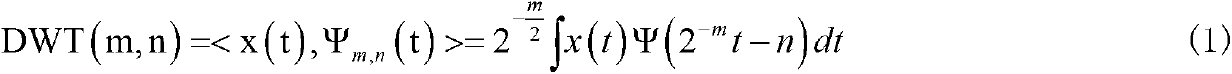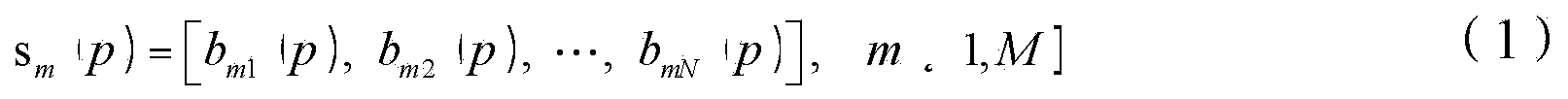Patents
Literature
186 results about "Communication source" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
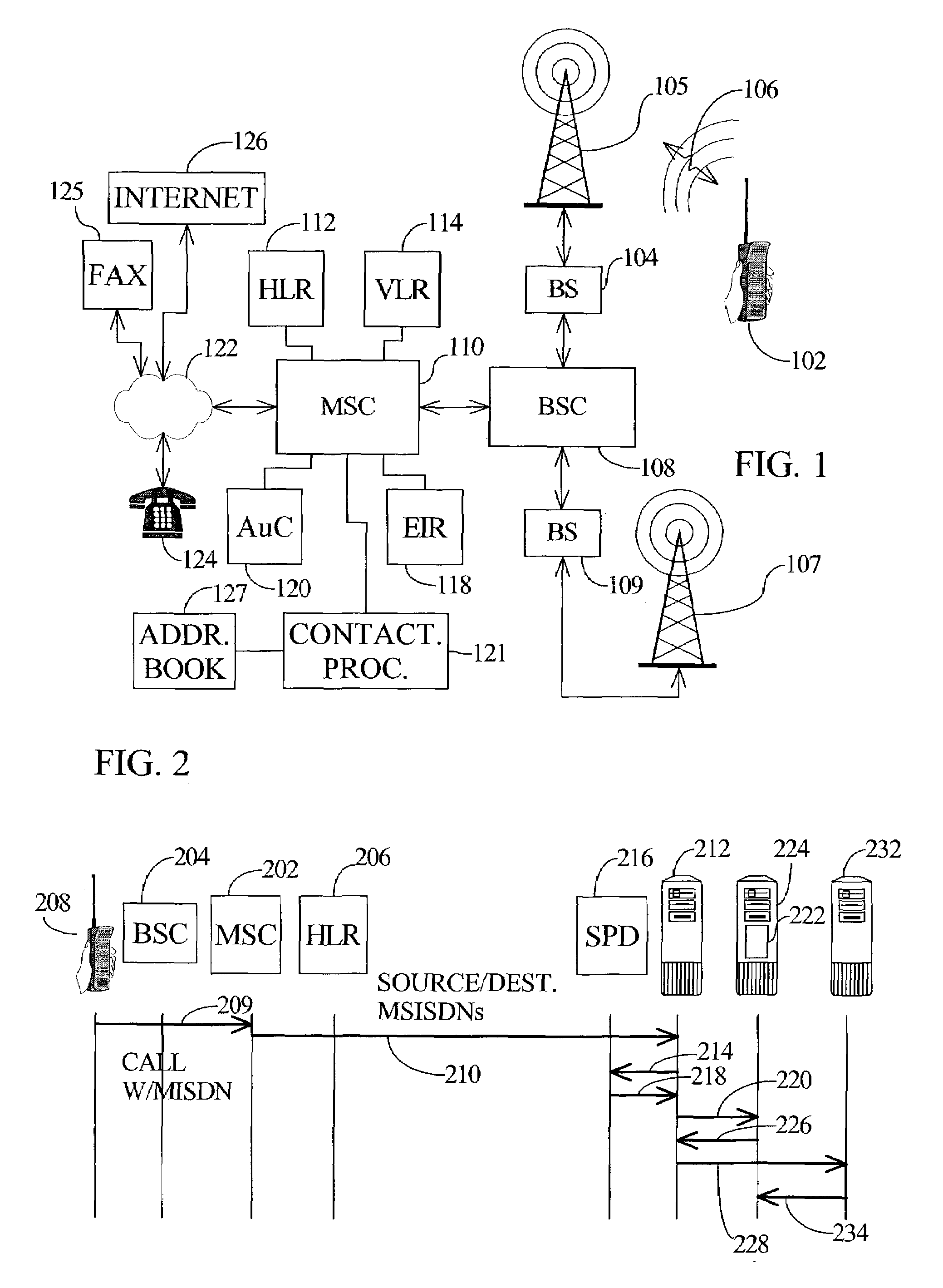
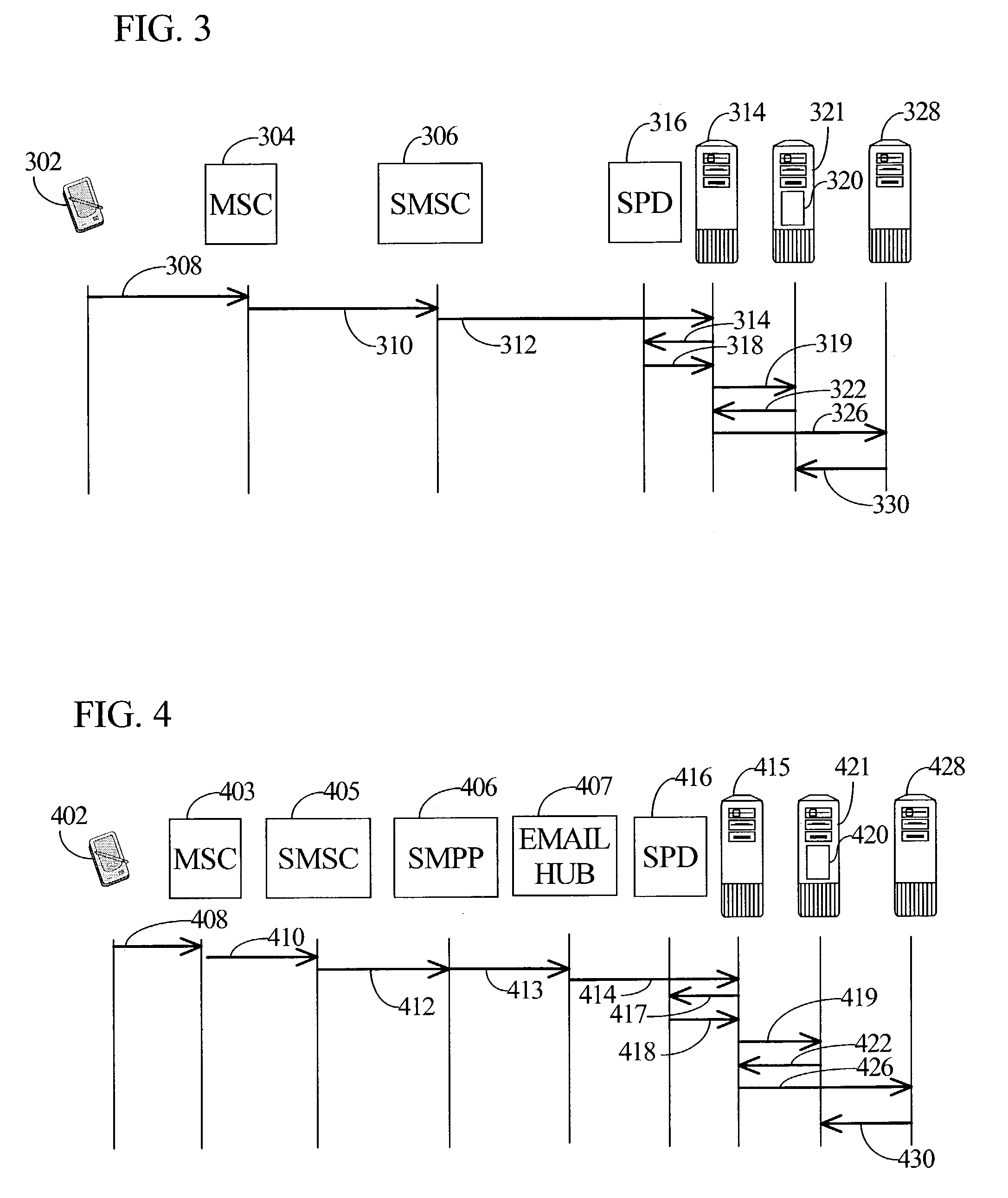
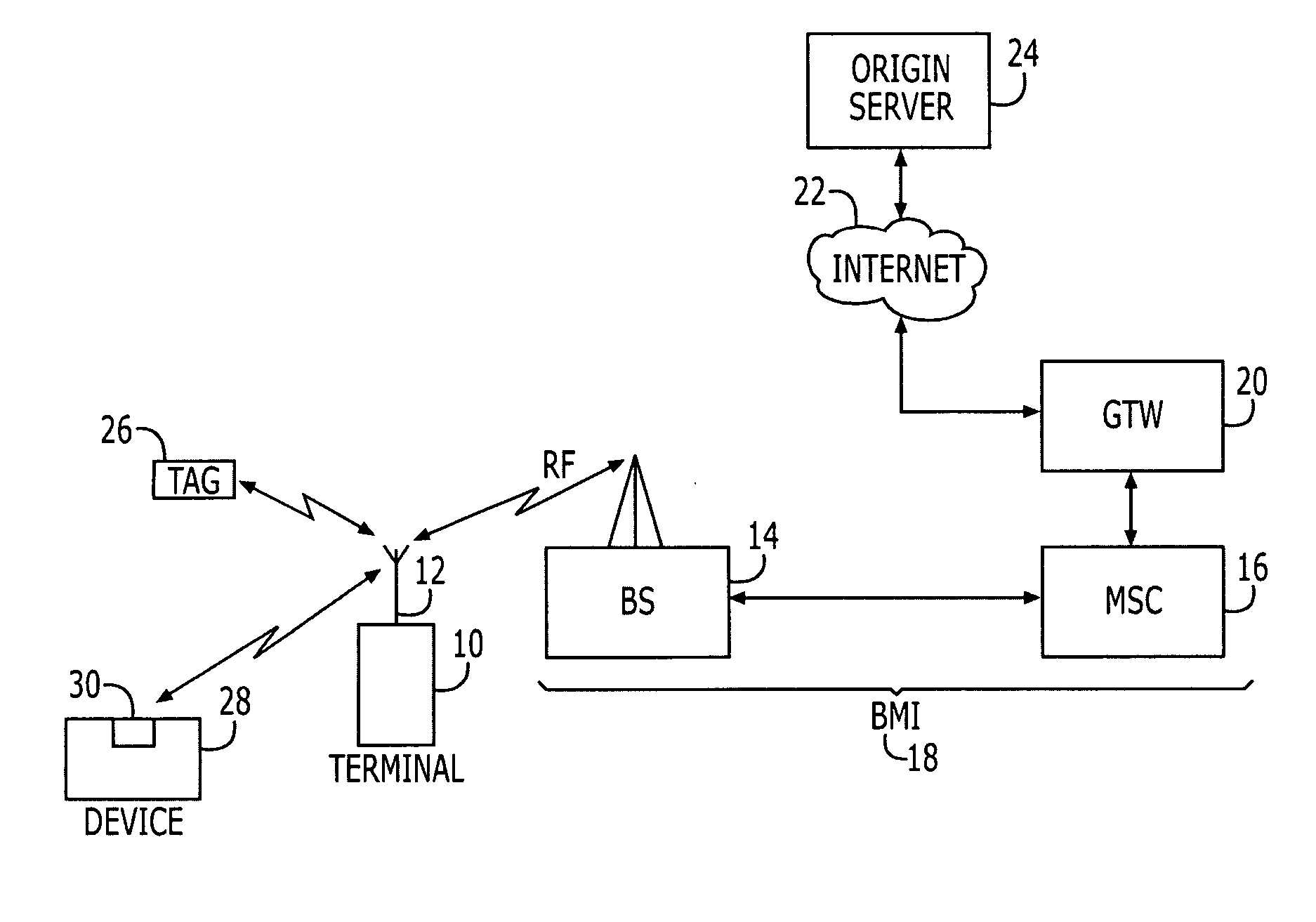
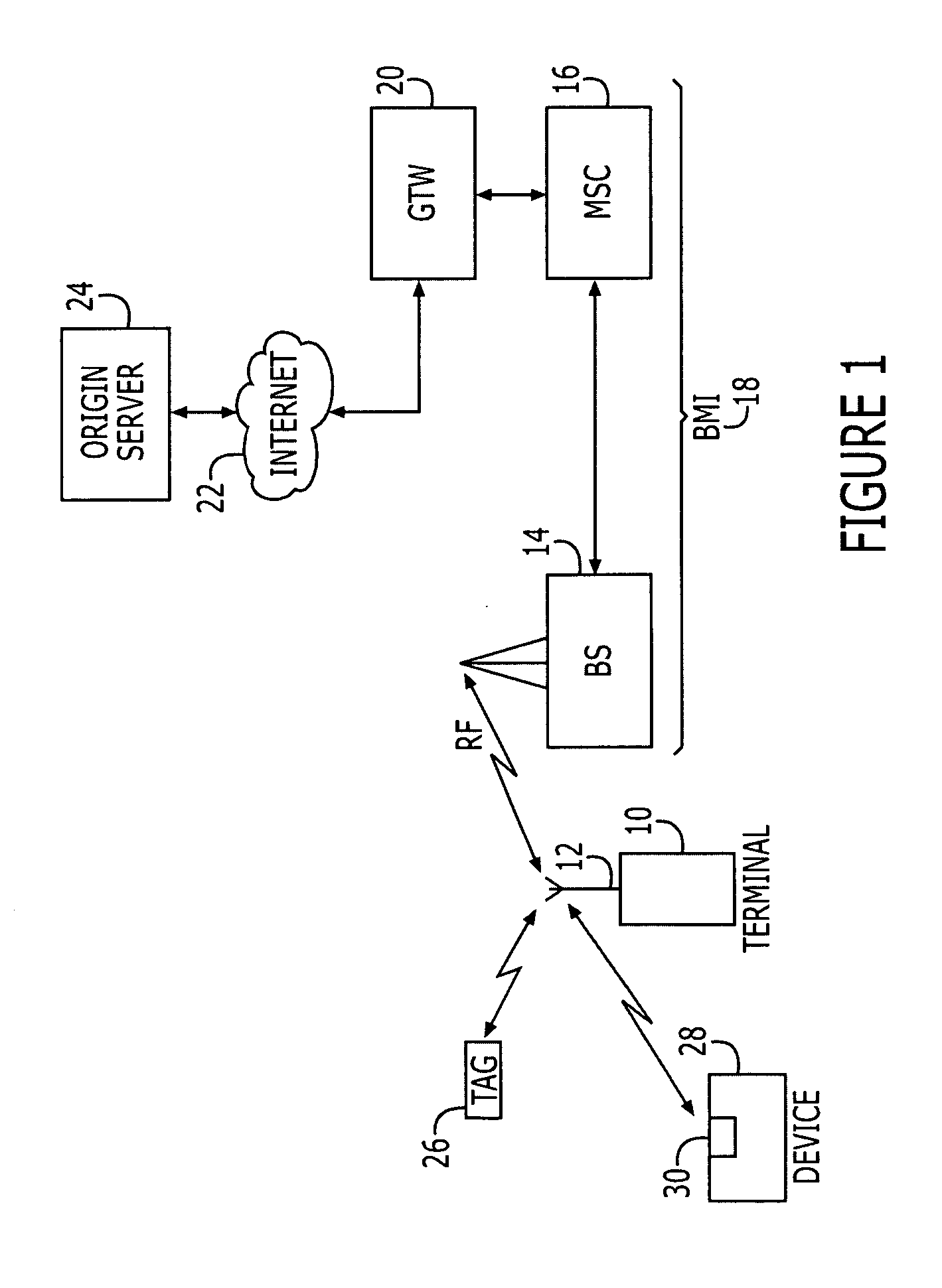
A source or sender is one of the basic concepts of communication and information processing. Sources are objects which encode message data and transmit the information, via a channel, to one or more observers (or receivers).
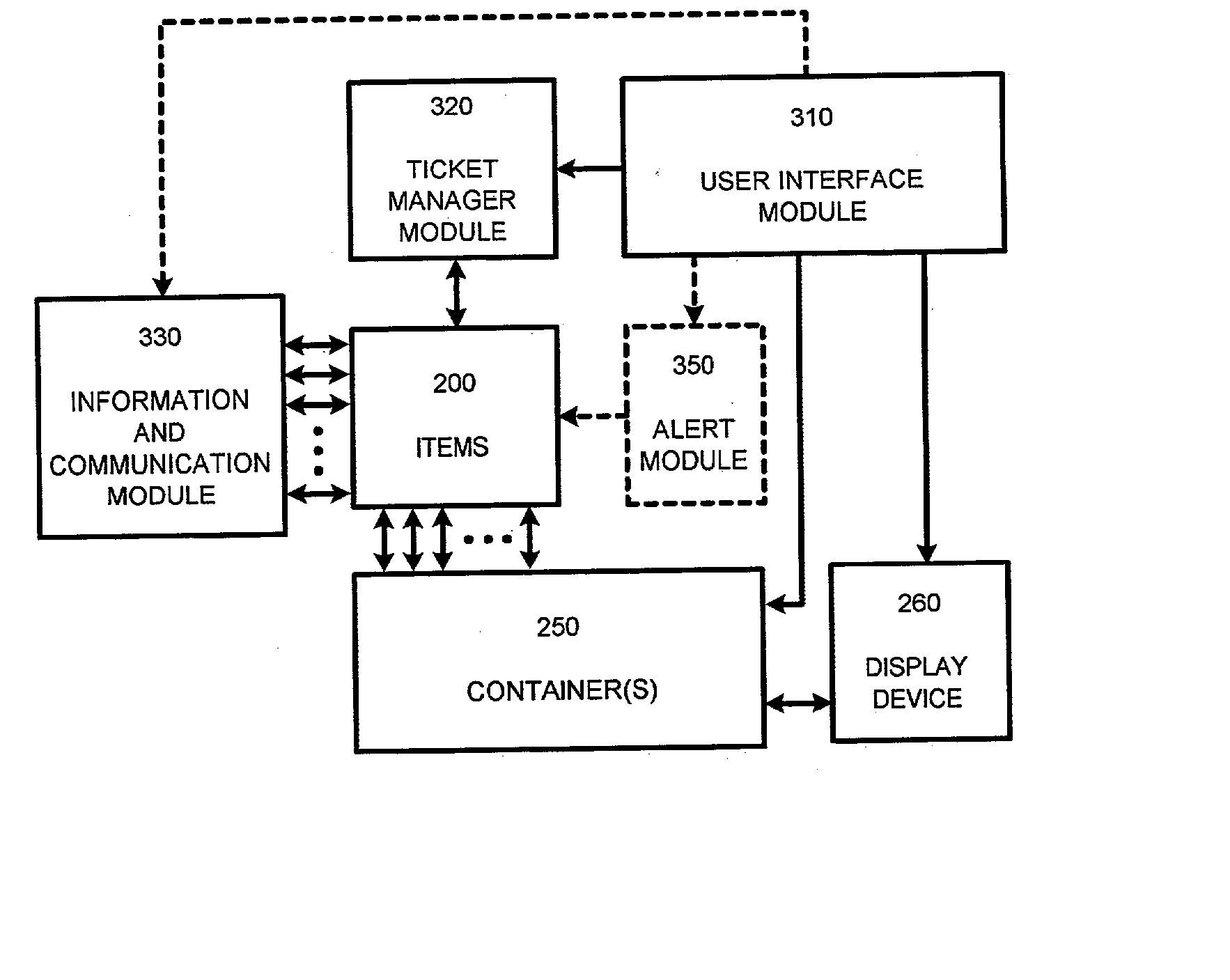
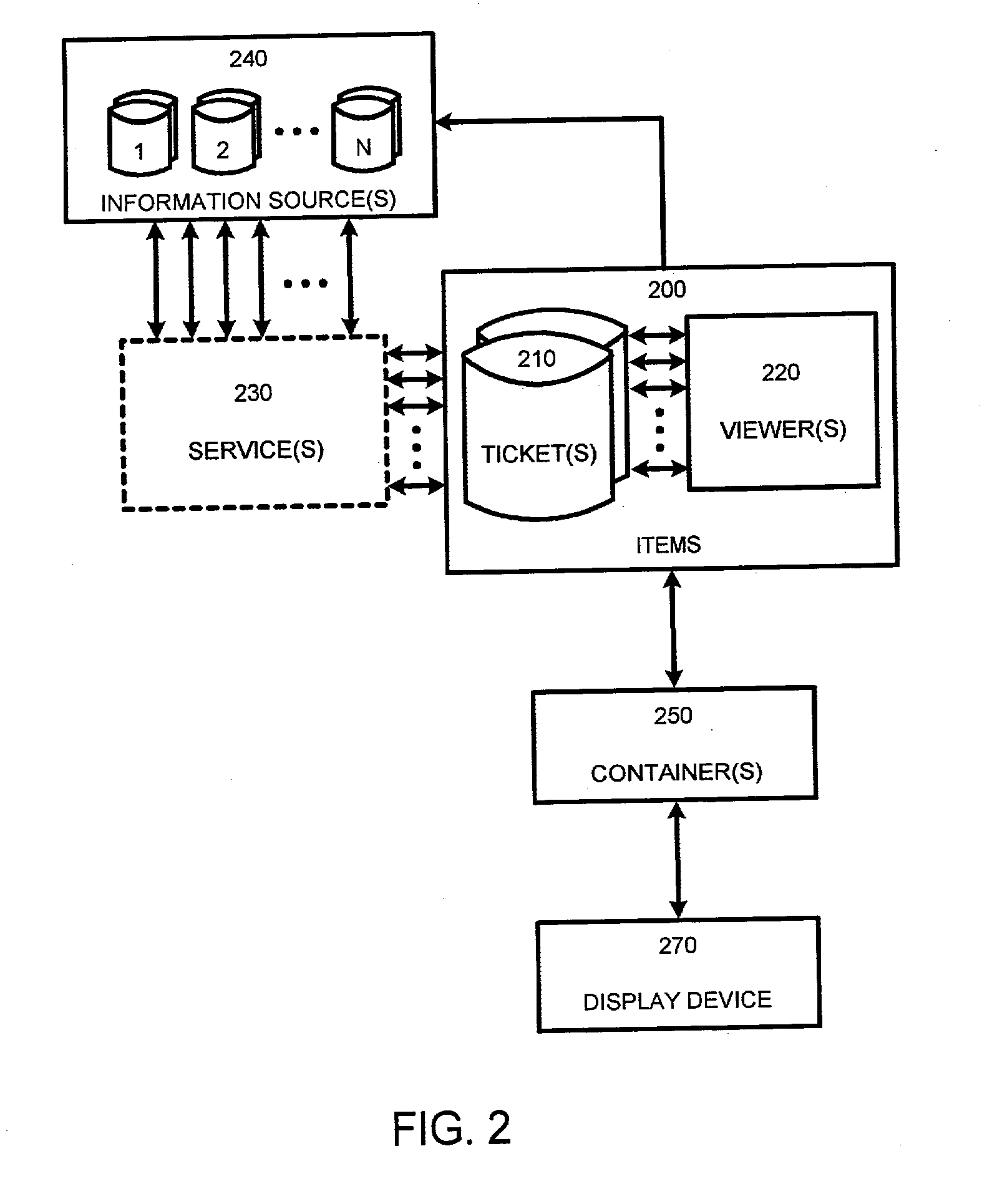
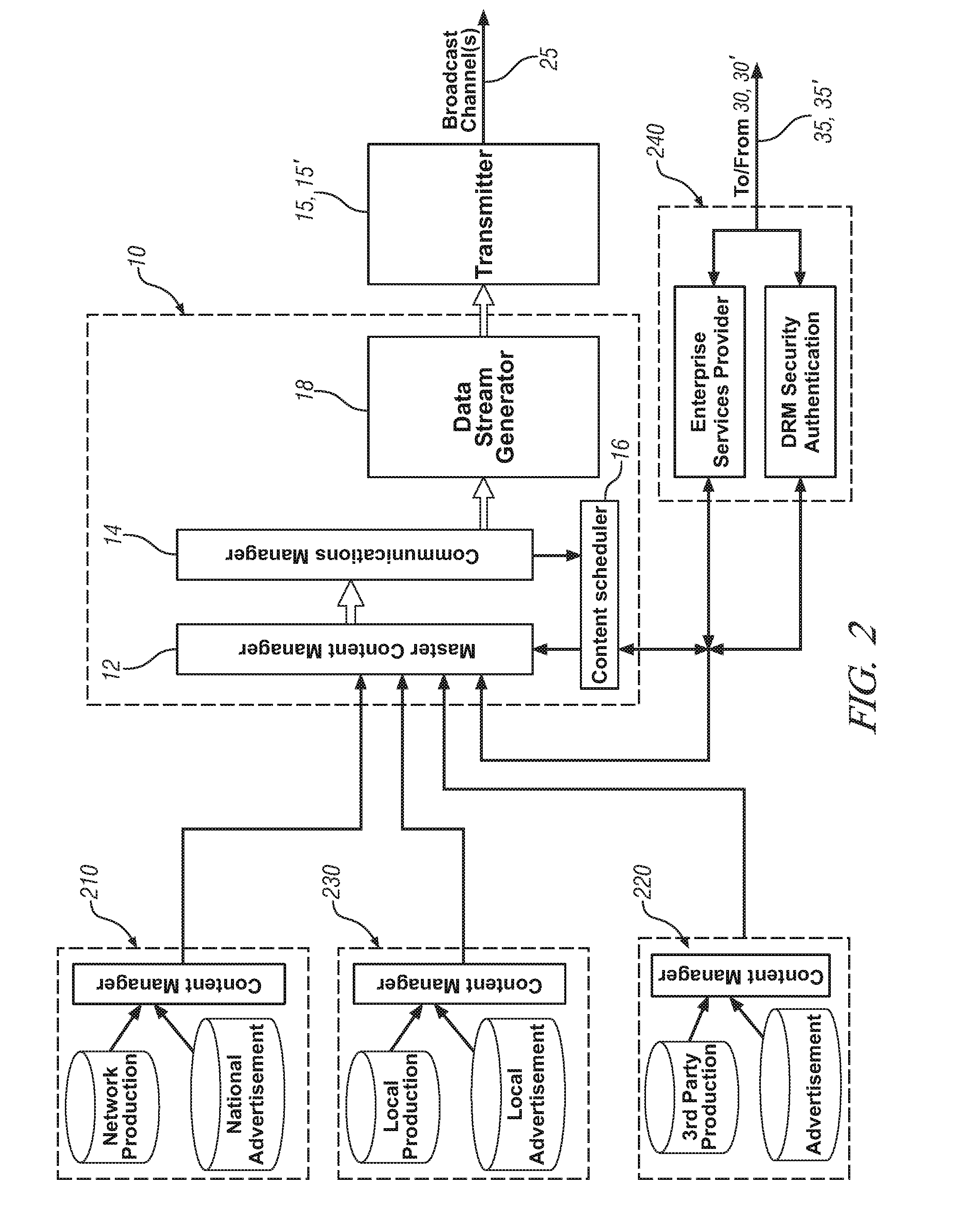
System and process for providing dynamic communication access and information awareness in an interactive peripheral display
InactiveUS20020186257A1Minimize distractionMinimize interruptionData processing applicationsDigital data information retrievalDrag and dropCommunication interface
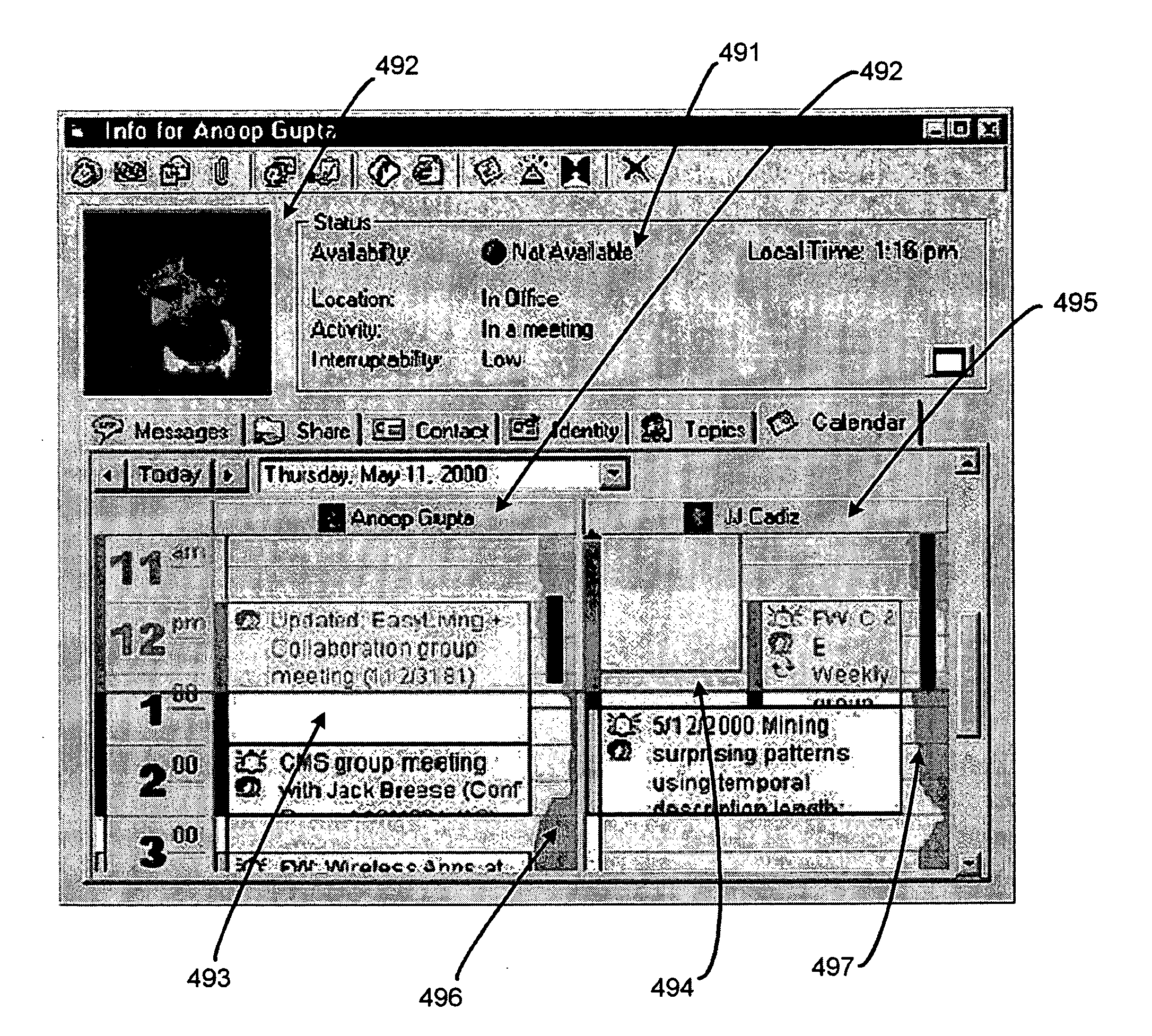
The system and method of the present invention provides peripheral awareness of information to a user. The information to be provided is either determined automatically, or specified by the user. Once the information to be provided is determined or specified, it is automatically tracked or watched via at least one conventional communications interface for accessing one or more conventional communications sources. Current information is then automatically dynamically provided in an interactive peripheral display which minimizes any potential distraction to the user. Determining or specifying, tracking or watching, and providing the information is accomplished using at least one customizable dynamic encapsulated object, a "ticket," that when paired with a "viewer," provides peripheral awareness of information to the user. Further, in one embodiment, the tickets are sharable among users, and may be copied, cut, pasted, saved, transmitted, dragged and dropped from web pages, etc., like any other electronic file using conventional techniques.
