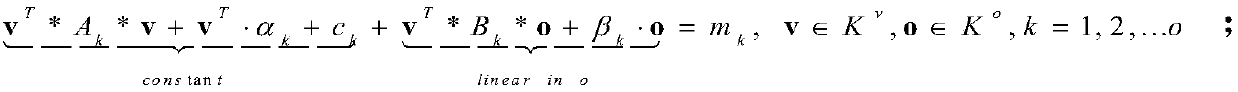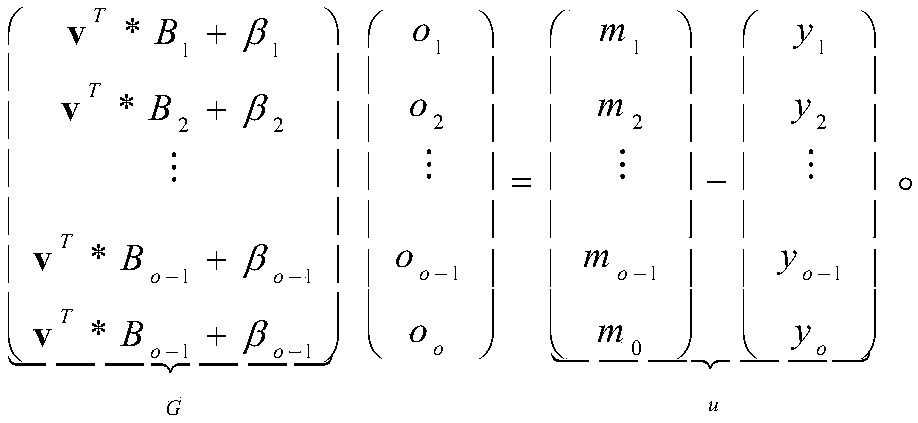Patents
Literature
55 results about "Online signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
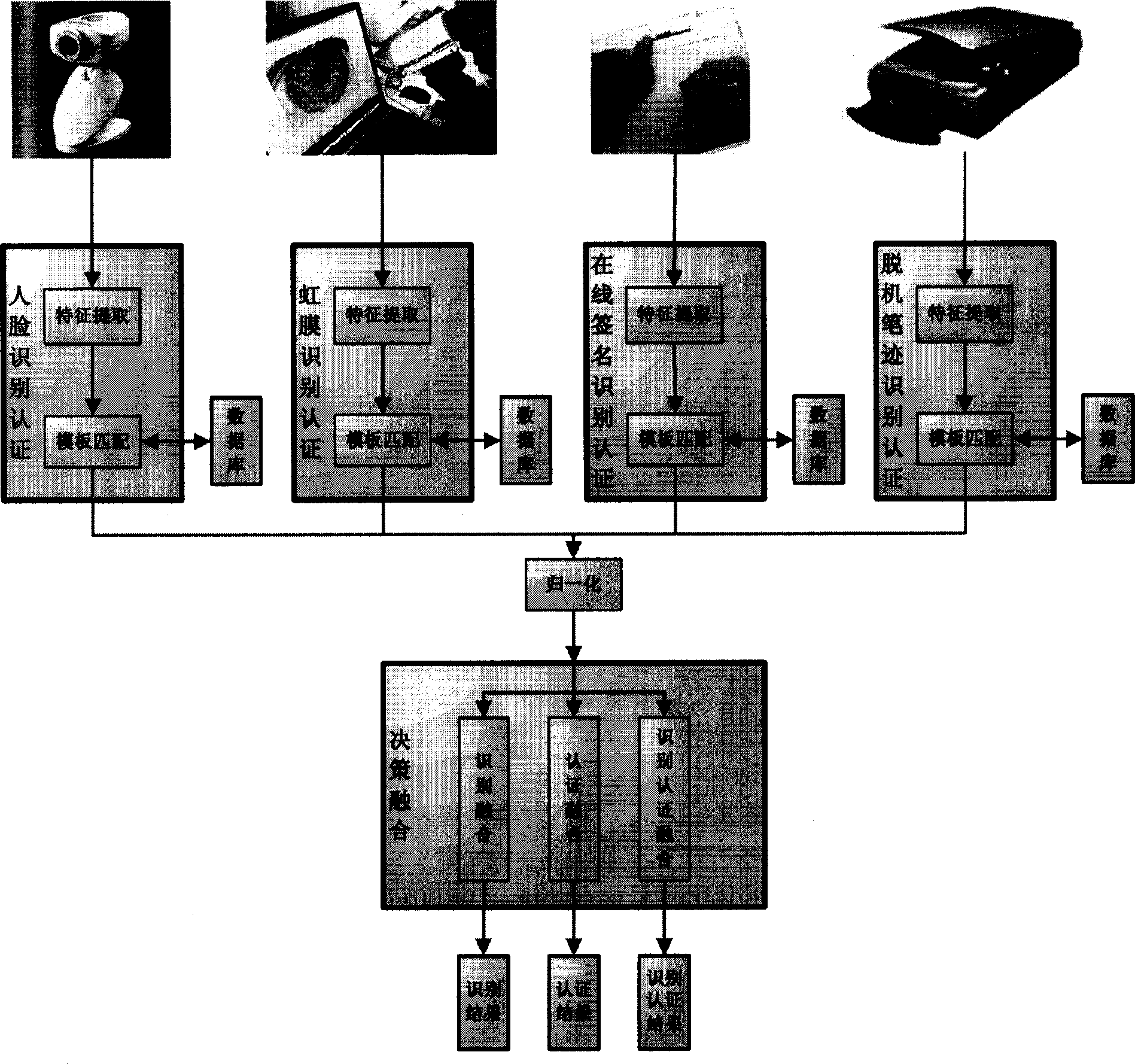
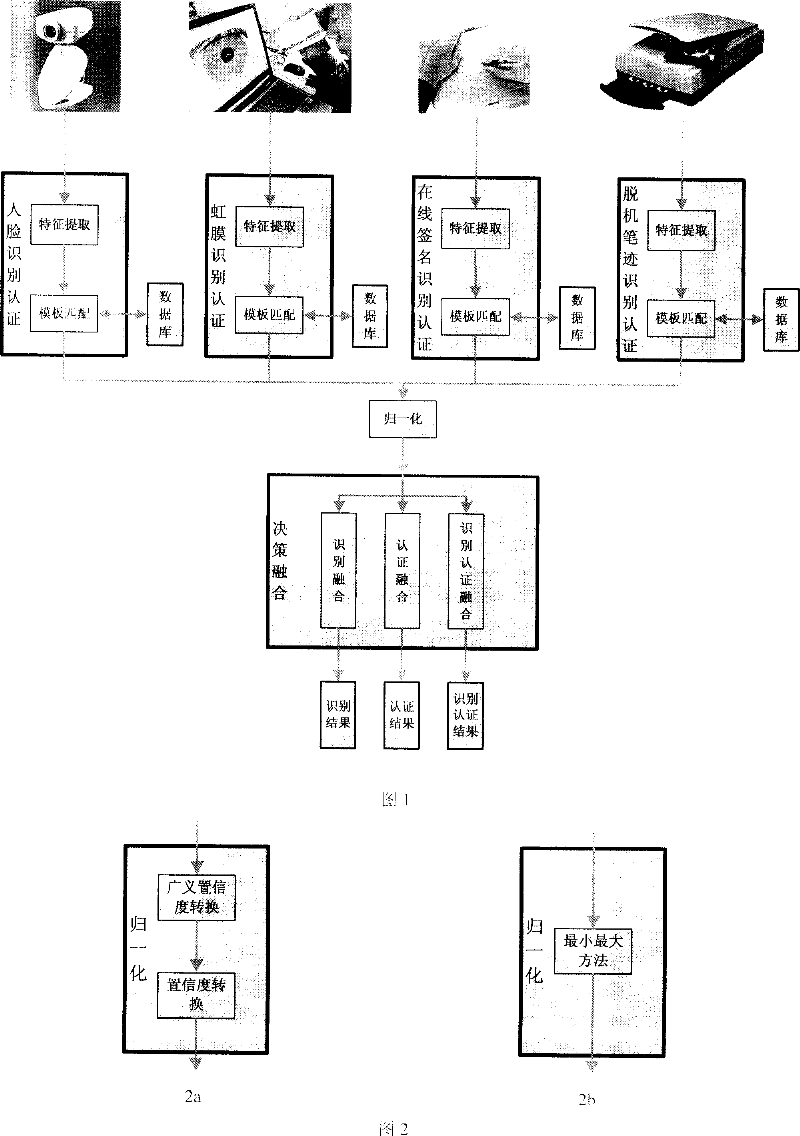
Biocharacteristics fusioned identity distinguishing and identification method
This invention relates to a sorter integration and mode identification field characterizing in obtaining characters of man-face, iris, on-line signature and off-line handwriting of a user by various collecting devices then sending them to corresponding certification sub-modules to pick up the characters and match with the molding boards and outputting the matched marks to be normalized and sent to an identification combined module to get the final identification result by confidence integration or sent to a certification module to be imaged to a multi-dimension space to be sorted by a sorter to get a final result or to be certified and combined to get the final identification result.
Owner:TSINGHUA UNIV
Identity-based safety signature method
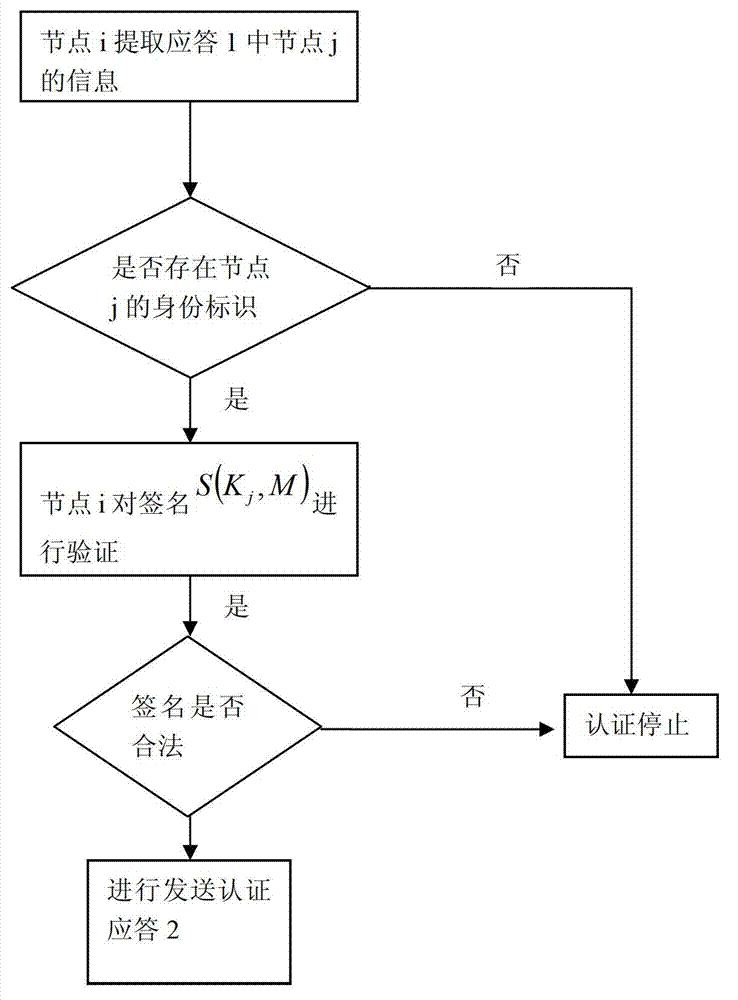
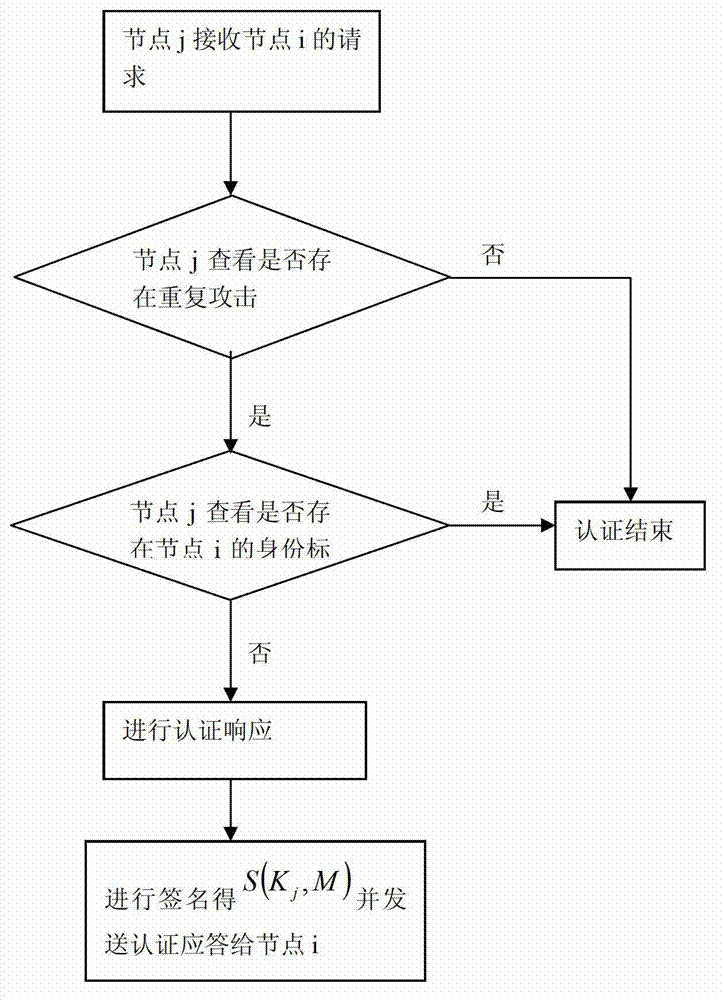
The invention relates to an identity-based safety signature method which comprises the steps of: allocating a secret key offline, signing online and setting a secret key service life for realizing updating of a communication group secret key, wherein a unique identification of a sensor node, i.e. a public key of the node, is used as identity information. Based on a public parameter of a system and a main secret key of the system and according to identity information of each node, a private key of the node is figured out. After a wireless sensor network is configured, a system parameter and a private key are stored in each node, when identity authentication is required between two or among more nodes, a sender can use the private key of the sender to sign a pre-appointed authentication quantity. With identity information of the sender as a public key, a receiver verifies the received information according to a signature verification algorithm in the signature scheme so as to determine the identity of the sender. The storage space in the safety signature method is a constant, therefore, the safety signature method is more suitable for being used in a wireless sensor.
Owner:YUELIANG CHUANQI TECH CO LTD
Data transaction credit investigation platform and method on supply chain
PendingCN107423980AImprove maintainabilityImprove portabilityElectronic credentialsTamper resistanceOnline signature
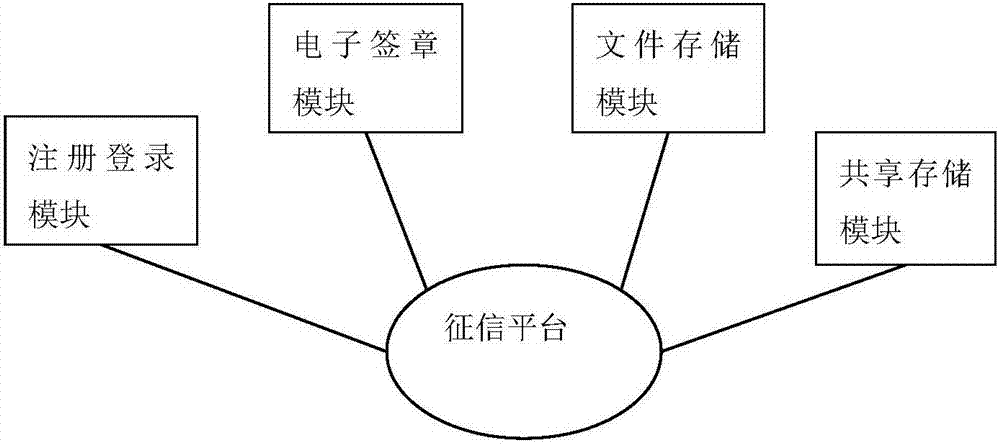
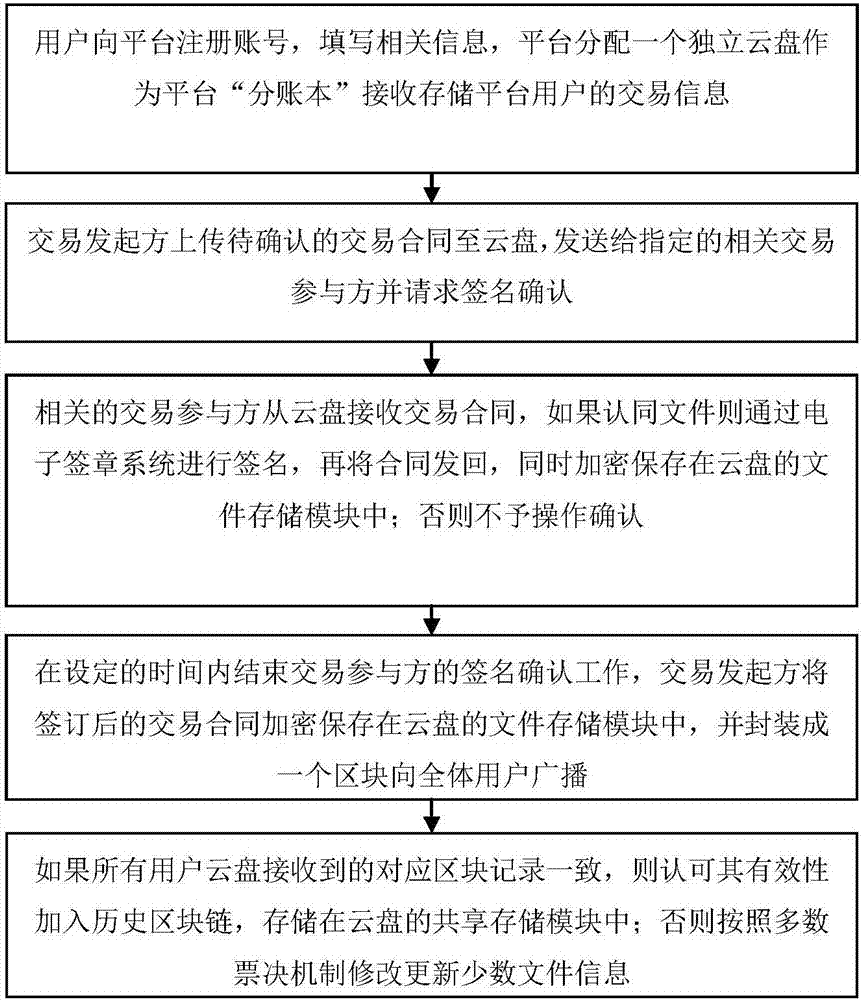
The invention discloses a data transaction credit investigation platform on a supply chain. The platform comprises a registration and login module which allows a user to register and use a platform function after login, an electronic signature module which allows the user to carry out online signature on a transaction contract, an encryption and authentication module which allows the user to authenticate the contract for a third party, a file storage module which is used for the encryption and storage of a contract file of the user, and a sharing storage module for storing shared contract abstract information. According to the platform architecture, the distributed management and sharing of credit data can be realized, and the querying, unforgeability and tampering resistance of data are ensured. The invention also discloses a data transaction credit investigation method on a supply chain.
Owner:易信(厦门)信用服务技术有限公司
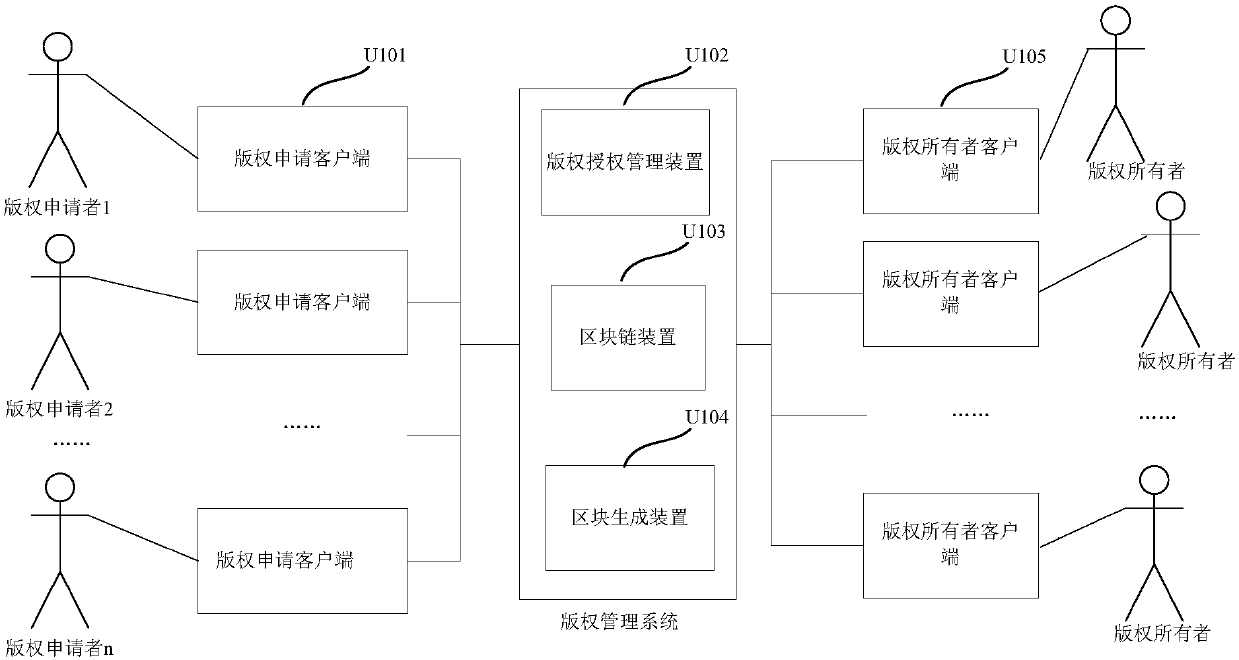
Copyright authorization management method and system
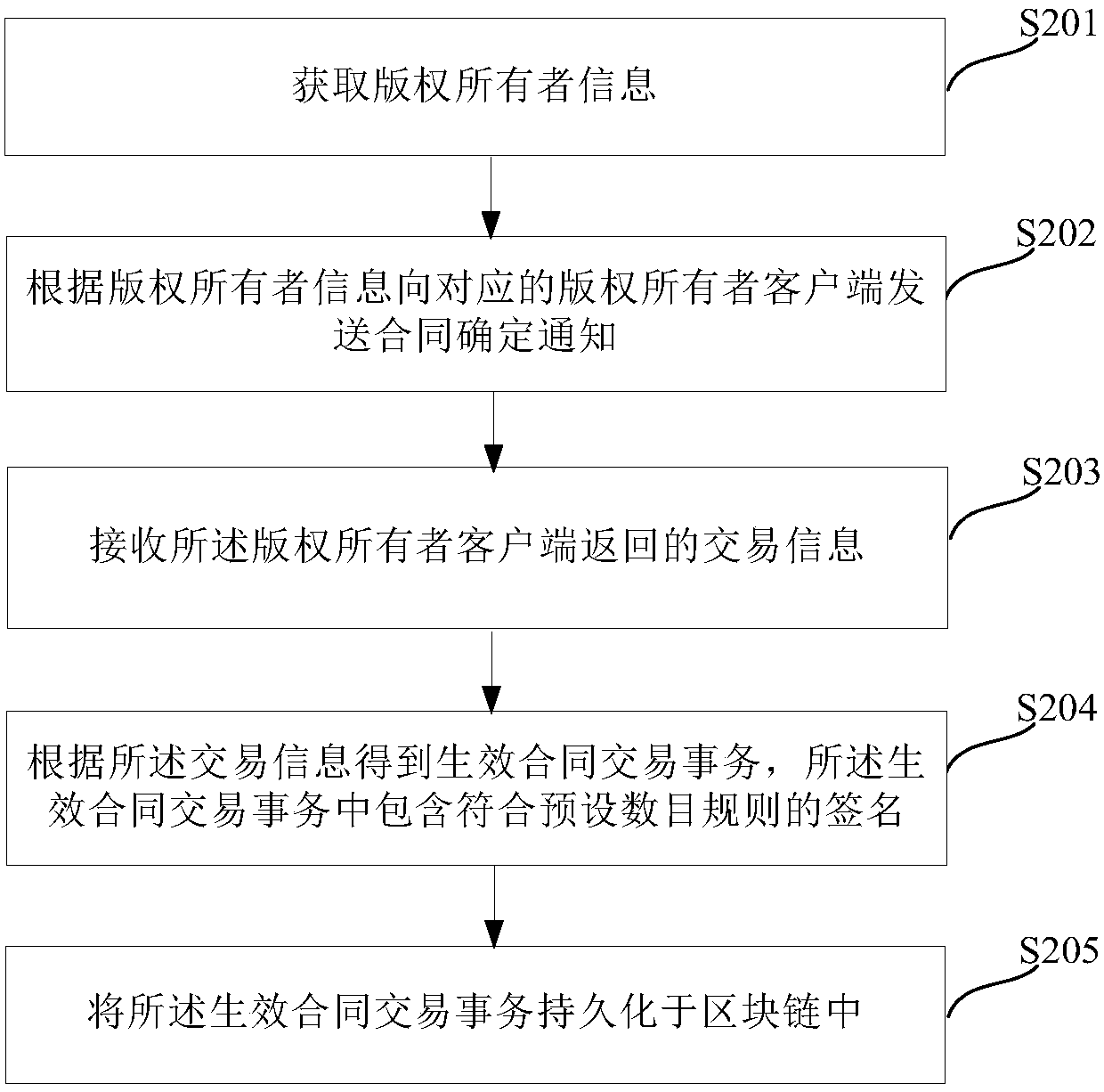
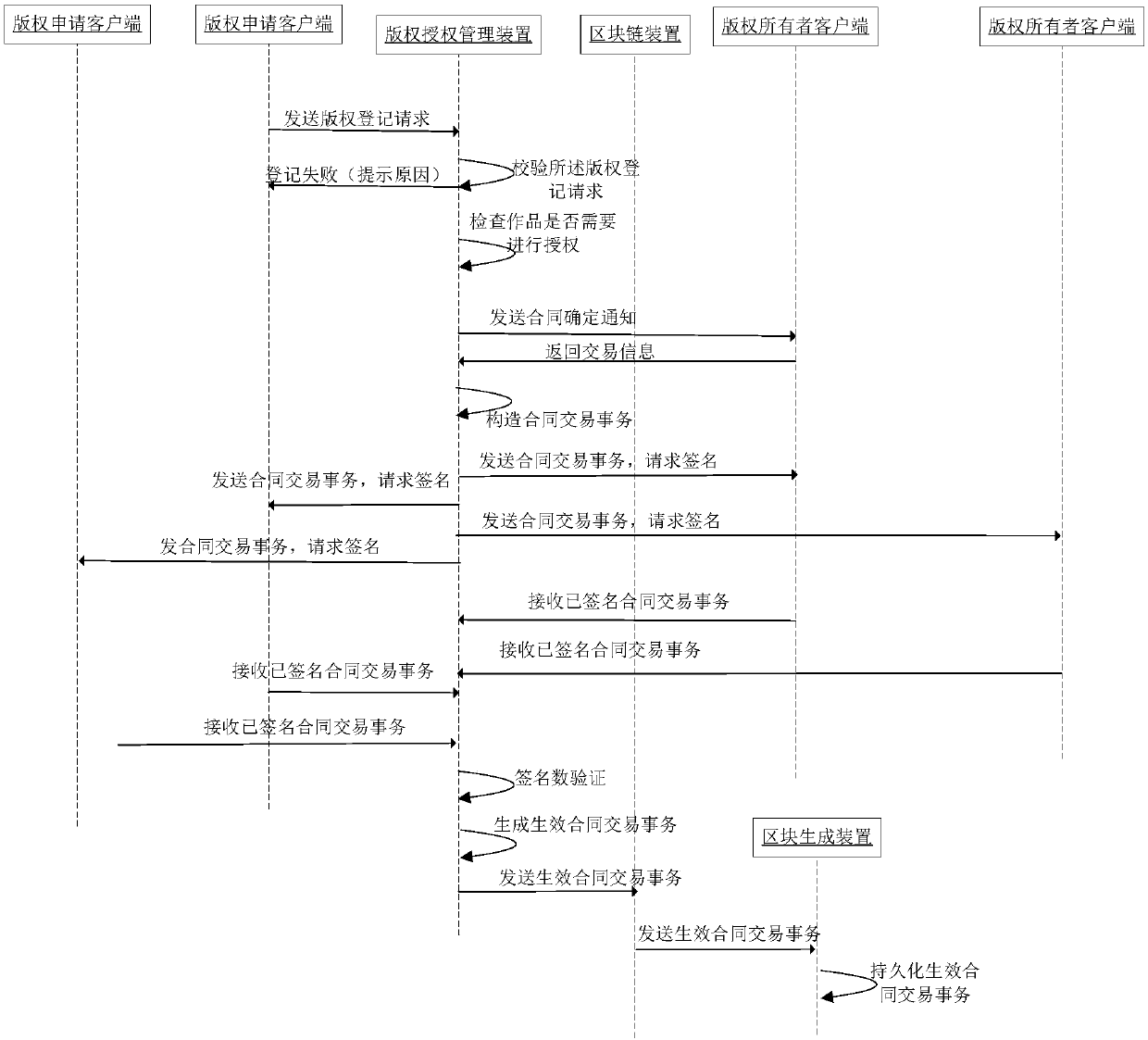
ActiveCN107679045AGuaranteed uniqueEnsure credibleDatabase distribution/replicationOffice automationOnline signatureRelevant information
The embodiment of the invention discloses a copyright authorization management method and system. The method comprises the steps that copyright owner information is acquired; a contract confirmation notice is sent to a corresponding copyright owner client according to the copyright owner information, wherein the contract confirmation notice carries copyright relevant information of authorized works; transaction information returned by the copyright owner client is received, wherein the transaction information contains contract information confirmed by a copyright owner according to the copyright relevant information; an operant contract transaction is obtained according to the transaction information, wherein the operant contract transaction contains signatures conforming to preset counting rules; and the operant contract transaction is persisted into a block chain. Through the technical scheme in the embodiment, online signing of a contract and persistence of the signed contract are realized based on the block chain, therefore, copyright authorization efficiency is improved, and it is guaranteed that the contract is unique and credible and cannot be tampered.
