Patents
Literature
487 results about "Trust network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
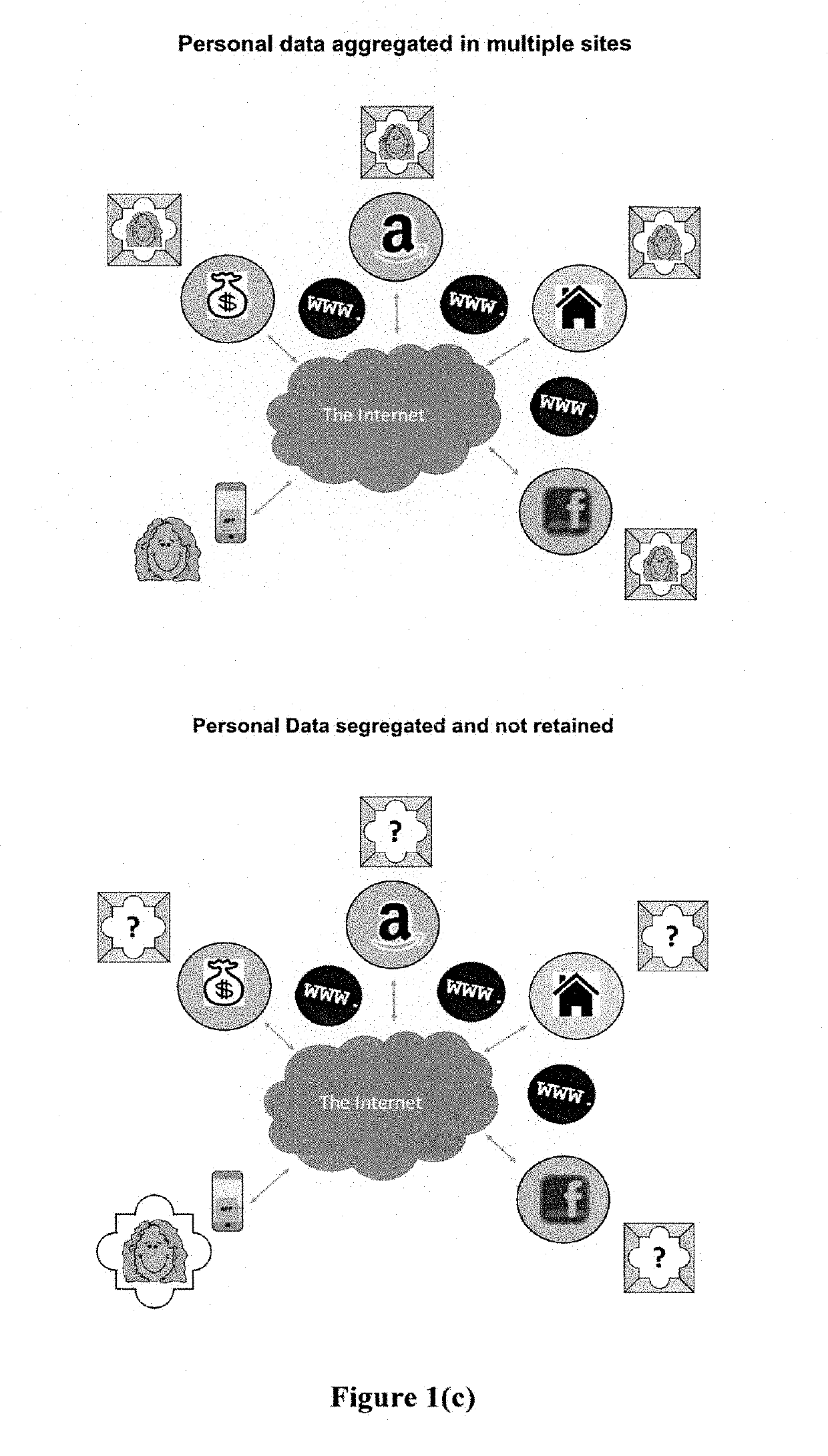
The Trust Network is a network for all independently run, state-funded schools providing its members with an opportunity to share best practice and exchange knowledge.
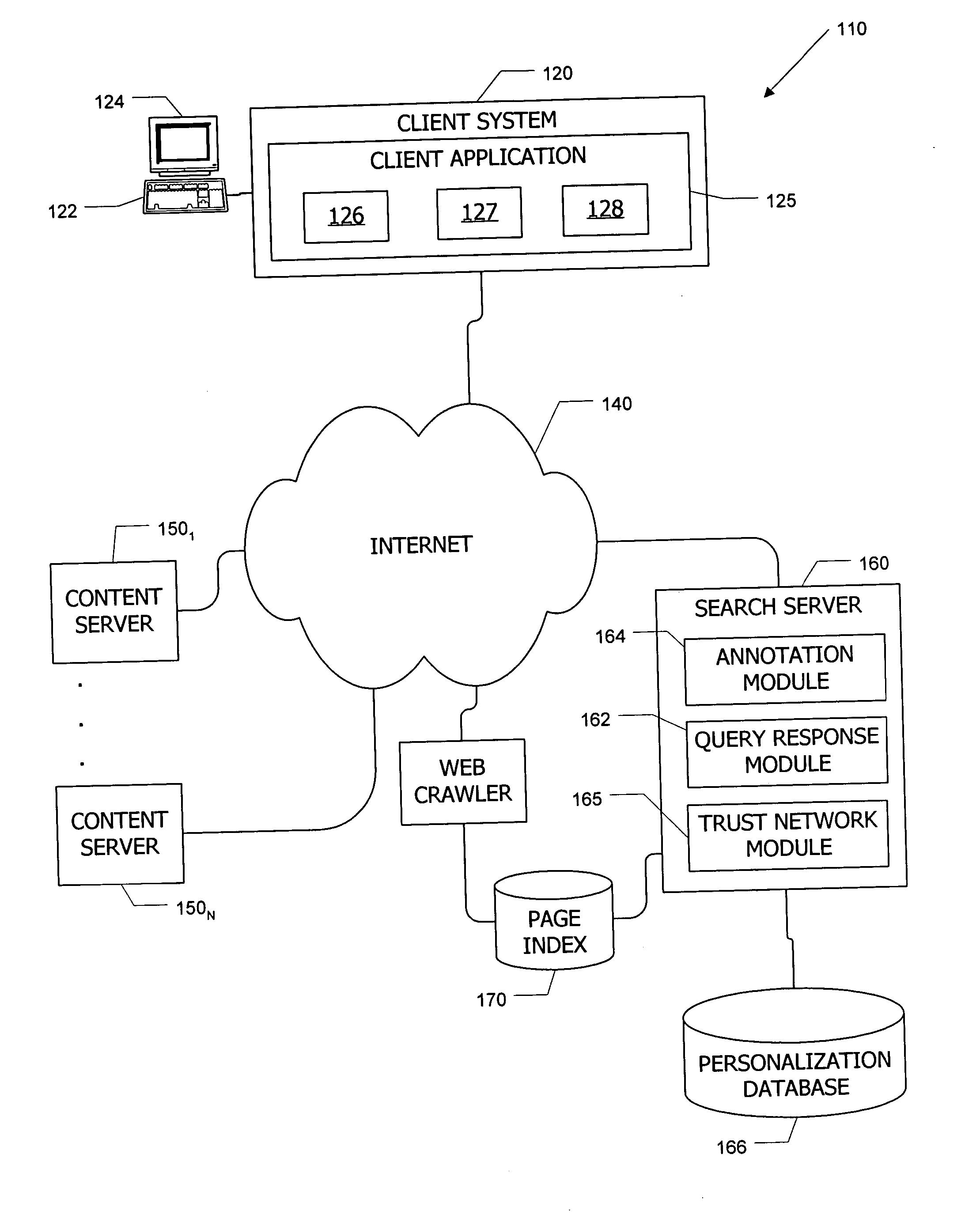
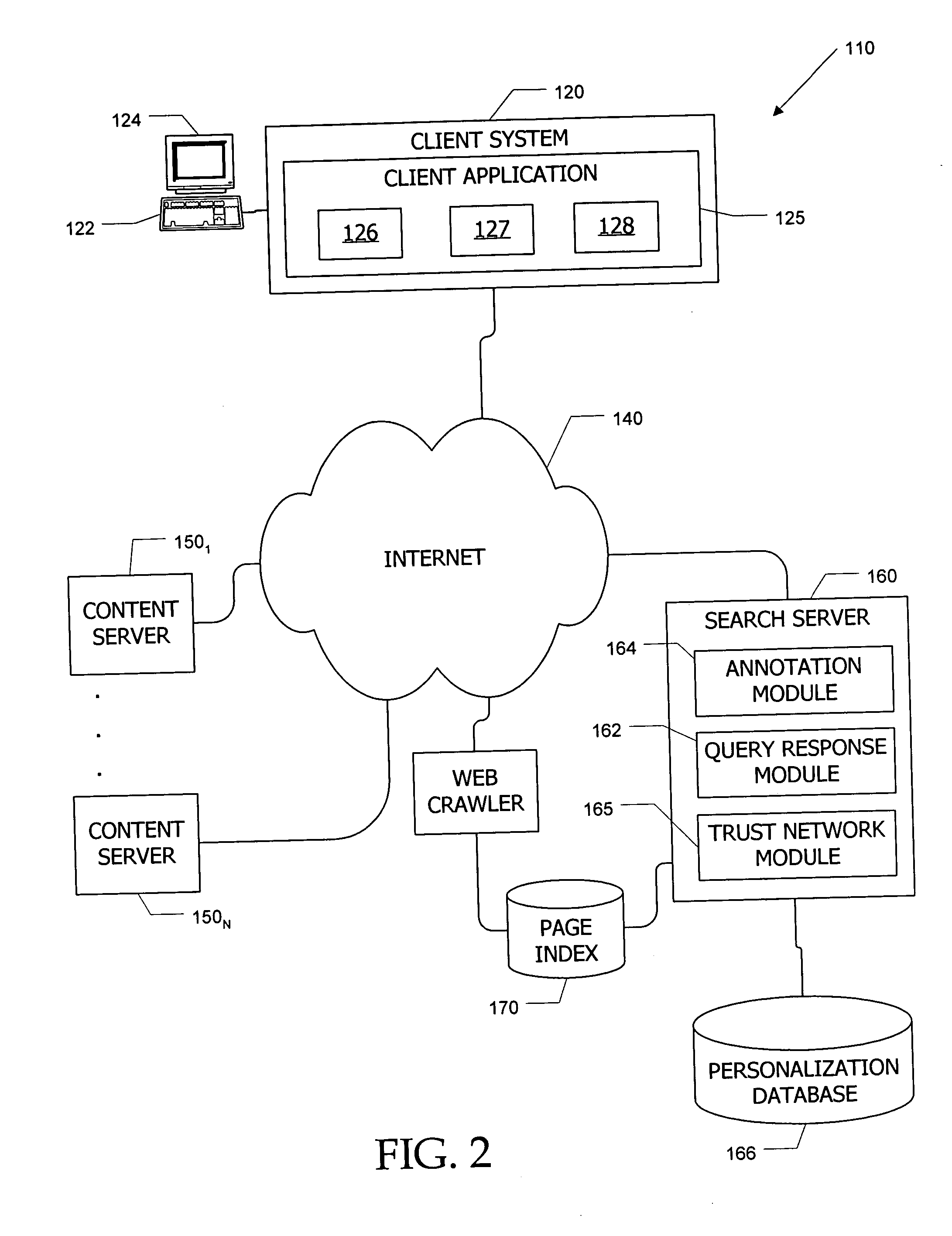
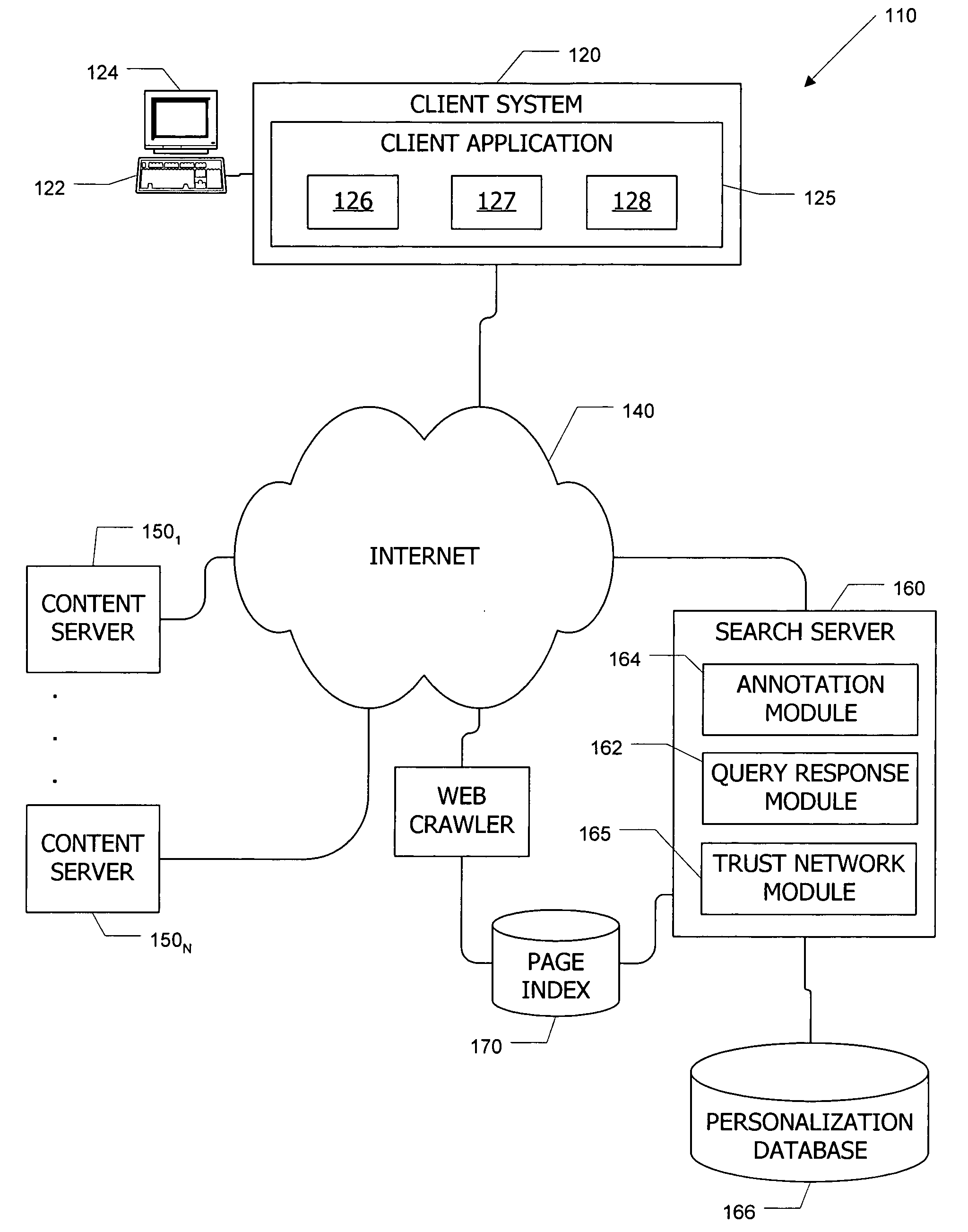
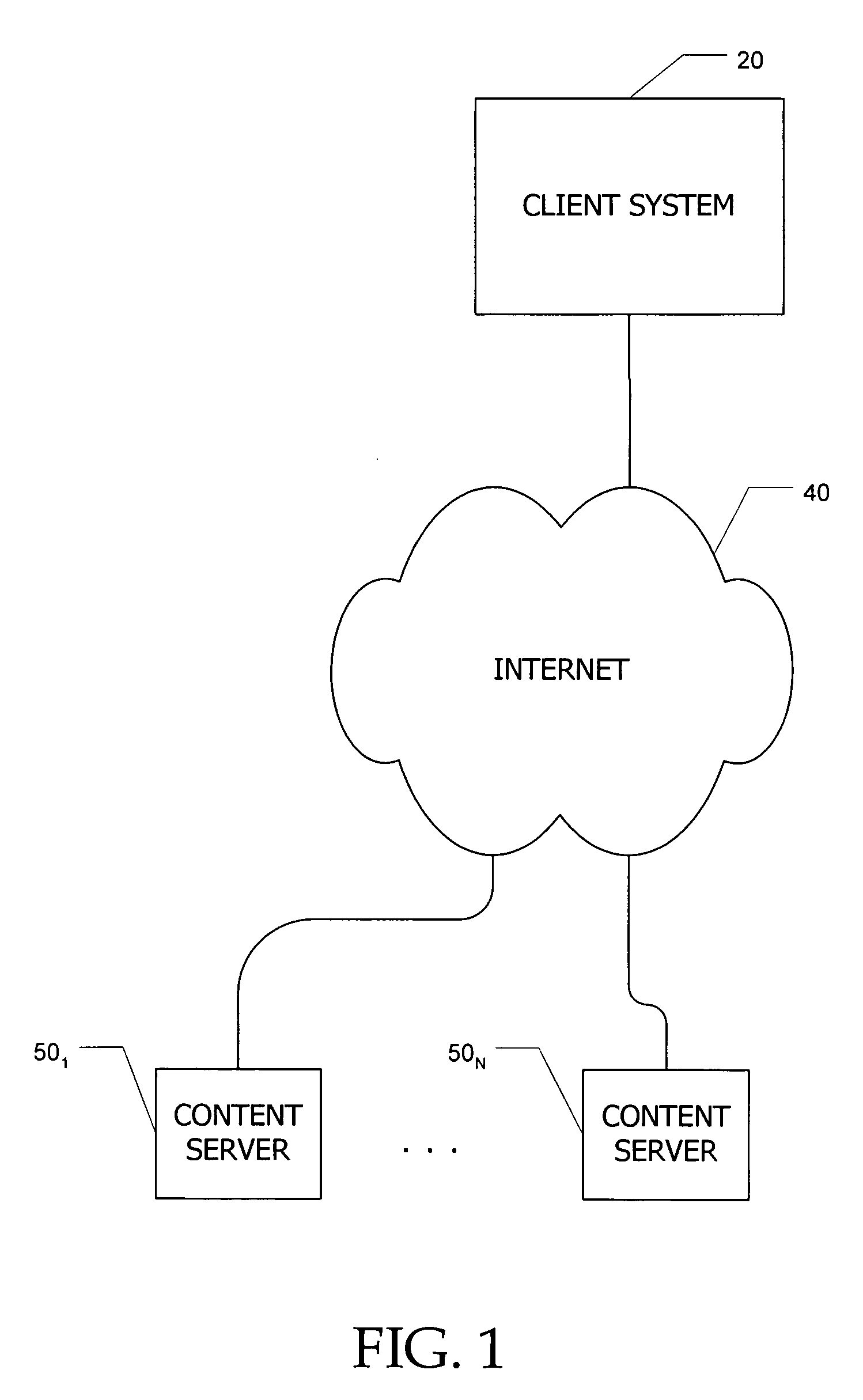
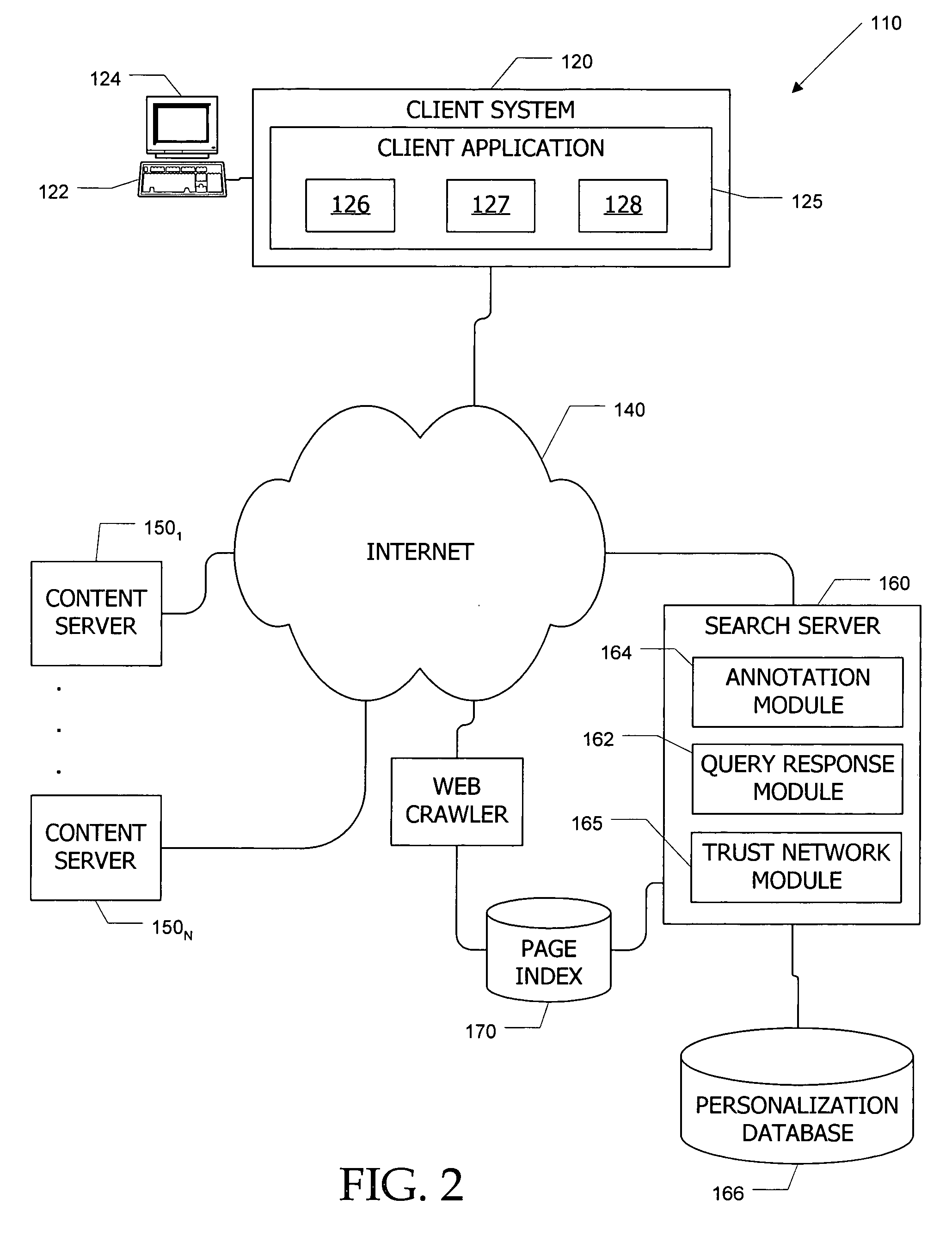
Search system and methods with integration of user annotations from a trust network
ActiveUS20050256866A1Enhance querying user 's experienceImprove browsing experienceData switching networksSpecial data processing applicationsTrust networkUser defined
Computer systems and methods incorporate user annotations (metadata) regarding various pages or sites, including annotations by a querying user and by members of a trust network defined for the querying user into search and browsing of a corpus such as the World Wide Web. A trust network is defined for each user, and annotations by any member of a first user's trust network are made visible to the first user during search and / or browsing of the corpus. Users can also limit searches to content annotated by members of their trust networks or by members of a community selected by the user.
Owner:SALESFORCE COM INC
Apparatus and method for content annotation and conditional annotation retrieval in a search context
InactiveUS20080005064A1Natural language data processingSpecial data processing applicationsDocumentationTrust network
Computer systems and methods incorporate user annotations (metadata) regarding various pages or sites, including annotations by a querying user and by members of a trust network defined for the querying user into search and browsing of a corpus such as the World Wide Web. A trust network is defined for each user, and annotations by any member of the querying user's trust network are made visible to the querying user during search and / or browsing of the corpus if the querying user and trust network members use similar queries to identify documents in the corpus. Users can also limit searches to content annotated by members of their trust networks or by members of a community selected by the user.
Owner:OATH INC
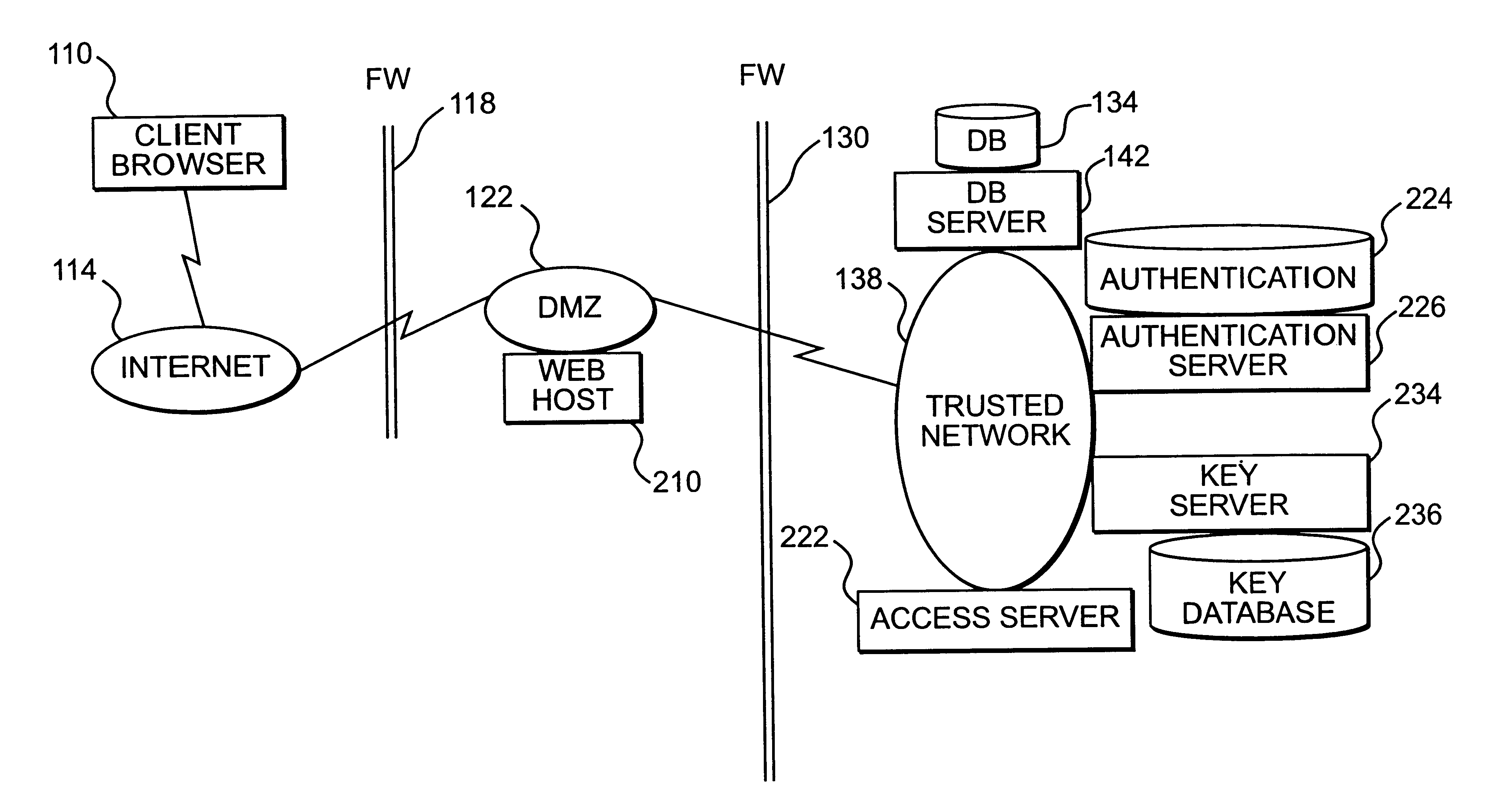
Apparatus and method for providing trusted network security
InactiveUS6199113B1Digital data processing detailsMultiple digital computer combinationsNetwork packetNetwork security policy
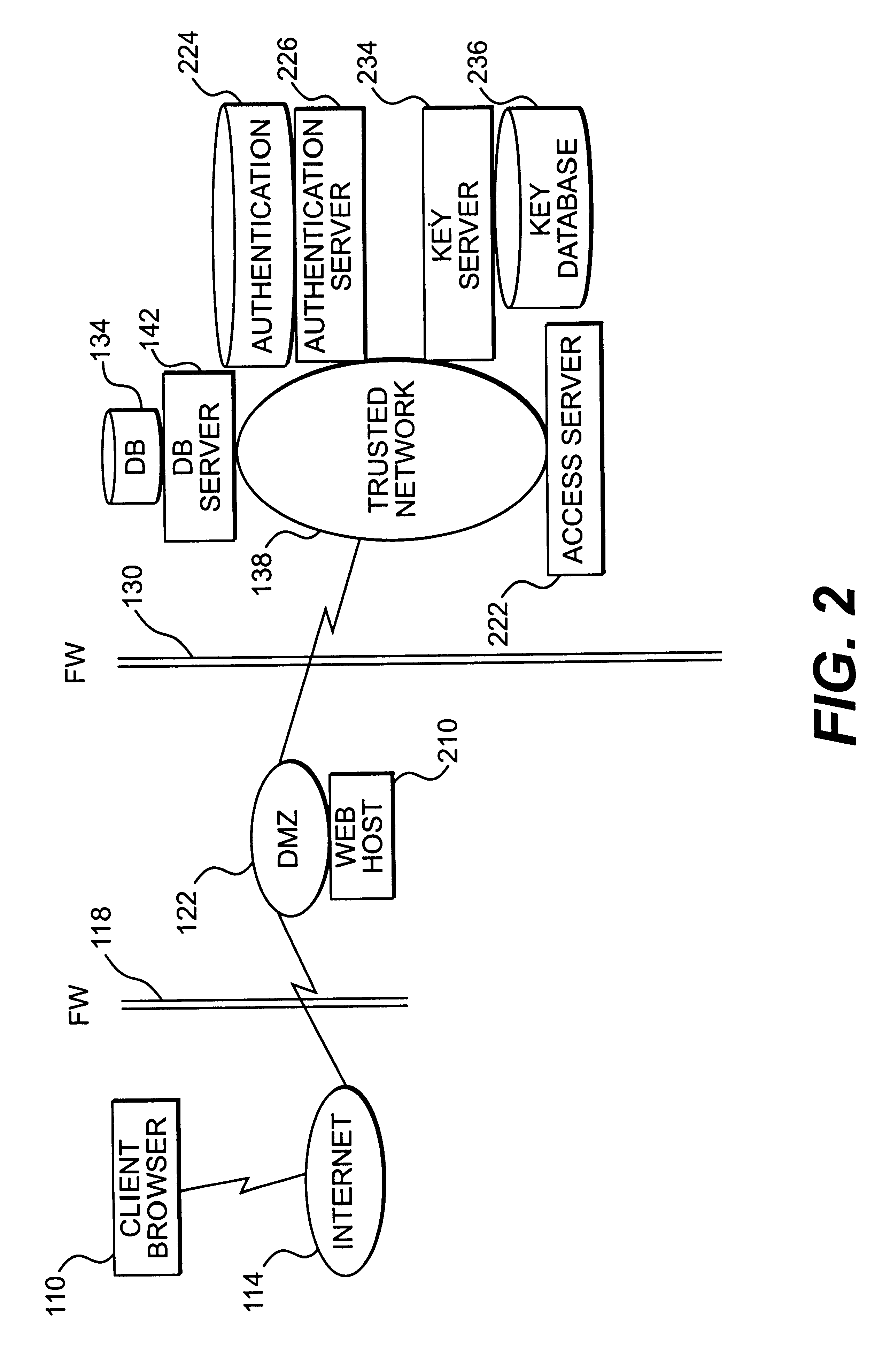
A session key is established for accessing a trusted network from a browser. An authentication process receives identification information from a user at the browser, and authenticates the user by checking the identification information against an authentication database. If the authentication database authenticates the user, a session key is created and stored at the browser. If the user is authenticated, a user profile defining access rights for the user is also retrieved. The user is then presented with access options based on the access rights defined in the user profile. In response to a user selection from the access page, the browser forwards an information request to the trusted network. The request includes a session key. A speaker object processes the information request and session key to form a network request packet. The network request packet is formed in a manner that allows authentication of the speaker object. The session packet is forwarded to a trusted network and processed. The packet is first authenticated to determine if it originated from the speaker object, and then the key is checked for validity at the trusted server. If the key is valid, the information request is processed and the information is returned to the user for display on the browser.
