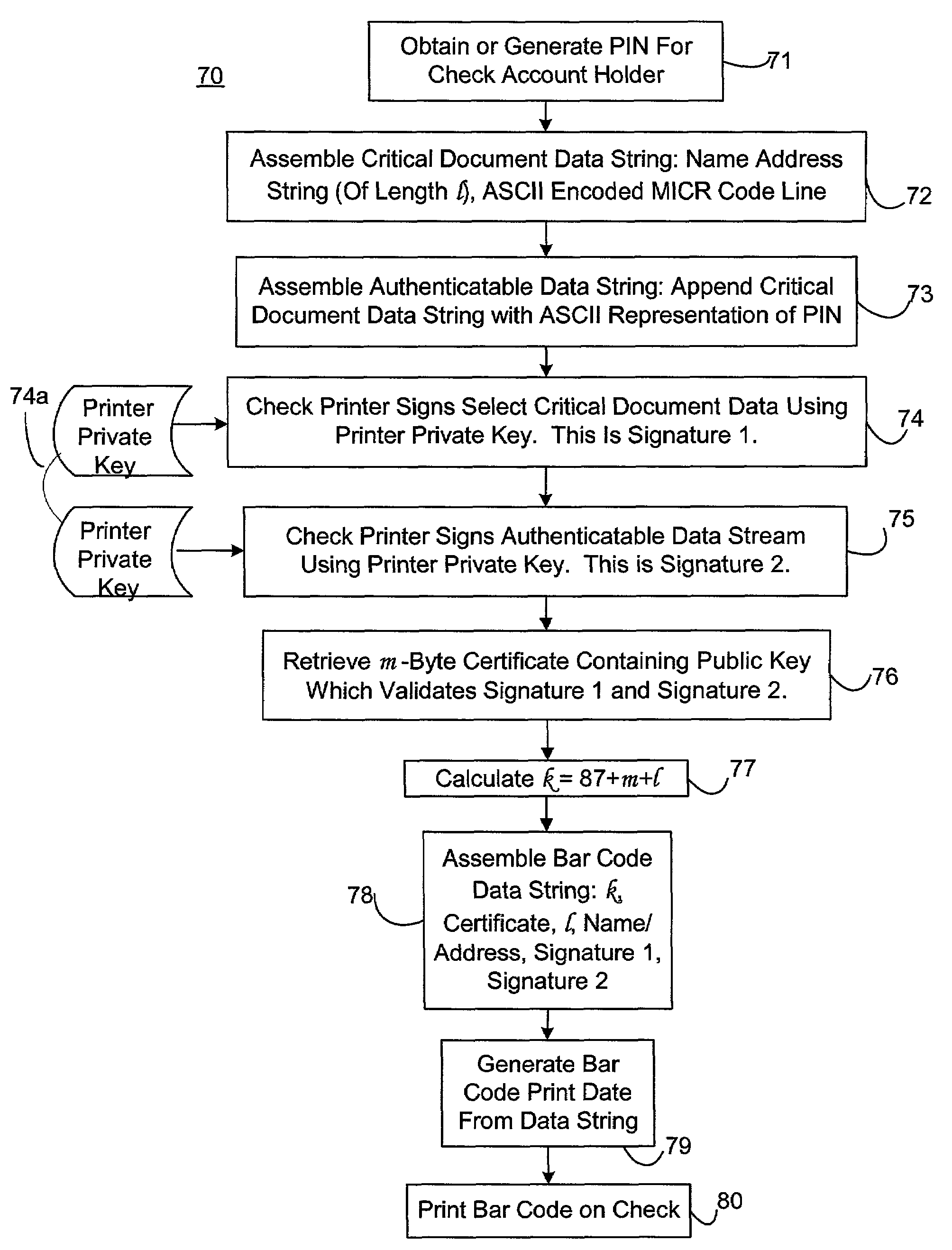
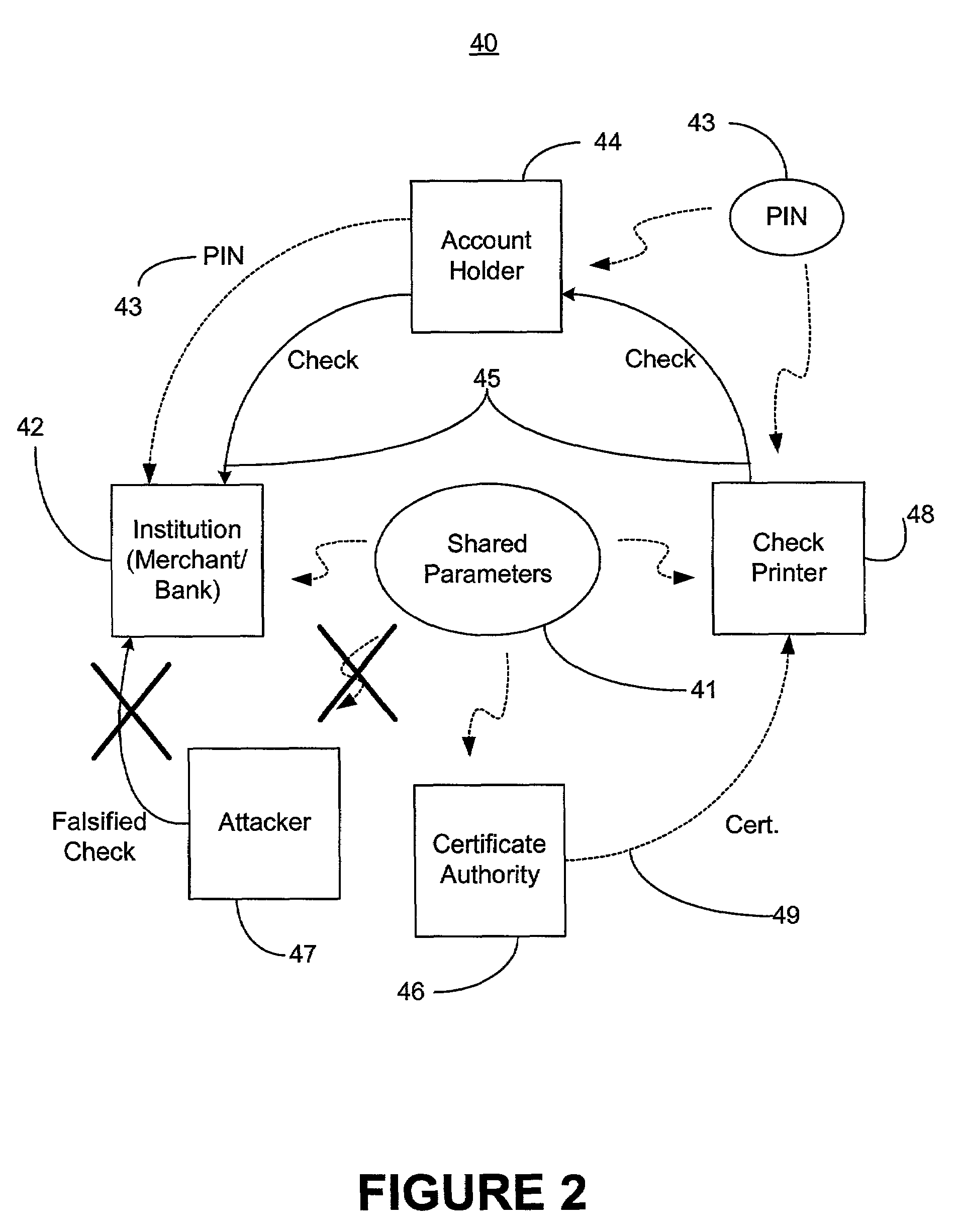
An encryption-free technique for enabling the self-authentication of value documents (including personal and commercial checks) presented at a point of purchase or financial institution. Certain data contained on the value document may be signed with a first digital signature and authenticated with a public key certificate issued from a trusted certificate authority. The signed data and public key certificate are stored on the value document, preferably in a two-dimensional bar code data format. In the case of certain personal value documents (such as checks, credit cards, passports, birth certificates, Social Security cards, etc.), a unique personal identification number (PIN) also may be included in the document data that is signed by a second digital signature. At a point of purchase, a merchant or teller can scan and read the data stored in the two-dimensional bar code and other magnetically recorded information, and together with the PIN the customer provides, can authenticate the value document thus presented using the second digital signature. Alternatively, if the customer is not present, if the personal value document contains the second digital signature, the document may be verified using a PIN-generating algorithm or other method that generates all permutations of PINs. The first digital signature alone may be used to authenticate selected data within the personal value document even when the PIN is not available. Similarly, in the case of a commercial value documents, authentication of pre-printed data may be based entirely upon only the first digital signature.
Owner:UNISYS CORP
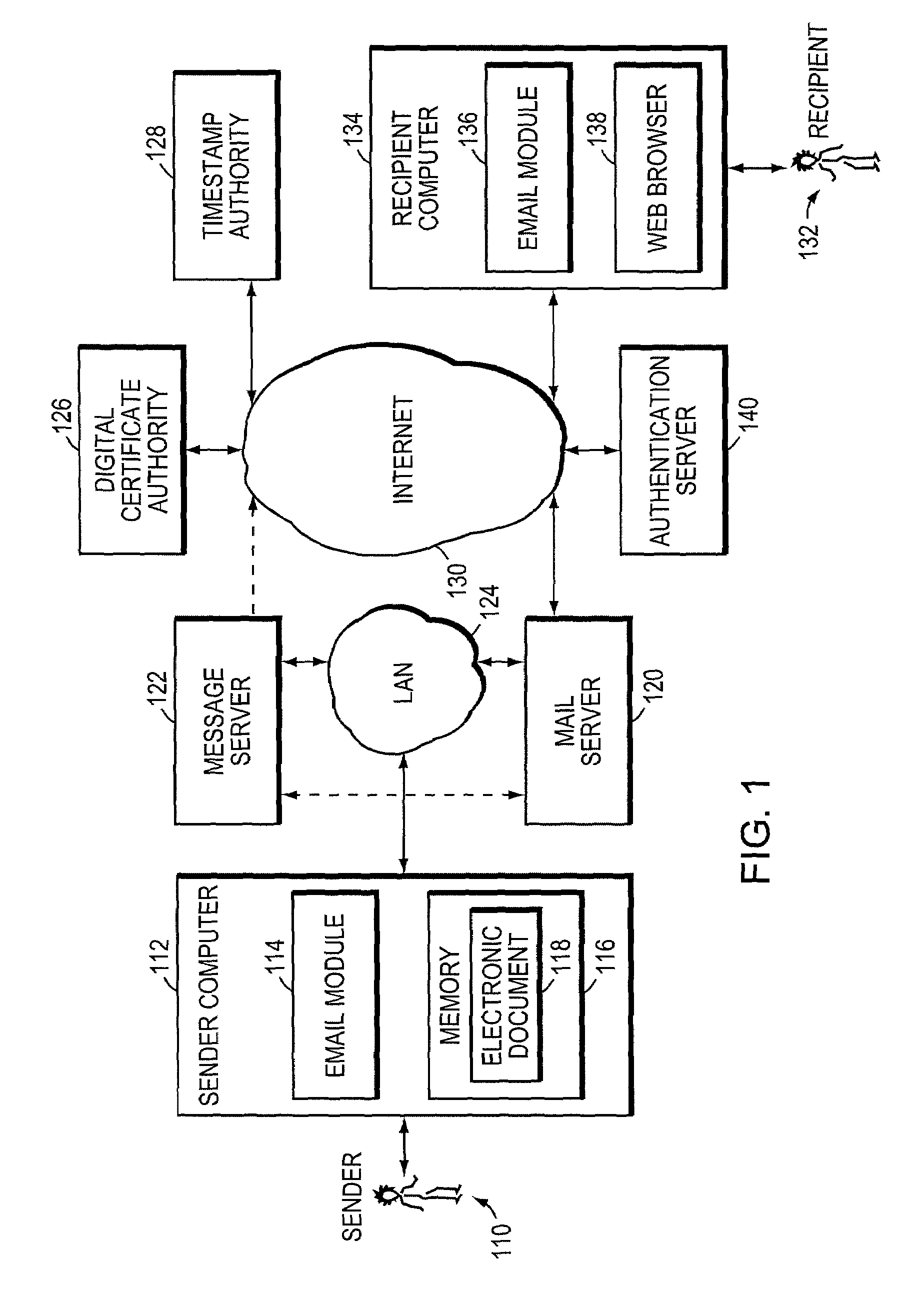
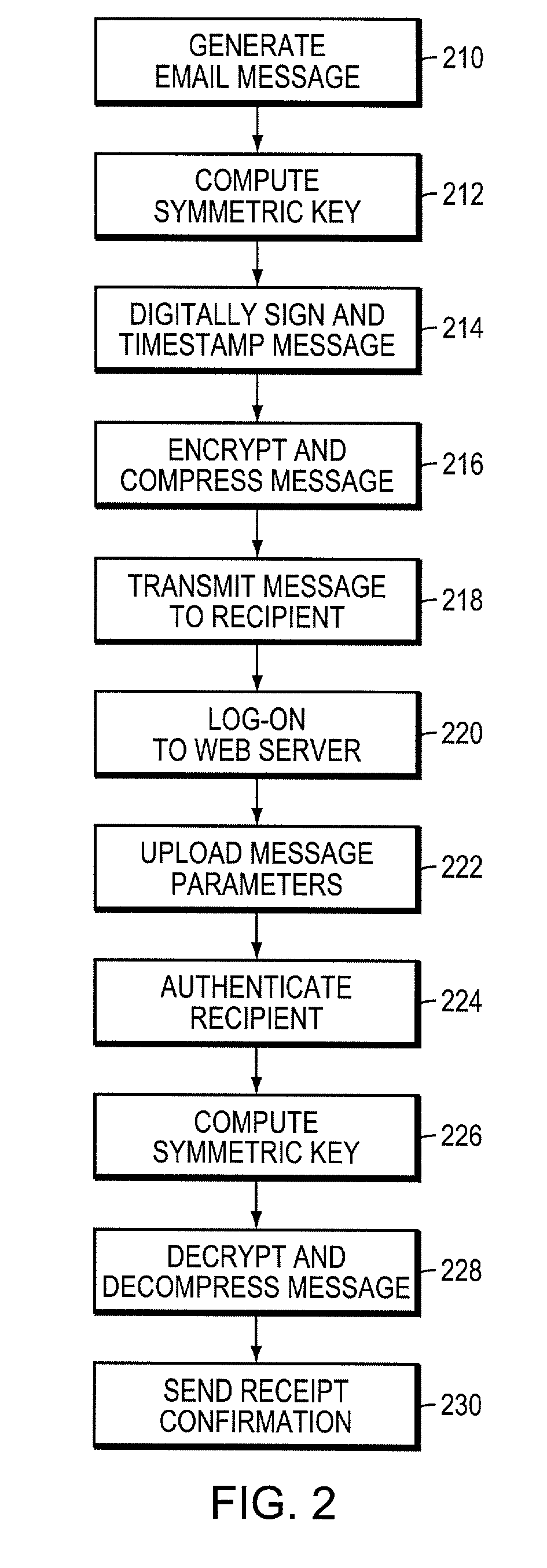
Electronically verified digital signature and document delivery system and method
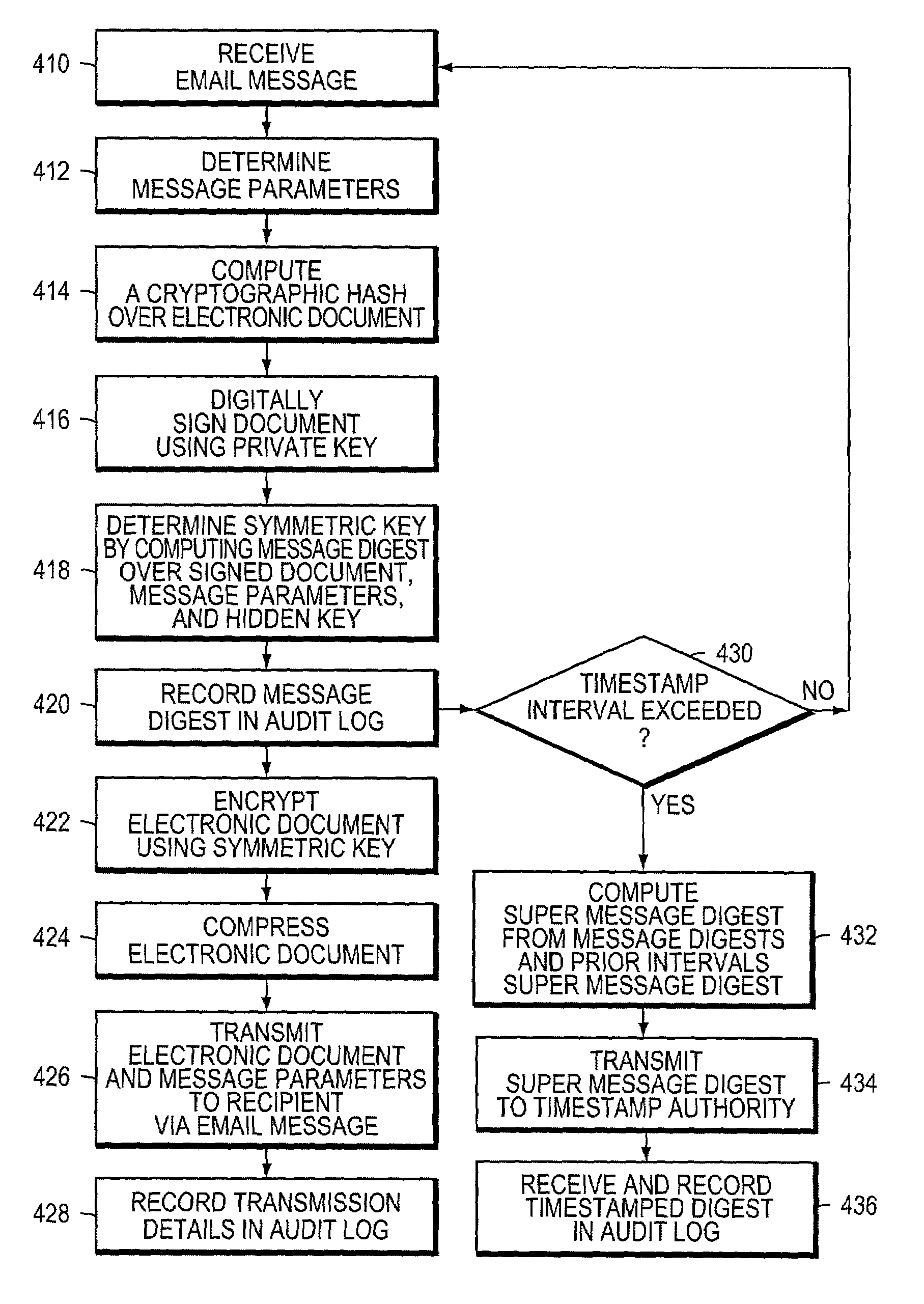
InactiveUS7082538B2Low costReduce complexityPublic key for secure communicationUser identity/authority verificationWeb serviceNetwork service
The secure messaging system of the invention encrypts an electronic document using a symmetric key and transmits the encrypted document and related message parameters to a recipient whose identity is then authenticated by a web server. The web server dynamically regenerates the symmetric key from a hidden key and from the message parameters accompanying the encrypted document, and thus avoids having to maintain a central repository of encrypted documents as required by typical “post and pick-up” encrypted messaging systems. Further, an audit trail produced while practicing the invention provides timestamped message digest data for a plurality of time intervals, where the message digests for adjacent time intervals are computationally linked together. The audit trail effectively enables timestamped message digest data to verify not only the existence of a document during a first time interval, but also to verify the existence of documents encountered in a prior time interval.
Owner:UPLAND SOFTWARE INC
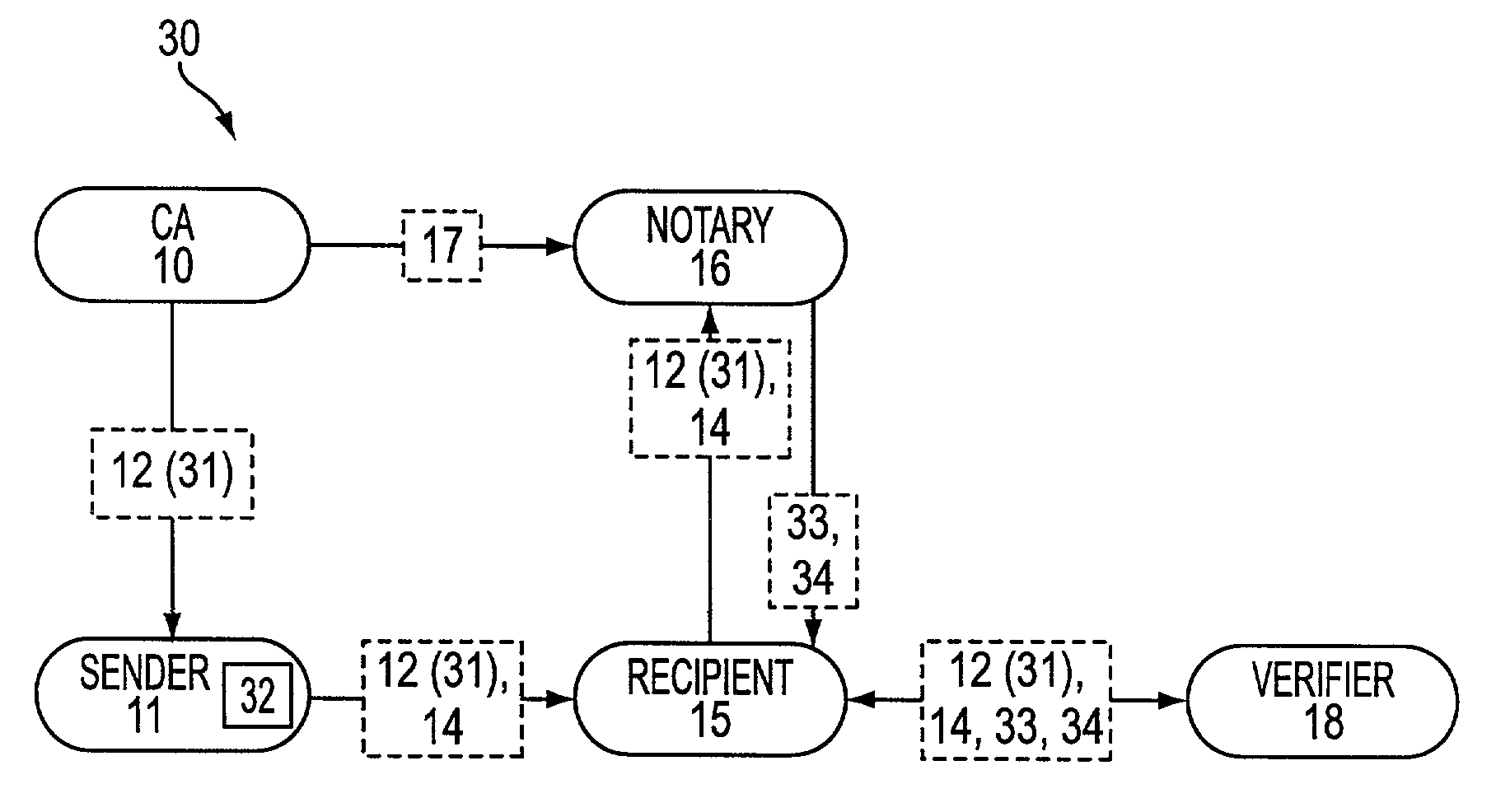
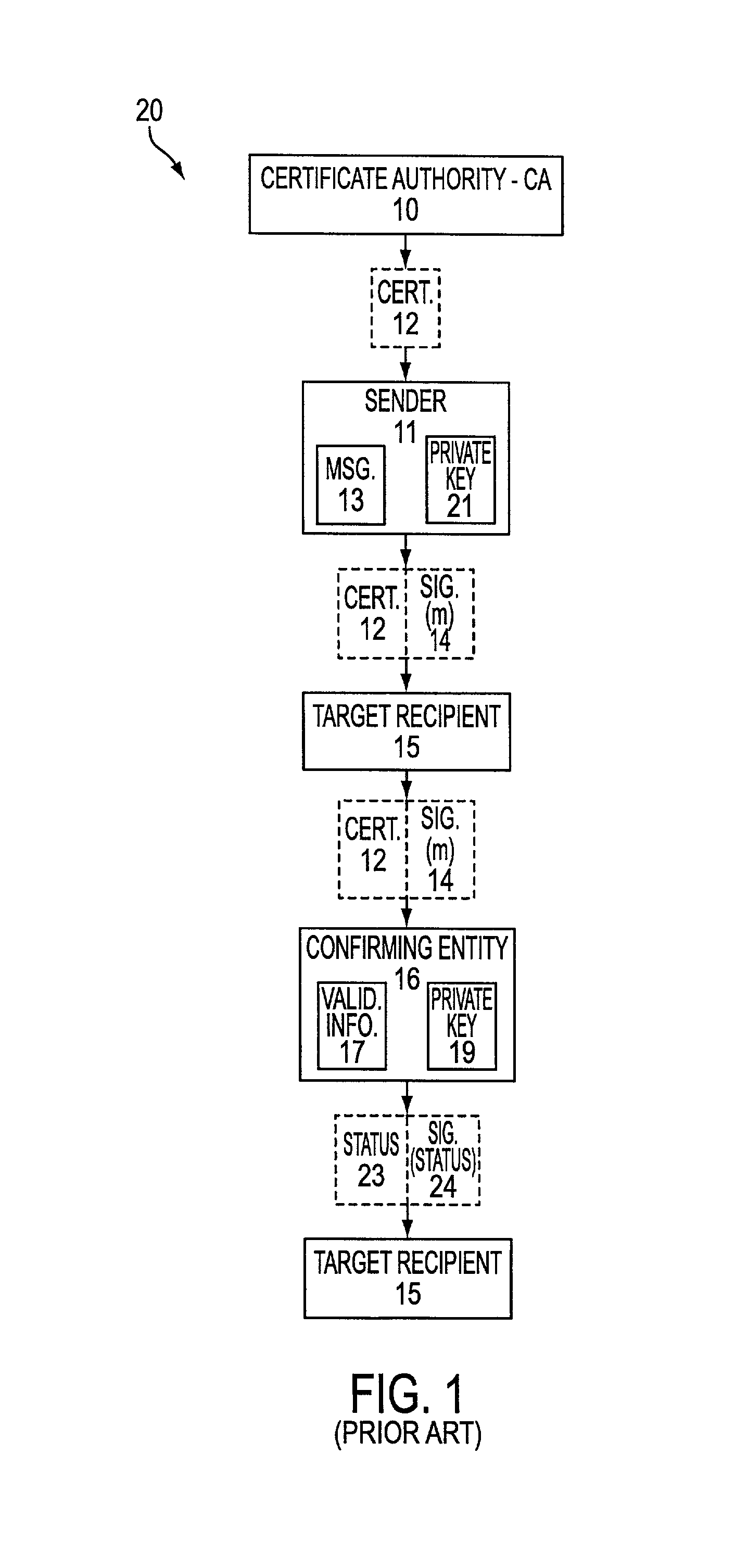
Method and apparatus for validating a digital signature
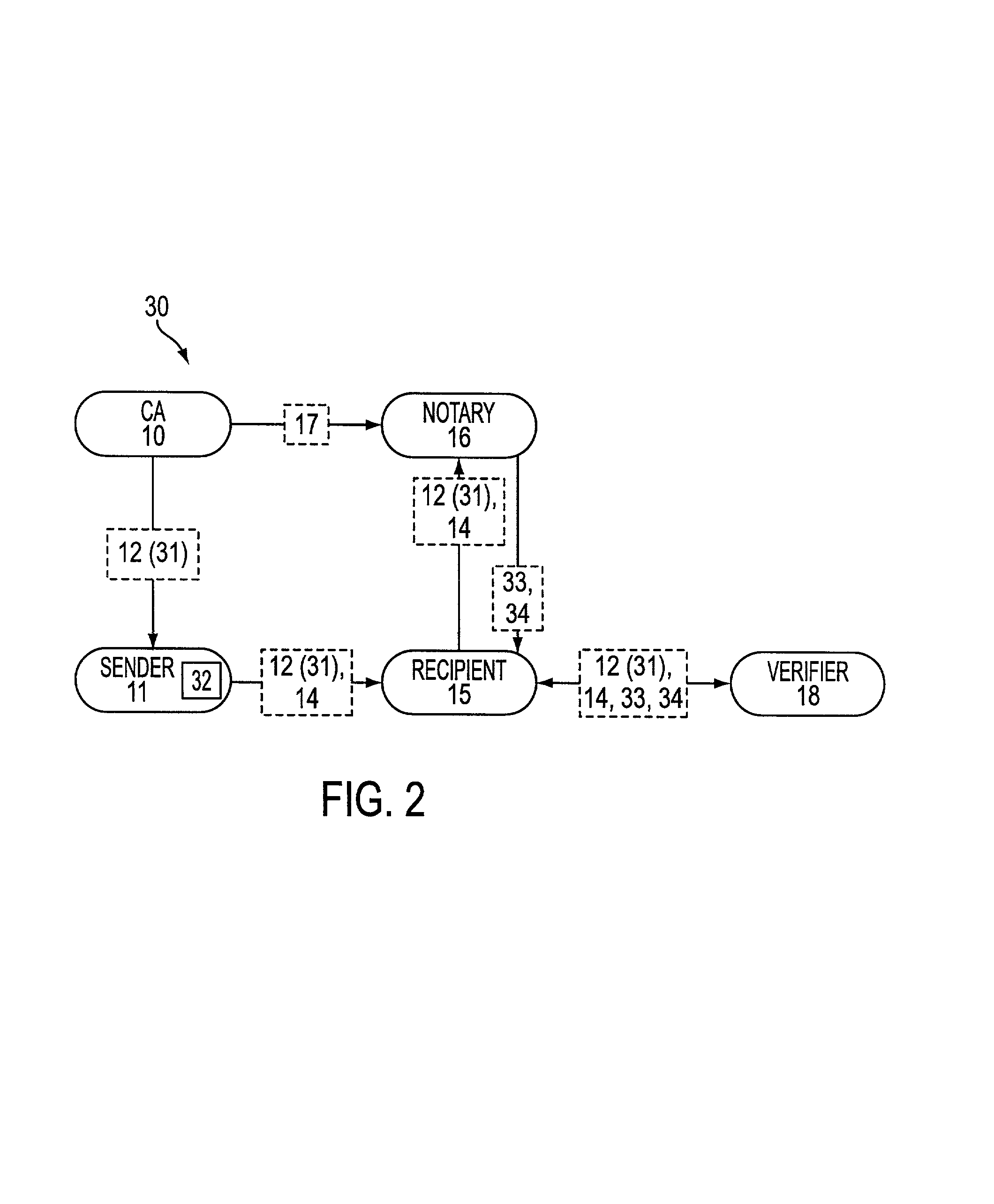
Method and system are described for validating a digital signature. More particularly, a signed message and a corresponding certificate are received. The certificate is checked for validation. A validation statement is generated, and the certificate validation and the signed message provide a status. This status represents a request for validation, and is provided along with a set of validations among which such status is an element. A digest is generated using a Merkle authentication tree corresponding to the set of validations, and this digest is signed with a private key. Accordingly, a notary may provide the signed digest, status and the set of validations for subsequent confirmation of the digital signature.
