Patents
Literature
206473results about "Data switching networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
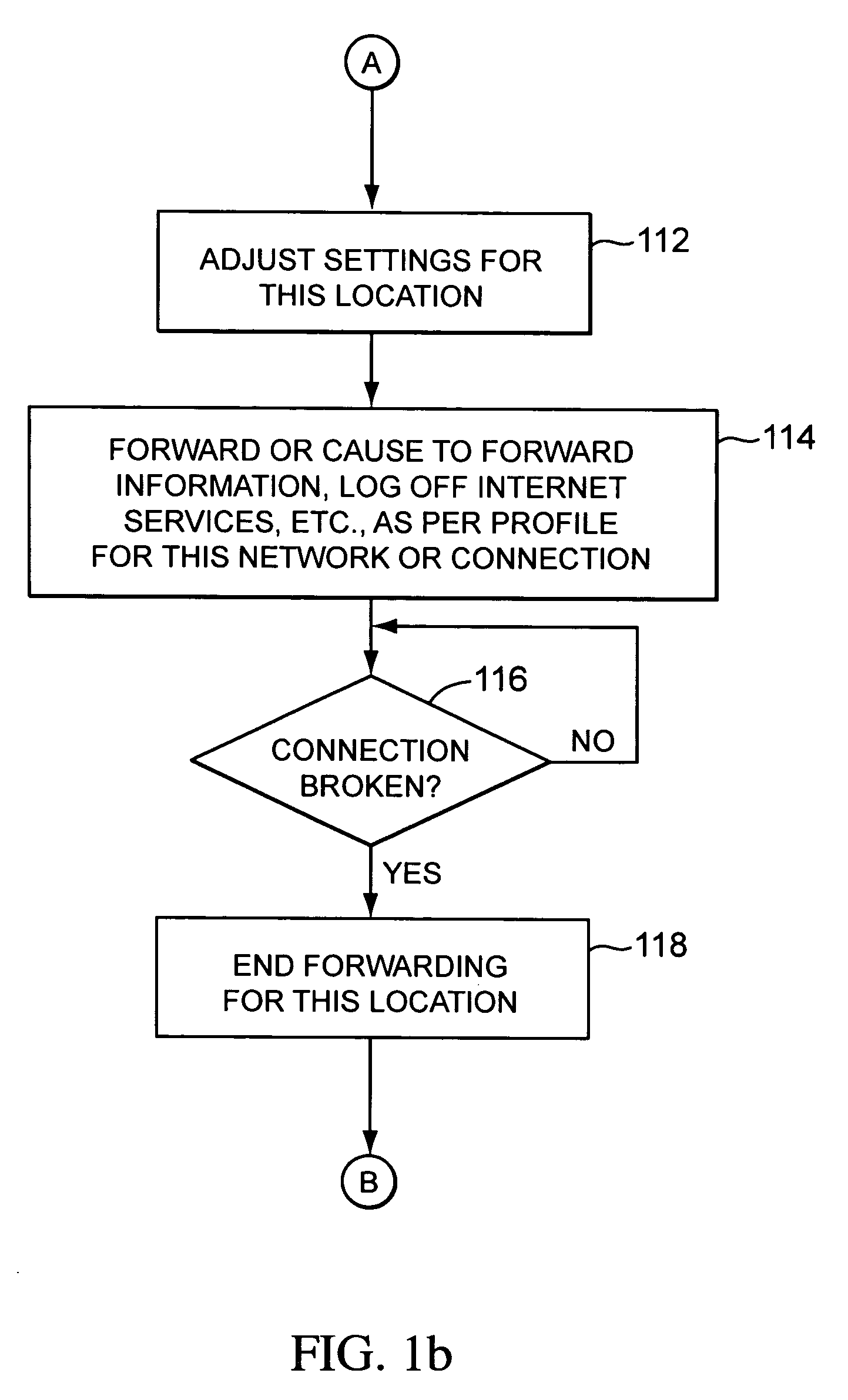
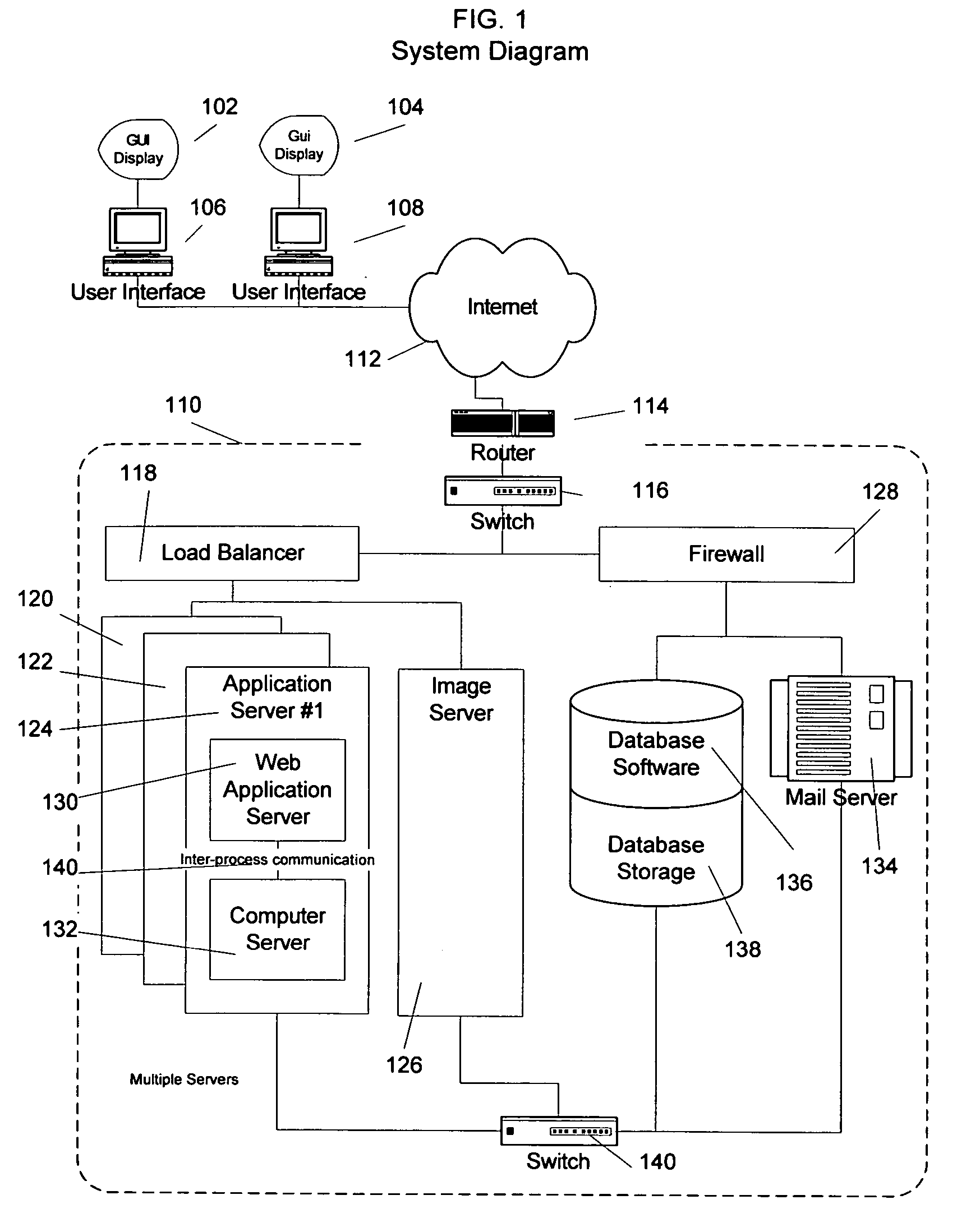
System for establishing plan to test components of web based framework by displaying pictorial representation and conveying indicia coded components of existing network framework
A system, method, and article of manufacture are provided for planning the testing of components of an existing network framework. First, a pictorial representation of an existing network framework is displayed along with a plurality of components of the existing network framework. Thereafter, the components of the existing network framework are indicia coded in order to convey a plan by which the components of the existing network framework are to be tested. The components may be indicia coded in order to convey an order of the testing or which components of the existing network framework are to be tested.
Owner:ACCENTURE GLOBAL SERVICES LTD
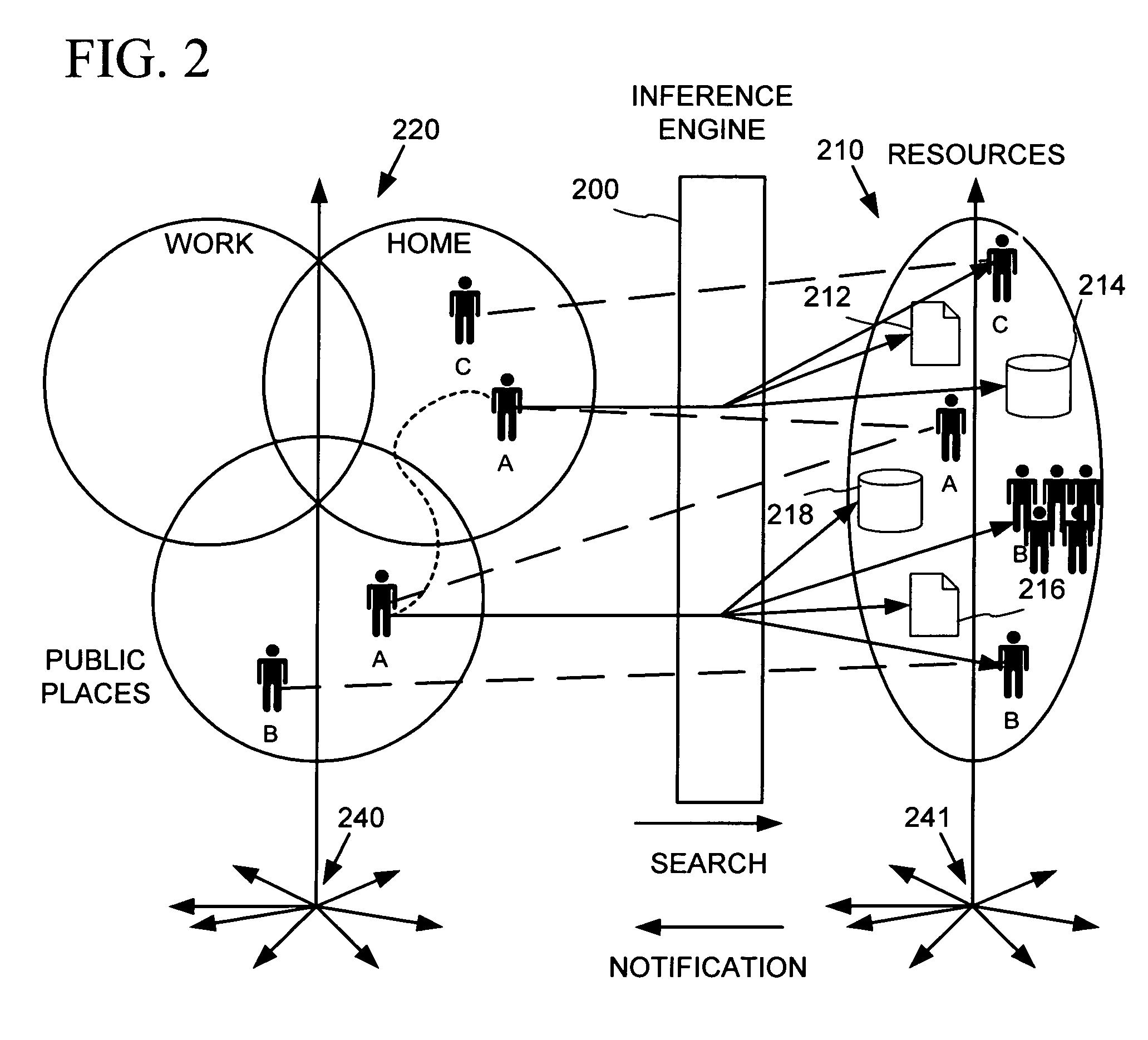
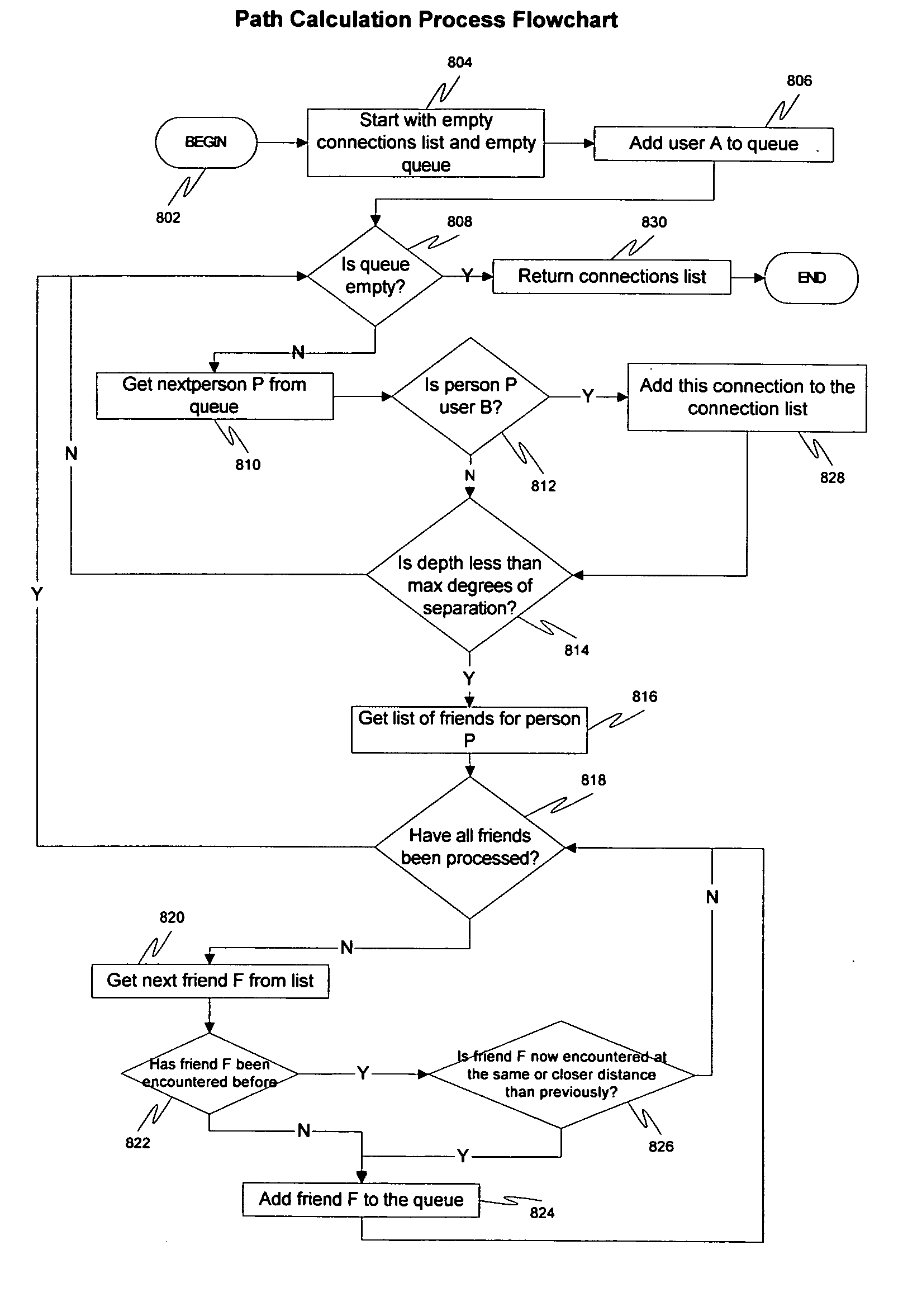
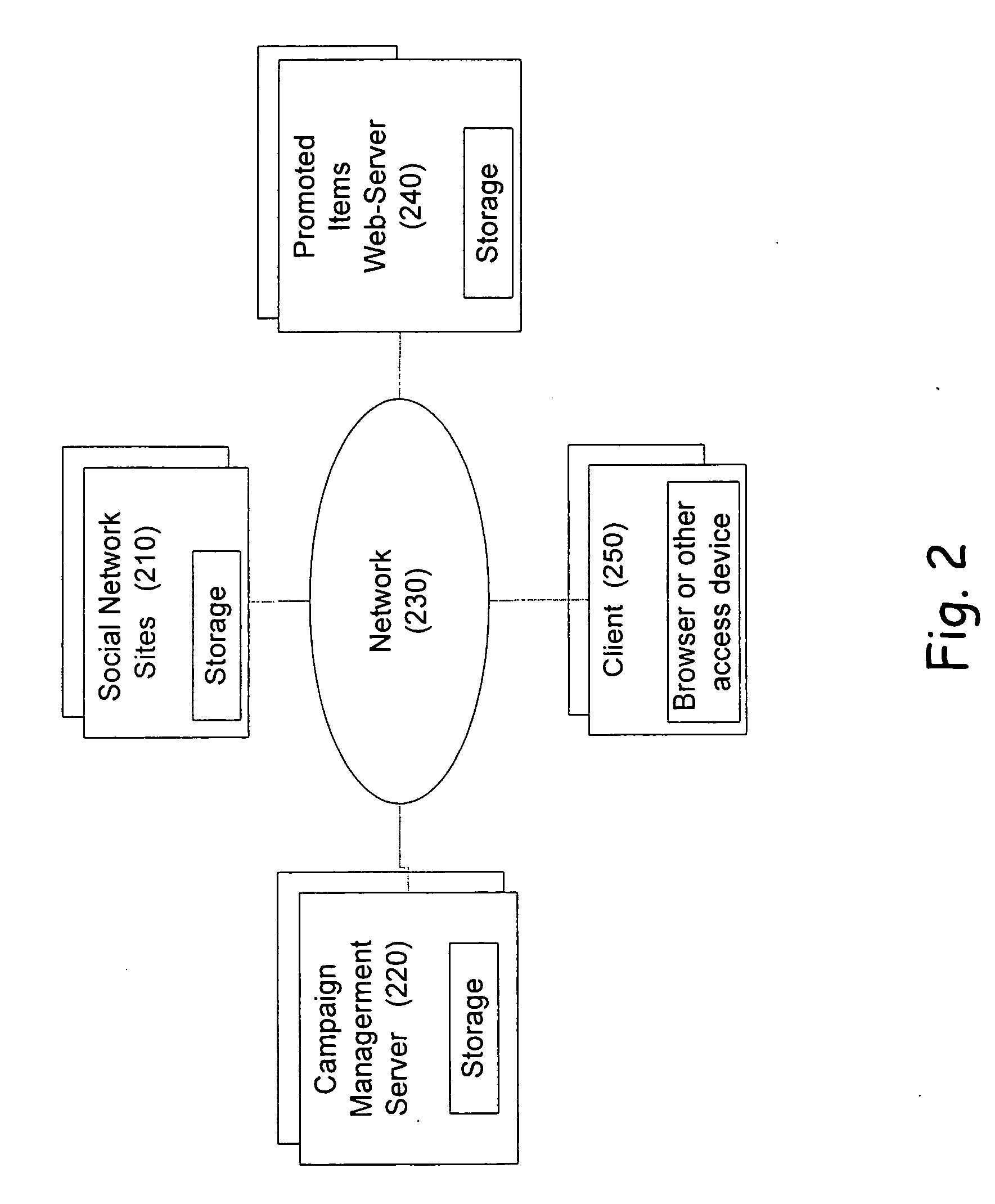
System, method and apparatus for connecting users in an online computer system based on their relationships within social networks
InactiveUS7069308B2Enhanced interactionIncrease valueMultiple digital computer combinationsOffice automationComputerized systemSocial network
A method and apparatus for calculating, displaying and acting upon relationships in a social network is described. A computer system collects descriptive data about various individuals and allows those individuals to indicate other individuals with whom they have a personal relationship. The descriptive data and the relationship data are integrated and processed to reveal the series of social relationships connecting any two individuals within a social network. The pathways connecting any two individuals can be displayed. Further, the social network itself can be displayed to any number of degrees of separation. A user of the system can determine the optimal relationship path (i.e., contact pathway) to reach desired individuals. A communications tool allows individuals in the system to be introduced (or introduce themselves) and initiate direct communication.
Owner:META PLATFORMS INC
Centrifugal communication and collaboration method
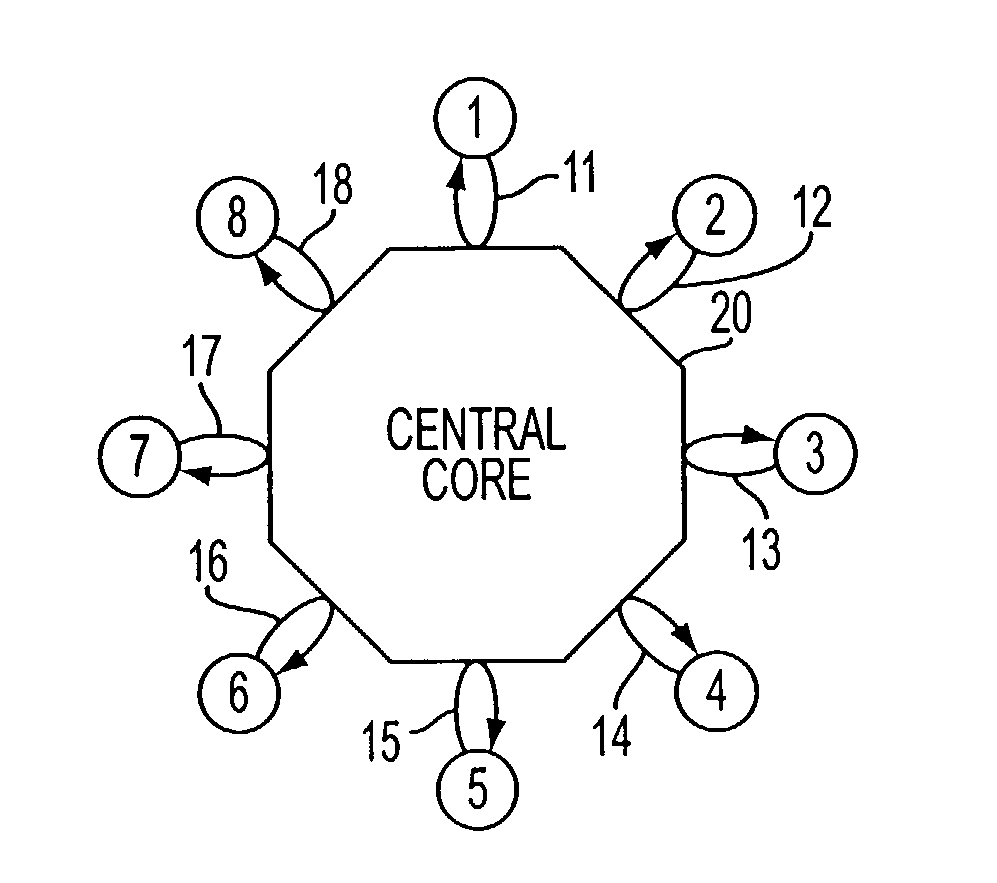
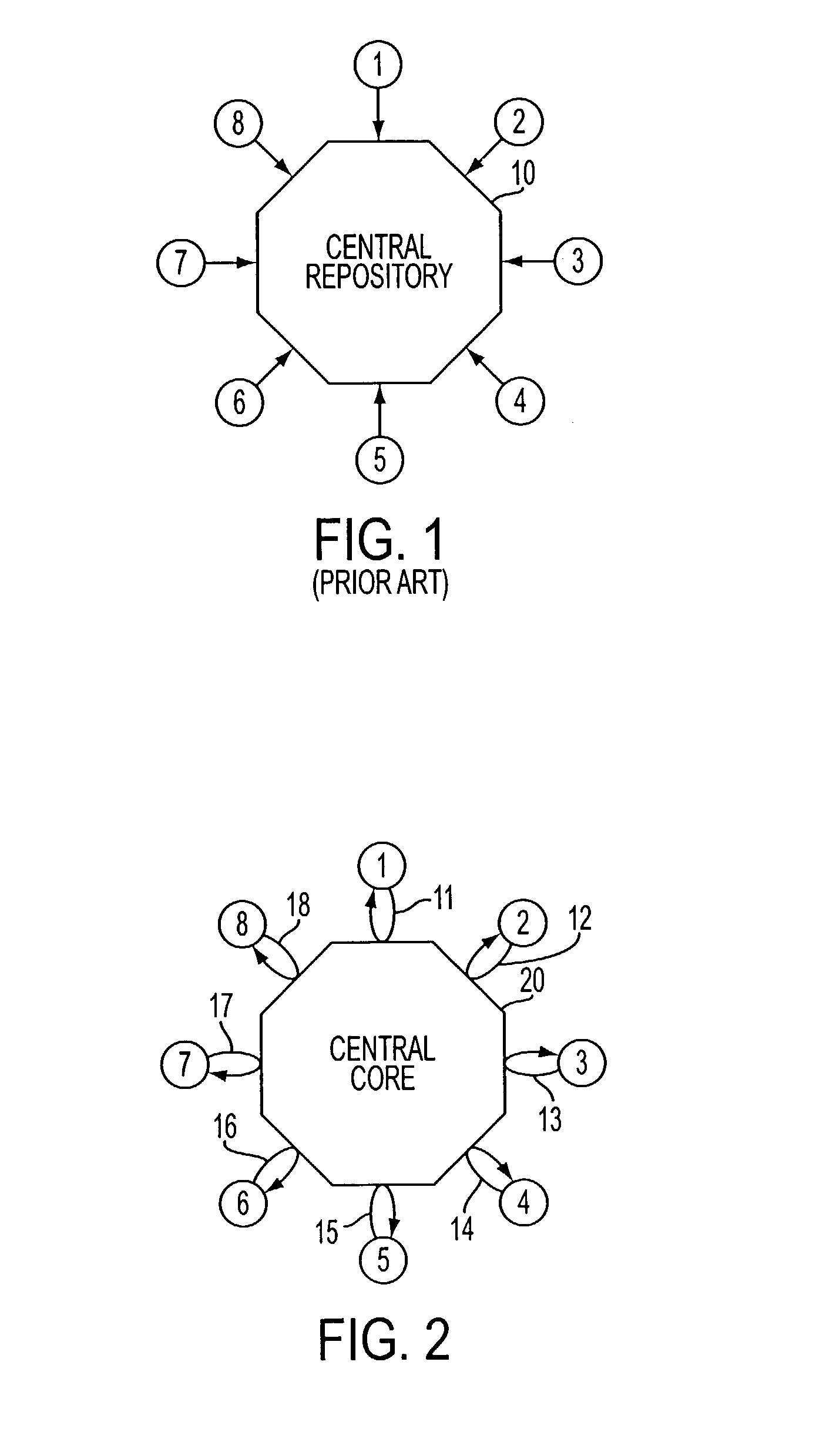
InactiveUS8015495B2Improve abilitiesBetter, cheaper, and fasterOffice automationData switching networksTelecommunicationsBiological activation
A method of facilitating communications and collaboration of a group of plural remote participants comprises steps of receiving information over an information communications network from a first group participant; pushing, over the network to at least one other group participant, an access via an access channel; and allowing the other group participant to access at least some of the received information via said access channel in response to selective activation of the access channel by the other group participant.
