Patents
Literature
305results about How to "Improve communication security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
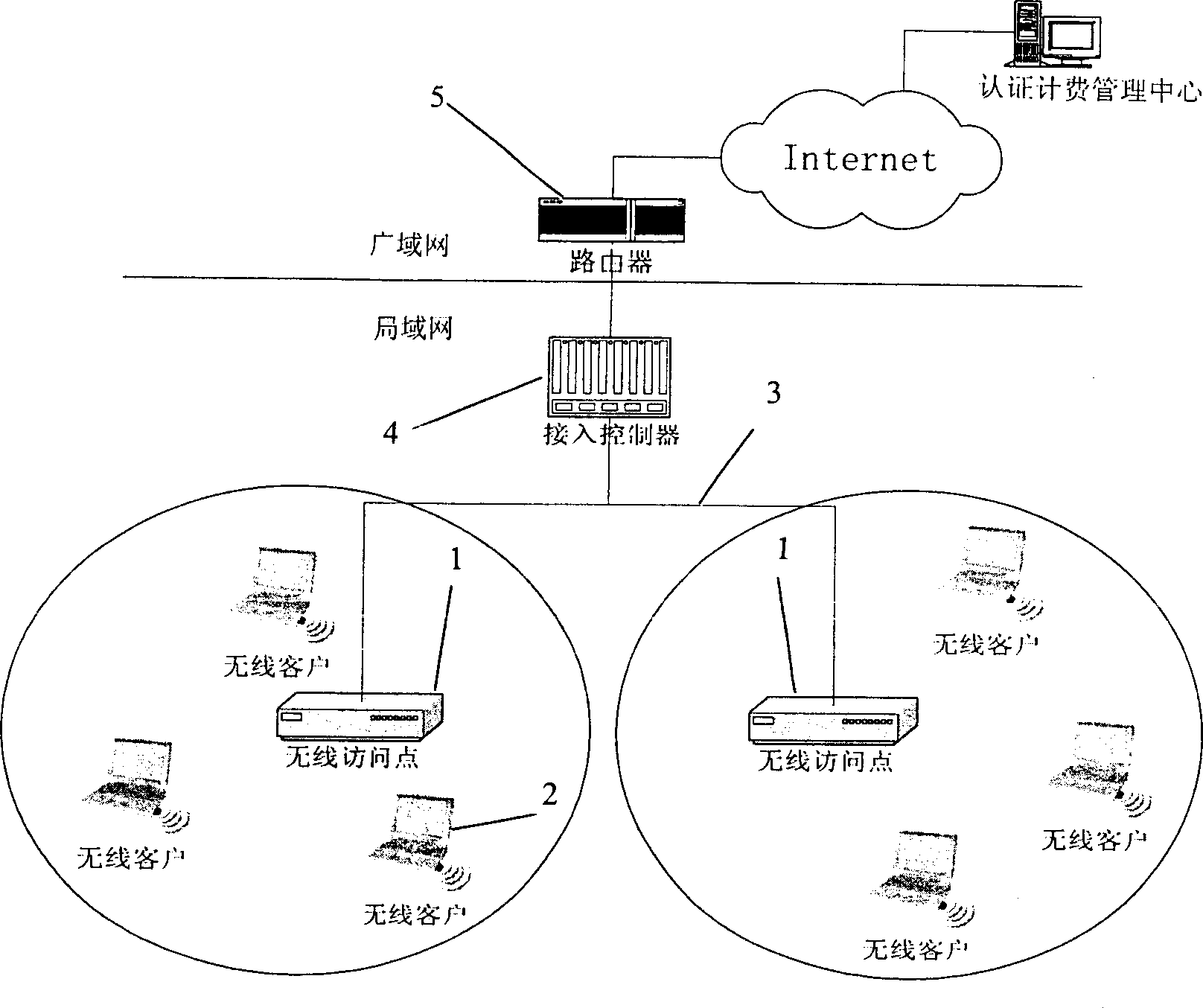
Authentication system and working method thereof
ActiveCN105847247APrevent leakageImprove communication securityTransmissionWorking setAuthentication server
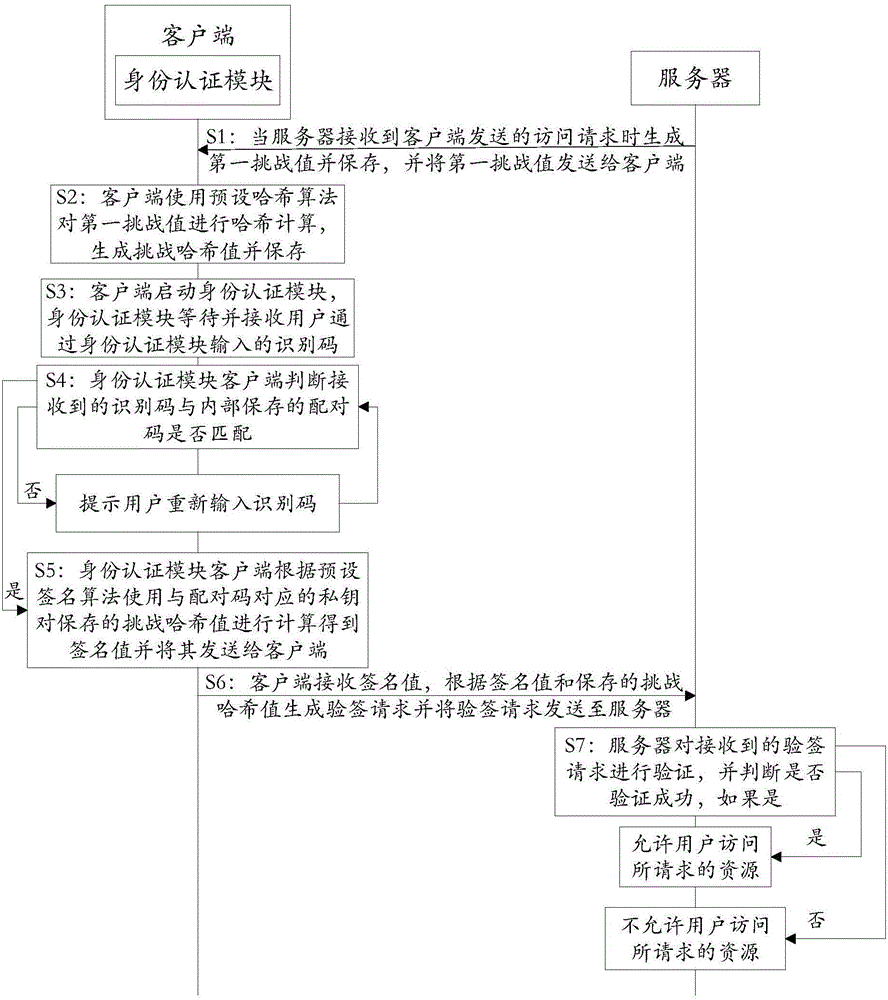
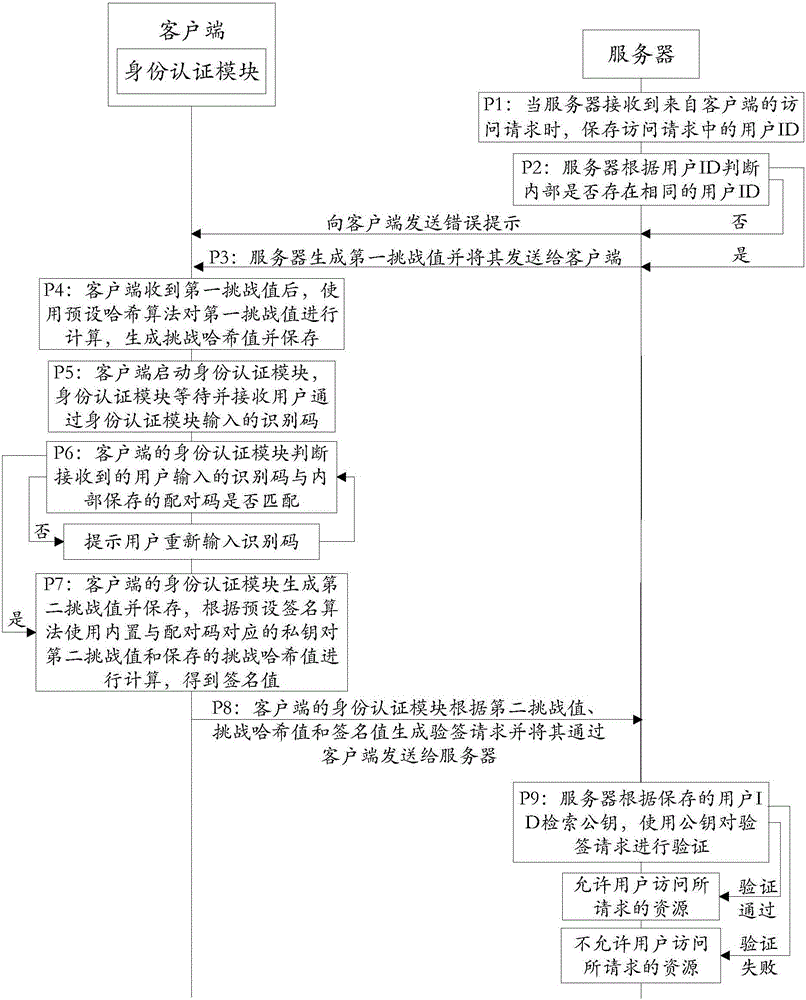
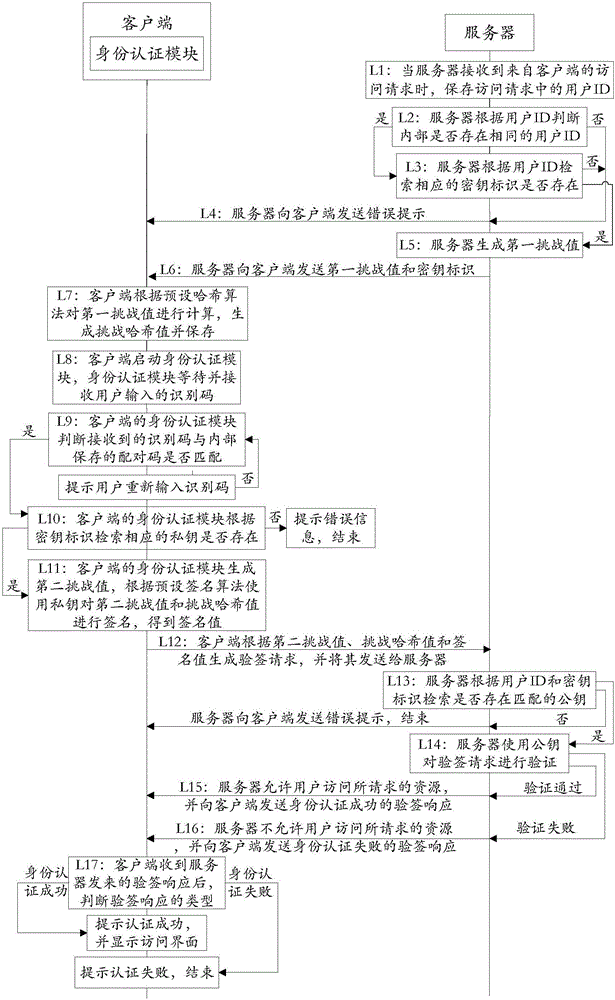
The invention discloses an authentication system and a working method thereof and belongs to the information security field. The method includes the following steps that: when receiving an access request, a server generates a first challenge value and sends the first challenge value to a client; the client uses a preset Hash algorithm to carry out Hash calculation on the first challenge value to generate a challenge Hash value; when judging that a received identification code is matched with a pairing code stored in an identity authentication module, the identity authentication module uses a private key corresponding to the pairing code to calculate the challenge the Hash value according to a preset signature algorithm so as to obtain a signature value; the client generates a signature verification request according to the signature value and sends the signature verification request to the server; and the server authenticates the signature verification request, and a user is allowed to access requested resources if the authentication is successful, and the user is not allowed to access the requested resources if the verification fails. With the authentication system and the working method thereof provided by the technical schemes of the invention adopted, communication can be continued as long as the identity authentication module completes local authentication, and therefore, the problem of data leakage in a data transmission process can be prevented, and the security of the communication can be improved.
Owner:FEITIAN TECHNOLOGIES
Method and system for quantum communication security
InactiveCN101820343AHighlight substantiveSignificant progressKey distribution for secure communicationCommunications securityPhoton emission
The invention relates to a method and a system for quantum communication security. An Alice terminal comprises a watchdog detector, an optical attenuator, a phase modulator, a reflector, a controller and a photon emitter; and a Bob terminal comprises a laser, a time division multiplex / demultiplex system, a phase modulator, a single photon detector, a controller, an optical switch and a reflector. The method and the system have the advantages that: (1) the two-way, stable and safe distribution of quantum keys is realized, the polarization and phase change of a single photon can be automatically compensated, and the aim of stable long-distance transmission is achieved; (2) the Alice terminal adopts the watchdog detector, on one hand, Trojan attack and intermediary attack can be detected by measuring the number of weak pulses reaching or leaving the Alice terminal, so that the communication security is improved greatly, and on the other hand, the communication speed and communication distance of the system are improved greatly; and (3) the Alice terminal and the Bob terminal can be adjusted and corrected respectively, can select mu independently without transmitting photons by means of unsafe optical fiber lines so as to ensure the system security.
Owner:BEIJING UNIV OF POSTS & TELECOMM
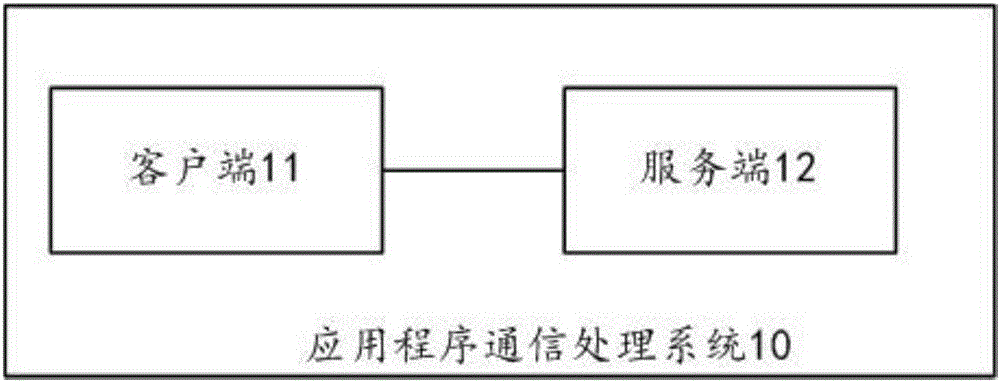
Application program communication processing system, an application program communication processing device, an application program communication processing apparatus and an application program communication processing method
InactiveCN105915342AImprove securityAbsolutely safeKey distribution for secure communicationGeneration processClient-side
The invention discloses an application program communication processing system, an application program communication processing device, an application program communication processing apparatus and an application program communication processing method. The application program communication processing system comprises a client and a server, wherein the client generates a request message including request information, signature information and a session key, carries out the signature and encryption by utilizing a client private key certificate, a session key and a server public key certificate in the generation process, transmits the request message to the server and receives a response message transmitted by the server after the request message is parsed; the server parses the received request message transmitted by the client and transmits the response message to the client, wherein the server performs the decryption and verification by utilizing a server private key certificate and a client public key certificate in the process of parsing the request message. By adopting the scheme provided by the invention, the application program communication safety can be improved.
Owner:GUANGZHOU AIJIUYOU INFORMATION TECH
V2X-based roadside unit system and information distribution method thereof
ActiveCN109672996ATraffic scene functions are simpleImprove distribution efficiencyParticular environment based servicesVehicle infrastructure communicationUnit systemHeterogeneous network
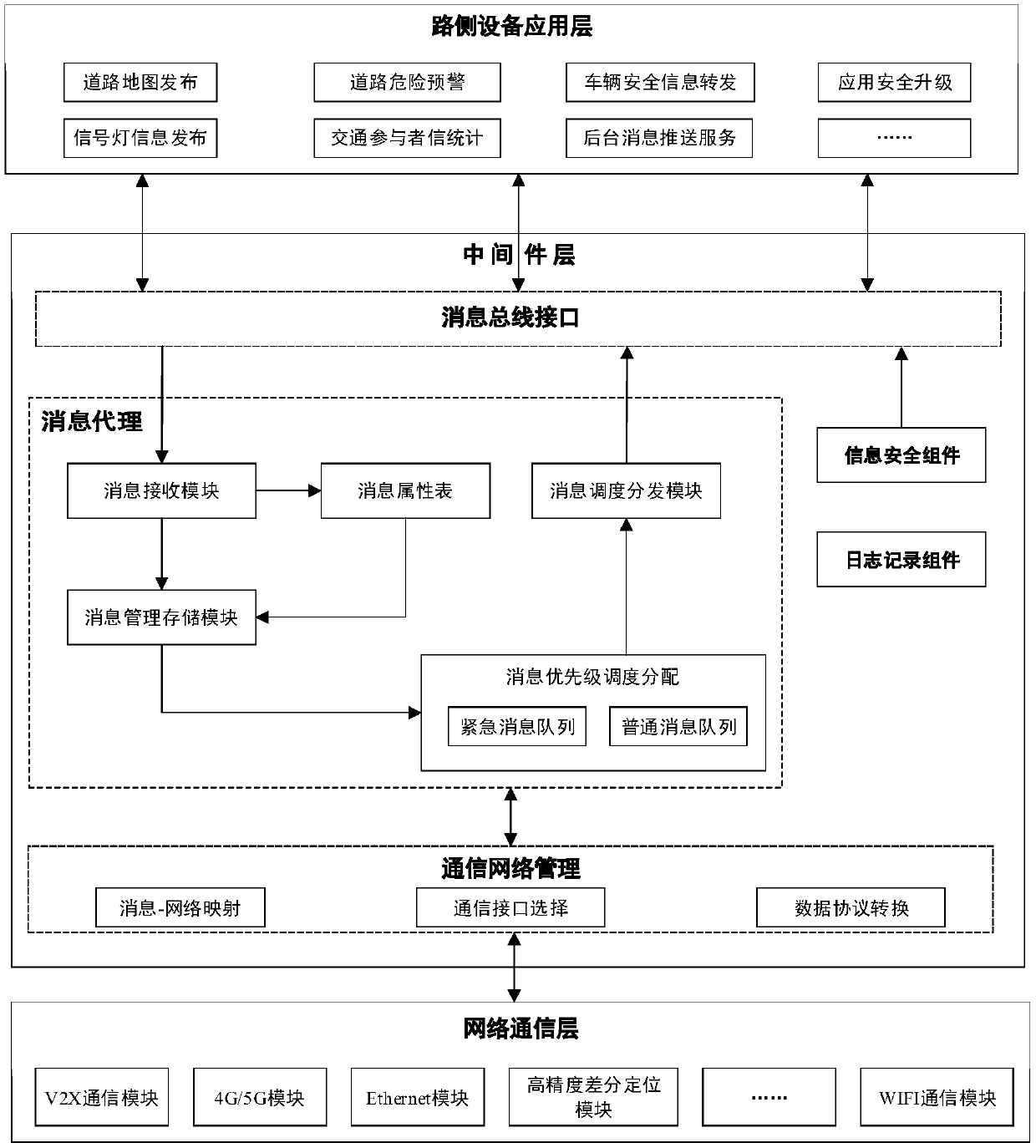
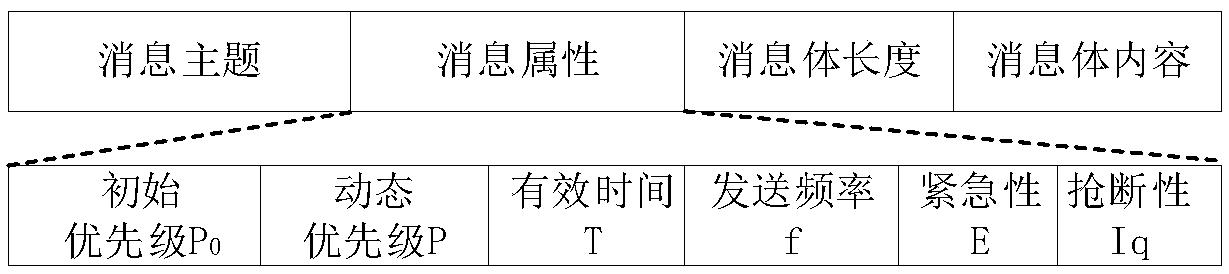
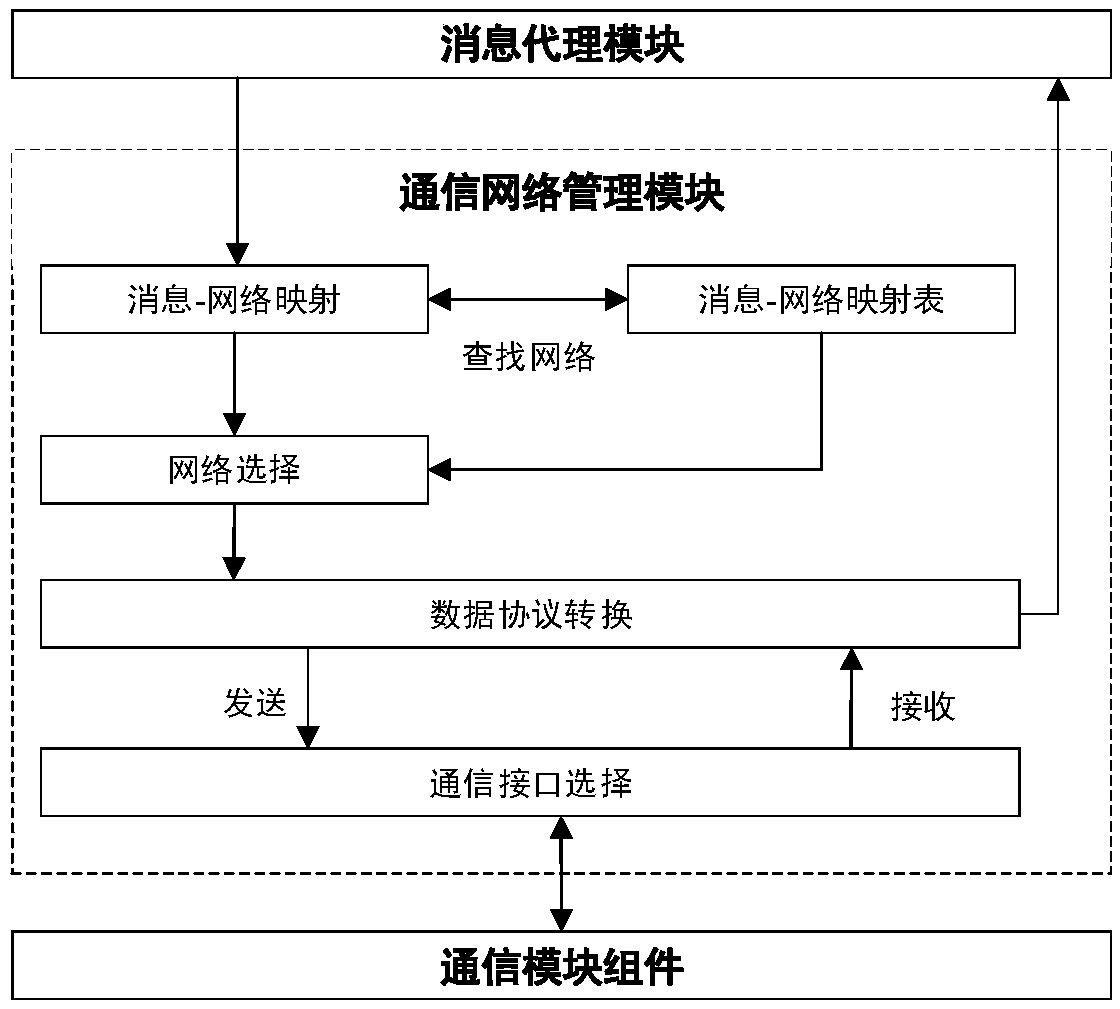
The invention provides a V2X-based roadside unit system and an information distribution method thereof. The system mainly comprises a communication network management module, a message proxy module, an information security component module, a log management component module, a message bus interface module and the like. An RSU (roadside unit) message proxy module is responsible for parsing, priority scheduling and distribution of messages, sent by an application layer through a message bus interface, to a message bus. The RSU communication network management module is responsible for shieldingprotocol difference of a platform and RSU auxiliary communication equipment, and a unified communication calling interface is provided for middleware message proxy. According to the system and the method in the invention, heterogeneous network multi-source information from a road sensor, a vehicle, a cloud platform, a differential positioning base station and the like is managed through the V2X RSU in a unified way, a unified communication calling interface is provided for an upper-layer application, and the application development efficiency and the function expandability are improved; the messages are scheduled on the basis of a priority policy so as to ensure that the information with relatively high information tightness is preferentially sent.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
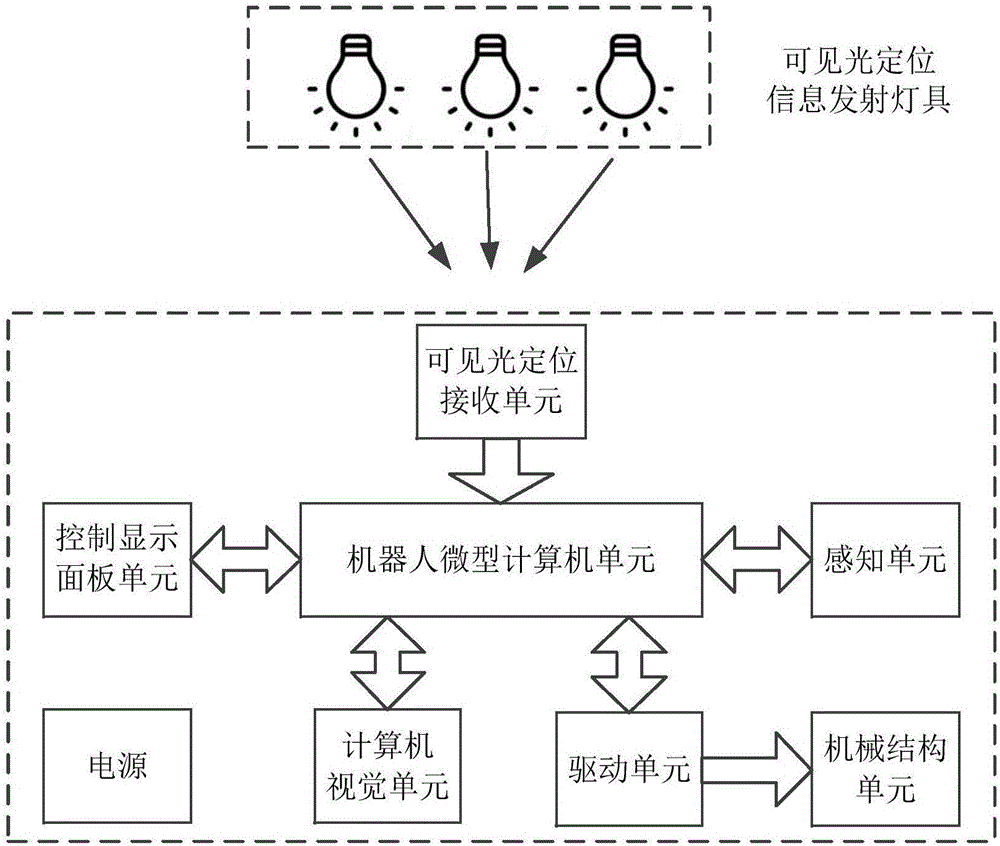
Indoor robot system based on visible light positioning and navigation
PendingCN106737687ANo radio frequency interferenceHigh precisionProgramme-controlled manipulatorRobotic systemsEngineering
The invention discloses an indoor robot system based on visible light positioning and navigation. The indoor robot system comprises a visible light positioning and emitting unit used for sending positioning information, a visible light positioning and receiving unit used for receiving a visible light signal to perform positioning and navigation, a drive unit for driving a robot to move, a mechanical structure unit used for moving the robot, a sensing unit used for monitoring an external environment, a computer visual unit used for obtaining image information, a robot micro type computer unit, a control display panel unit and a power supply, wherein the robot micro computer unit is used for firstly obtaining values of all sensors of the sensing unit, controlling the robot system to avoid obstacles during walking motion, obtaining and processing images acquired by the computer visual unit, and helping the robot system to predicate and avoid pedestrians better; and in a moving process, the visible light signal with coding information is extracted to perform positioning and navigation after a visible light image receiver performs quick image obtaining on an indoor visible light signal light source.
