Patents
Literature
755results about How to "Prevent forgery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
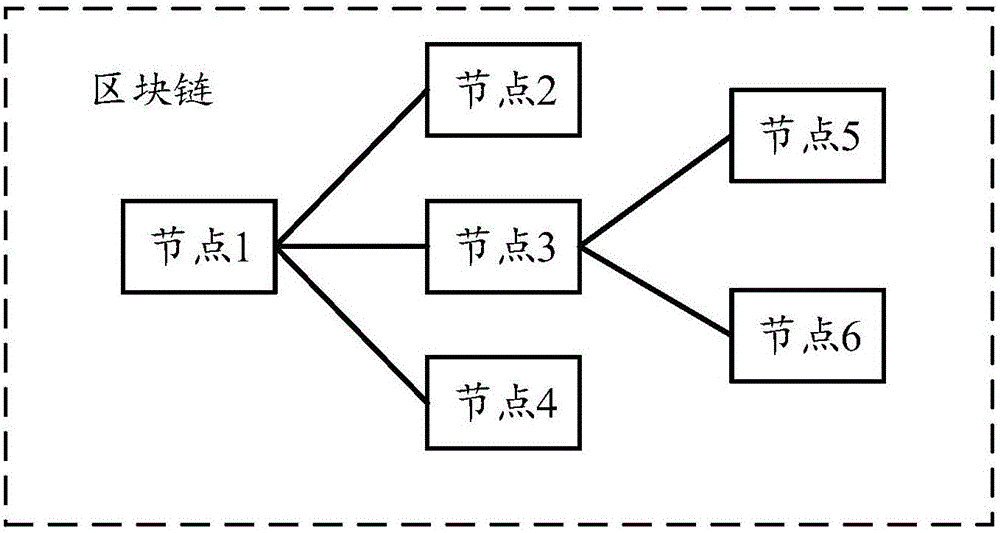
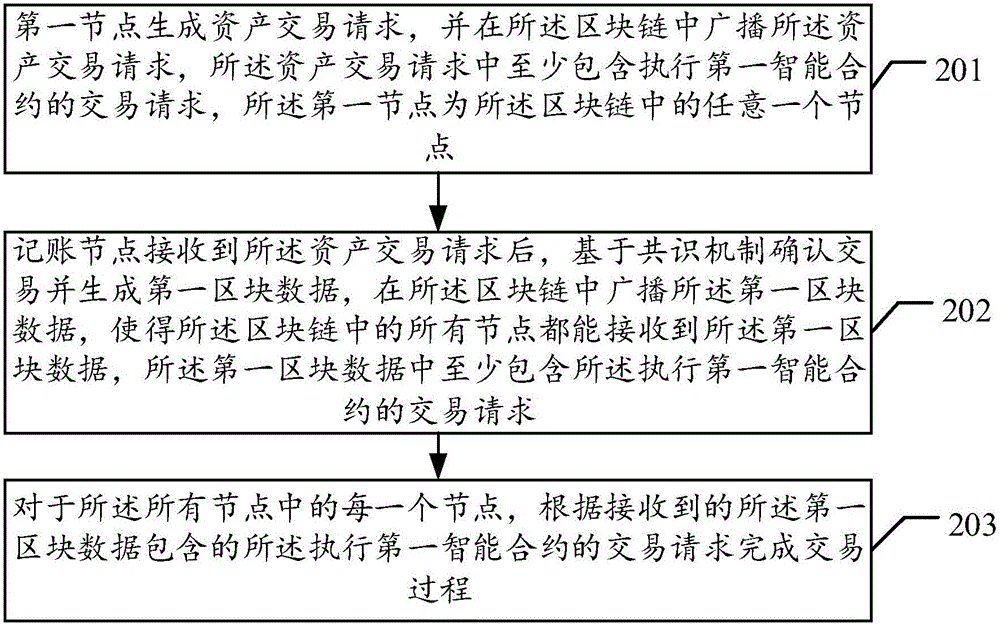
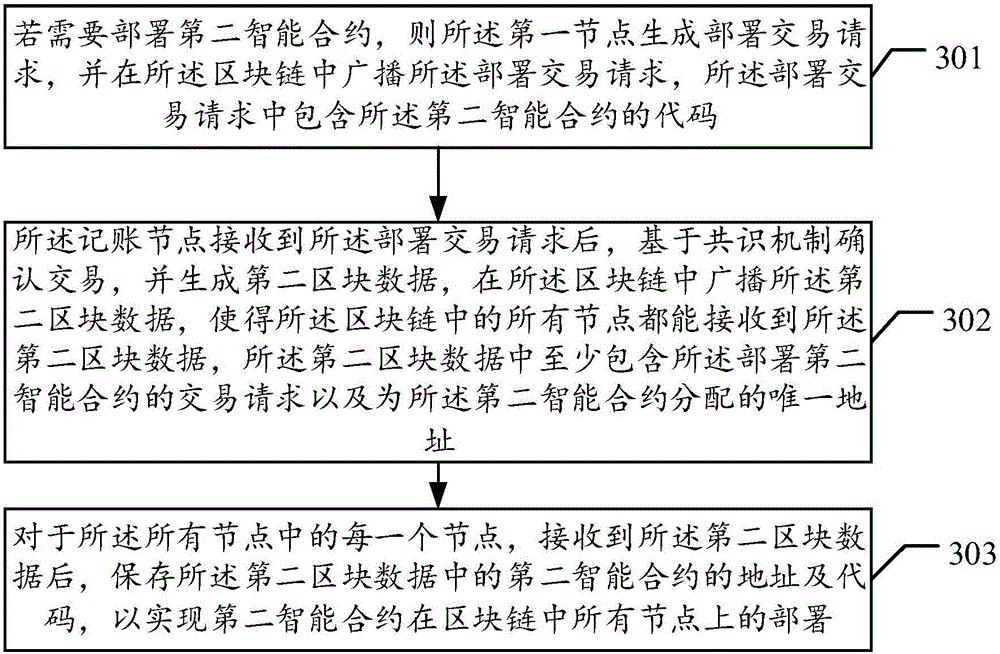
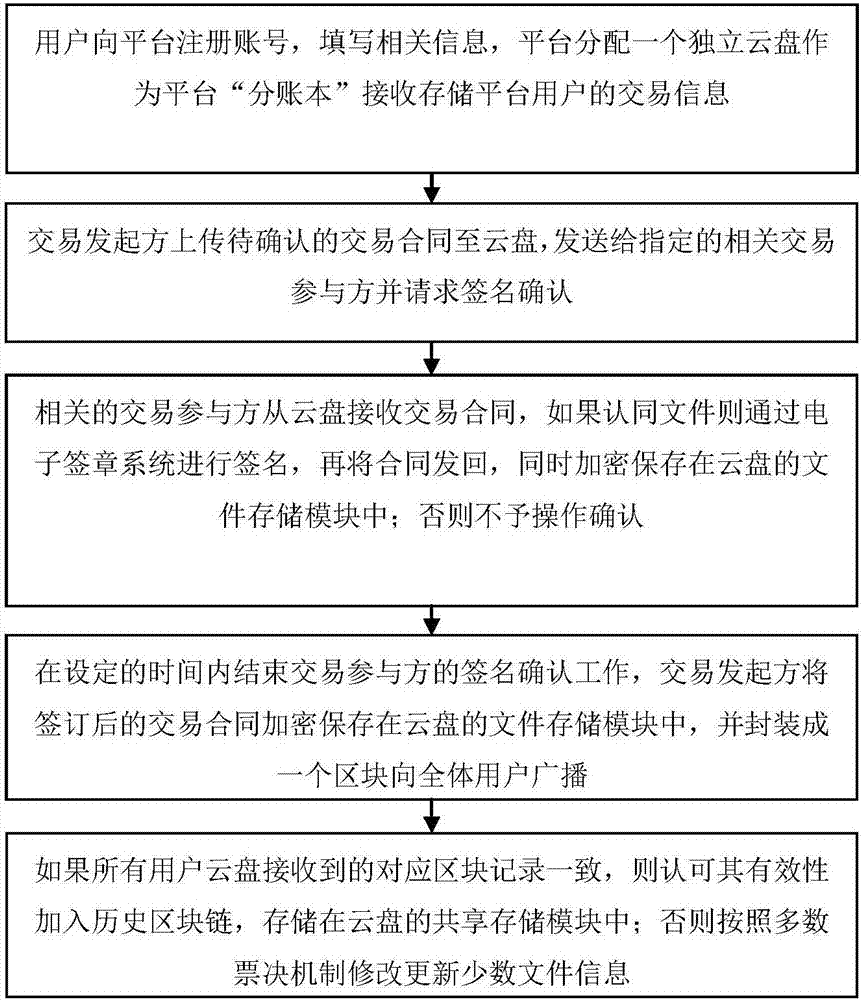
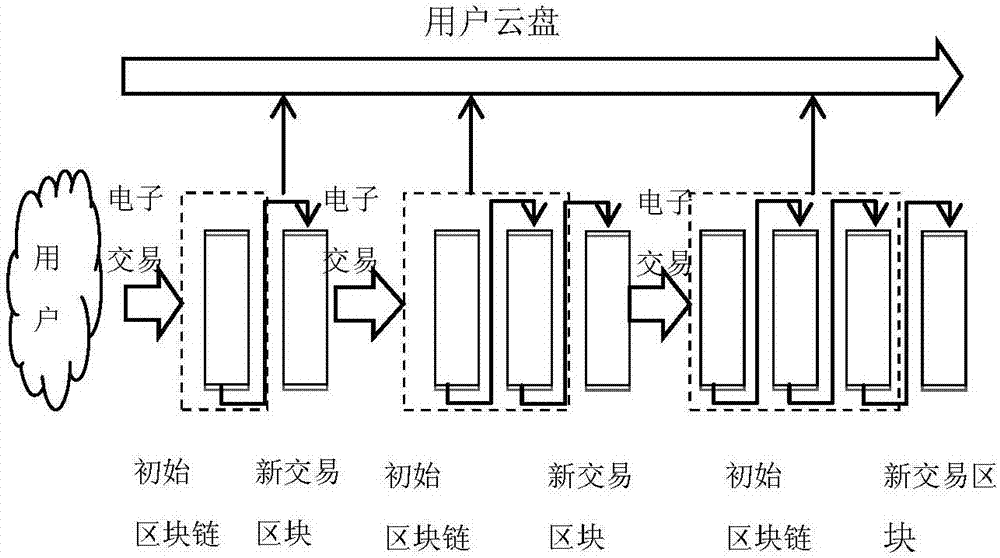
Asset management method based on intelligent block chain contracts and nodes
InactiveCN105976231ATransaction logic is open and transparentPrevent forgeryBuying/selling/leasing transactionsDistributed computingSmart contract
Owner:WEBANK (CHINA)
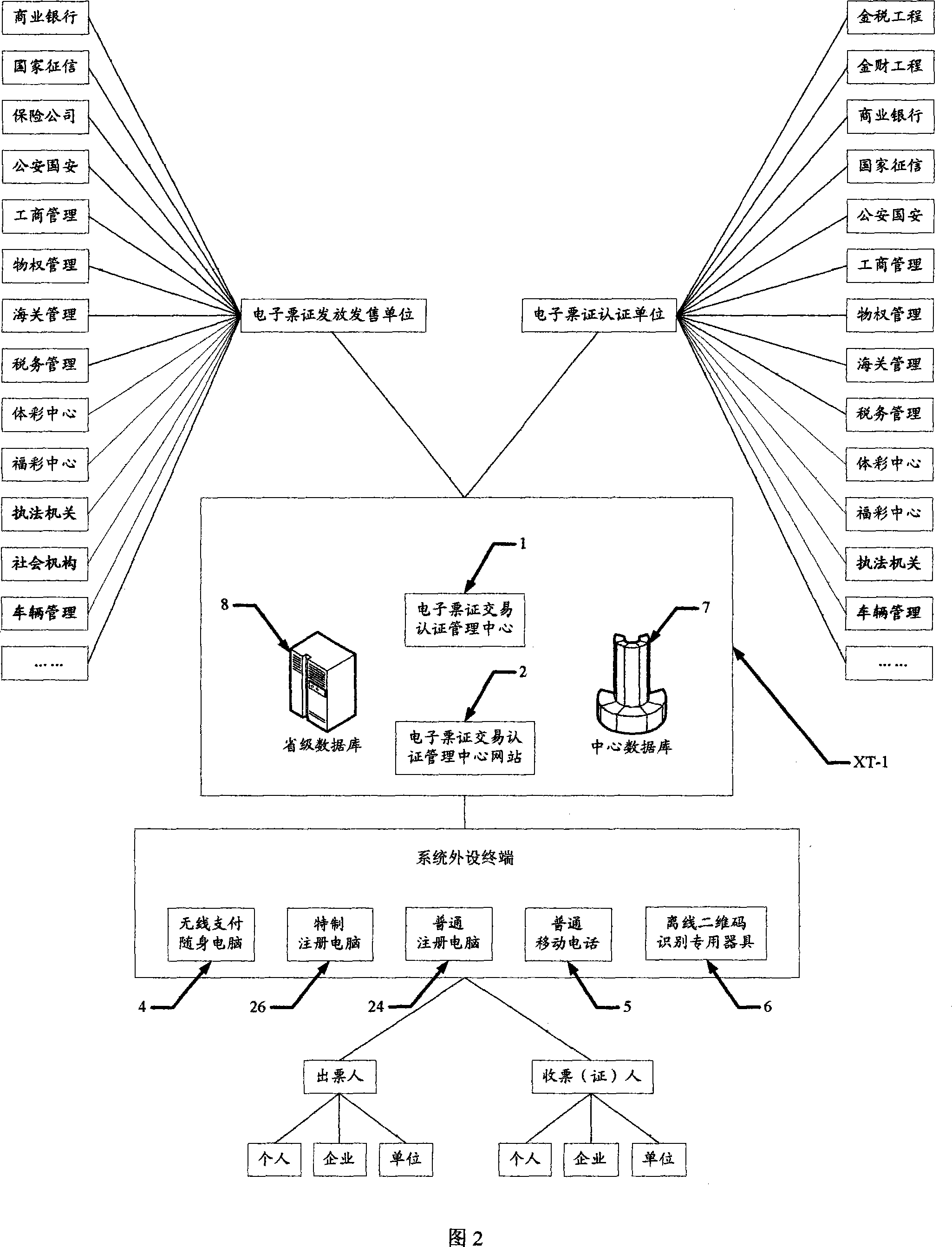
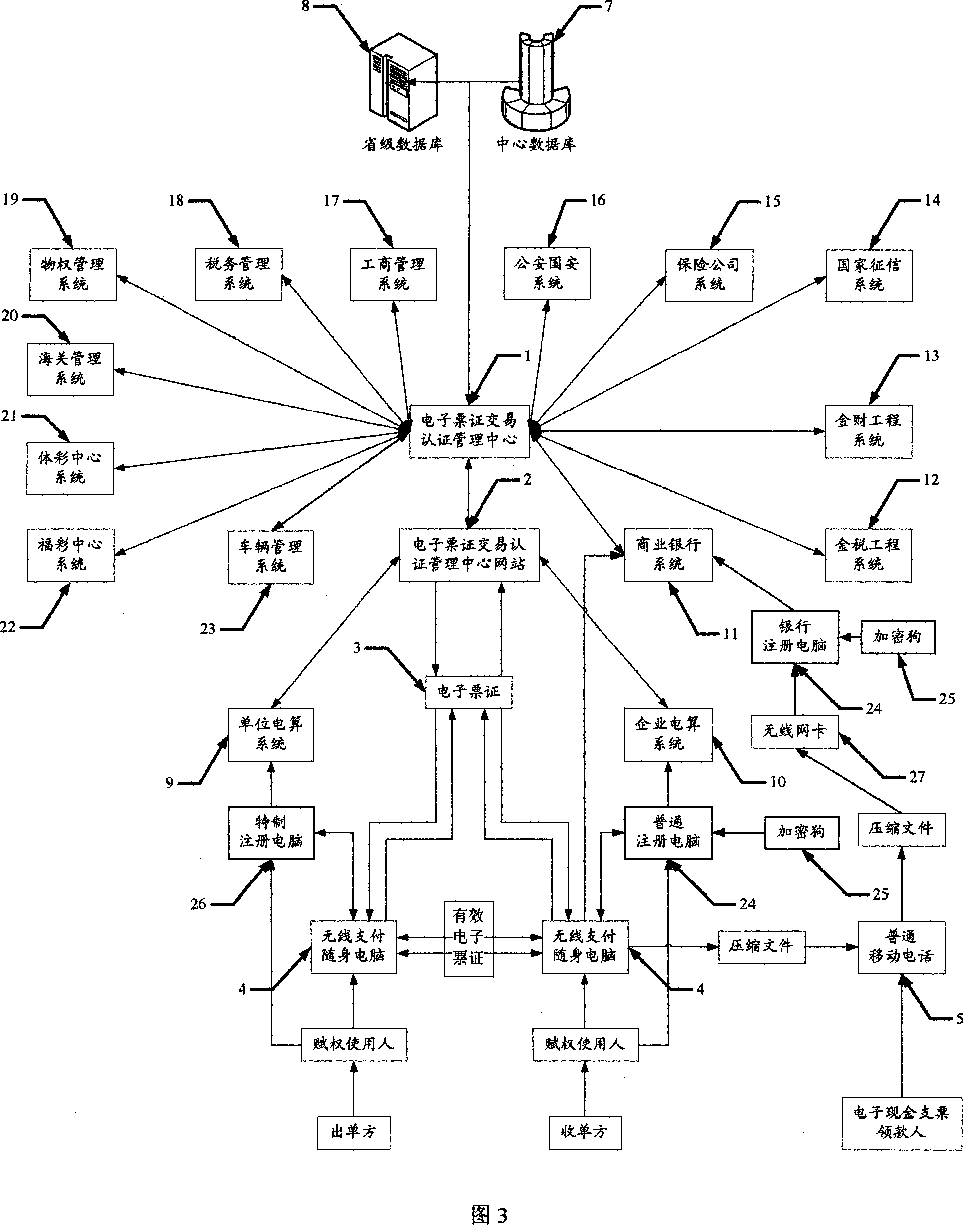
Method for managing electronic ticket trade certification its carrier structure, system and terminal
InactiveCN101075316APrevent forgeryPrevent tamperingAcutation objectsFinanceComputer scienceManagement system
A certification-managing method of electronic ticket transaction includes setting up certification-management center of electronic ticket transaction; connecting said center to fax office, financial office, commercial bank, public security, etc; registering user with real name on terminal; purchasing and downloading electronic ticket; finalizing ticket filling, certifying, electronic signing and locking; exchanging ticket through transaction-certification network station of ticket for realizing integrated certification in order to ensure truth of ticket.