Owner:PRIVADOR
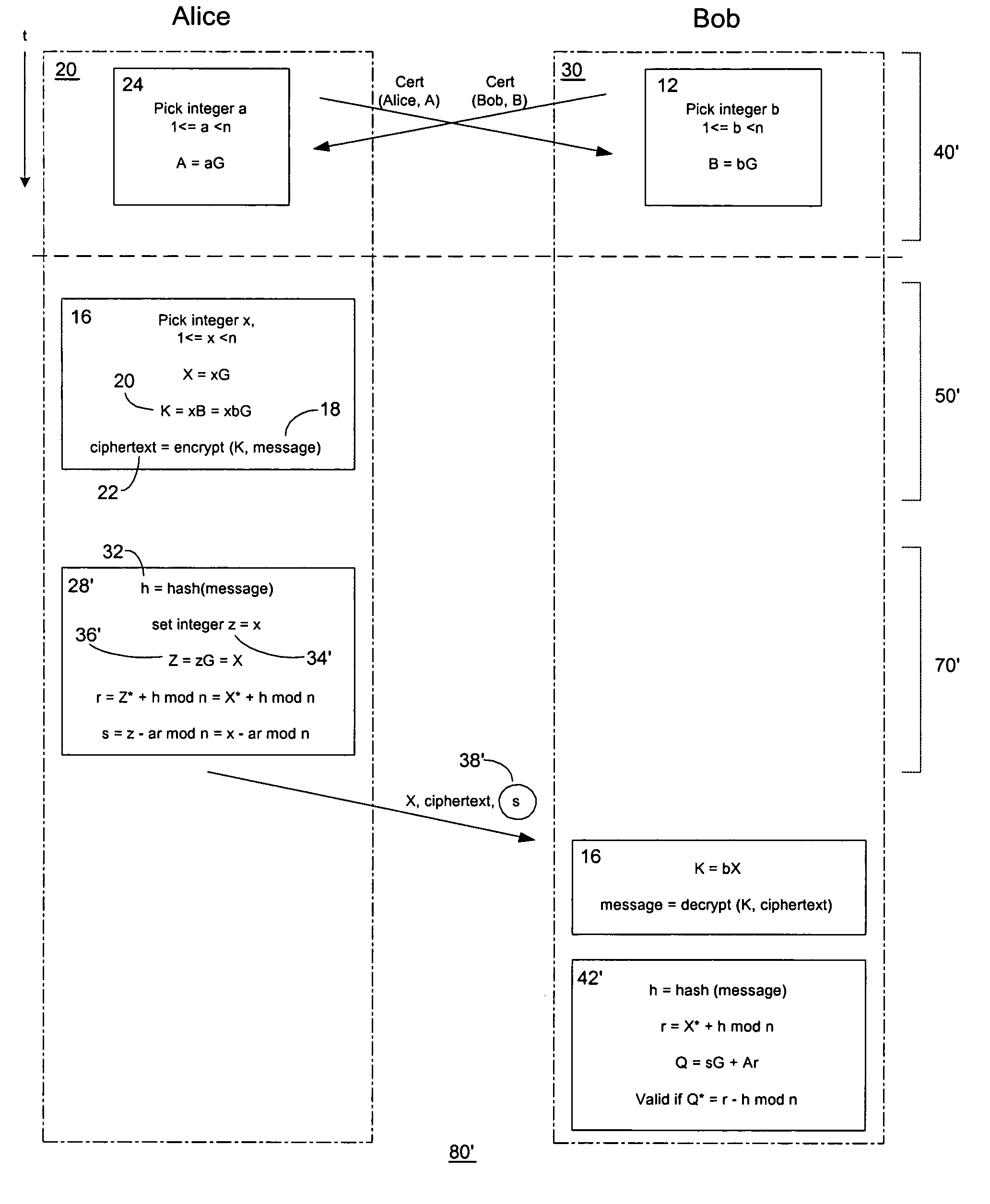
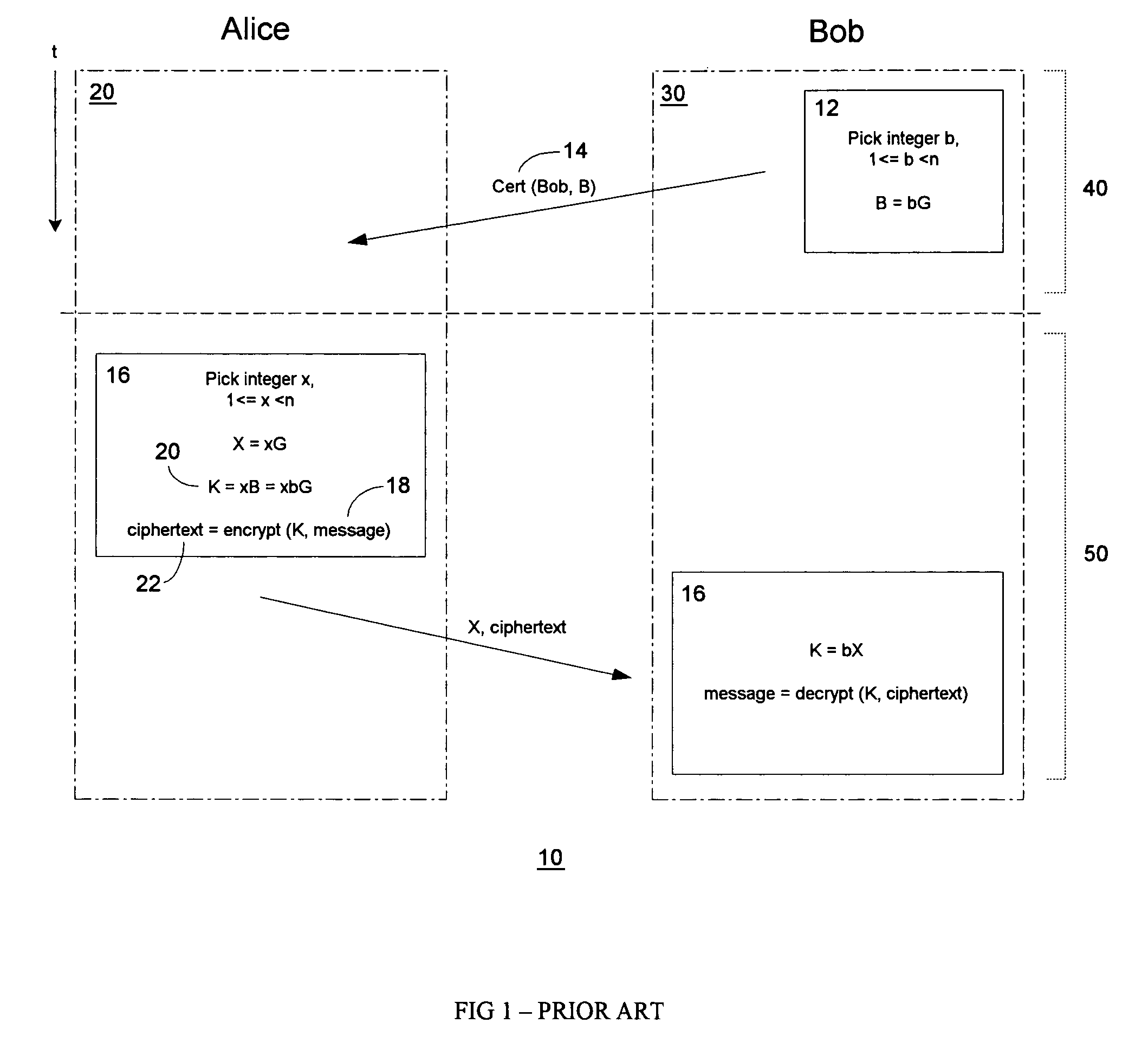
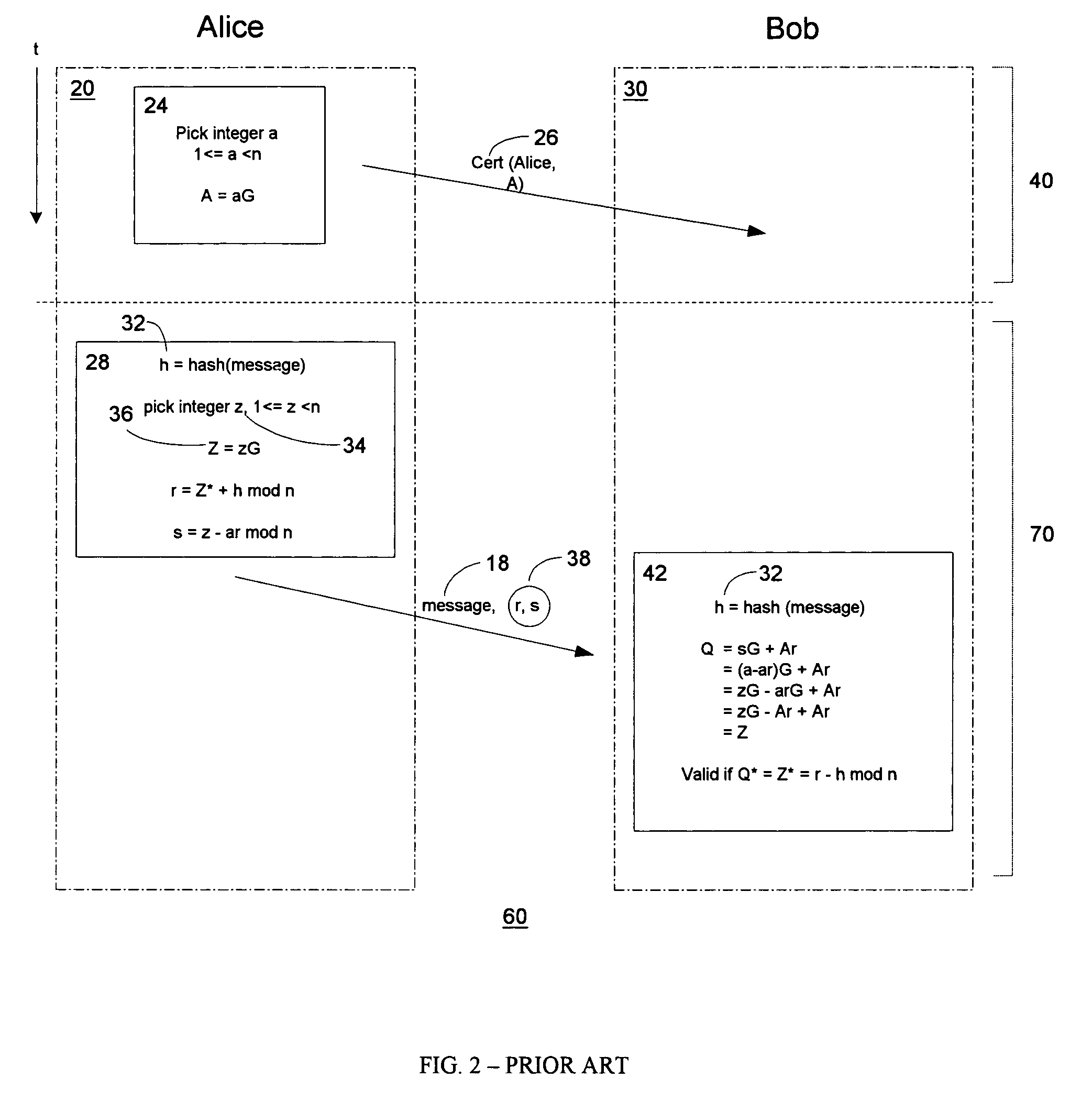
Public key encryption with digital signature scheme
InactiveUS7707420B1Mitigate such drawbackReduce computational processingPublic key for secure communicationUser identity/authority verificationDigital signatureDigital signature forgery
An improved encryption and digital signature system and method in accordance with the invention reuses an encryption ephemeral key pair from an encryption process in a digital signature process. The reuse of the encryption ephemeral key pair in the digital signature process advantageously results in reduced byte size of the digital signature and reduction of costly computation overhead. In a preferred embodiment, the invention is based on the El Gamal encryption scheme and the Nyberg-Rueppel signature scheme. The present invention is particularly useful for operation in conjunction with small communication devices having limited processing and storage, wherein such devices may communicate via bandwidth sensitive RF links.
Owner:MALIKIE INNOVATIONS LTD
System and method for verifying digital signatures on certificates
ActiveUS20060095388A1Efficient verificationCostly and time-consumeUser identity/authority verificationElectronic credentialsDigital signatureDigital signature forgery
A system and method for verifying a digital signature on a certificate, which may be used in the processing of encoded messages. In one embodiment, when a digital signature is successfully verified in a signature verification operation, the public key used to verify that digital signature is cached. When a subsequent attempt to verify the digital signature is made, the public key to be used to verify the digital signature is compared to the cached key. If the keys match, the digital signature can be successfully verified without requiring that a signature verification operation in which some data is decoded using the public key be performed.
Owner:MALIKIE INNOVATIONS LTD
Cloud storage data common auditing method possessing secret key leakage resistance characteristic
The invention belongs to the communication technology field and especially relates to a cloud storage data common auditing method possessing a secret key leakage resistance characteristic. The method mainly comprises the following steps of system initialization: blocking processing is performed on a data file so as to generate public and private key pairs of a cloud user and a cloud server; auditing identification generation: the cloud user sends the data file and a label, and a signature set of a data block to the cloud server; auditing challenge response: a third party auditor generates auditing challenge information and sends to the cloud server; the cloud server calculates combination information according to the auditing challenge information, gets signatures together and sends an auditing identification response information to the third party auditor; and the third party auditor verifies validity of the auditing identification response information. The method has advantages that a condition that digital signature forgery and auditing identification response information forgery caused by leakage of a user signature private key can be prevented; and a malicious cloud server is ensured not to generate the forged auditing identification response information to cheat a TPA and to pass through an auditing verification process.
Owner:SOUTHWEST PETROLEUM UNIV
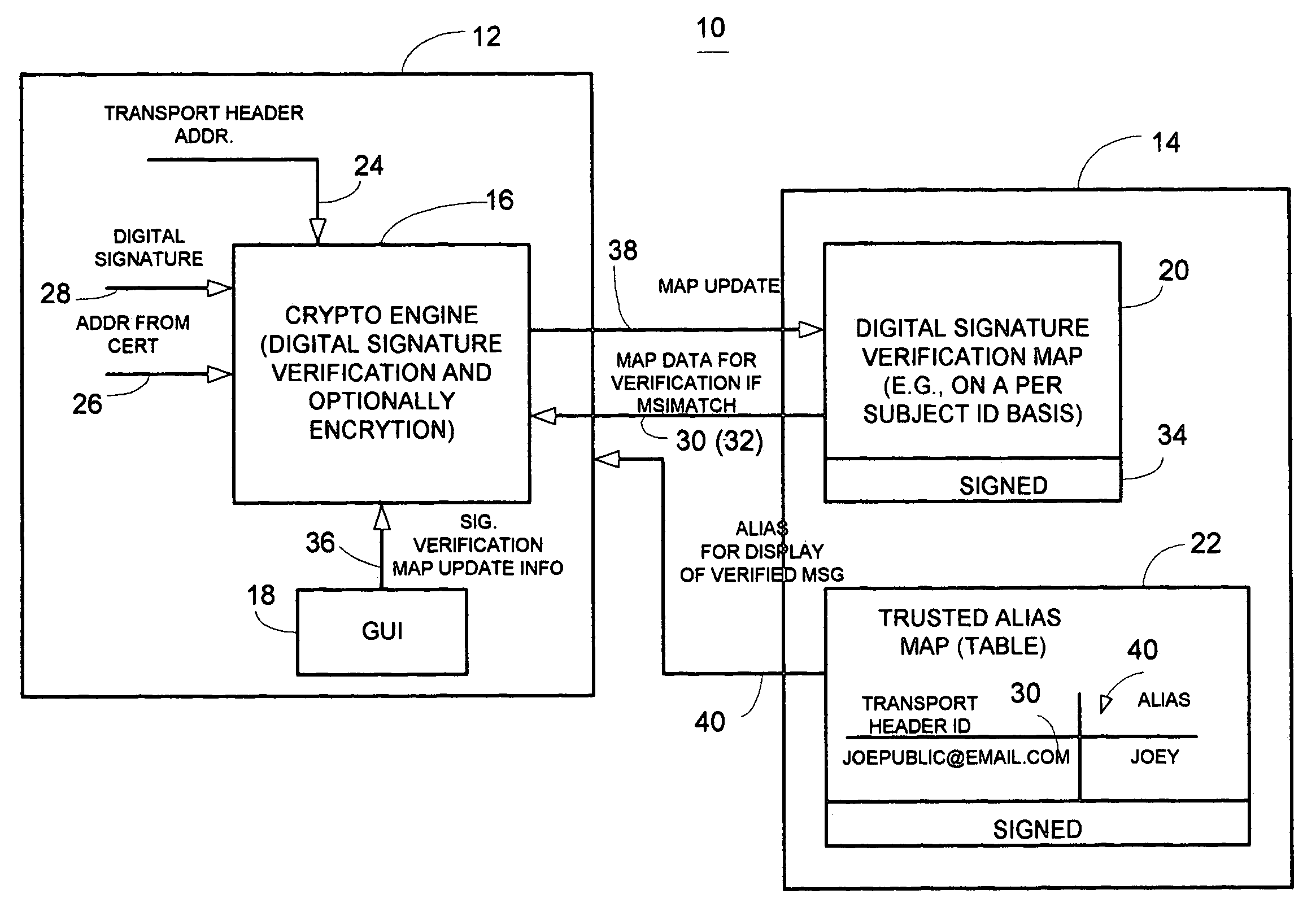
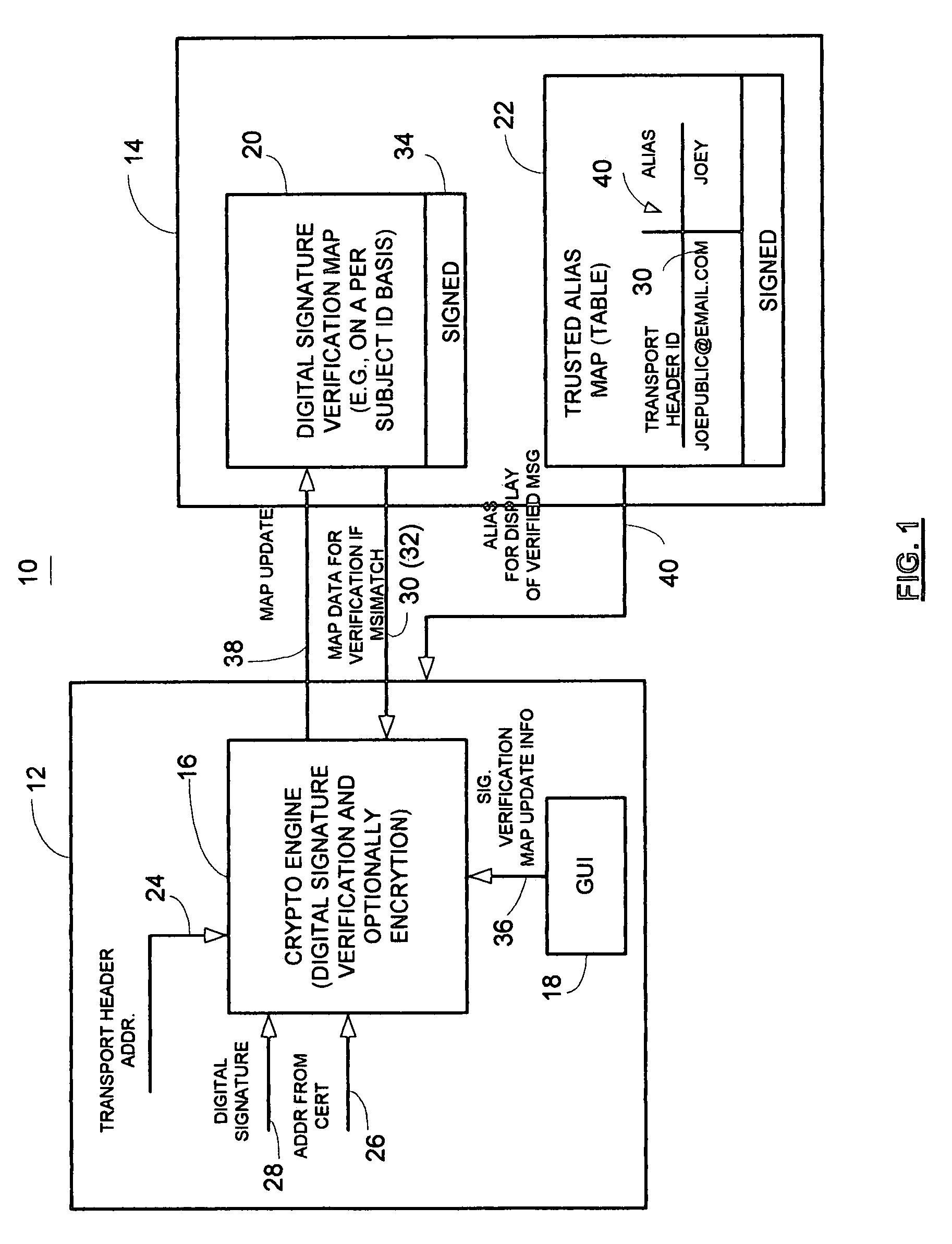
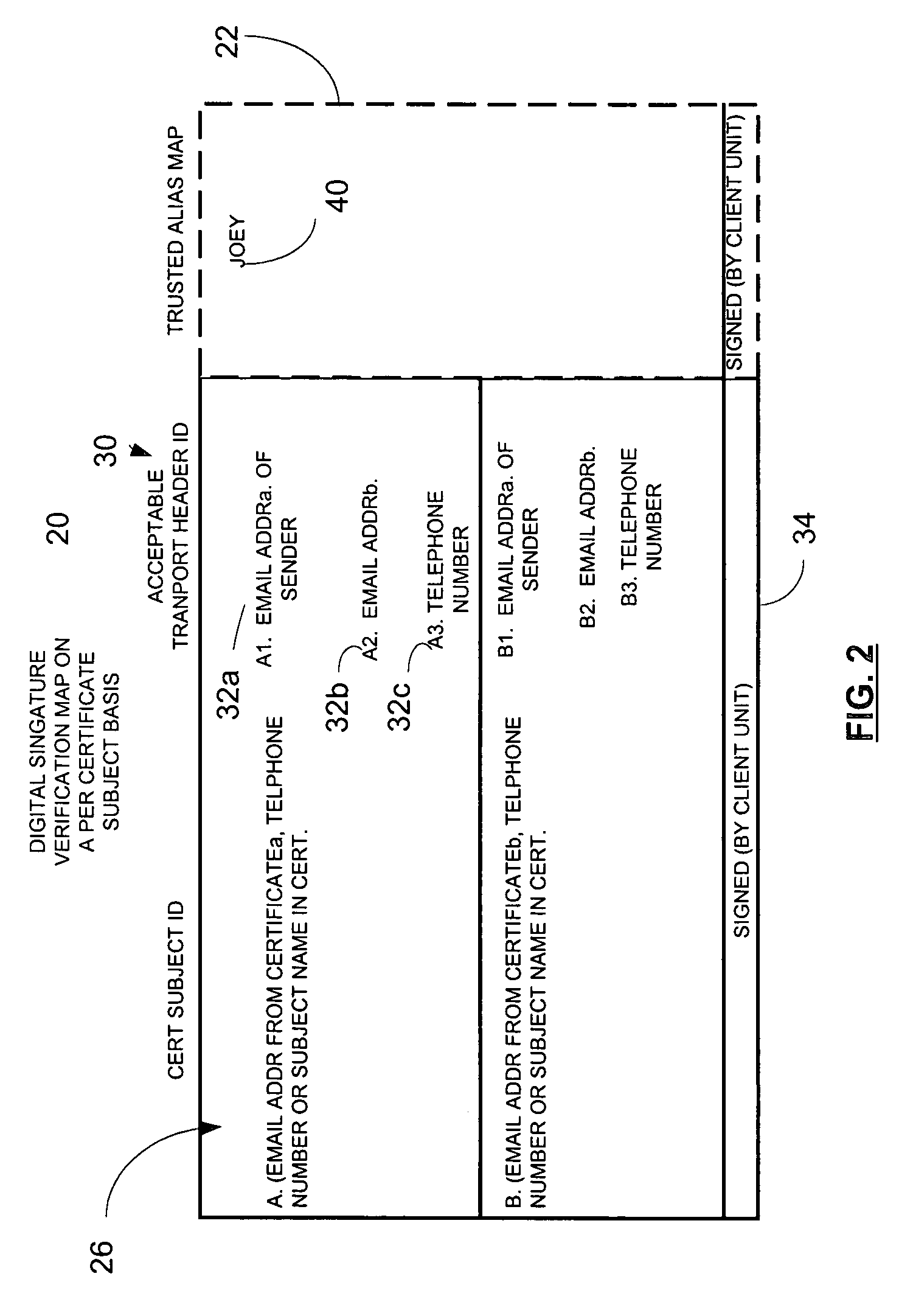
Method and apparatus for providing information security to prevent digital signature forgery
A method and apparatus utilizes a digital signature verification map containing a plurality of acceptable message header identifiers associated with a public key certificate identifier. In one embodiment, a method includes determining a digital signature verification error based on a received message header, such as transport header identifier associated with a public key certificate identifier, such as the subject field of the certificate. The method includes generating a signature verification map or updating a signature verification map containing a plurality of acceptable message header identifiers associated with the common public key certificate identifier in response to determining the digital signature verification error. Accordingly, a link is provided between a transport header and a digitally signed message. A digital signature verification map is continually updated to accommodate aliases to a common subject associated with the certificate. The digital signature verification map is preferably digitally signed to maintain a trusted verification map to operate as part of a secure communication system. If desired, a trusted alias map may also be used.
Owner:ENTRUST
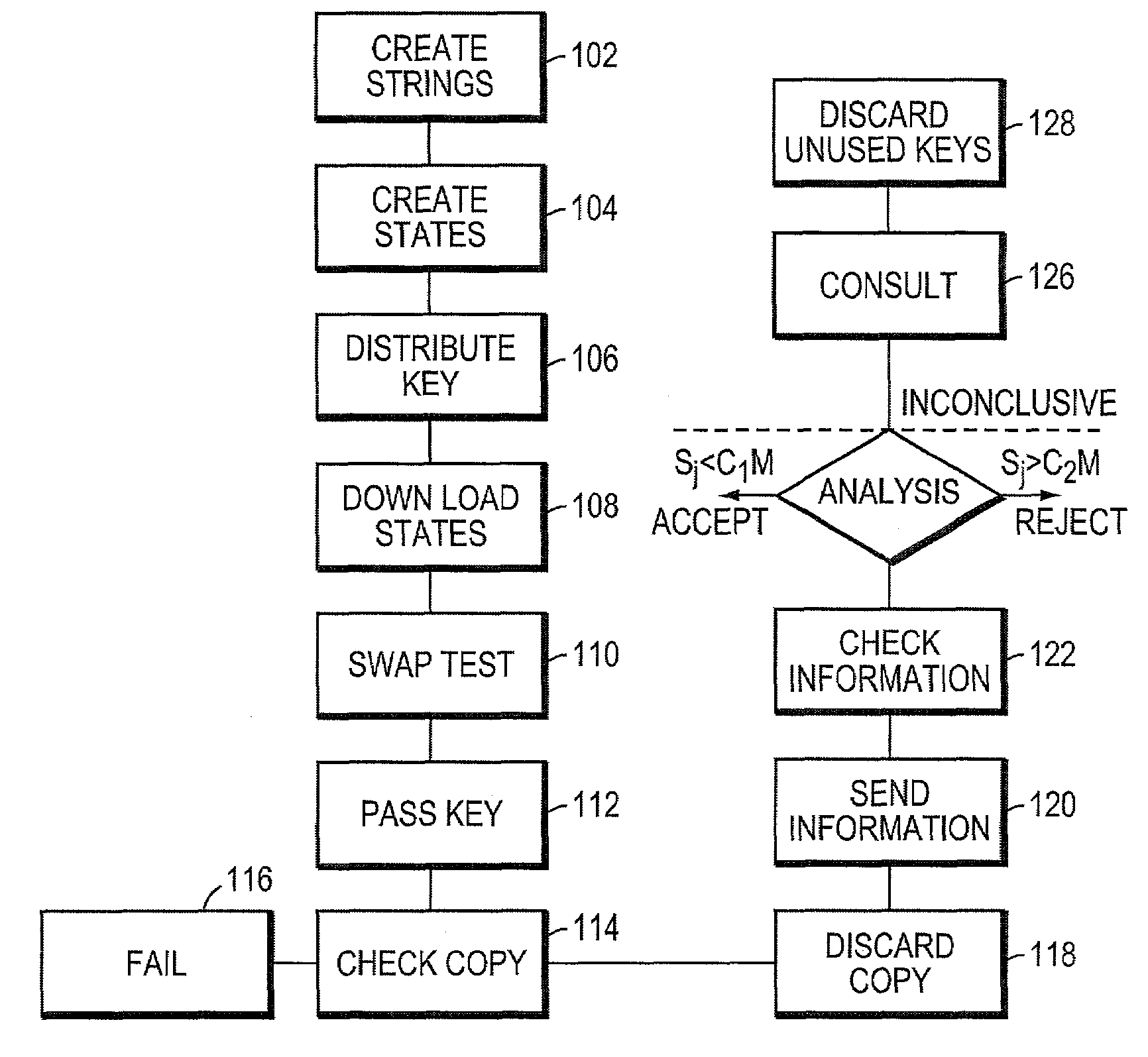
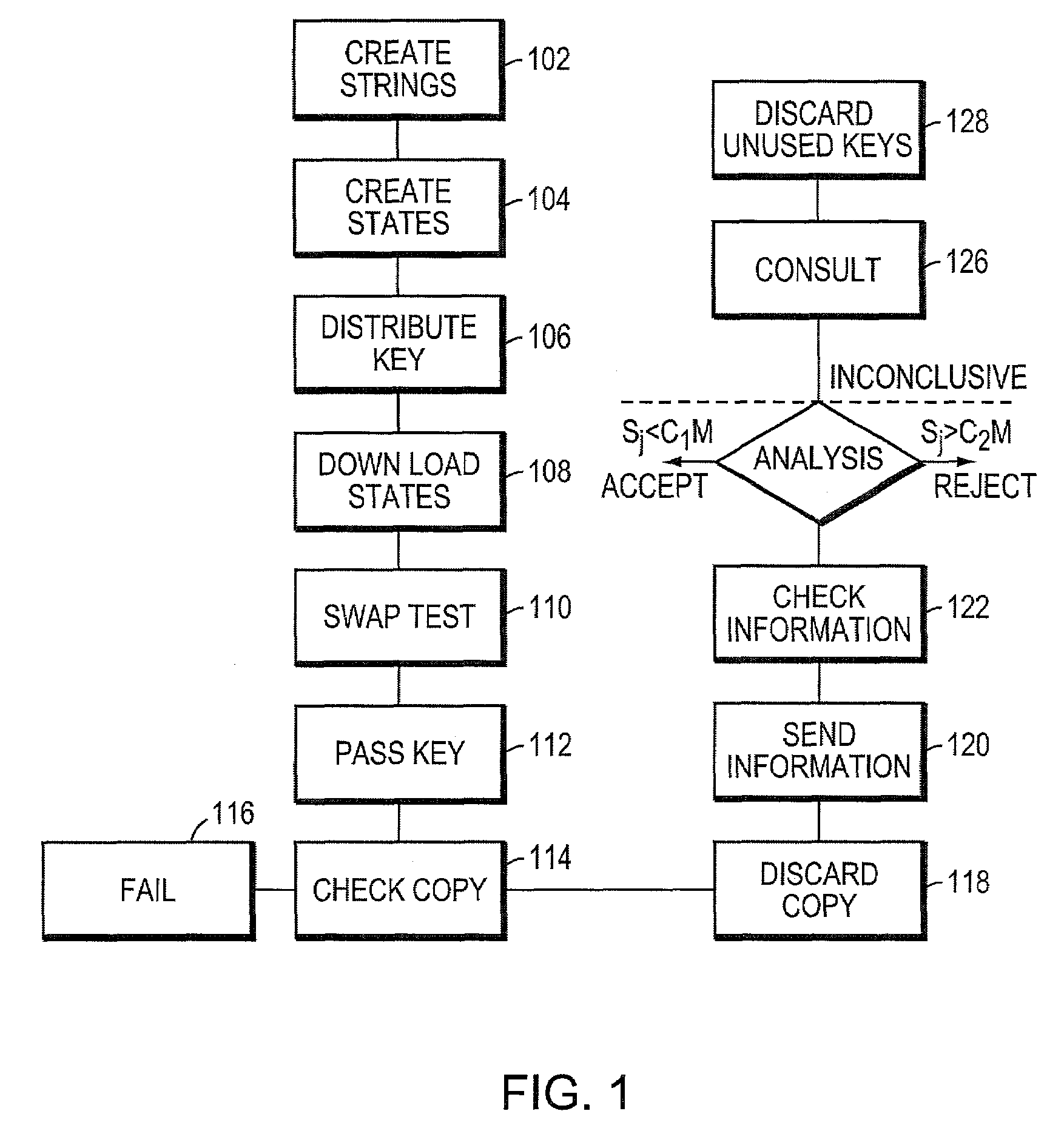
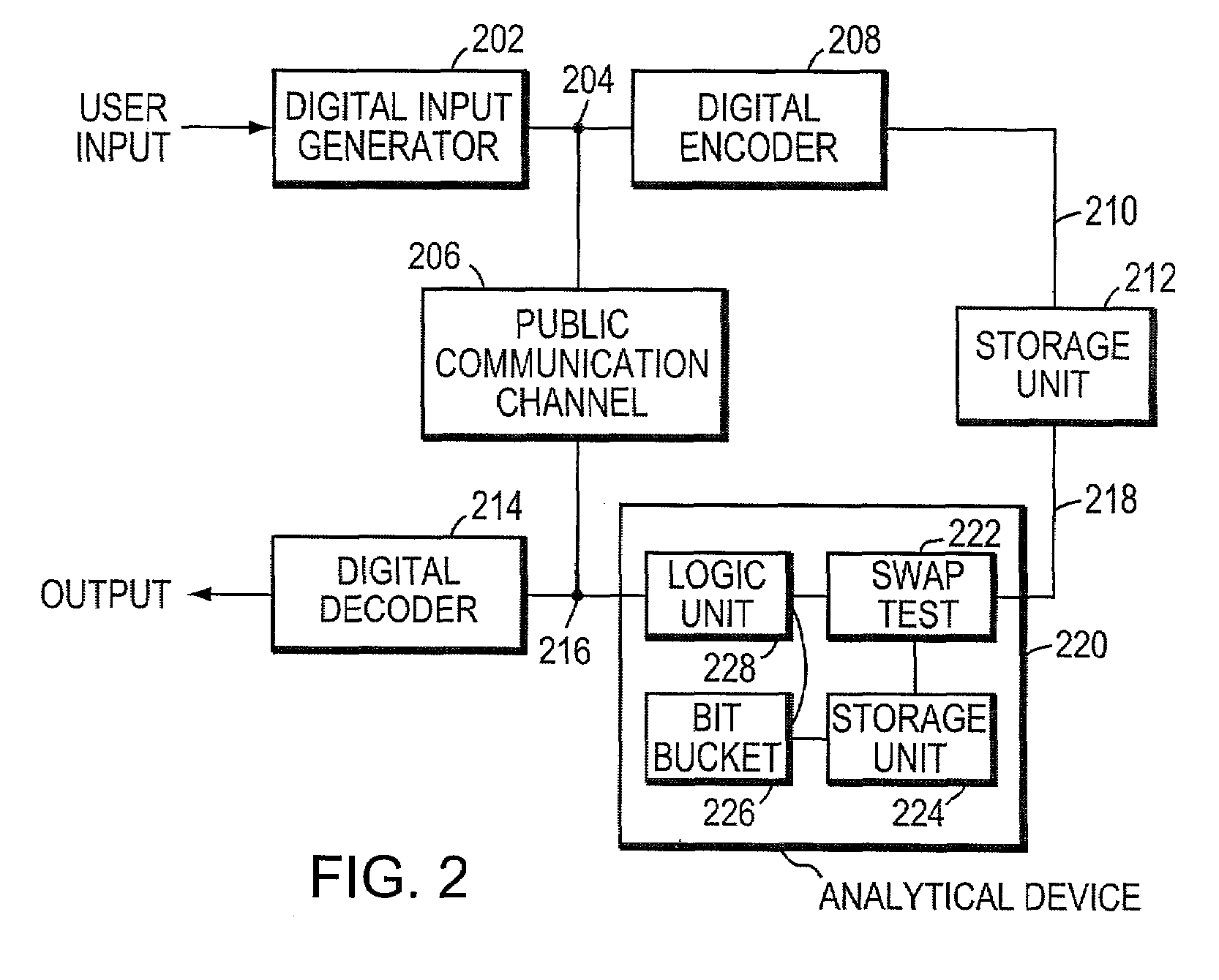
Quantum digital signatures
ActiveUS7246240B2User identity/authority verificationSecret communicationDigital signatureDigital signature forgery
Systems and methods for providing secure quantum digital signatures. In one embodiment, a digital signature user creates a plurality of identical “public” keys having one or more bits and a corresponding quantum mechanical one-way function. Quantum digital signature recipients use a “swap test” to check the validity of a copy of the key, and compare the test results with others. The quantum digital signature user sends a signed message over any channel, including an insecure channel. The recipients evaluate the signed message, and quantify the number of incorrect keys. The message is deemed valid and original, or forged and / or tampered with, when the number of incorrect keys is less than a lower threshold, or exceeds an upper threshold, respectively. For an intermediate number of incorrect keys, the recipients determine message authenticity by comparing observations. Hardware useful for application of the method is disclosed.
