Patents
Literature
2270results about How to "Protect interests" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
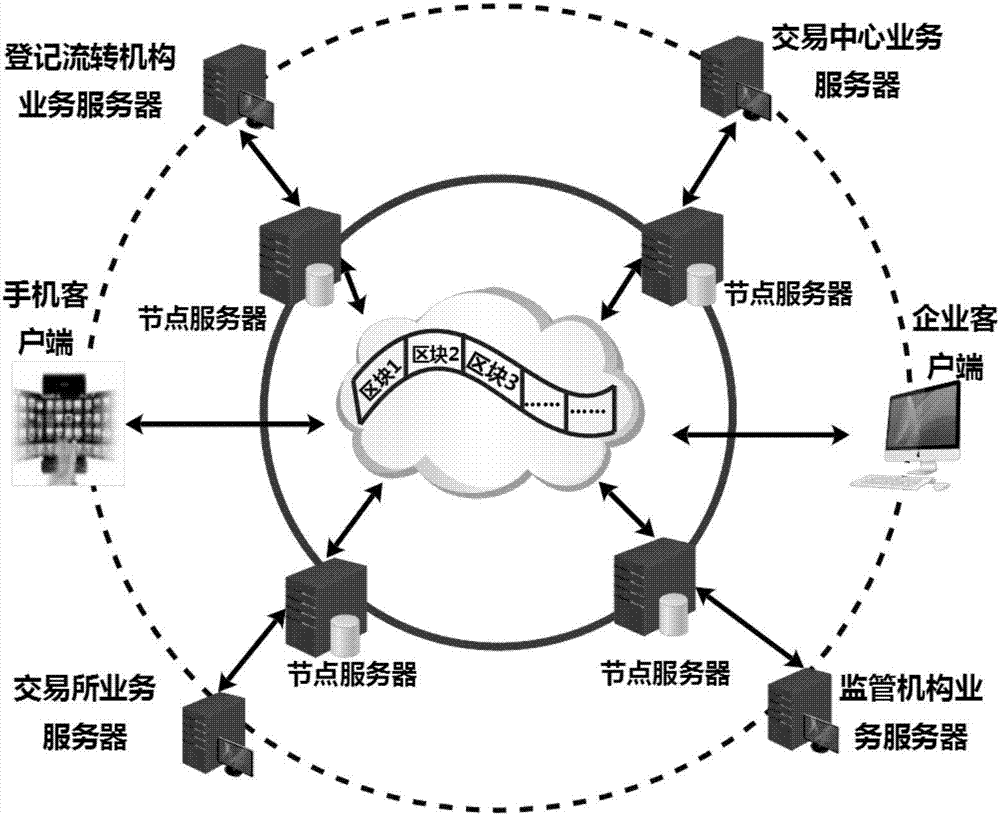
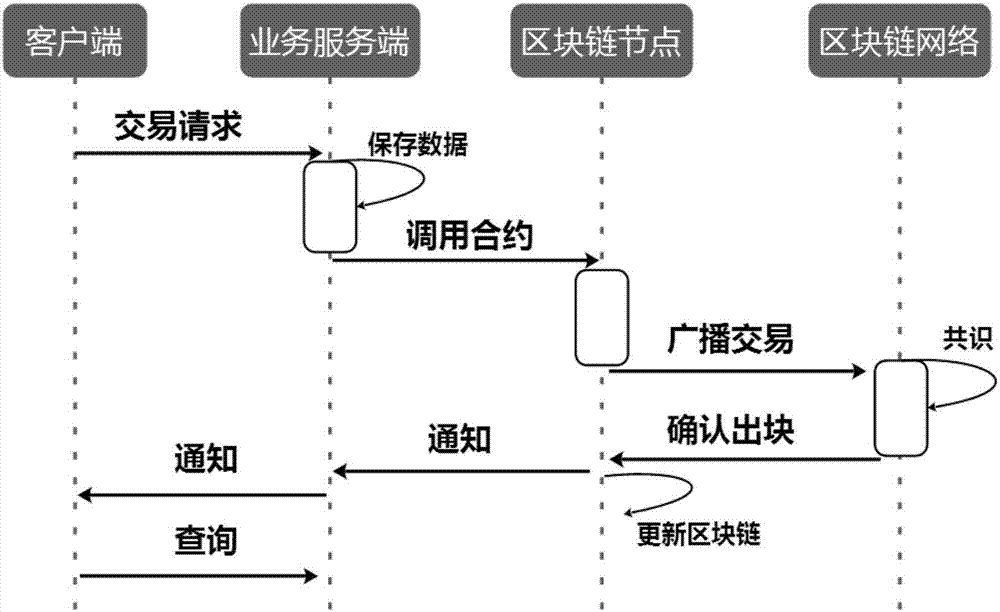
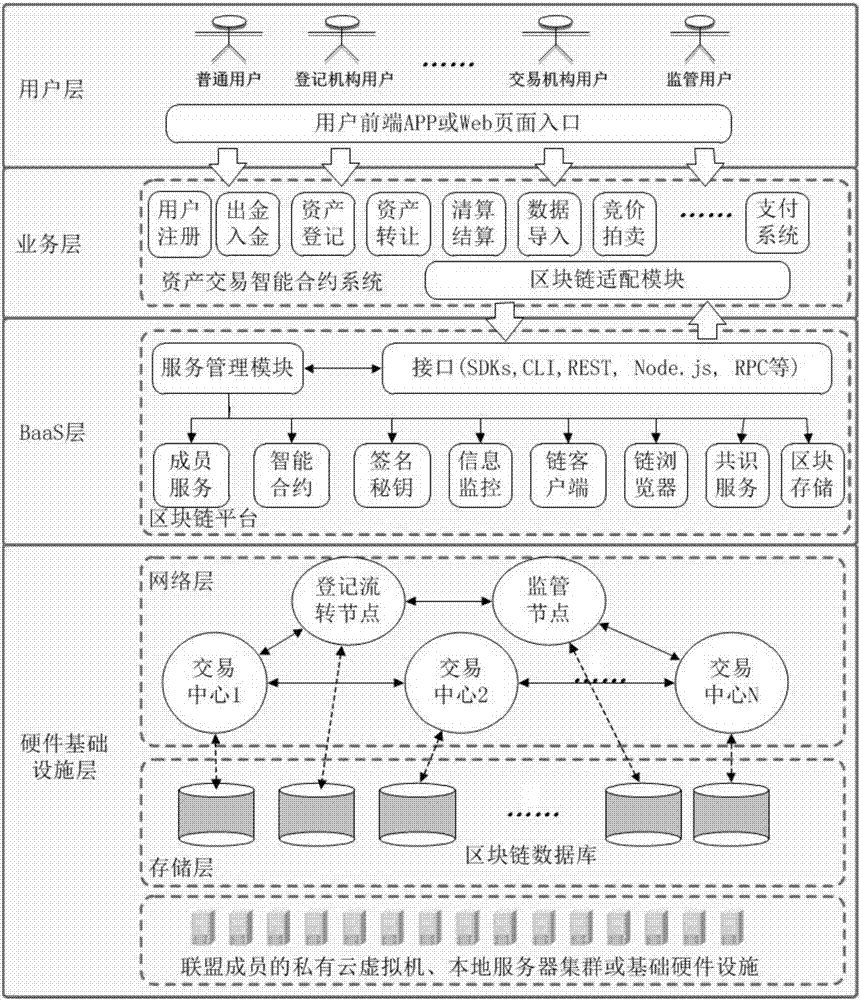
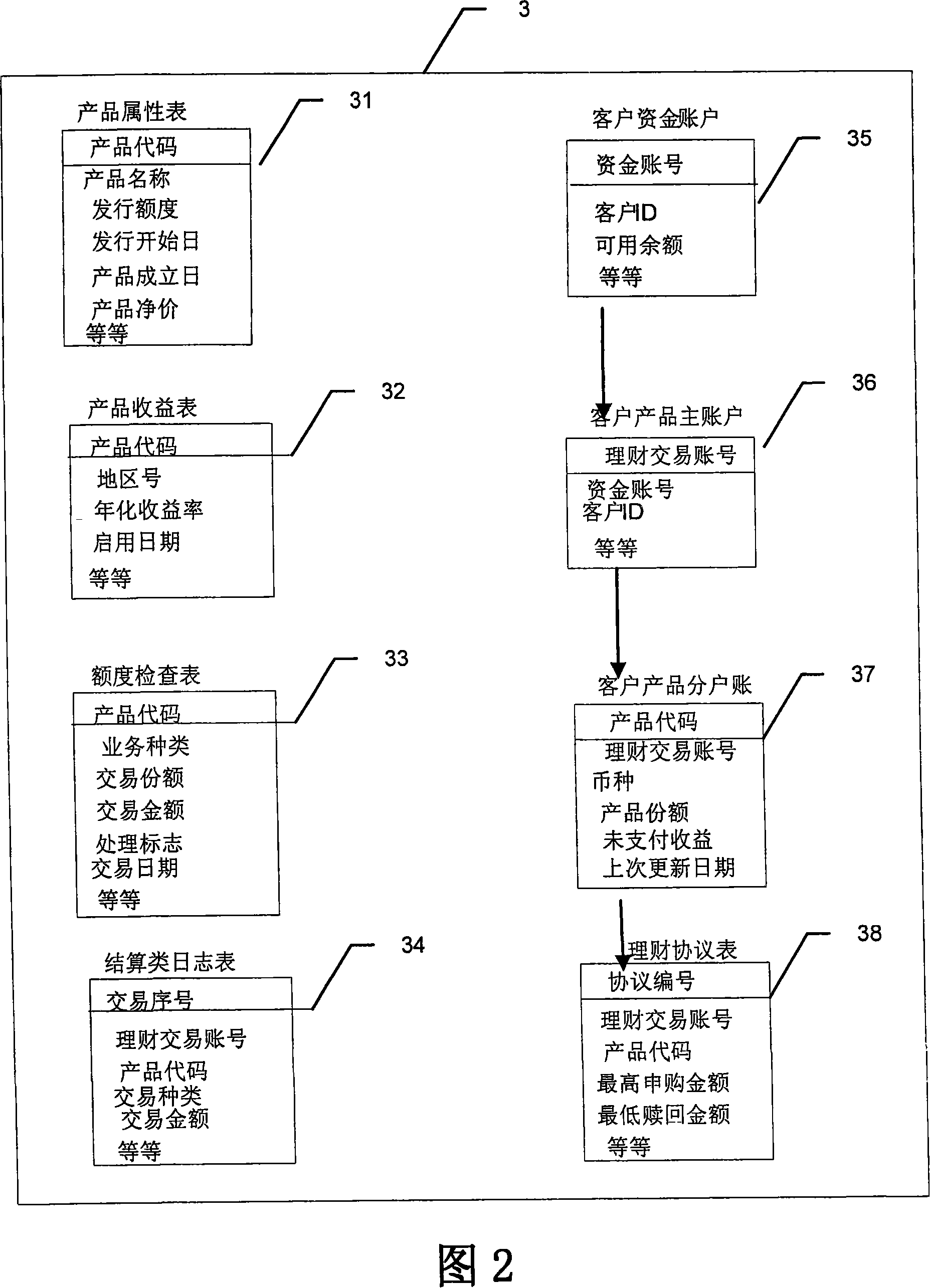
Method for constructing financial asset trading system based on alliance chain
InactiveCN107025602AProtect interestsReduce credit riskFinanceElectronic credentialsData miningComputer science
The invention discloses a method for constructing a financial asset trading system based on an alliance chain. With an alliance chain as a technical support, a novel financial asset digital unique certificate is provided based on the existing laws and regulations. The system uses a distributed technology architecture. All participants jointly maintain the ledger of financial asset trading. It is ensured that the trading of financial assets is open, transparent, real and credible. The credit risk of trading is reduced. The cross-platform and cross-region flow of financial assets is promoted. Tedious manual account checking work between platforms is omitted. In addition, the block chain technology is applied to the field of financial asset trading for the first time. A unified and standardized financial asset trading platform is established. Digital management of financial assets is realized. The credit risk of trading can be prevented effectively. The efficiency of trading and supervising is improved. The trading cost is reduced.
Owner:HANGZHOU YUNXIANG NETWORK TECH
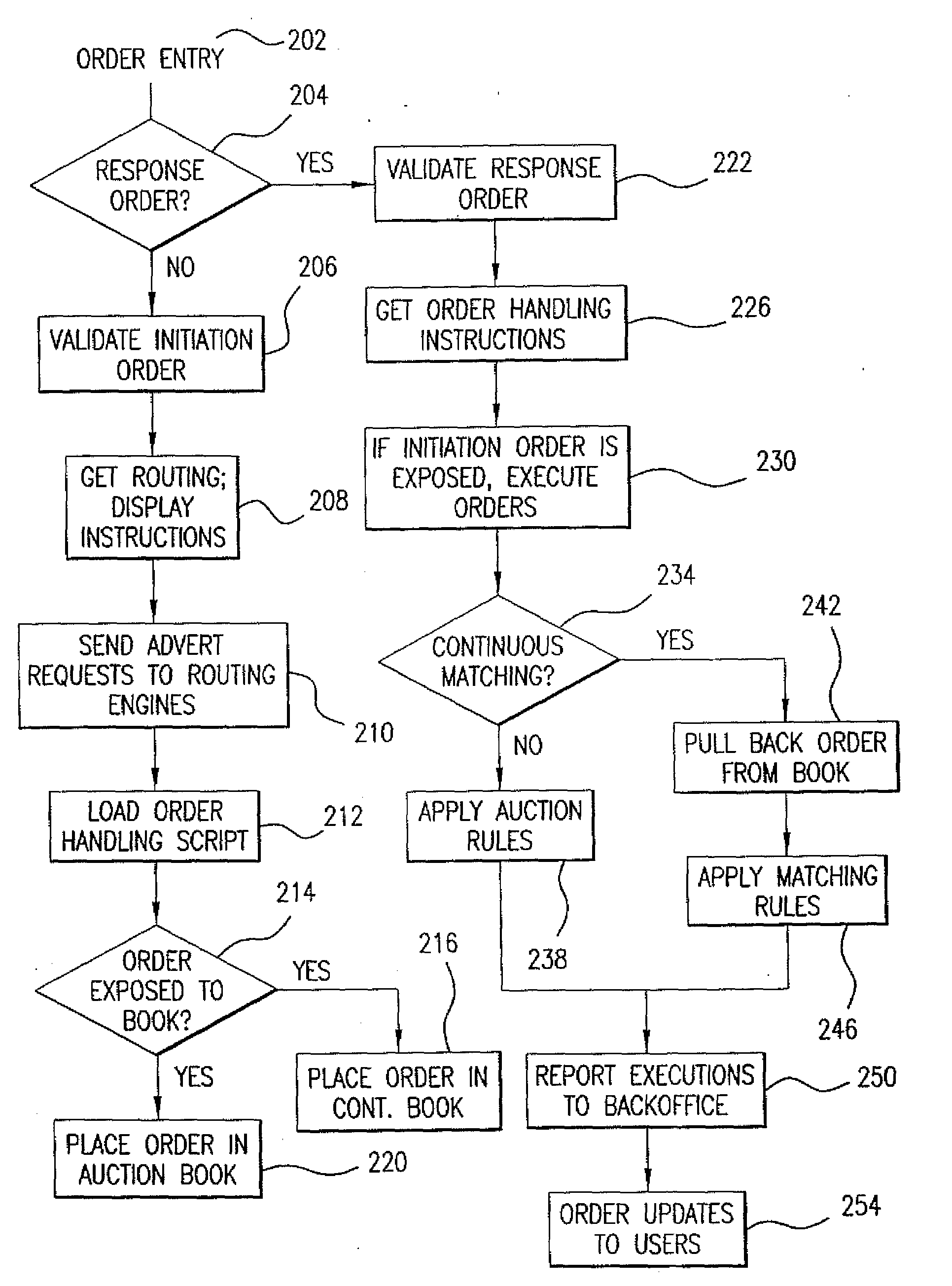
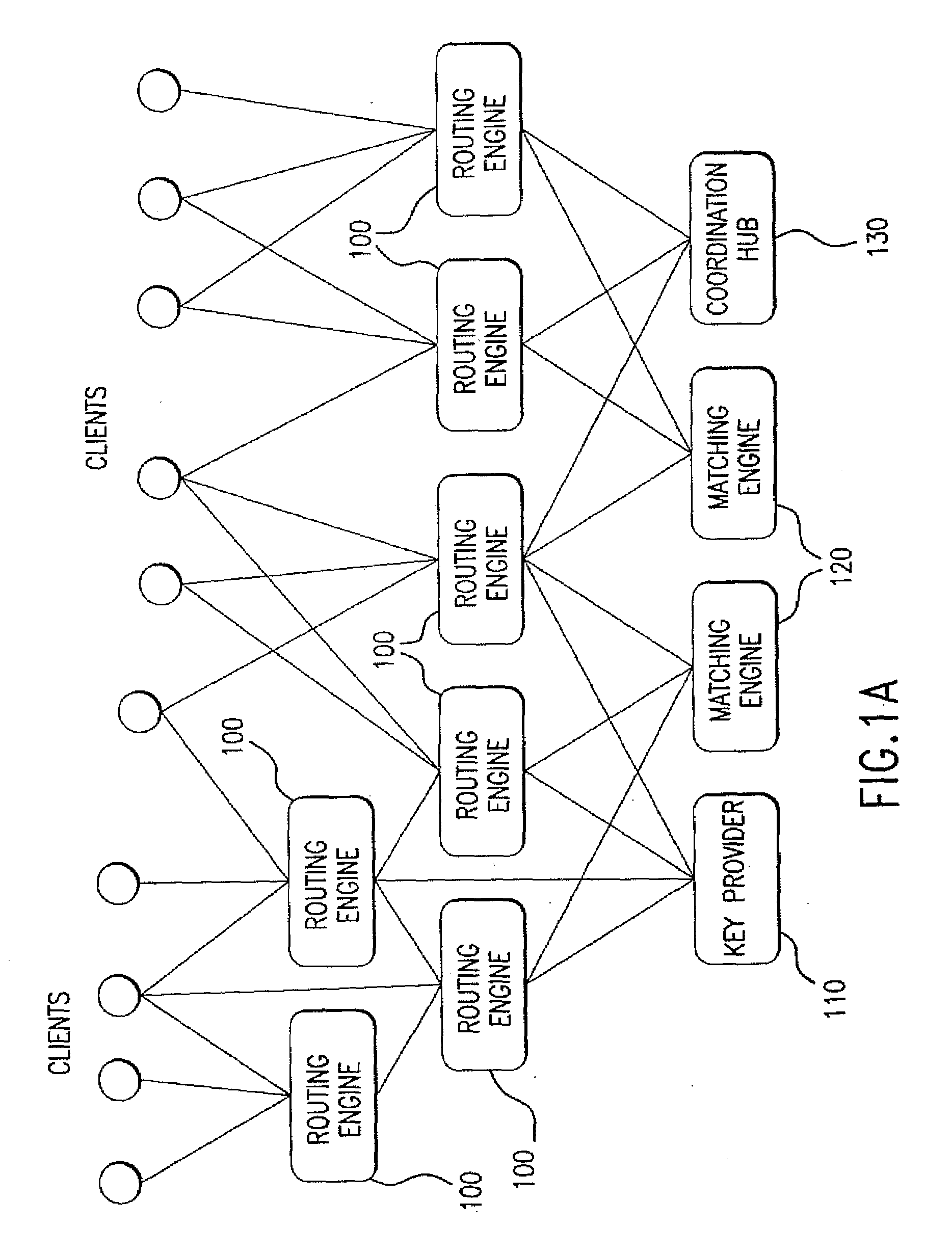
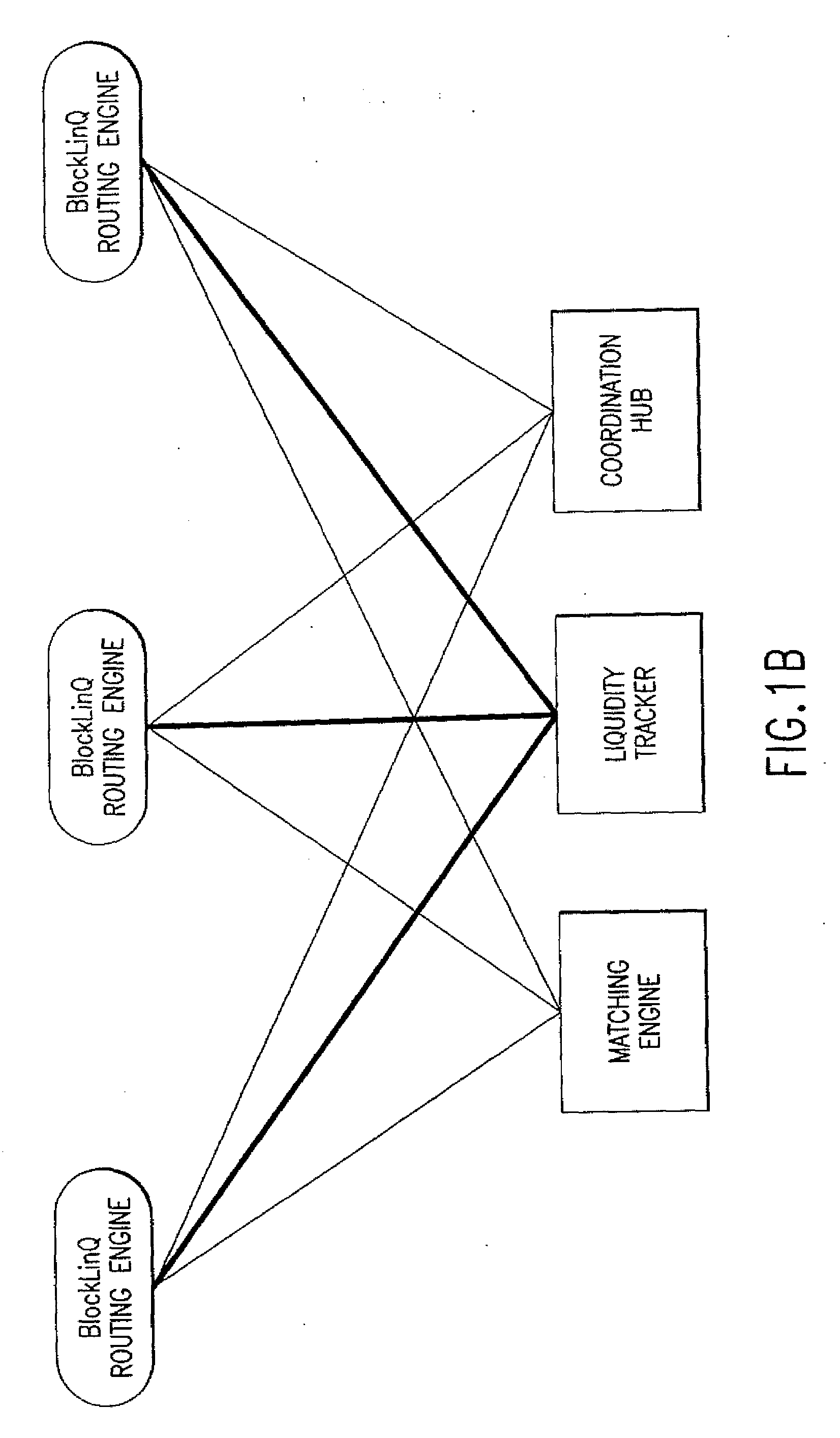
Method and system for managing distributed trading data
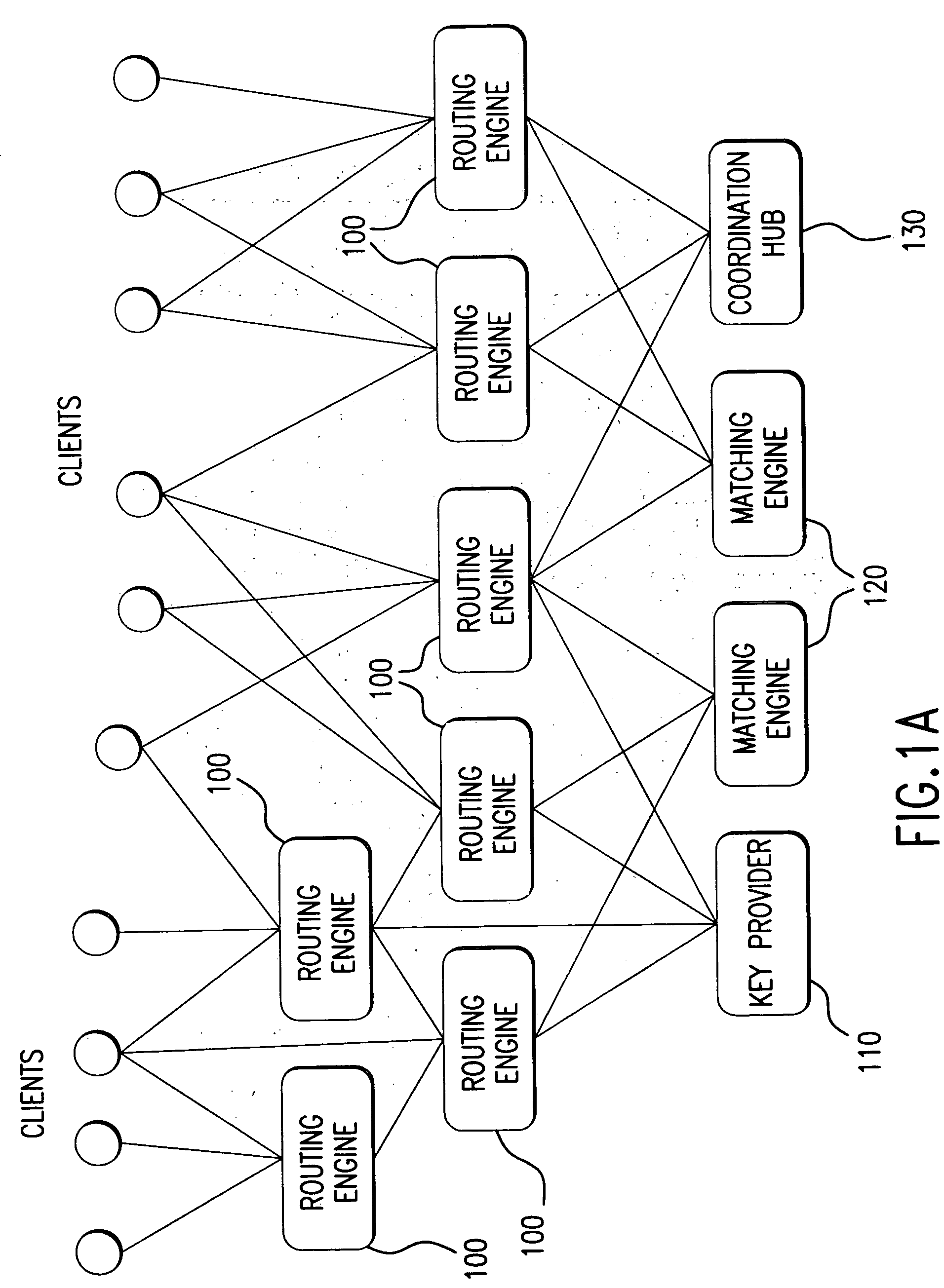
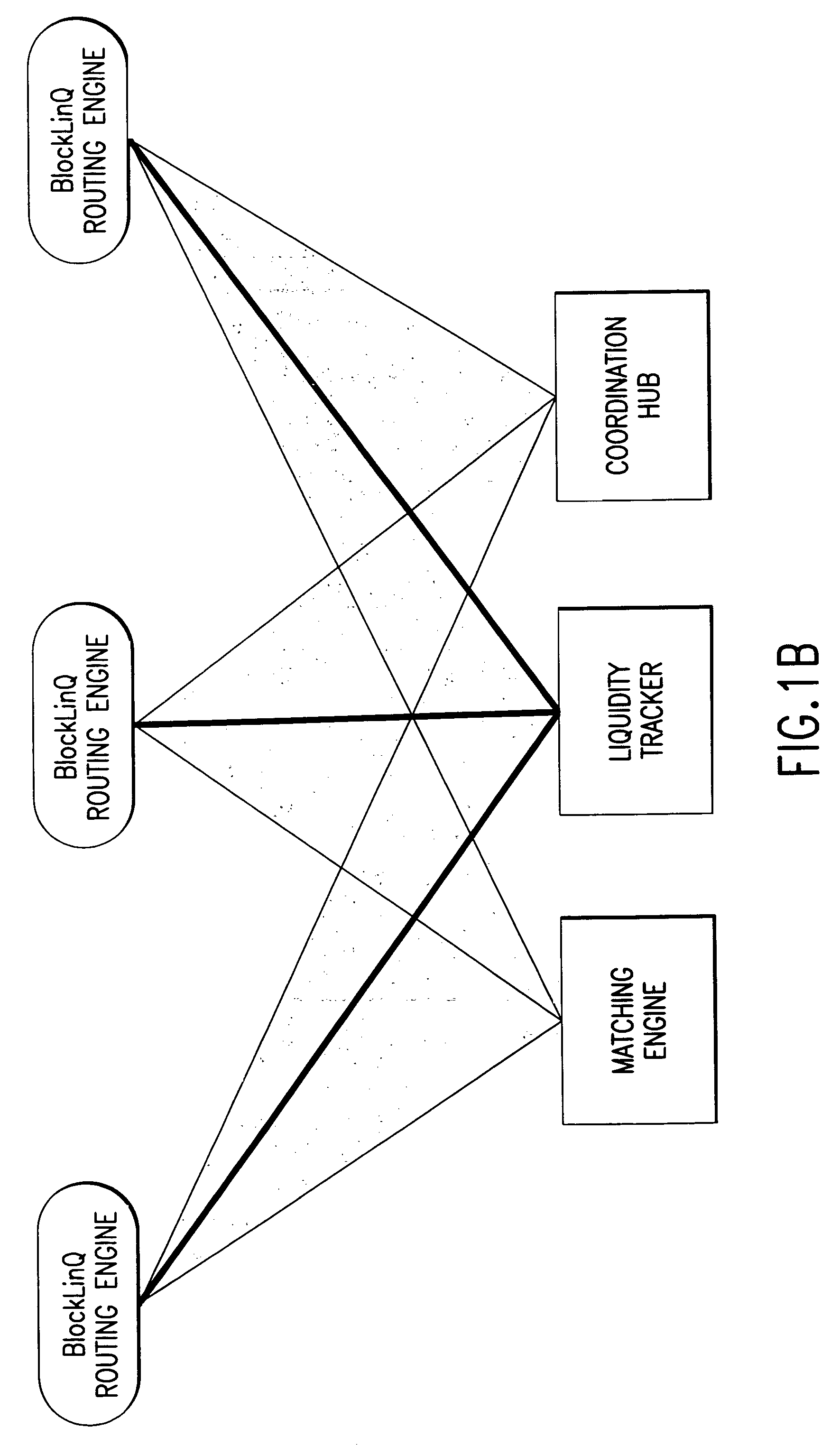
InactiveUS7565313B2Avoid misuseMaximizing internalization rateFinanceCommerceData providerTransaction data
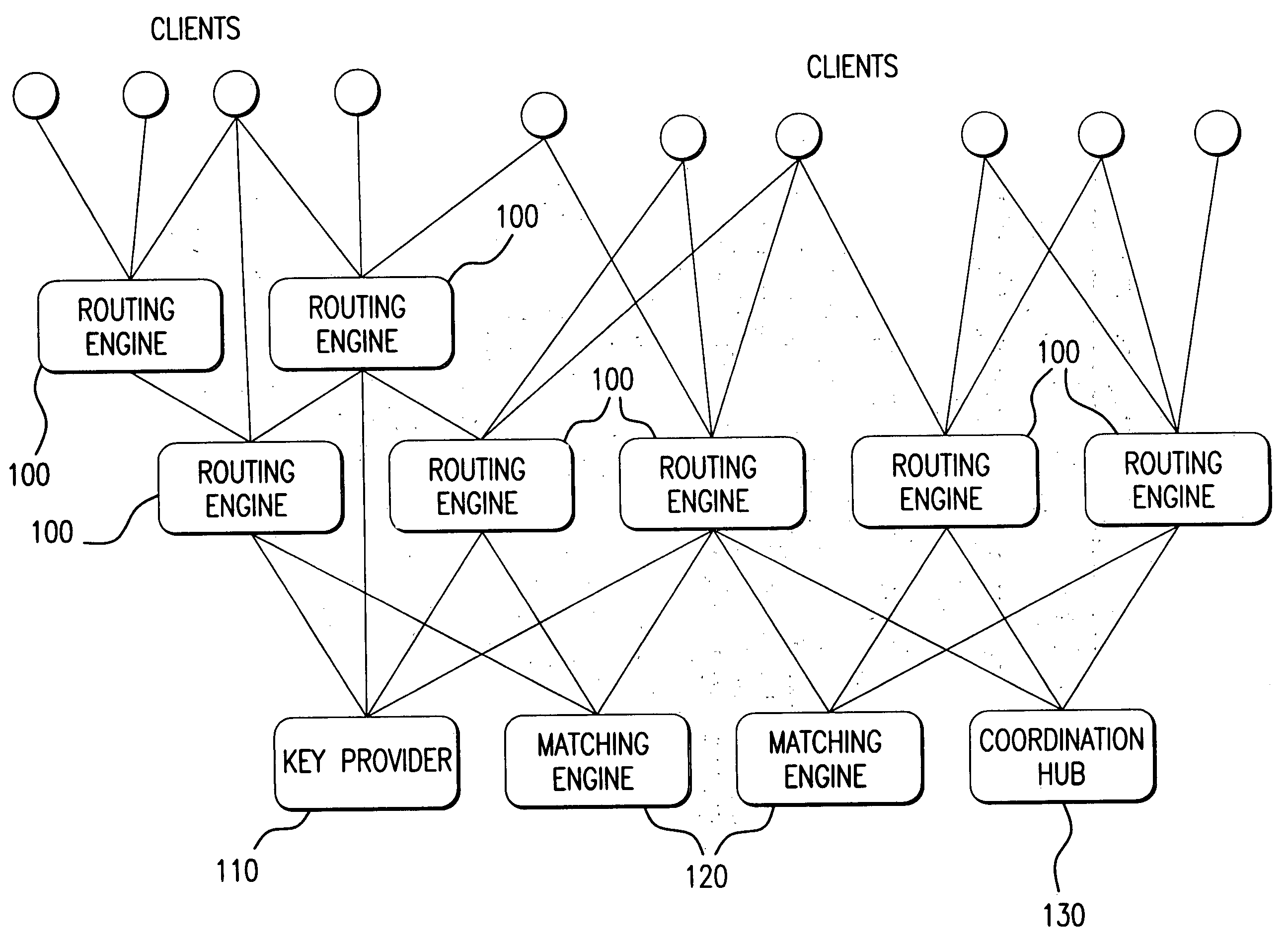
In a preferred embodiment, the invention comprises a computer-implemented system and method of managing market information across a network of data providers, comprising the steps of: (a) electronically receiving first data including confidential information regarding market participants in a first system that protects said first data behind a firewall; (b) electronically receiving second data including confidential information regarding market participants in a second system that protects said second data behind a firewall; (c) electronically receiving an order and targeting parameters from a first market participant; (d) electronically issuing an advertisement request message to said first system and said second system, said advertisement message comprising display attributes of said order and comprising said targeting parameters; (e) electronically prompting said first system and said second system via the advertisement request message to each send a coordination request message to a Coordination Hub, said coordination request message comprising information deduced from said confidential information regarding market participants in said first and second systems, wherein the selection of the information that is sent to the Coordination Hub is based at least in part on said