Owner:SICHUAN ZHENGDAOTIANHE INFORMATION TECH
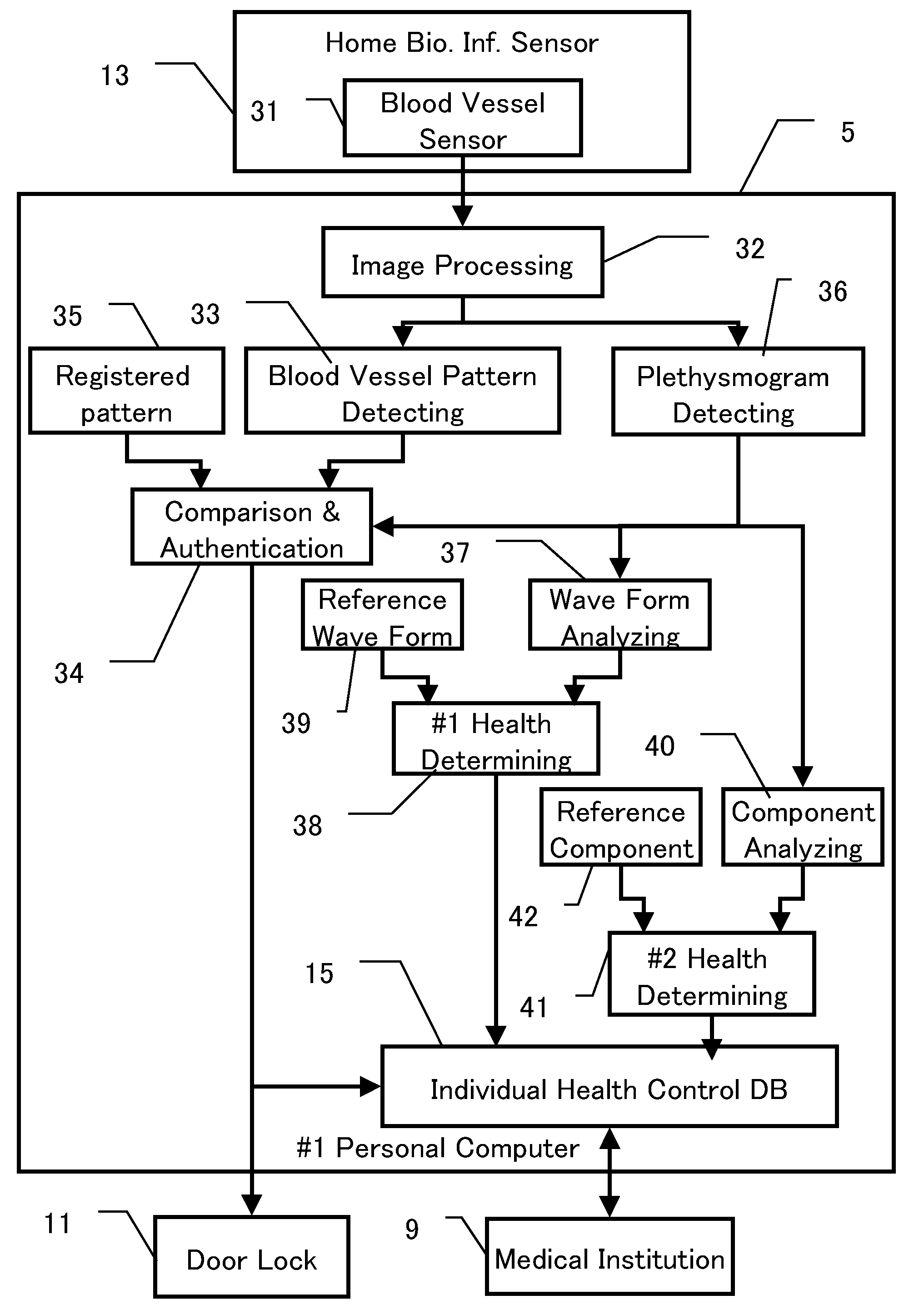
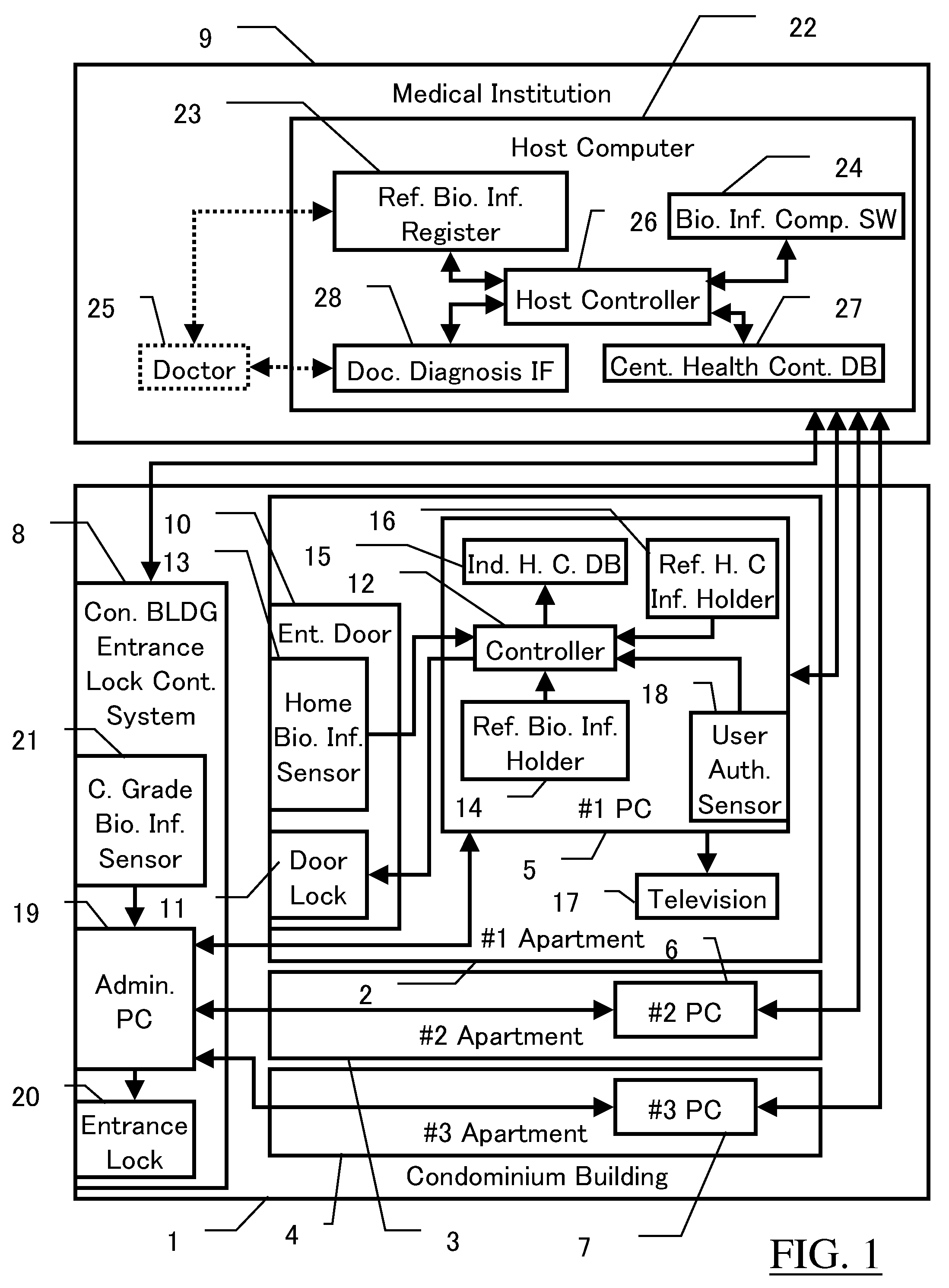
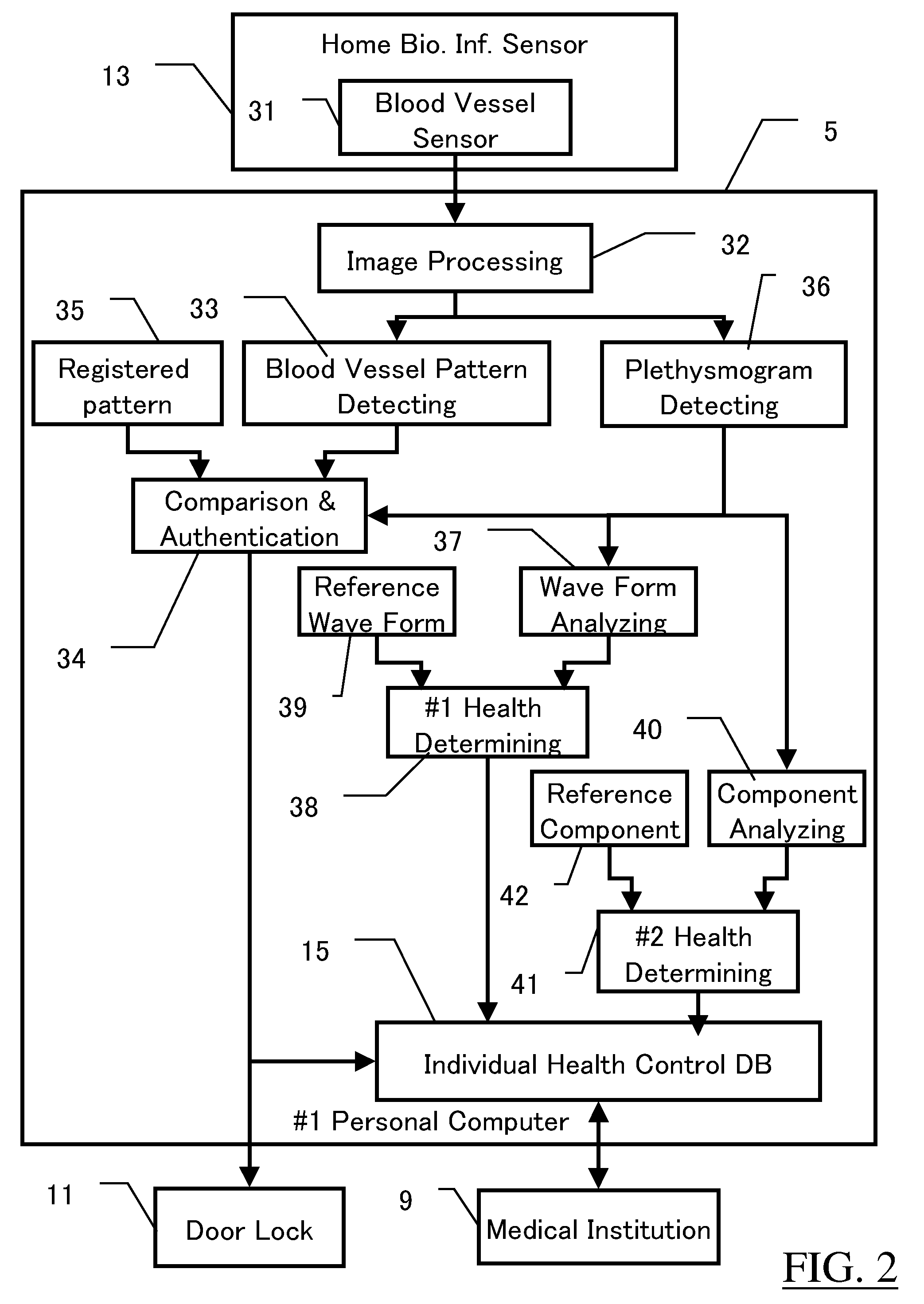
Biometrics System, Biologic Information Storage, and Portable Device
ActiveUS20070177771A1Improve securityPrevent forgeryPerson identificationDigital data authenticationSystems managementBank account
In a biometrics system for a building entrance unlocking or a bank account authentication, reference information registered under administration by the system is transmitted to a room or mobile-phone for private storage, with the original reference information deleted from the system. Biologic information gotten upon authentication is transmitted through wireless system to the room or mobile-phone for comparison with the reference, the result being returned to the system. Or, the reference is tentatively sent back to the system for comparison with the gotten biologic information. The biologic information sent to mobile-phone also includes health control information for storage and display. Mobile-phone also can receive blood pressure information at a waiting lounge of medical institution though wireless local communication even if the main power shut down. The communication between the biometrics system and the mobile-phone is encrypted. The system includes sensor unit and protection unit, the abnormality thereof being separately checked.
Owner:NL GIKEN
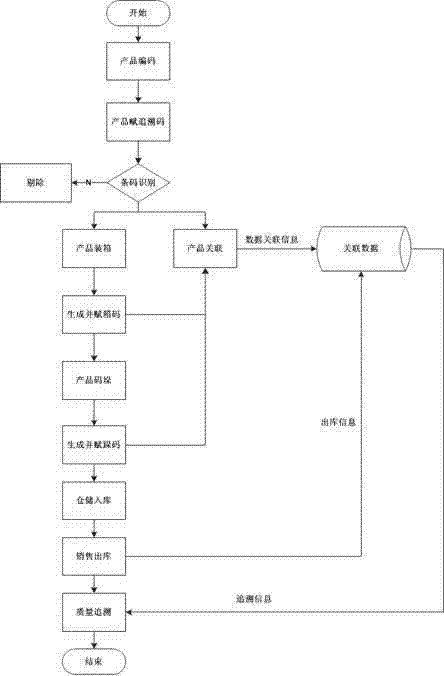
Quality safety tracing method for food processing enterprises
InactiveCN103761546ANo repeated codes appearMeet randomnessCo-operative working arrangementsDebit schemesProduction lineRelational database
The invention discloses a quality safety tracing method for food processing enterprises. The quality safety tracing method includes the steps that a laser coder generates random tracing codes according to a coding rule when a laser marking machine in a production line device is dynamically read in an on-line tagging mode; the laser marking machine carries out tracing mode marking on products on a production line, and two-dimension codes and plain codes are all marked on packages; a fixed reader is used for scanning and reading designated tagged code portions of the products; the two-dimension codes are successfully scanned and read, the tracing codes are recorded, and relevance between the tracing codes and commodity attribute information is completed; if the two-dimension codes fail to be scanned, the two-dimension codes will be removed through a removing device; the commodity tracing code information and the commodity attribute information are recorded into a relational database; after the products are packaged, package code data and product tracing code data are related; the products are stacked, stacking codes and tagged stacking codes are generated, and the stacking codes and the product package code data are related; the stacking codes are scanned, storage of the products is completed, delivery orders and the stacking codes are scanned to complete delivery, and the database records delivery information.
Owner:武汉华工赛百数据系统有限公司
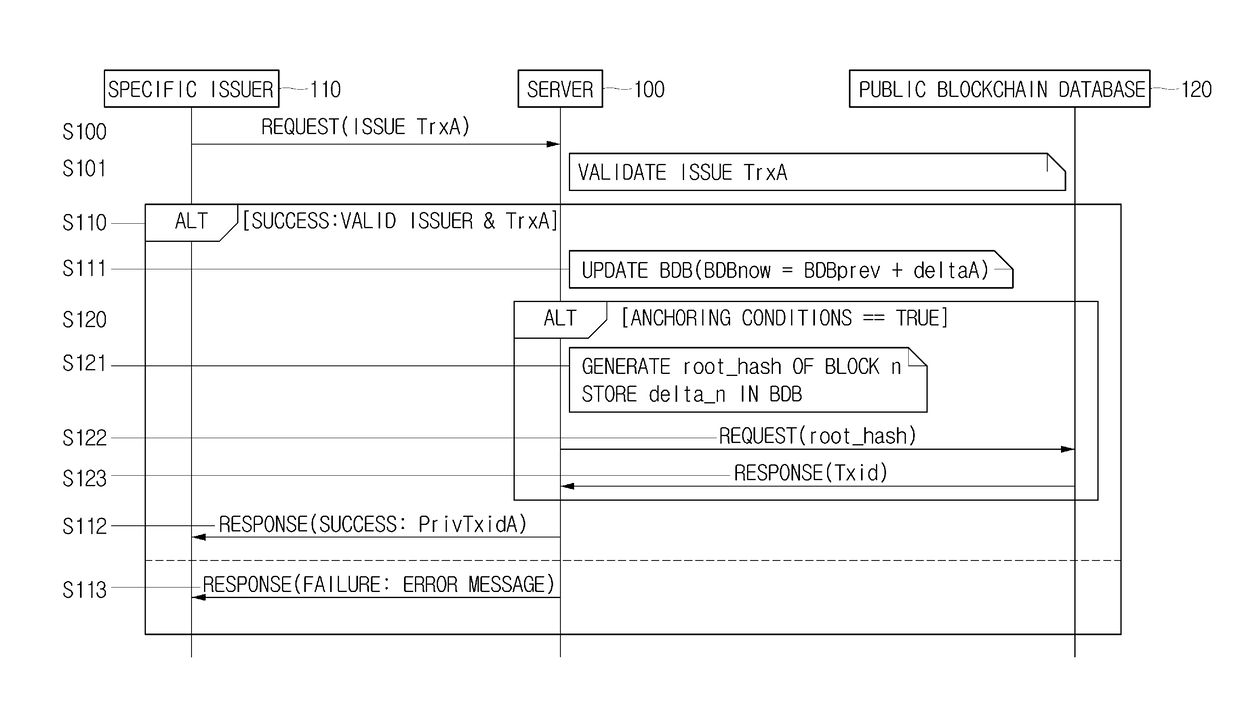
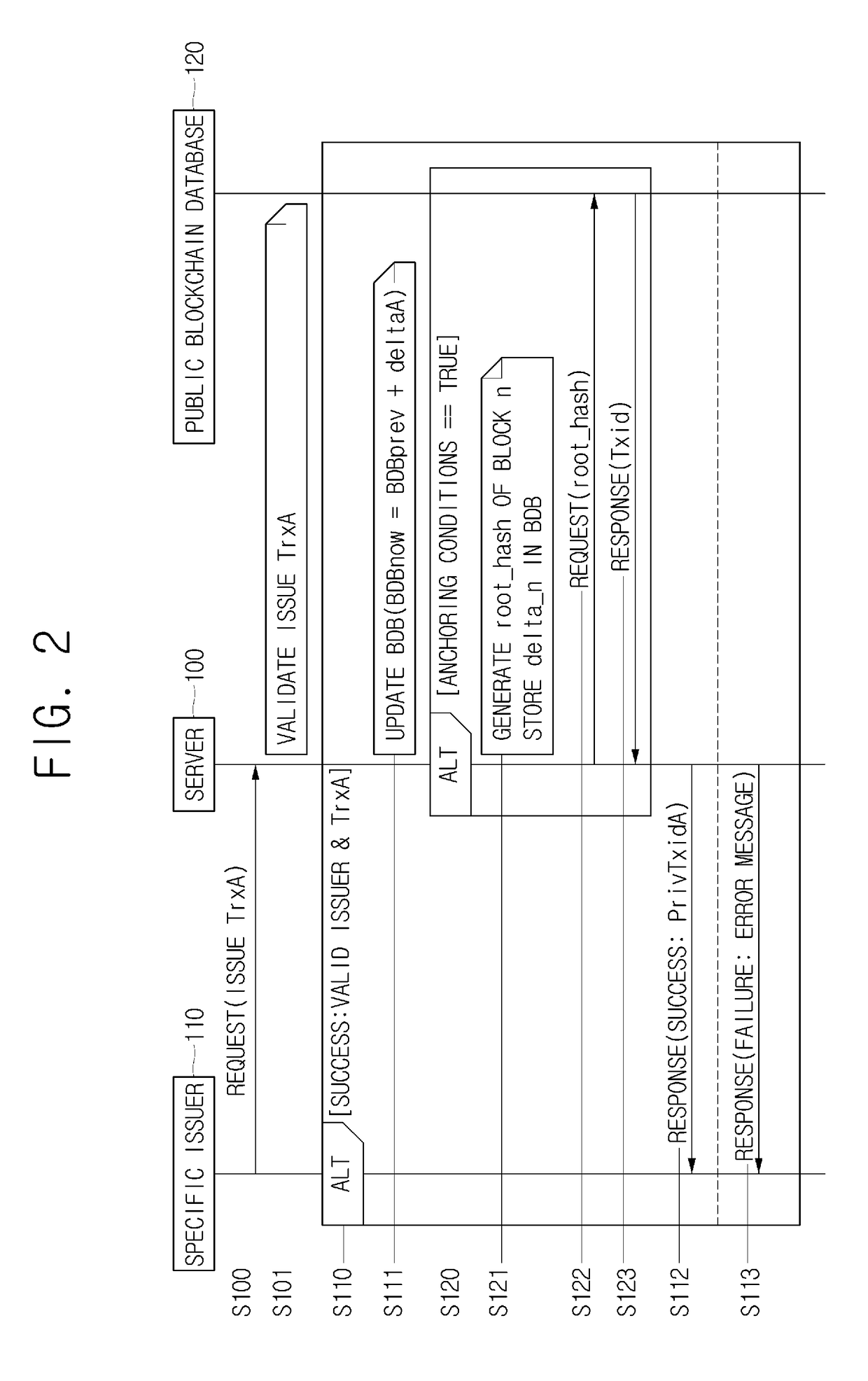
Method for issuing, using, refunding, settling and revocating electronic voucher using updated status of balance database by respective blocks in blockchain, and server using the same
ActiveUS20180101844A1Prevent forgeryPrevent illegal copyingKey distribution for secure communicationDigital data information retrievalVoucherData bank
A method of issuing an electronic voucher by an issuer is provided. The method includes steps of: (a) creating and registering a transaction including a voucher data, a public key and a signature value of the issuer, with a private blockchain database, providing the issuer with a PrivTxid locating the transaction in the private blockchain database, and updating and registering value information including a balance of the voucher data with a BDB; and (b) acquiring and registering a representative hash value calculated using a specific hash value, which is a hash value of the voucher data, the public key, and the signature value, and its corresponding hash values which include a hash value of a delta_n including all balances of all vouchers, identifiable by all PrivTxids locating their transactions, with a public blockchain database, and acquiring a Txid locating the representative hash value in the public blockchain database.
Owner:COINPLUG LNC
Authentication in a telecommunications network
InactiveUS7660772B2Easy to usePrevent forgeryAccounting/billing servicesData taking preventionTelecommunications networkTelecommunications link
The invention relates to an authentication method intended for a telecommunications network, especially for an IP network. From a terminal (TE1) in the network a first message (RR) containing an authenticator and a data unit is transmitted to the network, the data unit containing information relating to the manner in which the authenticator is formed. For carrying out authentication in the network, the data unit contained in the first message is used for determining a check value, which is compared with the said authenticator. To make it unnecessary for the terminal to perform any complicated and heavy exchange of messages when attaching to the network and for still obtaining the desired security characteristics for use, such an identification unit is used in the terminal which receives as input a challenge from which a response and a key can be determined essentially in the same manner as in the subscriber identity module of a known mobile communications system, a set of authentication blocks is generated into the network, of which each contains a challenge, a response, and a key, whereby the generation is performed in the same manner as in the said mobile communication system, at least some of the challenges contained by the authentication blocks are transmitted to the terminal, one of the challenges is chosen for use at the terminal, and, based on it, a response and key for use are determined with the aid of the terminal's identification unit, in the said first message (RR) the network is notified with the aid of the said data unit of which key corresponding to which challenge was chosen, and the authenticator of the first message and the said check value are determined with the aid of the chosen key.
Owner:CORE WIRELESS LICENSING R L
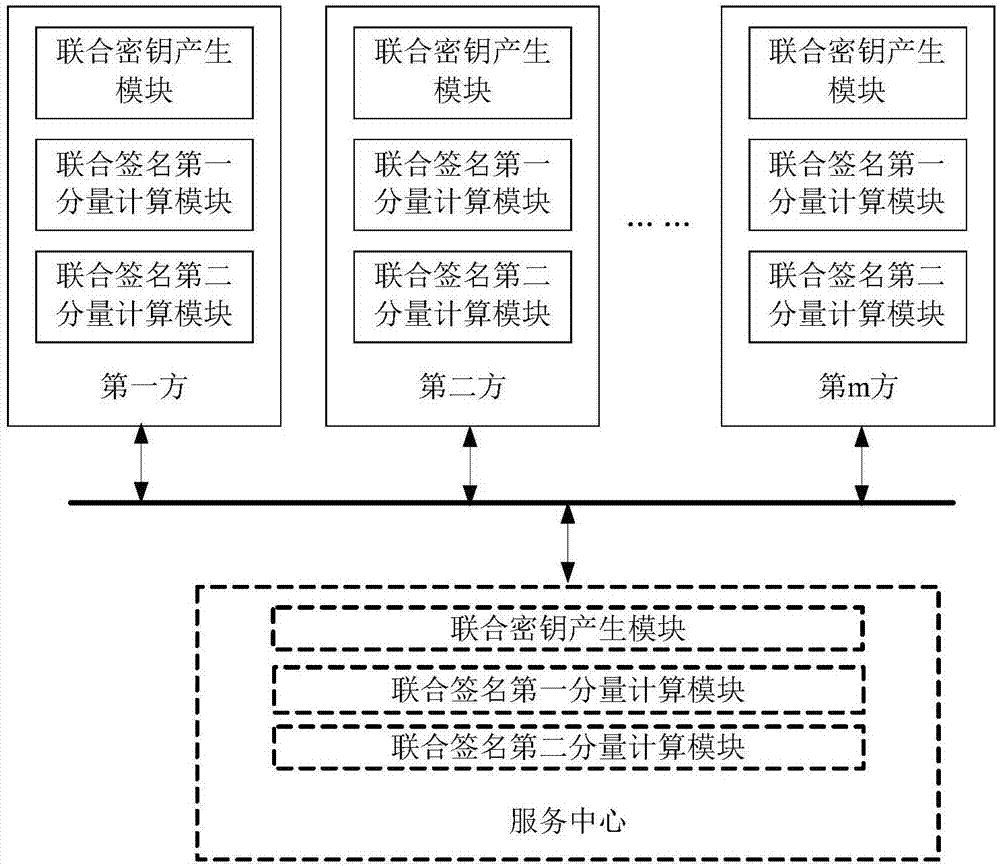
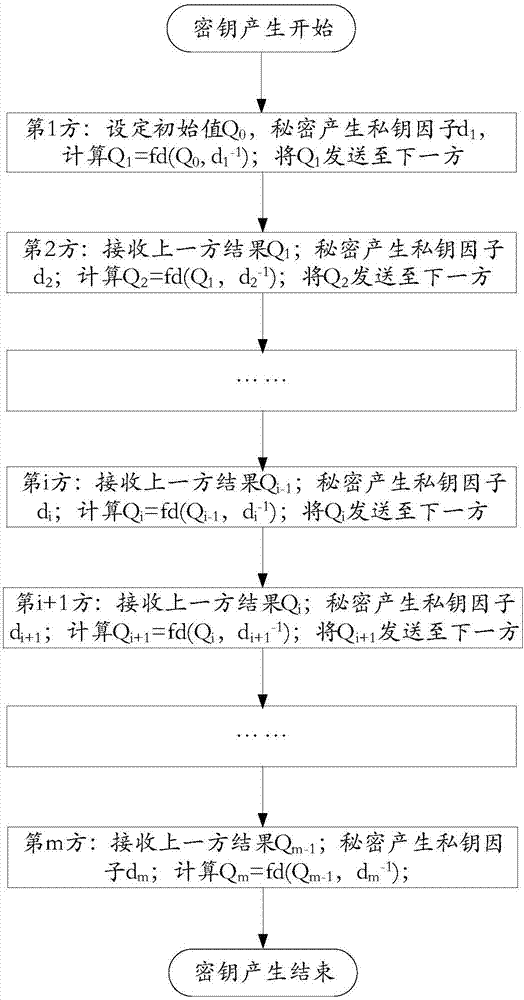
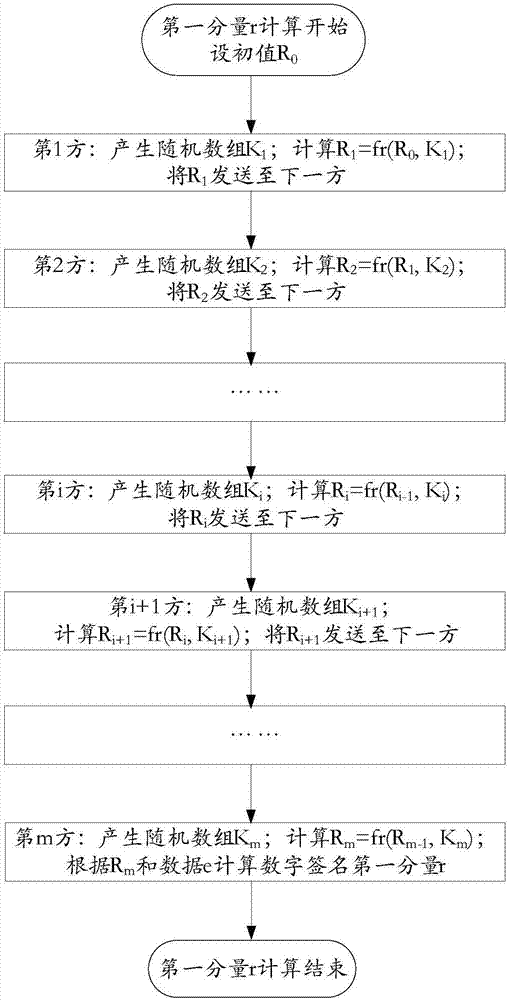
Multiparty joint key production and digital sign method and system
ActiveCN107017993AImprove protectionPrevention and control measures are effectiveKey distribution for secure communicationPublic key for secure communicationDigital signatureEngineering
The invention provides a multiparty joint key production and digital sign method and system. A joint sign private key d is composed of m private key factors di. The i is equal to [1, m]. The m is greater than or equal to 3. The m private key factors di are produced by the joint parties independently and secretly when the private key is produced and are stored in own devices secretly. The joint digital sign is finished by the parties according to a certain sequence and is finished jointly through utilization of the secretly stored key factors di based on calculation. The system comprises m joint parties. Each joint party has an independent subsystem. Each subsystem is composed of three parts: a joint key production module, a joint sign first component calculation module and a joint sign second component calculation module. According to the method and the system, the multiparty joint key production and digital sign method of an SM2 cryptographic algorithm and various formed systems: acentric and centered systems are realized. The digital sign is no longer finished by a single individual and is finished by multiple parities jointly.
