Patents
Literature
860 results about "Recovery procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In telecommunication, a recovery procedure is a process that attempts to bring a system back to a normal operating state.
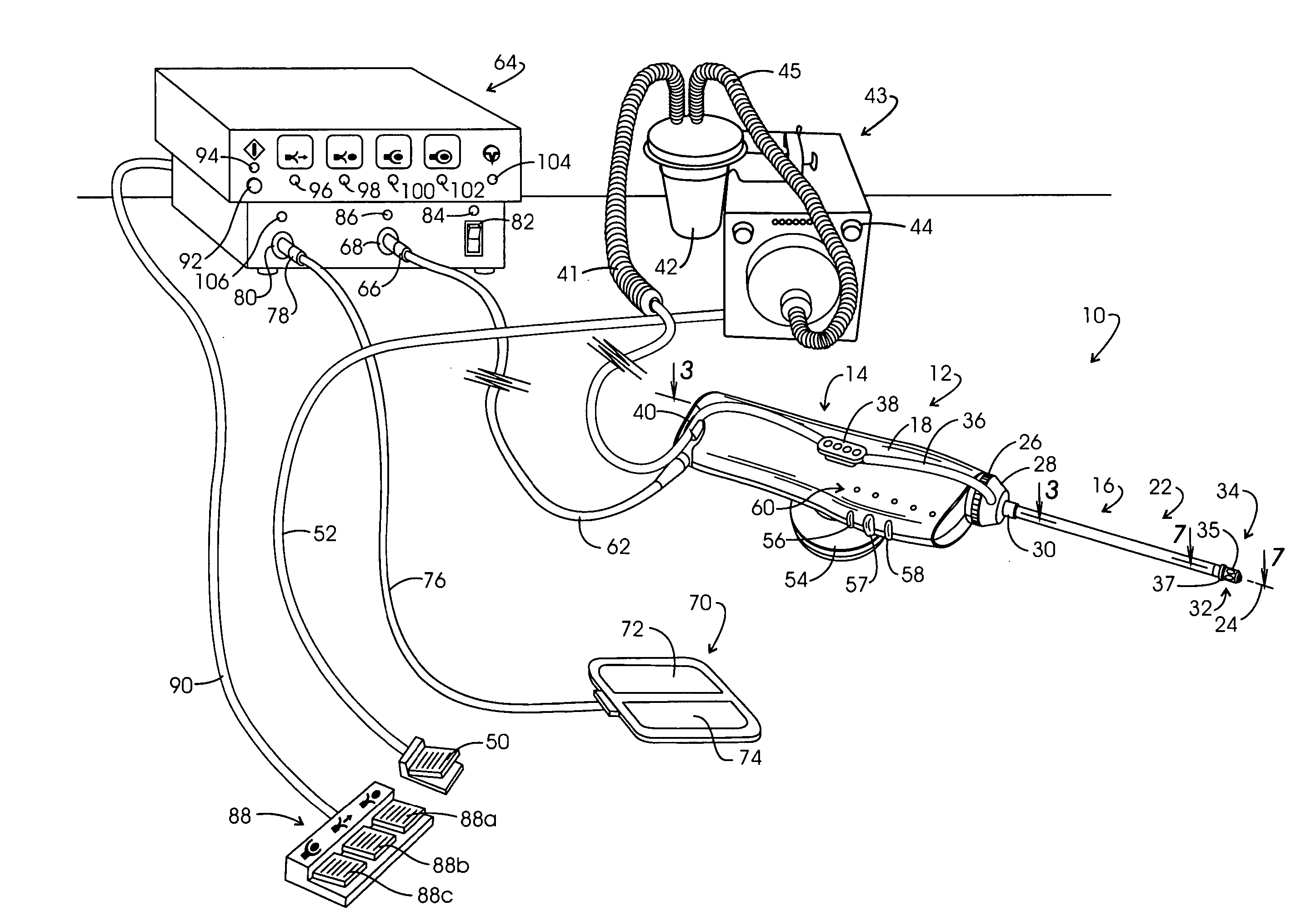
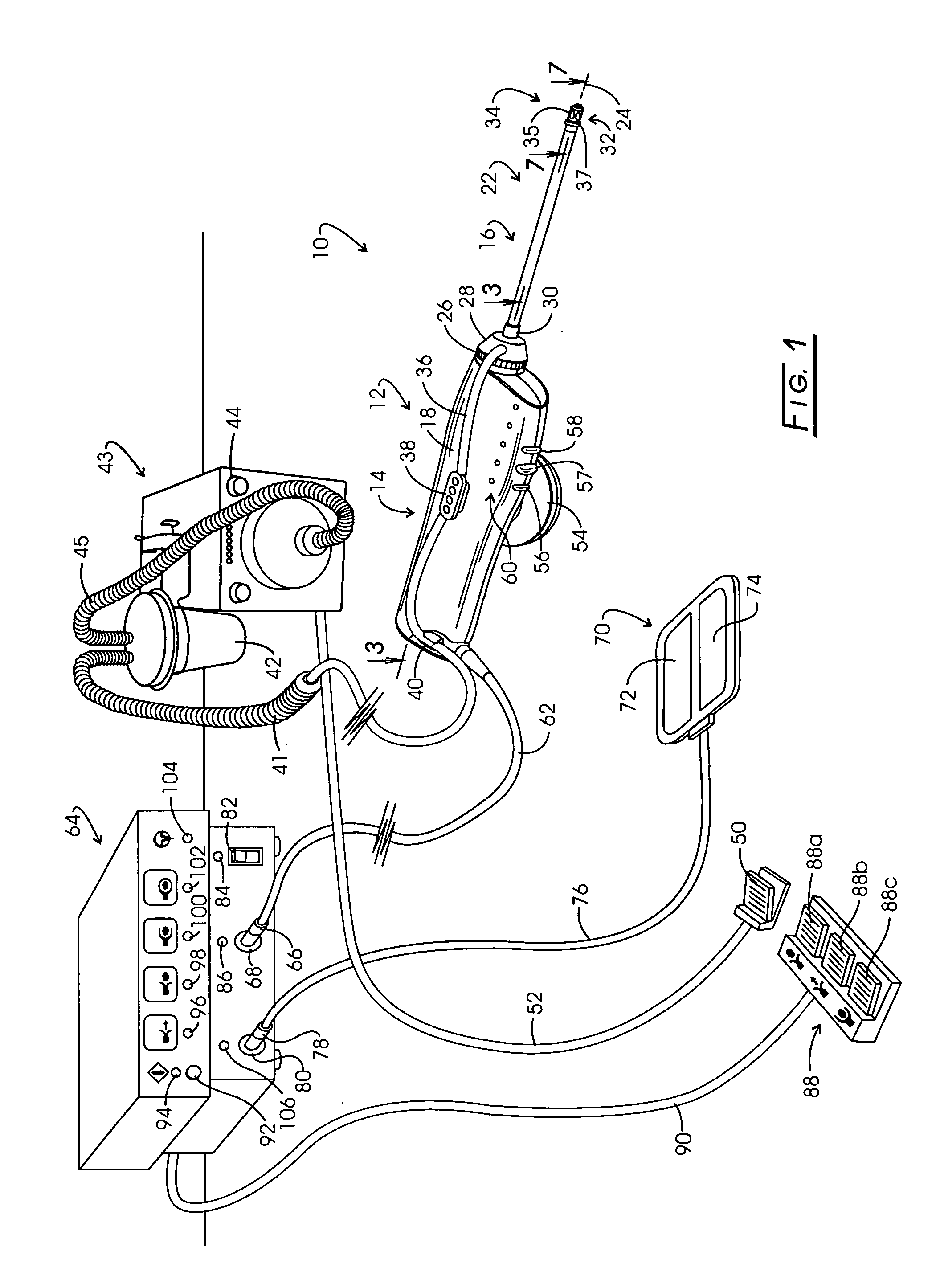
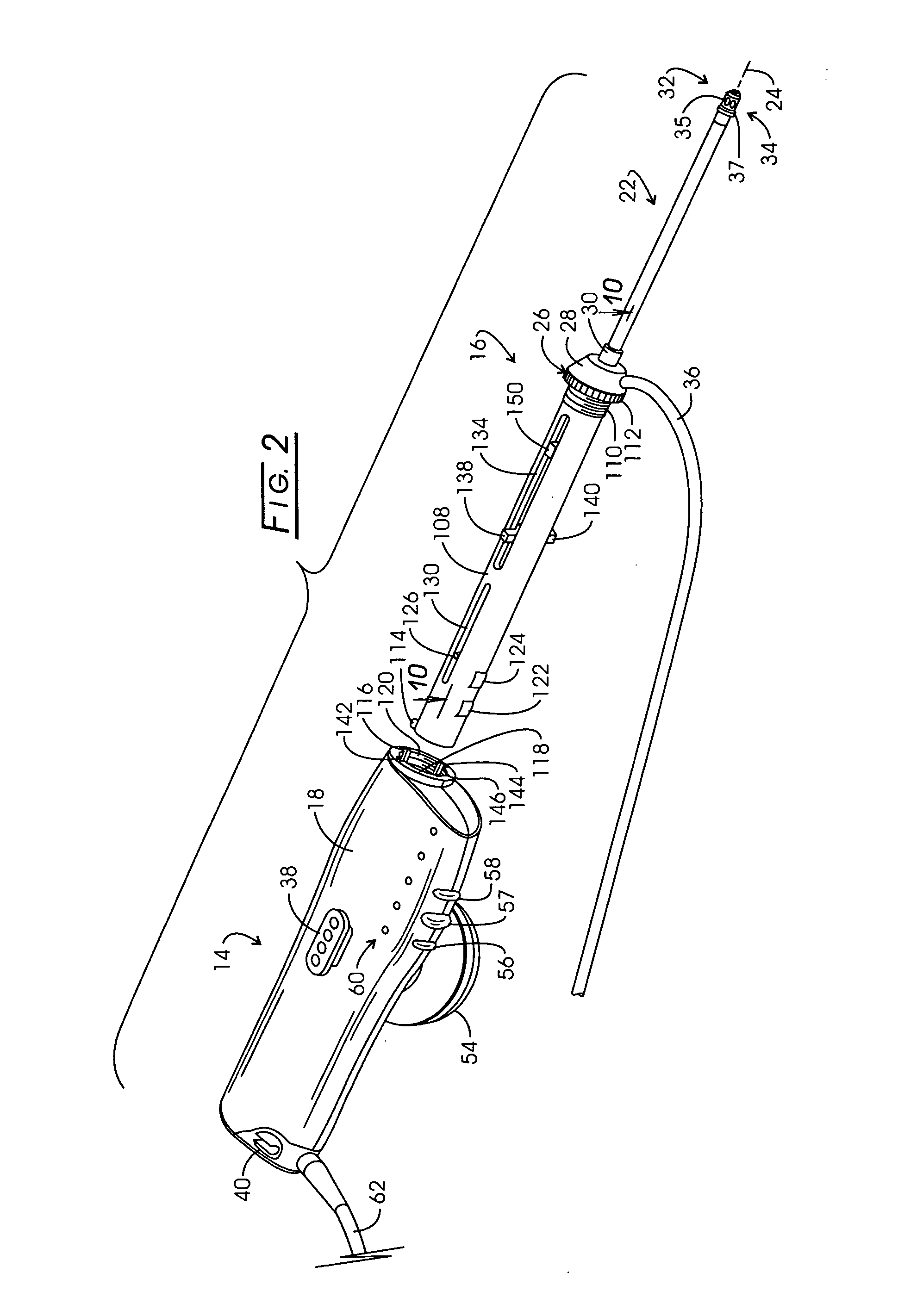
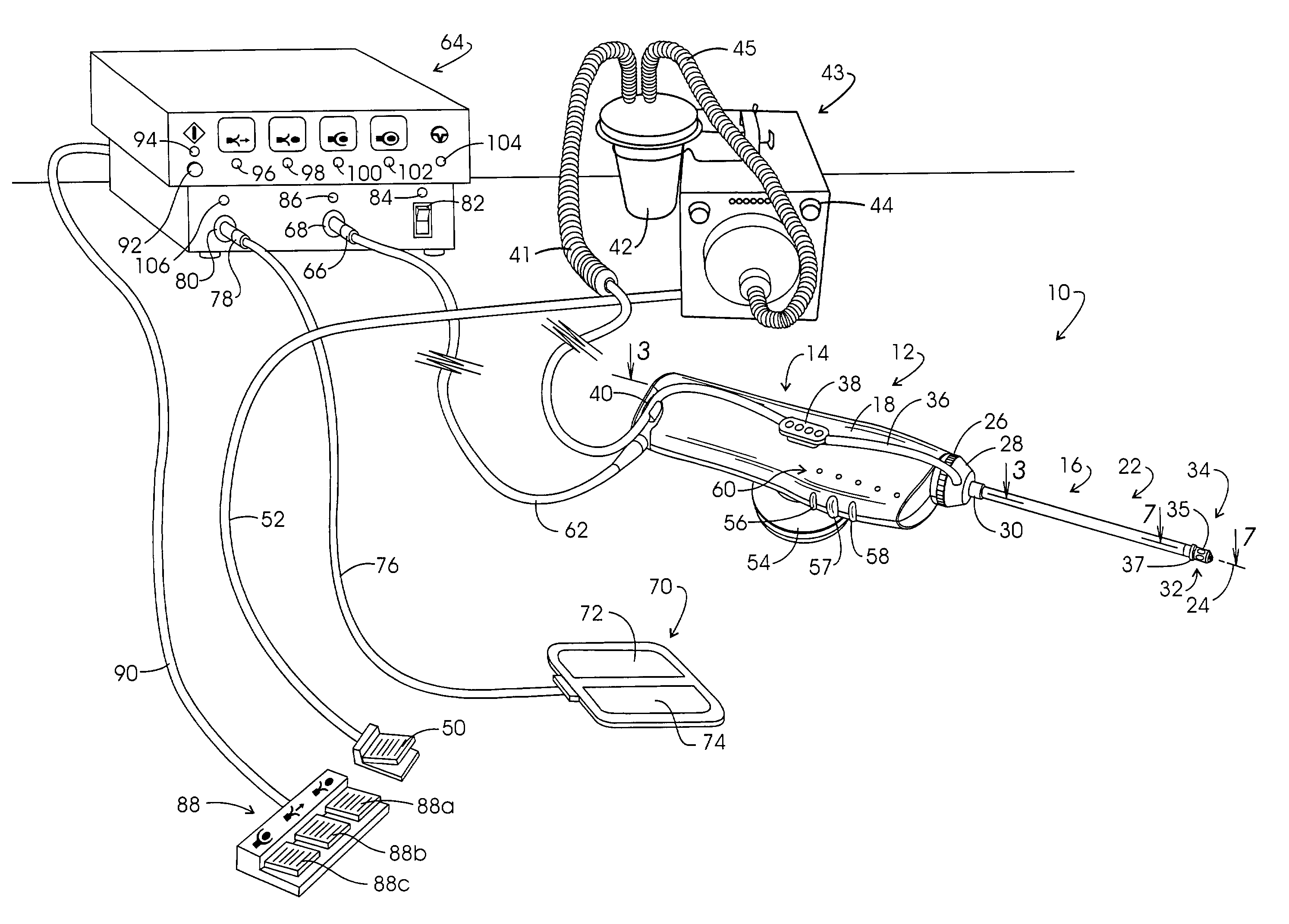
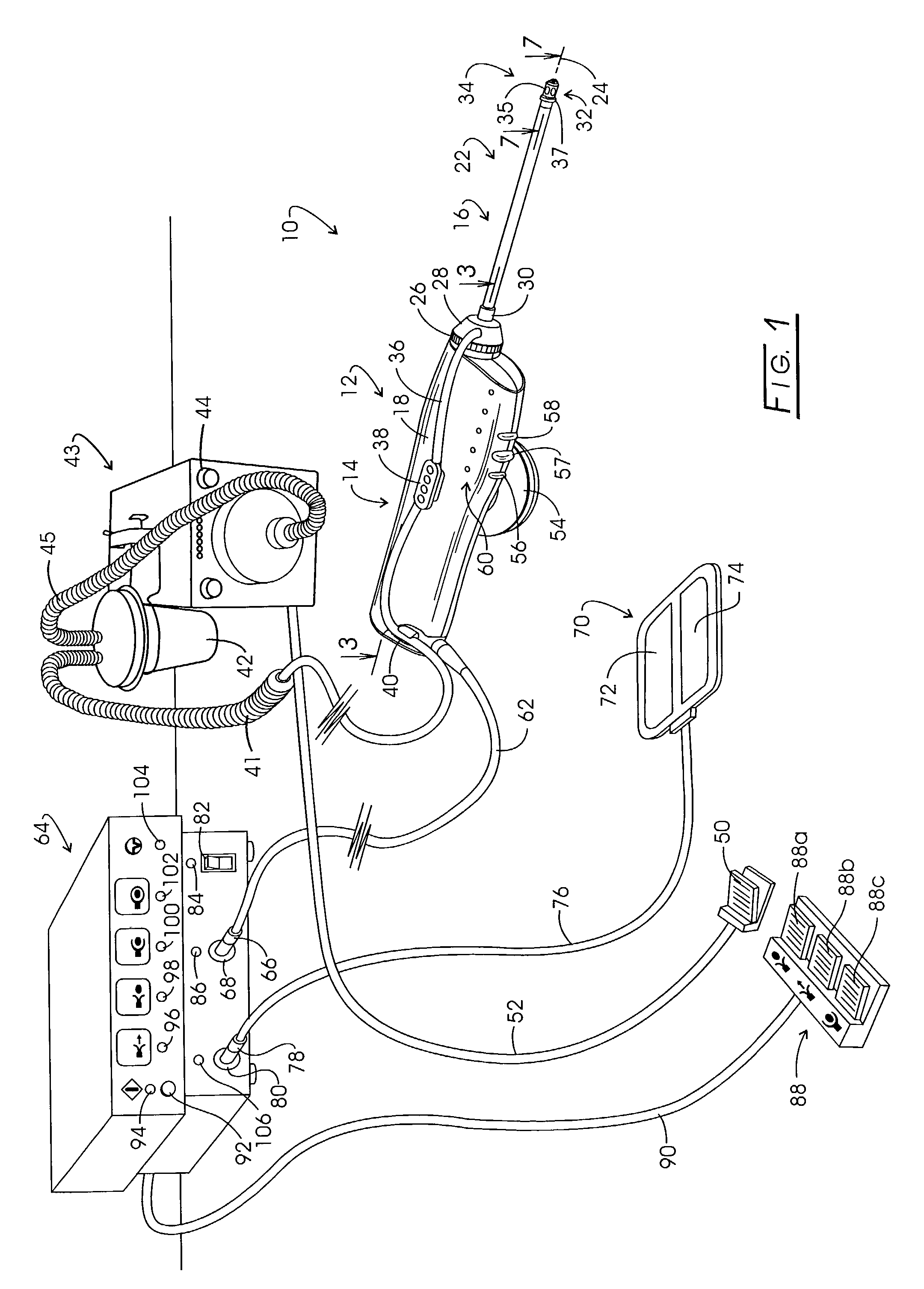
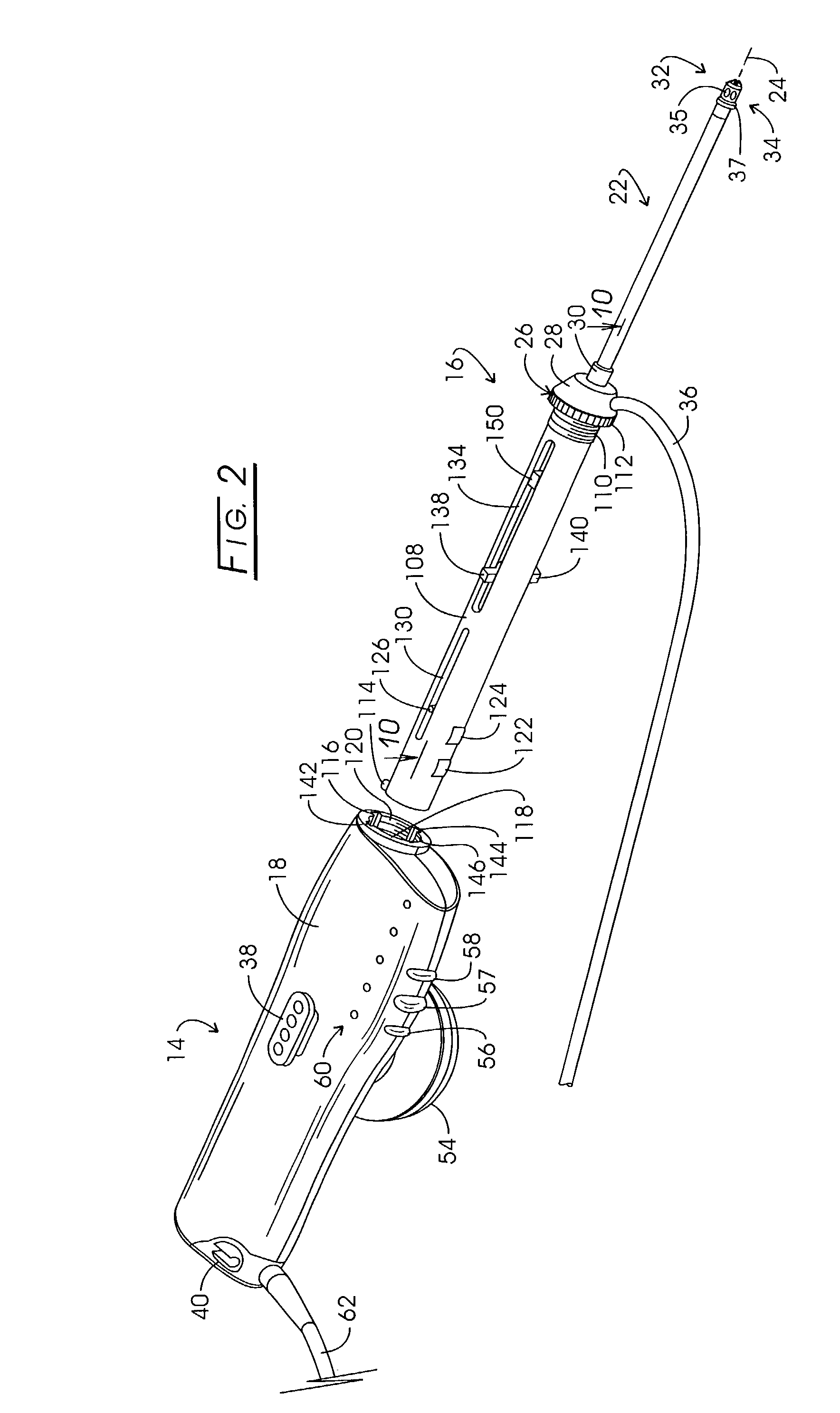
Electrosurgery with infiltration anesthesia
InactiveUS20050267455A1Reliable formationAnaesthesiaSurgical instruments for heatingElectrical resistance and conductanceElectrosurgery
Method for carrying out the recovery of an intact volume of tissue wherein a delivery cannula tip is positioned in confronting adjacency with the volume of tissue to be recovered. The electrosurgical generator employed to form an arc at a capture component extending from the tip is configured having a resistance-power profile which permits recovery of the specimen without excessive thermal artifact while providing sufficient power to sustain a cutting arc. For the recovery procedure, a local anesthetic employing a diluent which exhibits a higher resistivity is utilized and the method for deploying the capture component involves an intermittent formation of a cutting arc with capture component actuation interspersed with pauses of duration effective to evacuate any accumulation or pockets of local anesthetic solution encountered by the cutting electrodes.
Owner:INTACT MEDICAL
Electrosurgery with infiltration anesthesia
InactiveUS7004174B2AnaesthesiaVaccination/ovulation diagnosticsElectrical resistance and conductanceElectrosurgery
Method for carrying out the recovery of an intact volume of tissue wherein a delivery cannula tip is positioned in confronting adjacency with the volume of tissue to be recovered. The electrosurgical generator employed to form an arc at a capture component extending from the tip is configured having a resistance-power profile which permits recovery of the specimen without excessive thermal artifact while providing sufficient power to sustain a cutting arc. For the recovery procedure, a local anesthetic employing a diluent which exhibits a higher resistivity is utilized and the method for deploying the capture component involves an intermittent formation of a cutting arc with capture component actuation interspersed with pauses of duration effective to evacuate any accumulation or pockets of local anesthetic solution encountered by the cutting electrodes.
Owner:COVIDIEN AG
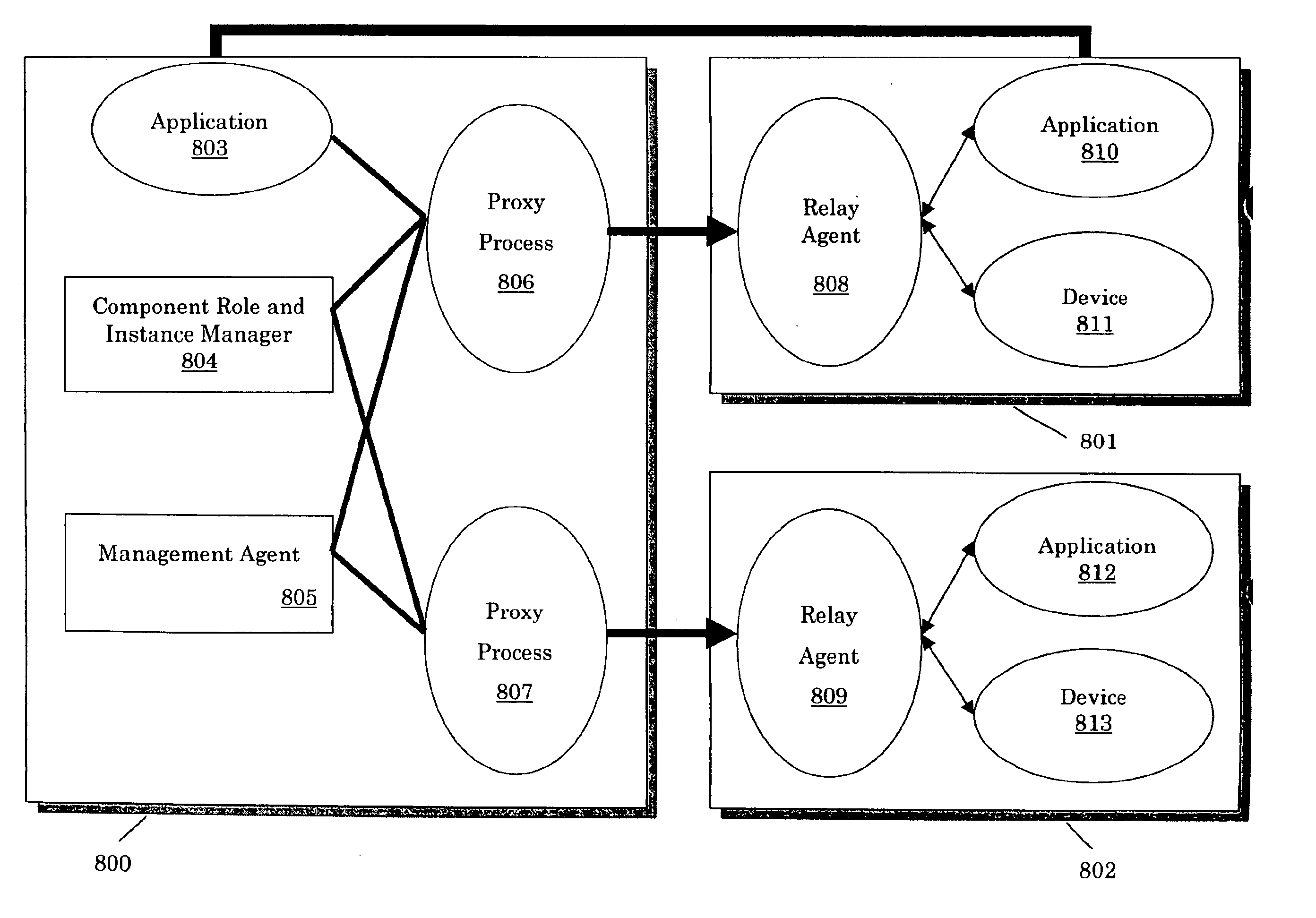
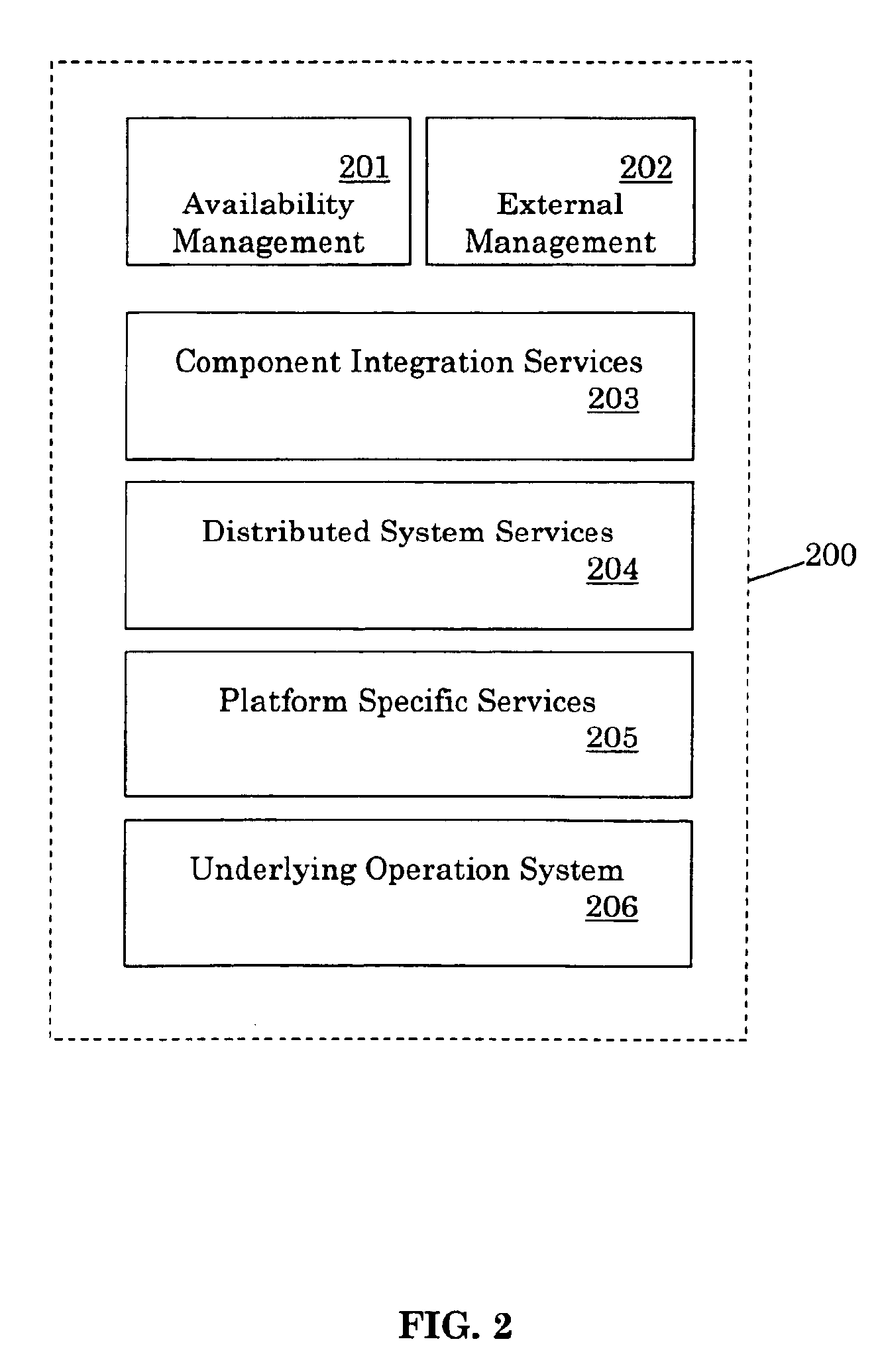
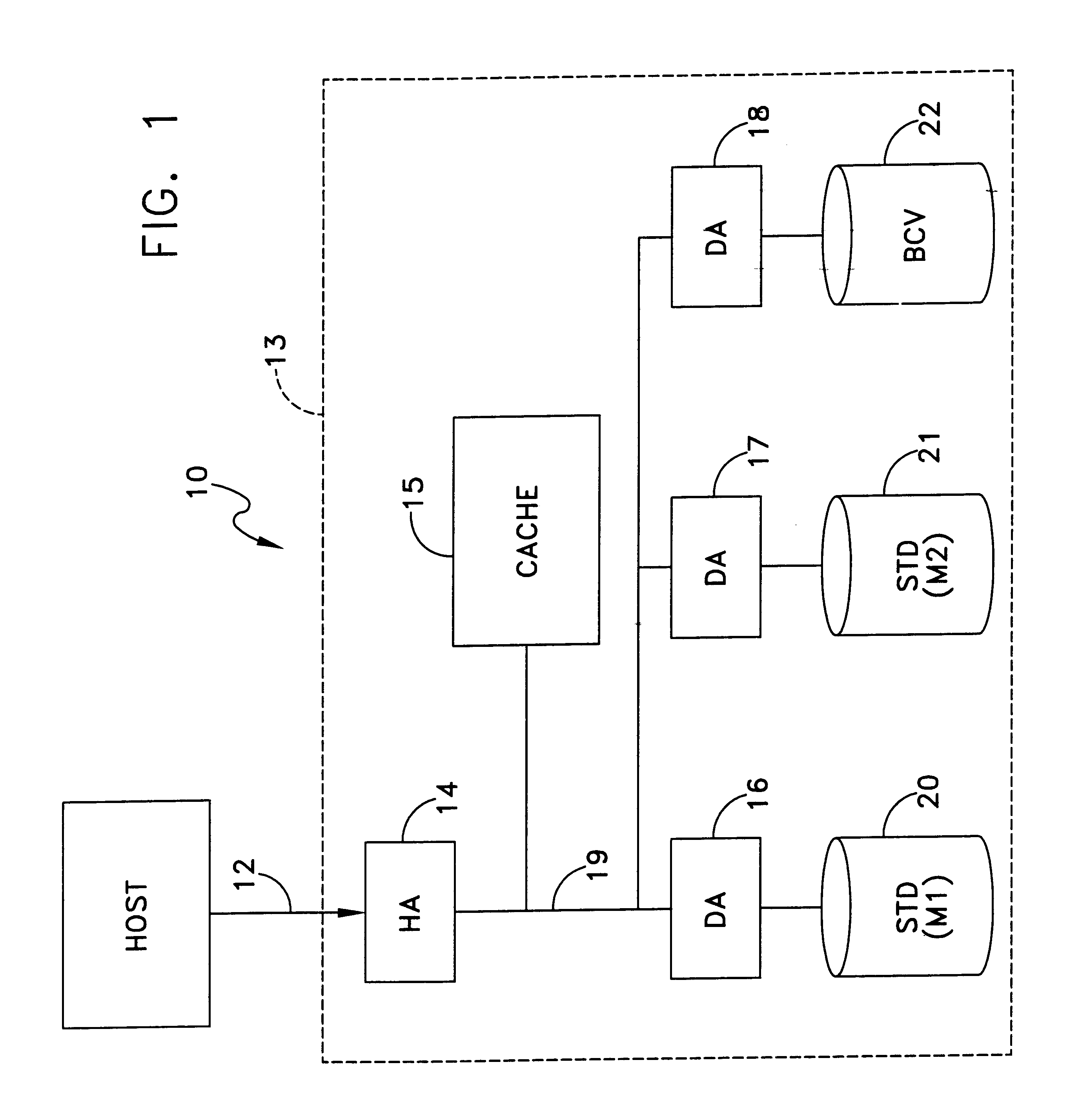
Method and system for achieving high availability in a networked computer system
InactiveUS6854069B2Improve portabilityImprove reusabilityError detection/correctionData switching networksNetwork connectionHigh availability
The present invention describes a method and system for achieving high availability in a networked computer system. In particular, the method for achieving high-availability is executed in a networked computer system. The networked computer system includes nodes connected by a network. The method includes using high-availability-aware components to represent hardware and software in the networked computer system, managing the components to achieve a desired level of redundancy, and monitoring health of the networked computer system, including health of components and nodes. The method further includes detecting a failure in the networked computer system. Failures detected by the method include failures of a component and / or node. Finally, the method includes recovering from the failure by performing an appropriate failure recovery procedure.
