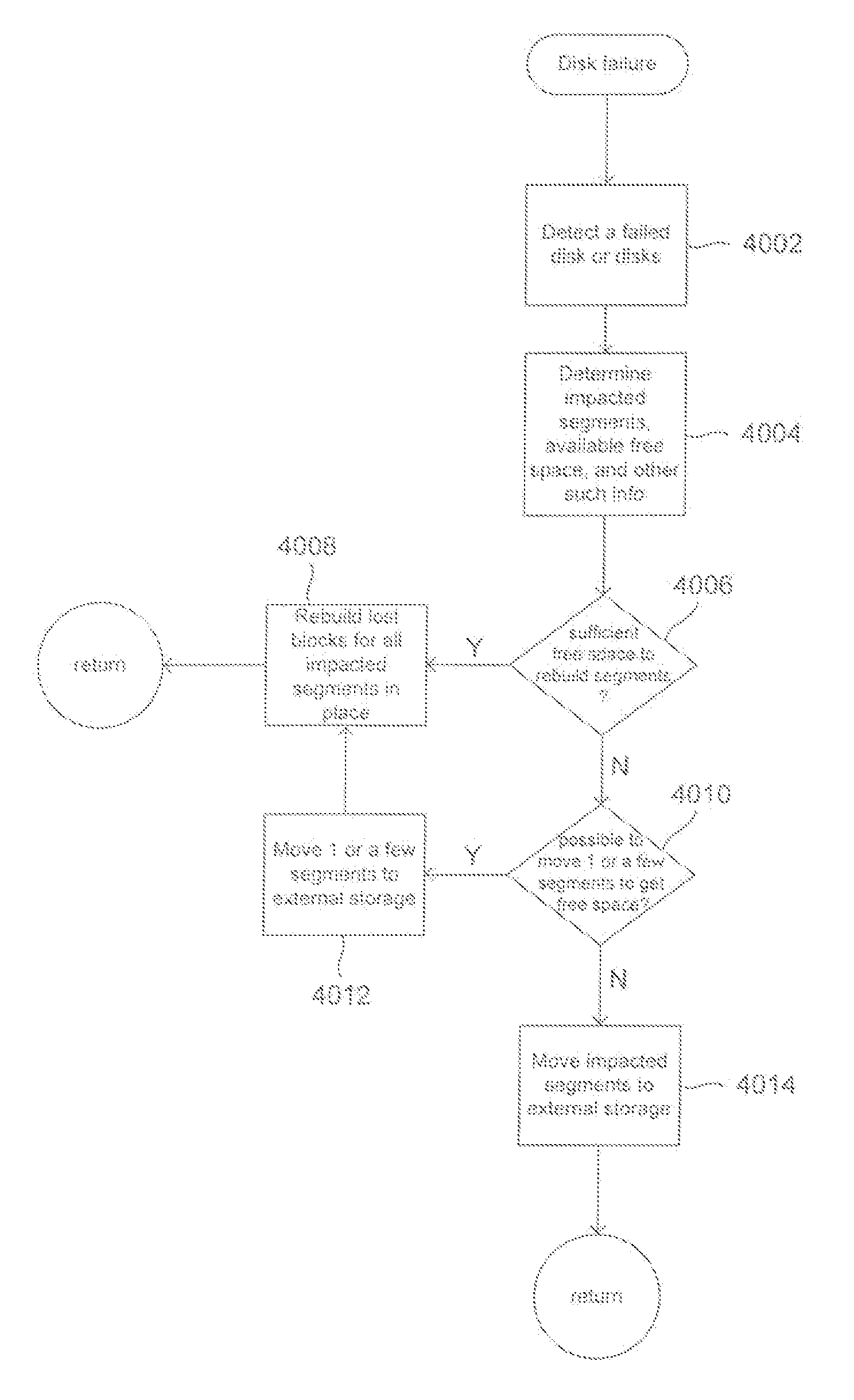Patents
Literature
1823results about How to "Effective recovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Adaptively controlled footwear
A method for controlling footwear, comprising cushioning a transient force during use of the footwear at a first period of a gait cycle, storing energy from said cushioning, and releasing the stored energy during use of the footwear at a second period of the gait cycle, and after said transient force has subsided. The control can be electronic, mechanical or hydraulic, and is preferably dependent on a sensed gait cycle phase. The control may be adaptive to the user or the use of the footwear. The stored energy can be used to assist in locomotion, to generate electrical energy, to drive a heat pump, or simply dissipated.
Owner:PROMDX TECH
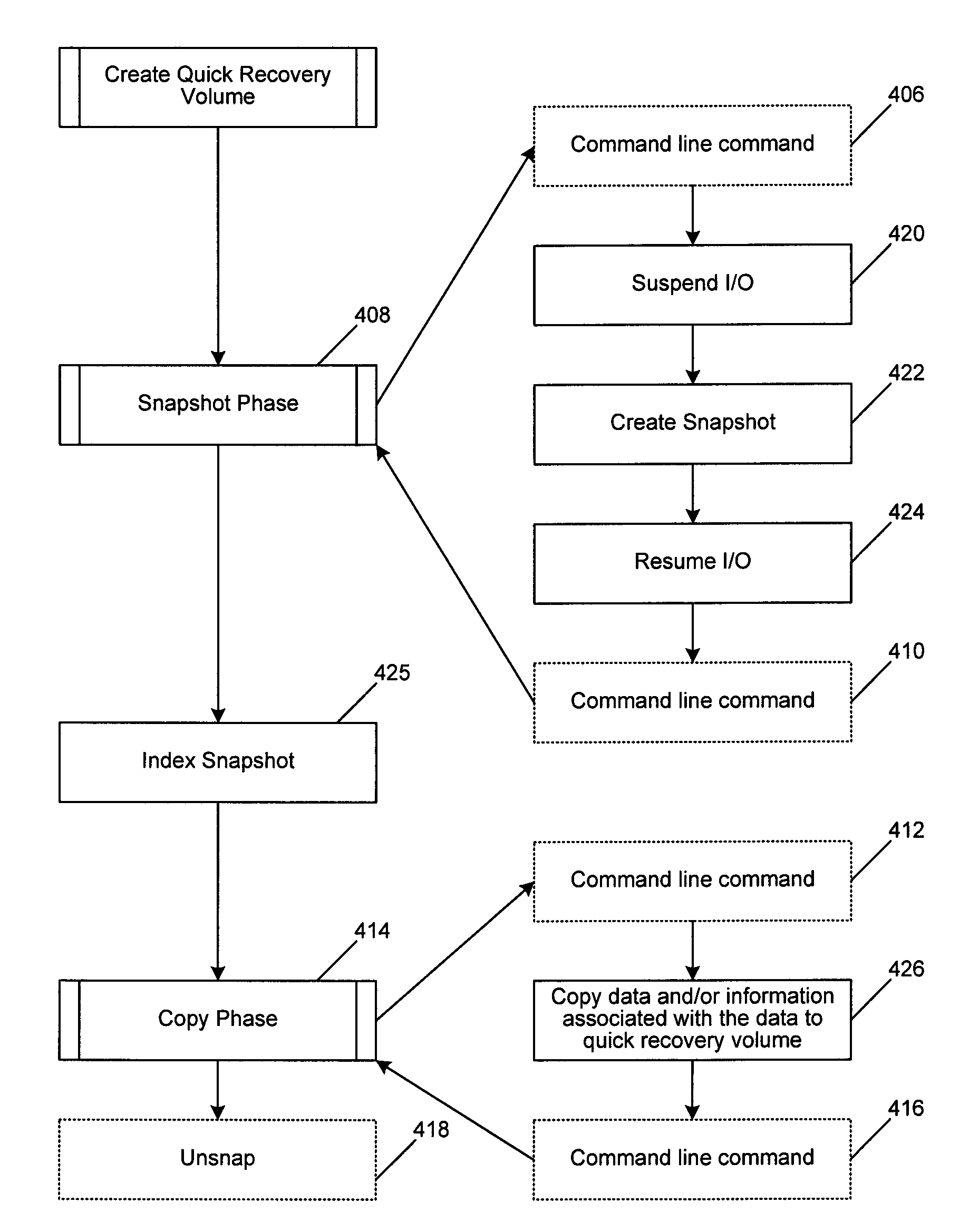
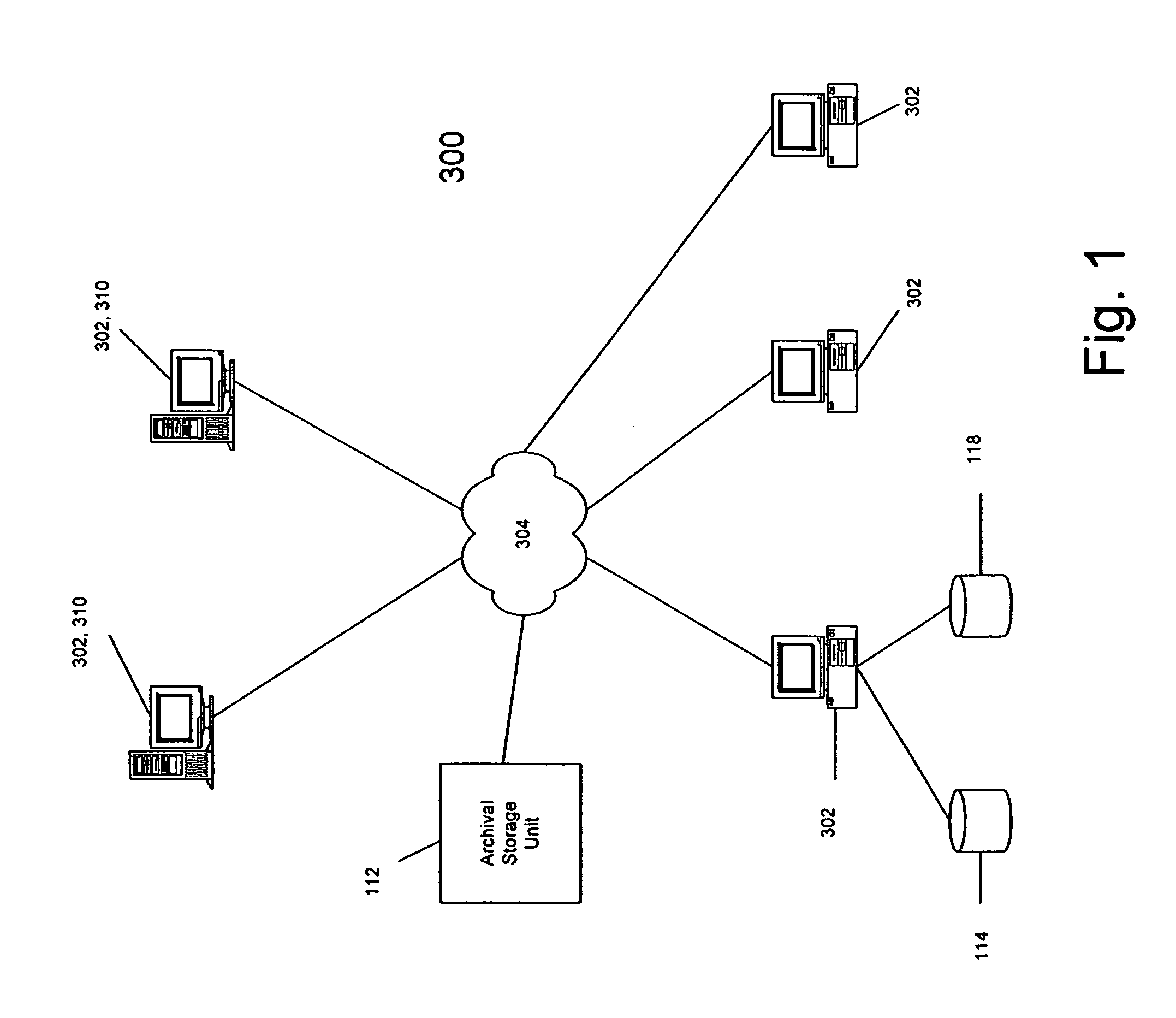
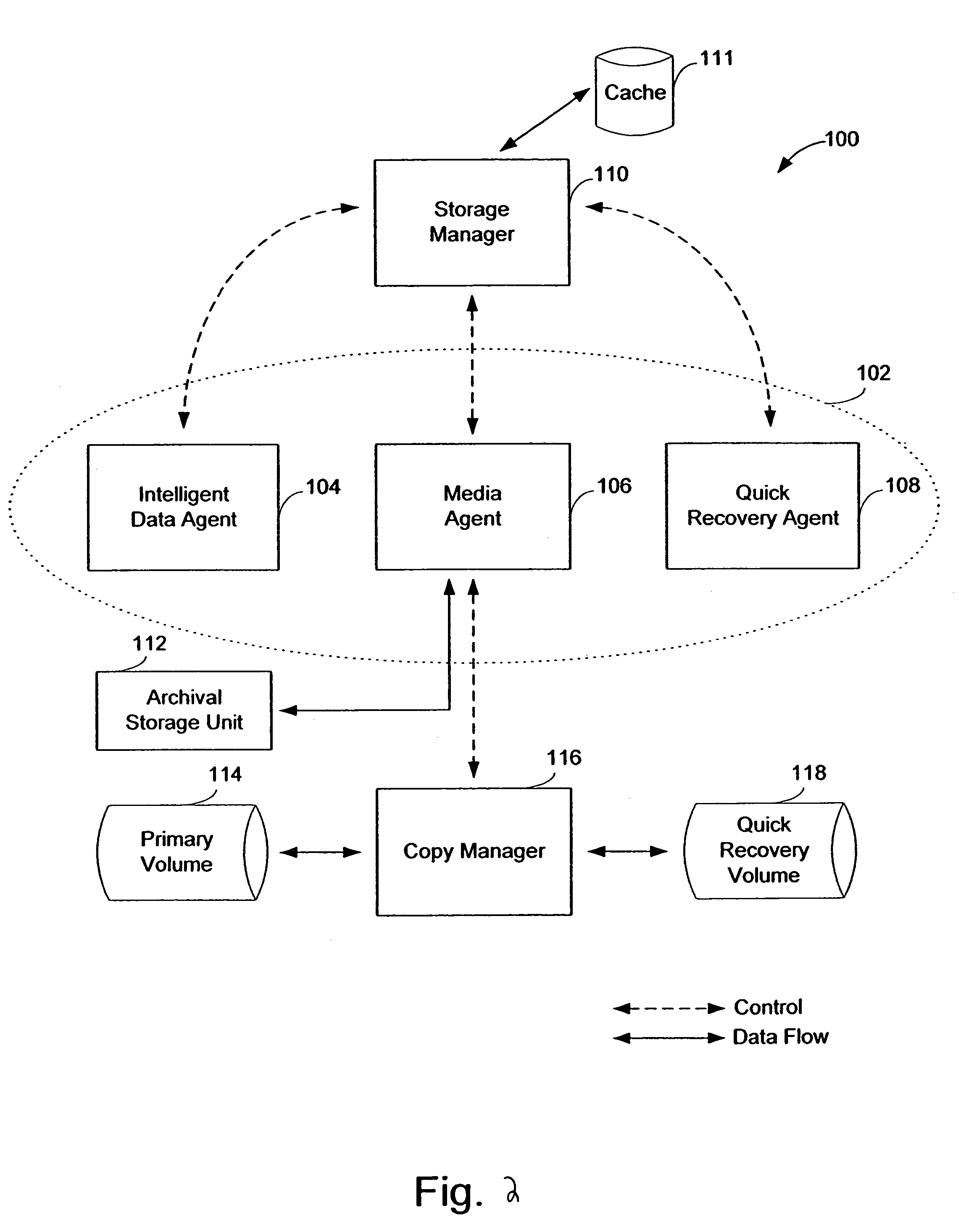
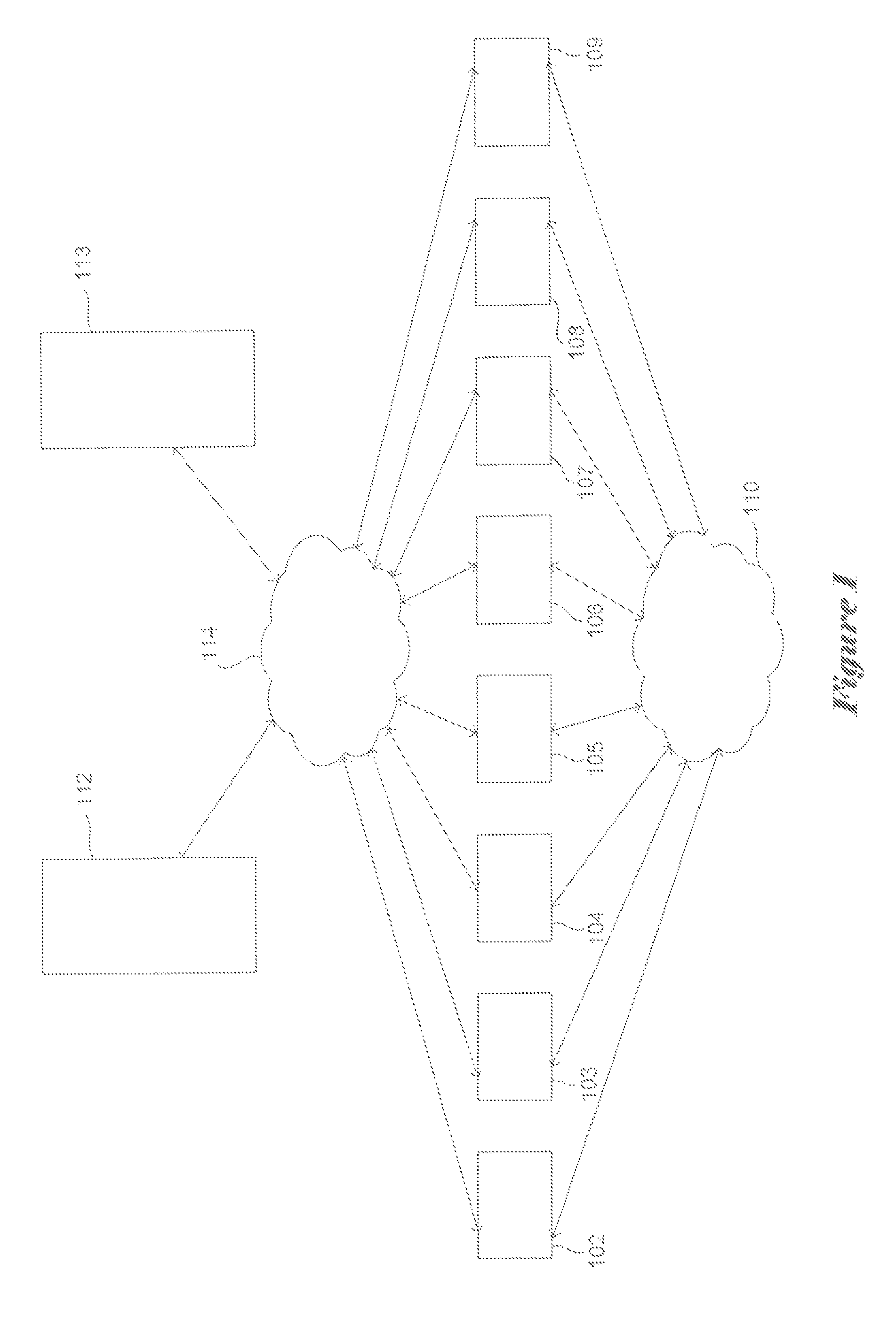
Snapshot storage and management system with indexing and user interface
InactiveUS7568080B2Create efficientlyEfficient managementData processing applicationsInput/output to record carriersStorage managementApplication software
A system and method of managing stored data in a storage management system. The storage management system includes a storage manager, a media agent connected to the storage manager, and a primary volume connected to the media agent. A plurality of snapshots are taken of the primary volume. The snapshots are indexed by associating respective information with the snapshot. The indexed snapshots are copied to a recovery volume. In this way, browsing features are enabled for the user. The user may view the snapshots in a hierarchical format, and may even view snapshot data in association with the corresponding application. The resultant recovery volume may be used to replace a primary volume.
Owner:COMMVAULT SYST INC
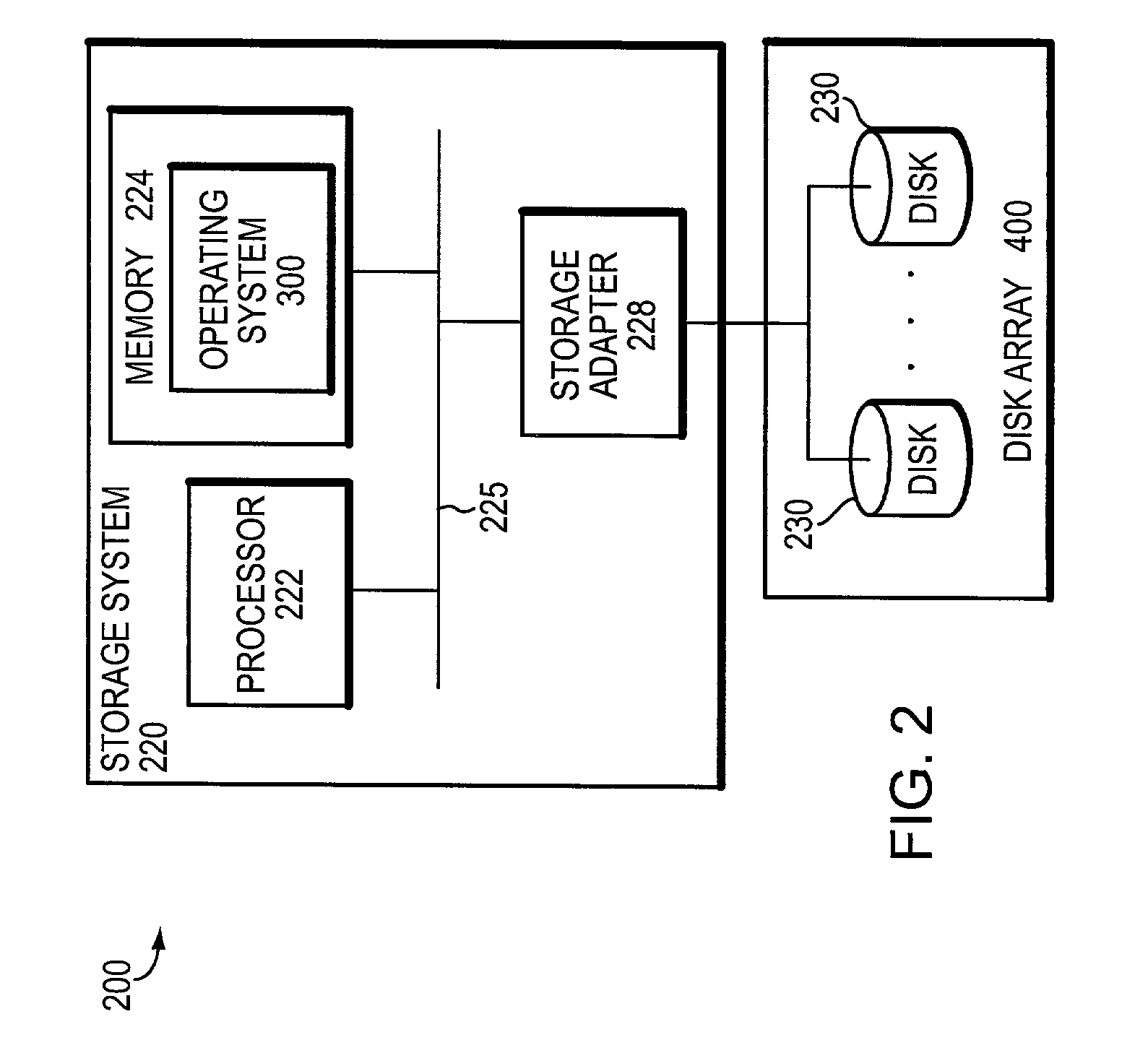
Sufficient free space for redundancy recovery within a distributed data-storage system
Embodiments of the present invention are directed to methods, and distributed data-storage systems employing the methods, for recovering redundancy within a distributed data-storage system upon failure of one or more mass-storage devices within a component data-storage system of the distributed data-storage system. In certain embodiments, failure of a mass-storage device within a component data-storage system elicits a redundancy-recovery operation in which segments affected by the mass-storage-device failure or failures are moved, by a process referred to as “migration,” to other component data-storage systems of the distributed data-storage system, and are recovered as a by-product of migration. Certain embodiments of the present invention more efficiently address redundancy recovery by moving only as many segments from the component data-storage system as needed to provide sufficient free space within the component data-storage system to recover the remaining segments affected by the mass-storage-device failure or failures within the component data-storage system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
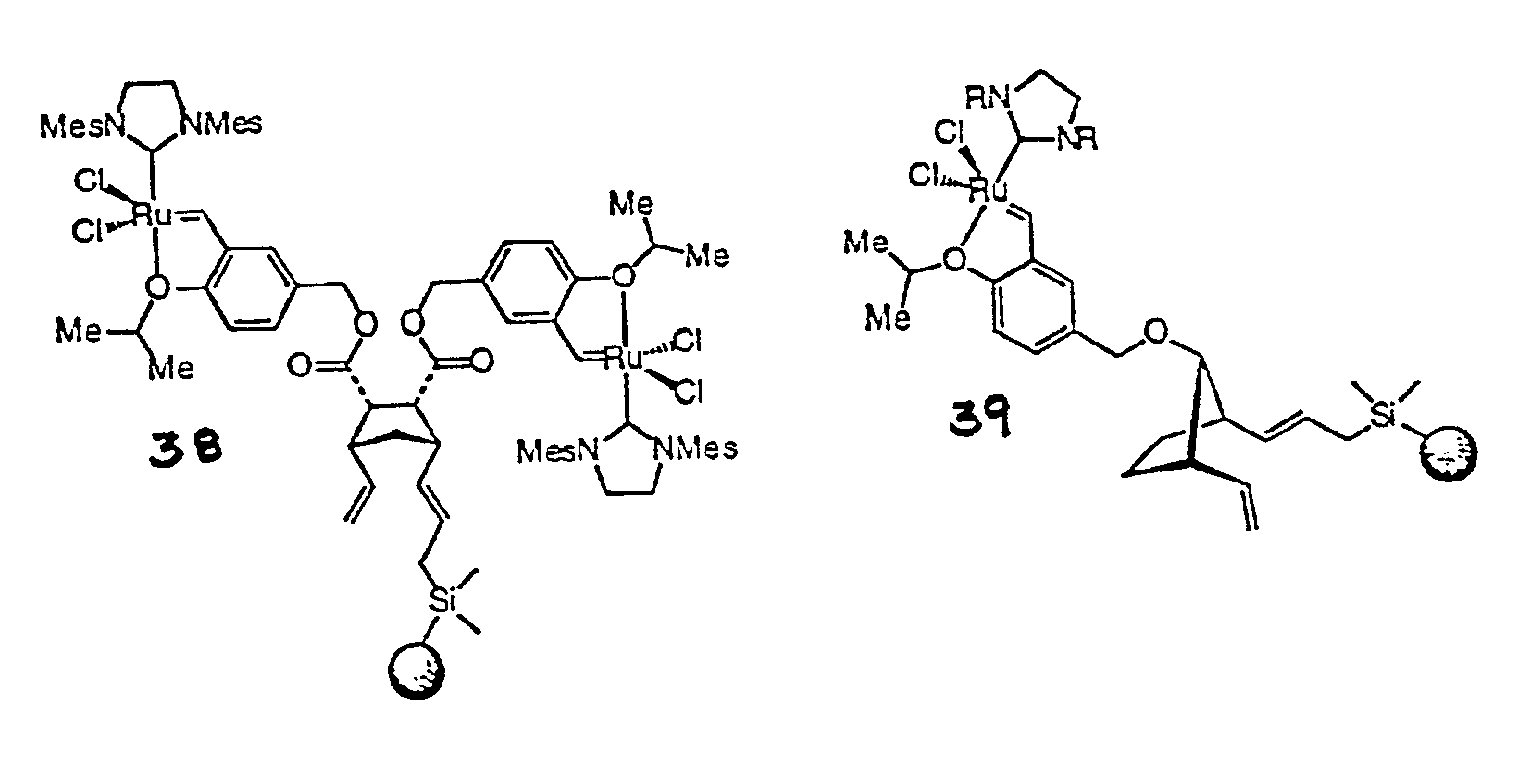
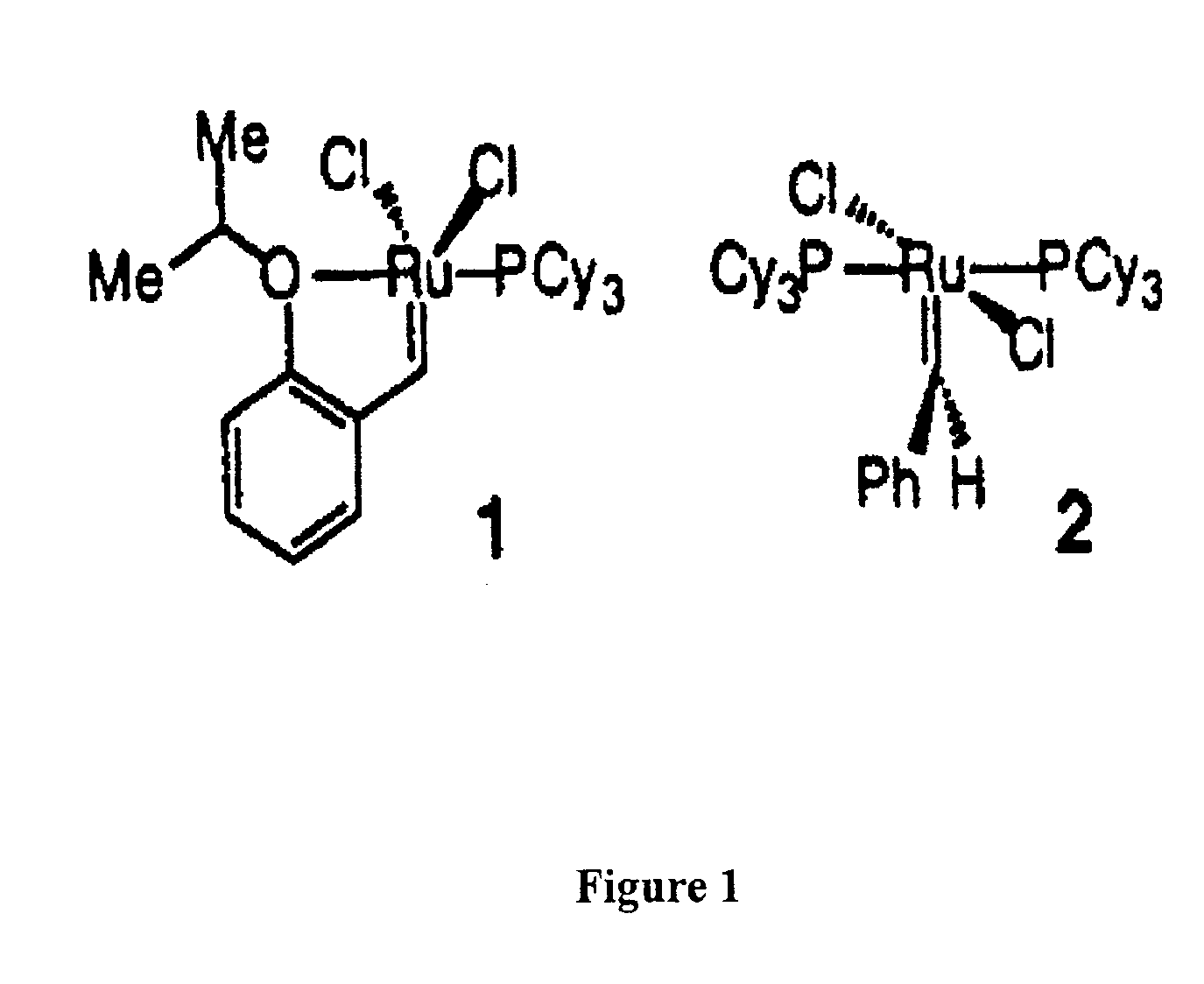
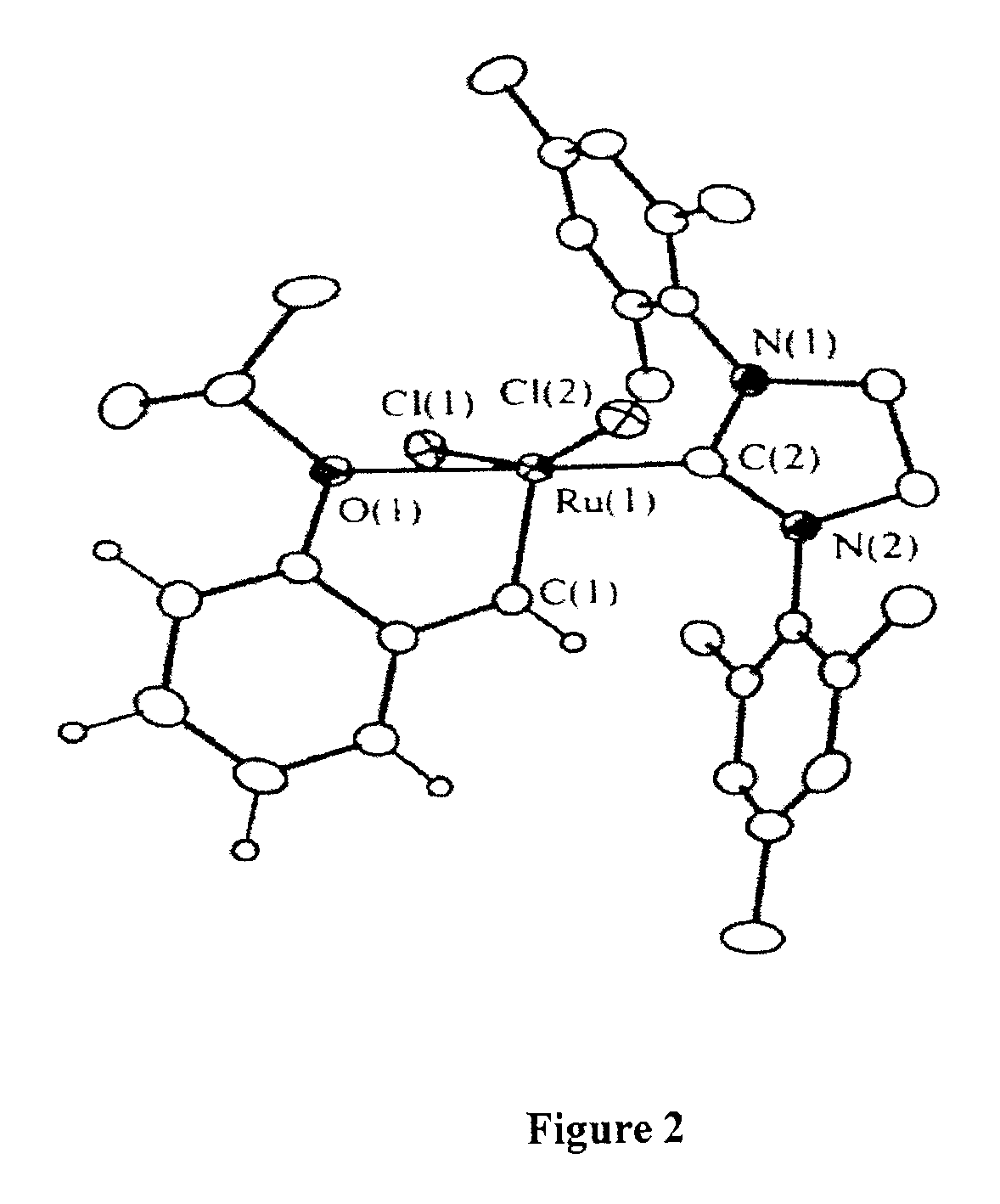
Recyclable metathesis catalysts
ActiveUS6921735B2Highly efficient mannerReadily isolableOrganic chemistry methodsCarboxylic acid esters preparationEtherCoordination complex
Highly active, recoverable and recyclable transition metal-based metathesis catalysts and their organometallic complexes including dendrimeric complexes are disclosed, including a Ru complex bearing a 1,3-dimesityl-4,5-dihydroimidazol-2-ylidene and styrenyl ether ligand. The heterocyclic ligand significantly enhances the catalytic activity, and the styrenyl ether allows for the easy recovery of the Ru complex. Derivatized catalysts capable of being immobilized on substrate surfaces are also disclosed. The present catalysts can be used to catalyze ring-closing metathesis (RCM), ring-opening (ROM) and cross metatheses (CM) reactions, and promote the efficient formation of various trisubstituted olefins at ambient temperature in high yield.