Owner:SAMPO IP
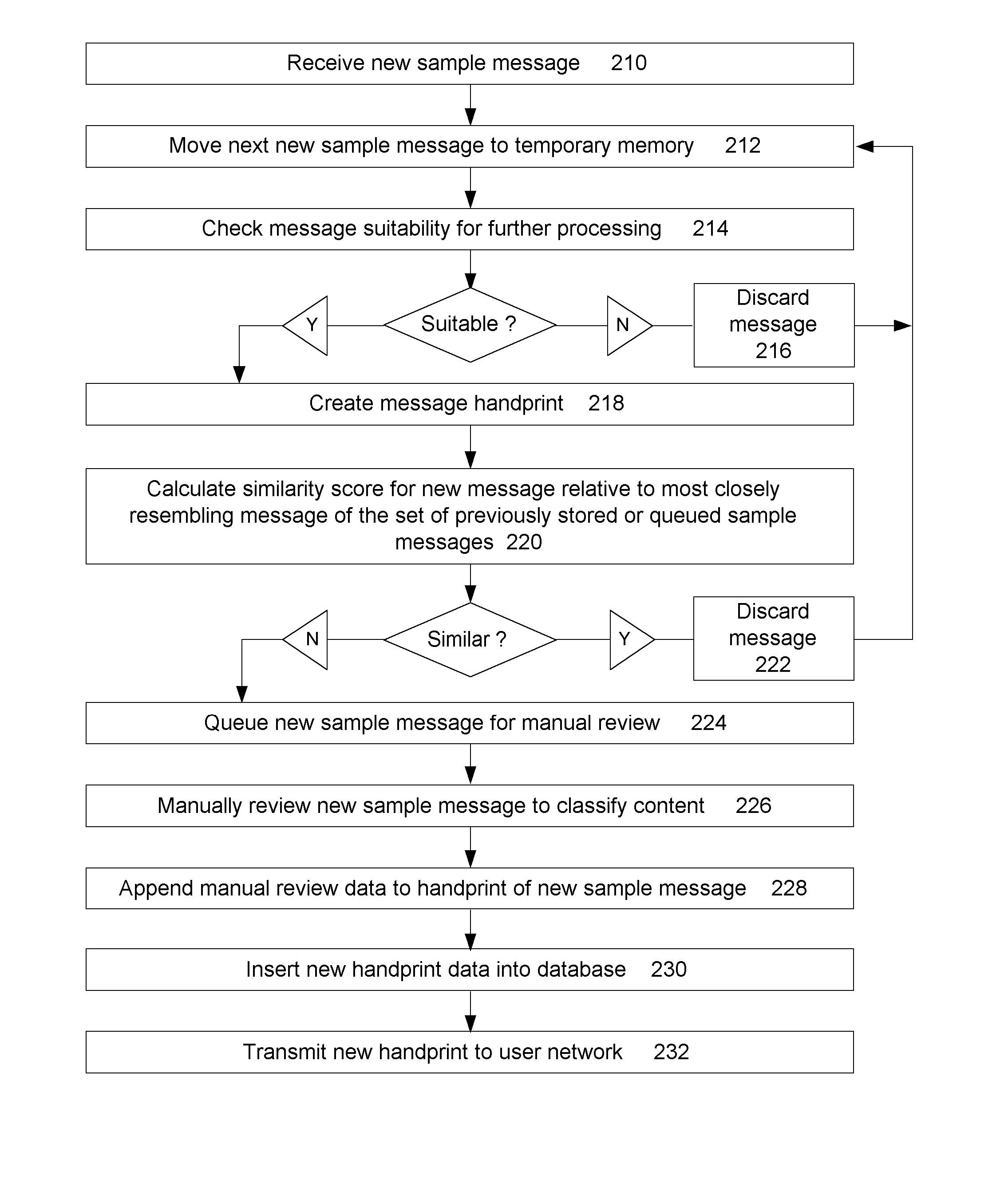
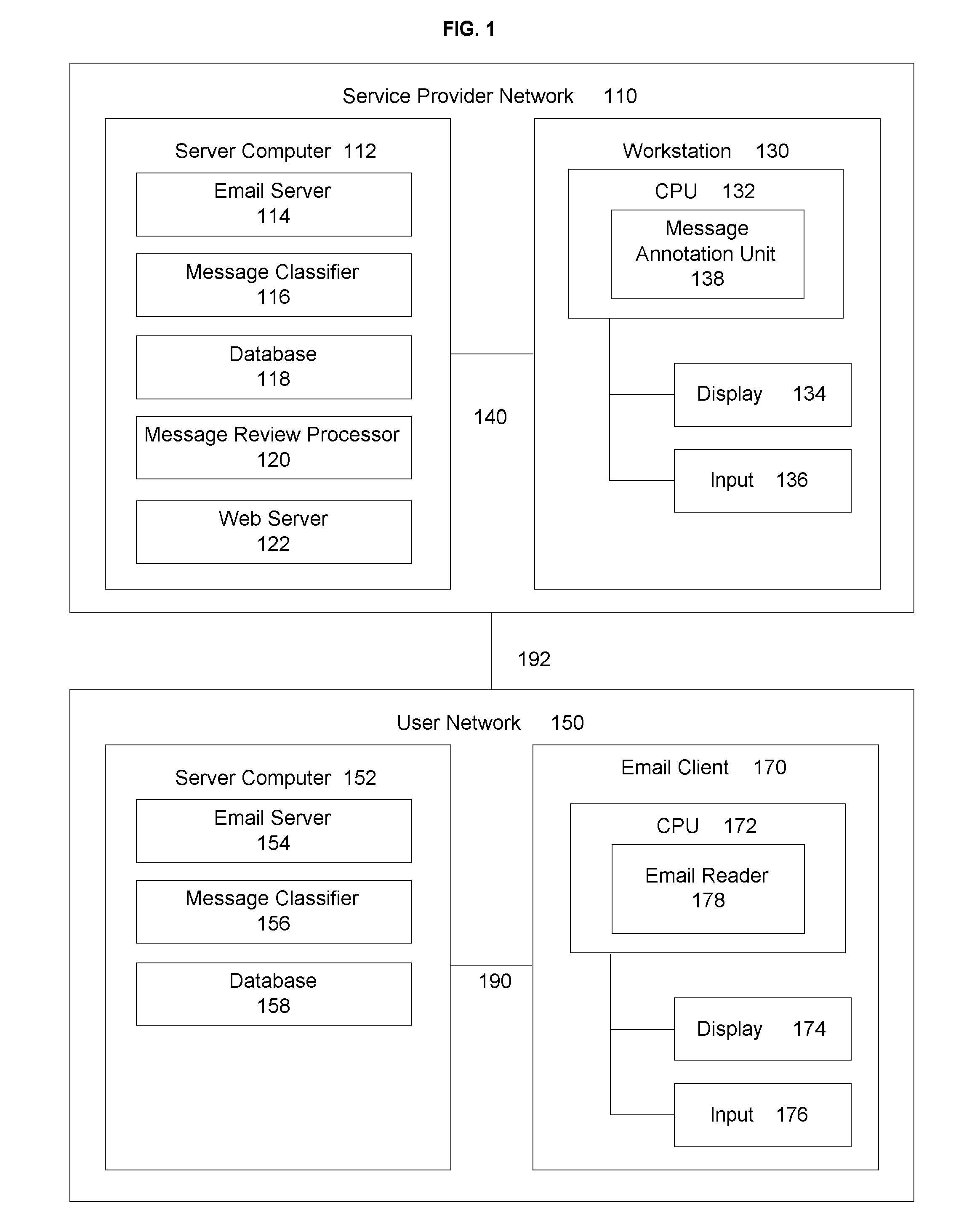
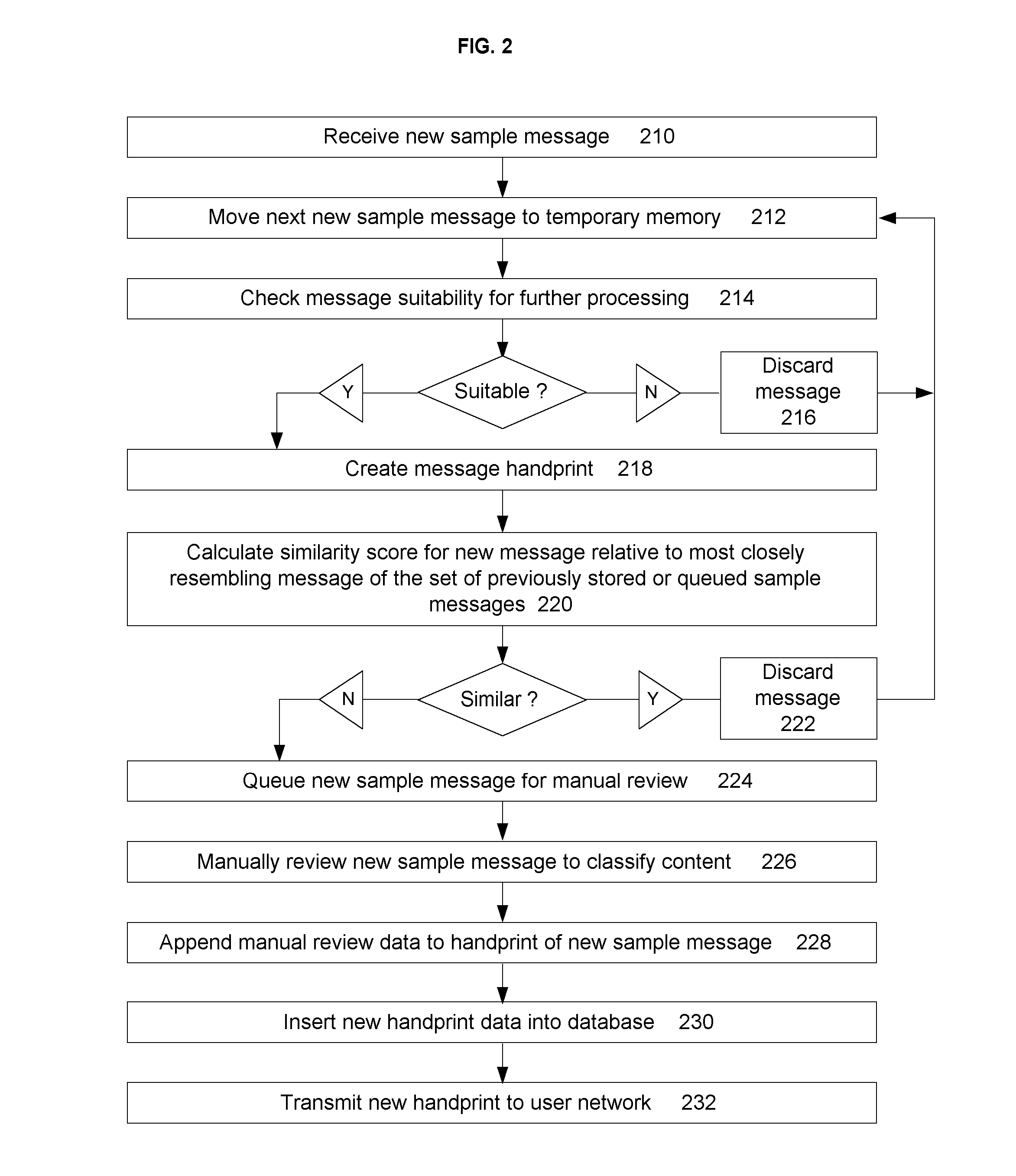
Document similarity detection and classification system
InactiveUS20050060643A1Natural language data processingData switching networksDocument similarityDocument preparation
A document similarity detection and classification system is presented. The system employs a case-based method of classifying electronically distributed documents in which content chunks of an unclassified document are compared to the sets of content chunks comprising each of a set of previously classified sample documents in order to determine a highest level of resemblance between an unclassified document and any of a set of previously classified documents. The sample documents have been manually reviewed and annotated to distinguish document classifications and to distinguish significant content chunks from insignificant content chunks. These annotations are used in the similarity comparison process. If a significant resemblance level exceeding a predetermined threshold is detected, the classification of the most significantly resembling sample document is assigned to the unclassified document. Sample documents may be acquired to build and maintain a repository of sample documents by detecting unclassified documents that are similar to other unclassified documents and subjecting at least some similar documents to a manual review and classification process. In a preferred embodiment the invention may be used to classify email messages in support of a message filtering or classification objective.
Owner:GLASS JEFFREY B MR
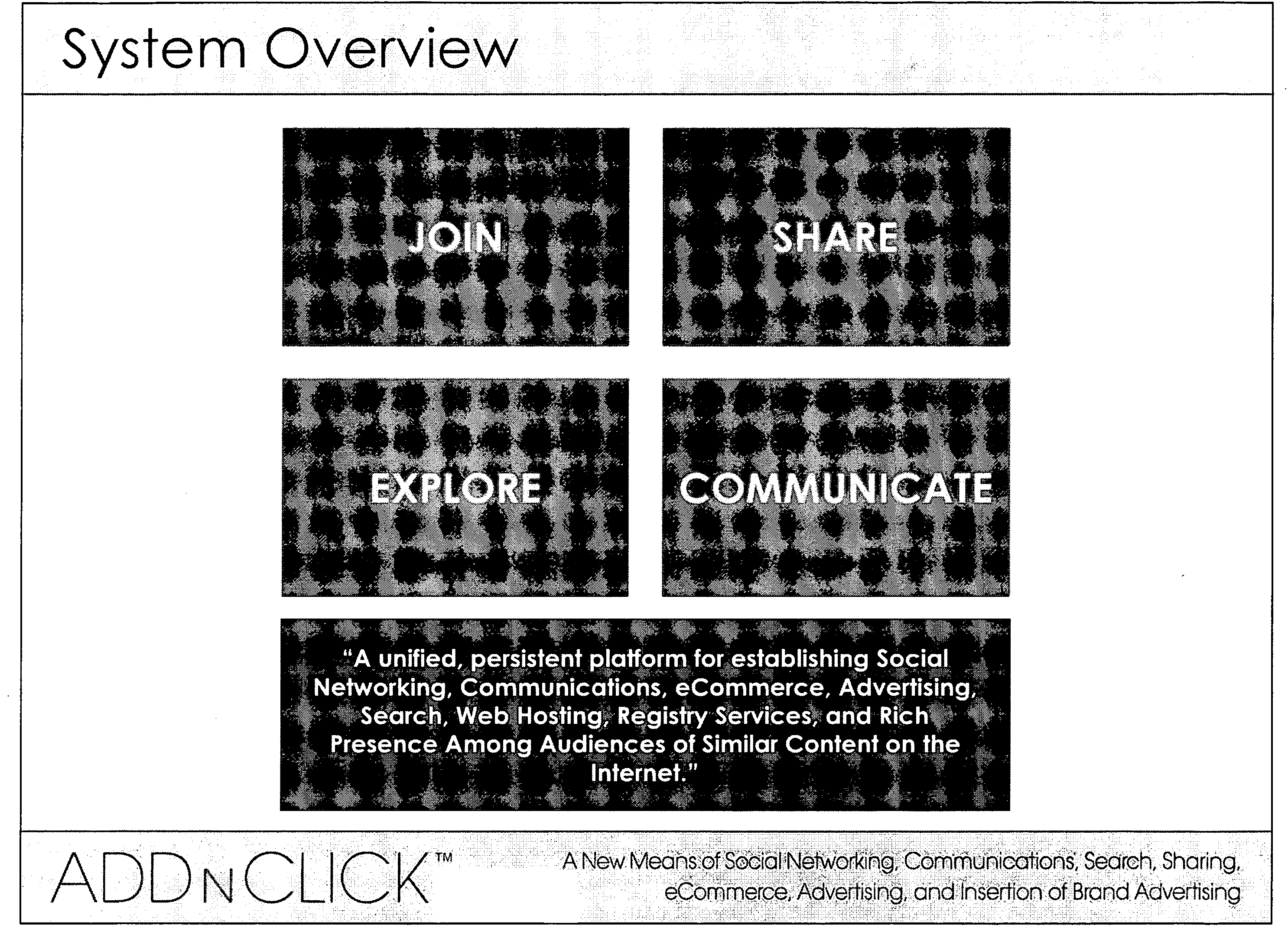
Using internet content as a means to establish live social networks by linking internet users to each other who are simultaneously engaged in the same and/or similar content
ActiveUS20080222295A1Low costReduced flexibilityMultiple digital computer combinationsOffice automationPush and pullInternet content
A system and method that uses internet content and / or content metadata as a means to establish social networks. Examples include linking internet users, searchers, viewers and / or listeners of the same and / or similar internet content to each other via a platform that enables any of the following in n-dimensional environments: social networking, communications, sharing, e-commerce, advertising, search, hosting and registry services, push and pull applications, anonymous communications, and rich presence.
Owner:NEONEKT LLC
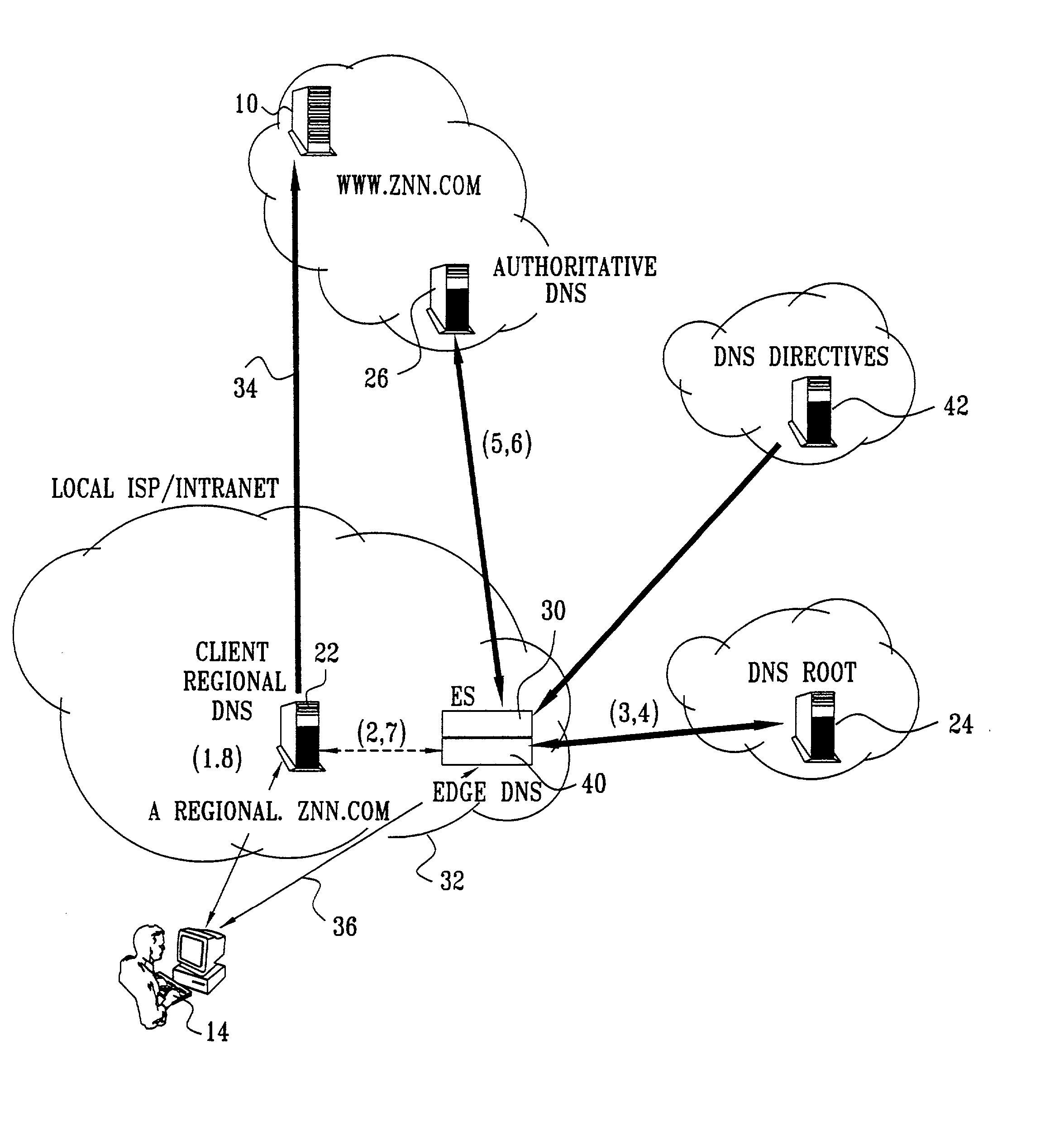
Differentiated content and application delivery via internet
InactiveUS20020010798A1Multiple digital computer combinationsWebsite content managementScalable systemEdge server
A technique for centralized and differentiated content and application delivery system allows content providers to directly control the delivery of content based on regional and temporal preferences, client identity and content priority. A scalable system is provided in an extensible framework for edge services, employing a combination of a flexible profile definition language and an open edge server architecture in order to add new and unforeseen services on demand. In one or more edge servers content providers are allocated dedicated resources, which are not affected by the demand or the delivery characteristics of other content providers. Each content provider can differentiate different local delivery resources within its global allocation. Since the per-site resources are guaranteed, intra-site differentiation can be guaranteed. Administrative resources are provided to dynamically adjust service policies of the edge servers.
Owner:CISCO TECH INC
Realtime, location-based cell phone enhancements, uses, and applications
ActiveUS20070032225A1Use minimizedMaximizing its battery powerMechanical apparatusLighting and heating apparatusMethod selectionComputer science