Owner:ORACLE INT CORP
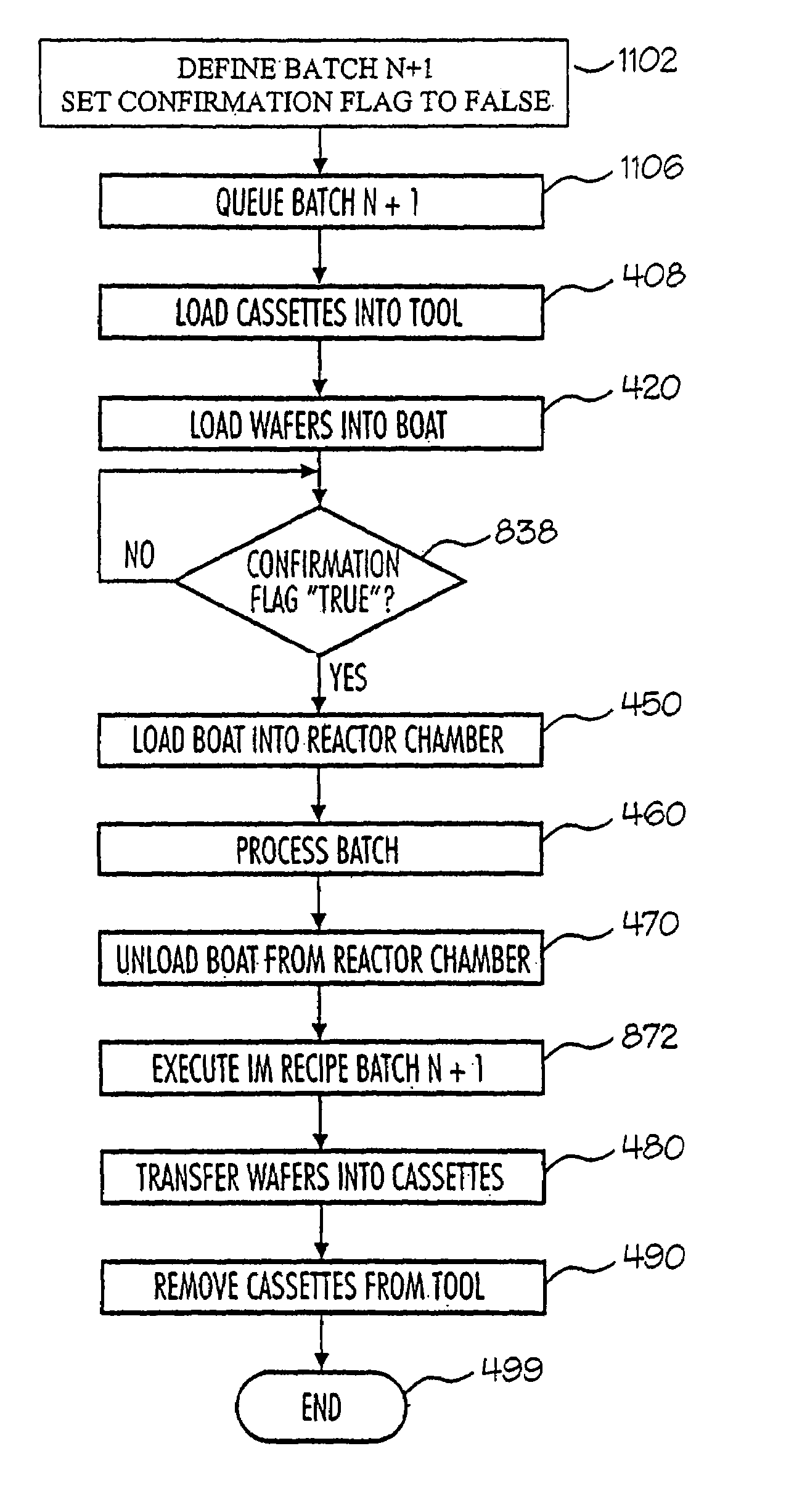
Method and system to process semiconductor wafers
InactiveUS6985788B2Smooth and flexible recoveryInterruption of started process is preventedElectric heatingSemiconductor/solid-state device manufacturingEngineeringRecovery procedure
A method and system for the processing of one or more wafers in a process tool is provided, the method comprising subjecting the one or more wafer in a reaction chamber to a process, generating an inhibit next load flag on predefined conditions, the inhibit next load flag not effecting already started processing of a wafer. Prior to the start of the processing of a wafer, a check is performed to see if an inhibit next load flag has been set. When upon checking it has been found that an inhibit next load has been set, the start of the process in the reaction chamber is prohibited. The method further includes providing pre-programmed recovery procedures, such that after execution of a pre-programmed recovery procedure the to be processed wafer of which the start of the processing is prohibited ends in a defined state such that the tool can be used for further processing.
Owner:ASM INTERNATIONAL
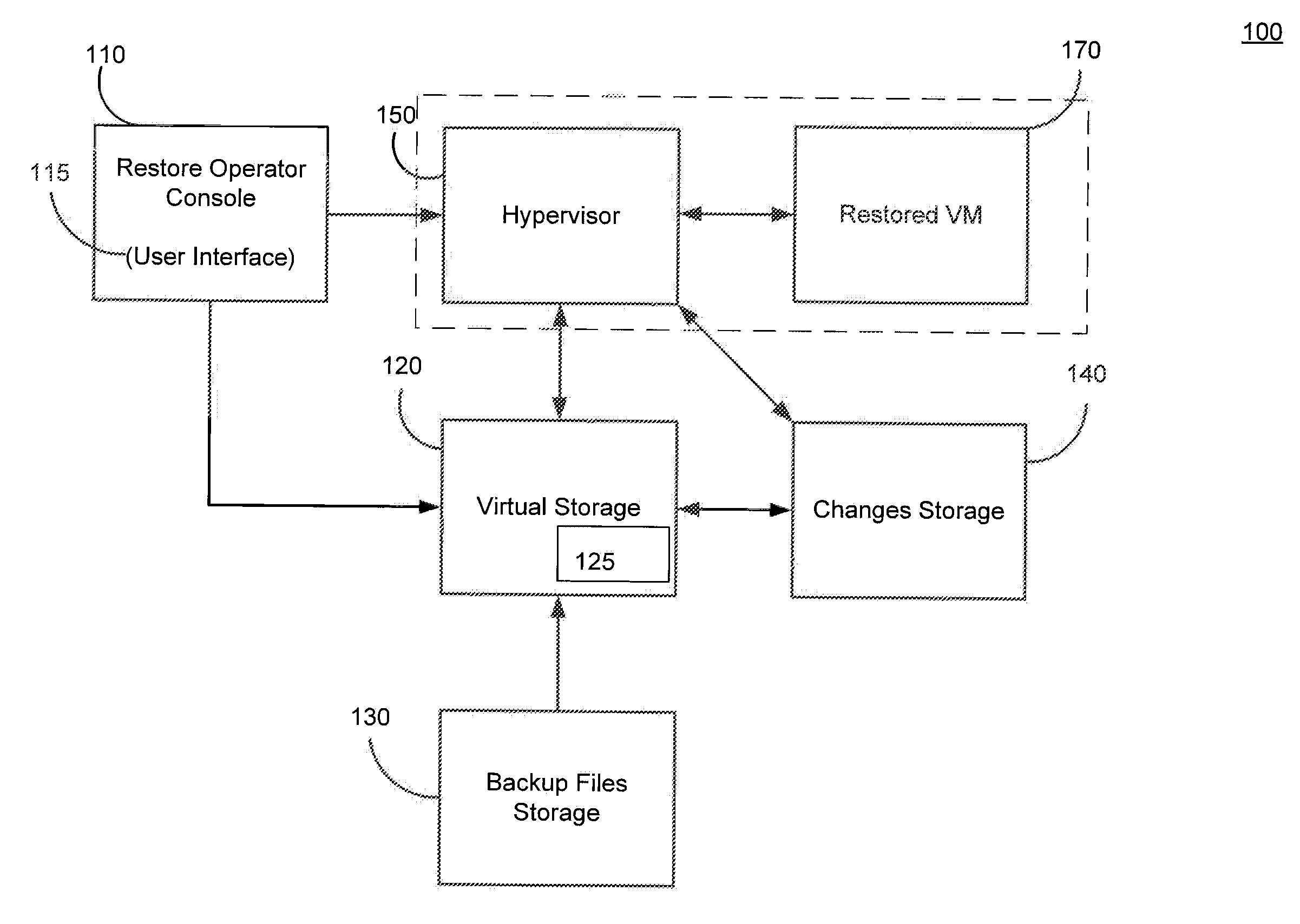
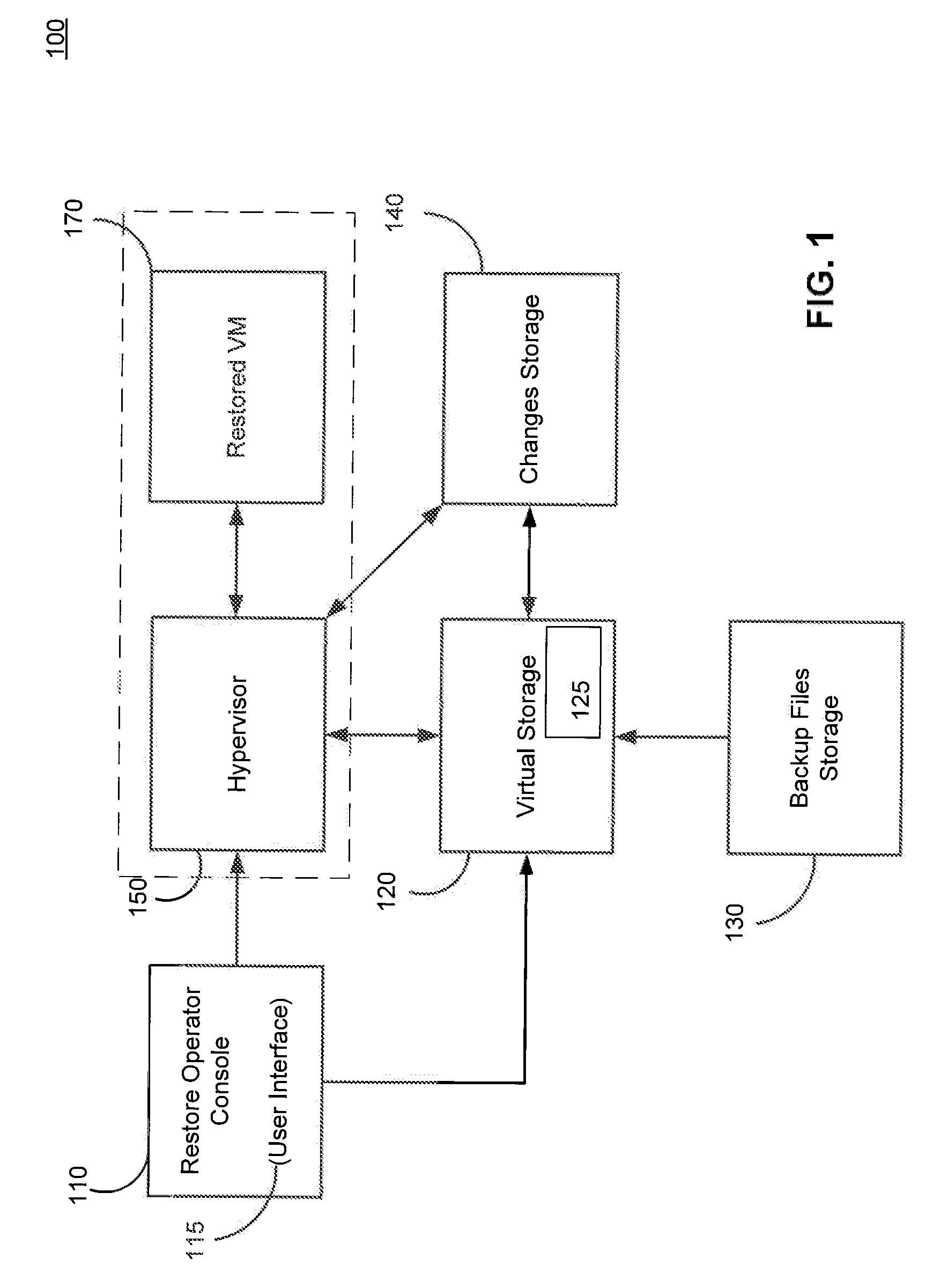
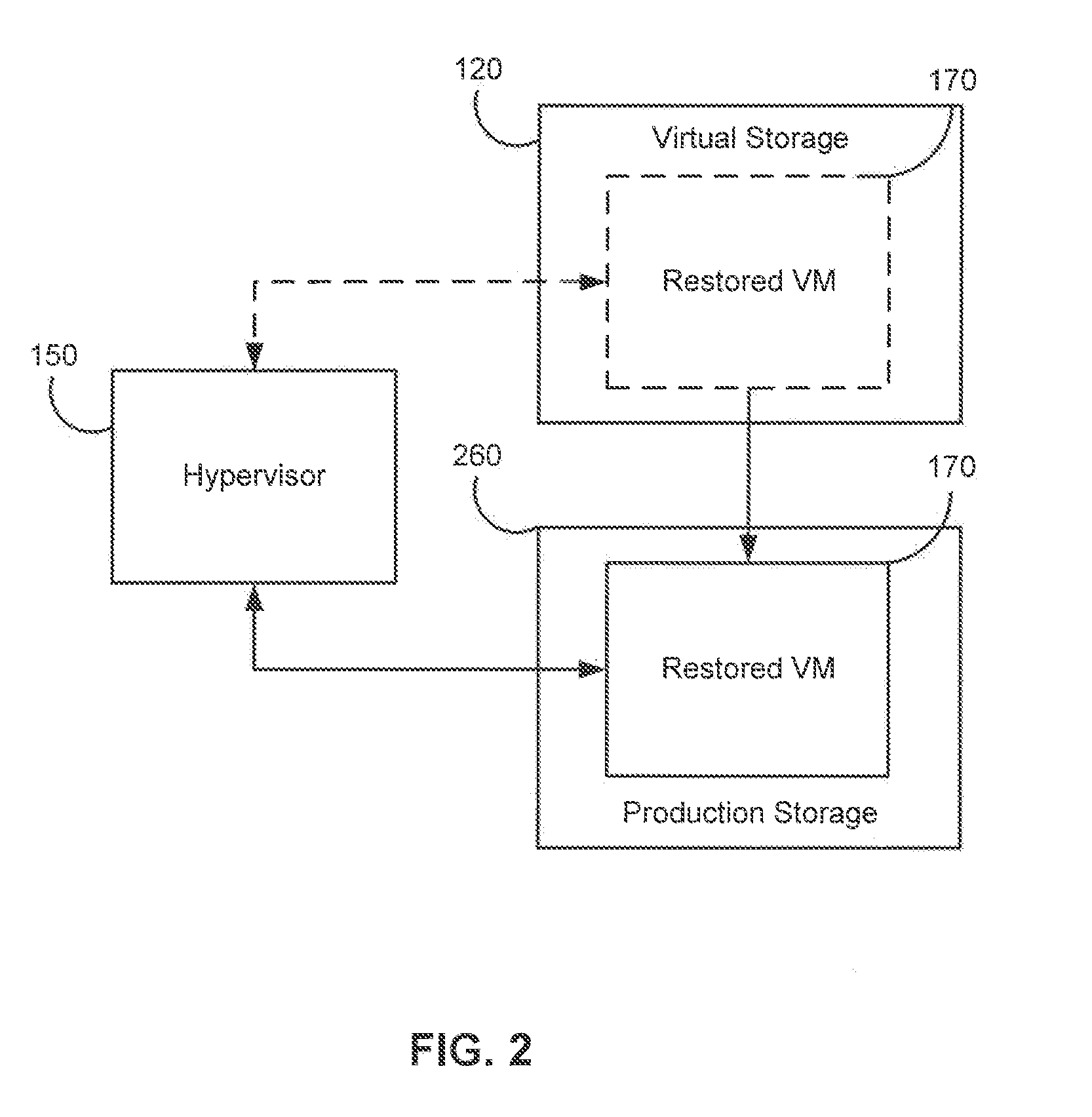
Systems, Methods, and Computer Program Products for Instant Recovery of Image Level Backups
ActiveUS20120017114A1Fault responseSoftware simulation/interpretation/emulationOperational systemDowntime
Systems, methods, and computer program products are provided for instant recovery of a virtual machine (VM) from a compressed image level backup without fully extracting the image level backup file's contents to production storage. The method receives restore parameters and initializes a virtual storage. The method attaches the virtual storage to a hypervisor configured to launch a recovered VM. The method stores virtual disk data changes inflicted by a running operating system (OS), applications, and users in a changes storage. The method provides the ability to migrate the actual VM disk state (taking into account changed disk data blocks accumulated in changes storage) so as to prevent data loss resulting from the VM running during the recovery and accessing virtual storage, to production storage without downtime. In embodiments, the method displays receives restore parameters in an interactive interface and delivers the recovery results via an automated message, such as an email message.
Owner:VEEAM SOFTWARE GROUP GMBH
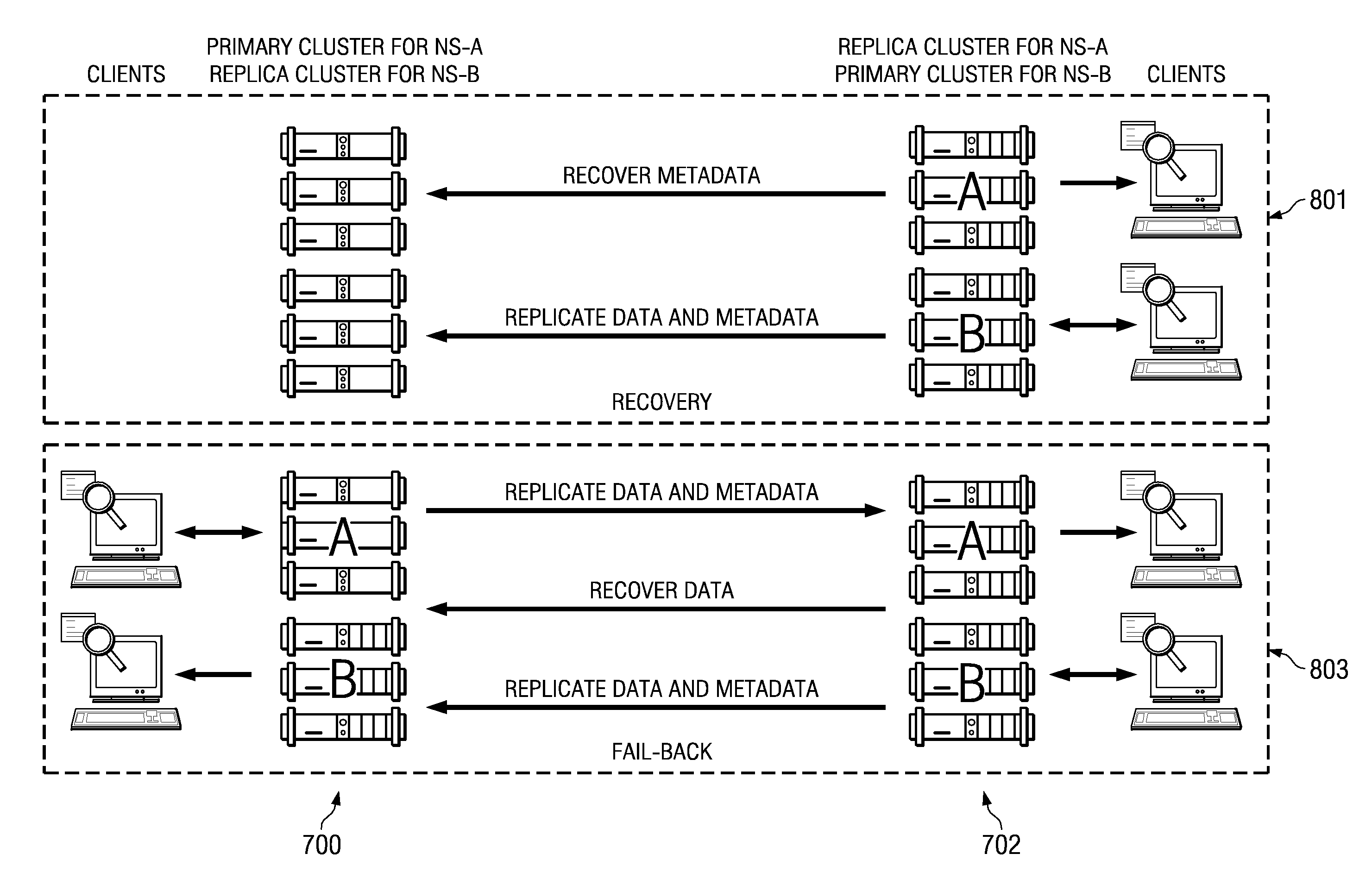
Fast primary cluster recovery
ActiveUS20090006888A1Easy to copyDigital data processing detailsRedundant data error correctionFailoverObject based
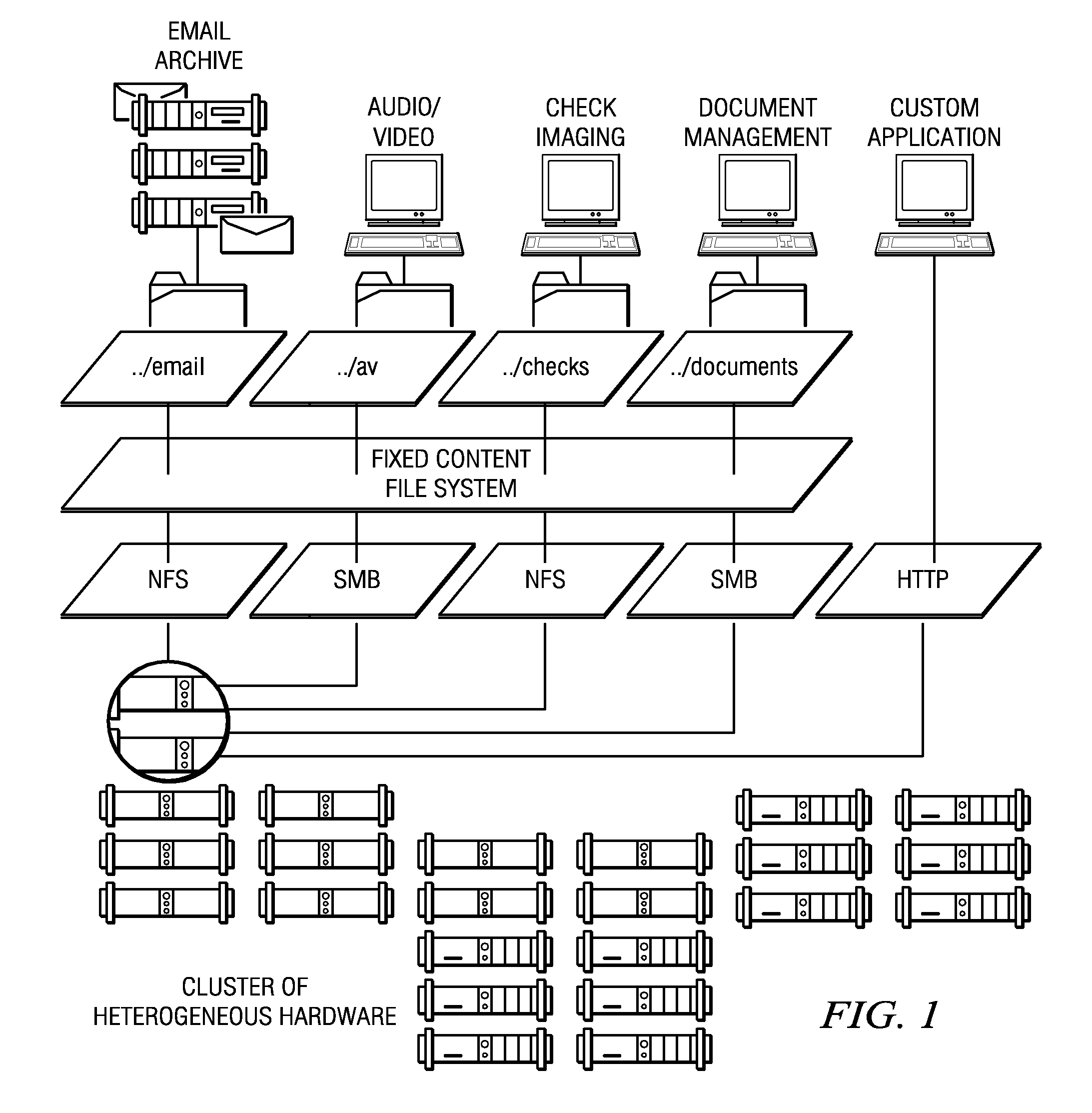
A cluster recovery process is implemented across a set of distributed archives, where each individual archive is a storage cluster of preferably symmetric nodes. Each node of a cluster typically executes an instance of an application that provides object-based storage of fixed content data and associated metadata. According to the storage method, an association or “link” between a first cluster and a second cluster is first established to facilitate replication. The first cluster is sometimes referred to as a “primary” whereas the “second” cluster is sometimes referred to as a “replica.” Once the link is made, the first cluster's fixed content data and metadata are then replicated from the first cluster to the second cluster, preferably in a continuous manner. Upon a failure of the first cluster, however, a failover operation occurs, and clients of the first cluster are redirected to the second cluster. Upon repair or replacement of the first cluster (a “restore”), the repaired or replaced first cluster resumes authority for servicing the clients of the first cluster. This restore operation preferably occurs in two stages: a “fast recovery” stage that involves preferably “bulk” transfer of the first cluster metadata, following by a “fail back” stage that involves the transfer of the fixed content data. Upon receipt of the metadata from the second cluster, the repaired or replaced first cluster resumes authority for the clients irrespective of whether the fail back stage has completed or even begun.
Owner:HITACHI VANTARA LLC
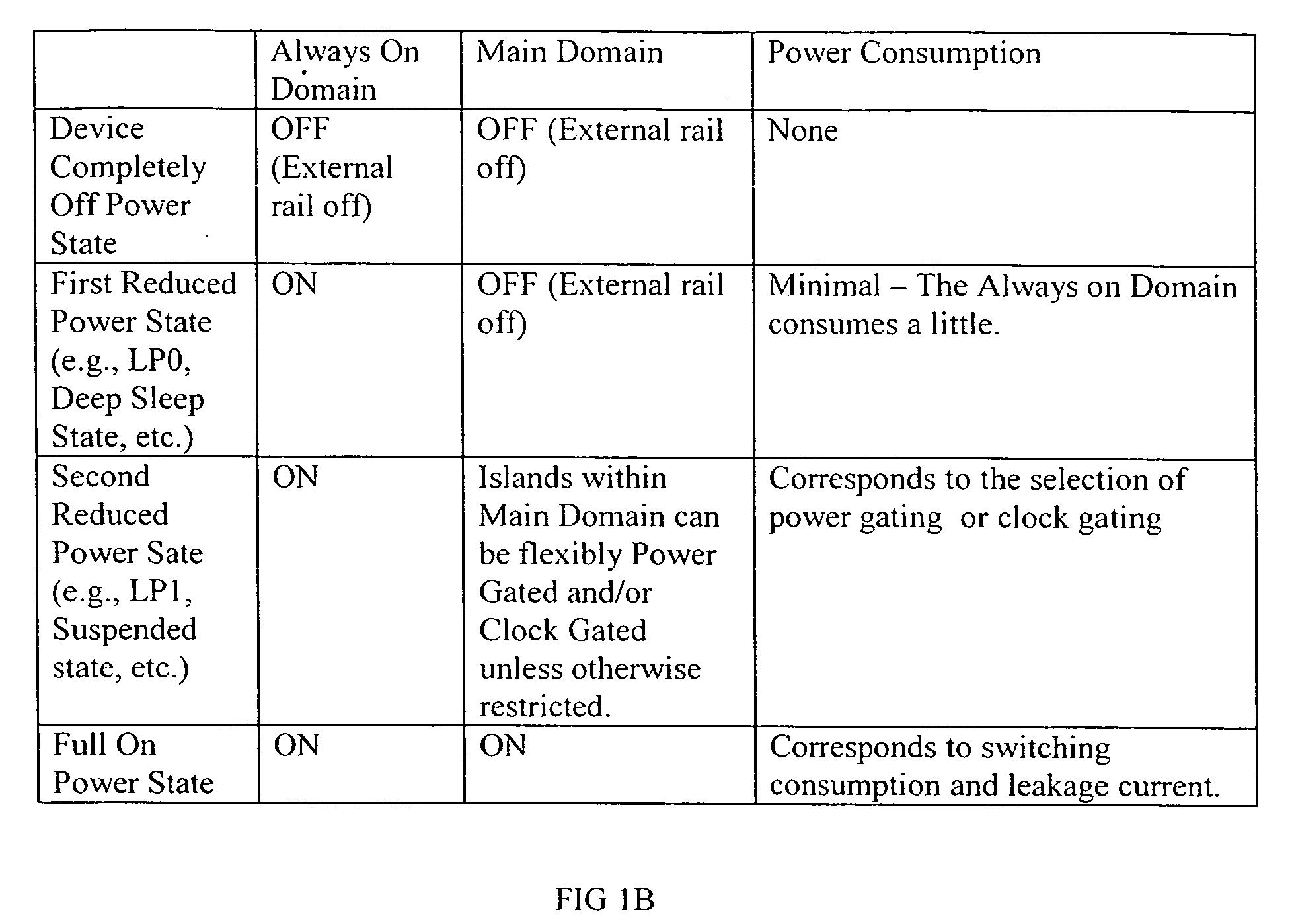
Power control system and method
An efficient and effective power control system method are described with expedited recovery from a reduced power state. In one embodiment, a present invention power control system includes performing a reduced power detection process for detecting a reduced power state, wherein the reduced power state is associated with an expedited recovery; performing a reduced power state entry process; performing a recovery detection process for detecting a recover indication event; and performing an expedited recovery process in accordance with detection of a recovery indication event. The reduced power state entry process comprises saving an expedited recovery information in registers of an always on domain and putting an external memory in self refresh mode to preserve a system context while a chip is turned off. The expedited recovery process comprises determining whether to proceed with the expedited recovery process; initializing memory controller registers and directing memory controller to exit self refresh; validating system context recovered from memory using keys stored in an always on domain; jumping to recovery instructions in memory; restoring operating system information and returning to operating system control.