Owner:BOSTON COLLEGE
Separation apparatus and separation method
InactiveUS20060000772A1Improve efficiencyHigh activityIon-exchange process apparatusSemi-permeable membranesBuffer solutionAnalytical chemistry
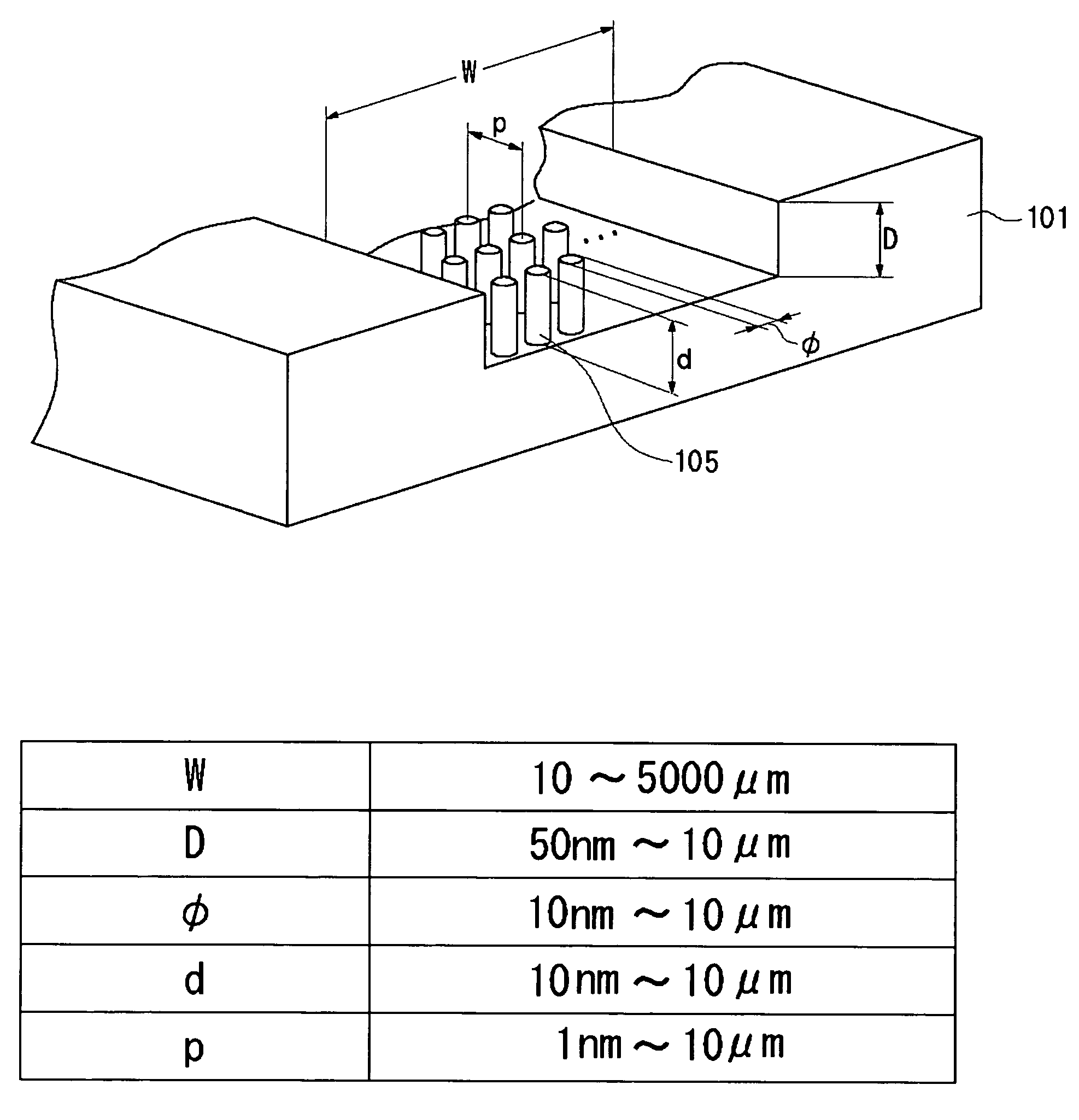
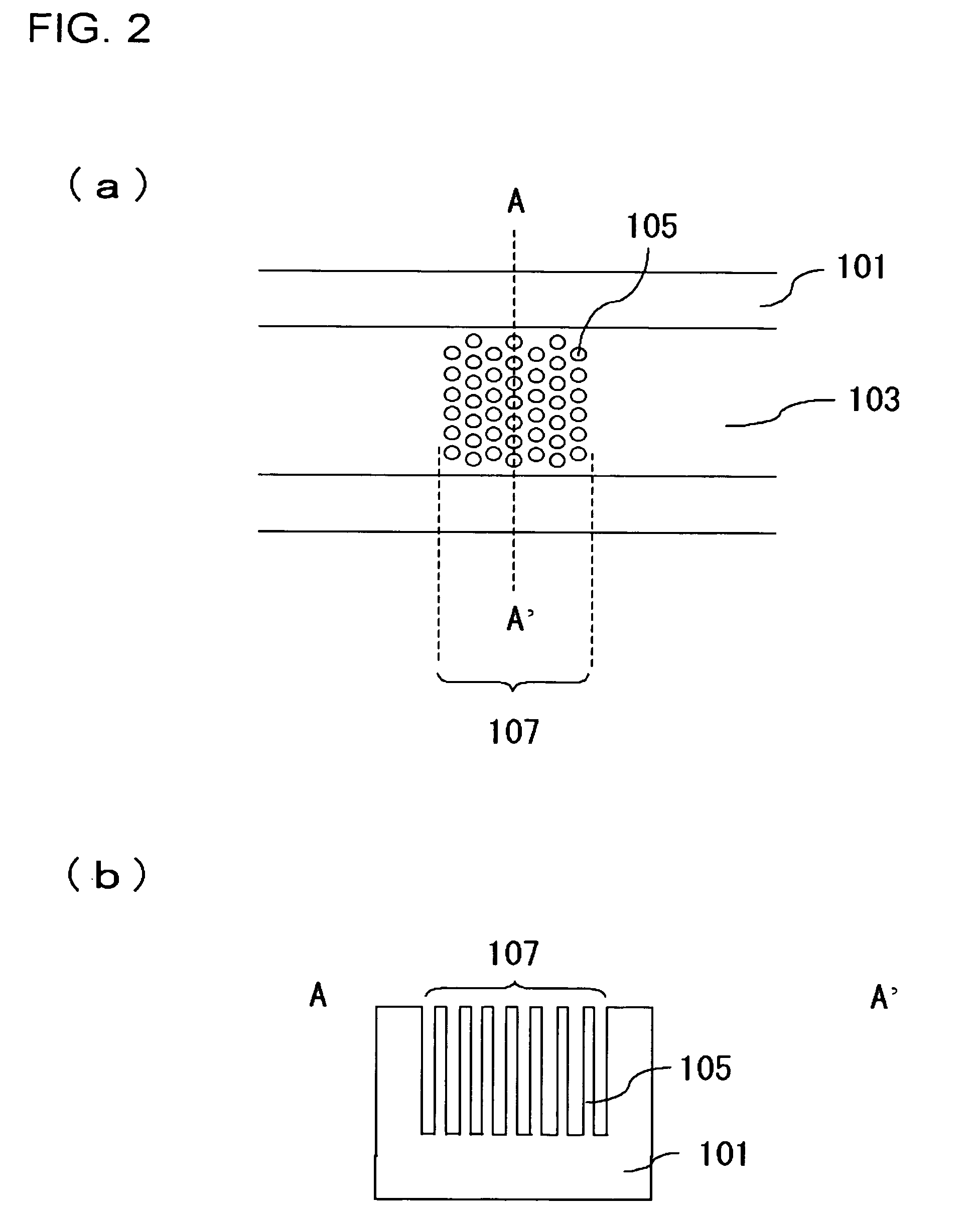
A channel (103) is formed in a substrate (101), and a portion of the channel (103) is provided with a separating portion (107). A number of pillars are formed in the separating portion (107), and an adsorptive substance layer having an adsorptive substance, which exhibits a specific interaction for a specific substance, immobilized on the surface thereof, is formed. Once a sample is introduced into the channel (103), the specific substance is adsorbed on the adsorptive substance layer to be separated from other components. After washing the inside of the channel (103) with a buffer solution, the specific substance is desorbed from the adsorptive substance layer by flowing a eluting solution through the channel (103) and the specific substance is recovered.
Owner:NEC CORP
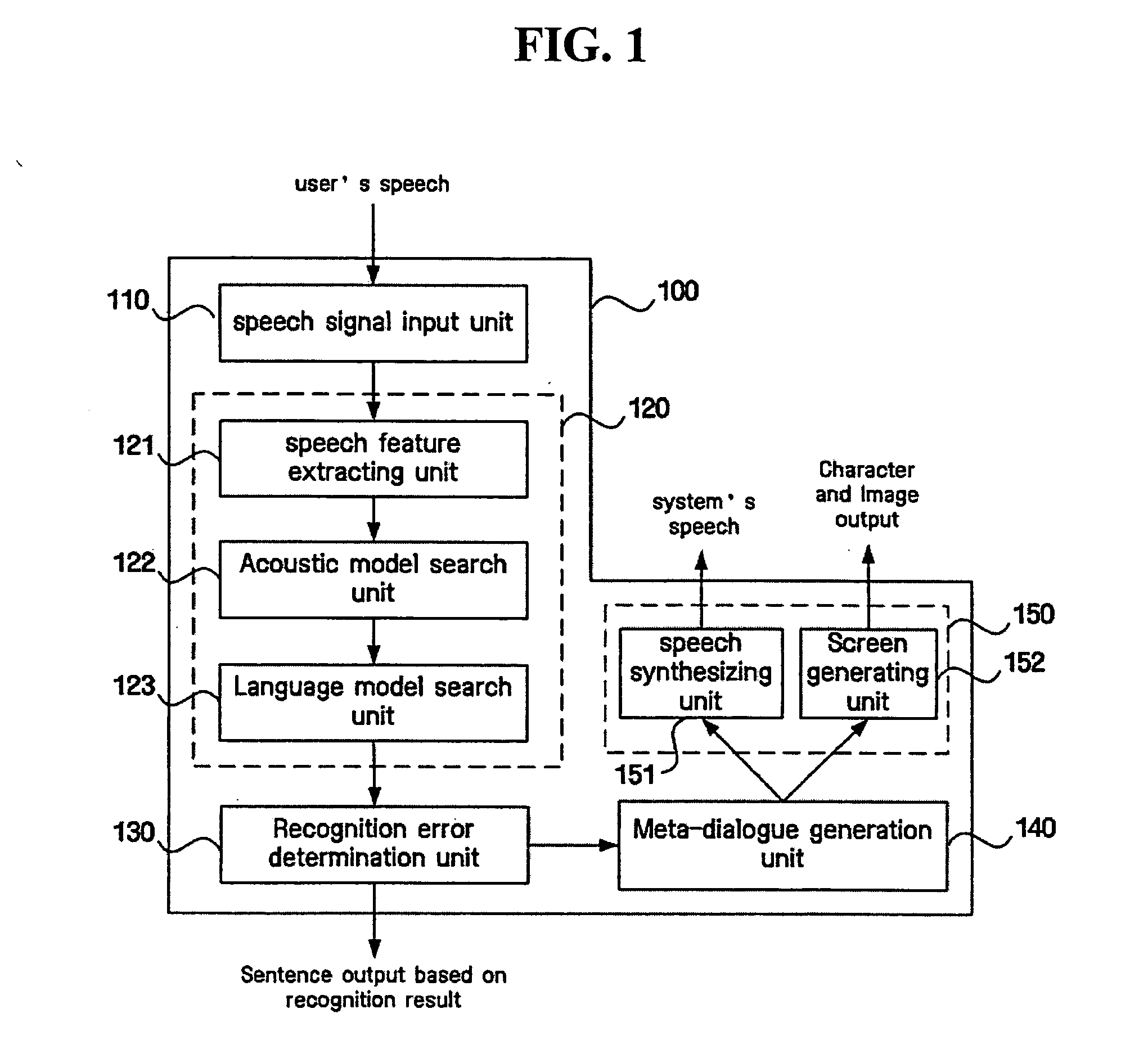
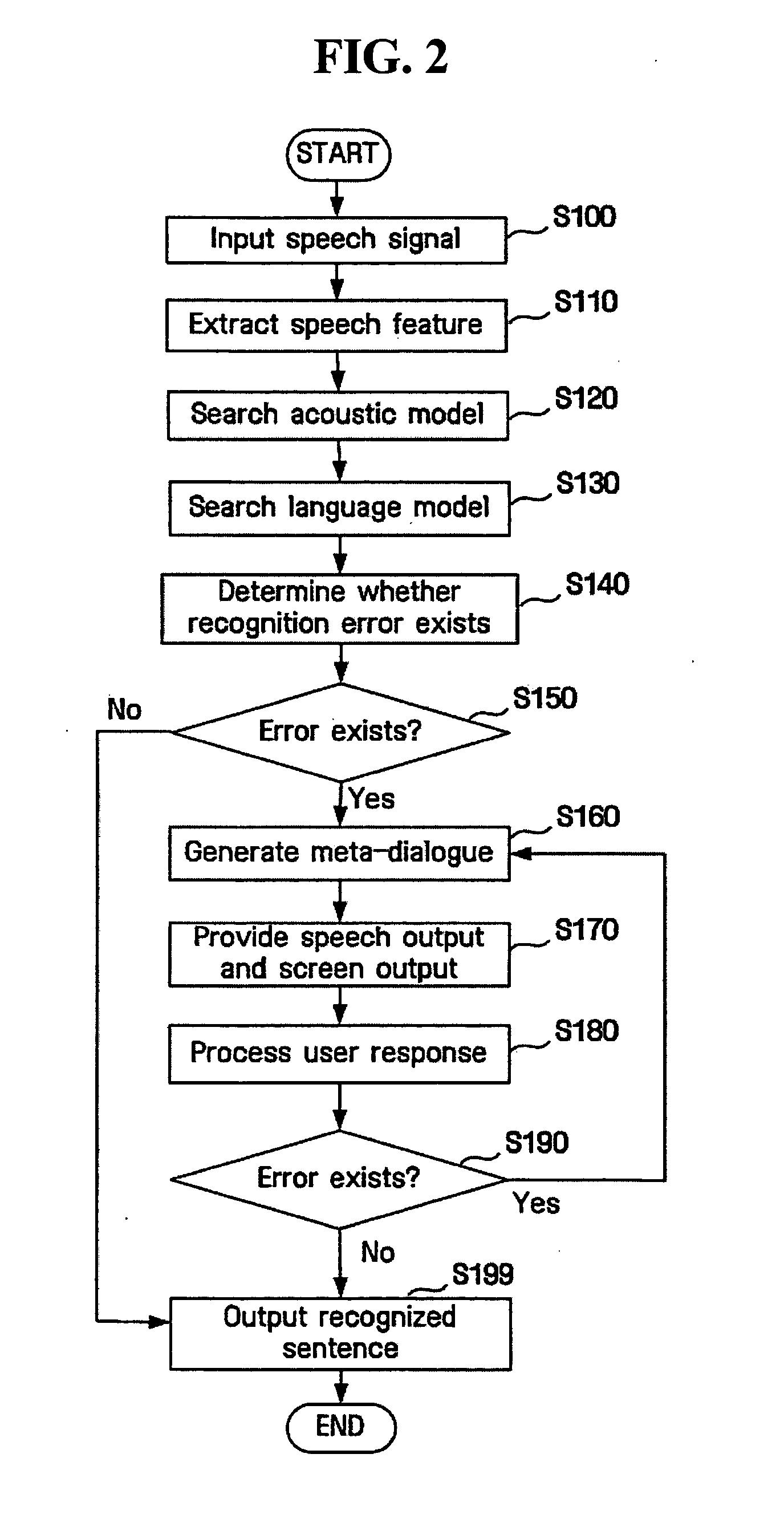
Method and apparatus handling speech recognition errors in spoken dialogue systems
ActiveUS20050033574A1Reliably resolvingEffective recoverySpeech recognitionDialog systemSpoken language
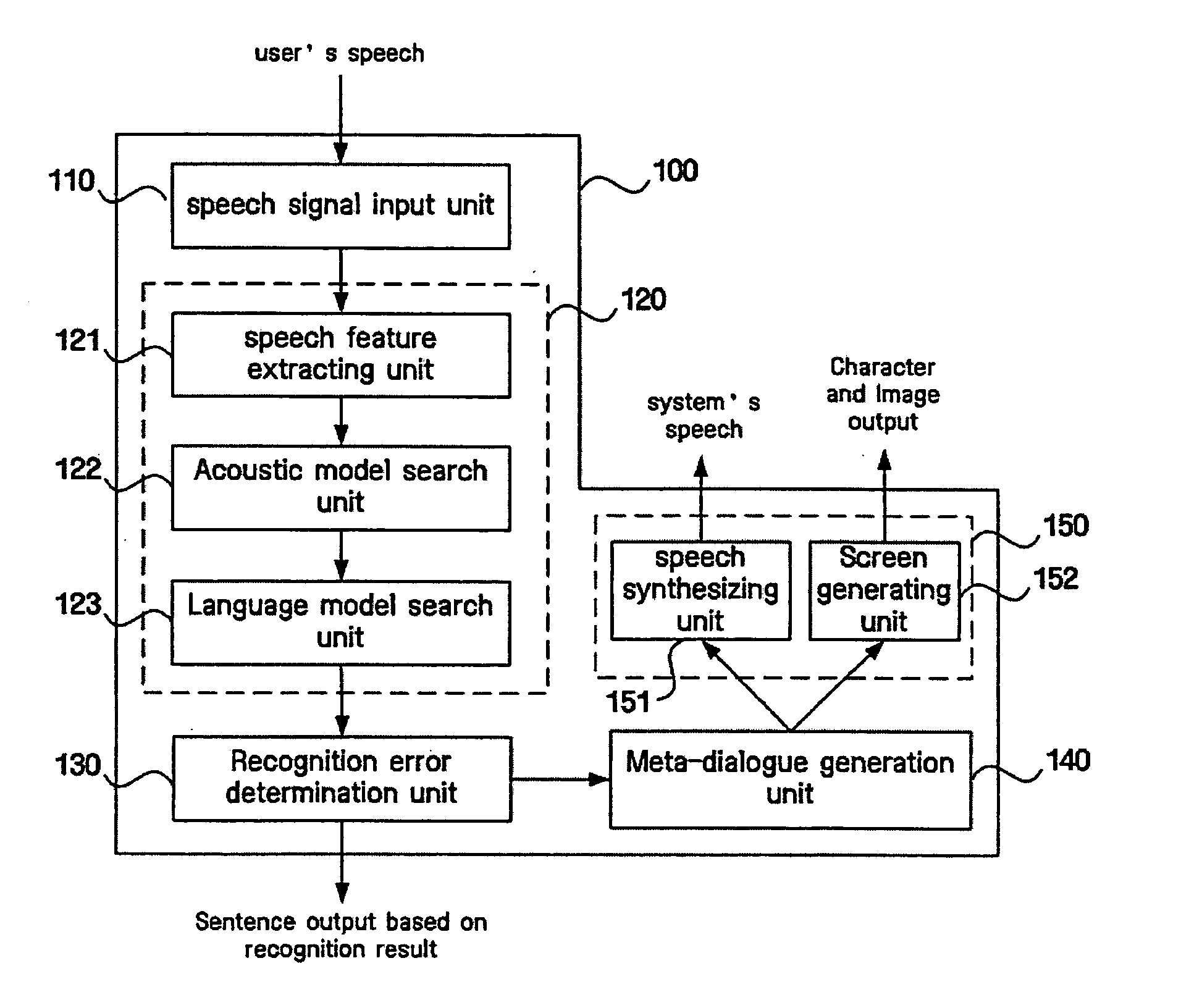
In order to handle portions of a recognized sentence having an error, a speaker or user is questioned about contents associated with the portions, and according to a user's answer a result is obtained. A speech recognition unit extracts a speech feature of a speech signal inputted from a user and finds a phoneme nearest to the speech feature to recognize a word. A recognition error determination unit finds a sentence confidence based on a confidence of the recognized word, performs examination of a semantic structure of a recognized sentence, and determines whether or not an error exists in the recognized sentence which is subject to speech recognition according to a predetermined criterion based on both the sentence confidence and a result of examining the semantic structure of the recognized sentence. Further, a meta-dialogue generation unit generates a question asking the user for additional information based on a content of a portion where the error exists and a type of the error.
