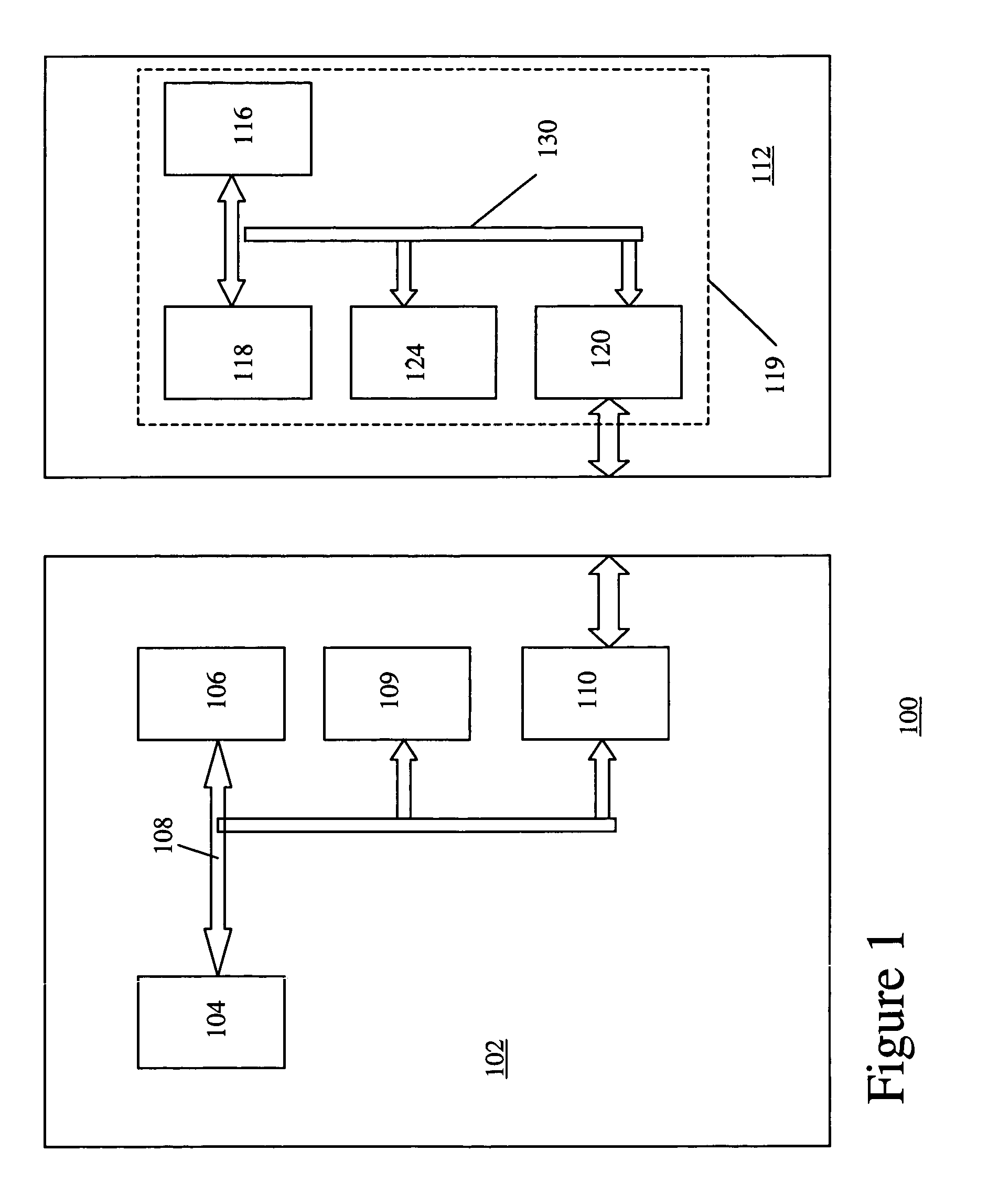
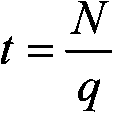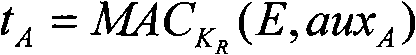Patents
Literature
1092 results about "Data breach" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A data breach is the intentional or unintentional release of secure or private/confidential information to an untrusted environment. Other terms for this phenomenon include unintentional information disclosure, data leak, information leakage and also data spill. Incidents range from concerted attacks by black hats, or individuals who hack for some kind of personal gain, associated with organized crime, political activist or national governments to careless disposal of used computer equipment or data storage media and unhackable source.
Smart contract protection method and system based on trusted environment
InactiveCN107342858ASolve the problem of smart contract versionSolve the problem of damage to rights and interestsKey distribution for secure communicationUser identity/authority verificationInformation processingInformation transmission
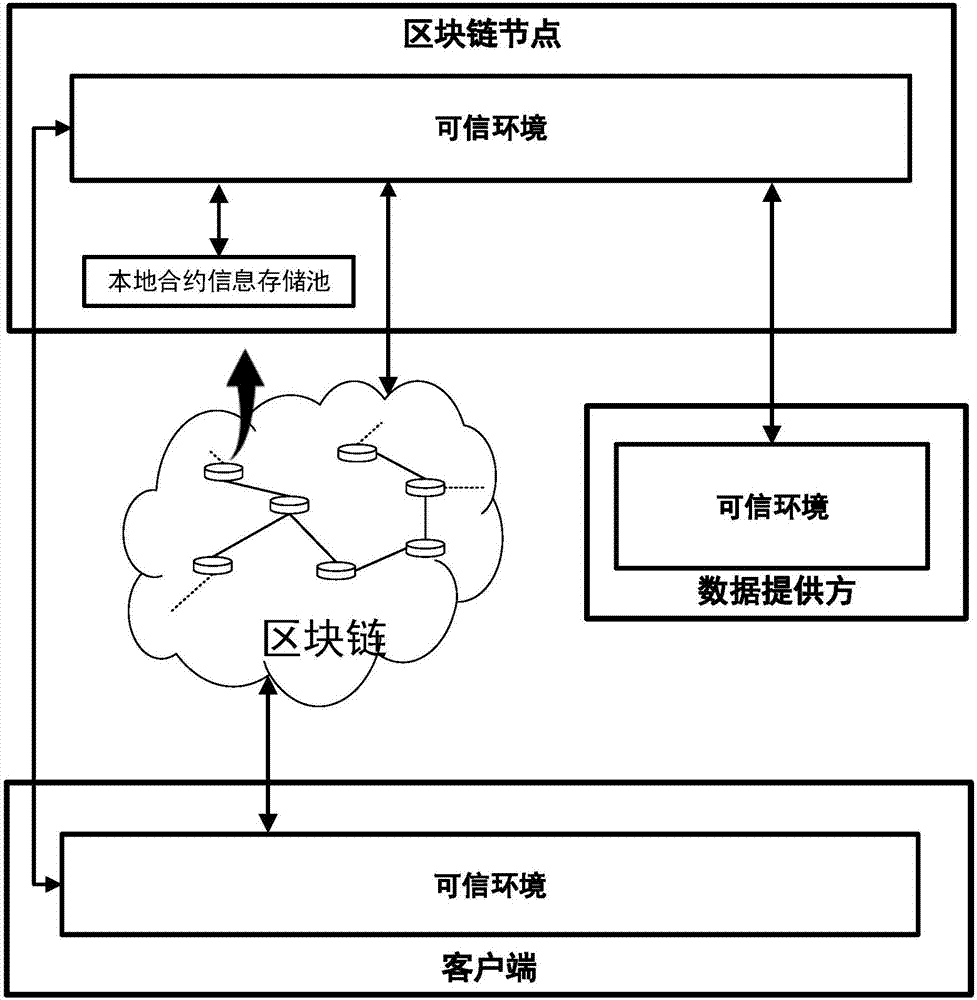
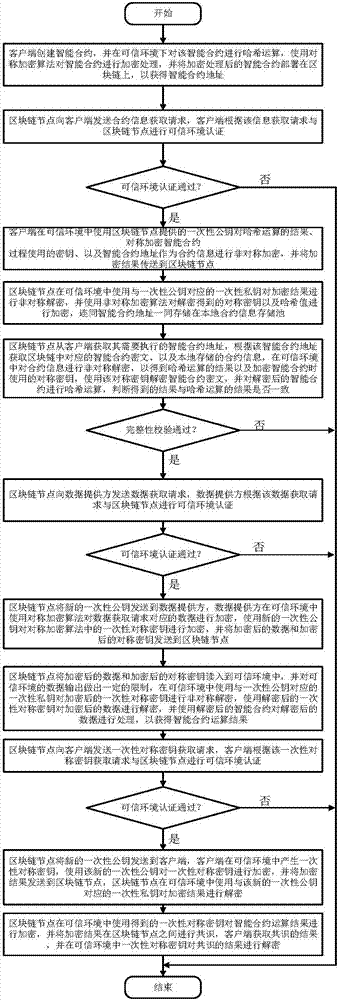
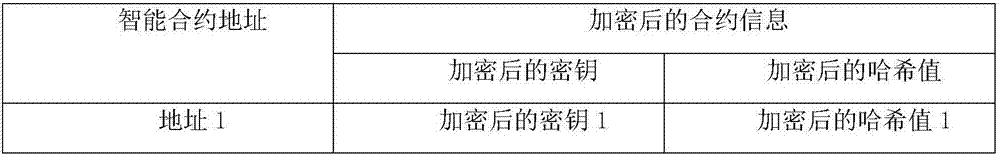
The invention discloses a smart contract protection system based on a trusted environment, including a client, block chain nodes, a data provider, a trusted environment, a non-trusted environment, a smart contract information processing module (A), a block chain node information transmission module (B) (such as a node interaction interface in the Ethereum), an input data transmission module (C), a smart contract execution module (D), a local contract information storage pool (E) and a block chain smart contract storage pool (F). The client is in communication connection with the block chain nodes. The data provider is in communication connection with the block chain nodes. The block chain nodes are in communication connection with one another. The technical problem that the copyright of smart contracts cannot be protected and the rights and interests of smart contract users are damaged due to the fact that the information of smart contracts may easily leak in the existing smart contract system and the technical problem that data may be stolen due to data leakage are solved.
Owner:武汉凤链科技有限公司
Automated Data Breach Notification
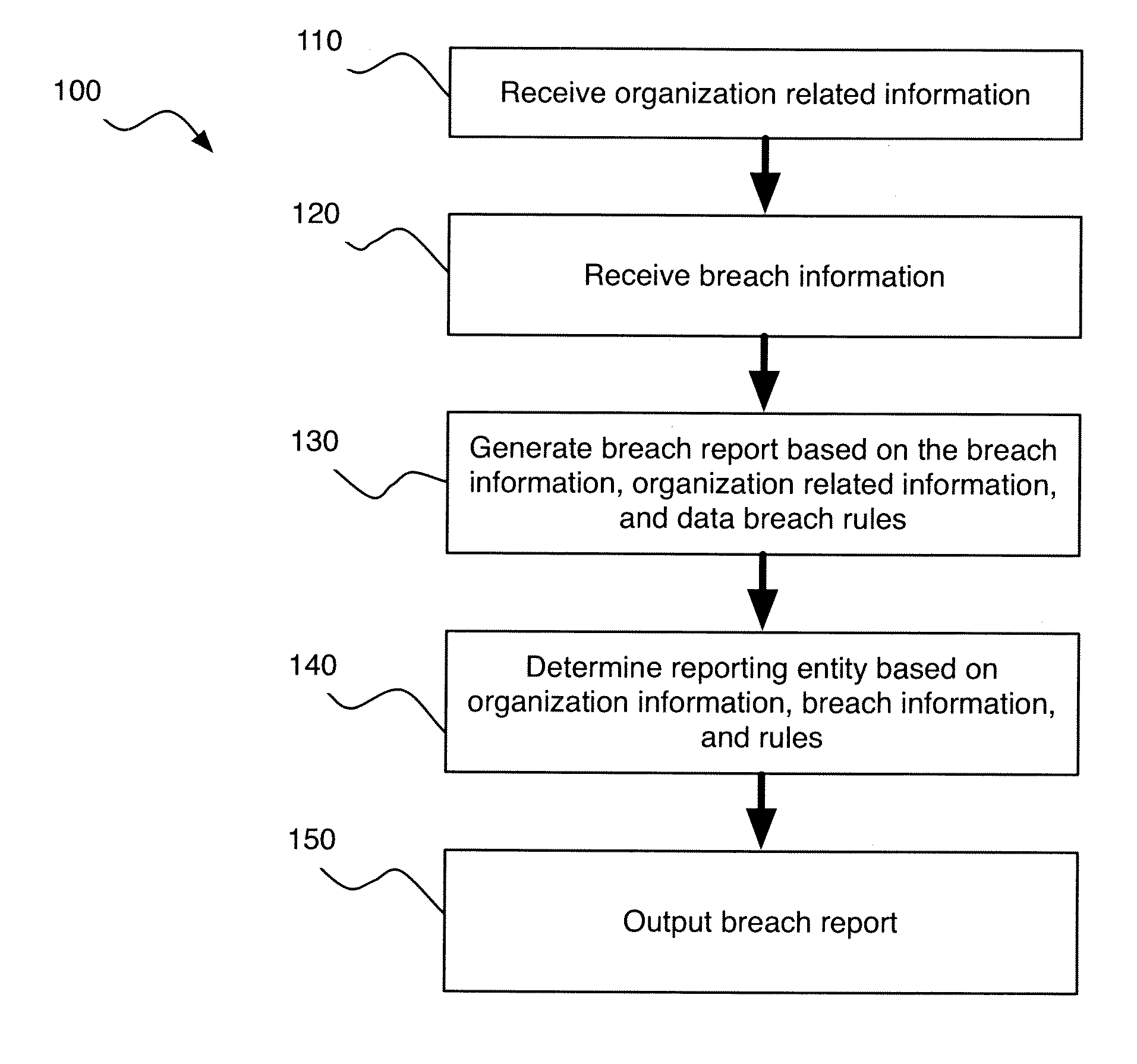
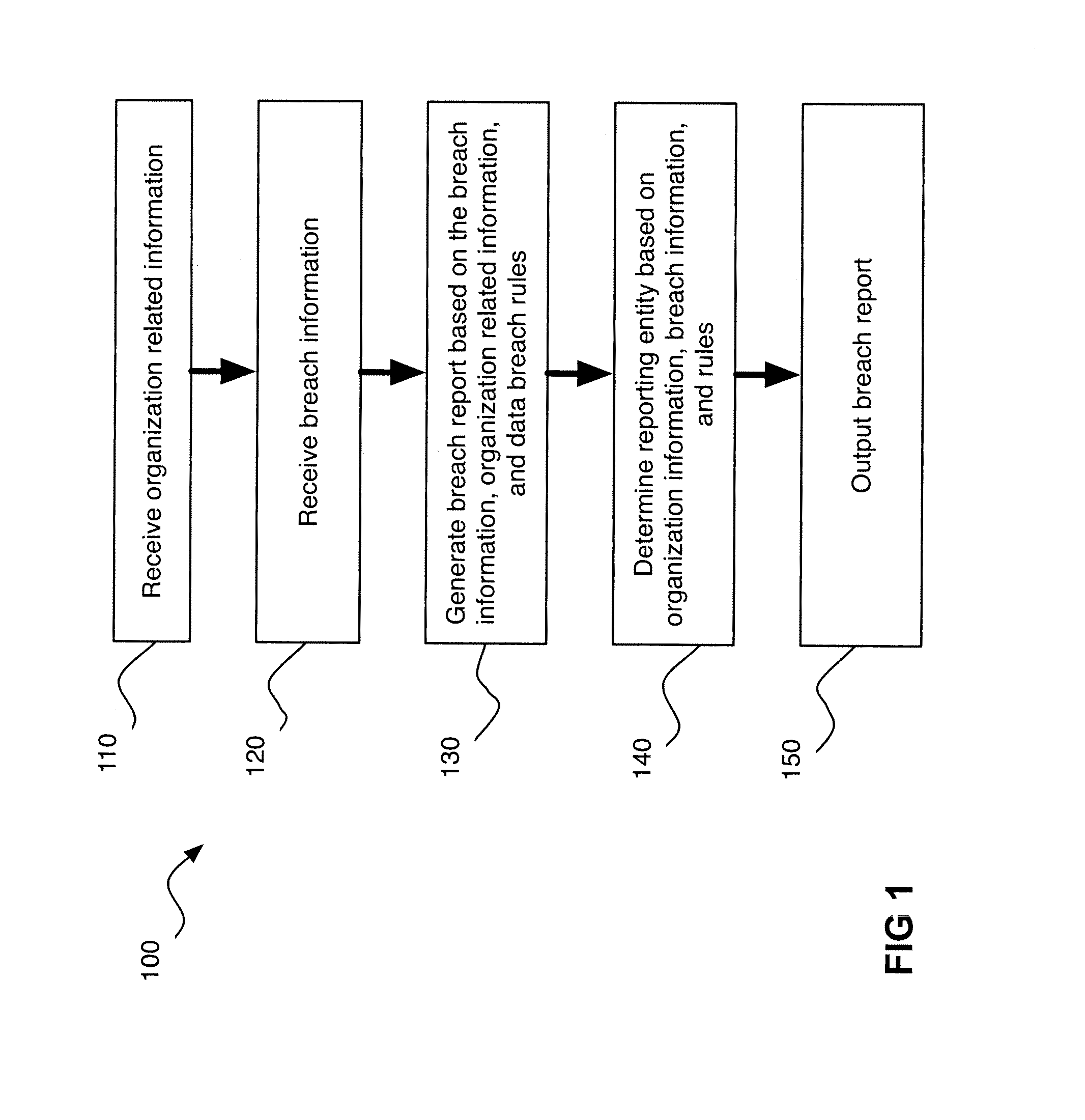
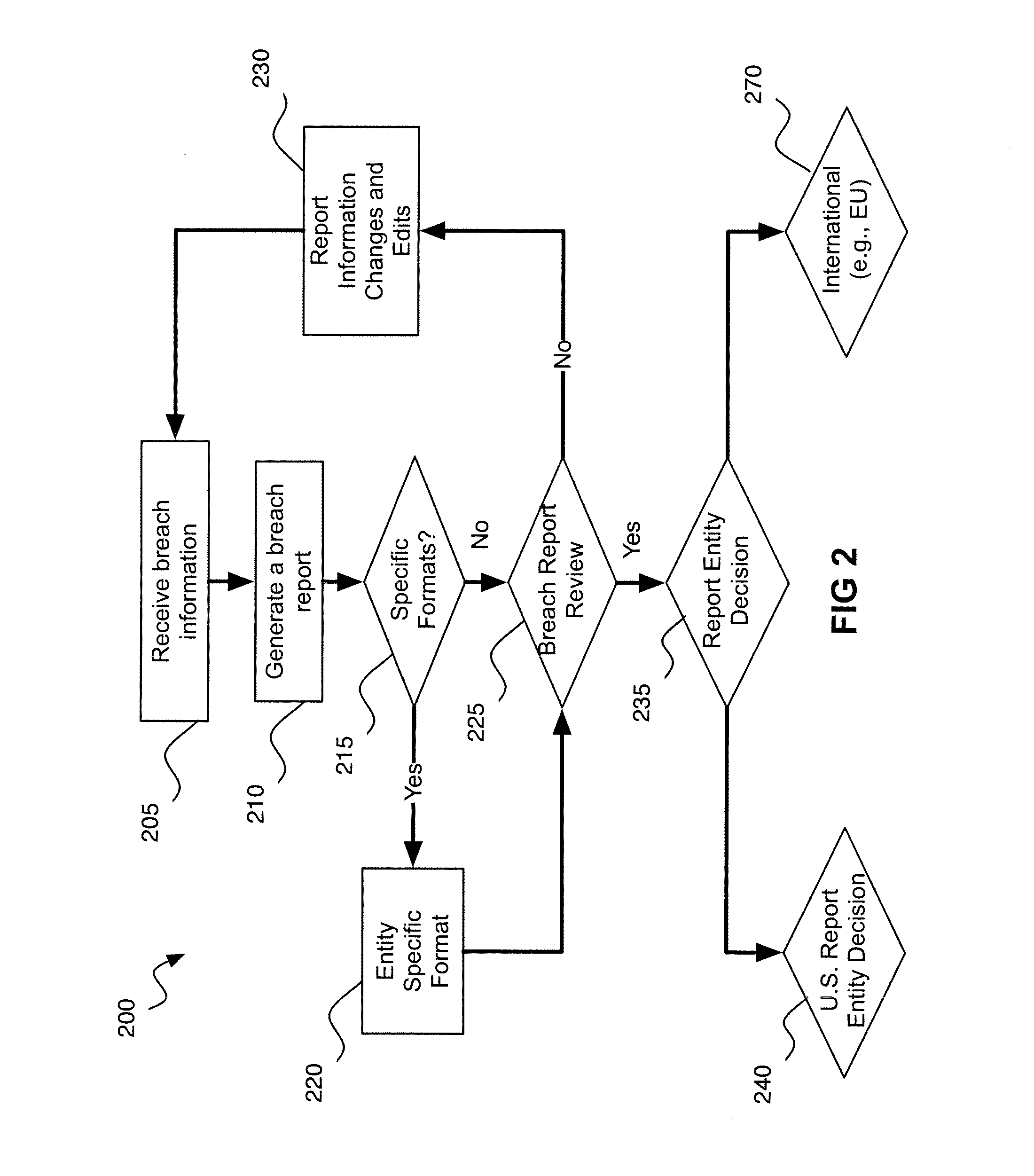
A computer-implemented system for data breach compliance comprises memory for storing computer executable program code; and a processor. The code comprises code for receiving electronic breach information (“EBI”), the EBI relating to a data breach, the EBI comprising data type information, geographic information, and data format information; code for analyzing the geographic information to choose an applicable set of regulatory rules; code for applying the rules to determine if a harm analysis is required; if the harm analysis is required, code for performing the harm analysis; code for analyzing the breach information and the volume of harm to determine if the volume of harm exceeds a harm threshold; and code for analyzing the breach information, the rules and the volume of harm to determine whether a consumer must be notified about the data breach.
Owner:CSR PROFESSIONAL SERVICES
Systems And Methods For Identifying Compliance-Related Information Associated With Data Breach Events
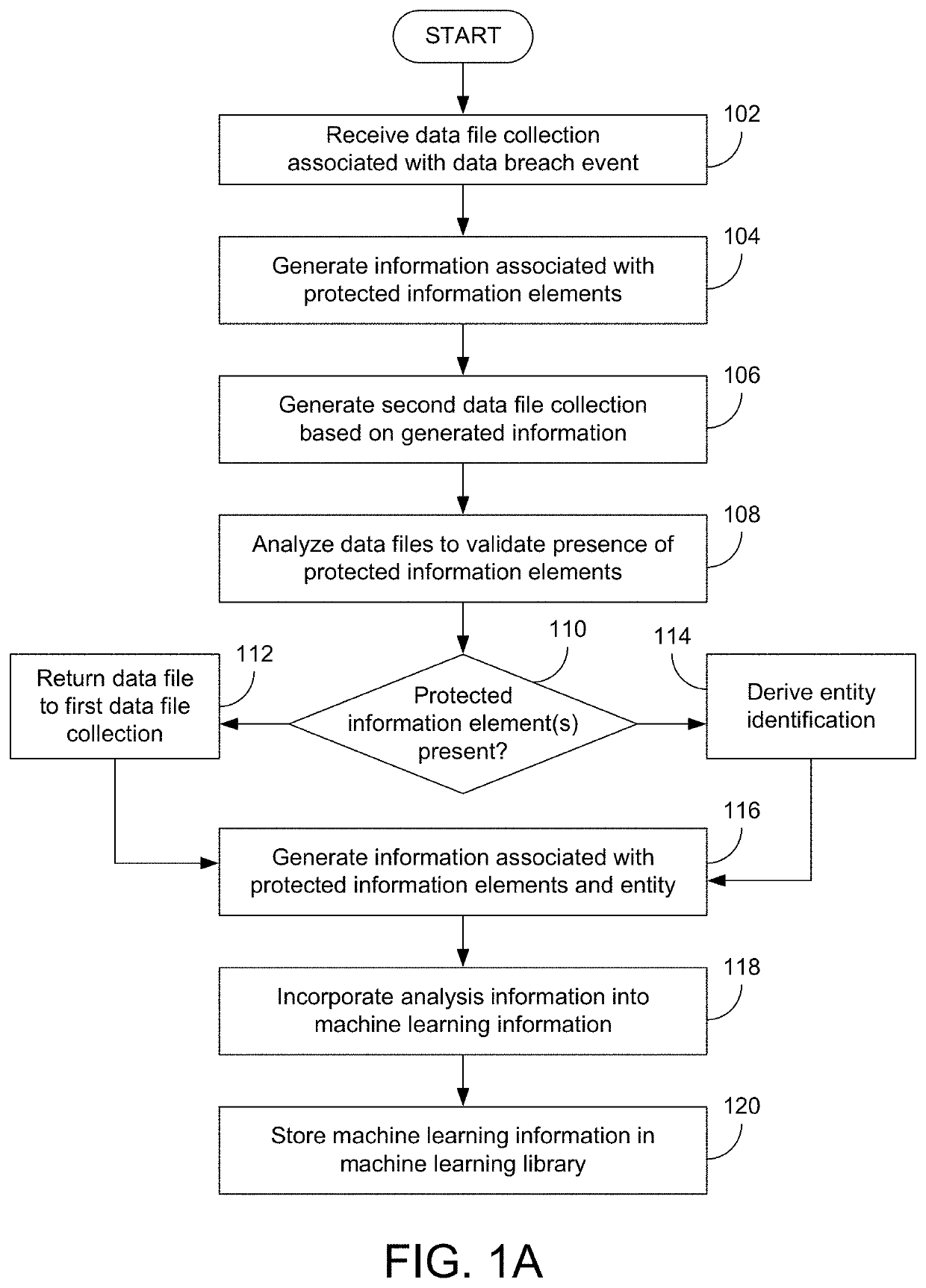
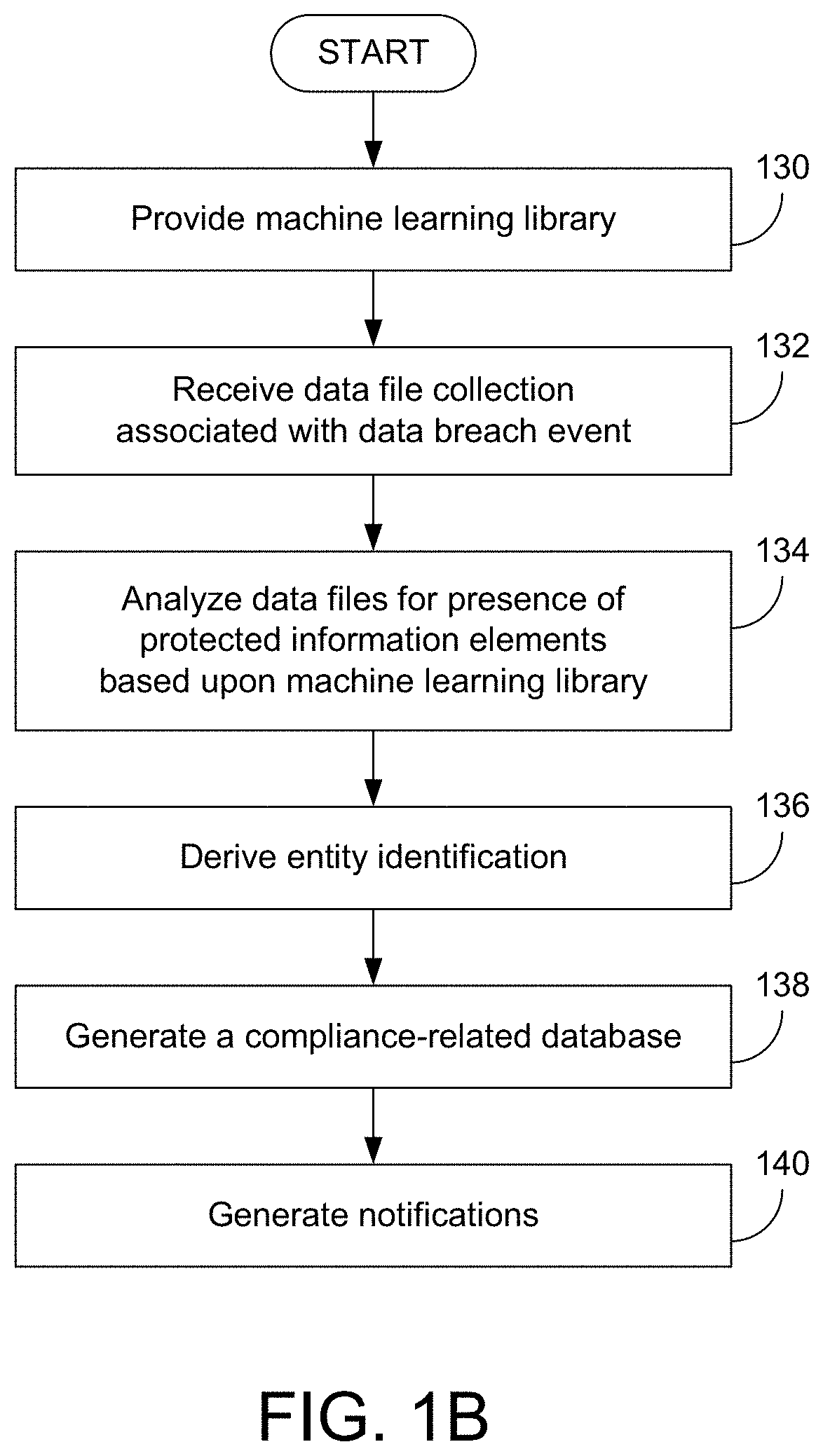
Various examples are provided related to identification and management of compliance-related information associated with data breach events. In one example, a method includes receiving a first data file collection associated with a first data breach event; generating information associated with presence or absence of protected information elements of all or part of the first data file collection and incorporating data files including the protected information elements in a second data file collection; analyzing data files selected from the second data file collection; and incorporating the information associated with the analysis into machine learning information that may be used for subsequent analysis of data file collections.