Owner:MICROSOFT TECH LICENSING LLC
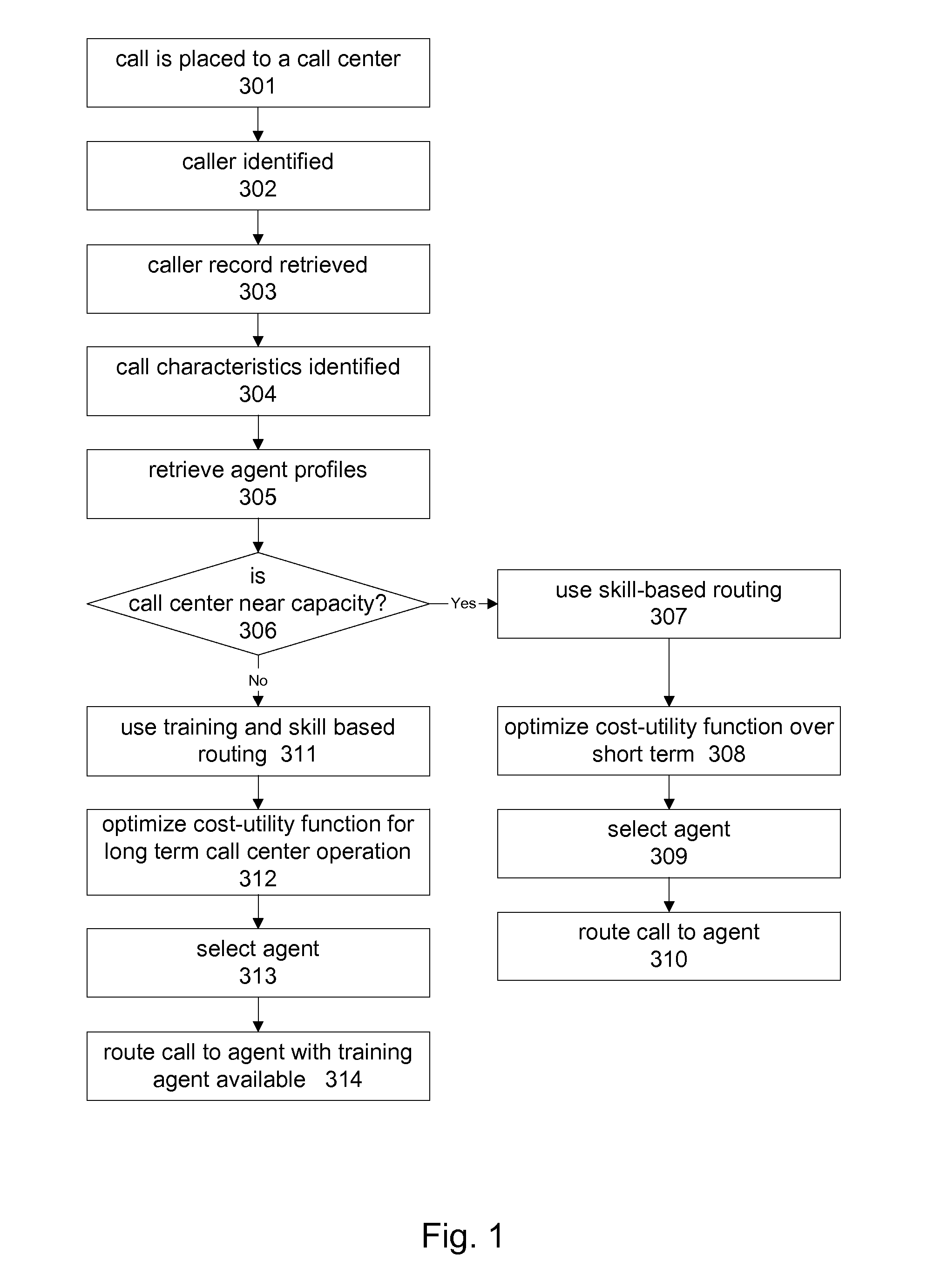
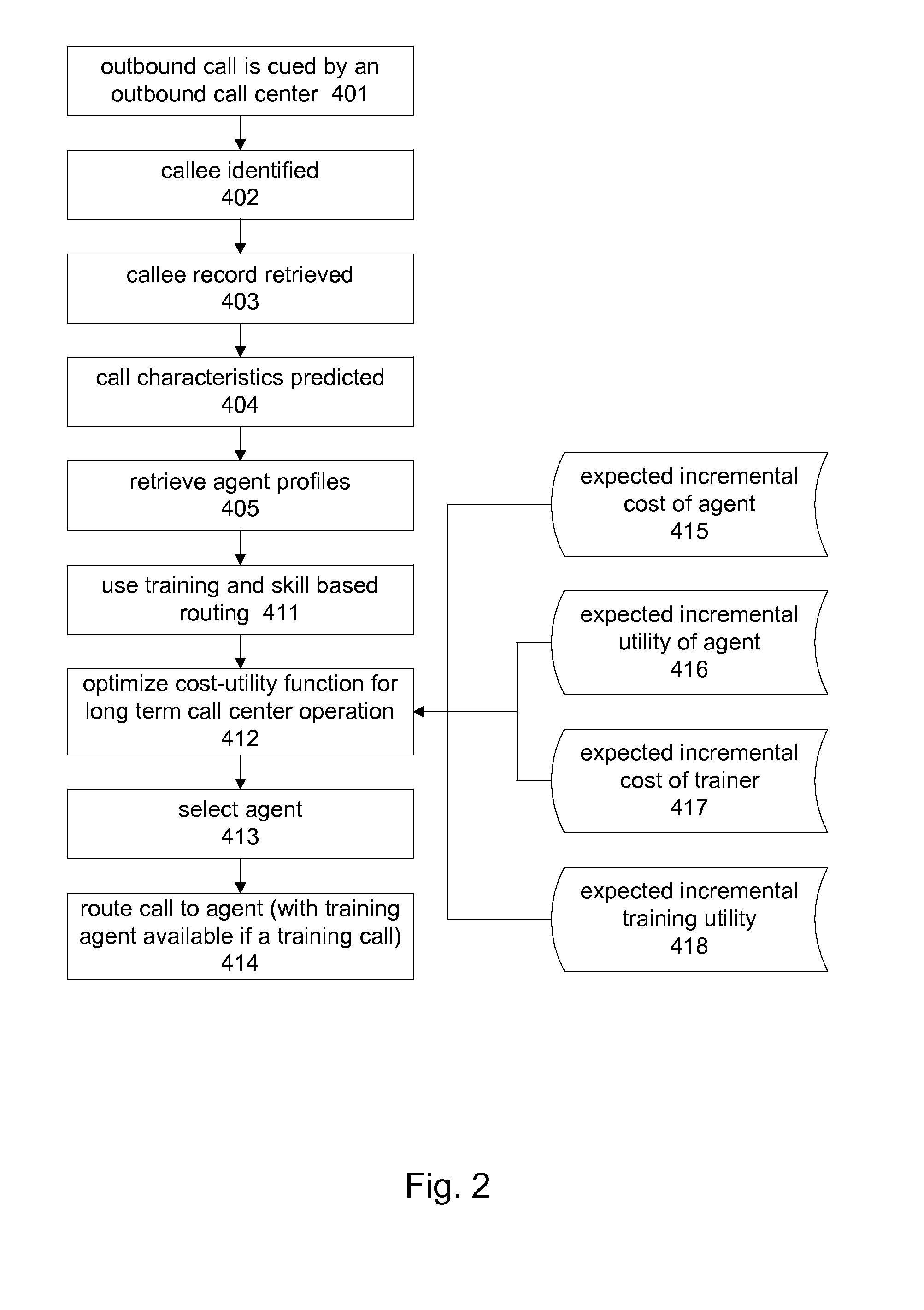
Intelligent communication routing system and method
InactiveUS8300798B1Reduce bandwidth requirementsReduce loadManual exchangesAutomatic exchangesCommunication sourceEconomic utility
A communications routing system, and method, for representing a plurality of predicted characteristics of a plurality of communications sources, each having an economic utility; representing a plurality of predicted characteristics of a plurality of communications targets each having an economic utility; and determining an optimal routing between the plurality of communications sources and the plurality of communications targets, by maximizing an aggregate utility with respect to the respective predicted characteristics of communications source and communications destination represented by linkages.
Owner:PATENT ARMORY INC
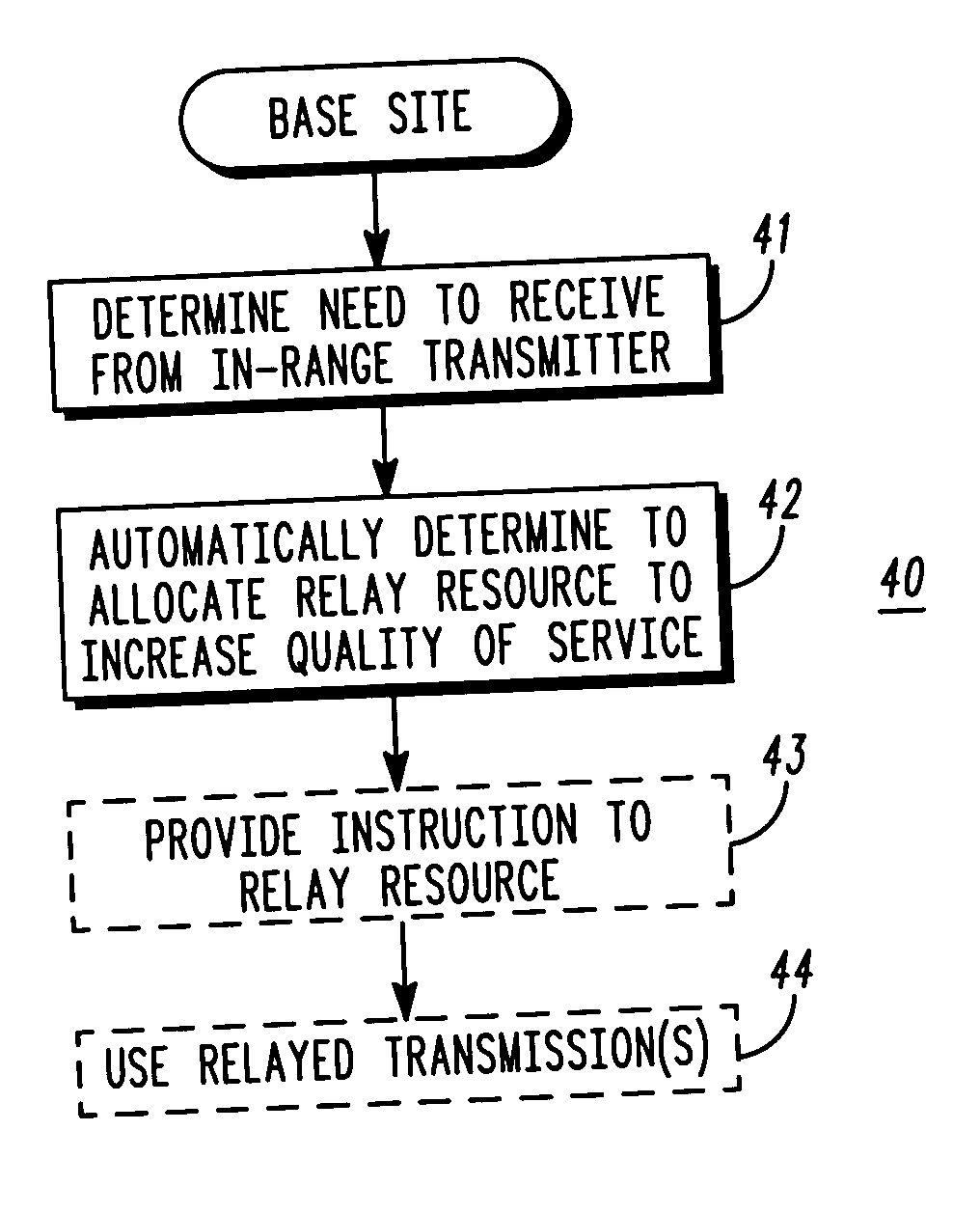
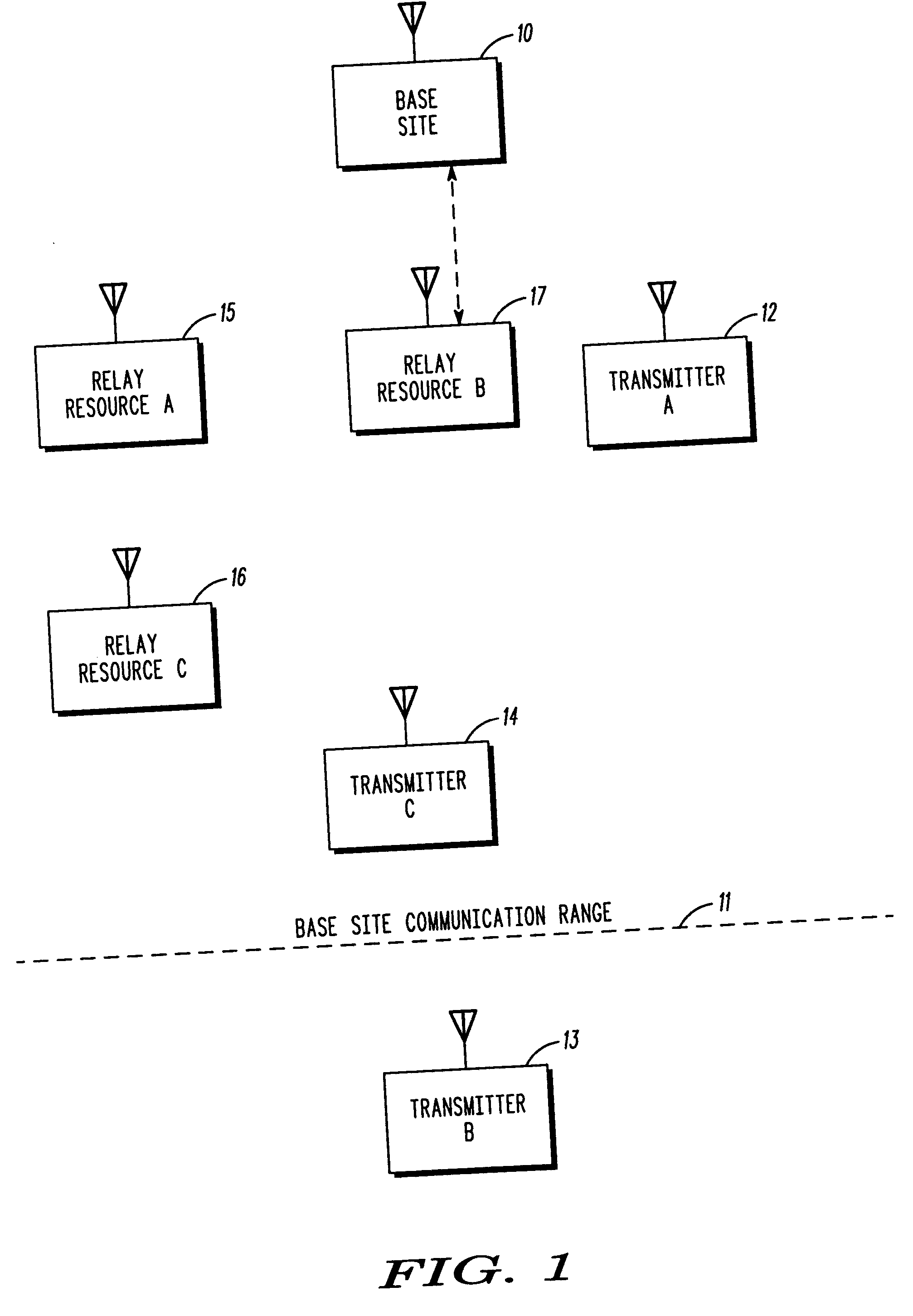
Method and apparatus for relay facilitated communications
InactiveUS20050048914A1Power managementFrequency-division multiplex detailsQuality of serviceData rate
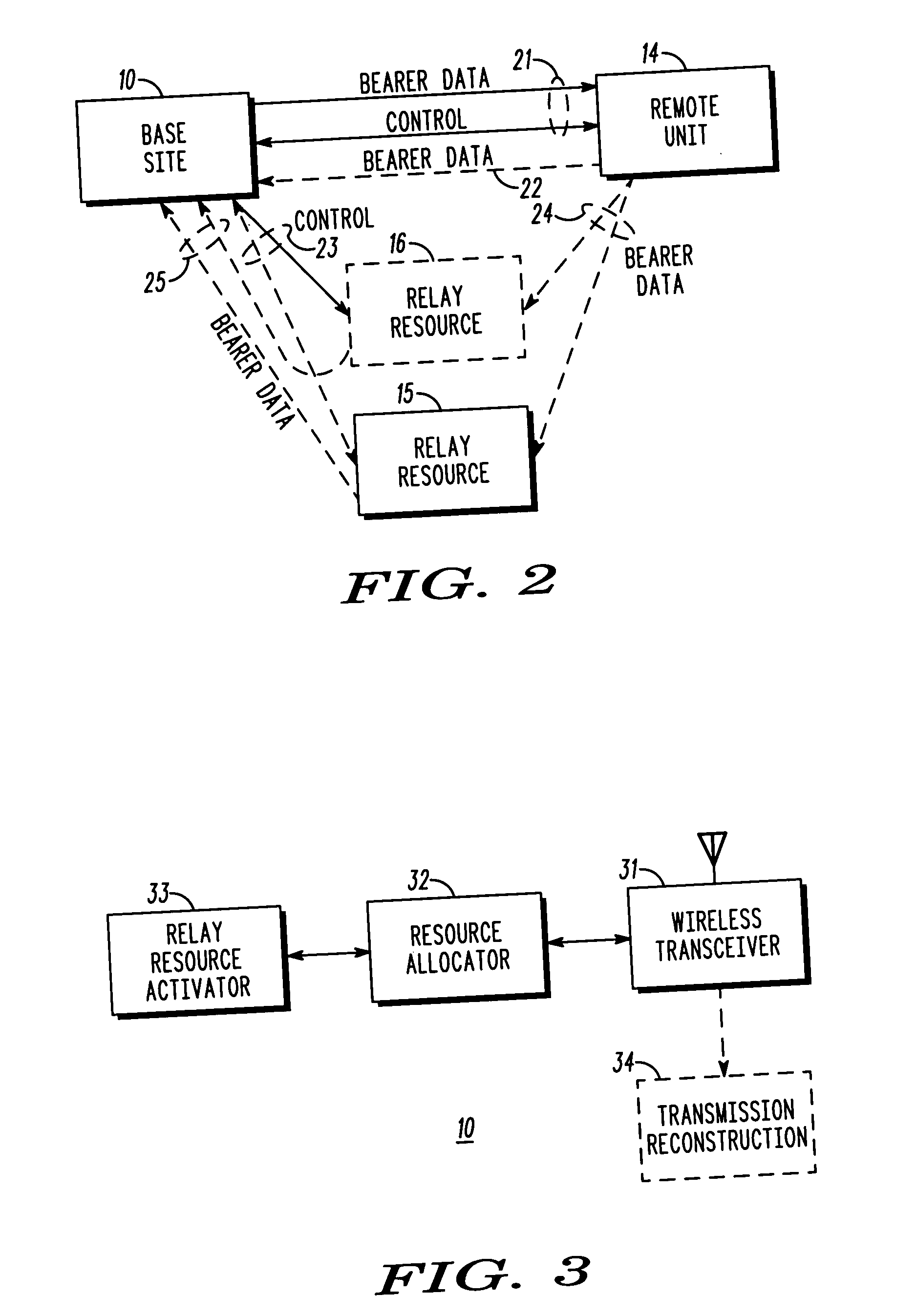
Communications sourced by a remote unit (14) that is already within reception range of a base site (10) can nevertheless be further facilitated through allocation of one or more relay resources (15, 16). Such relay resources, properly employed, then serve to effectively increase the quality of service for the facilitated communication. This, in turn, can permit the use of, for example, increased data rates for communications from a relatively low power remote unit.
Owner:GOOGLE TECH HLDG LLC
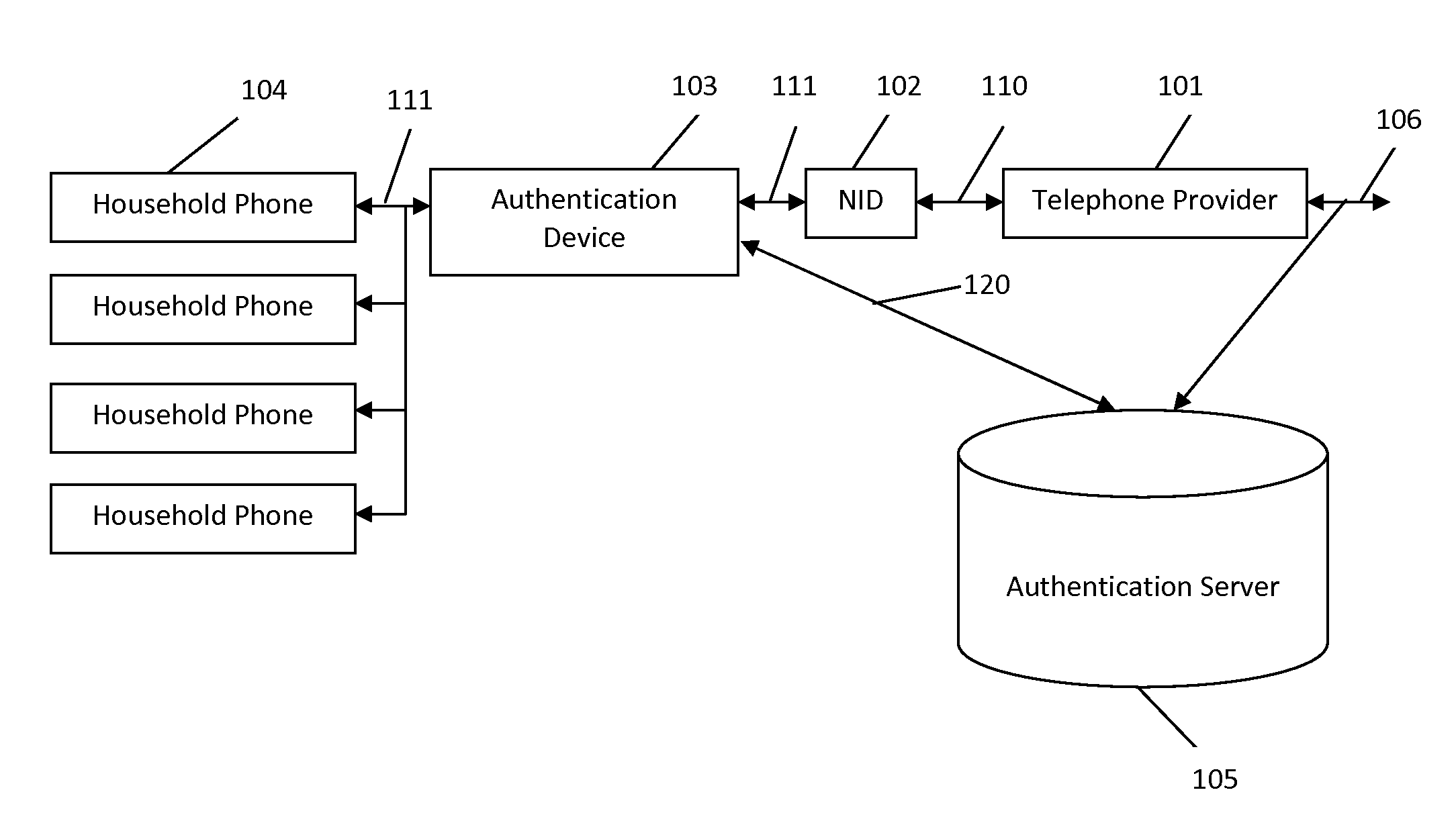
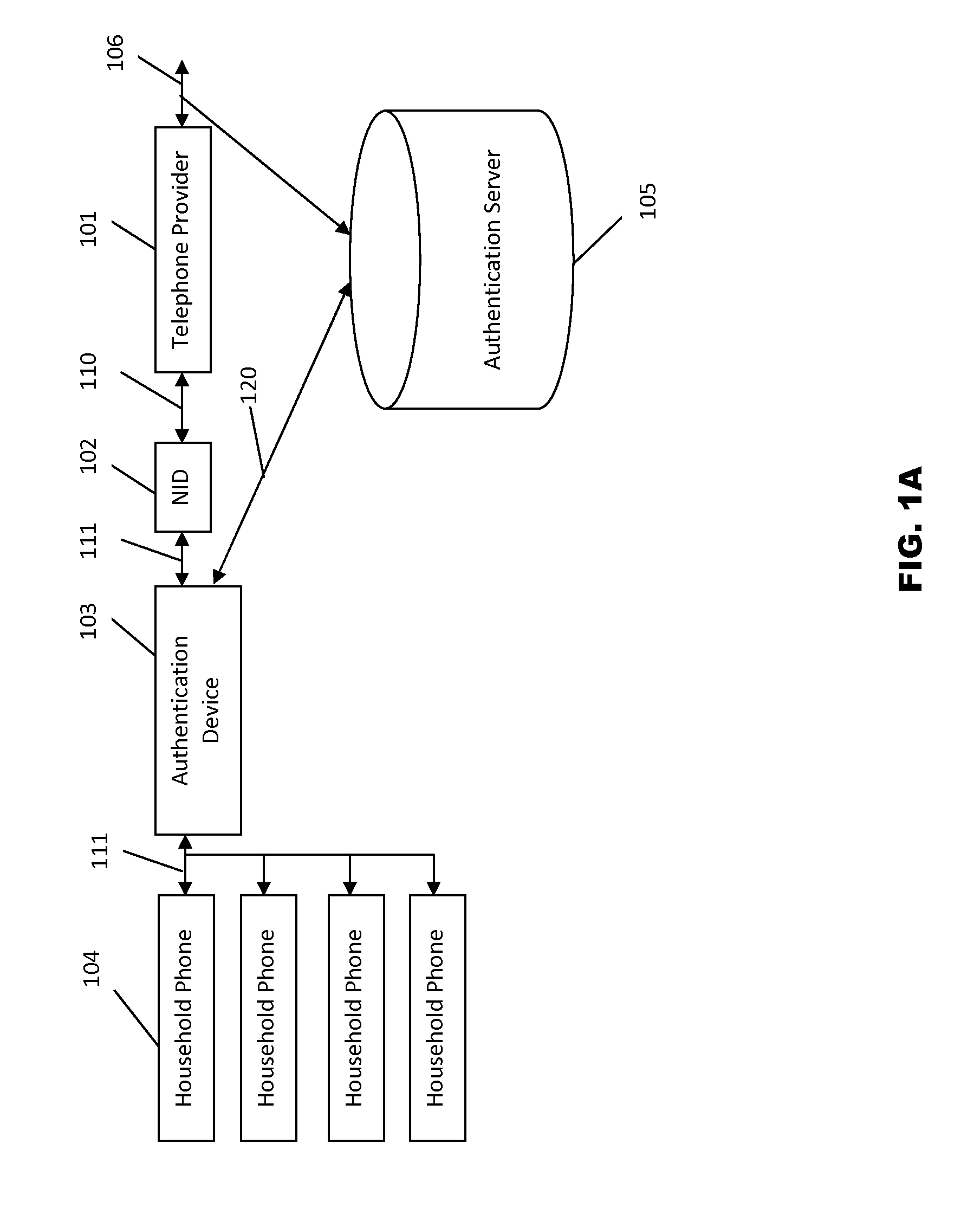
Systems and methods for caller ID authentication, spoof detection and list based call handling
ActiveUS9060057B1Special service for subscribersCalled number recording/indicationBase callingCommunication source
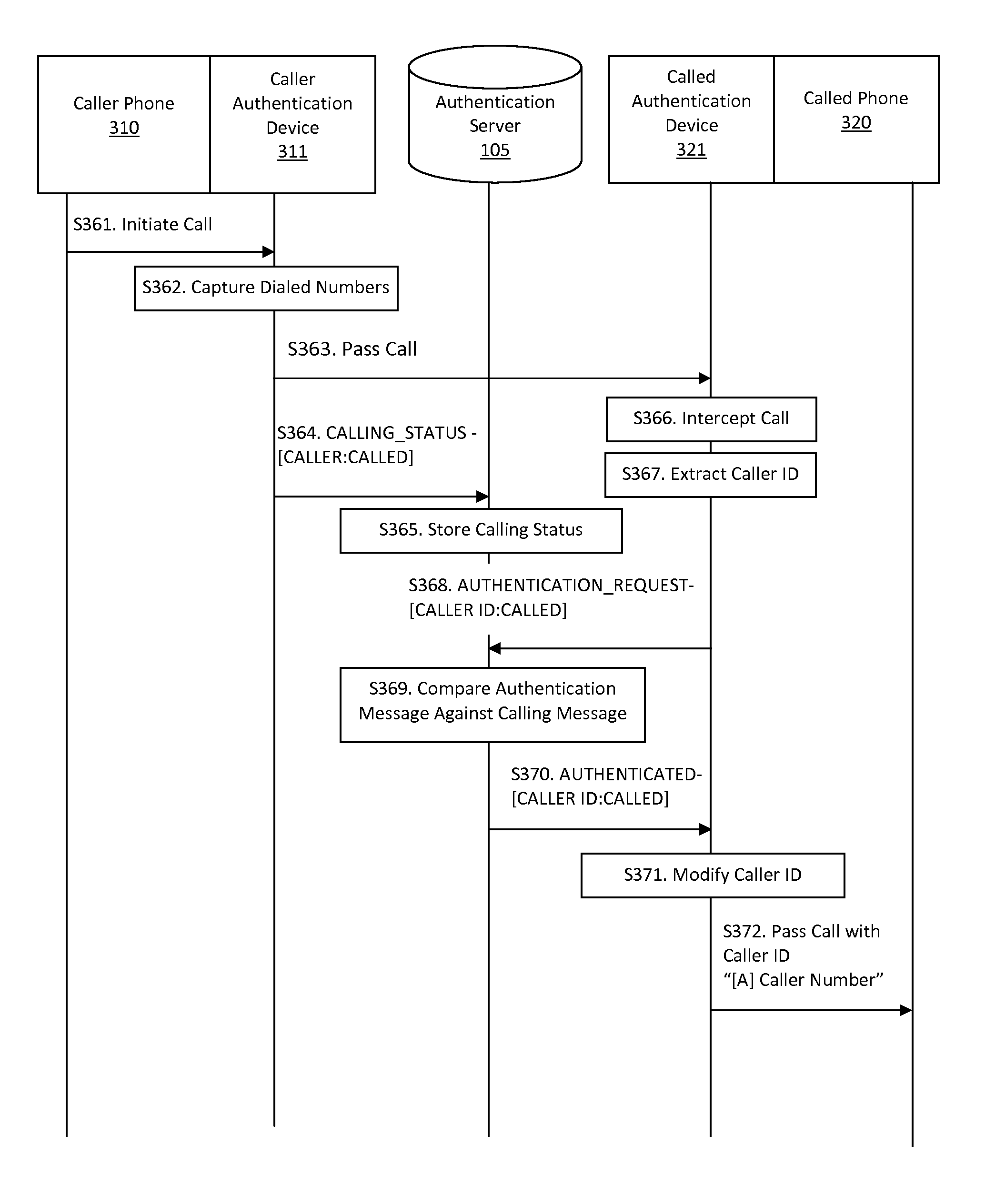
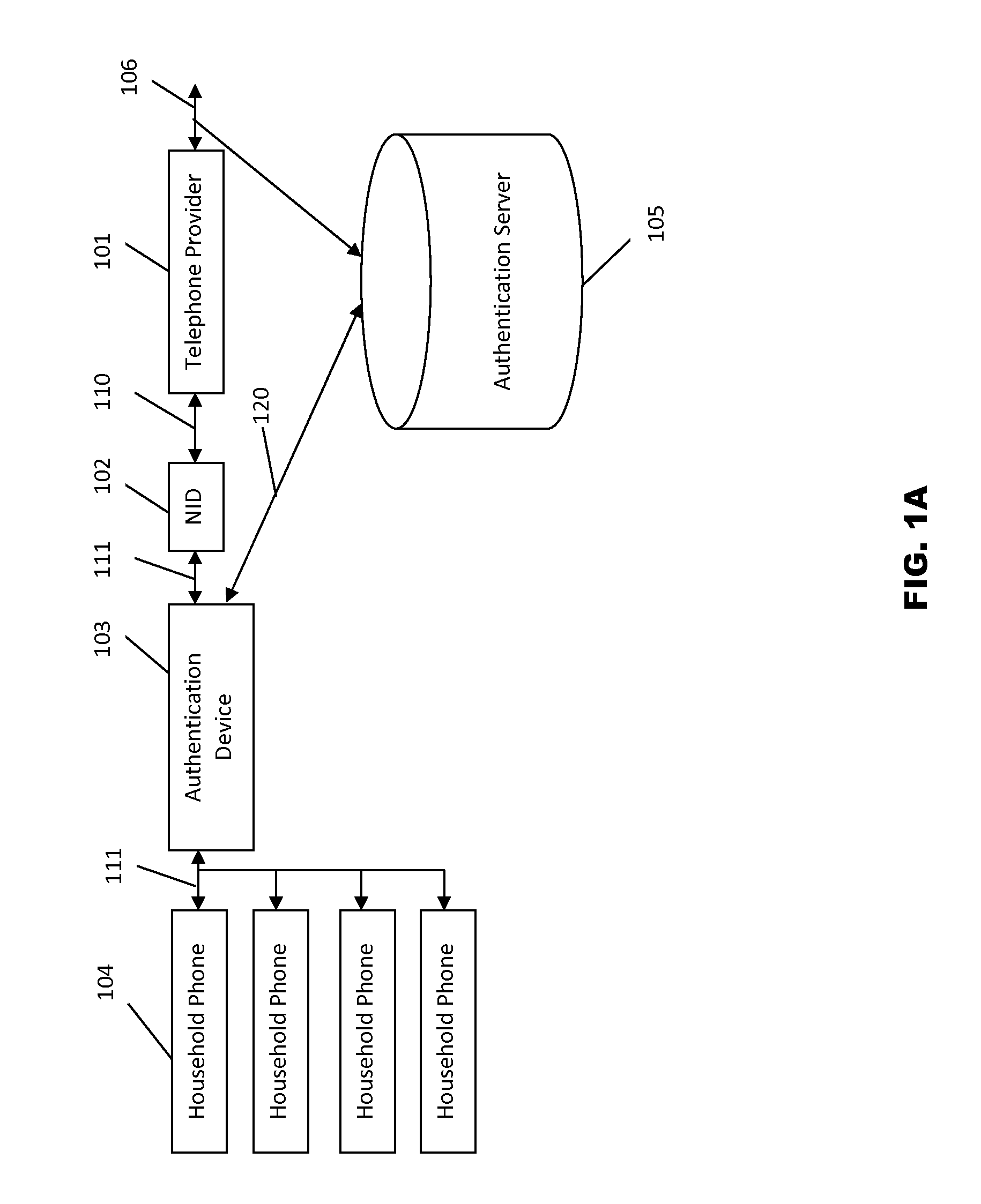
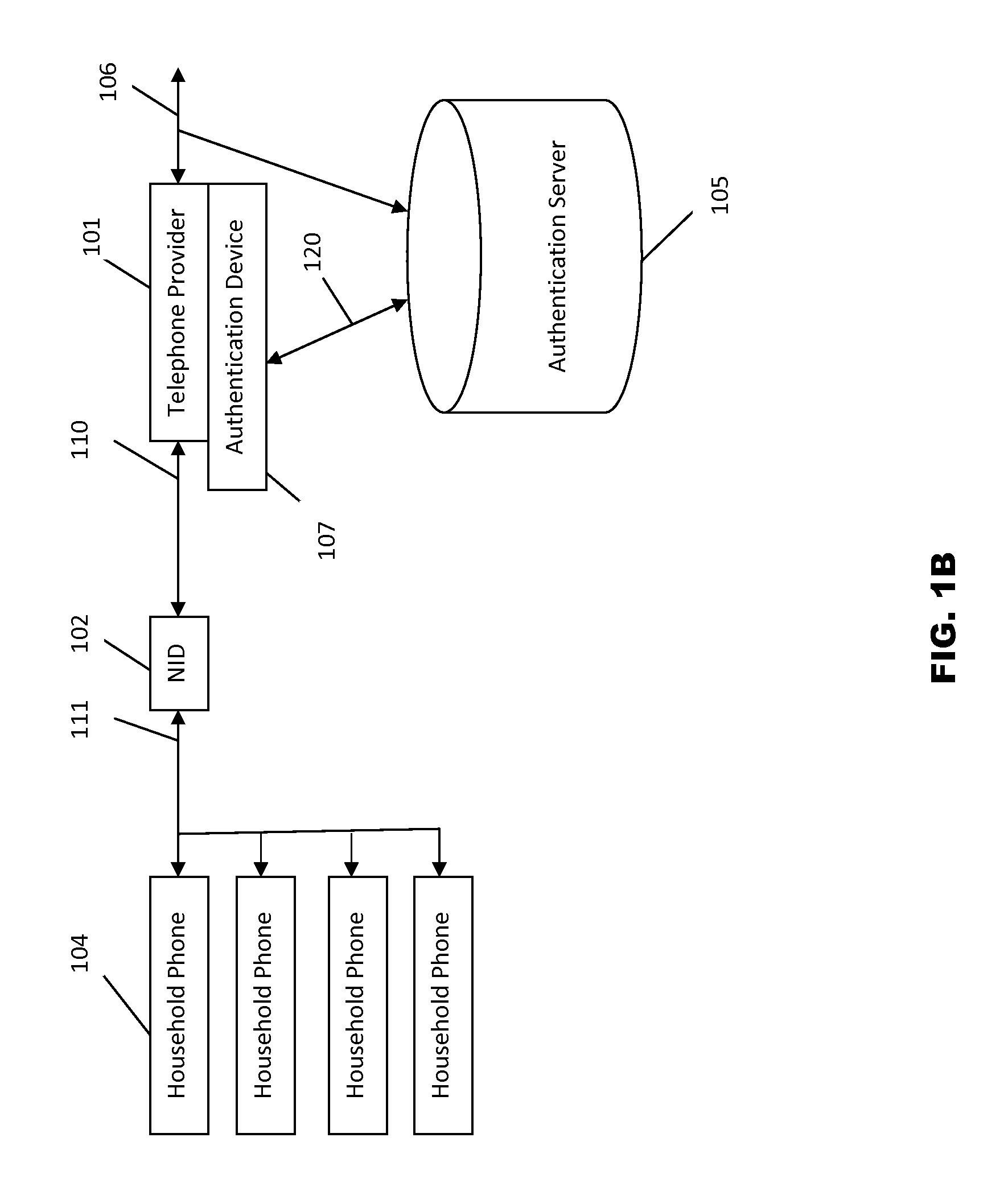
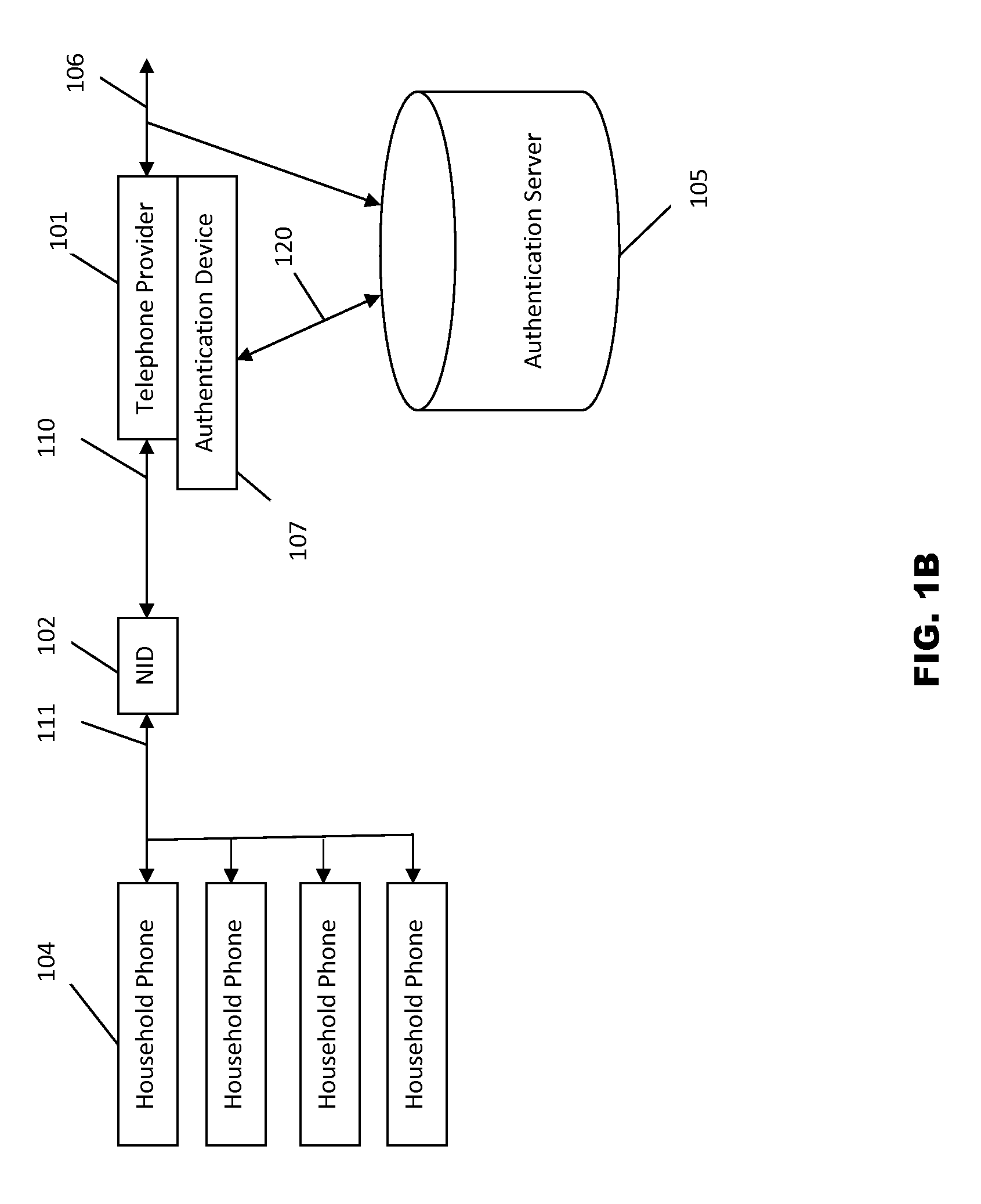
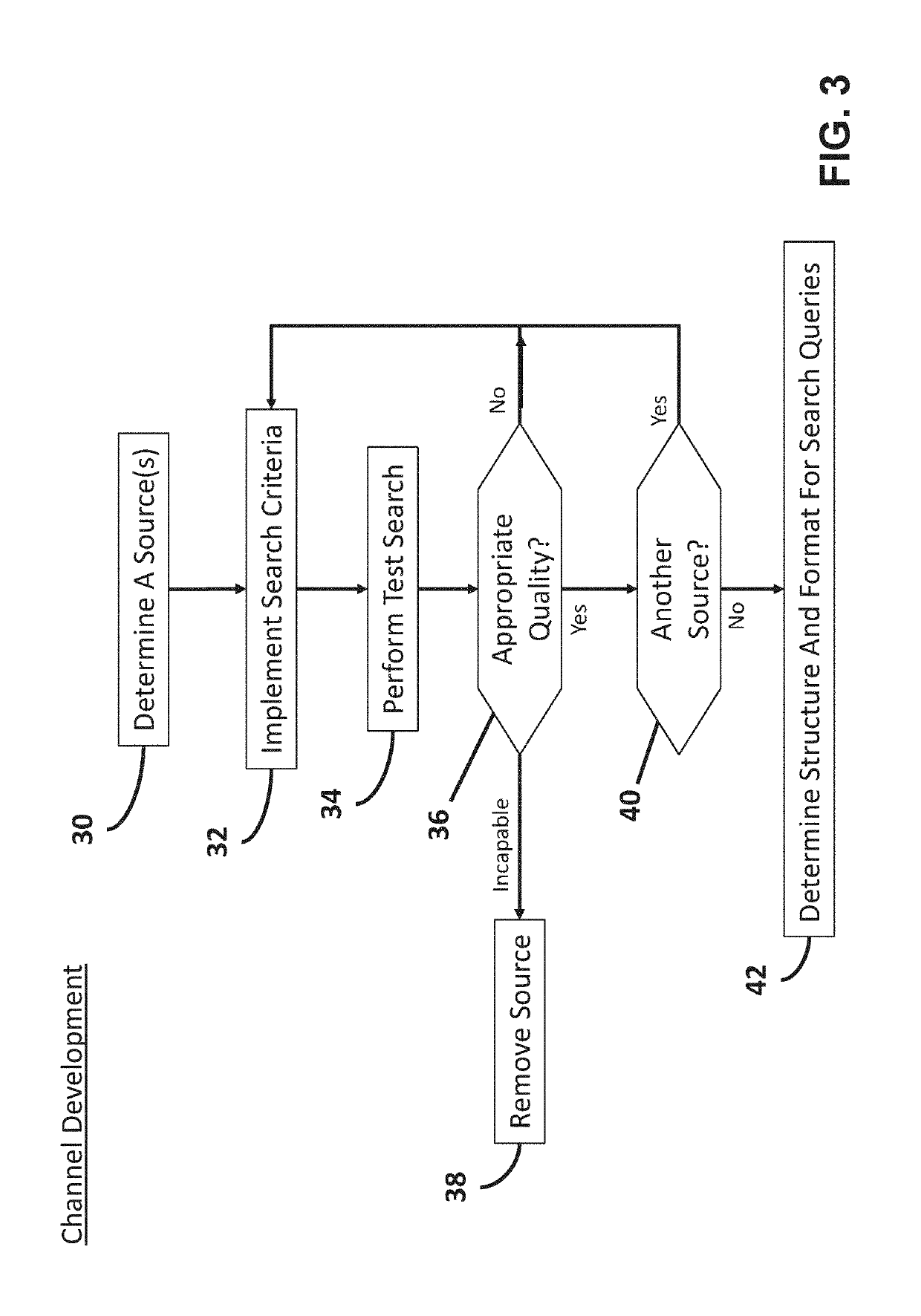
Systems and methods for caller id authentication, spoof detection and list based call handling are disclosed. The caller ID authentication is performed by an authentication device connected to the calling party telephone transmitting the source and destination telephone numbers of the call to an authentication server. The called party authentication device extracts the caller ID of the incoming call and transmits the caller ID of the caller and the telephone number of the called party to the authentication server. The authentication server analyzes the transmitted information from both devices and replies with the authentication status of the caller ID to the called party authentication device. Other embodiments are disclosed where the authentication server is not available and caller ID authentication is performed in a peer-to-peer manner. In another embodiment, the concepts of active and passive certification passwords are used to maintain the integrity of the system. Other embodiments allow for authenticating blocked caller ID's, reveling blocked caller ID's, VoIP implementations, legitimate caller ID spoofing, and placing a blocked caller ID on private white or black lists. Another embodiment combines the described caller ID authentication system within a call handling system utilizing internal, global and private white and black lists. Applications of caller ID authentication methodology to other forms of communication source address authentication, such as email, SMS, and postal mail are envisioned.
