IOT (Internet of Things) based equipment authentication method, device and system
An IoT device and authentication method technology, applied in the authentication field of IoT terminals and servers, can solve the problems of unsuitable symmetric key mechanism authentication, untrustworthy platform and IoT devices, and failure to verify server identity, etc., to ensure legality. The effect of equity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
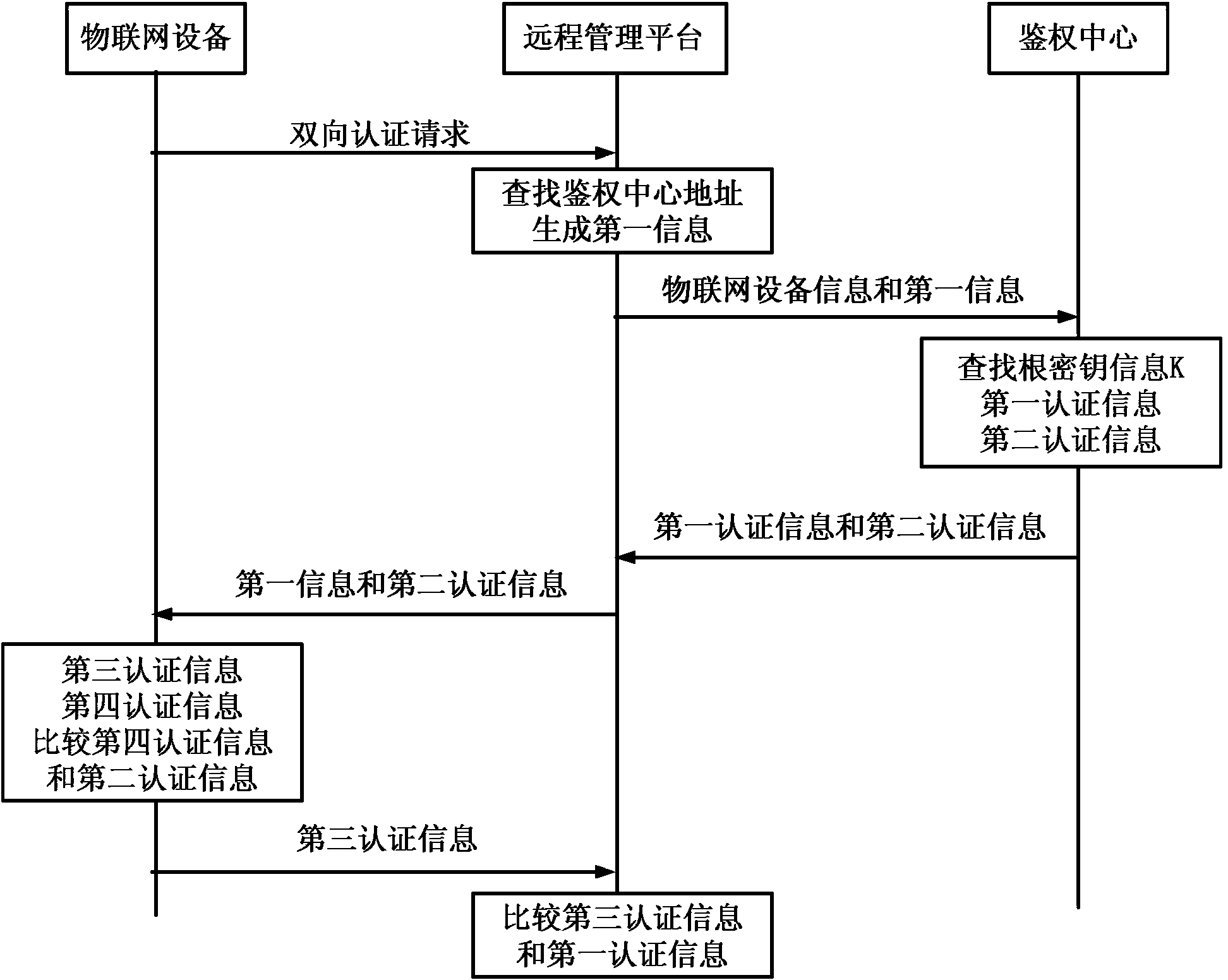
[0061] Example 1: Device A is bound to the card p through the registration stage. When the card p is put into the device B, if B is an illegal device and has not been registered on the remote management platform, it can be found in the table maintained by the Internet of Things management platform. Based on the information that B's device is bound to p, the platform directly rejects B's request, and can further blacklist B.
Embodiment 2
[0062] Example 2: Device B has been transformed by an attacker and can arbitrarily forge its ID and IMSI number, and send it to the remote management platform. The process of remotely managing and authenticating IoT device B needs to be compared with the result calculated by B, because B does not have the root key K , so it cannot pass the authentication, and the platform can judge that B does not have the claimed user subscription information, and device B is an illegal device.
Embodiment 3
[0063] Example 3: Device A is legal and the authentication has passed, but the user uses it to do illegal things. After the authentication, the authentication center can know that the illegal act is sent by device A and its bound card p, and can take further measures , such as freezing the function of the magnetic card or device, stopping the business, etc.
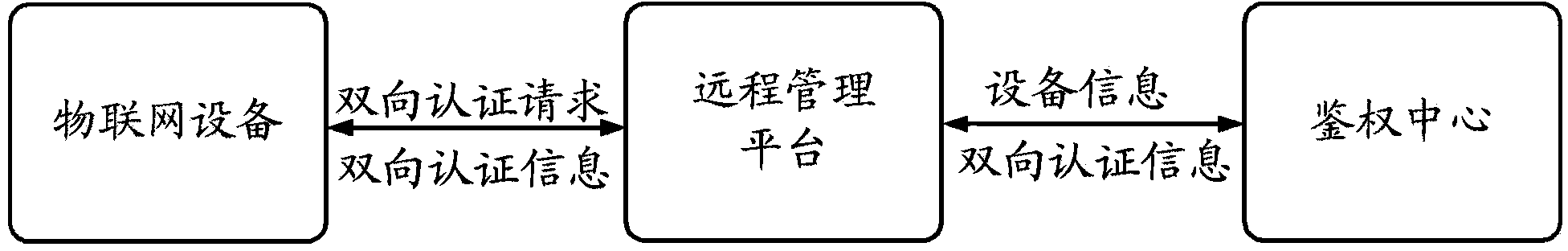
[0064] In the authentication method of the present invention, the IoT device and the bound user subscription information are registered on the remote management platform in advance, ensuring that only the legal remote management platform can be connected to the authentication center to obtain K information. The illegal remote management platform cannot be connected to the authentication center, cannot obtain K information, and cannot authenticate the remote management platform through IoT devices.
[0065] Before using the IoT device, it needs to sign a contract with the operator. The smart card in the IoT device is writt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com