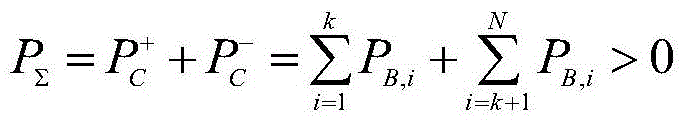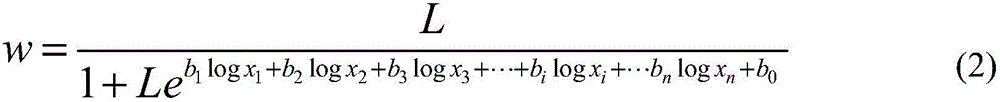Patents
Literature
177 results about "Strategy analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
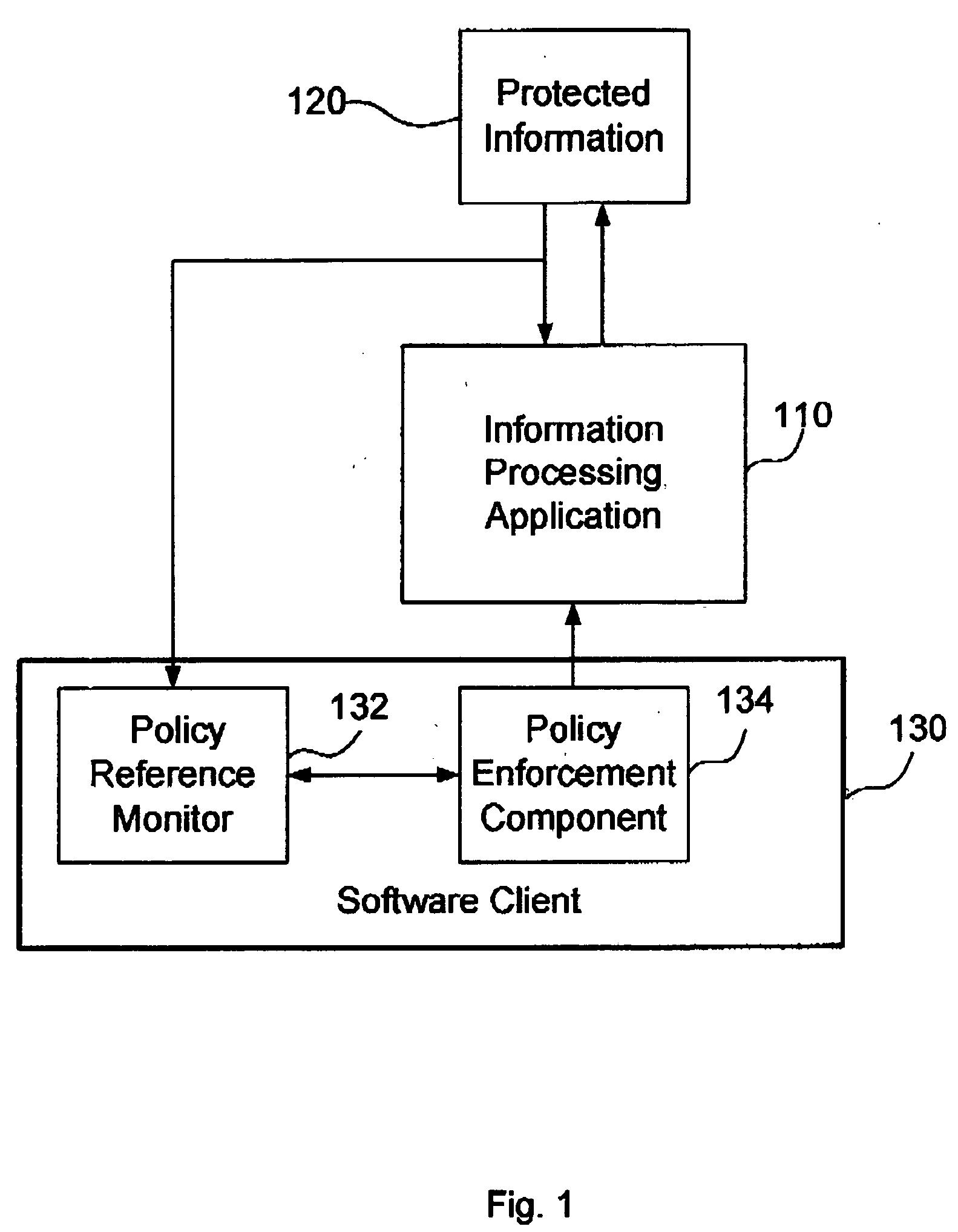
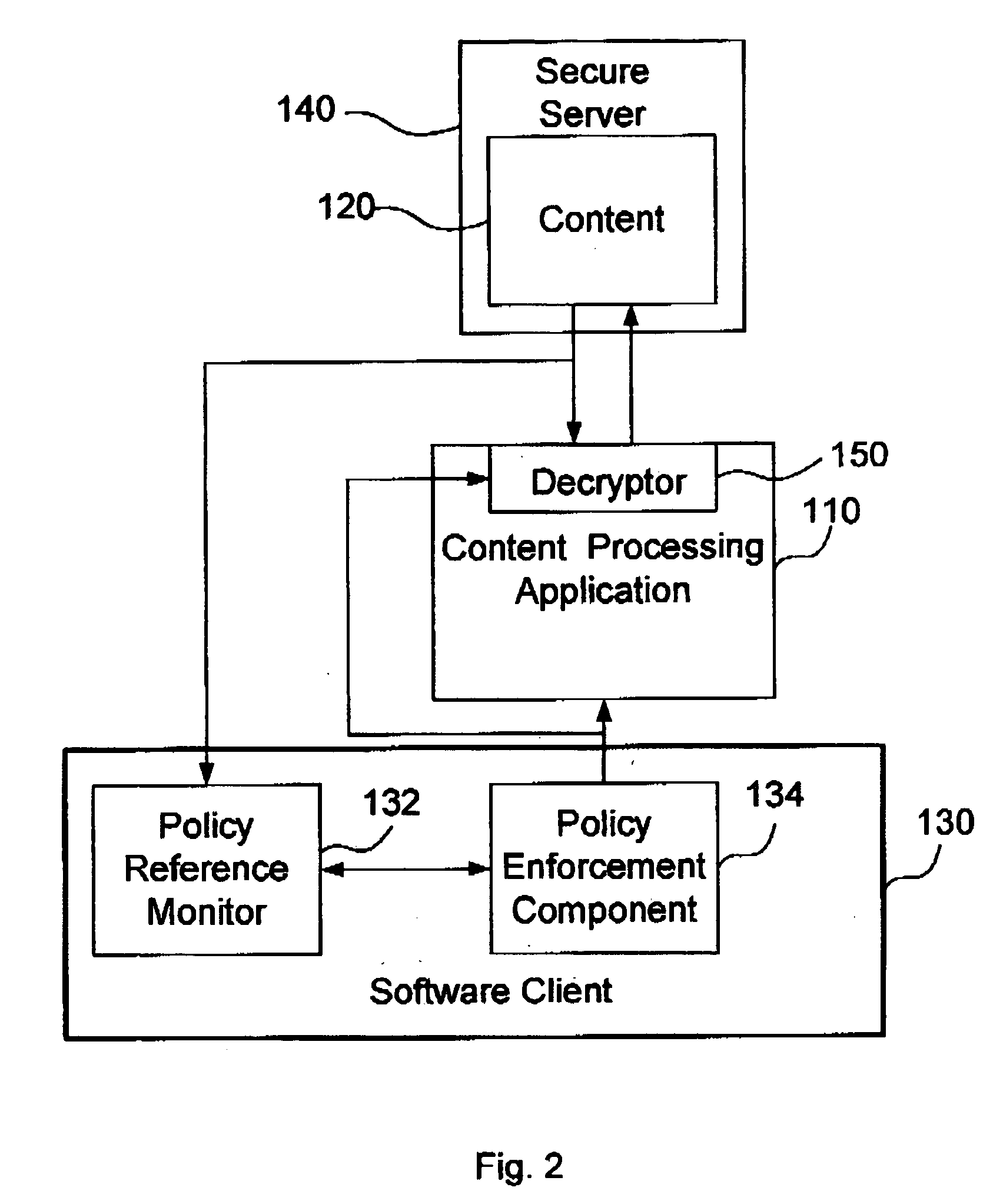
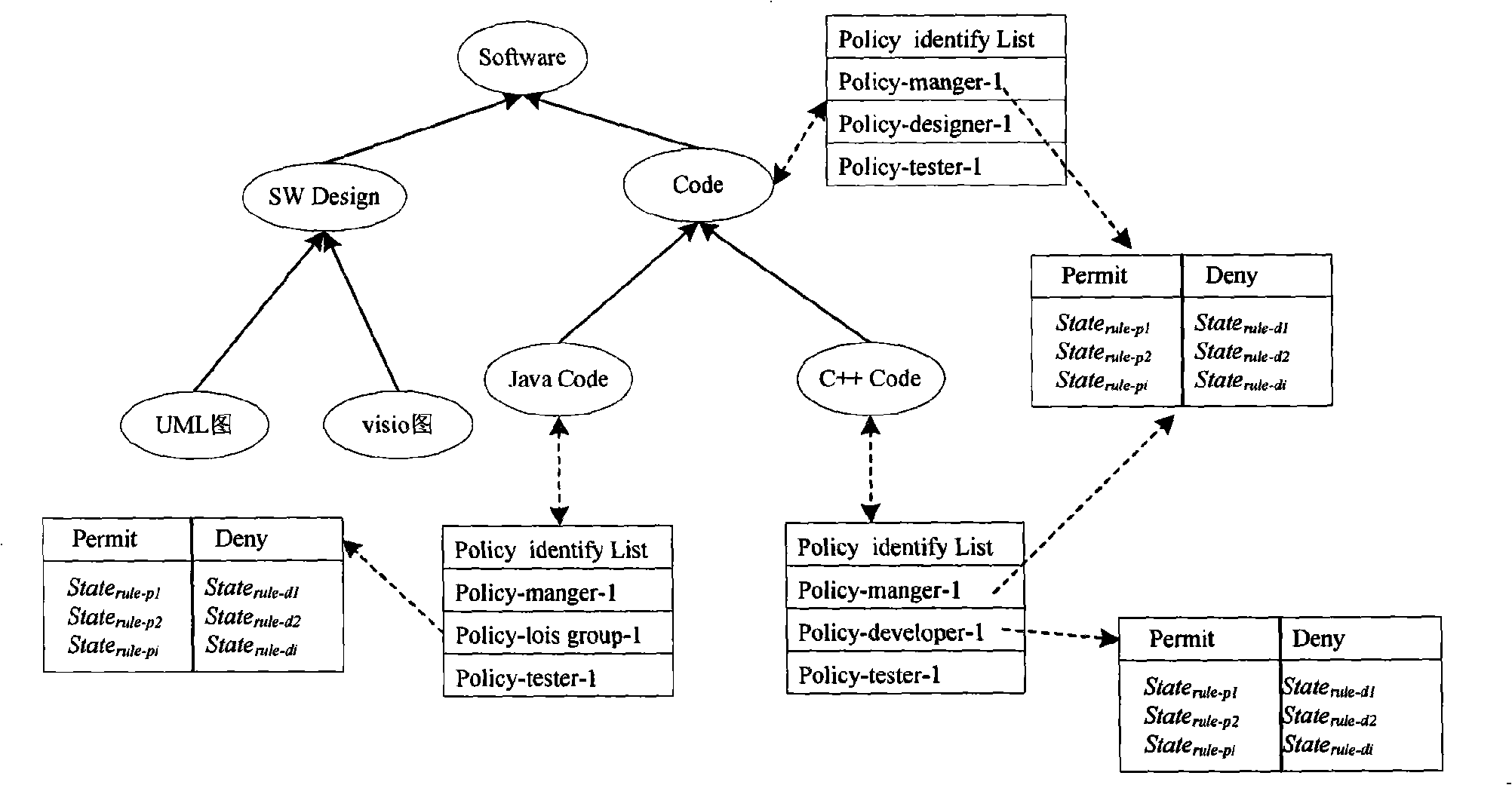
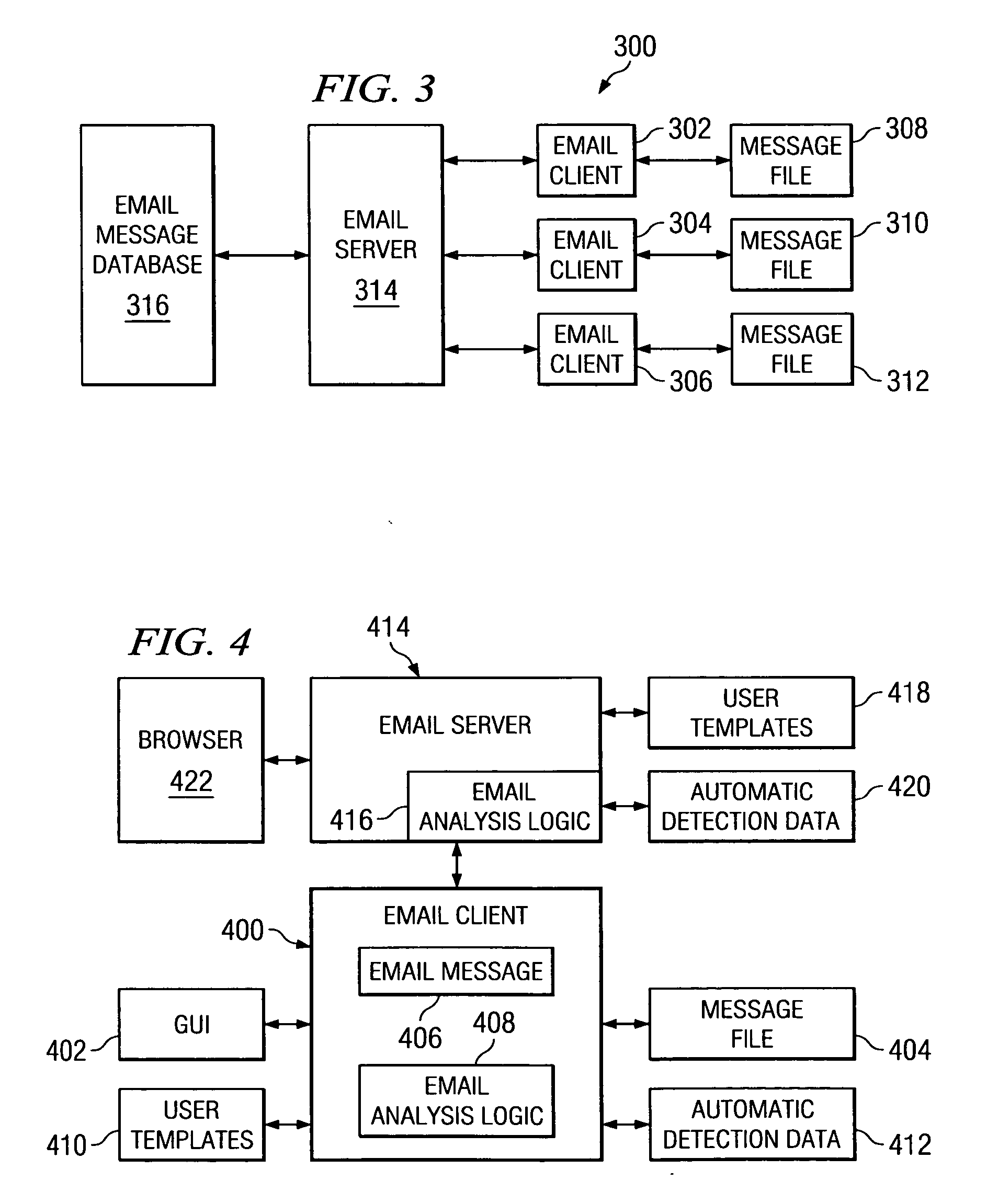
Method, system and apparatus for selecting encryption levels based on policy profiling
InactiveUS7010681B1Easily maintainable methodSelective encryptionSecuring communicationClient-sideSecurity level
The present invention depicts a method, system and program product for controlling levels of security and levels of encryption based on a predefined policy profile. This enables administrators and those who control the network to easily respond to changes in the requirements of the security levels for specific applications. It also allows for response to changes in personnel (such as someone being removed from a position that had topsecret security access) and accommodates variations in access by client devices.
Owner:IBM CORP
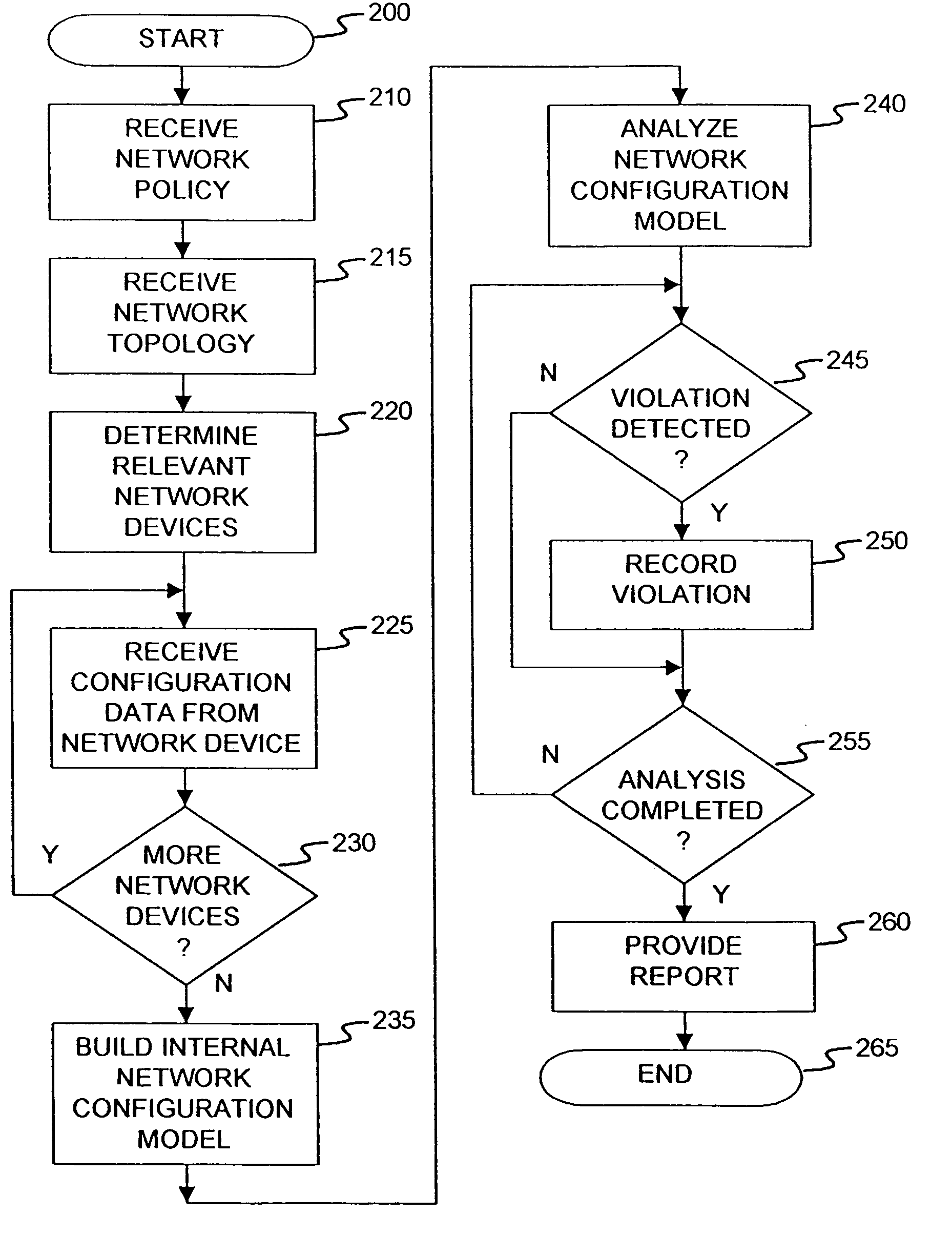
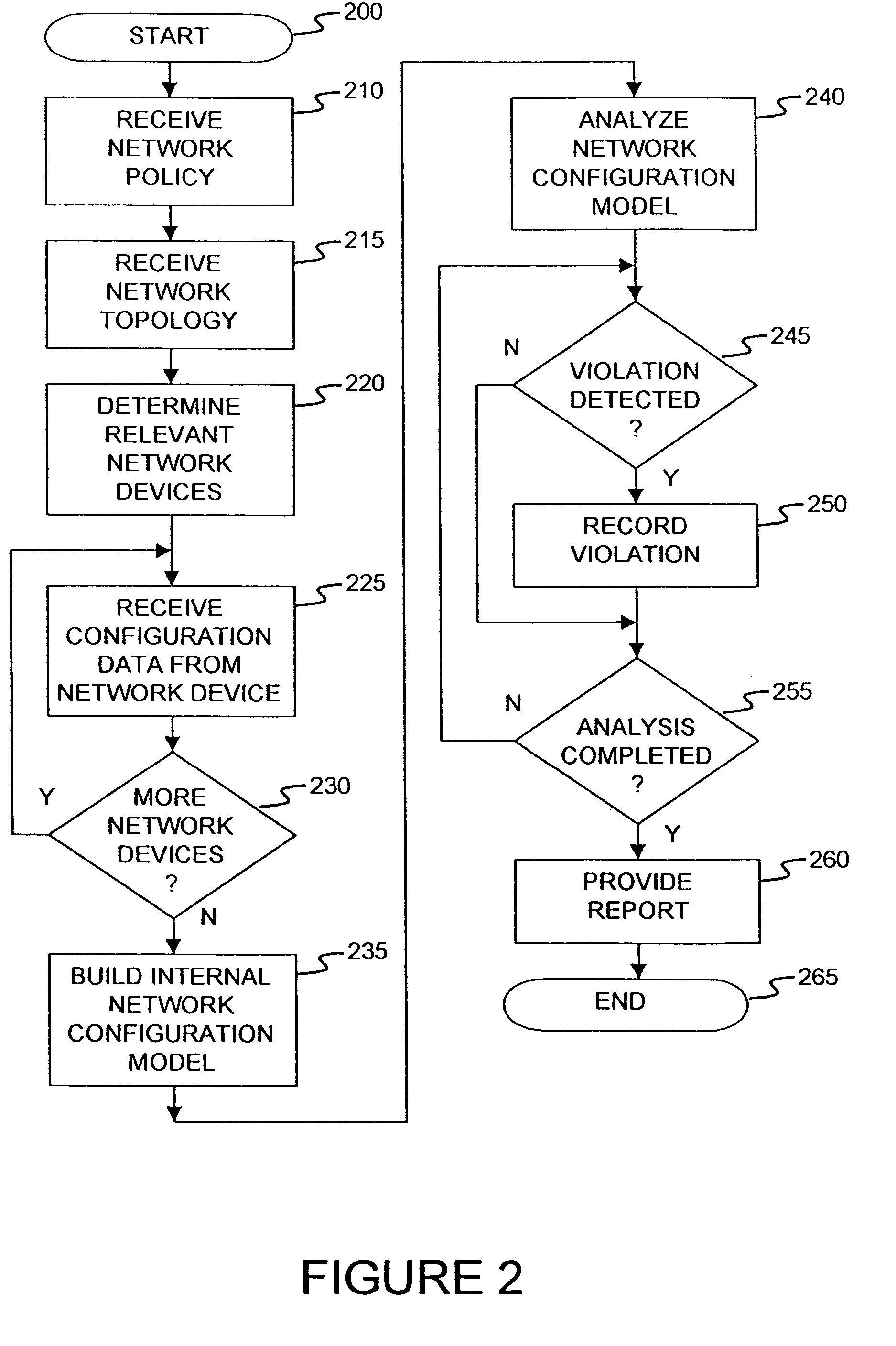
Method and apparatus for network wide policy-based analysis of configurations of devices
InactiveUS8135815B2Easy to determineAvoid problemsMultiple digital computer combinationsData switching networksApplication serverInternet traffic
A method for a computer system includes determining network devices within a network topology, wherein the network devices includes a first application server hosting a first application, receiving a policy for the network comprising requirements of a first application server including a description of a set of required network traffic, receiving a plurality of configuration files associated with the plurality of network devices, determining a network configuration model in response to the plurality of configuration files, computing network traffic on all network paths to and from the first application server to determine a plurality of computed paths, determining if the network traffic includes at least the set of required network traffic associated with the first server, and generating a report indicating whether the network traffic includes at least the set of required network traffic.