Owner:CANOPY SOFTWARE INC
Identification breach detection
InactiveUS9032531B1Low costDecrease in class action lawsuit lossMemory loss protectionError detection/correctionComputer scienceData breach
Owner:MIDDLEGATE
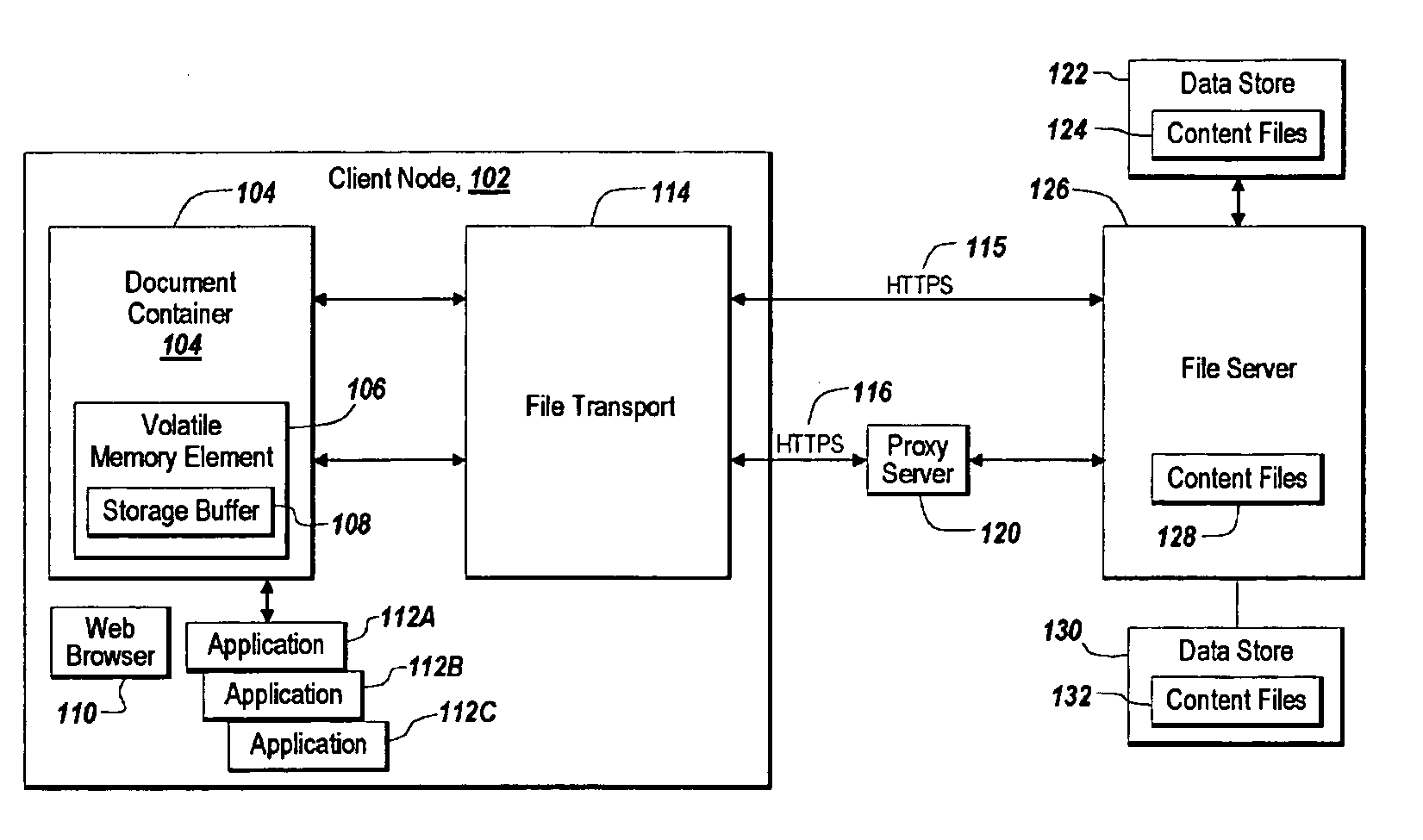
A method and apparatus for reducing disclosure of proprietary data in a networked environment
ActiveUS20060074837A1Reduce disclosureDigital data information retrievalInformation formatApplication serverClient-side
A method and apparatus for reducing disclosure of proprietary data in a networked environment includes a client node, an access control server, and an application server farm. The client node transmits a request for a file. The access control server receives the request for the file and makes an access control decision. An application server farm presents the contents of the file to the client node using an application program associated with a file type of the requested file.
Owner:CITRIX SYST INC
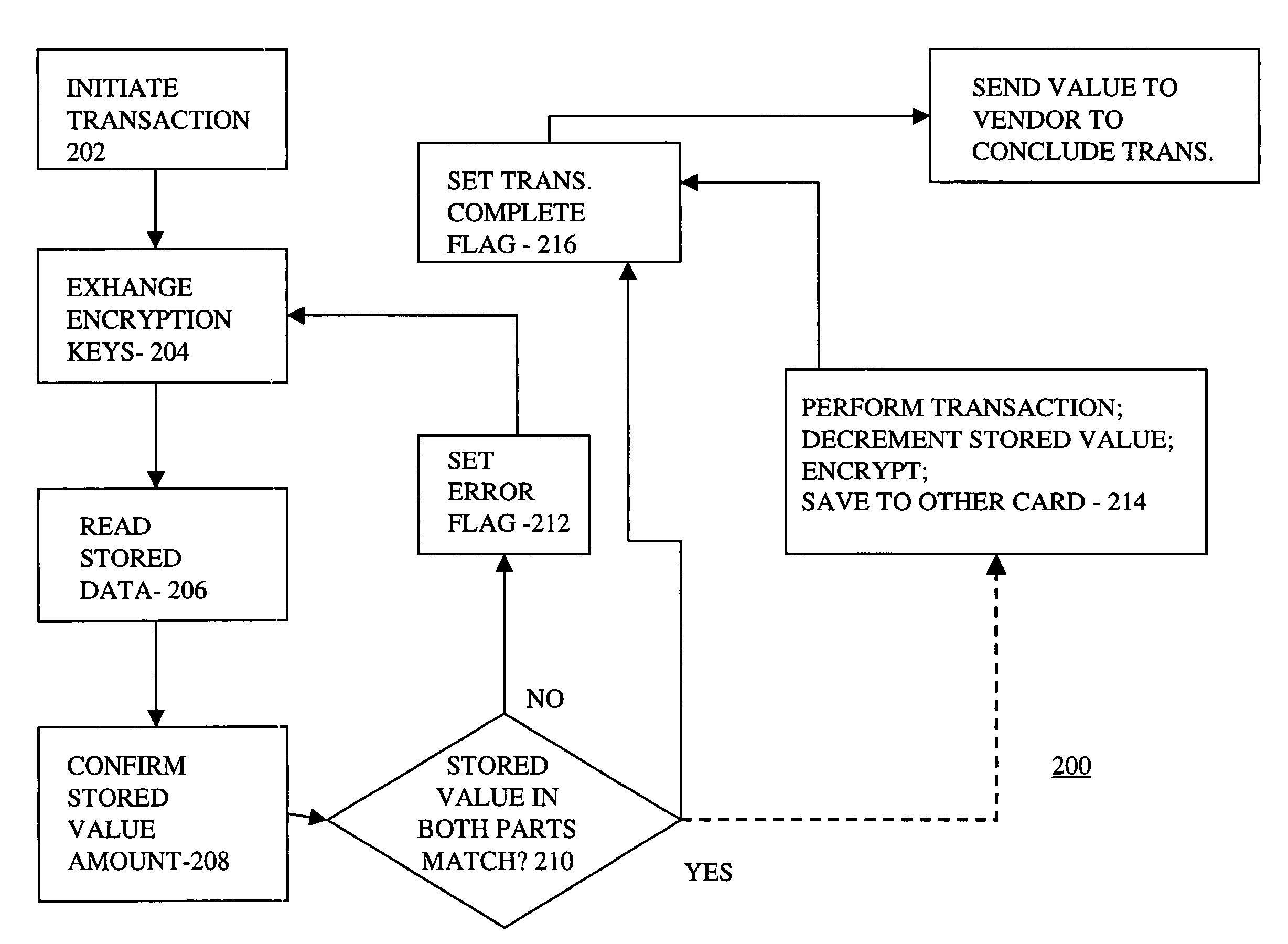
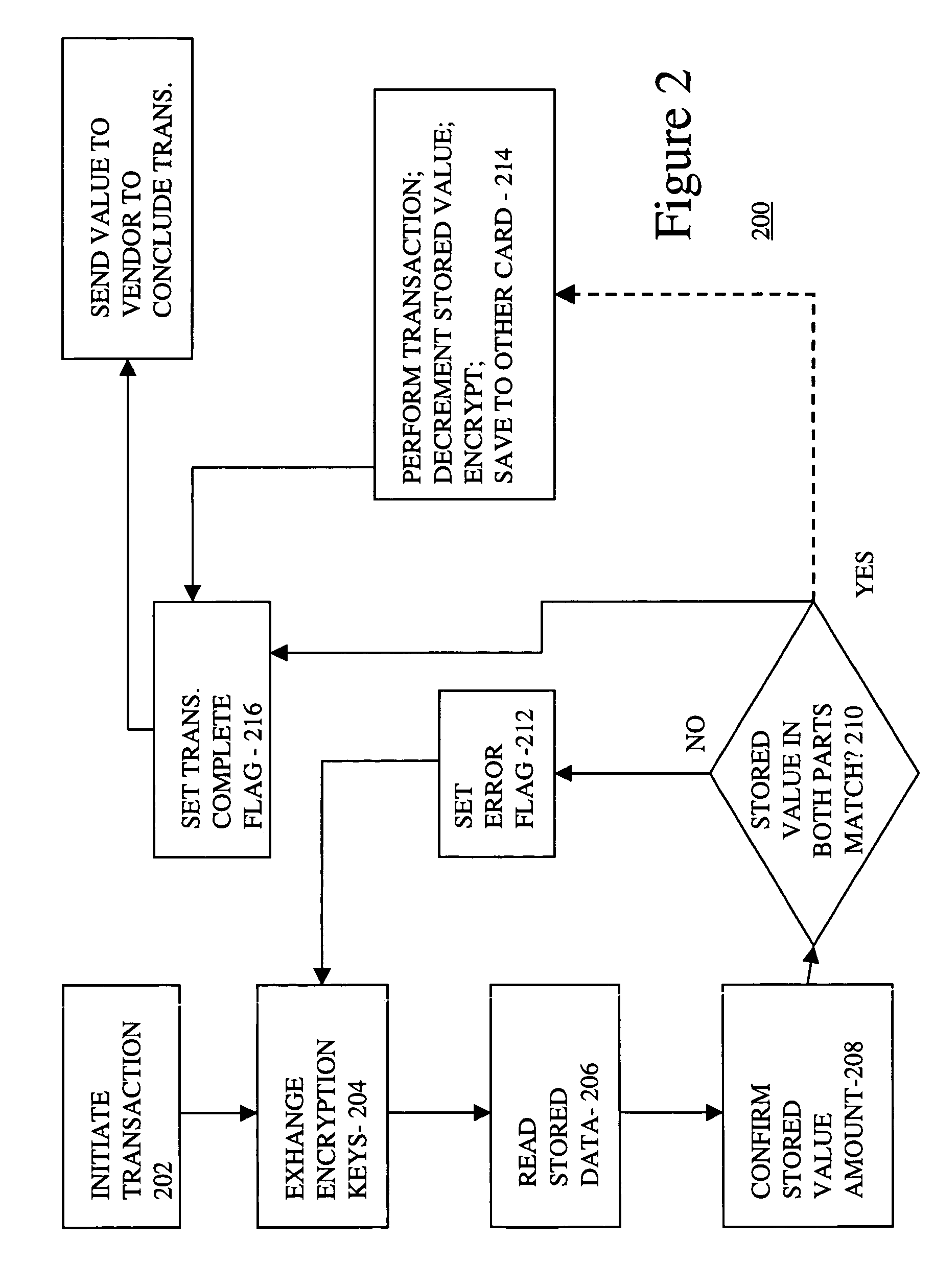
Smart card with back up
InactiveUS7206847B1Data SecurityImprove securityComplete banking machinesAcutation objectsProgram instructionSmart card security
Smart card security is enhanced by making the smart card a two-piece device. Both parts of the smart card contain copies of user data and a processor, which executes program instructions stored in the smart card half so as to give each part of the two-part smart card security and intelligence. Both parts must be in communication with each other for the data in either card to be accessible and useable. By separating the two pieces, data compromise is virtually impossible.
Owner:GOOGLE TECH HLDG LLC
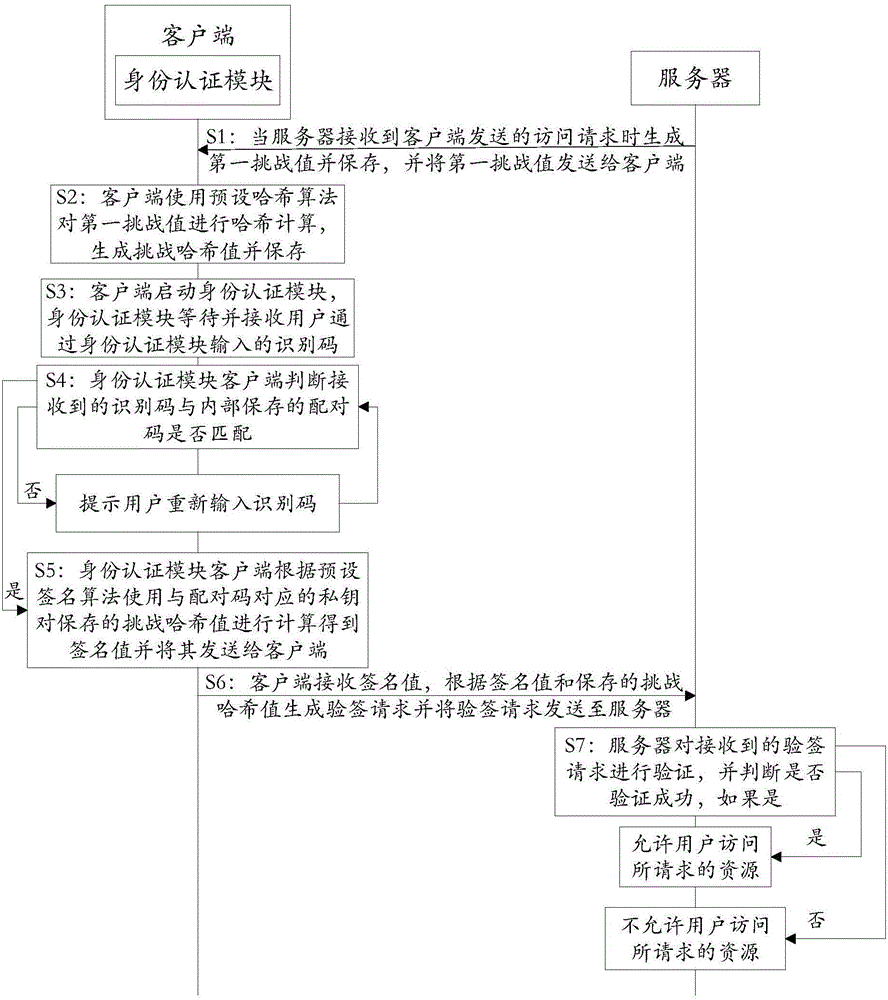
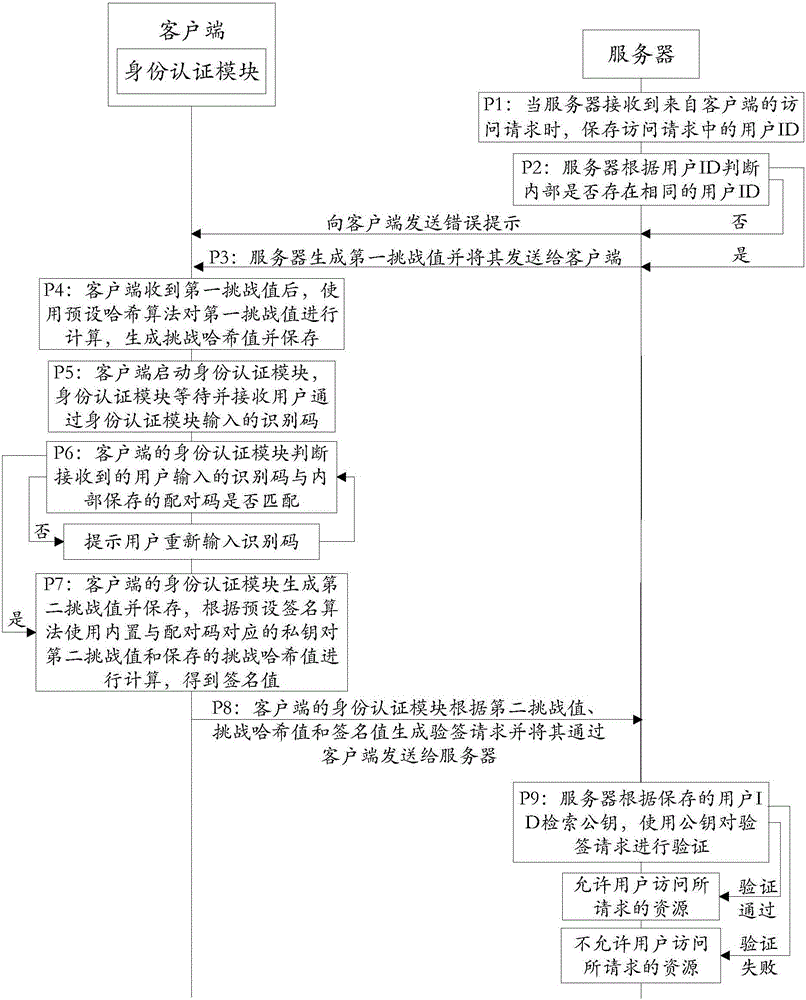
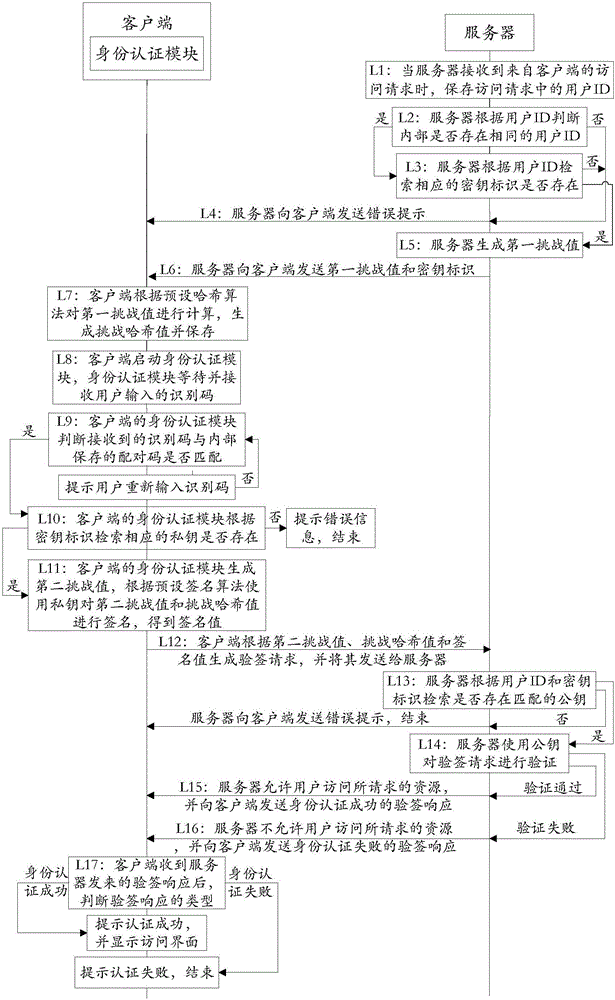
Authentication system and working method thereof
ActiveCN105847247APrevent leakageImprove communication securityTransmissionWorking setAuthentication server
The invention discloses an authentication system and a working method thereof and belongs to the information security field. The method includes the following steps that: when receiving an access request, a server generates a first challenge value and sends the first challenge value to a client; the client uses a preset Hash algorithm to carry out Hash calculation on the first challenge value to generate a challenge Hash value; when judging that a received identification code is matched with a pairing code stored in an identity authentication module, the identity authentication module uses a private key corresponding to the pairing code to calculate the challenge the Hash value according to a preset signature algorithm so as to obtain a signature value; the client generates a signature verification request according to the signature value and sends the signature verification request to the server; and the server authenticates the signature verification request, and a user is allowed to access requested resources if the authentication is successful, and the user is not allowed to access the requested resources if the verification fails. With the authentication system and the working method thereof provided by the technical schemes of the invention adopted, communication can be continued as long as the identity authentication module completes local authentication, and therefore, the problem of data leakage in a data transmission process can be prevented, and the security of the communication can be improved.