Owner:DANIS SERDAR ARTUN
User interface for a system and process for providing dynamic communication access and information awareness in an interactive peripheral display
InactiveUS20060179415A1Minimize distractionMinimize interruptionDigital data information retrievalData processing applicationsCommunication interfaceDistraction
The system and method of the present invention provides peripheral awareness of information to a user. The information to be provided is either determined automatically, or specified by the user. Once the information to be provided is determined or specified, it is automatically tracked or watched via at least one conventional communications interface for accessing one or more conventional communications sources. Current information is then automatically dynamically provided in an interactive peripheral display which minimizes any potential distraction to the user. Determining or specifying, tracking or watching, and providing the information is accomplished using at least one customizable dynamic encapsulated object, a “ticket,” that when paired with a “viewer,” provides peripheral awareness of information to the user. Further, in one embodiment, the tickets are sharable among users, and may be copied, cut, pasted, saved, transmitted, dragged and dropped from web pages, etc., like any other electronic file using conventional techniques.
Owner:MICROSOFT TECH LICENSING LLC
Autopopulation of address book entries
ActiveUS7187932B1Metering/charging/biilling arrangementsSpecial service for subscribersAddress bookCommunication source
Personal address book data is revised and updated based on communication sources and destination. An address tabulator compares a number of communications directed to a selected destination and based on a subscriber profile, determines if address or contact information associated with the destination is to be added to a personal address book or other contact database. Contact information can be obtained using a reverse phone number lookup in a white pages or yellow pages directory, or using an Internet-based search engine or database. The tabulator can be configured to access the subscriber profile prior to initiating a communication, during a communication, or after completion of the communication. In one example, subscriber billing records are delivered to the tabulator for identification of destinations for which contact information is to be added to the personal address book. Additional or revised contact information can be stored in the personal address book automatically, or in response to a subscriber instruction delivered from a mobile station.
Owner:AT&T WIRELESS SERVICES
RF base repeater for automated residence management system
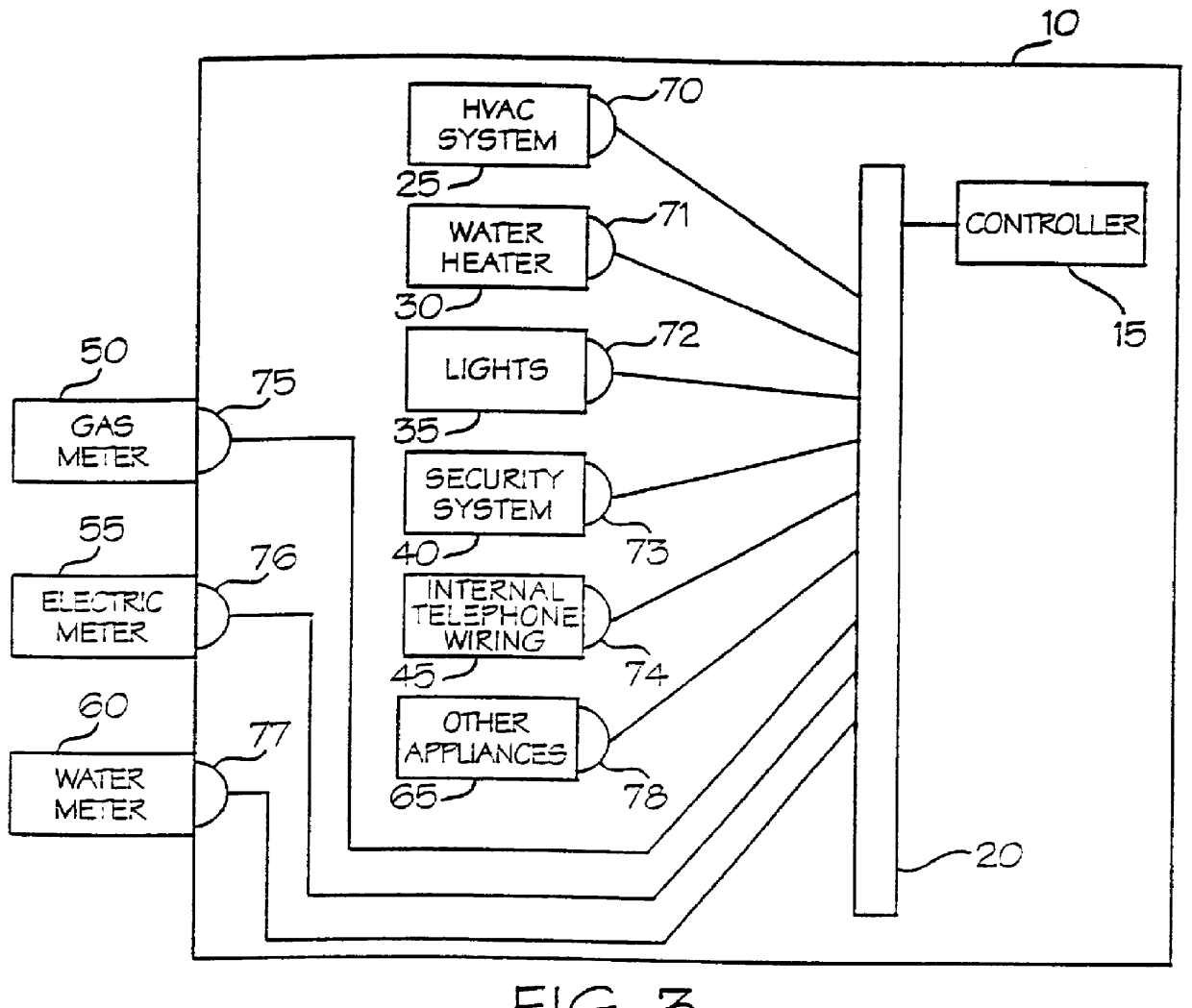
A multi-unit automated space management and communication system for use in association with a structure having a plurality of units. The system includes circuitry that monitors various utility related aspects of each of the plurality of units. The system further includes an automated subsystem disposed in each one of the plurality of units. This subsystem includes at least one appliance, at least one communication medium means, at least one interface means for connecting the at least one appliance apparatus into a signal exchanging relationship with the at least one communication medium means, at least one communication source, operably connected to the at least one communication medium means. The system further includes an external communication interface linking the automated subsystem to the monitoring means in a signal-exchanging relationship. The system still further includes data storage circuits.
Owner:SAFEGUARD DELAWARE
Communication device operation management
ActiveUS20050245236A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemCommunication source
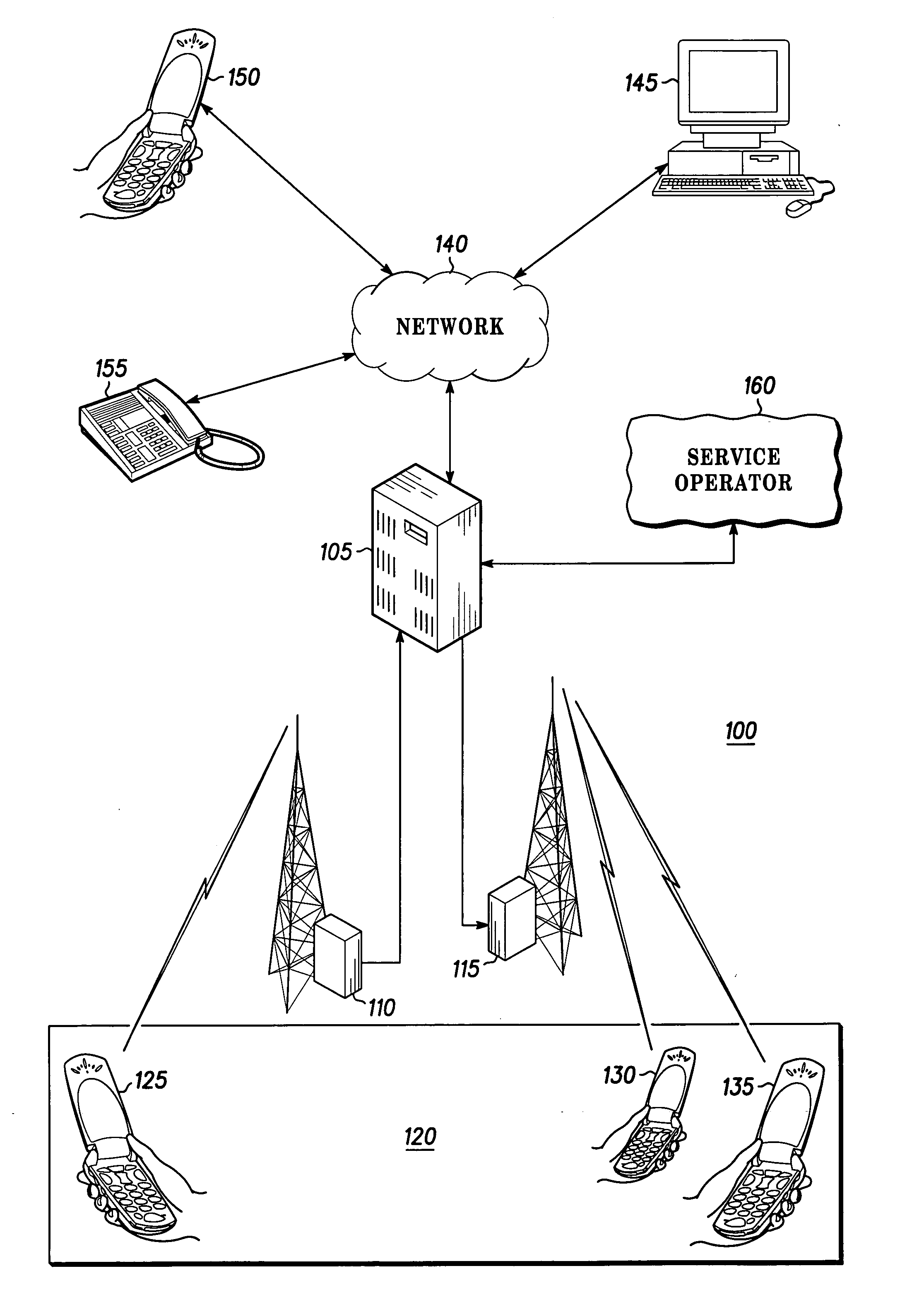
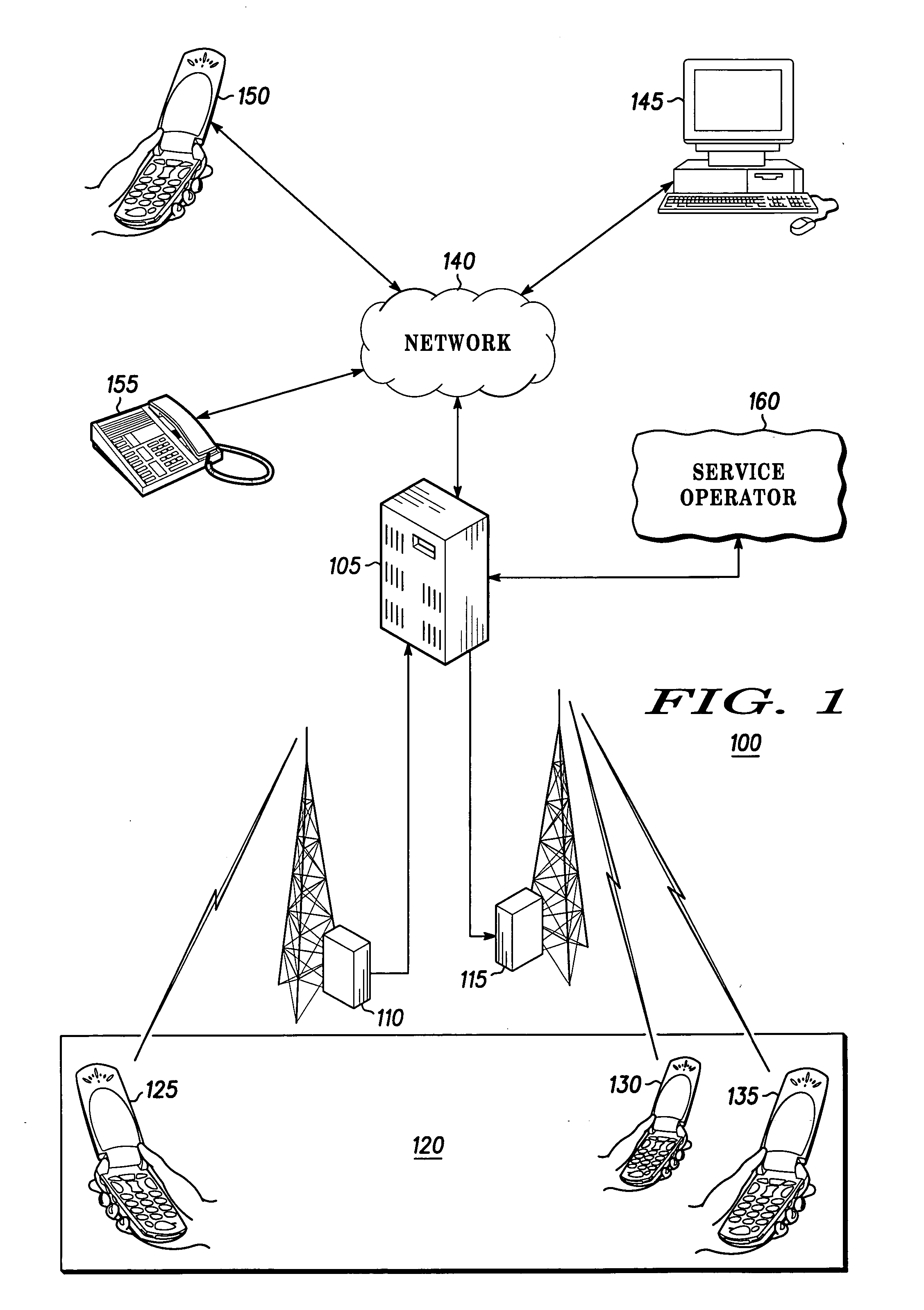
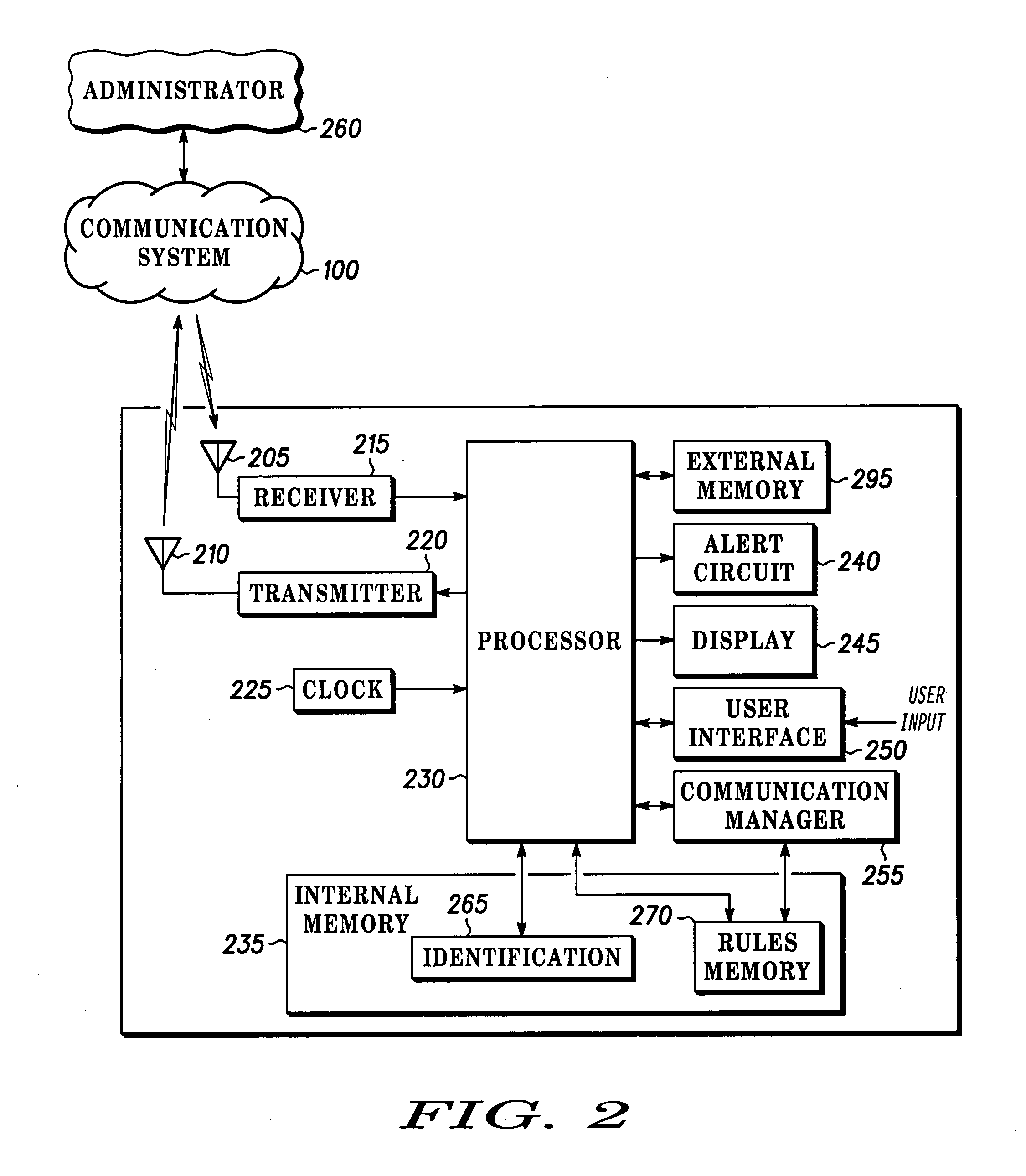
A communication group is activated within a communication system (100) including an administrator device (125) and at least one subordinate device (130,135). Each subordinate device (130,135) is programmed with a set of operation rules dependent upon communication source (300), information content (305), current time (310), or geographic location (315). The administrator device (125) dynamically changes the stored set of operation rules for the subordinate device (130,135) by communicating a change message.
Owner:GOOGLE TECH HLDG LLC
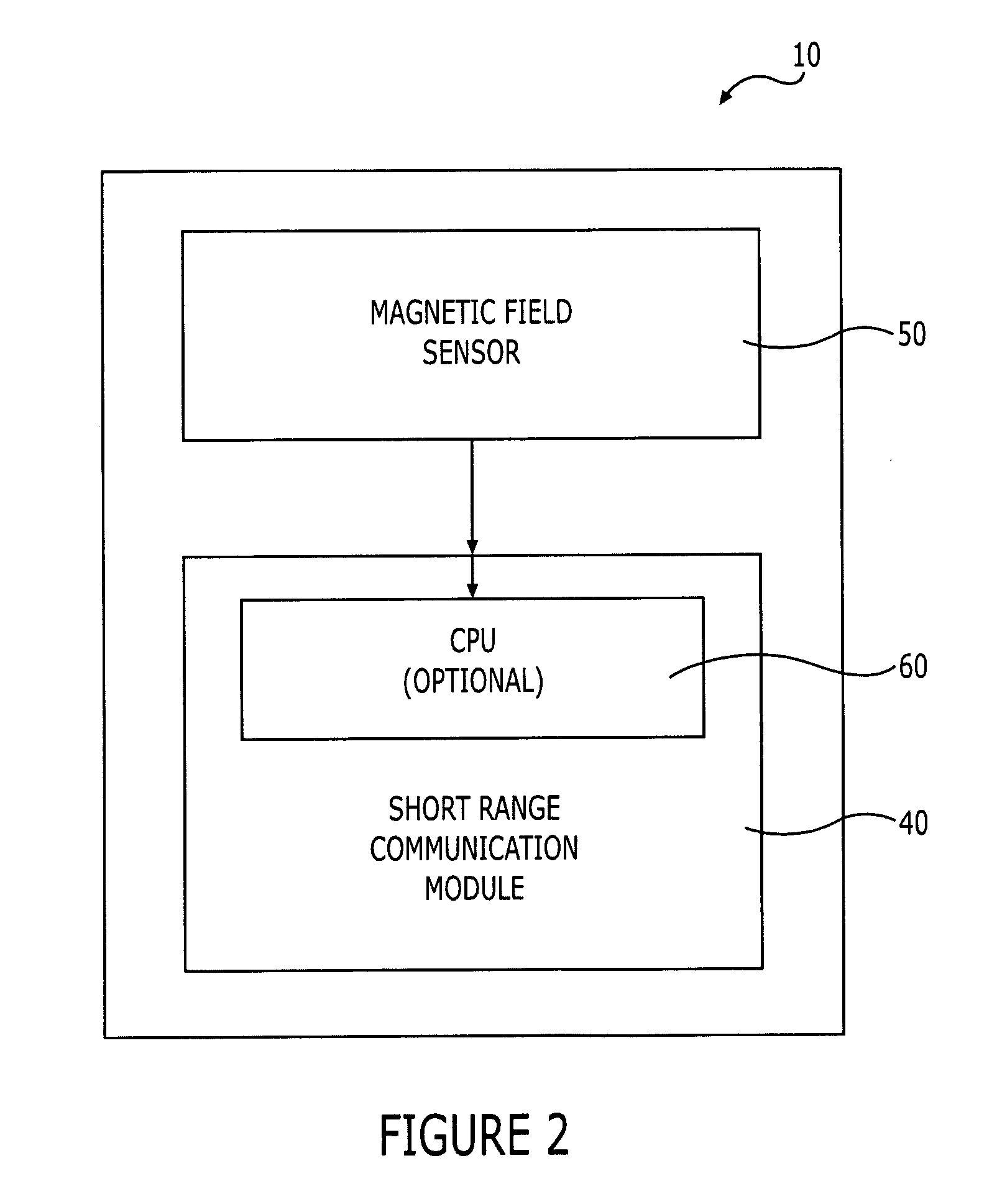
Methods, apparatus, systems and computer program products for energy management of short-range communication modules in mobile terminal devices
InactiveUS20060079180A1Less powerRaise the possibilityEnergy efficient ICTNear-field in RFIDTime segmentTerminal equipment
The methods, apparatus, systems and computer program products provide for sensing a magnetic field, emitted by a short-range communication source, to activate short-range communication modules in a mobile terminal. In addition to sensing the magnetic field, the terminal may rely on other parameters, such as operational state of the terminal, contextual information and the like, to determine if the short-range communication module should be activated. As such, the invention reduces the overall power consumption of the terminal by limiting the active state of the short-range communication module. By conserving power the mobile terminal is capable of operating for longer periods of time without requiring charging or replacement of the power supply.