Owner:JINAN UNIVERSITY
Method for transmitting and receiving image series digital content as well as transmitter and receiver
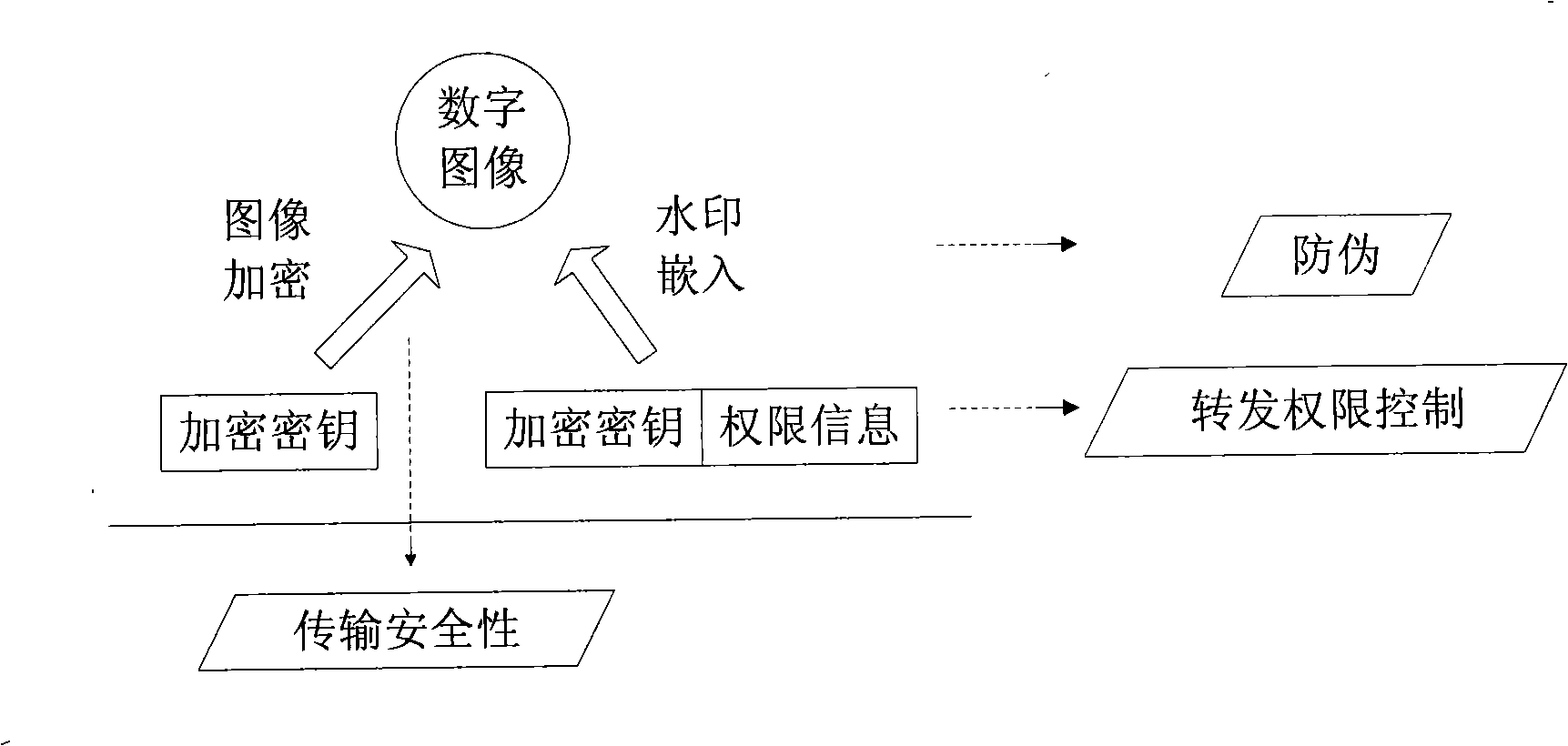
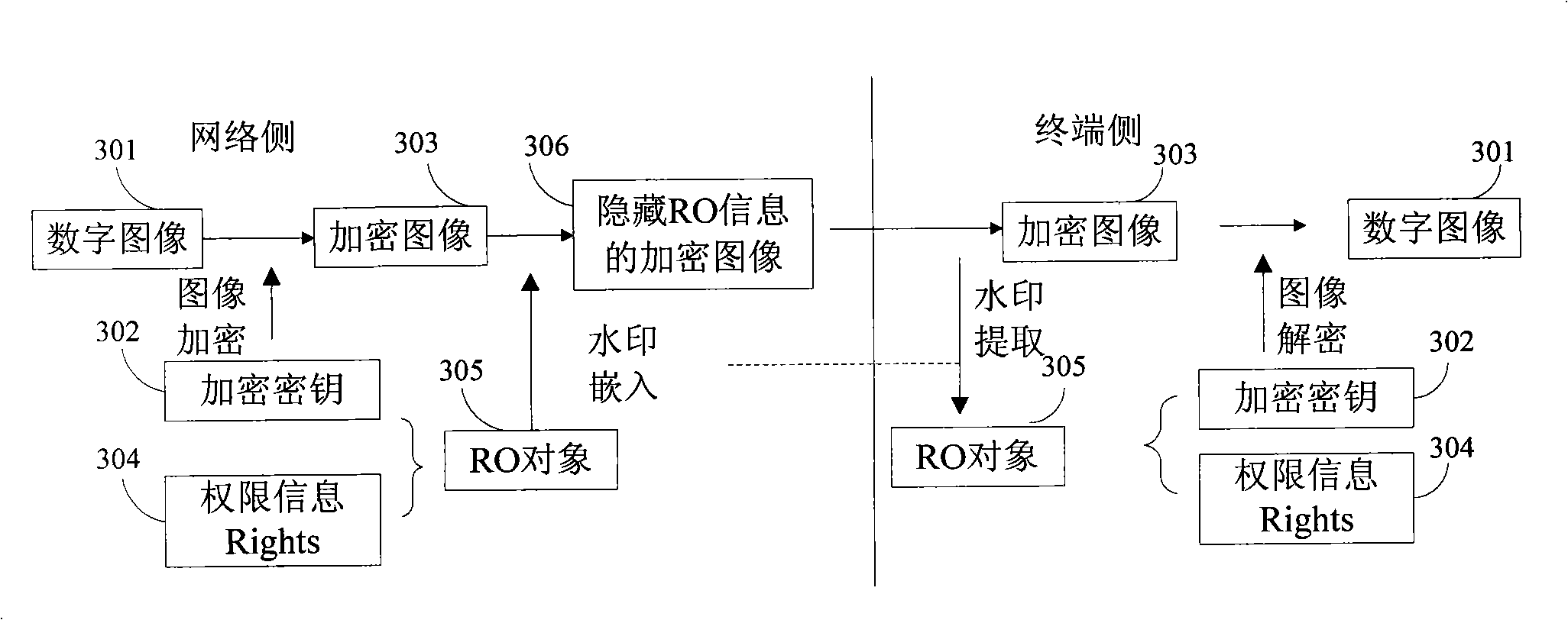
ActiveCN101355684AEnsure safetyImprove communication securityAnalogue secracy/subscription systemsCommunications securityComputer hardware
The invention discloses a method for sending image class digital contents and a method for receiving the image class digital contents, wherein the sending method is as follows: based on an encryption key, the digital image contents ready to be sent are encrypted; the encryption key is used as watermark information to be embedded in the encrypted digital image contents; and the encrypted digital image contents embedded with the watermark information are sent; the receiving method is as follows: the digital image contents are received; the watermark information containing the encryption key is picked up from the received digital image contents; based on the encryption key contained in the watermark information picked up, the received digital image contents are decrypted. In the technical proposal of the invention, the image encryption technology, the copyright management idea and the digital watermark technology are organically combined, thereby effectively improving the communication safety of image class digital services.
Owner:CHINA MOBILE COMM GRP CO LTD +1
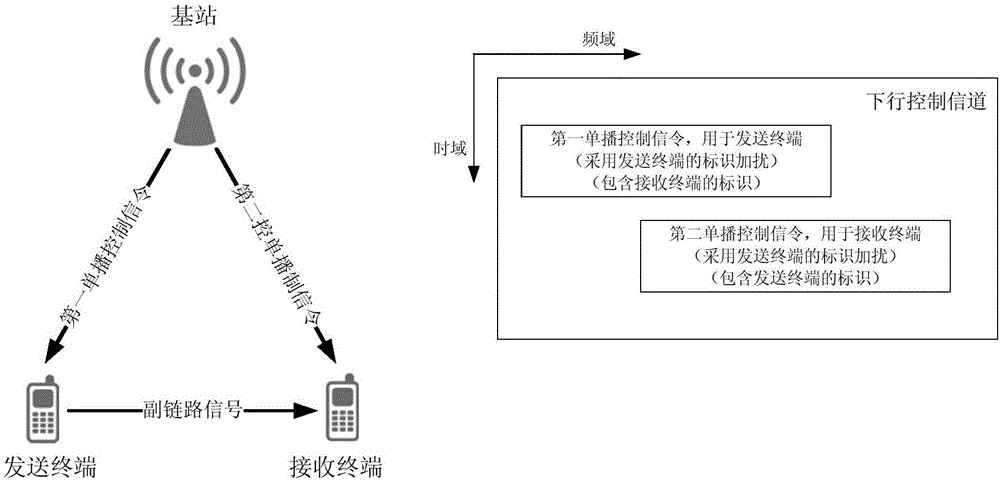
Direct terminal unicast control method mobile communication
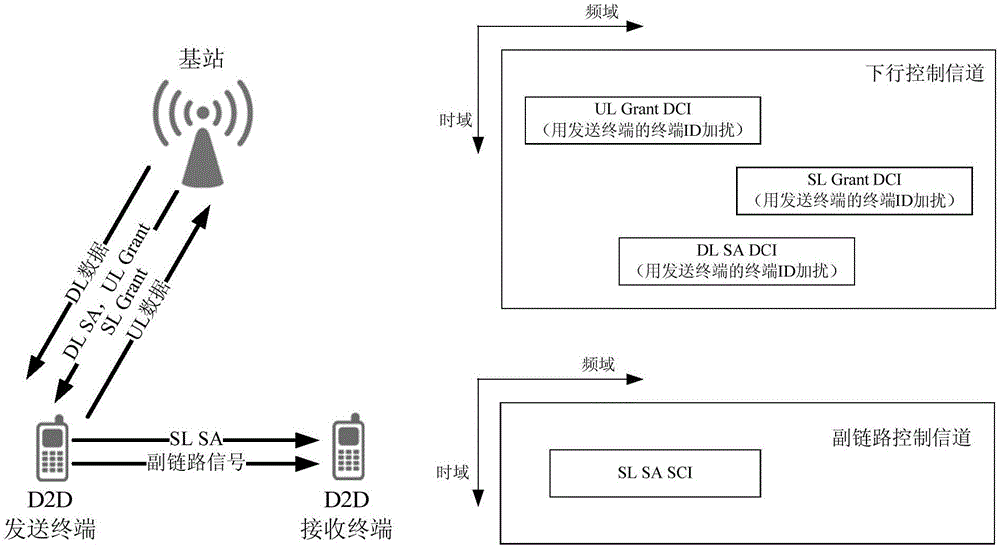
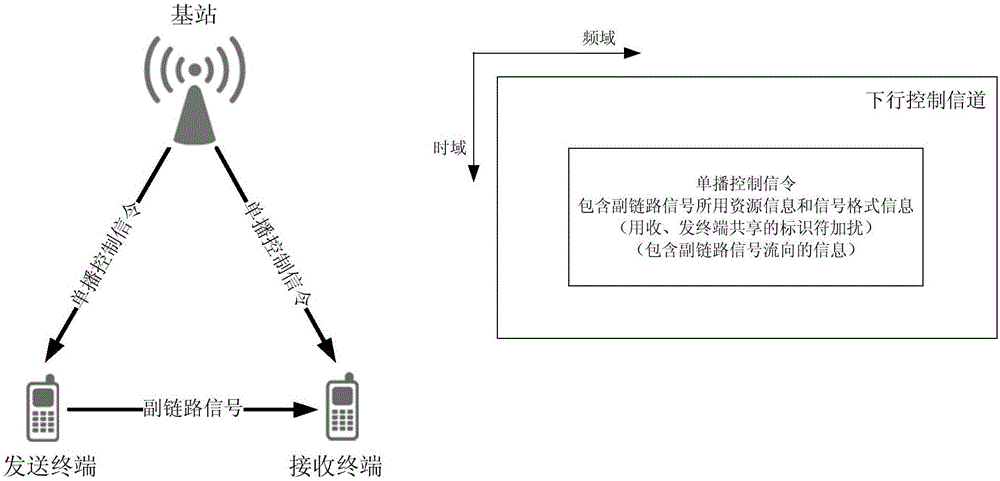
ActiveCN106793109ASolve the problem of reliable deliveryImprove communication securityConnection managementAir interfaceControl signal
The invention discloses a direct terminal unicast control method mobile communication, for solving the problem that unicast communication cannot be realized by the existing control signal. A base station sends a unicast control signal to at least one controlled terminal through a first type air interface, wherein the unicast control signal contains a resource information and signal format information occupied by an auxiliary link data signal, as well as unicast identification information; and the controlled terminal receives the unicast control signal, determines a communication object according to the unicast control signal, and sends or receives the auxiliary link data signal according to the resource and signal format, wherein the first type air interface is an air interface between the base station and the terminal, a second type air interface is an air interface between the terminal and the terminal, and the auxiliary link data signal is transmitted by the second type air interface. Compared with the existing technical scheme, the scheme disclosed by the invention can realize real unicast transmission, and the scheme is simple and high in security.