Owner:NVIDIA CORP
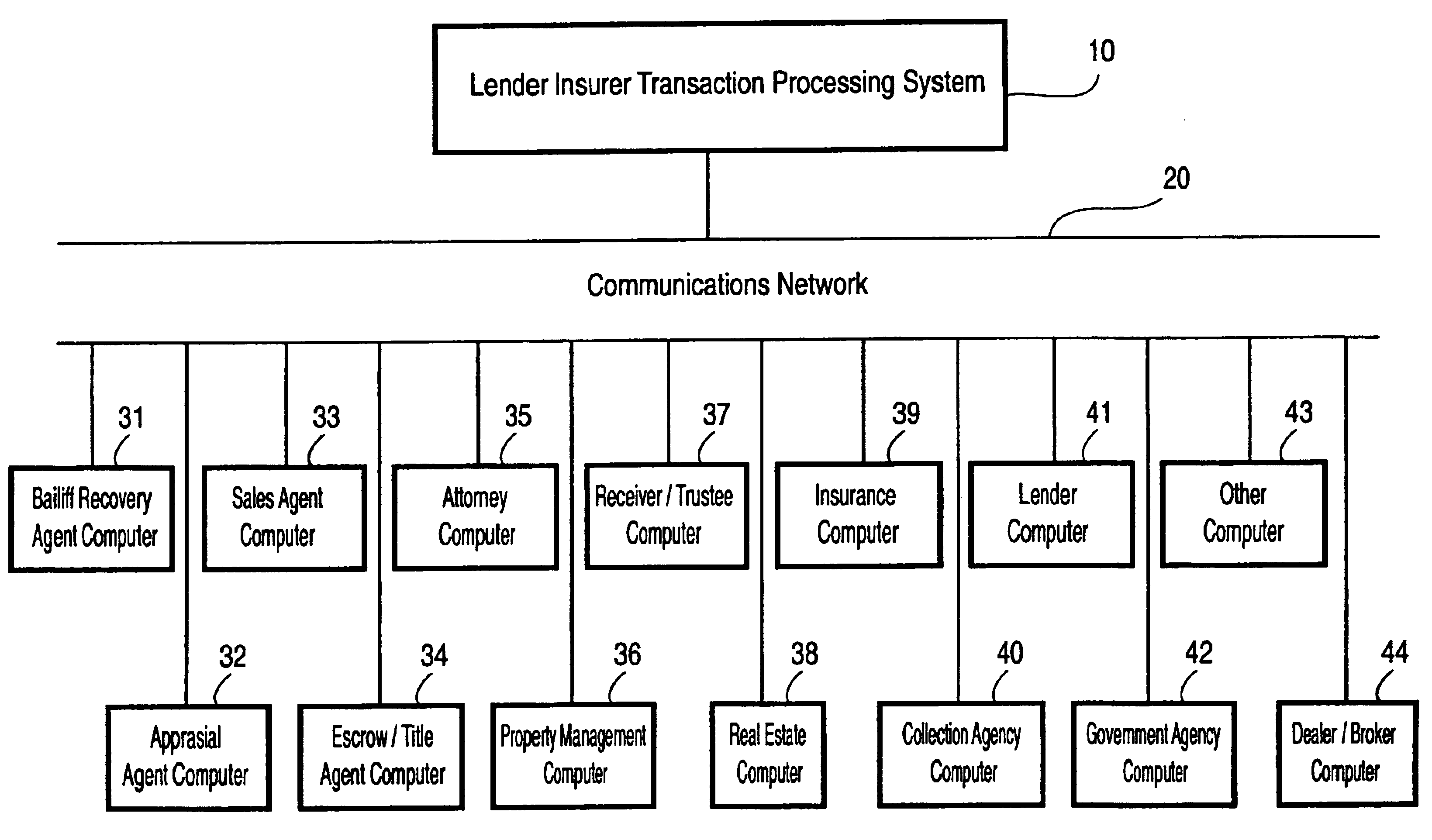
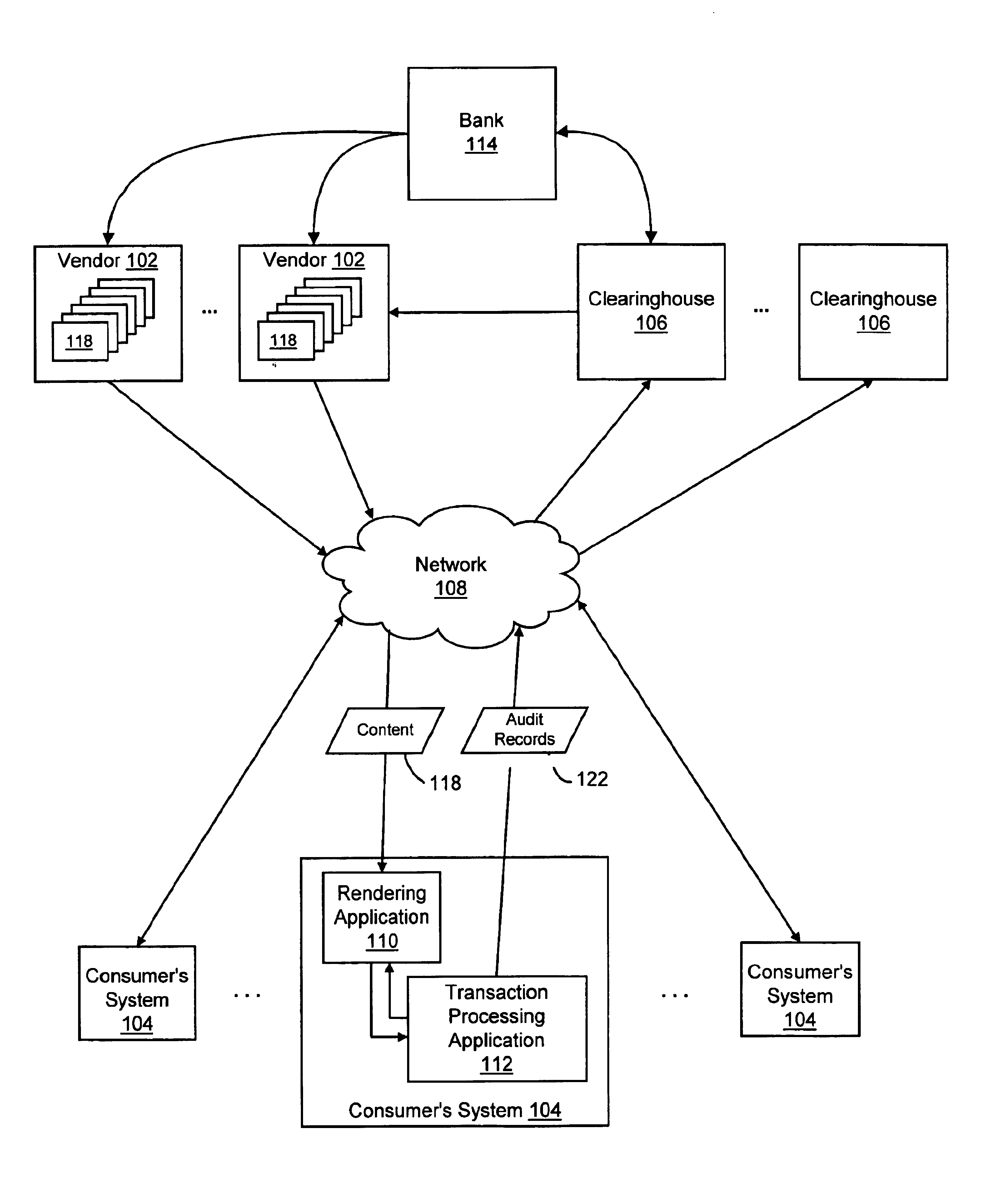
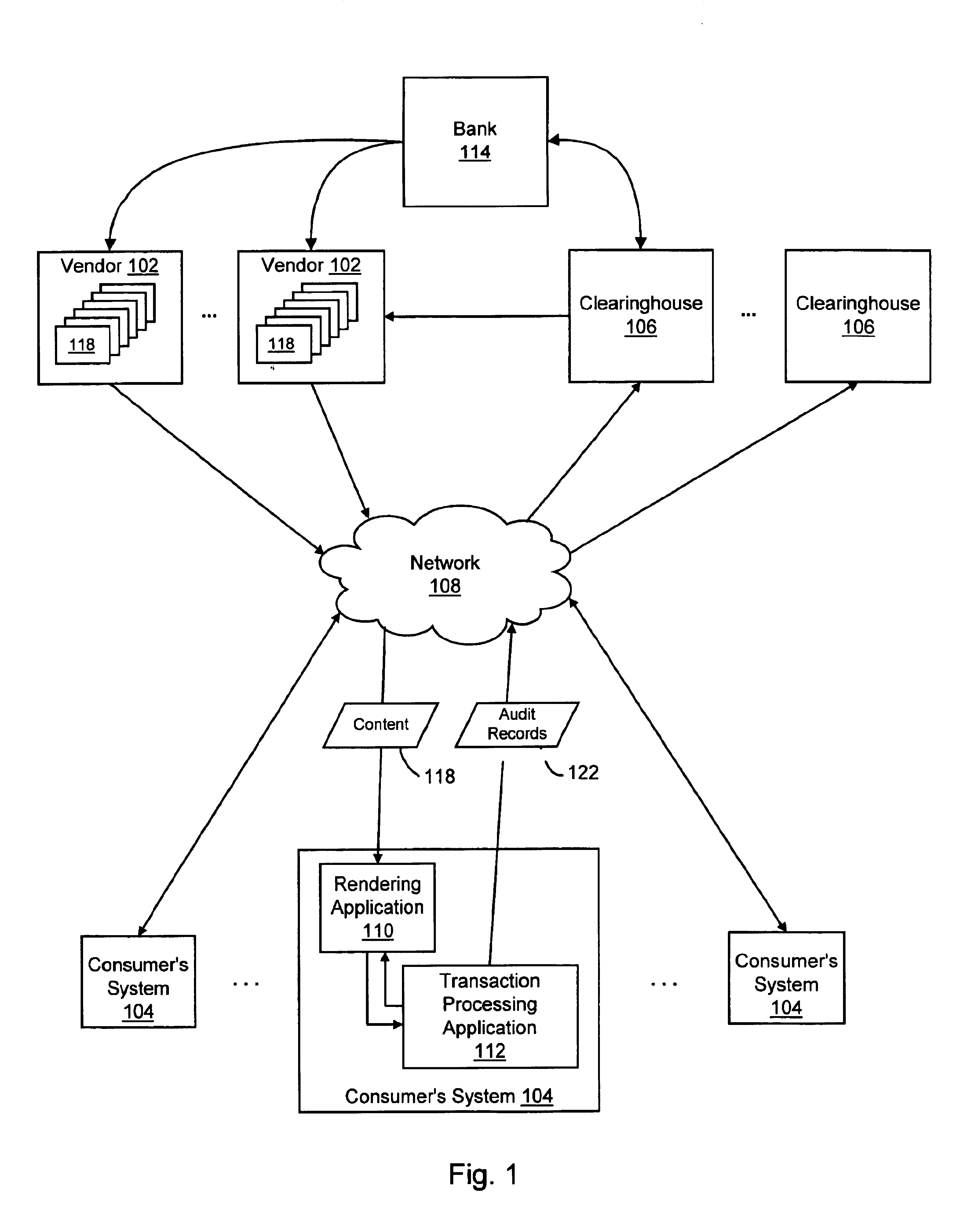
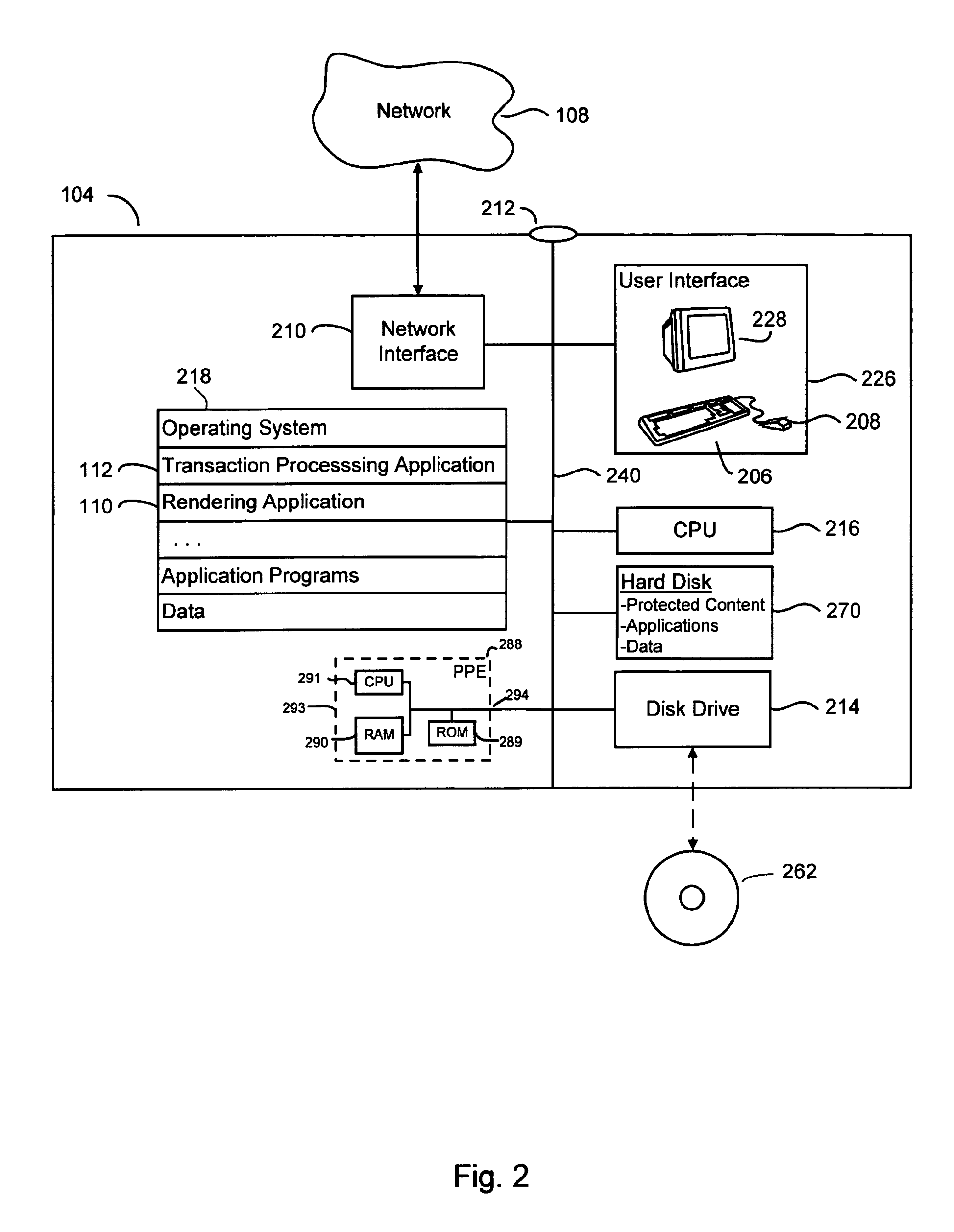
Lender and insurer transaction processing system and method
A system and method for transaction processing includes a central repository of transaction information which can be accessed by a variety of participants who may be located over a wide geographic area in the recovery process of a property unit such as a vehicle or other collateral. Interfacing with a variety of computer systems over a communication network, such as the Internet, allows interchange of data relating to the recovery process and centralized coordination of the recovery process.
Owner:DH COLLATERAL MANAGEMENT CORP
Optimizing order of error recovery steps in a disk drive
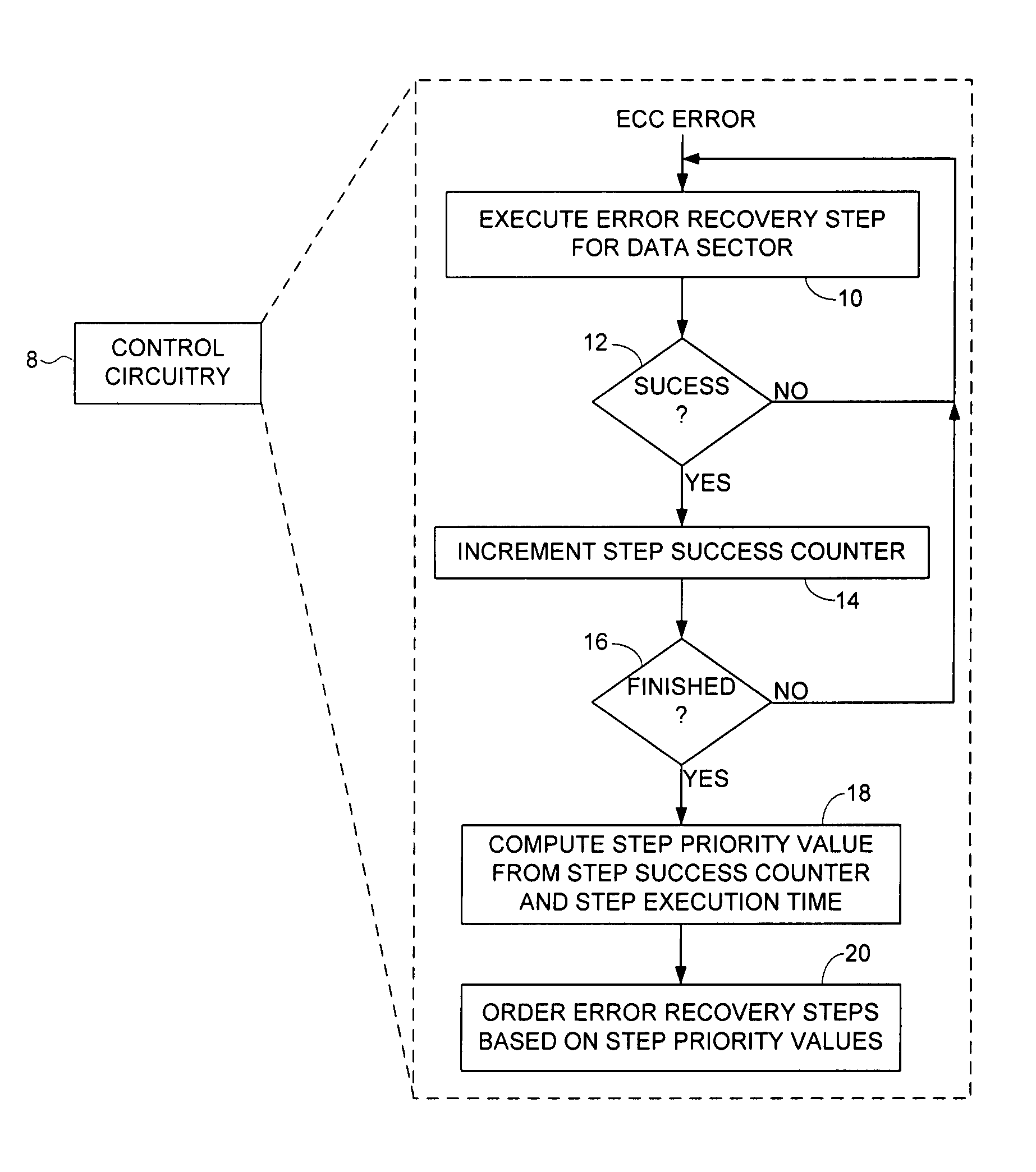
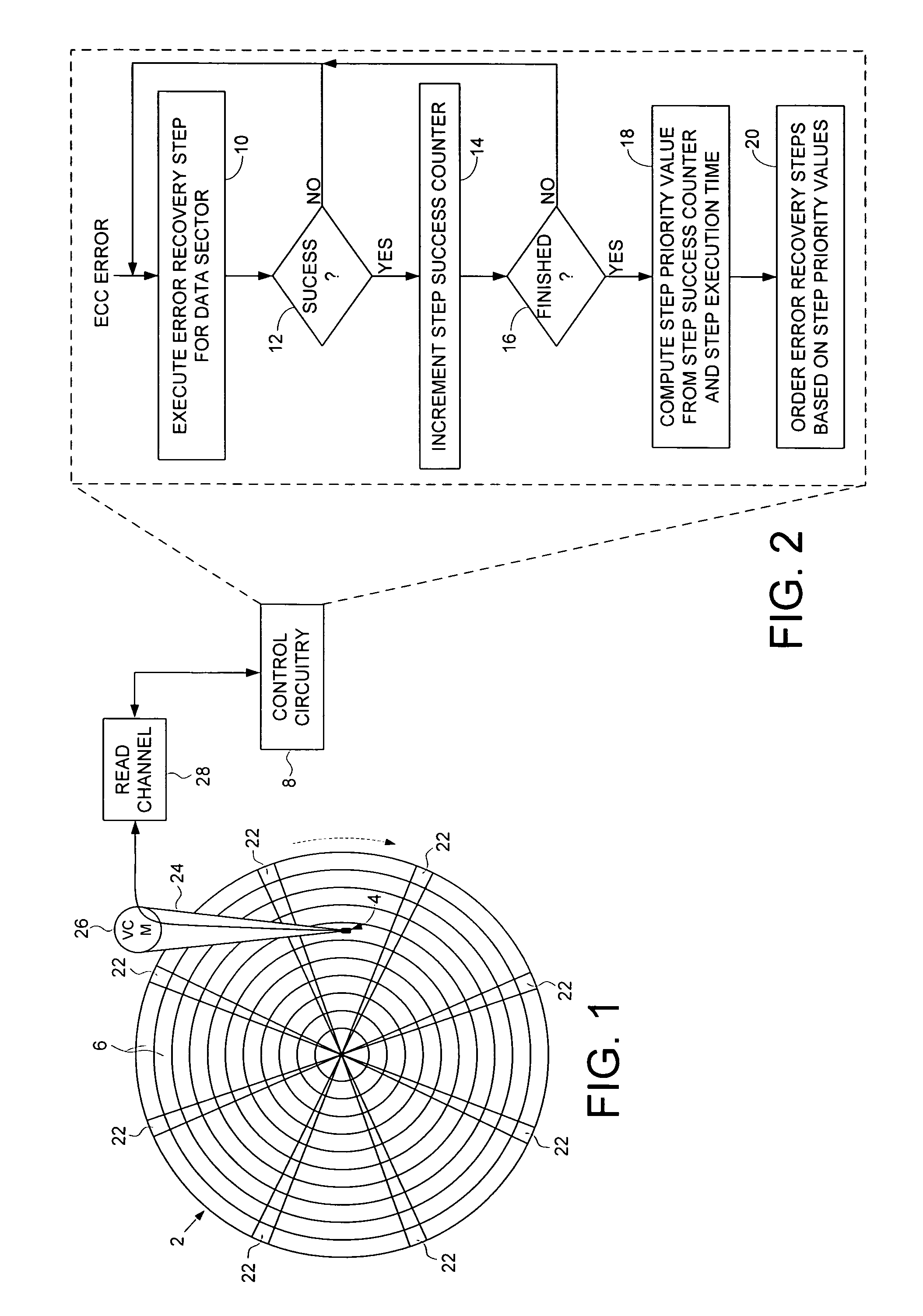
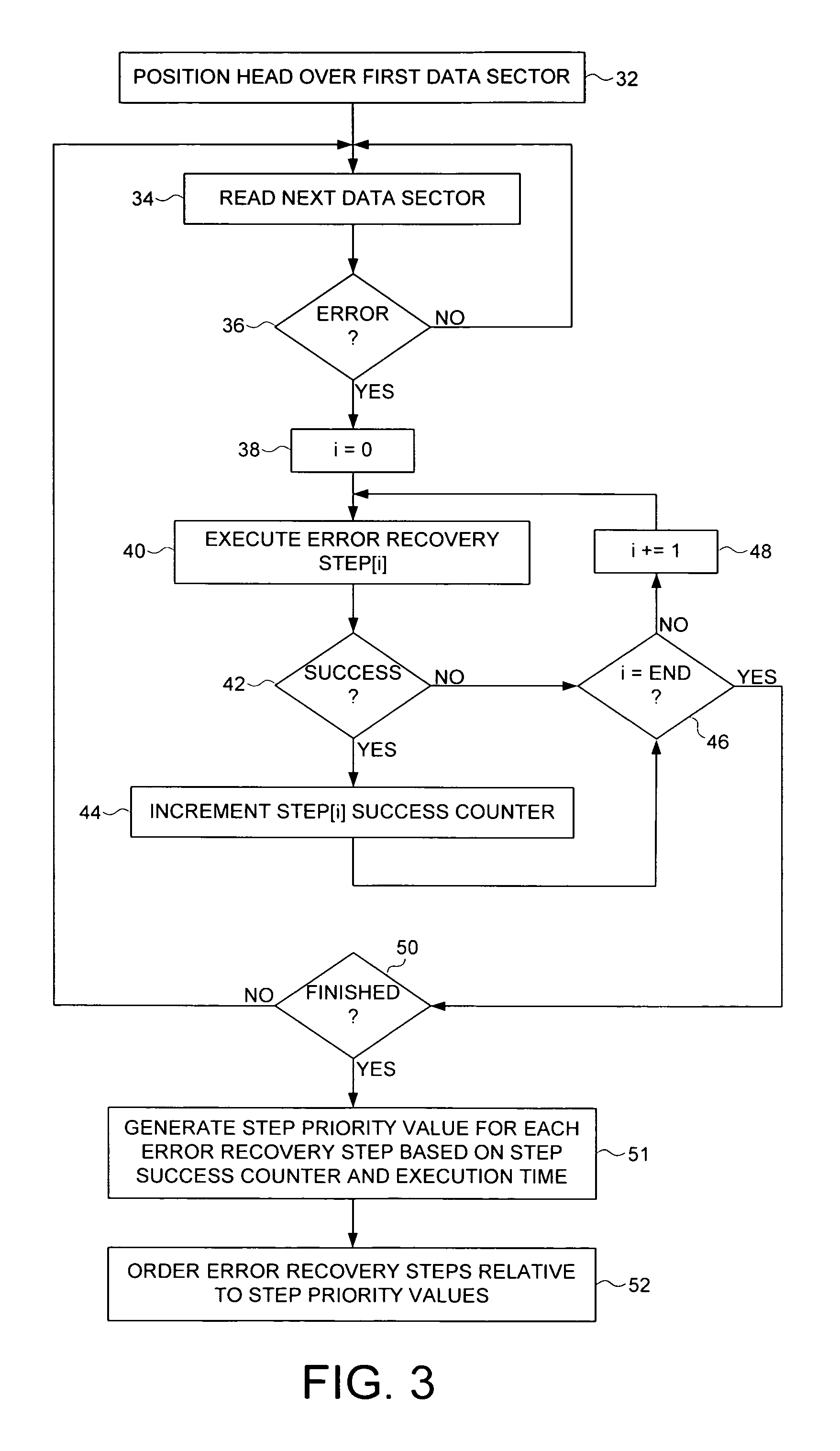
ActiveUS7451344B1Successful recoveryDisc-shaped record carriersError detection/correctionRecovery procedureComputer science
A method is disclosed for ordering error recovery steps of an error recovery procedure executed by a disk drive, wherein each error recovery step having an execution time. The disk drive comprises a disk having a plurality of tracks, wherein each track comprises a plurality of data sectors. A plurality of step success counters are initialized, wherein each counter corresponds to one of the error recovery steps. A plurality of the error recovery steps are executed, wherein if an error recovery step successfully recovers one of the data sectors the corresponding step success counter is incremented. A step priority value is computed for each error recovery step in response to the step success counter and execution time for each step. The error recovery steps are then ordered in response to the step priority values.
Owner:WESTERN DIGITAL TECH INC
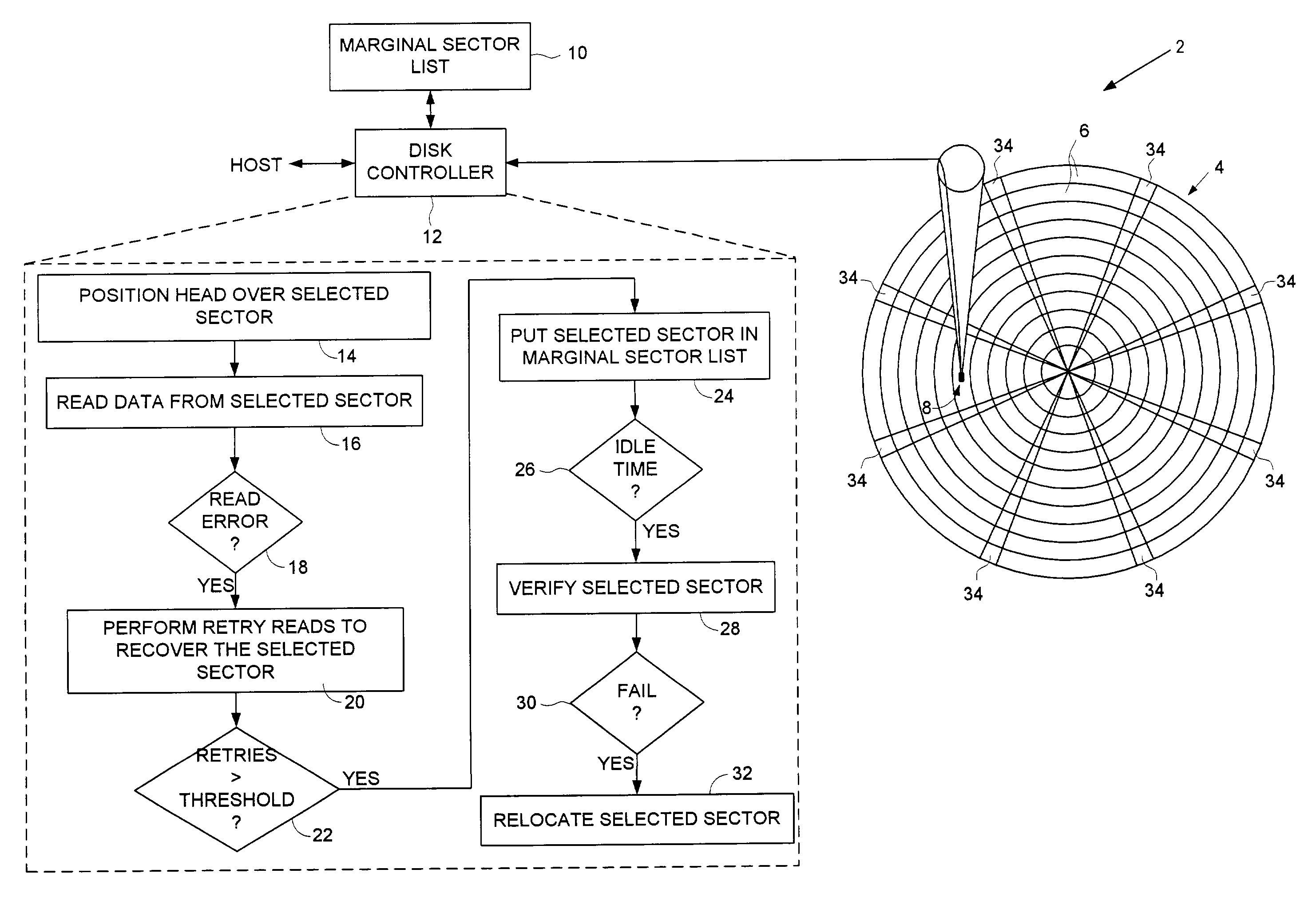
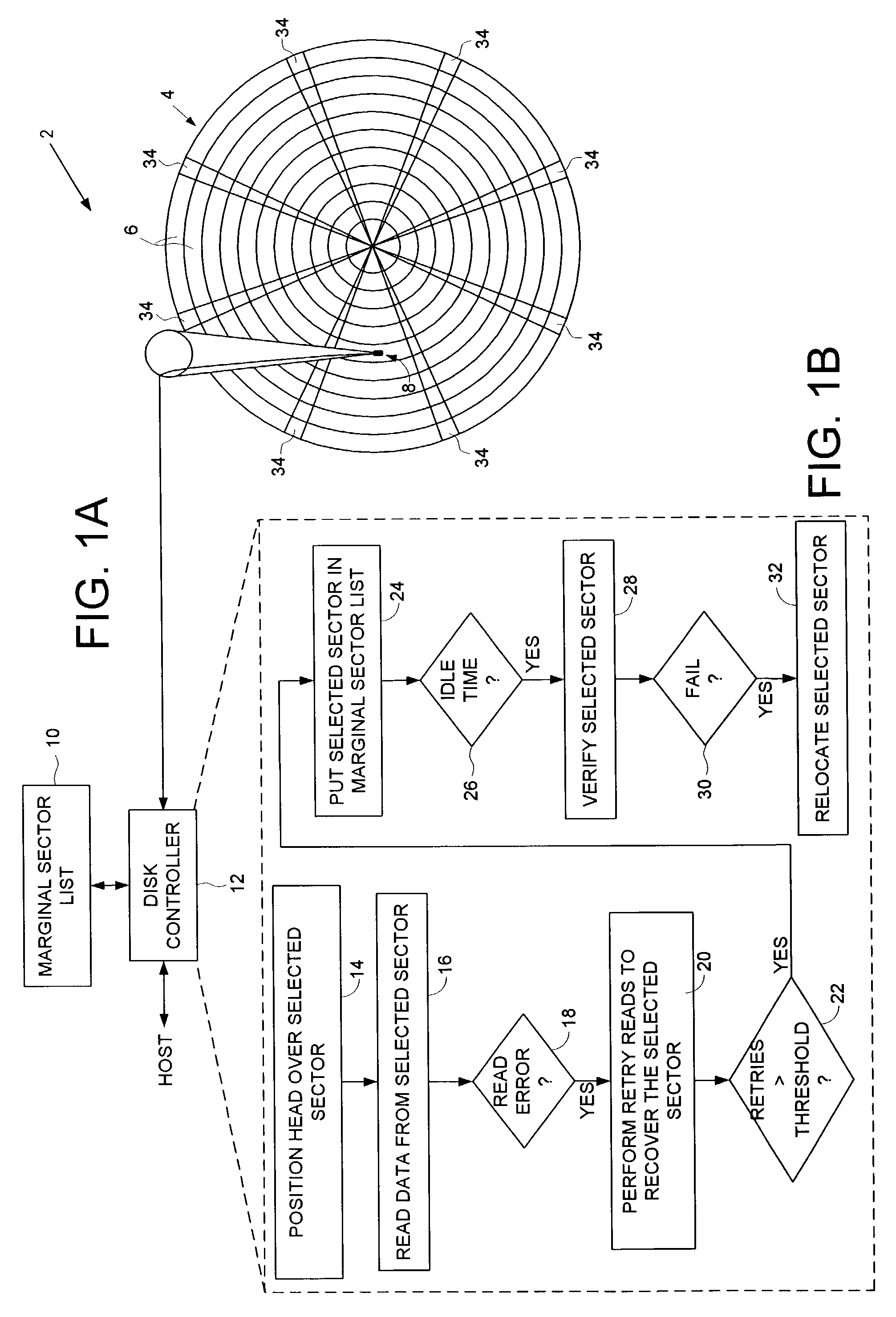
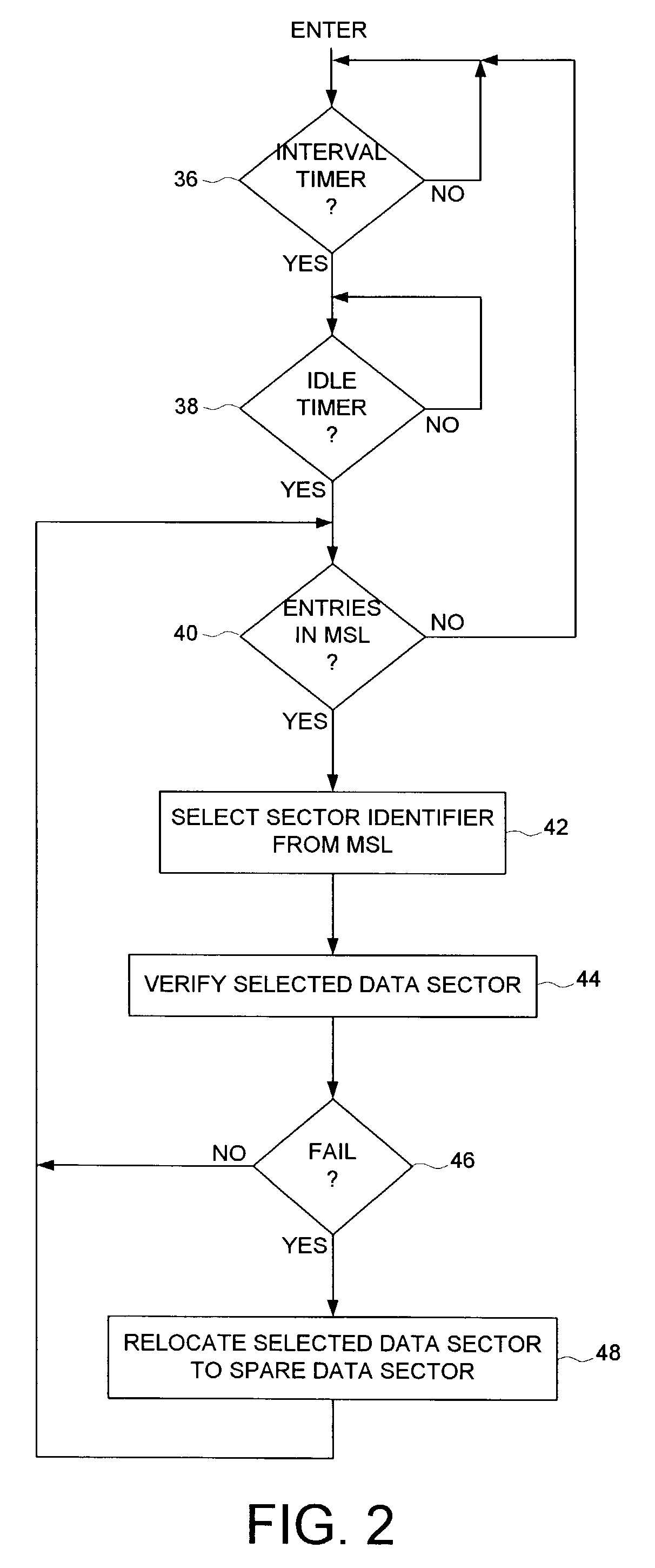
Disk drive employing off-line sector verification and relocation of marginal sectors discovered during read error recovery procedure
ActiveUS7050252B1Increase probabilityLower the thresholdDisc-shaped record carriersRecord information storageRecovery procedureLine scan
A disk drive is disclosed wherein if multiple retries beyond a threshold are required to recover a data sector during a normal read operation, the data sector is added to a marginal sector list. During an off-line scan, the data sectors in the marginal sector list are verified. If the verification of a data sector fails, the data sector is relocated.