Owner:FEITIAN TECHNOLOGIES
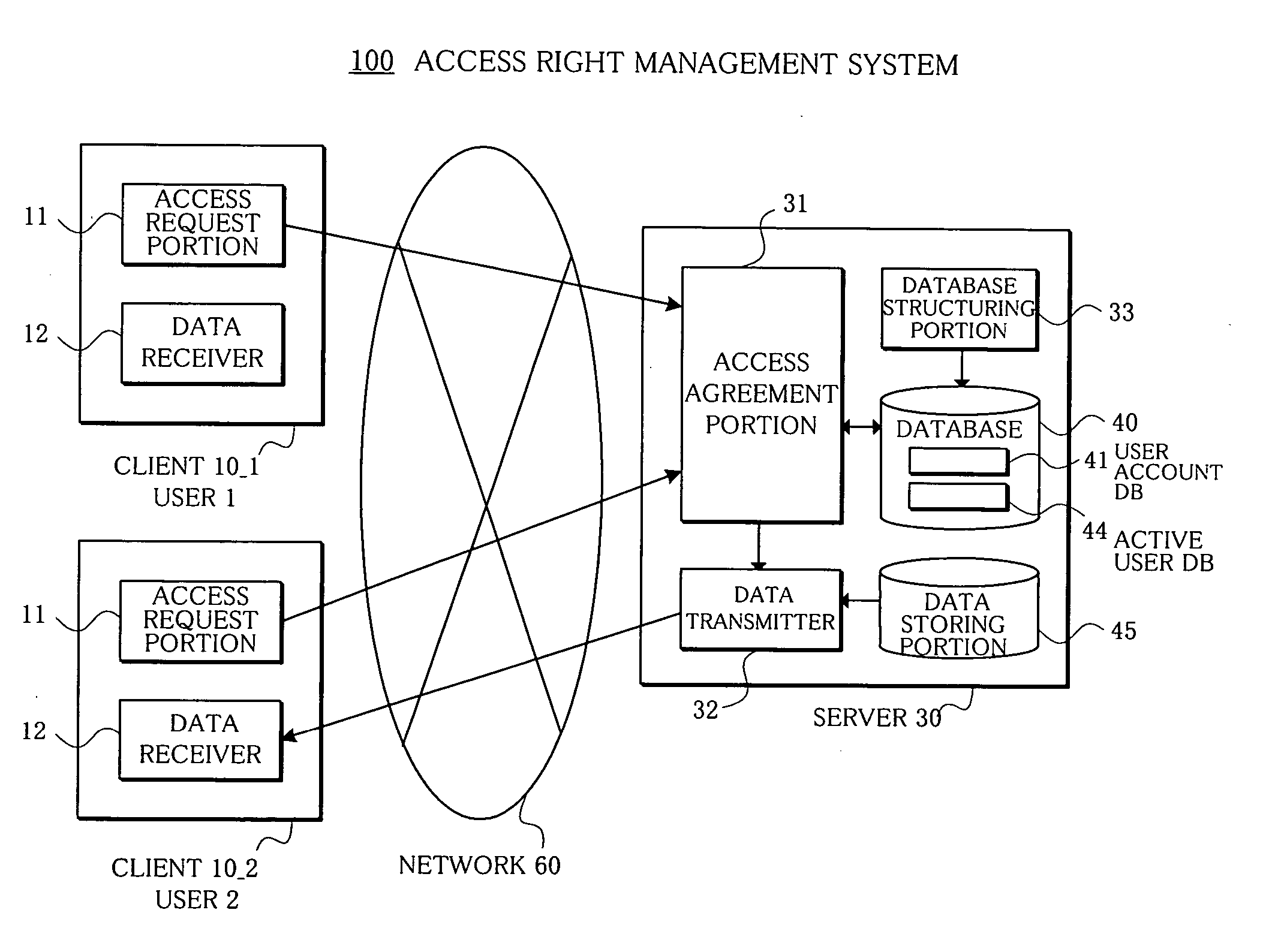
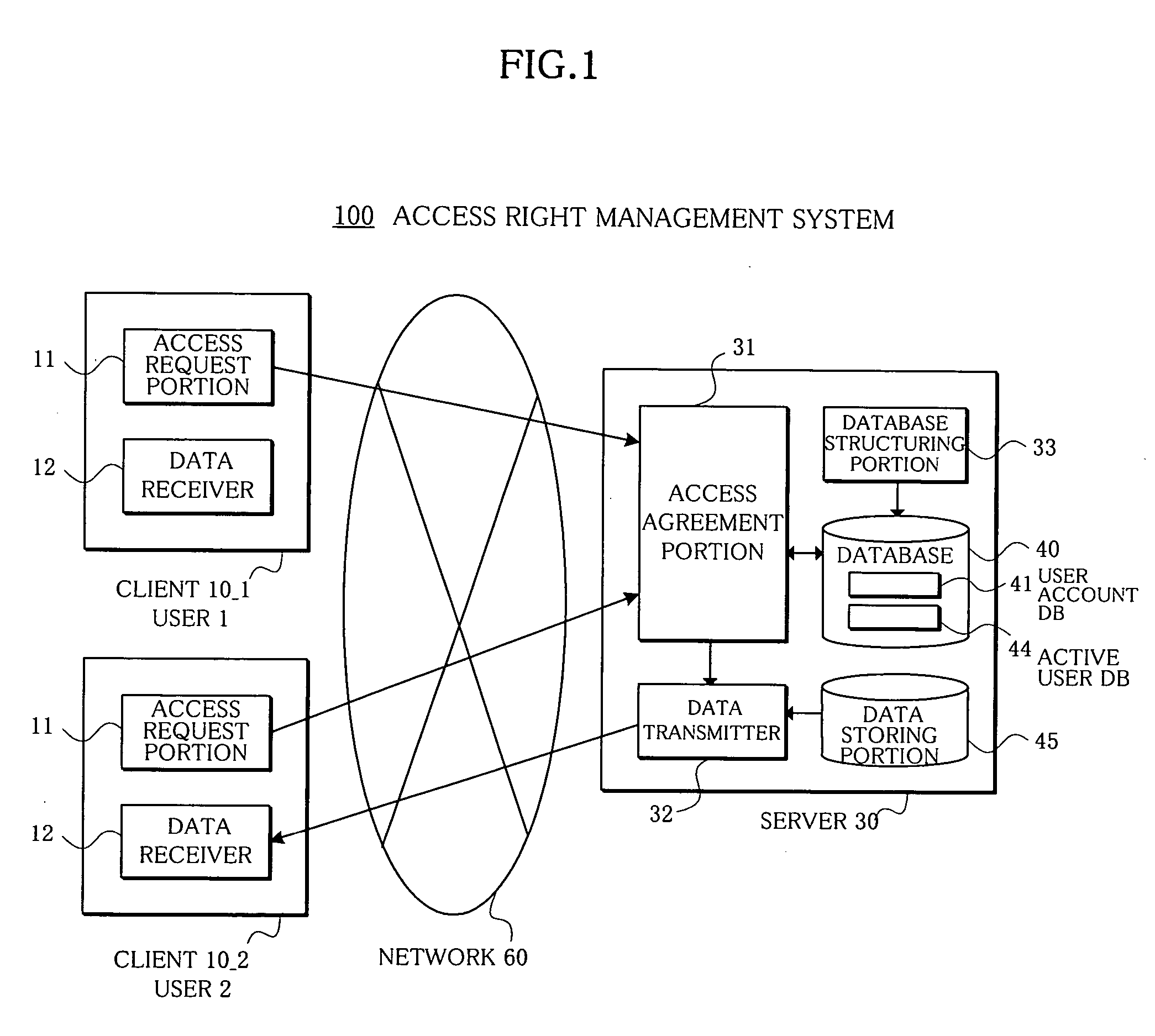
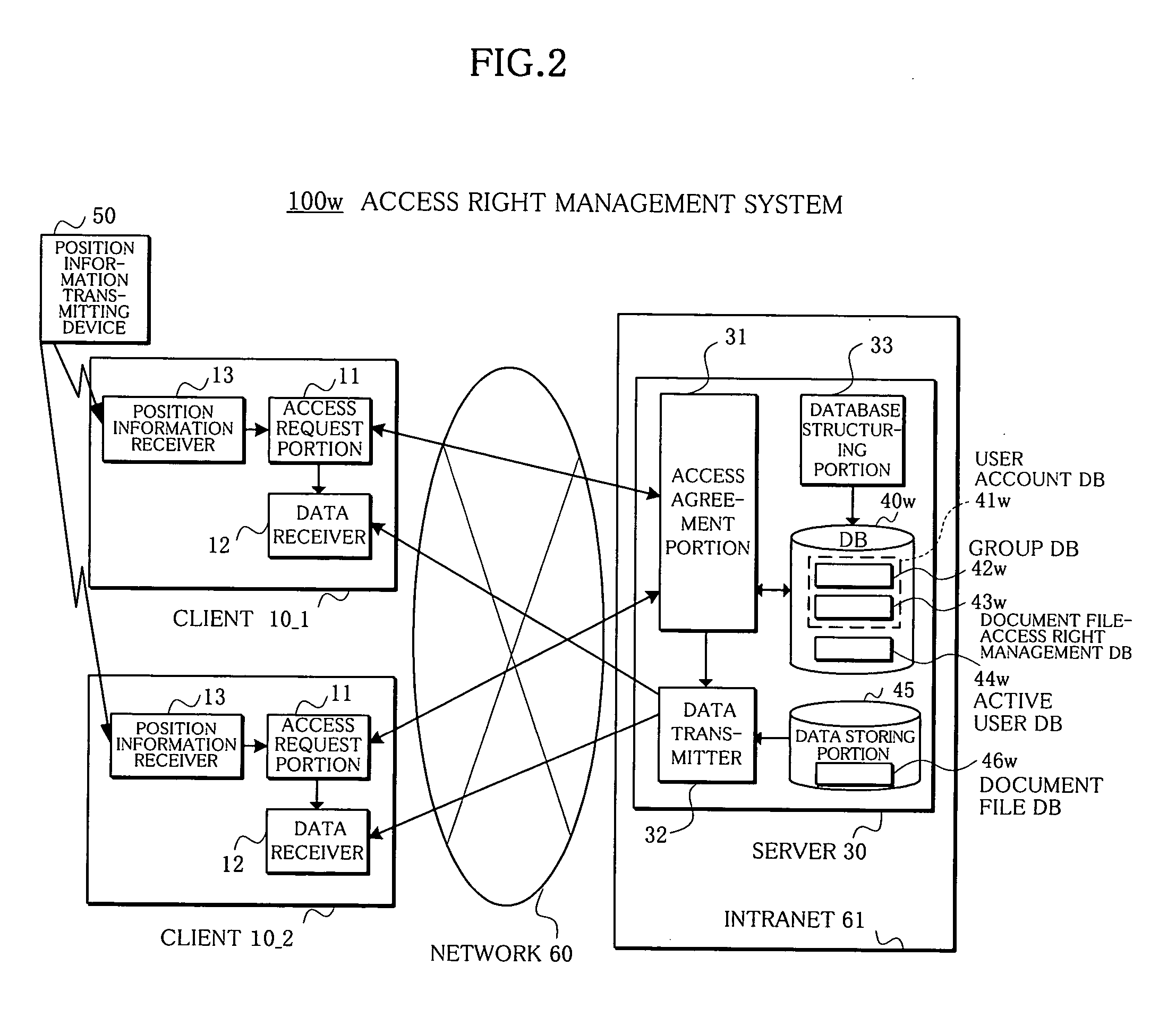
Access right management system and method
InactiveUS20050223008A1Avoid data breachesDigital computer detailsUnauthorized memory use protectionData accessRights management
In an access right management system and method which manage access to data and prevent the data from leaking, a plurality of associated users who possess access rights to data are registered in a user account database, users who agree to the access to the data at present among the access right possessing users are registered in an active user database, and an access agreement portion agrees, only when a present number of access right possessing users having agreed and registered in the active user database is plural, to the access to the data with access right possessing users who have requested the access to the data.
Owner:FUJITSU LTD
Data leakage prevention for resource limited device
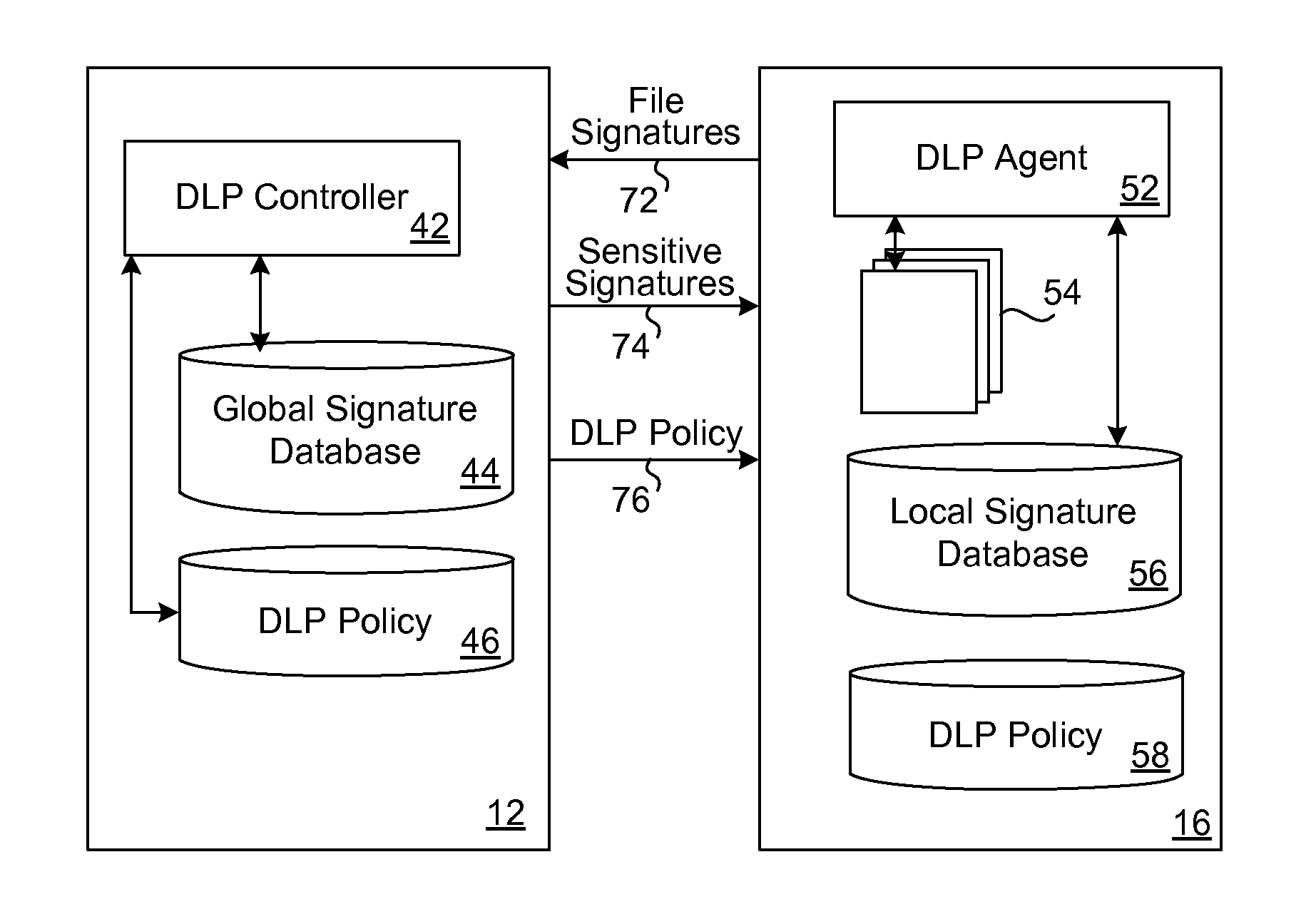
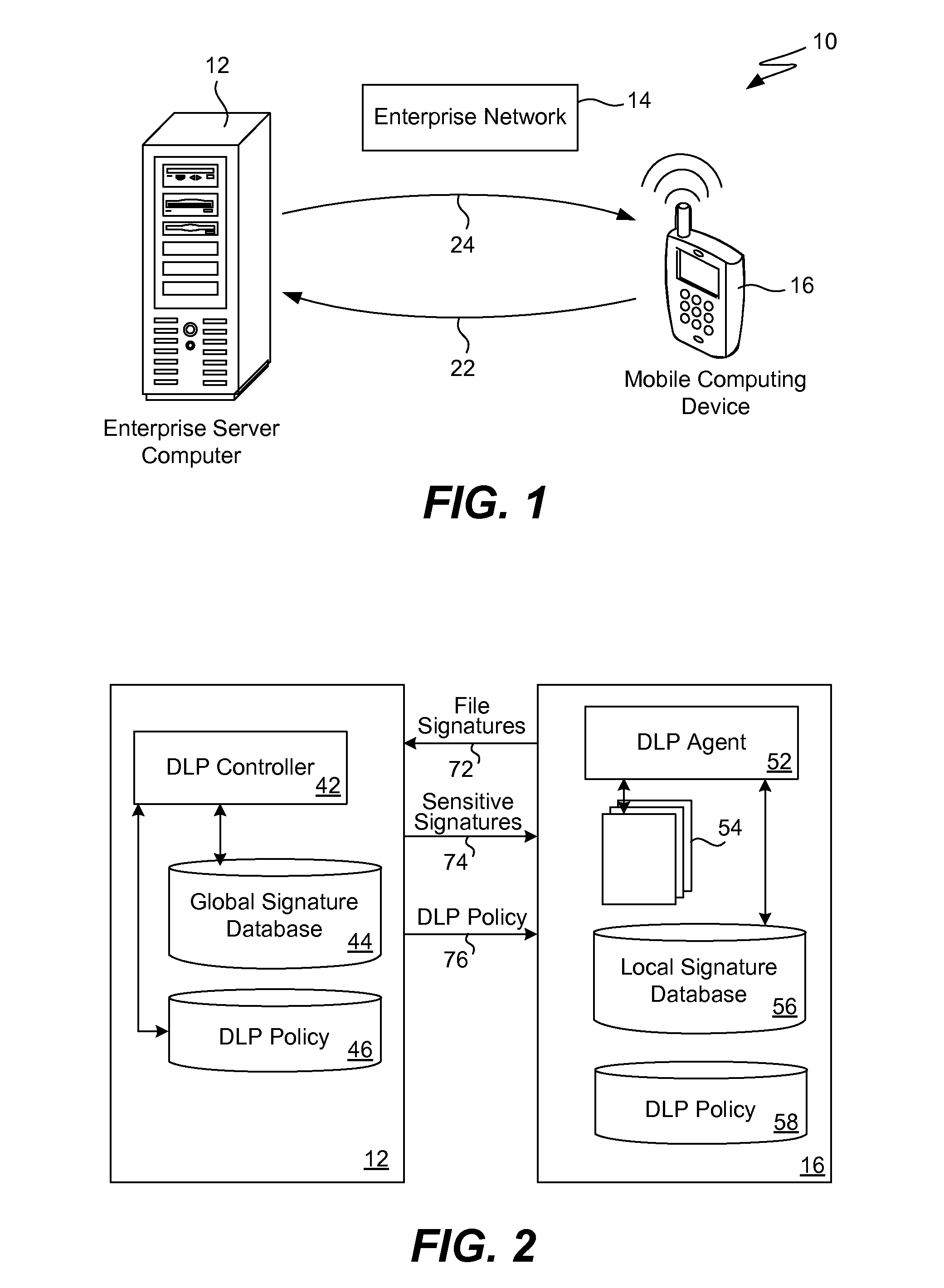
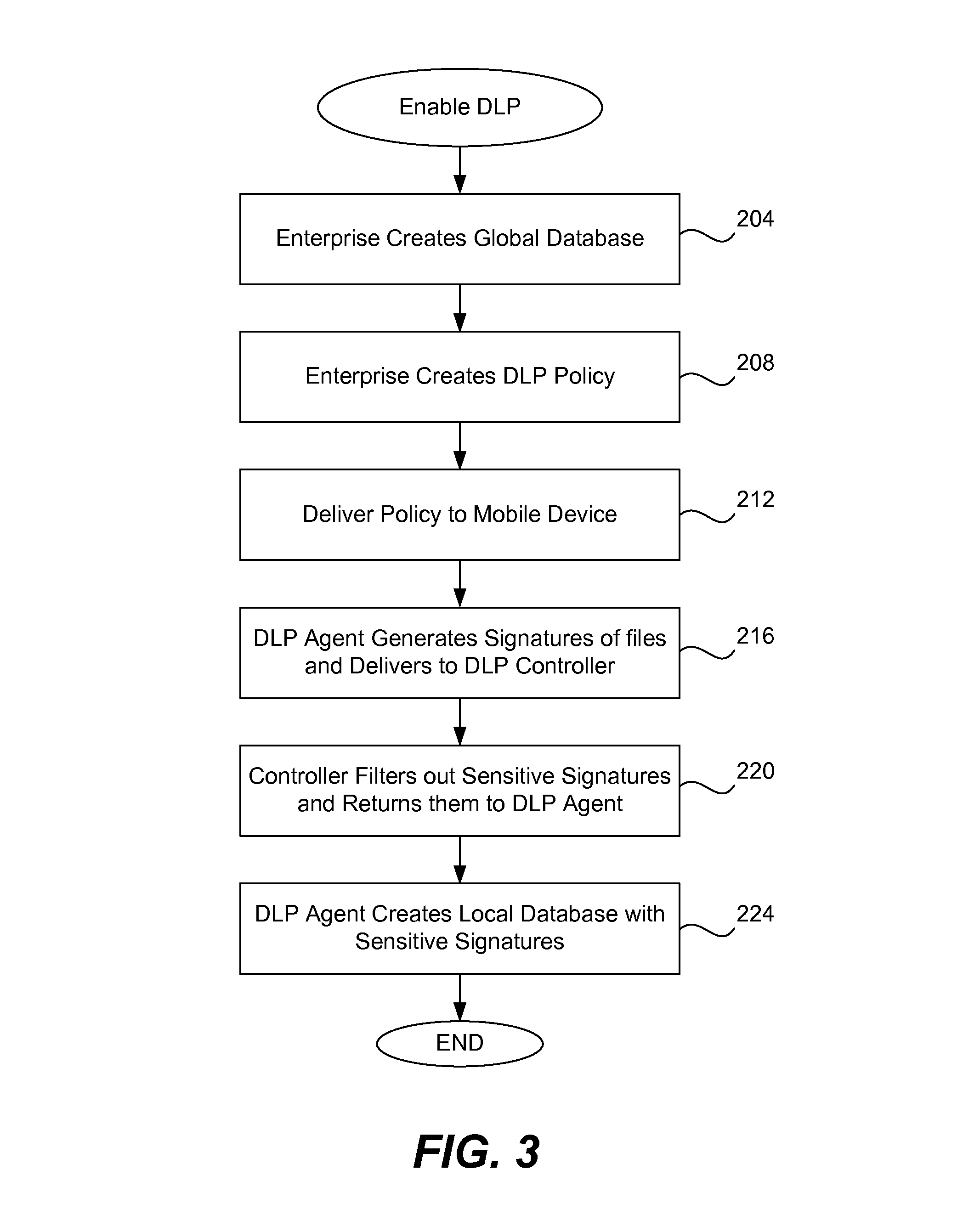
ActiveUS8286253B1Efficient and effectiveSimple to executeDigital data processing detailsDatabase distribution/replicationDigital signatureMobile telephony
When a resource-limited device (such as a mobile telephone) joins a network associated with an enterprise, the agent in the device generates digital signatures for all the files in the device and sends them to an enterprise controller. The controller compares them to the global signature database; it filters out the sensitive digital signatures and feeds them back to the agent in the device. The agent receives the feedback of digital signatures and consolidates them into its own local signature database. The agent analyzes each file that is attempting to be output from the device according to the local signature database and DLP policy. If the signature of the file is present in the local database then the action to output file is blocked. If a new file is created on the device, the agent generates and sends its digital signature to the controller for inspection. If the signature is sensitive, this new digital signature will be placed into the local signature database. If the DLP controller updates the global signature database, the device will send its signatures once again for comparison.
Owner:TREND MICRO INC
Android application vulnerability detection method and Android application vulnerability detection system
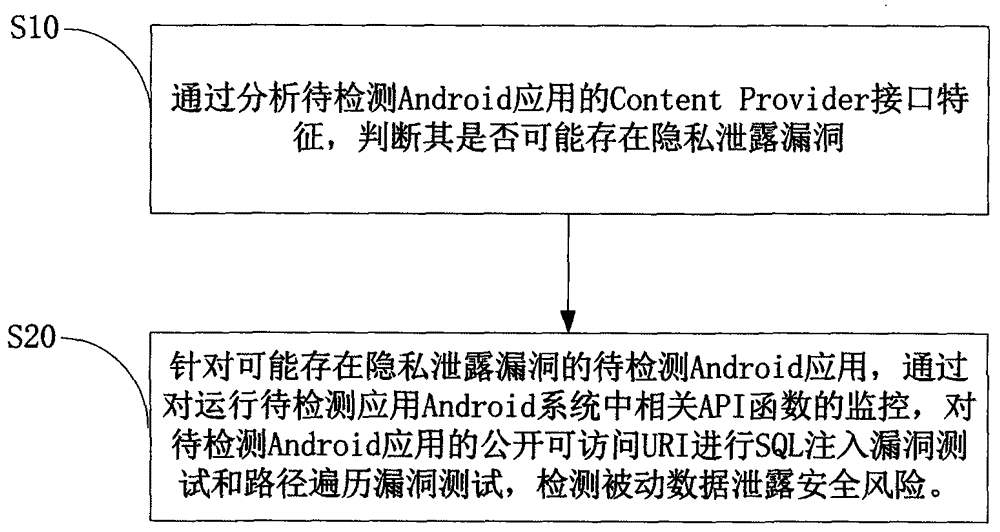
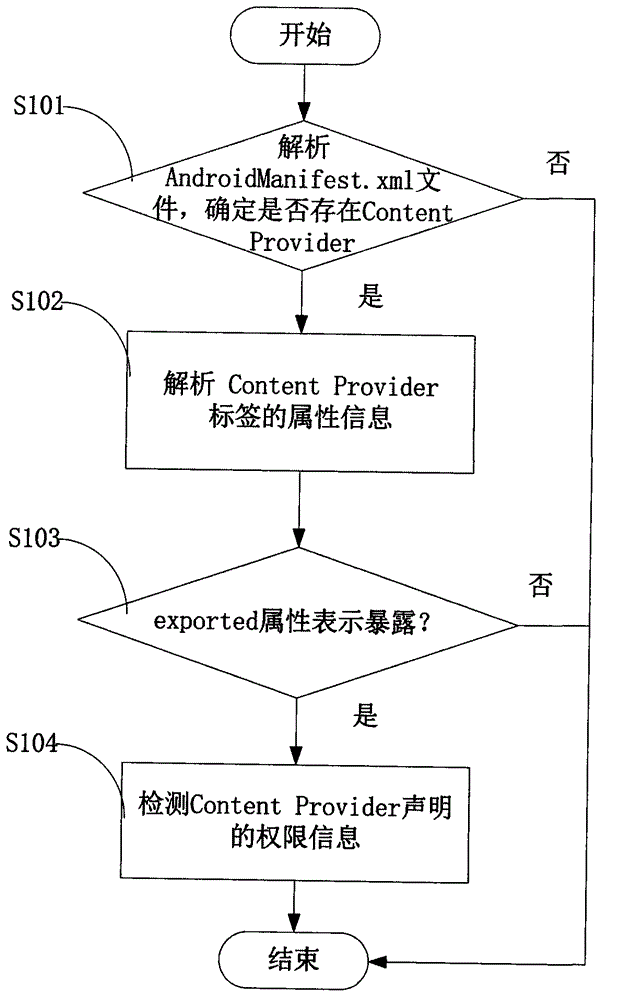
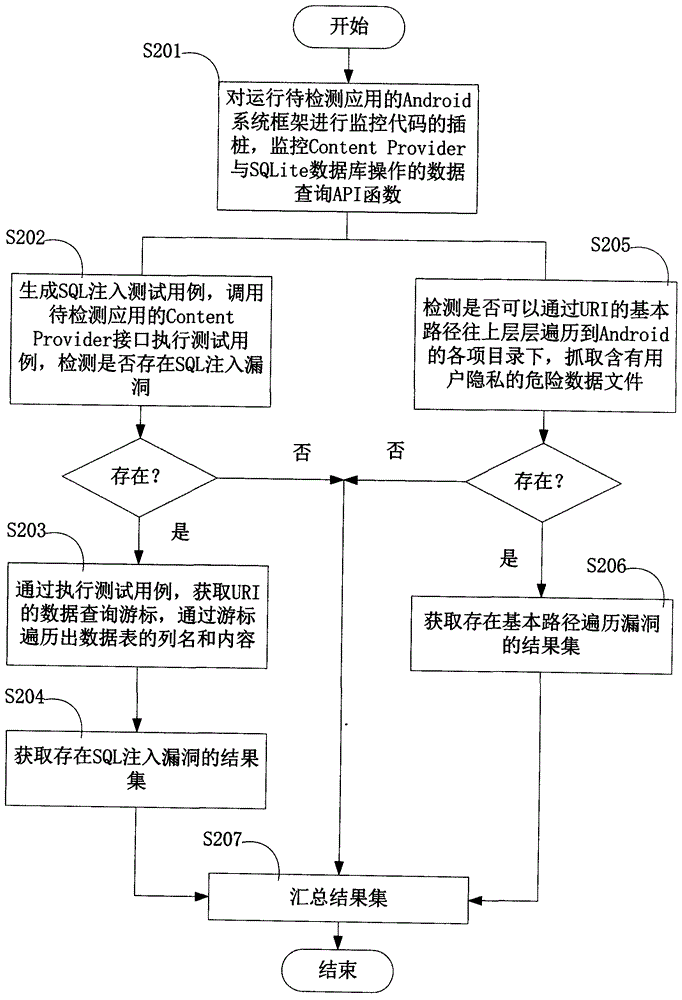
InactiveCN103984900AAvoid false positivesEfficient discoveryPlatform integrity maintainanceSQL injectionUniform resource identifier
The invention provides an Android application vulnerability detection method which comprises the following steps: 1, judging whether a privacy leakage vulnerability possibly exists or not by virtue of analyzing Content Provider interface characteristics of a to-be-detected Android application; 2, if the privacy leakage vulnerability possibly exists, performing an SQL (Structured Query Lanaguge) injection vulnerability test and a path traversal vulnerability test on a public accessible URI (Uniform Resource Identifier) of the to-be-detected Android application which possibly has the privacy leakage vulnerability by virtue of monitoring a related API (Application Program Interface) function in an Android system, and then detecting passive data leakage safety risks. The invention also provides an Android application vulnerability detection system. The method and the system can be used for rapidly discovering privacy leakage and data pollution vulnerabilities possibly existing in the Android application, avoiding misdeclaration, and providing a powerful support for discovering the privacy leakage and data pollution vulnerabilities in the Android application on a large scale.
