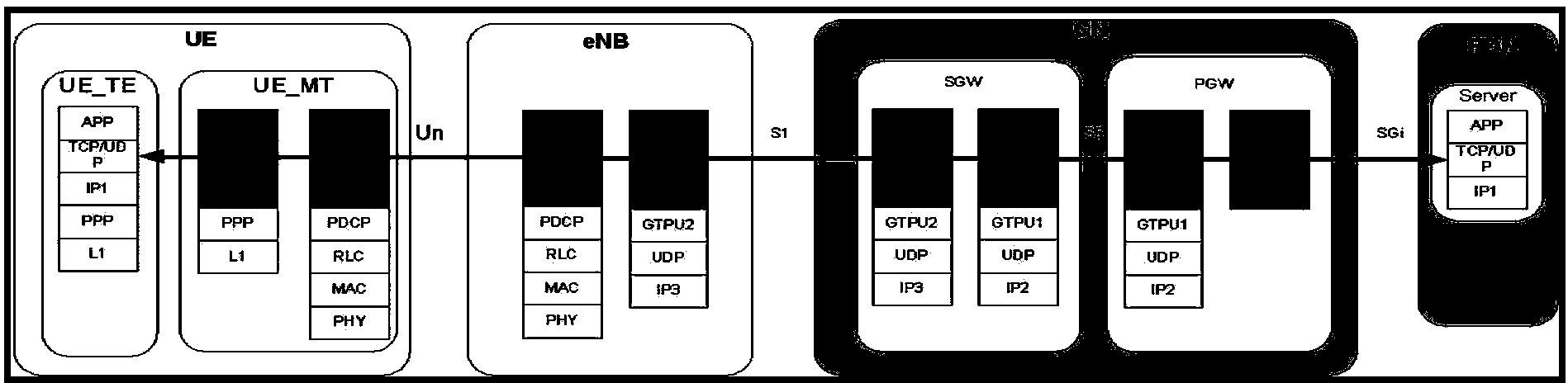
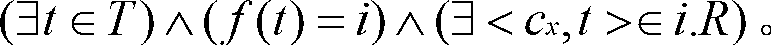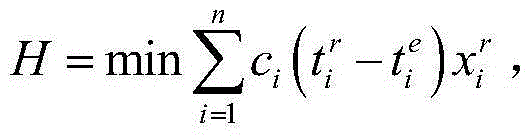Patents
Literature
239 results about "Strategy execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
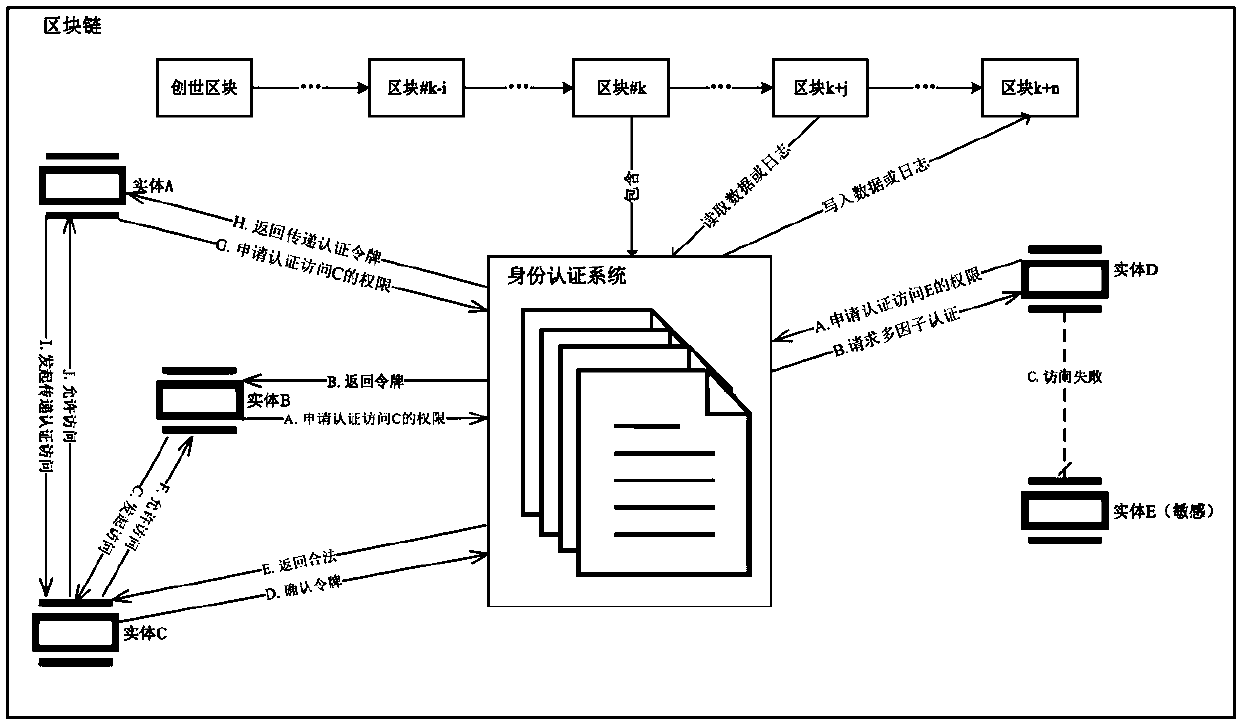
Internet of Things identity authentication method based on blockchain
The invention belongs to the technical field of identity authentication, and specifically provides an Internet of Things identity authentication method based on a blockchain. The basic steps of the Internet of Things identity authentication method provided by the invention are as follows: an entity calls an intelligent contract by means of an own key to accomplish the registration in an identity authentication system; each entity can call the intelligent contract to set an access strategy so as to limit the access of other entities to the entity and to form a trust network of the Internet of Things; when one entity accesses the data of the other entity, the entity needs to apply for a token from the intelligent contract to obtain the access qualification, and the intelligent contract checks whether the entity initiating the access has the access qualification according to the access strategy set by the accessed entity in the trust network between the entities, and if yes, the intelligent contract generates the token and returns the token to the entity initiating the access; or otherwise, the intelligent contract returns token application failure information. By adoption of the method provided by the invention, a centralized authority mechanism in an identity authentication process is removed, malicious tampering of records of identity authentication and data access is prevented, a strategy execution result is not manually manipulated, and a fair, transparent and credible execution environment is provided for the identity authentication of the entities in the Internet of Things.
Owner:FUDAN UNIV
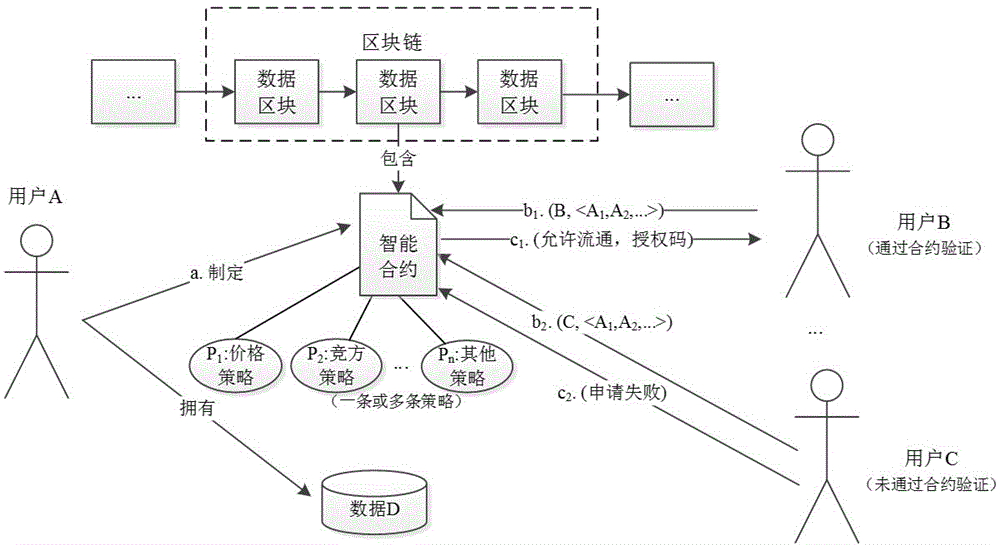
Block-chain-based data rights protection method
ActiveCN106600405ANot easy to tamper withNot easy to forgeFinanceDigital data authenticationThird partyStrategy execution
The invention belongs to the technical field of data security, and specifically relates to a block-chain-based data rights protection method. The steps of method are as follows: a user owning data formulates data circulation strategies according to data rights that need protection, compiles the circulation strategies into an intelligent contract, and deploys the intelligent contract on a block chain system; and before other users perform data circulation, the user serving as a data transferee needs to use identity information and related data circulation attributes to call the intelligent contract, and the intelligent contract automatically provides an approval result of a circulation application according to the established data circulation strategies: if circulation is allowed, a dynamic circulation authorization code is returned to the transferee user; otherwise application failure is returned. The block-chain-based data rights protection method provided by the invention is an application of a block chain system, removes dependence on a third-party authority organization in a data rights protection process, ensures that the data circulation strategies formulated by the data owner are not maliciously modified, and a strategy execution result is not manually manipulated, thereby providing a just, transparent and credible execution environment for data circulation processes of data transactions, data opening and sharing and the like.
Owner:FUDAN UNIV
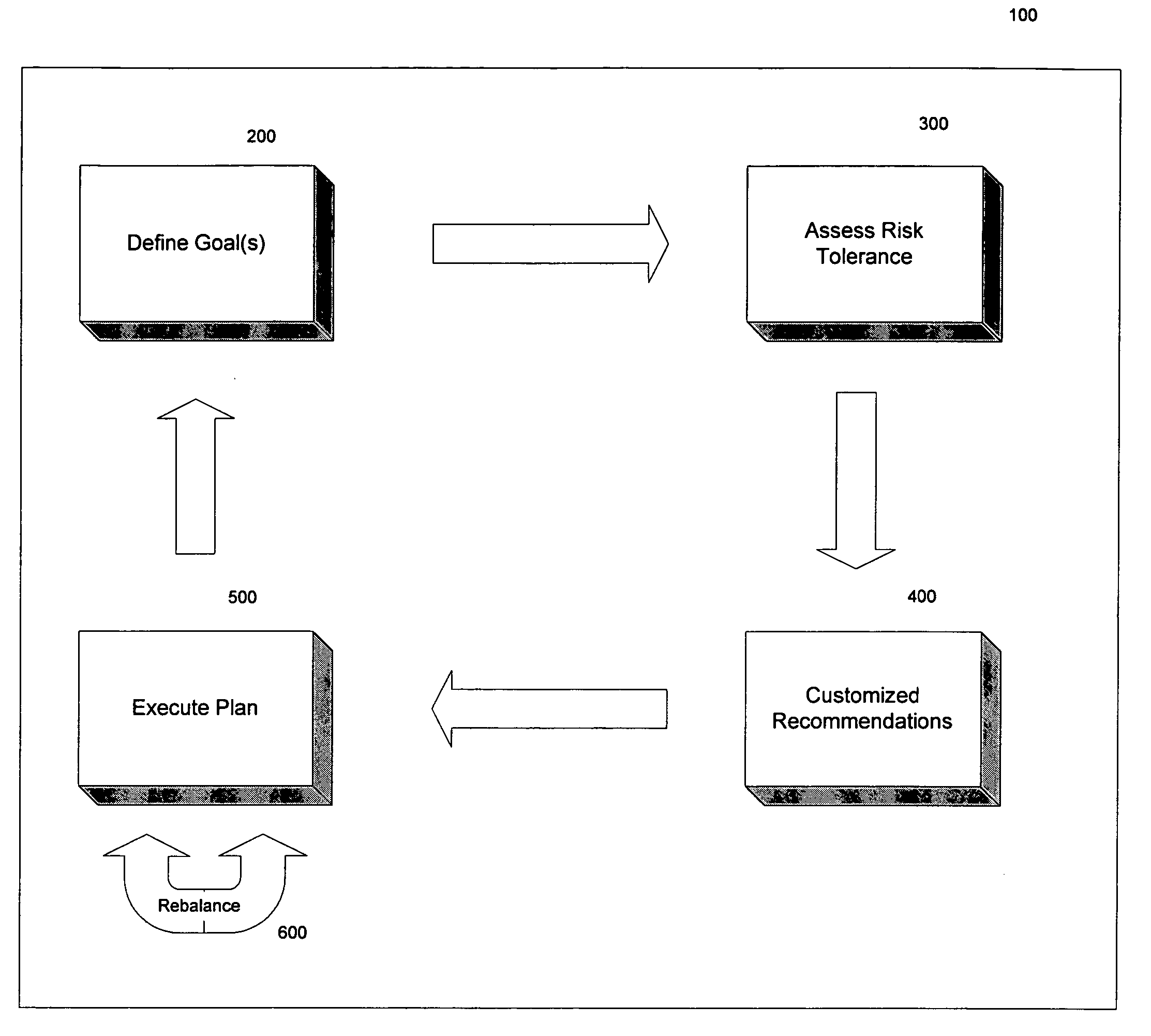
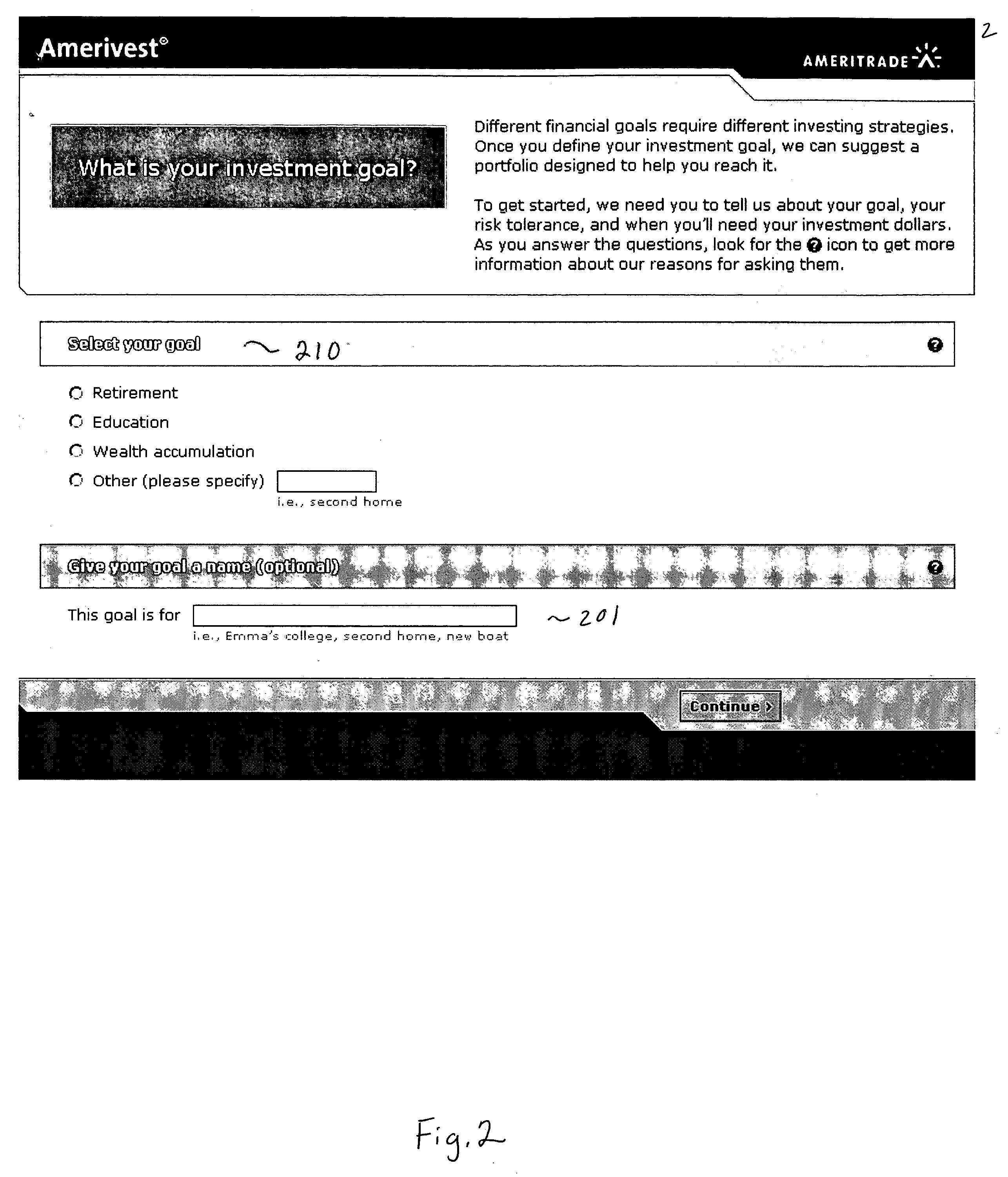
Dynamic rebalancing of assets in an investment portfolio
InactiveUS20050010516A1FinanceSpecial data processing applicationsStrategy executionComputer science
An portfolio investment management system comprising an asset allocation strategy recommendation module adapted to receive investment goal information and investor risk tolerance level information from a user, the investment goal information including at least one of an initial investment amount or estimated contributions, and an estimated withdrawal target date, the asset allocation strategy recommendation module determining a percentage allocation for a plurality of asset classes. The portfolio investment management system further comprises an asset allocation strategy execution module adapted to execute the determined asset allocation strategy. The portfolio investment management system also comprises a rebalancing execution module adapted to automatically rebalance the portfolio upon a predetermined condition without any further input from the user. The portfolio is automatically rebalanced without any further input from the user.
Owner:AMERITRADE HLDG CORP
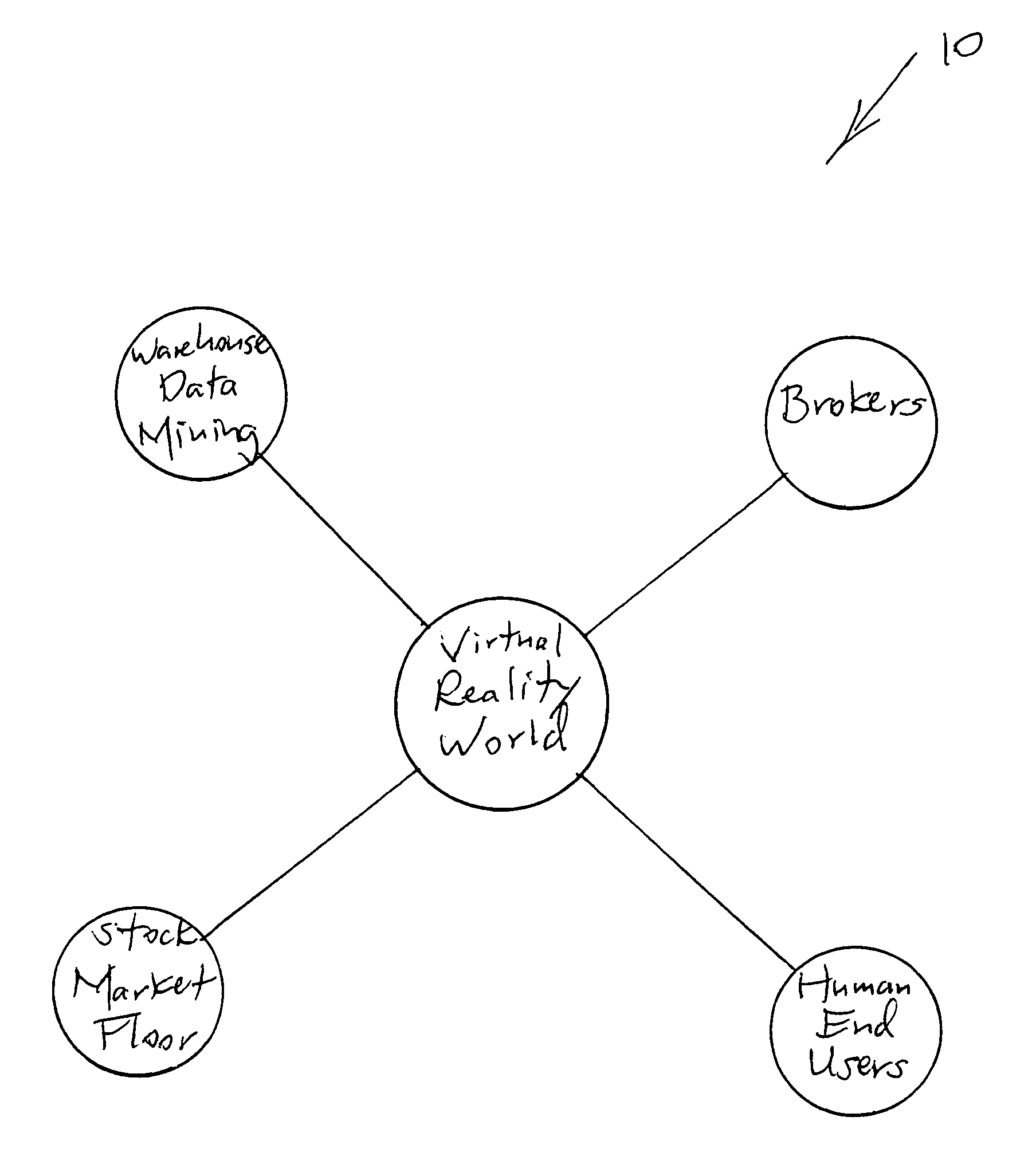
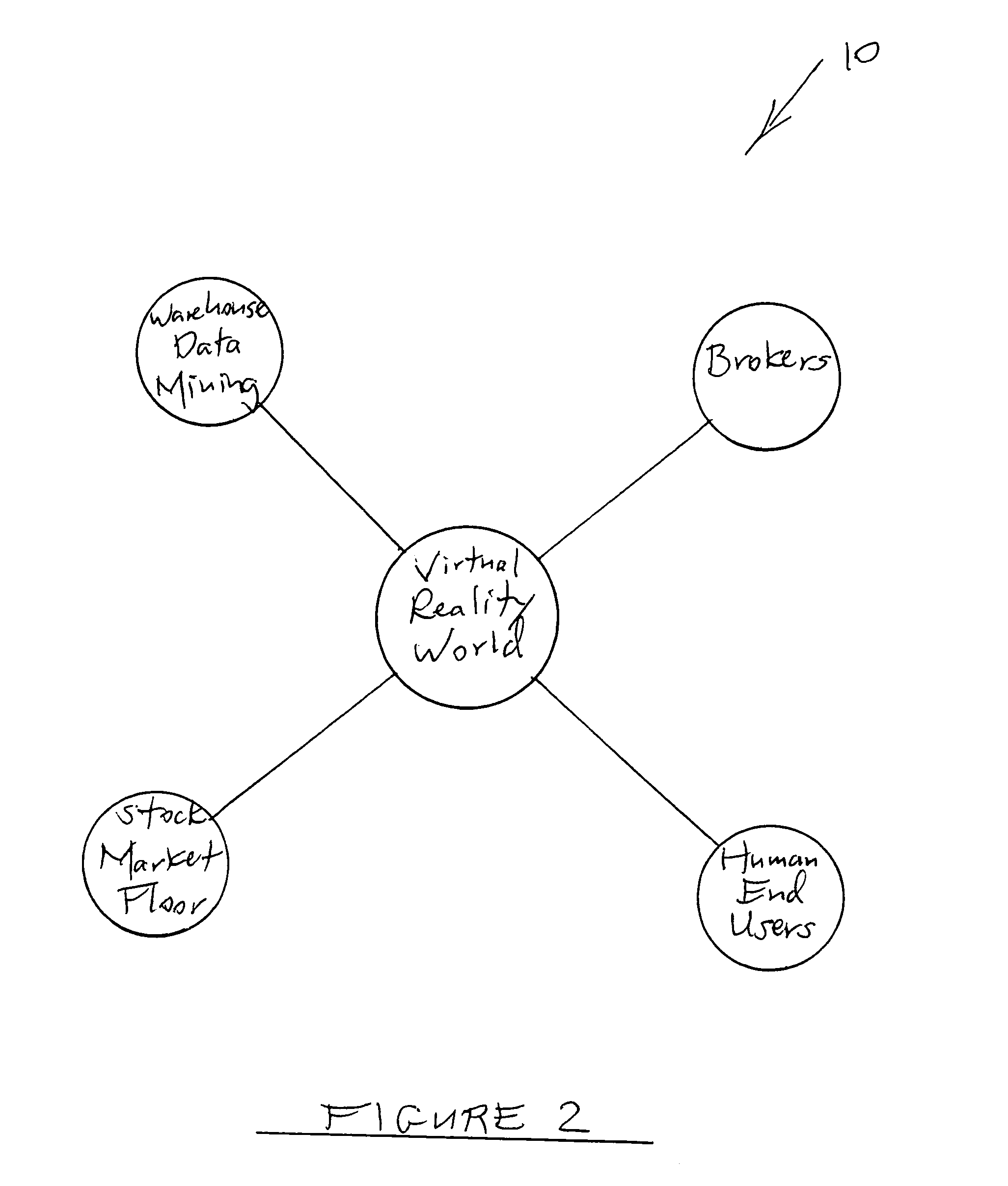
Continuous optimization and strategy execution computer network system and method
A computer network system within a virtual environment, includes several computers which are networked to each other to function as a single unit, including at least one parent computer synchronizing and delegating tasks among the several computers; so that the unit scans and gathers data from the virtual environment, and processes and organizes the data into an implementable representation of the data. The unit preferably additionally includes at least one dedicated computer for performing a specific task, and at least one processing computer for providing processing power to the unit. The unit alternatively delivers the implementable representation of the data in the form of a report to a user computer terminal and awaits a decision from a human user.