first market participant's targeting parameters; (f) electronically prompting based on the coordination request message said Coordination Hub to issue permissions to advertise the order to selected market participants, wherein market participants are selected based, at least in part, on said received information regarding market participants; and (g) electronically prompting based on the permission to advertise the order said first system and said second system to route information about said order from first participant to said selected market participants.
Owner:ITG SOFTWARE SOLUTIONS INC
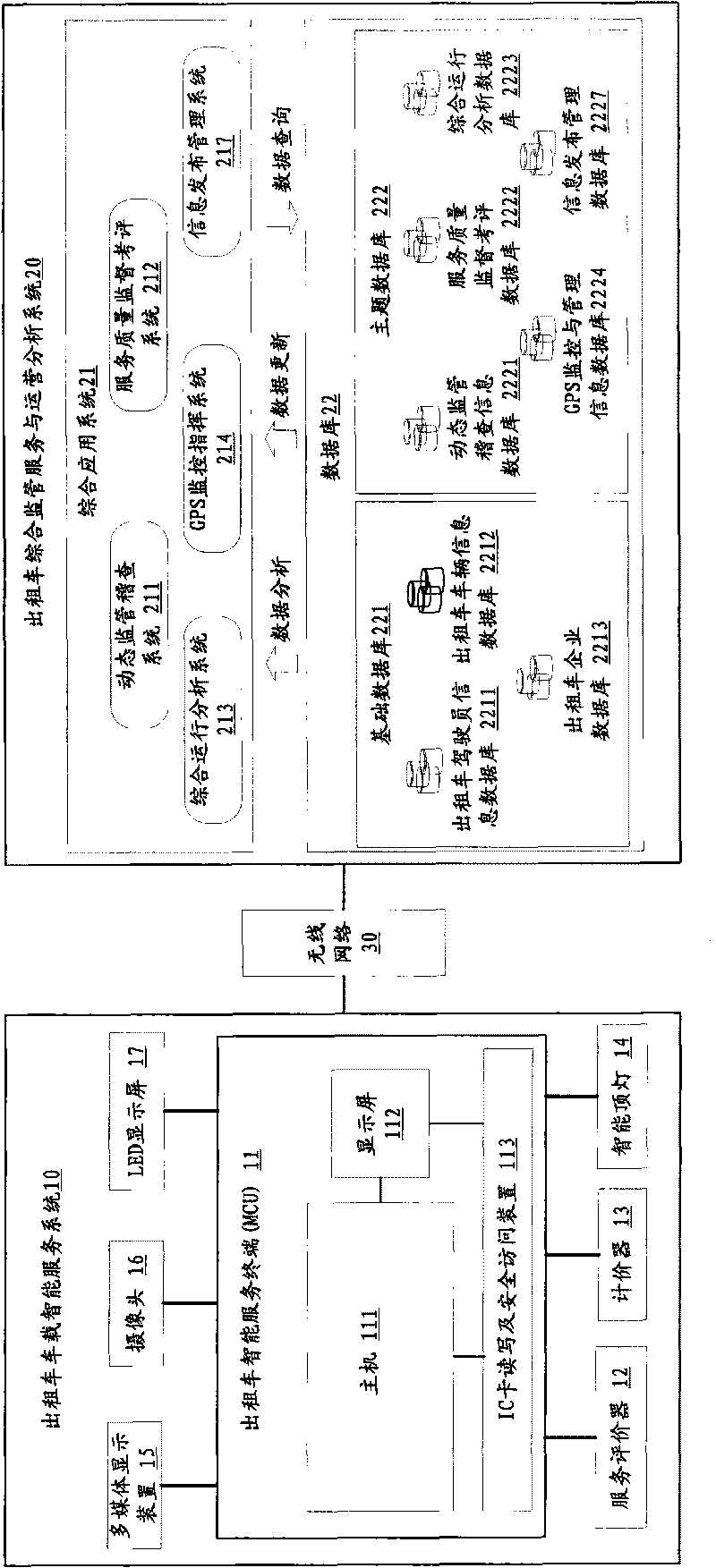
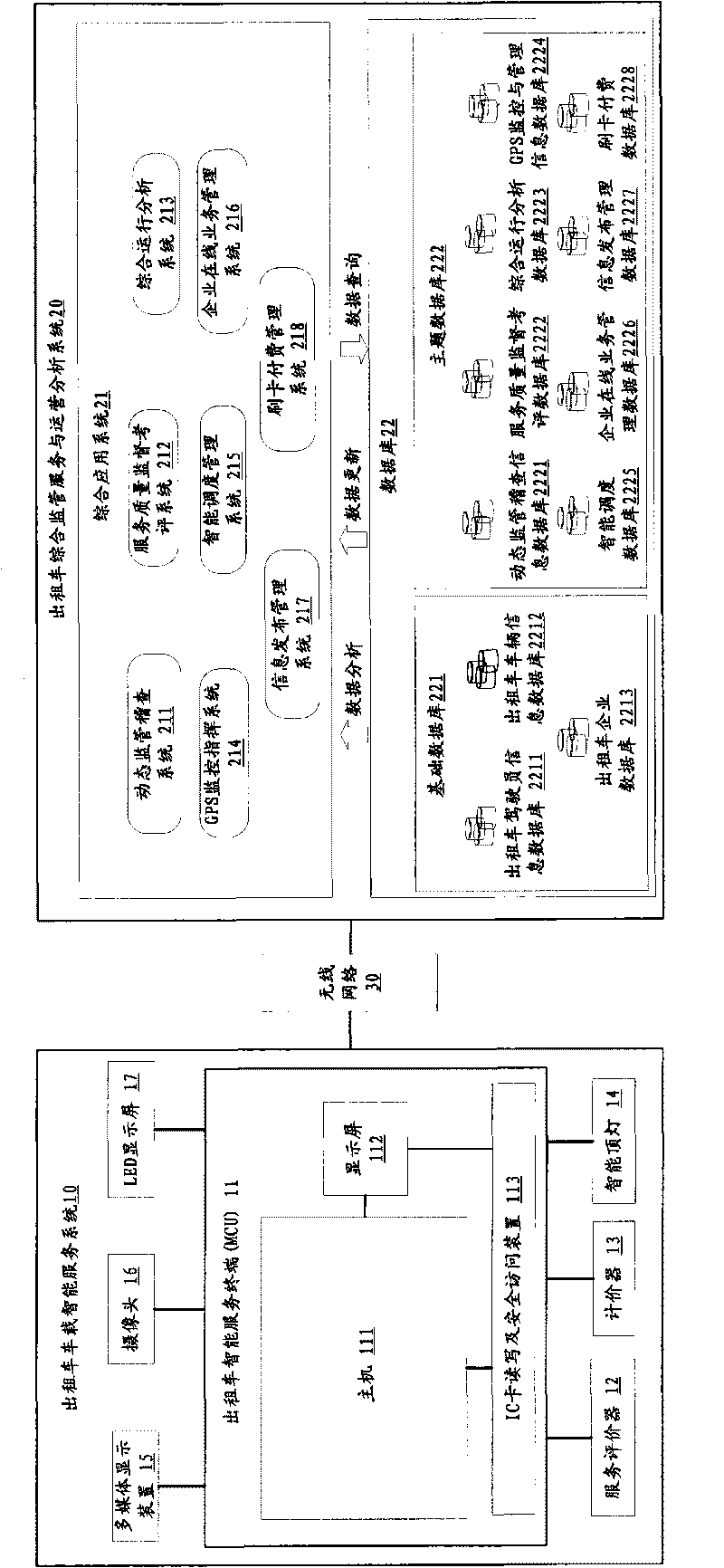
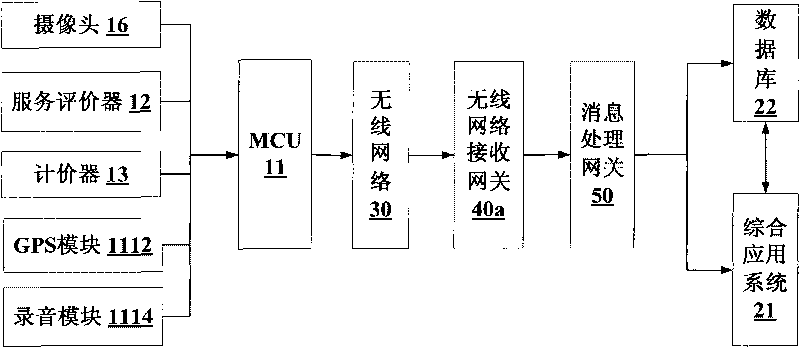
Taxi intelligent comprehensive supervision and service system
InactiveCN101739615AComprehensiveSolve the dilemma of unfounded complaintsResourcesDriver/operatorIn vehicle
The invention relates to a taxi intelligent comprehensive supervision and service system which comprises a taxi vehicle intelligent service system and a taxi comprehensive supervision service and operation analysis system. The taxi vehicle intelligent service system is connected with the taxi comprehensive supervision service and operation analysis system through a wireless network and sends on and off duty signing data of a driver, operation detail data, service evaluation data, passenger volume investigation and statistics data and alarm data to the taxi comprehensive supervision service and operation analysis system in real time; and the taxi comprehensive supervision service and operation analysis system receives and carries out mining analysis on the data and sends terminal control data, driver service quality star-level data, dynamic check data and public information data to the taxi vehicle intelligent service system, therefore, the invention can enhance the scientificity of industry management and decision and strengthen the supervision of a taxi industry, thereby enhancing the service level and the passenger satisfaction of the taxi industry.
Owner:交通部公路科学研究院
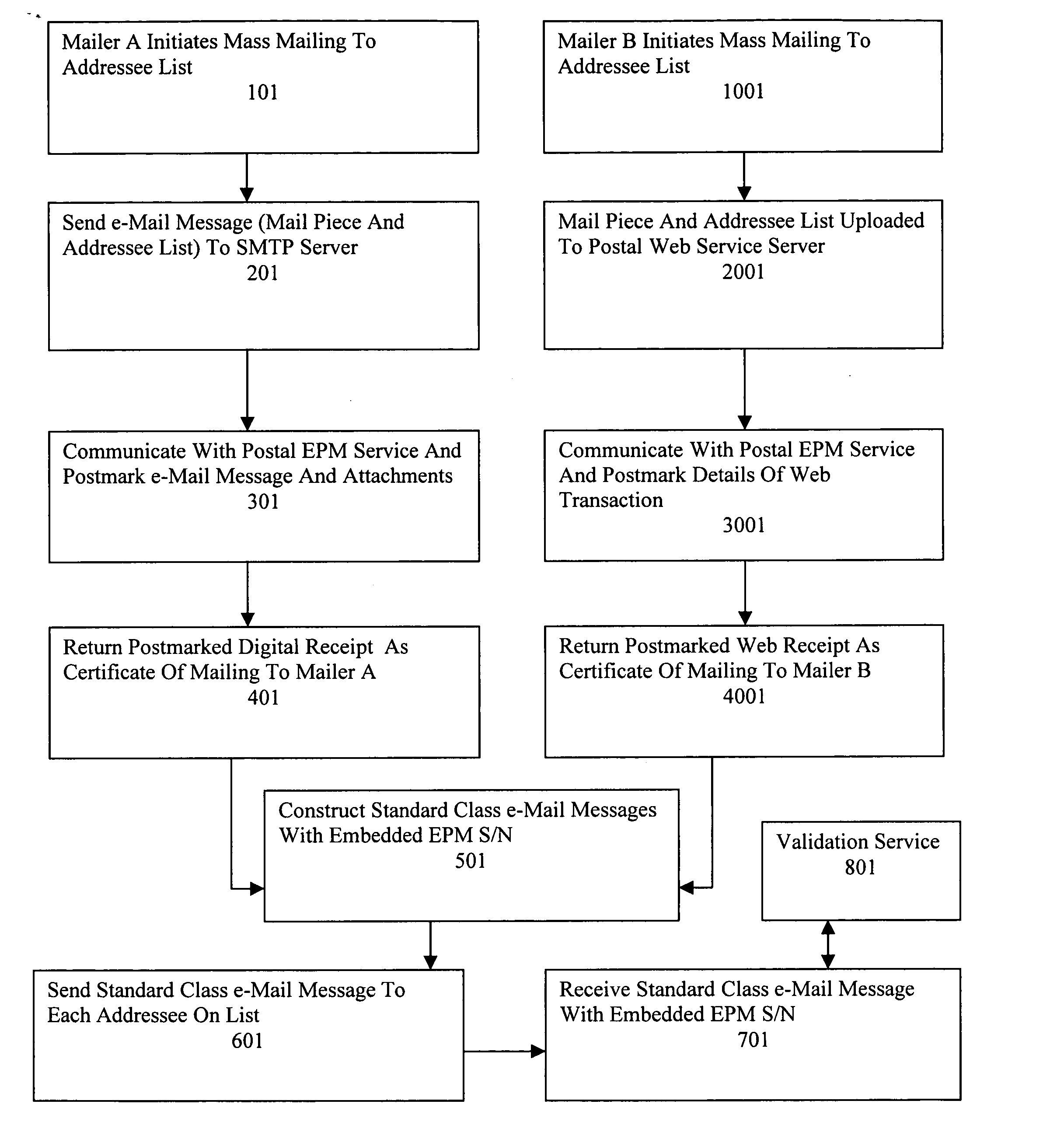
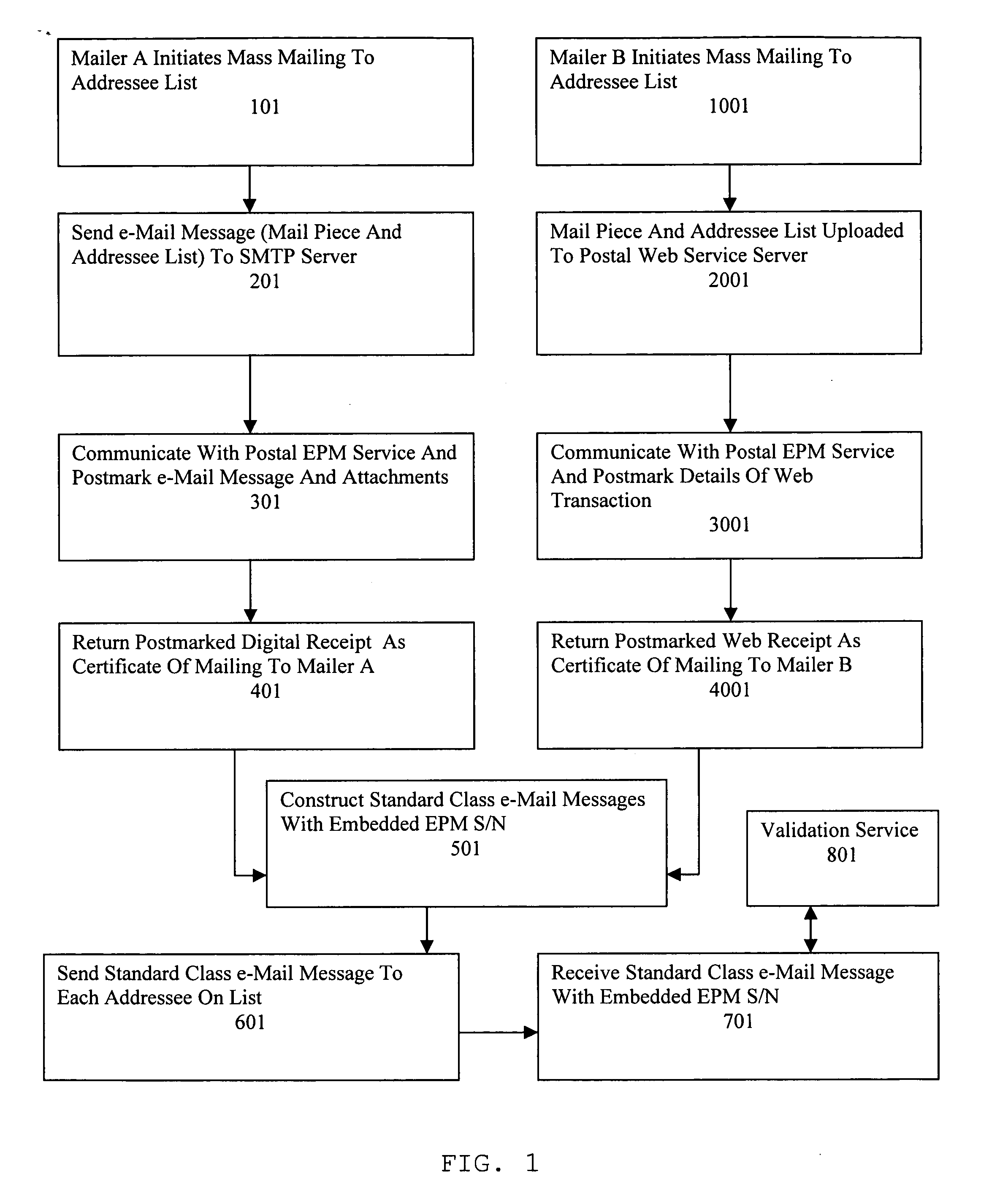
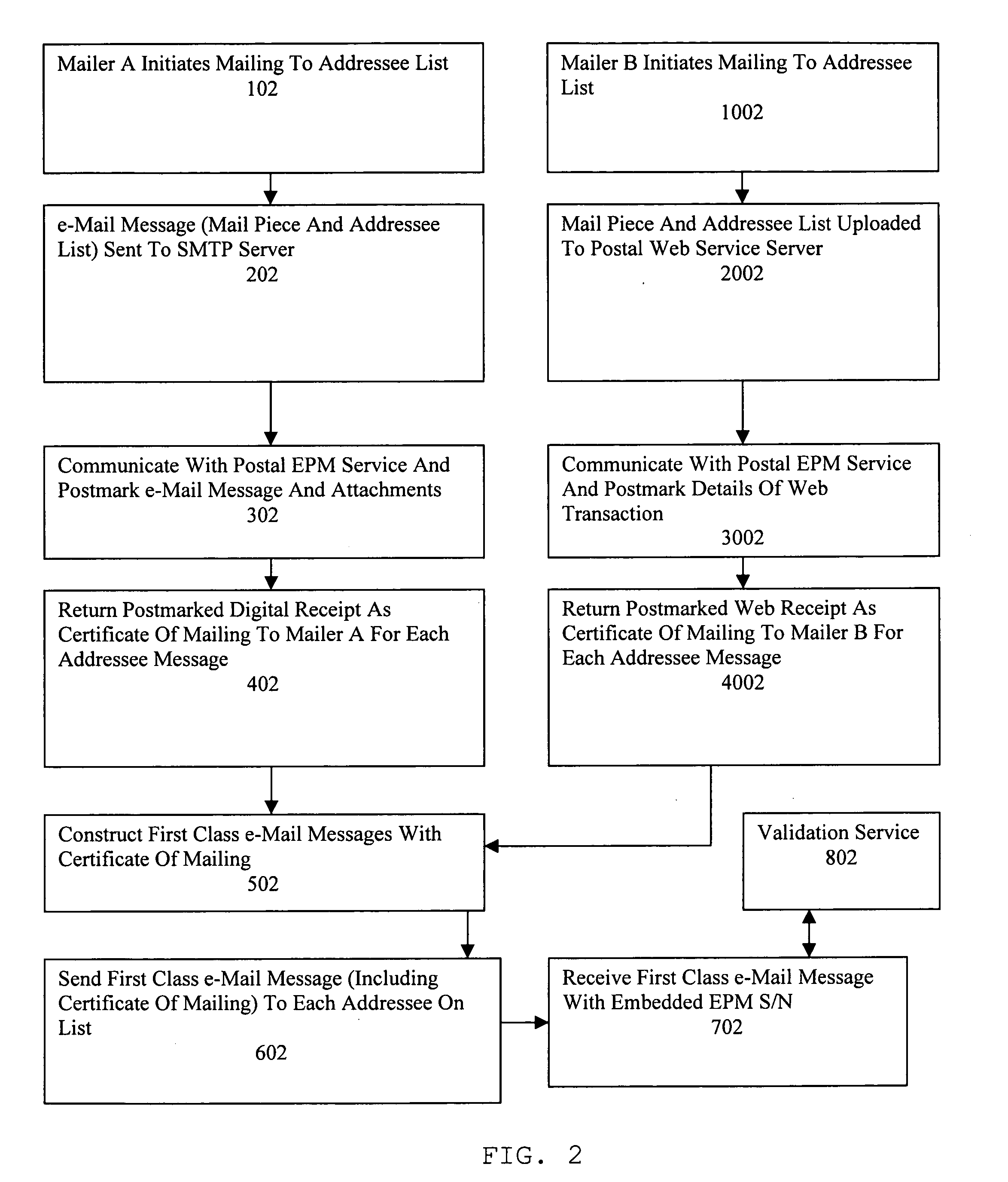
Method, apparatus and system for regulating electronic mail
ActiveUS20050193075A1Improve efficiencyImprove reliabilityMultiple digital computer combinationsTransmissionClass of serviceUnique identifier
A Postal Authority regulated e-Mail messaging application is provided over a public network to a plurality of mailers and addressees using authenticated transaction records. The application transmits at least one e-Mail message through at least one e-Mail account configured for a specific class of service. The application creates transaction records relevant to the specific class of service based upon details of completed transactions. Electronic postmarks are obtained to authenticate transaction records. Authenticated transaction records are sent to the mailer. A unique identifier of an electronic postmark is embedded in the e-Mail message. The e-Mail message incorporating the unique identifier is sent to at least one addressee. Authenticated e-Mail messages and transaction records are created and protected from undetectable modification.