Owner:南京赛宁信息技术有限公司 +1
Information processing device, information processing method, and program distribution system
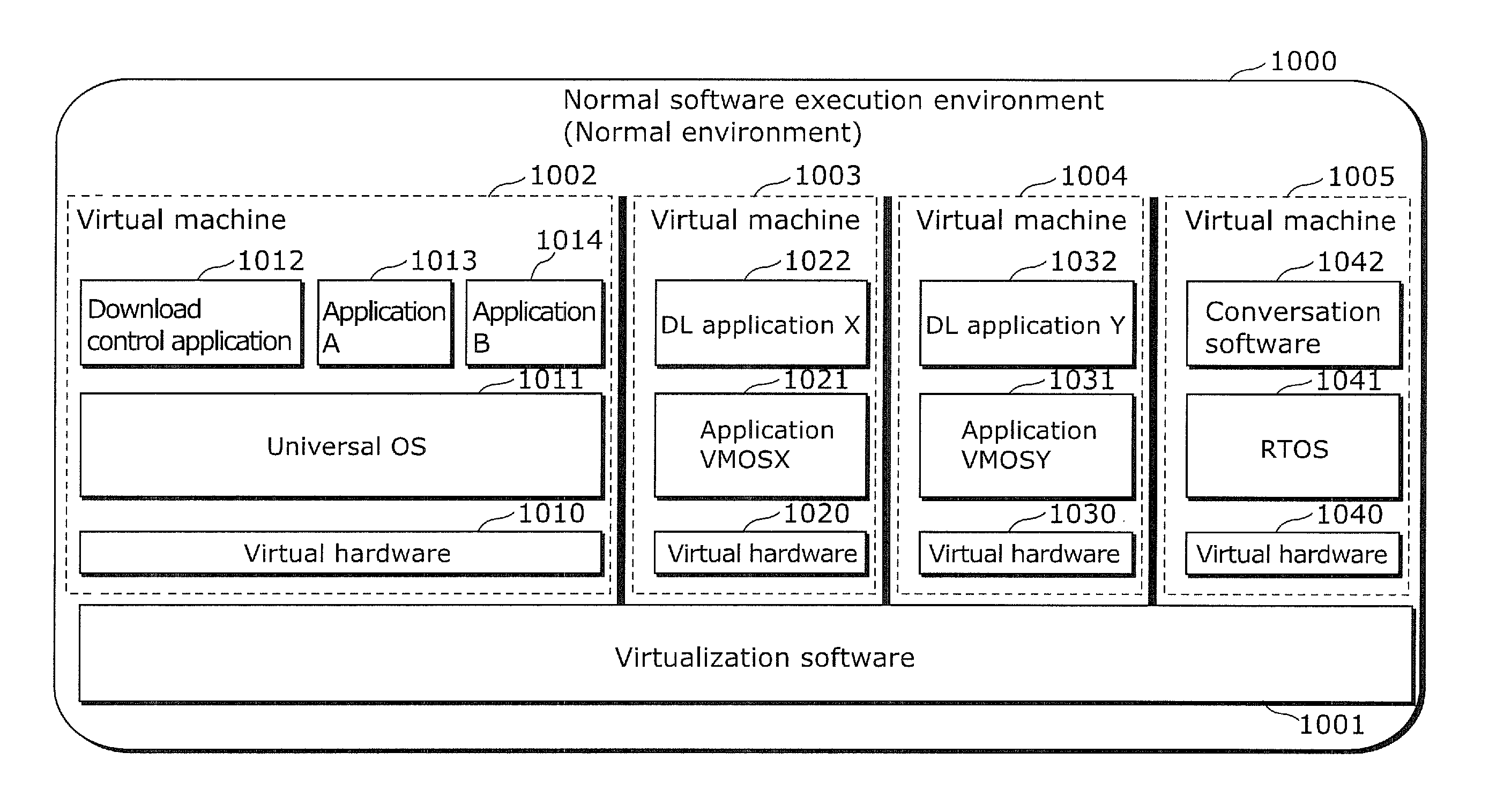
InactiveUS20120117566A1Avoid data breachesPlatform integrity maintainanceSoftware simulation/interpretation/emulationInformation processingData transport
Provided is an information processing device which is capable of preventing data leakage caused by a malicious application or malicious device driver and of allowing cooperation among virtual machines. The information processing device (110) includes: an external connection unit (1309) which connects to an external device; and a communication control unit which obtains data from a first virtual machine (1002), transmits the data to a second virtual machine (1003), and transmits, to the external connection unit, transmission completion information indicating that the data is already transmitted to the second virtual machine, wherein the external connection unit (i) determines, based on the transmission completion information, whether or not a virtual machine is the second virtual machine to which the data is already transmitted, when the external connection unit receives, from the virtual machine, a request for a connection to the external device, and (ii) permit a connection between the virtual machine and the external device, when the external connection unit determines that the virtual machine is not the second virtual machine to which the data is already transmitted.
Owner:SOVEREIGN PEAK VENTURES LLC
Development method and system based on mobile terminal application program security application
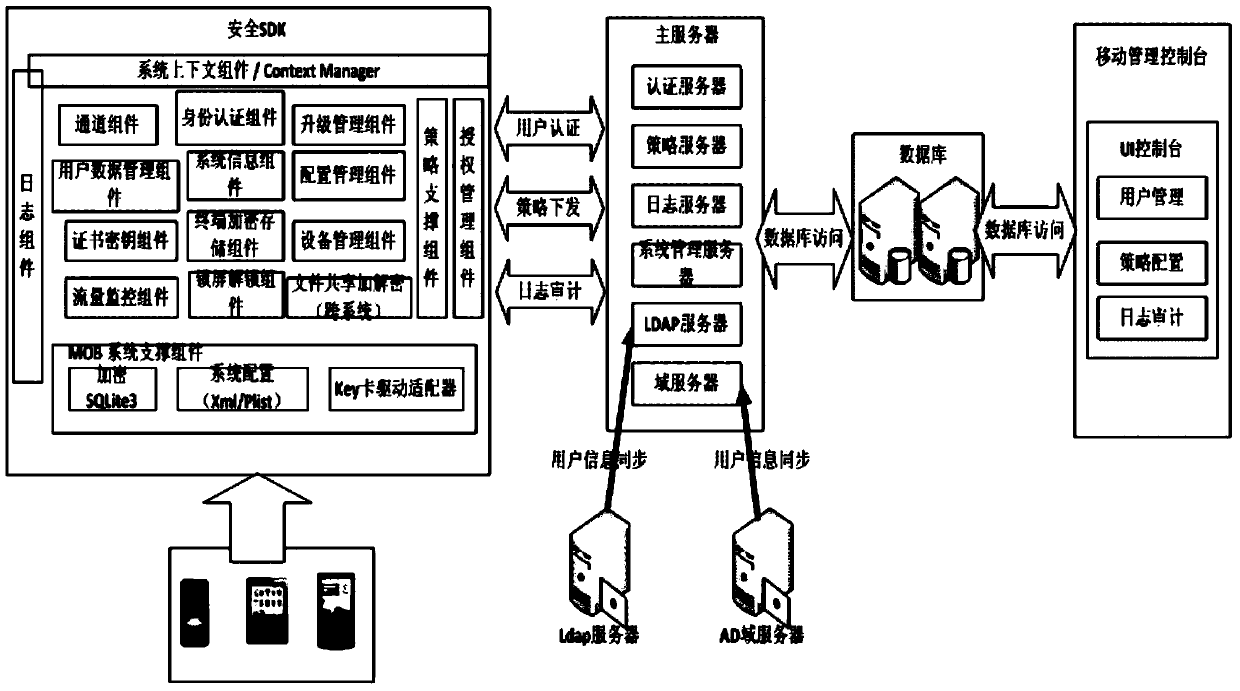
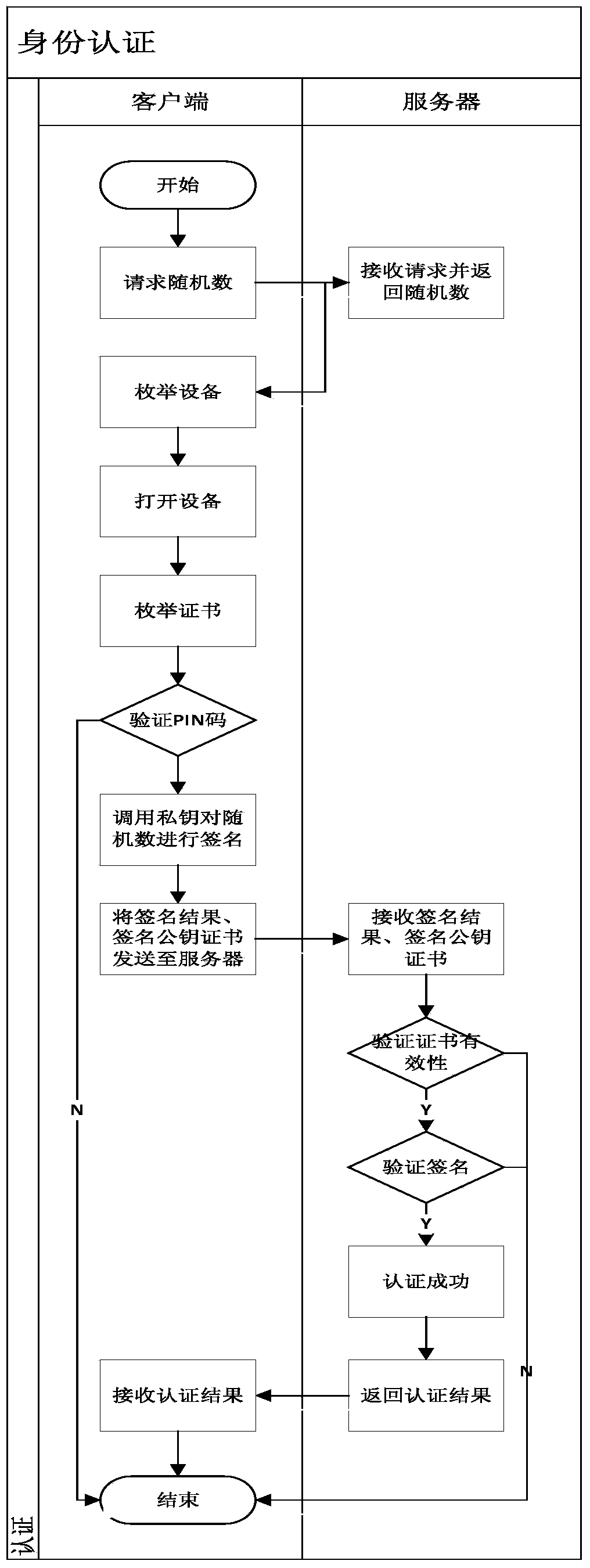
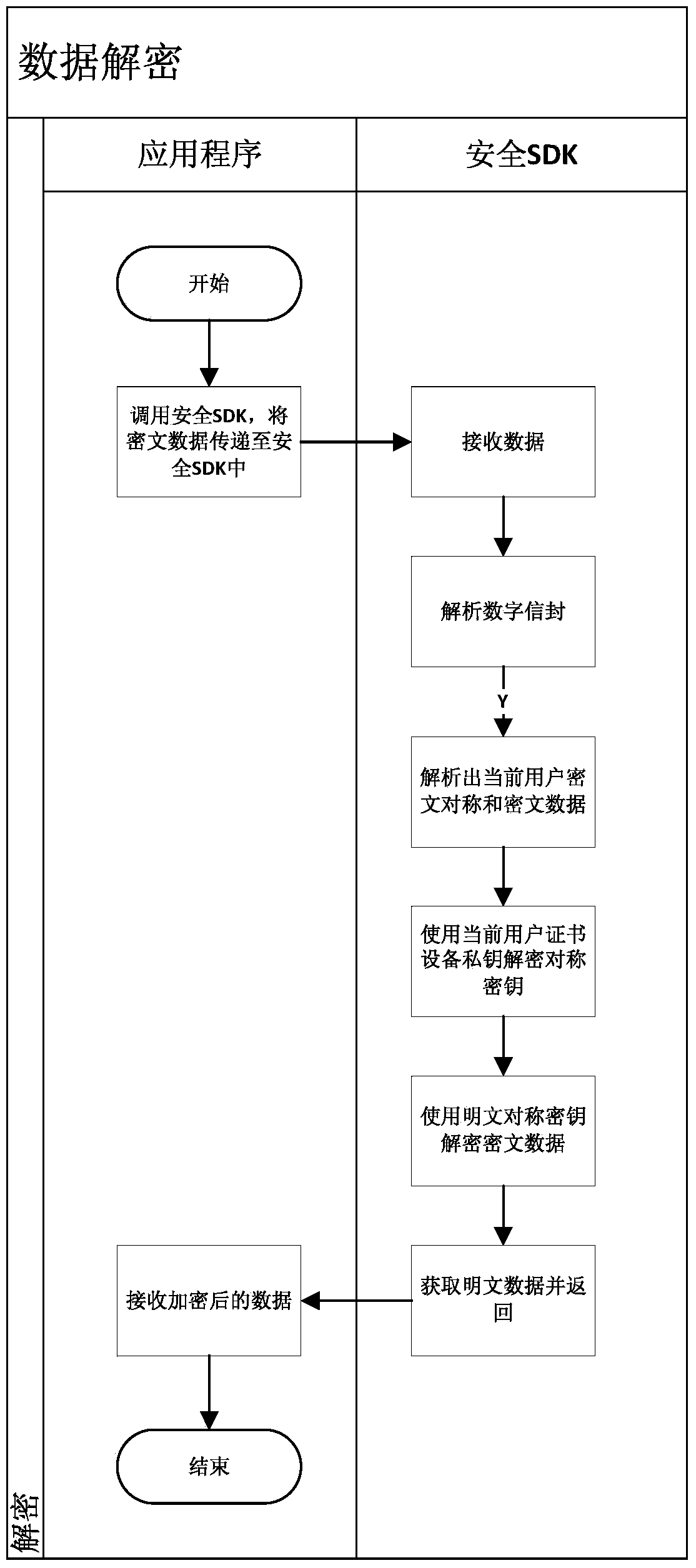
ActiveCN103812871AAvoid security issuesAvoid authenticationPublic key for secure communicationUser identity/authority verificationData informationCiphertext
The invention discloses a development method and system based on mobile terminal application program security application. The system comprises a sending terminal, a safe software development kit (SDK), a server and a receiving terminal. The method includes that the sending terminal requests a random number from the server, after the requested random number is received, a private key of the sending terminal is called to perform signing on the random number, and a signing result and a signing public key certificate are sent to the server; after the success of identity authentication, the safe SDK is called, received data information is encrypted through symmetric keys, the symmetric keys are encrypted by a public key of the receiving terminal, and encrypted symmetric keys and data information are sent to the receiving terminal; the receiving terminal calls the safe SDK to decrypt encrypted data. By means of the development method and system based on mobile terminal application program security application, related problems such as identity authentication, data breach and equipment controlling of data information safety are avoided.
Owner:北京明朝万达科技股份有限公司
Systems, methods and devices for providing device authentication, mitigation and risk analysis in the internet and cloud
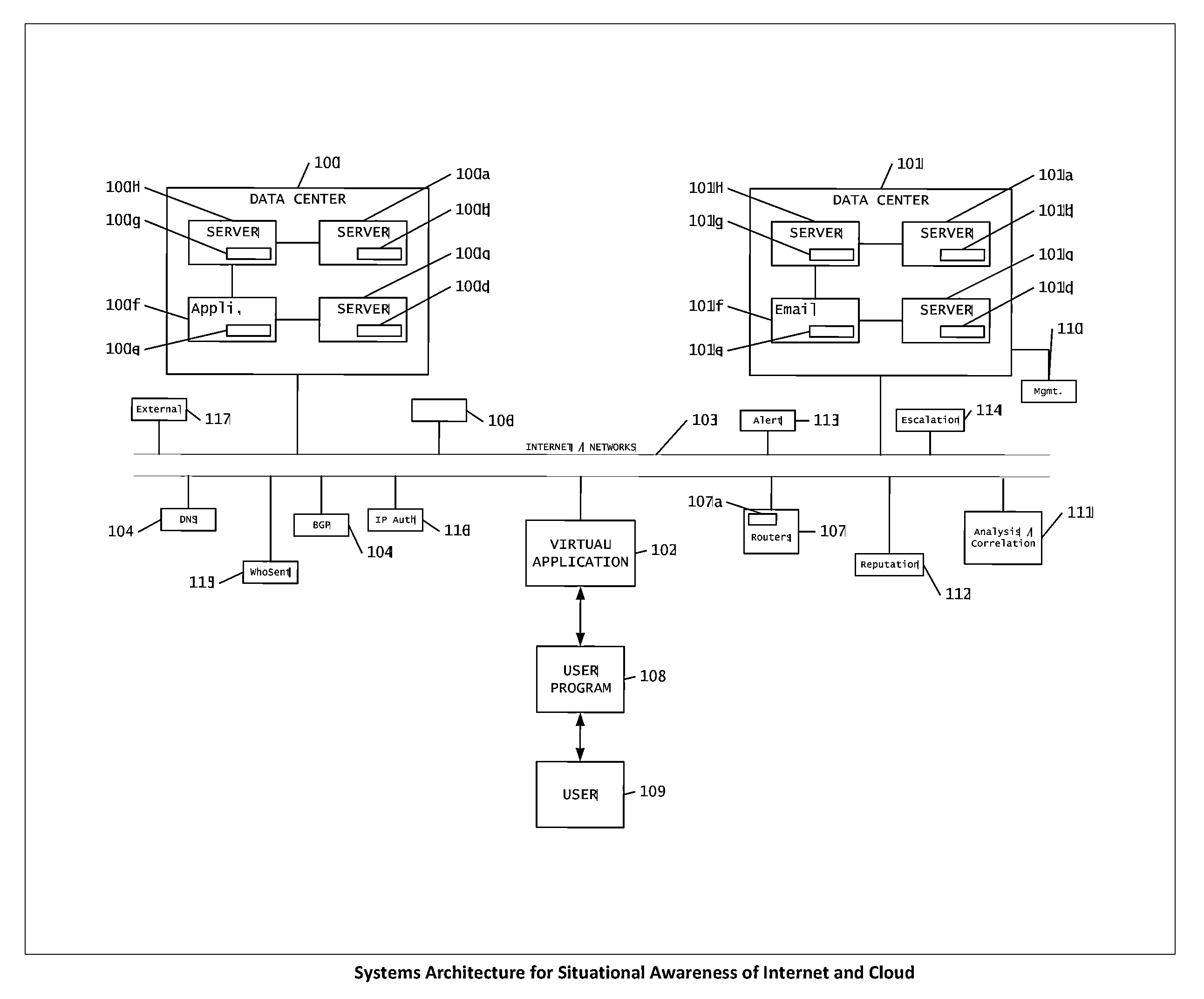
The present invention is a method to provide mechanisms and judgment to determine the ongoing veracity of “purported” devices (sometimes called spoofing) with such parameters as unique device ID, access history, paths taken and other environmental data (Device Authentication).This invention relies upon a previous invention “Reputation Database in the cloud and Internet”—the internet is comprised of collections of devices, data, applications and networks all dynamically exchanging information among users. We present a mechanism for real time observation, and putting or accessing those observations into a distributed virtual database for contextual evaluation and analysis of how the internet is being used or potentially subverted. This includes real time evaluation of DNS database changes, server logs, performance, path resolution, device logs, tip data and law enforcement data.This invention is particularly useful for helping detect and mitigate data compromises, networks, systems and other assets within the internet.
Owner:DONOVAN JOHN JOSEPH +2
Platform for live issuance and management of cyber insurance policies
ActiveUS20180322584A1Automatically analyzedMathematical modelsFinanceData integrityKnowledge management
A system for autonomous issuance and management of insurance policies for computer and information technology related risks, including but not limited to business losses due to system availability, cloud computing failures, current and past data breaches, and data integrity issues. The system will use a variety of current risk information to assess the likelihood of business interruption or loss due to both accidental issues and malicious activity. Based on these assessments, the system will be able to autonomously issue policies, adjust premium pricing, process claims, and seek re-insurance opportunities with a minimum of human input.