Owner:PAIZ RICHARD S
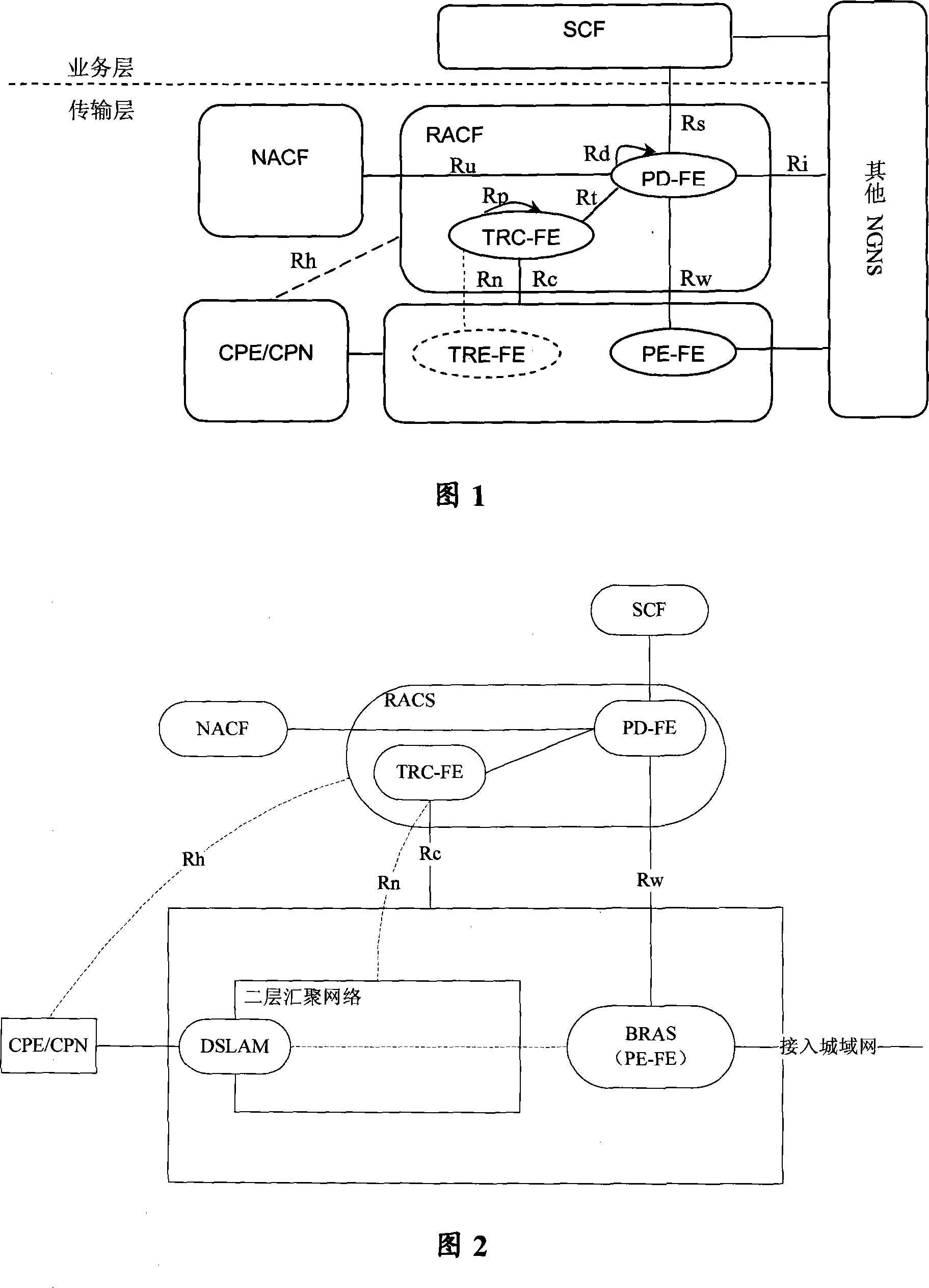
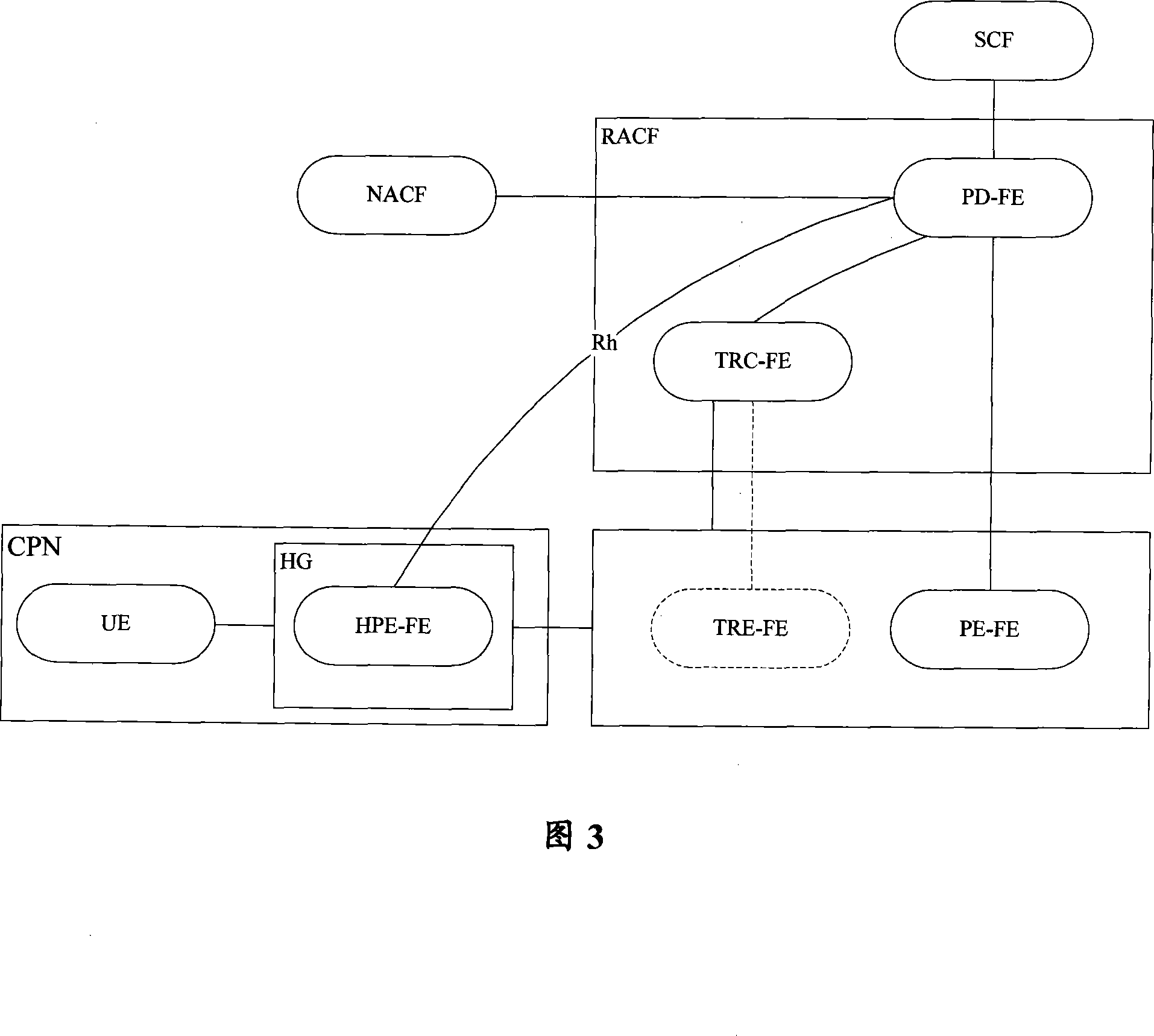
Household gateway policy control method and system
InactiveCN101222453ASolve the heavy loadNetwork traffic/resource managementData switching by path configurationStrategy executionComputer network
The invention discloses a home gateway strategy control method and a system thereof. The method comprises that: a resource and admission control function entity issues a strategy to a home gateway, the home gateway makes a strategy execution to an uplink message passing through the home gateway according to the received strategy. With the strategy control method and the system of the invention, the strategy is issued to the home gateway by a RACF, so the uplink message passing through the home gateway can be made a QoS control before a BRAS, which provides the uplink message with an effective QoS guarantee before the BRAS, and also solves the problem that the convergence layer of the MAN has heavier load in the prior art.
Owner:ZTE CORP
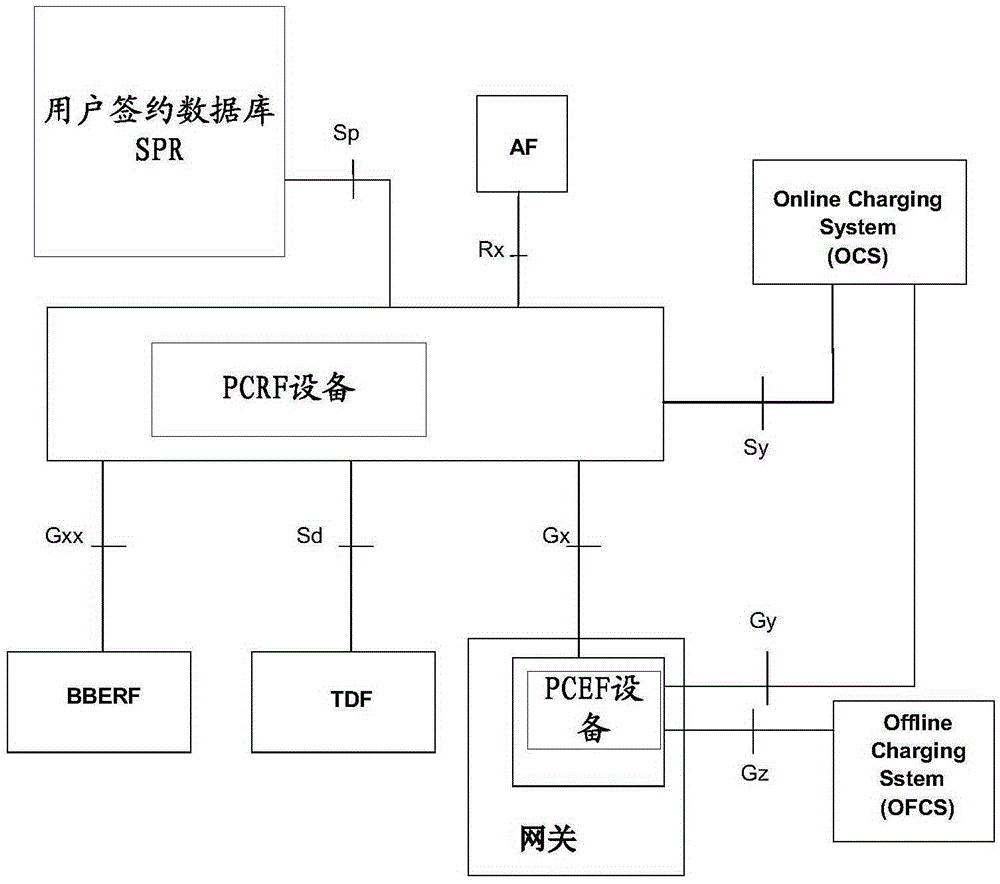
A system for charging control architecture based on network fusion policy and its processing method
InactiveCN101188504AMetering/charging/biilling arrangementsAccounting/billing servicesService flowStrategy execution
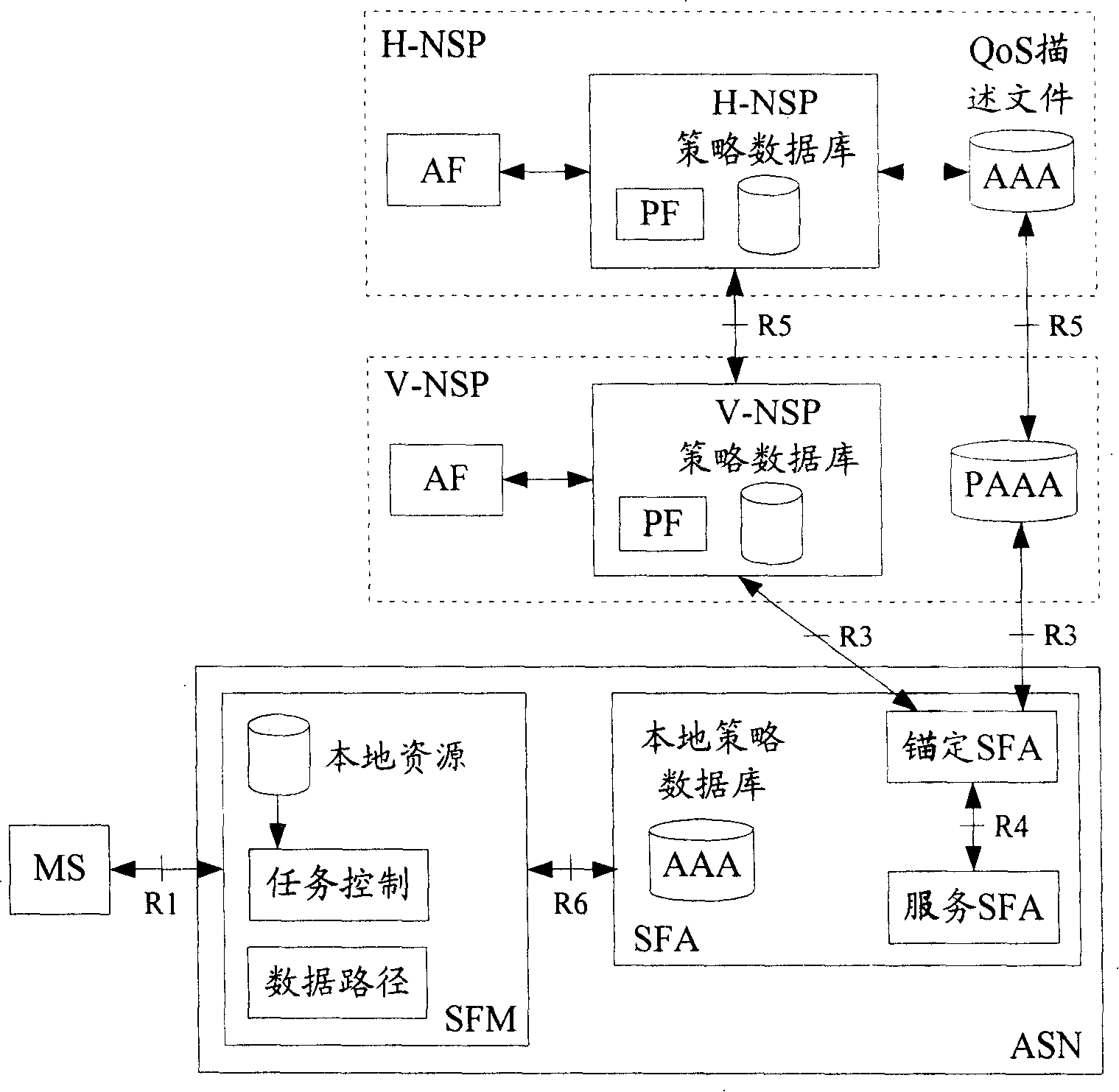
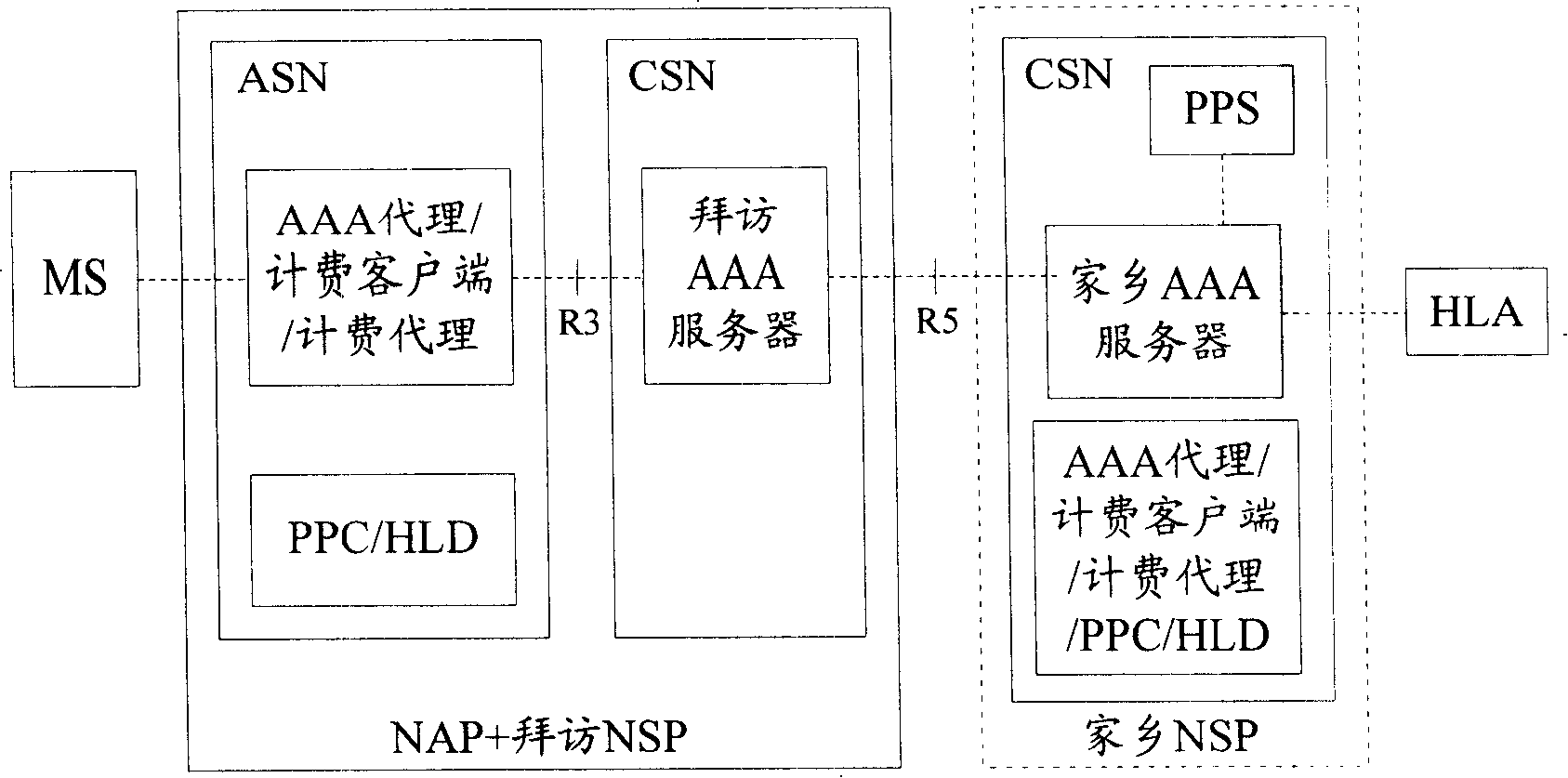
The invention discloses a network amalgamation strategy charging control framework system and the processing method thereof. PCRF ensures PCC rules according to the QoS parameters and charging strategy that are authorized by business layer and the information about user signature; and provides the PCEF with the PCC rules. The PCEF, which acts as the interface between the PCRF and the PCC strategy execution entities and / or the PCC strategy execution entity, and carries on protocol transfer, information retransmission and / or strategy charging execution; the PCC strategy execution entity executes the QoS authorization of service data flow and the detection and charging of service flow according to the PCC rules; the invention proposes a practical feasible solution for the integration of WiMAX network with 3GPP / 3GPP2 network the PCC framework, realizes the strategy control and charging control of the WiMAX network on business by using the PCC framework, and resolves the problems about the integration of functional entities, like functional entities in the PCC framework, strategy charging entities SFA , DPF, the charged client terminal / charging agents and hometown agent HA of the WiMAX network. The invention has the proposal of a processing flow and amalgamation solution for the WiMAX network to use the PCC framework for realizing the strategy control and charging control on business.
Owner:HUAWEI TECH CO LTD
Android authority management method and system based on calling chain
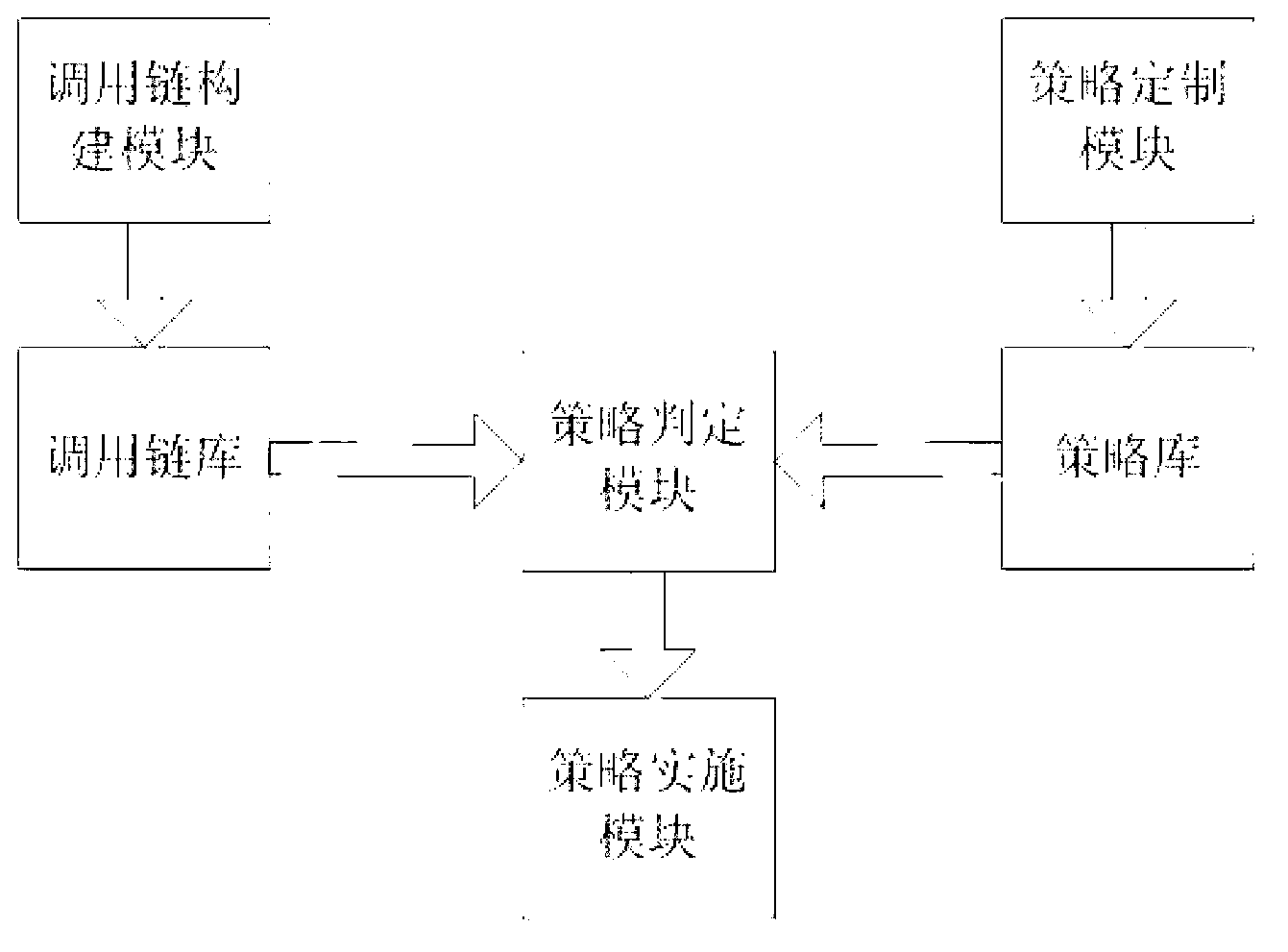
InactiveCN103268438AGuaranteed privacy and securityAvoid redundancyDigital data authenticationStrategy executionComputer module
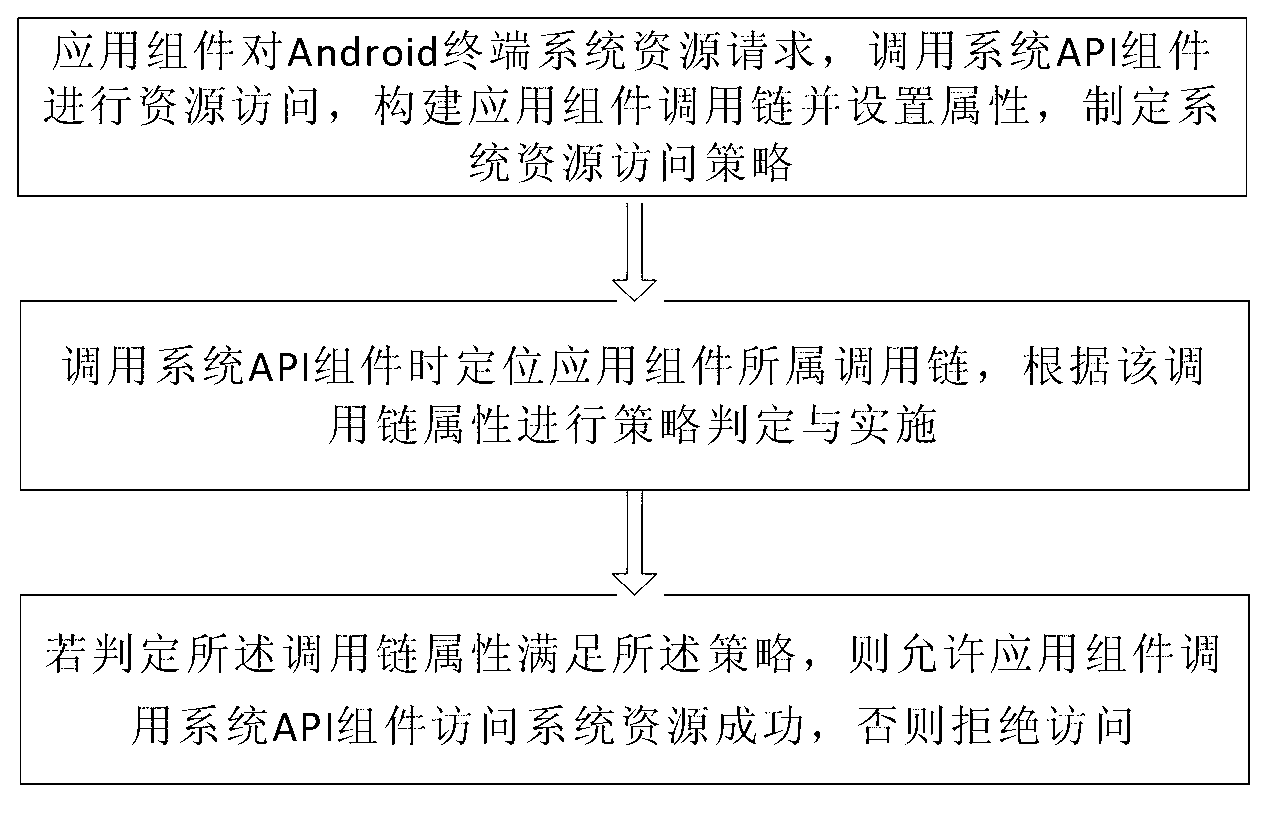
The invention relates to an android authority management method and an android authority management system based on a calling chain. The system comprises a calling chain construction module, a strategy making module, a strategy judging module and a strategy executing module. The method comprises the following steps that 1) an application component requests for resources of a terminal system, a system application program interface (API) component is called for resource accessing, an application component calling chain is constructed, the property of the application component calling chain is set, and a system resource access strategy is made; 2) when the system API component is called, the calling chain to which the application component belongs is positioned, and strategy judgment and strategy execution are performed according to the property of the calling chain; and 3) if the property of the calling chain meets the strategy, the application component is permitted to call the system API component to successfully access the system resources, or otherwise, the application component is refused to access the system resources. According to the calling chain construction method, redundancy caused by the construction of calling chain for each component is avoided, and the system burden is reduced; the text environment of the calling chain and the authority requirement of all components of the calling chain are considered through the diversification of strategy elements; and therefore, the authority lifting attack is avoided.