Owner:REDSEAL
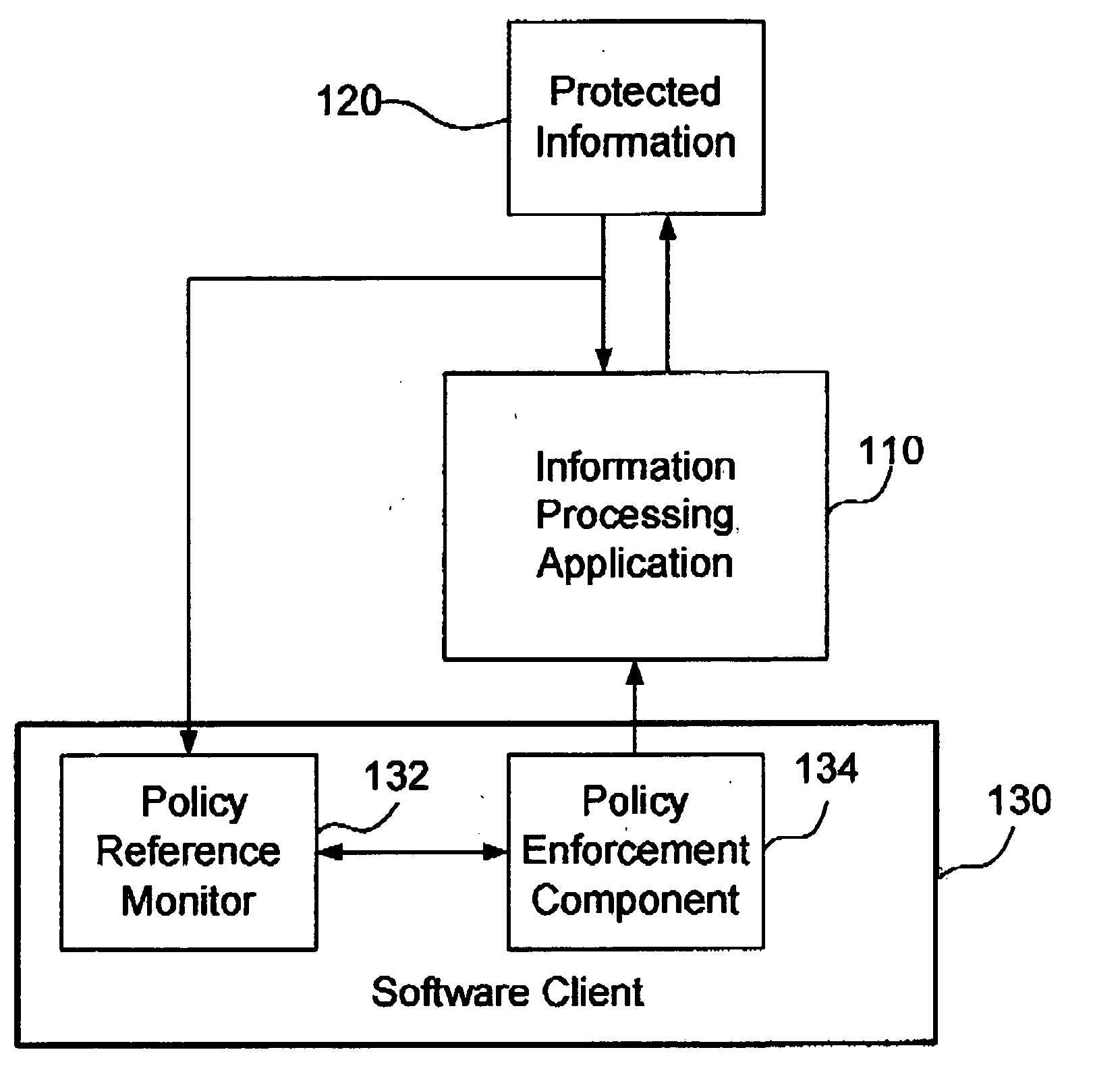
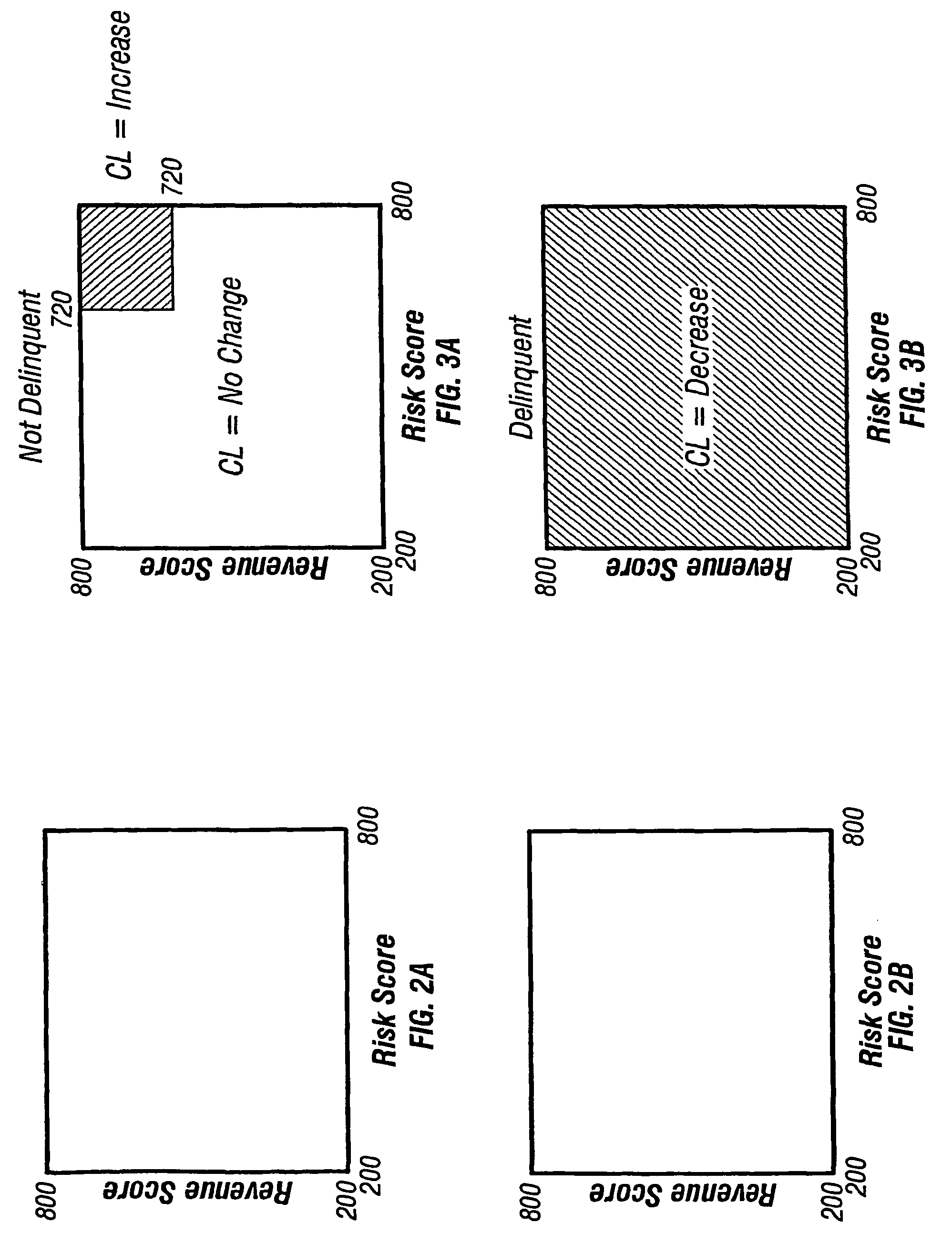
Method and system for protecting confidential information
ActiveUS20050066165A1Efficiently serve current needImprove protectionDigital data processing detailsAnalogue secracy/subscription systemsWorkstationStrategy analysis
A method for computer workstation based information protection is presented, the method comprises: a) monitoring user's actions on the computer workstation, b) analysis of the actions in respect to a pre-defined policy to determine whether the actions prejudice information to which the policy applies, and c) executing the policy in accordance with the results of the analysis to prevent or modify or restrict or monitor or log the actions.
Owner:FORCEPOINT LLC
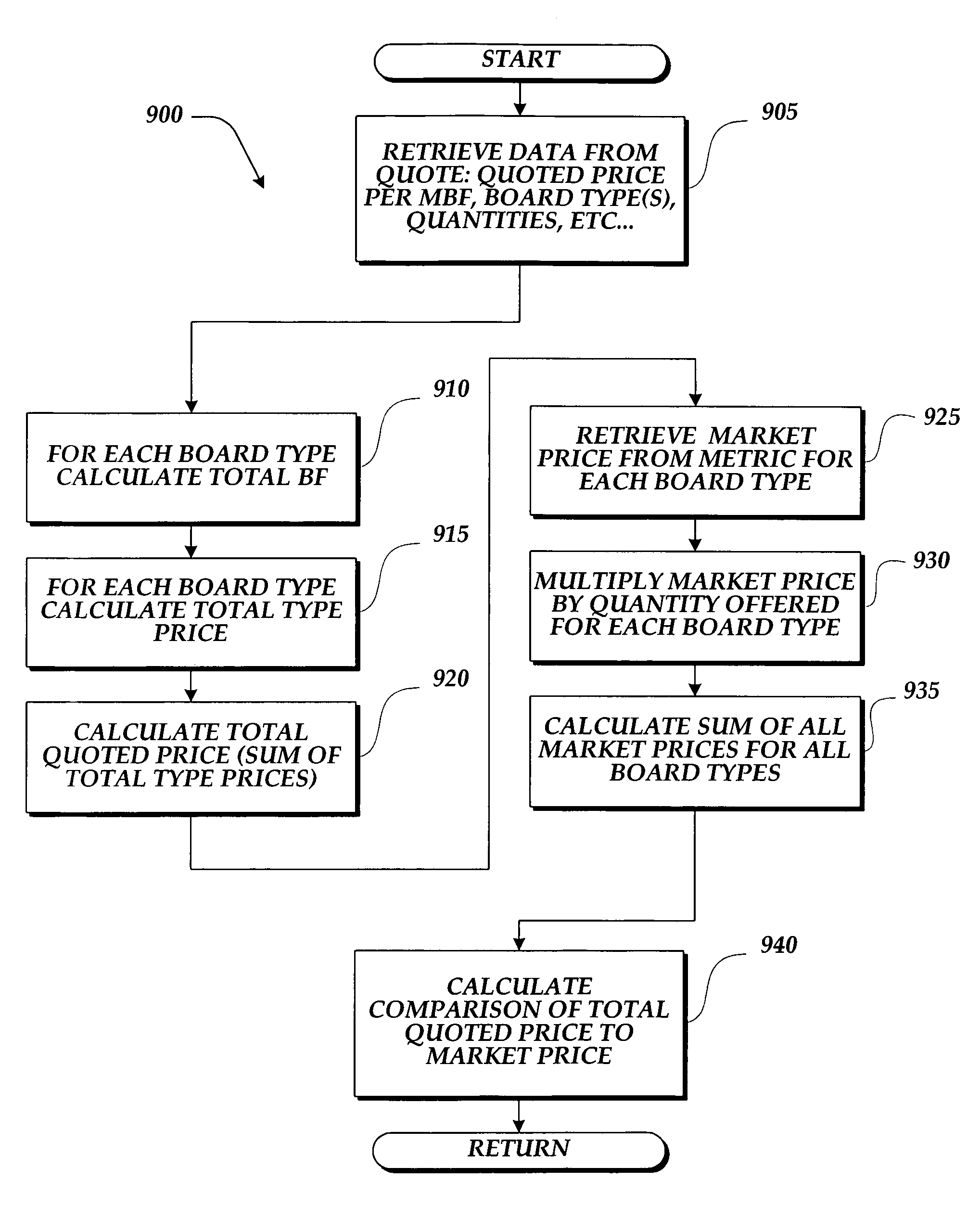
System and method for managing and evaluating network commodities purchasing
InactiveUS7043457B1Easy to compareSpecial service provision for substationMarket predictionsDistributed computingStandardization
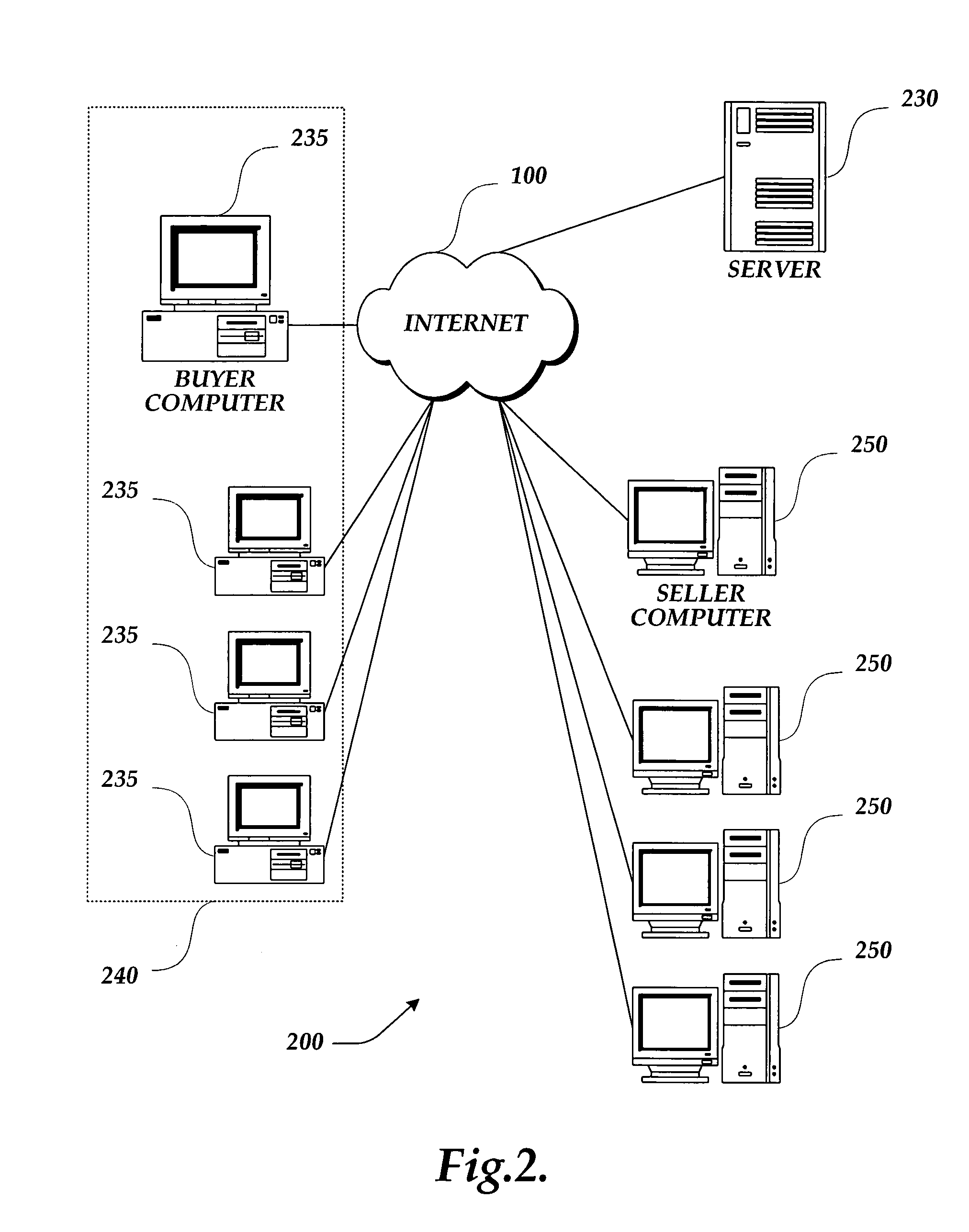
A method and system for managing and evaluating commodities purchasing over a network of distributed computing devices. In one embodiment, the method allows a plurality of buyers to generate one request for quote and, response to the request for quote, receive a quote from plurality of vendors. The system of the present invention provides a price normalization routine that allows buyers to evaluate and compare a normalized price for commodity products having different evaluation parameters. In an arrangement comprising a plurality of computers connected to a network said plurality of computers including at least one server, at least one buyer client computer and a plurality of seller client computers, the method for providing commodities exchange services first provides a web-based browsable display describing at least one commodities exchange service. The system then receives at least one request for quote from the buyer. The system then receives at least one quote from different sellers, wherein each quote may have a different price and quantity listed. The system then compares to one or more selected metrics and normalizes the prices received from the different quotes, thus, allowing the buyer to readily compare the prices of a number of commodity items having inherently different values. In one embodiment, the system of the present invention also provides a method for multi-value cross compilation of sales transactions, iterative quote information, and metric data for purposes of evaluation and strategy analysis.
Owner:BUYMETRICS
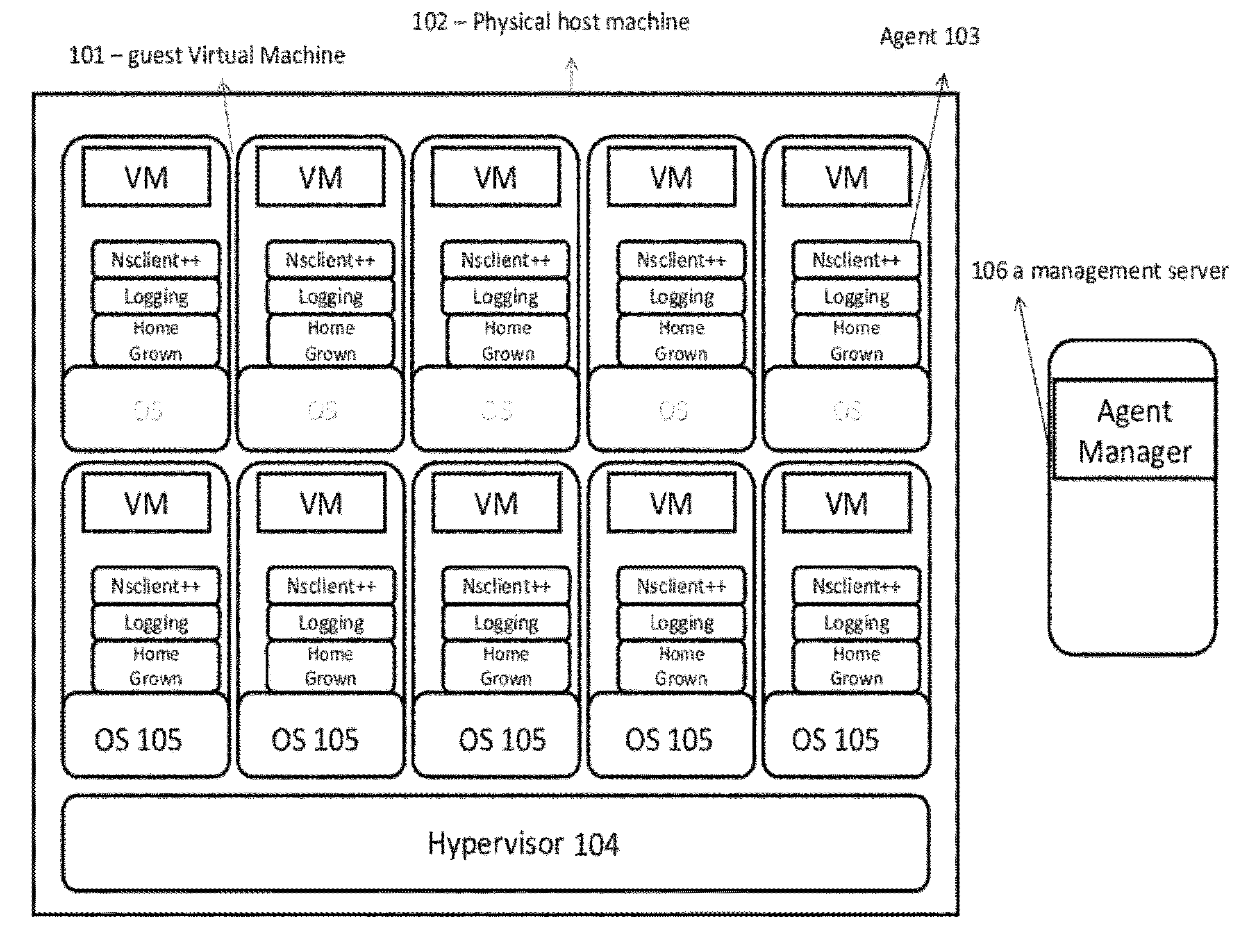
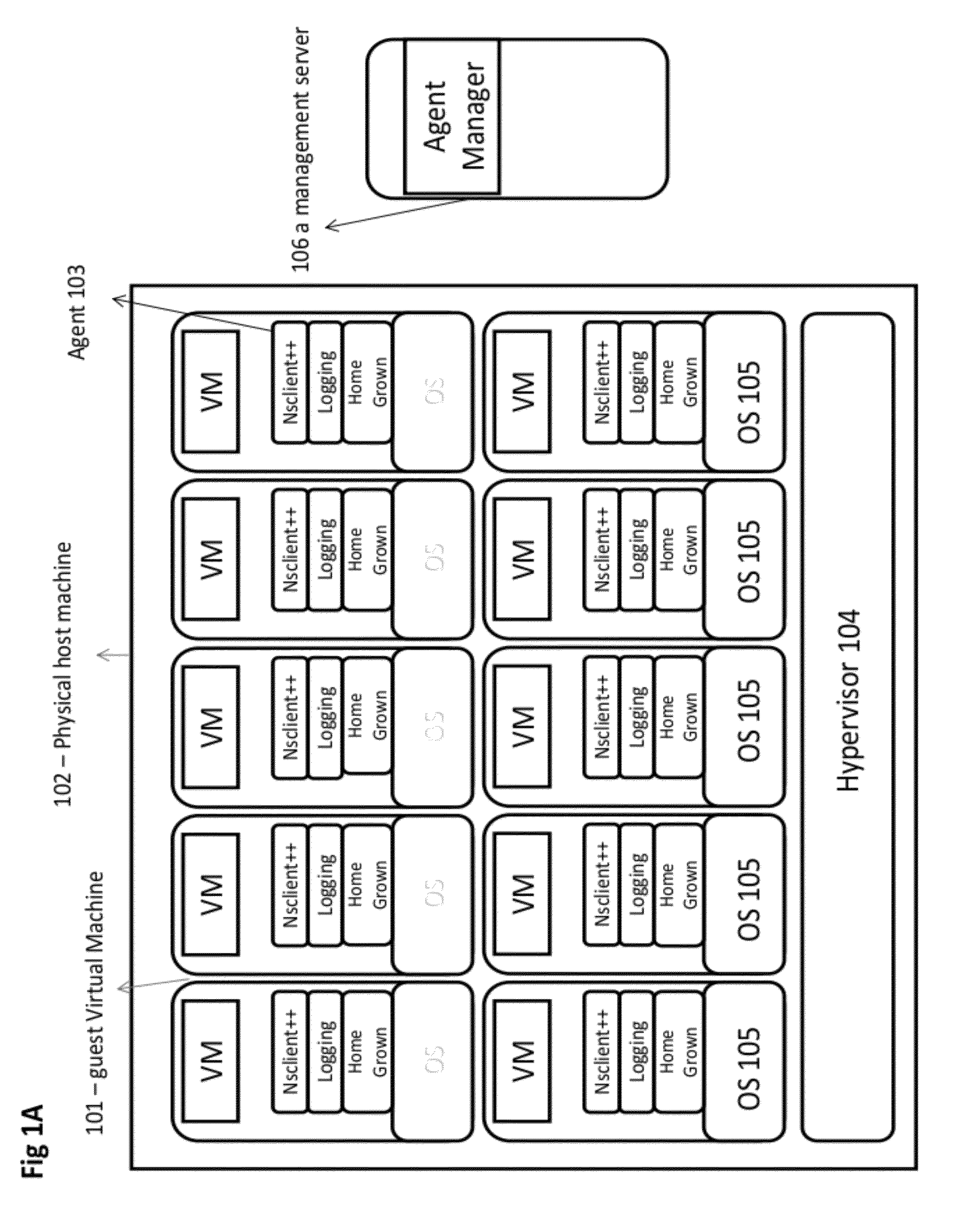
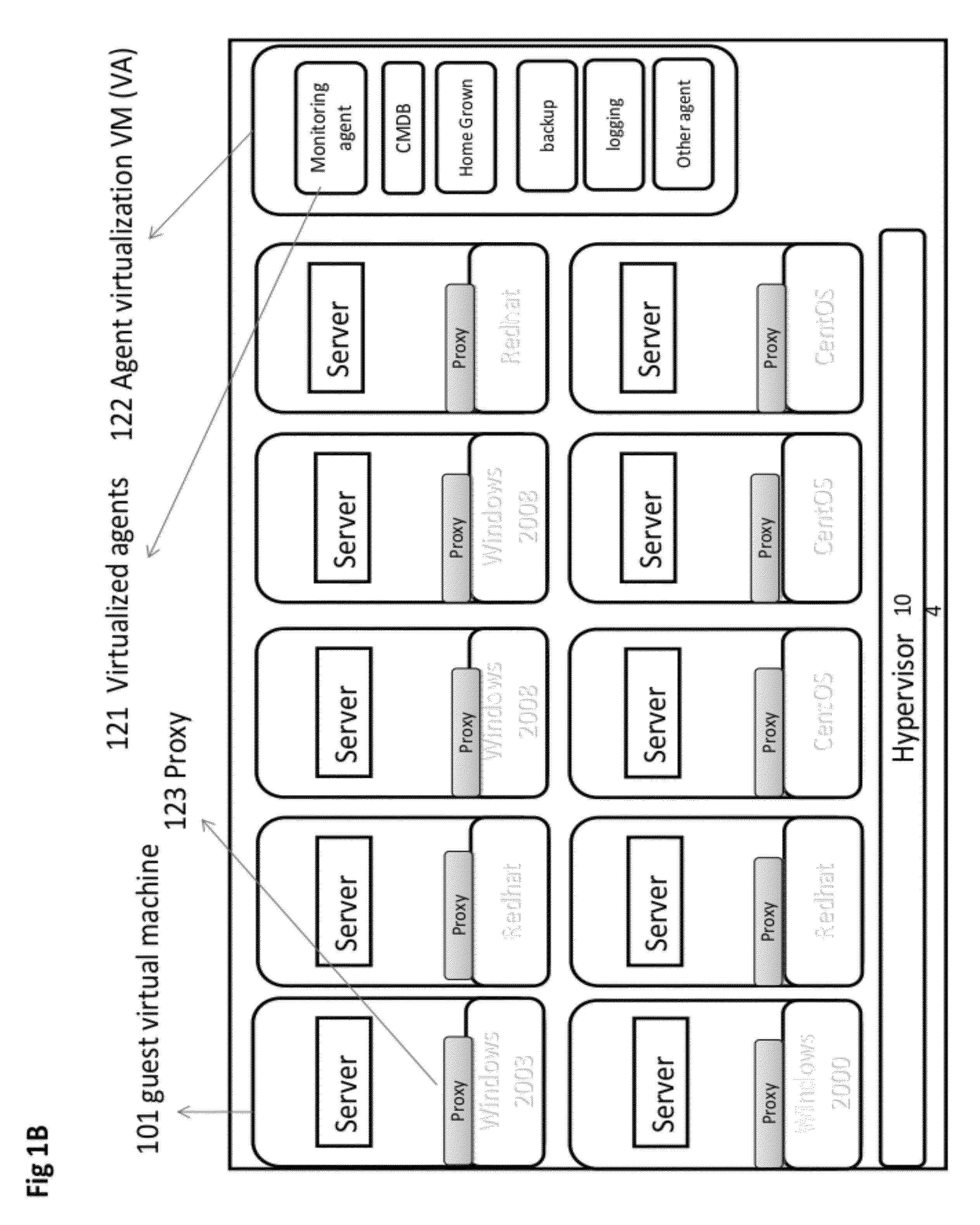
System and method for management of a virtual machine environment
InactiveUS20120066681A1Software simulation/interpretation/emulationMemory systemsHuman–computer interactionCode segment
A system and method for operating an agent. A policy may be generated based on an analysis of a code segment of an agent, analysis of the execution and / or installation of an agent. An interaction with the agent may be intercepted. The interaction may be analyzed according to the policy. A machine for performing an operation related to the interaction may be selected. A proxy on the selected machine may perform the operation and return a result to the agent. In some embodiments, a request to perform a task may be intercepted. A first portion of the task may be performed by an agent and a second portion of the task may be performed by a proxy.