Owner:WESTERN DIGITAL TECH INC
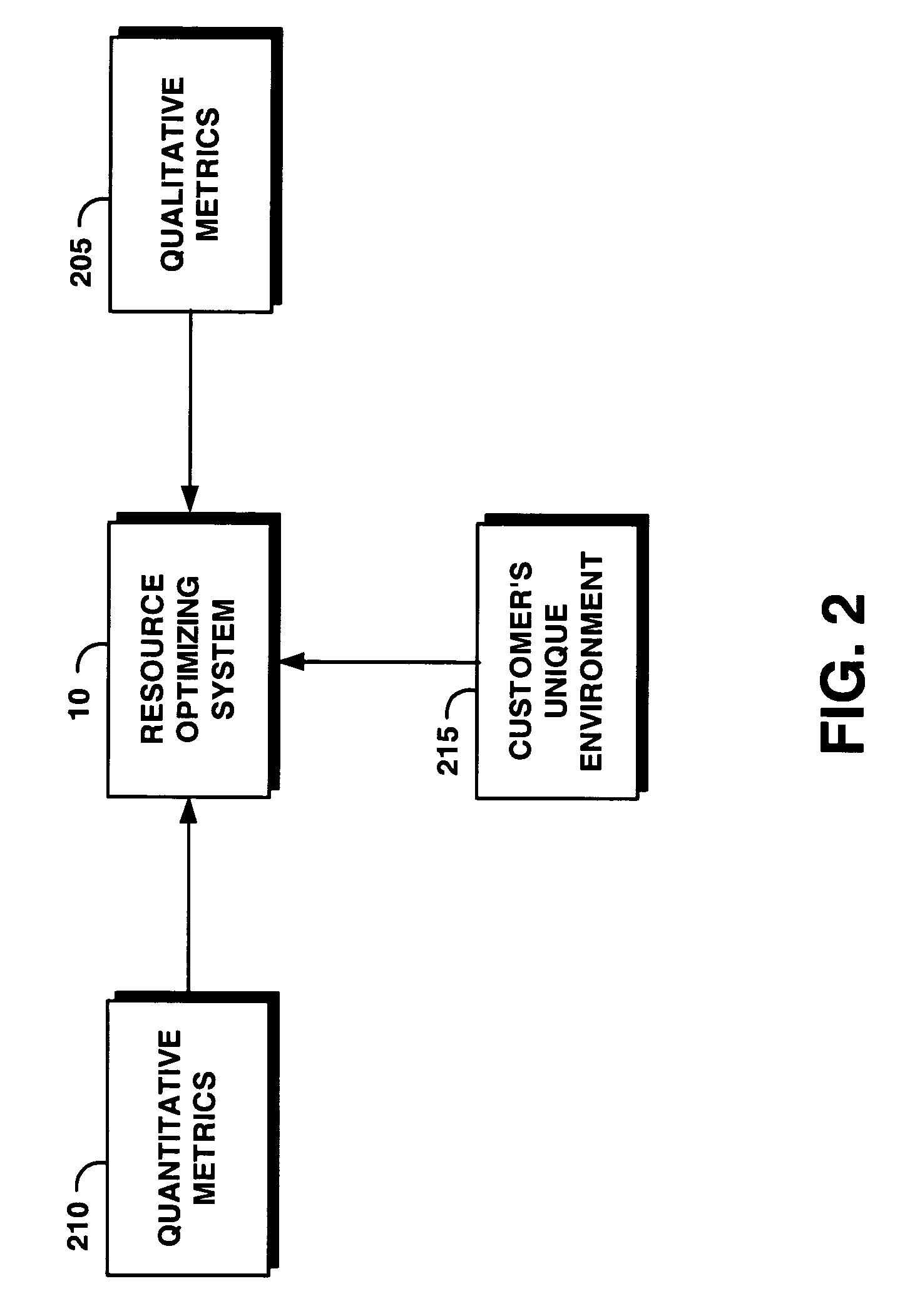
System and method for automatically and dynamically optimizing application data resources to meet business objectives
ActiveUS20050015641A1Provide flexibilityMinimize impactEmergency protective arrangements for automatic disconnectionSpecial data processing applicationsQuality of serviceData availability
A system and method to automatically and dynamically optimize available resources to meet application data availability and business objectives. In one embodiment, a backup and data recovery system continually and dynamically adjust to the backup and recovery or restore process depending on the customer's environment, workload, and business objectives. Acceptable tolerance of downtime due to recovery and backup impacts the customer's business or system operation. From this high-level business requirement, the present system determines the backup and recovery plan details. The present system accepts application data availability policies based on business objectives, and devises, executes and refines a resource optimal backup and recovery strategy required to deliver the desired quality of service in the environments that have dynamically changing application workloads, business objectives, and hardware / software infrastructure technologies. In addition, the present system performs backups outside blocked windows to minimize the impact on the customer's system.
Owner:TREND MICRO INC
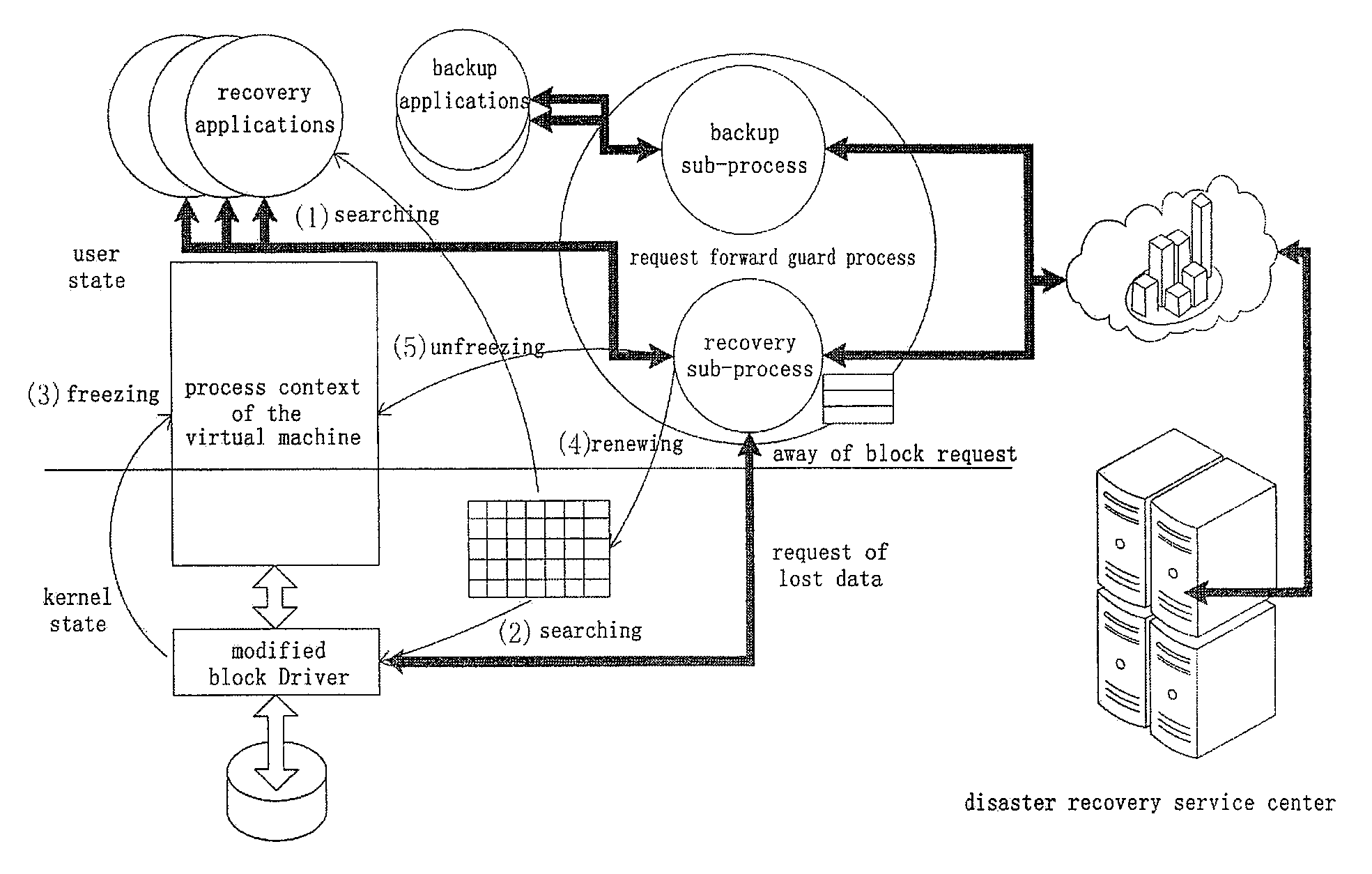
Virtual machine-based on-demand parallel disaster recovery system and the method thereof
InactiveUS20100115332A1Reduce dependenceStrengthen of backup dataDigital data processing detailsTransmissionFile systemApplication software
Owner:YU HONGLIANG +1
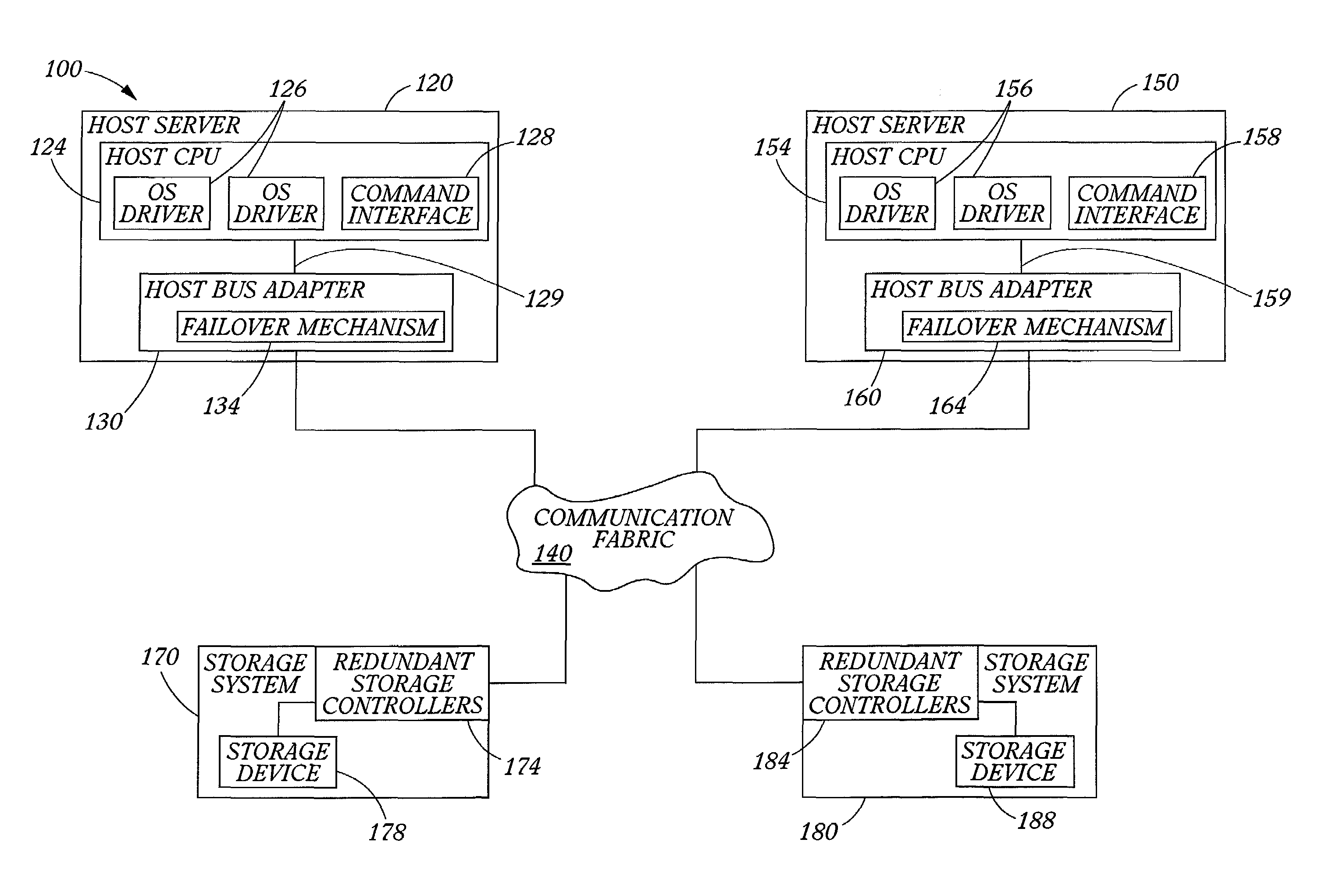
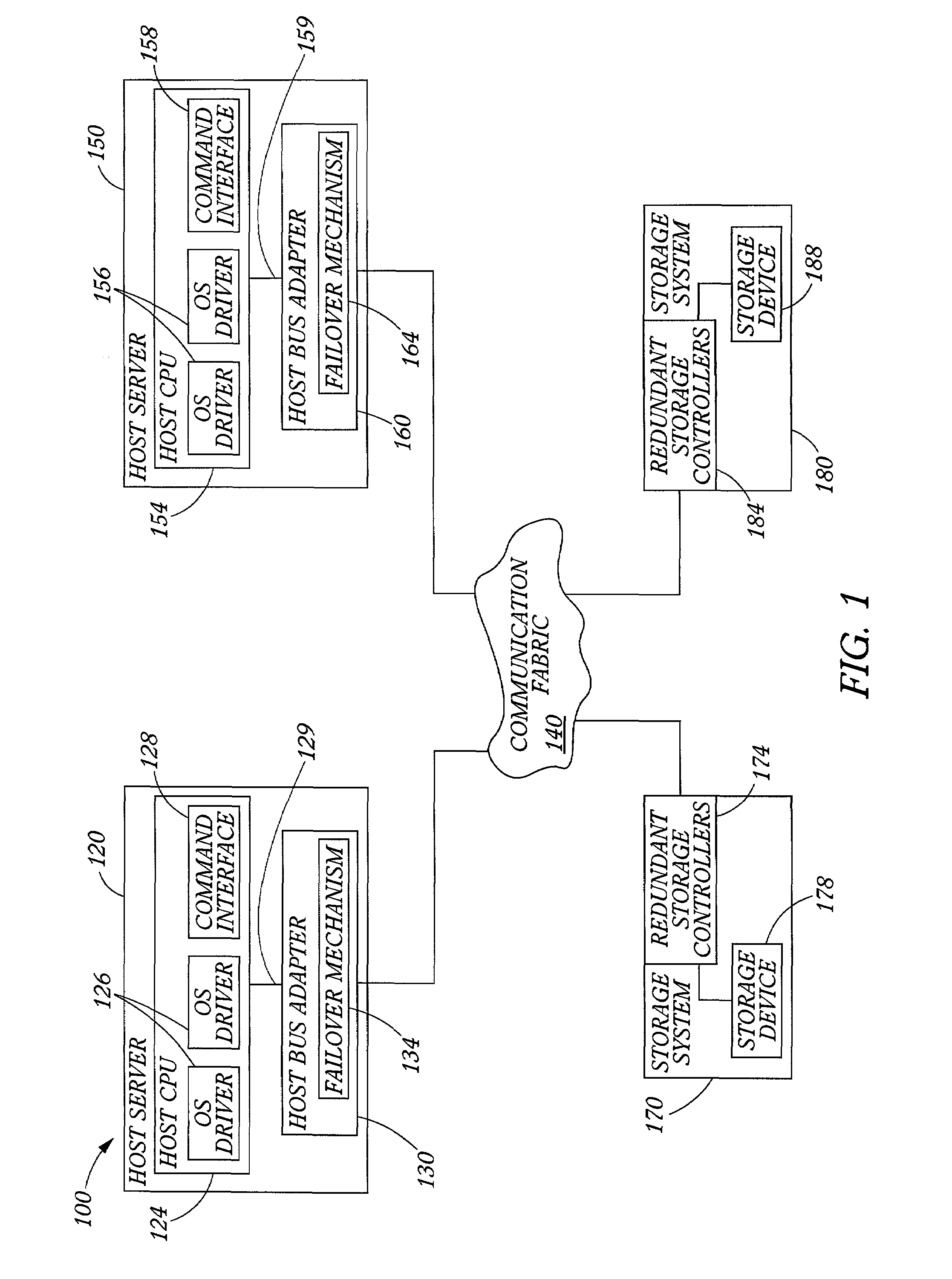
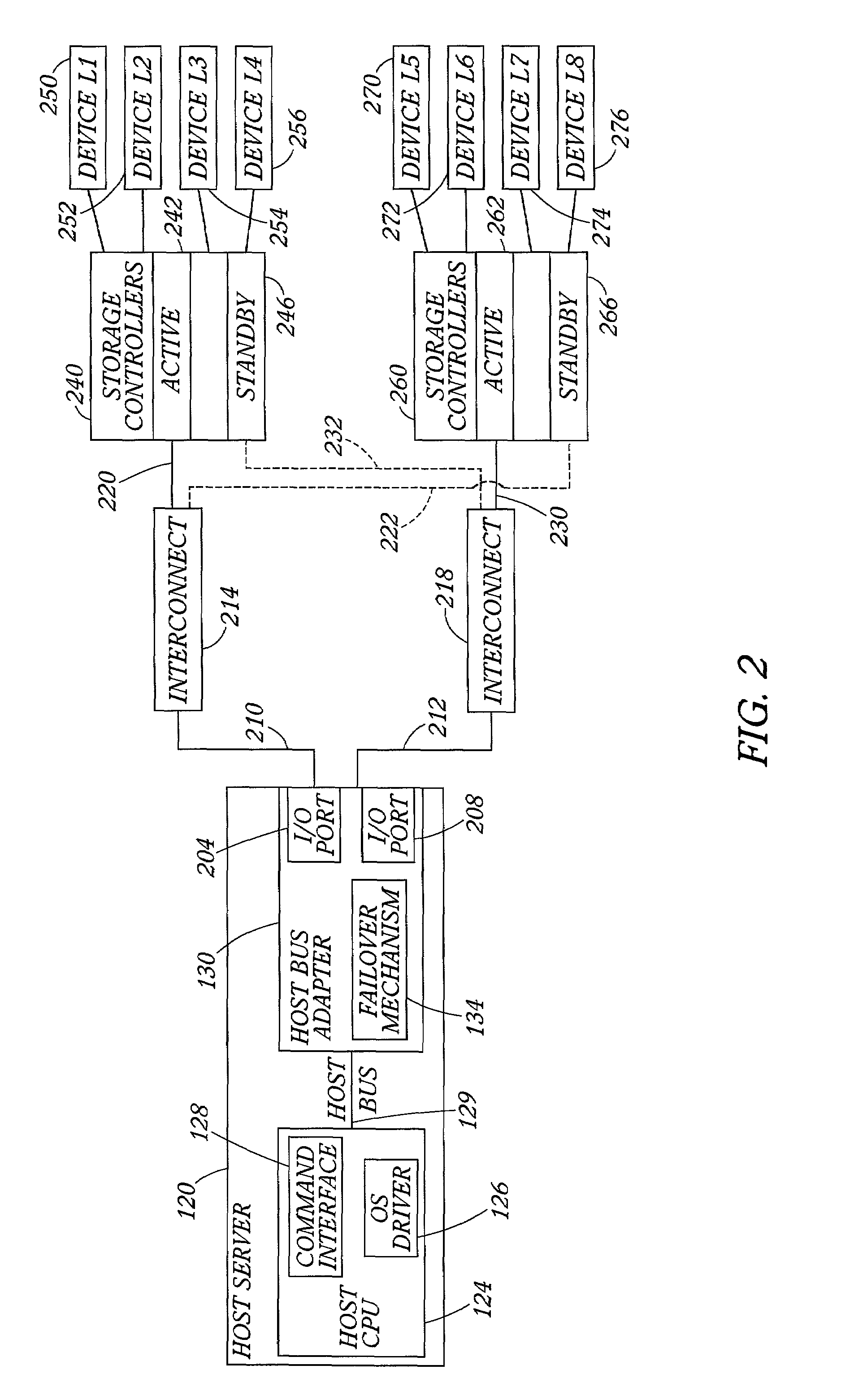
Data storage network with host transparent failover controlled by host bus adapter
ActiveUS7111084B2Facilitates consistent failbackFacilitates failover processingTransmissionRedundant hardware error correctionHard disc driveFailover
A method and host bus adapter for controlling failover and failback processes within a redundant data storage system. The method is carried out by a failover mechanism in a host bus adapter linked to a host server. The system includes a communication fabric providing data paths to pairs of redundant storage controllers managing access to storage devices (such as hard disk drives arranged as RAID). The method includes operating the host bus adapter to detect a failover condition and in response, to match the failover condition to a particular failover action. The failover conditions and corresponding actions are stored in a well-defined rule set accessed by the host bus adapter. The method continues with performing with the host bus adapter the matched failover action. The method is transparent to the host computer device, as the host is not required to participate in the failover processes.
Owner:VALTRUS INNOVATIONS LTD +1
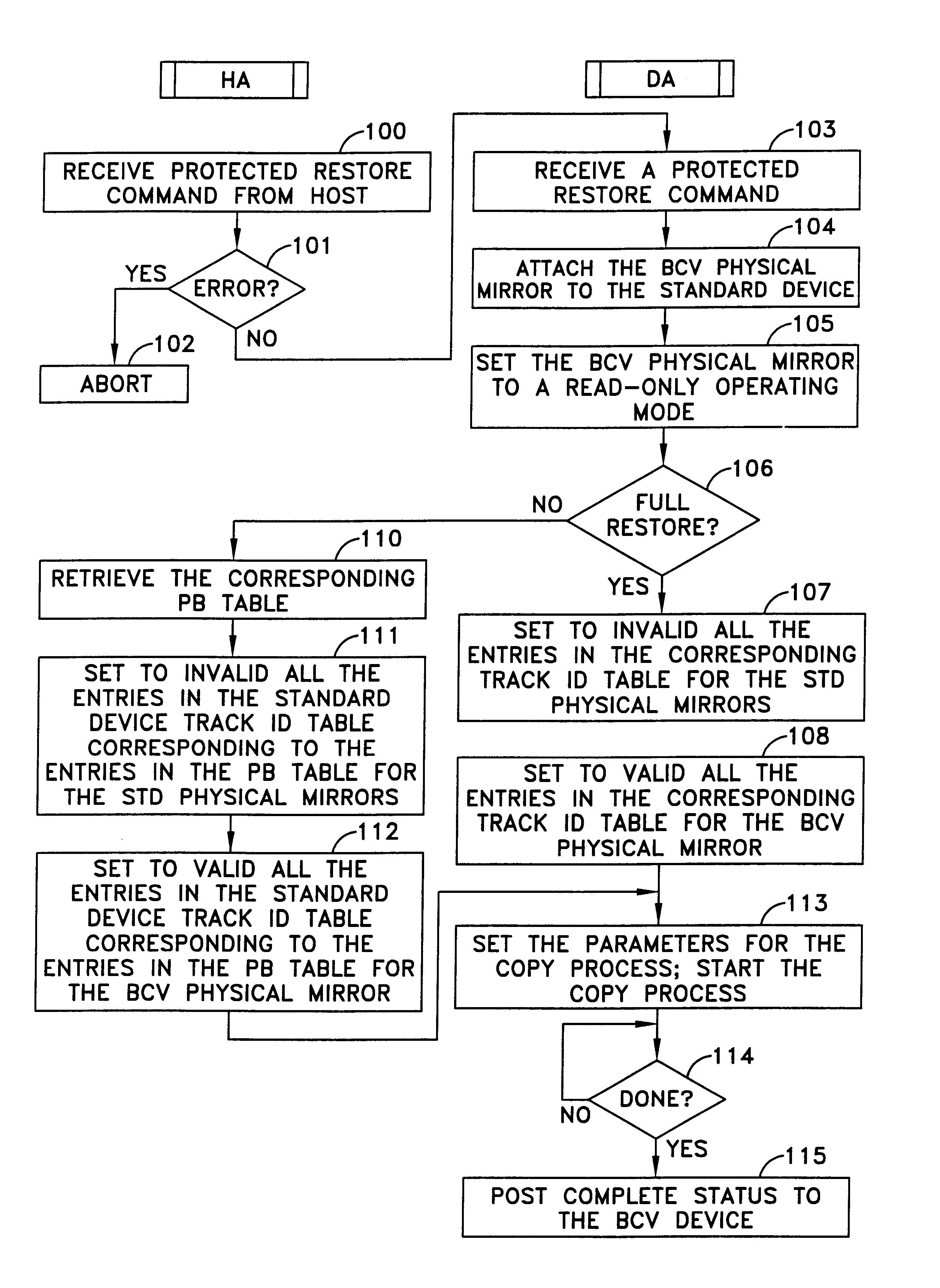
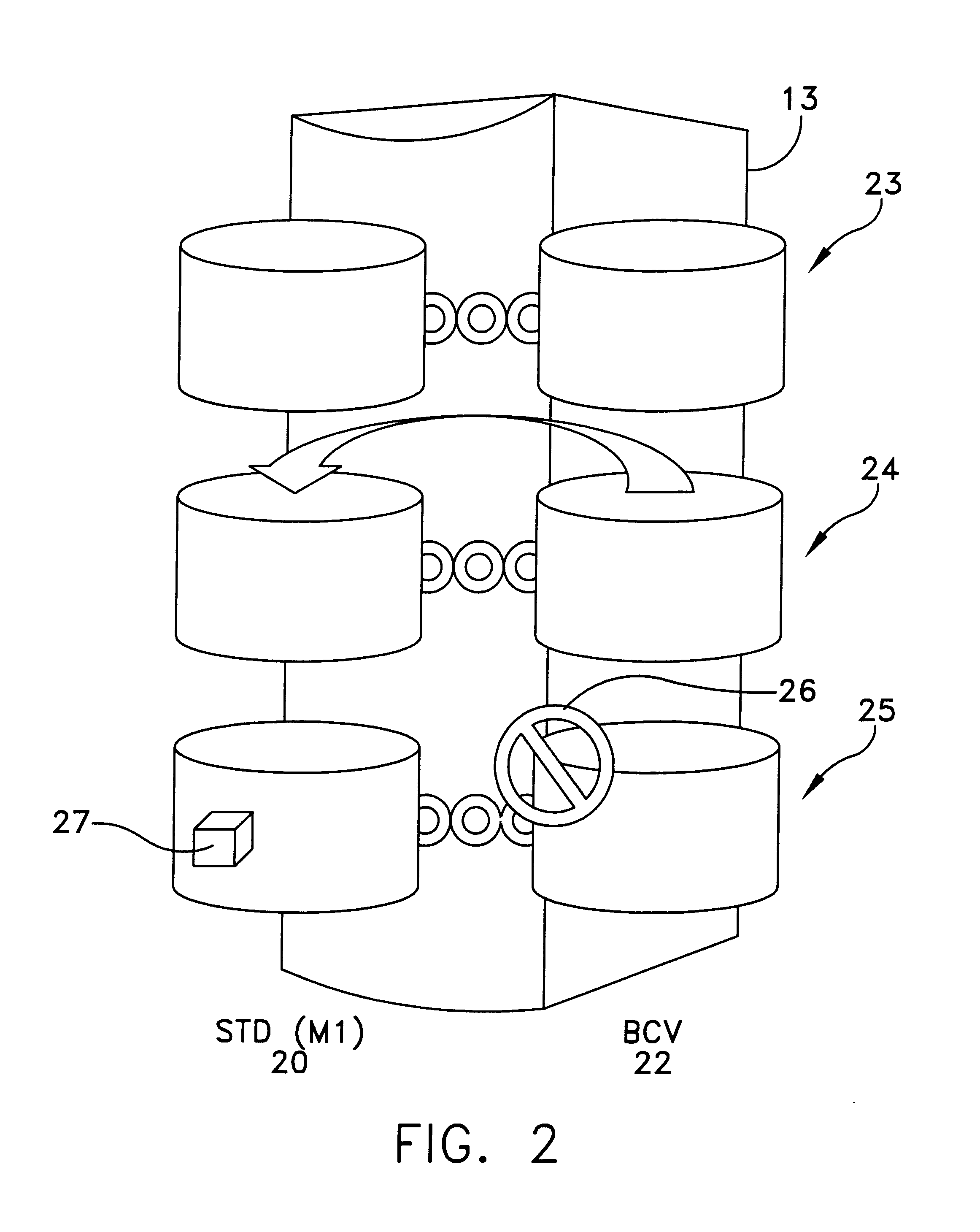
Data recovery method and apparatus
InactiveUS6742138B1Easy Data RecoveryAvoid data transferEmergency protective arrangements for automatic disconnectionRedundant operation error correctionRecovery methodData memory
A method and apparatus for data recovery in a system involving a first data store acting as a standard device and a physical moving mirror data store that operates as moving mirror with a first mode to be synchronized and in a second, isolated mode. In response to a command to establish a third or protected restore operating mode, the data to be transferred in response to that command is identified. A restoration procedure copies data from the second data store to the first store to recover any data that may have been corrupted in the second data store. An update procedure acts on the restored data concurrently with the restoration procedure.
