Patents
Literature
1149 results about "Black list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
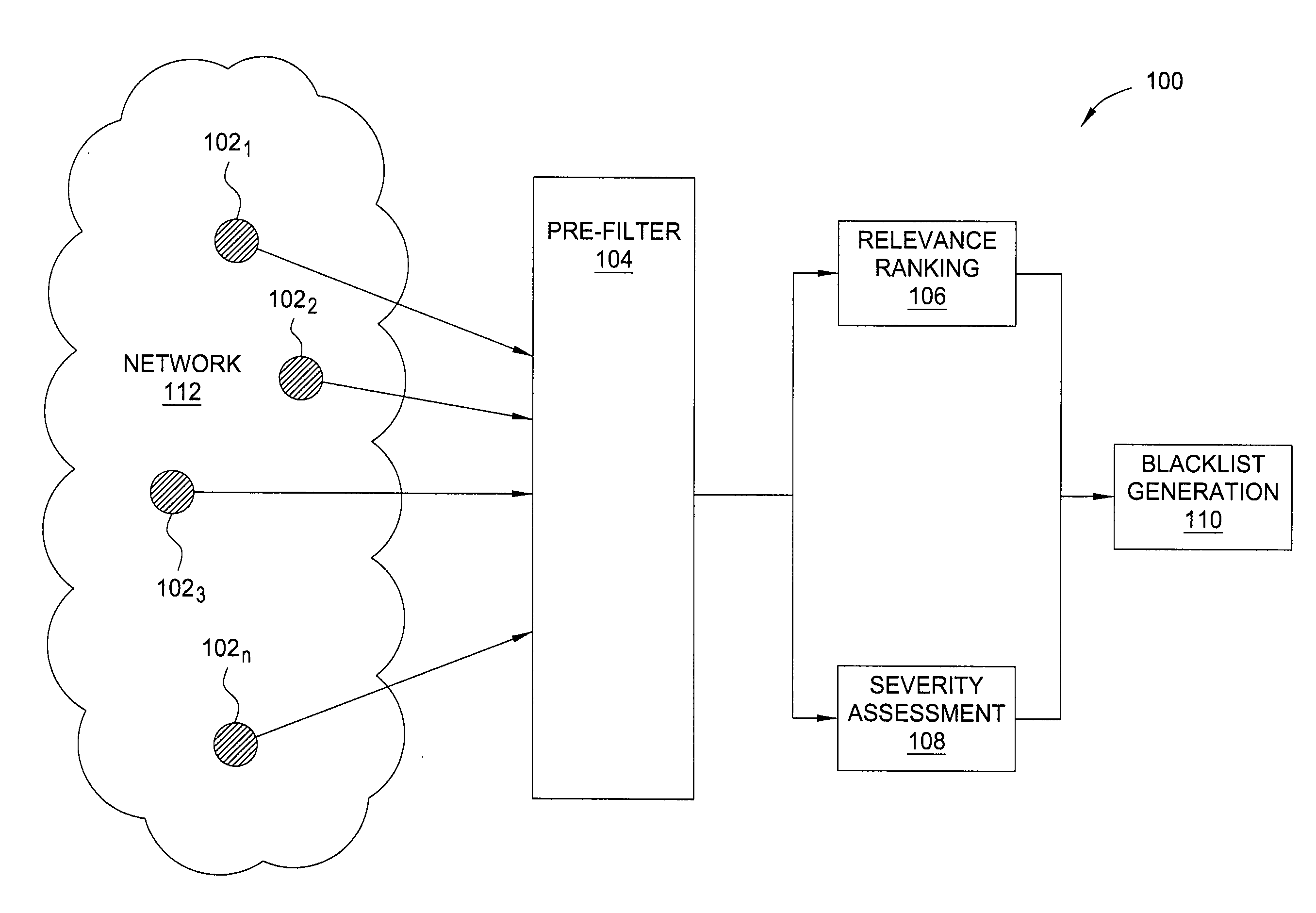
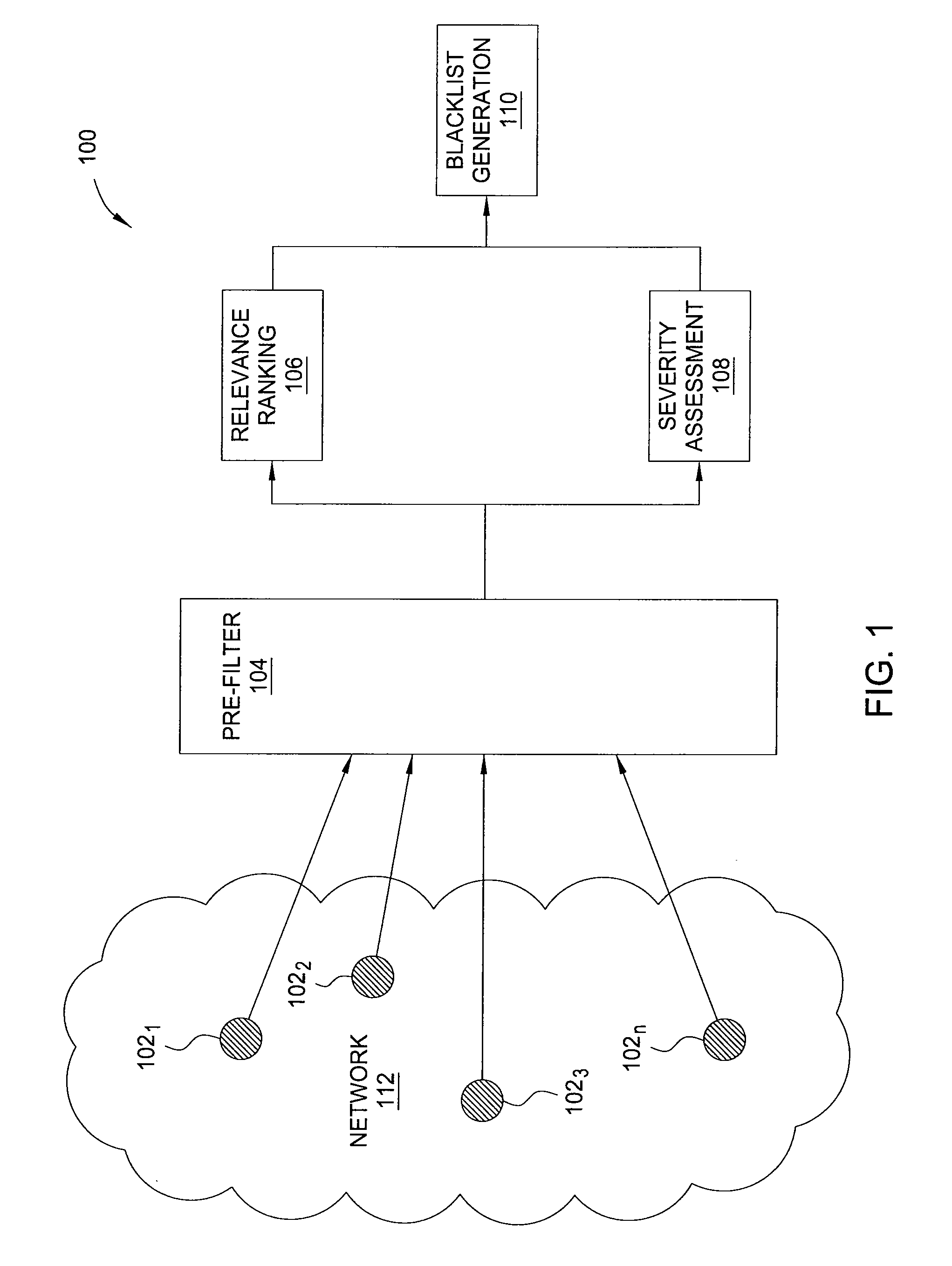
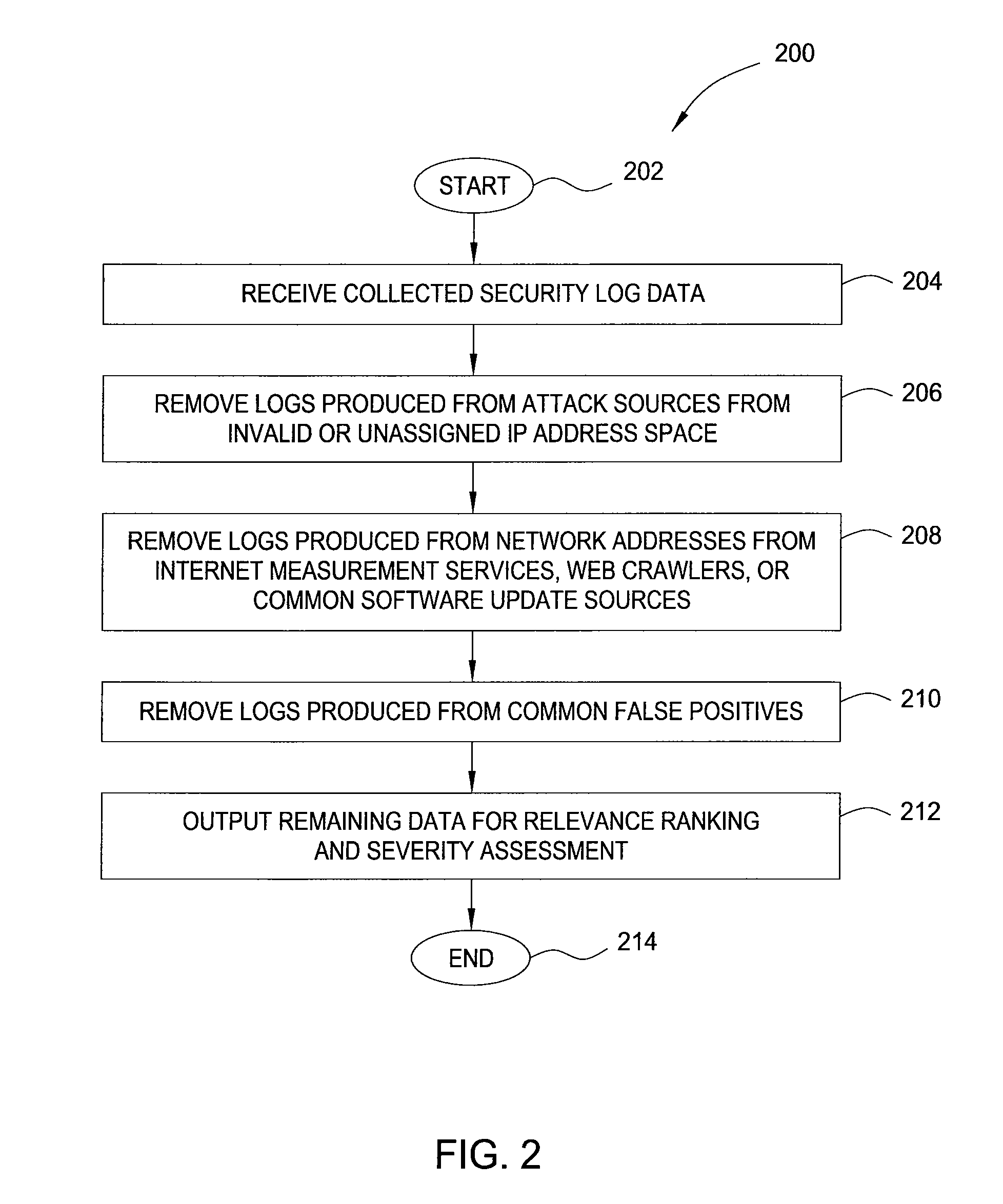
Method and apparatus for generating highly predictive blacklists
ActiveUS20090064332A1Memory loss protectionError detection/correctionNetwork addressingNetwork address
In one embodiment, the present invention is a method and apparatus for generating highly predictive blacklists. One embodiment of a method for generating a blacklist of network addresses for a user of a network includes collecting security log data from users of the network, the security log data identifying observed attacks by attack sources, assigning the attack sources to the blacklist based on a combination of the relevance each attack source to the user and the maliciousness of the attack source, and outputting the blacklist.
Owner:SRI INTERNATIONAL
Authorization and authentication based on an individual's social network
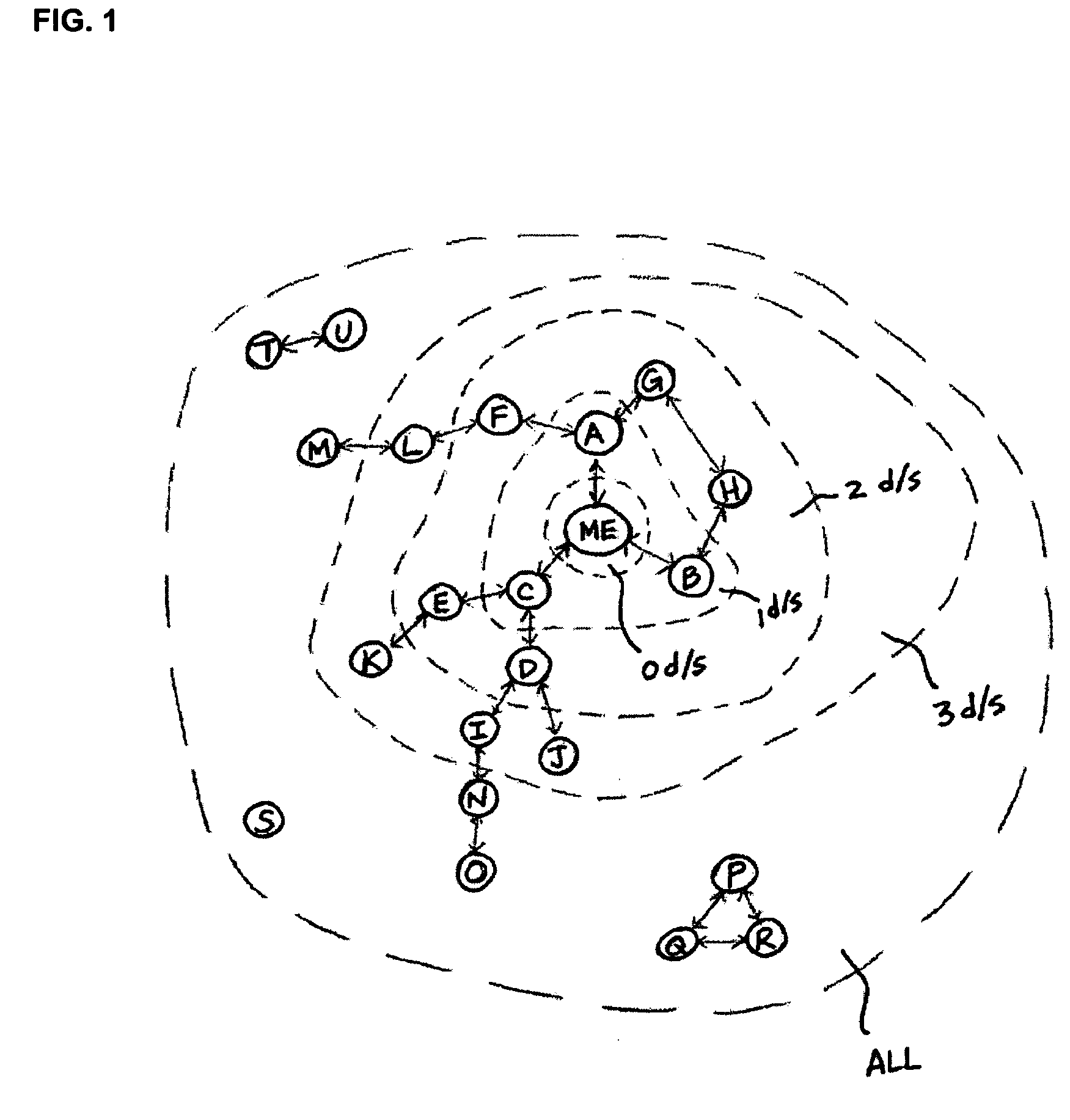
ActiveUS20060021009A1Limited accessFiltered outData processing applicationsDigital data processing detailsBlack listAuthorization
An individual's social network is used to authorize information flow to the individual and to authenticate the individual for access to certain information or services. Information flow to the individual is authorized if the source of the information is a member of the individual's social network who is connected to the individual along a path that does not traverse through anyone on a gray list of the individual. The black list identifies those members who previously sent unwanted communication to the individual or posted content that was deemed offensive by the individual. The gray list identifies those members who are one degree separated from any black list member. The individual is authenticated for access to certain information or services if a member of the individual's social network already has access and this member is connected to the individual along a path that does not traverse through anyone on a gray list of the individual, or if members of the individual's social network who are connected to the individual along a path that does not traverse through anyone on a gray list of the individual have an average authentication rating that is at least a minimum value.
Owner:META PLATFORMS INC
Dynamic message filtering
ActiveUS20050076084A1Reduce in quantityMake fastError detection/correctionGenetic modelsSpammingWhitelist
Dynamically filtering and classifying messages, as good messages, bulk periodicals, or spam. A regular expression recognizer, and pre-trained neural networks. The neural networks distinguish “likely good” from “likely spam,” and also operate at a more discriminating level to distinguish among the three categories above. A dynamic whitelist and blacklist; sending addresses are collected when the number of their messages indicates the sender is good or a spammer. A dynamically selected set of regular expressions input to the neural networks.
Owner:MAILGATE LLC
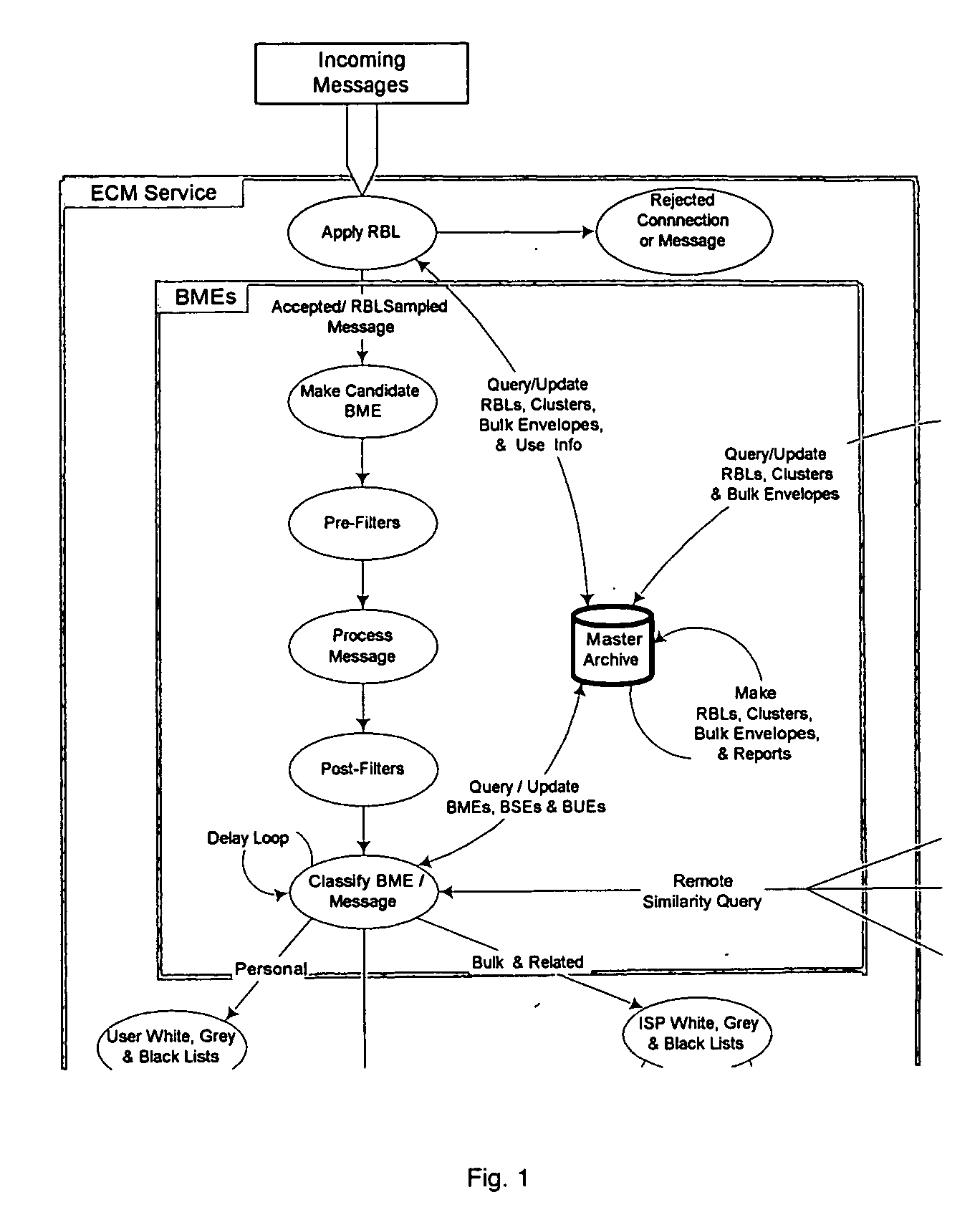
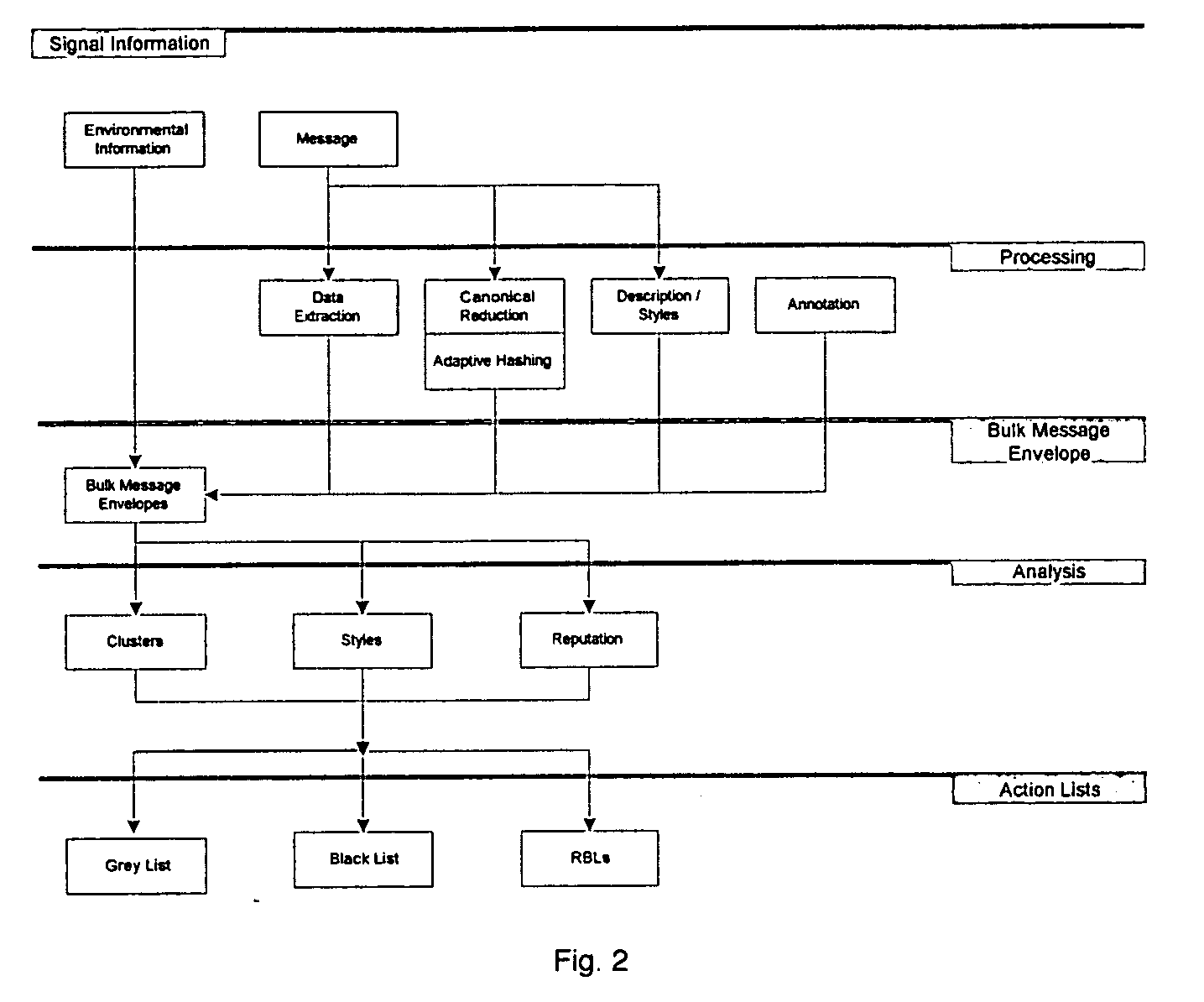
System and method for the classification of electronic communication
InactiveUS20060168006A1Multiple digital computer combinationsData switching networksElectronic communicationSpamming
From an electronic message, we extract any destinations in selectable links, and we reduce the message to a “canonical” (standard) form that we define. It minimizes the possible variability that a spammer can introduce, to produce unique copies of a message. We then make multiple hashes. These can be compared with those from messages received by different users to objectively find bulk messages. From these, we build hash tables of bulk messages and make a list of destinations from the most frequent messages. The destinations can be used in a Real time Blacklist (RBL) against links in bodies of messages. Similarly, the hash tables can be used to identify other messages as bulk or spam. Our method can be used by a message provider or group of users (where the group can do so in a p2p fashion) independently of whether any other provider or group does so. Each user can maintain a “gray list” of bulk mail senders that she subscribes to, to distinguish between wanted bulk mail and unwanted bulk mail (spam). The gray list can be used instead of a whitelist, and is far easier for the user to maintain.