Owner:HUAWEI TECH CO LTD +1
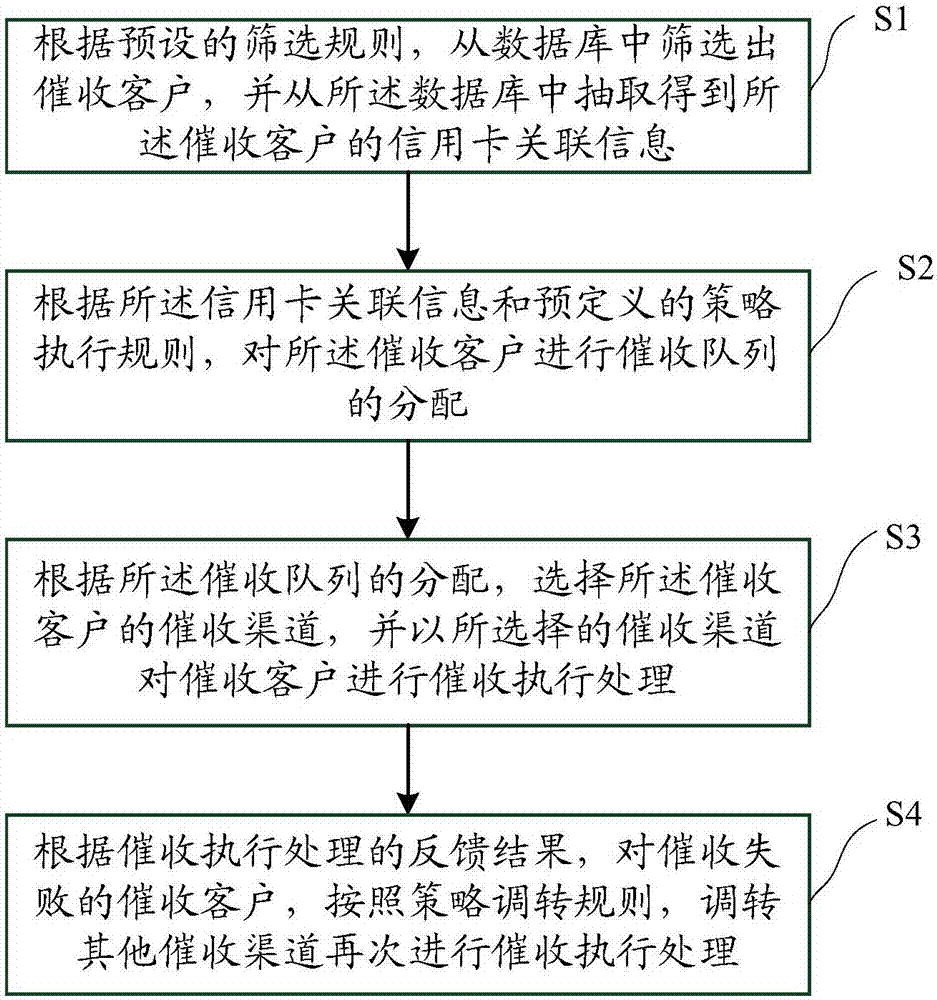
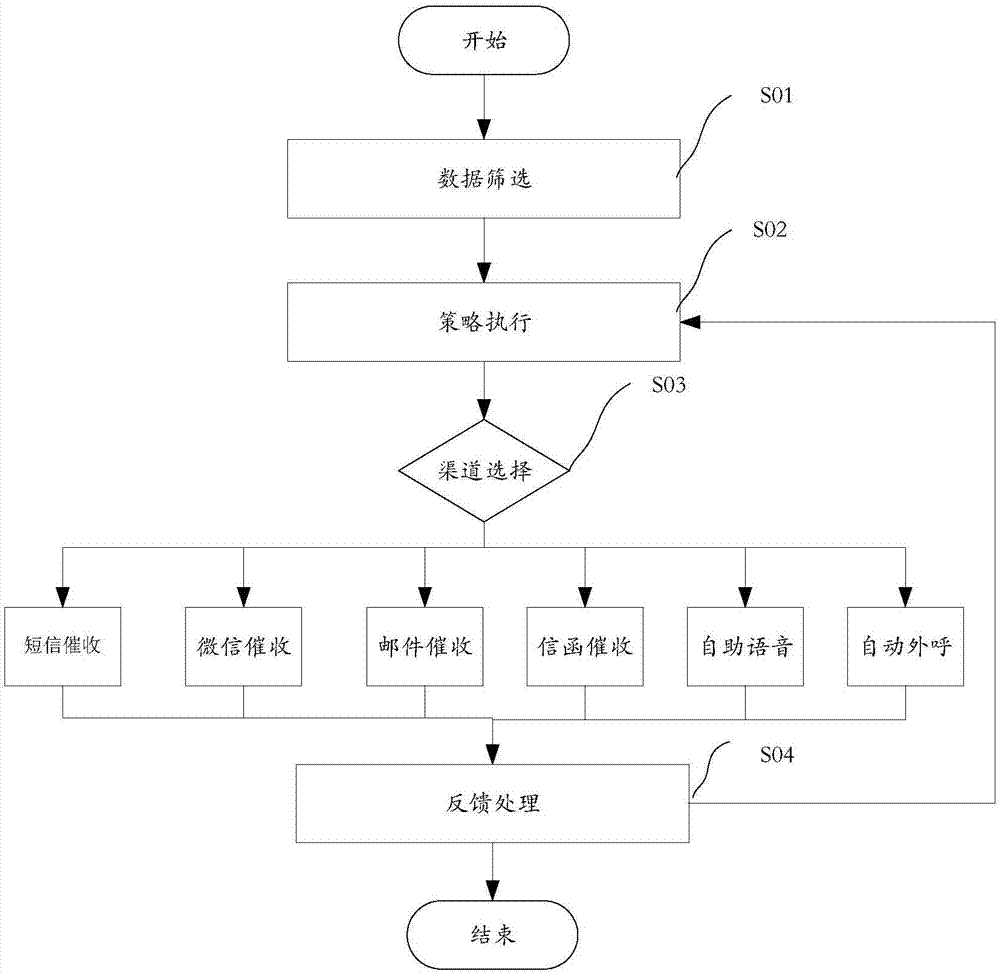
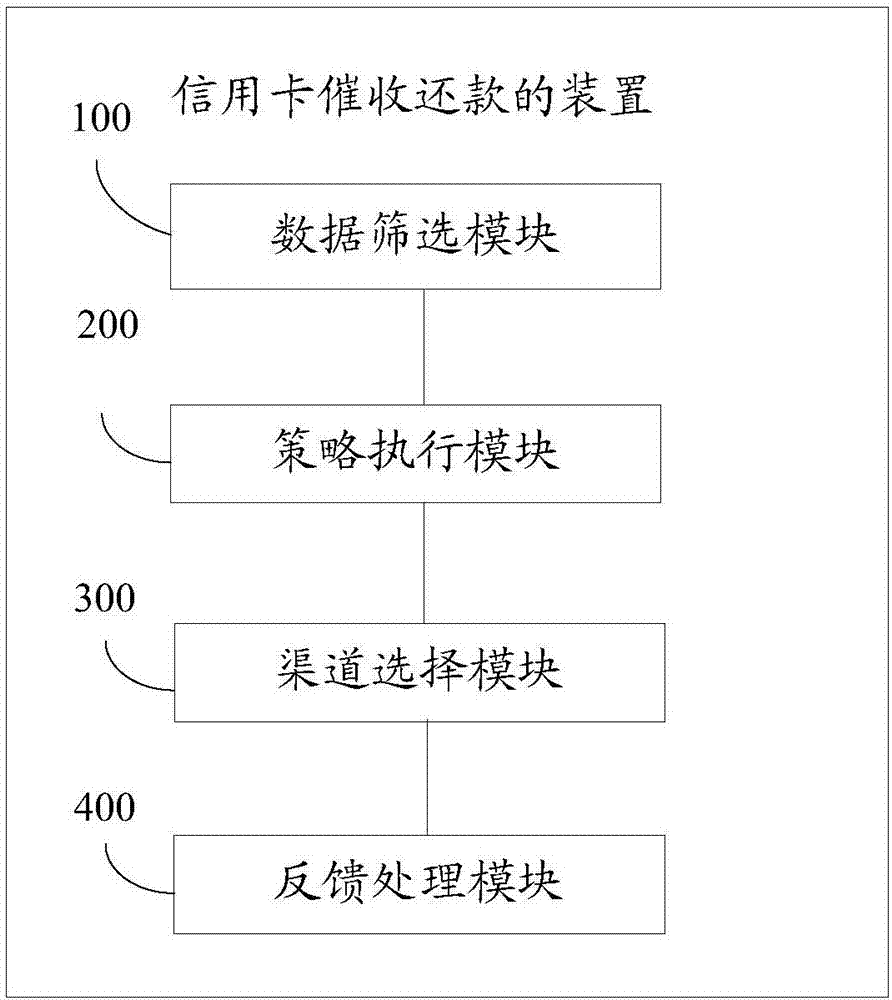
Credit card collection and repayment method and apparatus
InactiveCN107240013ARealize automatic collectionReduce labor costsFinanceCredit cardStrategy execution
The invention discloses a credit card collection and repayment method and apparatus. The method herein includes the following steps: based on preset screening rules, selecting a to-be-collected client from a database, extracting credit card-related information of the to-be-collected client from the database; based on the credit card-related information and the pre-defined strategy execution rules, allocating the to-be-collected client to a collection queue; based on the allocation to collection queue, selecting a collection channel of the to-be-collected client, and implementing collection on the to-be-collected client by means of the selected collection channel; based on the result of the implementation of the collection, for to-be-collected clients who fail to be collected, in accordance with strategy switching rules, switching to other collection channels and implementing collection. The method herein can realize automatic collection of credit card users, thus achieving the effects of labor reduction and higher collection efficiency.
Owner:CHINA CONSTRUCTION BANK
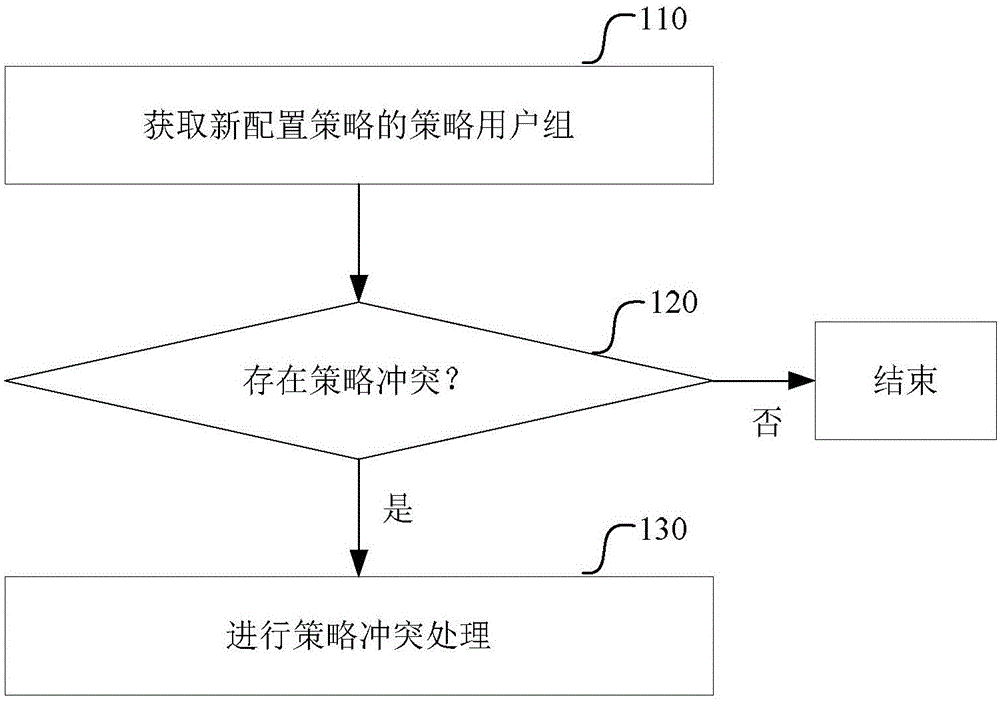
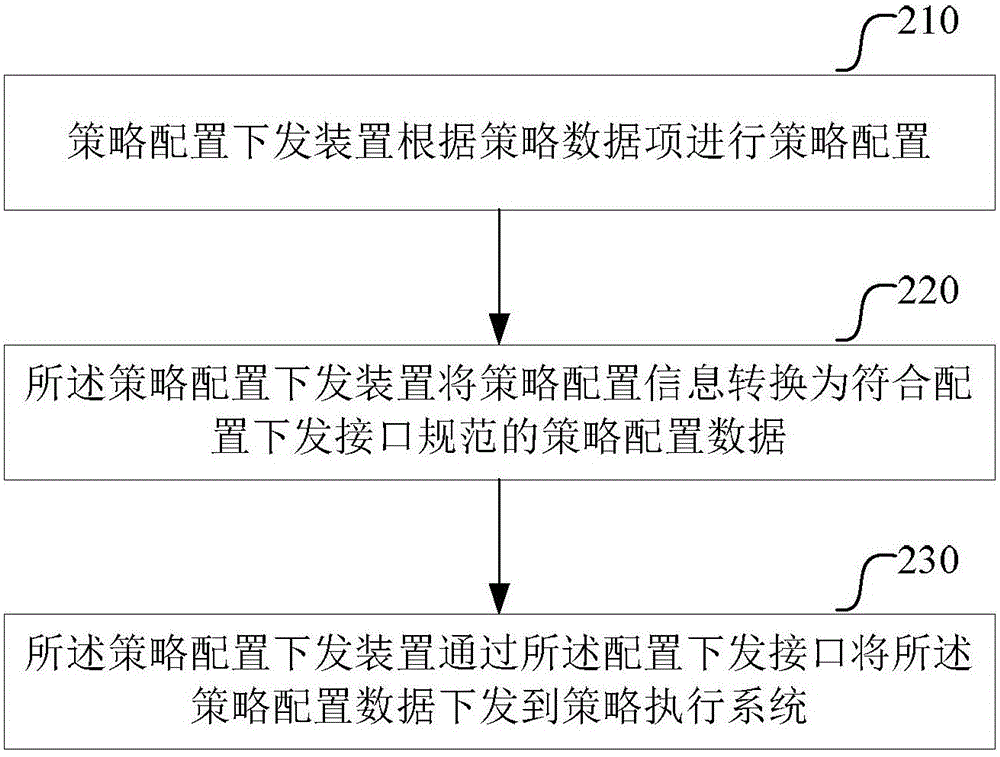
Strategy operation, configuration issuing, conflict resolution and closed-loop management method and system
InactiveCN105071964ALow costQuick configurationData switching networksStrategy executionStatistical analysis
The invention provides a strategy operation, configuration issuing, conflict resolution and closed-loop management method and system. The method comprises the following steps: when a strategy is newly increased in a strategy operation system, examining and approving the newly increased strategy; after passing the examination and approval, performing configuration and submission on the newly increased strategy, wherein the submission is realized through a standard configuration submission interface between the strategy operation system and a strategy execution system; monitoring a running state of the submitted strategy, and displaying the statistical analysis data executed by the submitted strategy. During the configuration process, the strategy conflict resolution can be performed, and after submission, the closed-loop management of the strategy can be performed. The scheme of the invention can enable operators to expand a strategy operation mode, configure and use strategies quickly, conveniently and safely, reduce the production cost of enterprises and enable end users to have a better user experience.
Owner:ZTE CORP
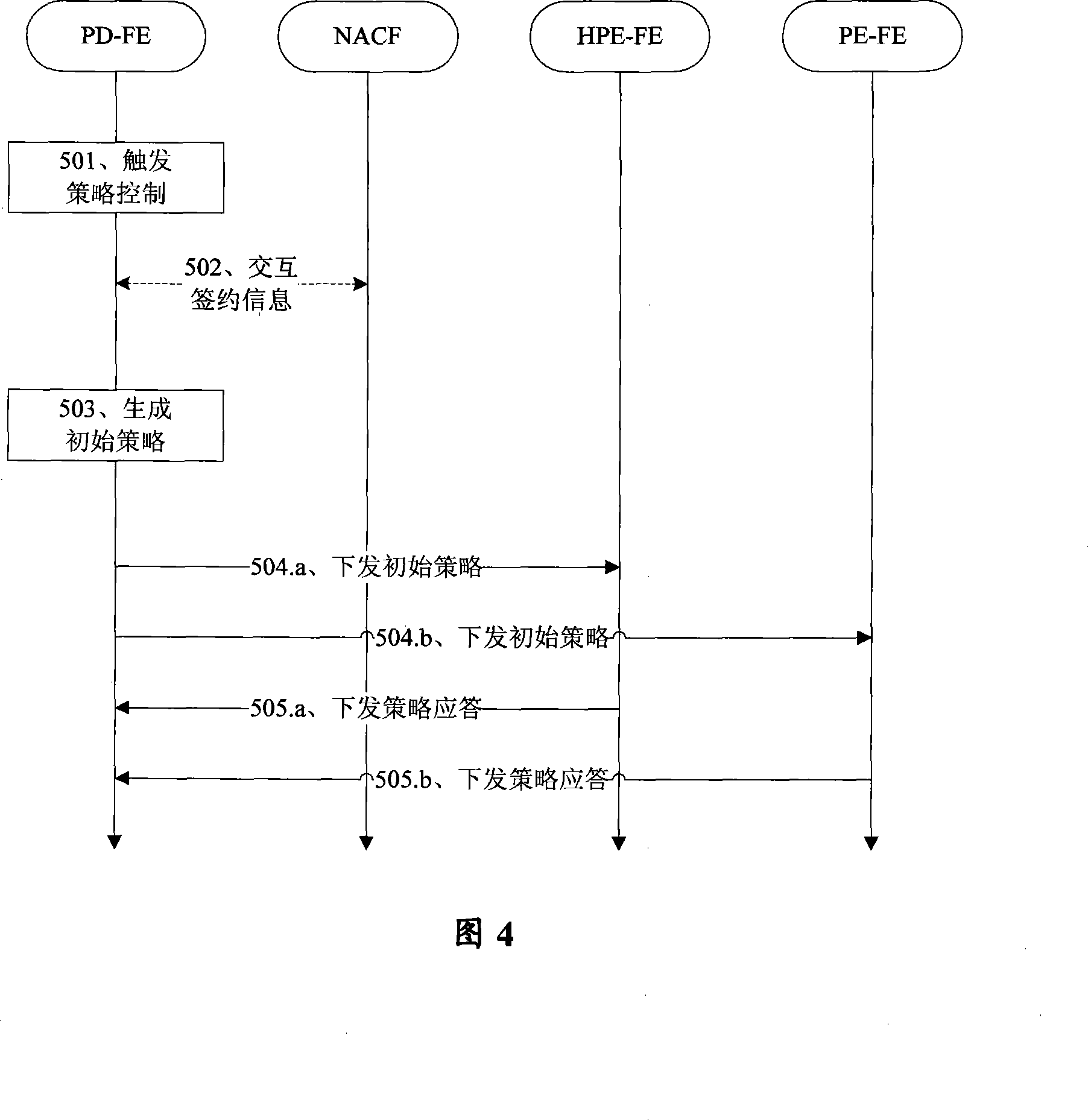
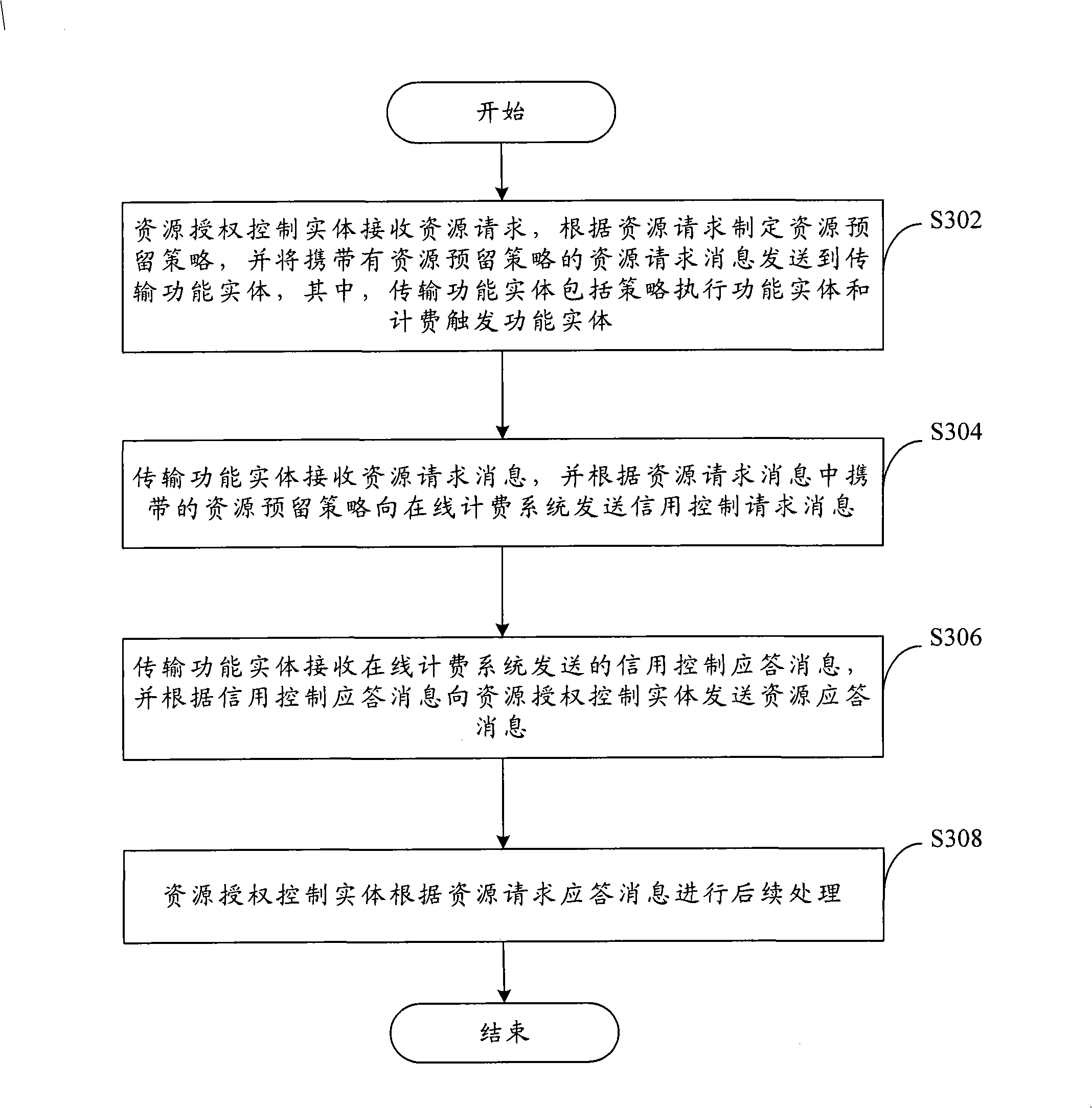
On-line charging method
ActiveCN101316175ARealization of online billingError prevention/detection by using return channelMetering/charging/biilling arrangementsStrategy executionComputer science
The invention discloses an on-line charging method, which includes the steps that: a resource-authorized control entity receives a resource request, formulates a resource reservation strategy according to the resource request, and transmits the resource request information containing the resource reservation strategy to a transmission functional entity, wherein, the transmission functional entity includes a strategy execution functional entity and a charging trigger functional entity; the transmission functional entity receives the resource request information and transmits credit control request information to the on-line charging system according to the resource reservation strategy contained in the resource request information; the transmission functional entity receives credit control response information transmitted by the on-line charging system and transmits resource response information to the resource-authorized control entity according to the credit control response information; the resource-authorized control entity makes subsequent processing according to the resource request response information. The invention can realize the on-line charging function.