Owner:EMC IP HLDG CO LLC
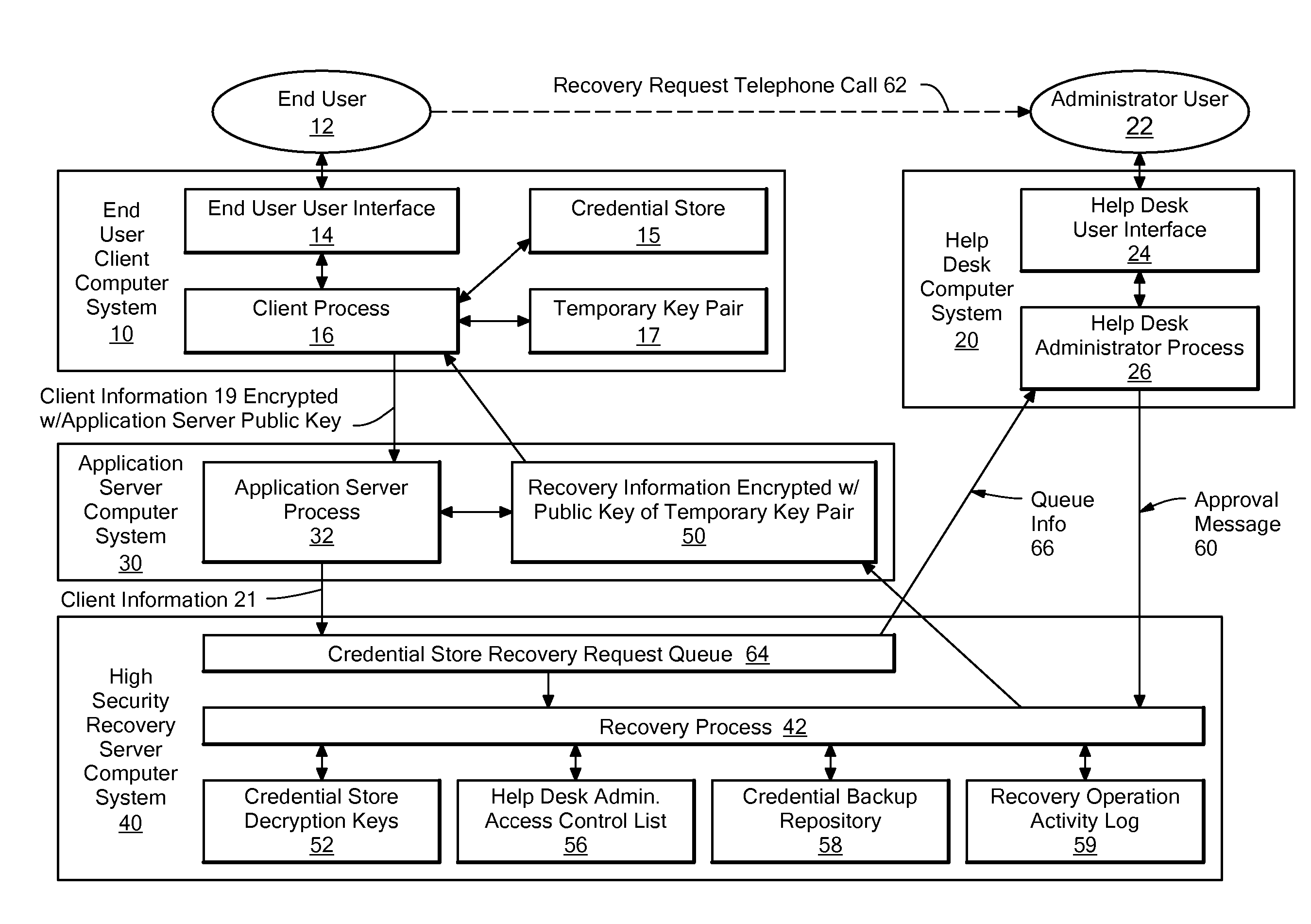
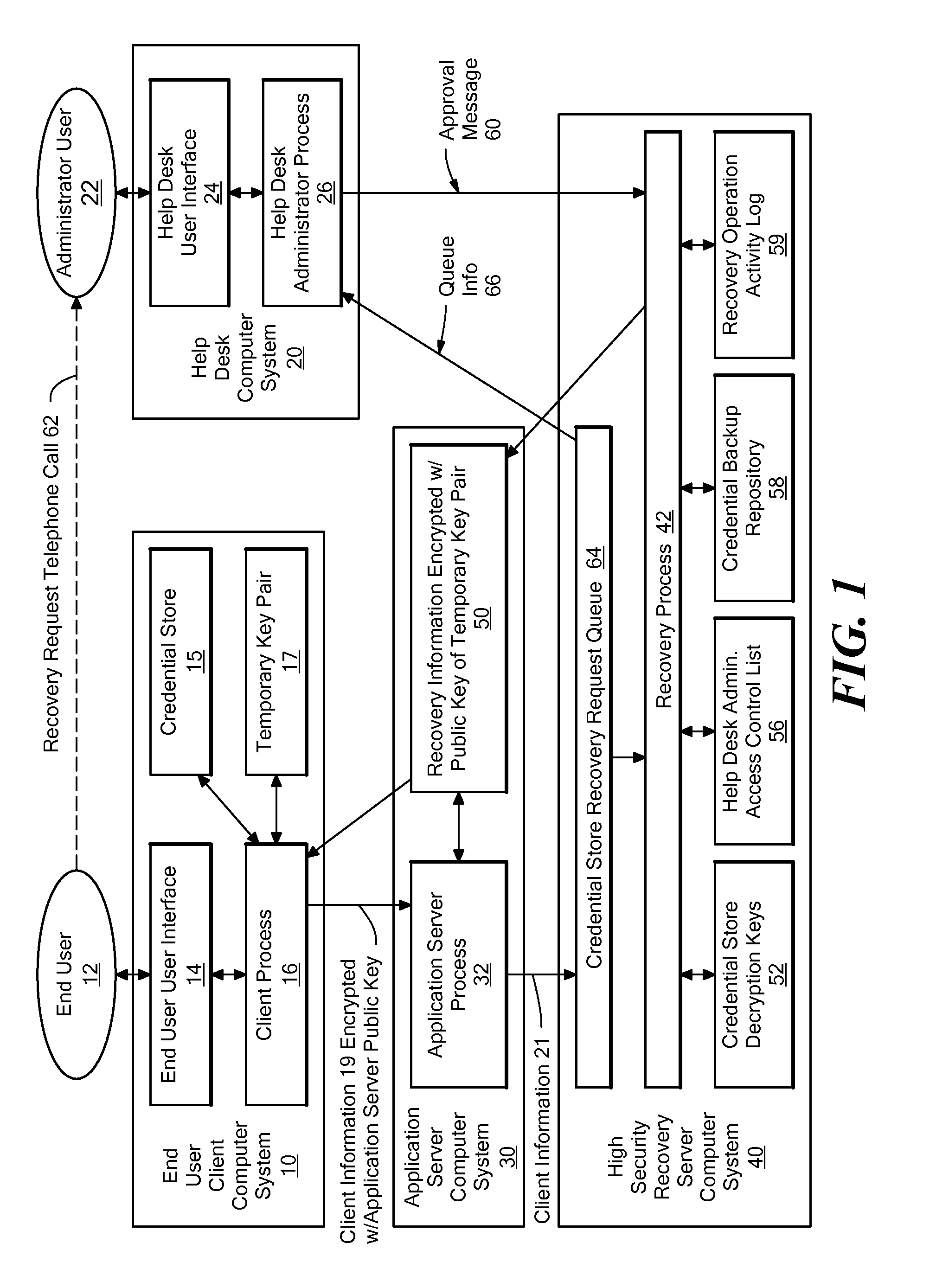
Method and system for automating the recovery of a credential store
A system for automating the recovery of a credential store, in which client software generates a temporary key pair based on a new password, and sends client information including the user's name, the public half of the temporary key pair, and the host name of the client computer system to a server system, from which the client information is passed to a recovery process. The client software process displays a prompt indicating that the user should call a help desk. A help desk administrator verifies the user's identity and approves the user's request by causing an approval message to be sent to the recovery process. The recovery process obtains recovery information consisting of either the decryption key(s) for the credential store, or a decrypted copy of the credential store, and encrypts the recovery information using the temporary public key. The client process downloads the recovery information from the server, and decrypts it using private key of the temporary key pair. The credential store can then be decrypted using the recovery information if necessary, then re-encrypted based on the new password. The encrypted recovery information is stored on the server and re-used for a certain period of time, after which it is deleted, thus allowing multiple copies of the credential store to be conveniently recovered.
Owner:IBM CORP
Data transfer and recovery process
ActiveUS20080016387A1Redundant operation error correctionRedundant hardware error correctionData transmissionNetwork-attached storage
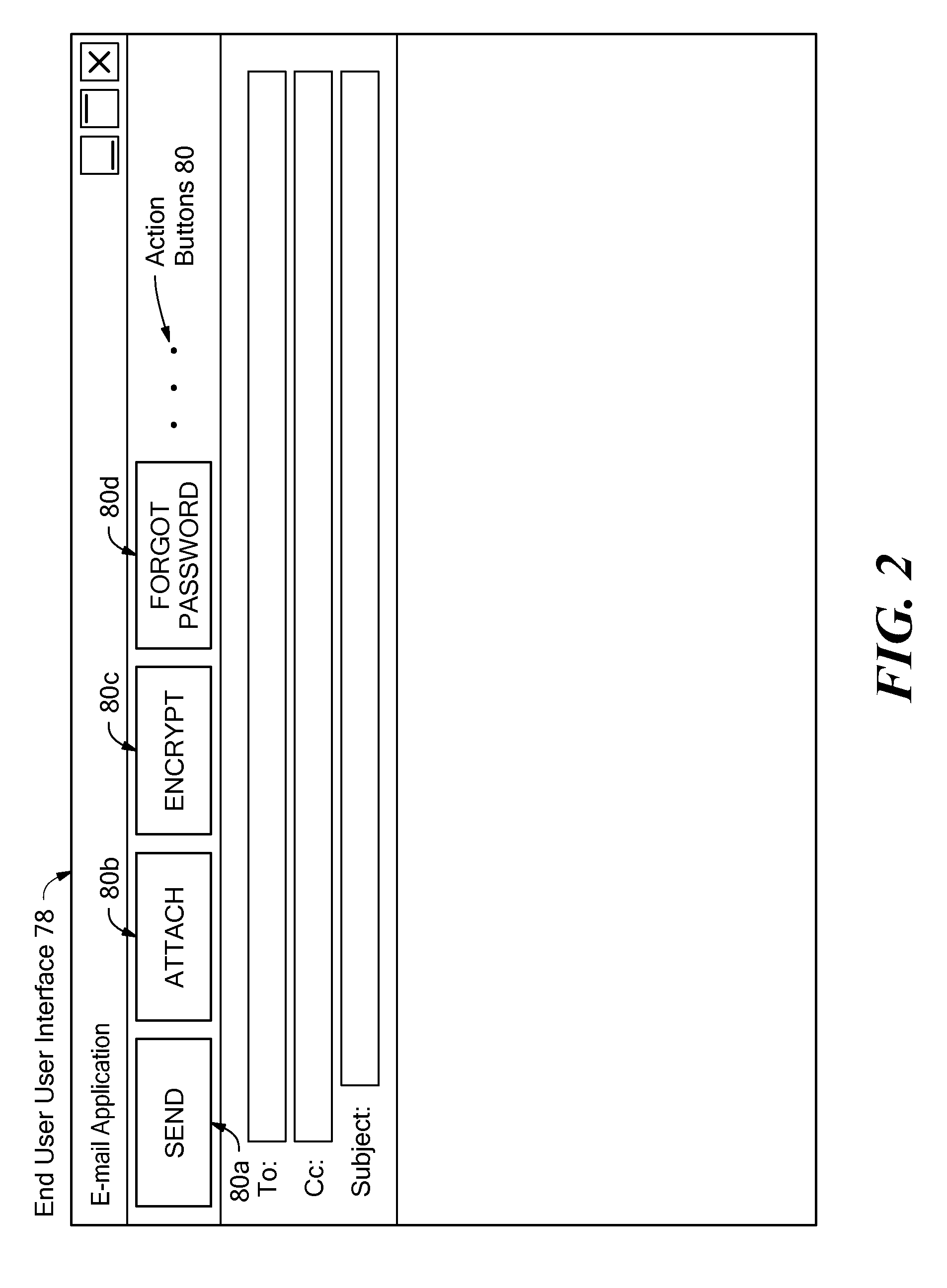
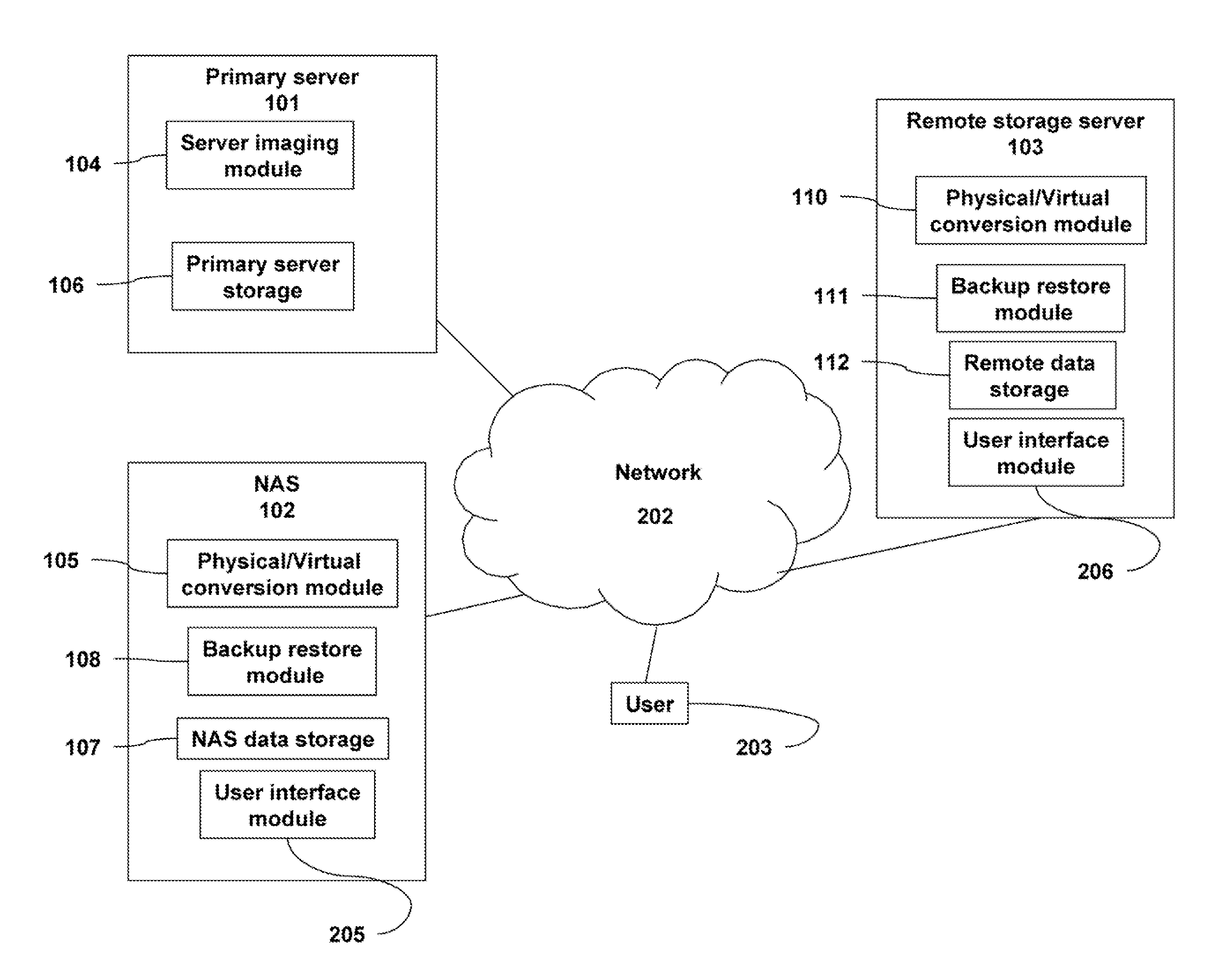
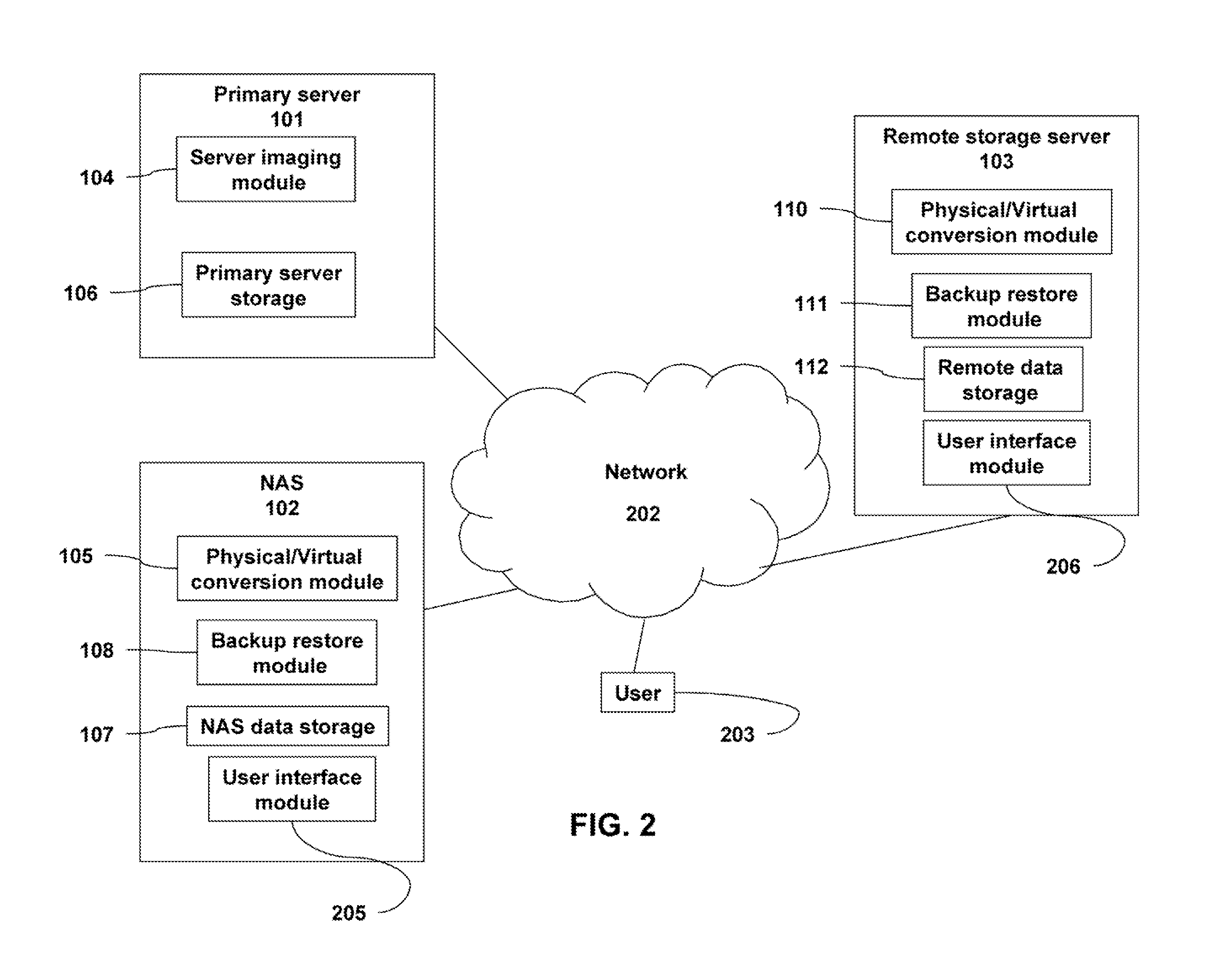
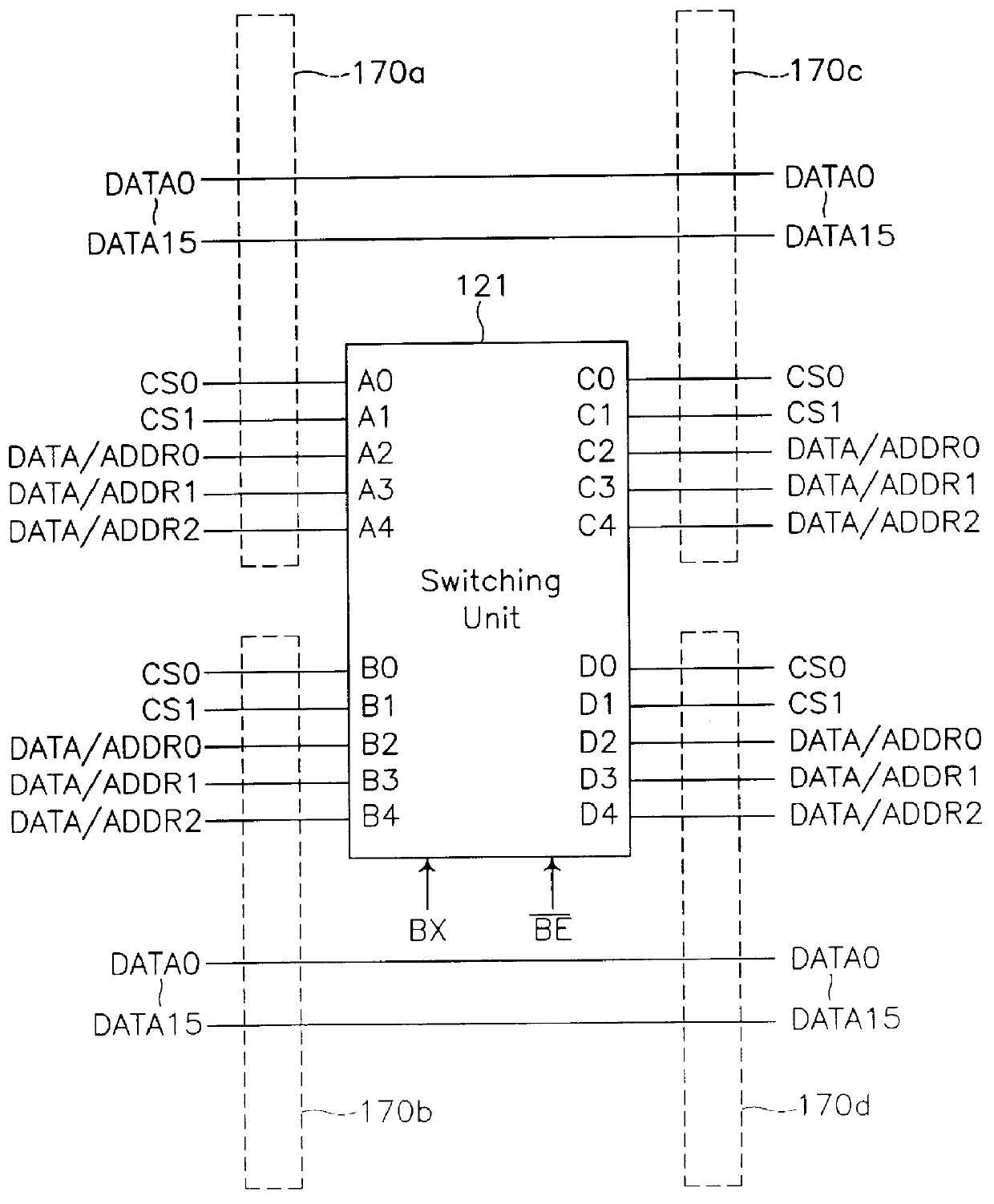
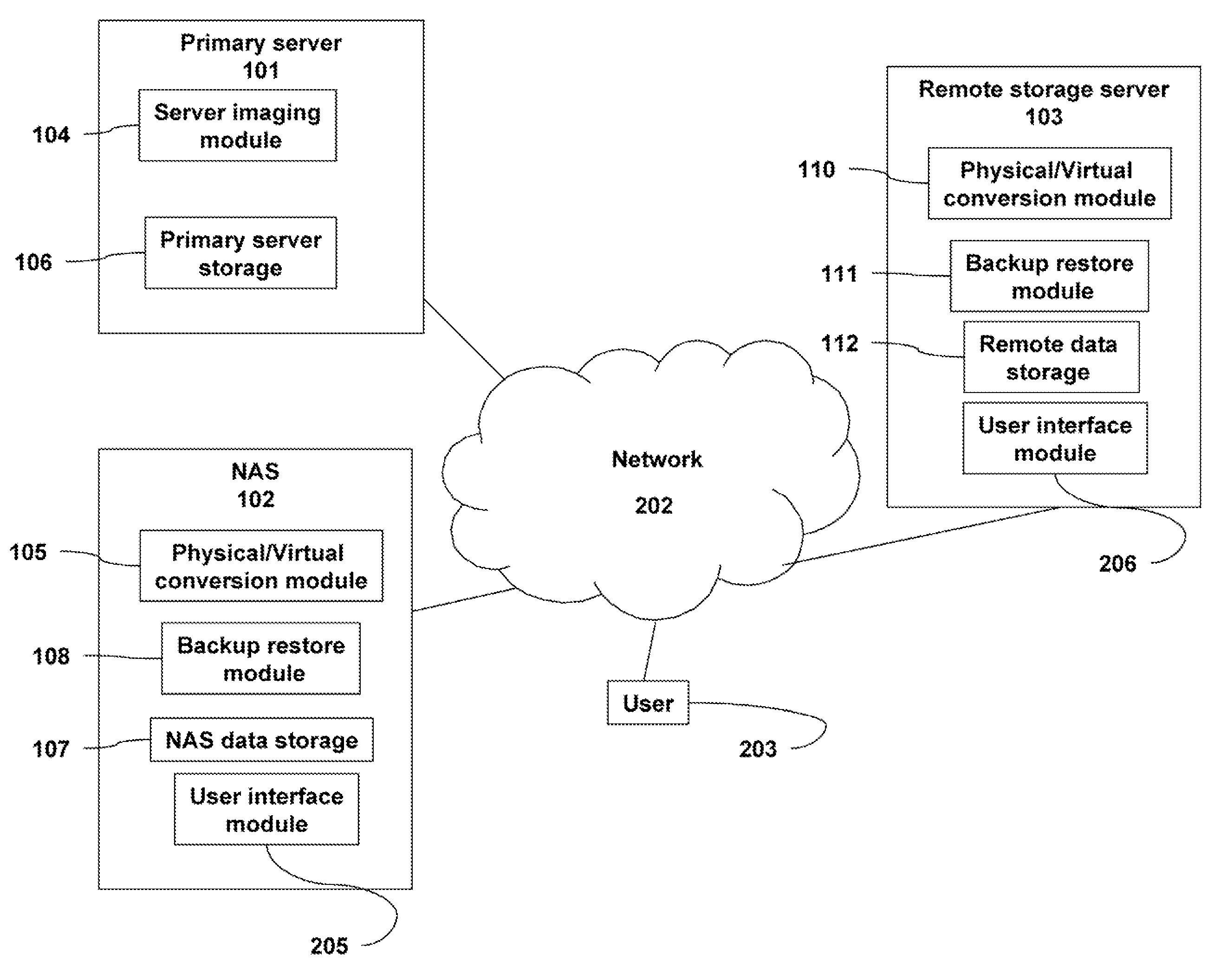
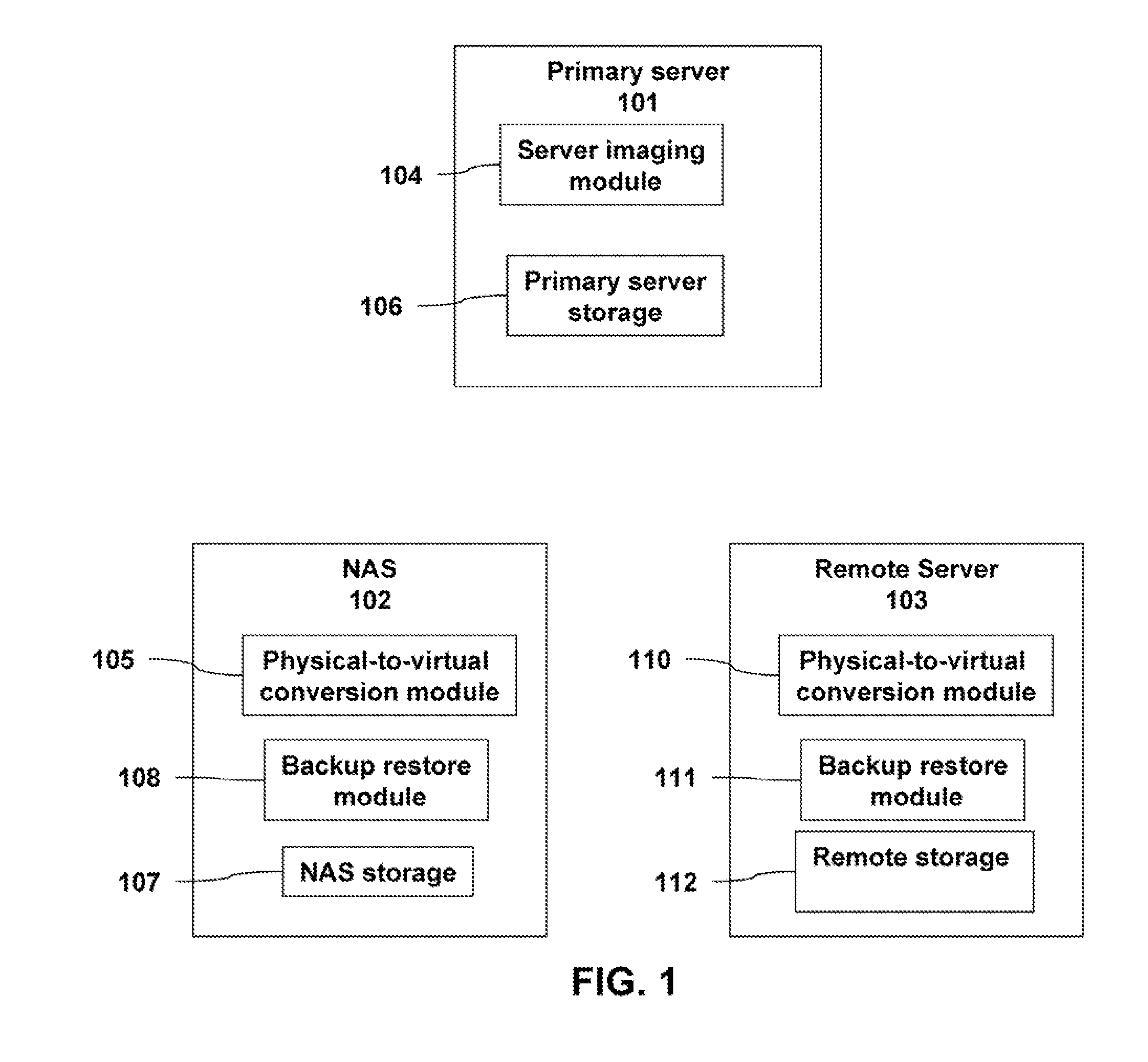
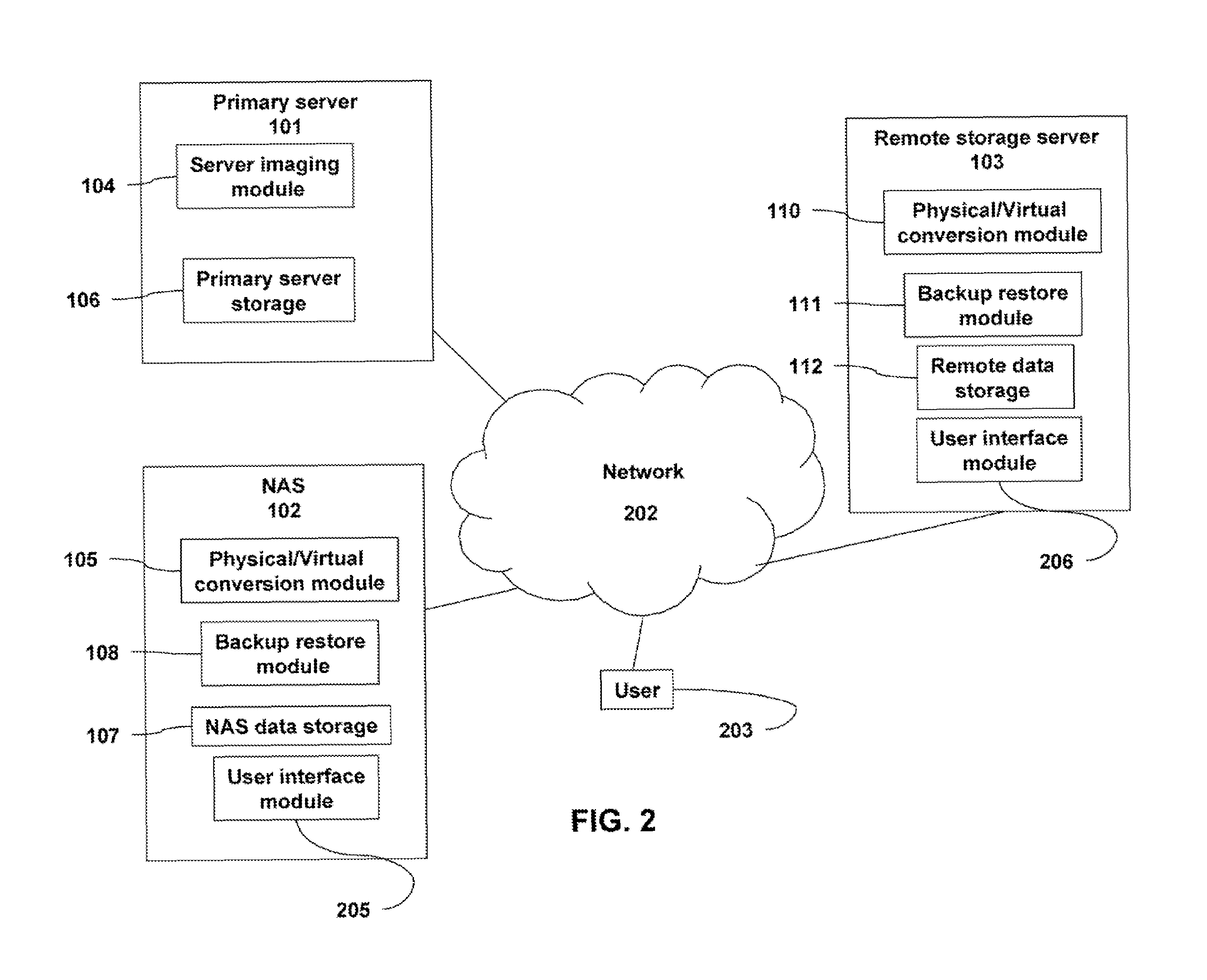
A backup image generator can create a primary image and periodic delta images of all or part of a primary server. The images can be sent to a network attached storage device and a remote storage server. In the event of a failure of the primary server, the failure can be diagnosed to develop a recovery strategy. Based on the diagnosis, at least one delta image may be applied to a copy of the primary image to generate an updated primary image at either the network attached storage or the remote storage server. The updated primary image may be converted to a virtual server in a physical to virtual conversion at either the network attached storage device or remote storage server and users may be redirected to the virtual server. The updated primary image may also be restored to the primary server in a virtual to physical conversion. As a result, the primary data storage may be timely backed-up, recovered and restored with the possibility of providing server and business continuity in the event of a failure.