Enhancements of and to cell phone operations are based in whole or in part on determining the location of the cell phone. Systems and methods select and determine locations or areas of importance or relevance, and based on that information and other programmed factors affect or alter the operations of the cell phone. While the systems and methods are illustrated by use of cell phone embodiments and applications, they are equally applicable to virtually any portable or mobile communication device, including for example, wireless laptop computers and PDAs.
Owner:RESIGHT LLC
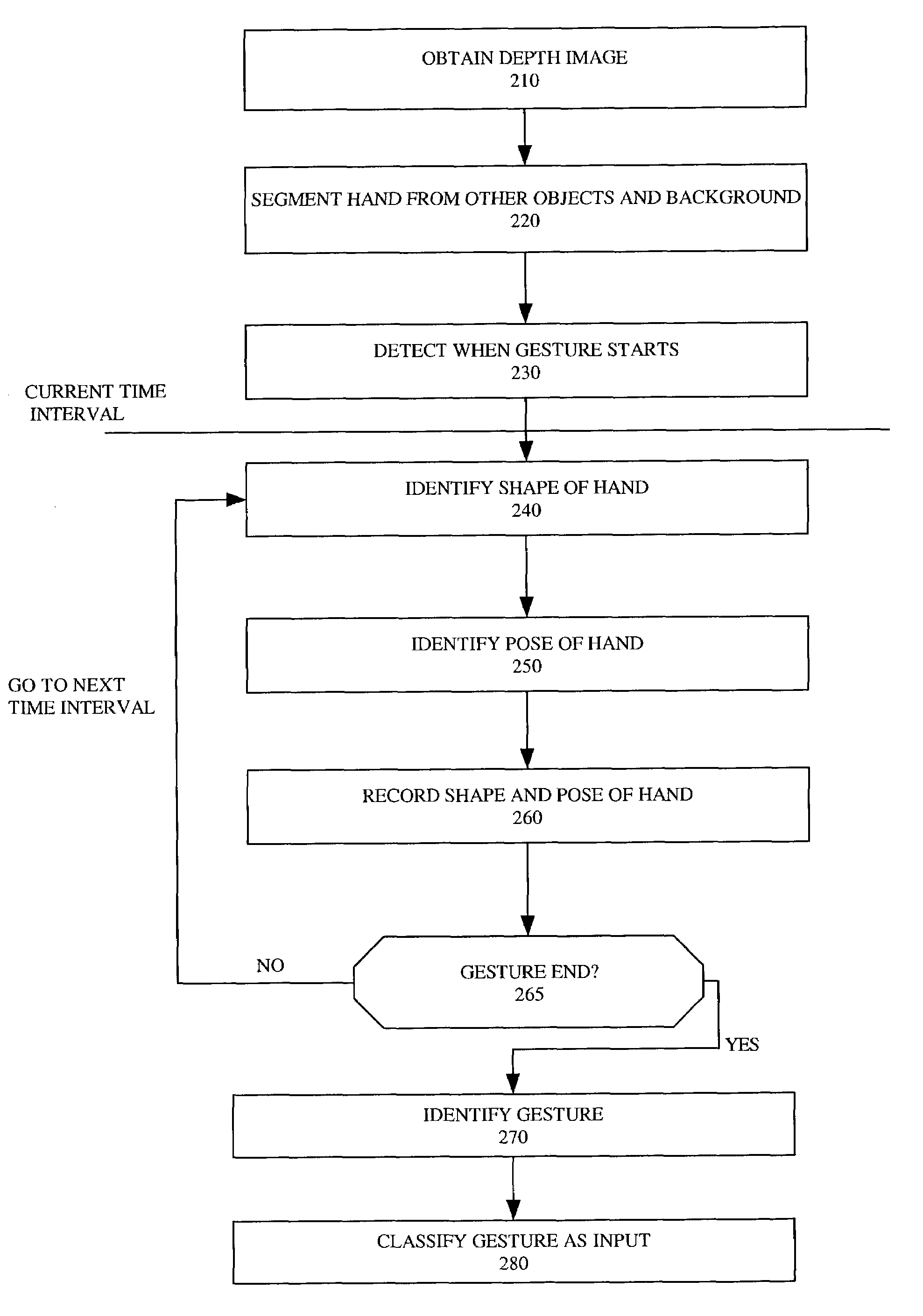
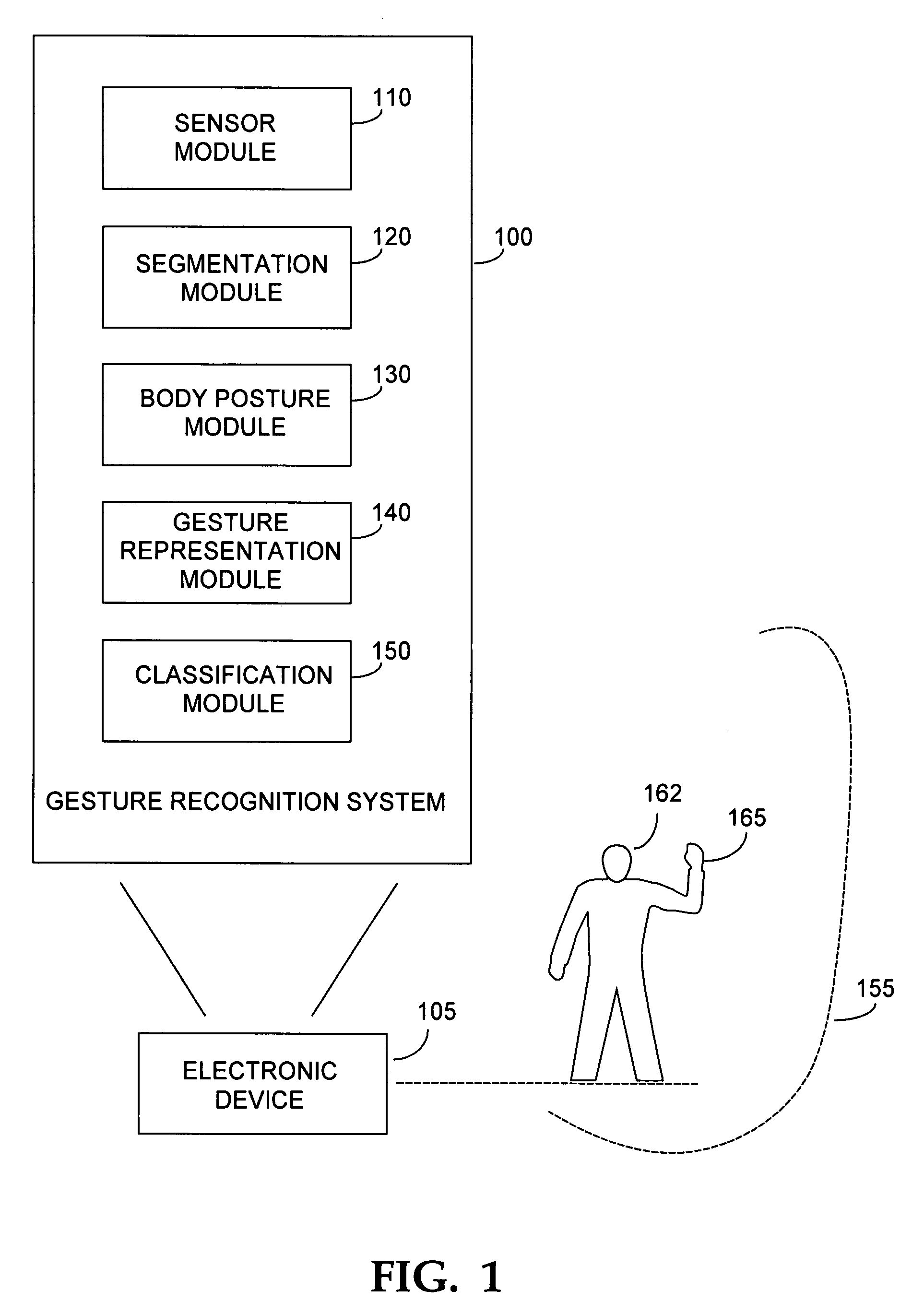
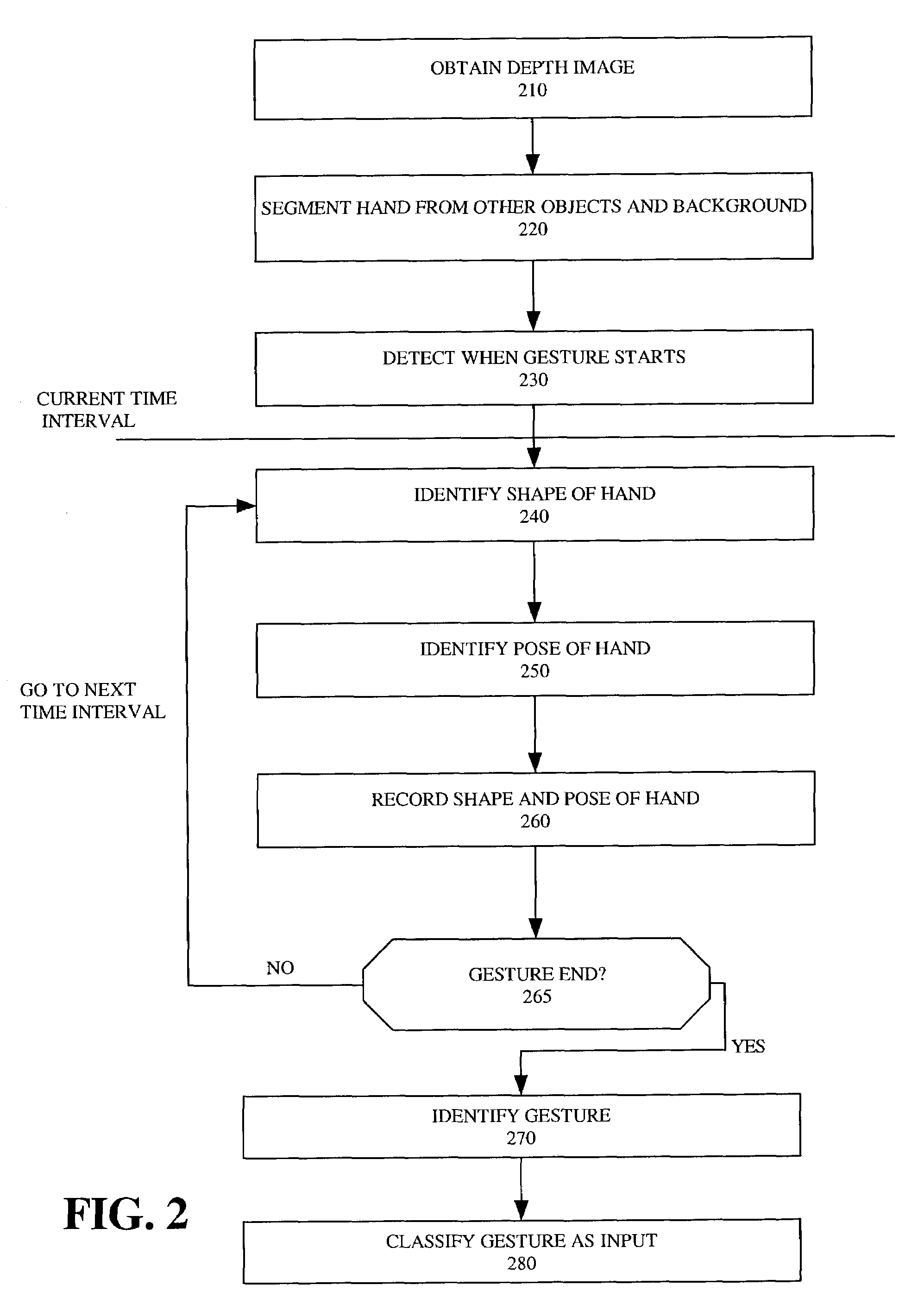
Gesture recognition system using depth perceptive sensors
ActiveUS7340077B2Input/output for user-computer interactionIndoor gamesPhysical medicine and rehabilitationPhysical therapy
Owner:MICROSOFT TECH LICENSING LLC
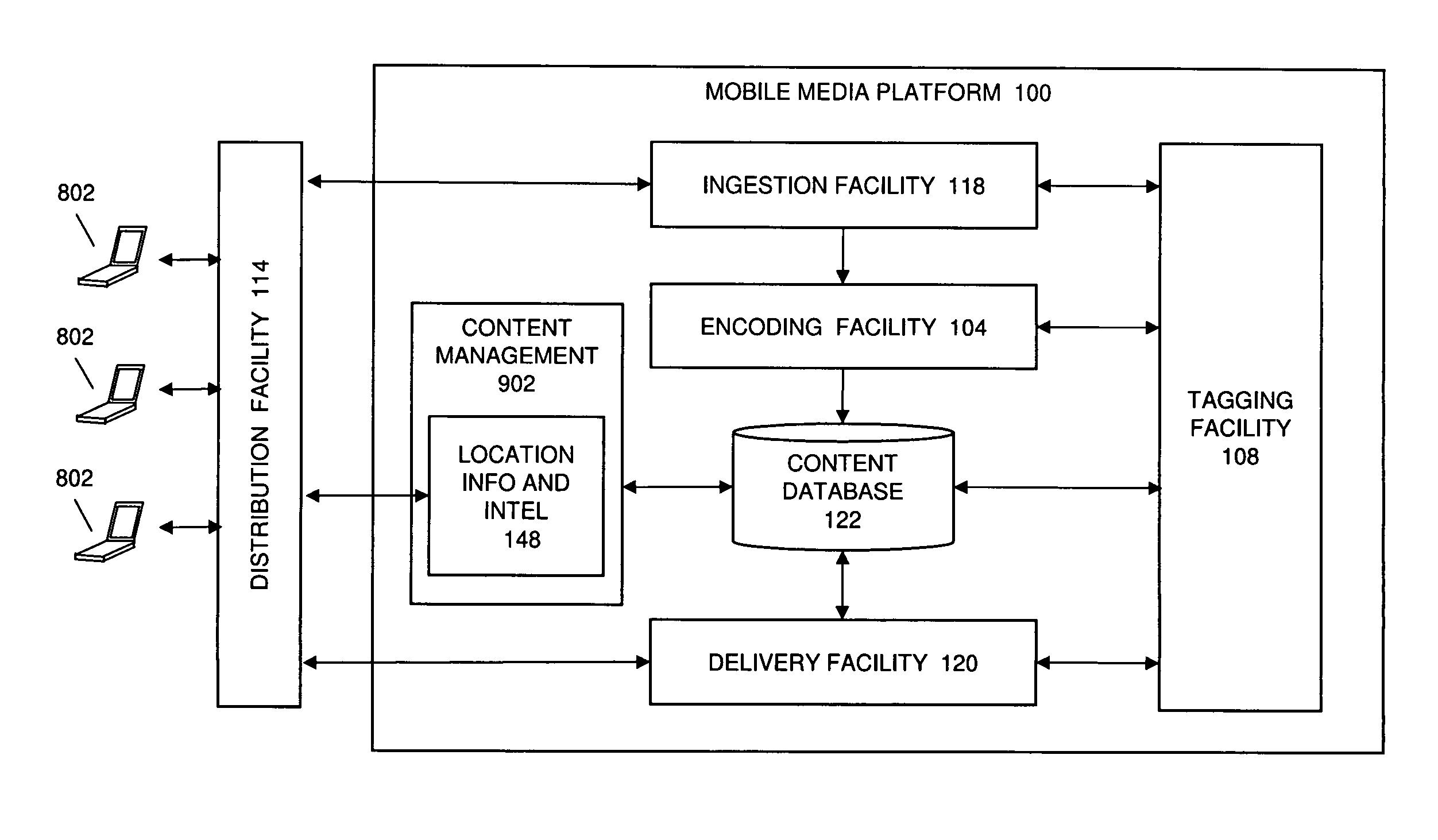
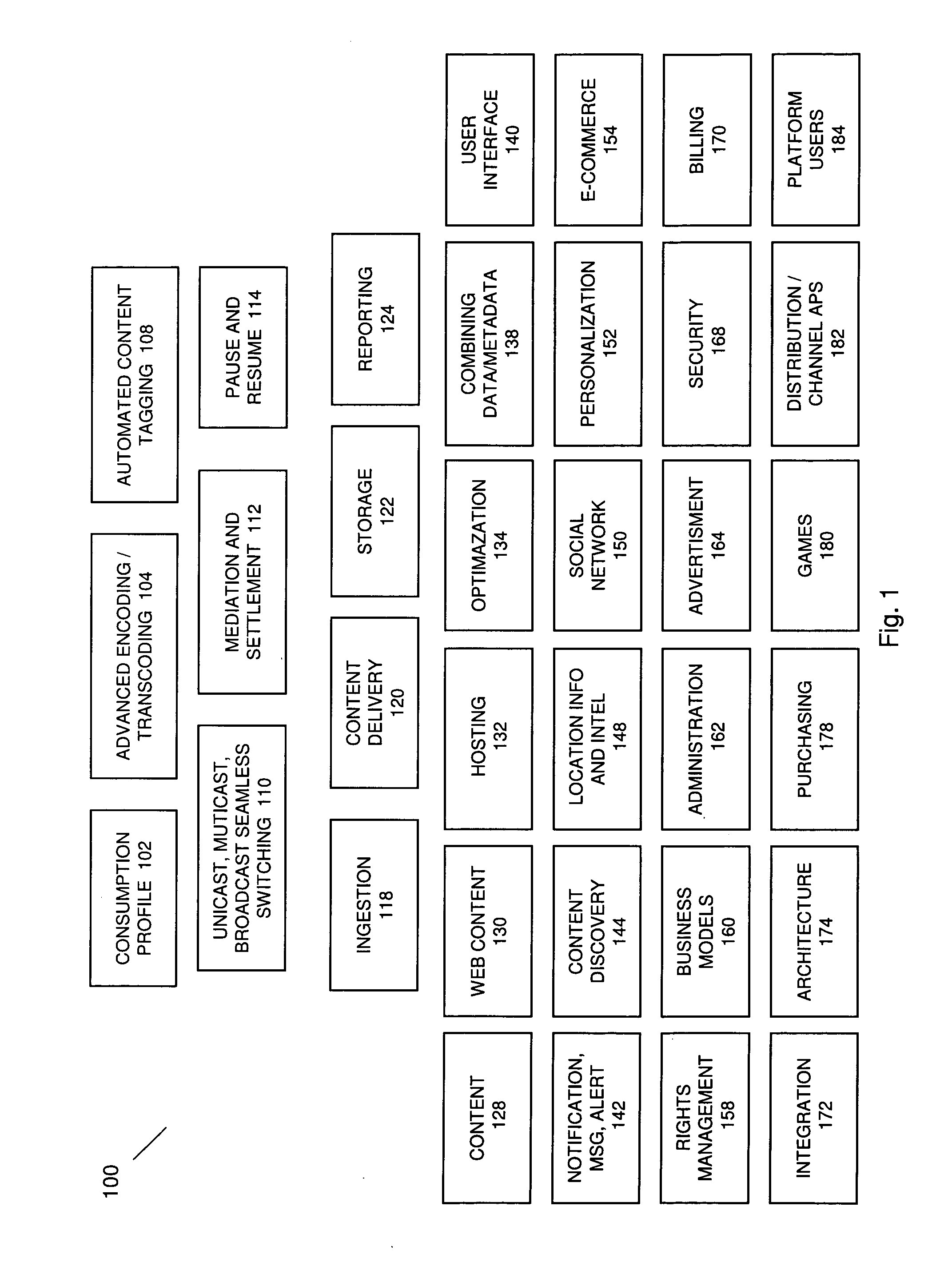
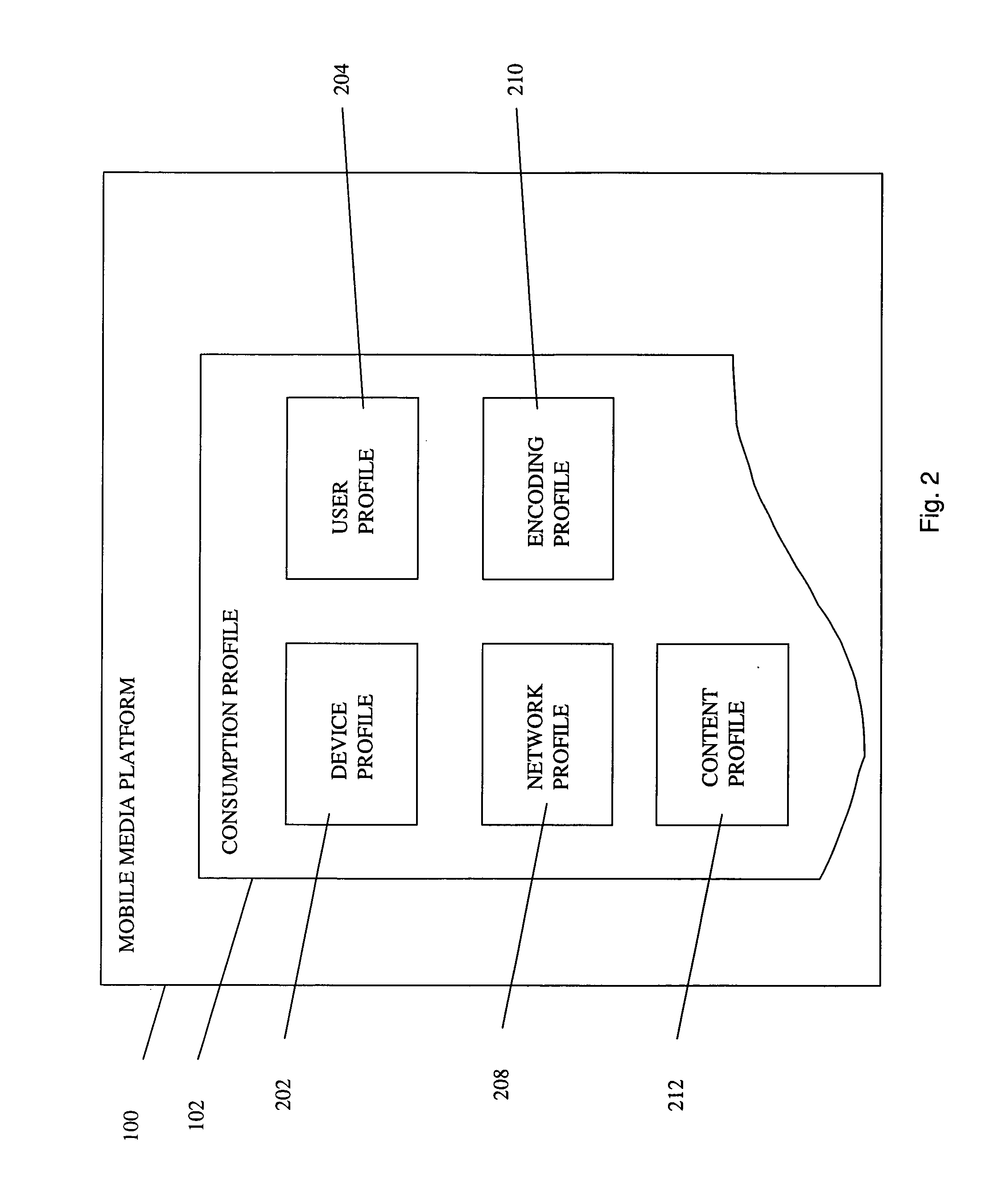
Automated Content Tag Processing for Mobile Media
InactiveUS20080195664A1Facilitating access to contentOptimization of content deliveryAdvertisementsDigital data processing detailsMobile deviceMobile media
In embodiments, the present invention provides a method and system for delivery of content on a mobile media platform, providing an automated tag processing facility, and delivering content to a mobile device, wherein content delivery is based at least in part on the automated tag processing.
Owner:THE DIRECTV GROUP
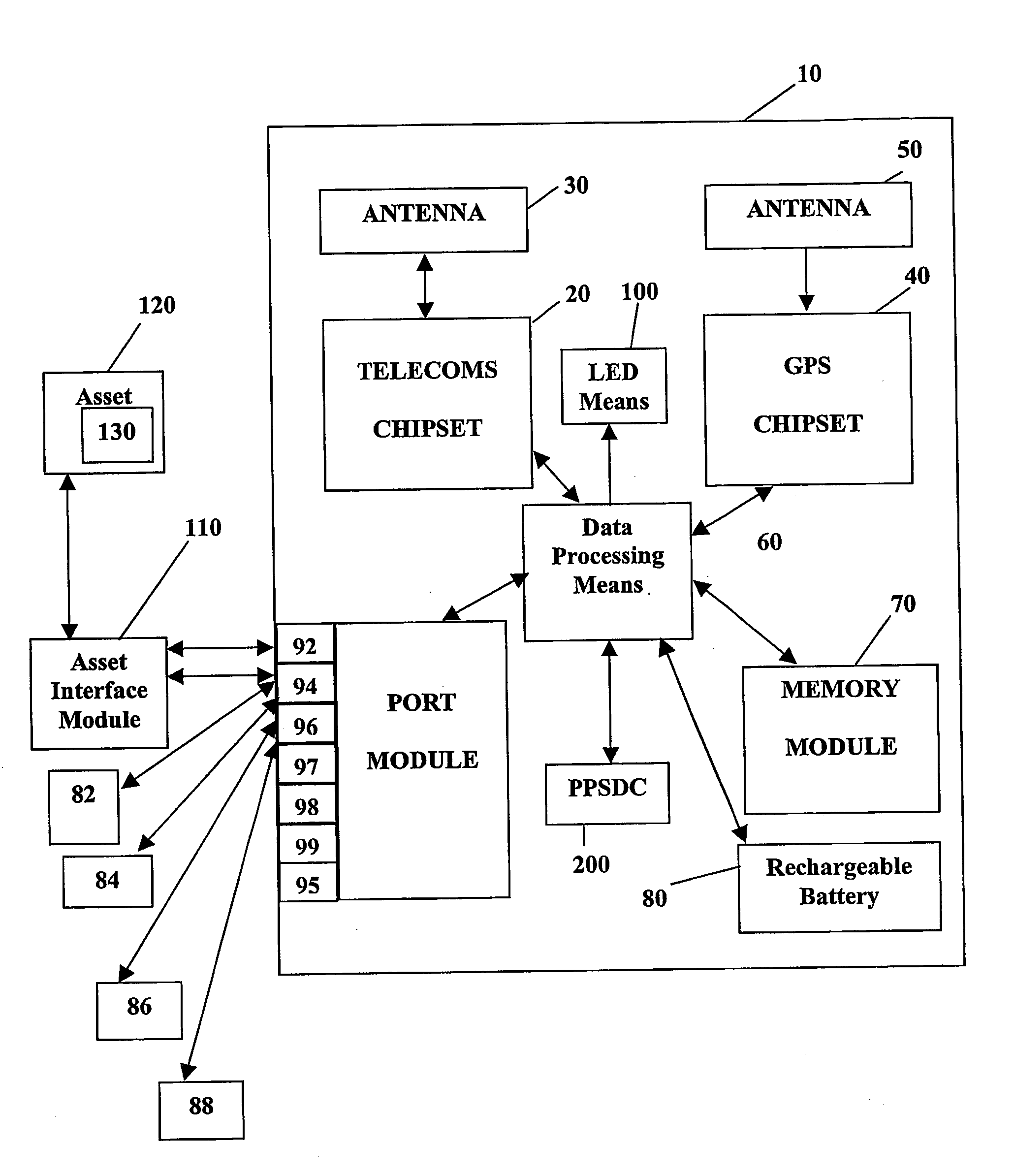
System and method for monitoring and control of wireless modules linked to assets
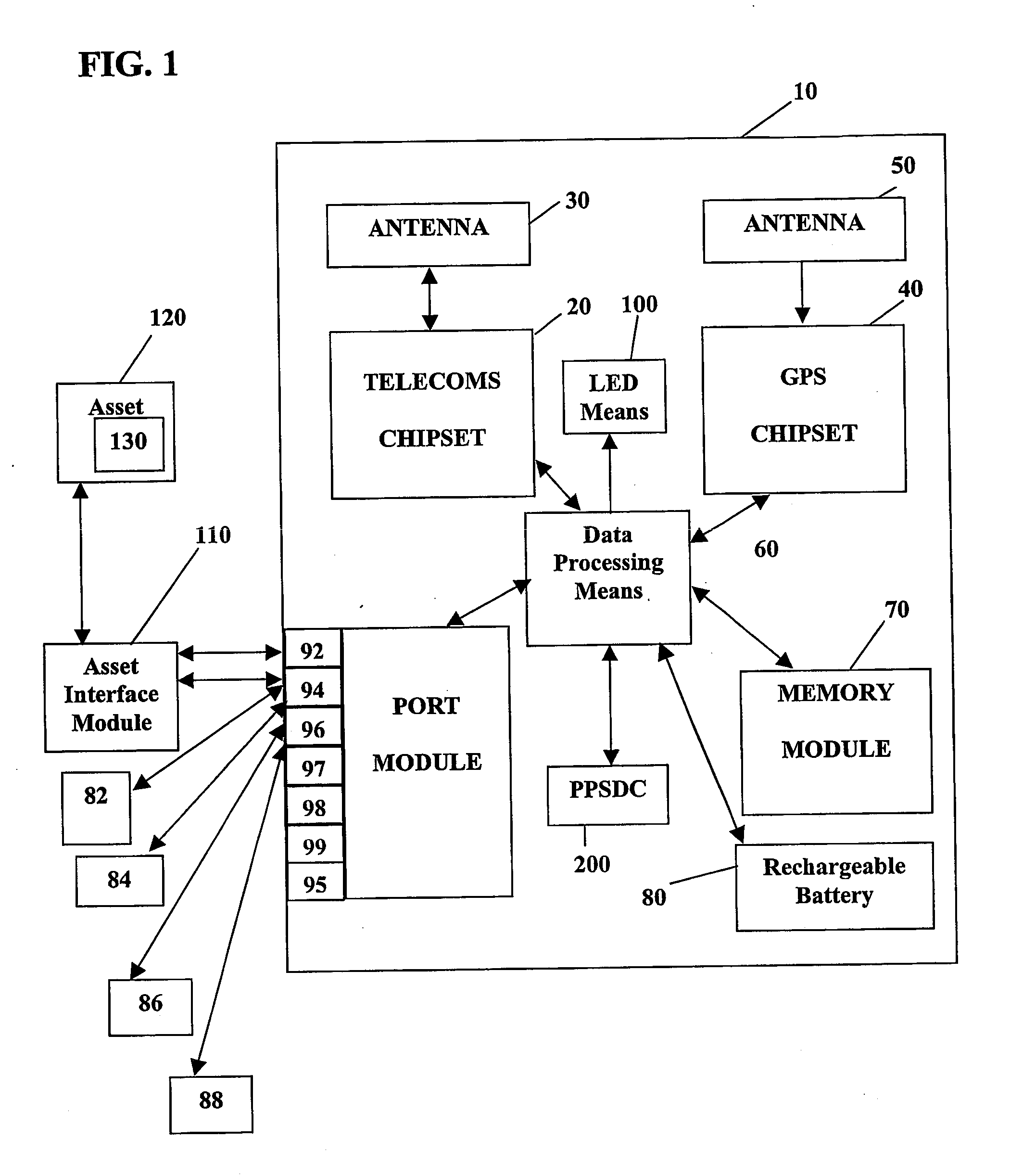
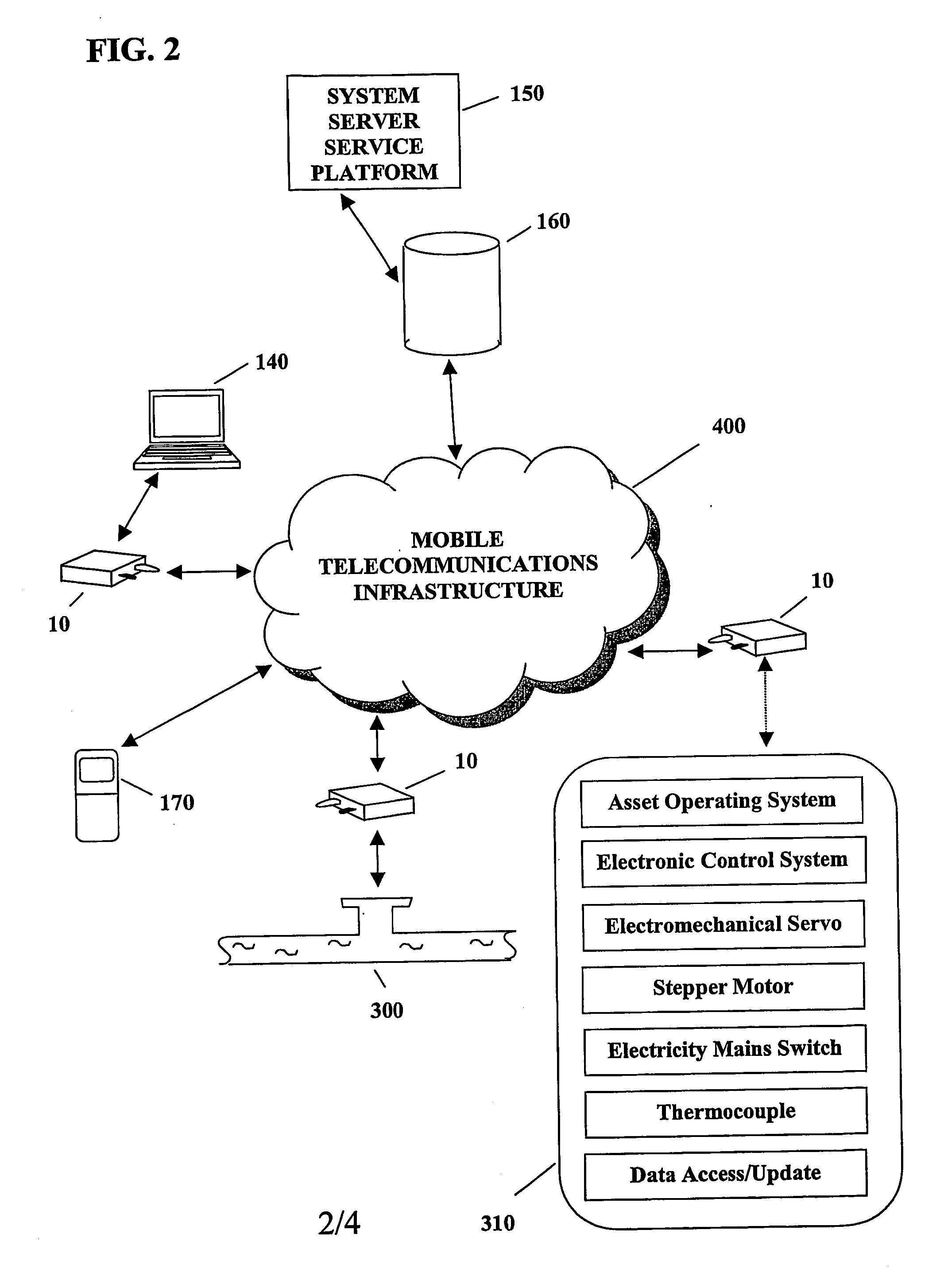
A system and method for remote asset management is described which can provide the basis for a diverse product group including an improved remote location monitoring system, a means for communicating with and for monitoring the status and or location of a plurality of diverse assets, as well as the means for communicating with said assets for the purpose of modifying the operational status of one or more of said assets according to one or more stored data parameters such as location, use, battery power, and such like. The remote asset management system comprise a wireless module, which is associated with at least one of the plurality of assets and which is interfaced with the operating system of said asset and or with an electromechanical control means, which may control one or more features of the operation of said assets. A supporting network-based, or internet-based service platform controls and manages the status of each of the plurality of assets, either automatically, or in response to received messages from fixed or wireless communication devices, and which is capable of selectively communicating data to said assets for changing the operational status of said assets according to pre-programmed conditions.
Owner:M2M SOLUTIONS
Television chat system
InactiveUS20050262542A1Television conference systemsAnalogue secracy/subscription systemsInteractive televisionTelevision equipment
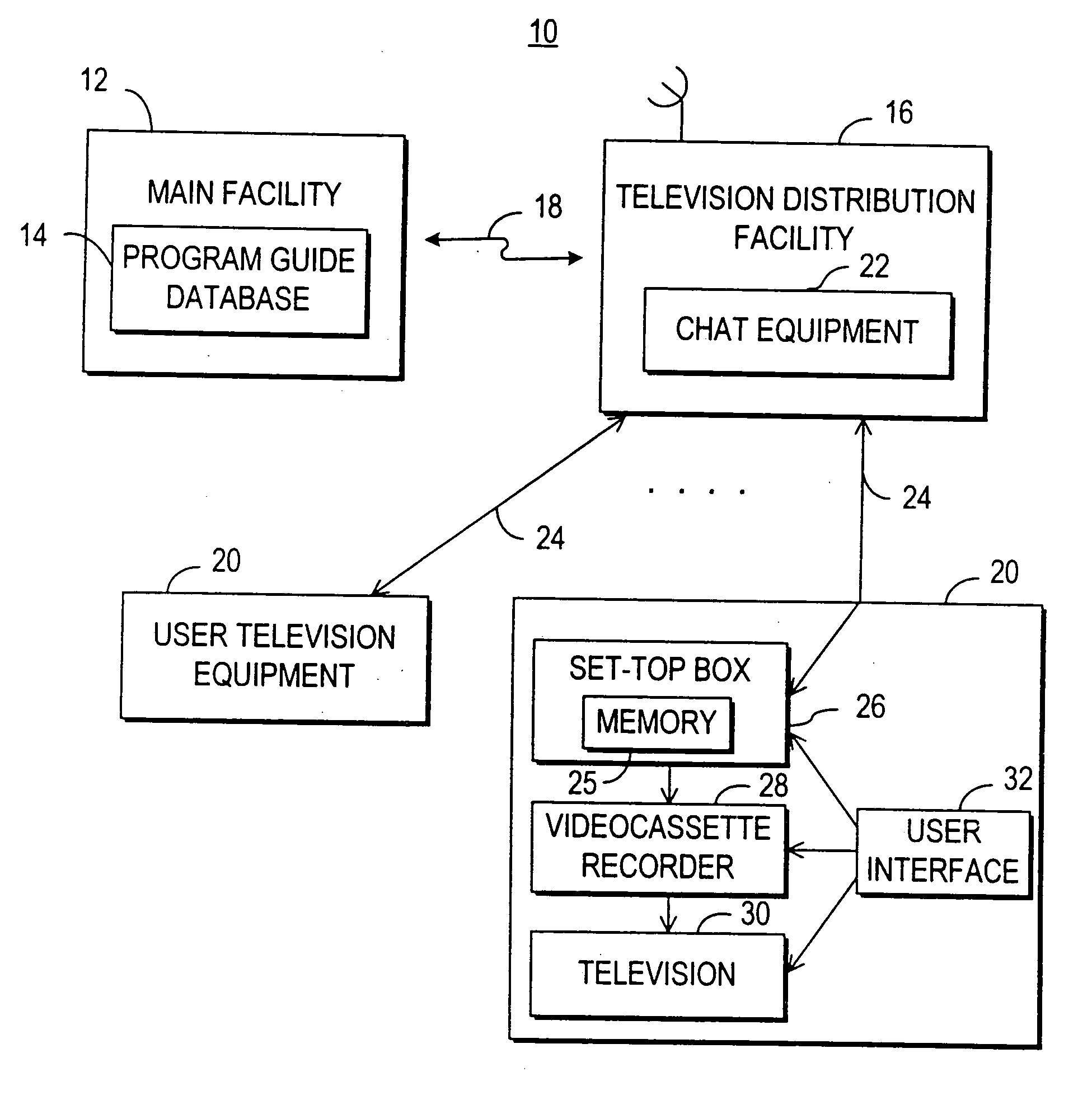
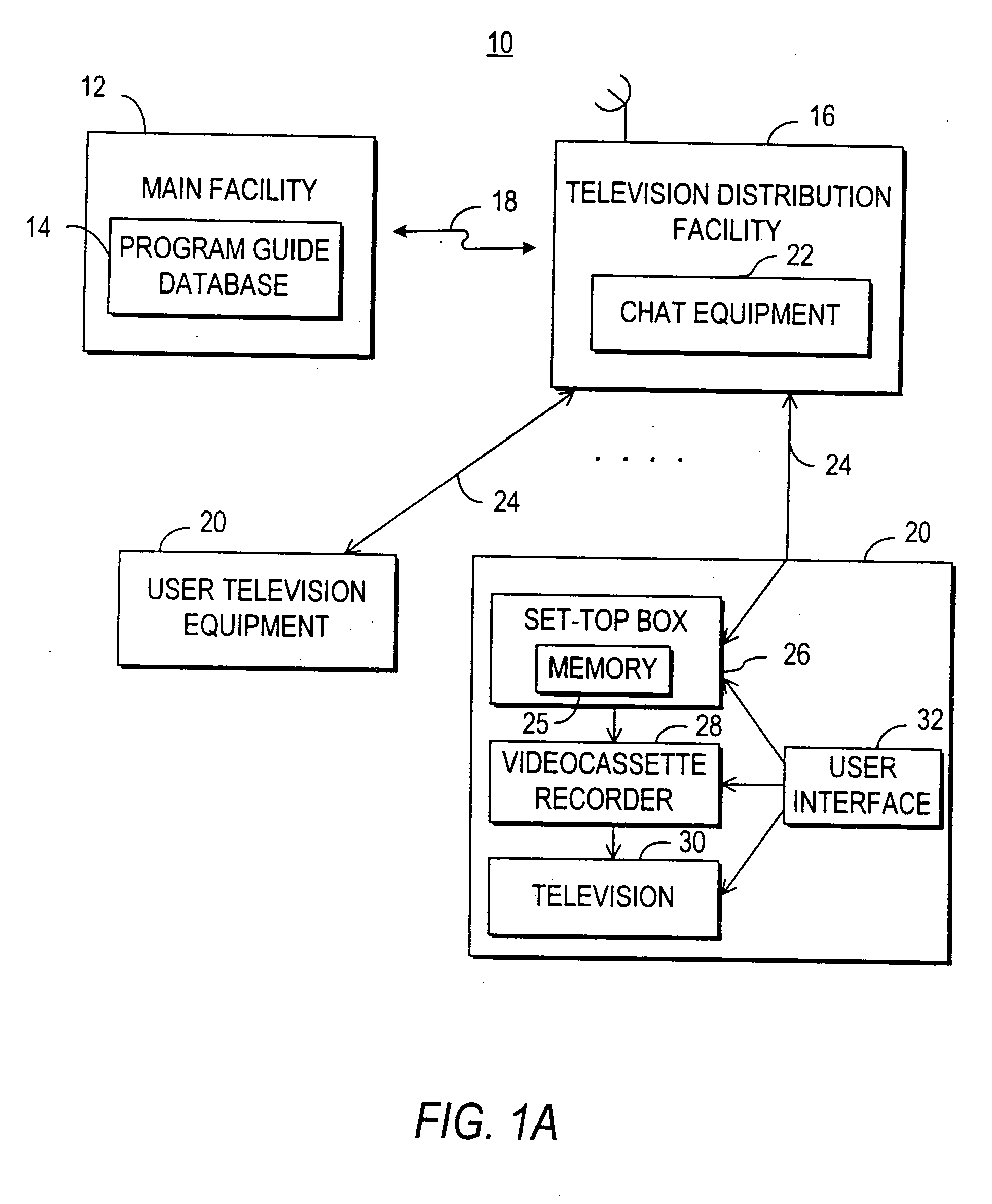
A television chat system is provided that allows television viewers to engage in real-time communications in chat groups with other television viewers while watching television. Users of the television chat system may engage in real-time communications with other users who are currently watching the same television program or channel. The system allows real-time communications in a chat group to be transmitted between users at user television equipment devices via a television distribution facility. The television chat system of the present invention permits users to join chat groups related to television programs, channels, or categories of programs that the user may be interested in. Real-time communications may be textual messages, audio communications, or video communications. The television chat system may also allow users to send chat requests to ask other users to enter a chat group. The system also permits users to establish chat groups that television viewers are permitted to join. The television chat system may be based on an interactive television program guide or set-top box application implemented on a set-top box.