Owner:ZTE CORP
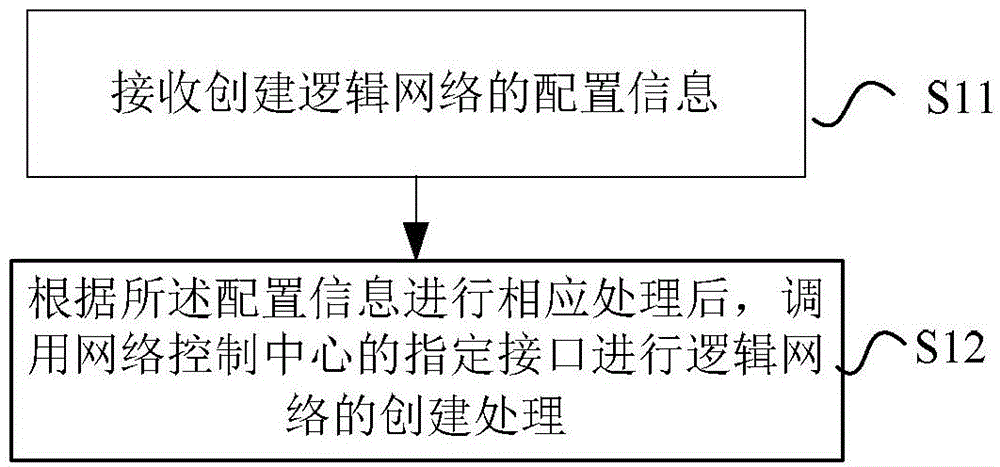
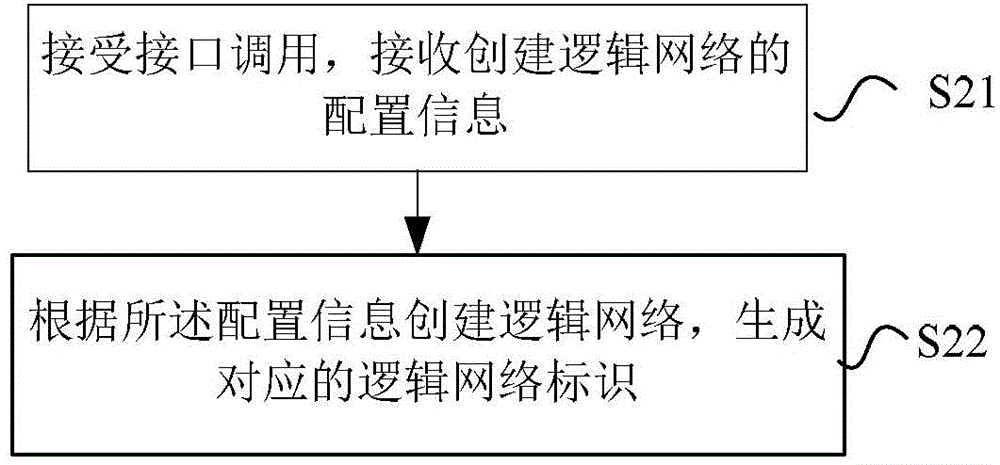
Network establishment method and system, and network control center
ActiveCN103607432AImprove automation performanceGranularityTransmissionStrategy executionNetwork control
The invention provides a network establishment method and a system, and a network control center. The method comprises the following steps of receiving configuration information used for establishing a logic network; according to the configuration information, after corresponding processing is performed, calling an assigned interface of the network control center to carry out establishment processing of the logic network. Through the method, the system and the network control center of the invention, the private and isolated logic network is established for different users; according to distribution of calculating resources owned by the user, network partition and connection are completed; network configuration is uniformly performed and strategy execution is controlled; a QOS demand needed by the user is satisfied and flexible expansion can be performed according to a need.
Owner:NANJING ZHONGXING SOFTWARE
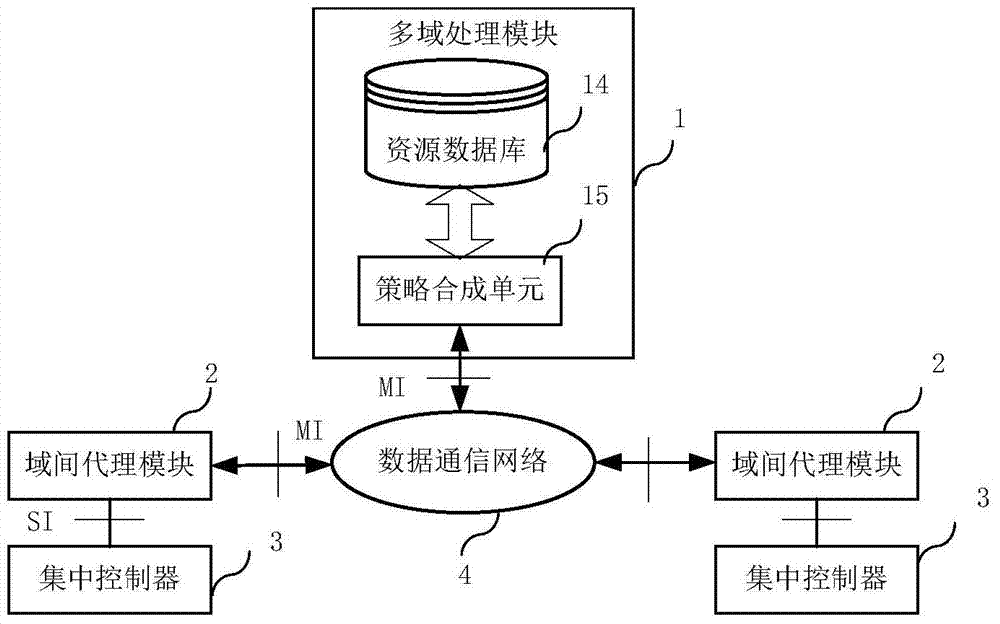
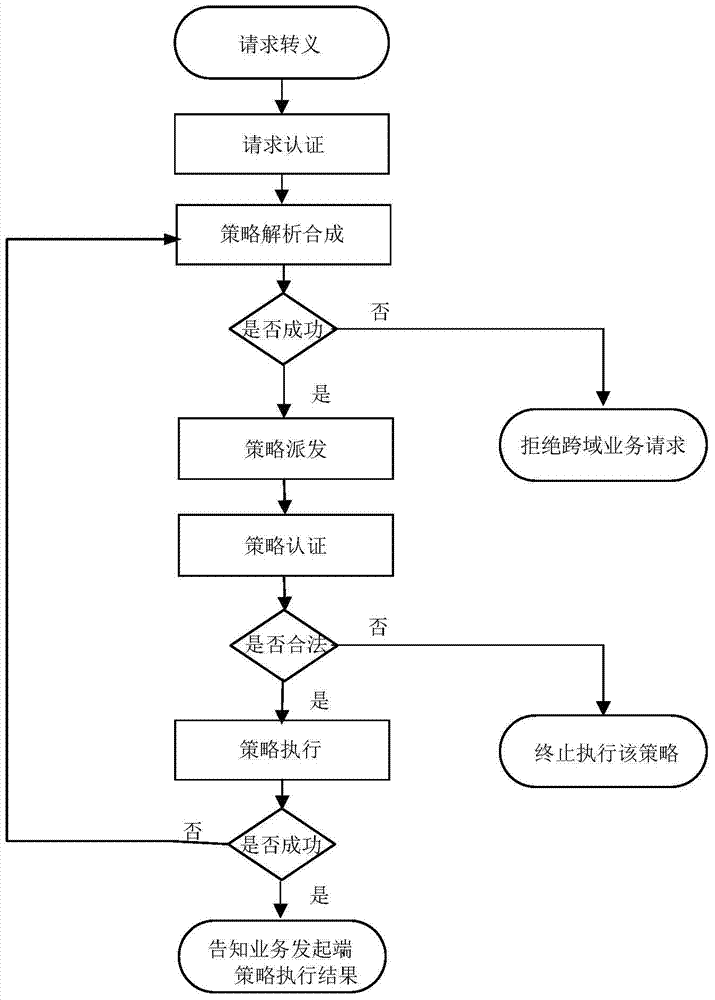
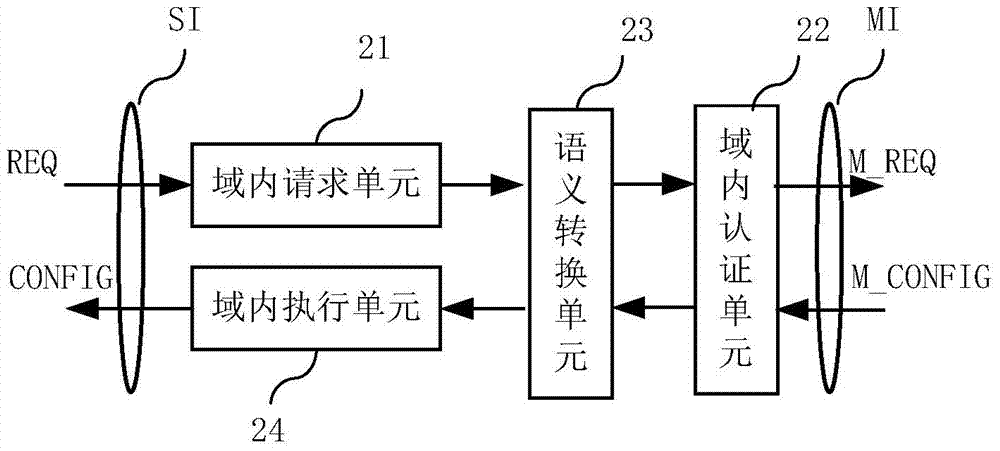
Software defined network cross-domain security agent method and software defined network cross-domain security agent system
ActiveCN104243496ASimplify the interaction processIntegrated reductionTransmissionStrategy executionSemantic translation
The invention provides a software defined network cross-domain security agent method and a software defined network cross-domain security agent system. Unified access control and management are performed on cross-domain shared resources, security policy conflict is eliminated, and strategy synthetic efficiency is improved. The software defined network cross-domain security agent system comprises at least two integrated controllers, at least one multi-domain processing module and at least two inter-domain agent modules, wherein the inter-domain agent modules transmit cross-domain business requests to the multi-domain processing modules after performing semantic translation; each multi-domain processing module comprises a resource database and a strategy synthesis unit; and after the strategy synthesis units receive the cross-domain business requests, the resource databases are queried, the strategy synthesis is carried out, and cross-domain strategy configuration commands are transmitted to the inter-domain agent modules. The software defined network cross-domain security agent method comprises the following steps of transferred meaning requesting, authentication requesting, strategy analysis and synthesis, strategy distribution, strategy authentication, strategy execution and the like. By the software defined network cross-domain security agent method and the software defined network cross-domain security agent system, information exchange of a heterogeneous network is simplified, information integration and synchronization difficulty of the heterogeneous network are reduced, resource scheduling safety is guaranteed, multi-domain resource sharing is realized, and business load of the centralized controllers in various domains can be adjusted.
Owner:BEIJING UNIV OF POSTS & TELECOMM
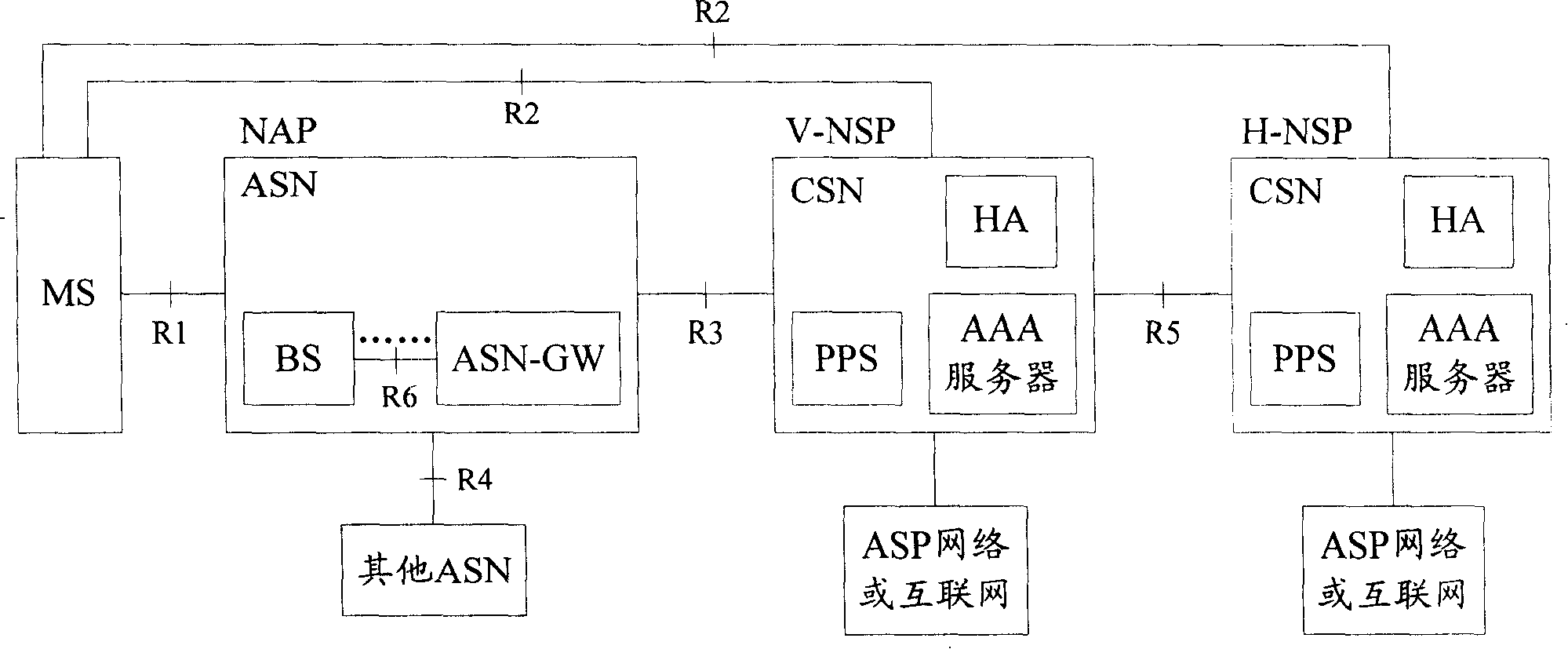
Wireless network user access processing method, device and system
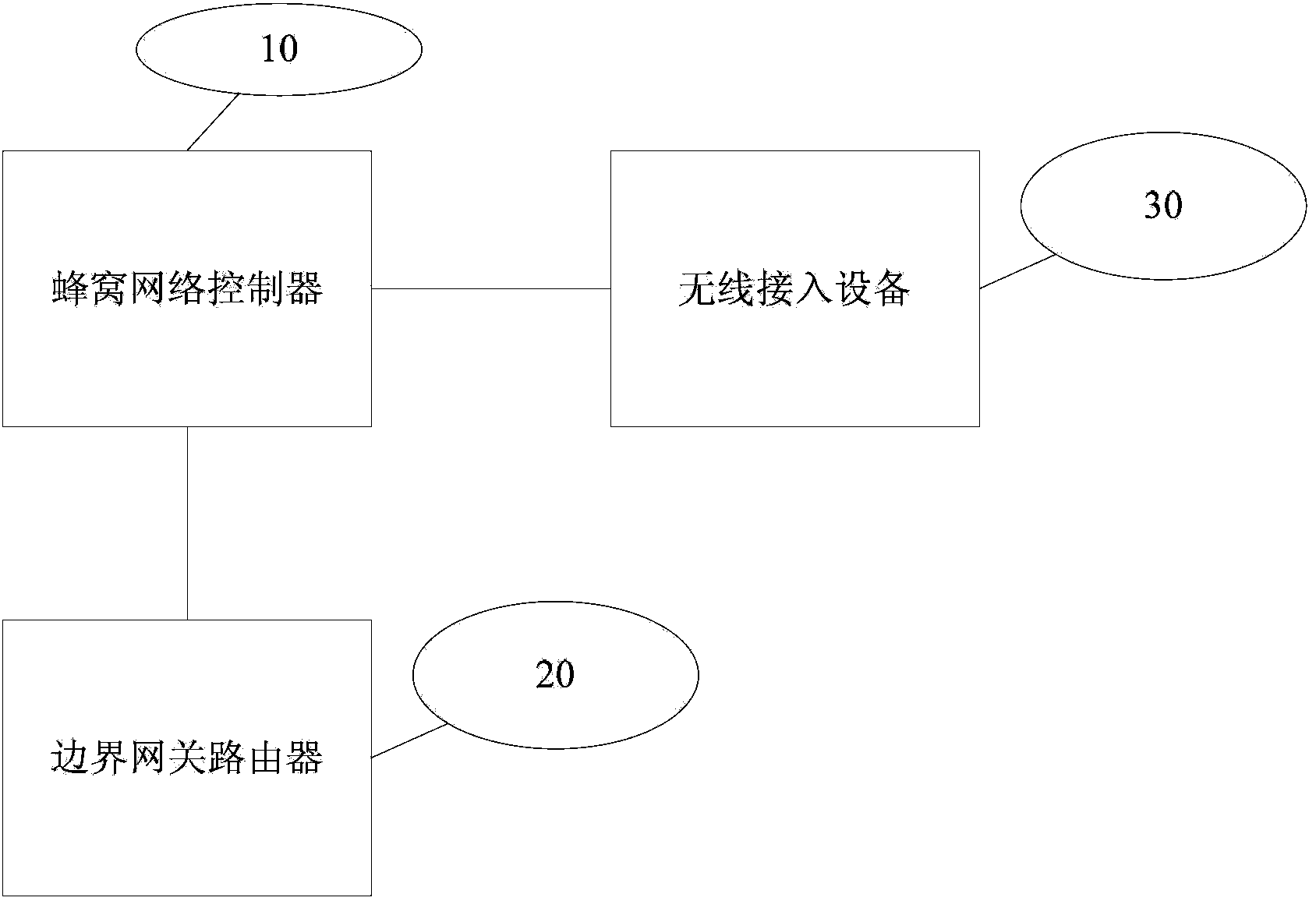
InactiveCN103857004AAchieve separationReduce signaling negotiationAssess restrictionNetwork topologiesCellular networkStrategy execution
The embodiment of the invention provides a cellular network controller. The cellular network controller comprises a wireless protocol processing module, a control decision module and a strategy issuing module, wherein the wireless protocol processing module is used for processing a wireless switching request coming from a wireless network user or wireless network access network and reporting processing results, the control decision module is used for formulating a bearing forwarding strategy of the switched user according to event information pre-stored in the cellular network controller and the processing results reported by the wireless protocol processing module, the strategy issuing module is used for issuing the bearing forwarding strategy formulated by the control decision module to a strategy execution body corresponding to the switched user for execution to enable a data package sent to the switched user to be forwarded according to the bearing forwarding strategy. The embodiment of the invention further provides a related wireless network user access processing method, device and system. By means of the scheme, signaling negotiation among multiple control entities is reduced, and network resource waste is reduced.
Owner:HUAWEI TECH CO LTD
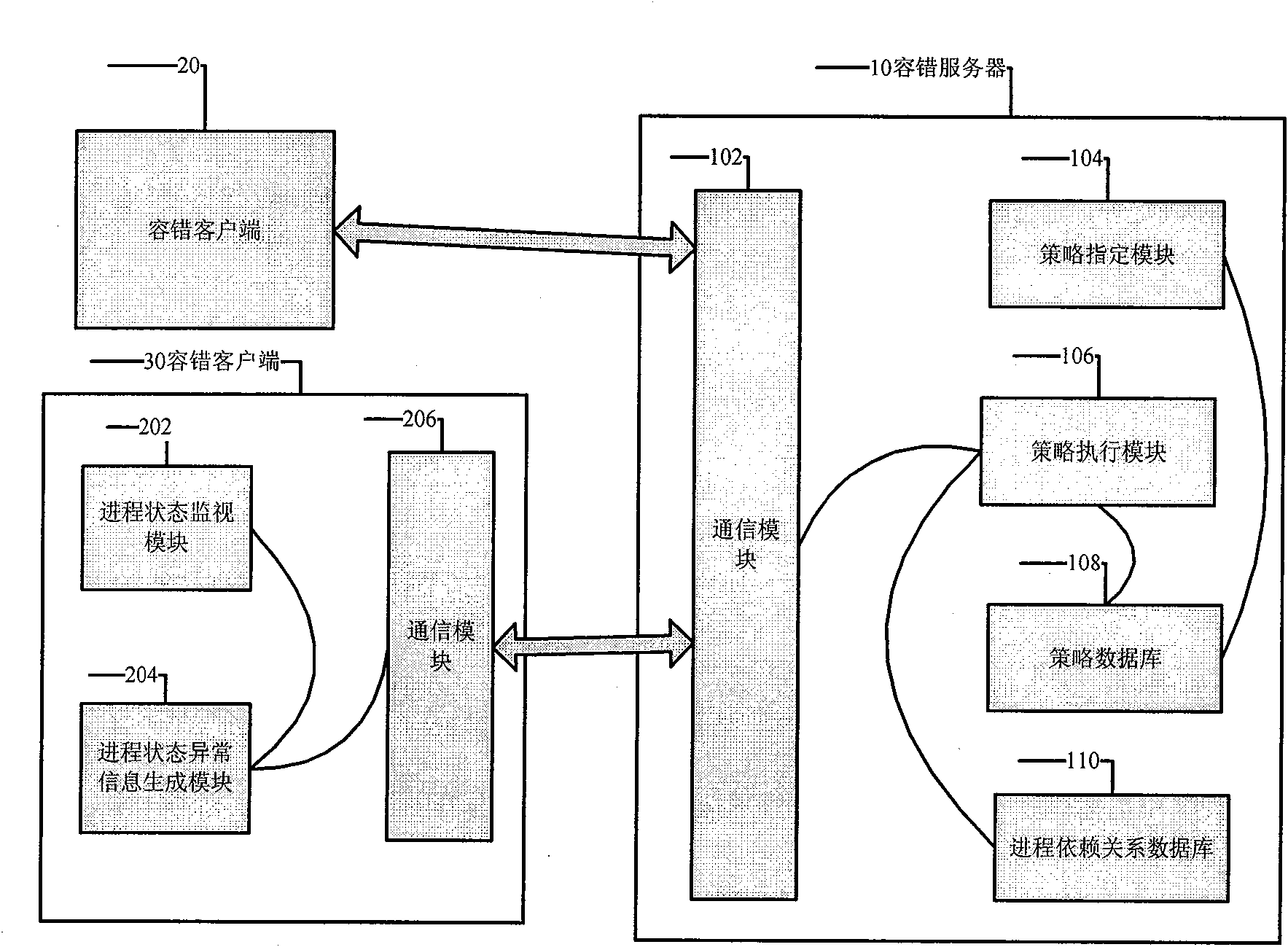
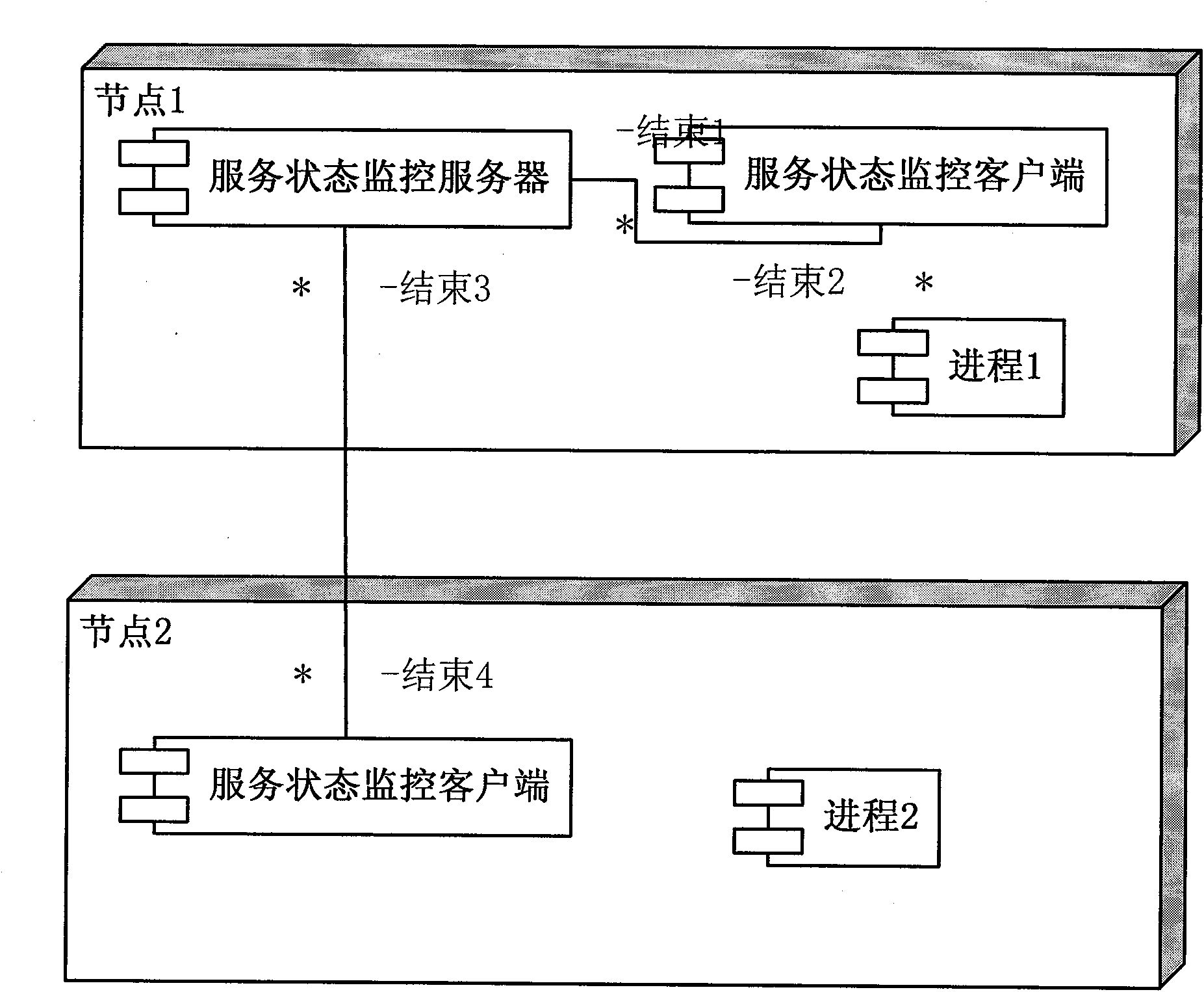
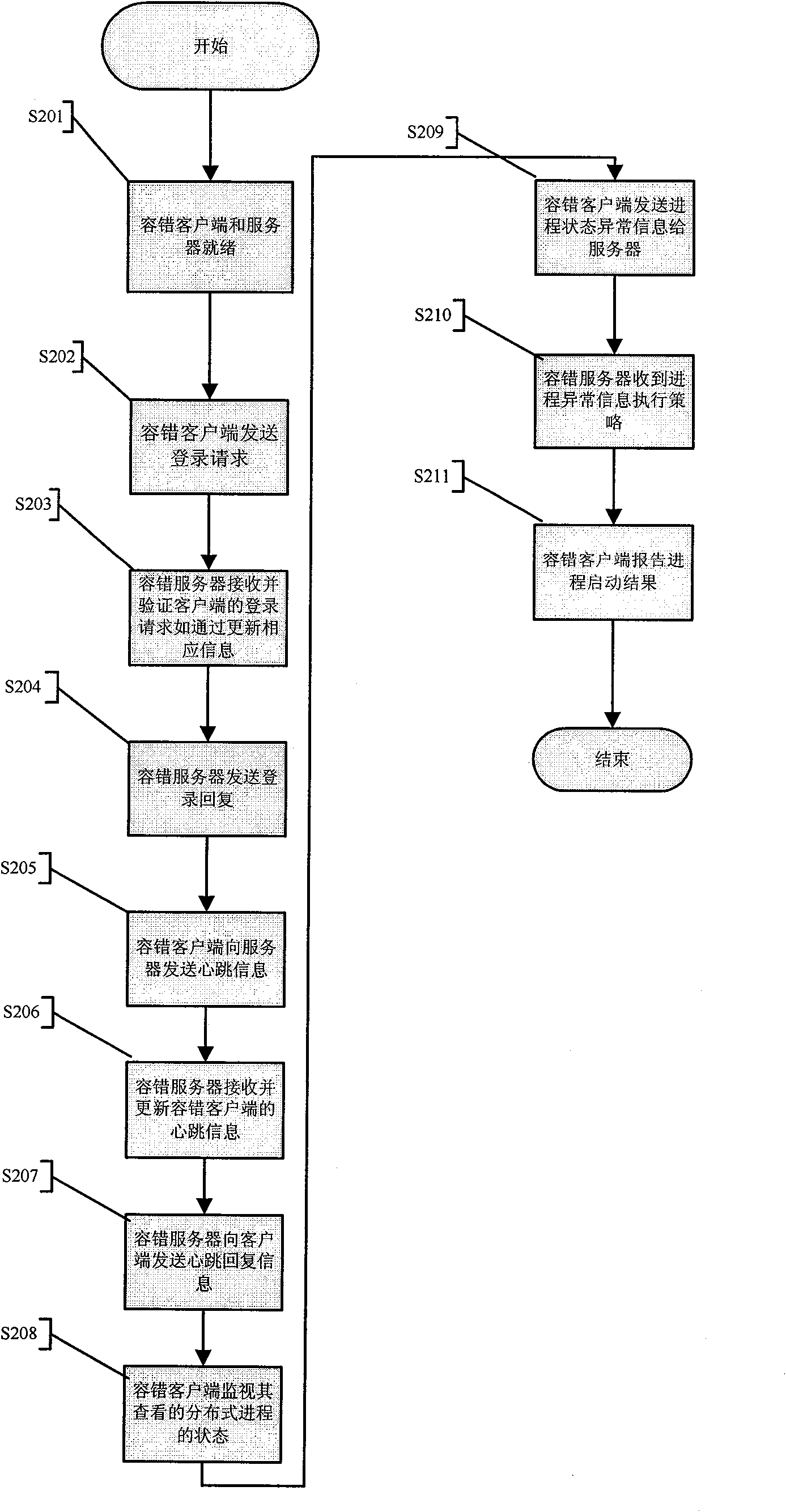
Fault tolerance method and system used for distributed program
ActiveCN101777020AEliminate the step of viewing process health status individuallySkip the step of viewing process healthSoftware testing/debuggingFault toleranceStrategy execution
The invention aims to provide a fault tolerance method and a system used for a distributed program, which can start program processes disposed on different fault tolerance clients according to a sequence. When any one process with a dependency relationship is collapsed, a fault tolerance server can execute the corresponding operation according to a strategy configured on the fault tolerance server, and the fault tolerance clients can start the processes according to the sequence as long as the fault tolerance clients utilize a traditional monitoring program to execute monitoring, take charge of reporting the process status and receive and execute an instruction transmitted by the fault tolerance server or issued by the operation maintenance personnel so as to ensure that the operation canbe normally carried out. The system is provided with a fault tolerance server and at least one fault tolerance client, wherein the fault tolerance clients monitor the status of the processes of the distributed program run by the fault tolerance clients per se. When the abnormity of the status is monitored, the fault tolerance clients inform the fault tolerance server, and the fault tolerance server utilizes a strategy execution module to execute restarting fault-tolerance treatment according to an automatic restarting strategy or a manual restarting strategy and the interprocess dependency relationship specified in a process dependency relationship form.