Owner:INTELLECTUAL VENTURES I LLC
System and method for providing a futures/forward tradable market and bidded price negotiation for Internet advertising
ActiveUS20080154784A1More informed purchasing or sales decisionsProtect interestsAdvertisementsPayment architectureInteractive advertisingTargeted advertising
Owner:VEERARAGHAVAN PUTHUCODE S
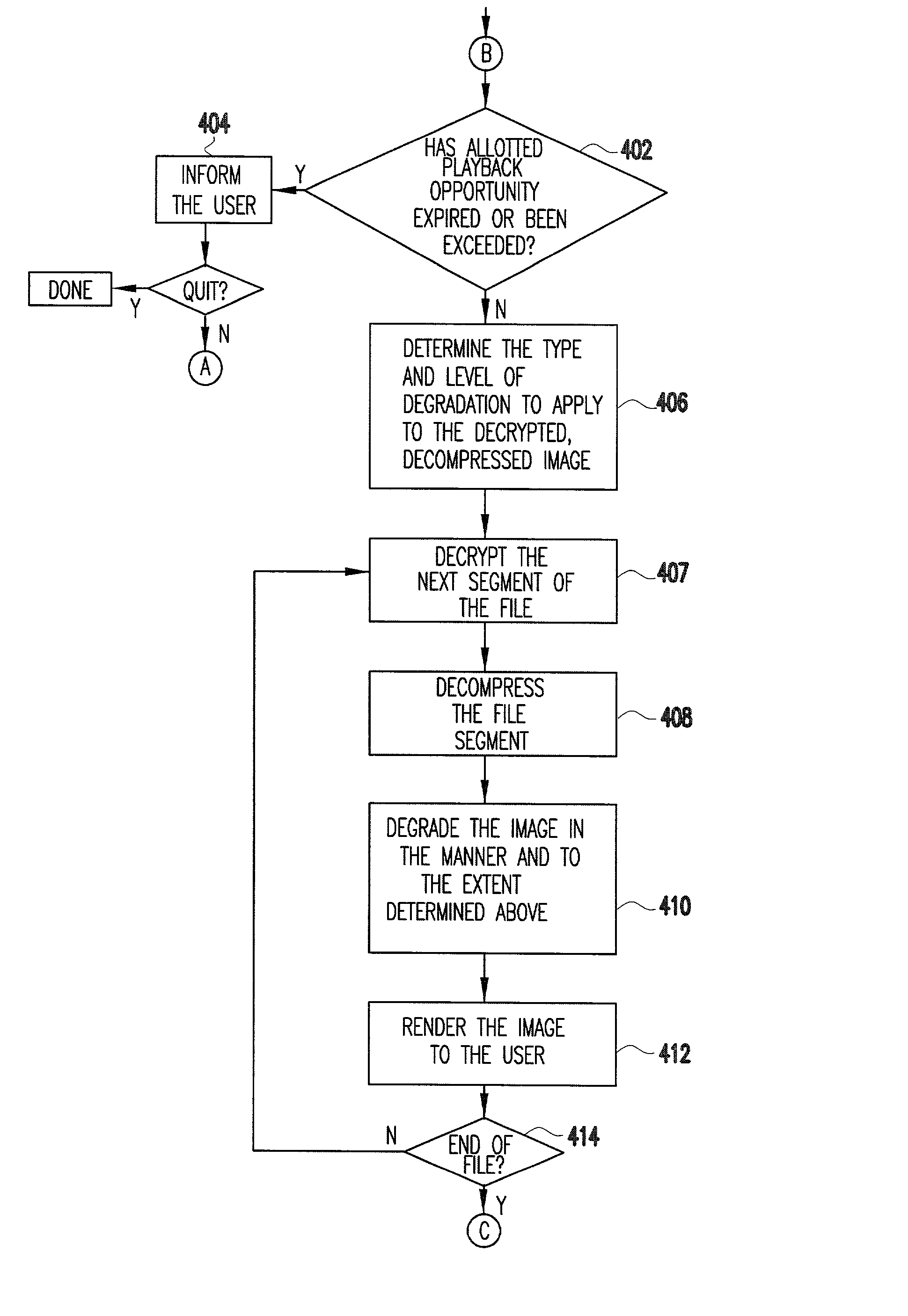
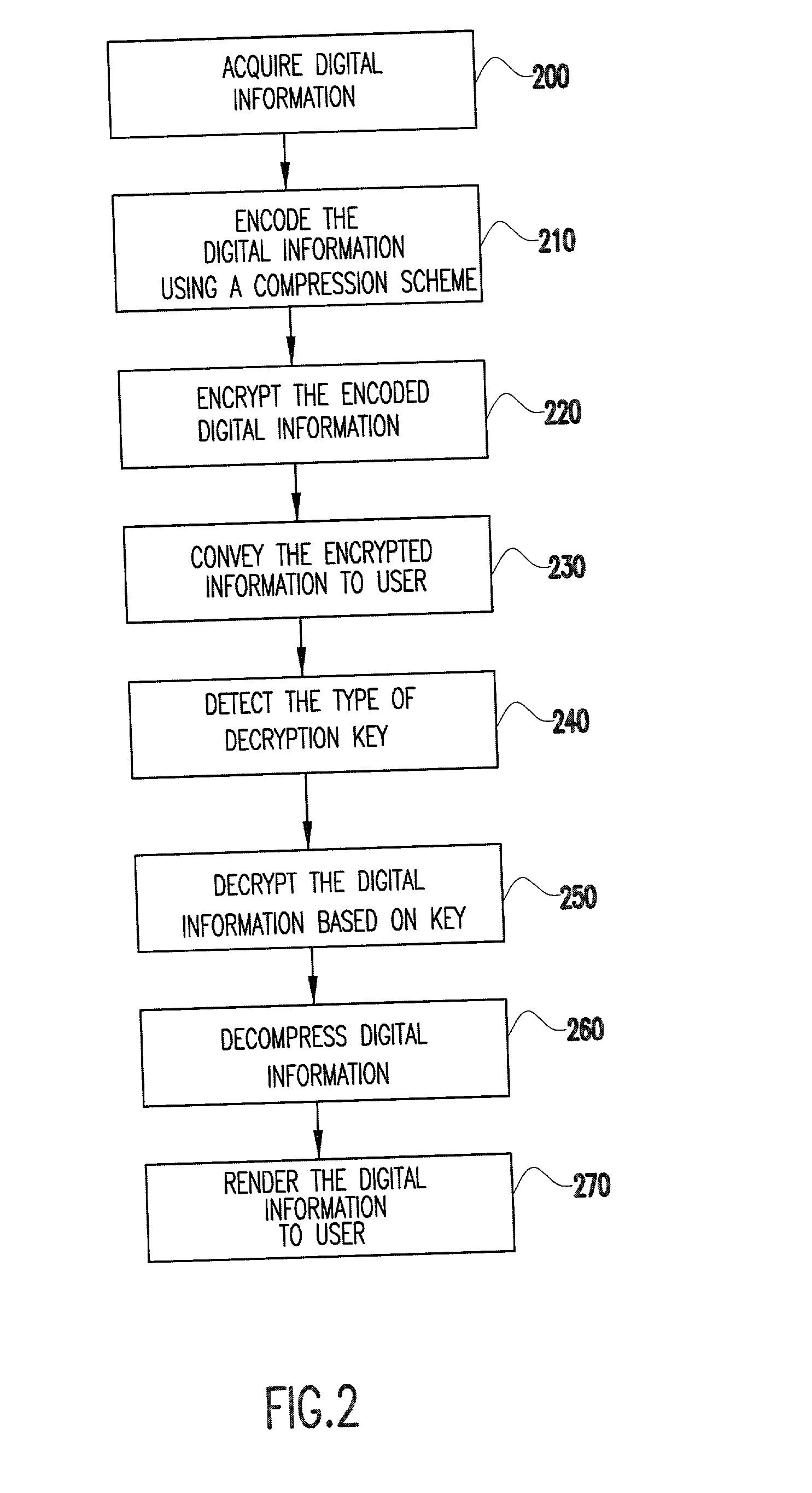
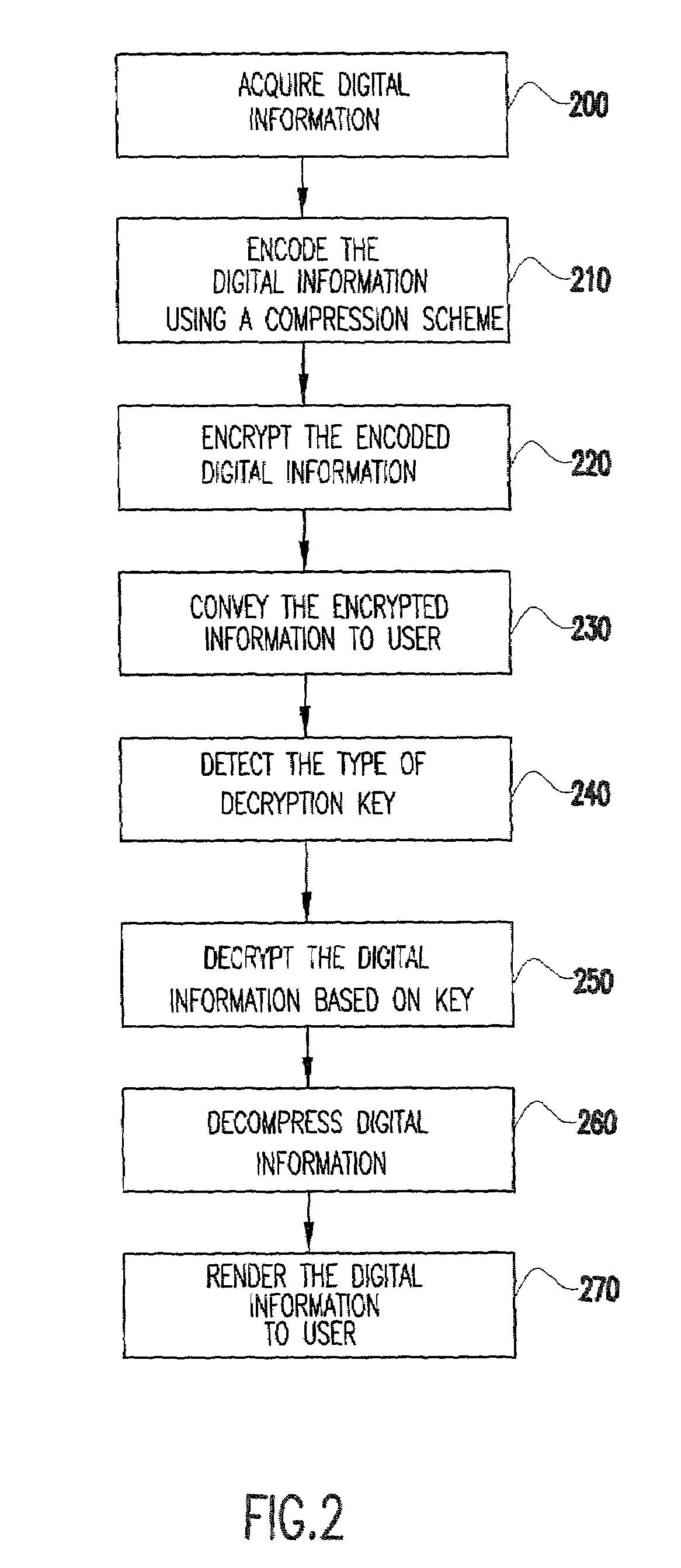
System and method for secure distribution and evalution of compressed digital information
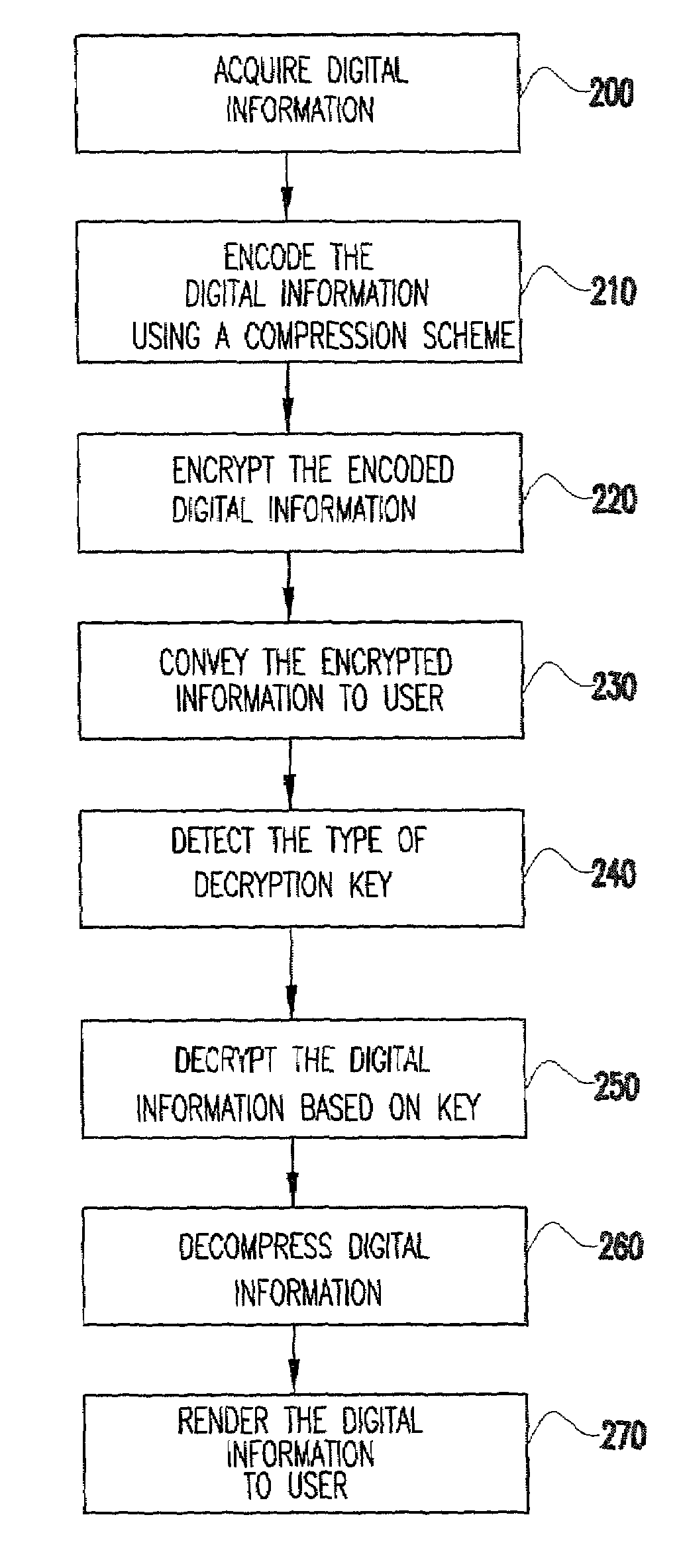
InactiveUS20030131251A1Reduce reproductionLimited accessKey distribution for secure communicationMultiple keys/algorithms usageTime conditionApplication software
A method for controlling access to digital information is performed based on a plurality of decryption keys sent by the information provider. A first type of decryption key instructs a user's host system to reproduce the digital information in accordance with a first level of reproduction quality degradation. Additional keys may specify other degradation levels. The quality of the digital information may be degraded by a fixed degree or a variable degree based on a function of a time condition and / or a use condition. Alternatively, only a portion of the information may be reproduced for a user or reproduction prevented. In order to obtain full and unrestricted access, the user must obtain a type of decryption key from the provider which removes all previous limitations on reproduction quality degradation. Preferably, the digital information is sent with a media player application program embedded with an initial decryption key. The program may include tamper-resistant features which provide a safeguard against hackers or other forms of unauthorized access. A business method uses a pricing structure which makes the decryption keys available for different prices.
Owner:IBM CORP
Real-time reminding method based on messages of different levels
The invention provides a real-time reminding method based on messages of different levels, and the method is applied to mobile equipment. According to the method, a mobile equipment system setting item or an instant messaging software setting item is configured with the levels of the messages to be received, the ranges of the different levels and the reminding modes of the levels; when the message of a high level is received and a mobile phone user does not give a response in time, the user is more efficiently reminded in time in the configured reminding mode of the corresponding level; if it is determined that a receiver cannot receive the message or cannot give a response in time, the receiver is reminded in a text message mode. The messages are processed according to the levels, the receiver is reminded of emergency messages of high levels in time in the modes like increasing volume, prolonging sound playing time and vibrating for a long time, then the receiver can receive the messages and give a response as soon as possible, efficiency is improved, risks are reduced, user experience is improved, and user benefits are guaranteed.
Owner:BEIJING SENSESHIELD TECH
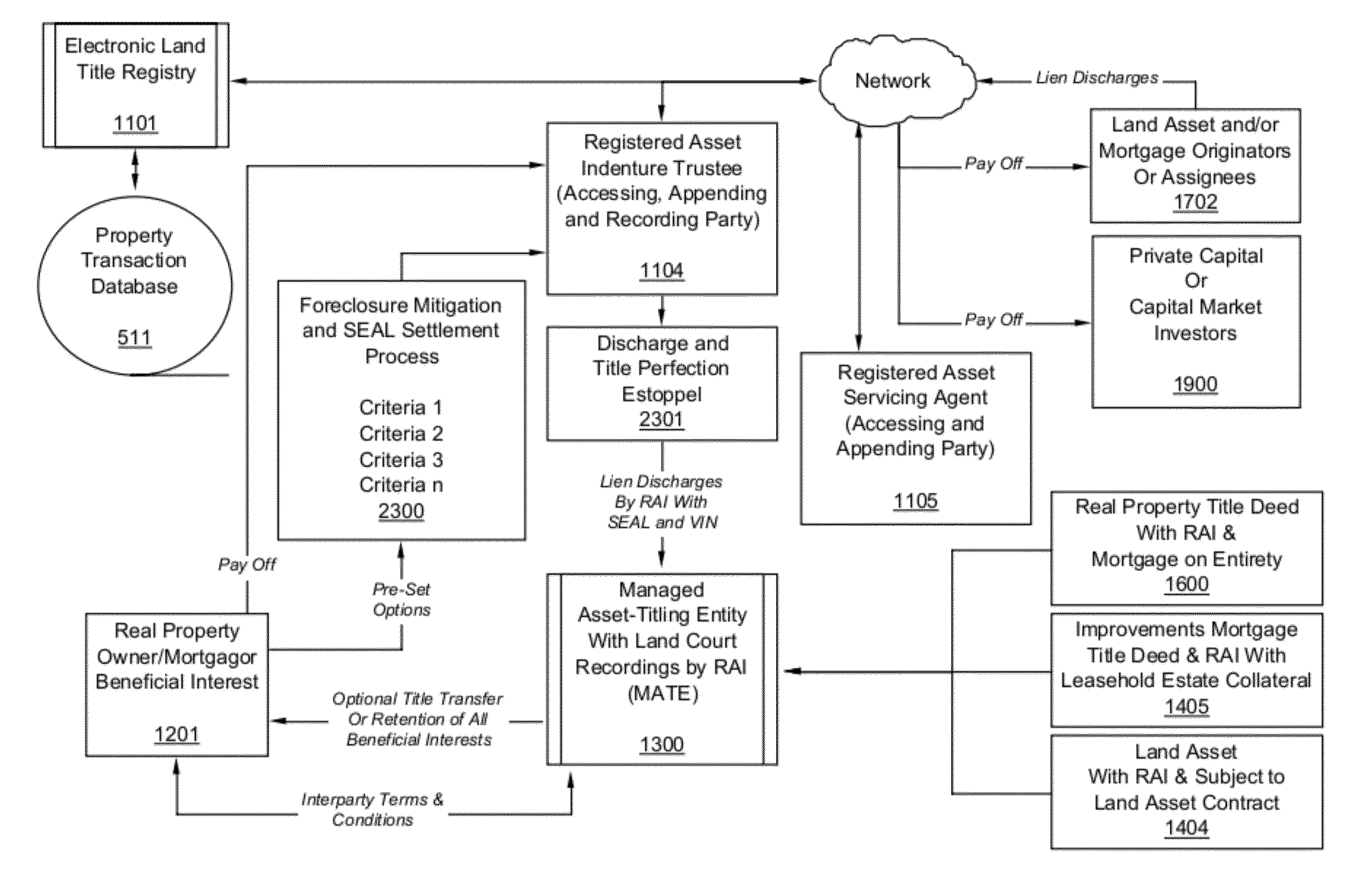
System and method for managing electronic real estate registry information
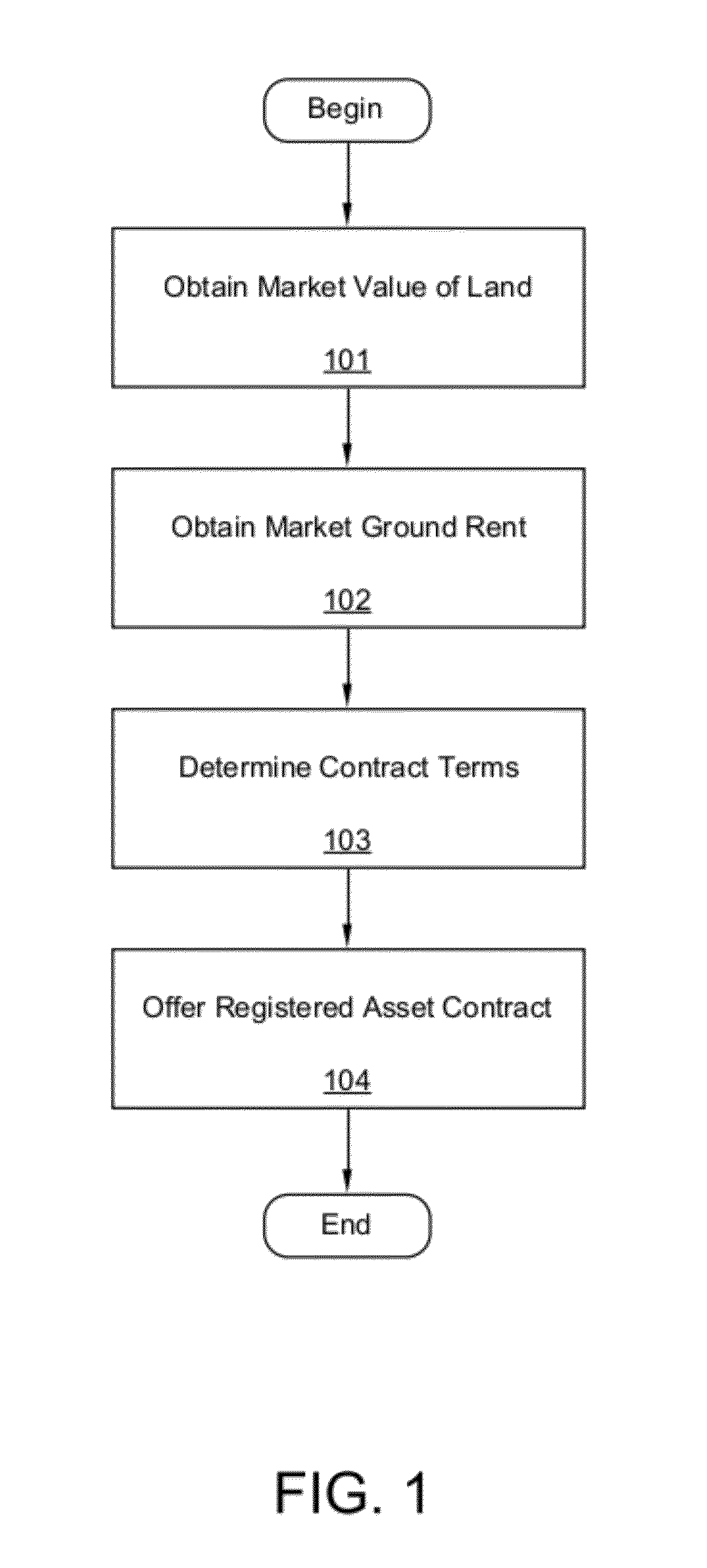
ActiveUS20120254045A1Improve efficiencyReduce the amount requiredFinanceBuying/selling/leasing transactionsRegistration systemRating system
Electronic real estate registration systems include property transaction and location characteristic databases communicating via computer networks providing information related to transactions associated with registered real property interests linked to publicly recorded documentation that protect legal interests of parties and counterparties engaged in the public exchange of real property rights. Real property rights can be held or owned by a managed asset-titling entity thus share a registered asset identifier providing locational coordinates identifying real property interest assignments and transactional documentation in association with asset underwriting, asset performance, and asset class rating systems. Electronic real estate registry database devices capture, process, store, retrieve, transmit, and report useful and timely information concerning registered property interests, responding in a manner typically associated with exchange traded securities, providing borrowers, creditors, investors and governing regulators ready access to fair and clear valuation, underwriting and transactional records delineated by time, apportionments, and pricing of real property interests.