Owner:SAMSUNG ELECTRONICS CO LTD
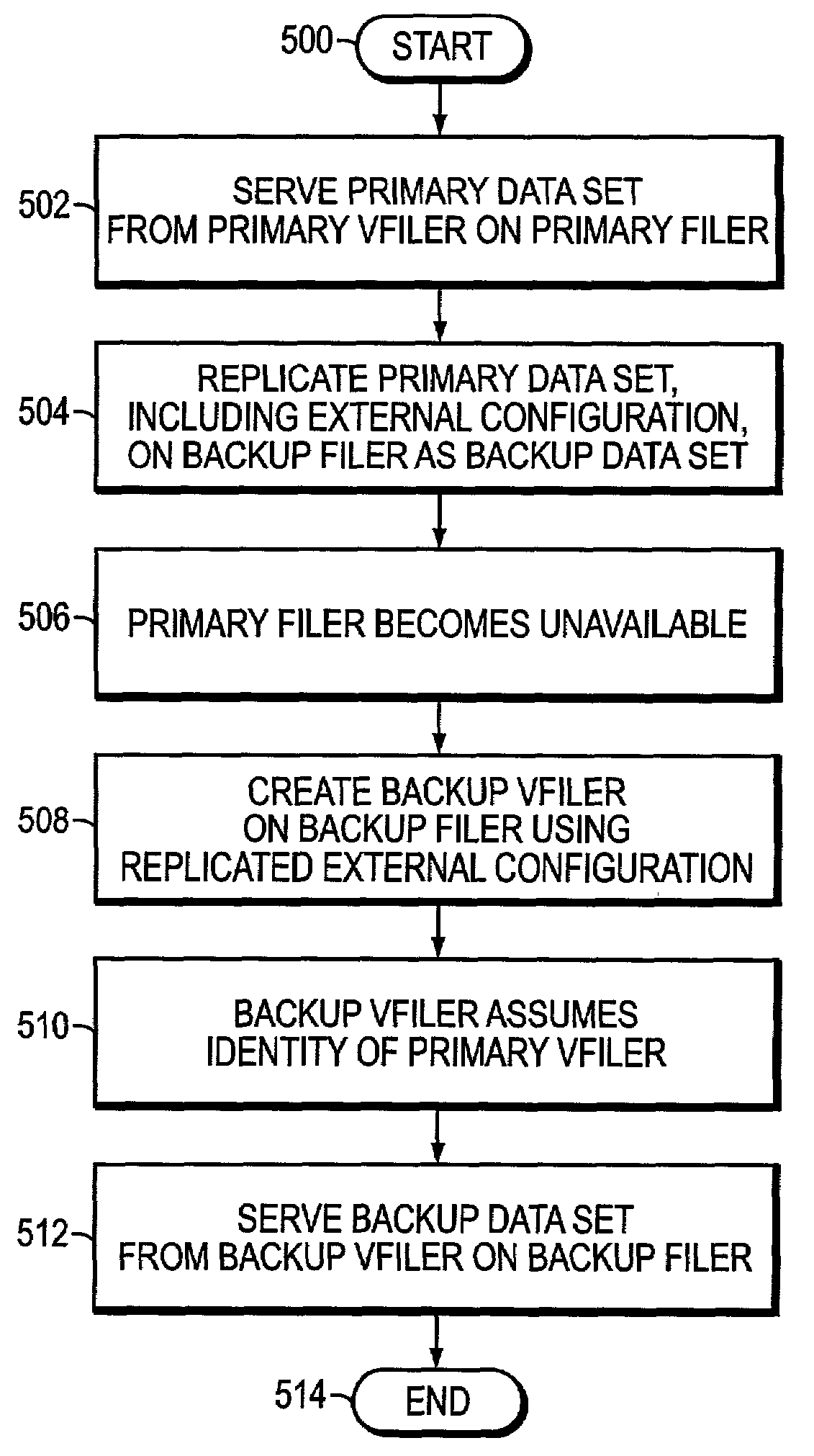
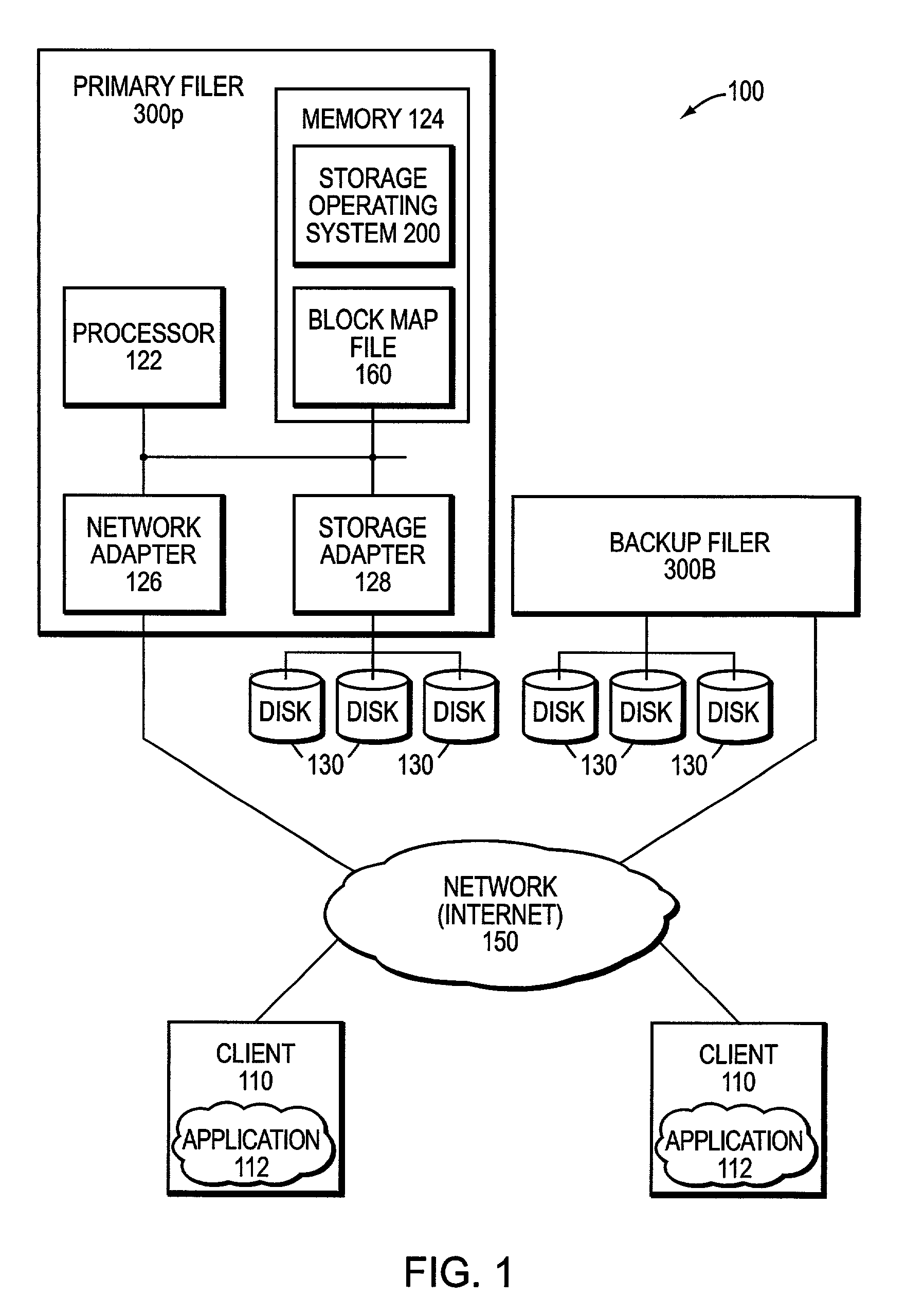
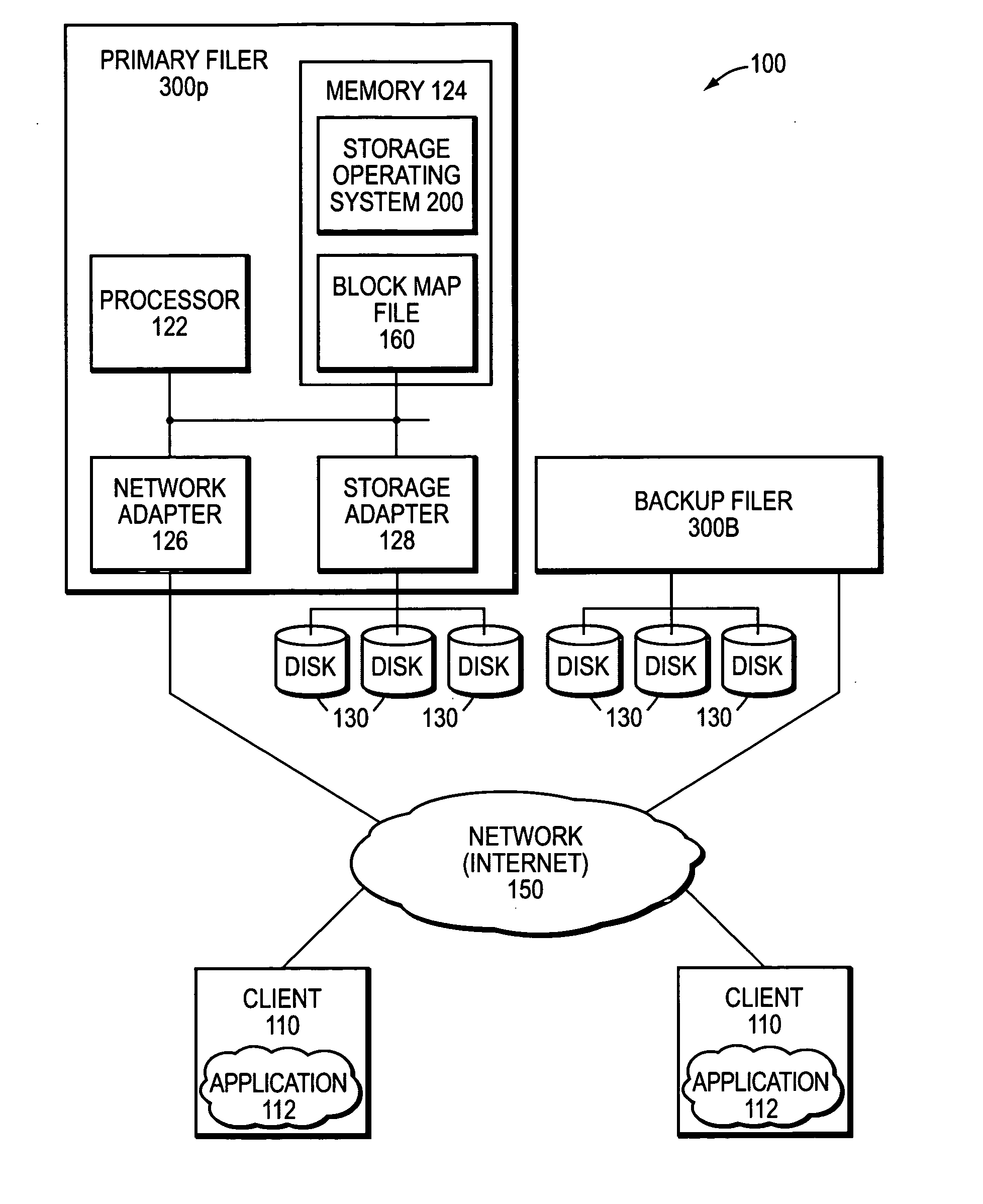
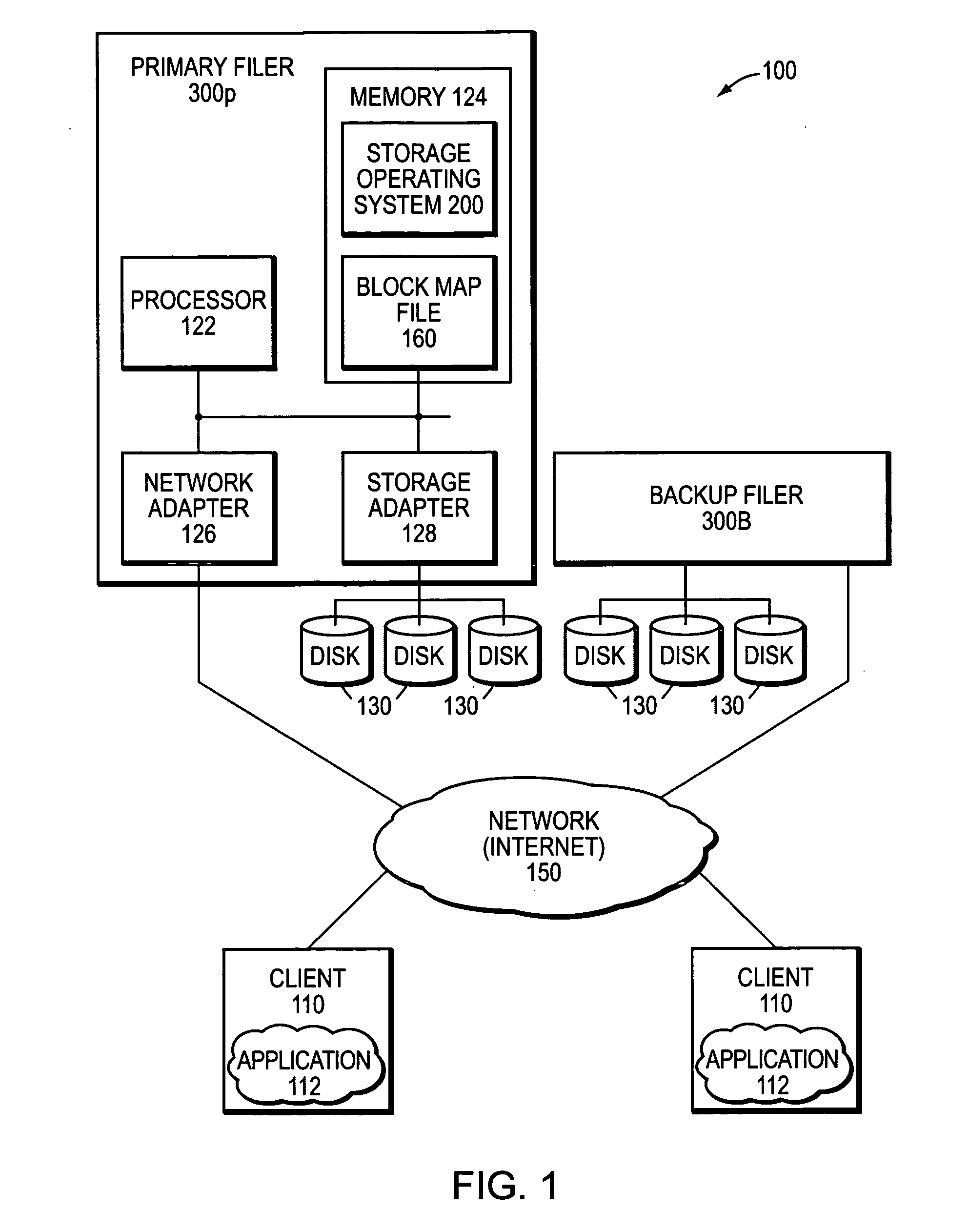
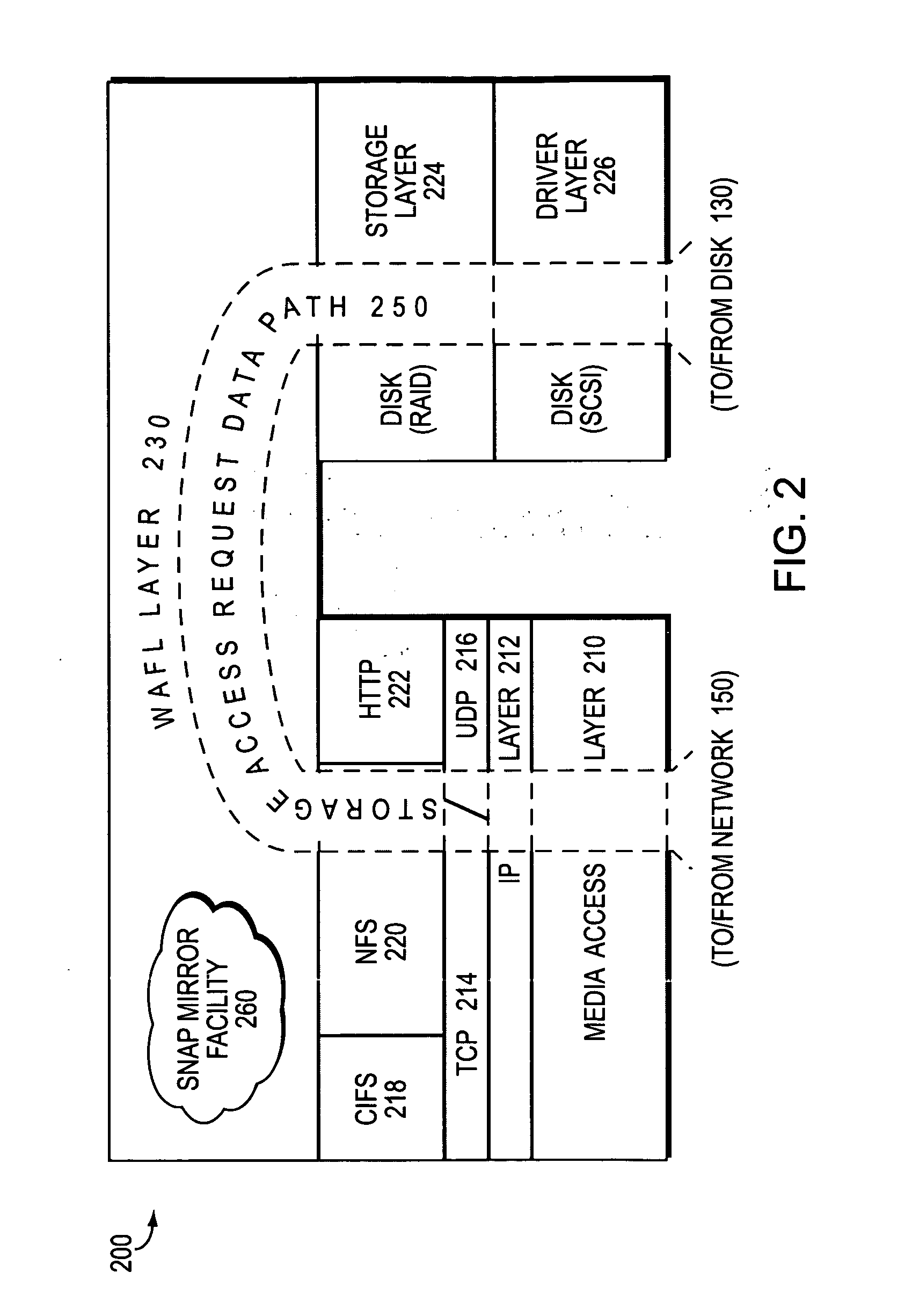
Remote disaster recovery and data migration using virtual appliance migration
A technique efficiently creates and serves a backup data set on a backup filer located at a remote site from a primary filer by essentially moving an entire operating environment of a primary data set to the backup filer. The primary filer is organized into one or more virtual filers (vfilers), one of which (the primary vfiler) is configured to serve data, such as the primary data set, for a client. In the event that the primary filer or primary vfiler becomes unavailable, the technique may be implemented as a disaster recovery or data migration sequence to enable efficient instantiation of a backup vfiler to serve the backup data set for the client.
Owner:NETWORK APPLIANCE INC
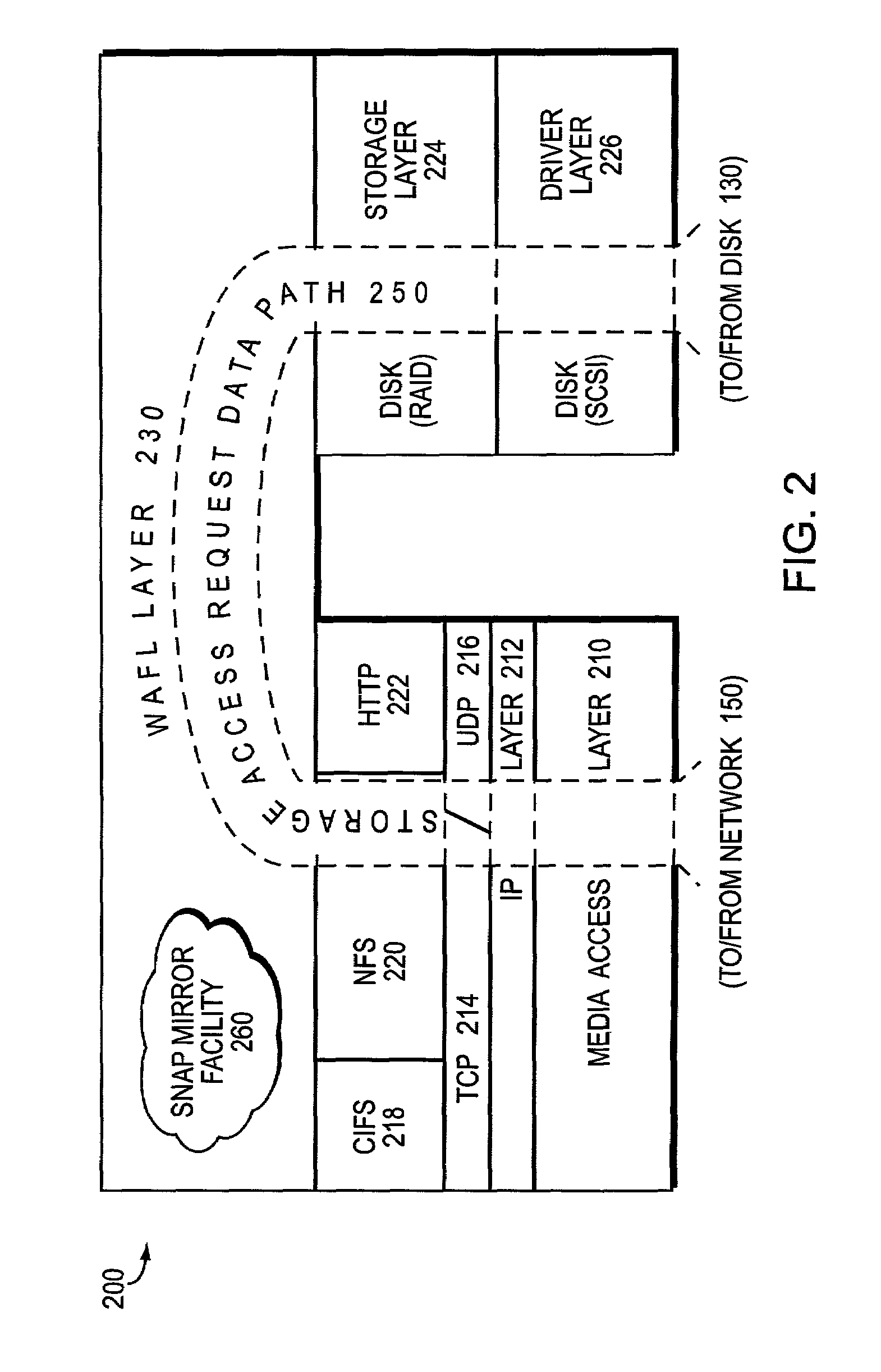
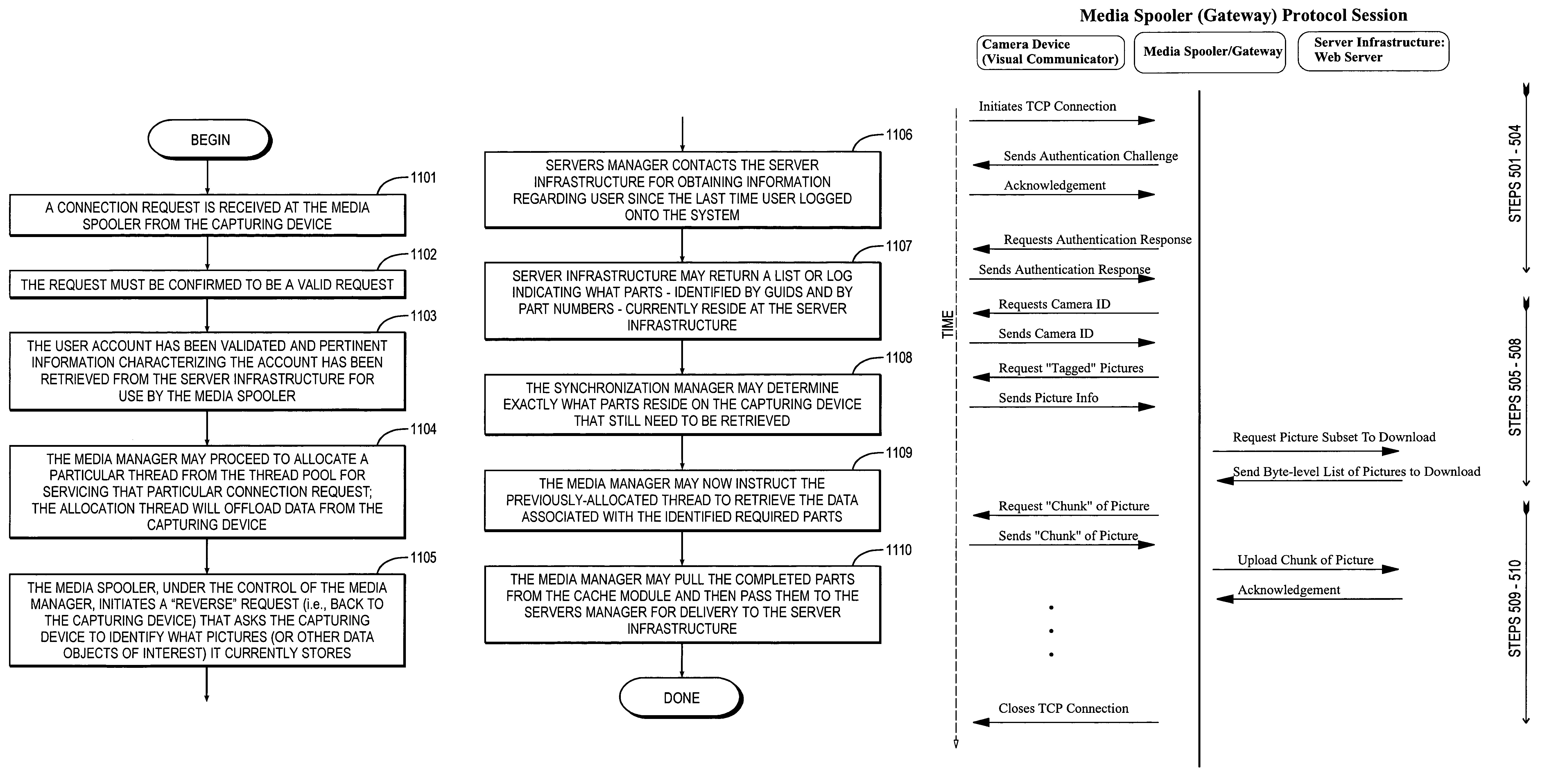
Media spooler system and methodology providing efficient transmission of media content from wireless devices
InactiveUS7103357B2Guaranteed normal transmissionEffective recoveryTelevision system detailsTelevision system scanning detailsStructure of Management InformationNetwork service
A media spooler system is described that provides a methodology for efficient transmission of media content from client devices, such transmission of digital images from wireless digital cameras. The media spooler or gateway addresses wireless transmission problems by acting as a protocol gateway between a thin-client device and a target host or server (supported by a server infrastructure). More particularly, the media spooler of the present invention acts as a protocol gateway between thin-client devices (e.g., “mobile visual communicator” in the form of a wireless digital camera) and server infrastructure (e.g., server-based computer systems or “Web servers” of a photographic service provider). This task entails accepting multiple, simultaneous connections from various client devices (e.g., wireless digital cameras), extracting information from those devices (e.g., digital photographs or other media content), and then uploading that information to the target server infrastructure. In basic operation, the media spooler queries each client device for the information (e.g., media, such as pictures) the client device thinks should uploaded, and then the media spooler queries the server infrastructure for the subset of pictures that have not been already uploaded. This improved coordination or synchronization of information between a device and target host allows for efficient recovery of dropped cellular data calls by essentially allowing the media spooler to “pick up where it left off.”