Owner:METASWARM INC
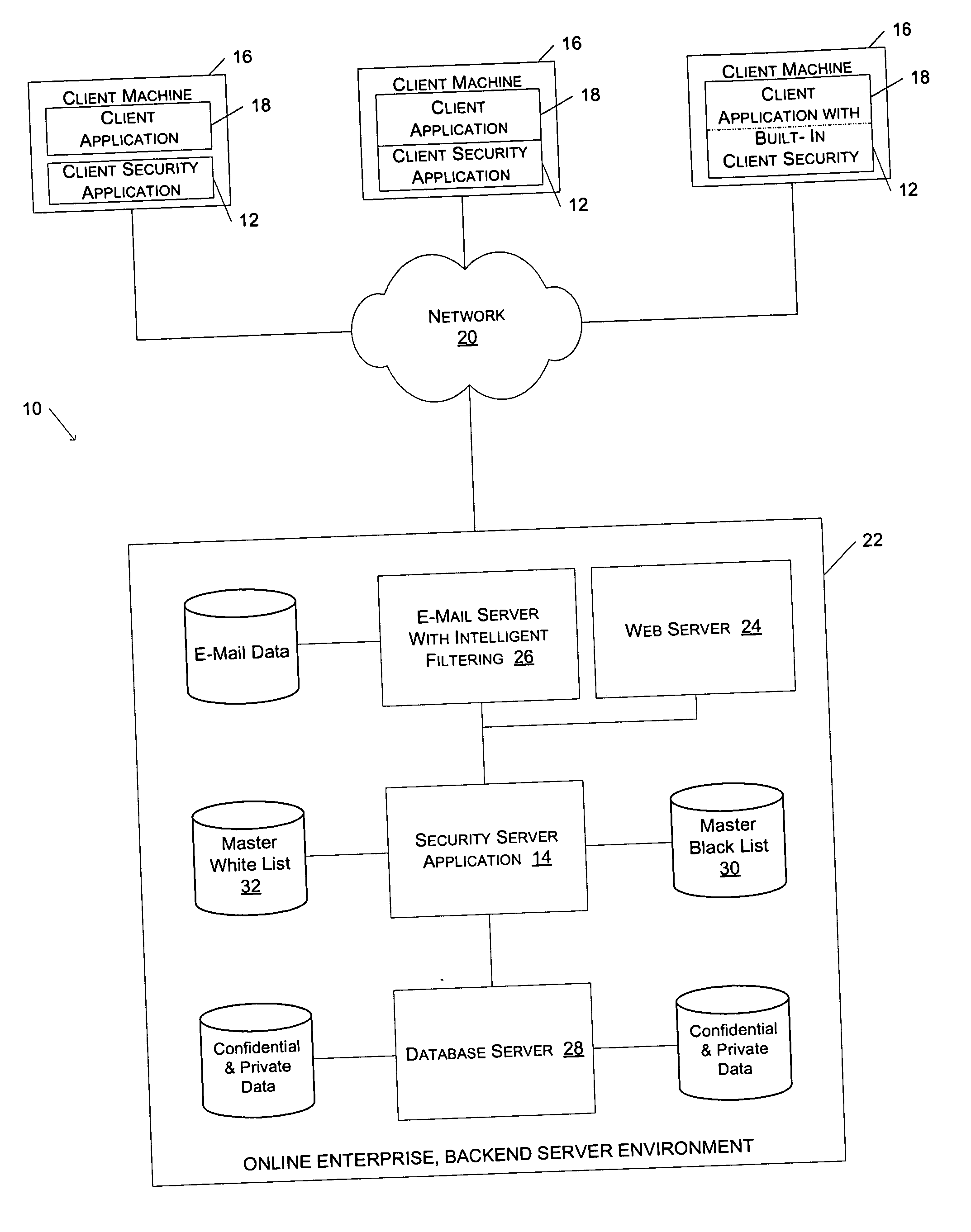
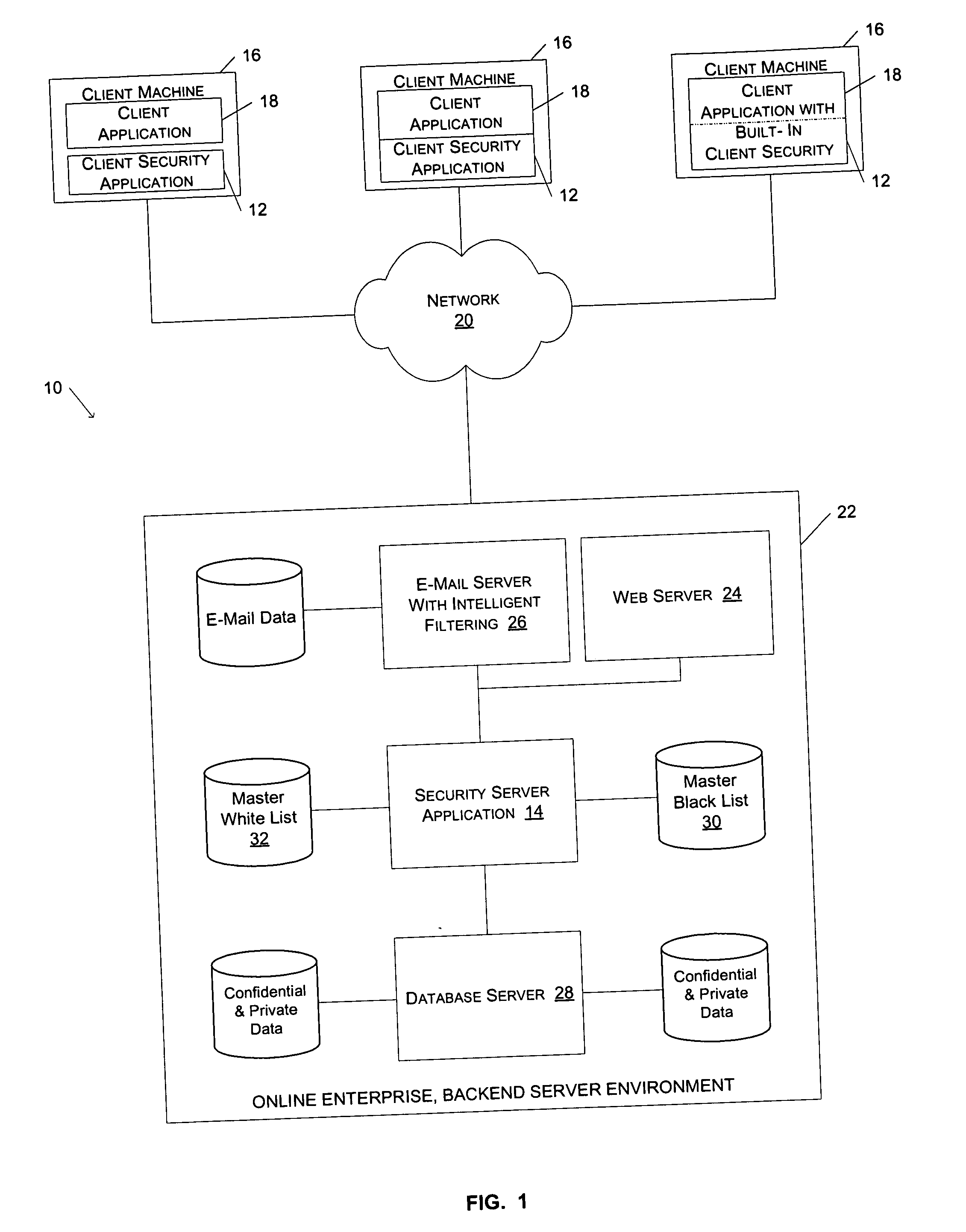
Method and system for preventing fraudulent activities
ActiveUS20060021031A1The process is simple and effectiveAbility to detectDigital data processing detailsAnalogue secracy/subscription systemsWeb siteWeb browser
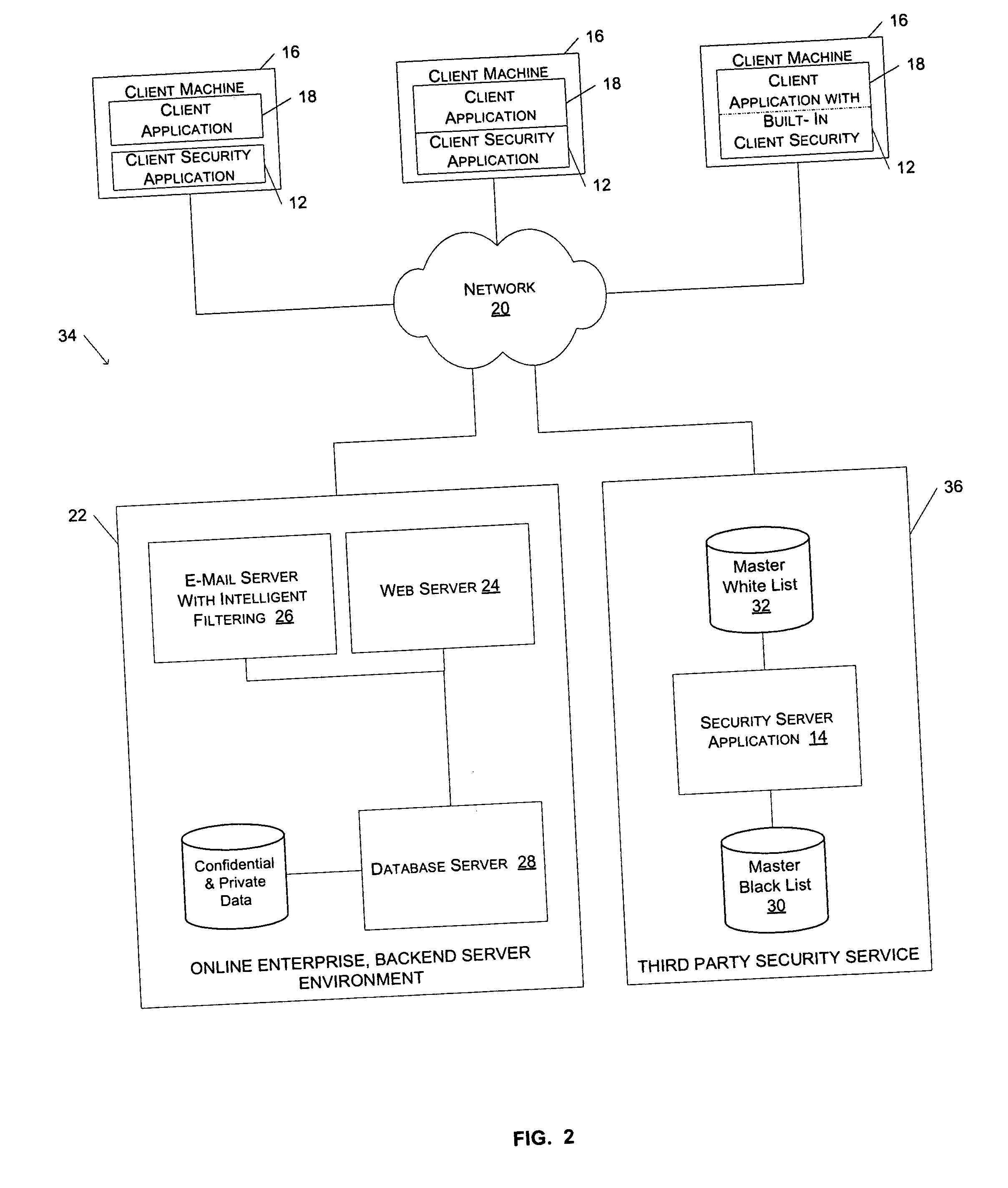
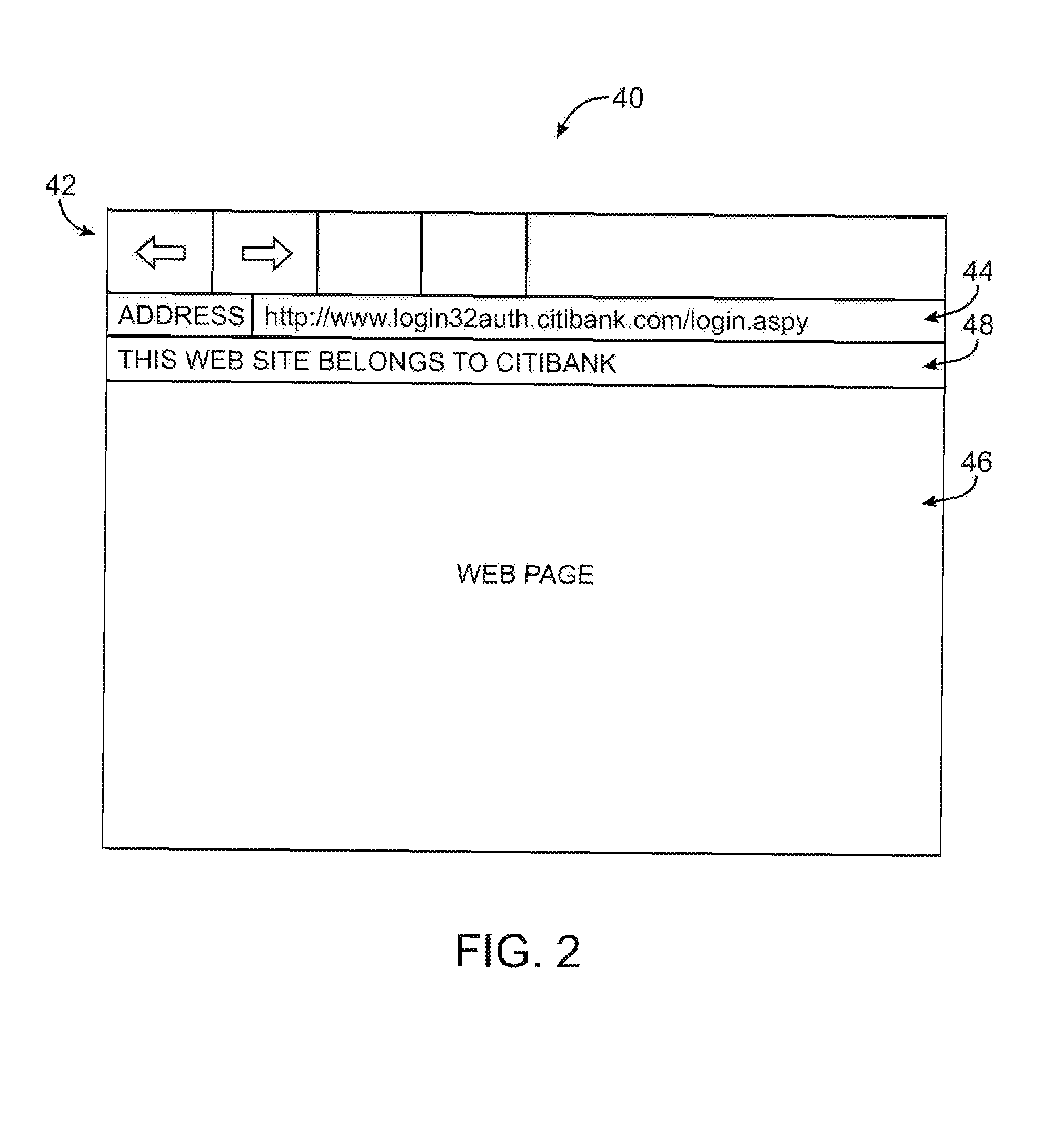
A method and system to protect users against potentially fraudulent activities associated with spoof web sites are described. According to one aspect of the present invention, the URL of a document downloaded via a web browser client is compared to the URLs in a list of URLs for known spoof sites. If the URL for the downloaded document is found in the list of URLs for known spoof sites, a security indicator is displayed to the user to indicate to the user that the downloaded document is associated with a known spoof site. According to another aspect of the invention, a security server maintains a master black list and periodically communicates updates of the master black list to the local list of a client security application.
Owner:EBAY INC
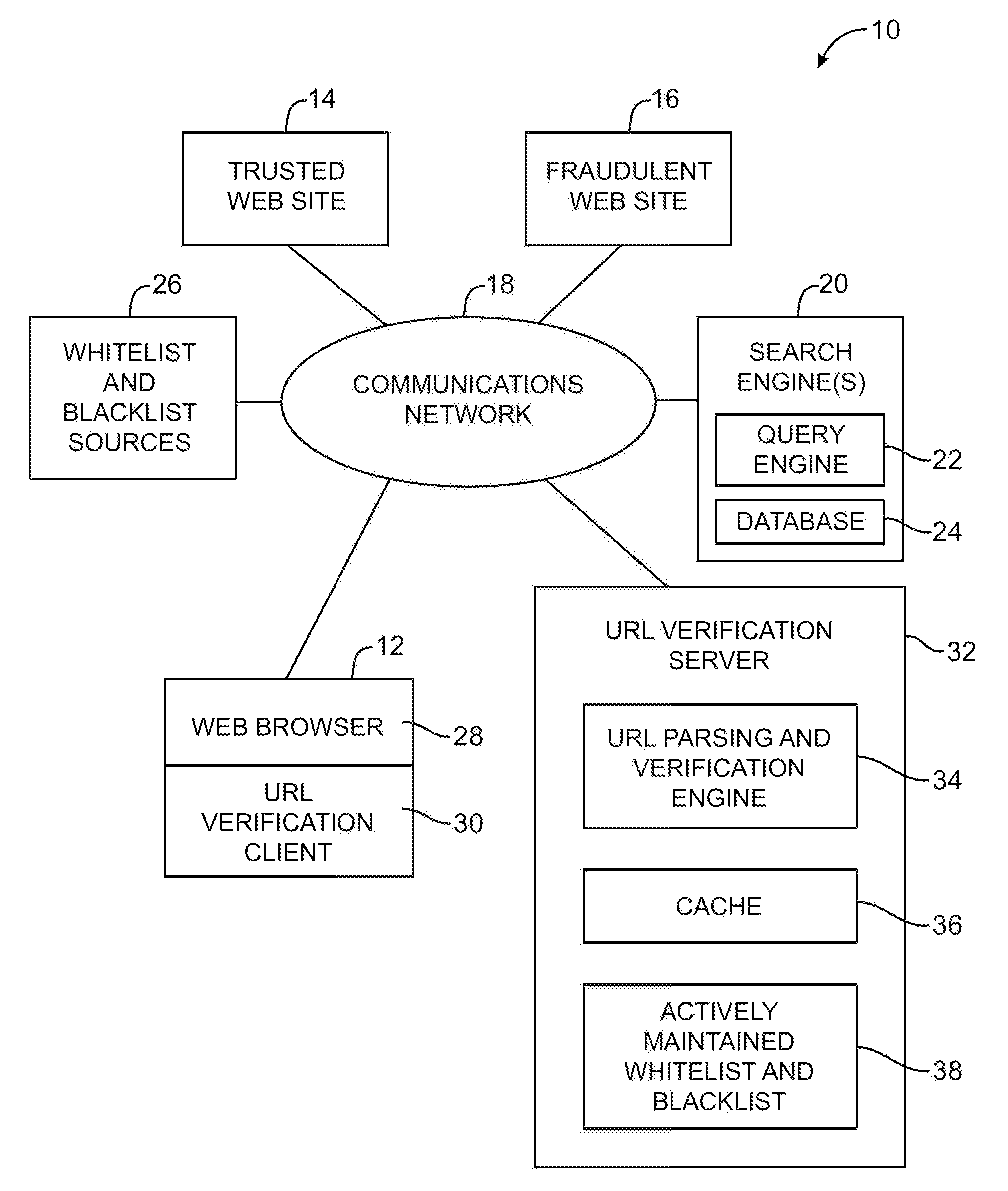
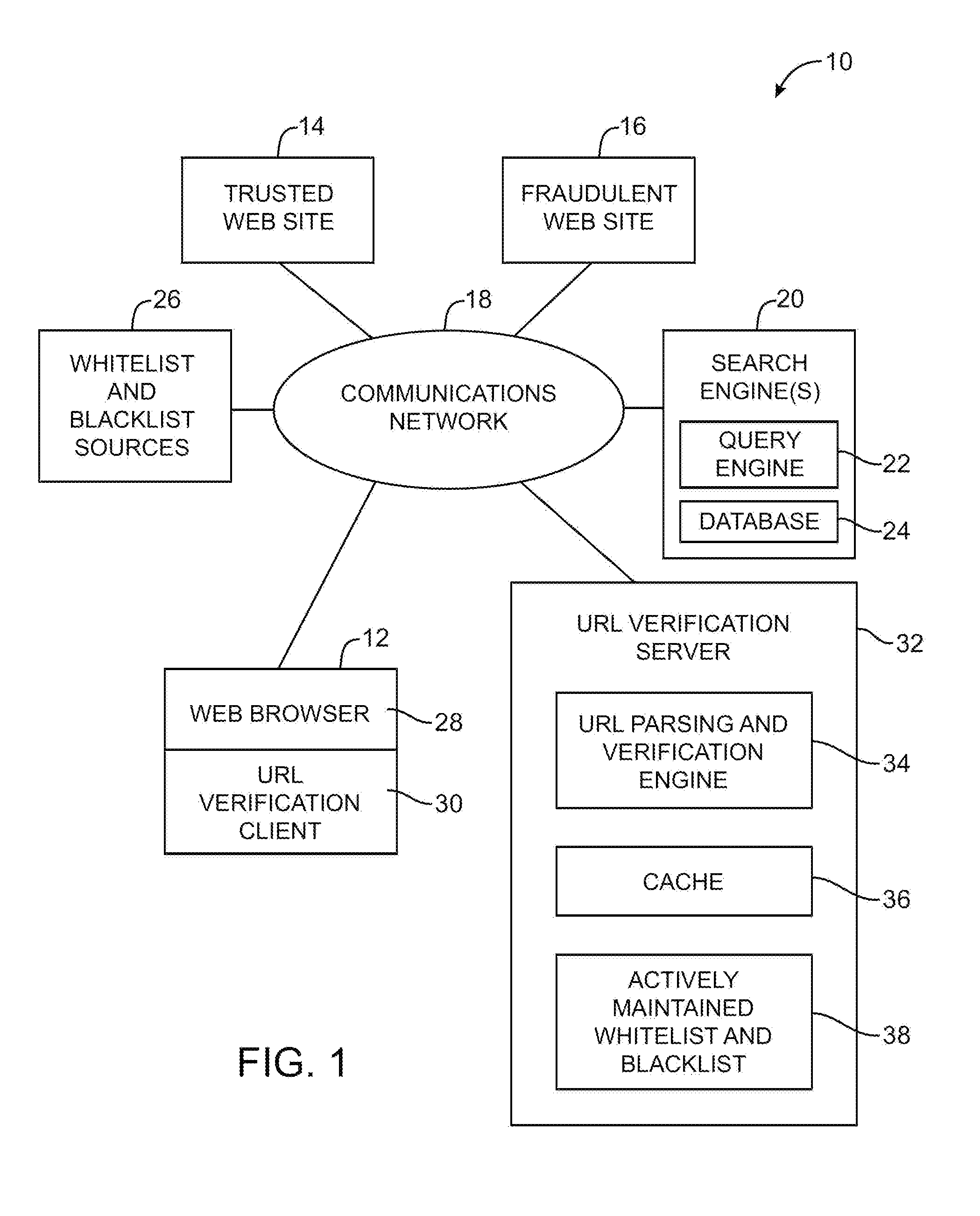
Server-based universal resource locator verification service
A URL verification service is provided that is used to evaluate the trustworthiness of universal resource locators (URLs). As a user browses the world wide web, a URL verification client captures a URL associated with a web page of unknown authenticity. The URL verification client transmits the captured URL to a URL verification server. The URL verification server compares the URL to actively maintained whitelist and blacklist information. The server also uses the URL and a user-supplied or automatically-extracted brand to query a search engine. The URL verification server processes the response of the search engine to the search engine queries and the results of cache and whitelist and blacklist comparisons to determine whether the captured URL is legitimately associated with the brand. The results of the URL evaluation process are transmitted from the URL verification server to the URL verification client, which notifies user.
Owner:MICRO FOCUS LLC
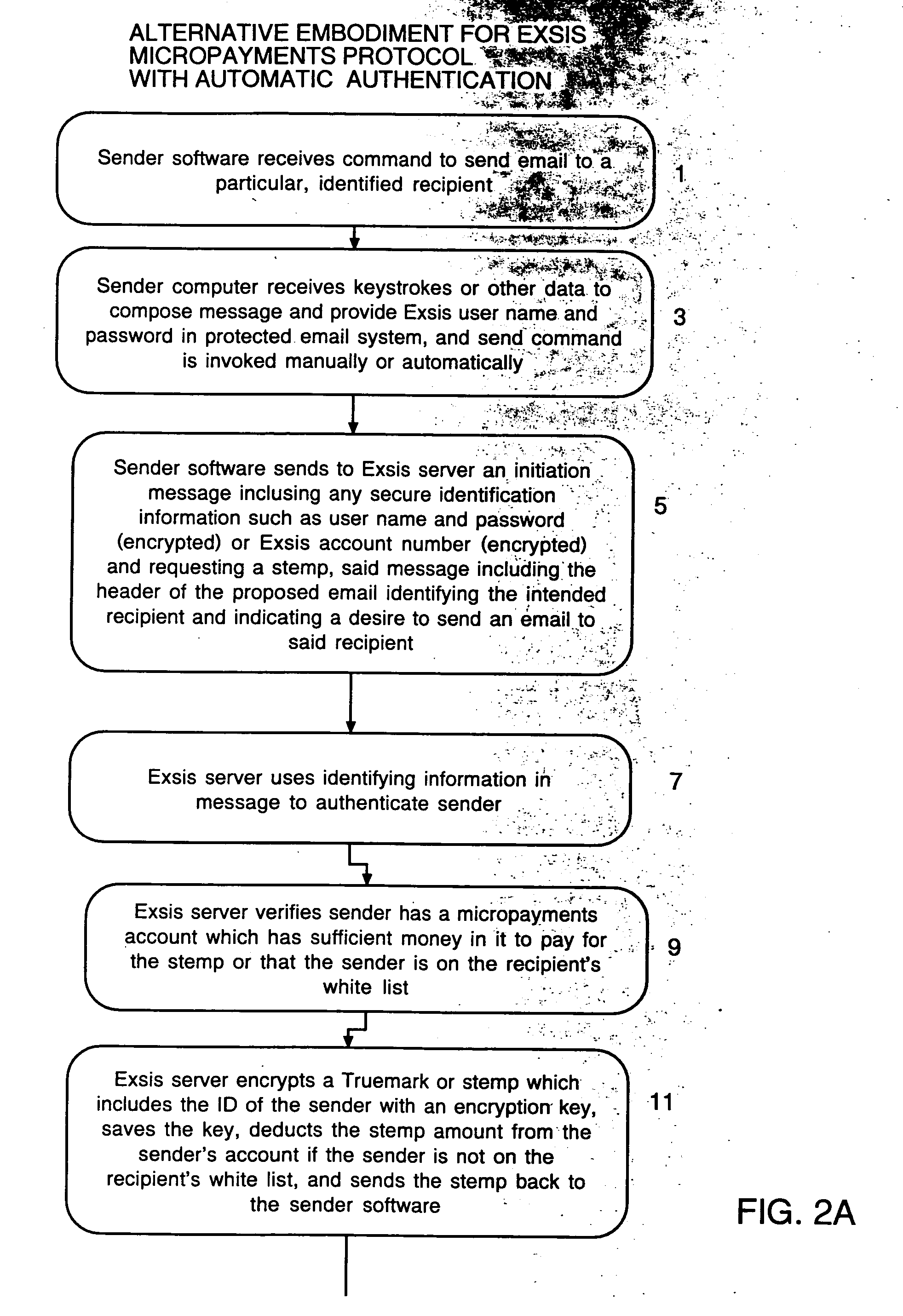
User interface and anti-phishing functions for an anti-spam micropayments system
ActiveUS20060075028A1Control contentEffective controlMultiple digital computer combinationsFlotationTrademarkSpamming
Owner:ICONIX INC
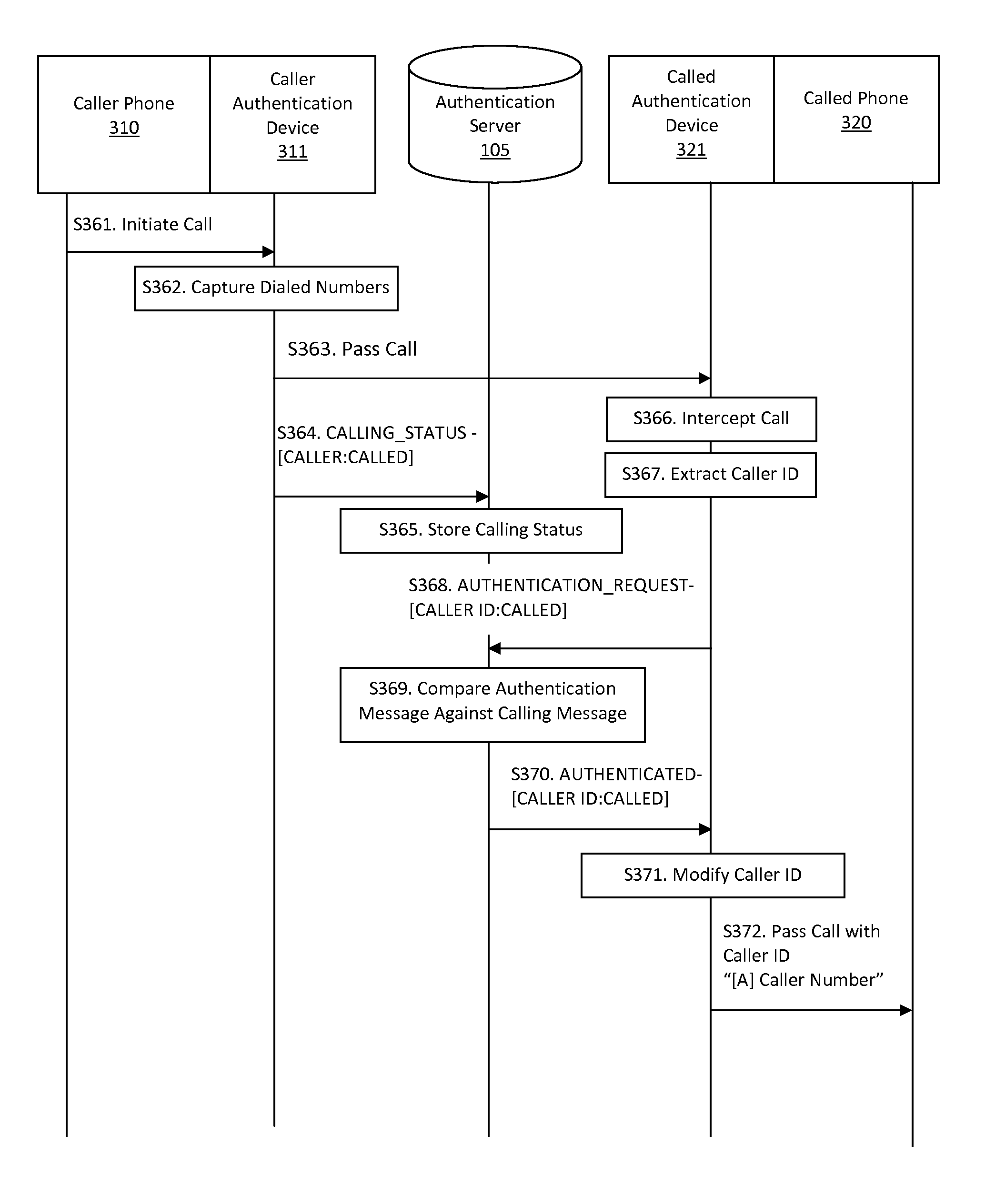
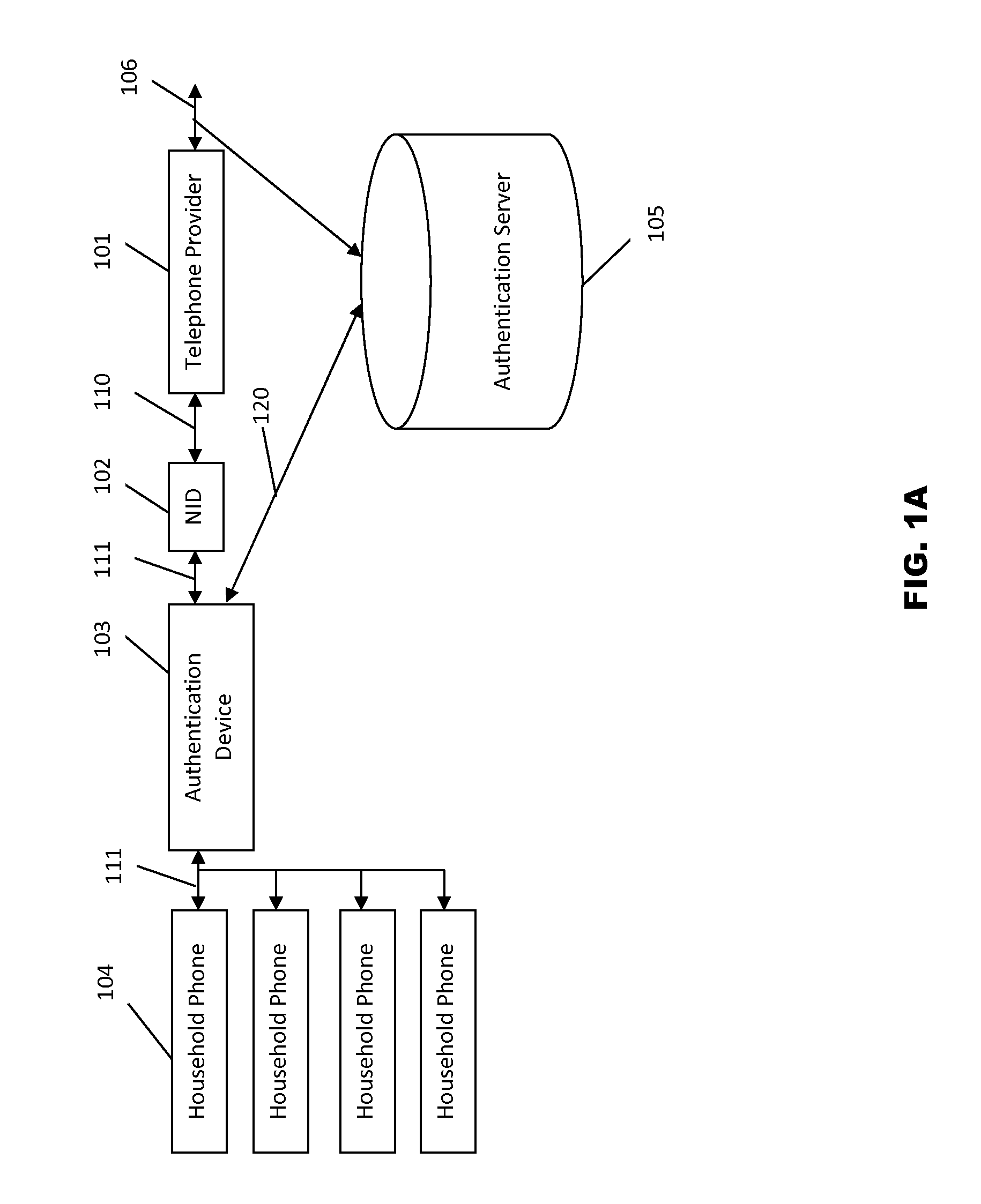
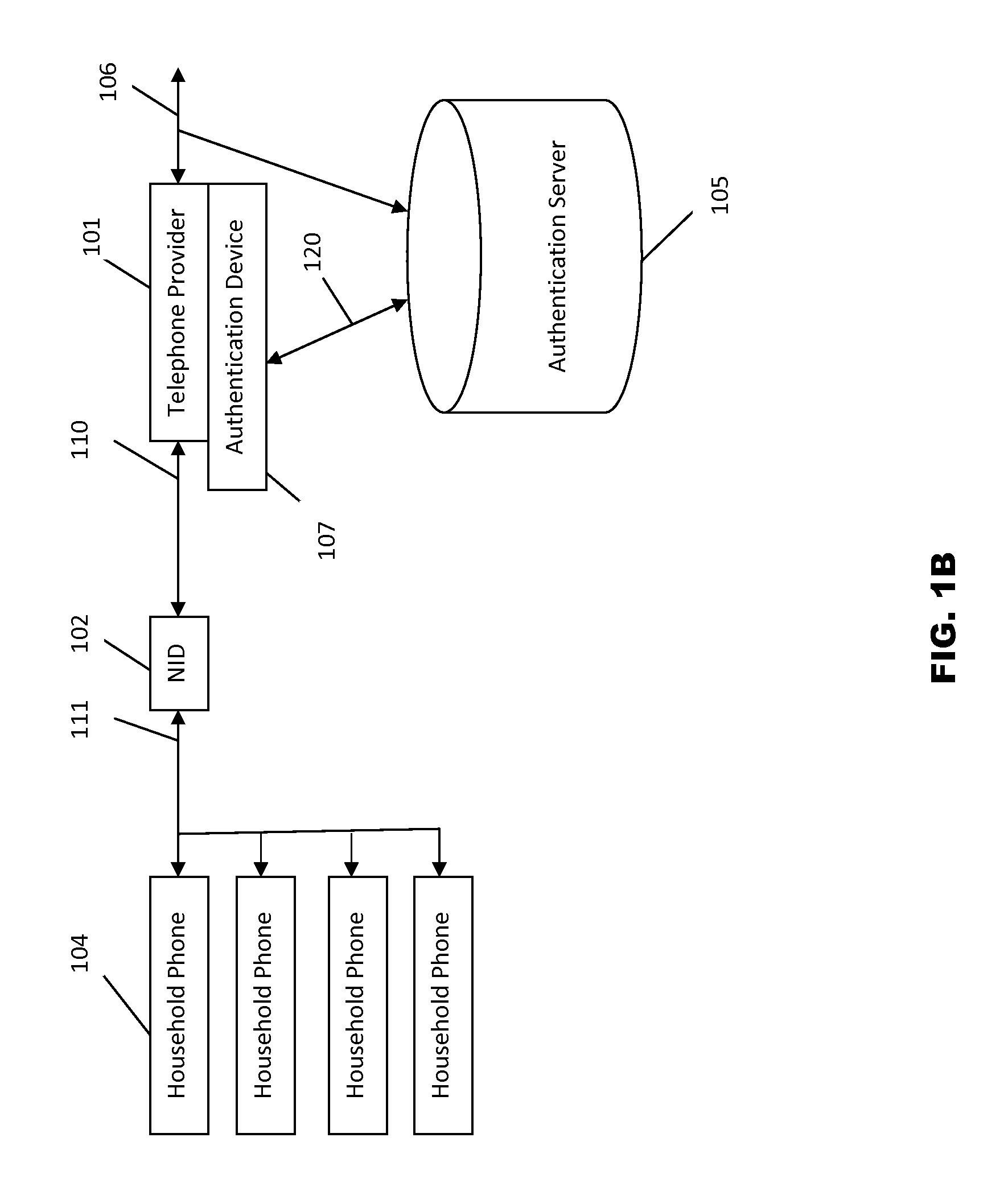
Systems and methods for caller ID authentication, spoof detection and list based call handling
ActiveUS9060057B1Special service for subscribersCalled number recording/indicationBase callingCommunication source
Systems and methods for caller id authentication, spoof detection and list based call handling are disclosed. The caller ID authentication is performed by an authentication device connected to the calling party telephone transmitting the source and destination telephone numbers of the call to an authentication server. The called party authentication device extracts the caller ID of the incoming call and transmits the caller ID of the caller and the telephone number of the called party to the authentication server. The authentication server analyzes the transmitted information from both devices and replies with the authentication status of the caller ID to the called party authentication device. Other embodiments are disclosed where the authentication server is not available and caller ID authentication is performed in a peer-to-peer manner. In another embodiment, the concepts of active and passive certification passwords are used to maintain the integrity of the system. Other embodiments allow for authenticating blocked caller ID's, reveling blocked caller ID's, VoIP implementations, legitimate caller ID spoofing, and placing a blocked caller ID on private white or black lists. Another embodiment combines the described caller ID authentication system within a call handling system utilizing internal, global and private white and black lists. Applications of caller ID authentication methodology to other forms of communication source address authentication, such as email, SMS, and postal mail are envisioned.