Owner:ORFANO MICHAEL DELL
System and method for secure distribution and evaluation of compressed digital information
InactiveUS7088823B2Effectively and securely controlsImprove convenienceKey distribution for secure communicationMultiple keys/algorithms usageTime conditionReproduction
Owner:INT BUSINESS MASCH CORP
Method for managing distributed trading data
InactiveUS20090281954A1Protect interestsAvoid misuseFinancePayment architectureData providerTransaction data
In a preferred embodiment, the invention comprises a computer-implemented system and method of managing market information across a network of data providers, comprising the steps of: (a) electronically receiving first data including confidential information regarding market participants in a first system that protects said first data behind a firewall; (b) electronically receiving second data including confidential information regarding market participants in a second system that protects said second data behind a firewall; (c) electronically receiving an order and targeting parameters from a first market participant; (d) electronically issuing an advertisement request message to said first system and said second system, said advertisement message comprising display attributes of said order and comprising said targeting parameters; (e) electronically prompting said first system and said second system via the advertisement request message to each send a coordination request message to a Coordination Hub, said coordination request message comprising information deduced from said confidential information regarding market participants in said first and second systems, wherein the selection of the information that is sent to the Coordination Hub is based at least in part on said first market participant's targeting parameters; (f) electronically prompting based on the coordination request message said Coordination Hub to issue permissions to advertise the order to selected market participants, wherein market participants are selected based, at least in part, on said received information regarding market participants; and (g) electronically prompting based on the permission to advertise the order said first system and said second system to route information about said order from first participant to said selected market participants.
Owner:E XCHANGE ADVANTAGE
Method for controlling distribution network closed loop
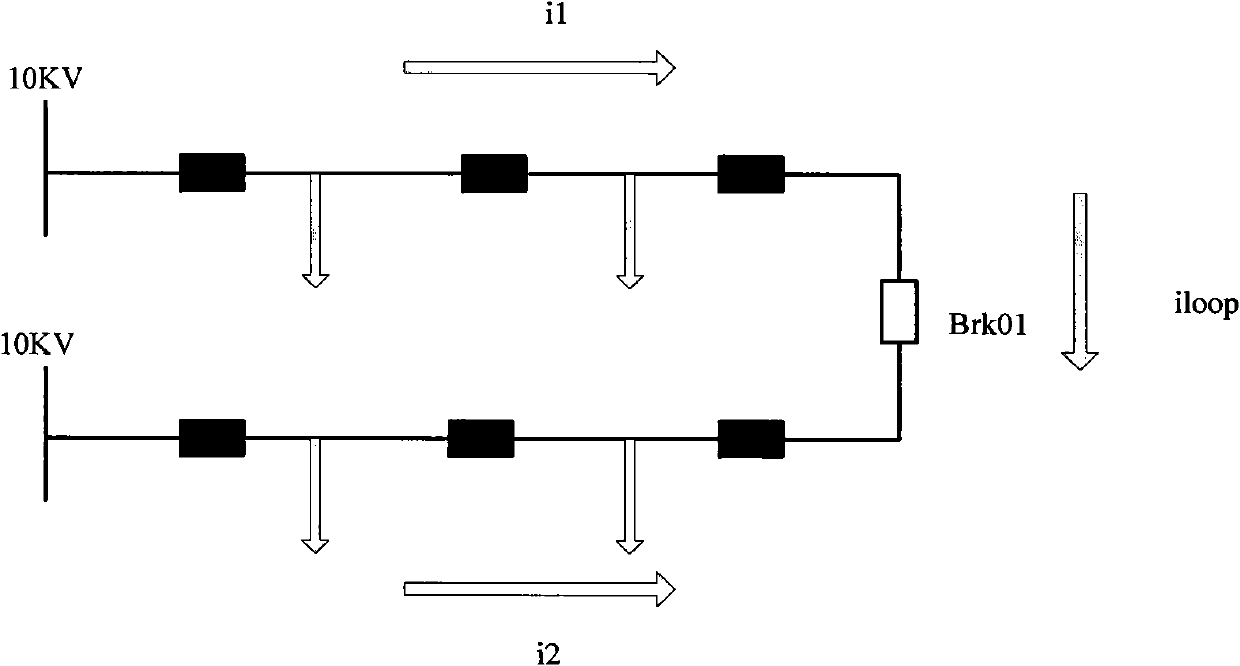
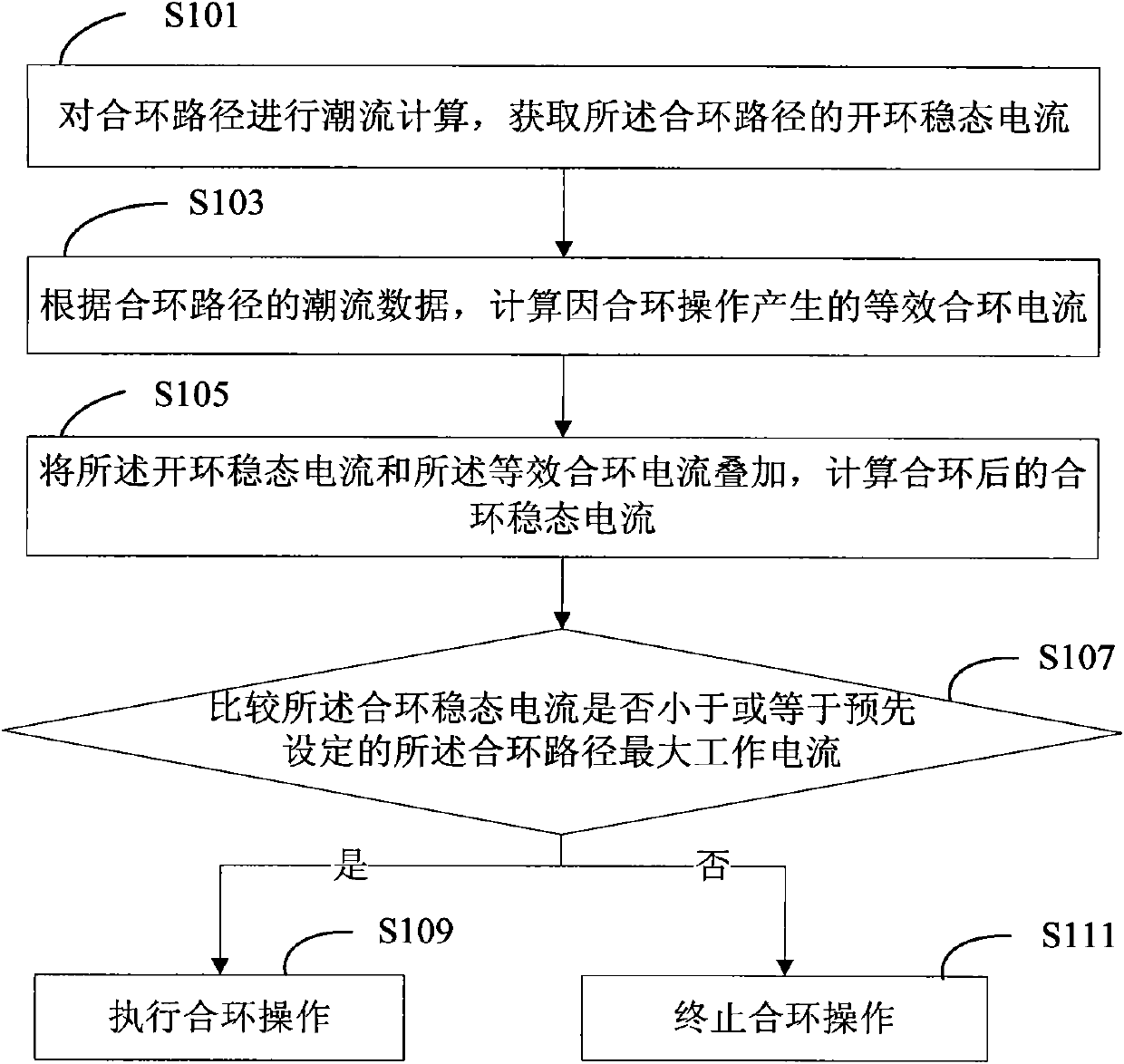
ActiveCN101908763AImprove reliabilityProtect the interests of usersAc networks with different sources same frequencyTidal currentClosed loop
The invention provides a method for controlling a distribution network closed loop. The method comprises the following steps of: performing load flow calculation on a closed loop path to acquire open loop steady-state current of the closed loop path; calculating equivalent closed loop current generated by closed loop operation according to flow data of the closed loop path; superimposing the open loop steady-state current and the equivalent closed loop current, and calculating closed loop steady-state current after closing a loop; comparing the closed loop steady-state current with the preset maximum operating current of the closed loop path; and if the closed loop steady-state current is less than or equal to the maximum operating current, performing the closed loop operation, and if the closed loop steady-state current is more than the maximum operating current, ending off the closed loop operation. The method for controlling the distribution network closed loop can realize safer distribution network closed loop operation, and is helpful for a distribution network dispatcher to perform safe adjustment on a regional electric power network.
Owner:ZHONGSHAN POWER SUPPLY BUREAU OF GUANGDONG POWER GRID
A system and method for real time ultra-short term financing
The invention provides a system and a method for a real-time ultrashort-term financing system so as to settle problems on poor liquidity of client capital in the prior art caused by no real-time communication between a bank fund distribution server and a fund transaction server of a fund corporation. A client sends a service request via a service handling terminal; a service processing device receives the service request in bank network; the service processing device inquires the data bases of a data storing device positioned at the same bank network, calculates in real time the service data related to the client and the bank, and processes the service request of the client. The invention has the advantages that the purchase and the redemption request of cliental financing products from the client can be responded in real time; the product sale condition can be monitored in real time via the system so as to prevent liquidity risk of product operation; and subsequent redemption operation can be stopped in time when a big amount of redemption occurrence so as to prevent the damage to benefits of the client and the bank.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
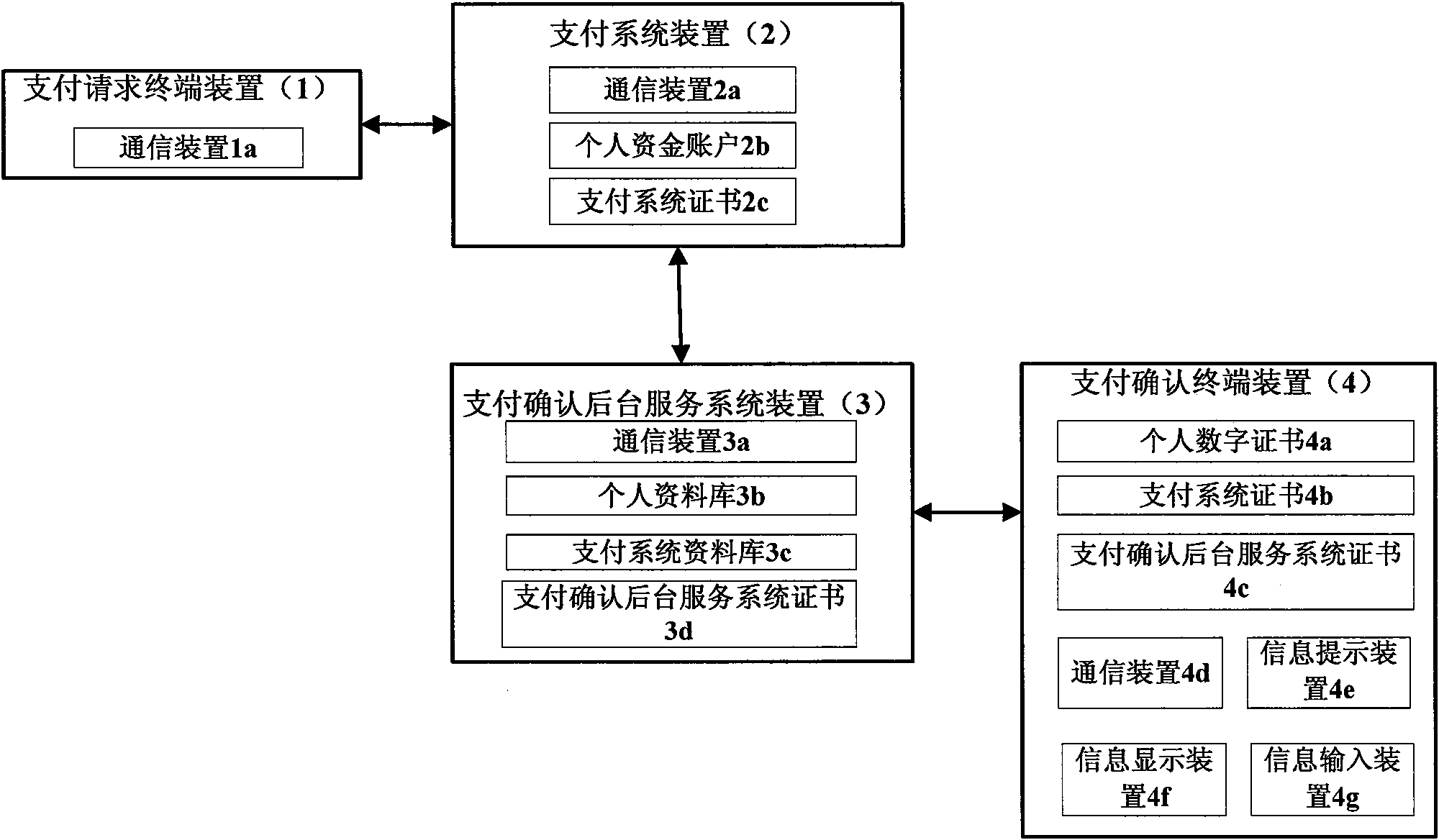
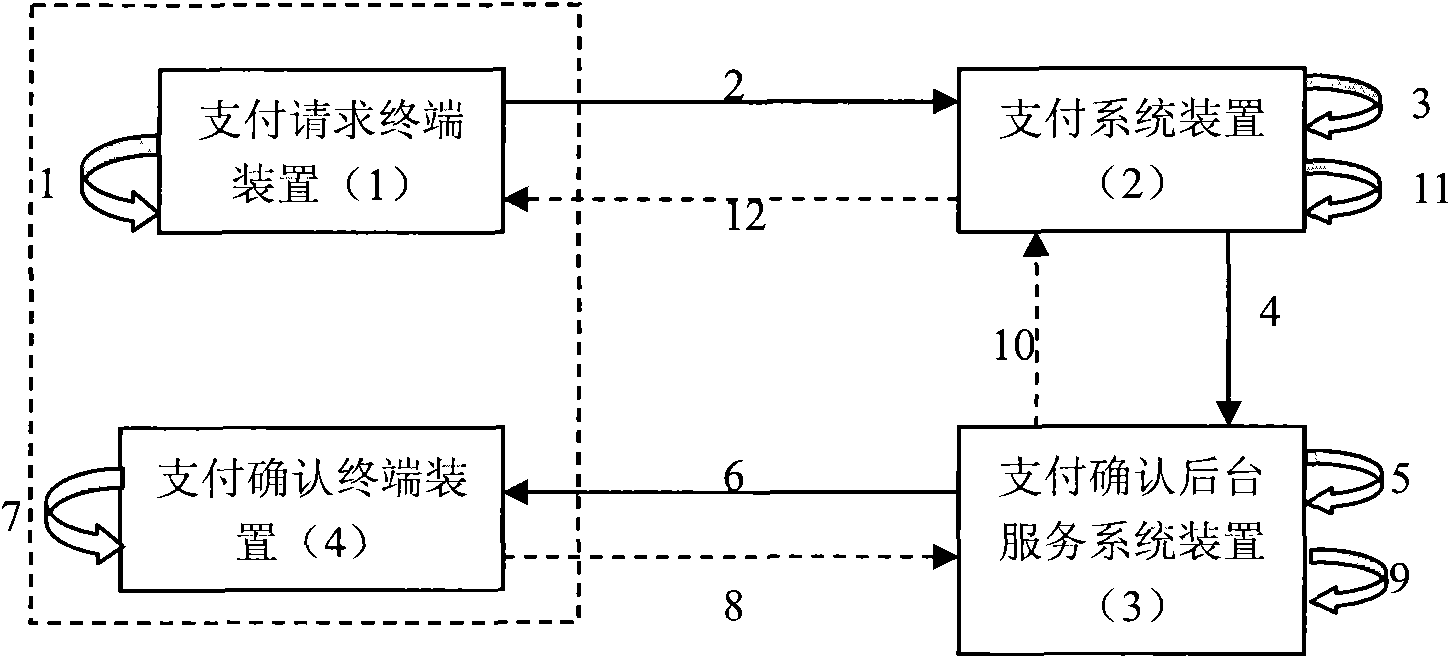
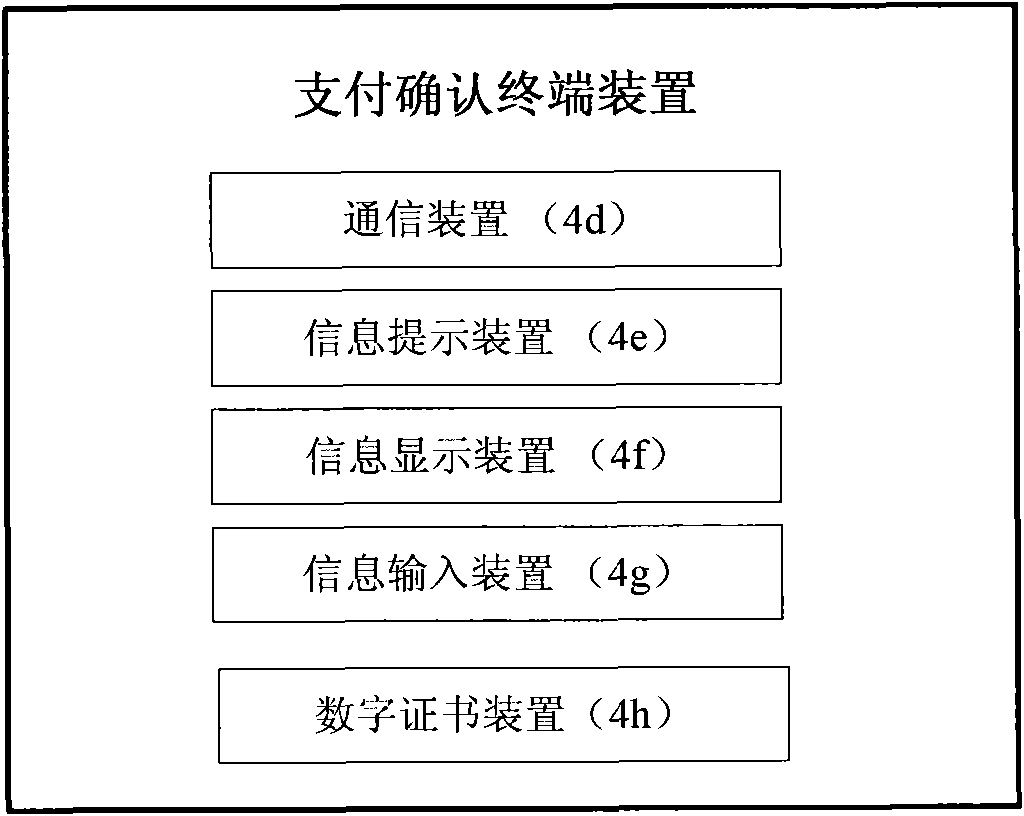
Method and device for realizing secure payment based on payment confirmation terminal and digital certification
InactiveCN101814169AProtect interestsUser identity/authority verificationPayment architectureDigital signaturePayment transaction
The invention provides a method and device for realizing secure payment based on a payment confirmation terminal and digital certification technology. The method is characterized in that in the electronic payment transaction, when the subscriber starts electronic payment at the electronic terminals such as the mobile terminal of the mobile phone, the PC terminal on the internet, the telephone terminal and the like, the payment information is transferred to the payment confirmation terminal independent of payment starting equipment via an independent payment confirmation channel, the subscriber checks the payment information through the payment confirmation terminal and submits the payment confirmation information to a payment system through the payment confirmation terminal and the payment confirmation channel, the payment system can only execute payment operation after receiving the payment confirmation information, and the payment confirmation terminal carries out digital signature protection on the confirmation information. The method can effectively prevent hackers from attacking electronic payment and the transaction process, thereby ensuring the payment and fund security of the subscriber.
