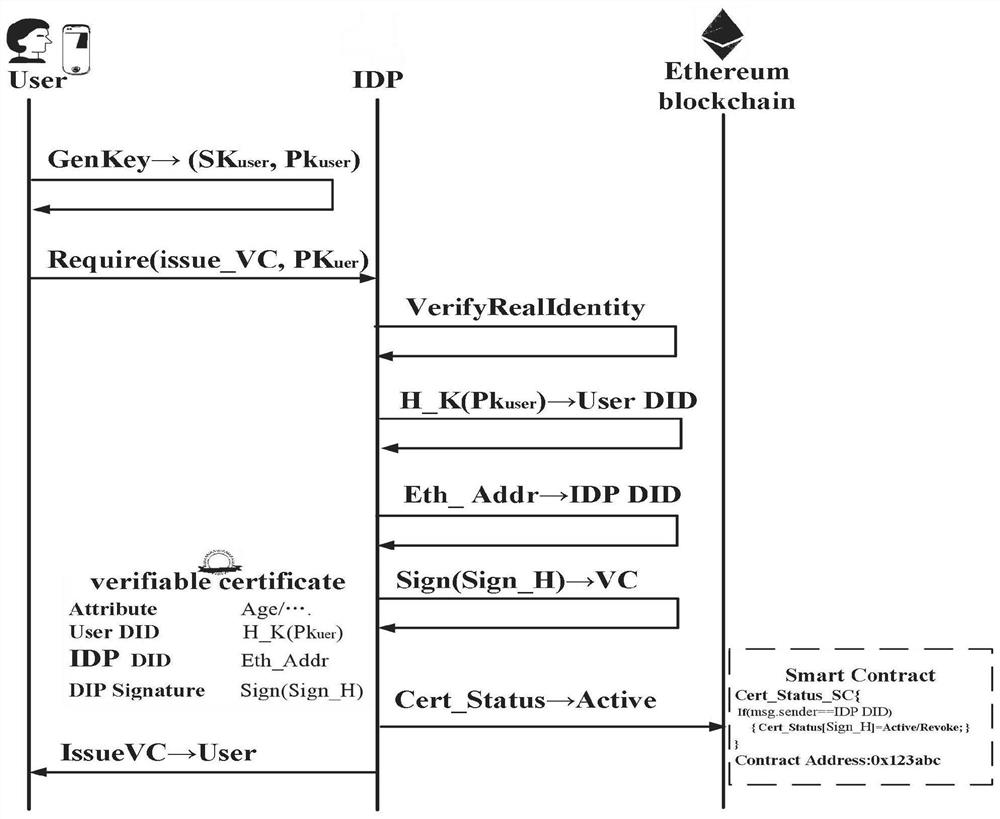
Patents
Literature
114results about How to "Ensure credible" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
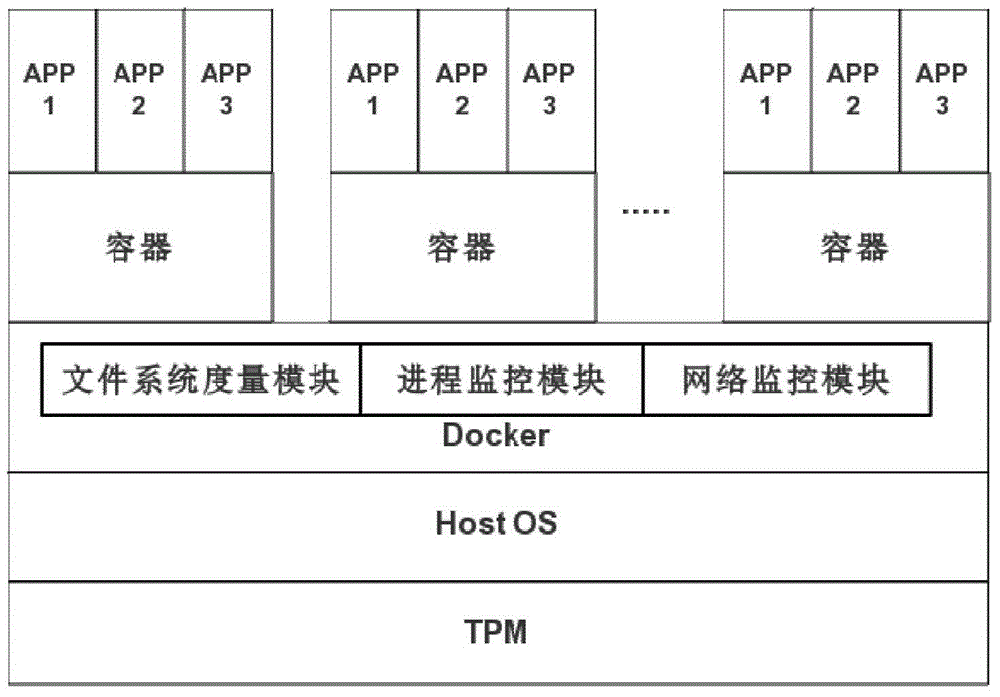
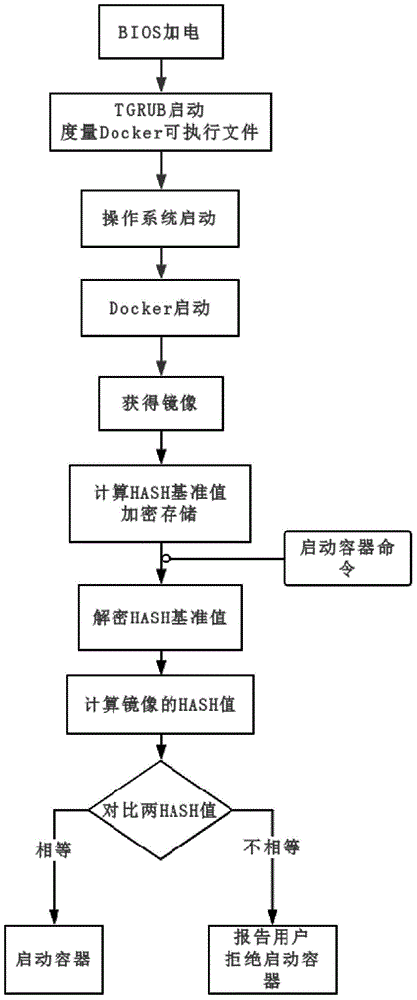
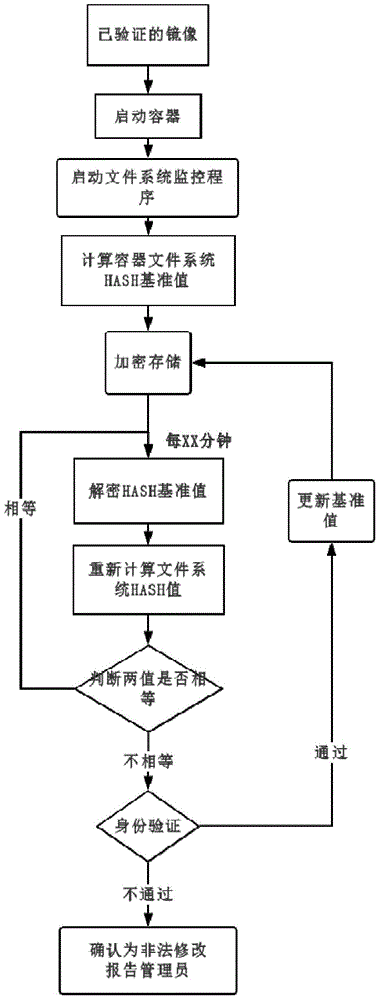
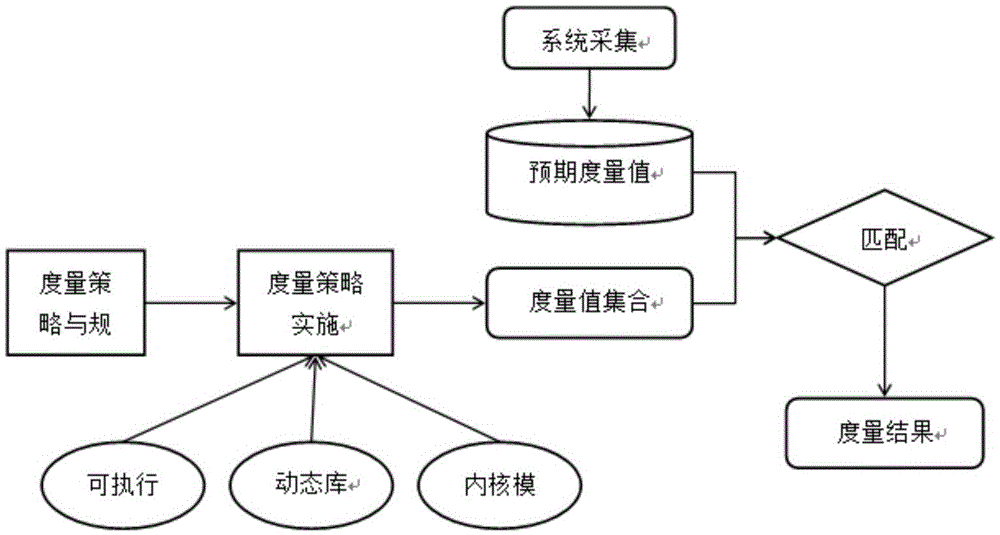
Security reinforcement method for credible container based on Docker
ActiveCN105069353ATrusted bootGuaranteed normal startupPlatform integrity maintainanceNetwork communicationMirror image
The invention discloses a security reinforcement method for a credible container based on Docker used for performing security reinforcement on a Docker container system, and realizes the credible container based on the Docker, as well is applied to a server cluster based on the Docker. The credible container based on the Docker comprises a container program Docker, a container credible measurement module, a progress monitoring module and a network communication monitoring module, wherein the container credible measurement module comprises a credible booting sub-module and a file measurement sub-module. The reinforcement method focuses on the credibility of the Docker container; a credible computing and integrity measurement technology is matched with a real-time monitoring module to reinforce the container system based on the Docker, so that the container and a mirror image are prevented from tampering; and meanwhile, a network communication behavior of the container is limited, and an inner progress of the container is monitored, so as to realize the security reinforced credible container.
Owner:WUHAN UNIV
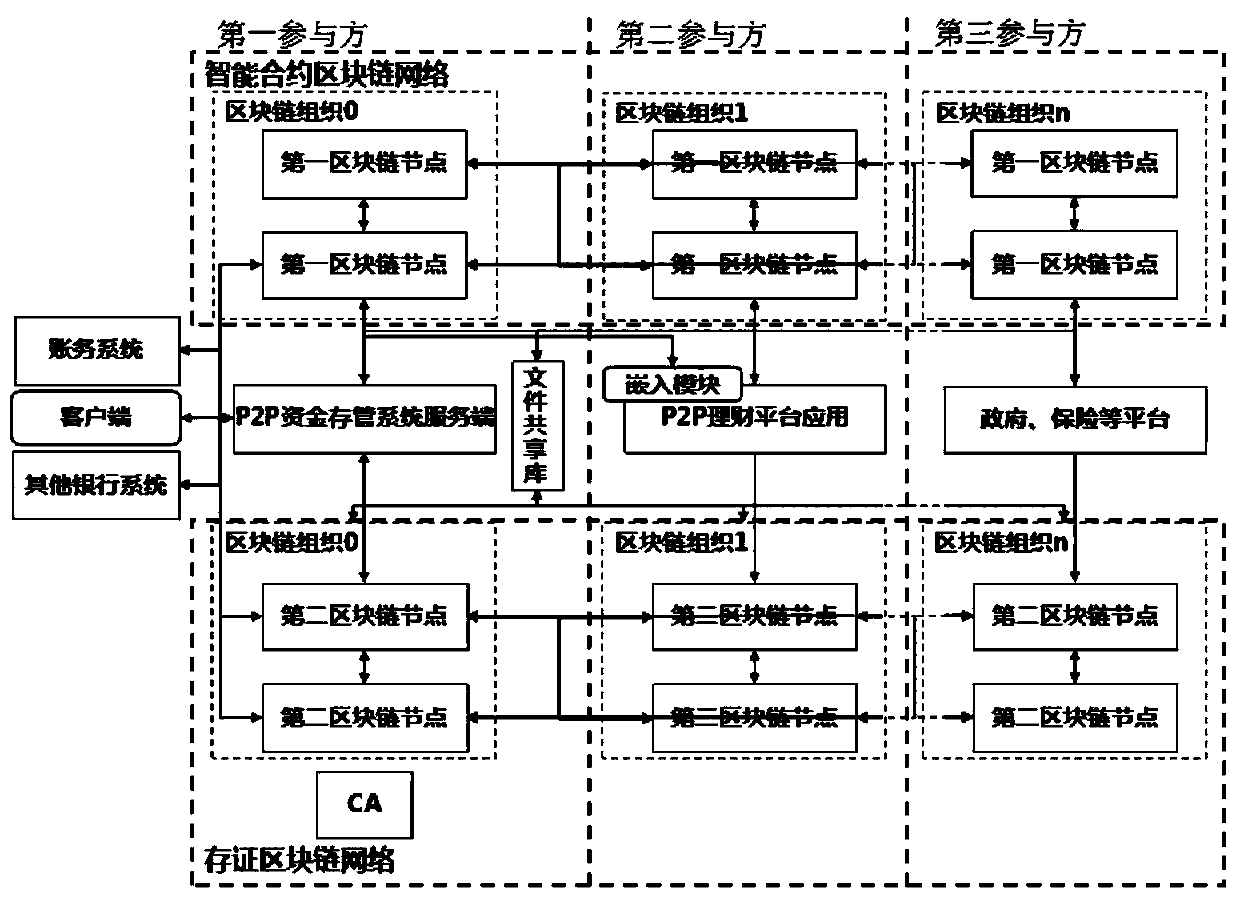
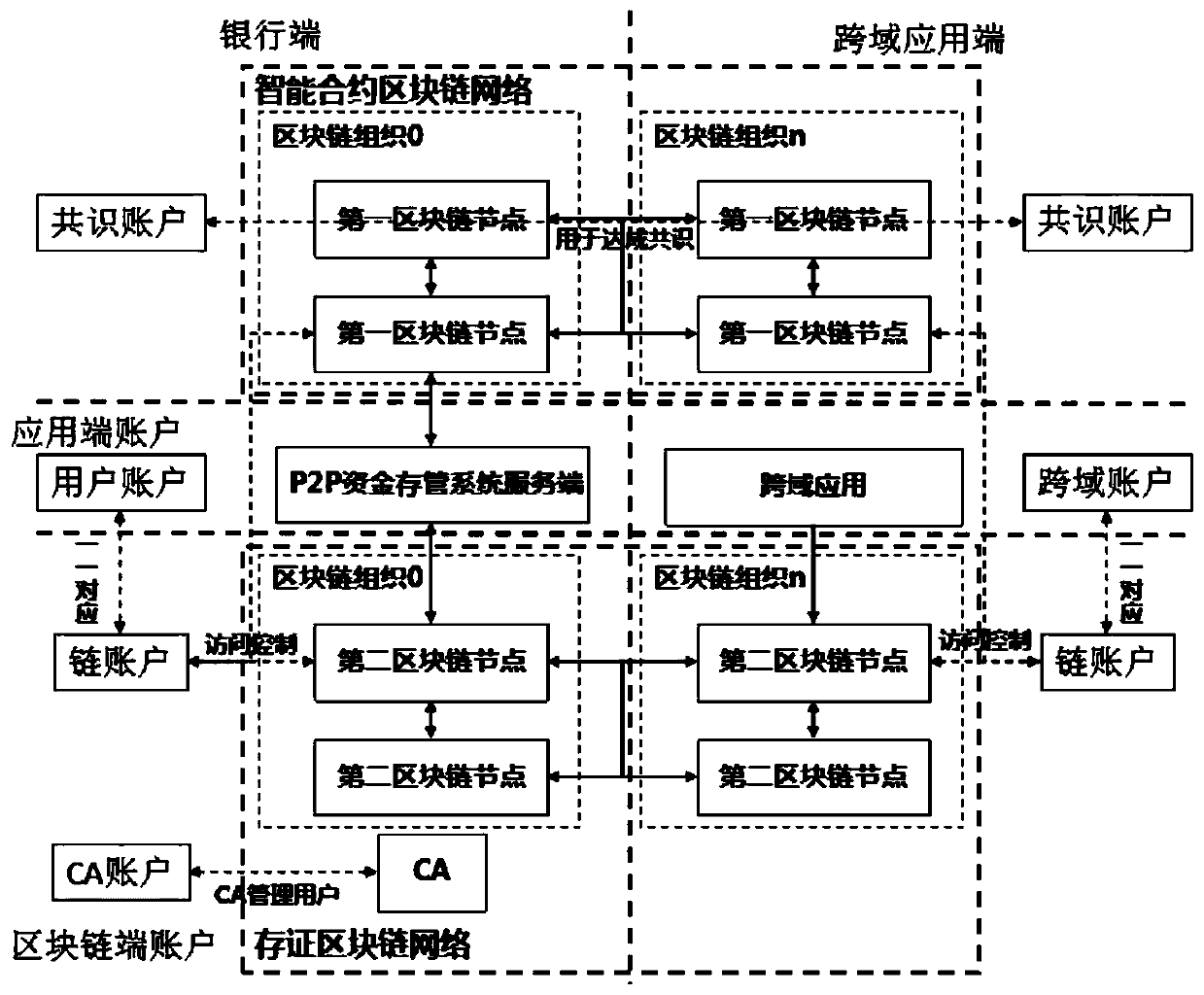
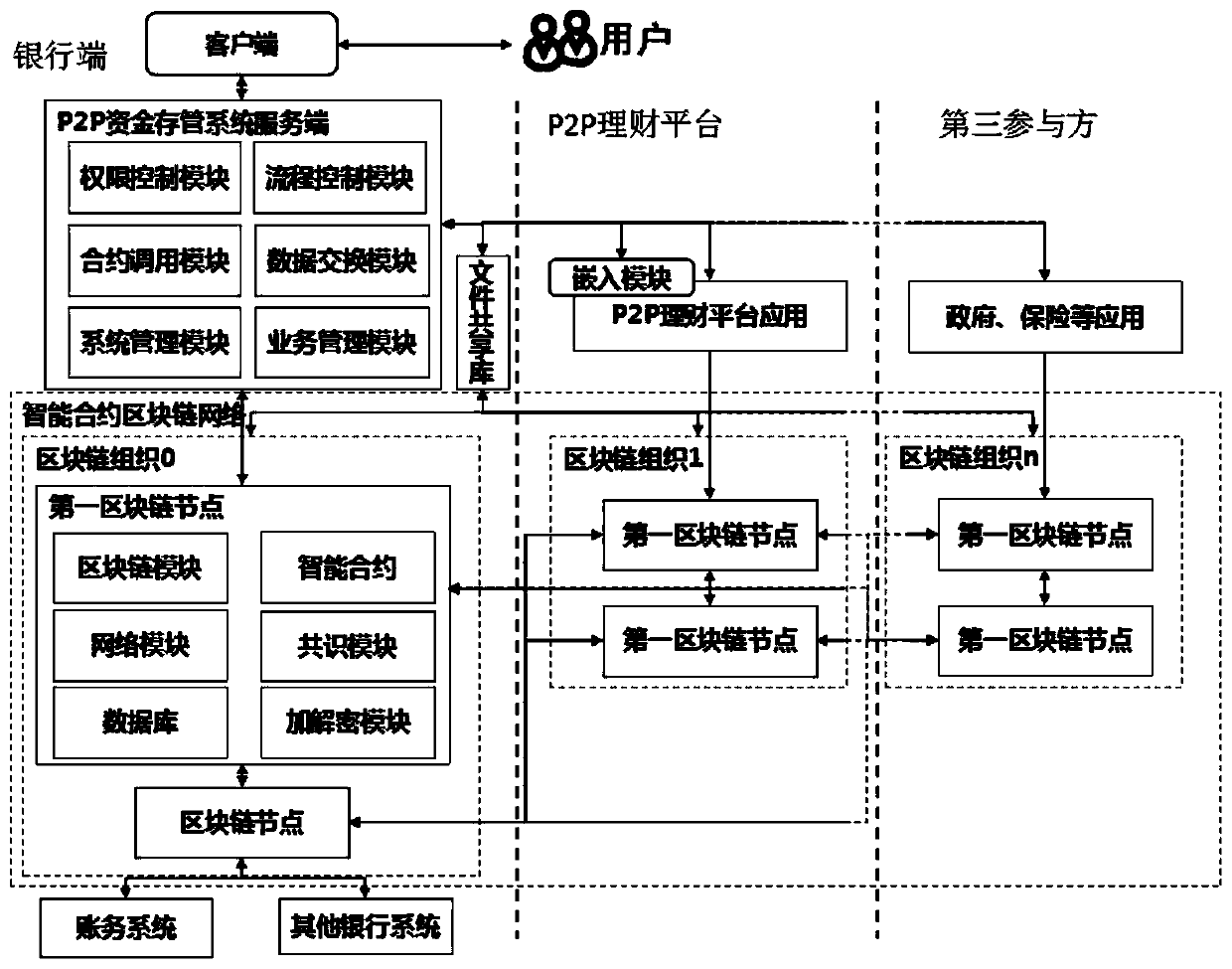
P2P financing platform fund bank storage management method based on block chain
InactiveCN109767336AEasy to operateEasy to open an accountFinancePayment protocolsInformation transparencyStorage management
The invention provides a P2P financial platform fund bank storage management method based on a block chain, a P2P fund storage management system of a first participant, a P2P financial platform application of a second participant, a government platform and an insurance platform of a third participant and the like need to be provided, and all the participants are mutually connected through the block chain network. The block chain network comprises an intelligent contract block chain network and a certificate storage block chain network; after the P2P financing platform application executes thepoint-to-point network borrowing and loan service, the P2P fund storage and management system performs storage and management; and the insurance platform provides insurance service, performs service scheduling and storage through the P2P fund storage and management platform, inquires and analyzes storage data through the government platform, and audits and supervises P2P services. According to theinvention, the whole-process legal management of P2P fund bank storage and management is realized, the data storage difficulty of P2P transaction is reduced, the system performance based on the blockchain technology is improved, the approval process and business transaction complexity of multiple participants in fund hosting are simplified, and the information transparency and the supervision strength are improved.