Owner:ORACLE INT CORP
Resilient trust network services
ActiveUS8843997B1Digital data processing detailsUser identity/authority verificationComposite applicationIntegration platform
A Resilient Trust Network (RTN) is a set of servers that provide: an application integration platform for developing and publishing services and user interface for services, building derived services, subscribing to services, and embedding services into host applications, and building composite applications composed from multiple diverse services. The RST can also provide a platform for defining security requirements and accessing shared trust services that implement those requirements for services regardless of where or how those services are used.
Owner:DATA443 RISK MITIGATION INC
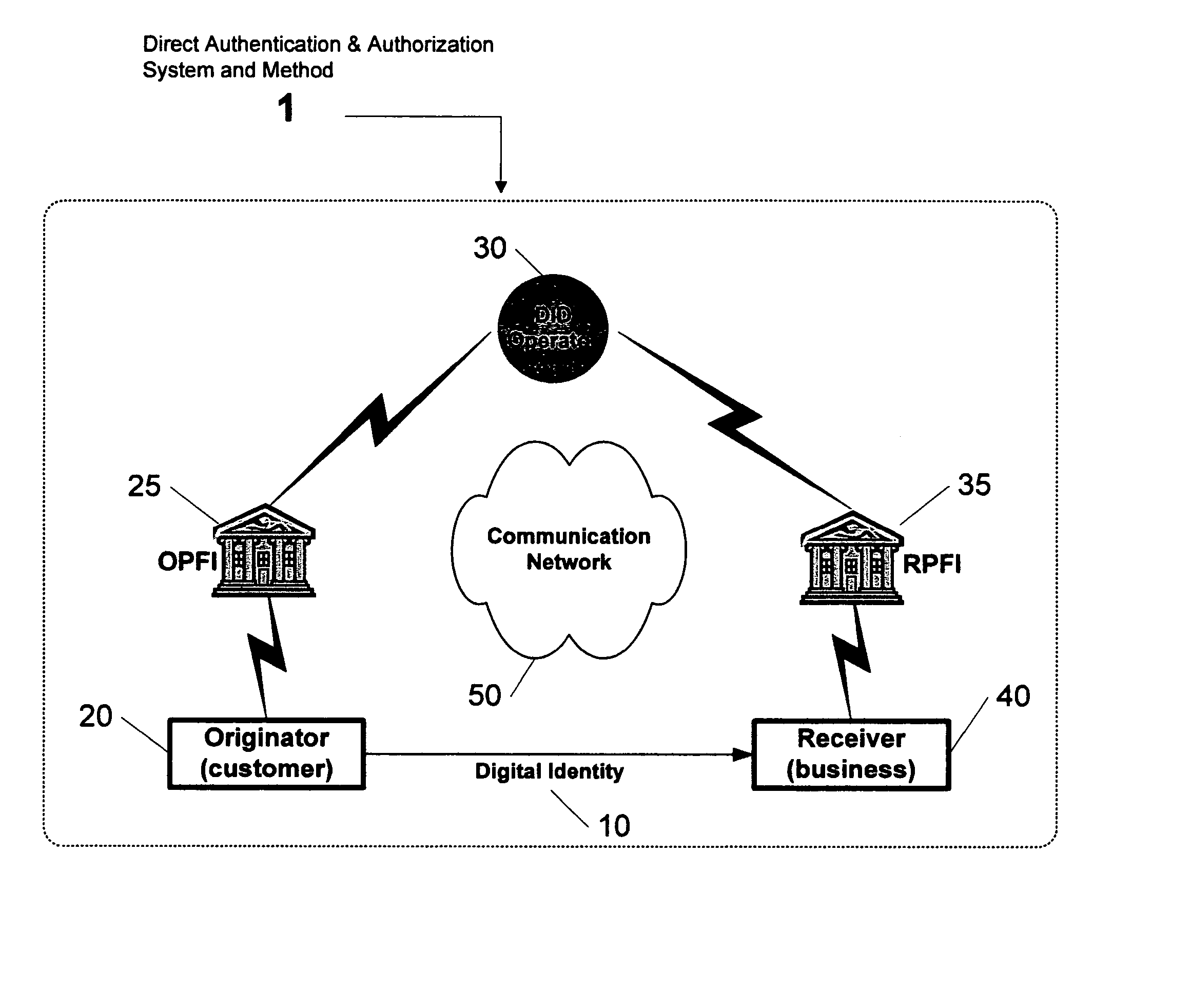
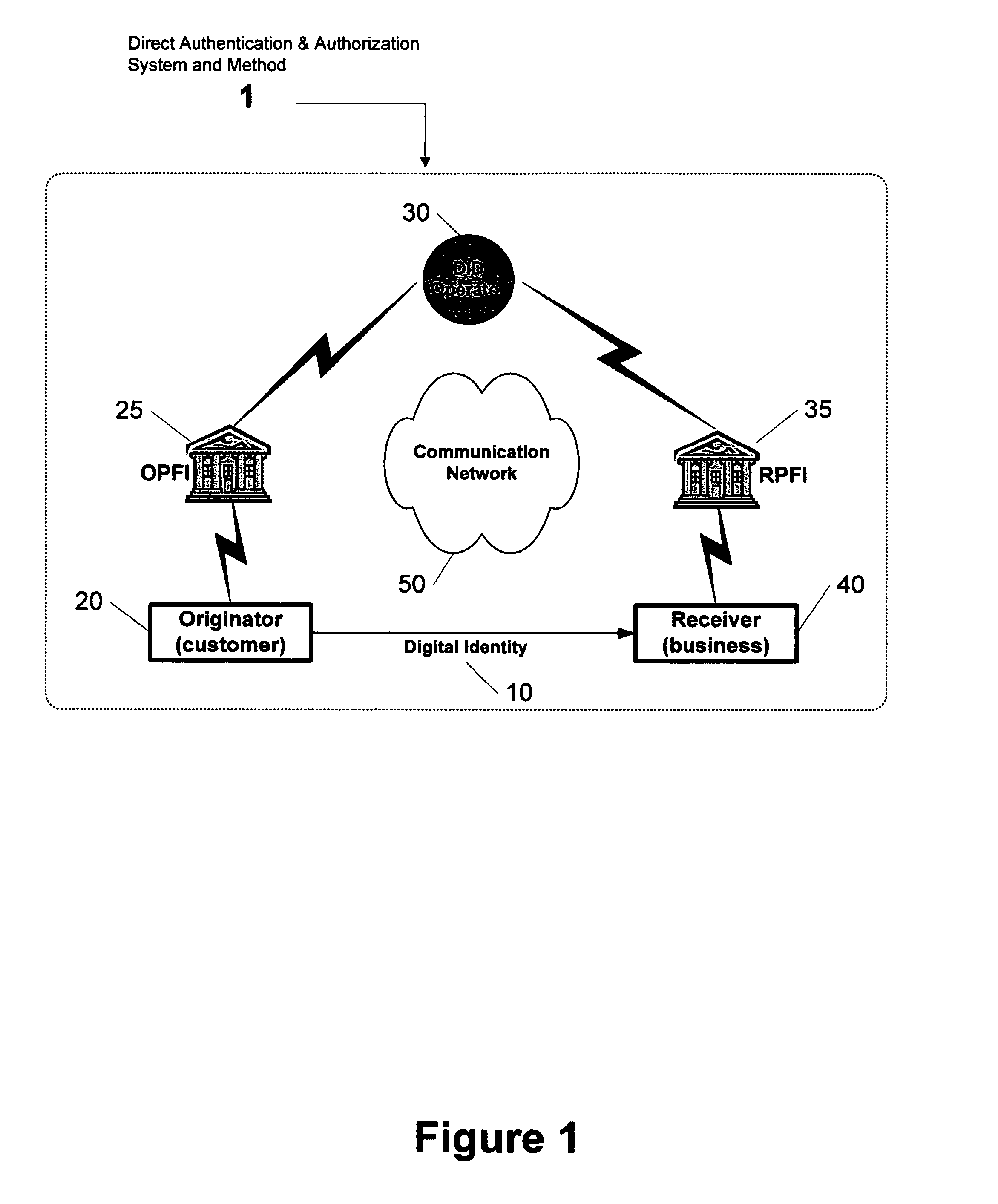
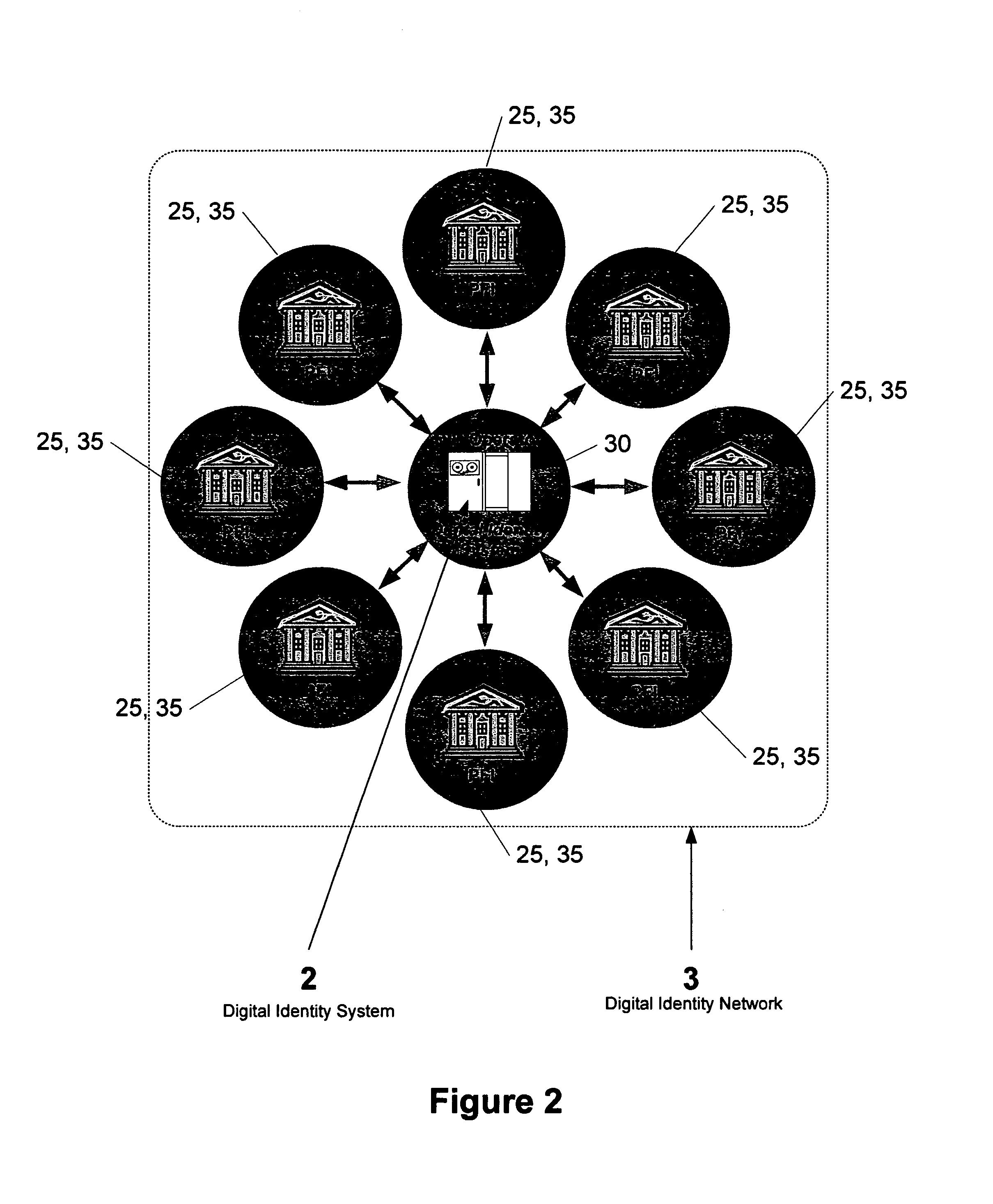
Direct authentication and authorization system and method for trusted network of financial institutions
A system and method for direct authentication and / or authorization of transactions. The system includes a trusted Digital Identity (DID) Network connecting an Originating Participating Financial Institution (OPFI) and a Receiving Participating Financial Institution (RPFI) through a DID Operator. The DID Operator may further be coupled to a DID System that calculates digital identities for Originators. According to the method, direct authentication of the Originator and / or authorization of the transaction is initiated upon the Originator communicating its digital identity to the Receiver. The Receiver subsequently provides the digital identity to the RPFI. The RPFI is then able to communicate with the OPFI for authentication of the Originator and / or authorization of the transaction through the DID Operator based on Originator's digital identity. The transaction between the Originator and Receiver can be financial or non-financial and may include, for example, account-to-account transfers, identity authentication or express agreements. In another embodiment, authentication and / or authorization may be performed in real time.
Owner:ASGHARI KAMRANI NADER +1
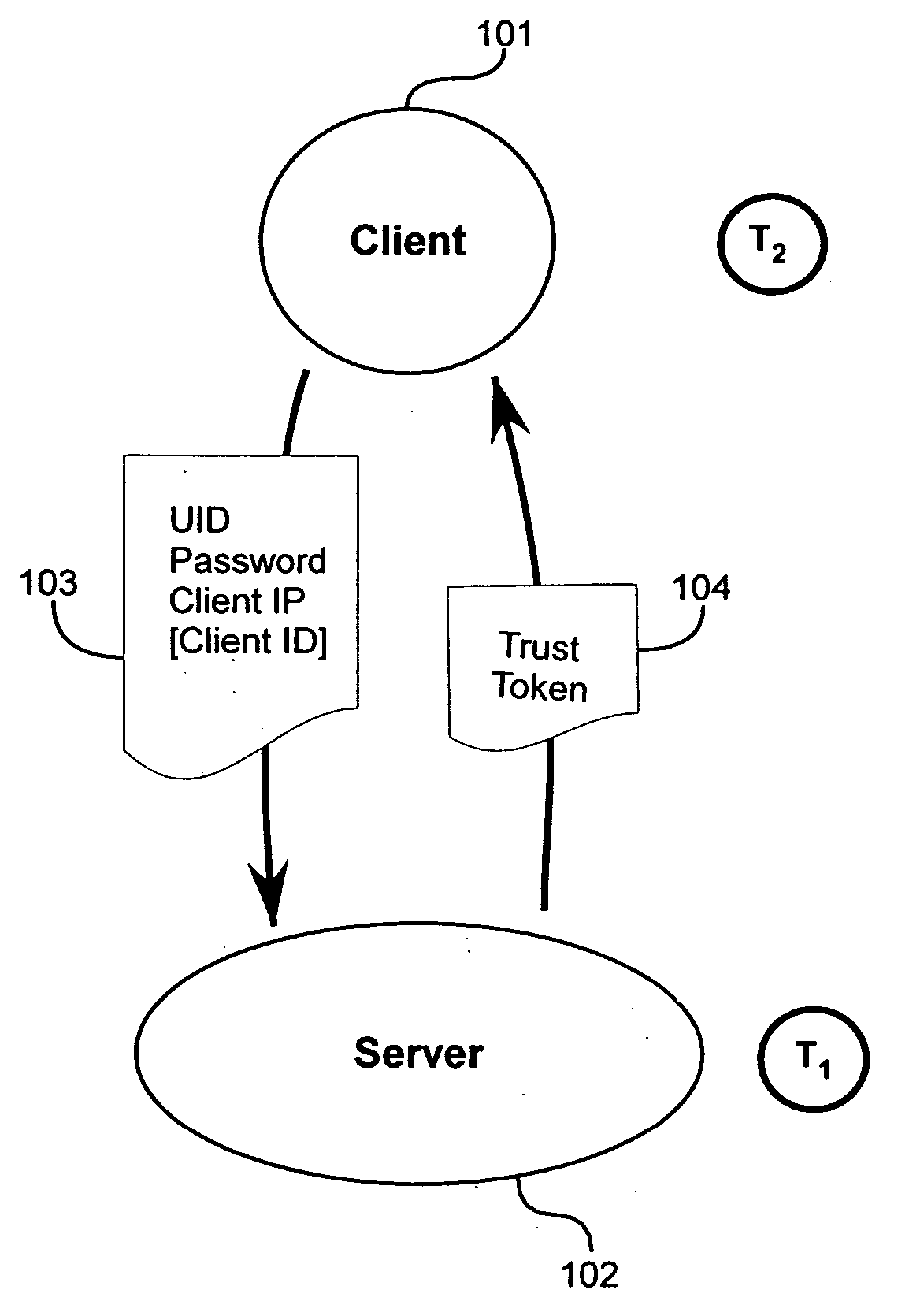
Method and apparatus for trust-based, fine-grained rate limiting of network requests
ActiveUS20050108551A1Digital data processing detailsUser identity/authority verificationRate limitingInternet traffic
A method and apparatus for fine-grained, trust-based rate limiting of network requests distinguishes trusted network traffic from untrusted network traffic at the granularity of an individual user / machine combination, so that network traffic policing measures are readily implemented against untrusted and potentially hostile traffic without compromising service to trusted users. A server establishes a user / client pair as trusted by issuing a trust token to the client when successfully authenticating to the server for the first time. Subsequently, the client provides the trust token at login. At the server, rate policies apportion bandwidth according to type of traffic: network requests that include a valid trust token are granted highest priority. Rate policies further specify bandwidth restrictions imposed for untrusted network traffic. This scheme enables the server to throttle untrusted password-guessing requests from crackers without penalizing most friendly logins and only slightly penalizing the relatively few untrusted friendly logins.
Owner:META PLATFORMS INC
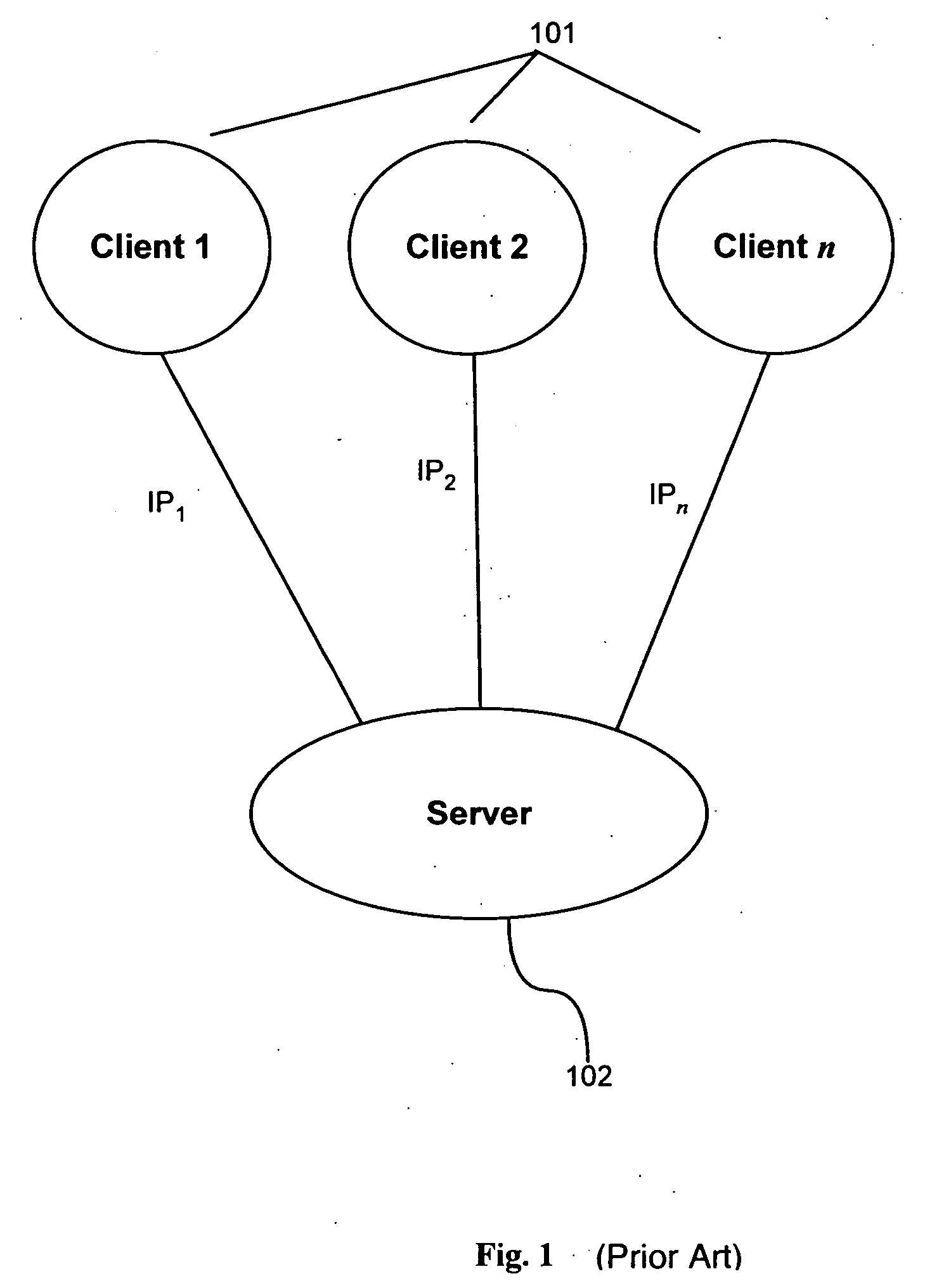
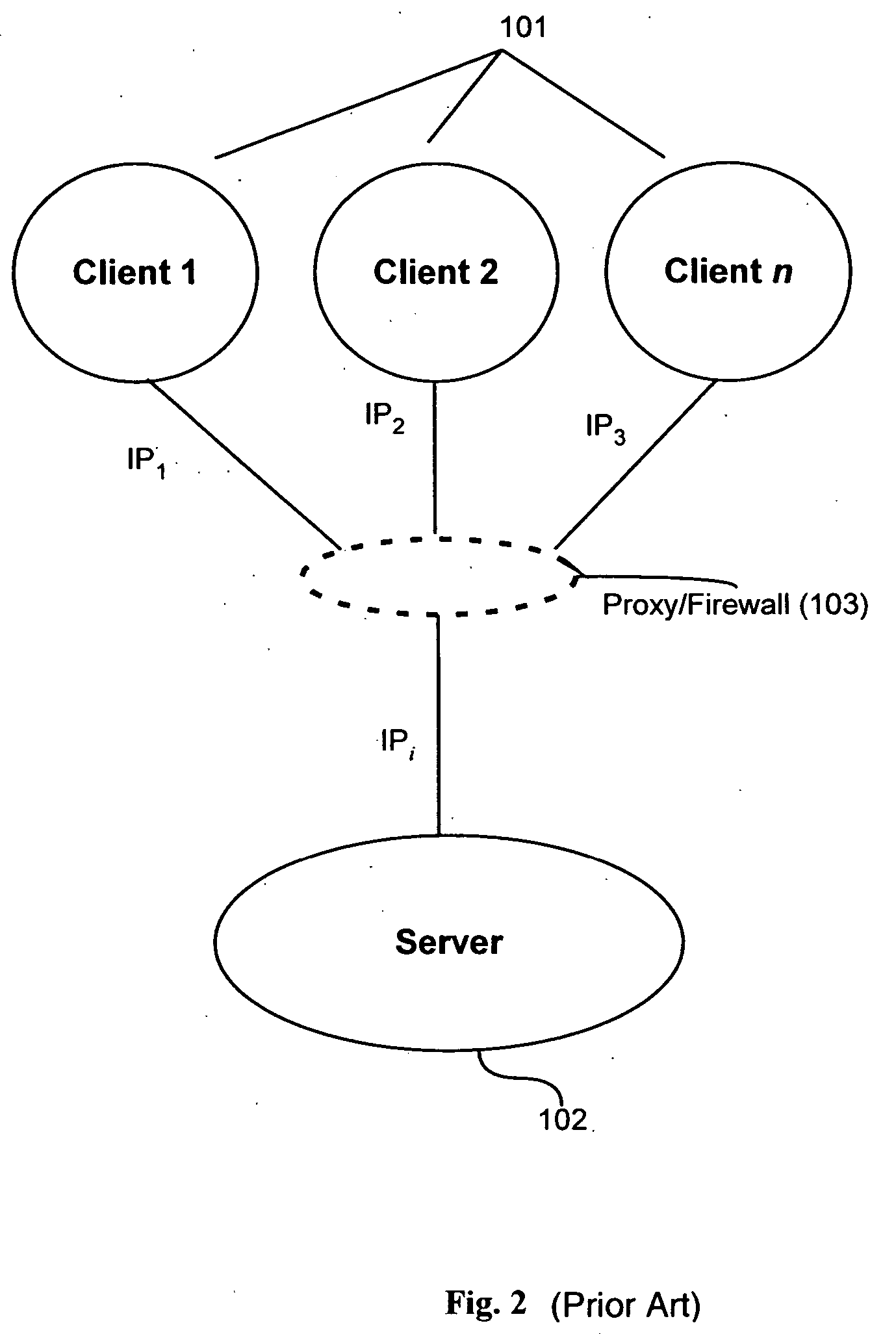
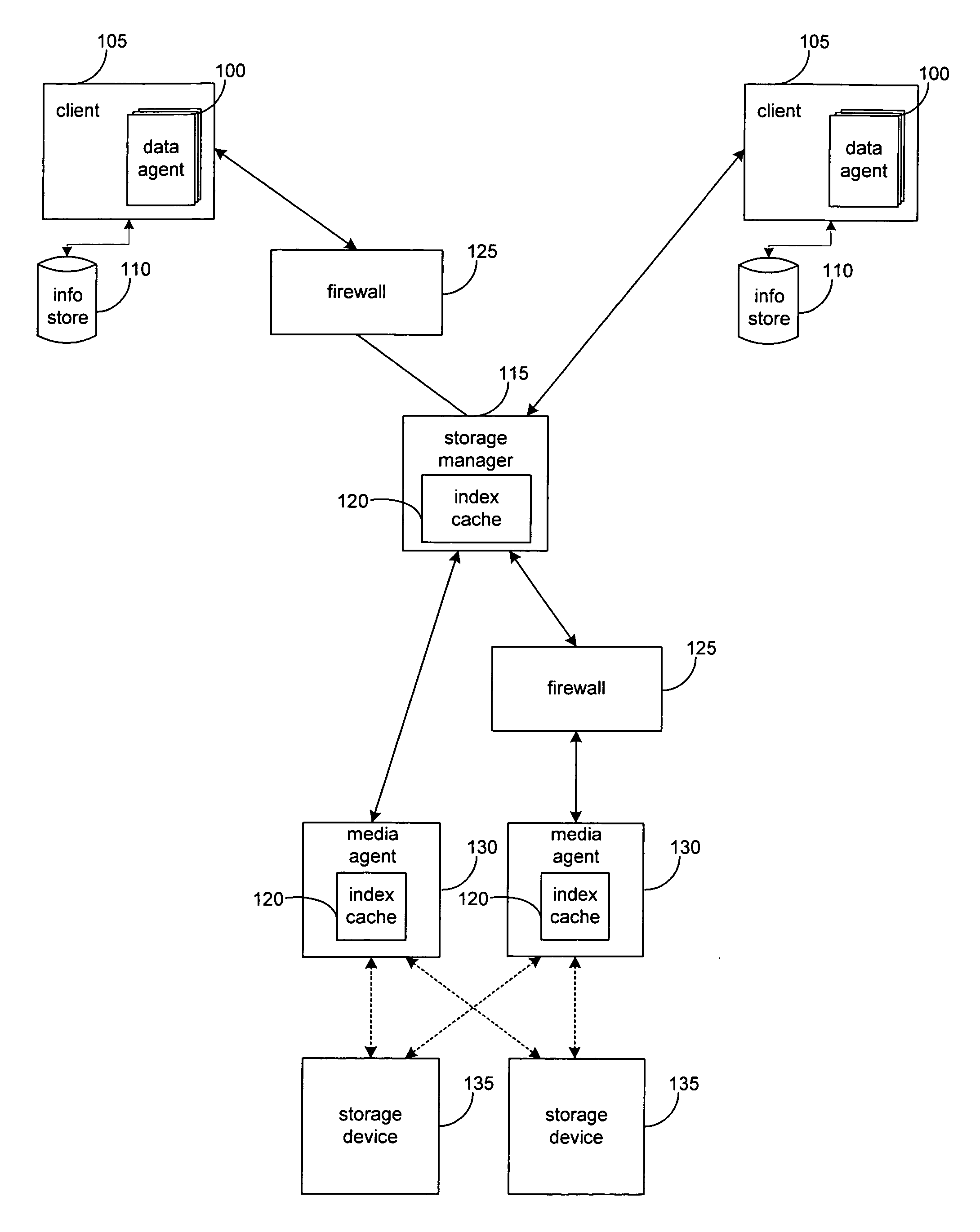
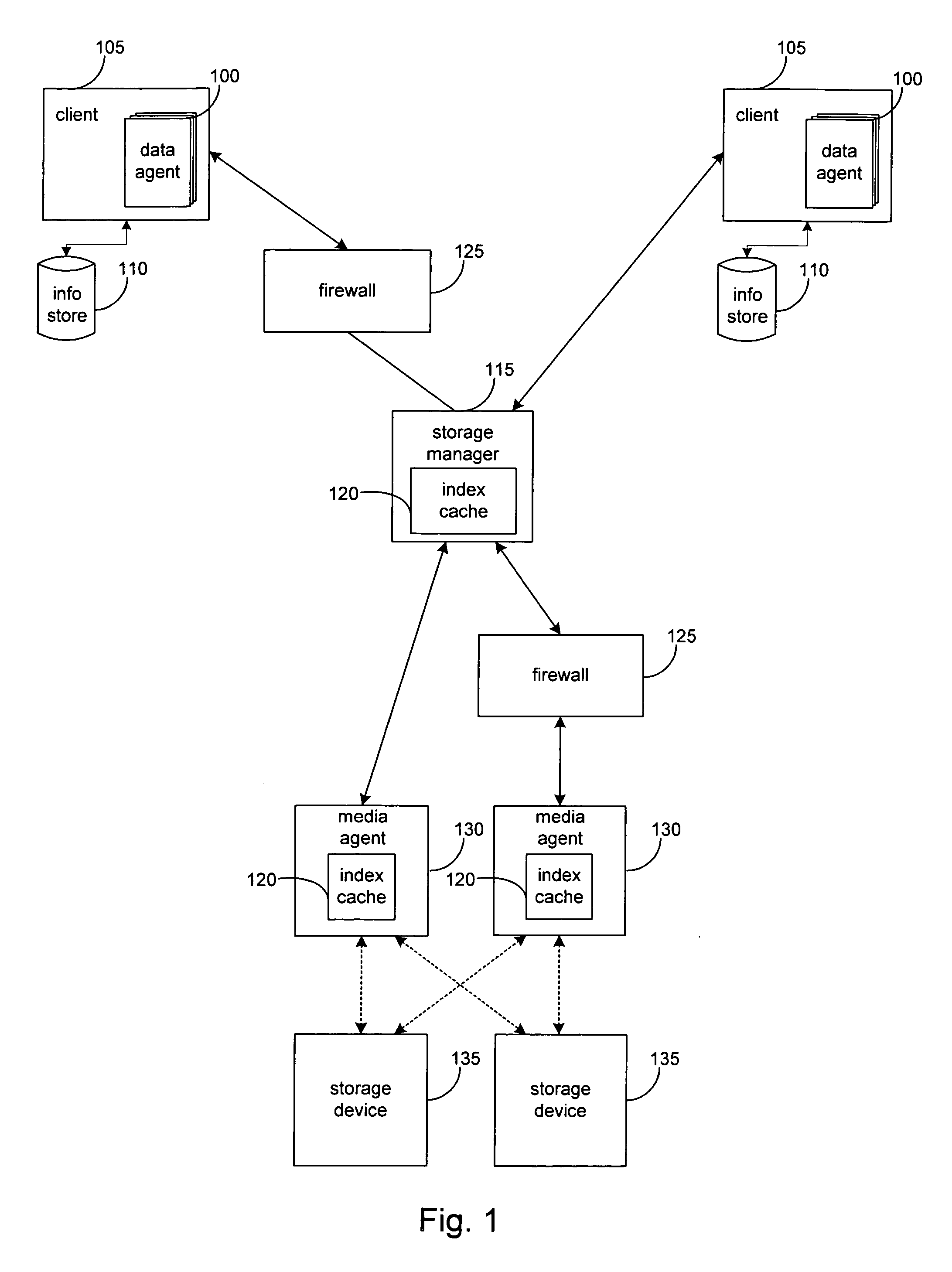
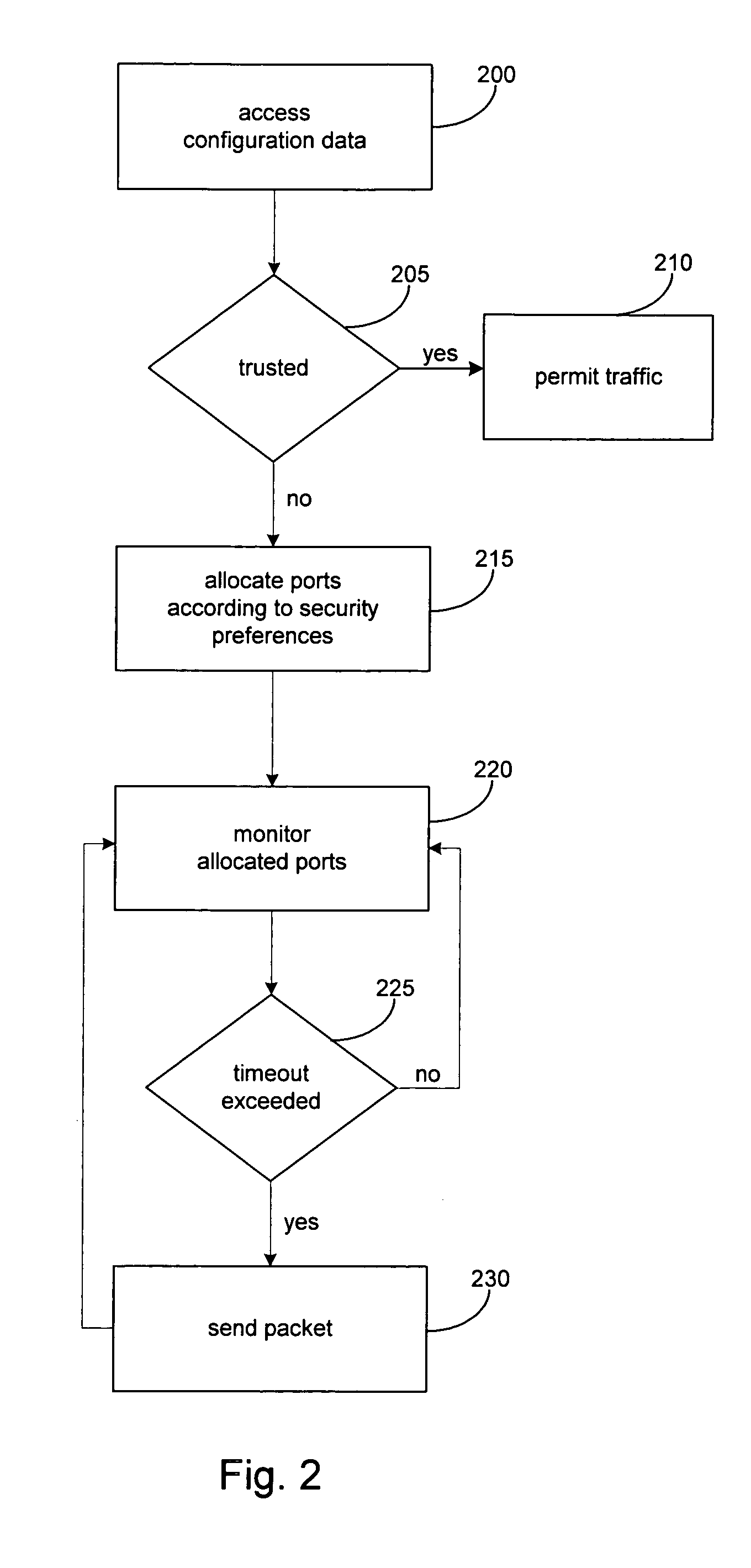
System and method for performing storage operations through a firewall
InactiveUS7631351B2Memory loss protectionDigital data processing detailsTraffic capacityComputerized system
The present invention provides systems and methods for performing storage operations through a firewall. Methods are provided that include, in a networked computer system, identifying, based on configuration data, whether each of a set of network elements is within a trusted network or not within the trusted network. Traffic between elements within the trusted network and elements not within the trusted network must pass through a firewall. The methods also include, prior to performing a storage operation through the firewall, allocating a specific set of ports, in accordance with at least one security parameter, for use in performing the storage operation. Methods are also provided which include monitoring traffic through the specific ports, and, if traffic is determined to be inactive through a first port of the specific ports, sending a packet through the first port.