Owner:SYNIVERSE ICX LLC
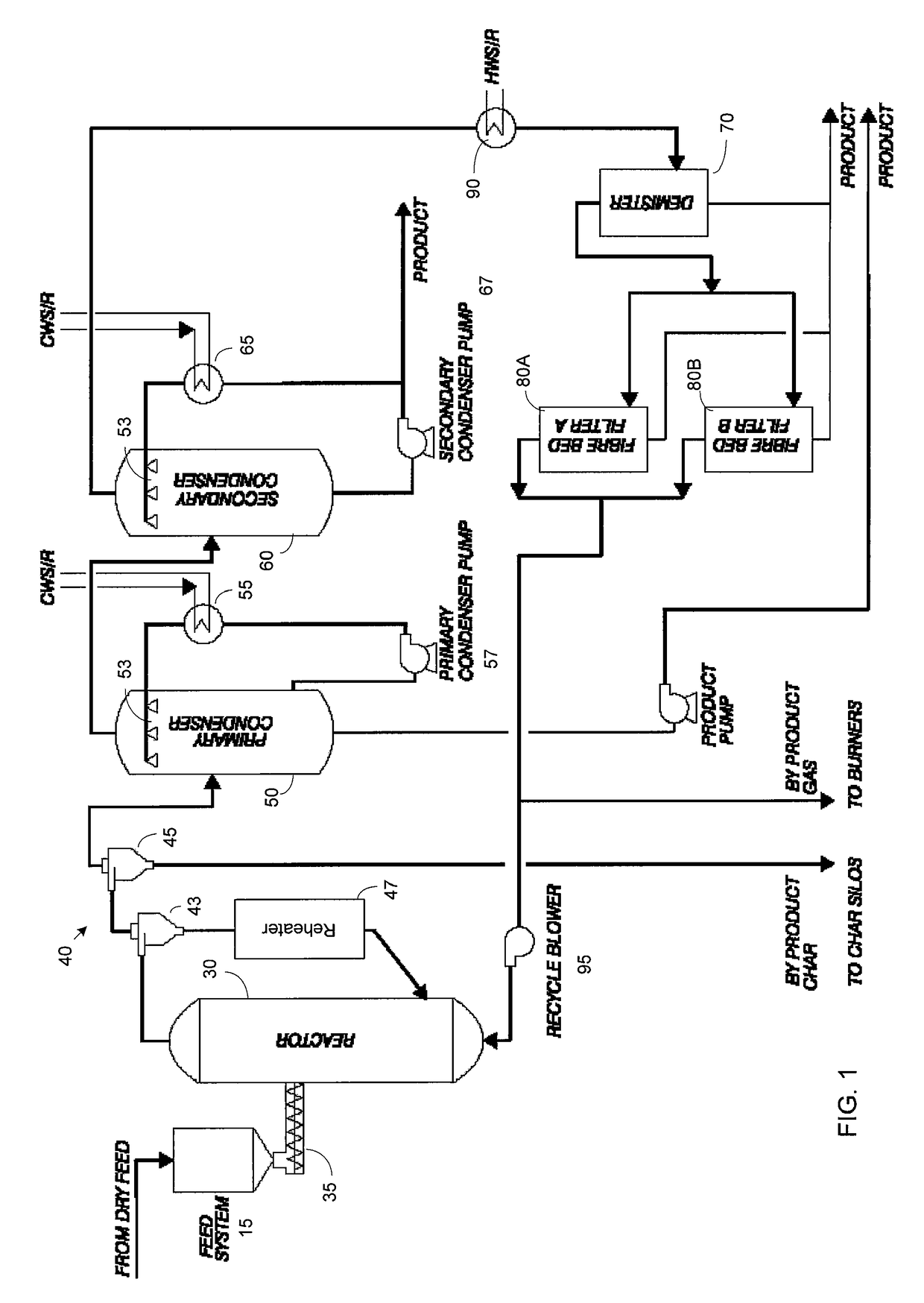
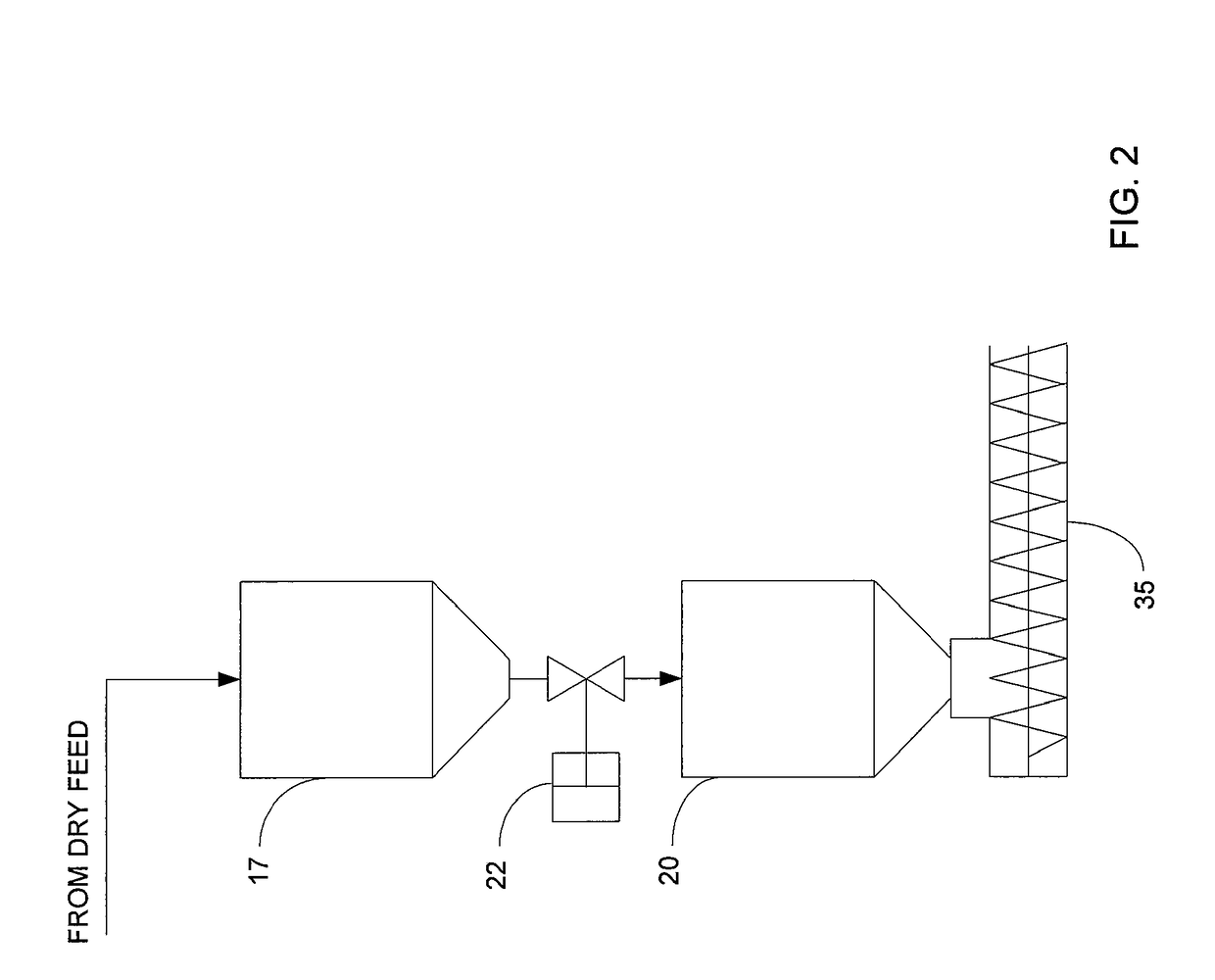
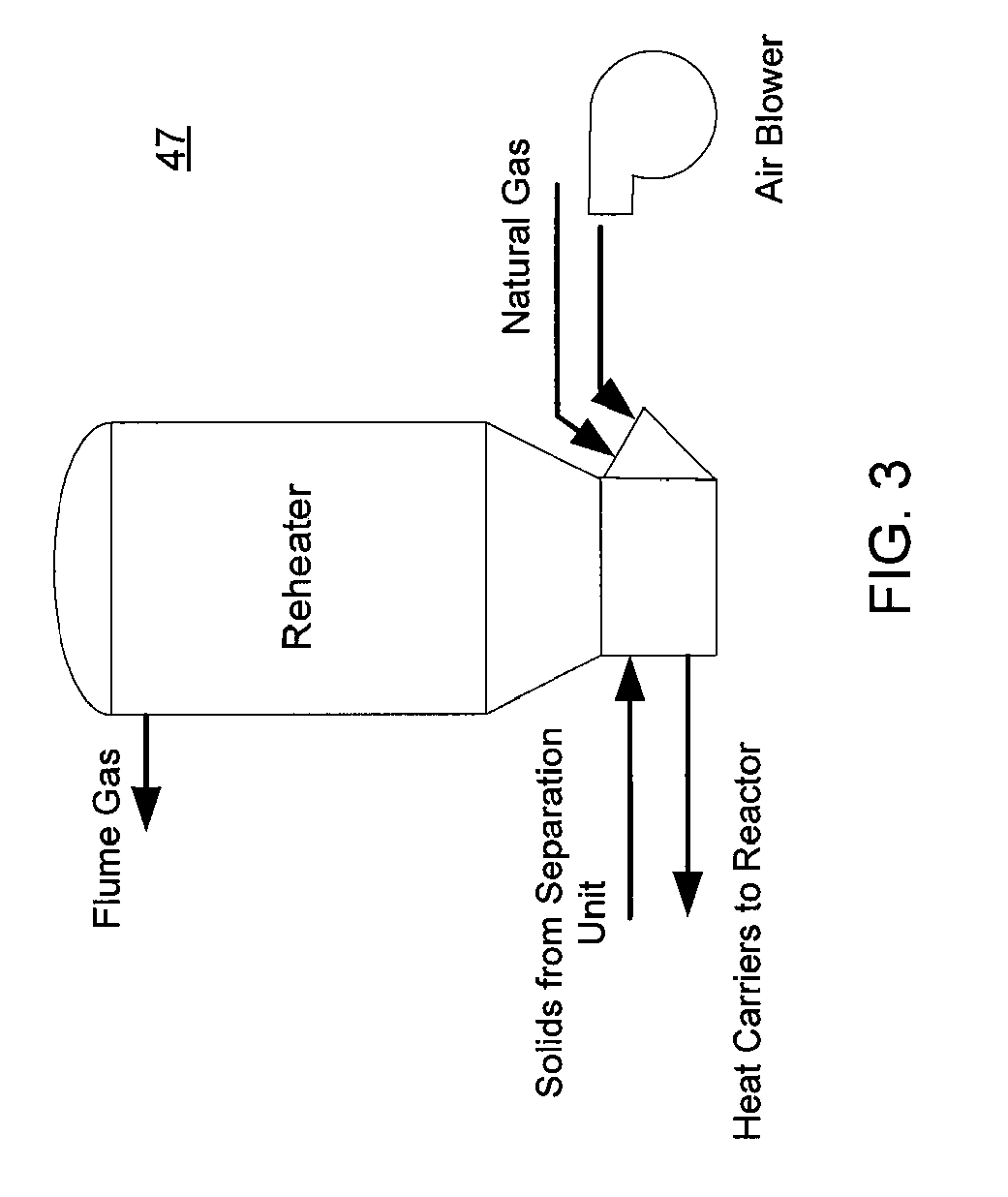
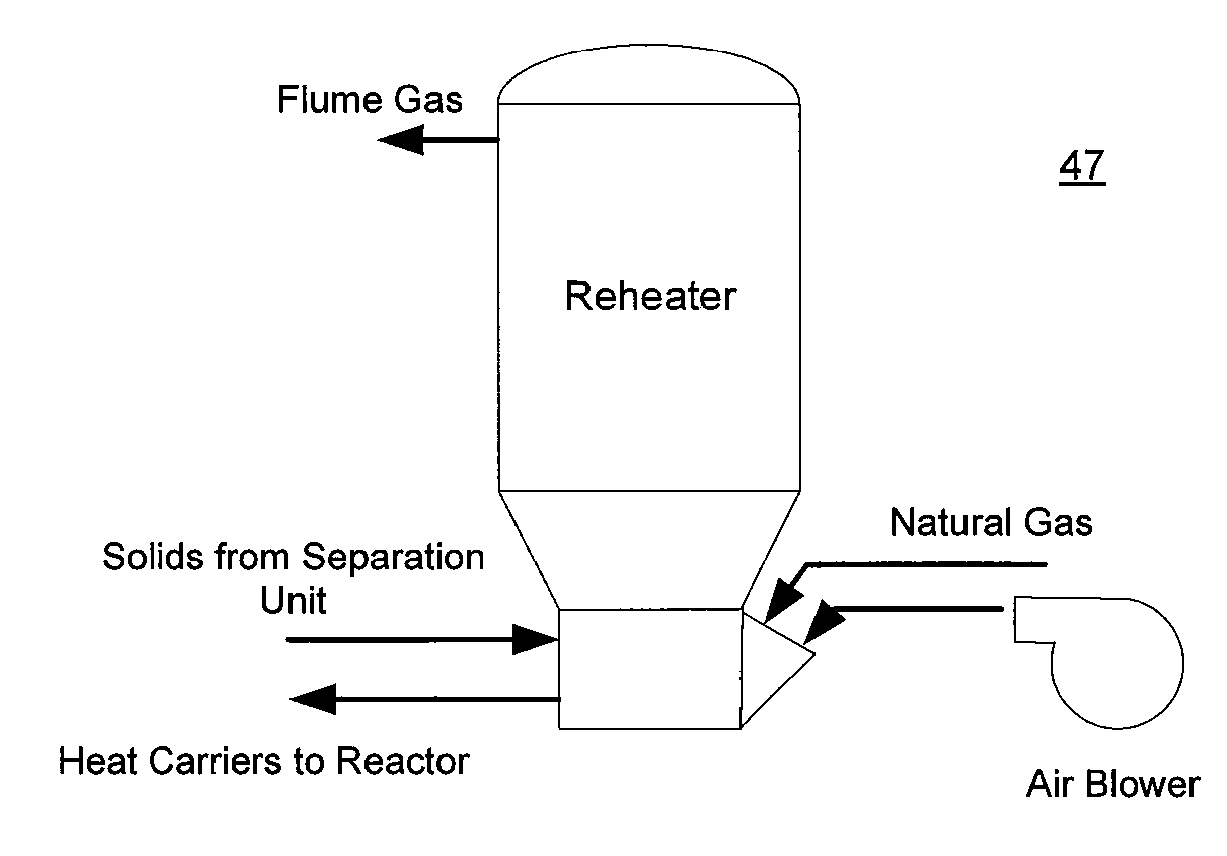
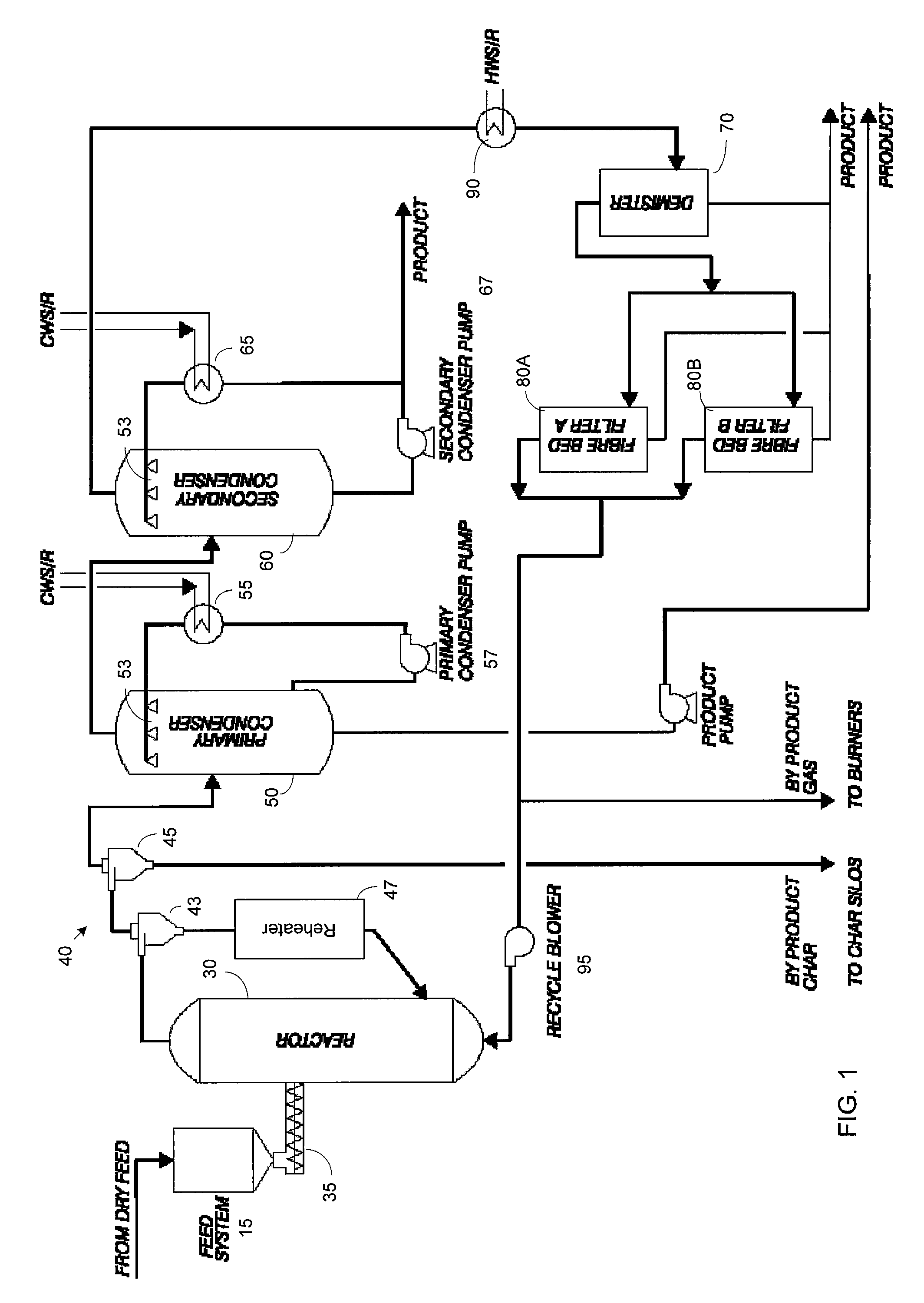
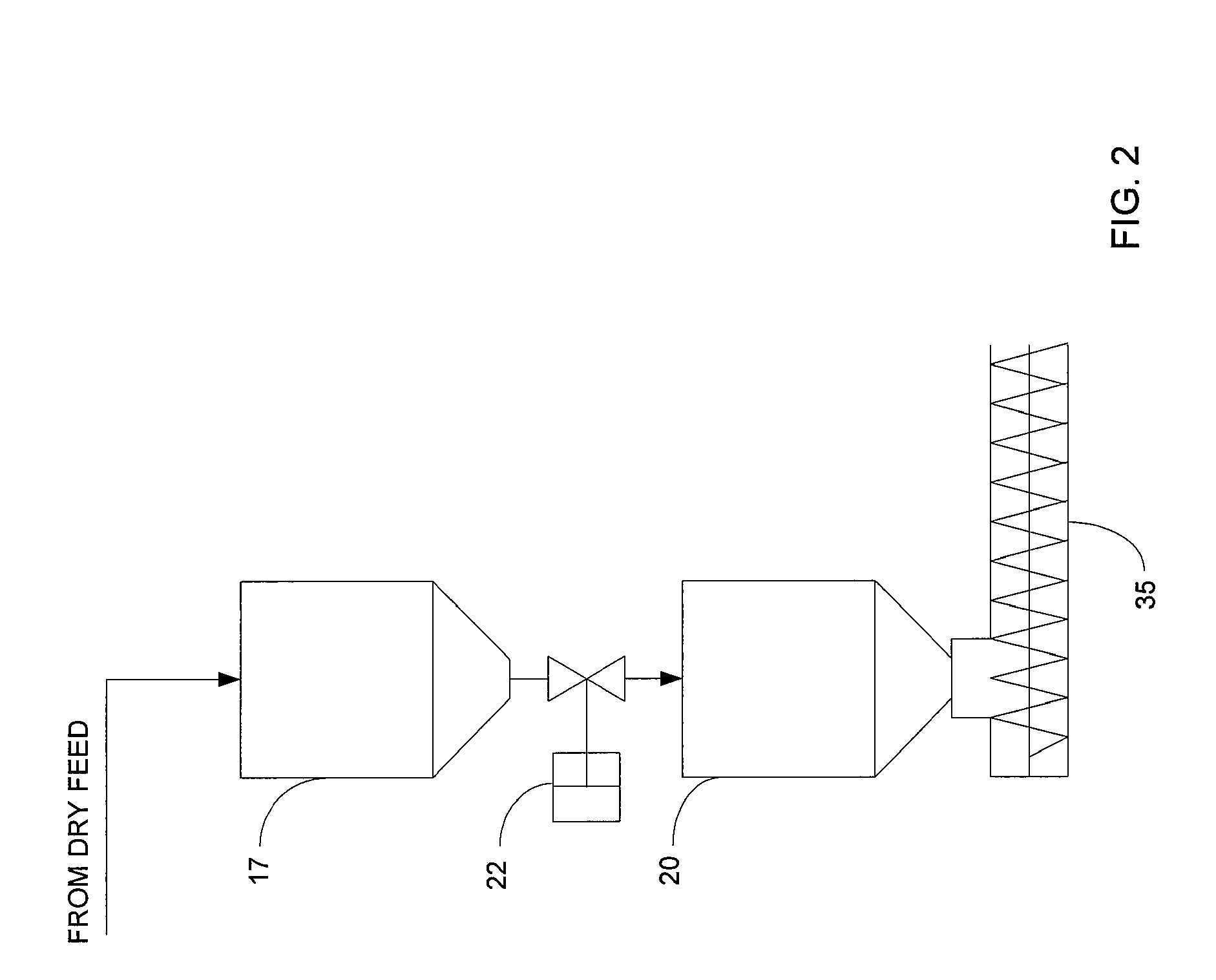
Rapid thermal conversion of biomass
ActiveUS7905990B2Improved rapid thermal conversion processEffective recoveryThermal non-catalytic crackingSolid waste disposalLiquid productHeat carrier
A rapid thermal conversion process for efficiently converting wood, other biomass materials, and other carbonaceous feedstock (including hydrocarbons) into high yields of valuable liquid product, e.g., bio-oil, on a large scale production. Biomass material, e.g., wood, is feed to a conversion system where the biomass material is mixed with an upward stream of hot heat carriers, e.g., sand, that thermally convert the biomass into a hot vapor stream. The hot vapor stream is rapidly quenched with quench media in one or more condensing chambers located downstream of the conversion system. The rapid quenching condenses the vapor stream into liquid product, which is collected from the condensing chambers as a valuable liquid product. The liquid product may itself be used as the quench media.
Owner:ENSYN RENEWABLES
Differentiation-suppressive polypeptide
InactiveUS6337387B1Improve physiological activityEasily mutatePeptide/protein ingredientsDepsipeptidesGeneMedical treatment
A polypeptide which contains the amino acid sequence described in SEQ ID NO: 1 in the Sequence Listing encoded by a gene originating in human being. Because of serving as a chemical efficacious in the supression of the proliferation and defferentiation of undifferentiated blood cells. this polypeptide is expected to be usable in medicines and medical supplies.
Owner:ASAHI KASEI KK
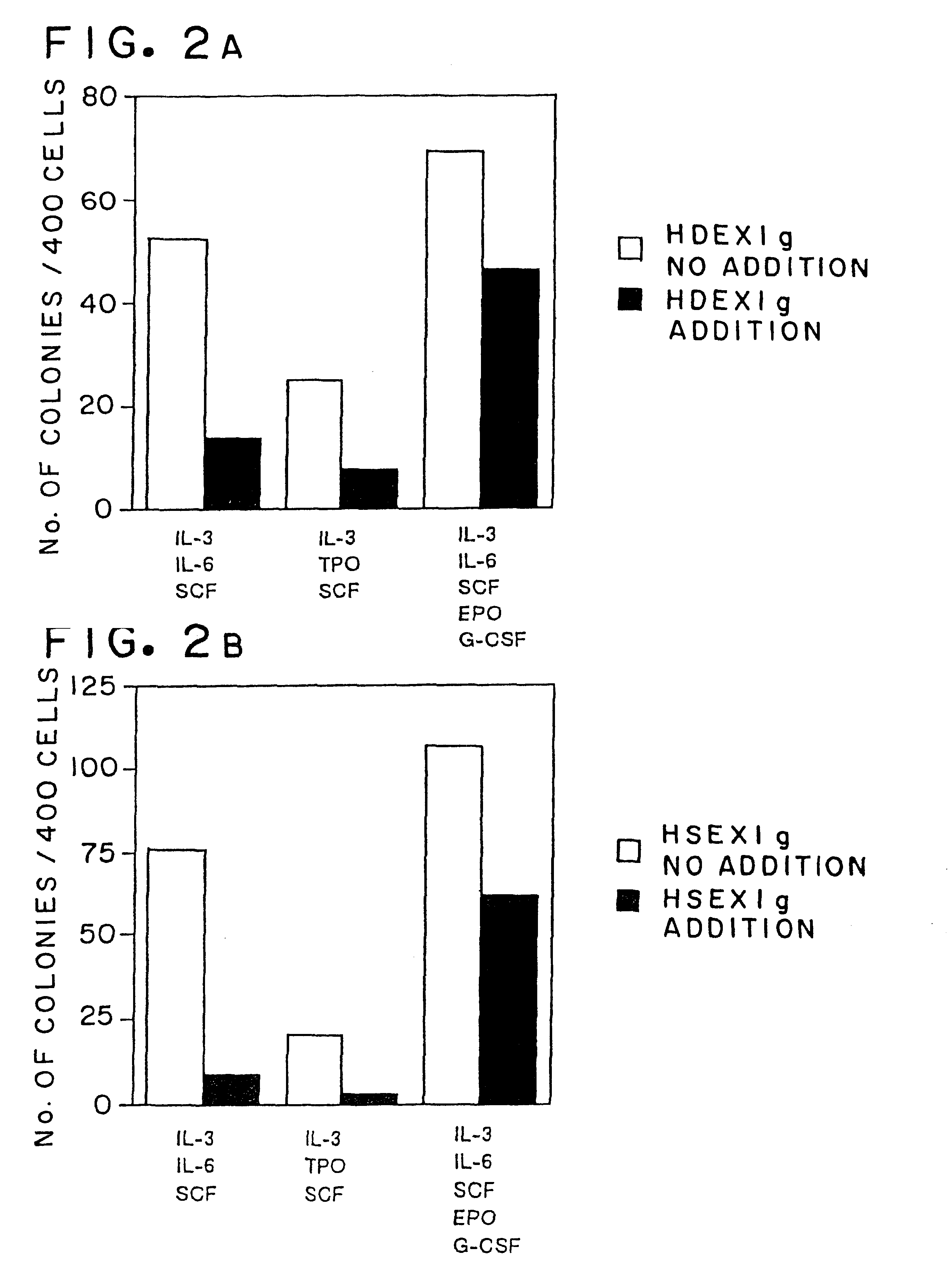
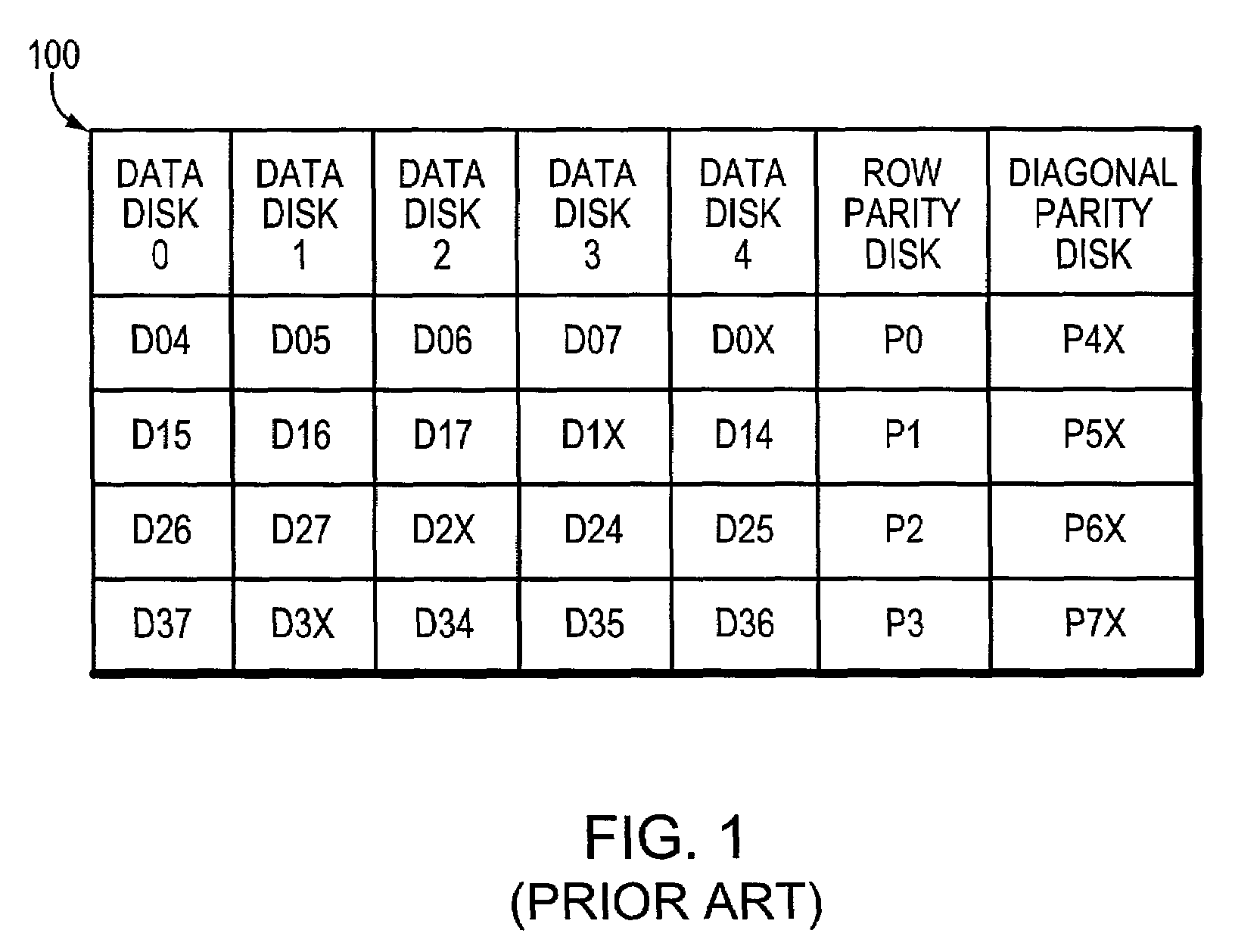
Row-diagonal parity technique for enabling efficient recovery from double failures in a storage array
ActiveUS6993701B2Reduce overheadEffective recoveryInput/output to record carriersStatic storageTheoretical computer scienceDouble fault
A “row-diagonal” (R-D) parity technique reduces overhead of computing diagonal parity for a storage array adapted to enable efficient recovery from the concurrent failure of two storage devices in the array. The diagonal parity is computed along diagonal parity sets that collectively span all data disks and a row parity disk of the array. The parity for all of the diagonal parity sets except one is stored on the diagonal parity disk. The R-D parity technique provides a uniform stripe depth and an optimal amount of parity information.