Owner:CHINA ACADEMY OF INFORMATION & COMM
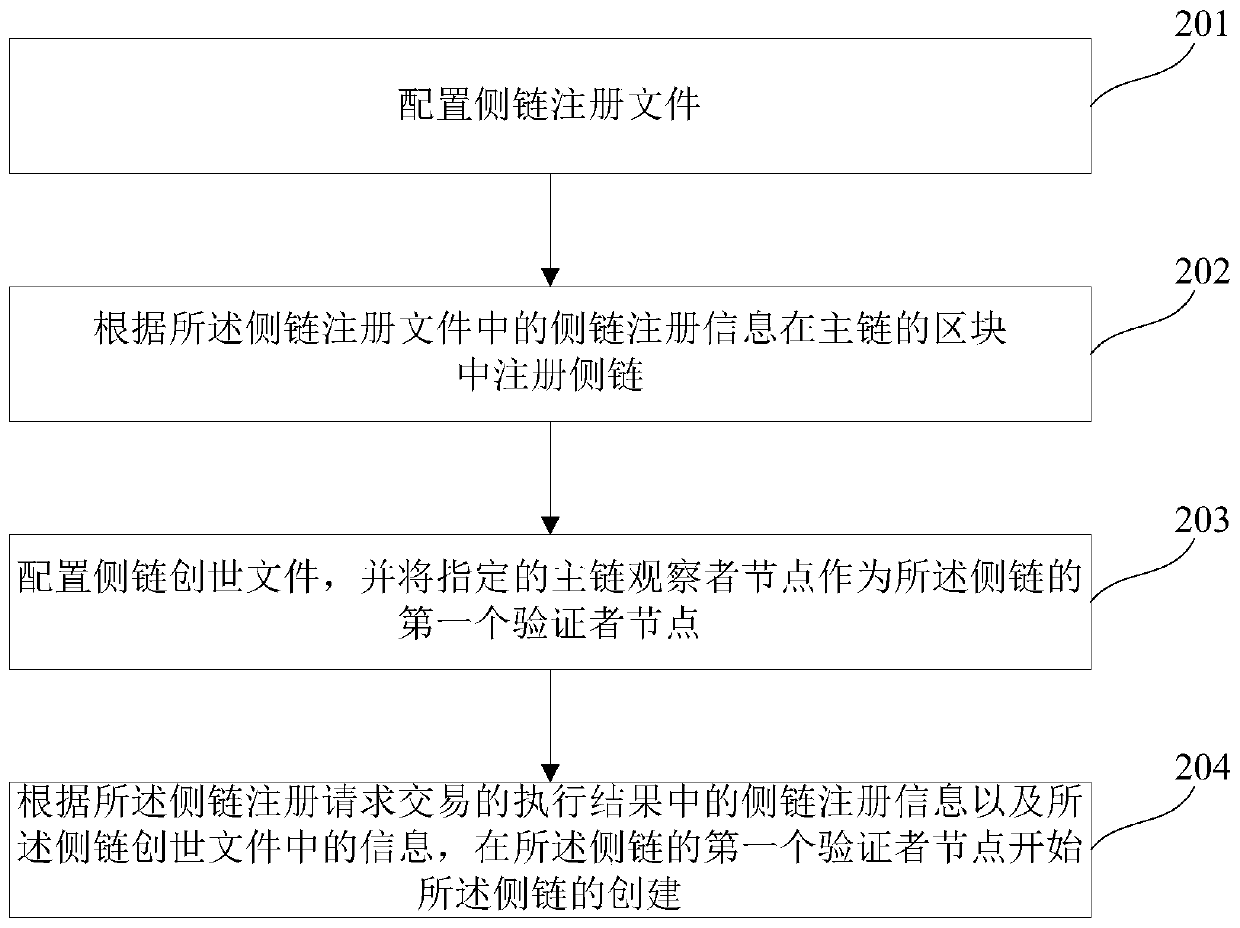
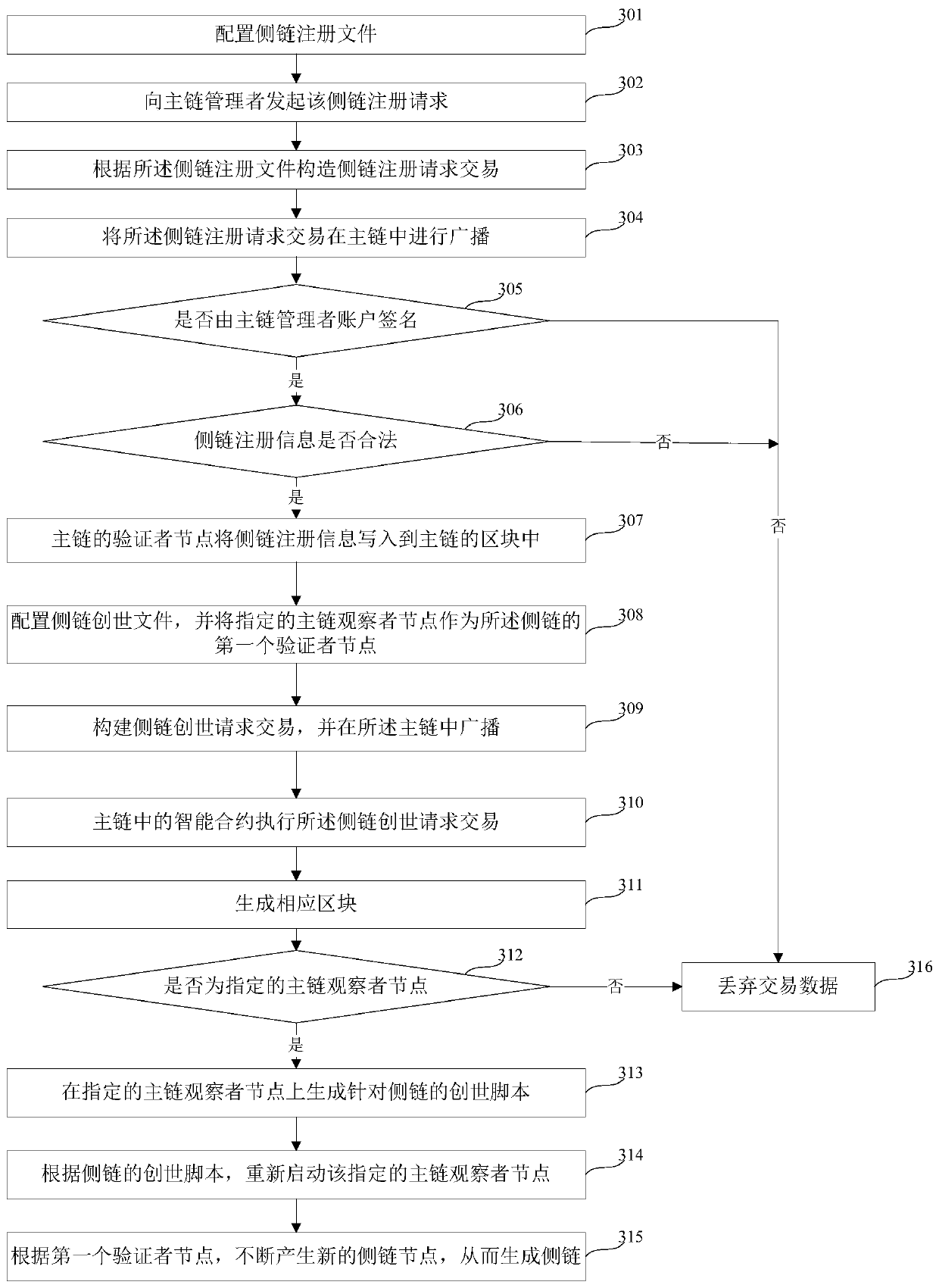
Method and device for generating side chain based on main chain and computer readable storage medium
PendingCN111414210AIncrease storage spaceImprove communication securityFinanceDatabase distribution/replicationSecure communicationComputer network
The invention relates to the technical field of block chains, in particular to a method and a device for generating a side chain based on a main chain and a computer readable storage medium. In orderto generate a side chain belonging to a main chain more quickly and conveniently, the method provided by the invention comprises the following steps: configuring a side chain registration file which comprises side chain registration information; registering a side chain in a main chain block according to the side chain registration information in the side chain registration file; configuring a side chain creation file, and taking a specified main chain node as the first verifier node of the side chain; and according to the side chain registration information in the execution result of the sidechain registration request transaction and information in the side chain creation file, starting creation of the side chain at the first verifier node of the side chain. Therefore, the side chain belonging to the main chain is generated, safe communication between the main chain and the side chain is ensured, and the side chain can be quickly generated according to the main chain.
Owner:北京新创智链科技有限公司
Two-dimensional bar code duplex communication method
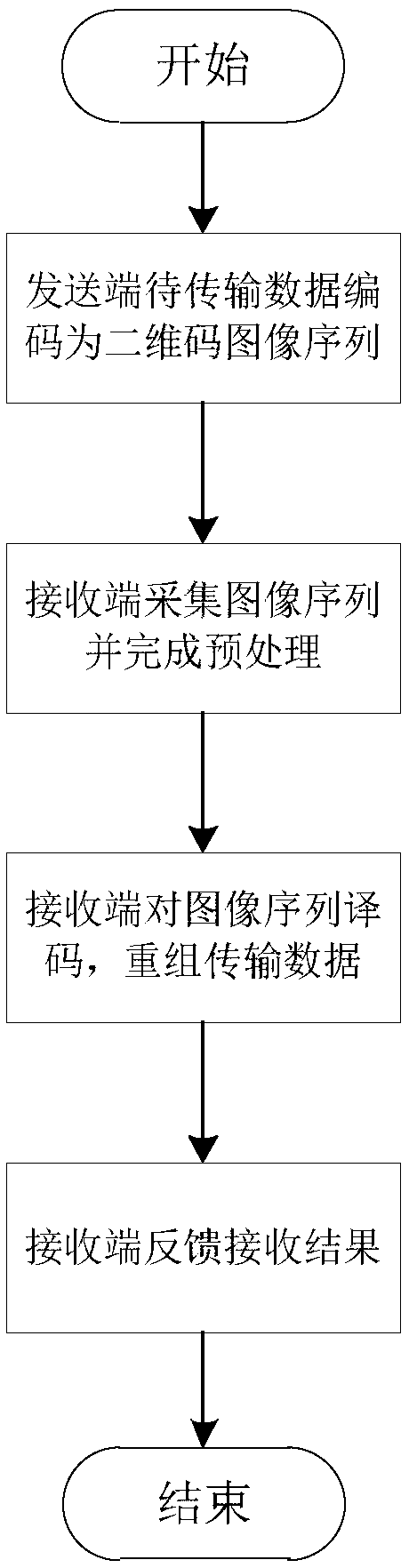
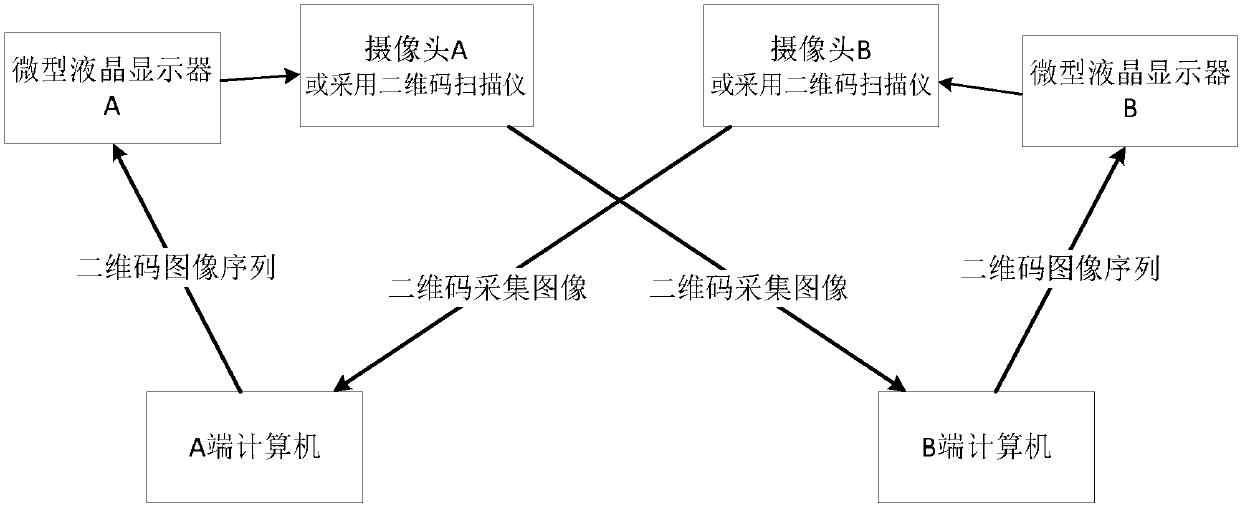
InactiveCN108055116AEquipment is cheapLow priceRecord carriers used with machinesDuplex signal operationData transmissionLiquid-crystal display
The invention discloses a two-dimensional bar code duplex communication method and aims at providing the duplex communication method based on two-dimensional bar codes. According to the duplex communication method, the communication security is high and the data transmission efficiency and reliability are high in a scene with a relatively high confidentiality demand. The method is realized throughutilization of the following technical scheme that a sending end codes to-be-transmitted data into a two-dimensional bar code image sequence and displays the two-dimensional bar code image sequence in sequence through utilization of a miniature liquid crystal display; a receiving end collects the two-dimensional bar code image sequence through utilization of a vision camera or a two-dimensional bar code scanner, carries out repeated frame elimination, image graying, median filtering and binarization preprocessing on collection results and decodes the collection results according to a two-dimensional bar code coding format, thereby acquiring decoding results; the receiving end integrates the decoding results according to frame serial numbers and the frame number, thereby acquiring a sending end source transmission file; and the receiving end carries out real-time feedback or delayed feedback on a receiving result according to system transmission configuration. According to the method,the defect of a data transmission security hinge is solved.
Owner:10TH RES INST OF CETC
Method of isolating user in radio local network
InactiveCN1414742ARealize functionAchieve isolationData switching by path configurationSecuring communicationWireless dataPacket filtering
A method to isolate the clients within the local area network transfers all the radio data packets that are realized for relay transmission originally by the firmwrok of IEEE802, 11 MAC to the radio mail bridge module of radio call-in point, and the judging the received source address and destination MAC address information of the data packet. According to the items of mail bridge retransmitting table and the items of MAC data packet filtering table, whether the data packet is retransmitted or discarded, these items are decided to realize the isolation for the radio clients within the same distributed system DS. The method uses a radio fire wall mechanism so that it not only can be used for the isolation of the radio client, but also can be used to define the incoming filtering and to retransmitt the MAC data packet by the method of rule matching and processing.
Owner:北京朗通环球科技有限公司
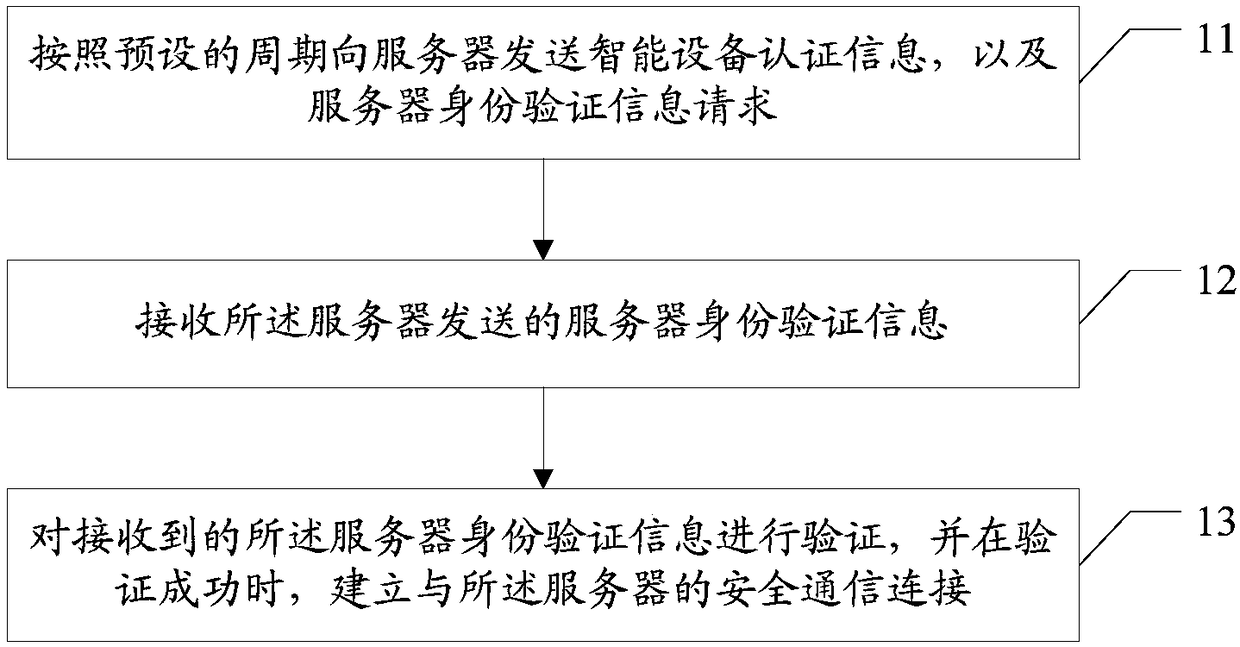
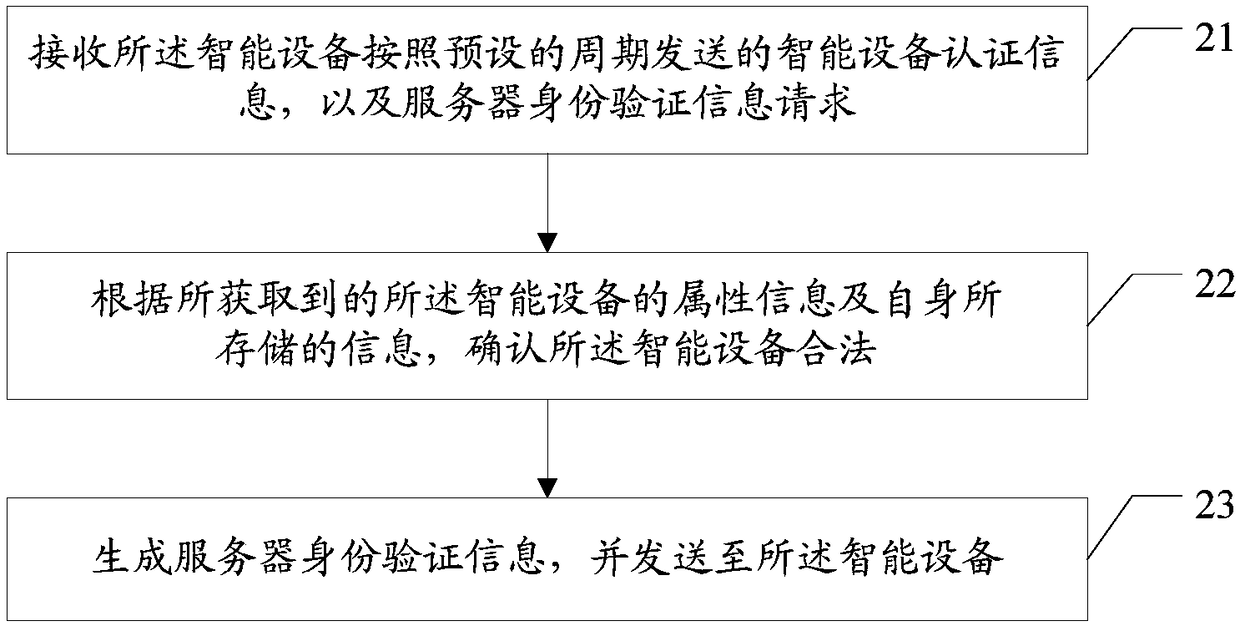
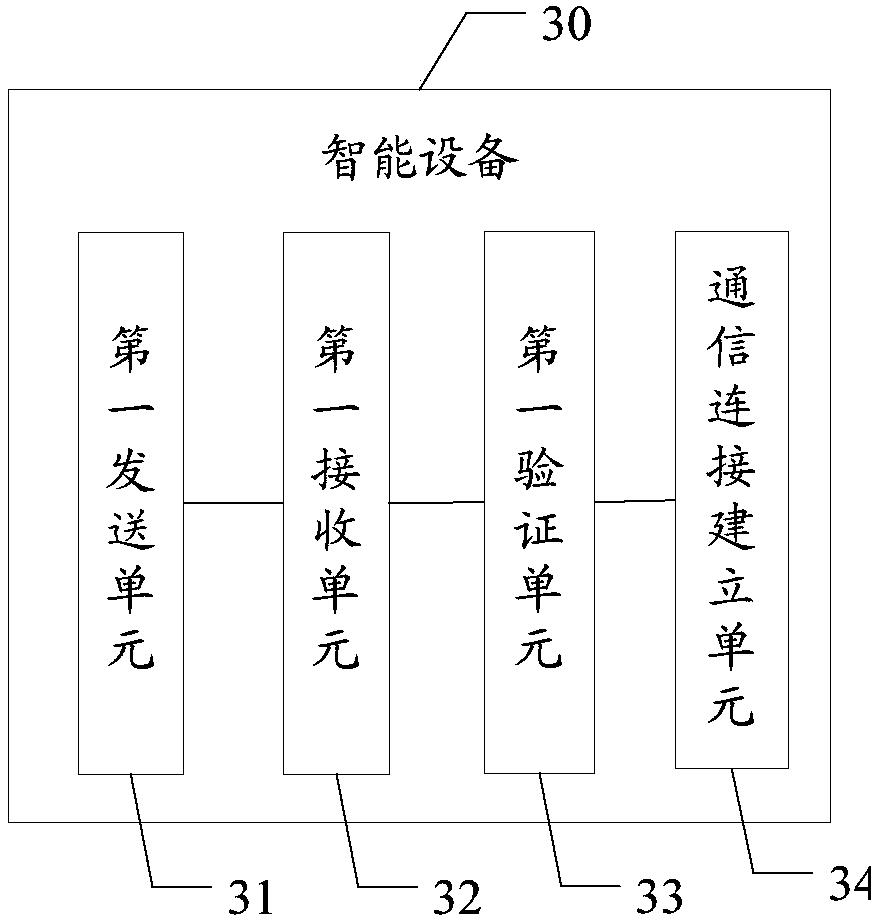
Data safety protection method, intelligent device, server and readable storage medium
InactiveCN109286599AFacilitate communicationAvoid attackKey distribution for secure communicationUser identity/authority verificationSecure communicationIntelligent equipment
The invention provides a data safety protection method, an intelligent device, a server and a readable storage medium. The data safety protection method comprises the steps of when over-the-air firmware updating is required, transmitting intelligent device authentication information and a server identity verification information request to a server according to a preset period, wherein the intelligent device authentication information comprises the attribute information of the intelligent device; receiving server identity verification information transmitted from the server, wherein the serveridentity verification information is generated by the server in confirming validity of the intelligent device according to the obtained attribute information of the intelligent device and the storedinformation itself after receiving the server identity verification information request; verifying the received server identity verification information, and when verification succeeds, establishing asafe communication connection with the server. The data safety protection method, the intelligent device, the server and the readable storage medium can improve communication safety in the system upgrading process of the intelligent device.