Owner:MASSACHUSETTS INST OF TECH
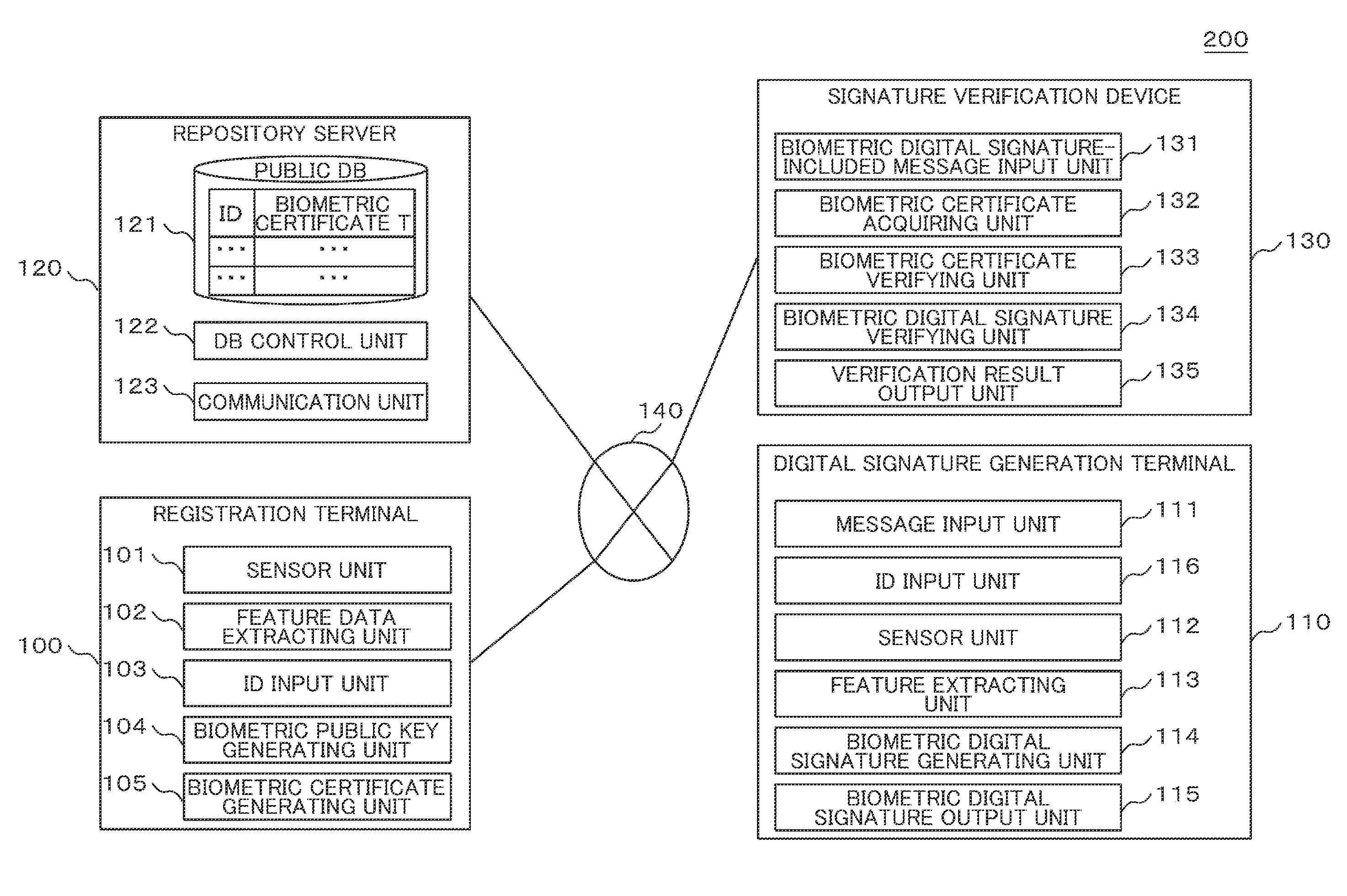
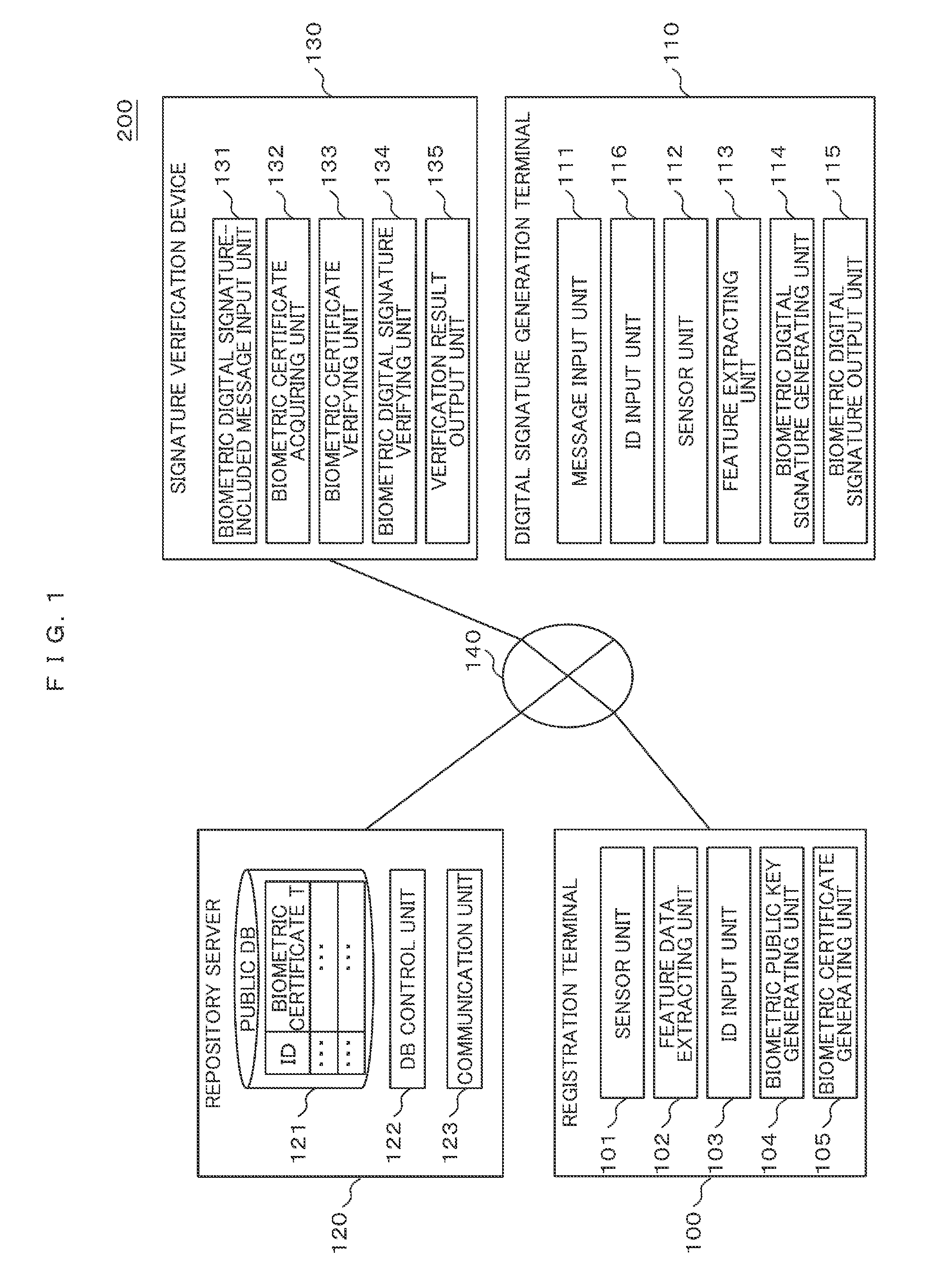
Biometric signature system, signature verification method, registration terminal, signature generation terminal, and signature verification device
ActiveUS20160094348A1Facilitate performance improvementsReduce management costsKey distribution for secure communicationUser identity/authority verificationElectronic documentDigital Signature Algorithm
A biometric signature system generates a digital signature for electronic documents using biometric information as a secret key. Registration commitment information is generated by performing expansion conversion on a predetermined secret key and embedding the resulting secret key in feature data of biometric information of a user, and a set with a corresponding public key. A pair of one-time secret and public keys is generated for digital signature feature data of the biometric information of the user, and a digital signature for a message is generated using the one-time secret key. A digital signature commitment is generated and a set of the one-time public key and the digital signature is output as the biometric digital signature. The digital signature is verified using the one-time public key. A differential secret key is calculated and a correspondence of the differential secret key, the one-time public key and the public key is verified.
Owner:HITACHI LTD
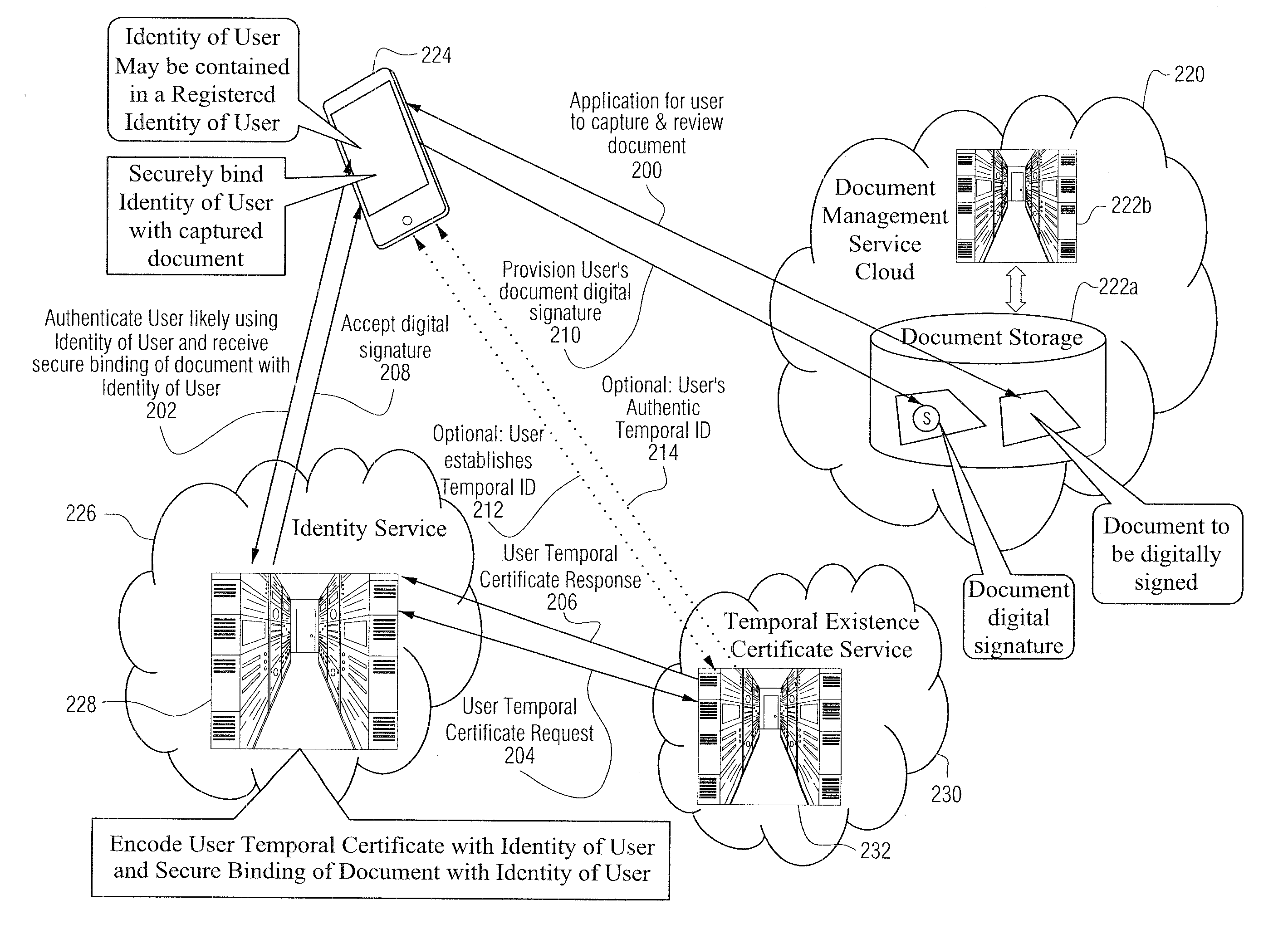
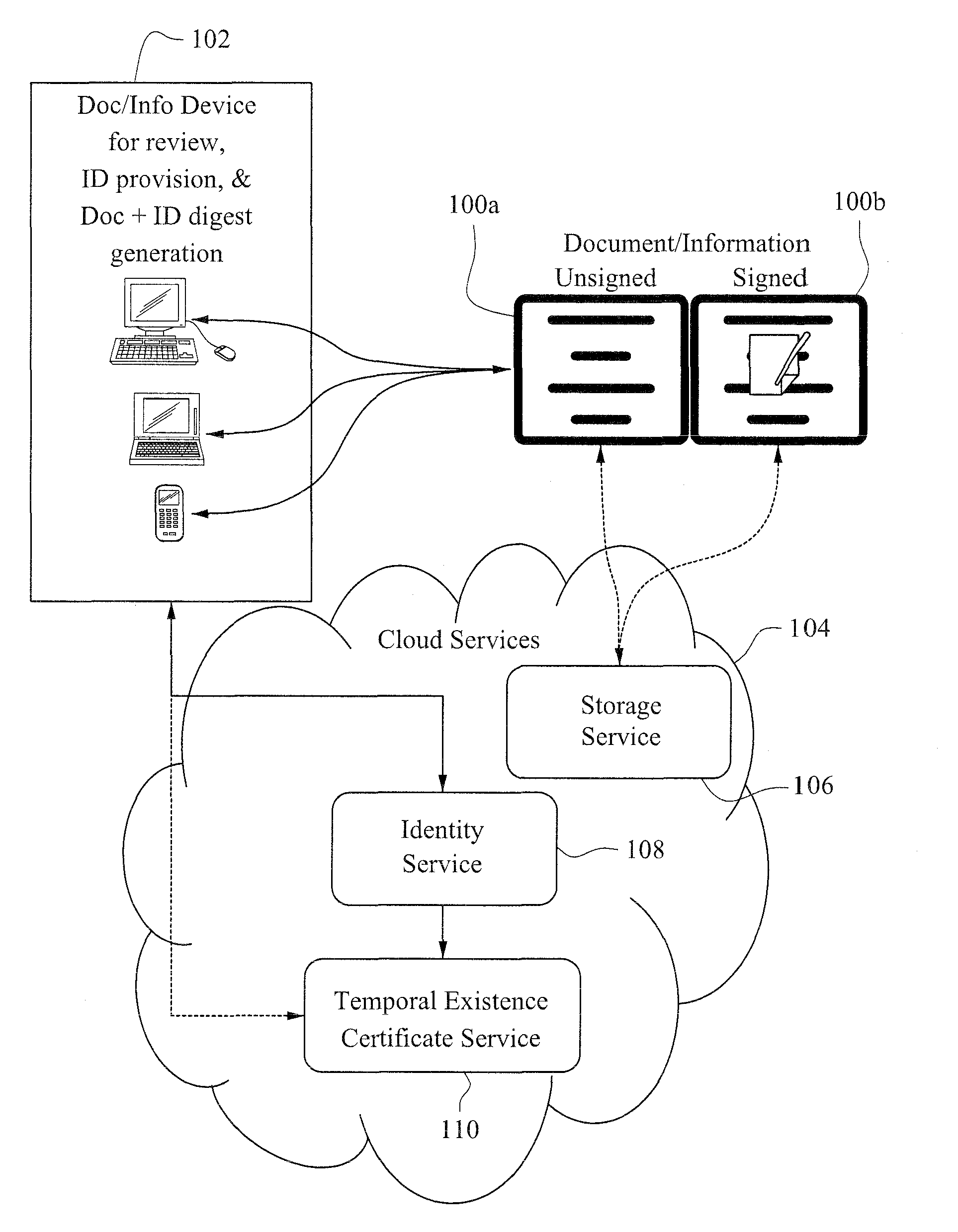
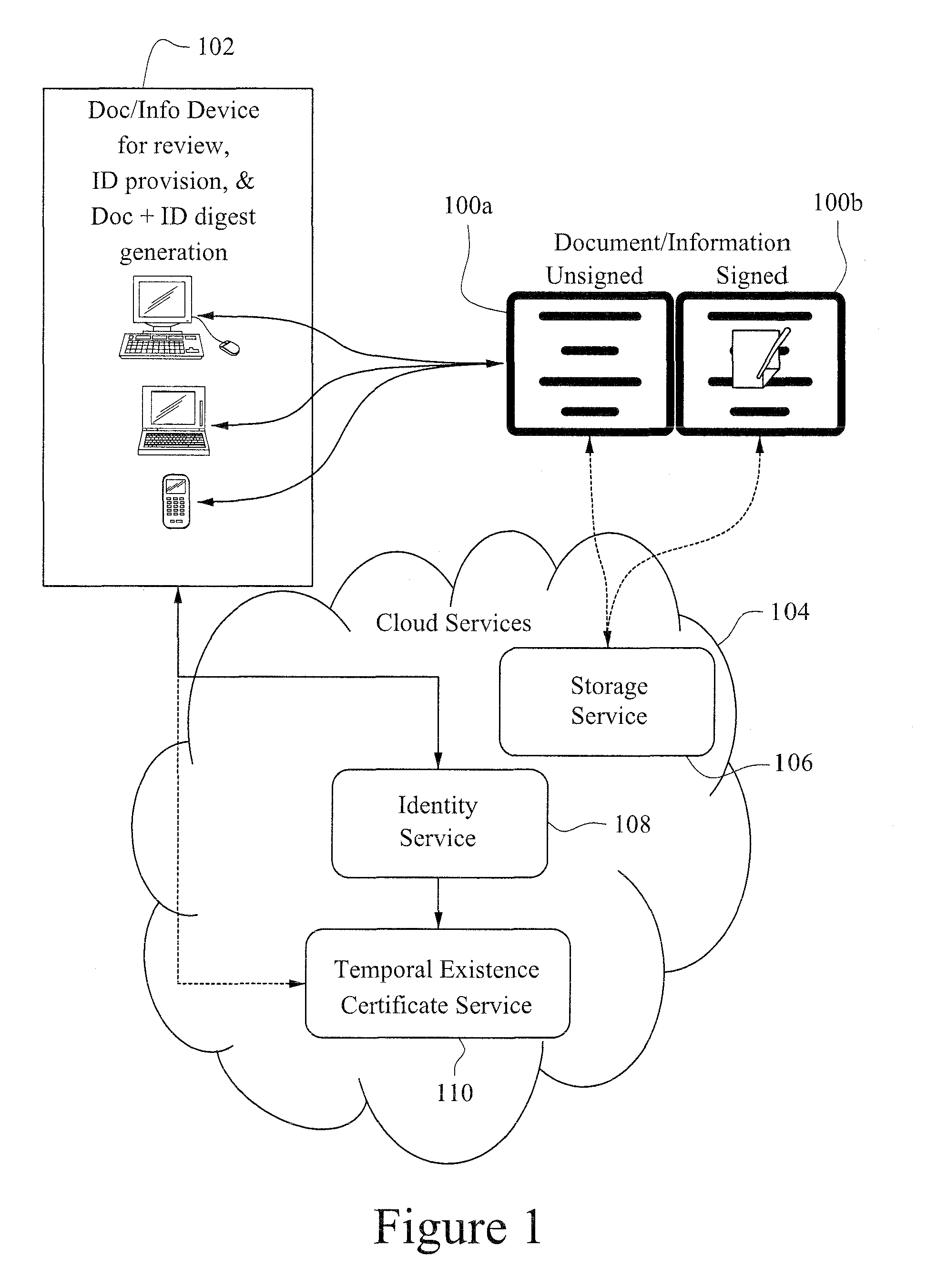
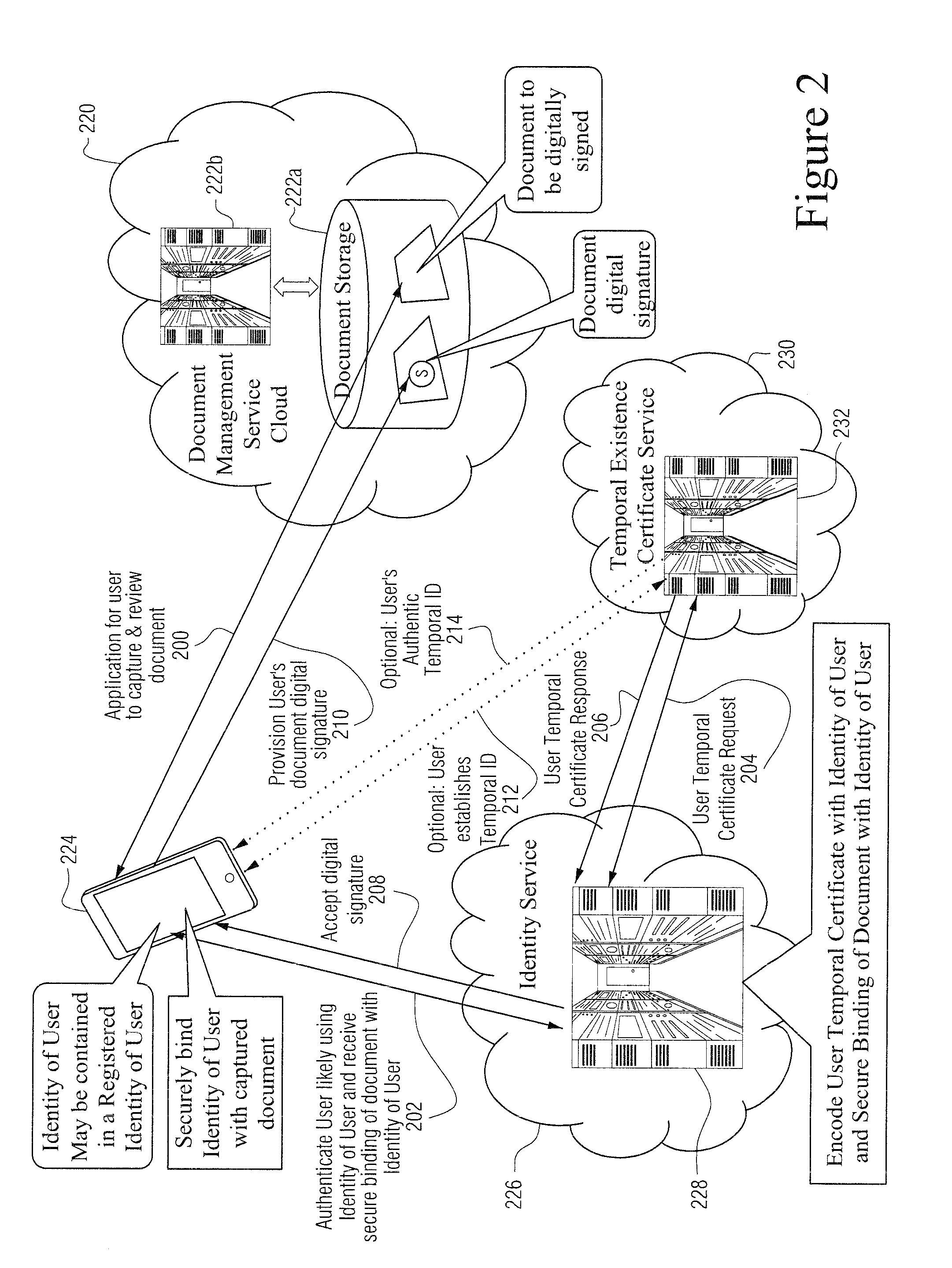
Non-PKI digital signatures and information notary public in the cloud
InactiveUS20130311772A1High user acceptanceMinimizes user information coordinationUser identity/authority verificationDocumentation procedureDigital signature
A digital signature is applied to digital documents / information. In certain instances, juridically strong digital signatures are achieved. Cloud computing technologies may be used to aid in the production of the cryptographically secure, authenticated digital signatures. Digital signatures may be produced with a digital notarization. The techniques of generating a digital signature may not require the use of traditional public key infrastructure (PKI).