Owner:FUJIAN RURAL CREDIT UNION
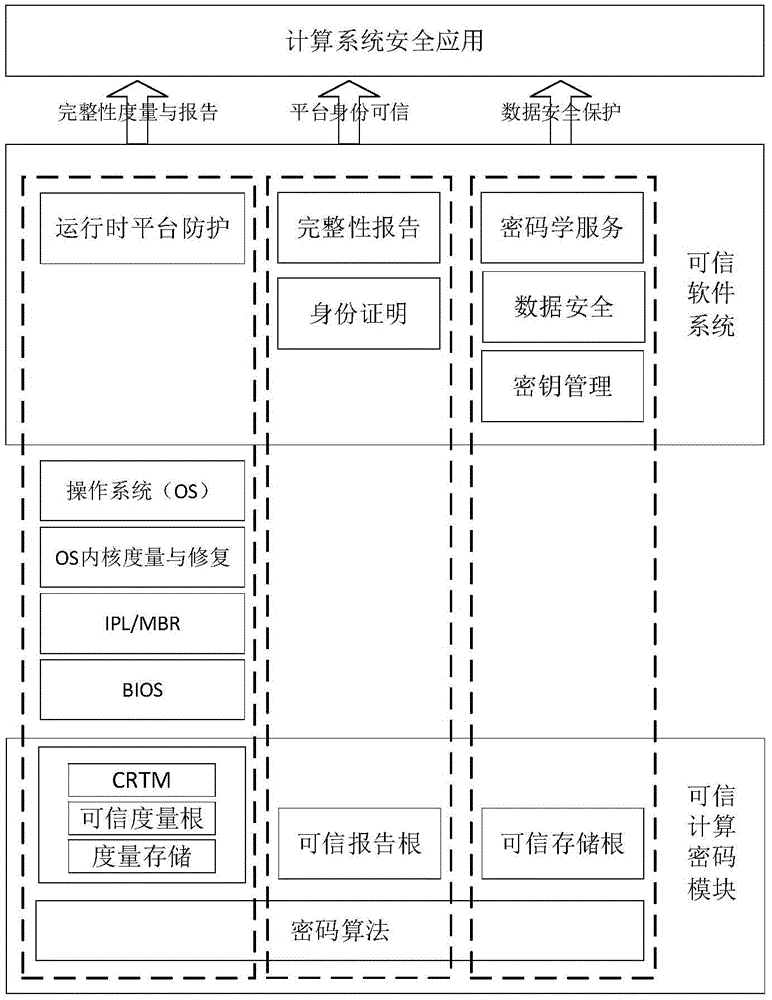
Trusted computing cryptogram platform suitable for general computation platform of electric system
ActiveCN105468978AEnsure credibleGuaranteed recognition effectPlatform integrity maintainanceOperational systemSoftware system
The invention provides a trusted computing cryptogram platform suitable for a general computation platform of an electric system. The cryptogram platform comprises a trusted computing cryptogram module and a trusted software system, wherein the trusted computing cryptogram module comprises a trusted measurement root, a trusted storage root and a trusted report root and is a transferring starting point of a platform trust chain; and the trusted software system comprises a trusted computing cryptogram driving module, a measurement module and an auditing module and provides an interface which uses the trusted computing cryptogram platform for an operating system and application software. The trusted computing cryptogram module is the trusted root which provides trusted environment for the operation of the trusted computing cryptogram platform, and the trusted software system is a core for realizing the functions and the service of the trusted computing cryptogram platform and provides guarantee for the management of the trusted computing cryptogram platform. The trusted computing cryptogram platform can provide functions including static measurement, dynamic measurement, white lists, access control and the like for a business system, and manages the sources and the operation of the system software to guarantee that the software is trusted, recognizable and controllable.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +5
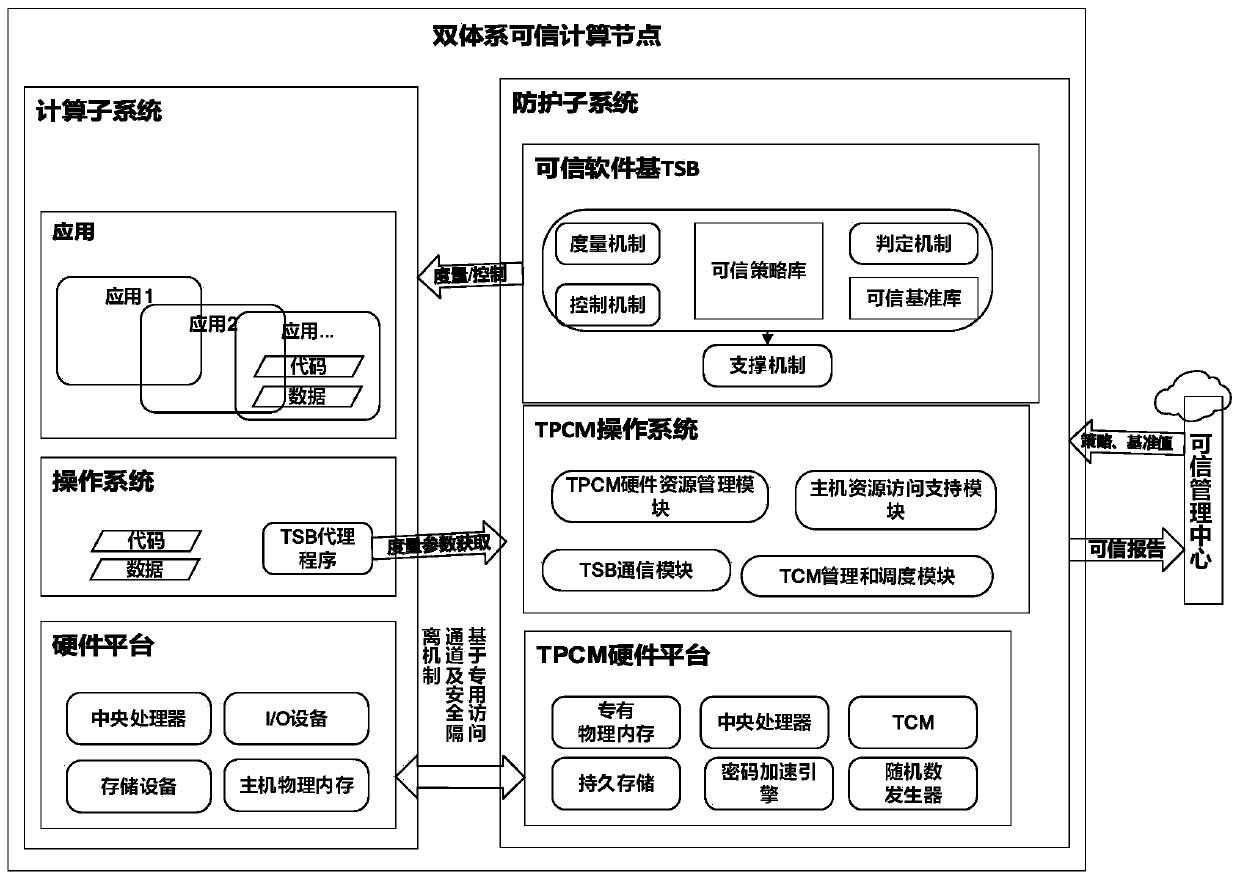
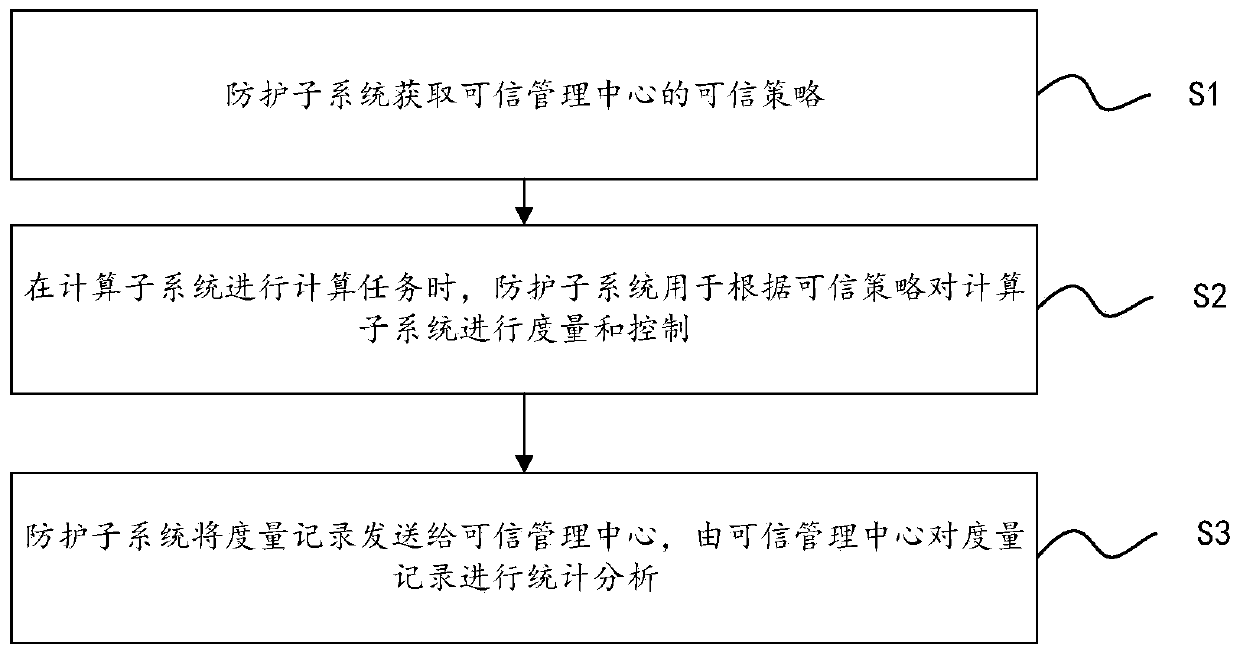
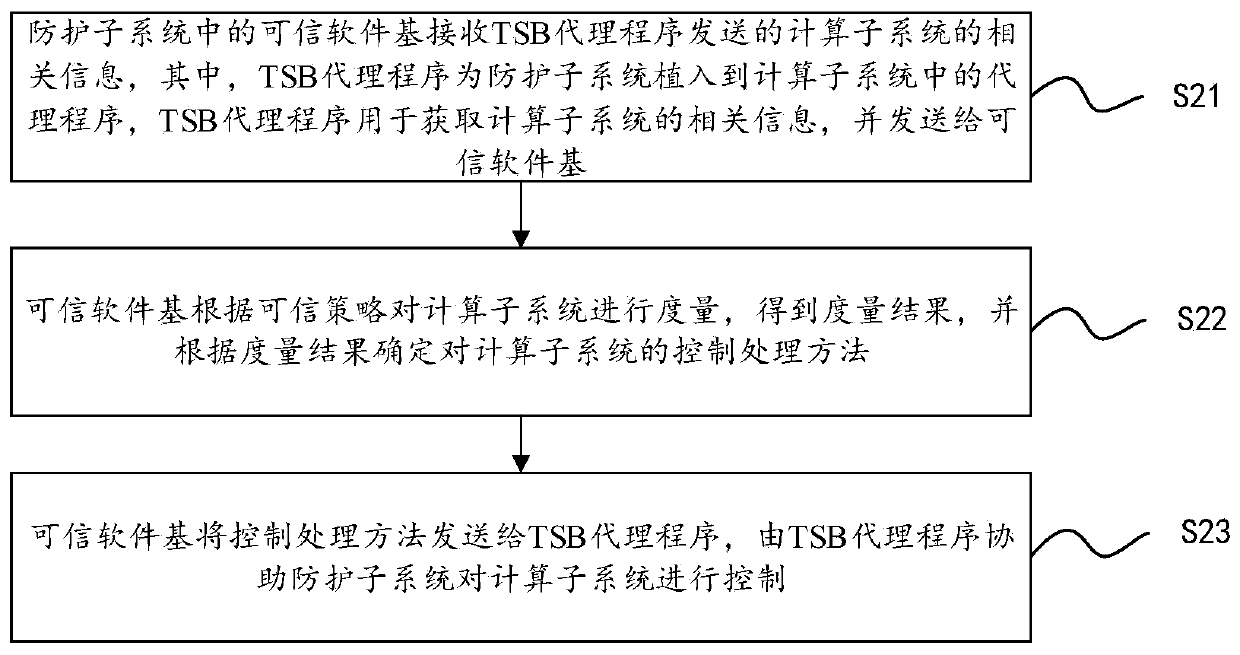
Dual-system trusted computing system and method
ActiveCN109918916AReverse the passive situation of "blocking and killing"Ensure crediblePlatform integrity maintainanceActive safetyStatistical analysis
The invention discloses a dual-system trusted computing system and method. The system comprises a trusted management center and at least one dual-system trusted computing node connected with the trusted management center, the dual-system trusted computing node comprises a computing subsystem and a protection subsystem which are parallel to each other, a security isolation mechanism is arranged between the computing subsystem and the protection subsystem, and interaction is carried out through a special access channel; wherein the computing subsystem is used for executing a computing task, theprotection subsystem is used for measuring and controlling the computing subsystem according to a credible strategy in the credible management center and sending a measurement record to the credible management center, and the credible management center is used for carrying out statistical analysis on the measurement record. According to the system and the method provided by the invention, active safety protection is carried out while calculation is carried out through the parallel calculation subsystem and the protection subsystem, so that calculation tasks are not interfered and damaged, andvarious known and unknown attacks can be resisted.
Owner:北京自主可信科技有限公司
Credible virtual machine platform
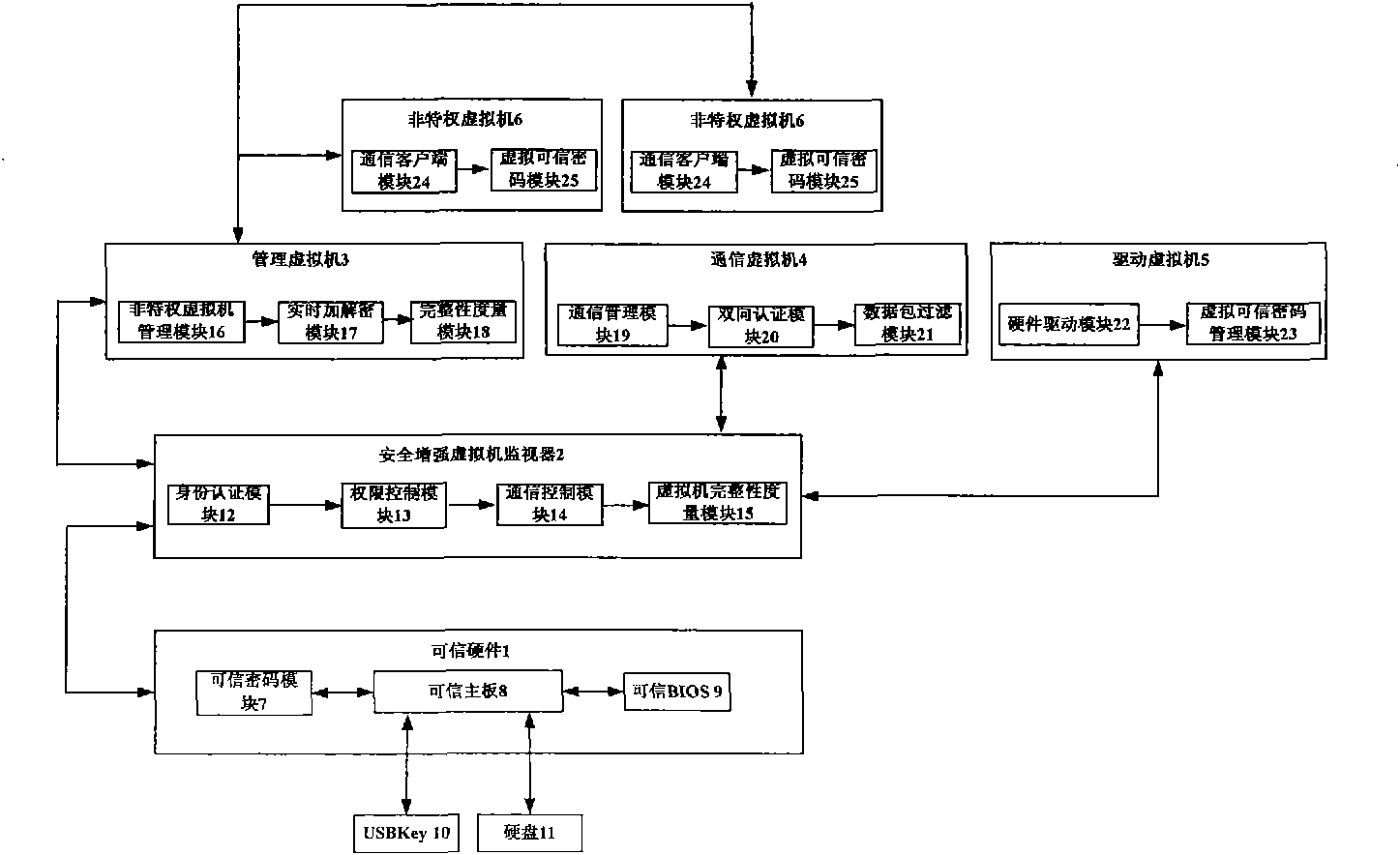
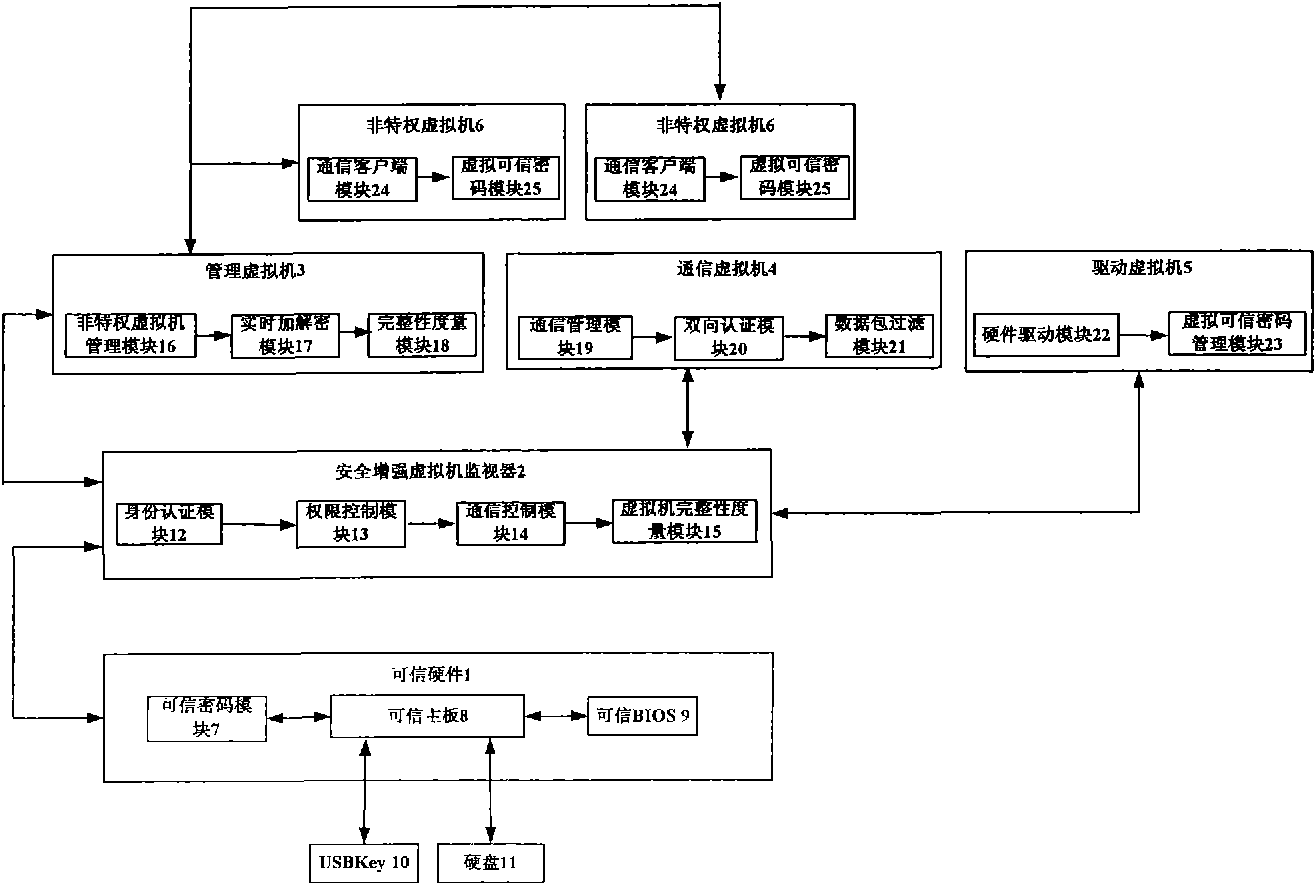
InactiveCN101957900AImprove stability and attack resistanceImprove securityInternal/peripheral component protectionVirtual machineOperating environment
The invention discloses a credible virtual machine platform, which comprises a hard disk (11), a USB Key (10) and a nonprivileged virtual machine (6), and also comprises credible hardware (1), a security enhancement virtual machine monitor (2), a management virtual machine (3), a communication virtual machine (4) and a driving virtual machine (5). The security enhancement virtual machine monitor (2) is bidirectionally connected with the credible hardware (1) and the management virtual machine (3) respectively; the management virtual machine (3), the driving virtual machine (5) and the communication virtual machine (4) are privileged virtual machines; the management virtual machine (3) creates, manages, destroys and transfers other virtual machines; the driving virtual machine (5) provides driving needed by the operation of the virtual machine and management of a virtual credible password module; and the communication virtual machine (4) takes charge of communication between inner virtual machines and a virtual machine platform. The credible virtual machine platform has the advantages of effectively guaranteeing the safety and credibility of an operating environment of the virtual machine platform and realizing effective management and control of communication between virtual domains.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