Owner:BEIJING SPREADTRUM HI TECH COMM TECH CO LTD
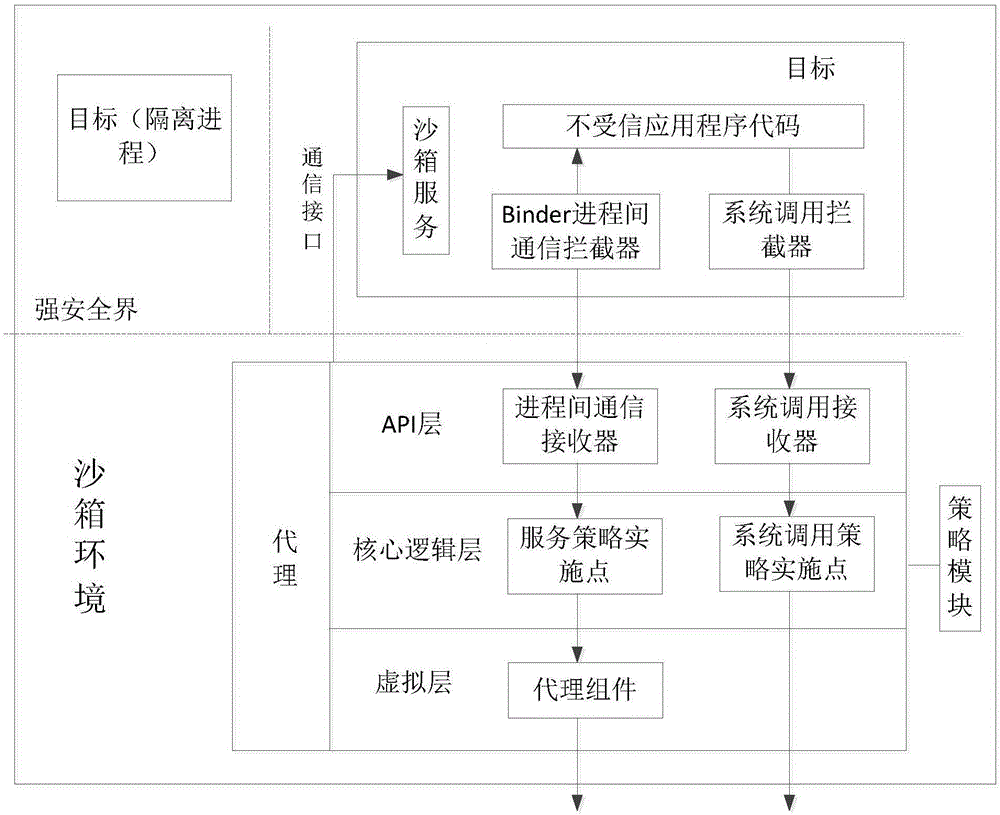
Android storage application sandbox based on application program virtualization, and communication method thereof
ActiveCN106384045AOvercomes the disadvantage of restricting the permissions of untrusted applicationsImprove communication securityPlatform integrity maintainanceVirtualizationOperational system
The invention discloses an Android storage application sandbox based on application program virtualization. The Android storage application sandbox comprises an agent and a target, wherein a strong secure boundary used for securely isolating untrusted application programs exists between the target and the agent; the agent is an application program process, owns all platform permissions distributed by a system, can normally interact with Android middleware and is used as all interactive compulsory agents between the target and an Android system; the agent comprises an API (Application Program Interface) layer, a core logic layer and a virtual layer; and the target does not have a platform permission, can not access Android firmware, can not change a file system and comprises sandbox service, a Binder interprocess communication interceptor and a system calling interceptor. Safety provided by an isolation process is used, and the untrusted application programs are dynamically loaded and executed in the process to avoid revising an operating system and the untrusted application programs. Meanwhile, a controllable method is used for permitting the untrusted application programs to execute an input / output operation and access system resources, and the untrusted application programs are packaged in the sandbox environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
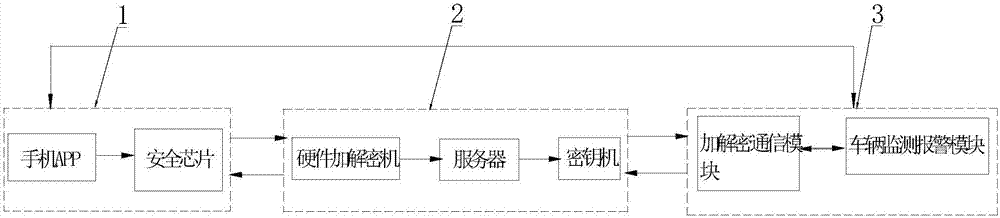
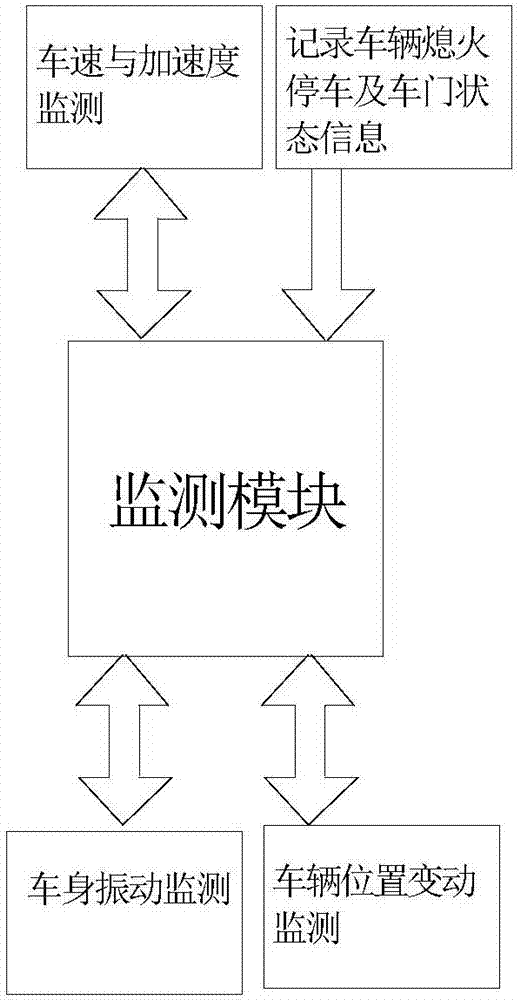
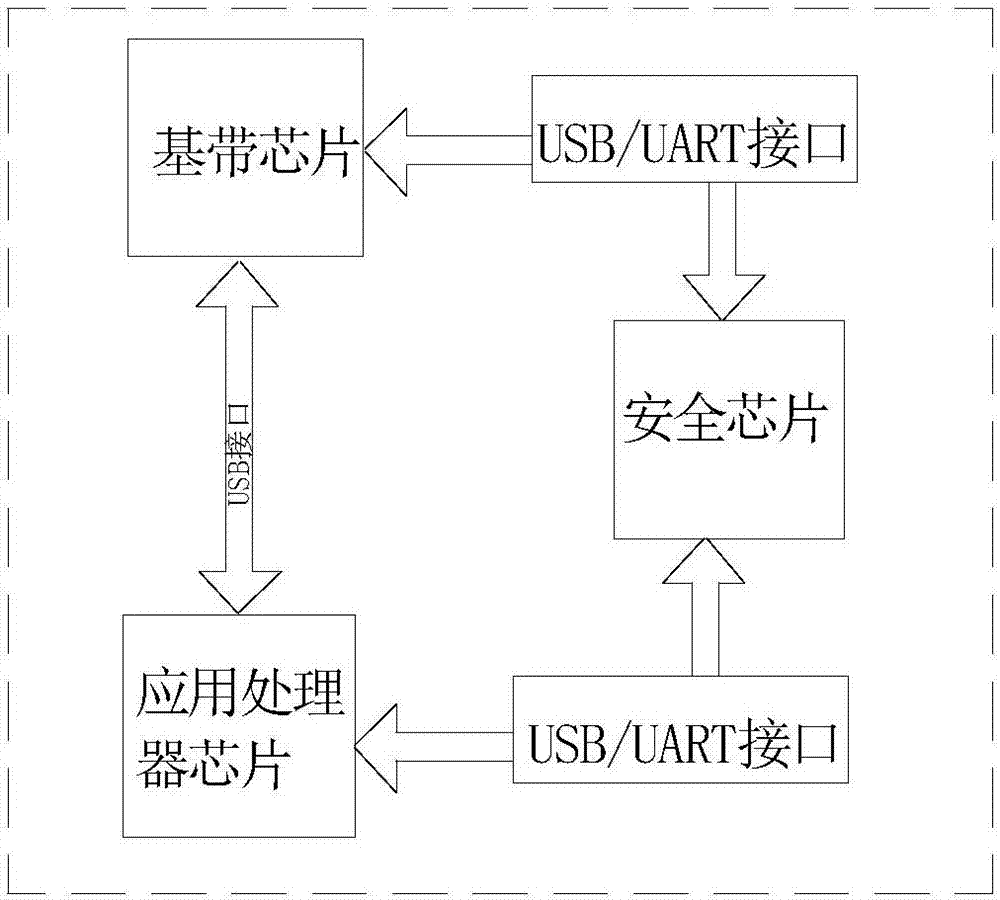
Low-power and high-security vehicle anti-theft tracking system and method thereof
ActiveCN107539271AReal-time monitoringSolve the problem of limited alarm distanceRegistering/indicating working of vehiclesAnti-theft devicesCommunications securityEngineering
The invention discloses a low-power and high-security vehicle anti-theft tracking system and a method thereof and belongs to the technical field of automobile anti-theft technology. The low-power andhigh-safety vehicle anti-theft tracking system comprises a monitoring and management platform, a mobile phone terminal and an anti-theft vehicle monitoring module, wherein the monitoring and management platform is respectively connected with the mobile phone terminal and the anti-theft vehicle monitoring module through wireless network for communication; the anti-theft vehicle monitoring module isarranged in a vehicle and comprises a vehicle monitoring and alarming module and an encryption and decryption communication module; the vehicle monitoring and alarming module is connected with an actuator in the vehicle; the encryption and decryption communication module is connected with the mobile phone terminal to realize data communications; a security chip is arranged inside the mobile phoneterminal; the security chip is positioned on a motherboard in the mobile phone terminal and connected with an application processor chip and a baseband chip on the motherboard for communication; andthe mobile phone terminal is provided with a mobile terminal app for supporting the use of the security chip. The low-power and high-safety vehicle anti-theft tracking system can monitor the conditionof the vehicle in real time and take corresponding protection measures when the vehicle is stolen, so as to achieve high communication security and solve the problems in the prior art.
Owner:济宁中科智能科技有限公司
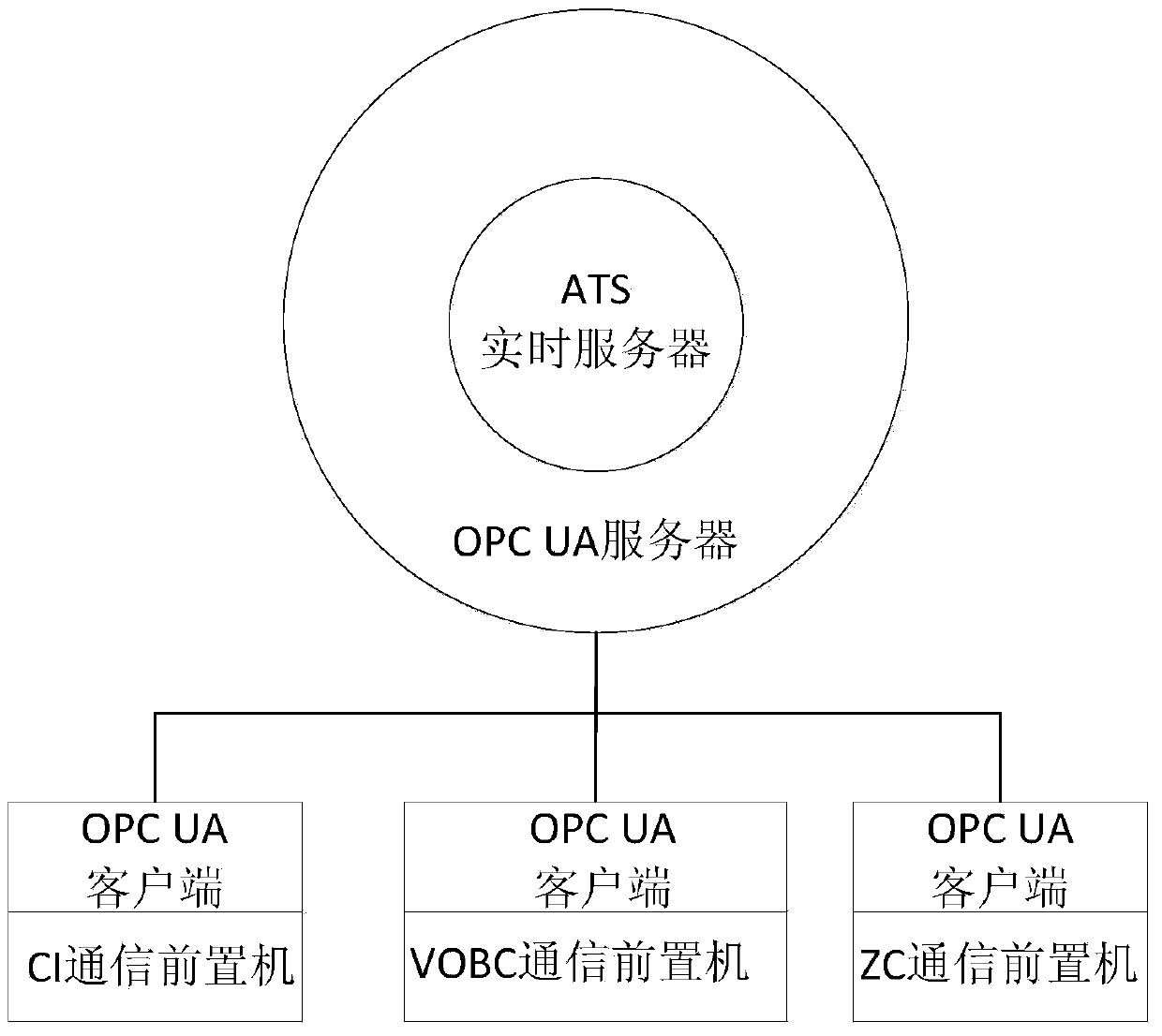
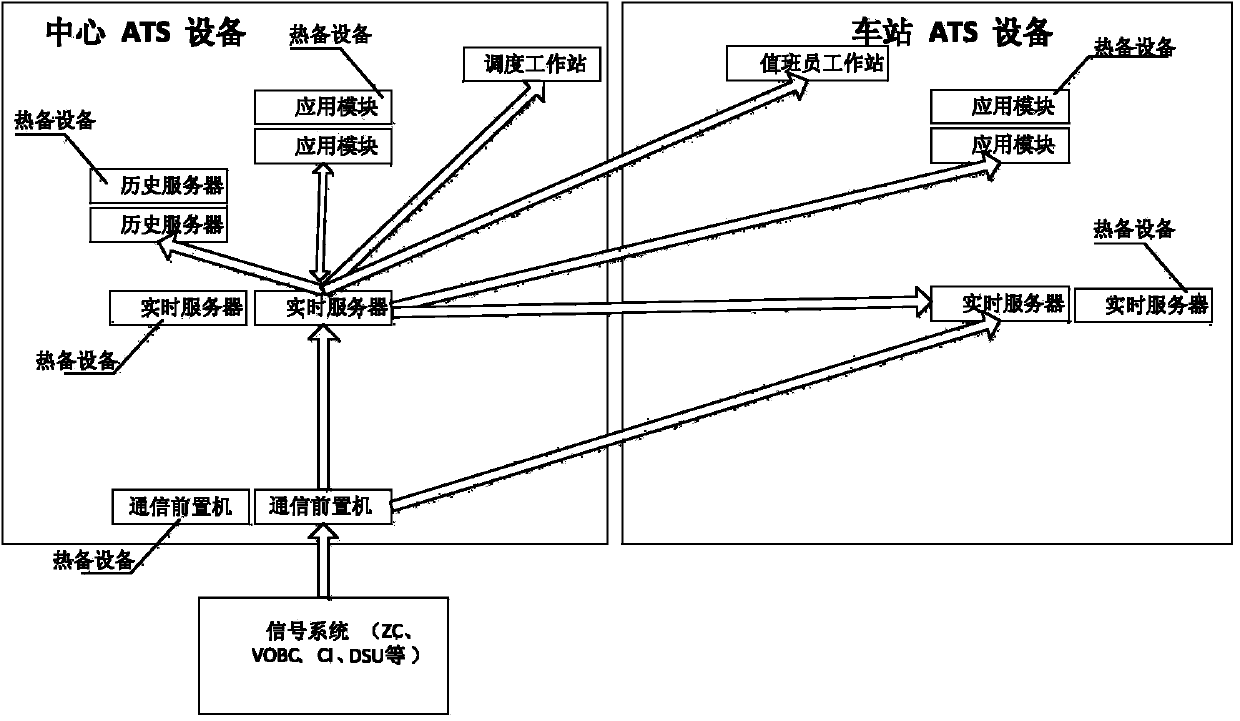
ATS device and system based on OPC UA technology
ActiveCN103738369AReduce development costsImprove scalabilityAutomatic systemsAutomatic controlMonitoring system
The invention discloses an ATS device and system based on an OPC UA technology and relates to the technical field of train automatic control. The metro ATS device comprises an ATS real-time server, and the ATS real-time server is in communication with a communication front-end processor in a signal system through an OPC UA. An OPC UA standard service interface is utilized to replace an original private protocol; after communication modes of every system are unified, various interfaces do not need defining, and the development cost is reduced; if changes occur in a monitoring system, access can be performed only by conforming to an OPC UA standard, and system expansibility is improved.
Owner:TRAFFIC CONTROL TECH CO LTD
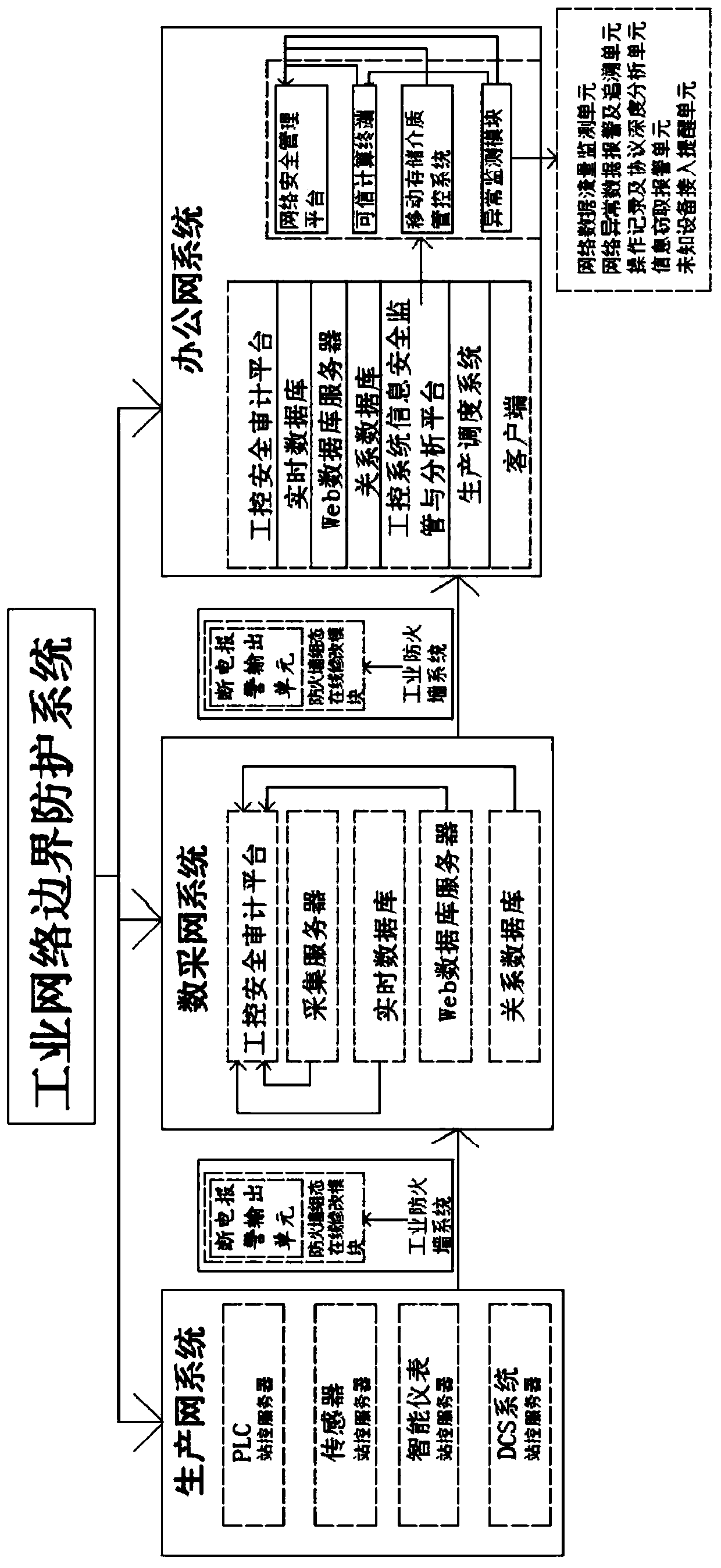
Industrial network boundary protection system
ActiveCN109739203AImprove securityRemarkable attack defenseTotal factory controlProgramme total factory controlCommunications securityData acquisition
The invention provides an industrial network boundary protection system. The industrial network boundary protection system comprises a production network system, a data acquisition network system, anoffice network system and an industrial firewall system; the production network system is connected to the data acquisition network system through the industrial firewall system, so that one-way datatransmission can be realized; both control and operation on equipment can be completed in a production network; the data acquisition network system comprises an industrial control safety audit platform; and the office network system further comprises an industrial control system information security supervision and analysis platform, a production scheduling system and a client side. According to the industrial network boundary protection system provided by the invention, behaviour analysis on the data acquisition network system, the production network system and communication of the data acquisition network system is made through the industrial control safety audit platform; the communication link state in a network can be monitored in real time through an abnormal monitoring module; the security of the industrial network boundary protection system is improved; depth inspection on a data packet based on an application layer can be carried out through the industrial firewall system; thecommunication security is improved; and the industrial network boundary protection system has the obvious effect for core asset protection of the production network system.
Owner:南京世界村云数据产业集团有限公司
Data processing method and device for realizing cross-domain request at webpage end and related equipment
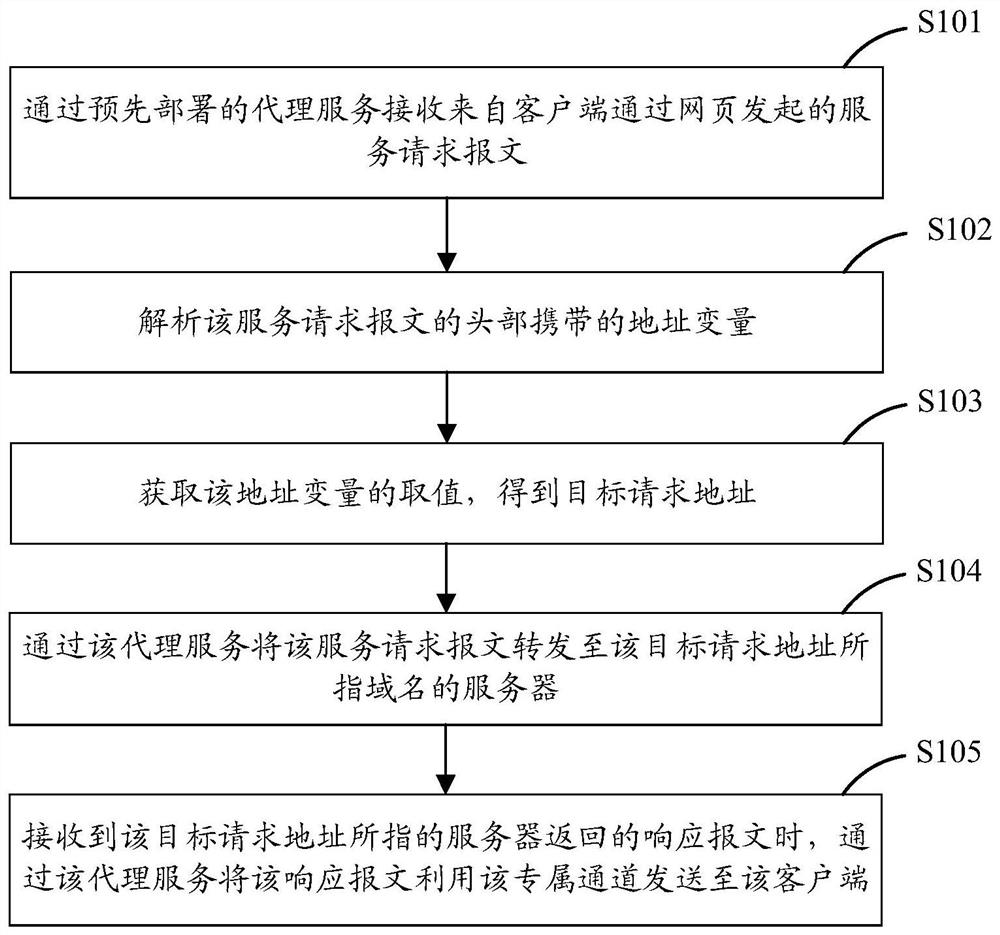
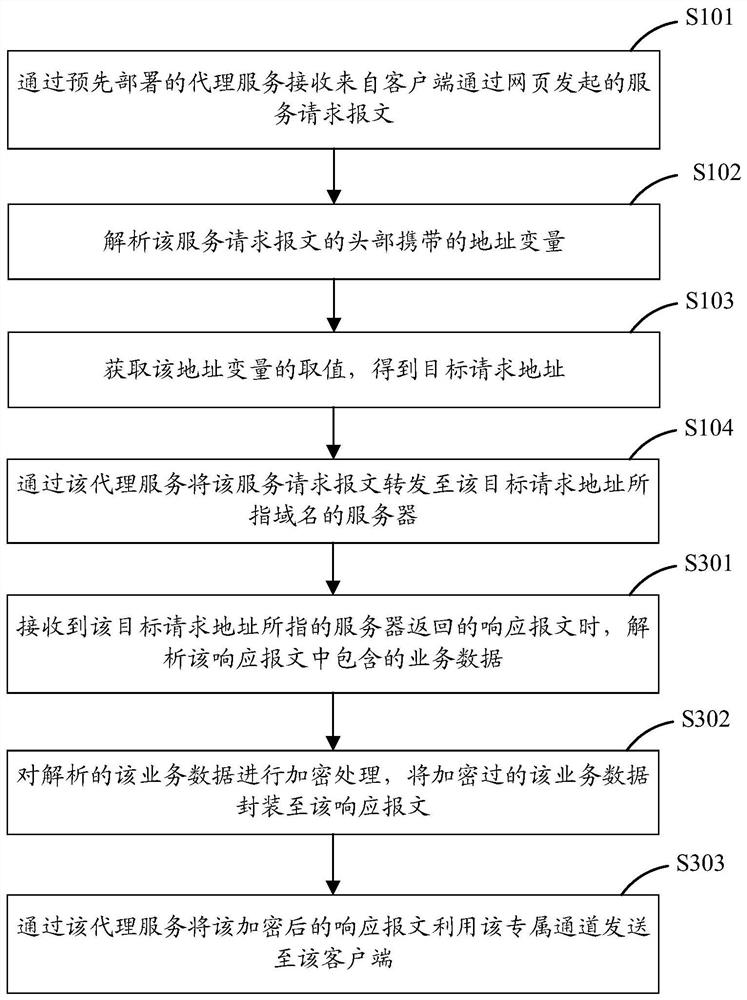
PendingCN111666514AImprove securityRealize communication interactionDigital data protectionSpecial data processing applicationsDomain nameEngineering
The invention discloses a data processing method and device for realizing a cross-domain request at a webpage end, computer equipment and a storage medium, is applied to the technical field of computers, and is used for improving the expansibility and safety of realizing the cross-domain request at the webpage end. The method provided by the invention comprises the steps that a service request message initiated by a client through a webpage is received through a pre-deployed proxy service, the proxy service is deployed on a server with the same domain name as the webpage, and the proxy serviceon the server receives the service request message through a pre-created exclusive channel; analyzing an address variable carried by the head of the service request message; obtaining a value of theaddress variable to obtain a target request address; forwarding the service request message to a server of a domain name pointed by the target request address through the proxy service; and when a response message returned by the server indicated by the target request address is received, sending the response message to the client by using the exclusive channel through the proxy service.