Owner:INTIGUA
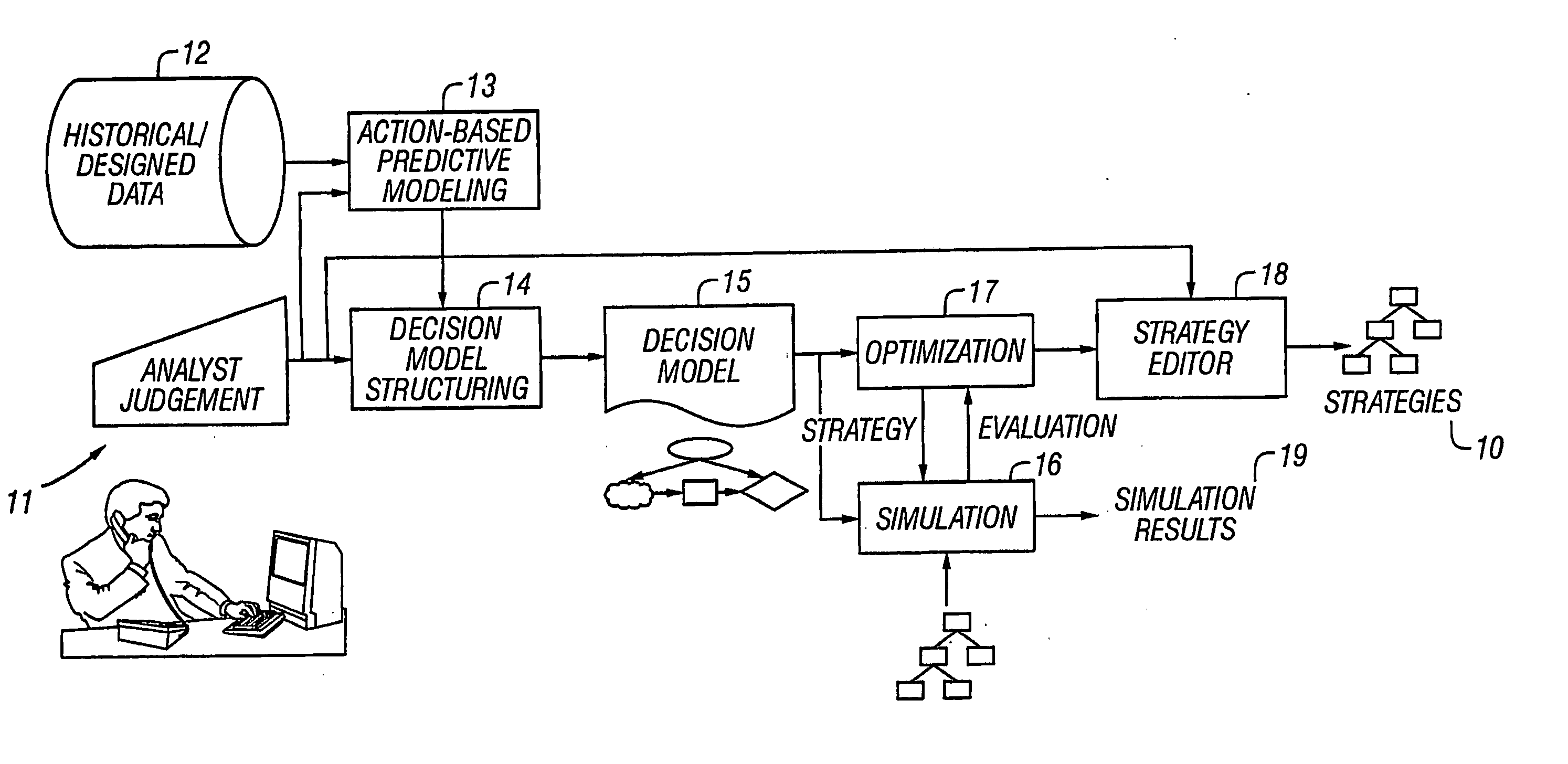
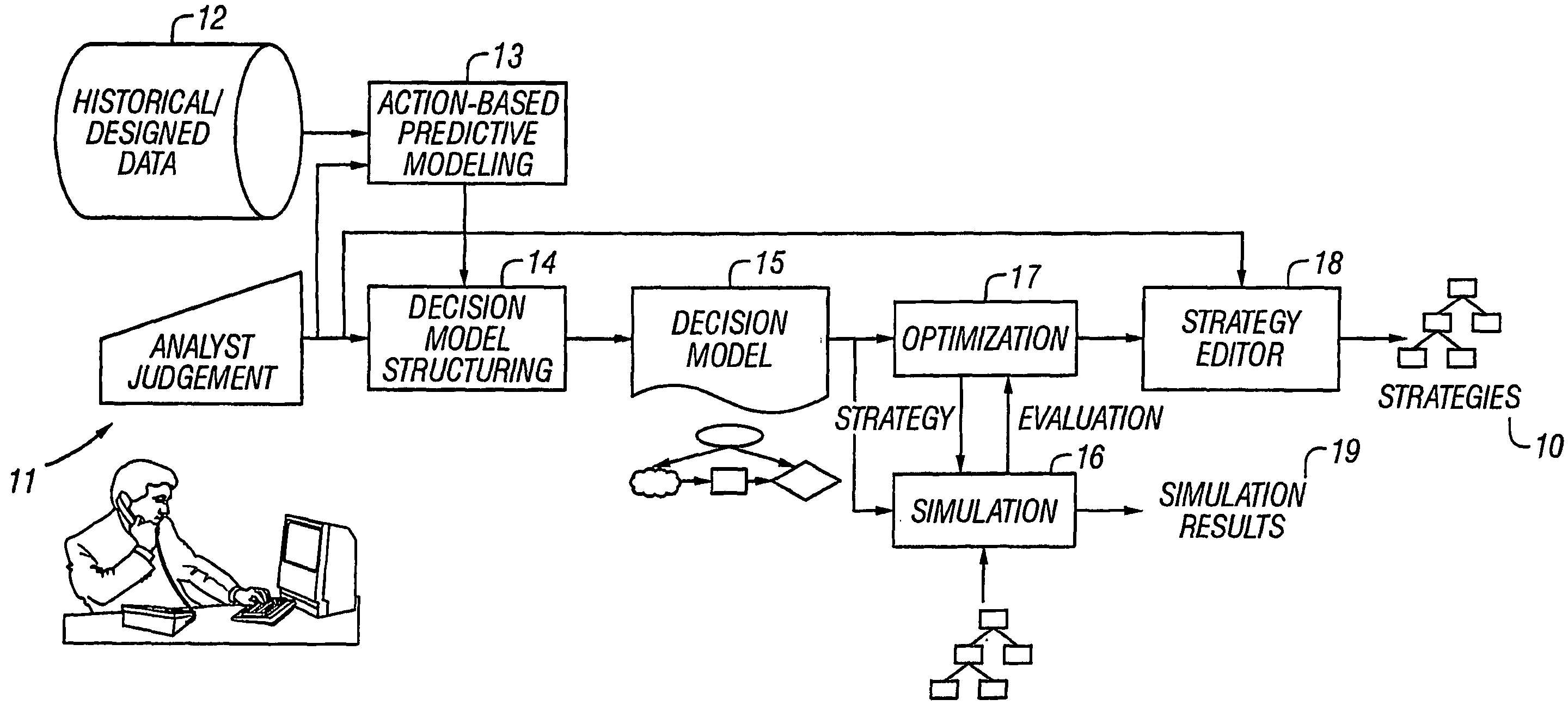
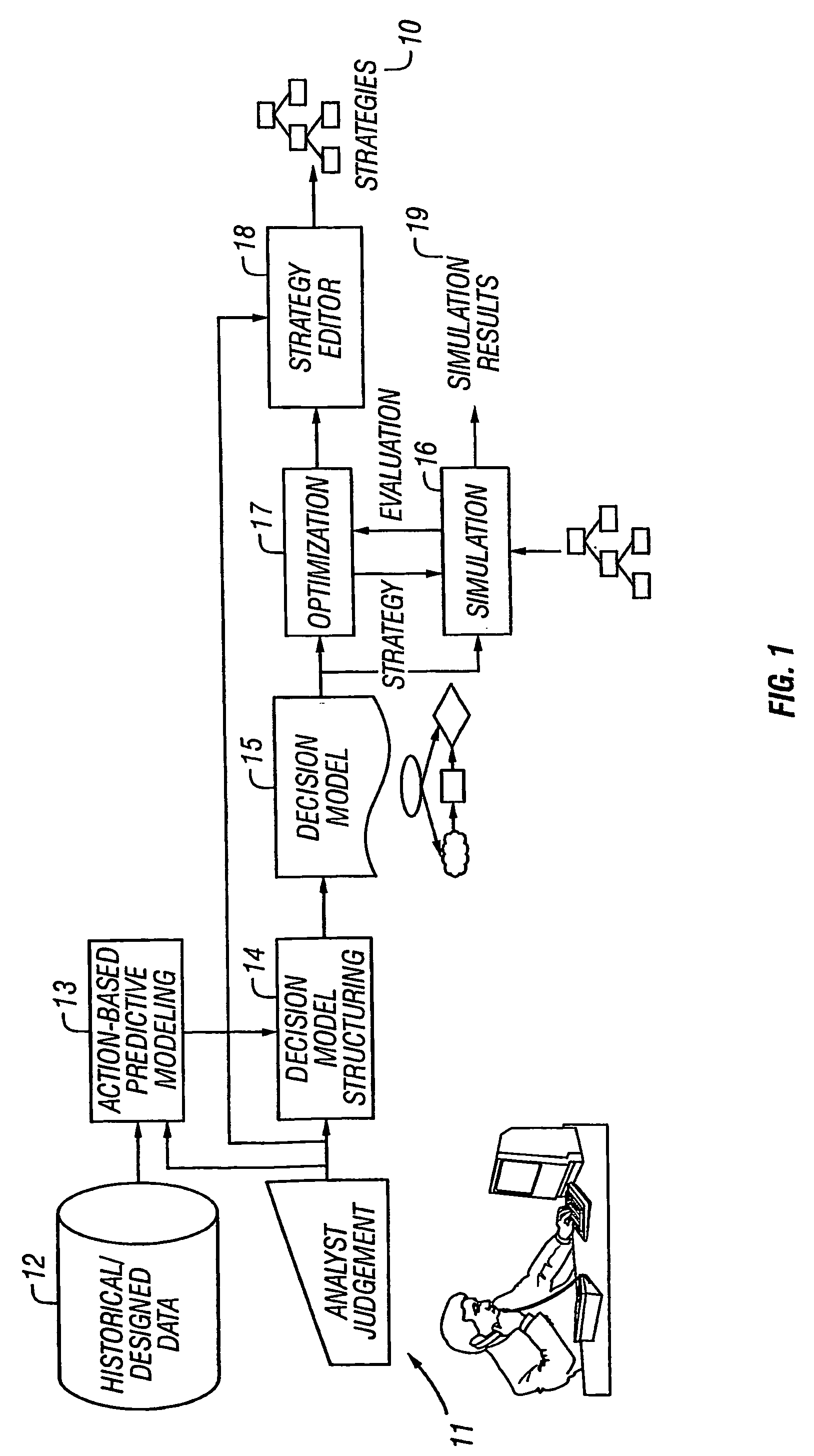
Model-based and data-driven analytic support for strategy development
The invention provides an overall architecture for optimal strategy design using both historical data and human expertise. The presently preferred architecture supports the tasks of strategy design and strategy analysis, and provides extensions to influence diagrams, translation of an influence diagram as a nonlinear optimization problem, and use of induction after optimization to derive decision rules.
Owner:FAIR ISAAC & CO INC
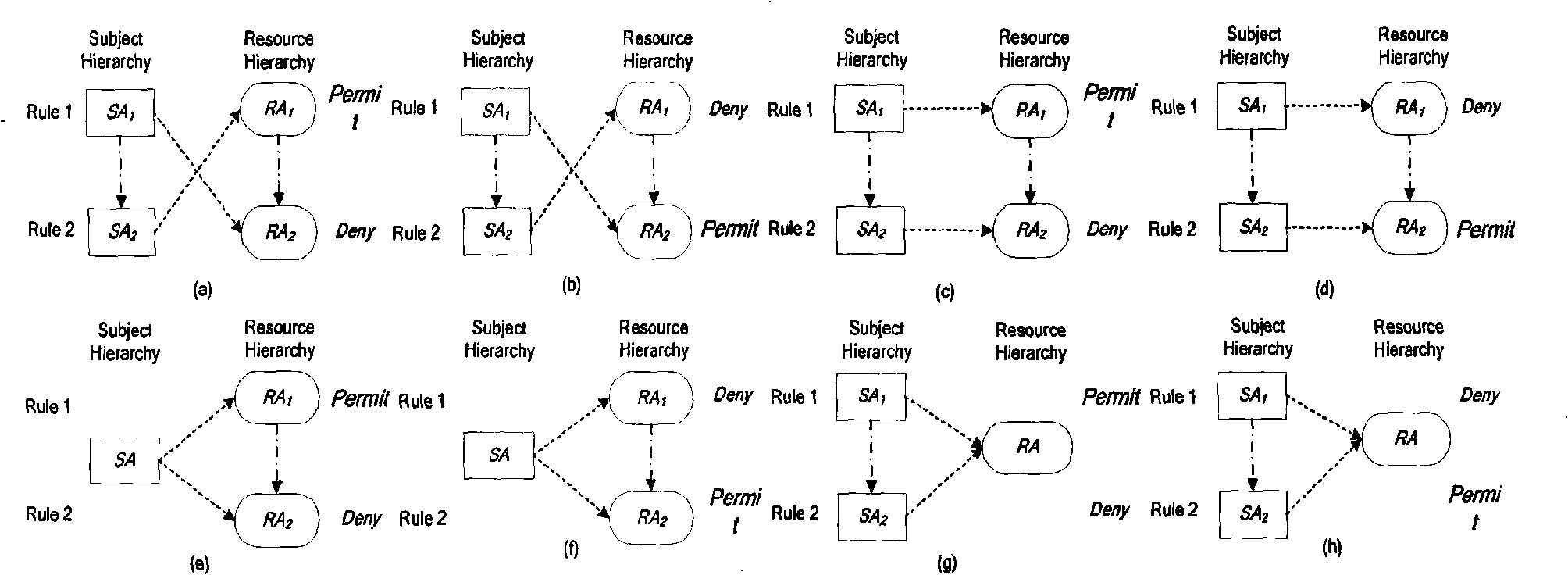
XACML policy rule checking method
InactiveCN101339591AOptimize strategy structureImprove the efficiency of strategy judgmentDigital data authenticationSemantic treeState dependent
The invention provides an XACML strategy rule detecting method, belonging to the field of authorized strategy analysis in information safety. According to the XACML strategy rule, the method has a rule status definition, a rule status correlation definition and a conflict type analysis; on the basis, a strategy index based on a semantic tree is established, a concrete XACML strategy rule detection is carried out and the rule conflict and the rule redundancy are analyzed; the detection method comprises two types: a conflict detection method based on a property level operation correlation and a detection method for other typed conflicts based on the status correlation. In the redundancy analysis, the analysis determining method of the rule redundancy is given respectively in the algorithms of allowing priority, refusing priority and the first-time application dispelling. By adopting the detection method, the strategy manager can precisely locate the rules causing the conflict and the reasons for the conflict; in the redundancy analysis, according to the analysis result, the strategy structure can be optimized and the redundancy rules which has no influence on accessing the determining result can be deleted, therefore, the strategy determining efficiency is improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
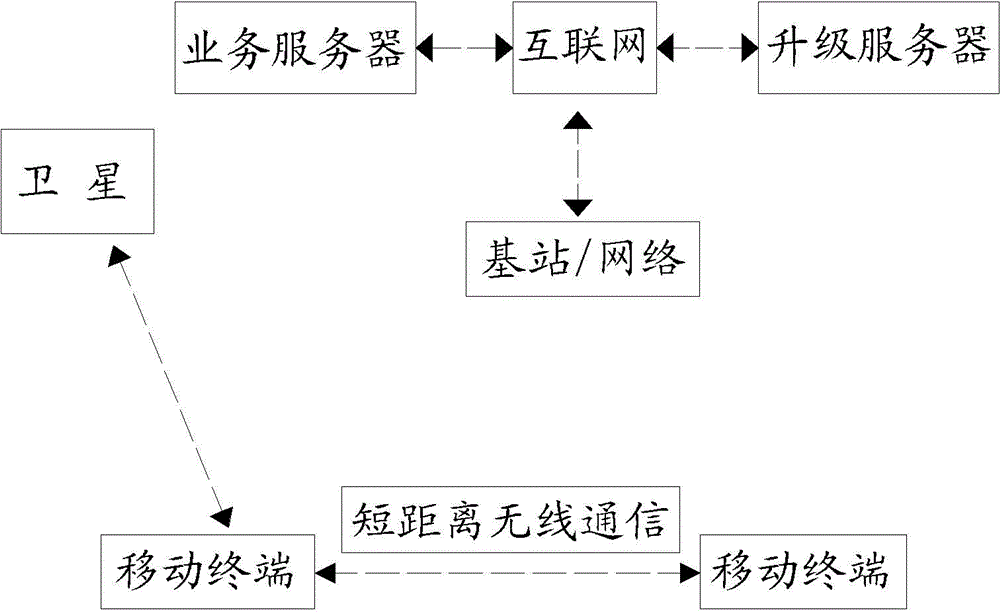
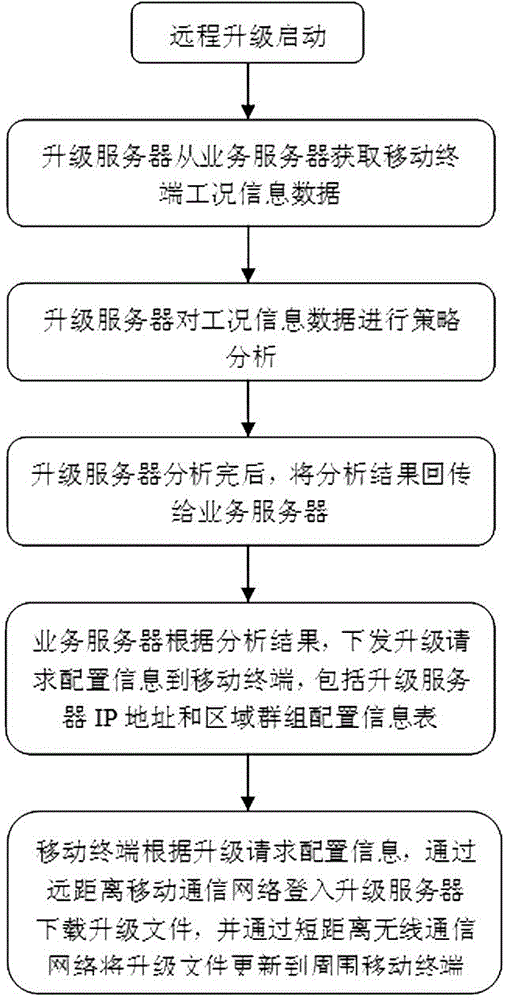
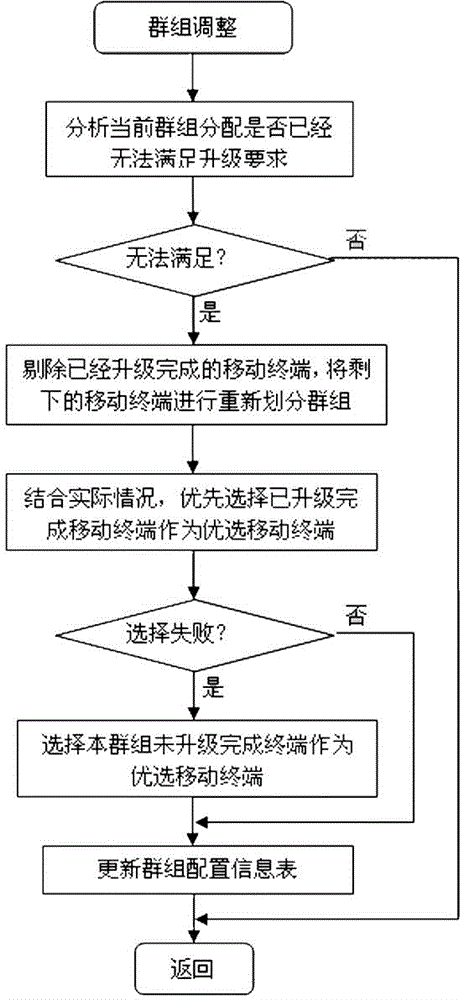
Remote software upgrade method for clustered mobile terminals
ActiveCN103607456AReal-time dynamic adjustment of download strategySolve the problem that cannot be upgraded remotelyProgram loading/initiatingTransmissionShortest distanceComputer terminal
The invention discloses a remote software upgrade method for clustered mobile terminals. The method comprises steps that: step 1, condition information data of the mobile terminals is acquired by an upgrade server in real time from a business server; step 2, dynamic strategy analysis on the condition information data is carried out by the upgrade server; step 3, upgrade request configuration information is issued by the business server to the mobile terminals according to the analysis result of the upgrade server; and step 4, the preferable mobile terminal registers the upgrade server to download an upgrade file according to the upgrade request configuration information, upgrade updating on self software is carried out, and the upgrade file is updated to surrounding mobile terminals through a short distance wireless communication network. According to the method, characteristics of slow speed of long distance mobile communication and fast speed of short distance wireless communication are utilized, real-time dynamic strategy analysis in combination with the condition information data of the mobile terminals is carried out, downloading strategy is dynamically adjusted in real time during a downloading process, and scientific dynamic scheduling and reasonable distribution are realized. The remote software upgrade method is applied to rapid reliable upgrade of mobile terminal software.