Owner:COMMVAULT SYST INC
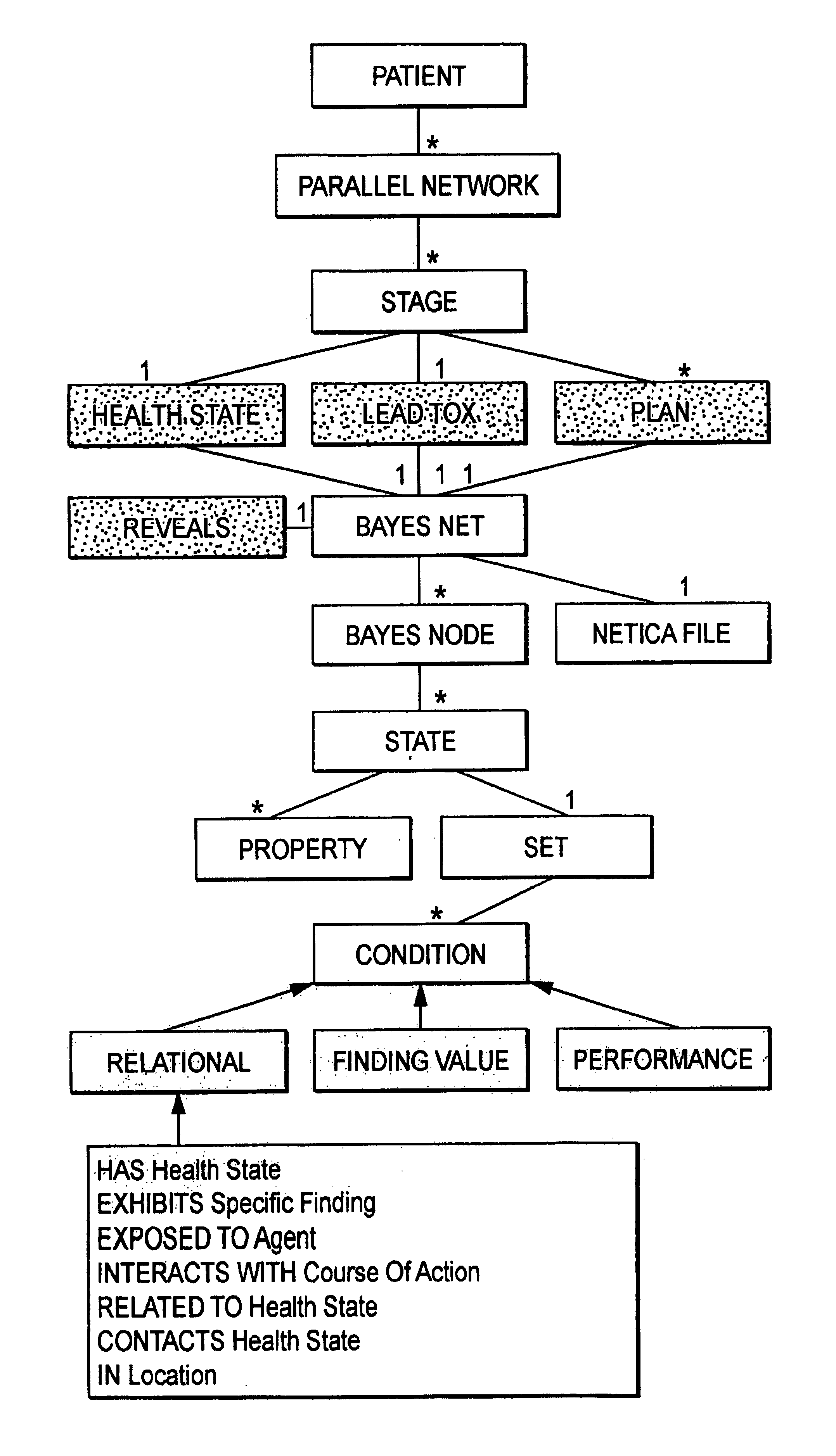
Computer architecture and process of patient generation, evolution, and simulation for computer based testing system using bayesian networks as a scripting language
InactiveUS7024399B2Economical and simpleReduce maintenance costsBiological neural network modelsComputer-assisted treatment prescription/deliveryScripting languageComputer access
A method and system for patient generation and evolution for a computer-based testing system and / or expert system. One or more belief networks, which describe parallel health state networks are accessed by a user or a computer. A knowledge base, at least in part, is scripted from the one or more belief networks by the computer. A model patient at least in part, is instantiated by the computer from the scripted knowledge base. Optionally, the model patient is evolved by the computer in accordance with the parallel health state networks and responsive to a received course of action.
Owner:AMERICAN BOARD OF FAMILY MEDICINE
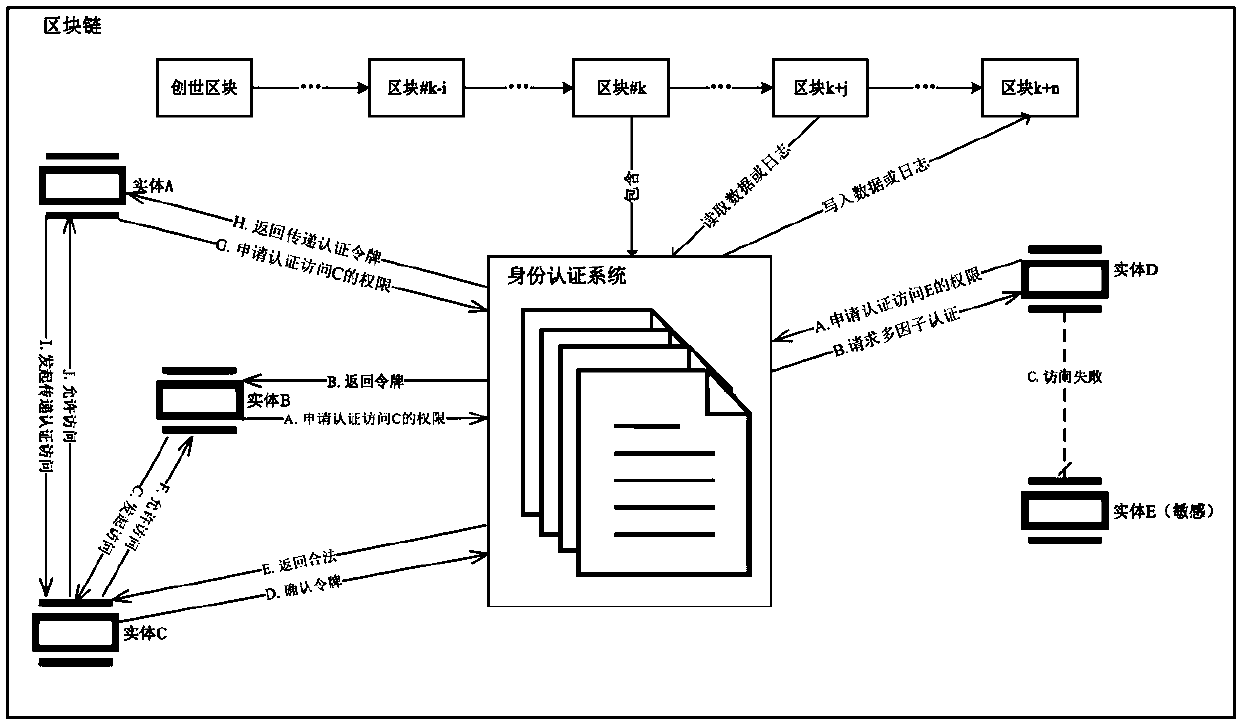
Internet of Things identity authentication method based on blockchain
The invention belongs to the technical field of identity authentication, and specifically provides an Internet of Things identity authentication method based on a blockchain. The basic steps of the Internet of Things identity authentication method provided by the invention are as follows: an entity calls an intelligent contract by means of an own key to accomplish the registration in an identity authentication system; each entity can call the intelligent contract to set an access strategy so as to limit the access of other entities to the entity and to form a trust network of the Internet of Things; when one entity accesses the data of the other entity, the entity needs to apply for a token from the intelligent contract to obtain the access qualification, and the intelligent contract checks whether the entity initiating the access has the access qualification according to the access strategy set by the accessed entity in the trust network between the entities, and if yes, the intelligent contract generates the token and returns the token to the entity initiating the access; or otherwise, the intelligent contract returns token application failure information. By adoption of the method provided by the invention, a centralized authority mechanism in an identity authentication process is removed, malicious tampering of records of identity authentication and data access is prevented, a strategy execution result is not manually manipulated, and a fair, transparent and credible execution environment is provided for the identity authentication of the entities in the Internet of Things.
Owner:FUDAN UNIV
Arrangement and method for transport sharing
ActiveUS20120290652A1ReservationsMultiple digital computer combinationsInternet privacyTrust network