Owner:BEIJING JN TASS TECH
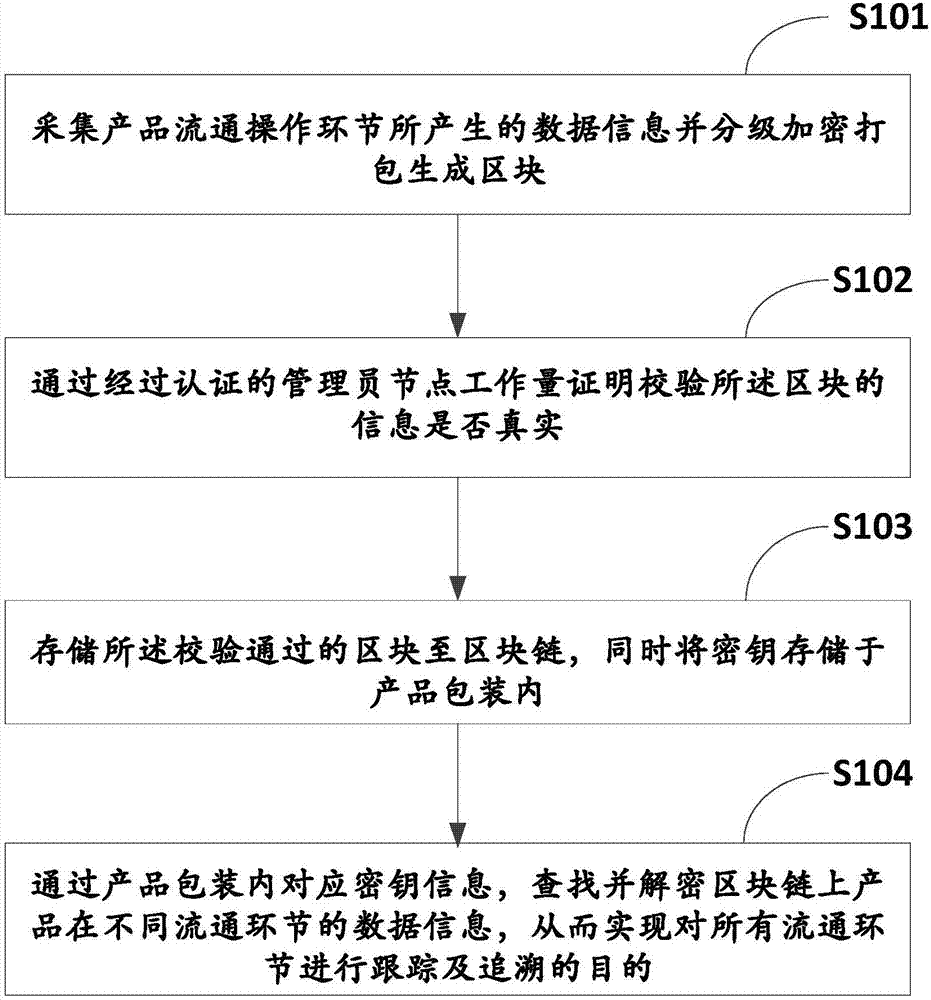
Product circulation tracking method and system based on block chain
InactiveCN108009830APrevent forgeryEnsure safetyKey distribution for secure communicationDigital data protectionData informationWorkload
The invention provides a product circulation tracking method based on a block chain. The method comprises the steps that data information generated in product circulation operation links is collected,graded, encrypted and packaged to generate blocks; whether the information of the blocks is true is verified through authenticated manager node workload proof; the blocks passing verification are stored into the block chain, and meanwhile keys are stored in product packages; and the data information of the products on the block chain in different circulation links is found and decrypted through corresponding key information in the product packages, so that the purpose of tracking and tracing all the circulation links is achieved. The invention furthermore provides a corresponding system. According to the product circulation tracking method and system based on the block chain in the embodiment, the whole production and circulation process of the products can be monitored, and source tracing can be performed no matter which link has a problem; moreover, the network system divides product information into three different levels, supervision is realized hierarchically, and information security is guaranteed; and meanwhile, a strict verification process is available for information input, multiple management nodes cooperate mutually, a single management node cannot impose a great influence on the whole system, and therefore the distributed network tracking system has high practicability in terms of product monitoring and is suitable for large-range popularization.
Owner:SHANGHAI DINGMING CONTAINER STORAGE & TRANSPORTATION CO LTD
Biometric Authentication Apparatus
InactiveUS20090304237A1FocusSimple configurationCharacter and pattern recognitionDiagnostic recording/measuringImaging processingImaging lens
A biometric authentication apparatus having a simple configuration, able to easily focus on a fingerprint or a vein or other blood vessel pattern and able to clearly capture an image of the same, able to prevent forgery, and in addition able to realize high precision authentication, which biometric authentication apparatus 100 having a transparent plate 110 formed by for example glass or plastic for placement of the finger of the authenticated person, that is, the inspected specimen OBJ, downward in the figure (surface where fingerprint is located facing downward), a fingerprint capturing use illumination apparatus 120, a vein capturing use illumination apparatus 130, and an image capturing apparatus 140, which image capturing apparatus 140 has an imaging lens apparatus capturing a dispersed image of an object passing through the optical system and phase plate, an image processing apparatus generating a dispersion-free image signal from a dispersed image signal from the imaging element, and an object approximate distance information detection apparatus generating information corresponding to the distance to the object, and which the image processing apparatus generating a dispersion-free image signal from the dispersed image signal based on the information generated by the object approximate distance information detection apparatus.
Owner:KYOCERA CORP +1
Semiconductor device
InactiveUS20060261331A1Prevent forgerySimple structureTransistorSemiconductor/solid-state device detailsOrganic compoundSimple Organic Compounds
It is an object of the present invention to provide a semiconductor device capable of additionally recording data at a time other than during manufacturing and preventing forgery due to rewriting and the like. Moreover, another object of the present invention is to provide an inexpensive, nonvolatile, and highly-reliable semiconductor device. A semiconductor device includes a first conductive layer, a second conductive layer, and an organic compound layer between the first conductive layer and the second conductive layer, wherein the organic compound layer can have the first conductive layer and the second conductive layer come into contact with each other when Coulomb force generated by applying potential to one or both of the first conductive layer and the second conductive layer is at or over a certain level.
Owner:SEMICON ENERGY LAB CO LTD
Intermediate transfer recording medium, method of forming print, and print
InactiveUS6308630B1Quality improvementSimple formatCylinder pressesPlaten pressesComputer scienceRecording media
An intermediate transfer recording medium is comprised by providing a transfer portion having a receptor layer on a substrate film. The transfer portion is printed with the image and thereafter transferred on a surface of a transfer-receiving material. In the first aspect of the intermediate transfer recording medium, the transfer portion is provided with plural hologram patterns 21 with a hologram mark 22 allocated to each the hologram pattern. According to the first aspect of the invention, since an image is formed on the receptor layer through positioning process using the hologram mark and then the transfer portion is transferred to the surface of the transfer-receiving material, no joint of a print plate appears in the hologram pattern and accuracy of transfer is remarkably excellent. On the other hand, In the second aspect of the intermediate transfer recording medium, peeling strength required to peel the transfer portion from the substrate film at the time when transferring the transfer portion to the transfer-receiving material is controlled in the range of 10 to 150 gf / inch. According to the second aspect of the invention, any transfer failure such as tail-extension or chip of the transfer portion is not caused.
Owner:DAI NIPPON PRINTING CO LTD
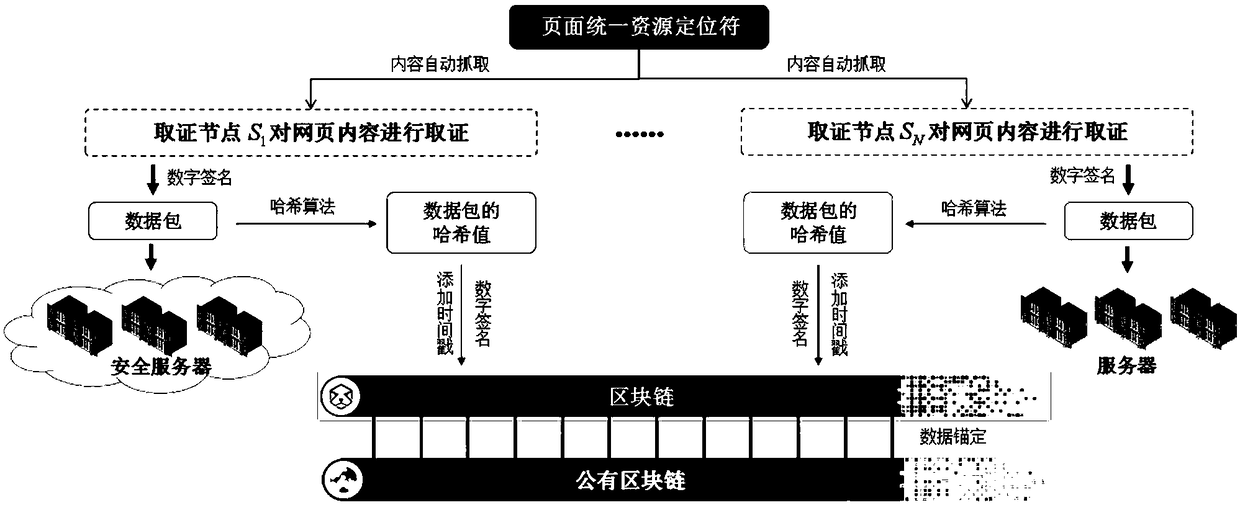
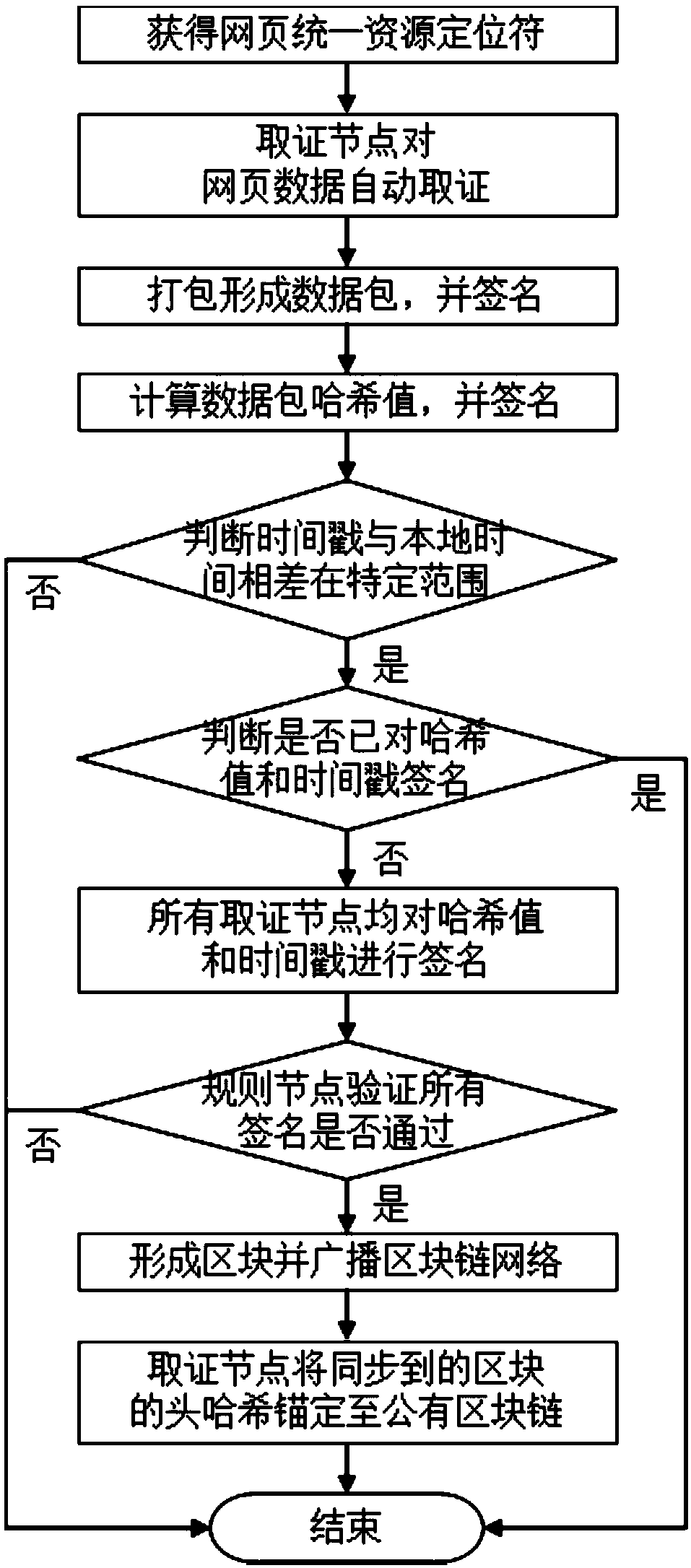
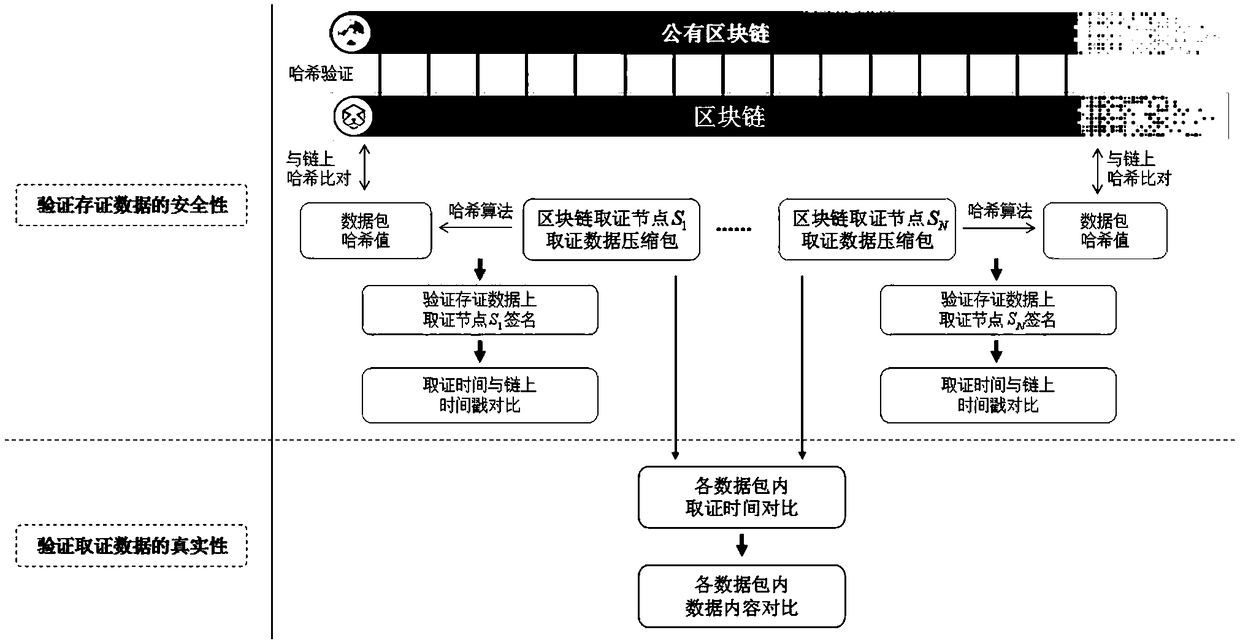
Webpage data automatic evidence obtaining and storing method based on block chain
ActiveCN108959416AEasy to collect evidencePrevent forgeryDigital data protectionSpecial data processing applicationsData compressionTimestamp
The invention discloses a webpage data automatic evidence obtaining and storing method based on a block chain. A user sends a uniform resource locator of a webpage which needs evidence obtaining to all evidence obtaining nodes in a block chain network, and the evidence obtaining nodes carry out automatic evidence taking on the webpage; the evidence obtaining nodes generate a preservation certificate and a data compression package for the evidence obtaining data, and the data compression package is signed and then stored in a server, the hash value of the data compression packet is calculated,a timestamp is added, and the data compression packet is broadcast to a block chain network after being signed; the evidence obtaining nodes verify the timestamp of the hash value, and if the condition is met and the signature is not signed, the signature is signed and broadcast to the block chain network; a rule node receives the data signed by all the evidence obtaining nodes, and the signatureis verified, after verification is passed, the data are formed into blocks and broadcast to the block chain network; and the evidence obtaining nodes anchor the blocks to a public block chain. The method can be used for carrying out automatic evidence obtaining and evidence storage on webpage data, and the authenticity of the evidence taking data and the safety of the evidence storage data are ensured.
Owner:浙江数秦科技有限公司
System and methods providing secure delivery of licenses and content
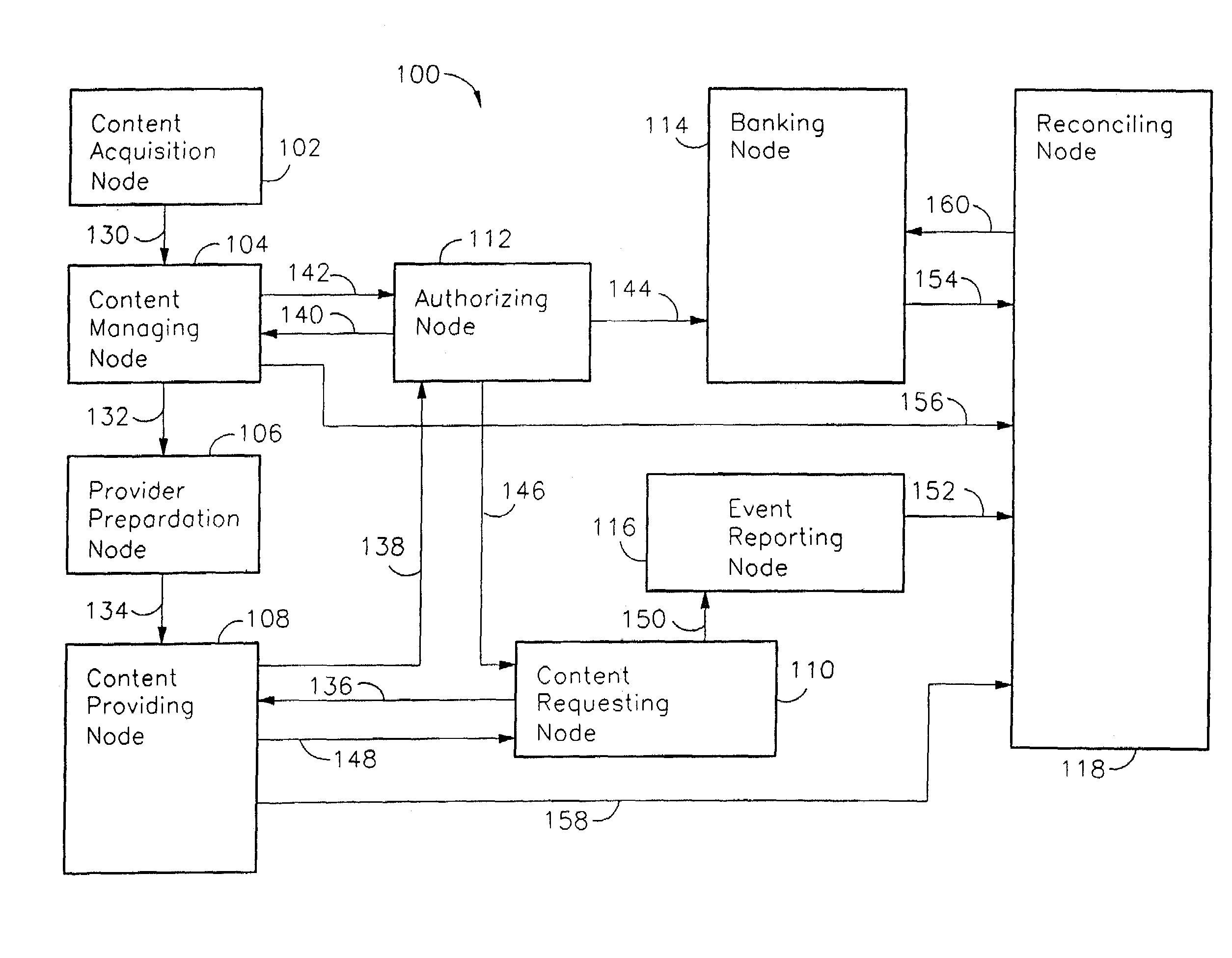
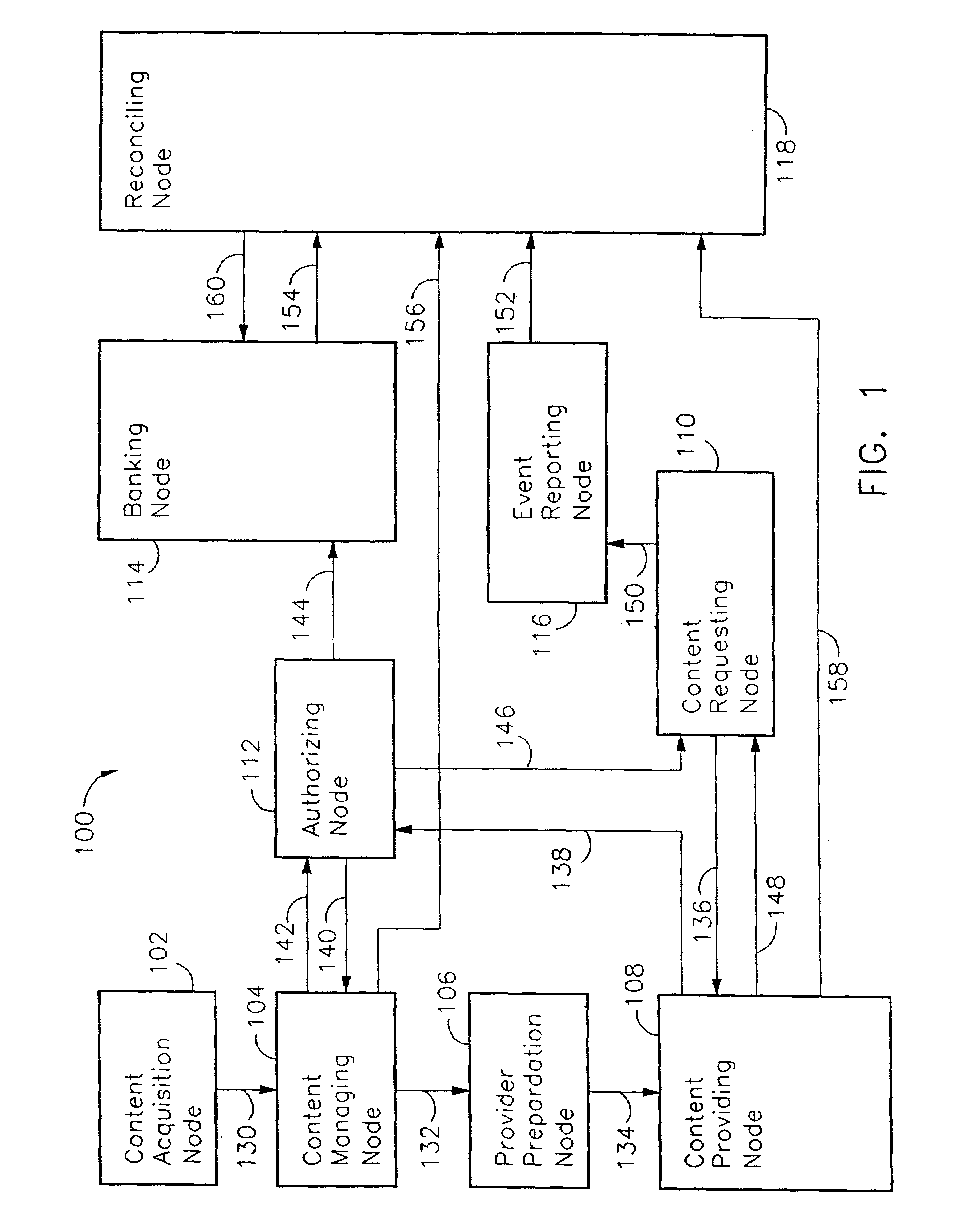
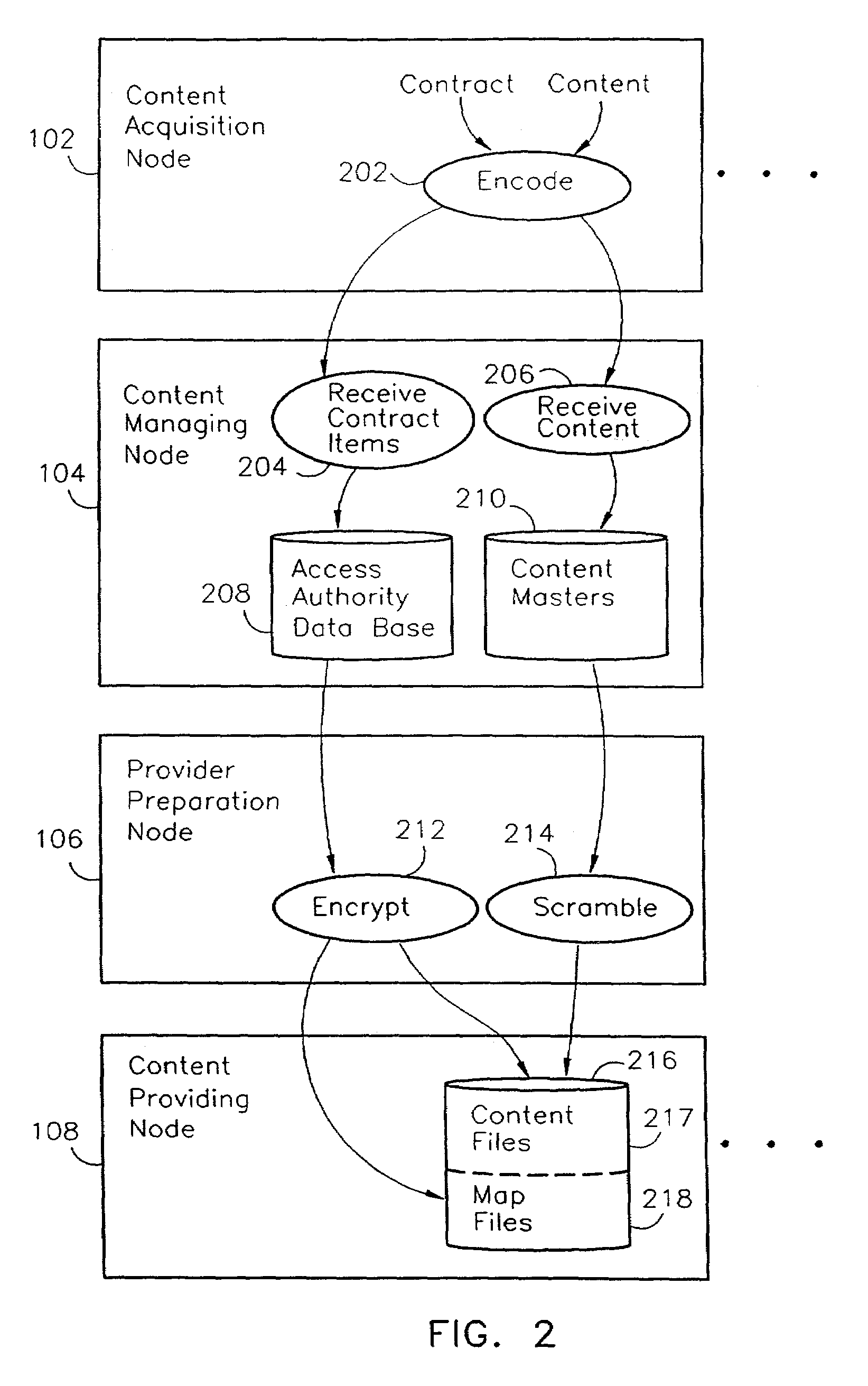
InactiveUS7051004B2Accurate calculationInhibitory contentDigital computer detailsDigital storagePaymentData transmission
A computer network having a requesting node and a providing node permits data transfer therebetween when permitted by an authorizing node. Reports generated in response to authorizations and reports generated in response to data transfers are reconciled at a reconciliation node to improve the accuracy of payments collected and paid for use of the data. Such payments include copyright royalties for audio, video, and other works recorded in digital format.