Owner:刘辛越 +1
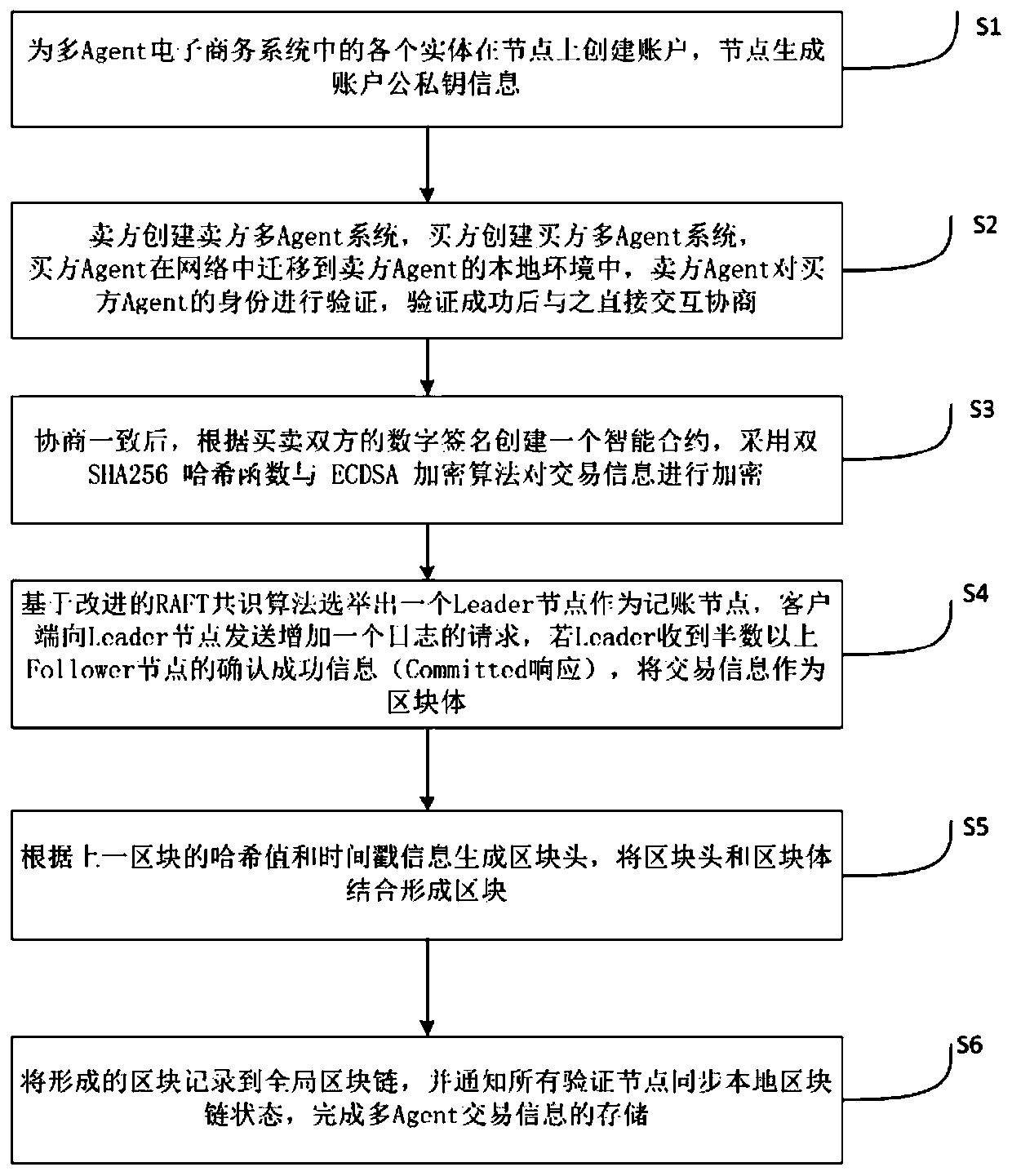
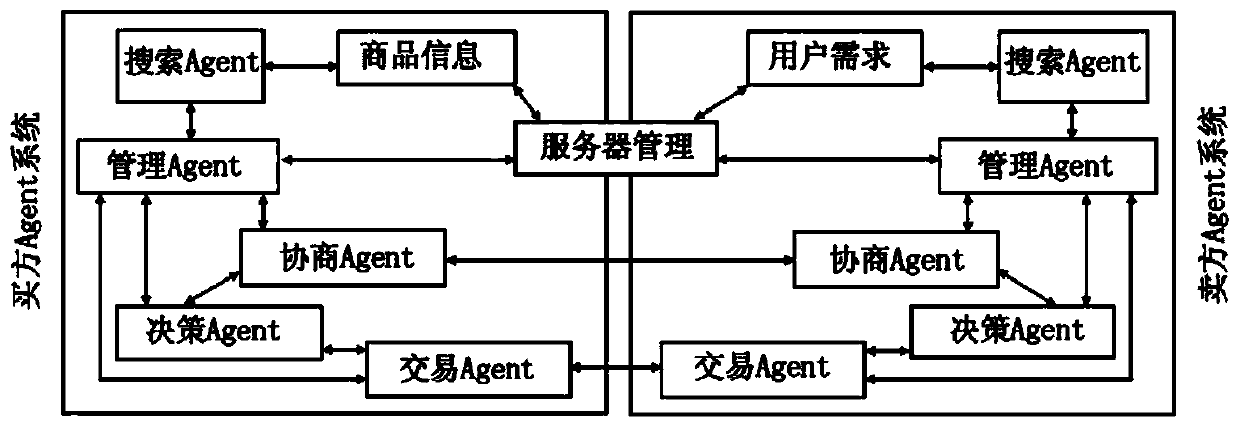
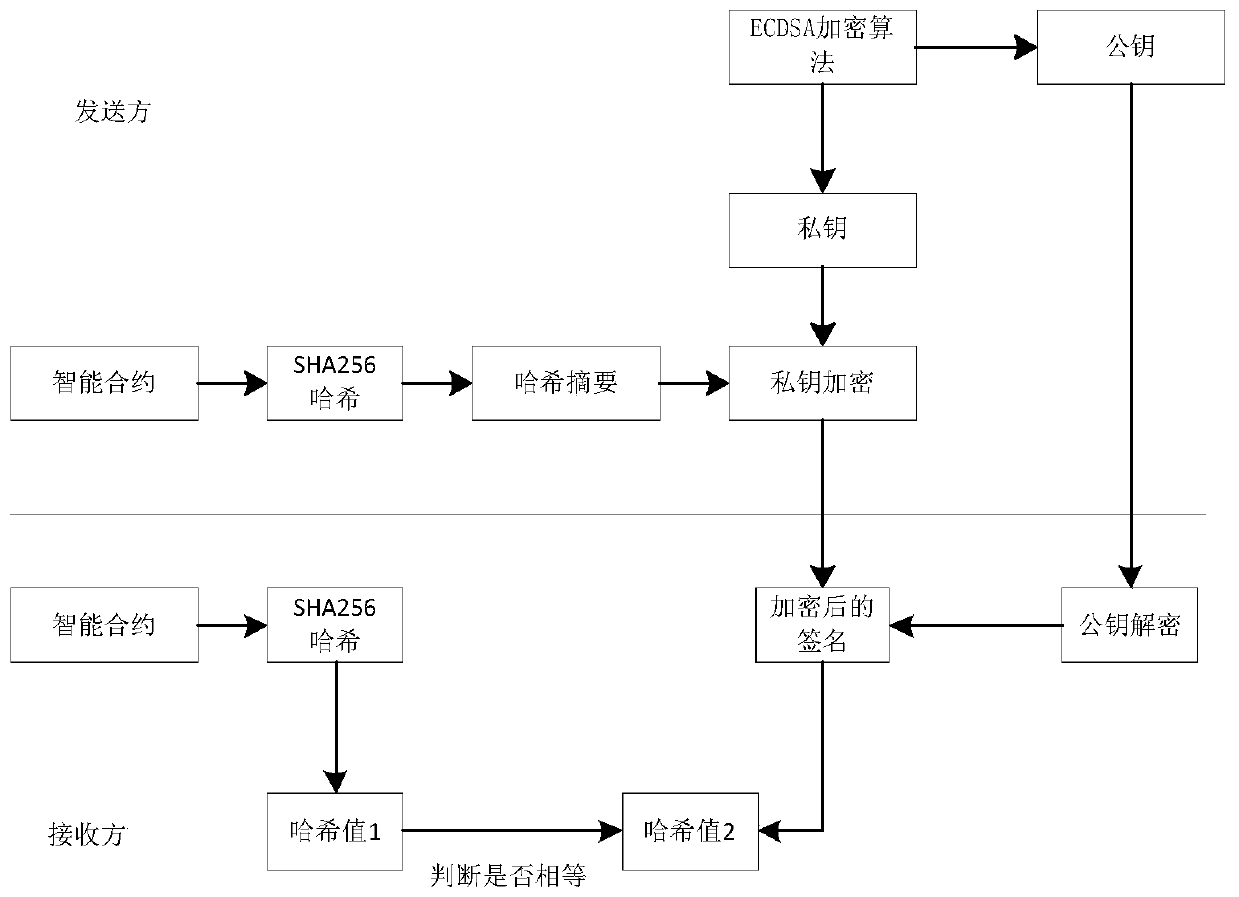
Multi-Agent transaction information protection method based on block chain technology
ActiveCN110569675AReduce in quantitySolve the consensus problemFinanceDigital data protectionByzantine fault toleranceDigital signature
The invention discloses a multi-Agent transaction information protection method based on a block chain technology. According to the method, a transaction execution platform which only has credible andsafe transaction information protection execution environment is established by utilizing a block chain. A transaction process between the buyer and the seller is realized by using the transaction execution platform. Besides, a BFT-Raft consensus algorithm based on Byzantine fault tolerance is adopted, and the method has the advantages that due to the establishment of a multi-Agent e-commerce system, the transaction cost and the user time can be remarkably reduced, and illegal authorization acquisition, use and leakage of transaction information are effectively prevented. The BFT-Raft consensus algorithm ensures that the log is not tampered by applying a digital signature technology and incremental hash in a log replication link. Through a Committed proving mechanism, it is ensured that aselected Leader node must have all log items reaching consensus, the BFT-Raft consensus algorithm can solve the consensus problem in a Byzantine fault-tolerant environment, the number of nodes participating in verification and accounting is greatly reduced, and second-level consensus verification can be achieved.
Owner:SHANGHAI MARITIME UNIVERSITY
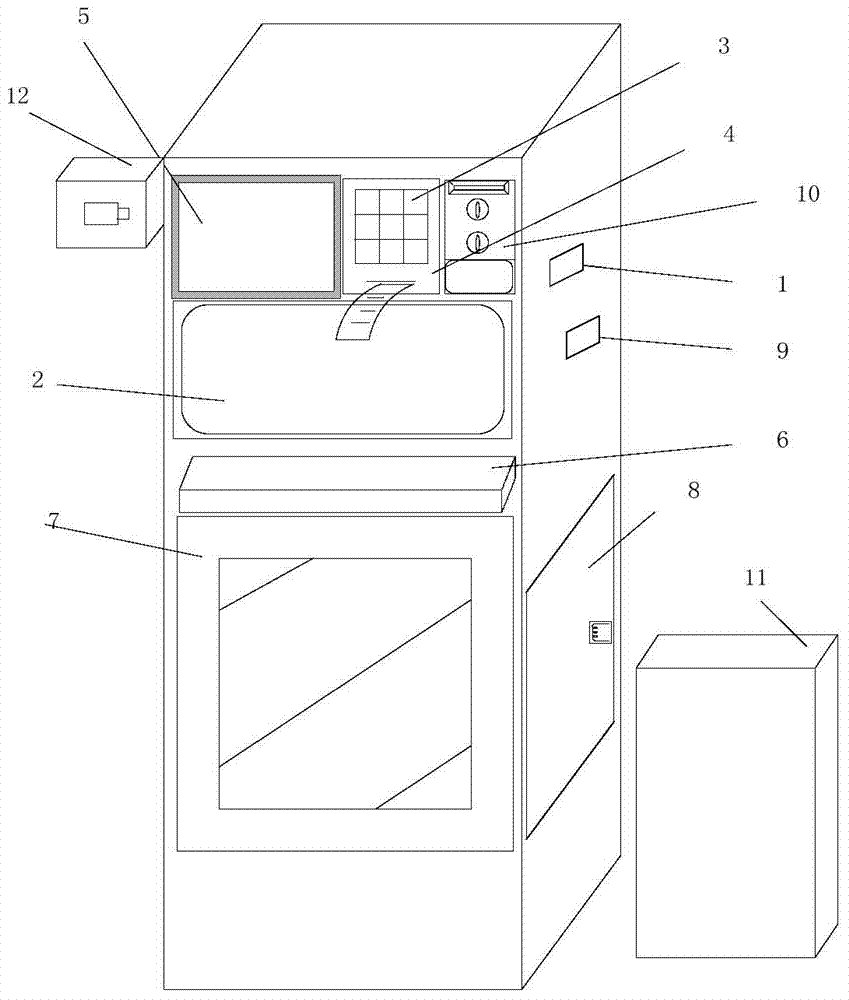
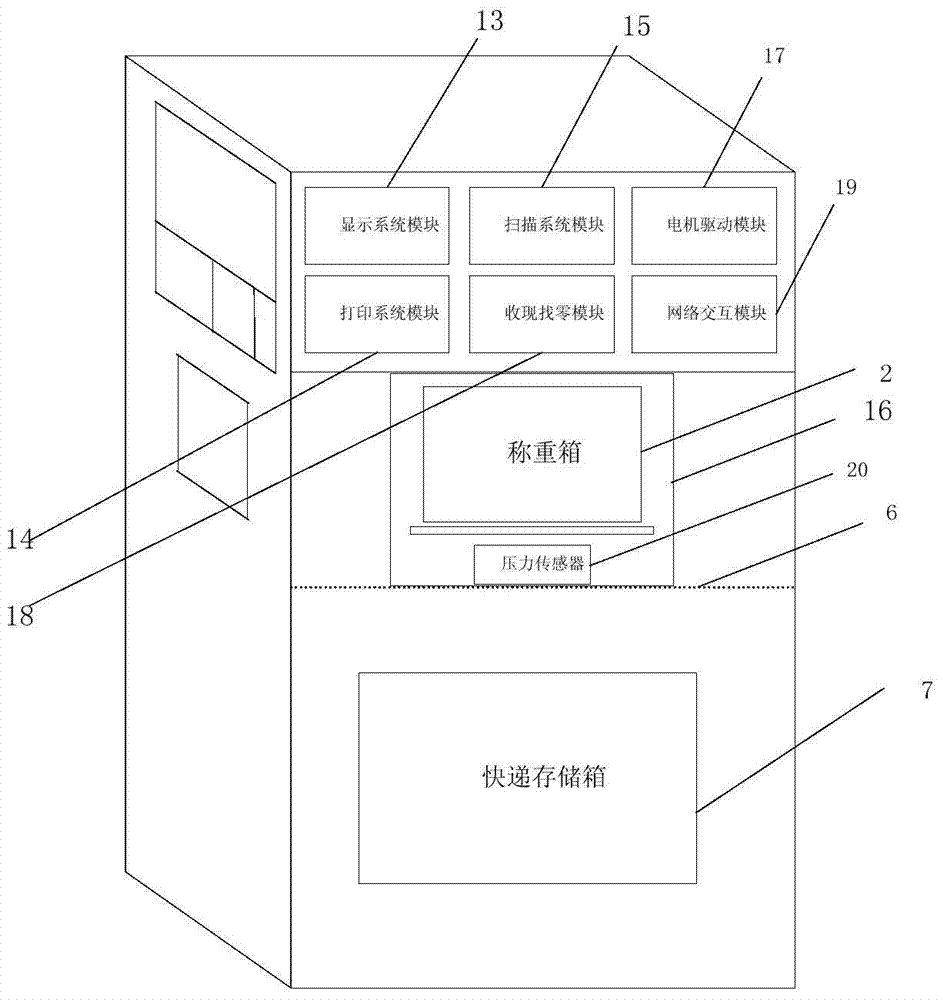
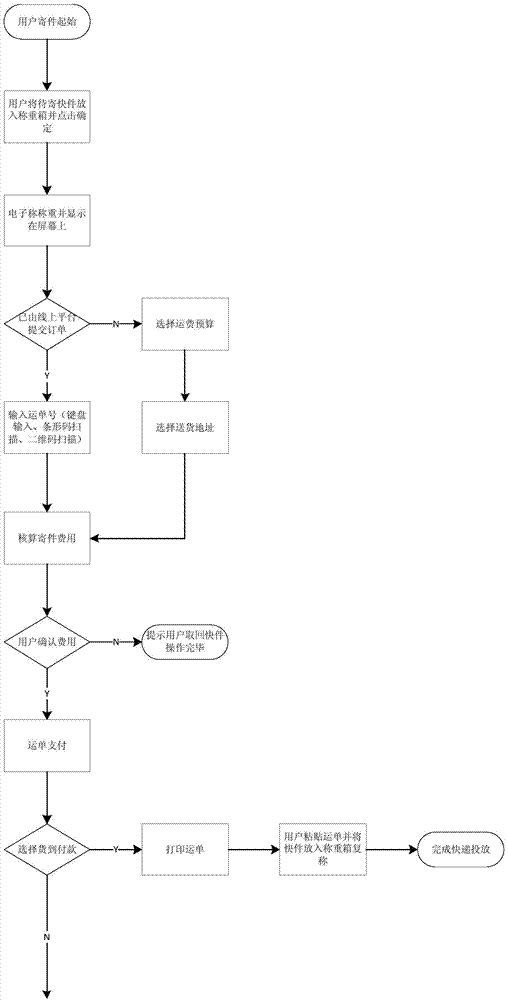
Self-service express pickup system and method based on O2O logistics platform
InactiveCN103927641AThe collection system is simpleSimple structurePayment architectureApparatus for meter-controlled dispensingMotor driveData processing
A self-service express pickup system and method based on an O2O logistics platform comprises a pickup machine communicating with the on-line logistics platform instantly. The pickup machine is connected with a terminal module through a network interaction module and comprises a pickup machine body provided with an express throwing opening and an express pickup opening, a display system module, a printing system module, a scanning system module, a weighing module, a background data processing module and a motor driving module, wherein the display system module, the printing system module, the scanning system module, the weighing module, the background data processing module and the motor driving module are arranged on the pickup machine body. The pickup system is simple in structure and low in cost. According to the pickup method, pickup services are standardized and automated, so that service links form an O2O closed loop, efficiency of mailing an express is improved for a customer, and information construction of the logistics industry is facilitated. The problem that because visiting pickup efficiency of a courier is low, and bag personal quality and good personal quality are intermingled, customer churn are caused is effectively solved, and meanwhile a basis and the method are provided for customer management of a logistics company.
Owner:高恬溪
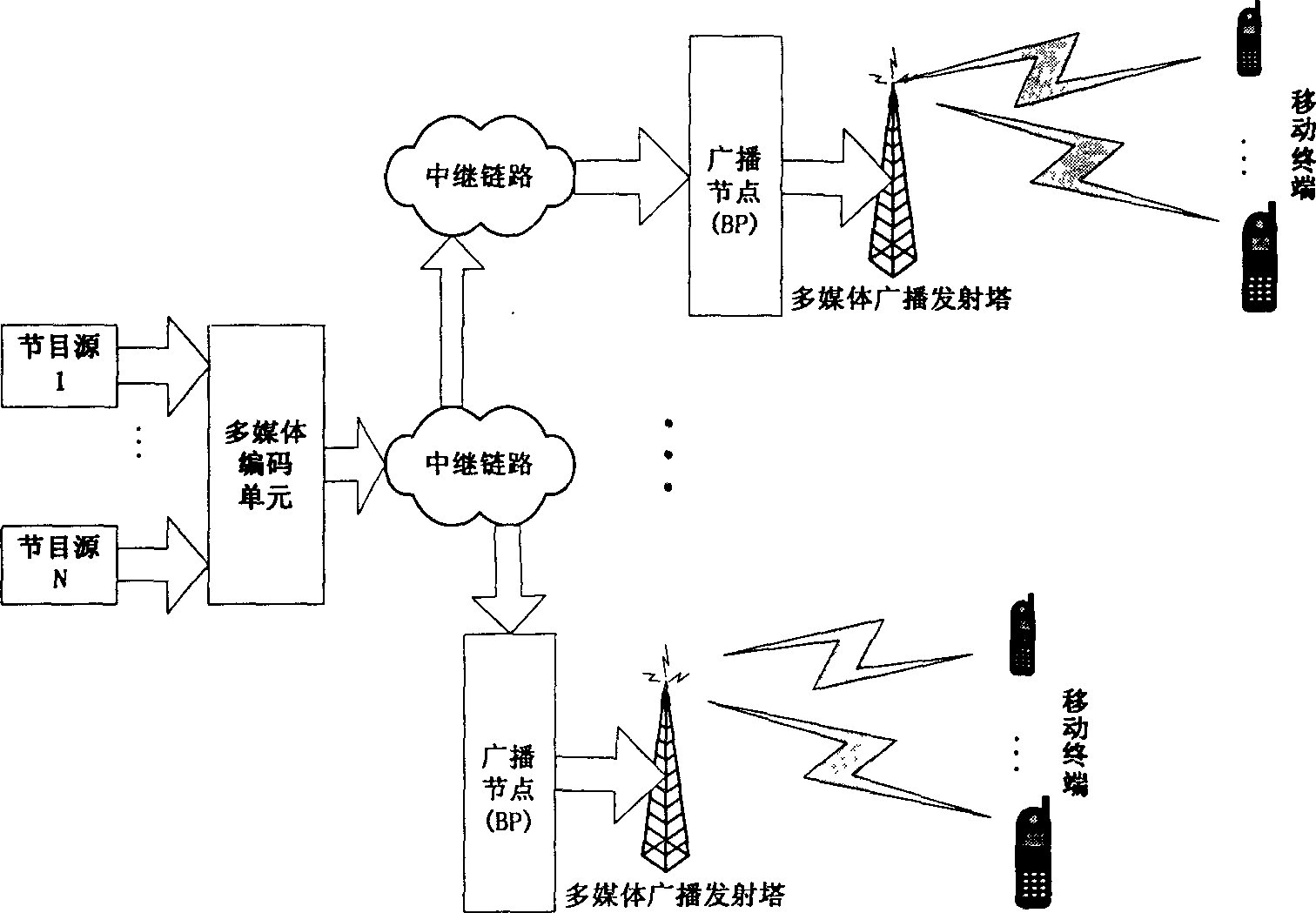
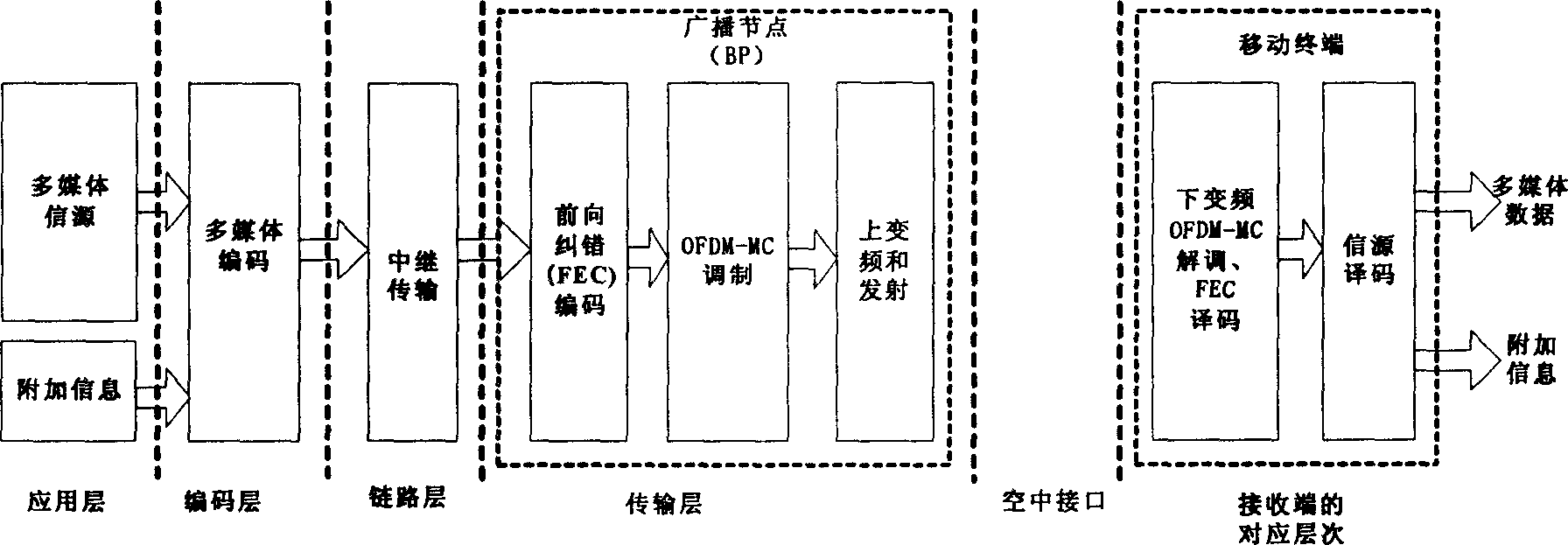
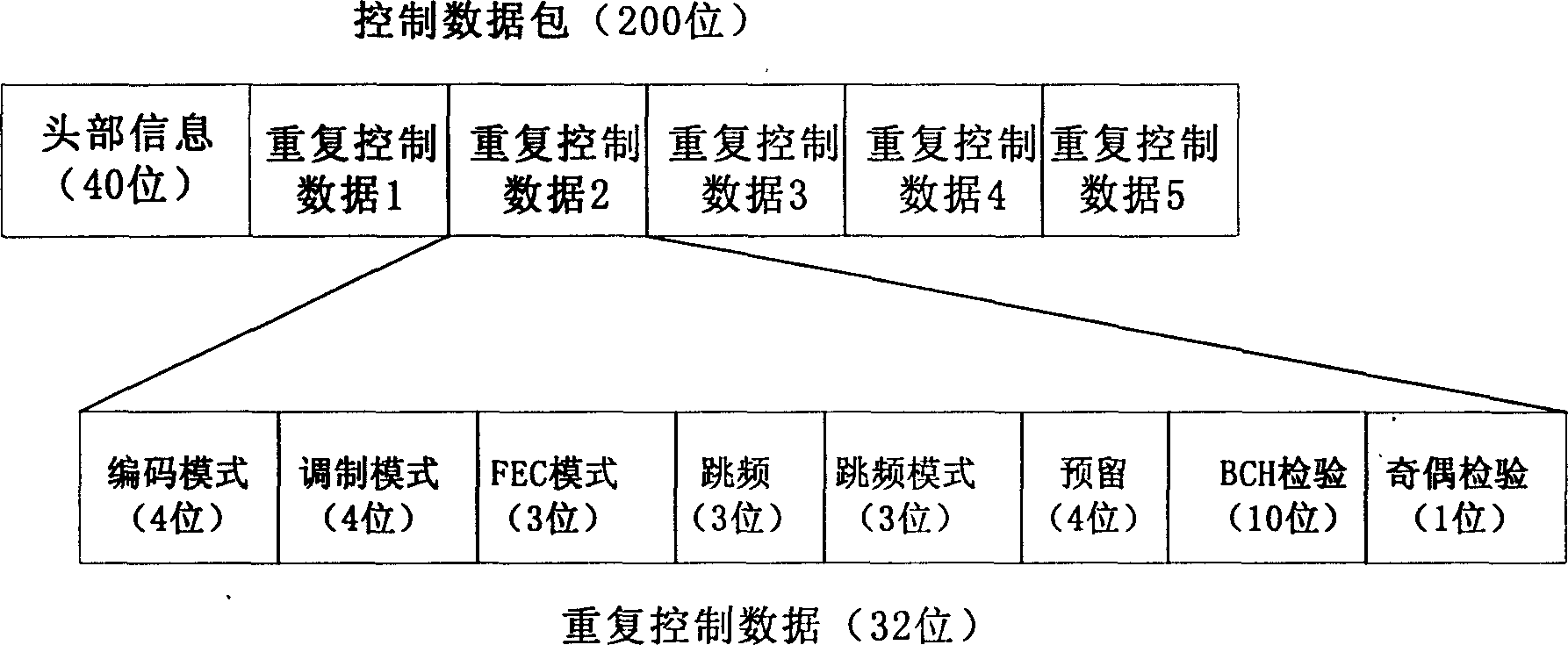
Mobile terminal oriented multimedia broadcasting system and implementing method thereof
InactiveCN1571512AQuality improvementQuality assurancePulse modulation television signal transmissionOrthogonal multiplexPersonalizationCarrier signal
This invention is a multimedia broadcasting system and its realizing method that facing mobile terminal. It belongs to multimedia broadcasting field. Its feature is that it is based on orthogonal frequency division multiplexingí¬multiple channel system. multiple broadcasting service is provided to mobile terminal by the IFFT of emission terminal and the FFT of receive terminal. The transformation is done by allocating different channels on different sub carrier wave groups by using the frequency range of existing common television broadcasting system and big zone broadcasting type. It can provide media program of scores of channels efficiently and economically, and the utility factor is high. Individualization broadcasting can be realized for different quality needs subscriber. Dynamic power control, modulation, forward error correction encoding and frequency hopping can be realized to ensure the transmission quality. The receive terminal can be simply design and the power consumption can be reduced in this invention.
Owner:TSINGHUA UNIV
Preparation and uses of false proof highly-effective insecticide and bactericide
InactiveCN1788569AProtect interestsLow toxicityBiocideFungicidesOrganophosphorus pesticidesAgriculture
The anti-fake pesticide-germicide is prepared with boron, saponin, pyrethroid, organophosphorus pesticide and alcohol. After the pesticide-germicide is set into various kinds of dry small mouth bottle with the lid opened for 0.25-2 hr, white snowflake-like crystal will grow around the bottle mouth, and this makes it possible for the user to identify the truth of the pesticide-germicide. Compared with pesticide-germicide of alone pyrethroid and organophosphorus pesticide, the pesticide-germicide of the present invention has greatly raised effect, lowered toxicity, lowered cost and reduced consumption.