Owner:ALL MEDIA GUIDE +10
Differentiated content and application delivery via internet
InactiveUS6976090B2Decentralized and differentiatedAdvanced technologyMultiple digital computer combinationsWebsite content managementScalable systemEdge server
Owner:CISCO TECH INC
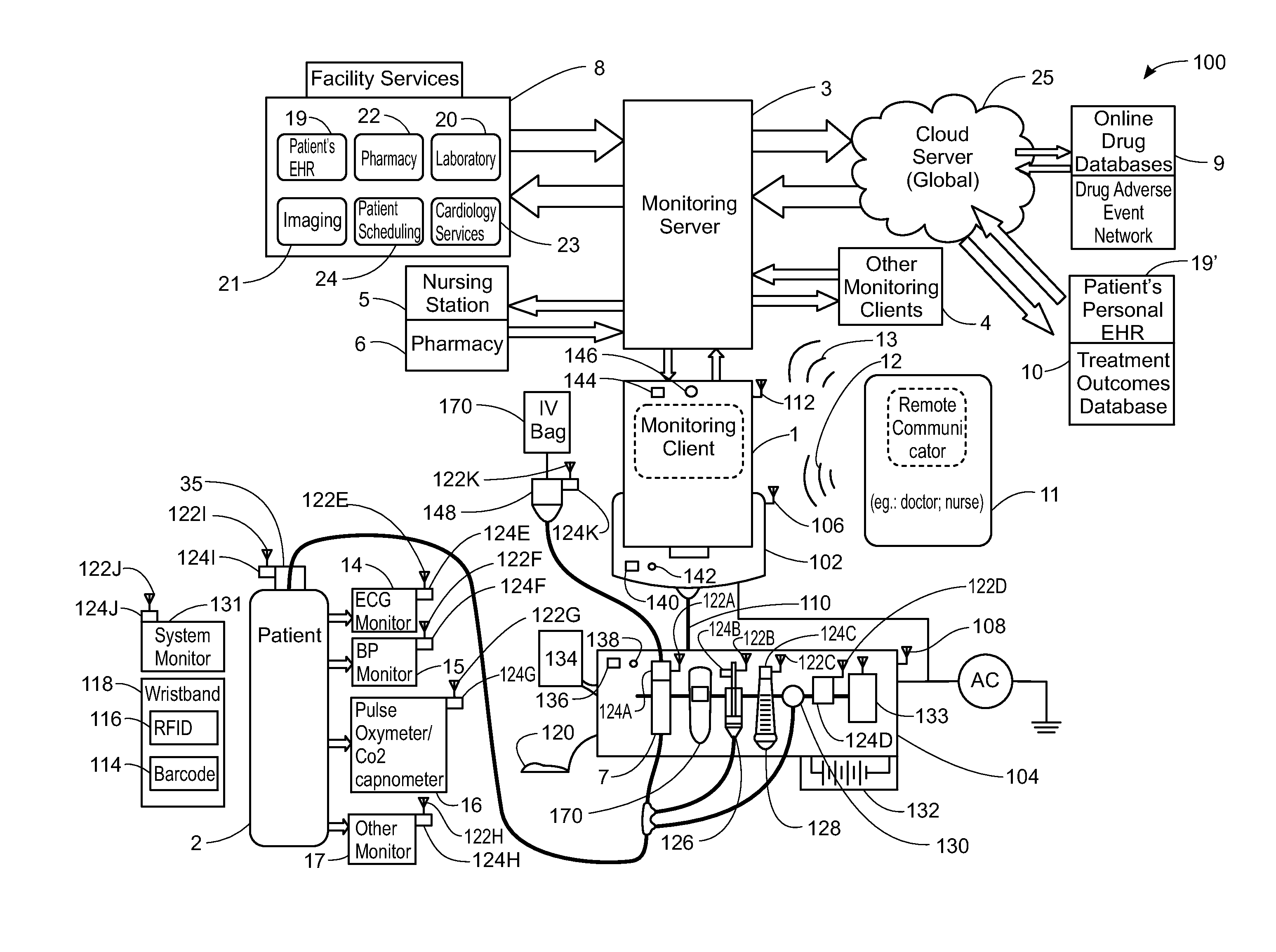
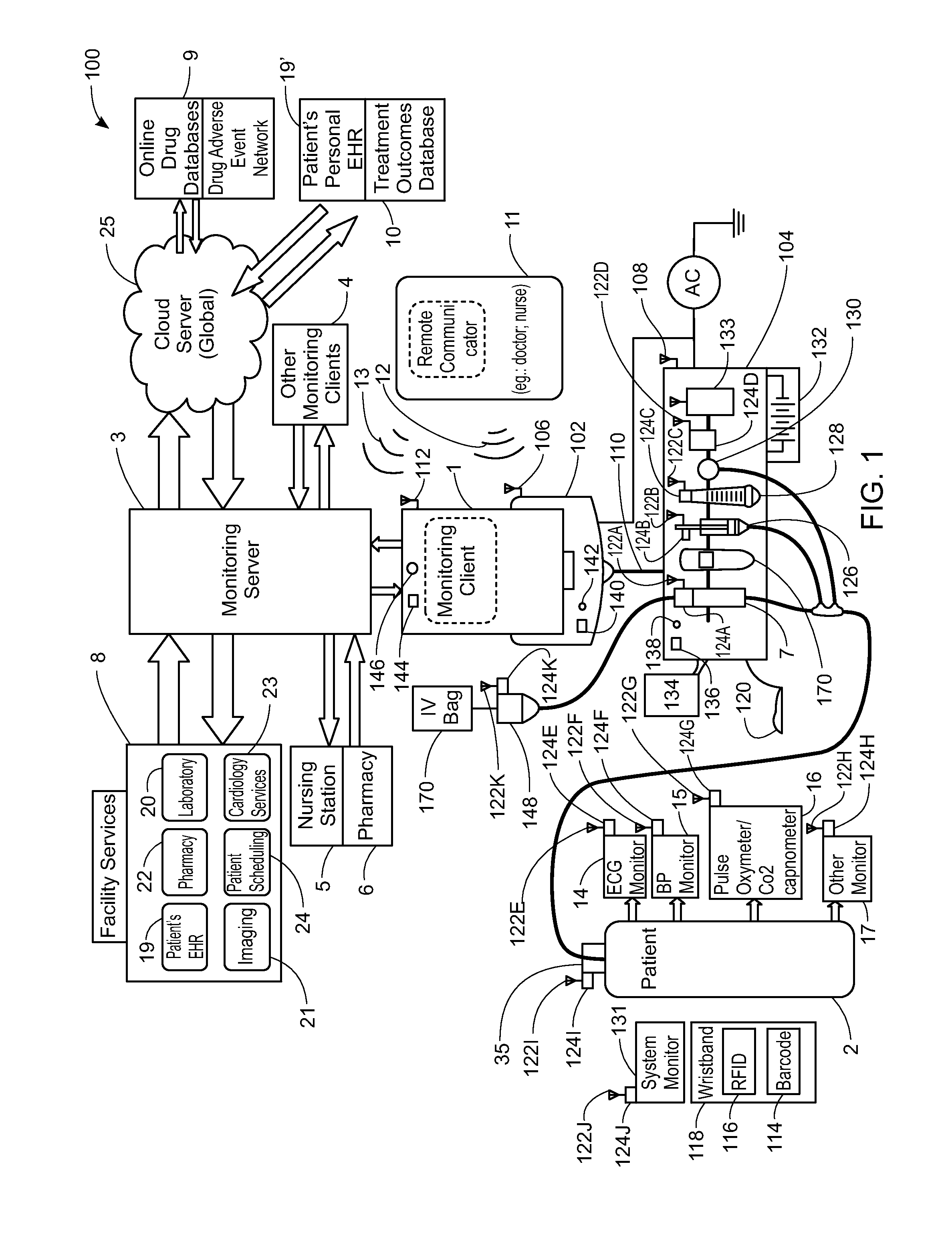
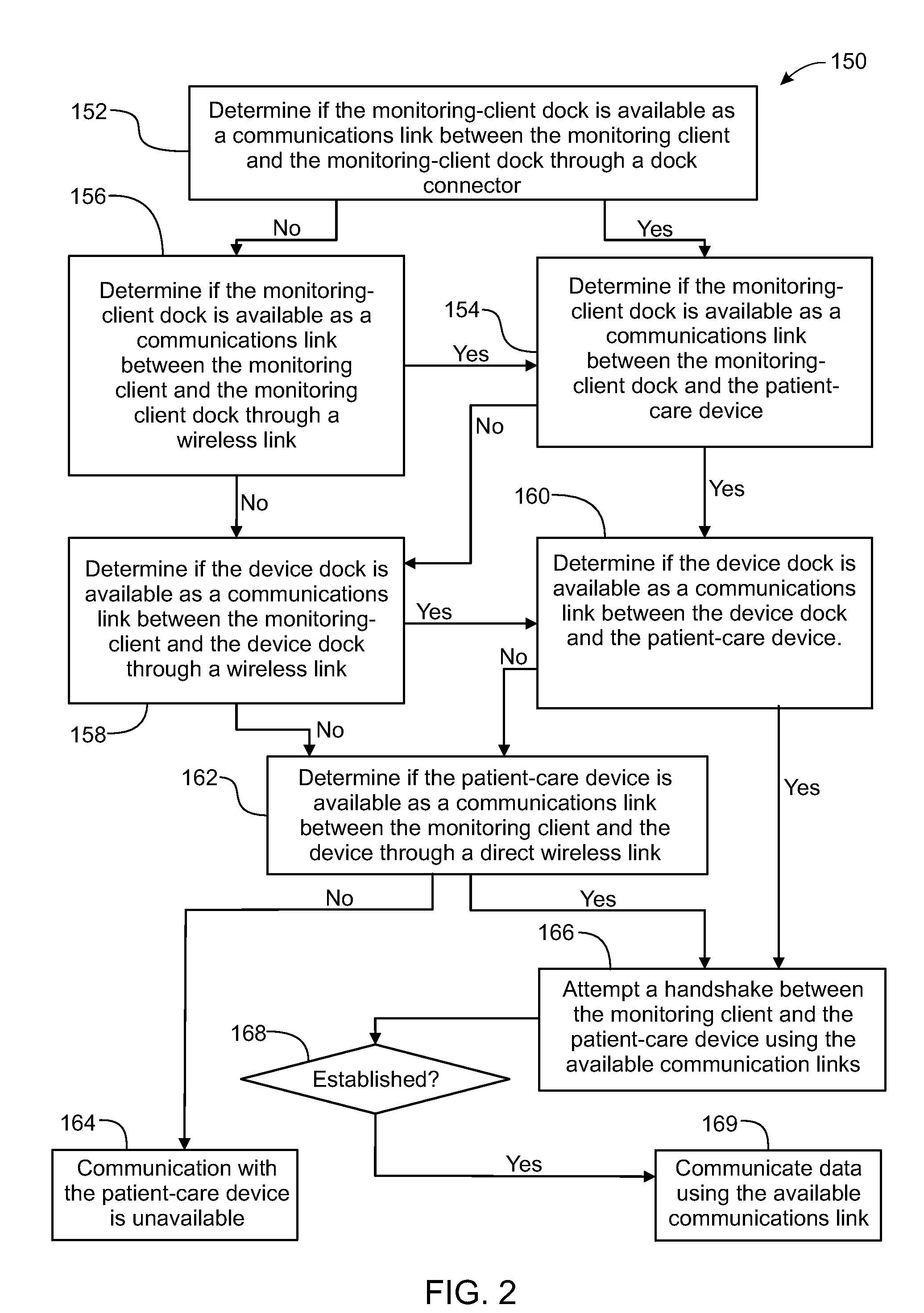
System, Method, and Apparatus for Electronic Patient Care
ActiveUS20130317753A1Quantity minimizationPerson identificationDigital computer detailsComputer hardwareCommunication link
A method implemented by an operative set of processor executable instructions configured for execution by a processor includes: determining if a monitoring client is connected to a base through a physical connection; establishing a first communications link between the monitoring client and the base through the physical connection; updating, if necessary, the interface program on the monitoring client and the base through the first communications link; establishing a second communications link between the monitoring client and the base using the first communications link; and communicating data from the base to the monitoring client using the second communications link.
Owner:DEKA PROD LLP
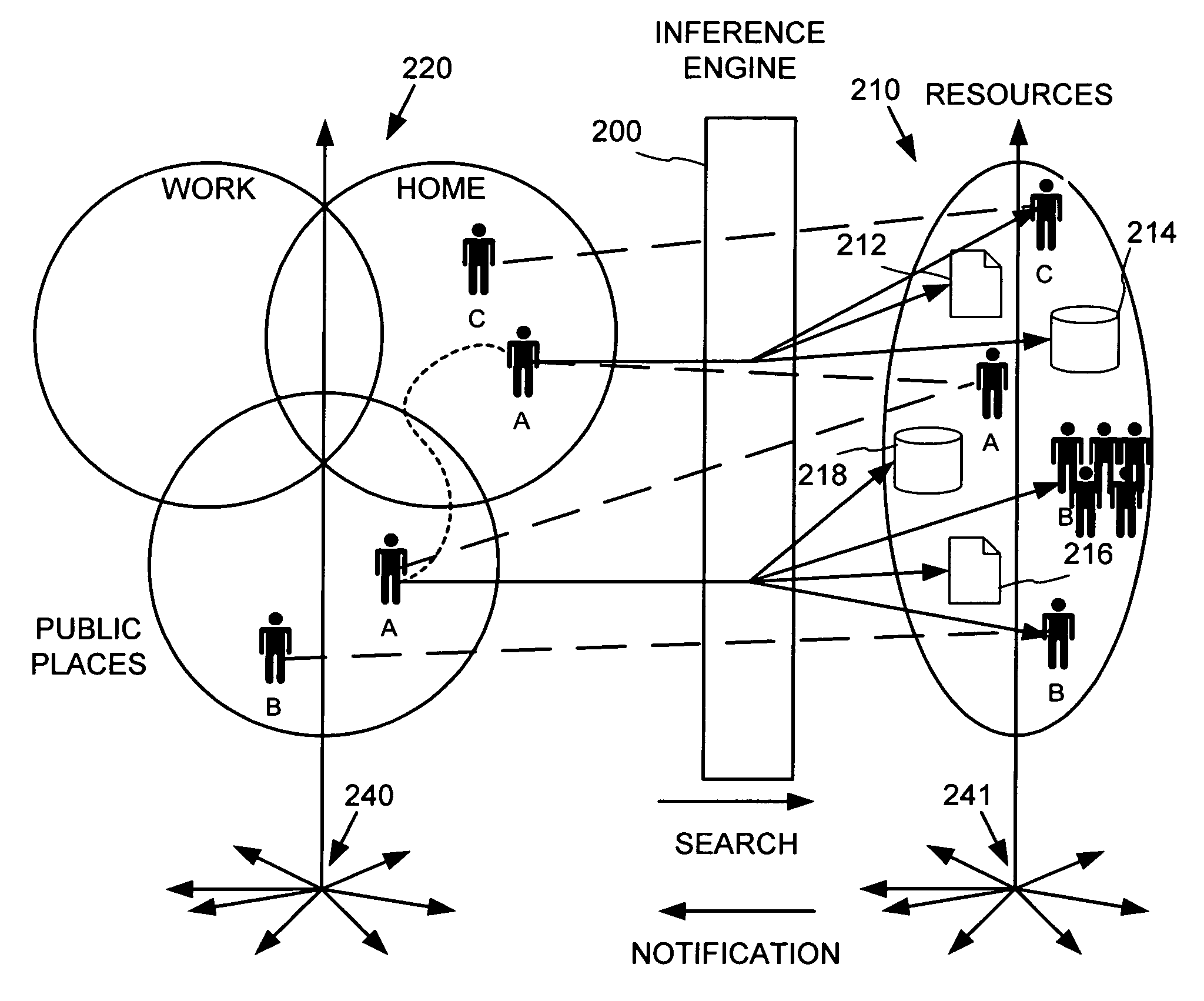
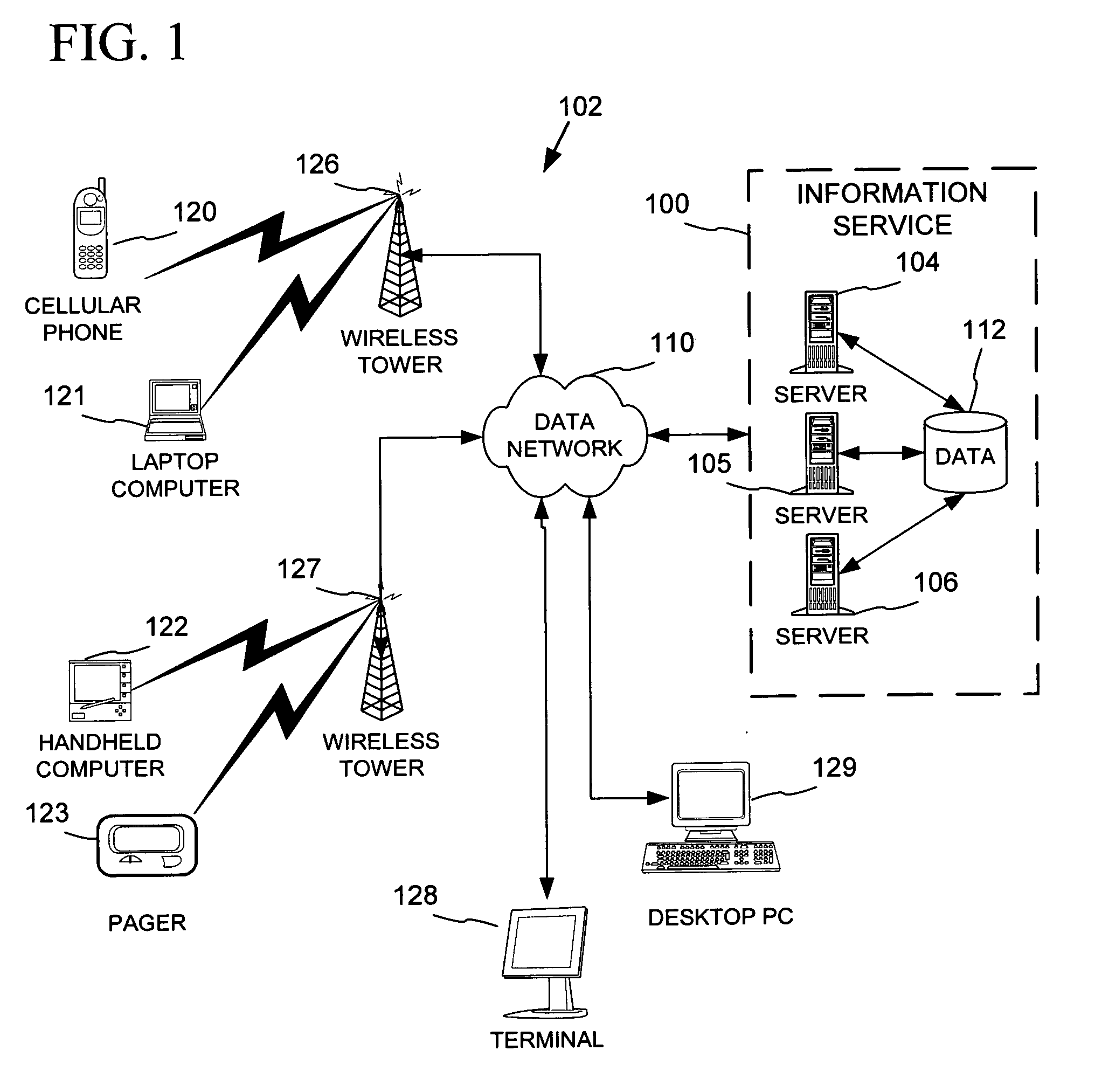
Place specific buddy list services
InactiveUS6968179B1Information formatSpecial service for subscribersWorld Wide WebPositioning equipment
An information service provides search and notifications to inform when certain people (e.g., friends, family, business contacts, etc.) are nearby so as to facilitate communications with those people. Users may define lists of people whose locations may be tracked by positioning equipment based on personal communications / computing devices carried by the people. The information service processes this people and place data to identify those of the listed people that are in the user's vicinity, and provide notifications and user-initiated search results informing the user such as via the user's personal communications / computing device.
Owner:MICROSOFT TECH LICENSING LLC
System, method and apparatus for connecting users in an online computer system based on their relationships within social networks
ActiveUS20050021750A1Enhanced interactionIncrease valueMultiple digital computer combinationsOffice automationDirect communicationSocial internet of things
A method and apparatus for calculating, displaying and acting upon relationships in a social network is described. A computer system collects descriptive data about various individuals and allows those individuals to indicate other individuals with whom they have a personal relationship. The descriptive data and the relationship data are integrated and processed to reveal the series of social relationships connecting any two individuals within a social network. The pathways connecting any two individuals can be displayed. Further, the social network itself can be displayed to any number of degrees of separation. A user of the system can determine the optimal relationship path (i.e., contact pathway) to reach desired individuals. A communications tool allows individuals in the system to be introduced (or introduce themselves) and initiate direct communication.