Owner:NETWORK APPLIANCE INC
Wellbore rig generator engine power control
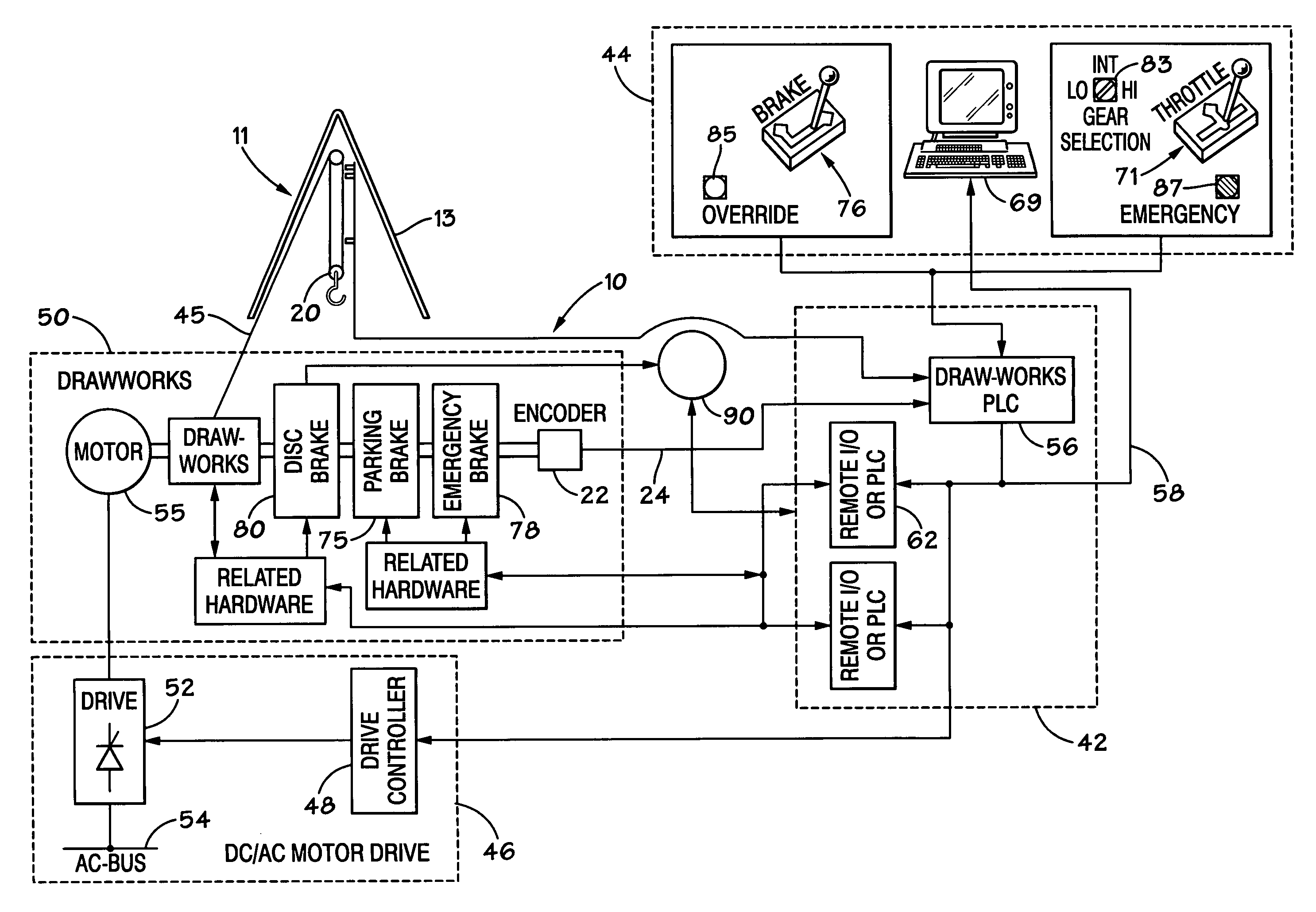
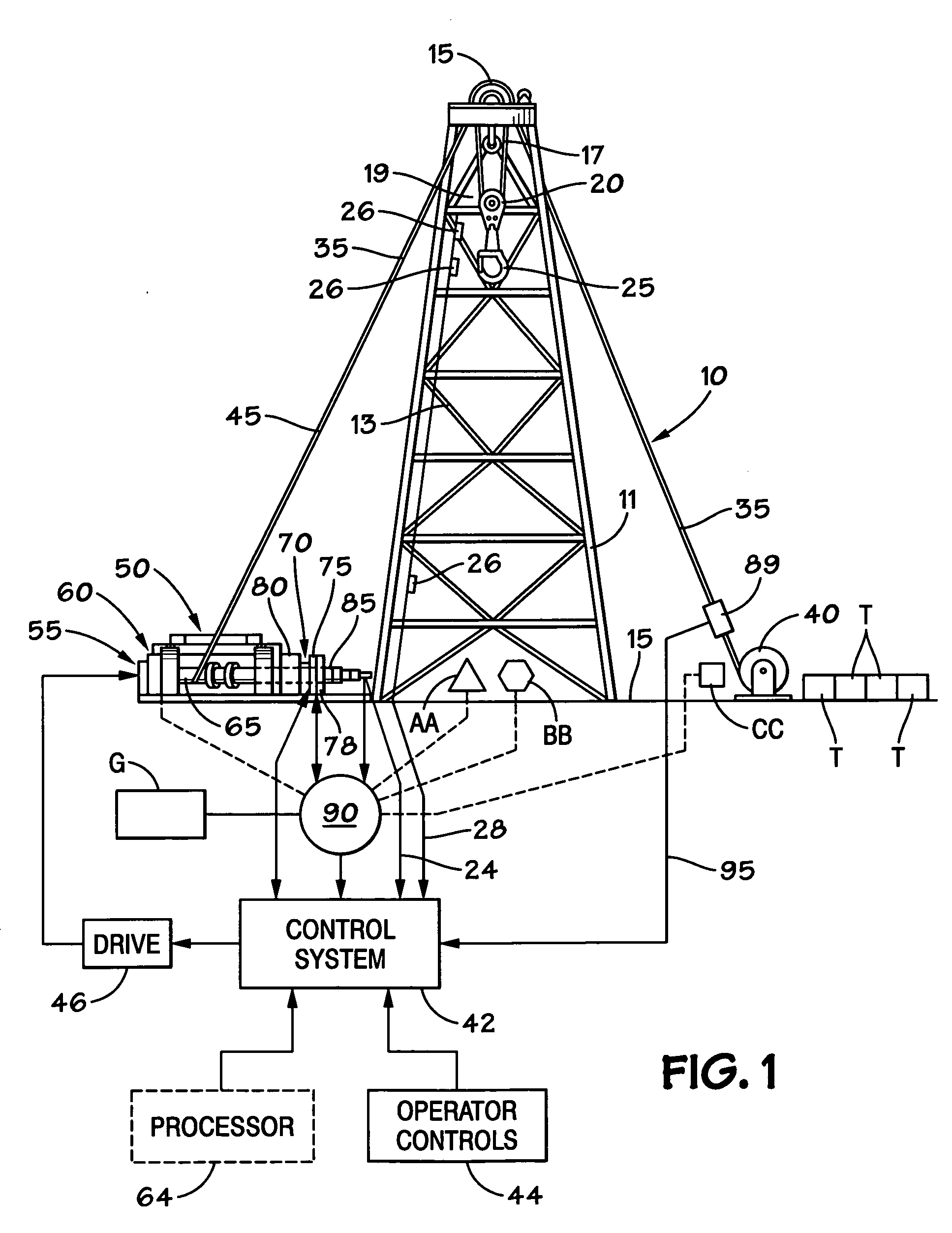
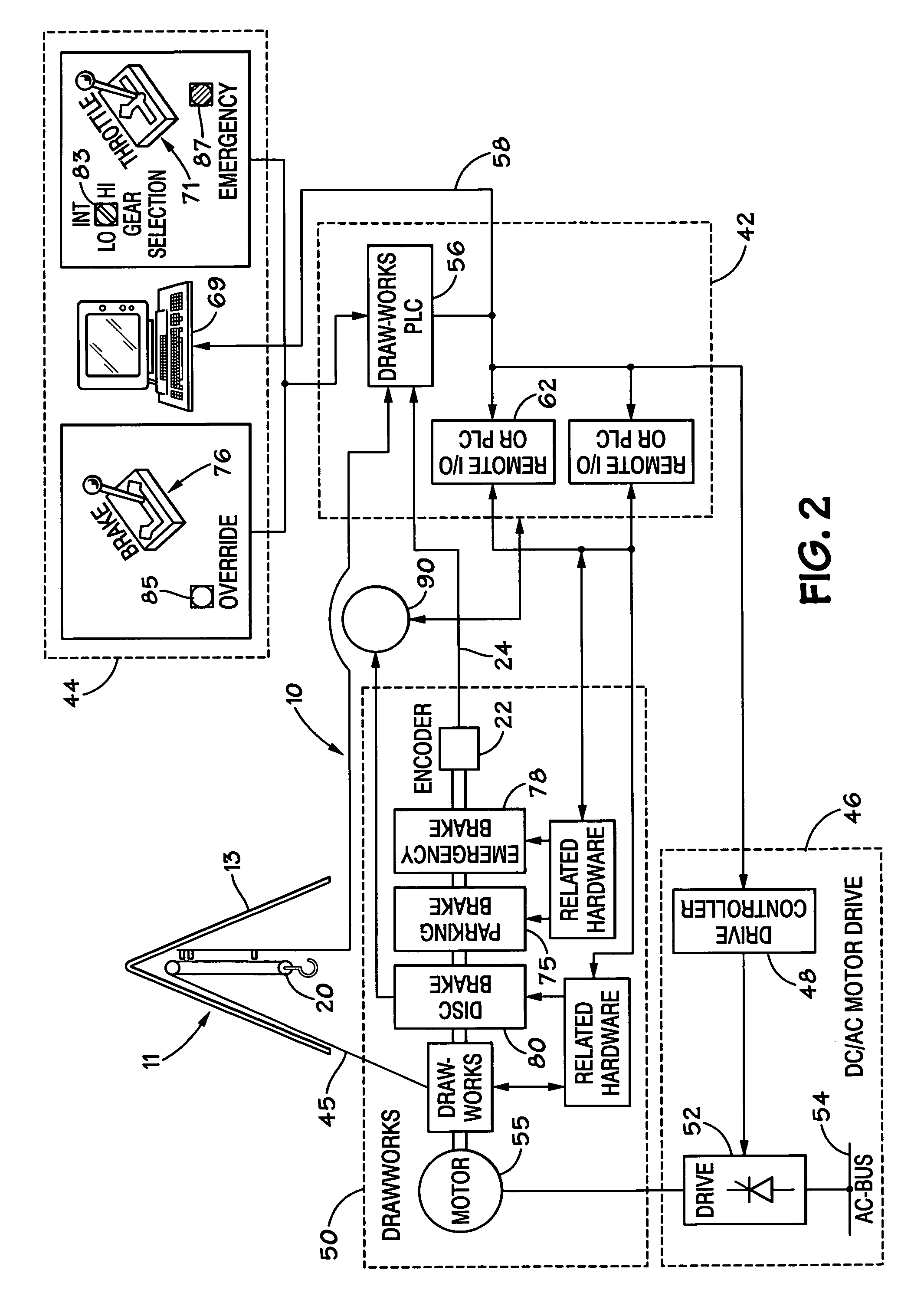
InactiveUS20080203734A1Improve and optimize engine responseEfficient engine operationAnalogue computers for vehiclesElectrical controlPower controlElectric generator
A system for controlling power load to a rig engine of a wellbore rig, the system including a controller for controlling a rig engine, a sensor for sensing the exhaust temperature of a rig engine, the sensor in communication with the controller for providing to the controller signals indicative of the exhaust temperature, and the controller maintaining power load to the rig engine based on said exhaust temperature. This abstract is provided to comply with the rules requiring an abstract which will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims, 37 CFR 1.72(b).
Owner:VARCO I P INC
Electronic invoice management system and method based on distributed accounting
InactiveCN106952124APrevent tamperingAvoid attackUser identity/authority verificationBilling/invoicingTamper resistanceInvoice
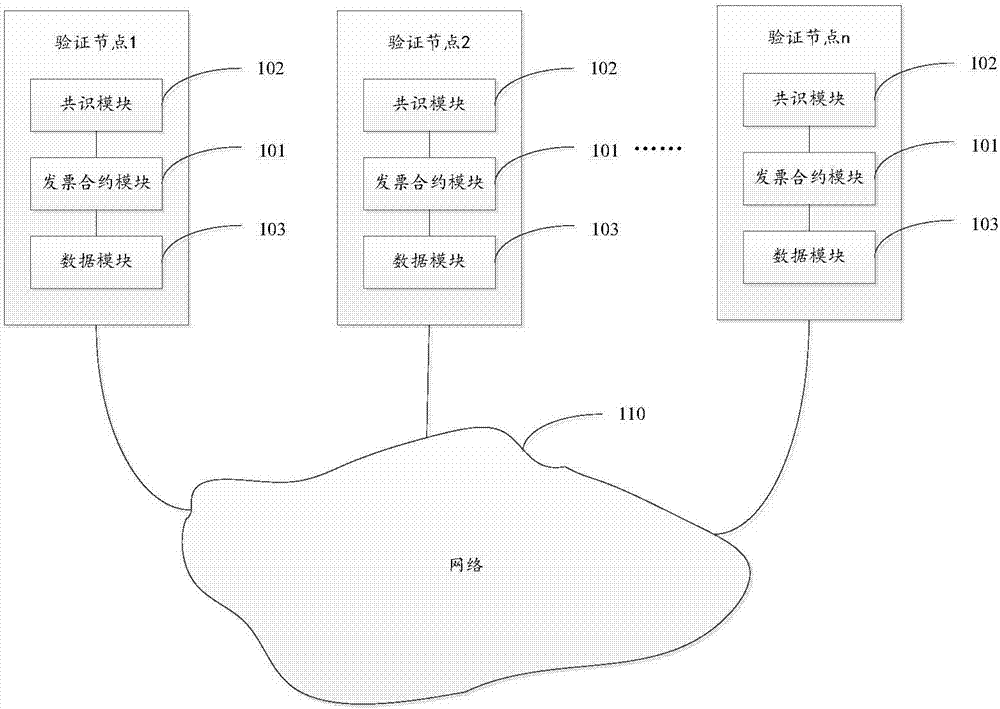
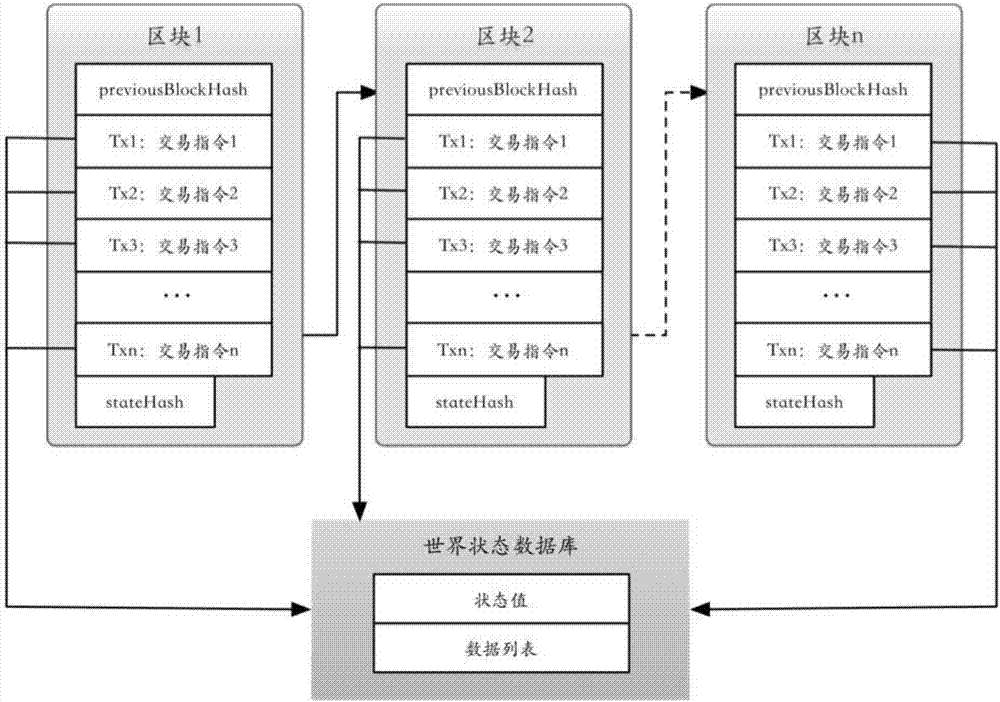
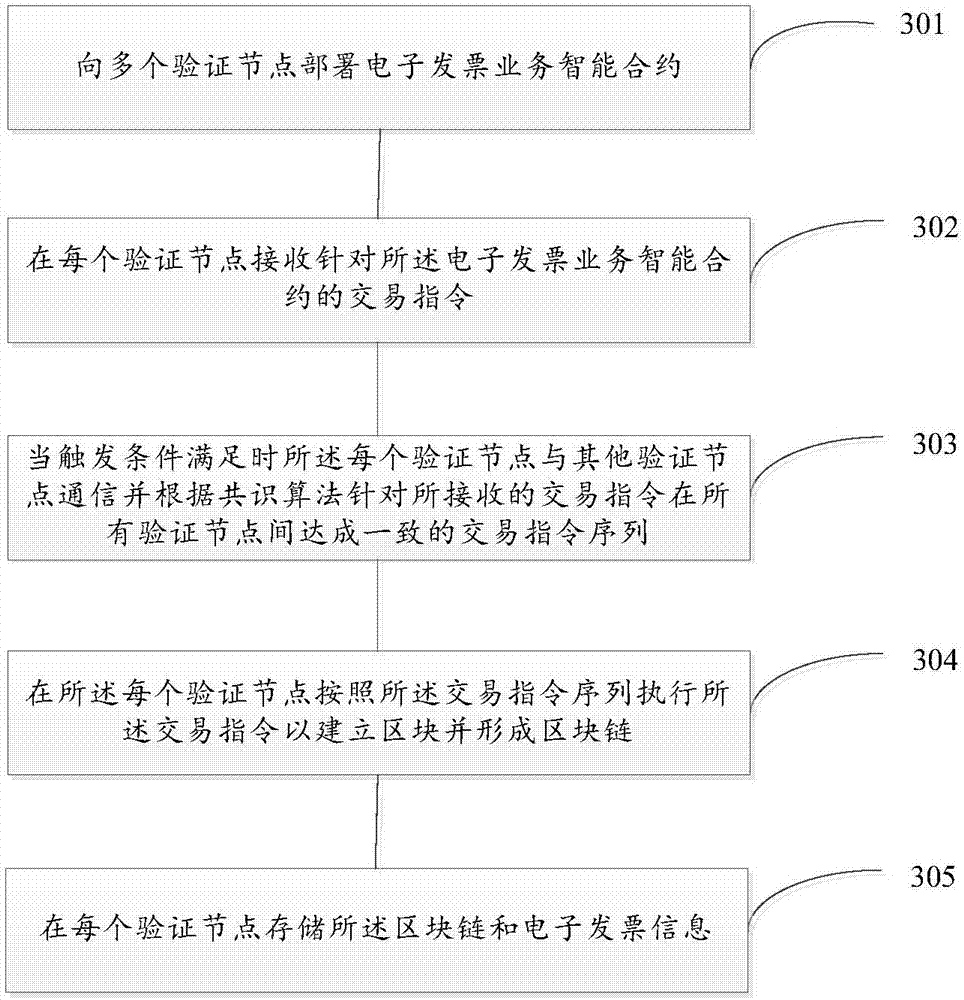
The invention discloses an electronic invoice management system and a method based on distributed accounting. The system comprises multiple verification nodes. Each verification node comprises an electronic invoice contract module and an agreement module, wherein the electronic invoice contract module comprises an electronic invoice service intelligent contract and is configured to be used for receiving a transaction command of the electronic invoice service intelligent contract and executing the transaction command according to a result of the agreement module so as to establish a block and form a block link, and the electronic invoice service intelligent contract is operation performed on an electronic invoice. The agreement module is configured to be used for communicating with other verification nodes when being triggered and making an agreement on a transaction command sequence between all verification nodes for the received transaction command according to an agreement algorithm. According to the invention, tamper-proofing is realized and the system and the method are cost-effective.
Rapid thermal conversion of biomass
ActiveUS20090139851A1Improved rapid thermal conversion processEffective recoveryThermal non-catalytic crackingCoke quenchingLiquid productHeat carrier
The present invent provides improved rapid thermal conversion processes for efficiently converting wood, other biomass materials, and other carbonaceous feedstock (including hydrocarbons) into high yields of valuable liquid product, e.g., bio-oil, on a large scale production. In an embodiment, biomass material, e.g., wood, is feed to a conversion system where the biomass material is mixed with an upward stream of hot heat carriers, e.g., sand, that thermally convert the biomass into a hot vapor stream. The hot vapor stream is rapidly quenched with quench media in one or more condensing chambers located downstream of the conversion system. The rapid quenching condenses the vapor stream into liquid product, which is collected from the condensing chambers as a valuable liquid product. In one embodiment, the liquid product itself is used as the quench media.
Owner:ENSYN RENEWABLES
Composition and method for fluid recovery from well
InactiveUS7893010B2Effective in permeabilityEffective recoveryOther chemical processesMixing methodsAlcoholCarrier fluid
Owner:SCHLUMBERGER TECH CORP
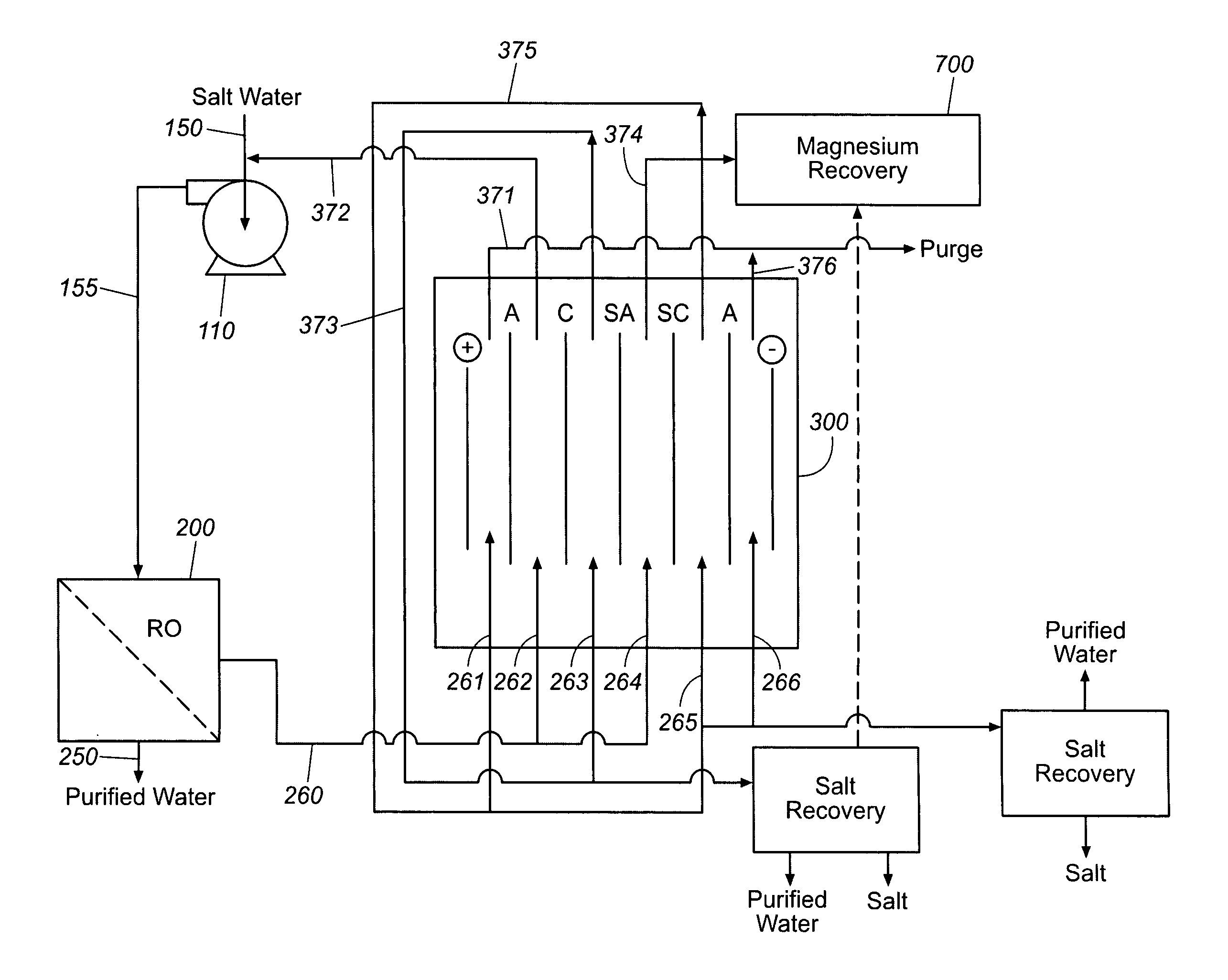
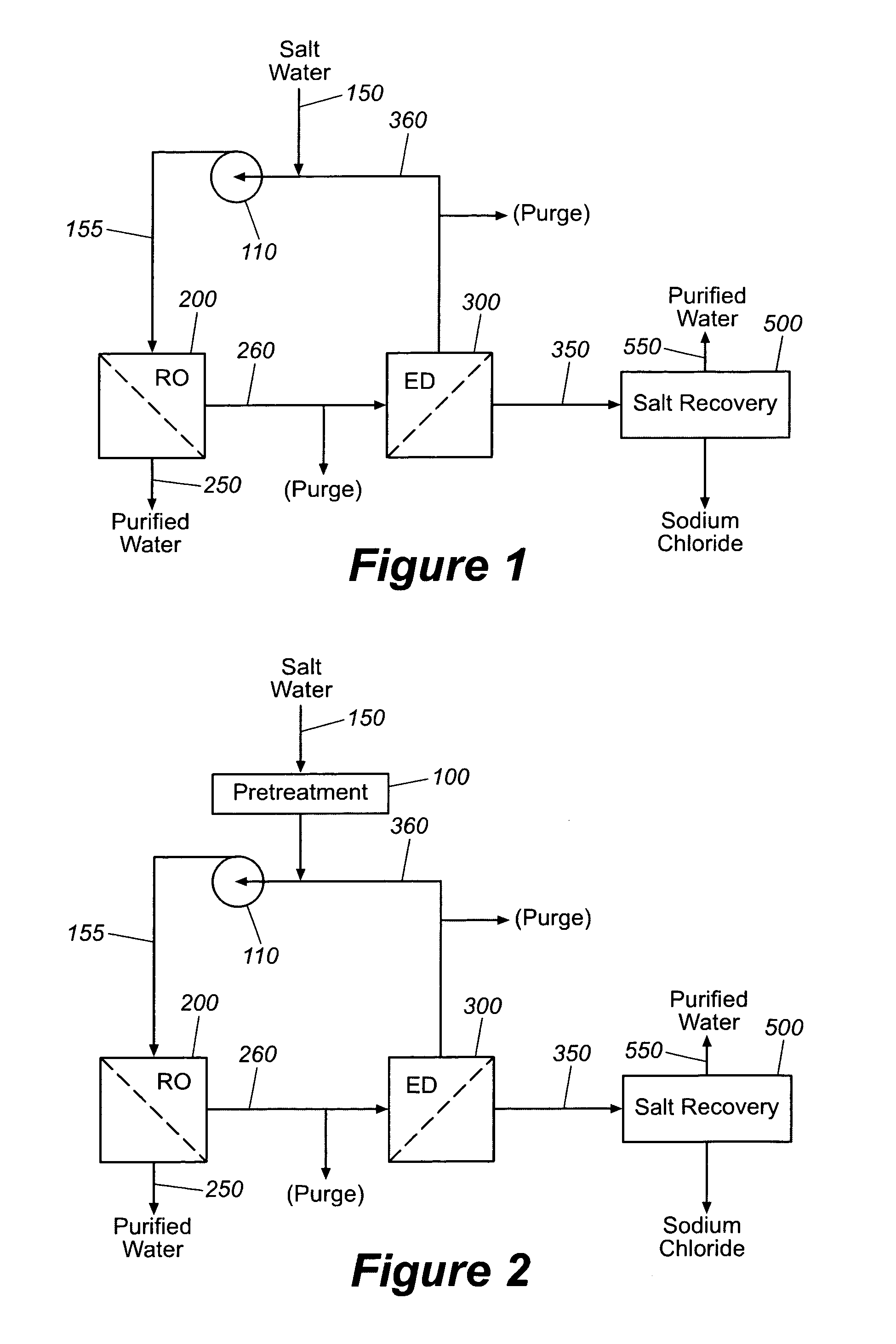
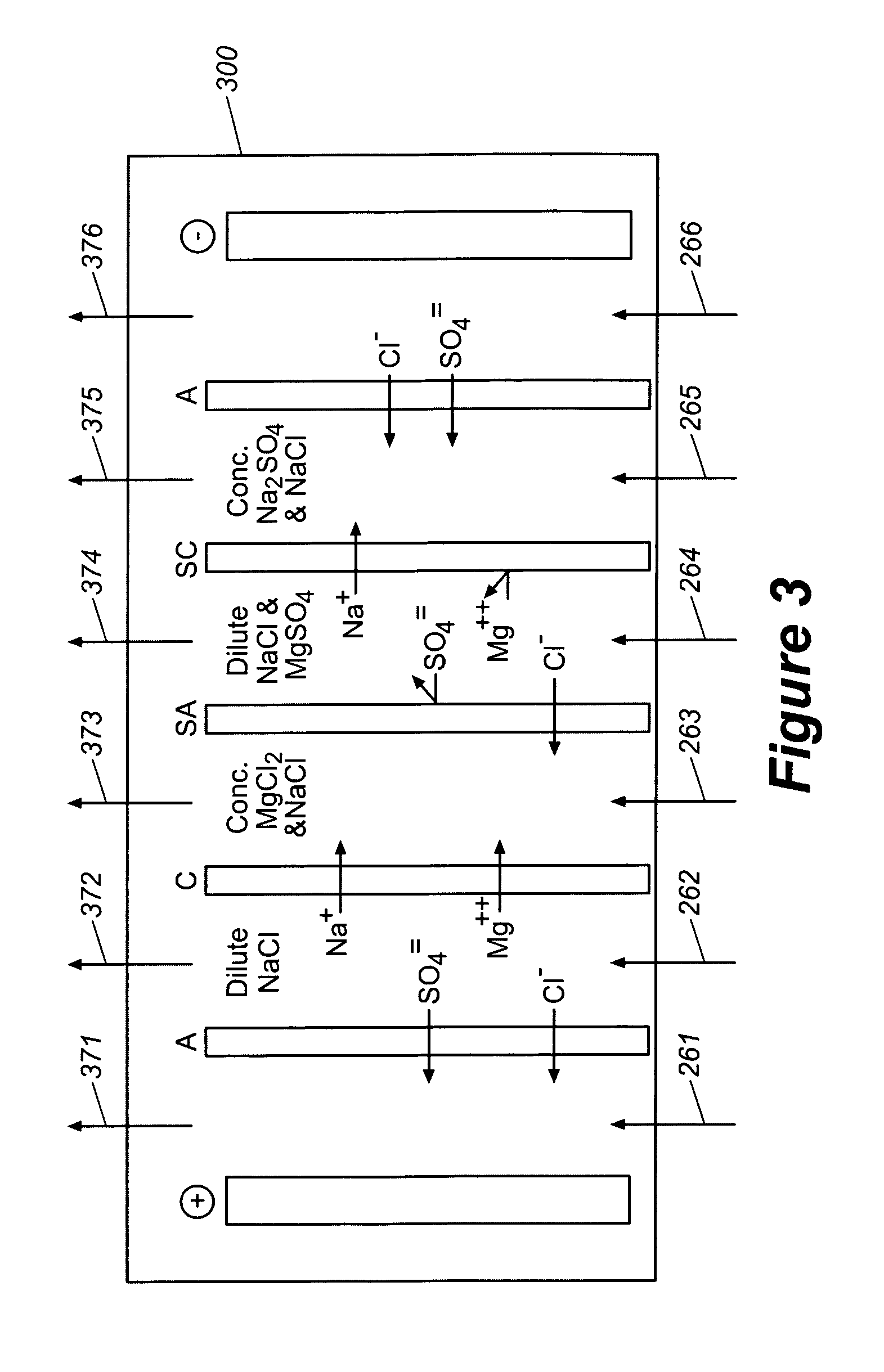
Production of purified water and high value chemicals from salt water
ActiveUS7083730B2Effective recoveryElectrolysis componentsSolvent extractionReverse osmosisHigh pressure
Sodium chloride and purified water are recovered by treating salt water that contains sodium chloride with an integrated reverse osmosis and electrodialysis system, which includes an efficiency-enhancing feature that is one or more of the following: the use of univalent anion and univalent cation selective membranes in the electrodialysis unit; the addition of a nanofiltration unit to process the diluate from the electrodialysis unit; or operation of the electrodialysis unit at an elevated pressure. Magnesium and bromine can optionally be produced when the salt water contains these materials.