Owner:QOMPLX INC
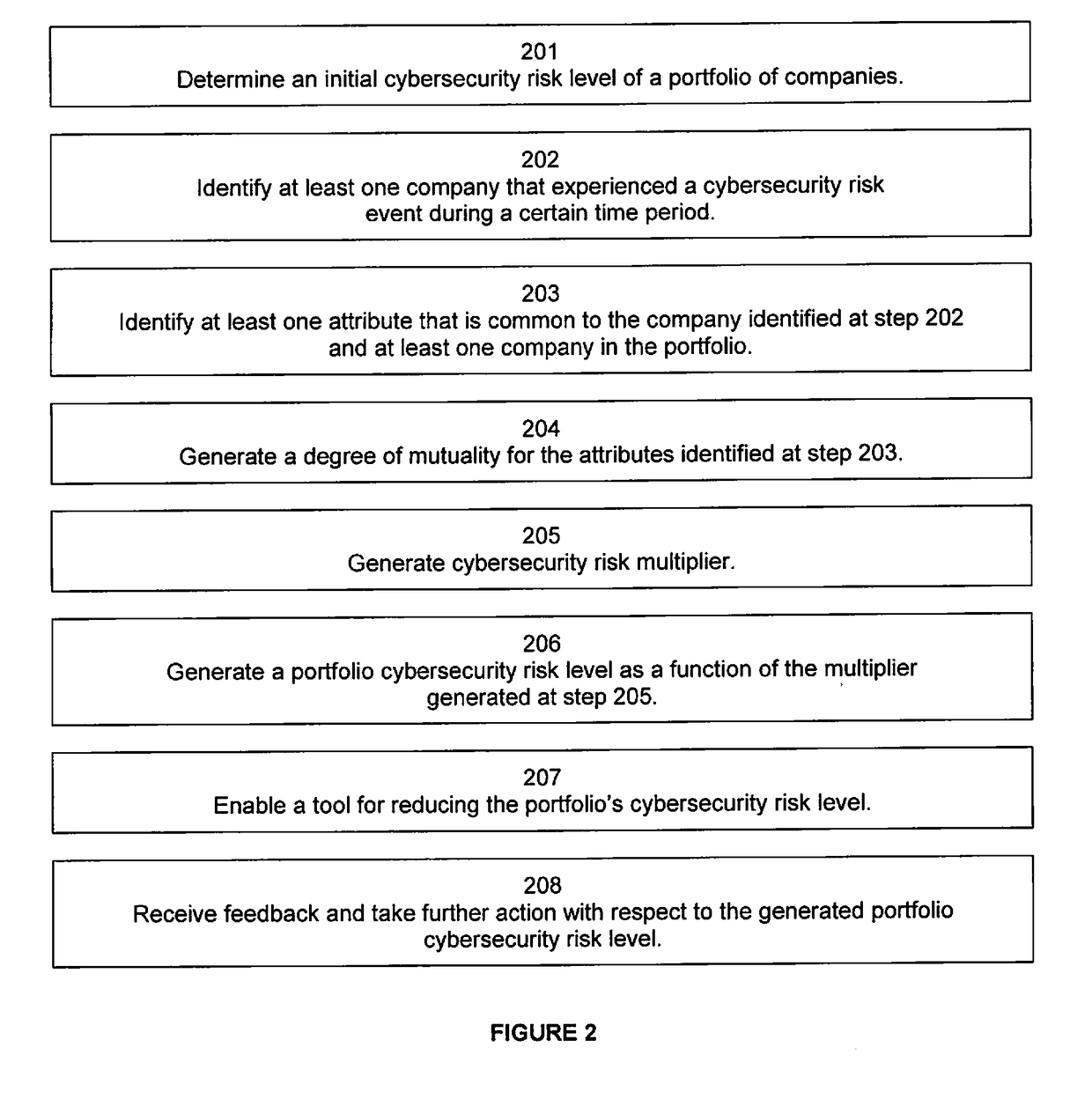
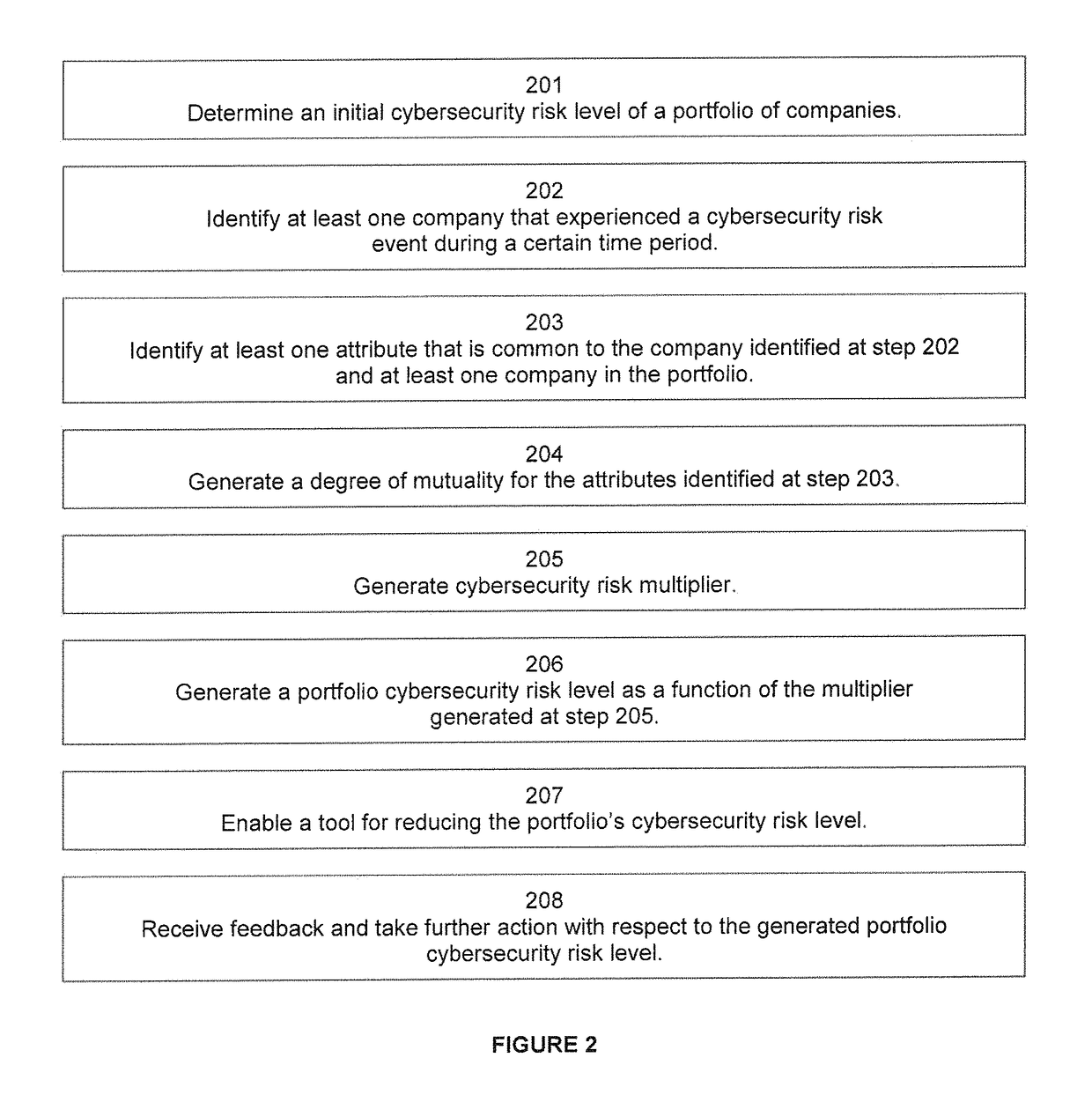
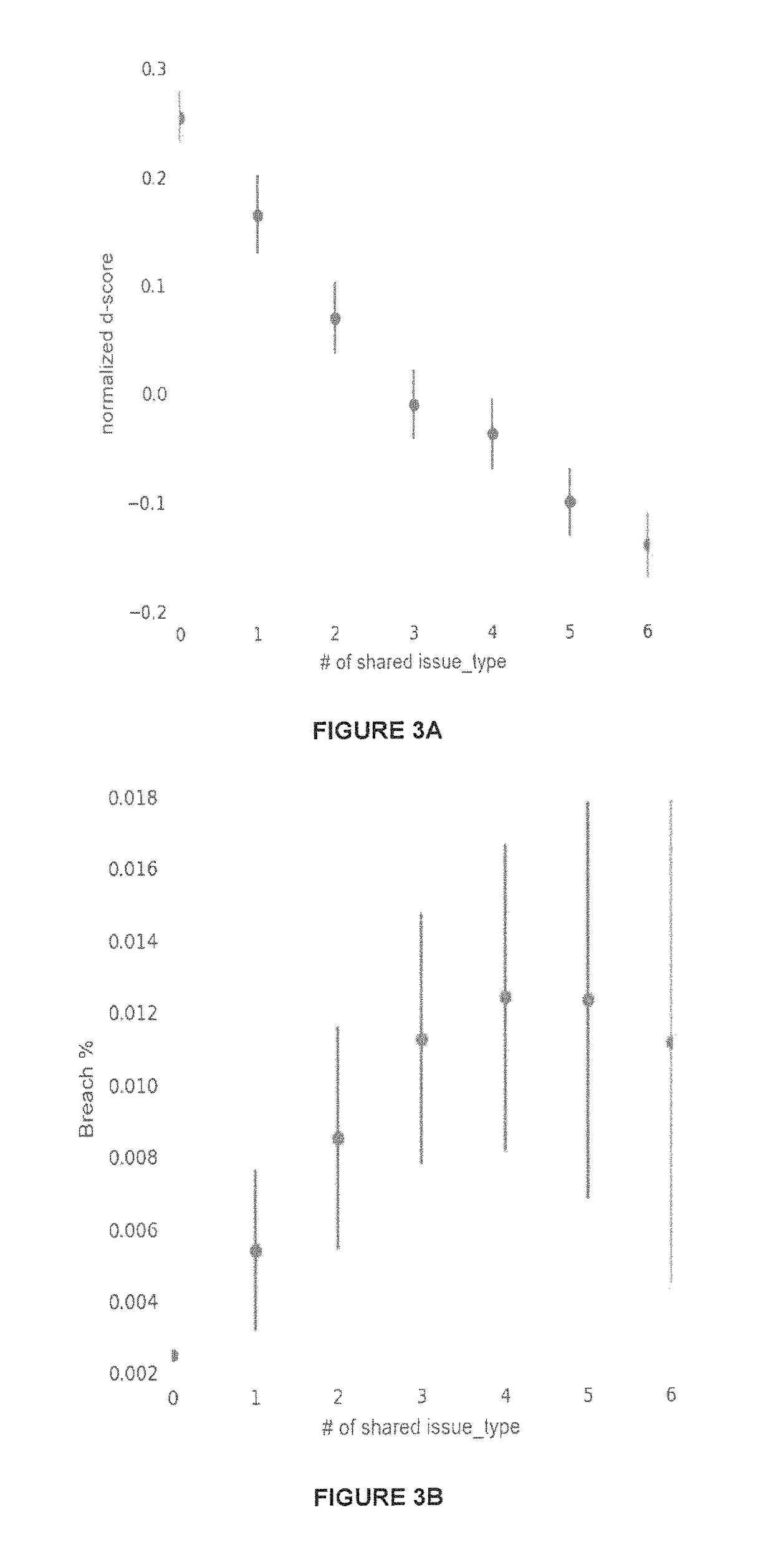
Reducing cybersecurity risk level of a portfolio of companies using a cybersecurity risk multiplier
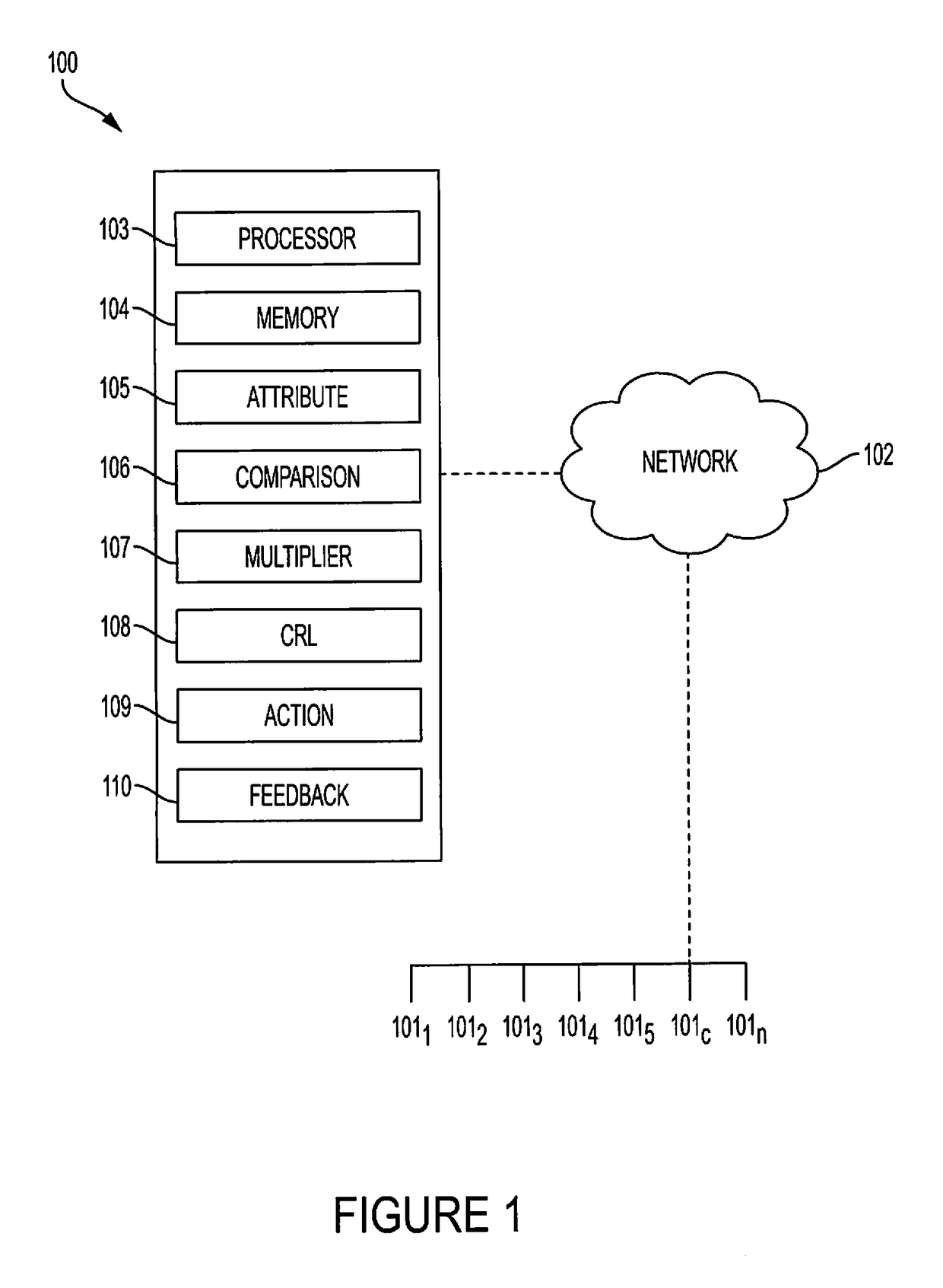
A multiplier is utilized to quantify a cybersecurity risk level of a portfolio of entities (e.g., companies) and enable actions to mitigate that quantified risk. In doing so, features or attributes of one or more companies in a portfolio are compared to features or attributes of one or more companies that experienced an adverse cybersecurity event (e.g. a data breach). Further, a degree of dependency, such as a matrix of a number of shared vendors and the proximity of those vendors to the companies, can be measured between (1) portfolio companies and one or more companies that experienced a cybersecurity event, and / or (2) the portfolio companies themselves to better quantify the risk. That is, to more meaningfully analyze a cybersecurity event that occurred at one or more companies and better predict the likelihood of an occurrence at portfolio companies, embodiments can determine an n-degree interdependency between companies. I
Owner:SECURITYSCORECARD
System for data leak prevention from networks using context sensitive firewall
InactiveUS20120180120A1Prevent leakageComputer security arrangementsMultiple digital computer combinationsWeb siteWeb application
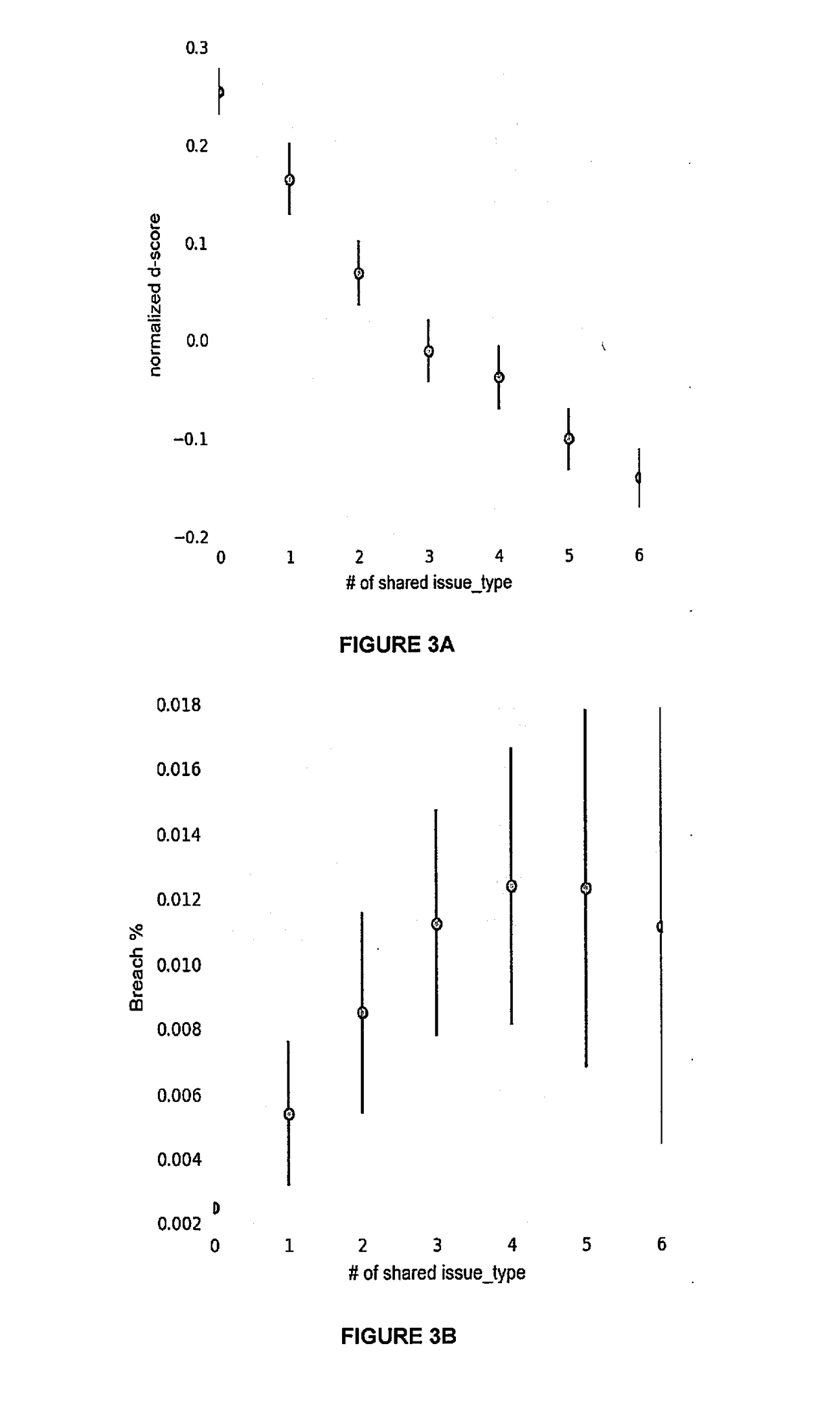
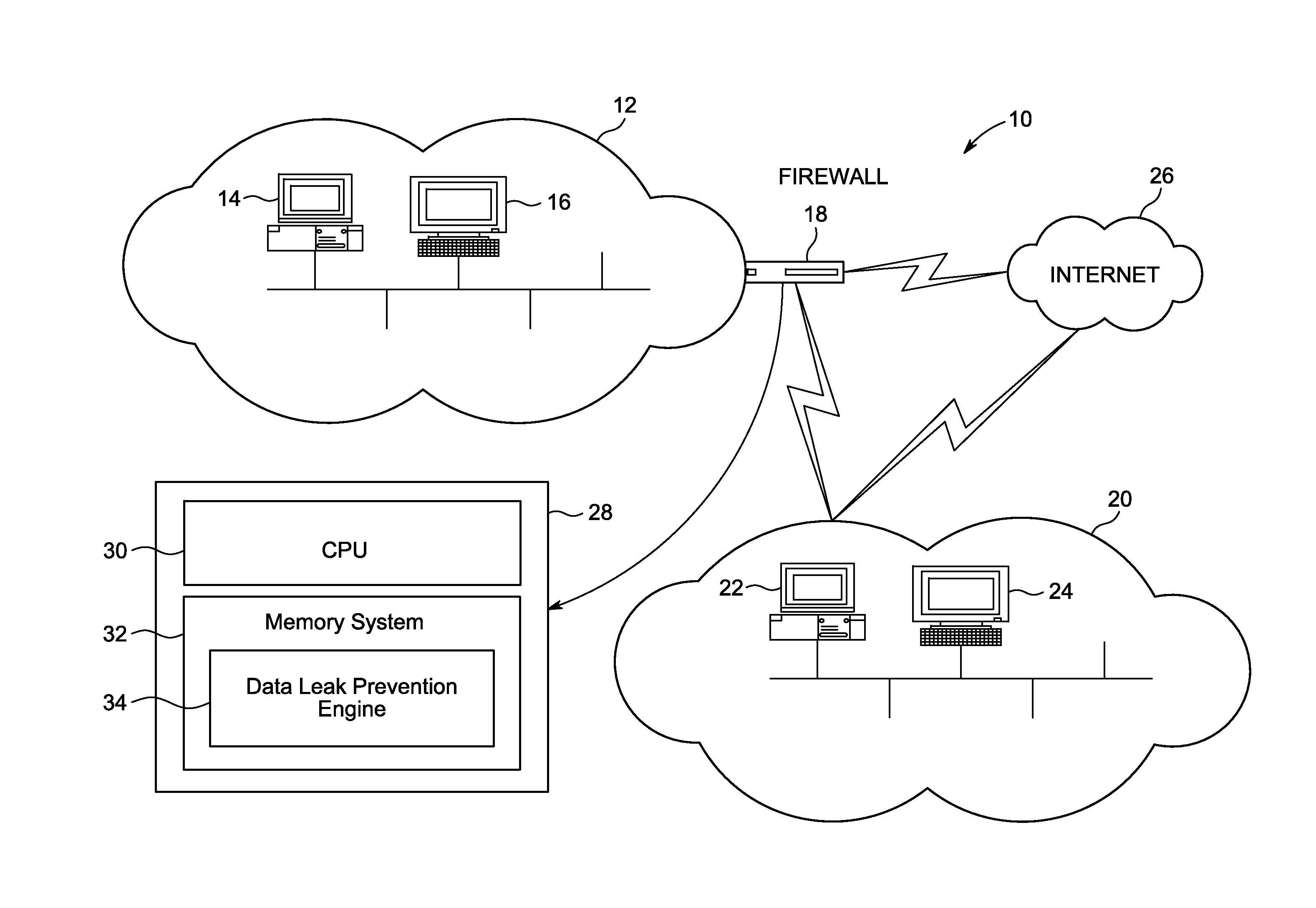
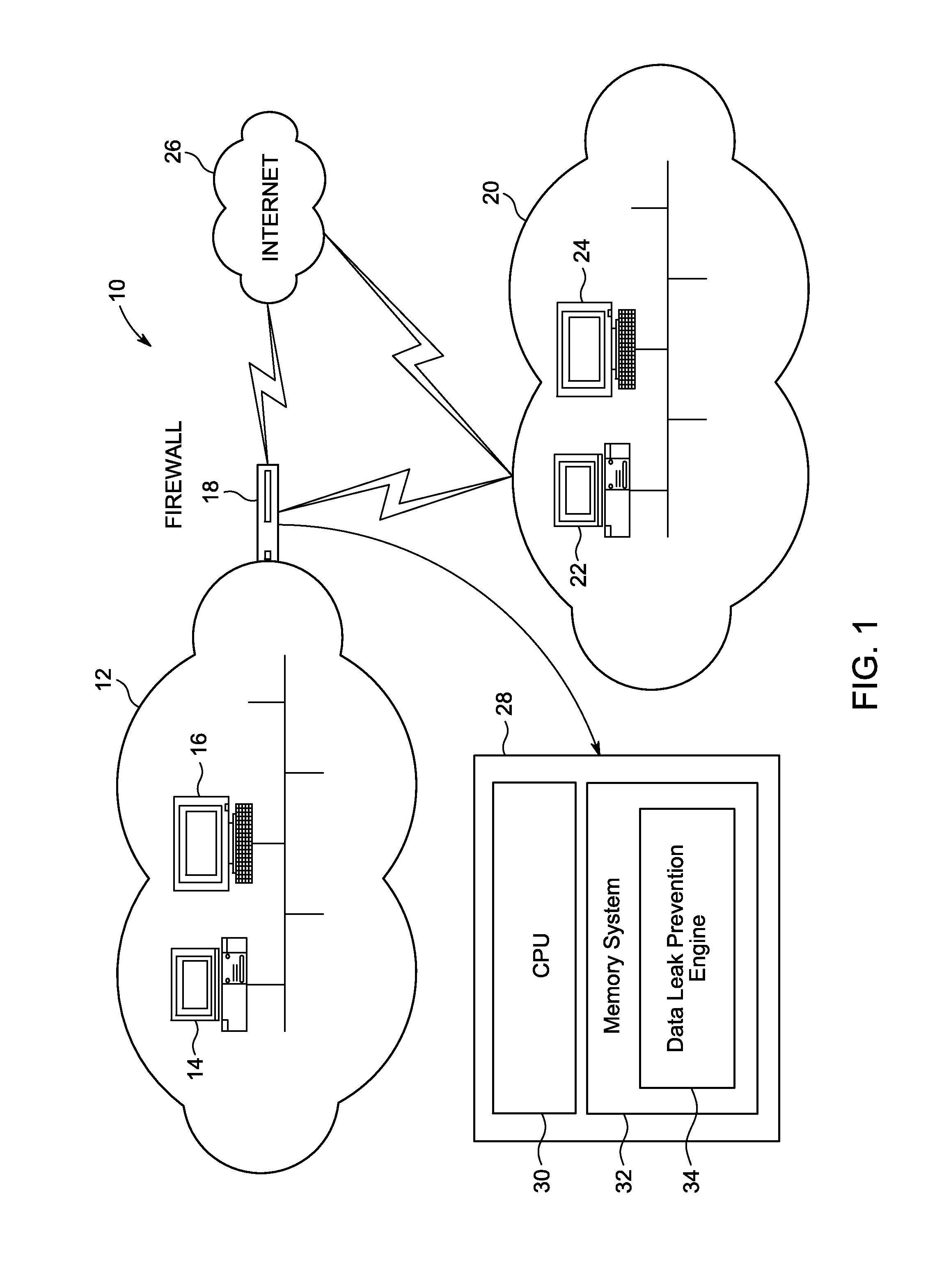
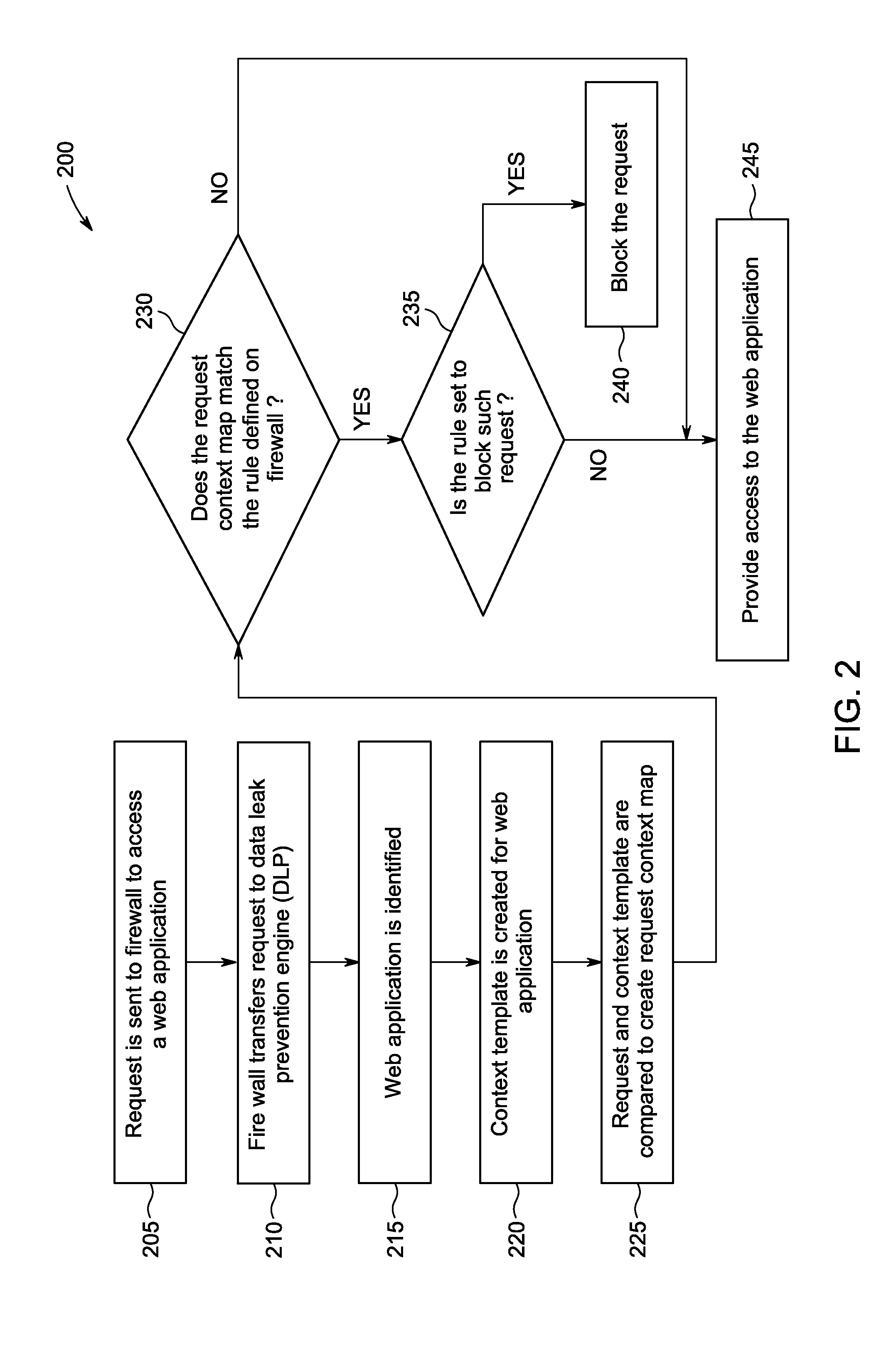
Method and system of preventing data leak in a network that allows for context based access of network resources by network users is provided. Where the communication network can be an open network like the internet or a closed network like a company's Local Area Network (LAN). The network resource may be any application, website, program, communication means etc. available by accessing the network. A request is sent to a network firewall to access a web application, where the web application is identified. A context template is created for the web application, and compared with the request to create a request context map. The request context map is compared to a request context rule on the network firewall. Access is provided to the web application when the request context map matches the request context rule.
