Patents
Literature
279 results about "Central repository" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Central Repository, or Central Learning Object Repository (CLOR), is a core feature enabled by default in your Docebo LMS. Therefore, it is available for both Growth and Enterprise clients.
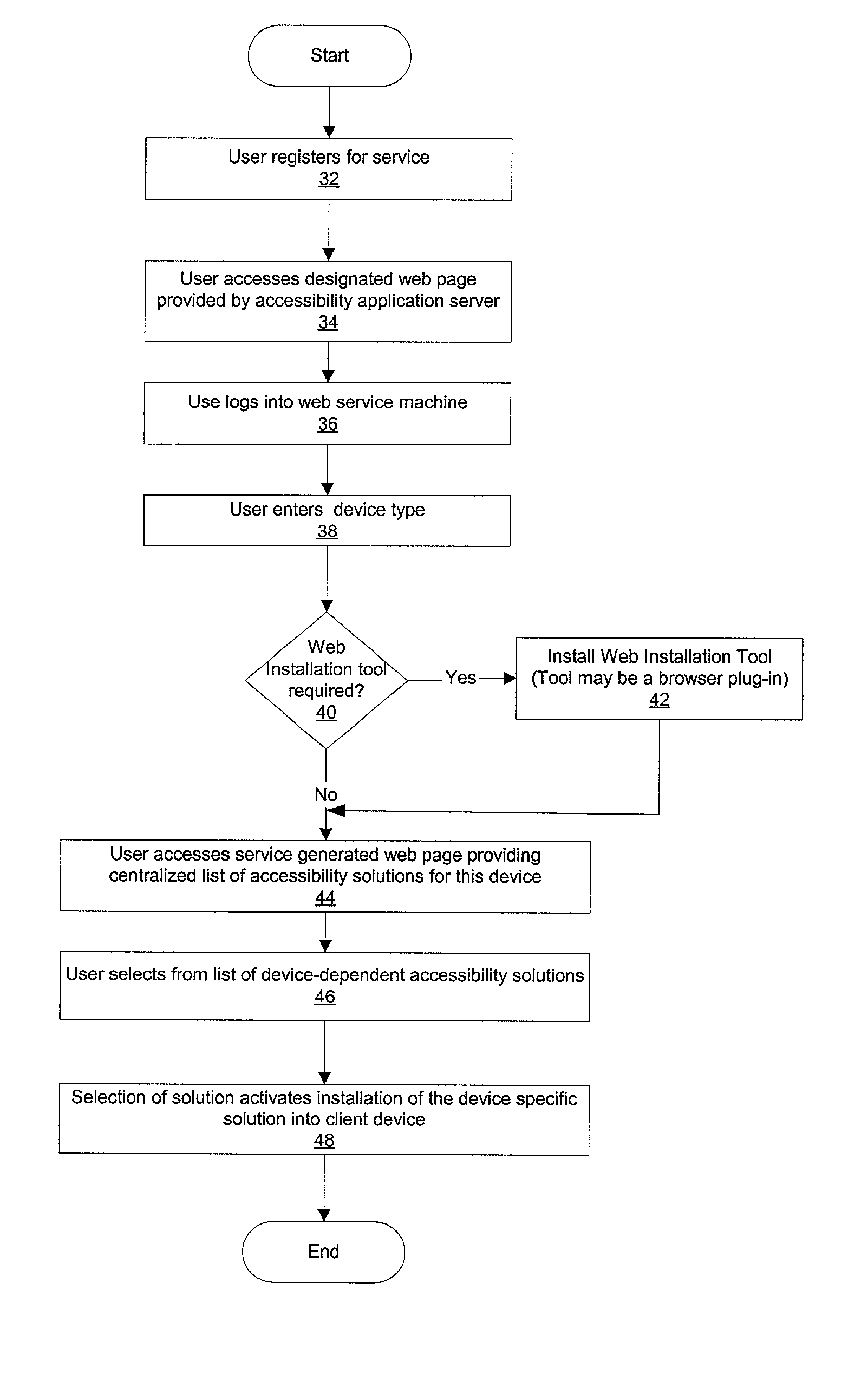
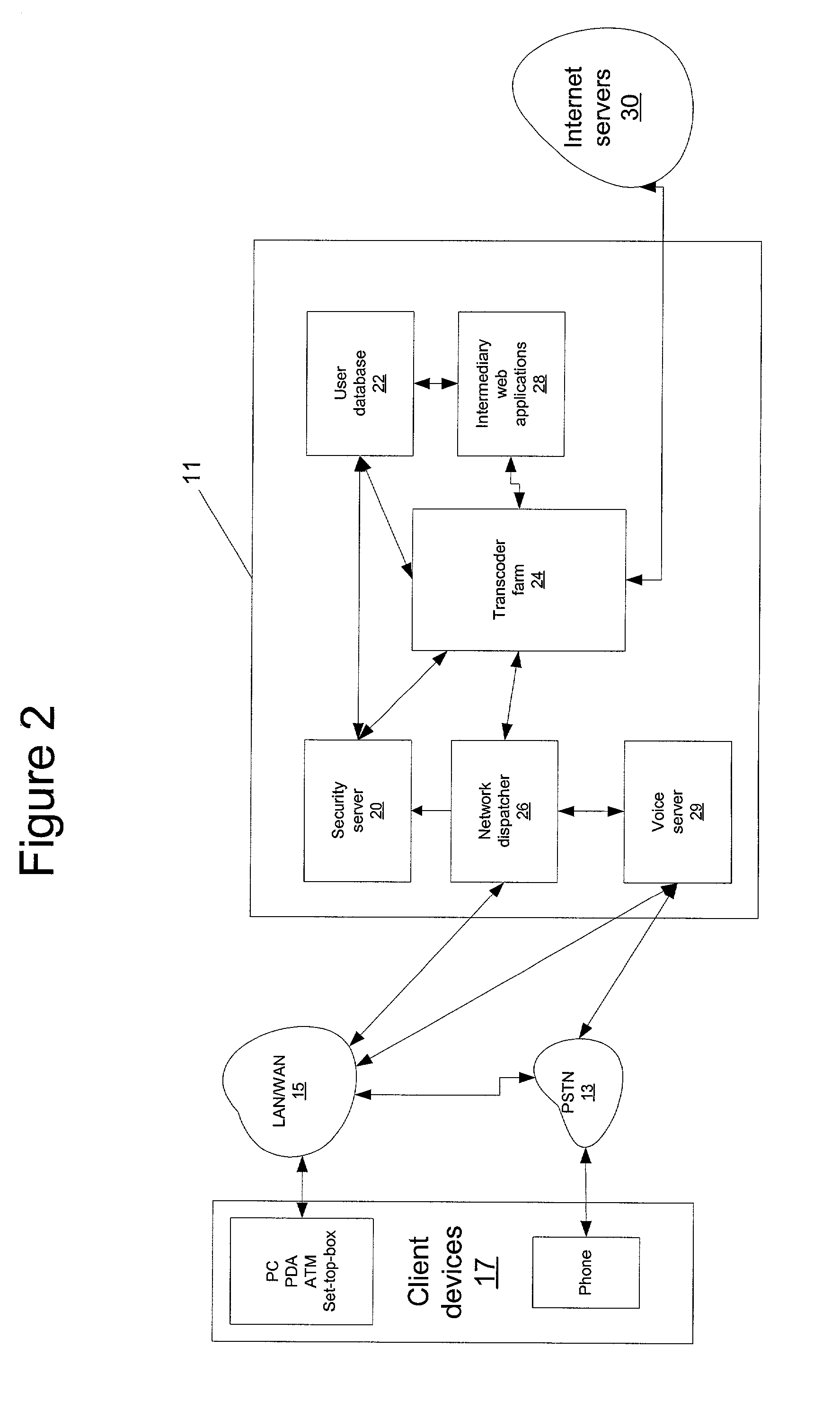
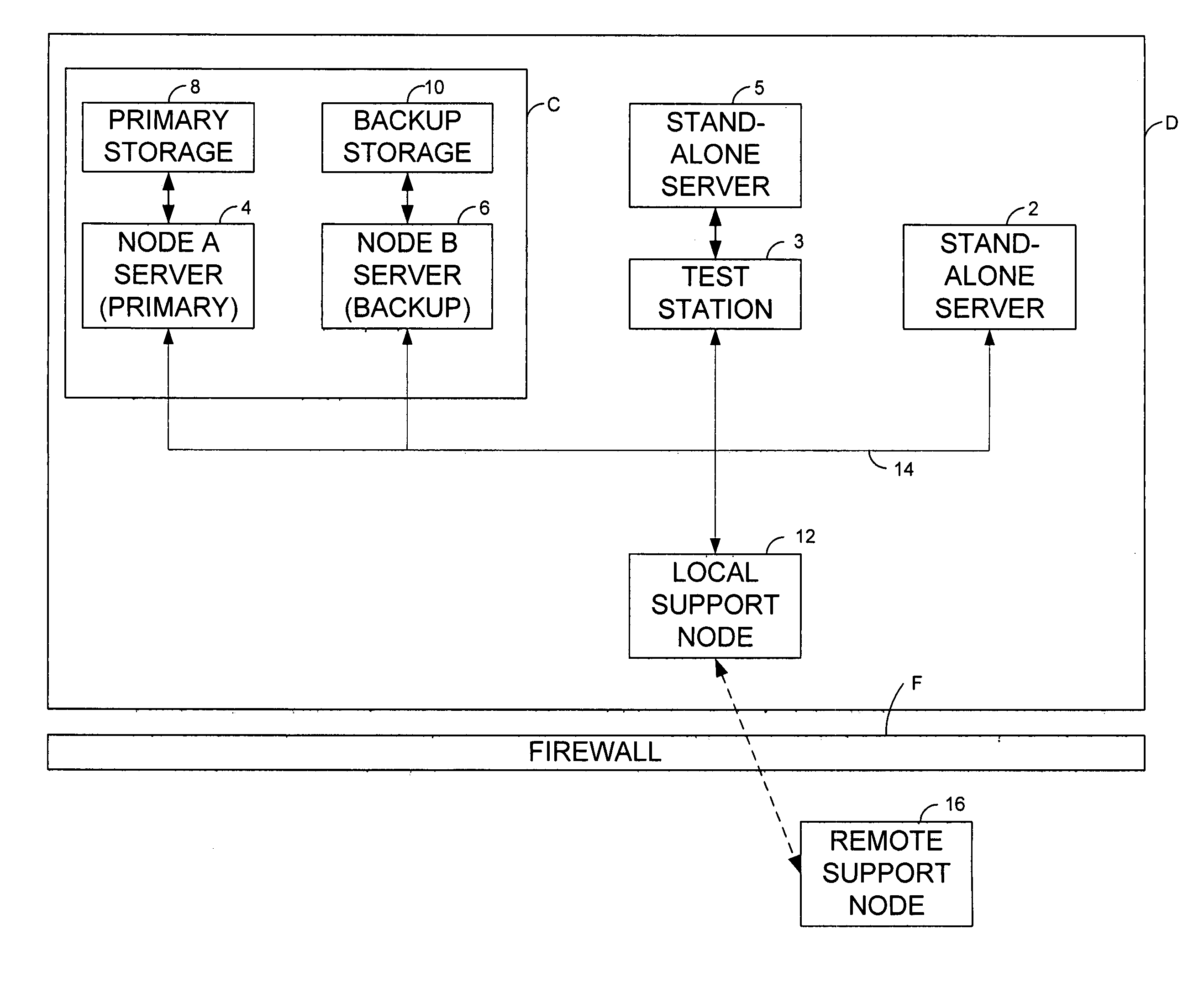
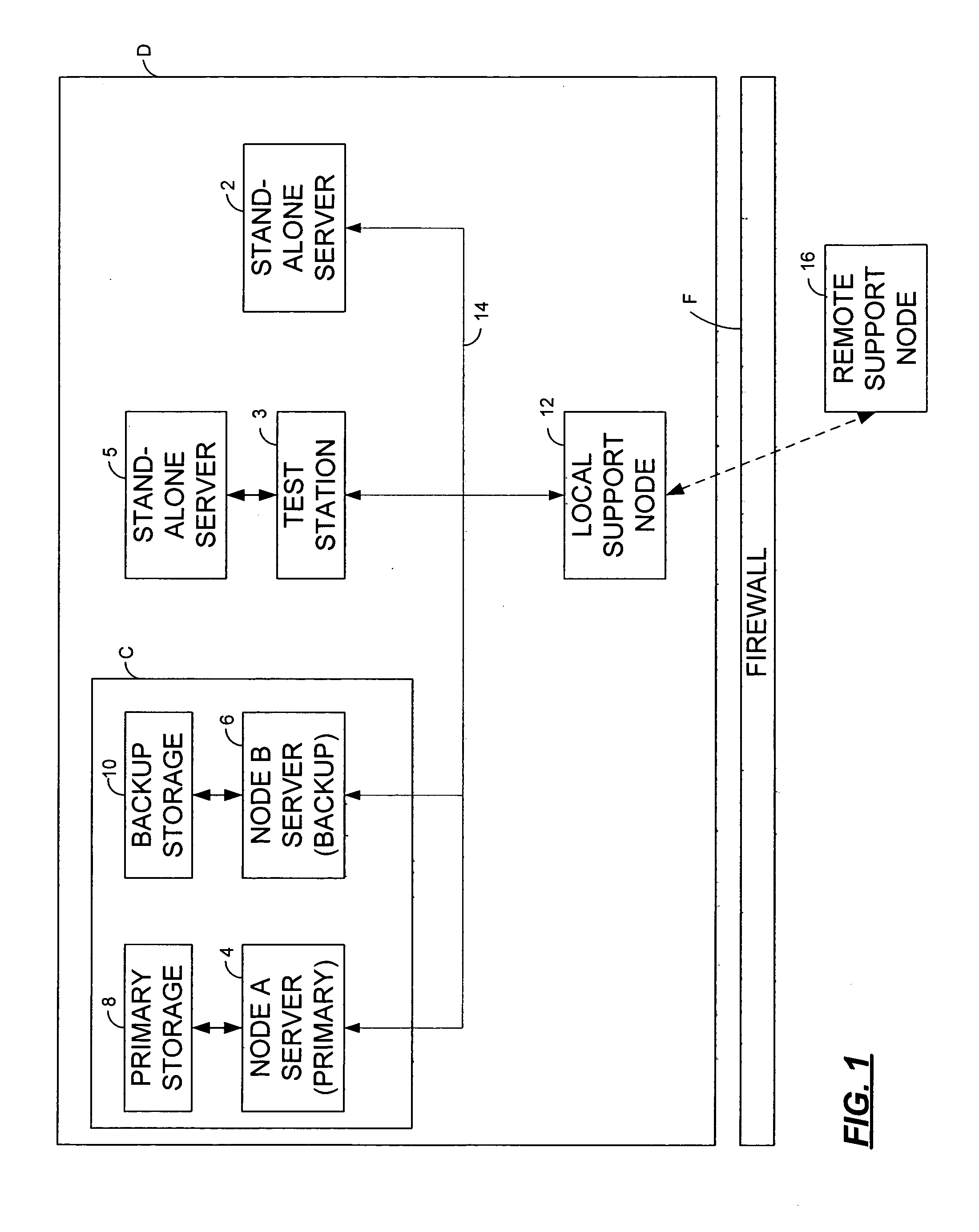
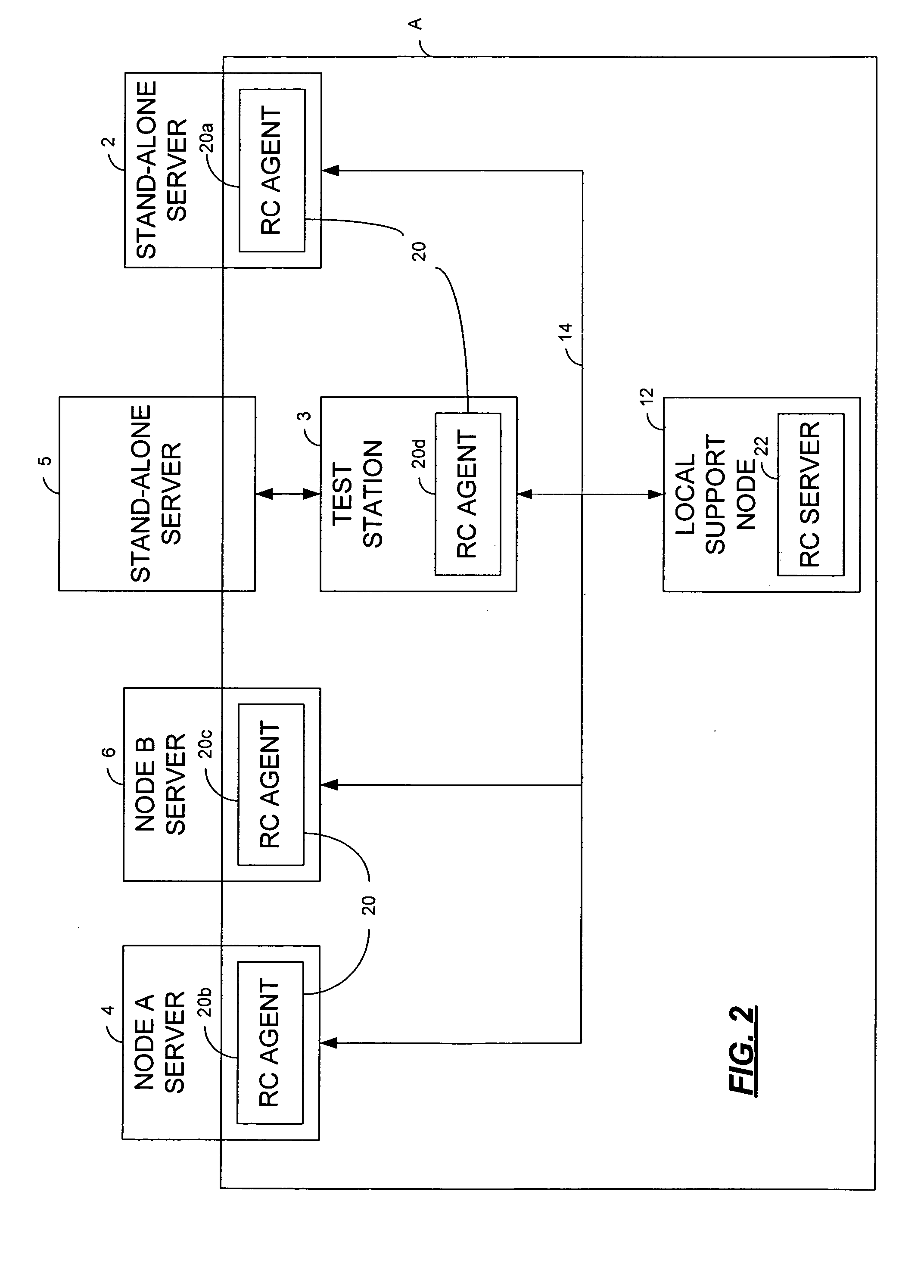
Method and system for providing a central repository for client-specific accessibility
InactiveUS20030061317A1Digital data information retrievalMultiple digital computer combinationsService provisionTranscoding
A method and system that provide a central repository for client specific accessibility applications to a user from an accessible server. The repository is updated on a periodic basis with new solutions provided by the service provider, who also manages licensing agreements between the user and the owner of the accessibility application. Accessibility programs, such as page magnification, screen readers, background changes, input modification, etc., are downloaded into the client device being used by the user customer by clicking link buttons from a web page generated by the service provider's server. The accessibility programs downloaded are then resident on the client device until changed by the user. In a preferred embodiment, the service provider also provides a universal transcoding service to apply the user selected accessibility transformations to any type of client device used by the user.