Owner:PING AN TECH (SHENZHEN) CO LTD
Vehicle safety communication method and device
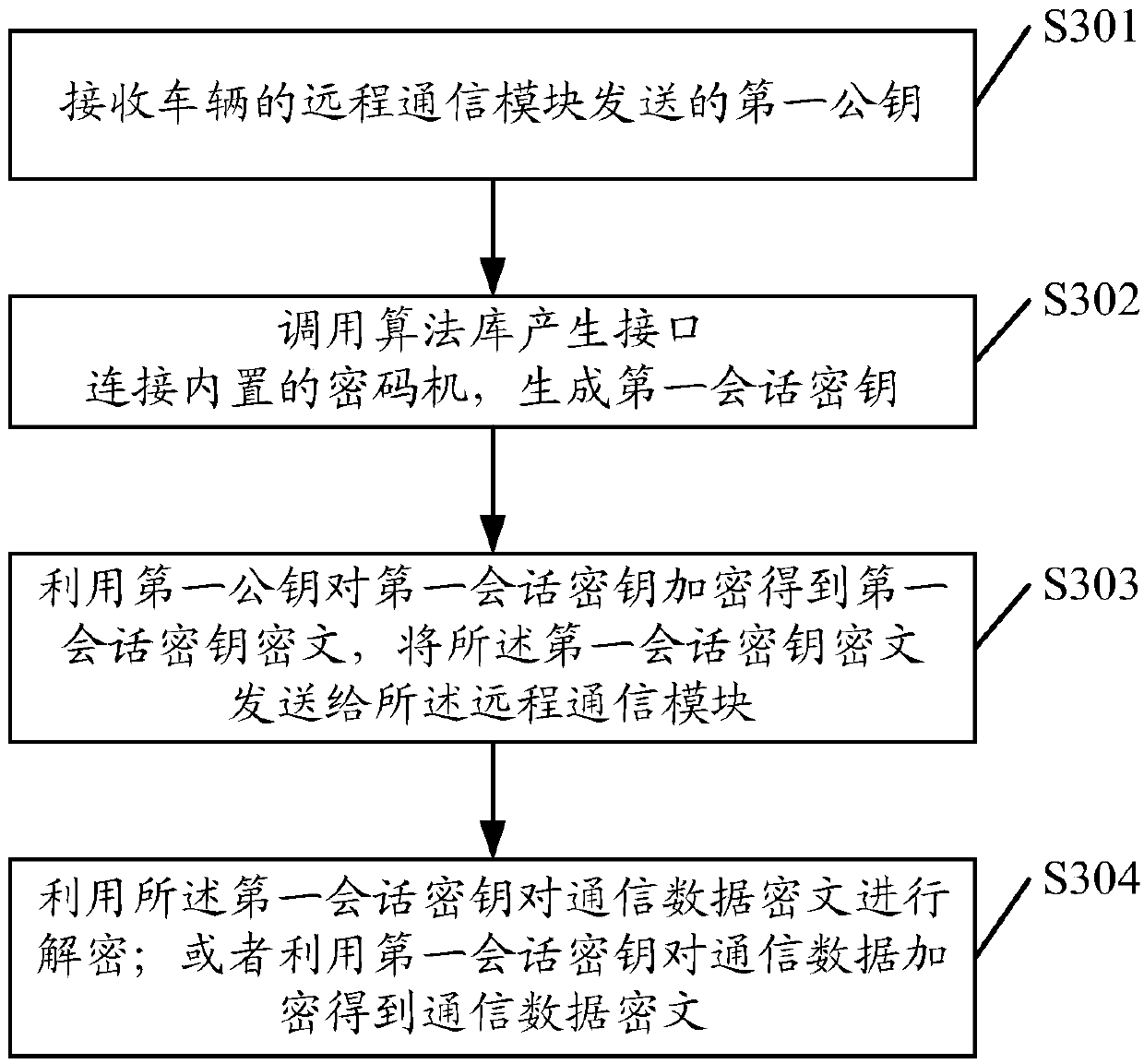
InactiveCN110768938AEnsure safetyEnsure driving safetyKey distribution for secure communicationUser identity/authority verificationCiphertextEngineering
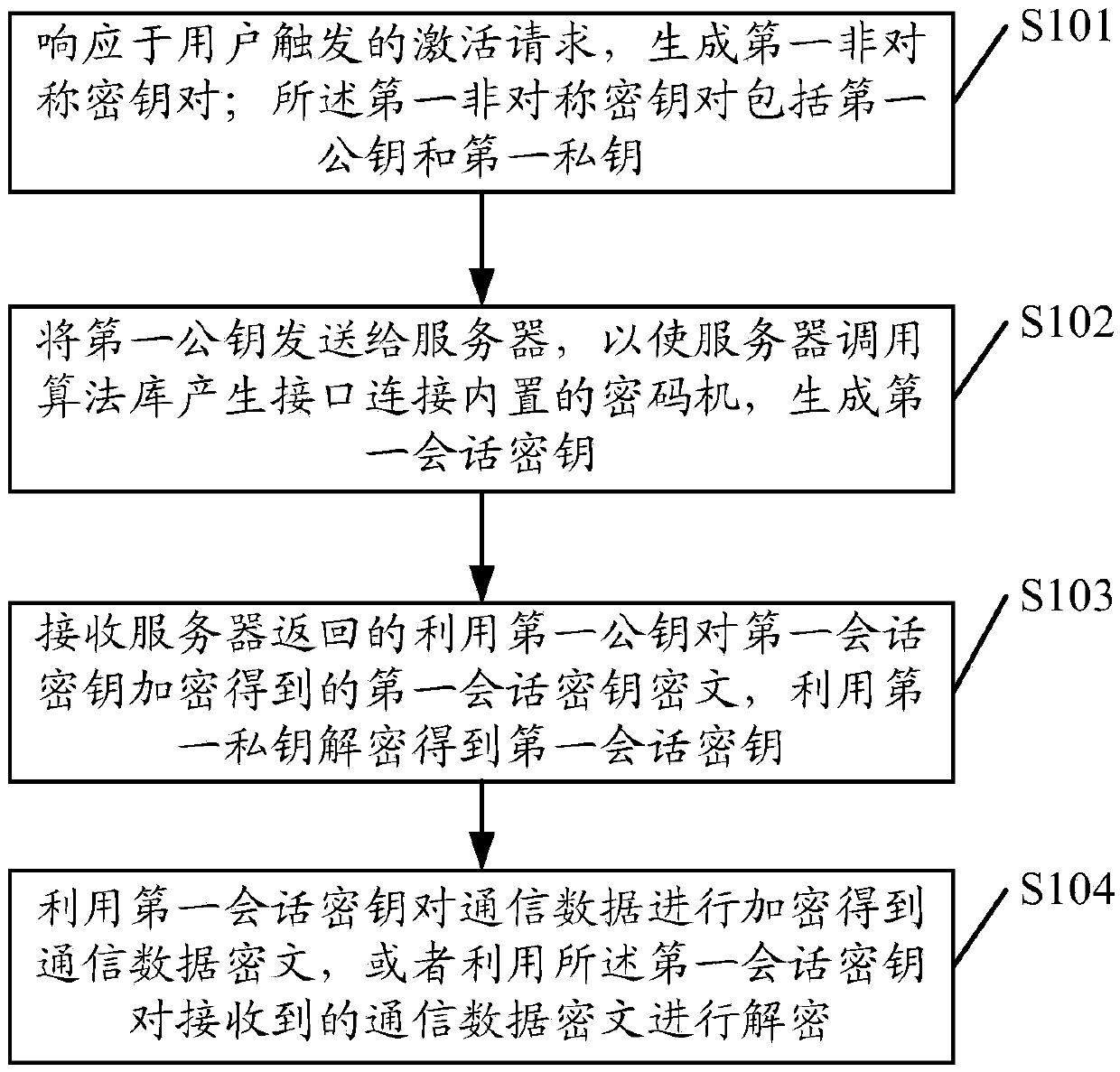
The embodiment of the invention discloses a vehicle safety communication method. A remote communication module of the vehicle and a server of the remote service platform can generate an asymmetric keypair; a public key in an asymmetric key pair is transmitted; the first session key can be encrypted or decrypted; the first session key is ensured to be transmitted in a ciphertext form; even if an illegal person obtains the ciphertext; the first session key cannot be obtained through decryption due to lack of the corresponding private key; when the remote communication module is communicated with the server of the remote service platform; the first session key is used for encrypting or decrypting the communication data, and the communication data is transmitted in a ciphertext form, so thatthe safety of communication between the vehicle and a remote service platform is guaranteed, and a phenomenon that a hacker or an illegal person simulates communication information to control a vehicle system to work is avoided, thereby guaranteeing the driving safety. The embodiment of the invention further discloses a vehicle safety communication device.
Owner:SAIC MOTOR
Safety communication method suitable for remote control with limited capability at controlled end
InactiveCN101931623AImprove confidentialityLimited number of solutionsError prevention/detection by using return channelSecure communicationTelecommunications link
The invention discloses a safety communication method suitable for remote control with a limited capability at a controlled end. The method comprises the following steps of: setting password sets at a control end and the controlled end and generating a password set according to an input initialization password by an irreversible method, wherein the password set comprises an index number and the password per se and encryption and decryption are performed by using the password corresponding to the recorded index number in a normal communication process; when the password is asynchronous, transmitting the index number by encrypting to perform password synchronization; and when a password set updating condition is met, negotiating about the update of the password set by transmitting a selected index number. A password set generating device for calculating the password set and communicating with the controlled end only when the password set is needed to be generated is arranged at the controlled end. Various attacks are resisted effectively by using a dynamic password and operation of real-time password calculation needed by the transmission of each data packet is avoided. Simultaneously, the password per se does not need to be transmitted on a communication link in password synchronizing and password set updating processes, so that simpleness and safety are realized.
Owner:SOUTH CHINA UNIV OF TECH
Method for realizing encryption communication
ActiveCN1881869AAvoid adverse effectsImprove communication security and user satisfactionSecuring communicationUser satisfactionEncryption
Owner:HUAWEI TECH CO LTD
Method for detecting false station in GSM and LTE network
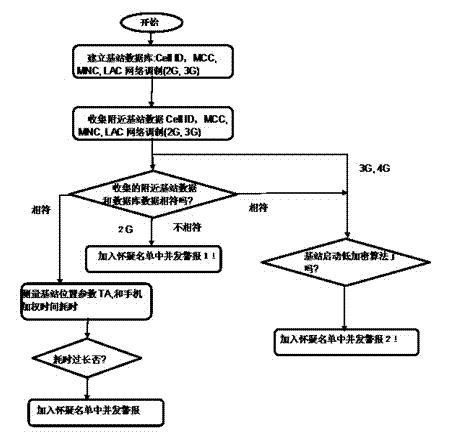
InactiveCN104270762AImprove communication securityVersatilitySecurity arrangementLow speedThird generation
The invention provides a method for detecting a false station in GSM and LTE networks. The new false station detection method provided can be used on 2G, 3G and 4G mobile equipment, such as cell phones adopting the GSM, WCDMA, LTE, LTEFDD or TD-LTE standard, so as to be universal to the Chinese market; safety performance for communication of using users or multiple users in a user area can be enhanced; the method can be used in a low-speed or static state; meanwhile, a final product has the characteristics of high portability and excellent price performance ratio.
Owner:信亚美科(南京)信息技术有限公司
Secure establishment method, system and device of wireless local area network
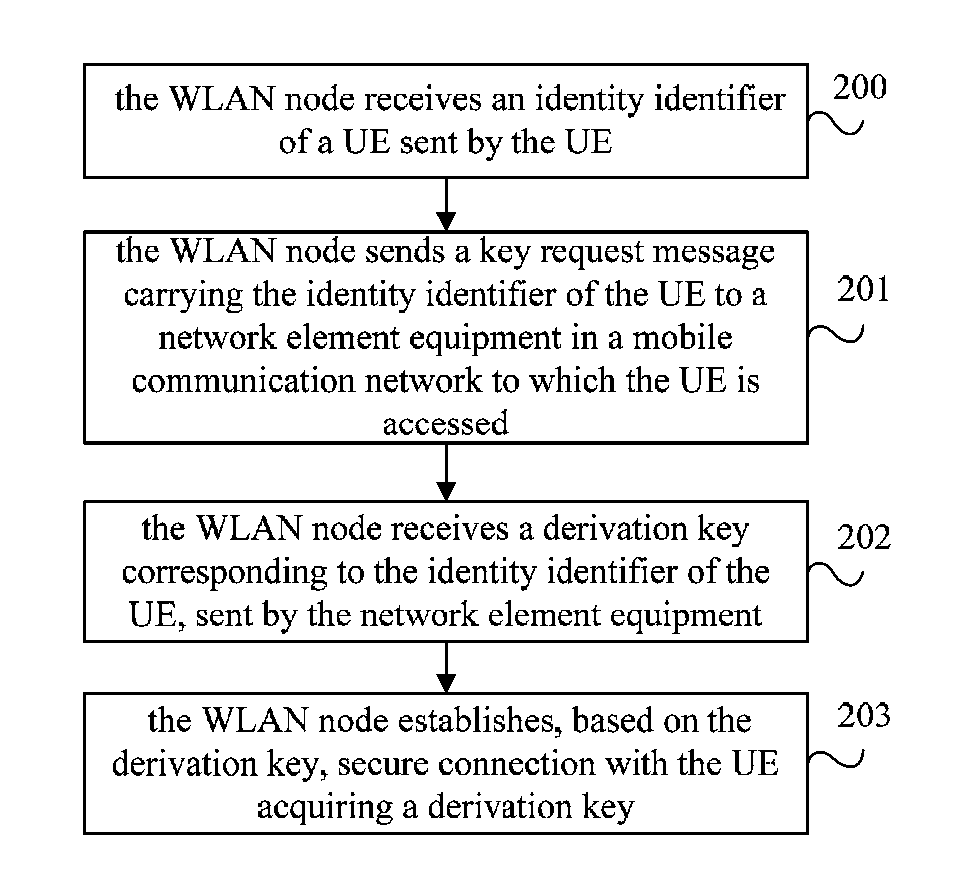
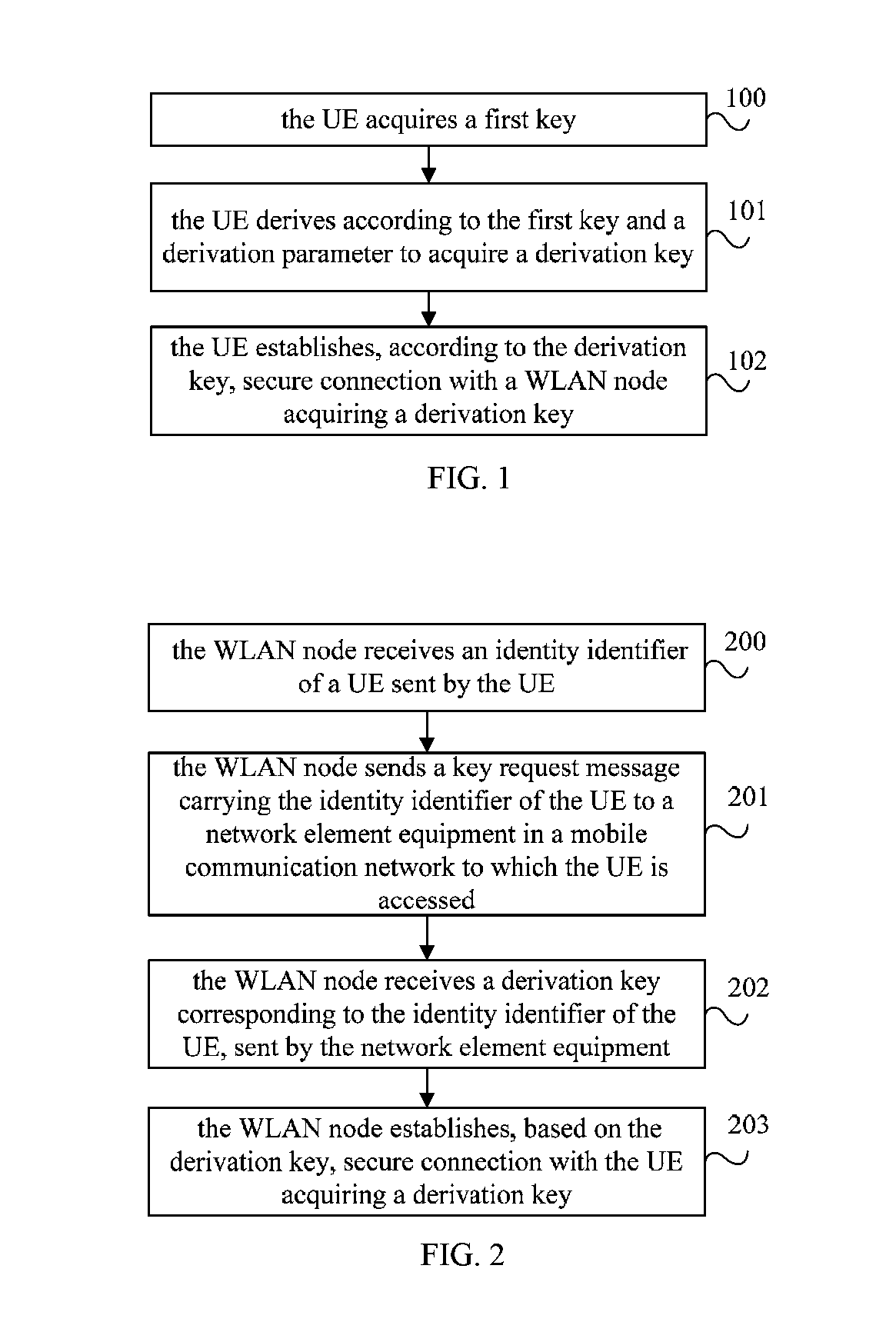
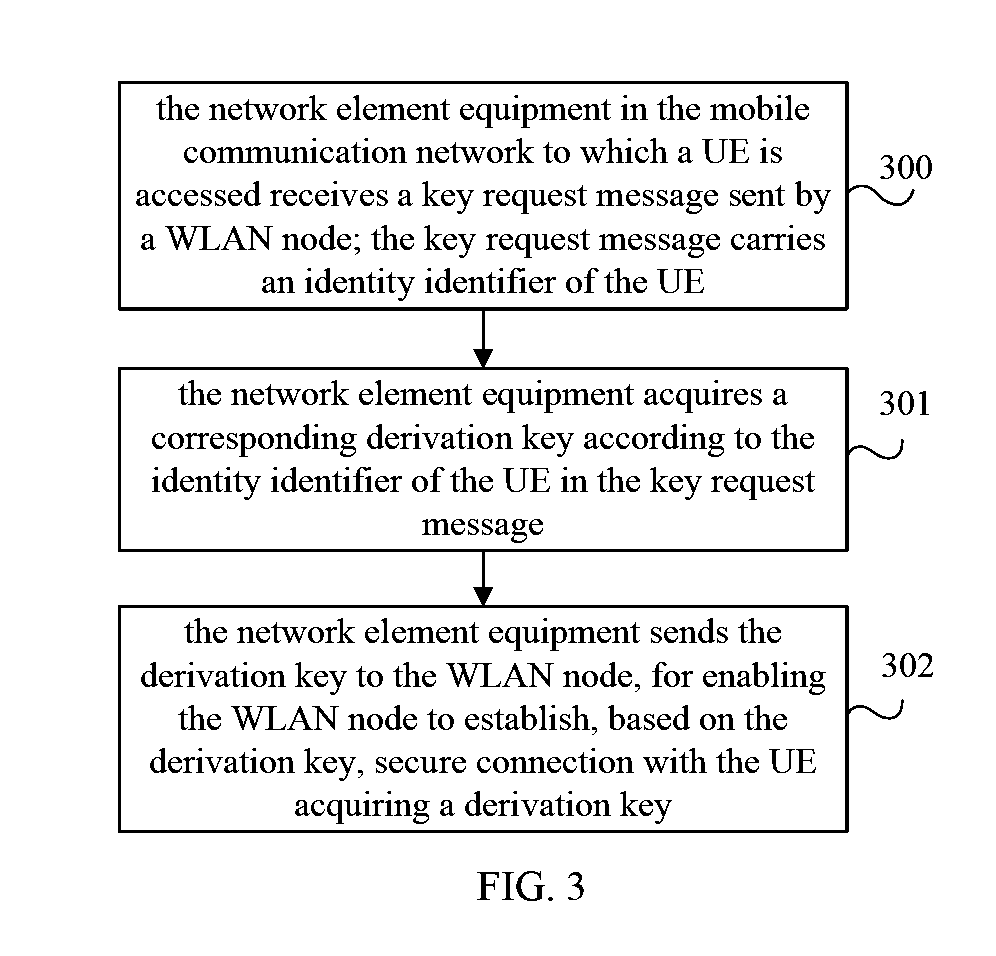
ActiveUS20150082393A1Improve communication securityImprove securityDigital data processing detailsNetwork topologiesAir interfaceNetwork element
The embodiments of the present invention provide a secure establishment method, system and device of a wireless local area network. The method includes: acquiring, by a UE, a first key; the first key is a shared key of the UE and a network element equipment in a mobile communication network to which the UE is accessed when implementing air interface security, or is derived according to the shared key; deriving, by the UE, according to the first key and a derivation parameter to acquire a derivation key; establishing, by the UE, according to the derivation key, secure connection with a WLAN node acquiring a derivation key, wherein the derivation key acquired by the WLAN node is the same as the derivation key acquired by the UE.