Owner:DANIS SERDAR ARTUN
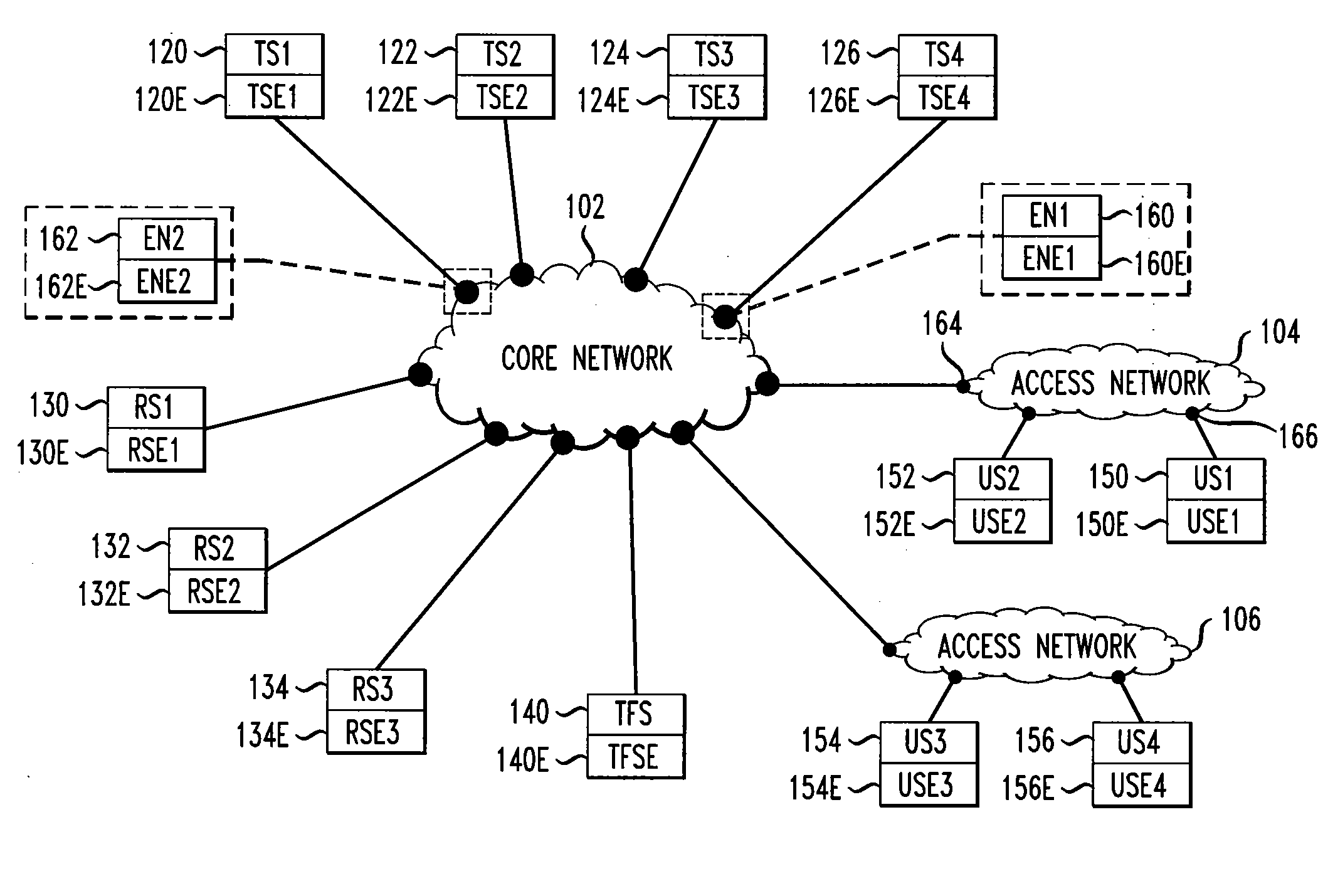
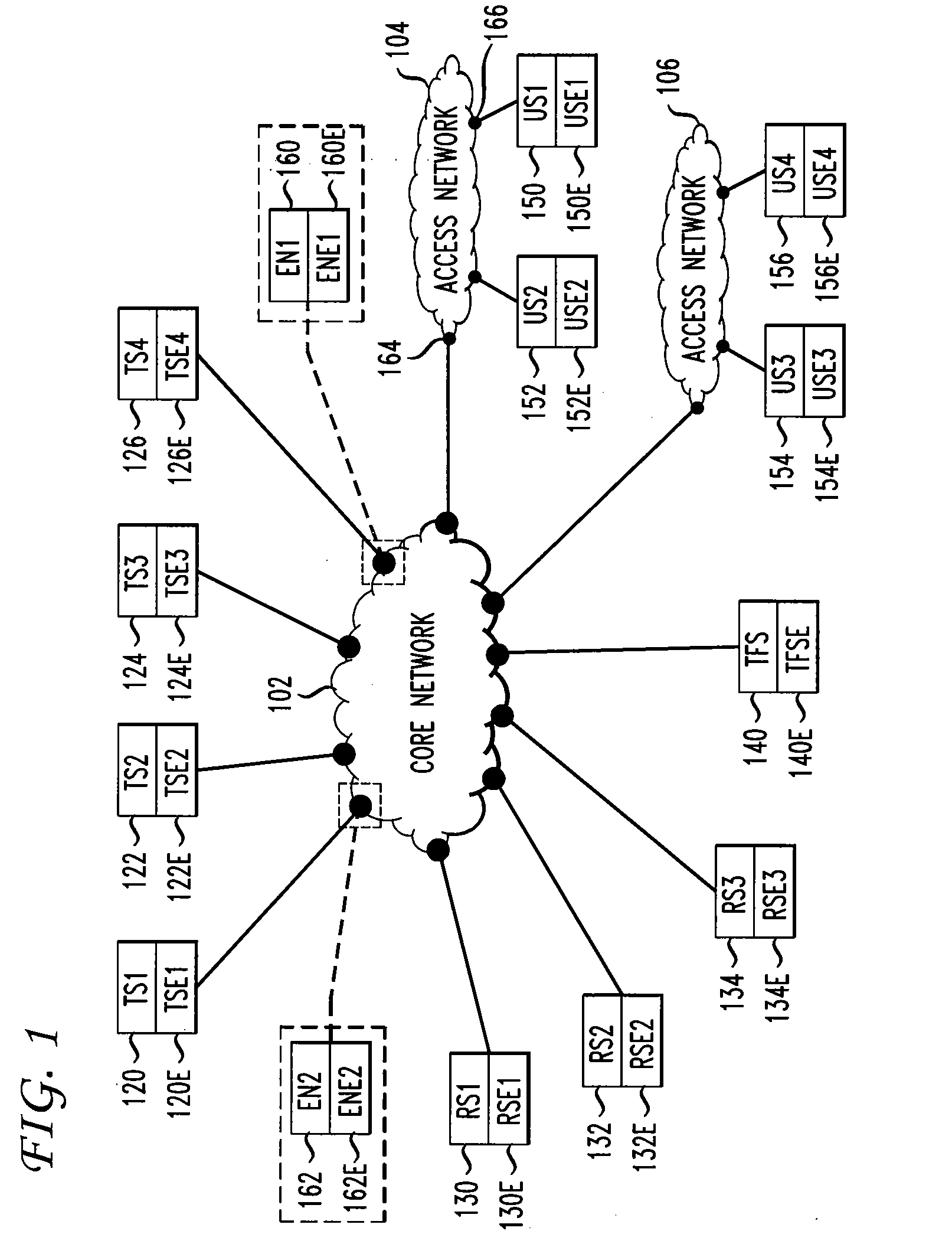
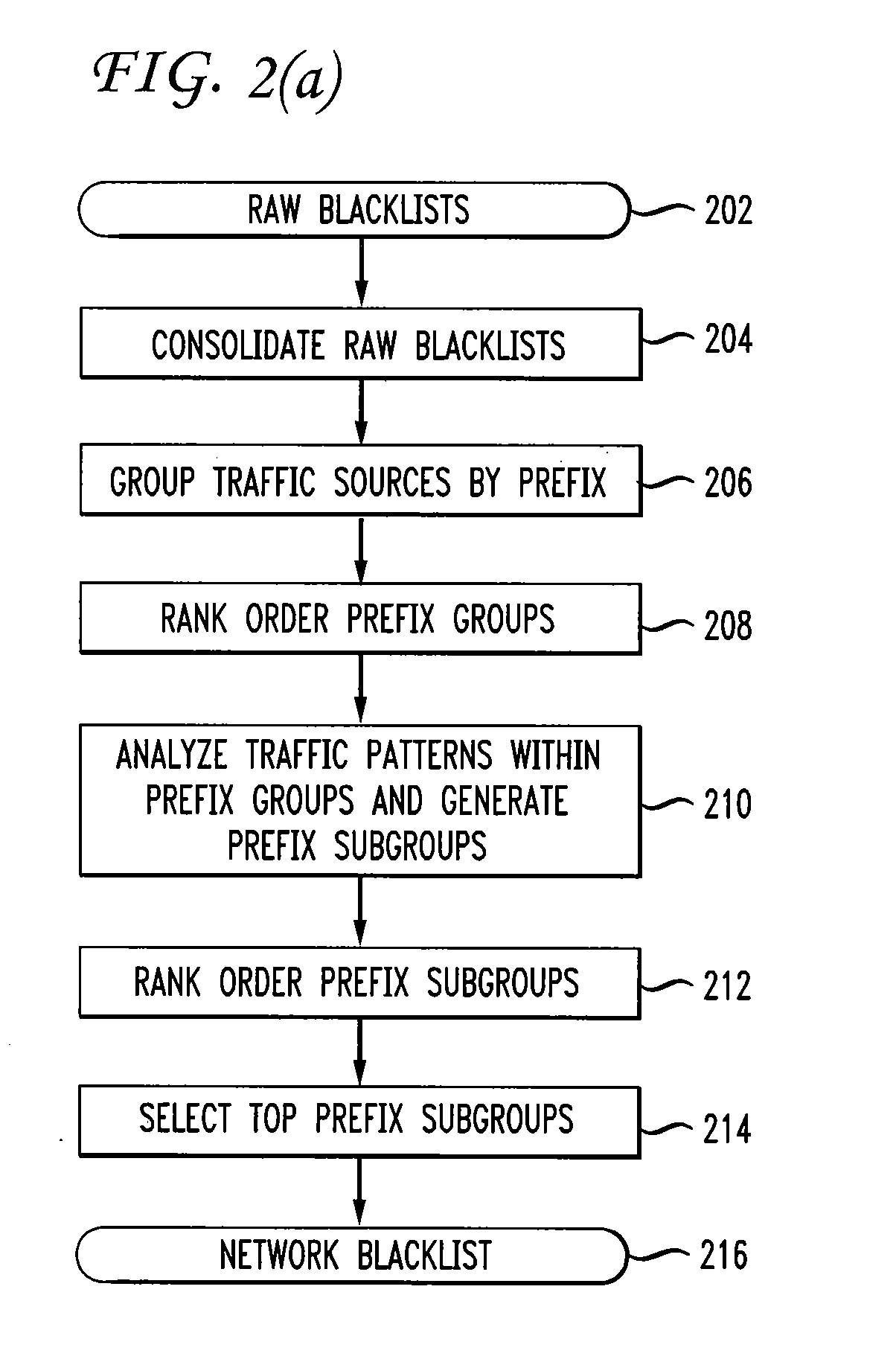
Filtering unwanted data traffic via a per-customer blacklist
ActiveUS20100082811A1Digital data information retrievalMultiple digital computer combinationsTraffic capacityIp address
Traffic flow from a traffic source with a source IP address to a customer system with a destination IP address is filtered by comparing the source IP address to a customer blacklist. If the source IP address is on the customer blacklist, then traffic to the customer system is blocked; else, traffic to the customer system is allowed. The customer blacklist is generated from a network blacklist, comprising IP addresses of unwanted traffic sources, and a customer whitelist, comprising IP addresses of wanted traffic sources. The customer blacklist is generated by removing from the network blacklist any IP address also on the customer whitelist. The network blacklist is generated by acquiring raw blacklists from reputation systems. IP addresses on the raw blacklists are sorted by prefix groups, which are rank ordered by traffic frequency. Top prefix groups are selected for the network blacklist.
Owner:AT&T INTPROP I L P
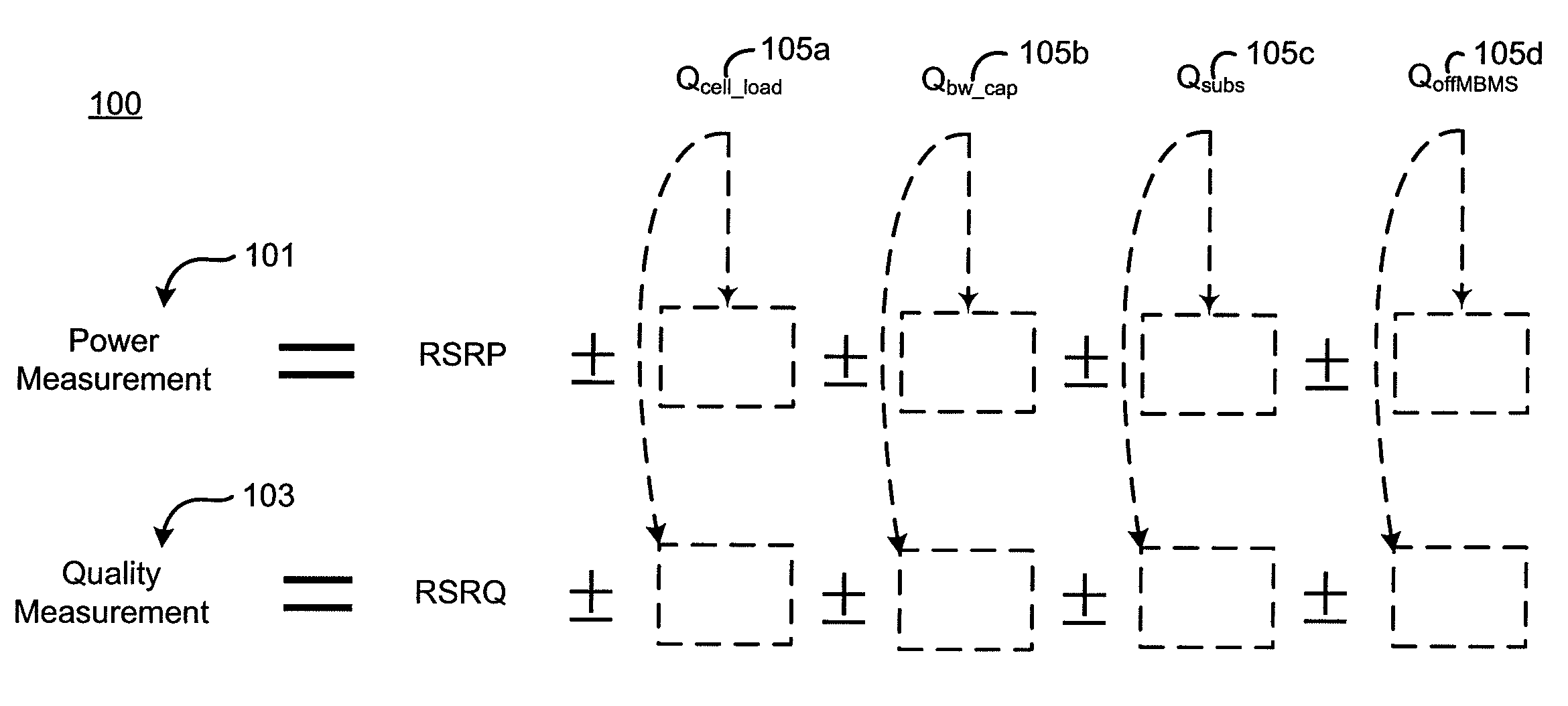
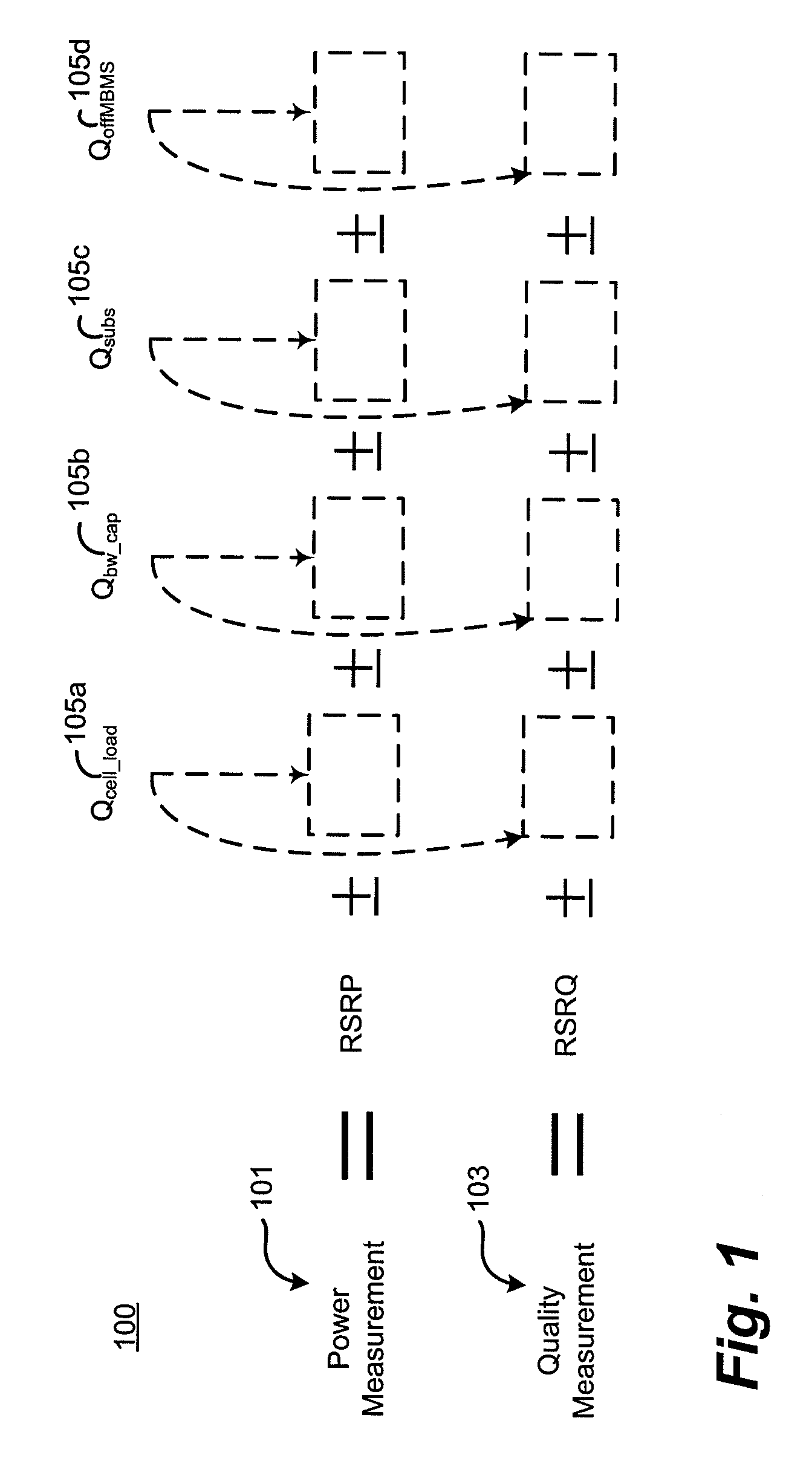
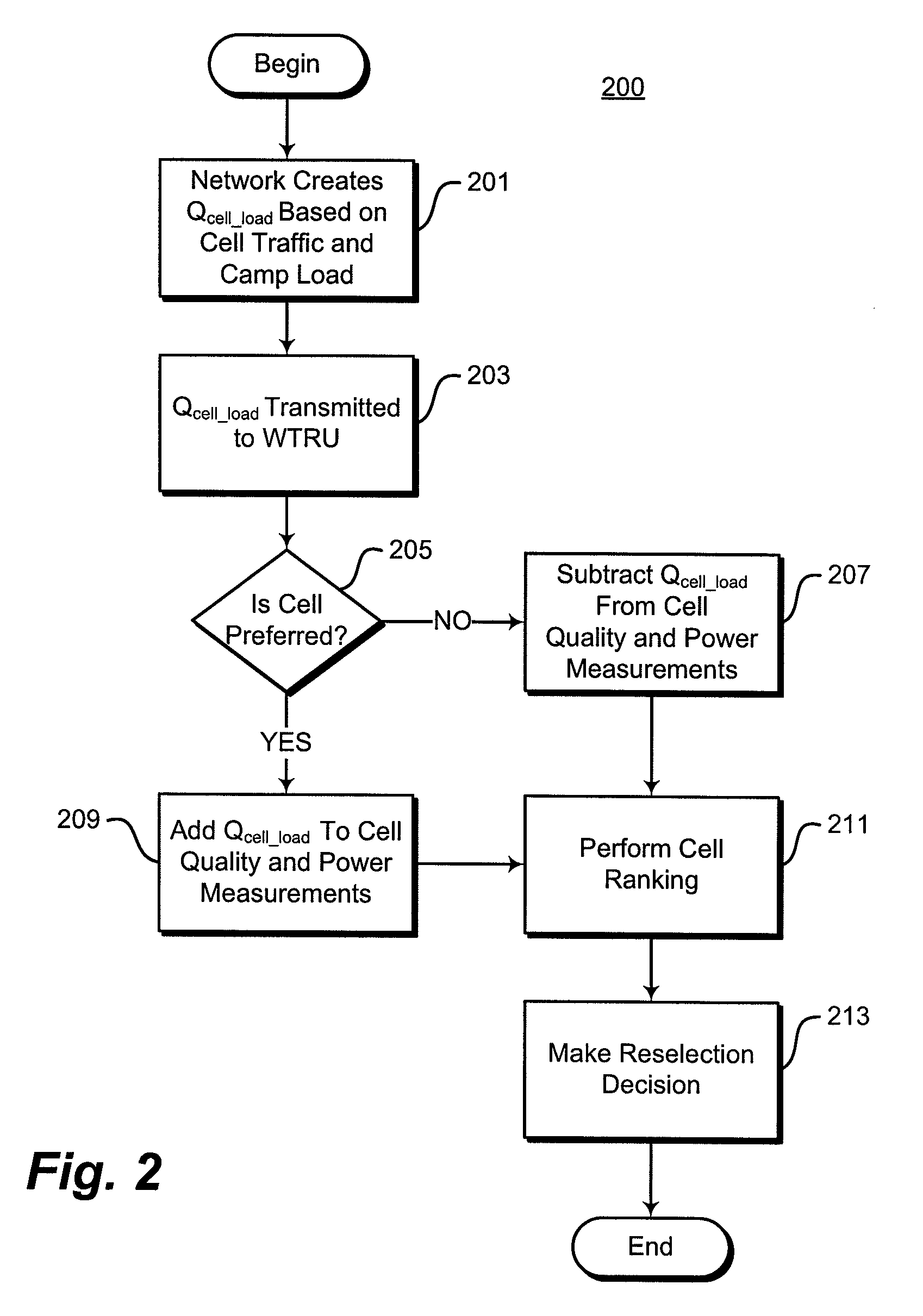
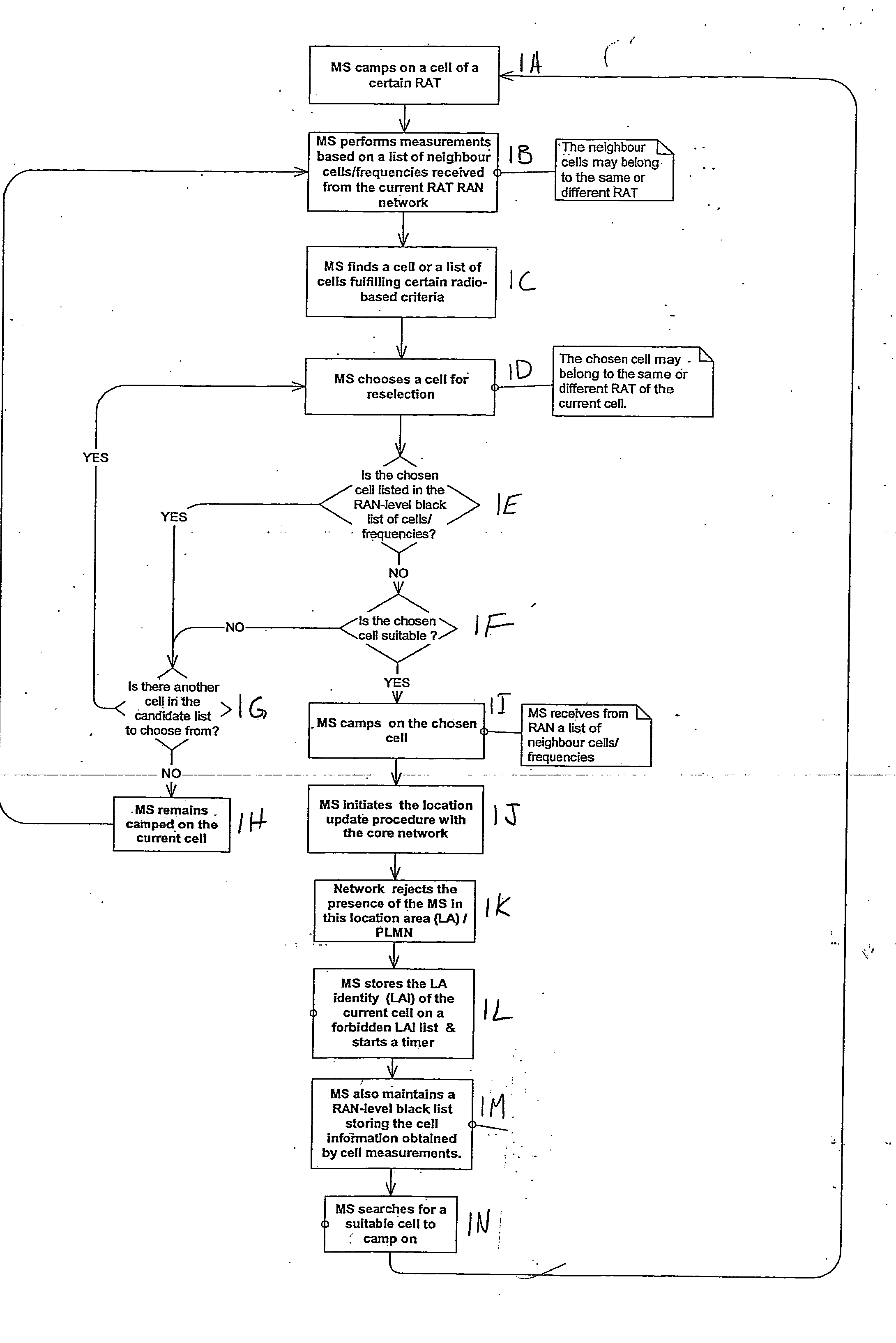
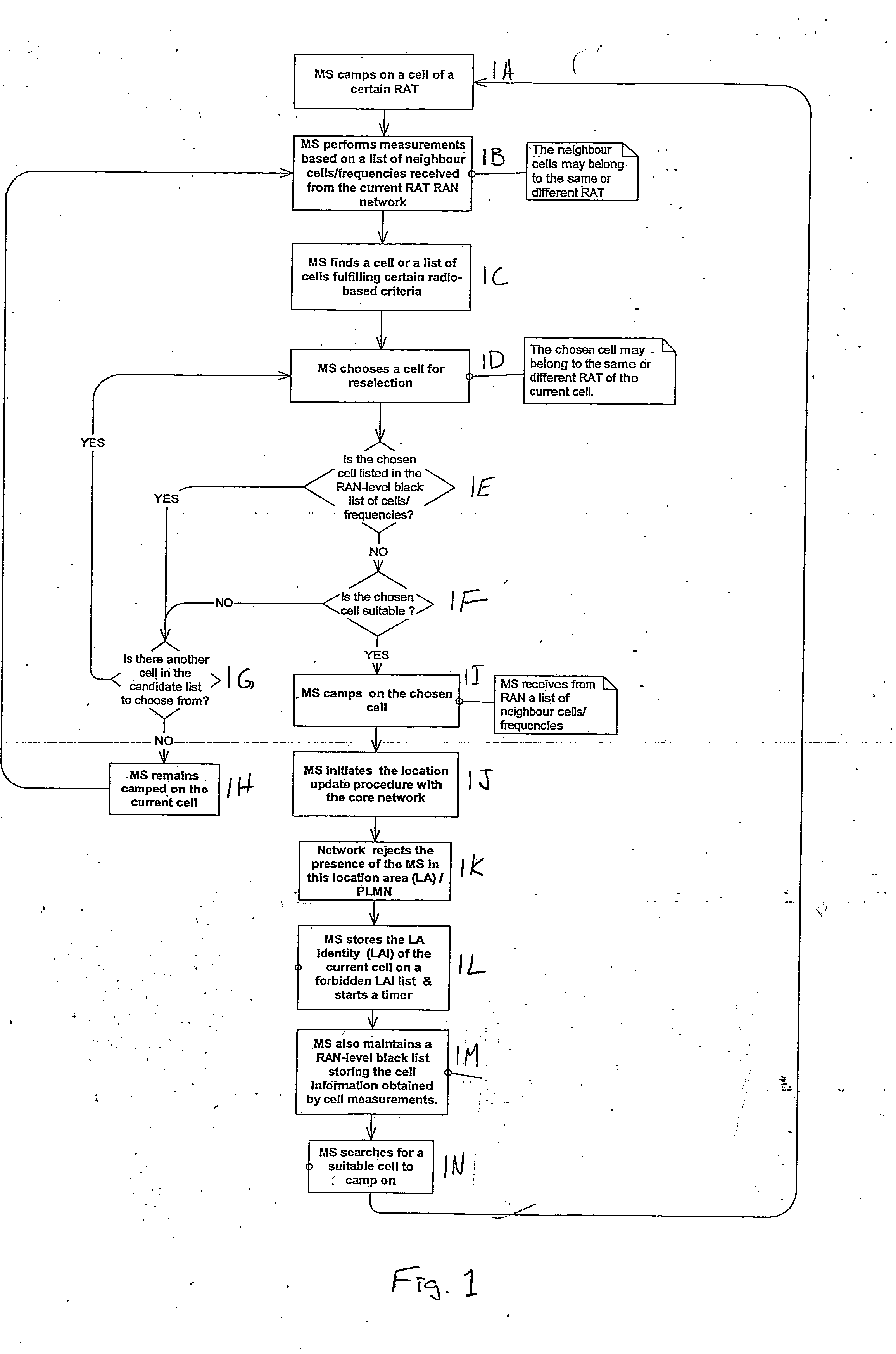
Cell reselection process for wireless communications
InactiveUS20080227453A1Assess restrictionRadio/inductive link selection arrangementsCommunications systemBlack list
A method of cell reselection in a wireless communications system where parameters are transmitted by the network in system information blocks to WTRU's on the network. Parameters are either added or subtracted from an equation representing the signal power and / or quality of a cell. Parameters may be prioritized. The results of the calculations are used to rank the servicing cell and neighboring cells. If a neighboring cell has a higher quality than the servicing cell, then the WTRU reselects the better cell. The network may transmit a blacklist of cells where the WTRU cannot camp as well as a barring timer for each cell where if the timer expires, the cell may again be considered for reselection. Information germane to the reselection decision may be transmitted and used by the network.