Owner:IBM CORP
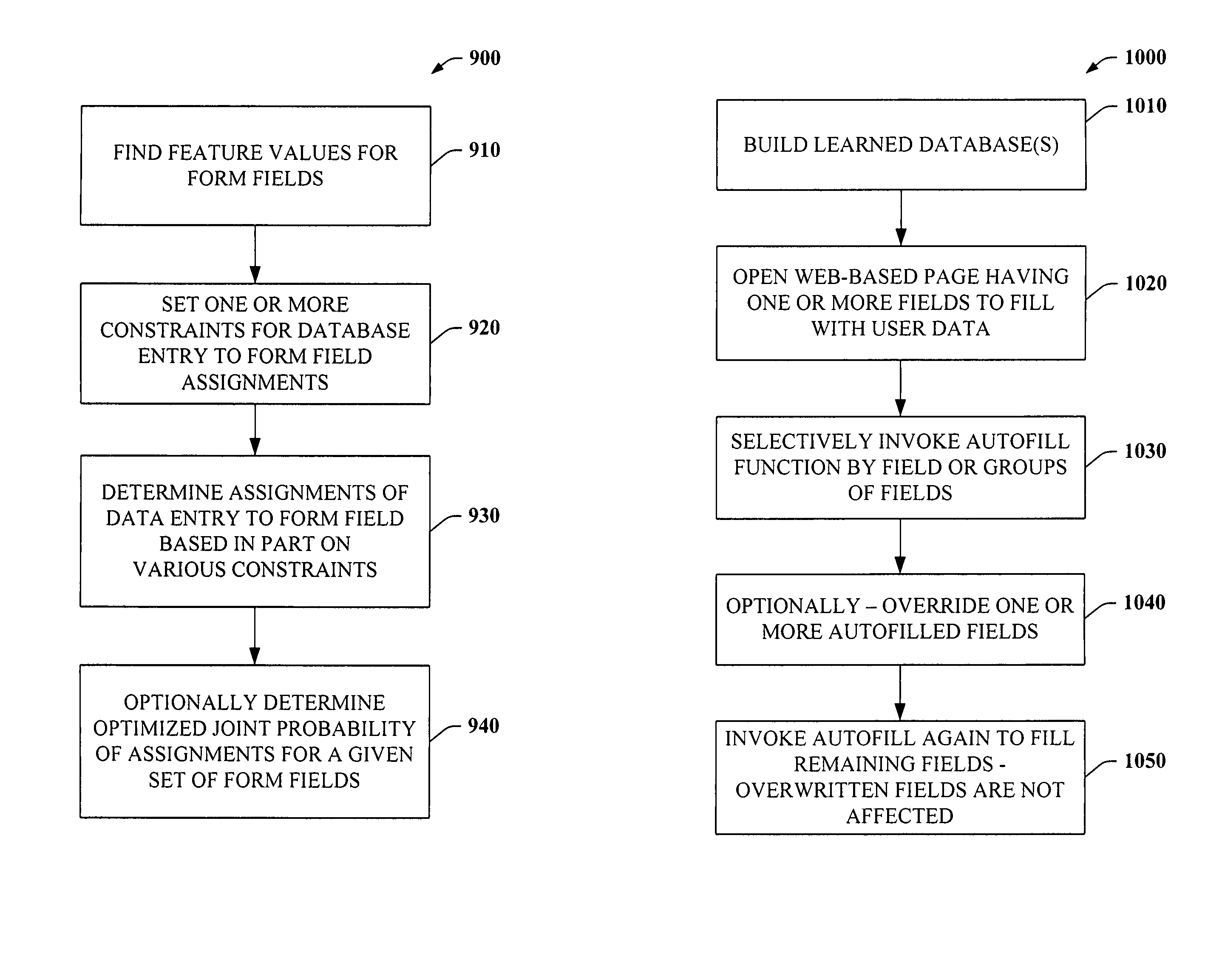
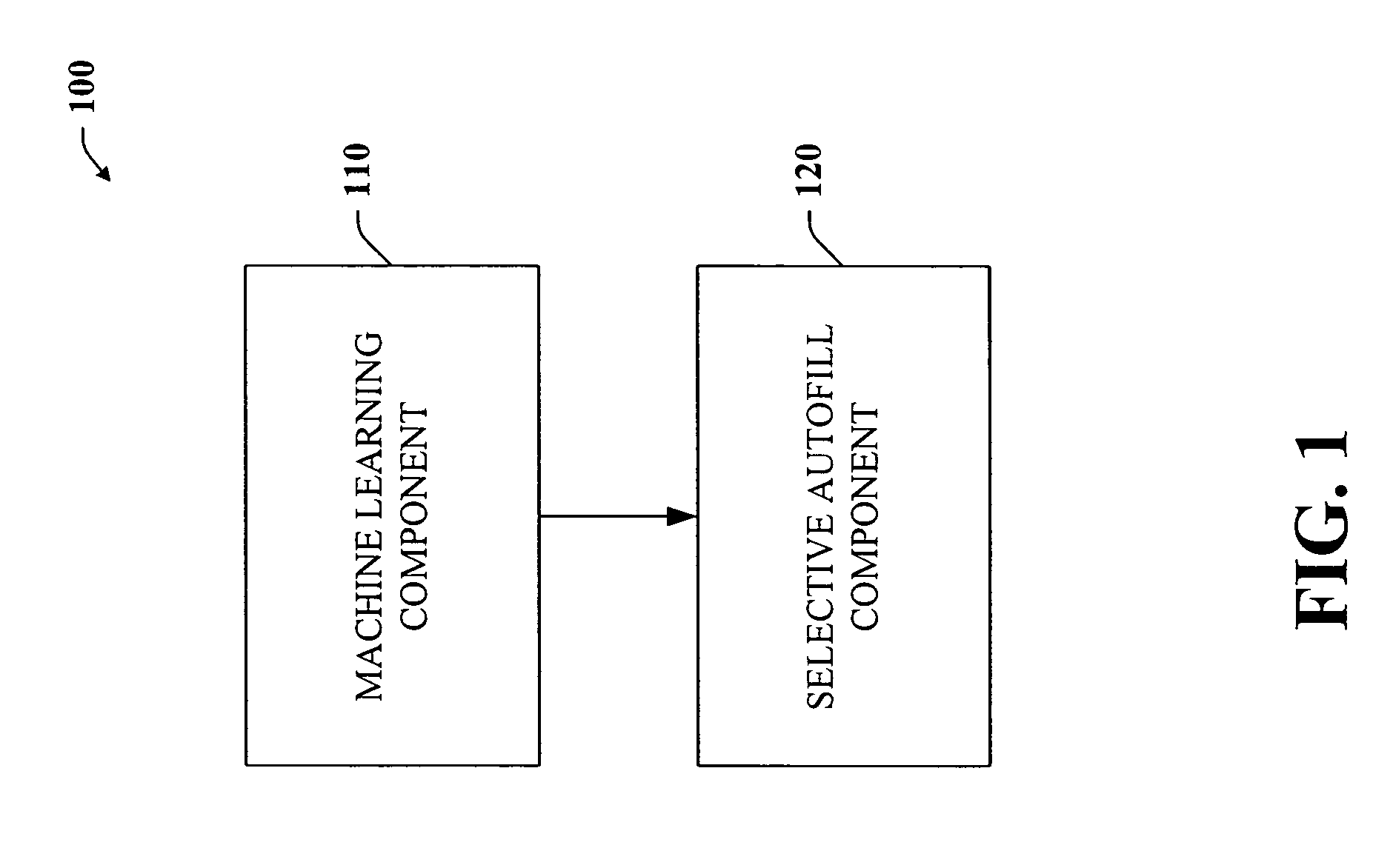
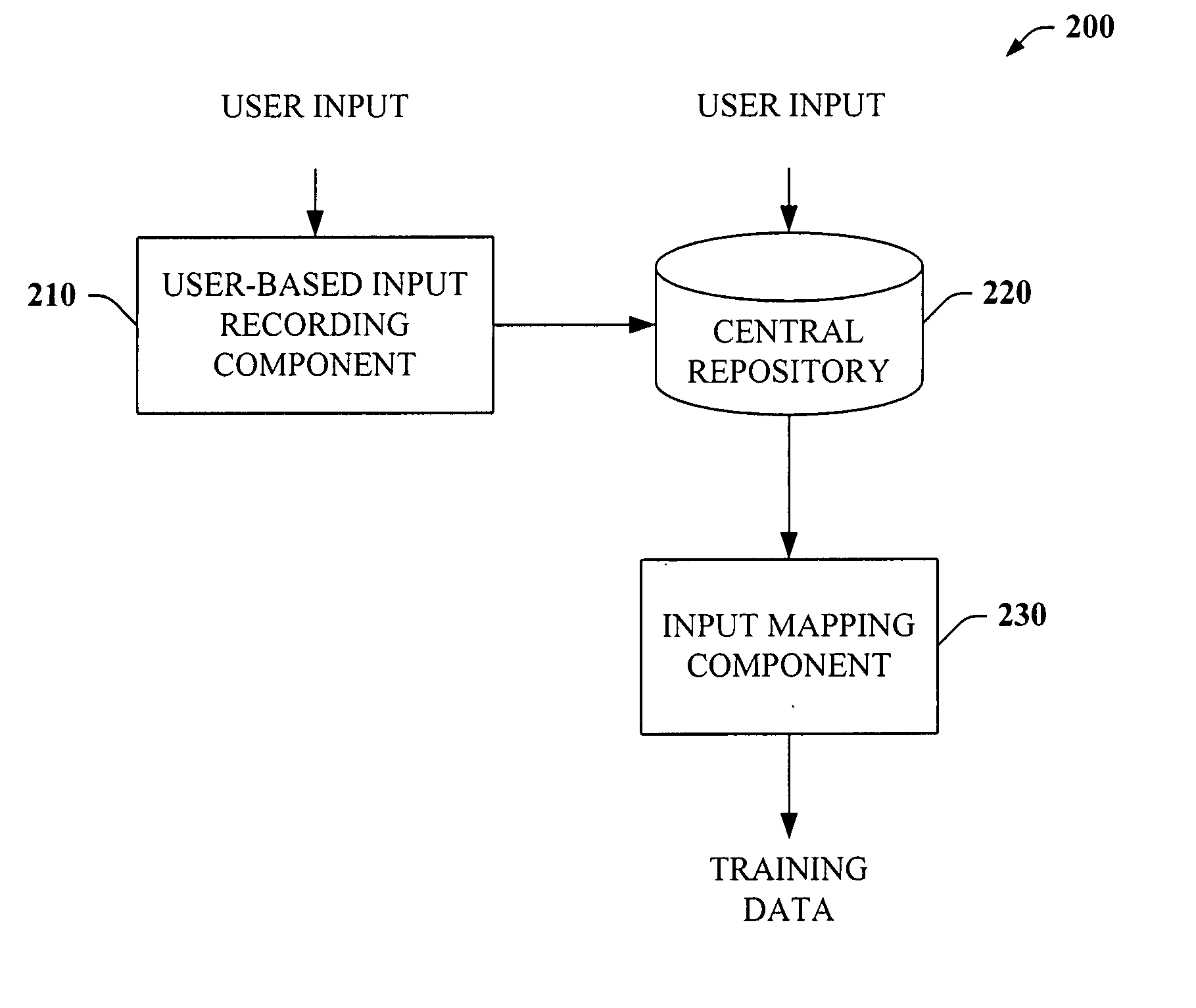
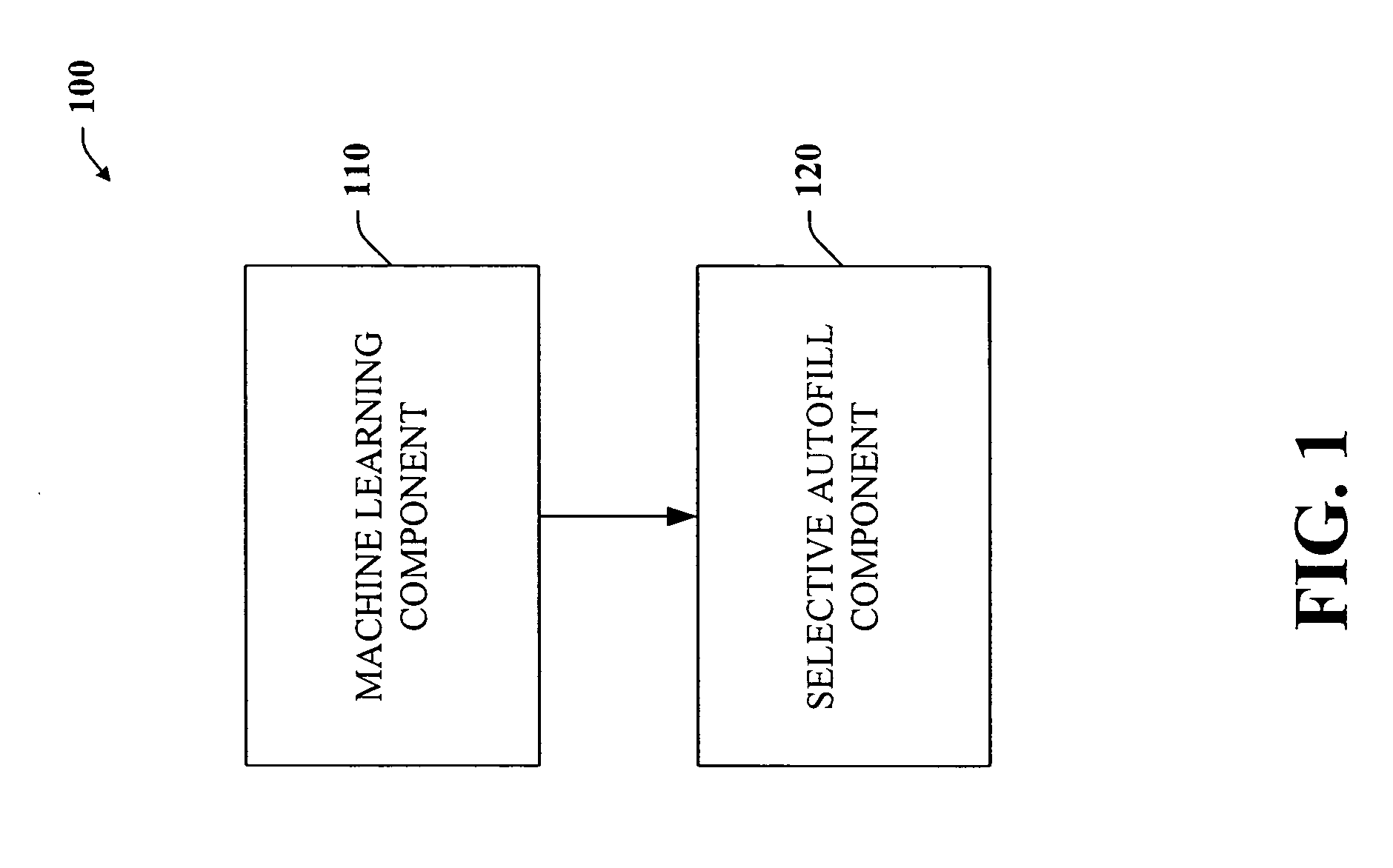
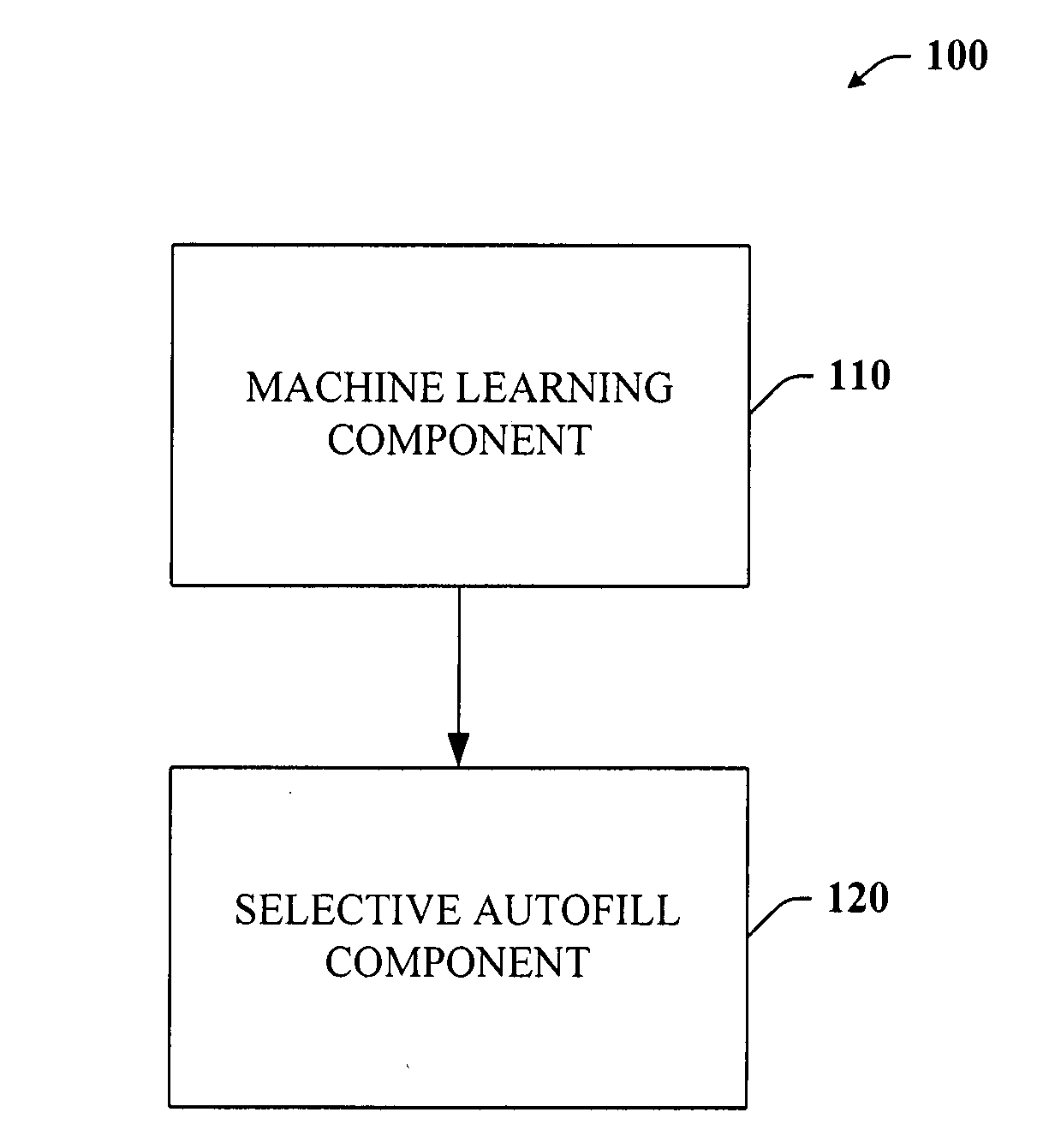
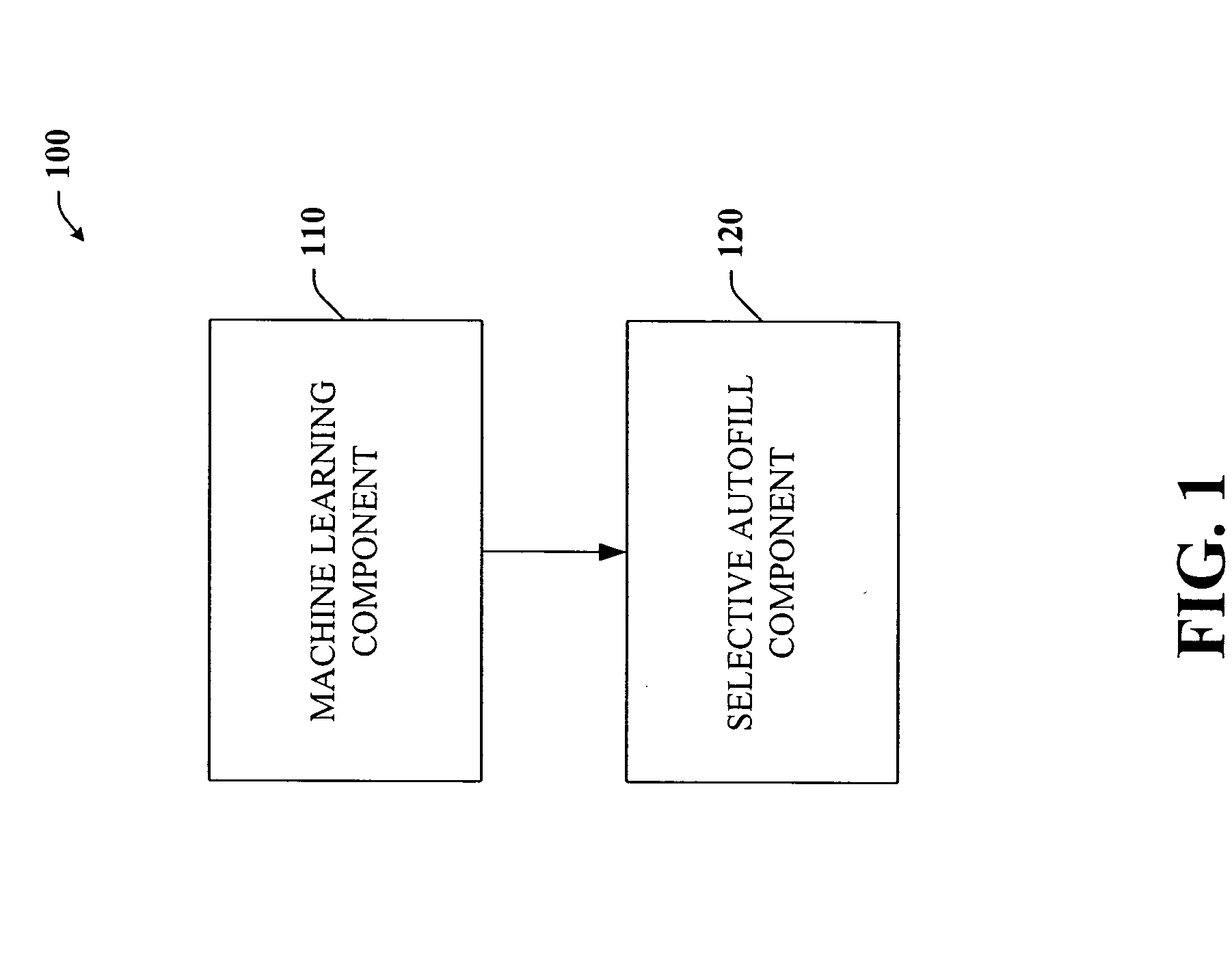
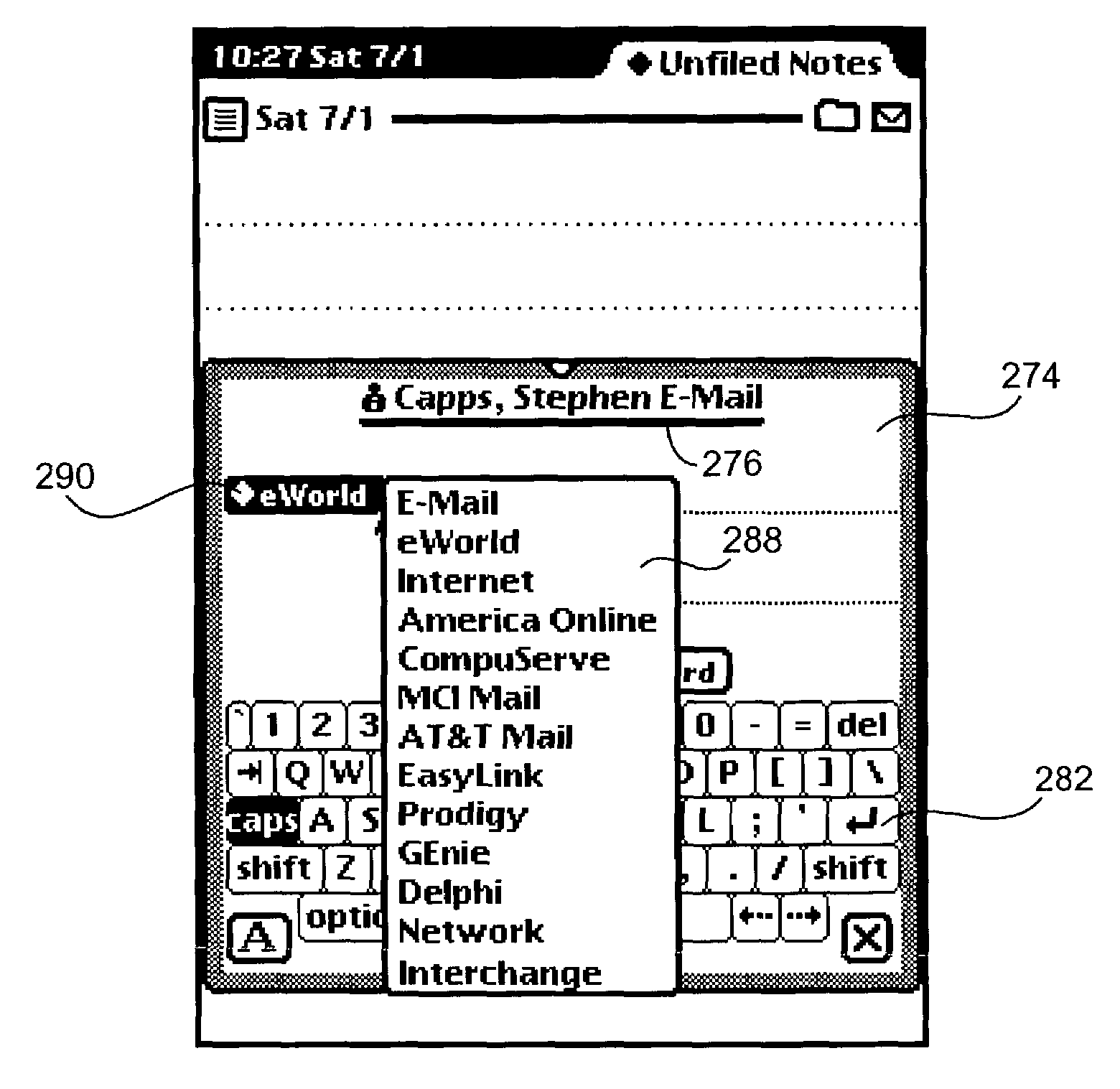
Intelligent autofill
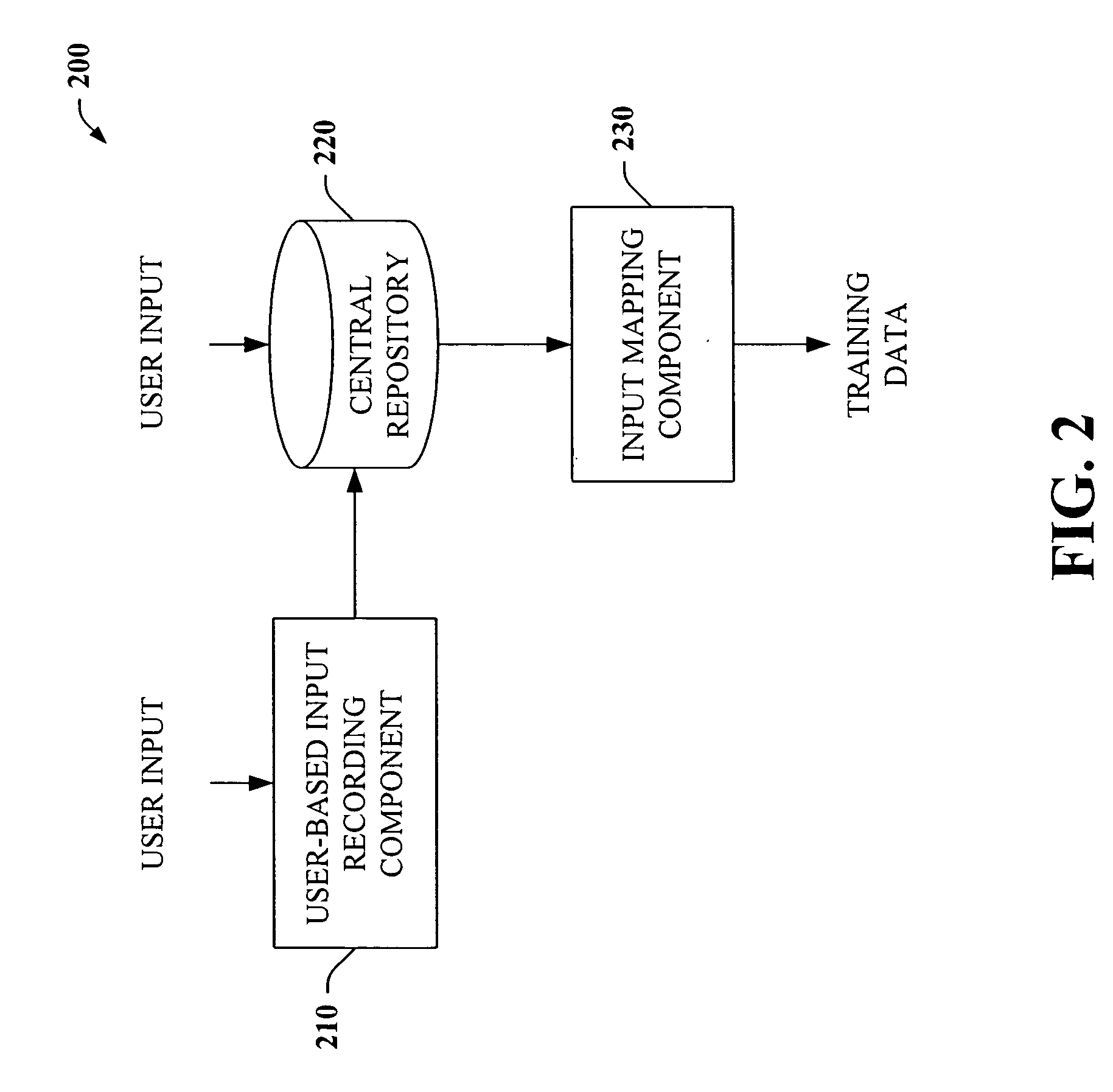
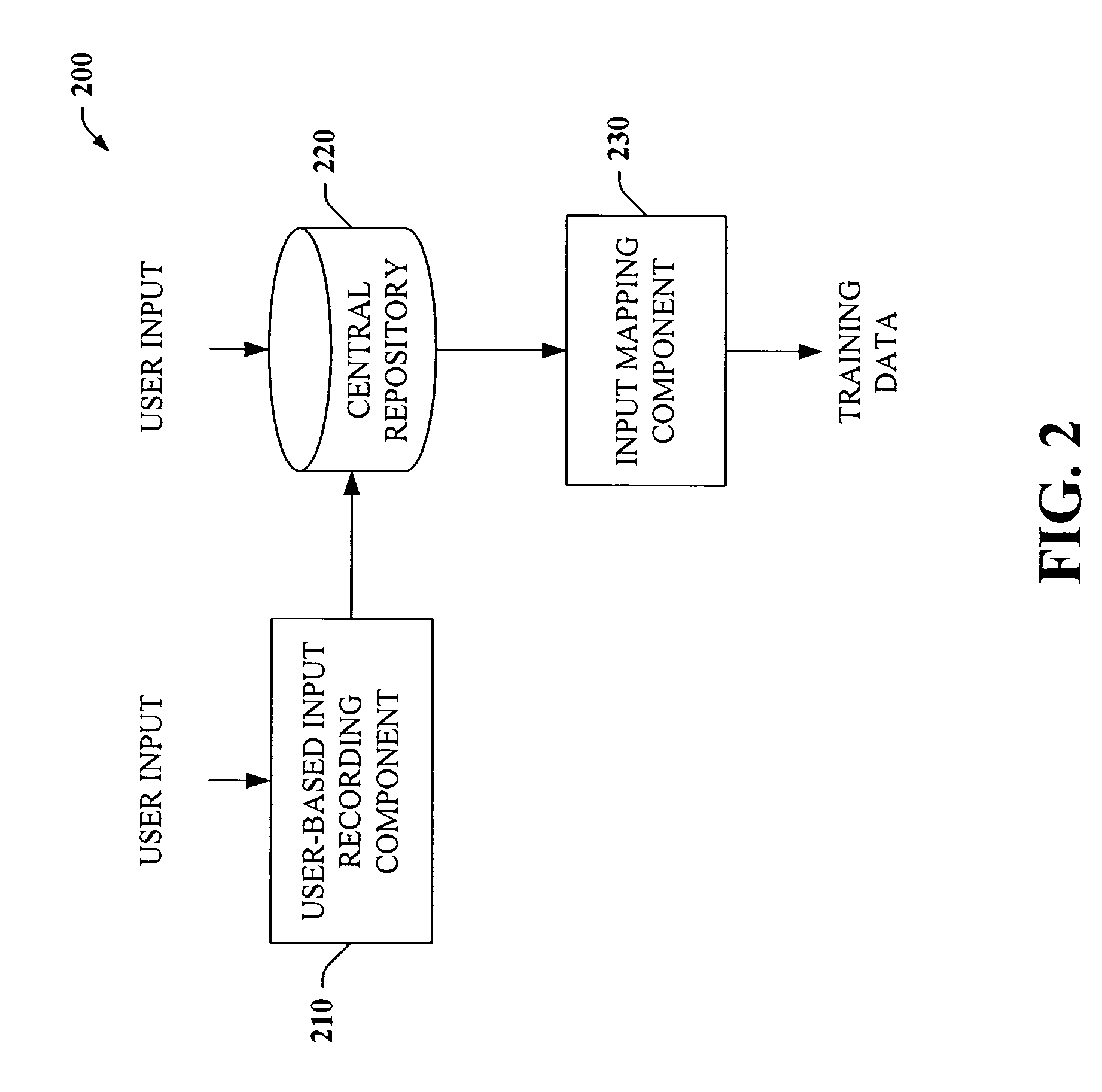
InactiveUS7254569B2Minimize effortData augmentationData processing applicationsMetal-working feeding devicesData miningData entry