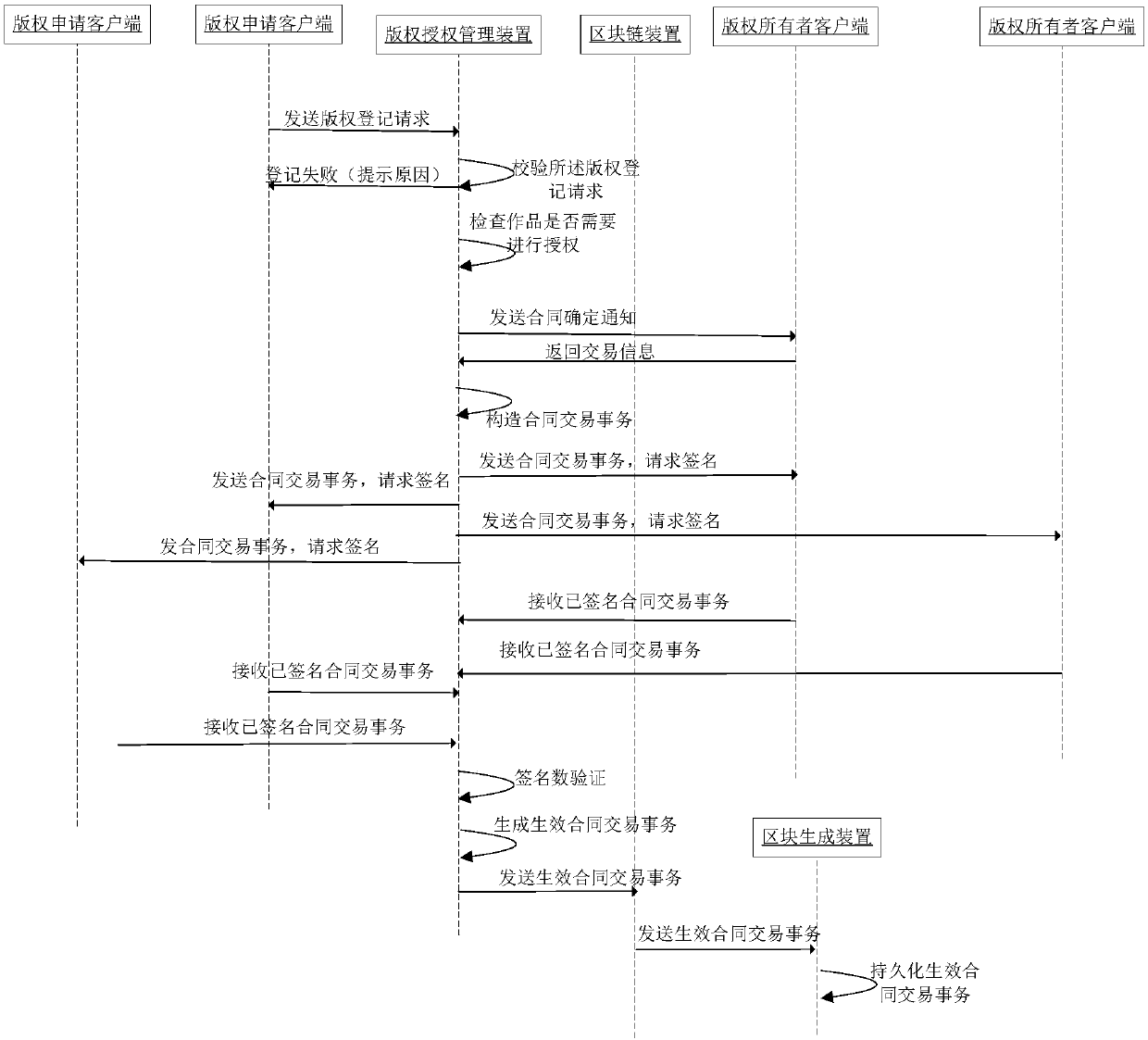
Copyright authorization management method and system
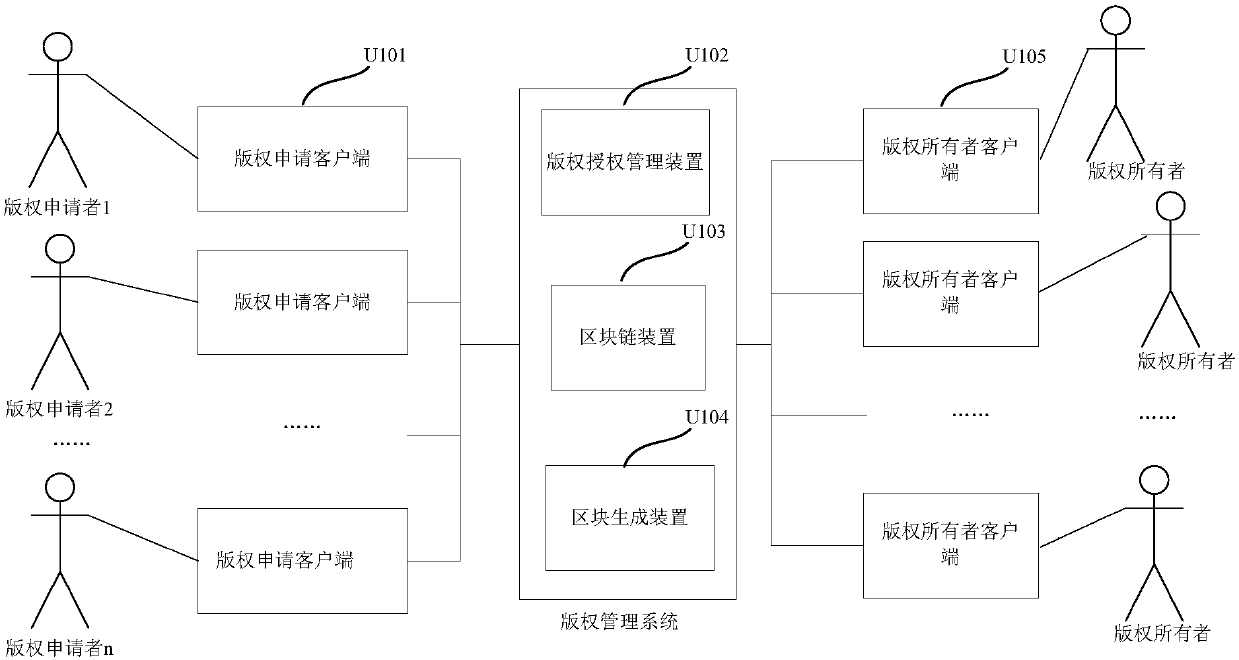
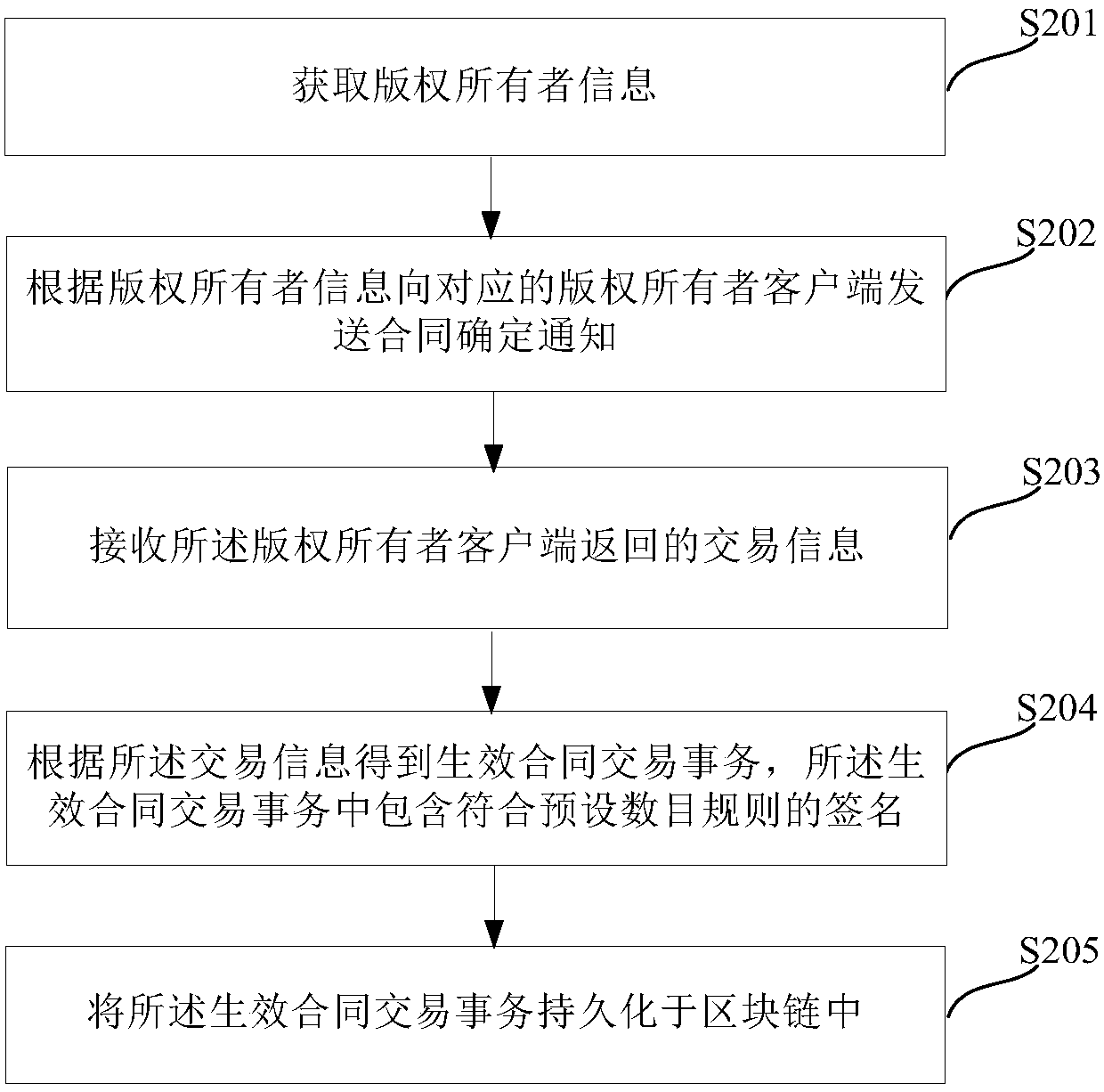
ActiveCN107679045AGuaranteed uniqueEnsure credibleDatabase distribution/replicationOffice automationOnline signatureRelevant information
The embodiment of the invention discloses a copyright authorization management method and system. The method comprises the steps that copyright owner information is acquired; a contract confirmation notice is sent to a corresponding copyright owner client according to the copyright owner information, wherein the contract confirmation notice carries copyright relevant information of authorized works; transaction information returned by the copyright owner client is received, wherein the transaction information contains contract information confirmed by a copyright owner according to the copyright relevant information; an operant contract transaction is obtained according to the transaction information, wherein the operant contract transaction contains signatures conforming to preset counting rules; and the operant contract transaction is persisted into a block chain. Through the technical scheme in the embodiment, online signing of a contract and persistence of the signed contract are realized based on the block chain, therefore, copyright authorization efficiency is improved, and it is guaranteed that the contract is unique and credible and cannot be tampered.
Owner:HUAWEI TECH CO LTD
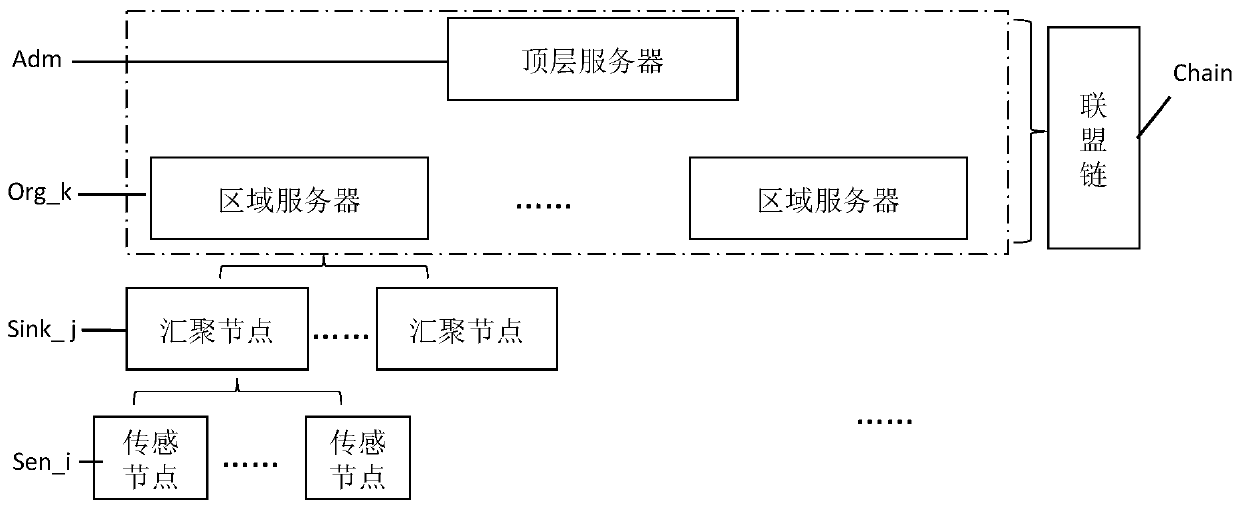
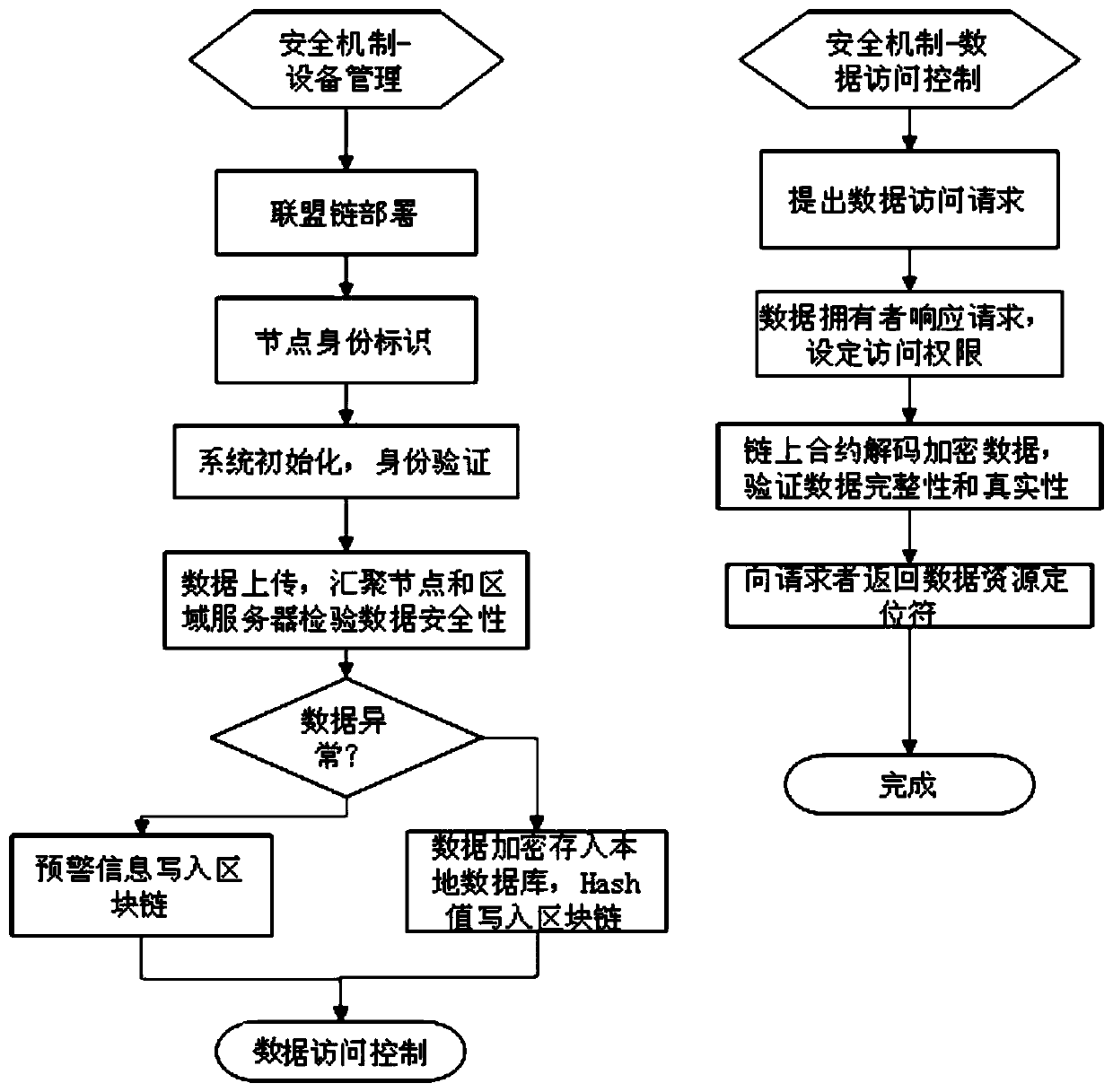
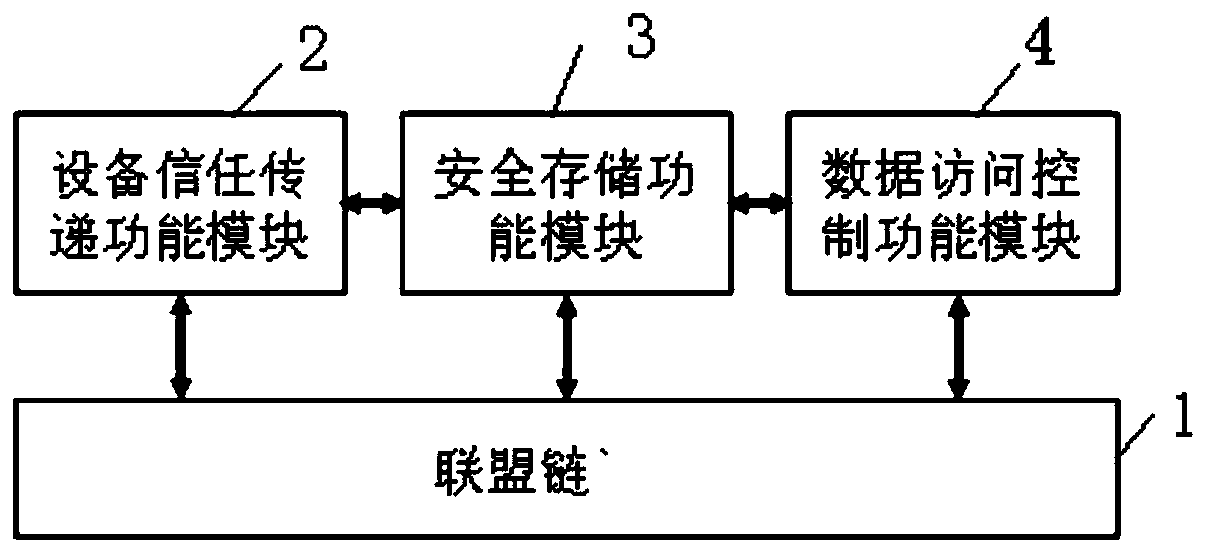
Distributed account book technology-based sensor network safety management method and safety system
ActiveCN110445827ASolve centralized management problemsAddress shared access controlDigital data protectionTransmissionData setUniform resource locator
The invention provides a distributed account book technology-based sensor network safety management method. The method comprises the following steps of selecting a top layer and a regional server as alliance chain nodes to establish an alliance chain, and storing a distributed account book; generating an asymmetric key for a sensing and aggregation node at the lower layer of the regional server, solidifying a private key in a memory, and writing a public key into an alliance chain; uploading the data collected by the sensing nodes to a regional server through the aggregation node, storing thedata set in an off-chain database of the regional server and encrypting the data set after the verification is passed, calculating a hash value of the data set and writing the hash value into an alliance chain to serve as an evidence; and S3, decrypting the data set, calculating a hash value of the data set, comparing the hash value with the evidence in the step S3 to verify the correctness of thedata set, and returning a uniform resource locator. The invention further provides a safety system. According to the safety management method, a centralized and effective equipment management mechanism and data safety verification are provided for a large-scale sensor network. The problem of data sharing access control is solved.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
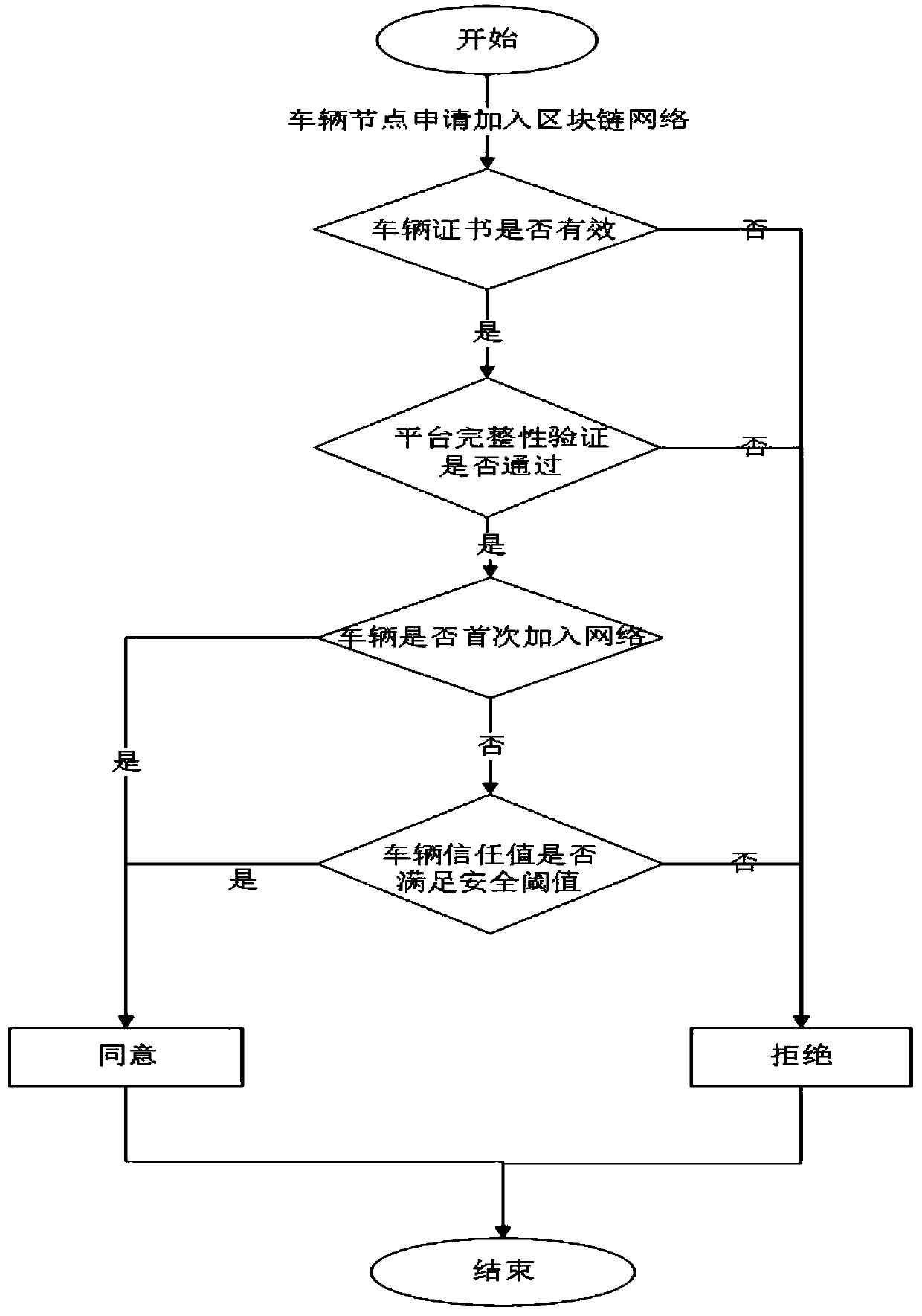
Credible node joining method in VANET based on block chain
ActiveCN111405011AEnsure credibleEnsure transparencyFinanceUser identity/authority verificationData informationAttack
The invention discloses a credible node joining method in VANET based on a block chain, belongs to the field of VANET safety, and aims to improve traffic jam and assist safe driving. If the vehicle isa malicious node, hidden dangers are buried for traffic safety, for example, the malicious node scatters false or attack data information, so that the reliability of related data information receivedby the vehicle is difficult to guarantee. And if the malicious node is rejected when the malicious node is added into the VANET, the security can be improved to a great extent. The invention providesa credible node joining method in VANET based on a block chain, and a roadside unit performs distributed verification on an applied vehicle. the method comprises: firstly, verifying whether the vehicle has a legal identity or not; then, verifying the integrity of the vehicle-mounted platform by utilizing a trusted computing technology; and finally, evaluating the reputation value of the vehicle in the last certificate validity period, namely evaluating whether the vehicle is a malicious node or not through historical performance; and allowing the verified vehicle to join, otherwise refusing.