Owner:NOKIA TECHNOLOGLES OY
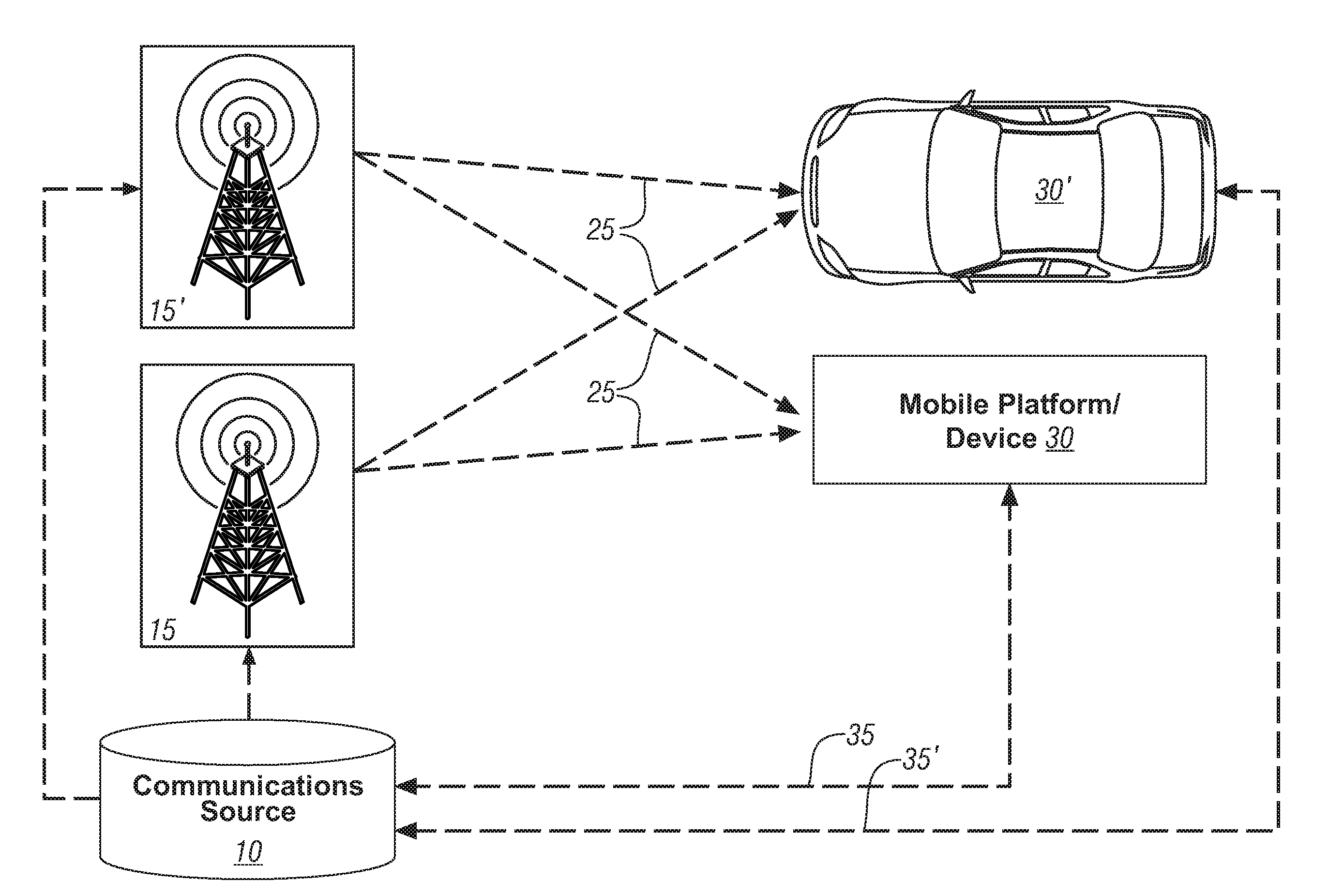
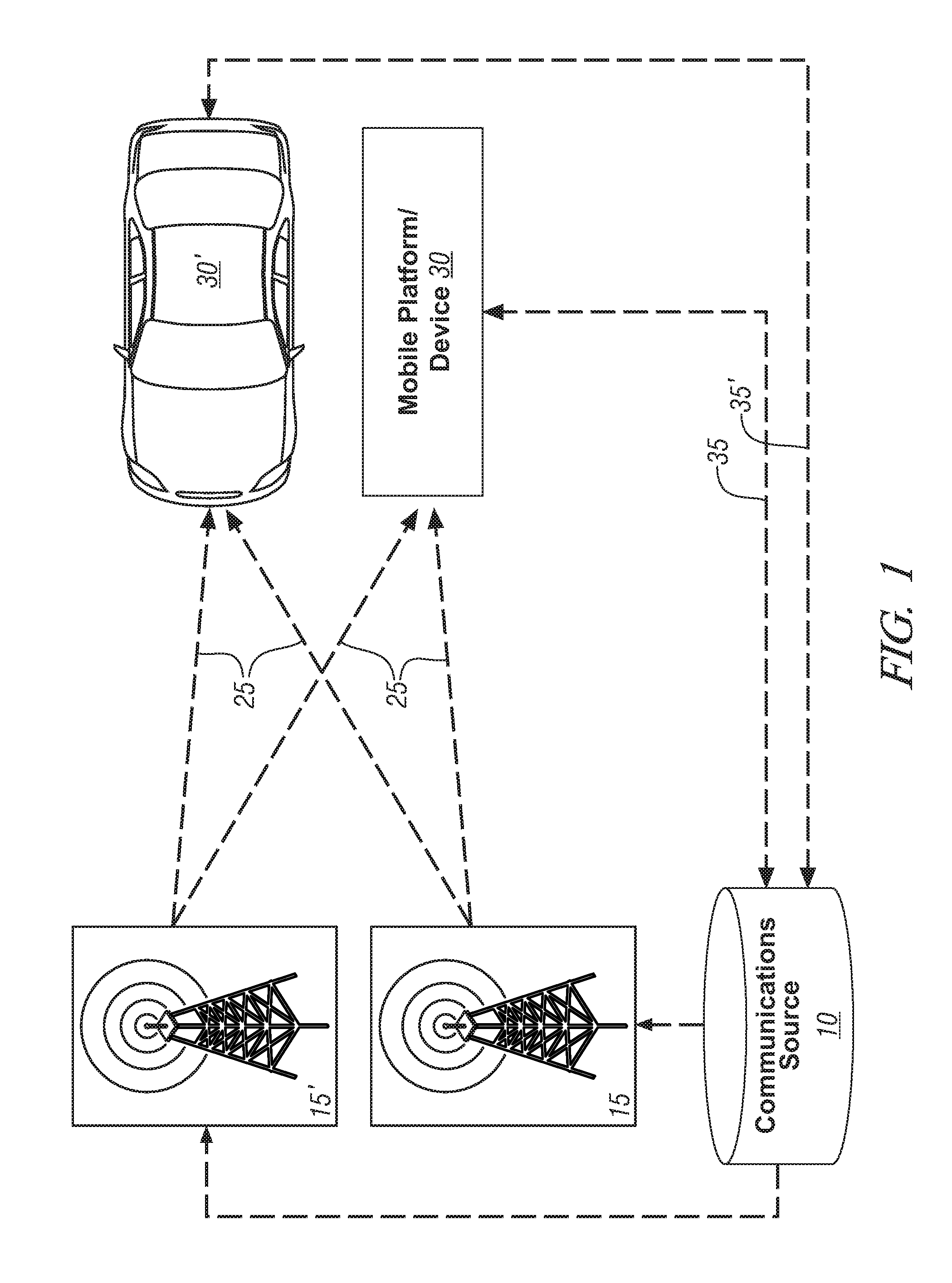
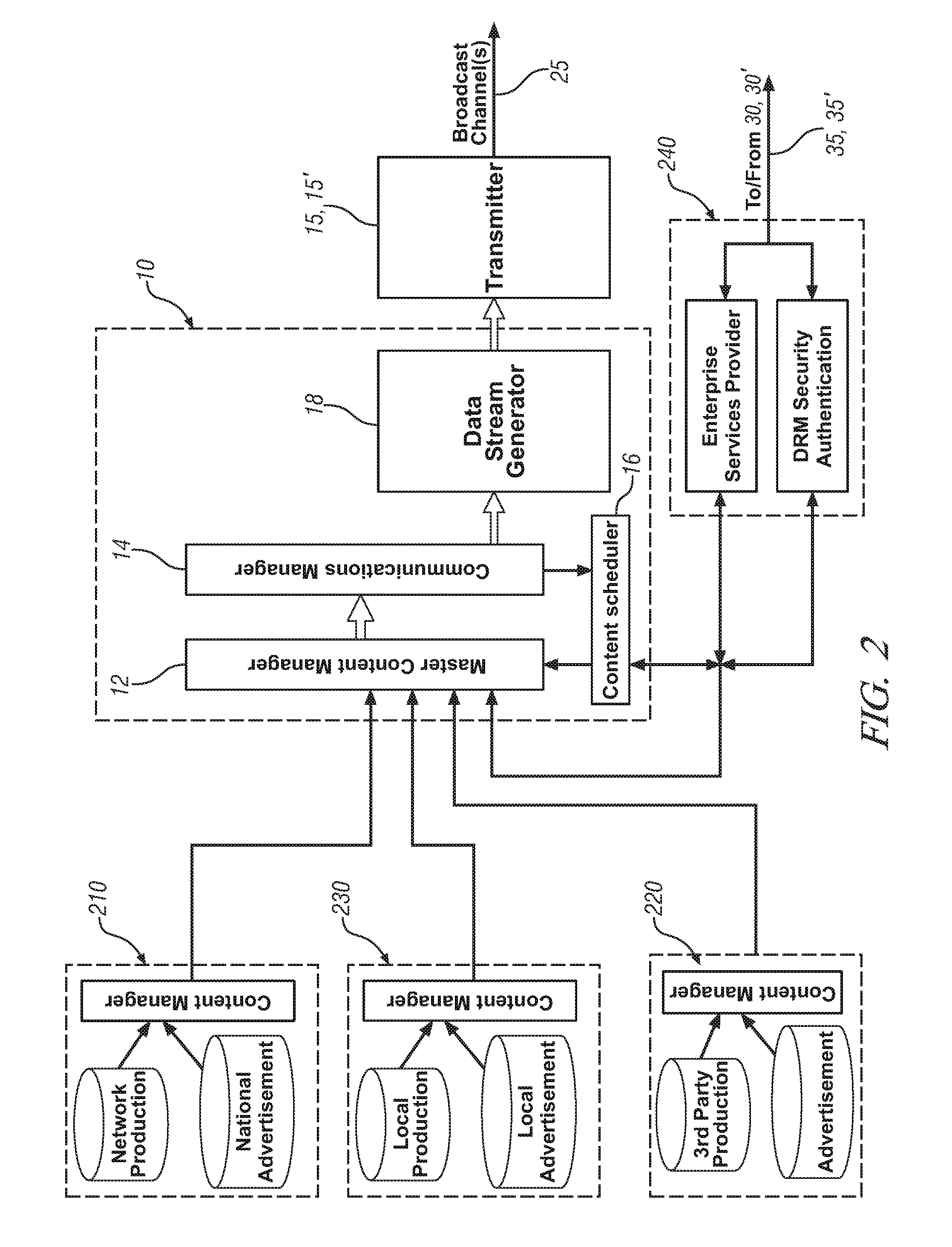
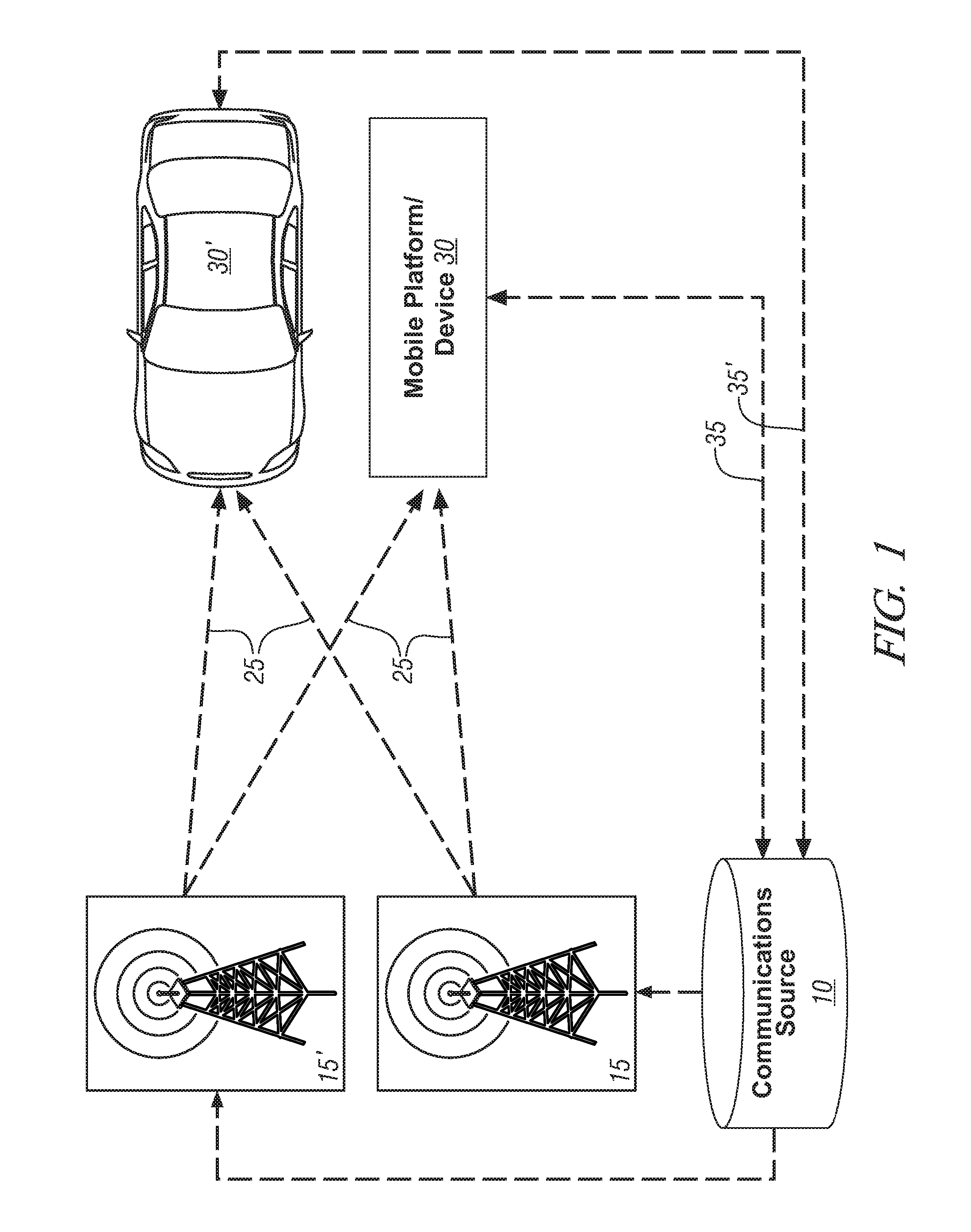
Method and system for communicating information to a user of a mobile platform via broadcast services
ActiveUS20080032721A1Radio/inductive link selection arrangementsWireless commuication servicesHuman–machine interfaceTransceiver
A mobile platform is equipped with a transceiver to receive a broadcast message and to execute two-way wireless communications. The mobile platform is also equipped with an electronic memory storage device, a processor, and a human-machine interface. A first message is formed at the communications source, broadcasted, and received at the mobile platform by way of the transceiver. A portion of the first message is selectively cached in the electronic memory storage device and selectively communicated to the human-machine interface. A second message is formed and wirelessly communicated between the communications source and the mobile platform by way of the two-way wireless communications device.
Owner:GM GLOBAL TECH OPERATIONS LLC
Systems and methods for caller ID and call destination authentication
ActiveUS9277049B1Special service for subscribersGraded-service arrangementsBase callingCall forwarding
Systems and methods for caller id authentication, caller id spoof detection, call destination authentication and call forwarding detection are disclosed. Embodiments include legitimate caller ID spoofing, authenticating blocked caller ID's and revealing caller ID's to certain parties. Other embodiments utilize caller ID authentication within a list based call handling system. Applications of caller ID authentication methodology to other forms of communication source address authentication, such as email, SMS, and postal mail are described.
Owner:DANIS SERDAR ARTUN
Establishing traffic priorities in a voice over IP network
InactiveUS20050281277A1Speed up upstream voice packetAlleviate packet congestionMultiplex system selection arrangementsData switching by path configurationTraffic capacityVoice over IP
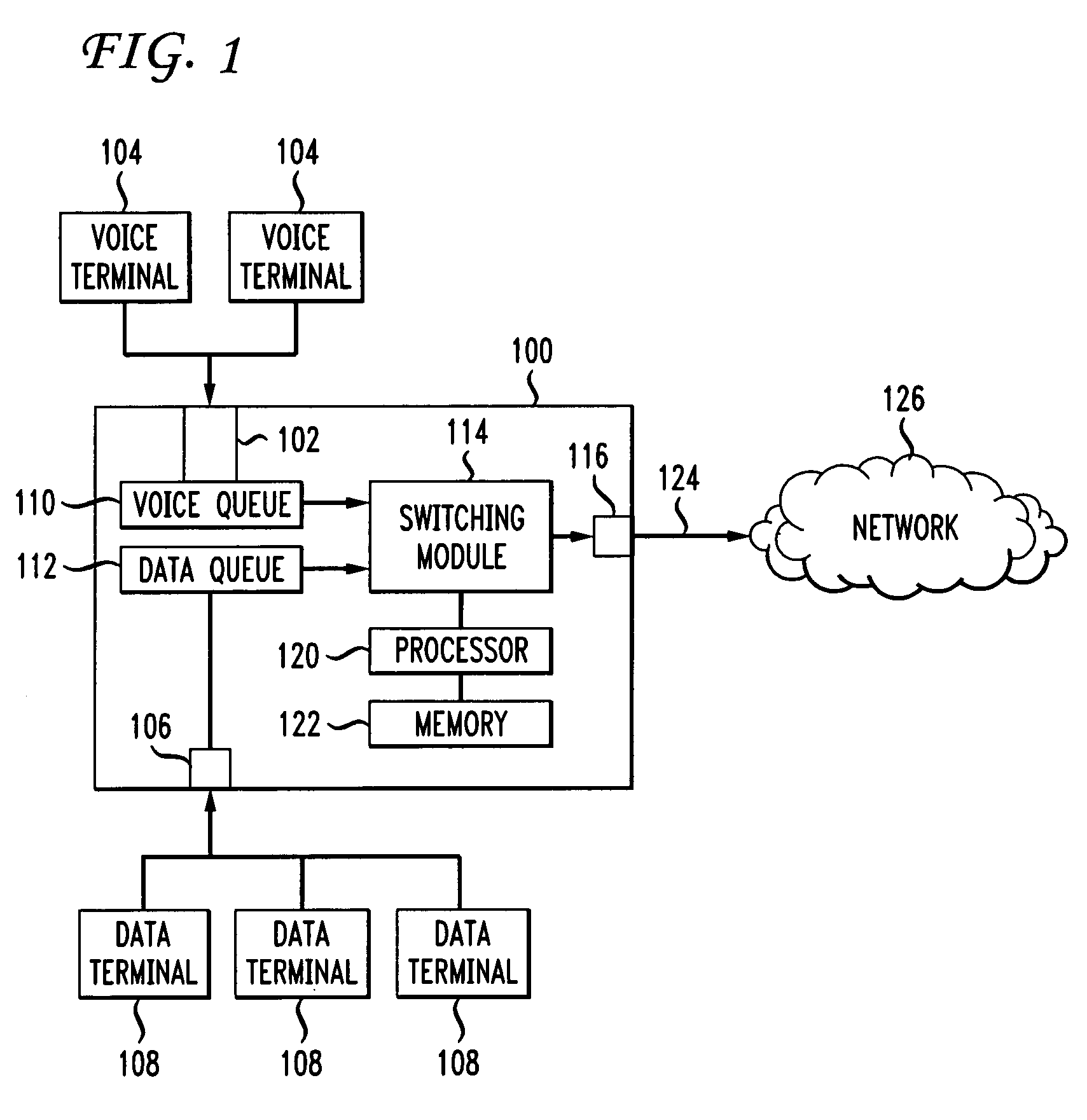
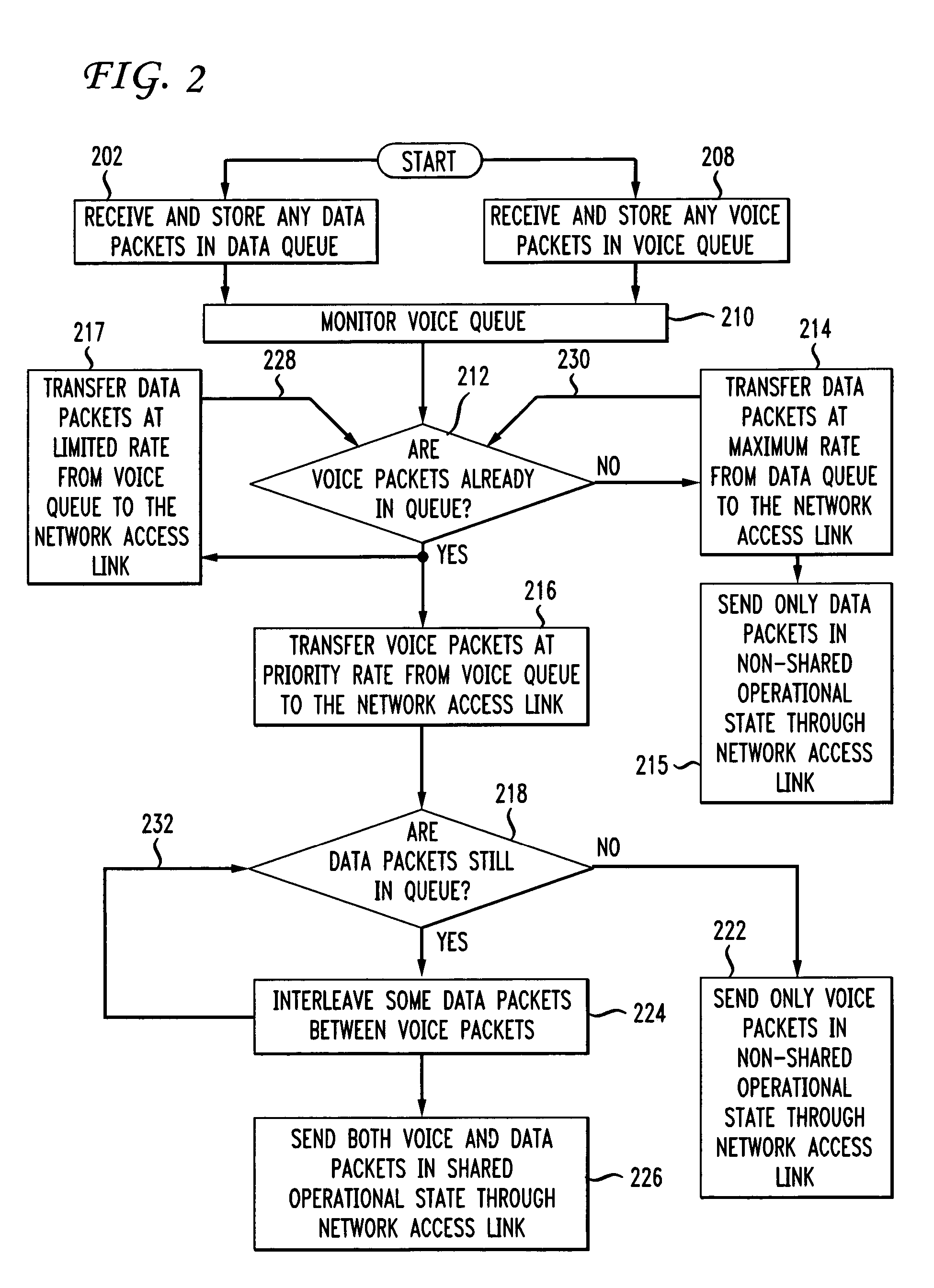
A method and apparatus for establishing traffic priorities in an IP network connected with multiple communication sources is disclosed. Different types of packets such as voice packets and data packets are received for transmission over a single network access link. In order to assure quality voice transmissions, voice packets are given priority over data packets by limiting a transmission rate from a data input queue whenever voice packets are detected in a voice input queue. Different combinations of interleaved voice and data packets help to alleviate packet congestion while maintaining priority for voice packets. In one aspect of the invention, priority for voice packets is further accomplished by limiting the size of data packet frames. In some instances when no voice packets are awaiting transmission, data packets are transmitted at a maximum rate in order to make full use of the network access link bandwidth. The invention is particularly beneficial when implemented over cable and DSL network access links with slow upstream feed rates.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Intra-domain and inter-domain network interconnecting method and system thereof
InactiveCN101459698ARealize interconnectionData switching networksInterconnectionHeterogeneous network
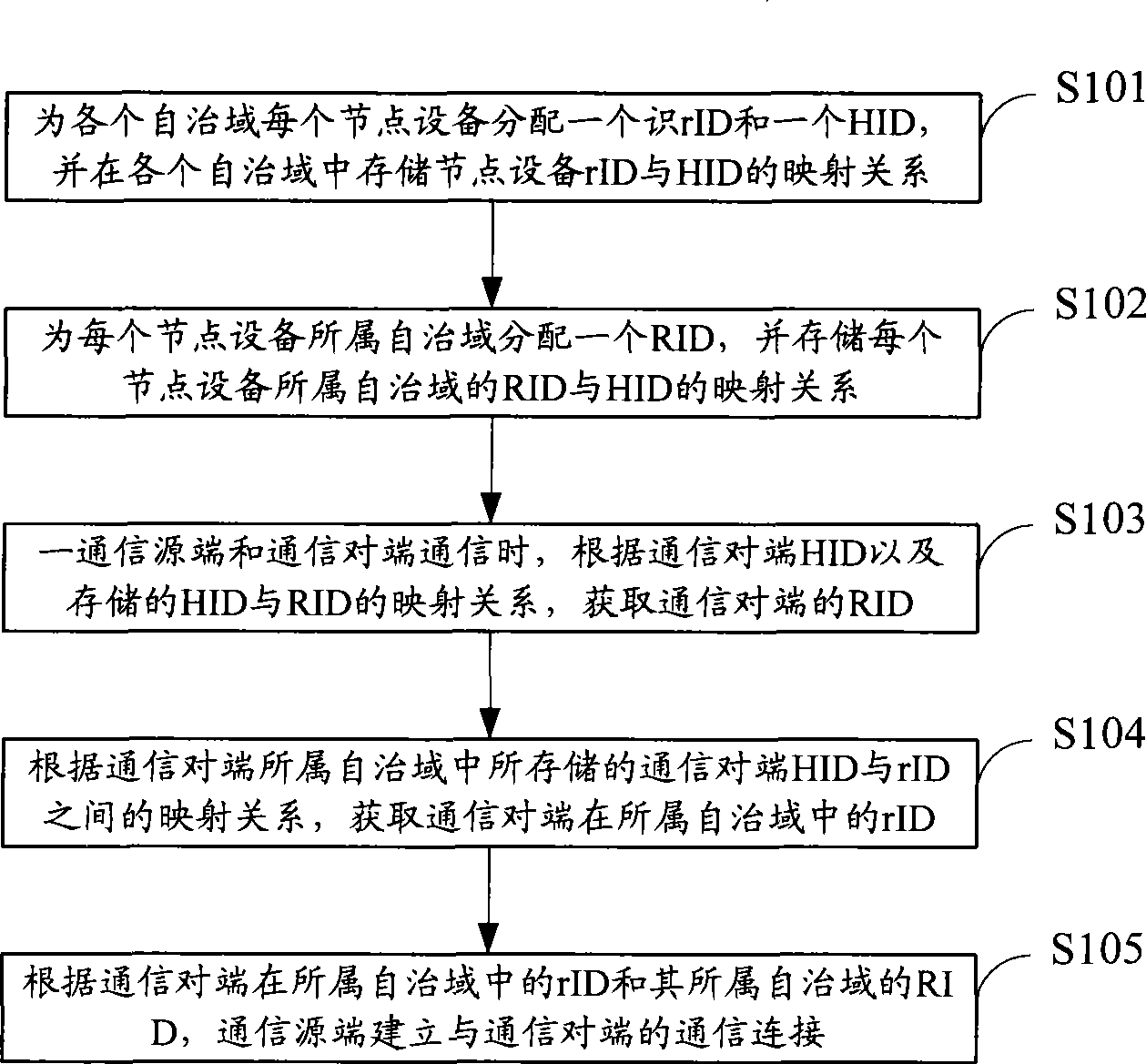
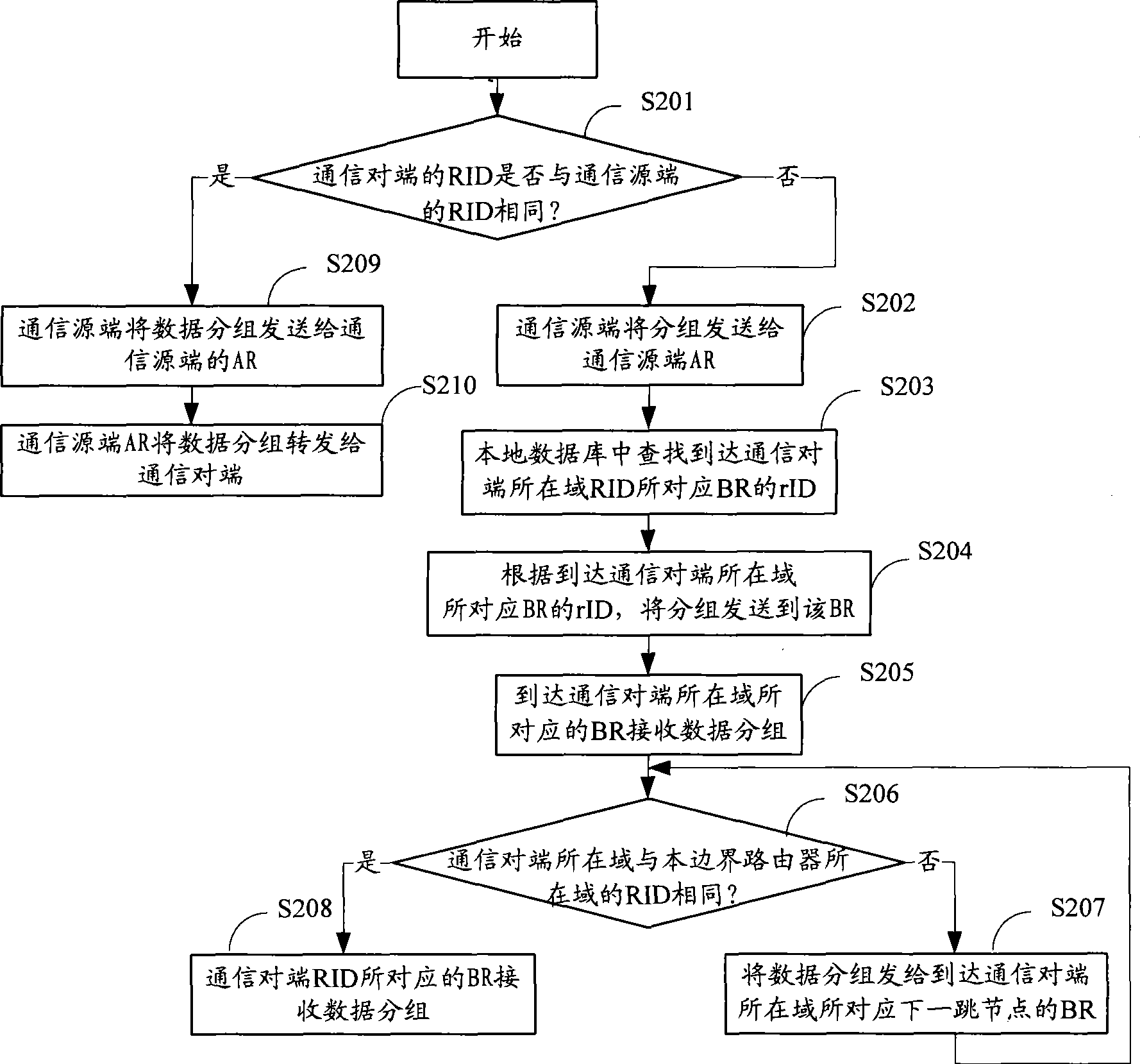
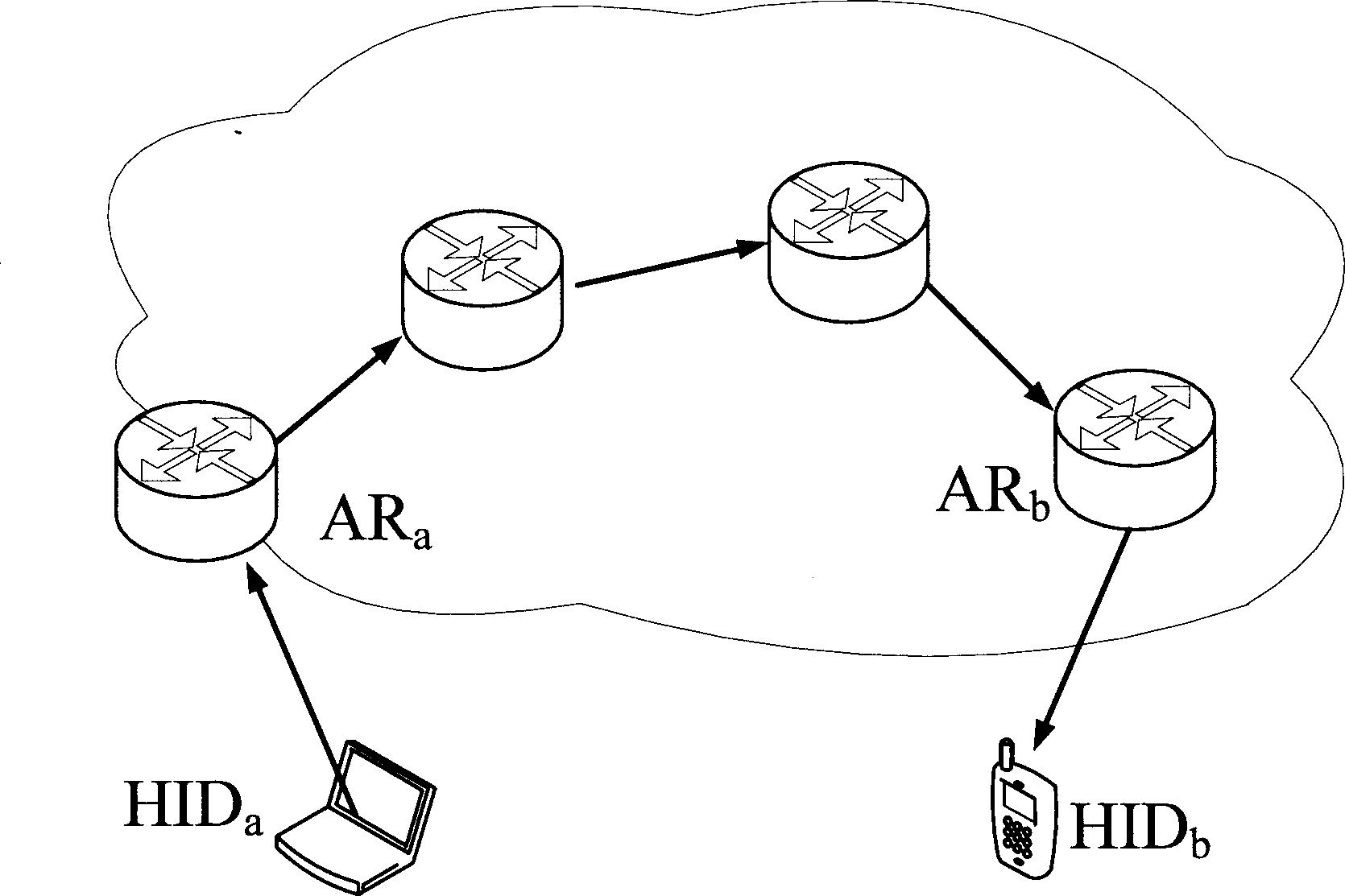
The invention discloses a method for interconnecting networks in domains and between domains, which comprises the steps: distributing a RID to each autonomous domain, distributing a rID and an HID to each node device in each domain, storing the mapping relation between the HID and the RID, and between the HID and the rID of each node device, obtaining a communication end RID according to the HID on the communicating end and the stored mapping relation between the HID and the RID when a communication source end is communicated with the communication end, obtaining the rID of the communication end in the autonomous domain according to the mapping relation between the HID and the rID of the communication end, and building communication with the communication end by the communication source end according to the rID of the communication end in the domain and the RID of the communication end the domain. The invention also discloses a system for interconnecting networks in domains and between domains. The routing between the domains is independent from an addressed mode in the domain and details of a routing protocol through the method and the system, and integral interconnection of a heterogeneous network is implemented.
Owner:THE PLA INFORMATION ENG UNIV
Containing disinformation spread using customizable intelligence channels
ActiveUS20190179861A1Digital data information retrievalSpecial data processing applicationsCommunication sourceData science
Techniques are provided for rating the veracity of content distributed via digital communications sources by creating an ontology and selecting keywords for a topic of the content, creating a customizable intelligence channel for the topic, and extracting from the customizable intelligence channel a first list of potential experts on the topic sorted by at least relevance and influence. The list of experts may be supplemented by mining trusted media sources to extract a second list of potential experts or witnesses on the topic. The first and second lists of potential experts are evaluated as a function of at least one of professionalism, reliability, proximity, experience, responsiveness, and lack of self-interest in the topic to identify a short list of experts. The content is provided to the short list of experts, who are polled about the veracity of the content to create a veracity score for delivery with the content.