An arrangement, of functionally connected electronic devices includes: a data input entity, configured to obtain user in-formation relative to a plurality of users, data indicative of trust between multiple users and data indicative of a number of ride requests and ride offers by the users, a trust network knowledgebase entity configured to establish and manage a number of trust networks on the basis of the obtained data. The knowledgebase entity groups a plurality of users into a number of trust networks, a scheduling entity configured, on the basis of the obtained data, to determine a potential transport sharing scenario for a plurality of users belonging to the same trust network. The scheduling entity is configured to find potential matches between the ride requests and ride offers to determine the scenario, and a data output entity configured to indicate the scenario to multiple users of the plurality.
Owner:BRAVIOZ
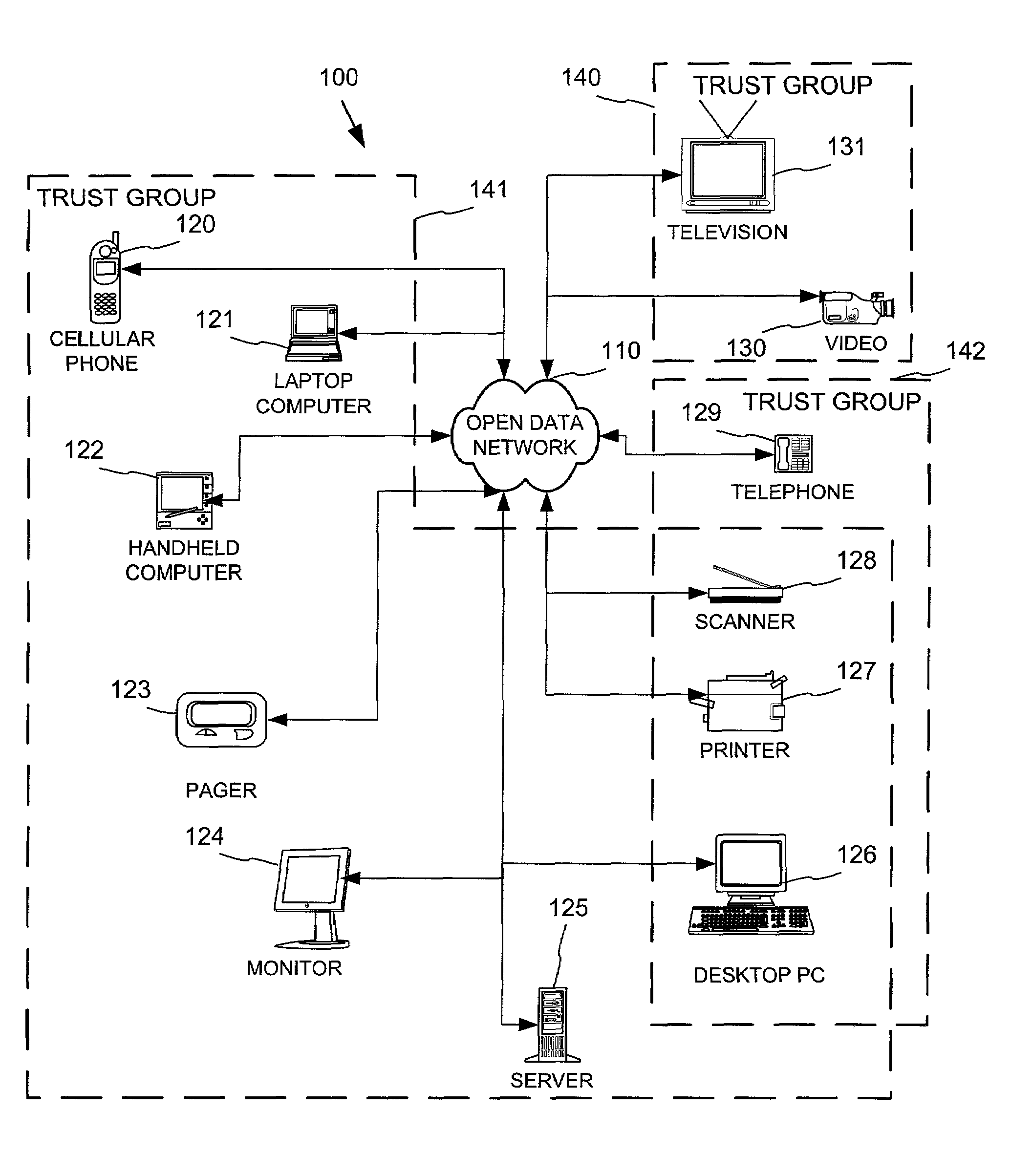
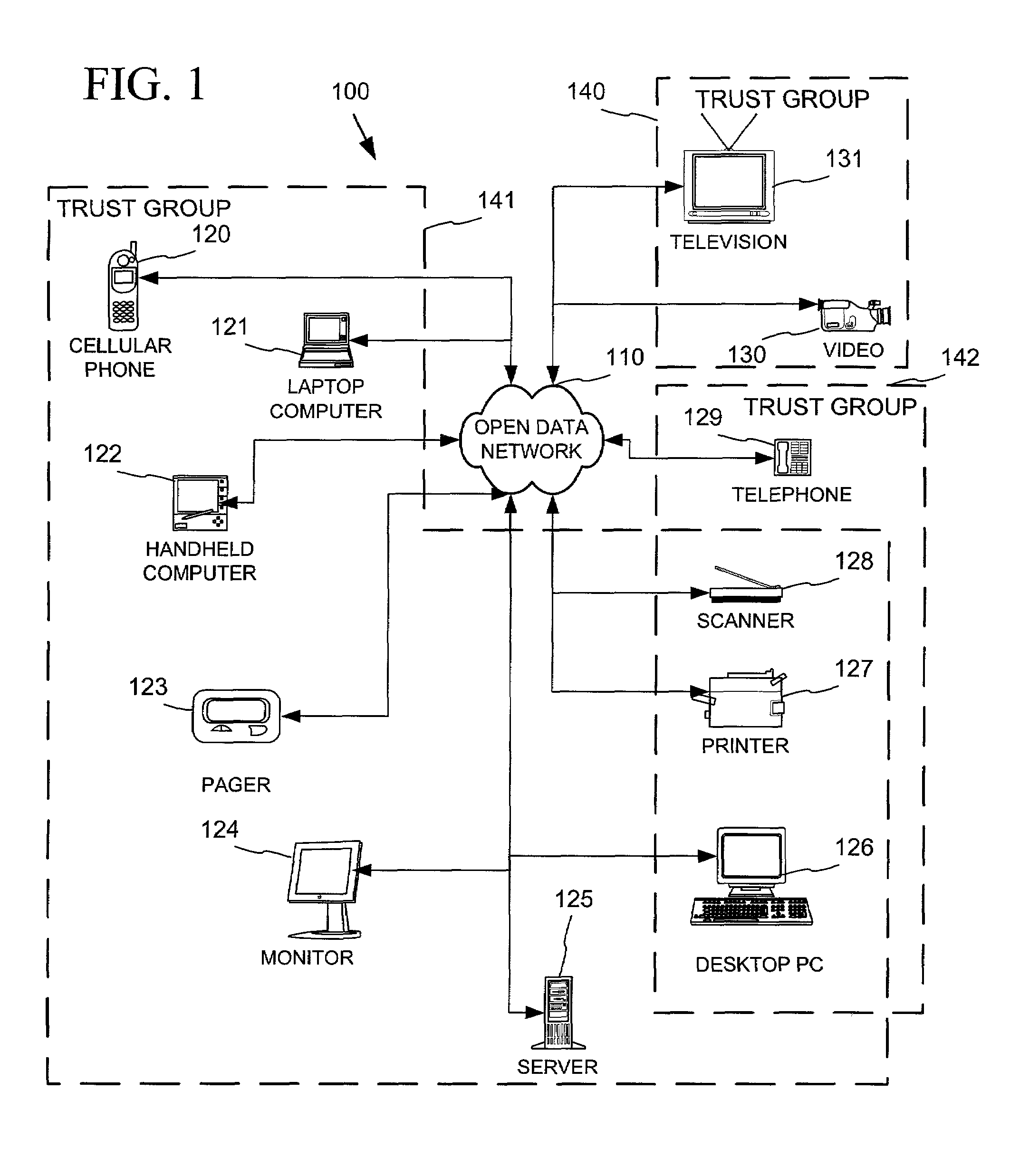
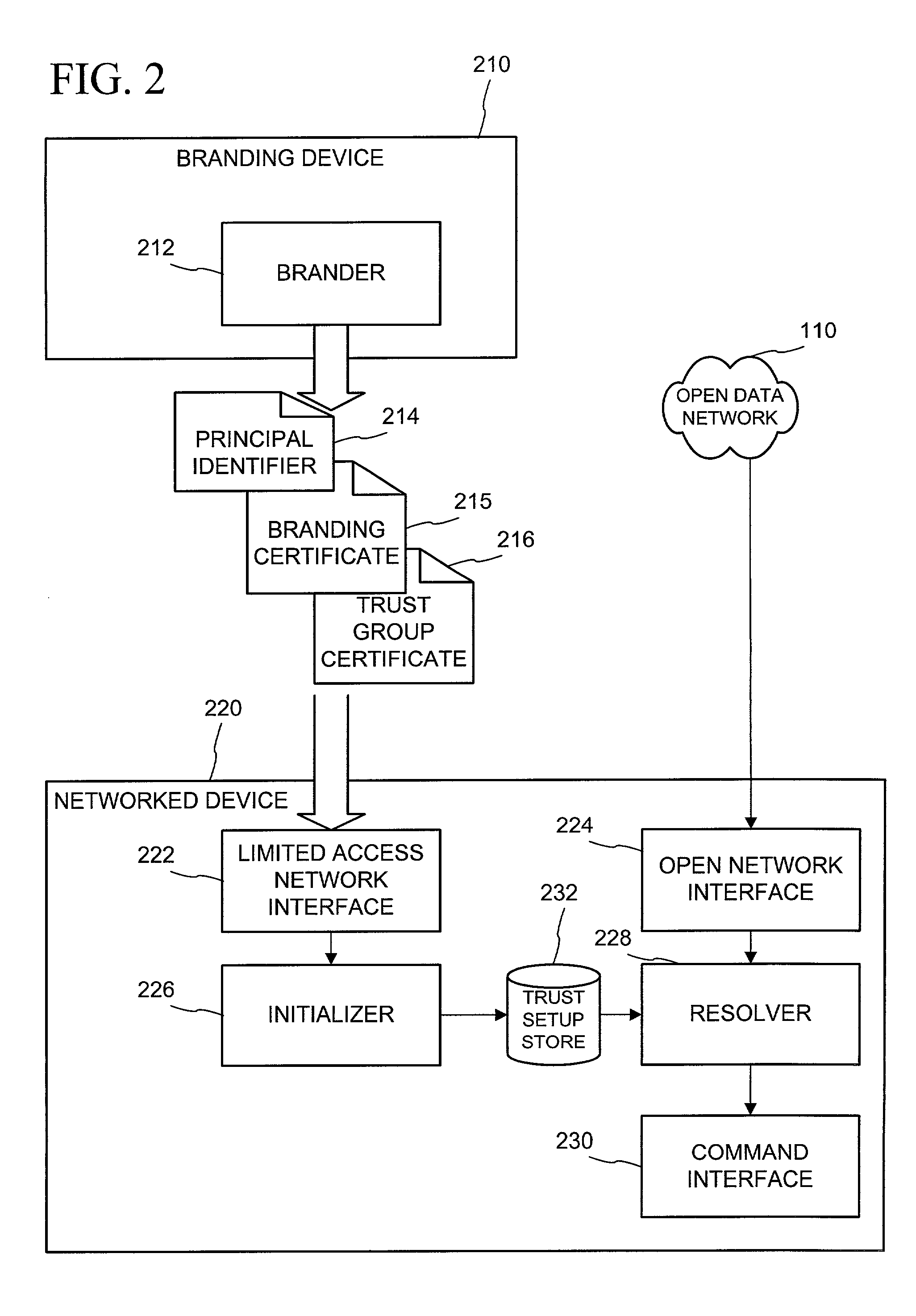
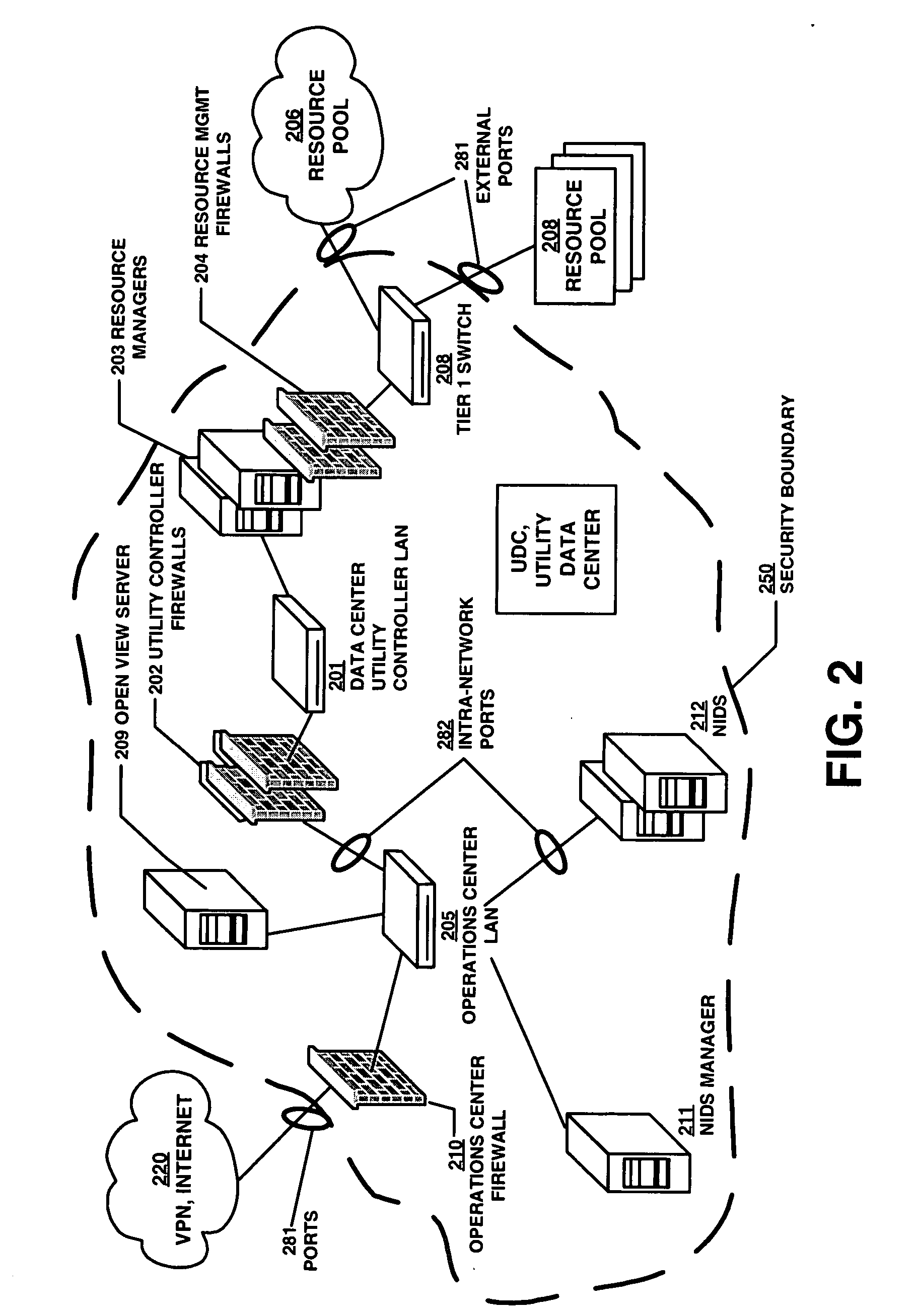
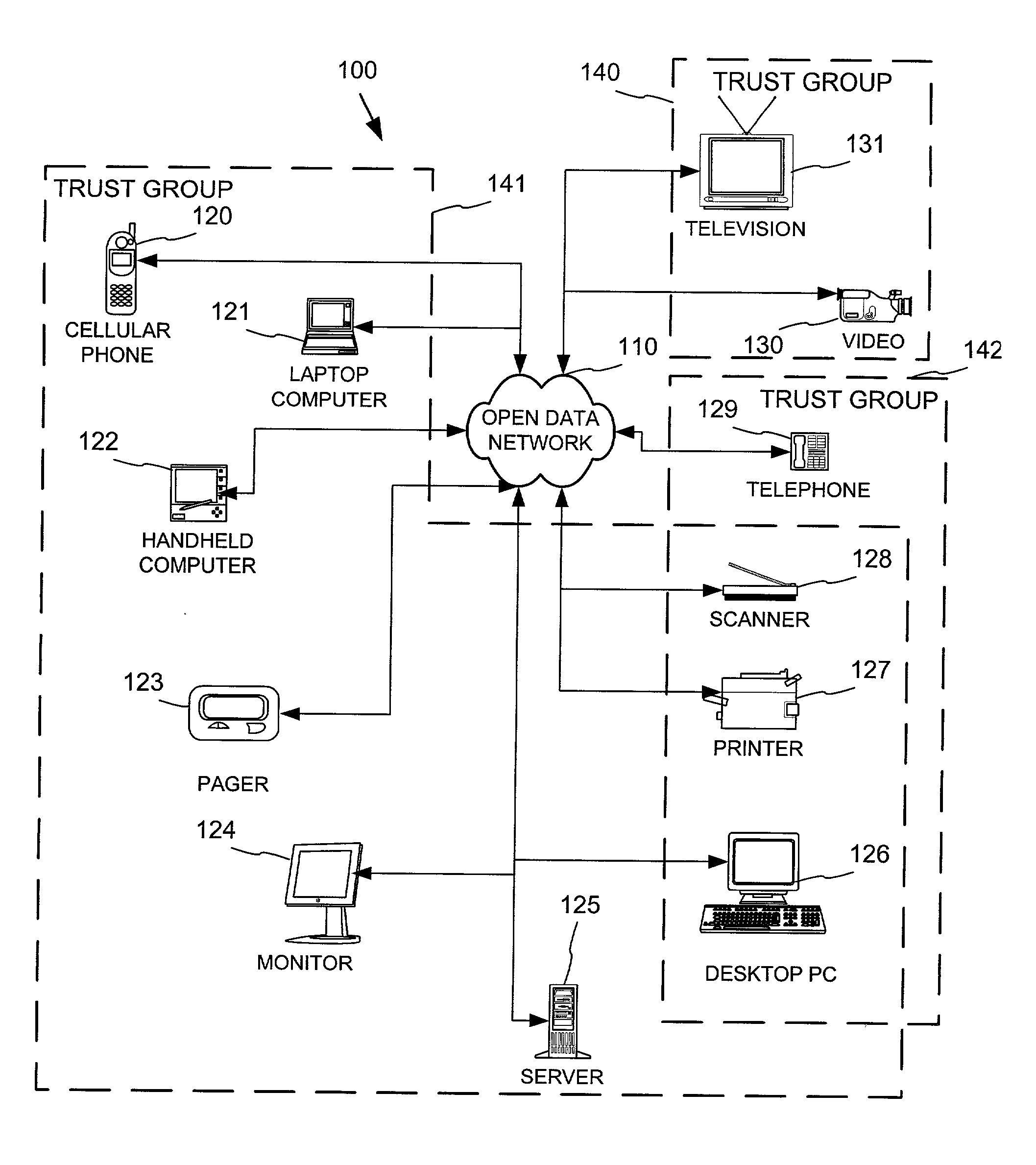
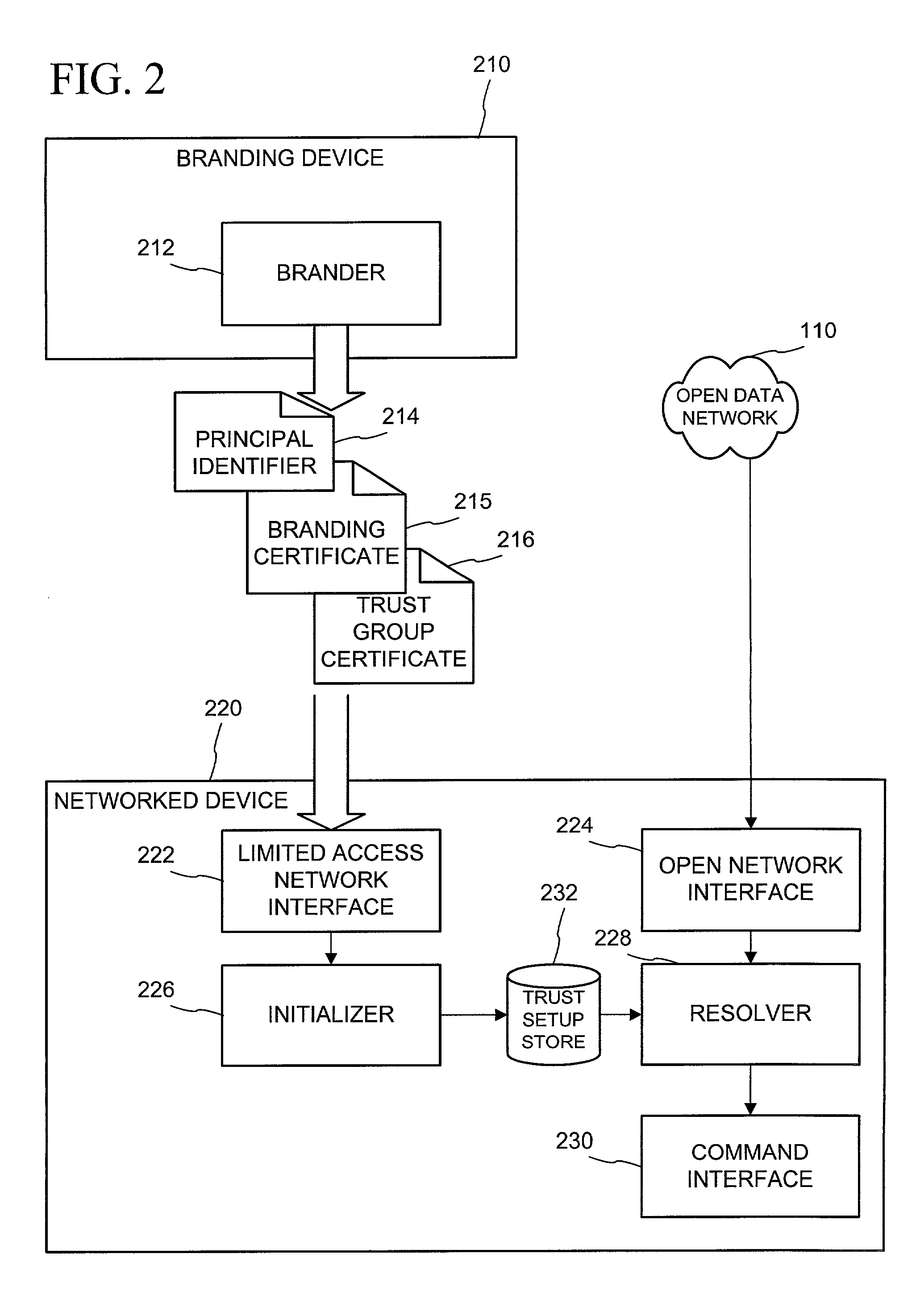
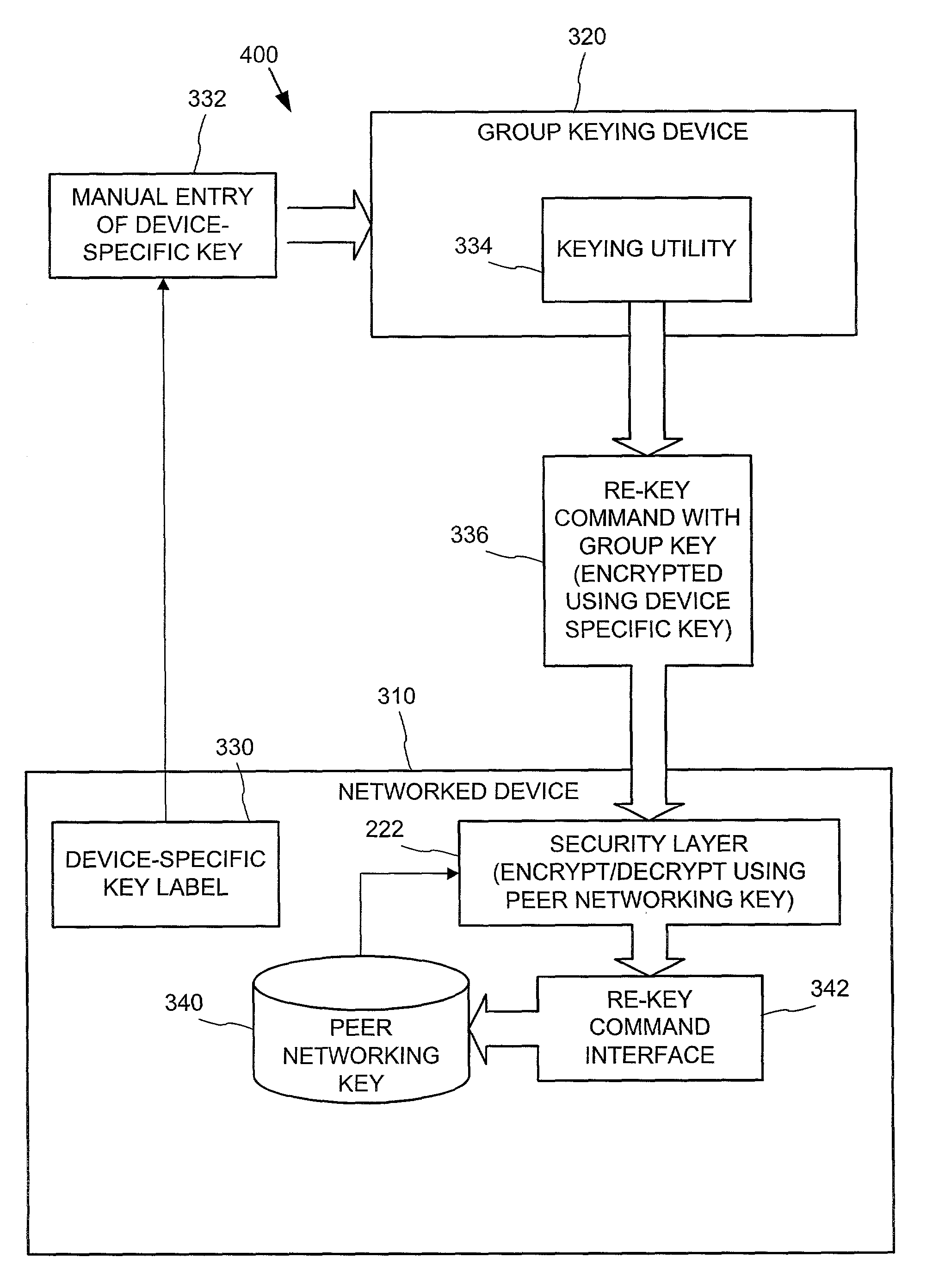
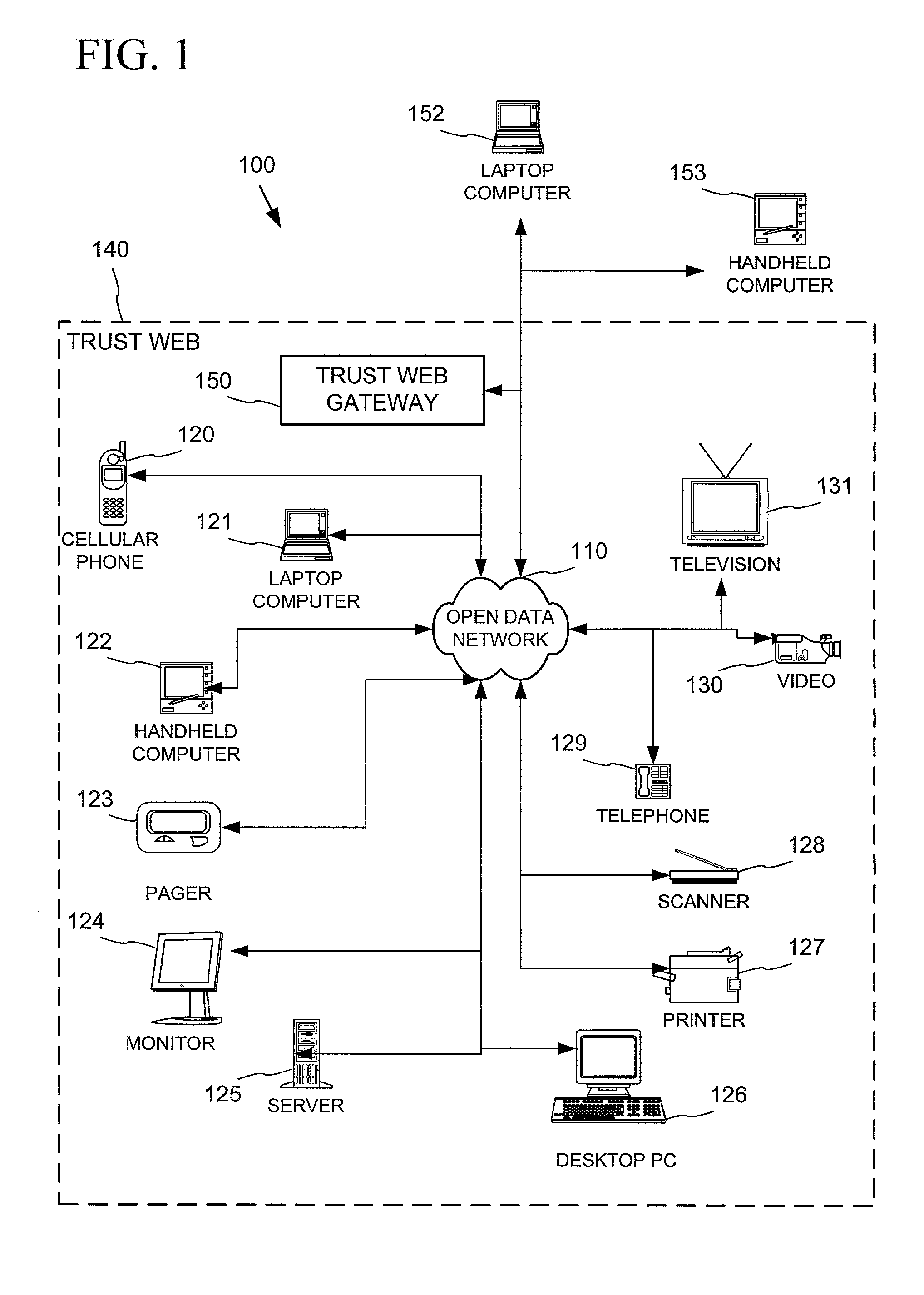
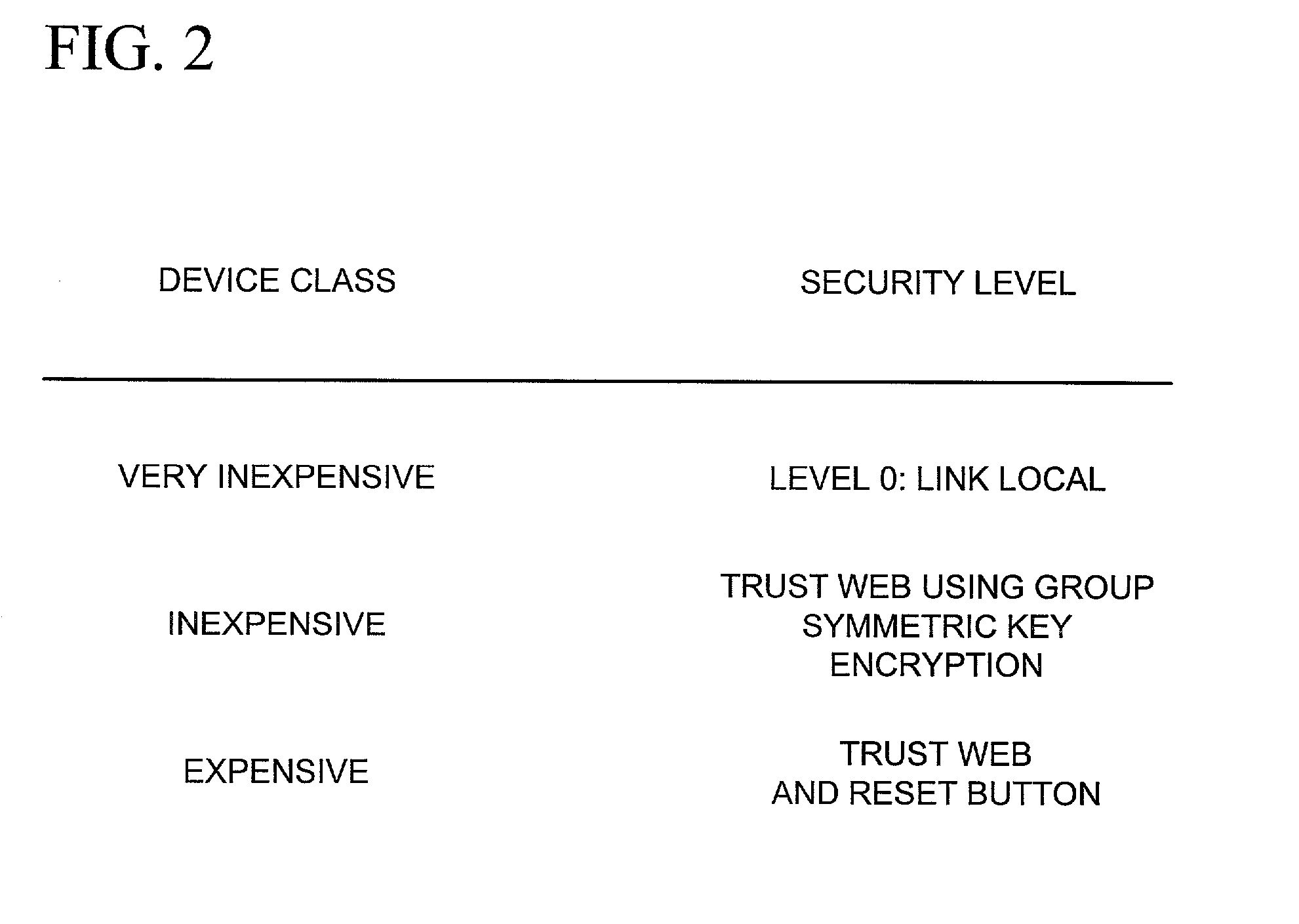
Networked device branding for secure interaction in trust webs on open networks
InactiveUS7500104B2CostSynchronising transmission/receiving encryption devicesDigital data processing detailsLimited accessNetwork media
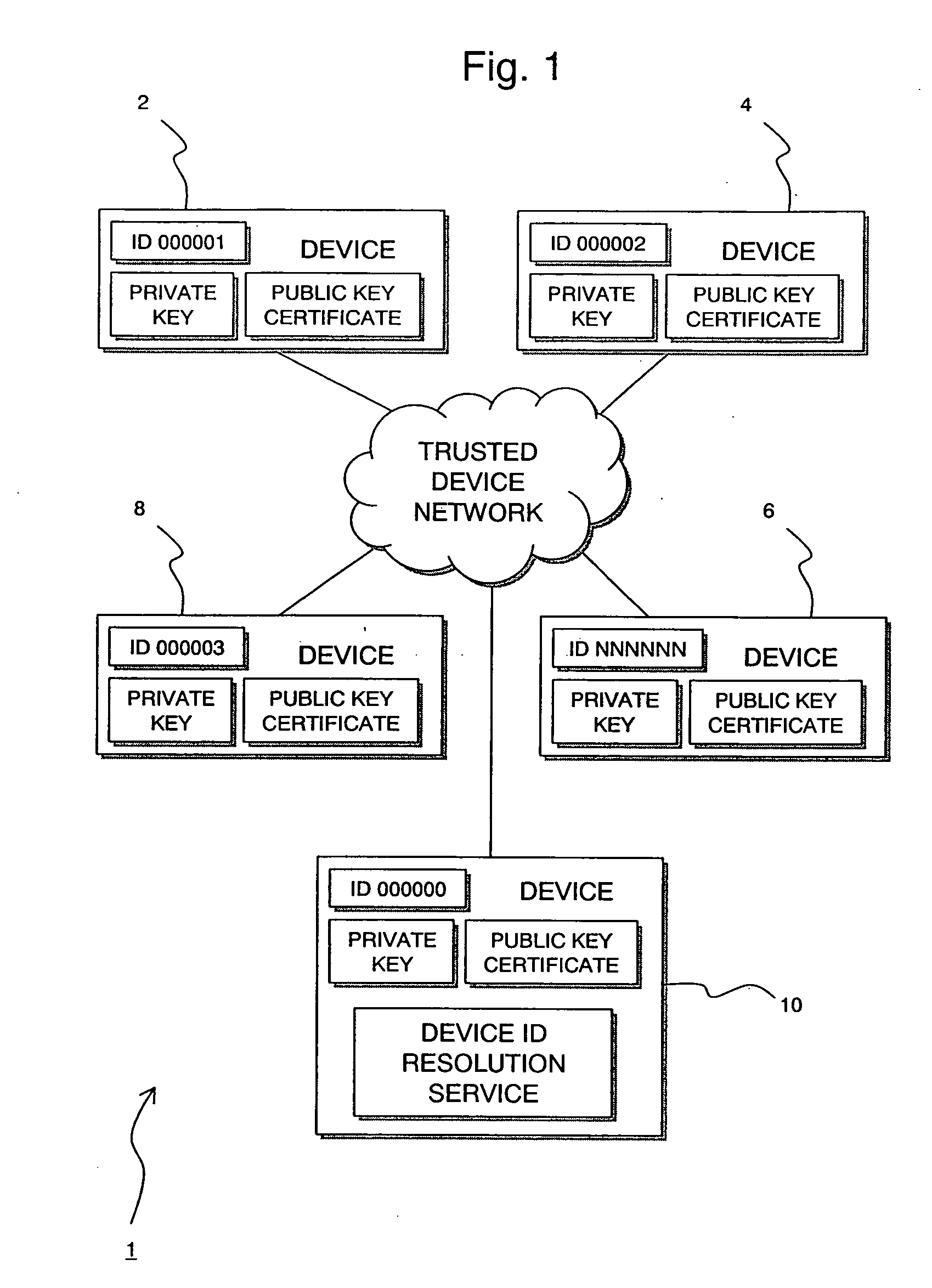
A branding process provides a networked computing device with initial set up information, including a name, a public / private key pair, and a set of certificates the device will need to inter-operate with other devices in the trust group. A branding device conveys the initial set-up information to the networked computing device via a limited access network interface, or alternatively via a broadcast network media with the device enclosed in a wave guide and / or Faraday cage. The networked computing device can then use the set up information to verify that other devices on the network that seek to interact with the device are also members of the trust group, with which networked computing device can interact.
Owner:MICROSOFT TECH LICENSING LLC
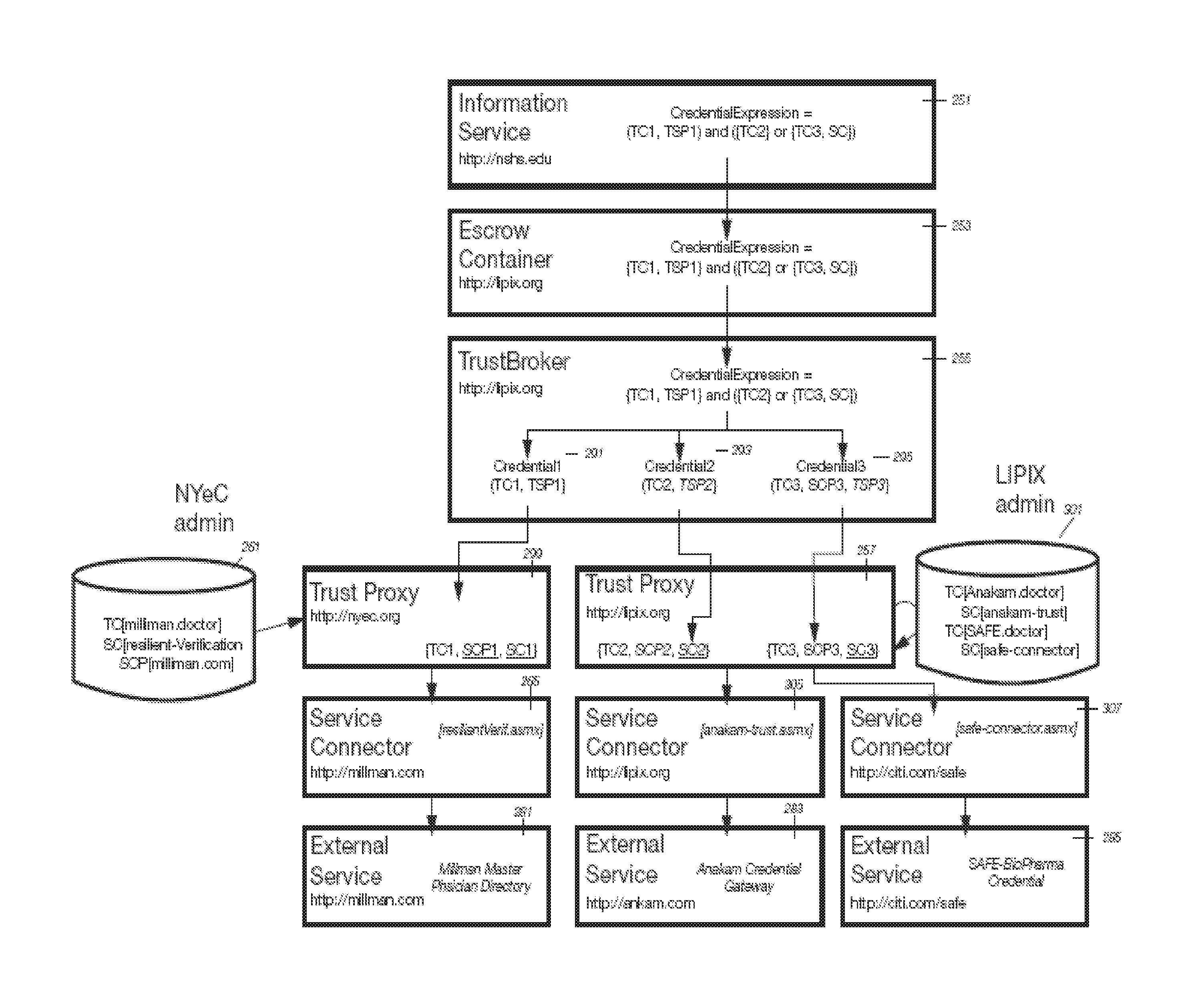
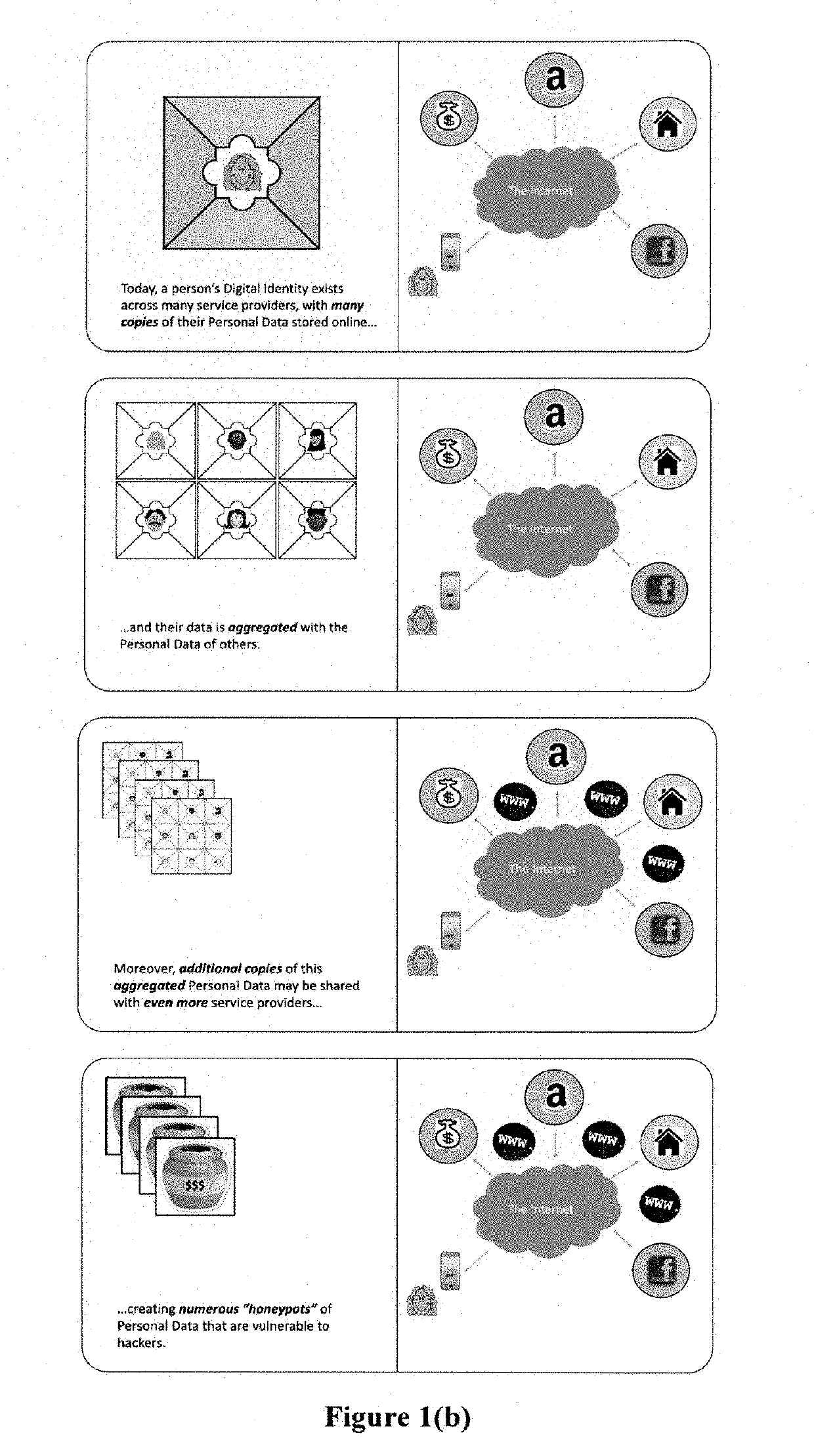
System for verification of pseudonymous credentials for digital identities with managed access to personal data on trust networks
InactiveUS20190333054A1Key distribution for secure communicationUser identity/authority verificationDigital identityThird party
The invention advantageously provides a system for the verification a user's identity and qualifications and authentication of credentials associated with a user's digital identity on a trust network (where service providers involved in a transaction may be independent parties operating with limited trust), in which a pseudonymized transaction record may be created for that digital identity and stored in a shared ledger; identifying information for a user may be retained in a custodial escrow account for that user; and transactions may be re-correlated with identifying information for authorized third parties under established “due process” rules that are appropriate for the applicable jurisdiction(s).