Owner:EFOLDER INC
Decoding Order Recovery in Session Multiplexing
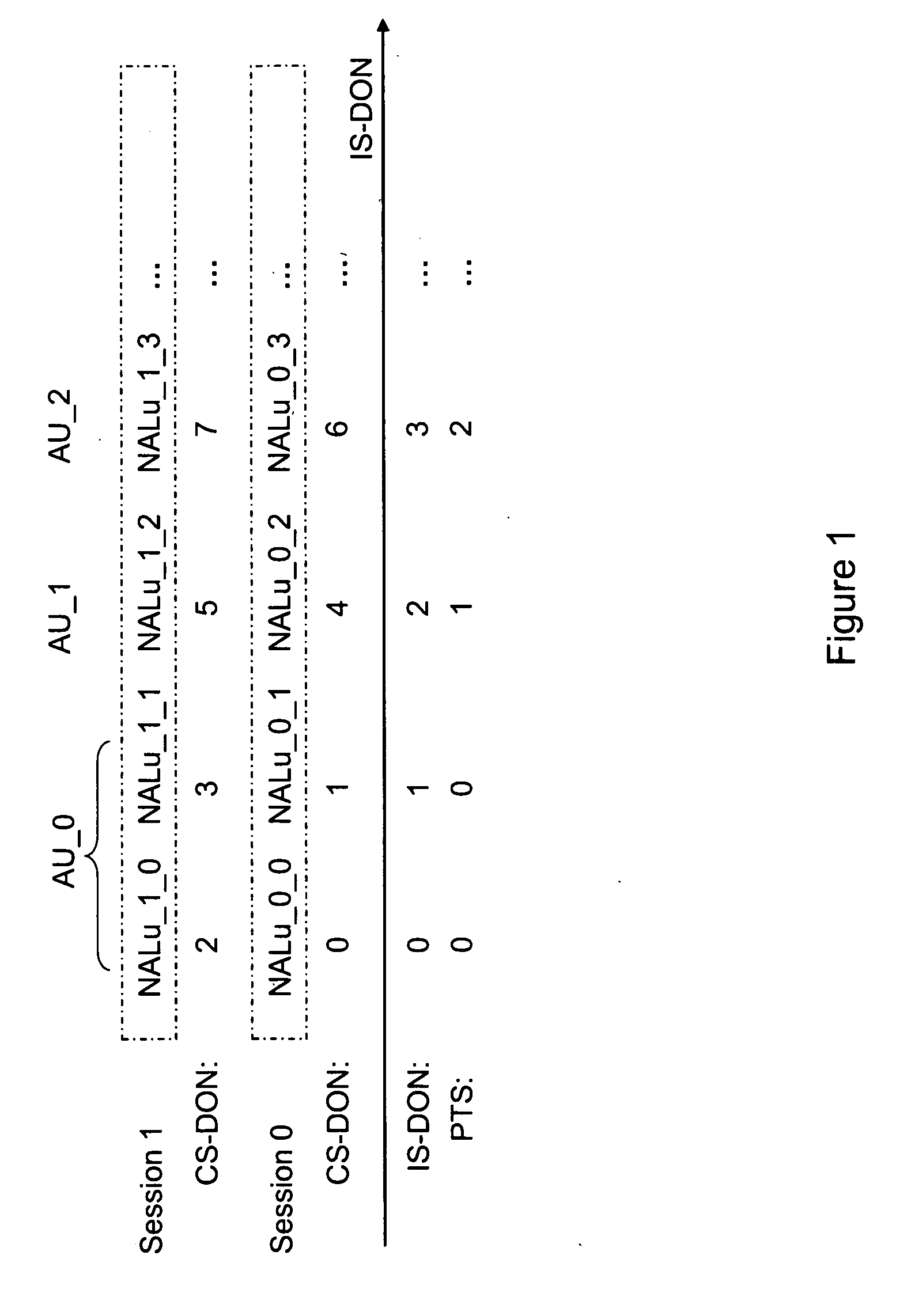
InactiveUS20100049865A1Speed up recoveryEffective recoveryMultiple digital computer combinationsTransmissionRecovery procedureComputer science
Systems and methods are provided for signaling the decoding order of ADUs to enable efficient recovery of the decoding order of ADUs when session multiplexing is in use. A decoding order recovery process in a receiver is improved when session multiplexing is in use. For example, various embodiments improve the decoding order recovery process of SVC when no CS-DONs are utilized. First information associated with a first media sample to identify a second media sample is signaled upon packetization to indicate / aid in recovering. Upon de-packetizing, a decoding order of the first media sample and the second media sample is determined based on the received signaling of the first information.
Owner:NOKIA CORP
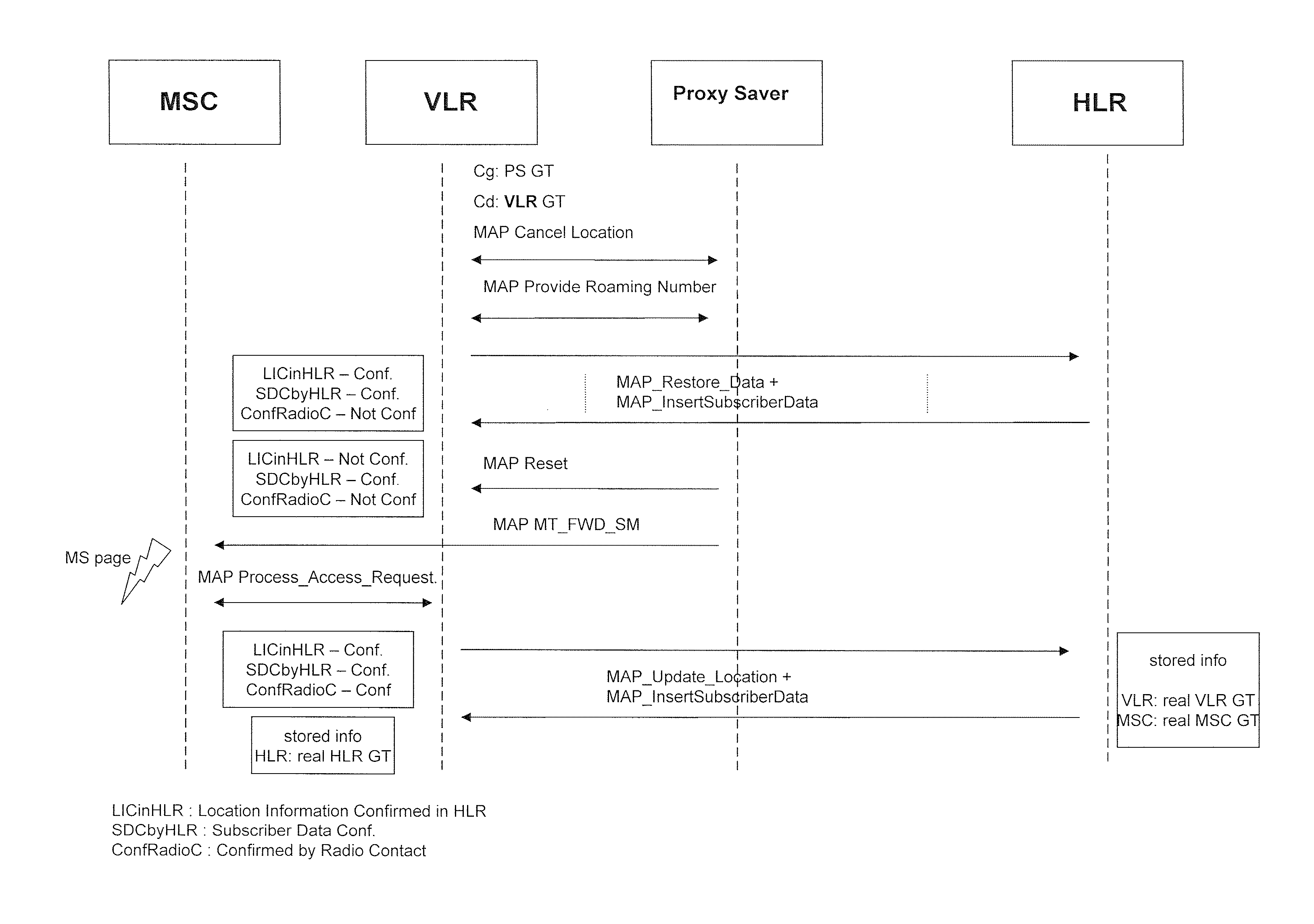
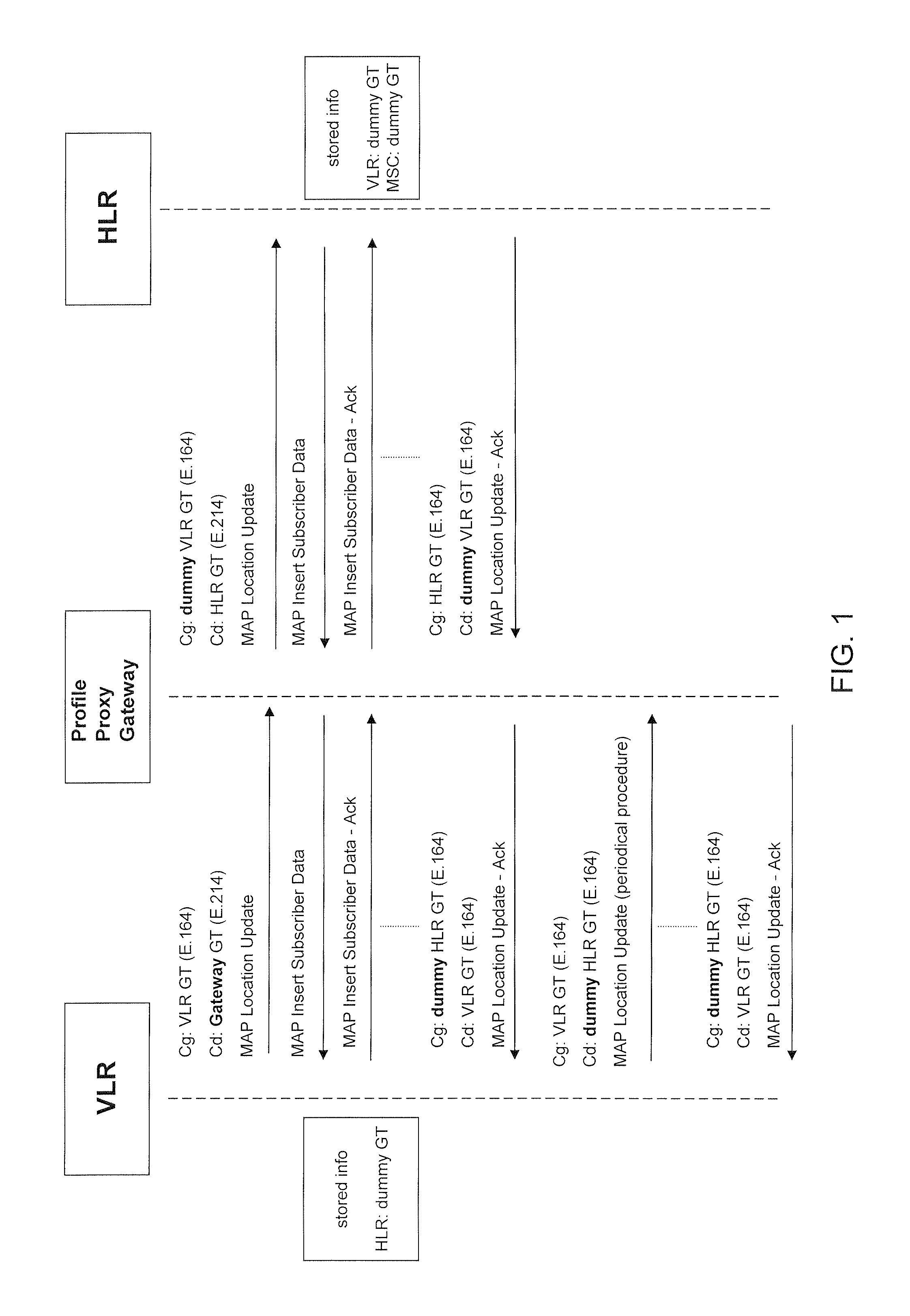
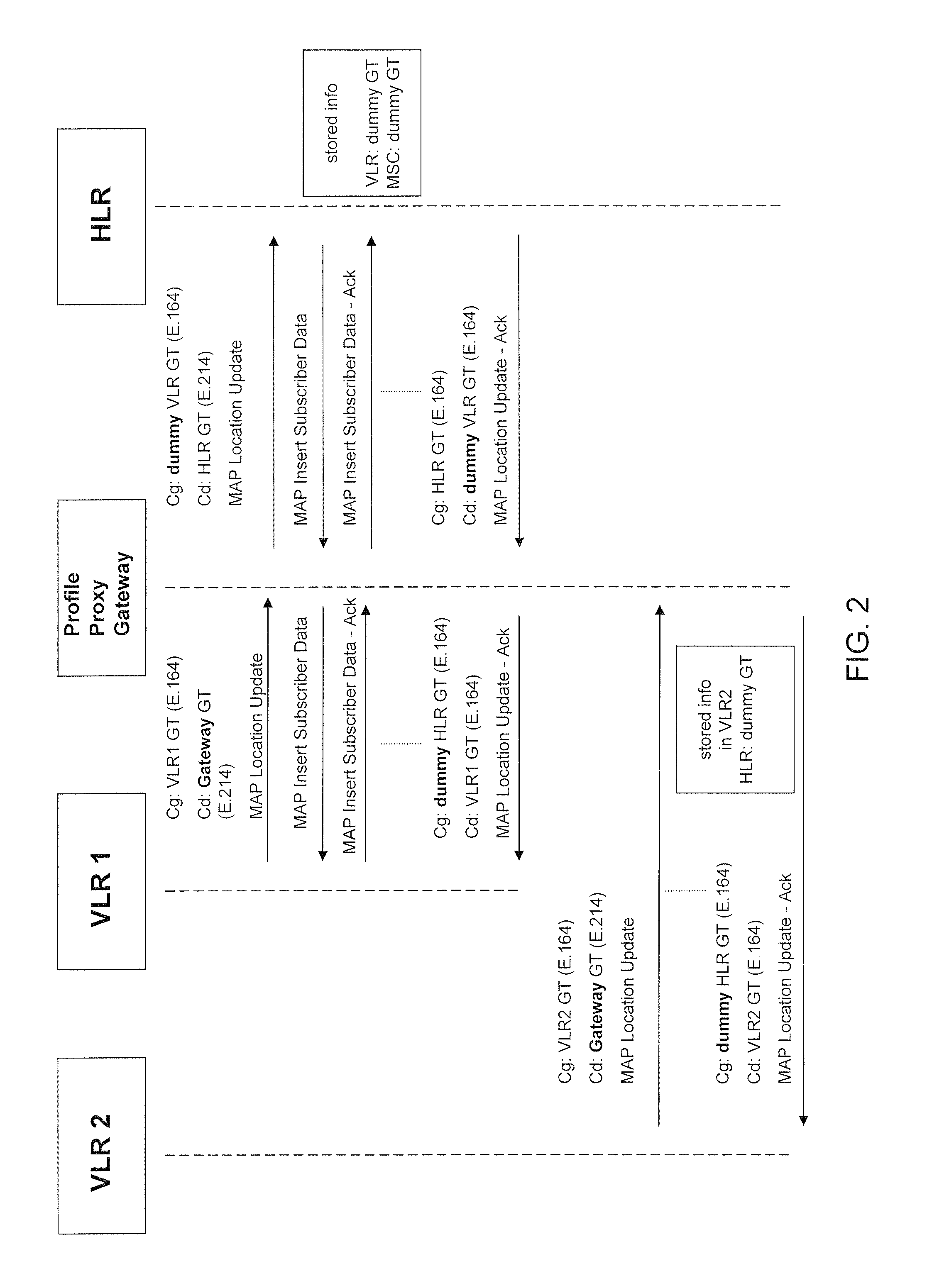
Method and system for ensuring service continuity in case of a proxy profile gateway failure or interruption
Aspects of the present invention relate to methods, systems and computer products that guarantee the availability of basic services to subscribers during the failure of a Proxy-Profile Gateway. An independent module equipped with monitoring probes for tracking the actual location of the end-customer, an interface for controlling the Gateway availability, and an active SS7 signaling interface are also provided, in order to initiate the recovery procedures, along with a database for storing the relevant information necessary to apply the restoration procedures.
Owner:MOBILEUM INC
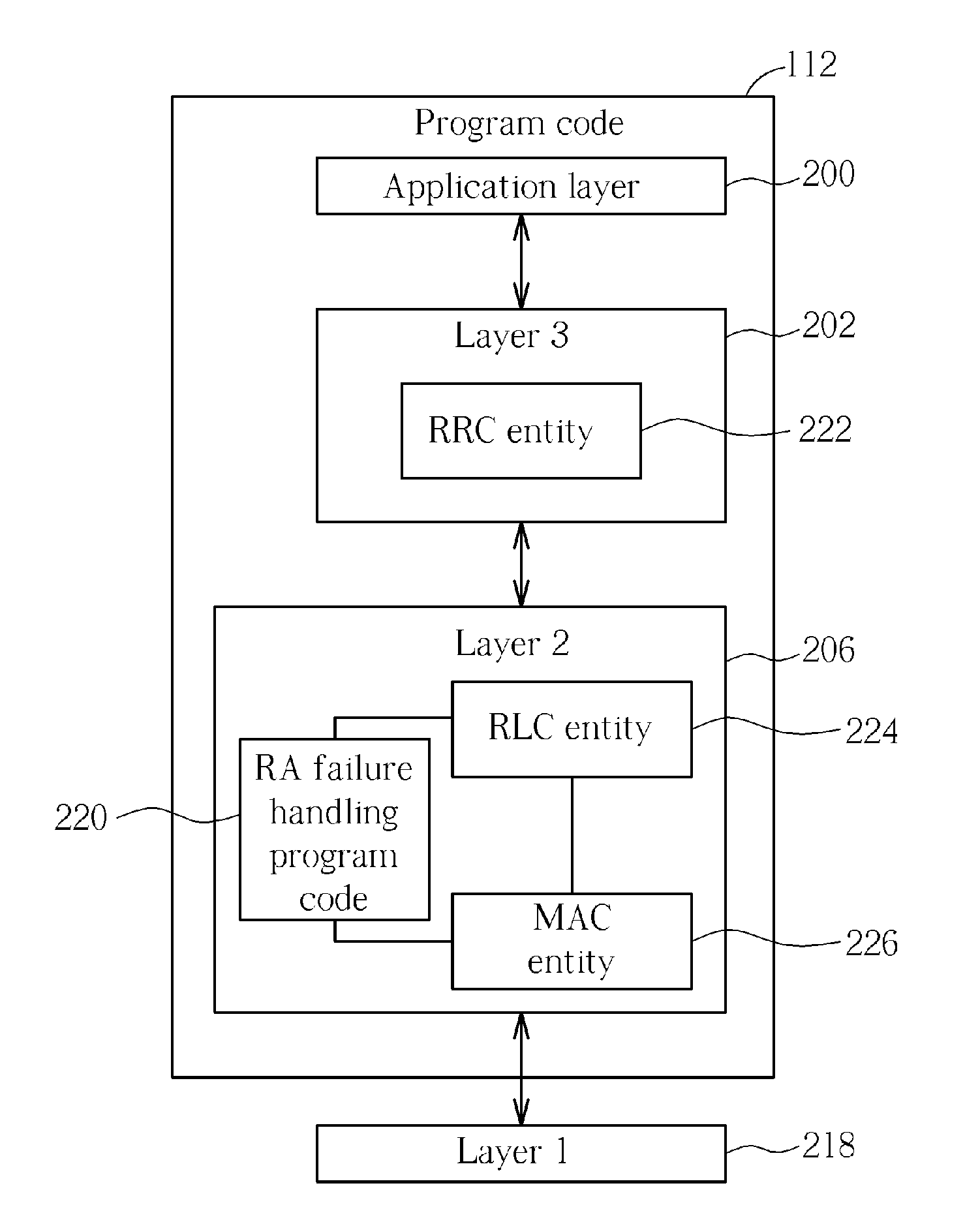
Method of Handling Random Access Procedure Failure and Related Communication Device
InactiveUS20090109838A1Avoid mistakesError preventionTransmission systemsCommunications systemRadio link failures
A method of handling random access procedure failure for a user equipment in a radio resource control connected state in a wireless communication system includes initiating a random access procedure corresponding to uplink or downlink data arrival, and then, when the random access procedure fails, determining that a radio link failure is detected and performing a radio link recovery procedure.
Owner:INNOVATIVE SONIC
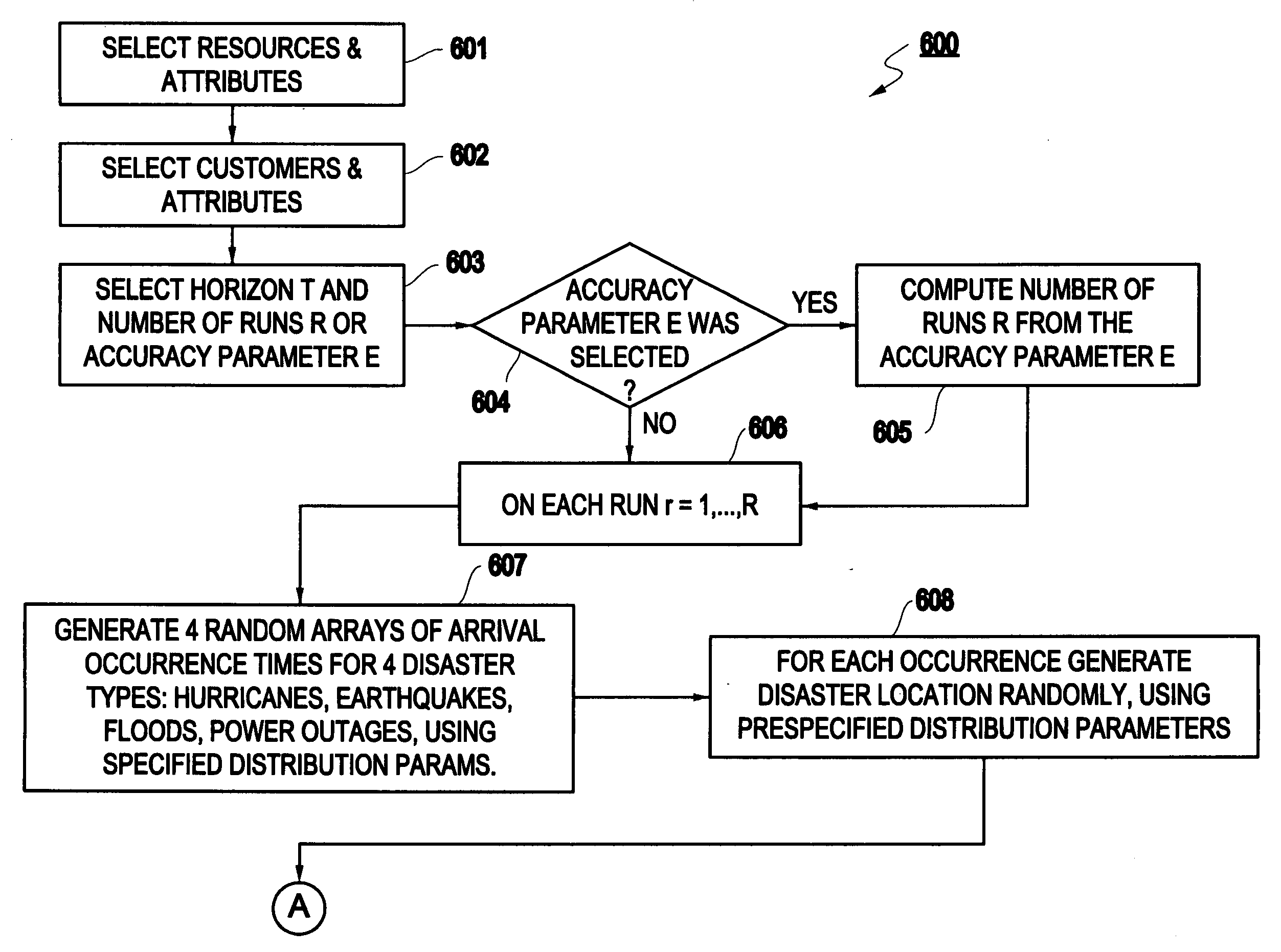
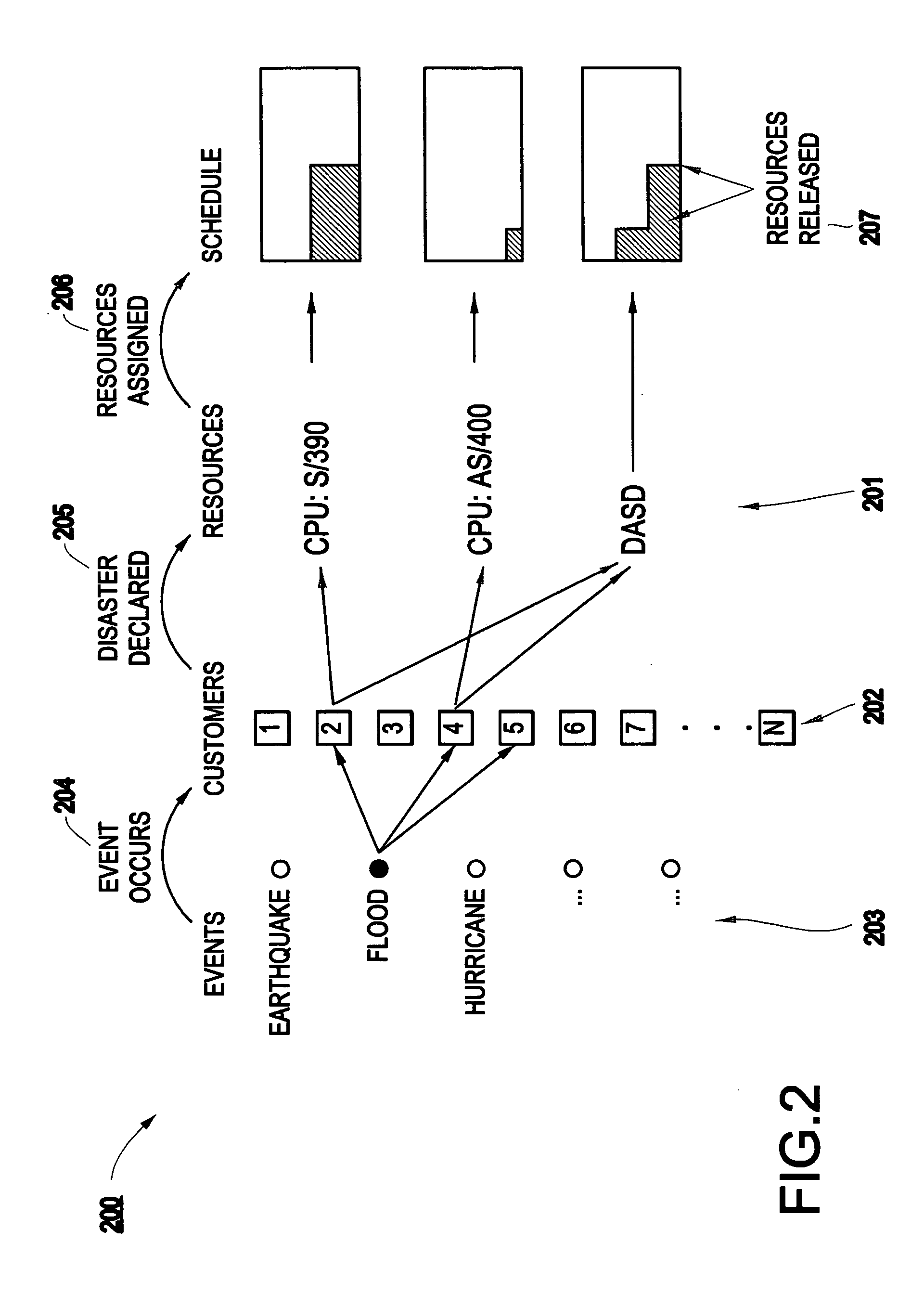
Method and apparatus for risk assessment for a disaster recovery process
InactiveUS20050027571A1Improve abilitiesGreat level of customer satisfactionFinanceElectric/magnetic detectionRisk exposureRisk model
A method and structure for calculating a risk exposure for a disaster recovery process, including loading a user interface into a memory, the user interface allowing control of an execution of one or more risk models. Each risk model is based on a specific disaster type, and each risk model addresses a recovery utilization of one or more specific assets identified as necessary for a recovery process of the disaster type. One of the risk models is executed at least one time.
Owner:IBM CORP
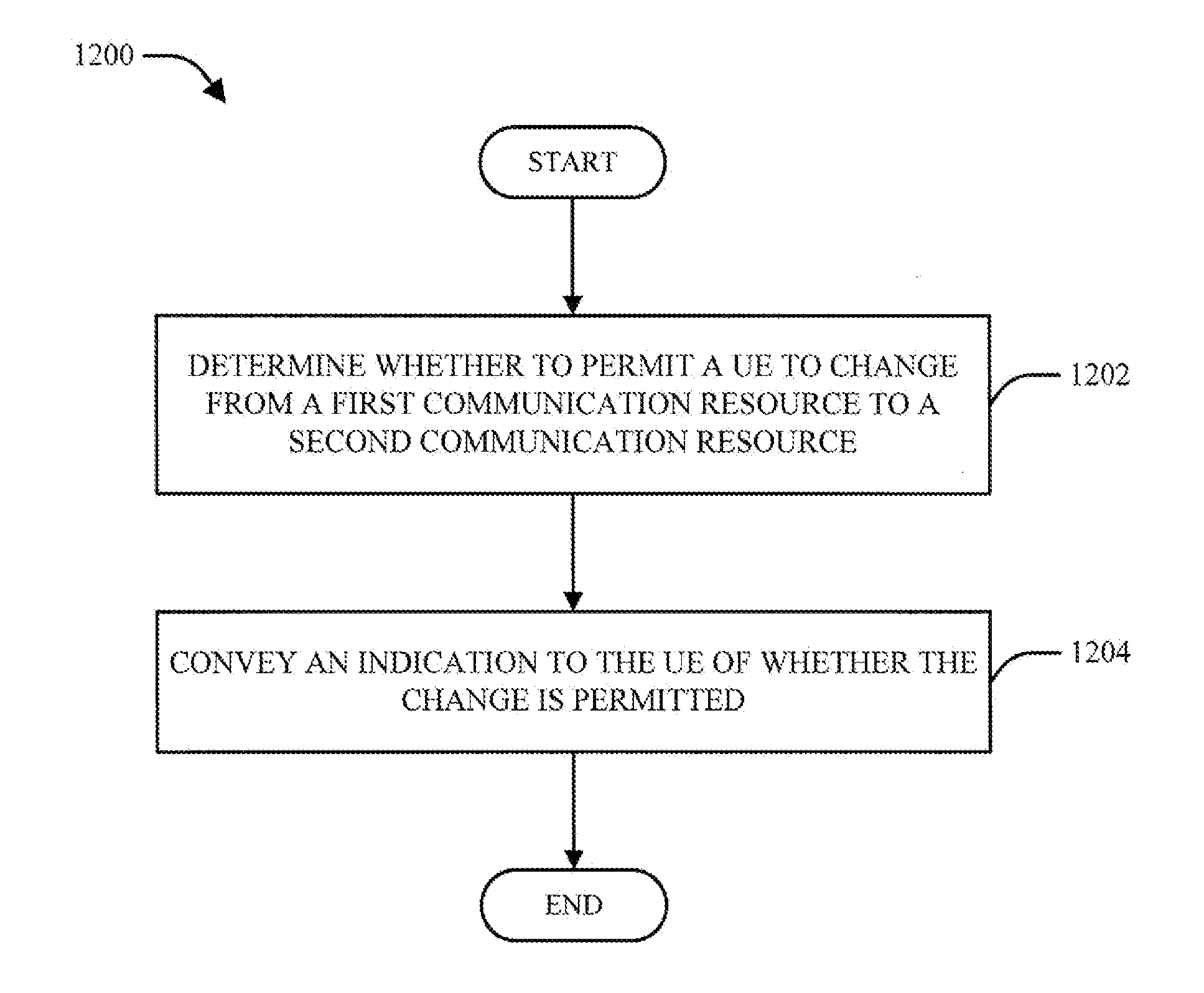
Method and apparatus to facilitate support for multi-radio coexistence
ActiveUS20110242969A1Error preventionFrequency-division multiplex detailsRadio access technologyTelecommunications
A user equipment (UE) monitors coexistence issues of one or more associated communication resources. The UE initiates link recovery procedures (e.g., declaring a Radio Link Failure (RLF)) in response to the monitoring when a coexistence issue is detected. The UE can also access a new channel or a new Radio Access Technology (RAT) in response to initiating the link recovery. The network may have the ability to control whether the UE can initiate the link recovery.