Owner:INTERDIGITAL TECH CORP
Introducing a new message source into an electronic message delivery environment
ActiveUS20180219830A1Reduce riskMaximizing numberMathematical modelsAdvertisementsMessage deliveryBlack list
Owner:HUBSPOT
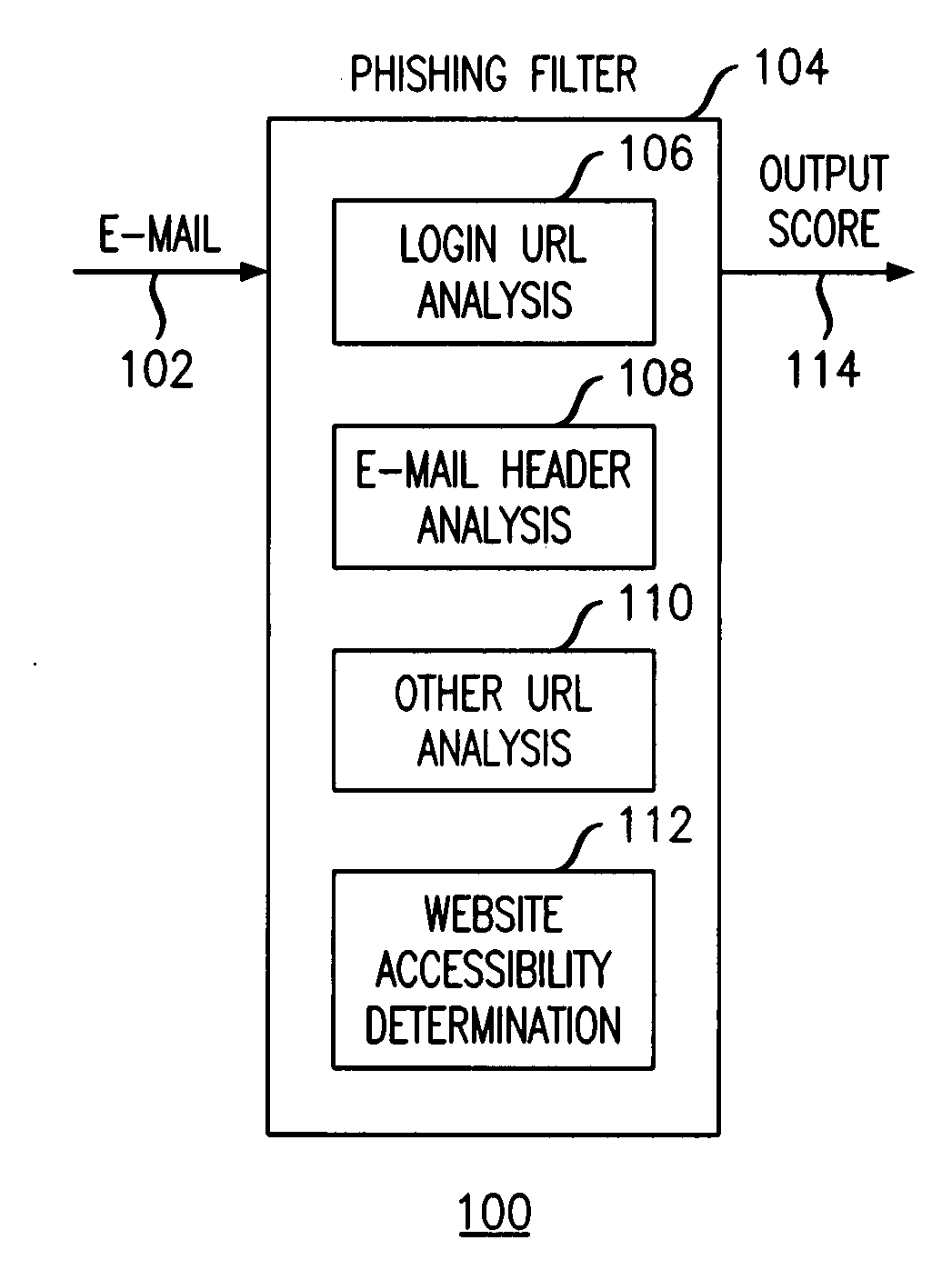
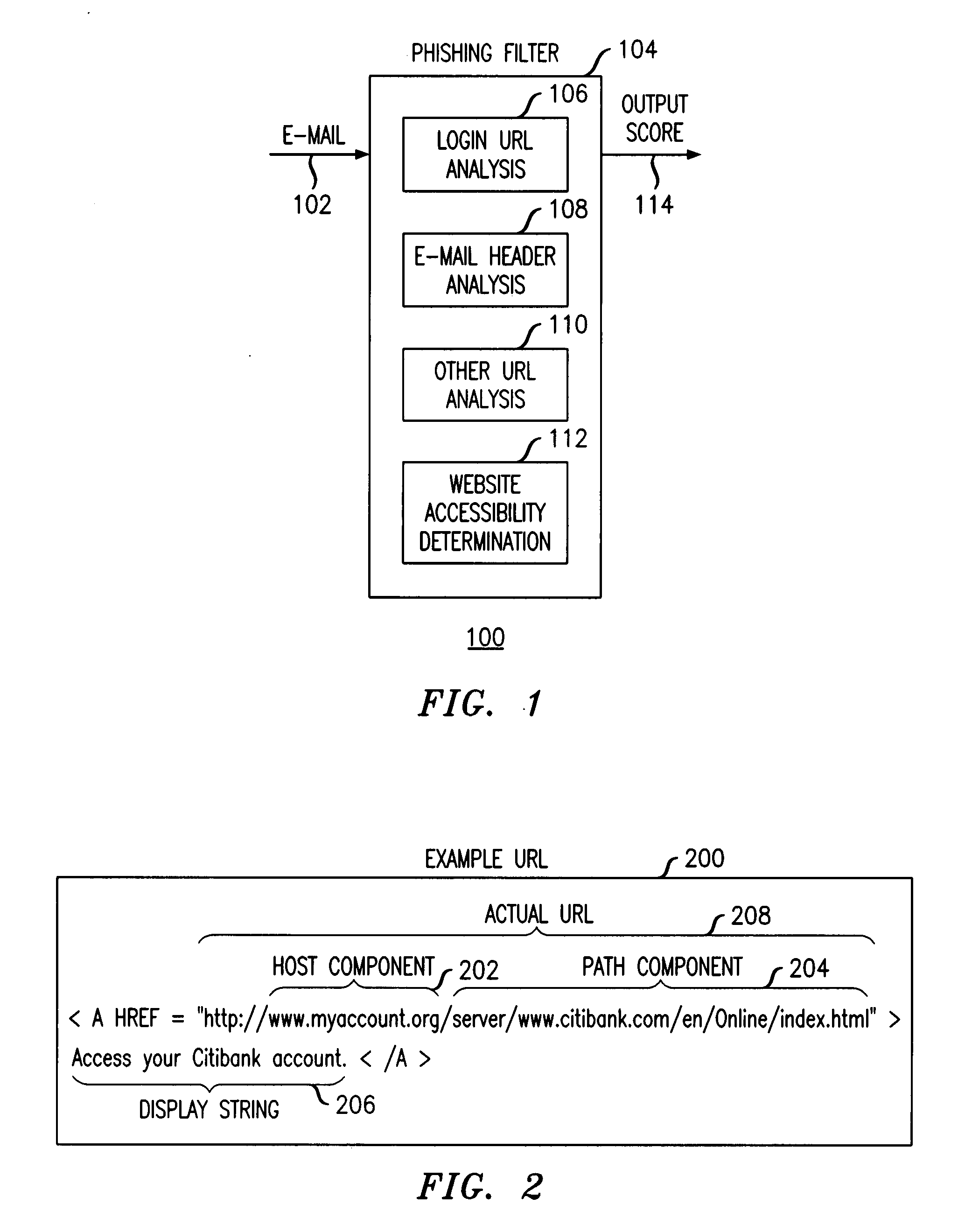
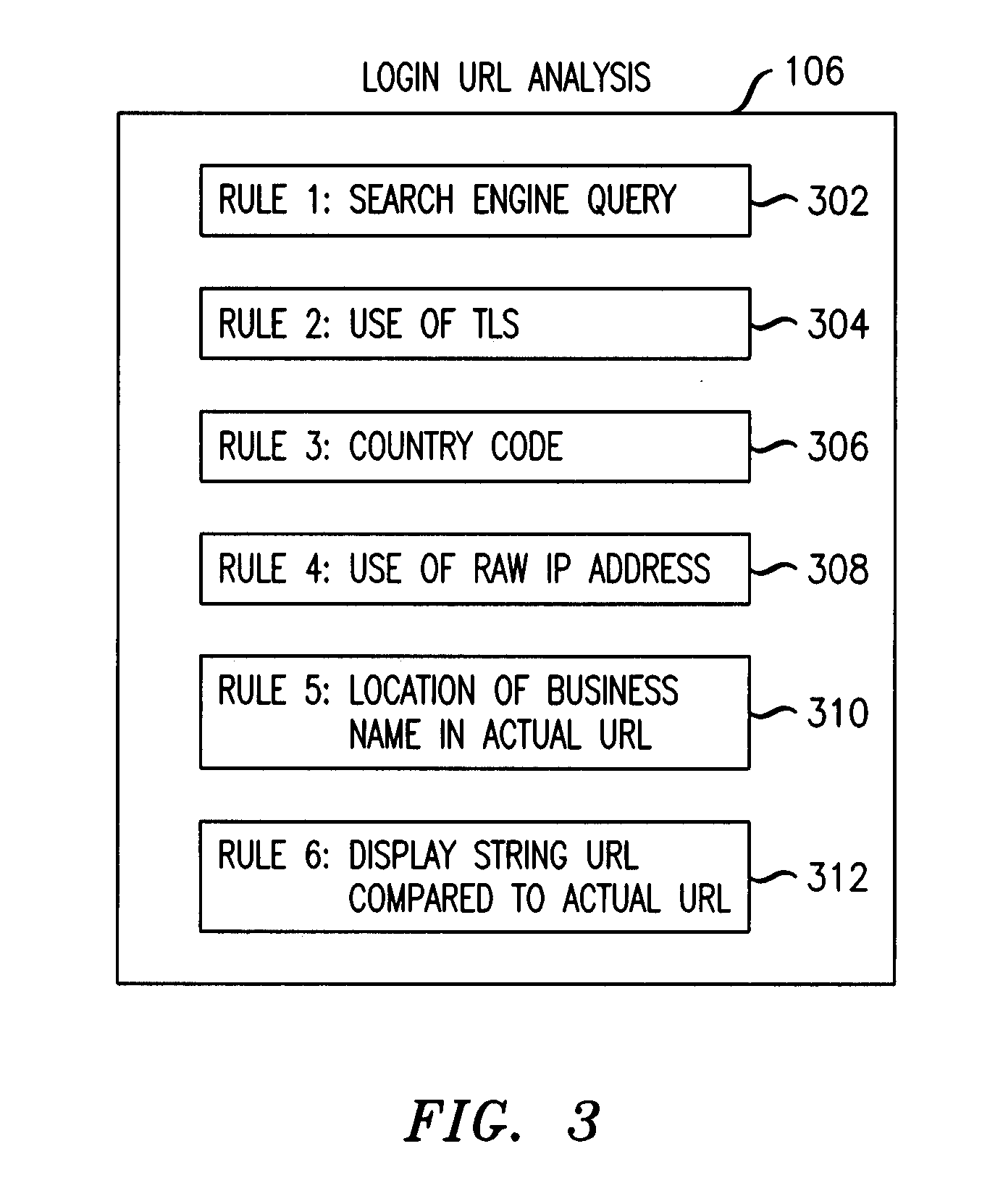
Method and apparatus for detecting phishing attempts solicited by electronic mail
InactiveUS20090089859A1Digital data processing detailsUser identity/authority verificationKeyword analysisHeuristic
A phishing filter employs a plurality of heuristics or rules (in one embodiment, 12 rules) to detect and filter phishing attempts solicited by electronic mail. Generally, the rules fall within the following categories: (1) identification and analysis of the login URL (i.e., the “actual” URL) in the email, (2) analysis of the email headers, (3) analysis across URLs and images in the email other than the login URL, and (4) determining if the URL is accessible. The phishing filter does not need to be trained, does not rely on black or white lists and does not perform keyword analysis. The filter may be implemented as an alternative or supplemental to prior art spam detection filters.
Owner:ALCATEL-LUCENT USA INC
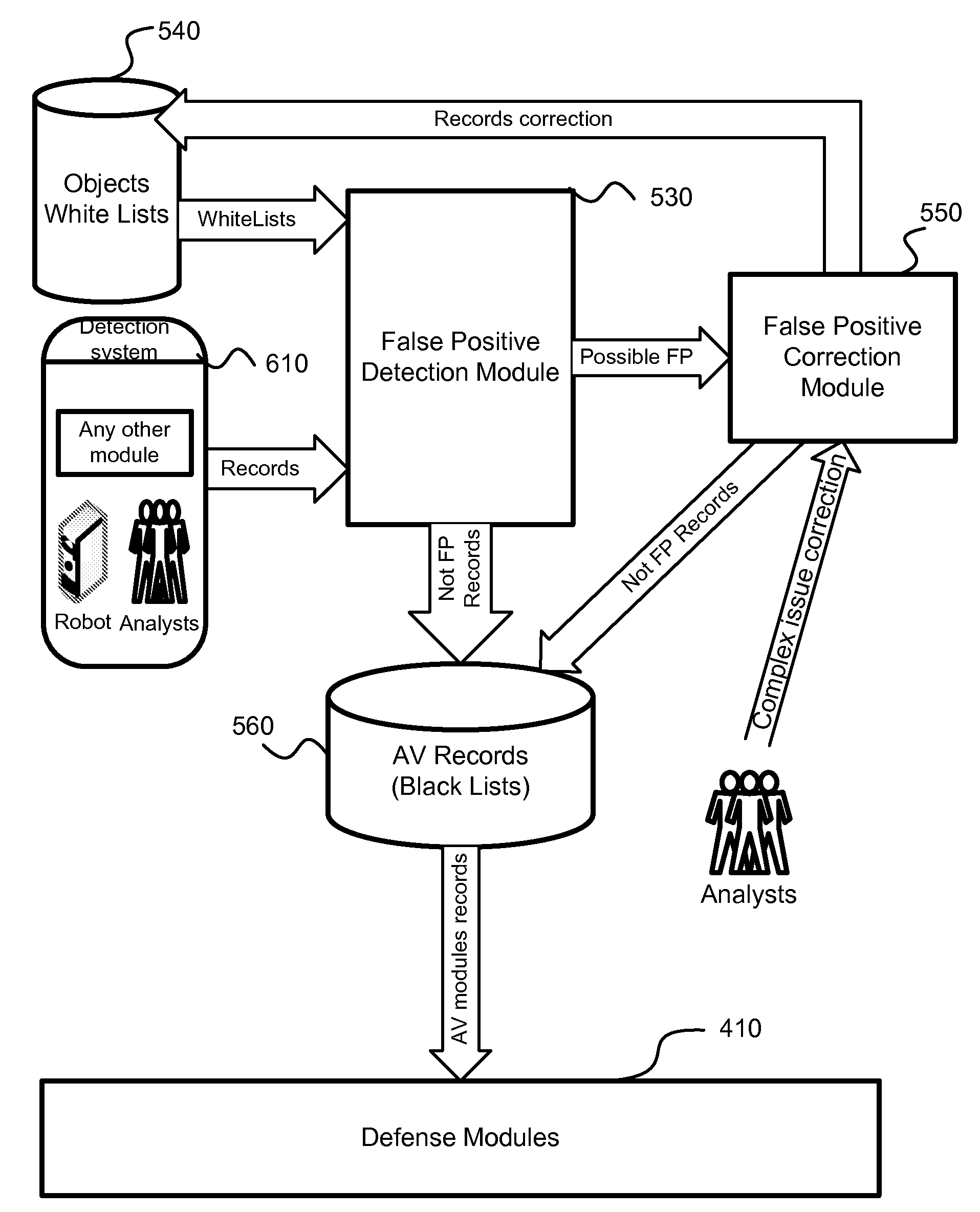
Detection and minimization of false positives in anti-malware processing
ActiveUS7640589B1Eliminate disadvantagesMemory loss protectionError detection/correctionAnti virusMalware
A system, method and computer program product for detection of false positives occurring during execution of anti-malware applications. The detection and correction of the false positives is implemented in two phases, before creation of new anti-virus databases (i.e., malware black lists) or before creation of new white lists, and after the anti-virus databases or new white lists are created and new false positives are detected. The system calculates a probability of detection of a certain potential malware object. Based on this probability, the system decides to either correct a white list (i.e., a collection of known clean objects) or update a black list (i.e., a collection of known malware objects). A process is separated into a several steps: creation and update (or correction) of white lists; creation and update of black lists; detection of collisions between these lists and correction of black lists or white lists based on the detected collisions.
Owner:AO KASPERSKY LAB
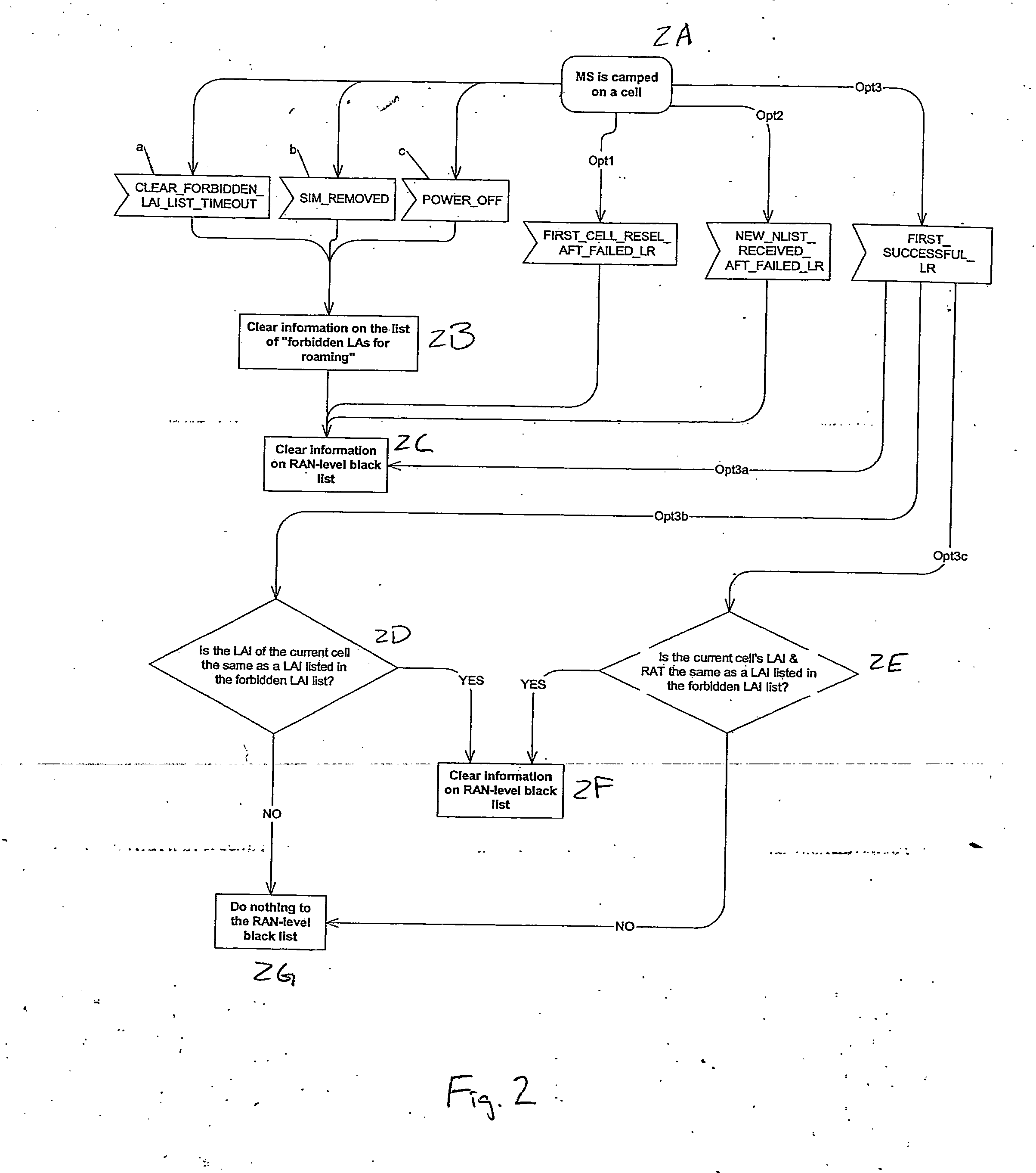
Apparatus, method and computer program product providing inclusion of local area information in broadcast messages and maintenance of radio access network black list
ActiveUS20070037577A1Avoid selectionAssess restrictionRadio/inductive link selection arrangementsRadio access networkLocation area
A method includes receiving location area-related information, associating the location area-related information with a neighbor cell information to determine if a cell belongs to a forbidden location area, and avoiding selection of the cell if the cell is determined to belong to the forbidden location area. Embodiments described include a UE, network element, computer program product, and integrated circuit.