Owner:ZENERJI
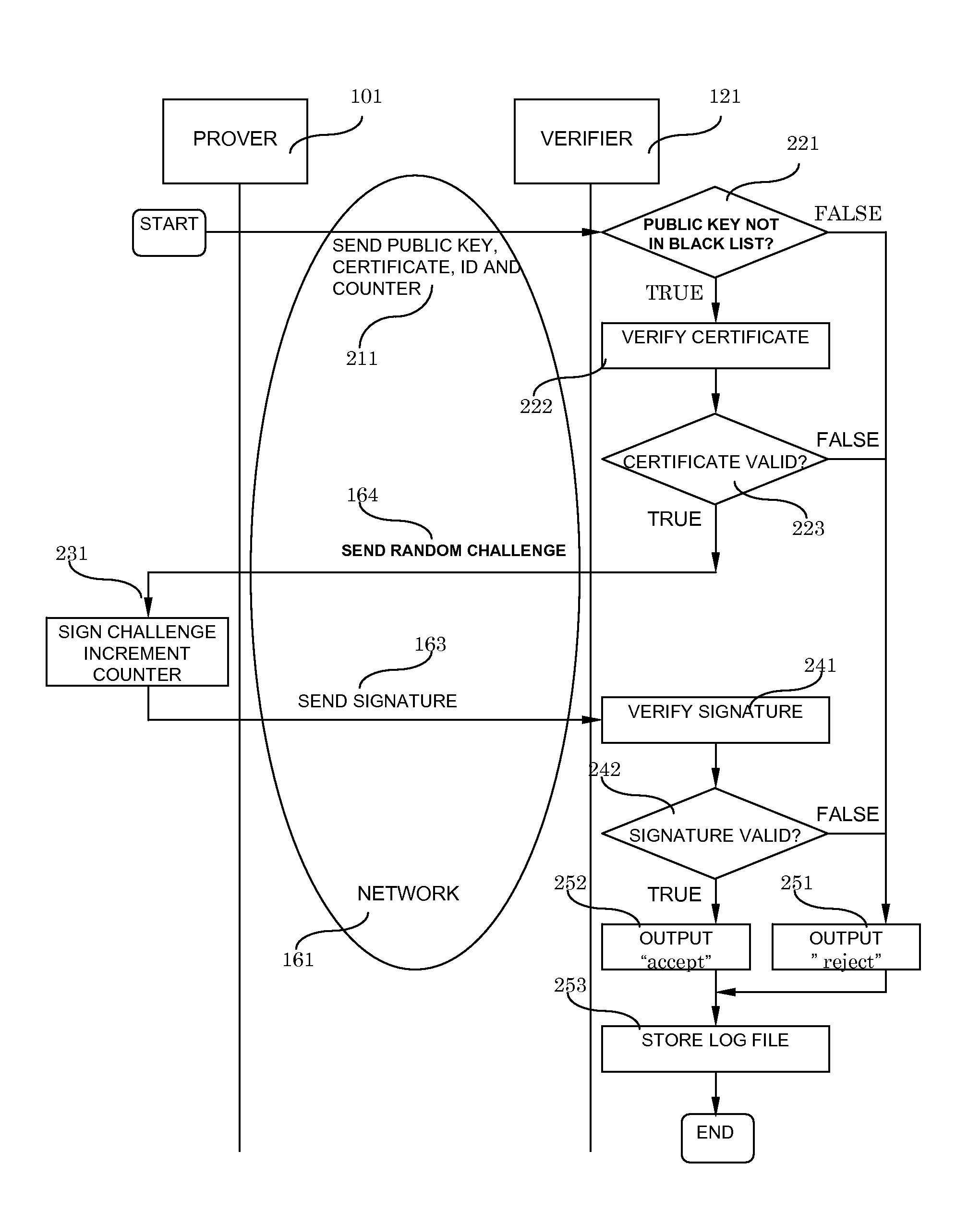
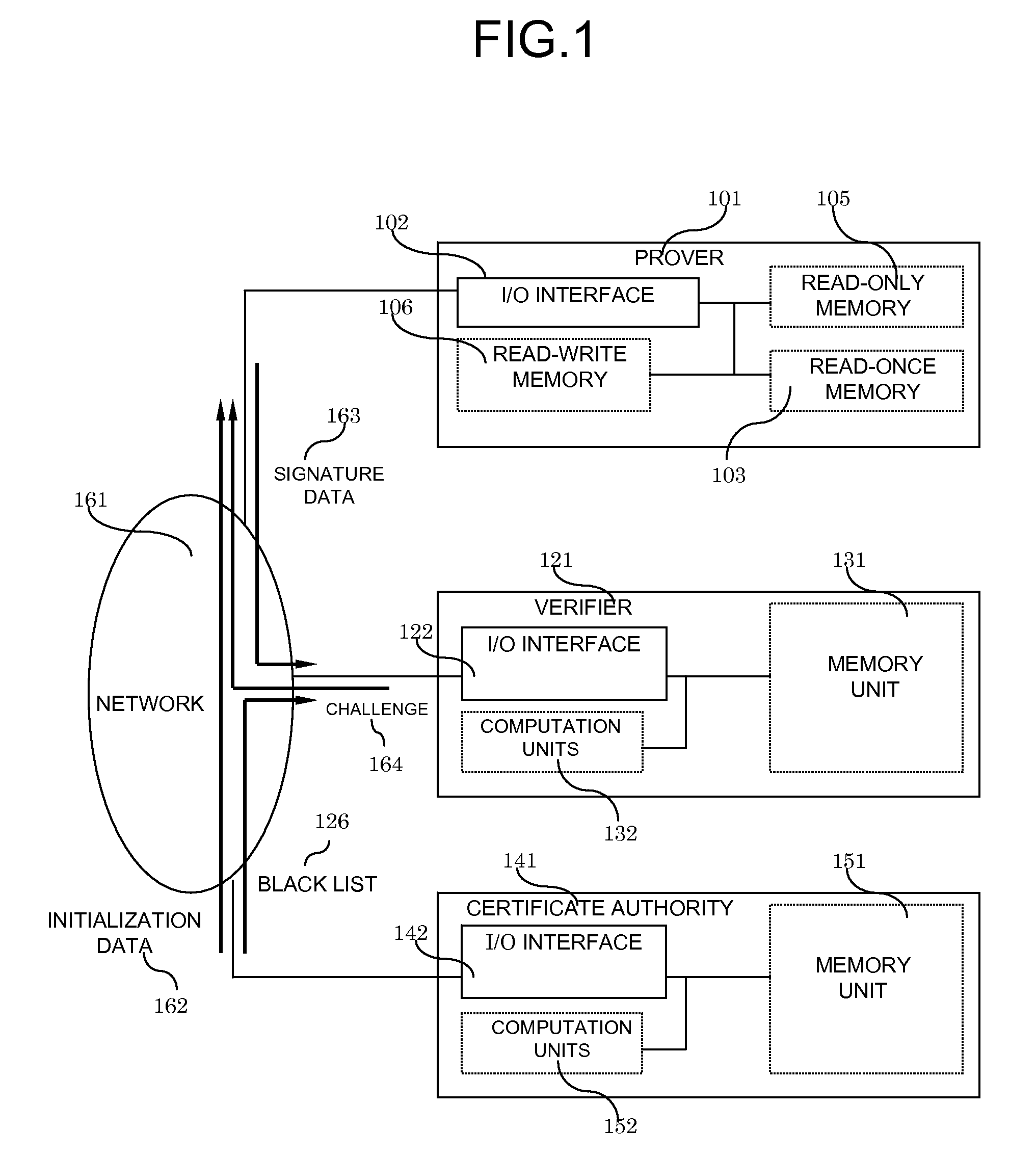
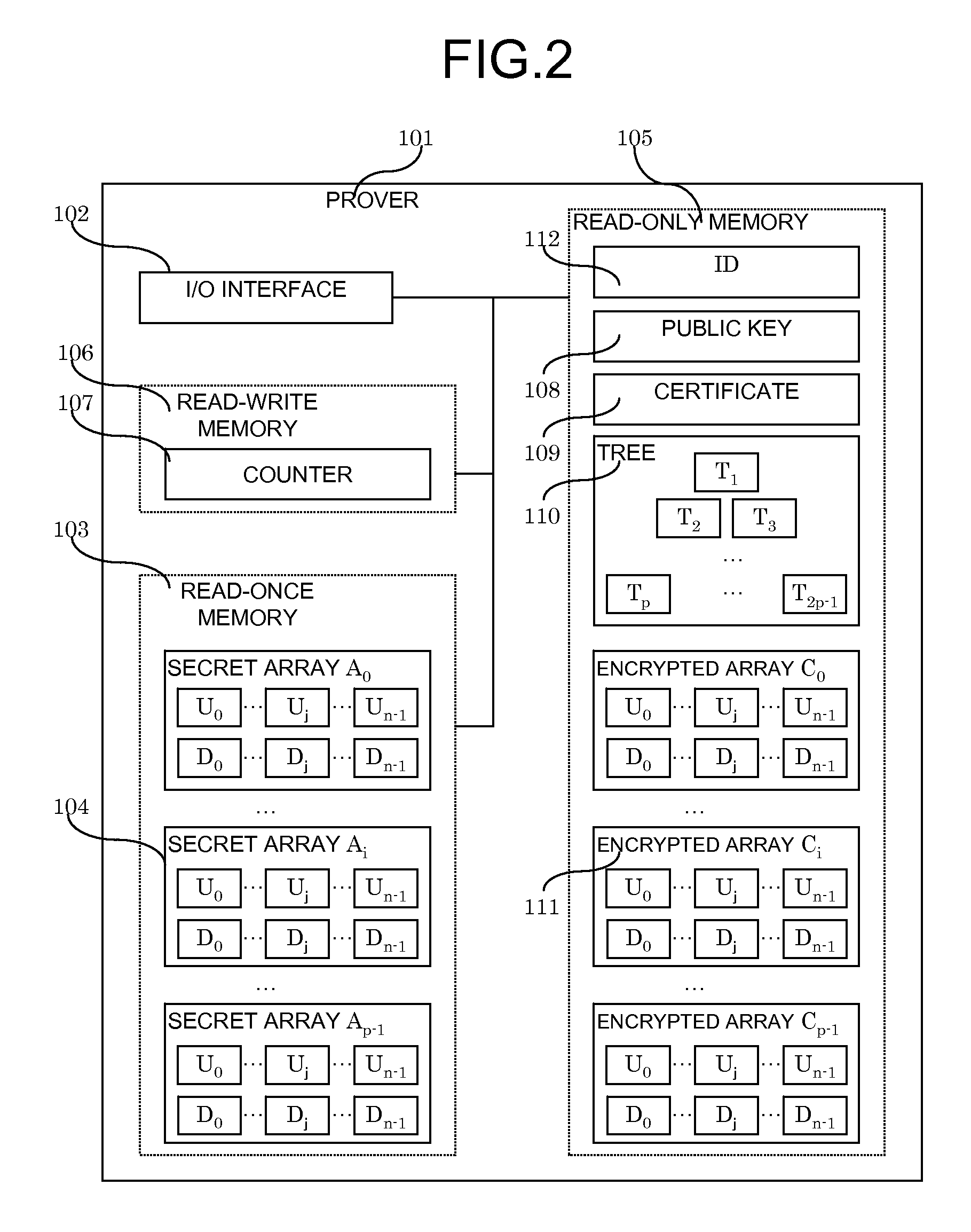
System and method for digital signatures and authentication
InactiveUS8291229B2Simple memory controllerPublic key for secure communicationUser identity/authority verificationDigital signatureKey issues
A system and method for authentication and digital signatures on memory-only supports, comprising a read-once memory unit storing secret arrays, whose contents are destroyed upon reading, a standard memory unit storing encrypted arrays, tree data authenticating the encrypted arrays to one single public key, and a certificate of the public key issued by a certificate authority. The memory support sends its public key and certificate to a verifier, receives a challenge which is signed by elements from secret arrays in the read-once memory. The verifier system checks the authenticity of the data revealed from the read-once memory by encrypting it and comparing the result to one of the encrypted arrays, and verifies that the encrypted array authenticates to the public key using tree data. Finally, the verifier checks the authenticity of the public key using the certificate.
Owner:HITACHI LTD
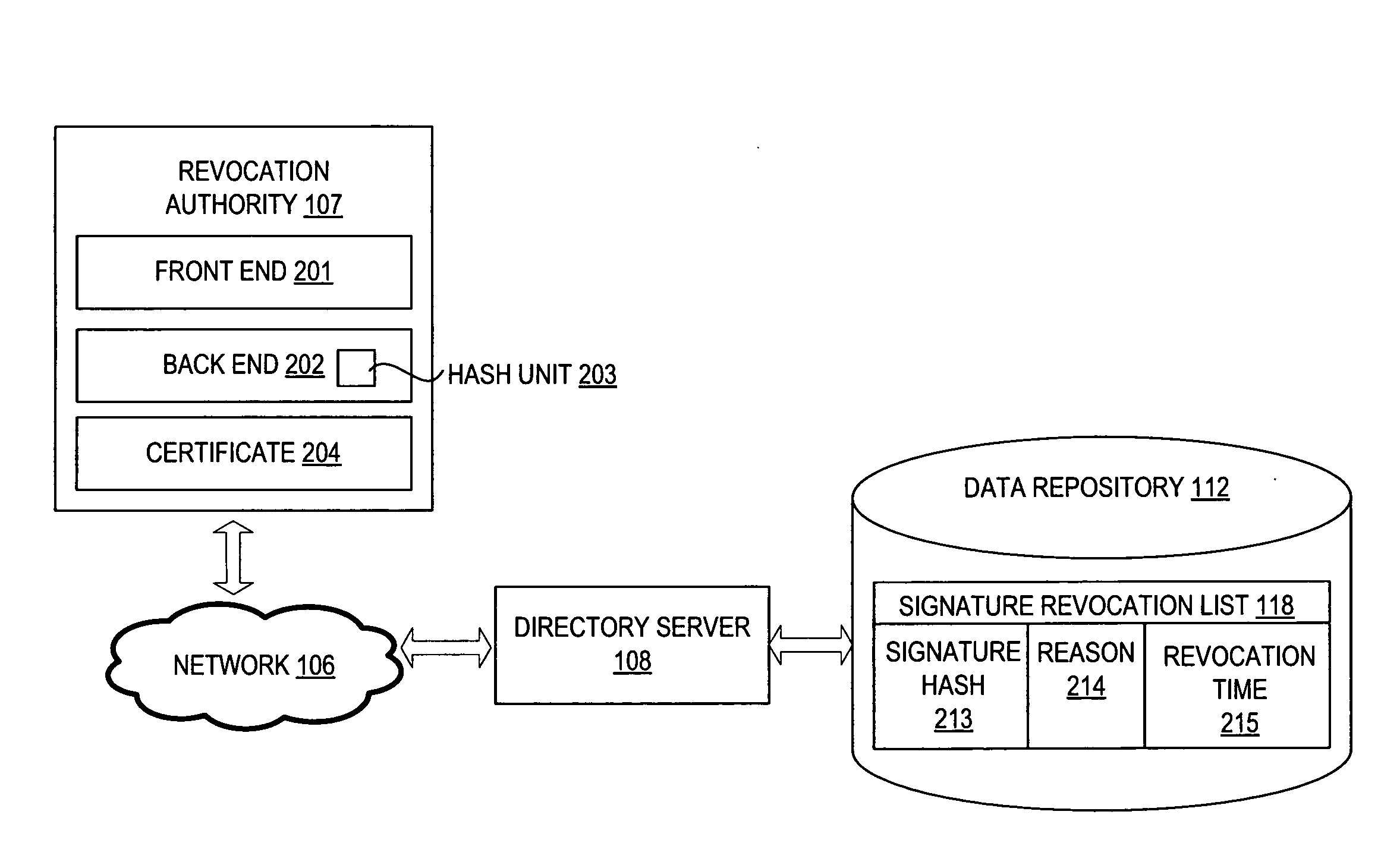
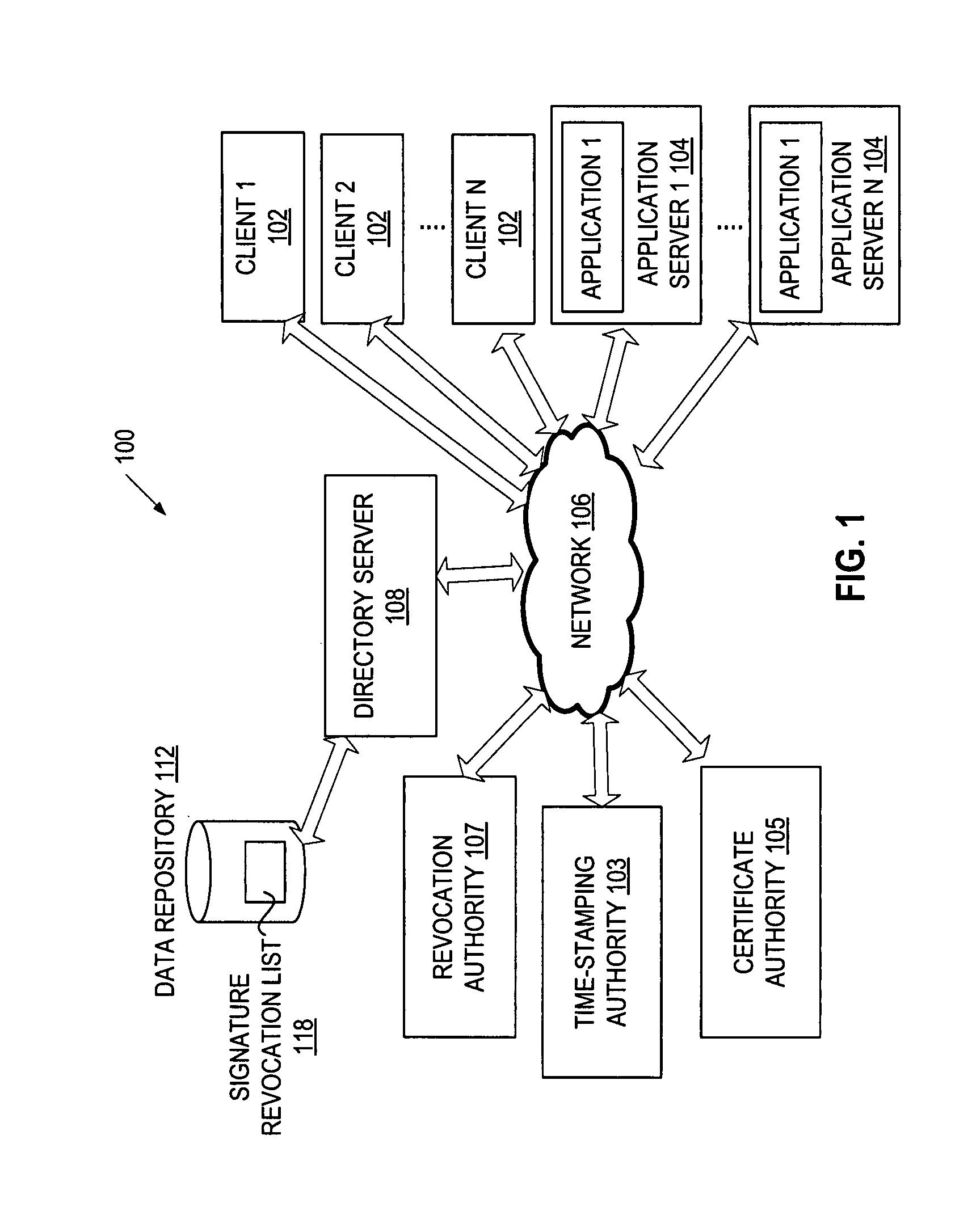
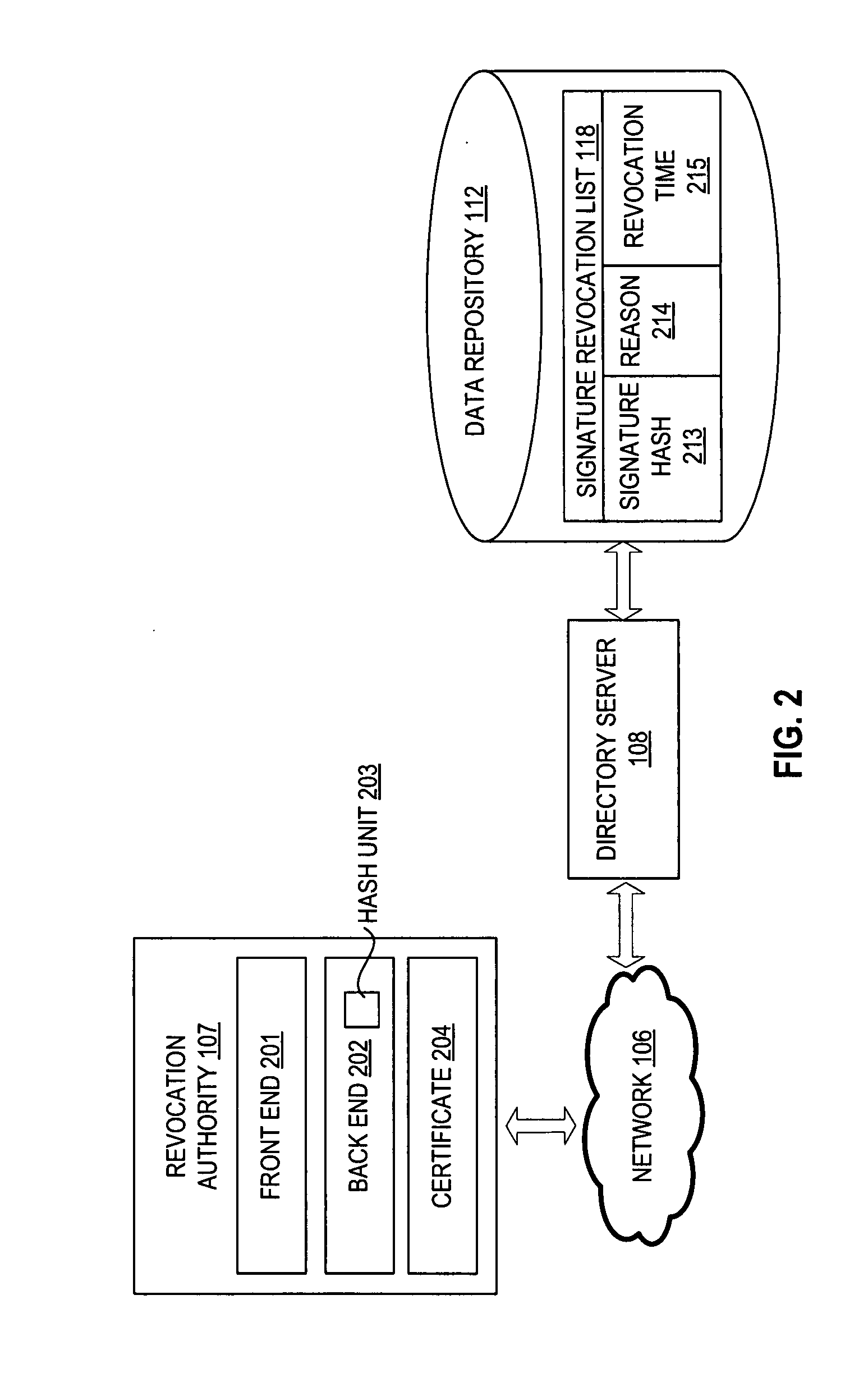
Method for revoking a digital signature
A method and apparatus for revoking a digital signature using a signature revocation list. In one embodiment, the method includes generating the signature revocation list to indicate revocation status of a signature. The signature is created from an encryption key and a document. The method also includes computing an identifier of the signature in the signature revocation list based on contents of the signature. The method further includes publishing the signature revocation list for access by users of the document.
Owner:RED HAT
Public Key Encryption with Digital Signature Scheme
InactiveUS20100174910A1Mitigate such drawbackReduce computational processingKey distribution for secure communicationMultiple keys/algorithms usageDigital signatureDigital signature forgery
An improved encryption and digital signature system and method in accordance with the invention reuses an encryption ephemeral key pair from an encryption process in a digital signature process. The reuse of the encryption ephemeral key pair in the digital signature process advantageously results in reduced byte size of the digital signature and reduction of costly computation overhead. In a preferred embodiment, the invention is based on the El Gamal encryption scheme and the Nyberg-Rueppel signature scheme. The present invention is particularly useful for operation in conjunction with small communication devices having limited processing and storage, wherein such devices may communicate via bandwidth sensitive RF links.
Owner:MALIKIE INNOVATIONS LTD
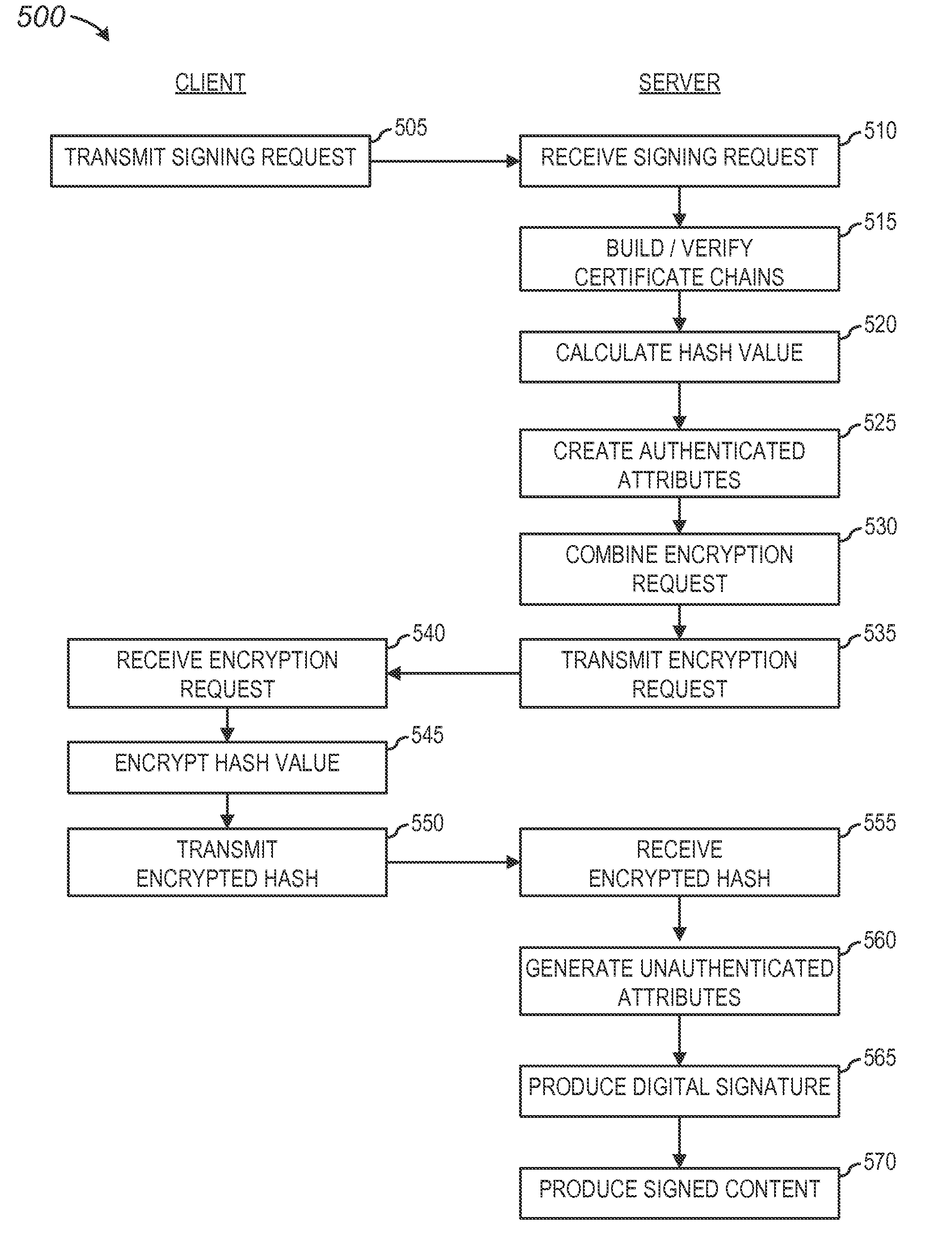
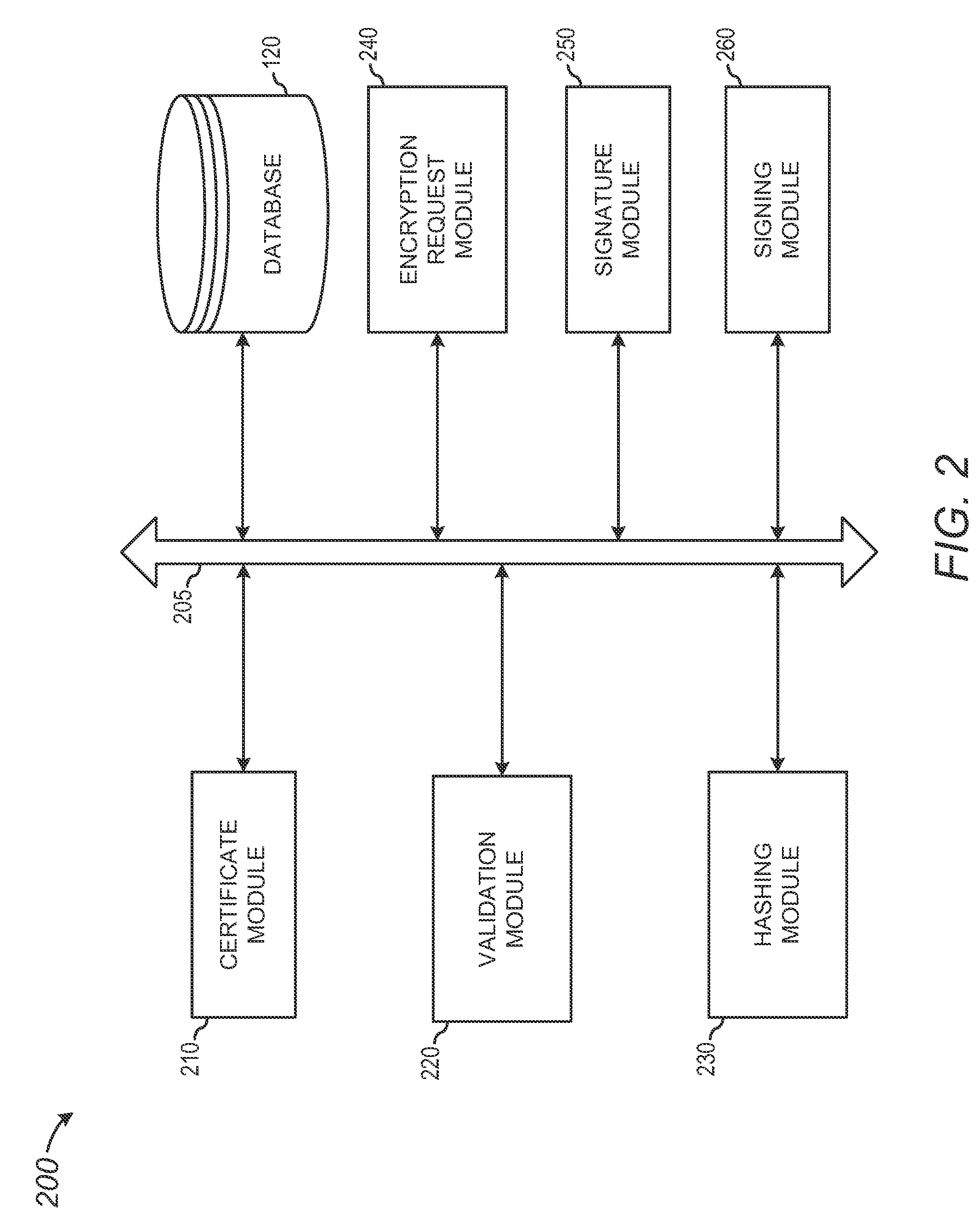
Distributive computation of a digital signature
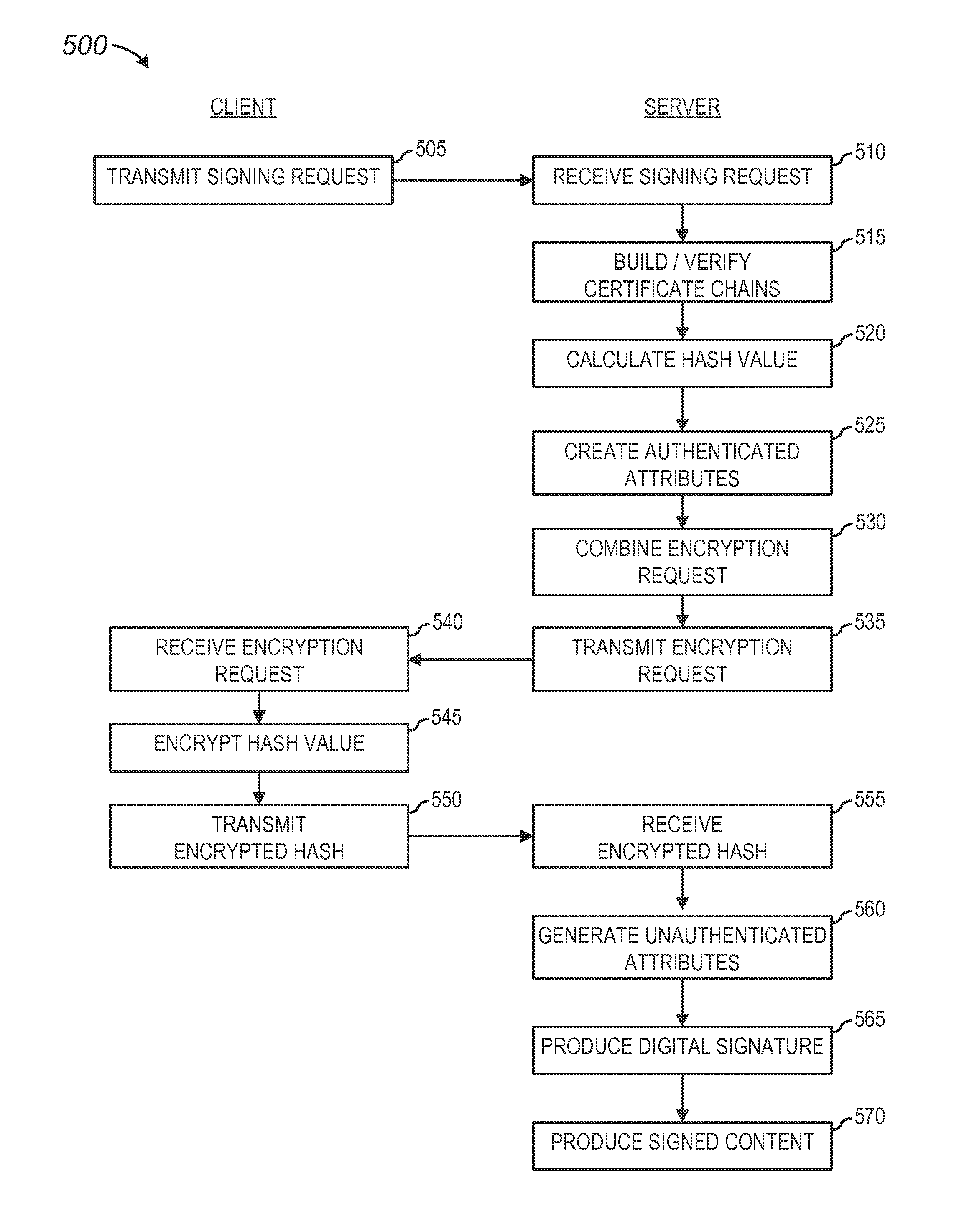
A method and apparatus are presented to perform a distributive computation of a digital signature in a document signing process. A signing request from a remote device initiates the document signing process including the distributive computation. The server verifies digital certificates corresponding to a signer's public key. An encryption request including a set of authenticated attributes and a hash value based on the to-be-signed content is transmitted to the remote device. A signer at the remote device encrypts the hash value in the encryption request with an encryption process utilizing a private key. The resulting encrypted hash value is transmitted to the server to produce the digital signature used to sign the subject content. This distributive computation process minimizes the amount of data transmitted between devices, while minimizing remote device resource requirements, and maintains the integrity of the signer's private key during generation of the digital signature.