Owner:META PLATFORMS INC
Distributed administration of access to information
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
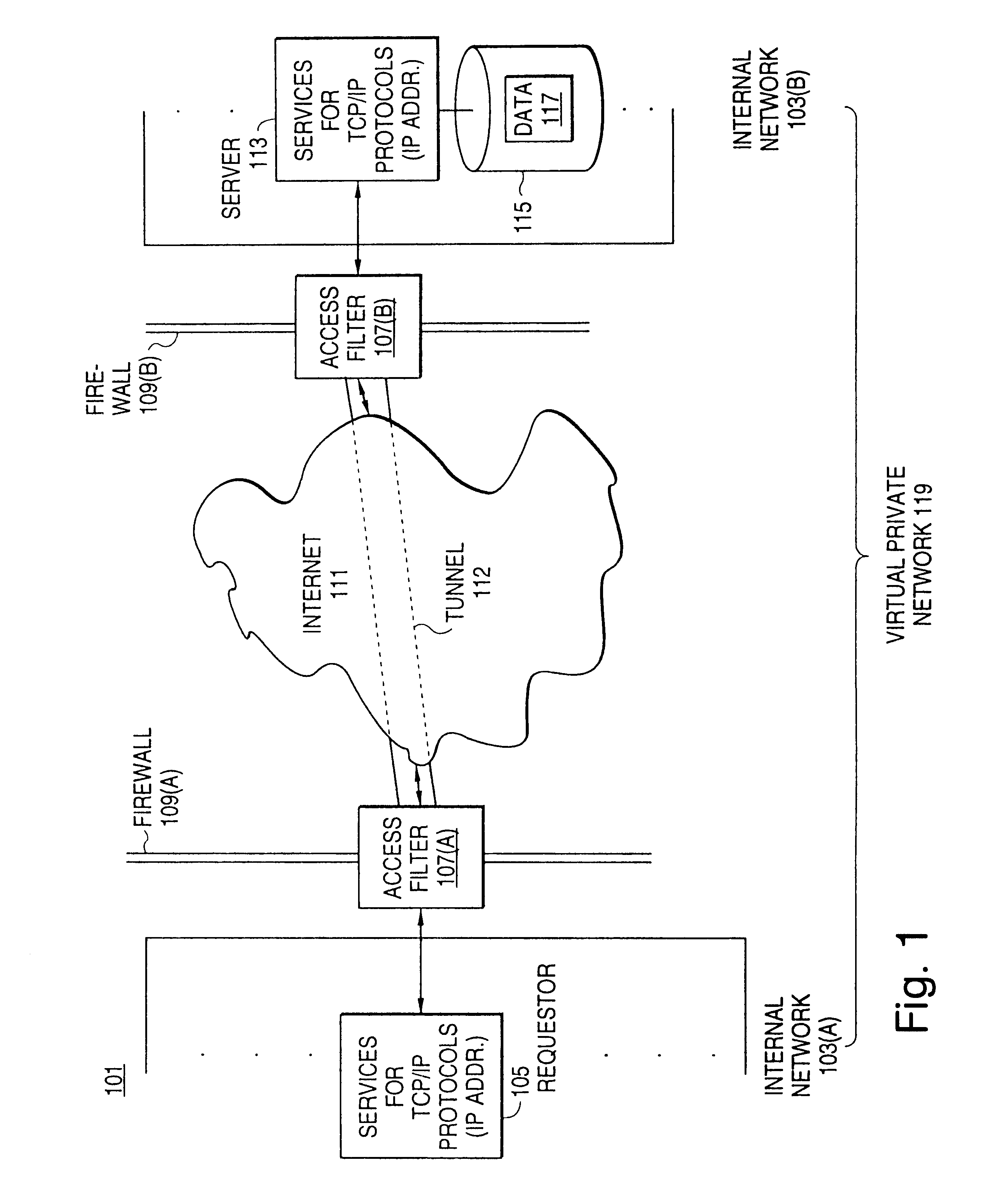
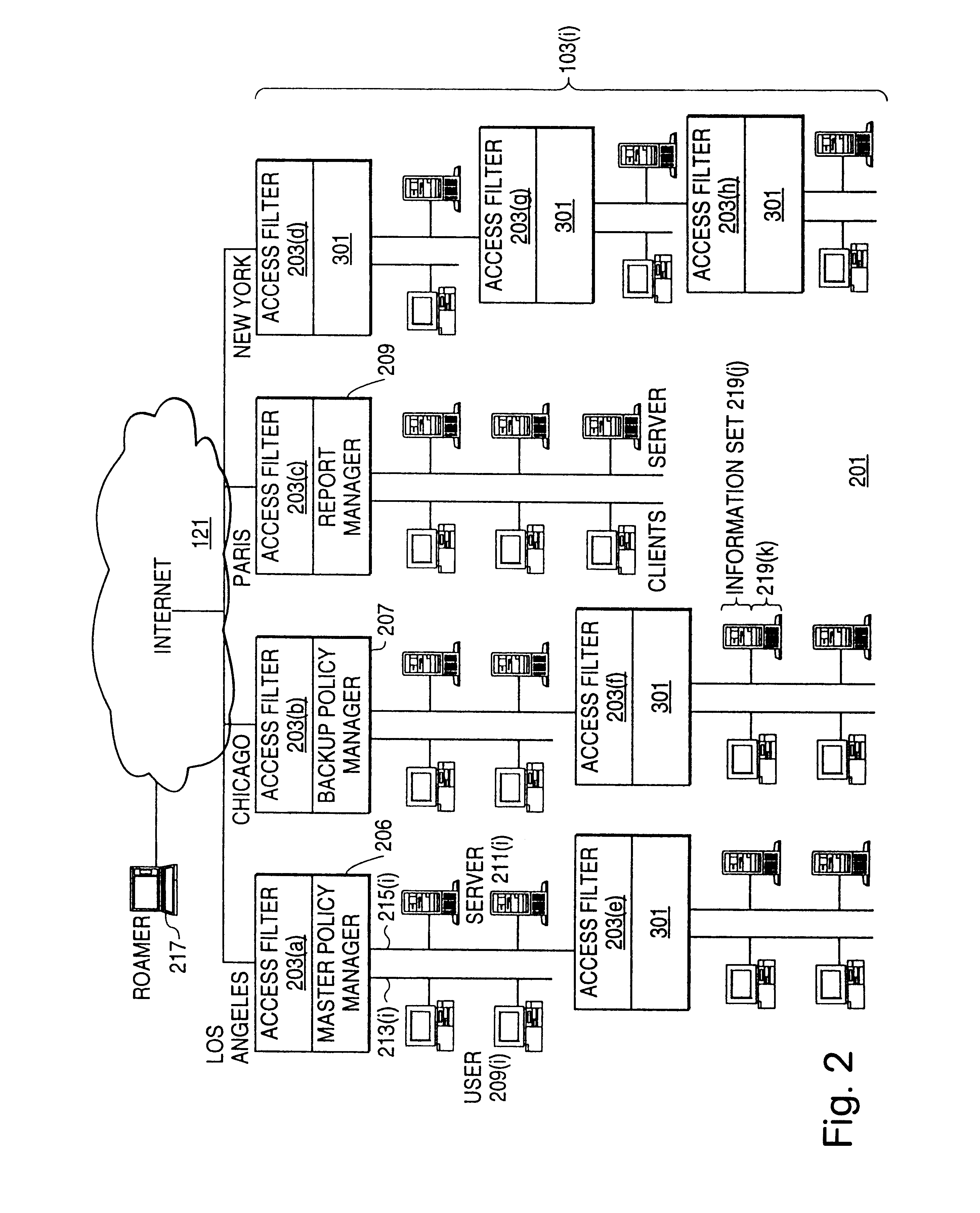
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
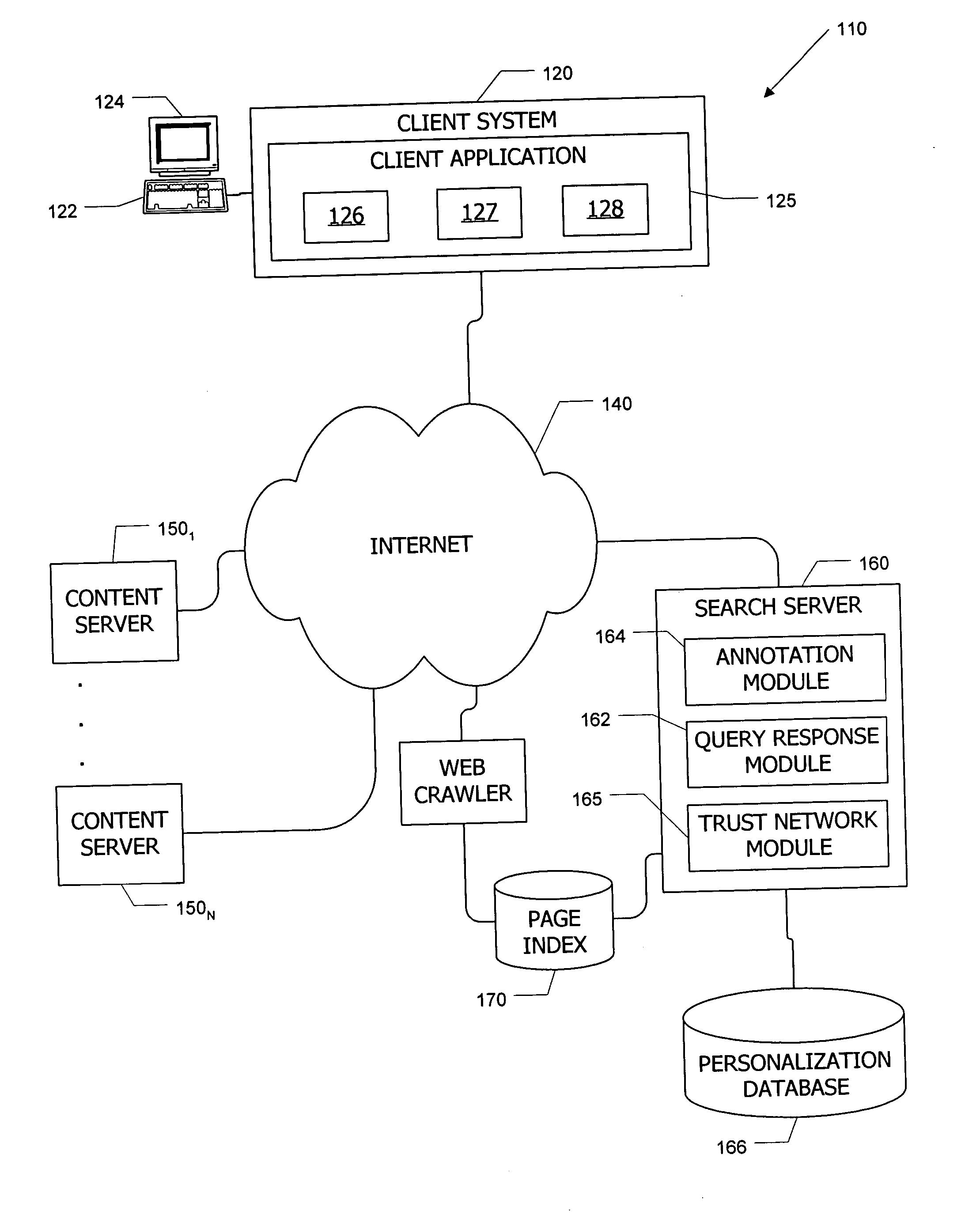
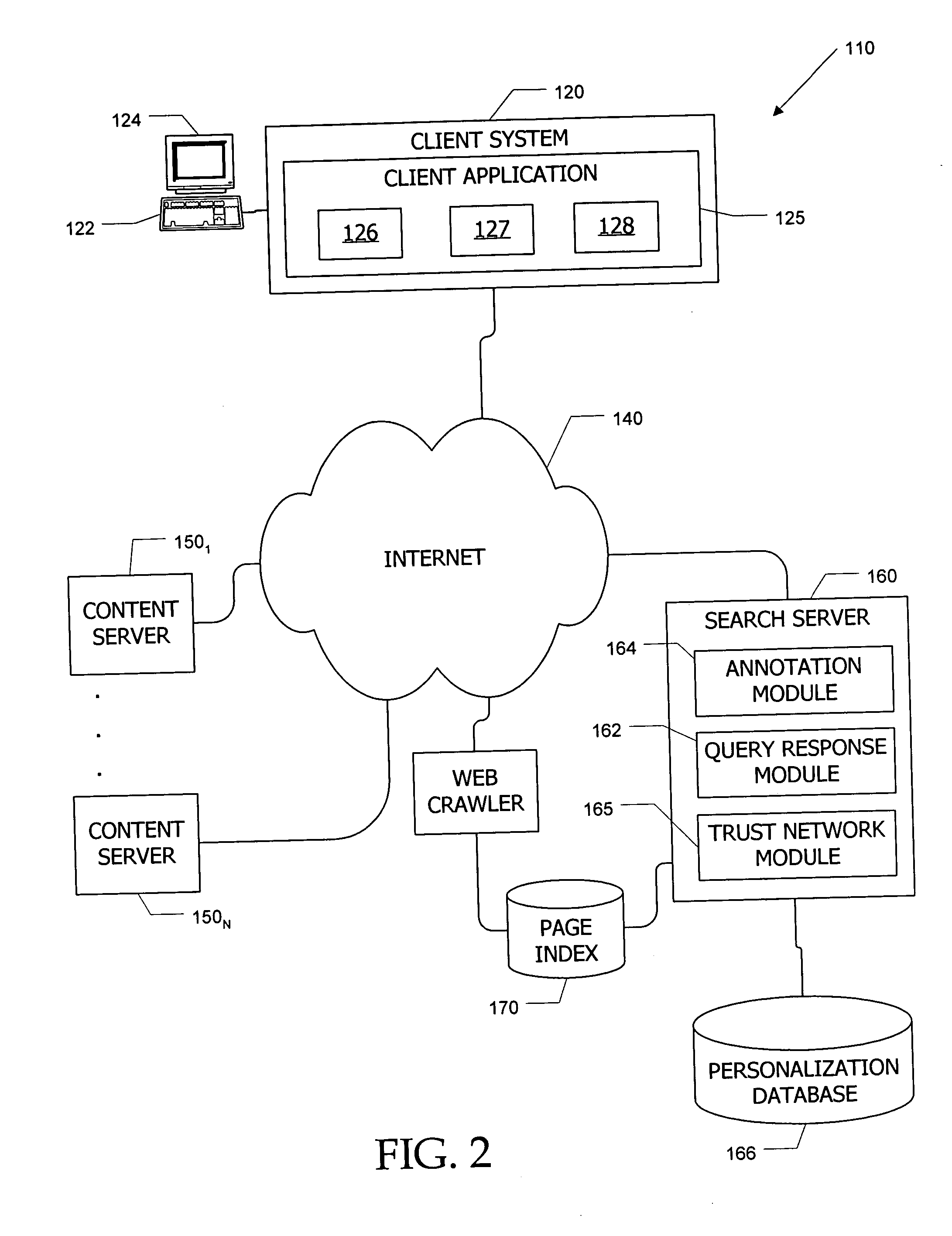
Search system and methods with integration of user annotations from a trust network
ActiveUS20050256866A1Enhance querying user 's experienceImprove browsing experienceData switching networksSpecial data processing applicationsTrust networkUser defined
Computer systems and methods incorporate user annotations (metadata) regarding various pages or sites, including annotations by a querying user and by members of a trust network defined for the querying user into search and browsing of a corpus such as the World Wide Web. A trust network is defined for each user, and annotations by any member of a first user's trust network are made visible to the first user during search and / or browsing of the corpus. Users can also limit searches to content annotated by members of their trust networks or by members of a community selected by the user.
Owner:SALESFORCE COM INC
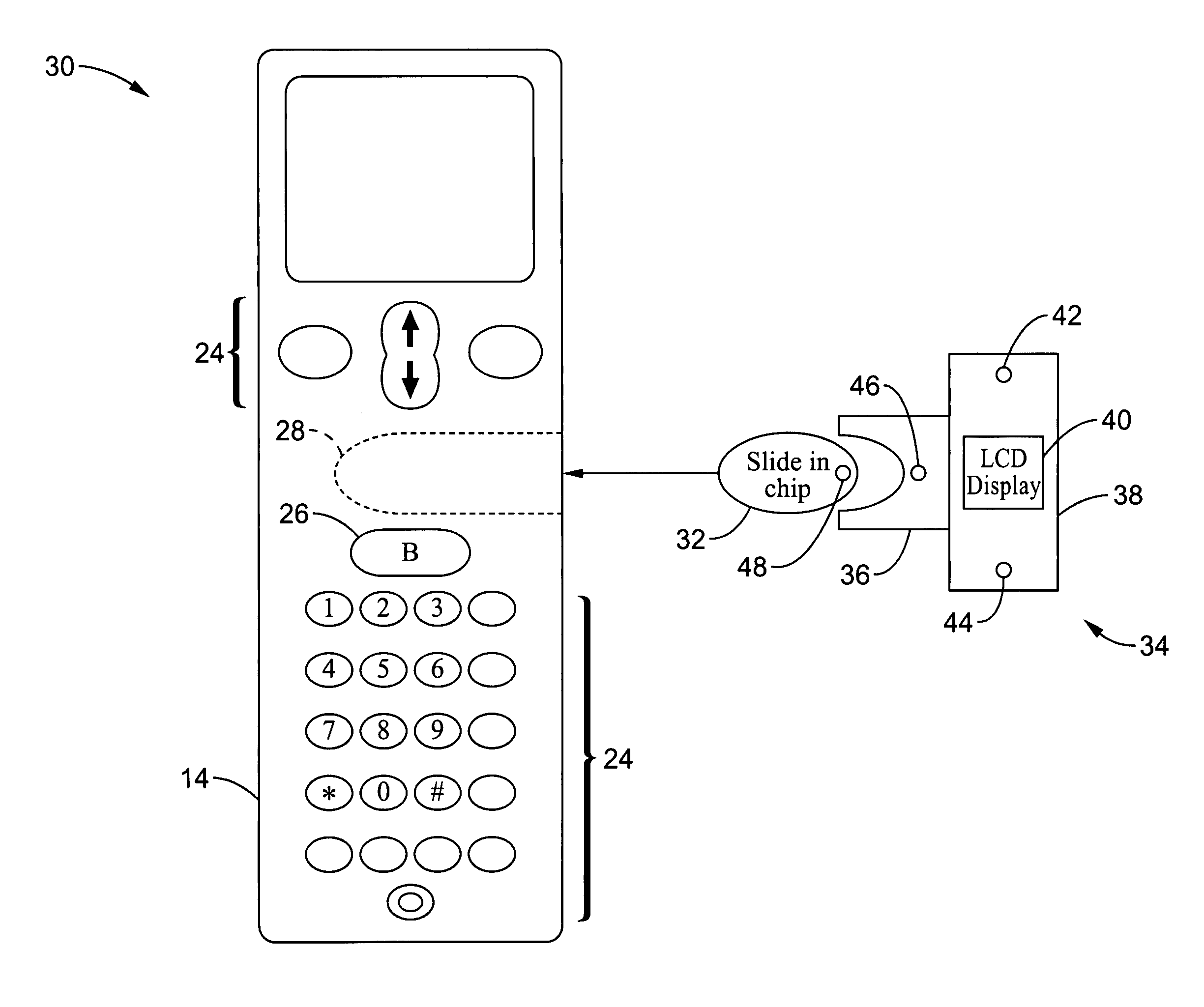
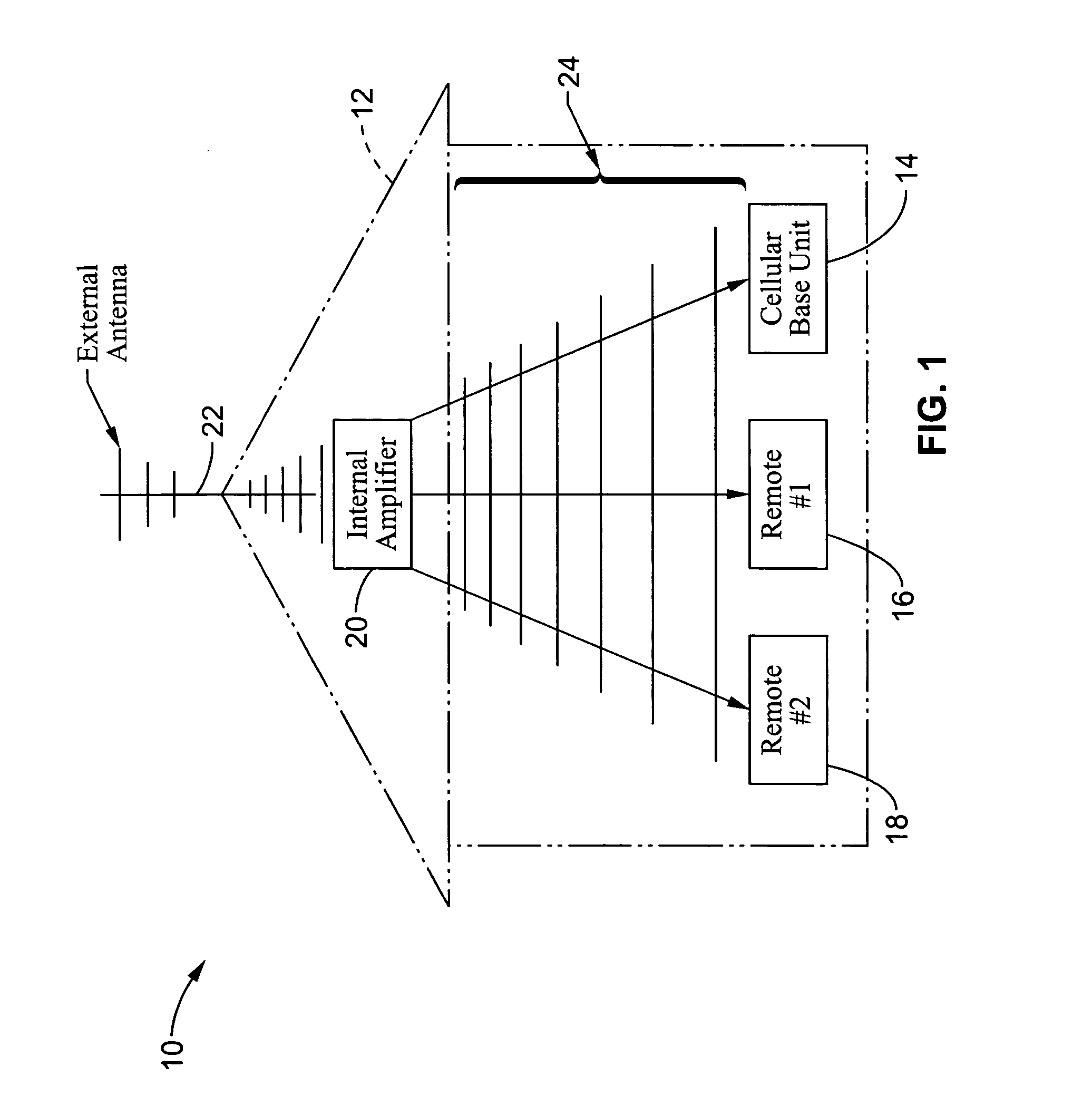
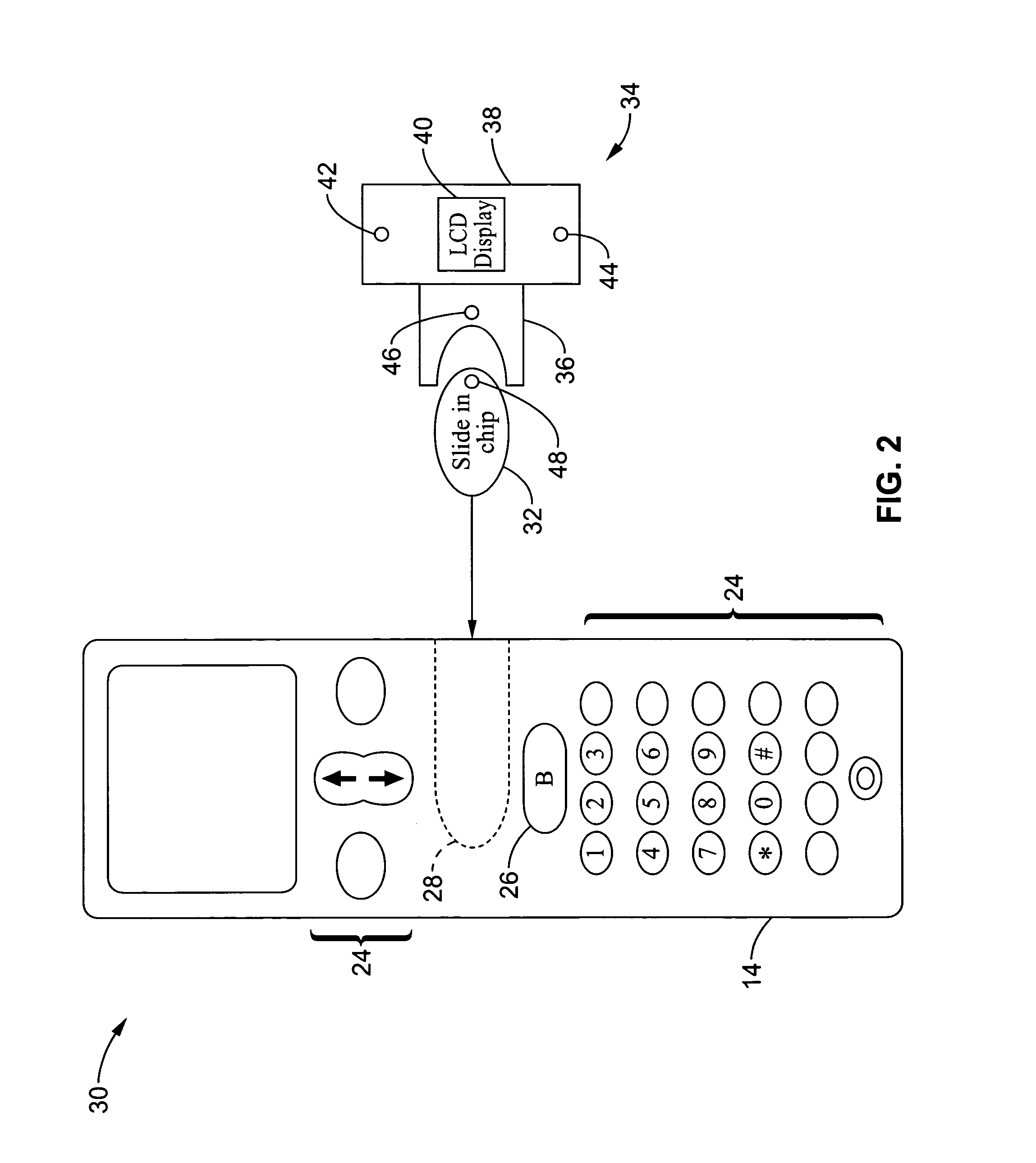
Wireless communications apparatus and method
InactiveUS7146191B2Easy to be stolenProcess safetyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInterconnectivityDisplay device
A wireless communication method and apparatus are described for increasing security for communication devices utilizing identification chips for accessing wireless networks and the associated billing for services. One aspect of the invention is an enhanced phone chip and a communications device adapted to engage the enhanced phone chip, which then cannot be installed or removed from the wireless communications device by unauthorized users. In one embodiment a security key mates to the identification chip and is utilized for installing and removing the enhanced phone chip. The security key preferably has a display upon which information about the communication device is displayed prior to removing the security key after installing the enhanced phone chip. Other aspects of the invention include wireless base station communication devices which support wired (dedicated and non-dedicated), and more preferably wireless extensions, while providing sharing of wireless network resources and interconnectivity between base station and extensions.
Owner:US THERMOELECTRIC CONSORTIUM
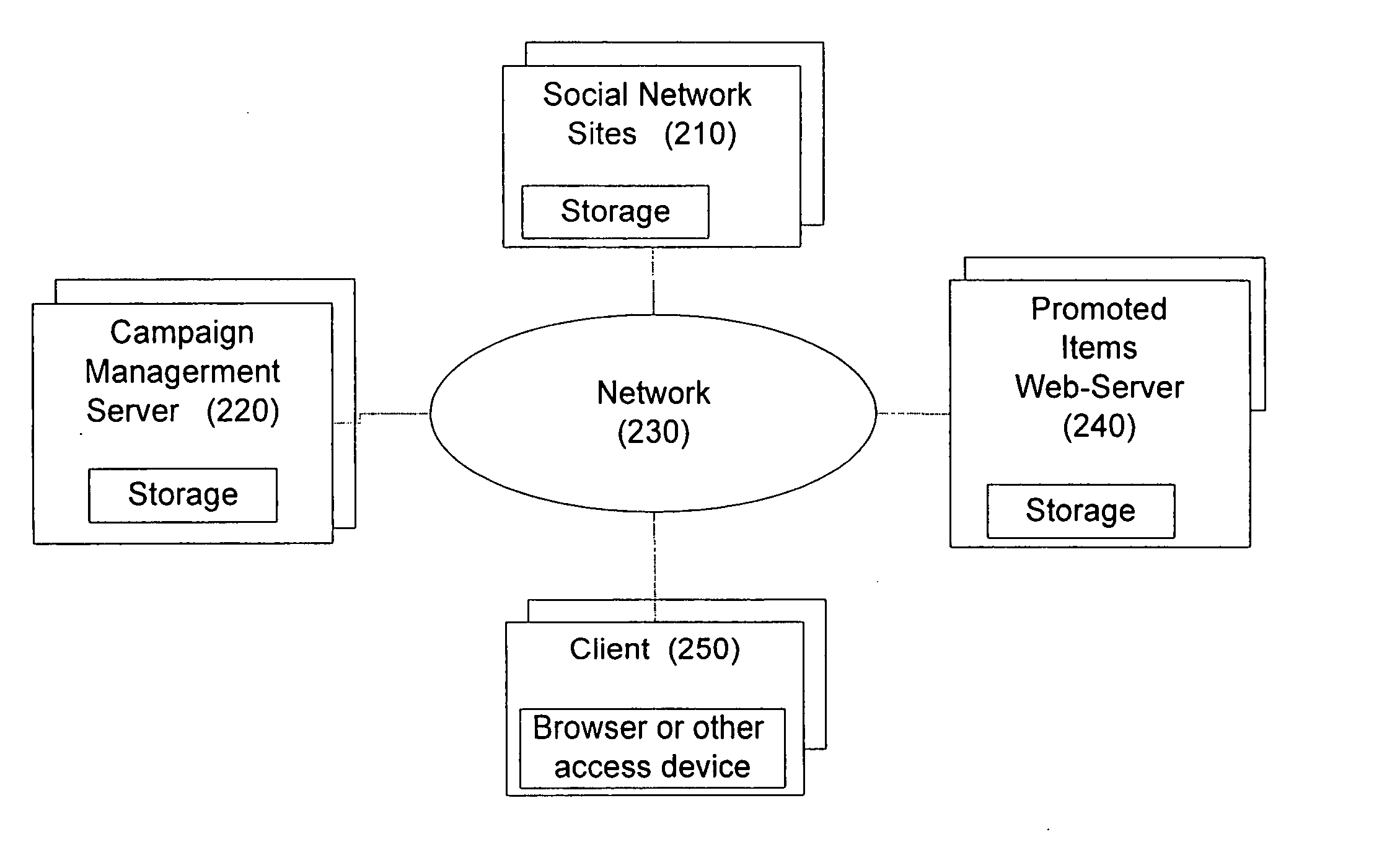
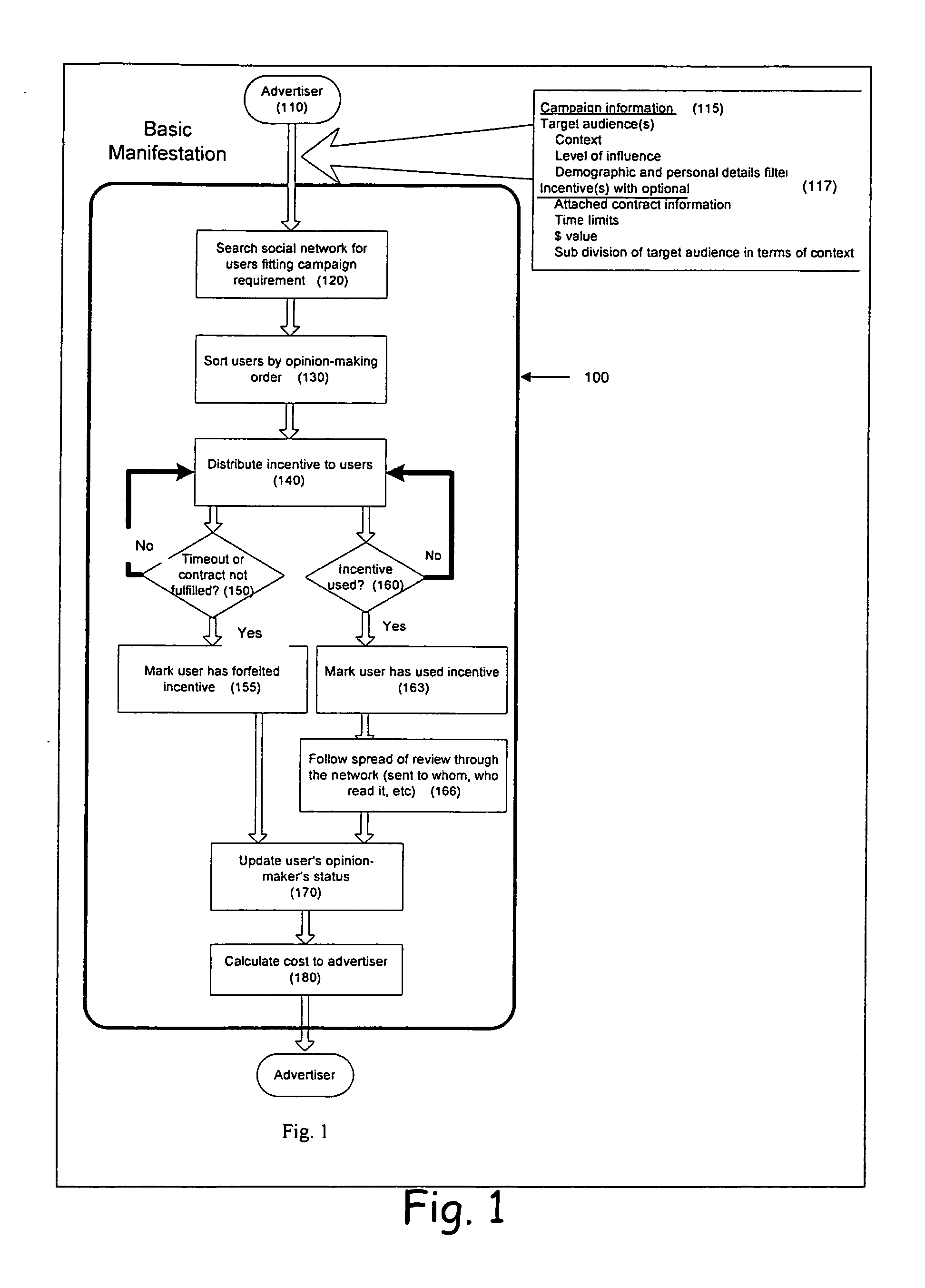
Advertising and incentives over a social network
A method whereby advertisers wish to deliver at least one of offerings and advertising messages relative to at least one of a product and a service to a target audience of users selected by a system operator during an advertising campaign. The method includes defining the users within the context of a social network, selecting the users from among the users of the social network, storing the information relevant to the defined users and utilizing the information stored / defined within the social network to deliver the messages to the users in an optimal manner.