Owner:JAIN SONIT BASANTKUMAR
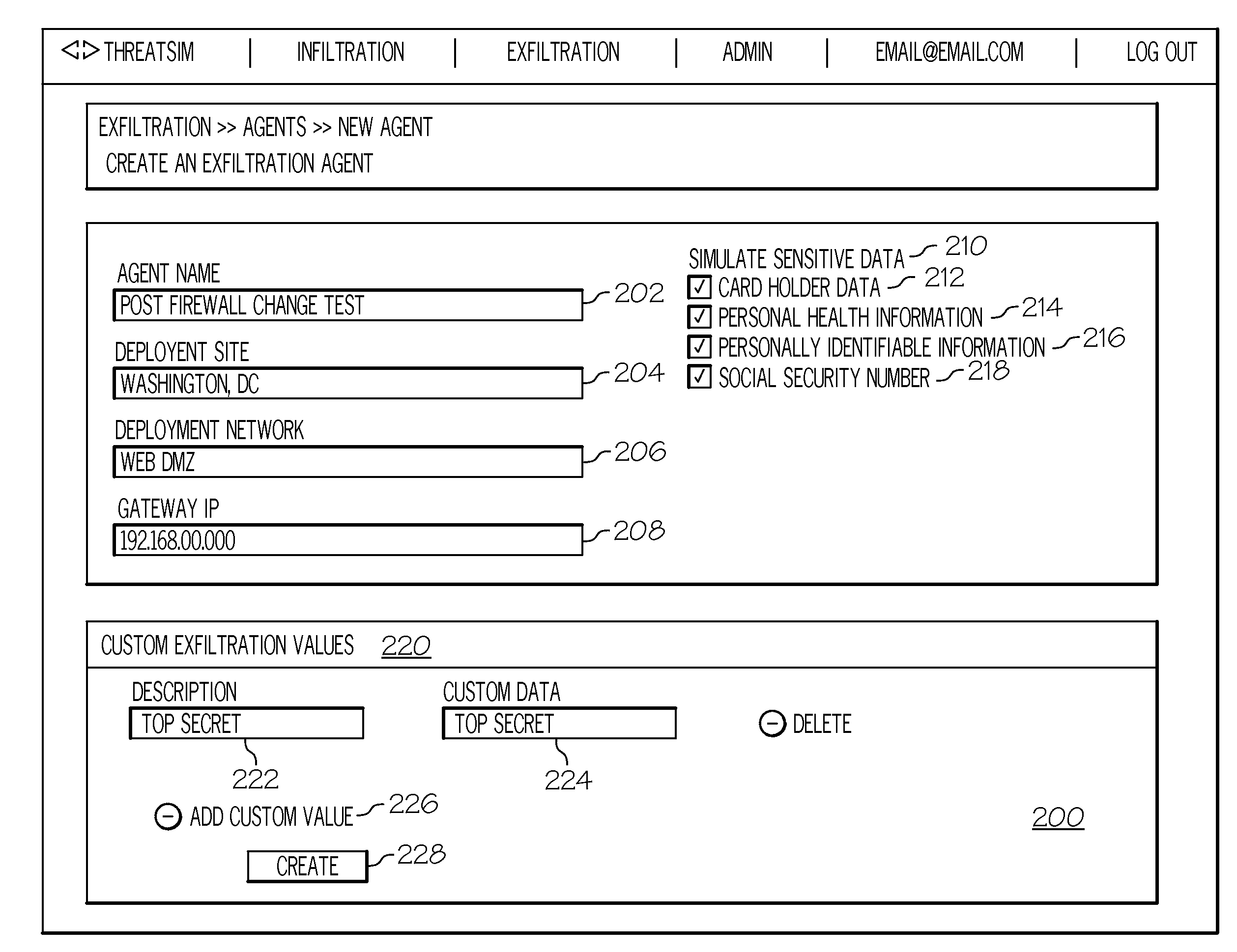
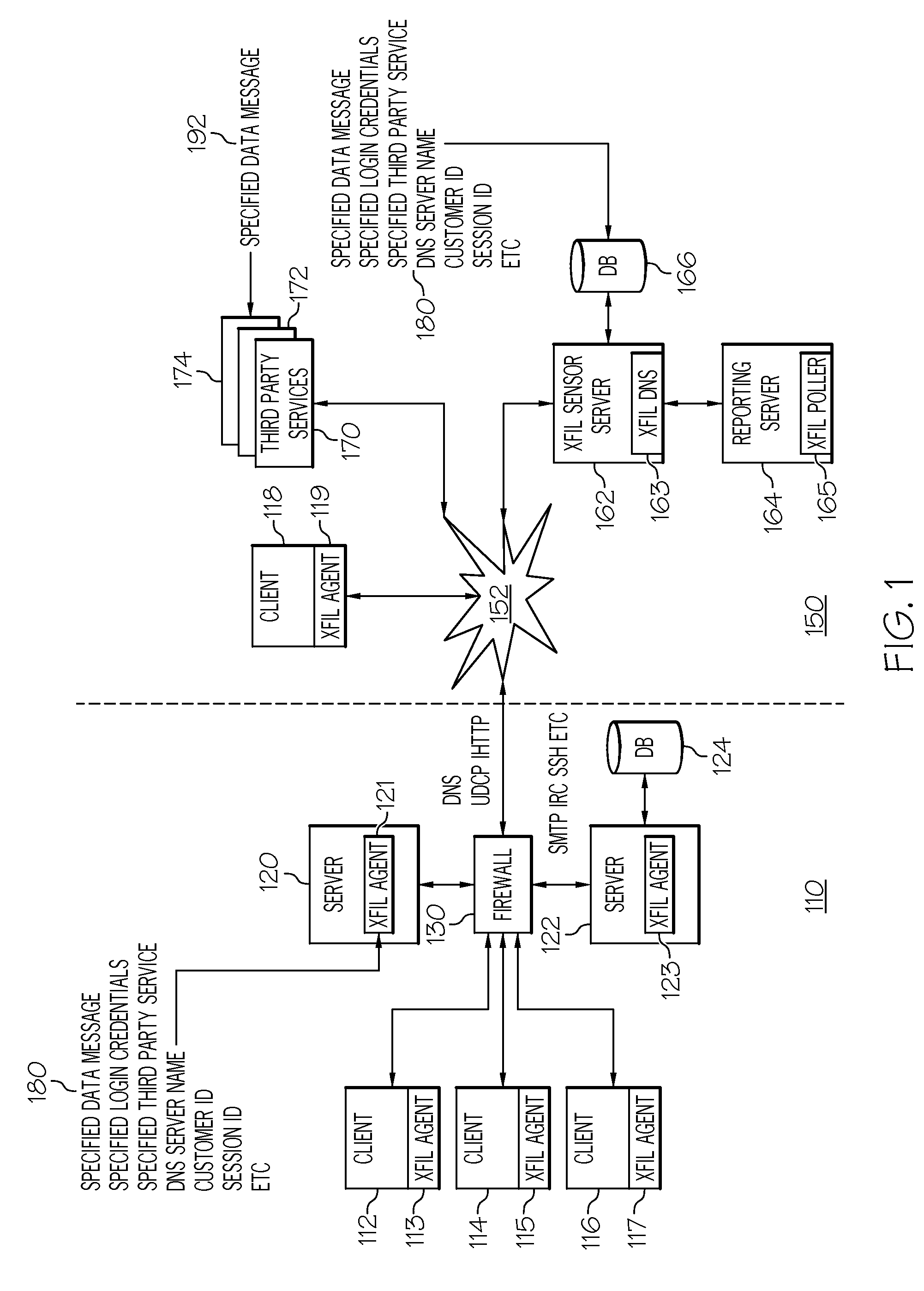
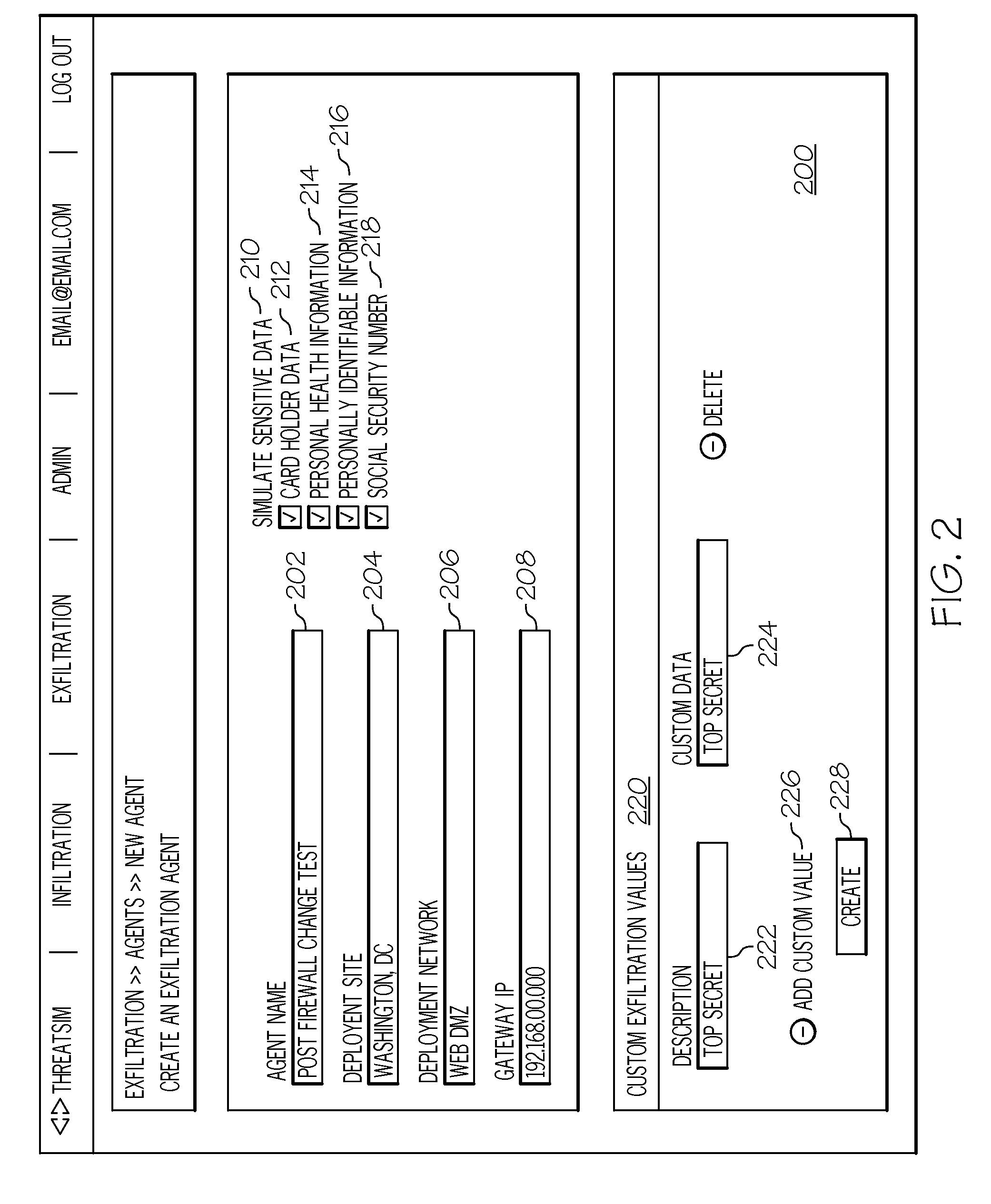
Data exfiltration attack simulation technology
InactiveUS20130347085A1Digital data processing detailsComputer security arrangementsThird partyData breach
Novel systems and methods for testing network security are disclosed. In one example, at least one specified data message and at least one specified access credential to at least one third-party web-based service is stored on a monitoring system. At least one software agent configured with the specified data message and the specified access credential to the third-party web-based service is installed on at least on system to be tested. The software agent is executed on the testing system to send the specified data message to the third-party web-based service using the specified access credential. A monitoring system which is independent of the network, access the third-party web-based service with the access credential. The monitoring system compares, if data on the third-party web-based service is equivalent to the specified data message sent by the software agent. In another example, the software agent is configured with a custom start-logging command.
Owner:STRATUM SECURITY
Reducing cybersecurity risk level of a portfolio of companies using a cybersecurity risk multiplier
ActiveUS10217071B2Lower risk levelReduce riskError detection/correctionResourcesRisk levelData breach
A multiplier is utilized to quantify a cybersecurity risk level of a portfolio of entities (e.g., companies) and enable actions to mitigate that quantified risk. In doing so, features or attributes of one or more companies in a portfolio are compared to features or attributes of one or more companies that experienced an adverse cybersecurity event (e.g. a data breach). Further, a degree of dependency, such as a matrix of a number of shared vendors and the proximity of those vendors to the companies, can be measured between (1) portfolio companies and one or more companies that experienced a cybersecurity event, and / or (2) the portfolio companies themselves to better quantify the risk. That is, to more meaningfully analyze a cybersecurity event that occurred at one or more companies and better predict the likelihood of an occurrence at portfolio companies, embodiments can determine an n-degree interdependency between companies.
Owner:SECURITYSCORECARD
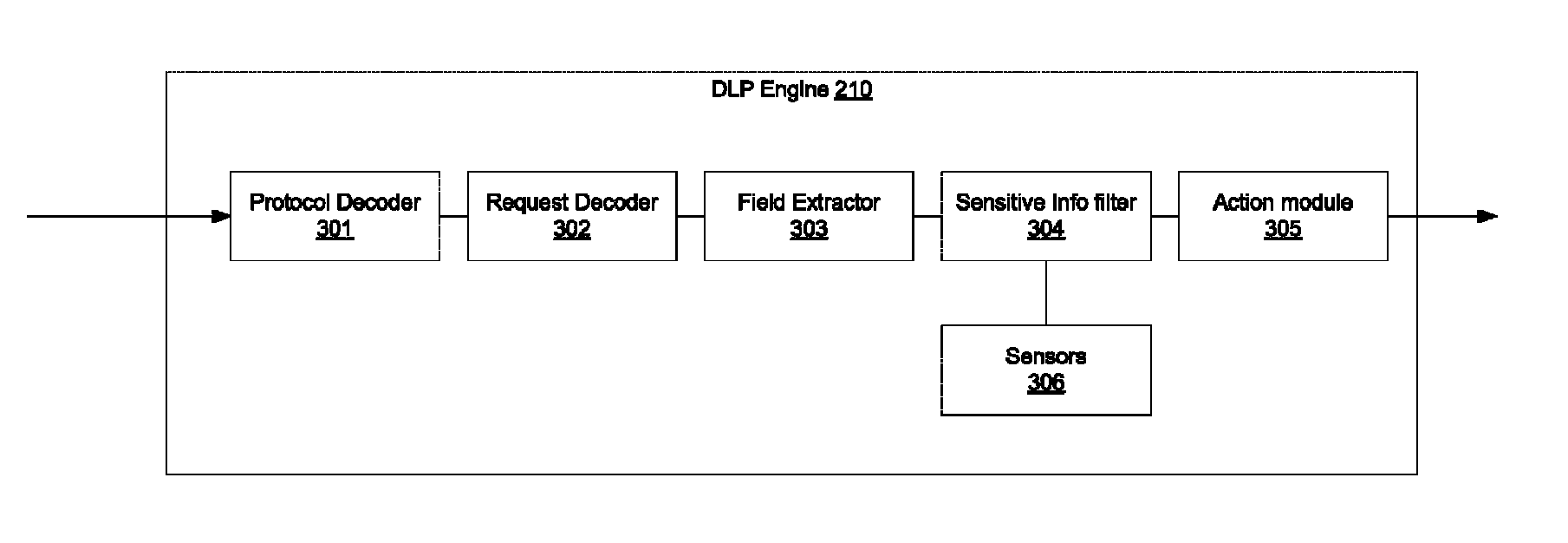
Data leak protection in upper layer protocols
Methods and systems for Data Leak Prevention (DLP) in a private network are provided. According to one embodiment, information is received from an administrator (i) defining a DLP rule to be applied to packets associated with an upper layer protocol and (ii) defining an action to take when a condition associated with the rule is satisfied. The rule includes a regular expression and / or a string that is configured to detect existence of sensitive information. A packet originated by a host device is received. The packet is determined to be associated with the upper layer protocol. A command, request or method of the protocol is identified that is specified by or represented by the packet. The packet is scanned for sensitive information based on the rule. When the scanning results in a conclusion that sensitive information is contained within the packet, then the defined action is performed.
Owner:FORTINET
Data leakage protection in cloud applications
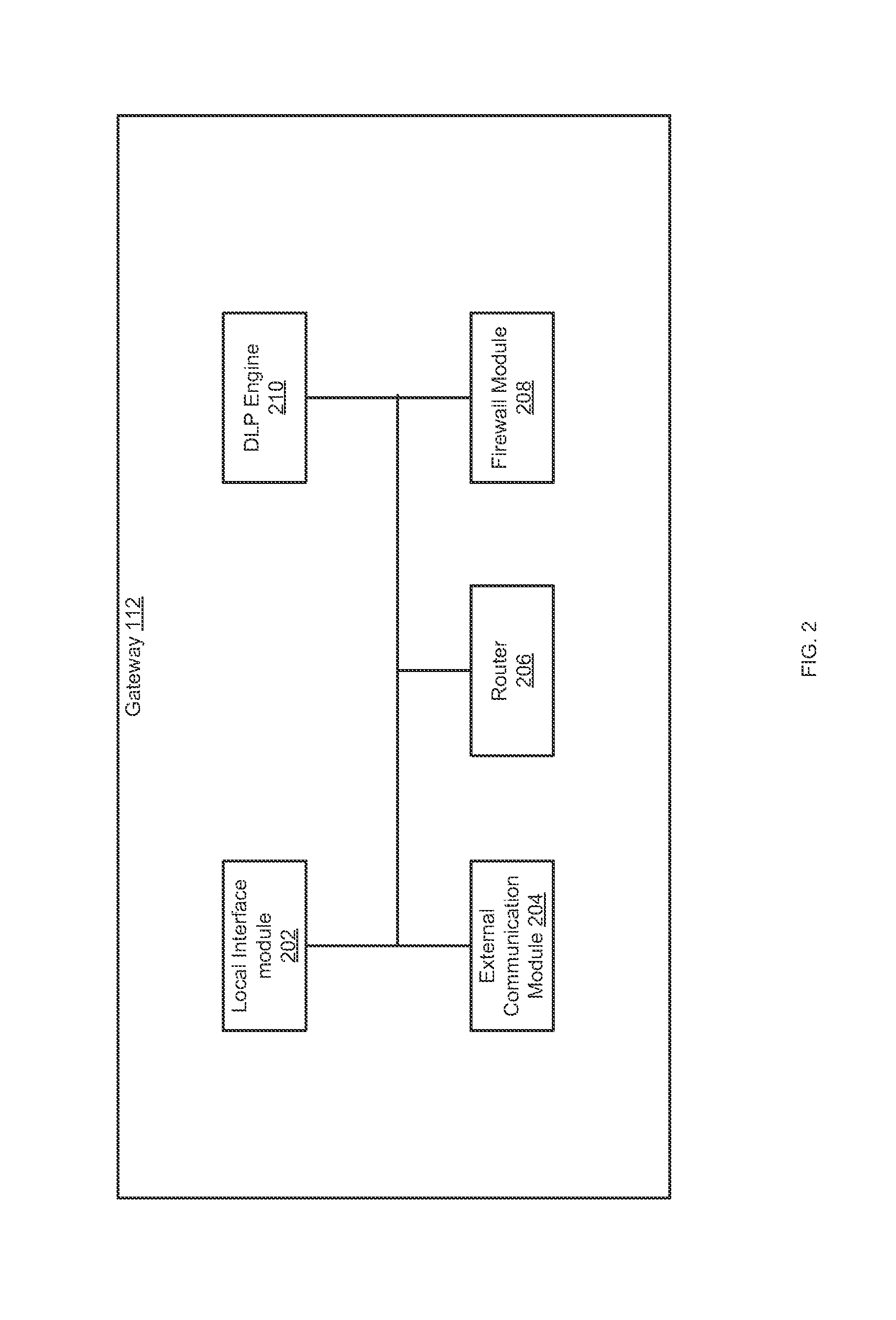
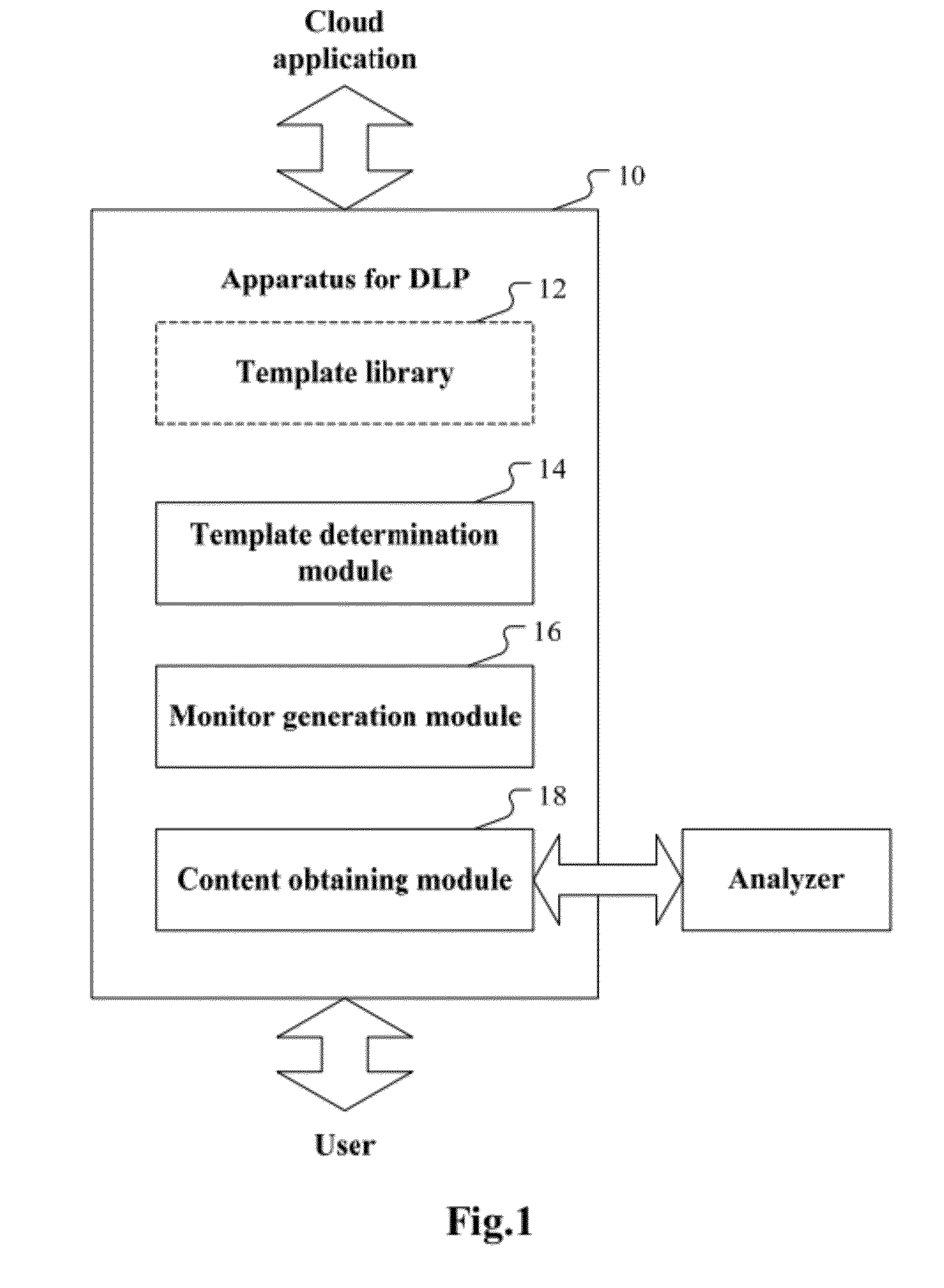
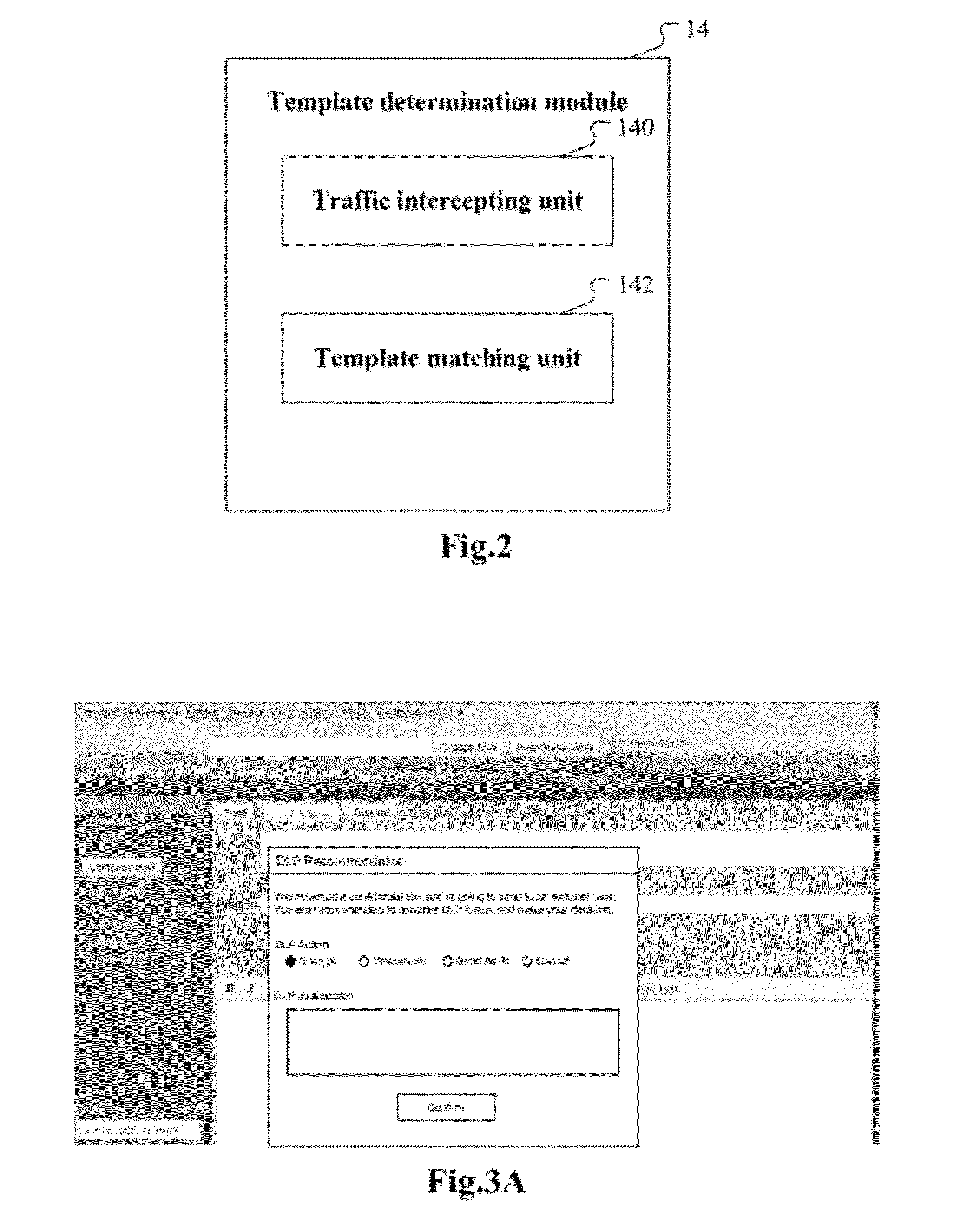
ActiveUS20120222110A1Memory loss protectionError detection/correctionSecurity analysisComputer science
A computer-implemented method for data leakage protection is disclosed. A monitoring template corresponding to the cloud application is selected based upon communication between a user and a cloud application and from a plurality of monitoring templates. A monitor is generated using the selected monitoring template. Identifying information of content shared between the user and the cloud application is obtained using the generated monitor. Data about the shared content for security analysis is obtained according to the identifying information of the shared content.