Owner:INFONETWORKS LLC
Method and apparatus for performing a secure transaction in a trusted network
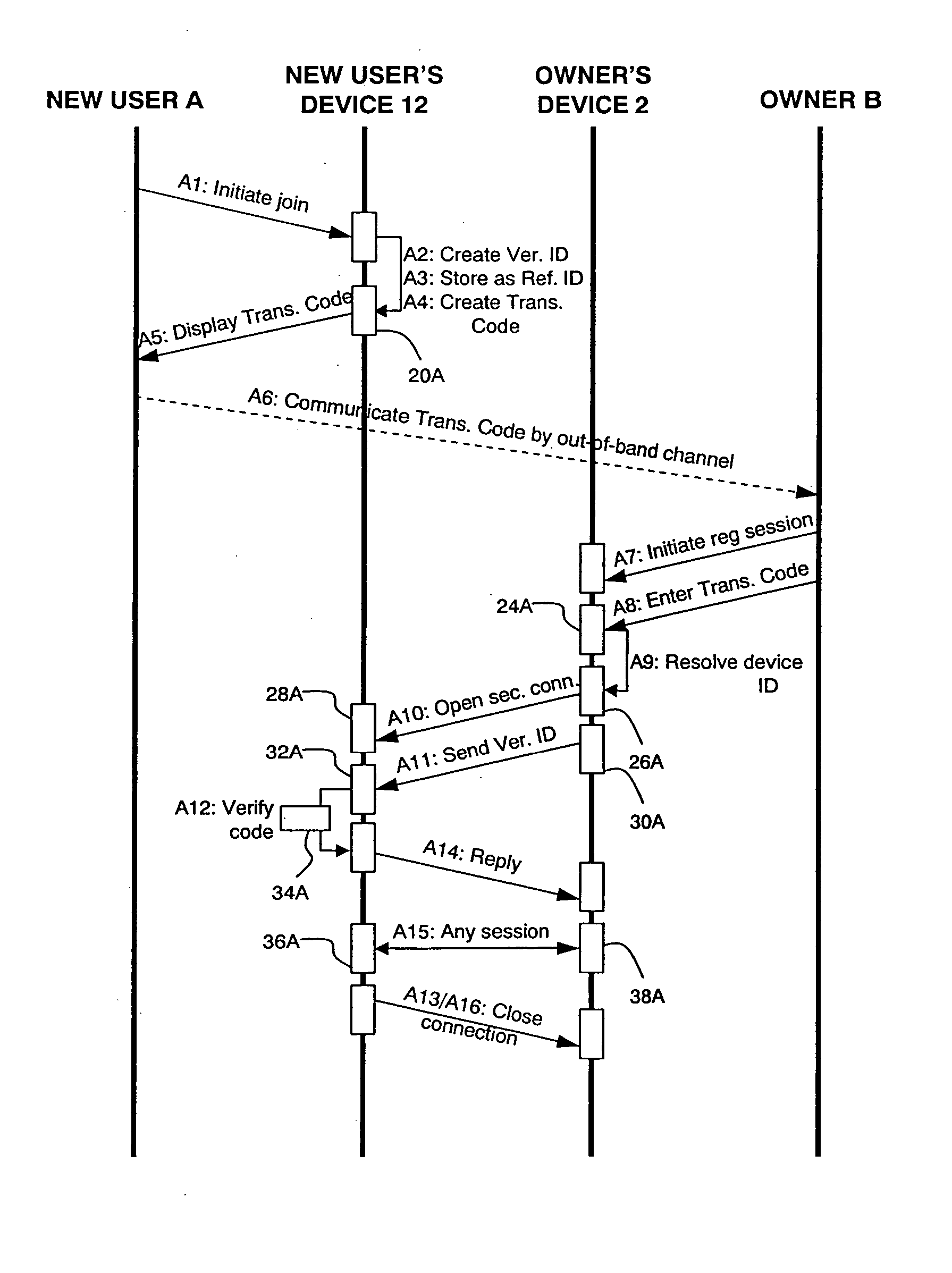
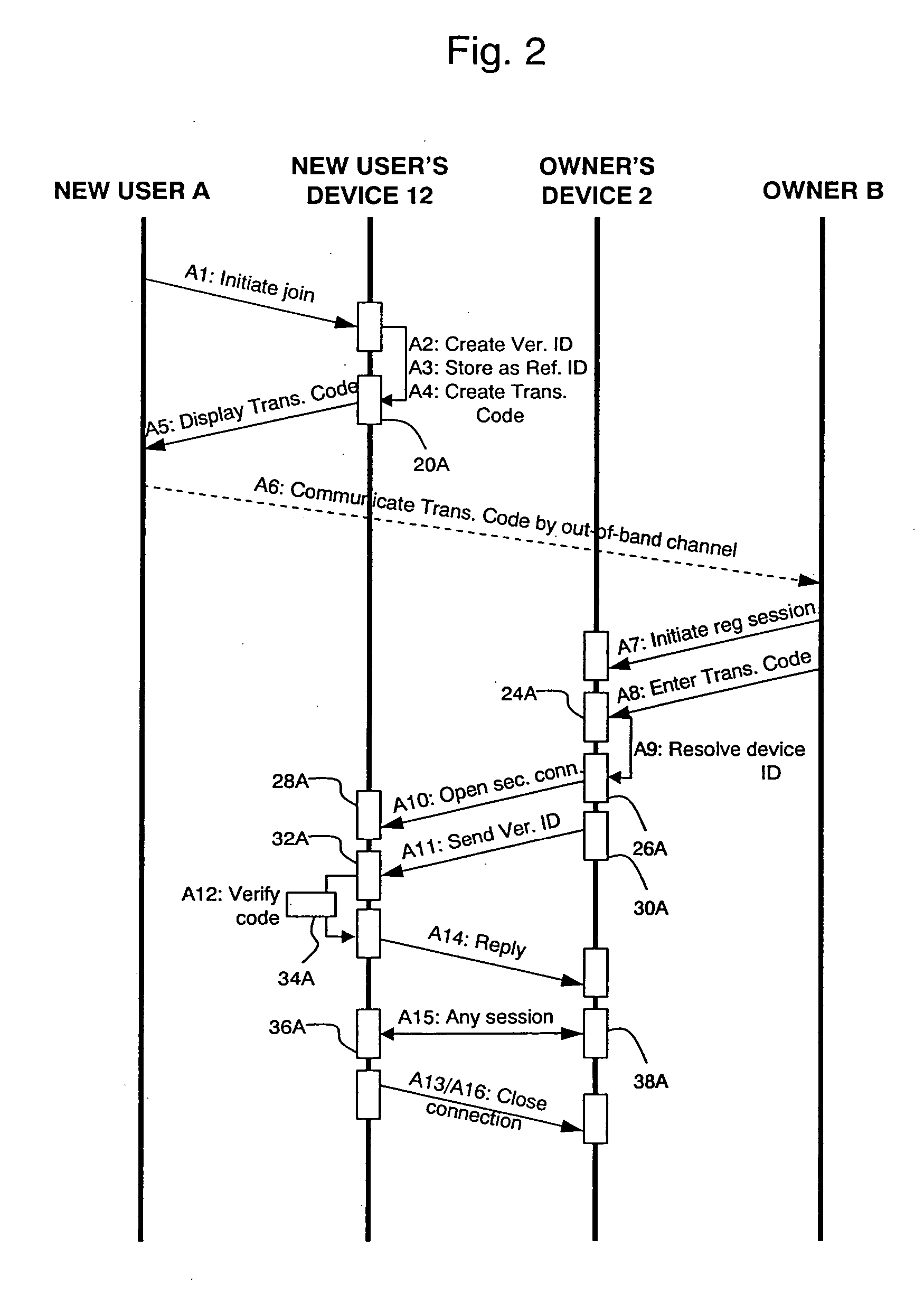
InactiveUS20060090067A1Straightforward and convenient for to initiate transactionImprove user experienceDigital data authenticationSecuring communicationTrust networkTelephony
A method is provided of enabling respective users (A, B) of first and second devices (12, 2) of a trusted network to perform a secure transaction between them. A communications channel, such as a telephone conversation, is established between the users (A, B). A verification identifier for the transaction is communicated between the users (A, B) using the communications channel (A6). The verification identifier is stored (A3) at the first device (12) as a reference identifier for the transaction. A secure connection is opened between the two devices (12, 2) over the trusted network (A10), the secure connection being different to the communications channel between the users (A, B). The verification identifier is sent (A11) from the second device (2) to the first device (12) over the secure connection. The verification identifier received over the secure connection is compared (A12) with the reference identifier at the first device (12). The secure transaction is performed over the secure connection (A15) in dependence upon the comparison.
Owner:SHARP KK
Systems and methods for communication, storage, retrieval, and computation of simple statistics and logical operations on encrypted data
InactiveUS20110264920A1Unauthorized memory use protectionHardware monitoringLogical queryData system
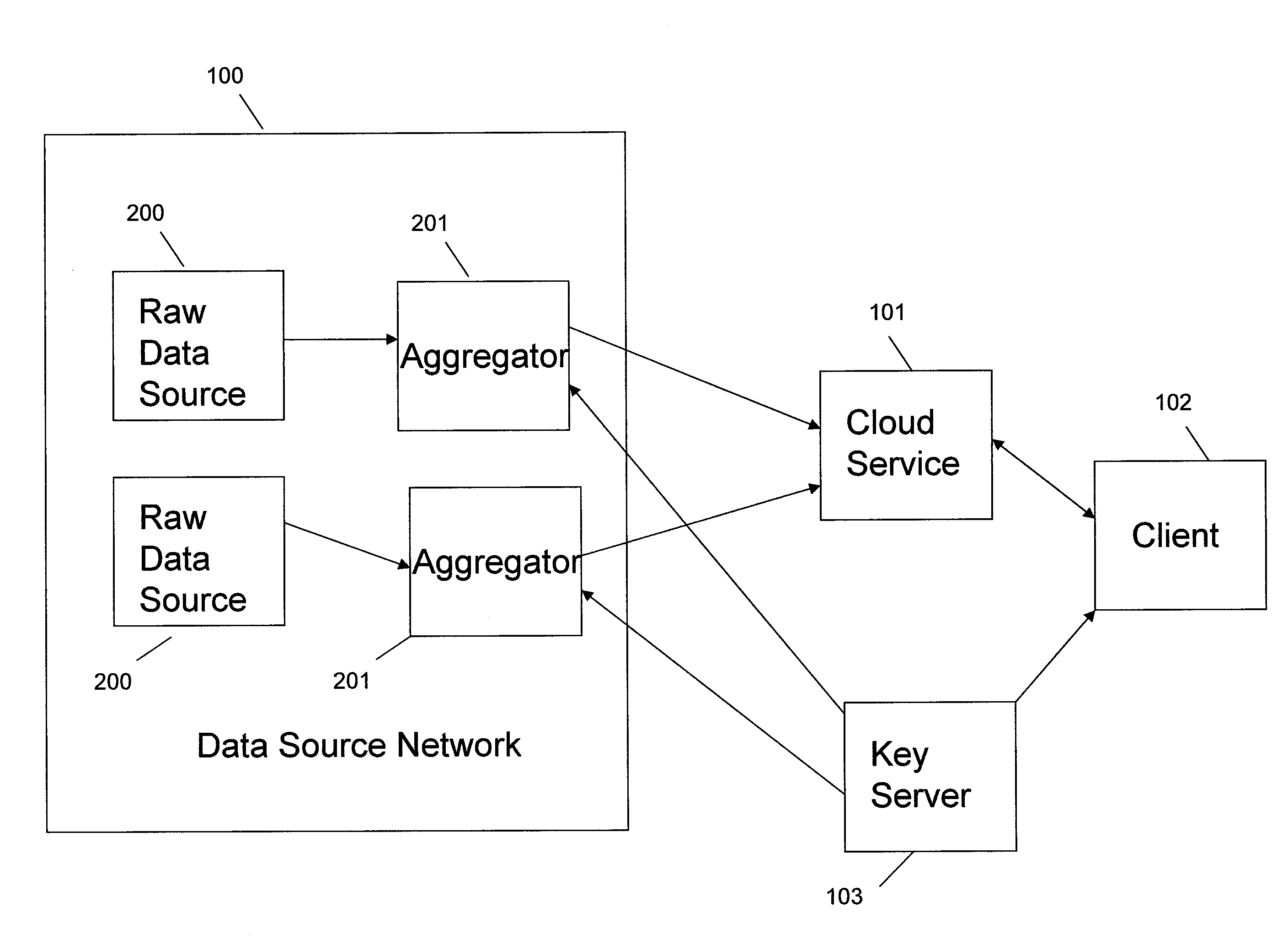
Systems and methods provide for a symmetric homomorphic encryption based protocol supporting communication, storage, retrieval, and computation on encrypted data stored off-site. The system may include a private, trusted network which uses aggregators to encrypt raw data that is sent to a third party for storage and processing, including computations that can be performed on the encrypted data. A client on a private or public network may request computations on the encrypted data, and the results may then be sent to the client for decryption or further computations. The third party aids in computation of statistical information and logical queries on the encrypted data, but is not able to decrypt the data on its own. The protocol provides a means for a third party to aid in computations on sensitive data without learning anything about those data values.
Owner:FUJIFILM BUSINESS INNOVATION CORP
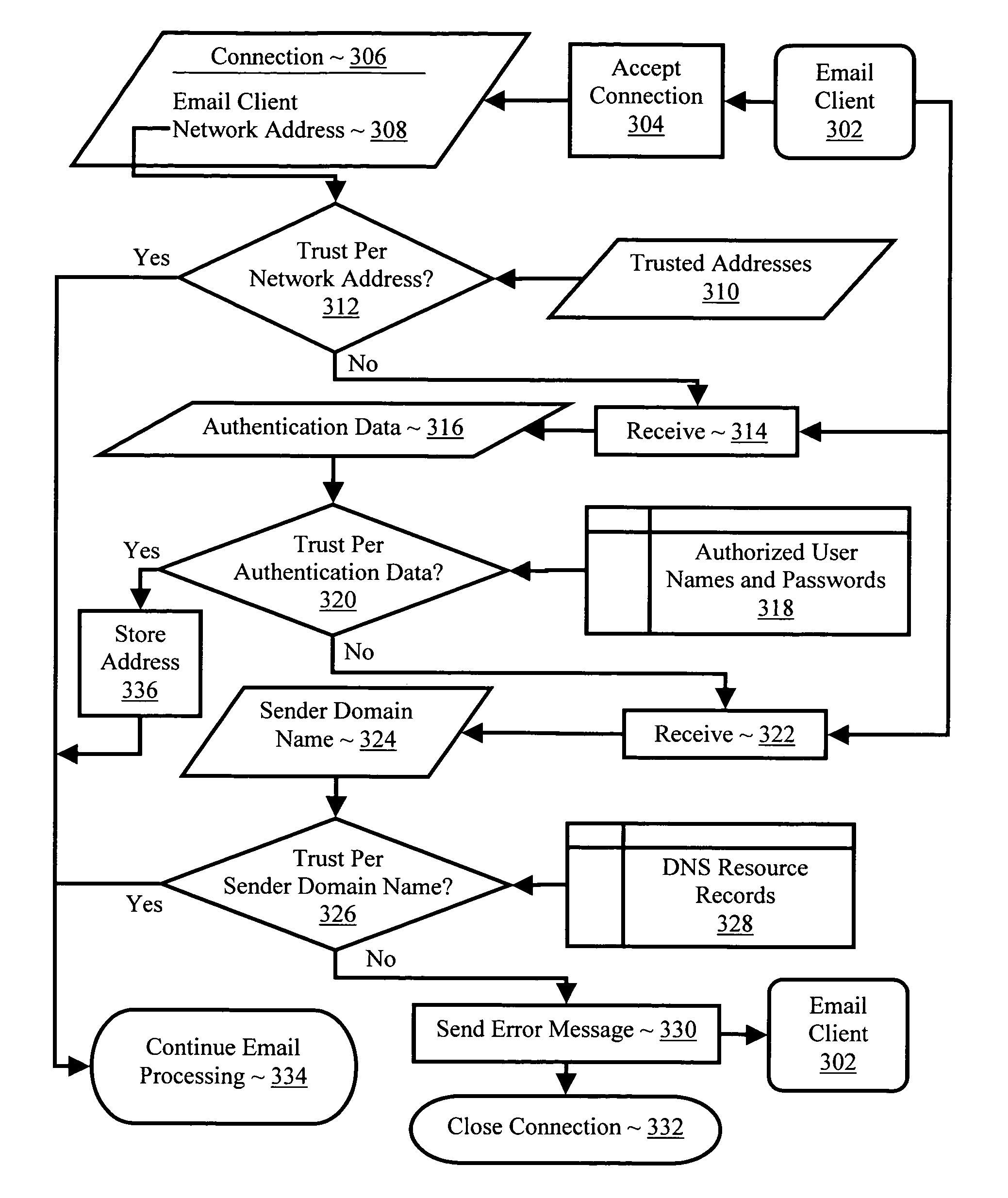
Establishing trust in an email client
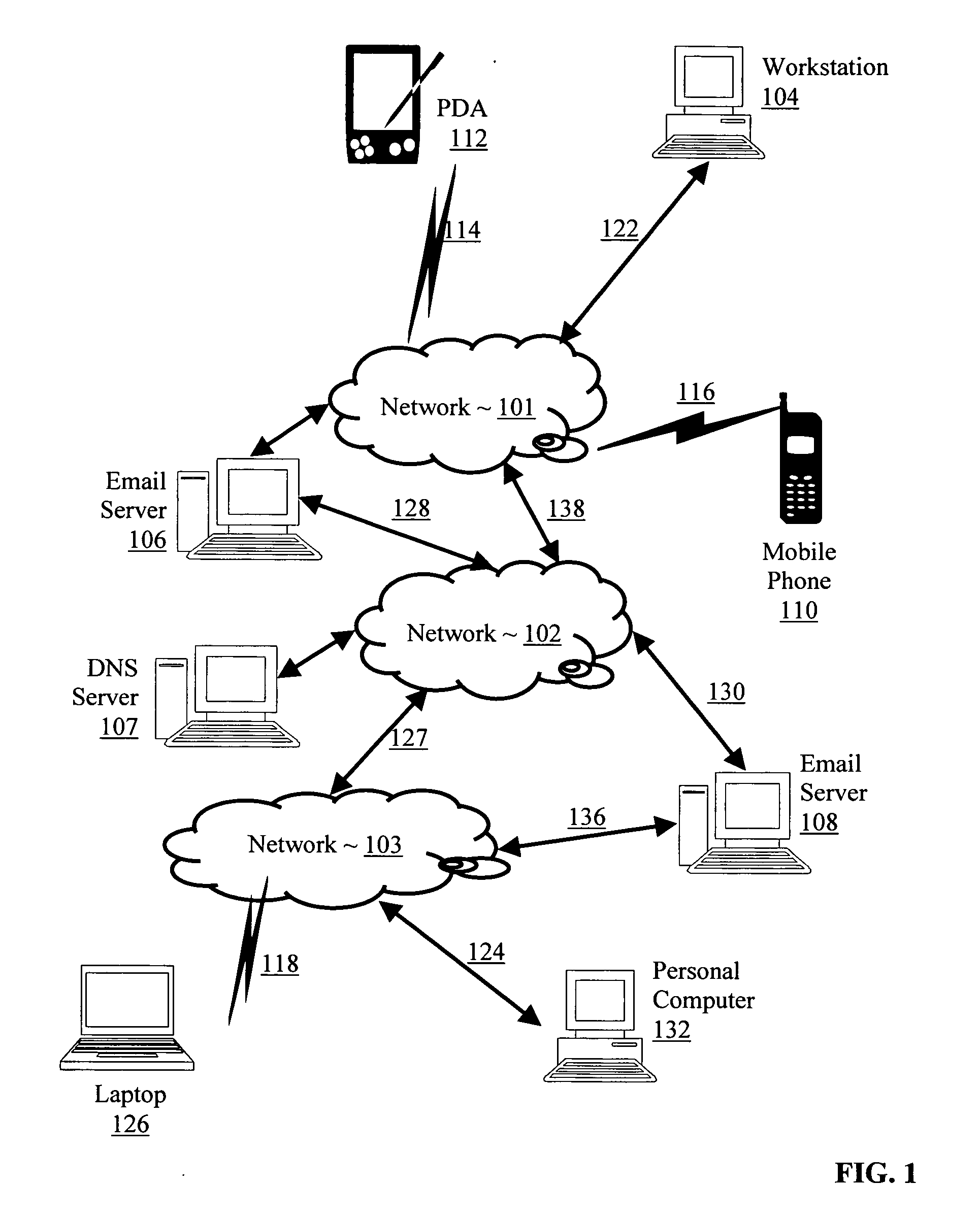
InactiveUS20050216587A1Multiple digital computer combinationsData switching networksDomain nameInternet privacy
Establishing trust in an email client including accepting in an email server a data communications connection from an email client, where the connection includes the email client's network address; determining from a stored list of trusted network addresses whether the email client is trusted according to the email client's network address; if the email client is not trusted according to the email client's network address, receiving authentication data from the email client and determining whether the email client is trusted according to the authentication data; and if the email client is not trusted according to the email client's network address and the email client is not trusted according to the authentication data, receiving a sender domain name for an email message from the email client and determining whether the email client is trusted according to the sender domain name.
Owner:IBM CORP
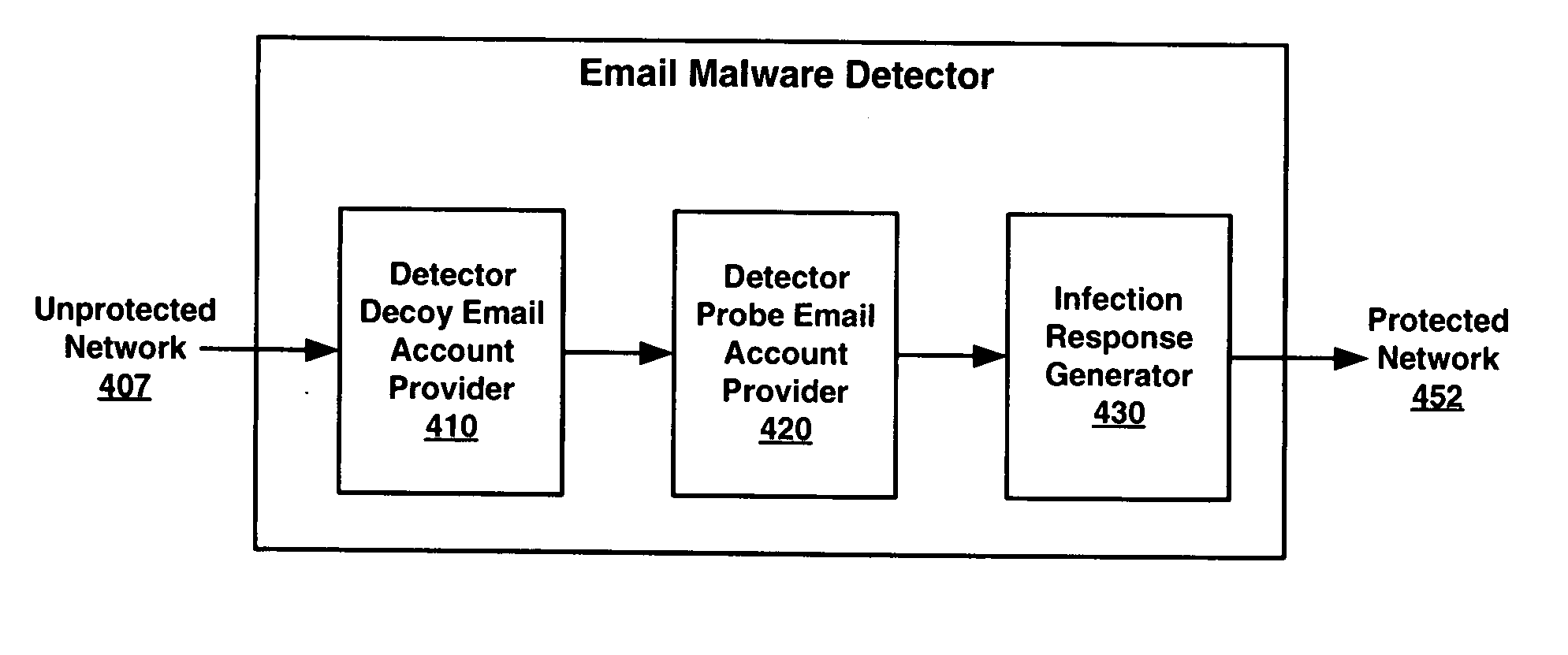
Method and apparatus for detecting and responding to email based propagation of malicious software in a trusted network
ActiveUS20070101430A1Memory loss protectionUser identity/authority verificationDecoyInternet privacy
Embodiments of the invention provide a method and an apparatus for detecting and responding to email based propagation of malicious software (malware) in a trusted network. One embodiment provides a detector decoy email account to serve as generic bait for malicious software for a domain within the trusted network. In addition, at least one email account for the domain within the trusted network is provided as a detector probe account. In so doing, when the detector decoy email account receives an email from the detector probe account within the trusted network a policy based infection response rule is generated.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Networked device branding for secure interaction in trust webs on open networks
InactiveUS20030056114A1CostInexpensive and reliableDigital data processing detailsUser identity/authority verificationLimited accessNetwork media
A branding process provides a networked computing device with initial set up information, including a name, a public / private key pair, and a set of certificates the device will need to inter-operate with other devices in the trust group. A branding device conveys the initial set-up information to the networked computing device via a limited access network interface, or alternatively via a broadcast network media with the device enclosed in a wave guide and / or Faraday cage. The networked computing device can then use the set up information to verify that other devices on the network that seek to interact with the device are also members of the trust group, with which networked computing device can interact.
Owner:MICROSOFT TECH LICENSING LLC
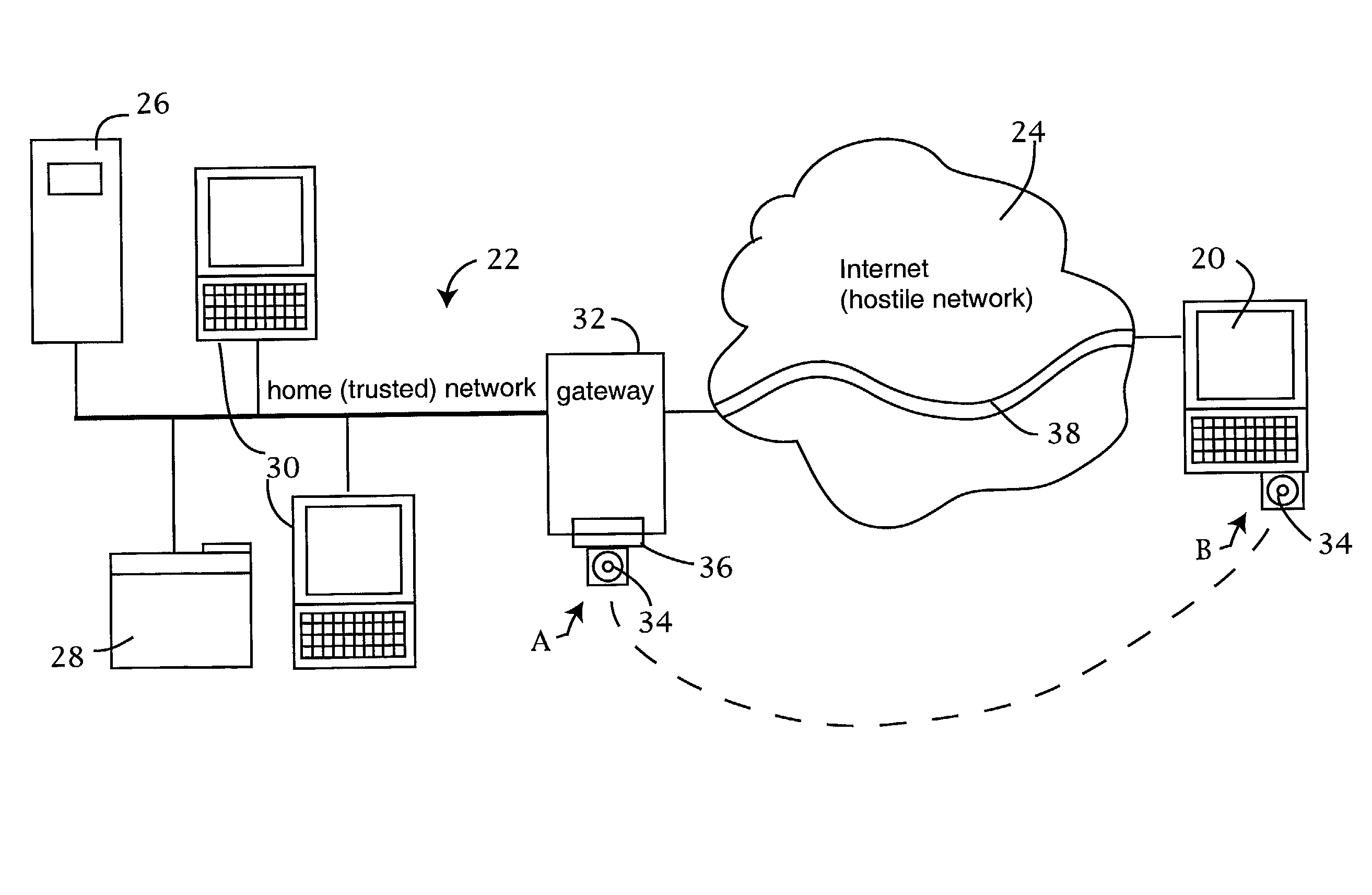
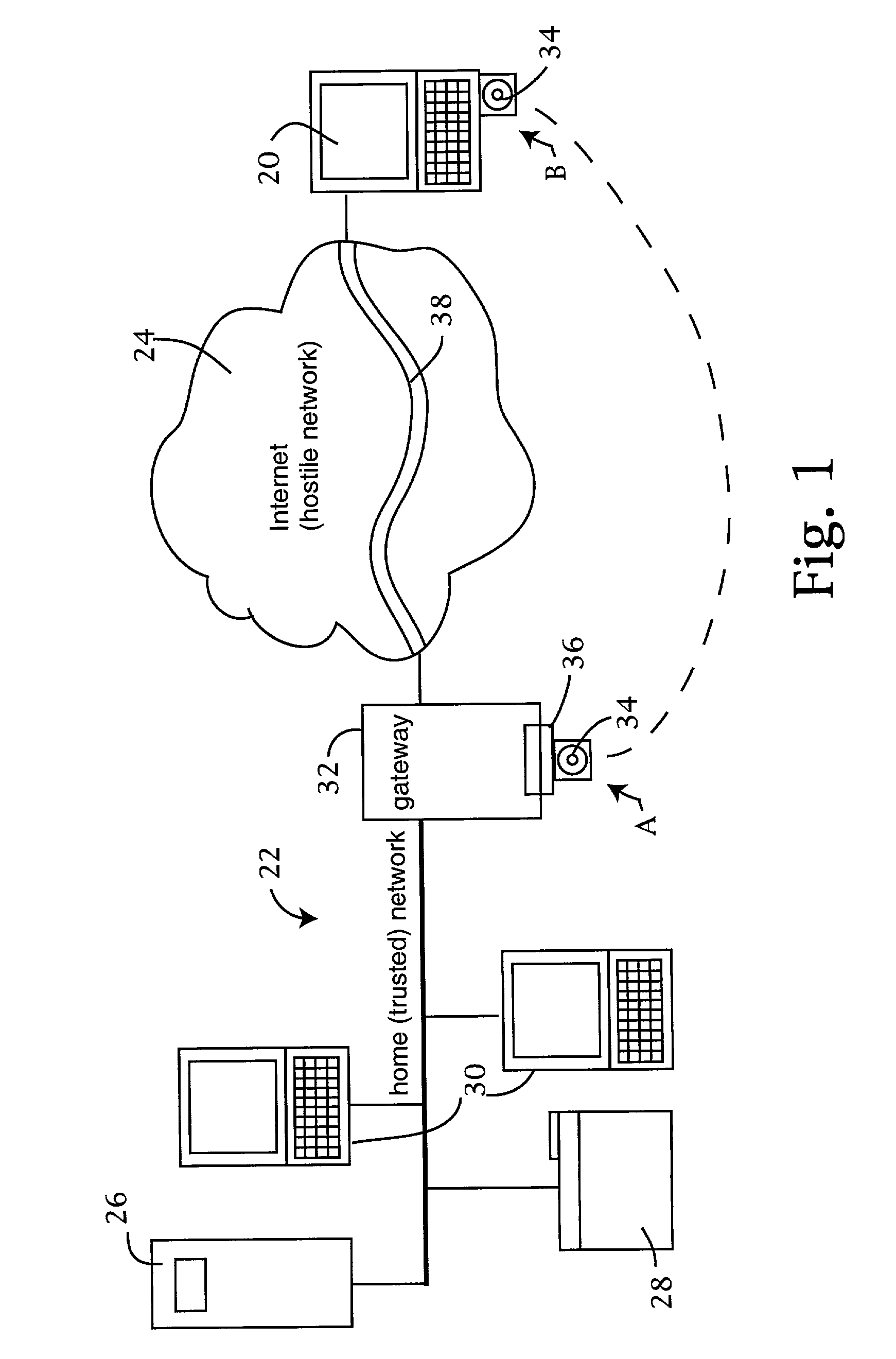
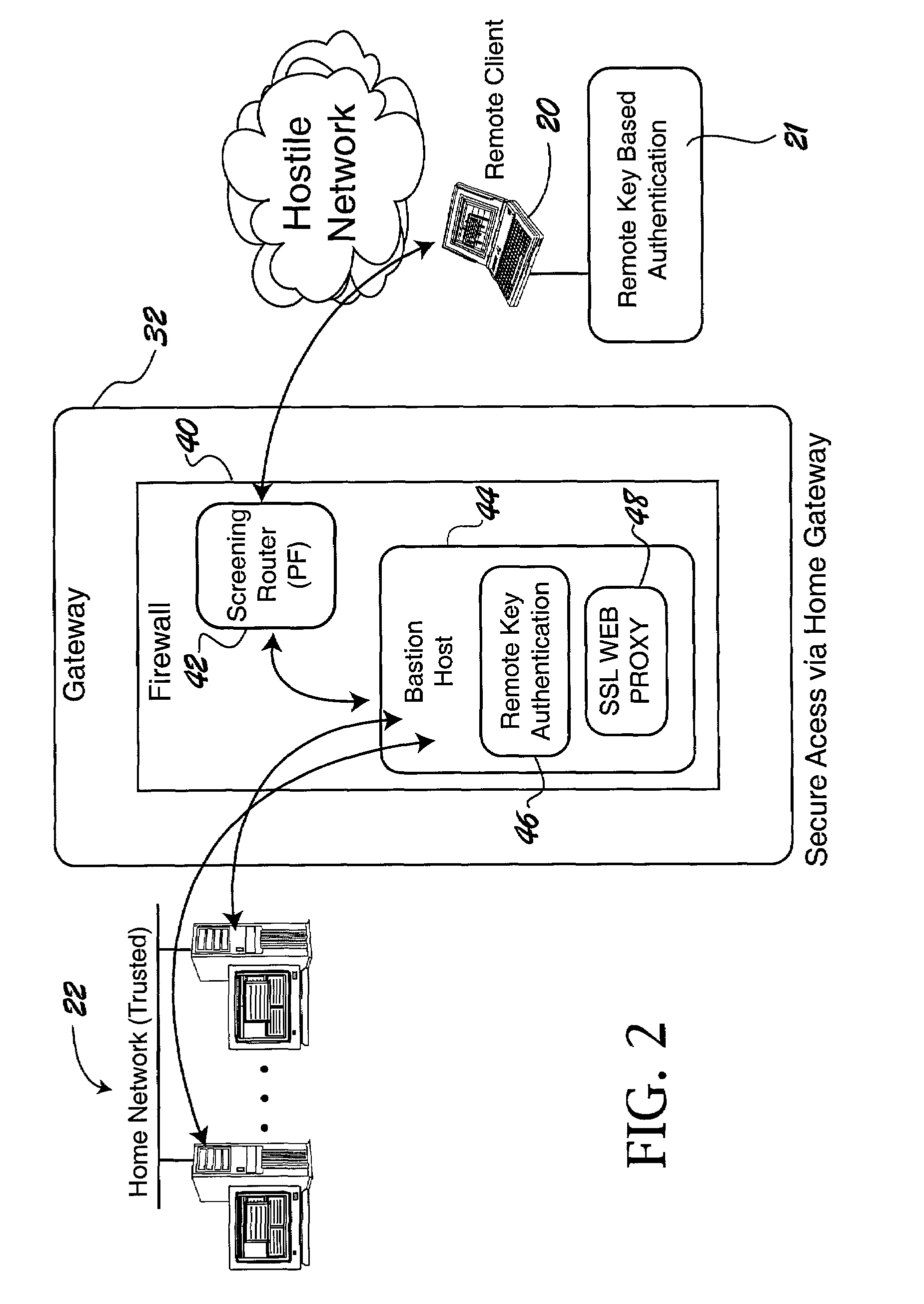
Computer network security system employing portable storage device
ActiveUS7228438B2Easy to useRaise security concernsUser identity/authority verificationUnauthorized memory use protectionUniform resource locatorClient machine
The trusted computer network is protected behind a gateway that includes a bastion host and screening router which blocks all URLs associated with the trusted network. The bastion host includes a remote client authentication mechanism and web proxy component that verifies and translates incoming URL requests from authenticated remote clients. Authentication is performed using one-time passwords that are stored on a portable storage device. The user configures the portable storage device by operating configuration software from the protected side of the gateway. The portable storage device also stores plug-in software to enable the client computer to properly retrieve the one-time password and exchange authentication messages with the bastion host. Further security is obtained by basing the one-time password on an encrypted version of the user's PIN. A symmetric key used to encrypt the PIN is stored in a protected area within the portable storage device.