Owner:北京讯鸟软件有限公司
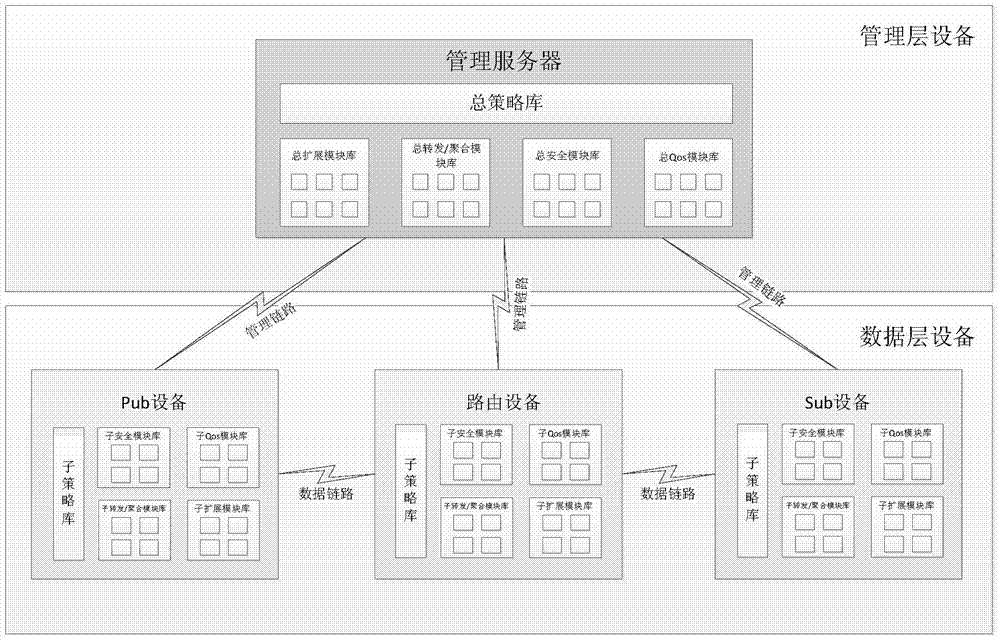
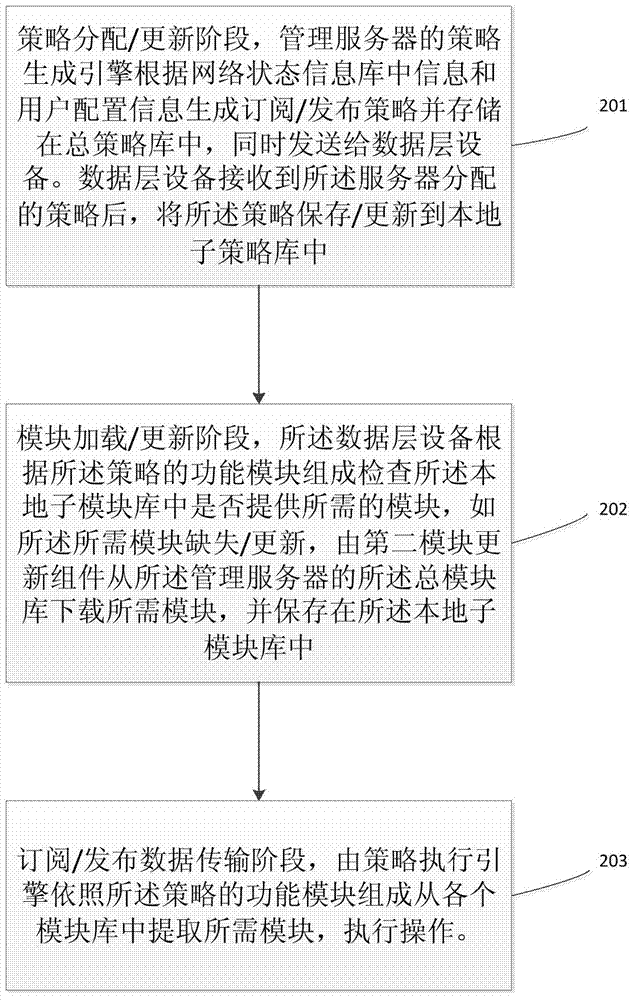
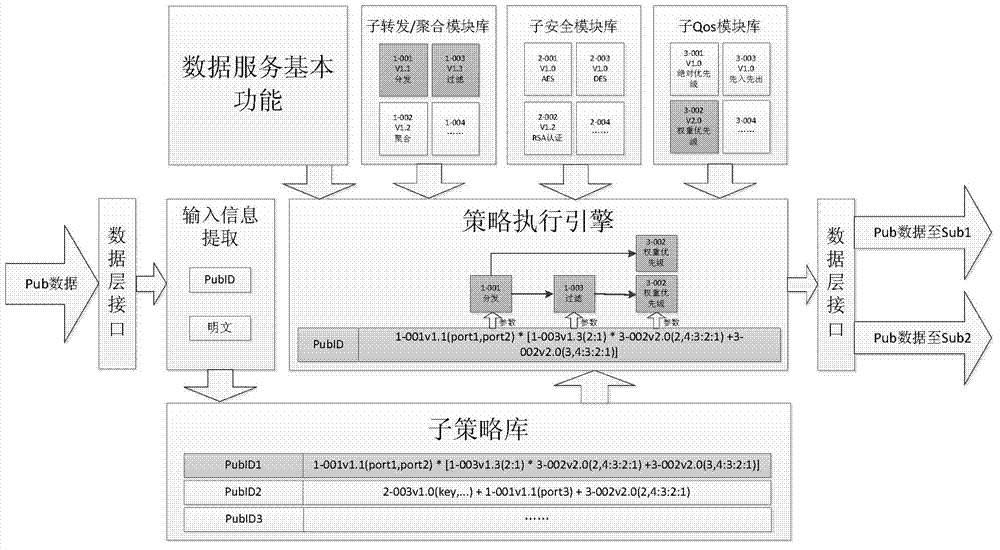
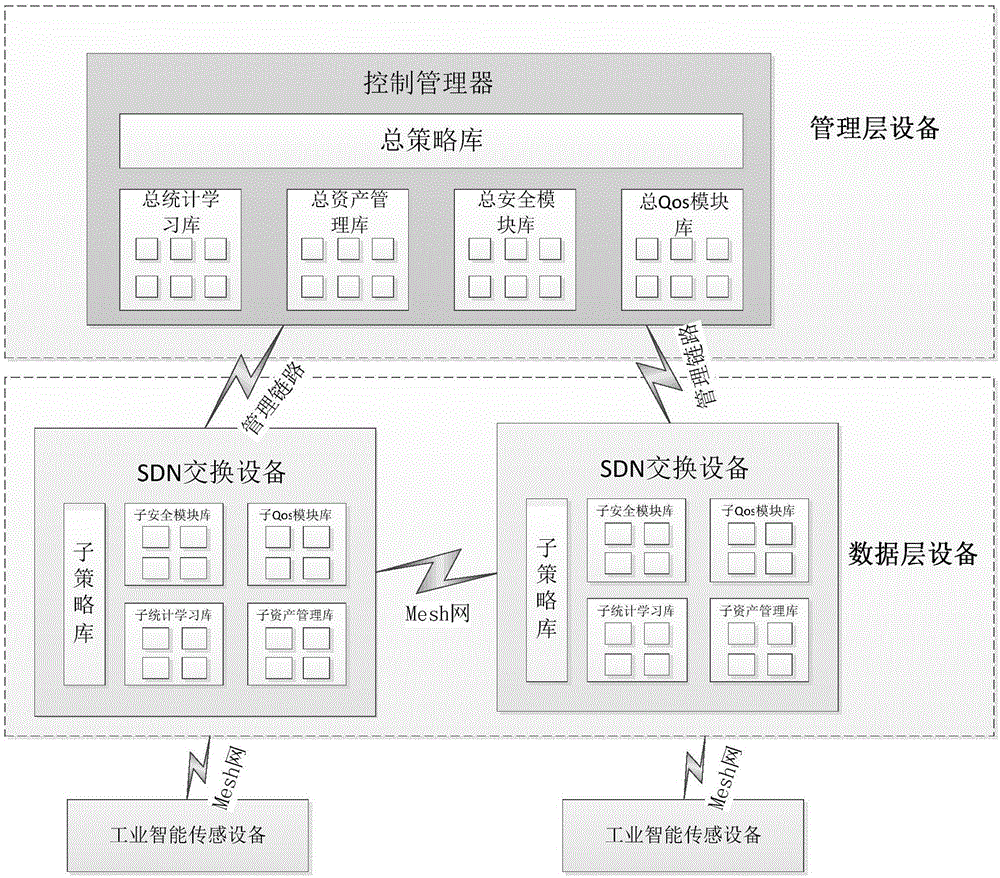
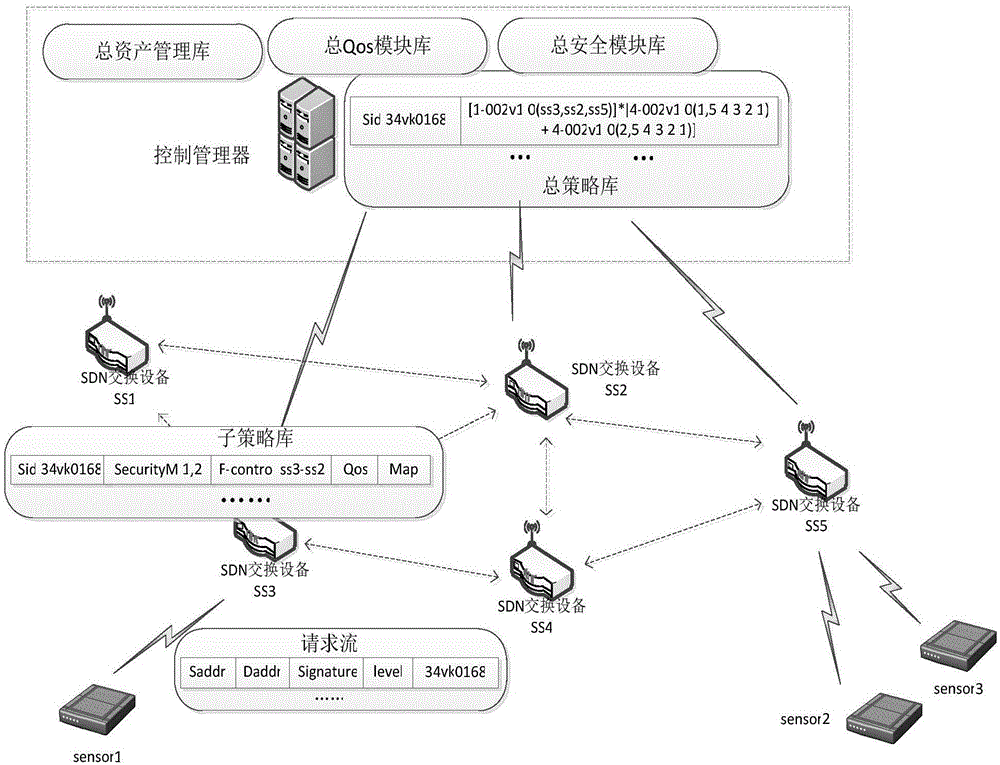
Industrial backhaul network realizing method and system based on software-defined network
ActiveCN104734872AIncrease flexibilityReduce maintenance costsData switching networksStrategy executionLayer interface
The invention discloses an industrial backhaul network realizing method and system based on a software-defined network. The method comprises the strategy distributing / updating stage, the module loading / updating stage and subscription / publication data transmission stage. The system comprises a management server and a data layer device, wherein the management server comprises a user interface unit, a data layer interface unit, a first module updating unit, a first strategy updating unit, a total module library unit, a total strategy library unit, a strategy generation engine unit, a user configuration unit and the like. The data layer device comprises an input information extraction unit, a strategy execution unit, a sub-strategy library unit, a sub-module library unit, a second strategy updating unit, a second module updating unit, a data layer interface unit and the like. By means of the method and system, the subscription / publication network functions can be achieved and updated dynamically and flexibly, and the problems that an existing network is poor in flexibility, high in maintenance cost and hard to update are solved.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Network fault detection and repair method based on SDN architecture
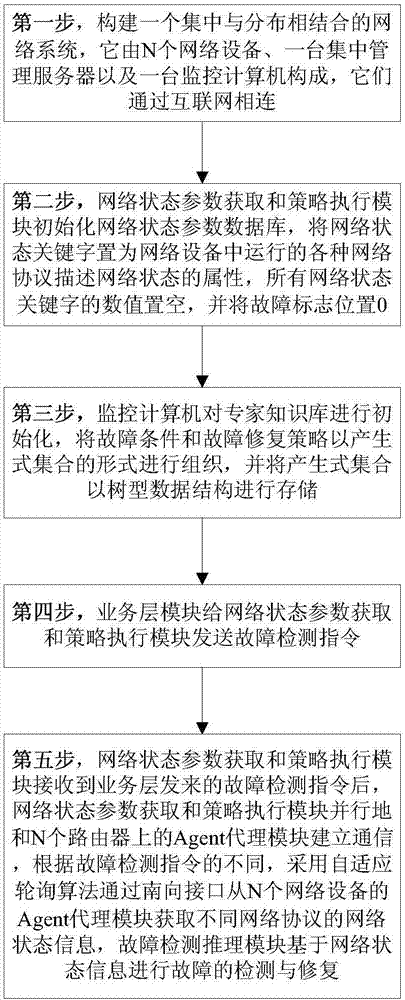
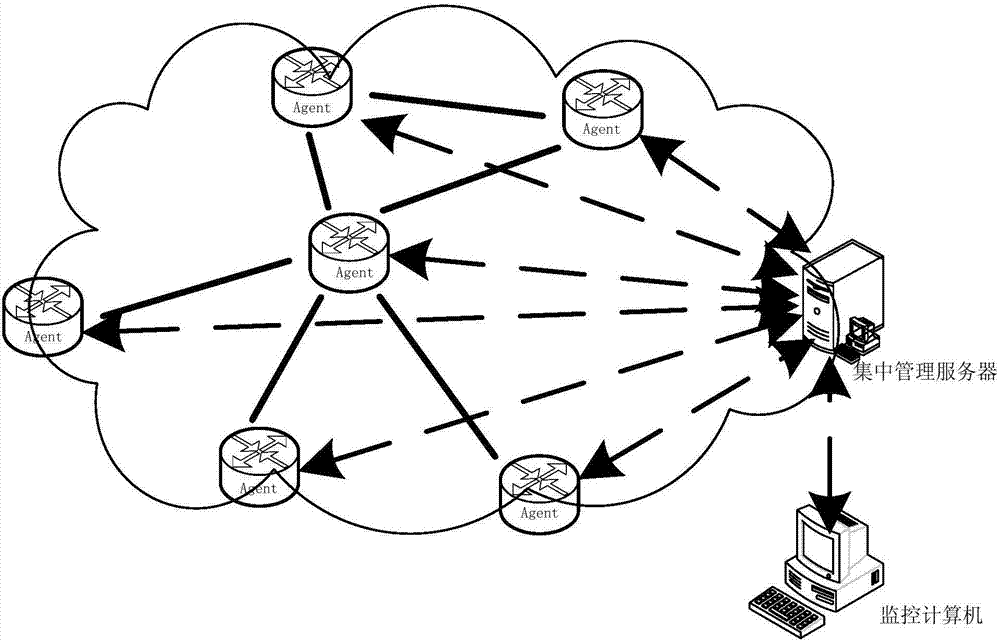
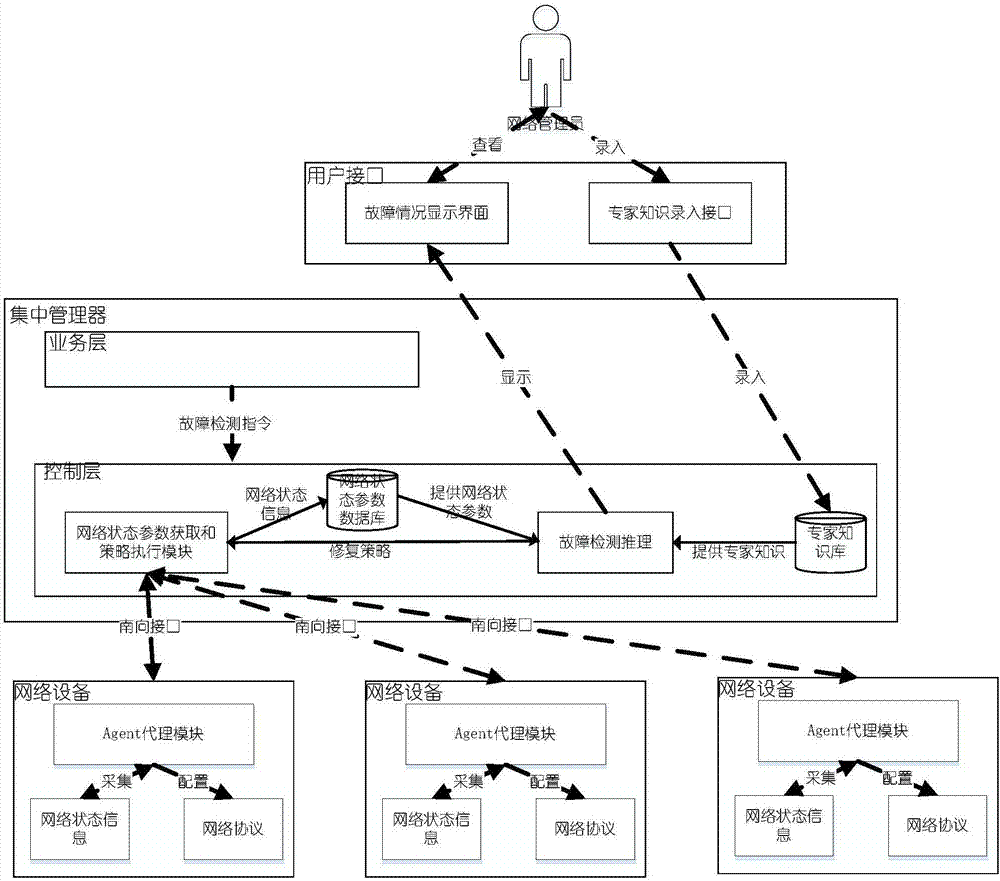
ActiveCN106992877AReduce overheadIncreased maximum failure recovery timeData switching networksStrategy executionState parameter
The invention discloses a network fault detection and repair method based on an SDN architecture. The technical scheme of the method is to build a network system consisting of network equipment, a concentrated management server and a monitoring computer, wherein an agent module is deployed on the network equipment; a business layer module, a network state parameter acquisition and strategy execution module, a fault detection reasoning module, a network state parameter database and an expert knowledge base are installed in the concentrated management server; after the network state parameter acquisition and strategy execution module receives a fault detection command sent by a business layer, the network state parameter acquisition and strategy execution module builds communication with the agent module on a router in parallel, and acquires network state information of different network protocols from the agent module by using a self-adaptive roll polling algorithm; and the fault detection reasoning module performs fault detection and repair. By using the method provided by the invention, a known fault can be accurately positioned, fault detection overheads can also be reduced, and automatic repair of the fault can also be ensured.