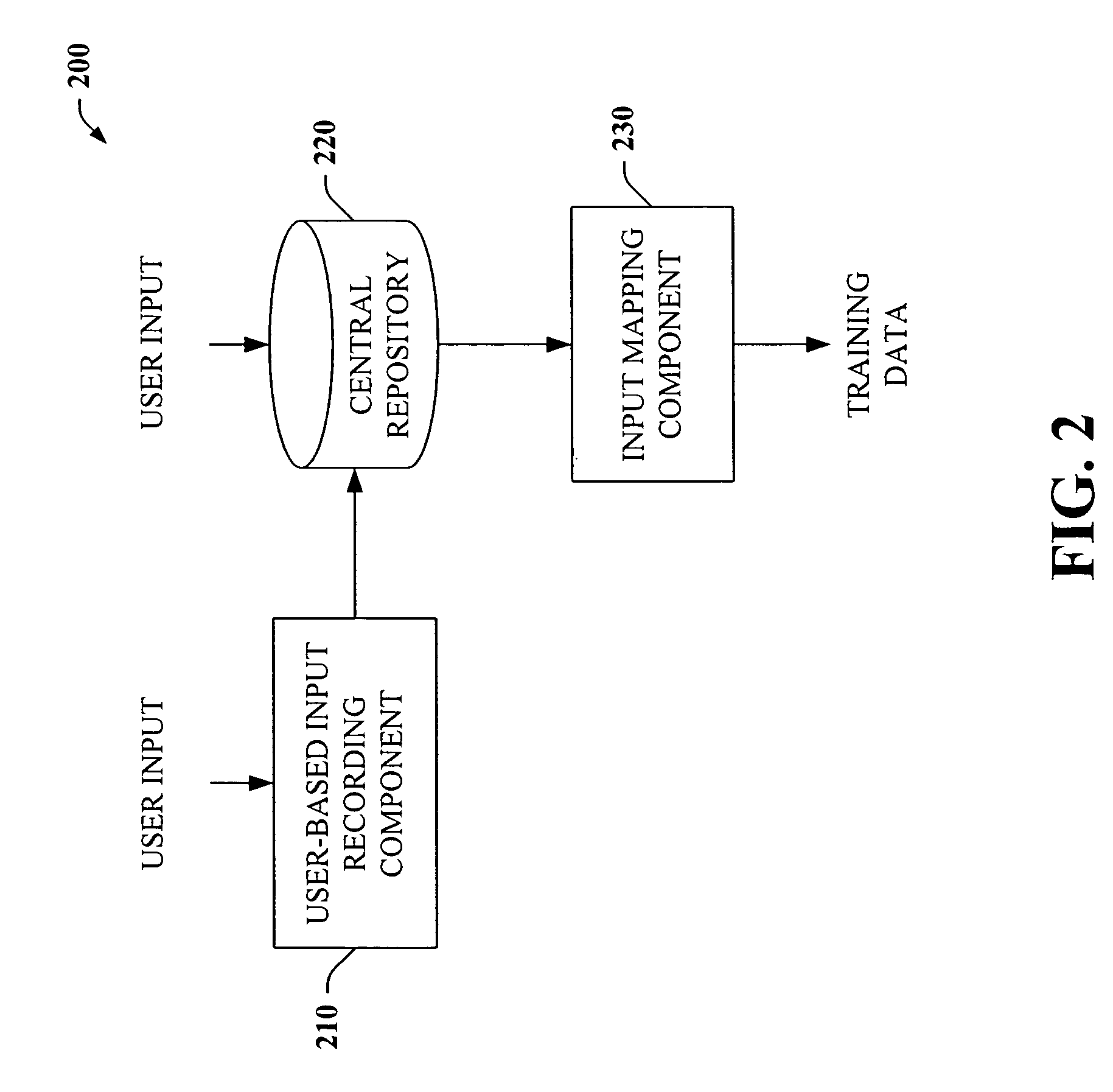
The present invention provides a unique system and method that can employ machine learning techniques to automatically fill one or more fields across a diverse array of web forms. In particular, one or more instrumented tools can collect input or entries of form fields. Machine learning can be used to learn what data corresponds to which fields or types of fields. The input can be sent to a central repository where other databases can be aggregated as well. This input can be provided to a machine learning system to learn how to predict the desired outputs. Alternatively or in addition, learning can be performed in part by observing entries and then adapting the autofill component accordingly. Furthermore, a number of features of database fields as well as constraints can be employed to facilitate assignments of database entries to form values—particularly when the web form has never been seen before by the autofill system.
