Trusted platform for wireless terminal, and method
A wireless terminal and trusted technology, applied in the field of communication, can solve the problems of loss of user calls, malicious subscriptions, automatic dialing of voice stations, etc., to avoid intrusion and data leakage, and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
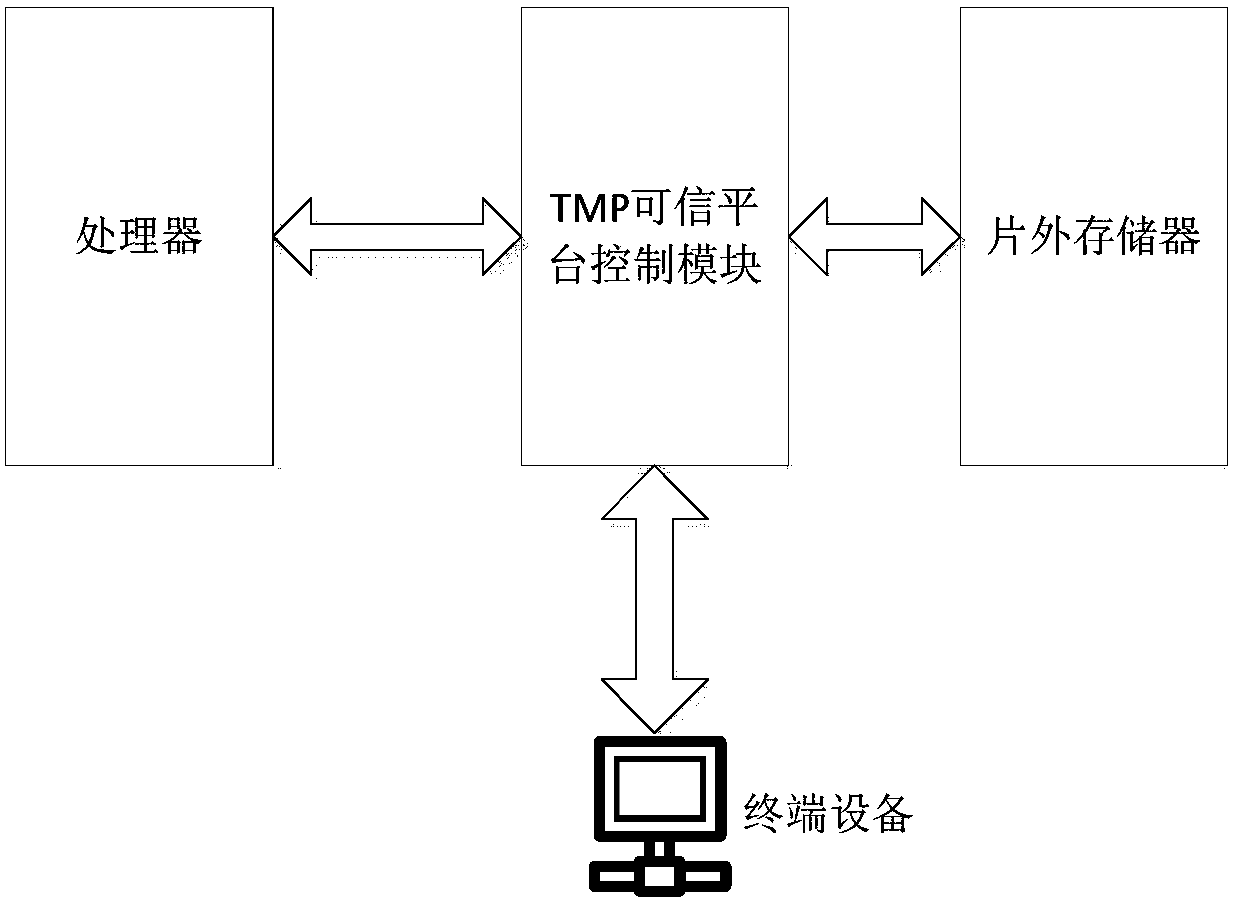
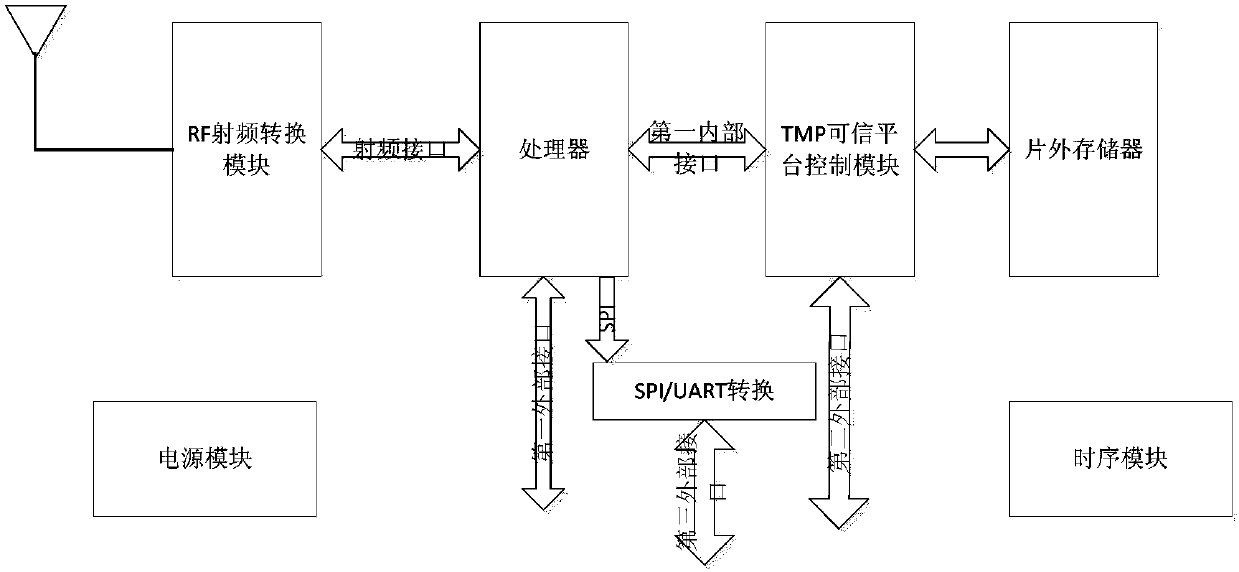
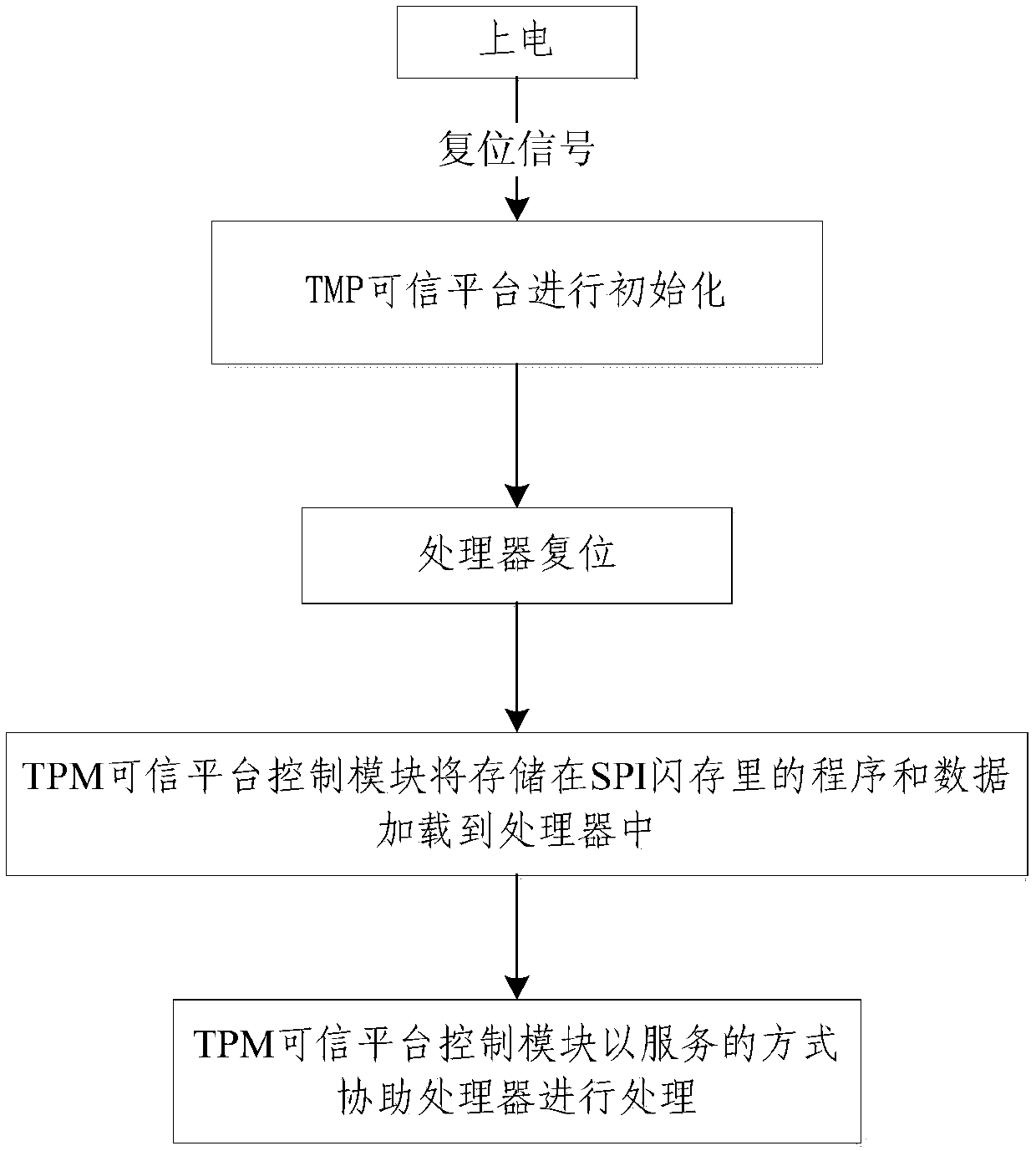
[0019] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
[0020] In order to create a more secure mobile smart terminal, two standard organizations, Trusted Computing Group (TCG) and Global Platform (GP), have successively proposed TPM (Trusted Platform Module, Trusted Platform Module) and TEE (Trusted Execution Environment, Trusted Execution Environment). ) as the representative solution.
[0021] Among them, the purpose of TCG is to widely use trusted computing platforms supported by hardware security modules in computing and communication systems to improve overall security. The TCG specification defines a chip device called Trusted Platform Module (TPM) as a "trust base" for protected activities. TPM is the core of the TCG s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com