Owner:ROVI SOLUTIONS CORP
Method and apparatus for authentication of client server communication
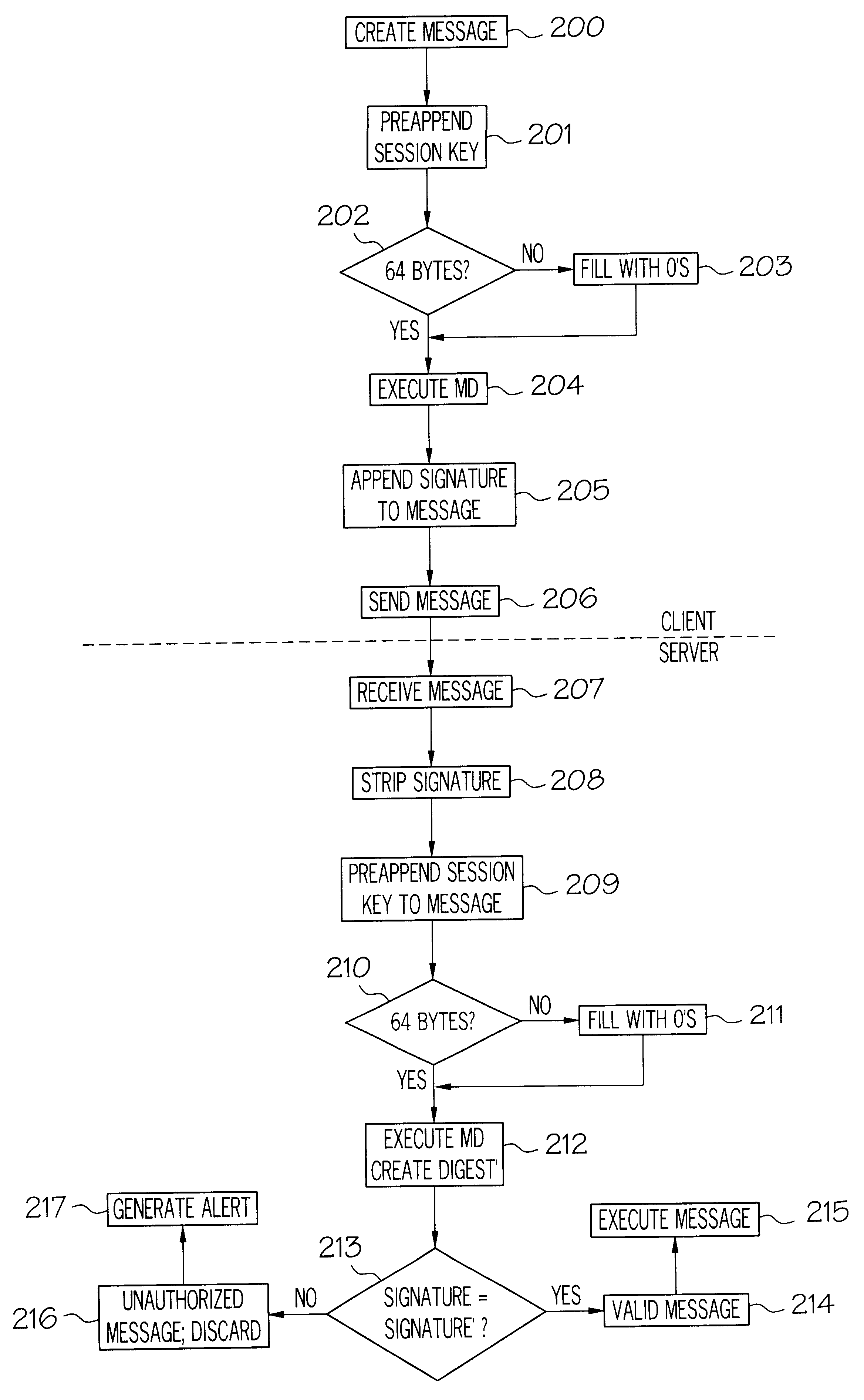
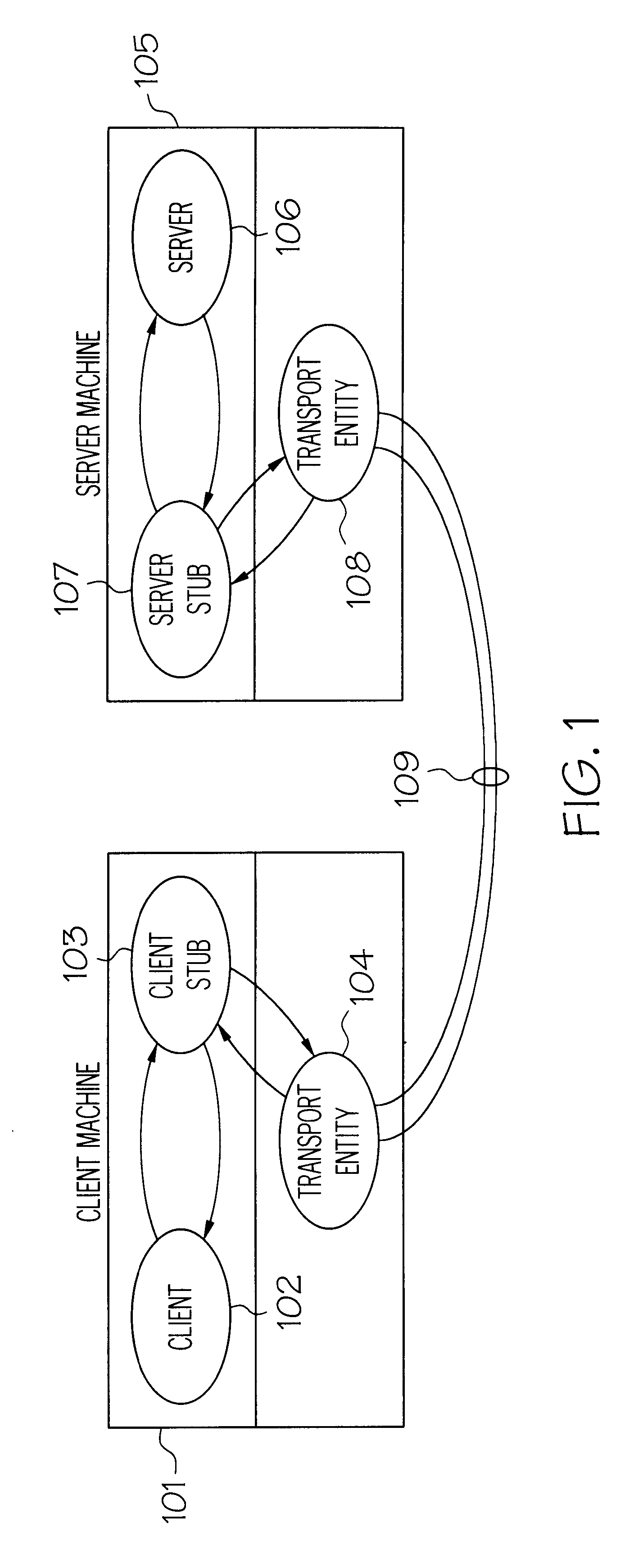
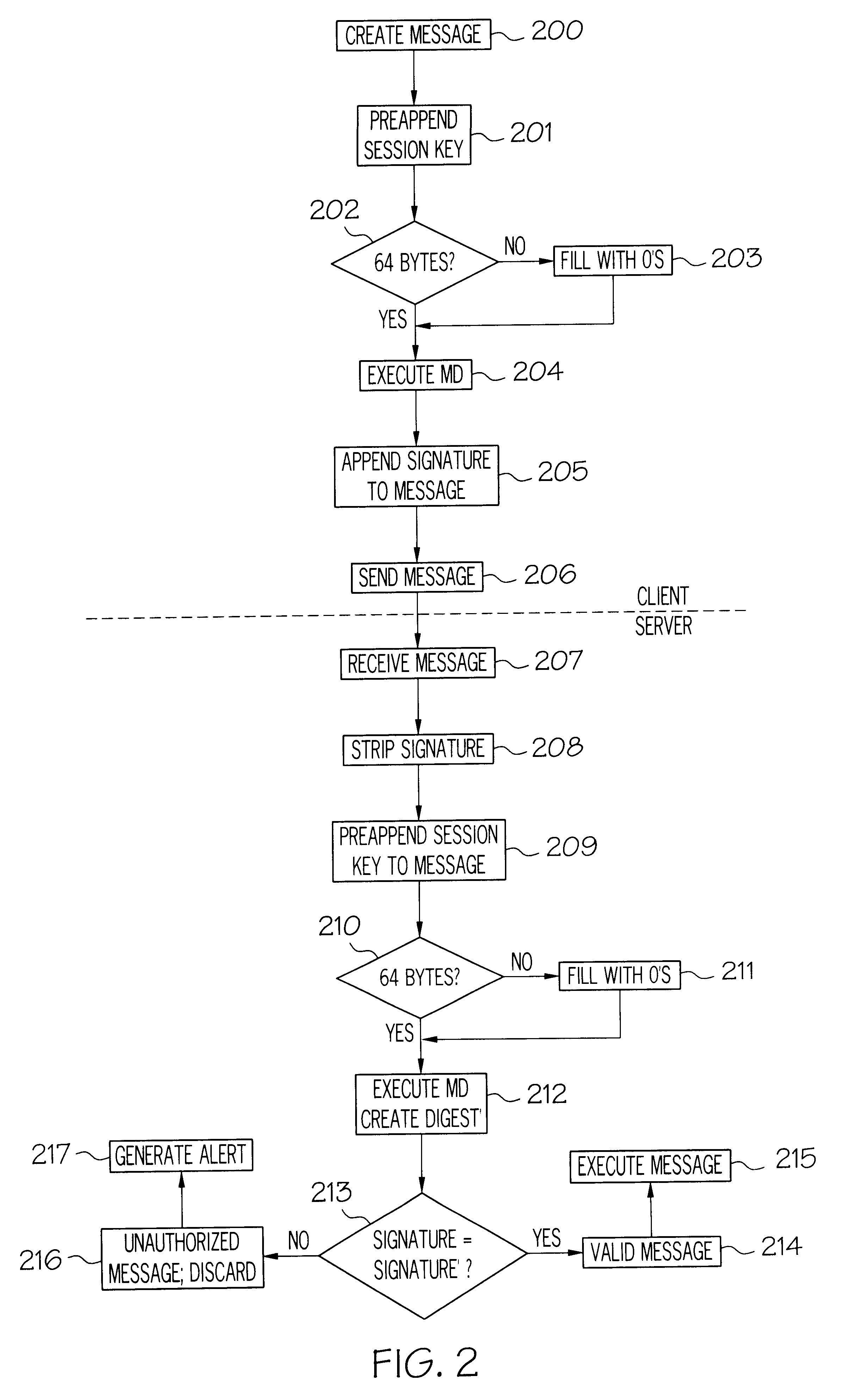
InactiveUSRE37178E1Prevent forgeryKey distribution for secure communicationPublic key for secure communicationClient-sideSession key
The present invention provides a method and apparatus for message packet authentication to prevent the forging of message packets. After a message packet is created, a secret session key is preappended to the message, and a message digesting algorithm is executed on the altered message to create a message digest. A portion of the message digest, referred to as the signature, is then appended to the actual message when it is sent over the wire. The receiving station strips the signature from the message, preappends the same secret session key and creates its own message digest. The signature of the digest created by the receiving station is compared to the signature of the digest appended by the sending station. If there is a match, an authentic message is assumed. If there is no match, the message is considered as invalid and discarded. An advantage of the present invention is that the session key is never transmitted over the wire. The receiving station (server) already has the key and uses the key along with the message data to recalculate the message digest upon receiving the packet. The shared secret key (session key) is generated during initiation of the NCP session. In addition, cumulative state information is maintained by both the sending station and the receiving station. This state information is also used to authenticate messages.
Owner:EMC CORP
Semiconductor device and driving method of the same
InactiveUS7499305B2Well formedPrevent forgeryNanoinformaticsSolid-state devicesBit lineSimple Organic Compounds
The present invention provides a semiconductor device including a memory that has a memory cell array including a plurality of memory cells, a control circuit that controls the memory, and an antenna, where the memory cell array has a plurality of bit lines extending in a first direction and a plurality of word lines extending in a second direction different from the first direction, and each of the plurality of memory cells has an organic compound layer provided between the bit line and the word line. Data is written by applying optical or electric action to the organic compound layer.
Owner:SEMICON ENERGY LAB CO LTD
Adhesive tape structure for sealing and keeping secrecy
InactiveUS20060066096A1Keeping secrecyPrevent forgeryOther printing matterFlexible container closureAdhesiveLettering
An adhesive tape structure for sealing and keeping secrecy comprises a releasable paper film, an upper adhesive layer, a separation layer, a film and a lower adhesive layer sequentially combined downwardly from above; the separation layer has thereon warning letters, when the releasable paper film is torn off, the upper and the lower adhesive layers of the adhesive tape can be stuck respectively on the inner side of the flap and the edge to be sealed at the opening of a bag; and when the edge at the opening of the bag is detached, the separation layer shows the printed letters or pattern for warning. The structure suits postal matters, express delivery bags, package bags and cash bags for sealing and keeping secrecy.
Owner:KAN SHEN NAN
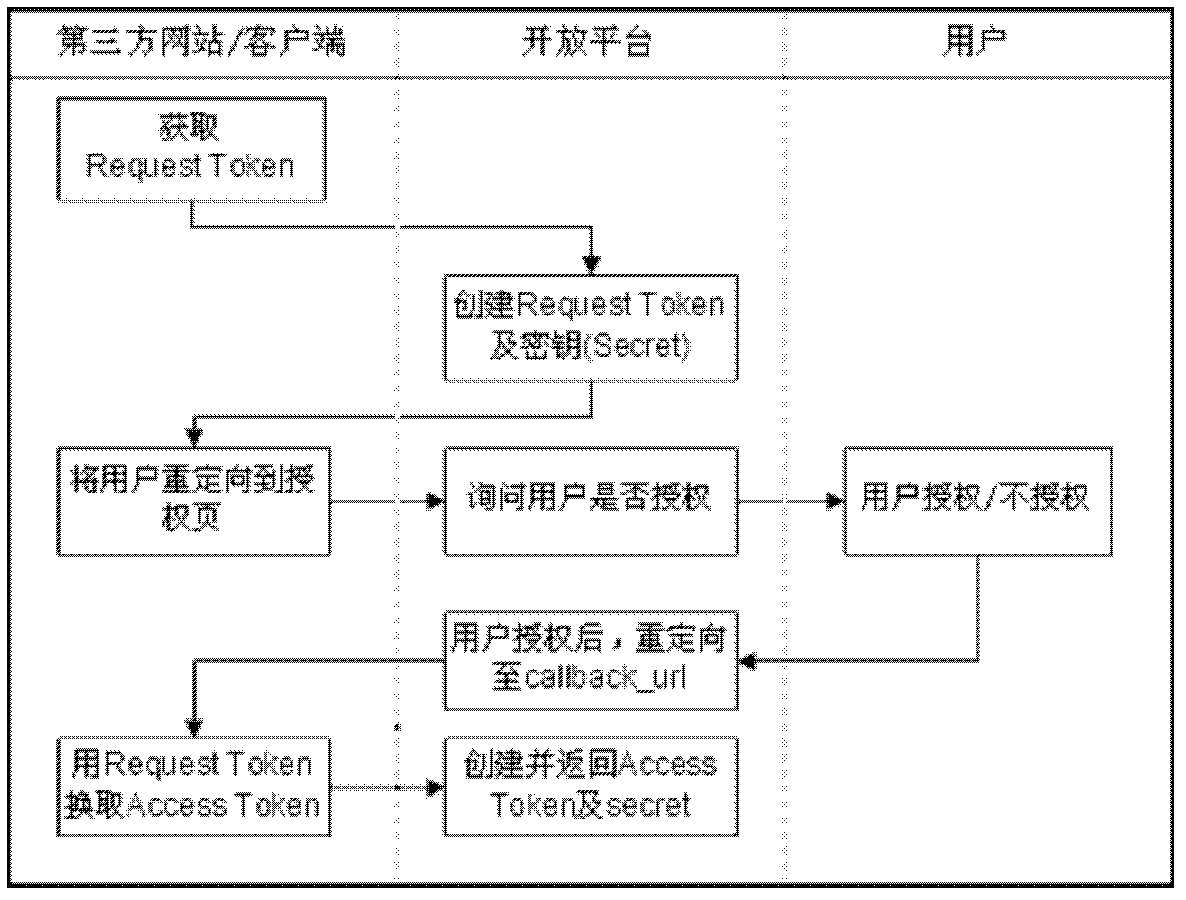
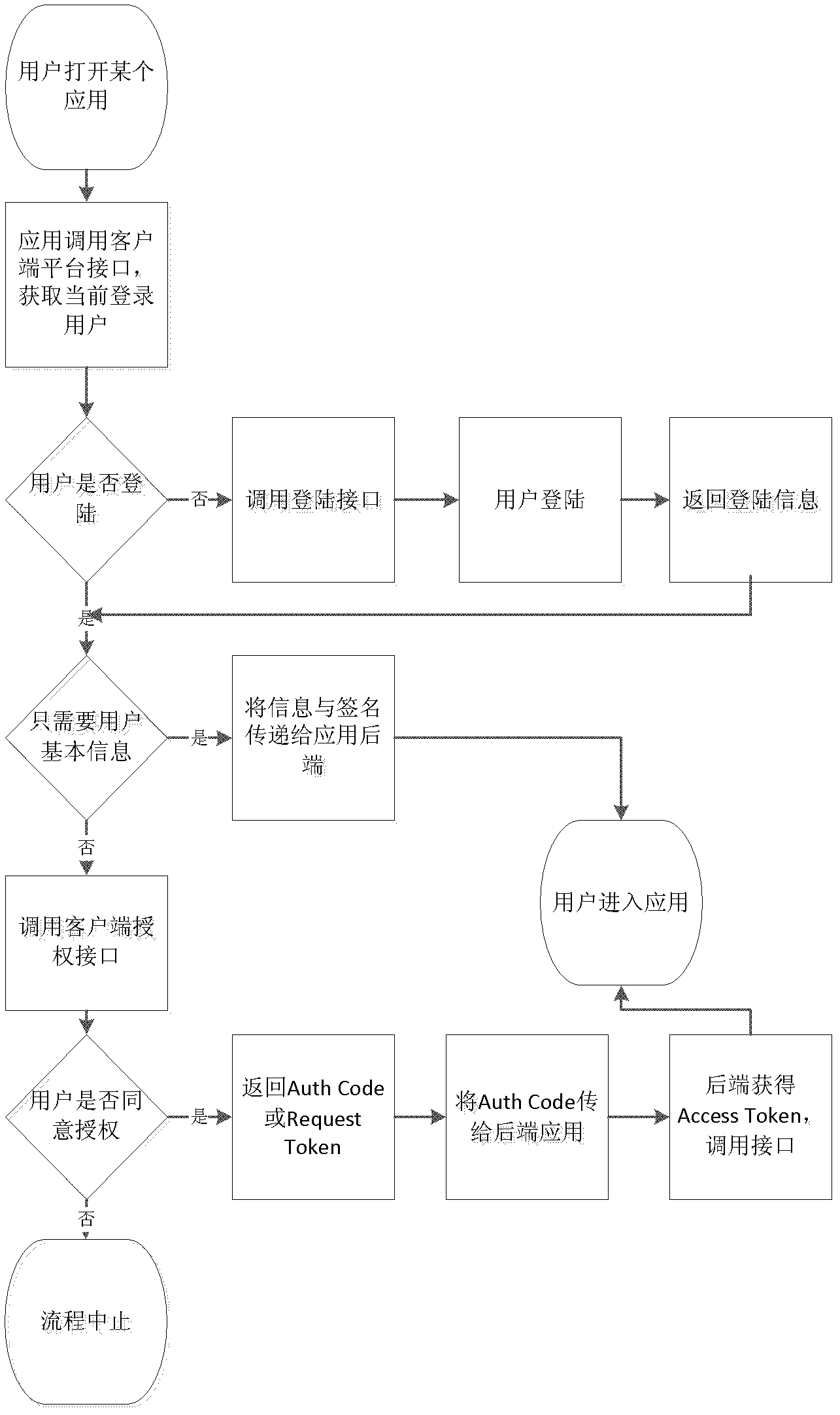
Authentication and authorization method and system applied to client platform
The invention discloses an authentication and authorization method and an authentication and authorization system applied to a client platform. The method and the system are modified on the basis of a protocol in a way that the client platform provides a Javascript (JS) interface for an access application party for user login, authorization and authentication. The method comprises the following steps of: starting at least one application program of the client platform; calling the JS interface of the client platform to acquire the basic information at least comprising the username of a current login user by using the application program; if information indicating that the user does not log in is returned and the user is required by the application program to log in, calling a login JS interface by using the application program; calling back and returning the basic information of the signature of the user to the application program through the JS interface; and if the application program determines that only the information of the username and the signature are required, allowing the user to access the application program. Therefore, a plurality of users can share a plurality of pieces of application, the authorization page counterfeiting of the application is avoided, user experiences are improved, the advanced background entry of a calling-back address is avoided, and the basic information can be acquired without the official authorization of the user after the addition of the application.