Owner:SWAAYED INC
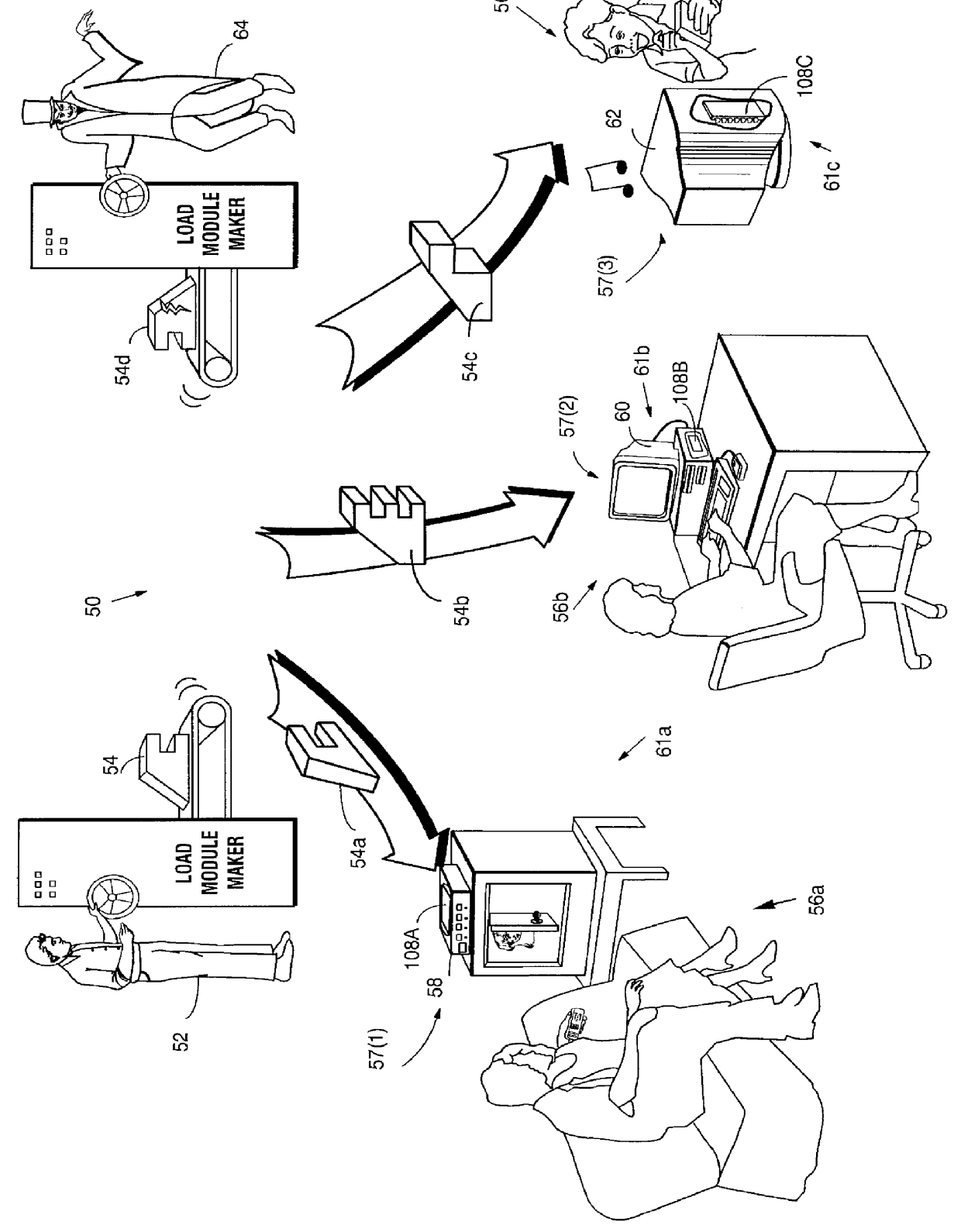
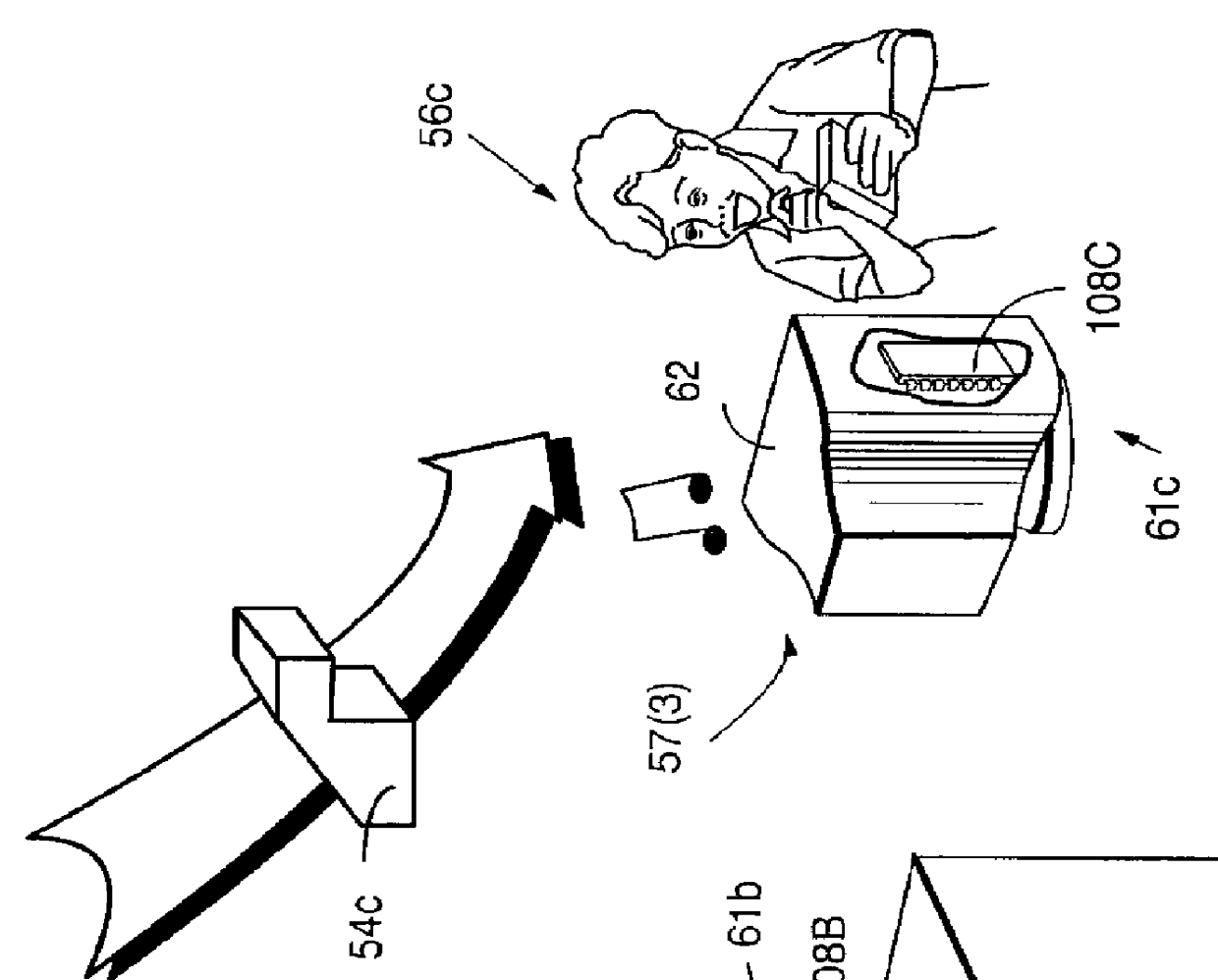
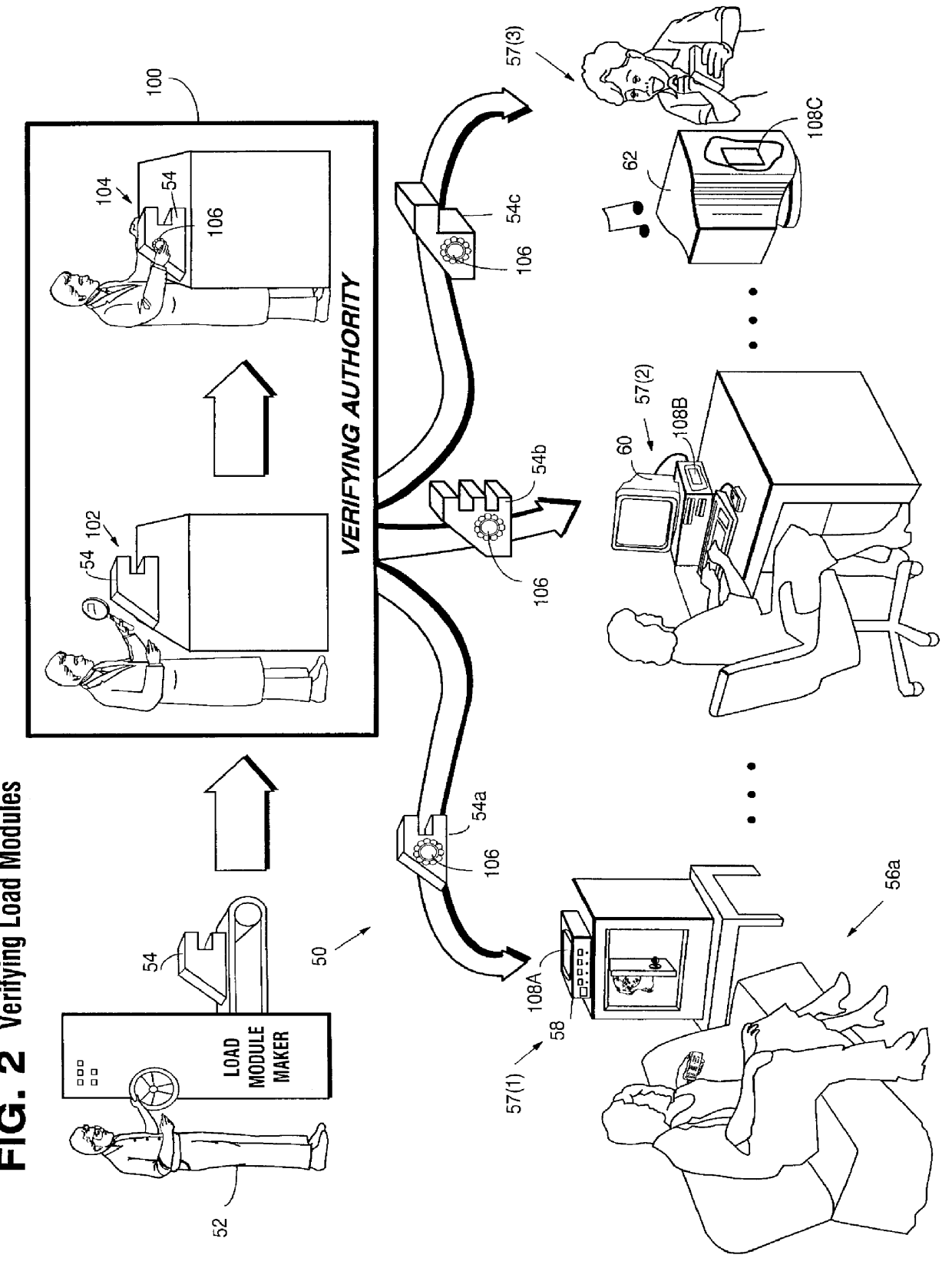
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
Programmable multimedia controller with programmable services
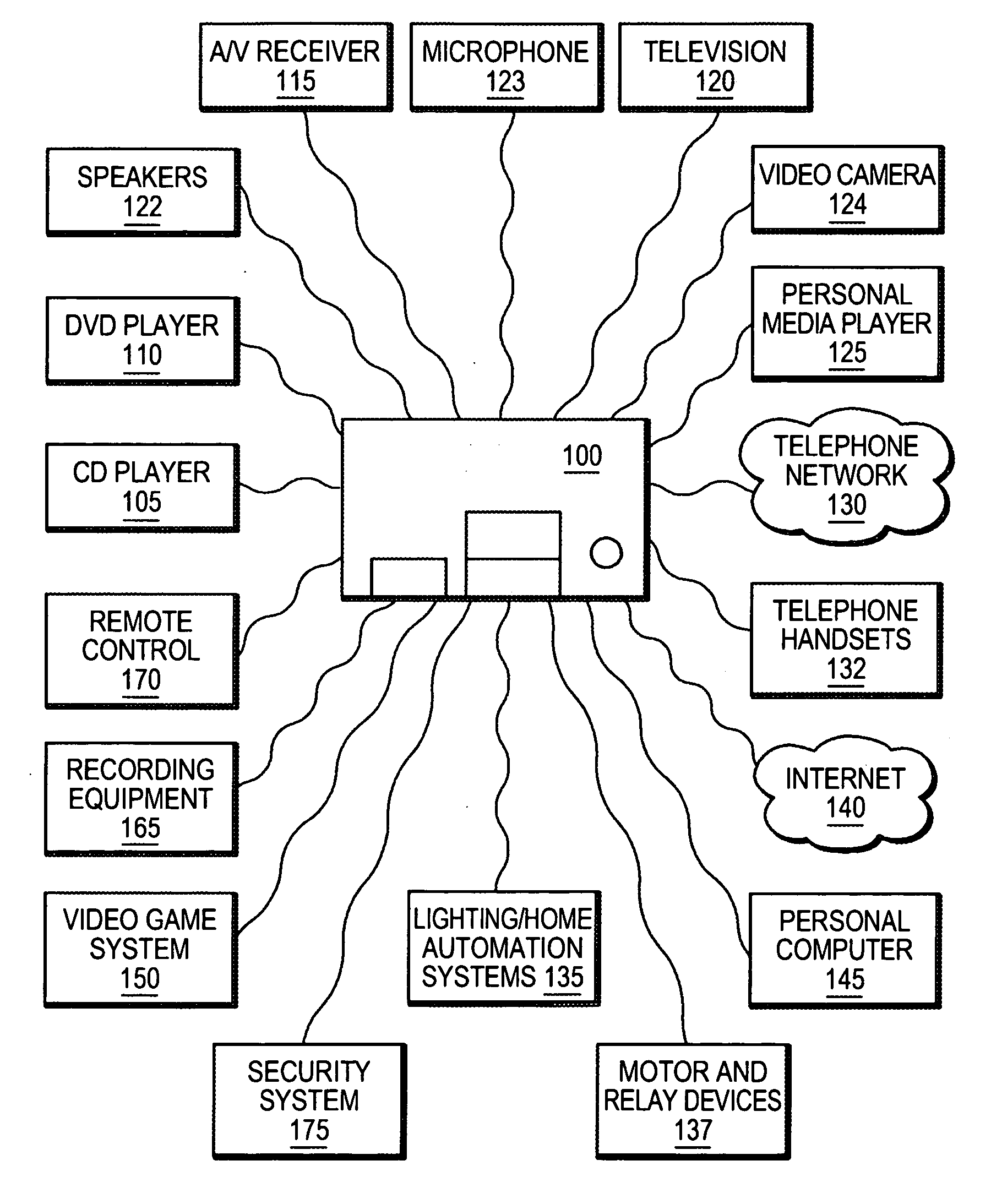
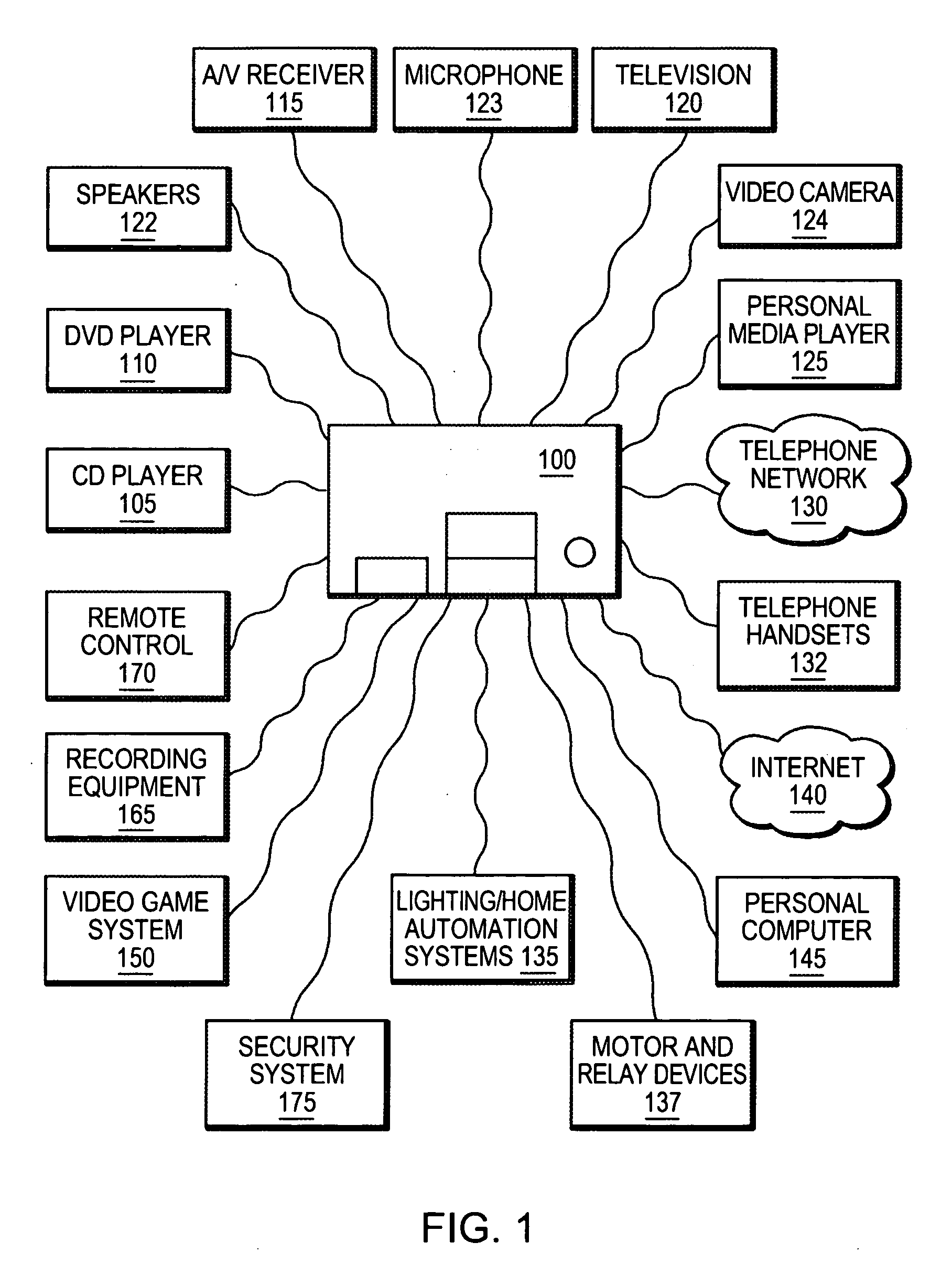
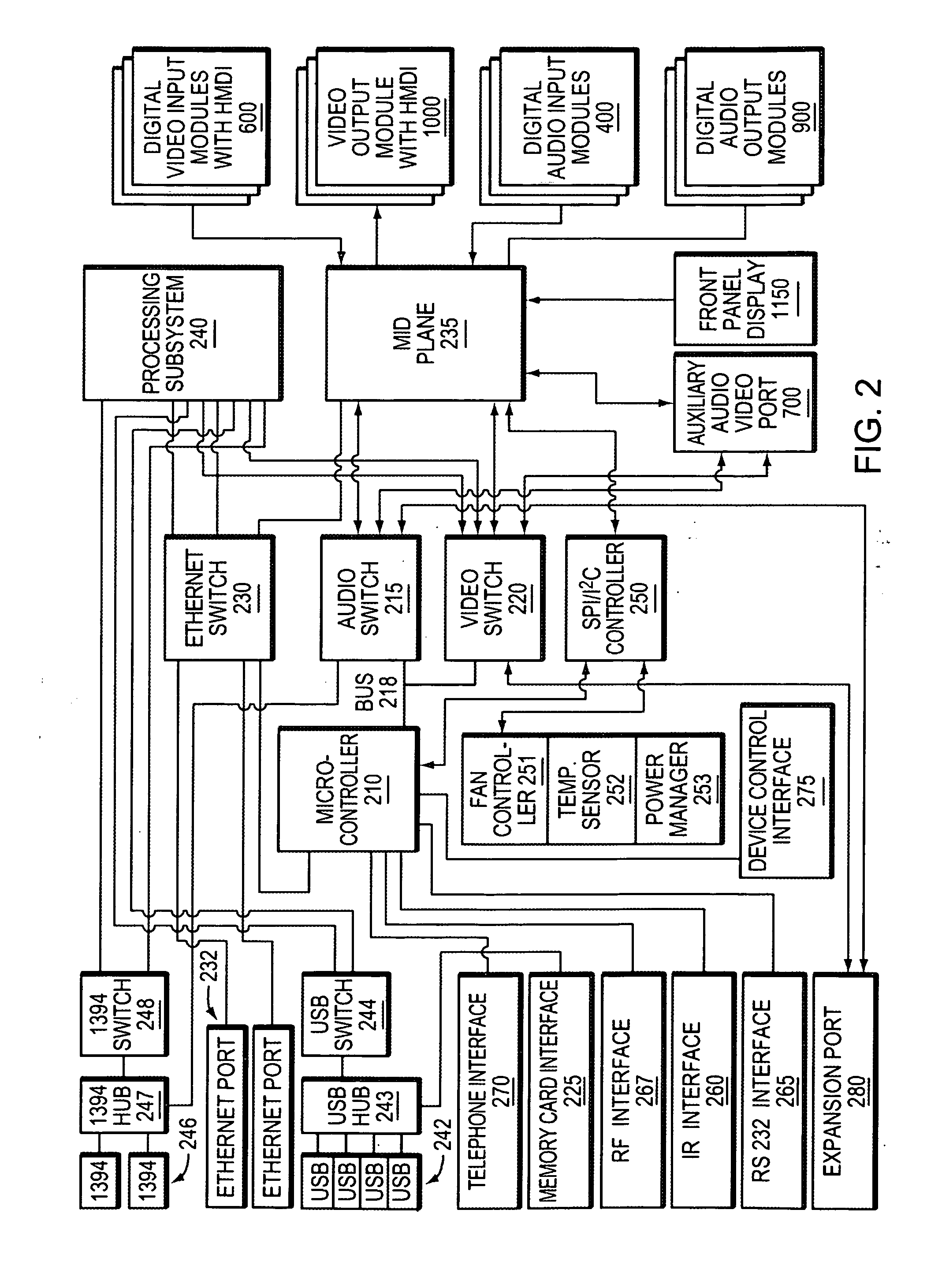
ActiveUS20070142022A1Easy to useEfficient modificationLink editingTransmission systemsControl systemProgrammable logic device
An integrated multimedia, entertainment, communications and control system. The system is based on a general purpose computer and is capable of interfacing with, controlling or managing a wide variety of audio, video, telecommunications, data communications or other devices. The system includes a programming environment for creating services or user experiences that may incorporate features or functionalities of several devices that are conventionally operated as separate, standalone devices.