Owner:BEIJING UNIV OF TECH
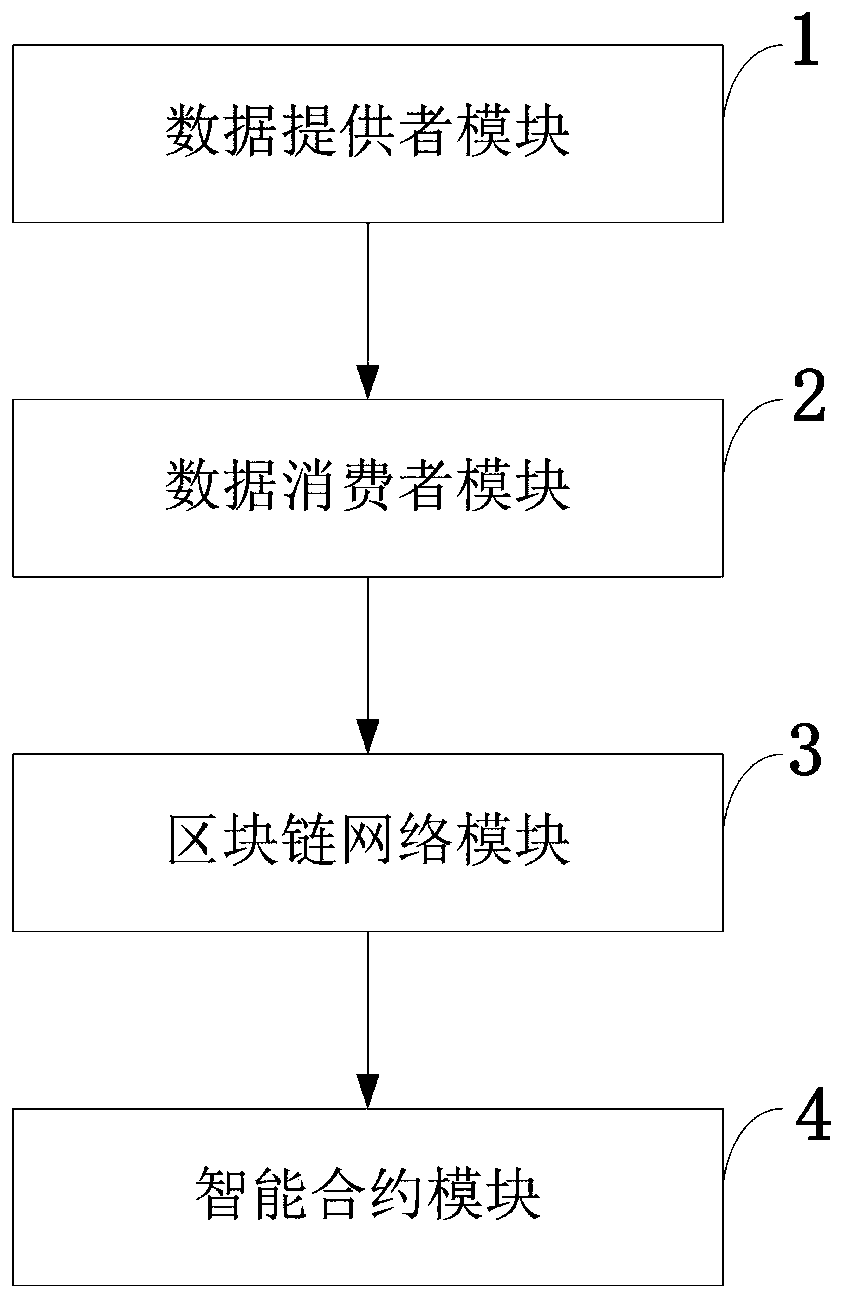
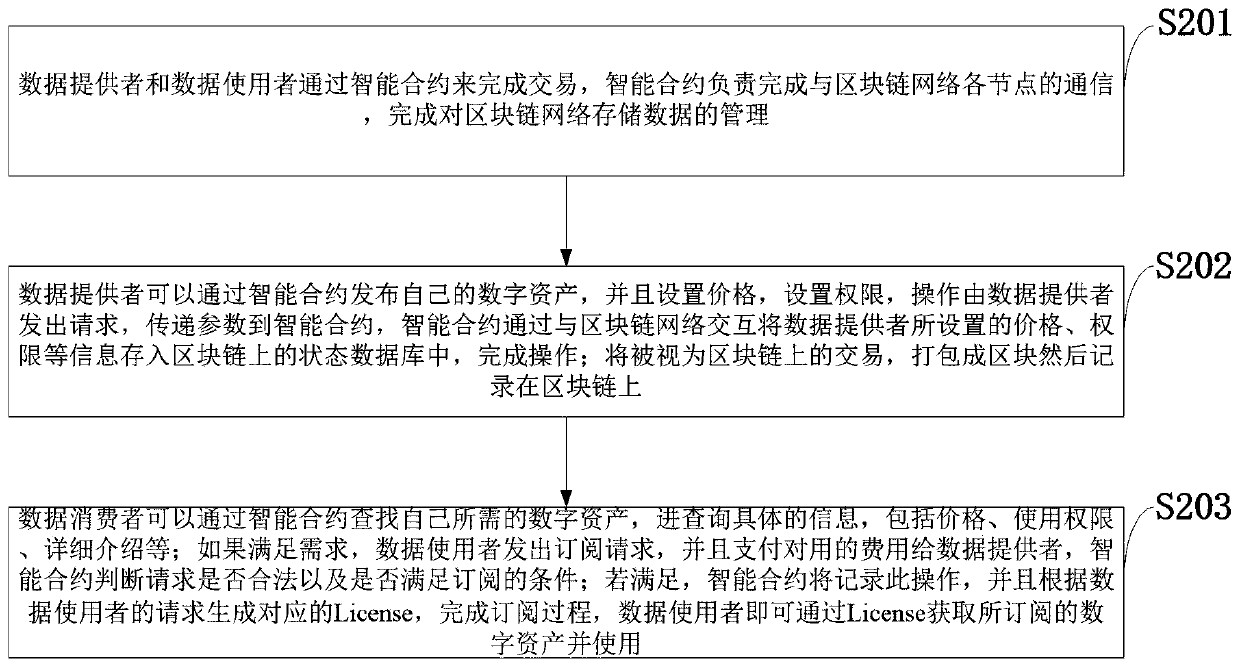
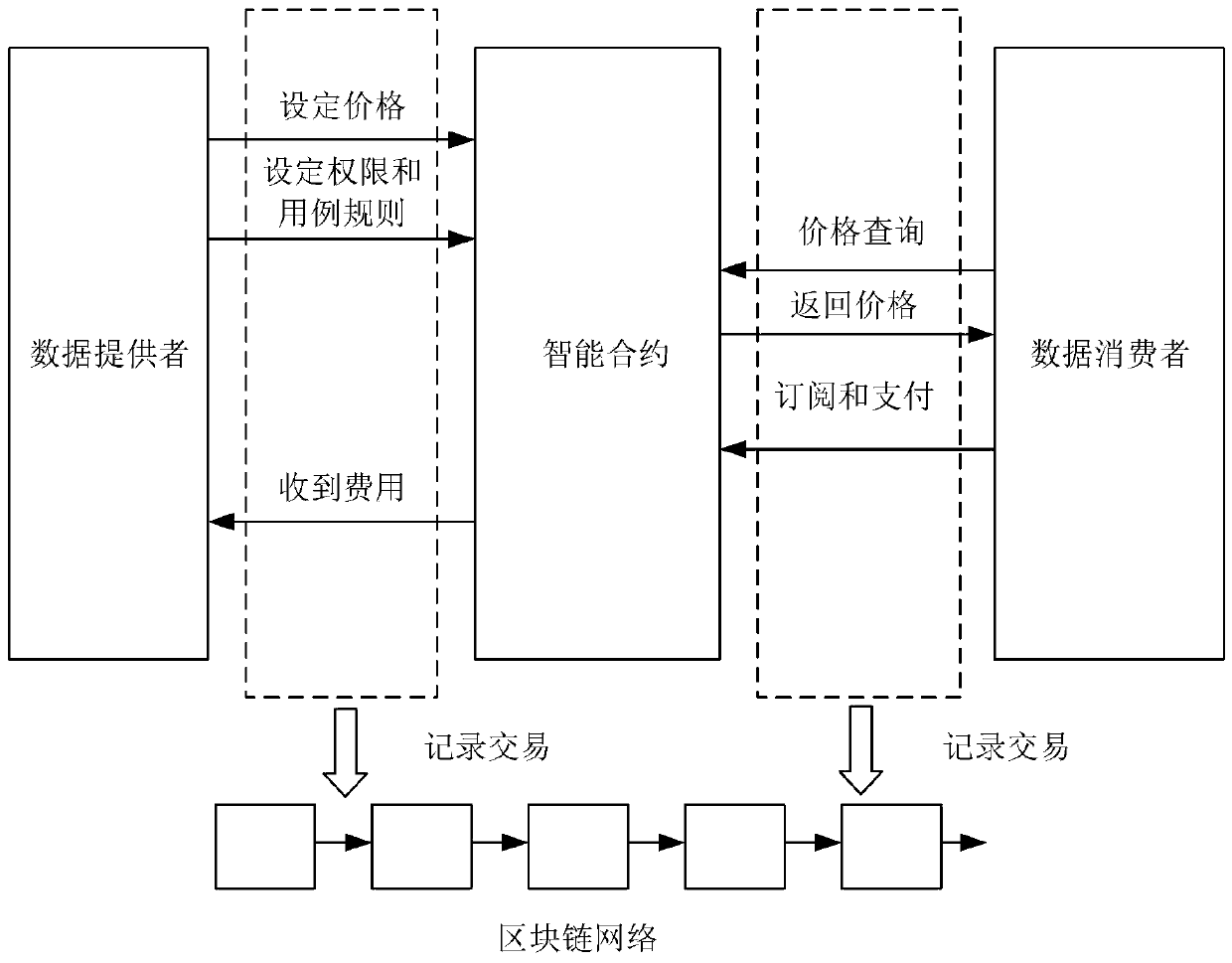
Digital asset information exchange system and method based on block chain
PendingCN110335147AReliable recordReliable exchangeFinancePayment circuitsData providerConfidentiality
The invention belongs to the technical field of block chains and internet information, and discloses a digital asset information exchange system and method based on a block chain. The digital asset information exchange system based on a block chain comprises a data provider module, a data consumer module, a block chain network module, and a smart contract module. The digital asset information exchange system provides a preset digital asset exchange mode based on the intelligent contract technology of the block chain, does not need to consider the trust problem between subjects, aiming at the problems that a traditional data exchange mechanism depends on a third-party payment mechanism, and data records are prone to being tampered and forged. Based on an exchange medium of the block chain cryptocurrency, multiple subjects jointly maintain an account book, so as to guarantee that records are real, reliable and not tampered. According to the digital asset exchange mechanism disclosed by the invention, the digital asset exchange mechanism is developed on the basis of the characteristics of confidentiality, integrity, non-repudiation and the like of the block chain, and data asset exchange and sharing are promoted.
Owner:XIDIAN UNIV
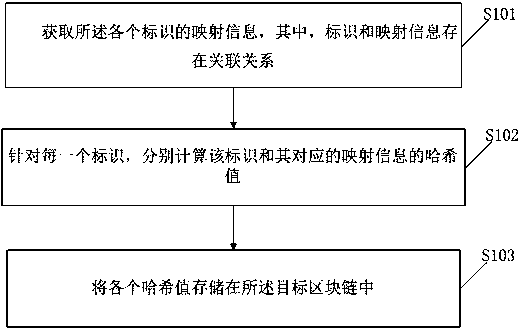
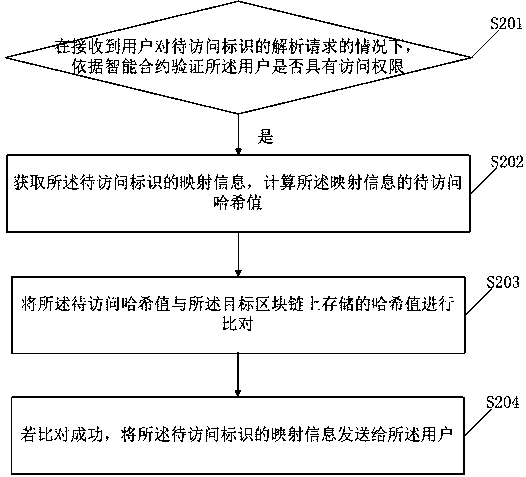
Industrial Internet identifier analysis access control method based on block chain
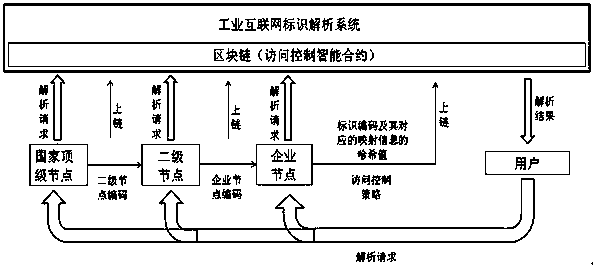
InactiveCN111209596AEnsure credibleAvoid distortionDigital data protectionIndustrial InternetEngineering
The invention discloses an industrial Internet identifier analysis access control method based on a block chain. Relevant information of each identifier in the industrial Internet is stored in a target block chain in advance, and the method comprises the steps of verifying whether a user has an access permission or not according to an intelligent contract under the condition of receiving an analysis request of the user for a to-be-accessed identifier; if yes, obtaining mapping information of the to-be-accessed identifier, and calculating a to-be-accessed hash value of the mapping information;comparing the hash value to be accessed with the hash value stored on the target block chain; and if the comparison is successful, sending the mapping information of the identifier to be accessed to the user. According to the method, each identifier is stored in the target block chain, so that credibility of identifier resources is ensured, and whether a user has access permission or not is verified according to the smart contract; if yes, comparing the hash value to be accessed with a hash value stored on the target block chain; and if the comparison is successful, sending the mapping information of the identifier to be accessed to the user, so that distortion of an analysis result is avoided.
Owner:STATE GRID E COMMERCE CO LTD +2
Clean room environment-based safe virtual machine migration method
ActiveCN105700945AEnsure credibleImprove migration efficiencyProgram initiation/switchingSoftware simulation/interpretation/emulationConfidentialityTransfer procedure
The invention provides a clean room environment-based safe virtual machine migration method. Through the method, the credibility of physical computers is validated before the migration of a virtual machine, so that the virtual machine can be migrated onto a credible physical computer, and the confidentiality and integrity of the virtual machine data in the transmission process can be ensured. According to the method, the number of migration iterations can be decreased to a certain extent, so that the migration efficiency is improved; and the method is simple in realization process and easy to operate.
Owner:CENT SOUTH UNIV
OTP and user behavior-based certification and authorization method in mobile cloud computing environment
InactiveCN105099690ASolve the problem of not being able to resist decimal attacksEnsure credibleUser identity/authority verificationMobile cloudClient-side
The present invention discloses an OTP and user behavior-based certification and authorization method in a mobile cloud computing environment. The method is characterized in that various intelligent mobile terminals available for users are enabled to be accessed to the cloud service via a wireless network in the mobile cloud computing environment and the bidirectional identity authentication between a client and a server is realized through improving the one-time password (OTP) technology. In this way, the safety and the reliability of the identity authentication process are improved. Meanwhile, according to the specific behavior habits of a user accessed to the cloud service, the features of historical behavior data of the user are analyzed and extracted based on the data mining technology. In this way, a knowledge database of the normal behavior patterns of the user is formed. When the user behaves abnormally or suspiciously, the identity of the user is authenticated again. Only when the user passes the identity authentication process, the corresponding service is authorized for the user. Therefore, the illegal operation of others is avoided, and the information security of the user is fully ensured.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
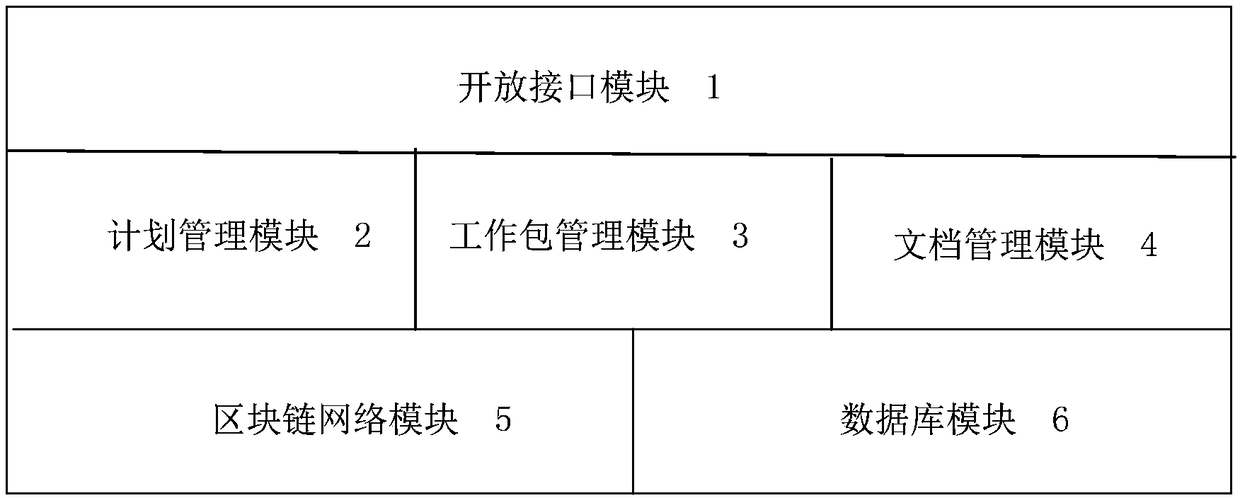
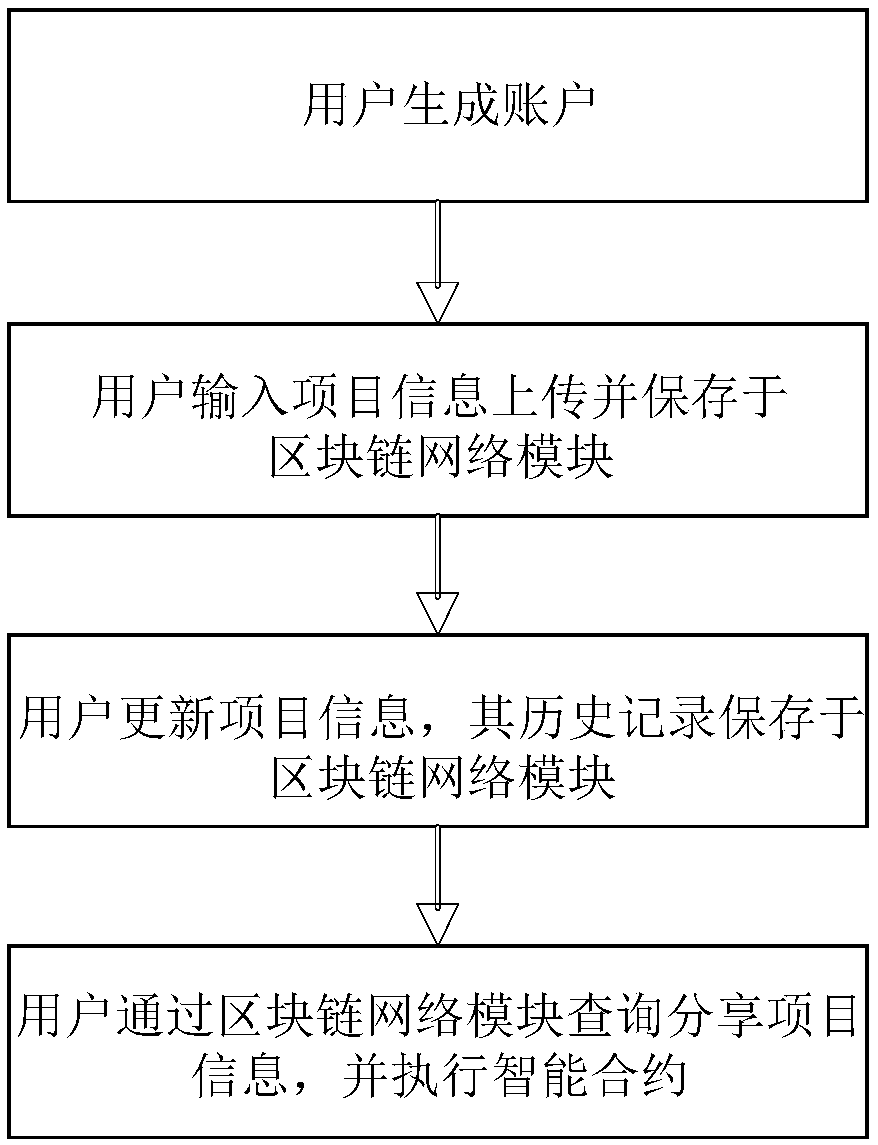
Project completion management system based on block chain and implementation method thereof
The invention relates to a project completion management system based on a block chain and an implementation method thereof. The system comprises an open interface module, a plan management module, awork package management module, a document management module, a block chain network module, and a database. The open interface module is a channel for interaction between the system and an external application, and the external application accesses the system through the open interface module. A project owner, a contractor and a construction party digitally sign project plan information through the plan management module, and the digital signatures are stored in the block chain network module. The work package management module is used for dividing and assigning work packages to different construction parties, and updates of work package states are stored in the block chain network module. The document management module is used for saving and tracking design documents of system components,and after the design documents are performed by hash calculation, eigenvalues are sent to the block chain network module. The block chain network module adopts a trusted authorization access federation chain system, and is used for storing of a project plan, work package states and design document change information. The information is stored in the database. The system effectively shares projectcompletion information, records changes, and records a completion status.