Owner:HUAWEI TECH CO LTD
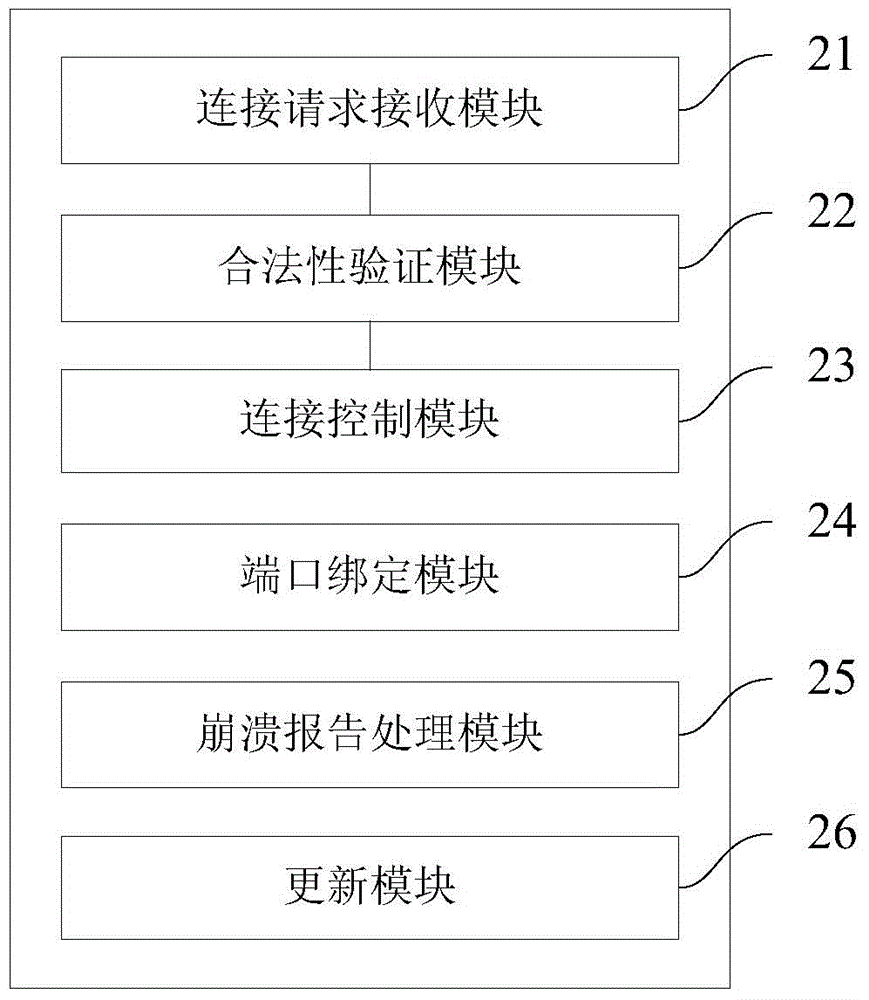
Method, device and system for invoking local service assembly by means of browser
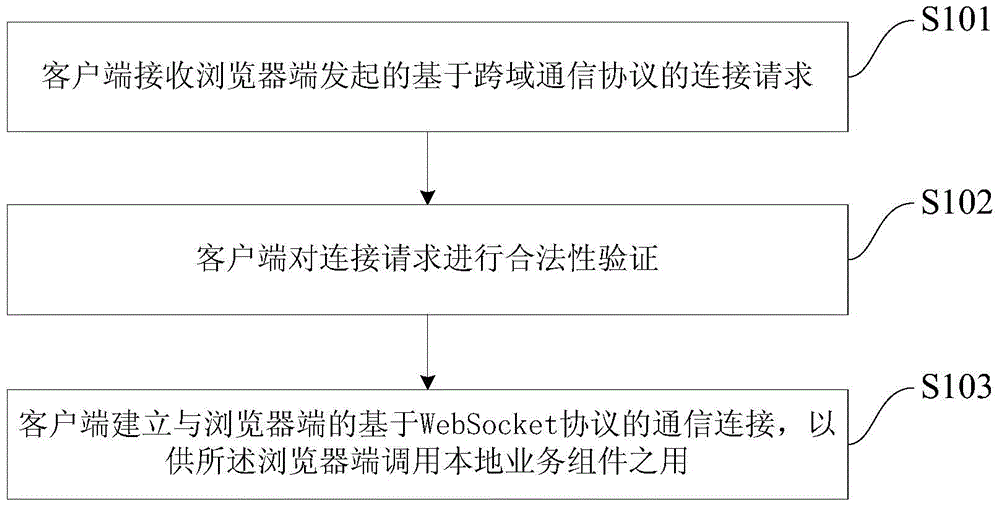
InactiveCN105471824AReduce total usageImprove communication securityHardware monitoringSecuring communicationCommunications securityNetwork Communication Protocols
The embodiment of the invention provides a method, a device and a system for invoking a local service assembly by means of a browser. The method comprises the steps that: a client receives a connection request which is based on a cross-domain communication protocol and initiated by a browser end; the client conducts validity verification on the connection request; and if the connection request has passed the validity verification, the client establishes a communication connection based on the cross-domain communication protocol with the browser end for the browser end to invoke the local service assembly. The embodiments of the method, the device and the system can realize invoking of the local service assembly by means of most popular browsers and the communication security is better.
Owner:ALIBABA GRP HLDG LTD
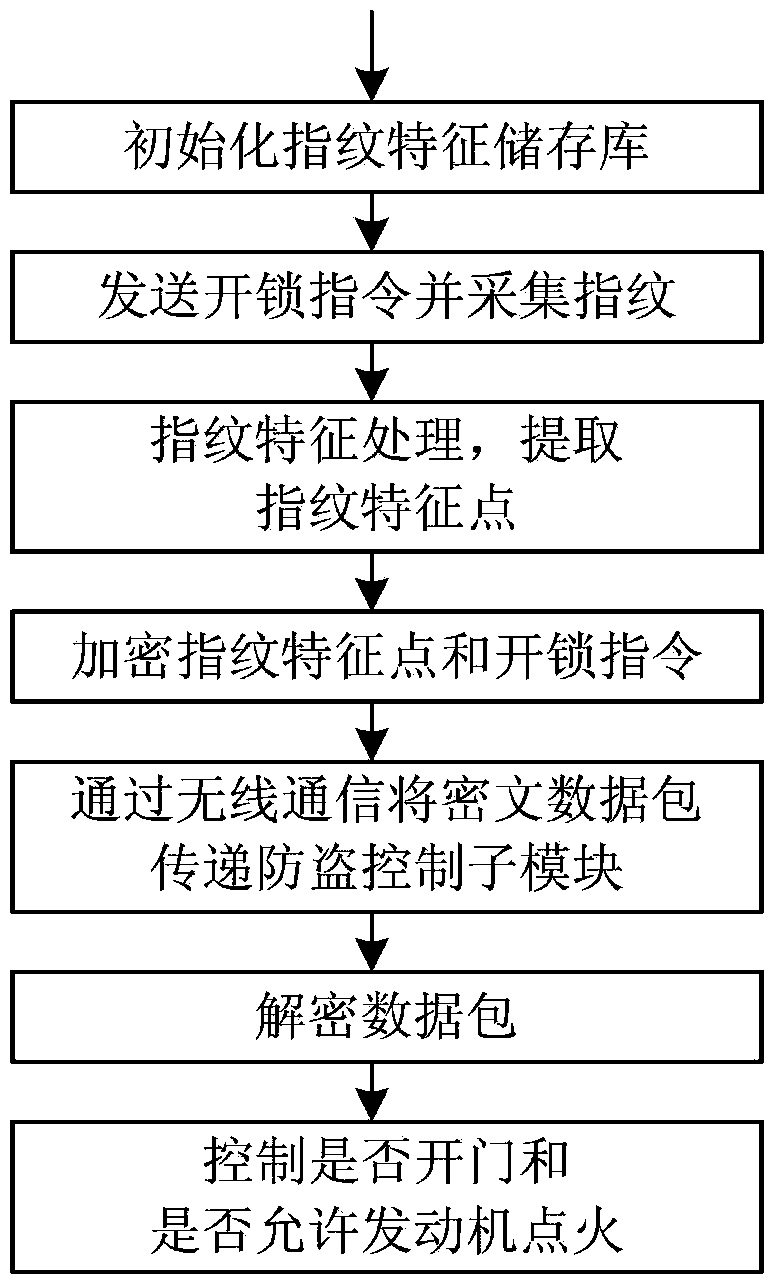
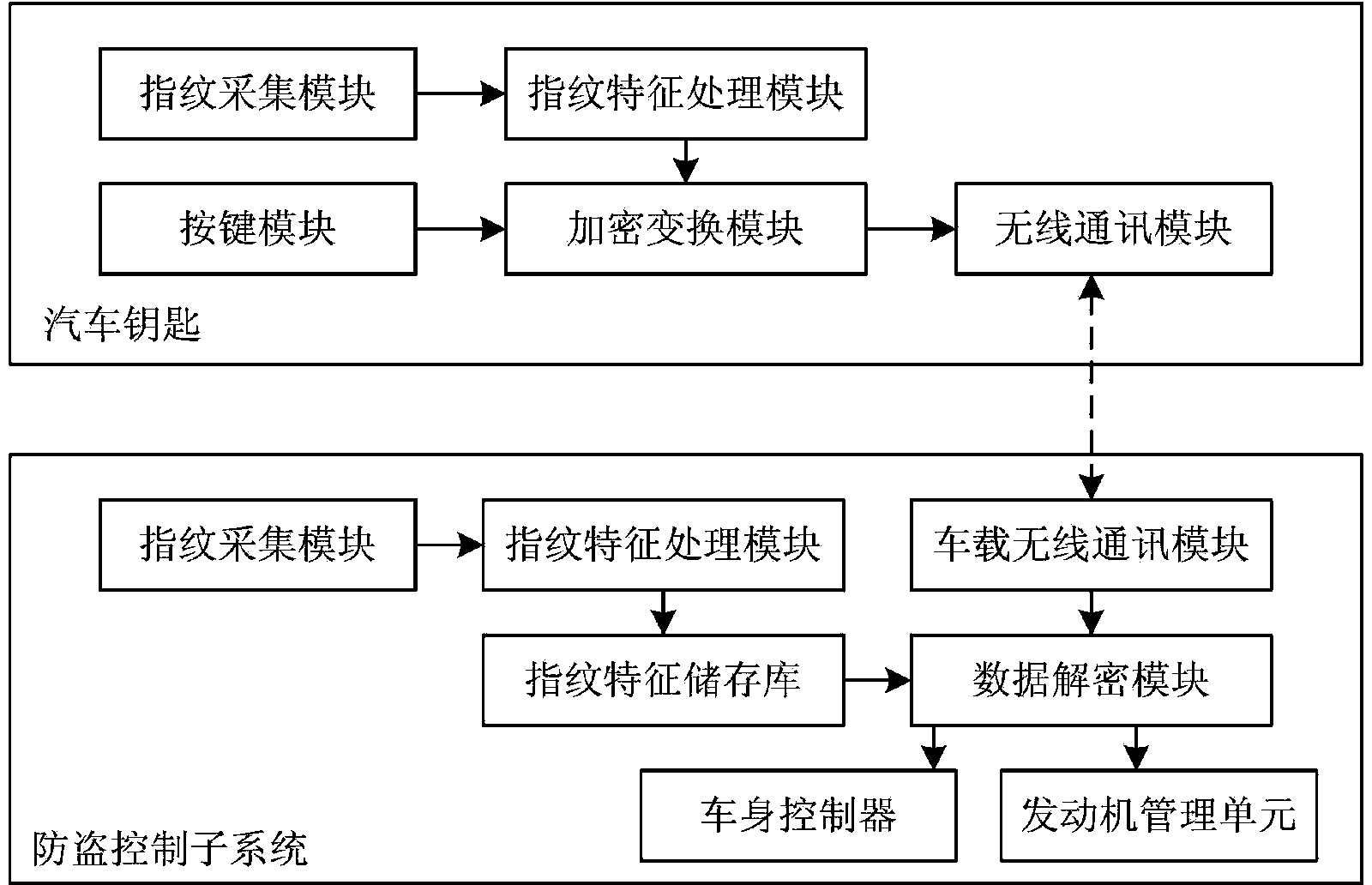
Car anti-theft method and system based on fingerprint secret key encryption technology
InactiveCN104029654AImprove communication securityImprove anti-theft performanceAnti-theft devicesFingerprintAnti theft
The invention relates to a car anti-theft method and system based on a fingerprint secret key encryption technology. The car anti-theft system based on the fingerprint secret key encryption technology is composed of a car key and an anti-theft control sub-system, a user sends an unlocking command on the key and inputs the fingerprint on a fingerprint collection module, a fingerprint image is converted into finger characteristic points through a fingerprinting characteristic processing module, an encryption conversion module generates a ciphertext data package through a fingerprint secret key technology, the ciphertext data package is transmitted to a data decryption module of the anti-theft control sub-system in a wireless communication mode, the data decryption module calls all the fingerprint characteristic points stored in a fingerprint characteristic repository to decrypt the ciphertext data package, a car body controller determines whether to execute a door opening operation according to received plaintext data, and an engine management unit determines whether to allow an engine to prepare for ignition according to the received plaintext data. According to the car anti-theft method and system based on the fingerprint secret key encryption technology, based on the uniqueness of the fingerprint characteristics, the fingerprint secret key encryption technology is adopted, communication safety is improved, engine ignition authority verification is added, and the anti-theft performance of the car is effectively improved.
Owner:JIANGSU UNIV
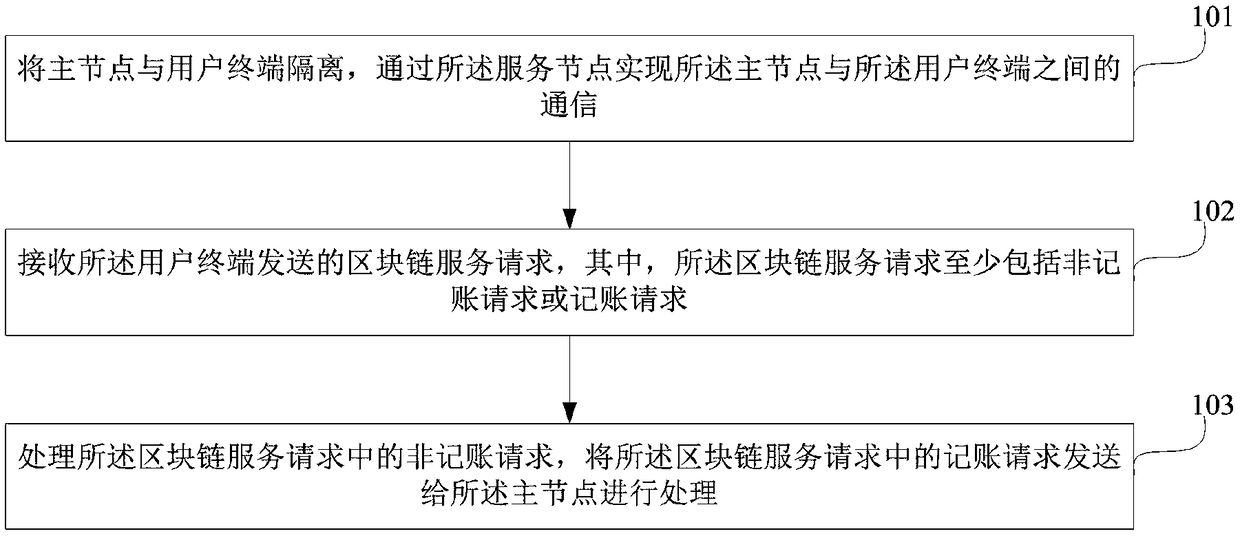
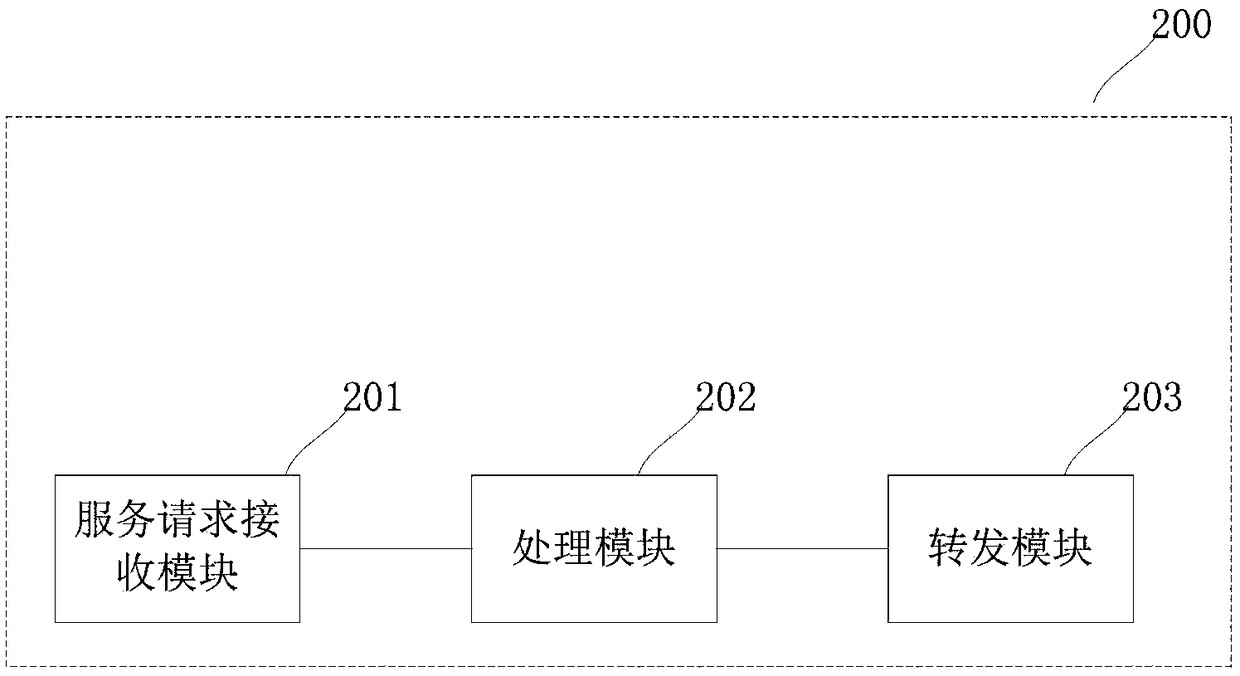
Blockchain secure communication method and system, and service node
ActiveCN109451036AAddressing VulnerabilityHigh speedFinanceTransmissionCommunications securityBlockchain
The invention relates to the technical field of blockchain security, and in particular to a blockchain secure communication method and system, and a service node. The method comprises the following steps: isolating a master node from a user terminal; receiving a blockchain service request sent by the user terminal, wherein the blockchain service request at least comprises a non-accounting requestor an accounting request; processing the non-accounting request in the blockchain service request, and sending the accounting request in the blockchain service request to the master node for processing. By adoption of the method and system, and the service node provided by the embodiment of the invention, the problem that the master node in a blockchain network is easily attacked can be solved, and the communication security of the master node in the network is improved.