Owner:BEIJING QIHOO TECH CO LTD +1
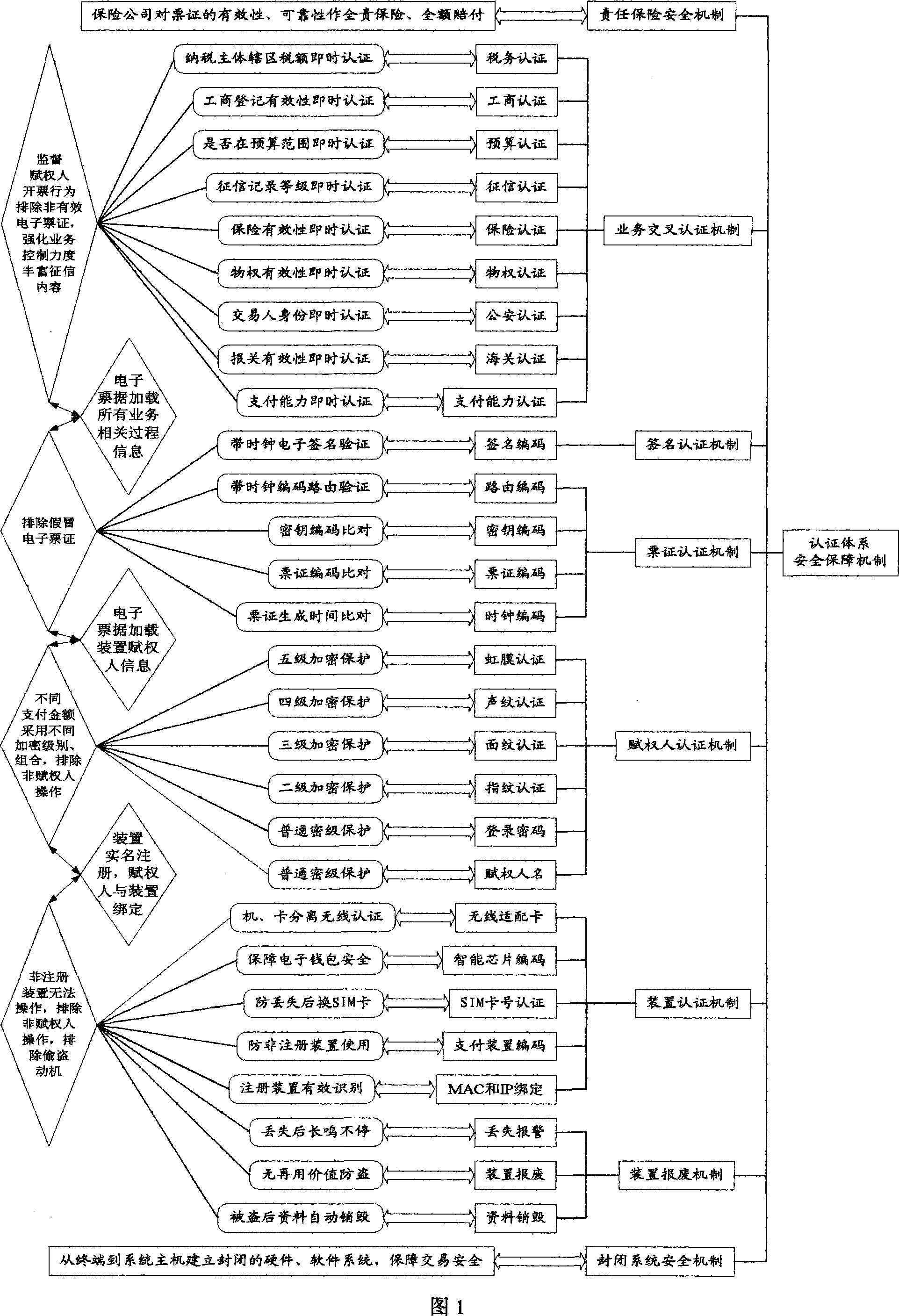
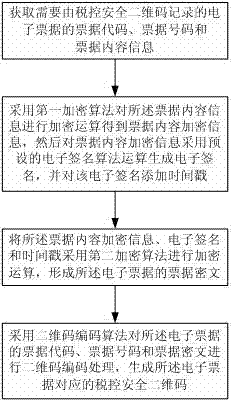
Tax-control safety two-dimensional code encoding and decoding processing method
InactiveCN103198344APromote exchangeEasy transferRecord carriers used with machinesSensing by electromagnetic radiationProgramming languageThe Internet
The invention discloses a tax-control safety two-dimensional code encoding and decoding processing method. By means of the method, a tax-control safety two-dimensional code generated through the method has a plurality of levels of tax-control safety protection, anti-counterfeiting and safety performance of the tax-control safety two-dimensional code is improved, electronic signature information carried by the code can serve as a tool carrying out off-line authenticity identification on the condition of separation from the internet, the problem that when electronic bill information is transmitted through the two-dimensional code in the prior art, the authenticity identification is limited by network conditions and time is solved, and tax-control safety of the tax-control safety two-dimensional code is effectively enhanced. The tax-control safety two-dimensional code decoding processing method not only can prevent illegal leakage of useful information in the tax-control safety two-dimensional code, but also can immediately identify authenticity of the electronic bill information contained in the tax-control safety two-dimensional code off-line on the condition that the internet is not relied on, and therefore the tax-control safety of the tax-control safety two-dimensional code during the decoding process is further improved.
Owner:CHONGQING FARSIGHT PRINTING +1
Cloud storage data common auditing method possessing secret key leakage resistance characteristic
The invention belongs to the communication technology field and especially relates to a cloud storage data common auditing method possessing a secret key leakage resistance characteristic. The method mainly comprises the following steps of system initialization: blocking processing is performed on a data file so as to generate public and private key pairs of a cloud user and a cloud server; auditing identification generation: the cloud user sends the data file and a label, and a signature set of a data block to the cloud server; auditing challenge response: a third party auditor generates auditing challenge information and sends to the cloud server; the cloud server calculates combination information according to the auditing challenge information, gets signatures together and sends an auditing identification response information to the third party auditor; and the third party auditor verifies validity of the auditing identification response information. The method has advantages that a condition that digital signature forgery and auditing identification response information forgery caused by leakage of a user signature private key can be prevented; and a malicious cloud server is ensured not to generate the forged auditing identification response information to cheat a TPA and to pass through an auditing verification process.
Owner:SOUTHWEST PETROLEUM UNIV
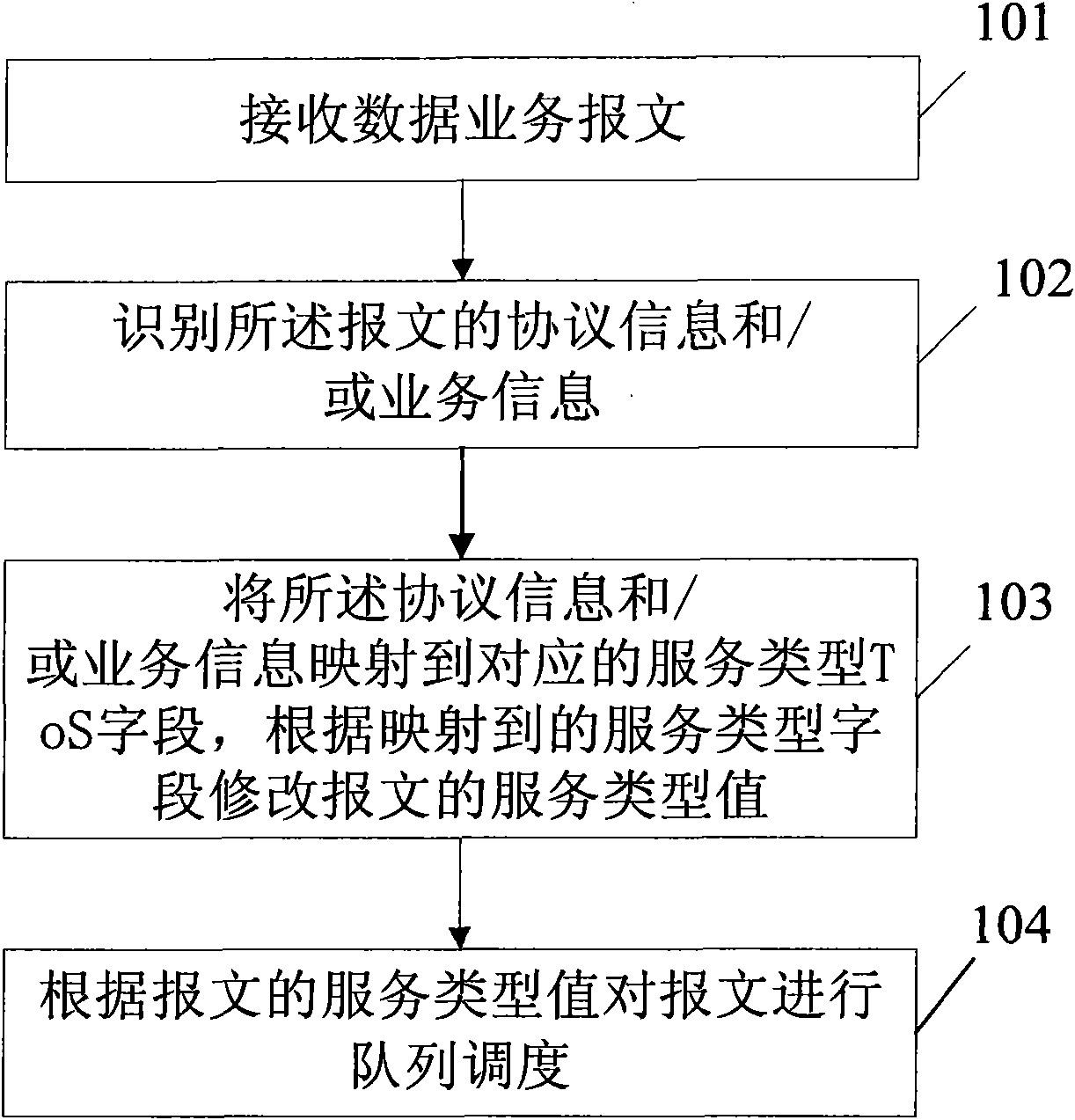
Data traffic processing method, network device and network system
InactiveCN102143035APrevent forgeryAvoid bearerData switching networksApplication serverNetworked system
The invention provides a data traffic processing method, a network device and a network system, wherein the data traffic processing method comprises the steps of: receiving a data traffic message; recognizing protocol information and / or traffic information of the message; mapping the protocol information and / or traffic information to a corresponding traffic type field, and modifying a traffic type value of the message according to the mapped traffic type field; and carrying out queue scheduling and forwarding on the message according to the service type value of the message. The invention hasthe advantages of effectively lowering cost of a QoS (Quality of Service) implementation scheme, preventing a traffic of falsifying high priority by a low-priority application server, and avoiding using the traffic of loading low-priority by using a high-priority port.
Owner:HUAWEI TECH CO LTD
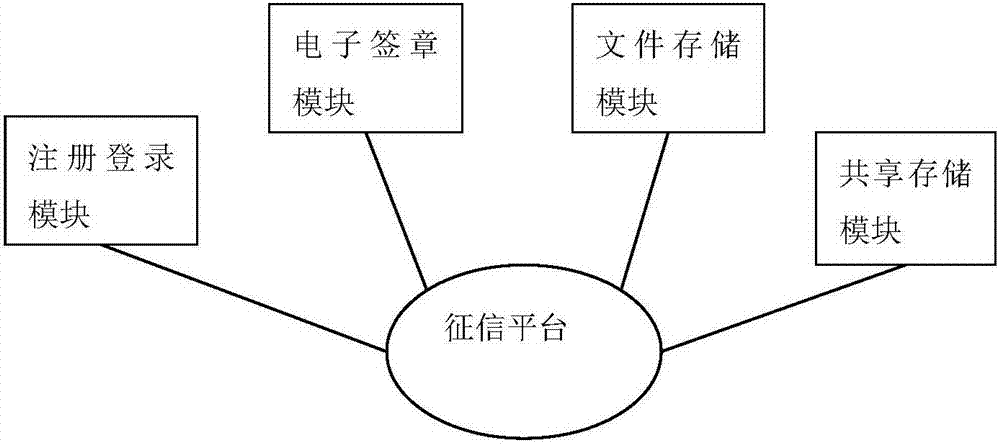
Data transaction credit investigation platform and method on supply chain
PendingCN107423980AImprove maintainabilityImprove portabilityElectronic credentialsTamper resistanceOnline signature
The invention discloses a data transaction credit investigation platform on a supply chain. The platform comprises a registration and login module which allows a user to register and use a platform function after login, an electronic signature module which allows the user to carry out online signature on a transaction contract, an encryption and authentication module which allows the user to authenticate the contract for a third party, a file storage module which is used for the encryption and storage of a contract file of the user, and a sharing storage module for storing shared contract abstract information. According to the platform architecture, the distributed management and sharing of credit data can be realized, and the querying, unforgeability and tampering resistance of data are ensured. The invention also discloses a data transaction credit investigation method on a supply chain.
Owner:易信(厦门)信用服务技术有限公司
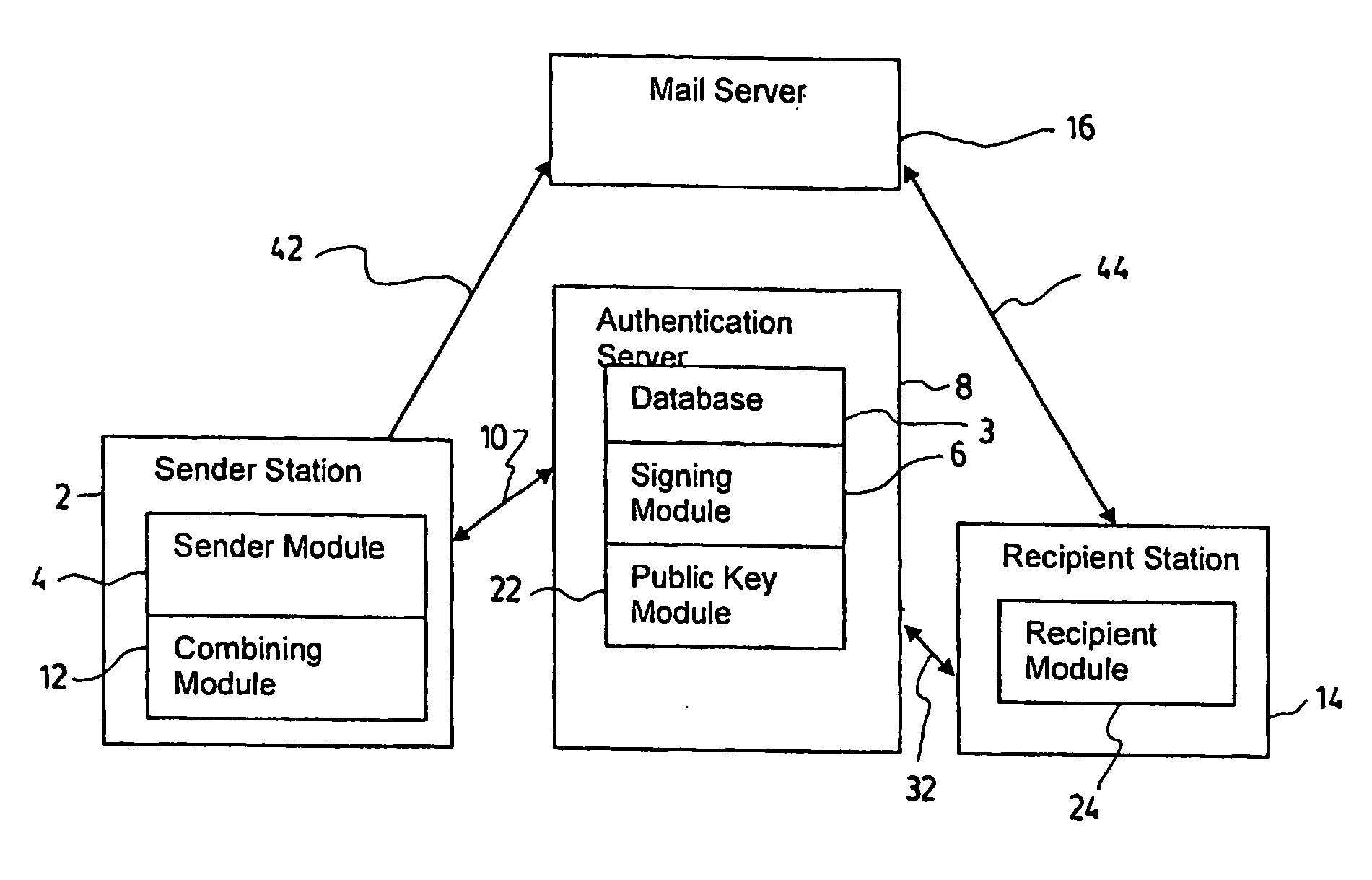
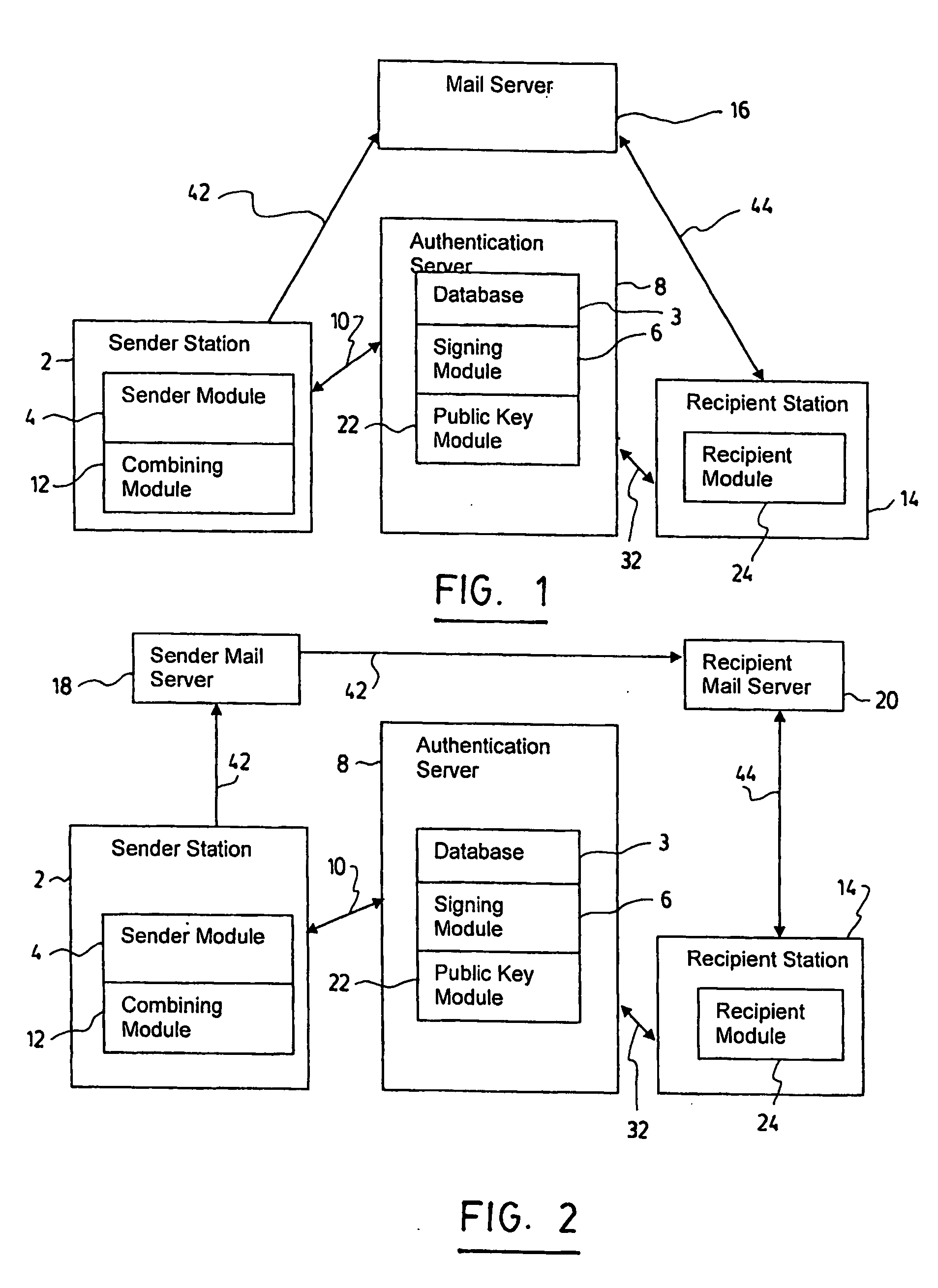
System and method for warranting electronic mail using a hybrid public key encryption scheme
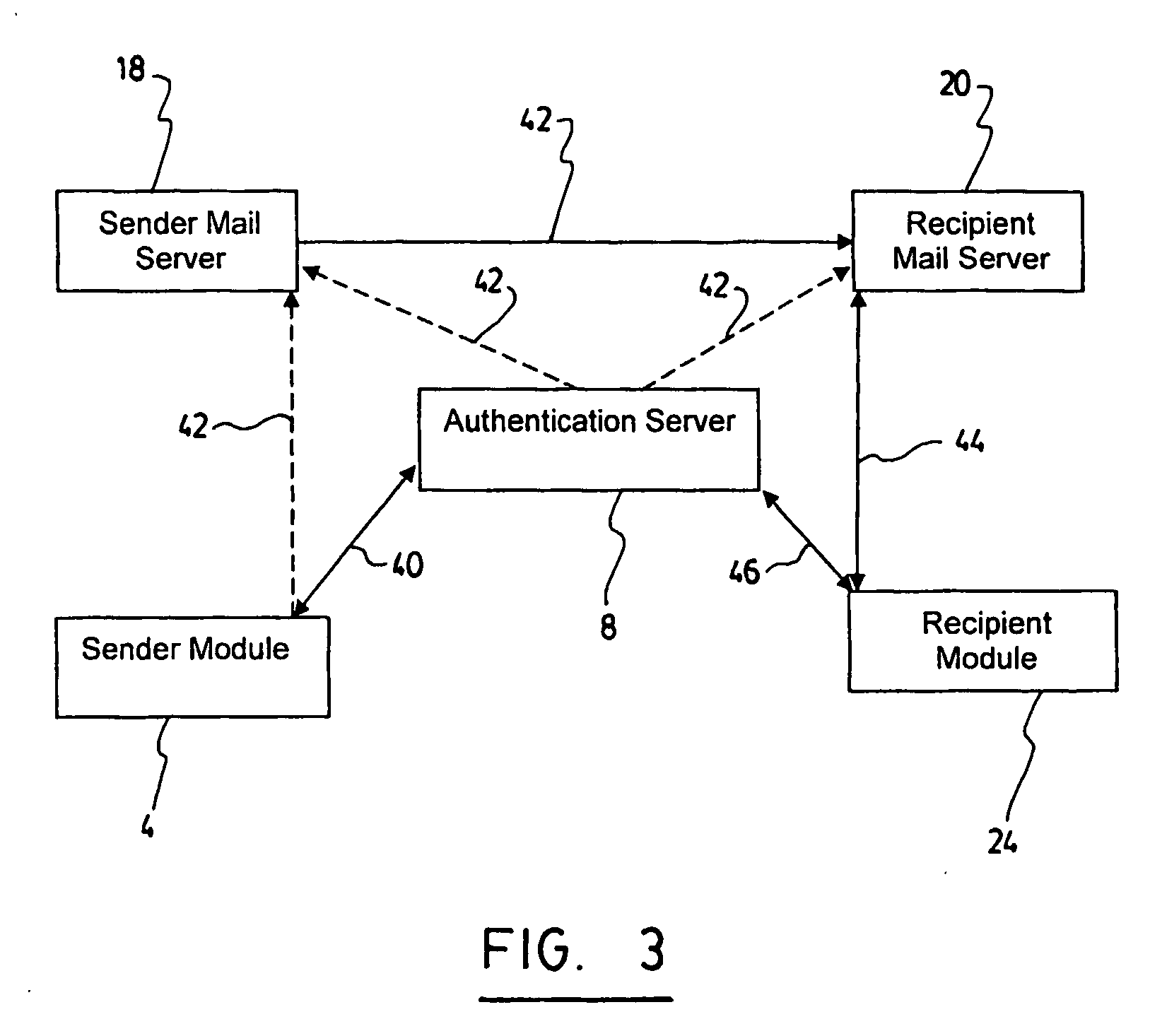
InactiveUS20060123476A1Prevent forgeryMemory loss protectionPublic key for secure communicationAuthentication serverElectronic mail
The present invention provides a method and system for warranting electronic mail using a hybrid public key encryption scheme. In one embodiment, the sender contacts an authentication server which first identifies the sender as being allowed to send through the server, and secondly signs his email using a private key in order to send to the recipient. Upon receipt, the recipient can then verify that the sender is indeed authenticated by the authentication server by contacting the authentication server, requesting the sender's public key and using this public key to validate the signature contained in the email. It is possible that the authentication server may itself send the email to the existing mail servers, or it may simply return the signature to the sender for sending to the recipient along with the original email using the sender's existing outgoing email server.