Owner:XIAMEN YAXON NETWORKS CO LTD
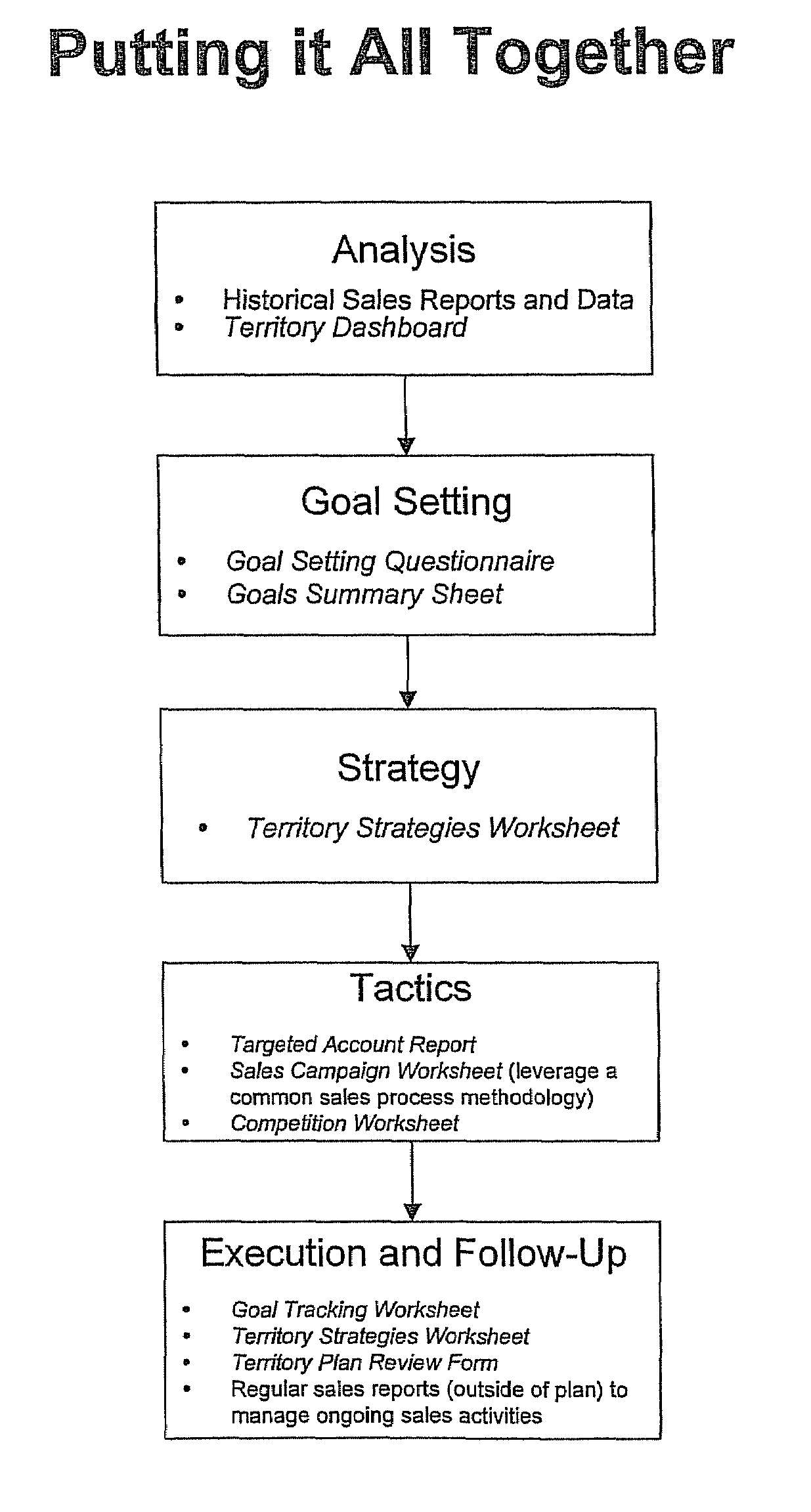
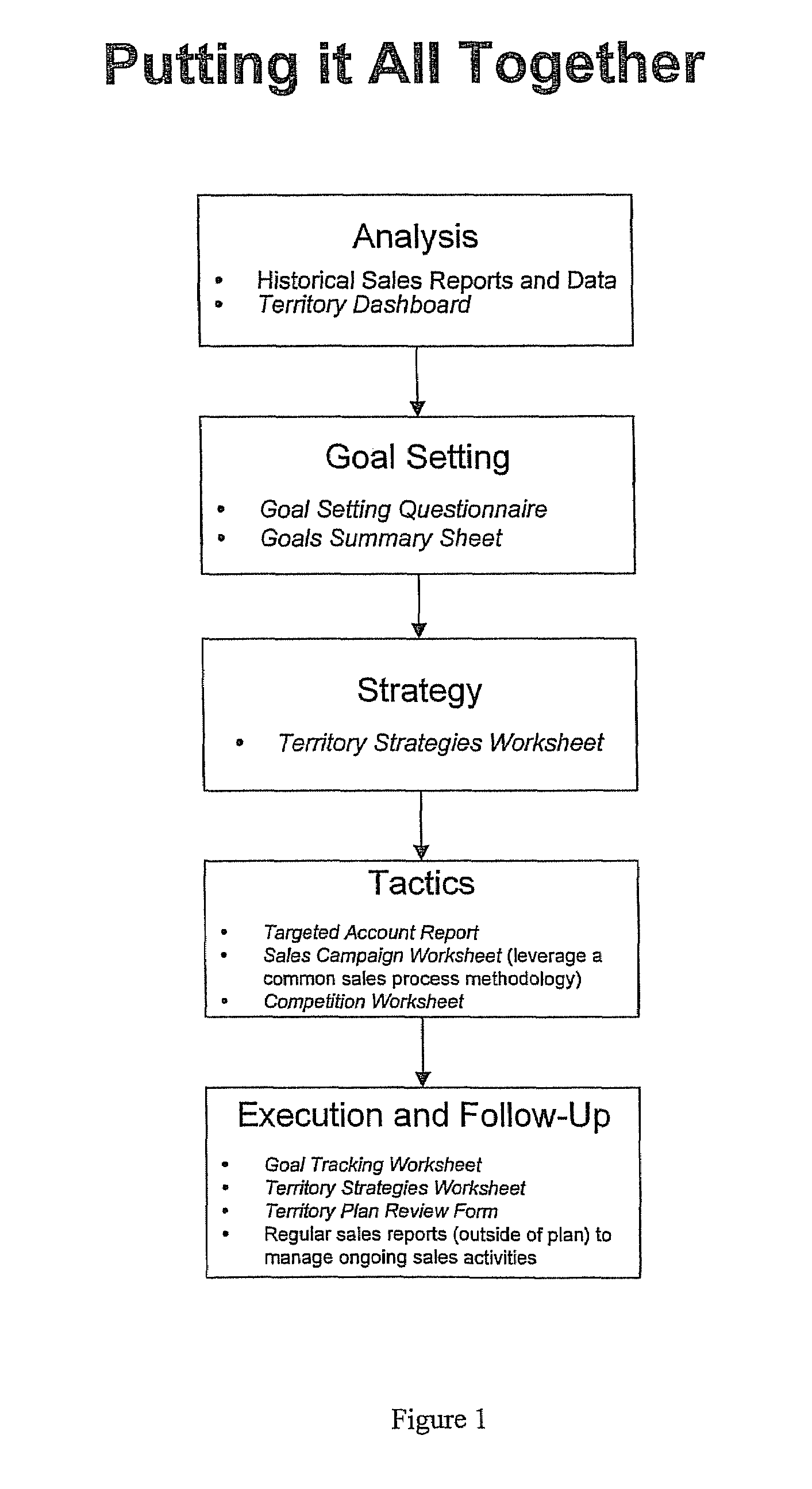
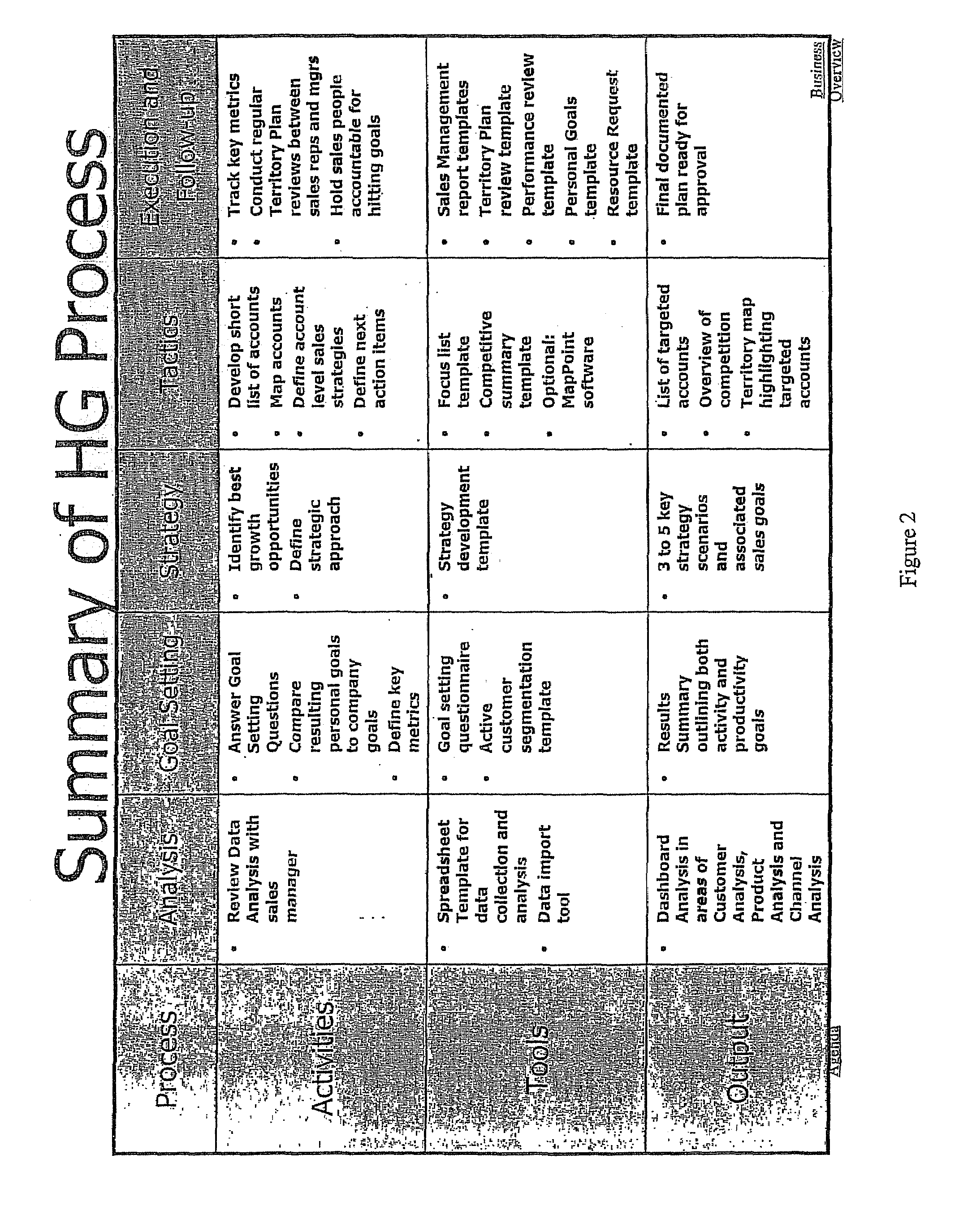
Sales territory planning tool and method
InactiveUS7620564B1Increase productivityImprove sales efficiencySpecial data processing applicationsMarket data gatheringDashboardAction plan
Owner:HARVESTGOLD
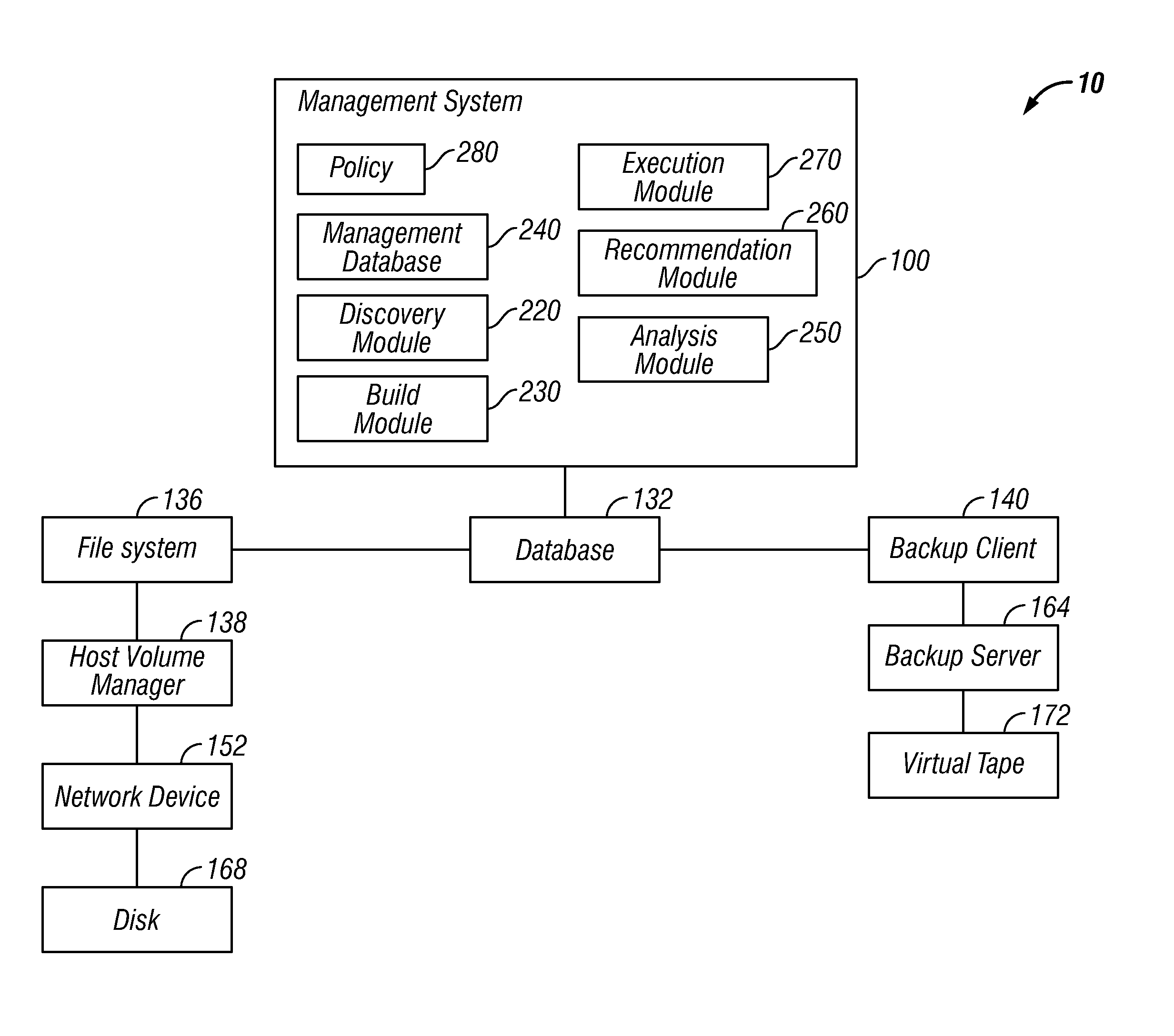
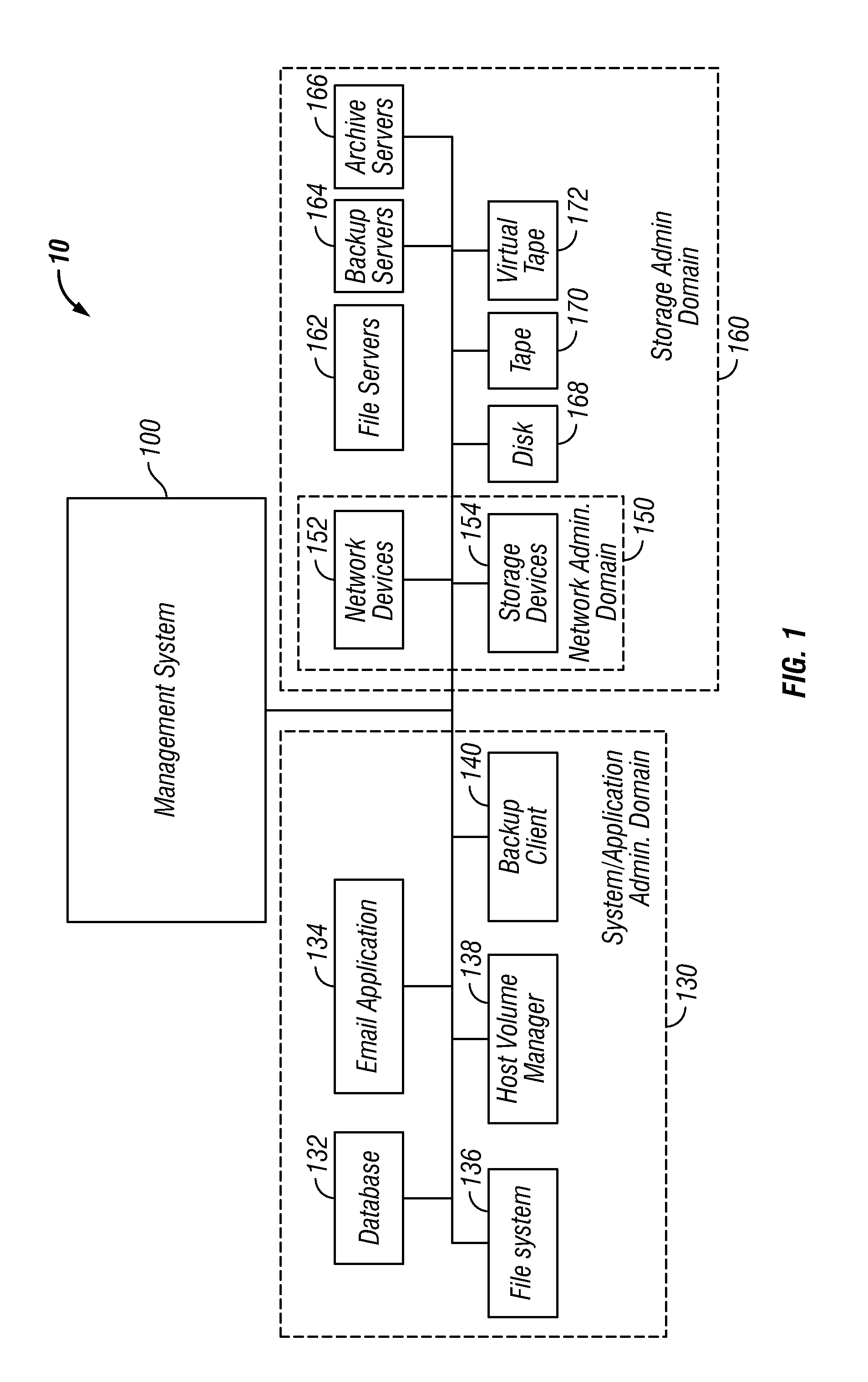
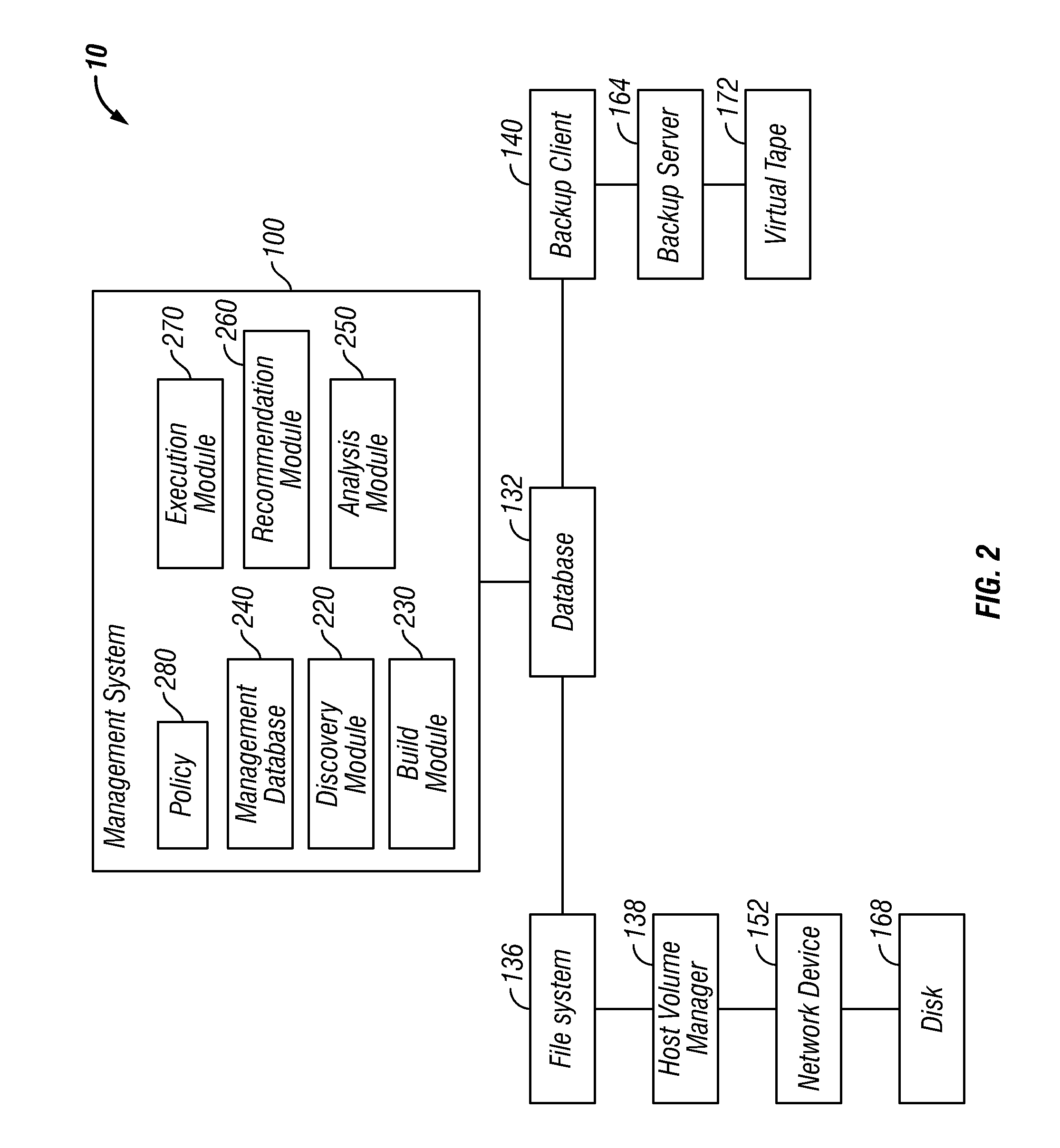
Optimization of a Computing Environment in which Data Management Operations are Performed
InactiveUS20110138154A1Digital data information retrievalDigital computer detailsData managementDatapath
Described are embodiments of an invention for optimizing a computing environment that performs data management operations such as encryption, deduplication and compression. The computing environment includes data components and a management system. The data components operate on data during the lifecycle of the data. The management system identifies all the data components in a data path, how the data components are interconnected, the data management operations performed at each data component, and how many data management operations of each type are performed at each data component. Further, the management system builds a data structure to represent the flow of data through the data path and analyzes the data structure in view of policy. After the analysis, the management system provides recommendations to optimize the computing environment through the reconfiguration of the data management operation configuration and reconfigures the data management operation configuration to optimize the computing environment.
Owner:IBM CORP
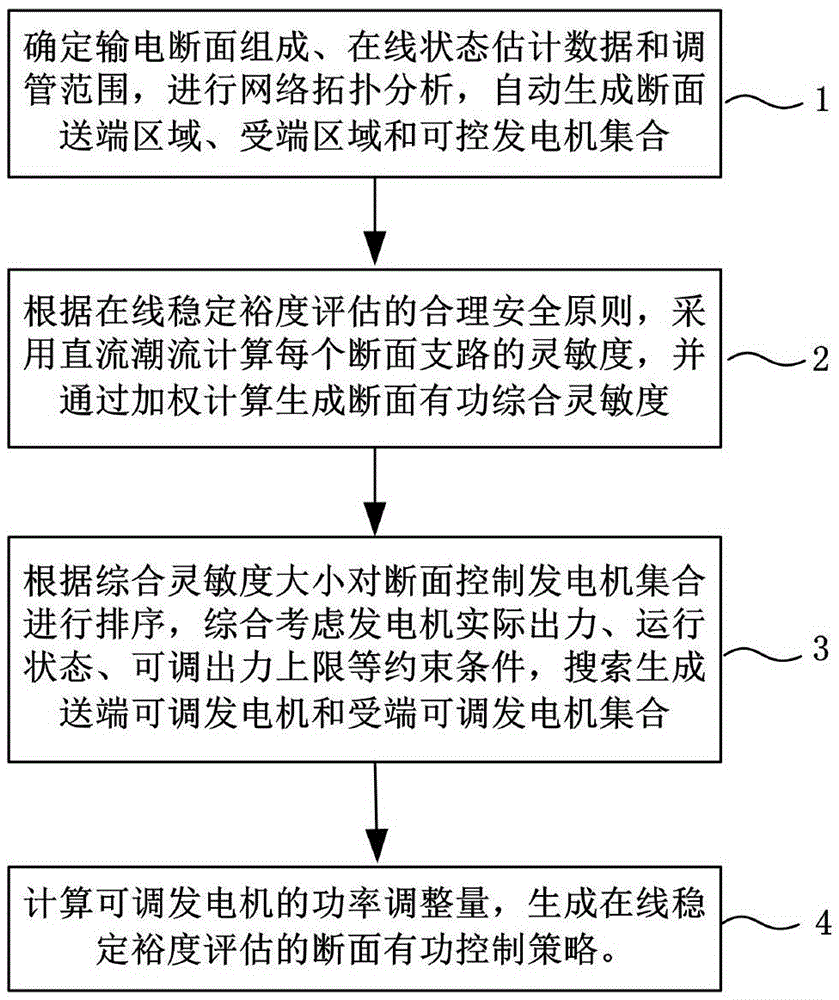
Section active control strategy analysis method for online stability margin evaluation
The invention relates to a section active control strategy analysis method for online stability margin evaluation. The method comprises following steps: determining power distribution section compositions, online state evaluation data and an adjusting and managing range, carrying out network topology analysis, automatically generating section sending end region, section receiving end region and control generator set; calculating the sensitivity of each section branch through using direct current load flow according to online stability margin evaluation rational and safe rules, generating a section active comprehensive sensitivity; screening the section control generator set according to the value of the comprehensive sensitivity, through comprehensively considering the actual output, the operation state and the adjustable output upper limit constraint conditions of a generator, searching to generate a sending end adjustable generator set and a receiving end adjustable generator set; calculating the power adjusting amount of an adjustable generator and generating the section active control strategy for online stability margin evaluation. According to the method of the invention, the problem that the existing online stability margin evaluation functions depend more on dispatching the off-line calculating experiences of specialists and cannot carry out self-adaption to the changes of the operation modes of a power grid is solved.