Owner:鹰投(上海)海洋科技发展有限公司
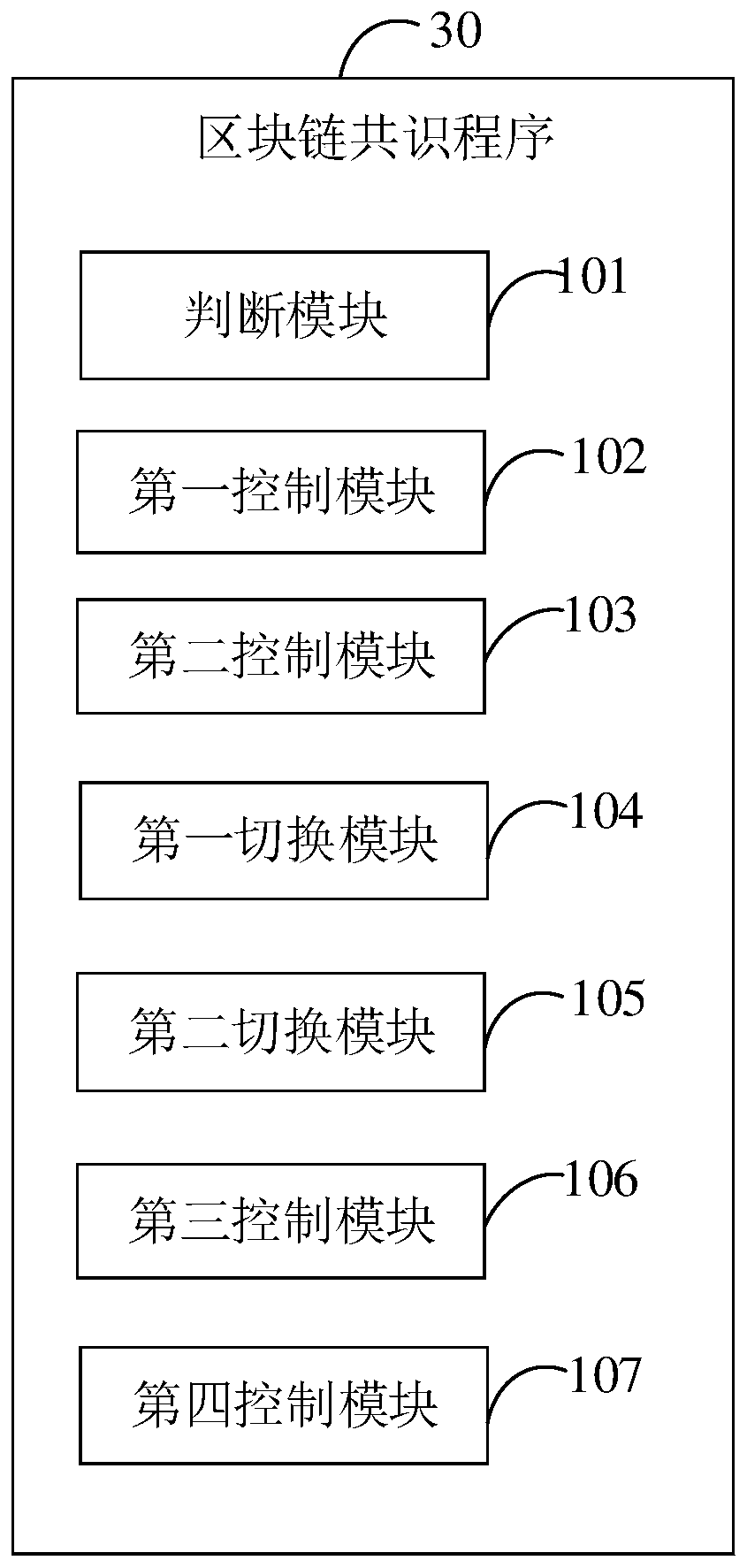
Block chain consensus device and method and computer readable storage medium
InactiveCN110336707AEnsure credibleUser identity/authority verificationData switching networksData synchronizationSource Data Verification
The block chain consensus method comprises the steps of judging whether an undetermined master node exists in a system or not; if so, controlling each slave node to send a data synchronization requestto the undetermined master node; controlling each slave node to verify the received synchronous data block, and if the verification is passed, broadcasting a verification passing message; when the slave node receives more than a first preset number of verification passing messages and the abstract of the last block contained in each piece of verification passing information accords with consistency, switching the slave node from a search state to a slave state, storing the synchronization data block, and sending a synchronization completion message to the undetermined master node; and when the undetermined master node receives more than a first preset number of synchronization completion messages, switching the state to a leader state, and changing to a formal master node. The invention further provides a block chain consensus device and a computer readable storage medium. According to the invention, after the main node is selected, data synchronization and synchronous data verification can be carried out, so that each node keeps data synchronization.
Owner:卓尔智联(武汉)研究院有限公司
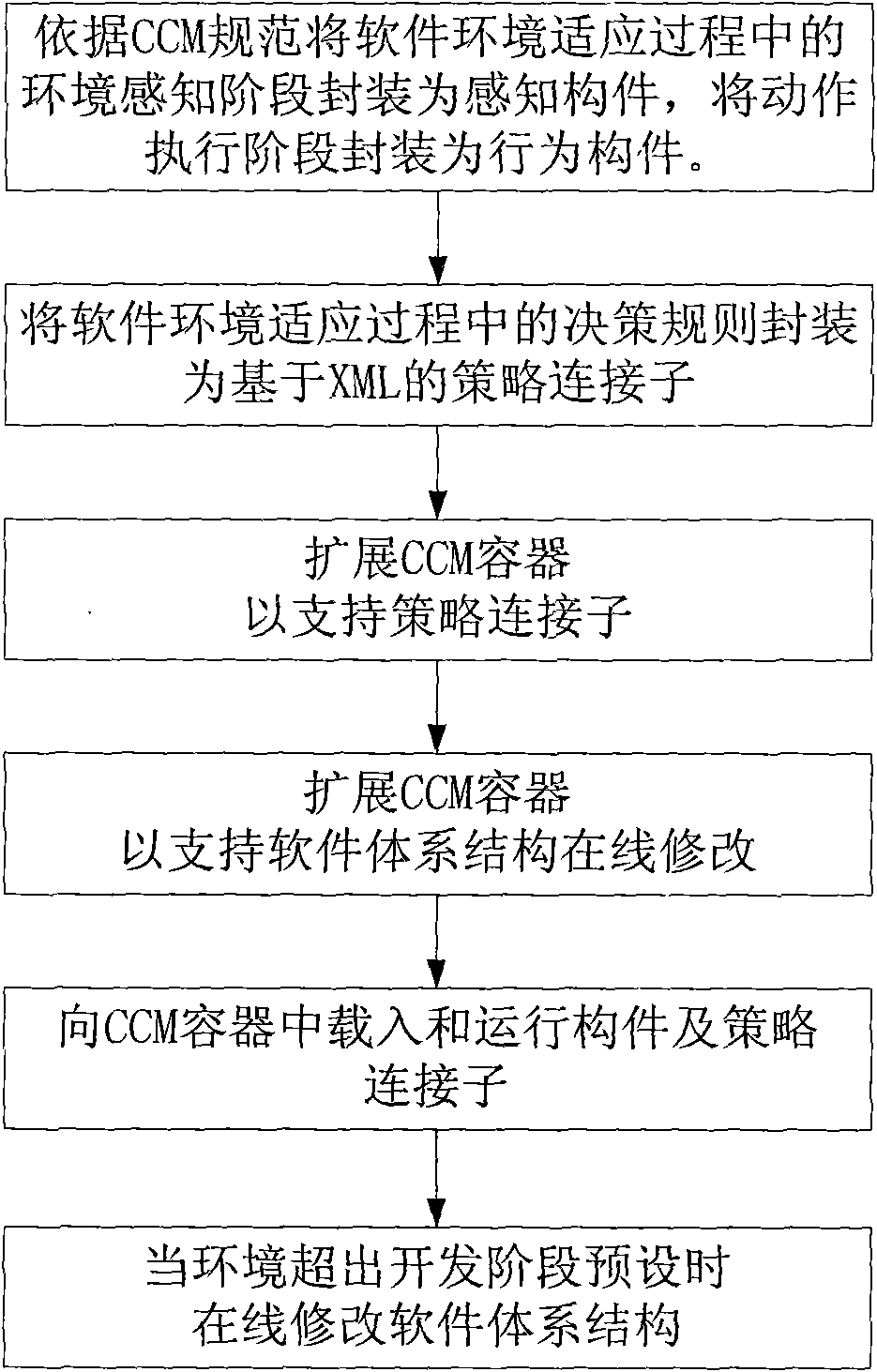
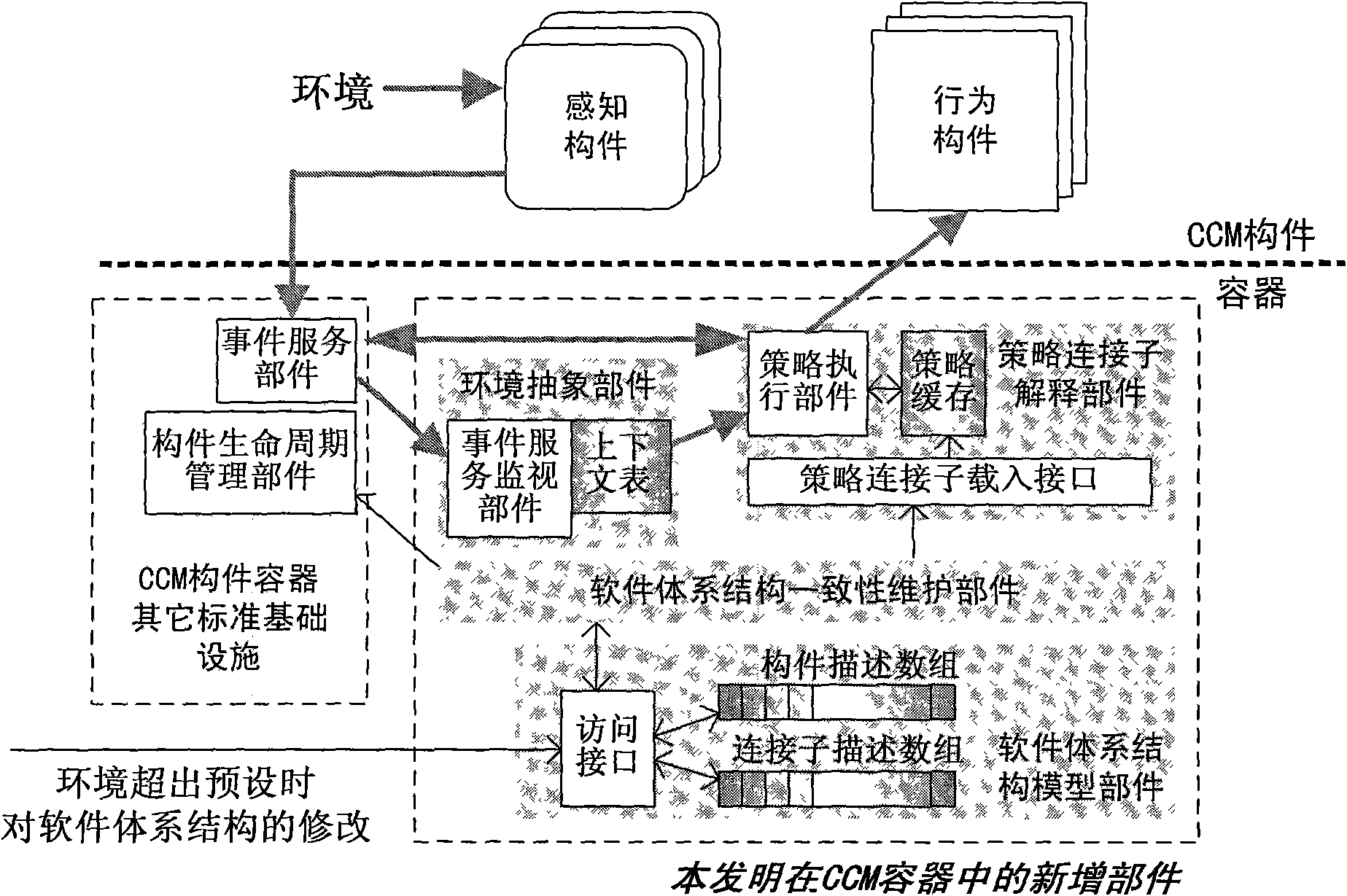
Software trust ensuring method based on system structure evolution
InactiveCN101673197AMeet needsEnsure credibleInternal/peripheral component protectionPlatform integrity maintainanceThird partySoftware engineering
The invention discloses a software trust ensuring method based on system structure evolution, aiming to provide a method for modifying each stage in a software environment adapting process on line toensure software trust when the environment exceeds the presetting environment of a development stage. The invention adopts the technical scheme that a perceptive stage and an executive stage in the software environment adapting process are packaged into different members, and the rule for software to make action decision according to the environment is packaged into a strategy connector; then, a member container is extended for supporting the interpretive execution of the strategy connector and allowing a third party to selectively add or delete and replace the members and the connectors whenrunning so that each stage in the software environment adapting process is independently modified on line. The invention can be used for adjusting the software environment adapting process when the software runs and can ensure the software trust with low modifying cost.
Owner:NAT UNIV OF DEFENSE TECH
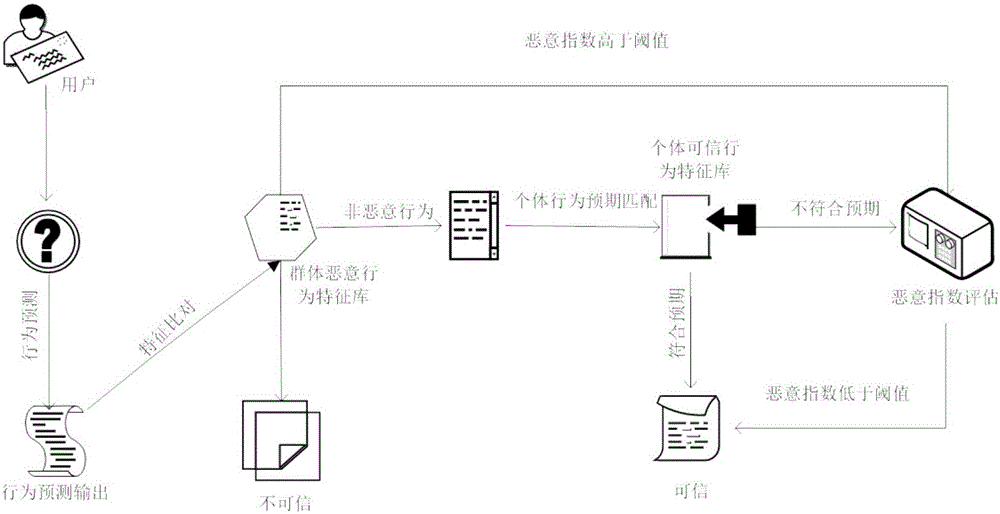
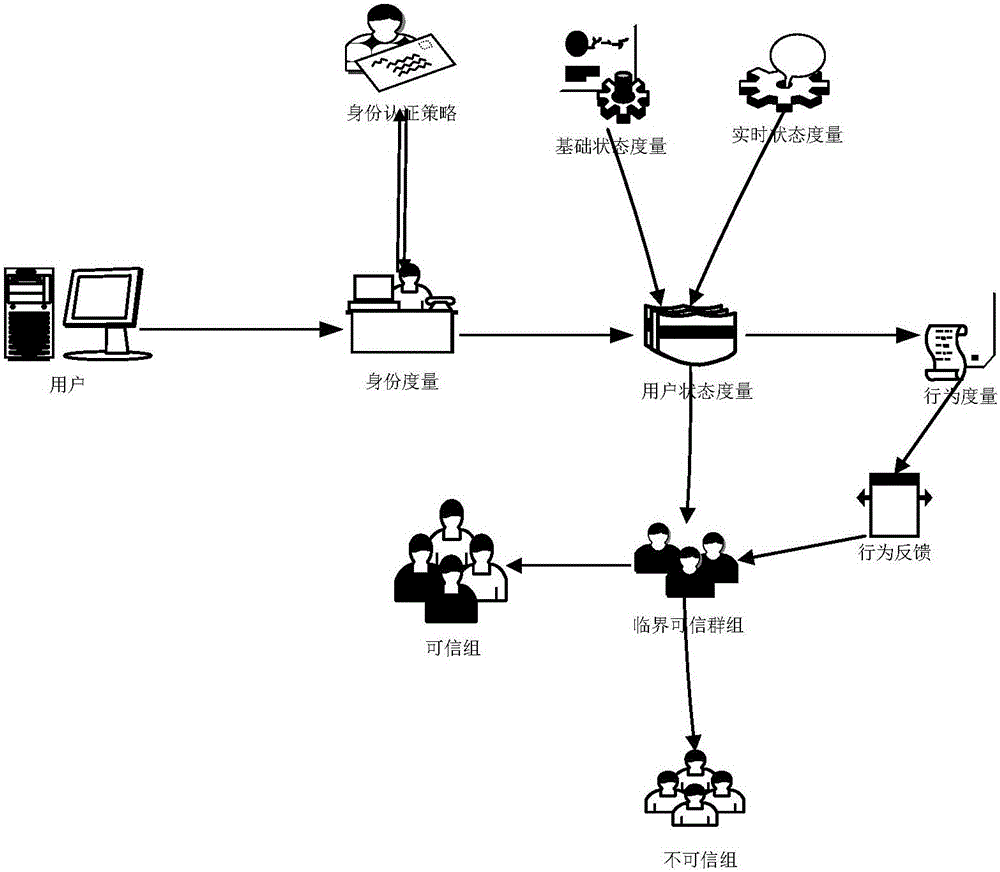
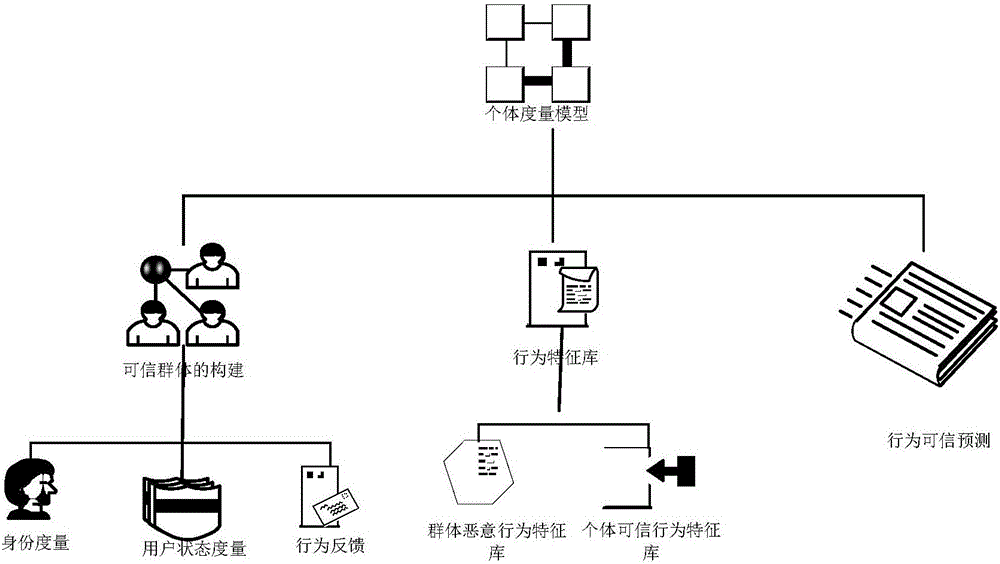
Behavior prediction control based trusted network group construction method
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
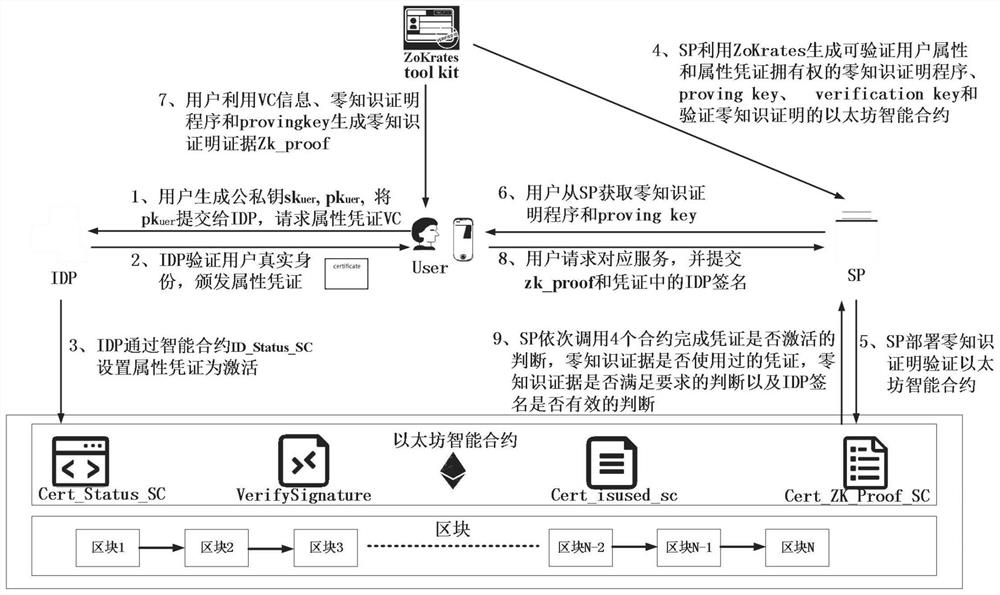
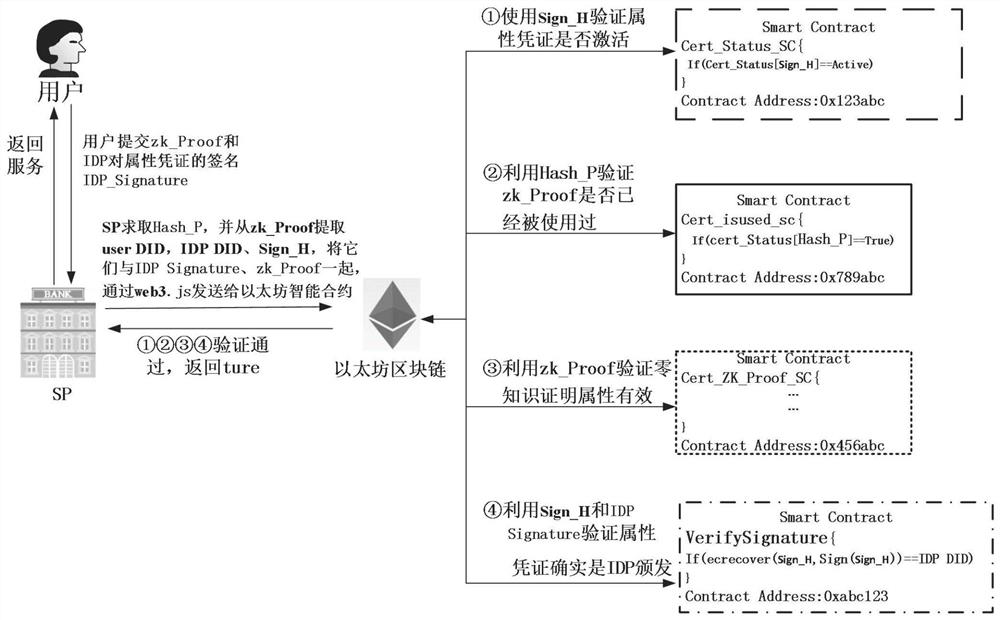
Zero-knowledge proof verifiable certificate digital identity management system and method based on block chain smart contract
ActiveCN114186248AImproved Identity Privacy FeaturesIdentity attribute requirements are metDigital data protectionDigital data authenticationDigital identityEngineering
The invention discloses a zero-knowledge proof verifiable certificate digital identity management system and method based on a block chain smart contract. The system comprises a zero-knowledge smart contract and a certificate client. The zero-knowledge smart contract comprises a voucher state smart contract, a zero-knowledge evidence use state smart contract, a zero-knowledge evidence validity verification smart contract and a verifiable voucher validity verification smart contract; the voucher client is provided with three roles: an identity provider, a user and a service provider. The description program for proving the zero-knowledge problem is constructed by the service provider according to the identity attribute requirement of the service, and the user only needs to generate the zero-knowledge evidence according to the zero-knowledge problem program constructed by the service provider and the attribute voucher of the user and submits the evidence to the service provider to obtain the service. And the attribute in the evidence is proved to meet the identity attribute requirement of the service, and meanwhile, the user is proved to be the holder of the generated evidence, so that the dual guarantee of privacy and security is realized.