Owner:SOUTH CAROLINA UNIV OF
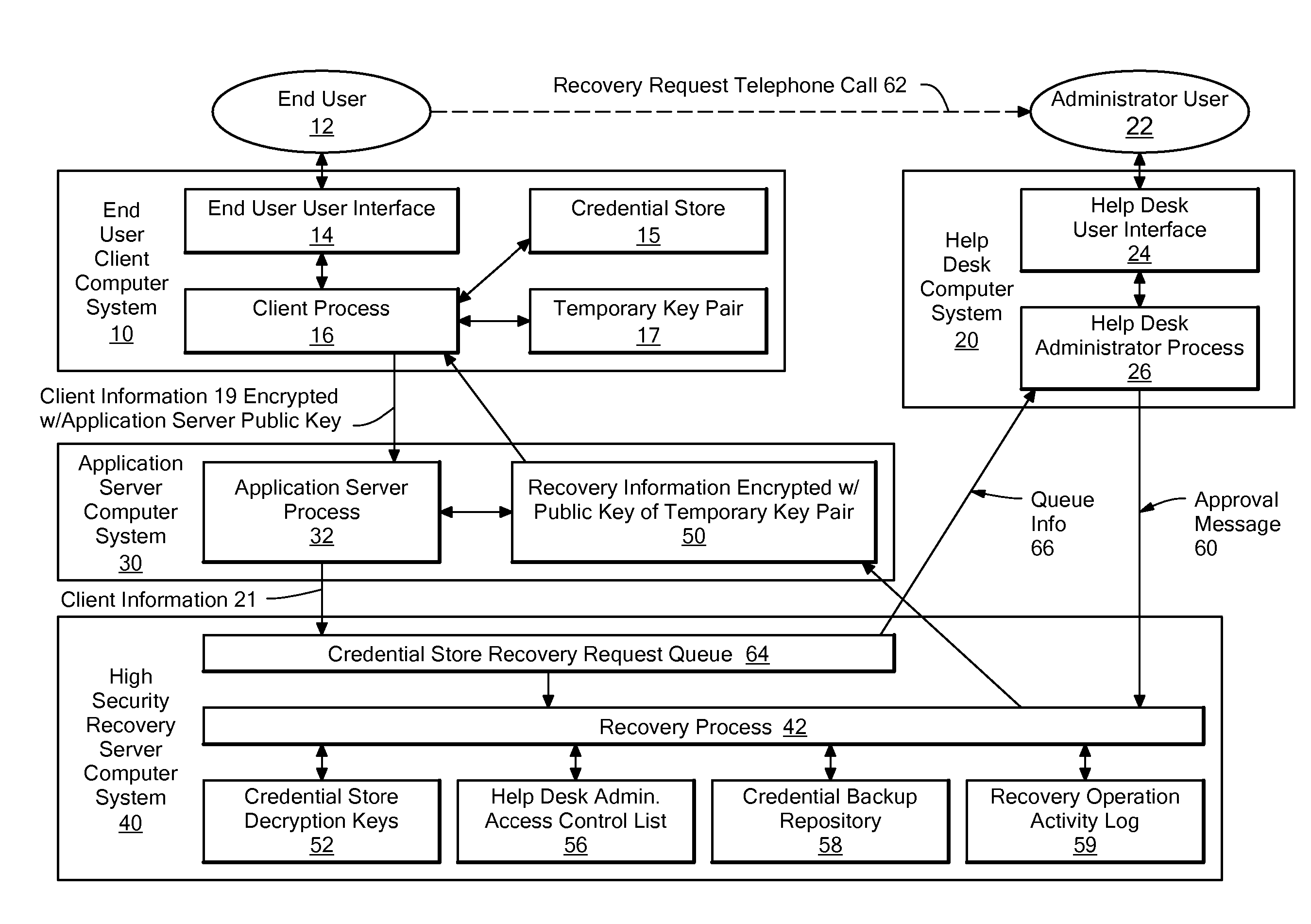
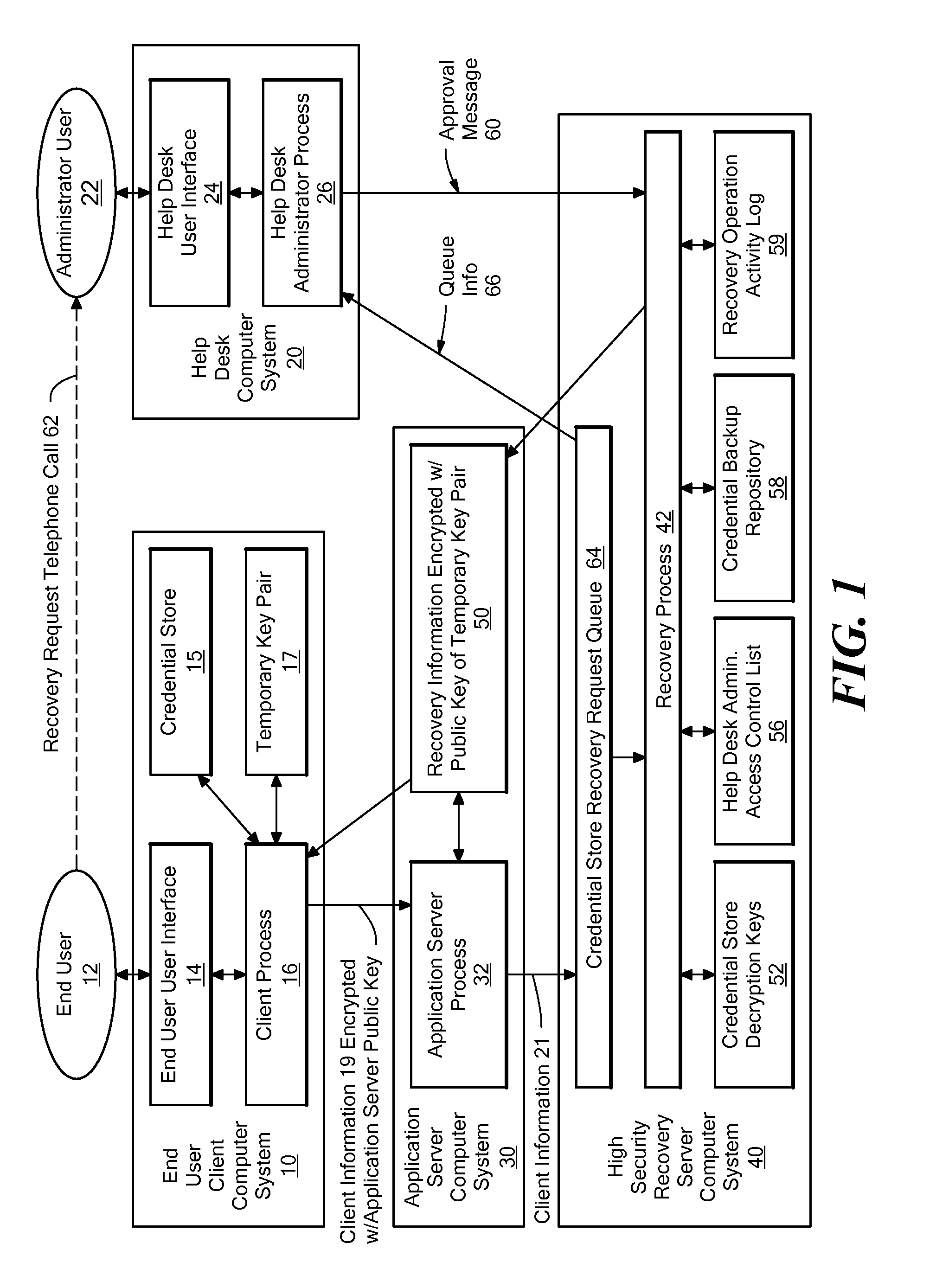
Method and system for automating the recovery of a credential store
A system for automating the recovery of a credential store, in which client software generates a temporary key pair based on a new password, and sends client information including the user's name, the public half of the temporary key pair, and the host name of the client computer system to a server system, from which the client information is passed to a recovery process. The client software process displays a prompt indicating that the user should call a help desk. A help desk administrator verifies the user's identity and approves the user's request by causing an approval message to be sent to the recovery process. The recovery process obtains recovery information consisting of either the decryption key(s) for the credential store, or a decrypted copy of the credential store, and encrypts the recovery information using the temporary public key. The client process downloads the recovery information from the server, and decrypts it using private key of the temporary key pair. The credential store can then be decrypted using the recovery information if necessary, then re-encrypted based on the new password. The encrypted recovery information is stored on the server and re-used for a certain period of time, after which it is deleted, thus allowing multiple copies of the credential store to be conveniently recovered.
Owner:IBM CORP
Composition and Method for Fluid Recovery from Well
InactiveUS20090281004A1Improve propertiesEffective in permeabilityOther chemical processesMixing methodsAlcoholCarrier fluid
A well treatment microemulsion for use in a subterranean formation is disclosed, the microemulsion comprises a solvent blend comprising a solvent and a co-solvent; a surfactant blend comprising a surfactant, wherein the surfactant blend is able to give formation intermediate wettability properties; an alcohol; and a carrier fluid; wherein the alcohol, the solvent and surfactant blends are combined with the carrier fluid to produce the well treatment microemulsion. By intermediate wettability it is meant that the water has an advancing contact angle on the surface between 62 and 133 degrees. The associate method of treating a subterranean formation of a well with the microemulsion and the associate method of modifying the wettability of the formation with the microemulsion are also disclosed.
Owner:SCHLUMBERGER TECH CORP
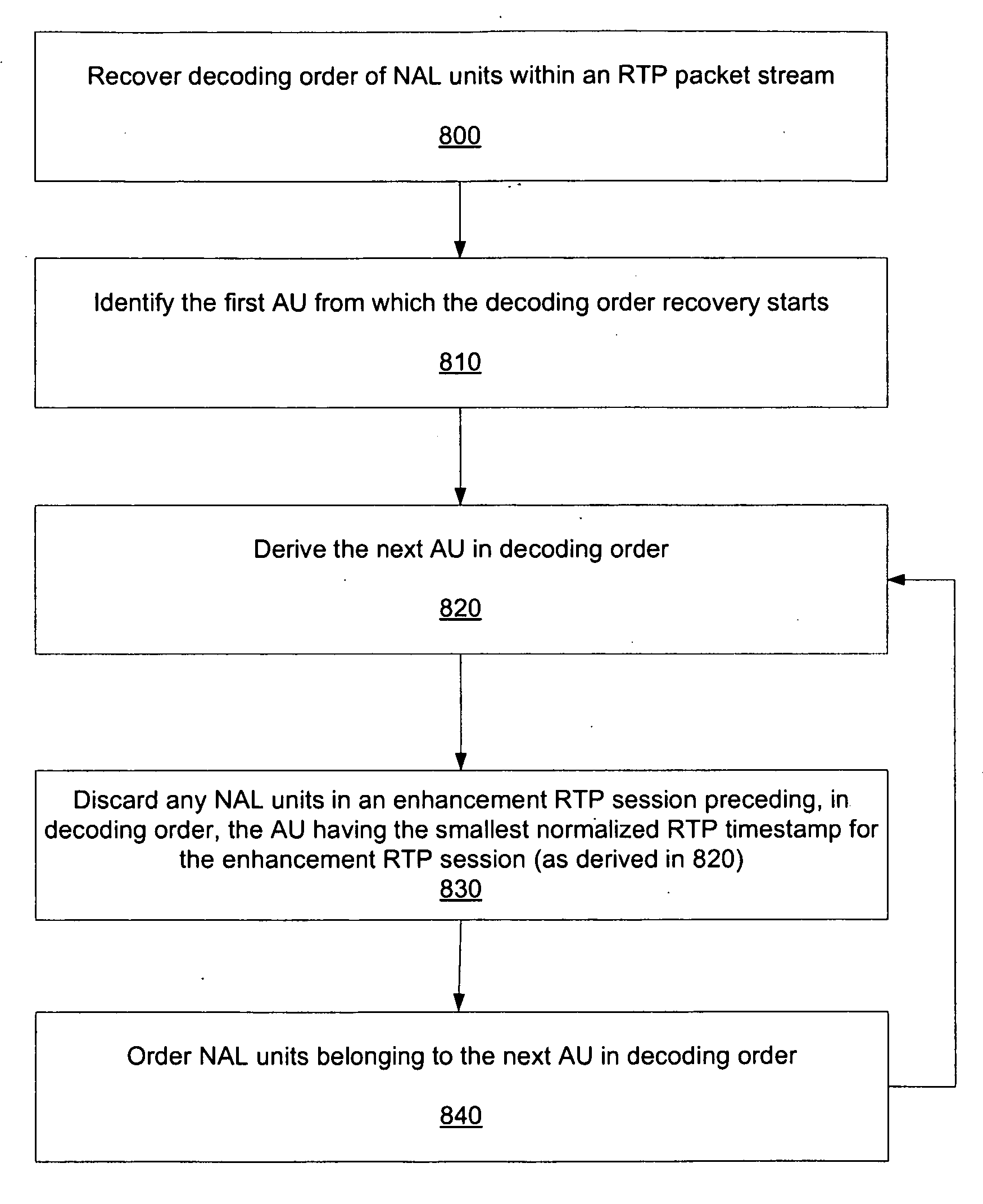
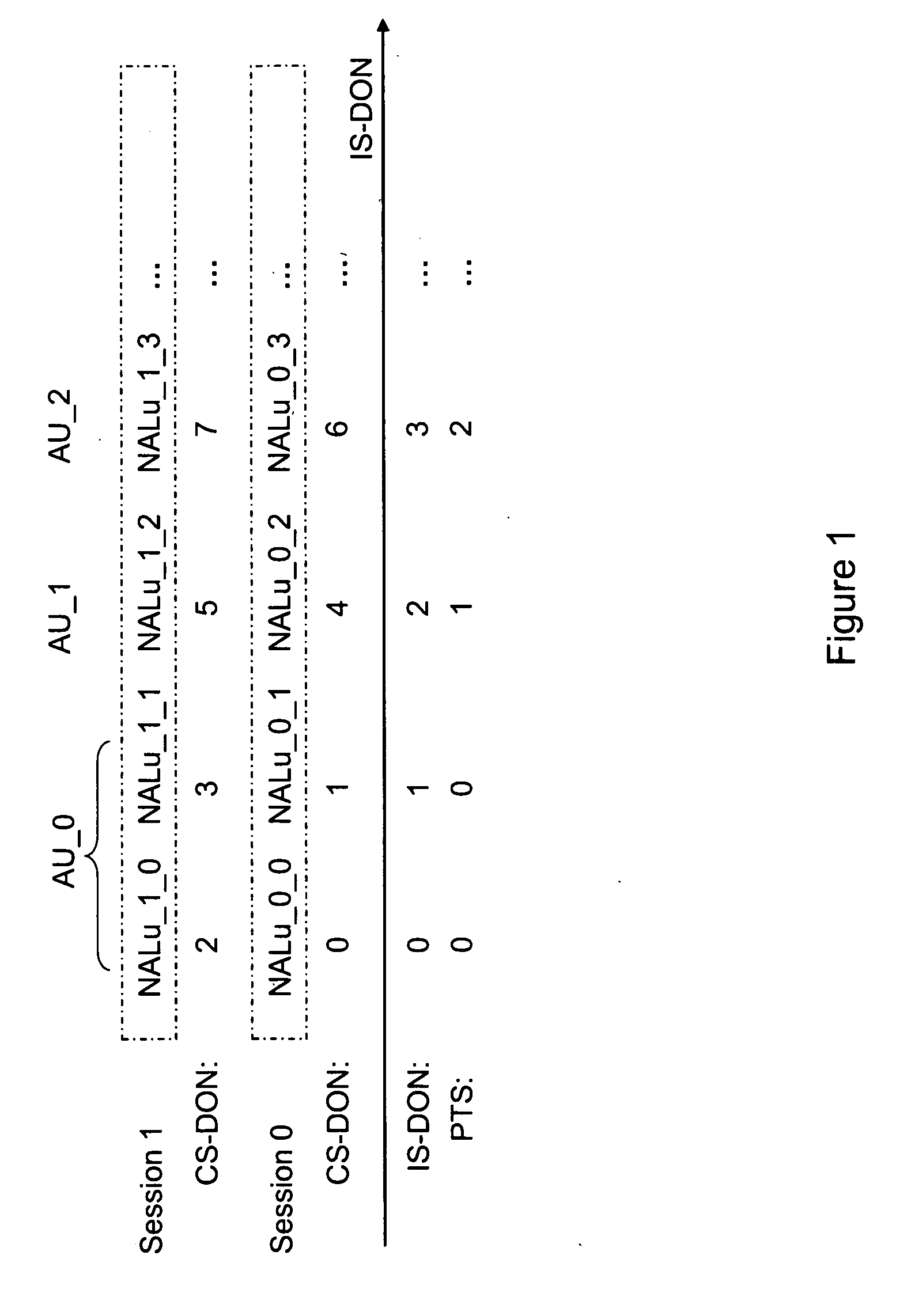
Decoding Order Recovery in Session Multiplexing
InactiveUS20100049865A1Speed up recoveryEffective recoveryMultiple digital computer combinationsTransmissionRecovery procedureComputer science
Systems and methods are provided for signaling the decoding order of ADUs to enable efficient recovery of the decoding order of ADUs when session multiplexing is in use. A decoding order recovery process in a receiver is improved when session multiplexing is in use. For example, various embodiments improve the decoding order recovery process of SVC when no CS-DONs are utilized. First information associated with a first media sample to identify a second media sample is signaled upon packetization to indicate / aid in recovering. Upon de-packetizing, a decoding order of the first media sample and the second media sample is determined based on the received signaling of the first information.
Owner:NOKIA CORP
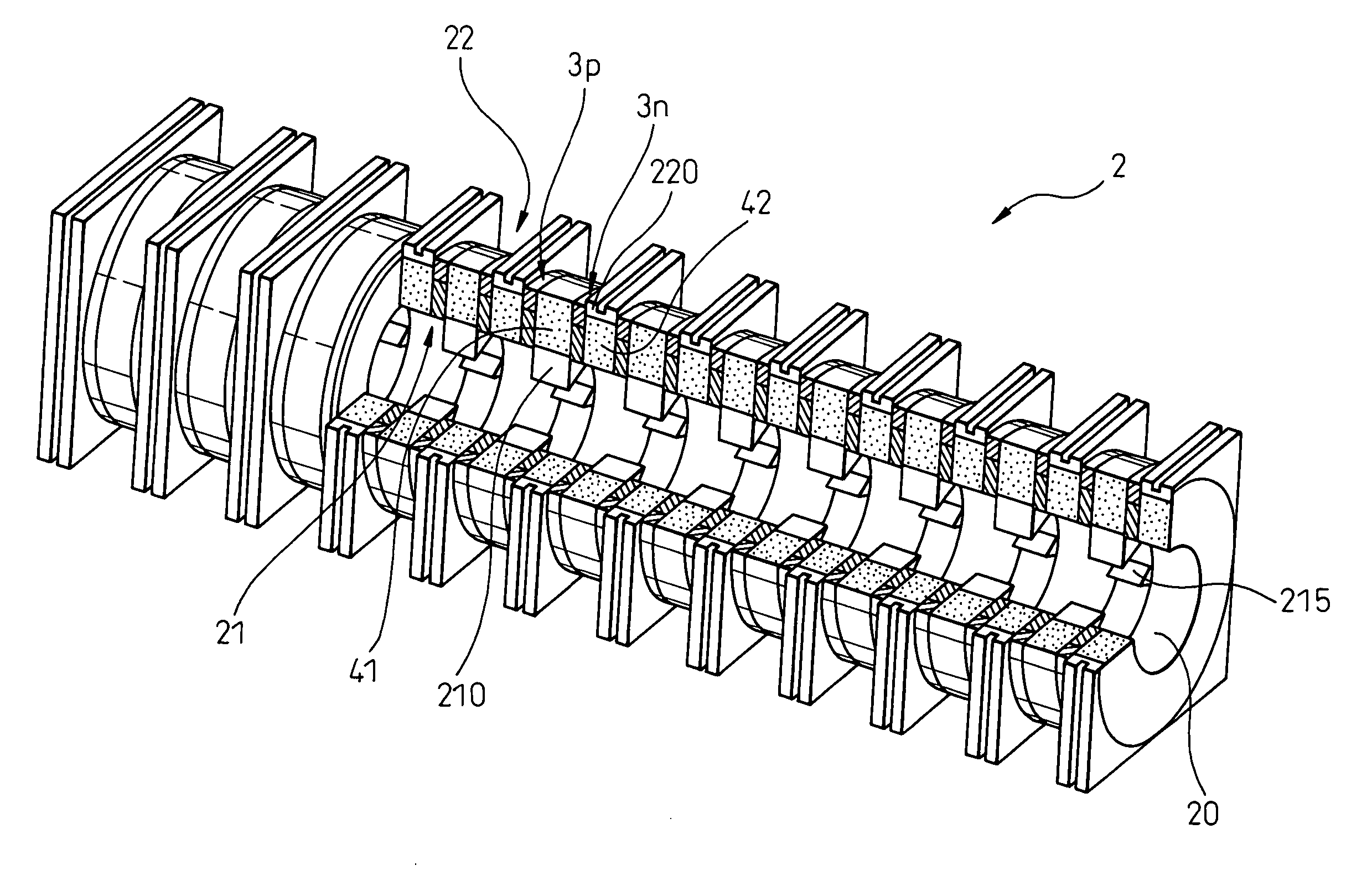
Exhaust heat recovery system
InactiveUS20050217714A1Efficiently exhaust heatEffective recoveryInternal combustion piston enginesThermoelectric device with peltier/seeback effectElectricitySemiconductor
A thermoelectric module 2 constituting an exhaust heat recovery system has p-type semiconductors 3p and n-type semiconductors 3n which both constitute thermoelements 3 for converting a difference in temperature between high temperature side end portions 21 and low temperature side end portions 22 into electricity. The thermoelectric module 2 is constructed such that the n-type semiconductors 3n and the p-type semiconductors 3p are stacked alternately along a longitudinal direction of an exhaust pipe portion 20 with heat insulating support portions 41, 42 being interposed therebetween, and the n-type semiconductors 3n and the p-type semiconductors 3p are electrically connected to each other via electrode members at the high temperature side end portions 21 and the low temperature side end portions 22.
Owner:DENSO CORP
Remote disaster recovery and data migration using virtual appliance migration
InactiveUS20070038887A1Create efficientlyEfficiently servingError detection/correctionData setClient-side
A technique efficiently creates and serves a backup data set on a backup filer located at a remote site from a primary filer by essentially moving an entire operating environment of a primary data set to the backup filer. The primary filer is organized into one or more virtual filers (vfilers), one of which (the primary vfiler) is configured to serve data, such as the primary data set, for a client. In the event that the primary filer or primary vfiler becomes unavailable, the technique may be implemented as a disaster recovery or data migration sequence to enable efficient instantiation of a backup vfiler to serve the backup data set for the client.