Owner:NOKIA TECHNOLOGLES OY
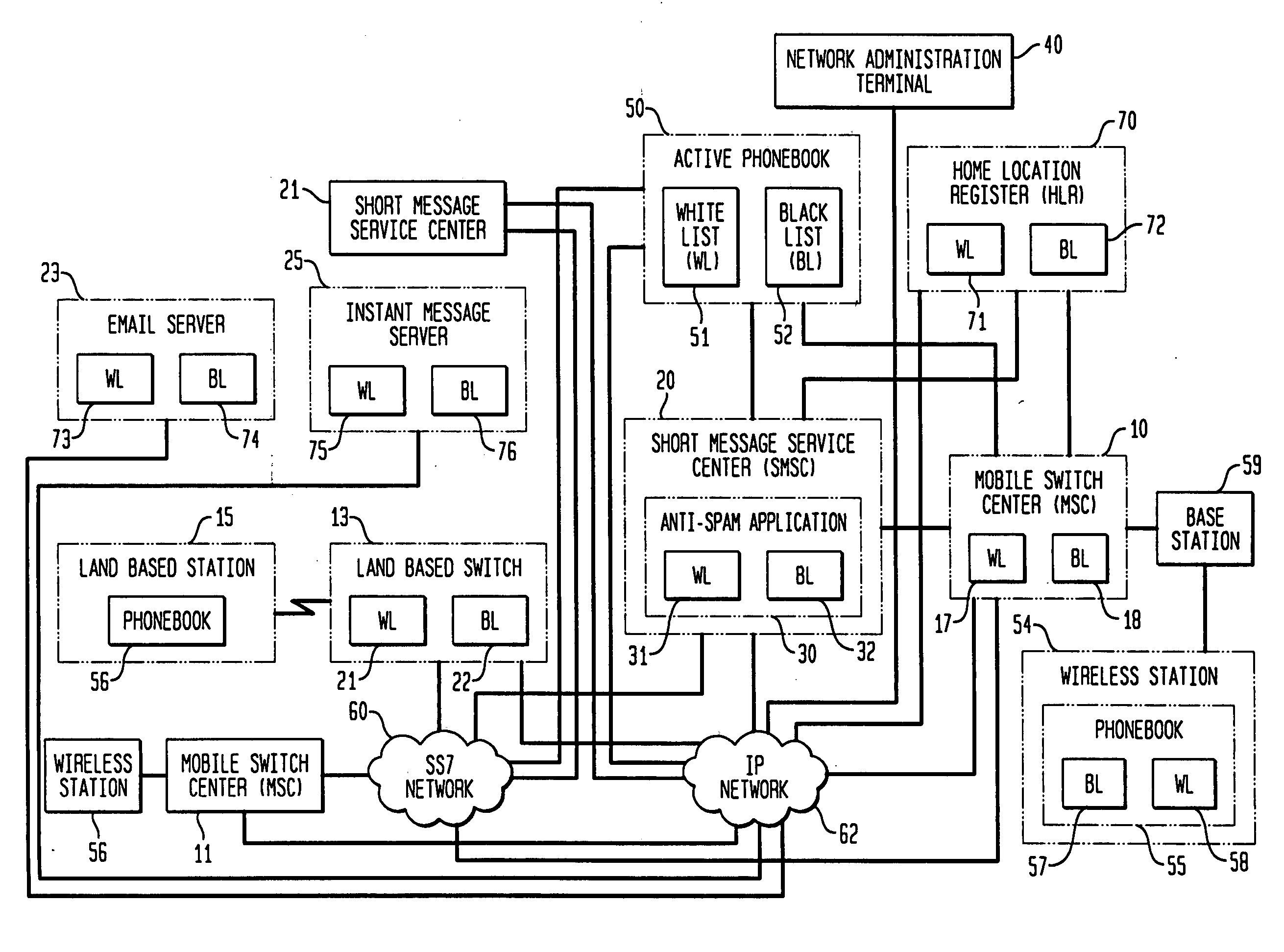
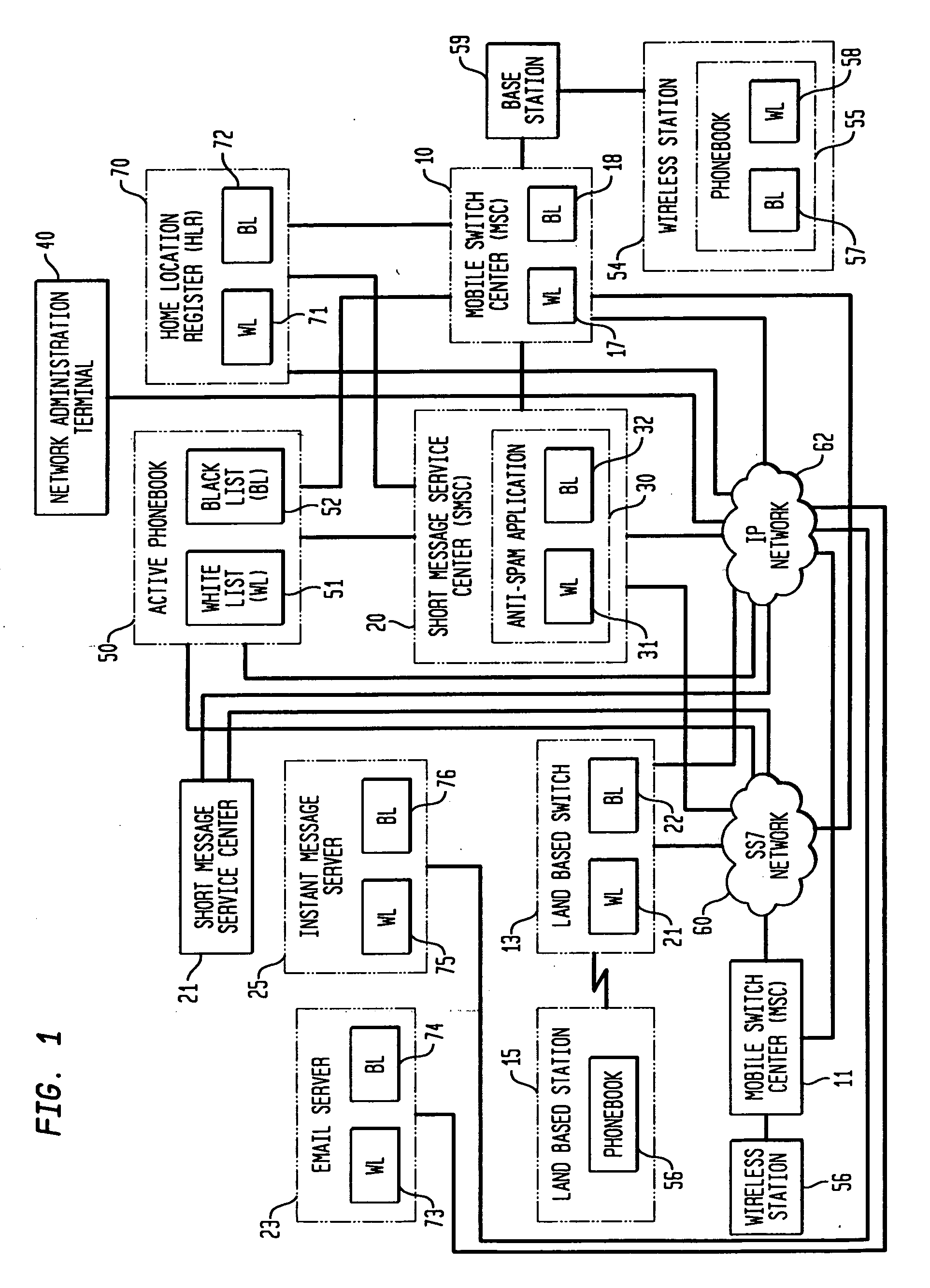
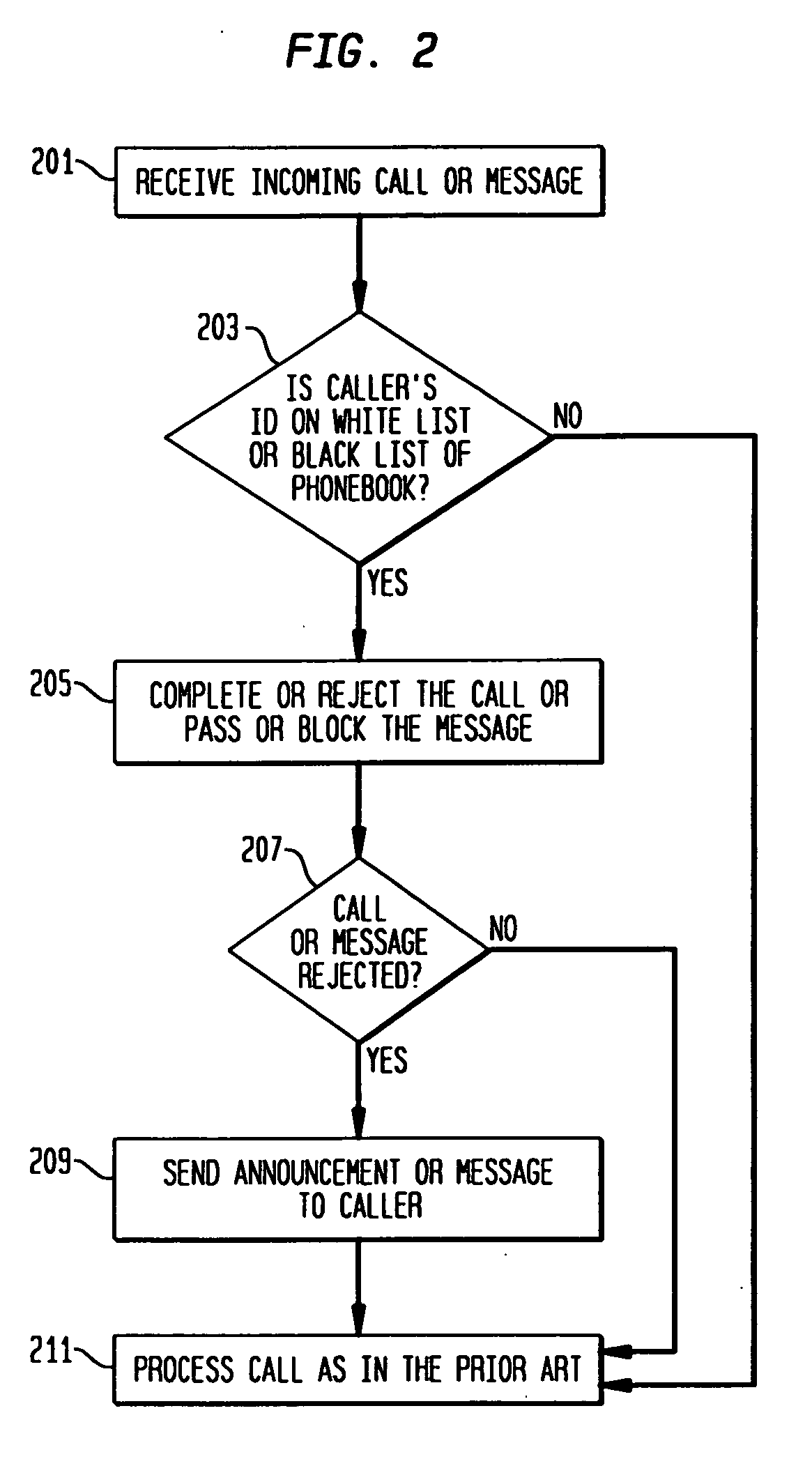
Phonebook use to filter unwanted telecommunications calls and messages
InactiveUS20070143422A1Minimizes and eliminates processingImprove network efficiencyMultiple digital computer combinationsSubstation equipmentTelecommunicationsWhitelist
This invention relates to the use of a customer phonebook feature for storing white lists and black lists for filtering unwanted voice calls or data messages. It also relates to the automatic population of a customer phonebook of identifications of a destination of outgoing calls. Advantageously, the phonebook can be rapidly and effortlessly populated with white lists and black lists to reduce processing for determining whether incoming calls or messages should be blocked or passed to the called destination.
Owner:LUCENT TECH INC
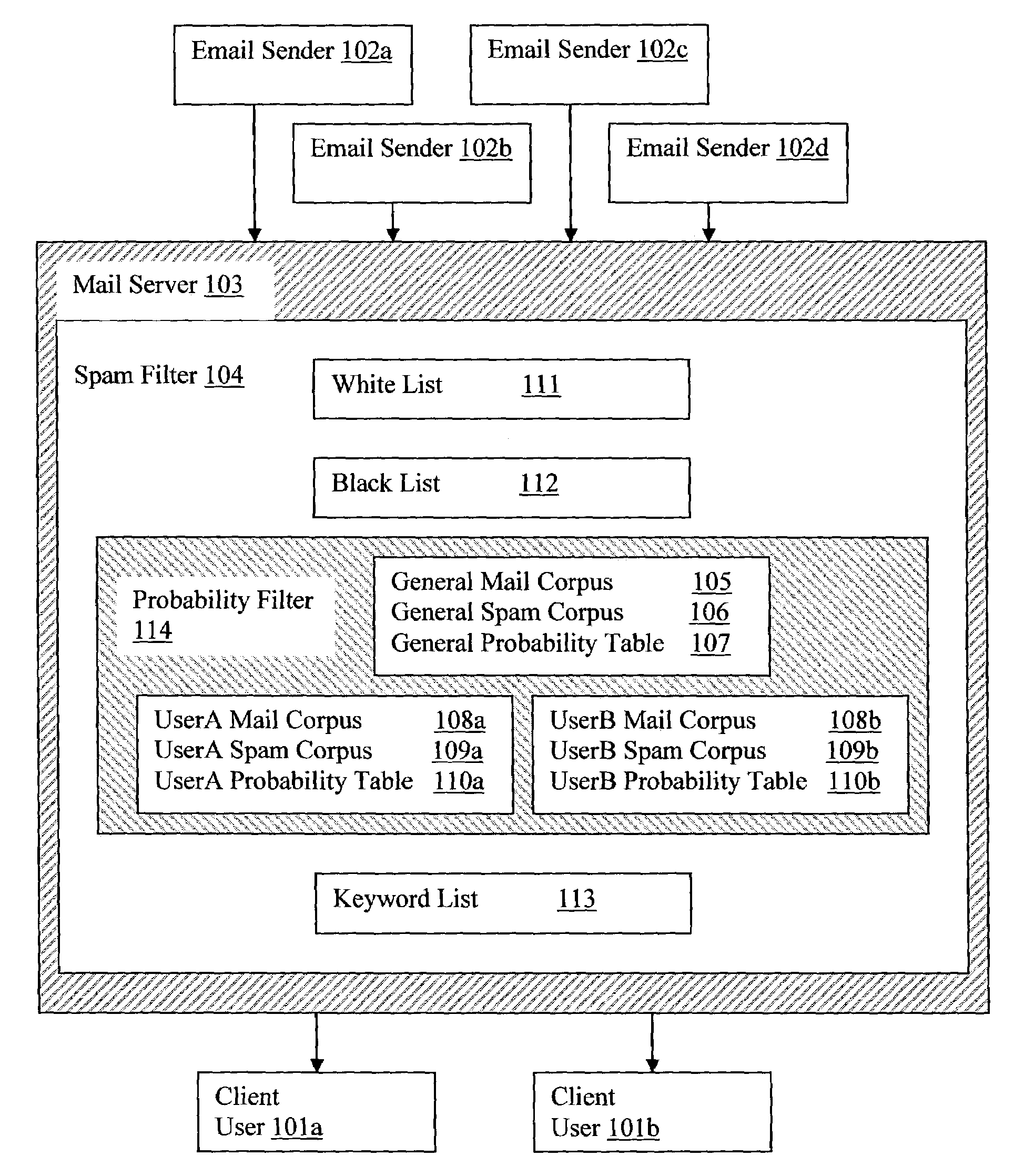
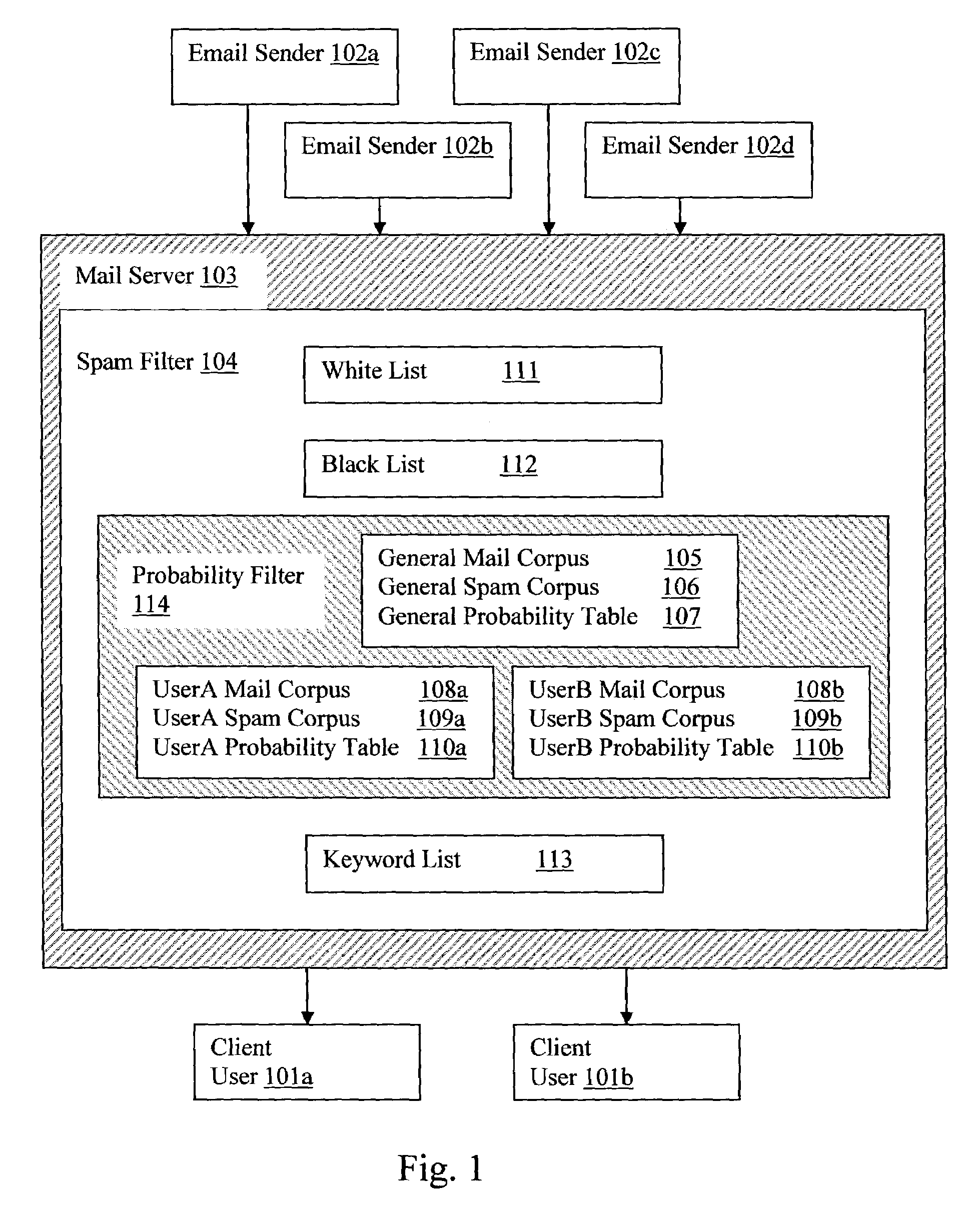
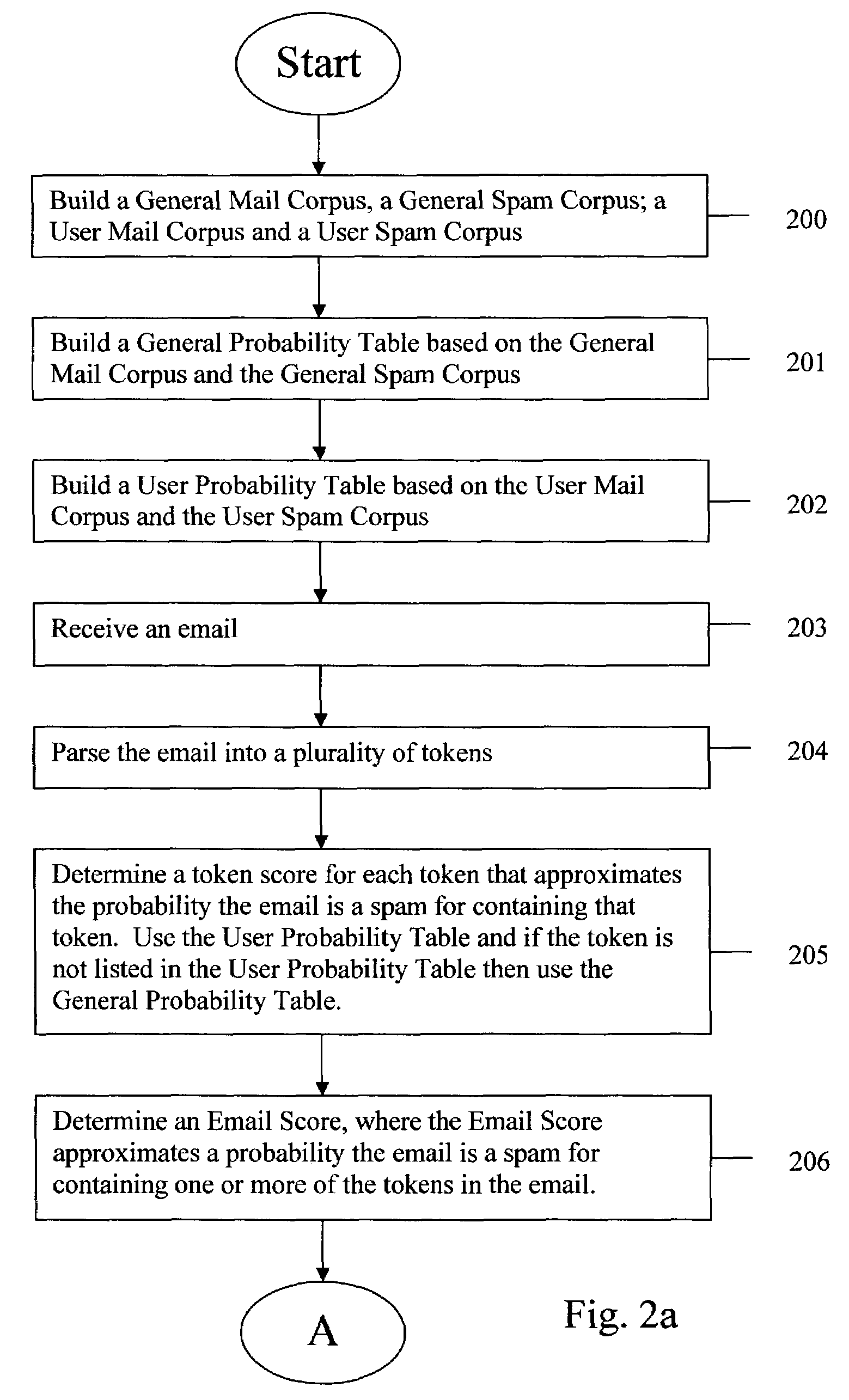
Mail server probability spam filter
InactiveUS7320020B2Multiple digital computer combinationsData switching networksThe InternetClient-side
Email senders may transmit emails over the internet to a mail server that handles emails for a plurality of users (clients). The mail server may use a spam filter to remove the spam and then transmit the filtered emails to the addressed clients. The spam filter may use a white list, black list, probability filter and keyword filter. The probability filter may use a user mail corpus and a user spam corpus for creating a user probability table that lists tokens and the probability that an email is a spam if the email contains the token. The probability filter may also use a general mail corpus and a general spam corpus for creating a general probability table that. Tokens of incoming emails may be searched for in the user probability table, and if not found, the general probability table to calculate the probability that the email is a spam.
Owner:GO DADDY OPERATING
Methods and apparatus for redirecting attacks on a network
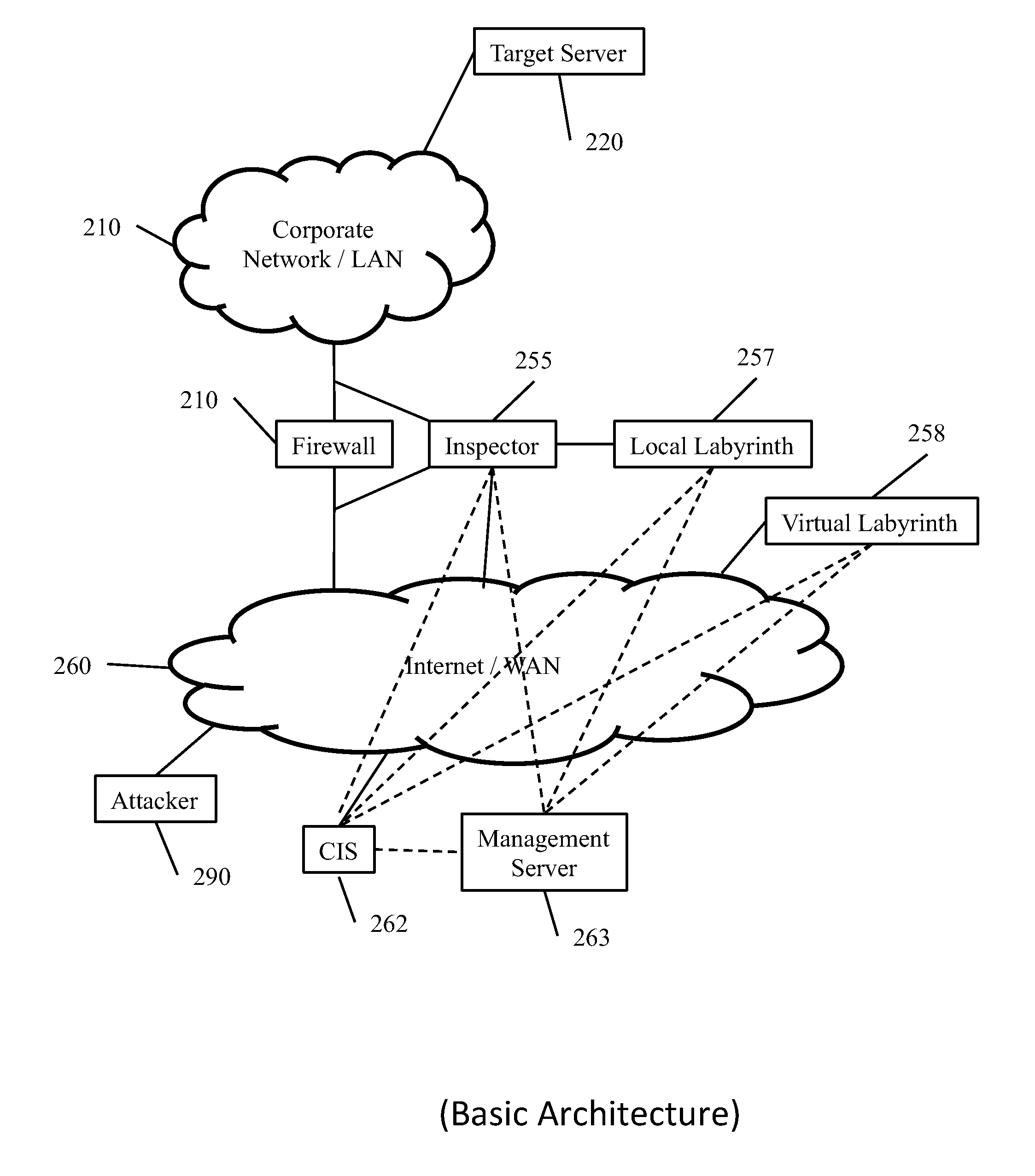
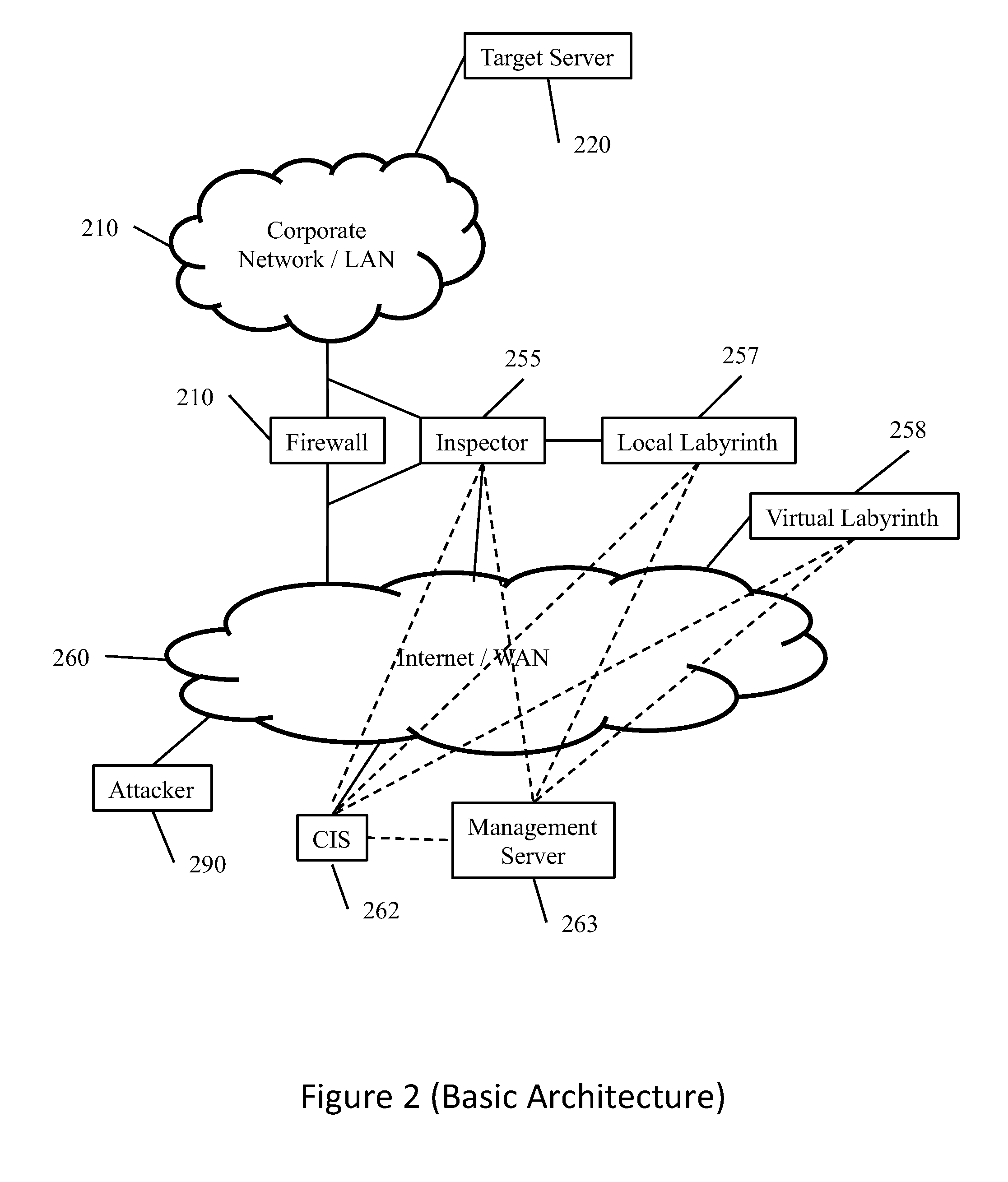
A system is disclosed for protecting a network against malicious attacks or attempts for unauthorized access. A network is connected to an external network by a number of firewalls. Inspectors detect packets blocked by the firewalls and some or all of the packets are detected to a labyrinth configured to emulated an operational network and response to the packets in order to engage an attacker. Blocked packets may be detected by comparing packets entering and exiting a firewall. Packets for which a corresponding packets are not received within a transit delay may be identified as blocked. Entering and exiting packets may be compared by comparing only header information. A central module may receive information from the inspectors and generate statistical information and generate instructions for the inspectors, such as blacklists of addresses known to be used by attackers.