Owner:MICROSOFT TECH LICENSING LLC
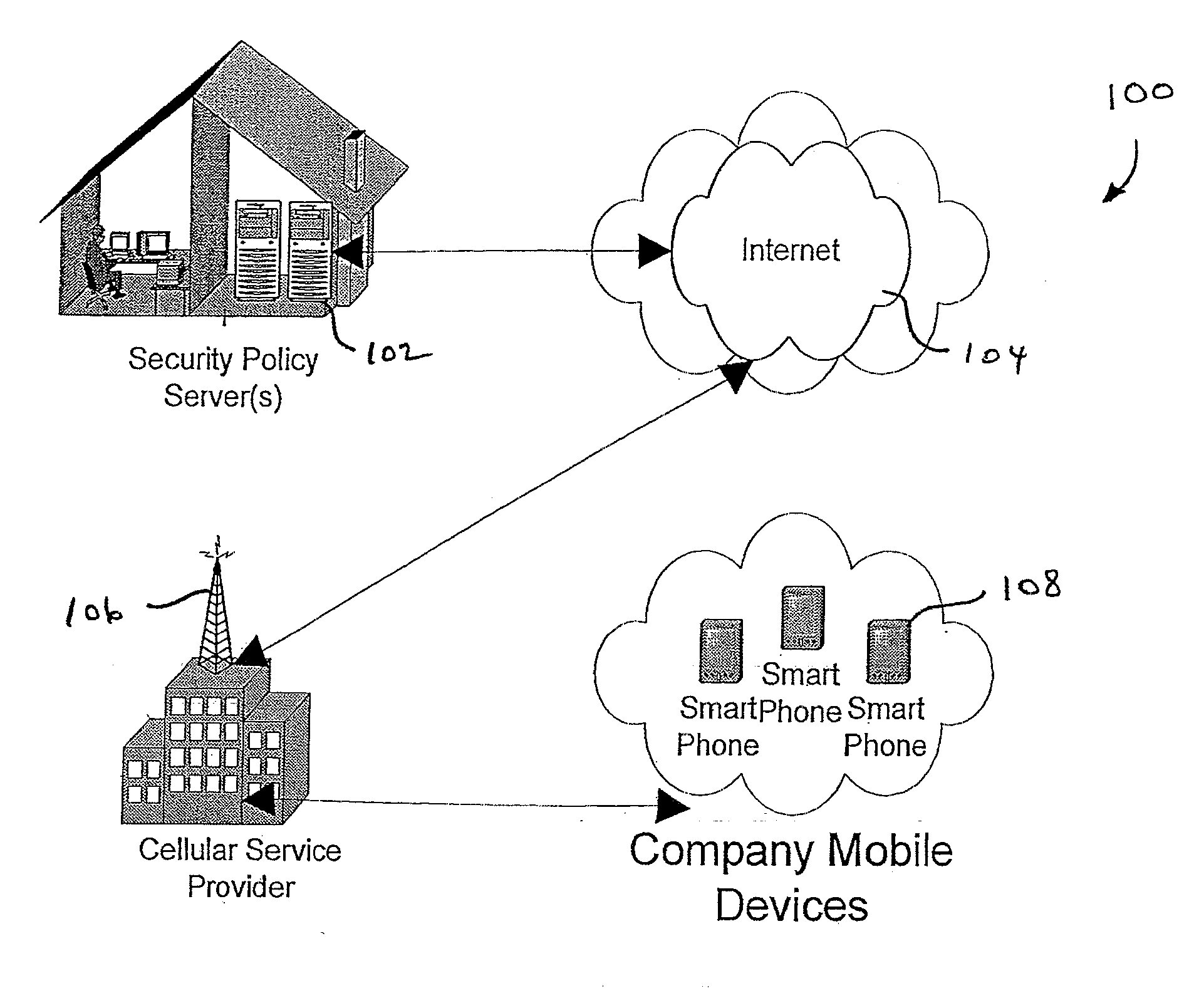
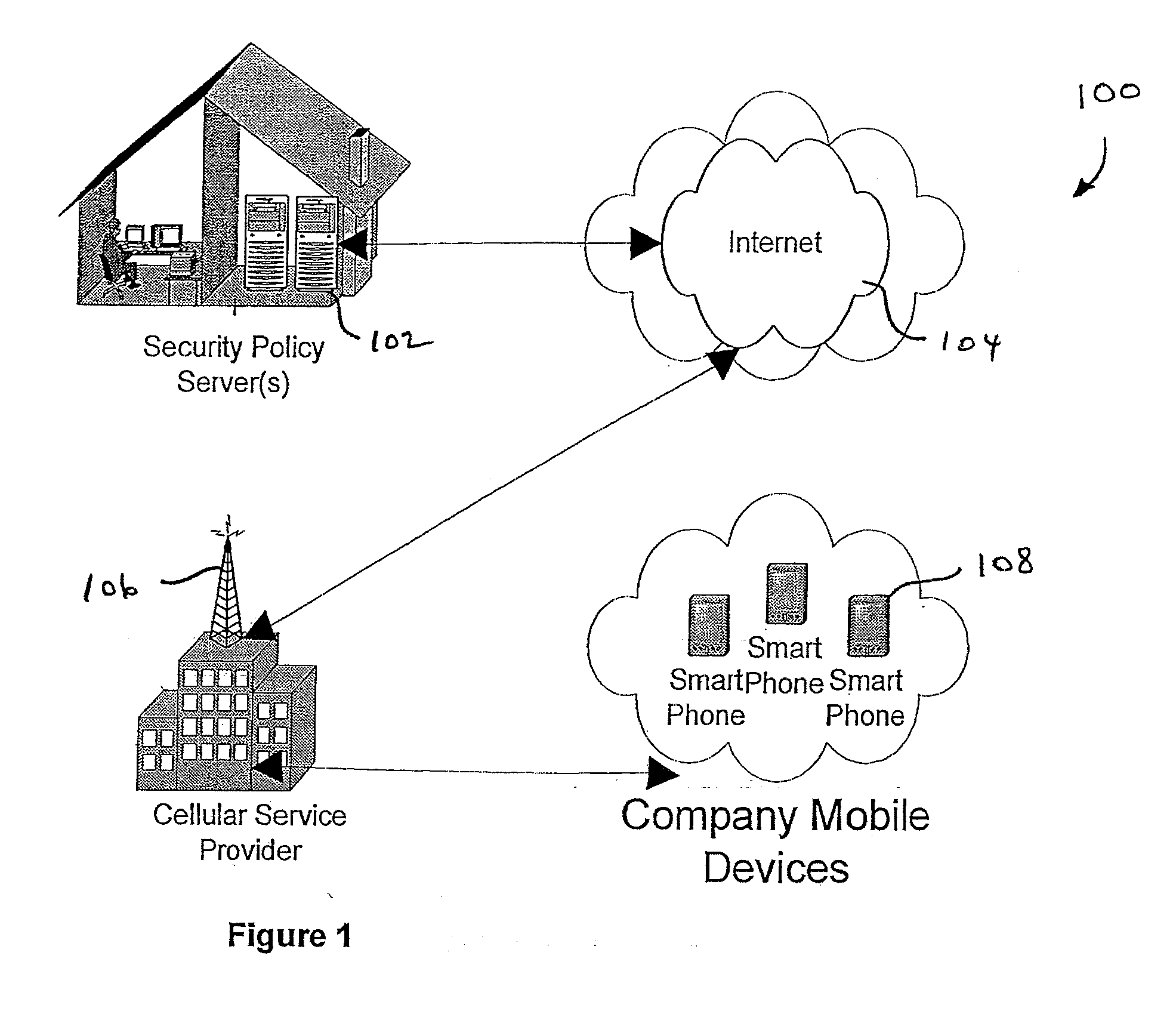
Centralized Dynamic Security Control for a Mobile Device Network
InactiveUS20070266422A1Well formedSecurity arrangementSpecial data processing applicationsTimerSecurity system
An security system for an enterprise network and data automates the revision, deployment, enforcement, auditing and control of security policies on mobile devices connected to said enterprise network, through automated communication between a security policy server and the mobile device. Control of the security system is centralized through administrative control of security policies stored on the security policy server. Automation of deployment of security policies to mobile devices occurs through transparent background communication and transfer of updated policies either triggered by a change in a security policy within the central repository of security policies or upon the expiration of a certain time period during which no policies were downloaded to the mobile device. When the mobile device is not in compliance with a security policy, a software security agent operating thereon limits access to said enterprise network and enterprise data. To aid in preventing the overwhelming of the enterprise network and the security policy server as a result of to many synchronization communications coming from too many mobile devices, a randomized timer is set by the software security agent upon receipt by the mobile device of a synchronization command from the security policy server.
Owner:SQUARE 1 BANK
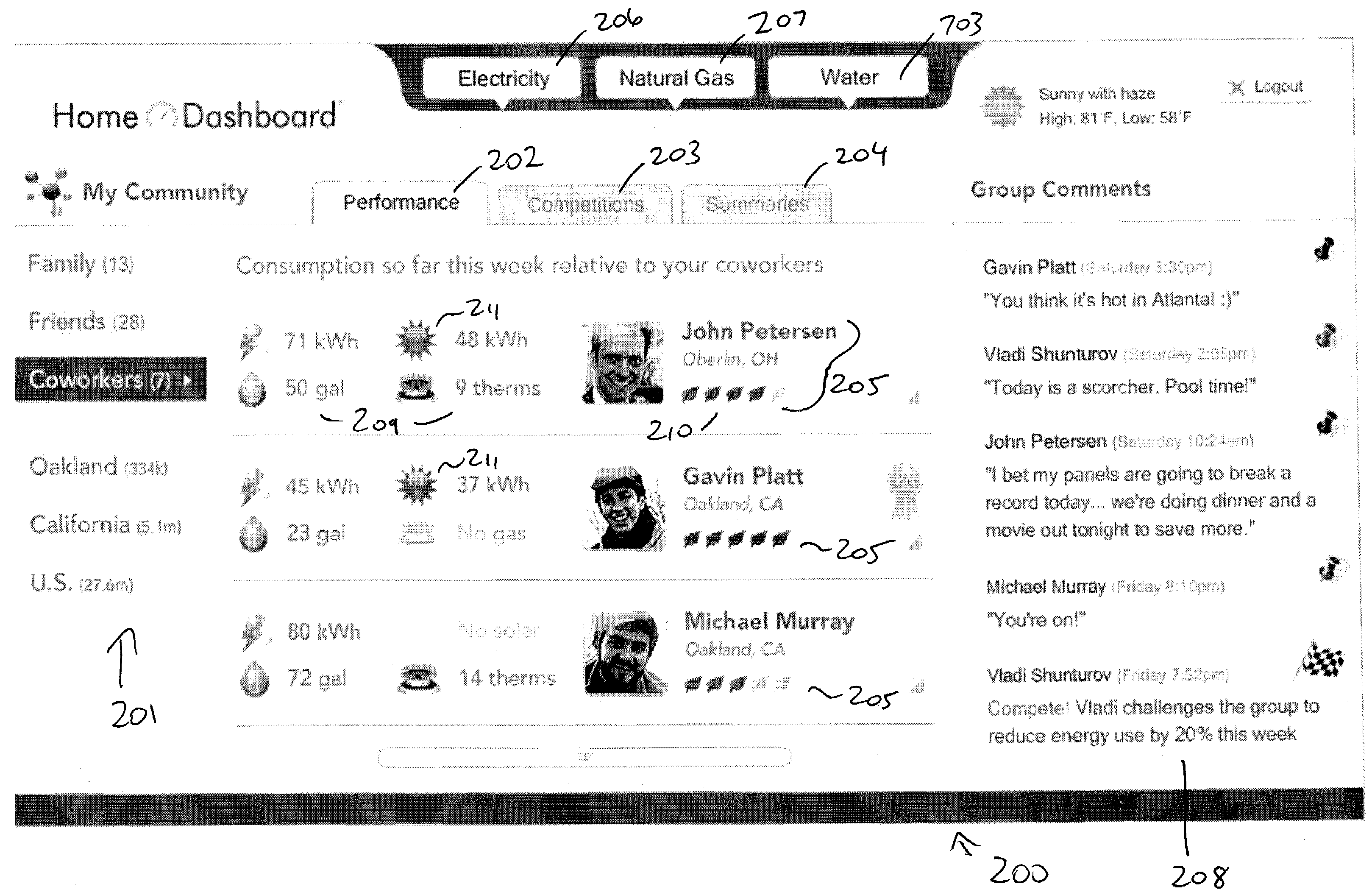
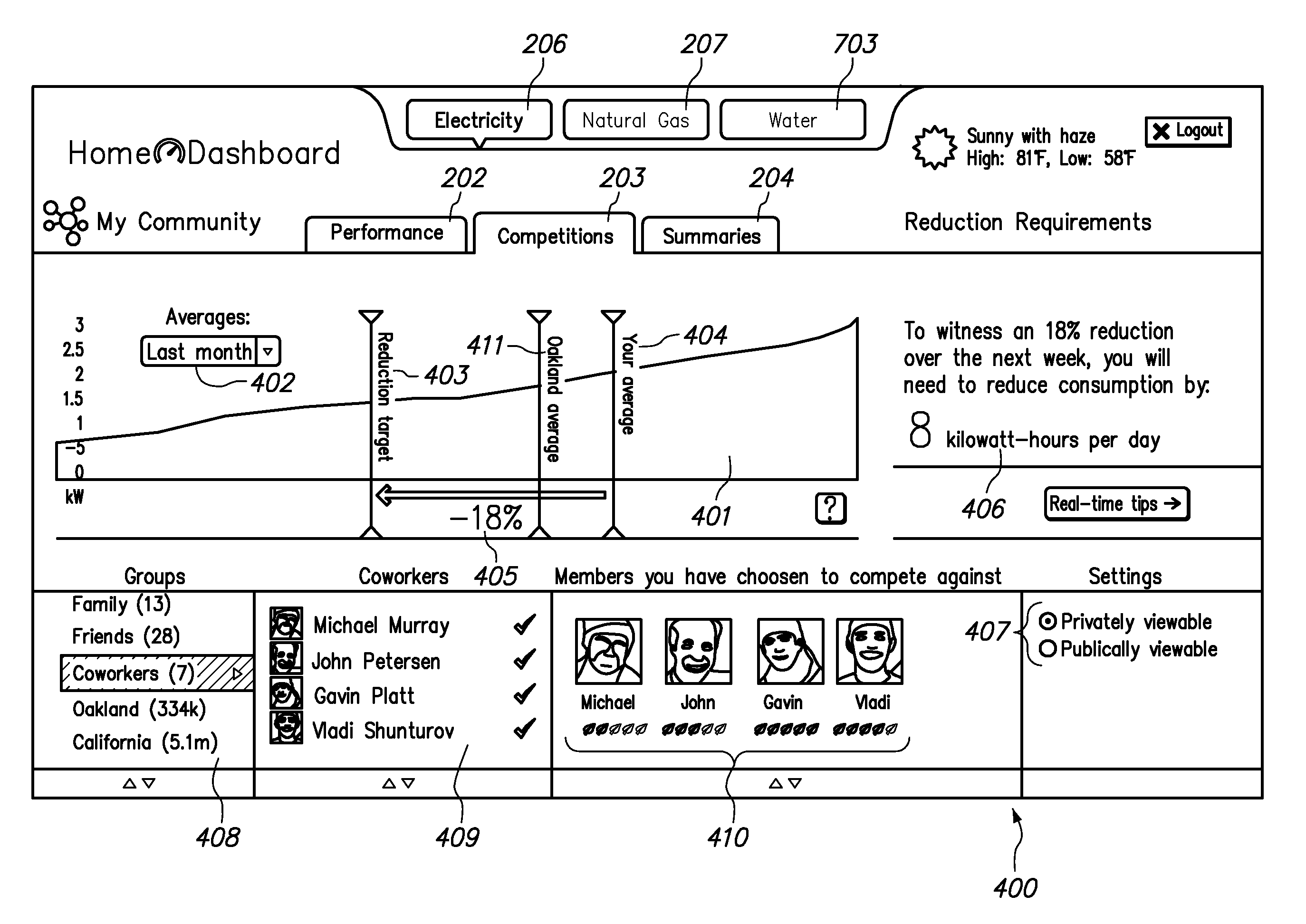
Collecting, sharing, comparing, and displaying resource usage data
ActiveUS20080306985A1Easy to compareThe effect is highlightedOffice automationCommerceGraphicsInteractive displays
Resource usage data is automatically collected for an individual, house-hold, family, organization, or other entity. The collected data is transmitted to a central repository, where it is stored and compared with real-time and / or historical usage data by that same entity and / or with data from other sources. Graphical, interactive displays and reports of resource usage data are then made available. These displays can include comparisons with data representing any or all of community averages, specific entities, historical use, representative similarly-situated entities, and the like. Resource usage data can be made available within a social networking context, published, and / or selectively shared with other entities.