Owner:ADOBE SYST INC
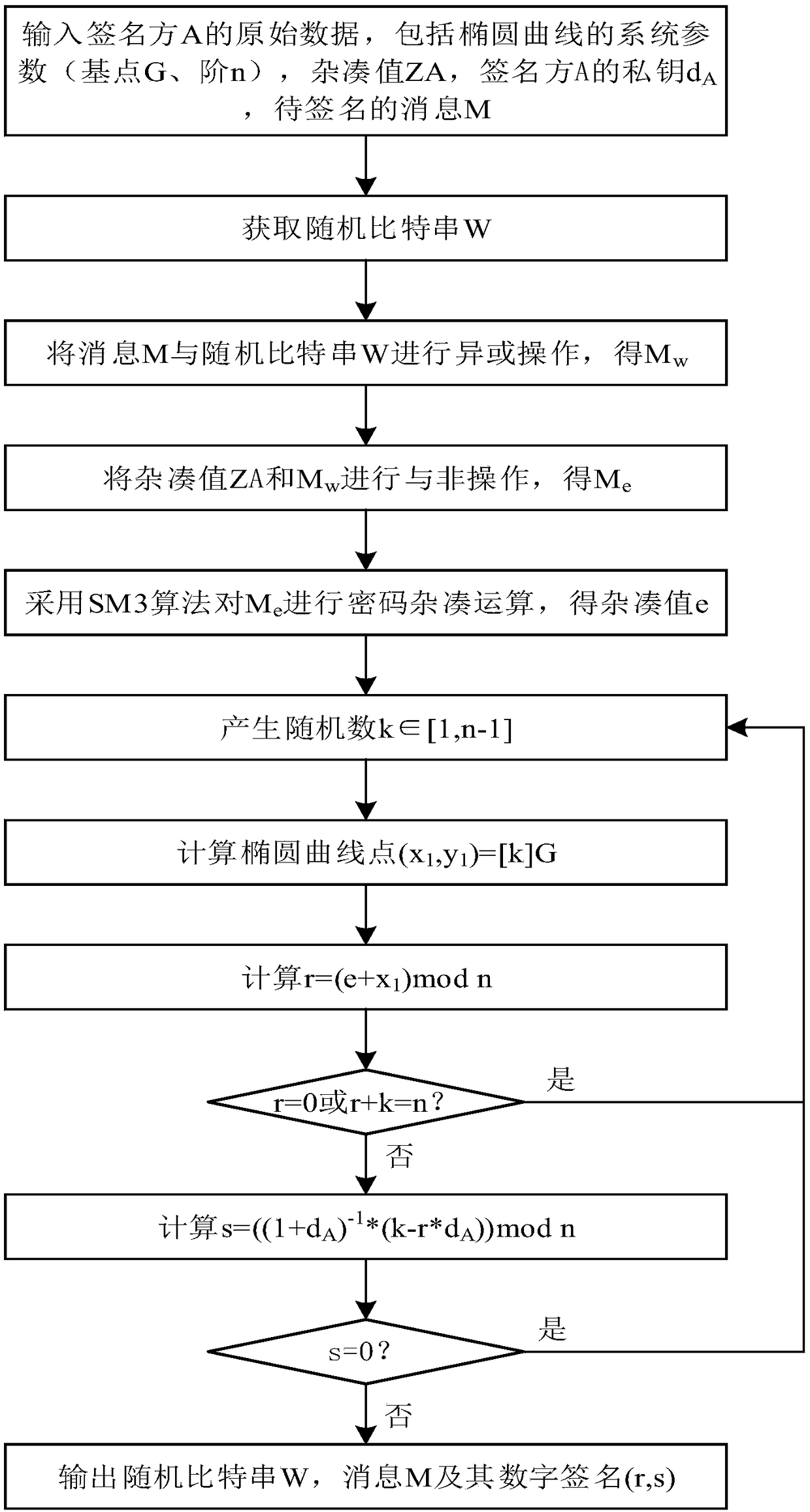
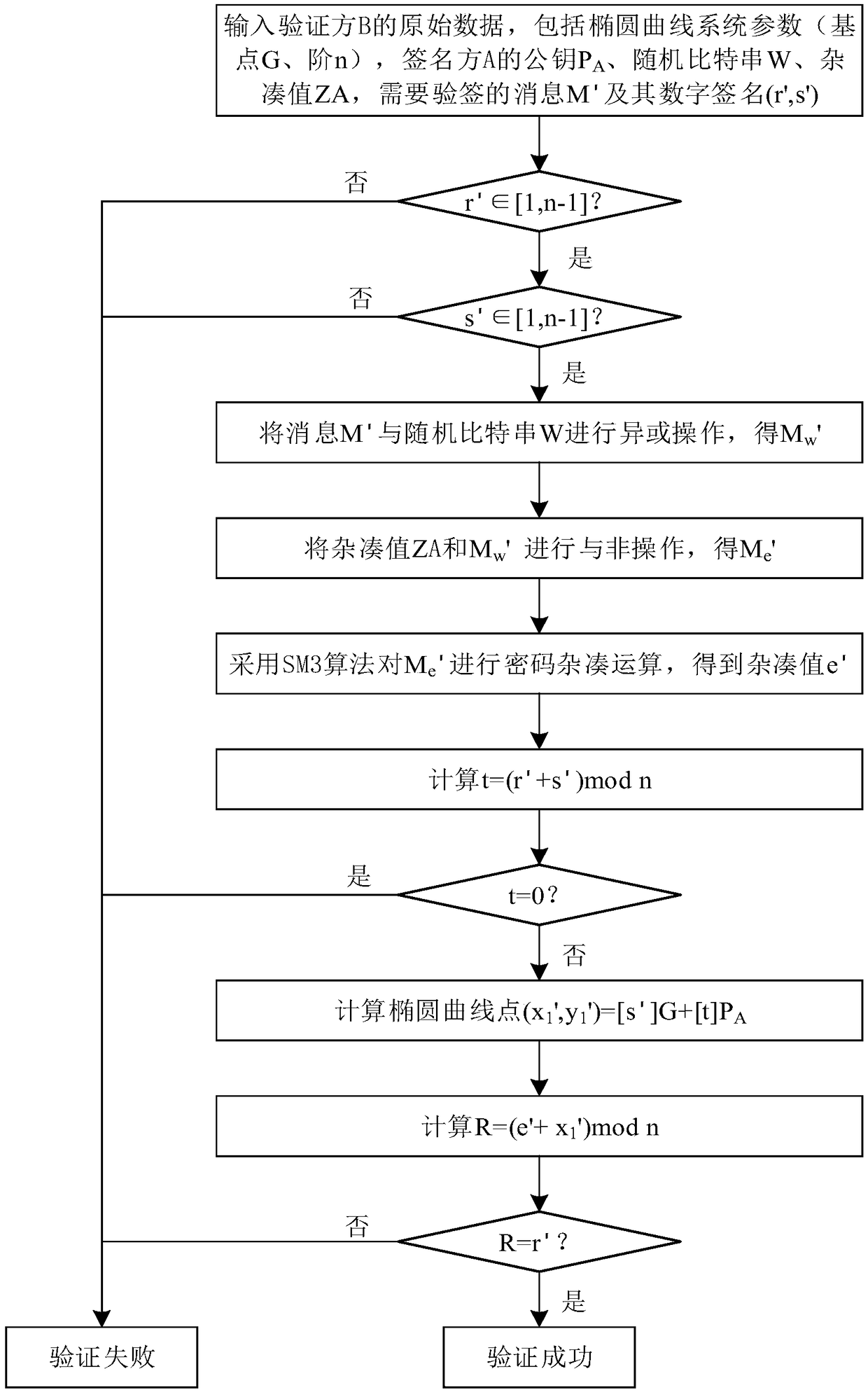
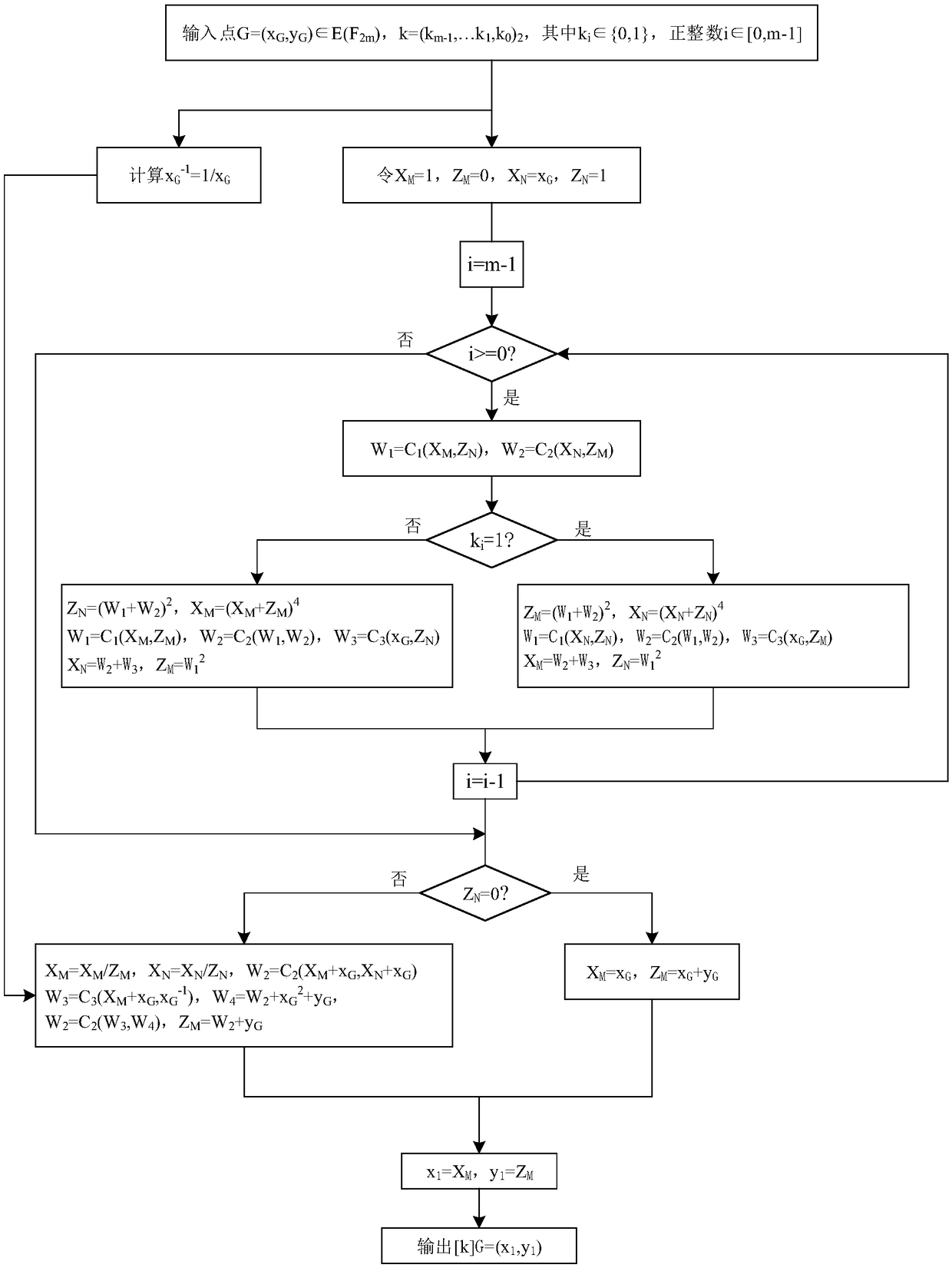
SM2 elliptic curve signature verification algorithm
ActiveCN108667623AImprove securityAvoid crackingPublic key for secure communicationUser identity/authority verificationOriginal dataDigital Signature Algorithm
The invention discloses an SM2 elliptic curve signature verification algorithm. The SM2 elliptic curve signature verification algorithm comprises the following steps: a digital signature generation algorithm: inputting the original data of a signature party A, comprising system parameters (base point G, order n) of an elliptic curve, a hash value ZA, a private key dA of the signature party A and amessage M to be signed; and obtaining a random bit string W. In a process of generating a digital signature, a segment of random bit string is obtained at first, then after an XOR operation is performed on the message to be signed and the random bit string, a NAND operation is performed with the hash value, if the signature information is intercepted by a lawbreaker in a transmission process, thelawbreaker cannot completely crack or counterfeit the signature information without knowing the XOR operation and the NAND operation in the signature process, thereby improving the security of the signature information and preventing the lawbreaker from cracking and counterfeiting the signature information after intercepting the signature information.
Owner:GUANGDONG UNIV OF TECH
Small public-key based digital signatures for authentication
ActiveUS8437473B2Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital signatureDigital signature forgery
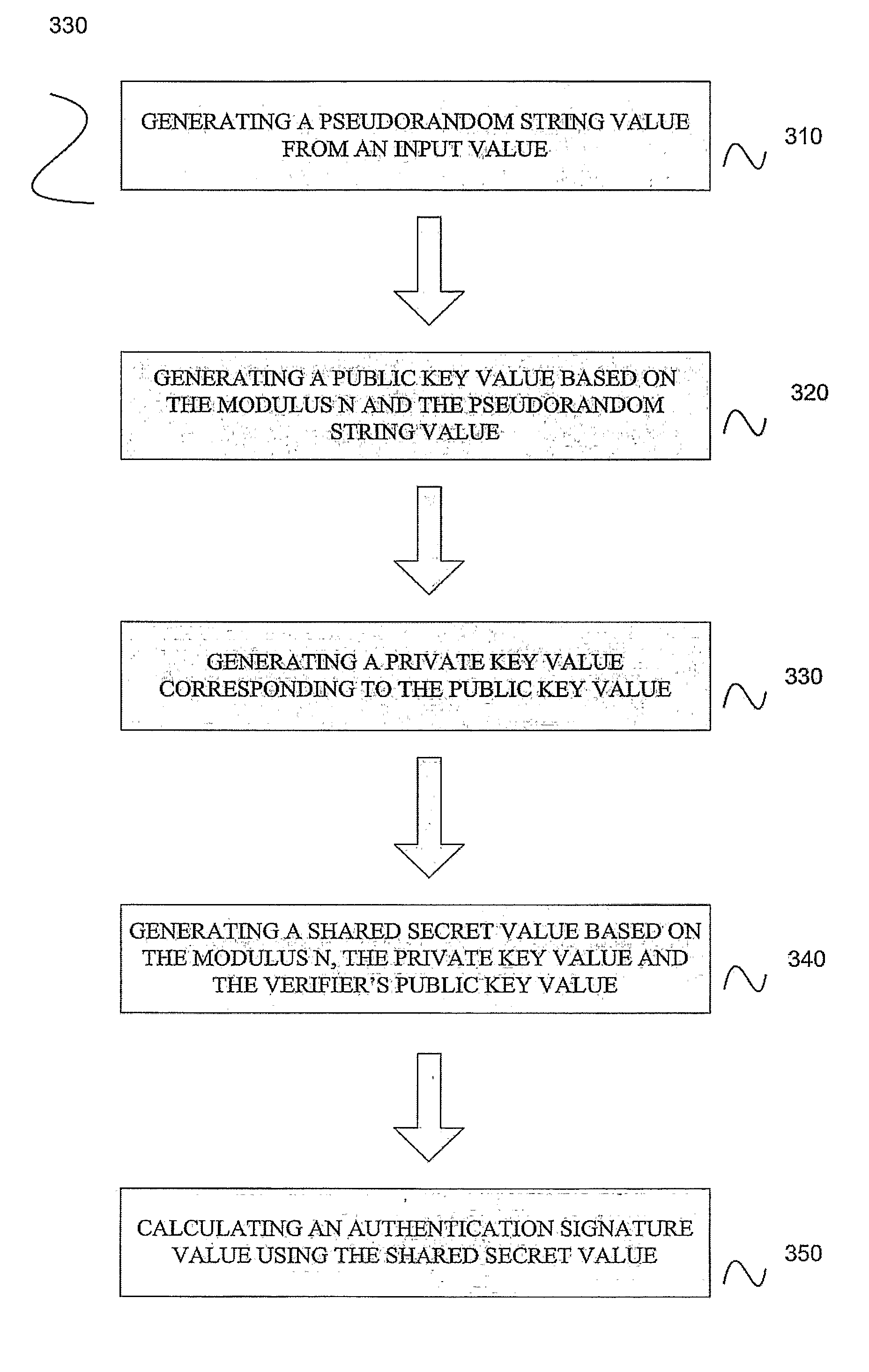
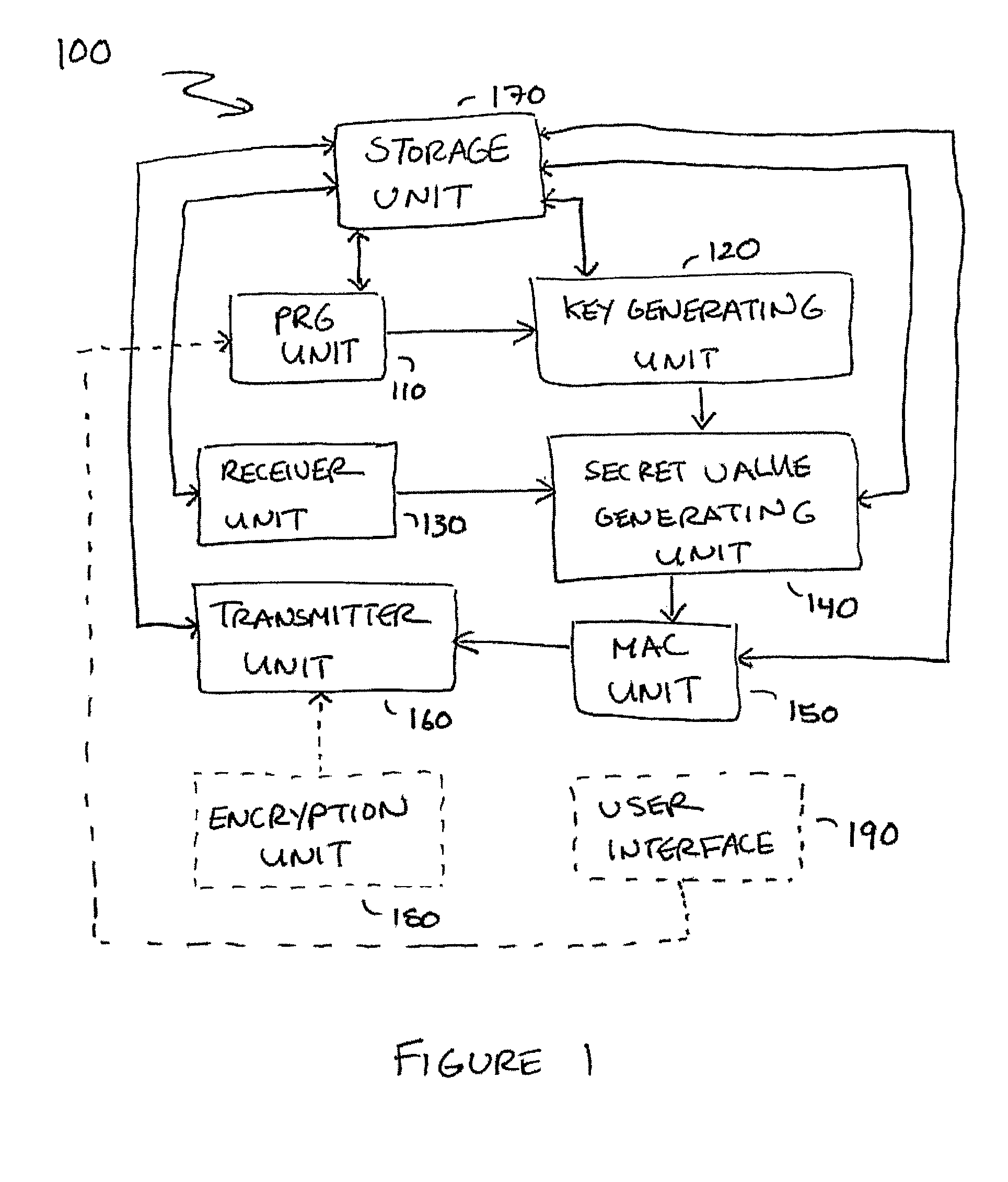
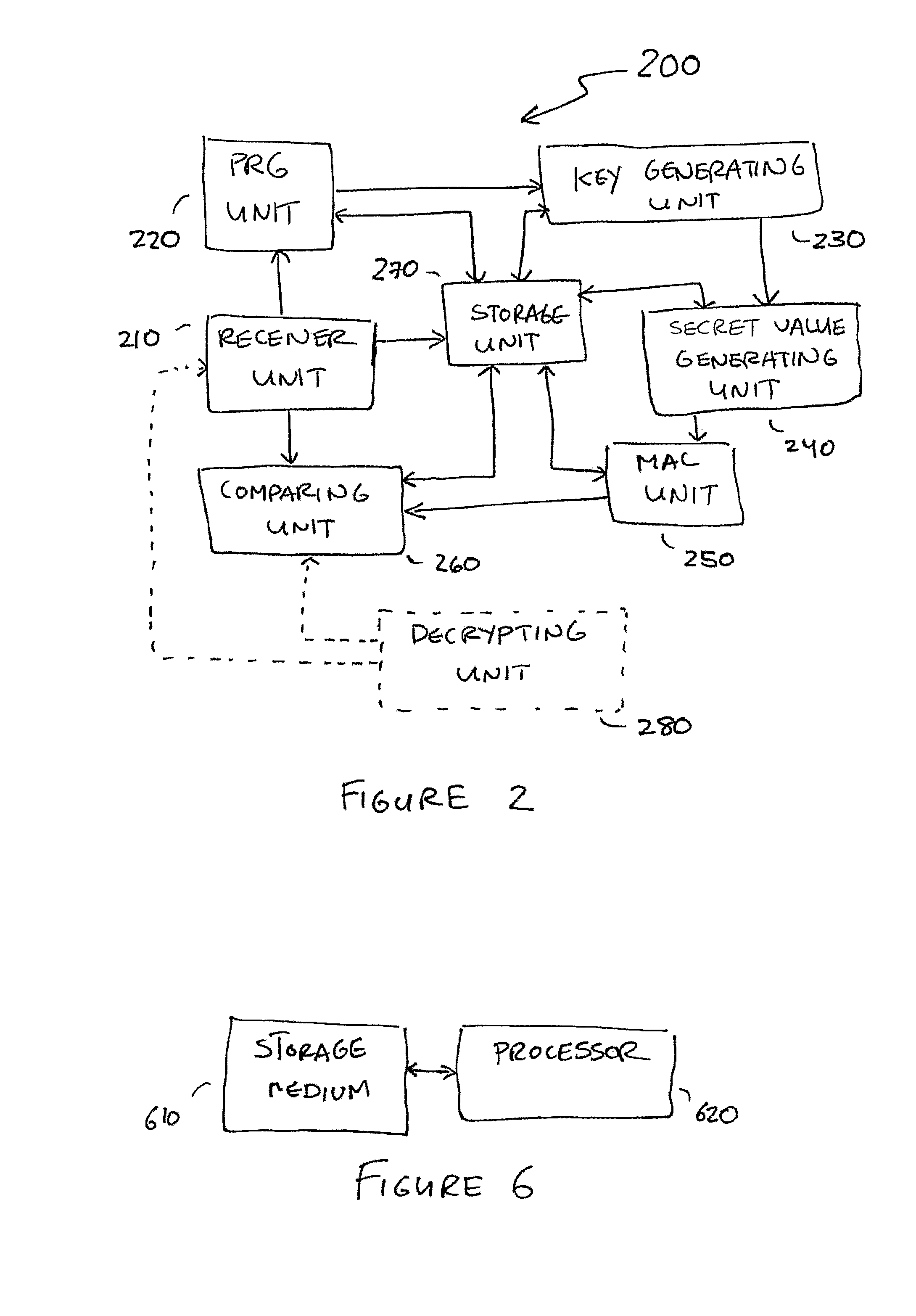
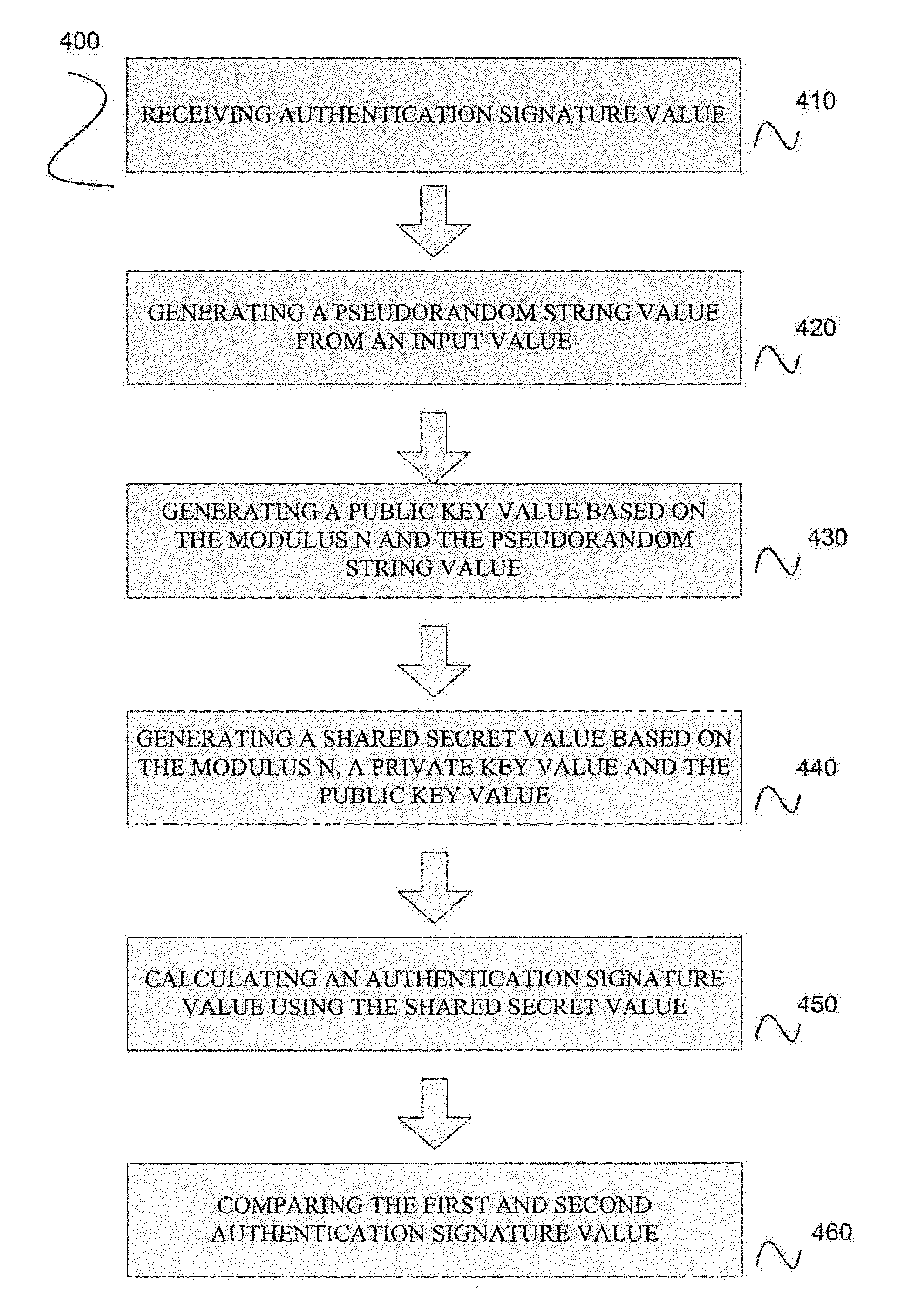
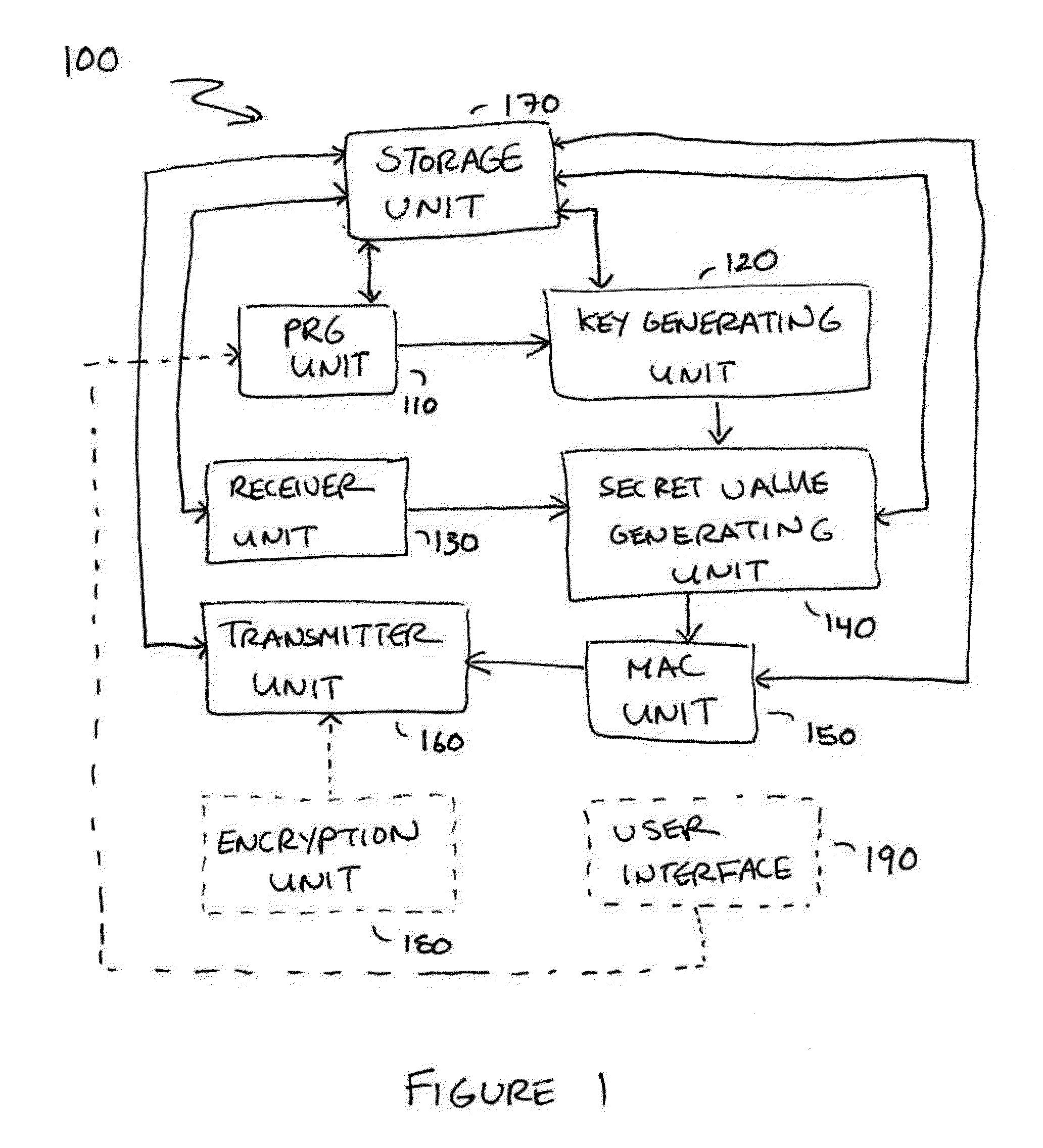
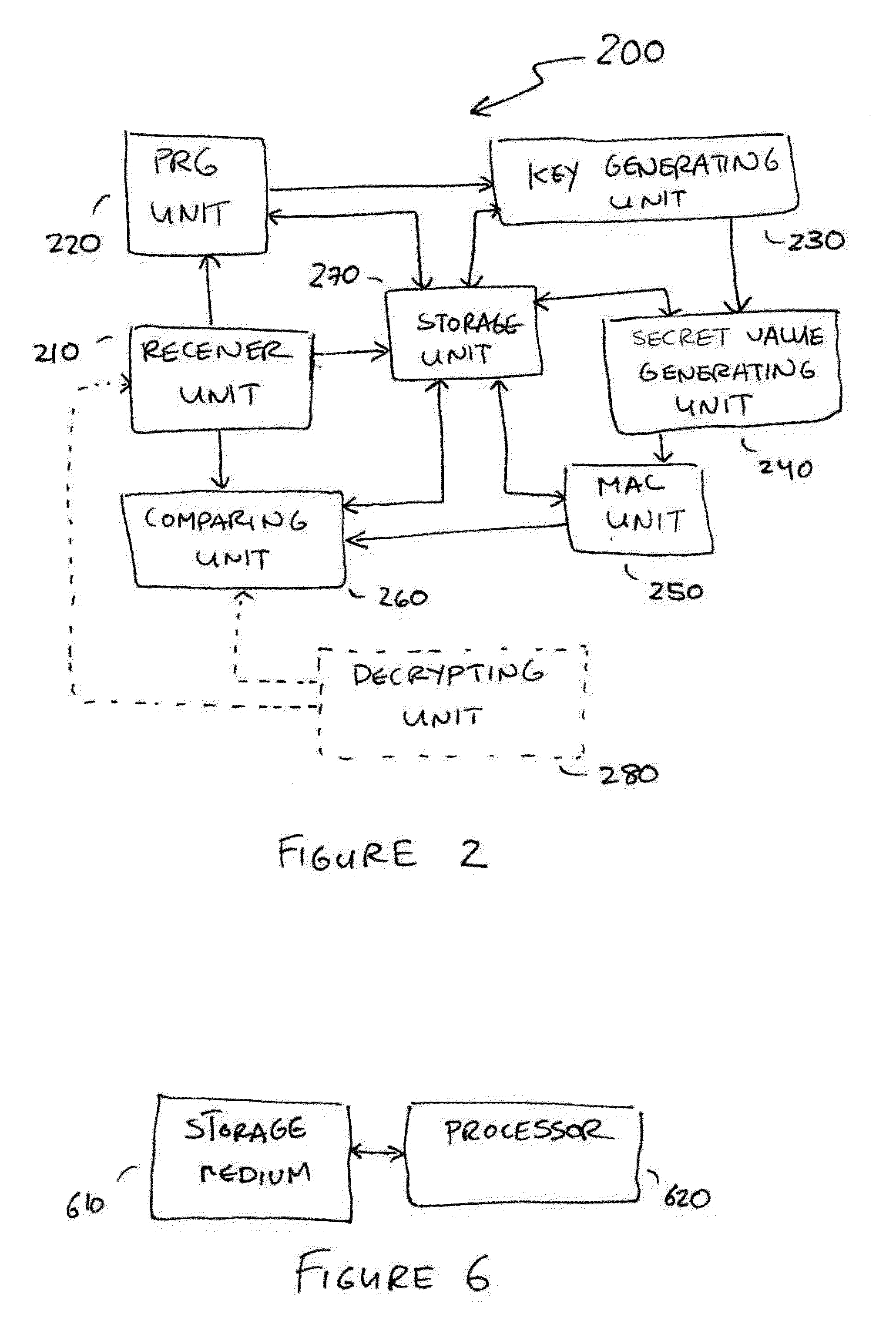
Embodiments disclosed allow authentication between two entities having agreed on the use of a common modulus N. The authentication includes generating a pseudorandom string value; generating a public key value based on the modulus N and the pseudorandom string value; generating a private key value corresponding to the public key value; receiving a verifier's public key value; generating a shared secret value based on the modulus N, the private key value and the verifier's public key value; calculating an authentication signature value using the shared secret value; and transmitting the authentication signature value for authentication. When the authentication signature is received, the public key value and the shared value are generated to calculate an authentication signature value. Thereafter, the authentication signature values are compared and authenticated.