Owner:HUAWEI TECH CO LTD
Methods and systems for performing deduplication in a data storage system
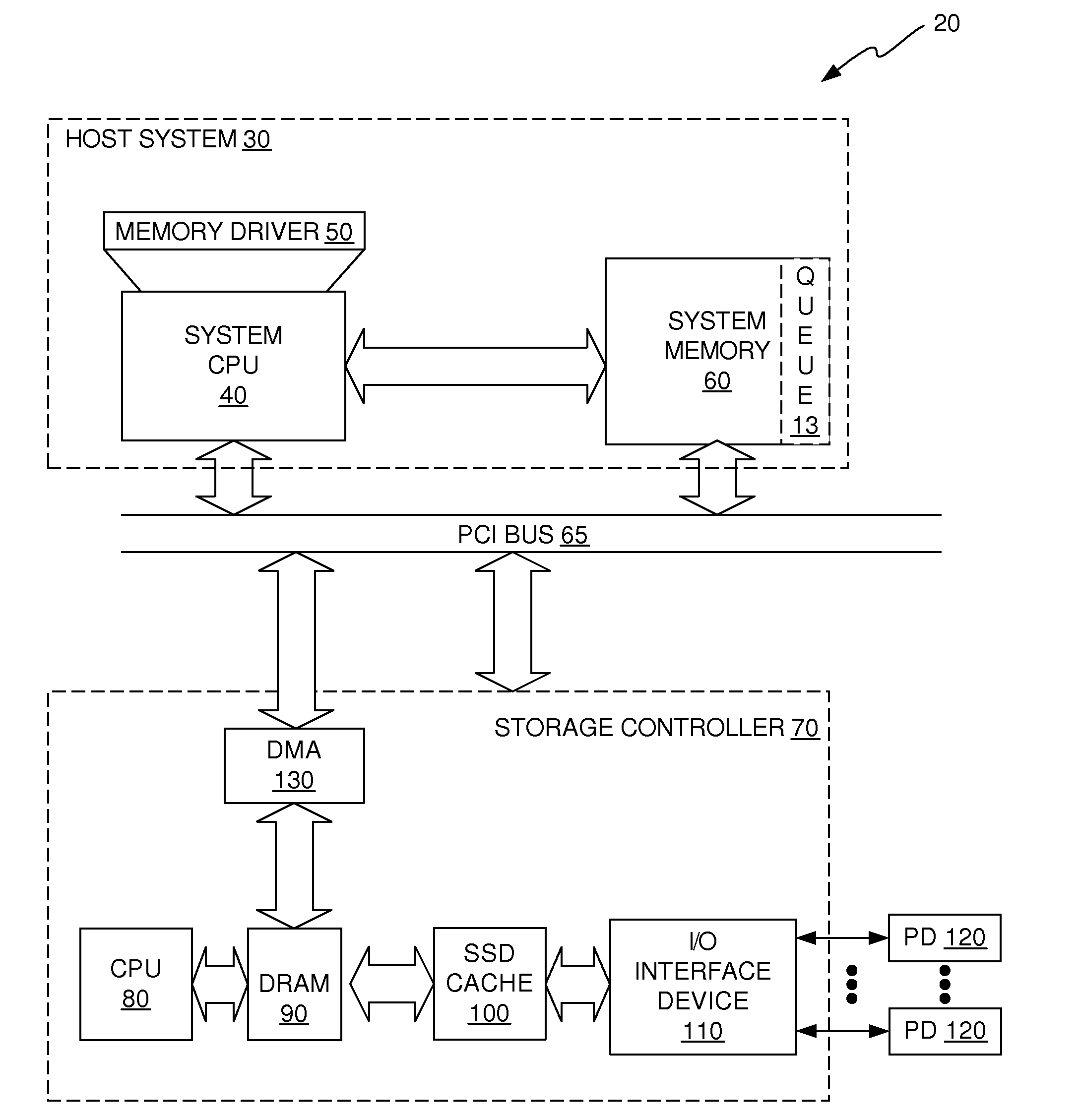
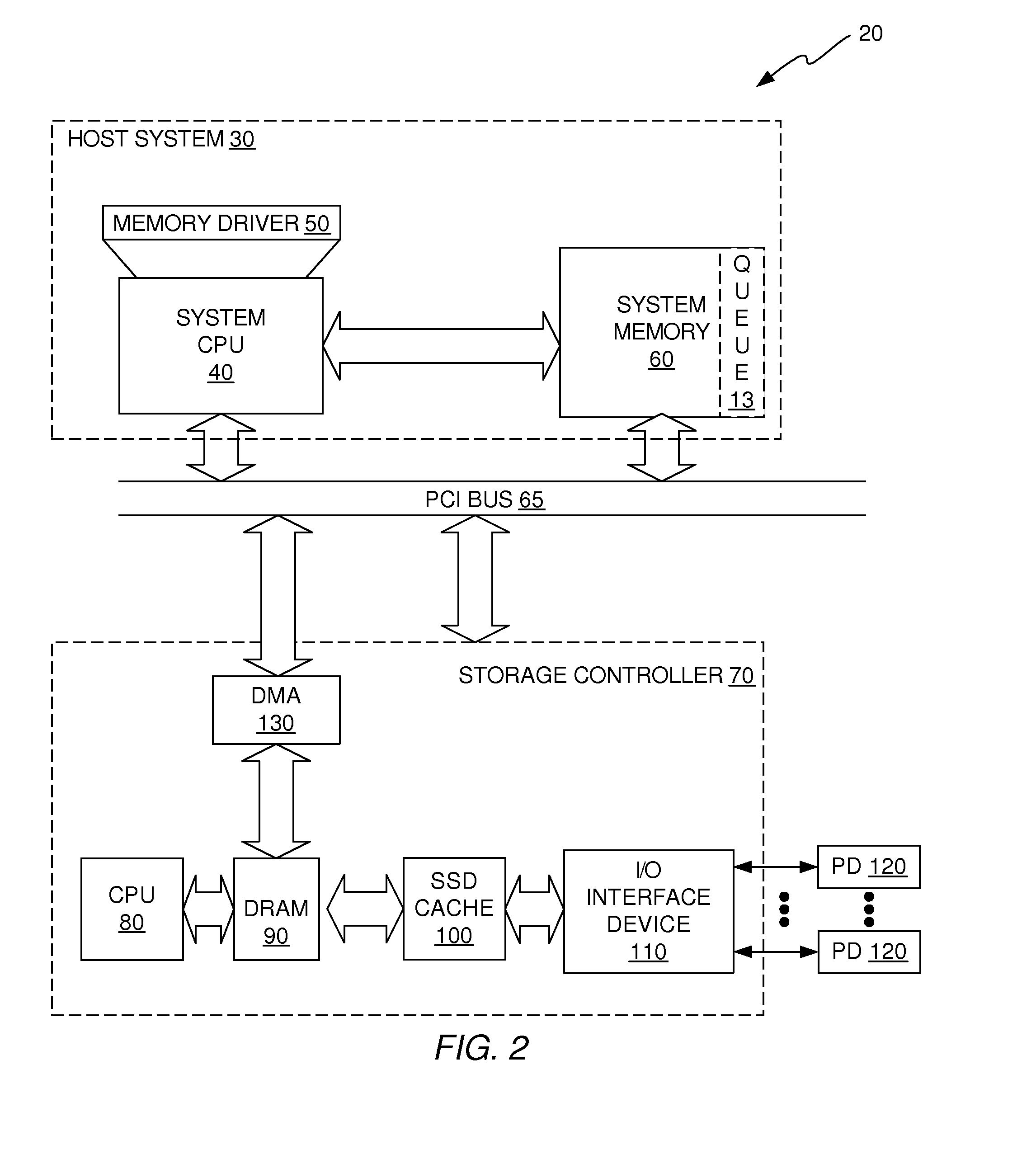
A dedupe cache solution is provided that uses an in-line signature generation algorithm on the front-end of the data storage system and an off-line dedupe algorithm on the back-end of the data storage system. The in-line signature generation algorithm is performed as data is moved from the system memory device of the host system into the DRAM device of the storage controller. Because the signature generation algorithm is an in-line process, it has very little if any detrimental impact on write latency and is scalable to storage environments that have high IOPS. The back-end deduplication algorithm looks at data that the front-end process has indicated may be a duplicate and performs deduplication as needed. Because the deduplication algorithm is performed off-line on the back-end, it also does not contribute any additional write latency.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Cellphone sensing based online signature identity authentication method and system
InactiveCN105912910AAddress insecurityAvoid complexityCharacter and pattern recognitionDigital data authenticationHandwritingOnline signature
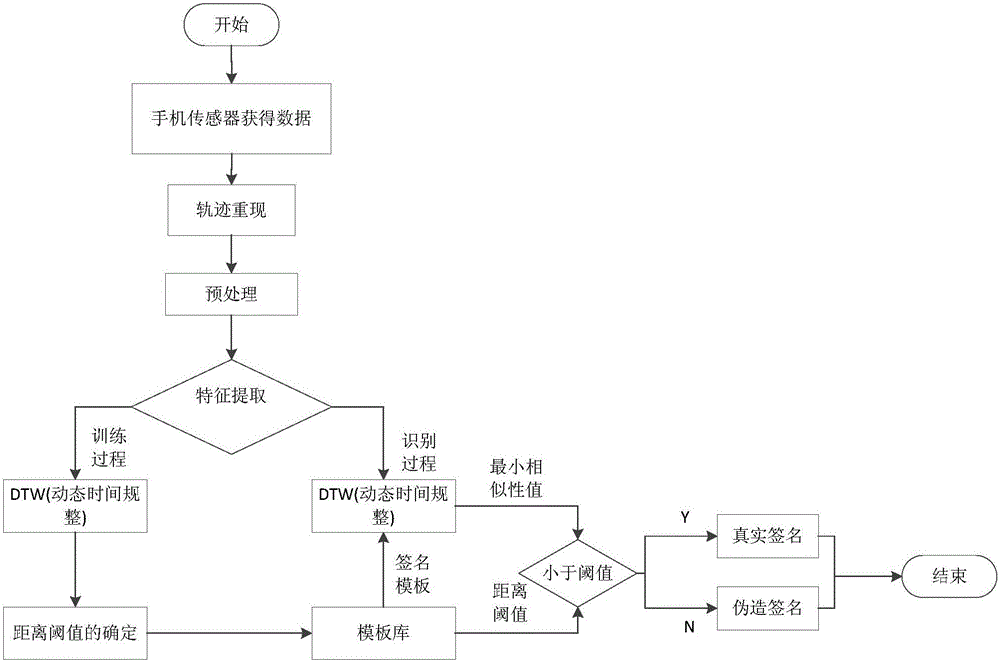
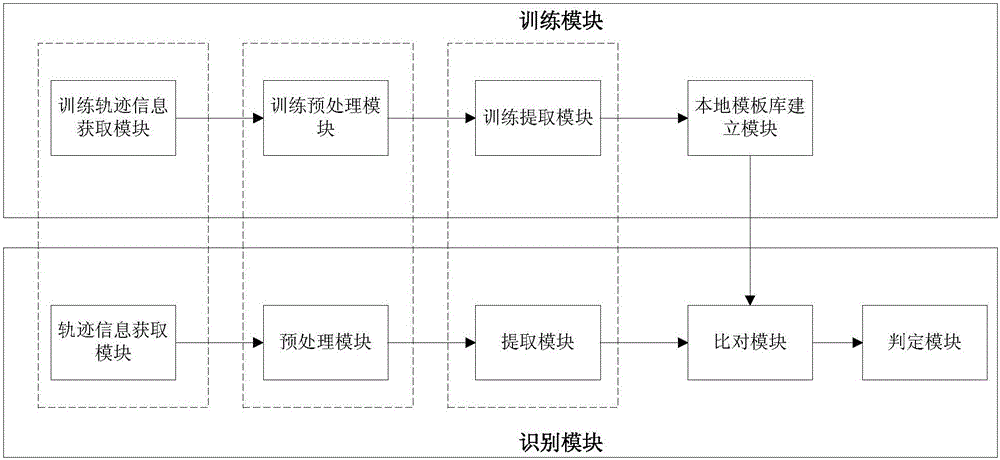
The present invention discloses a cellphone sensing based online signature identity authentication method and system. The method comprises: firstly training handwriting tracks of a real user and a fake user so as to obtain a similarity threshold, and storing the threshold and real user information used for training in a local user template library; and in a user identity authentication process, collecting user track information through a cellphone sensor, after extracting feature information of the tracks, carrying out similarity matching on the feature information and feature information in the user template library by using a DTW algorithm to obtain a minimum similarity value, and comparing the similarity value with the threshold stored in the local template library to determine whether the current user is the real user.
Owner:WUHAN UNIV OF TECH
Online signer identity authentication system, device and method based on mobile terminal
InactiveCN109190351AImprove recognition efficiencyImprove recognition accuracyDigital data authenticationDigital ink recognitionHandwritingOnline signature
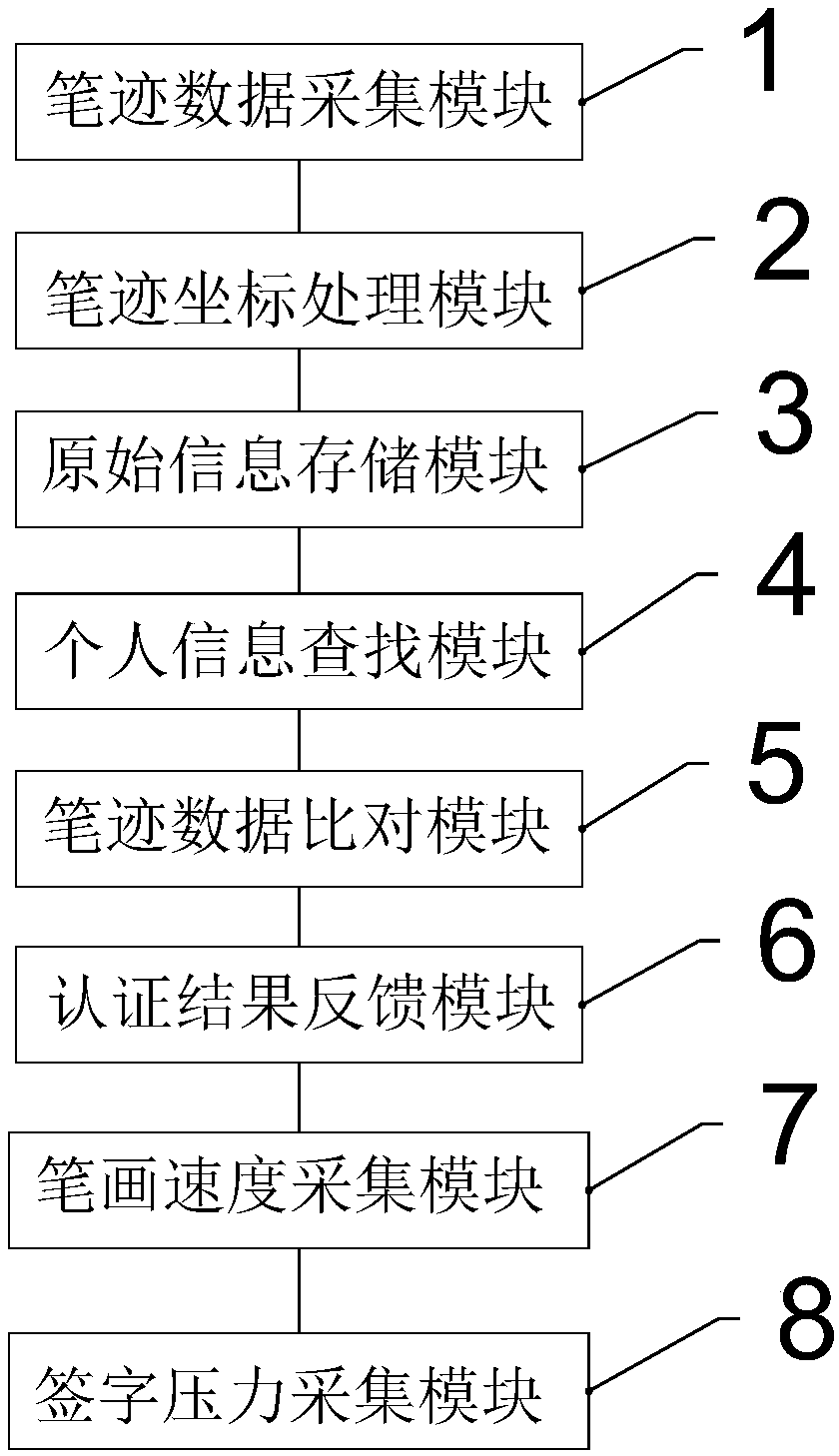
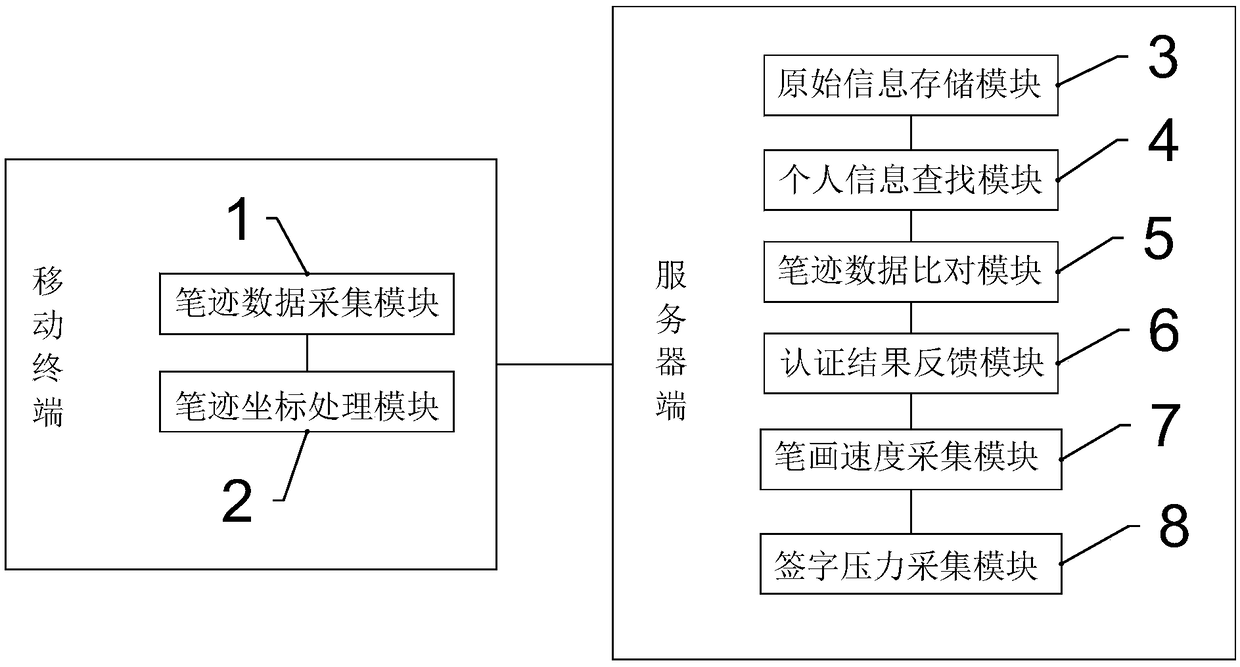
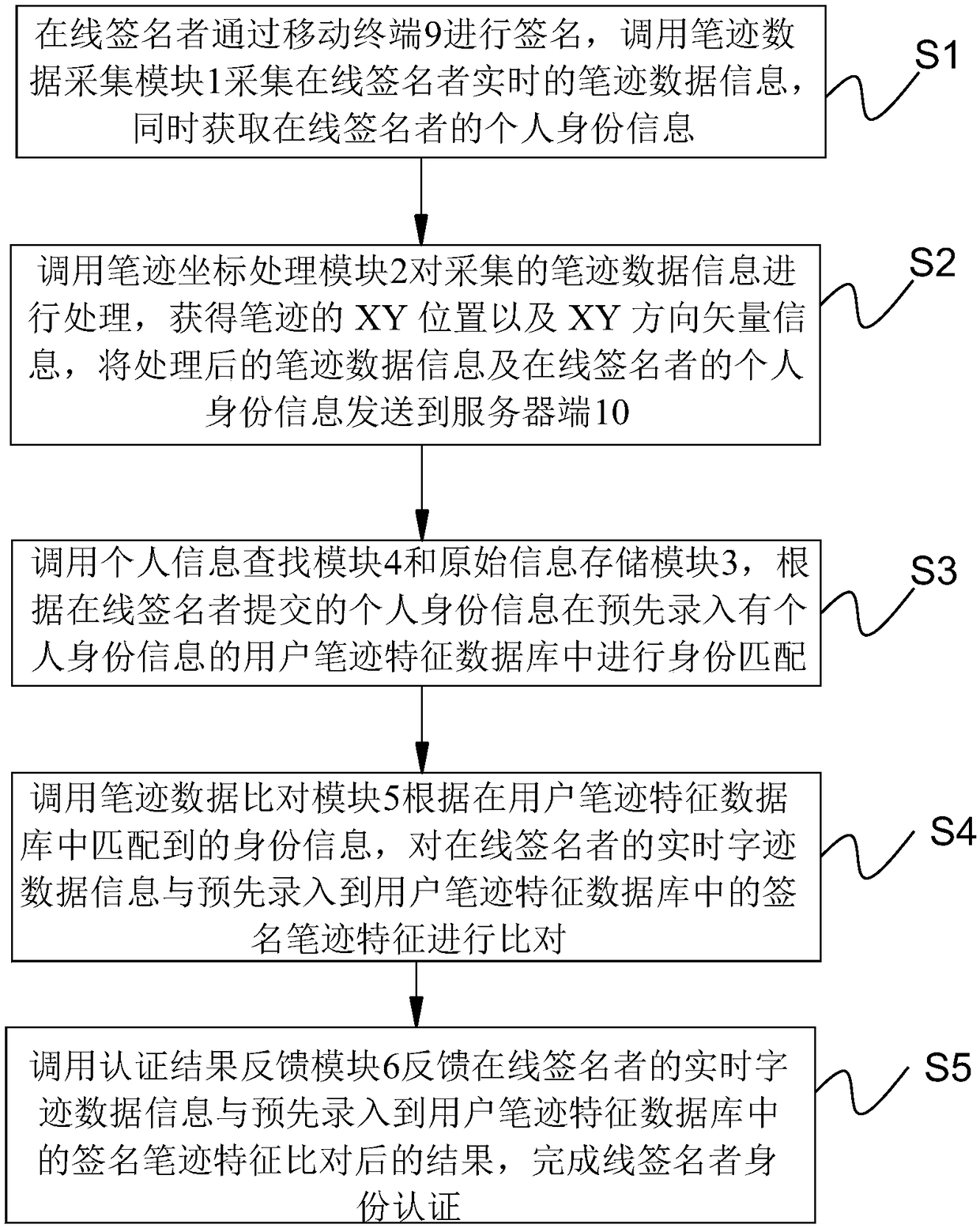
An online signer identity authentication system, device and method based on mobile terminal are provided. The method comprises the steps of: calling handwriting data acquisition module to collect real-time handwriting data information of online signer, and obtaining personal identity information of online signer at the same time; obtaining the XY position and the XY direction vector information ofthe handwriting, and sending the processed handwriting data information and the personal identity information of the online signer to the server;according to the personal identity information submitted by the online signer, matching the identity in the user handwriting characteristic database with the personal identity information recorded in advance; according to the identity information matchedin the user handwriting feature database, comparing the real-time handwriting data information of the online signer with the signature handwriting features recorded in the user handwriting feature database in advance; feeding back the online signer signature handwriting feature matching results to complete line signer authentication. The method has the advantages of fast identification speed, high precision, high safety factor, imitation prevention and more reliable safety.