Owner:SOVEREIGN PEAK VENTURES LLC
System and method for providing extension of network coverage
ActiveUS20160073271A1Emergency connection handlingUnauthorised/fraudulent call preventionTrust levelPoint of presence
An approach is provided for causing an extension of secure emergency network resources via one or more trusted point of presence. The approach involves determining a networking context, wherein the networking context initiates a request to join an extension mesh network to a currently trusted network. The approach also involves determining a target network trust level associated with the networking context, the currently trusted network, or a combination thereof. The approach further involves selecting the extension mesh network based on the target network trust level. The approach also involves initiating a joining of the extension mesh network to the currently trusted network.
Owner:VERIZON PATENT & LICENSING INC
Decentralized public key management method and system based on trusted network
ActiveCN107070644AEfficient verificationEfficient queryKey distribution for secure communicationStructure of Management InformationUser identifier
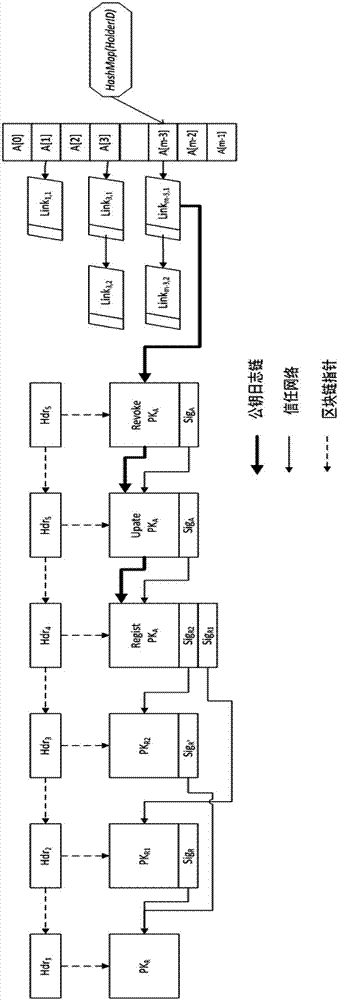
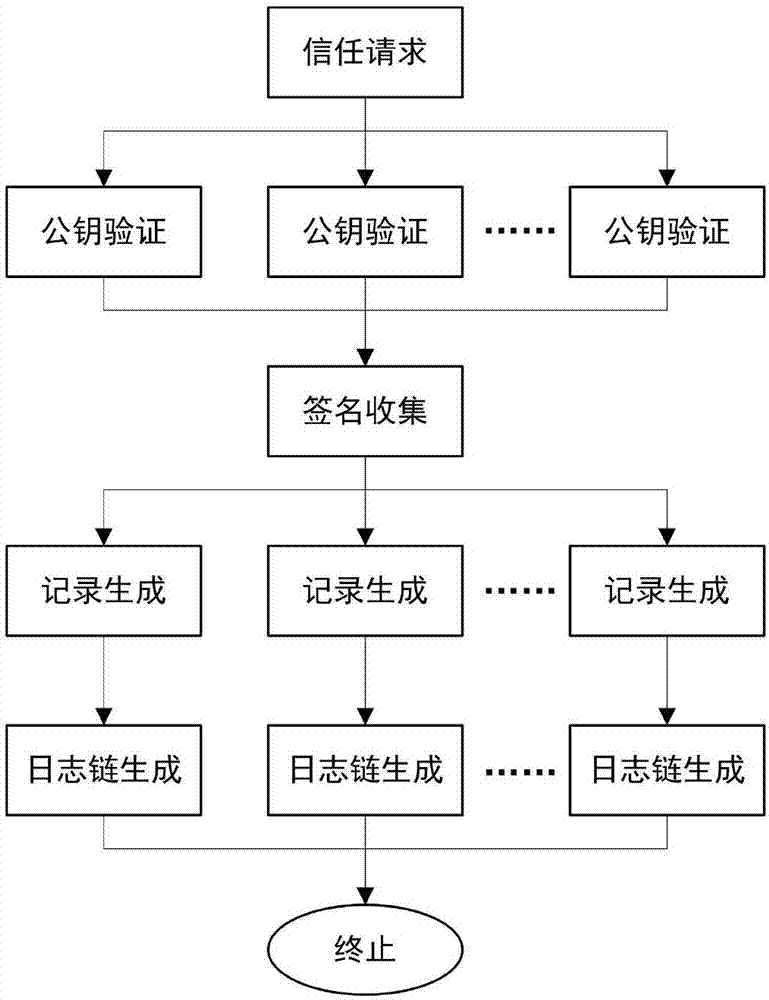
The invention mainly belongs to the technical field of information security, and specifically relates to a novel decentralized public key management method and a trusted model. The method is constructed on distributed data network platforms such as a block chain and P2P (Peer to Peer) in order to ensure that all nodes in the platforms can participate in maintenance of whole-life-cycle management of public keys of users, and the changes of the public keys of the users in various states in a life cycle are recorded in a bill form. Through the method, public keys passing verification can be recorded and added into a consistent public key storage structure of a platform to be saved; a public key log chain is generated for all public key records of the same user according to a time sequence, and an authentication chain and a trusted network are formed on the basis of a referrer signature; and efficient search of the public keys can be realized on the basis of user identifiers. Through adoption of the method, the public keys of the users can be issued and acquired conveniently and accurately, and the effectiveness, correctness, consistency and non-fraudulence of acquired public keys are ensured. The method can be taken as an infrastructure supporting authentication, encryption, integrity and accountability services.
Owner:UNIV OF SCI & TECH BEIJING
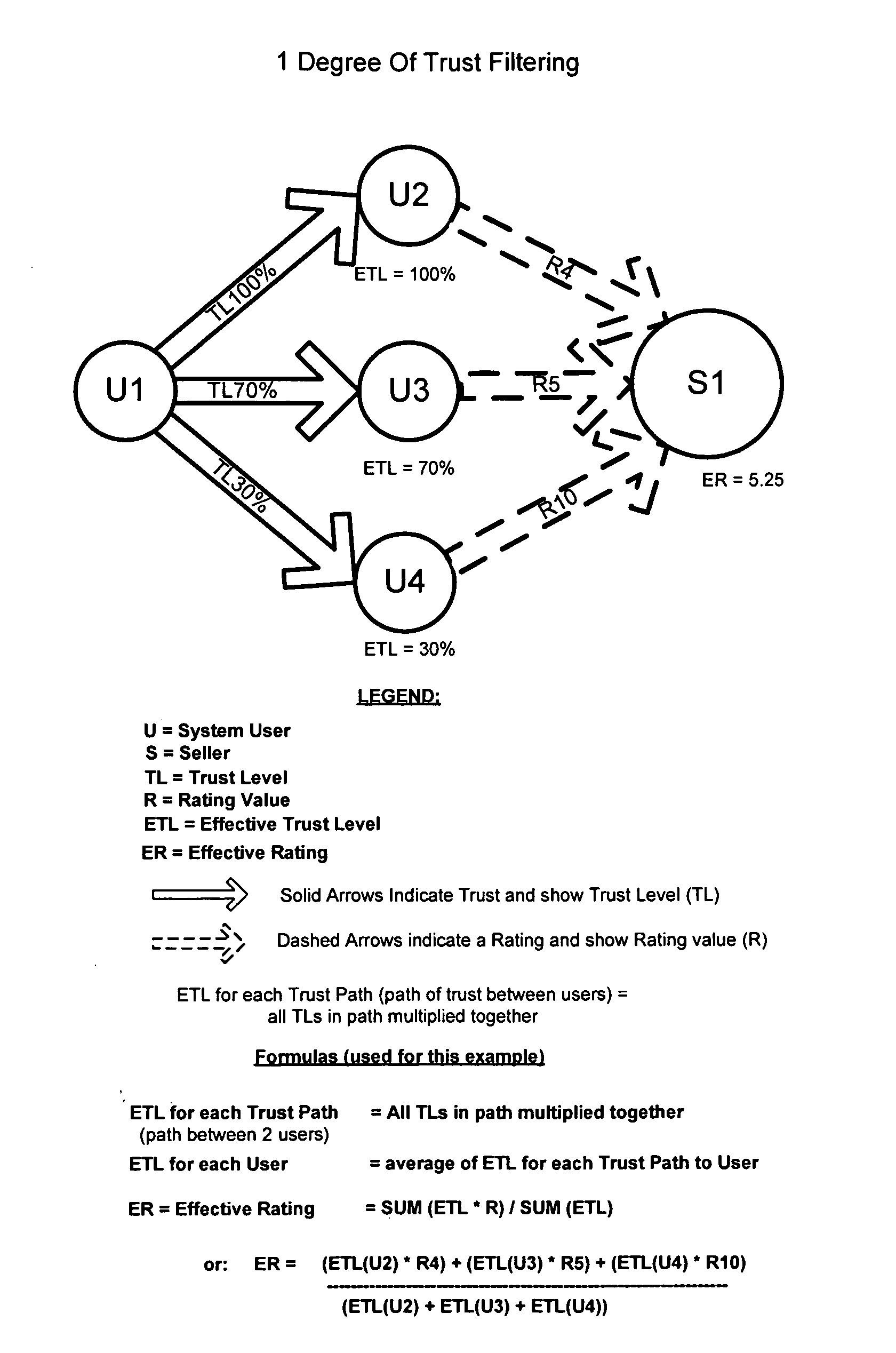
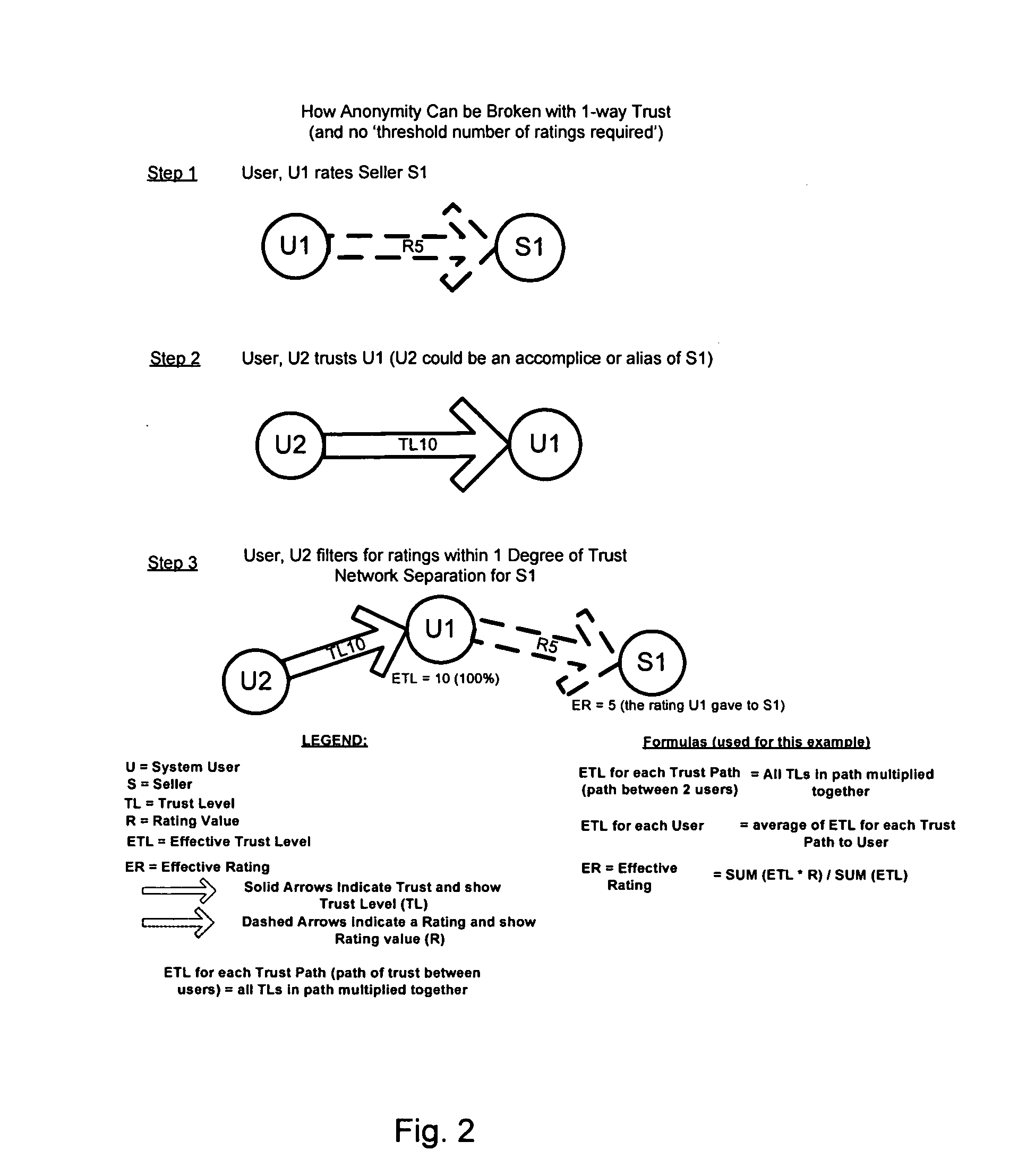
Trust-based Rating System
A trust-based communication and information filtering system having rating features is user customizable. It is a system in which the raters remain anonymous. The anonymous ratings mimic real life person-to-person recommendation methods wherein recommendations are personal and cannot be controlled by persons or items being rated. The system uses contextually meaningful rating which are filtered explicitly by the end-user or implicitly based upon the environment of the end-user to facilitate discovery and minimize the potential for fraud and deception. Trust networks are constructed between the participants and the rating or information filtered or weighted according to the user's relative trust of the raters in the system. Ratings made by the inventive system can be for goods, services, people, businesses or virtually any item that can be rated and / or recommended.
Owner:DAVIS JOHN STANNARD
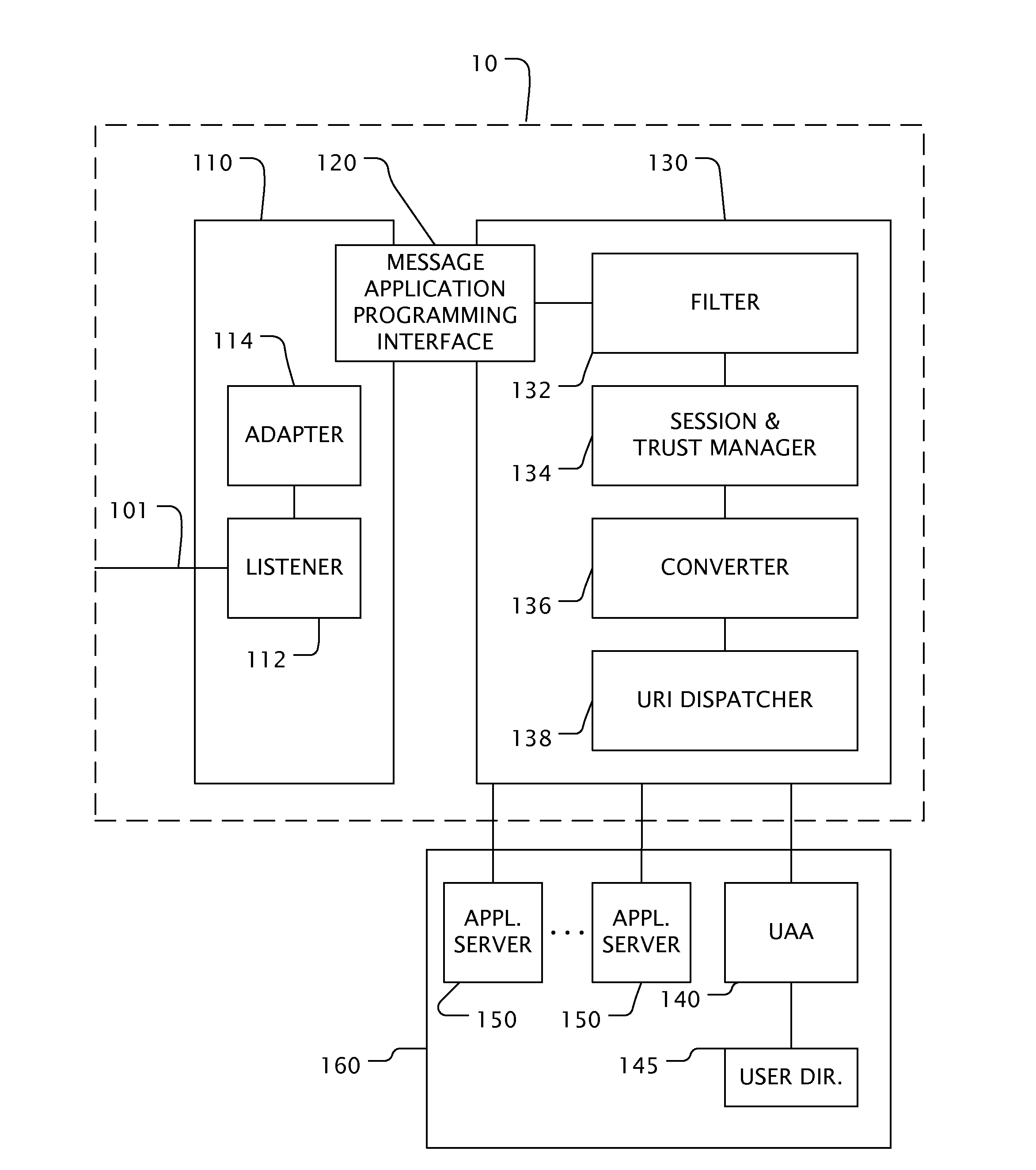
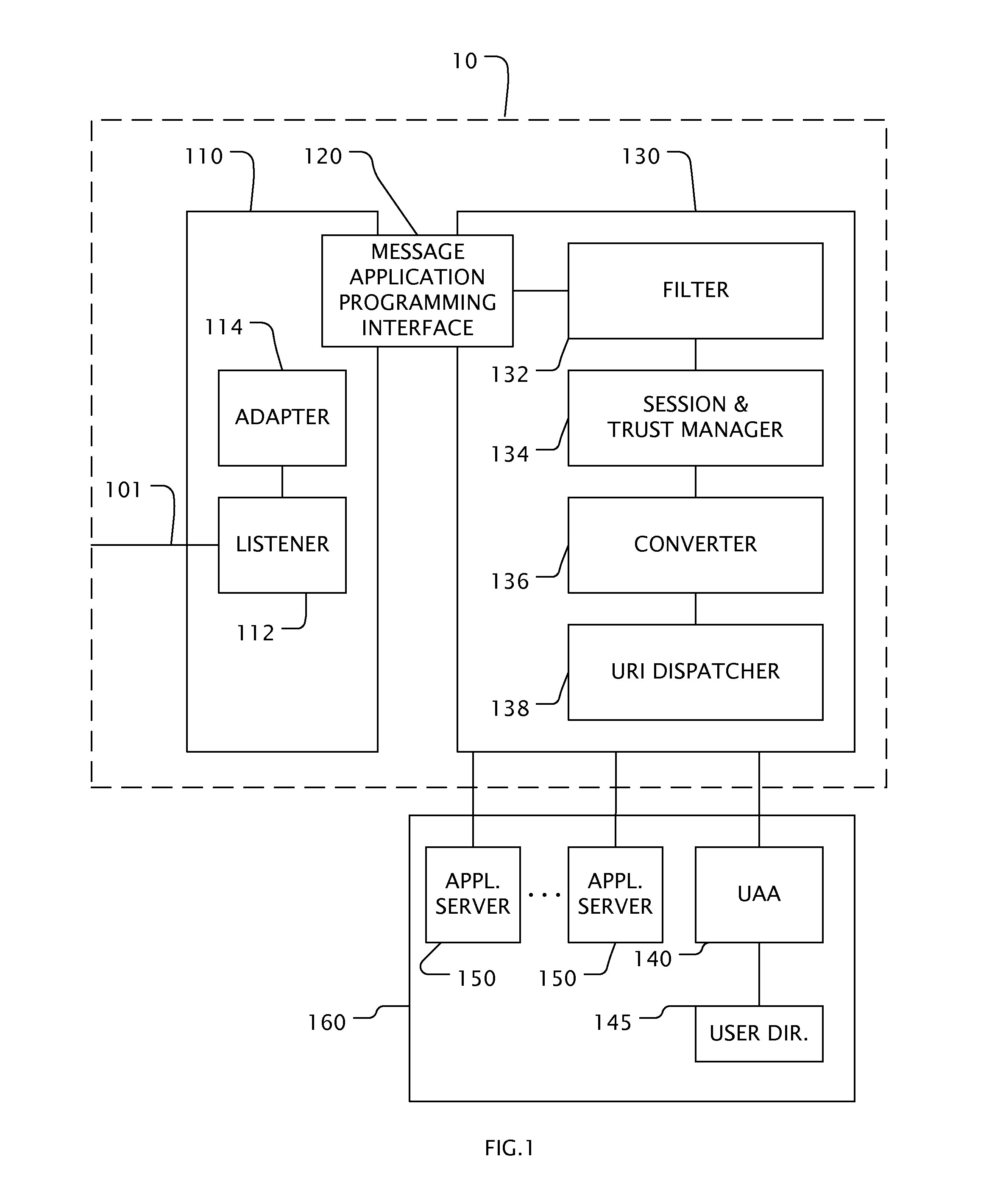
Method and apparatus for passing security configuration information between a client and a security policy server
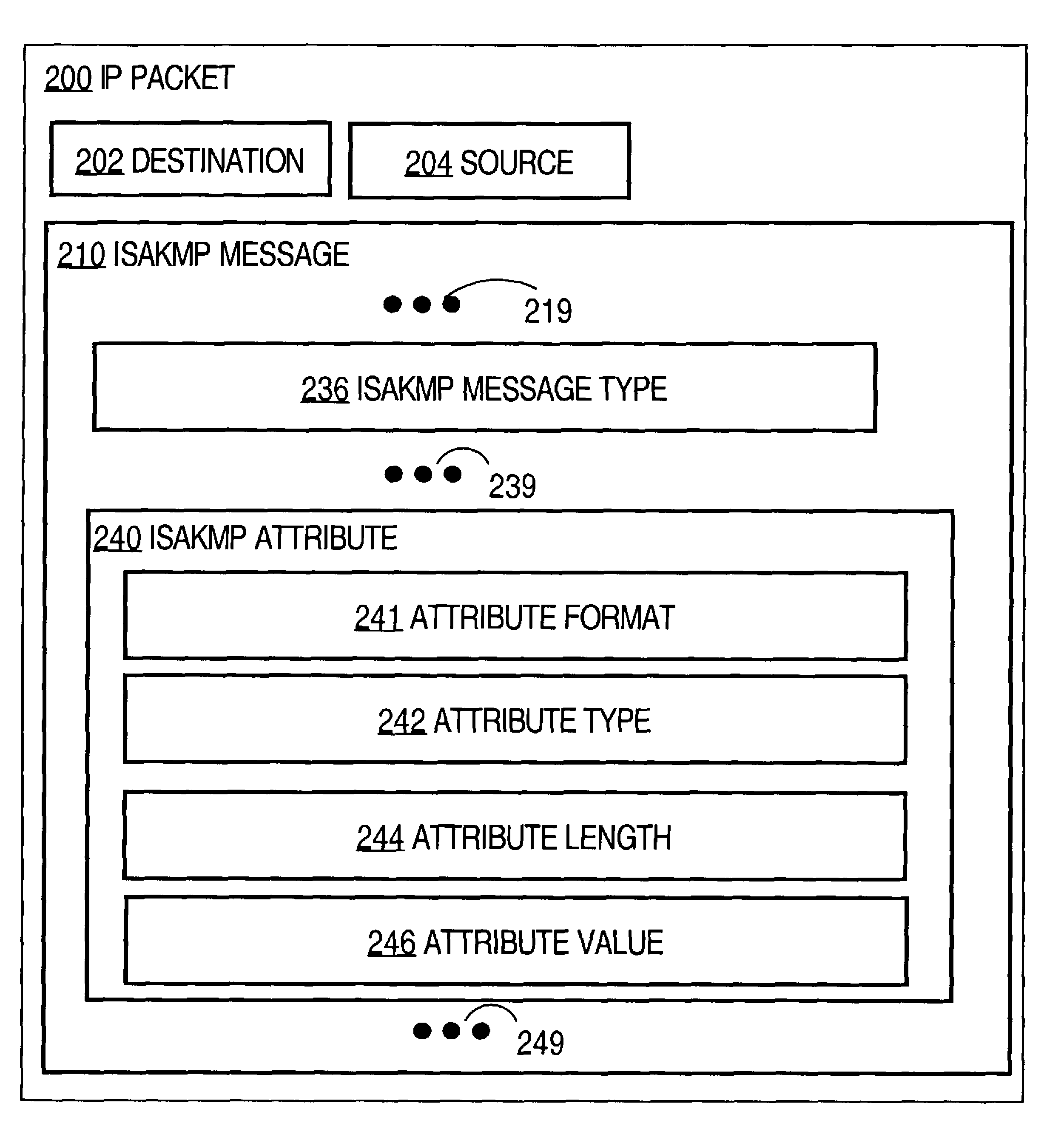
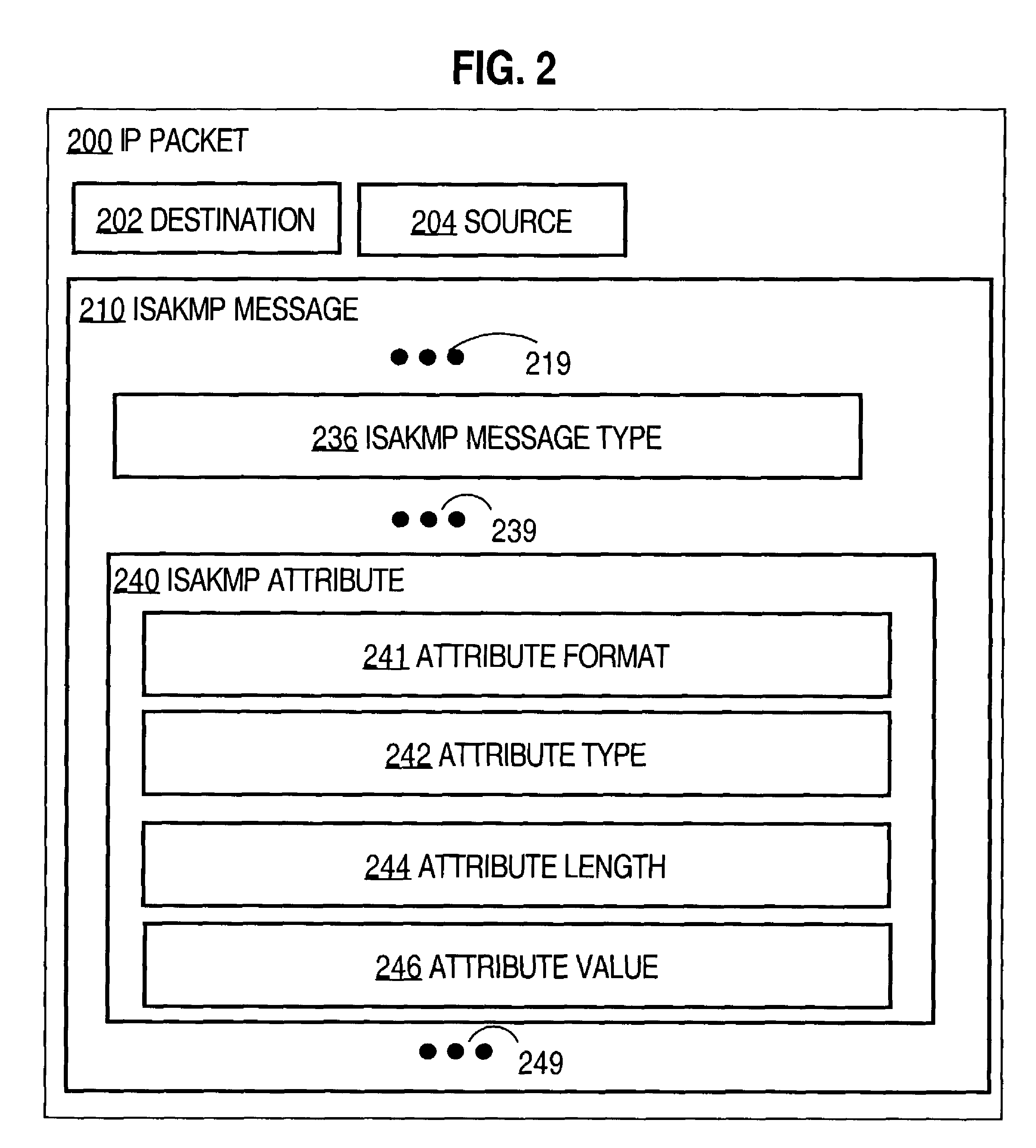
ActiveUS7849495B1Special data processing applicationsSecuring communicationSecure communicationInternet Security Association and Key Management Protocol
Techniques for passing security configuration information between a security policy server and a client includes the client forming a request for security configuration information that configures the client for secure communications. The client is separated by an untrusted network from a trusted network that includes the security policy sever. A tag is generated that indicates a generic security configuration attribute. An Internet Security Association and Key Management Protocol (ISAKMP) configuration mode request message is sent to a security gateway on an edge of the trusted network connected to the untrusted network. The message includes the request in association with the tag. The gateway sends the request associated with the tag to the security policy server on the trusted network and does not interpret the request. The techniques allow client configuration extensions to be added by modifying the policy server or security client, or both, without modifying the gateway.