Owner:CREOPOINT
System and method for managing location of assets equipped with transponder
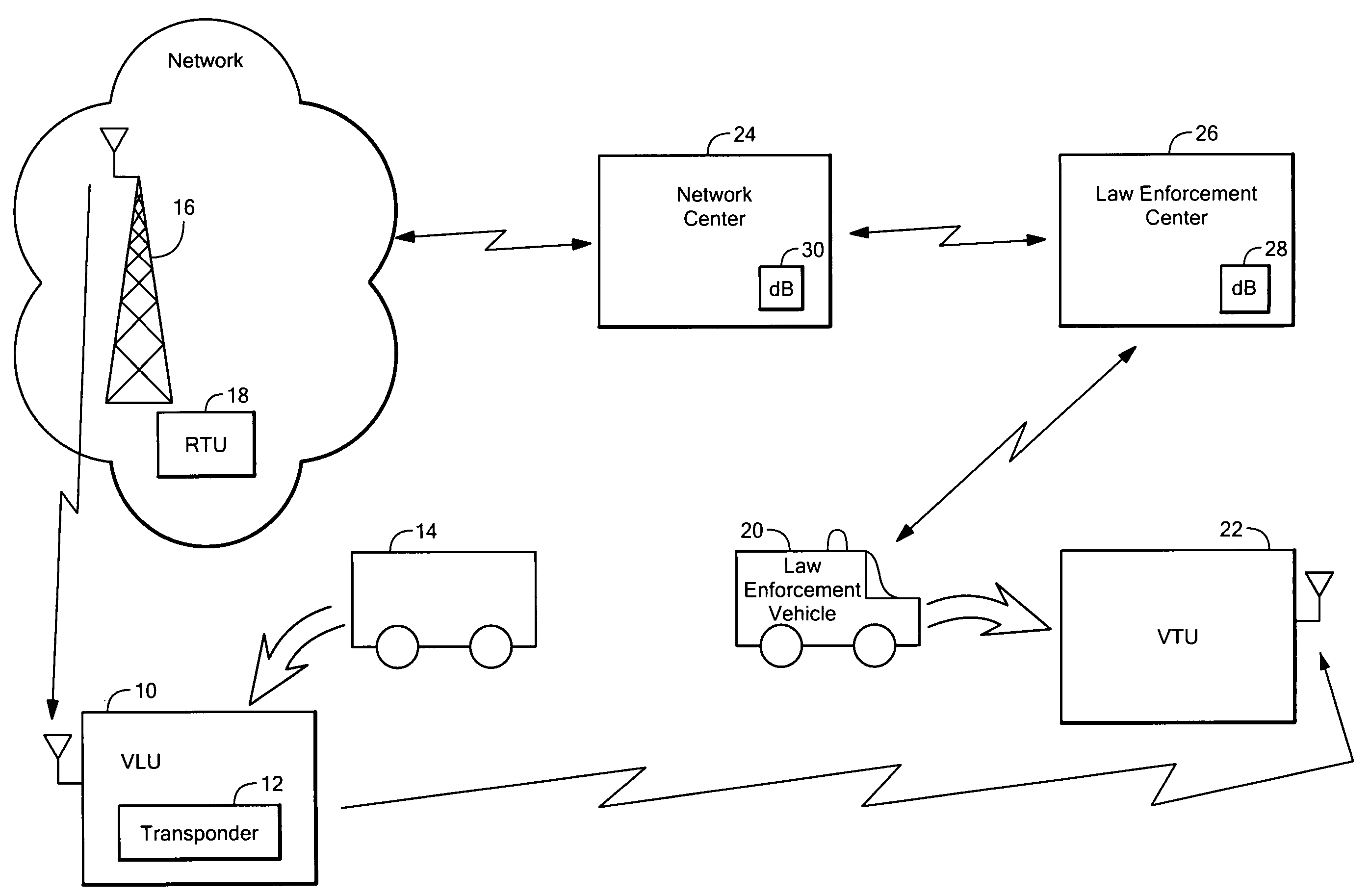
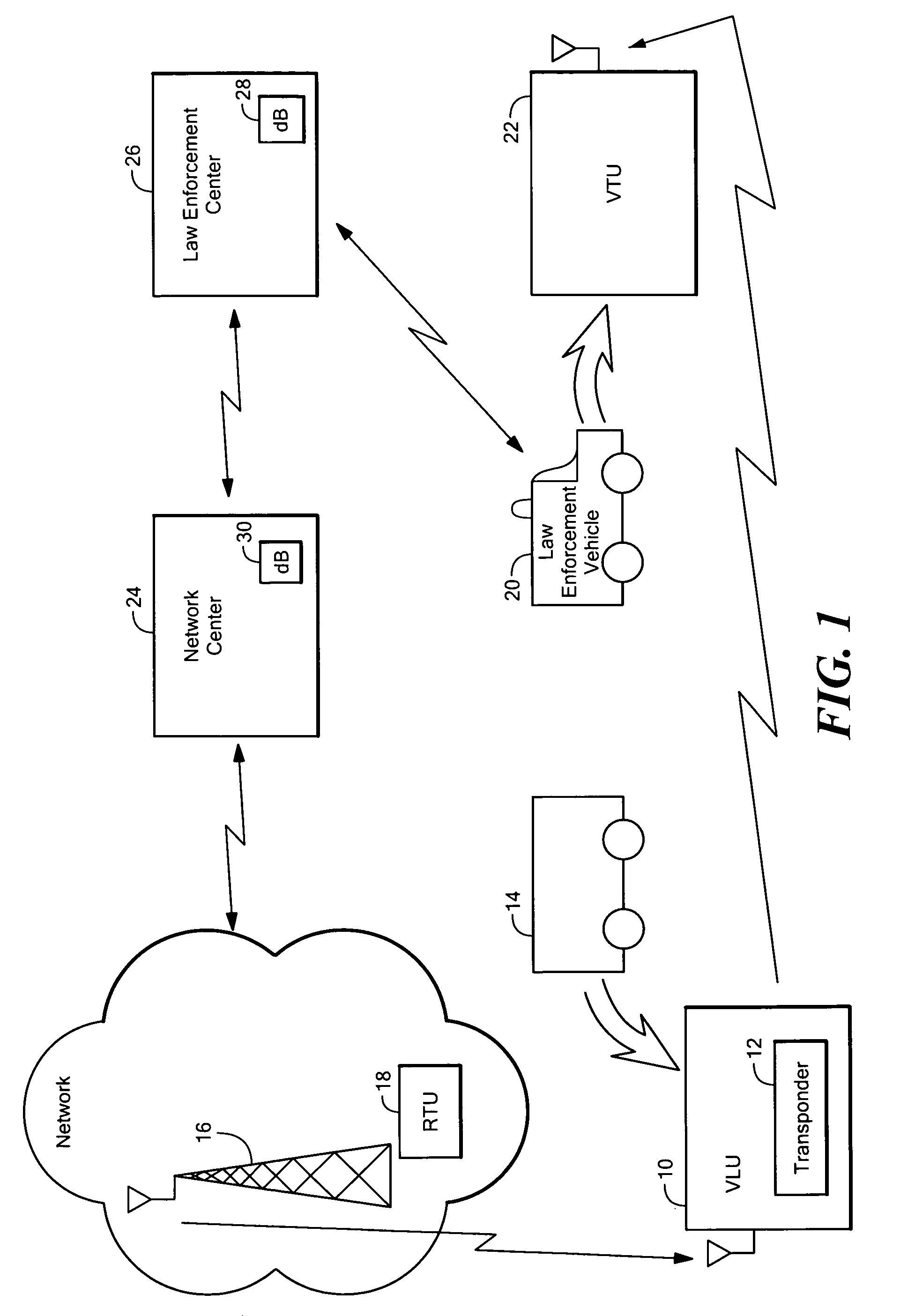
InactiveUS20150168173A1Instruments for road network navigationRegistering/indicating working of vehiclesControl communicationsOn board
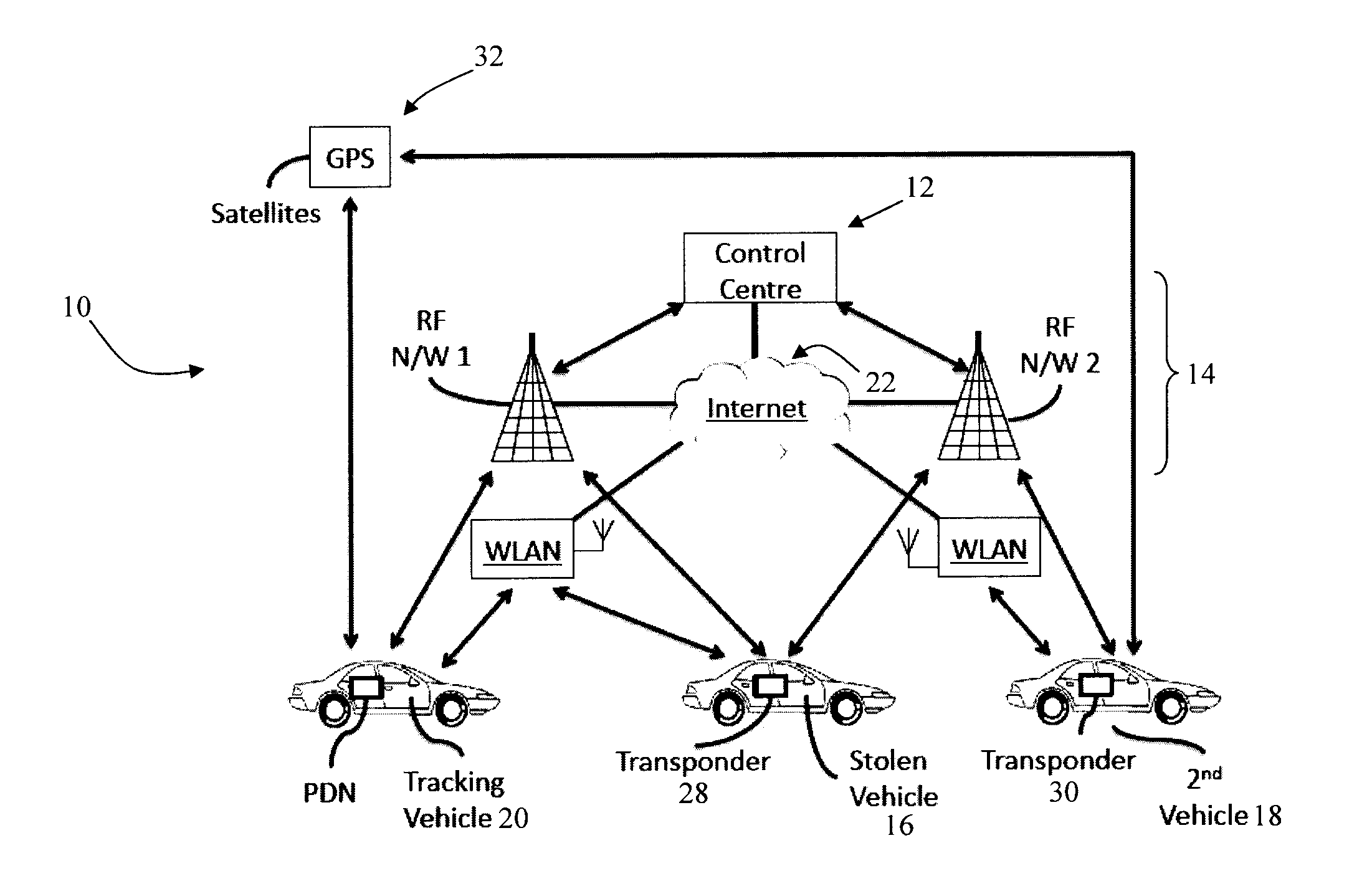
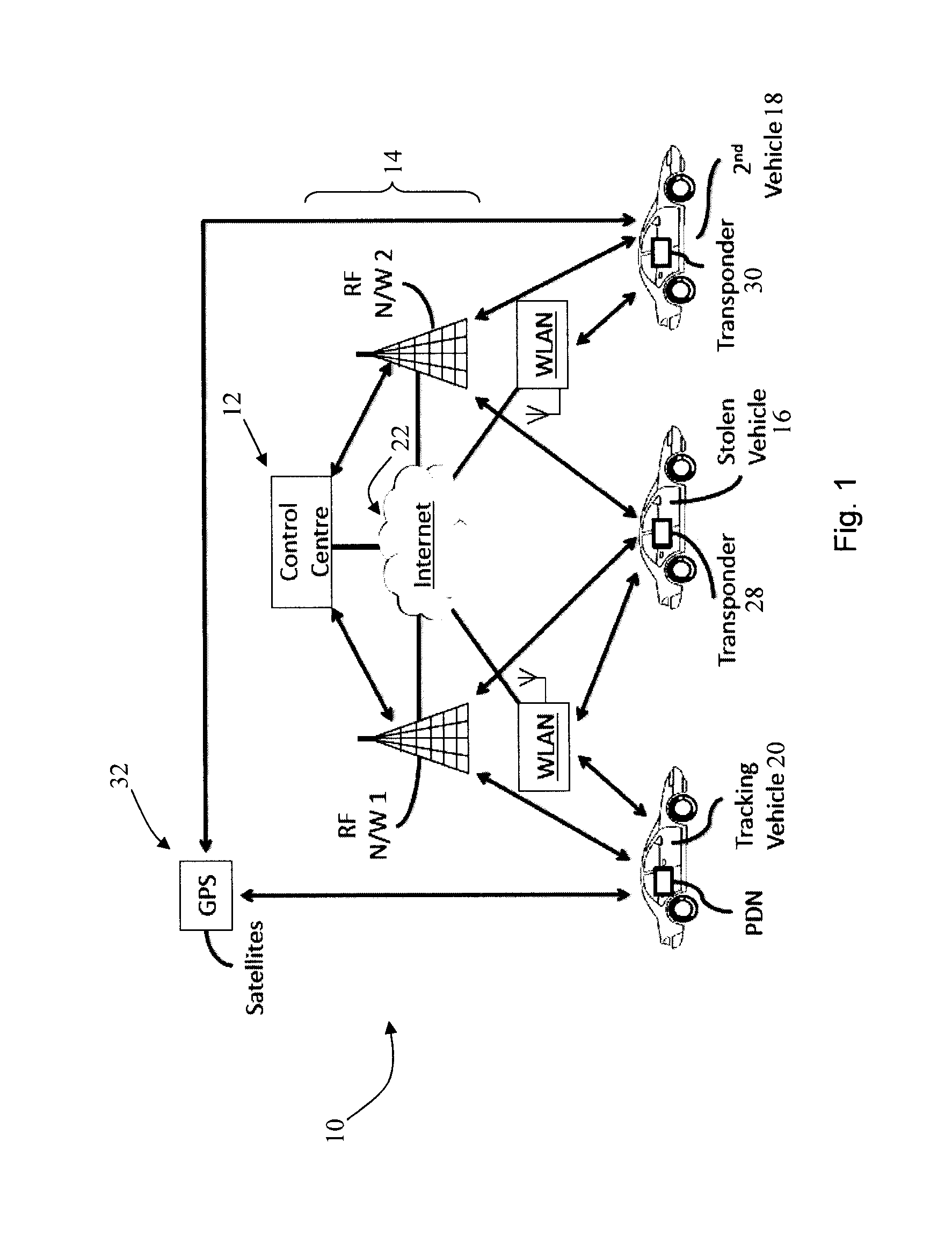
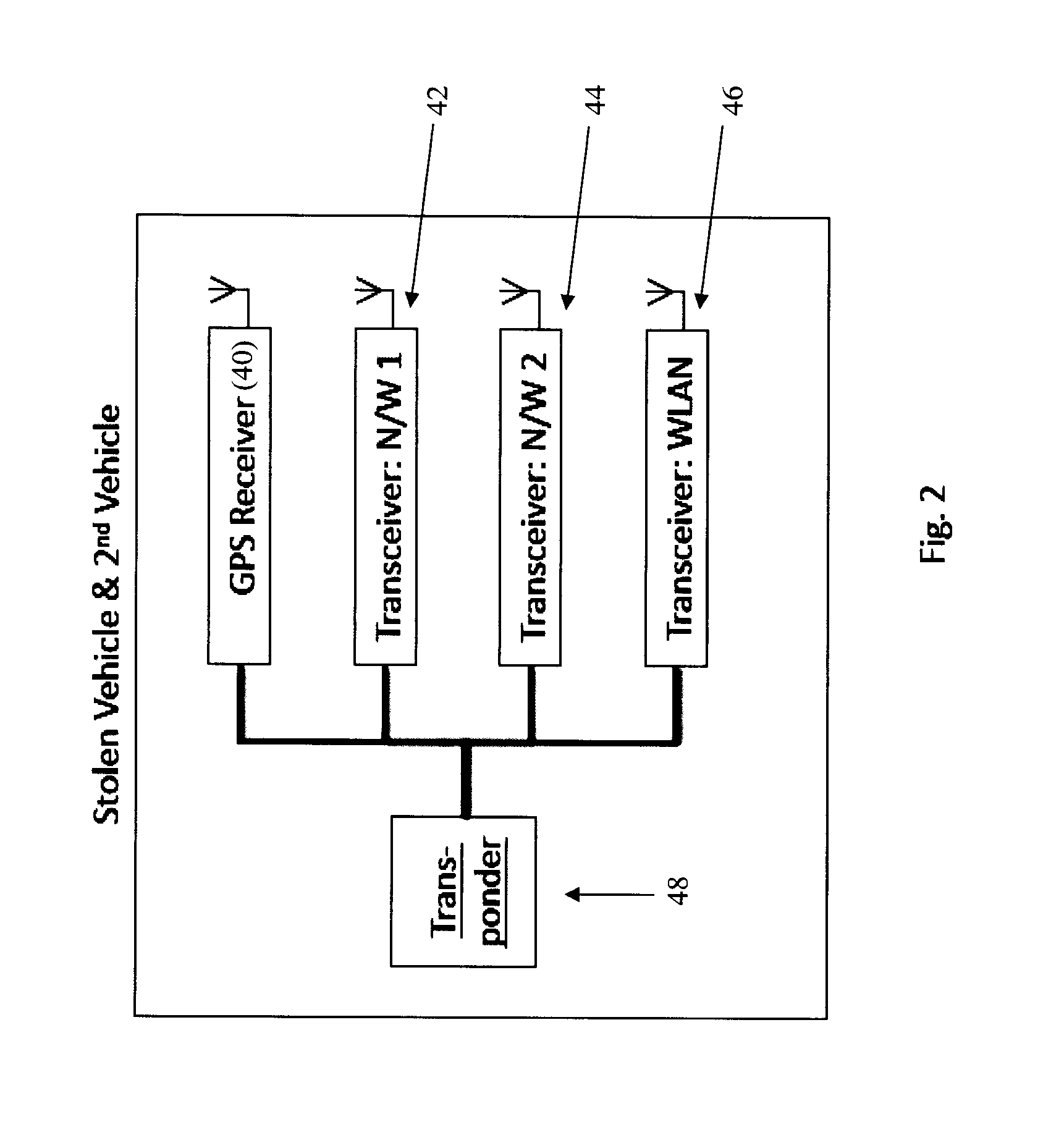
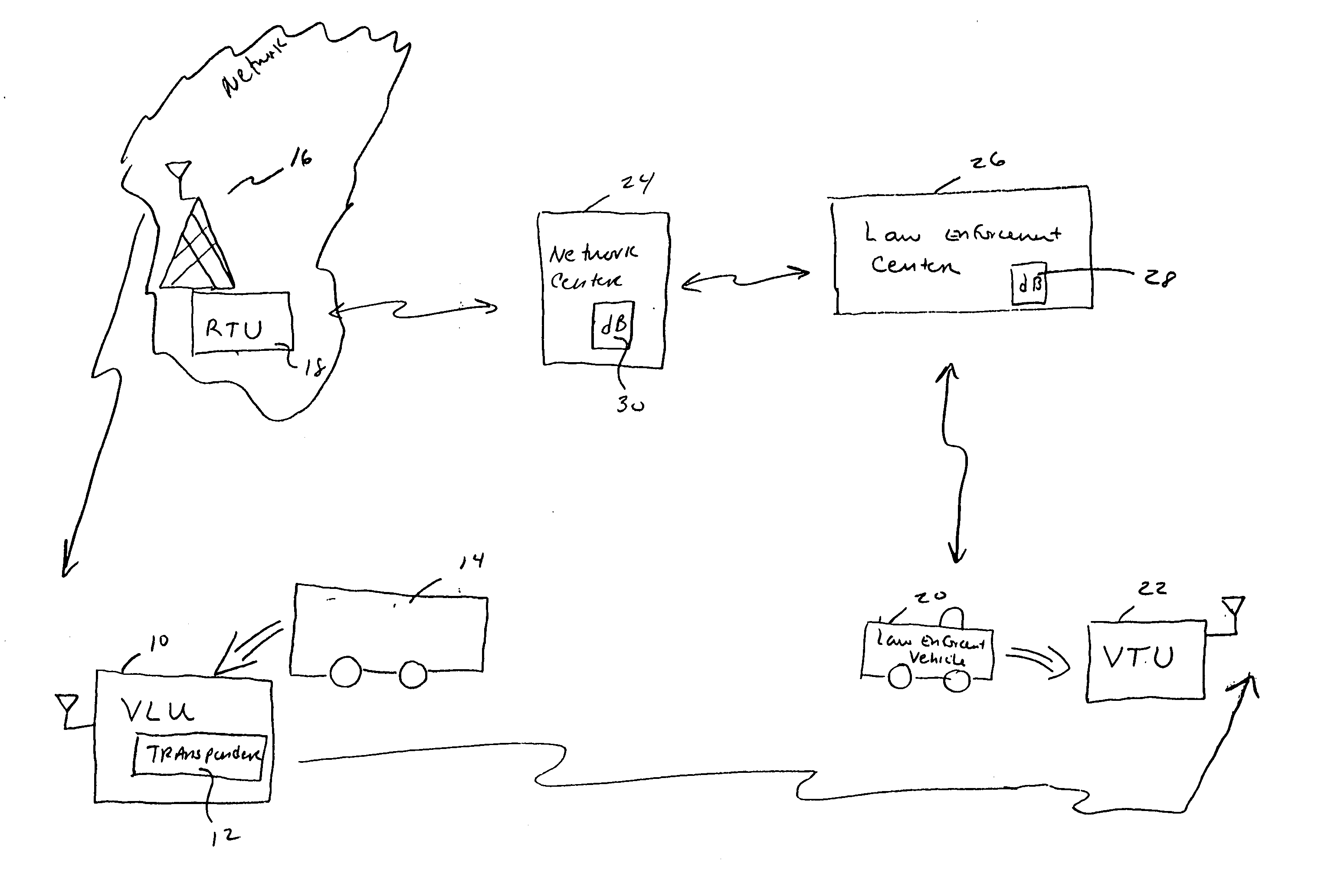
A method is provided for locating an asset equipped with a transponder which issues coded signals when activated by a control communication received from a communication source or by a local event. The coded signals enable a tracking unit to direction find said asset. The method comprises the steps of: providing said tracking unit with map data compatible with a navigation system on-board the tracking unit; and displaying a location indicated by said map data on a map display of said navigation device, wherein said map data is indicative of a search location for the asset and the likely best route for recovery of the asset.
Owner:CHINAPAC
TCP data package transmission method
InactiveCN101217493AFacilitate transmissionImprove efficiencyData switching networksStream socketTraffic capacity
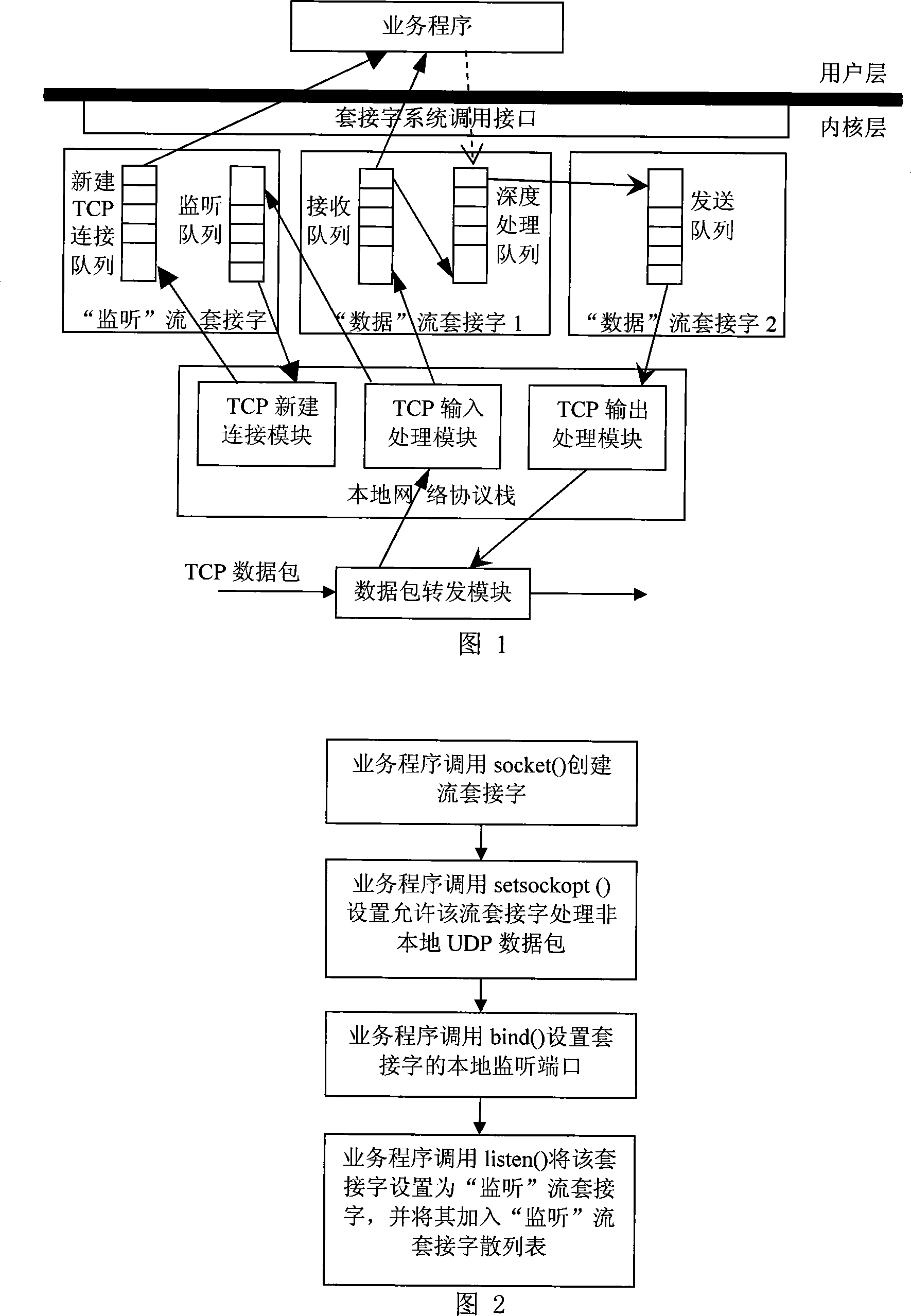
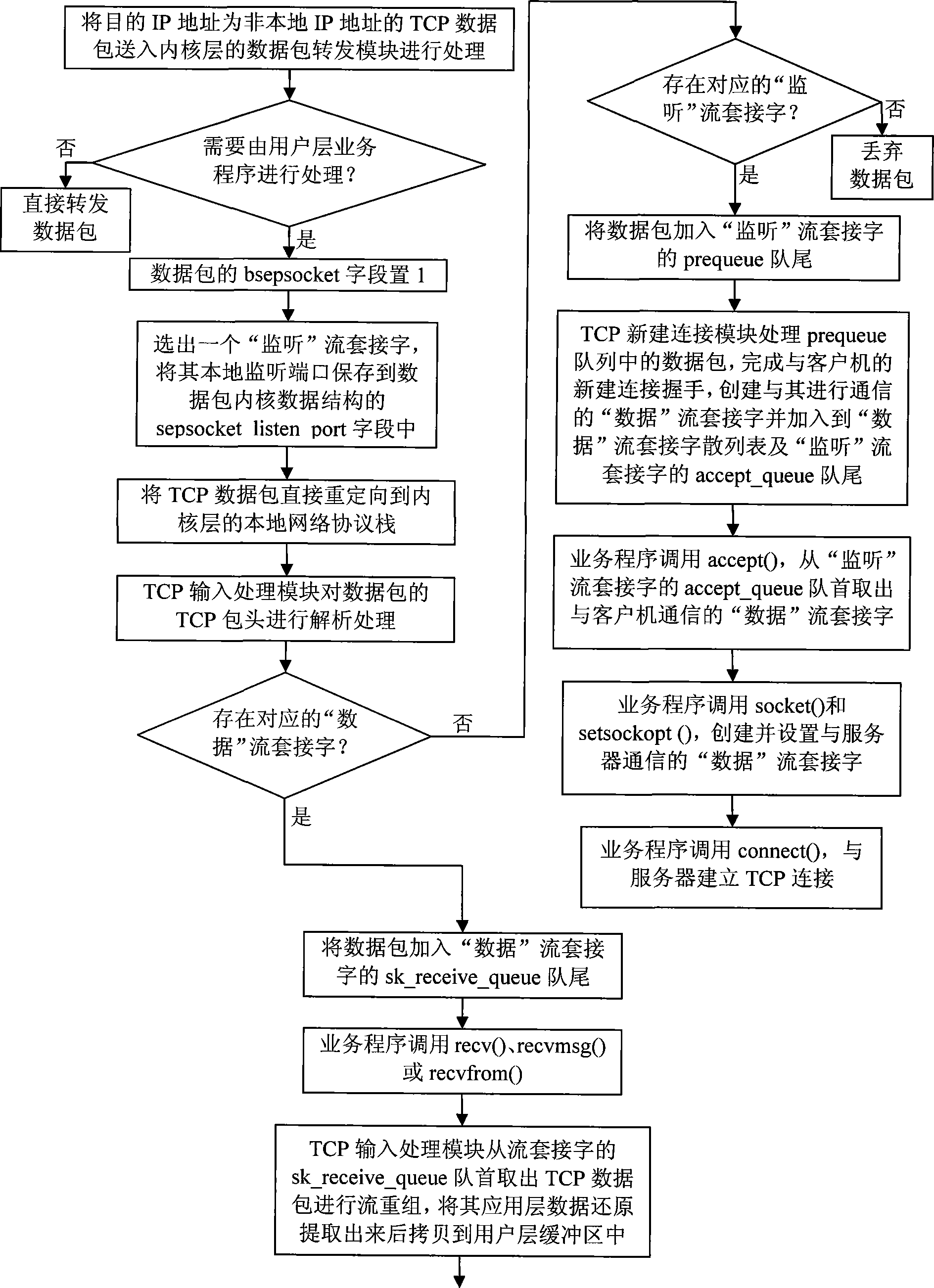
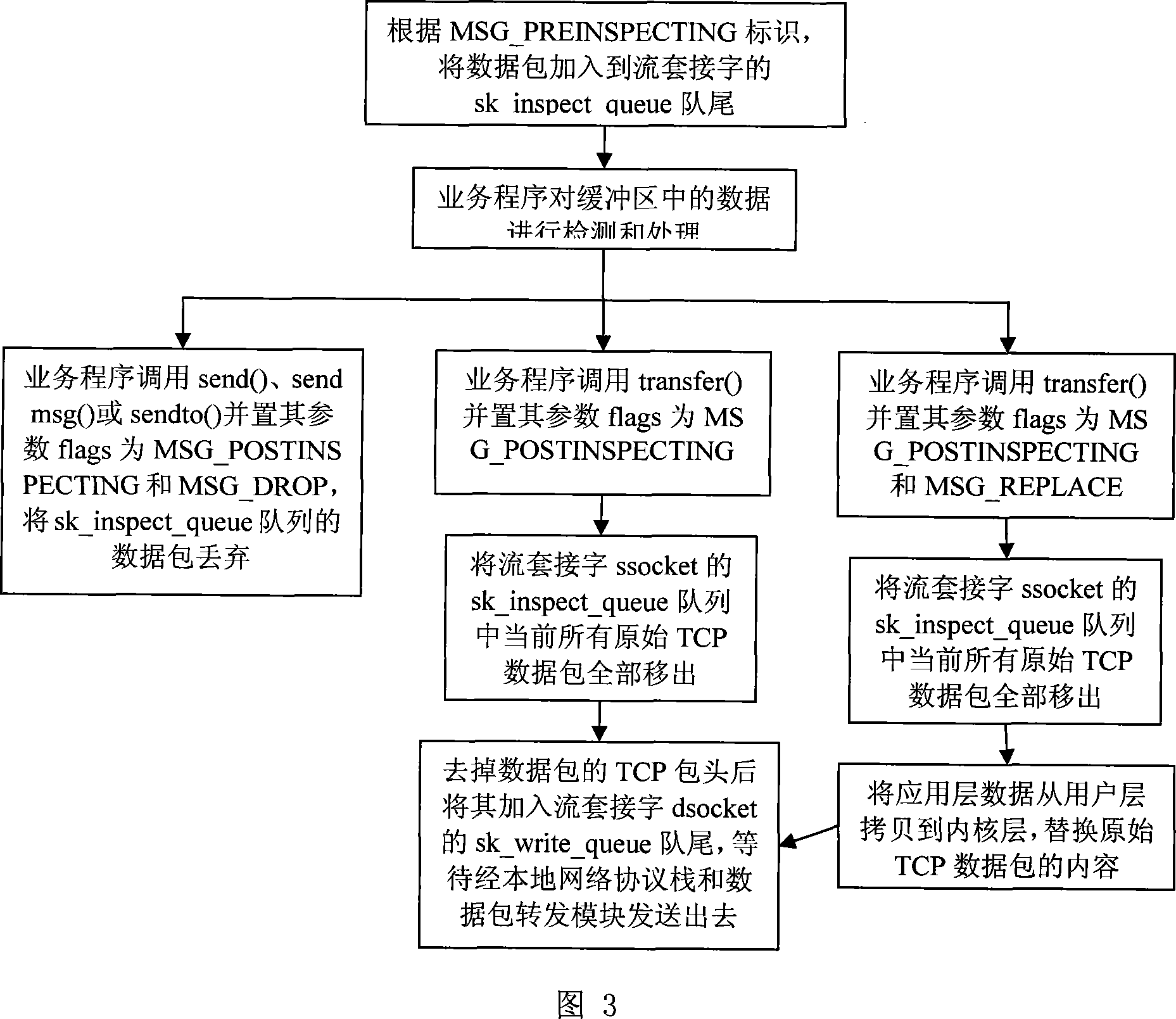
The invention aims at providing a transmission method of a TCP data packet. By directly redirecting a non local TCP data packet to a local network protocol stack to process (not dependent on the network address translation technique), stream socket loading equilibrium, reducing the data copying and transmitting between an inner nuclear layer and a user layer, transmitting the TCP data packet directly among the stream sockets of the inner nuclear layer and reducing the cost of the complicated operations such as executing the construction of the data packet in the network protocol stack, the method improves the efficiency of transmitting and processing of the TCP among the modules inside the inner nuclear layer and the efficiency of transmitting data among the business programs of the inner nuclear layer and the user layer, realizes the online high-speed processing of an application gateway to the data of the TCP flow application layer, the rapid retransmission of the TCP data packet and the support on the concurrence of the TCP conversation with a large amount, and guarantees the transparency of the application gateway to a communication source end and a target end.