Owner:NETWORK APPLIANCE INC
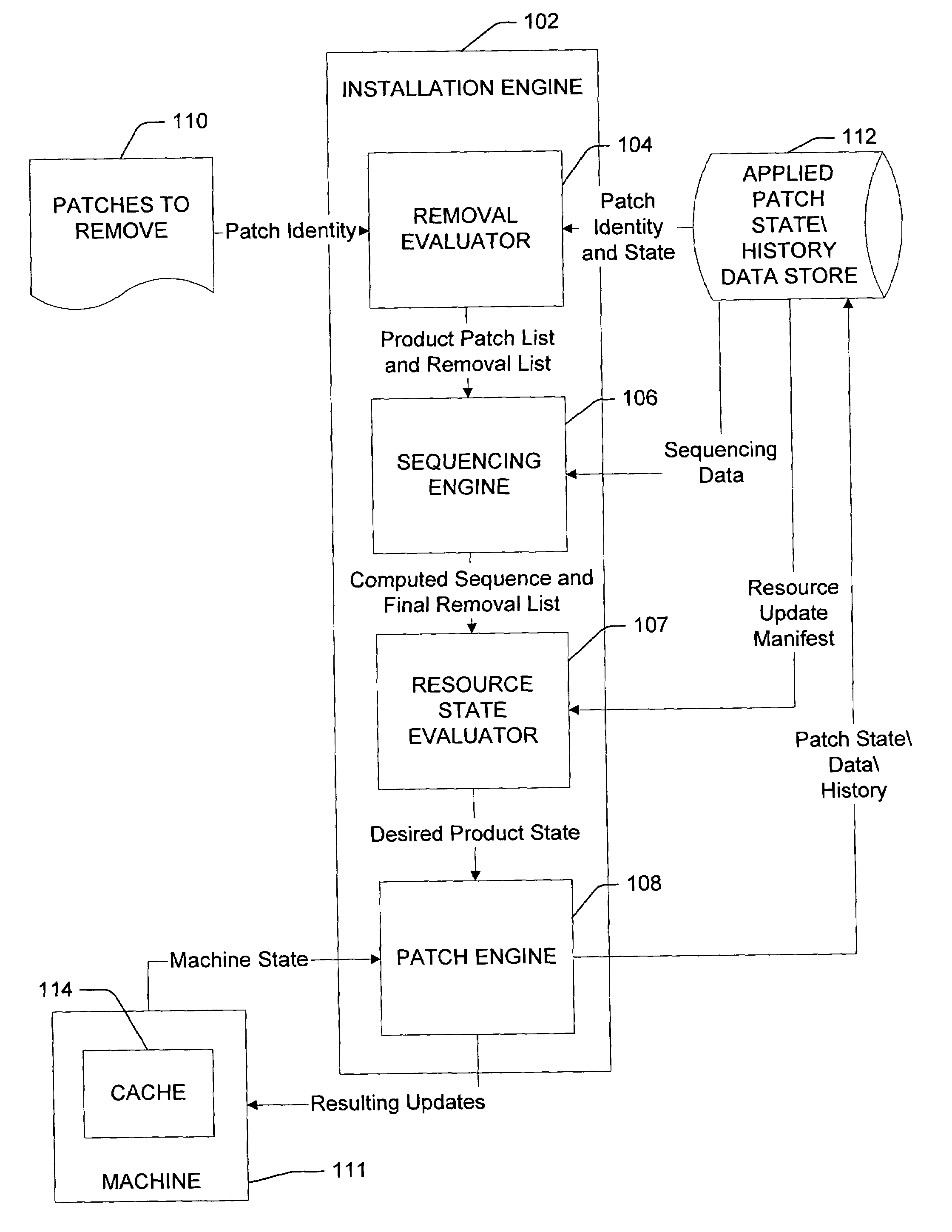
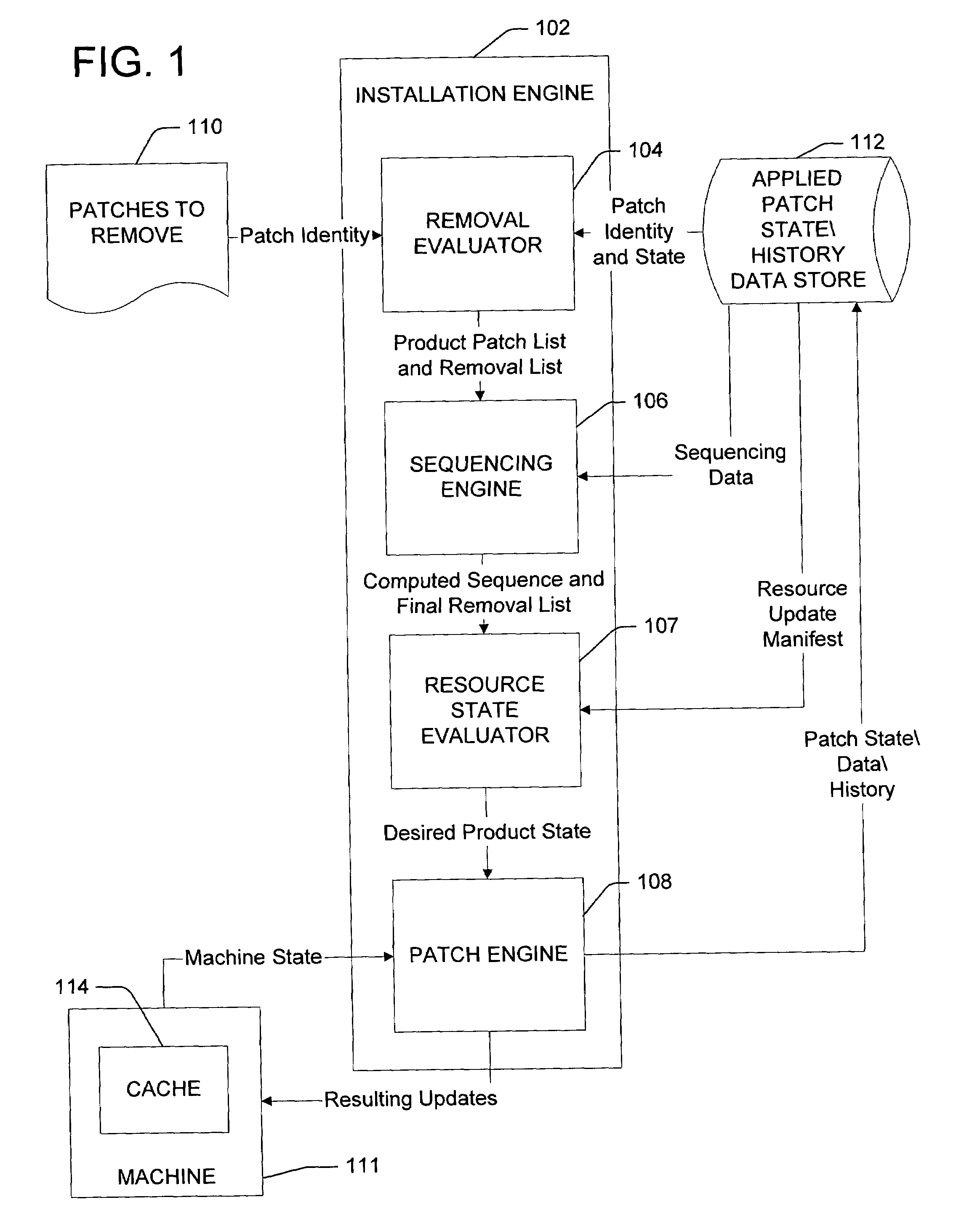
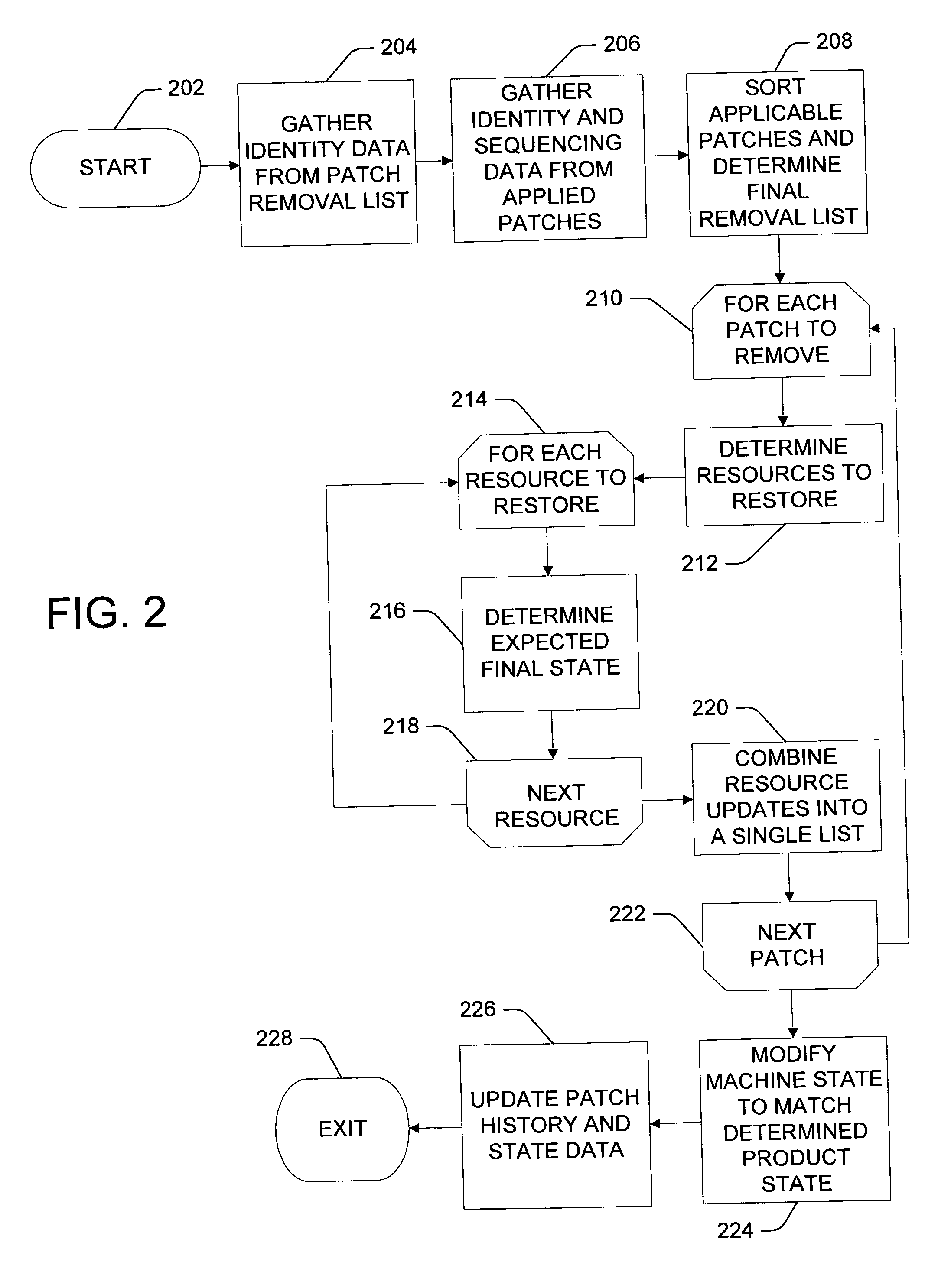
Patch un-installation
ActiveUS7703090B2Effective recoveryWithout negative side effectDigital computer detailsStatic storageSoftware engineeringSoftware
Uninstalling a patch applied to a software product installed on a computer. A current state of a software product is identified. A desired state of the software product is determined. The desired state of the software product represents a state of the software product when a patch applied to the software product is removed from the software product. The patch is removed from the software product to transition the software product from the identified current state to the determined desired state.
Owner:MICROSOFT TECH LICENSING LLC
Corpectomy implant
ActiveUS20090138089A1Inhibit migrationEffective recoveryJoint implantsSpinal implantsCorpectomyLumbar spine
The present invention describes an expandable vertebral implant and the method of use. The longitudinally expandable vertebral implant includes telescoping sections adapted for incremental expansion and ease of securement at any desired increment in situ, and constructed and arranged to engage opposing vertebrae. The corpectomy device is a distractible vertebral body replacement for the thoracic and lumbar spine. The device is cylindrical shaped having an inner and outer sleeve made adjustable by use of locking pads formed integral with the outer sleeve for use in engaging parallel circumferential locking grooves formed along the outer side surface of the inner sleeve.
Owner:ORTHO INNOVATIONS
Systems and methods for collaborative tag suggestions
InactiveUS7685198B2Promote aggregationIncrease coverageMetadata text retrievalDigital data processing detailsCommon CriteriaWorld Wide Web
A set of general criteria have been defined to improve the efficacy of a tagging system, and have been applied to present collaborative tag suggestions to a user. The collaborative tag suggestions are based on a goodness measure for tags derived from collective user authorities to combat spam. The goodness measure is iteratively adjusted by a reward-penalty algorithm during tag selection. The collaborative tag suggestions can also incorporate other sources of tags, e.g., content-based auto-generated tags.
Owner:R2 SOLUTIONS
Correcting multiple block data loss in a storage array using a combination of a single diagonal parity group and multiple row parity groups
InactiveUS7073115B2Promote recoveryEffective recoveryInput/output to record carriersStatic storageComputer hardwareDiagonal
A technique efficiently corrects multiple storage device failures in a storage array using a combination of a single diagonal parity group and multiple row parity groups. The storage array includes a plurality of concatenated sub-arrays, wherein each sub-array includes a set of data storage devices and a parity storage device. Each row parity group is associated with a sub-array of the array. The array further includes a global parity storage device holding diagonal parity computed across the concatenation of the sub-arrays. Instead of requiring that each parity group contain both a row parity device and a diagonal parity device, the array is composed of a collection of row parity groups. Diagonal parity is calculated across the full array.
Owner:NETWORK APPLIANCE INC
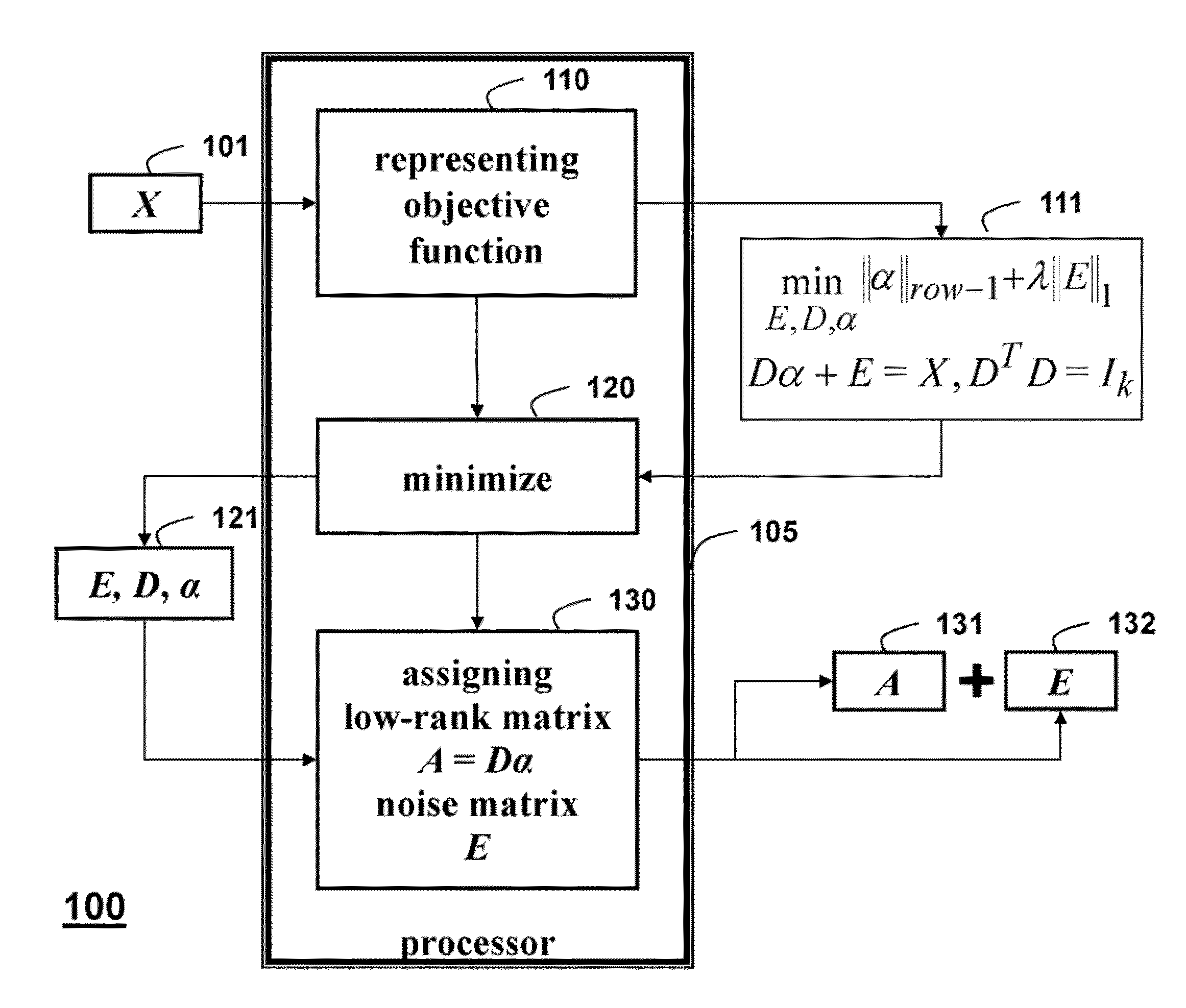
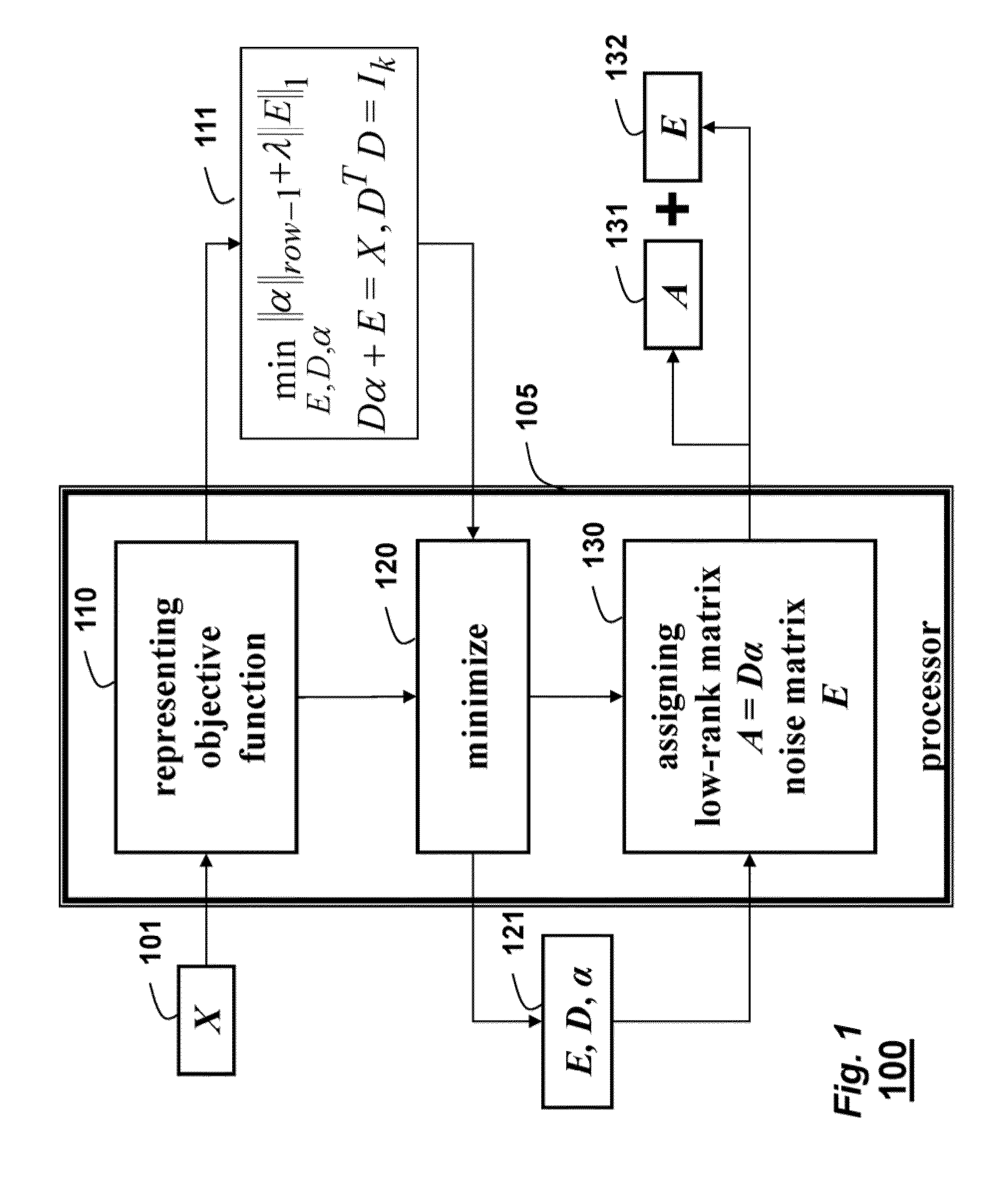
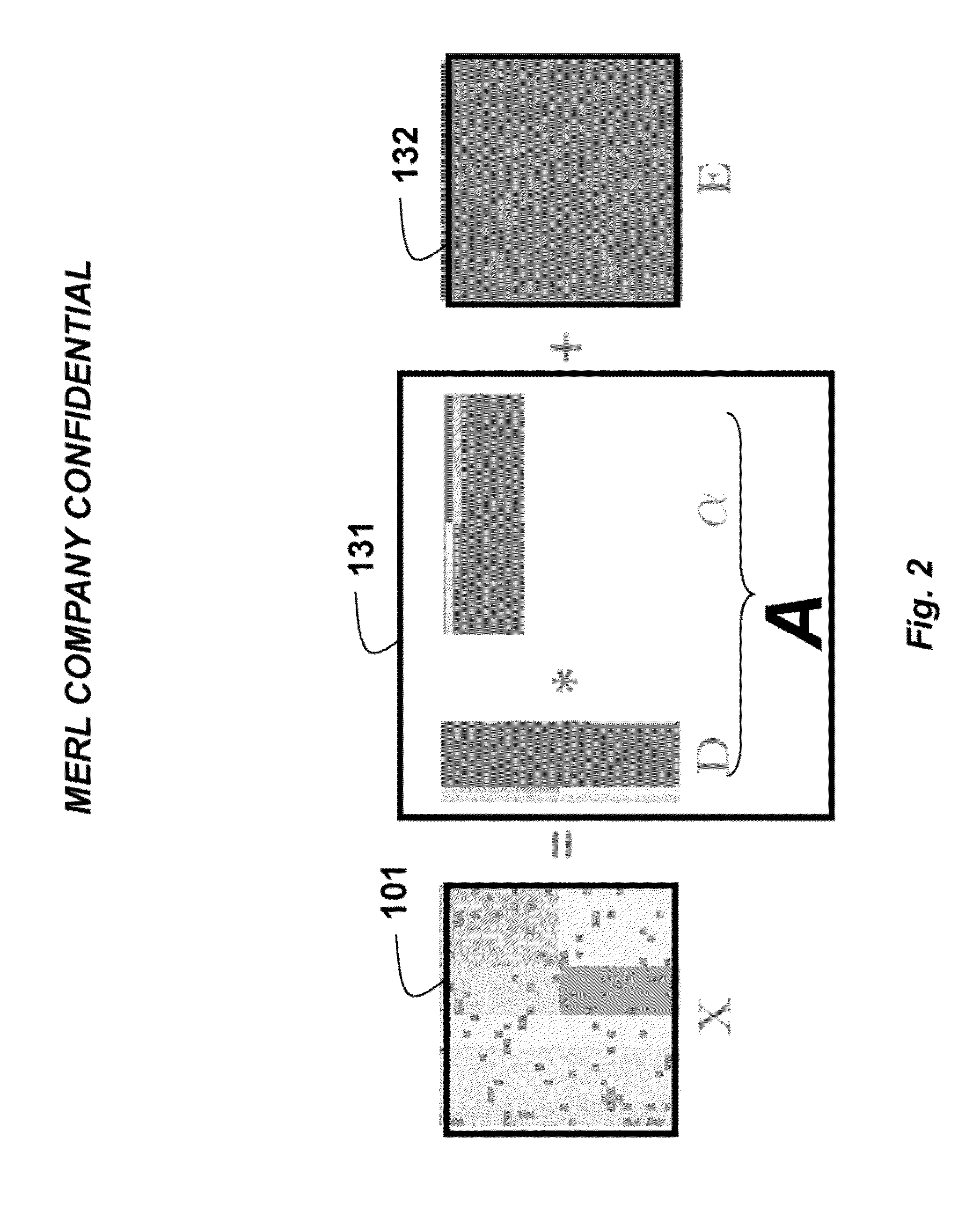
Method for Recovering Low-Rank Matrices and Subspaces from Data in High-Dimensional Matrices
InactiveUS20130191425A1Effective recoveryFaster robust low-rank recoveryDigital data processing detailsDigital computer detailsAugmented lagrange multiplierAlgorithm
A method recovers an uncorrupted low-rank matrix, noise in corrupted data and a subspace from the data in a form of a high-dimensional matrix. An objective function minimizes the noise to solve for the low-rank matrix and the subspace without estimating the rank of the low-rank matrix. The method uses group sparsity and the subspace is orthogonal. Random subsampling of the data can recover subspace bases and their coefficients from a much smaller matrix to improve performance. Convergence efficiency can also be improved by applying an augmented Lagrange multiplier, and an alternating stepwise coordinate descent. The Lagrange function is solved by an alternating direction method.
