Internet of Things identity authentication method based on blockchain
A technology of identity authentication and authentication method, which is applied in the direction of electrical components, transmission systems, etc., can solve problems such as the inability to decentralize the authentication process, the inability to support multi-factor authentication, and access to delivery authentication scenarios, etc., to achieve both ease of use and security Sexuality, quickness, high efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be described in detail below in conjunction with the accompanying drawings.
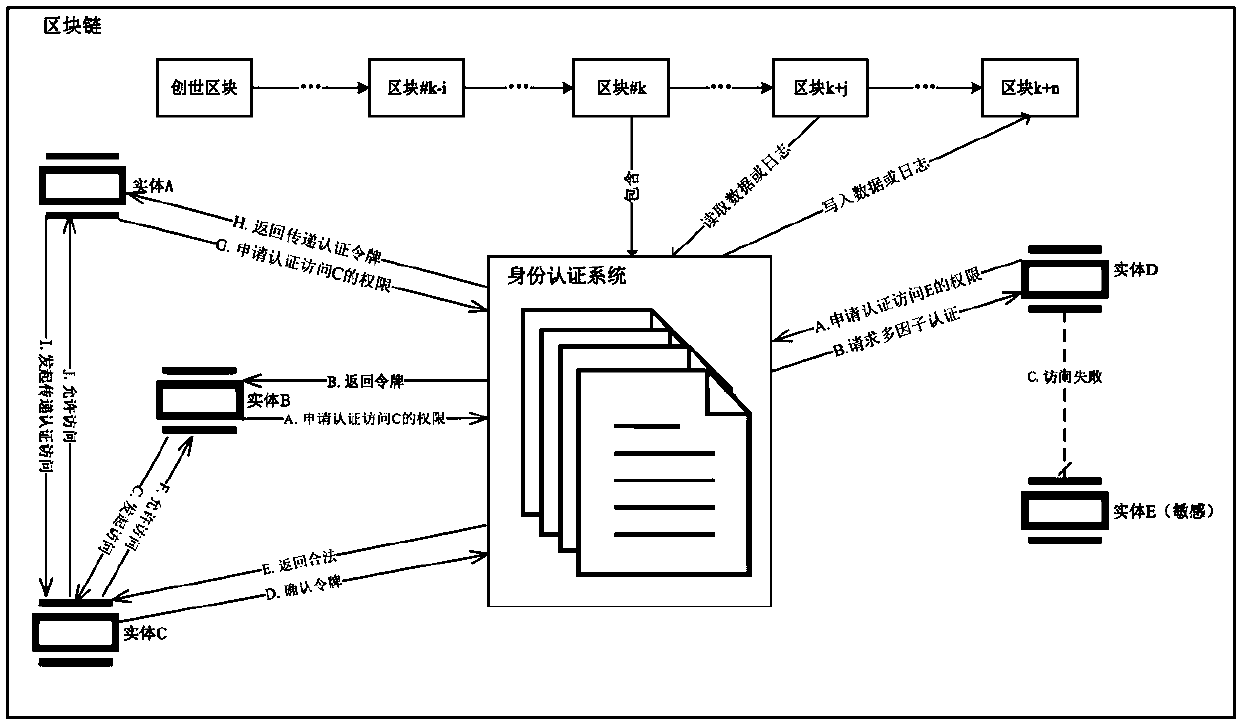
[0037] exist figure 1 On the left side, Entity B wishes to access a resource on Entity C via transitive access, and Entity A wishes to access a resource on Entity C.
[0038] (1) Entity B first uses the address of its own blockchain node and the address of entity A as authentication information to call the identity authentication smart contract;
[0039] (2) After receiving the request, the smart contract will apply for access to the decentralized cloud storage system to obtain the conditions for accessing entity C. After cloud storage returns the access conditions set by entity C, the smart contract compares the access conditions with the identity authentication information sent by entity B. figure 1 If the smart contract finds that entity C allows the entity represented by the address of entity B to access the resources of entity C, then the smart contract will g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com