Owner:刘起麟
System for Transmitting Syndicated Programs over the Internet
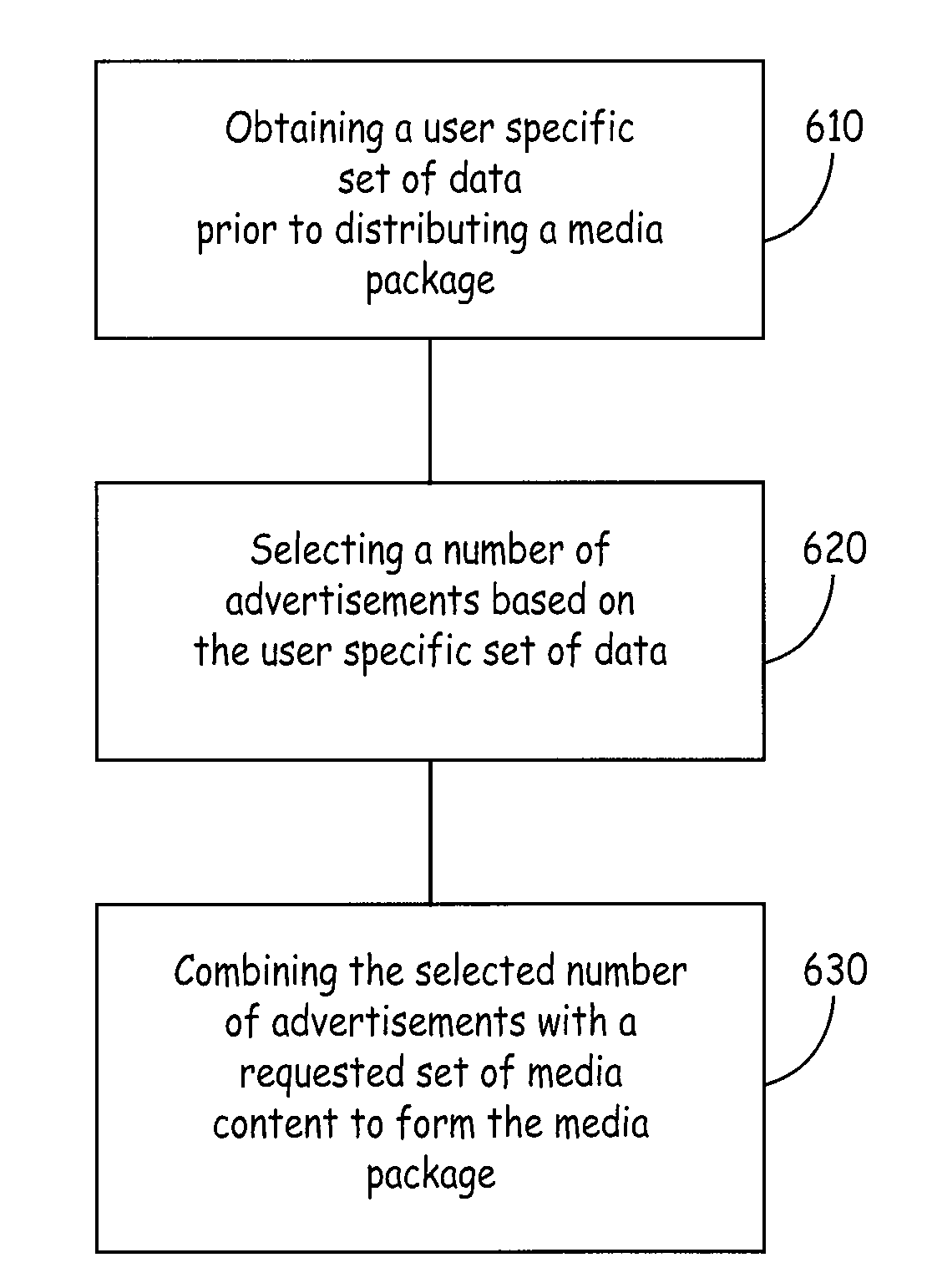
ActiveUS20080319828A1Protect interestsPreserve its investmentResourcesSelective content distributionIt investmentData set
A system and method are provided for exposing Internet users to advertisements together with the distribution of media content in a manner which is germane to conventional syndicated broadcast agreements. The system includes a processor coupled to a memory device. The system further includes software means operable on the processor and memory device. The software means is operable on the processor for obtaining a user specific set of data prior to distributing a media package. The software means is operable for selecting a number of advertisements from a data bank containing a plurality of advertisements based on the user specific set of data. The software means is operable for combining the selected number of advertisements with a requested set of media content to form the media package. The software means is further operable for distributing the media package. In this manner a regional broadcasting station can preserve its investment in purchasing national syndicate broadcast rights by ensuring regional advertisers a penetration of their advertisements across a regional Internet audience. Methods for performing the same are similarly included.
Owner:SYNDICAST CORP
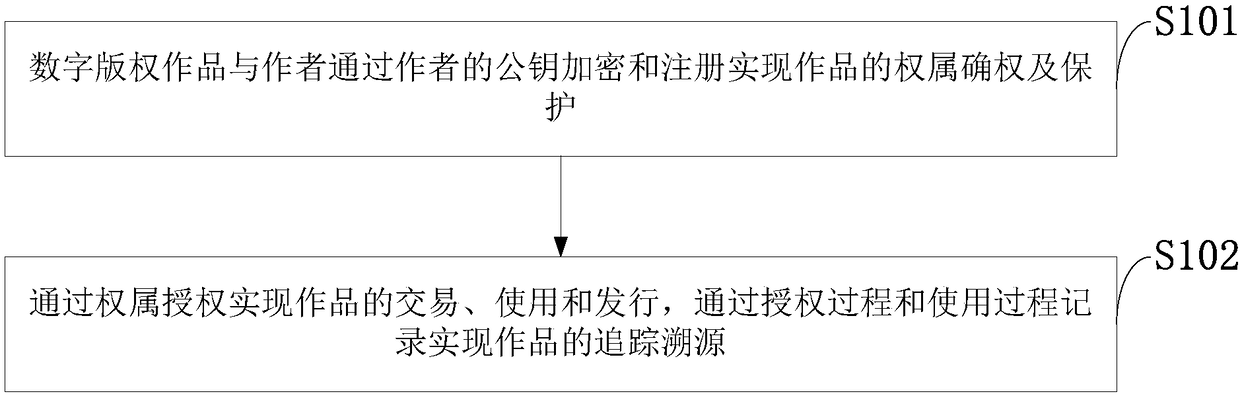
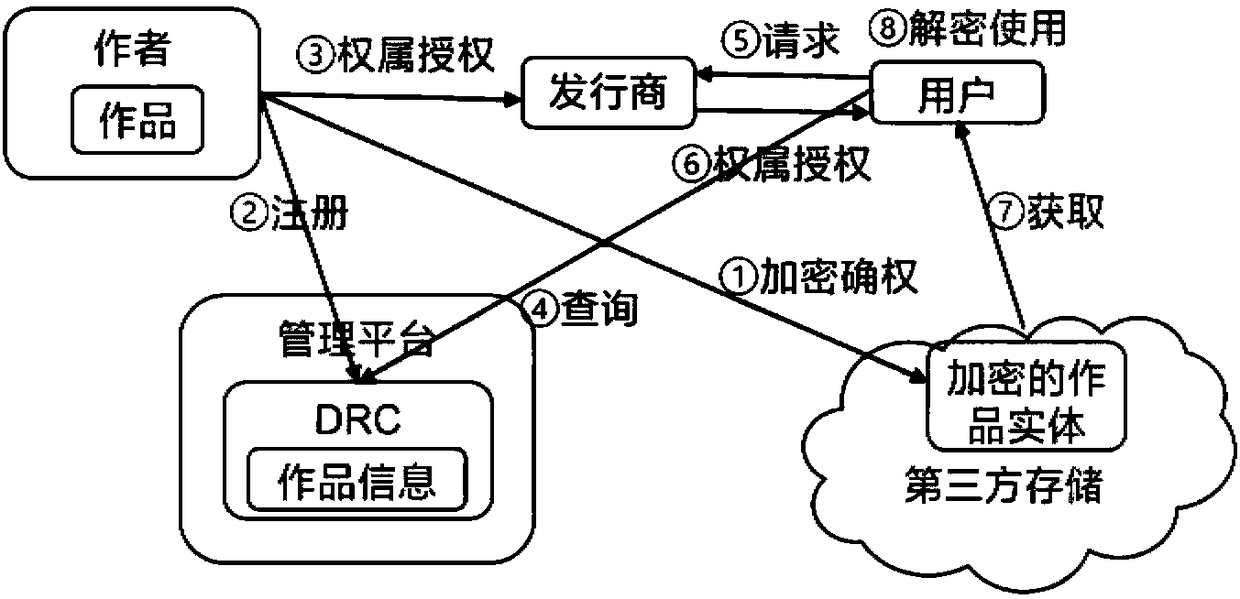
Ownership based digital copyright work protection-transaction-issuing method and system
InactiveCN108389059AProtect interestsProtection of rights and interestsTransmissionCommerceAuthorizationEncryption
The invention discloses an ownership based digital copyright work protection-transaction-issuing method and system, and belongs to the technical field of direction data protection. According to the method, an author declares and protects the ownership of a digital copyright work by public key encryption and registration; and the work is transacted, used and issued by authorization, and the work istracked and traced via recording in authorization and using processes. Via the encrypted ownership declaration and authorization methods, the problem that a traditional digital copyright protection method has deficiency in the aspects of preventing non-authorized use and pirates, help is provided for protection and shared use of the digital copyright work, and benefit and rights of the author canbe protected.
Owner:CHENGDU UNIV
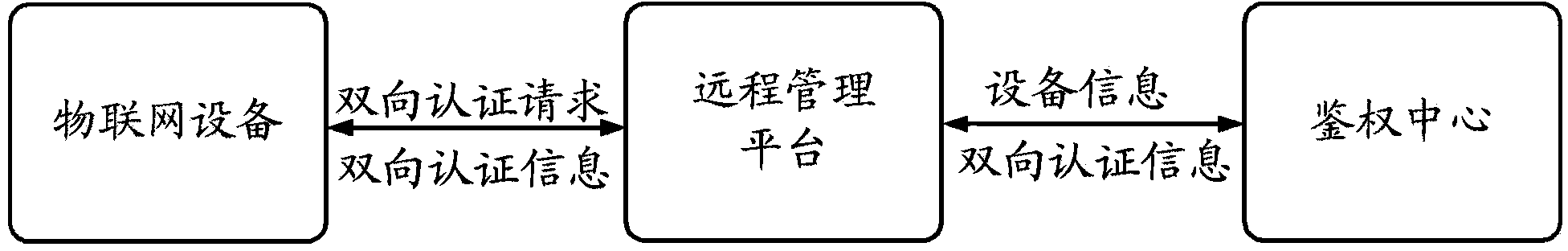
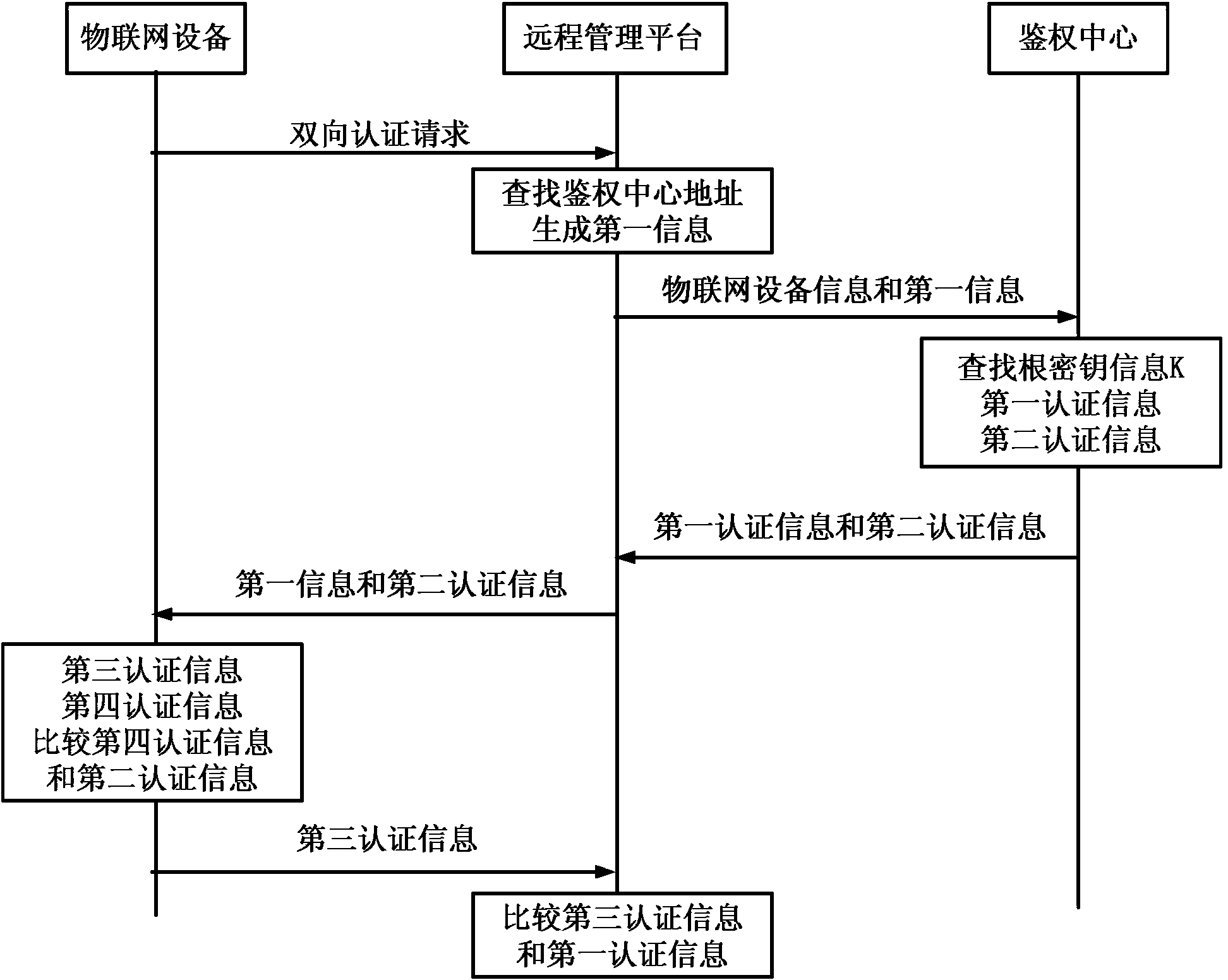
IOT (Internet of Things) based equipment authentication method, device and system
InactiveCN103532963AAffect normal operationNo lossUser identity/authority verificationComputer terminalAuthentication information
The invention discloses an IOT based equipment authentication method, device and system, and relates to the field of authentication of IOT terminals and servers. In order to guarantee the safety of an IOT system and the authentication effectiveness, a remote management platform generates a first message when receiving a bidirectional authentication request of IOT equipment; an IOT equipment message and the generated first message are sent to an authentication center; the authentication center seeks a root key message K corresponding to the IOT equipment according to the IOT equipment message, generates a bidirectional authentication message according to the root key message and the first message and returns the bidirectional authentication message to the remote management platform; and the remote management platform finishes bidirectional authentication according to the bidirectional authentication message and the IOT equipment. According to the provided method and system, only legal IOT equipment can be accessed to the management platform, illegal equipment can be prevented from being accessed, and simultaneously, the legitimate right of a user using the IOT equipment can be protected from loss.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
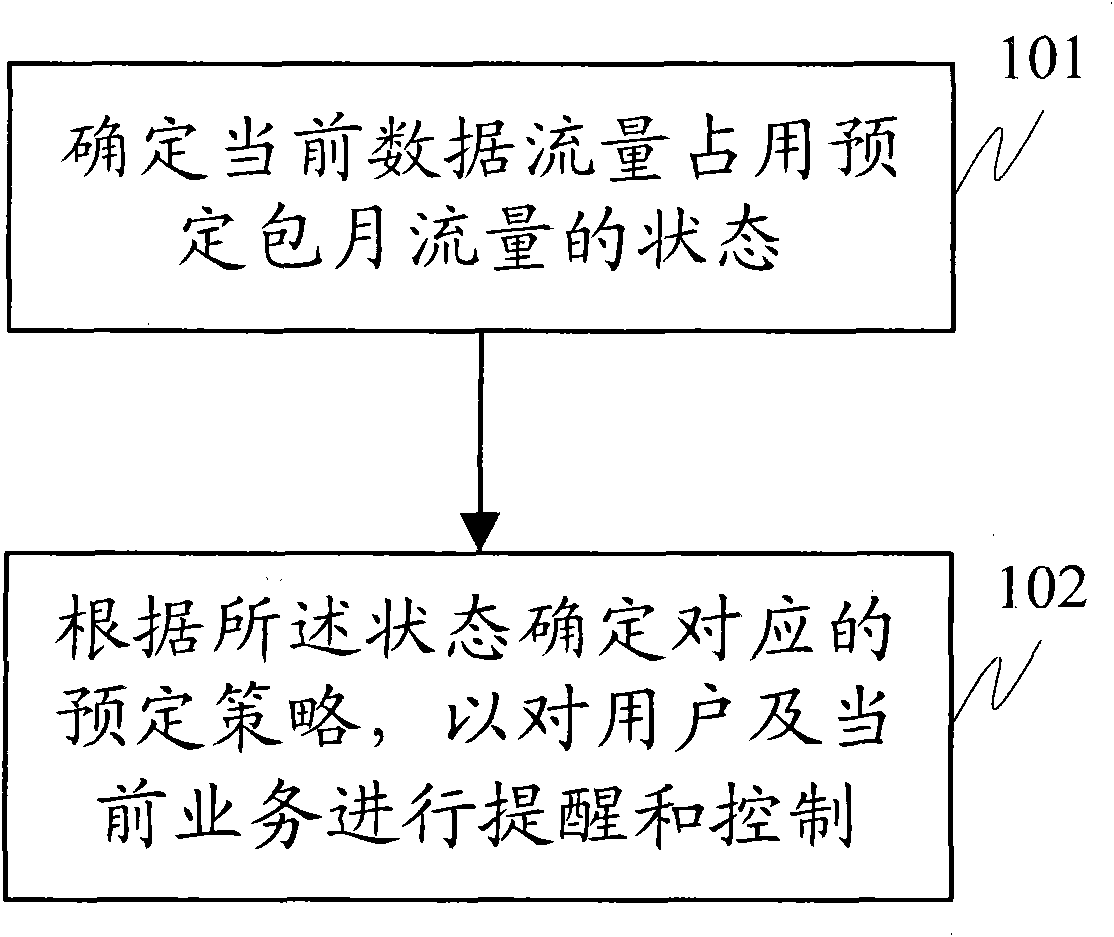
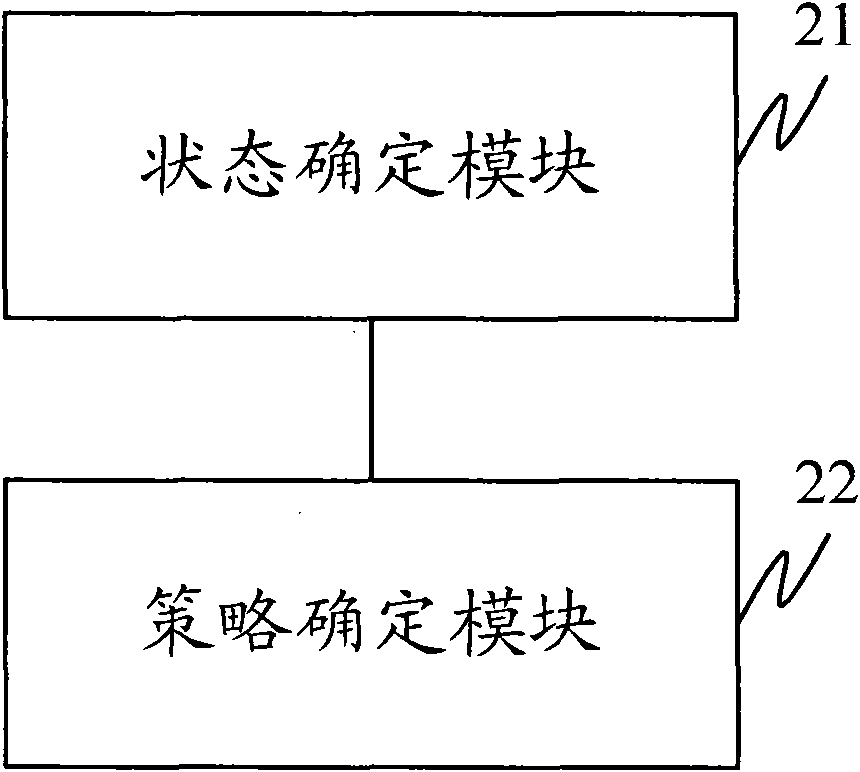
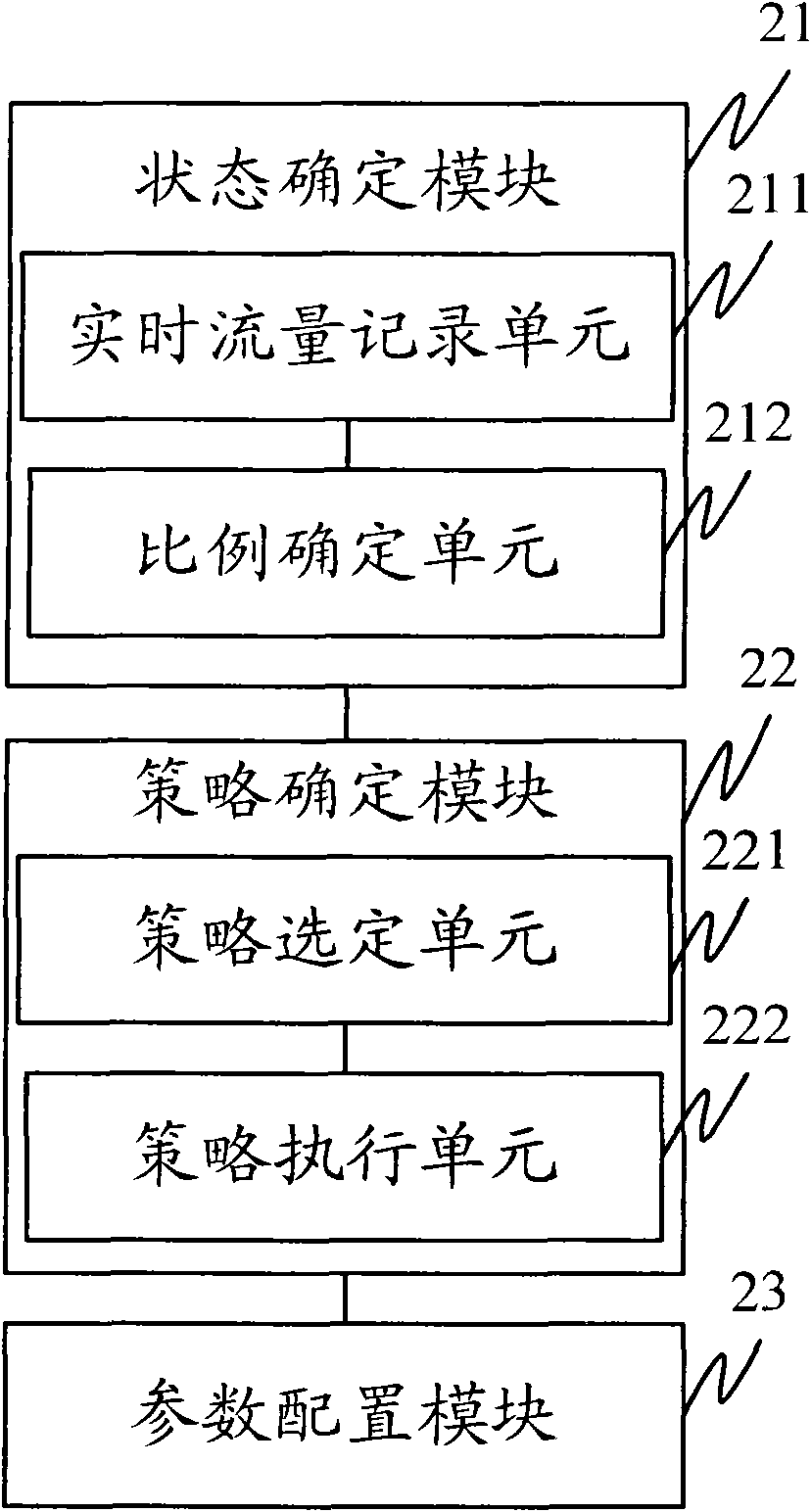
Method and device for controlling data traffic
InactiveCN101820641AProtect interestsAvoid high feesNetwork traffic/resource managementData switching networksTraffic capacityData traffic
The embodiment of the invention discloses a method and a device for controlling data traffic. The method comprises the following steps of: determining a state that current data traffic occupies scheduled monthly subscription traffic; and determining a corresponding scheduled policy according to the state, reminding a user and controlling a current service. The device comprises a state determining module used for determining the state that the current data traffic occupies the scheduled monthly subscription traffic; and a policy determining module used for determining the corresponding scheduled policy according to the state acquired by using the state determining module, reminding the user and controlling the current service. By adopting the method and the device of the invention, the data traffic of the user can be reminded aiming at monthly subscription actively and the benefits of the user can be protected by adopting a control policy after monthly subscription traffic is exceeded.