Owner:KRYPTIVA
Digital authentication control method for access control system and access control system using the same
InactiveCN101246607AWill not leakImprove convenienceUser identity/authority verificationIndividual entry/exit registersElectricityCiphertext
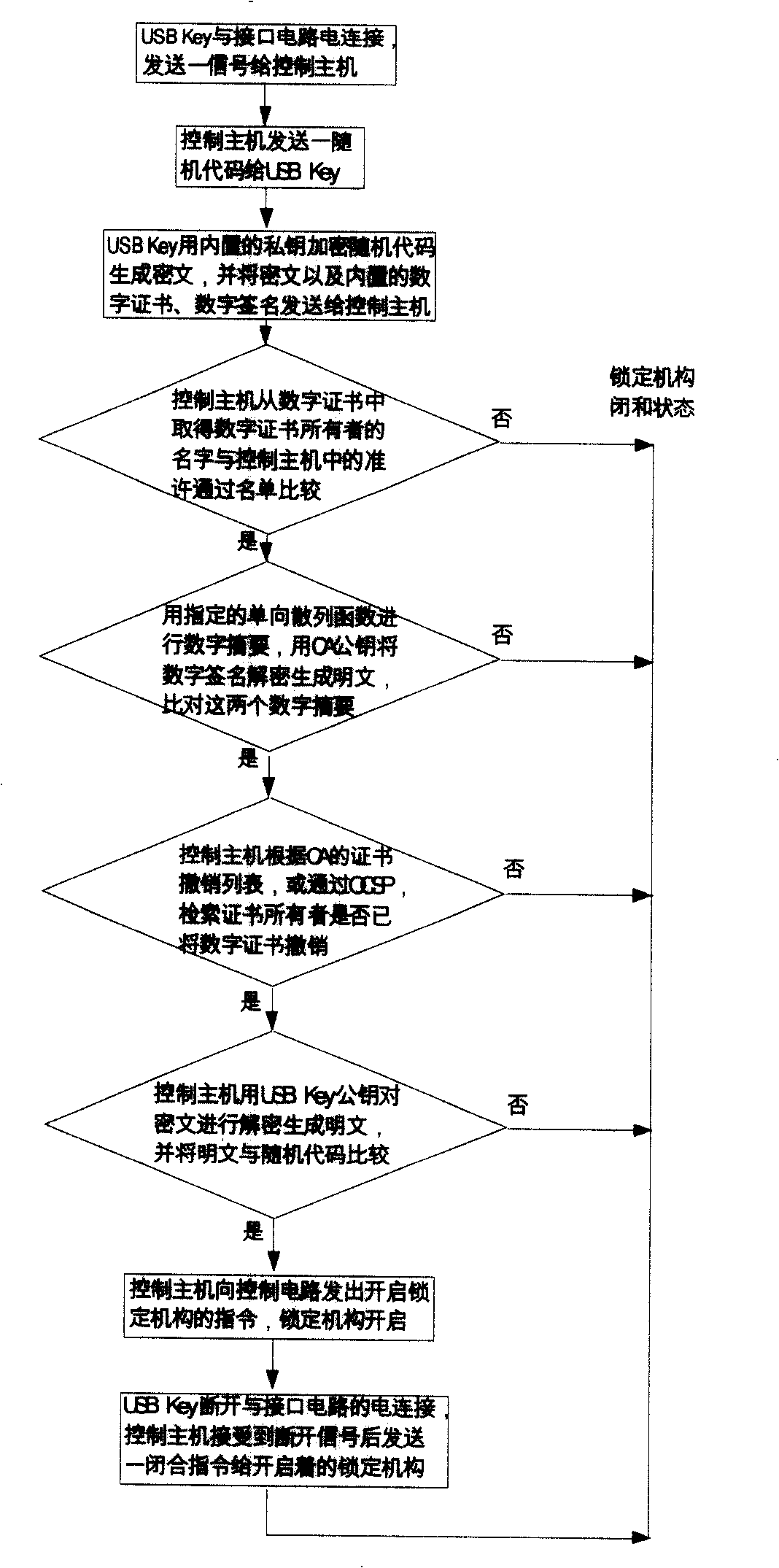
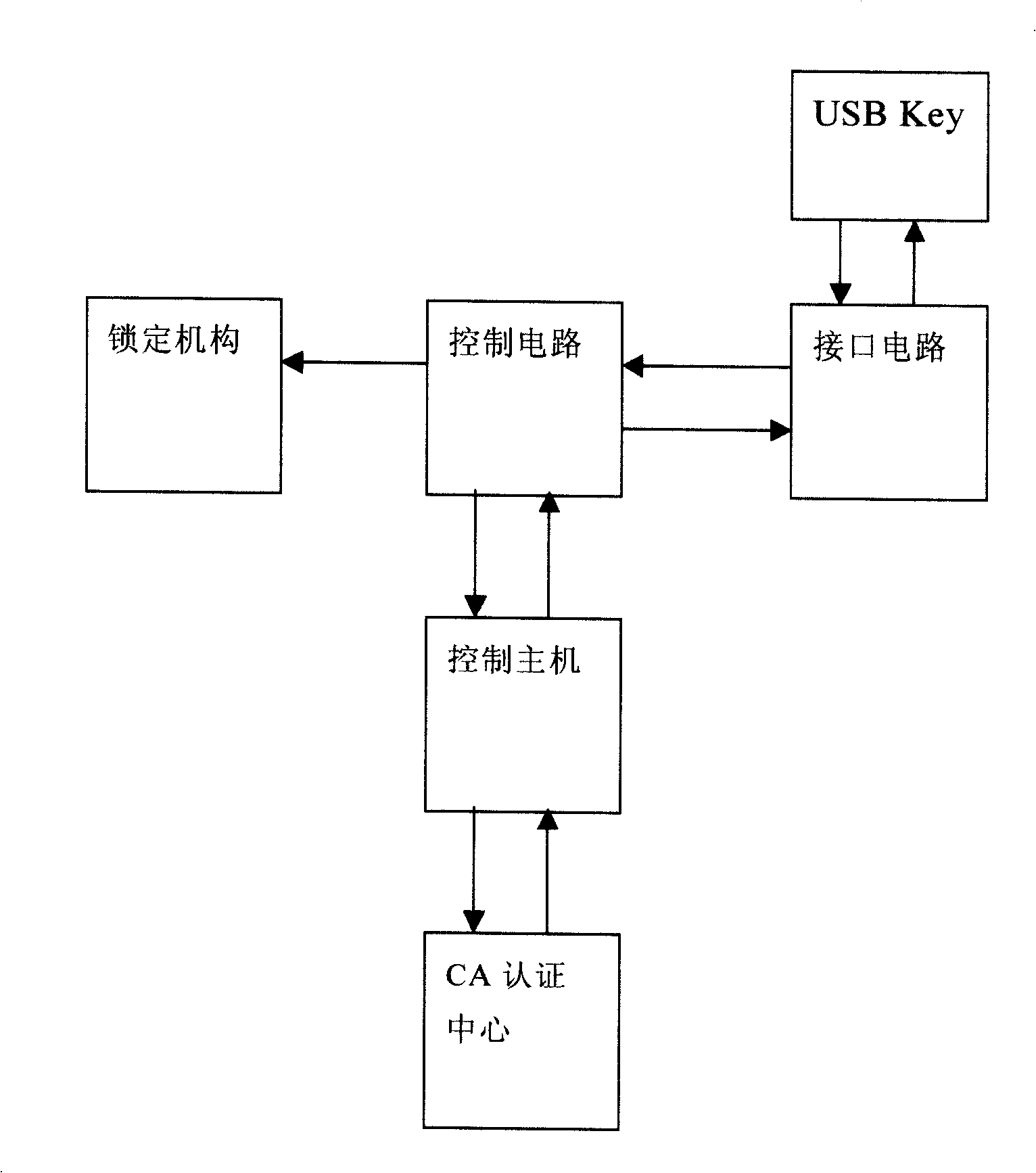
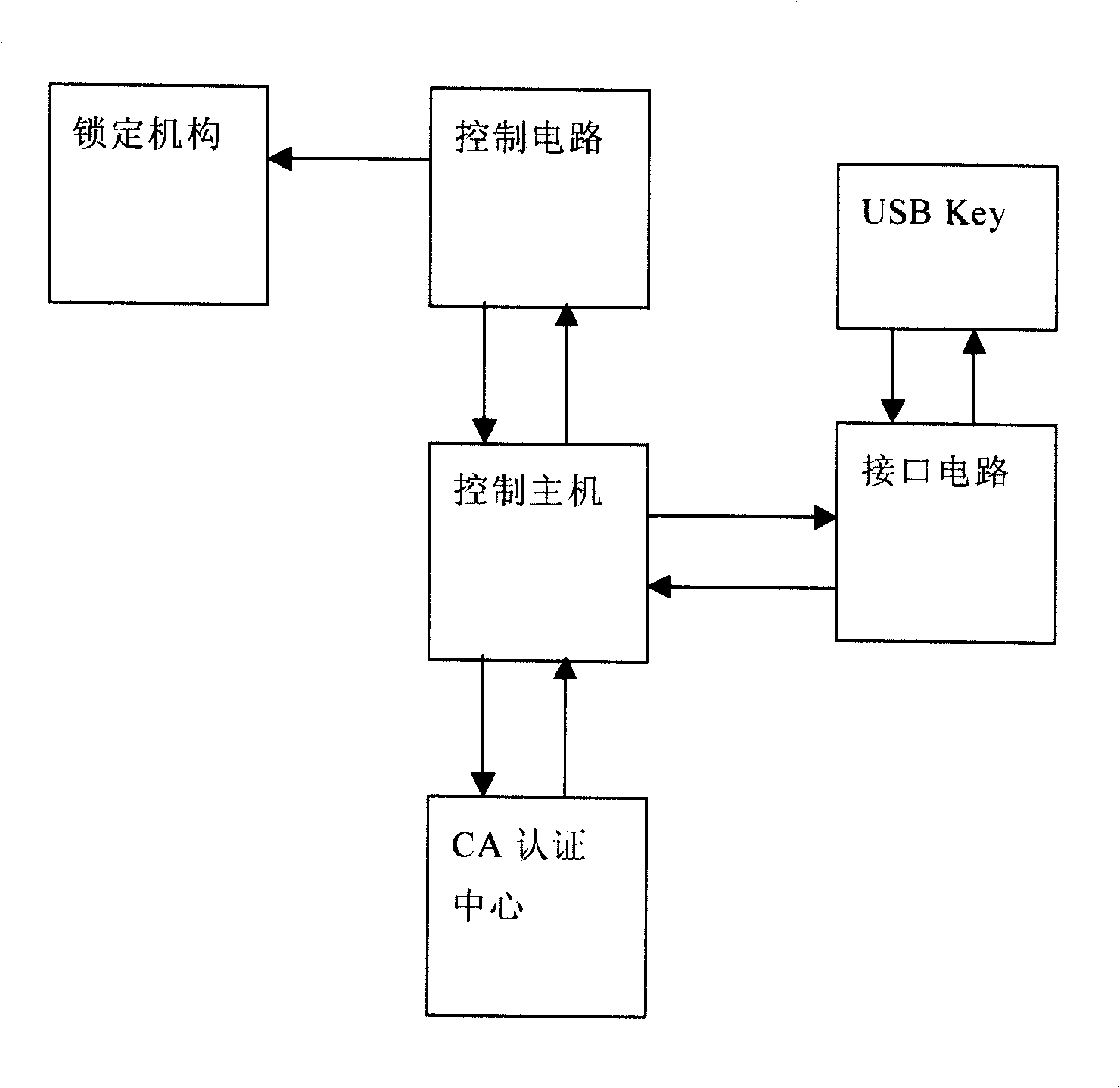
The present invention provides a digital certificate control method of access control system, the control master transmits a random code to USB Key when the USB Key is connected to the interface circuit, the USB Key uses inner key encryption to generate cryptograph and transmits to the control master, the control master USB Key of the digital certificate and decoding the received cryptograph to cleartext, the control master compares the cleartext with the random code, when the comparing result is identical, the indentity of USB Key holder is determined; the control master transmits opening command to open lock mechanism after determining legal identity and access permision of the holder, when USB Key breaks the connection with the interface circuit, the control master transmits closing command, the locking mechanism is closed. The invention also provides an access control system applying the above method, including an access control system, an inner key, a digital certificate and a USB Key of digital signature and a locking mechanism. The access control method and system of the invention has convenience, high security and high credibility.
Owner:陈年
System and method for multi-system authentication and synchronization in mobile equipment
ActiveCN107172008AGuaranteed experienceAvoid enteringEncryption apparatus with shift registers/memoriesUser identity/authority verificationMobile endBiological activation
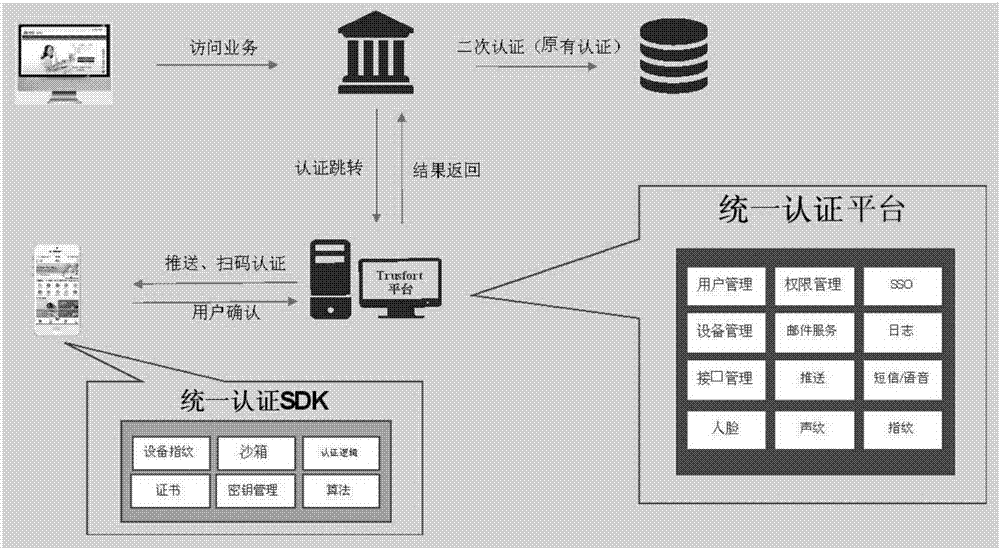
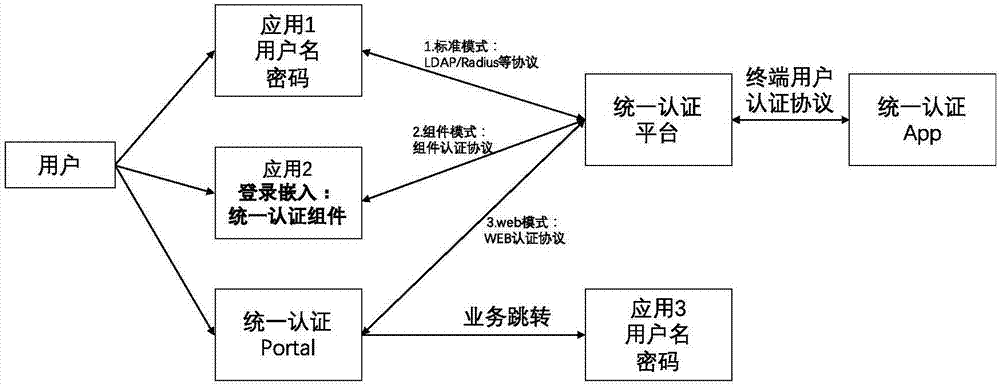
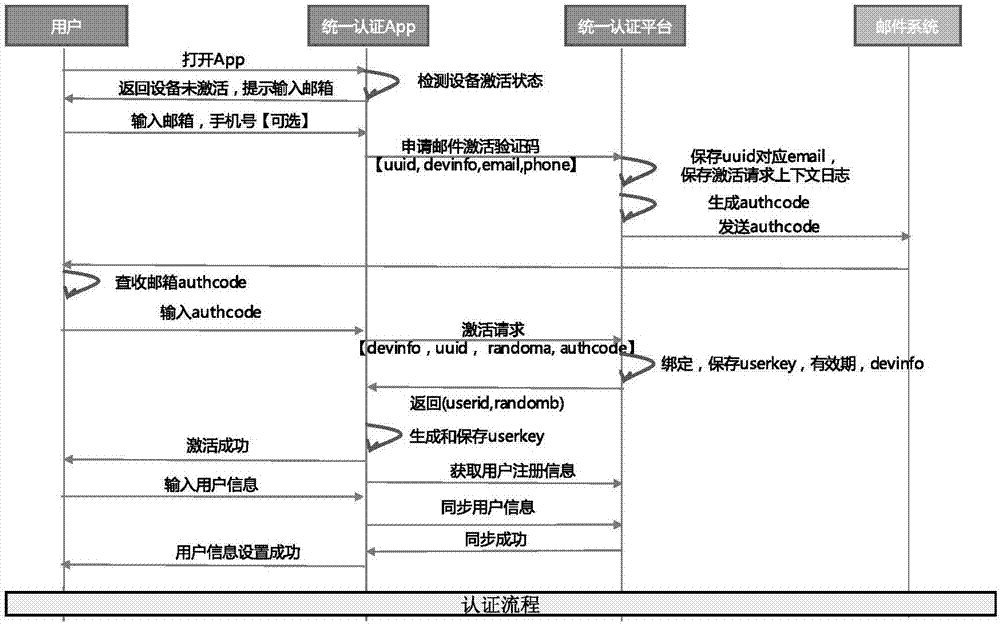
The invention discloses a system and method for multi-system authentication and synchronization in mobile equipment. The system is composed of a unified authentication assembly SDK and a unified authentication platform, wherein the unified authentication assembly SDK comprises an equipment fingerprint module, a sandbox module, a certificate module, a secret key management module, an algorithm module and an authentication logic module; and the unified authentication platform comprises a user management module, an authority management module, an SSO module, an equipment management module, a mail service module, a log module, an interface management module, a push module, a text message / voice module, a face module, a voiceprint module and a fingerprint module. The system and method can be applied to service scenes where existing enterprise services migrate to mobile ends, provide authentication and state synchronization on the mobile ends for enterprise users, through an innovative equipment fingerprint generation algorithm, a matching algorithm and a system activation process, the users can bind their mobile phones with enterprise accounts, and thus the enterprise accounts can realize login and state synchronization on the mobile equipment.