Owner:NAT UNIV OF DEFENSE TECH
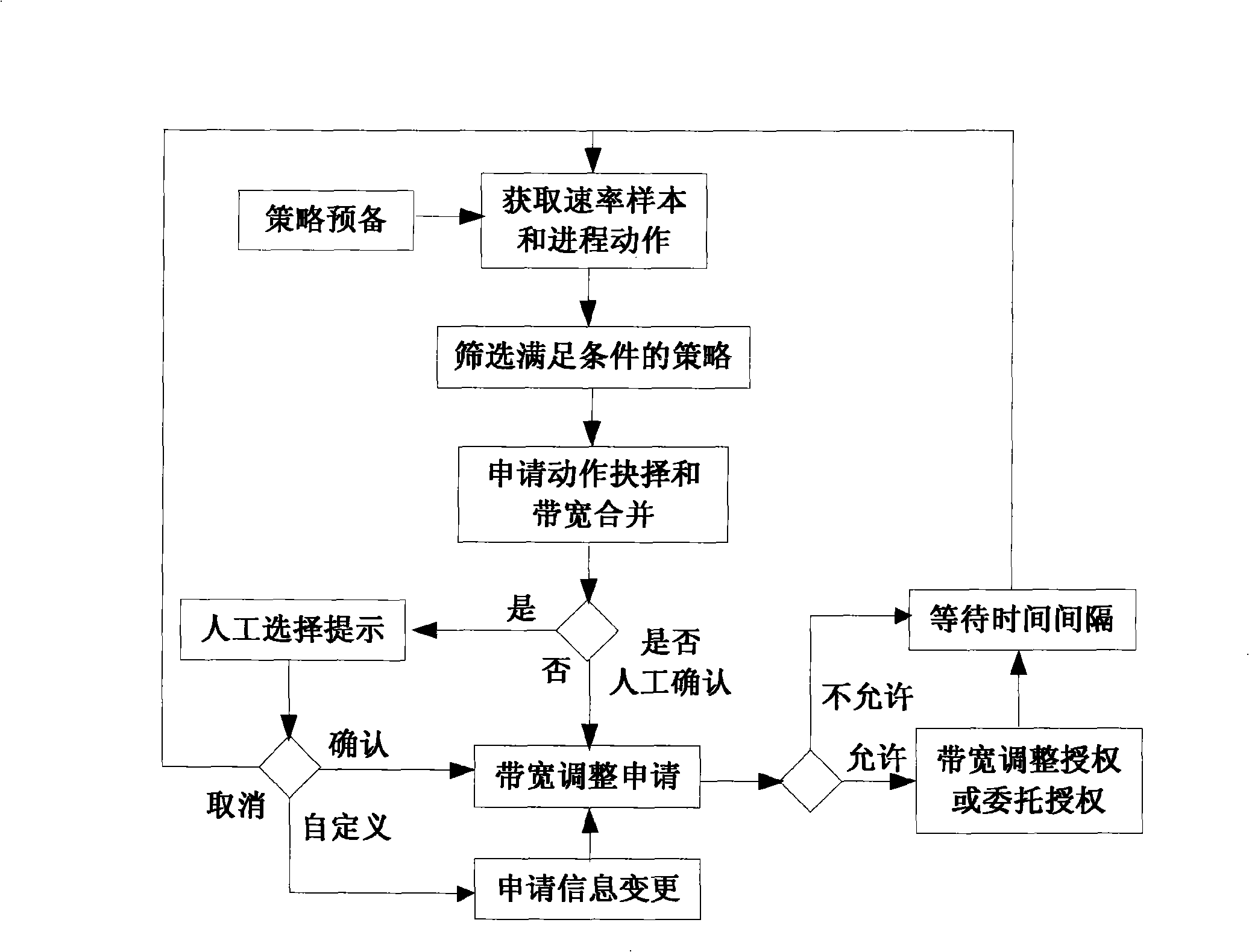
Apparatus, system and method for implementing access bandwidth dynamic regulation
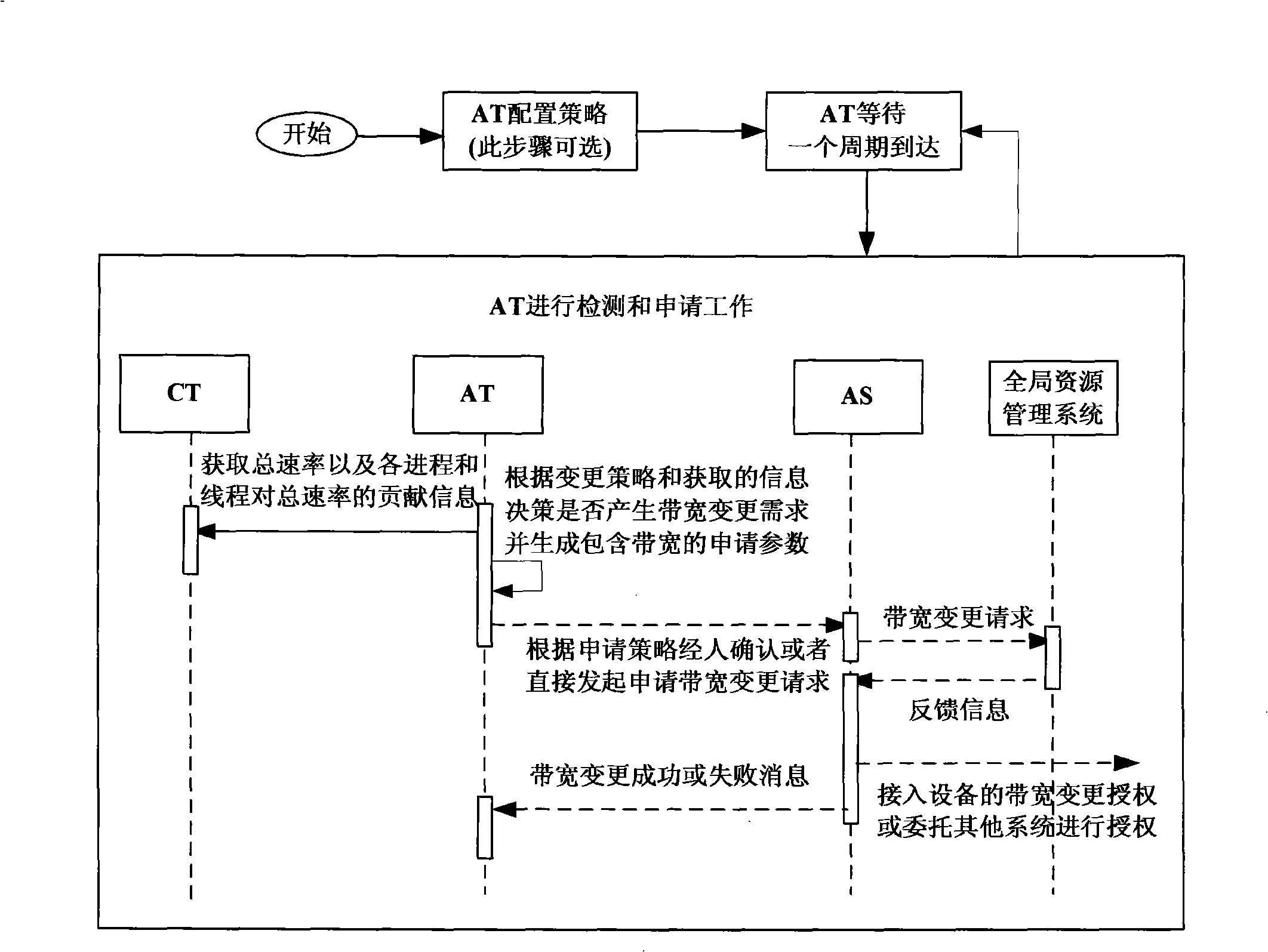
ActiveCN101409674AOptimizationLower the thresholdError preventionData switching by path configurationStrategy executionResource Management System
The invention discloses a method for realizing the access bandwidth dynamic adjustment. In the method, a device for realizing the access bandwidth dynamic adjustment captures current uplink and downlink rate information of a user host, matching is carried out according to the rate information and locally preserved change strategies and whether the bandwidth is required to be changed is judged. If yes, a bandwidth change request is initiated to a bandwidth application service node, wherein, applied bandwidth adjustment parameters are included in the request. The bandwidth application service node sends the received bandwidth change request to a global resource management system and judges that whether the bandwidth change request is allowed according to a feedback result which is returned by the global resource management system. If yes, a bandwidth change instruction with new bandwidth value is sent to a strategy execution system. The strategy execution system adjusts the bandwidth of the user host according to the bandwidth change instruction. With the method adopted, the threshold of the on-demand bandwidth in use is lowered greatly and users can enjoy optimized access bandwidth under the condition that the users do not contact the bandwidth change technology.
Owner:ZTE CORP
Service information based resource demand admittance controlled method
InactiveCN101136864AFlexible Billing PrinciplesMeet the needs of refined operationsData switching networksStrategy executionService control
Owner:ZTE CORP
Method, equipment and system for resisting wireless network flooding attack
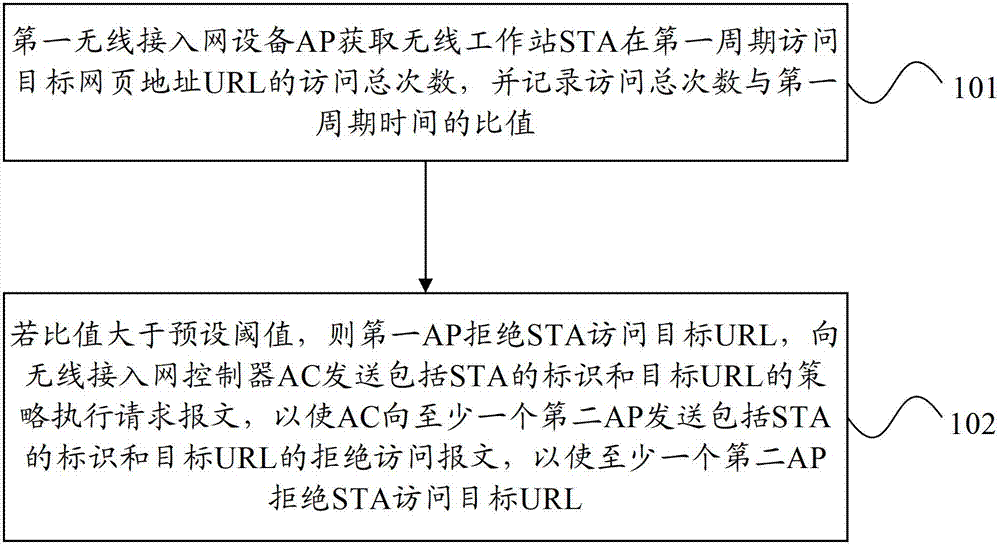
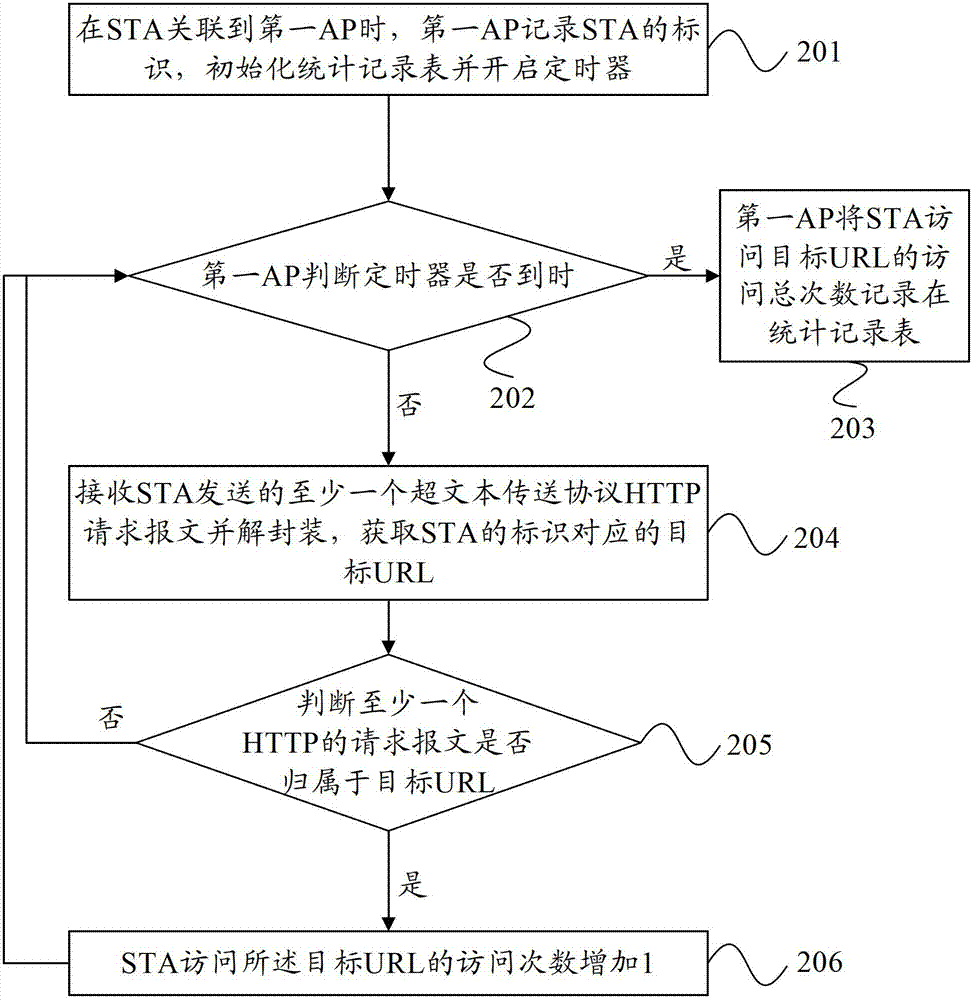
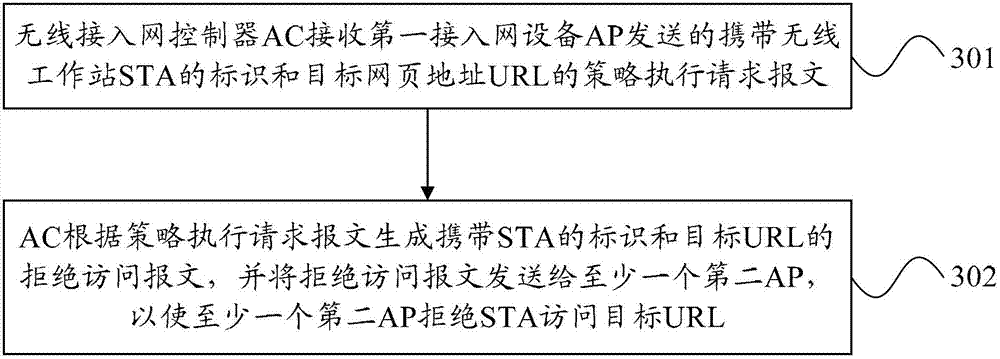
ActiveCN102833268AImprove securityImprove reliabilityClimate change adaptationTransmissionStrategy executionAccess time
The embodiment of the invention provides a method, equipment and a system for resisting the wireless network flooding attack. The method for resisting the wireless network flooding attack comprises the following steps of: a first access point (AP) obtains the total target webpage address URL (uniform resource locator) number of access times of a wireless station (STA) in a first period; the ratio of the total number of access times and the period time is recorded; if the ratio is more than a preset threshold value, the first AP refuses STA to access the target URL; an identification comprising STA and a strategy execution request message of target URL is sent to an access controller (AC); therefore the AC sends an access denying message comprising the STA identification and the target URL to at least one second AP; and at least one second AP refuses the STA to access the target URL. According to the embodiment of the invention, the safety and the reliability of the access equipment of the whole network can be improved.
Owner:RUIJIE NETWORKS CO LTD
Active safety guaranteeing method for Linux server
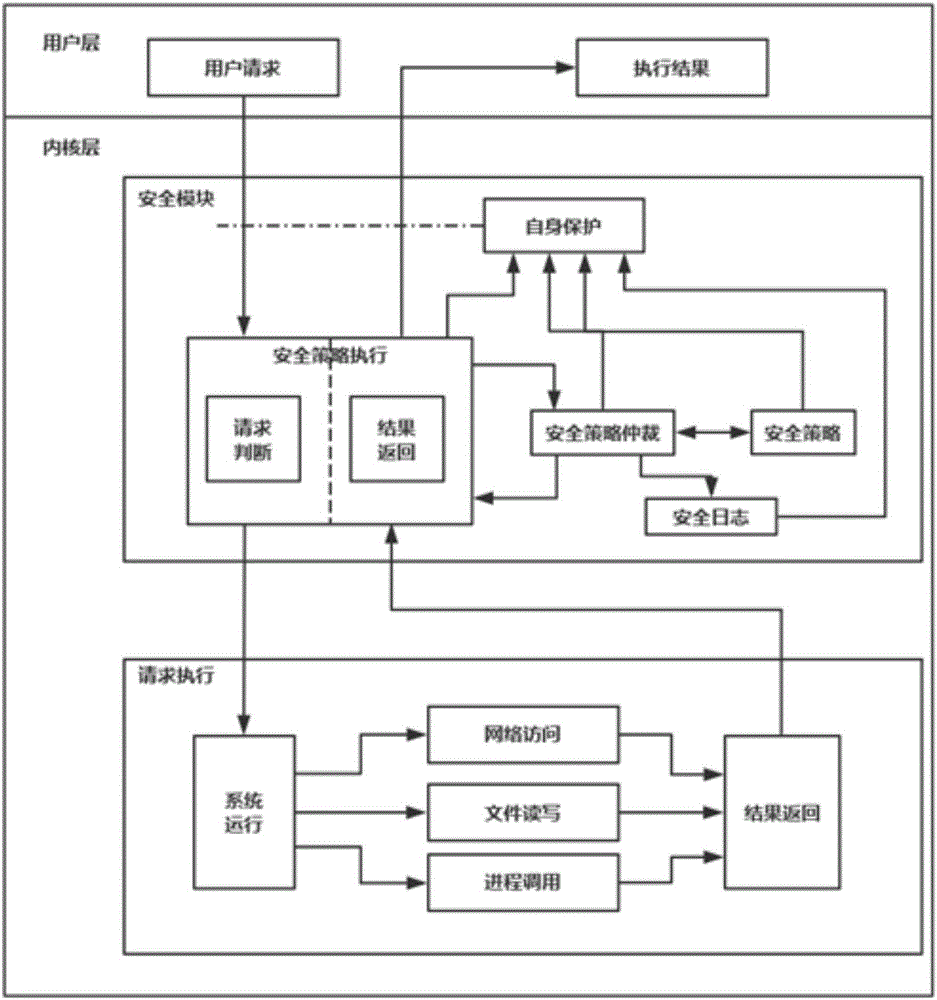
ActiveCN106295355AImprove the defect that system resources cannot be managed uniformlyImprove defects that cannot detect and analyze processes in real timePlatform integrity maintainanceTransmissionActive safetyStrategy execution
The invention provides an active safety guaranteeing method for a Linux server. An embedded system kernel and an operating system are tightly combined through a safety module capable of being operated independently, the defects existing in system resource management, process management, firewall management, user management, file management, log safety auditing, condition monitoring and the like of an existing Linux operating system are overcome, a multi-module working mode is adopted, strategy execution, strategy arbitration, strategy storage and log recording are independent from one another, and it is ensured that the system is operated normally.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
A method and system for controlling network service
ActiveCN101166153AEasy to controlSolving the control strategy is too simpleError preventionNetwork traffic/resource managementStrategy executionQuality of service
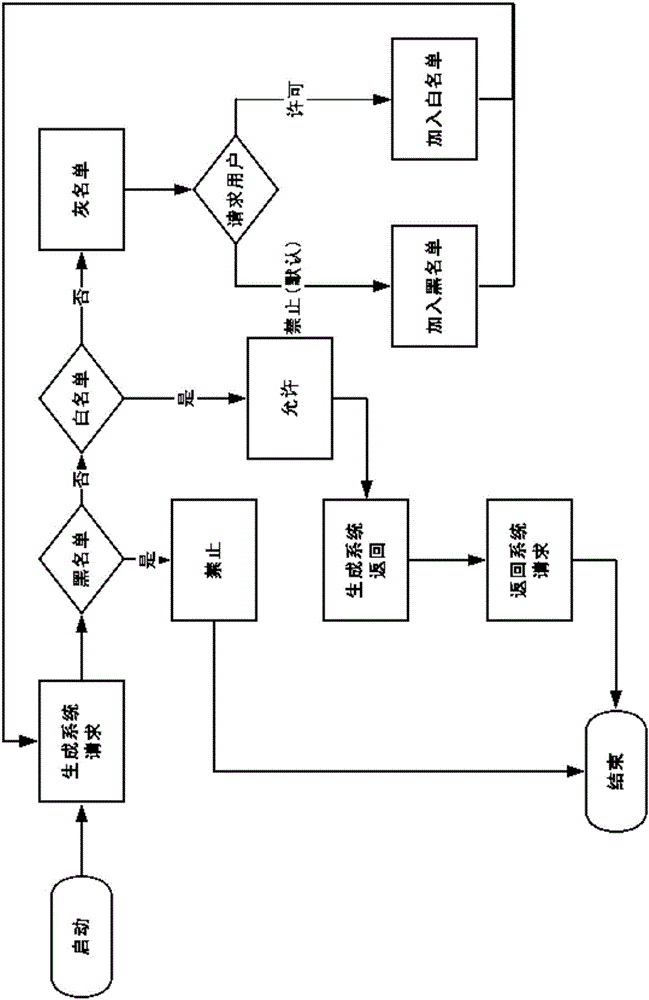
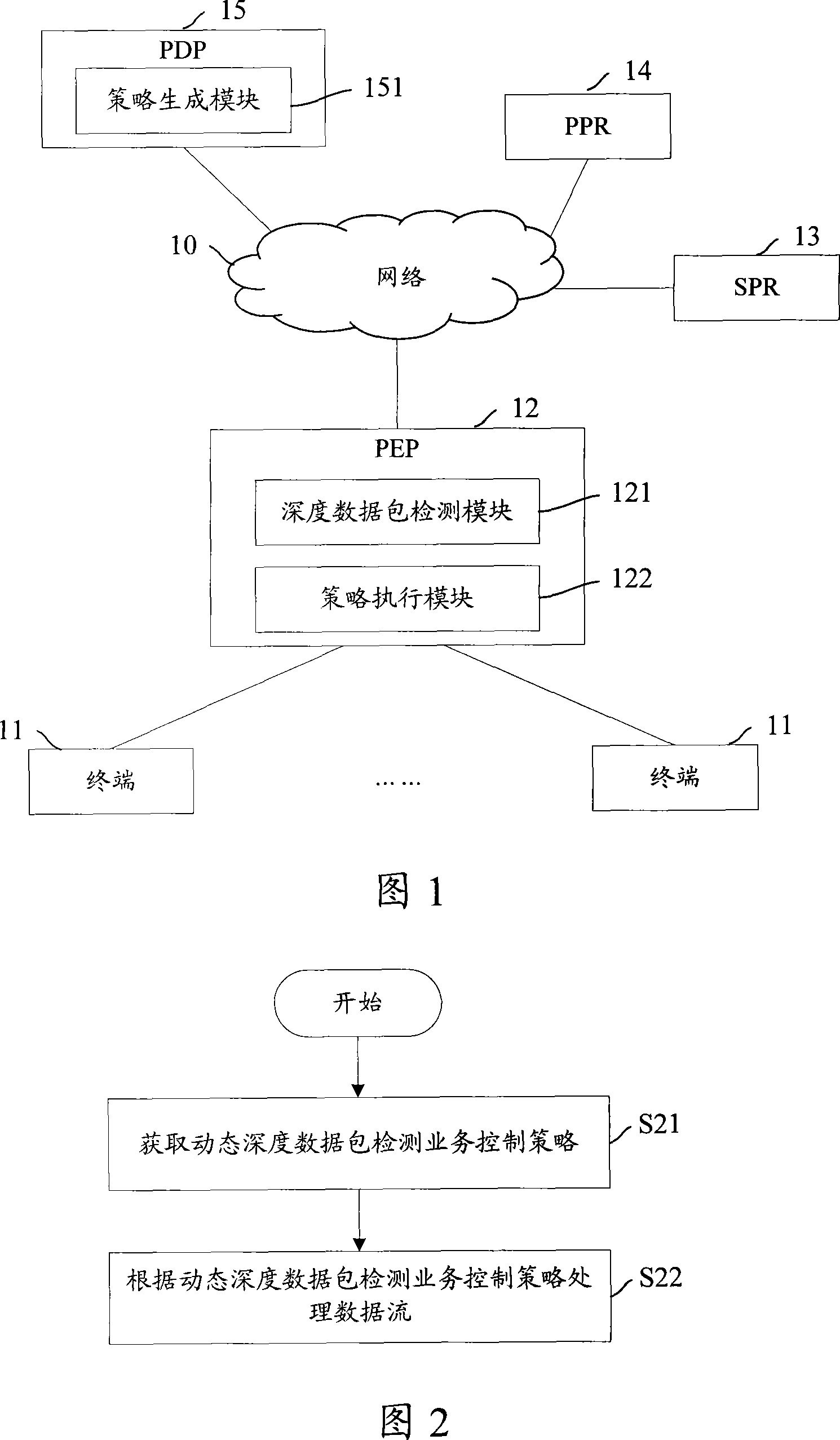
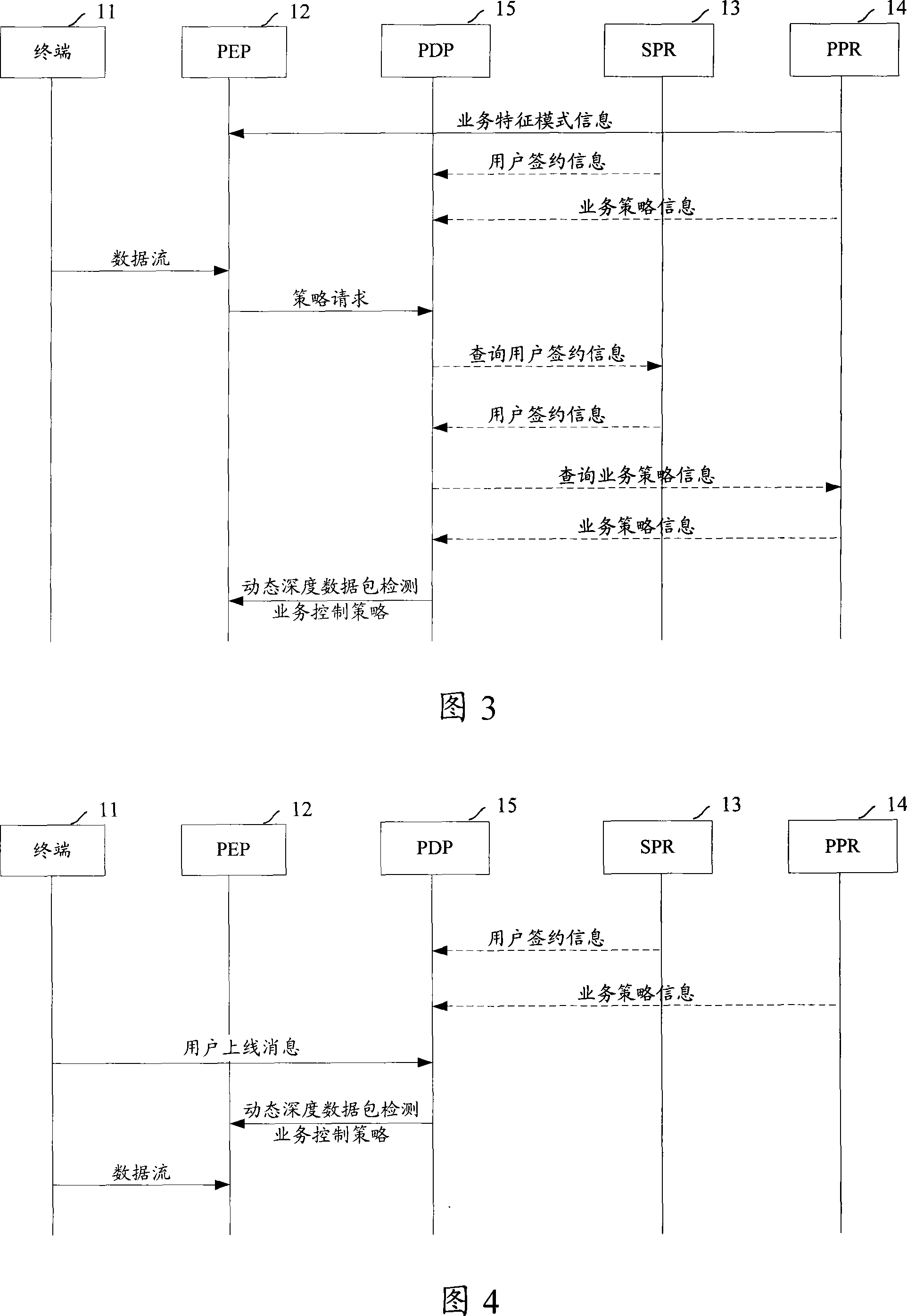
Through the strategy execution point, network services are transferred among terminals. The method includes steps: (1) the strategy execution point obtains strategy for controlling service of detecting data packets in dynamic deepness from the strategy decision point; (2) the strategy execution point processes data flow from terminal based on strategy for controlling service of detecting data packets in dynamic deepness. The invention also discloses a corresponding system for controlling network service. Using strategy for controlling service of detecting data packets in dynamic deepness to process data flow, the invention realizes different qualities of services when different users use network services. Through dynamic strategy control, the invention implements controlling services in network so as to reduce cost for operating network.