Owner:SAVANT SYST INC
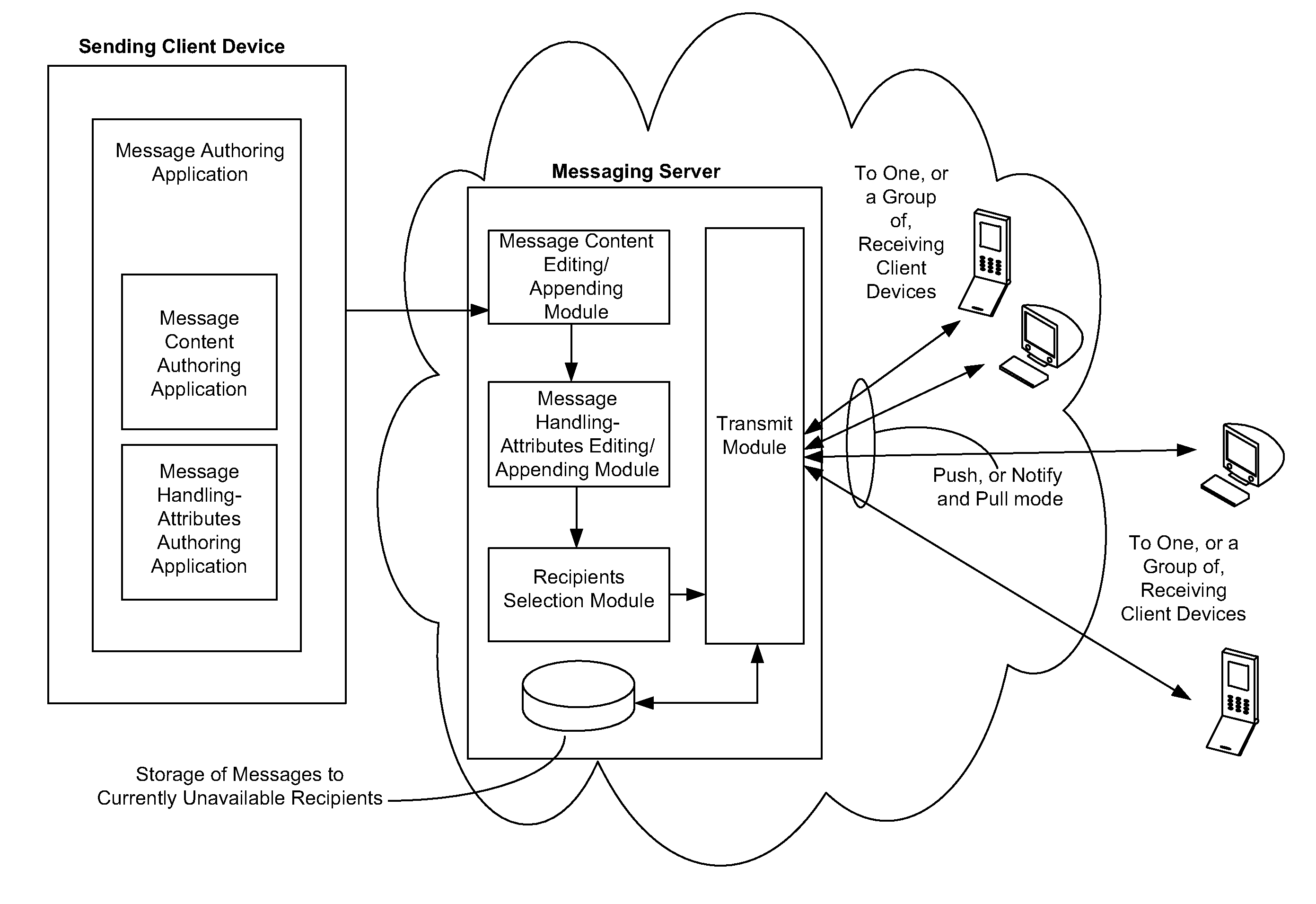
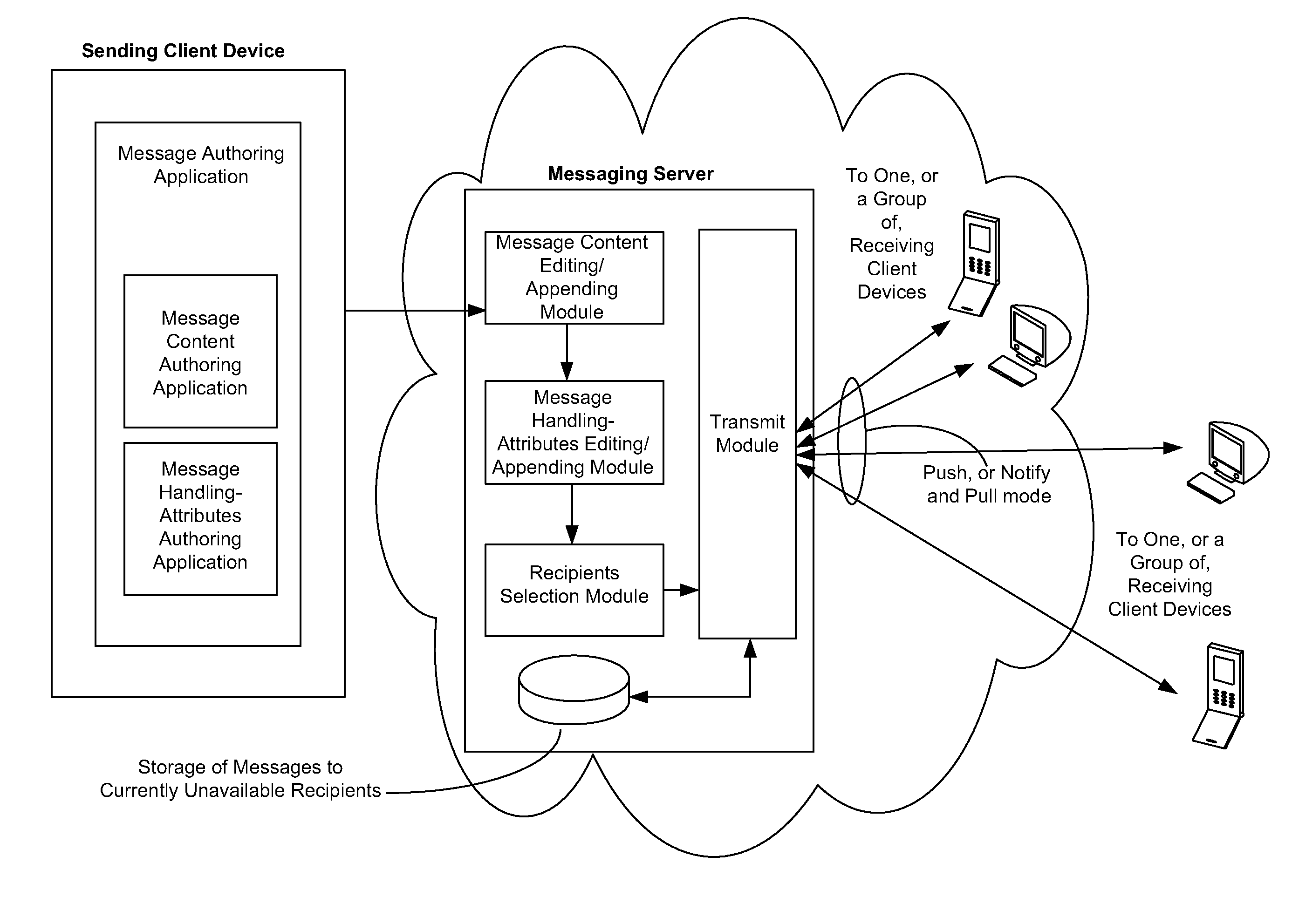
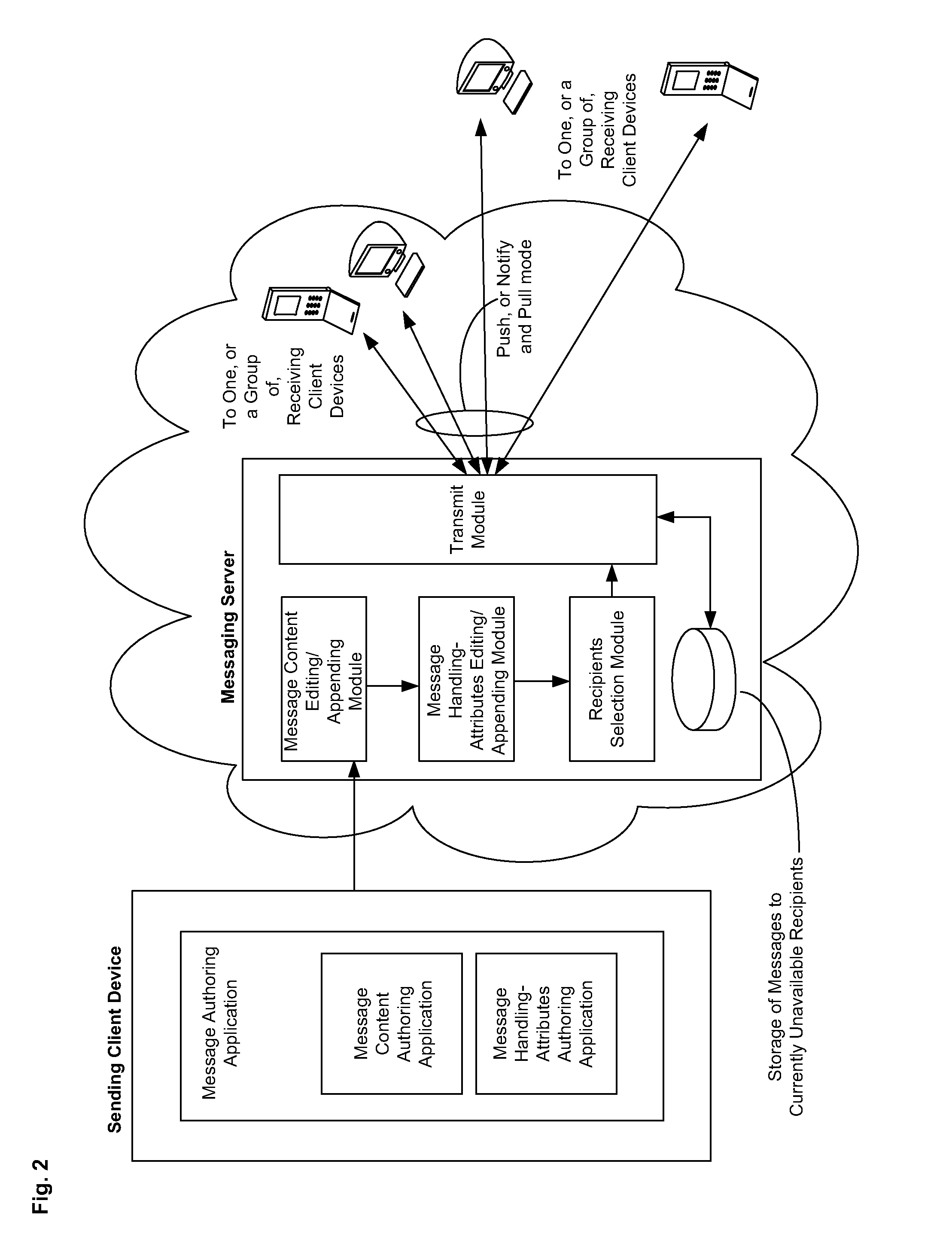
Messaging System Apparatuses Circuits and Methods of Operation Thereof
ActiveUS20120209924A1Multiple digital computer combinationsMessaging/mailboxes/announcementsClient-sideMessage passing system
Owner:TIGERCONNECT INC
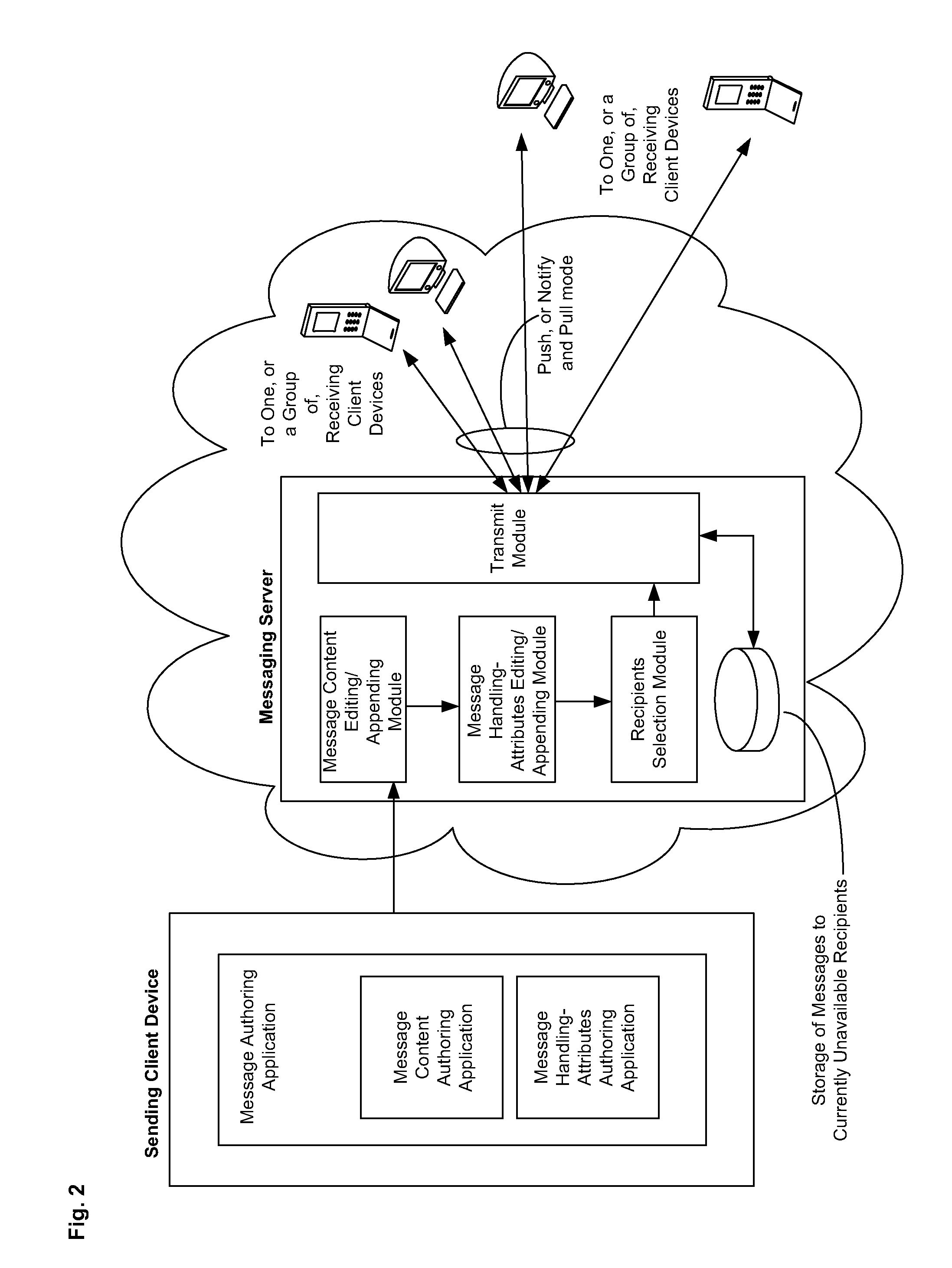
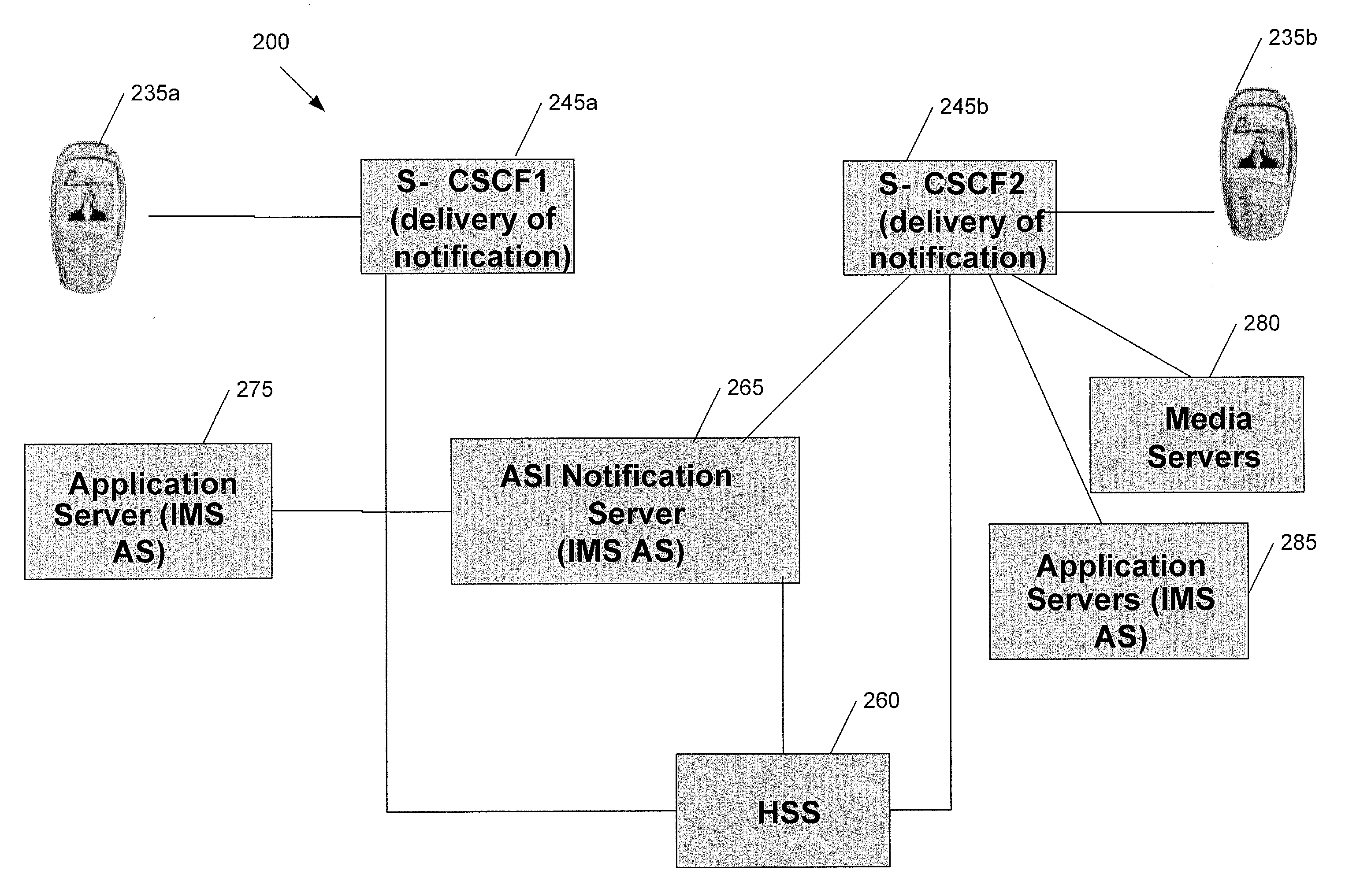
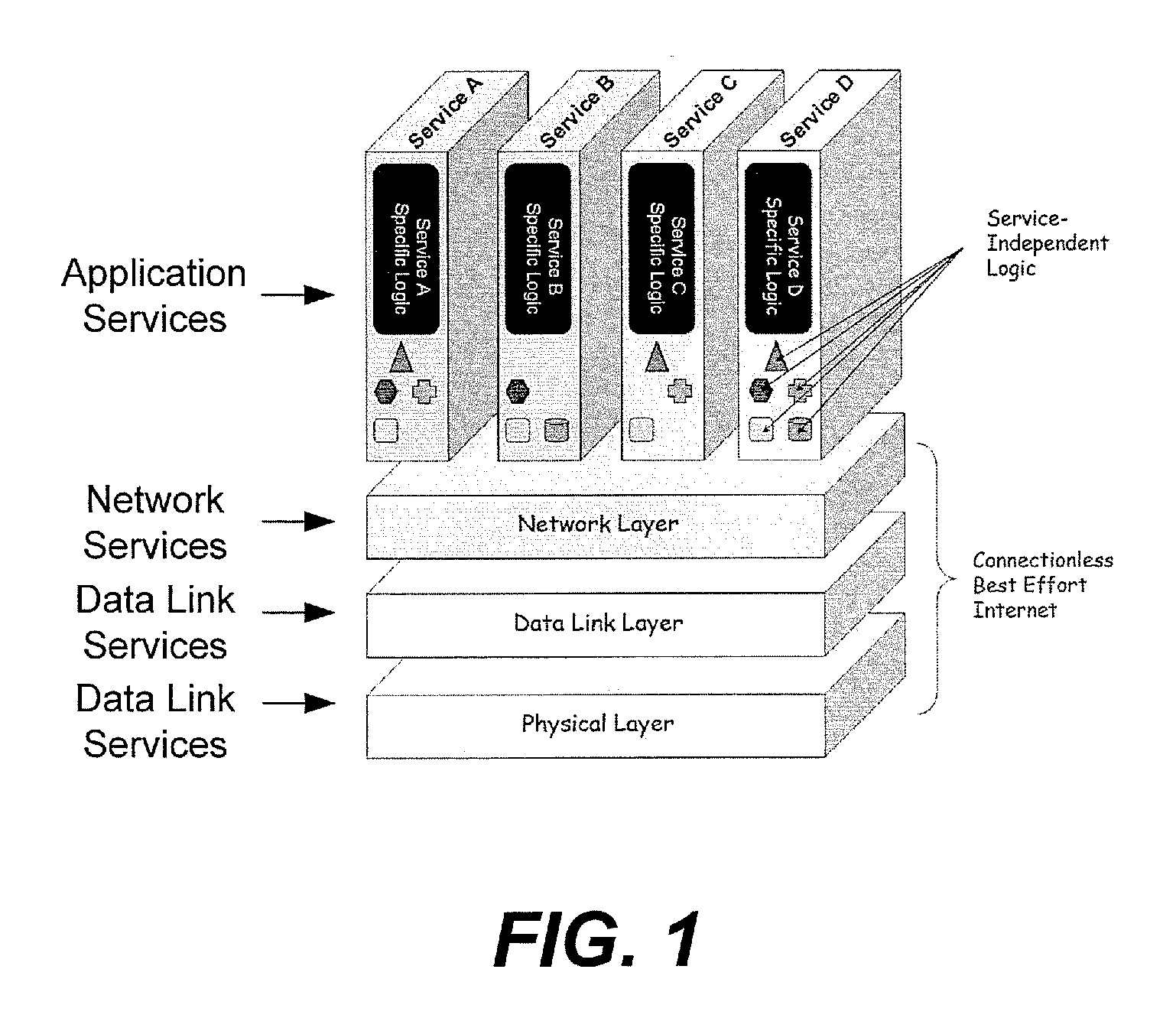
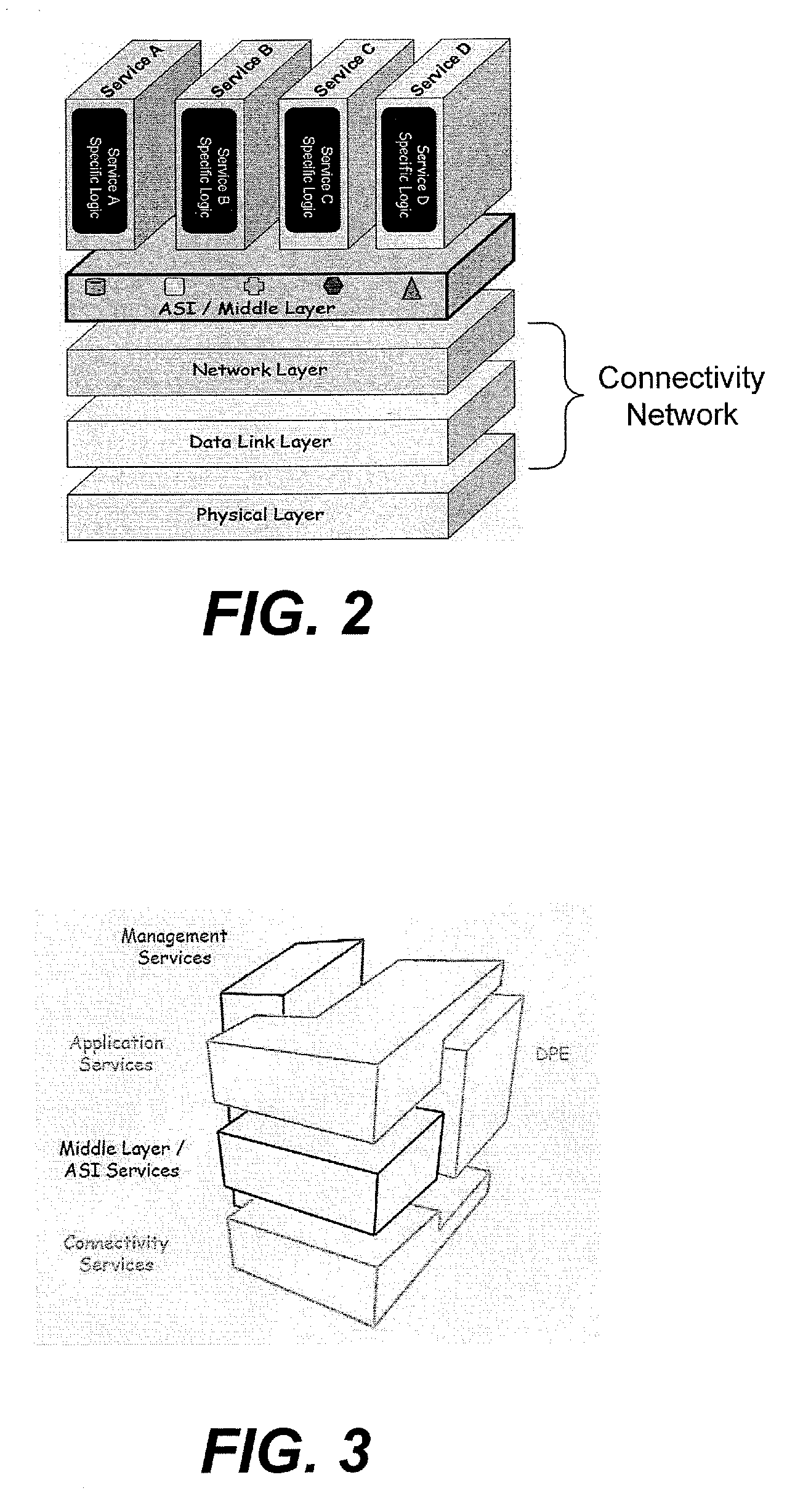
Application services infrastructure for next generation networks including a notification capability and related methods and computer program products
ActiveUS20080162637A1Facilitate sending of messageMultiple digital computer combinationsData switching networksService infrastructureNetwork layer
A system for supporting a notification capability for a plurality of applications utilizing a next generation network having a network layer includes an application services middleware between the applications and the network layer comprising a plurality of common infrastructure elements usable by the applications. The common infrastructure elements provide both services associated with use of the network and services that are not associated with use of the network. The plurality of common infrastructure elements includes a notification service that is configured to facilitate the sending of messages from authorized services to recipients.
Owner:AT&T INTPROP I L P
Messaging system and method
InactiveUS8332475B2Reduce deliveryInformation formatComputer security arrangementsCommunications systemClient-side
Owner:T PLAY HLDG LLC
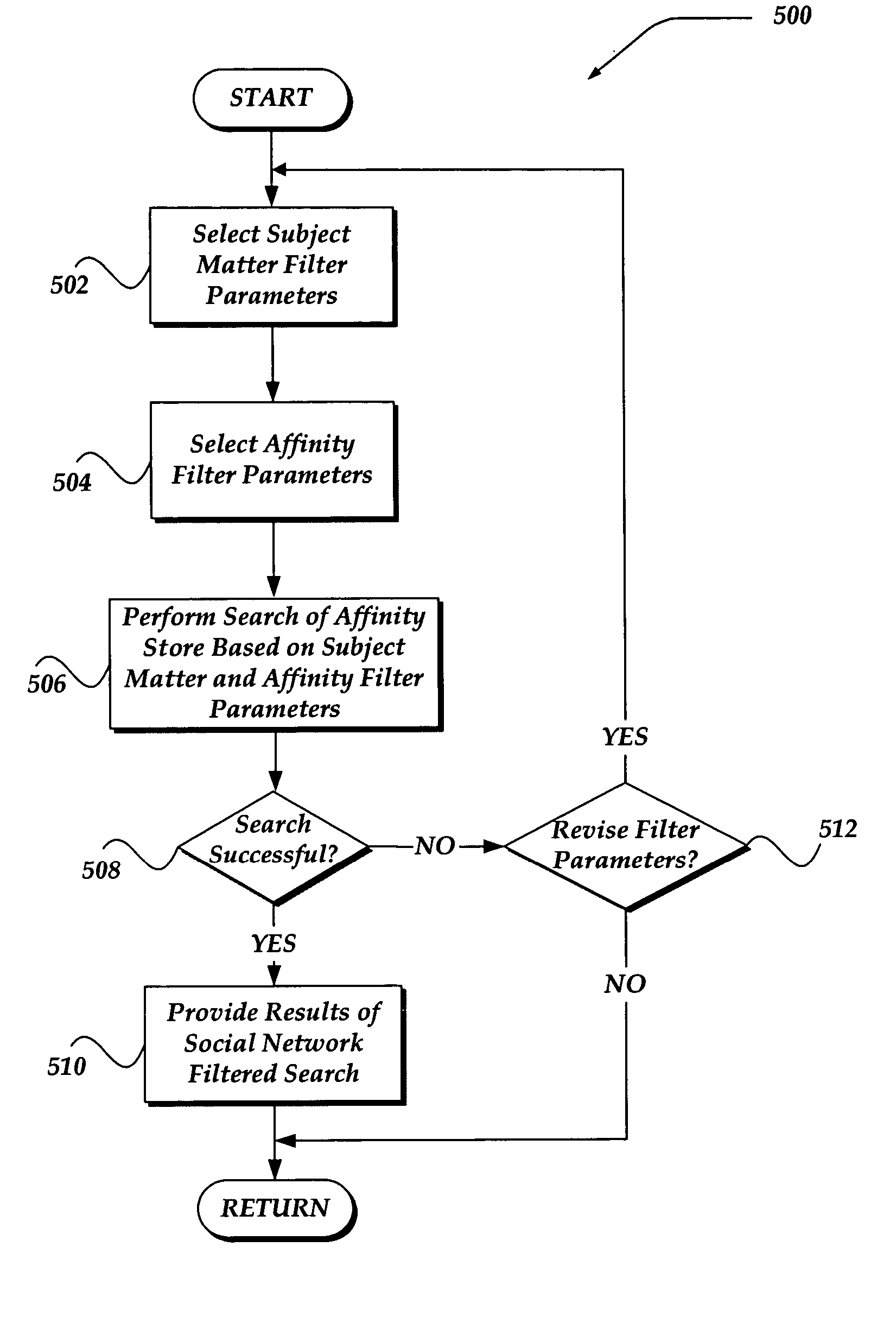
System and method of information filtering using measures of affinity of a relationship
ActiveUS20050171955A1Data processing applicationsData switching networksAffinity measurementSpamming
A system, apparatus, and method are directed towards enabling information filtering using measures of an affinity of a relationship between subscribers of an online portal system. The affinity of a relationship may be determined based, in part, on the tracking of various online behaviors of and between subscribers of the portal system. Any of a variety of behaviors may be tracked, including message communications between subscribers, participation in instant messaging groups, purchases, activities, categories, and so forth. Such behaviors may be employed to determine a level of trust (or affinity) between subscribers of the portal system. This affinity measurement may be used to filter various information, including, but not limited to, product recommendations, ratings, polling queries, advertising, social network communications, personal ads, search results, and the like. Moreover, this affinity measurement may also be employed to perform message spam detection.