Owner:CHINA ELECTRIC POWER RES INST +2
Method for realizing event alert and storm-proof policy of monitoring system
The invention provides a method for realizing an event alert and a storm-proof policy of a monitoring system. The weight grading of a final event is realized by formulating a set of service policy, and a storm is prevented by using alert merging and a monitoring policy rule. The method comprises the following steps of: (1) collecting the data of specific indexes by using a data collector; (2) analyzing the collected data through the service policy to form different grades of alert events; (3) carrying out event merging in a cache in order to ensure that the alert events are not generated repeatedly; and (4) analyzing the alert information subjected to alert merging through a health policy to form a final required event, and sending the final required event to an event flow for processing.
Owner:INSPUR SOFTWARE CO LTD
Method of testing online recommender system
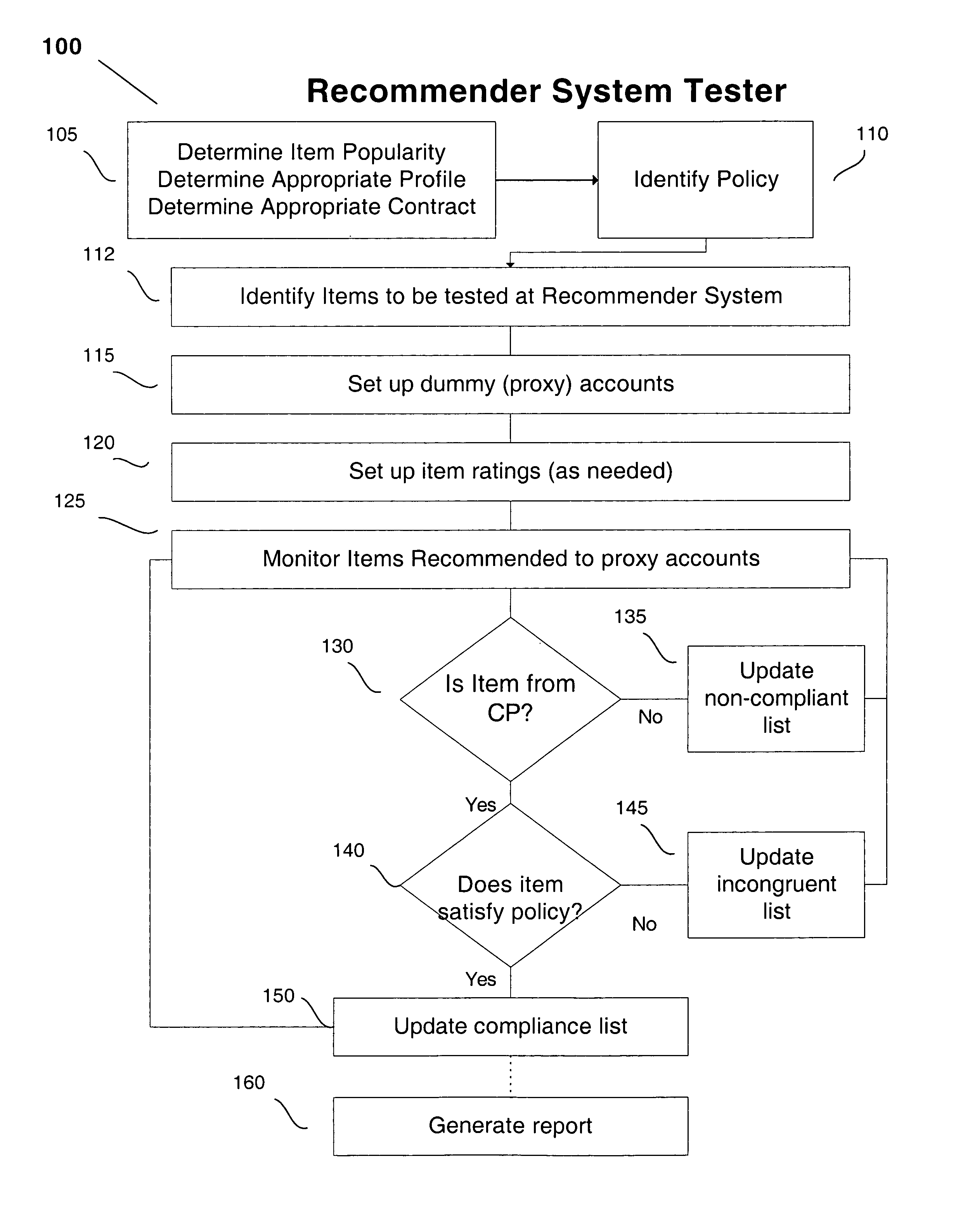
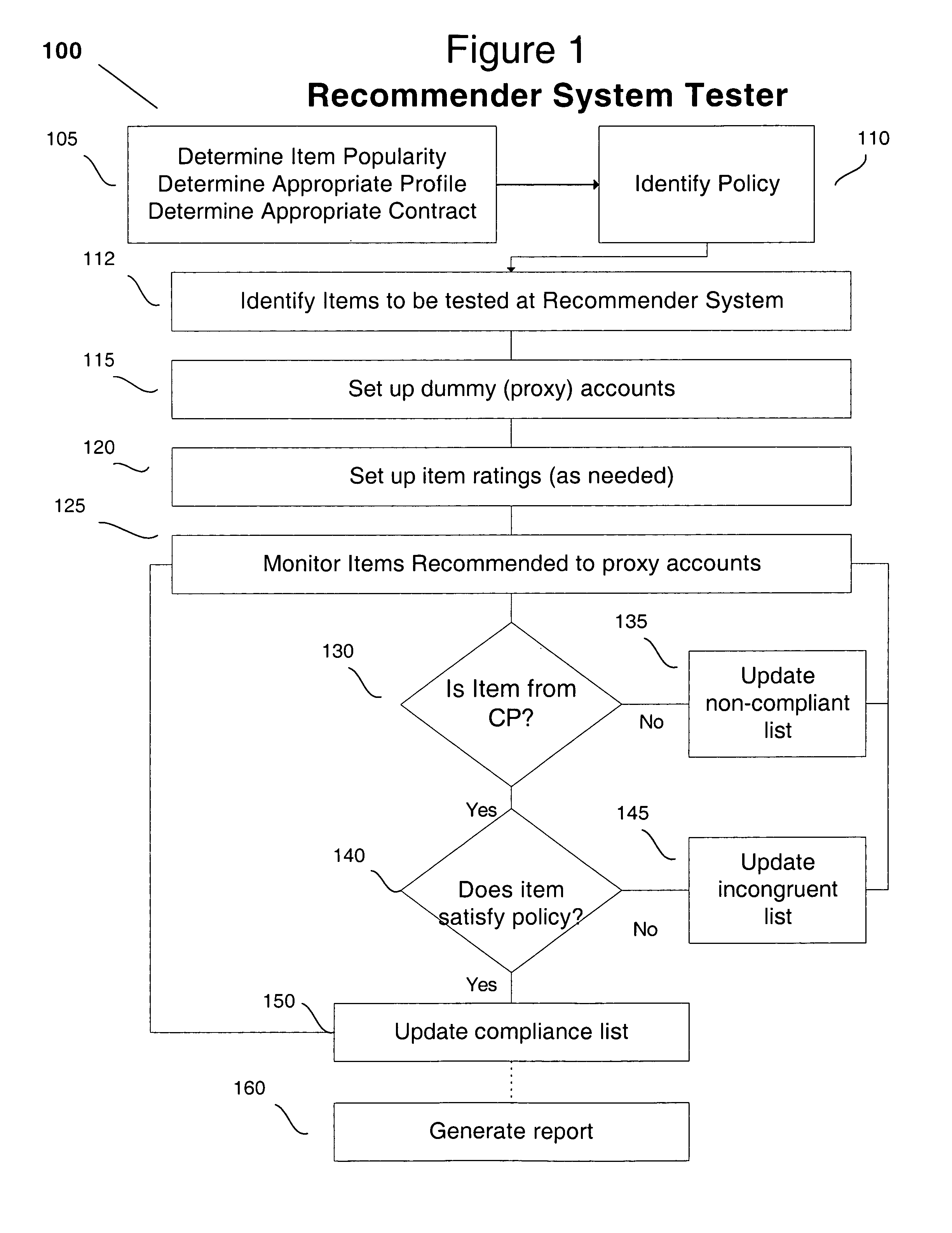
ActiveUS8630960B2Determine delayDetermine latencyMarketingSpecial data processing applicationsService provisionDependability
A recommender system can be analyzed to determine various performance characteristics of an online content service provider. The recommender system is analyzed using a predetermined policy, to determine if it satisfies such policy, and / or has other measurable intended and / or unintended biases. The policy can include such parameters as whether a particular profile is presented with certain particular types of items by the recommender system. The reliability of search engines can also be tested using a similar approach.
Owner:JOHN NICHOLAS & KRISTIN GROSS
Alarm monitoring strategy analysis method based on data mining technology
InactiveCN106603317APerfect mining processImprove integrityData miningData switching networksData dredgingNetwork structure
The invention discloses an alarm monitoring strategy analysis method based on a data mining technology and belongs to the field of communication alarm monitoring. Through data mining, valuable knowledge can be extracted from enormous fuzzy data comprising noise, alarm data of a communication network is enormous and dynamic and is rich in knowledge, the alarm data of the communication network is mined without reliance on a network structure, and dynamic change of the network can be adapted. Data mining comprises the following steps: obtaining and preprocessing the alarm data; converting the obtained alarm data into a set of transaction items, and carrying out frequent item set data mining by use of a correlation algorithm; and through combination with actual application, performing compression, merging and classification processing on a result of a frequent item set. According to the invention, through merging and converting alarms, the multiple alarms are merged into one alarm with a larger information amount so as to replace the multiple alarms, and assistance is provided for network management personnel in analyzing fault information and rapidly positioning faults.
Owner:SHANDONG INSPUR COMML SYST CO LTD
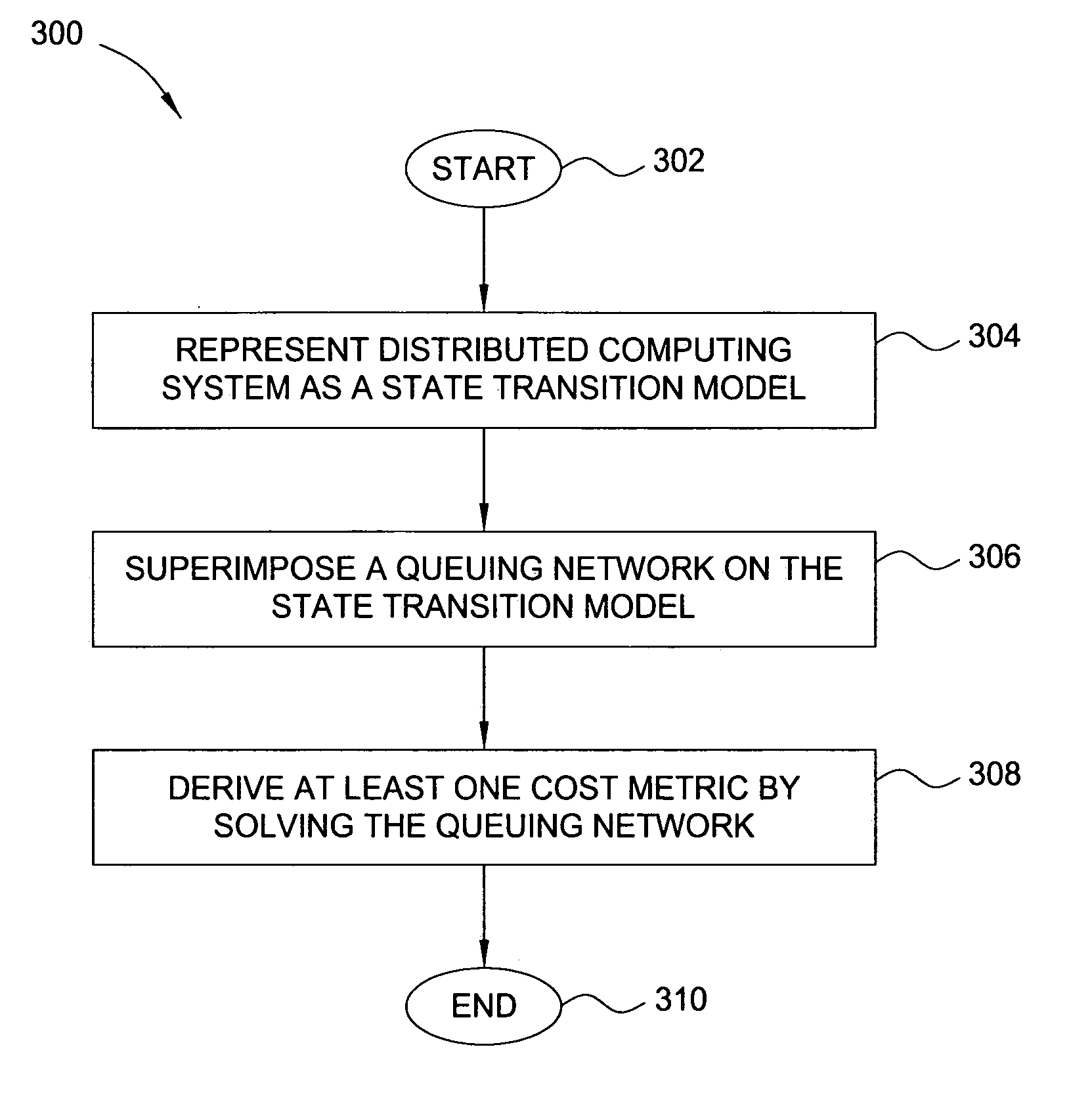
Method and apparatus for performance and policy analysis in distributed computing systems
One embodiment of the present method and apparatus for performance and policy analysis in distributed computing systems includes representing a distributed computing system as a state transition model. A queuing network is then superimposed upon the state transition model, and the effects of one or more policies on the distributed computing system performance are identified in accordance with a solution to the queuing network.
Owner:IBM CORP
System and method for the automatic evaluation of existing security policies and automatic creation of new security policies
InactiveUS20080201760A1Preventing unnecessary authorization requirementComputer security arrangementsSpecific program execution arrangementsRunning timeSecurity policy
Owner:IBM CORP
Software defined network cross-domain security agent method and software defined network cross-domain security agent system
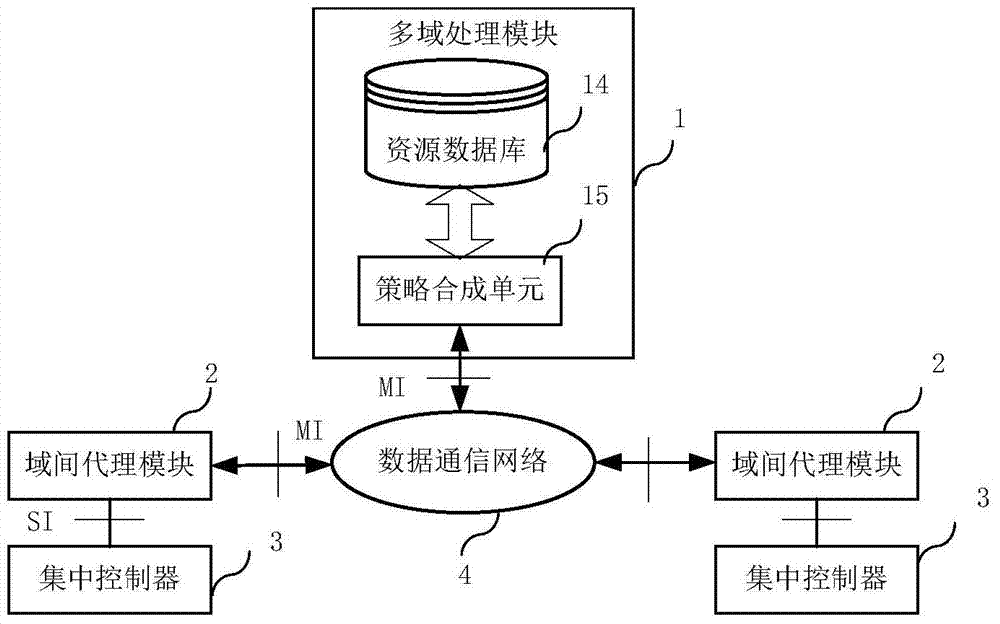
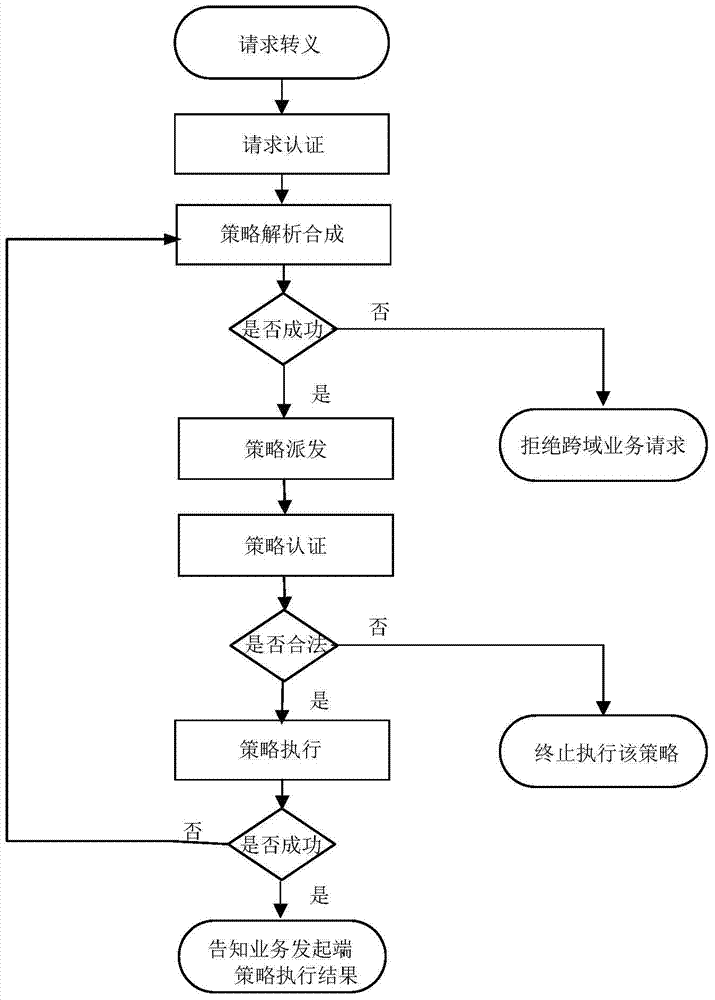
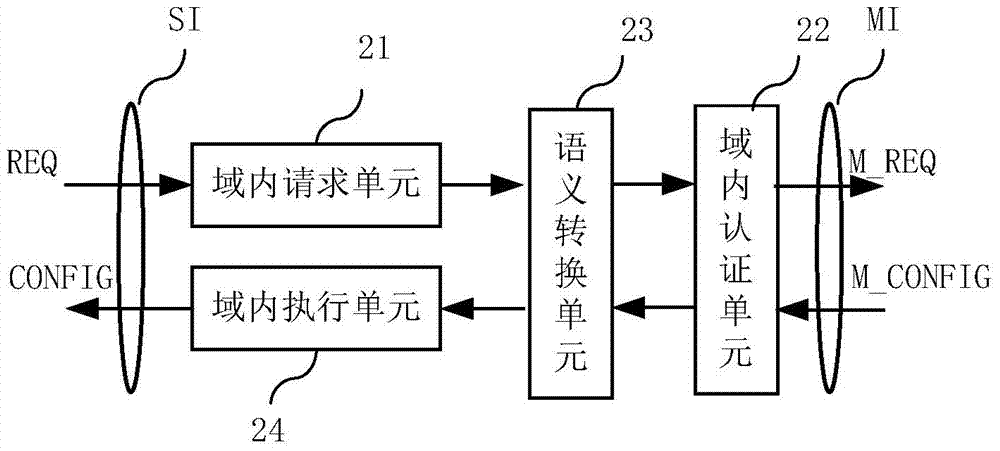
ActiveCN104243496ASimplify the interaction processIntegrated reductionTransmissionStrategy executionSemantic translation
The invention provides a software defined network cross-domain security agent method and a software defined network cross-domain security agent system. Unified access control and management are performed on cross-domain shared resources, security policy conflict is eliminated, and strategy synthetic efficiency is improved. The software defined network cross-domain security agent system comprises at least two integrated controllers, at least one multi-domain processing module and at least two inter-domain agent modules, wherein the inter-domain agent modules transmit cross-domain business requests to the multi-domain processing modules after performing semantic translation; each multi-domain processing module comprises a resource database and a strategy synthesis unit; and after the strategy synthesis units receive the cross-domain business requests, the resource databases are queried, the strategy synthesis is carried out, and cross-domain strategy configuration commands are transmitted to the inter-domain agent modules. The software defined network cross-domain security agent method comprises the following steps of transferred meaning requesting, authentication requesting, strategy analysis and synthesis, strategy distribution, strategy authentication, strategy execution and the like. By the software defined network cross-domain security agent method and the software defined network cross-domain security agent system, information exchange of a heterogeneous network is simplified, information integration and synchronization difficulty of the heterogeneous network are reduced, resource scheduling safety is guaranteed, multi-domain resource sharing is realized, and business load of the centralized controllers in various domains can be adjusted.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and system for issuing gray level
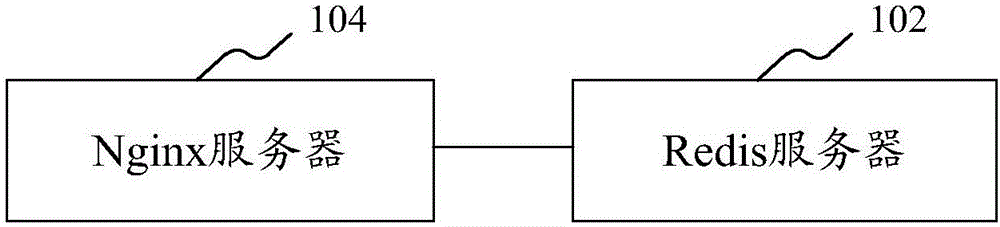
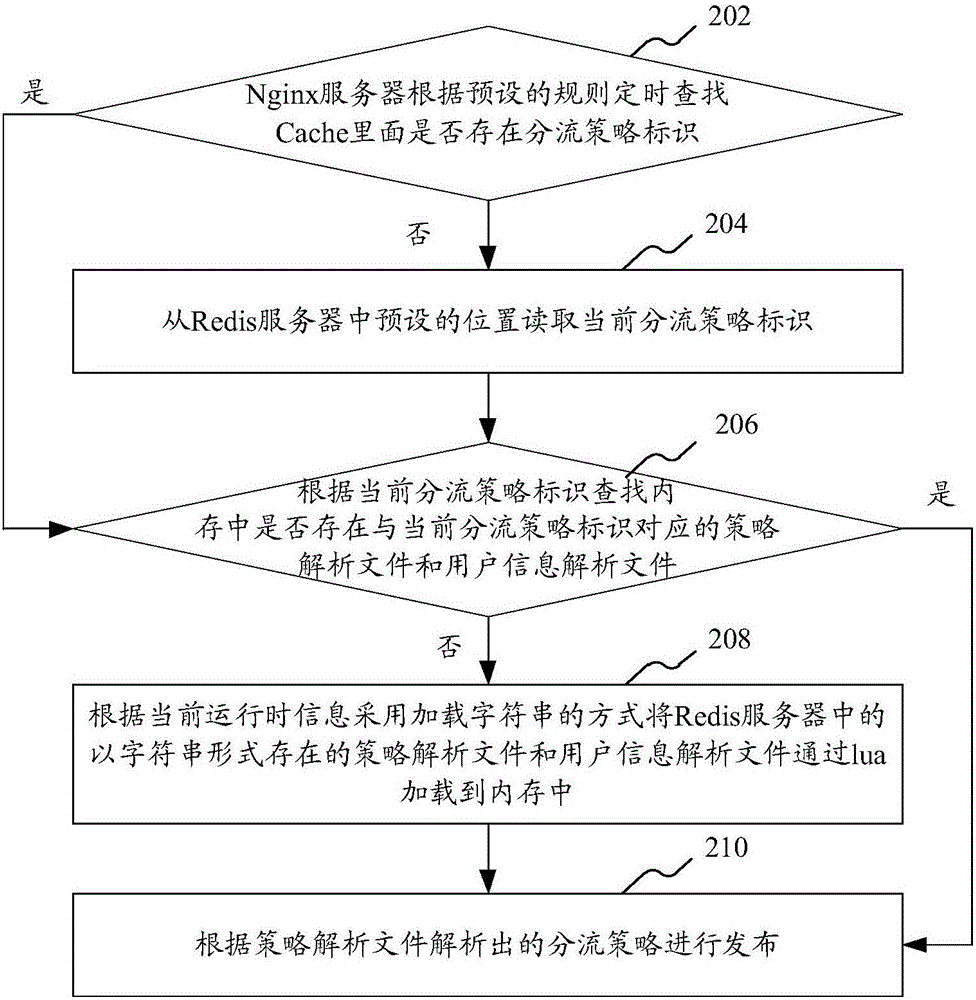
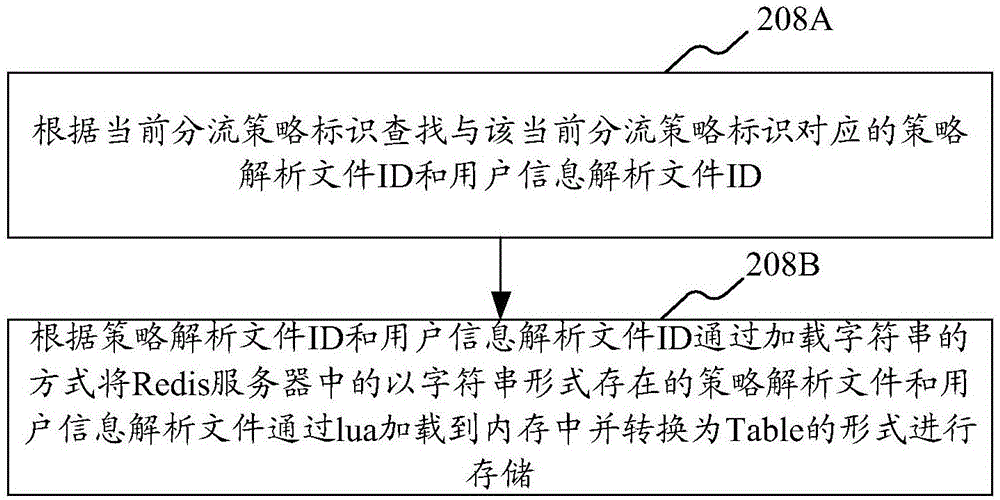
ActiveCN106775859AEasy to operateShorten the timeVersion controlProgram loading/initiatingGray levelOperating system
The invention provides a system for issuing a gray level. The system comprises a Redis server and an Nginx server, wherein the Nginx server is used for checking if a shunt strategy identity exists in Cache; if the shunt strategy identity does not exist, the Nginx server is capable of reading a present shunt strategy identity from a preset position in the Redis server and checking if a strategy analysis file and a user information analysis file corresponding to the present shunt strategy identity exist in a memory according to the present shunt strategy identity; and if the strategy analysis file and the user information analysis file do not exist, the Nginx server is capable of loading the strategy analysis file and the user information analysis file existing in a form of character string in the Redis server into the memory through lua in the manner of loading the character string according to the present shunt strategy identity and then issuing according to the shunt strategy analyzed by the strategy analysis file. In the process, when a new shunt strategy is added, the reload or the restarting of the Nginx server is not required. Besides, the invention also provides a method for issuing the gray level.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
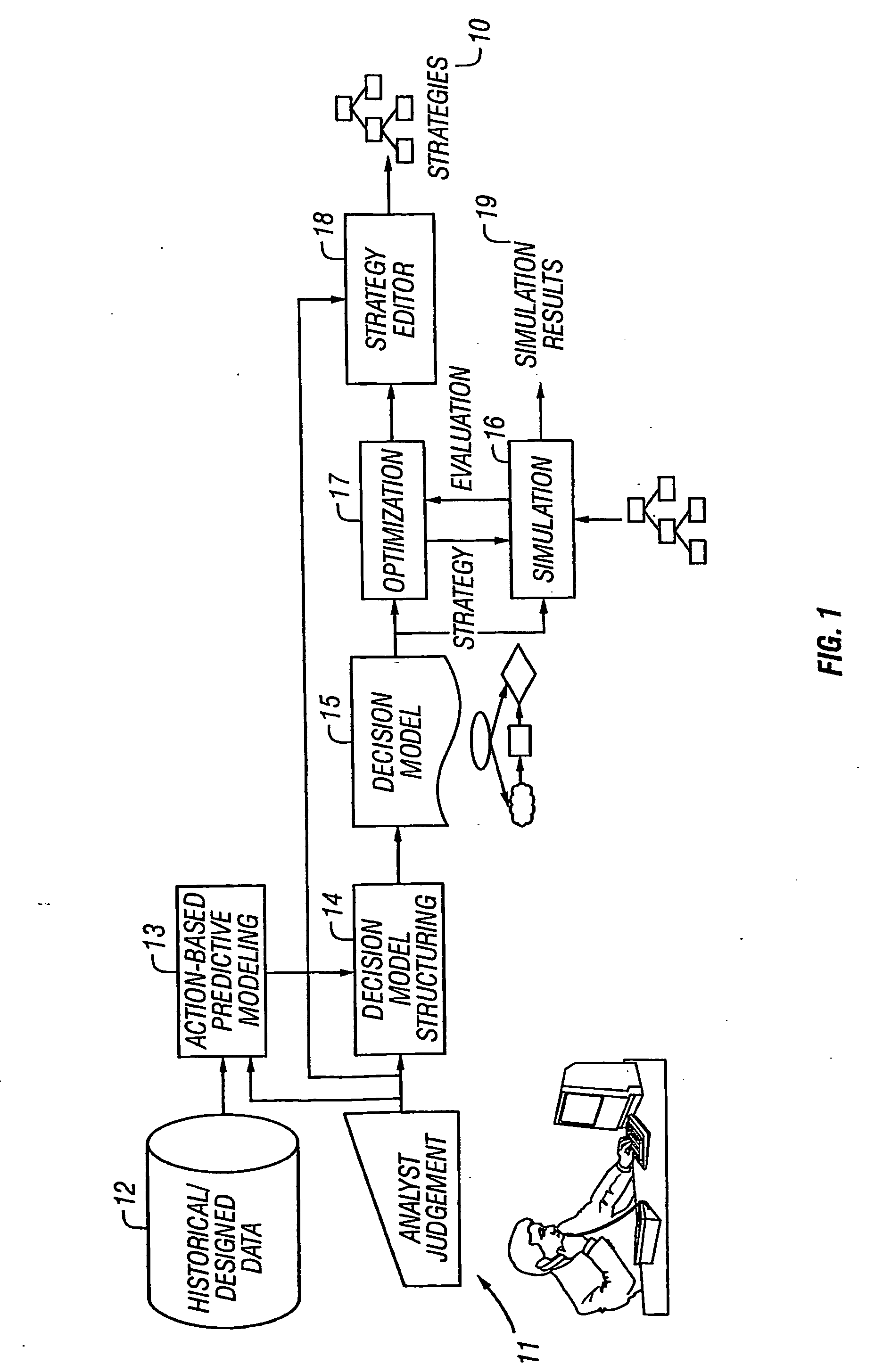
Model-based and data-driven analytic support for strategy development
The invention provides an overall architecture for optimal strategy design using both historical data and human expertise. The presently preferred architecture supports the tasks of strategy design and strategy analysis, and provides extensions to influence diagrams, translation of an influence diagram as a nonlinear optimization problem, and use of induction after optimization to derive decision rules.