Owner:YUNNAN UNIVERSITY OF FINANCE AND ECONOMICS +1
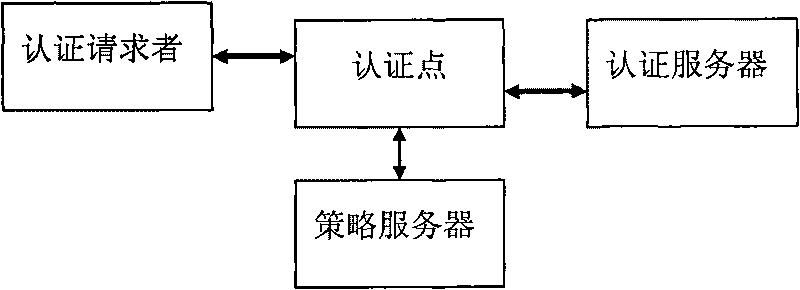
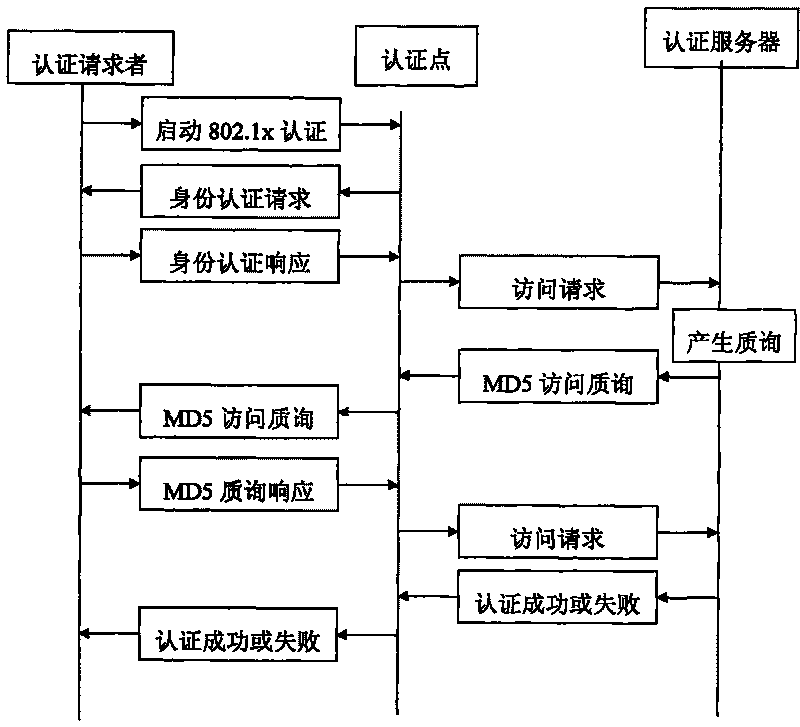
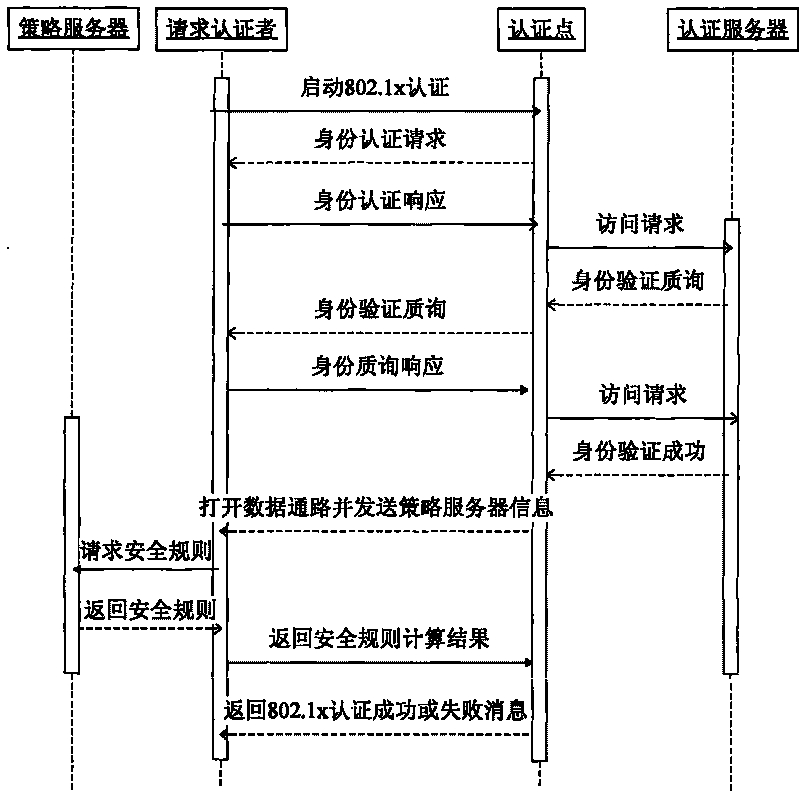
Safe access method based on extended 802.1x authentication system
ActiveCN101764788AMeet Access ControlGuaranteed to be trueUser identity/authority verificationAccess networkAccess method
The invention discloses a safe access method based on a extended 802.1x authentication system, wherein the method which is based on EAPOL standard protocol expands EAPOL protocol identity authentication response message of authentication requestor and adds secure access mark to ensure that the authentication point control enters the safe access procedure; and an authentication server and a strategy server adopt authentication point mutual security level information message to realize that the authentication requestor, namely the terminal user accesses the network through a two-level access device safely and reliably. The invention can better satisfy the access control of the two-level access device to the terminal by expanding standard EAPOL protocol; and the truth and credibility of edgedevice of access network can be fully guaranteed while the traditional access authentication mode is not changed.
Owner:MAIPU COMM TECH CO LTD
Internet-of-Things data management method based on block chain and edge computing
InactiveCN113055456AImprove performanceEnsure auditabilityNetwork topologiesDatabase distribution/replicationNetwork architectureCollections data
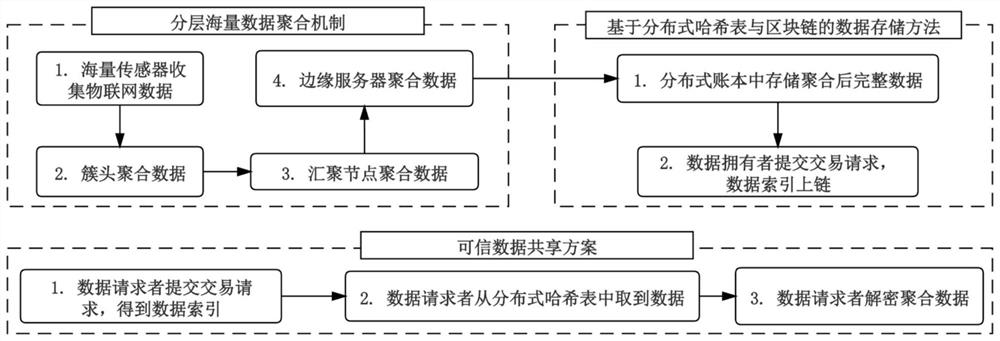
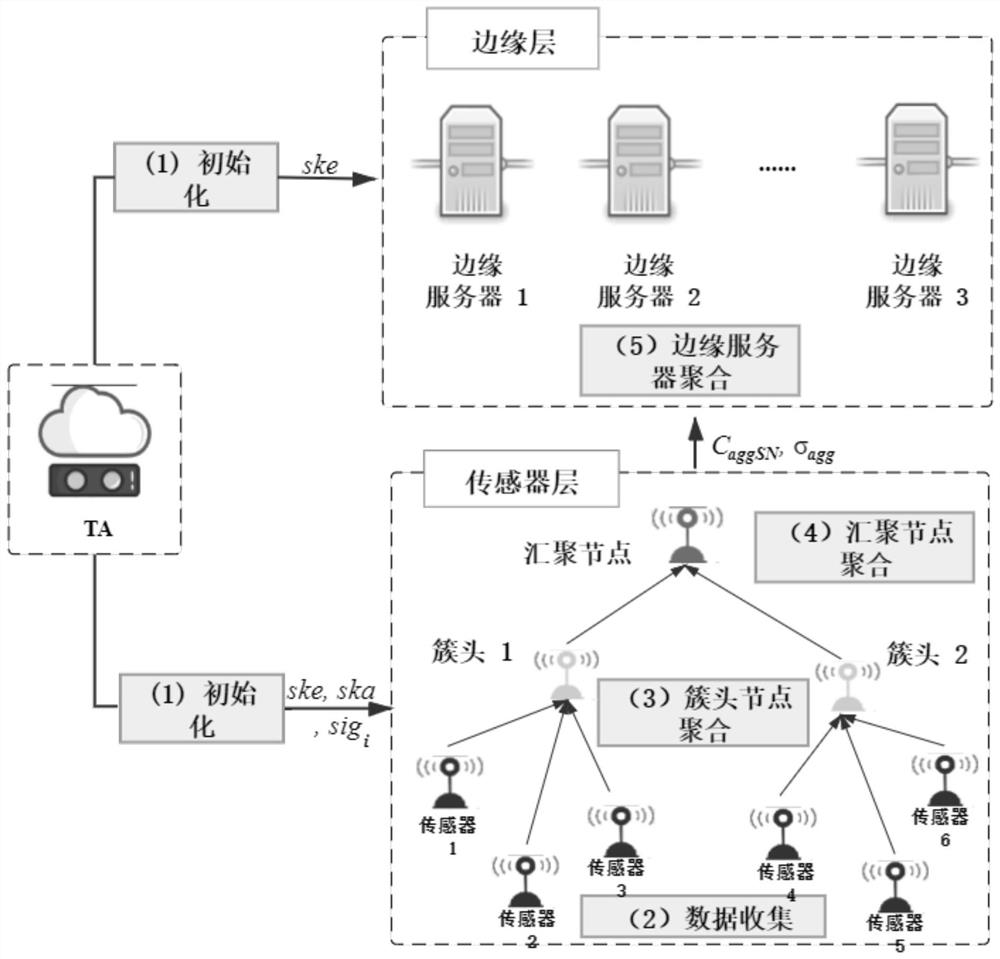
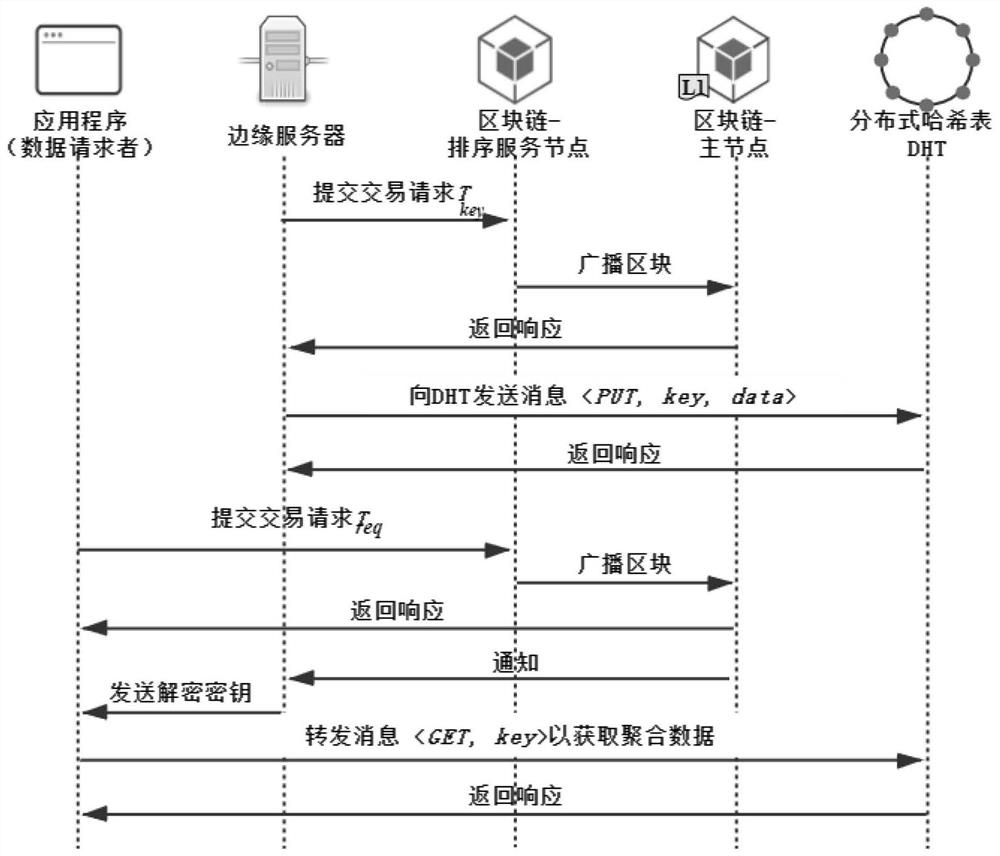
The invention belongs to the technical field of block chains and the technical field of Internet of Things, and relates to an Internet-of-Things data management method based on block chains and edge computing. The method has the advantages that firstly, an efficient, safe and low-consumption layered mass Internet-of-Things data collection and aggregation mechanism is designed based on the advantages of Internet-of-Things network architecture and edge computing; secondly, complete data is stored outside the chain, the block chain storage pressure is relieved, and the performance is improved; an index hash value is stored in the block chain, so that a credible, safe and traceable data storage method is ensured; and finally, the credible data sharing method is provided, and auditing, credibility and traceability of a data sharing process are ensured based on an intelligent contract technology of a block chain.
Owner:DALIAN UNIV OF TECH
Unified authentication and authorization scheme
InactiveCN111131301ARealize unified managementEasy to controlTransmissionUser PrivilegeBusiness enterprise
The invention discloses a unified authentication and authorization scheme, which is composed of an authorization module, a resource module and a client sdk, wherein the authorization module is mainlyresponsible for client verification, user information authentication and issuing of a JWT token after successful authentication; the resource module is mainly responsible for managing open resources by the server; the client sdk cooperates with the server authorization module to complete an authentication and authorization process, obtains the JWT token issued by the server, obtains the user information, and can obtain the specified open resources of the server through the JWT token. A barrier between systems developed based on Java in an enterprise can be broken through, unified management and control of basic information such as user authority are achieved, and the operation management cost of the enterprise is reduced. The access of each subsystem and the access of an external system are finely controlled through a unified authentication and authorization center, so that the credibility of the access system is ensured; basic information sources such as user authority are consistent,communication of all systems in an enterprise can be achieved, and the use cost of staff is reduced.
Owner:徐工汉云技术股份有限公司
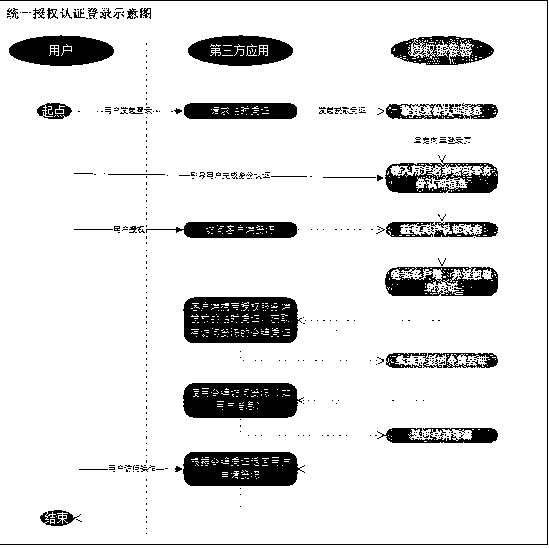
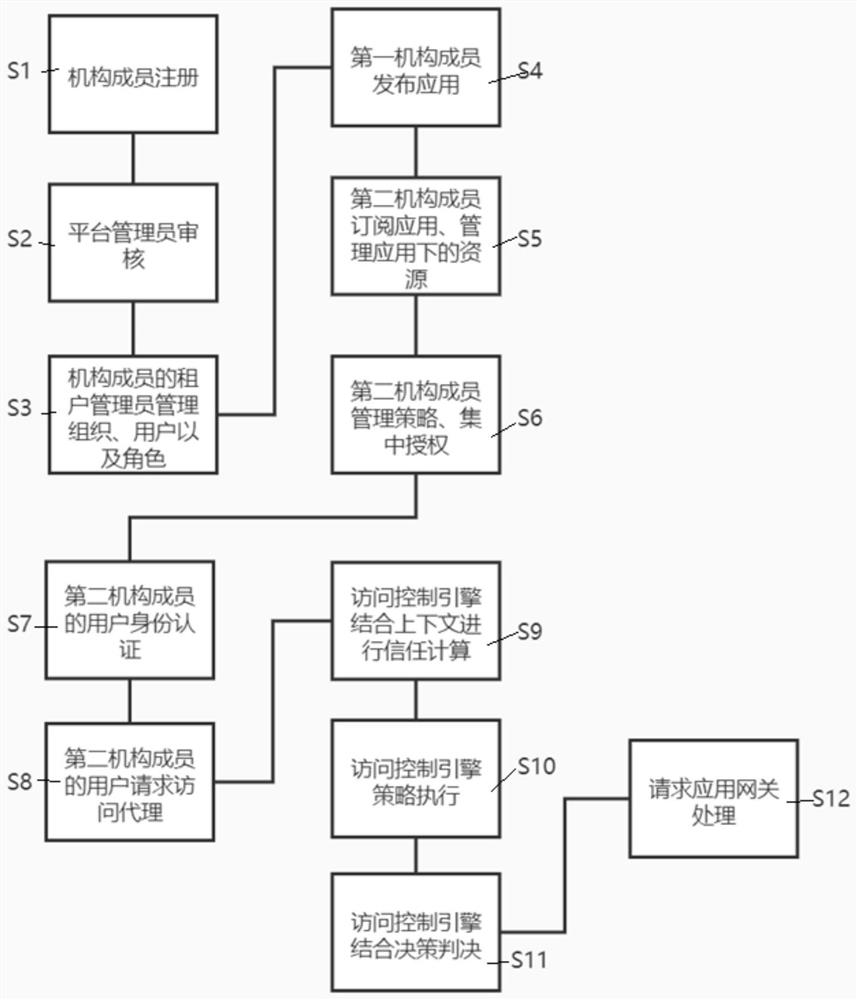
Industrial internet field identity access control method based on zero-trust model
PendingCN114070600AEnsure credibleAvoid attackSecuring communicationIndustrial InternetManagement strategy
The invention relates to an industrial internet field identity access control method based on a zero-trust model. The method comprises the steps of registration, auditing, management, application publishing, subscription and management, management strategy and centralized authorization, user identity authentication, request access proxy, trust calculation, strategy execution, judgment and application gateway processing. According to the invention, a zero-trust model in the technical field of network security is applied to the field of the industrial internet industry, so that the defects of identity verification, authority control and data protection during data access among clients, industrial equipment, application systems and services are overcome, and a set of efficient and complete user access control system is formed.