Owner:CISCO TECH INC
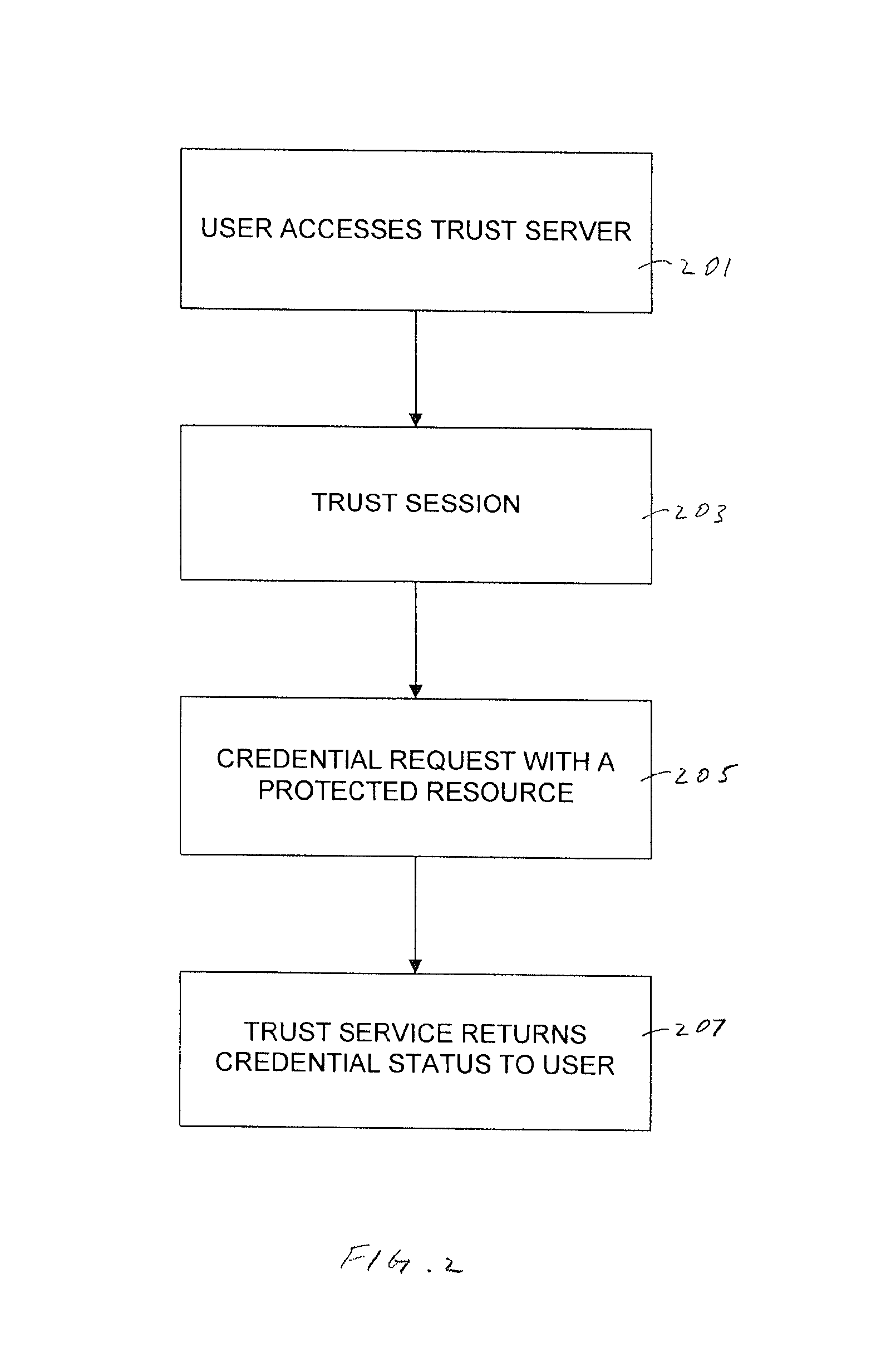
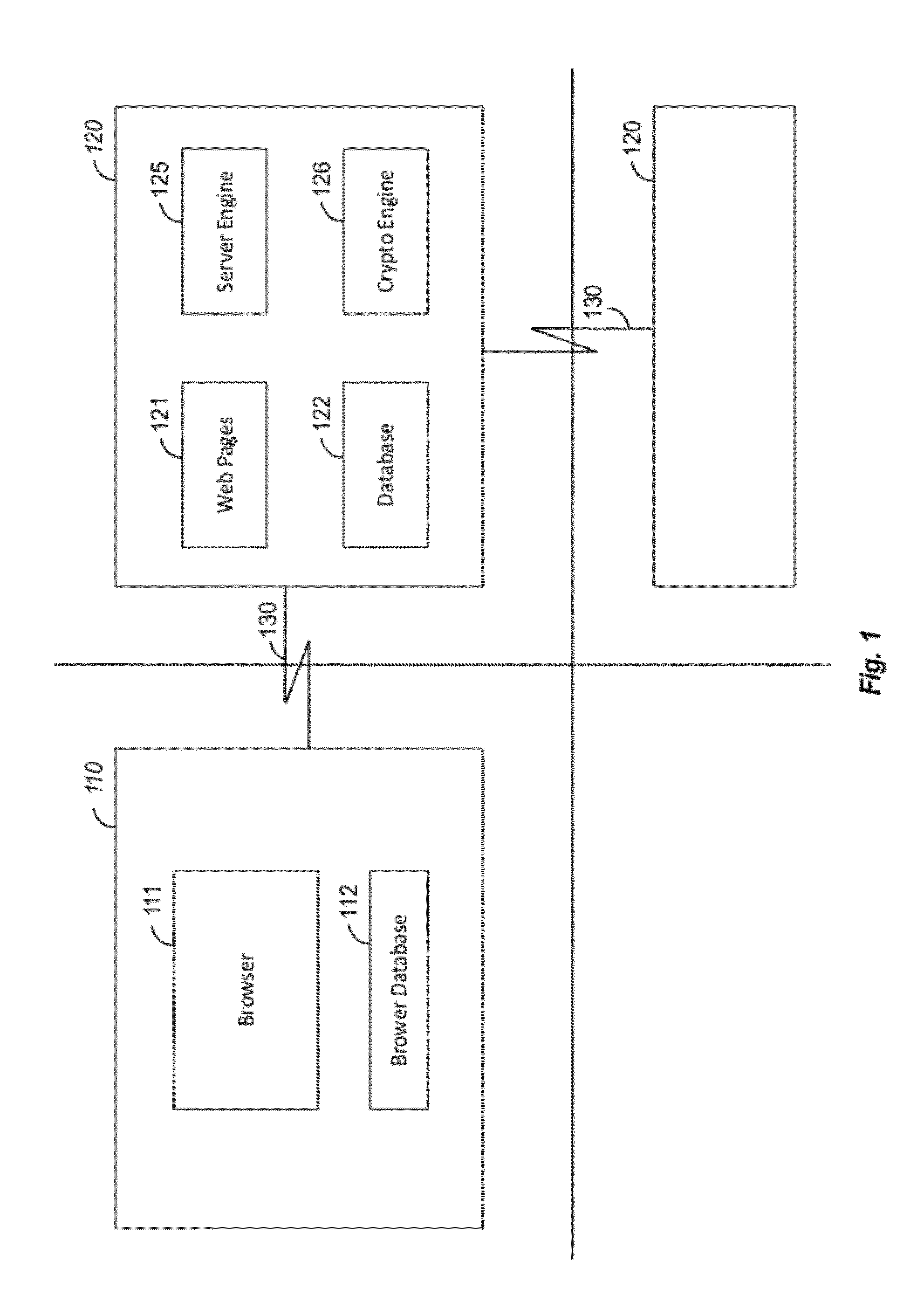
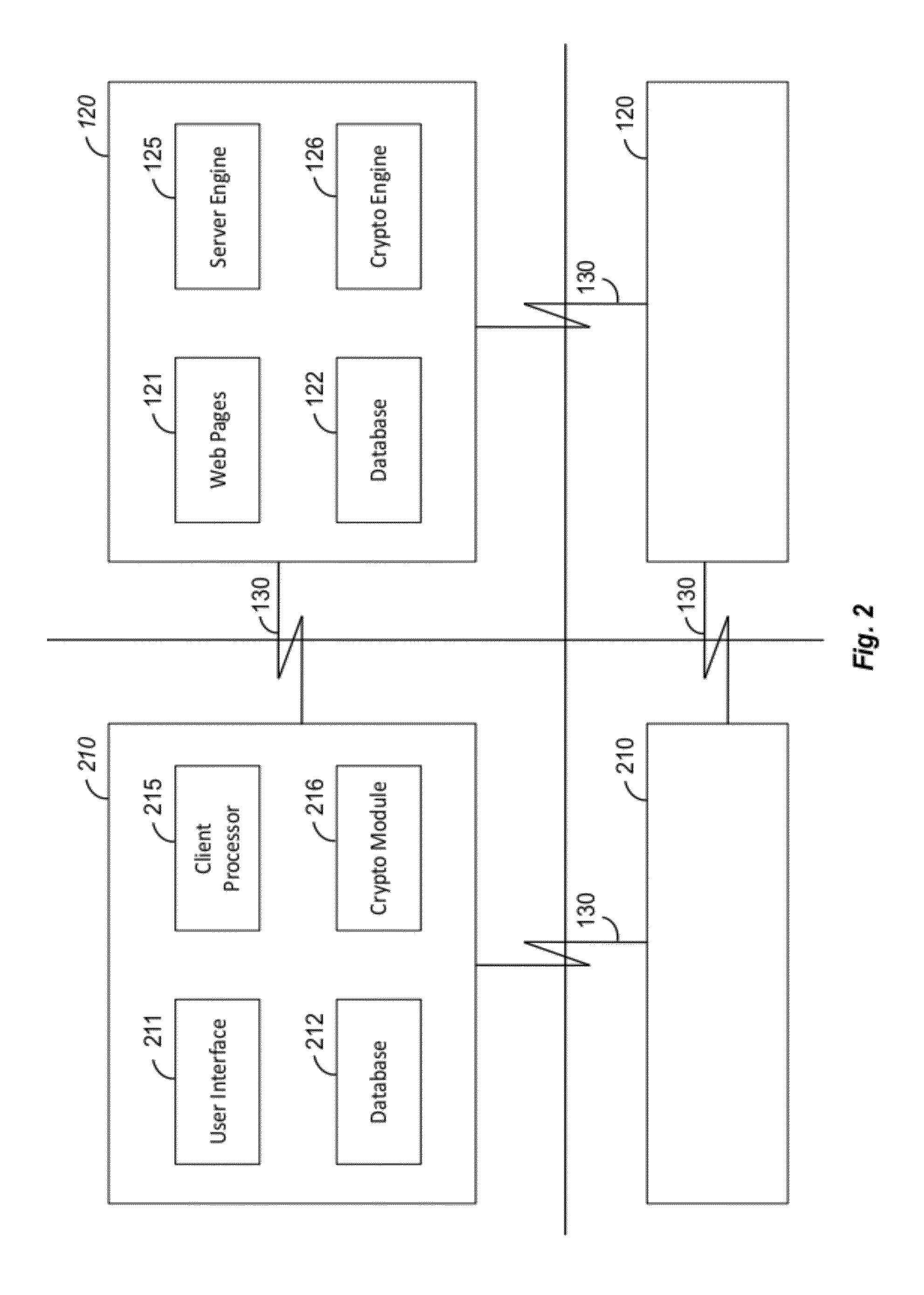
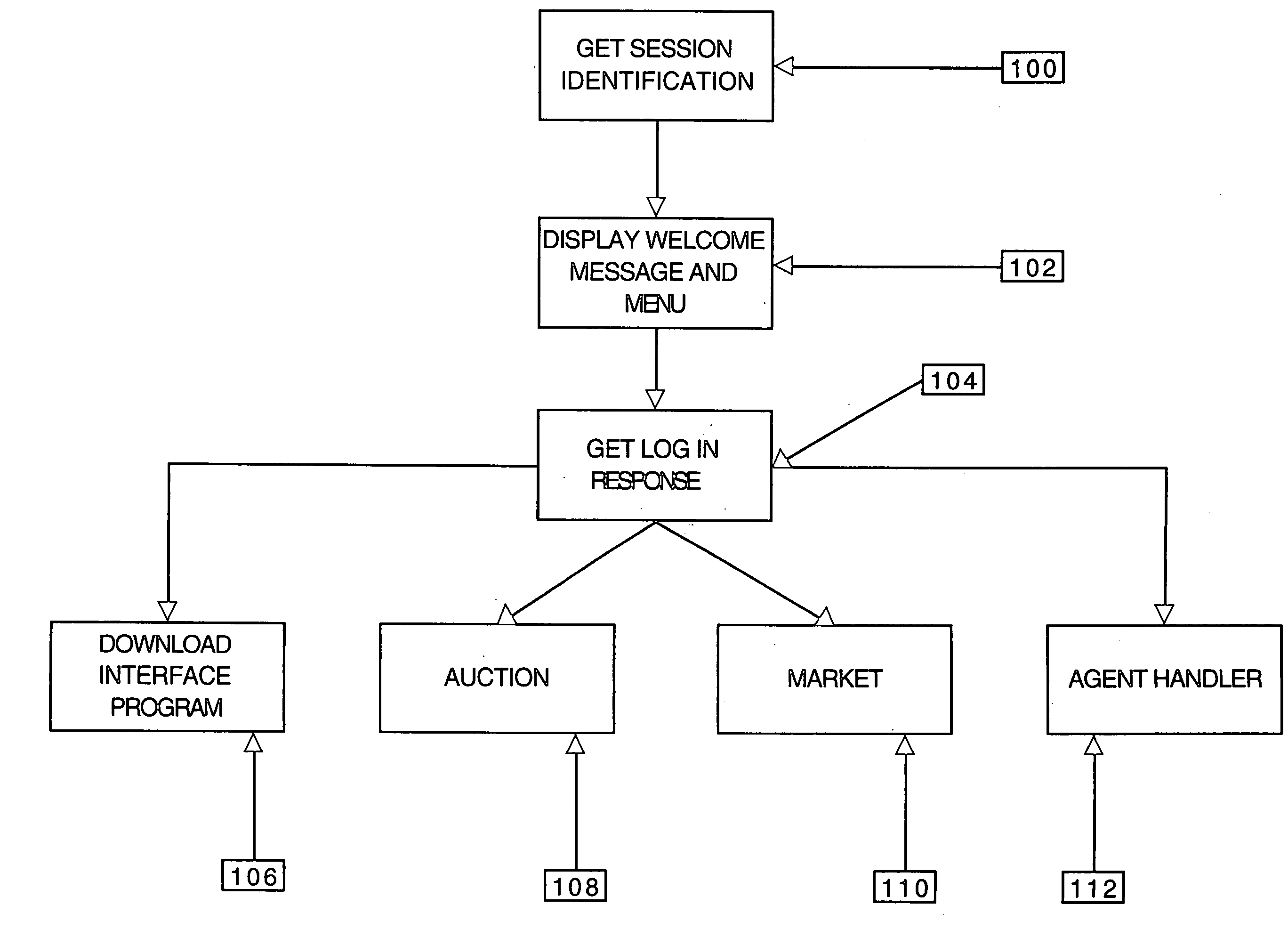
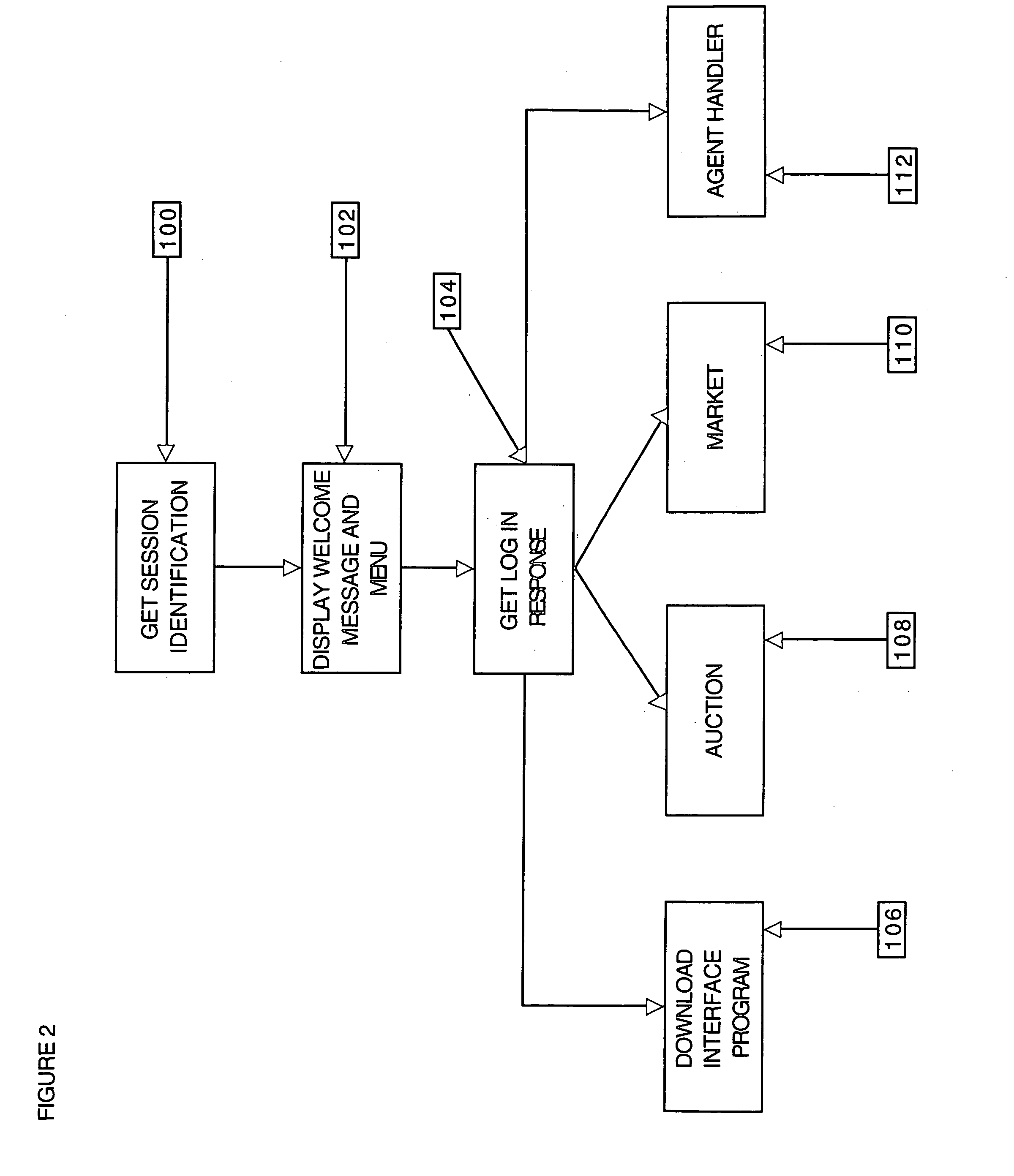
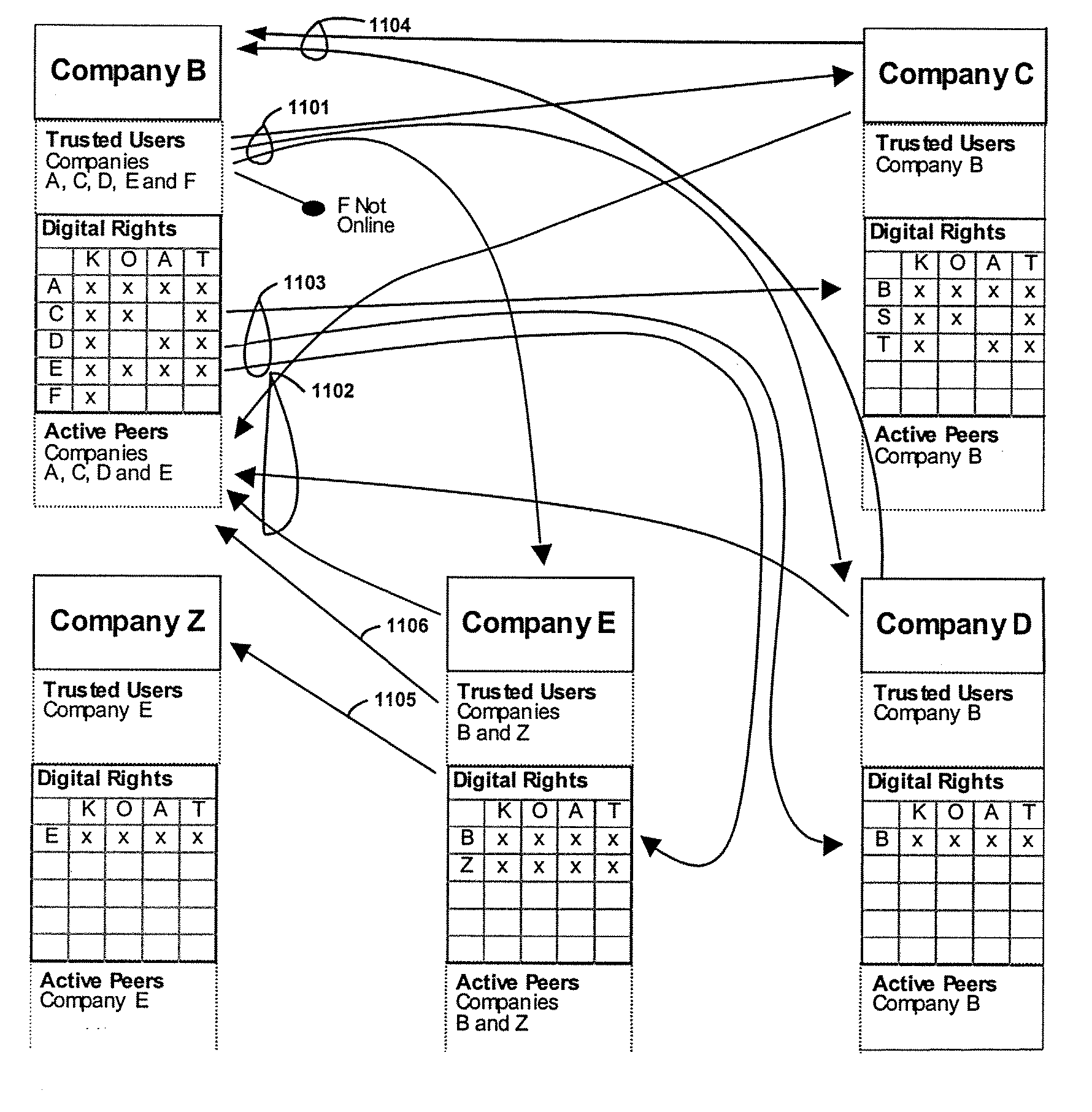
Apparatus and Method for Managing a Trust Network
A computer readable storage medium includes instructions to receive a request from a client to enroll in a trust network. A registration form is supplied to the client in response to the request. Client data in the registration form received from the client is processed to load the client data as parameters in a managed trust network. The managed trust network includes a vouch system, a complaint resolution mechanism, relationship value exchange and endorsements.
Owner:RESPECT NETWORK CORP
Secure extranet server
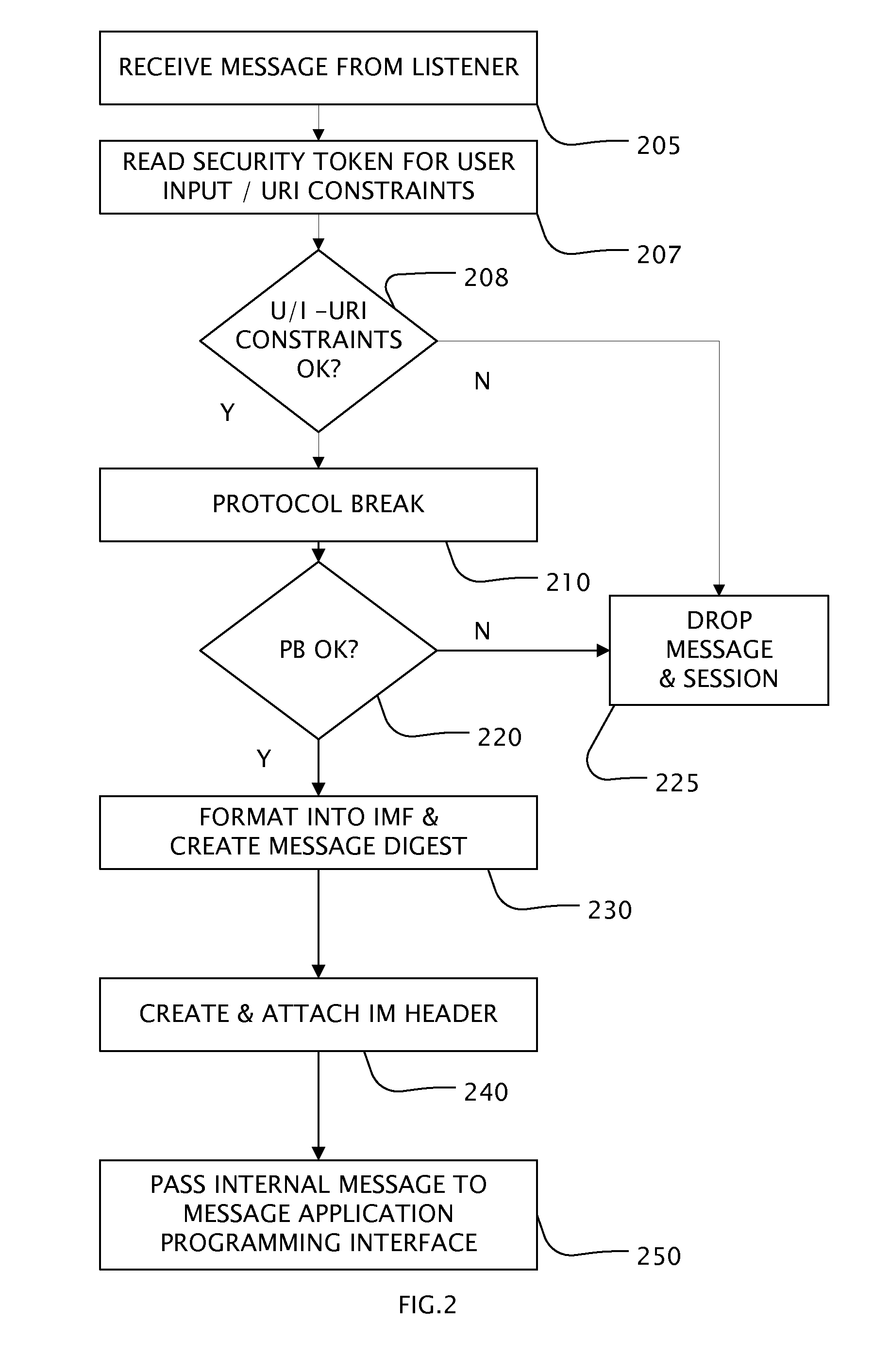
A Secure Extranet Server (SES) provides for secure and traceable communication and document exchange between a trusted network and an untrusted network by authenticated users. The SES includes a first partition in communication with the untrusted network and a second partition in communication with the trusted network. The second partition maintains a session table and is in communication with a user authentication and authorization module. Communication between the first and second partition is preferably initiated by a request from the second partition. Security tokens attached to messages provide constraint checking on user inputs, access to documents and servers within the trusted network, checkout and checkin of controlled documents, and a single sign-on capability for on-line applications as well as local applications operating on protected files at remote user computers.