Owner:SENTINELONE INC
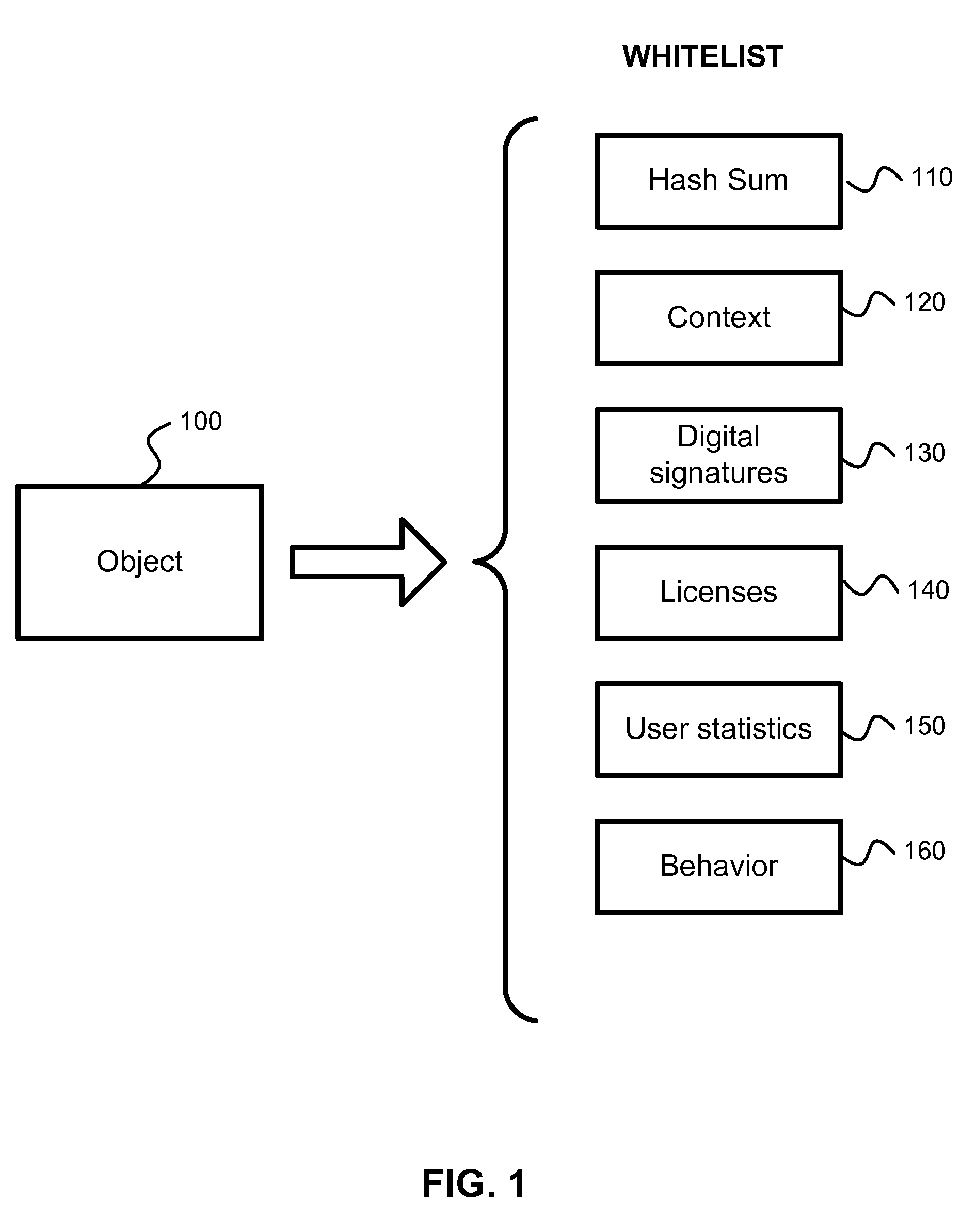
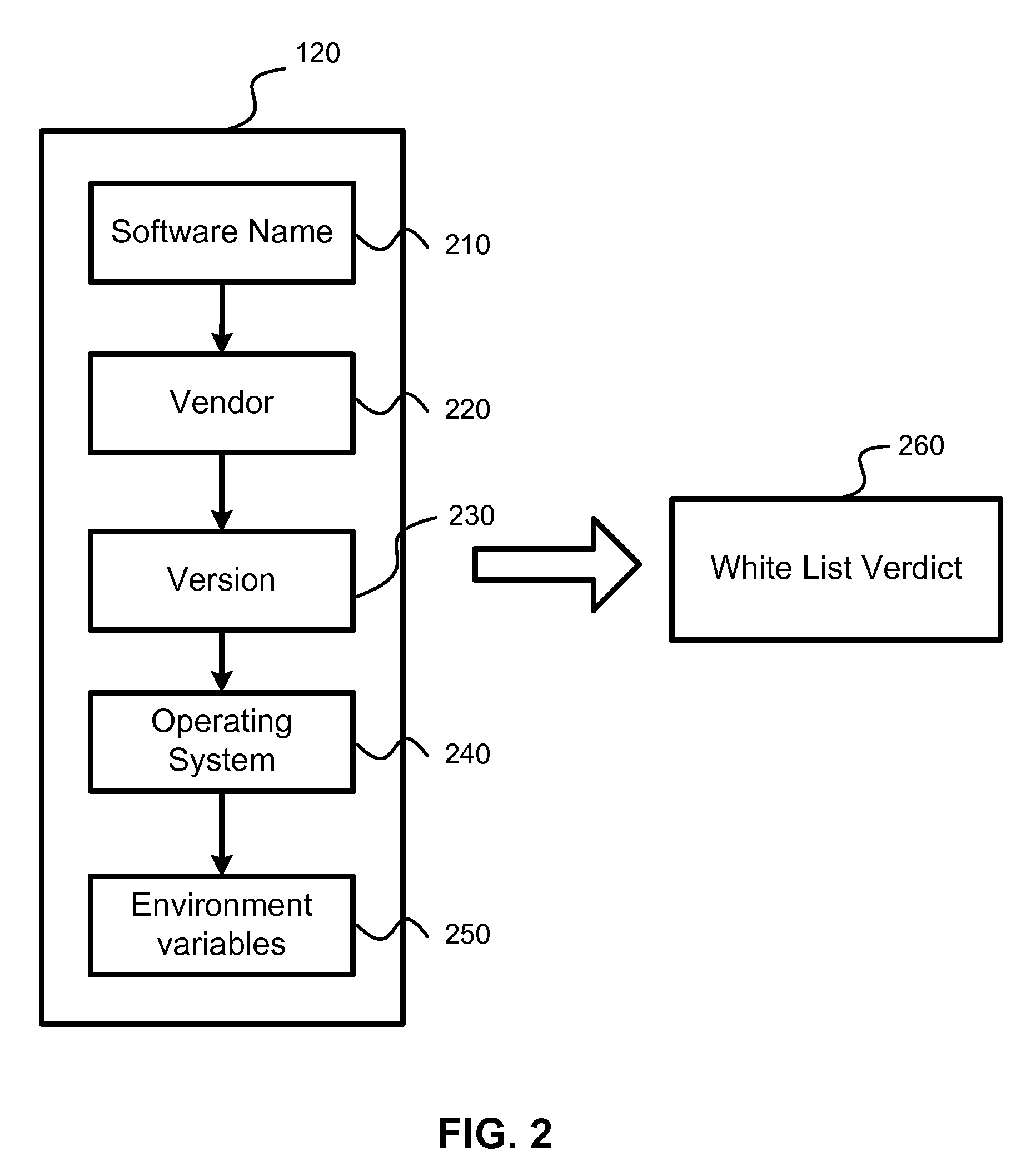
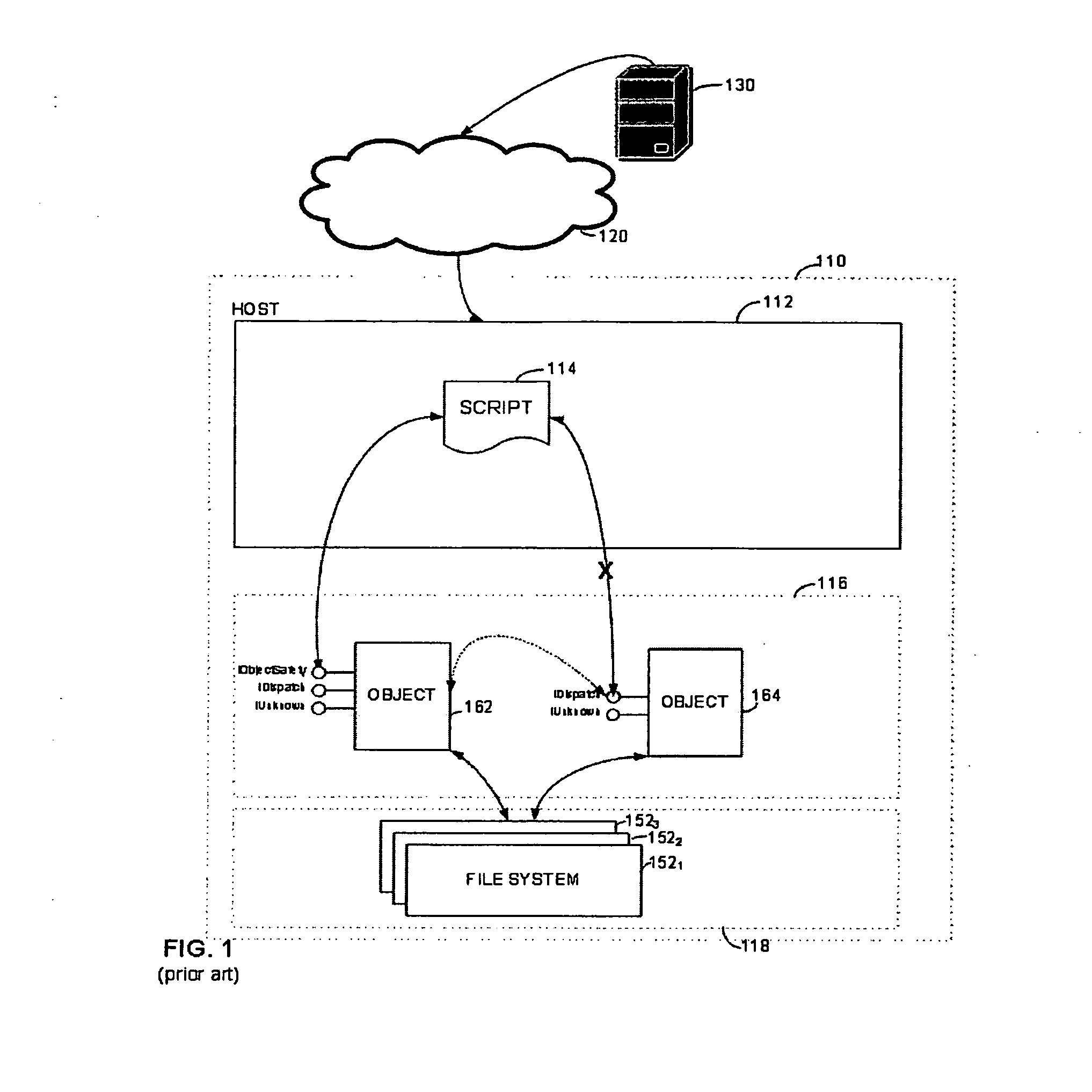
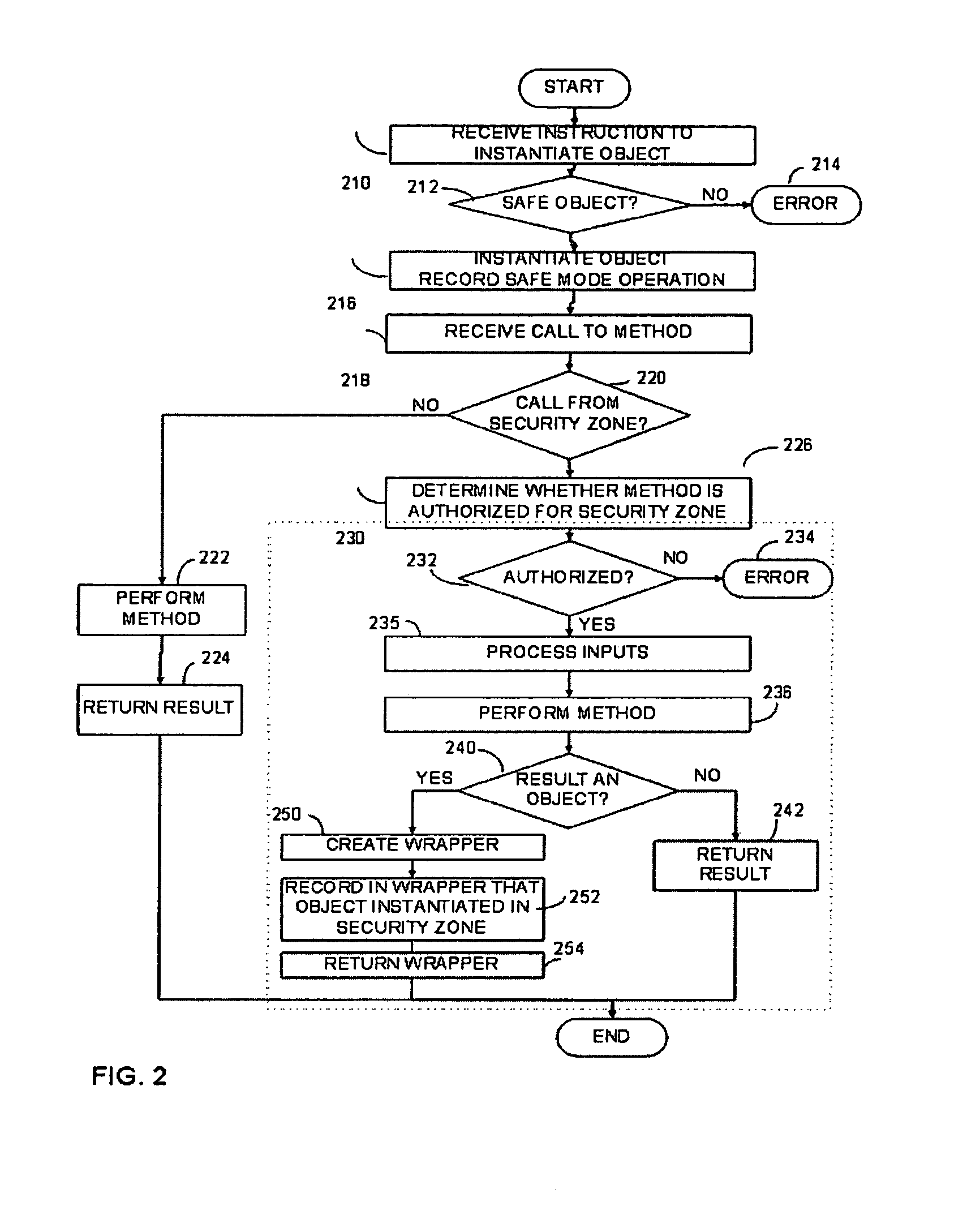
Software system with controlled access to objects
ActiveUS20070199000A1Easy to useImprove developmentSpecific access rightsProgram control using stored programsSoftware systemWhitelist
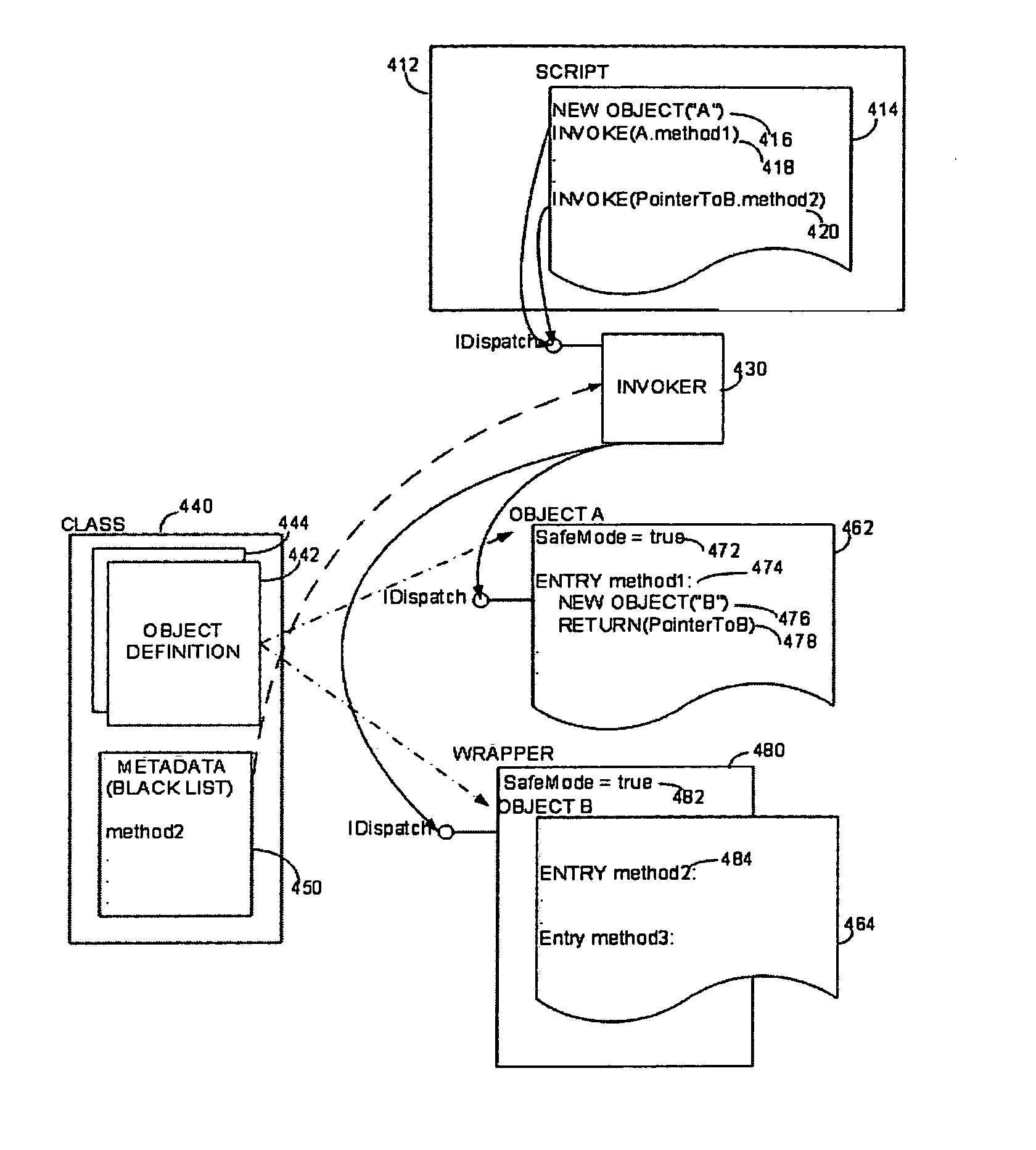
A computer system configured to intercept method calls placed on an object. By intercepting method calls, processing may be performed on a method call-by-method call basis. As part of the processing, metadata for an object is consulted to partition the methods for that object into subsets. The processing performed in response to any specific method call may be based on the subset to which the method belongs. The type of metadata may depend on the desired operation of the computer system. Metadata representing a white list or black list may be used in a computer system that implements a security zone that allows access to methods deemed to be safe or to deny access to methods deemed to be unsafe. In a performance monitoring system, metadata may identify methods to be logged or methods for which execution cost are to be measured. Values returned by a method call may also be processed when the method calls are intercepted. The returned value may be wrapped with a wrapper that holds data useful in implementing a security zone or for performing other processing.
Owner:MICROSOFT TECH LICENSING LLC
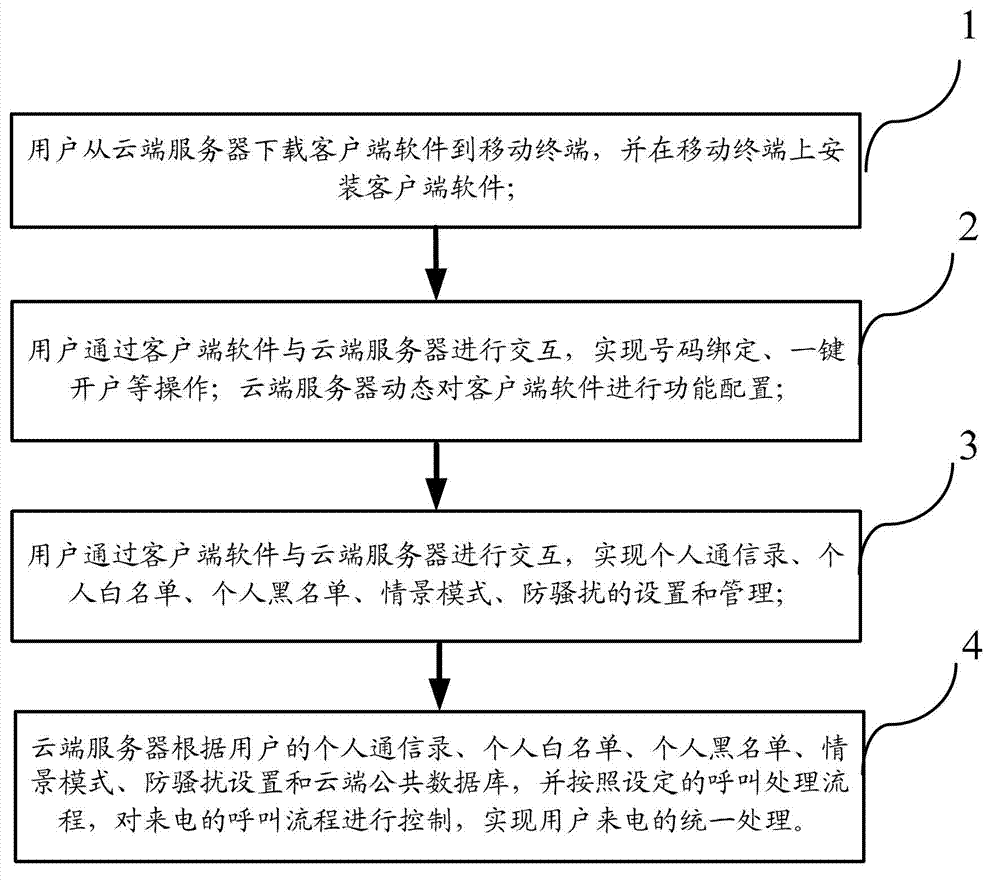
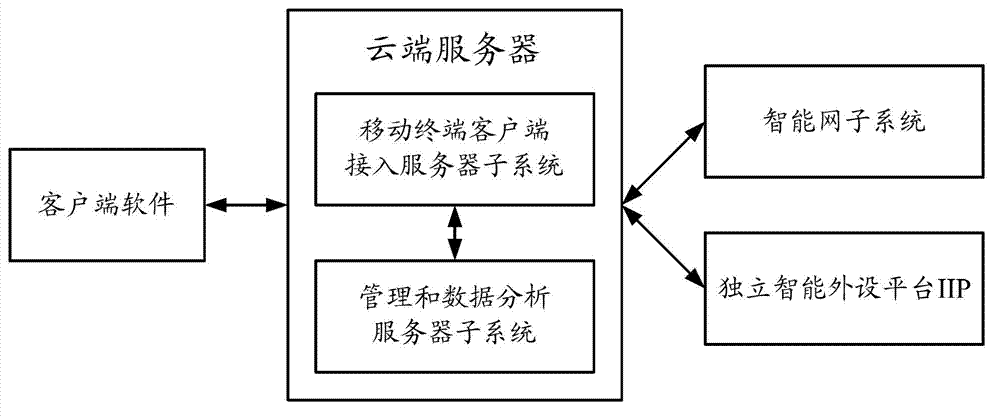
Method and system achieving united processing of mobile phone
ActiveCN103167500AAchieving unified processingRealize integrated processing functionSubstation equipmentTransmissionIntelligent NetworkAddress book
A method achieving united processing of a mobile phone comprises steps as below: a user installs client terminal software on a mobile terminal; achieving operations like number binding and establishing an account simply with pressing of one key and the like, and a cloud server carries out functional configuration to the client terminal software; achieving setting and management of a personal address book, a personal white list, a personal black list, contextual models, and harassment prevention; the cloud server carries out united controlling and processing of the calling process of the incoming calls of the user according to a set calling processing scheme and a calling process of an incoming call. The system achieving the united processing of the mobile phone comprises a subsystem of an intelligent network, an independent peripheral platform, a cloud server, and client terminal software, wherein the cloud server comprises a mobile terminal access service subsystem and a management and data-analyzing server subsystem. The method and the system achieving the united processing of the mobile phone achieve united processing functions of harassment prevention, disturb prevention, call transfer, a voice mail, a secretary station and the like.
Owner:EB INFORMATION TECH
Dynamic message filtering
ActiveUS7257564B2Reduce in quantityMake fastError detection/correctionGenetic modelsWhitelistData mining
Dynamically filtering and classifying messages, as good messages, bulk periodicals, or spam. A regular expression recognizer, and pre-trained neural networks. The neural networks distinguish “likely good” from “likely spam,” and also operate at a more discriminating level to distinguish among the three categories above. A dynamic whitelist and blacklist; sending addresses are collected when the number of their messages indicates the sender is good or a spammer. A dynamically selected set of regular expressions input to the neural networks.
