Authentication system and working method thereof
A technology of authentication system and working method, which is applied in the field of information security and can solve problems such as low security and data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
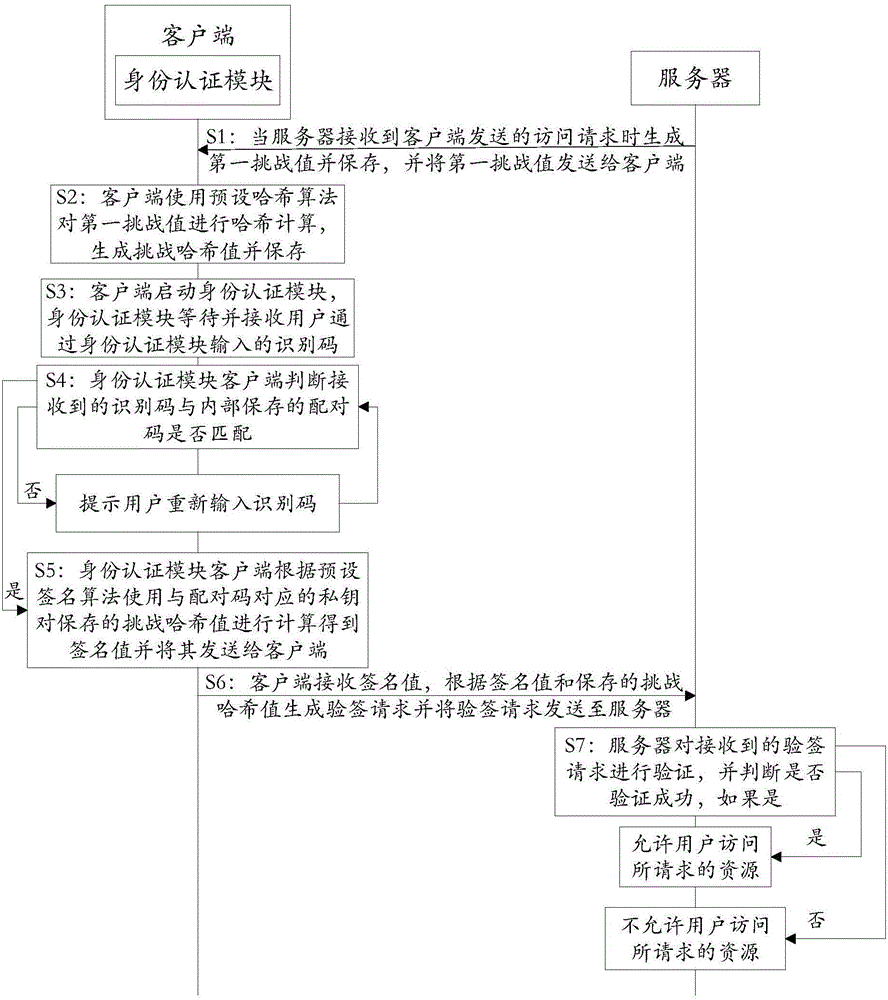
[0176] Embodiment 1 provides a working method of an authentication system, which is applied to a system composed of a client, an independently configured identity authentication module, and a server. As shown in 1, this method specifically includes:
[0177] Step S1: When the server receives the access request sent by the client, it generates and saves the first challenge value, and sends the first challenge value to the client;
[0178] Step S2: The client uses a preset hash algorithm to perform hash calculation on the first challenge value, generates a challenge hash value and saves it;
[0179] Step S3: the client starts the identity authentication module, and the identity authentication module waits for and receives the identification code input by the user through the identity authentication module;
[0180] Step S4: The identity authentication module judges whether the received identification code matches the internally stored pairing code, if yes, execute step S5, othe...