Owner:重庆重剑科技有限公司
System and method for monitoring integrated charger of multiplexed output coordination control electric automobile
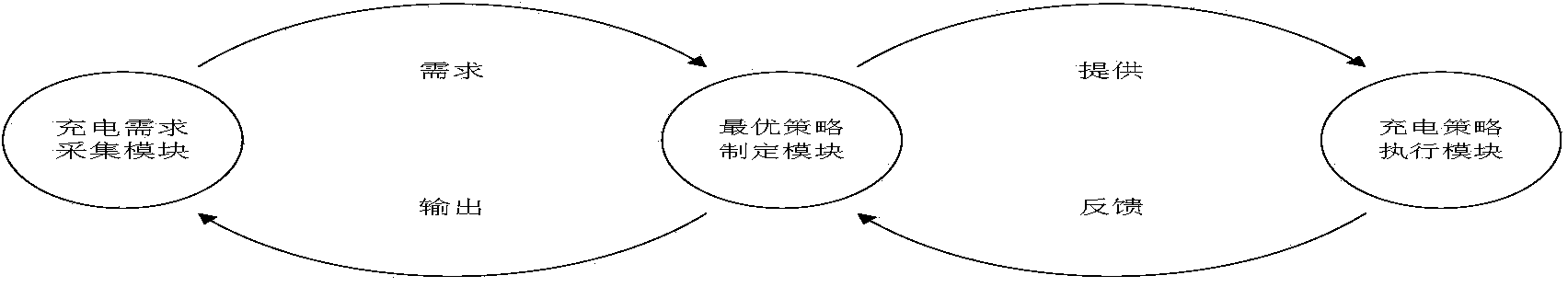
ActiveCN103475059APowerful strategy customizationAccurate processingCharging stationsElectric devicesStrategy executionStrategy making
The invention discloses a system and method for monitoring an integrated charger of a multiplexed output coordination control electric automobile. The system comprises a voltage and current real-time requirement acquisition module, an optimal strategy customizing module and a strategy execution module. The voltage and current real-time requirement acquisition module transmits requirements to the optimal strategy customizing module, the optimal strategy customizing module provides the requirements for the strategy execution module, the strategy execution module feeds an execution result back to the optimal strategy customizing module, and the optimal strategy customizing module outputs the result to the voltage and current real-time requirement acquisition module. The system and method for monitoring the integrated charger of the multiplexed output coordination control electric automobile has the advantages that an optimal power output strategy is selected by adopting an intelligent power allocation mode and adjusting voltage and current of the modules and multiple-module on-line and off-line states in real time, and the problems of the safety, the real-timeliness and the variety of the power, voltage and current requirements in the charging process of the electric automobile are solved.
Owner:SHANDONG LUNENG SOFTWARE TECH
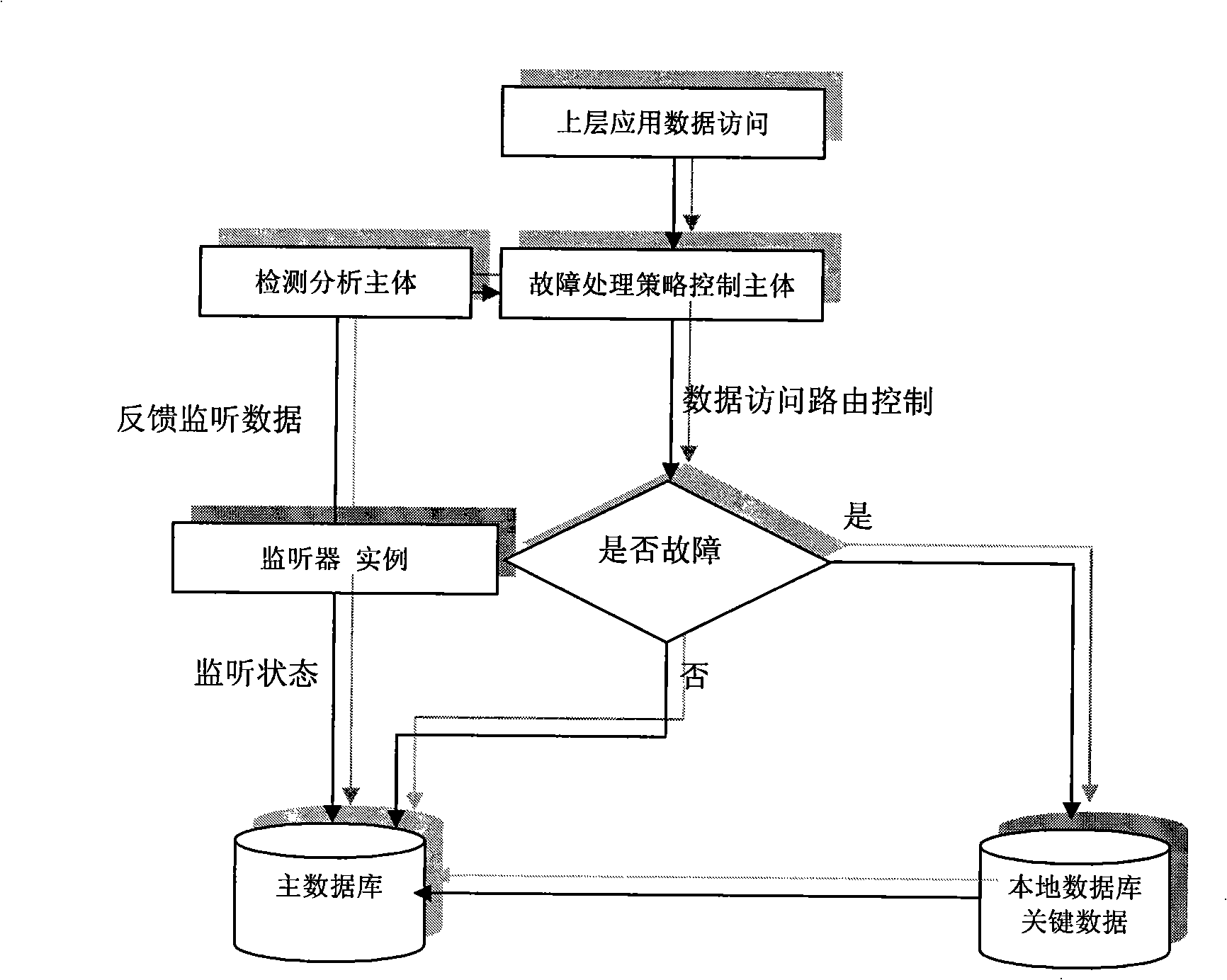
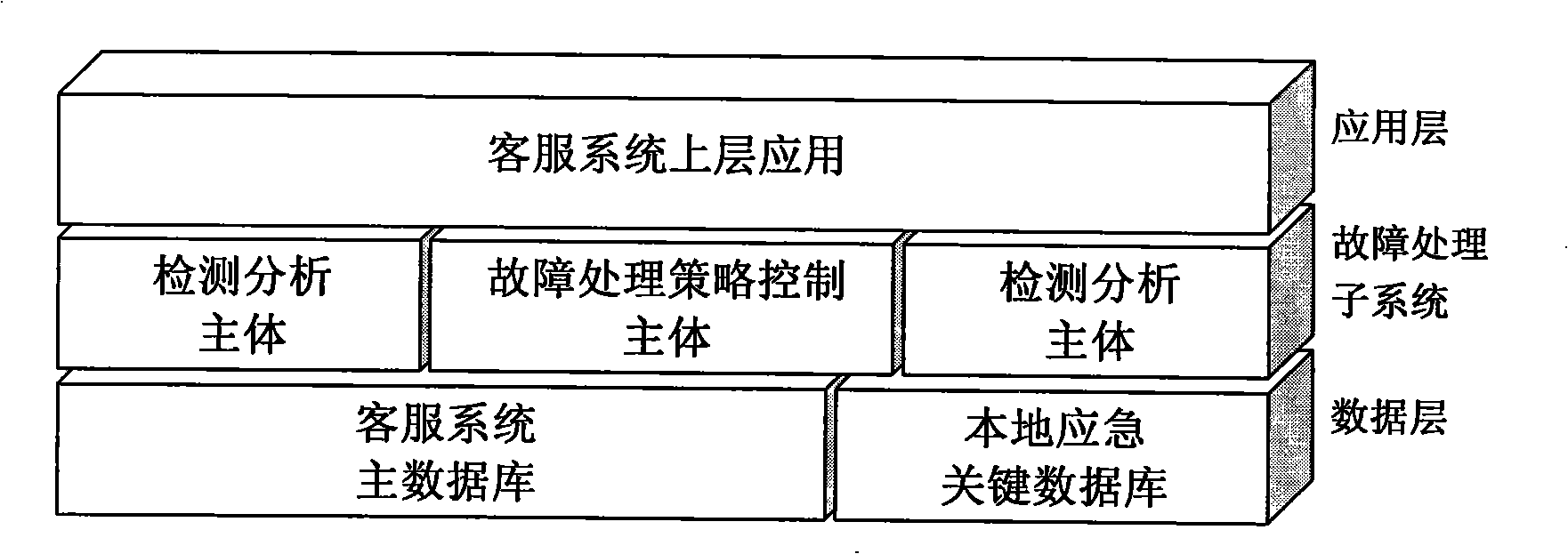
Failure processing method of telecommunication customer service system database
ActiveCN101321207AGuaranteed uptimeContinuous operationSpecial service for subscribersSupervisory/monitoring/testing arrangementsStrategy executionData access
The invention provides a method for treatment of failures in a telecommunication customer service system database, comprising: a step of accessing upper layer application data, an automatic voice interaction server IVR and artificial seat software access a main customer database to acquire call treatment logic configuration data; a step of monitoring, a monitor collects periodically status data associated with the database and feeds the data to a detection analyzing main body as evidences for analysis, judgment and strategy execution; a step of detection analyzing, the detection analyzing main body on a strategy control service analyzes the status data of the database and judges normality of the database on the ground of own knowledge database; if the judging result is abnormal, enter into failure treatment flows; a step of strategy control service, a strategy control server sends a local emergency key database an instruction to synchronize the key data of the main database, just in case of occurrence of the failures.
Owner:CHINA MOBILE GROUP JIANGSU
Method, device and system for configuring network resources
ActiveCN105682069AReduce in quantityReduce interactive signalingAccounting/billing servicesStrategy executionData stream
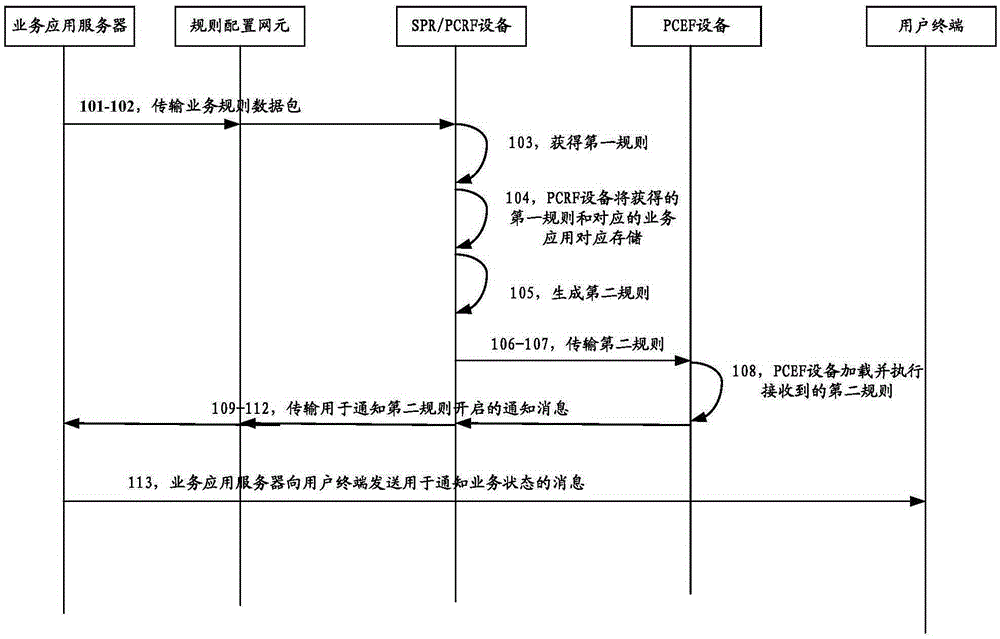
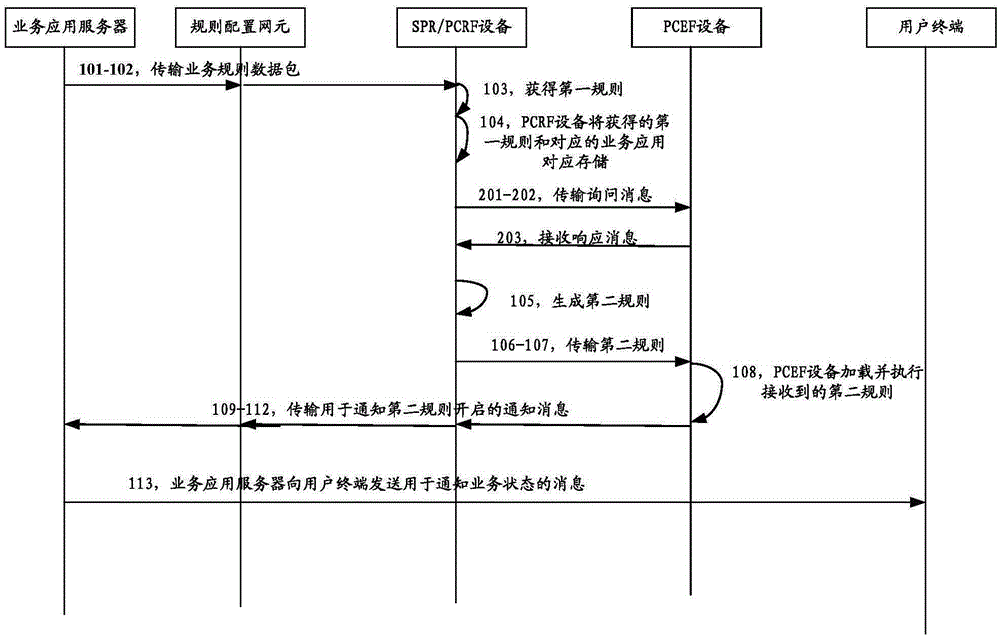
The invention discloses a method, a device and a system for configuring network resources. The method comprises the steps of when a first server receives a business rule data packet, acquiring a first rule; according to the first rule, generating at least one second rule, wherein the second rule is used for processing data flows; and sending the second rule to a second server, and instructing the second server to execute a business application corresponding to the second rule according to the second rule, wherein the first server has a strategy control function, and the second server has a strategy execution function. According to the method, the problems that the execution delay of the business application is large, and the storage quantity of the business rules and the quantity of interface signaling configured by the transmission rules are large when the business rule is set and the network service capability is fit for the business application are solved.
Owner:CHINA MOBILE COMM GRP CO LTD
Marketing strategy launching method and system
Owner:CHENGDU WANGDING SCI & TECH
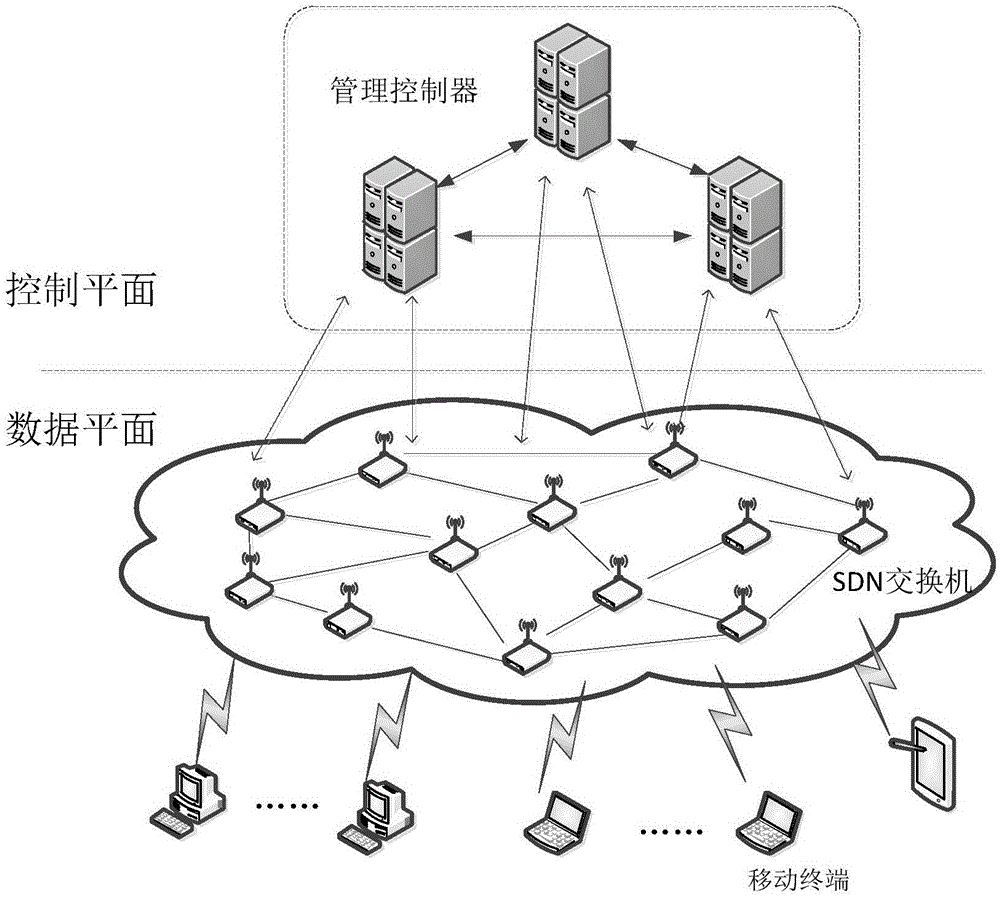
Wireless mesh safety hierarchical transmission method based on SDN
ActiveCN106412880ASecure Hierarchical Transmission GuaranteeImprove protectionSecurity arrangementStrategy executionNetworking protocol
The invention discloses a wireless mesh safety hierarchical transmission method based on an SDN. The method includes: a strategy generation stage, a strategy distribution / maintenance stage, a strategy update / loading stage and a strategy execution stage. According to the method, transmission requirements of data flows with different safety demands can be flexibly met based on an SDN architecture, problems of poor flexibility of the network function and high update cost are solved, the method is in accordance with safety hierarchical transmission of the conventional network protocol, safety hierarchical transmission of wireless data messages is guaranteed, and better protection is provided for the data messages with high safety level.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
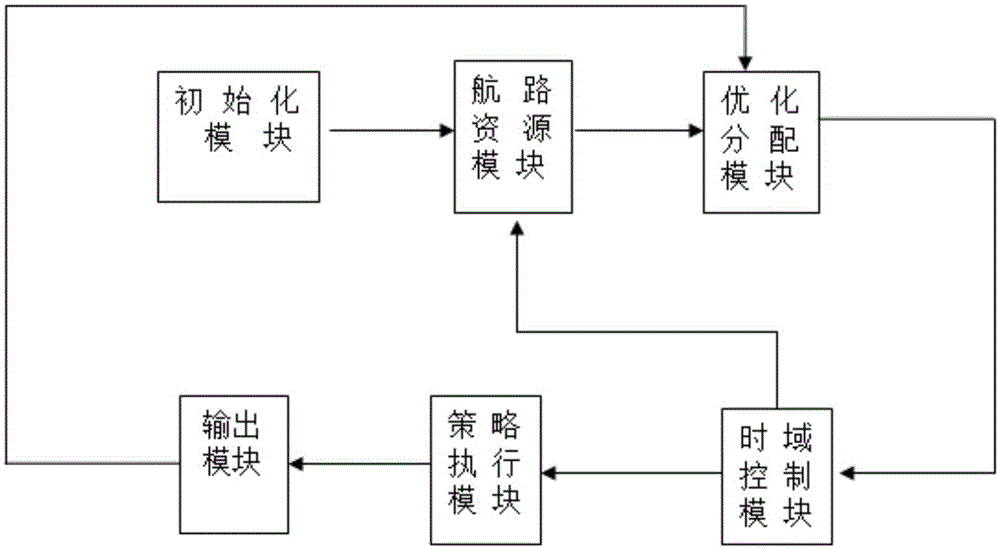
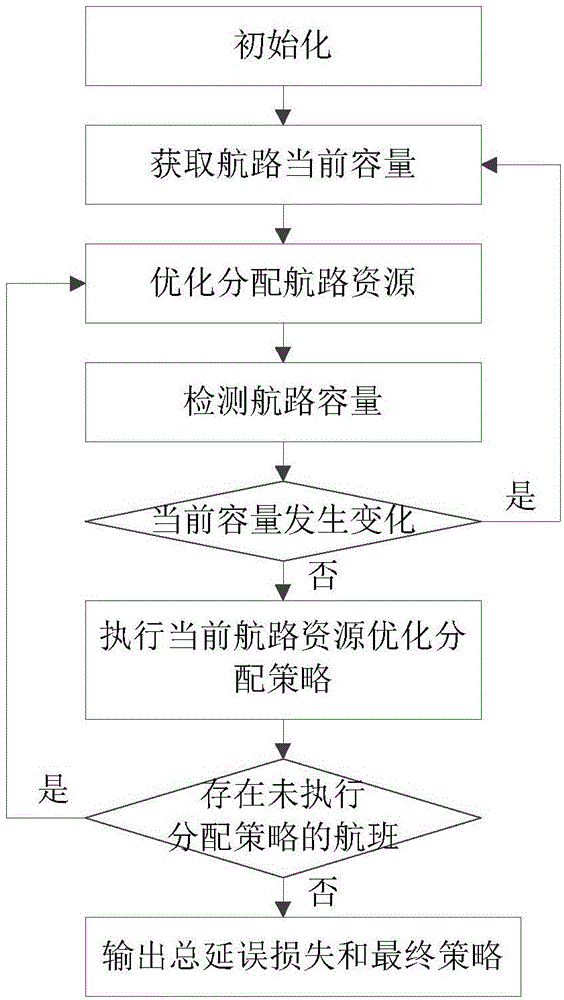
Dynamic allocation tool of air route resources and realization method thereof
ActiveCN105160944AIncrease profitImprove efficiencyAircraft traffic controlTraffic capacityTime domain