Owner:ABL IP HLDG
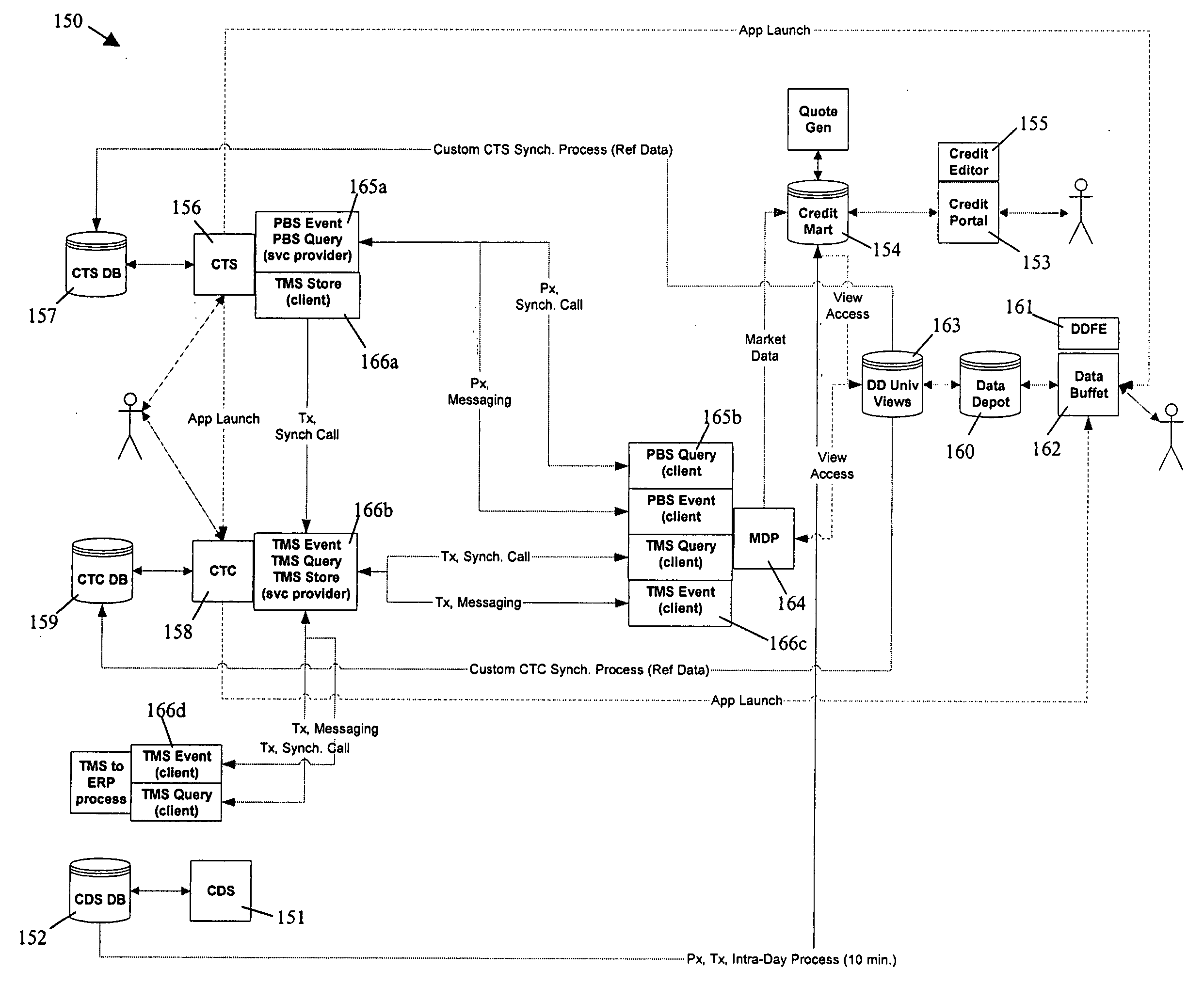
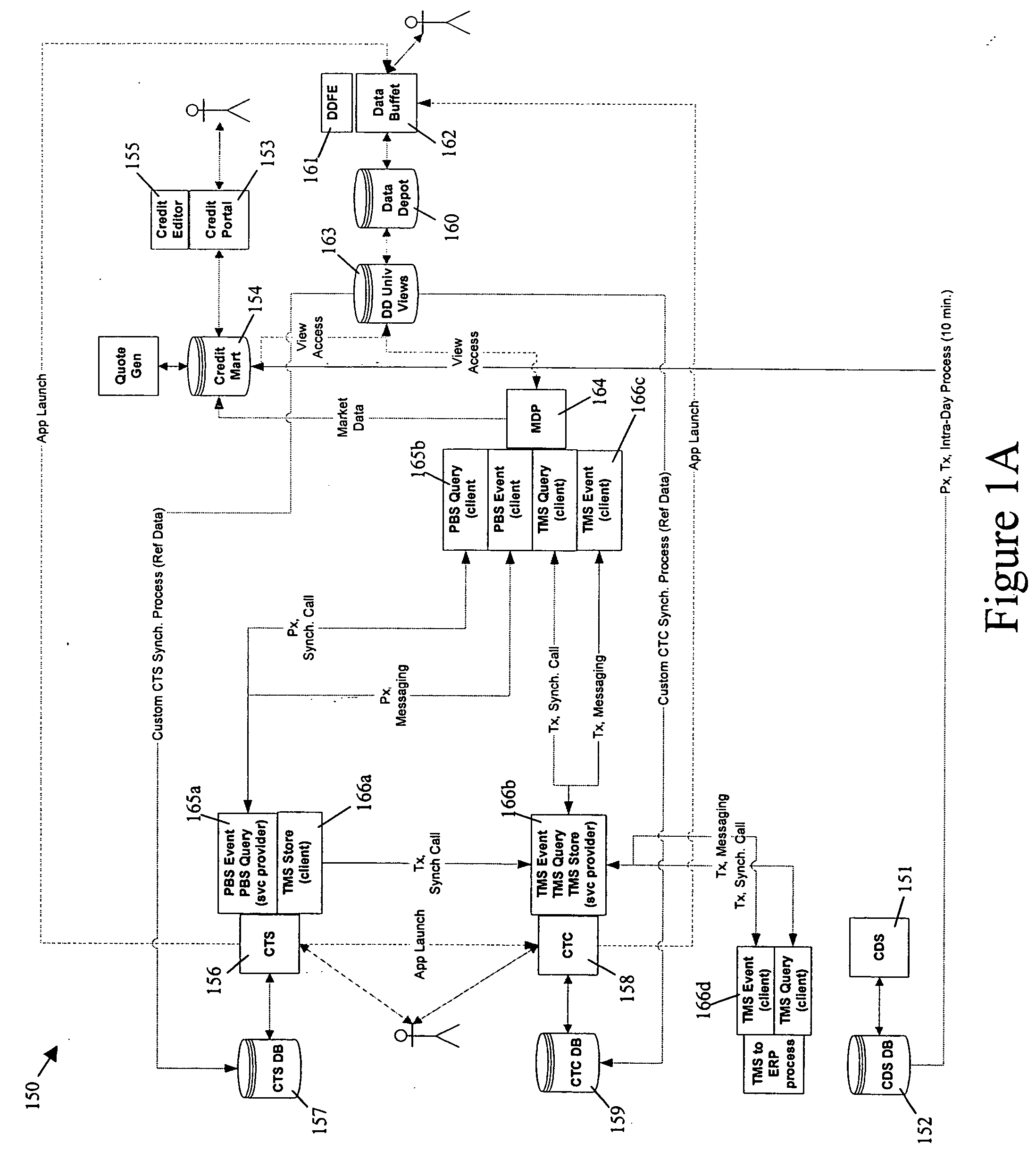
Apparatus, method and system for providing an electronic marketplace for trading credit default swaps and other financial instruments, including a trade management service system
ActiveUS20050149428A1Improve accessibilityEasy to deployFinanceCoin/paper handlersTransaction managementTransaction data
A method and system for providing integrated credit derivative brokerage services, the method or system including or using a credit trading arrangement, a credit trade capture arrangement, a trade management service arrangement to process trade data for the credit trading arrangement and the credit trade capture arrangement, and a central repository arrangement to store market data and shared reference data.
Owner:GFI GROUP INC
Intelligent autofill
InactiveUS20050257148A1Minimize effortData augmentationData processing applicationsMetal-working feeding devicesDatabaseCentral repository
The present invention provides a unique system and method that can employ machine learning techniques to automatically fill one or more fields across a diverse array of web forms. In particular, one or more instrumented tools can collect input or entries of form fields. Machine learning can be used to learn what data corresponds to which fields or types of fields. The input can be sent to a central repository where other databases can be aggregated as well. This input can be provided to a machine learning system to learn how to predict the desired outputs. Alternatively or in addition, learning can be performed in part by observing entries and then adapting the autofill component accordingly. Furthermore, a number of features of database fields as well as constraints can be employed to facilitate assignments of database entries to form values—particularly when the web form has never been seen before by the autofill system.
Owner:MICROSOFT TECH LICENSING LLC
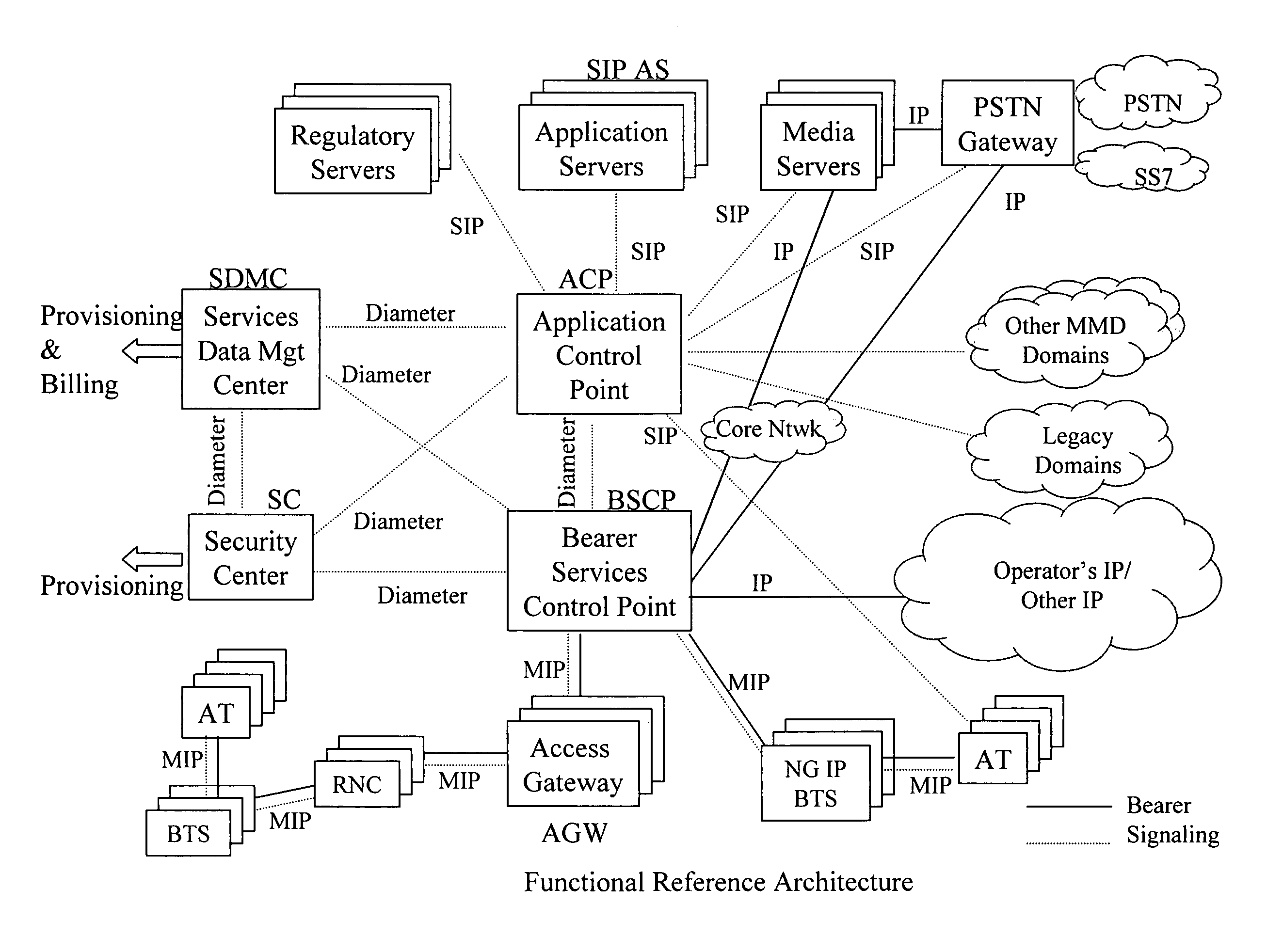