Owner:IBM CORP
Bidirectional authentication method of radio frequency identification system
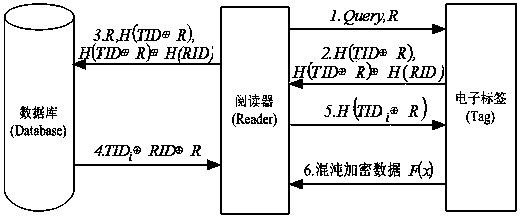
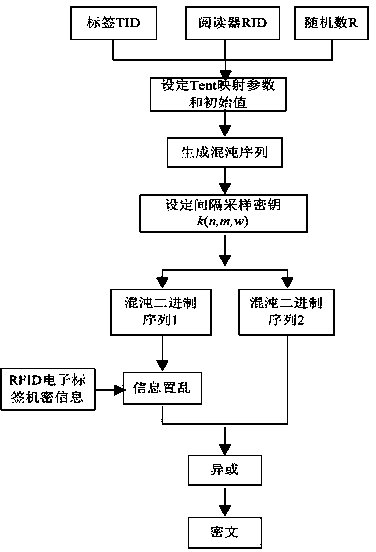
ActiveCN103413109AImprove securityHigh utility valueUser identity/authority verificationSensing record carriersHash functionAttack
Disclosed is a bidirectional authentication method of a radio frequency identification system. The simple and rapid method with chaotic mapping combined with the Hash function, the exclusive-or operation and the like is adopted, filter operation is conducted together with bidirectional authentication, search and computing loads of a back-end data base are reduced, the safety problems of impersonation, retransmission attack, tracing and the like are avoided, a label of the radio frequency identification system and TID and RID of the unique mark amount of a reader are used as an initial value and parameters of the chaotic mapping, and chaotic scrambling and exclusive-or encryption are performed on confidential information of the label by being combined with the authentication process. On the basis of taking full consideration of saving the cost of the passive radio frequency identification label, data encryption and safety authentication are organically combined, and accordingly the safety problems such as illegal access, counterfeiting and cheating and data leakage in the radio frequency identification system can be solved.
Owner:徐州虹智智能科技有限公司
Hive platform user safety management system and application
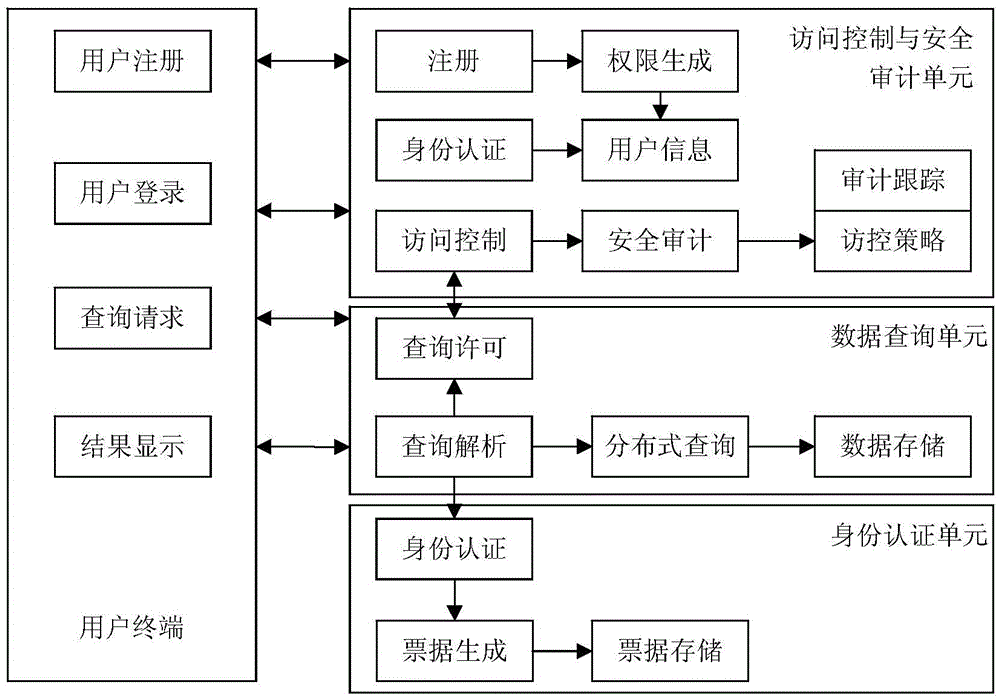
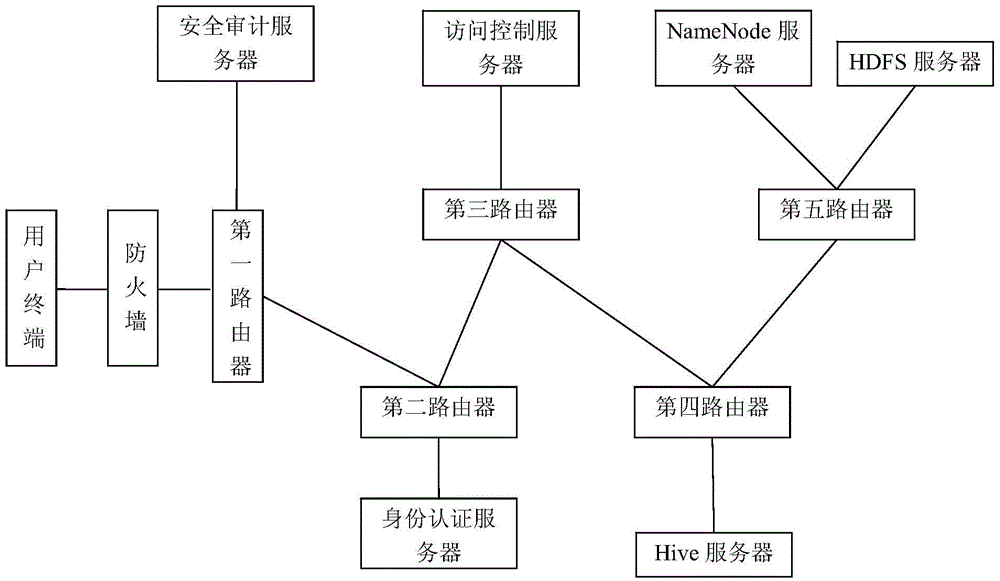
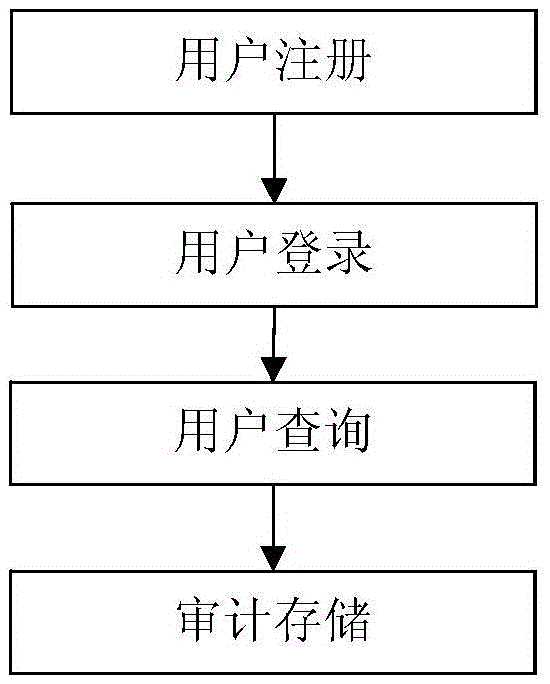
InactiveCN105656903AMeet safety requirementsAvoid the shortcomings of intertwined functions and reduced business efficiencyTransmissionSafety management systemsData query
The invention discloses a Hive platform oriented user safety management system. The Hive platform oriented user safety management system comprises an access control and safety audition unit, a data query unit and an identify authentication unit, wherein the access control and safety audition unit comprises a safety audition server and an access control server, the data query unit comprises an HDFS server, a NameNode server and a Hive server, and the identify authentication unit comprises an LDAP server. A Hive platform oriented user safety management method comprises four steps, including user registration, user login, user query and audition storage. According to the Hive platform oriented user safety management system and method, an exceed authority access action of the traditional user to a large-scale storage system is prevented, data leakage due to the fact that a data storage device is stolen can be safely and effectively prevented, and problems that data packets are captured illegally and private data is obtained after the traditional storage system is invaded by external personnel are prevented.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
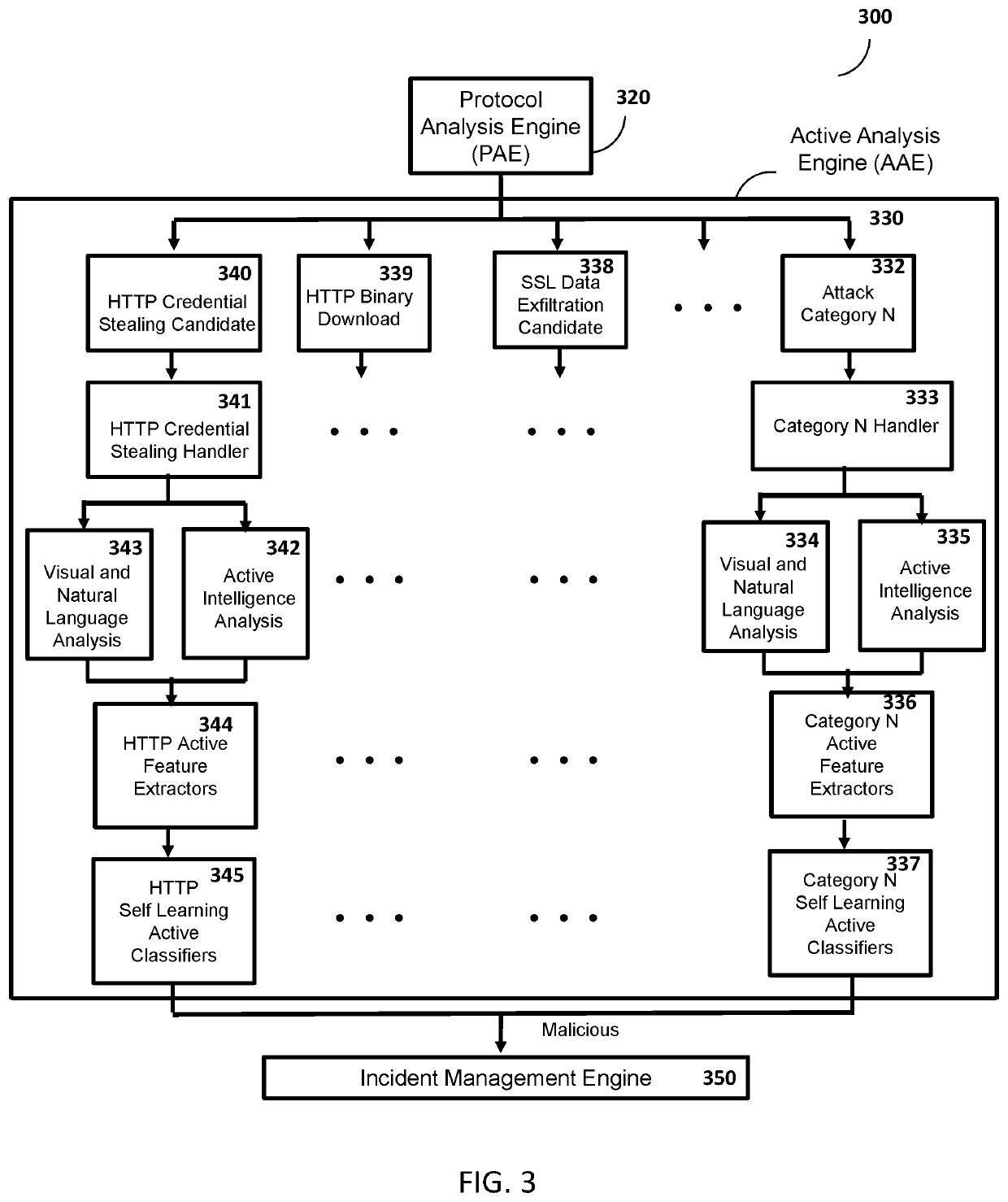
Method and system for protection against network-based cyber threats
An Active Cyber Defense method and system is provided for detecting and stopping malicious cyber activity including for example Drive-By Exploits, Malicious Binaries, Data Exfiltration, Social Engineering and Credential Stealing Attacks. The system disclosed herein can be configured to detect and block multi protocol network-based cyber attacks targeting different platforms or operating systems. The system can also be configured to be scalable. The system as disclosed herein can conduct real time inspection of network traffic and can self-learn and adapt as needed to a changing cyber threat landscape.
Owner:SLASHNEXT INC
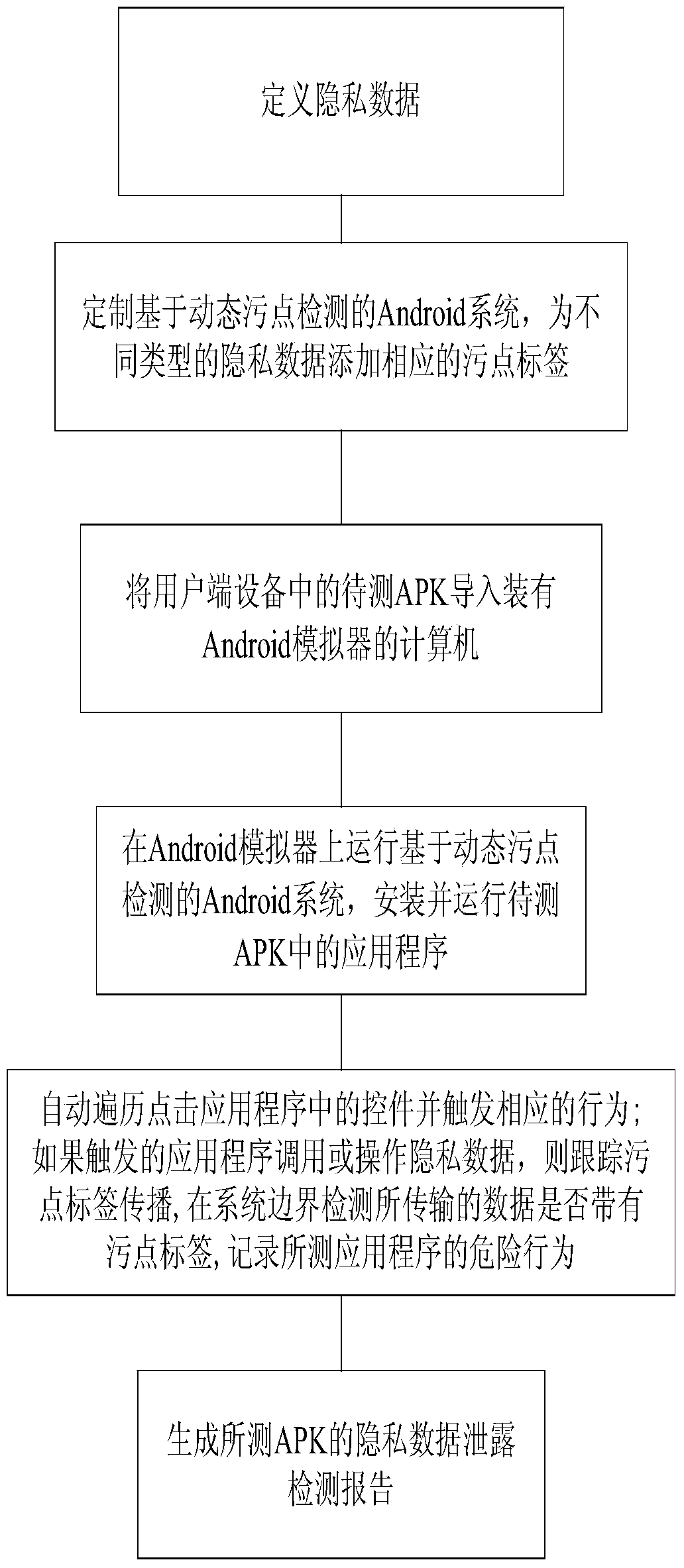
Method for offline detecting private data leakage of Android application program
InactiveCN103729595ANot infectedNot easy to cause false detectionDigital data protectionPlatform integrity maintainanceTest efficiencyApplication software
The invention discloses a method for offline detecting private data leakage of an Android application program. The method comprises the following steps that private data are defined; an Android system based on dynamic dirty point detection is customized, and corresponding dirty point labels are added to the private data of different types; an APK to be detected in user side equipment is guided into a computer; the system is operated on a simulator, and the application program in the APK to be detected is installed and operated; controls in the application program are automatically traversed and clicked by automatically testing scripts, corresponding behaviors are triggered, and the dangerous behavior of the detected application program are recorded; after traversal is finished, the private data leakage detection report of the detected APK is generated. The problems that the private data leakage can only be reminded in real time, a record detection result is not generated, and virtual detection and leak detection occur easily are solved, and meanwhile the problems that an existing detection scheme is low in test efficiency and poor in practicality, the real private data leakage can be caused, and the risk is large are solved.
Owner:SOUTHEAST UNIV
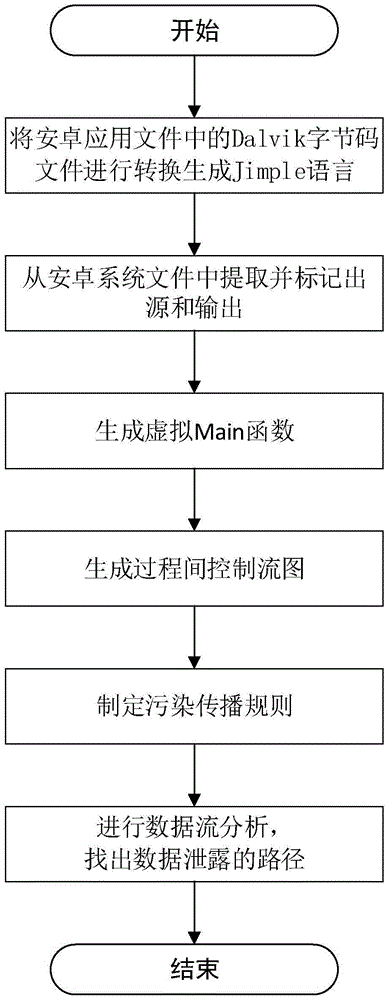
Security detection method for android application file
ActiveCN105550594AEasy to operateOvercoming the difficulties of analysisDigital data protectionOperating systemControl flow diagram
The invention discloses a security detection method for an android application file, and mainly solves the problem of privacy leakage vulnerability detection capability shortage of an existing android application file. The method is implemented by the steps of 1, converting a Dalvik byte code file in the android application file into a Jimple language; 2, extracting input and output functions related to sensitive data by classification from an android system file, classifying the input and output functions, and marking a source and an output; 3, generating a virtual Main function in the Jimple language and generating an interprocedural control flow diagram according to the function; 4, establishing a taint spread rule; 5, generating a taint access path according to the interprocedural control flow diagram; and 6, according to the marked source and output, executing the taint spread rule in the taint access path to find out a data leakage path. According to the method, the missing and false reporting of privacy leakage vulnerabilities is reduced and the security protection performance is improved, so that the method can be used for detecting the android application file.