Owner:MAILGATE LLC
Link exchange system and method
InactiveUS20110078550A1Enhancing search engine optimizationMore visibilityDigital data information retrievalSpecial data processing applicationsWeb siteWhitelist
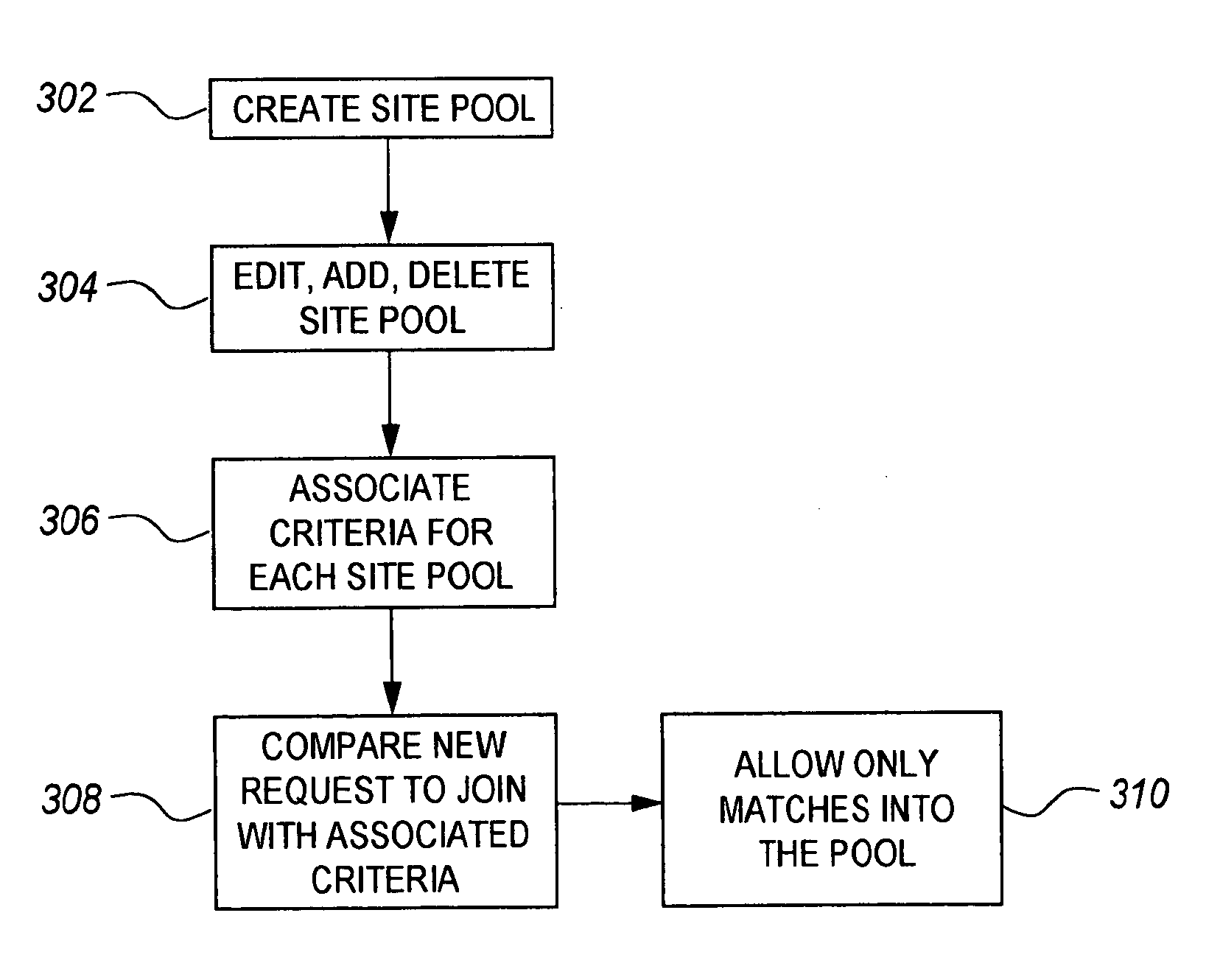
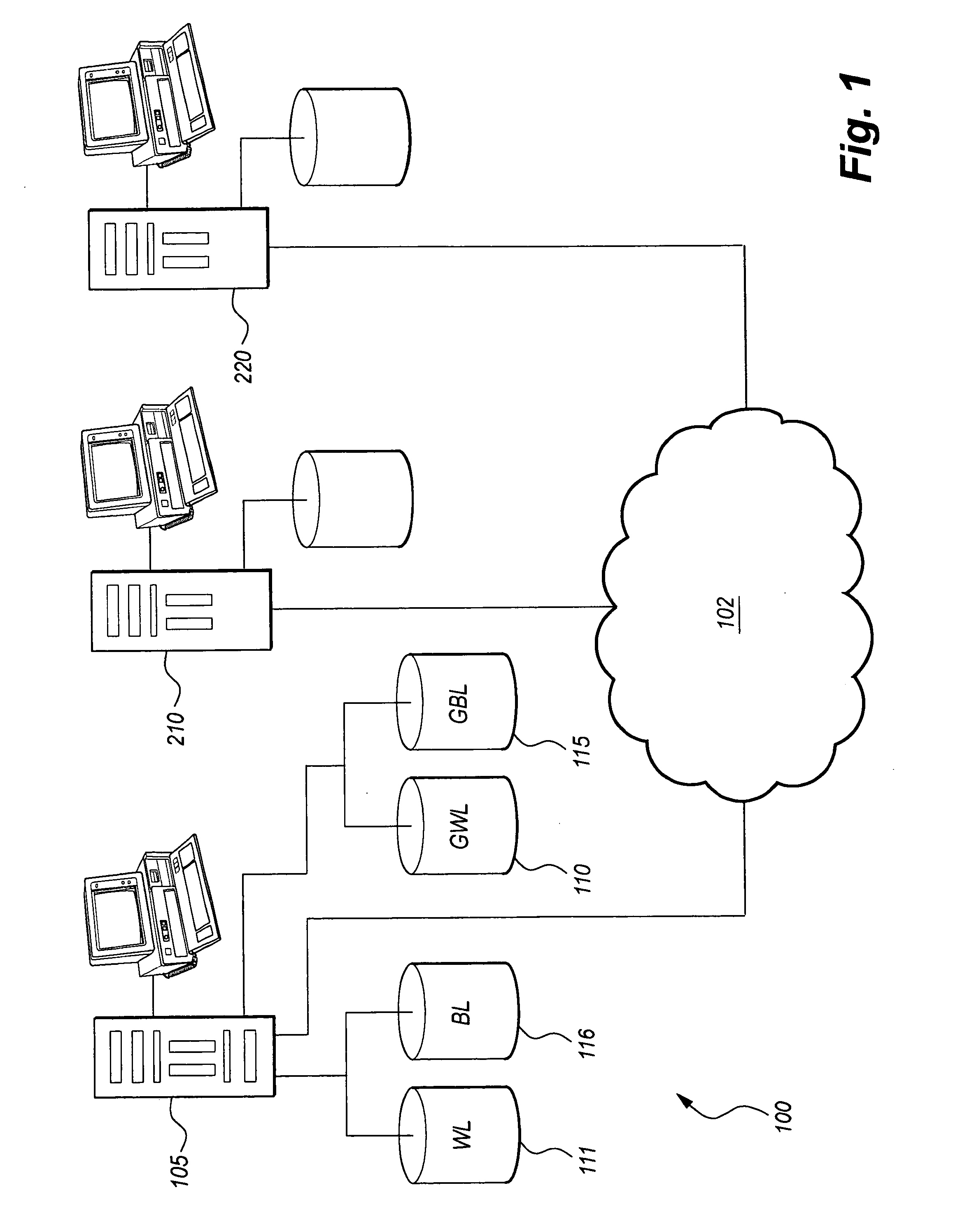
The link exchange system and method 100 automatically creates links between web sites. Specifically, the method of creating links includes providing an account Owner the opportunity to create and manage whitelists 111 and blacklists 116 which are used as filters to automatically accept or decline a proposed link according to criteria set forth in the respective lists. If the link request is accepted, the link is created on the account Owner's link page(s).
Owner:NABUTOVSKY SERGE
Method and system for detecting network security threat based on trusted business flow
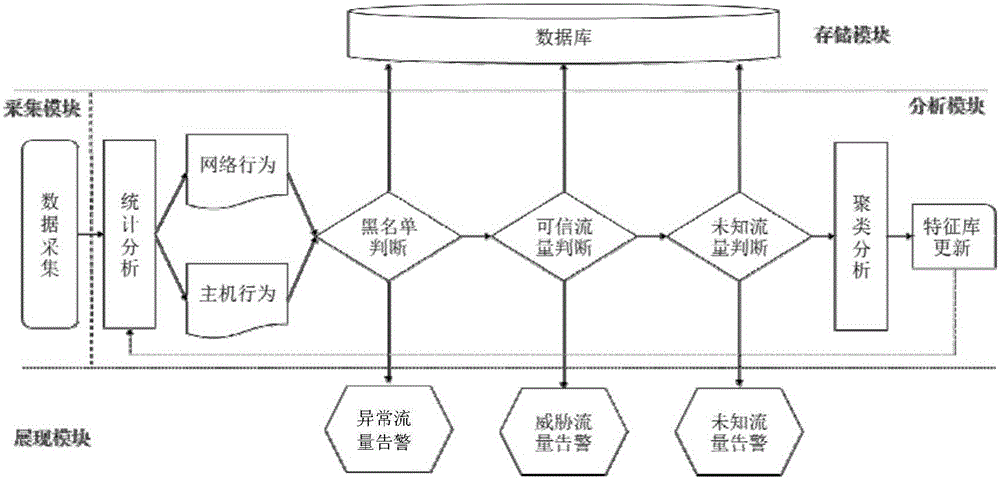
The invention discloses a method and a system for detecting a network security threat based on trusted business flow. The method comprises the following steps of establishing a blacklist and a white list of network flow and constructing a baseline model, wherein the white list is the trusted business flow and is a feature contour library of normal network behavior and host behavior; comparing real-time monitoring flow data and the baseline model; when the real-time data is matched with the blacklist, outputting an abnormal flow alarm; when the real-time data is matched with the white list and a deviation exceeds a preset threshold, outputting a threat flow alarm; and when the real-time data is mismatched with the blacklist and the white list, treating as a gray list and outputting an unknown flow alarm. According to the method and the system, the network security threat can be comprehensively and effectively detected at a low false alarm rate and high anti-virus efficiency, and the method and the system can adapt to a more granular network attack and defense confrontation environment.
Owner:STATE GRID CORP OF CHINA +1
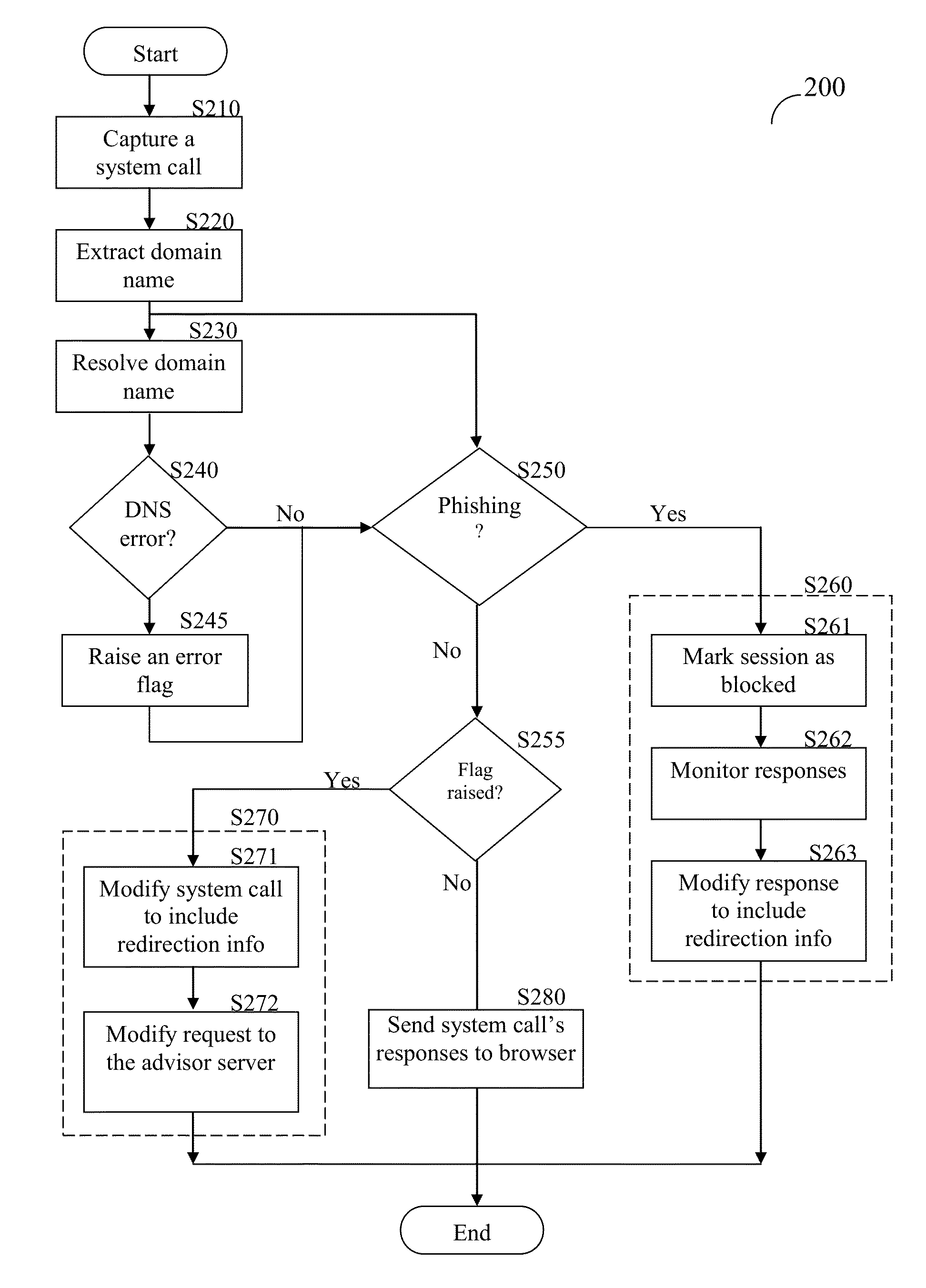
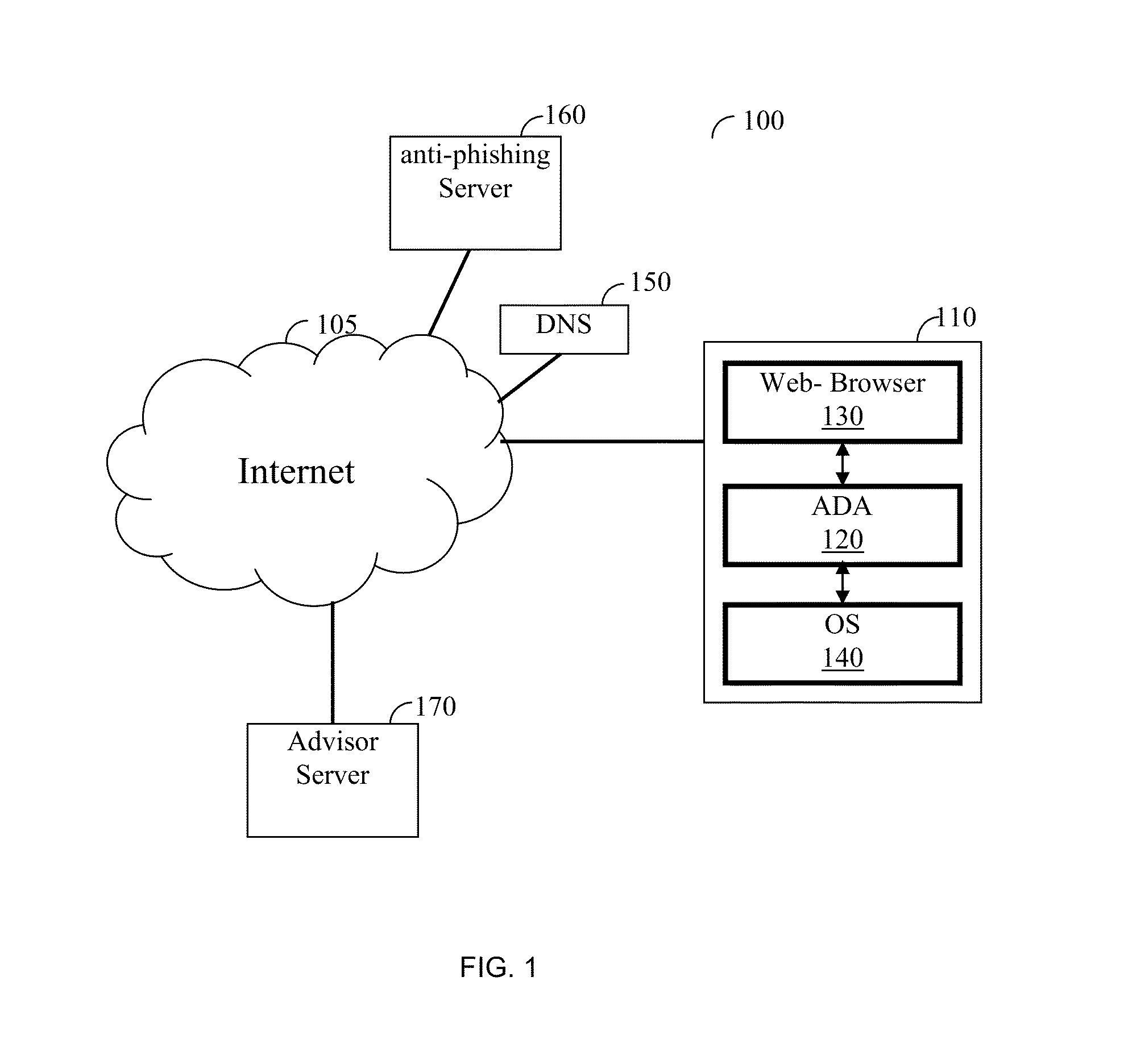
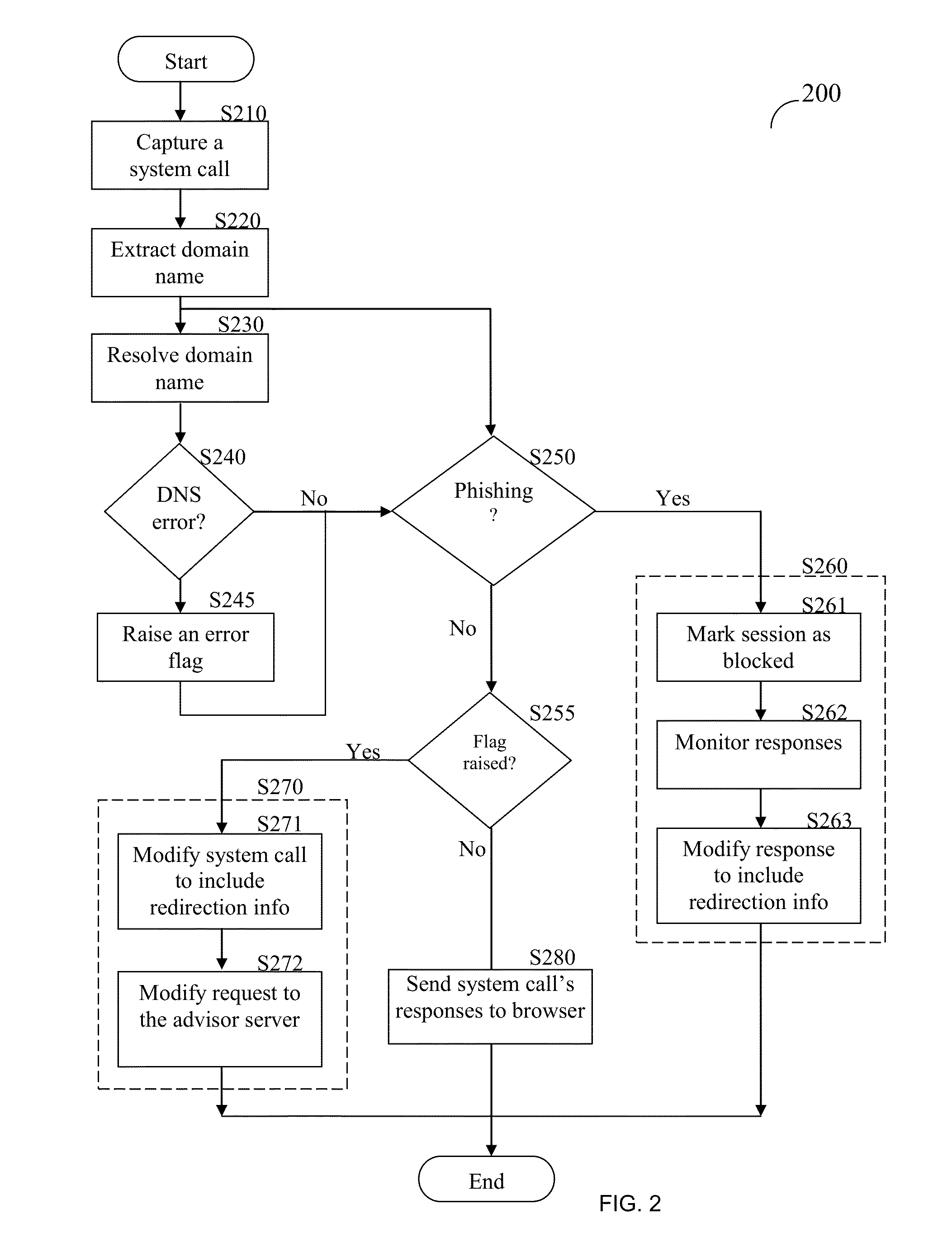
Anti-phishing domain advisor and method thereof
A method of anti-phishing and domain name protection. The method comprises capturing a system call sent to an operating system of a client by an application requesting an access to an Internet resource; extracting a URL included in the captured system call; capturing a response to the system call sent from operating system to the application; determining if the system call's response includes any one of a domain name system (DNS) error code and fake internet protocol (IP) address; checking the extracted URL against an anti-phishing blacklist to determine if the Internet resource is a malicious website; performing a DNS error correction action if any one of the DNS error code and the fake IP address was detected; and performing an anti-phishing protection action if the internet resource is determined to be a malicious website.
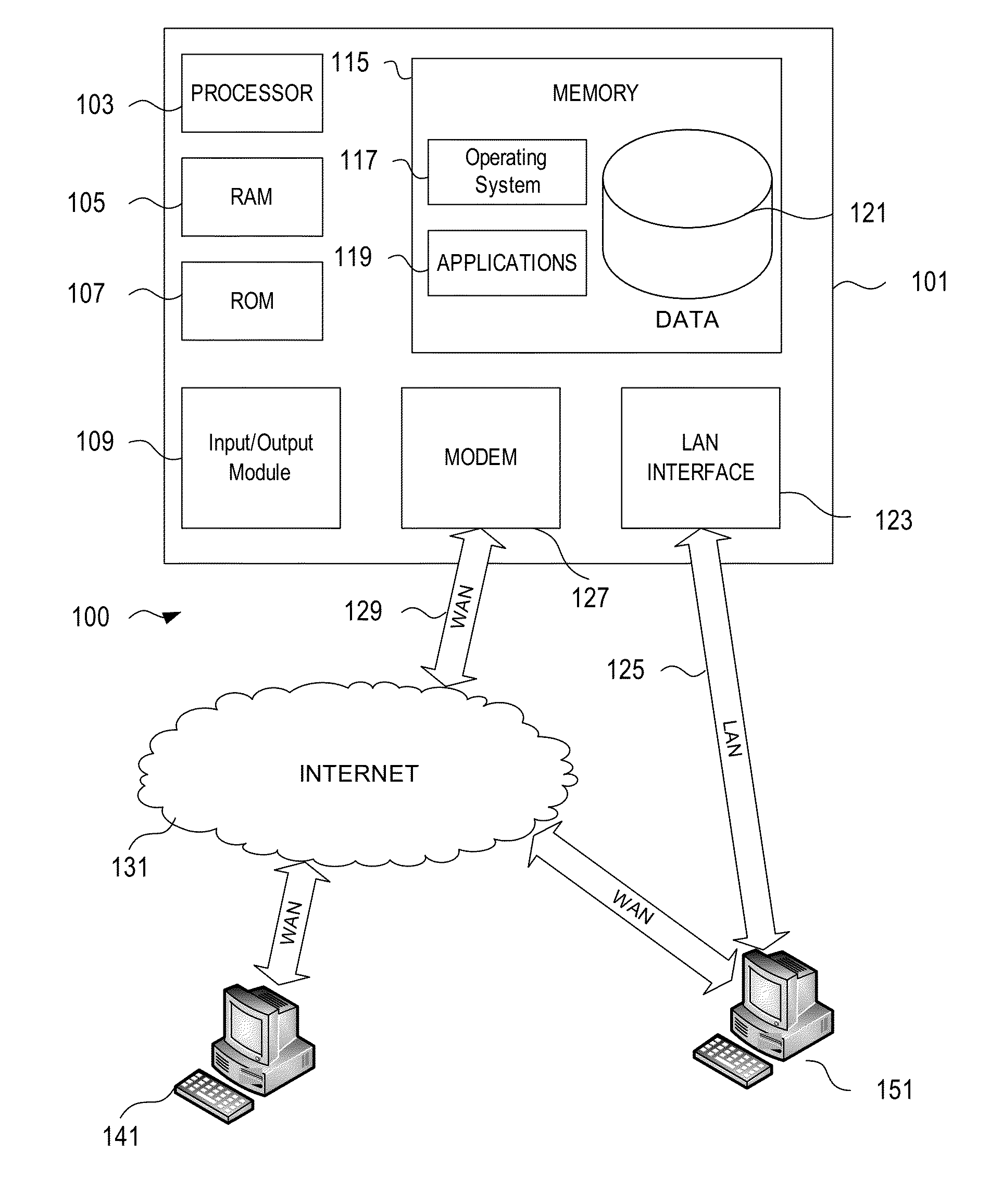
Owner:VISICOM MEDIA
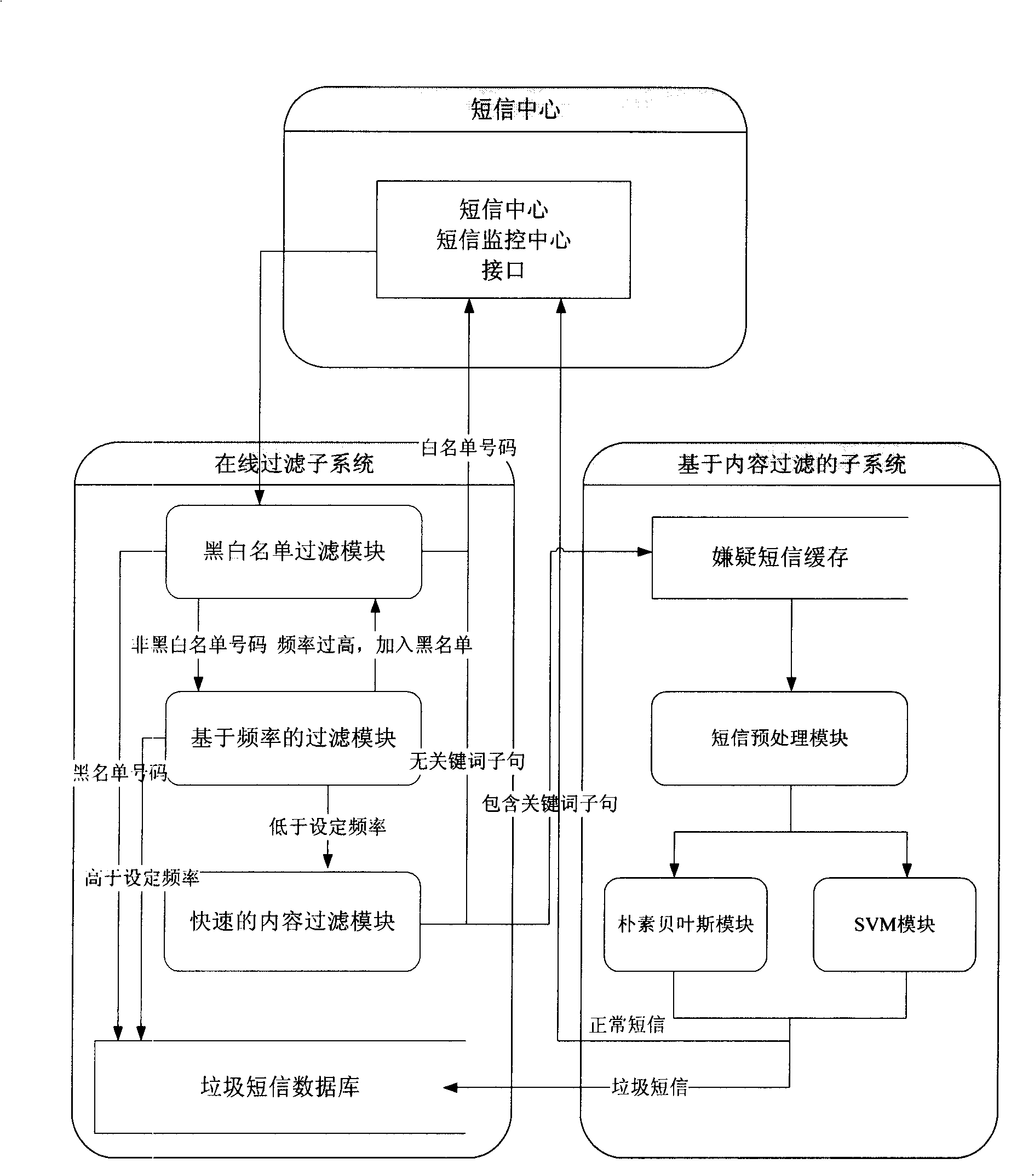
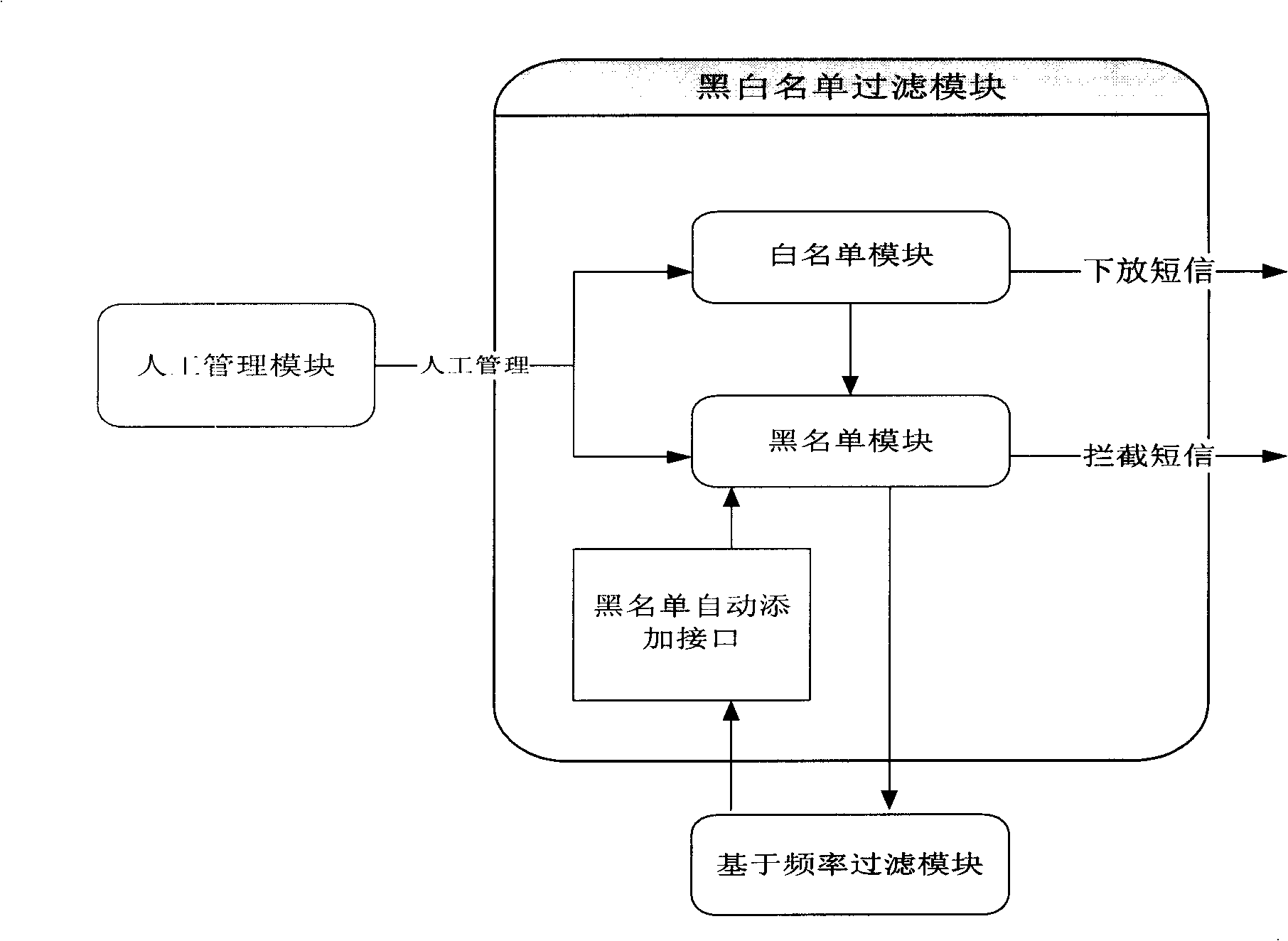
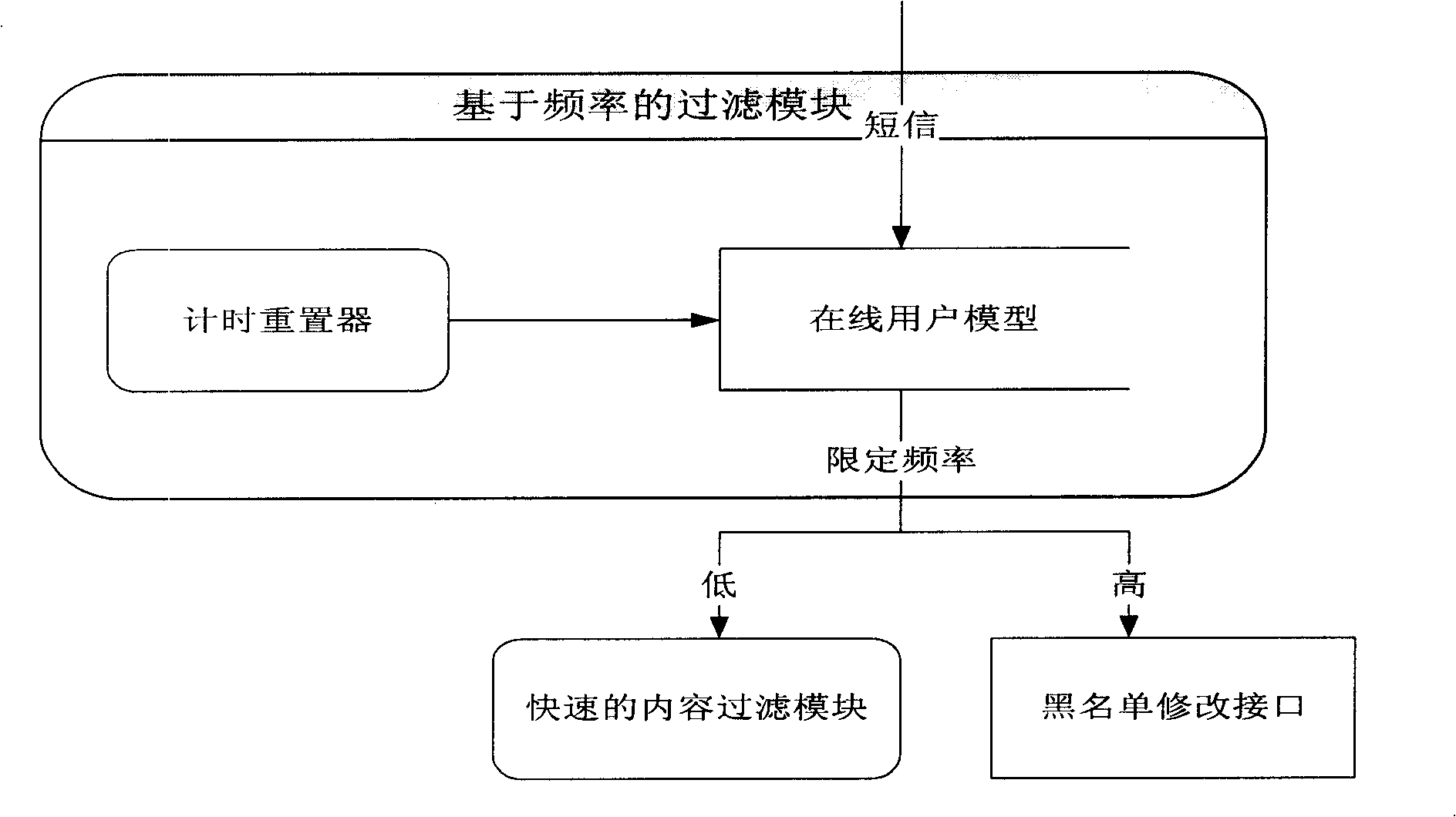
Method for real time filtering large scale rubbish SMS based on content
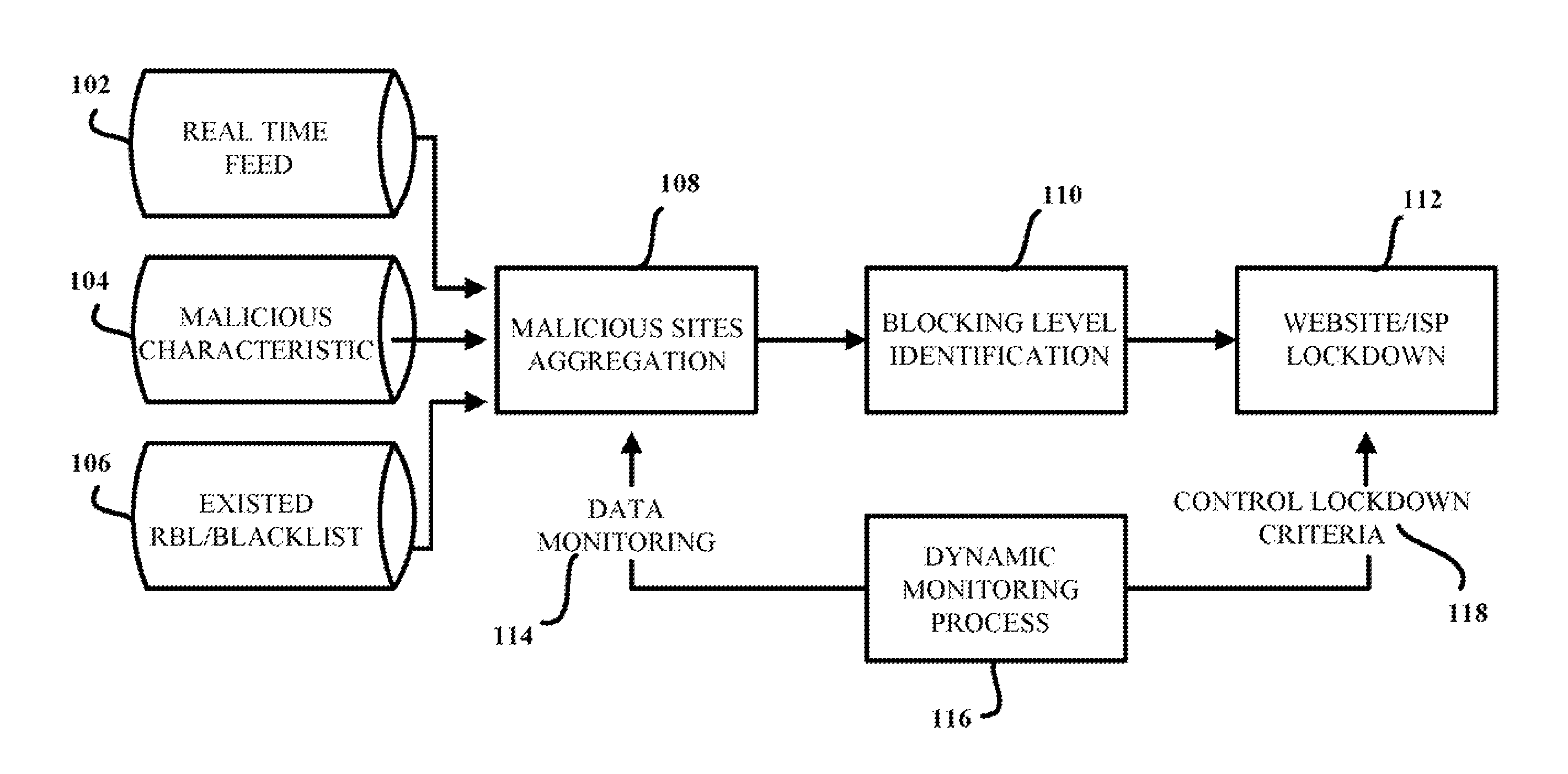
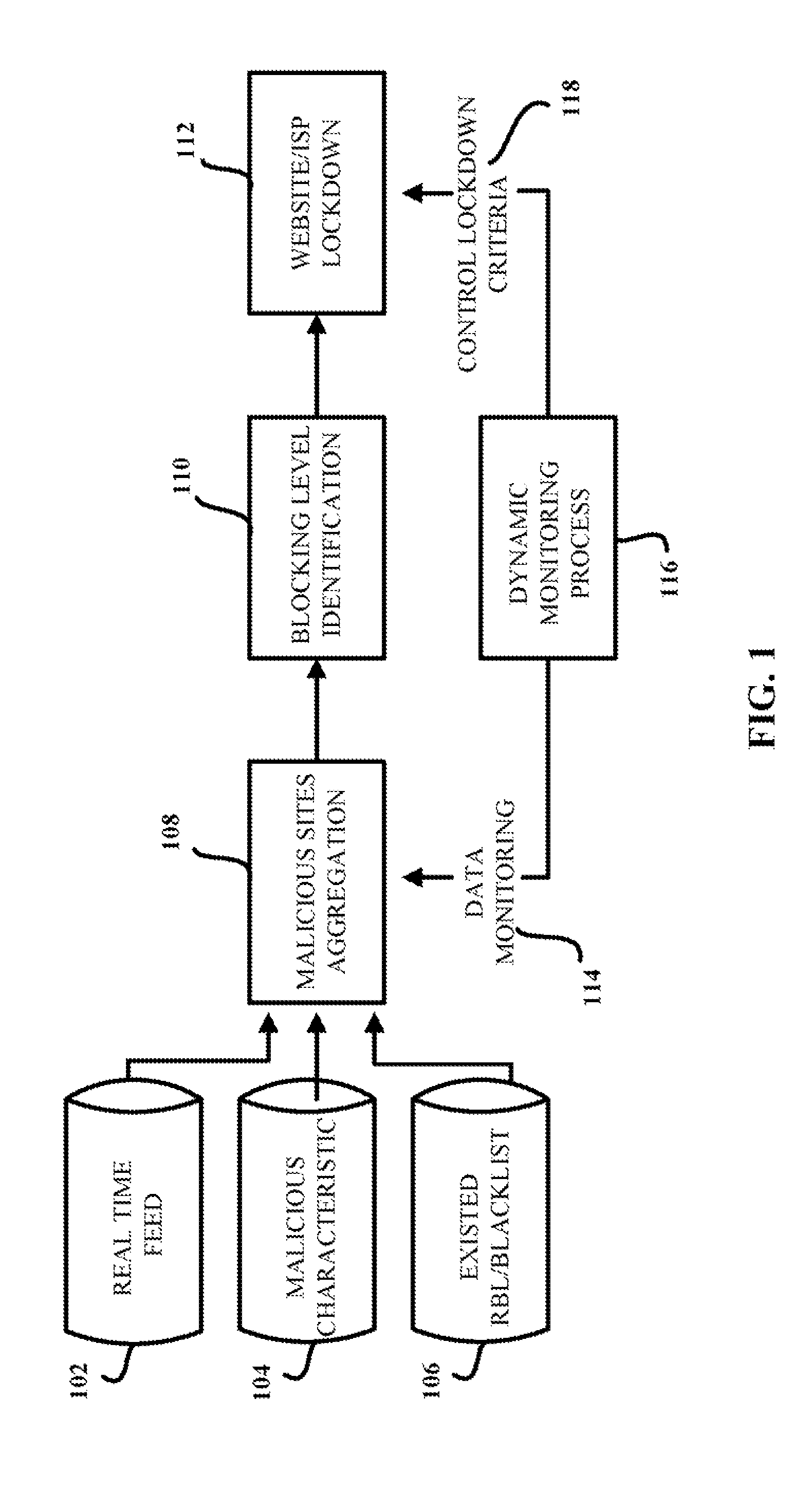
InactiveCN101257671AReduce false positive rateSpeed up filteringUnauthorised/fraudulent call preventionRadio/inductive link selection arrangementsSemanticsSupport vector classifier
The invention discloses a real time filtrating method for large-scale garbage message based on the content, including the steps as following: 1, pre-filtrating by using the black list and the white list; 2, carrying out the online filtrating by using the filtrating module based on the frequency; 3, carrying out the fast filtrating for the message content by using the method of twice hashing; 4, carrying out the pretreating of the message text for suspicion message, and converting the same into the phase vector; 5, judging the suspicion message by using the method of combination of Naive Bayesian classifier and support vector classifier. The invention can greatly improve the filtrating speed of garbage message, and efficiently reduce the produced erroneous judgement rate in the conventional key word filtrating method; can efficiently solve the problem of group sending garbage messages with malicious intent in the short time; can efficiently avoid to mistake the common message as the garbage message so as to reduce the erroneous judgement, and efficiently improve the filtrating accuracy of whole system by analyzing the message content on the semantics.
Owner:ZHEJIANG UNIV
Aggregation-based phishing site detection
InactiveUS7854001B1Reduce in quantityReduce attackMemory loss protectionError detection/correctionWeb siteBlack list
A computer-implemented method for reducing phishing attacks that employ malicious websites is provided. The computer-implemented method includes gathering information about potentially malicious websites from a plurality of sources. The computer-implemented method also includes reducing the number of potentially malicious websites gathered; thereby creating a malicious website database that tracks at least a subset of the potentially malicious websites. In addition, the computer-implemented method includes generating a malicious website blacklist from the malicious website database, each website in the malicious website blacklist satisfying inclusion criteria, wherein the malicious website blacklist is employed to decide whether an access request to a given website is permitted.