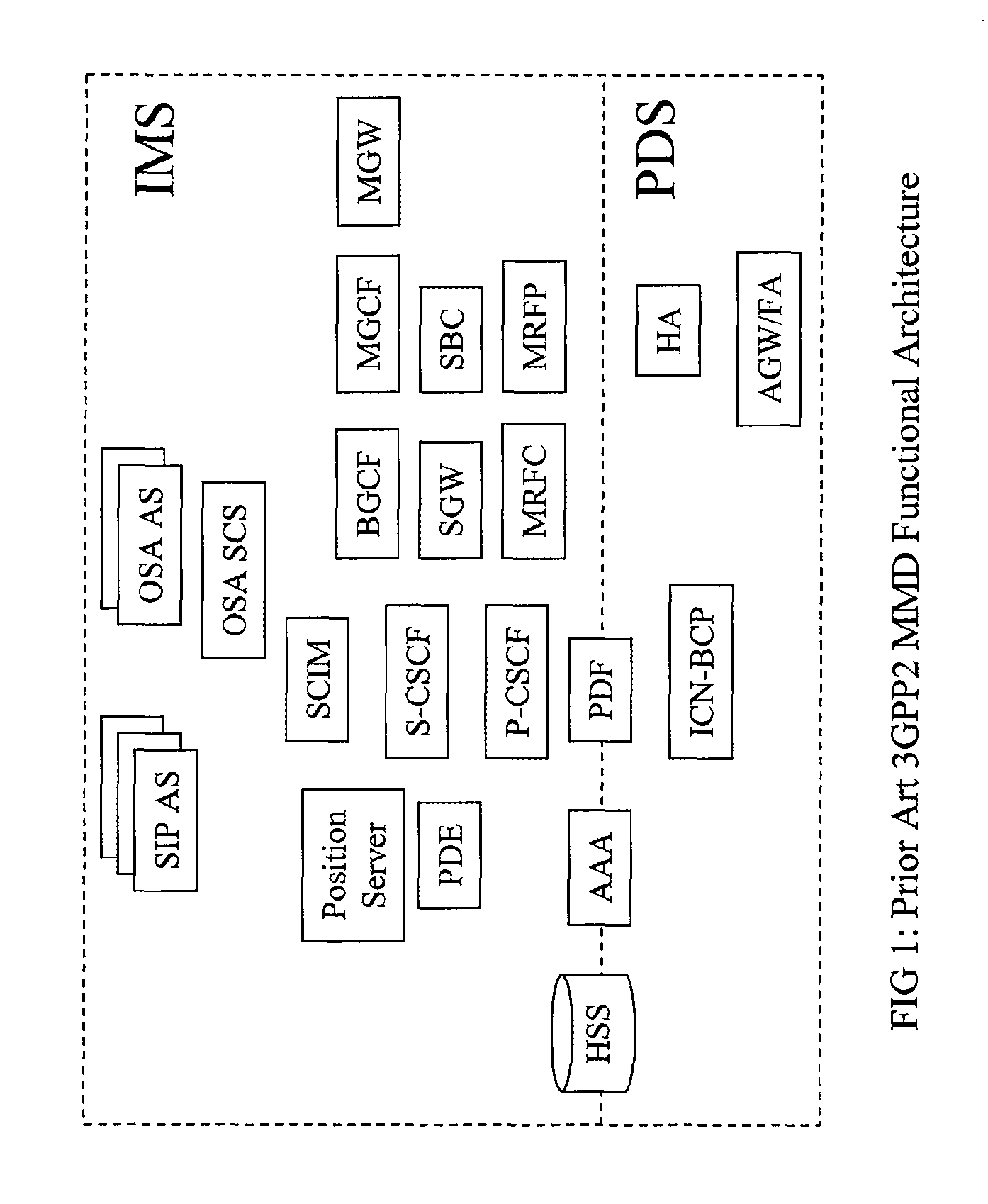
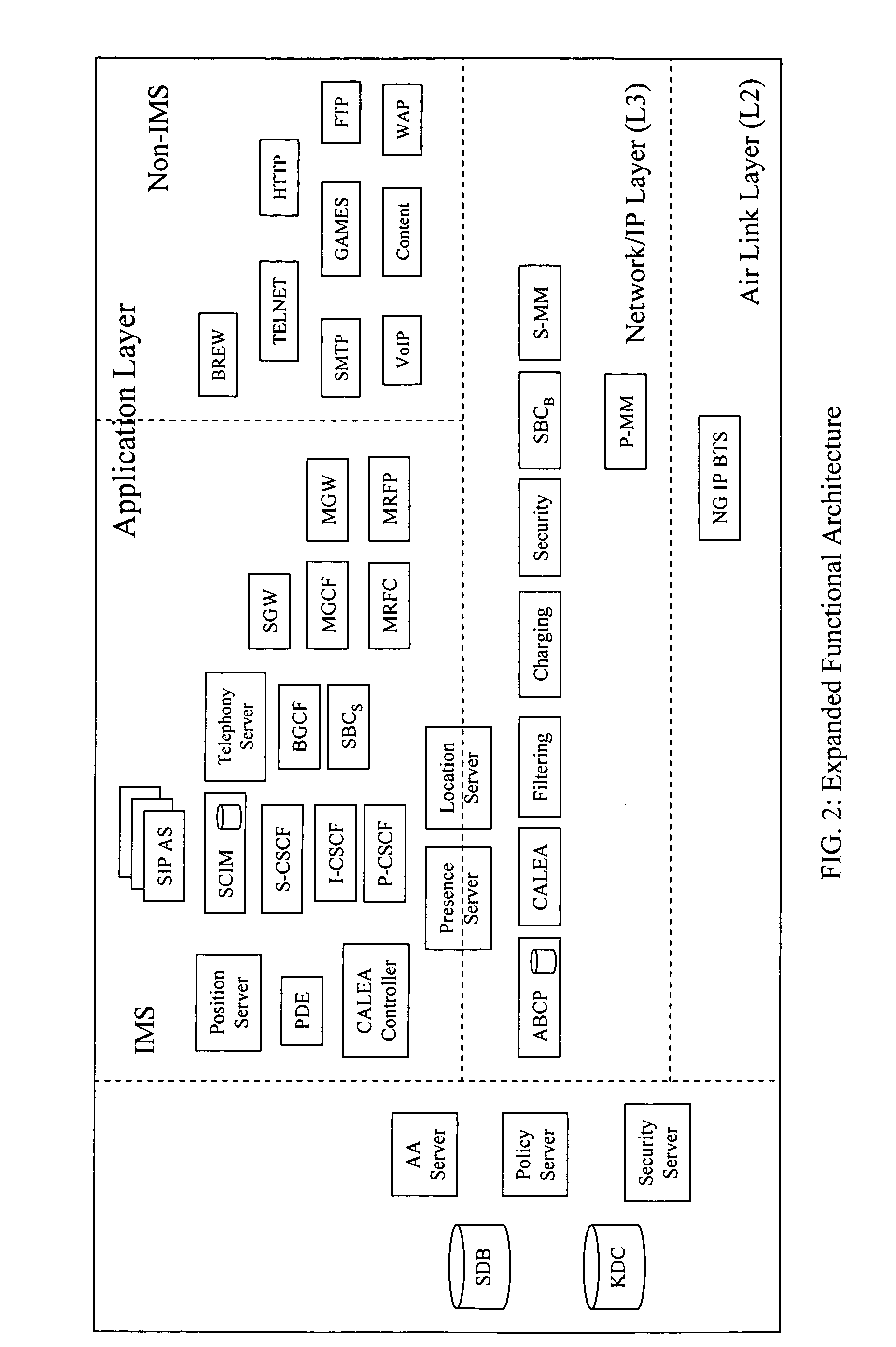
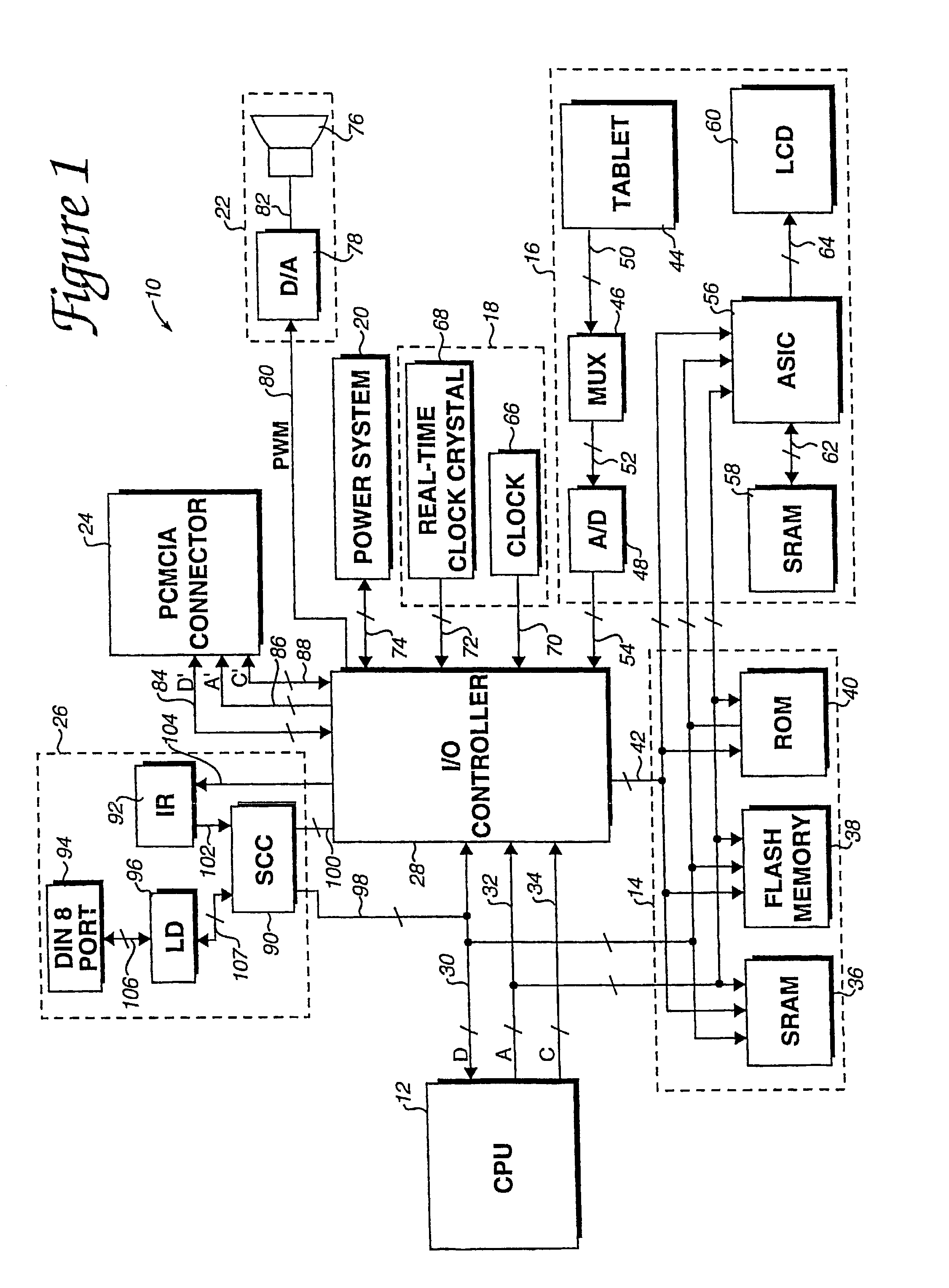
Multimedia next generation network architecture for IP services delivery based on network and user policy
InactiveUS7984130B2Network traffic/resource managementDigital computer detailsPolicy decisionService control
The exemplary Multimedia Next Generation Network architecture disclosed herein covers the entire next generation system, e.g. for wireless communication services, including application, signaling and bearer functionalities. The architecture addresses unification of subscriber databases for both SIP services and non-SIP services in a Services Data Management Center (SDMC). A Security Center (SC) provides a central repository for all security related databases and functions. An Application Control Point (ACP) provides a single point of services control for all active SIP services for all subscribers via state information and services interaction management. Policy decisions are made at the packet layer, for example in an Advanced Bearer Control Point (ABCP) clustered with other functions to form a Bearer Services Control Point (BSCP). Policy enforcement is implemented at various nodes at the network or packet layer (L3) and above, e.g. including the BSCP and ACP.
Owner:CELLCO PARTNERSHIP INC
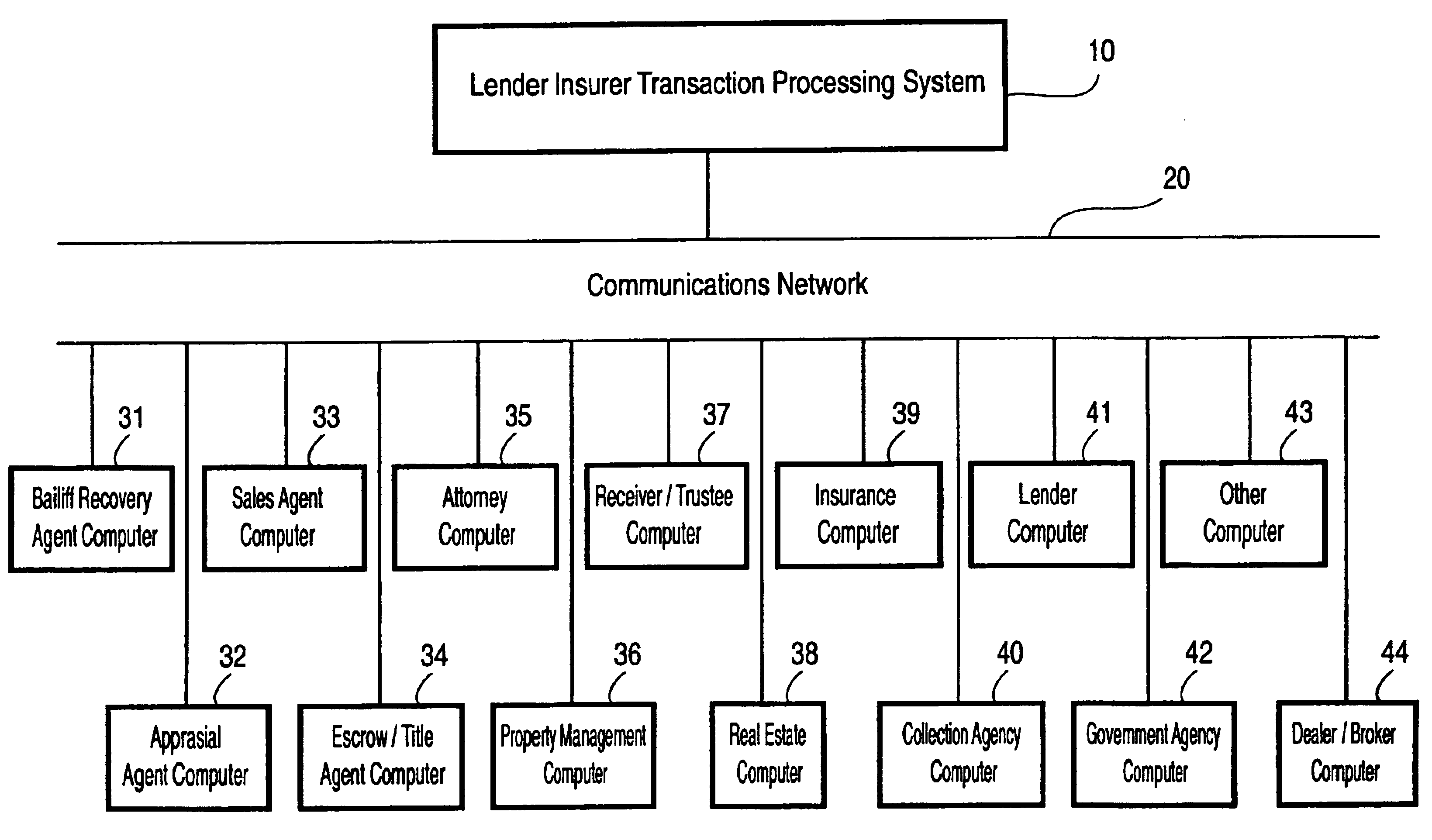
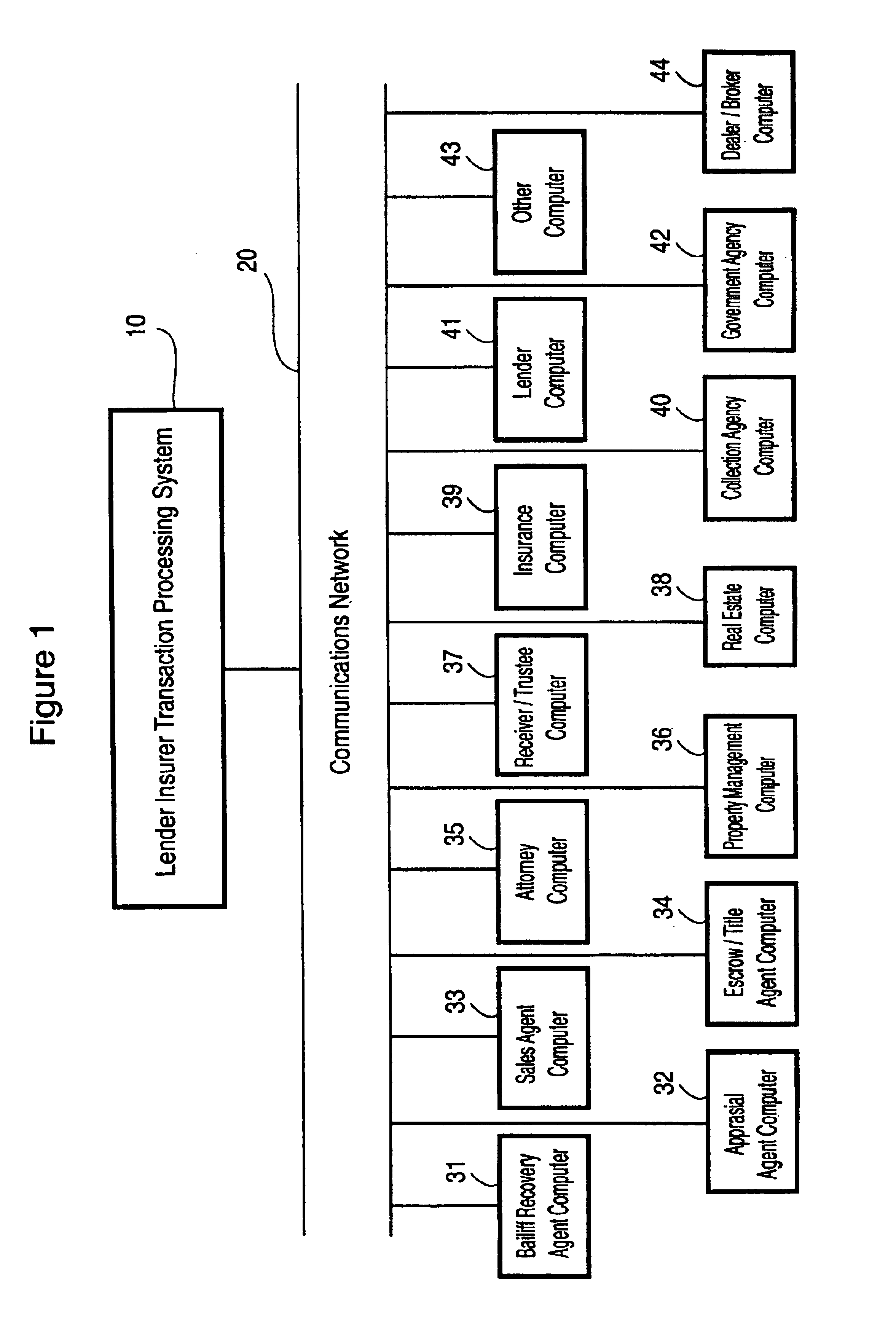
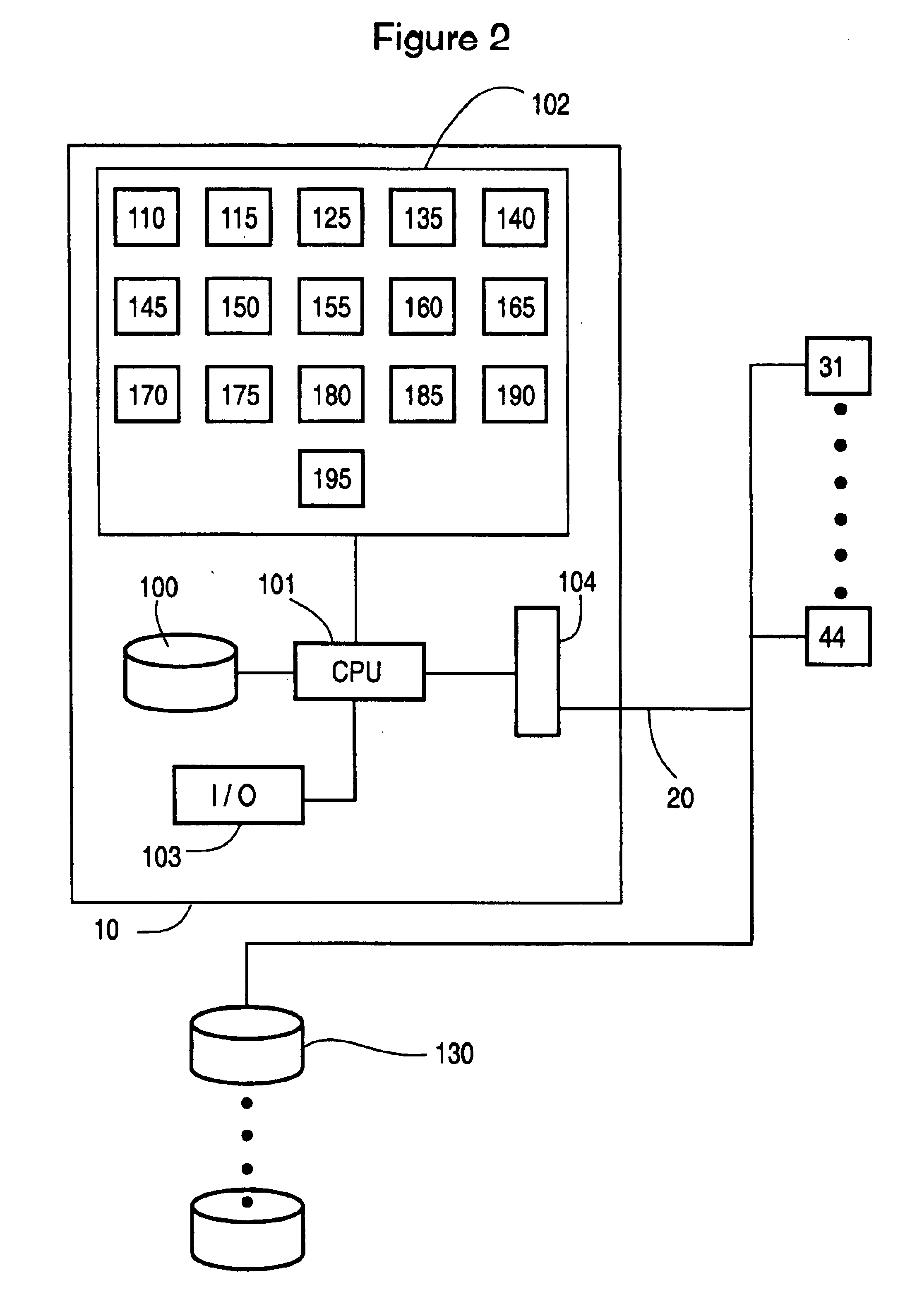
Lender and insurer transaction processing system and method
A system and method for transaction processing includes a central repository of transaction information which can be accessed by a variety of participants who may be located over a wide geographic area in the recovery process of a property unit such as a vehicle or other collateral. Interfacing with a variety of computer systems over a communication network, such as the Internet, allows interchange of data relating to the recovery process and centralized coordination of the recovery process.