Owner:MITSUBISHI ELECTRIC RES LAB INC
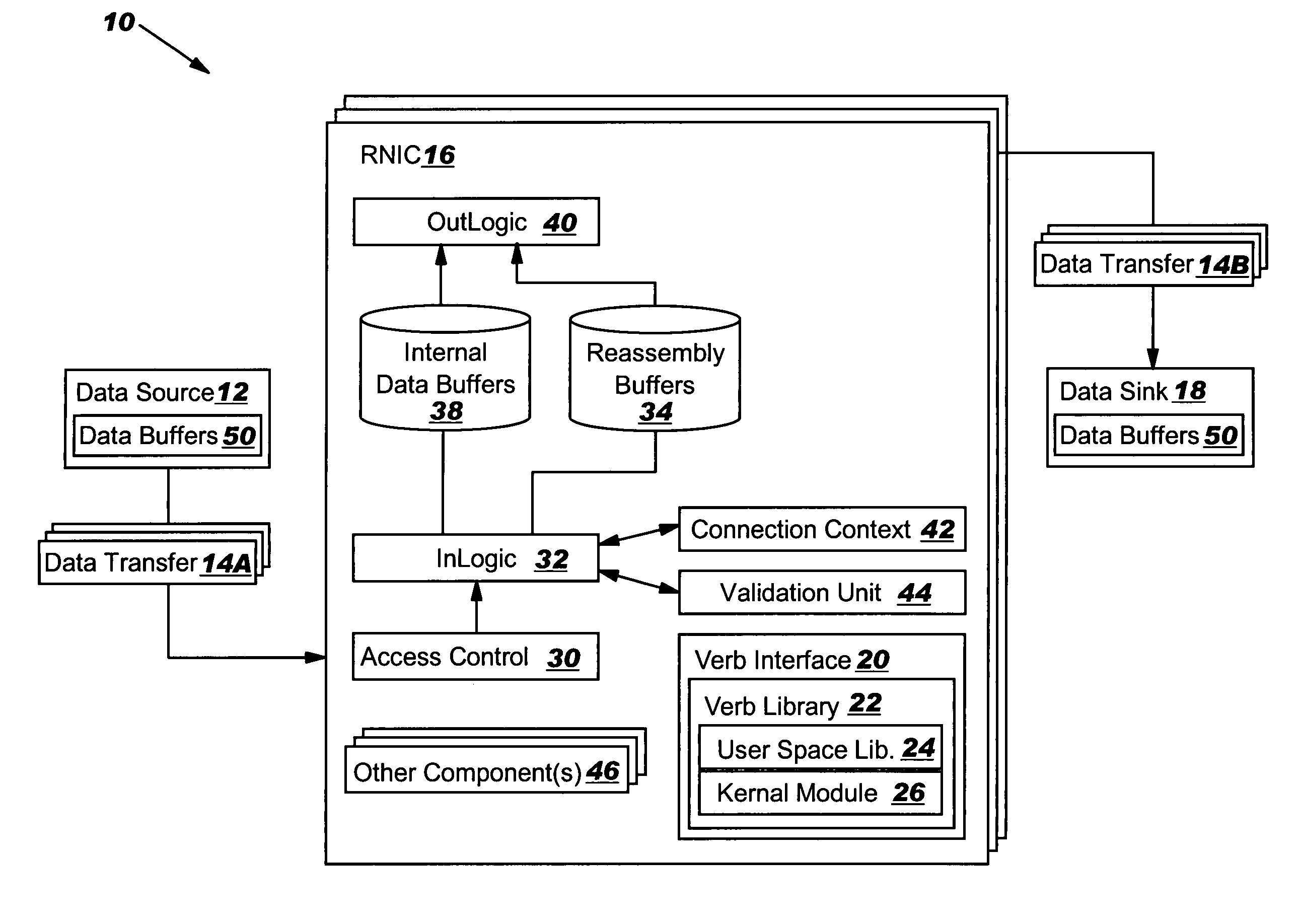
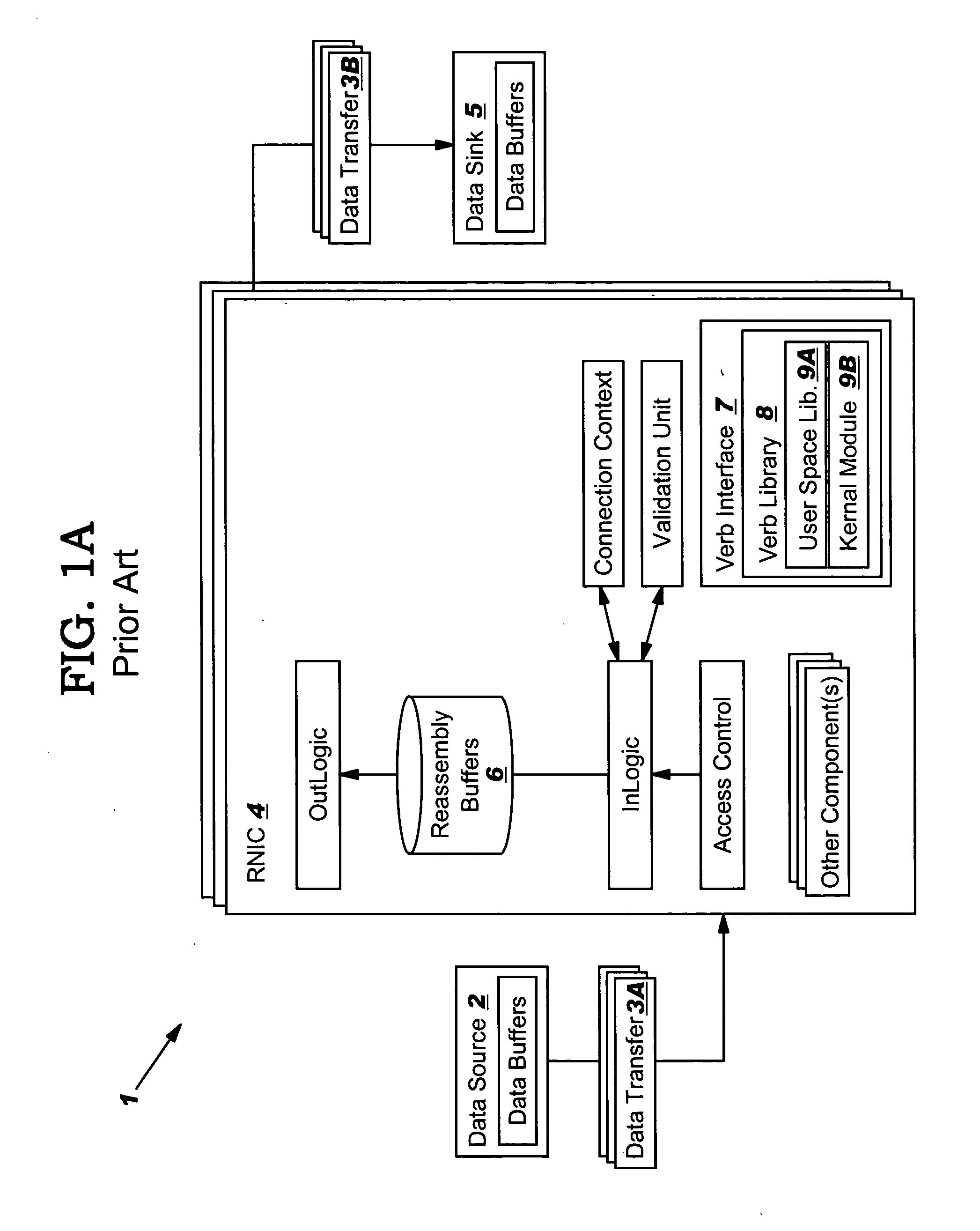
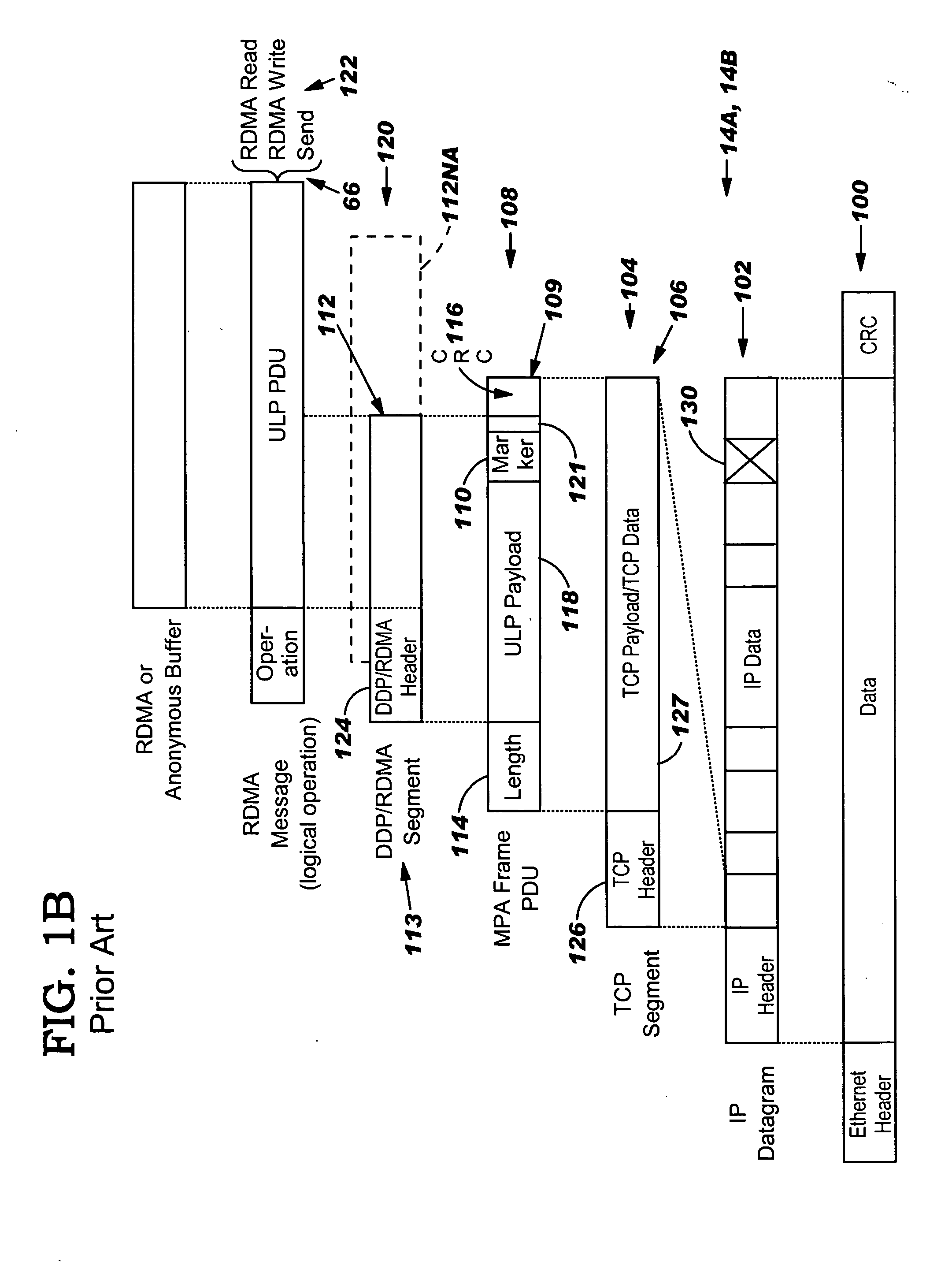
Data transfer error checking
InactiveUS20050149817A1Reduce memory bandwidthReduce latencyCode conversionError detection onlyConnection typeData placement
An RNIC implementation that performs direct data placement to memory where all segments of a particular connection are aligned, or moves data through reassembly buffers where all segments of a particular connection are non-aligned. The type of connection that cuts-through without accessing the reassembly buffers is referred to as a “Fast” connection because it is highly likely to be aligned, while the other type is referred to as a “Slow” connection. When a consumer establishes a connection, it specifies a connection type. The connection type can change from Fast to Slow and back. The invention reduces memory bandwidth, latency, error recovery using TCP retransmit and provides for a “graceful recovery” from an empty receive queue. The implementation also may conduct CRC validation for a majority of inbound DDP segments in the Fast connection before sending a TCP acknowledgement (Ack) confirming segment reception.
Owner:IBM CORP
Ethanol recovery process and apparatus for biological conversion of syngas components to liquid products
ActiveUS20090215139A1Efficiently and economically separateEffective recoveryBiofuelsWaste based fuelPervaporationSyngas
Ethanol and other liquid products produced by the contacting CO and / or a mixture of CO2 and H2 with a microorganism in a bioreactor are separated using a combination of distillation and vapor permeation membranes. The bioreactor passes an effluent with an ethanol concentration of 1 to 6 wt % to a distillation column that produces an overhead vapor stream enriched in ethanol. A series of vapor permeation membranes retain ethanol as retentate and produce a 99 wt % or higher ethanol product. Ethanol depleted permeate streams flow back to the column and the bioreactor. Coupling a bioreactor with distillation and pervaporation efficiently and economically separates ethanol when present at low concentration in an aqueous fermentation broth. The separation arrangement may also include a flash zone ahead of the distillation column to raise the concentration of the ethanol in the input stream to the distillation column.
Owner:SYNATA BIO INC
Method and System for Treating Brine Waste Water
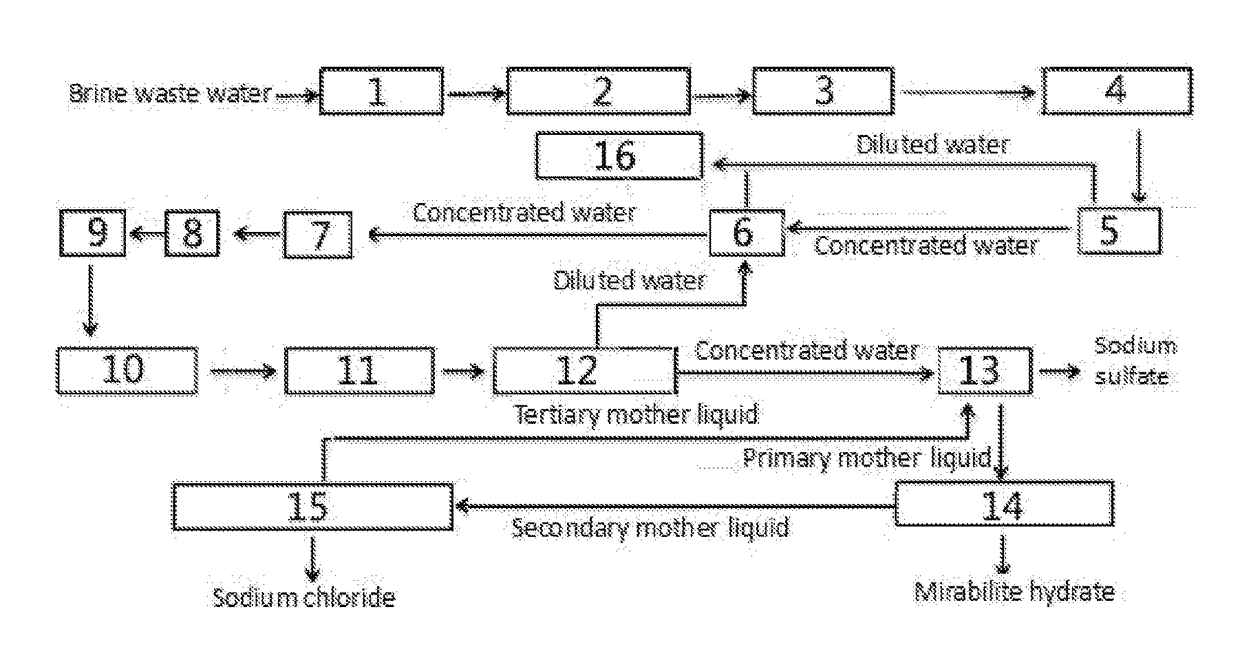
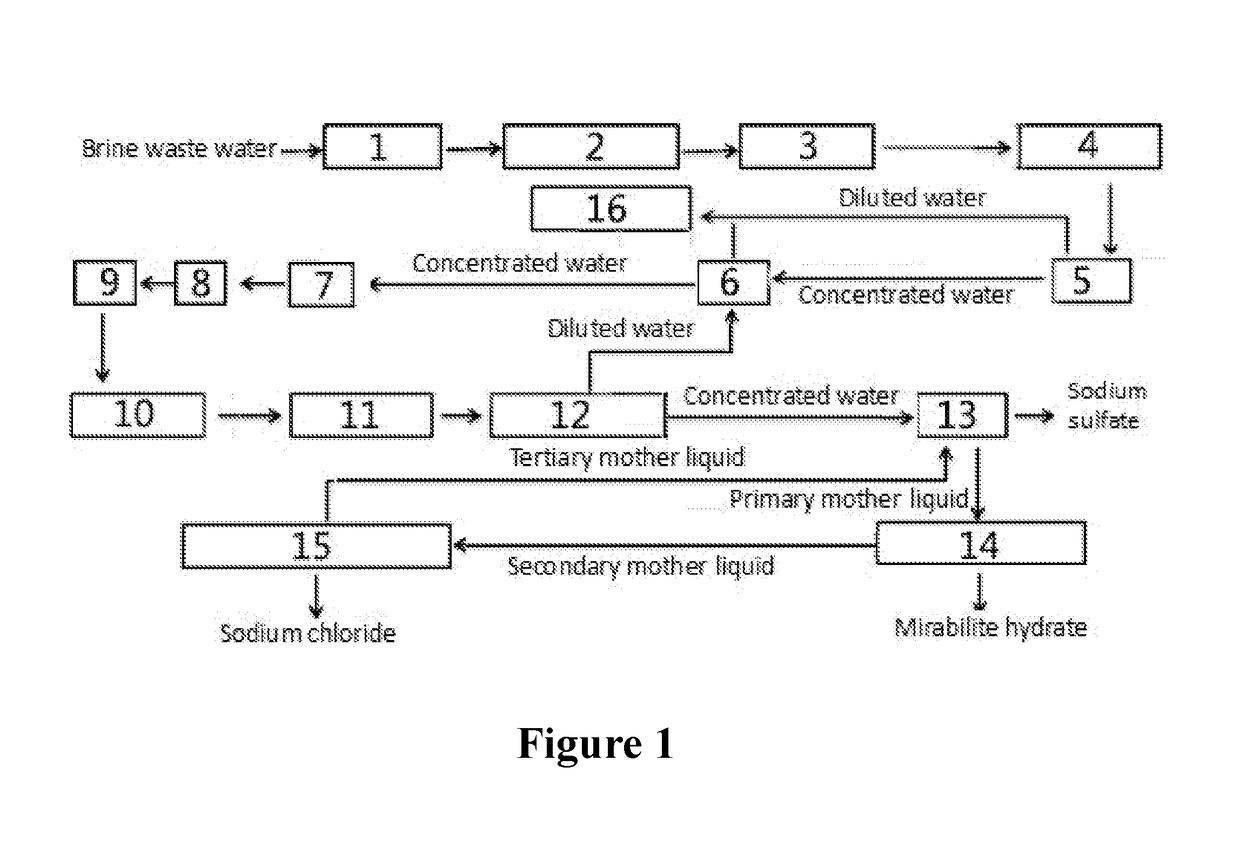
ActiveUS20180148350A1Reduce pollutionExtended service lifeScale removal and water softeningSustainable biological treatmentSaline waterWastewater
The present invention relates to a method for zero-release treatment of brine waste water, comprising: (1) pretreatment; (2) reverse osmosis treatment; (3) advanced oxidation treatment; (4) biochemical treatment; (5) electrodialysis concentration; (6) circulating crystallization. Compared with the prior art, the method for zero-release treatment of brine waste water provided in the present invention realizes zero release or near zero release of waste water, improves salt recovery efficiency, can recover high-quality sodium sulfate, mirabilite and sodium chloride, and turns crystalline salts into a resource; the membrane treatment unit can operates stably in the process for a long operation period at a low cost, and the entire process has high economic efficiency.
Owner:CHINA PETROCHEMICAL CORP +1
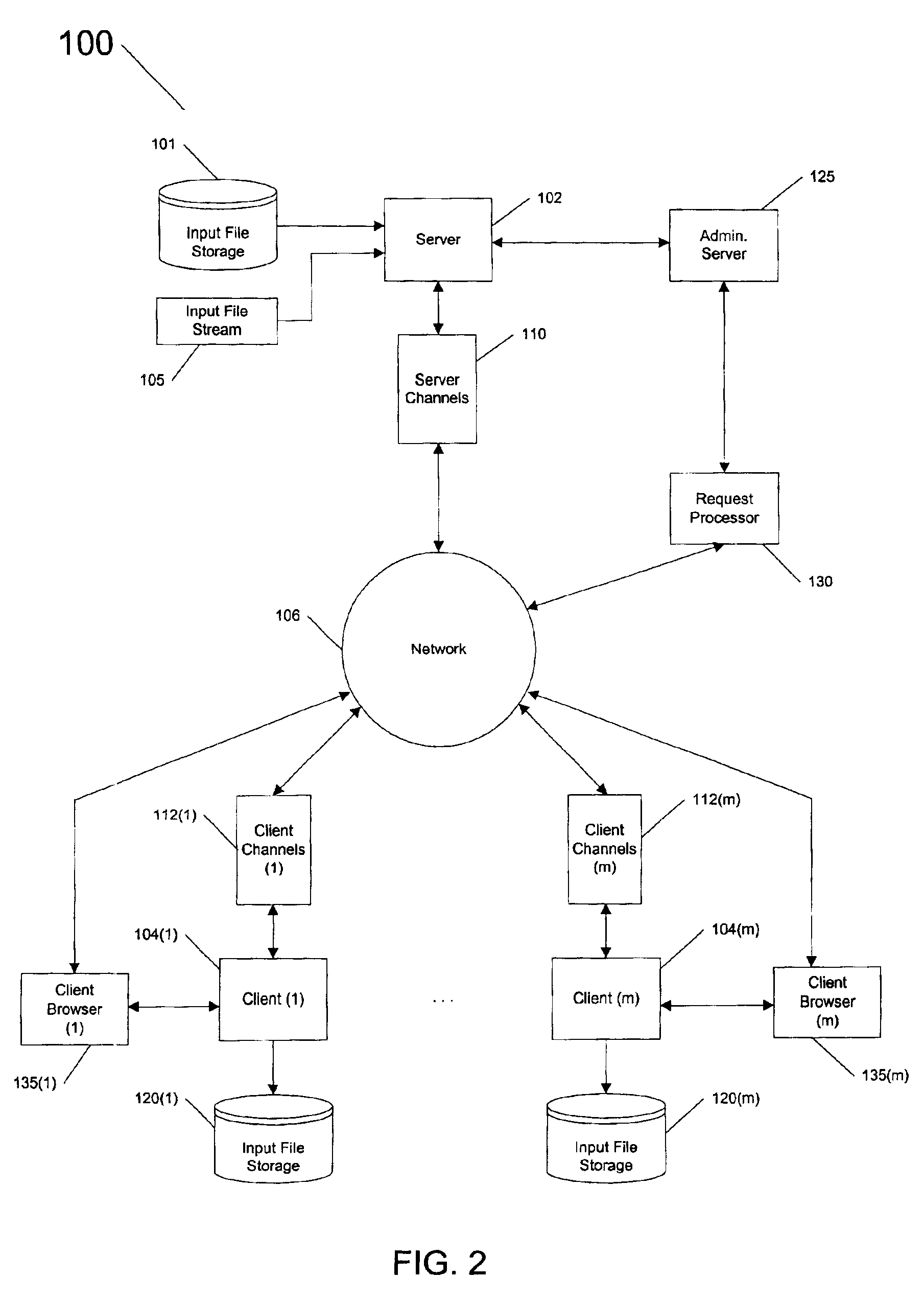
Scheduling of multiple files for serving on a server
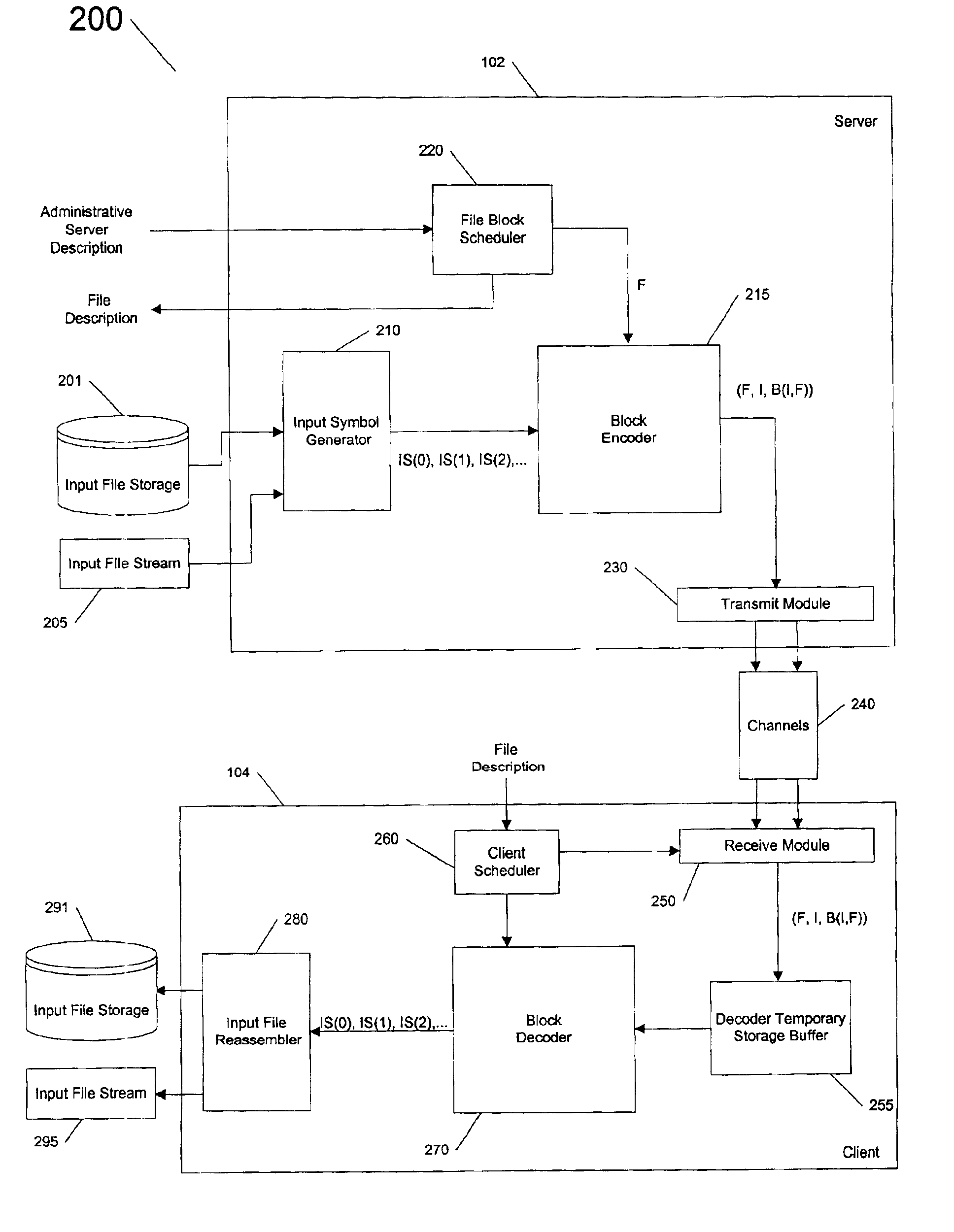
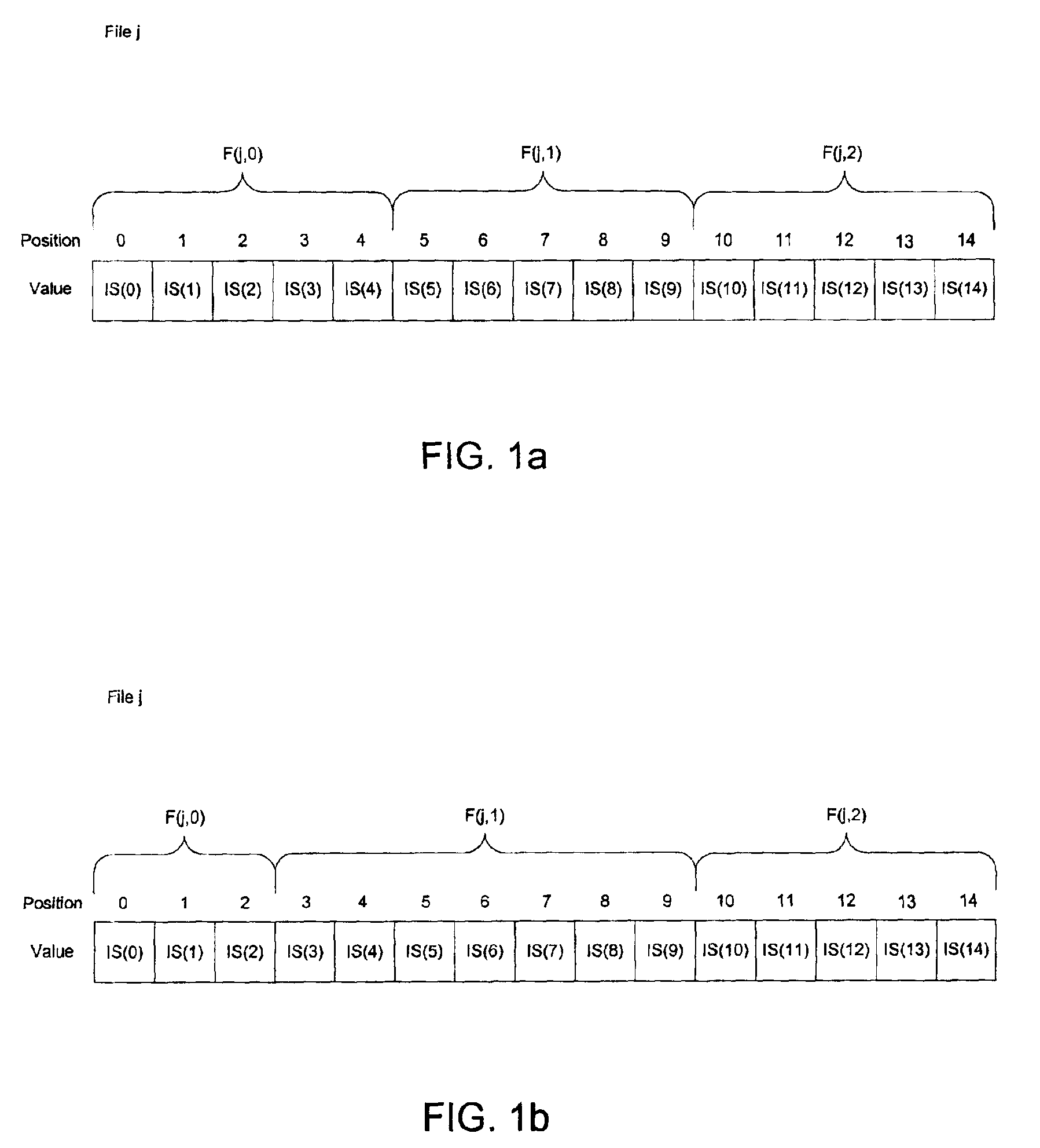
InactiveUS7072971B2Good serviceEffective recoveryIndividual digits conversionMultiple digital computer combinationsOperating system
Multiple files a served using a server coupled to a data network. A plurality of files is determined, wherein a file includes an integer number of blocks, and wherein each block includes at least one input symbol. For each file, an indication of at least one channel on which to serve the file is determined, and, for each file, a rate at which to serve the file is determined. Also, a schedule for processing the blocks is determined, and output symbols for the blocks are generated according to the schedule. The output symbols are transmitted on the corresponding at least one channel, wherein the files are concurrently served at their corresponding rates.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com