Owner:FAIR ISAAC & CO INC
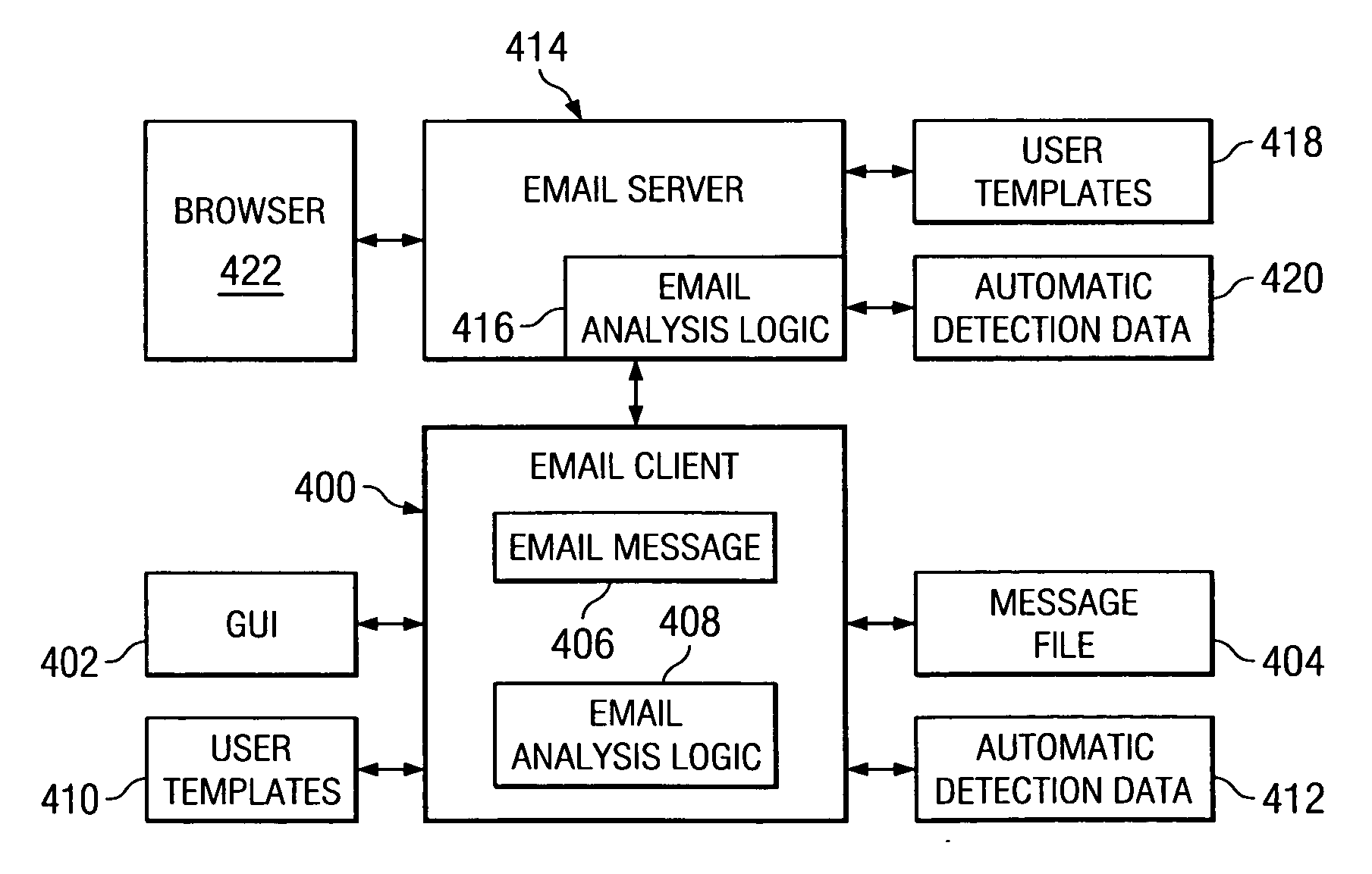
Method and apparatus for determining whether an email message is ready for transmission
A computer implemented method, apparatus, and computer usable program code to analyze an email message using a policy to form a result in response to detecting a request to send an email message. A determination is made as to whether the result indicates that the email message is complete. An alert is generated if a determination is present that indicates that the email message is incomplete.
Owner:MACHINES CORP INT BUSINESS
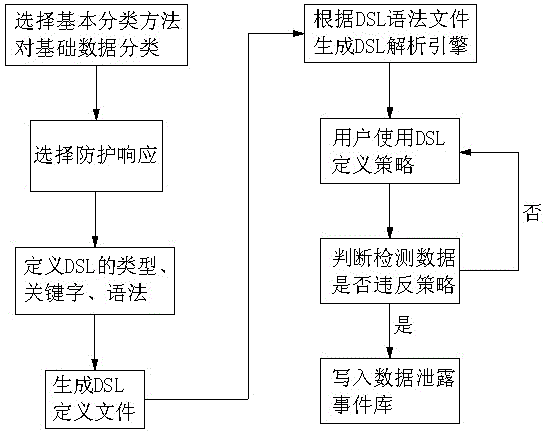
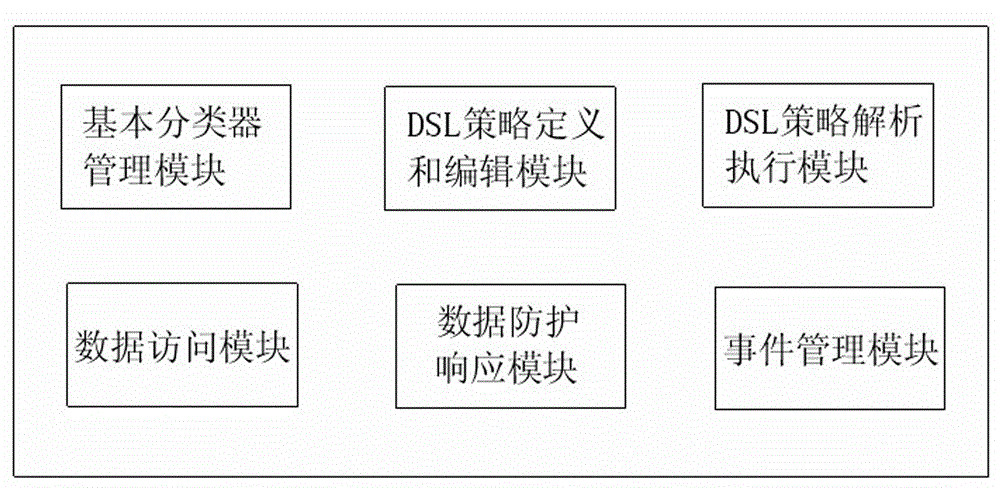
Data classification based data leakage prevention method and system
InactiveCN103336927AAccurate Data Leakage PreventionDigital data protectionStatistical classificationData access
The invention relates to a data classification based data leakage prevention method and system, which can further improve the data leakage prevention effect. The data classification based data leakage prevention method comprises the steps as follows: A, designing a basic data classifier, B, defining various elements of DSL (domain specific languages) to form a data leakage strategy library, C, detecting input data via the DSL strategy library, executing defined response in the strategy, and writing time which violates the strategy into a data leakage event database, D, obtaining data, E, executing defined corresponding operation on the violated data, and F, performing statistical classification on the violated data leakage events, and displaying at a client. The data classification based data leakage prevention system comprises a basic classifier management module, a DSL strategy defining and editing module, a DSL strategy analysis execution module, a data access module, a data protection response module and an event management module.
Owner:HANGZHOU SHIPING INFORMATION & TECH
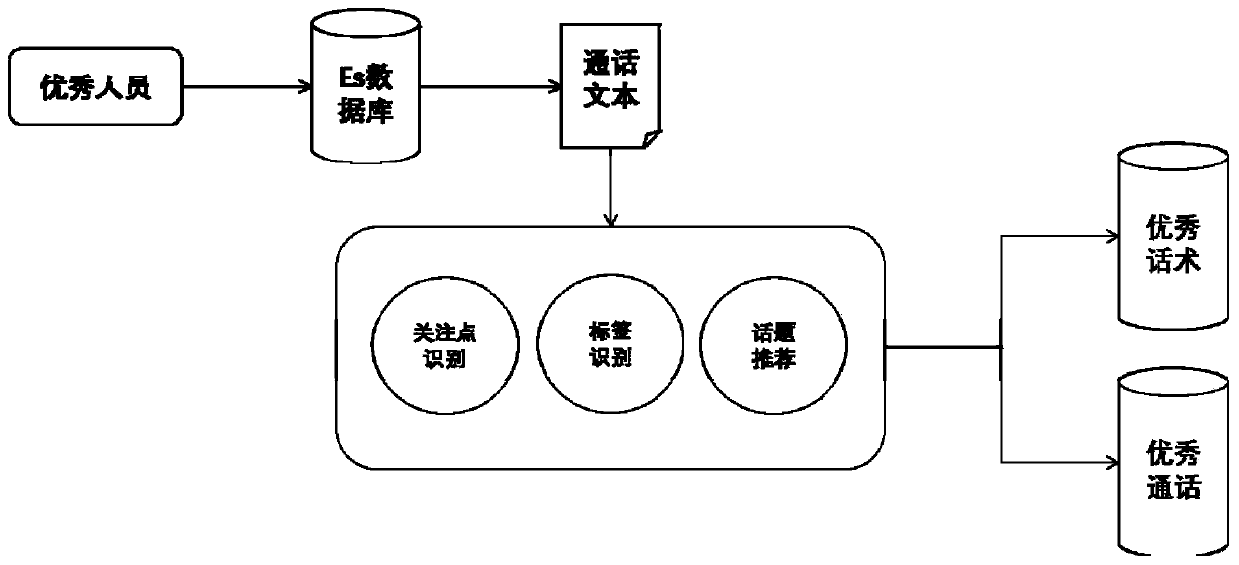
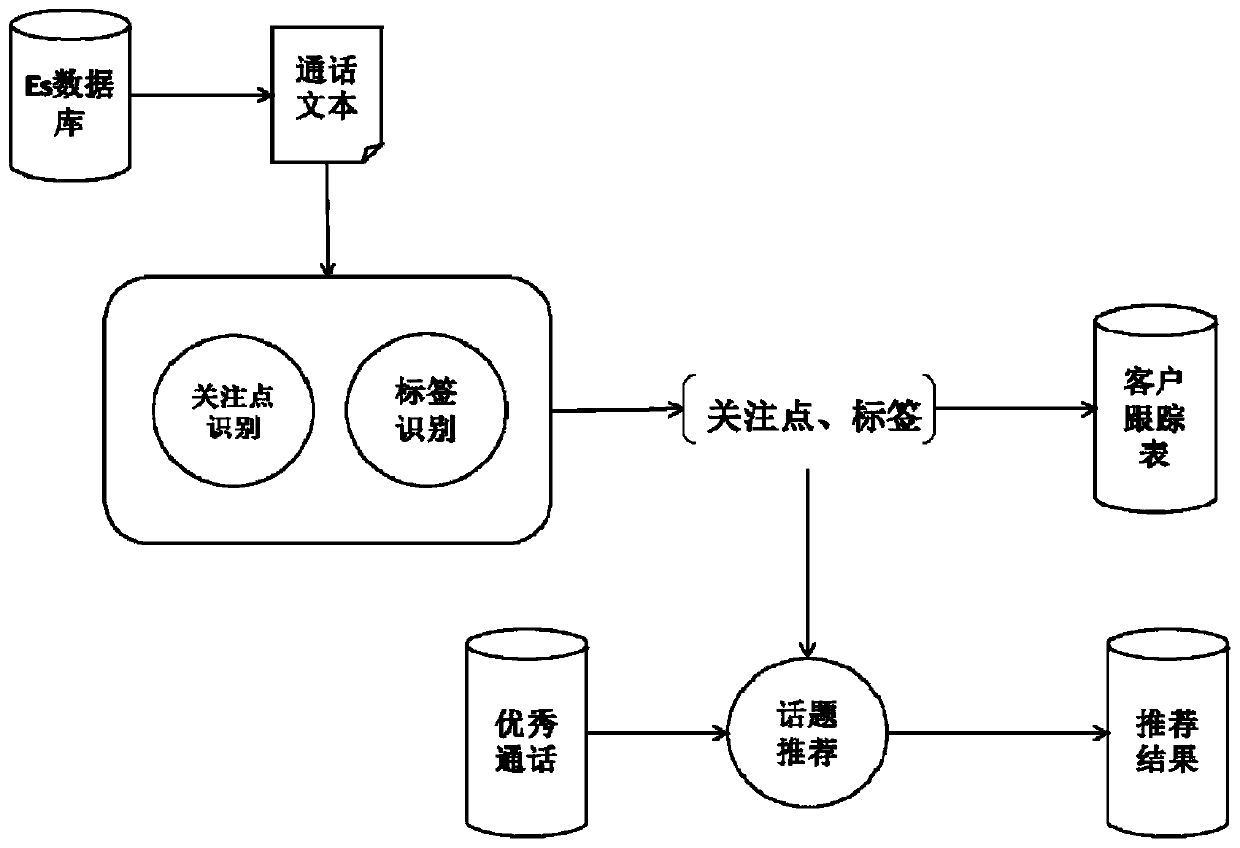
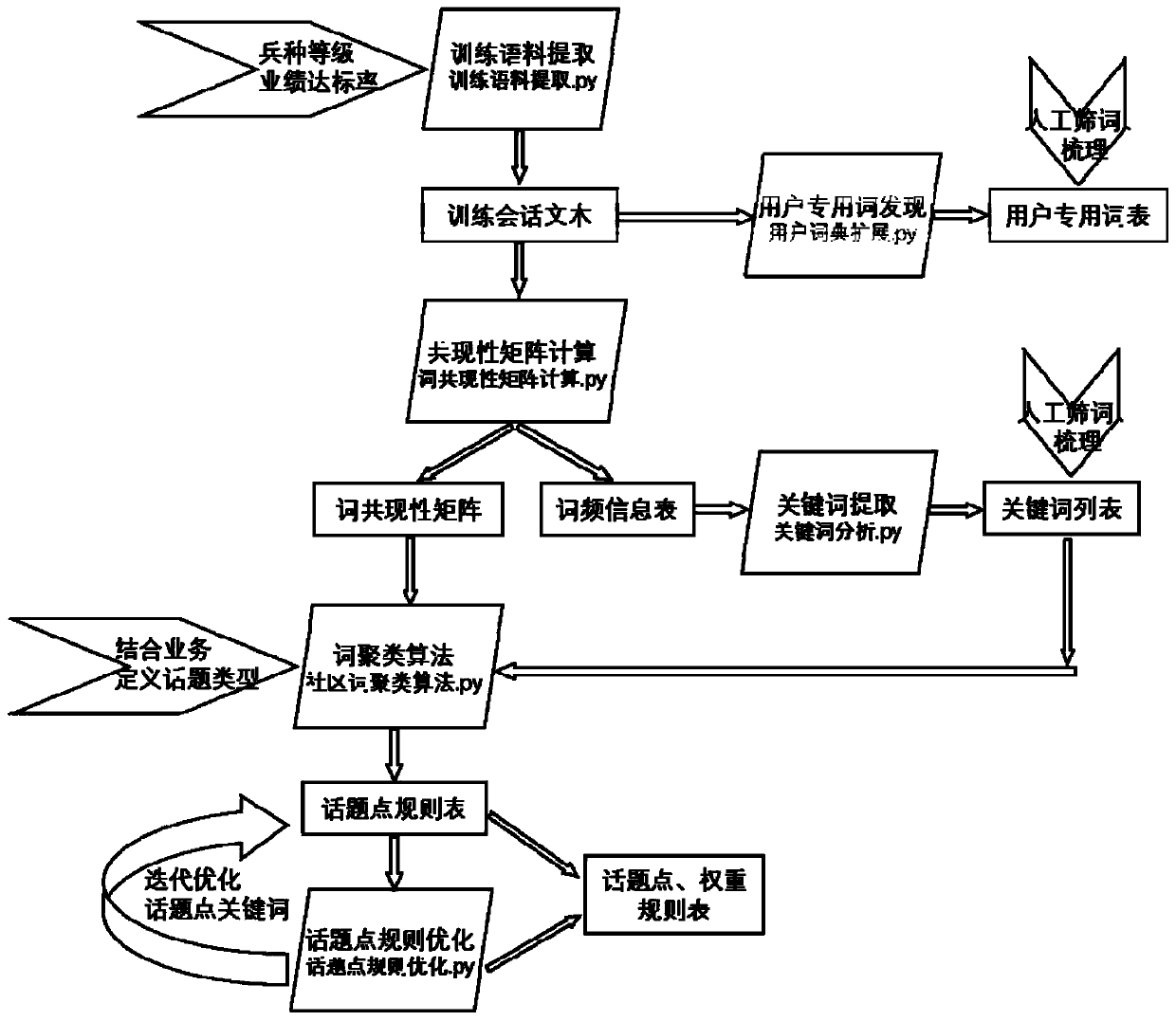
Verbal skill analysis and topic point identification matching method and system
InactiveCN110472017AStart fastRelieve pressureText database queryingSpecial data processing applicationsMaterial resourcesData science
The invention relates to a natural language processing technology, in particular to a verbal skill analysis and topic point recognition matching method and system. The method comprises the following steps: firstly, establishing a marketing verbal skill strategy analysis label library, respectively establishing a client label system and an agent label system for a client and an agent, and accurately identifying the willingness of the client; analyzing the marketing verbal skill strategy, completing automatic verbal skill extraction, and completing automatic verbal skill recommendation in combination with the client label and the excellent verbal skill library; and generating a marketing verbal skill analysis report according to the reference condition of the agent to the excellent verbal skill. According to the method, from verbal skill analysis to topic point identification, the client topic points are analyzed in a full-intelligent mode, excellent verbal skill is provided, the mode ofmanually extracting excellent verbal skill in the past is broken through, and a large amount of manpower and material resources are reduced.