Owner:PHION
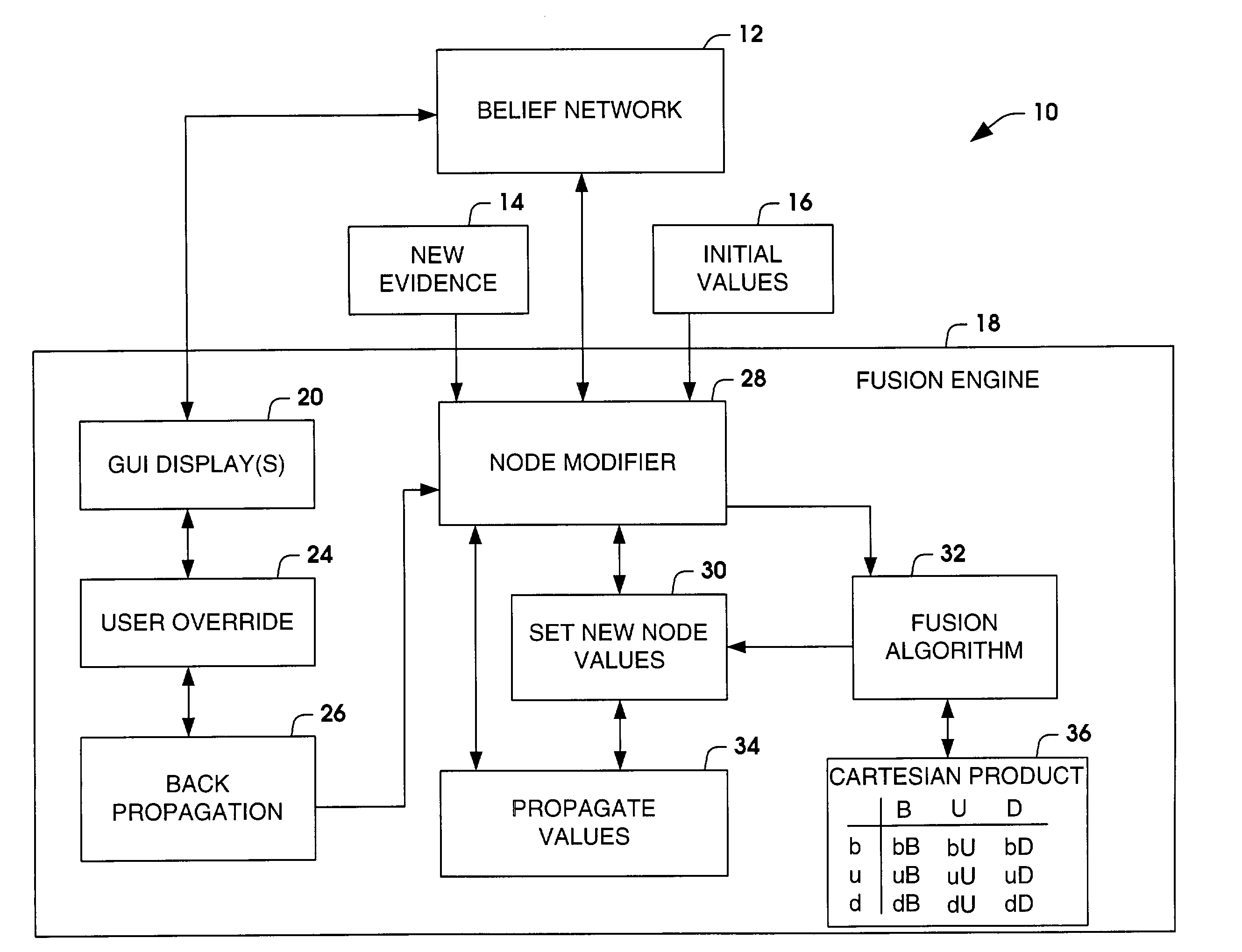
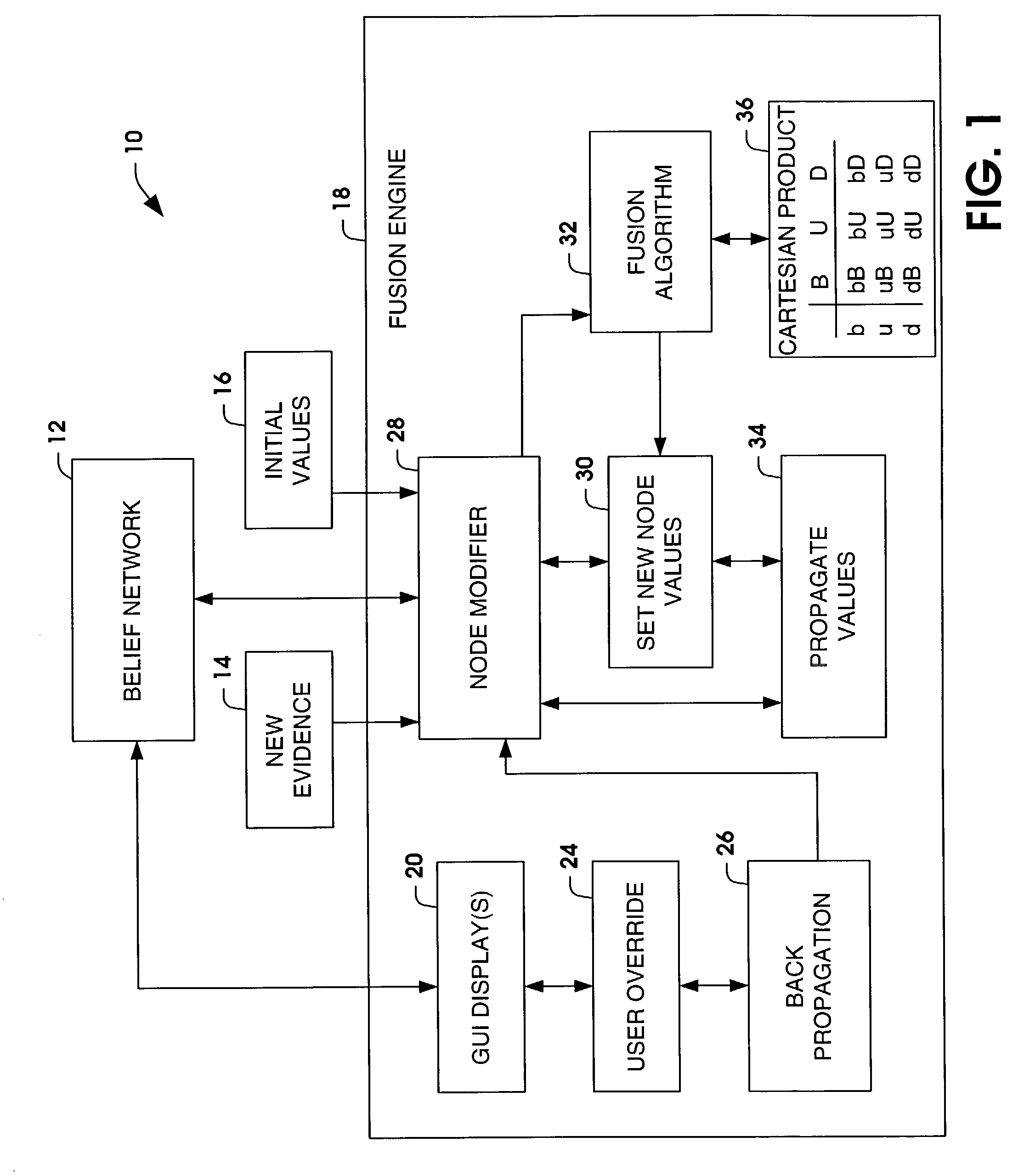
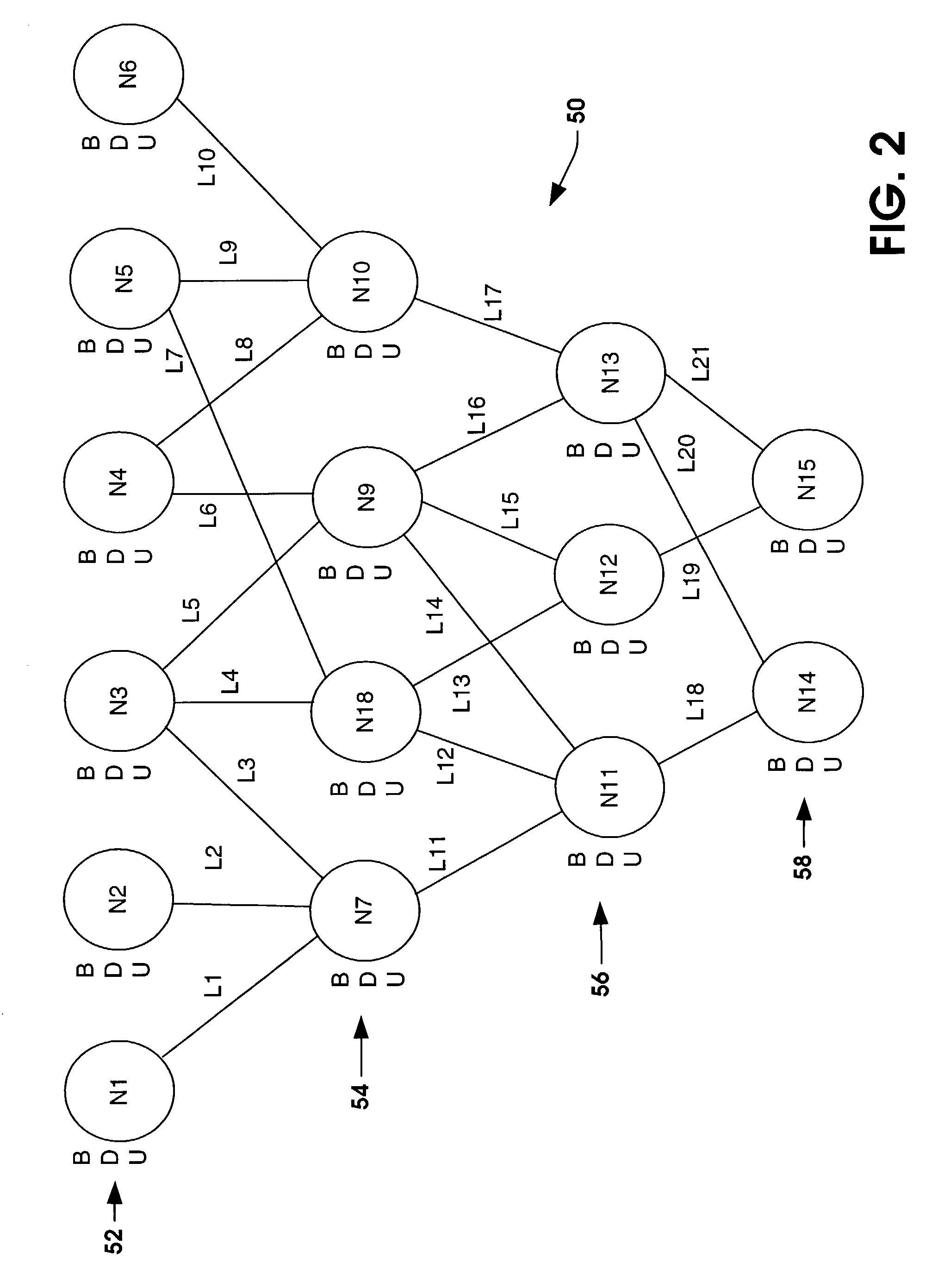
General purpose fusion engine
ActiveUS20040019575A1Probabilistic networksFuzzy logic based systemsDeep belief networkGeneral purpose
Systems and methods are provided for fusing new evidence and displaying node parameters of a decision network. The decision network can be a belief network, such as a Dempster-Shafer belief network. The Dempster-Shafer belief network includes node parameters that conform to the Dempster-Shafer combination rule, which is based on an evidential interval: the sum of a belief value, a disbelief value and an unknown value is equal to one. A user override is provided to allow a user to override node parameters associated with a hypothesis or outcome and the decision network self-adjusts the appropriate link values or learned to instantiate the override. The back-propagation algorithm is used to adjust the links.
Owner:NORTHROP GRUMMAN SYST CORP
Consignment nodes
InactiveUS20050033655A1Minimal costIncrease valueFinancePayment architectureLibrary scienceTrust network
Owner:EBAY INC
Establishing secure peer networking in trust webs on open networks using shared secret device key
InactiveUS7082200B2CostImprove connectivityKey distribution for secure communicationDigital data processing detailsS/KEYVia device
Owner:MICROSOFT TECH LICENSING LLC
Transitive trust network
Methods, data structures, and systems by which entities can efficiently discover, extend, validate and establish business relationships over a digital network are disclosed. A transitive trust system can be utilized by any number of interconnected entities in which at least two of the entities are capable of sharing information. One or more entity trust lists contain, for at least two of the entities, at least one characteristic. Each characteristic can, for example, describe or pertain to the actual or perceived dependability, reliability and / or credibility of an entity. The system also includes at least one transactional trust list that contains at least one parameter relative to an exchange between at least two of the entities through at least one degree of separation between the entities. The transactional trust list can, for example, be a listing of any type of parameters that define or describe business exchanges within a particular industry segment. The transactional trust list can also list information about the types of transactional activities that can take place and proxy actions available to cooperating entities. The system retrieves information from the entity trust list and the transactional trust list in order to provide a framework for at least two of the entities to establish relationships with one another.
Owner:ACCENTURE GLOBAL SERVICES LTD
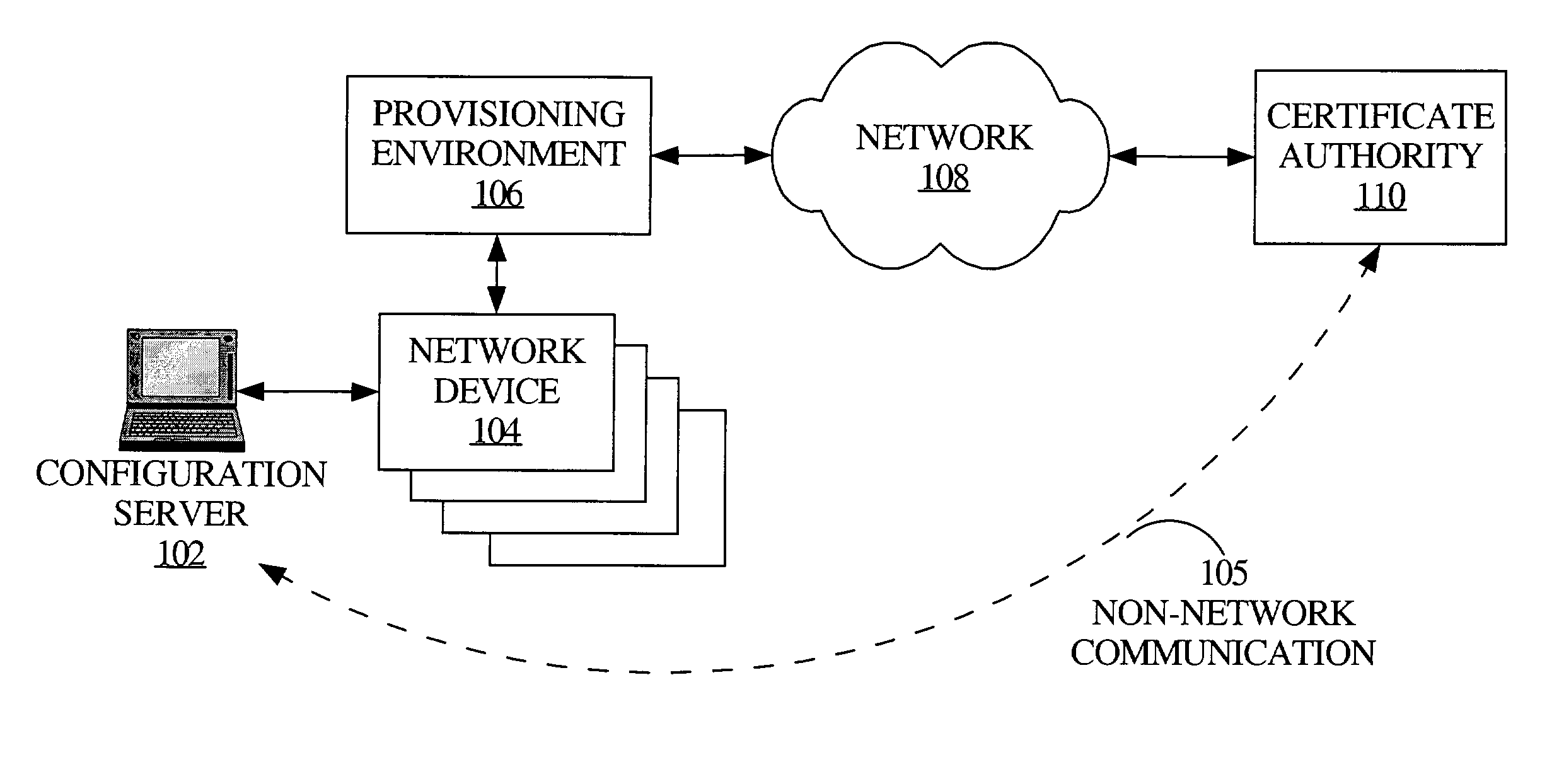
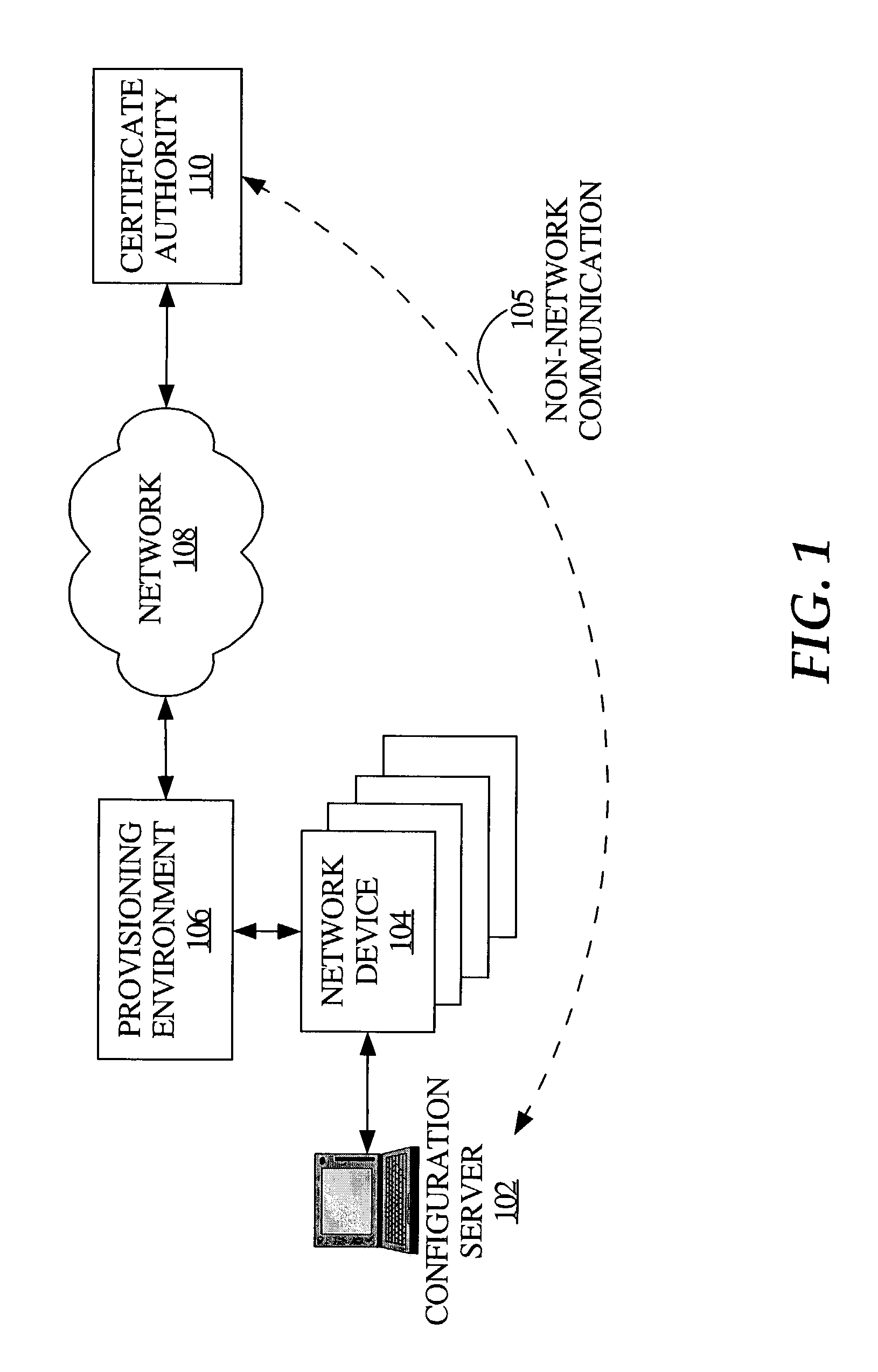
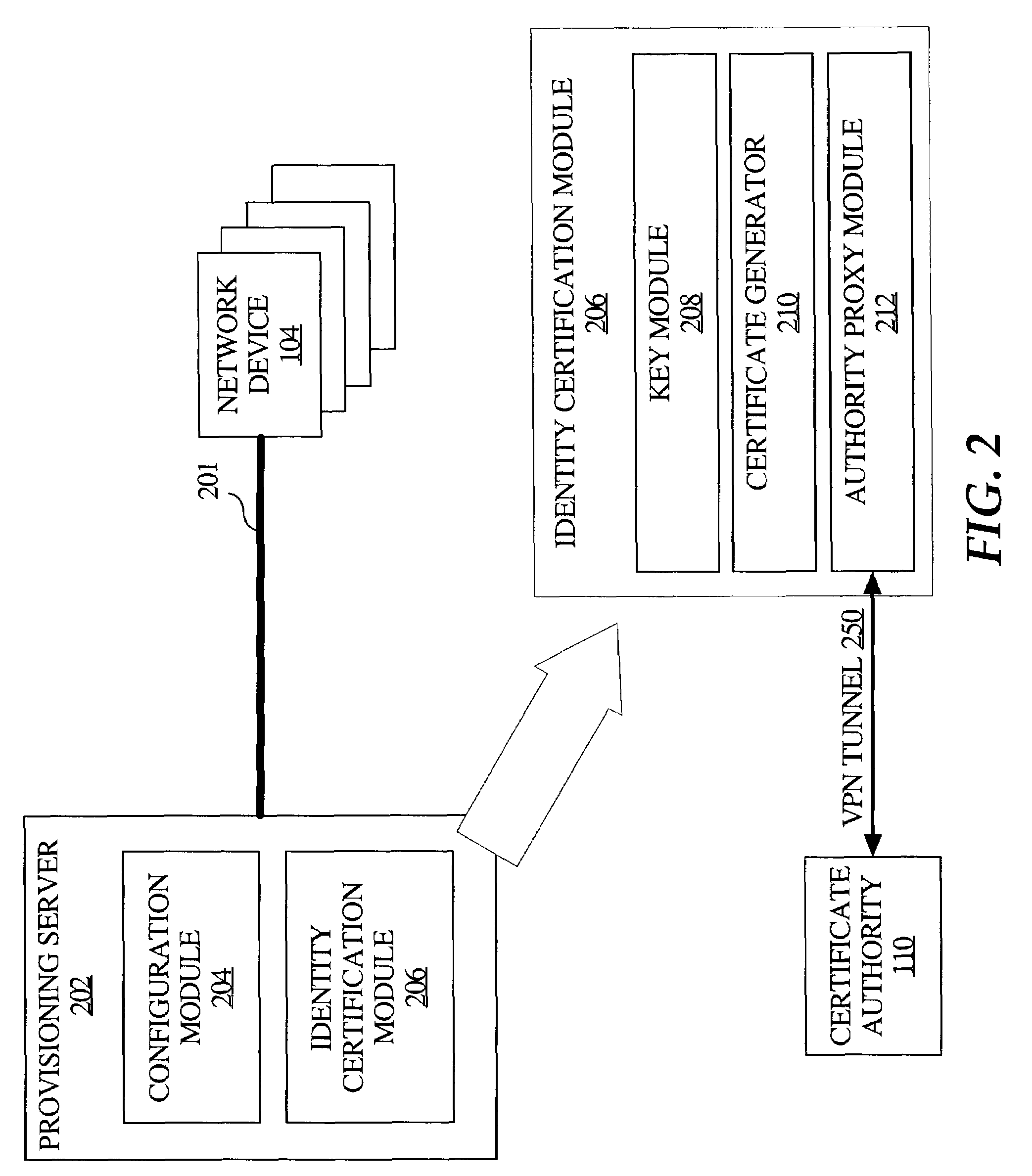
Method and apparatus for integrated provisioning of a network device with configuration information and identity certification
InactiveUS7386721B1Digital data processing detailsUser identity/authority verificationSecure communicationComputer module
According to one aspect, a provisioning server comprises a configuration module that configures a network device and an identification certification module that certifies the identity of the network device. With use of the provisioning server, the network device does not require configuration with network connectivity in order to obtain its certified identity. In one embodiment, configuration module configures the device for operation at the device's point of deployment in a network. In one embodiment, the identity certification module is configured to generate a digital certificate for the network device and the configuration module is configured to automatically configure the network device based on its digital certificate. The provisioning server is coupled to the network device with a secure communication link. As a result, a more trusted network device is ultimately deployed into its network of operation.
Owner:CISCO TECH INC
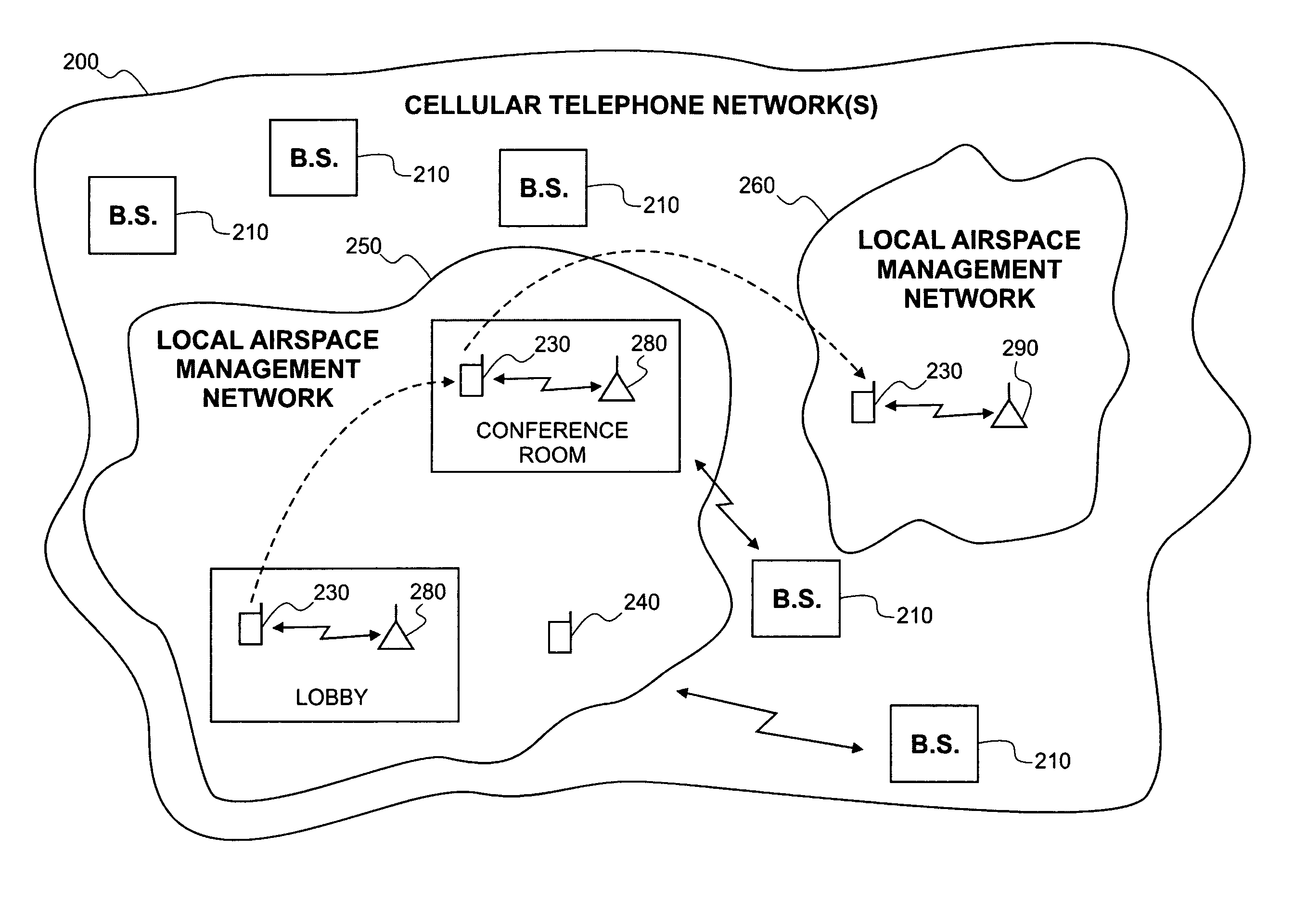
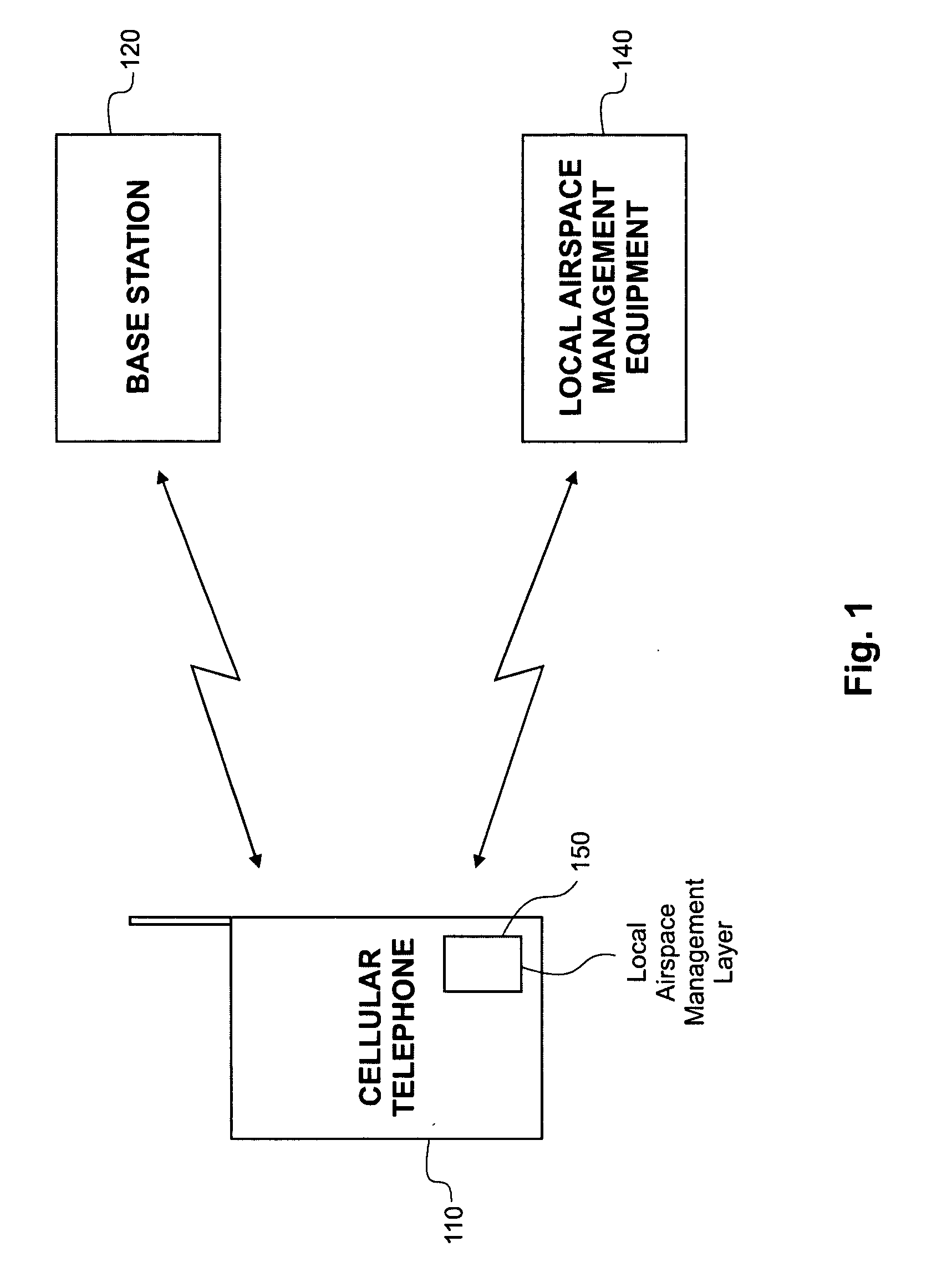
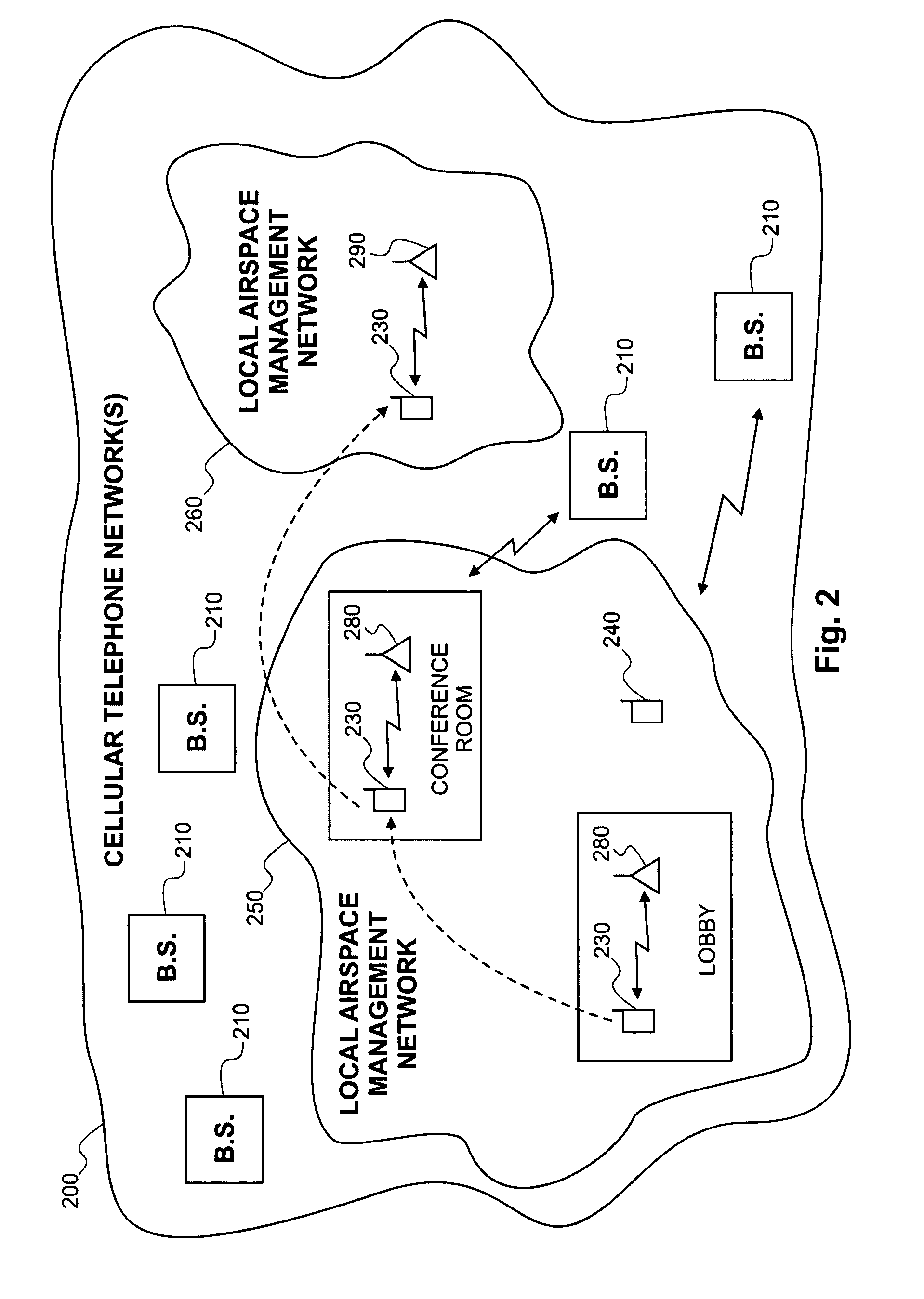
Local area wireless airspace management
A mobile wireless device that is implemented to provide personal communications services in a wireless communications network can be integrated with hardware and / or software to manage the device at the device level (e.g., control device usage or operation at the device) at the local level. Management can be implemented to be invisible to wireless device user such as to be implemented without requiring user initiation to acknowledge or allow management to proceed. Local management can be implemented on a real time basis to manage the usage or operation of a device, device components (hardware or software, peripherals (e.g., speaker, display, keyboard, microphone, etc.), or hardware (e.g., camera, voice recorder, etc.) or software integrated into the device. Different policies can be applied within a local airspace management network. A local airspace management network can be configured to interact with wireless devices to authenticate the user of a device. Security measures can also be implemented to assure that local airspace management is applied by a trusted network. Information associated with a local airspace management network such as user biometrics, trusted network certification, authentication information can be stored in a wireless device. A local airspace management network can include a transmitter and associated hardware and / or software that implement the local airspace management policy of an entity.
Owner:BALWANI RAMESH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com