The invention discloses a dynamic allocation tool of air route resources and a realization method thereof. The tool comprises an initialization module, an air route resource module, an optimized allocation module, a time domain control module, a strategy execution module, and an output module. The occupied or idle situation of the air route resources can be gotten timely and the air route resources can be allocated dynamically in an optimized mode; a technical support can be provided for airspace management, coordinated flow management, and control command automatic system development; and a rapid realization tool is also provided for effective mastering and dynamic control of the air route operation. According to the realization method, on the basis of cooperation of all modules, the air route capacity change information can be gotten timely and dynamically; dynamic optimized allocation of the air route resources is realized; the air route resources are utilized to the greatest extent; and losses can be reduced. The realization method has advantages of simpleness, fastness, easy operation, and high accuracy.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
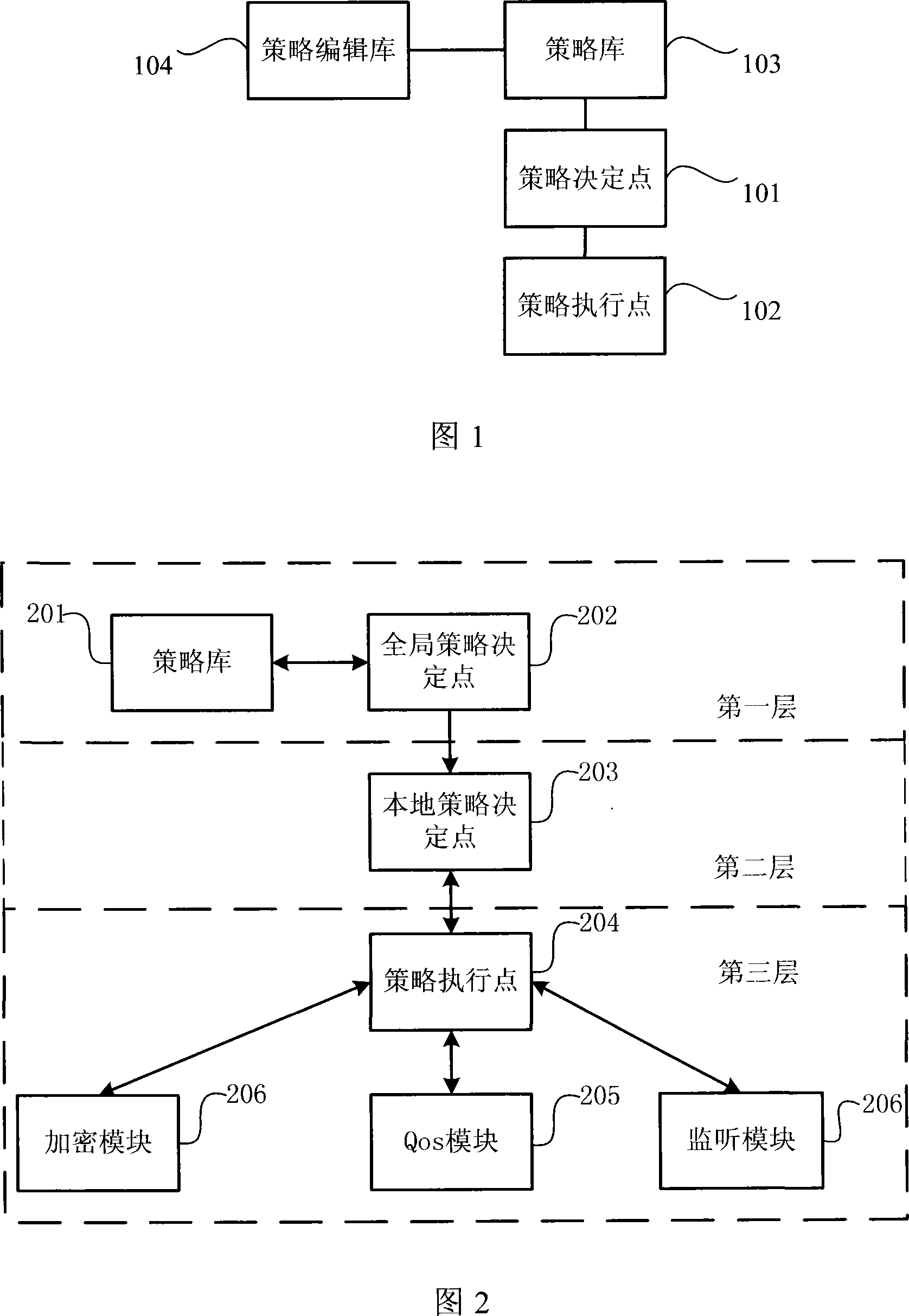
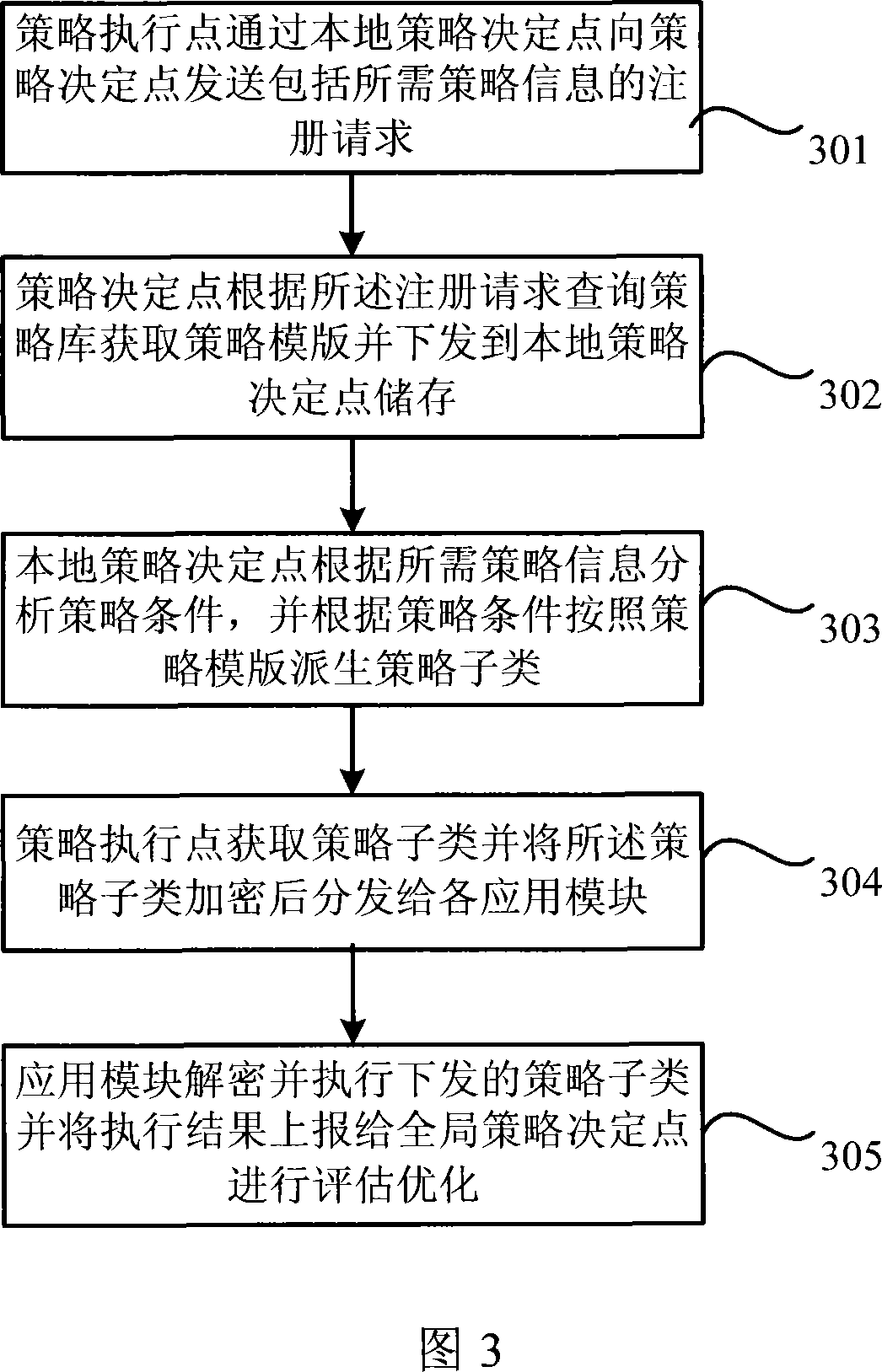
Network policy architecture for legal monitoring system and its policy processing method
InactiveCN101123534AReduce processing burdenPublic key for secure communicationUser identity/authority verificationStrategy executionMonitoring system
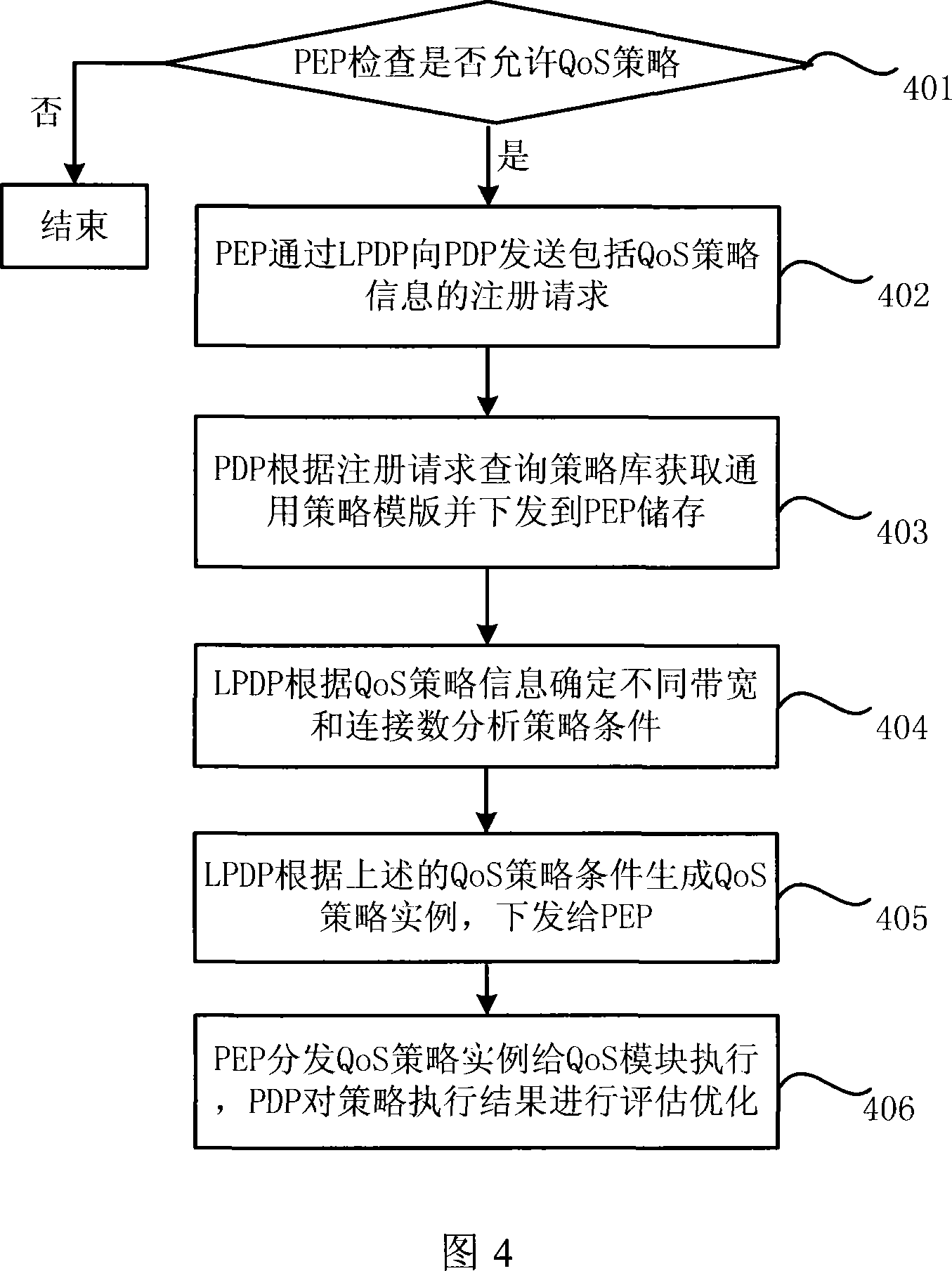
The present invention relates to a network strategy framework applied to a legal interception system, which comprises a strategy library, a global strategy decision point, a local strategy decision point connected with the global strategy decision point and a strategy execution point connected with the local strategy decision point. The present invention also relates to a strategy processing method, which has four steps. Firstly, the strategy execution point sends a registration request to the global strategy decision point via the local strategy decision point; secondly, according to the registration request, the global strategy decision point queries the strategy library to acquire a strategy template, which is then sent down; thirdly, the local strategy decision point analyzes strategy rules and, according to the strategy rules, derives strategy subclasses according to the strategy template; and finally, the strategy execution point obtains the strategy subclasses, which are then distributed. By means of a three-layer system strategy architecture, the present invention alleviates the processing load of the upper-layer global strategy decision point, flexibly loads various modules related to the strategy execution of the legal interception system and encrypts the sent-down strategy subclasses, thus protecting the safety of strategy information.
Owner:HUAZHONG UNIV OF SCI & TECH
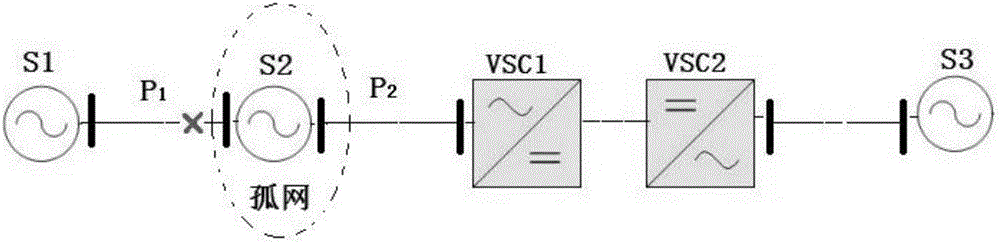
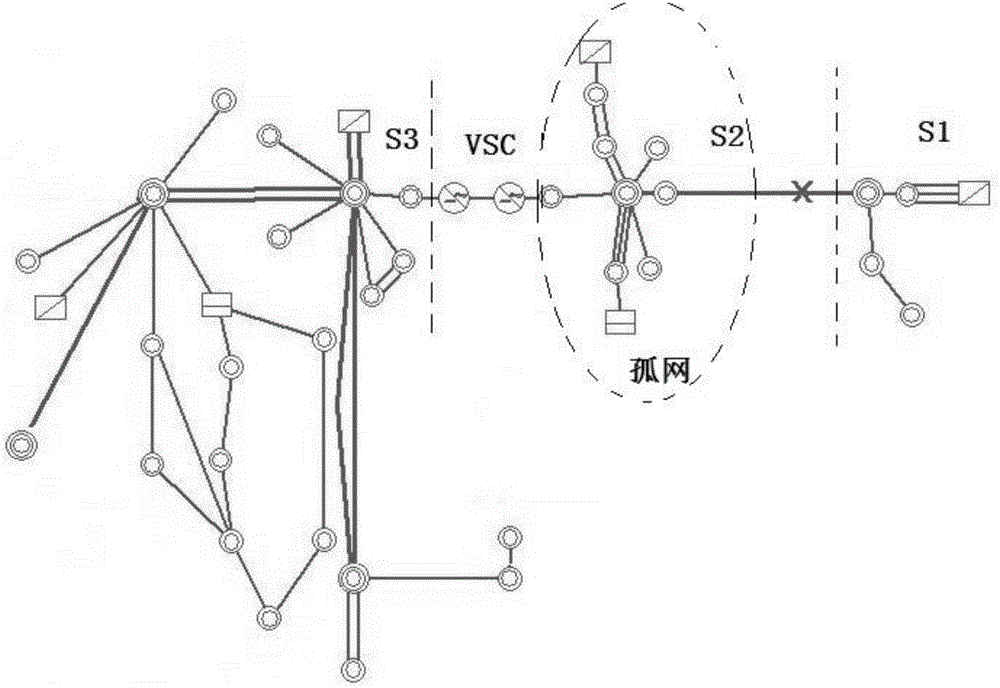
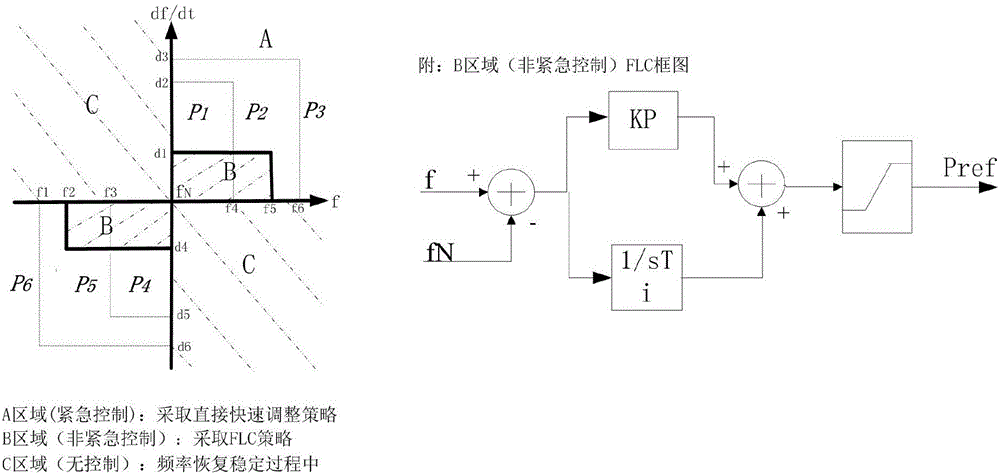
Fast control method of fault island containing flexible DC
ActiveCN106549425AImprove frequency stabilityImprove operating economySingle network parallel feeding arrangementsFrequency stabilizationStrategy execution
The invention discloses a fast control method of a fault island containing flexible DC. A control strategy execution scheme is formed through offline simulation calculation for the condition of an interconnected network of which regional network powers are connected with other power networks through AC and DC transmission channels separately; an offline control strategy is divided into an emergency control strategy and a non-emergency control strategy to correspond to control methods of different flexible DC; the strategy which is obtained through offline calculation in advance is searched according to frequency and frequency variation characteristics when the fault island is generated, execution is confirmed, a frequency and a frequency variation are continuously judged, and real-time complement can be carried out on an action result of a security and stability control device in a power system; and the stability of an island system is finally restored. The fast control method has the advantages that a flexible DC control method is directly determined in a manner of using an offline strategy searching scheme, the sampling calculation amount is small, judgment is fast and the control efficiency is high, thereby improving the frequency stability and the operation economy of the fault island.
Owner:ELECTRIC POWER SCHEDULING CONTROL CENT OF GUIZHOU POWER GRID CO LTD
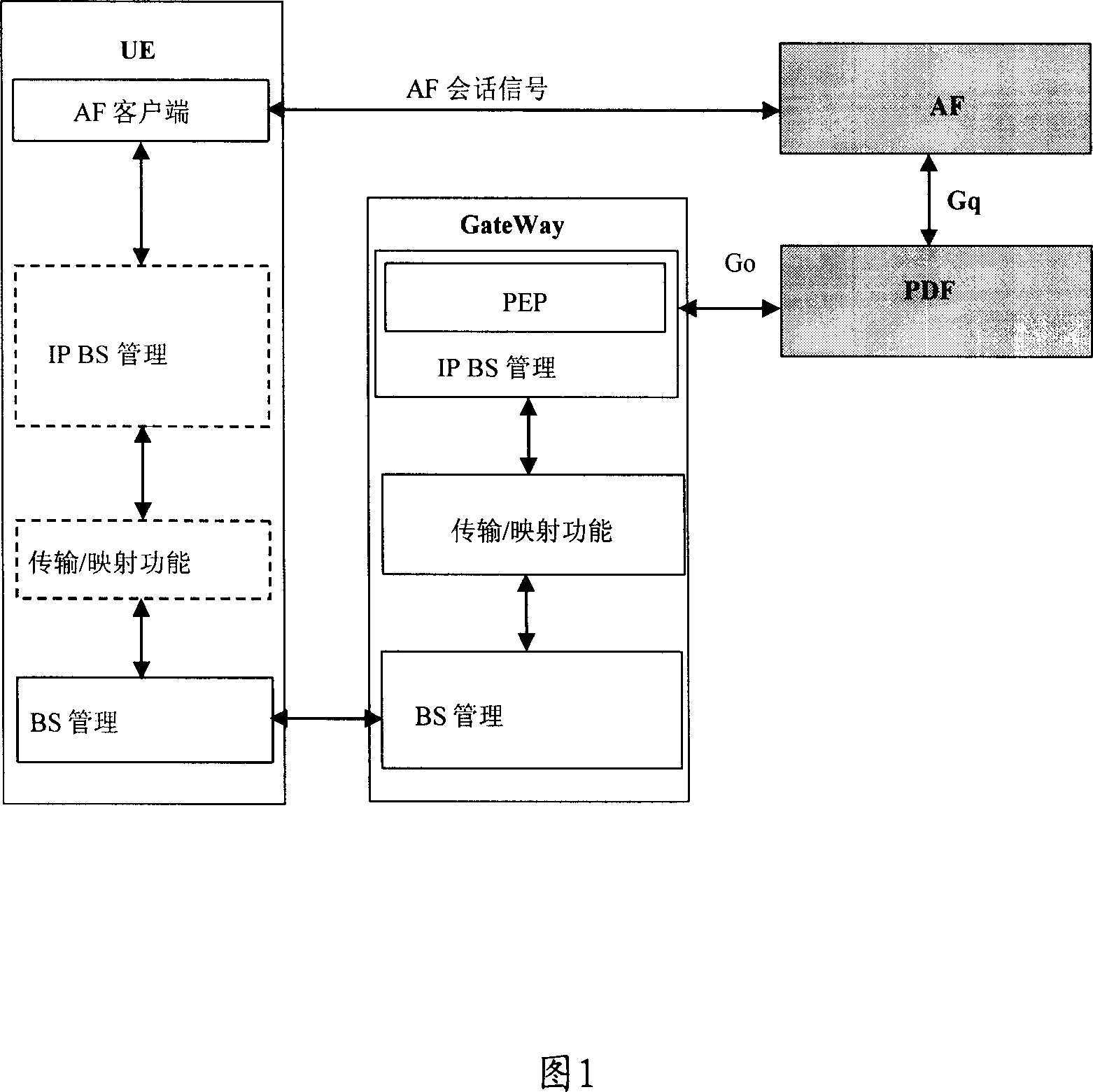
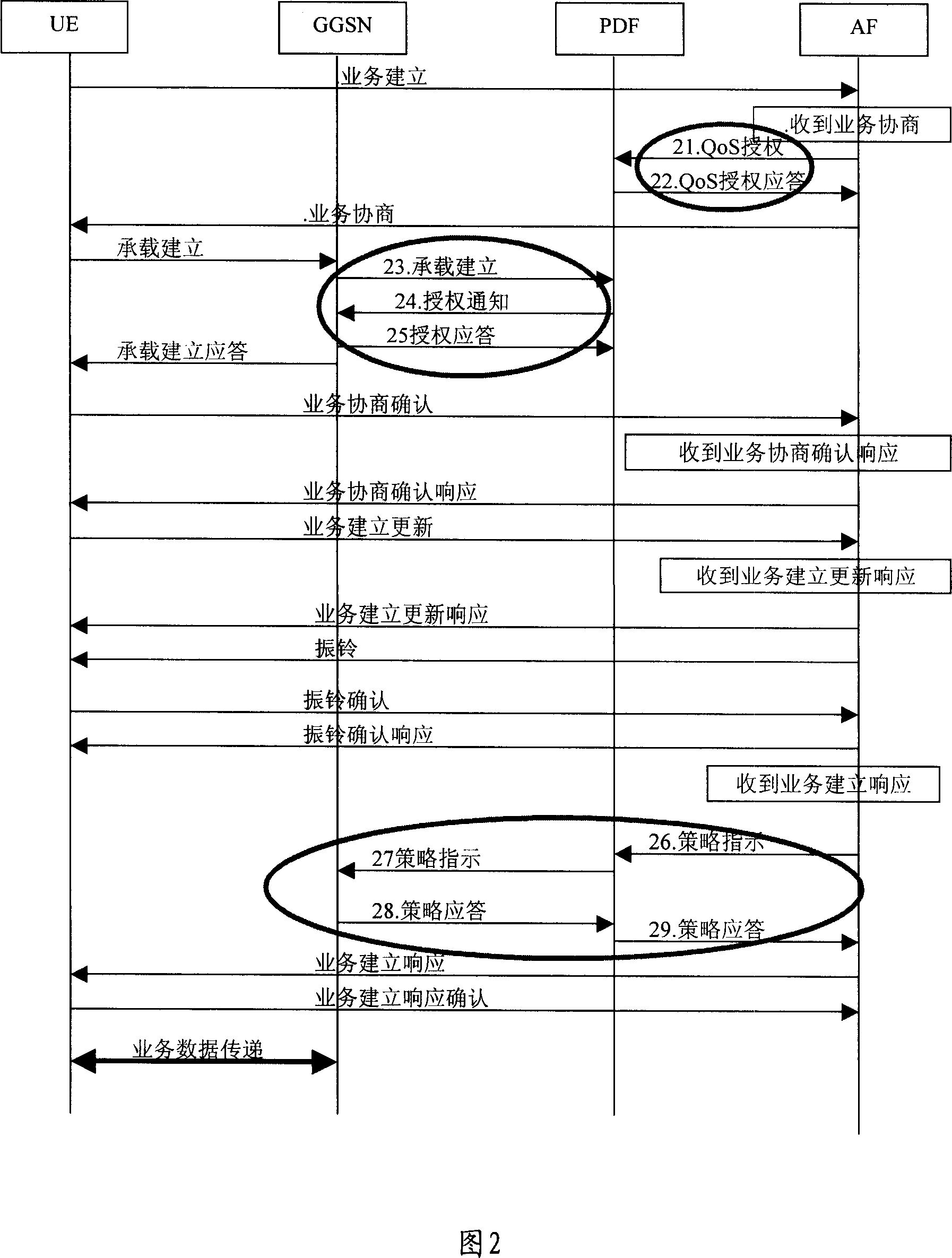
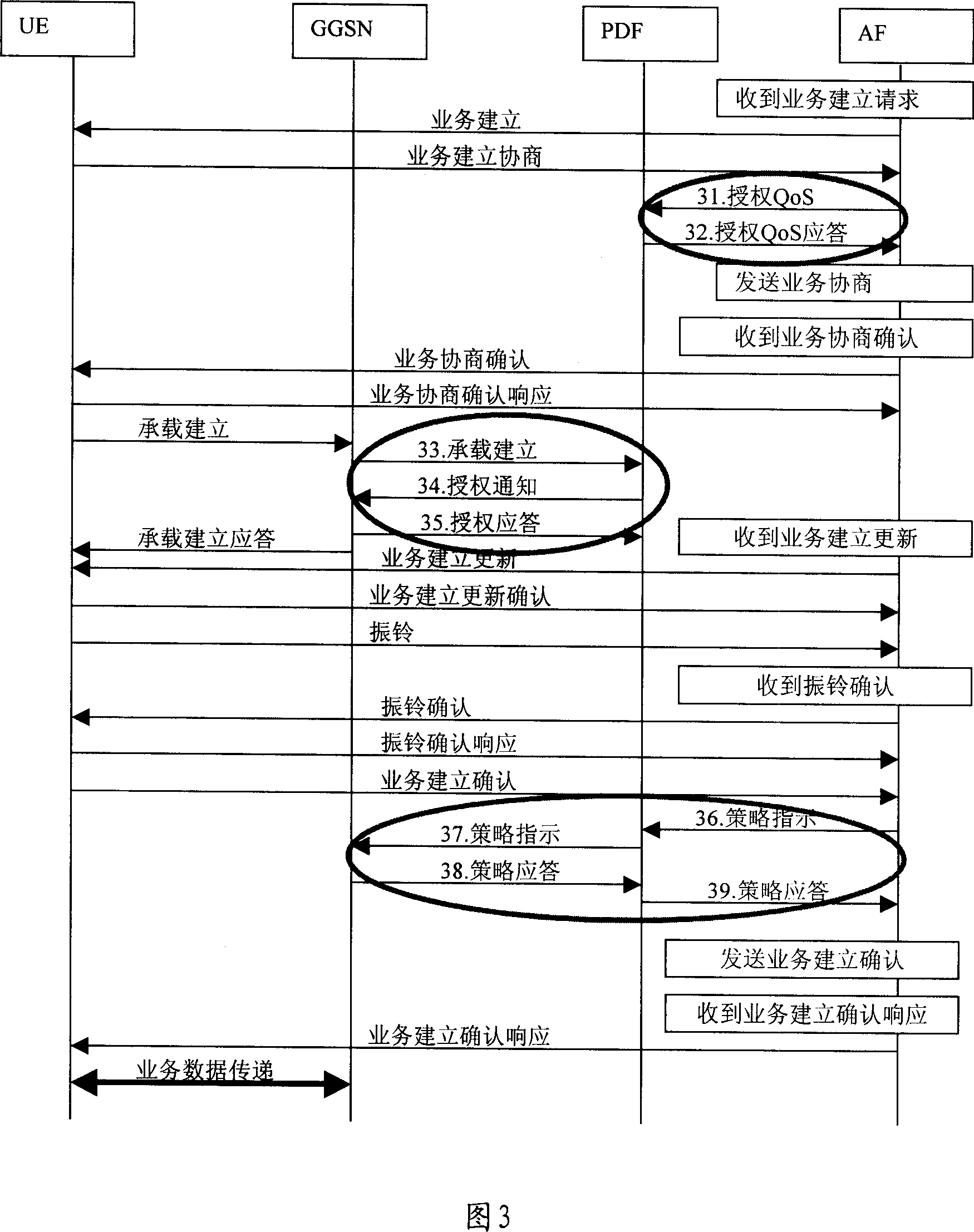
Method for realizing bearing set-up based on tactics control
ActiveCN1980150AReduce latencyOptimize the bearer establishment processData switching by path configurationStrategy executionTime delays
The method includes steps: application functional entity in comm. network sends pre authorized indication message to strategied decision functional entity for user terminal of initiating pre authorized request; receiving the pre authorized indication message, the strategied decision functional entity executes strategy control, and sends strategy indication message to strategy execution functional entity directly; then, based on received strategy indication message, strategy execution functional entity carries out admission control of establishing load procedure for user terminal directly in order to build operation for load of user terminal. Using mode of strategy negotiation in advance, the invention changes serial steps added to strategy control in prior art to not executing procedure or executing procedure in parallel. The invention shortens time delay for establishing service effectively, reduces and simplifies interactive message in procedure for establishing service load.
Owner:XFUSION DIGITAL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com