Embodiment 2
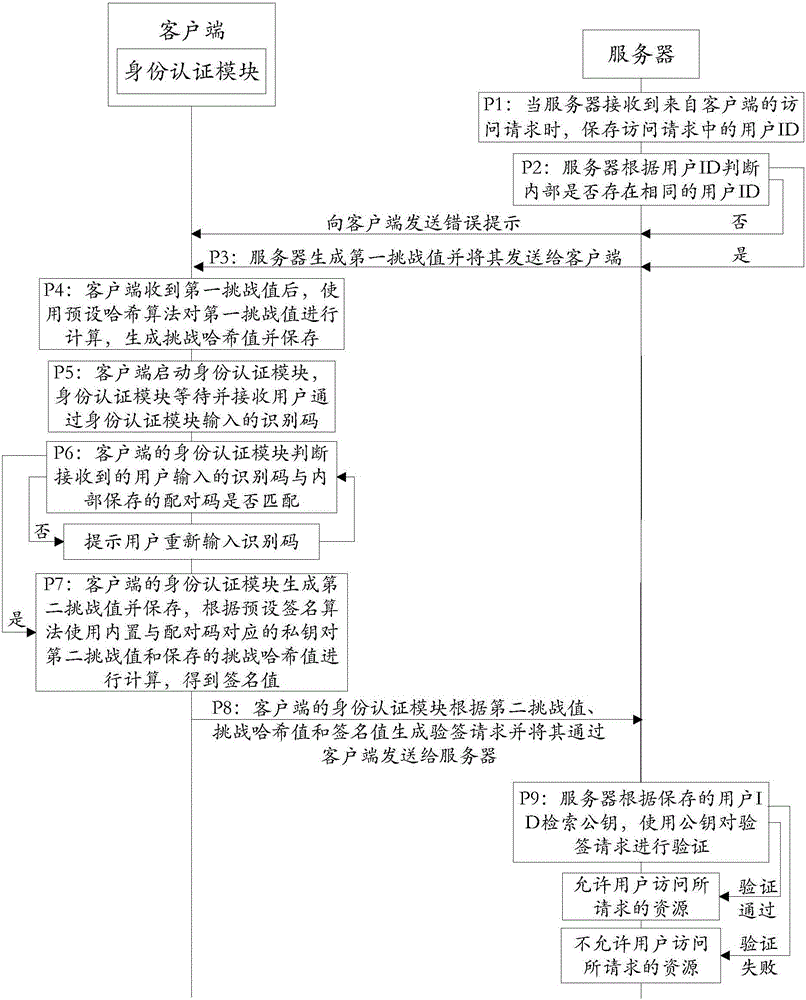
[0188] Embodiment 2 provides a working method of the authentication system, which is applied to a system composed of a client, an identity authentication module independently set on the client, and a server.
[0189] Specifically, in this embodiment, the client has an identity authentication function and has an independent identity authentication module built in.
[0190] Preferably, the identity authentication module can be used for fingerprint identification. Correspondingly, the identity authentication module compares the built-in pairing code (ie, information required for fingerprint identification) with the identification code (ie, fingerprint) input by the user. The identity authentication module can also be implemented in other ways, such as voiceprint, palmprint, iris, password, etc.
[0191] The identity authentication module has the functions of generating key pairs and digital signatures. During the registration process of the user on the server, the identity auth...
Embodiment 3
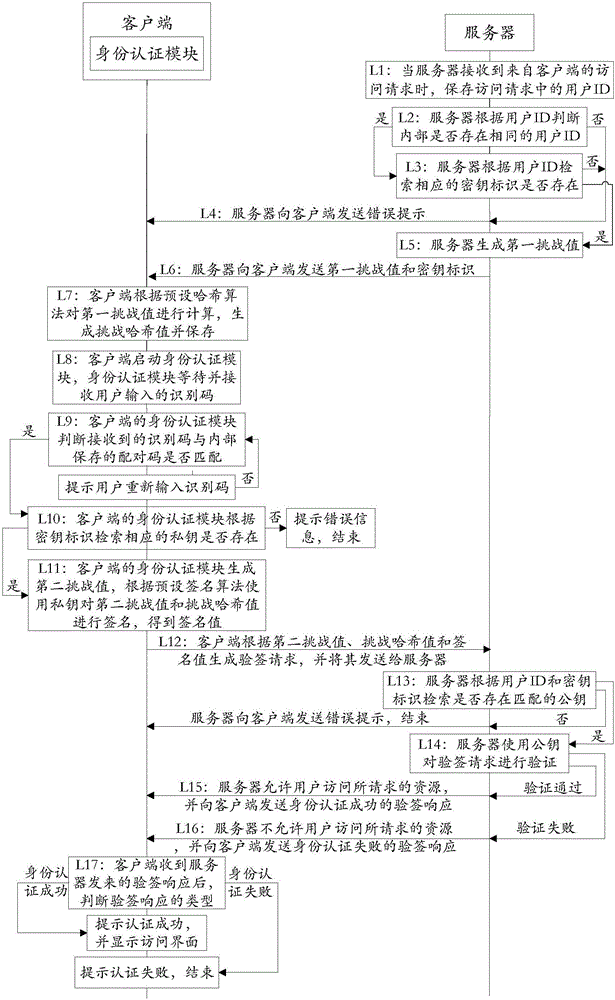
[0222] Embodiment 3 provides a working method of the authentication system, which is applied to a system composed of a client, an identity authentication module independently set on the client, and a server.
[0223] Preferably, in this embodiment, the identity authentication module is set in the client, and multiple key pairs are set in the identity authentication module, one key pair corresponds to one user, and the key pair is the same as the key identifier and the pairing code. One to one correspondence.
[0224] Such as image 3 As shown, the working methods of the authentication system specifically include:
[0225] Step L1: when the server receives an access request containing the user ID from the client, save the user ID;
[0226] For example, user ID: 13012345678;
[0227] Step L2: The server judges whether the same user ID exists internally according to the user ID, and if so, executes step L3, otherwise executes step L4;
[0228] Step L3: The server retrieves wh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com