Owner:HUAWEI DEVICE CO LTD
Virtual gift task scalping prevention system and method in live-broadcasting platform
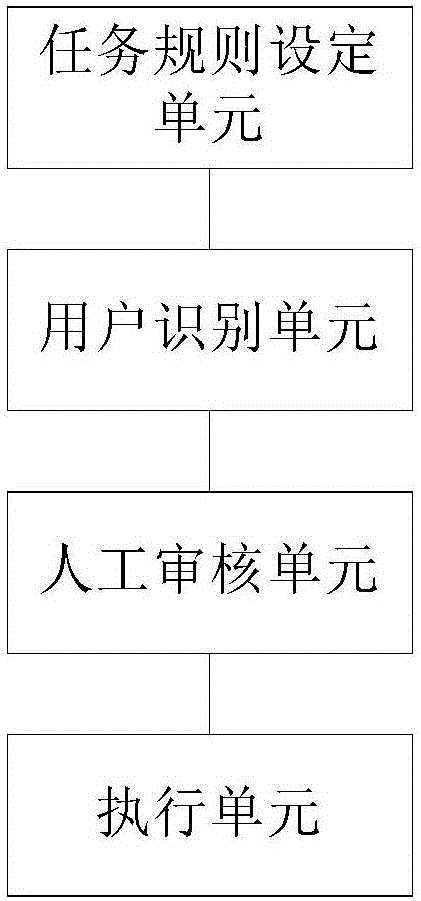
InactiveCN106228410AProtection securityProtect interestsDiscounts/incentivesError reductionThe Internet
The present invention discloses a virtual gift task scalping prevention system and method in a live-broadcasting platform, and relates to the internet live-broadcasting technology field. The system comprises: a task rule setting unit configured to configure the task rule of a virtual gift; a user identification unit configured to identify and divide the user classification which includes normal users and black list users; and an execution unit configured to allow the normal users to obtain the virtual gift and prohibit the black list from obtaining the virtual gift. The concrete steps of the method comprises: S1, the task rule setting unit configures the task rule of obtaining the virtual gift by a user, and writing into a database to generate buffer memory; S2, the user identification unit is configured to identify and divide the user classification into the normal users and the black list users according to the task rule; and S3, the execution unit allows the normal users to execute and obtain the virtual gift and prohibit the black list from obtaining the virtual gift. The virtual gift task scalping prevention system and method in live-broadcasting platform reduce the data bulk artificial screening, effectively improve the efficiency, reduce the manpower cost and decrease the error rate.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
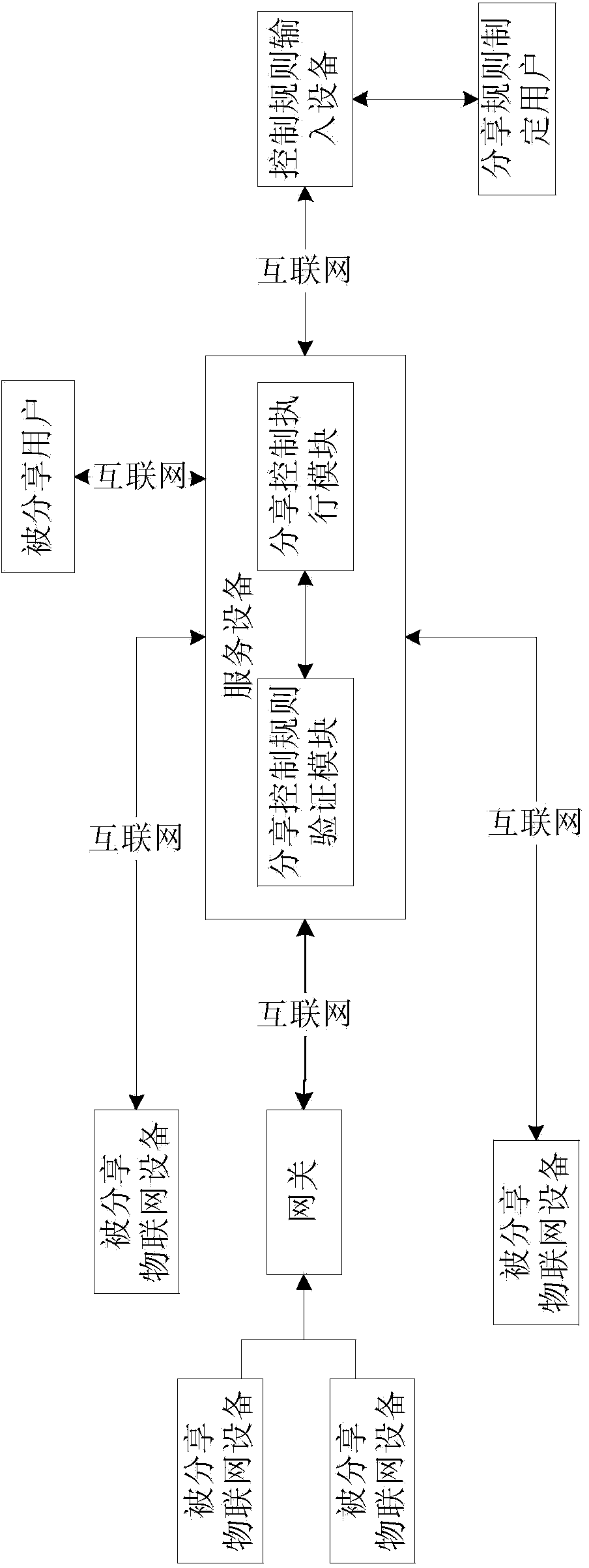
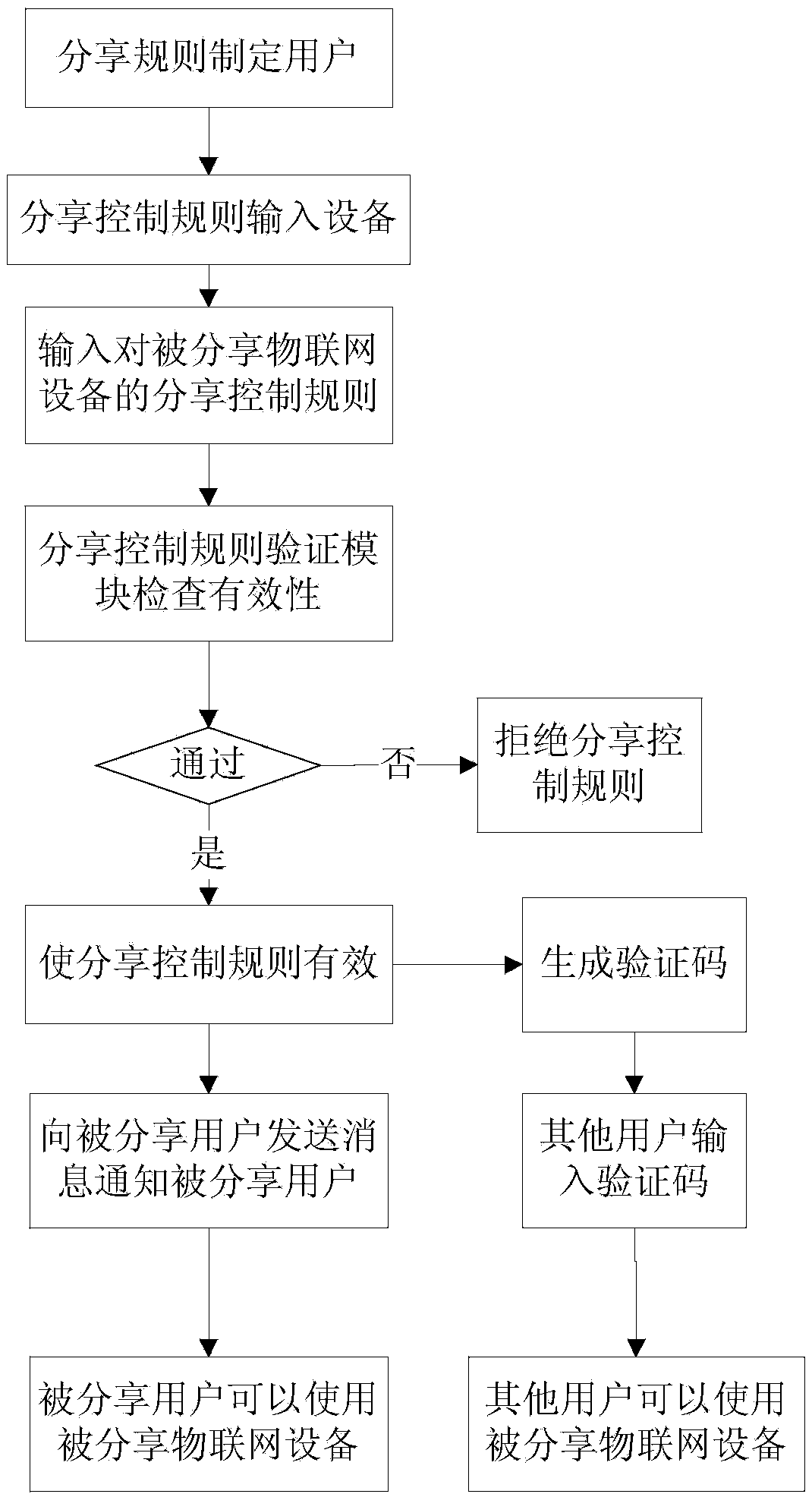
Sharing system and sharing method for internet-of-things device
ActiveCN104219328AReflect the characteristics of open sharingSave resourcesTransmissionThe InternetDistributed computing
The invention relates to a sharing system and a sharing method for an internet-of-things device. The sharing system comprises a shared internet-of-things device, a service device, a sharing rule designing user, a shared user and a sharing control rule input device, wherein the service device comprises a sharing control rule verification module and a sharing control execution module, the sharing control execution module is connected with the sharing control rule verification module, the sharing control execution module sends a message to the shared user to inform the shared user, thereby, the shared user can know that a control rule of the shared internet-of-things device is already shared to the shared user, and when the shared user logs in the service device, the shared user can automatically obtain a corresponding permission to the shared internet-of-things device in accordance with the regulations in the sharing control rule. Compared with sharing systems and sharing methods in the prior art, the sharing system and the sharing method for the internet-of-things device have the advantages that the permission of the internet-of-things device can be shared to other users within the internet for usage, internet open sharing feature can be really reflected, and the idea of making the best use of everything and saving resources is reflected.
Owner:NINGBO HAIBO GRP CO LTD
Ticket service system and method for preventing scalping train tickets
InactiveCN101546195AProtect interestsAvoid lossCharacter and pattern recognitionTotal factory controlPurchasingComputer science
A ticket service system and method for preventing scalping train tickets relate to ticket service management system. The system is composed of a ticket service center, ticketing subsystems, a ticket checking system, a mobile ticket service subsystem, communication network. The invention adopts a set of ticketing, ticket checking, loss reporting, offense reporting, punishing and rewarding method, provides ticket purchasing with good faith, ticket purchasing with certificate, self purchasing and deposit ticket purchasing and ticket checking rules, thus preventing scalping train tickets. The loss reporting function can avoid property loss and social resource loss for the ticket purchasing people after ticket losing or damaging. The ticket purchasing people can be found quickly based on the recorded ID information or identification code in ticket purchasing when the occurring public safety or sanitation event in the ticket applying course to control the influence range of the event.
Owner:乔超
Message processing protocol which mitigates optimistic messaging behavior
ActiveUS20180183901A1Increase transaction volumeMaintain performanceFinanceData switching networksMessage processingMessage passing
The disclosed embodiments relate to implementation, such as by a message processing system architecture, of a message handling system and / or protocol which mitigates optimistic messaging behavior. As used herein optimistic messaging behavior may at least refer to the transmission, in whole or in part, of a message, or of one or more messages of a sequence thereof, to a receiving system, such as the system implemented by the disclosed embodiments, prior to the sender determining that the message(s) is / are desired, alone or in conjunction with subsequently canceling or otherwise invalidating the message(s) once it has been determined that it is not desired. The disclosed embodiments mitigate such behavior by detecting and taking action with respect to these types of messages to deter optimizing behavior which may or may not be manipulative, while maintaining reliable message handling under increasing processing loads with minimal impact on users being able to send messages to the system.
Owner:CHICAGO MERCANTILE EXCHANGE
All-region parking lot information sharing and parking position reserving method and system for achieving method
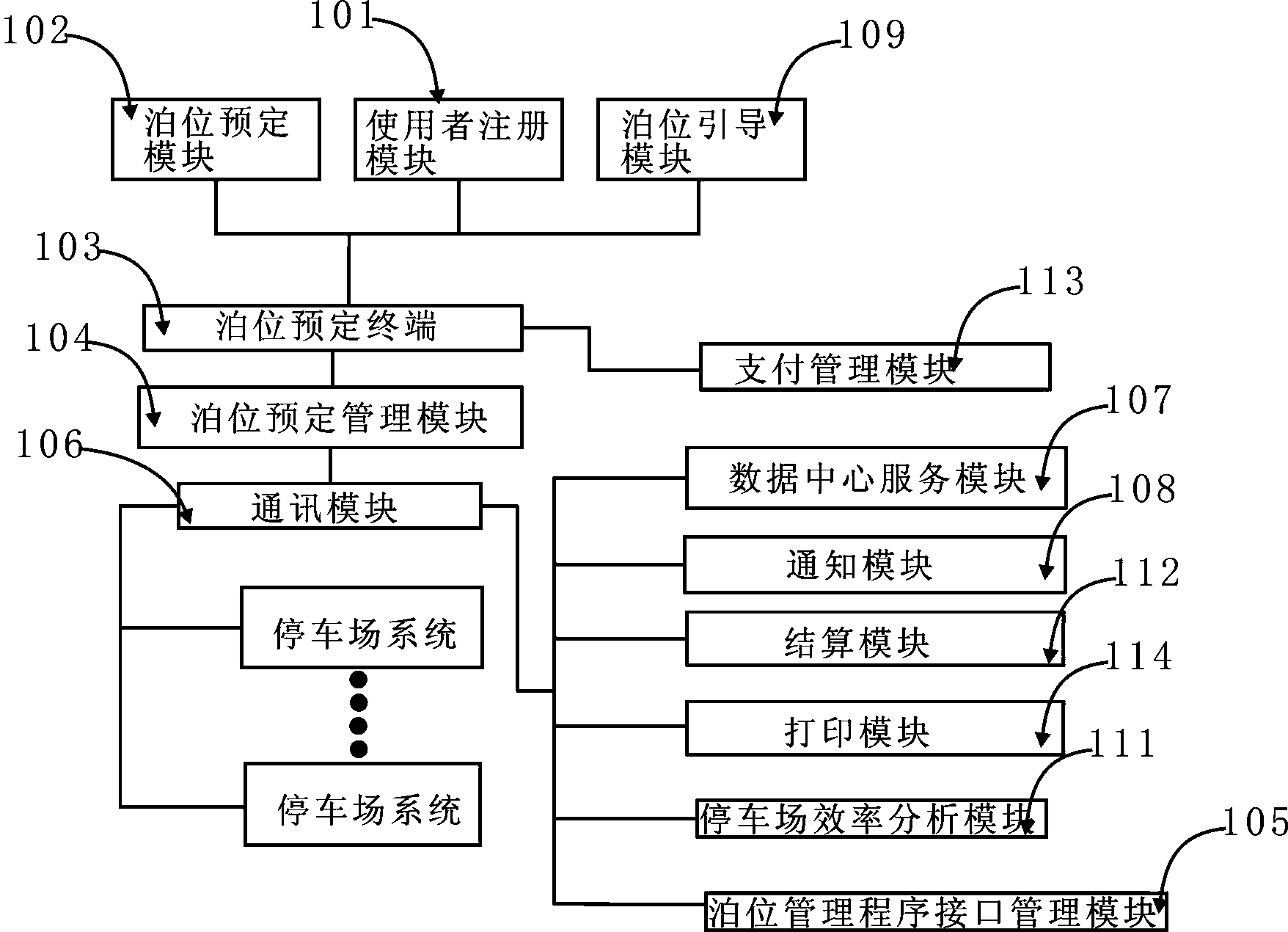
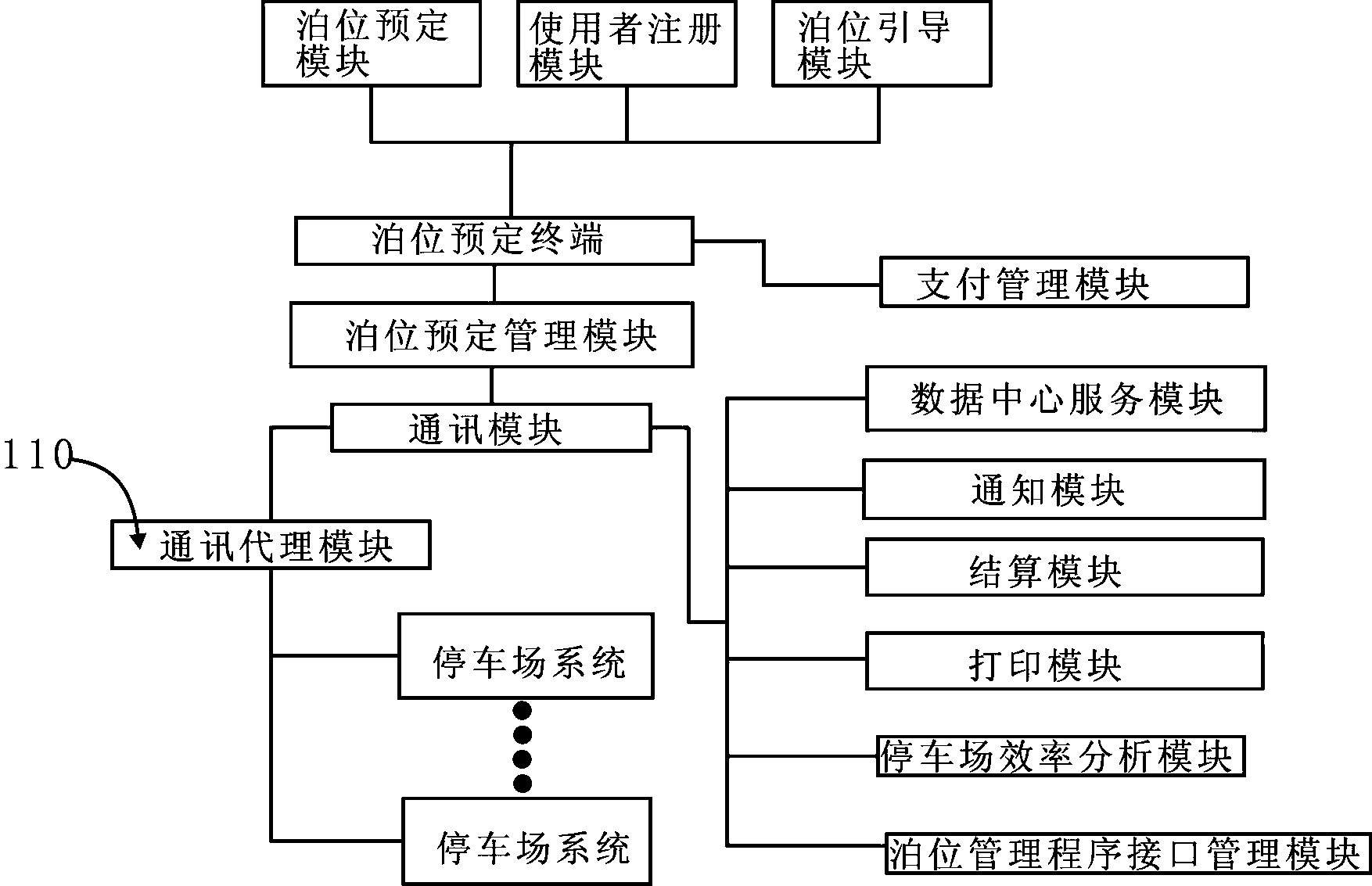
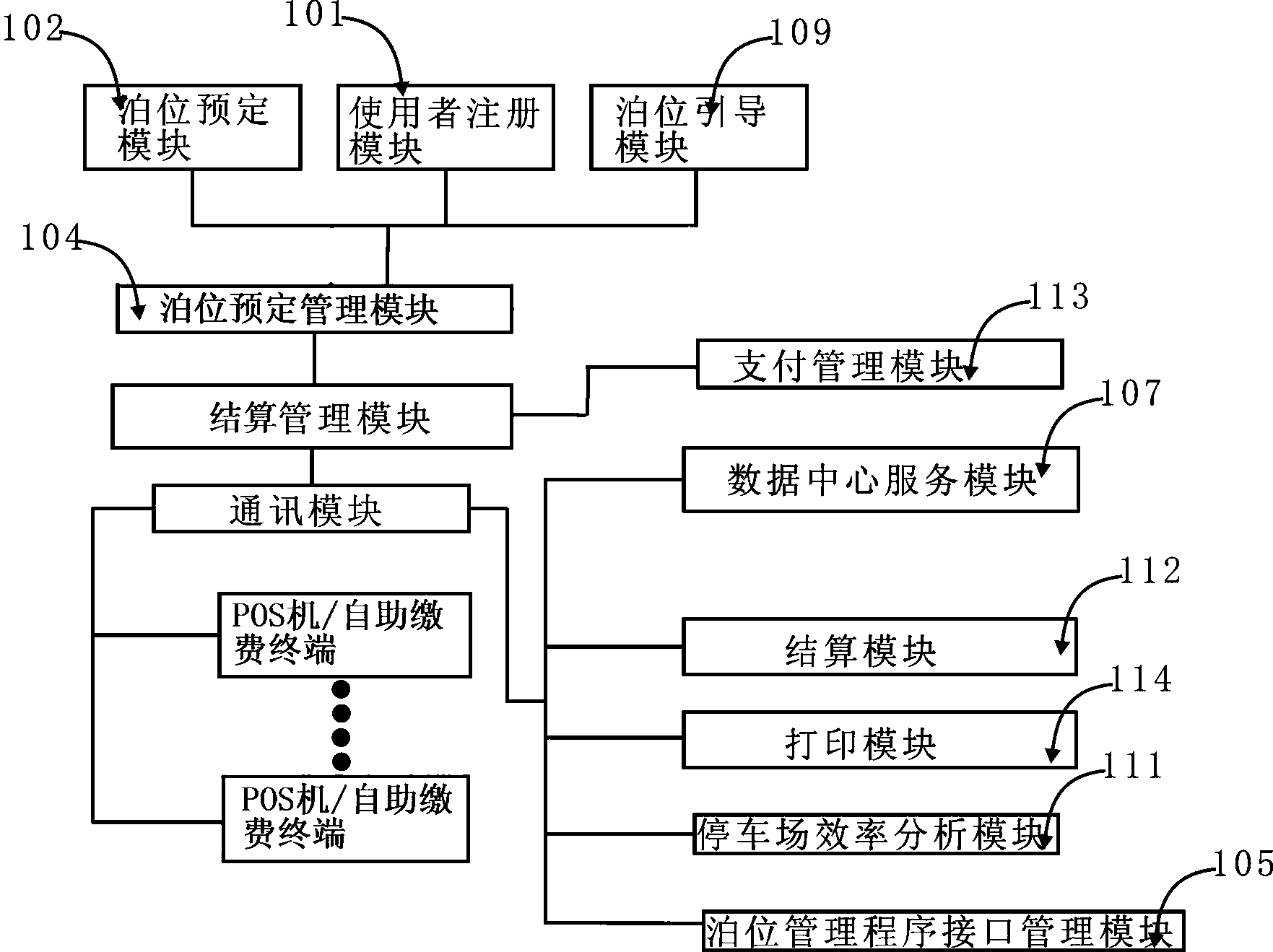
ActiveCN103413458AImproved berth bookingSimple methodTicket-issuing apparatusIndication of parksing free spacesPaymentInformation sharing
The invention relates to an all-region parking lot information sharing and parking position reserving method and a system for achieving the method. The system is jointly composed of a parking position reserving module, a parking position management module, a parking lot efficiency analysis module, a payment management module, a user register module, a communication module, a data centre service module, a settlement module, a bill printing module, a notification module, a parking position reserving terminal and a parking position guiding module. A client can operate the parking position reserving module to conduct parking position reserving through the parking position reserving terminal, the parking fee can be paid in advance through the payment management module, reservation can be completed by a parking position reserving service module in a time scope set when the client conducts reservation through the parking position management programming module, and notification is given to the client. If the reservation fails, the payment management module can send back the pre-paid parking fee in the same way. The parking lot efficiency analysis module is mainly used for conducting urban traffic situation auxiliary analysis on traffic flow analysis of a parking lot. The all-region parking lot information sharing and parking position reserving method and the system are low in cost, bring convenience to the client, and are convenient to operate and high in safety performance.
Owner:成都宜泊信息科技有限公司
Method and system for Intenet payment
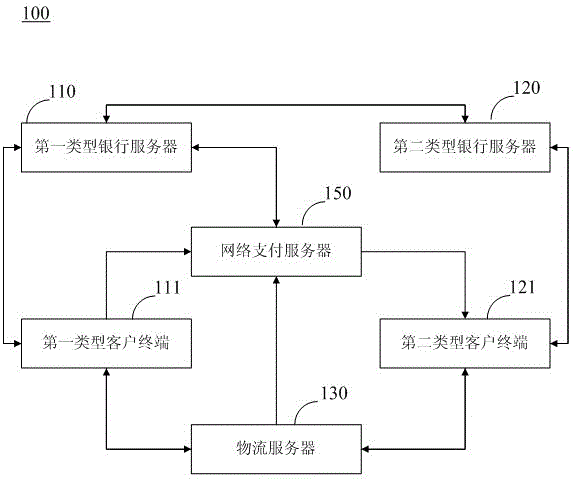
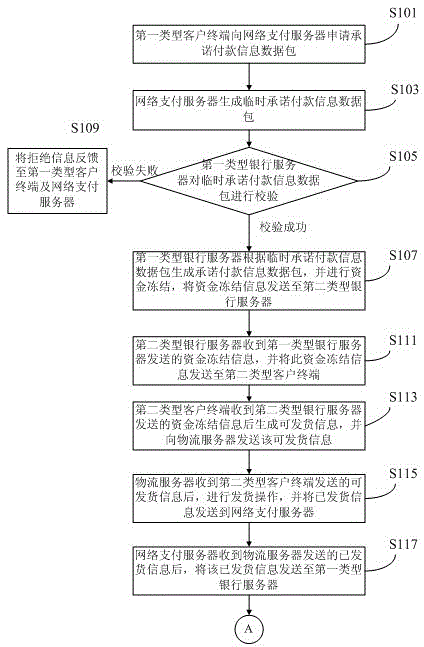
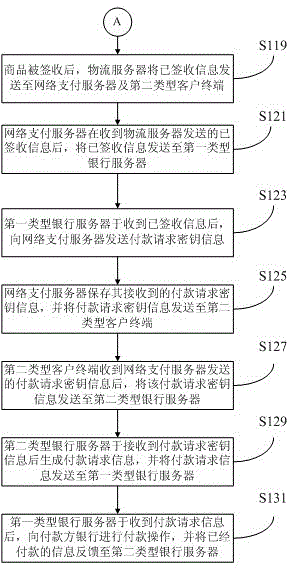
InactiveCN103827902AReduce capital riskProtect interestsFinancePayment architectureE-commerceNetwork packet
The invention is suitable for the field of electronc commerce technology, and provides a method and a system for Internet payment.The method comprises the following steps: a first type client terminal sends application information to an Internet payment server to apply a commitment payment information data package; based on the application information, the Internet payment server generates and sends a temporary commitment payment information data package to a first type bank server; the first type bank server verifies the temporary commitment payment information data package; and if verifies successively, the first type bank server generates a commitment payment information data package based on the temporary commitment payment information data package, carries out fund freezing and sends fund freezing information to a second type bank server. According to the invention, for a payment clinet, fund is just frozen and needs not to be paid, so fund risks are reduced and benefit of the payment client is ensured.