Owner:QUALCOMM INC
Method and computer system operated software application for digital signature
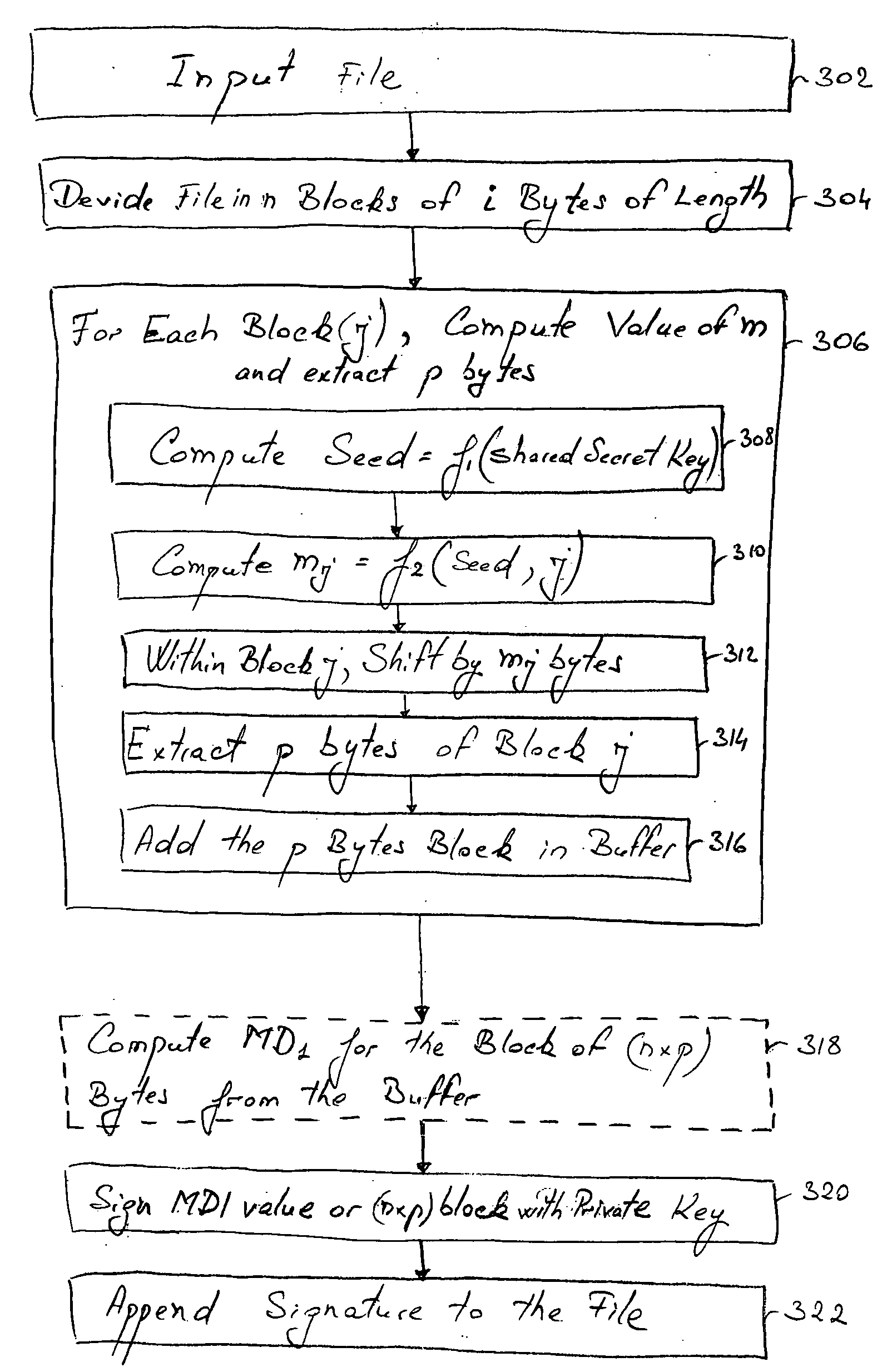
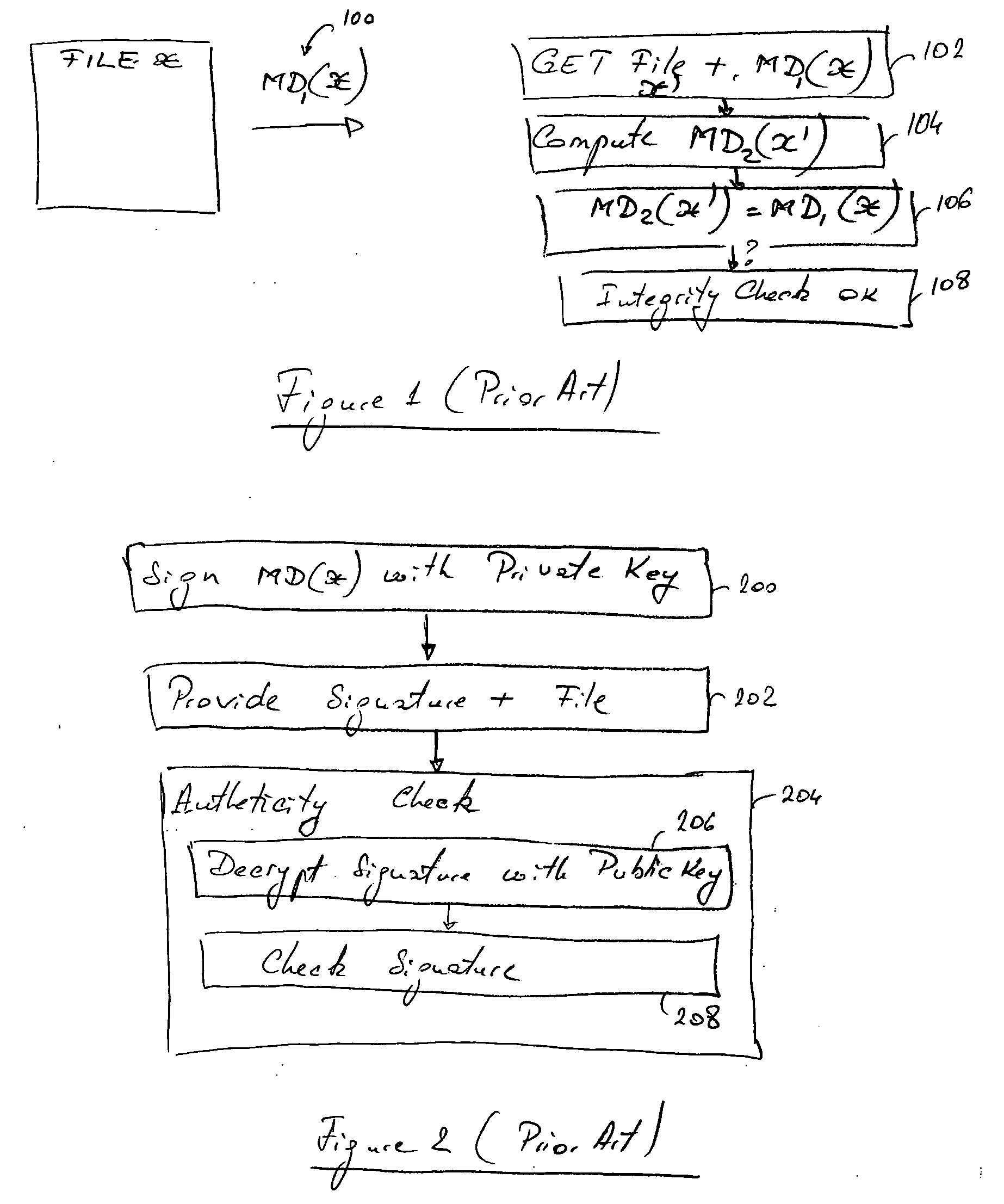
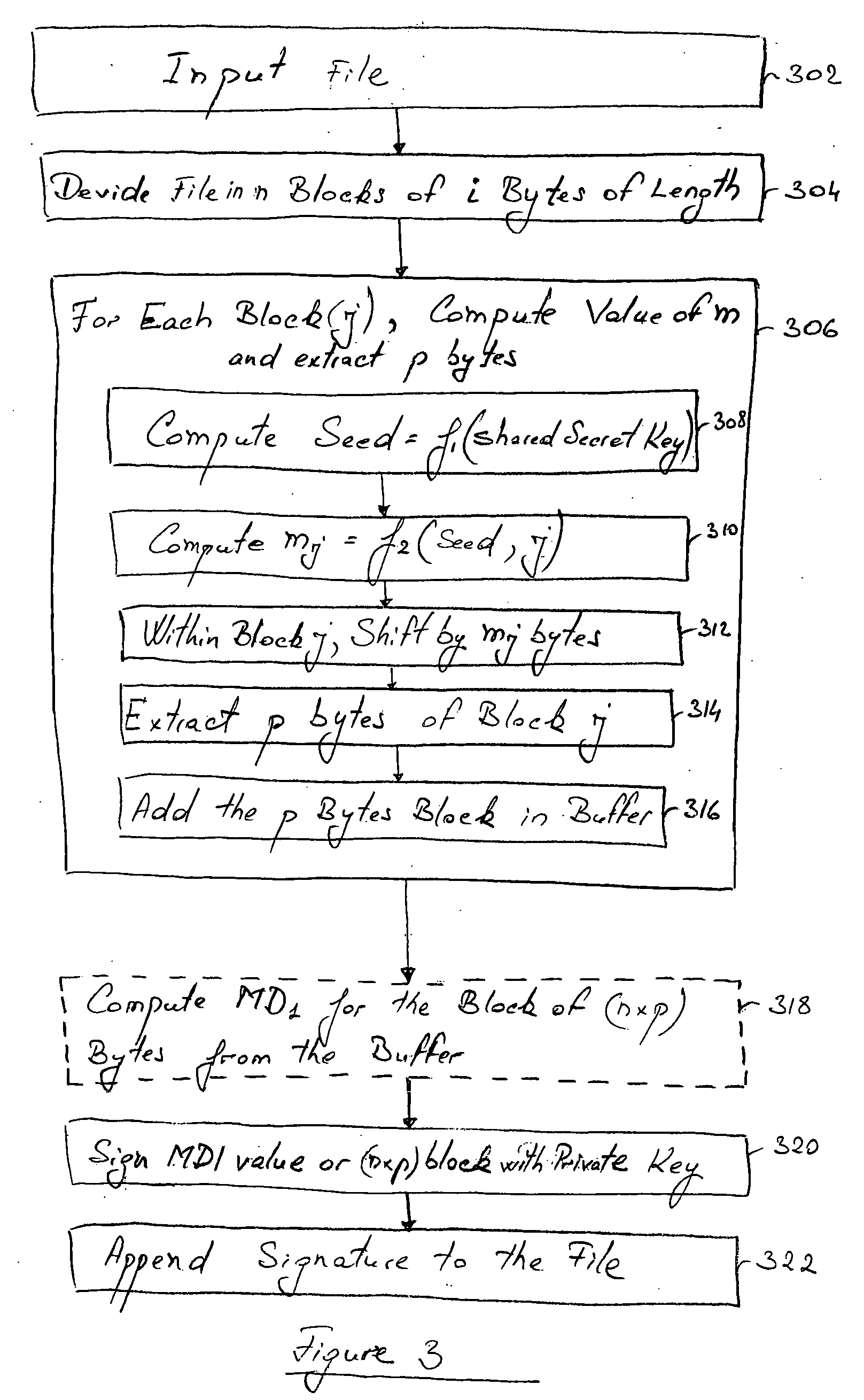
A method and computer operated software application for digitally signing a portion of an electronic file, and for verifying such a digital signature. A portion of the file to be signed is extracted based on a computation of one or more functions, and the file portion is used for being either directly digitally signed, or for calculating a Message Digest value (MD1) and for digitally signing the MD1 value with a private key of the signer. The so-formed digital signature is appended to the file. During verification, the digital signature is removed from the file, decrypted using the signer's public key, which is known to the verifier, and the portion of the file, or respectively MD1 is obtained. The portion of the file used for the signature is again obtained and used for a similar a computation based on the one or more functions, which are also known to the verifier, for calculating a corresponding portion of the file, or another Message Digest value (MD2). MD1 and MD2 are compared, or alternatively the file portions are compared, to determine the authenticity and integrity of the file.
Owner:TELEFON AB LM ERICSSON (PUBL)
Digital signature method, system and device
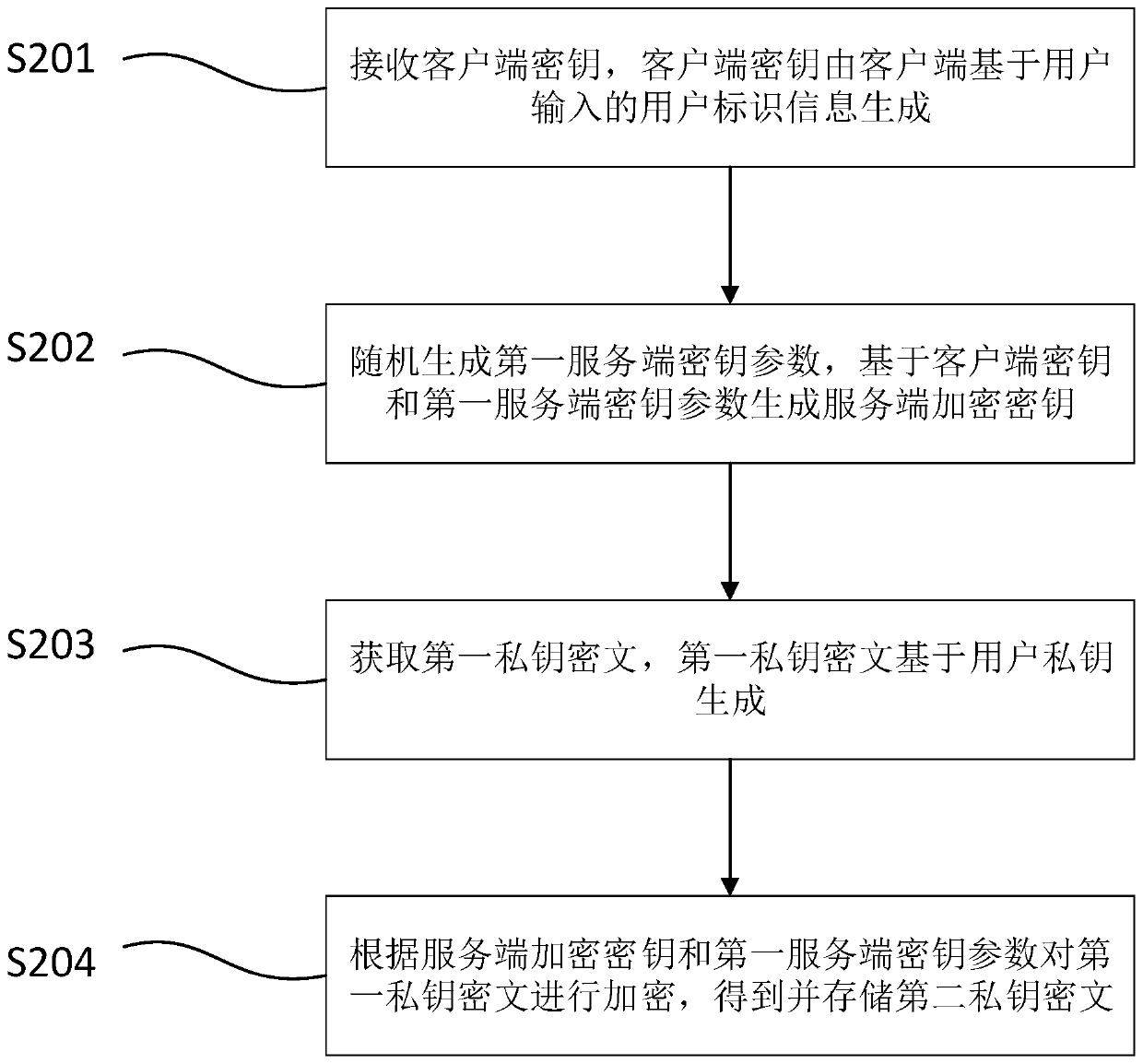
ActiveCN111130803AImprove securityKey distribution for secure communicationUser identity/authority verificationInternet privacyDigital signature
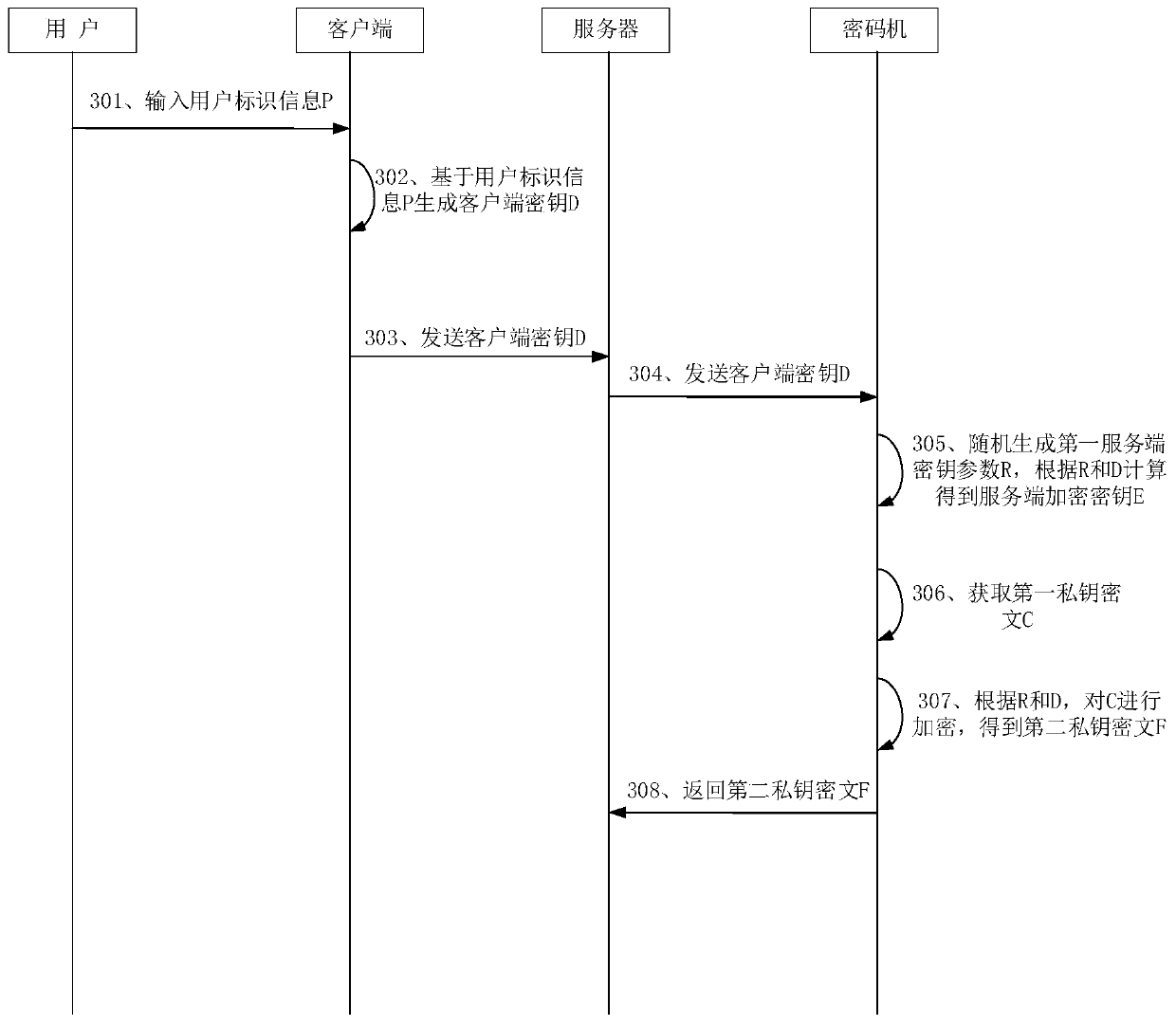
The invention relates to the technical field of cryptology, and particularly provides a digital signature method, system and device. The digital signature method is applied to a server, a second private key ciphertext is stored in the server, the second private key ciphertext comprises a first ciphertext fragment and a second ciphertext fragment, and the second ciphertext fragment is obtained by encrypting the first private key ciphertext according to user identification information input by a user. The first private key ciphertext is encrypted according to the user identification information;thus, the digital signature process is simplified; the second ciphertext fragment is decrypted according to a client decryption key generated by the client to obtain a first private key ciphertext; it is ensured that the second private key ciphertext can be decrypted only under the condition that the user participates in; therefore, the digital signature is completed according to the first private key ciphertext, a counterfeiter cannot forge the user signature singly, the use security of the user private key is improved, the second private key ciphertext is divided into a plurality of segments to be stored, and the security of the user private key is further improved.
Owner:信安神州科技(广州)有限公司
Small public-key based digital signatures for authentication
InactiveUS20130227297A1Key distribution for secure communicationUser identity/authority verificationDigital signatureDigital signature forgery
Embodiments disclosed allow authentication between two entities having agreed on the use of a common modulus N. The authentication includes generating a pseudorandom string value; generating a public key value based on the modulus N and the pseudorandom string value; generating a private key value corresponding to the public key value; receiving a verifier's public key value; generating a shared secret value based on the modulus N, the private key value and the verifier's public key value; calculating an authentication signature value using the shared secret value; and transmitting the authentication signature value for authentication. When the authentication signature is received, the public key value and the shared value are generated to calculate an authentication signature value. Thereafter, the authentication signature values are compared and authenticated.