Owner:TREND MICRO INC
Online Privacy Management
ActiveUS20130276136A1Simple processDigital data processing detailsAnalogue secracy/subscription systemsDashboardAnalysis data
A privacy management system (PMS) is disclosed for a Chief Privacy Officer (CPO) or other user to use in monitoring and / or controlling in realtime the flow of data (e.g., outflow) about the user and his / her online experience. The PMS may employ pattern recognition software to evaluate analytics data and potentially block private information from being sent within the analytics data. The PMS may provide a dashboard displaying a whitelist and / or blacklist indicating what destinations / sources are blocked or allowed as well as private information settings indicating what types of private information should be blocked. The PMS includes browser-client scripting code and may also include a PMS-certified verification icon and / or lock and unlock icons for display on webpages being monitored / controlled in realtime by the PMS.
Owner:ENSIGHTEN
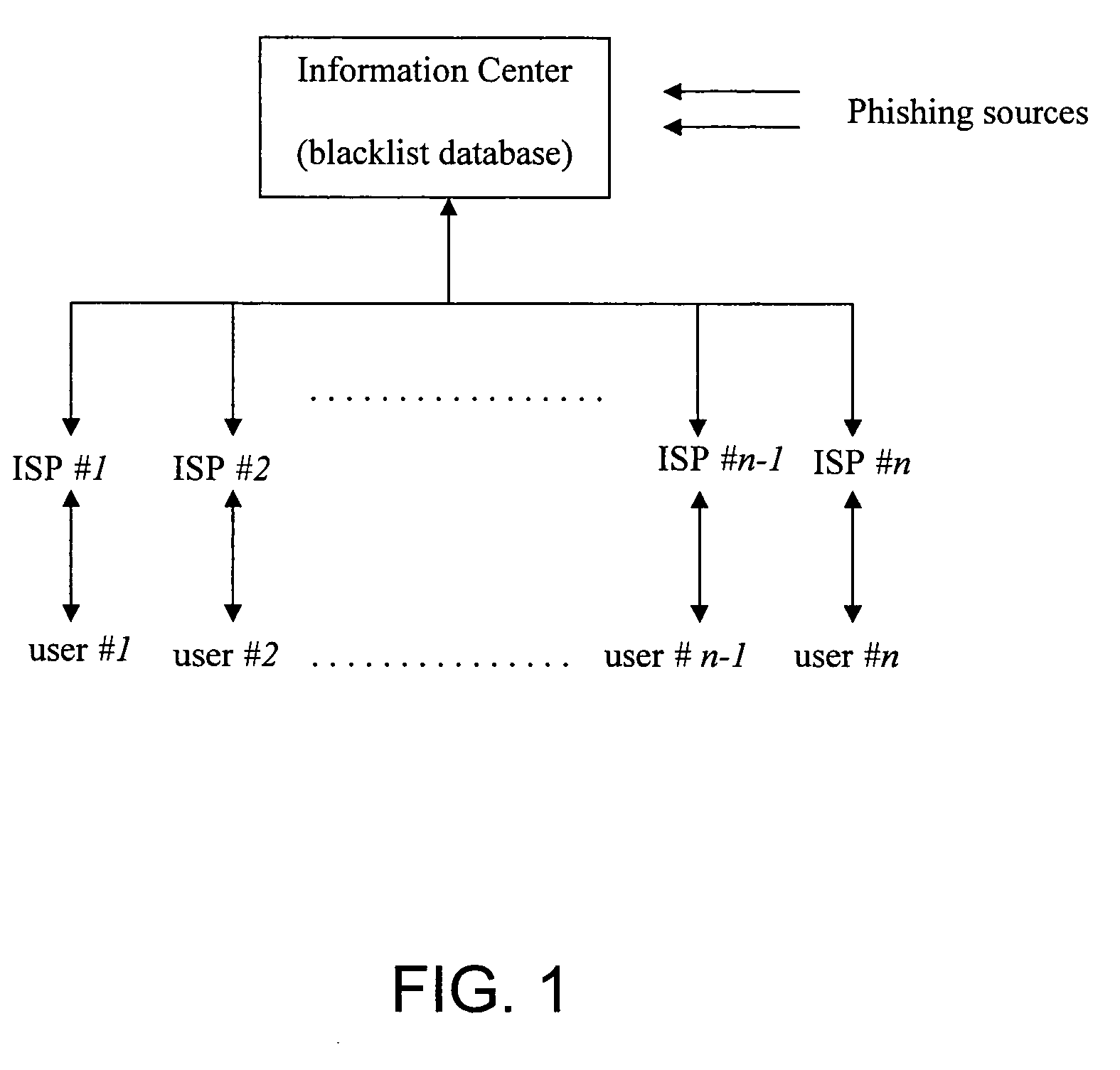
Jurisdiction-wide anti-phishing network service
InactiveUS20060095955A1Prevent theftPrevent users from being deceivedDigital data processing detailsUser identity/authority verificationWeb sitePhishing
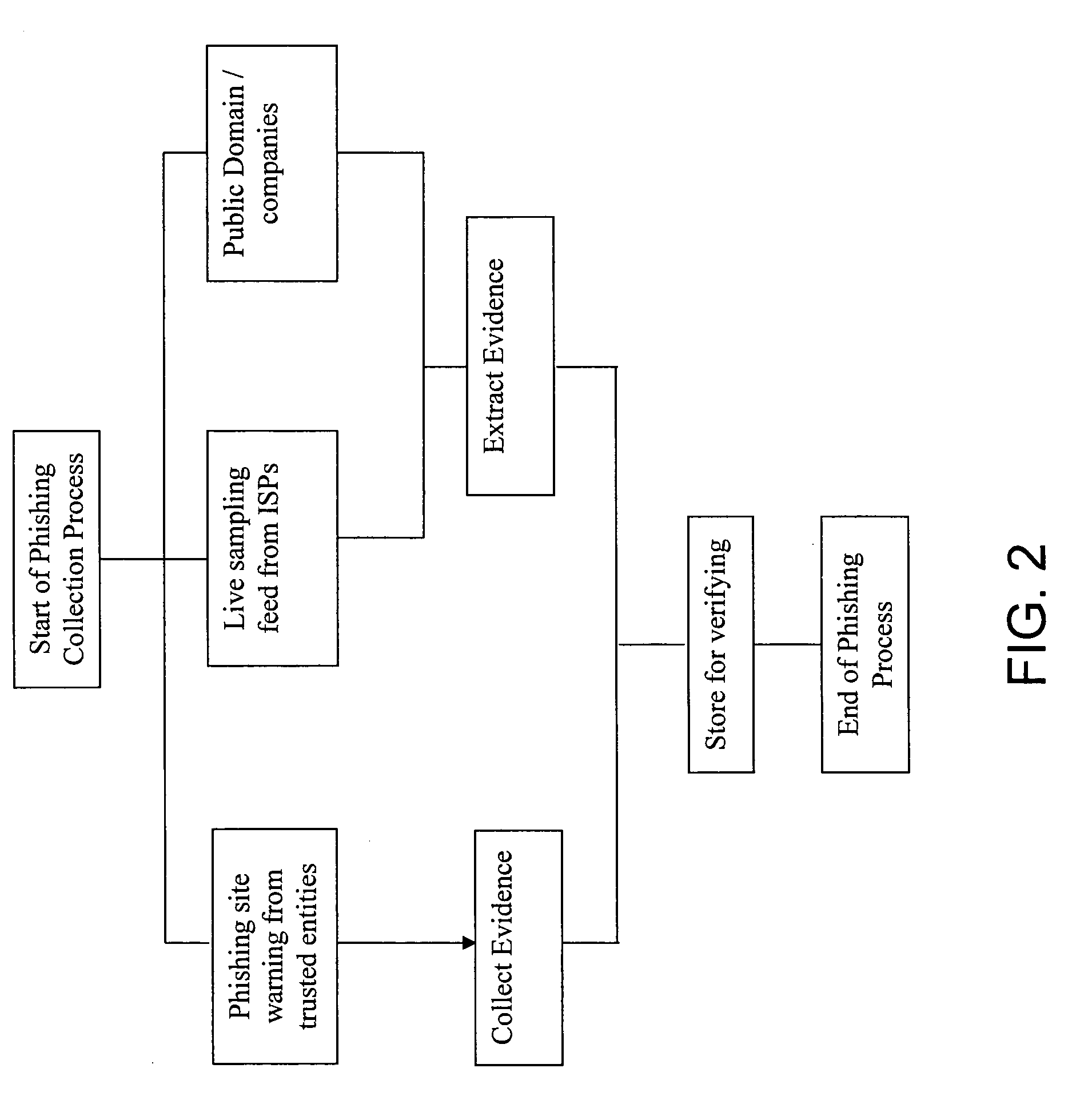
An anti-phishing method includes the steps of establishing an information center having a blacklist database, wherein the information center is liaising with at least an Internet service provider (ISP) through a communication network; collecting a plurality of phishing sources to be stored in the blacklist database to form a plurality of blacklist items therein; and sending the blacklist sources to the Internet service provider such that when a user of the Internet service provider tries to access a website source which matches with one of the blacklist items, the user receives a warning signal to inform the user that the website address is the phishing source.
Owner:MAIL PROVE
Determining source of side-loaded software
ActiveUS20160321452A1Digital data authenticationPlatform integrity maintainanceApplication softwareWhitelist
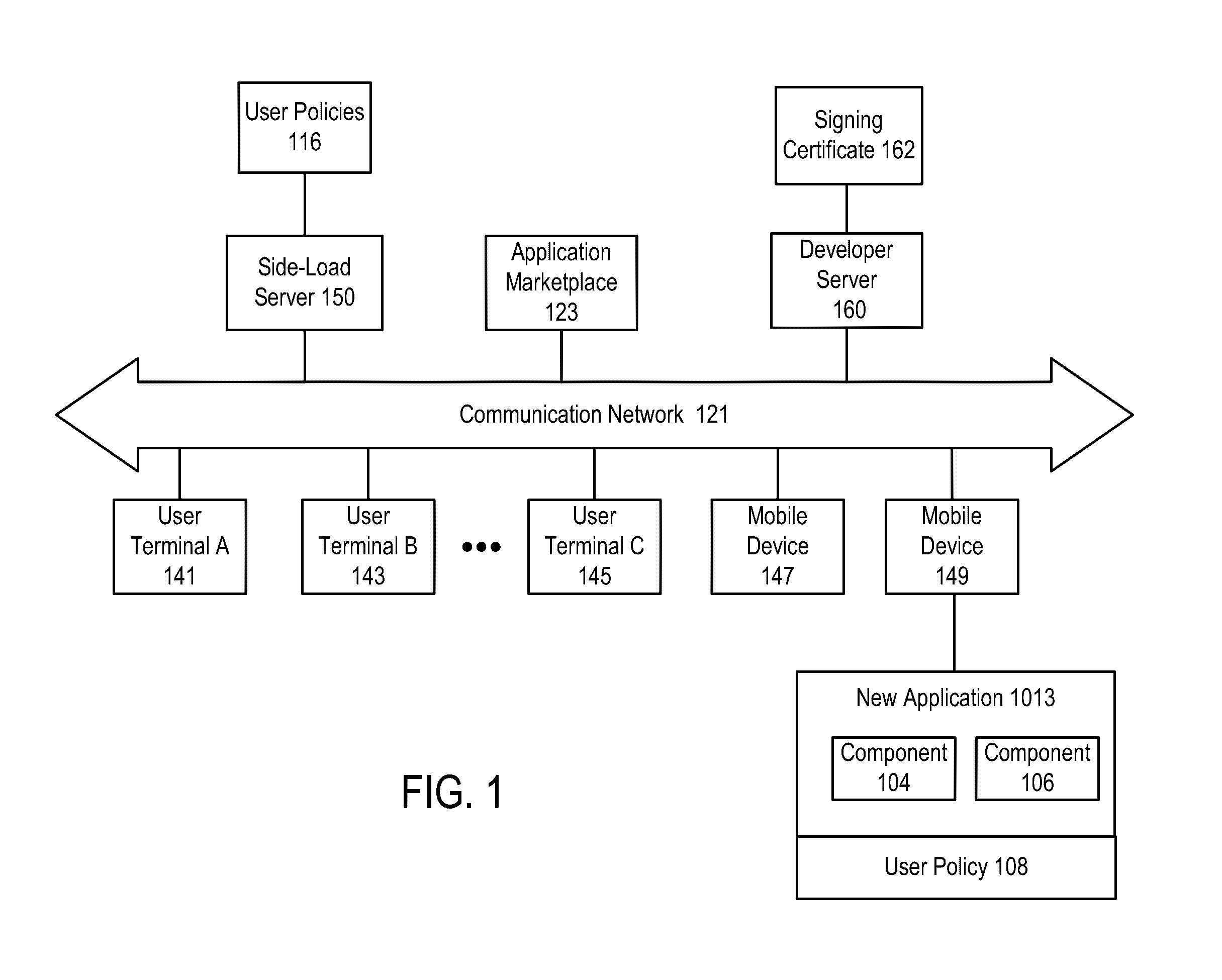
A source of side-loaded software is determined. An action may be performed in response to the determination of the source. In one case, the handling of an application on a mobile device may be based on whether the source of the application is trusted or untrusted. If a software application being newly-installed on a mobile device of a user is determined to be untrusted, installation or execution is blocked. In one approach, the determination of the source includes: determining whether a first source identifier of a first application matches a white list of source identifiers or a black list of source identifiers; and sending the first source identifier and a first application identifier for the first application to a different computing device.
Owner:LOOKOUT MOBILE SECURITY
Botnet detection method based on DNS (Domain Name System) flow characteristics
The invention discloses a botnet detection method based on DNS (Domain Name System) flow characteristics. The method of the invention comprises a Domain-Flux botnet detection method based on DNS flow characteristics. The method comprises steps: legal main domain names and illegal main domain names are combined to form a target set; a domain name whose length is larger than 6 is extracted and processed as a research target; the domain name entropy, word formation characteristics, phonetic characteristics and grouped characteristics are calculated respectively; and the above is put in a random forest classifier to obtain a training model. A Fast-Flux botnet detection method based on the Domain-Flux botnet detection method comprises steps: the original data of a DNS server are processed; the training model obtained before is used for evaluating a to-be-processed domain name, and a score for a DGA condition is acquired; a white list, a black list and a grey list are used for scoring the domain name and an IP; time characteristics of the IP address are calculated; the stability of the IP address is calculated; and the above is put in the random forest classifier to obtain a training model SFF. The experiment accuracy is high.
Owner:宁波知微瑞驰信息科技有限公司
Authorization and authentication based on an individual's social network
An individual's social network is used to authorize information flow to the individual and to authenticate the individual for access to certain information or services. Information flow to the individual is authorized if the source of the information is a member of the individual's social network who is connected to the individual along a path that does not traverse through anyone on a gray list of the individual. The black list identifies those members who previously sent unwanted communication to the individual or posted content that was deemed offensive by the individual. The gray list identifies those members who are one degree separated from any black list member. The individual is authenticated for access to certain information or services if a member of the individual's social network already has access and this member is connected to the individual along a path that does not traverse through anyone on a gray list of the individual, or if members of the individual's social network who are connected to the individual along a path that does not traverse through anyone on a gray list of the individual have an average authentication rating that is at least a minimum value.
Owner:META PLATFORMS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com