Owner:XIDIAN UNIV
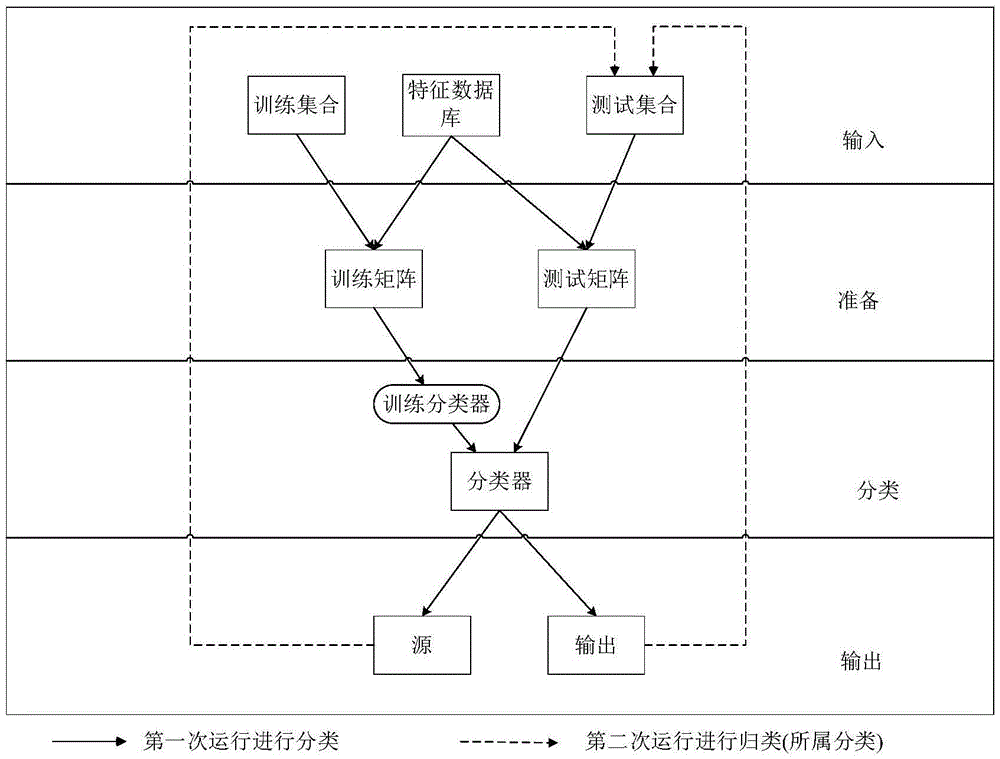
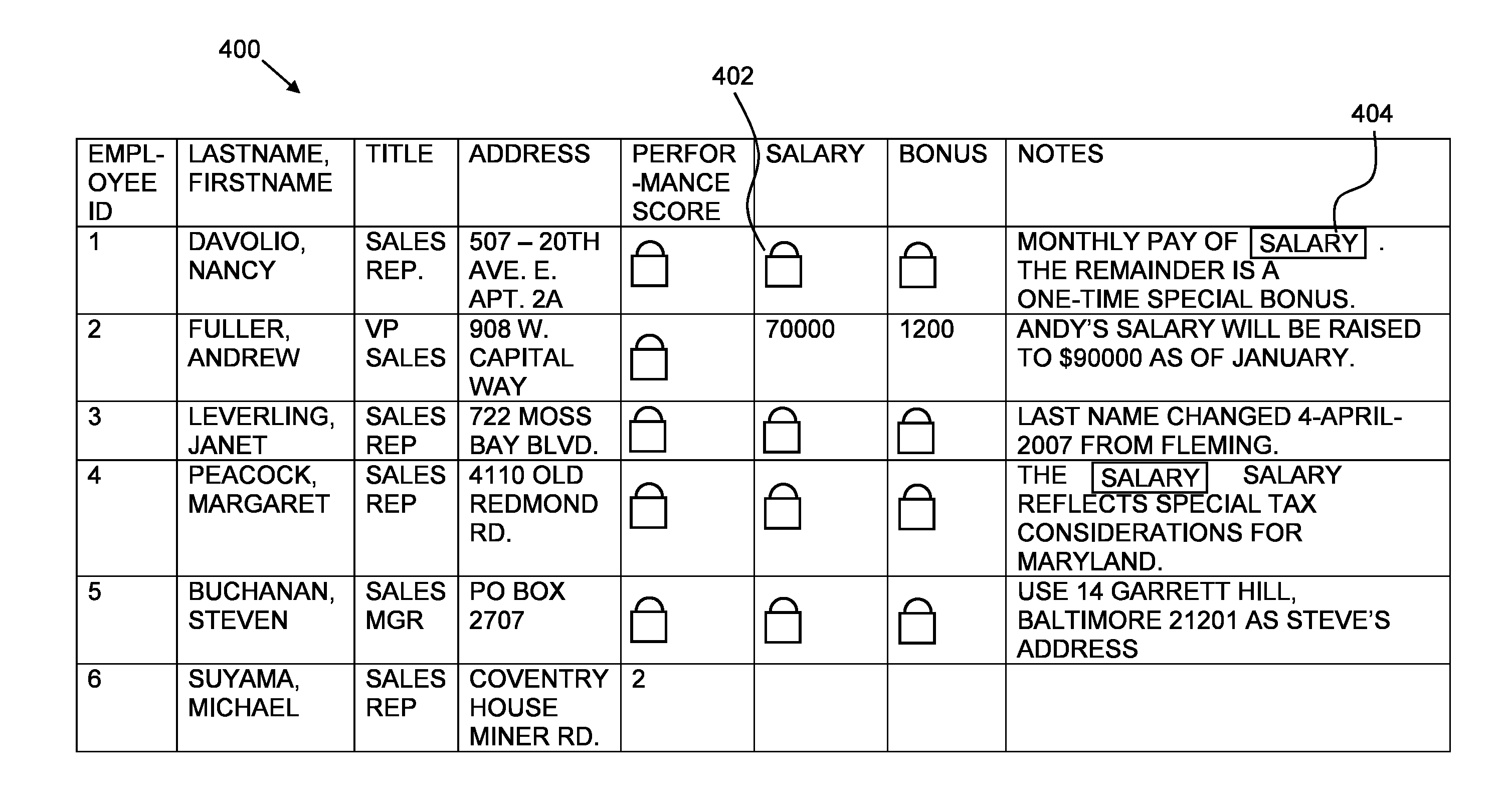
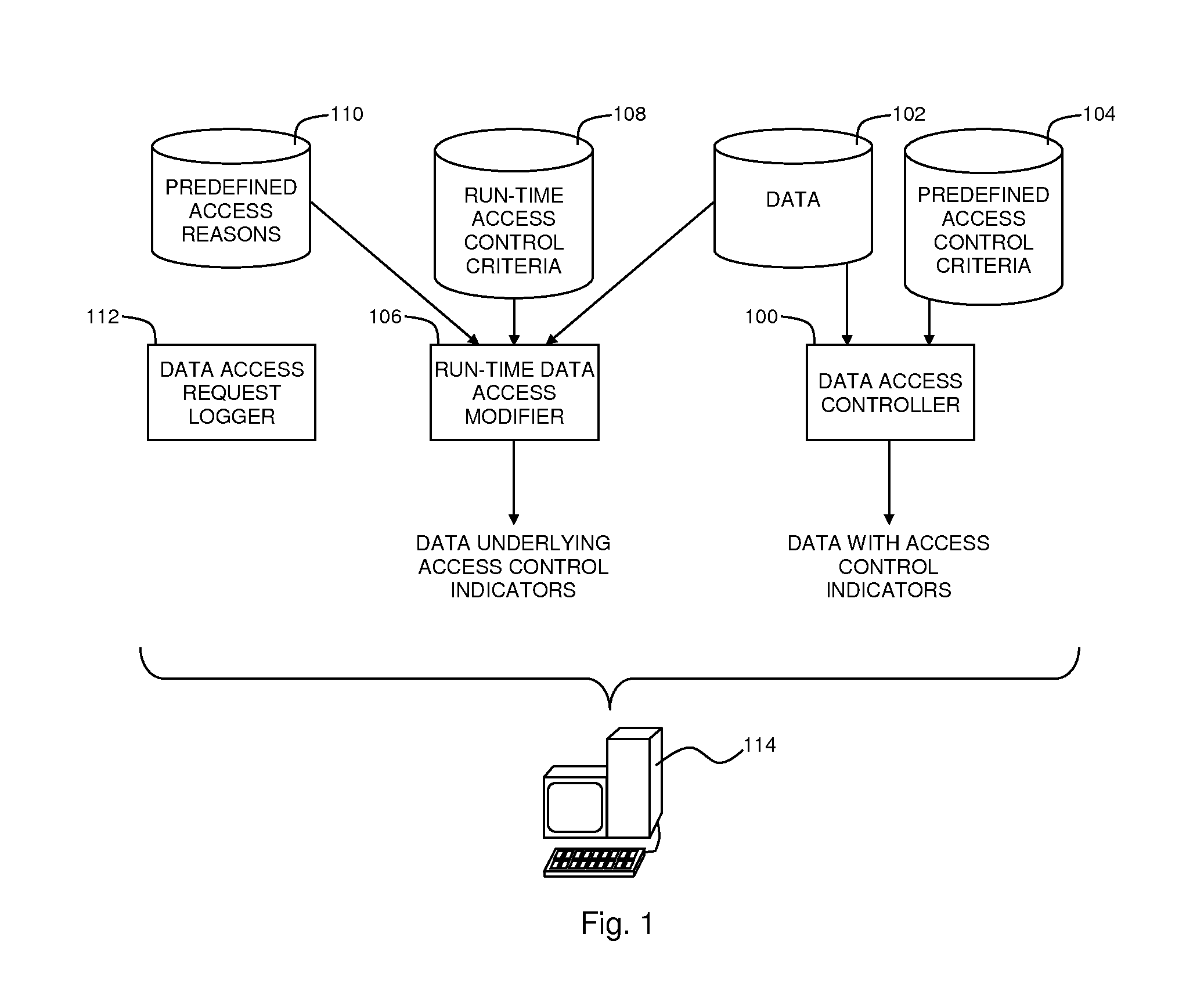
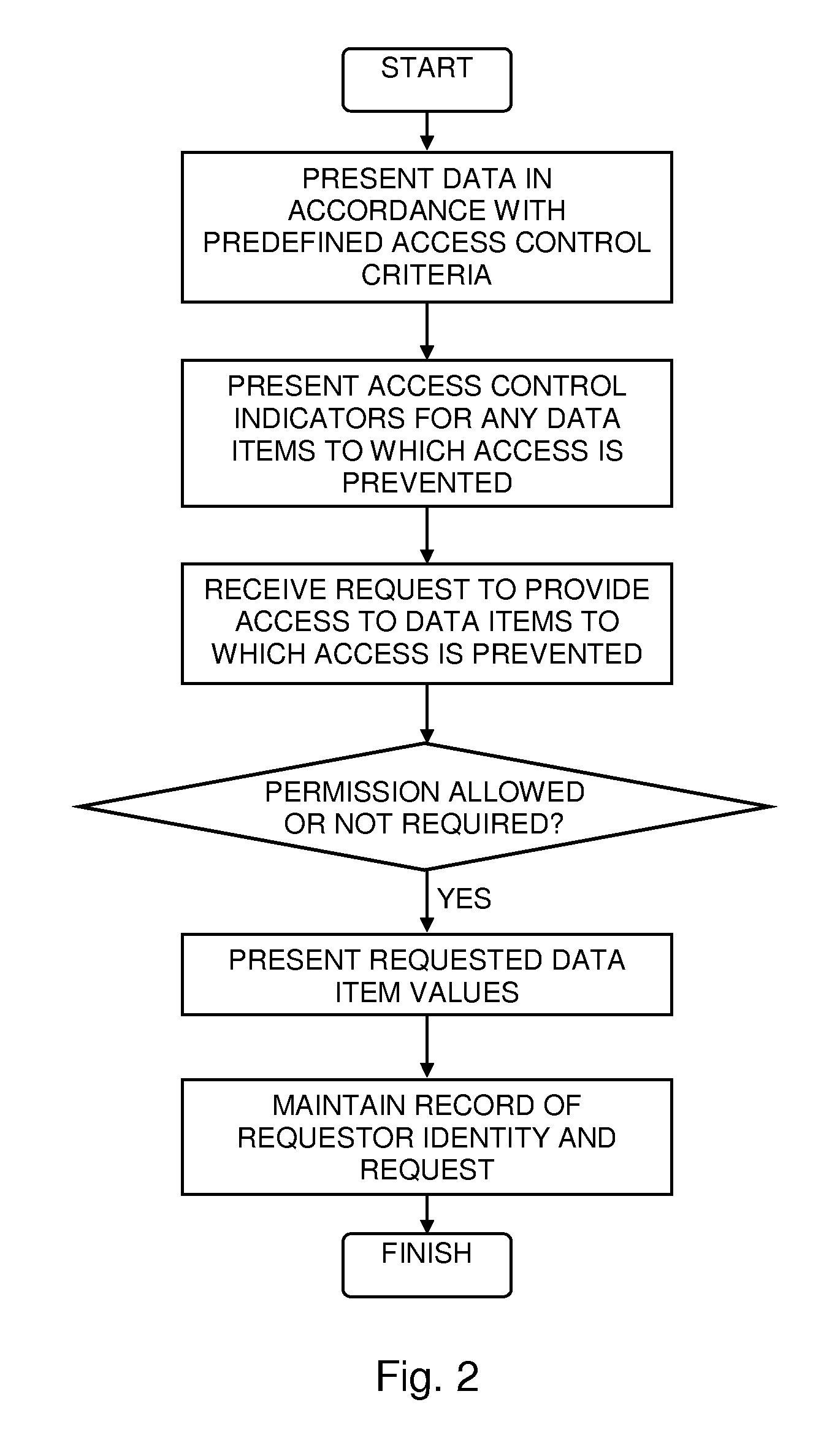
Data Access Control with Flexible Data Disclosure
ActiveUS20110055932A1Digital data processing detailsAnalogue secracy/subscription systemsData access controlOutput device
A method for presenting data, the method including presenting via a first computer output device an indicator indicating a data item whose value is prevented, in accordance with predefined access control criteria, from being presented via the first computer output device, receiving from a requestor a request to present the data item value, maintaining a record of an identity of the requestor together with a description of the requested data item, and presenting via a second computer output device the data item value.
Owner:IBM CORP
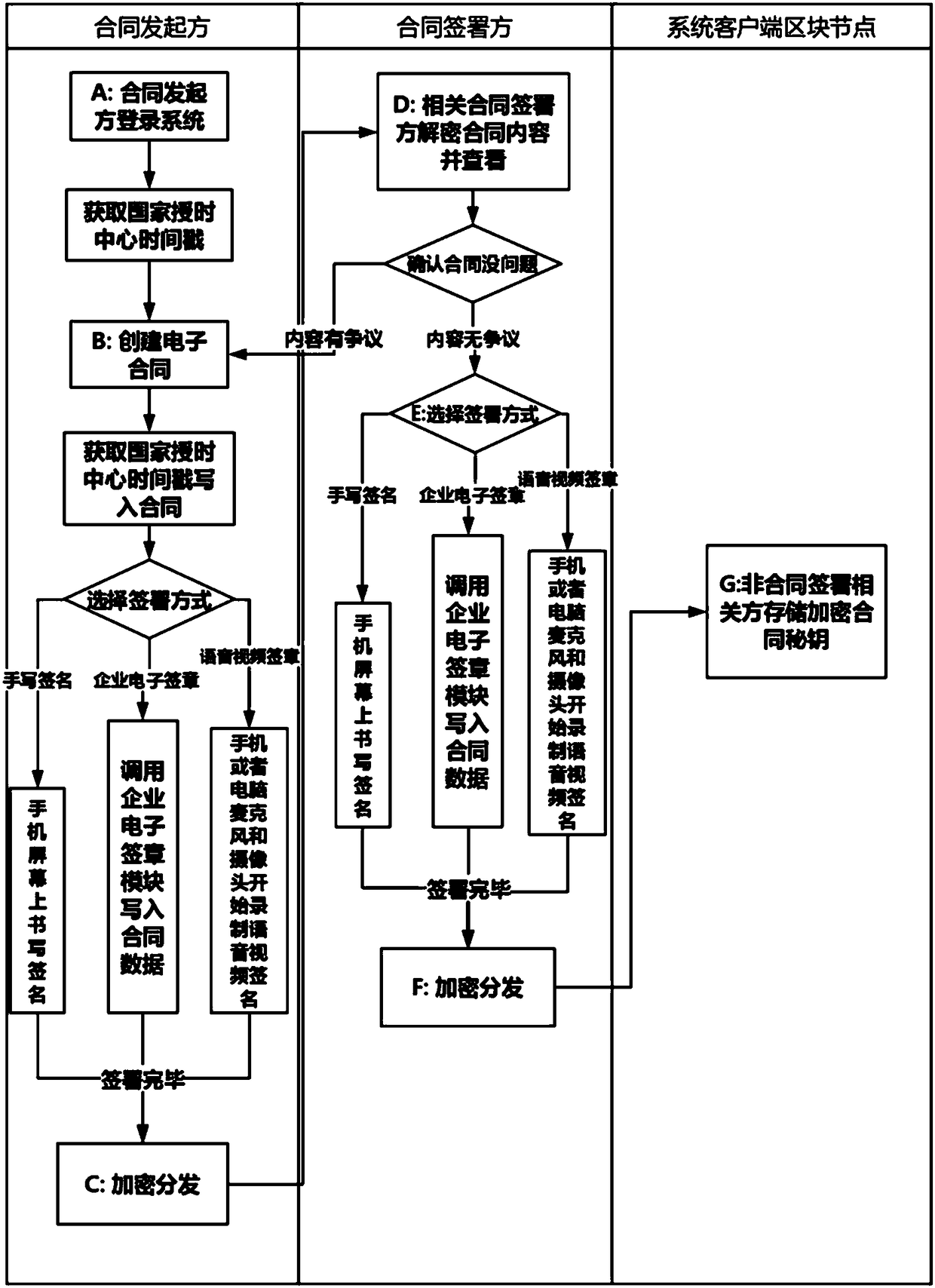
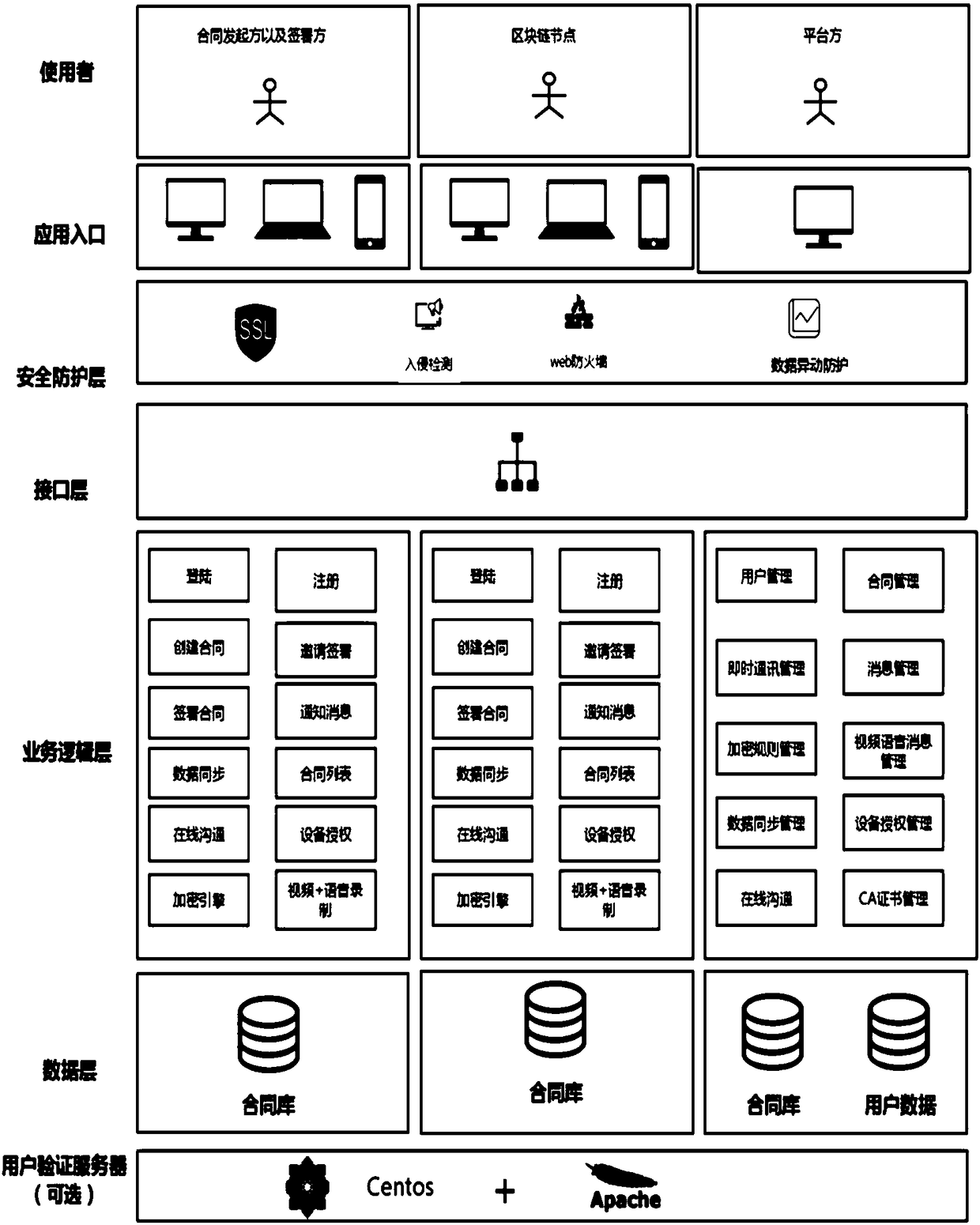
Online contract signing system and online contract signing method on basis of block chain technologies
InactiveCN108537046APrevent leakageData processing applicationsDigital data protectionThird partyElectronic contracts
The invention provides an online contract signing system and an online contract signing method on the basis of block chain technologies. The online contract signing method includes allowing contract initiators to log in systems; creating electronic contracts; carrying out encrypting and distributing, to be more specific, encrypting the electronic contracts by network engines of clients and then distributing the electronic contracts to clients of various contract signatories; decrypting contract contents by the related contract signatories and viewing the contract contents; selecting signing modes; carrying out encrypting and distributing; storing encrypted contract secret keys by non-contract-signing related parties so that anonymous encrypted unidentifiable contract data on networks can be synchronized after each client logs in the systems. The online contract signing system and the online contract signing method have the advantages that decentralization strategies are completely adopted, all operation is locally carried out, and accordingly the possibility that data leak to third parties can be prevented; anonymous encryption strategies are adopted for contract data, accordingly,encrypted data contents cannot be identified by clients of the non-contract-signing related parties, all global clients need to be tampered by optional protocol tampering operation, no optional client has the permission for operating data of the other clients, and the tampering possibility can be completely eradicated.
Owner:才信网络科技(上海)有限公司
Audit protection system for data leakage
InactiveCN102609637AImprove reliabilityImprove securityHardware monitoringDigital data protectionEnd systemComputer terminal
The invention discloses an audit protection system for data leakage, wherein a client system and a management end system are arranged on a user terminal and a server in an internal network manner; a client system is used to monitor the using situation of programs and files of the user terminal at any time to generate operation record and screenshot record of the target file or the program, and the operation record and screenshot record of the target file or the program are collected in operation historical record database and screenshot historical record data base of the server so as to form text and video track record during the target operation in the management end system, therefore, all process of data leakage are flexibly reproduced, so that the file leakage and responsibility track can be well documented, the anti-leaking effect is obvious, the protection process is safe and reliable, and the audit protection system is particularly suitable for being installed in units such as enterprises, institutions, offices and so on.
Owner:BEIJING UVIC SOFTWARE TECH
Method for authentication for resisting secrete data disclosure and key exchange based on passwords
InactiveCN101626364AImprove computing efficiencyPrevention analysisPublic key for secure communicationUser identity/authority verificationKey exchangeCryptographic protocol
The invention belongs to a cryptographic protocol, and in particular relates to a method for authentication for resisting secrete data disclosure and key exchange based on passwords. The method is superior to correlative American or international current standard in the aspects of user password protection, secrete data disclosure resistance, better user privacy protection, better online efficiency calculation, less communication bandwidth and higher security. The method for the authentication and the key exchange comprises sub-methods of an innovative method for public key encryption and signcryption based on passwords, a method for knowledge binding certification, a method for resisting temporary secrete data disclosure, a method for awarding a public key certificate. The method has the advantages of good systematicness, adaptability and compatibility.
Owner:赵运磊 +3
Data leakage detecting method, system, device and storage medium
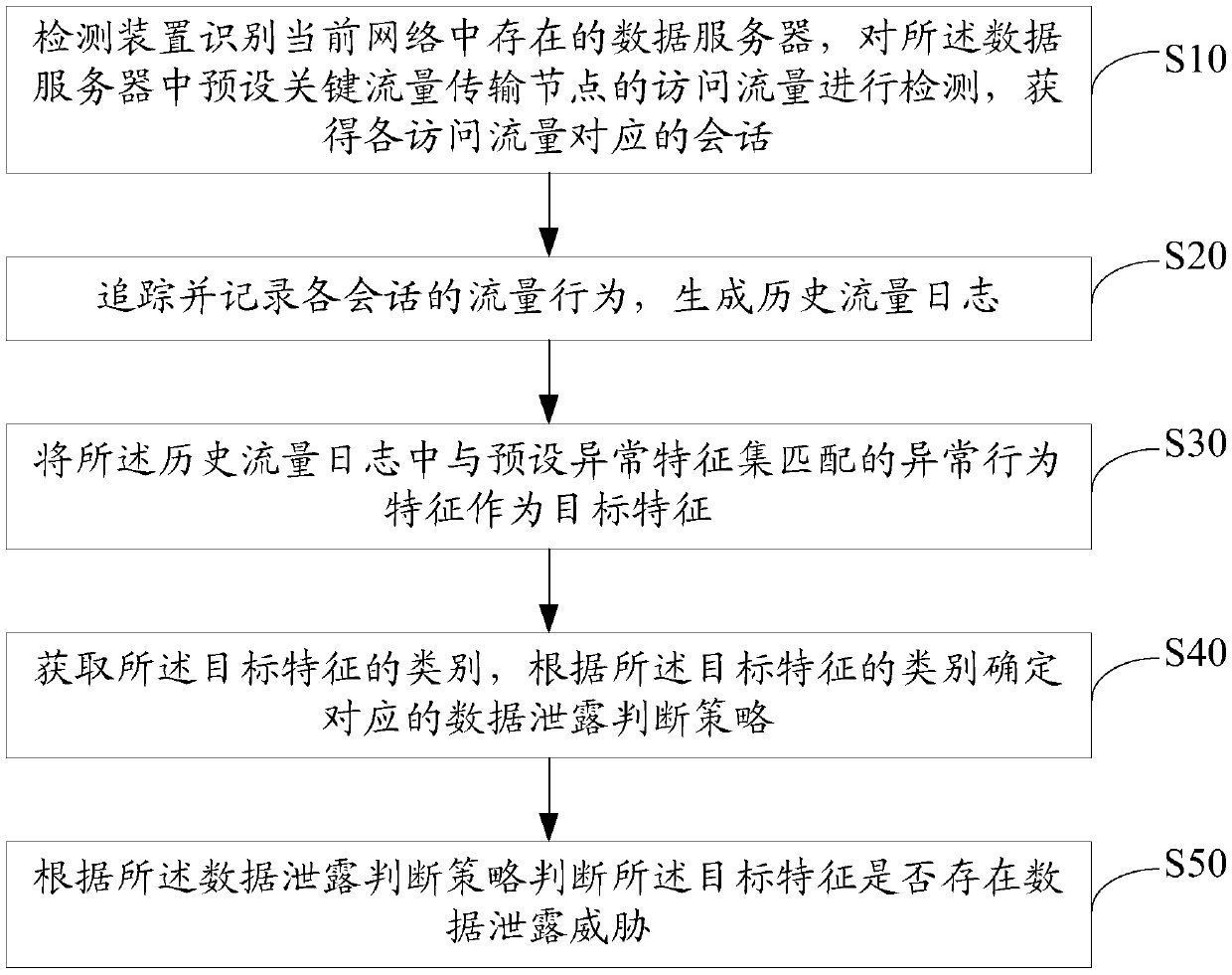
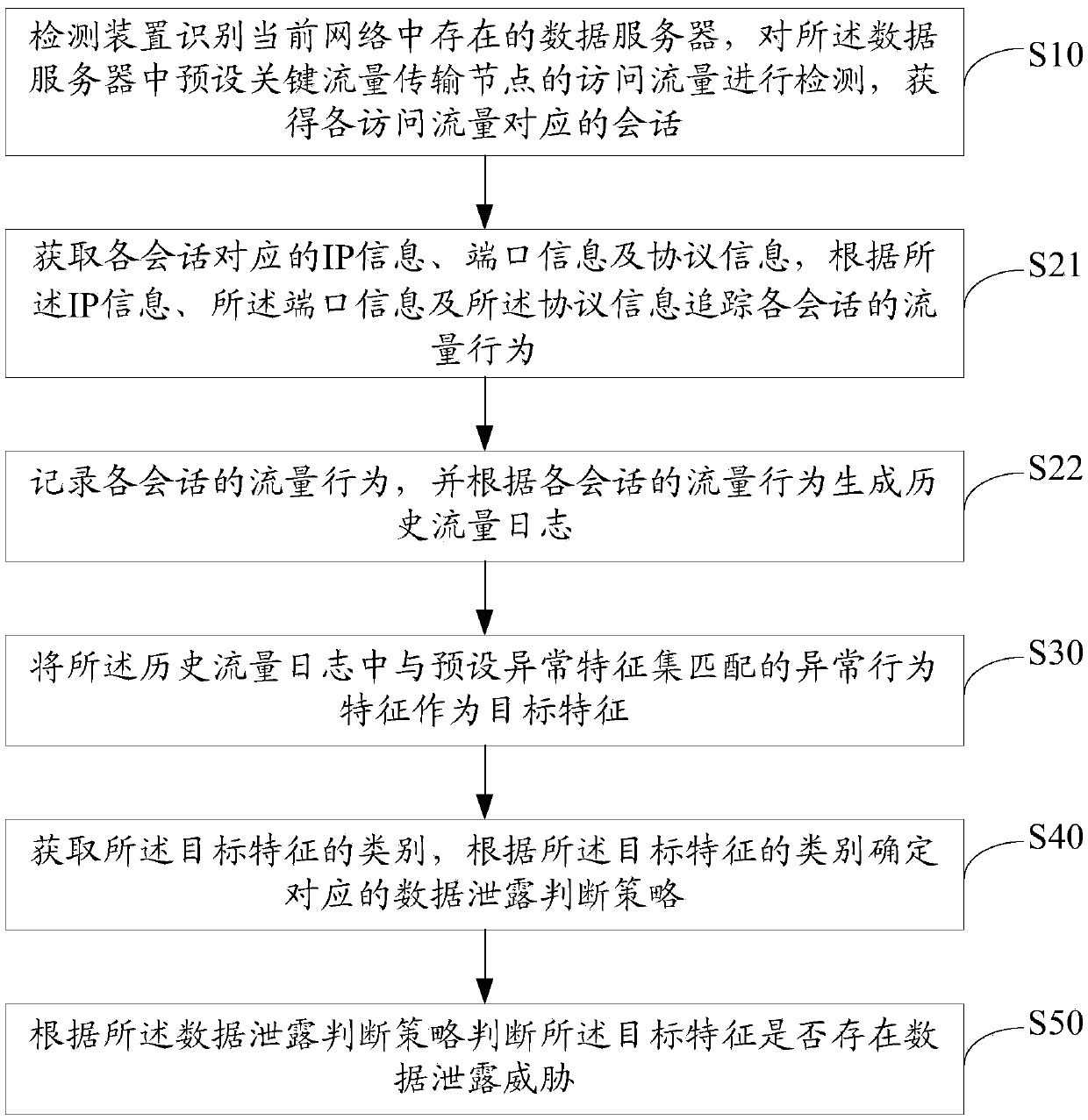
ActiveCN109525558AHigh precisionProtect against encryption attacksTransmissionTraffic capacityFeature set
Owner:SANGFOR TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com