Owner:北京创世智链信息技术研究院
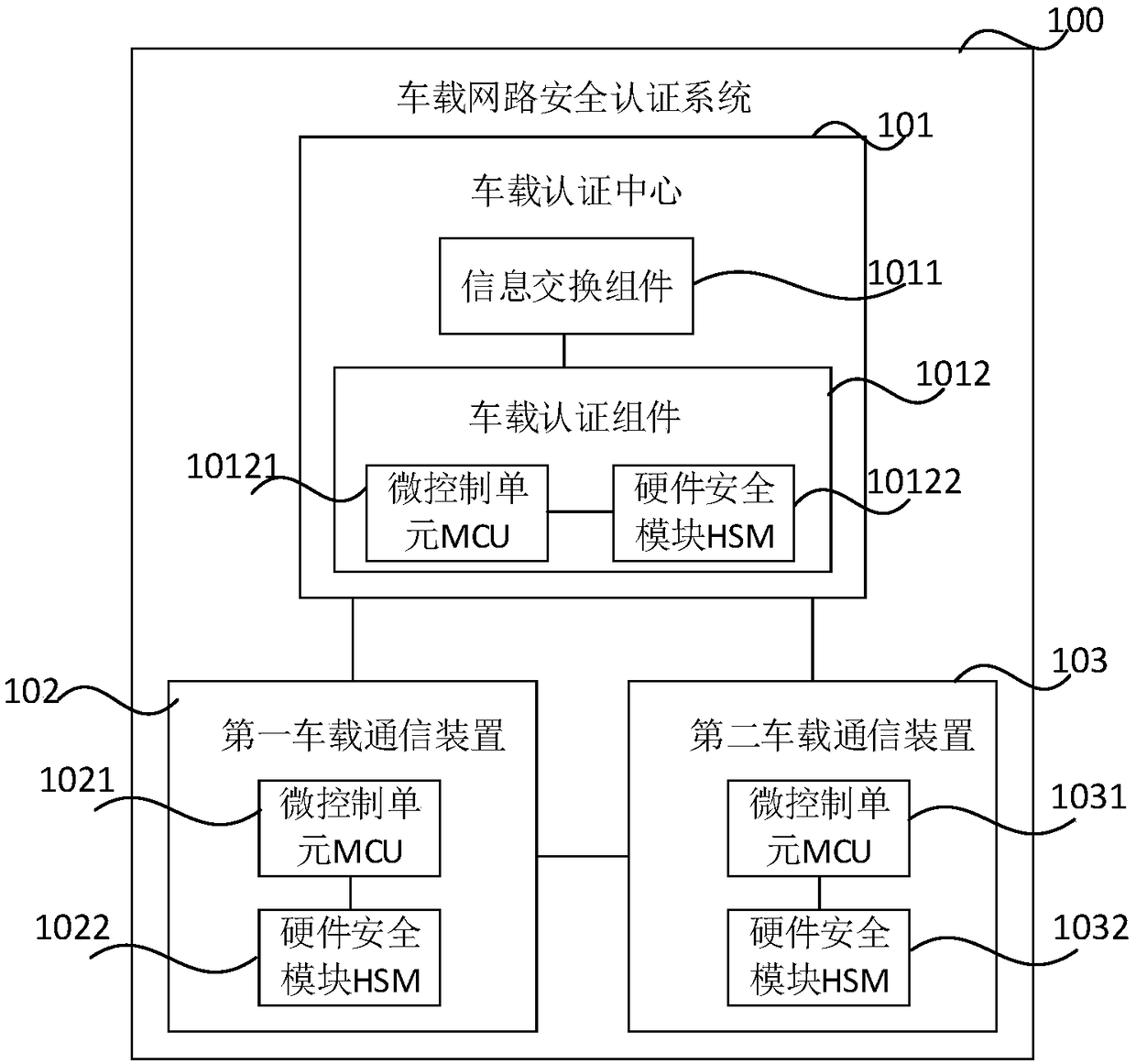
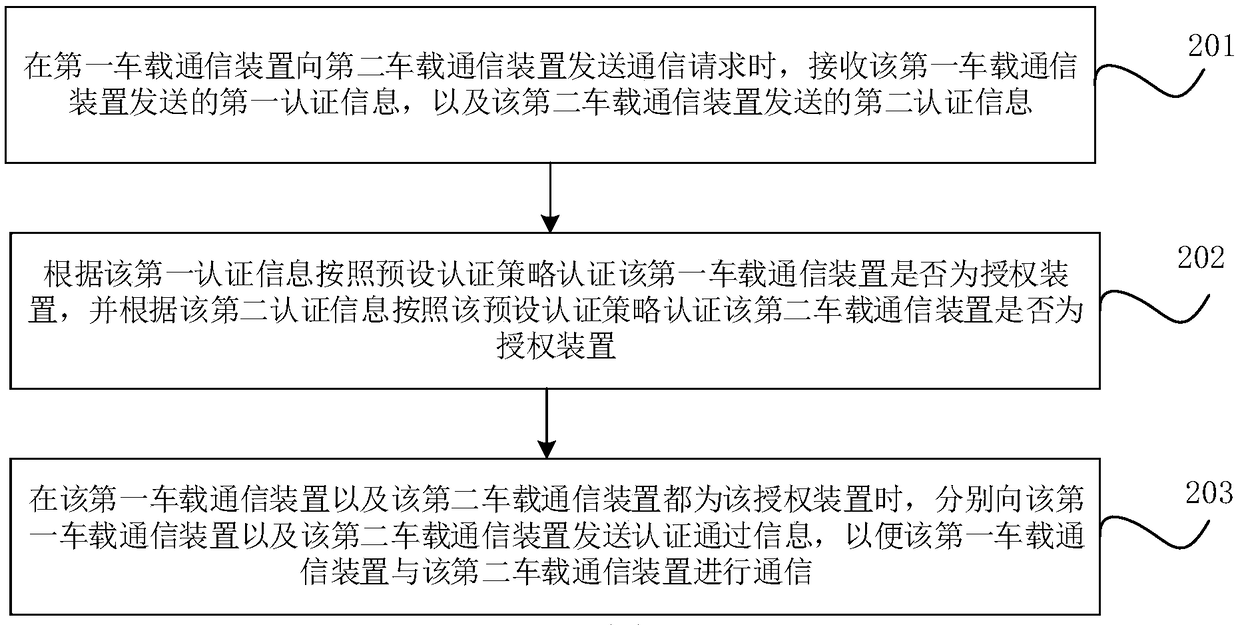
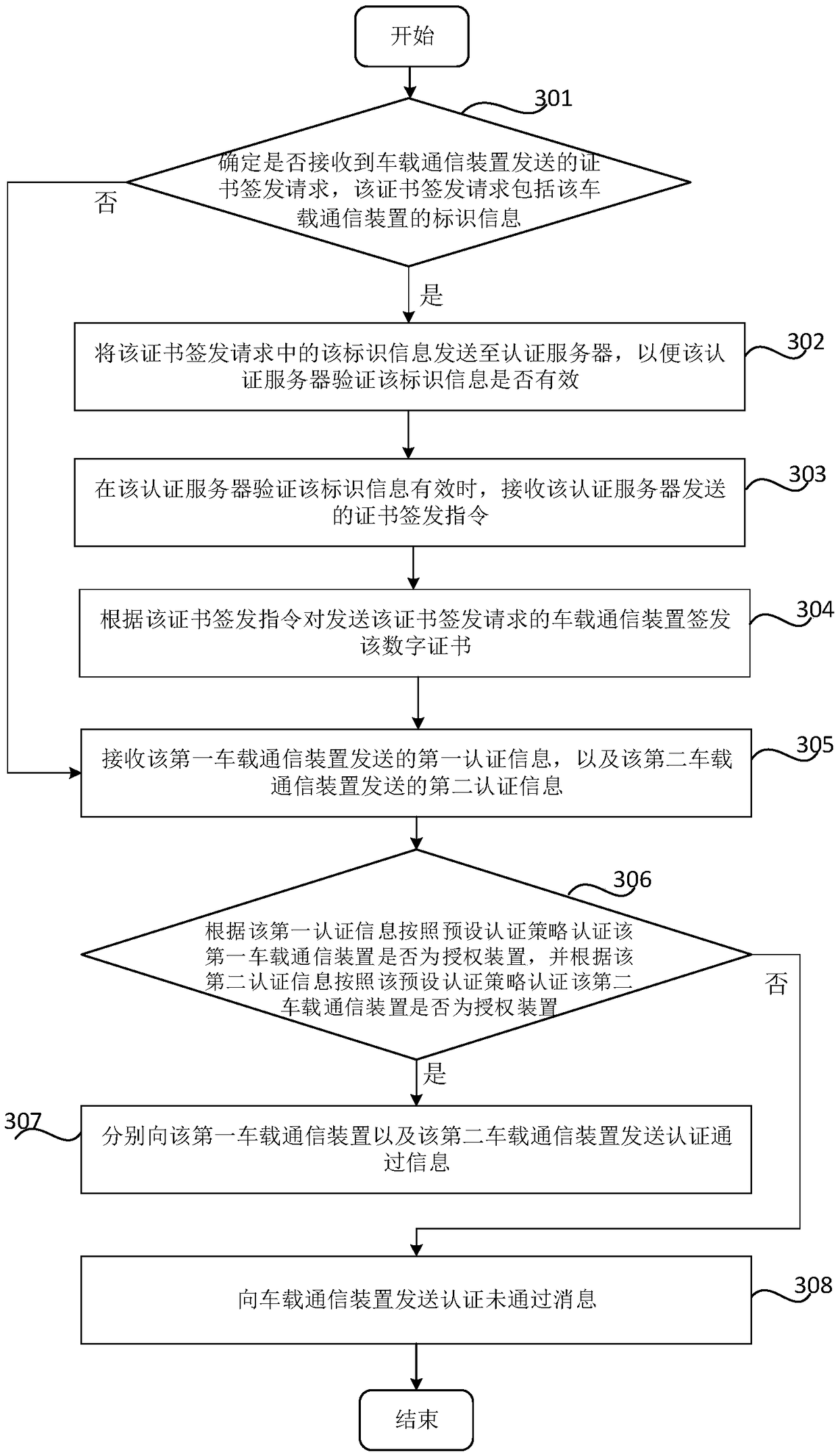
Vehicle-mounted network security authentication method, device, storage medium and vehicle
ActiveCN109040285AImprove communication securityAccess containmentTransmissionComputer hardwareIn vehicle
The invention relates to a method, a device, a storage medium and a vehicle for securing authentication of a vehicle-mounted network. When a first vehicle-mounted communication device sends a communication request to a second vehicle-mounted communication device, the first authentication information sent by the first vehicle-mounted communication device and the second authentication information sent by the second vehicle-mounted communication device are received. whether the first vehicle-mounted communication device is an authorizing device is authenticated by the preset authentication strategy according to the first authentication information and authenticating whether the second vehicle-mounted communication device is an authorizing device is authenticated by the preset authentication strategy according to the second authentication information; When both the first vehicle-mounted communication device and the second vehicle-mounted communication device are the authorization devices,authentication passing information is sent to the first vehicle-mounted communication device and the second vehicle-mounted communication device, respectively, so that the first vehicle-mounted communication device communicates with the second vehicle-mounted communication device.
Owner:BEIJING AUTOMOTIVE IND CORP +1
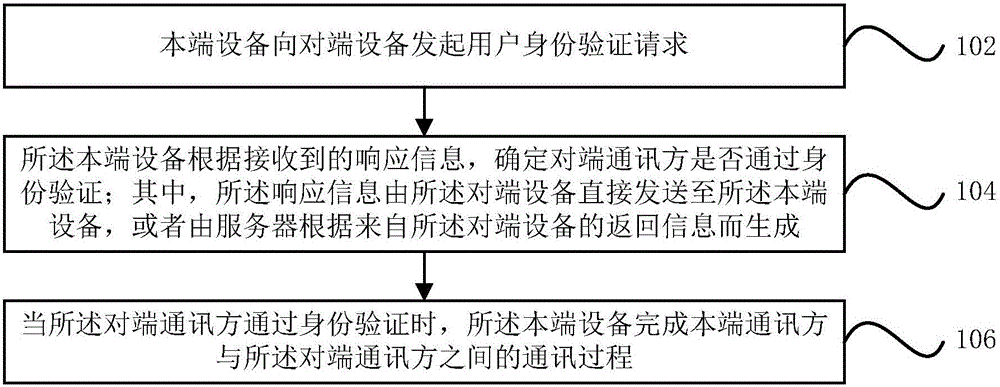
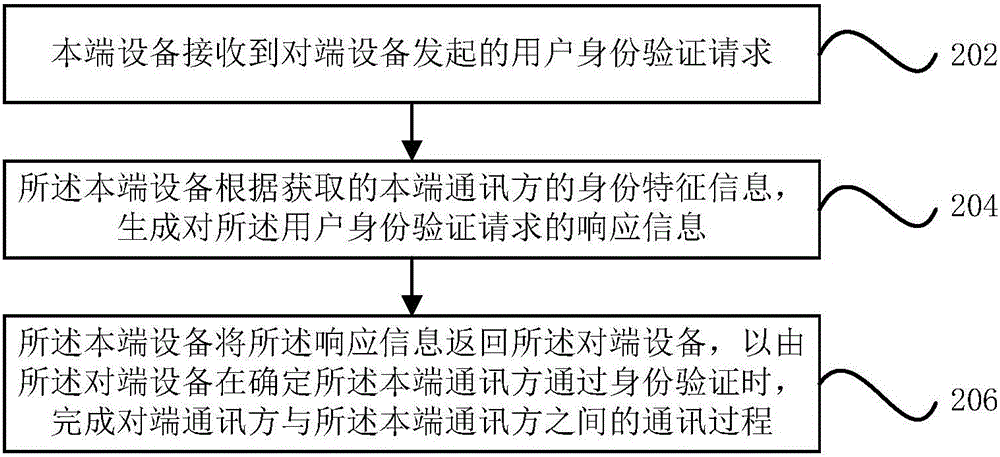
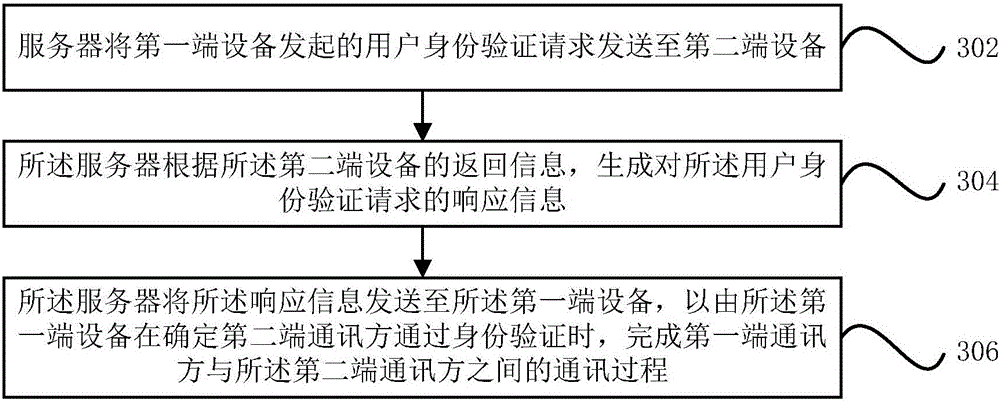
Communication method and device
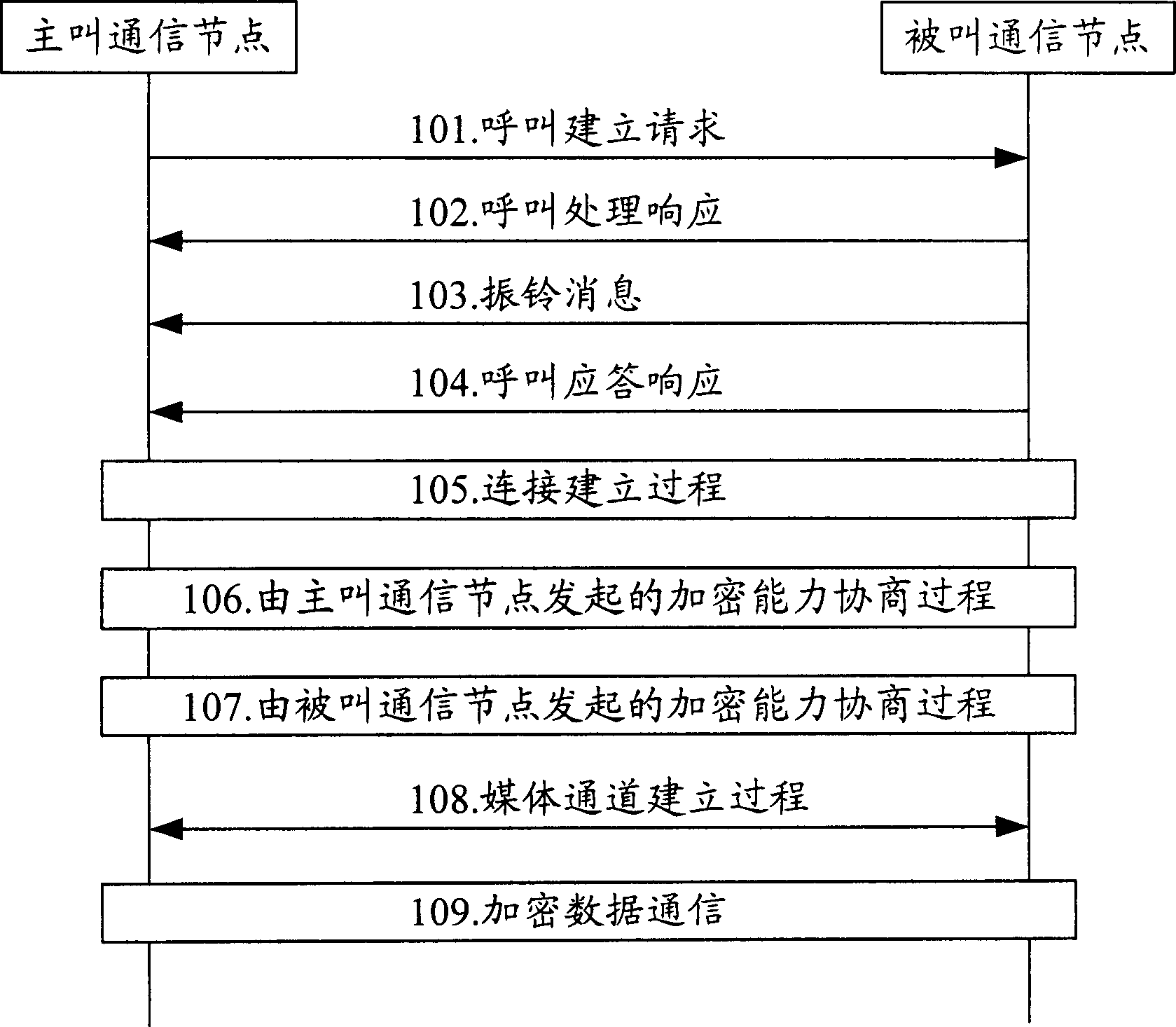
ActiveCN105721468AProtect interestsImprove communication securitySecuring communicationCommunications securityInternet privacy
The invention provides a communication method and device. The method may comprise that a local end device initiates a user identity verification request to an opposite end device; the local end device determines whether an opposite end communication party passes identity verification or not according to received response information, wherein the response information is directly sent to the local end device by the opposite end device, or is produced by a server according to the returned information from the opposite end device; and when the opposite end communication party passes identity verification, the local end device finishes a communication process between a local end communication party and the opposite end communication party. Through adoption of the technical scheme provided by the invention, the communication security is increased; and the benefits of the communication parties are ensured.
Owner:ALIBABA GRP HLDG LTD
Web management system for power LTE wireless terminal and terminal authentication method thereof
ActiveCN106972974AImprove securityImprove communication securityData switching networksHypertext Transfer Protocol over Secure Socket LayerPrivate network
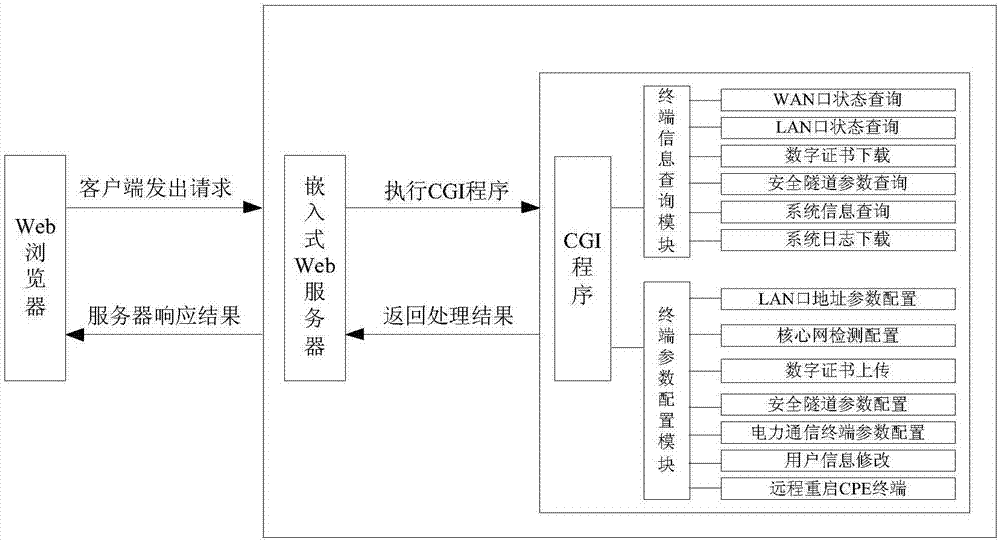
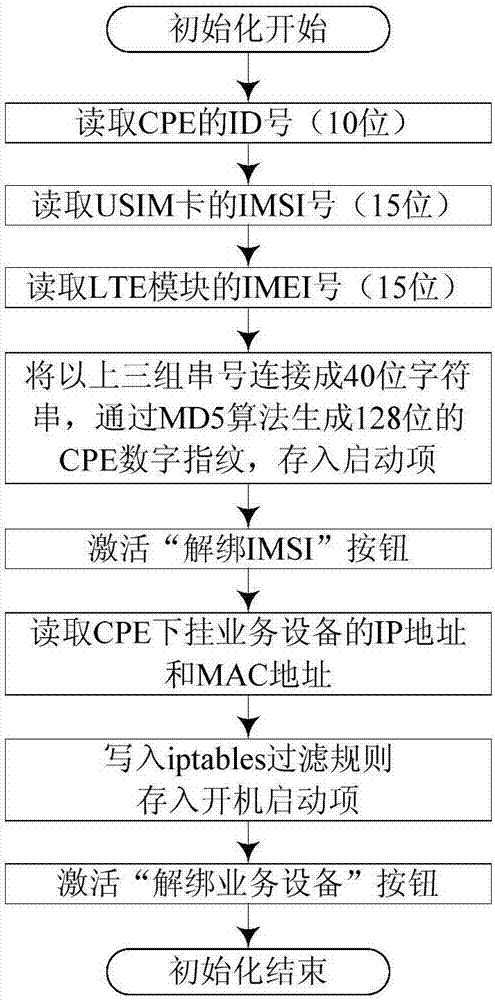
The invention provides a Web management system for a power LTE wireless terminal and a terminal authentication method thereof. The Web management system comprises a Web server. The Web server comprises a terminal identity authentication module and a CGI (Common Gateway Interface) program module. The Web server carries out terminal identity authentication on a CPE terminal through the terminal identity authentication module, so the CPE terminal can access a power LTE wireless private network. A private key and a certificate generated by an SSL (Secure Socket Layer) tool are stored in the Web server. A user accesses an HTML static webpage of the Web server in an HTTPS mode based on an SSL protocol through a client Web browser, and further the CGI program module is triggered to carry out a corresponding function unit program. According to the system and the method, the secure embedded Web server is established through utilization of the common gateway interface (CGI) and the secure socket layer (SSL); terminal information query and terminal parameter configuration functions are realized on a power LTE-1.8GHz wireless CPE terminal; and the system and the method adapt to a power service device well and have relatively good application prospect.
