SM2 elliptic curve signature verification algorithm
An elliptic curve and signature verification technology, applied in the field of information security, can solve problems such as low security, slow operation speed, and time-consuming, and achieve the effect of improving security and preventing cracking and forgery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The present invention will be further described in detail below in conjunction with the embodiments and the accompanying drawings, but the embodiments of the present invention are not limited thereto.
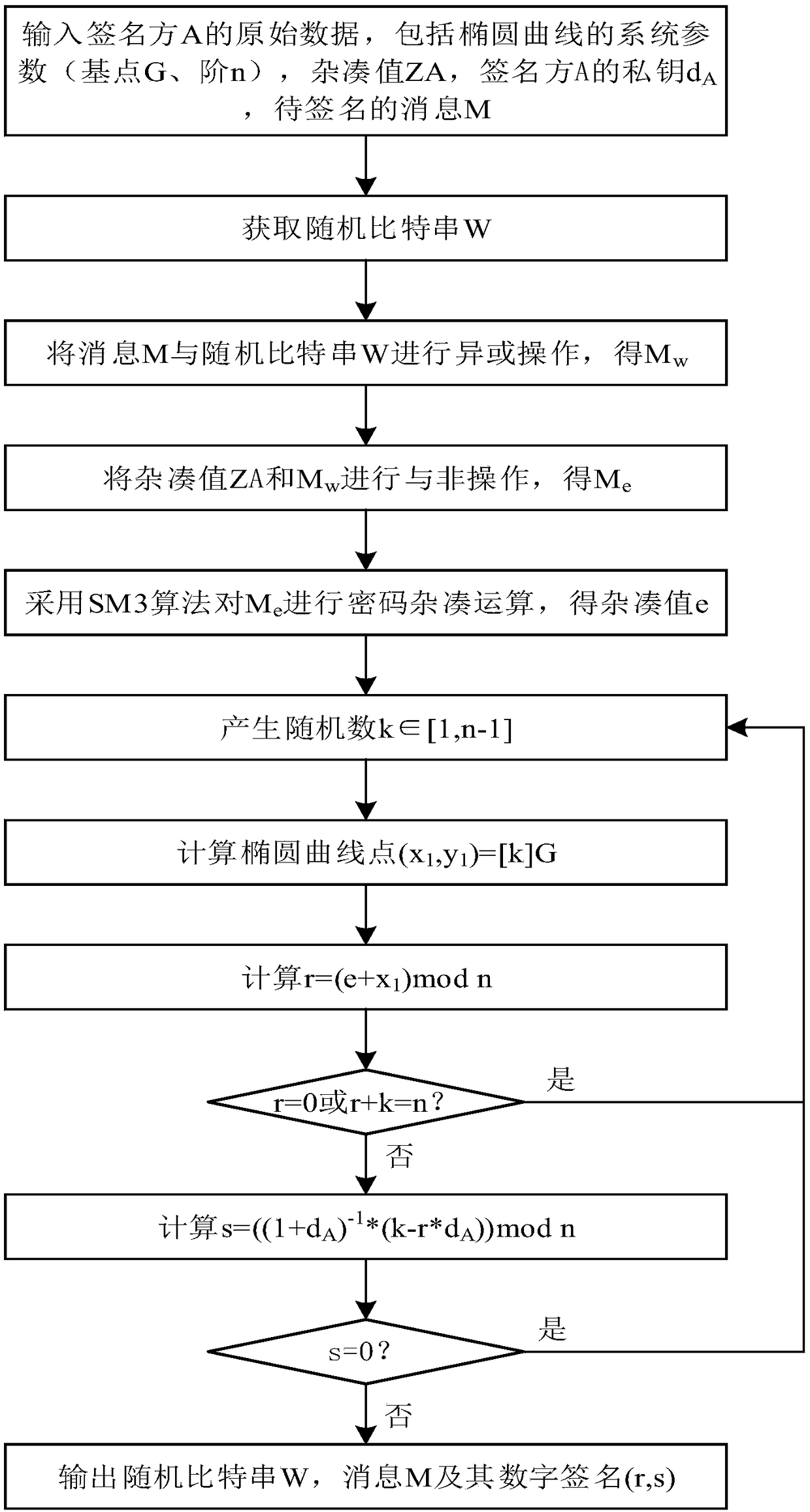
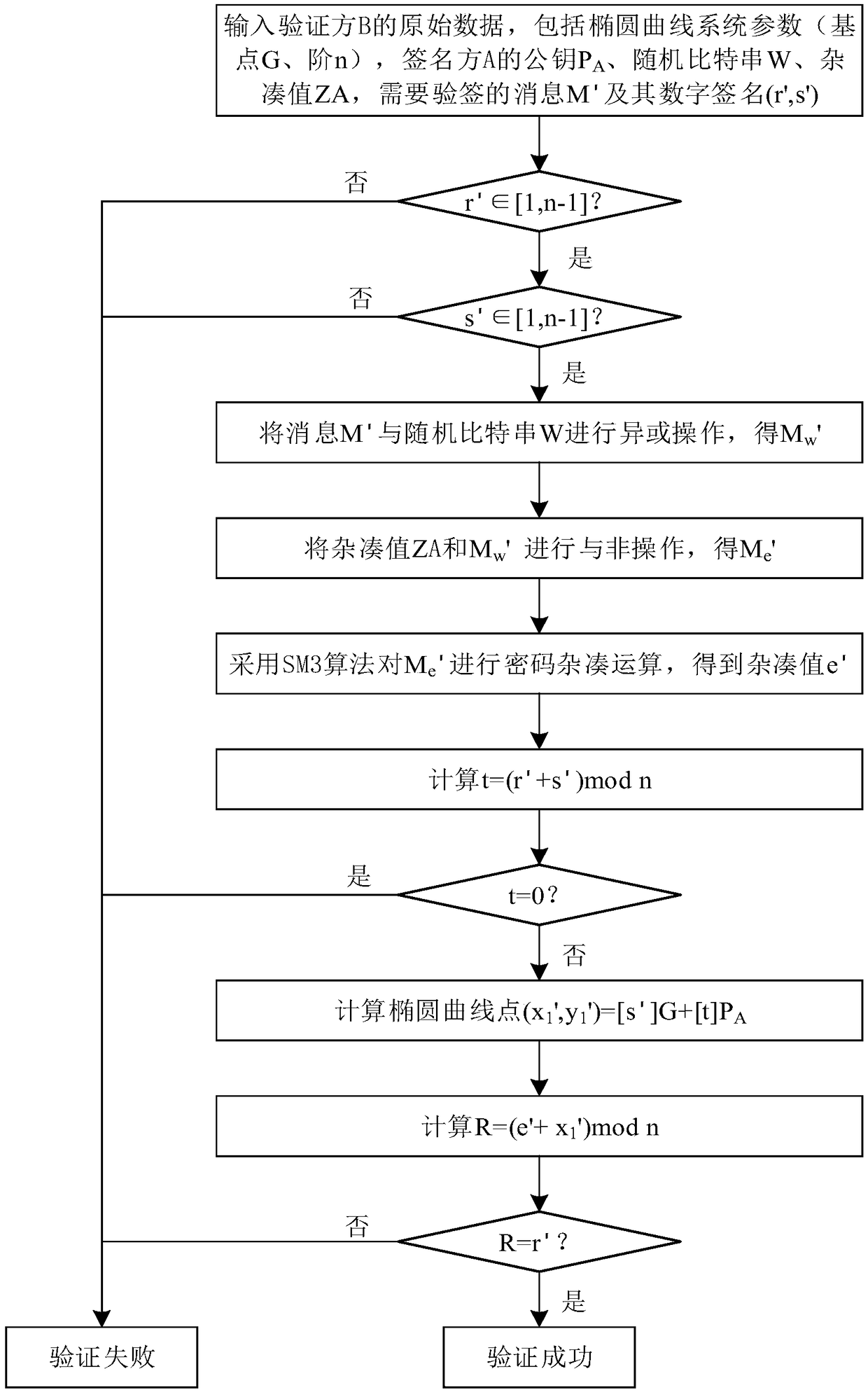
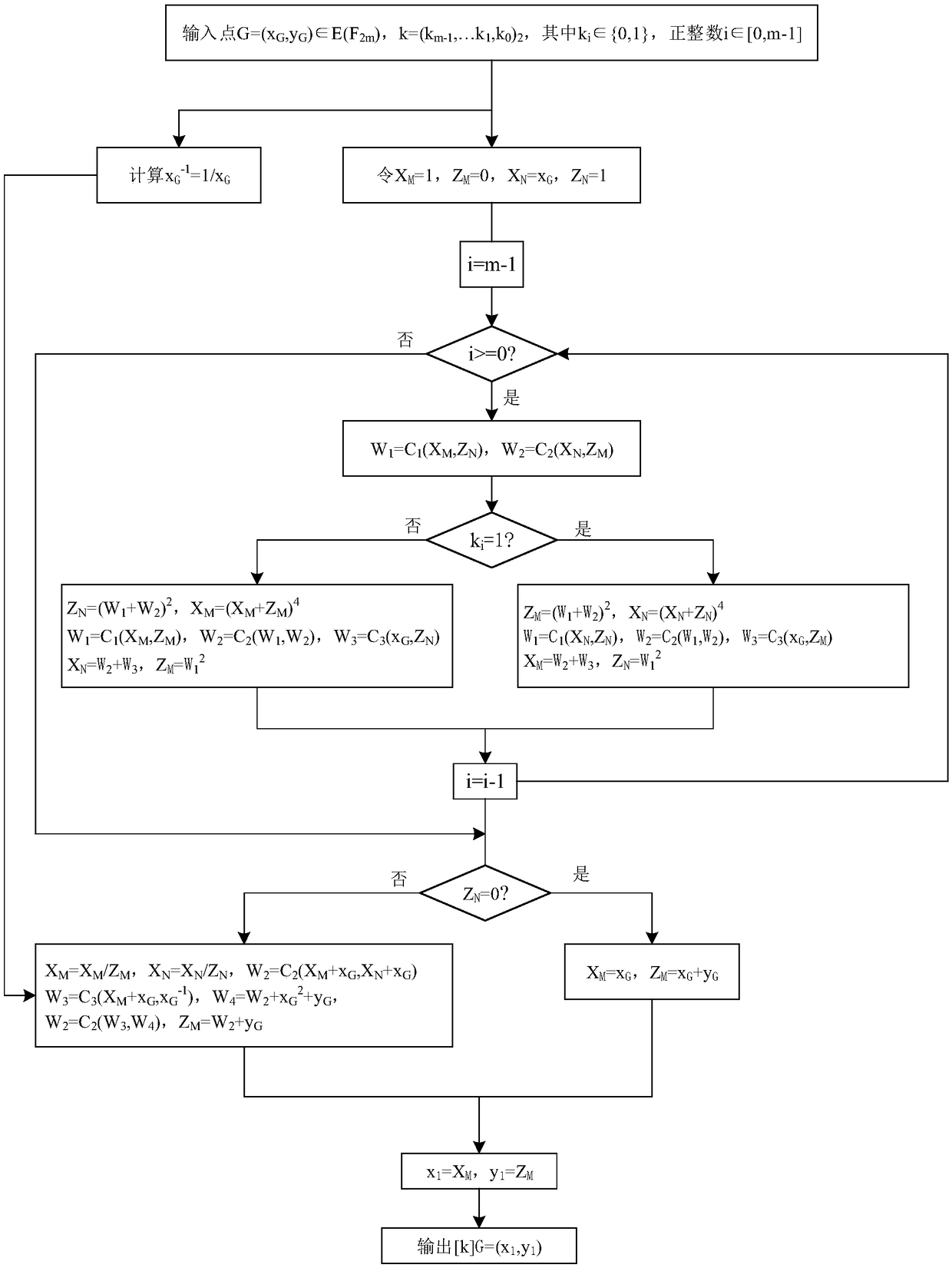
[0064] The technical problem to be solved by the present invention is to provide a SM2 elliptic curve signature verification algorithm, which improves the SM2 signature generation algorithm (signature verification algorithm). ) and the random bit string XOR operation, and then perform the NAND operation with the hash value, which improves the security of the signature verification system. The point product algorithm in the process of signature generation and signature verification adopts an improved Montgomery point product algorithm. Dot multiplication operation converts affine coordinates into standard projection coordinates, eliminates the modular inverse operation in the point operation (point addition, doubling point operation) in the dot multiplication operation, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com