Owner:SHENZHEN CIFPAY NETWORK BANK TECH
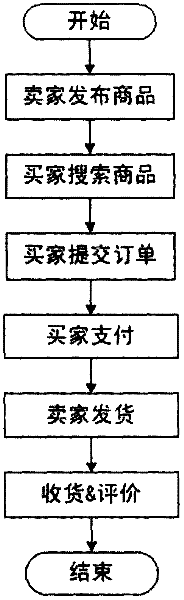
System and method for matchmaking and transaction of electronic commerce
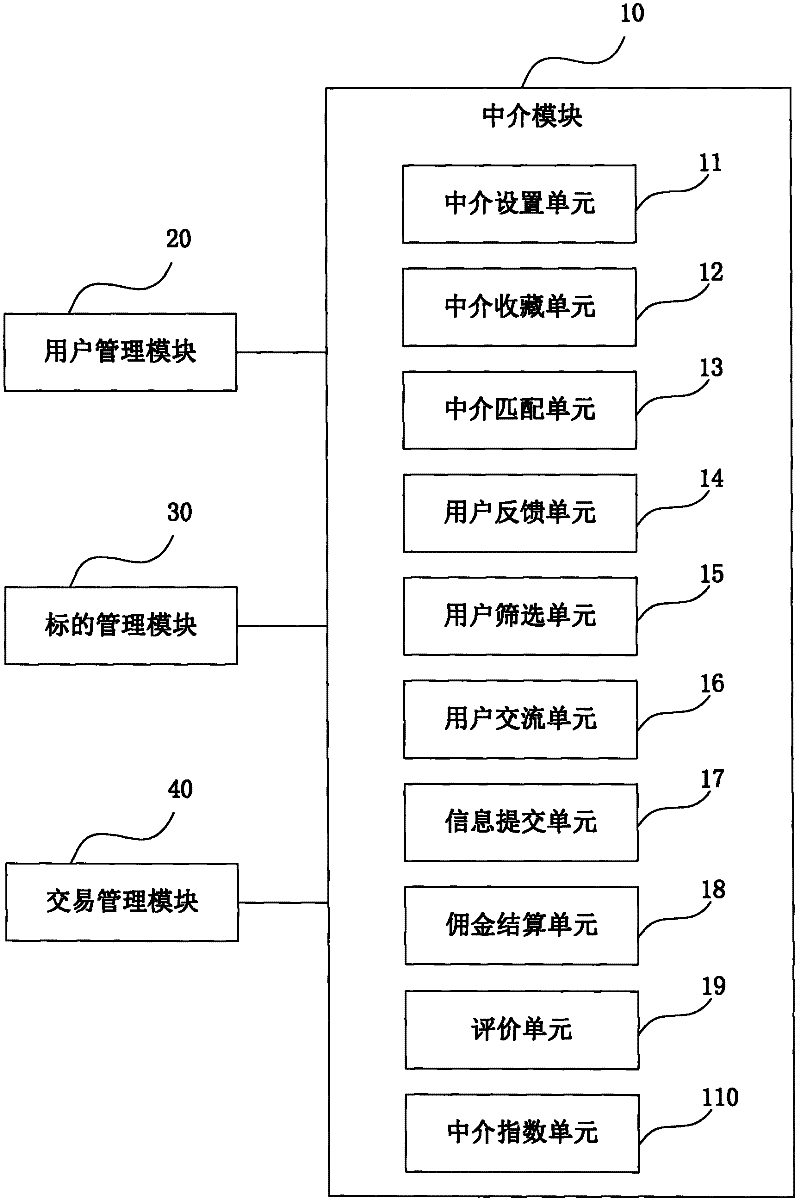
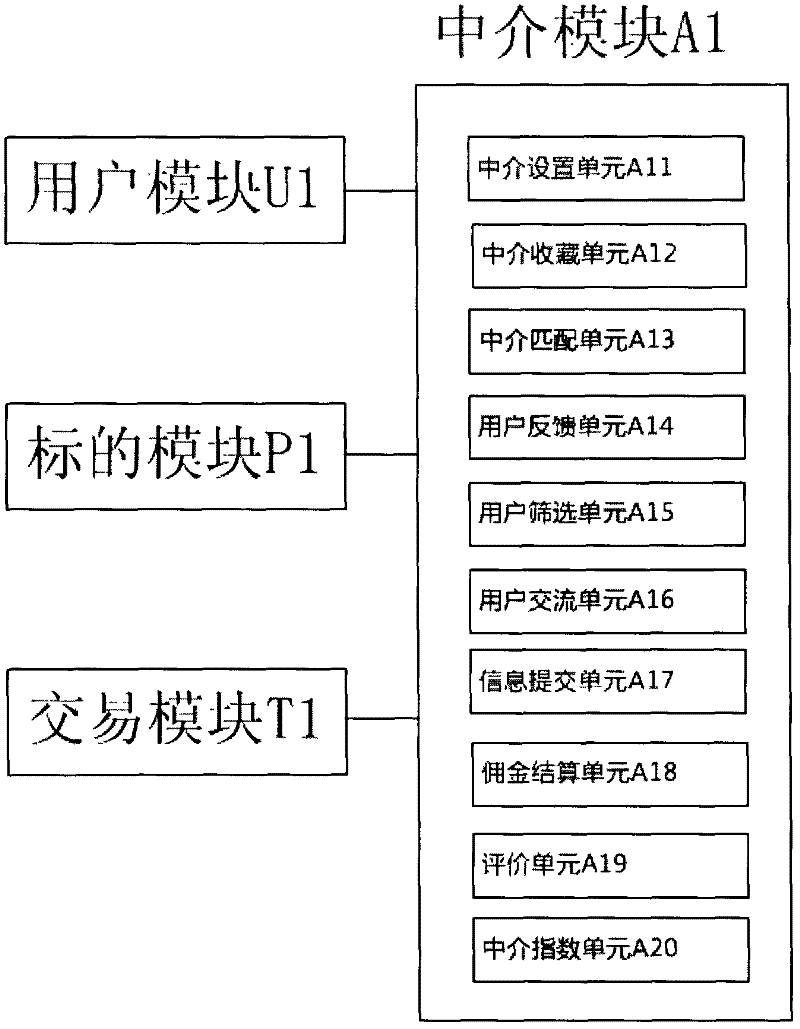
InactiveCN102609870AReduce query timeLow costBuying/selling/leasing transactionsDeep knowledgeTransaction management
The invention discloses a system and method for matchmaking and transaction of electronic commerce. The system comprises a user management module, a target management module, a transaction management module and an intermediary module, wherein an intermediary user provides commodities, services or user recommendation service for a buyer or a seller through the intermediary module; the commodities and services needing to be purchased or user parameter information provided by the buyer and the commodities, services or the user parameter information provided by the seller are received and stored into a database by the intermediary module; the commodities, services or user parameter information needed by the buyer and the commodities, services or user parameter information needed by the seller are matched, and the matching coincidence rate is calculated; and a group of commodities, services or user data or multiple groups of commodities, services or user data are selected for the two parties of the buyer and the seller to select according to the matching coincidence rate. According to the system and the method, the intermediary user who has deep knowledge of certain category products can effectively help the two trading parties reduce information query time and cost; and the success rate of on-line transaction is greatly improved due to the appearance of the intermediary user.
Owner:陈晓亮
Blockchain-based transaction method and a blockchain-based transaction system
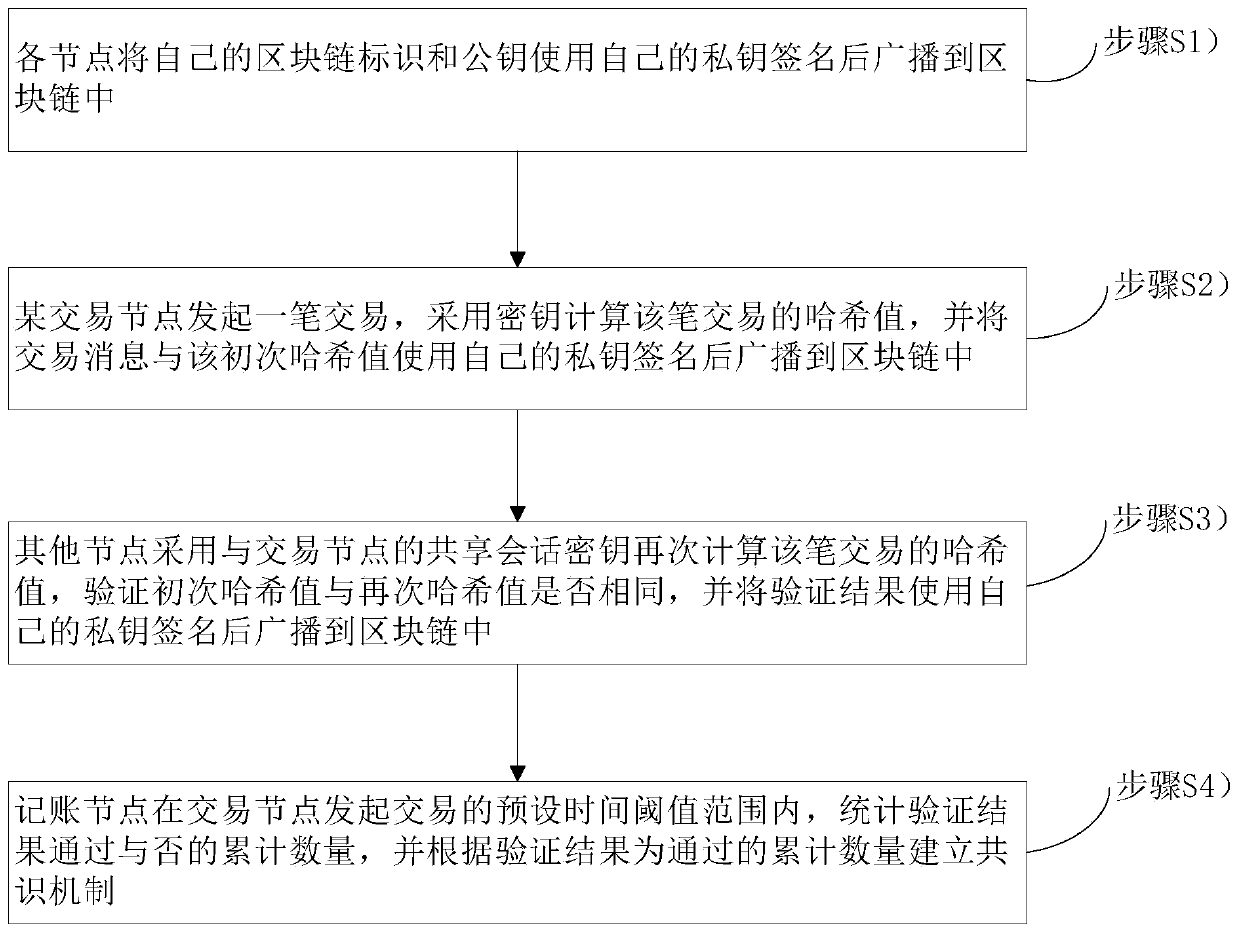
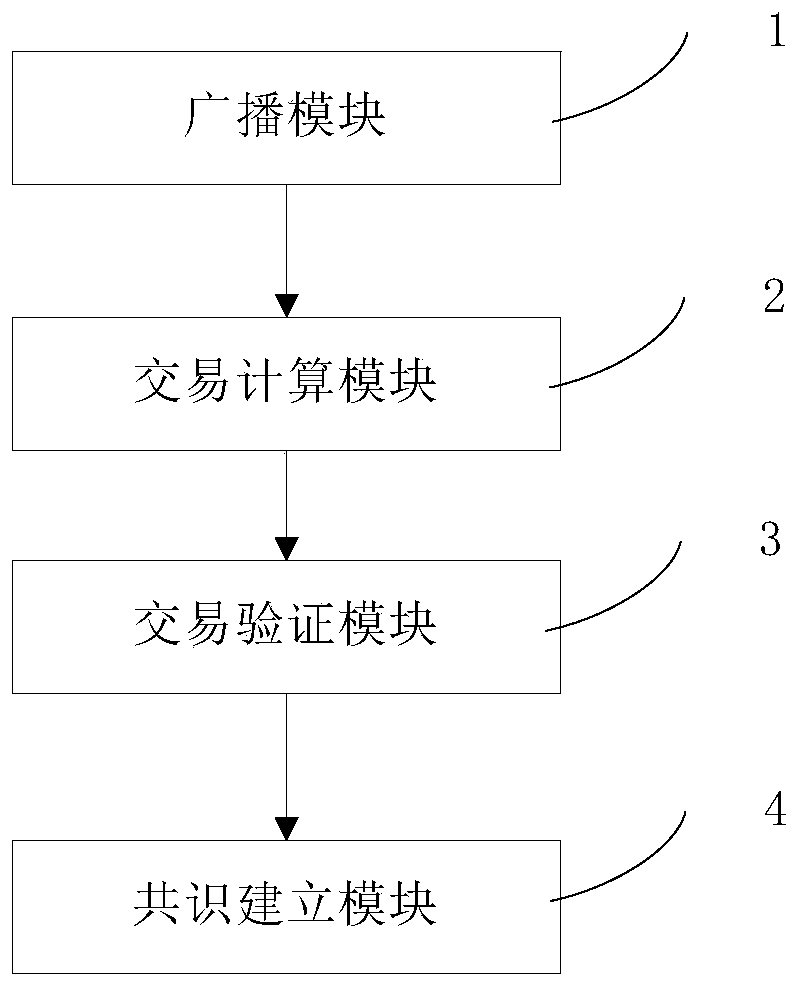
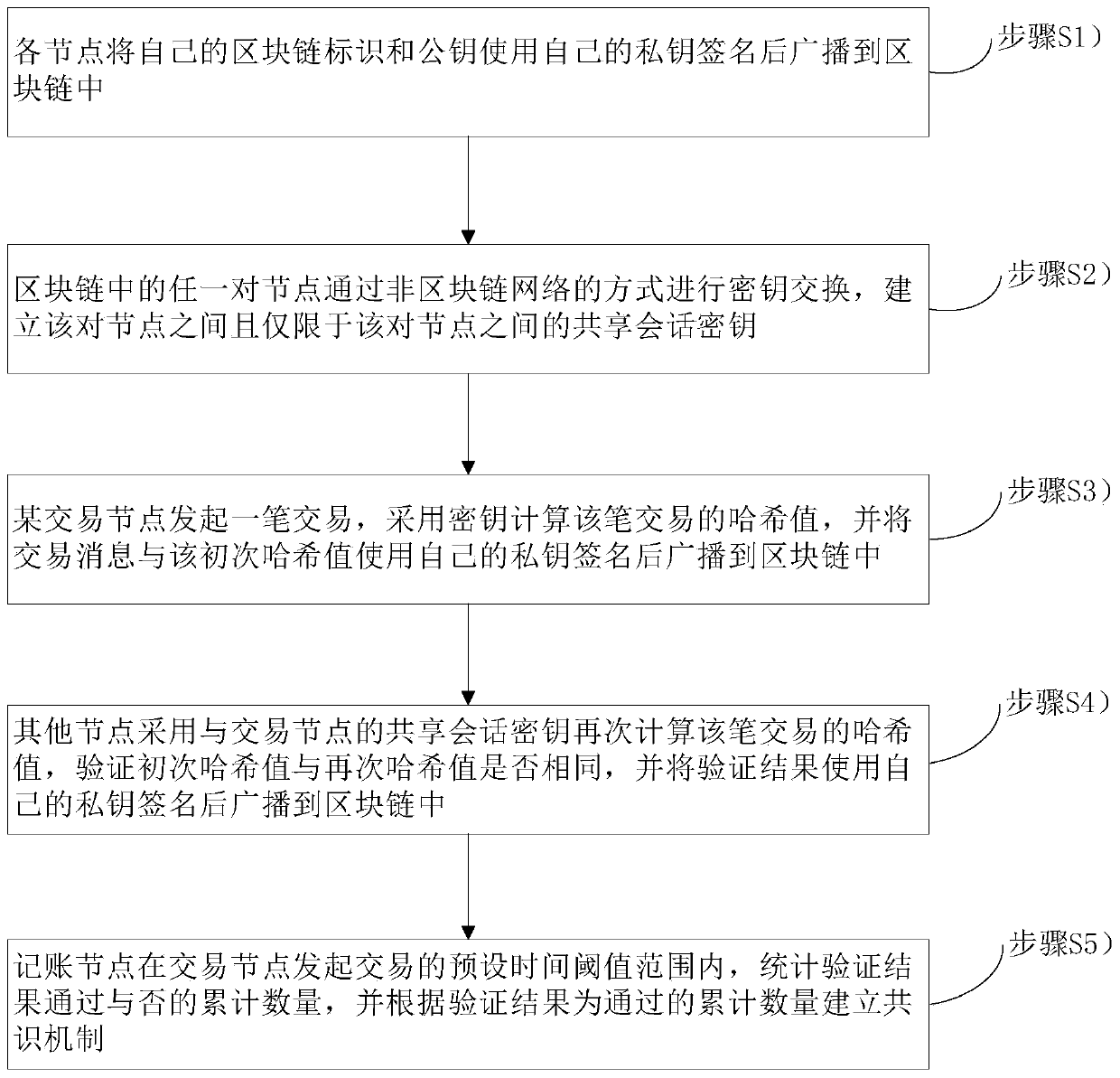
ActiveCN109767220AImprove transmission efficiencyIncrease communication loadPayment protocolsNode countSession key
The invention belongs to the technical field of block chains, and relates to a block chain-based transaction method and a block chain-based transaction system. The method comprises the following steps: each node signs a block chain identifier and a public key of the node by using a private key of the node and broadcasts the block chain identifier and the public key to a block chain; A certain transaction node initiates a transaction, calculates a Hash value of the transaction by adopting a secret key, signs the transaction message and the primary Hash value by using a private key of the transaction node, and broadcasts the transaction message and the primary Hash value to the block chain; The other nodes calculate the Hash value of the transaction again by adopting the shared session key with the transaction node, verify whether the primary Hash value is the same as the secondary Hash value or not, and broadcast the verification result to the block chain after using the own private keyto sign the verification result; And the accounting node counts whether the verification result is passed or not within a preset time threshold range of the transaction initiated by the transaction node, and establishes a consensus mechanism according to the verification result which is the passed accumulated number. The communication burden of the block chain and the size of the block can be reduced, and the transmission efficiency of the block chain is greatly improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
System and method for realizing software protection
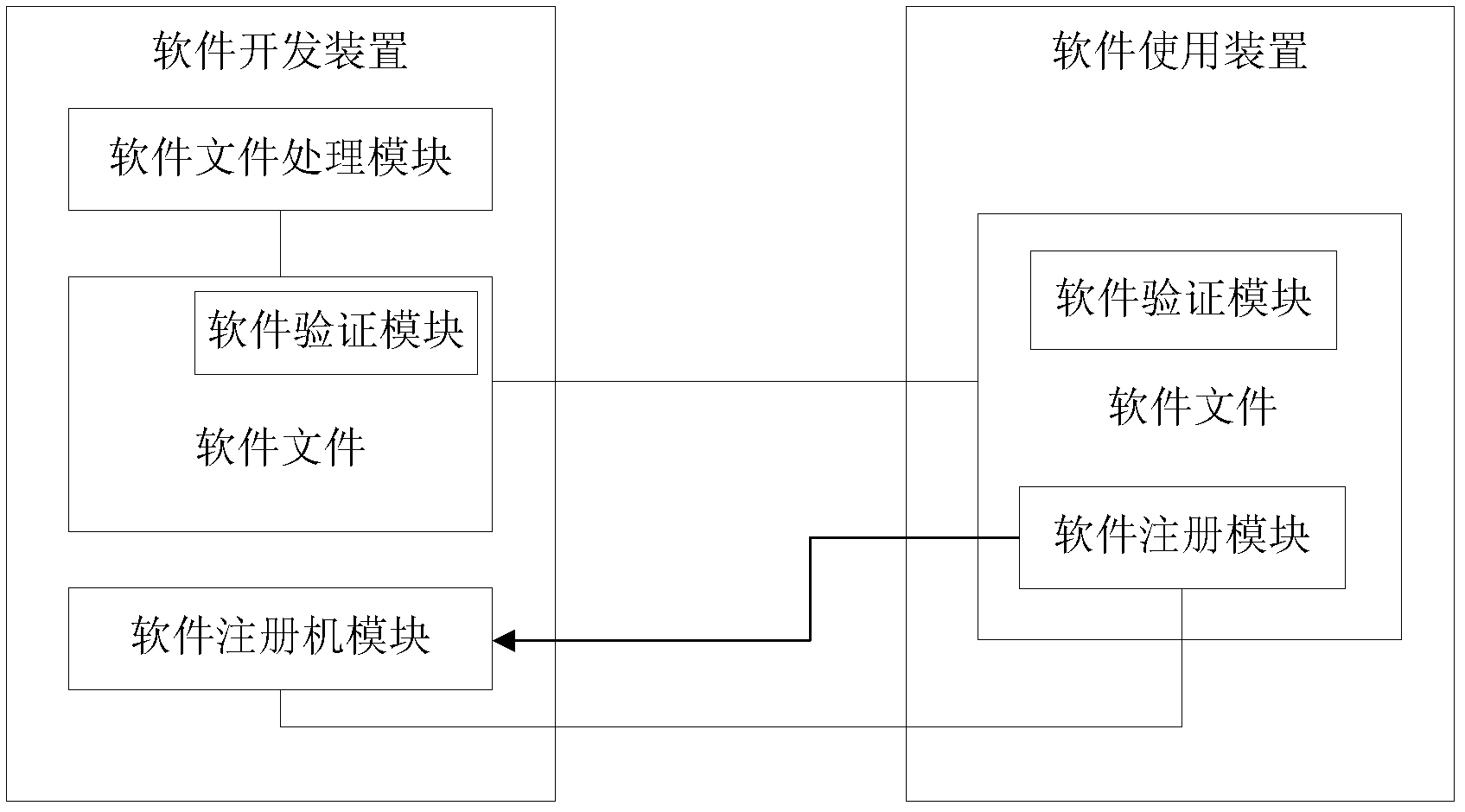
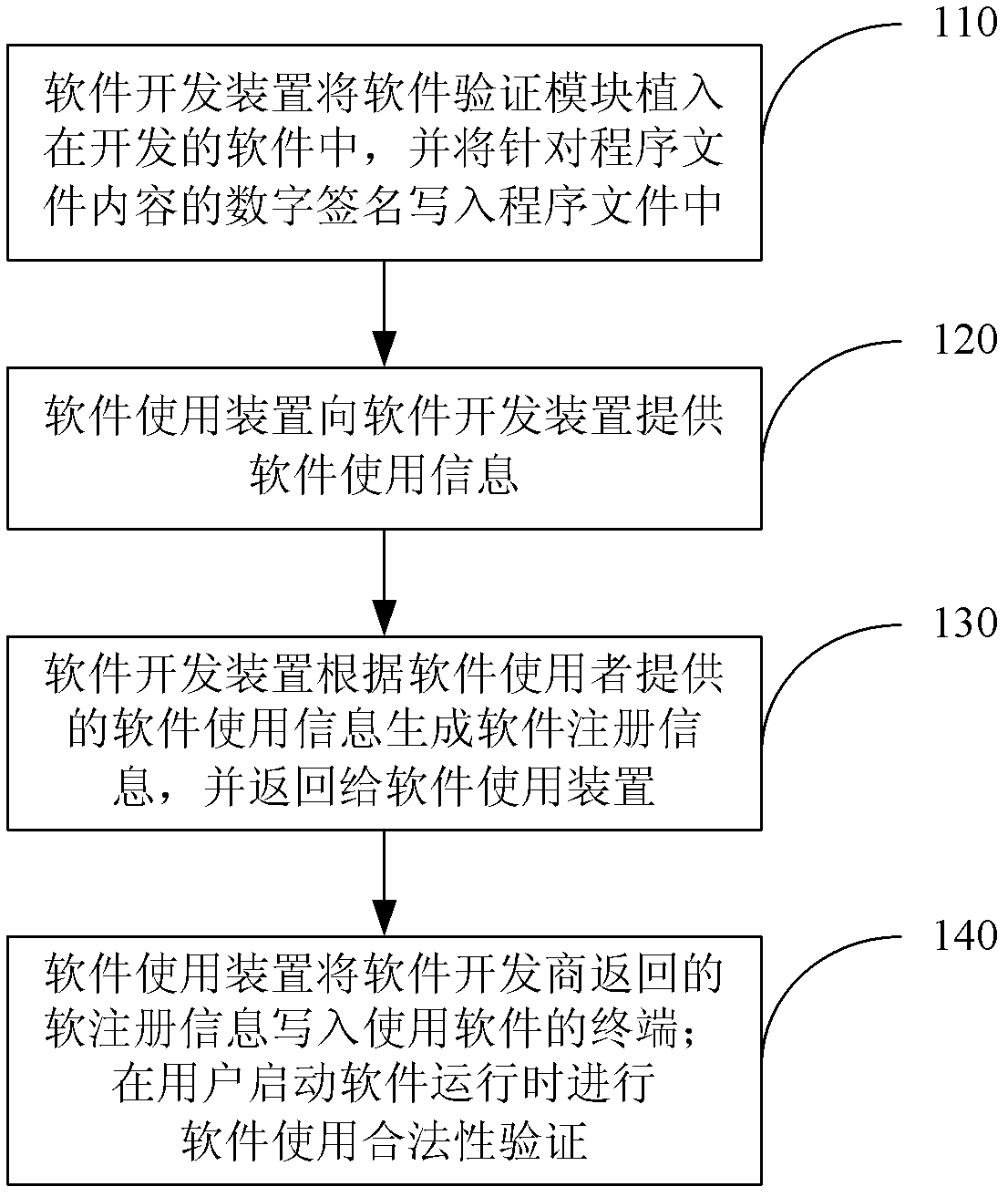
ActiveCN102314578AProtect interestsAvoid using effectsProgram/content distribution protectionDigital signatureComputer module
The invention provides a system and a method for realizing software protection, wherein the system comprises a software development device and a software application device; the software development device is used for implanting a software verification module into developed software and for writing a digital signature which is generated aiming at the content of a program file in the developed program file; and the software application device is used for carrying out authorization verification on the software through the implanted software verification module when the software is started to run by a user. With the adoption of the system and the method for realizing the software protection provided by the invention, the software can be greatly protected so as to prevent unauthorized users from using and unlocking the software, so that the benefit of software developers is greatly protected, and the software industry of China develops towards the healthy direction.
Owner:广西浪潮云计算服务有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com