Owner:BEIJING TRUSFORT TECH CO LTD
Identity authentication method and apparatus
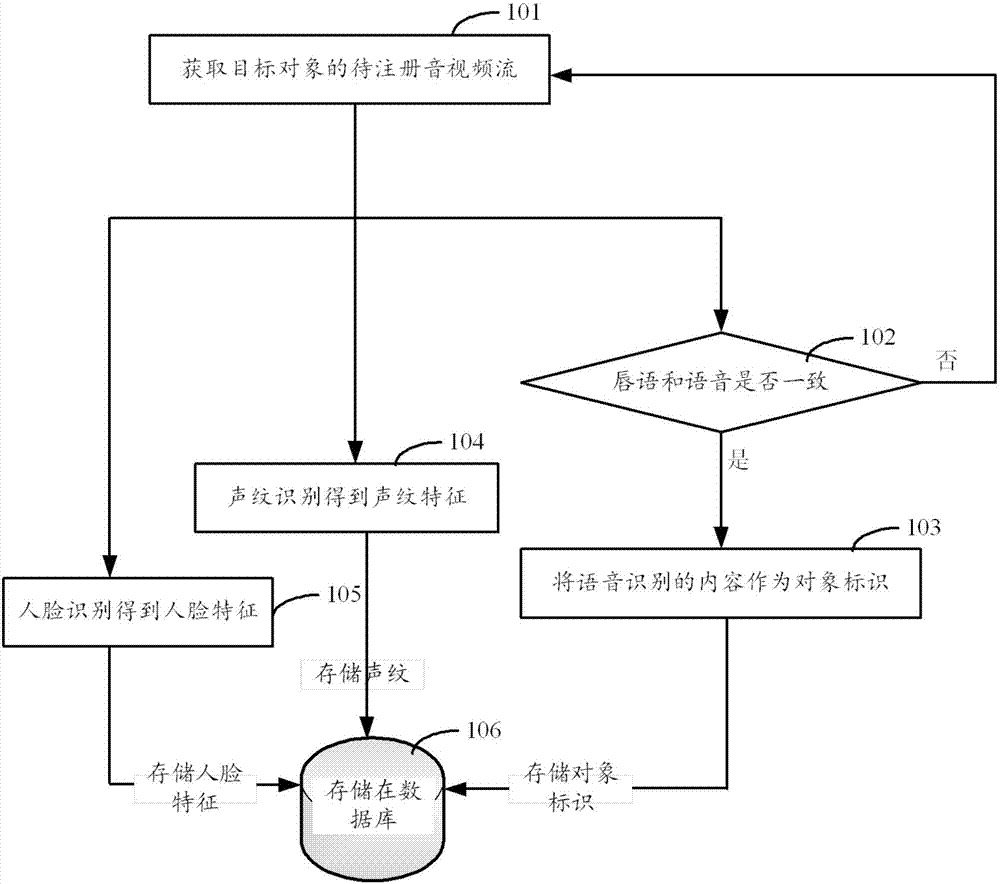
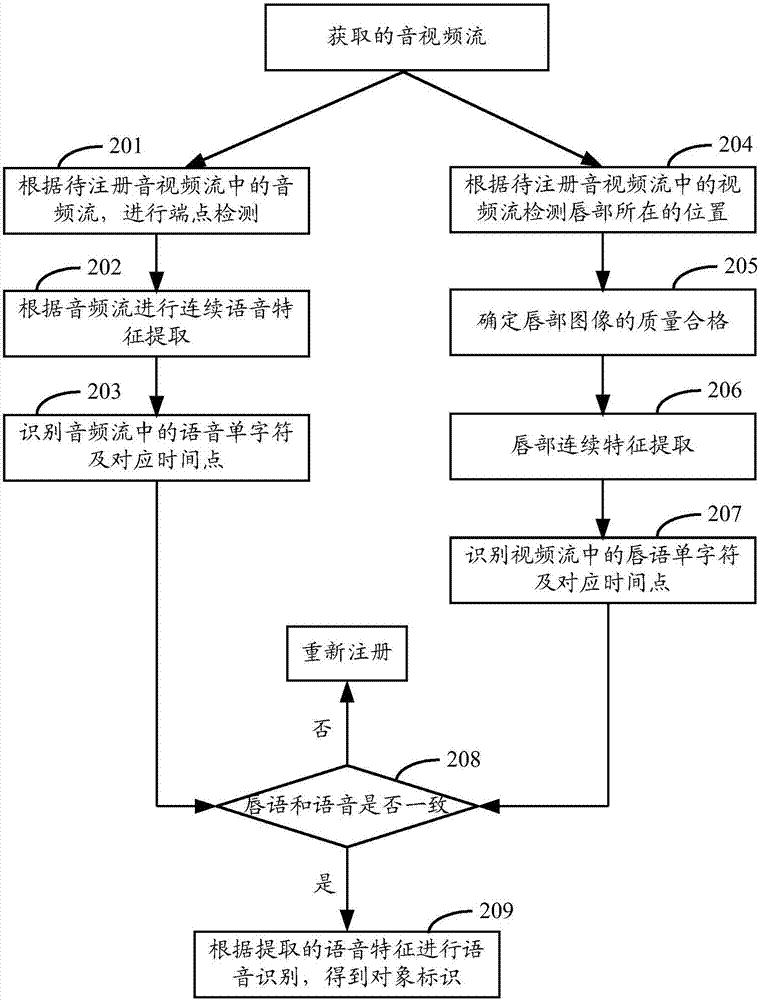
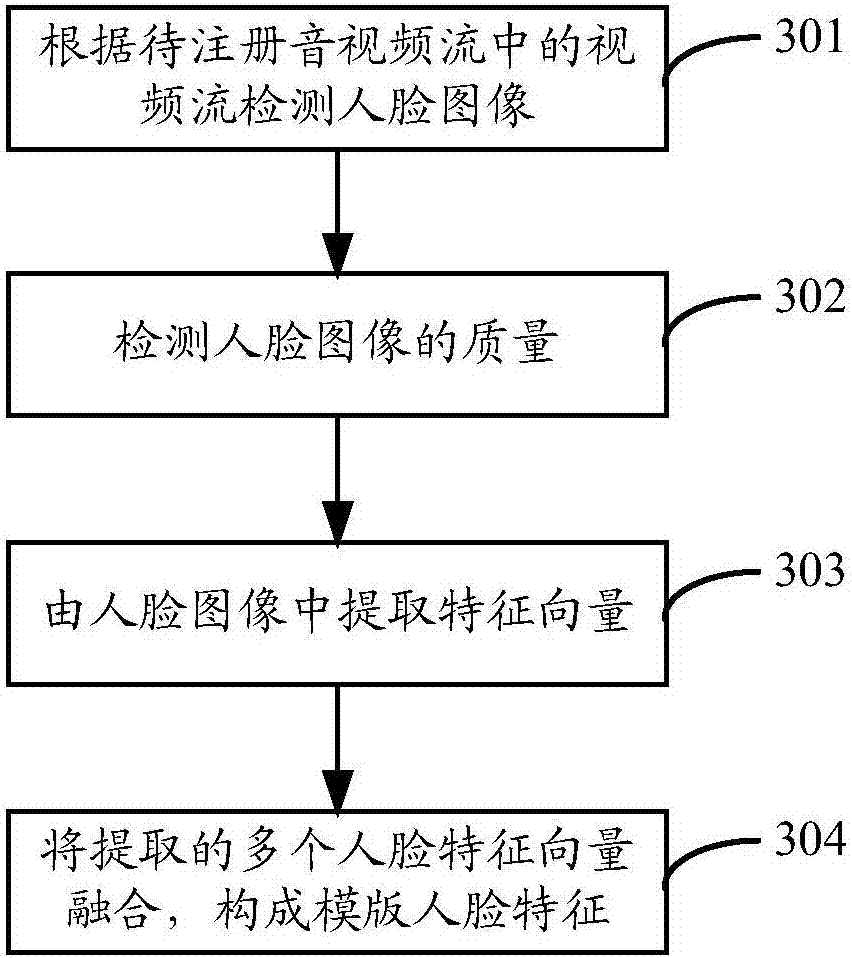
InactiveCN107404381AEasy to operatePrevent forgeryUser identity/authority verificationCharacter and pattern recognitionObject registrationObject identifier
The invention provides an identity authentication method and apparatus. The method comprises the steps of obtaining an audio / video stream which is collected and is generated by a to-be-authenticated target object, judging whether a lip language and a voice in the audio / video stream meet consistency, and if the lip language and the voice meet the consistency, taking a voice content which is obtained by performing voice recognition on an audio stream in the audio / video stream as an object identifier of the target object; if the object identifier is included in pre-stored object registration information, obtaining a template physiological characteristic corresponding to the object identifier in the object registration information; performing physiological recognition on the audio / video stream to obtain a physiological characteristic of the target object; and comparing the physiological characteristic of the target object with the template physiological characteristic to obtain a comparison result, and if the comparison result meets an authentication condition, confirming that the target object passes through authentication. According to the identity authentication method and apparatus provided by the invention, the efficiency and the reliability of the identity authentication are improved.
Owner:ALIBABA GRP HLDG LTD
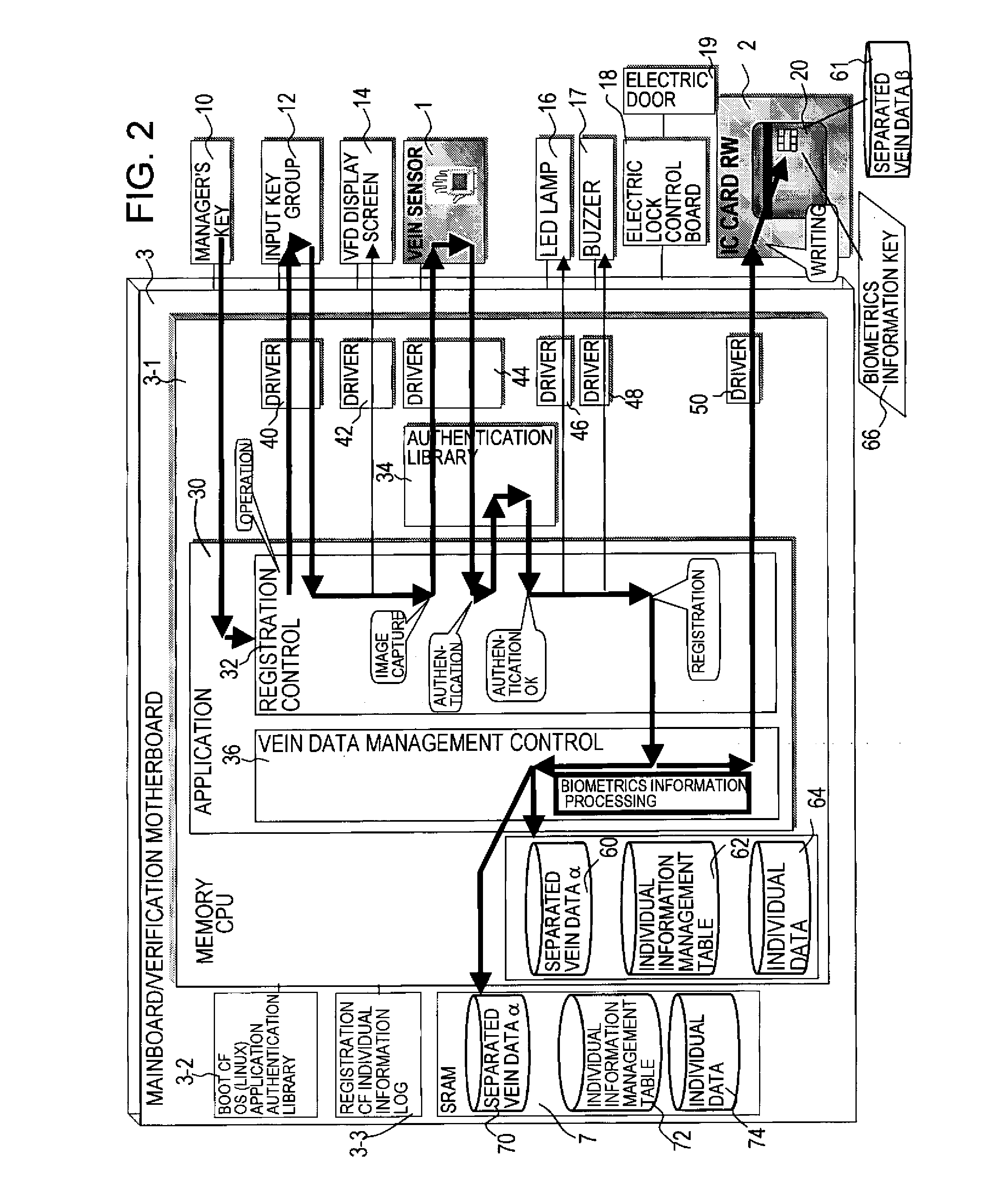
Biometrics authentication method, media for individual authentication, and biometrics authentication device
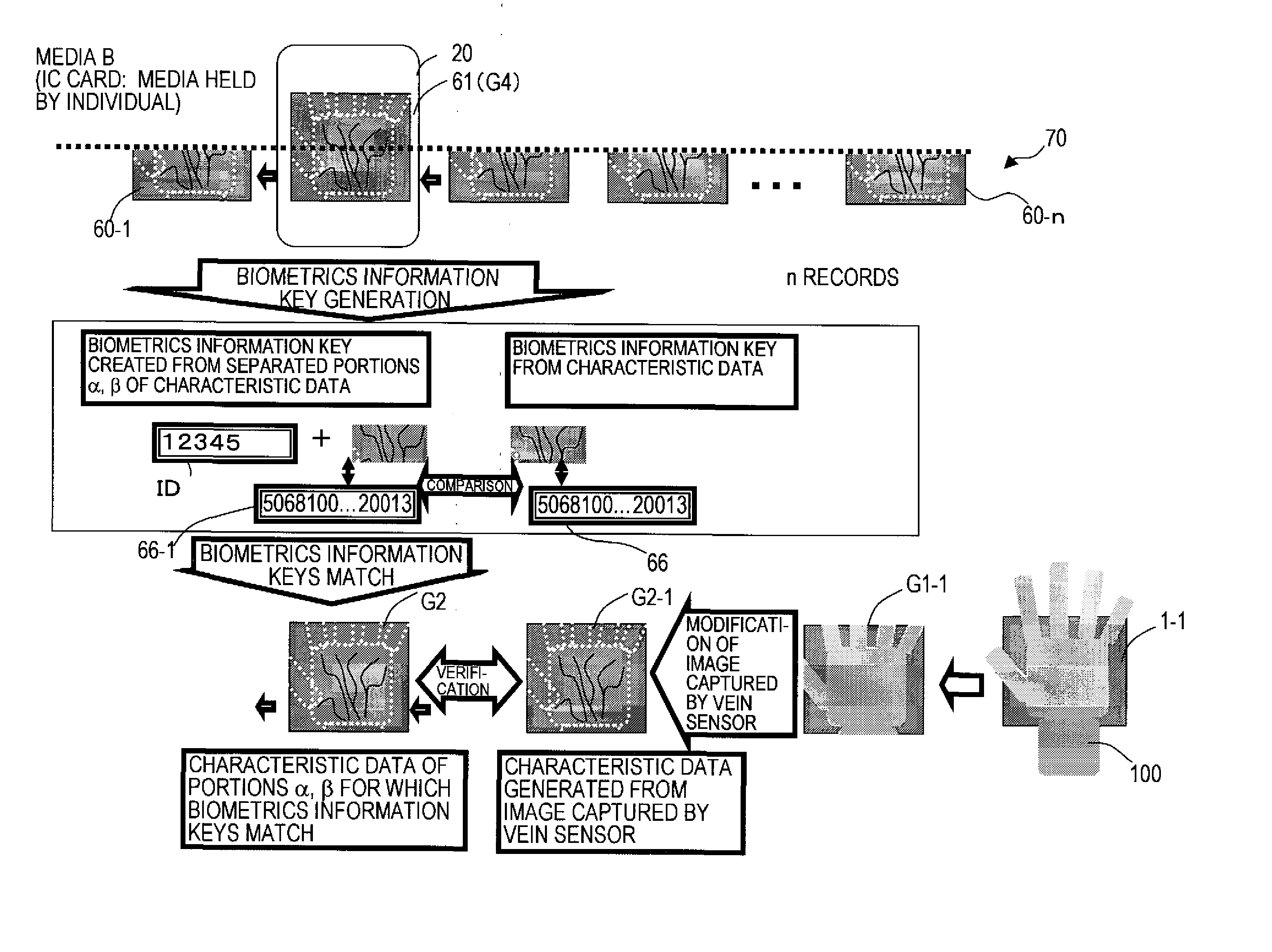
ActiveUS20080065901A1Prevent illegal usePrevent illicit acquisition and mergingUser identity/authority verificationPerson identificationBiometric dataConfidentiality
A biometrics authentication device which detects body characteristics, performs verification against registered biometrics data, and performs individual authentication, by which confidentiality is improved even when biometrics data is separated, distributed and stored. A biometrics information key is created from biometrics data detected by a detection device, the biometrics data is divided into a plurality of portions, and the portions are stored on different media. The biometrics information key is stored on one media, and at the time of authentication, the separated biometrics data portions are combined and a biometrics information key is created and is compared with the biometrics information key, to judge the linked relationship. Hence confidentiality of the association of the individual separated data portions can be improved even when the biometrics data is separated, distributed and stored, contributing to prevent illicit use resulting from leakage or theft of biometrics data.
Owner:FUJITSU LTD +1
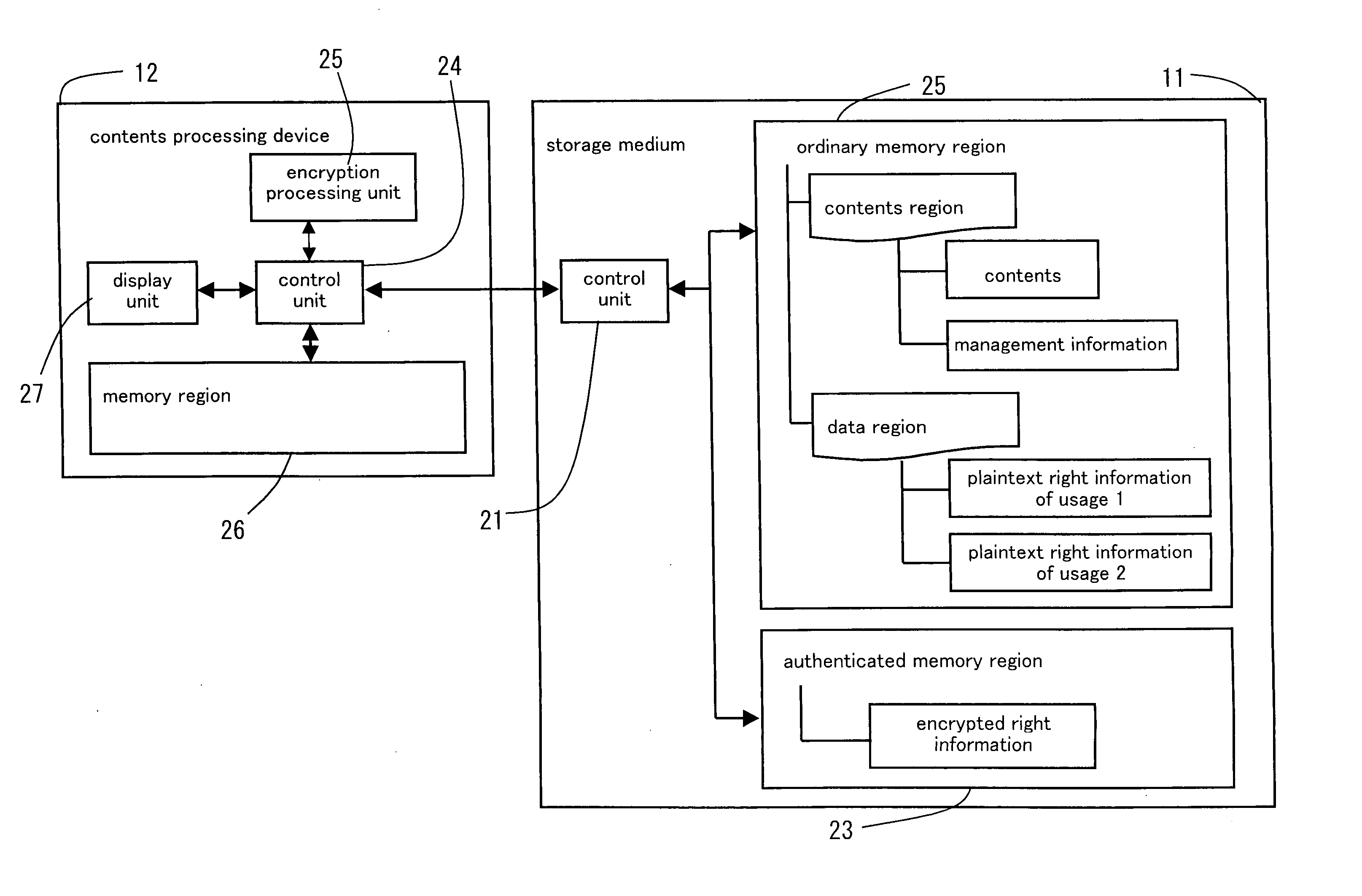
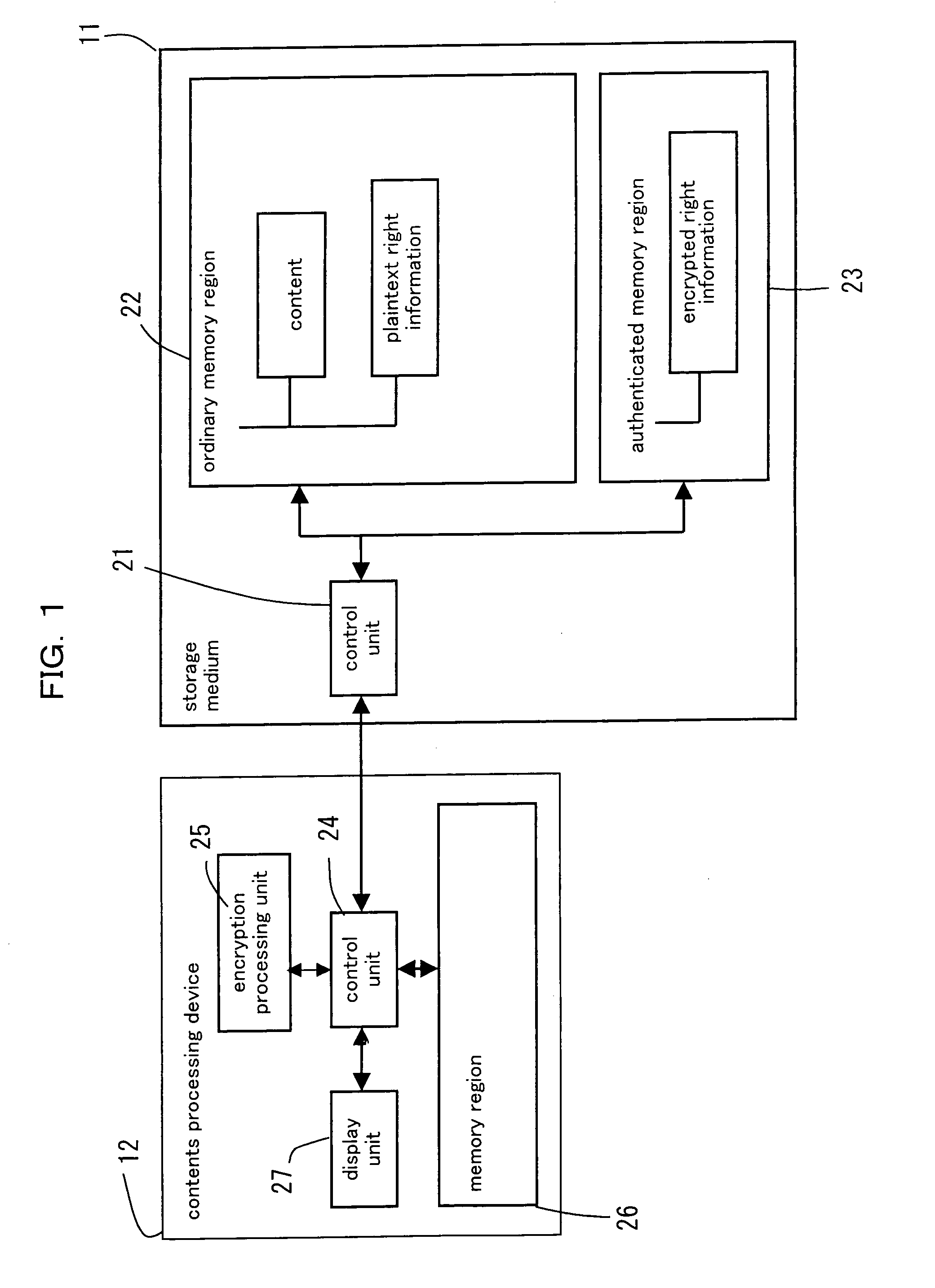
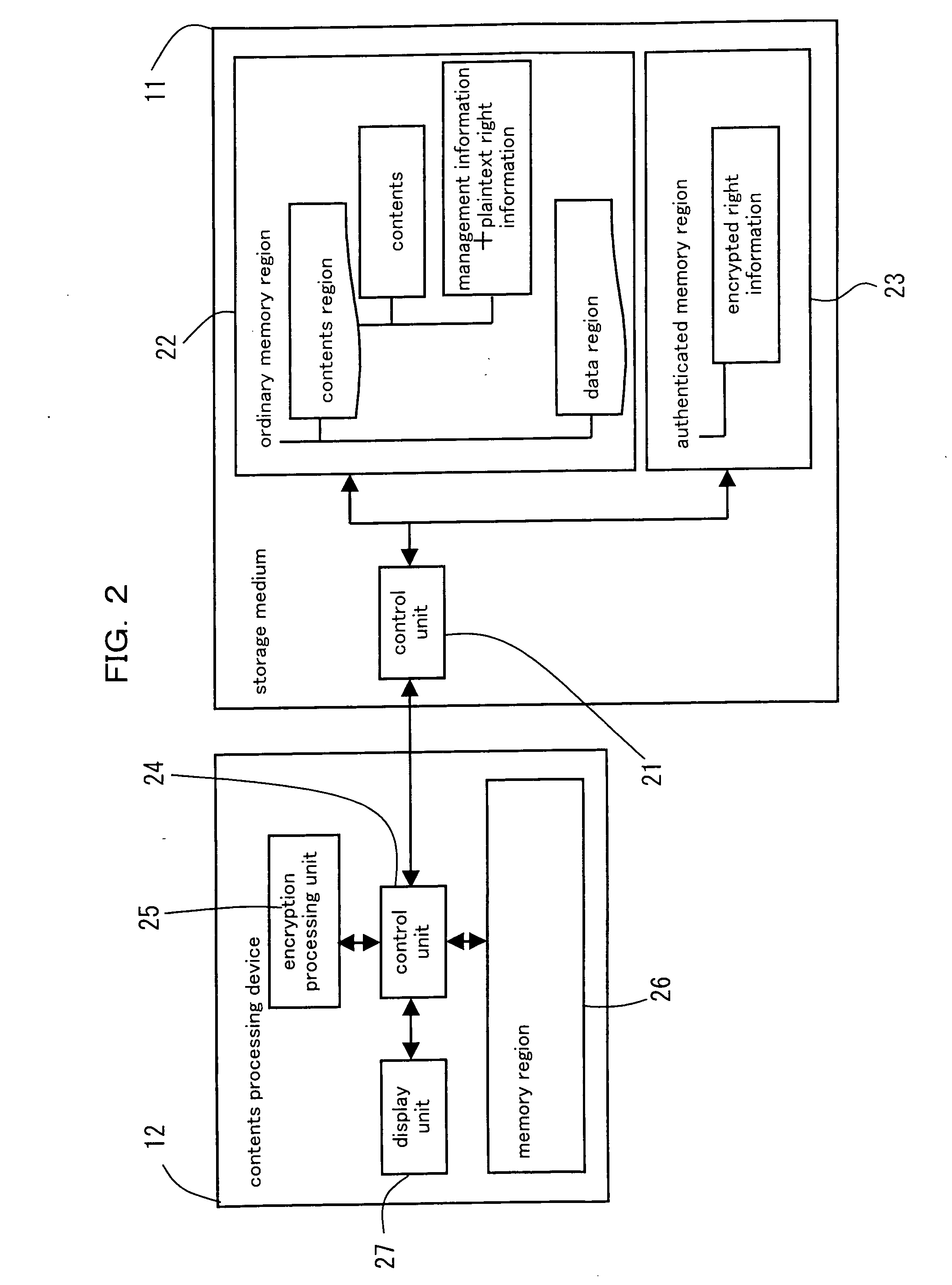
Right information management method and right information management device
ActiveUS20060117013A1Prevent forgeryGuaranteed legalityKey distribution for secure communicationDigital data protectionPlaintextWorld Wide Web
A right information management method for managing a right information of contents retained in a storage medium comprising an authenticated memory region accessible after a mutual authentication is obtained relative to a contents processing device and an ordinary memory region accessible without obtaining the mutual authentication, comprising a step of reading an encrypted right information retained in the authenticated memory region, a step of decoding the read encrypted right information and retrieving a plaintext right information, and a step of retaining the plaintext right information in the ordinary memory region. According to the right information management method, a user can be notified of the contents and the right information of the contents managed in the storage medium in a speedy manner via the contents processing device.