Owner:上海电气集团数字科技有限公司
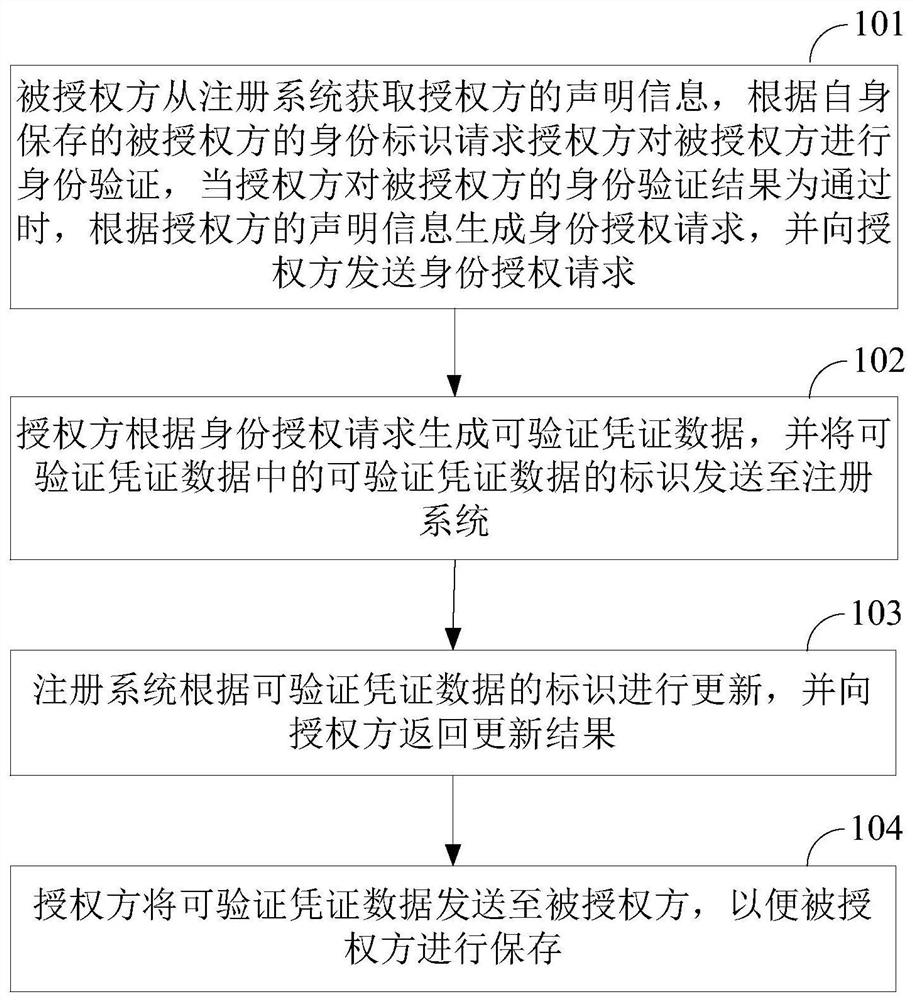
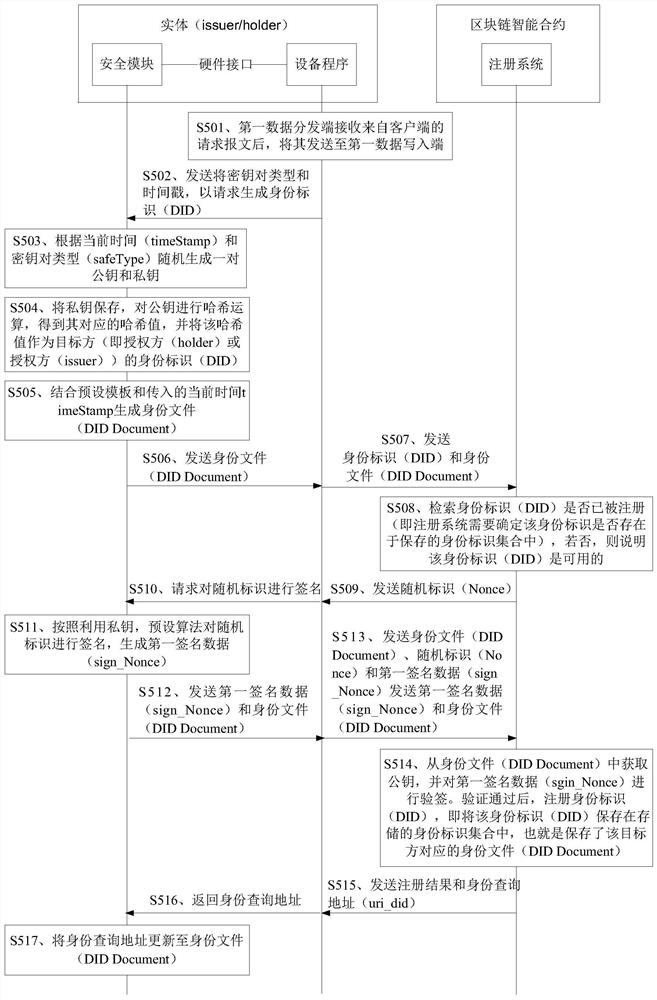
Identity authorization method and device, storage medium and equipment
ActiveCN112291245AImprove securityImprove reliabilityKey distribution for secure communicationDigital data authenticationInternet privacyVoucher
The invention discloses an identity authorization method and device, a storage medium and equipment, and the method comprises the steps of: enabling an authorized party to obtain the declaration information of an authorization party from a registration system, and requesting the authorization party to carry out the identity verification of the authorized party according to the stored identity identification of the authorized party, generating an identity authorization request according to the declaration information of the authorizing party and sending the identity authorization request to theauthorizing party when the identity verification result of the authorizing party to the authorized party is passed; enabling the authorization party to generate verifiable voucher data according to the identity authorization request and send an identifier of the verifiable voucher data to the registration system, so that the registration system updates according to the identifier of the verifiable voucher data; and enabling the authorizing party to send the verifiable credential data to the authorized party so that the authorized party can store the verifiable credential data. Therefore, based on the advantages of decentralization of the blockchain and incapability of being tampered by the outside of the registration system, the security and reliability of identity authorization between the authorizing party and the authorized party can be effectively improved.
Owner:BEIJING HUAHONG INTEGRATED CIRCUIT DESIGN
Distributed energy data management co-processing method and system based on block chain
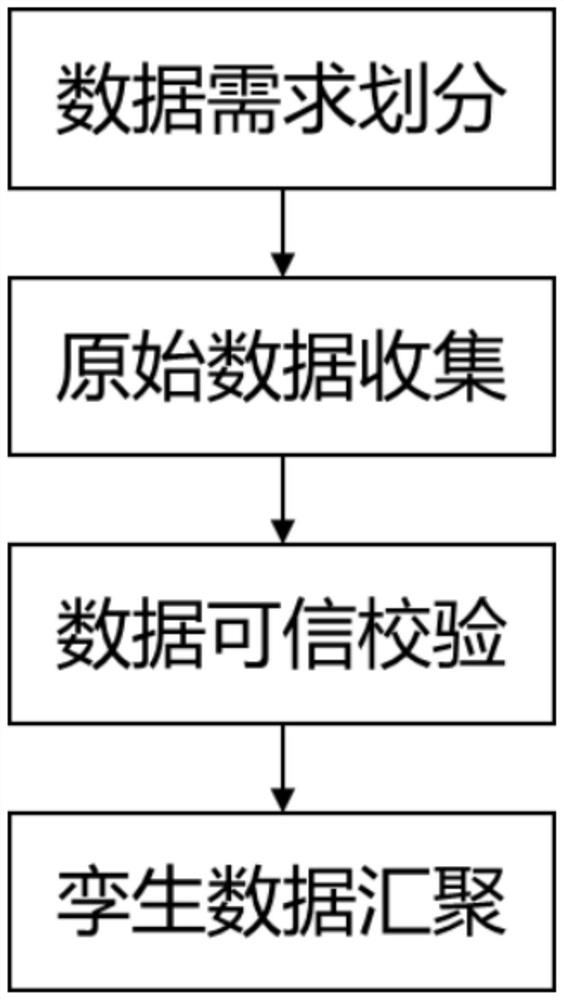
PendingCN114861167AEnsure the coordination of distributed data resourcesEnsure credibleDigital data protectionPlatform integrity maintainanceData verificationData processing
The invention discloses a distributed energy data management co-processing method and system based on a block chain, and belongs to the technical field of distributed energy data processing. According to the distributed energy data management co-processing method based on the block chain, the data of the distributed energy system terminal is acquired by constructing the distributed acquisition model, so that the credibility of data acquisition is ensured; a trusted computing distributed sandbox is constructed, an isolation environment is provided for data, and the trustworthiness of an operation environment is ensured; constructing a distributed data verification model, and performing credible verification on the isolated data to ensure that the off-chain data is not tampered or damaged; constructing a distributed data twinning model, and carrying out twinning convergence on the data so as to meet a refined optimization decision task; according to the optimization decision making task, a distributed optimization decision making contract model is constructed, the optimization decision making task is divided into micro-task services, cooperative processing of distributed energy data resources is completed, and the scheme is detailed and feasible.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY
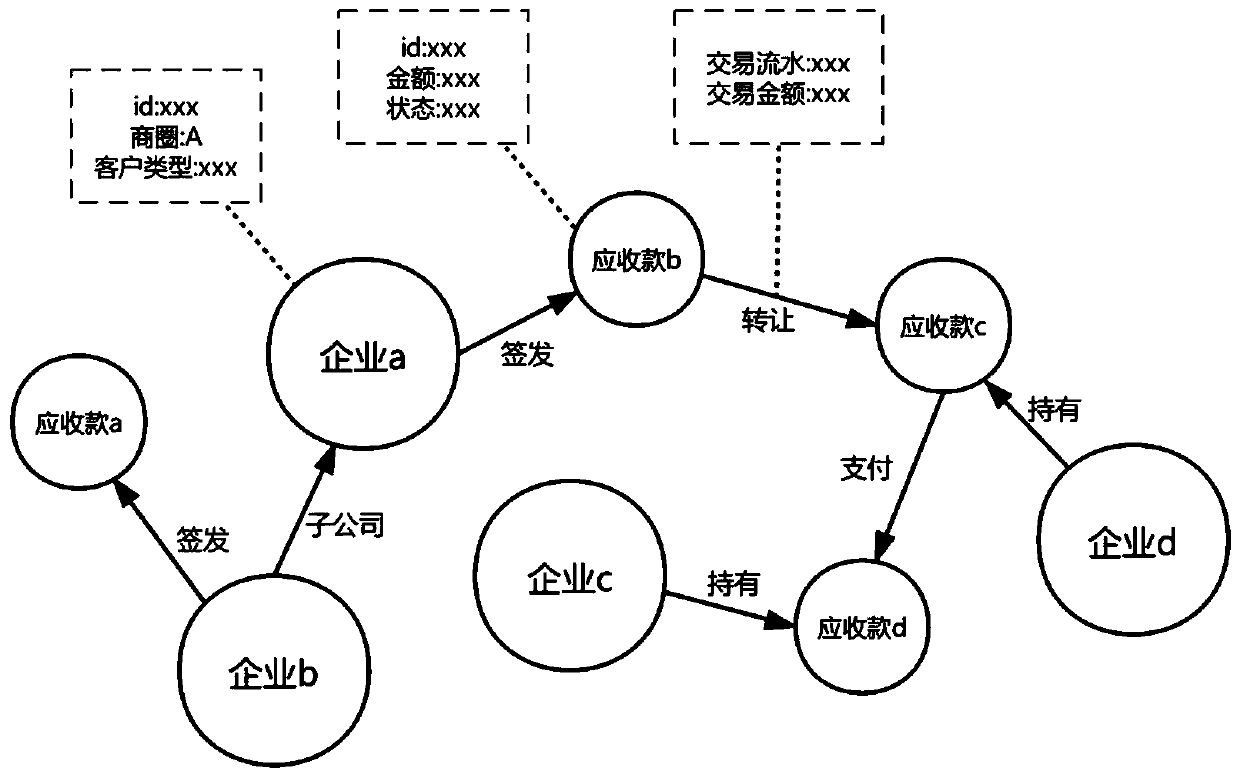
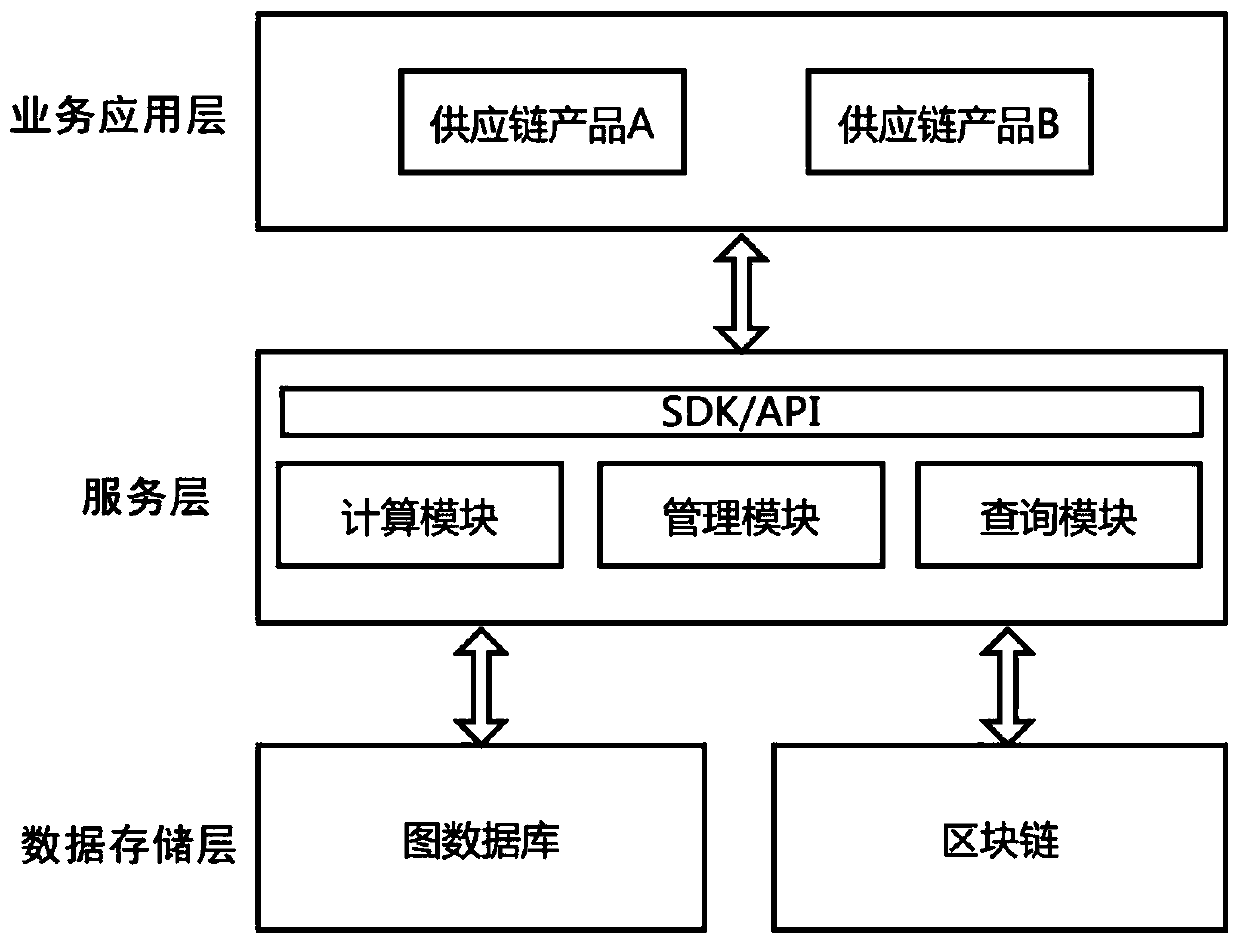
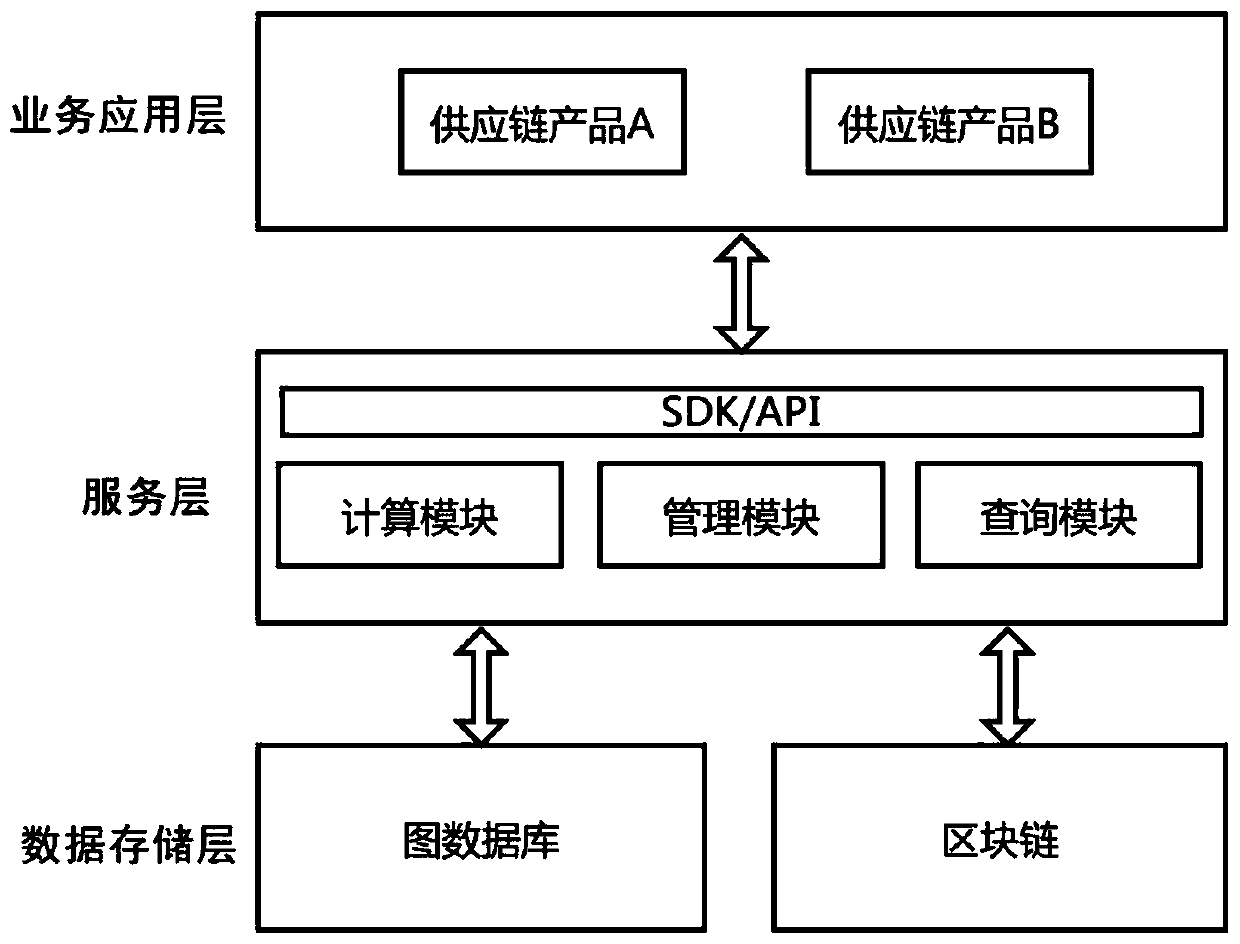
Supply chain financial system data query optimization method and platform based on block chain
PendingCN111177202AVisual inspectionEasy to analyzeDatabase distribution/replicationOther databases indexingGraph theoreticQuery optimization
The invention discloses a supply chain financial system data query optimization method and platform based on a block chain. The method comprises the following steps: customer data, product data and product circulation data involved in a supply chain financial system are stored in a block chain; association relationship data between customers, between customers and products and between products areobtained and stored in a graph database; on one hand, the association relationship data can be inquired from the blockchain through the service identifier to ensure the credibility and traceability of the data in the graph database, and on the other hand, the graph database is utilized to calculate and analyze the basic association data by using different graph theory algorithms according to different service requirements to provide an efficient and diversified inquiry function. According to the method, the blockchain provides a primary key query function, and the graph database provides an association relationship query function, so that the flexibility and high efficiency of data query in an actual supply chain scene can be met, and the system data query capability is effectively improved.