Owner:GUANGZHOU BAILING DATA CO LTD
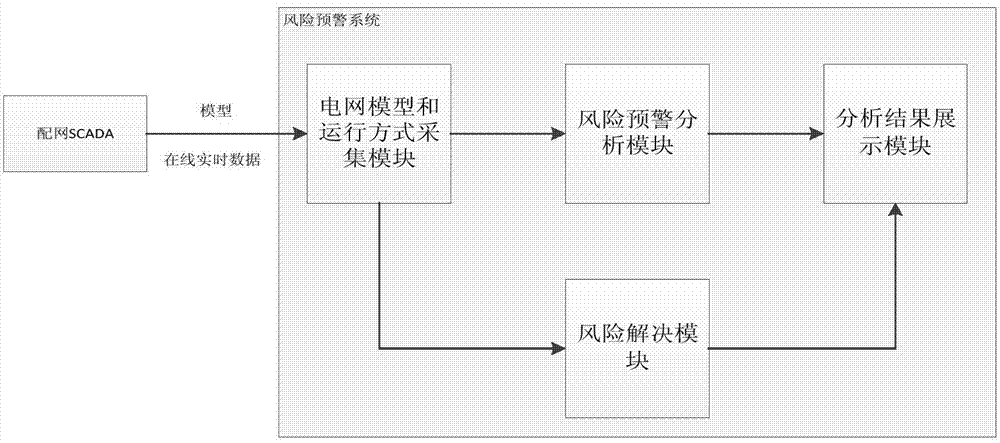
Real-time running status evaluation based power distribution network running risk warning system
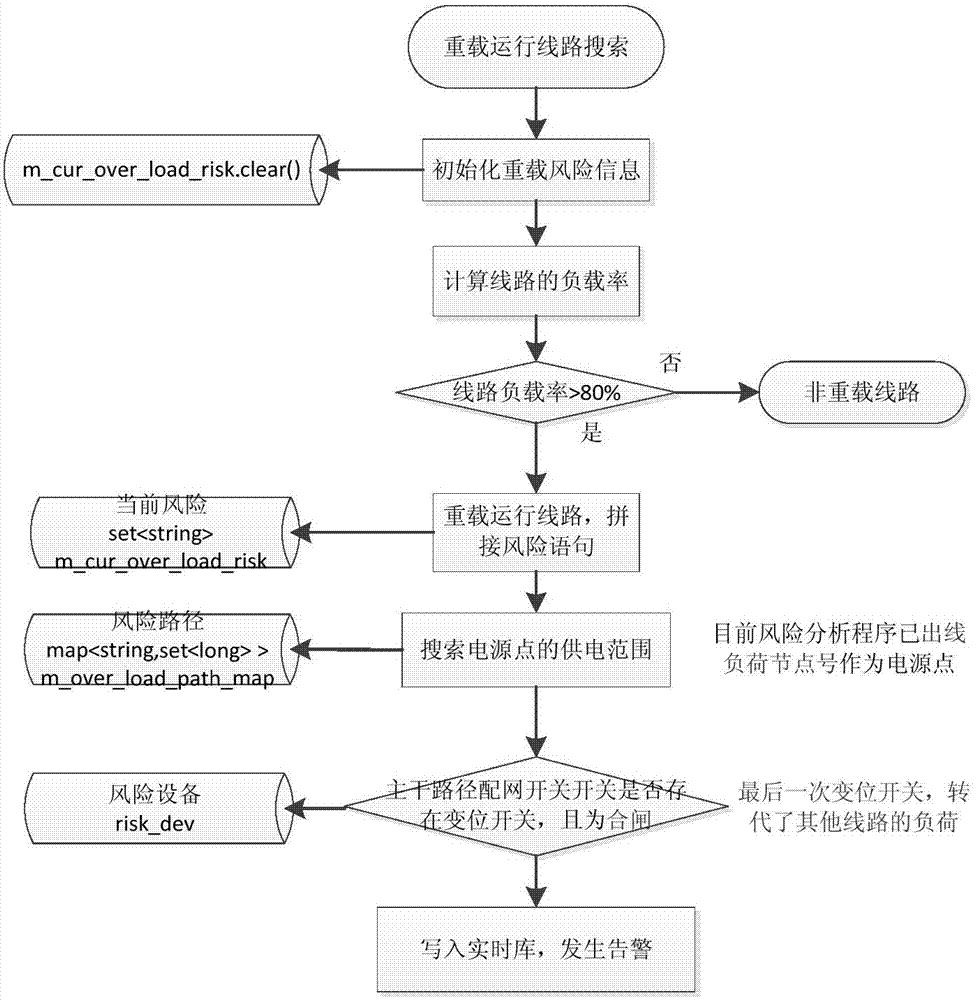
ActiveCN104218672AGuaranteed real-timeReduce power supply reliabilityCircuit arrangementsSustainable buildingsSCADAPower grid
The invention discloses a real-time running status evaluation based power distribution network running risk warning system. The system comprises a power grid model and running mode acquisition module, a risk warning analysis module, a risk solution module and an analysis result display module, the power grid model and running mode acquisition module is used for acquiring a power grid model and a running mode from a power distribution network SCADA (supervisory control and data acquisition) system; the risk warning analysis module is used for analyzing risks of the power distribution network according to the current power distribution network model and the running mode; the risk solution module is used for analyzing solution strategies for the power distribution network risks to obtain a power distribution network risk solution strategy; the analysis result display module is used for displaying a power distribution network risk analysis result and a power distribution network risk solution strategy analysis result. The power grid model and the on-line power grid running mode are synchronized in real time from the power distribution network SCADA system, and real-time performance of risk analysis is guaranteed; rich risk warning display means are provided, and users are assisted to quickly position a risky area; the risks of the power distribution network are analyzed from the perspective of the power grid running mode, advance discovering and timely processing are achieved, and power supply reliability of the power distribution network is improved.
Owner:STATE GRID CORP OF CHINA +4
Transitioning an organization to a service management oriented organization
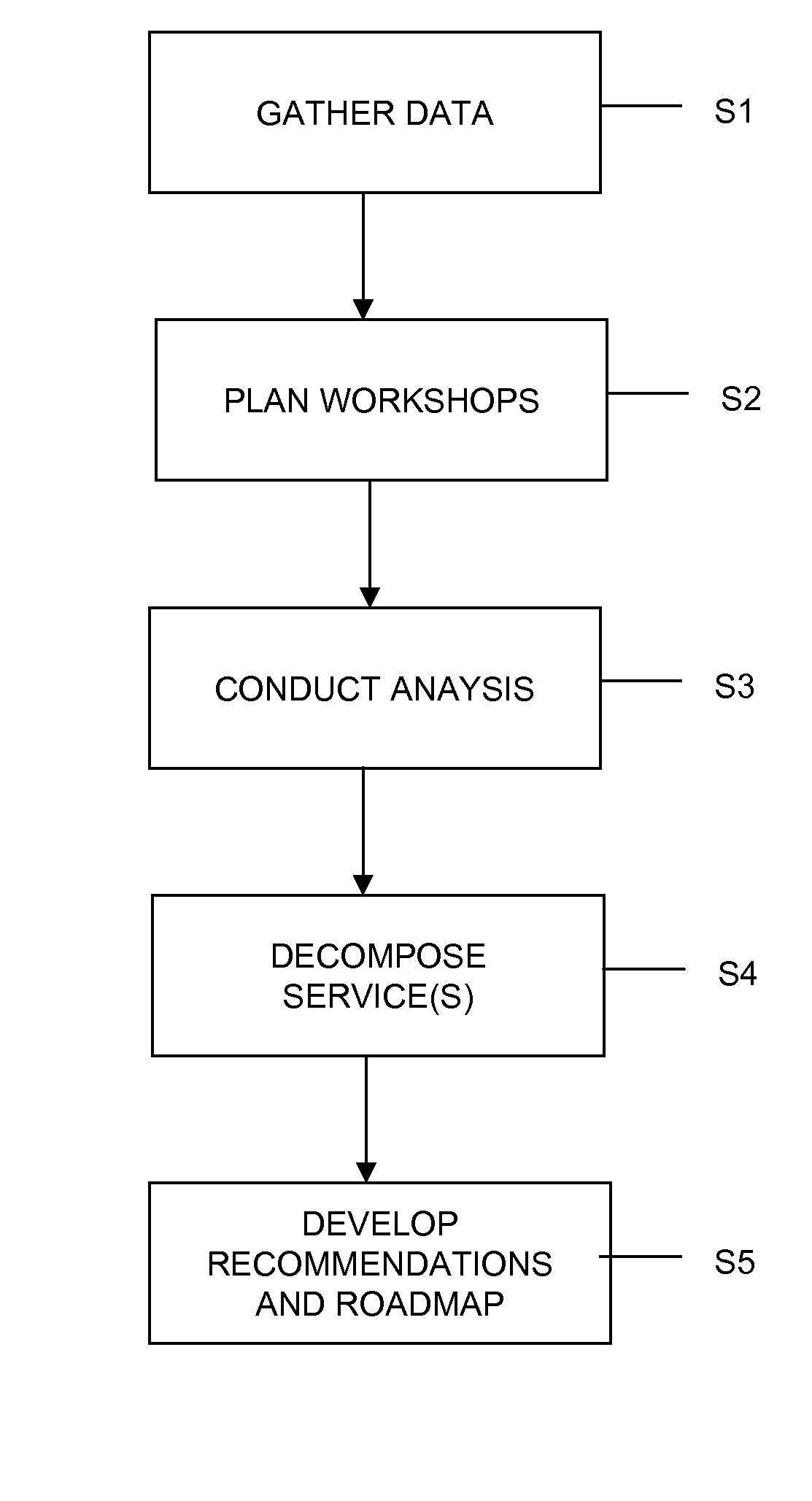
The present invention provides an approach to transition an IT organization such as a data center to a service management oriented organization. Specifically, under the present invention, data is gathered pertaining to how the organization is currently managed. Then a set of workshops is planned to provide education on IT service management, to establish service management nomenclature, to identify IT services that the organization is capable of providing internally, and to identify IT services that the organization is capable of providing externally. Thereafter, an IT services capabilities and strategy analysis is performed for the organization, predetermined quantity of the IT Services is decomposed into their constituent configuration item, and recommendations and a roadmap are developed for the organization to transition to the service management oriented organization.
Owner:IBM CORP
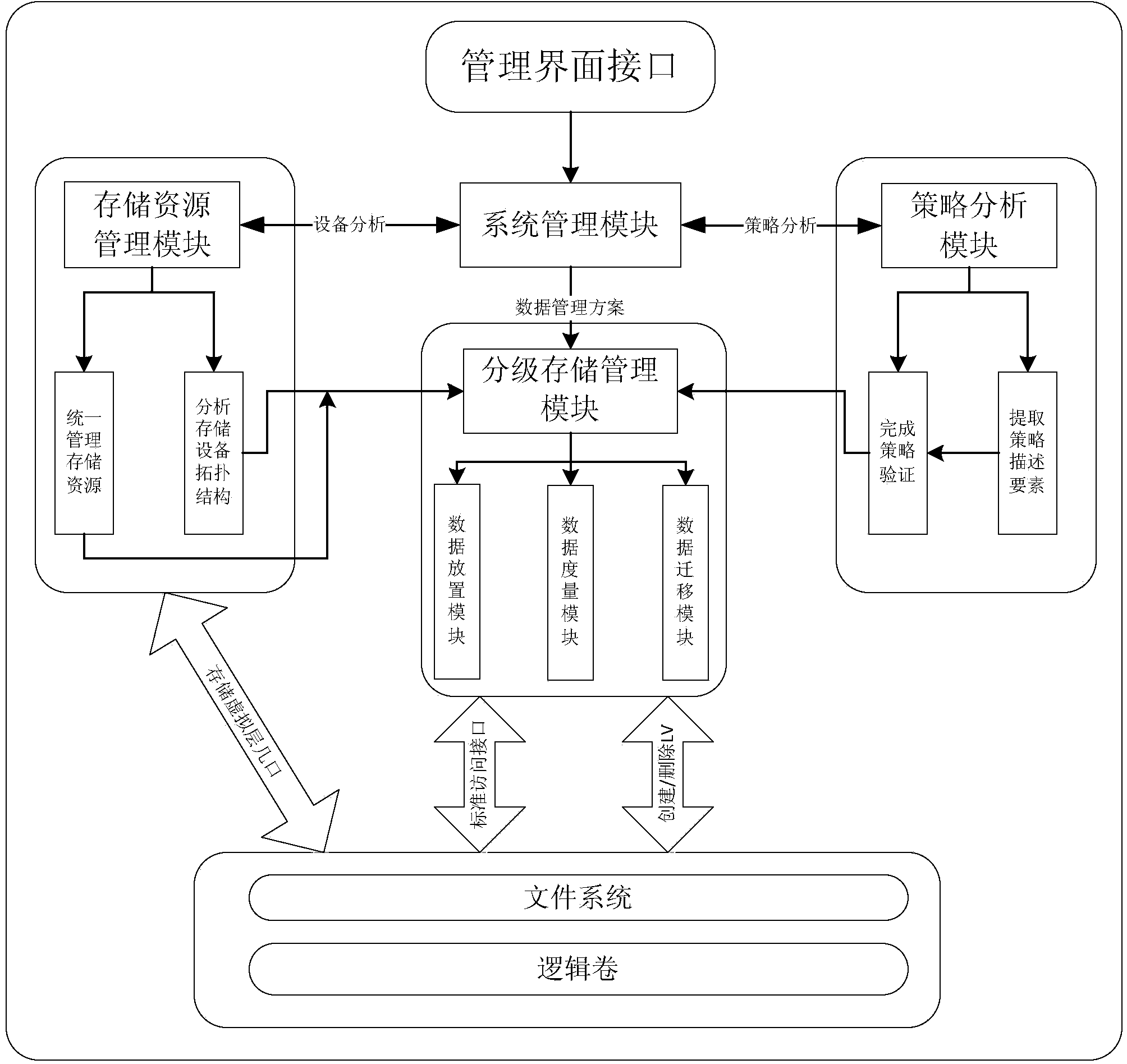
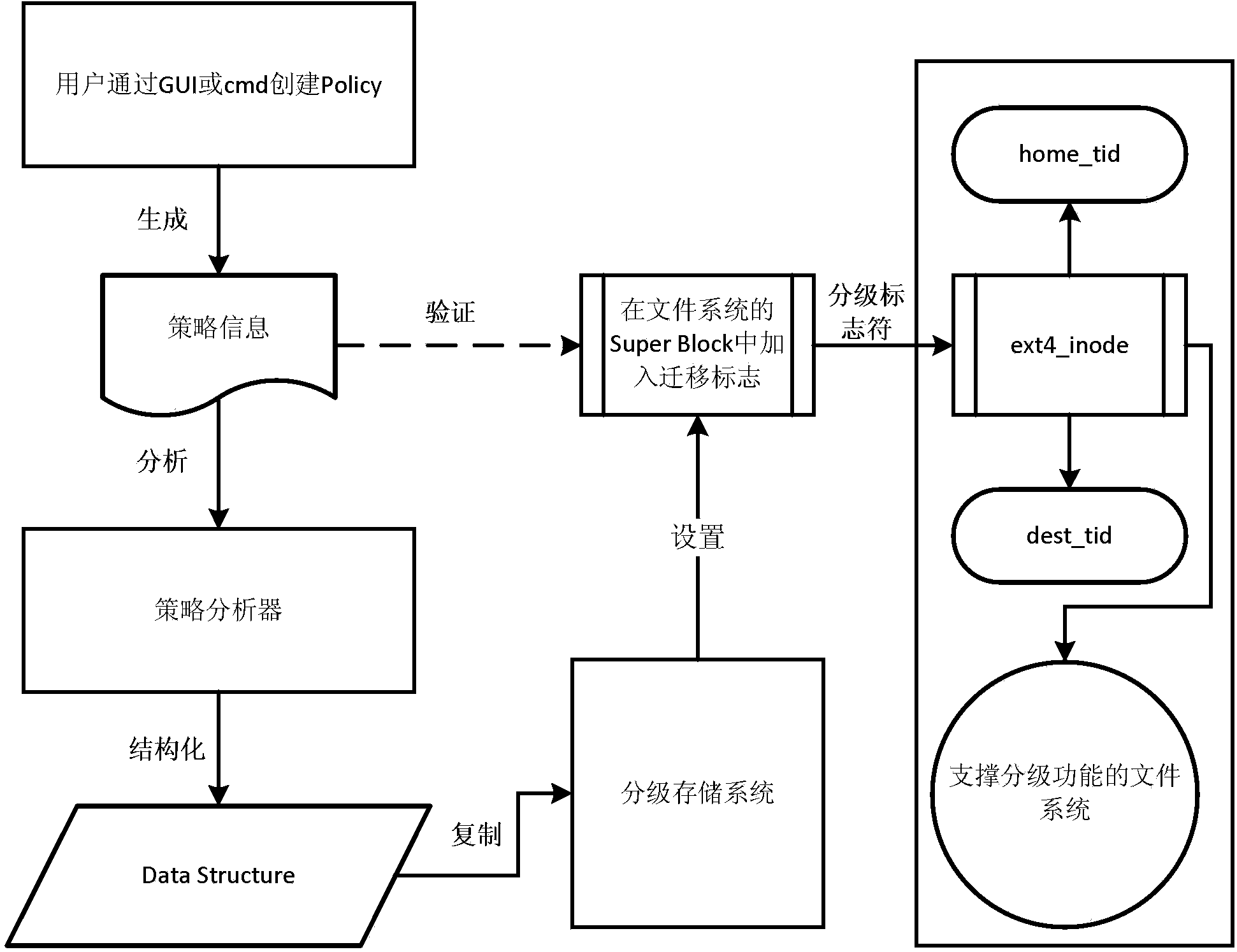
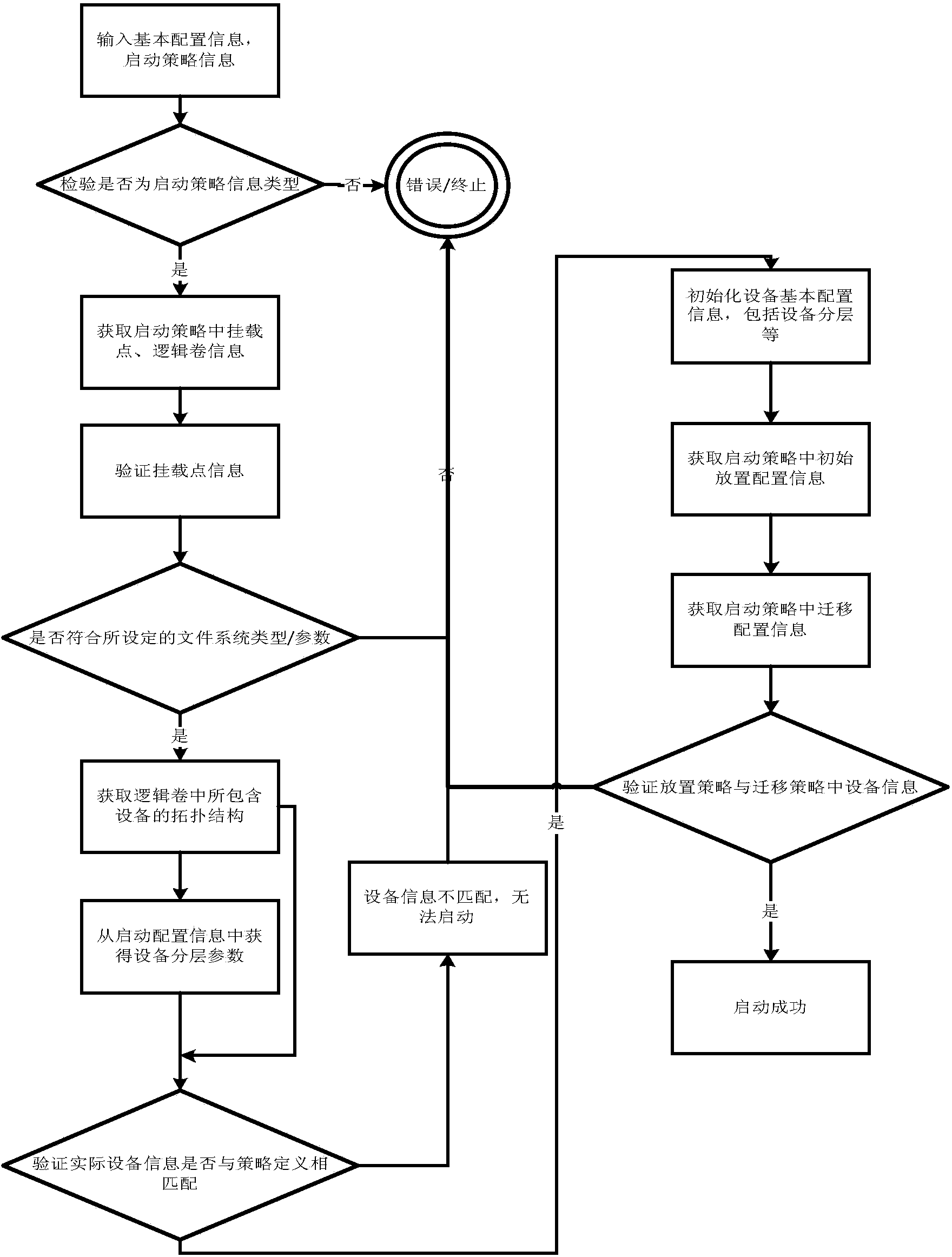
Method and system for hierarchically storing data
ActiveCN103631931AImprove usabilityImplement configuration managementMemory adressing/allocation/relocationSpecial data processing applicationsUsabilitySmart data
The invention provides a method for hierarchically storing data, which is applied to the field of intelligent data management. The method comprises the following steps that a strategy analysis module acquires an XML (Extensive Markup Language) strategy file, wherein the XML strategy file is generated by a management interface according to set strategy configuration information; the strategy analysis module detects and analyzes the strategy configuration information extracted from the XML strategy file to obtain an analysis result; a hierarchical storing management module acquires the analysis result and calls a sub-functional module to complete data processing according to the analysis result. According to the method, management methods such as data migration and the like can be integrated effectively, so that the configuration management of a plurality of file features, classified measurement and migration management functional collaboration are realized, and the usability of intelligent data management is effectively improved.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
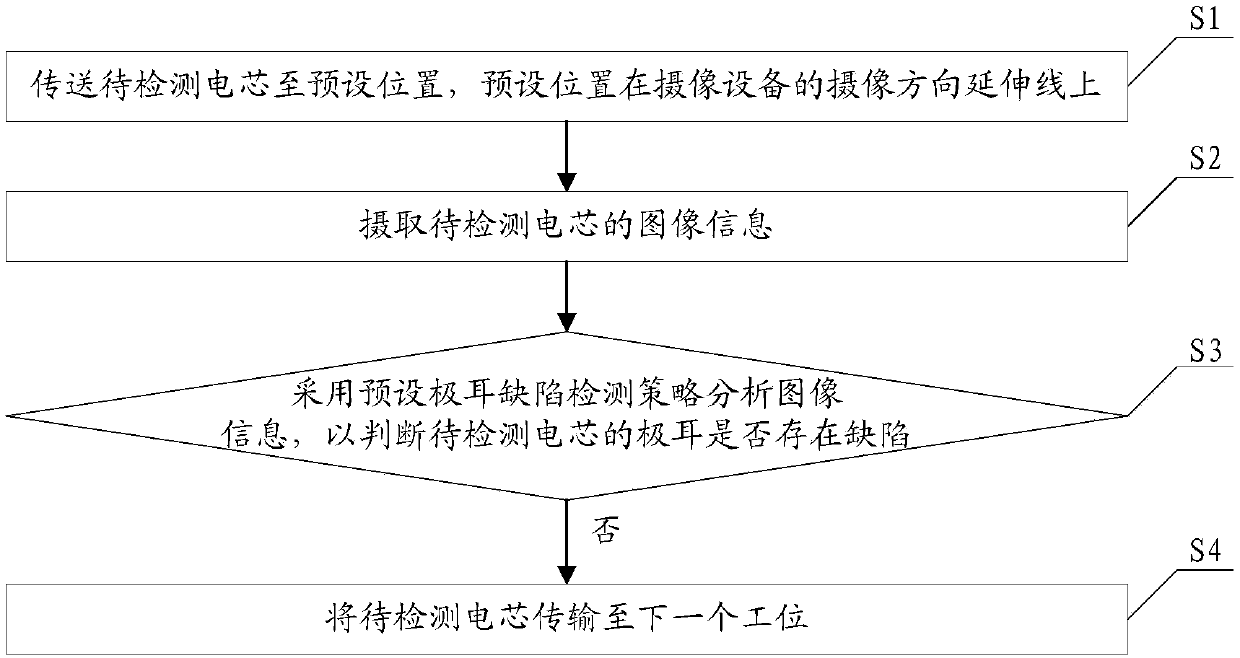
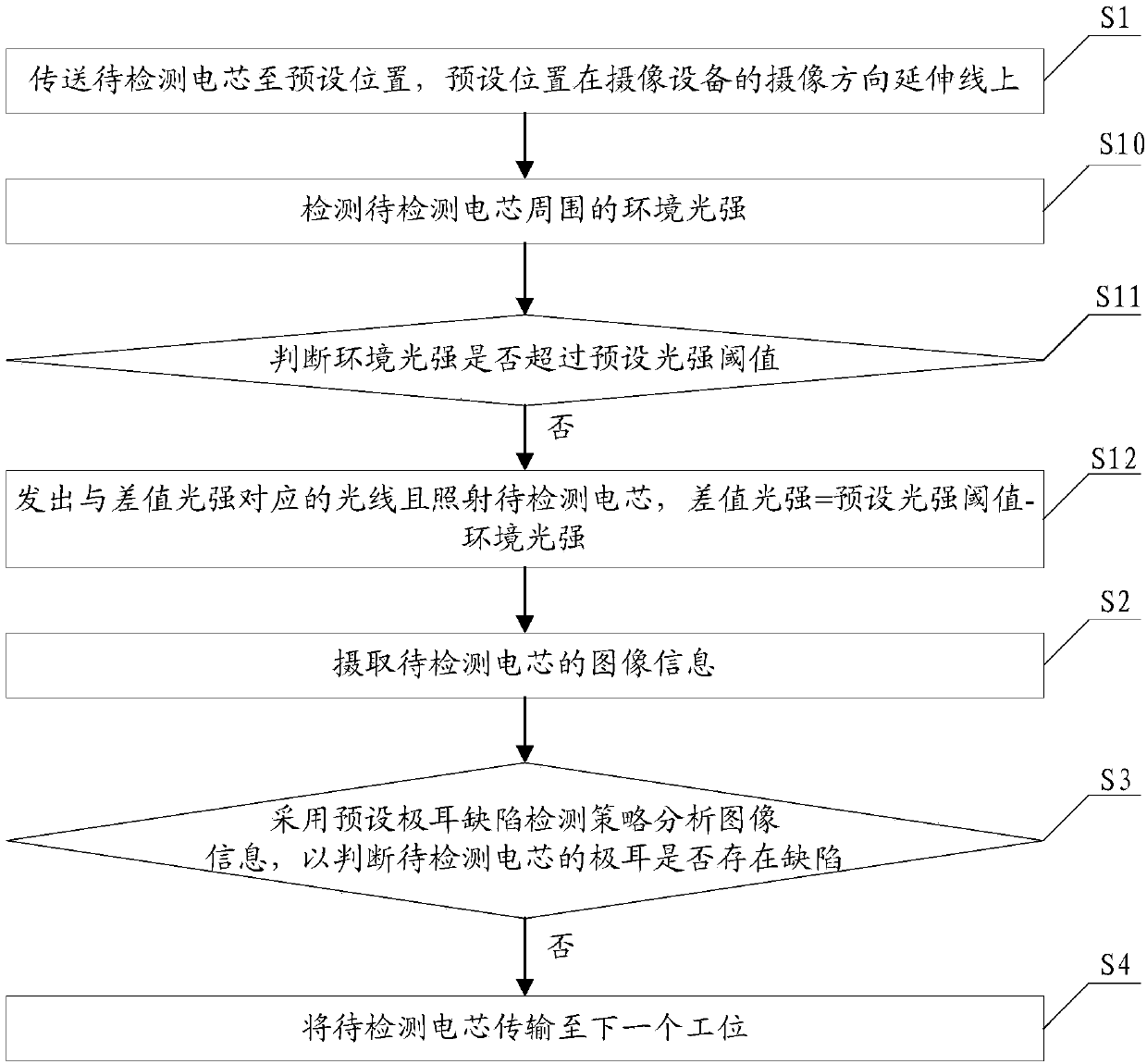
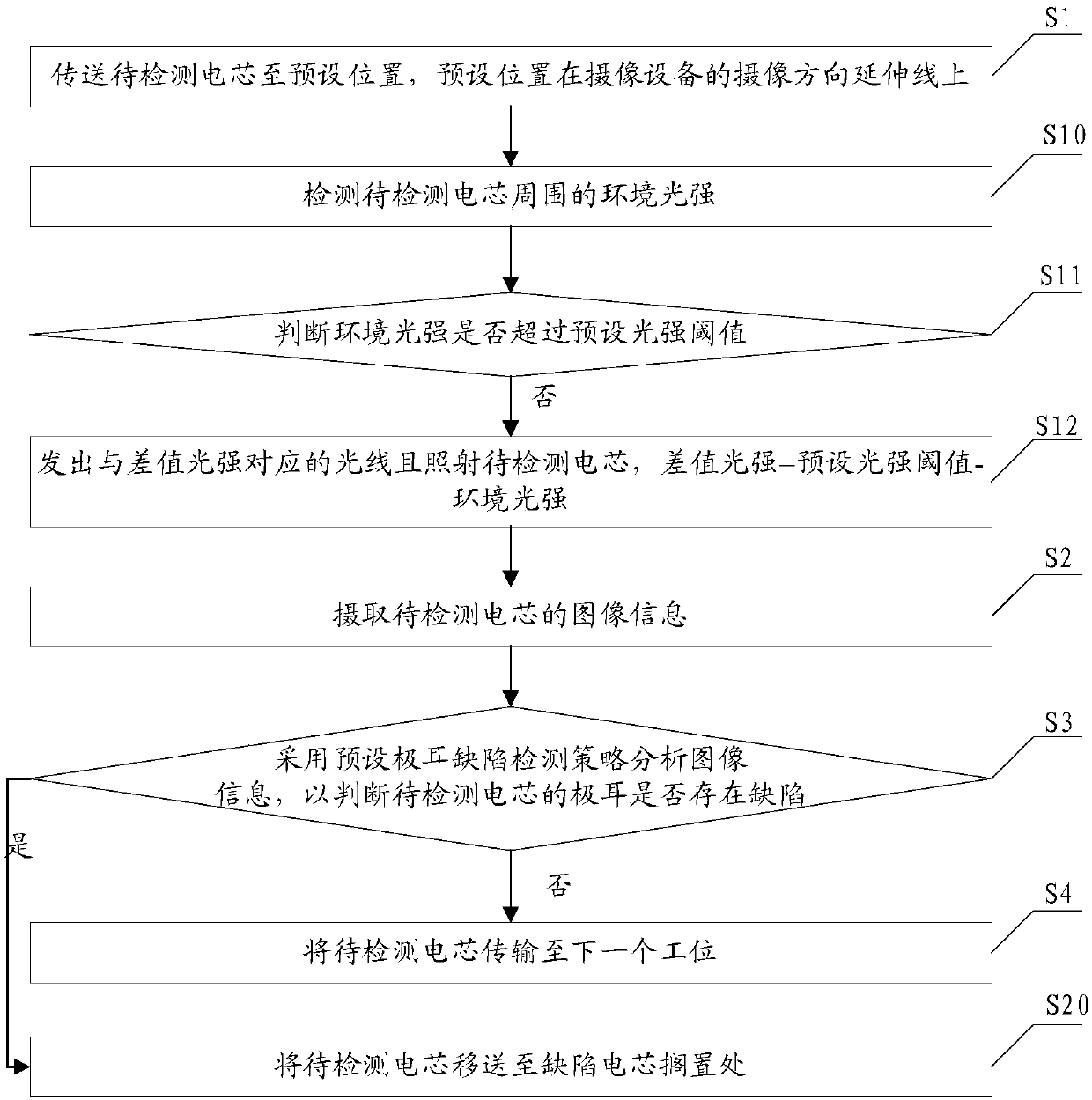
Automatic detection method and automatic detection device for cell tab defects
ActiveCN108037130AQuality improvementImprove assembly speedOptically investigating flaws/contaminationUsing optical meansComputer scienceStrategy analysis
The invention discloses an automatic detection method and an automatic detection device for cell tab defects. The method includes the steps: conveying a cell to be detected to a preset position in anextending line of a camera shooting direction of a camera shooting device; acquiring image information of the cell to be detected; judging whether a tab of the cell to be detected has the defects or not by the aid of preset tab defect detection strategy analysis image information; conveying the cell to be detected to next station if the cell to be detected does not have defects. The automatic detection method automatically analyzes whether the tab of the cell has shortcomings or not according to the image information acquired by the camera shooting device, labor cost is saved, judgment accuracy rate of the tab defects is increased, so that the quality of a battery module is improved, and the assembly rate of the battery module is increased.