Owner:PEKING UNIV
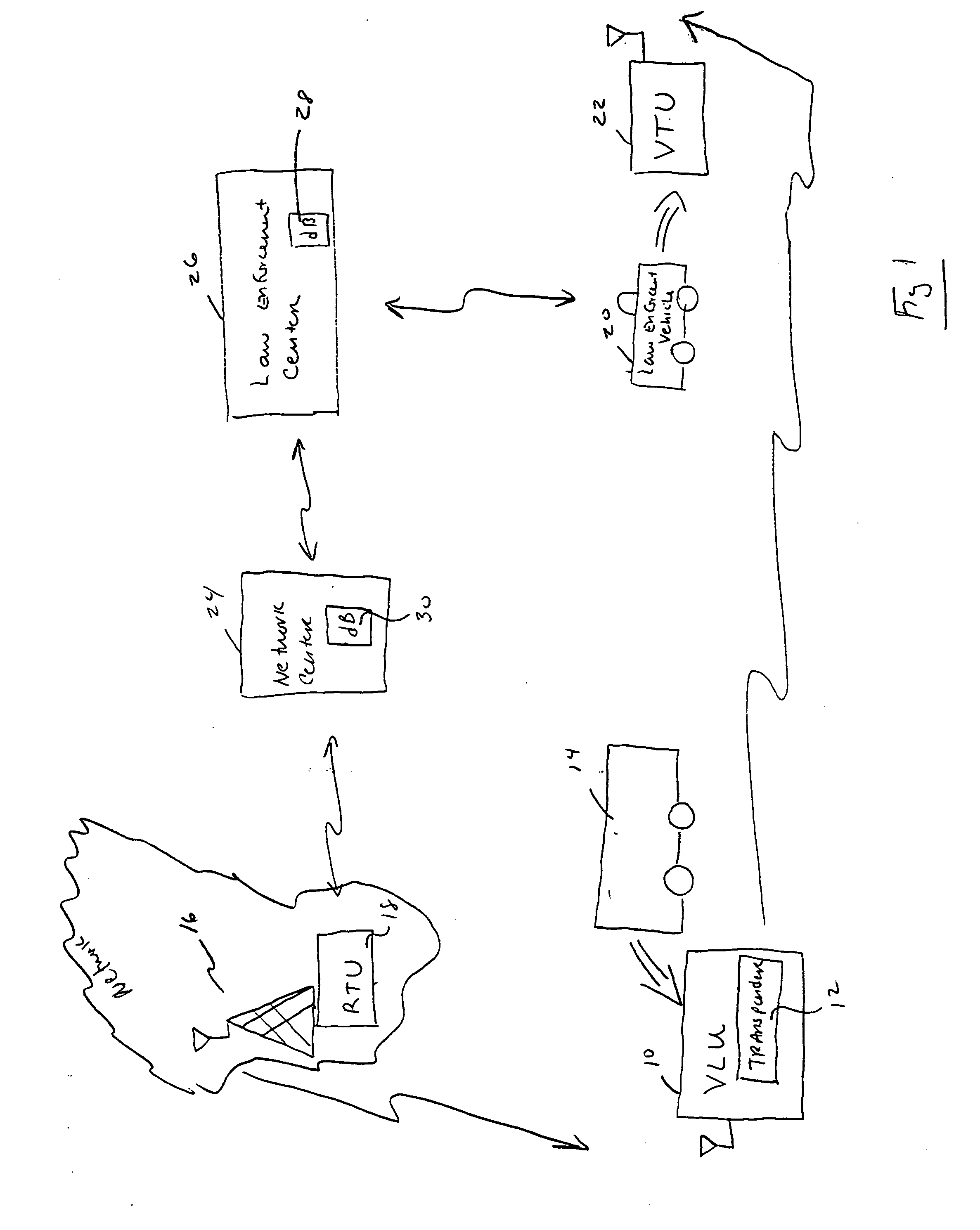
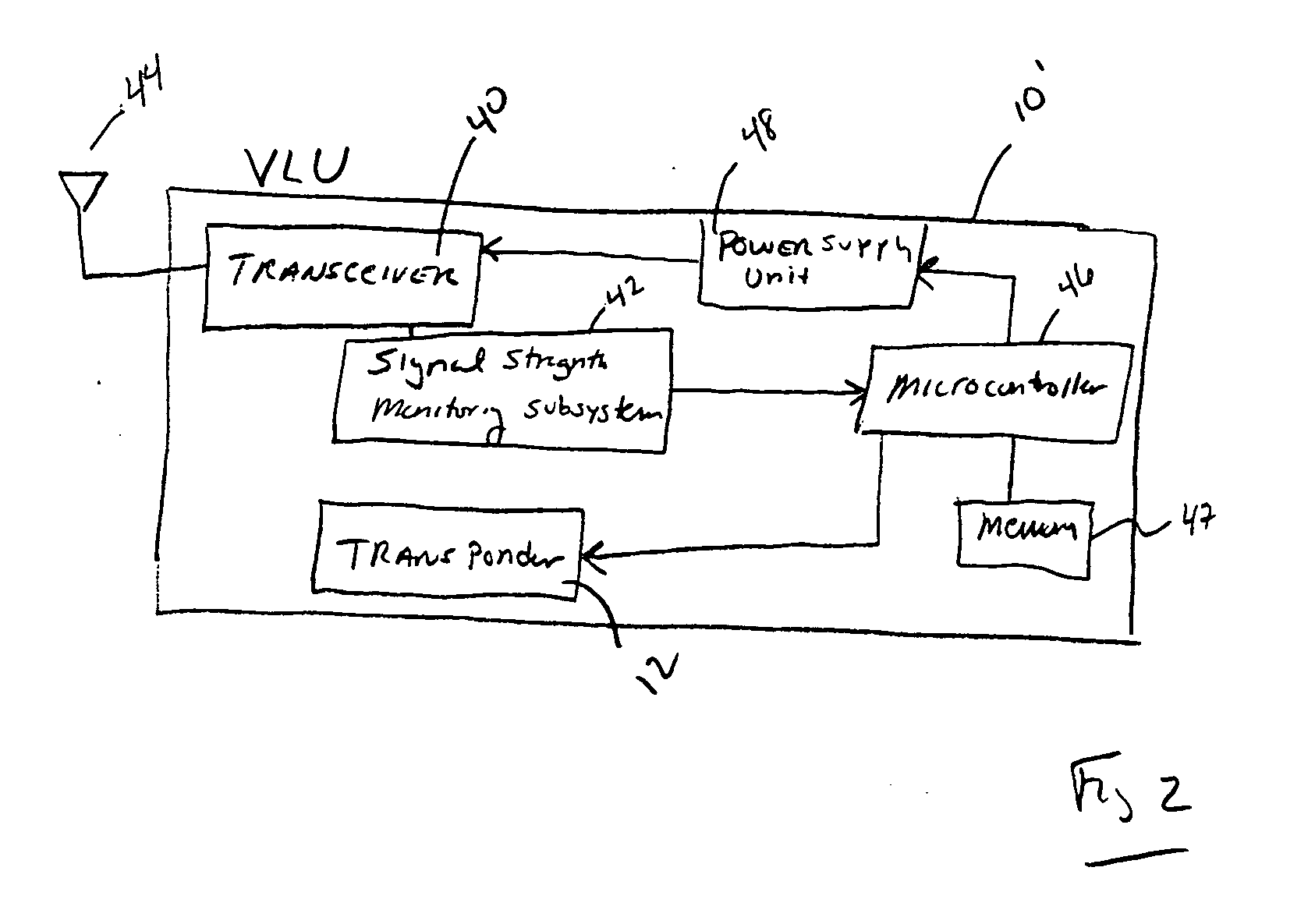
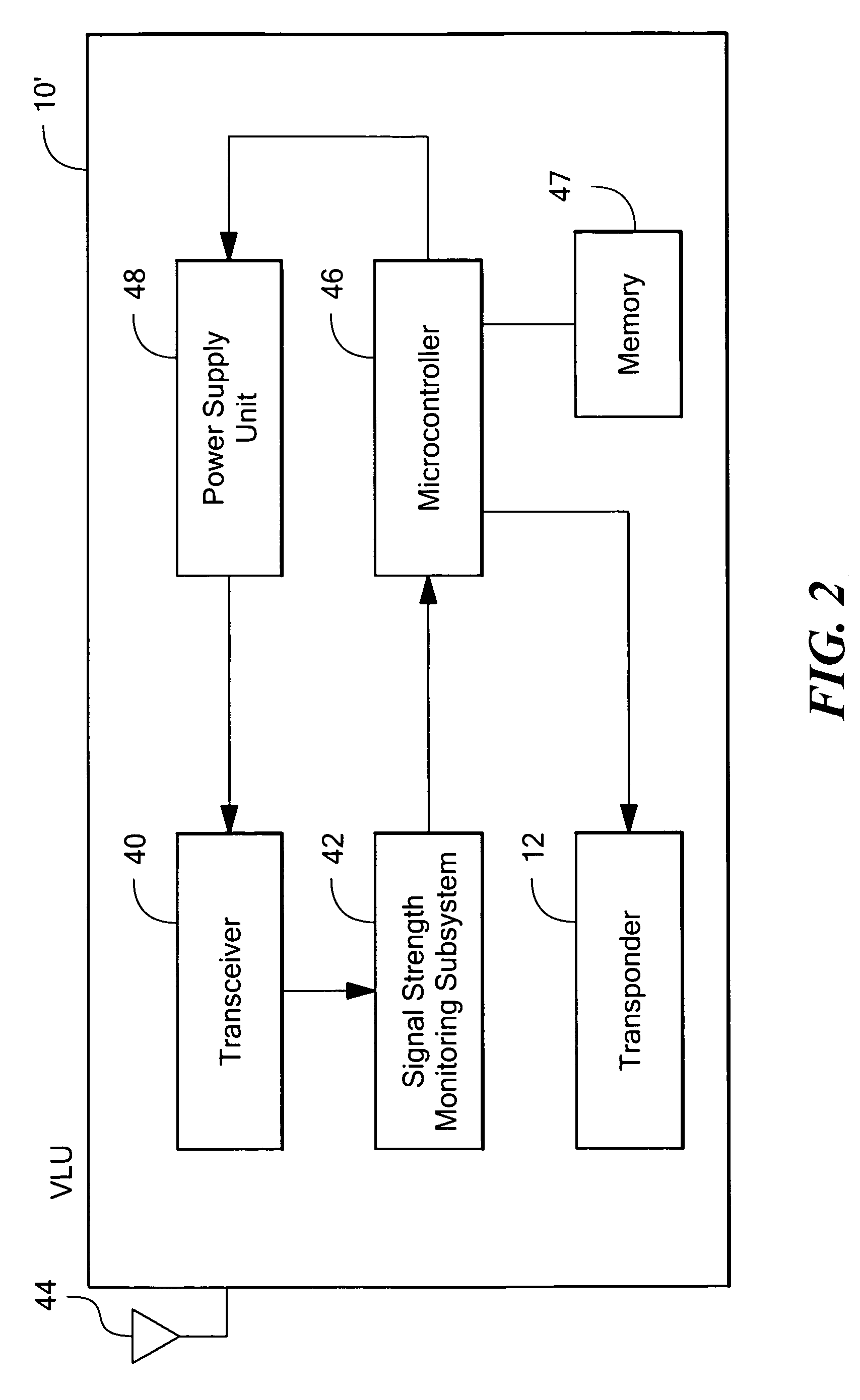
Vehicle locating unit with improved power management method
ActiveUS20060276160A1Improved power management techniquePower managementEnergy efficient ICTEngineeringCommunication source
A vehicle locating unit with improved power management. A receiver receives a signal from a network of communication sources. A signal strength monitoring subsystem determines which of the communication sources are transmitting the strongest signals. A power management subsystem is responsive to the signal strength monitoring subsystem and is configured to alternatively enter sleep and wake-up modes, synchronize the wake-up mode to the communication source transmitting the strongest signal, and test the signal strength of at least one additional communication source according to a predefined sequence.
Owner:CALAMP WIRELESS NETWORKS
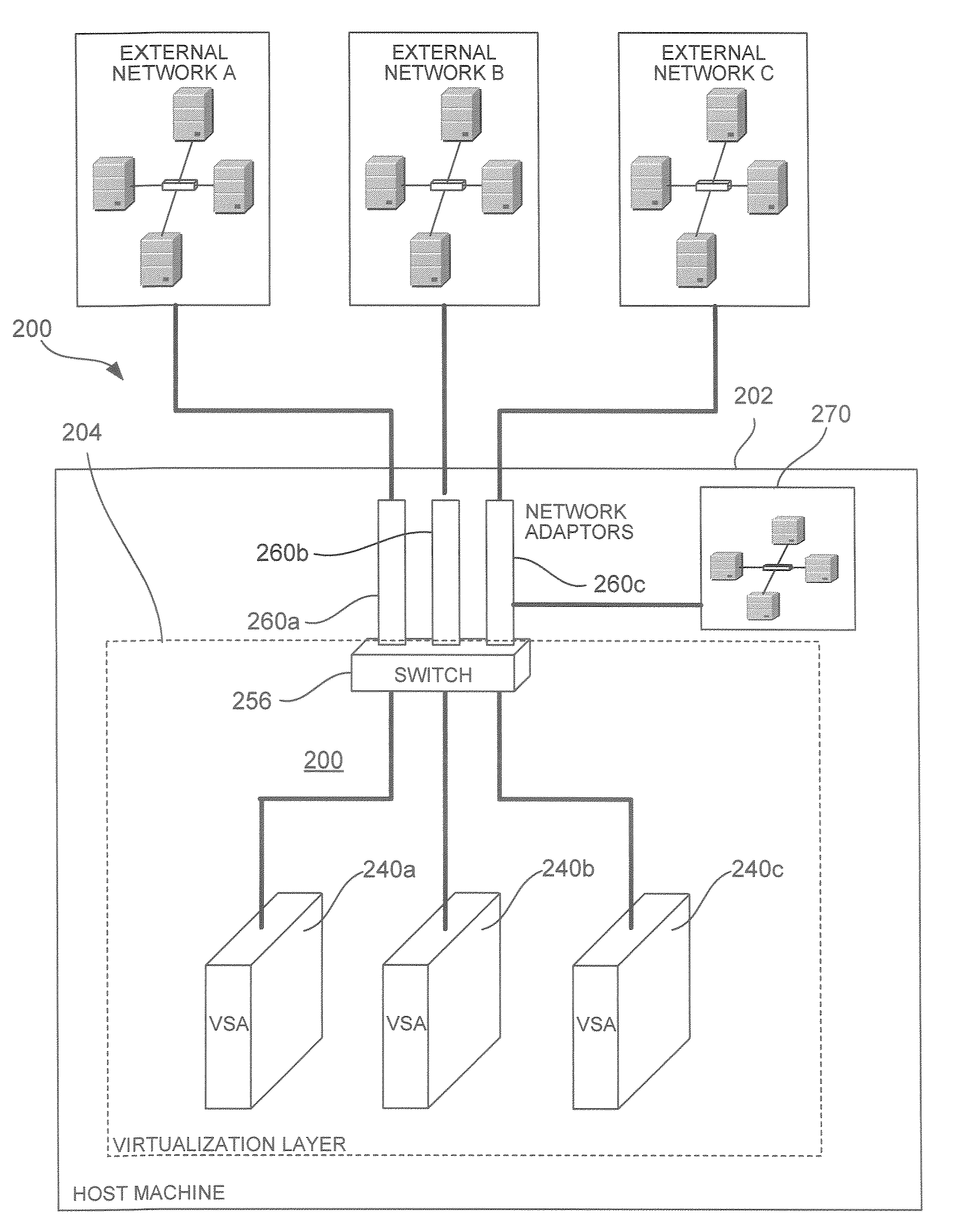
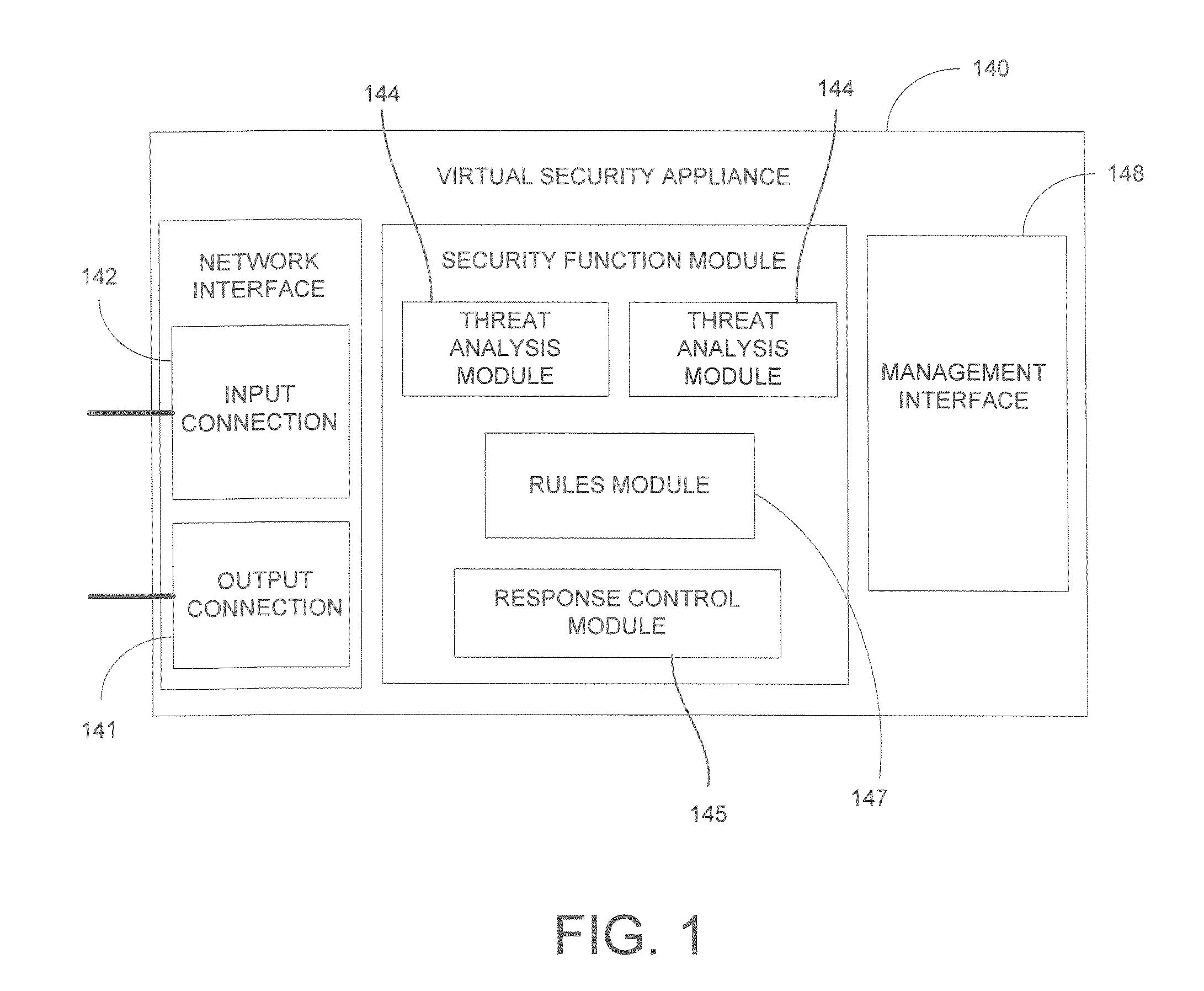
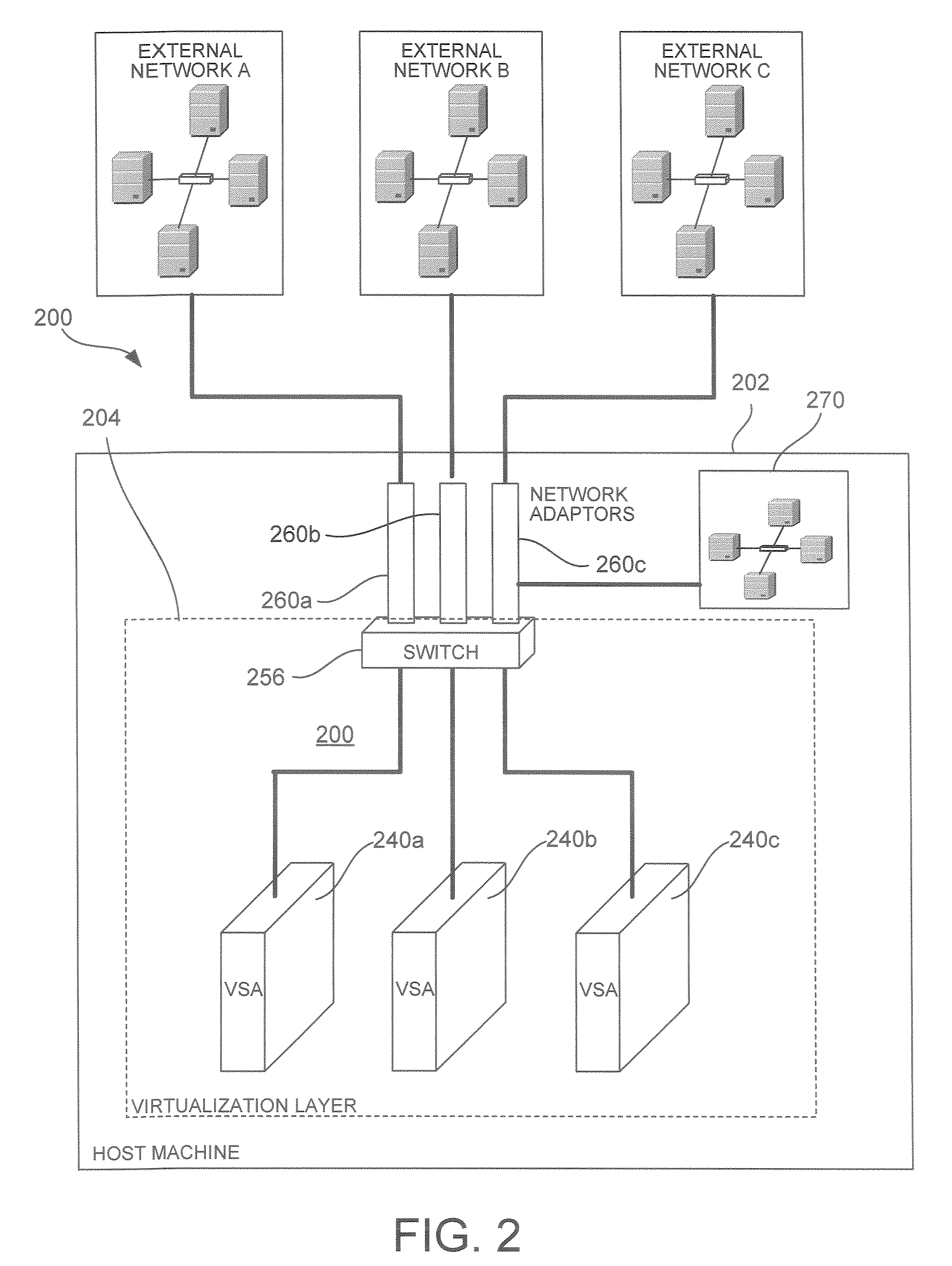
System and Method for Implementing a Virtualized Security Platform
InactiveUS20090328193A1User identity/authority verificationMultiple digital computer combinationsVirtualizationCommunication source
A virtual security platform residing in a virtualization layer on a host data processing machine is provided. The virtual security platform comprises at least one virtual security appliance, each of which is configured for receiving, via a network interface, data communications from at least one data communication source. Each virtual security appliance is also configured for initiating a security function responsive to one of said data communications meeting predetermined criteria.
Owner:STRATACLOUD
Electronic device shield and connector case
InactiveUS8690600B1Avoid obscuring purposeElectric discharge tubesDigital data processing detailsCommunication sourceUSB
An electronic device protective case with a built-in capability to have a connector or cable that enables it to interface to power and communication sources without the need for a separate cable. The connector can be an AC connector for power, or a DC connector for power and / or signals, such as an universal serial bus (USB) connector or similar connector. The connector or cable can the move between a stowed position within the protective case housing and a deployed positions where it is external to said case.
Owner:ZEOLLA GIORGIO
Communication processing apparatus, communication control method and computer program
InactiveUS20060063511A1Inhibitory contentUnauthorised/fraudulent call preventionEavesdropping prevention circuitsReference modelGeneration process
There is provided a configuration enabling prevention in advance of leakage and outflow of secret information in the local network, such as private data and content whose copyright and use right is restricted. A plurality of identification information of a communication destination device are acquired at different data processing levels. Identification information acquired by data processing at a level of a physical layer or a data link layer of the OSI reference model and identification information acquired by data processing at a layer level of a network layer or higher are received and these identification information are matched. In addition, at least one of identification information receives generated data generated by an encryption process or a hash value generation process based on secret information shared with the communication source device. By matching a plurality of identification information and in accordance with a satisfied or an unsatisfied state of the matching, it is determined whether or not the communication destination device is a device connected to the same local network.
Owner:SONY CORP
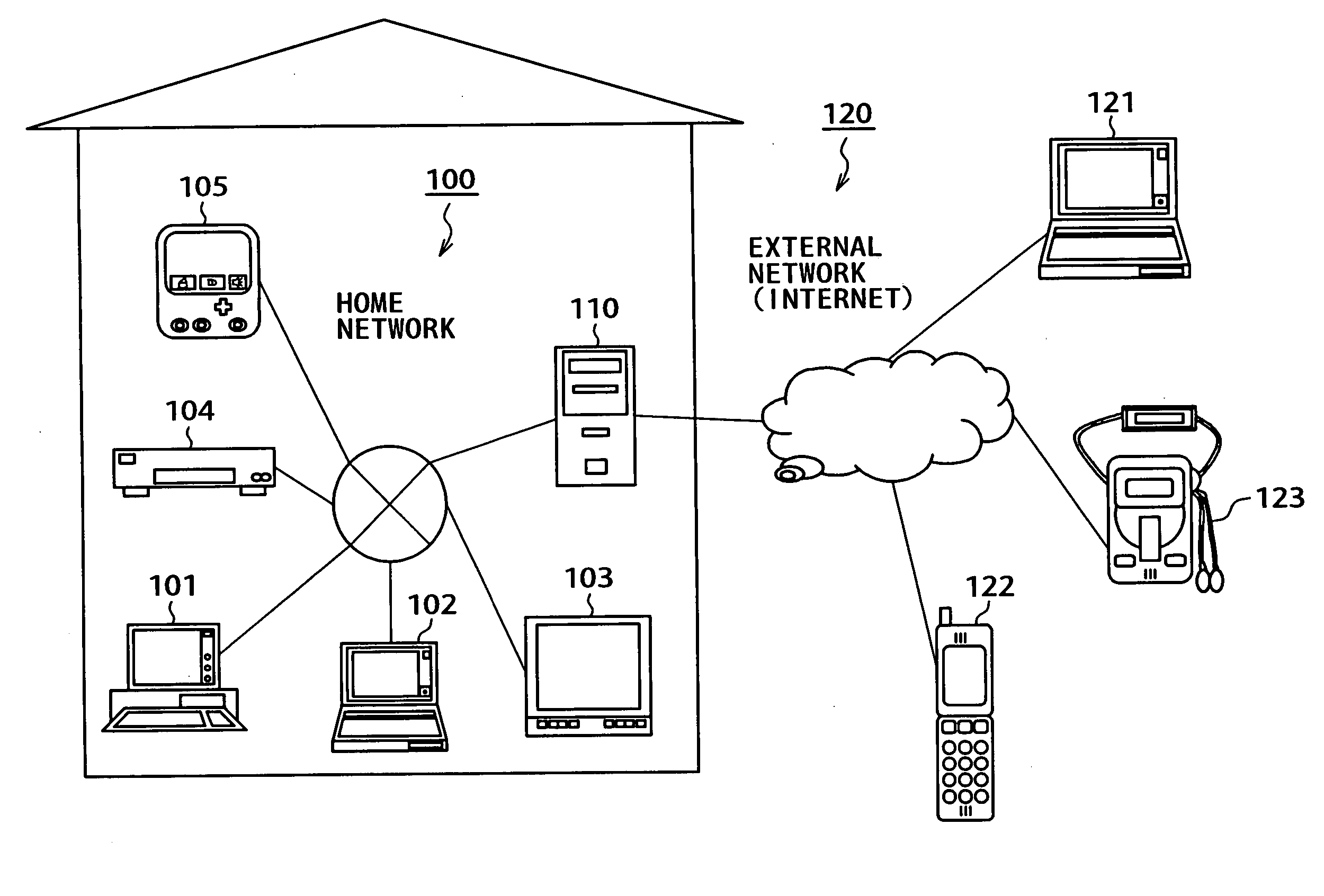
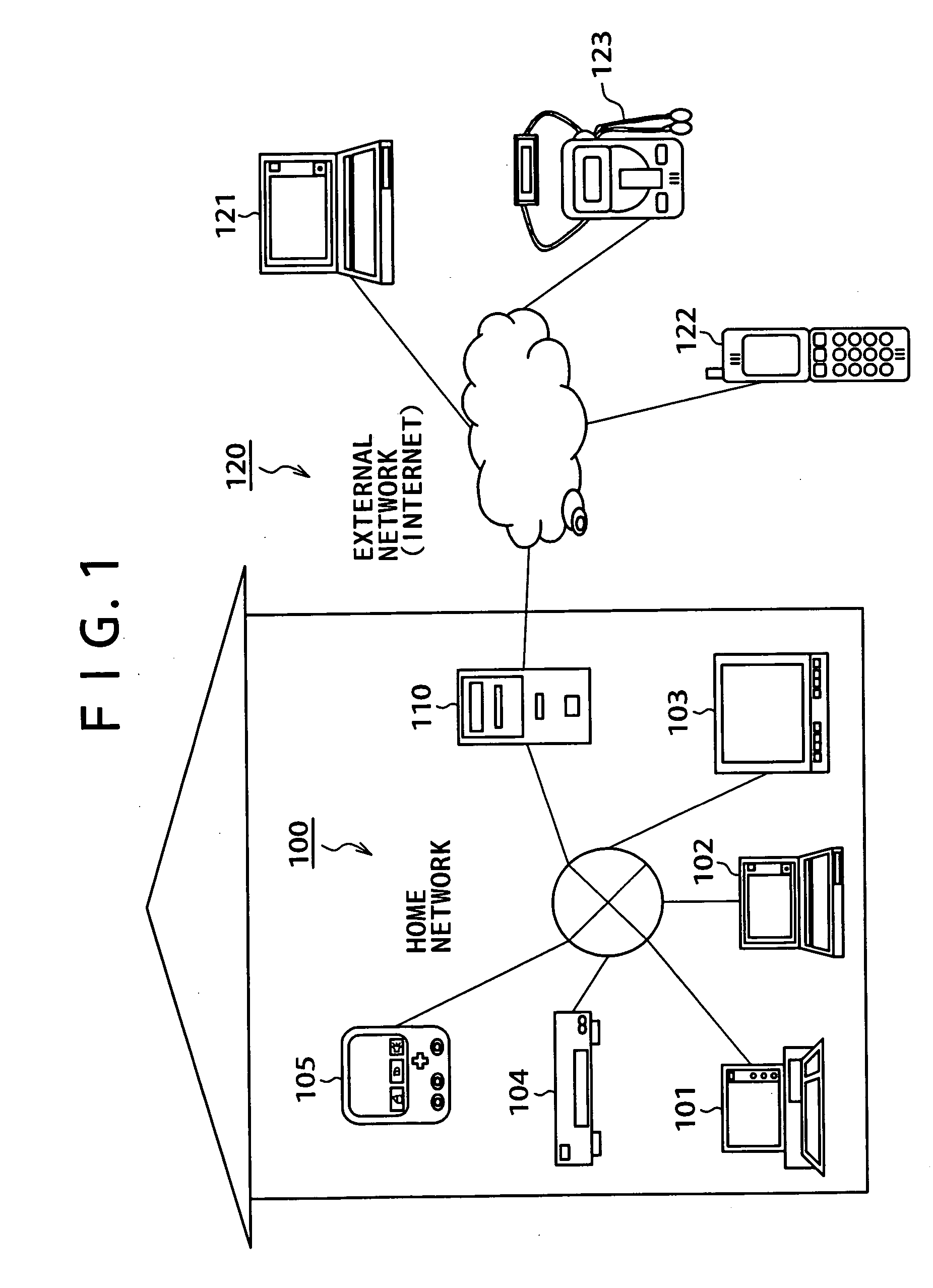
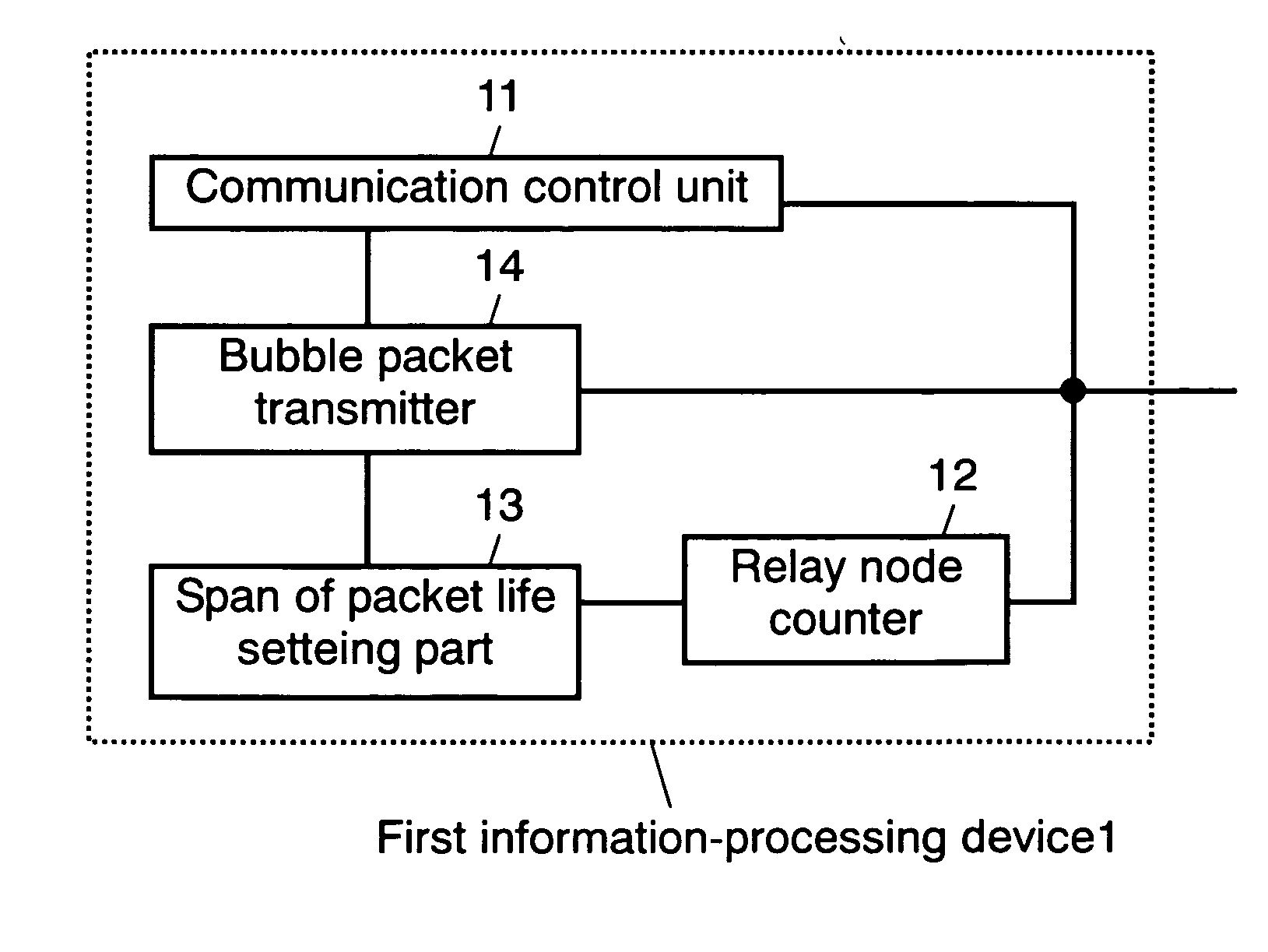
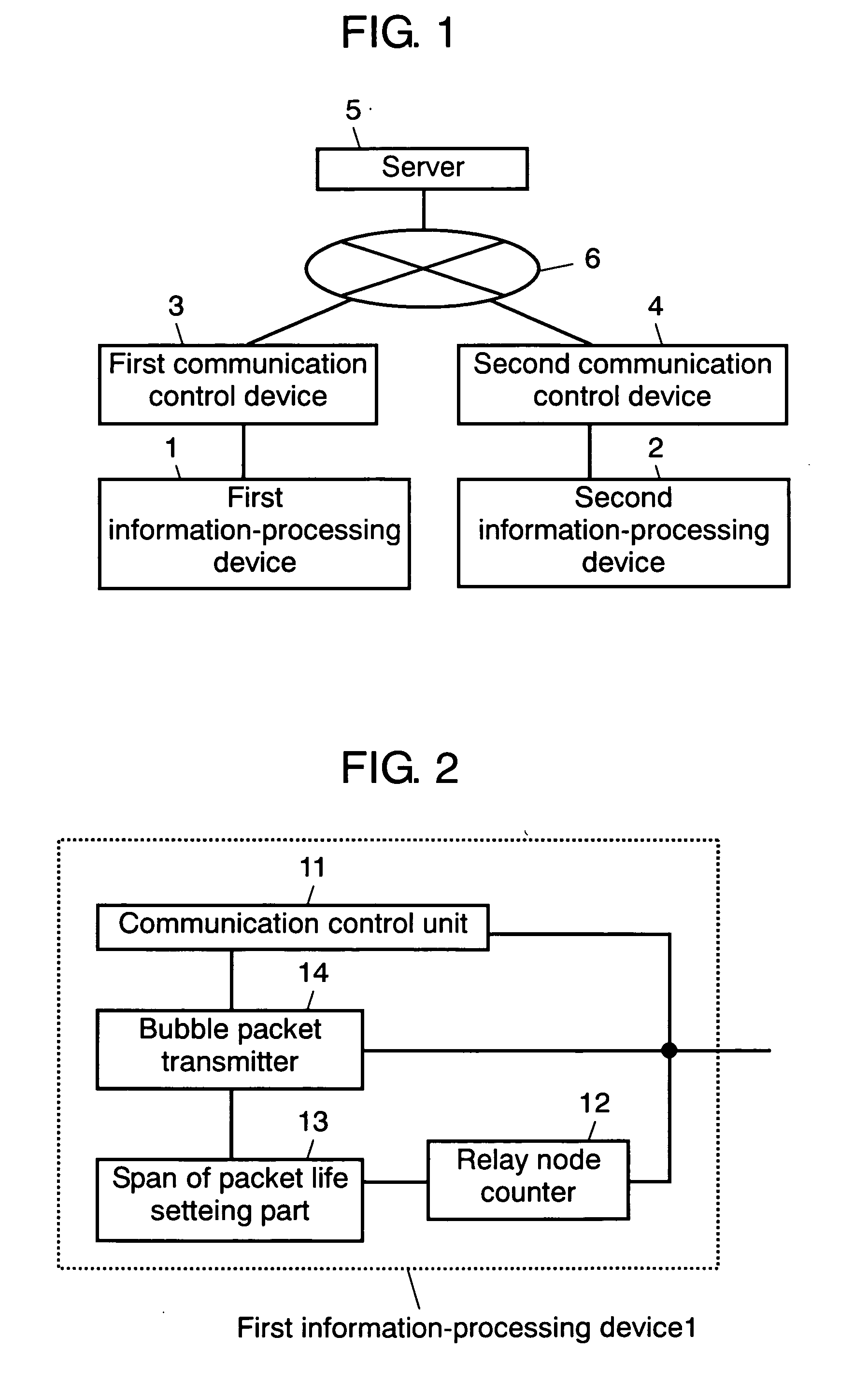
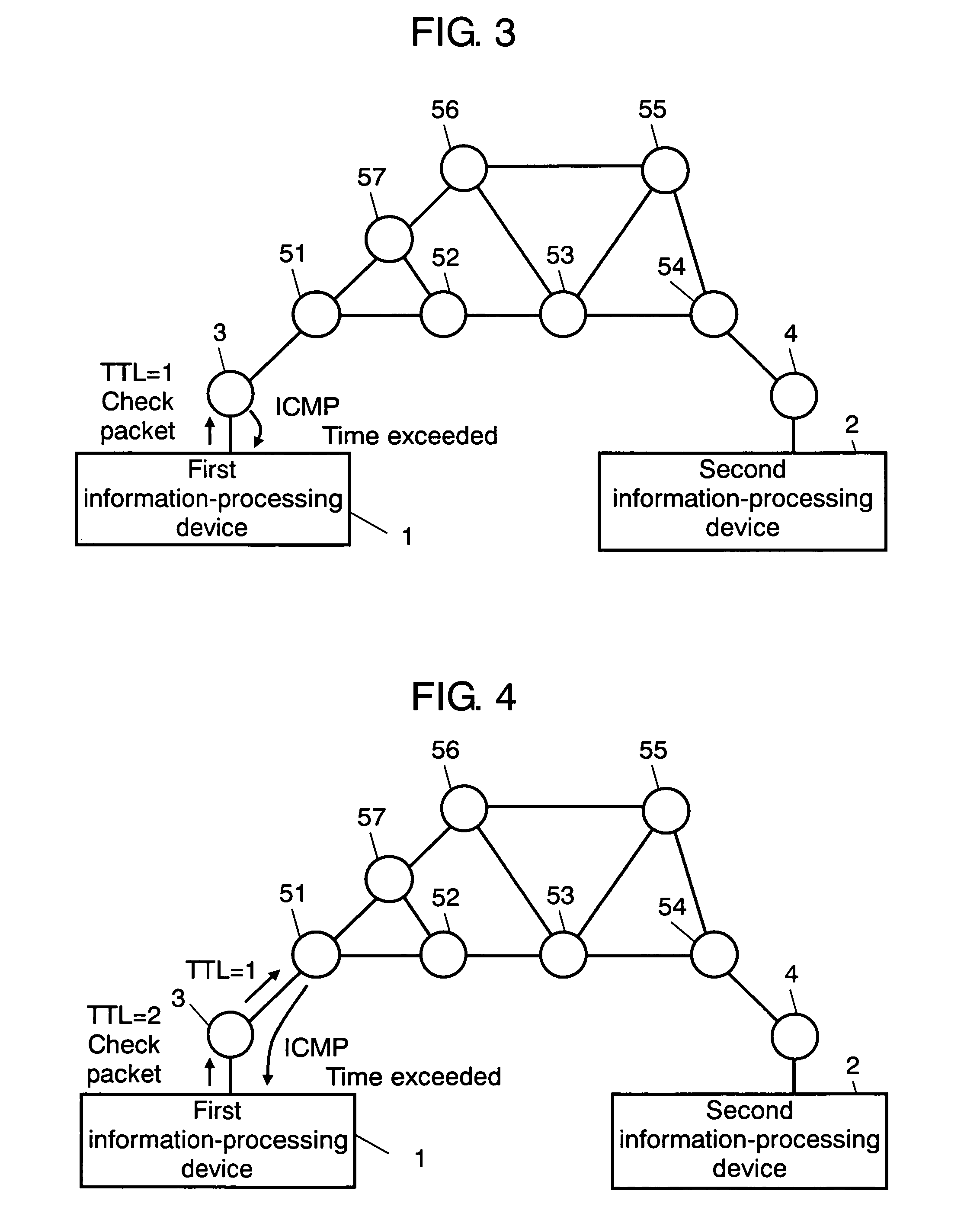
Information processing device, and bubble packet transmission method and program
ActiveUS20070171835A1Avoid communicationError preventionTransmission systemsInformation processingCommunication source
A first information-processing device at a communication source, is equipped with span of packet life setting part and bubble packet transmitter. The span of packet life setting part sets a span of packet life in a range where a bubble packet transmitted for leaving a transmission history in a NAT at the communication source so that a packet transmitted from the information-processing device at the communication destination, does not reach the information-processing device at the communication destination. Meanwhile, bubble packet transmitter transmits a bubble packet having the span of packet life set by span of packet life setting part through the NAT at the communication source. With such a configuration, the present invention provides an information-processing device that appropriately establishes communications through a NAT with high-level security.