Owner:宁辛
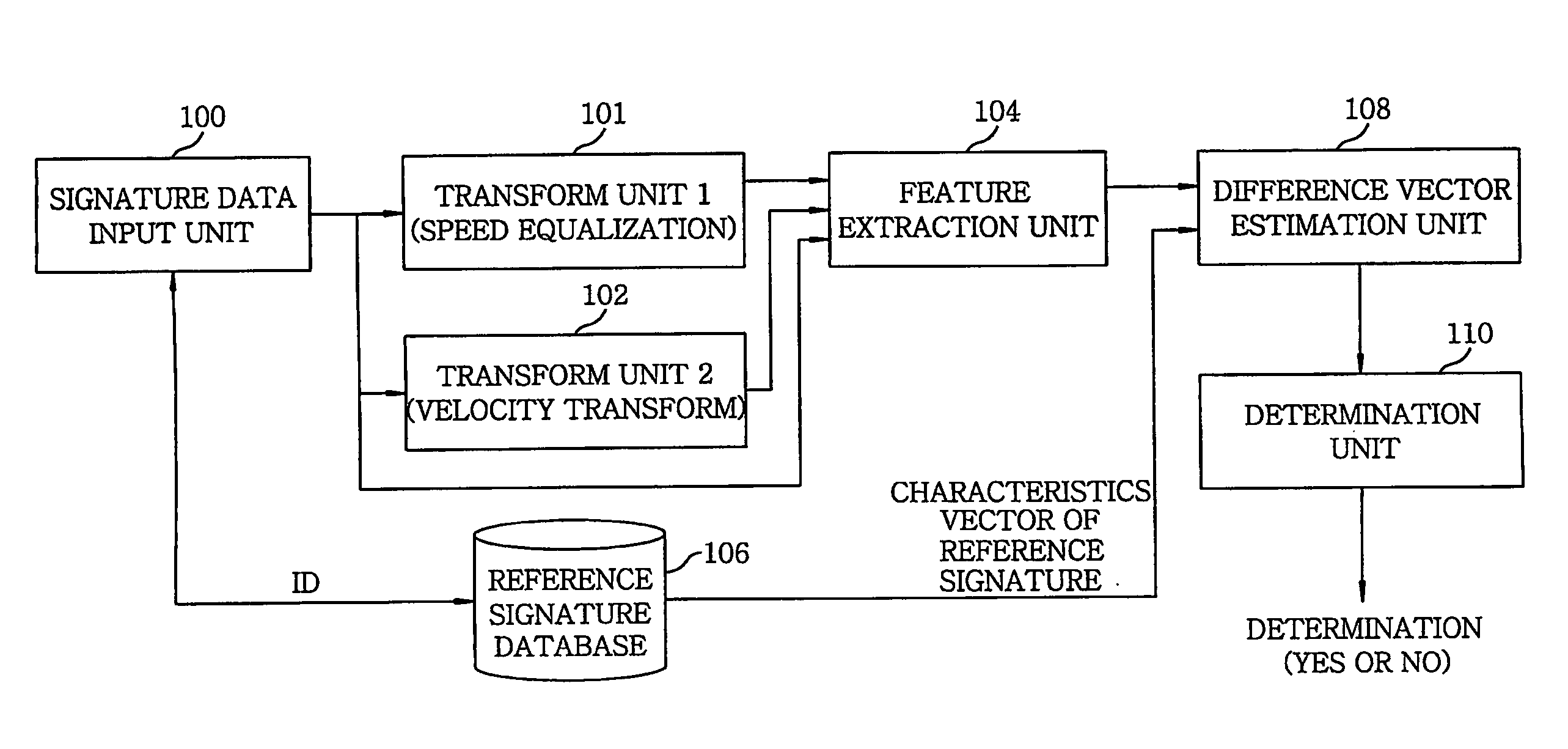
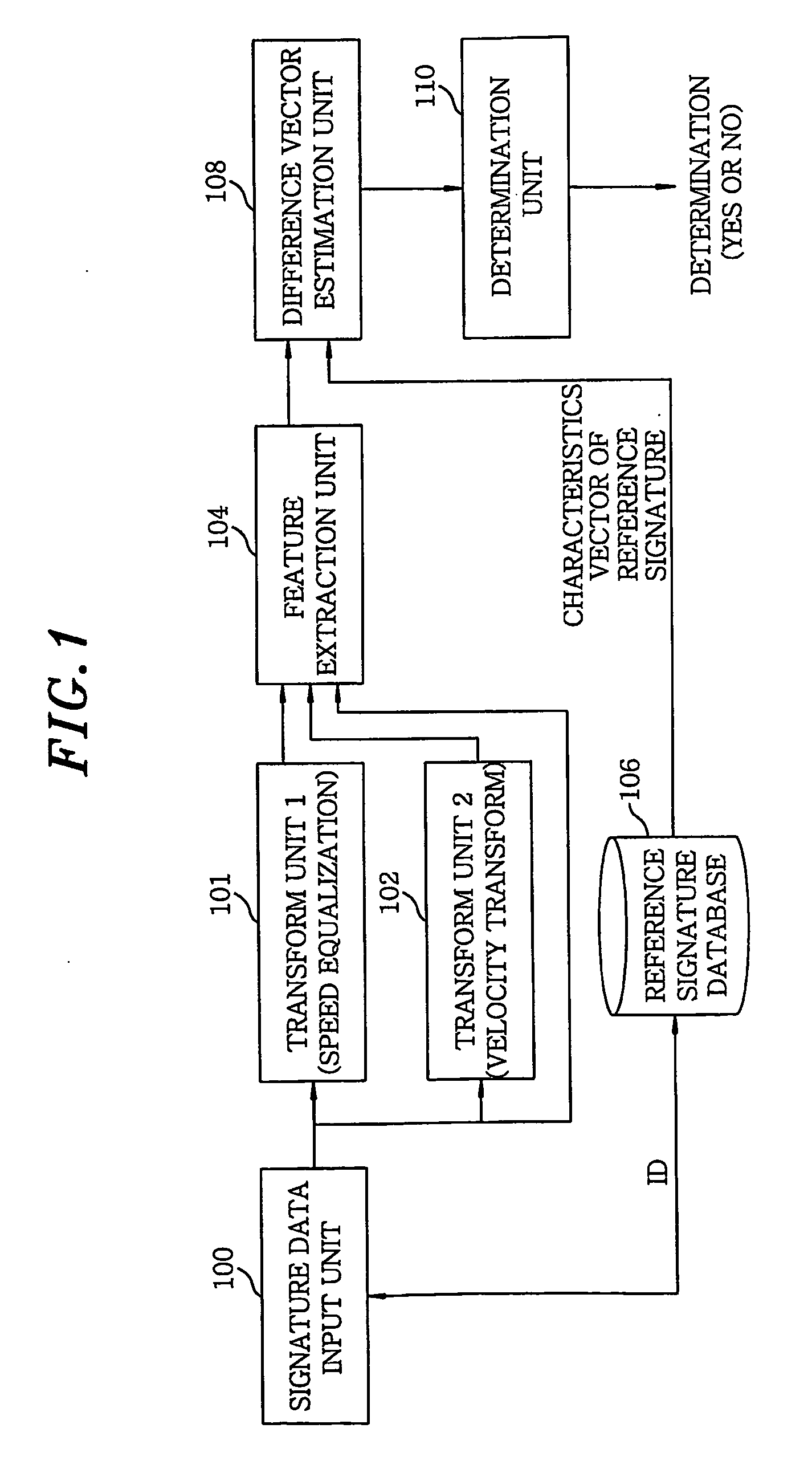
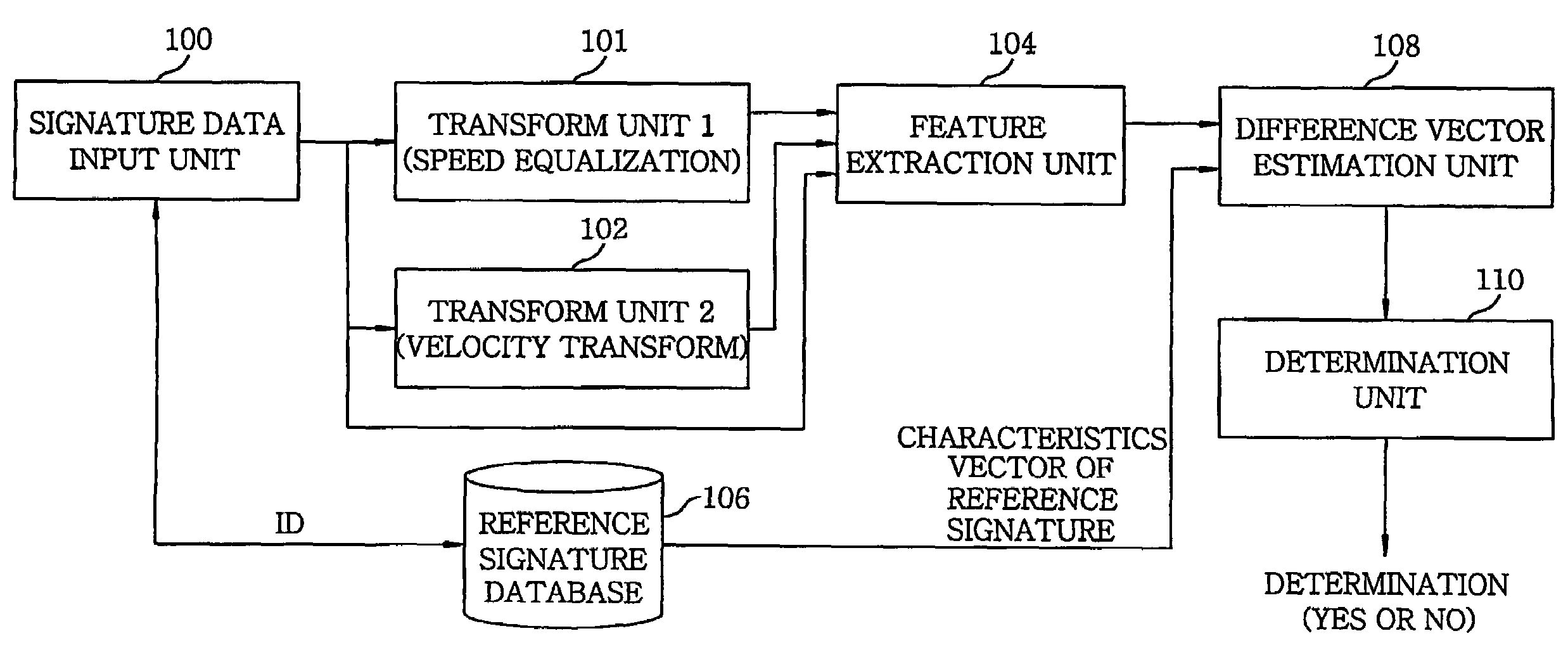
Apparatus for online signature verification using pattern transform technique and method therefor
InactiveUS20060088194A1Securely verifiesImprove discriminationDigital computer detailsElectric digital data processingPattern sequenceOnline signature
In an apparatus for online signature verification, a signature data input unit digitalizes a locus of a user signature and reads the locus as a sequence of points. A first and a second pattern transform unit performs a speed equalization and a velocity transform on the signature sequence and generates a first and a second transformed pattern sequence, respectively. A characteristics extraction unit extracts three characteristics vectors from the signature sequence, the first and the second transformed pattern sequence, respectively, to thereby generate the three characteristics vectors. A difference vector estimation unit generates a difference vector. A determination unit determines whether an input signature and the reference signature are signed by a single person.
Owner:ELECTRONICS & TELECOMM RES INST
A method for online signature verification using wrist-worn devices
ActiveUS20190121951A1Digital data authenticationDetails for portable computersOnline signatureTraining phase
A signature verification system, which comprises a plurality of worn devices of signing users, each provided with one or more motion sensors, and a processor for receiving motion signals from the sensors, the processor is adapted to define a set of features that describe a signature and distinguish one signature from another; perform a training phase by obtaining motion signals from one or more motion sensors of the worn devices; training a machine learning classifier using the instances and labels; obtain motion signals from motion sensors of the a worn device, the motion being of an allegedly genuine signature of one of the users; scale and domain transform the allegedly genuine signature; calculate values of the features describing the allegedly genuine signature with respect to scaled and transformed reference signatures of the one of the users; and apply the trained classifier on the feature values, thereby classifying the allegedly genuine signature as genuine or forged.
Owner:B G NEGEV TECH & APPL LTD +1
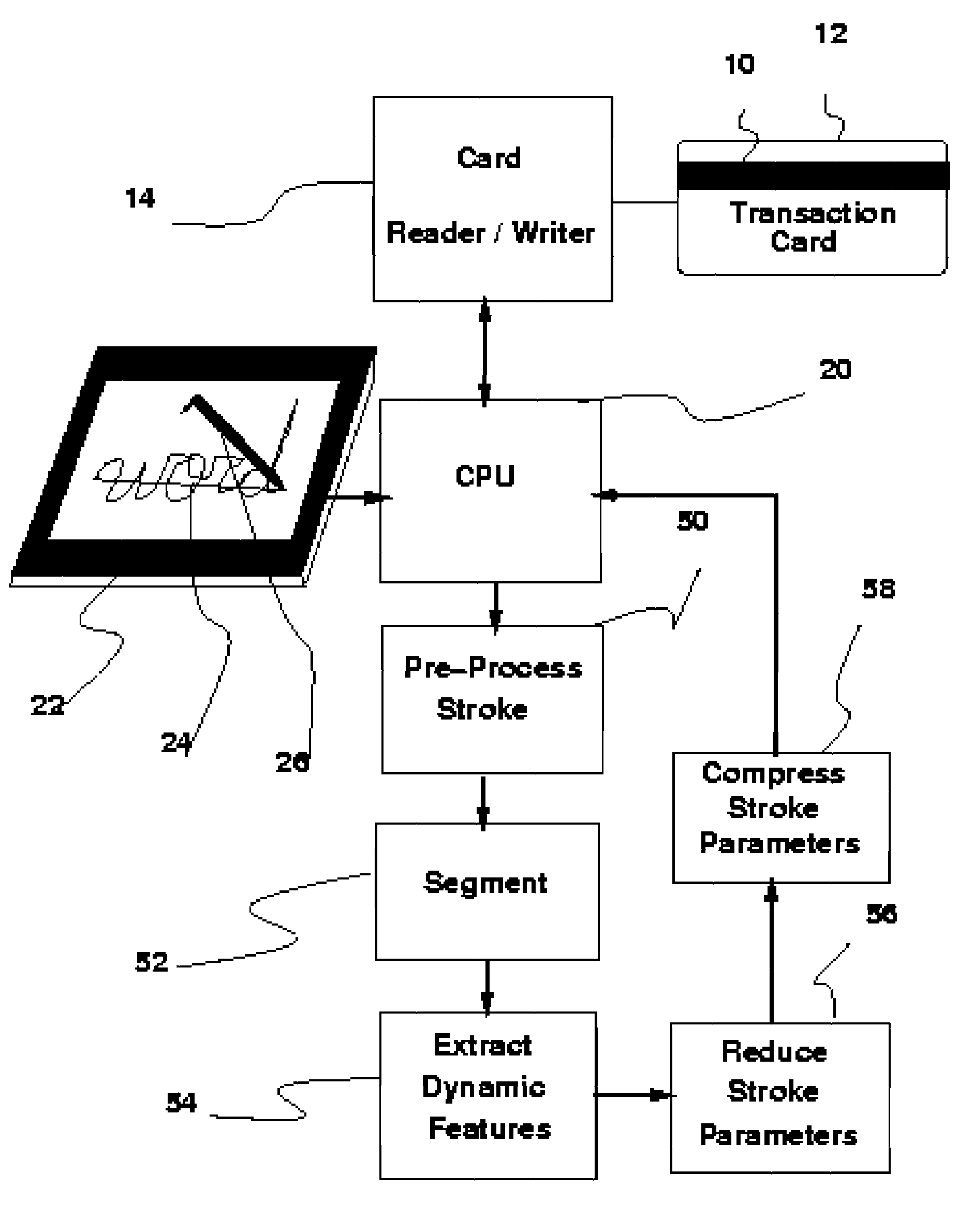
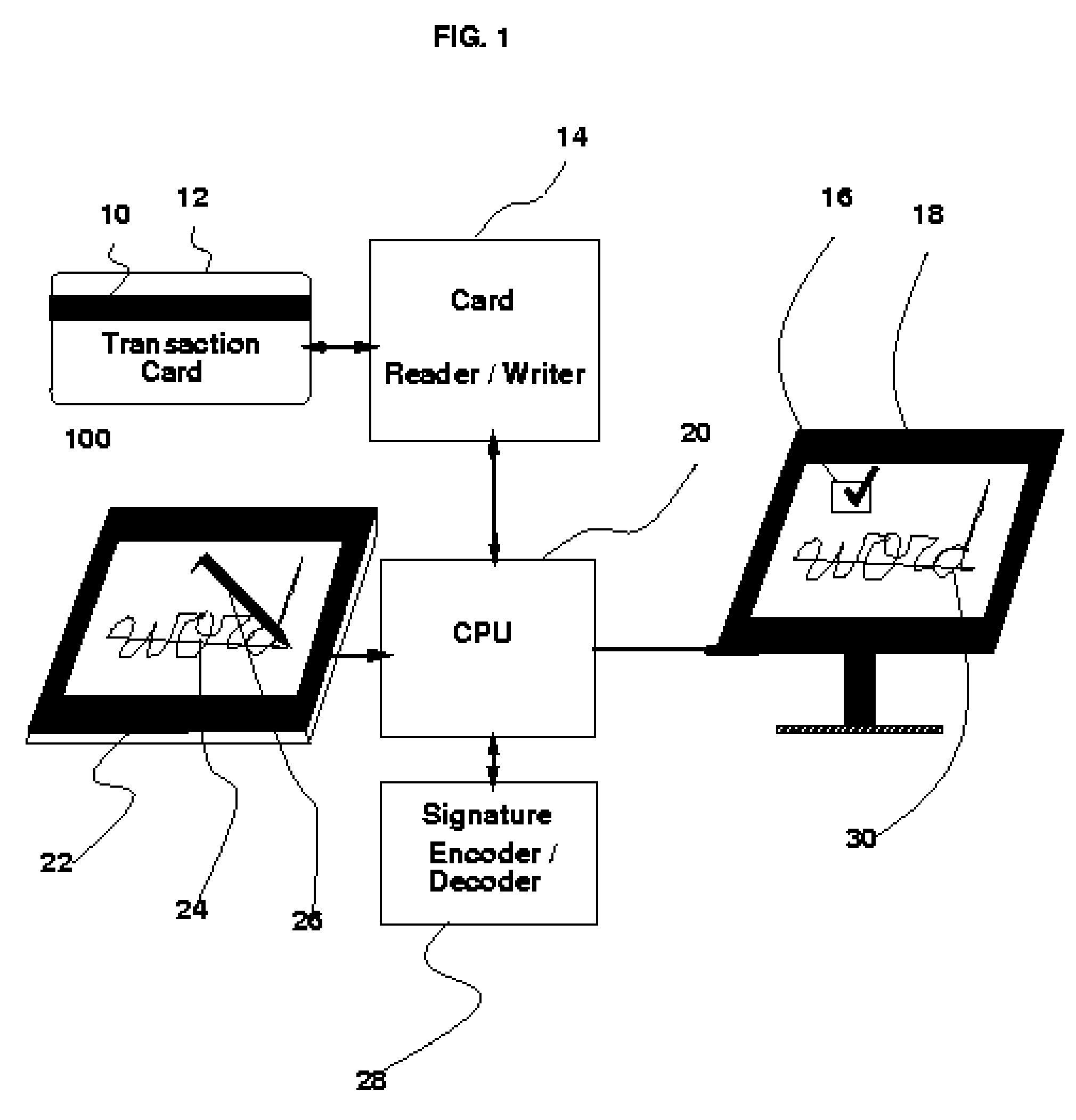
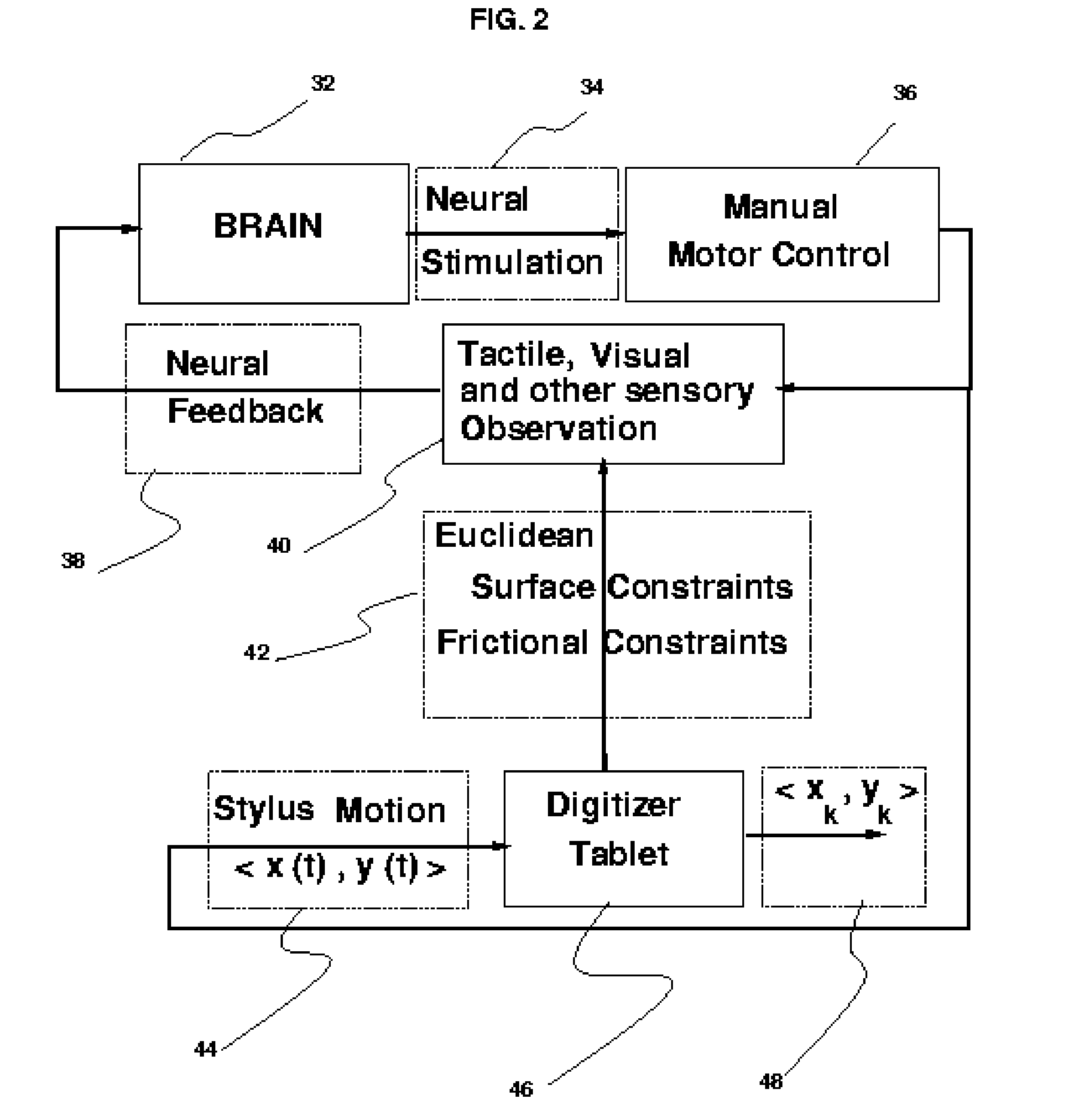
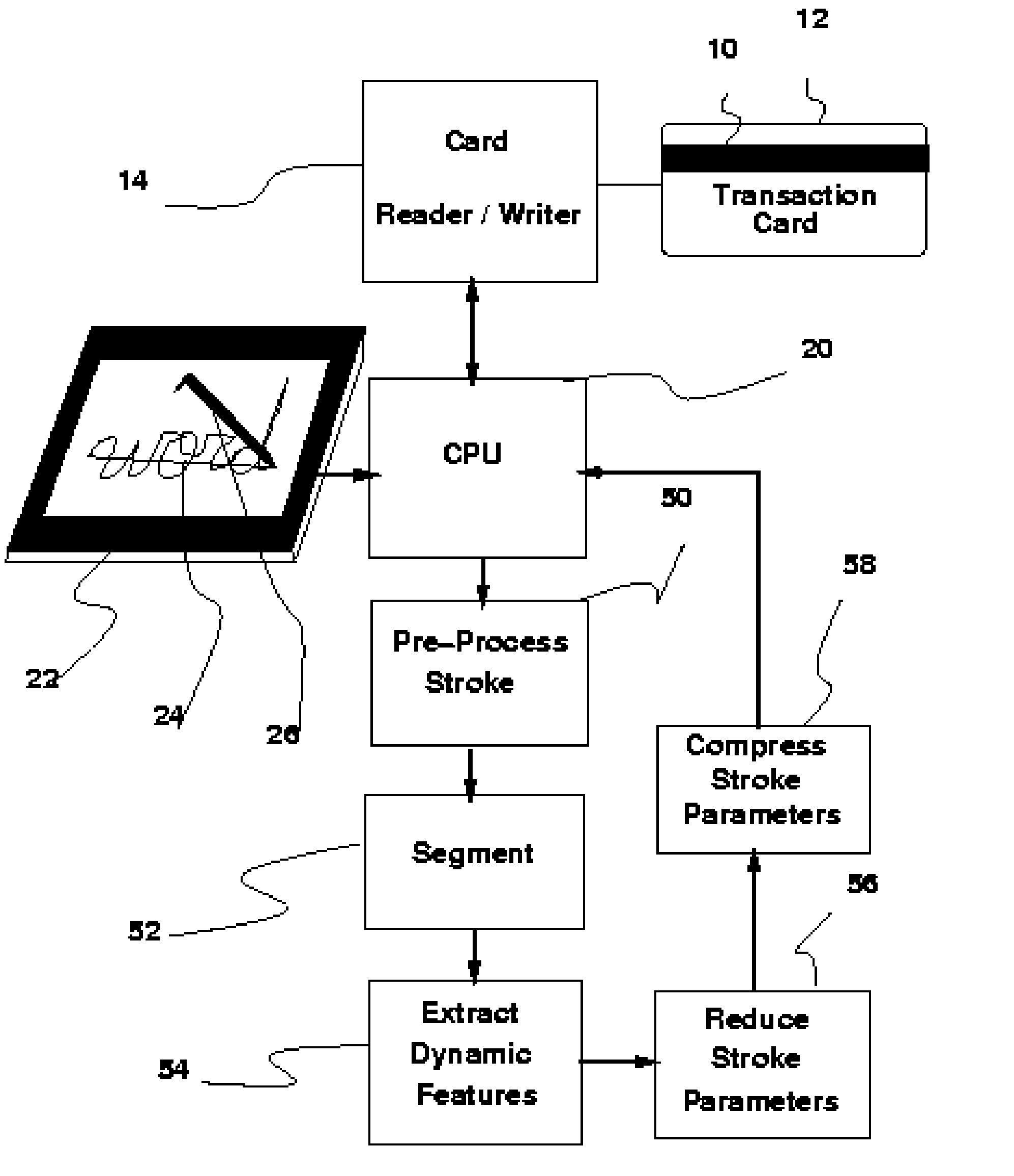
Method and apparatus for aggressive compression, storage and verification of the dynamics of handwritten signature signals
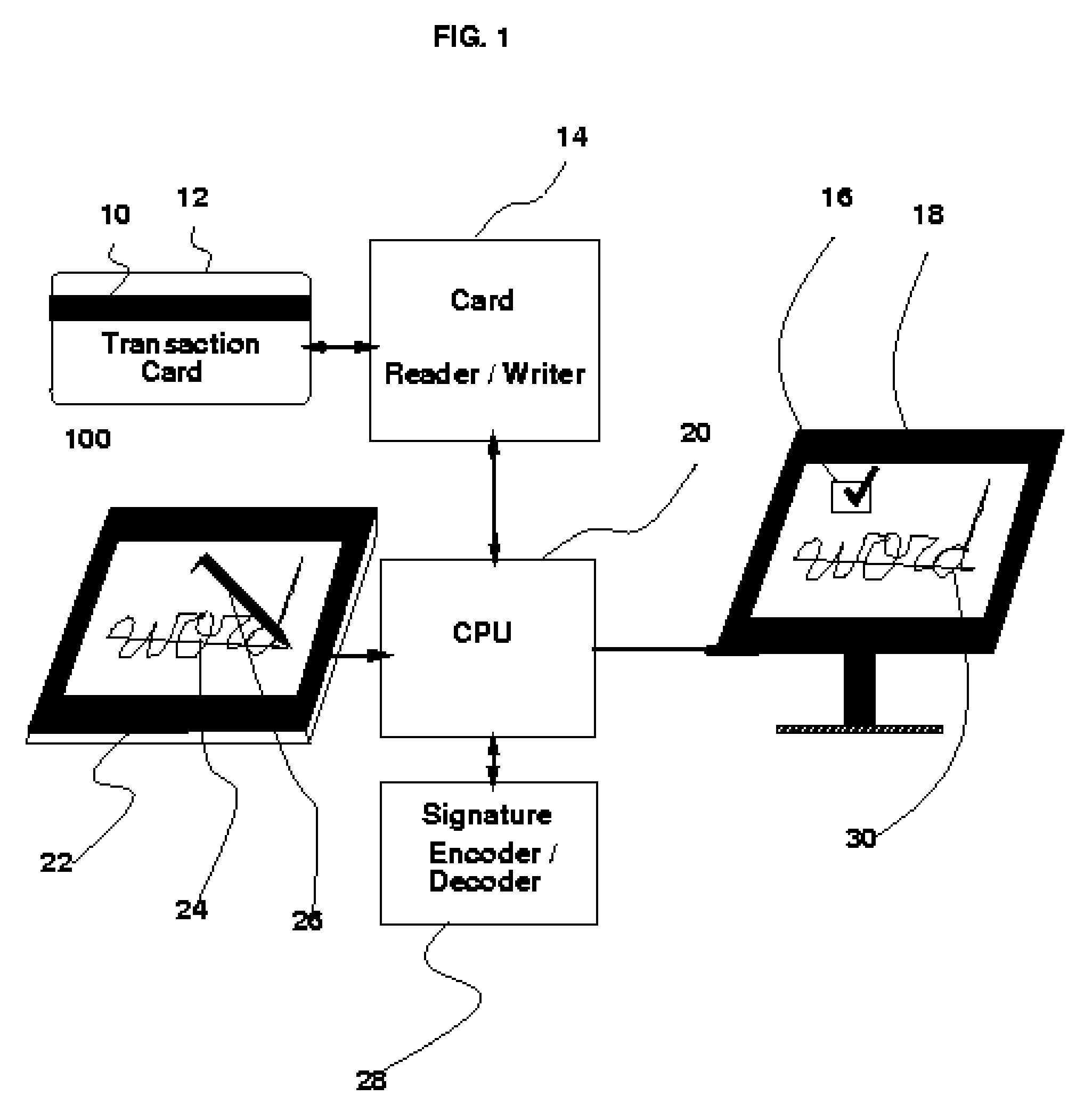
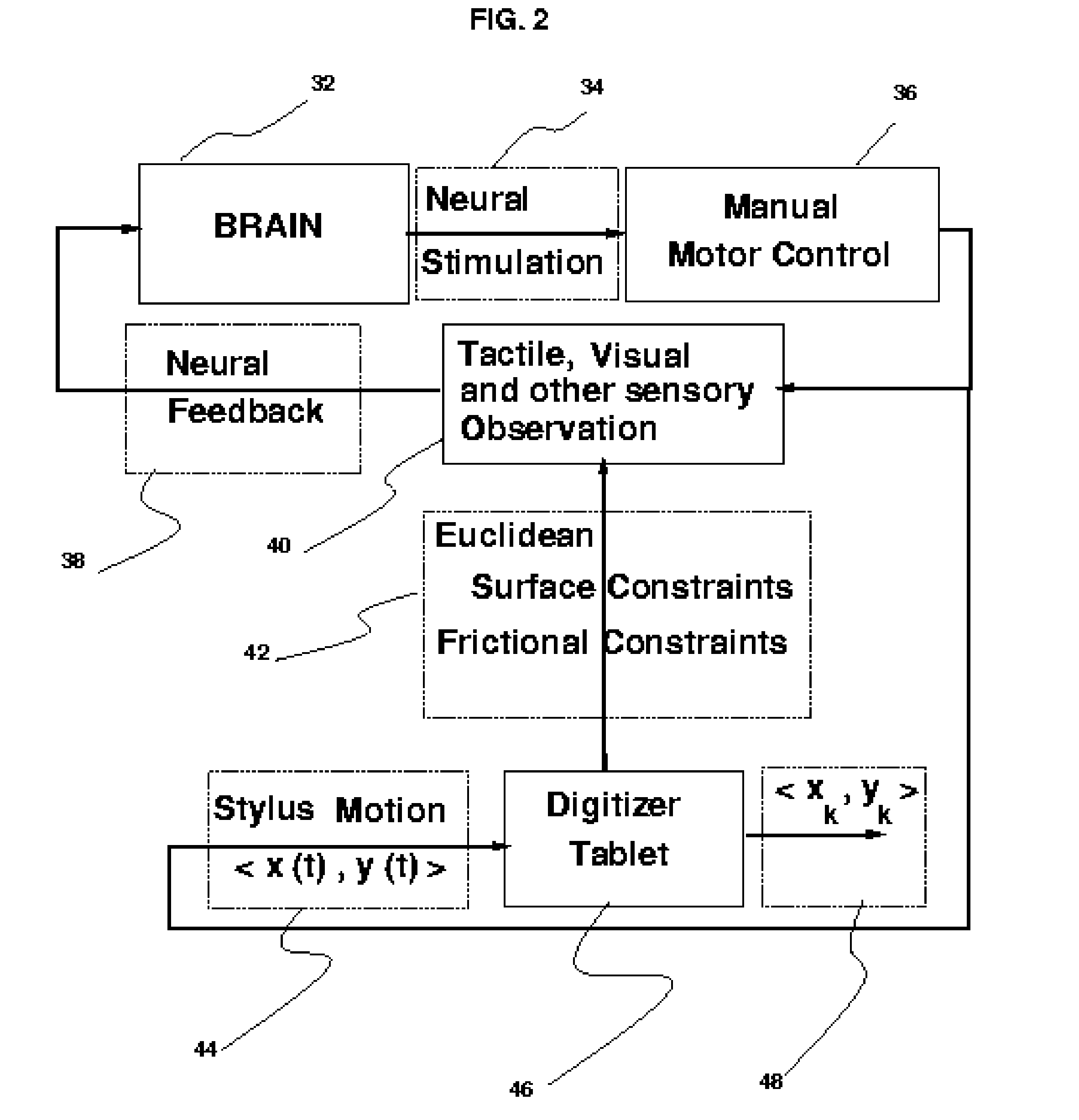
InactiveUS7474770B2Difficult to forgeImprove efficiencyPayment architectureCoded identity card or credit card actuationHandwritingOnline signature
The fields of biometrics and commerce can benefit from the aggressive compression techniques presented here. A novel approach to compressing the on-line handwriting signal without losing the dynamic information (i.e., velocity and order) is presented which provides the means to fit almost any signature sample within the 57-byte limit of one of the free magnetic strips on the back of conventional transaction cards such as credit or debit cards or other identity cards. The apparatus requires an on-line signature capture tablet capable of sampling the handwritten signature in a series of sampled X and Y coordinates. The compression method starts with segmenting the on-line handwriting signal into portions which may be approximated with a set of features from which the velocity and position may be reconstructed. These features are then compressed further using standard compression techniques. A Huffman coding technique is used to demonstrate this step. The size of the average signature including its dynamic information is stored in a space less than 57 bytes which is the magic limit imposed by conventional, magnetic transaction (credit or debit) card strips. This is by far less than about 1000 bytes required if only loss-less techniques were used. A loss-less compression technique is also briefly presented. Normally, out of the three strips which are provided on the back of a card, two strips are available and may be used for storing the template of the owner's signature for future verification.