Owner:SLACK TECH LLC
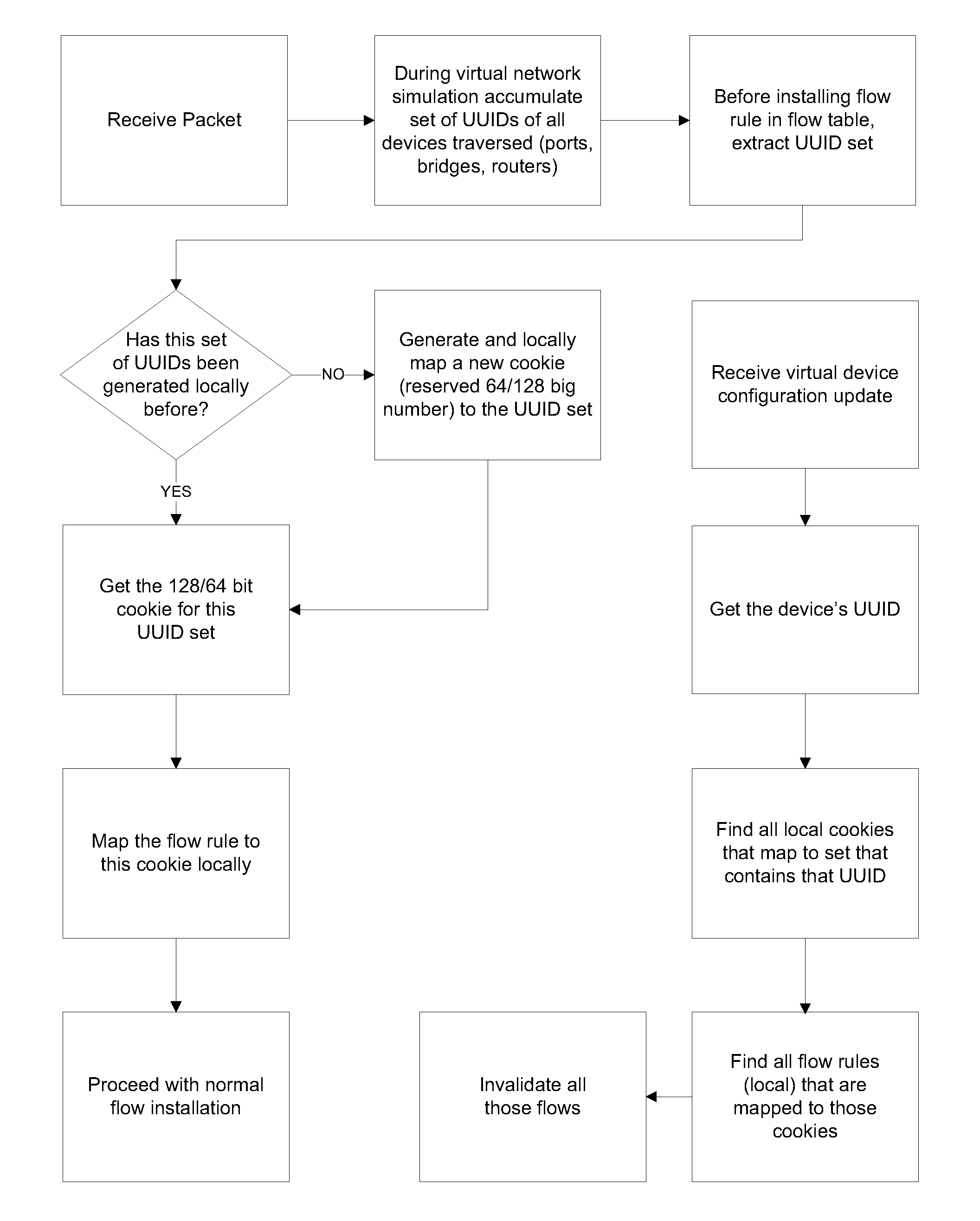
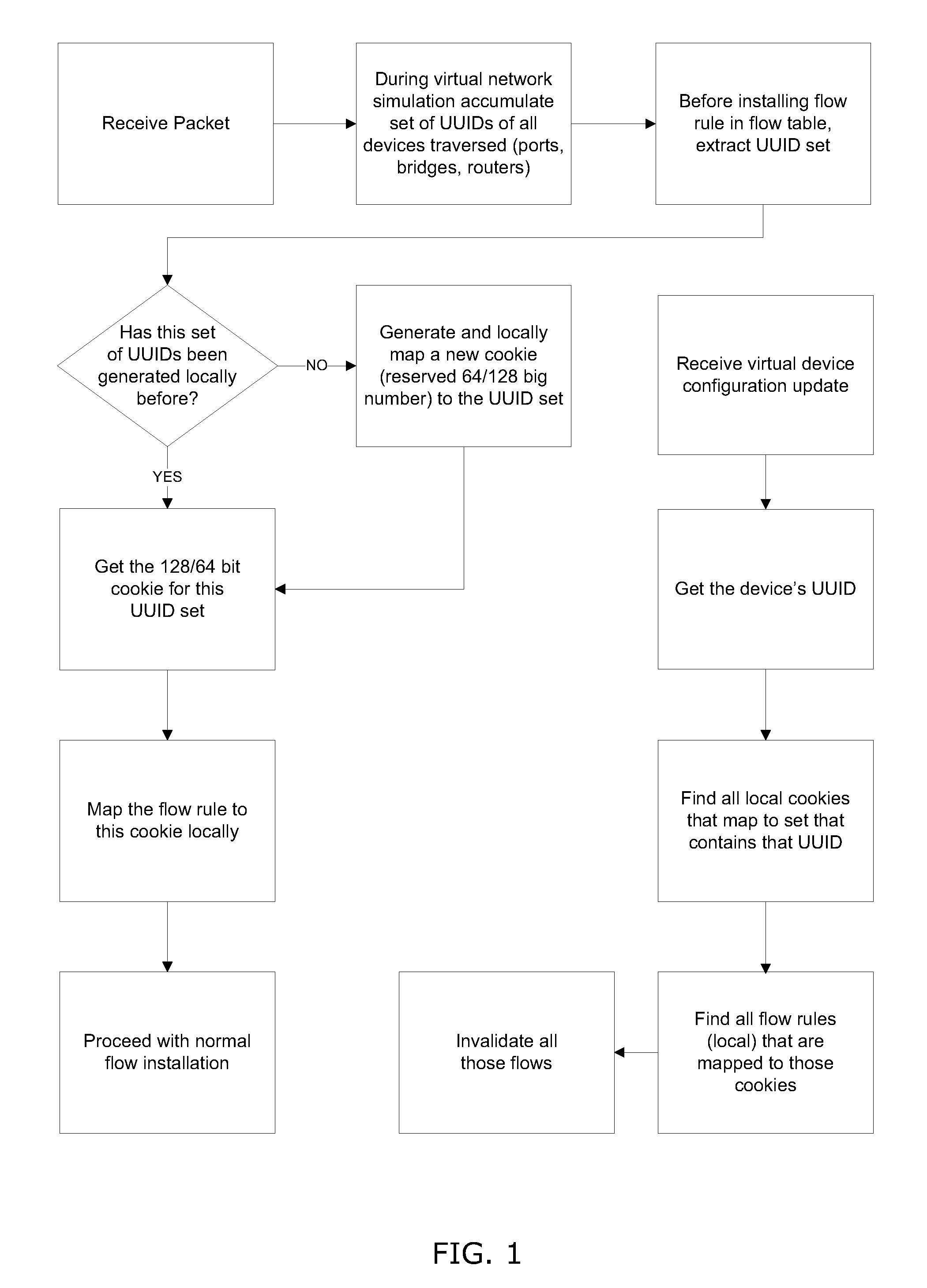
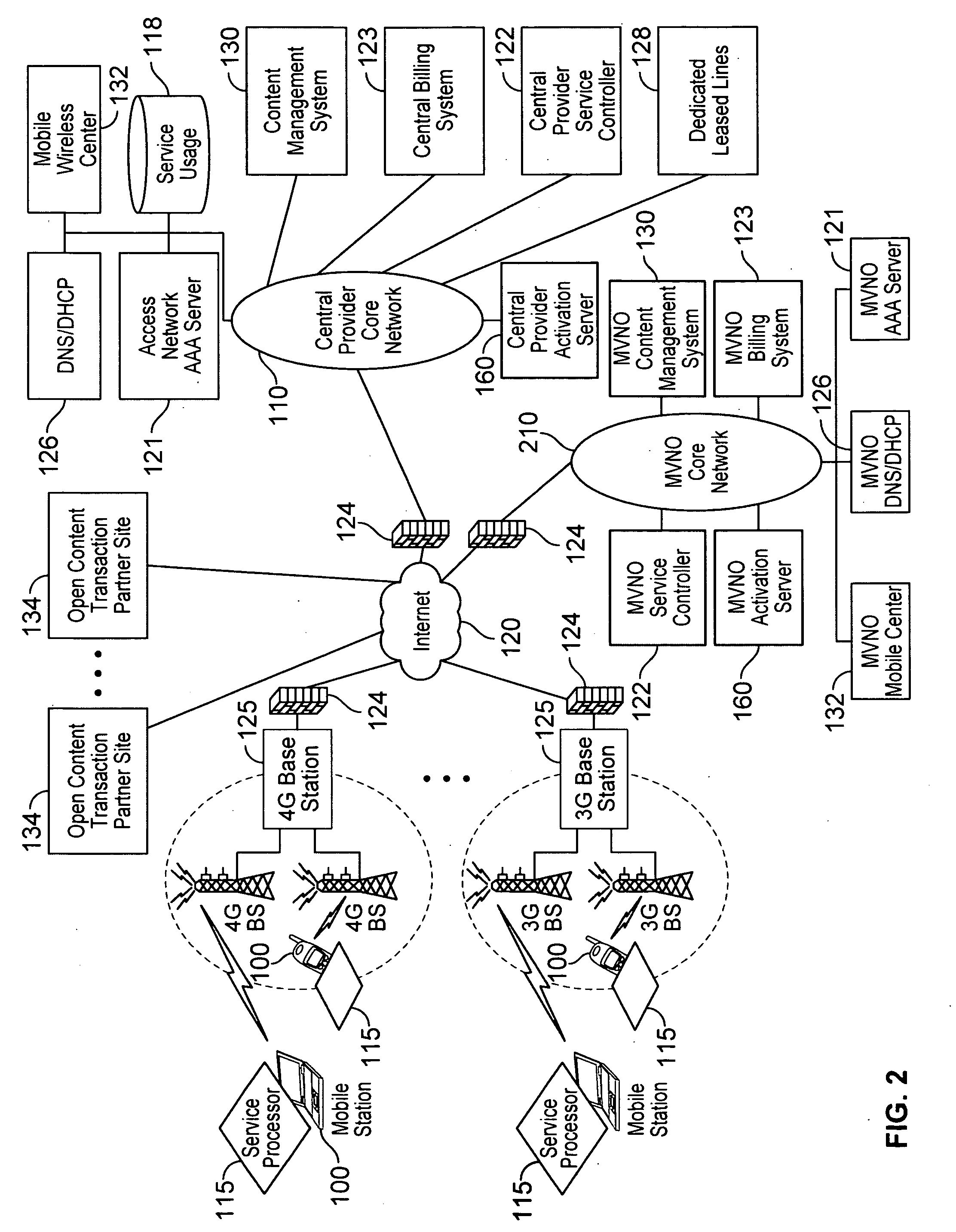
System and method for implementing and managing virtual networks
ActiveUS20140195666A1Digital computer detailsData switching networksVirtual network topologyDecision taking
A system and method for implementing and management virtual networks is disclosed. A method includes receiving a network packet arriving at a first network interface of a first node of an underlying network, communicating at least the packet and an identifier of the first network interface to a decision engine, determining how the packet should be processed based on a simulation by the decision engine of a traversal of a virtual network topology including a plurality of virtual network devices, wherein the decision engine communicates with a shared database accessible from the underlying network that stores the virtual network topology and virtual device configurations for the plurality of virtual network devices; and processing the packet based upon the simulation.
Owner:MIDO HLDG LTD
Systems and methods of blockchain transaction recordation
Owner:NASDAQ INC
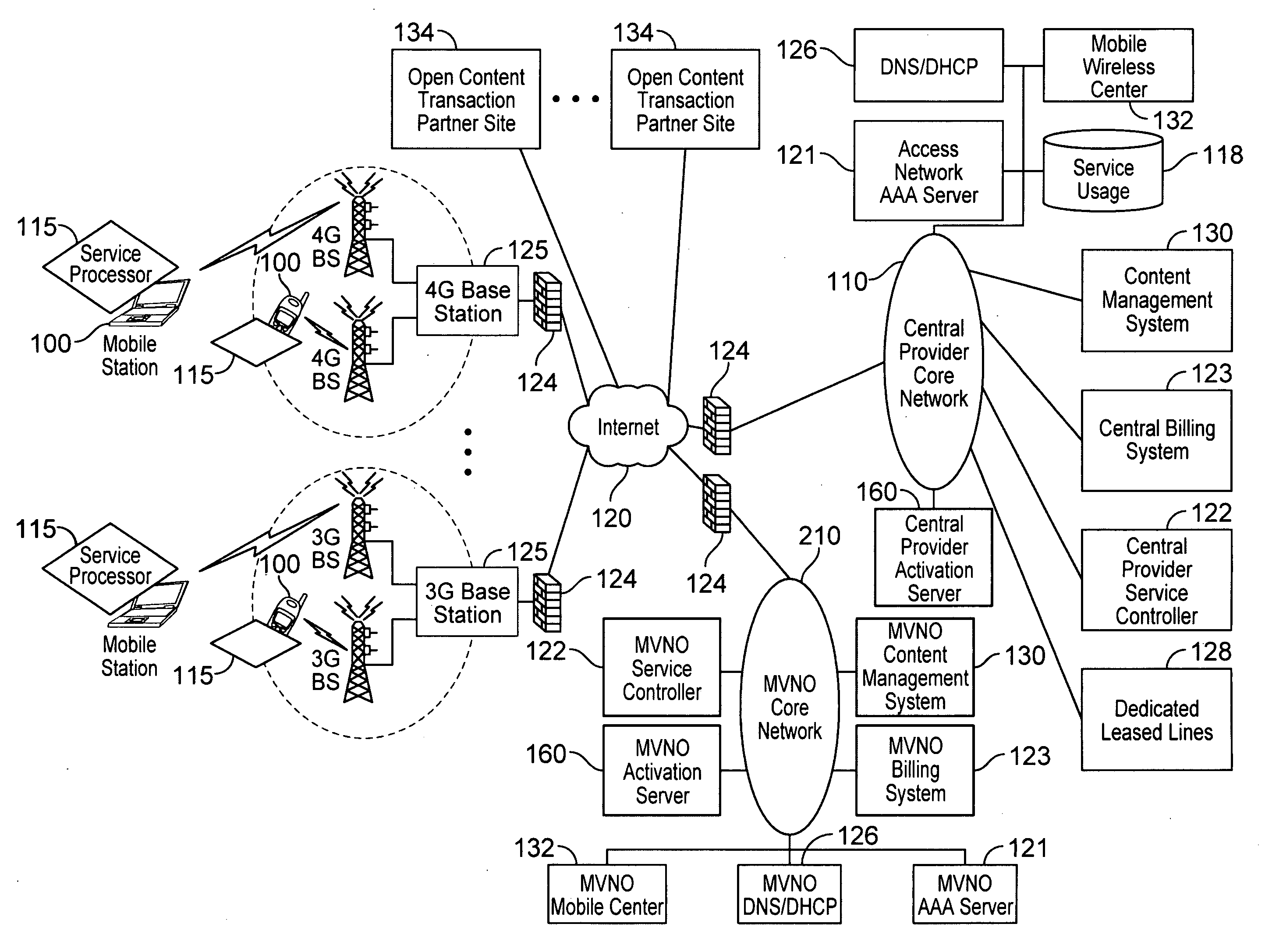
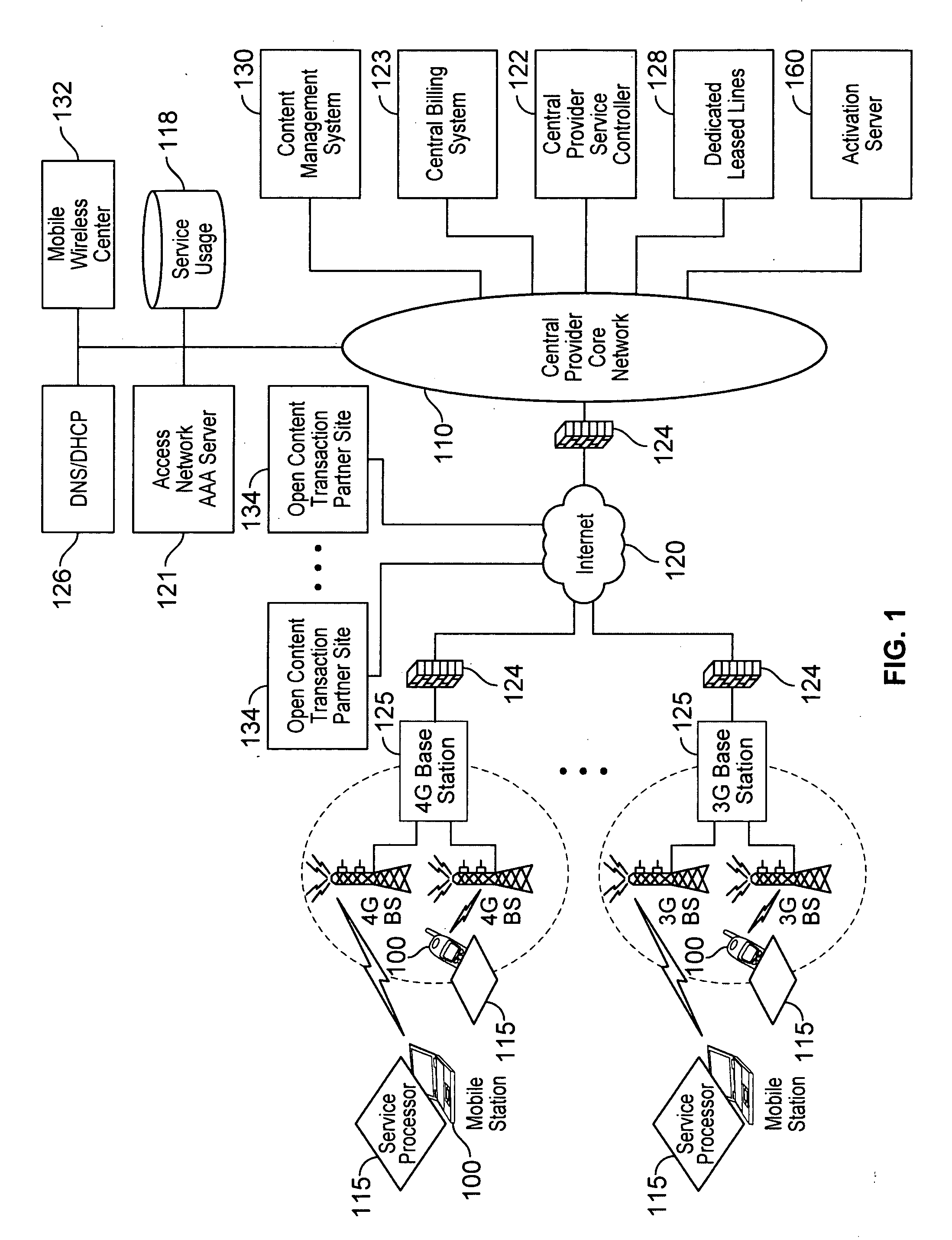
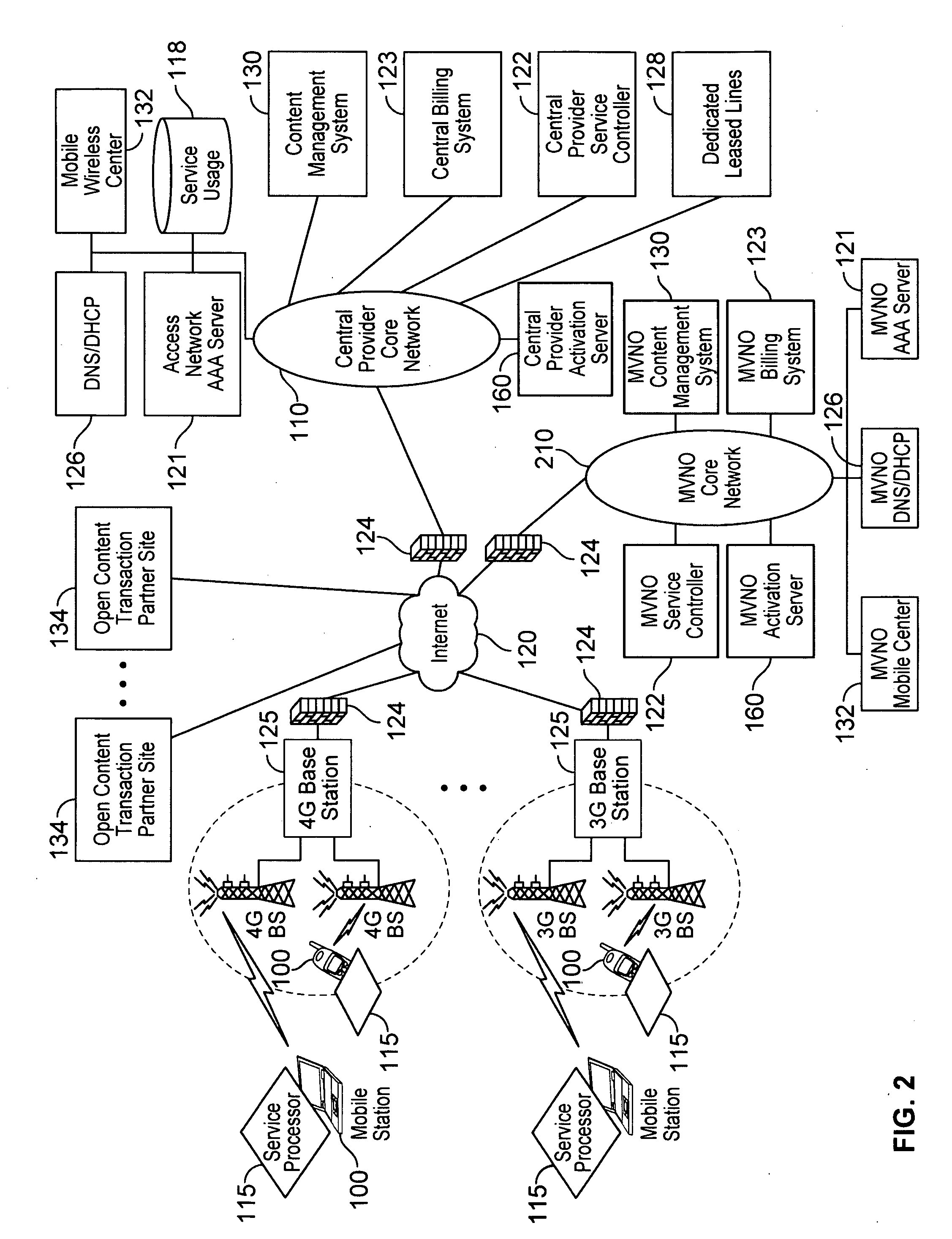
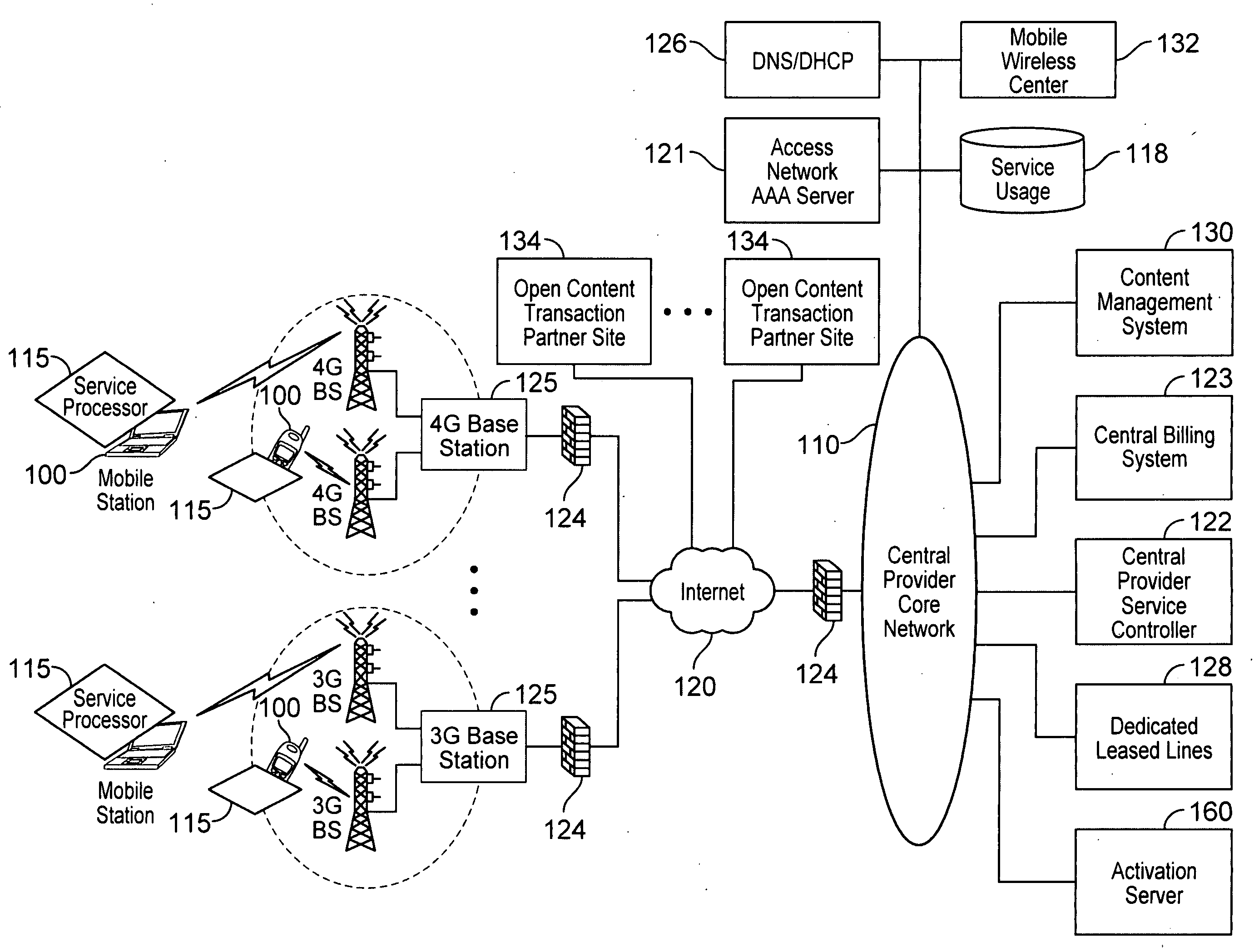
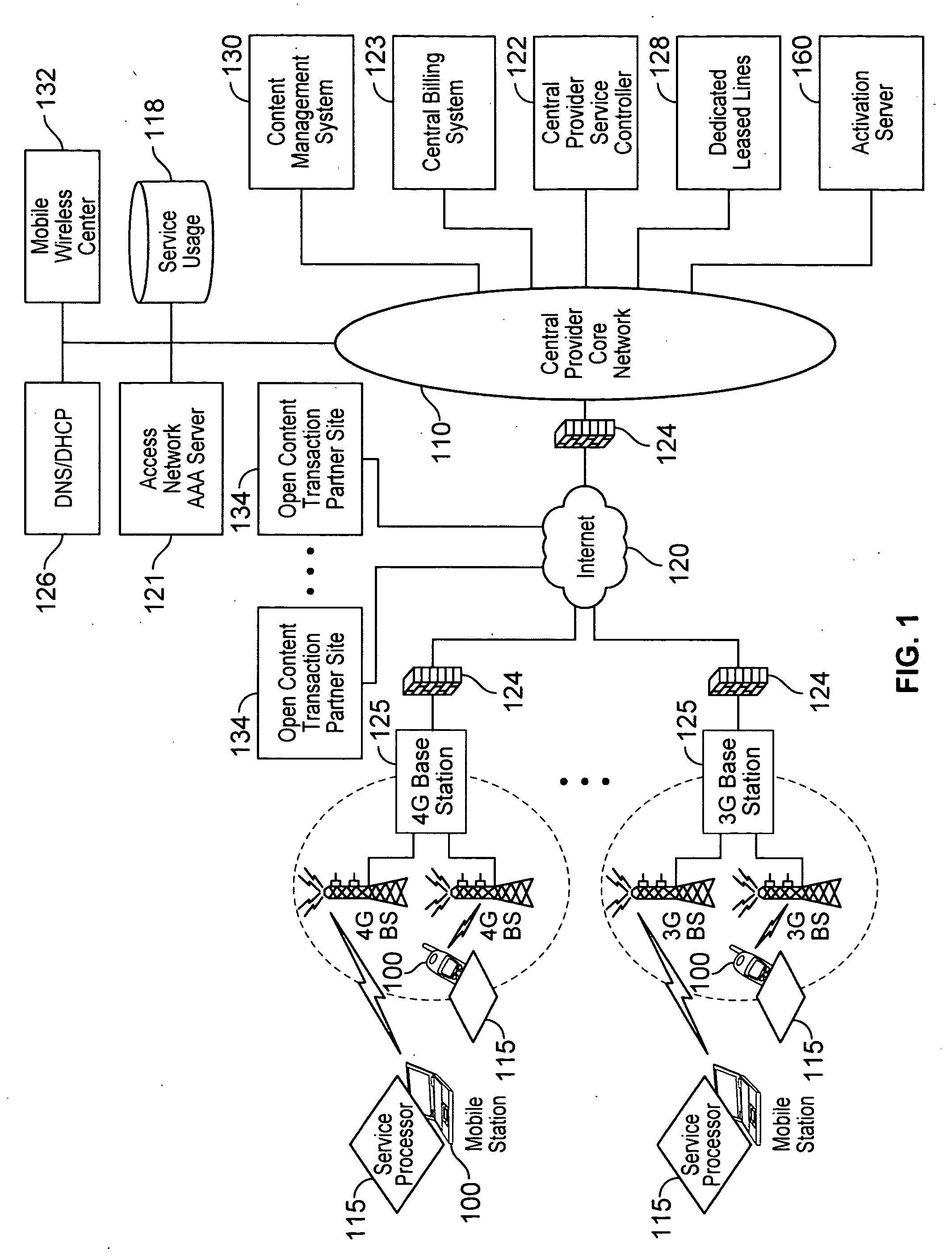
Automated device provisioning and activation
ActiveUS20100192212A1Digital data processing detailsTechnology managementCommunications systemBiological activation
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device stores a set of device credentials for activating the communications device for a service on a network; and sends an access request to the network, the access request including the set of device credentials.
Owner:HEADWATER RES LLC
Verifiable device assisted service policy implementation
ActiveUS20100188975A1Error preventionFrequency-division multiplex detailsCommunications systemCommunication device
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting control of the communications device use of a service on a network; and monitors use of the service based on the service policy, in which the implementation of the service policy is verified.
Owner:HEADWATER RES LLC
Messaging System Apparatuses Circuits and Methods of Operation Thereof
ActiveUS20110202598A1Multiple digital computer combinationsMessaging/mailboxes/announcementsClient-sideMessage passing
Disclosed are a messaging system, apparatuses circuits and methods of operation thereof. A messaging client device is adapted to receive an impermanent message and to manage the received message in accordance with a message management policy associated with the message. An impermanent messaging server is adapted to validate said messaging client device as complying with message management policies prior to authorizing transmission of the message to said messaging client device.
Owner:TIGERCONNECT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com