Owner:PANASONIC CORP
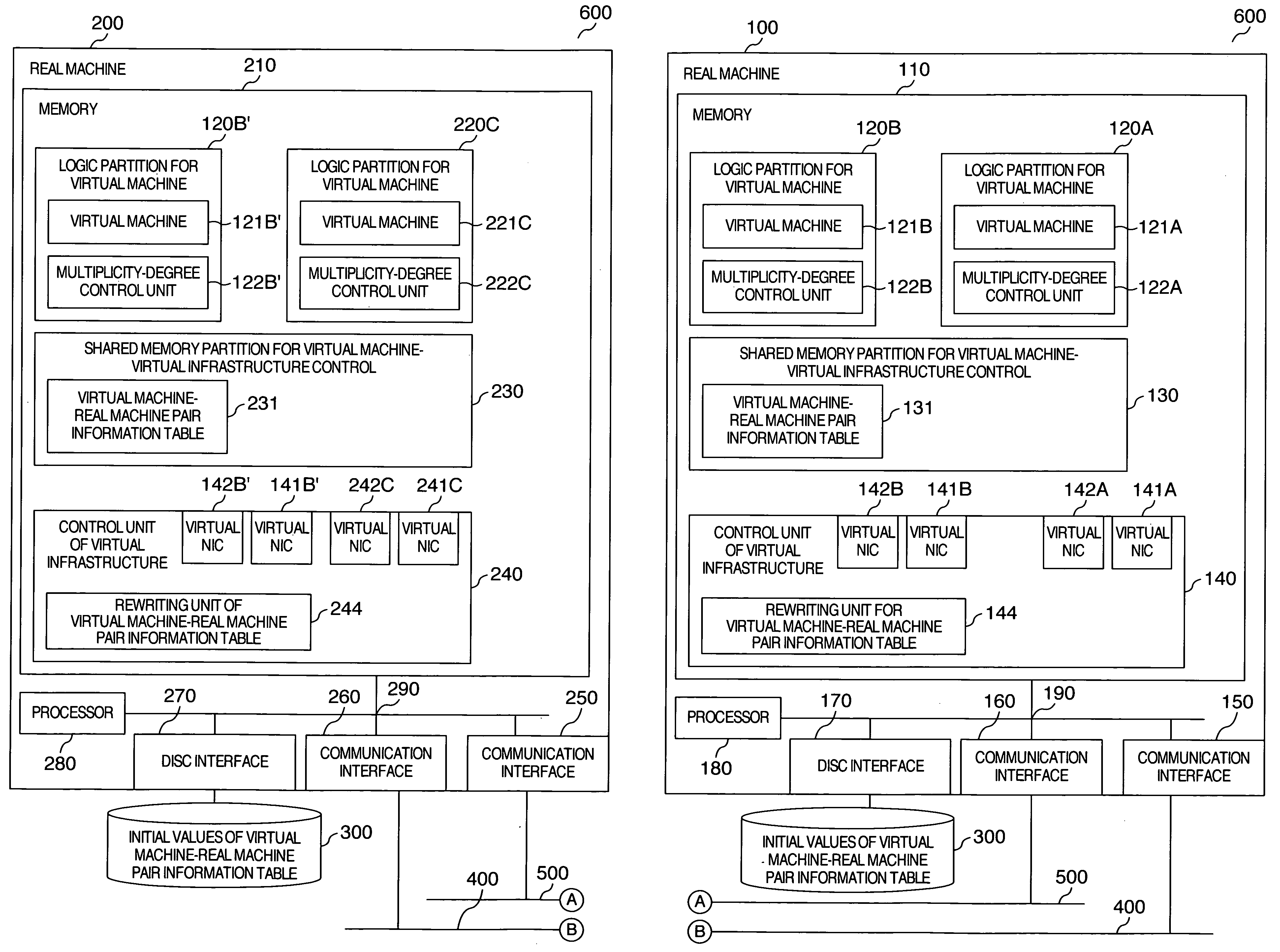
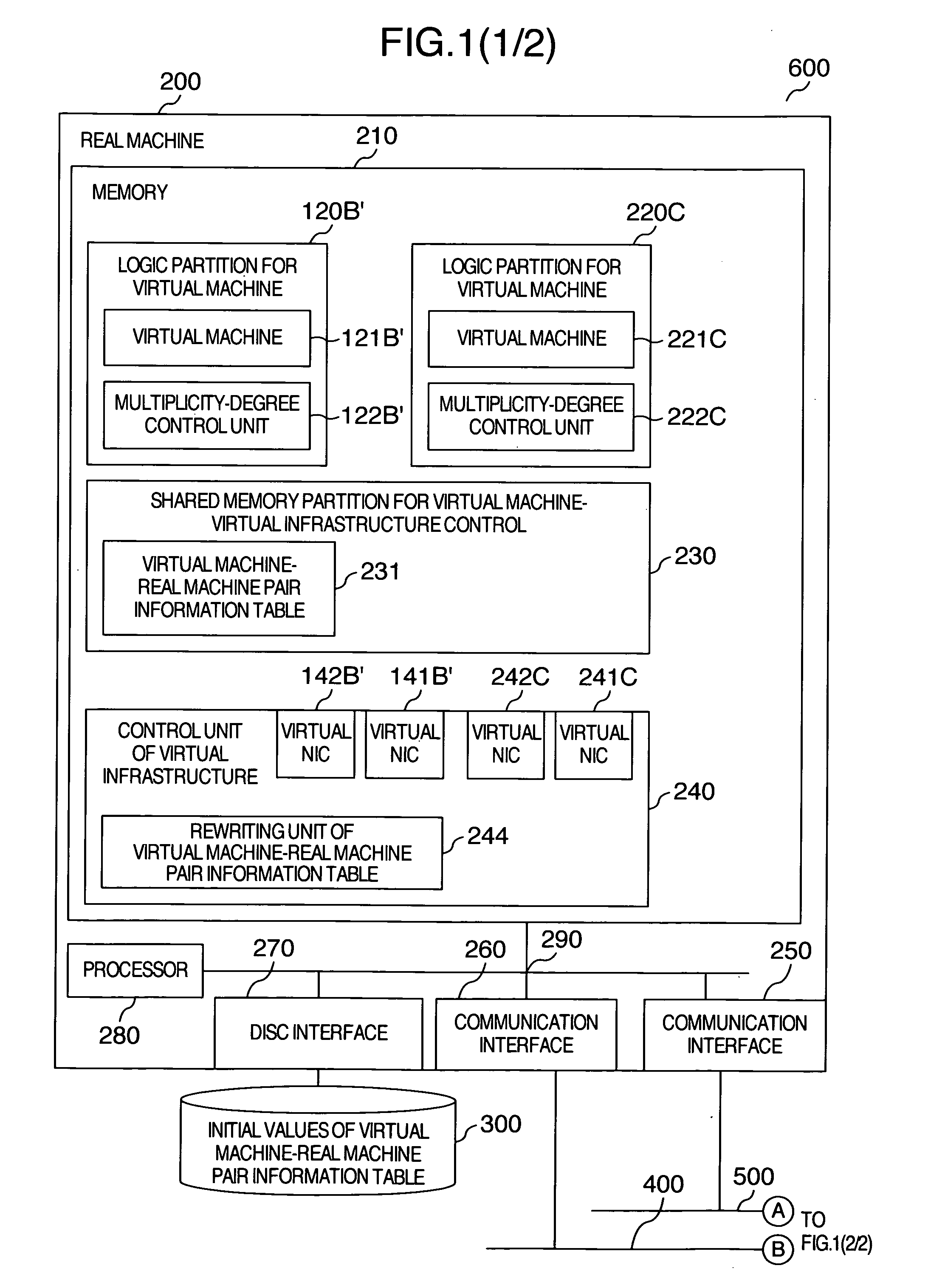
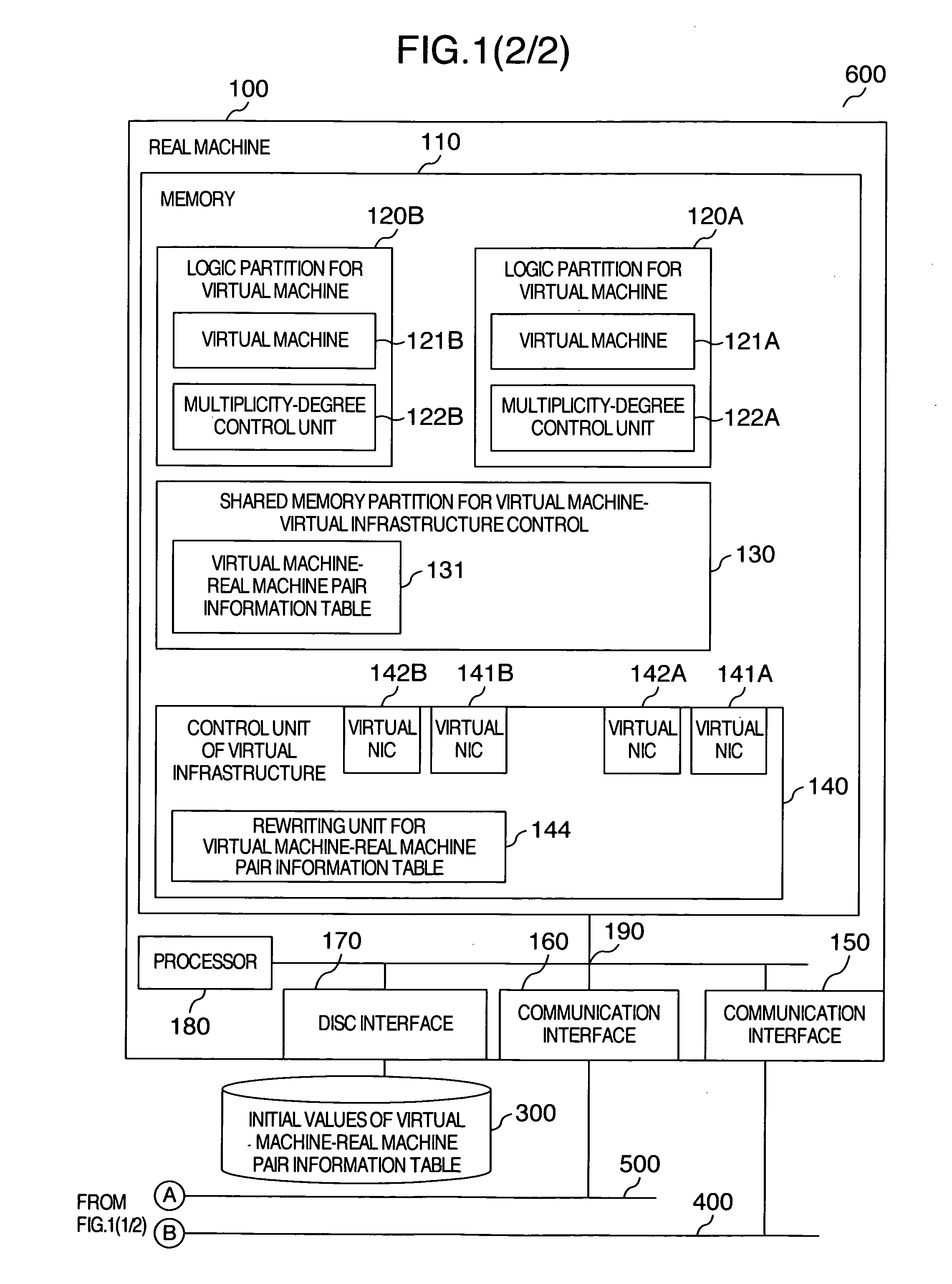
Computer system and communication control method
InactiveUS20080263544A1Reduction in CPU usage ratioAvoid lostSoftware simulation/interpretation/emulationMemory systemsComputerized systemCommunication source
A technology is provided, in which pair information of a virtual machine and a real machine on which the virtual machine operates are made related with each other, and are recorded into a shared memory partition of the virtual machine and a control function of virtual machine infrastructure, from the above-described recorded information, a judgment is made as to whether or not a communication-destination virtual machine exists on the same real machine as that of a communication-source virtual machine, and a technology for changing the multiplicity degree in accordance with this judgment, moreover, the above-described recorded information is written when the virtual machine has displaced to another real machine to implement a reduction in the CPU usage ratio in network processing between the operating virtual machines, and to dynamically control the multiplicity degree of the communication path by making full use of location information between the virtual machines.
Owner:HITACHI LTD
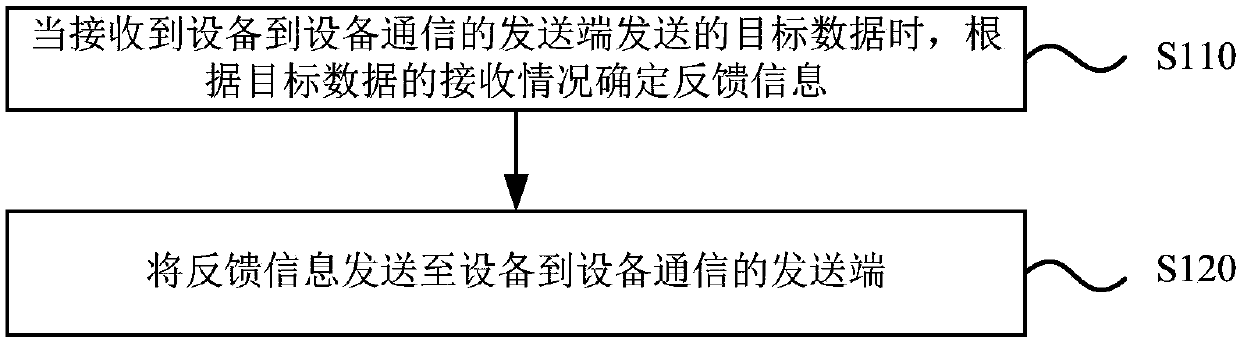
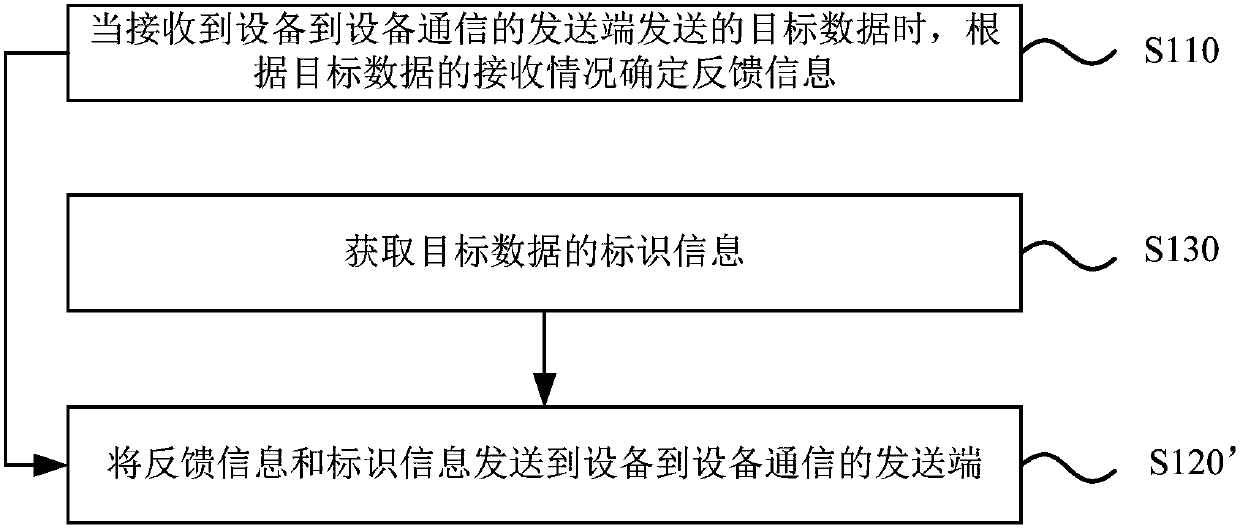
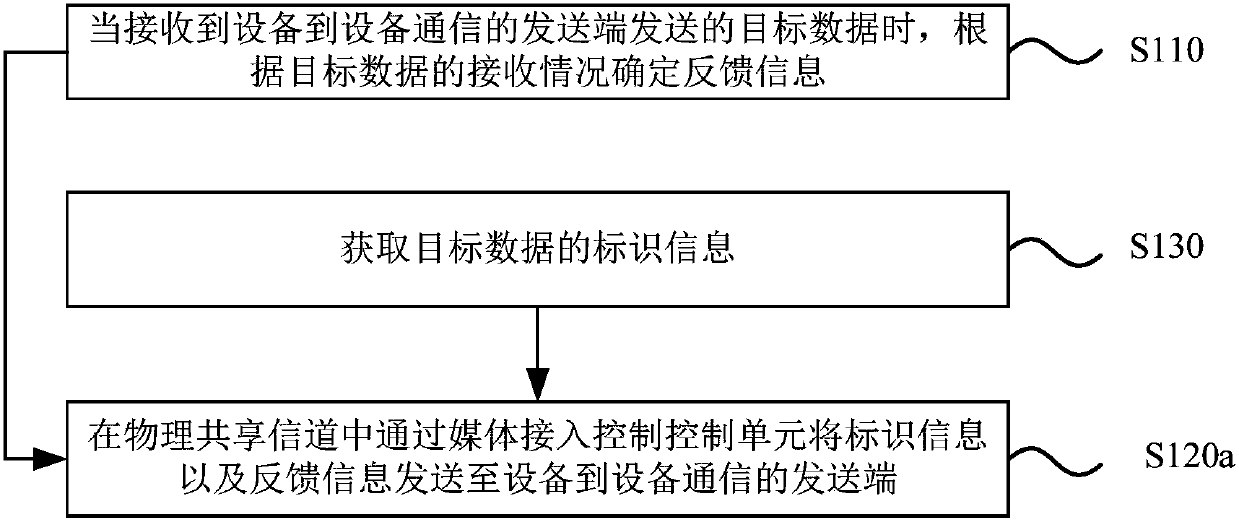
Device-to-device (D2D) communication feedback method and device
InactiveCN107733574AImprove reliabilityImprove service qualityError prevention/detection by using return channelWireless communicationQuality of serviceCommunication source
The invention discloses a device-to-device (D2D) communication feedback method and device. The method comprises the steps of determining feedback information according to receiving condition of targetdata when the target data sent by a D2D communication source is received; and sending the feedback information to the D2D communication source. According to the embodiment of the invention, a D2D communication destination can determine the feedback information according to the receiving condition of the target data when the target data sent by the source is received and feeds back the feedback information to the source, thereby feeding back the receiving condition of the target data. In the prior art, the destination cannot feed back the receiving condition of the D2D communication target data to the source, so the data transmission reliability and the quality of service are low. The D2D communication destination can feed back the feedback information of the target data sent by the sourceto the source, so the source can adjust data sending content according to the feedback information, and the data transmission reliability and the quality of service in the D2D communication are improved.
Owner:BEIJING XINWEI TELECOM TECH
Multi-beam laser communications system and method
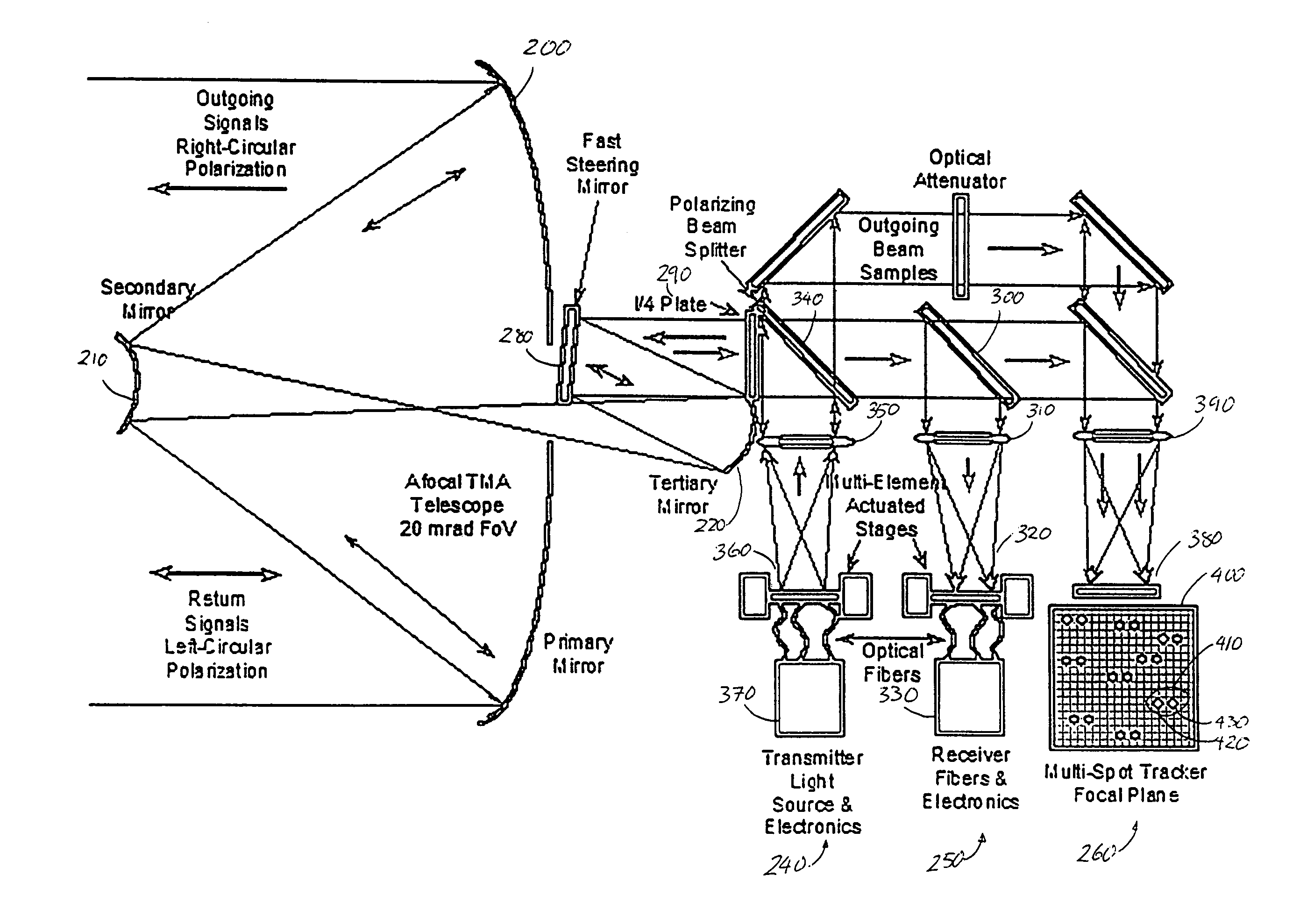
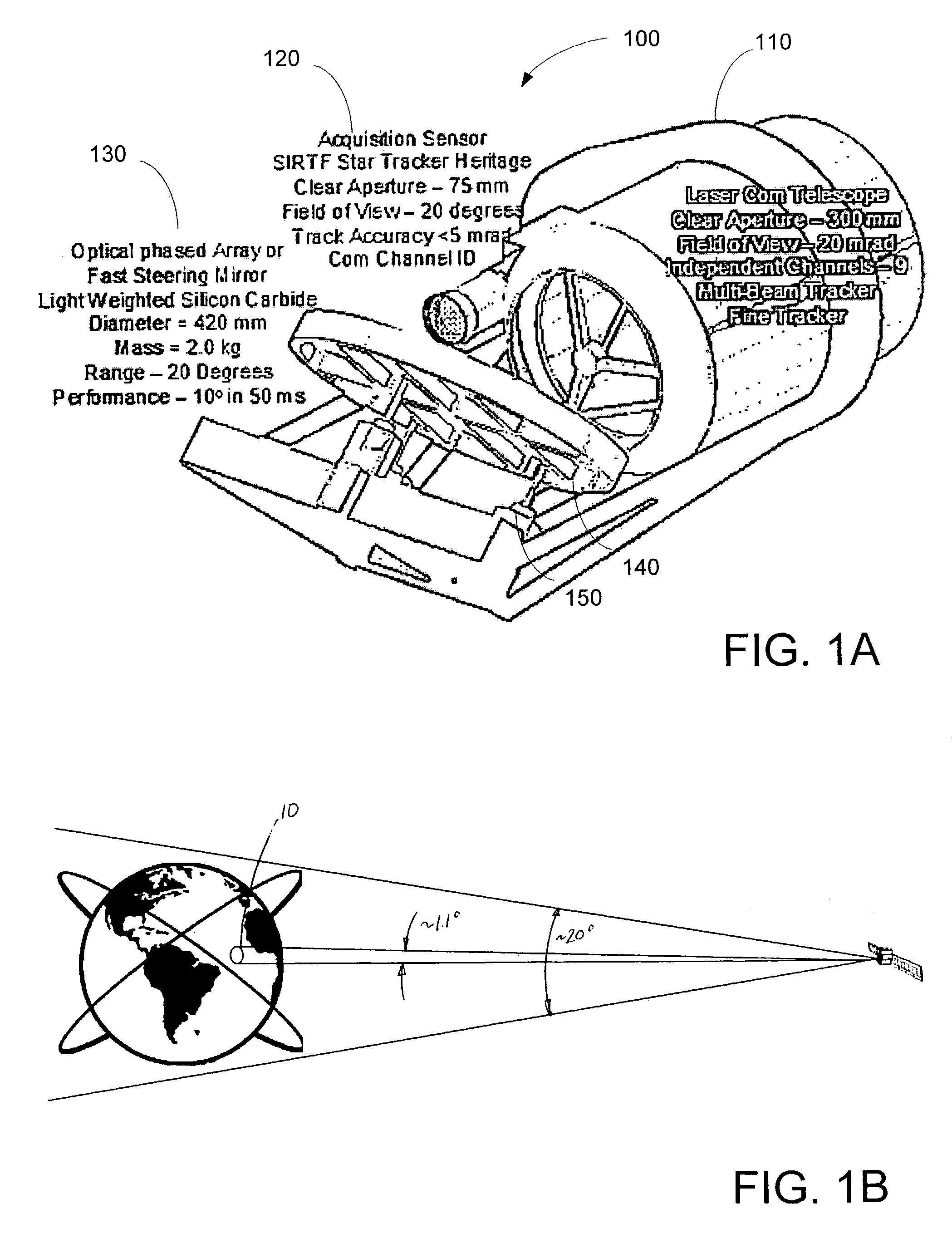
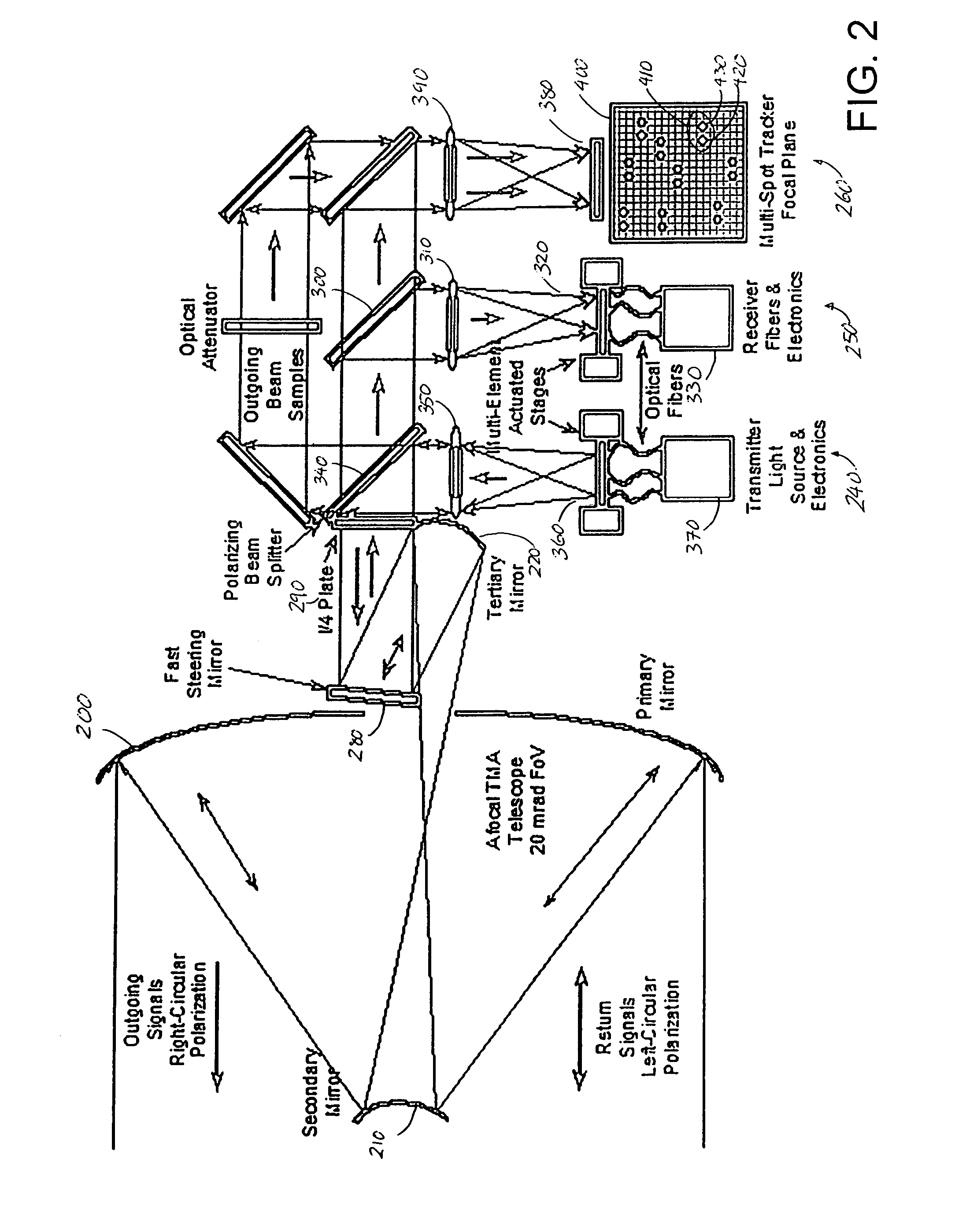
ActiveUS7292788B2Rapid and large angle retargetingImprove performanceElectromagnetic transmissionCommunications systemWide field
A laser communications system includes a wide-field sensor, configured to detect a first set of laser communications sources within a first field of view, a narrow-field sensor includes a tracking portion and a control portion configured to receive laser communications from a second set of laser communications sources within a second field of view, wherein the first field of view is larger than the second field of view, and wherein the second set of laser communications sources comprises at least a first source and a second source, and a redirection unit coupled to the narrow-field sensor configured to position the second field of view within the first field of view wherein the first receiving element is positioned in response to the first positioning signal for the first receiving element, and the second receiving element is positioned in response to the first positioning signal for the second receiving element.