Owner:BEIGI HOMAYOON S M
Method and Apparatus for Aggressive Compression, Storage and Verification of the Dynamics of Handwritten Signature Signals
InactiveUS20060291703A1Difficult to forgeImprove efficiencyPayment architectureCoded identity card or credit card actuationOnline signatureHandwriting
The fields of biometrics and commerce can benefit from the aggressive compression techniques presented here. A novel approach to compressing the on-line handwriting signal without losing the dynamic information (i.e., velocity and order) is presented which provides the means to fit almost any signature sample within the 57-byte limit of one of the free magnetic strips on the back of conventional transaction cards such as credit or debit cards or other identity cards. The apparatus requires an on-line signature capture tablet capable of sampling the handwritten signature in a series of sampled X and Y coordinates. The compression method starts with segmenting the on-line handwriting signal into portions which may be approximated with a set of features from which the velocity and position may be reconstructed. These features are then compressed further using standard compression techniques. A Huffman coding technique is used to demonstrate this step. The size of the average signature including its dynamic information is stored in a space less than 57 bytes which is the magic limit imposed by conventional, magnetic transaction (credit or debit) card strips. This is by far less than about 1000 bytes required if only loss-less techniques were used. A loss-less compression technique is also briefly presented. Normally, out of the three strips which are provided on the back of a card, two strips are available and may be used for storing the template of the owner's signature for future verification.
Owner:BEIGI HOMAYOON S M
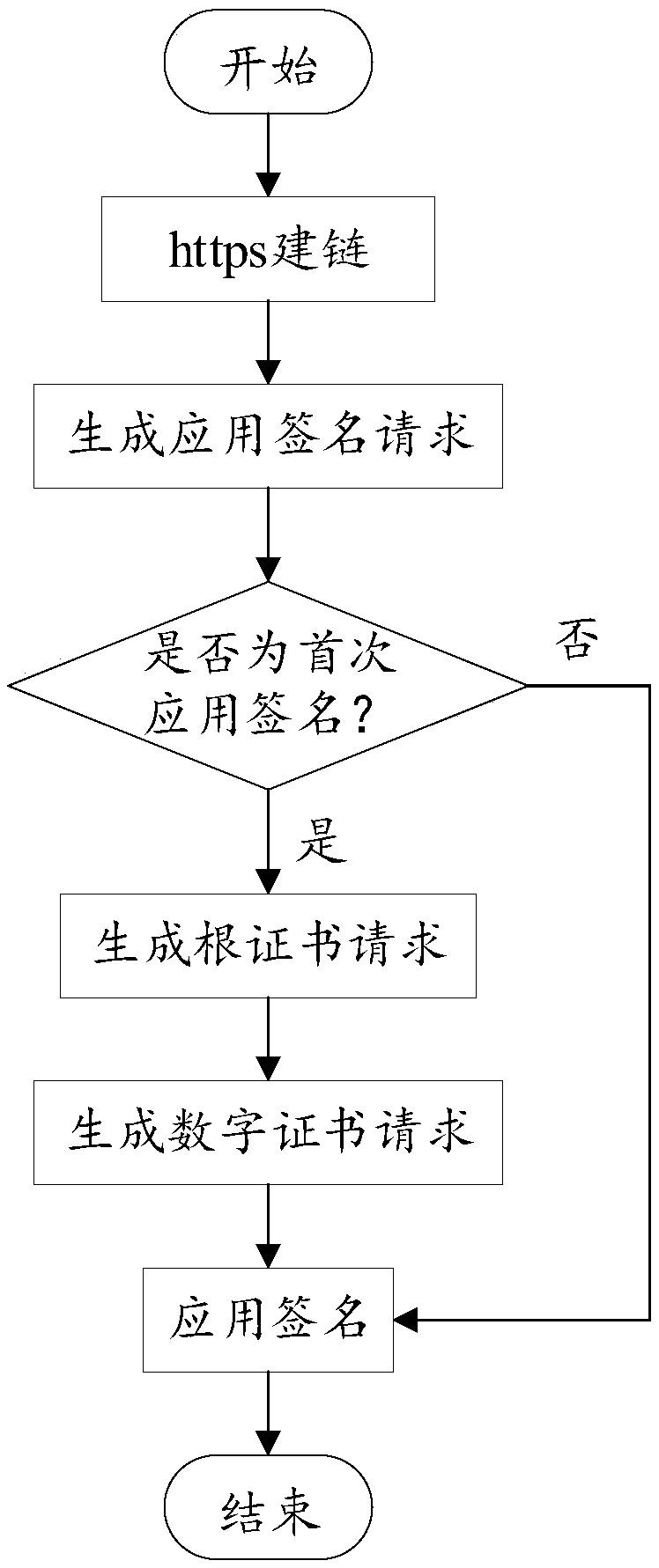
An application online signature method and system
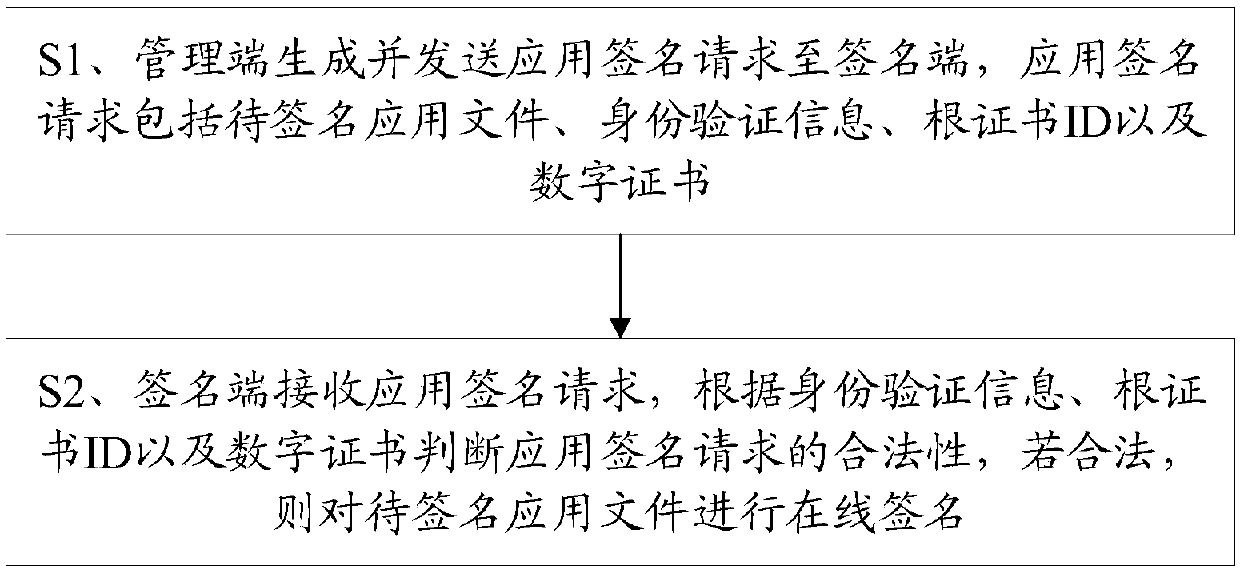
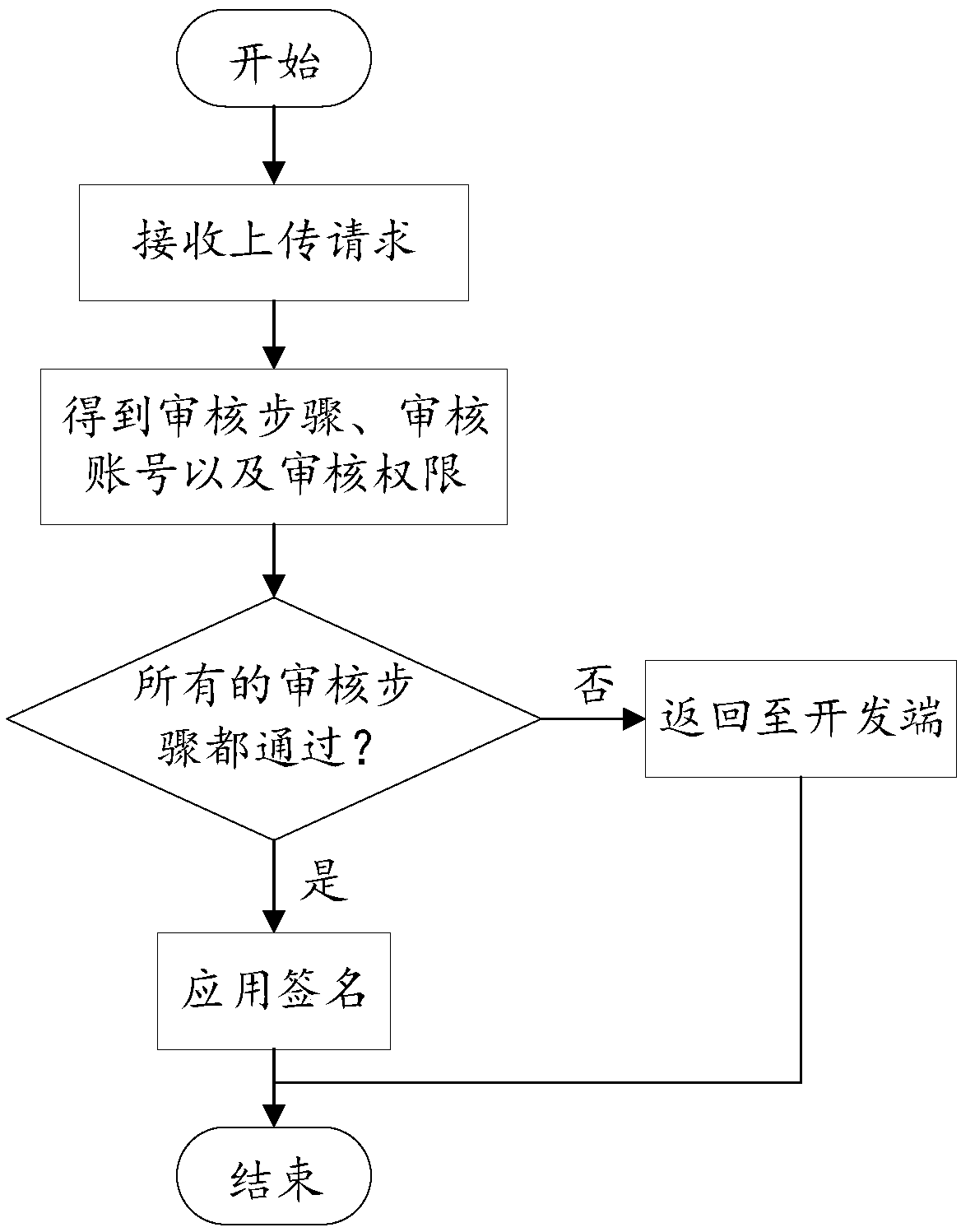
ActiveCN109670828AEnsure application securityReduce easy lossProtocol authorisationRoot certificateOnline signature
The invention discloses an application online signature method and system, and the method comprises the steps that a management end generates and sends an application signature request to a signatureend, and the application signature request comprises a to-be-signed application file, identity verification information, a root certificate ID, and a digital certificate; the signature end receives the application signature request, the legality of the application signature request is judged according to the identity verification information, the root certificate ID and the digital certificate, and if the application signature request is legal, the to-be-signed application file is signed online. According to the invention, the original offline UKEY application signature is replaced by the online application signature; the application security of the terminal is ensured, the informatization of terminal application management can be realized, the risk of easy loss and utilization caused by offline human factors is effectively reduced, and the problems of labor cost, management cost and operation disjunction caused by offline signatures are also avoided.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