Owner:SHENZHEN CLOU ELECTRONICS
Computer network emergency response safety strategy generating system
InactiveCN1655526AQuick buildImprove survivabilityData switching networksHandling systemSecurity policy
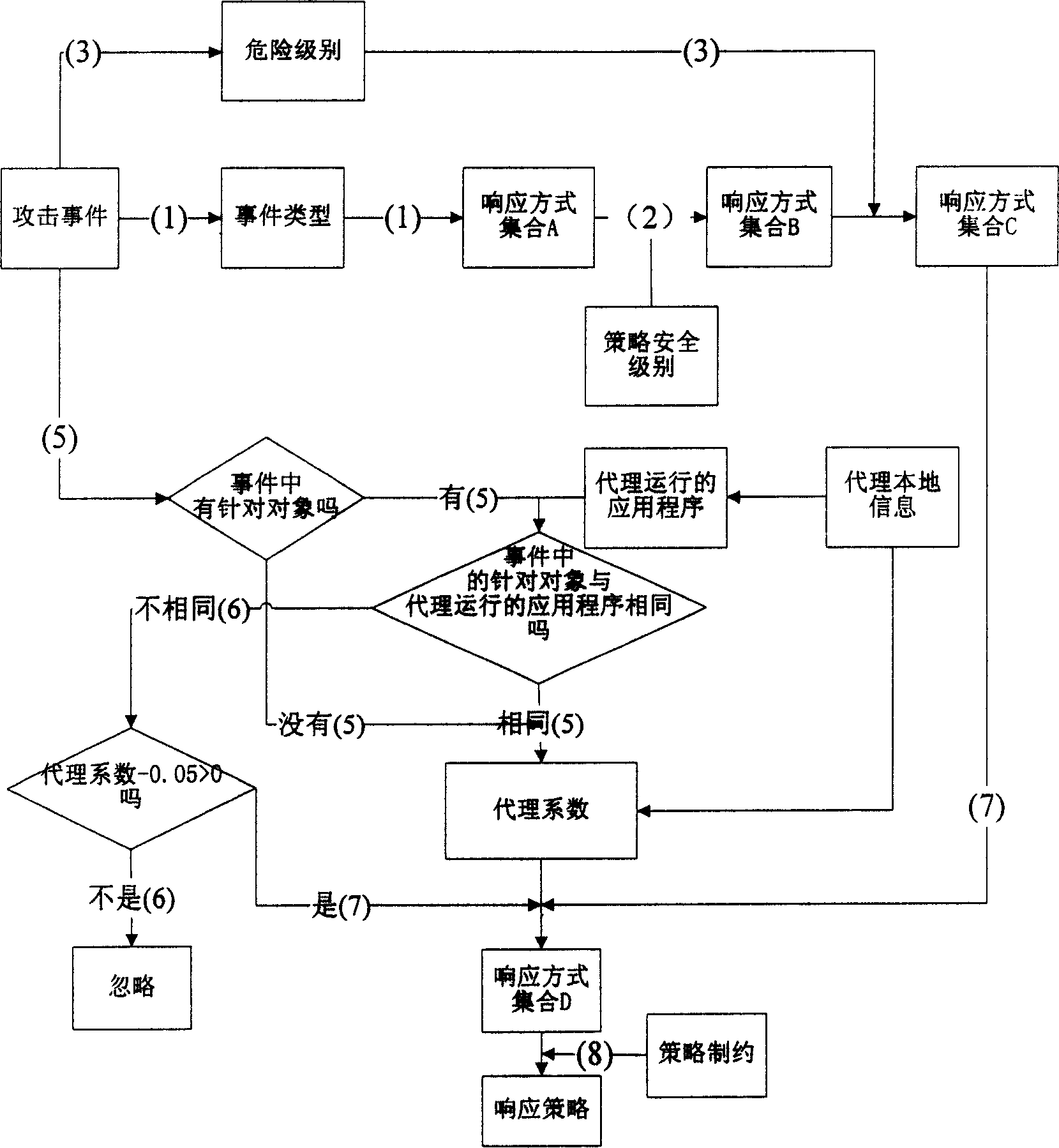
This invention discloses one computer emergency responding safety strategy generation system, which is characterized by the following: the module starting and receiving the attack affair information and transferring the pre-set definition information in the database; then comparing the attack affair information with the attack affair in the database to determine responding means assembly A for analysis and filtering; finally the module choosing the responding means with highest integration parameter to make the final responding means.
Owner:上海三零卫士信息安全有限公司
Collaborative defense method for network protection and system
ActiveCN109587174AGood for in-depth analysisGet the effect of defenseTransmissionCentralized managementProtection system
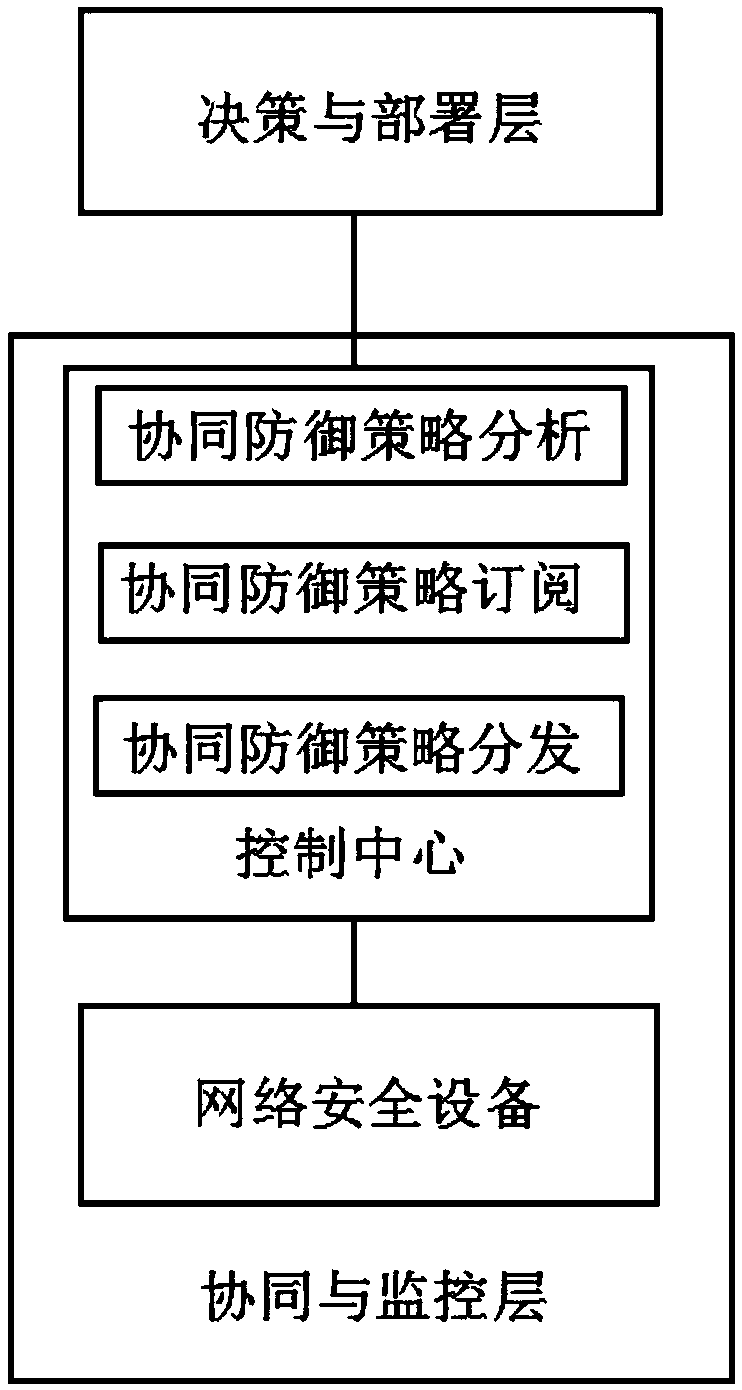
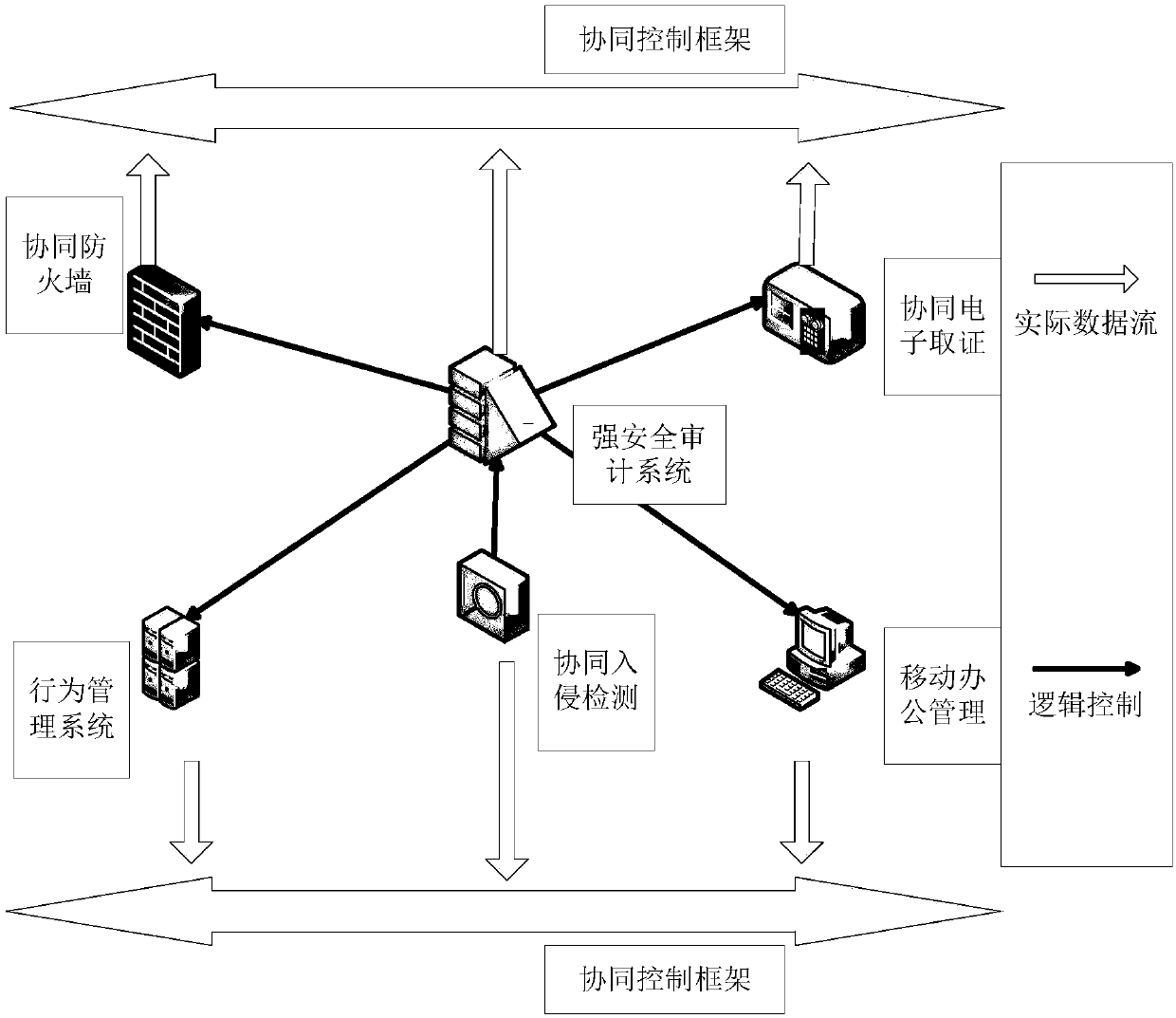
The invention discloses a collaborative defense method for network protection and system. The system comprises a decision-making and deployment layer and a collaboration and monitoring layer, whereinthe decision-making and deployment layer uses an acquired network security early warning event, a defense intension is formulated according to the defense purpose of the network security and the current situation of the network security, a network defense strategy is later generated by a decision-making engine, and a defense task is deployed according to the defense strategy; the collaboration andmonitoring layer comprises a control center and network security devices, thereby realizing collaborative task deployment between network security devices and real-time monitoring on the network defense condition; the control center is in communication connection with the decision-making and deployment layer and the network security devices for data flow control and logical control; and the control center comprises a collaborative defense strategy analysis module, a collaborative defense strategy subscription module and a collaborative defense strategy distribution module. A collaborative defense solution with security perception, collaborative protection and centralized management as the core can be given, and an active, integrated and comprehensive dynamic security protection system isrealized.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
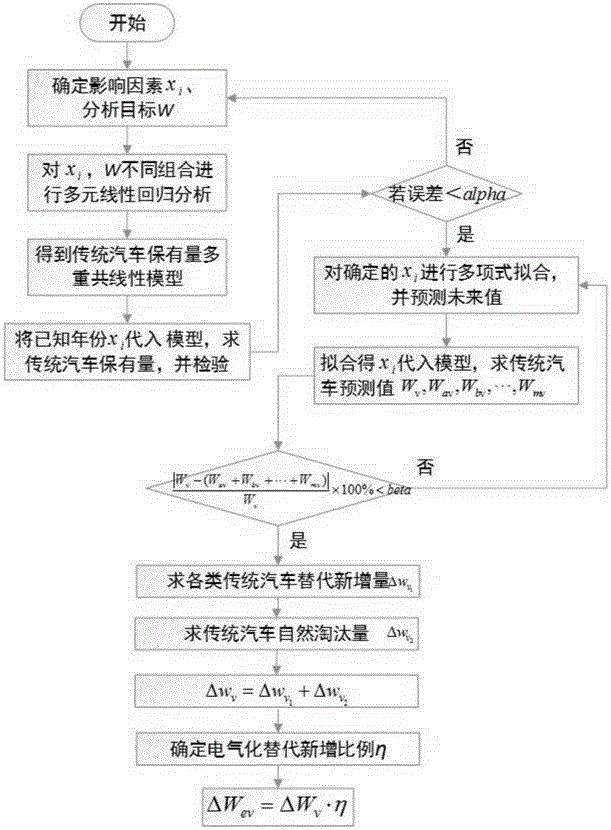
Electric vehicle parc prediction method based on multivariate linear regression method and proportional substitution method
InactiveCN105868865AEffective predictionFix limitationsForecastingObjective variablesSubstitution method
The invention belongs to the technical field of automobile industry data forecasting, and in particular relates to a method for forecasting electric vehicle ownership based on multiple linear regression and proportional substitution. Analyze the correlation with the target variable, establish and verify the multicollinearity model of traditional car ownership; according to the polynomial fitting results of the data of each influencing factor in known years, predict the unknown year data of each influencing factor, and substitute it into the above multiple After the collinear model, the traditional car ownership in the future years is predicted; combined with the local replacement ratio of electric vehicles and the actual growth of electric vehicles, new replacement increments are obtained, and then the total number of electric vehicles in the future years is predicted. The invention can use statistical data to calculate the number of traditional automobiles and calculate the number of electric vehicles, which is helpful for the planning of electric vehicle charging facilities and policy analysis.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
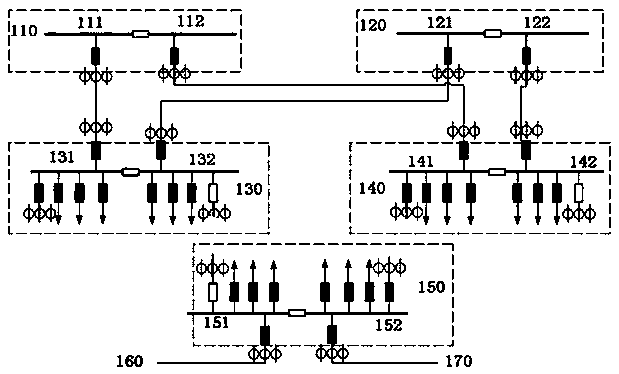
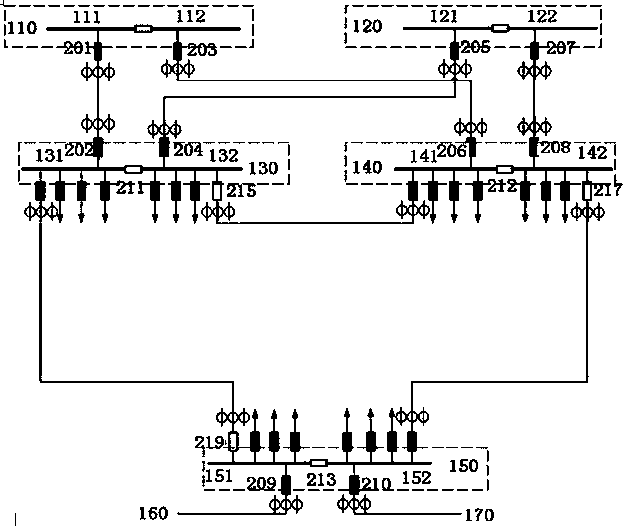
City center area power distribution network and load transfer method
InactiveCN105375465AMeet capacity requirementsMeet reliability requirementsAc network circuit arrangementsTransformerEngineering
The invention discloses a city center area power distribution network. Buses of a first switch station bus, a second switch station bus and a third switch station bus are respectively preset with a private line connection position, every two of the private line connection positions of the first switch station bus, the second switch station bus and the third switch station bus are in circuit connection through connection wires, and a first transformer station bus, a second transformer station bus, a third transformer station bus and a fourth transformer station bus form two main configurations and two standby configurations. The power distribution network employs grid design thinking, a corresponding target wiring load transfer strategy analysis model is established, power supply capacity and reliability requirements of important users are satisfied, and transfer scheme making efficiency of regulators and operators is improved.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com