Owner:LOCKHEED MARTIN CORP
Vehicle locating unit with improved power management method
ActiveUS7593711B2Improved power management techniquePower managementEnergy efficient ICTEngineeringCommunication source
A vehicle locating unit with improved power management. A receiver receives a signal from a network of communication sources. A signal strength monitoring subsystem determines which of the communication sources are transmitting the strongest signals. A power management subsystem is responsive to the signal strength monitoring subsystem and is configured to alternatively enter sleep and wake-up modes, synchronize the wake-up mode to the communication source transmitting the strongest signal, and test the signal strength of at least one additional communication source according to a predefined sequence.
Owner:CALAMP WIRELESS NETWORKS
Method and apparatus for communicating a graphic image to a mobile platform via broadcast services
InactiveUS20080046172A1Instruments for road network navigationRoad vehicles traffic controlGraphicsHuman–machine interface
A mobile platform is equipped with a broadcast signal receiver operative to receive a broadcast message, an electronic memory storage device, a processor, and, a human-machine interface comprising a visual display screen. A first message is broadcast from a communications source and received at the mobile platform via the broadcast signal receiver. The first message includes a graphic image which is cached in the electronic memory storage device and selectively displayed with the visual display screen of the human-machine interface.
Owner:GM GLOBAL TECH OPERATIONS LLC
Sparse matrix based compressed sensing processing method for hyperspectral remote sensing images
InactiveCN103024398AReduce sampling costsHigh gainTelevision systemsDigital video signal modificationData classSource encoding
The invention belongs to the field of mobile communication source coding and discloses a sparse matrix based compressed sensing processing method for hyperspectral remote sensing images. The method includes the steps of wavelet transform, data type transform, quantization, sparse matrix compressed encoding, OMP (orthogonal matching pursuit) decoding, data type inverse transform, inverse quantization and wavelet inverse transform, and the eight steps are executed sequentially. The method can be used for processing two types of remote sensing images, wherein the remote sensing images of the first type are not subjected to geometric correction, and the remote sensing images of the second type are subjected to geometric correction. Data type transform and data type inverse transform are added to the whole processing method aiming at the remote sensing images of the second type. The method for processing the hyperspectral remote sensing images has the advantages of high image compression proportion, saving of memory and computation space and high image restoration quality.
Owner:SHANDONG UNIV
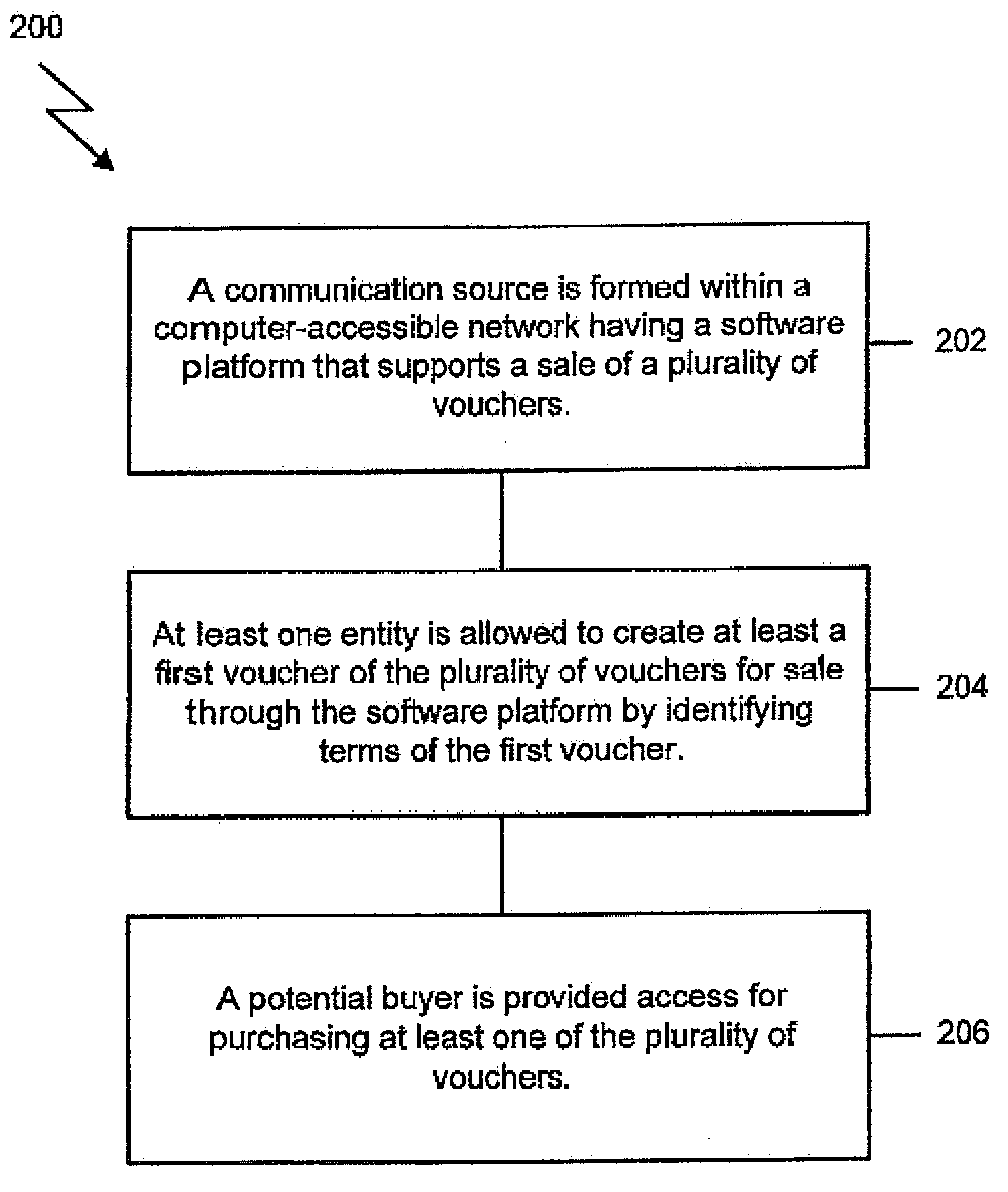
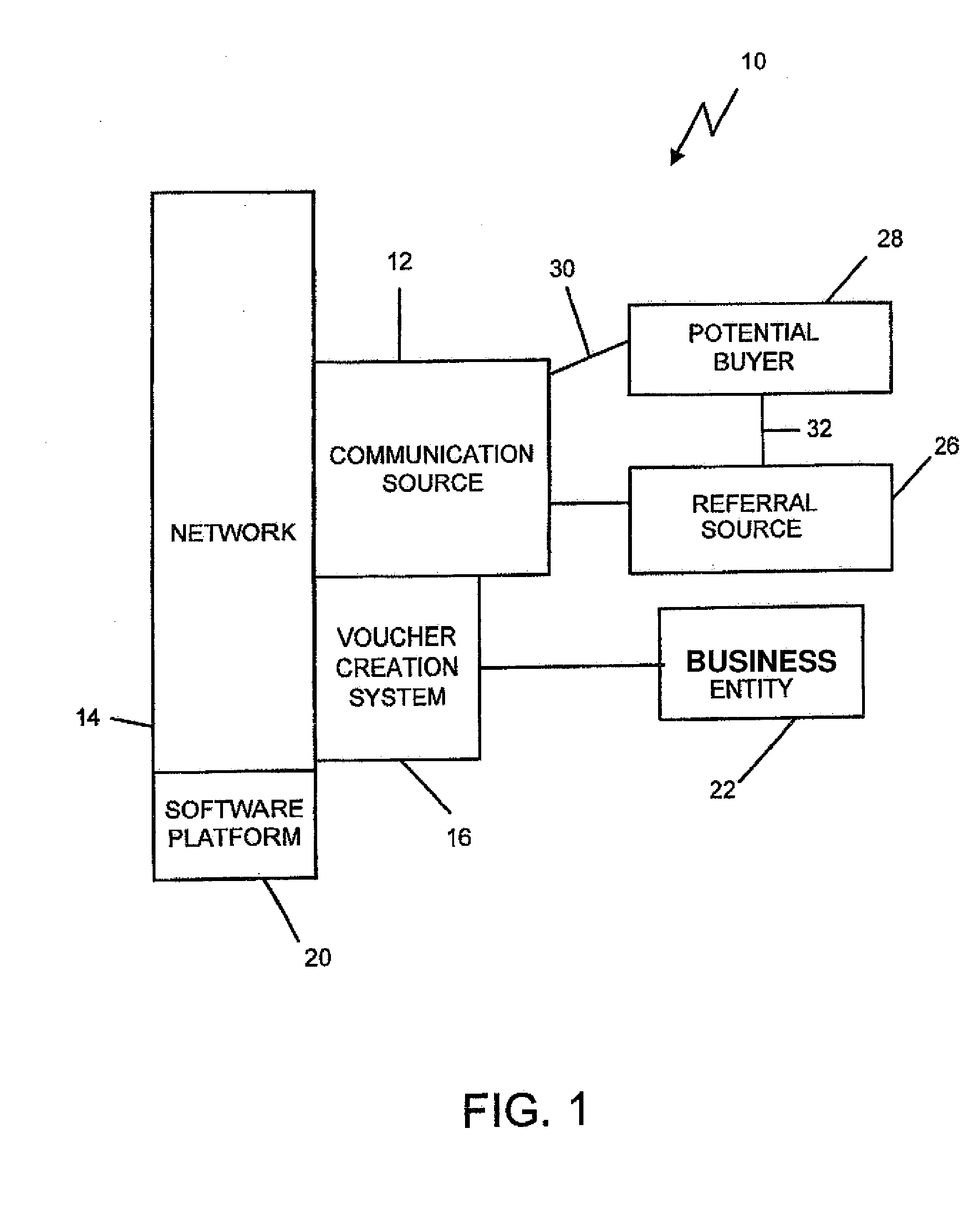
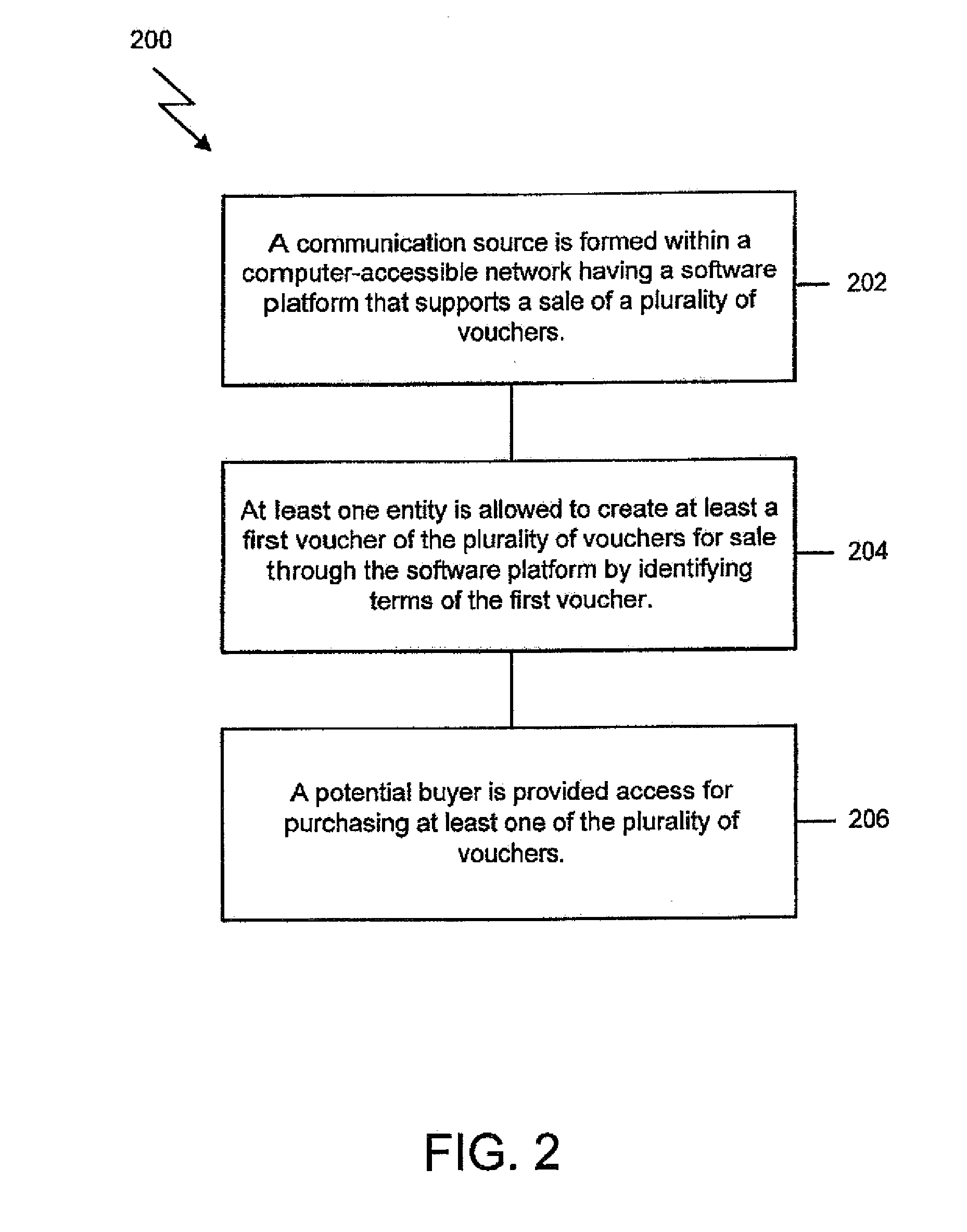
System and method for creating, promoting and tracking vouchers within a community
The system includes a communication source formed with a computer-accessible network having a software platform that supports a sale of a plurality of vouchers. A voucher creation system is in communication with the communication source. The voucher creation system allows at least one entity to create at least a first voucher of the plurality of vouchers for sale through the software platform by identifying terms of the first voucher. At least one potential buyer has sufficient access through the software platform to purchase the first voucher.
Owner:OFFERNODE
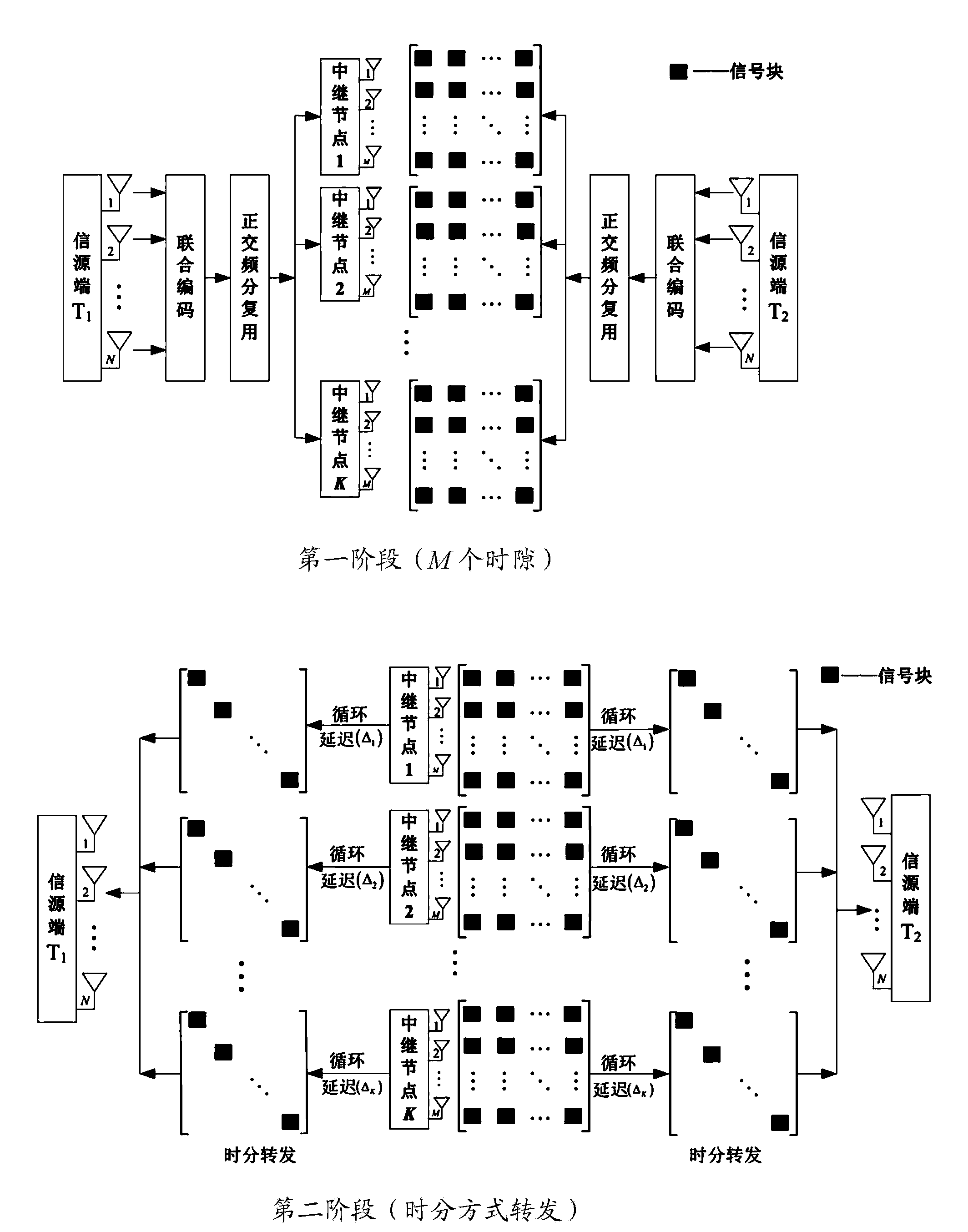
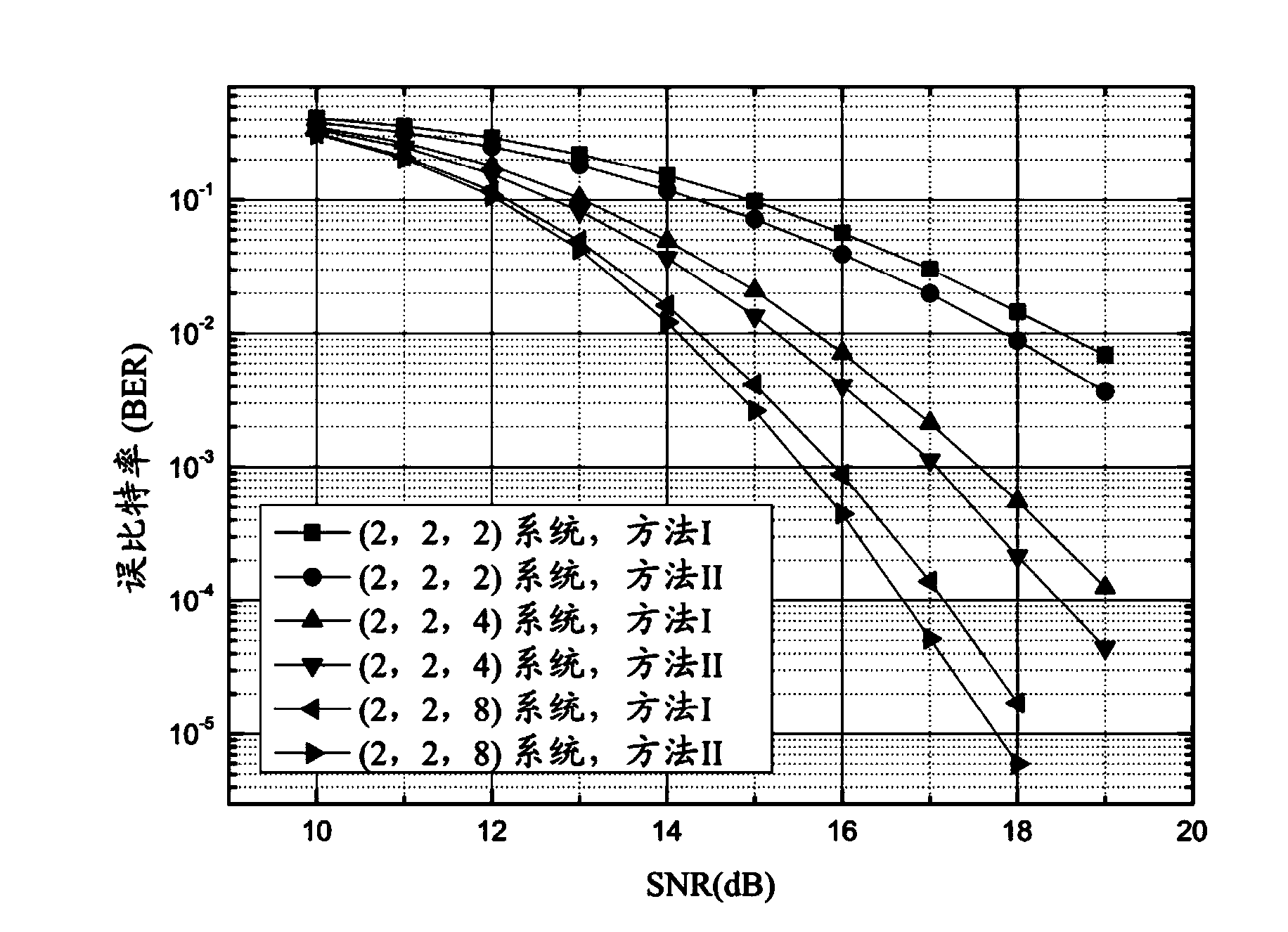
Full-rate distributed type multi-antenna bi-directional wireless cooperative relay transmission method
InactiveCN103973627ALow costSimplify the coding processError preventionMulti-frequency code systemsTime domainInformation transmission
A full-rate distributed type multi-antenna bi-directional wireless cooperative relay transmission method is suitable for a universal bi-directional relay communication network, wherein two communication source nodes and all relay nodes of the universal bi-directional relay communication network are respectively provided with a plurality of antennas. Information transmission between the nodes is carried out in an orthogonal frequency division multiplexing mode. A data communication process comprises two stages, wherein firstly, the communication source nodes conduct joint encoding on symbols to be transmitted in all sub-carriers and a plurality of time slots respectively and broadcast the encoded symbols to the relay nodes; secondly, each relay node conducts circular delay on received modulating signals in a time domain firstly, then the antennas on each relay node transmit processed signals to the communication source nodes sequentially in a time division working mode, and according to encoding and transmitting criterions, one source node obtains data transmitted by the other source node after eliminating signal interference of the former source node. The full-rate distributed type multi-antenna bi-directional wireless cooperative relay transmission method has the advantages that the expansibility is good, an encoding process is simple and easy to design, full-rate transmission can be achieved, the detection complexity is low, and very high application value is achieved.
Owner:ANHUI UNIVERSITY
Switching device for refrigerator
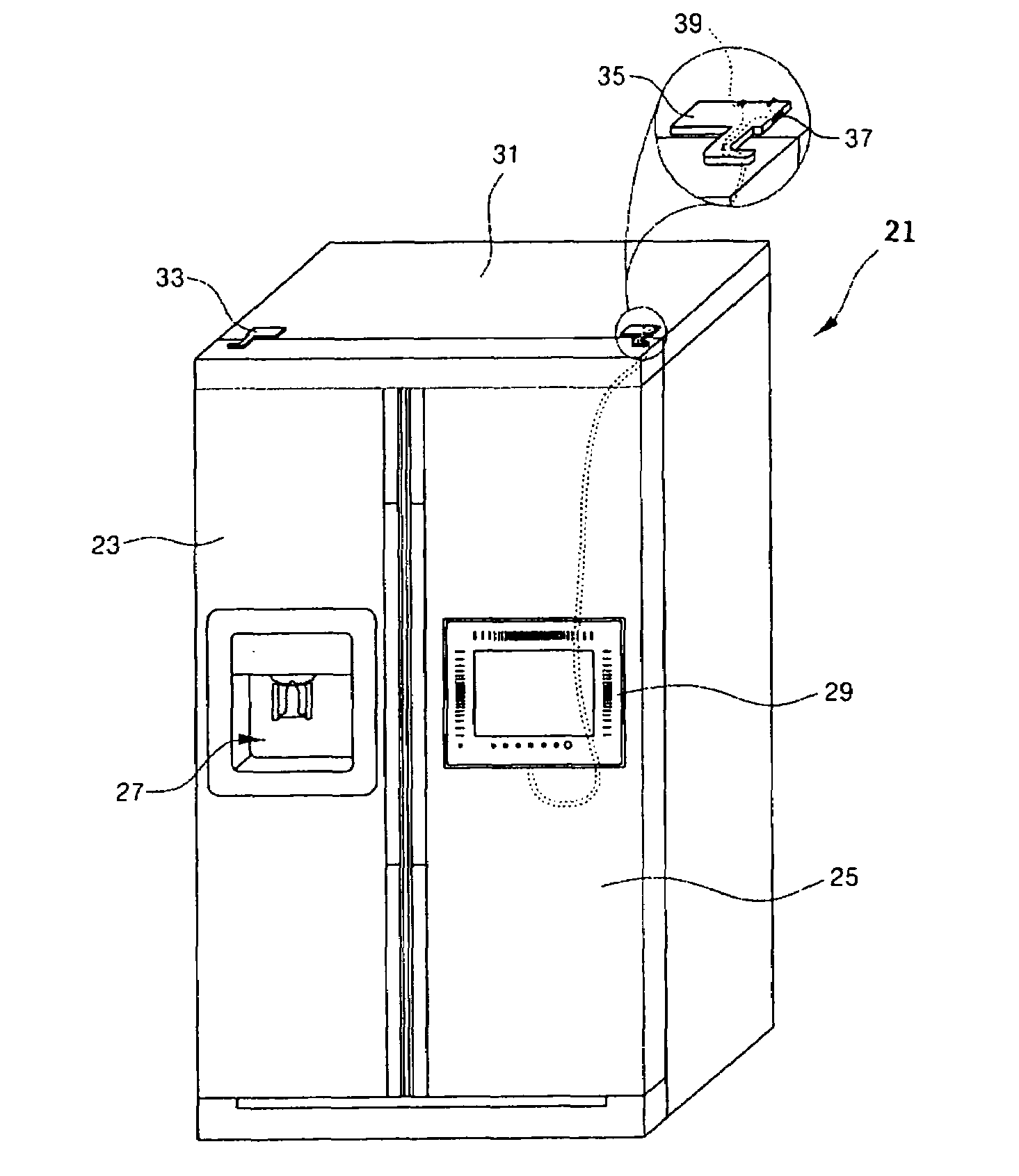
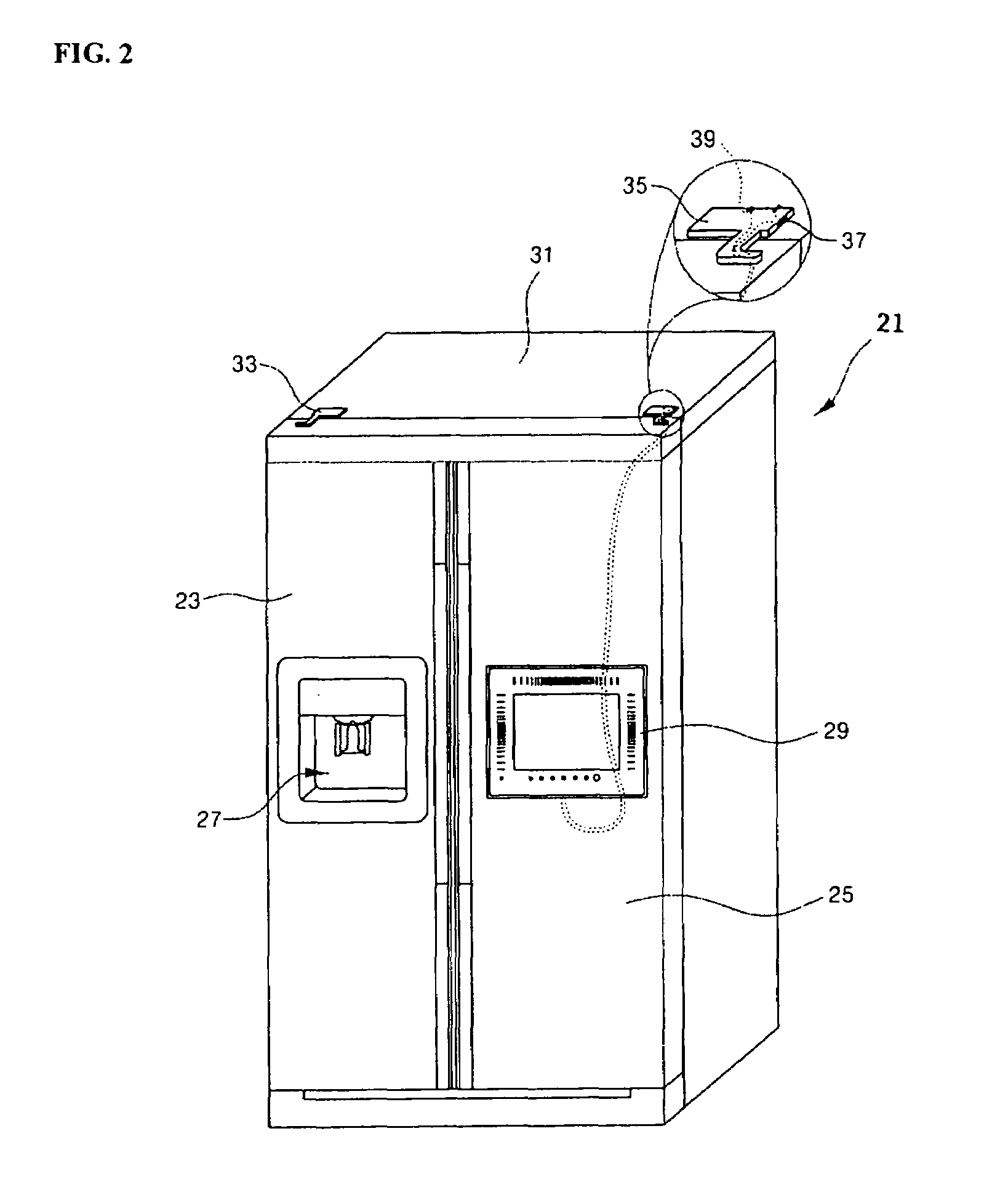
ActiveUS7266963B2Good lookingLighting and heating apparatusBuilding locksPower switchingDisplay device
A switching device for an integrated product, such as a display, installed on a front surface of a door of a refrigerator is provided. The switching device includes a hinge assembly which rotatably couples the door to the refrigerator. The hinge assembly includes a power switch that applies power to the display, and a connector that connects the display to an external signaling / communication source. The switch may be provided on a lateral surface of a hinge plate portion of the assembly, and the connector may be provided on a rear surface of the hinge plate. The power switch and the connector may be connected to the display by lead wires.
Owner:LG ELECTRONICS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com