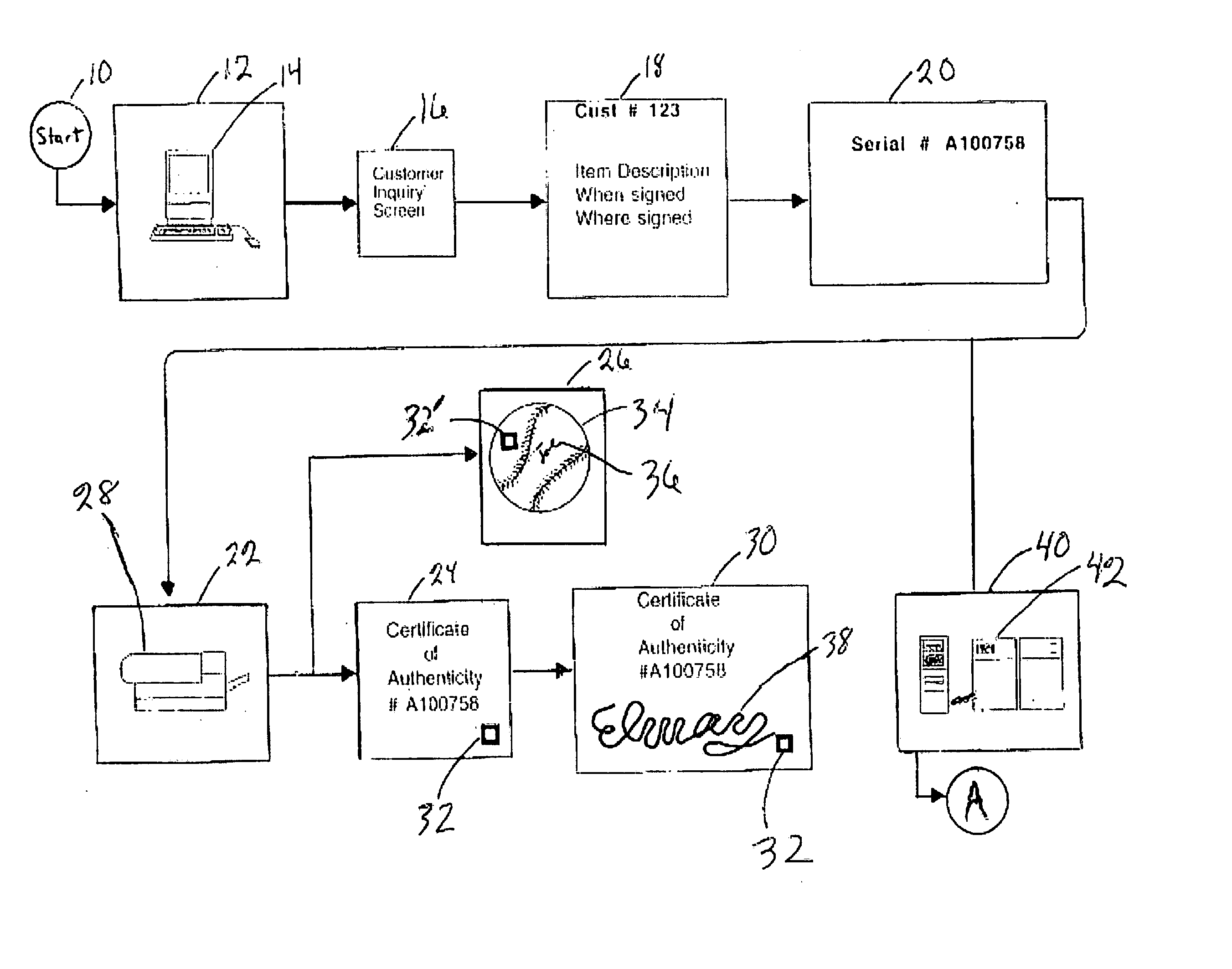
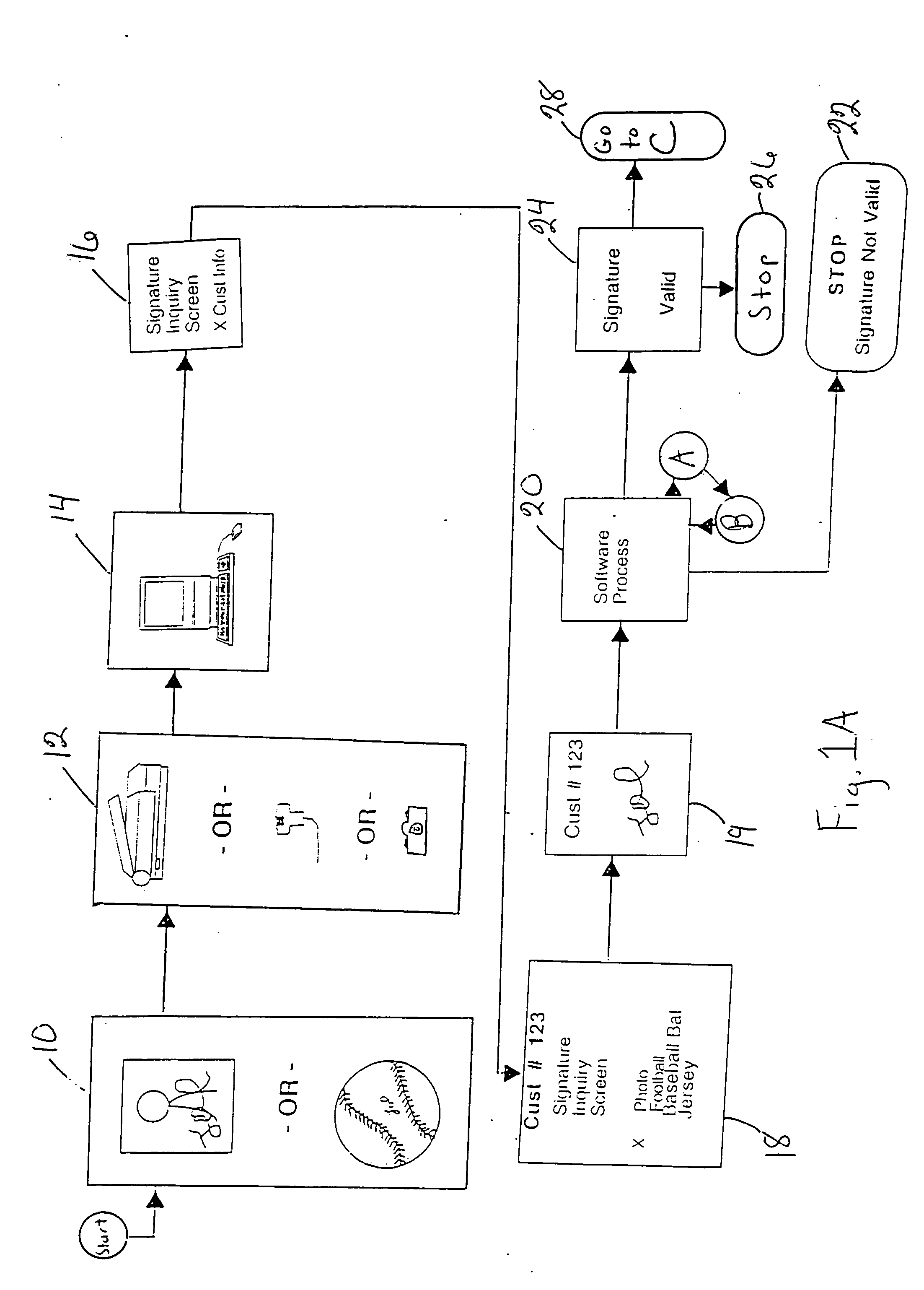
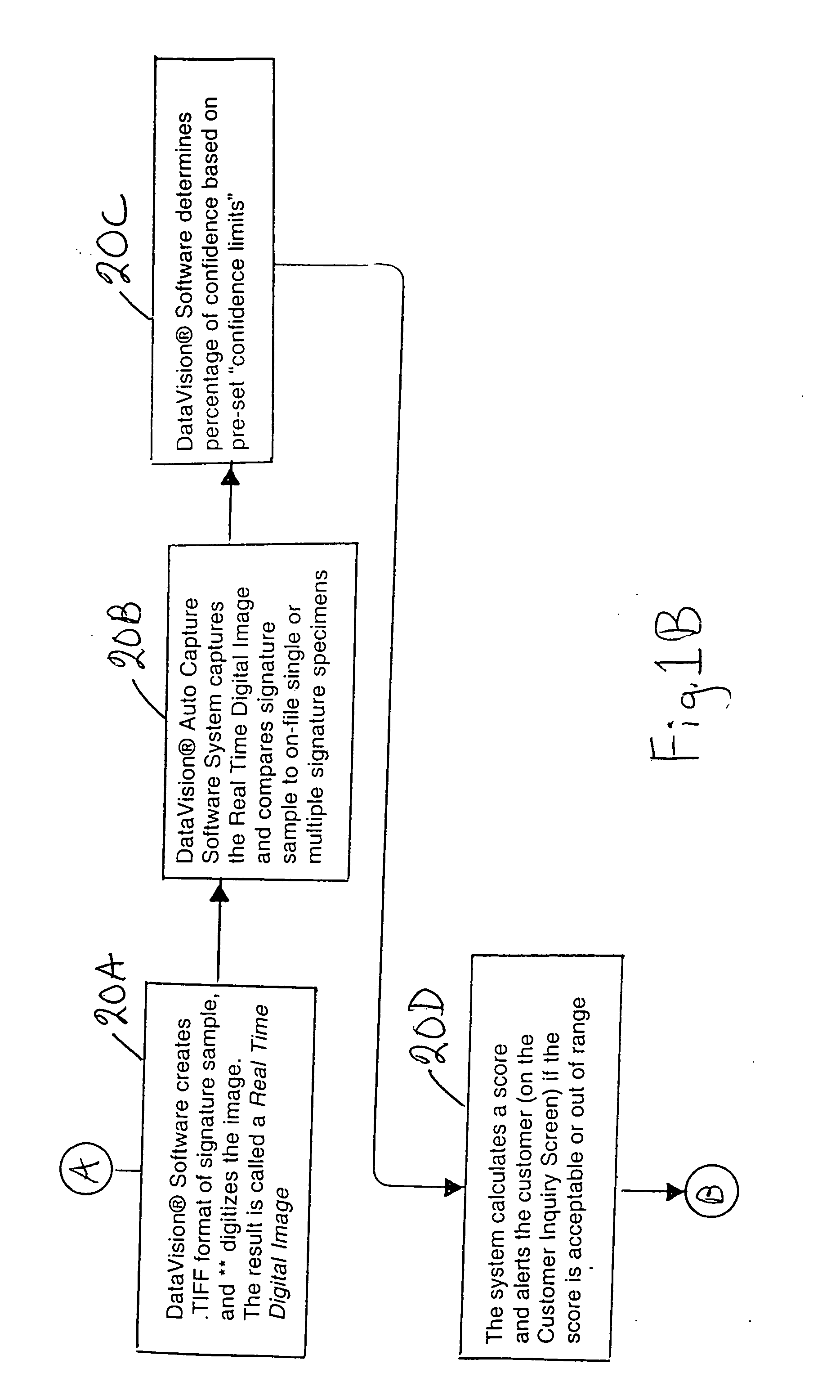
Method and system for on-line certificate of authenticity for collectibles and on-line signature verification of collectibles
InactiveUS20060239516A1Fast authenticationElectric signal transmission systemsImage analysisOnline signatureInternet privacy
An on-line method for issuing a certificate of authenticity for a collectible to a collector who has personally witnessed the collectible being signed and a verification system for authenticating a suspected signature on an object by scanning the suspected signature and transmitting to a central computer where the suspected signature is compared with a set of authentic reference signatures based on input as to the shape of the object. In embodiments, the collector provides information on the collectible via the Internet to a central computer which stores the information for future reference by potential purchasers of the collectible. The collector must sign a statement on the certificate of authenticity that declares, under penalty of perjury, the information that the collector provided regarding the collectible is correct. Subsequent purchasers can access the central computer via the Internet.
Owner:AUTHENTICSIG
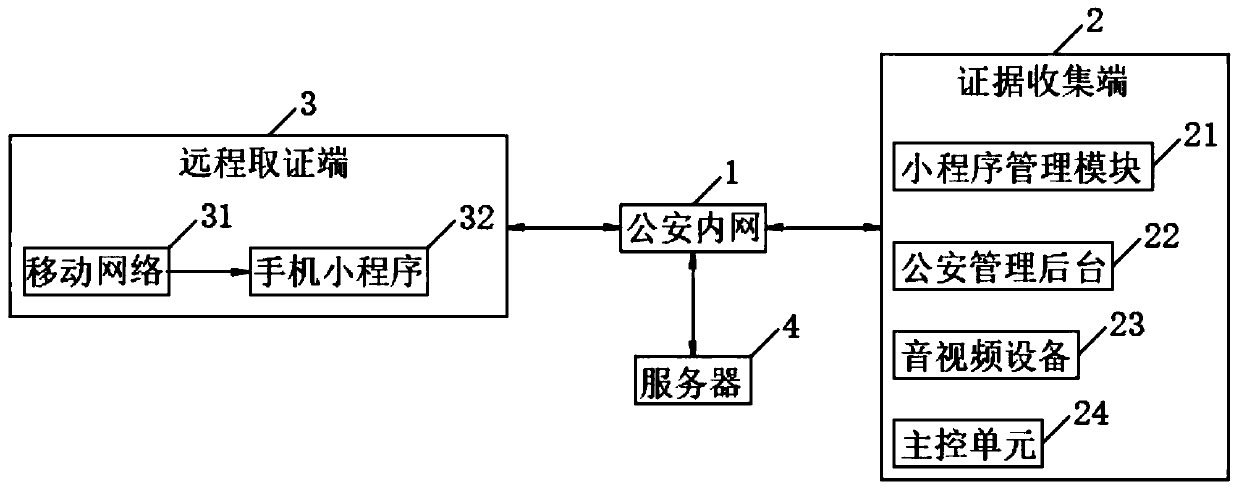
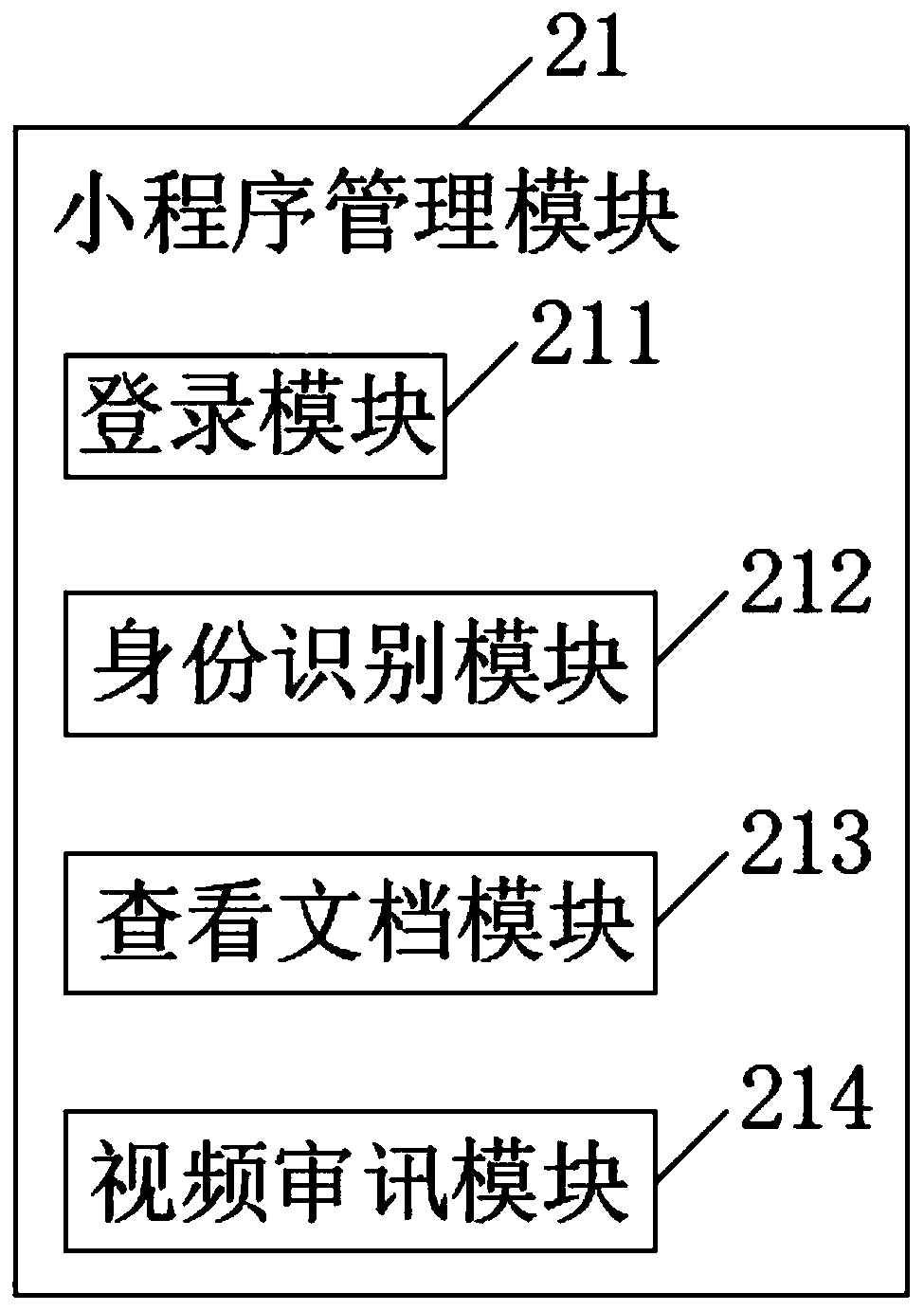
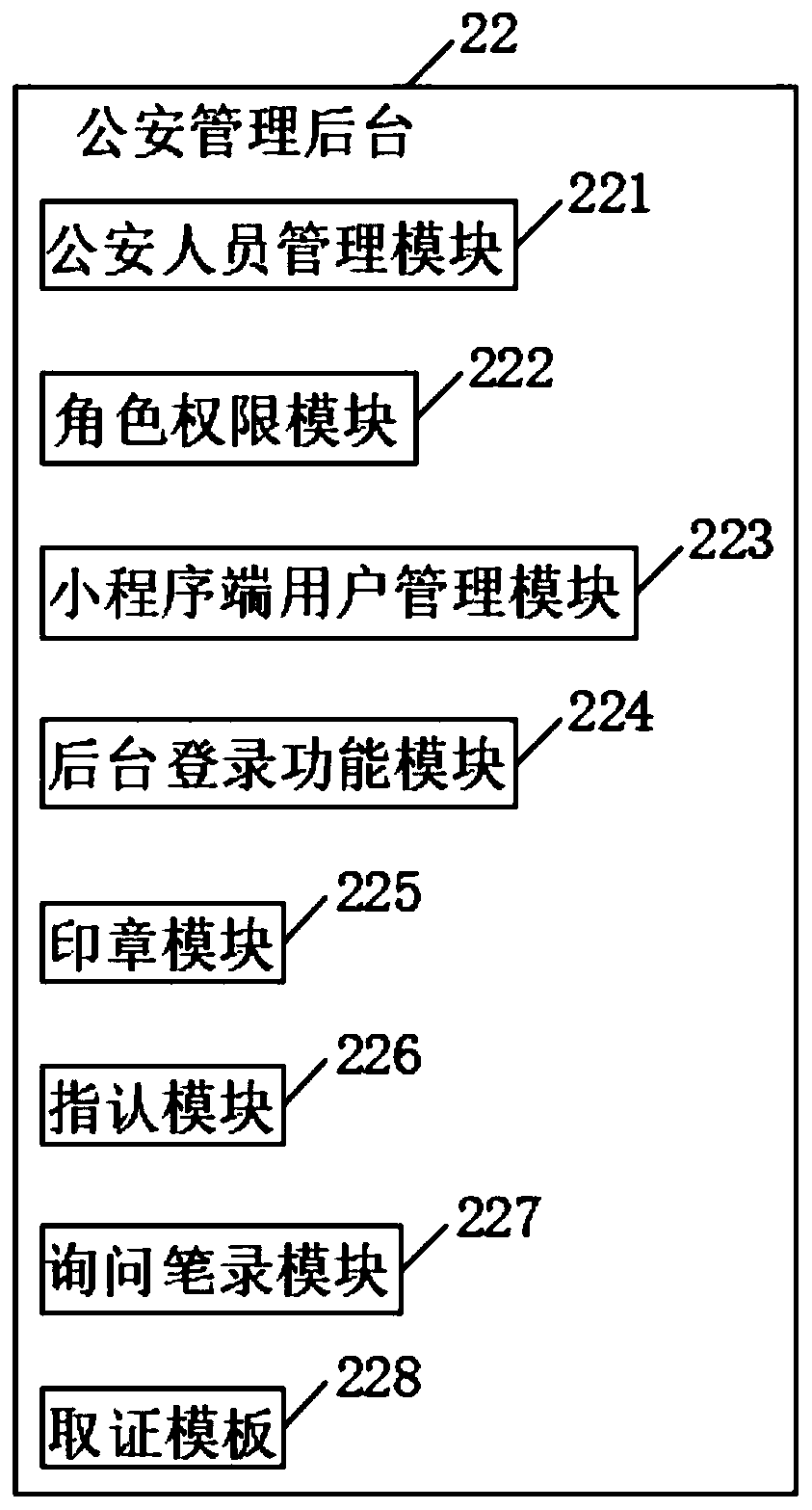
Remote online inquiry and evidence collection system and method
InactiveCN111294547ARealize online signatureImprove forensics efficiencyData processing applicationsFile system administrationOnline signatureEngineering
The invention relates to a remote online inquiry and evidence collection system and method. The system comprises a public security intranet, and an evidence collection end, a remote evidence collection end and a server which are in bidirectional connection with the public security intranet, the public security intranet is a public security encryption Internet private cloud network. The evidence collection end comprises a main control unit, and a applet management module, a public security management background and audio and video equipment which are electrically connected with the main controlunit, the audio and video equipment is uploaded to the server through the public security intranet, the server is a virtual server, and the remote evidence collection end comprises a mobile network and a mobile phone applet. According to the invention, a user can access the system as a party through a mobile phone applet, functions of online signature, evidence uploading, online identification and the like of a mobile phone screen can be realized, the evidence obtaining efficiency of public security personnel can be improved, and a large amount of time and case handling expenditure of case handling policemen can be saved.
Owner:江苏齐德隆智能科技有限公司
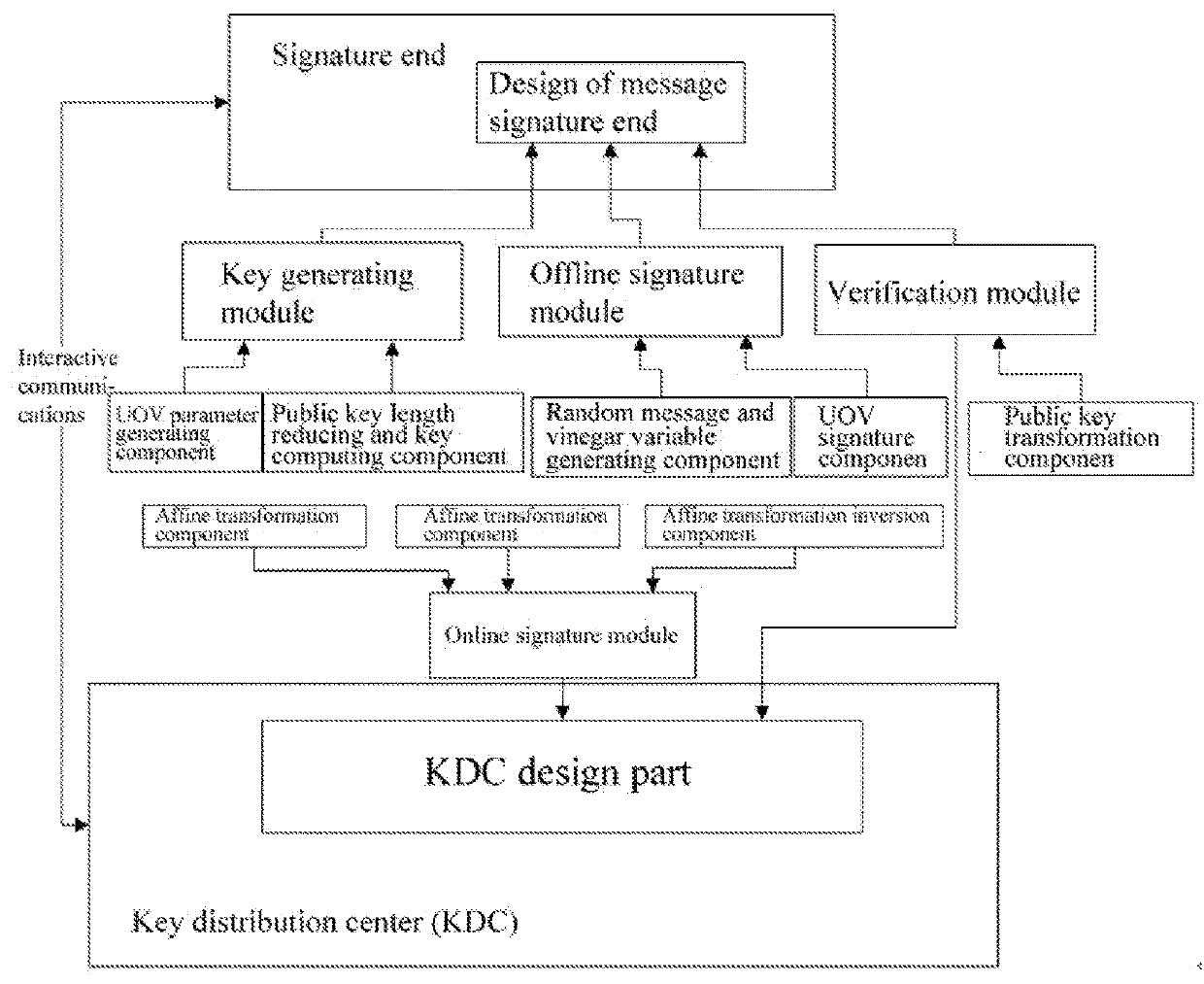
Online/Offline Signature System and Method Based on Multivariate Cryptography
ActiveUS20180278426A1Reduce computational overheadKey distribution for secure communicationPublic key for secure communicationOnline signatureSensor node
Disclosed is an offline / online signature system including a key distribution center (KDC) and a signature end, wherein the KDC includes a key generating module, an offline signature module, and a verification module; and the signature end includes an online signature module and a verification module. The key generating module generates a temporary signature required for online signature, and transmits the result to a sensor node for storage. The online signature module generates a signature for a specific message; and the verification module includes a processor and a public key transformation component, wherein the processor transmits the signature to the public key transformation component and determines whether the signature is valid.