Owner:QUALCOMM INC
Target type estimation in target tracking
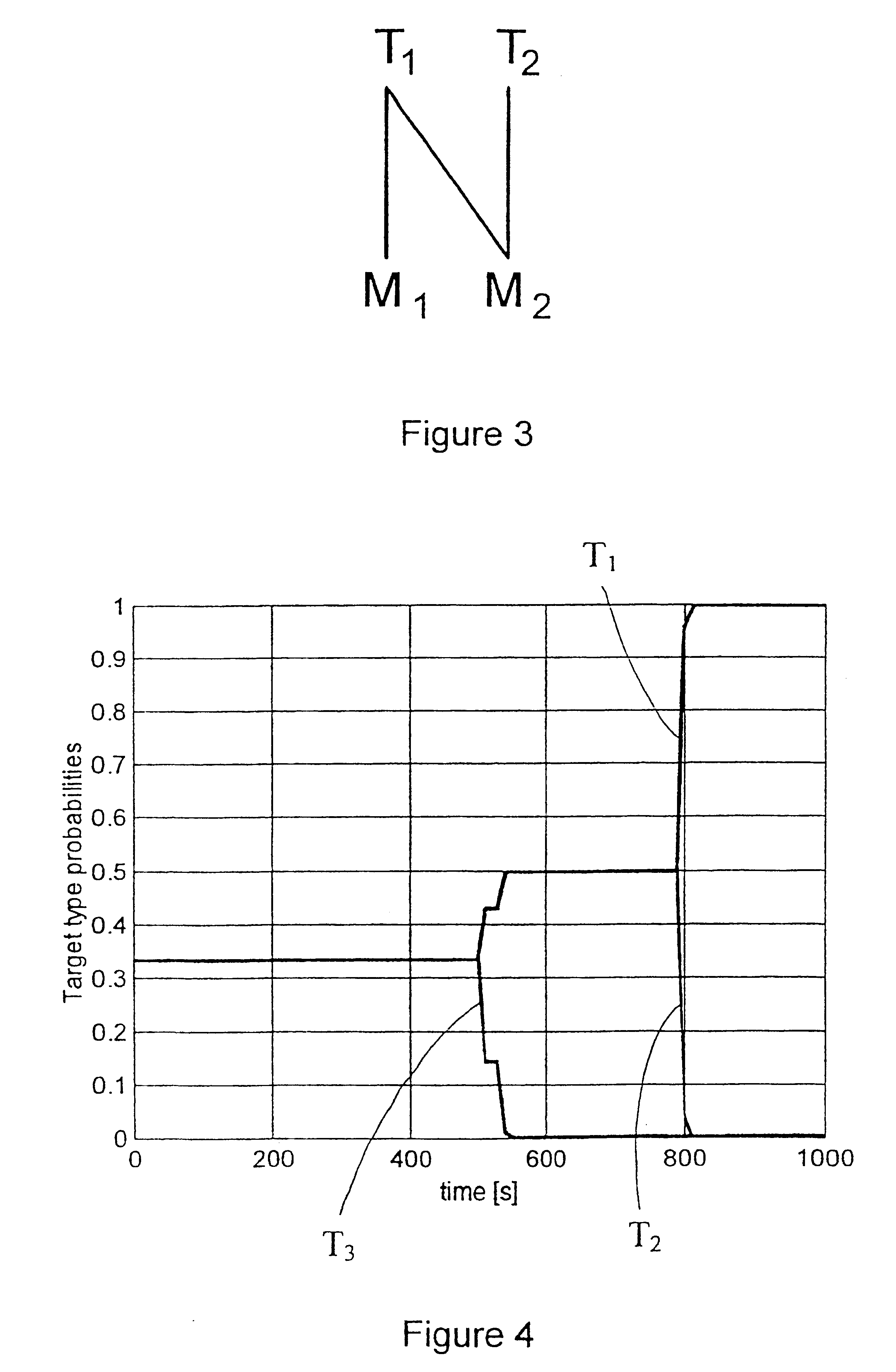
InactiveUS6278401B1Easy to integrateEase of evaluationRadio wave direction/deviation determination systemsDirection/deviation determining electromagnetic systemsMultiple hypothesis trackingPattern recognition
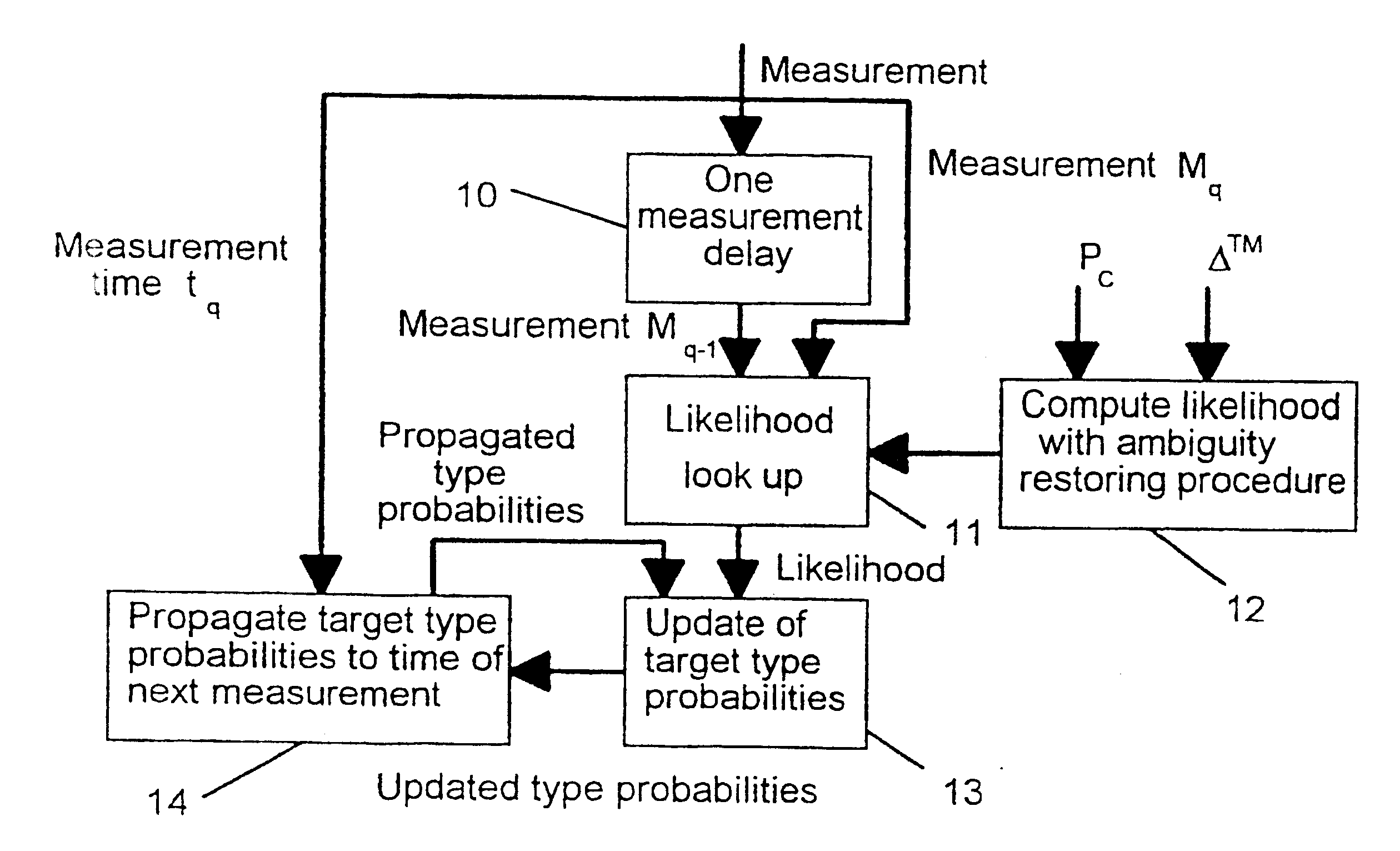
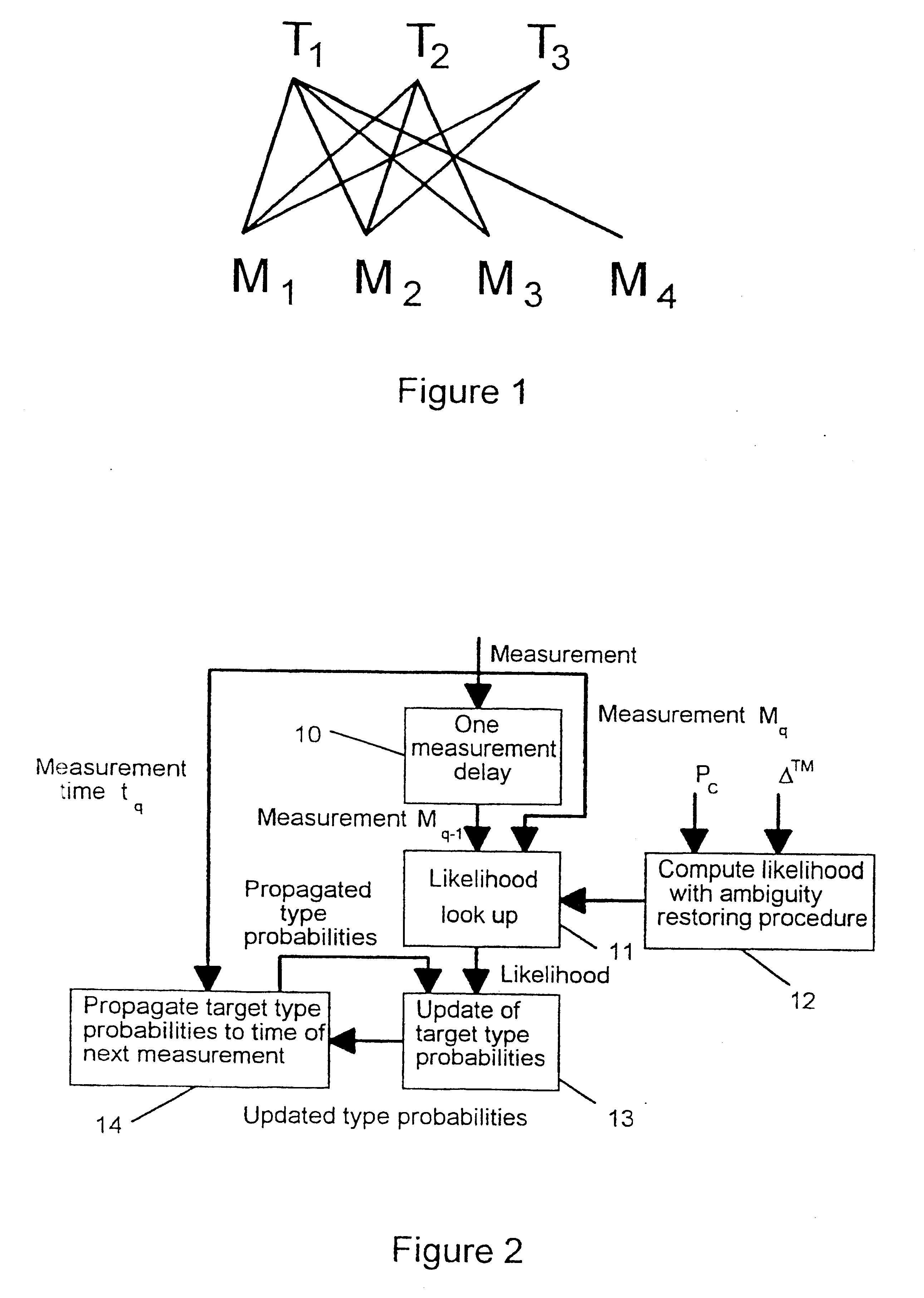
The present invention is in general related to target type estimation in target tracking systems. The invention enables a low complexity estimation of target type, using, e.g. ESM sensor data, by the introduction of an ambiguity restoring procedure in certain likelihood calculations. The invention further enables the systematic use of target type probability information in the calculation of strobe track crosses and their associated quality which is particularly useful for deghosting purposes. Methods for utilisation of target type probability information in the processes of strobe tracking, association, track quality evaluation and multiple hypothesis tracking are also disclosed.
Owner:SAAB AB
Read error recovery utilizing ECC and read channel quality indicators
PCT No. PCT / US97 / 04906 Sec. 371 Date Oct. 21, 1997 Sec. 102(e) Date Oct. 21, 1997 PCT Filed Mar. 27, 1997 PCT Pub. No. WO97 / 43835 PCT Pub. Date Nov. 20, 1997An apparatus and method for recovering from read errors detected by a read channel (70) in a sequence of data read from a disc (18) of a disc drive (10) by using read channel quality indicators to determine the appropriateness of using error correction in combination with other corrective actions utilized in the recovery process. Upon the detection of an uncorrected error in the retrieved data, the disc drive (10) enters a read error recovery routine wherein one or more corrective actions (102, 122) are applied in an effort to resolve the error. One of the channel quality indicators comprises a channel quality measurement (108, 128) determined as the sum of the square of the sampled data bit error values recovered during the read operation. When the channel quality measurement is at or below a threshold value indicative that the probability of passing undetected erroneous data is at an acceptable level (110, 130), error correction is applied to the data (112, 138); otherwise, error correction is disallowed (118, 140). Additional channel quality indicators comprise erasure pointers (132) which identify a particular set of symbols that are suspected of containing a read error. In such a case, the disc drive determines that the total number of symbols identified by the erasure pointers is below a predetermined erasure threshold before applying error correction (134, 136, 138), the erasure threshold selected to be within the correction capability of error correction circuitry 90.
Owner:SEAGATE TECH LLC
System and method for managing transaction record delivery using an acknowledgement-monitoring process and a failure-recovery process with modifying the predefined fault condition
InactiveUS6950867B1Conduct electronic transactionsFinanceFault responseRemote systemDistributed Computing Environment
The present invention provides systems and methods for conducting electronic transactions in a distributed computing environment. A communications protocol is provided that enables reliable transactional state synchronization for peers participating in a distributed transaction. A transaction processing application is deployed on a local computer system to manage transactions thereon. The local computer system contacts a remote computer system to obtain authorization to execute a transaction. The local computer system initiates a failure-recovery job that is operable to automatically resend status signals and other information to the remote system if the communication with the remote system exhibits certain predefined fault conditions. The remote system is able to dynamically adjust the definition of the predefined fault conditions. If the transaction concludes without triggering the predefined fault conditions, the failure-recovery job is cancelled. The transaction processing application may also allow deferred transactions between remote parties. The transaction processing application maintains a record of the transactions performed by the consumer on the consumer's local system. Upon the occurrence of predefined conditions, transactional records are sent to a remote vendor or clearinghouse. The vendor or clearinghouse can manage the risk it bears by setting the predefined conditions appropriately.
Owner:INTERTRUST TECH CORP
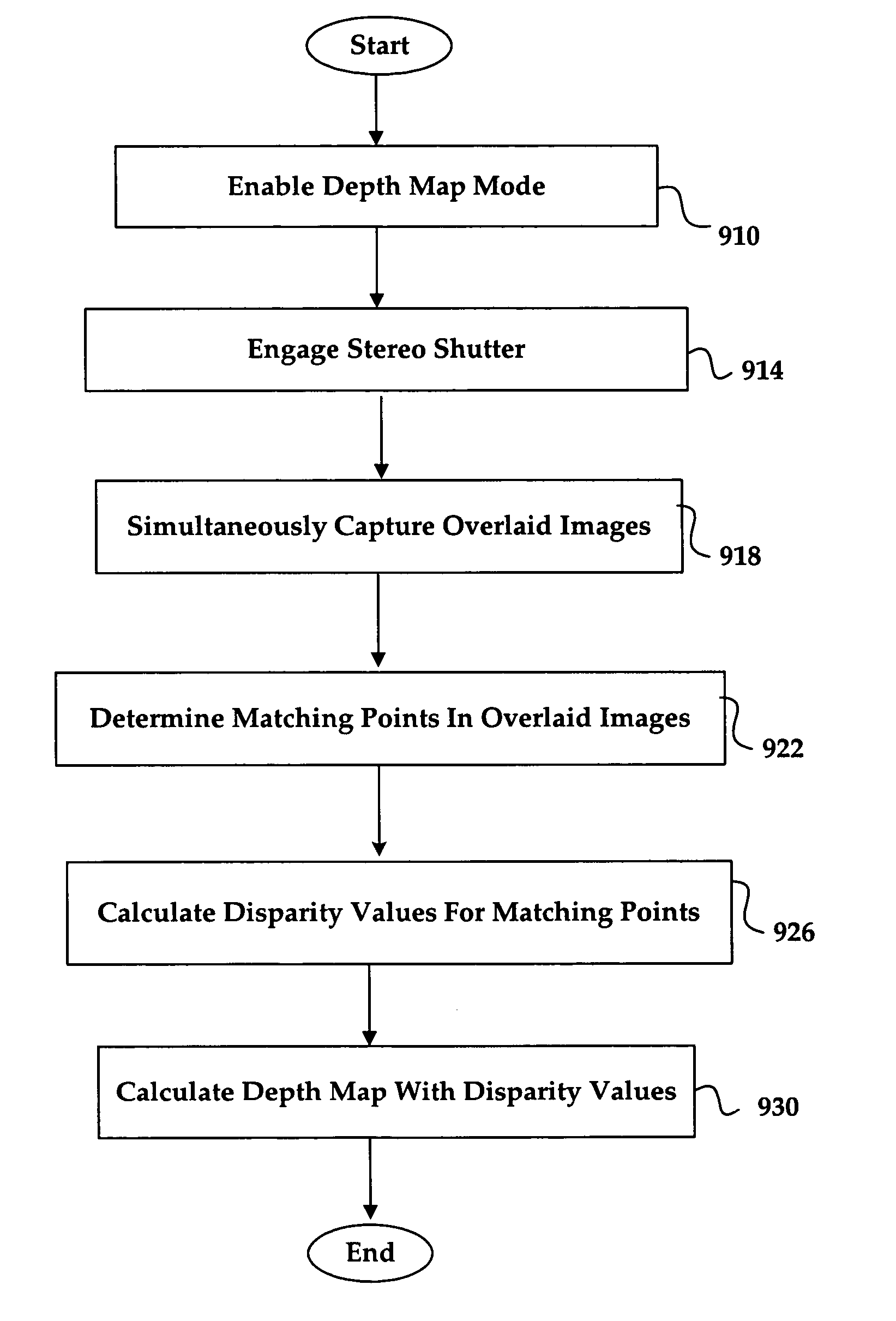
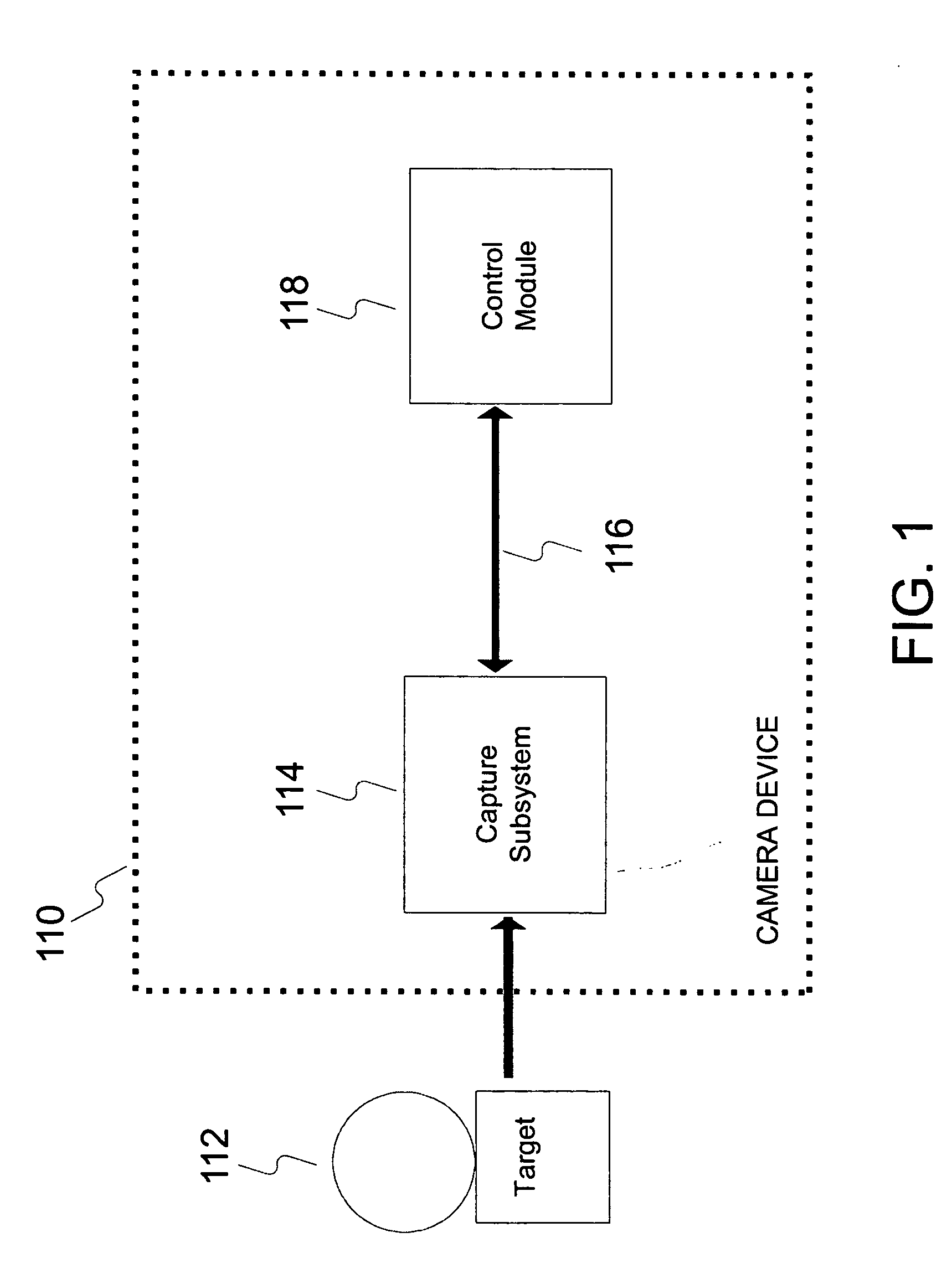
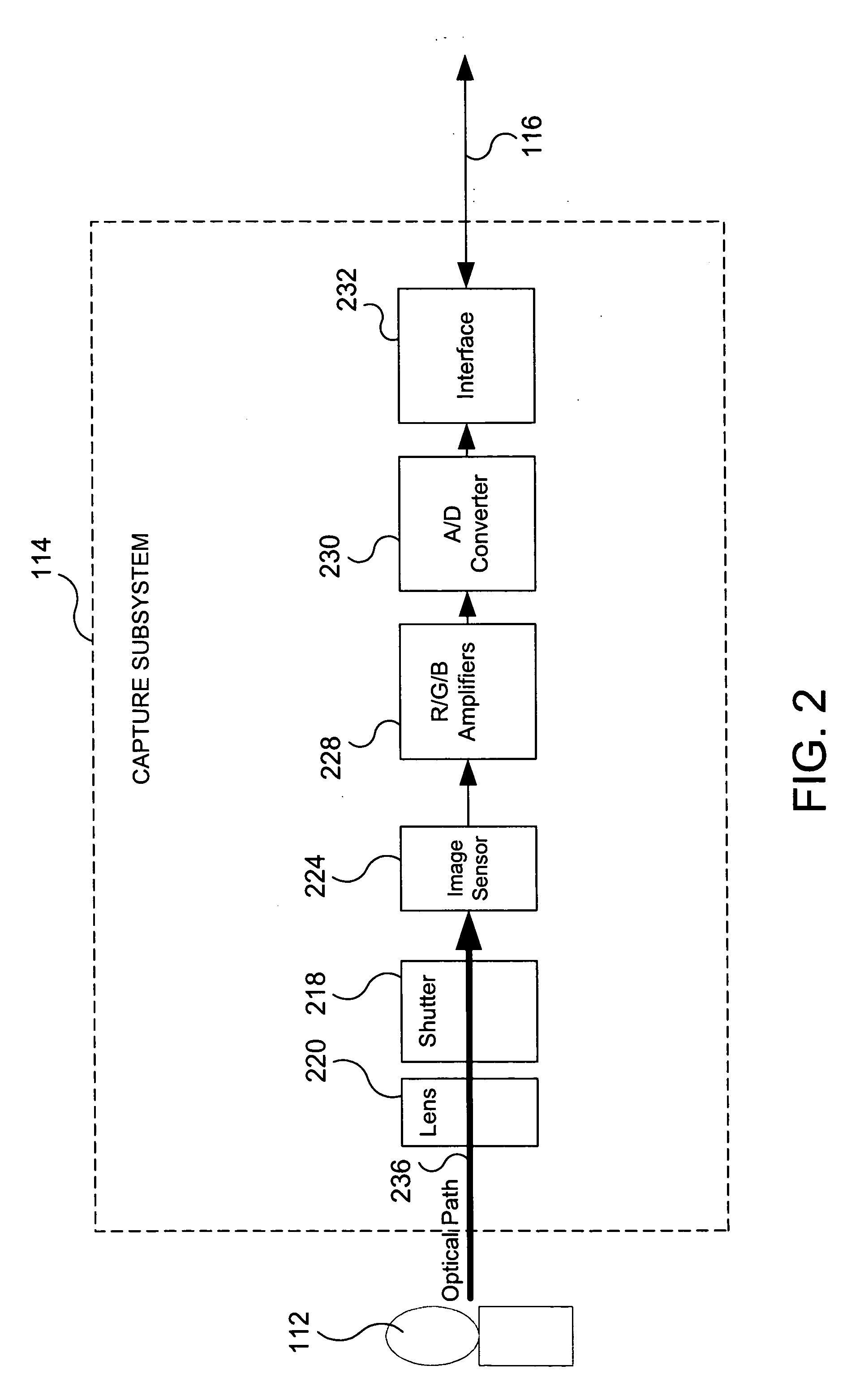
System and method for efficiently performing a depth map recovery procedure
ActiveUS20060029270A1Efficient procedureEfficient executionImage analysisCharacter and pattern recognitionParallaxImaging equipment
A system and method for efficiently performing a depth map recovery procedure includes an imaging device that is implemented in a single-lens stereo-shutter configuration for simultaneously capturing overlaid images corresponding to a photographic target. A depth map generator is configured to analyze the overlaid images to determine disparity values corresponding to separation distances between matching points in the overlaid images. The depth map generator then utilizes the disparity values to calculate depth values that correspond to locations in the photographic target. The depth map generator may then utilize the foregoing depth values for creating a depth map corresponding to the photographic target.
Owner:SONY CORP +1
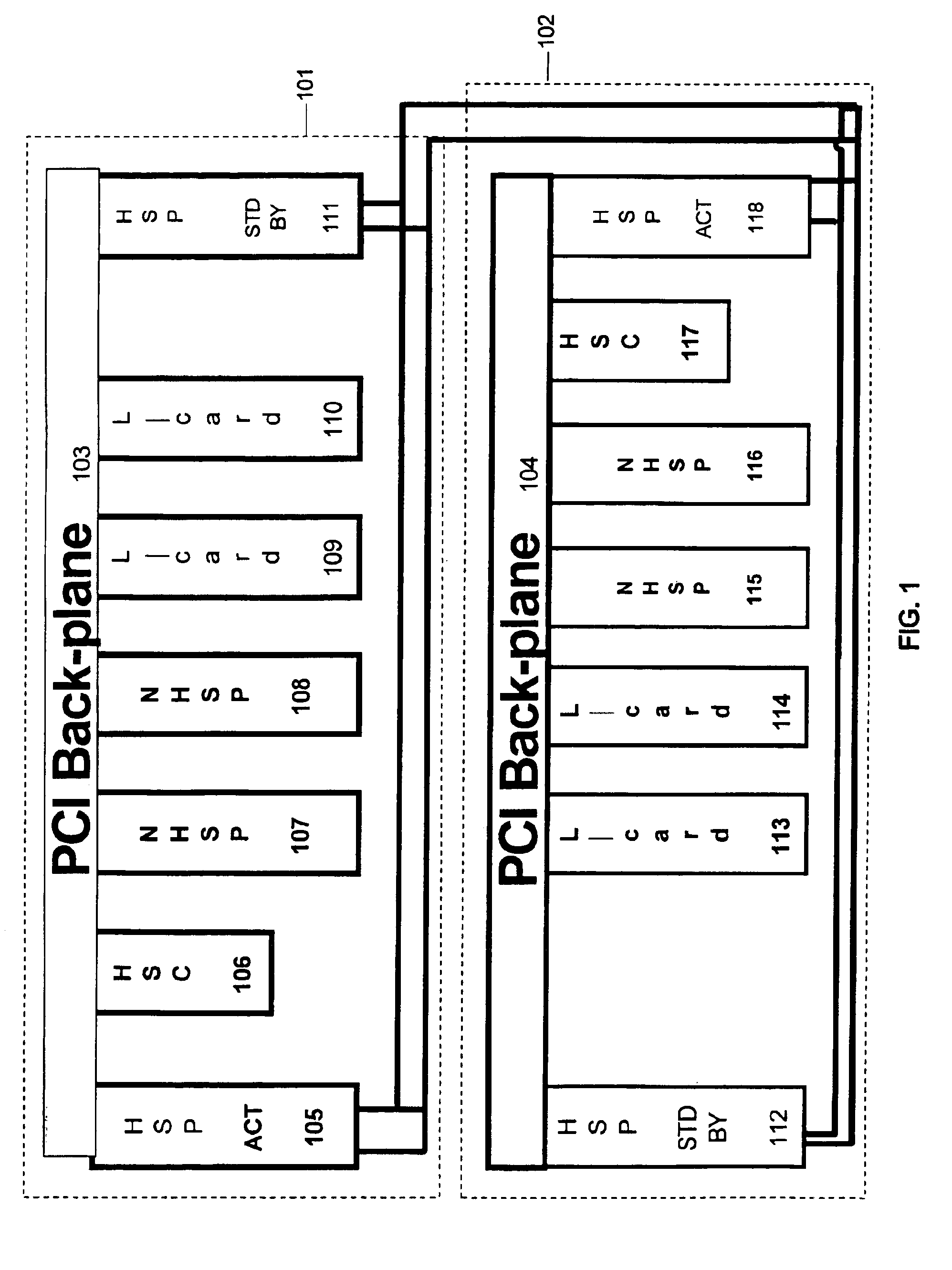
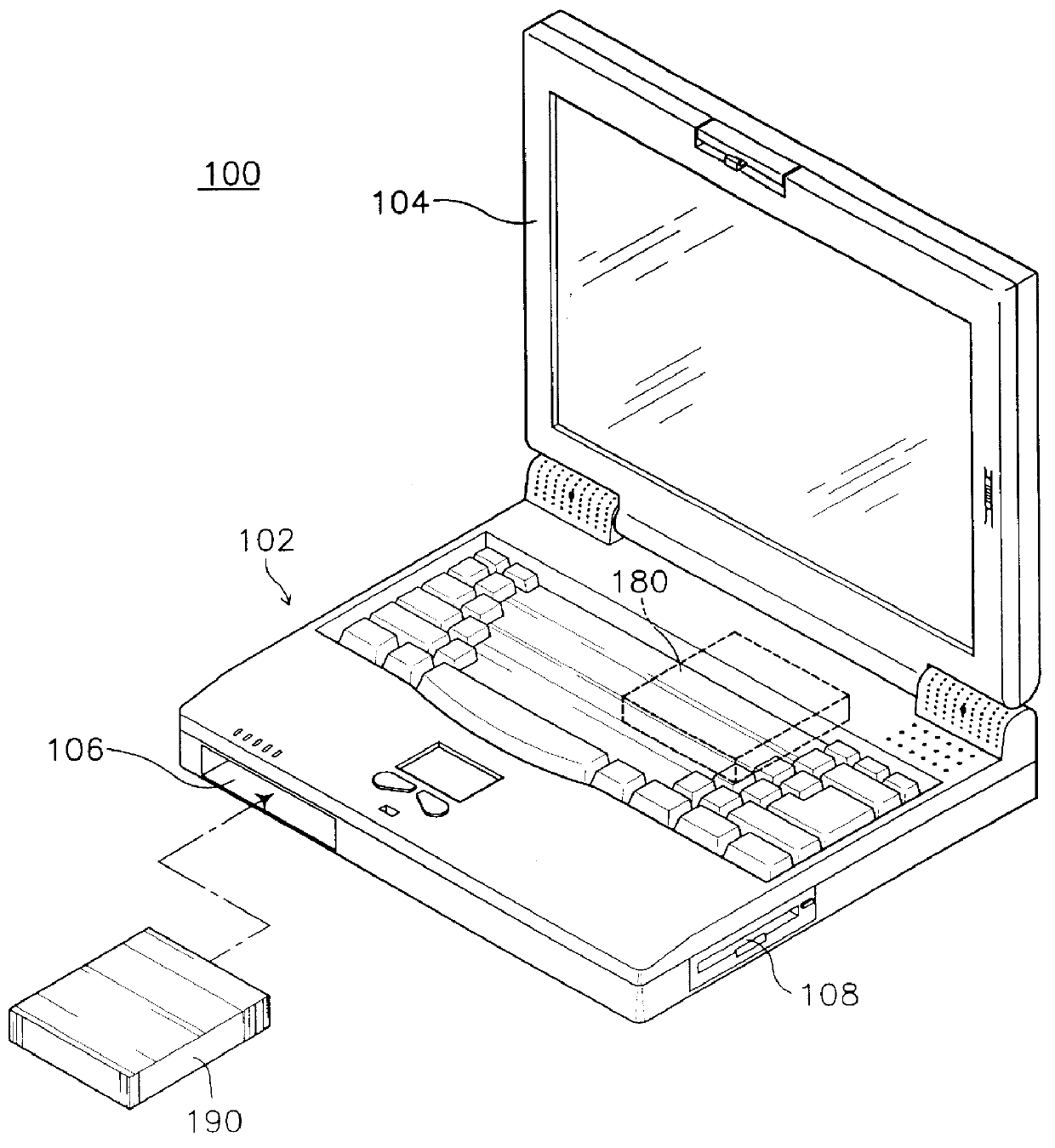
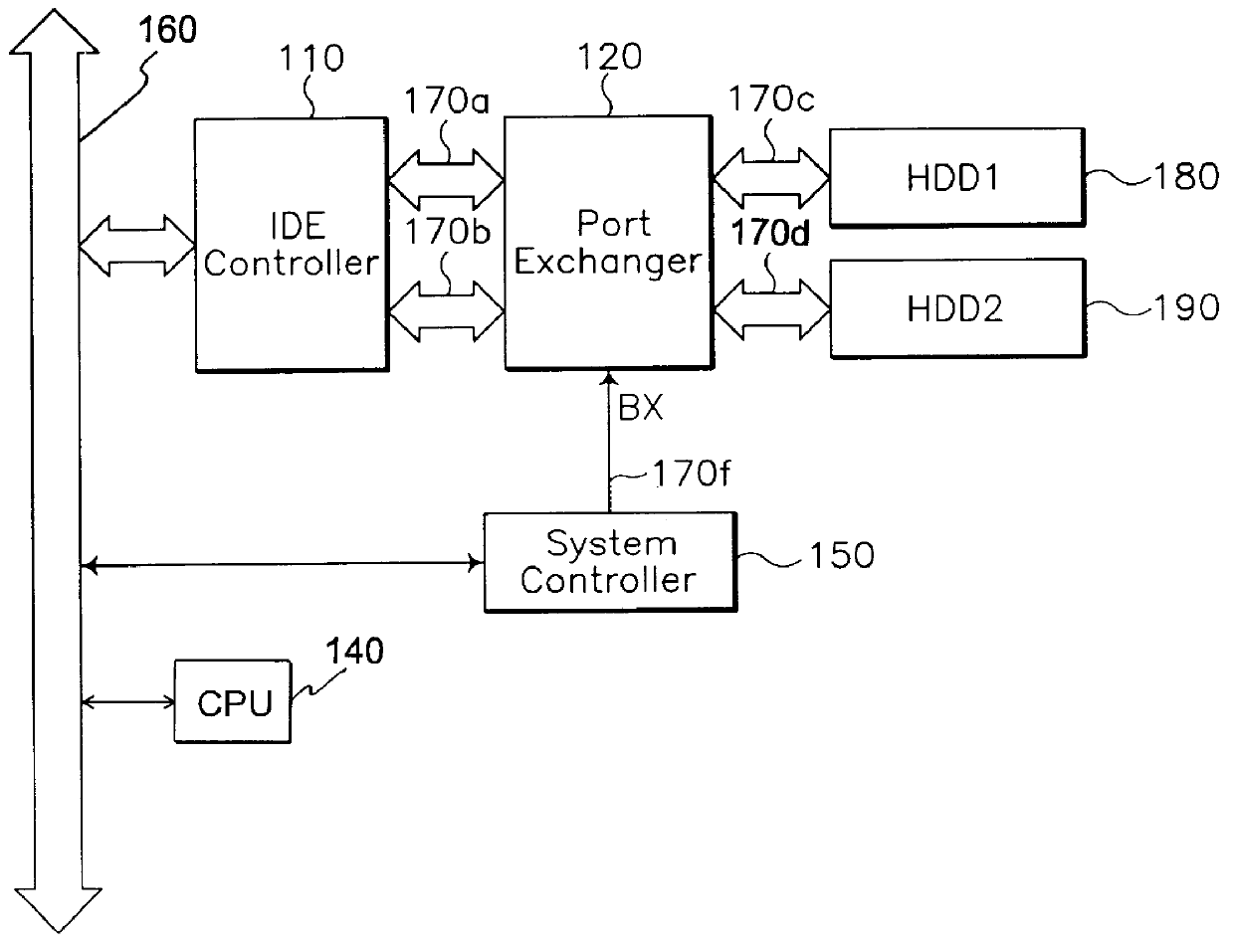
Computer system capable of selective booting from two hard disk drives
InactiveUS6088794AEasy and efficientEasy to useEnergy efficient ICTInput/output to record carriersHard disc driveOperational system
A computer system having two fixed disk drives and with a different operating system stored in each disk drive, in which selective booting and suspend / resume operation of the power management can be preformed through the two fixed disk drives. The computer system comprises a first hard disk drive storing a first operating system and a second hard disk drive storing a second operating system, each of the first and second hard disk drive has a reserved data storage area for the suspend operation. A port exchanger intervenes in the master and slave integrated drive electronics (IDE) interface signal lines leading from an integrated drive electronics (IDE) controller to the first and second hard disk drives, in response to a bus exchange control signal fed from a system controller to pass or cross switch the integrated drive electronics (IDE) interface signal paths directed to the first and second hard disk drives. The computer system further includes a controller for producing the bus exchange control signal, under control of the system management part by referring to the first and second hard disk drive status information during booting or resuming process.
