Computer network emergency response safety strategy generating system
A computer network, security policy technology, applied in the field of security policy generation system, can solve the problem of lack of automatic effective response and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
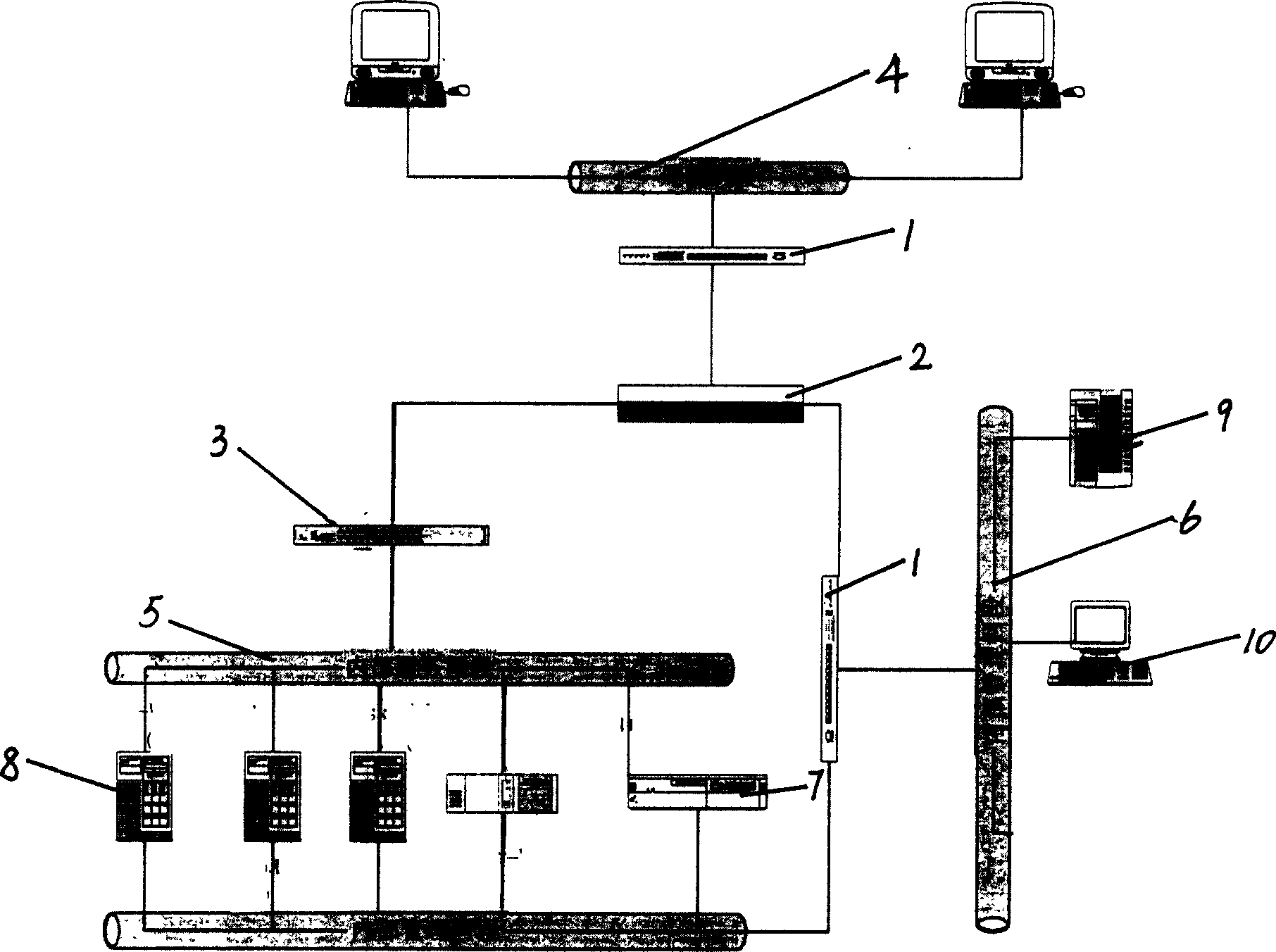
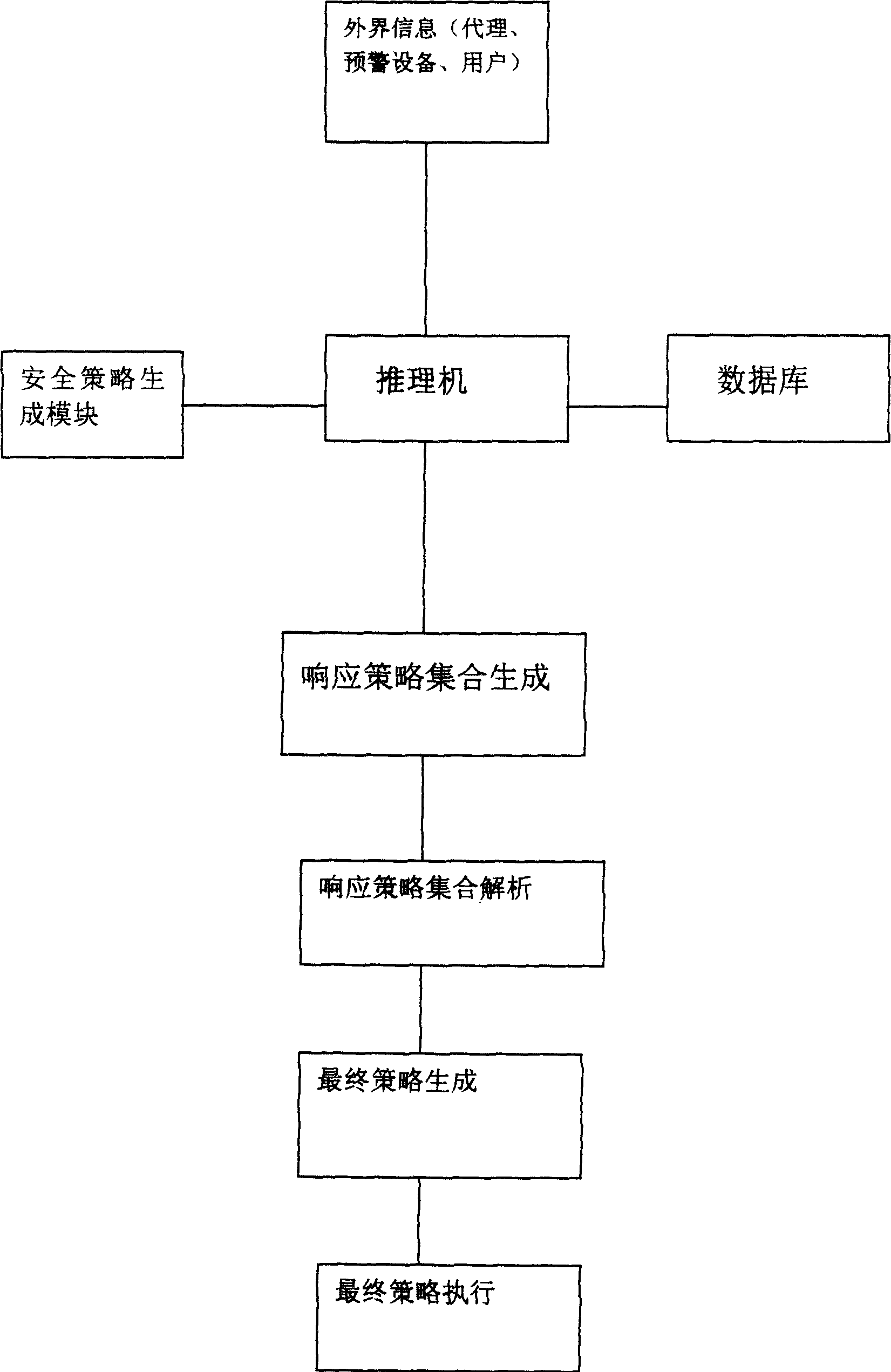
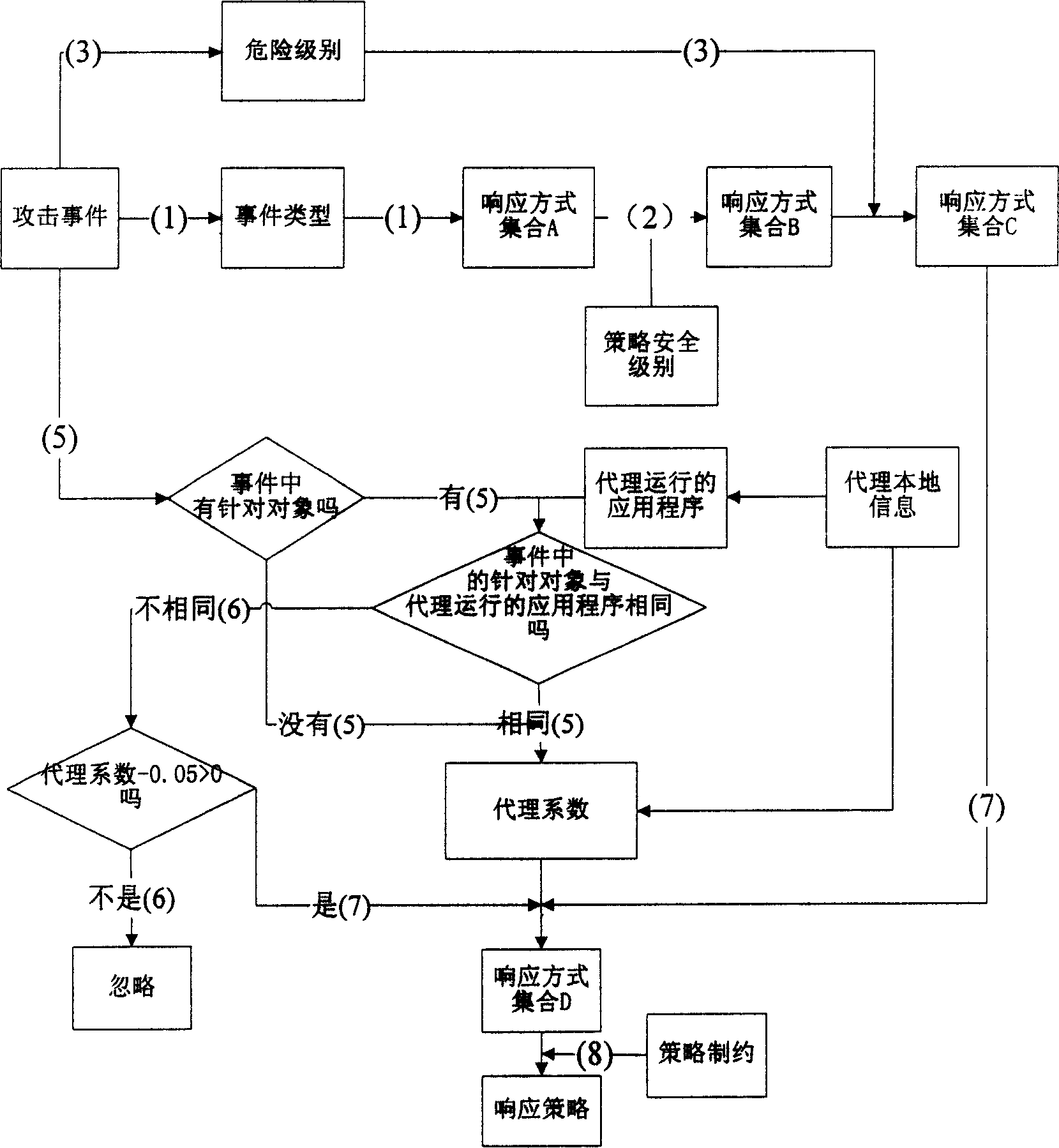
[0012] The present invention is a security policy generation system for computer network emergency response, which mainly includes a switch 1, a router 2, an Ethernet hub 3, and an external network segment 4, which is different from the prior art in that: the security of the computer network emergency response The policy generation system connects the external network segment with the internal service network segment 5 through switches, routers, and Ethernet hubs, and the internal service network segment is connected with the internal management network segment 6 through switches, wherein the internal service network segment is equipped with an eagle-eye network intrusion The detector 7 and several servers 8, the control center server 9 and the log terminal 10 are set in the internal management network segment, and the early warning processing module is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com