Owner:SOUTH CHINA UNIV OF TECH
AI-based unmanned intervention approval system
InactiveCN112184145AExempt from submittingNatural language data processingOffice automationText recognitionEngineering
Owner:上海浦东临港智慧城市发展中心 +1
Lightweight online and offline certificateless signature method
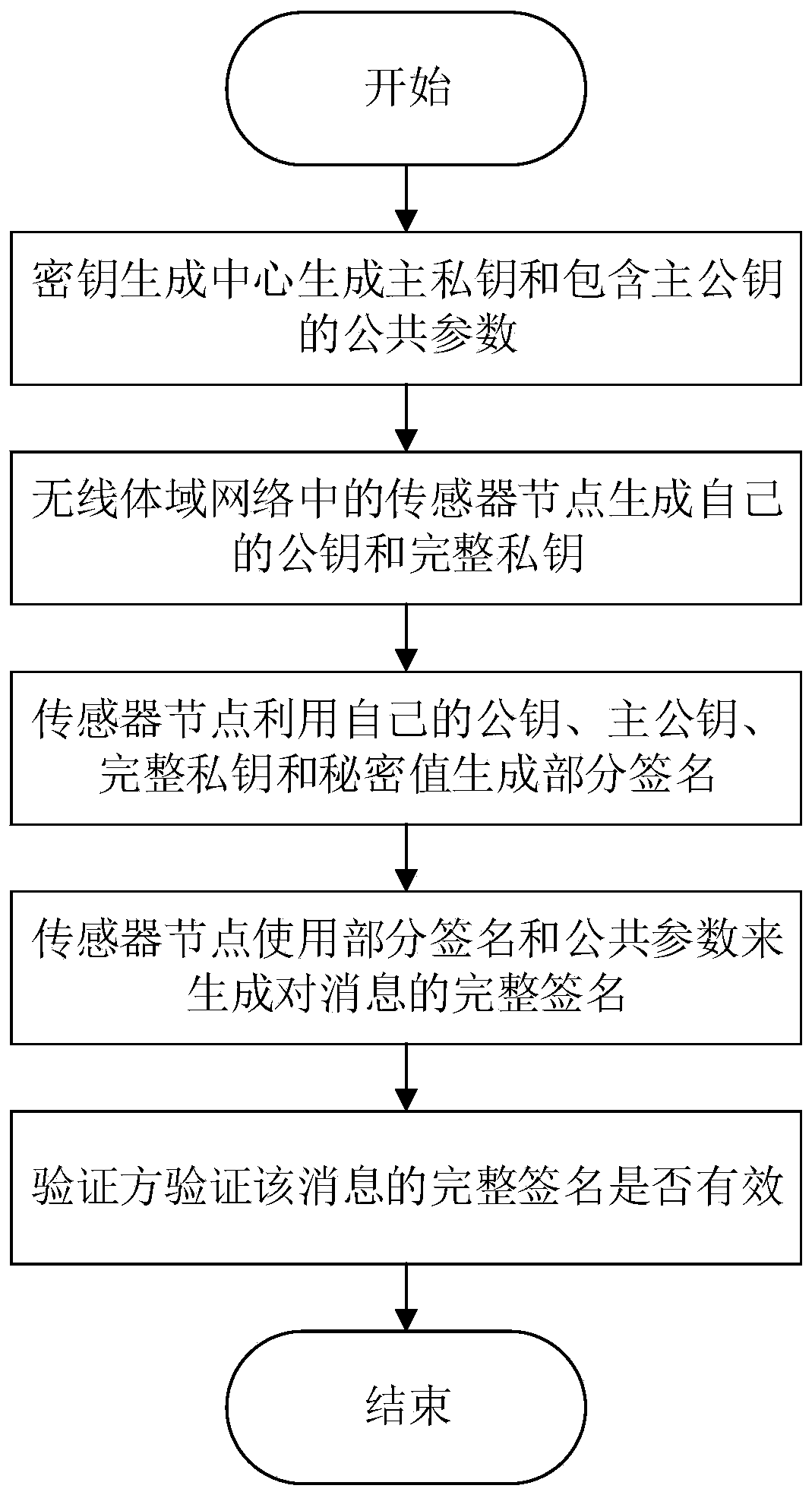
ActiveCN110808833AResistant to Substitution AttacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesOnline signatureComputer network
The invention discloses a lightweight online and offline certificateless signature method, which comprises the following steps: (1) in an initialization stage, a key generation center generates a mainprivate key and a public parameter containing a main public key; (2) a key generation stage: a sensor node in the wireless body area network generates a public key and a complete private key of the sensor node; (3) an offline signature stage: before the message is known, the sensor node generates a partial signature by using the own public key, the main public key, the complete private key and the secret value; (4) in an online signature stage, the sensor nodes use partial signatures and public parameters to generate complete signatures for the messages; and (5) a verification stage: the verifier verifies whether the complete signature of the message is valid or not. The online and offline certificateless signature method provided by the invention can resist forgery attacks and public keyreplacement attacks, and is proved to be safe under two attacks of a malicious client and a malicious key generation center.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
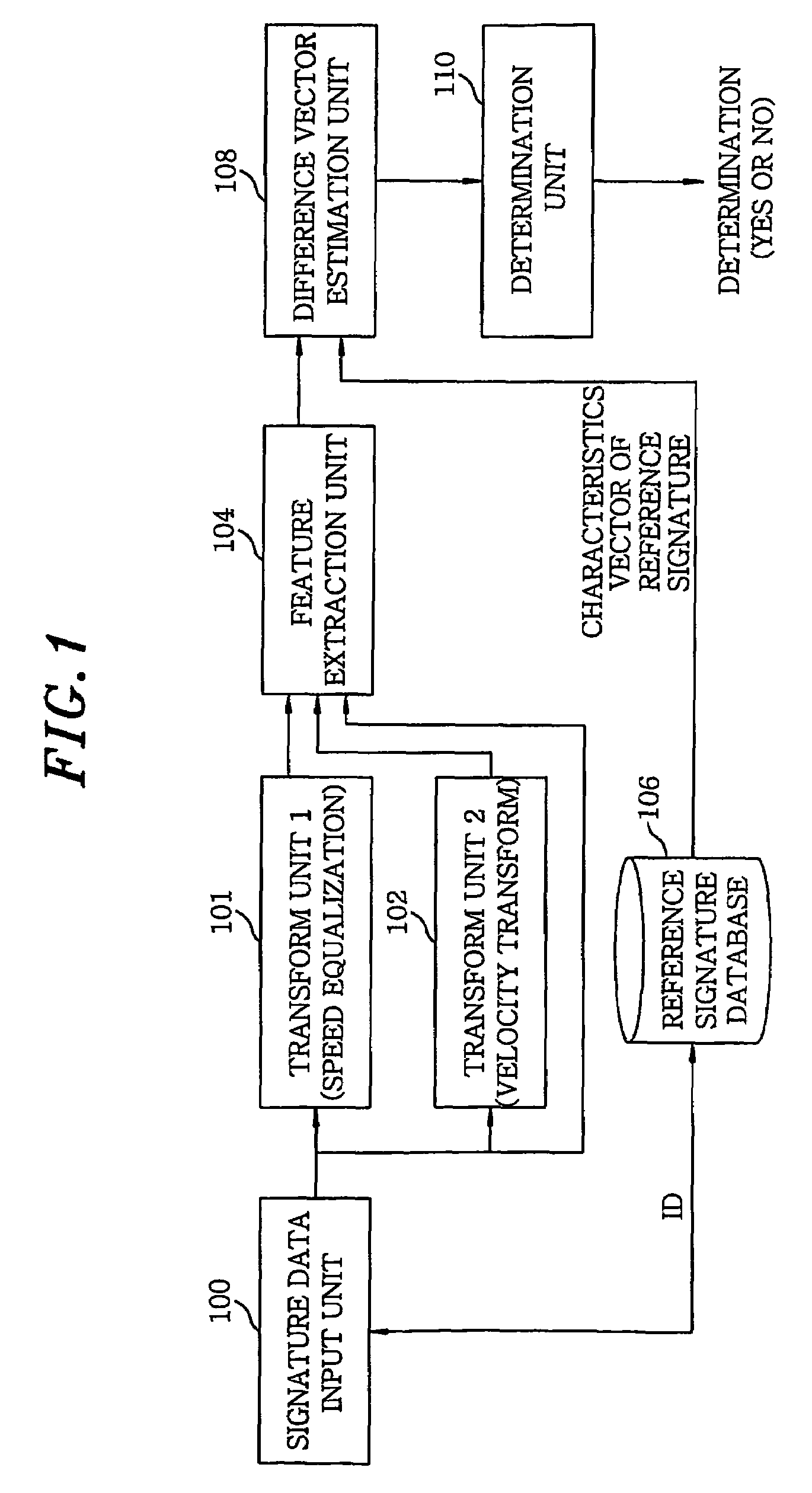
Apparatus for online signature verification using pattern transform technique and method therefor
InactiveUS7454042B2Securely verifiesImprove discriminationDigital computer detailsElectric digital data processingPattern sequenceOnline signature
In an apparatus for online signature verification, a signature data input unit digitalizes a locus of a user signature and reads the locus as a sequence of points. A first and a second pattern transform unit performs a speed equalization and a velocity transform on the signature sequence and generates a first and a second transformed pattern sequence, respectively. A characteristics extraction unit extracts three characteristics vectors from the signature sequence, the first and the second transformed pattern sequence, respectively, to thereby generate the three characteristics vectors. A difference vector estimation unit generates a difference vector. A determination unit determines whether an input signature and the reference signature are signed by a single person.
Owner:ELECTRONICS & TELECOMM RES INST
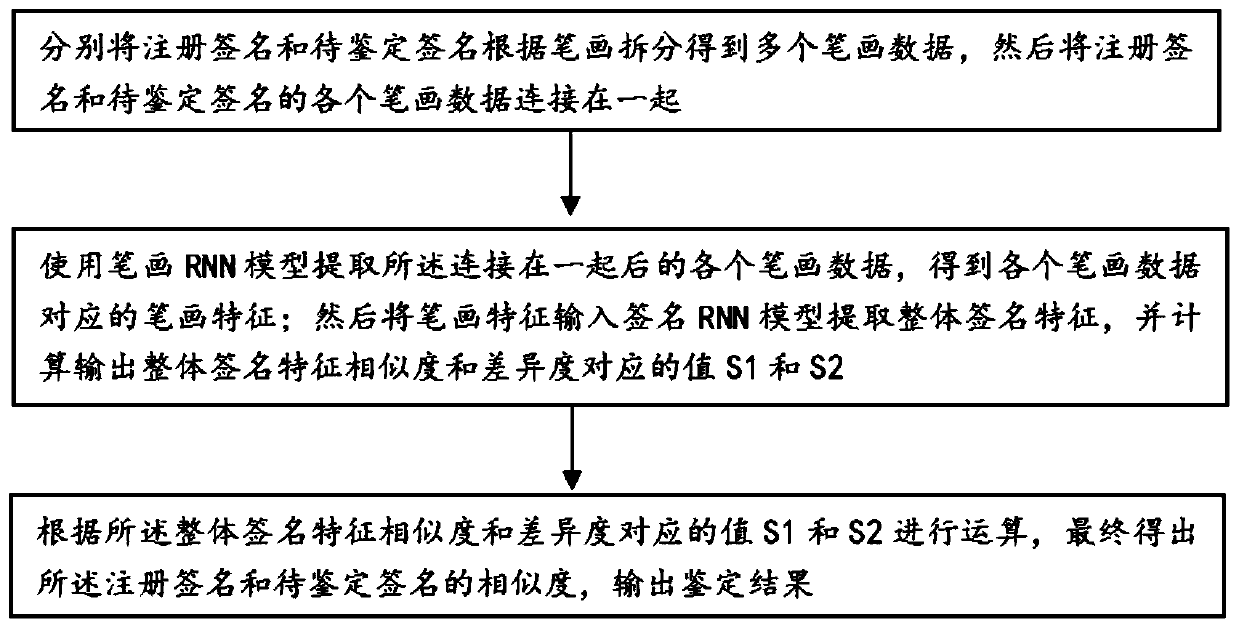
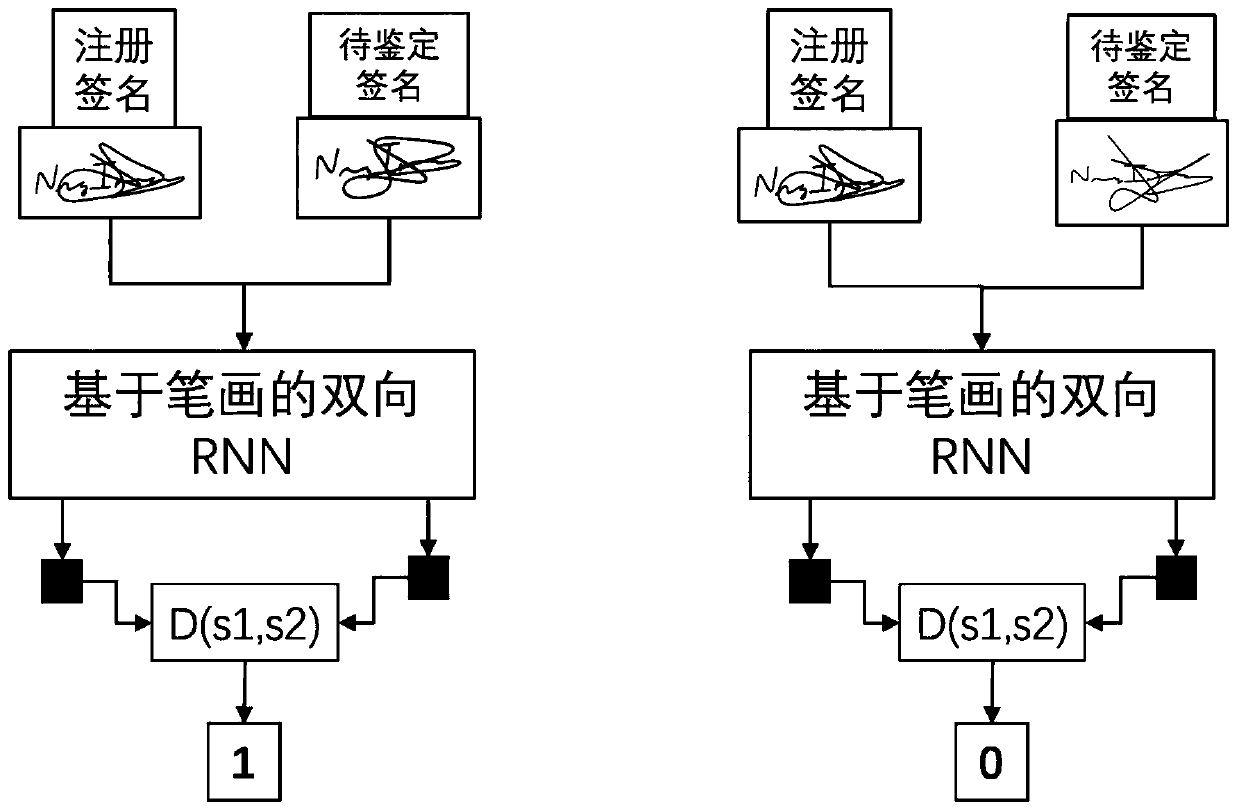
User-independent online signature recognition method and device based on RNN model
PendingCN111461015AImprove accuracyStrong anti-overfitting abilityCharacter and pattern recognitionNeural architecturesOnline signatureData connection
The invention provides a user-independent online signature recognition method and device based on an RNN model. The method comprises the steps that a registration signature and a to-be-authenticated signature are split according to strokes to obtain multiple parts of stroke data, then the stroke data of the registration signature and the stroke data of the to-be-authenticated signature are connected together, and the registration signature is a signature registered by a user in advance; extracting the connected stroke data by using a stroke RNN model to obtain stroke features corresponding tothe stroke data; inputting the stroke features into a signature RNN model to extract overall signature features, and calculating values S1 and S2 corresponding to similarity and difference of the overall signature features; and performing operation according to the values S1 and S2 corresponding to the overall signature feature similarity and the difference degree, finally obtaining the similaritybetween the registered signature and the signature to be authenticated, and outputting an authentication result. According to the method, fewer features and fewer training samples are used, the precision is improved, and the training speed and the running speed are higher.
Owner:CHINA FINANCIAL CERTIFICATION AUTHORITY
Method and system for signature authentication based on elliptical curve
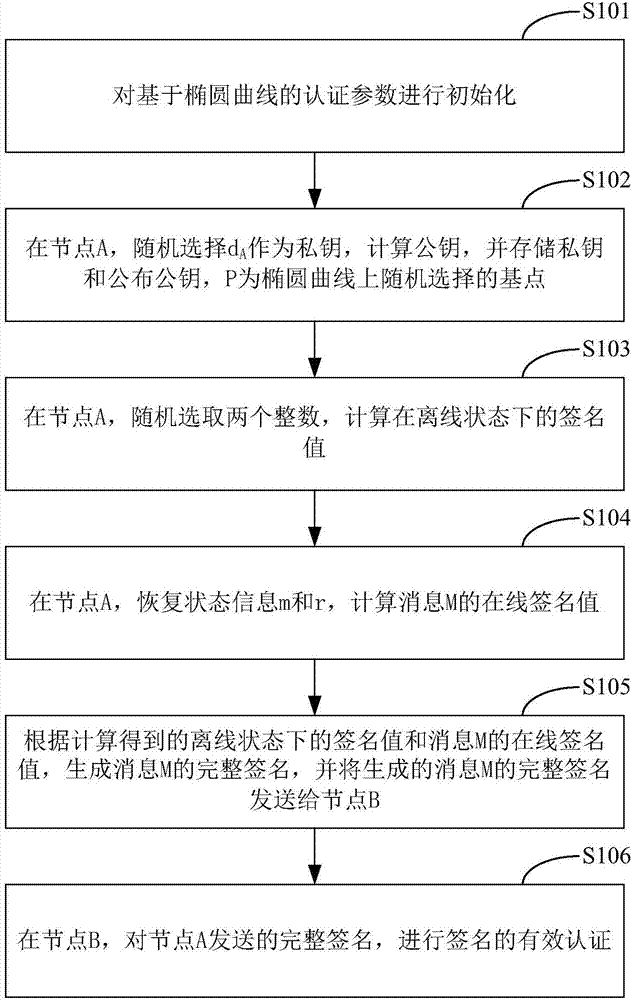
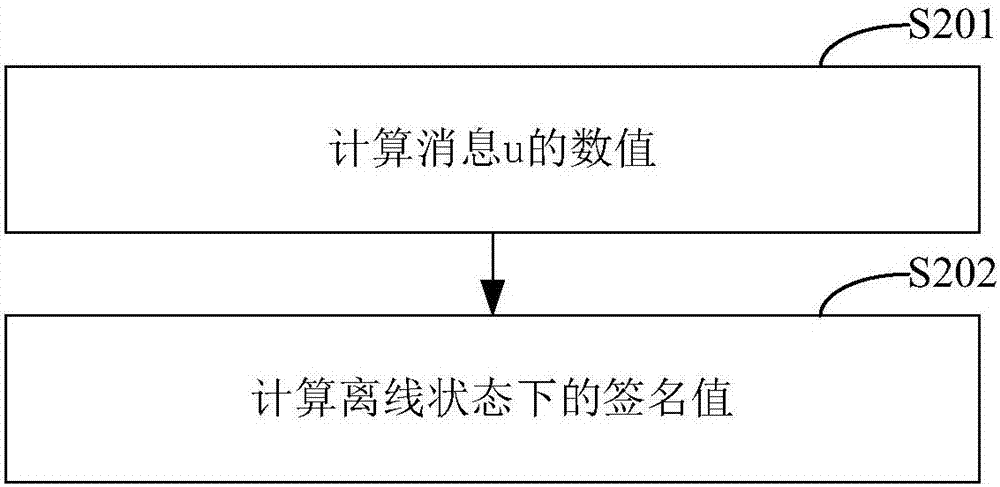
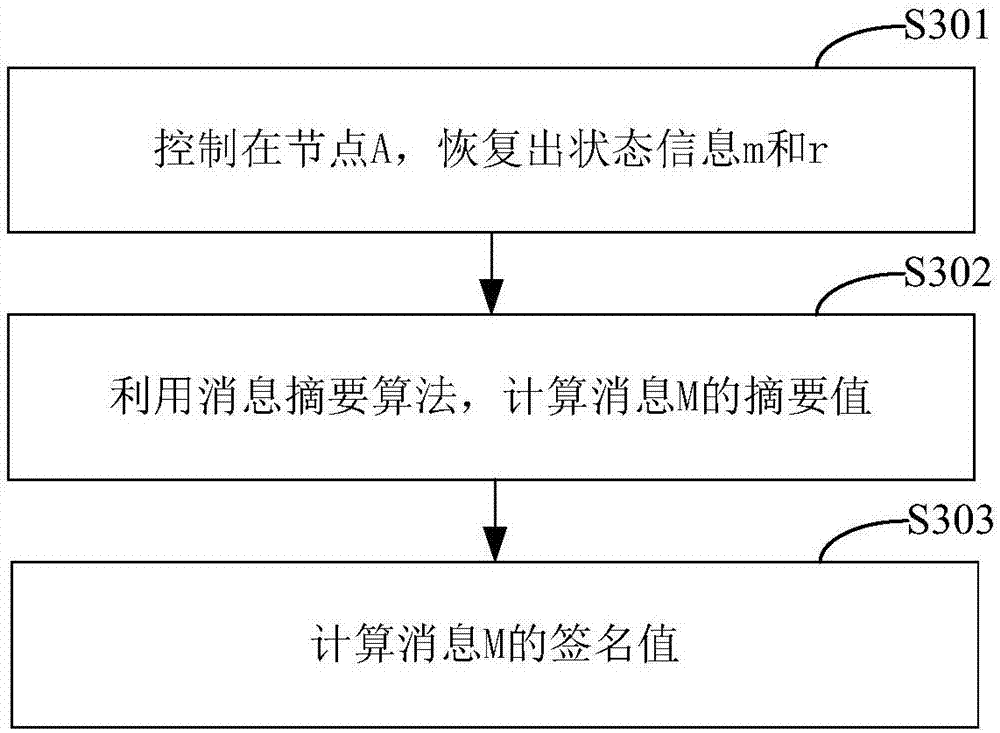
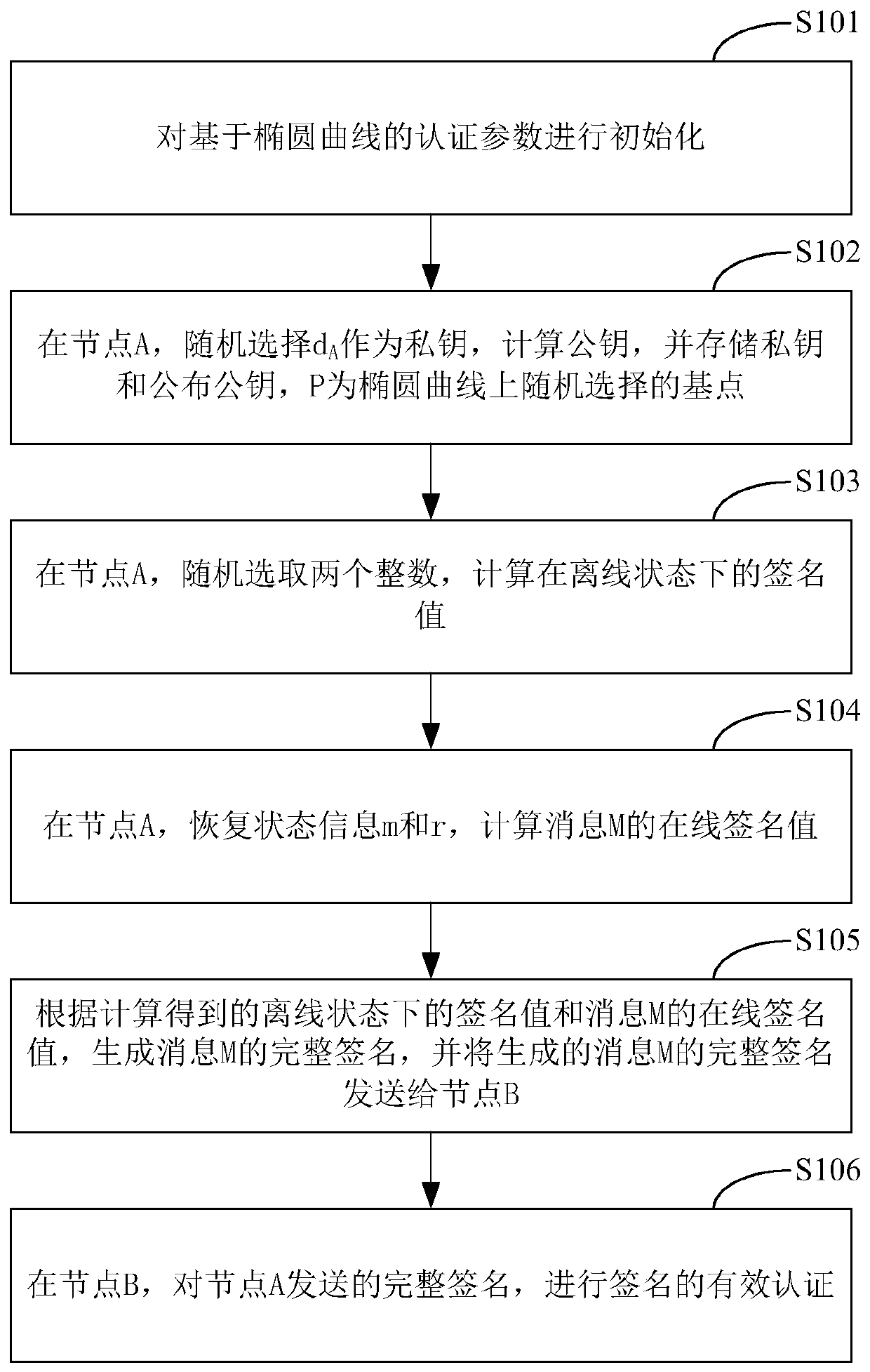
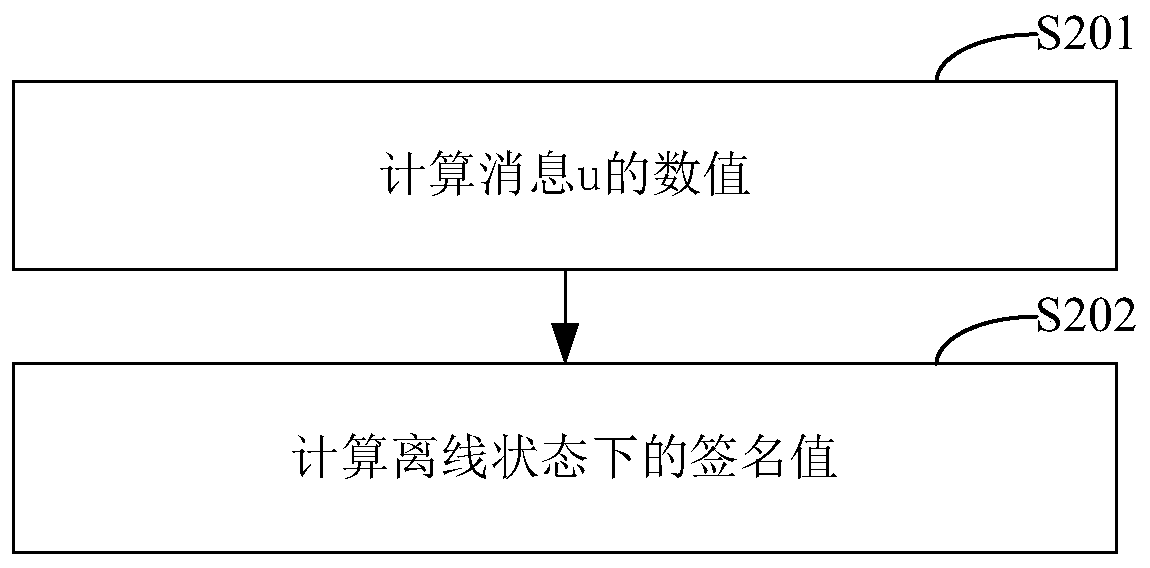
ActiveCN107171807AImprove verification speedEncryption apparatus with shift registers/memoriesPublic key for secure communicationOnline signatureBody area network
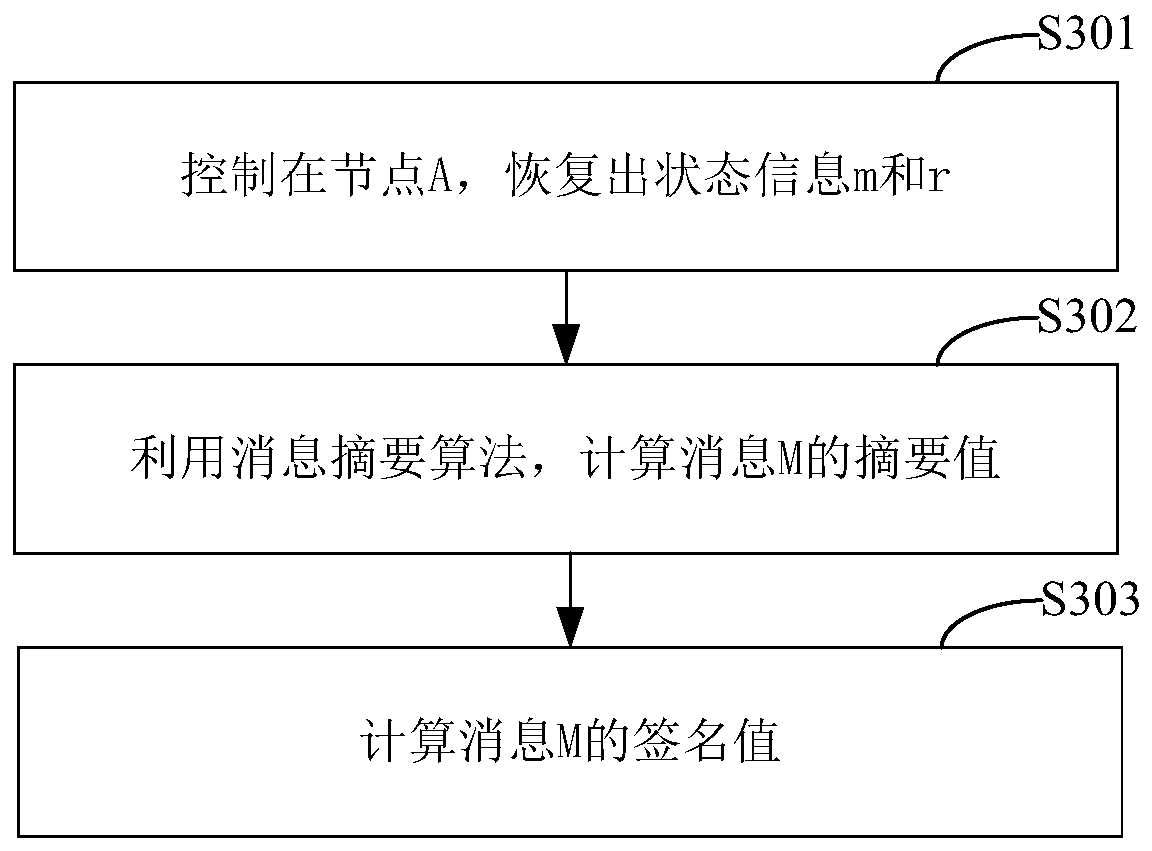
The invention belongs to the technical field of body area network node authentication and provides a method and a system for signature authentication based on an elliptical curve. The method comprises the following steps of initializing authentication parameters based on the elliptical curve; at a node A, randomly selecting (formula) as a private key, computing a public key QA=Dap=(QAx, QAy), storing the private key and publishing the public key (G1, G2, H, P, QA); at the node A, randomly selecting two integers m, wherein r belongs to ZP, and computing a signature value sigma' in an offline state; at the node A, recovering state information m and r and computing an online signature value r' of a message M; generating a complete signature sigmaM of the message M according to the signature value sigma' in the offline state and the online signature value r' of the message M which are obtained by computation, and sending the generated complete signature sigmaM of the message M to a node B; and at the node B, carrying out effective authentication of the signature on the complete signature sigmaM sent by the node A. according to the method and the system, the signature authentication based on the elliptical curve is realized, and the calculated quantity for signature and verification is effectively reduced and the signature verification speed is improved.