Owner:SAMSUNG ELECTRONICS CO LTD
Data transfer and recovery process
A backup image generator can create a primary image and periodic delta images of all or part of a primary server. The images can be sent to a network attached storage device and a remote storage server. In the event of a failure of the primary server, the failure can be diagnosed to develop a recovery strategy. Based on the diagnosis, at least one delta image may be applied to a copy of the primary image to generate an updated primary image at either the network attached storage or the remote storage server. The updated primary image may be converted to a virtual server in a physical to virtual conversion at either the network attached storage device or remote storage server and users may be redirected to the virtual server. The updated primary image may also be restored to the primary server in a virtual to physical conversion. As a result, the primary data storage may be timely backed-up, recovered and restored with the possibility of providing server and business continuity in the event of a failure.
Owner:EFOLDER INC
Dead on demand disk technology
InactiveUS7099110B2Avoid retrievingApparatus modification to store record carriersUndesired vibrations/sounds insulation/absorptionMagnetic mediaData storing
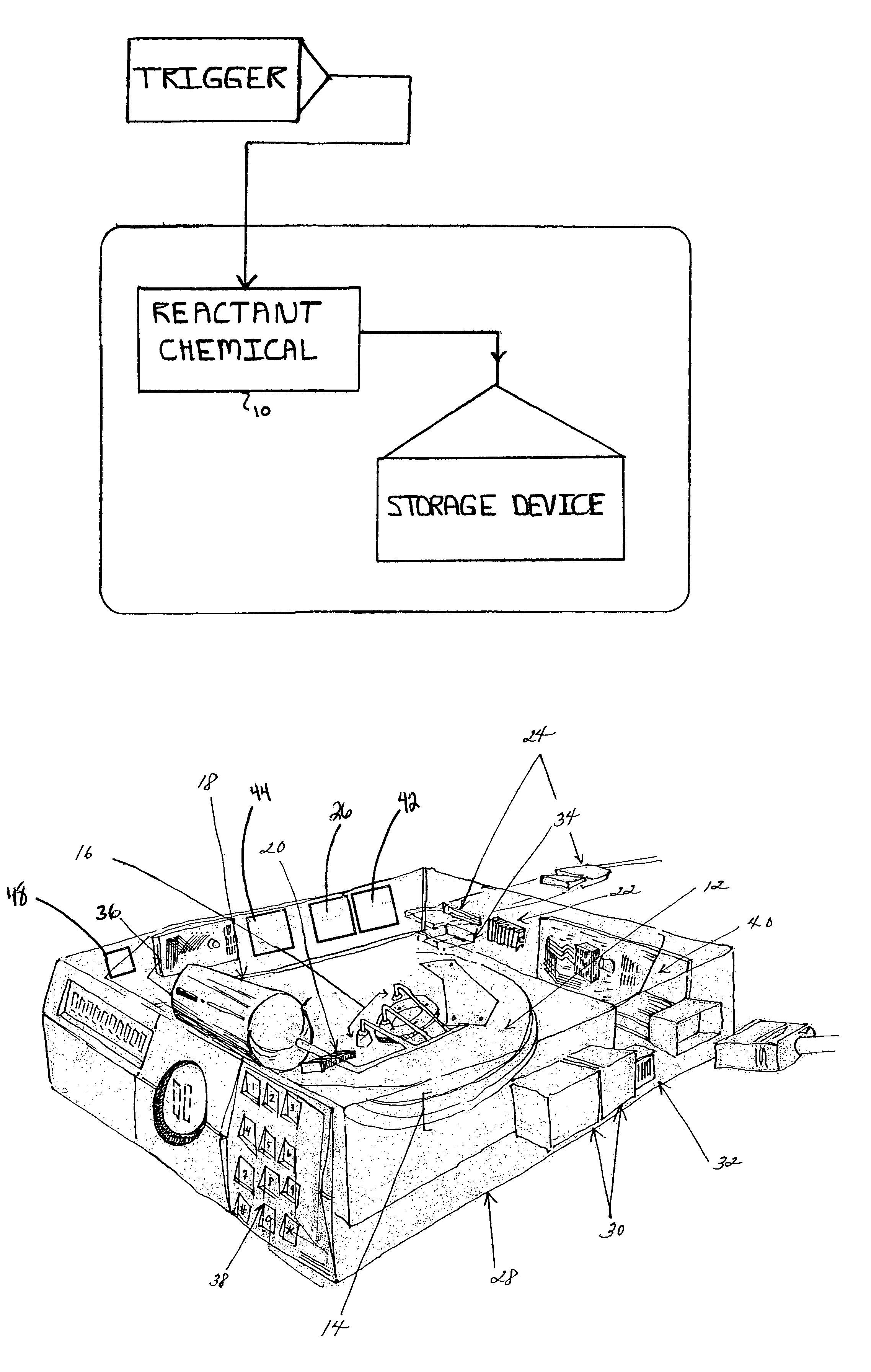
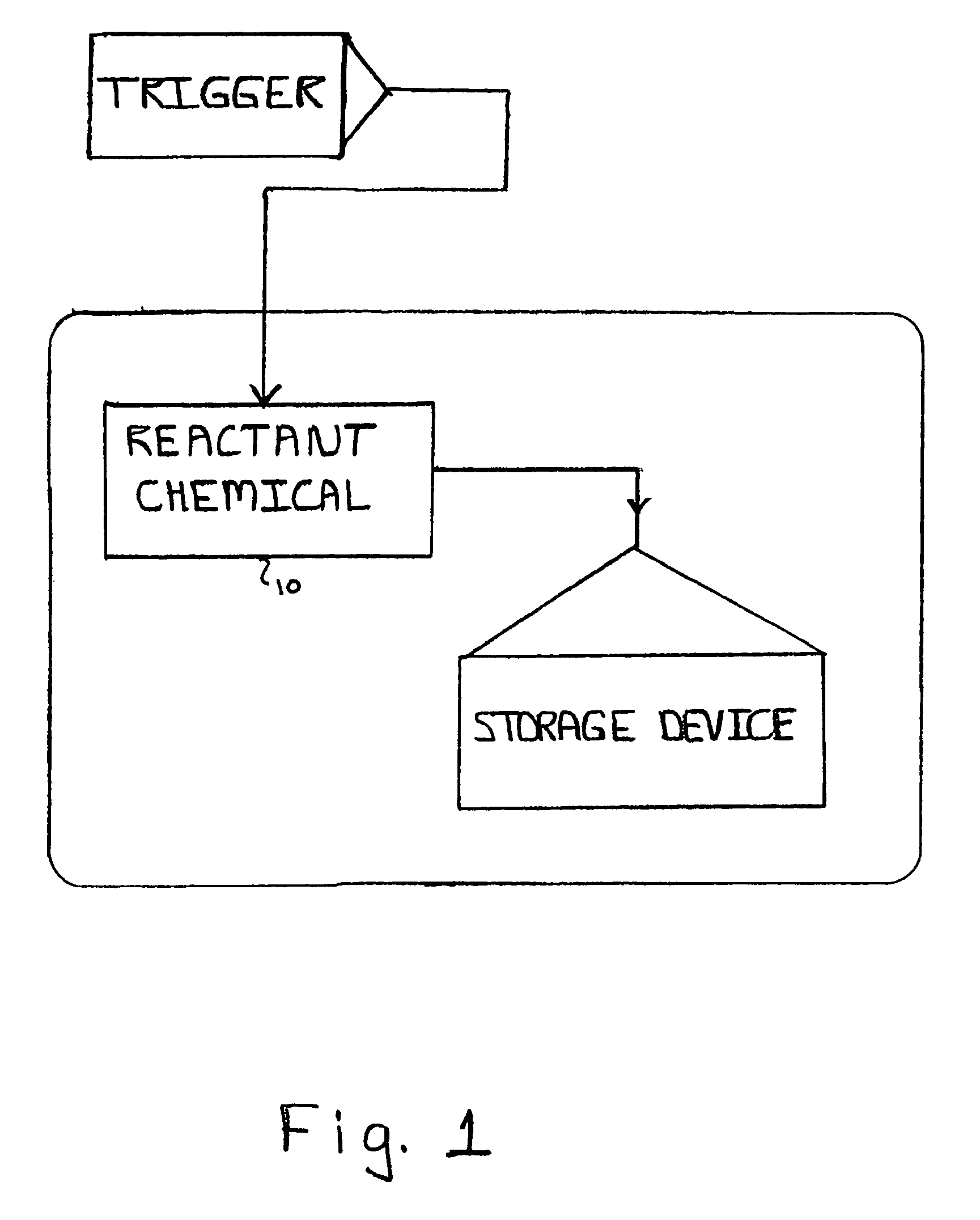
The present invention relates to a system and method for permanently and generally instantaneously destroying at least the data contained on magnetic data storage media upon the occurrence of certain events. Unauthorized access to data stored on magnetic media is prevented by destruction of the media with a reactant chemical. This approach may be initiated as a response to tampering or intentionally by using any one of several triggering interfaces described herein. Destruction of the media is quick and permanent, rendering the data unrecoverable even to aggressive recovery procedures.
Owner:ENSCONCE DATA TECH
Information transmission method and information transmission device
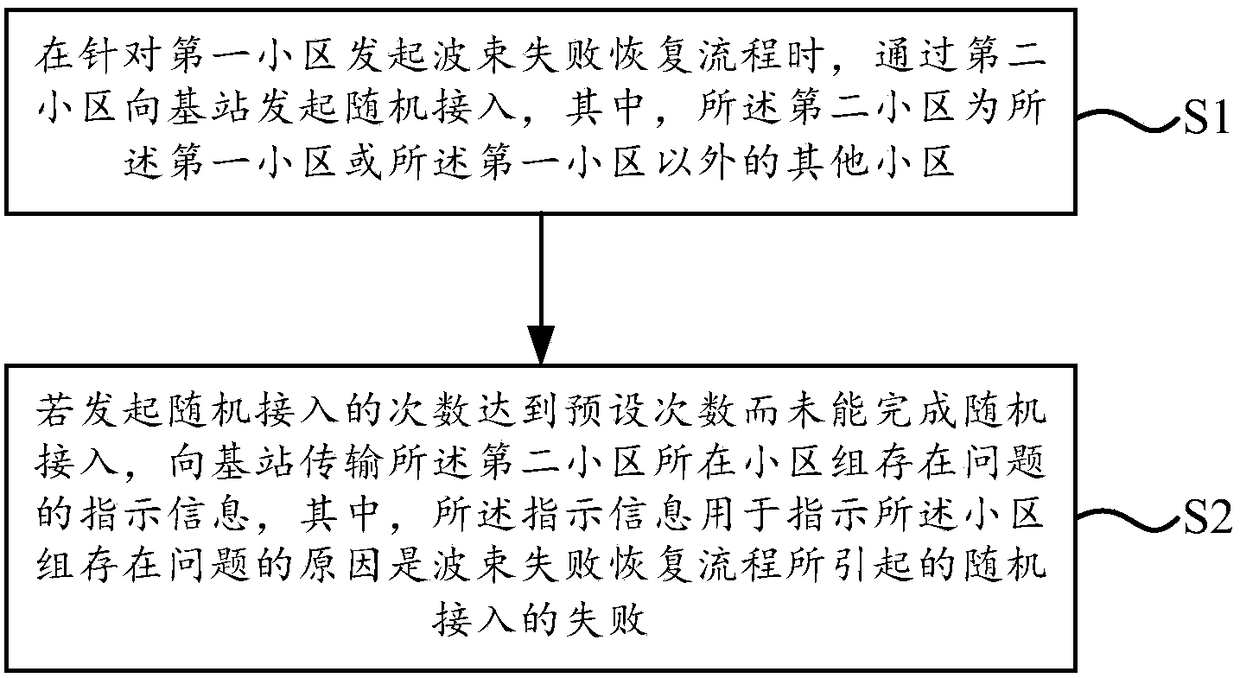
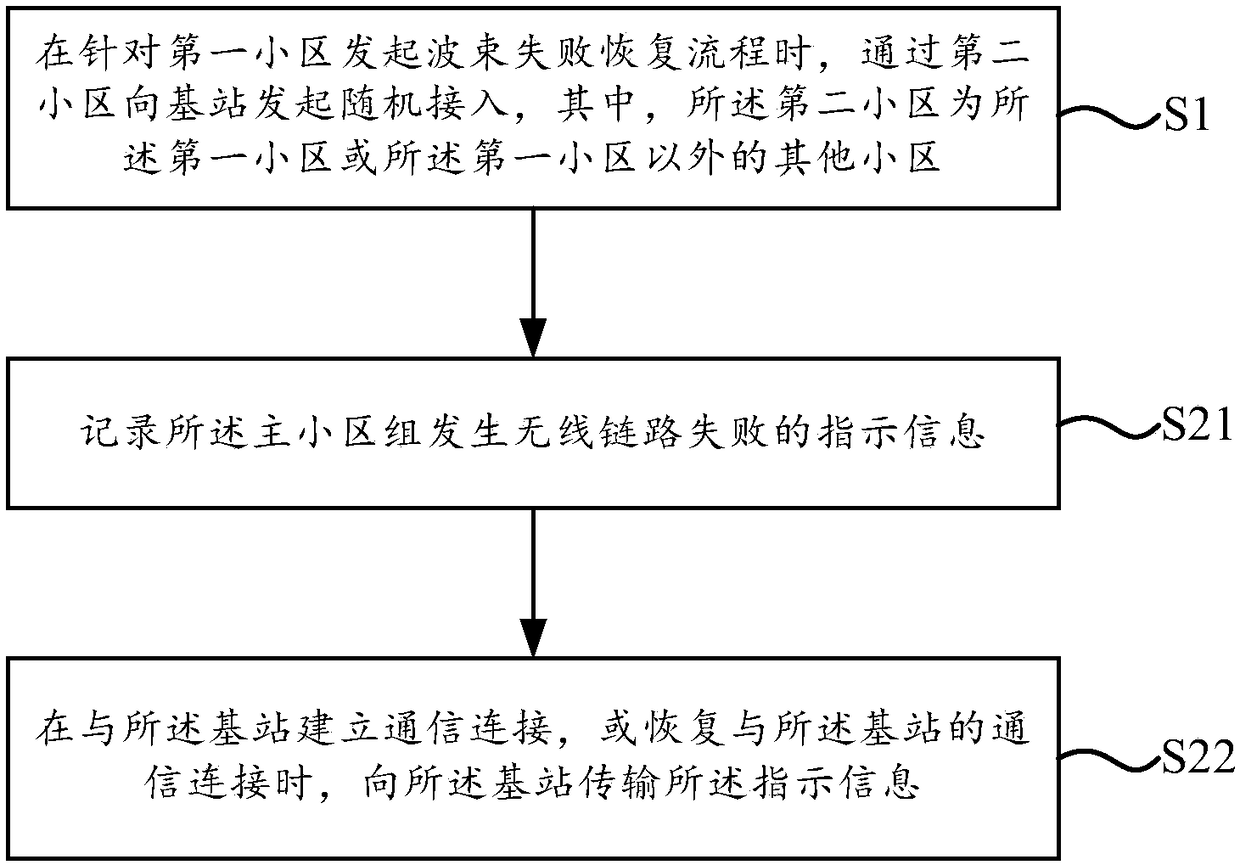
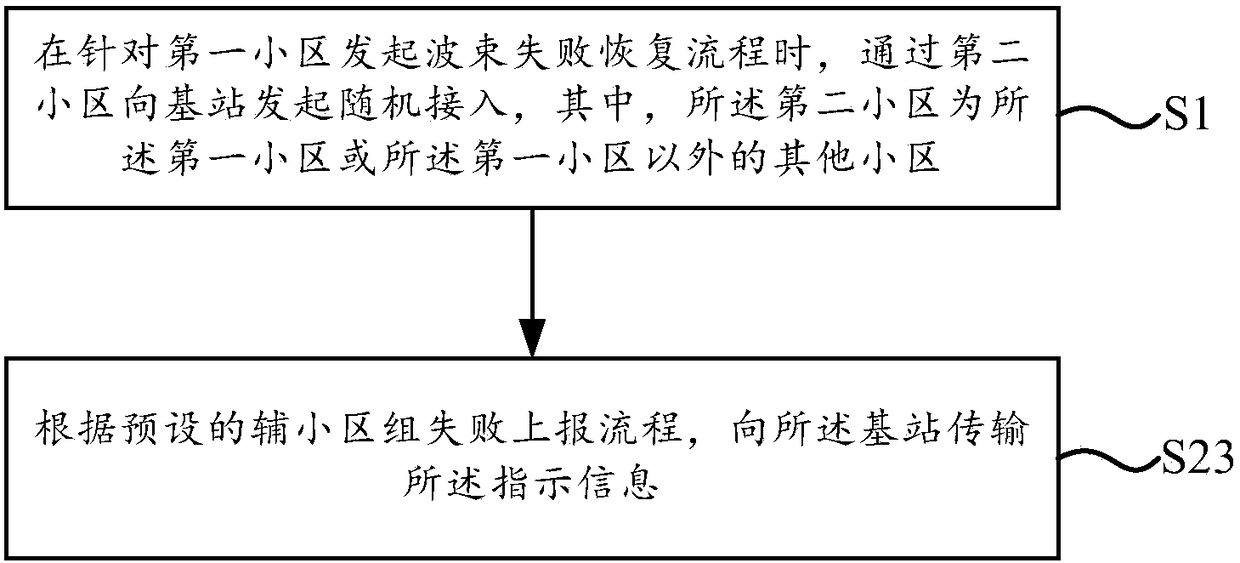
ActiveCN108513737AGuaranteed reasonablenessConnection managementRadio transmissionInformation transmissionUser equipment
The present disclosure relates to an information transmission method, which is applicable to a user equipment, the method includes: when a beam failure recovery procedure is initiated for a first cell, a random access is initiated to a base station by a second cell, where the second cell is the first cell or another cell other than the first cell; if the number of times of the random access is upto a preset number of times and the random access is not completed, to a base station, the indication information is used to indicate the reason why the problem exists in the cell group and the reasonis a failure of the random access caused by the initiation of the beam failure recovery process. According to the embodiment of the present disclosure, the reason that the indication of the cell group indicates that the cell group has a problem is the failure of the random access caused by the beam failure recovery process, so that the base station can define the reason for the random access failure to ensure that the subsequent configuration of the base station is reasonable.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Method of providing cyber security as a service
InactiveUS20140259095A1Memory loss protectionError detection/correctionChange managementNetworked system
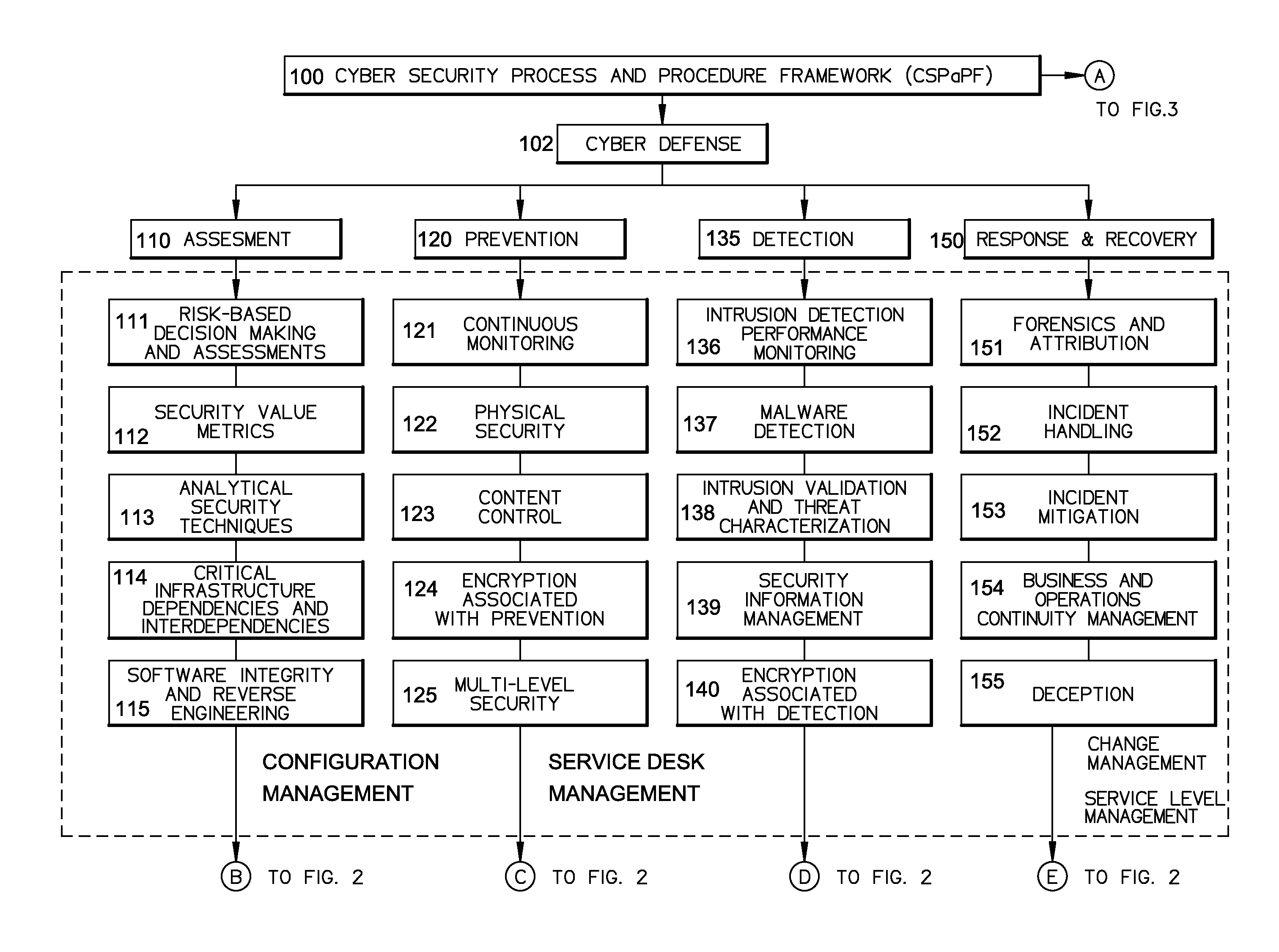
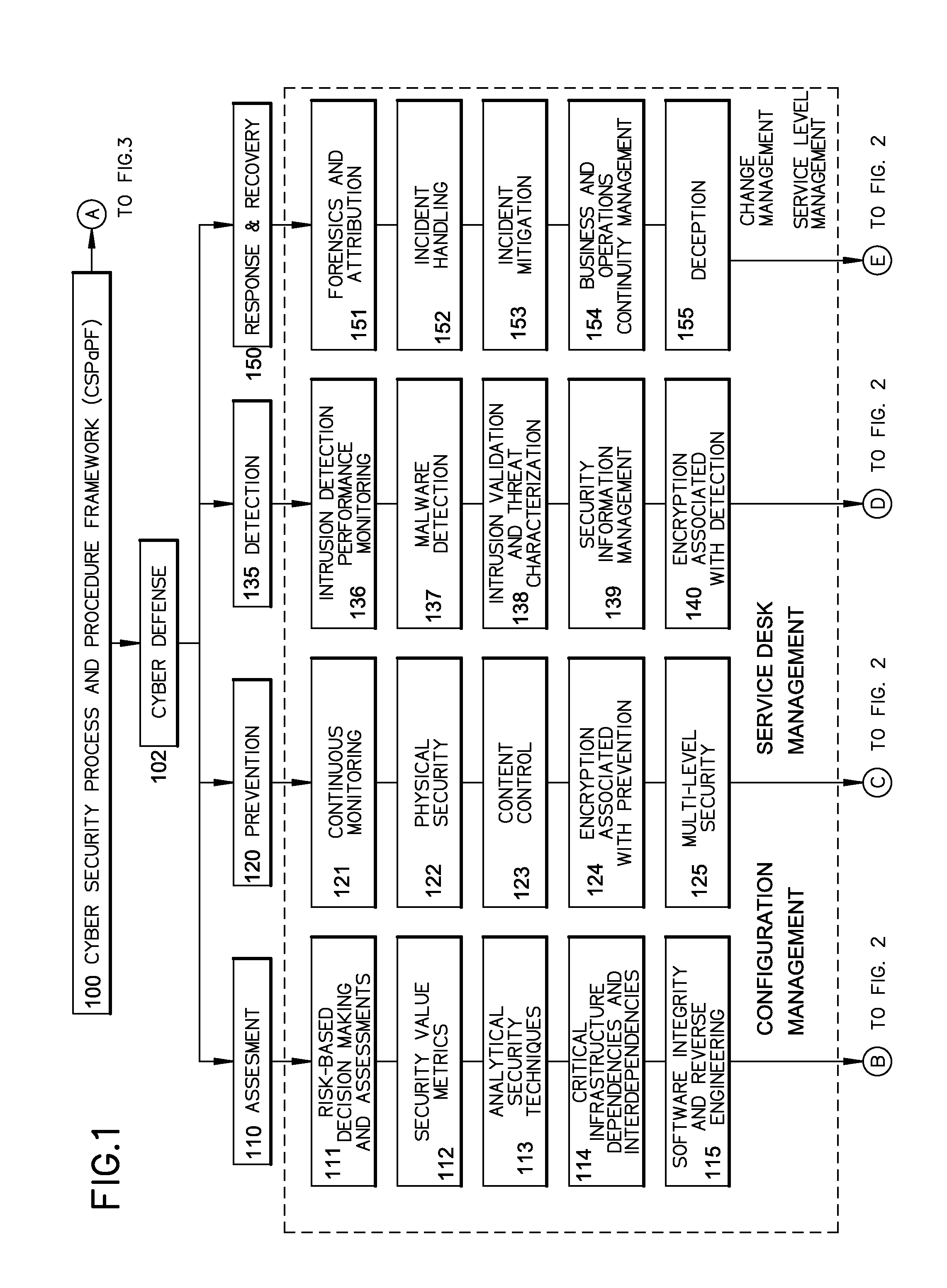
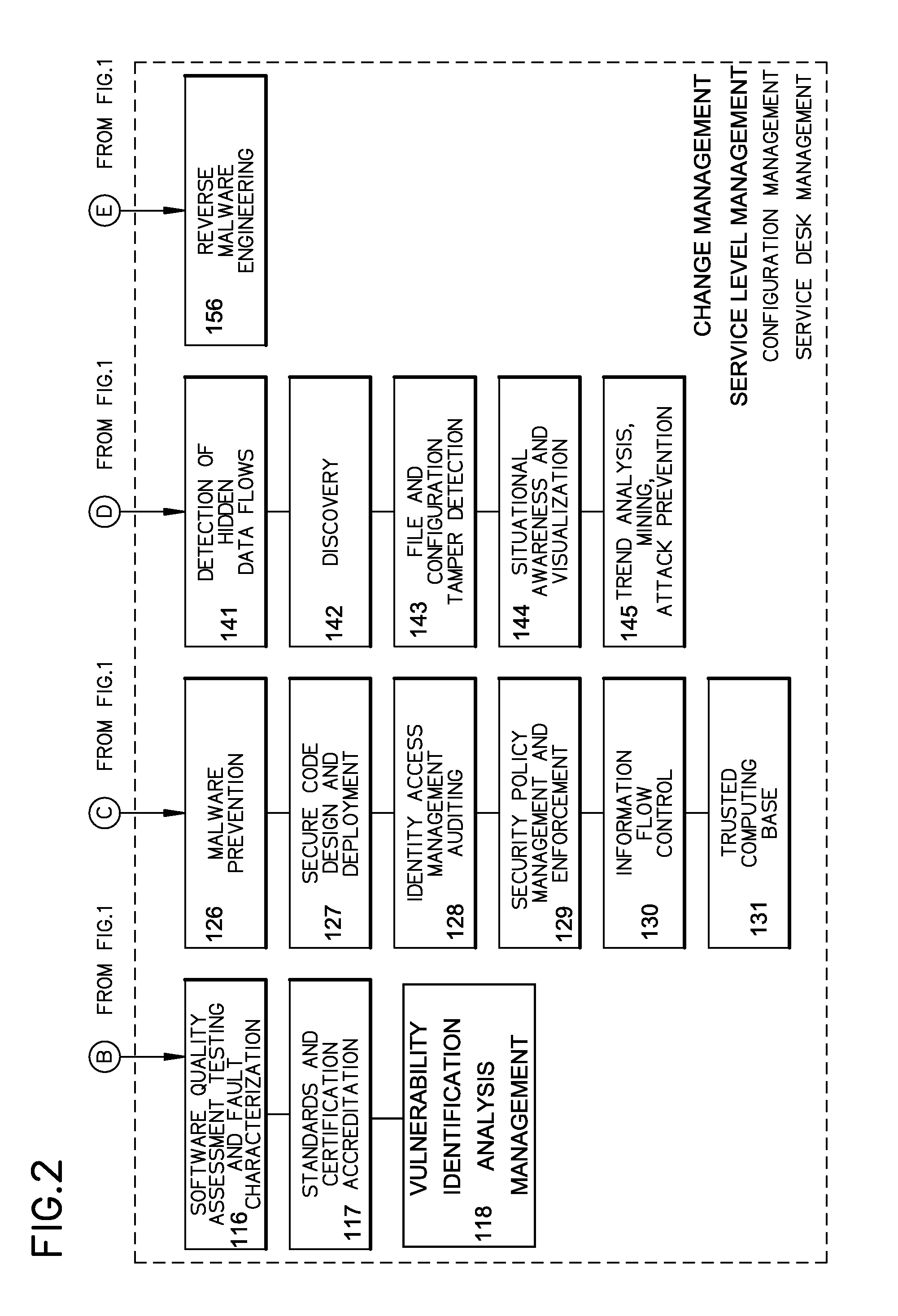
A cyber system including a method of providing cyber security as a service is provided. The cyber system may include an integrated architecture of defensive and offensive security procedures and processes that enable enterprises to practice safe, holistic security techniques. The plurality of cyber defense procedures may include a plurality of risk-based assessment procedures, a plurality of attack-prevention procedures, a plurality of detection procedures and a plurality of response and recovery procedures. The plurality of cyber offense procedures may include a plurality of cyber weapon procedures, a plurality of cyber Intelligence, surveillance and reconnaissance procedures, a plurality of information operations target exploitation procedures and a plurality of information operations attack procedures. The cyber system may also include a plurality of overlapping processes interconnecting the plurality of cyber offense procedures and plurality of cyber defense procedures. The plurality of overlapping processes may include a change management, a configuration management, a service desk and a service-level management. The change management may be structured within an enterprise for ensuring that changes in people, facilities, technology and / or processes are smoothly and successfully implemented to achieve lasting benefits. The configuration management may establish and maintain the consistency of a product's performance, functional and physical attributes with its requirements, design and operational information throughout its life. The service desk may provide the communication needs of the users, employees and customers. Service-level management may assess the impact of change on service quality and establish performance metrics and benchmarks.
Owner:BRYANT JAMES ALVIN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com