Owner:SOCIONEXT INC
Non-contact CPU (Central Processing Unit) card entrance guard reader
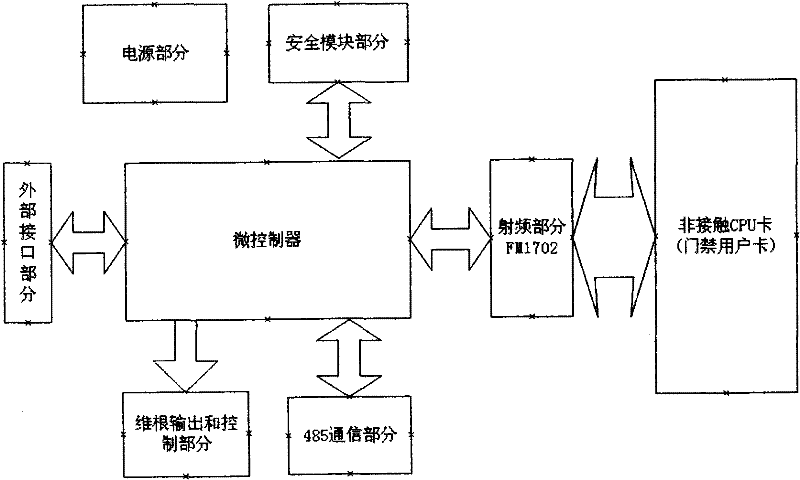
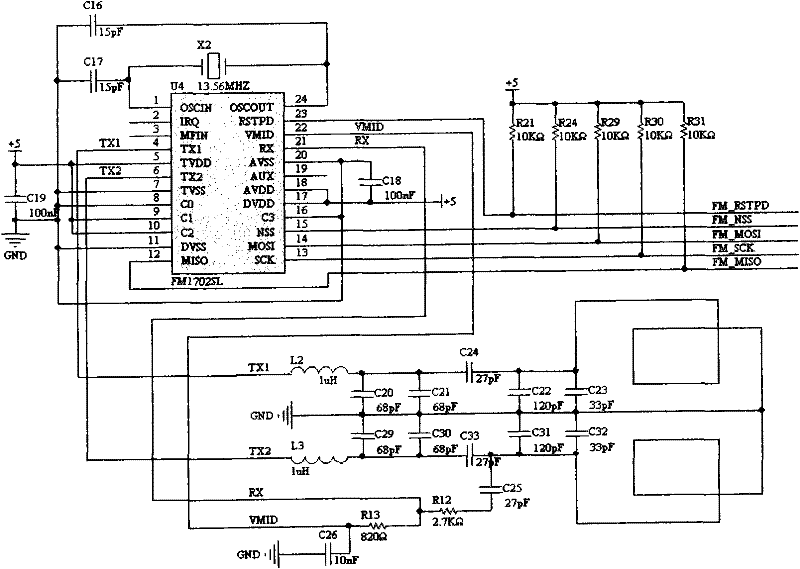
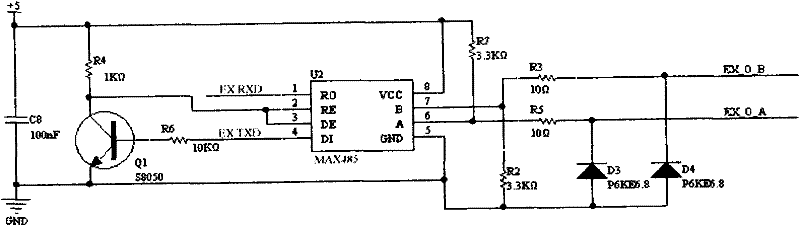
InactiveCN102129730AMake the most of security featuresImprove security levelSensing record carriersIndividual entry/exit registersMicrocontrollerComputer module
The invention discloses a non-contact CPU (Central Processing Unit) card entrance guard reader comprising a radio frequency part, a 485 communication part, a security module part, a Wigan output and external control part, a power supply part, an external connection part, a microcontroller part and other parts. The non-contact CPU card entrance guard reader is internally provided with a PSAM (Pilot Symbol Assisted Modulation) card and applies security certification read-write mechanisms of the PSAM card and a CPU card. The CPU card entrance guard reader builds an integral and strict key management system by adopting the security certification of the PSAM card and the CPU card, sufficiently uses the security characteristics of the CPU card and comprises key systems of the CPU card and the PSAM card; after a key is input into the PSAM card, the key cannot be externally read, the PSAM card is inserted into card reading equipment, two-way validation is carried out through the PSAM card and the CPU card, a verified message is calculated through the participation of random data, and a same card is different every time when swiped on one equipment, therefore a counterfeit card is thoroughly prevented.
Owner:SHANGHAI ZTRON ELECTRONICS
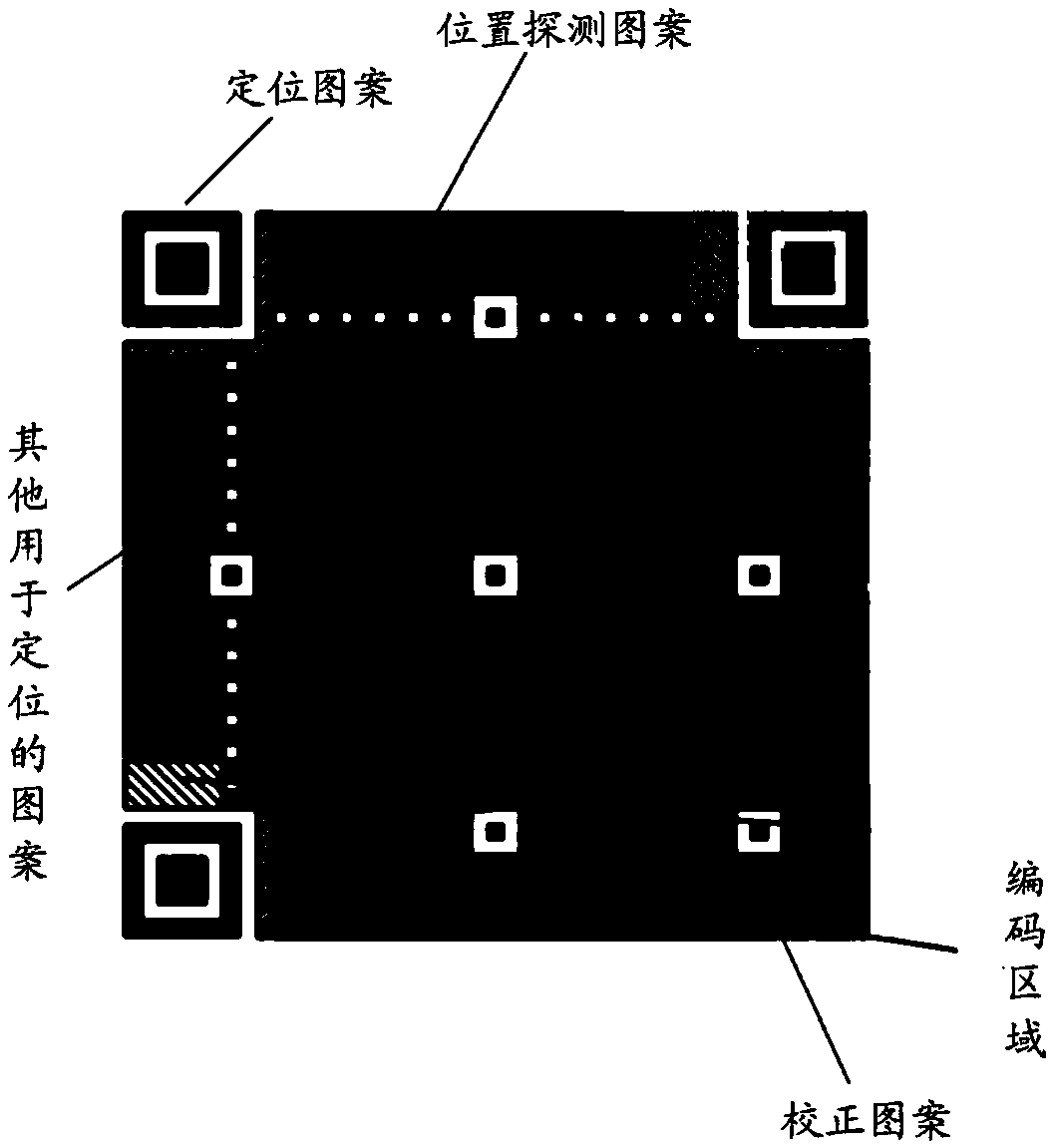
Two-dimensional code, encoding and identification method thereof and product with anti-counterfeiting function
ActiveCN108764420ARich Personalization FeaturesFlexible Personalization FeaturesRecord carriers used with machinesGraphicsDimensional modeling
Owner:CHINA BANKNOTE SECURITY PRINTING TECH RES INST CO LTD +1
Interactive process for content class service
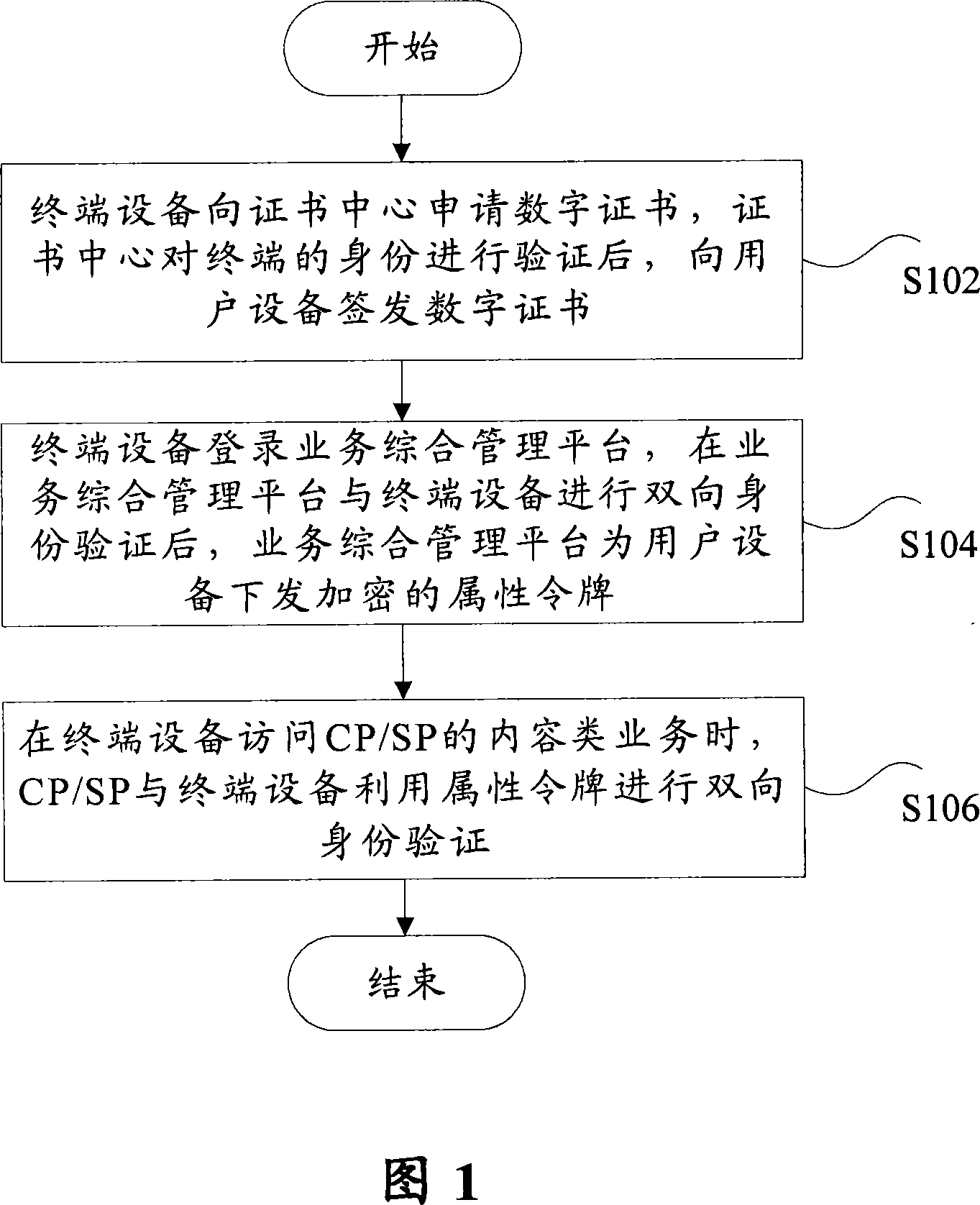
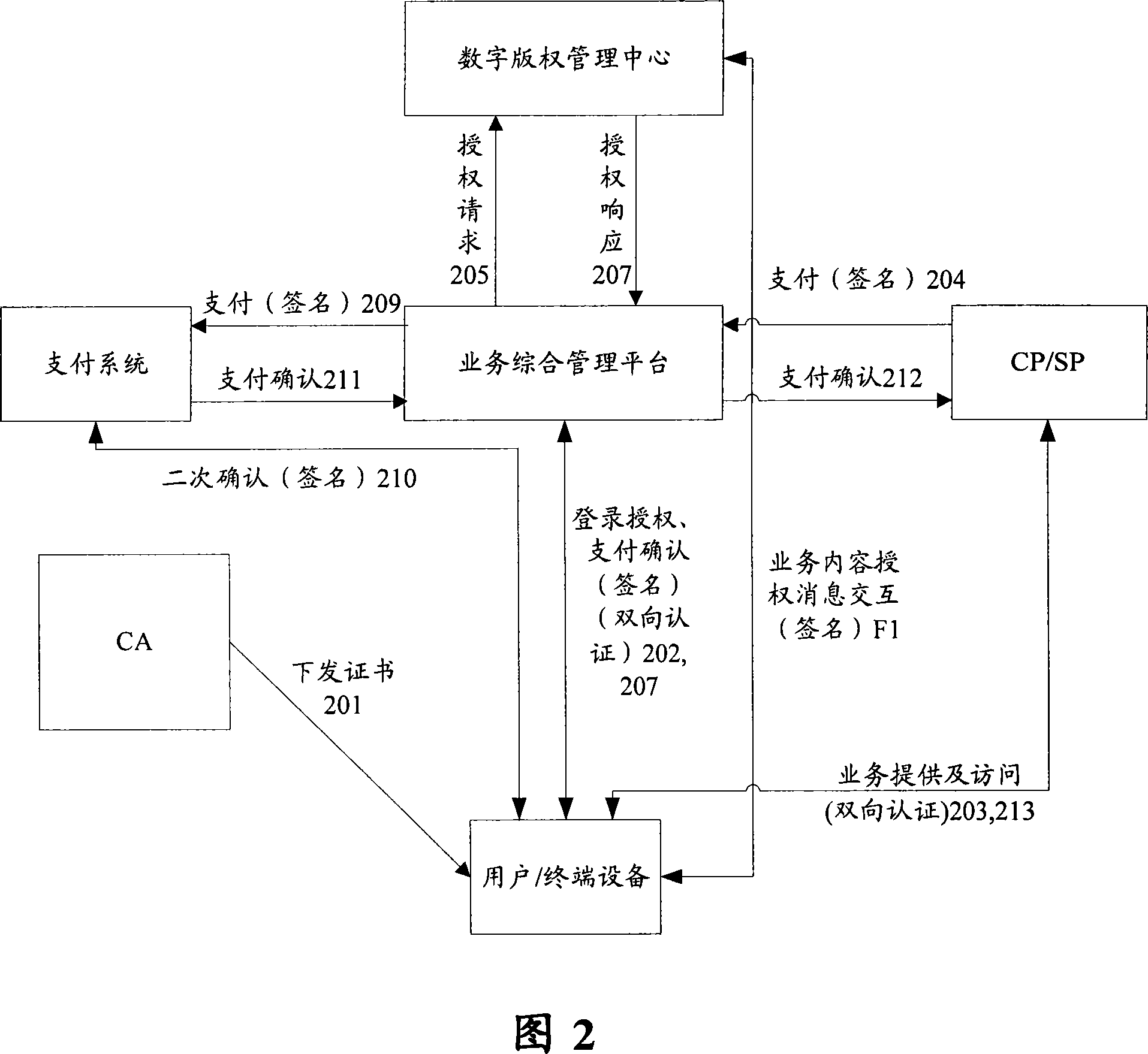
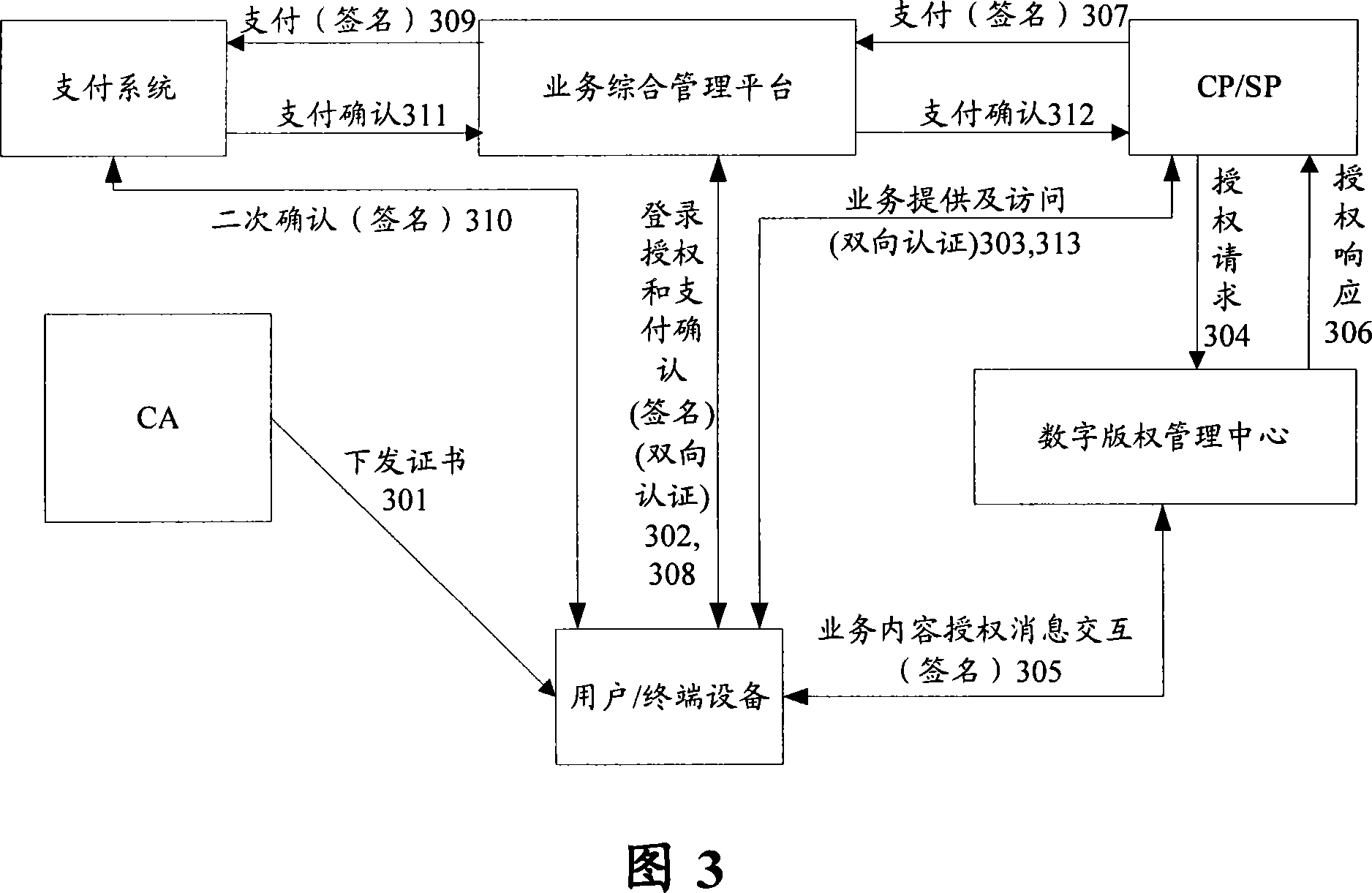
InactiveCN101043337AEnsure safe interactionPrevent forgeryPublic key for secure communicationUser identity/authority verificationComputer securityMutual authentication
The invention discloses an interactive mode for the content business which includes: step S102, the terminal device applies for the digital certificate from the certificate center, and the certificate center issues the digital certificate for the user's device after the ID of terminal device has been passed, and the digital certificate includes the public key and private key; step S104, the terminal device logs on the business general management platform, when the two-way ID checking between the business general management platform and the terminal device has been passed, the business general management platform sends out the encrypted property board for the user's device; and the step S106, when the terminal device accesses the content business which is provided by the content provider / service, the two-way ID checking between the content provider / service and the terminal device will be done by the property board. Using the invention, it can assure the safe interactive between the each business entities of the content business and prevent the counterfeit of service web.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com