Owner:国康中健(北京)科技有限公司
Financial management system and method based on real supply chain
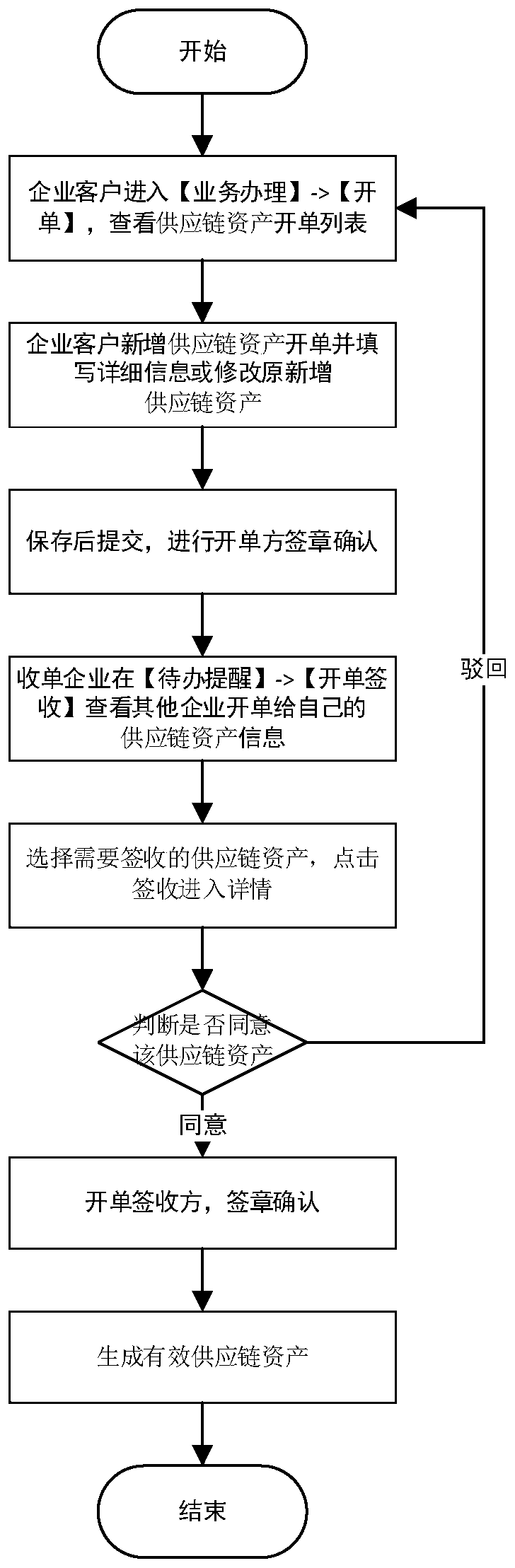
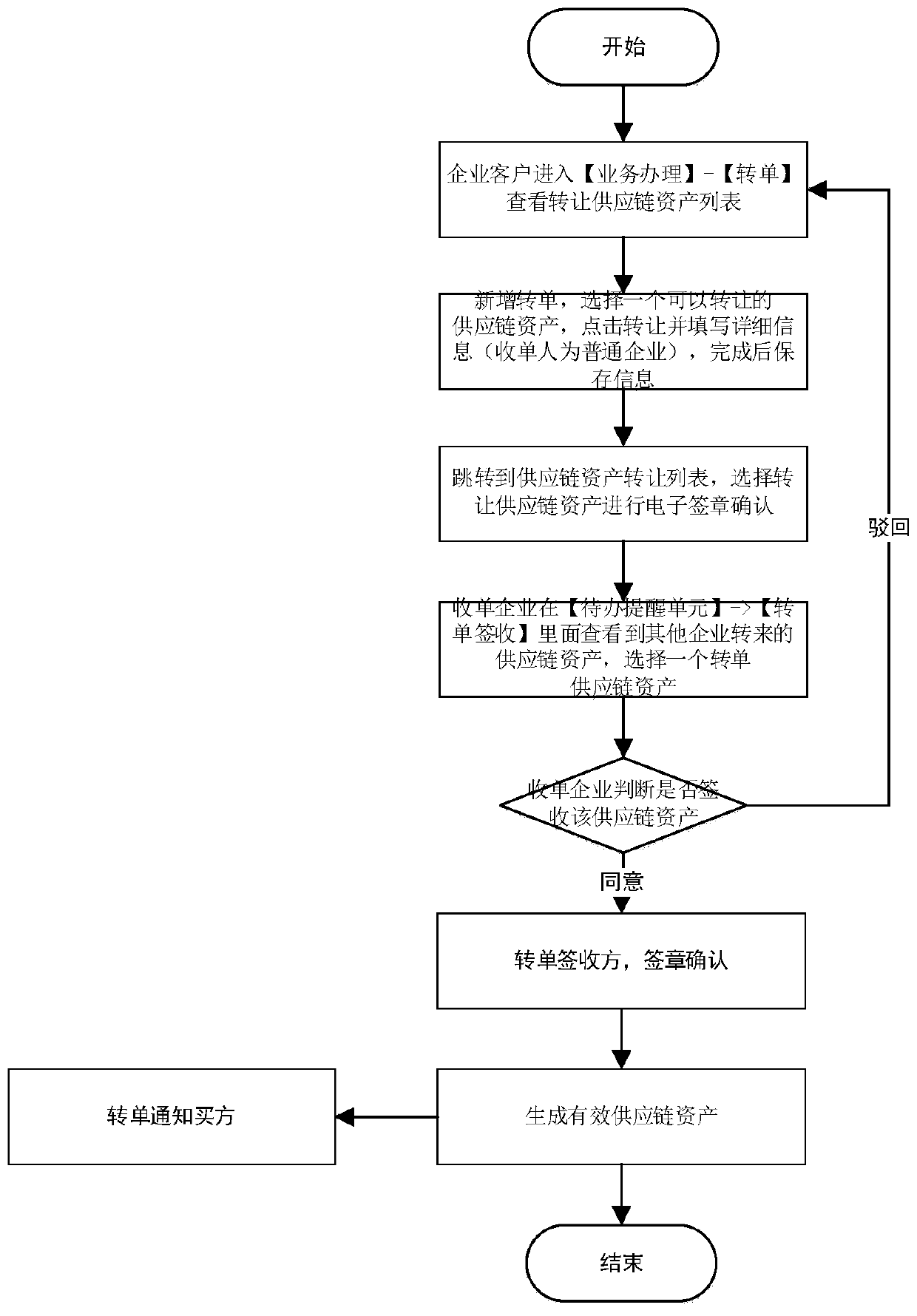
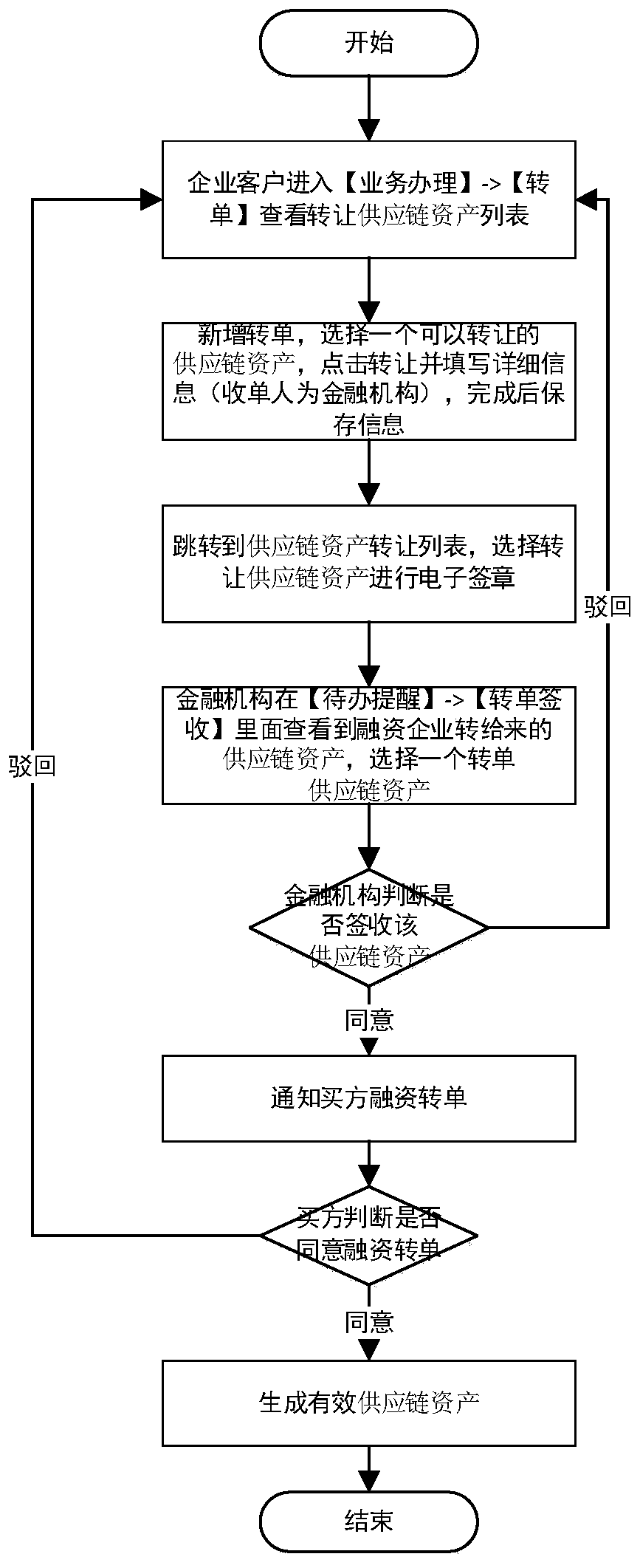
PendingCN110610427AGuarantee authenticityIncrease payment commitmentFinanceOffice automationOnline signatureThird party
The invention relates to the field of financial data management. The invention provides a financial management system and method based on a real supply chain. The invention discloses a financial management system based on a real supply chain and a financial management method based on the real supply chain. Asset financing can be completed only by using a supply chain financing user of a financialmanagement system intelligent terminal provided with a mobile supply chain, a certificate is generated on line from underlying supply chain assets based on real transaction of buyers and sellers, andthe certificate is confirmed by online signature of the buyers and sellers; the buyer or the seller uploads an invoice, the buyer or the seller corresponding to the invoice, the invoice amount and theinvoice number can be automatically recognized through a self-built OCR invoice recognition system, and a third-party platform is called according to the invoice number to verify the authenticity ofthe invoice; generated supply chain asset buyers and sellers can initiate, any party initiates, the other party confirms and finances that complete trade information is contained, and payment commitments of the buyers are increased. And splitting, transferring and financing the supply chain asset voucher on line.
Owner:深圳宏鹏数字供应链管理有限公司
Online signature identification method based on sample synthesis and sorting learning
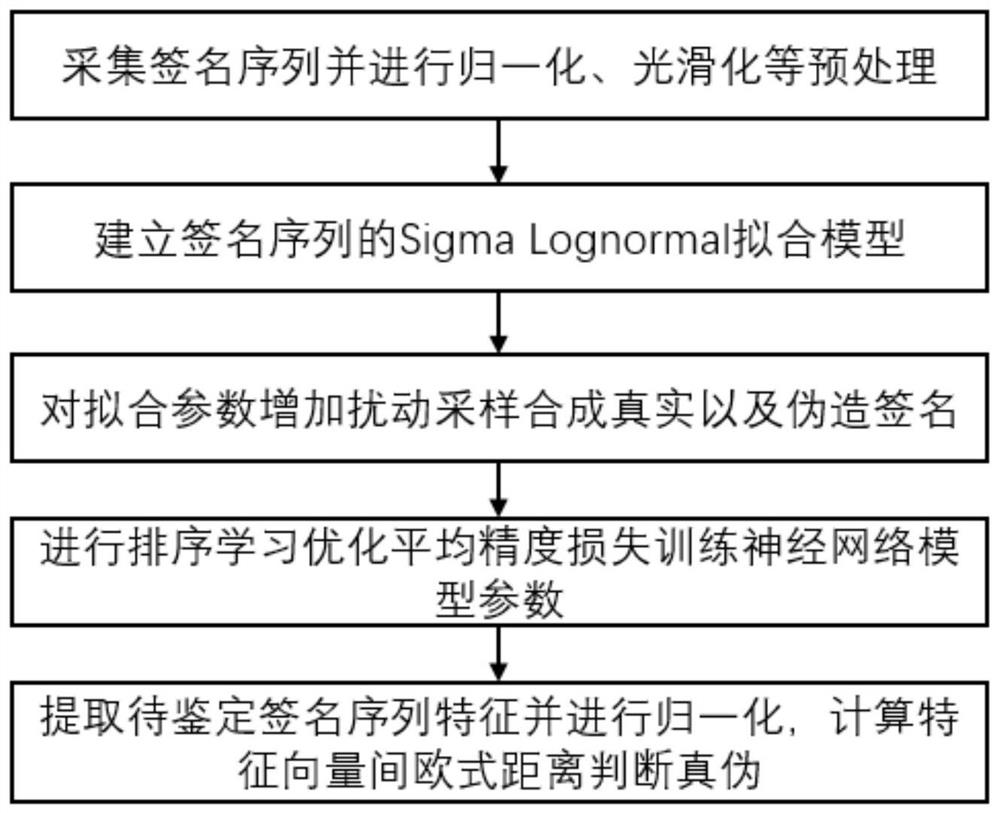
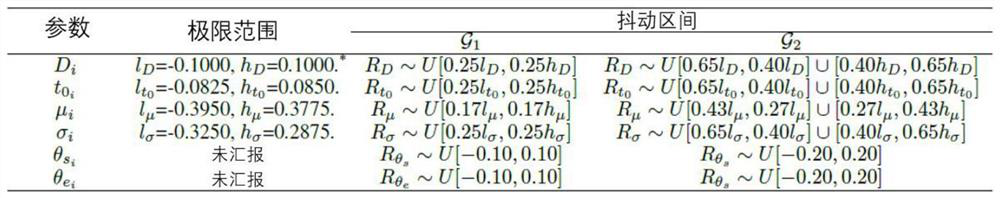
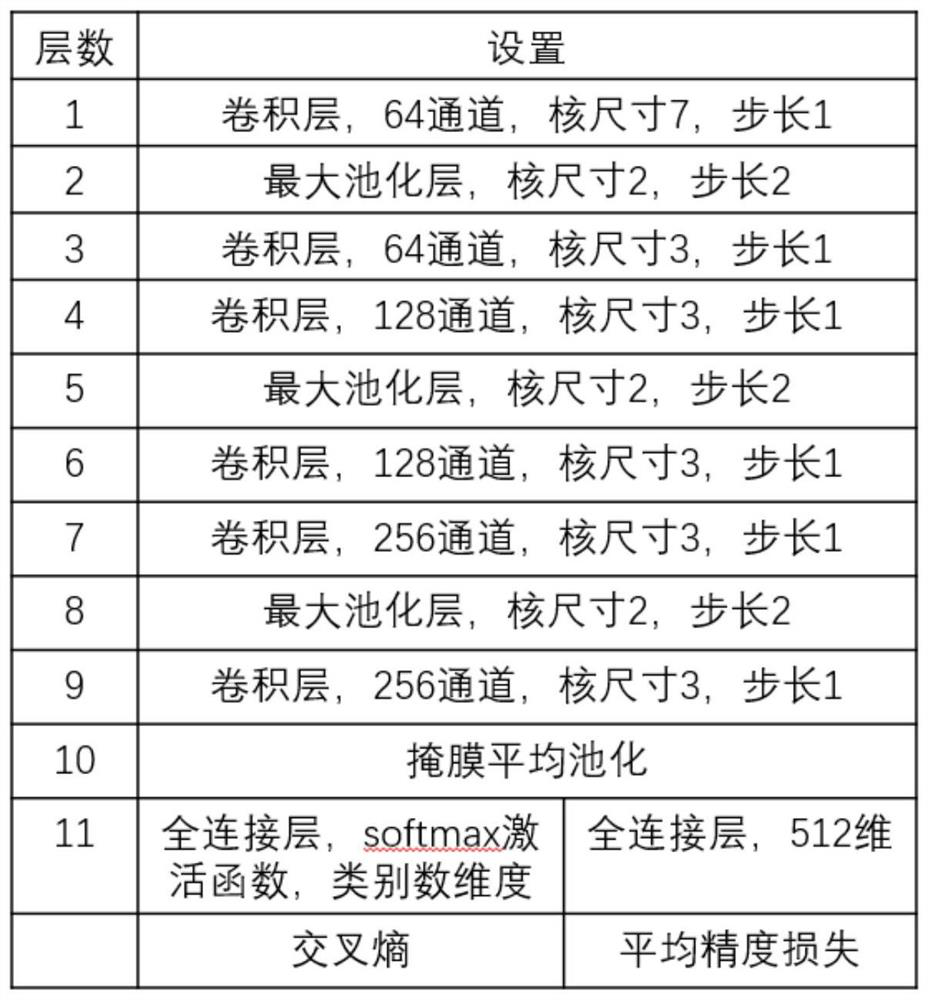
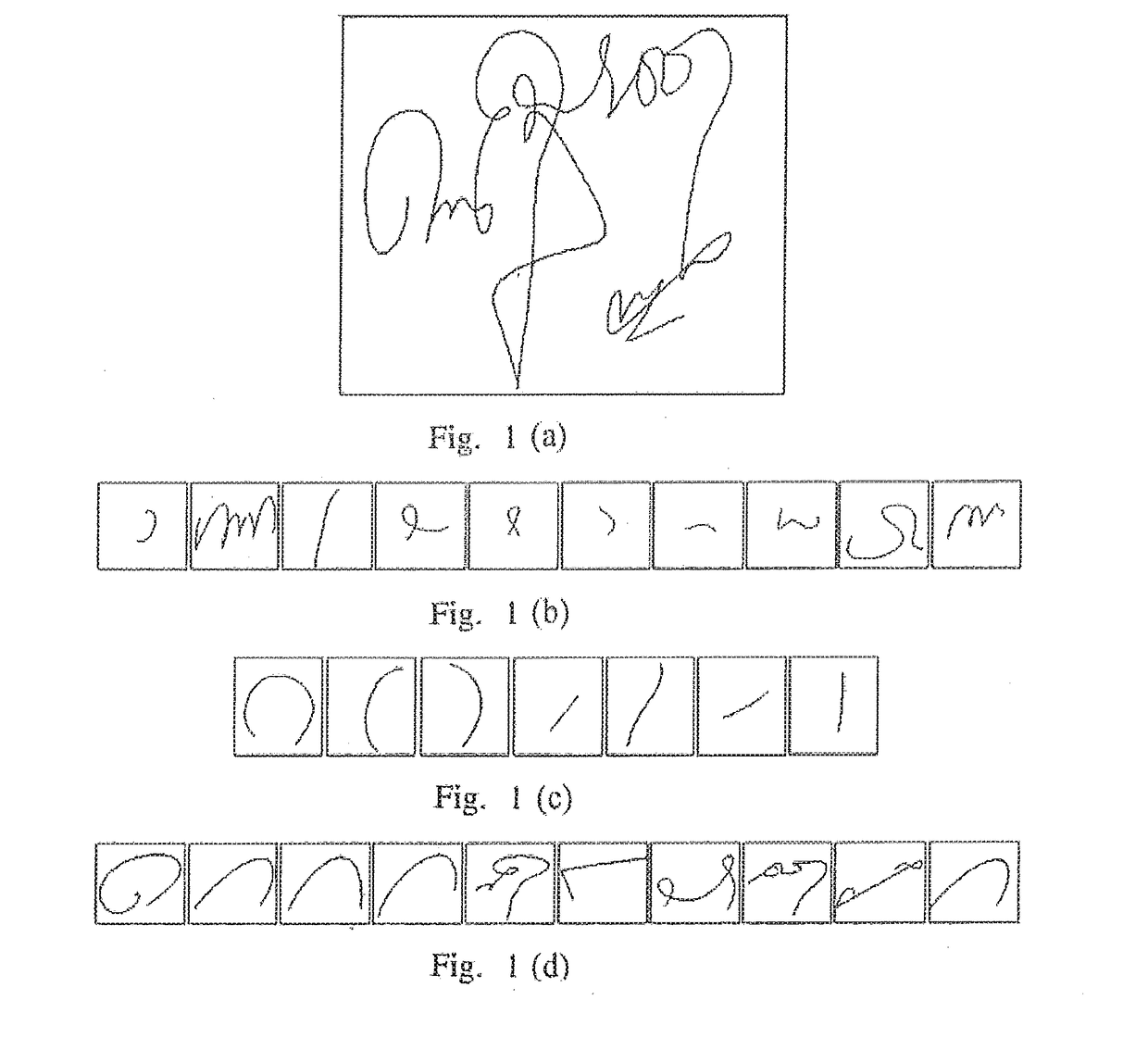
PendingCN112699349ASolve difficult to obtain difficultiesSolve problems that are prone to ambiguityDigital data authenticationNeural architecturesOnline signatureFeature vector
The invention discloses an online signature identification method based on sample synthesis and sorting learning. The method comprises the following steps: acquiring a signature sequence and preprocessing the signature sequence; establishing a Sigma Lognormal fitting model of the signature sequence; adding disturbance sampling to the fitting parameters to synthesize a real signature and a forged signature; carrying out sorting learning to optimize average precision loss training neural network model parameters; and for the signature sequence to be identified, extracting features by using the trained neural network model, normalizing the features, and calculating an Euclidean distance between feature vectors to judge authenticity. According to the online signature identification method, the problem that forged samples are difficult to obtain in an online signature identification task is solved, the Sigma Lognormal model is used for generating the samples, collection of forged signature data is not depended on any more, sorting learning is carried out to learn correlation and similarity information between the signature samples, and the high-precision online signature identification method is achieved. The invention has the characteristics of high accuracy, good adaptability and the like, and has good practical value.