Owner:NANJING NARI GROUP CORP +1
Communication method and related product
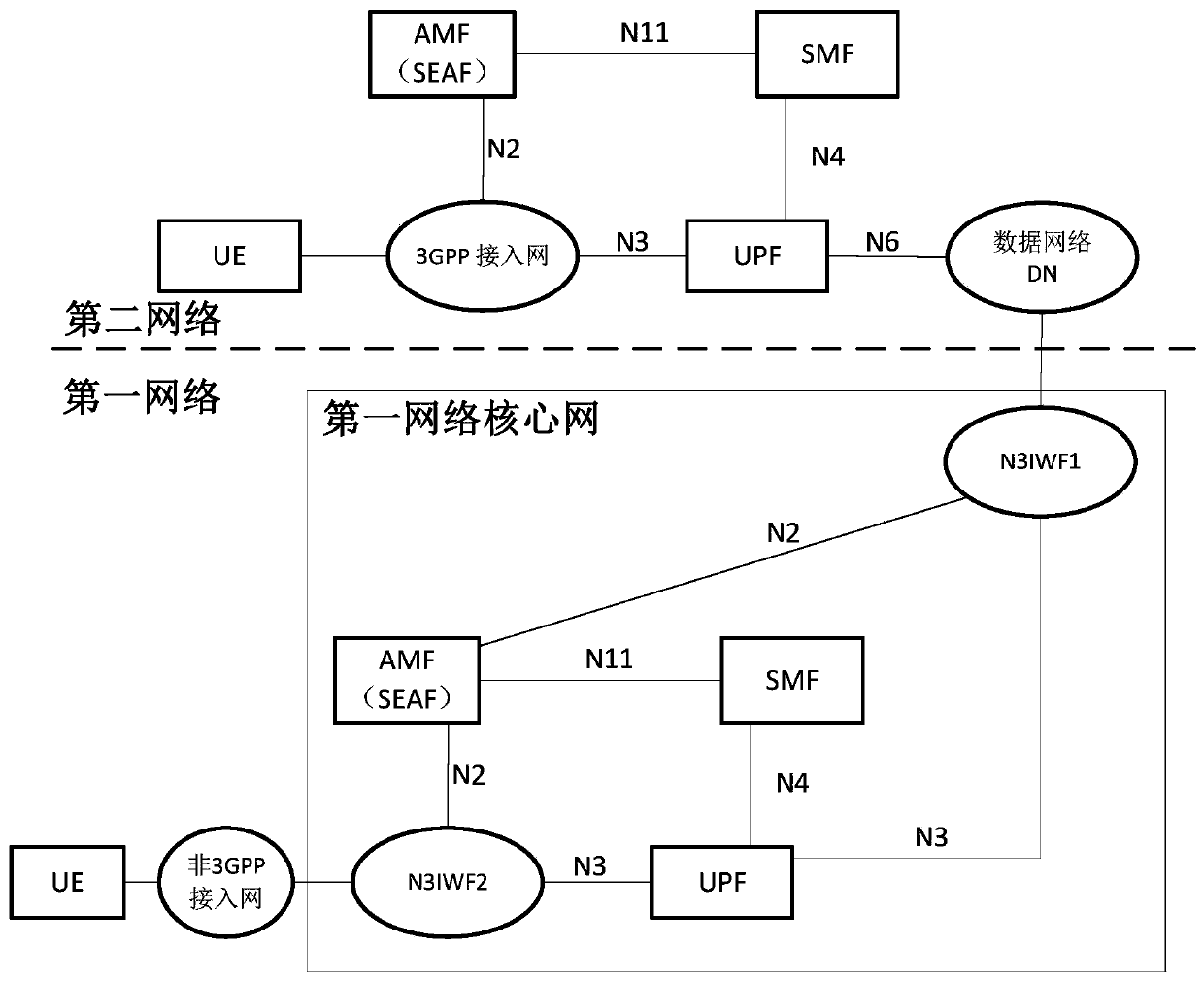
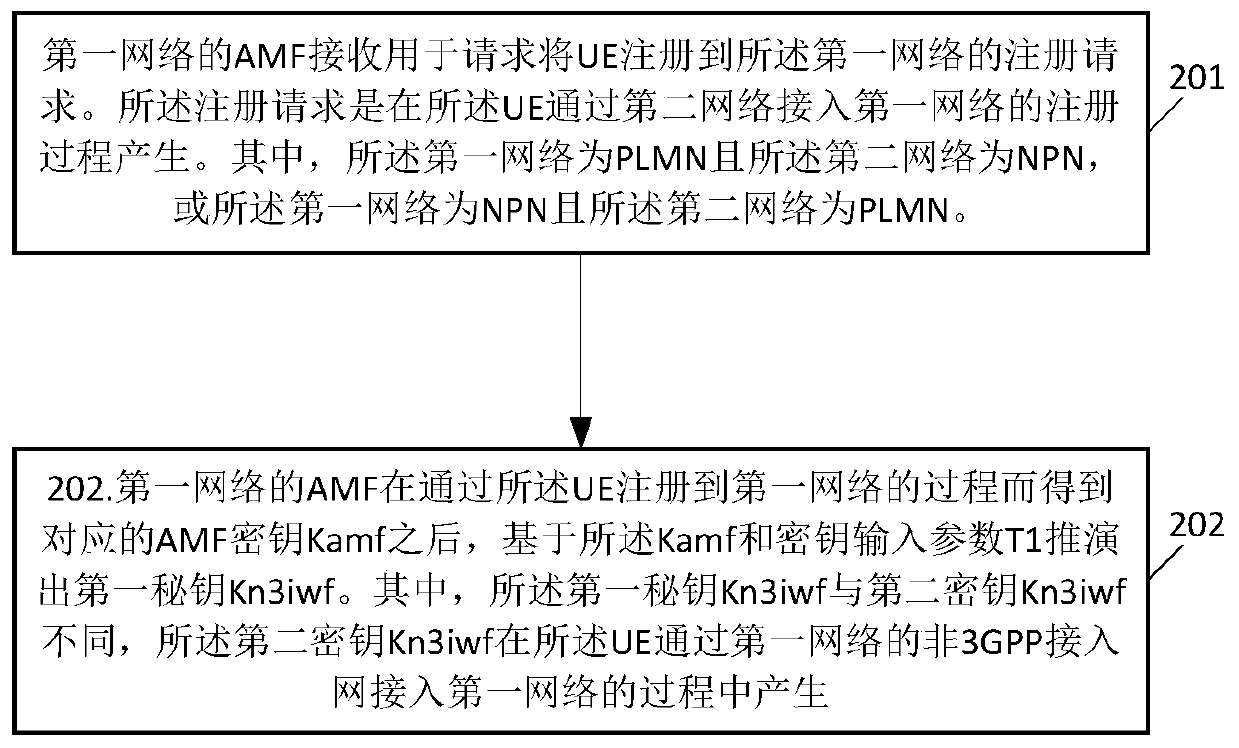
ActiveCN111447675AResistance to leakage risksImprove communication securityAssess restrictionSecurity arrangementCommunications securityAccess network
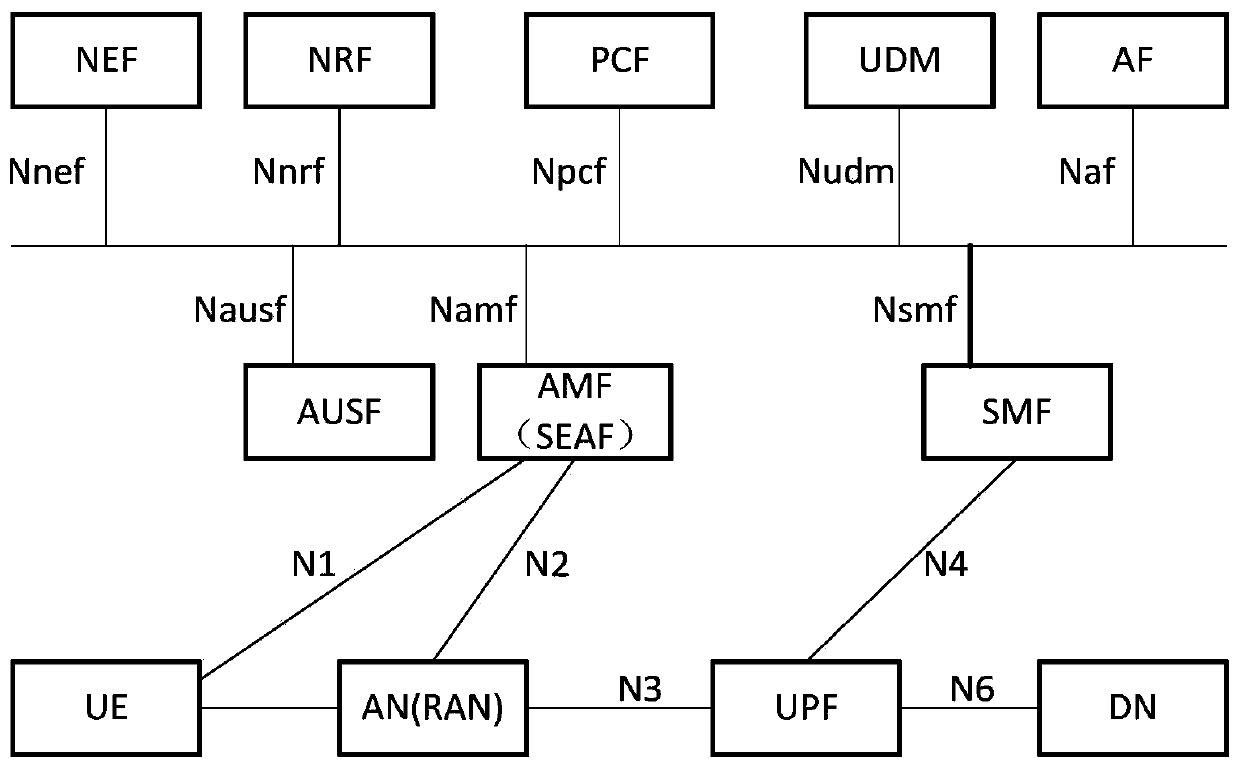
The embodiment of the invention discloses a communication method and a related product. The communication method comprises the following steps: receiving, by the AMF of a first network, a registrationrequest for requesting registration of UE to the first network, the registration request being generated in a registration process in which the UE accesses the first network through a second network,the first network being a PLMN and the second network being an NPN, or the first network being an NPN and the second network being a PLMN; and after the AMF of the first network obtains a corresponding AMF key Kamf through a process of registering the UE to the first network, deducing a first key Kn3iwf based on the Kamf and the key input parameter T1, wherein the first secret key Kn3iwf is different from the second secret key Kn3iwf, and the second secret key Kn3iwf is generated in the process that the UE accesses the second network through the non-3GPP access network of the second network.According to the scheme, the Kn3iwf key isolation in a cross-network access scene can be improved, and the communication security is further improved.
Owner:HUAWEI TECH CO LTD
Method for encrypting communication between UAV (unmanned aerial vehicle) and ground station
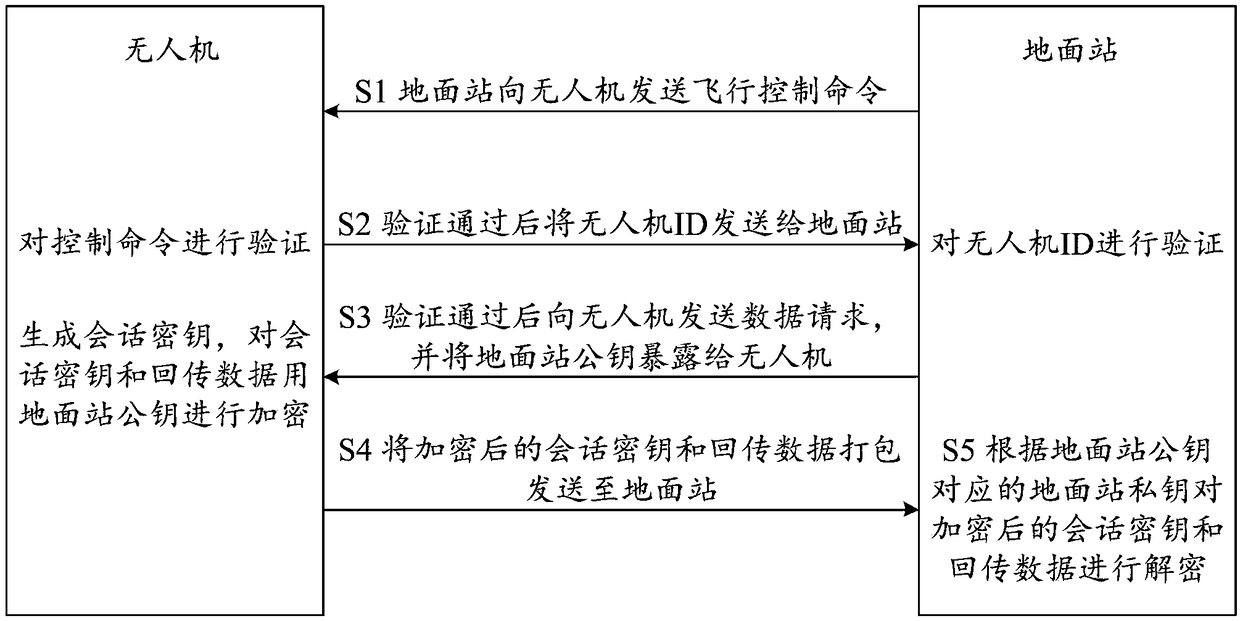
InactiveCN108966174AImprove communication securityPrevent theftParticular environment based servicesVehicle wireless communication serviceData transmissionCiphertext
The invention relates to a method for encrypting the communication between a UAV (unmanned aerial vehicle) and a ground station. The method comprises the steps that the ground station sends a controlcommand to the UAV; the UAV verifies the control command, and after verification succeeds, the UAV sends a UAV ID to the ground station; the ground station verifies the UAV ID, after verification succeeds, the ground station sends a data request to the UAV, and reveals a ground station public key to the UAV; the UAV receives the data request and the ground station public key, then generates a session key, encrypts the session key and returned data by using the ground station public key, then packs and sends the encrypted session key and returned data to the ground station; and the ground station performs decryption according to a ground station private key. According to the method, data transmitted between the UAV and the ground station is encrypted based on an asymmetrical encryption method, uplink data and downlink data between the UAV and the ground station are guaranteed to be transmitted in a form of ciphertext, so that the UAV is prevented from being controlled maliciously and data is prevented from being stolen and being used illegally, and communication between the UAV and the ground station is safer.
Owner:长春草莓科技有限公司
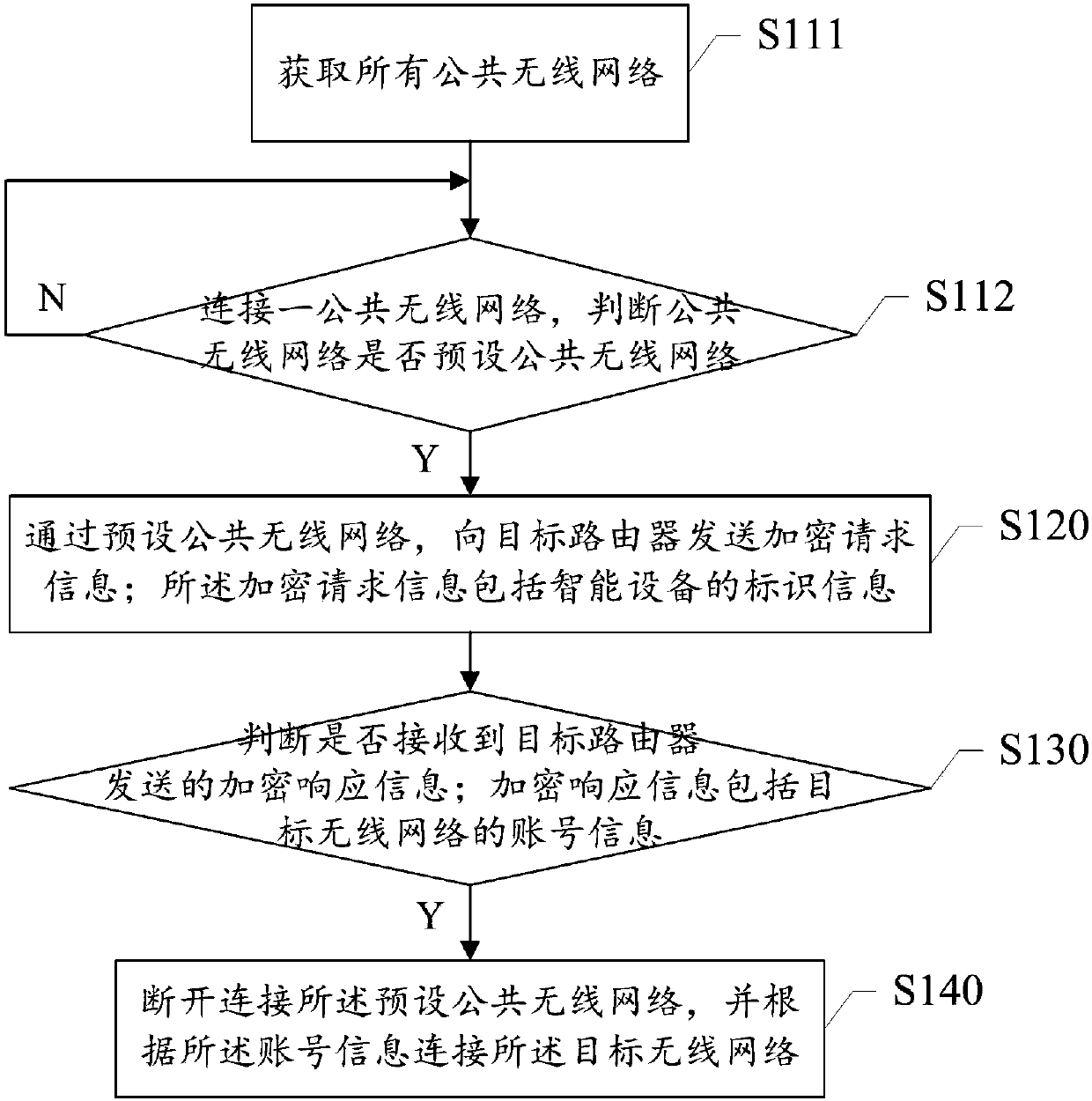
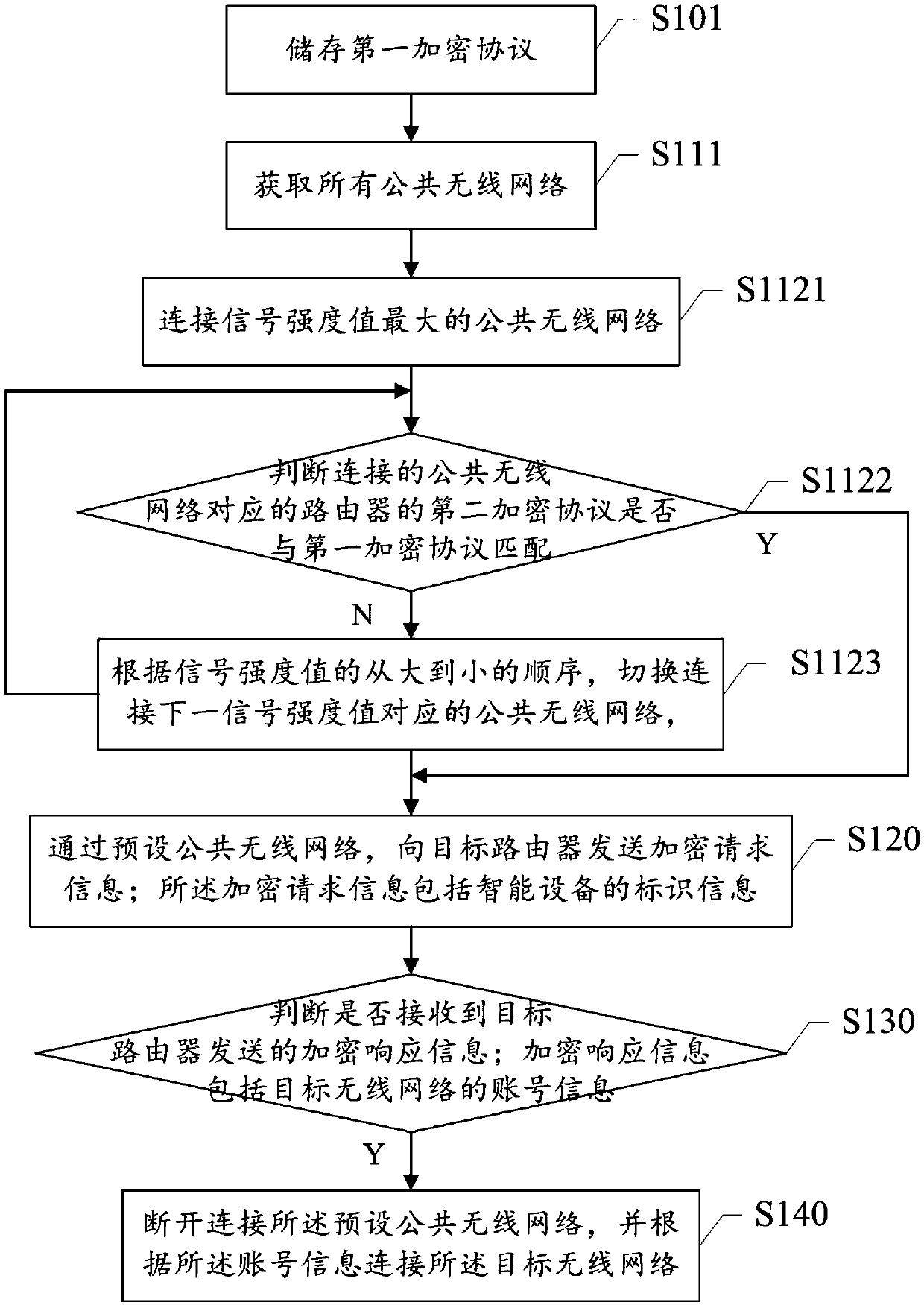
Method for connecting target wireless network, intelligent device and router
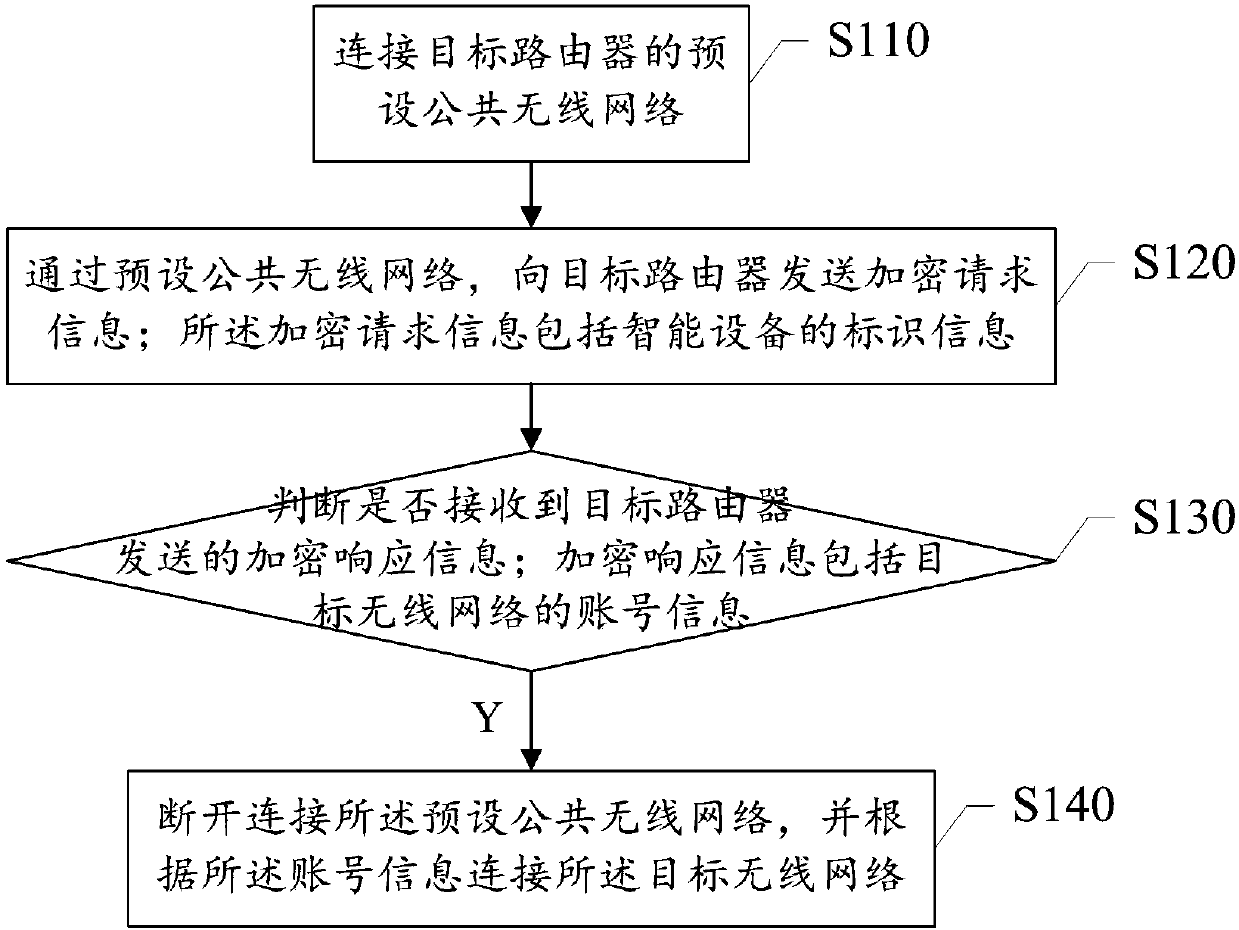
InactiveCN107872802AReduce manual input operationsEasy to operateAssess restrictionSecurity arrangementEmbedded systemSmart device
The invention provides a method for connecting a target wireless network, an intelligent device and a router. The method includes the steps: S110 connecting a preset public wireless network of a target router; S120 transmitting encryption request information comprising identification information of the intelligent device to the target router through the preset public wireless network; S130 judgingwhether encryption response information transmitted by the target router is received or not, and entering a step S140 if the encryption response information is received; S140 disconnecting the presetpublic wireless network and connecting the target wireless network according to account information. The encryption response information comprises the account information of the target wireless network. Participation of a mobile terminal is omitted, the intelligent device is connected with the target wireless network of the router, connecting operation is simplified, and connecting efficiency isimproved.
Owner:台州市吉吉知识产权运营有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com