Owner:QUALCOMM INC
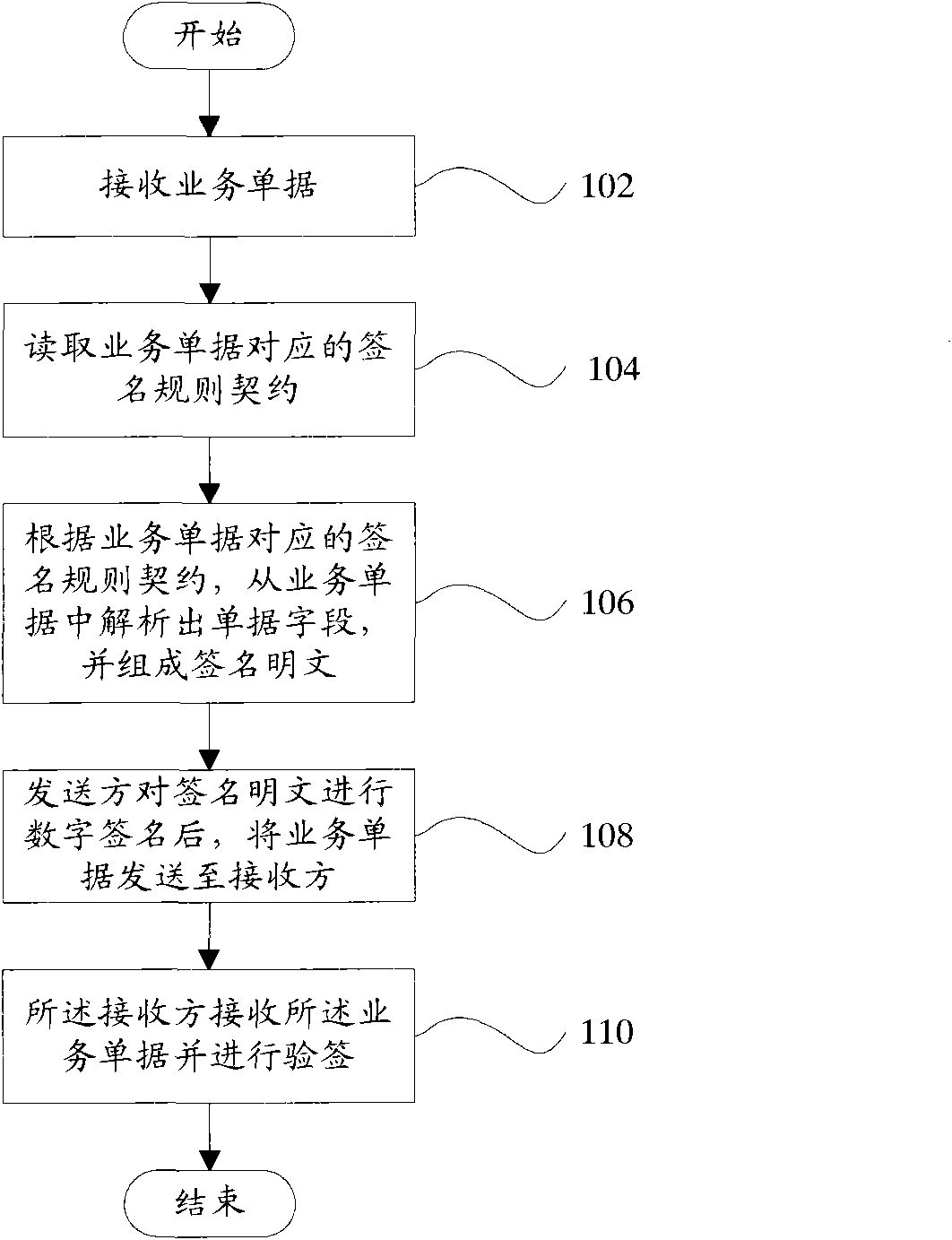
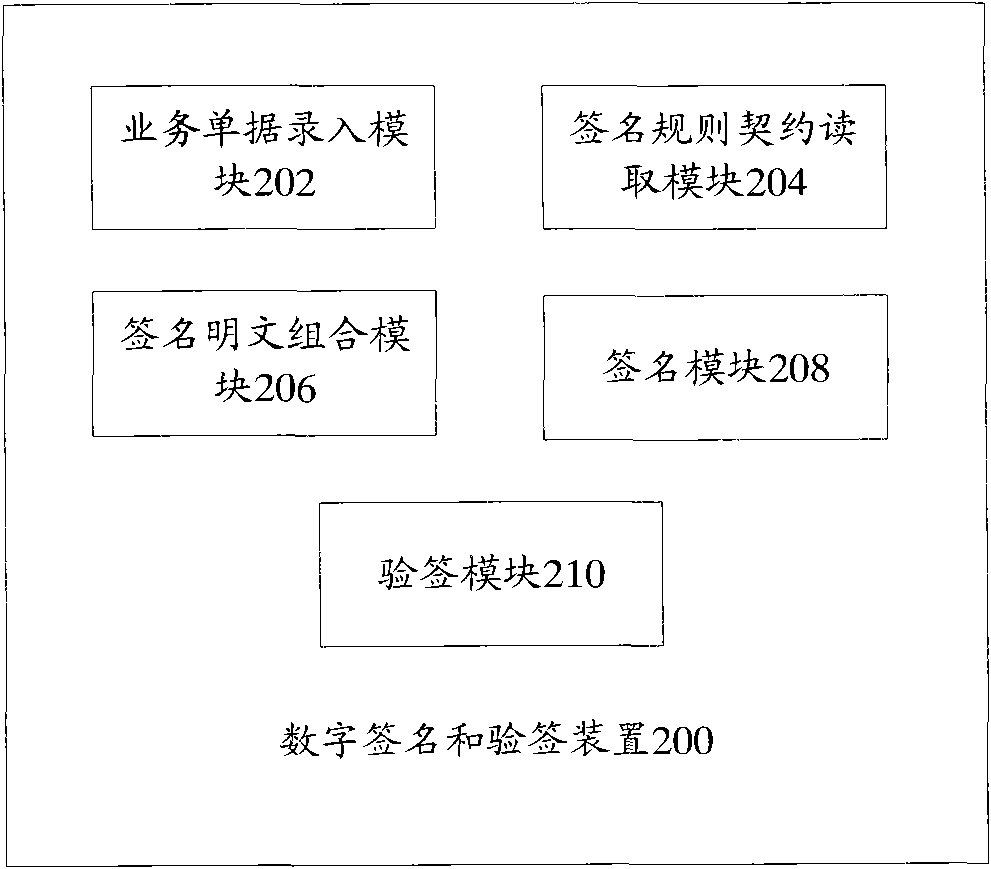
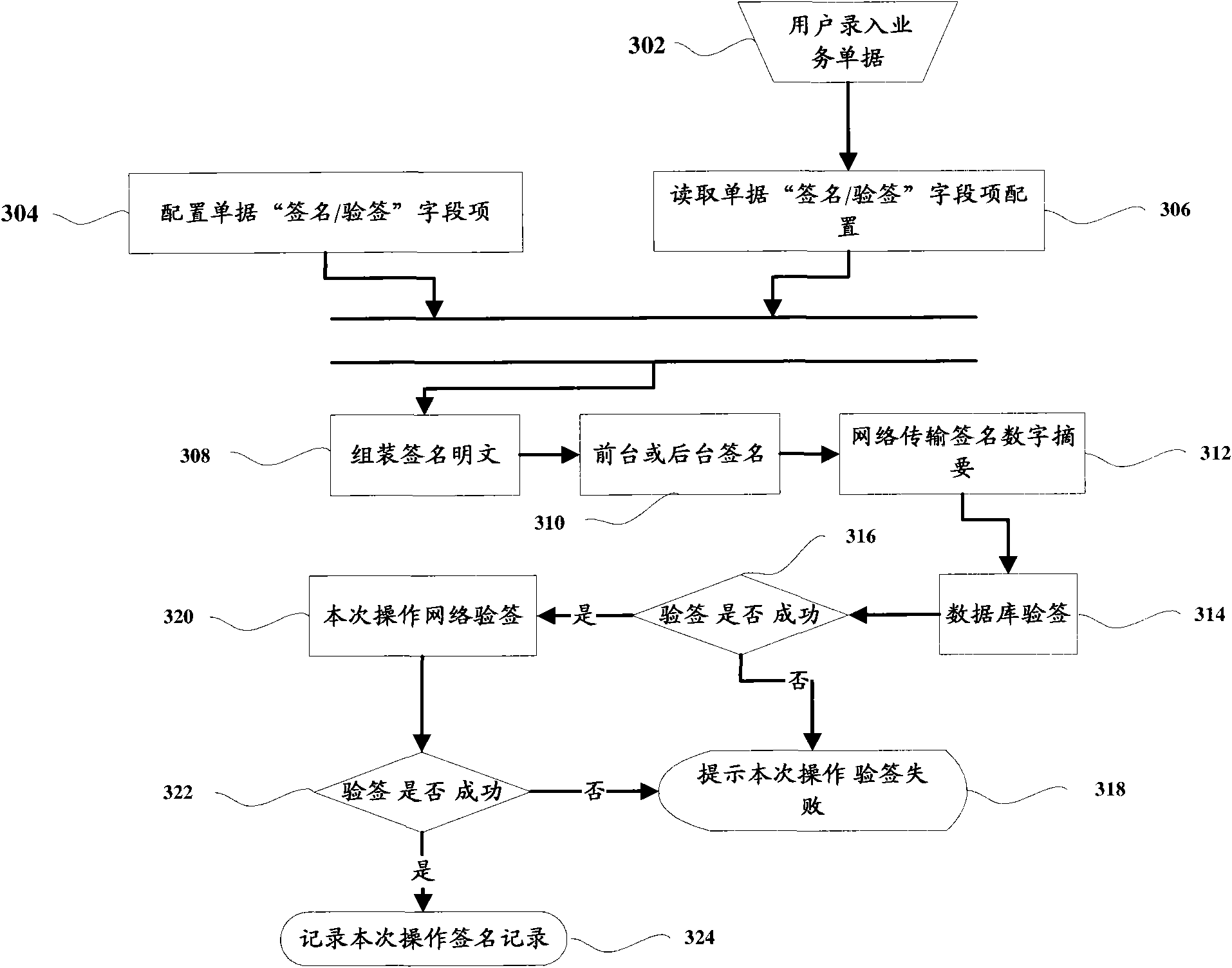
Digital signature and signature authenticating method
The invention provides a digital signature and a signature authenticating method which comprises the following steps: step 102, receiving business documents; step 104, reading the signature rule contract corresponding to the business documents; step 106, according to the signature rule contract corresponding to the business documents, resolving the document fields from the business documents and forming a plain text of signature; step 108, after a sender digitally signs on the plain text of signature, sending the business document to a receiver; and step 110, receiving the business documents by the receiver and authenticating the signature. The invention also provides a digital signature and a signature authenticating device. According to the invention, a user can dynamically configure the field rules of 'signature / signature authentication', relative independence of business demands and an authentication function is realized, and a uniform log record for the authenticating operation is provided, thus ensuring that all signature records can be looked up with a basis.
Owner:YONYOU NETWORK TECH
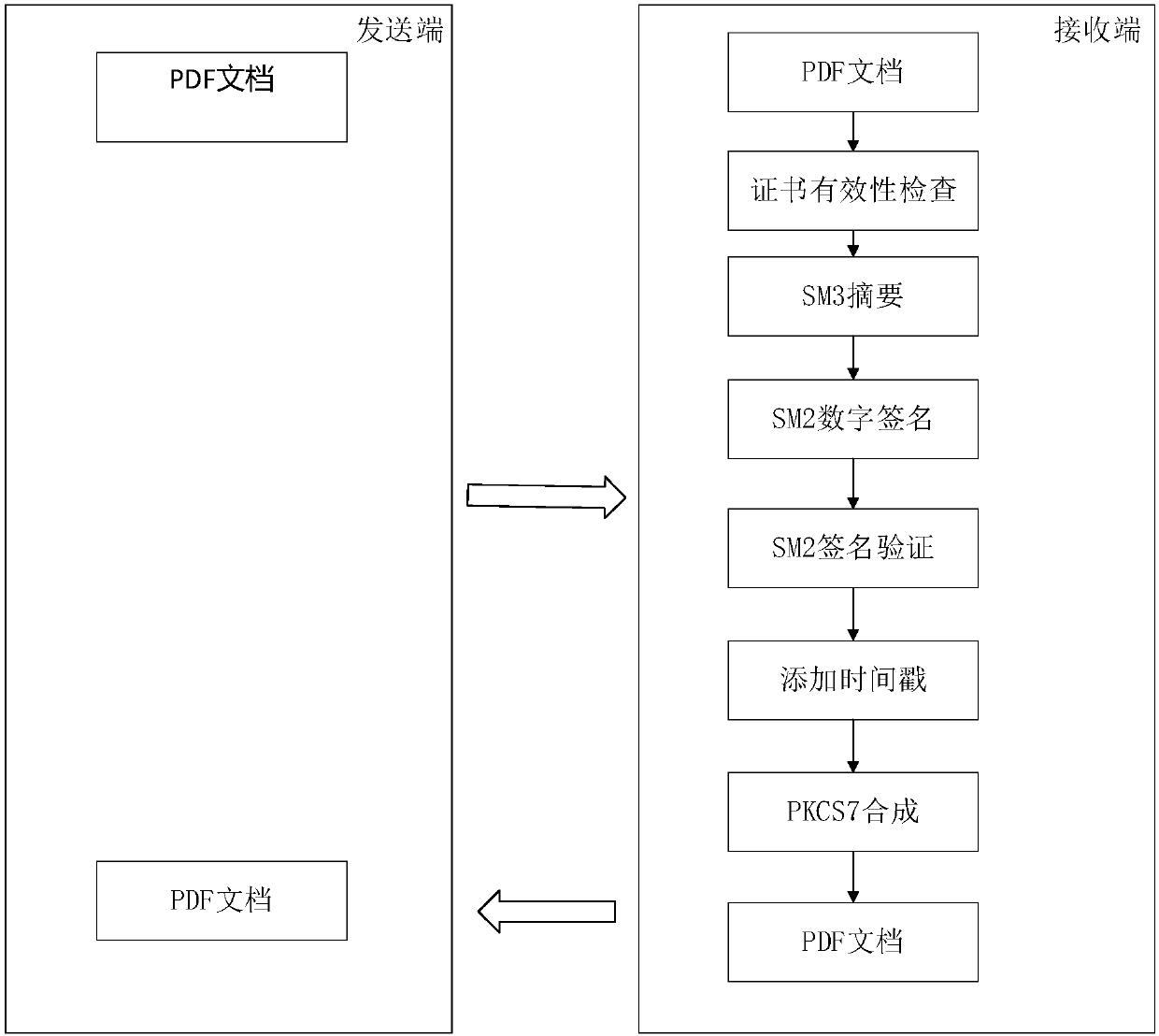
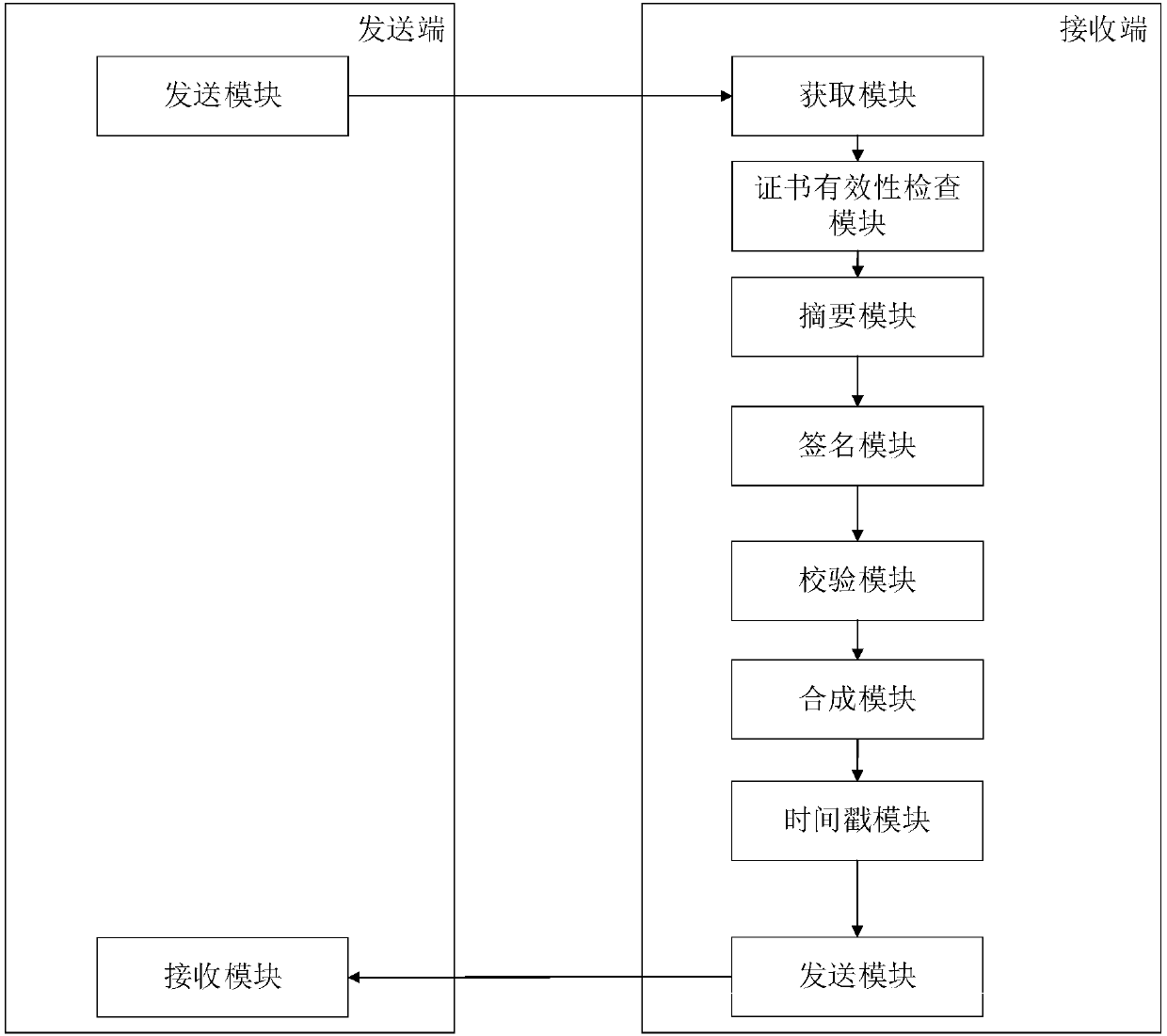
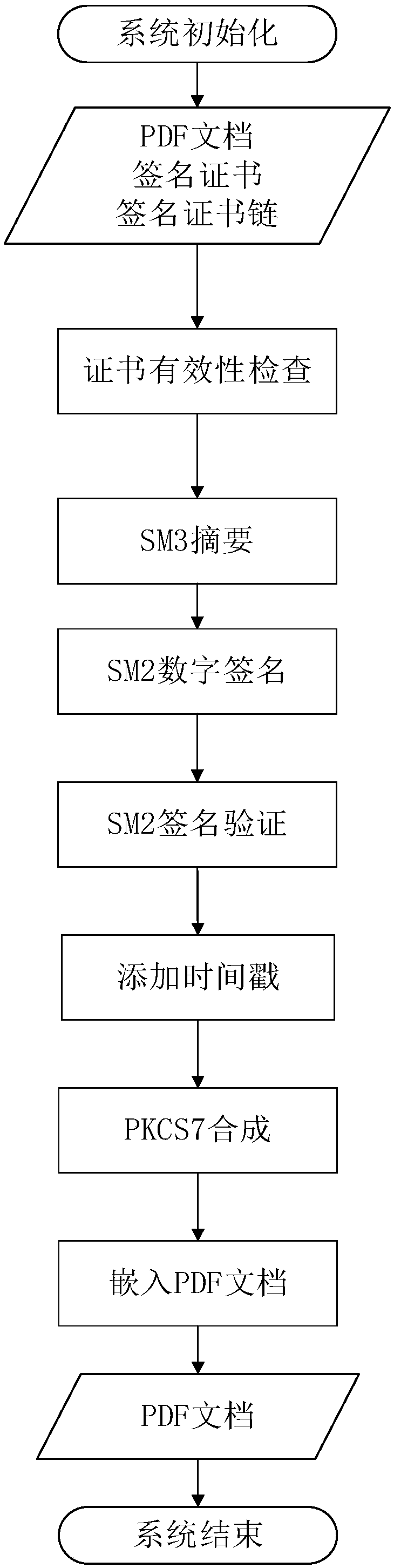
PDF signature method and system supporting SM3 password hash algorithm and SM2 digital signature algorithm
InactiveCN107947939ASolve the problem of signingSignature Efficiency LimitsUser identity/authority verificationDigital data protectionPasswordDigital Signature Algorithm
The invention discloses a PDF signature method and system supporting the SM3 password hash algorithm and the SM2 digital signature algorithm. The method comprises the following steps that a sending end sends a PDF document to be signed; a receiving end is provided with a digital certificate of a signer, the receiving end acquires the PDF document and checks the validity of the digital certificateof the signer; the SM3 password hash algorithm is used for carrying out abstract on the obtained PDF document, and an abstract message to be signed is generated; the SM2 digital signature algorithm and a private key are used for signing the abstract message to be signed, and a digital signature value is generated; the digital signature value is verified; and a signature body of the CAdES format isgenerated by using the generated digital signature value and the digital certificate of the signer, a PDF document containing the digital signature is synthesized, and the PDF signature is completed.According to the PDF signature method and system, the SM3 password hash algorithm and the SM2 digital signature algorithm are applied to the PDF signature, so that the digital signature is safer, fast and reliable.
Owner:杭州尚尚签网络科技有限公司
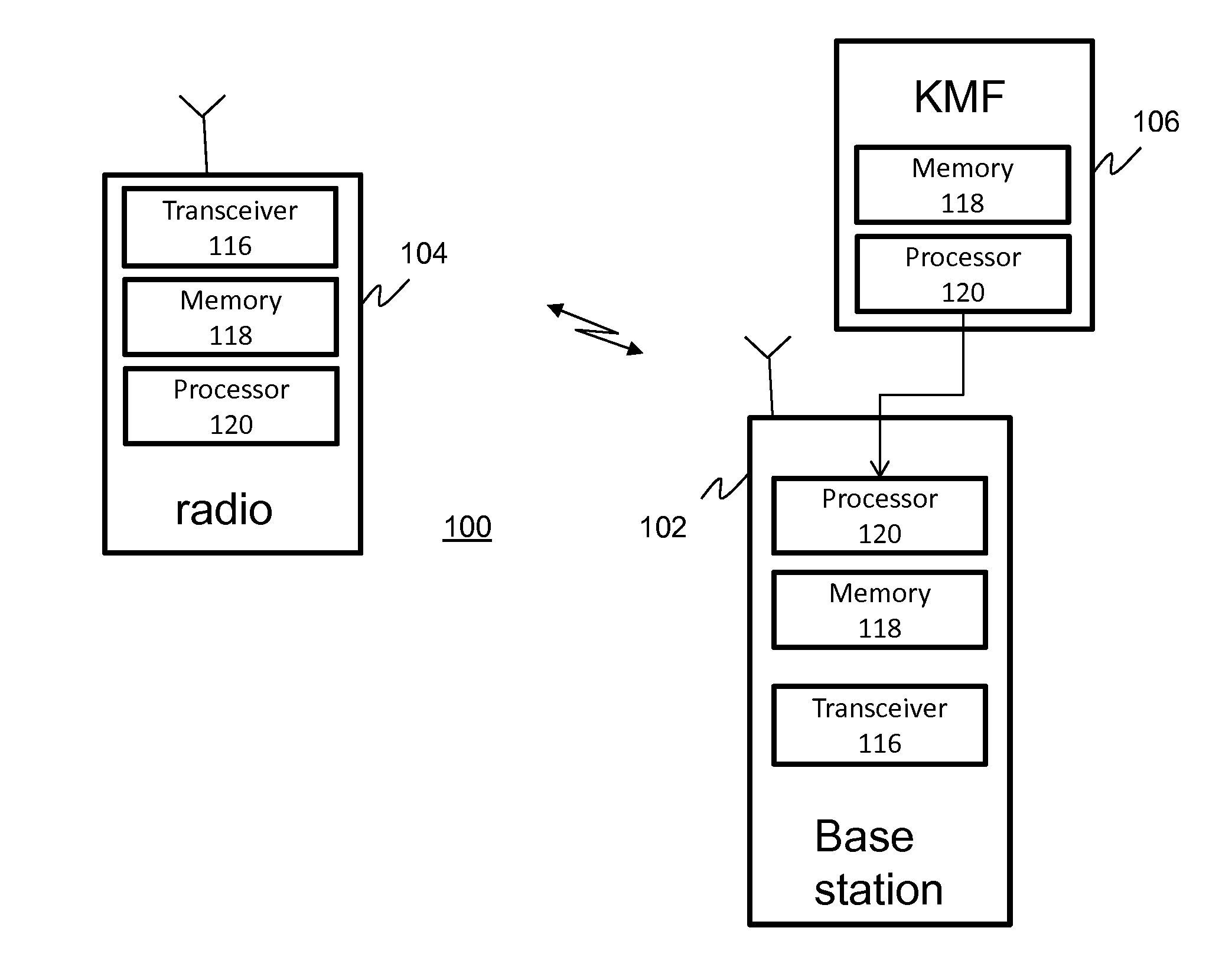
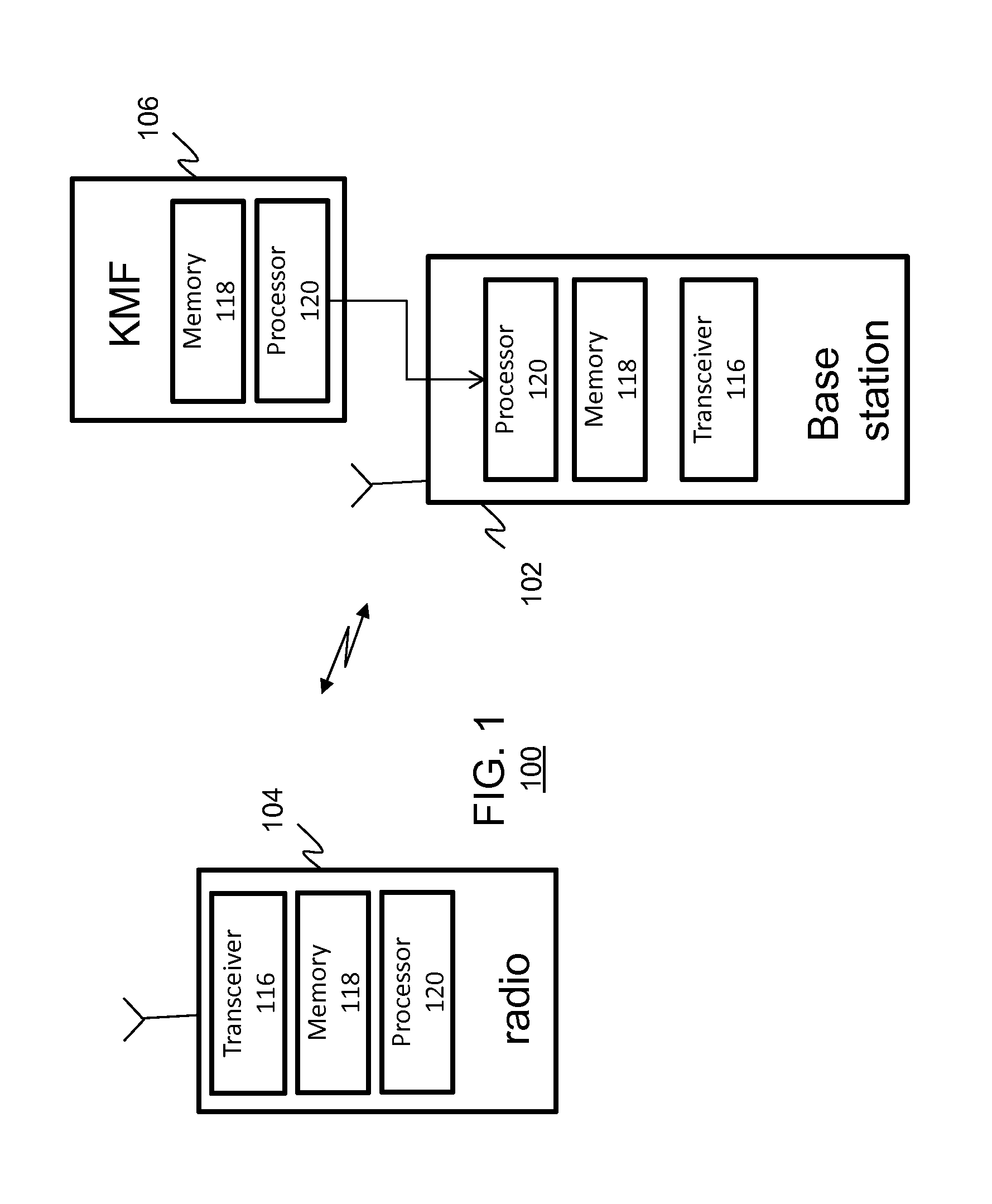
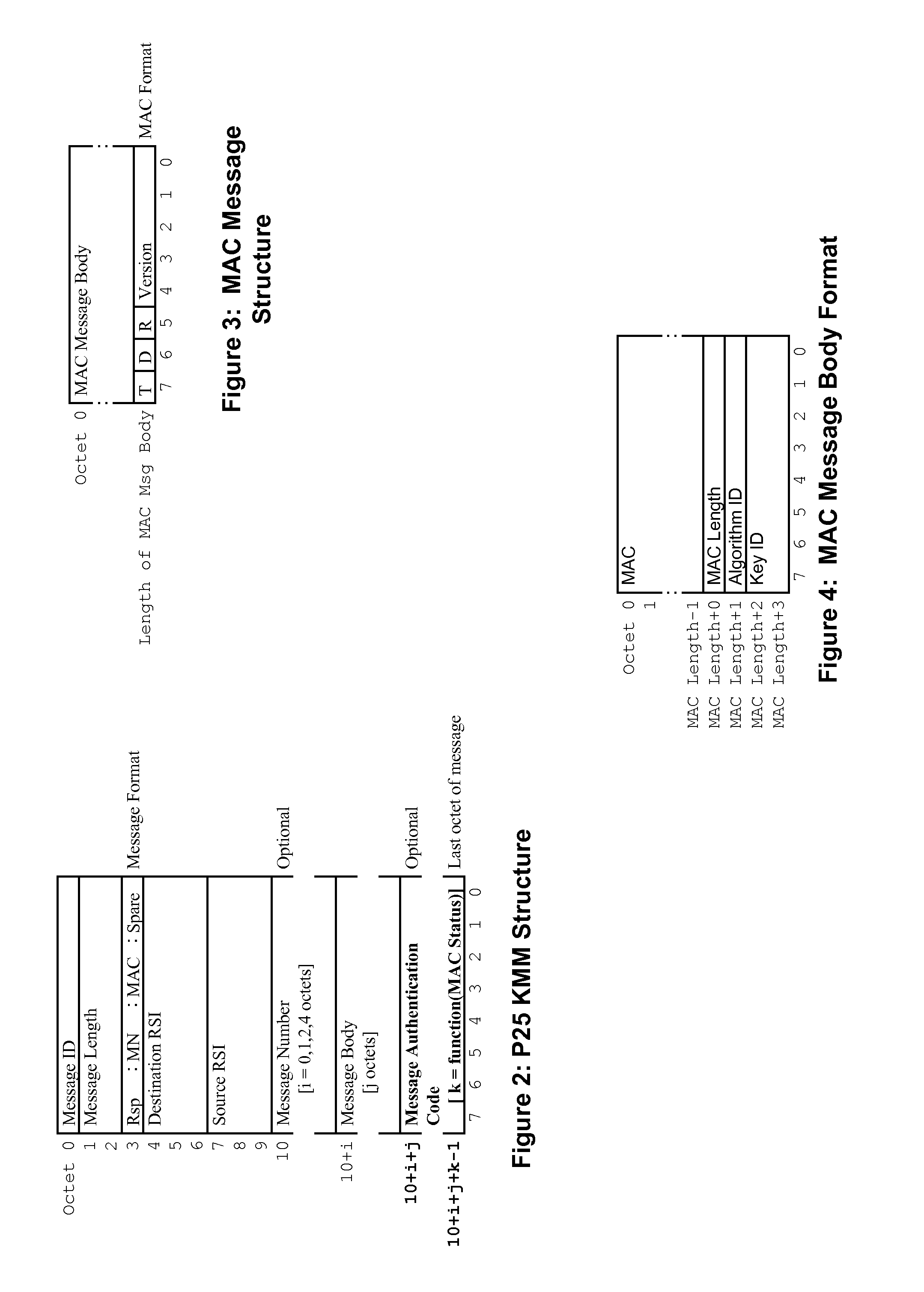
Communication protocol for secure communications systems
ActiveUS20130227294A1User identity/authority verificationSecurity arrangementDigital signatureNetwork Communication Protocols
A method and apparatus for authenticating a key management message within a secure communication system is provided herein. During operation, a digital signature for message authentication of a Project 25 Key Management Message (KMM) is utilized. In particular, the digital signature will be used to authenticate the KMM in scenarios where there is no Message Authentication Code (MAC). The MAC will be utilized to authenticate the KMM when available. Because authentication of KMMs take place, even when no MAC is available, it becomes increasingly more difficult to tamper or spoof the delivery of encryption keys.
Owner:MOTOROLA SOLUTIONS INC
Novel identity identification and digital signature method
InactiveCN101197669ASolve the identification problemFix workKey distribution for secure communicationUser identity/authority verificationPasswordDigital signature
The invention aims to provide a novel method for the identity authentification and the digital signature. The invention provides a method for the safe identity authentification and the digital signature under the circumstance that the challenge times are not revealed. An RSA number or an RSA magic number can compose a safer method for the identity authentification and the digital signature. In addition, the RSA number or the RSA magic number can be adopted to accomplish the authentification and the digital signature of a plurality of websites. Besides, a method for generating a user password (a private key) corresponding to the website through the information provided by the website is provided.
Owner:NANJING E SECURITY TECHNALOGY
Distributive computation of a digital signature
A method and apparatus are presented to perform a distributive computation of a digital signature in a document signing process. A signing request from a remote device initiates the document signing process including the distributive computation. The server verifies digital certificates corresponding to a signer's public key. An encryption request including a set of authenticated attributes and a hash value based on the to-be-signed content is transmitted to the remote device. A signer at the remote device encrypts the hash value in the encryption request with an encryption process utilizing a private key. The resulting encrypted hash value is transmitted to the server to produce the digital signature used to sign the subject content. This distributive computation process minimizes the amount of data transmitted between devices, while minimizing remote device resource requirements, and maintains the integrity of the signer's private key during generation of the digital signature.