Owner:SOUTH CHINA UNIV OF TECH +1
Online signature identification method and system
The invention discloses an online signature identification method and system. In different application occasions of electronic signature identification, contradiction between accuracy and cost is solved. The method comprises the steps that electronic signature sample collection is carried out by taking population as a target; when each person in the population is registered, multiple samples are collected to form a sample library of the population; whether a specified signature is corresponding to a designated person object is identified; if the specified signature is not corresponding to the designated person object, an identification process is ready to start; before identification starts, an identification algorithm is adjusted according to a preset straying rate and false rejection rate; and the identification process is carried out to find out the real signer from the sample library of the population. According to the invention, a flexible electronic signature judging method is ultimately realized; a reasonable work method is selected according to different application occasions; and high identification accuracy or low cost is realized.
Owner:SOUTHWEST UNIVERSITY
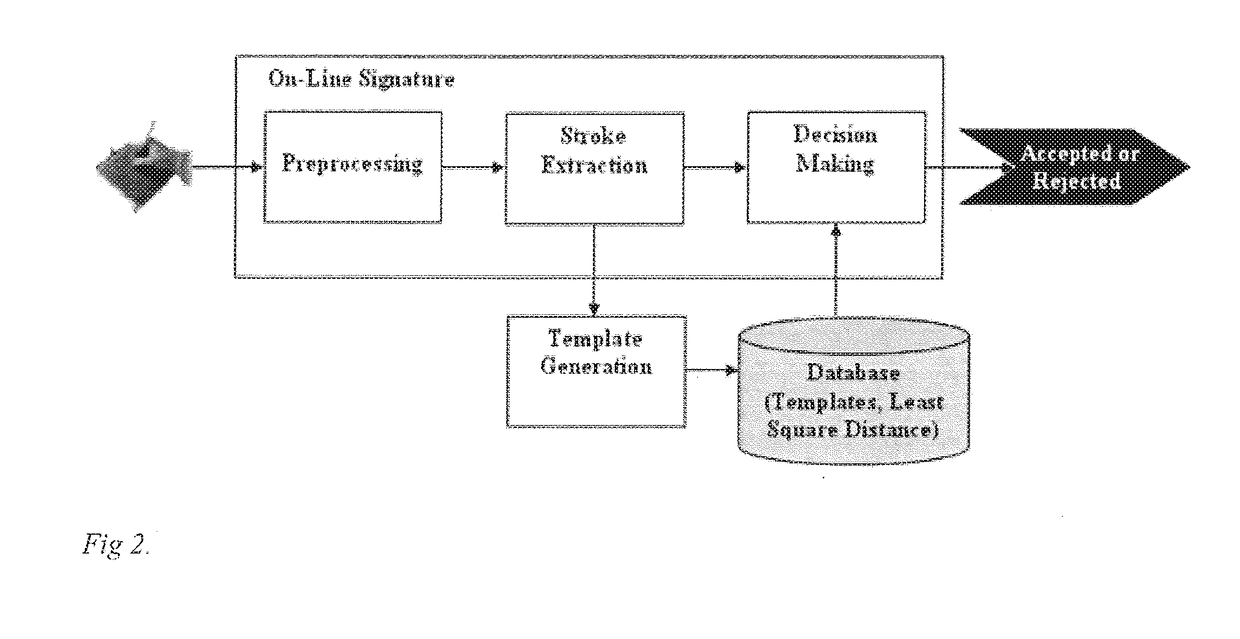
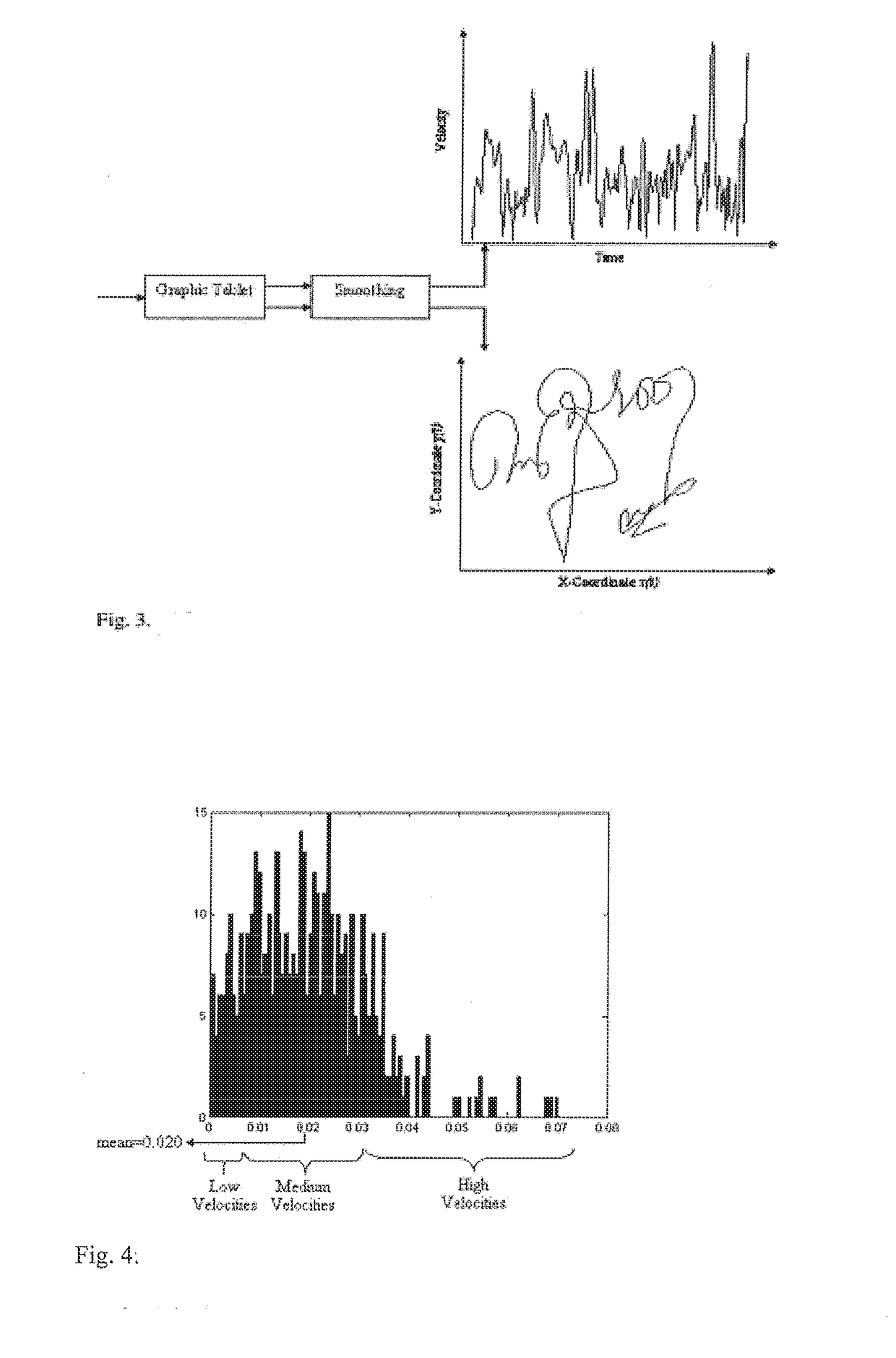
Velocity-based online signature verification system and method
InactiveUS20180349677A1Reduced implementation timeSave computing resourcesCharacter and pattern recognitionDigital data authenticationOnline signatureVerification system
A method of calculating the authenticity of a signature acquired online from a touch sensitive computer display within a mobile or stationary device comprises comparing extracted strokes from a second signature to those of a known genuine signature to determine the degree of matching. The strokes are obtained by decomposing the velocity image of each signature into low medium, and high velocity portions; decomposing the medium velocity portion into two partitions; and extracting strokes from each partition into contiguous parts.
Owner:EFFAT UNIVERSITY
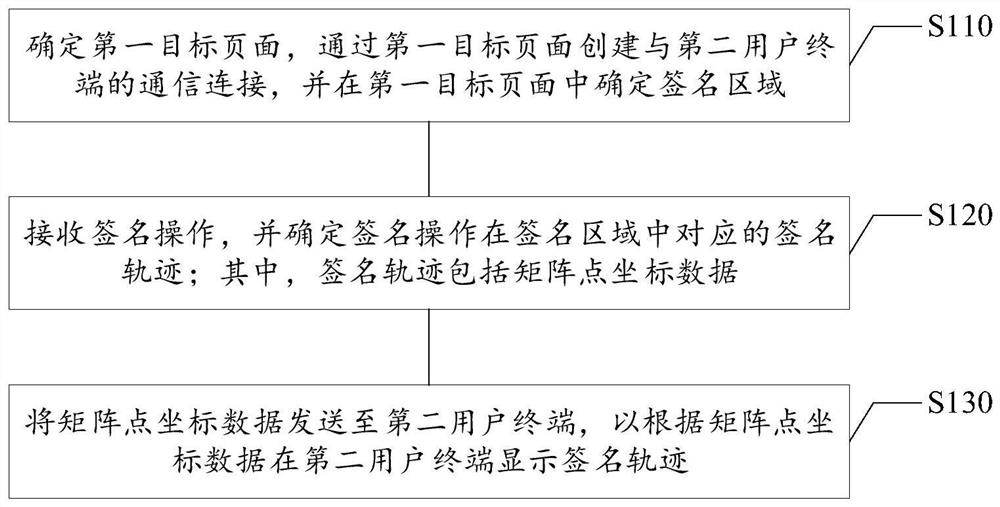
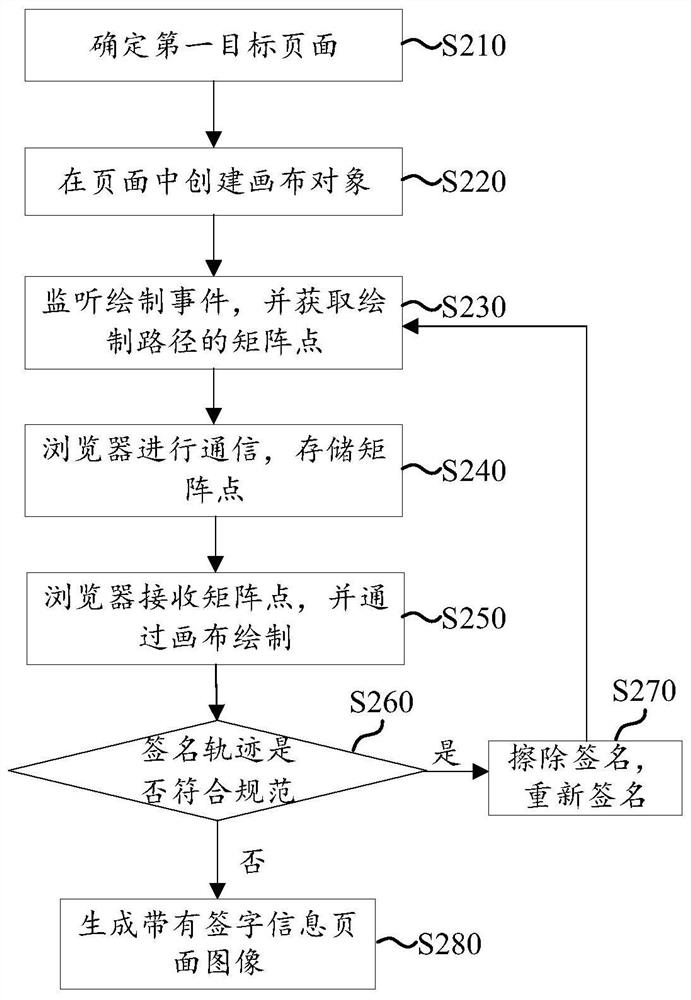
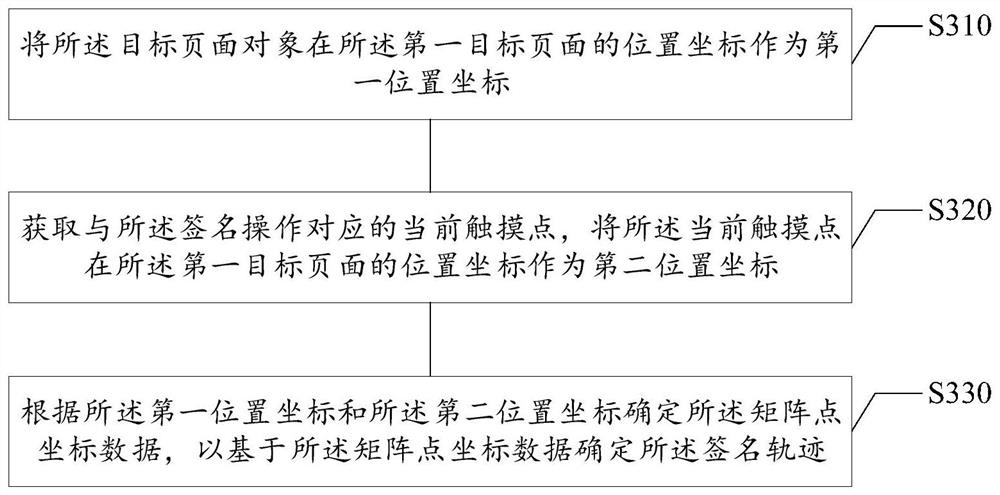
Online signature method and device, electronic equipment and computer readable storage medium
PendingCN111756787AImprove experienceShorten the timeTransmissionSignature reading/verifyingOnline signatureComputer network
The invention relates to an online signature method and device, electronic equipment and a computer readable storage medium, relates to the technical field of computers, and can be applied to a sceneof online signature of a user. The online signature method comprises the following steps: determining a first target page, creating a communication connection with a second user terminal through the first target page, and determining a signature area in the first target page; receiving a signature operation, and determining a signature track corresponding to the signature operation in the signature area, wherein the signature track comprises matrix point coordinate data; and sending the matrix point coordinate data to a second user terminal so as to display the signature track at the second user terminal according to the matrix point coordinate data. According to the invention, a solution for realizing online signature can be provided, so that the user can sign online in real time, an opposite user can check the current signature state in real time, and the user does not need to go to the scene personally or print a signature page to send the signature to the opposite user.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
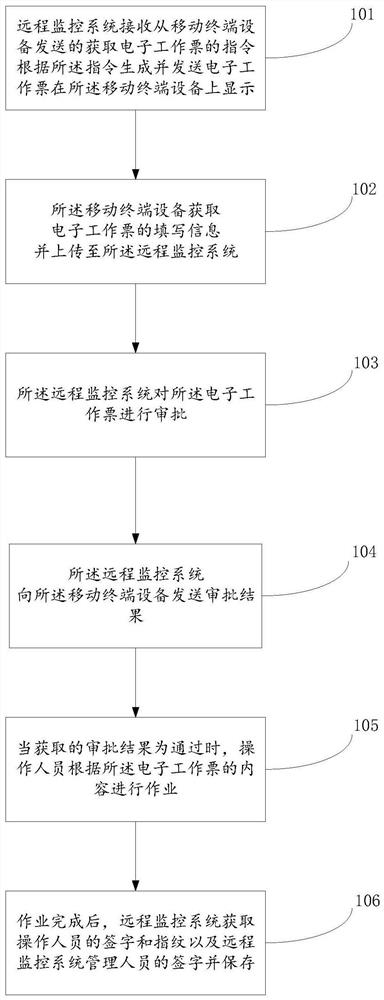
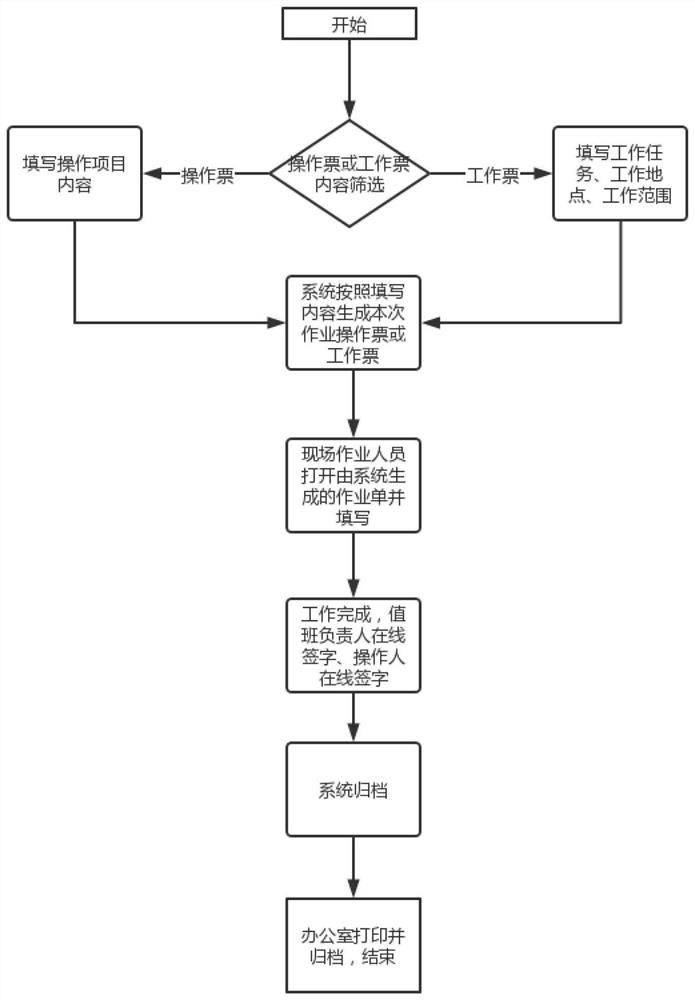
Electronic work ticket management method
PendingCN113850569ARealize paperless operationImprove work efficiencyOffice automationTicketPaperless office
The embodiment of the invention discloses an electronic work ticket management method. A database and a work ticket auditing system are established in a remote monitoring system, various electronic work tickets are preset in the database, all operation tickets and work tickets are fused to form a unified management interface, and corresponding work forms can be generated according to different work contents. An electronic work ticket is obtained through mobile terminal equipment, an operator is guided to work according to the content of the electronic work ticket, and after the work is completed, online signature and fingerprint recording are performed to confirm that the work is directly uploaded to the remote monitoring system. The working process of backfilling an operation ticket is replaced, paperless operation is achieved, and the working efficiency is improved.
Owner:GUANGDONG POWER GRID CO LTD DONGGUAN POWER SUPPLY BUREAU
Biocharacteristics fusioned identity distinguishing and identification method
This invention relates to a sorter integration and mode identification field characterizing in obtaining characters of man-face, iris, on-line signature and off-line handwriting of a user by various collecting devices then sending them to corresponding certification sub-modules to pick up the characters and match with the molding boards and outputting the matched marks to be normalized and sent to an identification combined module to get the final identification result by confidence integration or sent to a certification module to be imaged to a multi-dimension space to be sorted by a sorter to get a final result or to be certified and combined to get the final identification result.
Owner:TSINGHUA UNIV
Online and offline circulating unbalanced oil and vinegar signature method
ActiveCN107947943ALow computing resource requirementsReduce performanceUser identity/authority verificationComplex mathematical operationsOnline signatureDigital signature
The invention discloses an online and offline circulating unbalanced oil and vinegar signature method. The method decomposes a traditional unbalanced oil and vinegar signature process into an offlinepart and an online part, wherein offline steps are independent of a signature message and can be performed in advance, and a circulating computation method is combined and used during a computing process for enhancing performance. When the online part needs the signature, a computing result stored in the offline steps are combined and used for completing final signature operation. The method provided by the invention is an unbalanced oil and vinegar signature scheme based on a multi-variable public key cryptosystem, a lightweight digital signature scheme applicable to low-performance electronic equipment. The method provided by the invention divides an unbalanced oil and vinegar signature algorithm is divided into the offline part and the online part, the computation of the offline steps can be performed in advance, and the online signature process can be accelerated while the energy can be more fully utilized. According to the method provided by the invention, in the computation of the offline steps, the circulating computation method is used, the size of he secret key is greatly reduced, and meanwhile the signature period is shortened.
Owner:SOUTH CHINA UNIV OF TECH
An online sign-off method, device and equipment
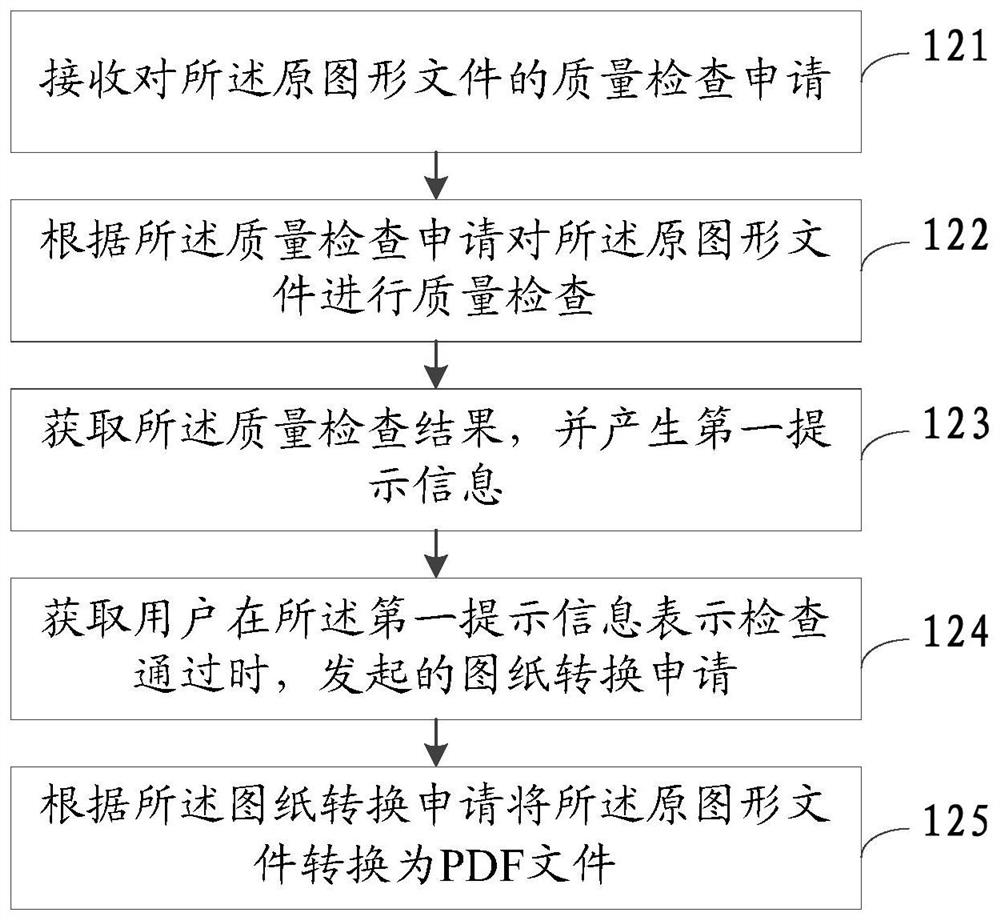
ActiveCN108388546BEnsure safetyImprove work efficiencyDigital data protectionNatural language data processingOnline signatureSoftware engineering
The invention discloses an online approval method, device and equipment. The online approval method includes: obtaining the original graphic file of the file to be approved uploaded by the user; After passing the inspection, convert the original graphics file into a PDF file for the user to review; obtain the graphics file re-uploaded after the user modifies the original graphics file according to the review comments, and convert it into PDF format; the graphics file in PDF format Add an electronic signature. The online signing and approval method of the embodiment of the present invention standardizes the format of the system drawings compared with paper signing drawings, ensures data security and standardization, saves costs, and improves the work efficiency of engineers.
Owner:BAIC GRP ORV CO LTD
A signature authentication method and system based on elliptic curve
ActiveCN107171807BImprove verification speedRealize Signature SeriouslyEncryption apparatus with shift registers/memoriesPublic key for secure communicationOnline signatureBody area network
The invention belongs to the technical field of body area network node authentication and provides a method and a system for signature authentication based on an elliptical curve. The method comprises the following steps of initializing authentication parameters based on the elliptical curve; at a node A, randomly selecting (formula) as a private key, computing a public key QA=Dap=(QAx, QAy), storing the private key and publishing the public key (G1, G2, H, P, QA); at the node A, randomly selecting two integers m, wherein r belongs to ZP, and computing a signature value sigma' in an offline state; at the node A, recovering state information m and r and computing an online signature value r' of a message M; generating a complete signature sigmaM of the message M according to the signature value sigma' in the offline state and the online signature value r' of the message M which are obtained by computation, and sending the generated complete signature sigmaM of the message M to a node B; and at the node B, carrying out effective authentication of the signature on the complete signature sigmaM sent by the node A. according to the method and the system, the signature authentication based on the elliptical curve is realized, and the calculated quantity for signature and verification is effectively reduced and the signature verification speed is improved.
Owner:国康中健(北京)科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com