Owner:CHINA ZHESHANG BANK
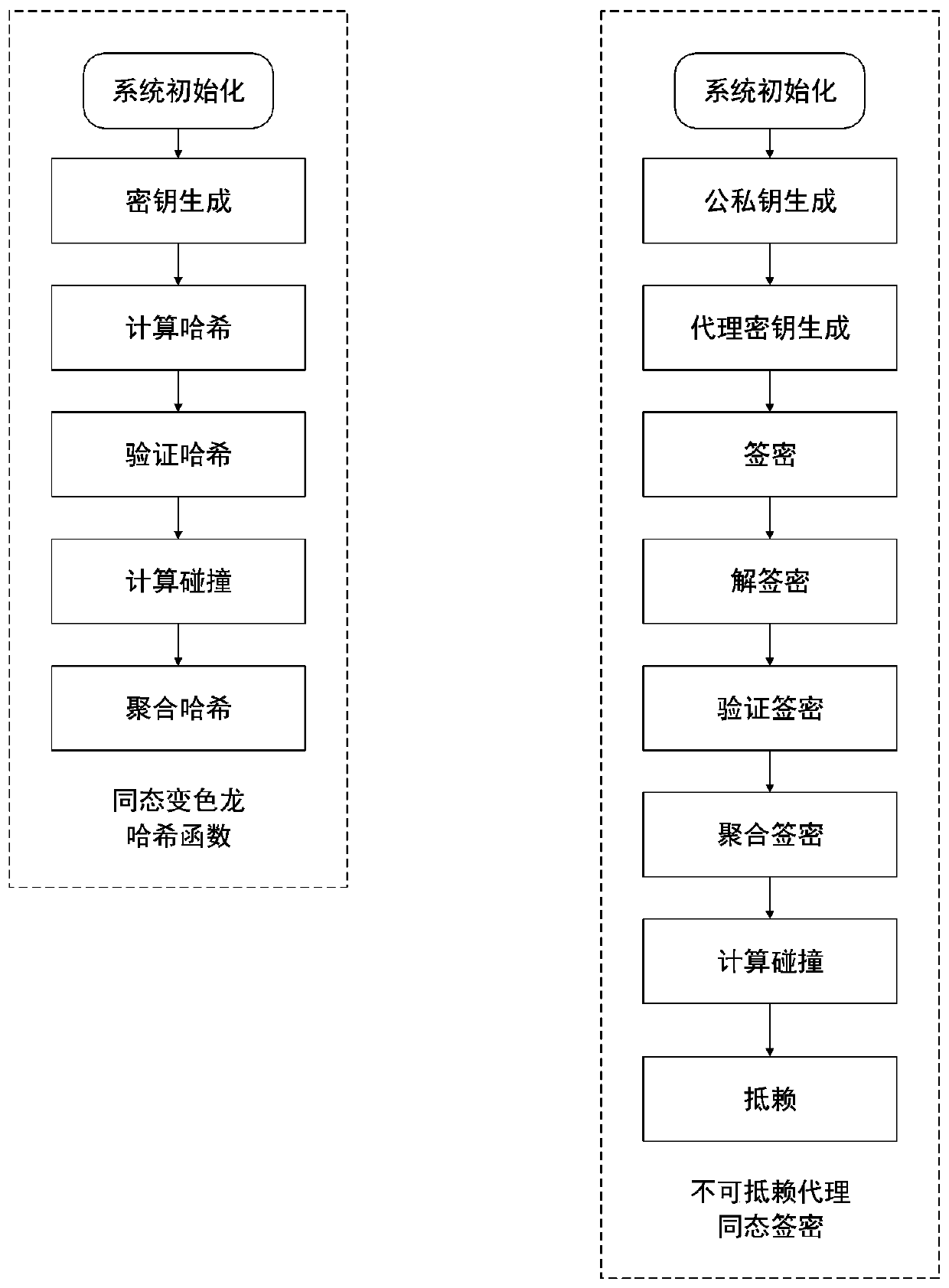
Hash calculation method and signcryption method based on homomorphic chameleon Hash function
ActiveCN110086599AComputationally efficientFunctionalKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionSurrogate key
The invention discloses a Hash calculation method and a signcryption method based on a homomorphic chameleon Hash function. According to the provided homomorphic chameleon hash function, a chameleon hash value result adopts a logarithm form, a signcryption result based on the hash in the signcryption method is also a logarithm form, so that the homomorphic property is achieved, the homomorphic aggregation can be conducted in hash calculation, hash is more efficiently calculated, and the homomorphic chameleon hash function has both the homomorphic state and the key leakage prevention characteristics. The signcryption method is realized on the basis of the homomorphic chameleon hash function, the homomorphic aggregation signcryption ensures the homomorphism, the system public parameters generated by the system initialization are used together by the chameleon hash function and the signcryption, and two password schemes share one set of system parameters, so that multiple function effectscan be realized under one set of shared system parameters, and multiple functions are supported under the same framework. Secondly, the proxy key generation and proxy re-signature steps realize the proxy re-signature, and the non-repudiation is realized through a repudiation step.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
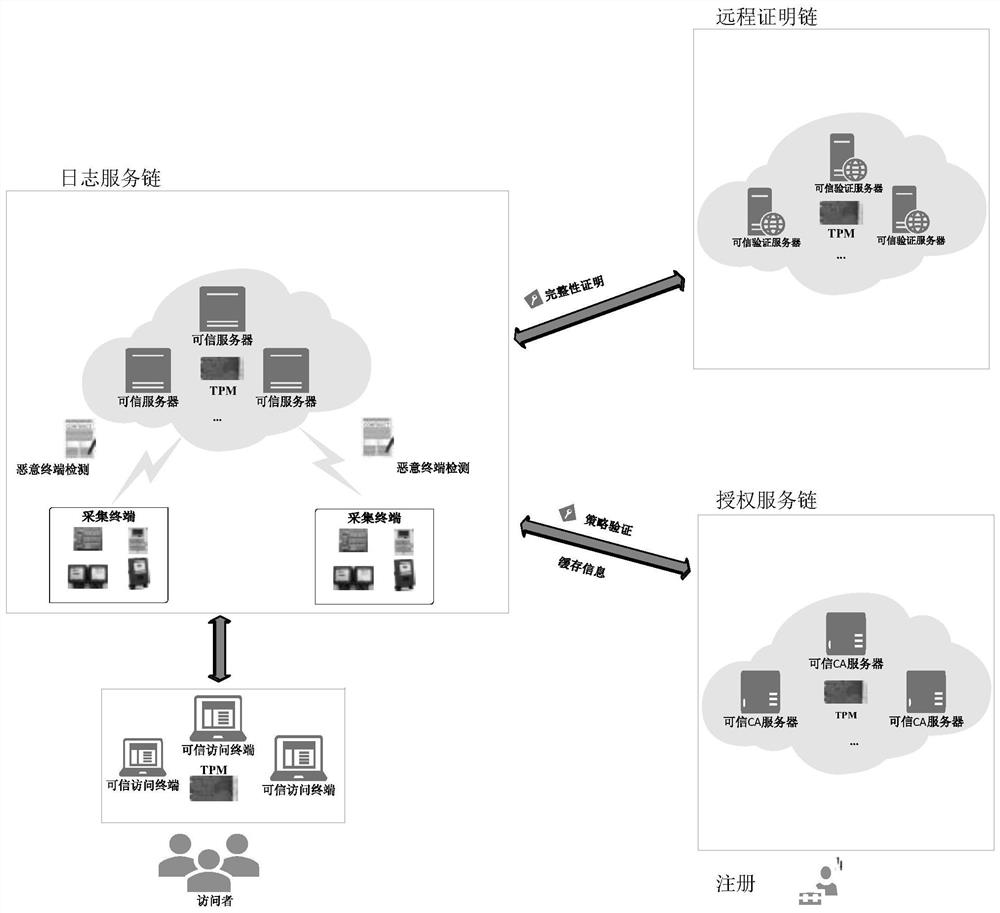
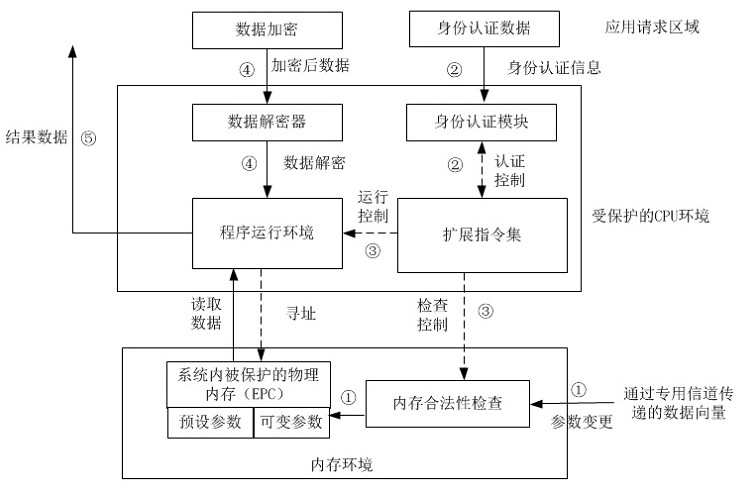
Trusted computing-based electric power block chain system
PendingCN112417494AGuaranteed privacy dataEnsure crediblePublic key for secure communicationDigital data protectionTrusted ComputingSmart contract
The invention relates to the technical field of trusted authentication, and provides a trusted computing-based electric power block chain system, which comprises an authorization service chain, a logservice chain and a remote certification chain, trusted chips are arranged in blockchain nodes of the authorization service chain, the log service chain and the remote certification chain; the log service chain measures the reputation value of the collection layer terminal in real time through a malicious node detection mechanism based on an intelligent contract, discovers that the terminal can befound in time and removes the terminal out of the network, and prevents the malicious terminal from publishing malicious data. The log service chain and the remote verification chain perform remote integrity verification on the terminal requesting to access the system through the trusted chip; the authorization service chain carries out strategy verification on the terminal requesting to access the system. The system detects the access authority of a visitor through two aspects of integrity proof and access strategy verification, guarantees the credibility of an access terminal, comprehensively maintains the safe and credible operation of the power block chain system, and protects the private data in the power block chain.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
Data trusted processing method and system fusing trusted computing and block chain
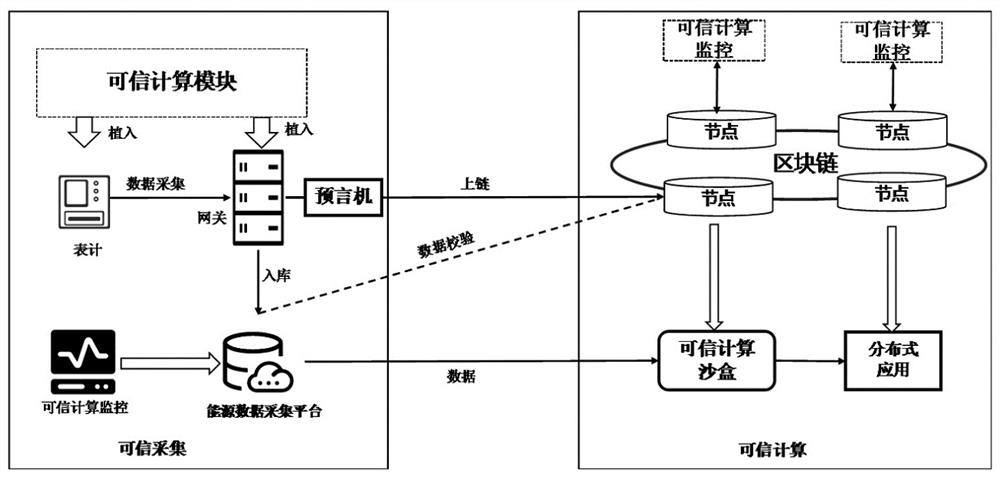
ActiveCN114499895ARealize trusted acquisitionRealize computingUser identity/authority verificationInstrumentsPrivacy protectionData acquisition
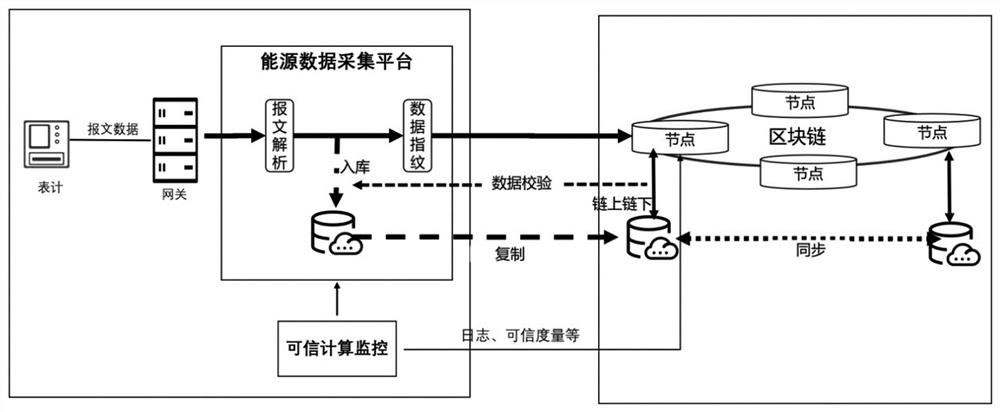
The invention discloses a data trusted processing method and system fusing trusted computing and a block chain, and belongs to the technical field of energy data processing. The invention discloses a data trusted processing method and system fusing trusted computing and a block chain. The data trusted processing method and system are mainly used for solving the energy data trust problem before energy data is chained in the current block chain application process and the environment trusted problem of service computing. Aiming at the problem of credibility of uplink energy data, starting from two aspects of an Internet of Things acquisition end or an Internet of Things energy data acquisition platform, a method of fusing a credible computing technology and a block chain technology is adopted, and Internet of Things acquisition equipment, an oracle machine and an on-chain and off-chain energy data credible verification model are embedded through credible computing; the credibility of energy data collection, transmission and storage processes is realized, and the credibility of energy data collection is ensured in combination with security monitoring of credible computing. In order to solve the problem of a service computing environment, the invention provides a computing architecture combining trusted computing and a state channel, so that service computing is carried out on energy data under the condition of privacy protection.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
Trusted platform for wireless terminal, and method
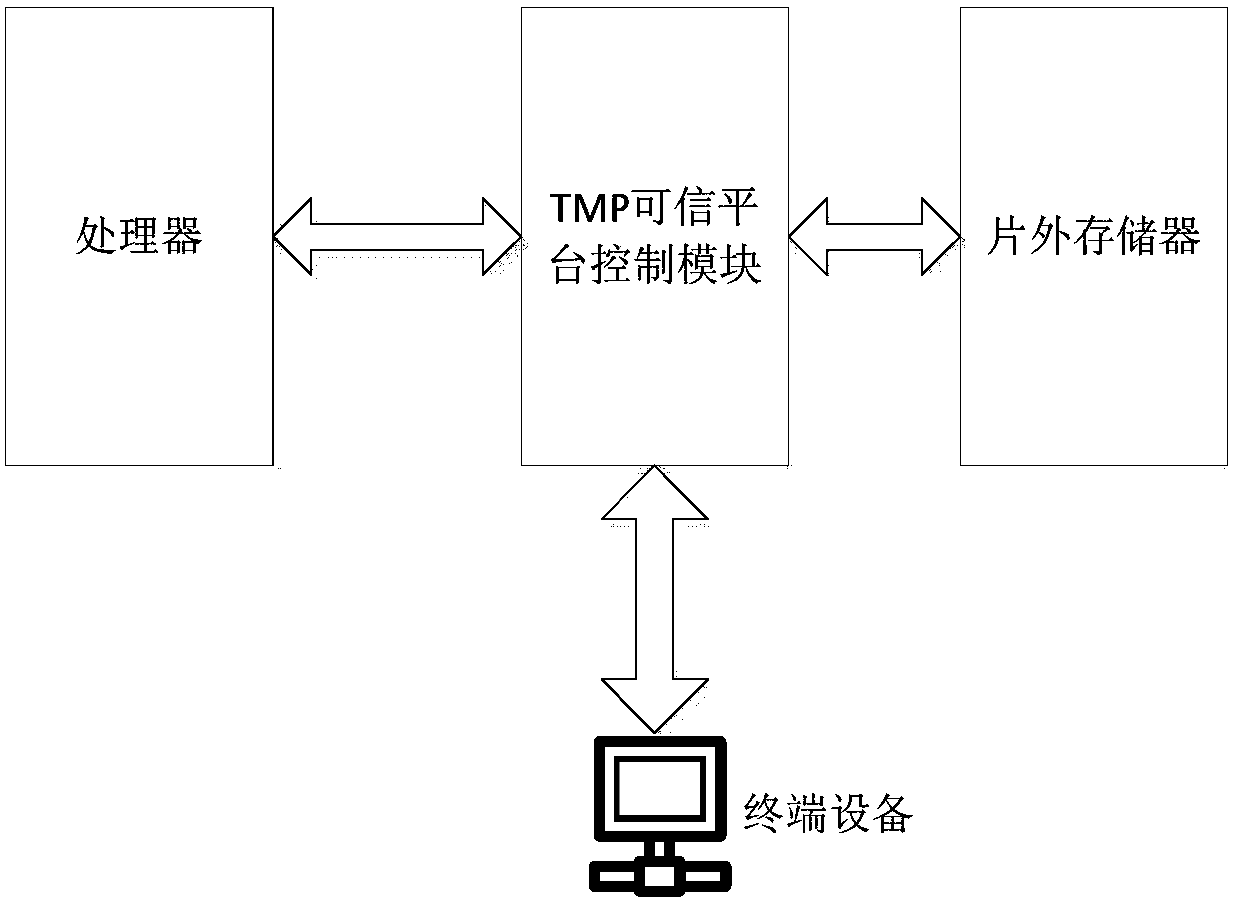
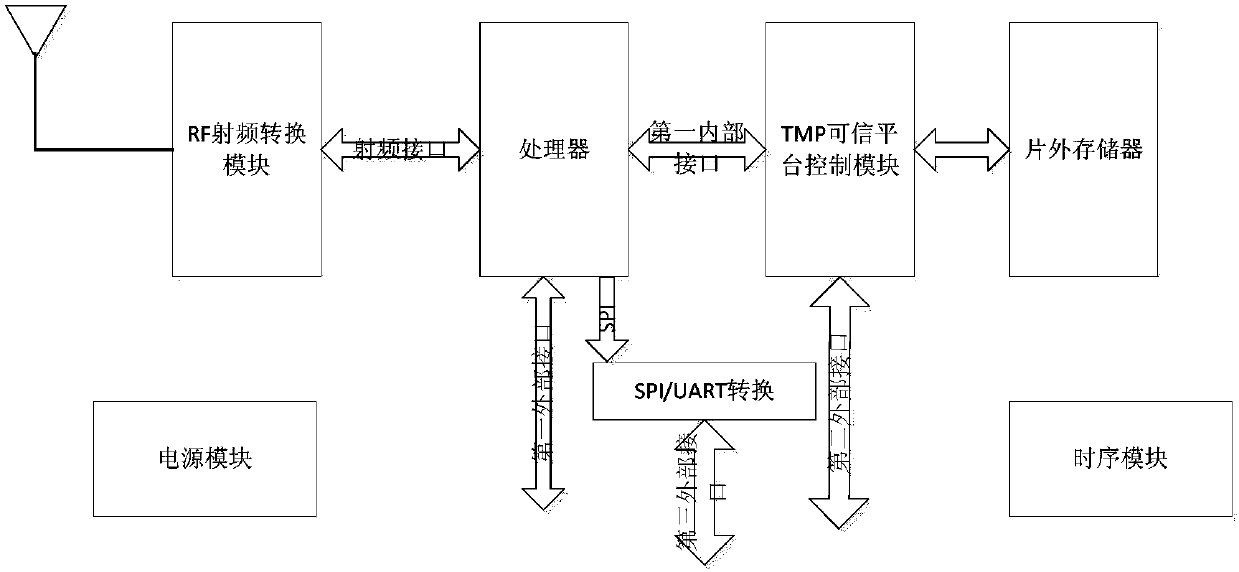
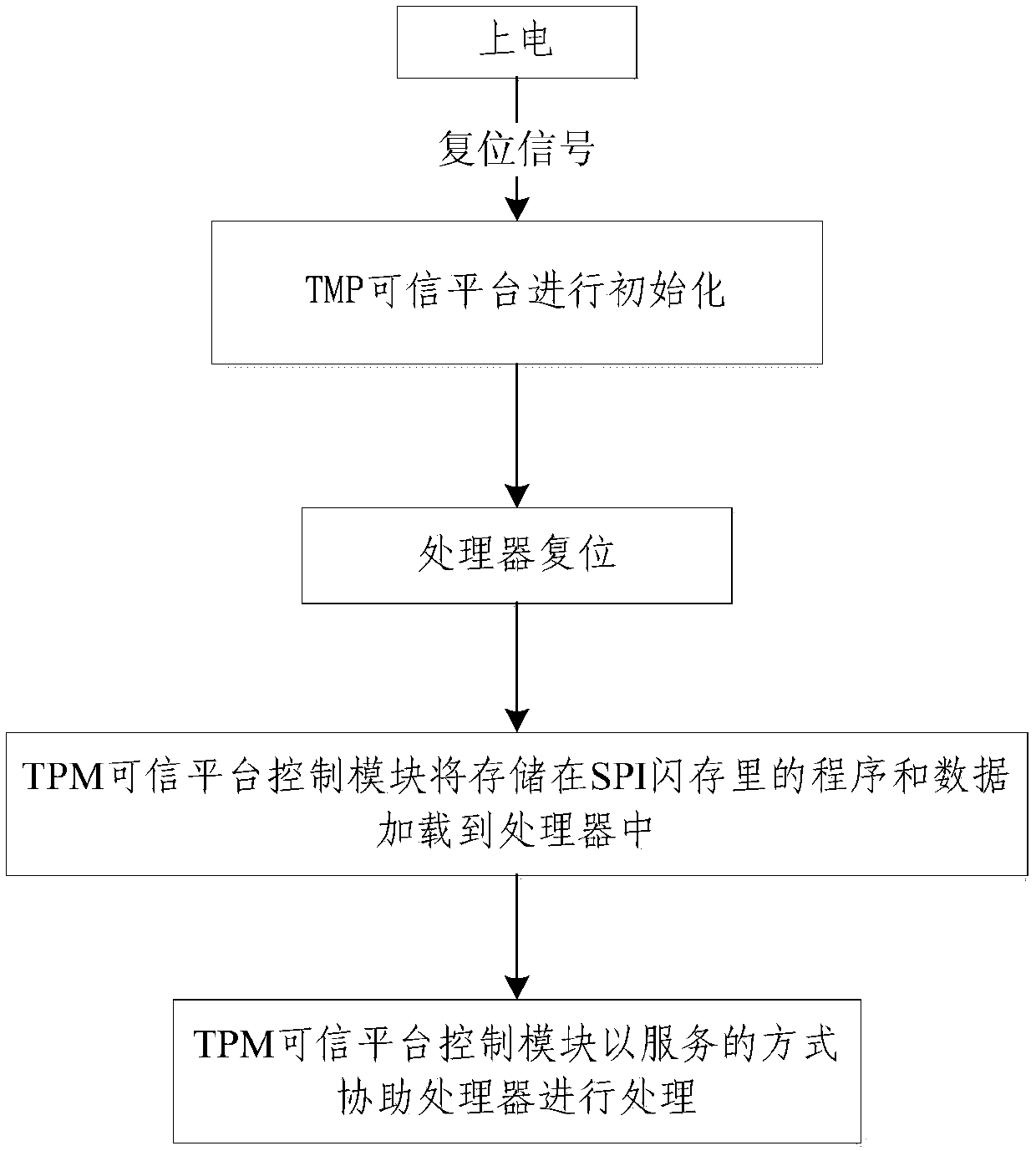
InactiveCN107769917AEnsure credibleTrusted implementationKey distribution for secure communicationTerminal equipmentComputer terminal
The invention provides a trusted wireless terminal platform, and a method for realizing trustworthiness of a wireless terminal. The platform comprises a trusted platform control module used for safelycalling programs and configuration data stored in an off-chip manner, triggering a processor to perform loading and assisting the execution of the processor. Therefore, a terminal device can avoid intrusion and data leakage from the source, and the security of the platform and a network system is guaranteed.
Owner:POTEVIO INFORMATION TECH CO LTD
Ticket managing method using bar code
InactiveCN1658213AEnsure credibleNot abiding by the lawCo-operative working arrangementsSpecial data processing applicationsRelevant informationPassword
This invention discloses a method for to managing the securities though the bar code. In order to be served, the administrant of the securities has to bring the certificate and enter the password. The program can show the basic information of the administrant and remind the staff to handle with it on time. When the securities are sold, the staff of the tax bureau will have to scan the bar code of the receipt invoice with a bar code scan device. The information such as the serial number, the total number and the price of the securities, the time when the securities are sold will be collected automatically. Then the safety of the securities is in the charge of the administrant. This method can be used with only one window and only to one customer. It also needs a certain person to guarantee the safety of the securities. Though the information exchange between the customer and the service centre, it connect the securities with a certain person, so as to make sure the securities are safe.
Owner:ZHEJIANG UNIV
Control method for Bluetooth security management
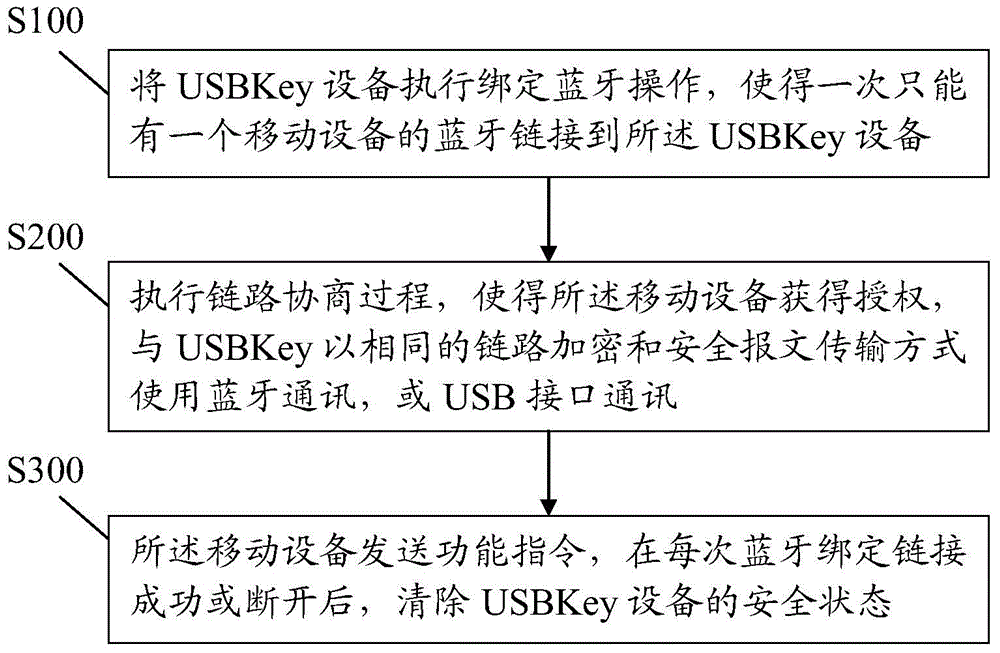
ActiveCN104902476AFix security issuesEasy to implementWireless commuication servicesSecurity arrangementPasswordSecure state
The application discloses a control method for Bluetooth security management. The method comprises the following steps: I, executing Bluetooth binding operation on USBKey equipment in order that the Bluetooth of only one piece of mobile equipment can be linked to the USBKey equipment; II, executing a link negotiation process in order that the mobile equipment acquires authorization, and communicates with USBKey via Bluetooth or a USB (Universal Serial Bus) interface in the same link encryption and security message transmission way; and III, transmitting a function command by the mobile equipment, and clearing the security state of the USBKey equipment after successful connection or disconnection of every Bluetooth binding. The control method has the advantages that an implementation method is simple, and the problems of security matching and credible communication between mobile intelligent equipment and intelligent password equipment is solved through the Bluetooth security management.
Owner:神州融安科技(北京)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com