Owner:ADOBE SYST INC
Using public keys provided by an authentication server to verify digital signatures
ActiveUS20180254889A1Key distribution for secure communicationMultiple keys/algorithms usageDigital signatureAuthentication server
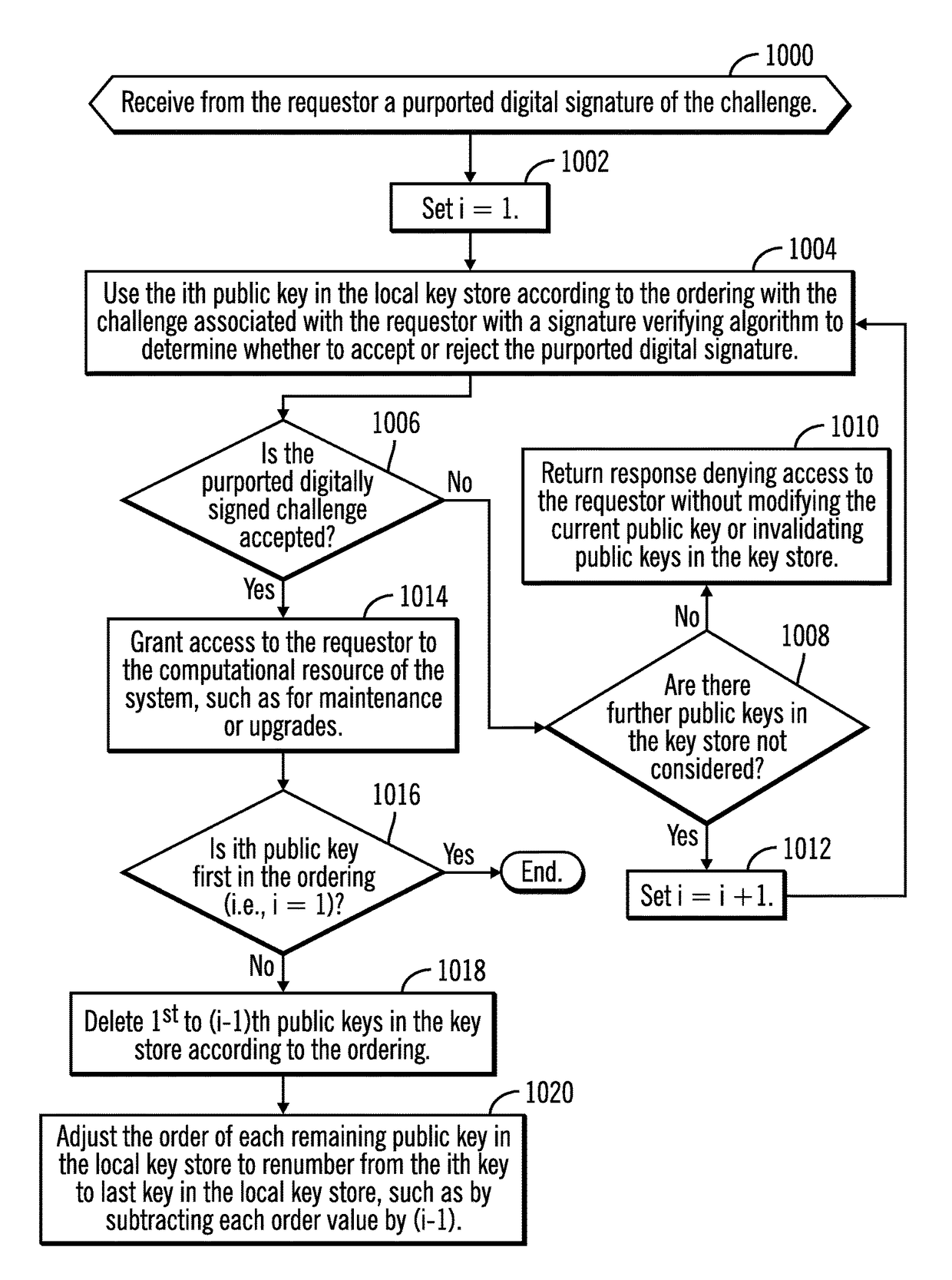
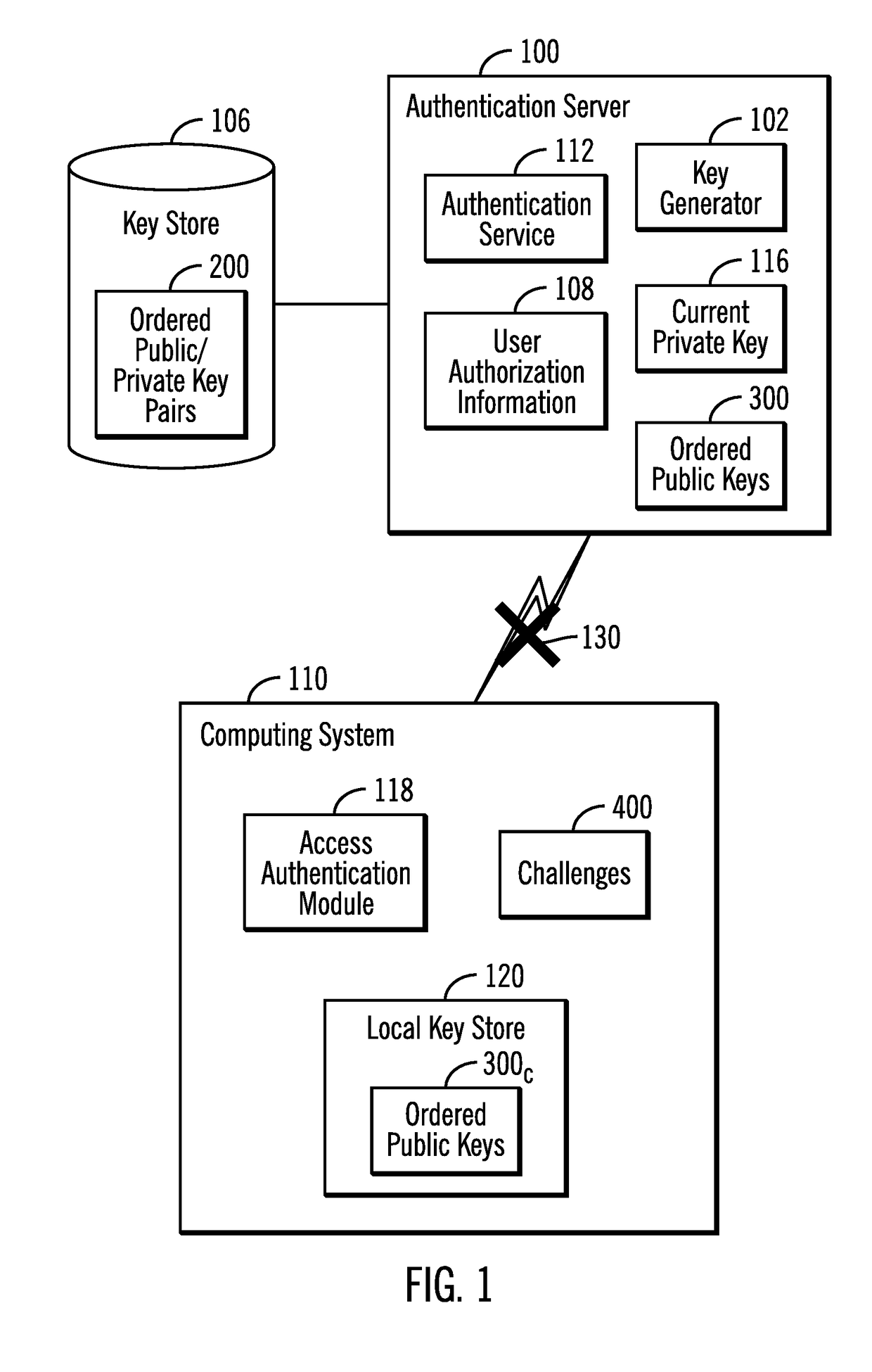
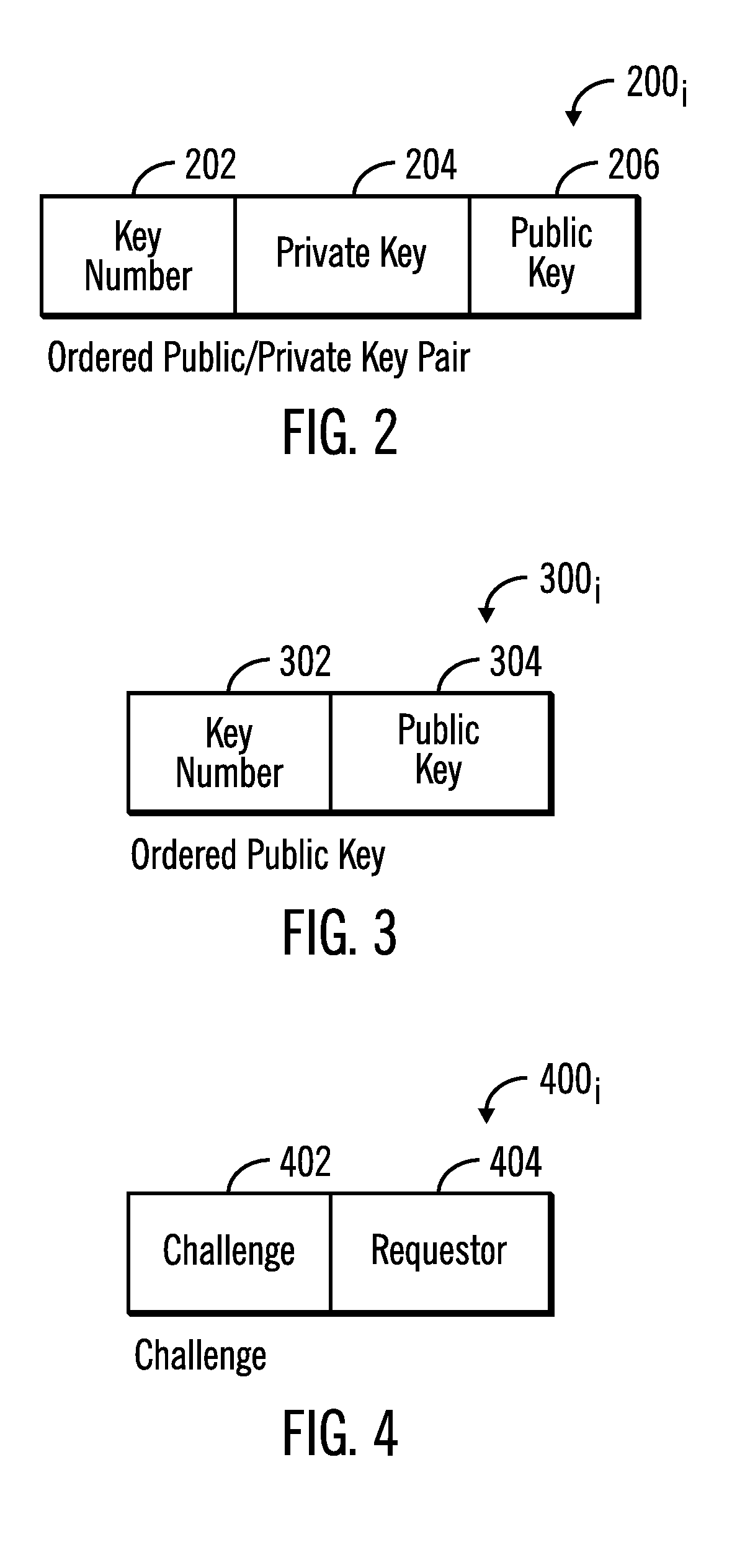
Provided are a computer program product, system, and method for using public keys provided by an authentication server to verify digital signatures. A plurality of public keys from a plurality of public-private key pairs and stored in a local key store. A request is received to access computational resources in the system. A challenge is returned in response to the request. A response to the challenge is received comprising a purported digitally signed challenge. A determination is made as to whether the purported digitally signed challenge is verified using a first public key of the public keys in the local key store. A determination is made as to whether the purported digitally signed challenge is verified using a second public key of the public keys in the local key store in response to determining that the first public key did not verify the purported digitally signed challenge.
Owner:IBM CORP
Method, system, and program product for generating and validating digital signatures
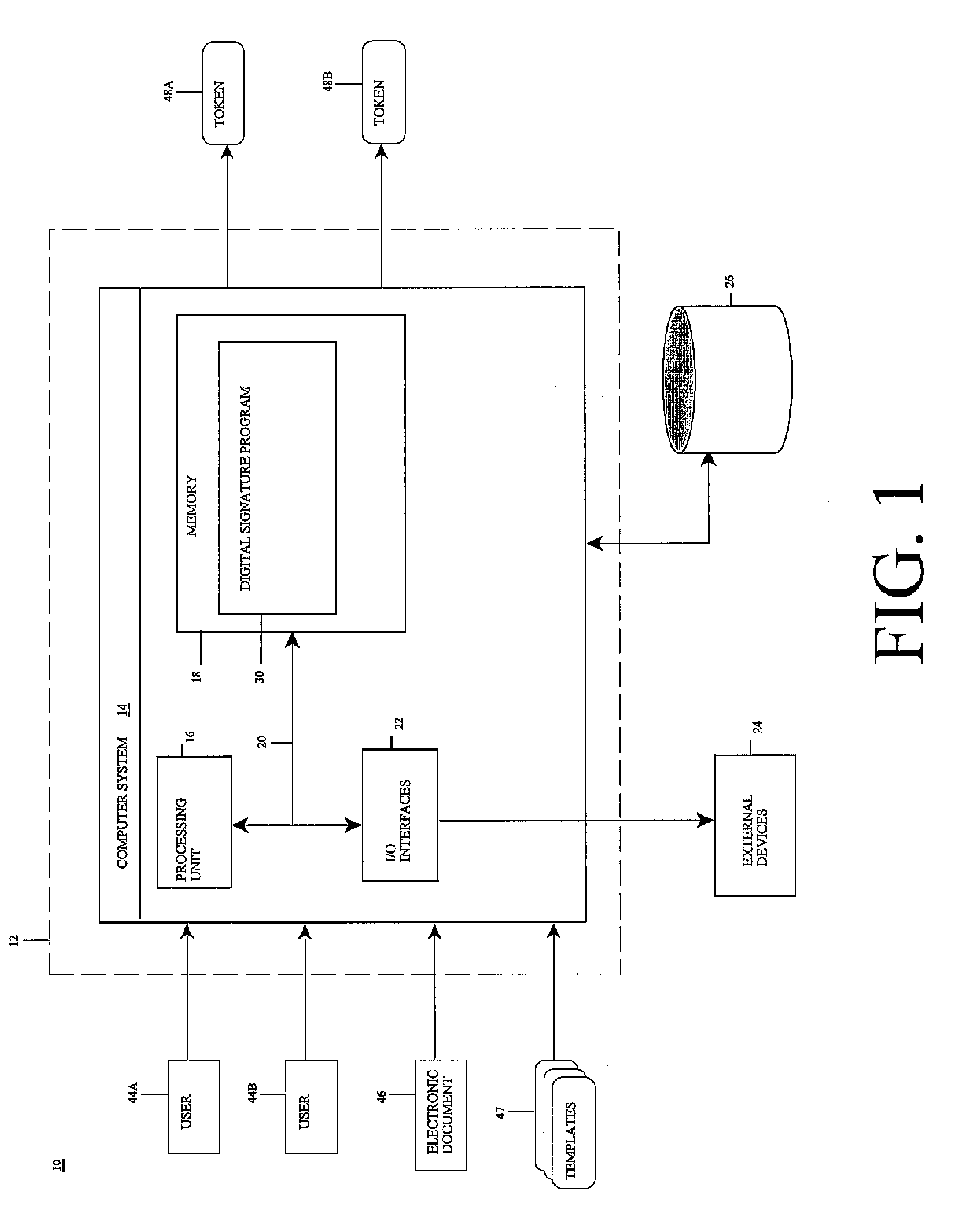
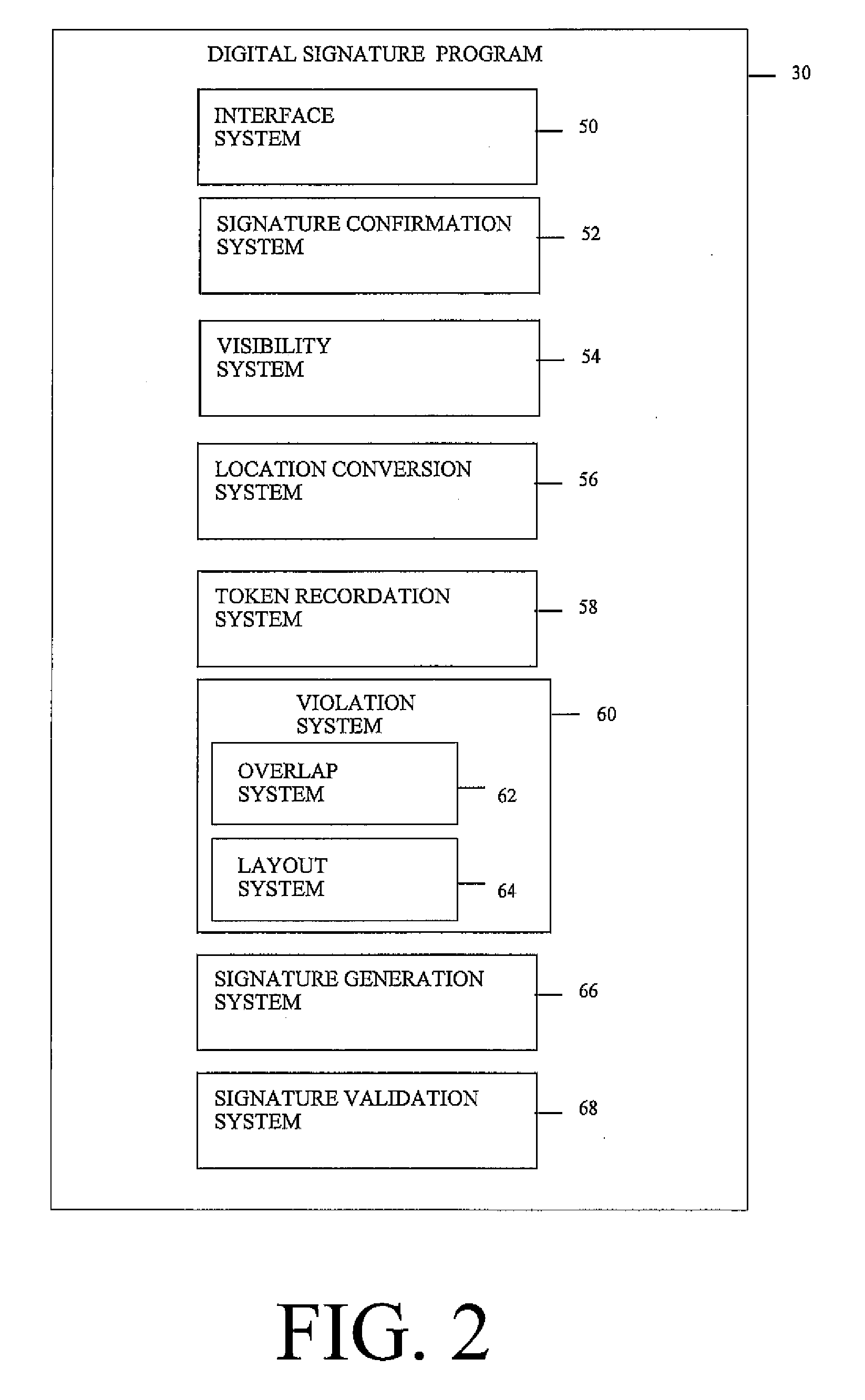
InactiveUS20070288393A1User identity/authority verificationDigital data protectionElectronic documentDigital signature
Under the present invention, an electronic document is accessed. Each user interface control (UIC) in the electronic document is confirmed to be operationally classified as signed or unsigned by a given digital signature based on whether the UIC is associated with a data node that is signed by the digital signature. It is then determined whether the signed UIC is visible. A token representing a geometric location of the visible signed UIC within a visual representation of the electronic document and a relative location of the visible signed UIC to other visible signed UICs in the electronic document is then recorded. However, if the UIC is contained within any hierarchic UICs, the location thereof is first converted to the geometric location within the visual representation prior to recording the token. The digital signature can then be generated and / or validated unless a UIC overlap and / or layout violation is committed.
Owner:IBM CORP
A method for secure and resilient distributed generation of elliptic curve digital signature algorithm (ecdsa) based digital signatures with proactive security
Described is system for generation of elliptic curve digital signature algorithm (ECDSA) based digital signatures. A. Secret-Share protocol is initialized between a client and a set of servers to share a set of shares of a private key s among the set of servers. The set of servers initializes a protocol to generate a digital signature on a message using the set of shares of the private key s without reconstructing or revealing the private key A. The set of servers periodically initialises a Secret-Redistribute protocol on each share of the private key A- to re- randomize the set of shares. A Secret-Open protocol is initialized to reveal the private key s to an intended recipient, wherein the private key A is used to compute the digital signature.
Owner:HRL LAB
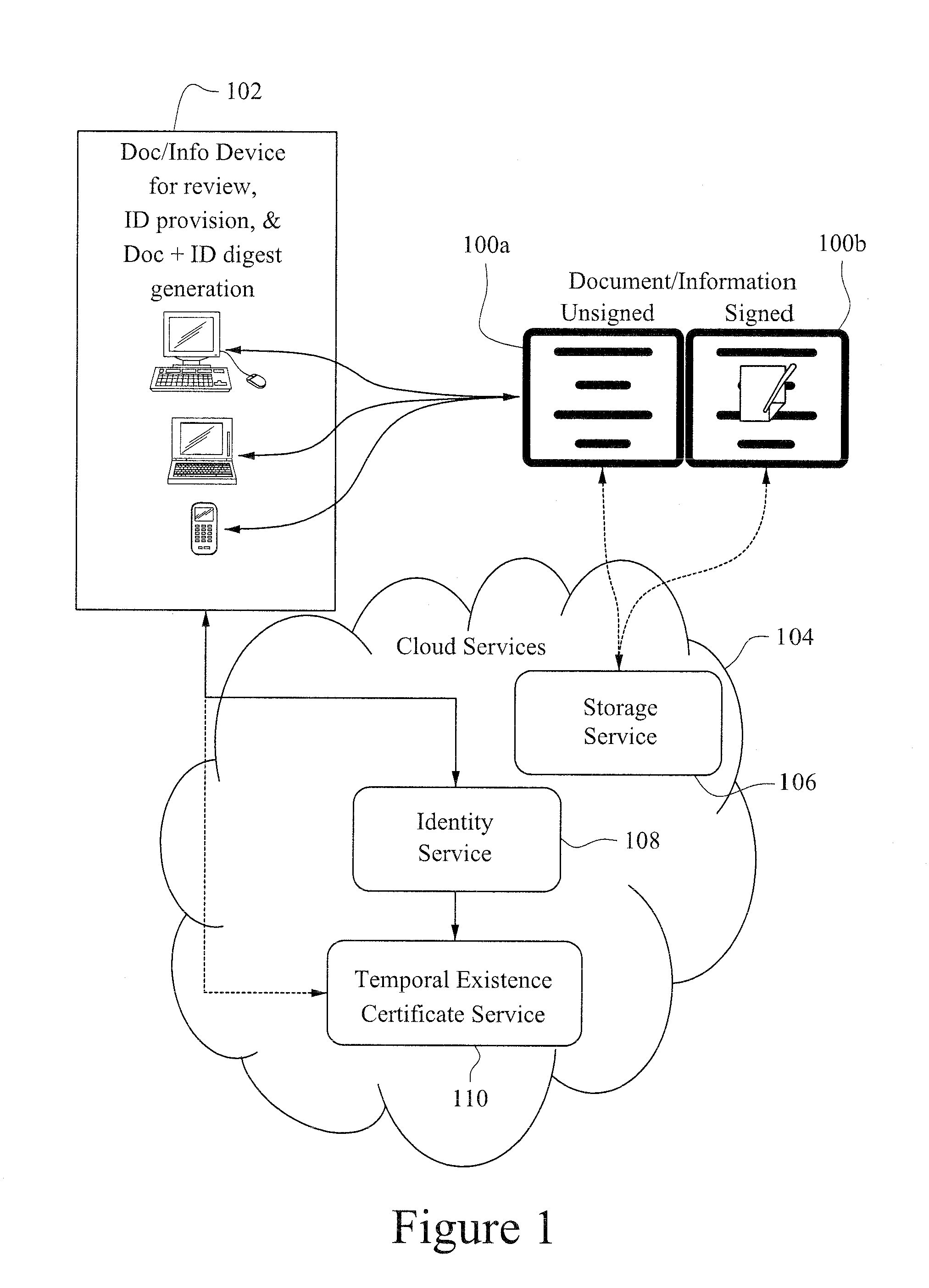
Non-PKI digital signatures and information notary public in the cloud
InactiveUS9049027B2High user acceptanceMinimizes user information coordination and managementUser identity/authority verificationDocumentation procedureDigital signature
A digital signature is applied to digital documents / information. In certain instances, juridically strong digital signatures are achieved. Cloud computing technologies may be used to aid in the production of the cryptographically secure, authenticated digital signatures. Digital signatures may be produced with a digital notarization. The techniques of generating a digital signature may not require the use of traditional public key infrastructure (PKI).
Owner:ZENERJI
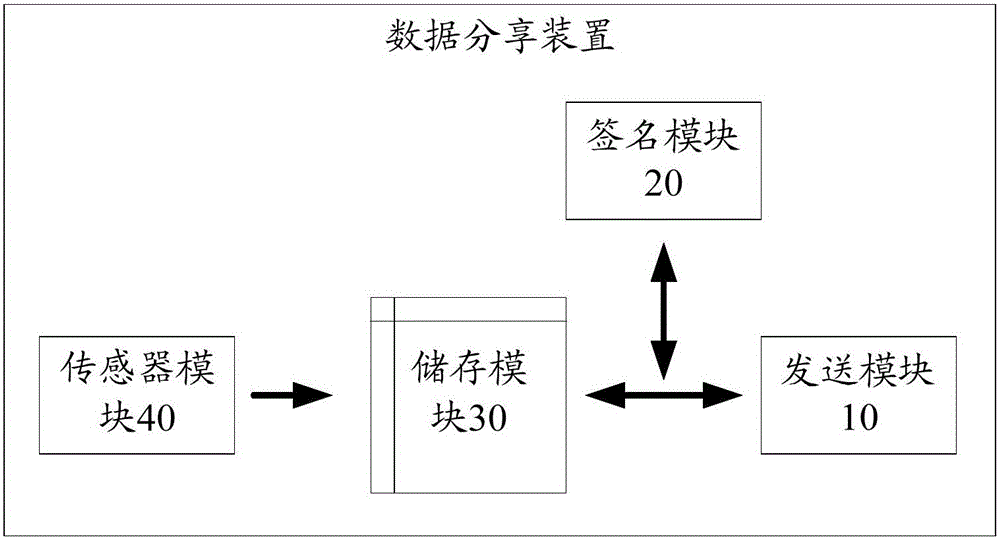
Data sharing method and device
InactiveCN105847254AProtect interestsEnsure understandabilityUser identity/authority verificationTamper resistanceDigital signature
The invention discloses a data sharing method and device. The method comprises following steps: performing digital signature cryptography on hardware sensor data and performing digital signature tamper-proofing publishing in combination with added information by a publisher. By means of the device and method, the fidelity of hardware sensor data in the internet sharing propagation process can be verified by public keys for internet programs; and information added by information publishers is involved so that the benefit of information publishers is guaranteed and the data is comprehensible to people.
Owner:山东集博智能科技有限公司
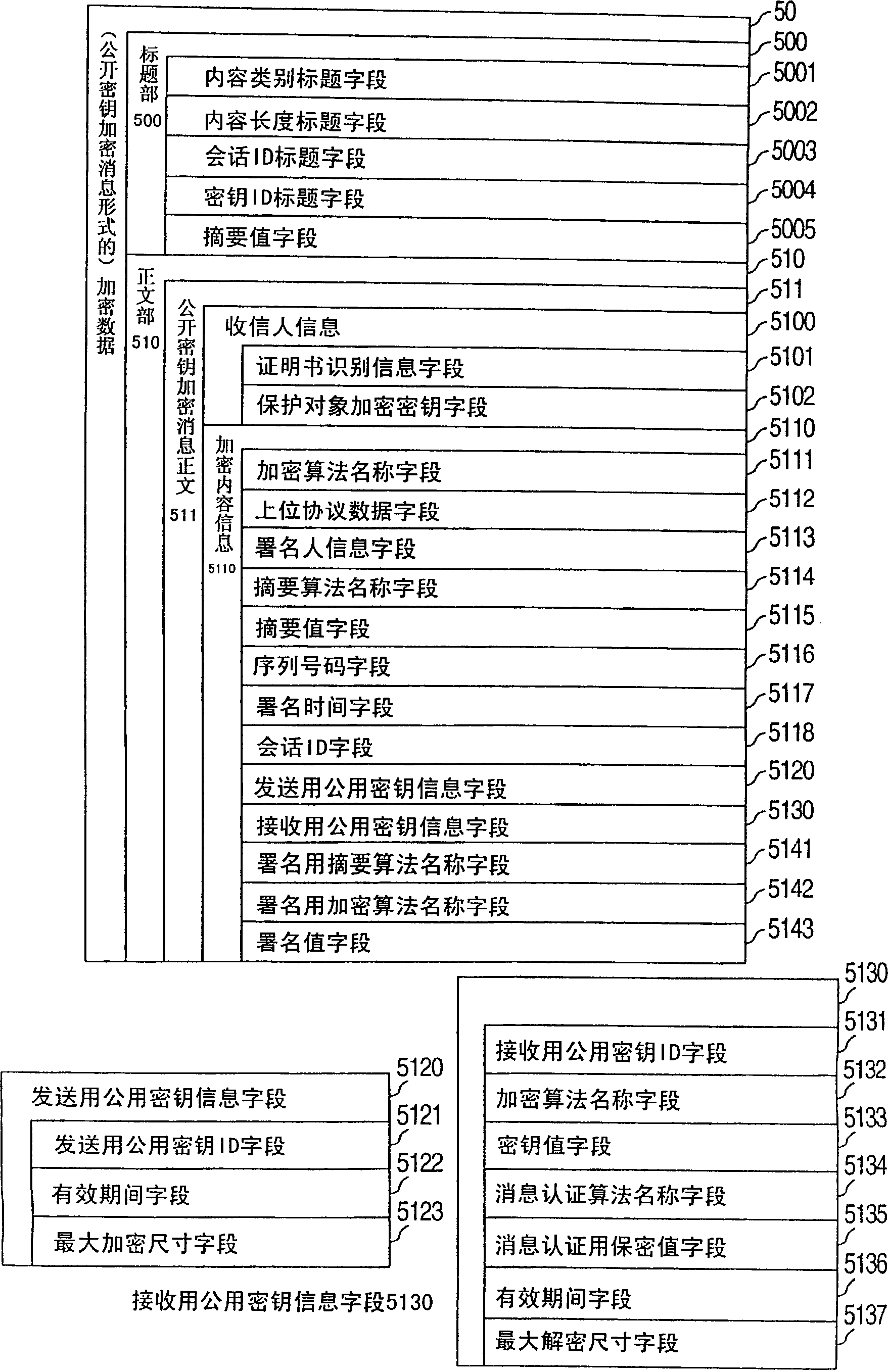
Encryption method for sip message and encrypted sip communication system
InactiveCN1855805AEasy to handleImprove confidentialityUser identity/authority verificationCommunications systemDigital signature
It takes time for an encryption data communication system to transfer encrypted data, because negotiations of security parameters are necessary prior to communications in order to protect security and integrity of a SIP message or public key cryptography is required to be used for an encryption process, a decryption process, an digital signature process and an digital digital signature verification process each time a SIP message is transmitted / received. When a SIP message is transferred between two entities, the message is encrypted by shared information if the information is being shared between the entities, or the message is encrypted by the public key of the transmission destination entity if the shared information is not being shared. The encrypted message contains shared information to be used for the transmission destination entity of the encrypted data to encrypt or decrypt the message, during communications after the encrypted data is generated.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com