Owner:DH COLLATERAL MANAGEMENT CORP
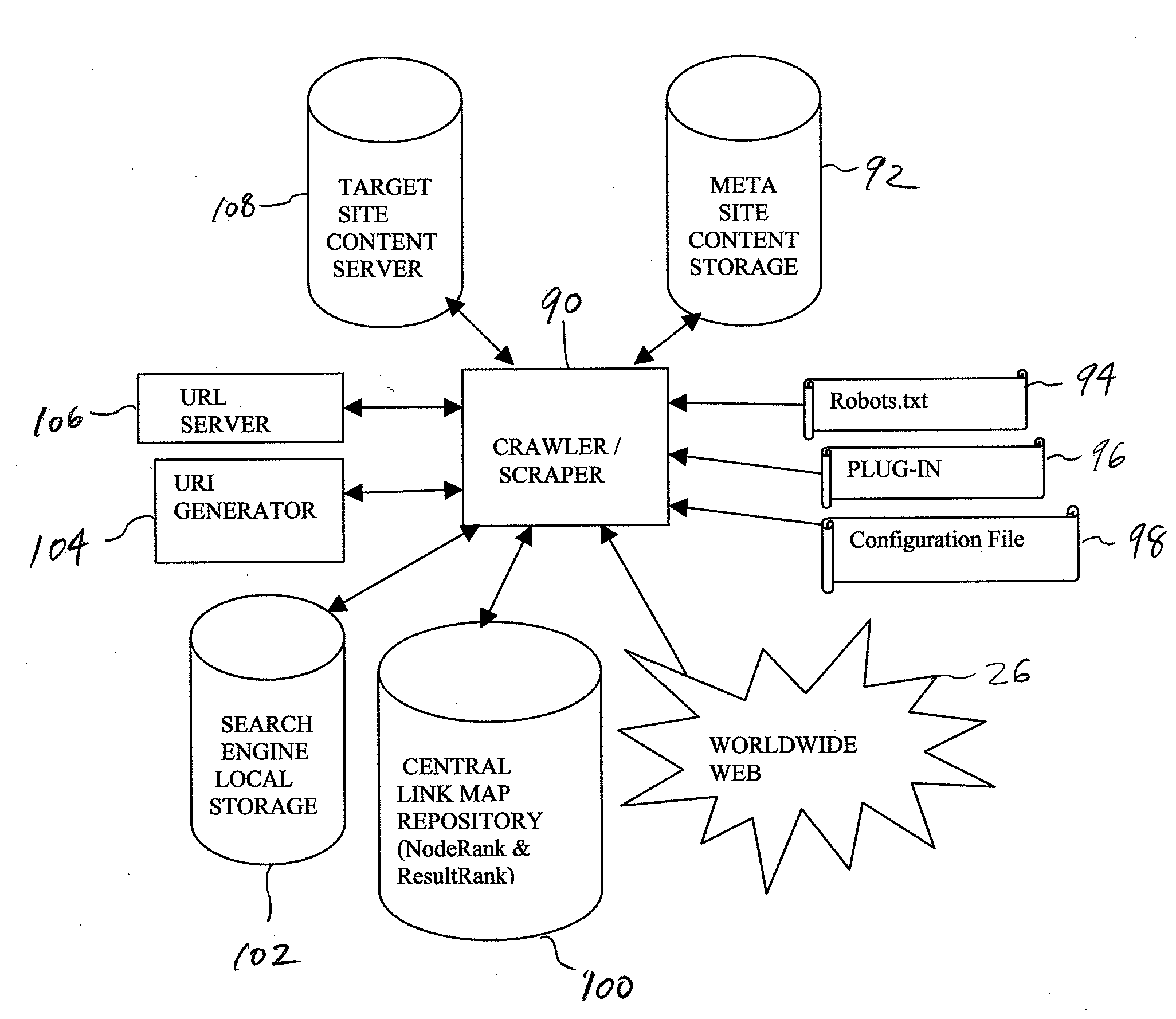
System and Method for Searching for Internet-Accessible Content
InactiveUS20080114739A1Secure transmissionMotivate userWeb data indexingDigital data processing detailsWeb siteWeb browser
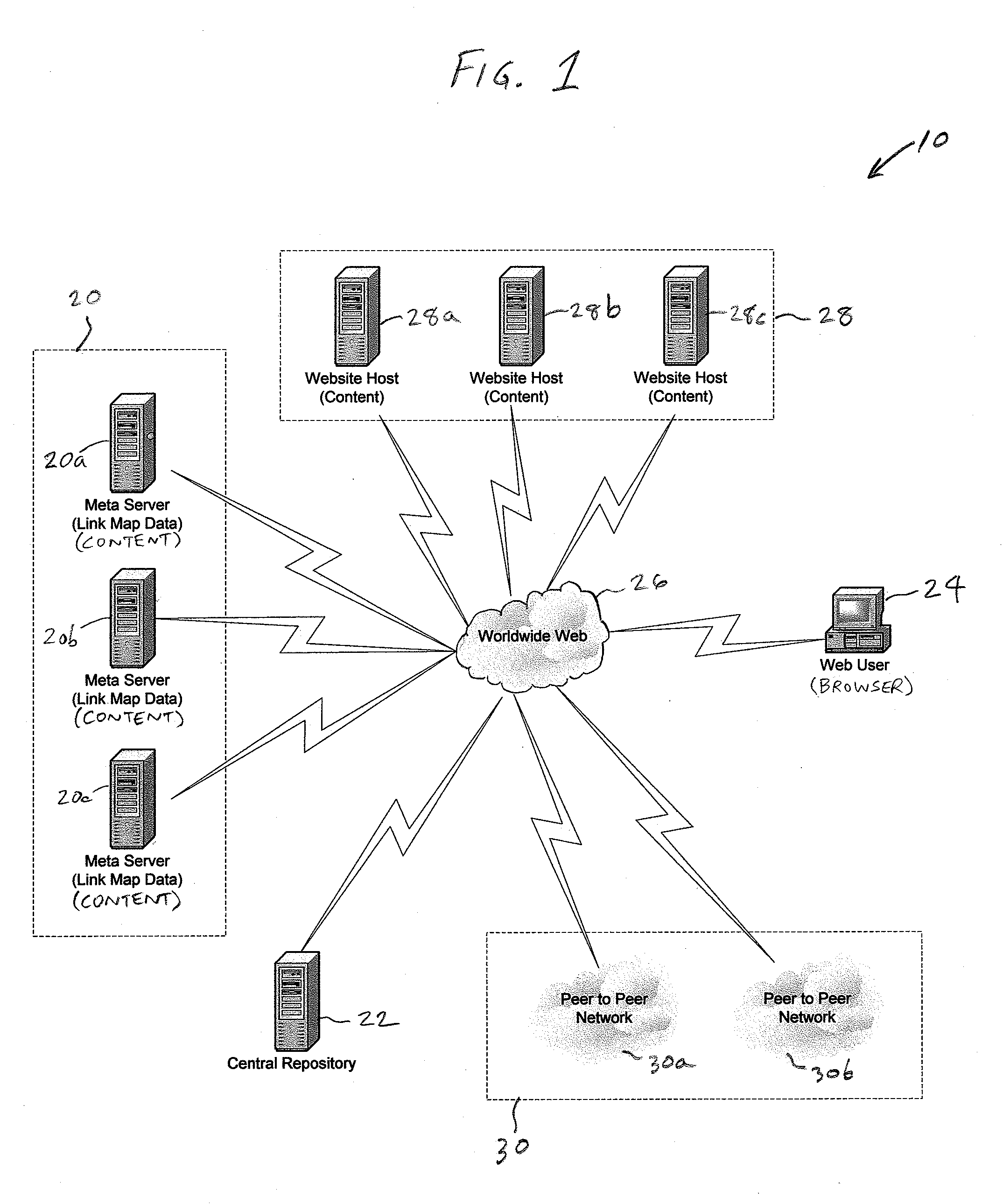
A system and method for searching and voting on Internet-accessible content is presented. One or more meta servers or sites store information about the structure and location of content on one or more Internet host servers. HTML-linked content on the one or more Internet host servers is indexed and stored on the one or more meta servers, and non-HTML content on the one or more Internet host servers is processed by the present invention into HTML content, indexed, and stored on the one or more meta servers. Each meta server includes a local search engine that can be queried by a user. A plurality of different types of queries can be conducted by the user, including local queries, global queries, and peer-to-peer network queries. The user is provided with search results which point to relevant content on one or more of the meta server and / or one or more of the Internet host servers. After viewing the content, the user can cast votes relating to the user's satisfaction with the search results. The present invention also includes a central repository which tracks user votes, query progressions, and information about content on each of the meta sites. The present invention also provides a plurality of enhancement plug-ins for standard web robots, including a toolbar for conventional web browsers. The toolbar can be used to securely solicit and collect authenticated user votes from standard web sites, as well as to vote-check top results returned by supported search engines. The plug-ins facilitate interoperability between existing Internet software (and technology) and the present invention.
Owner:HUDSON BAY WIRELESS
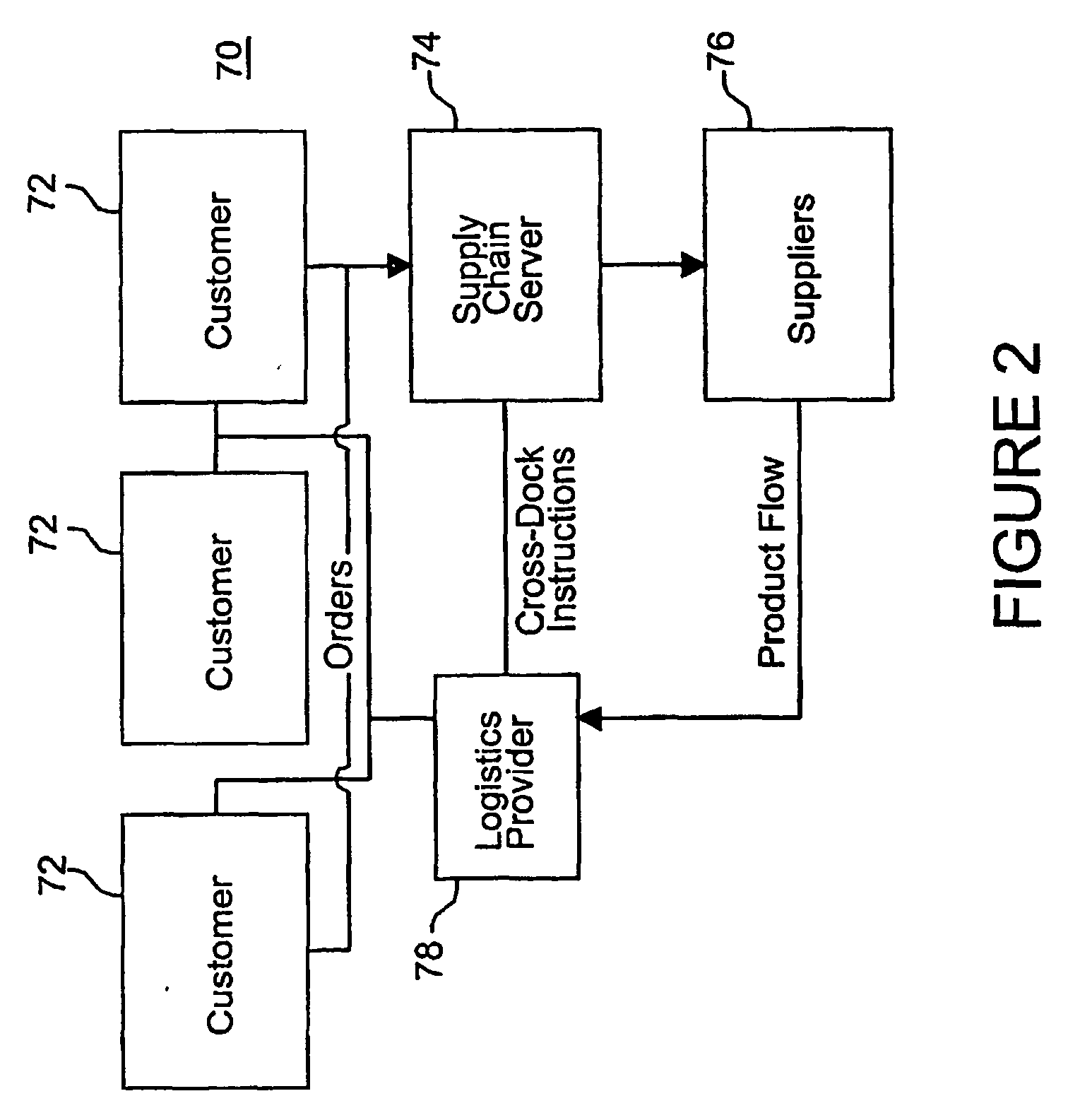
Supply chain network
InactiveUS20050177435A1Improve economyReduce the numberHand manipulated computer devicesPayment architectureChain networkComputer science
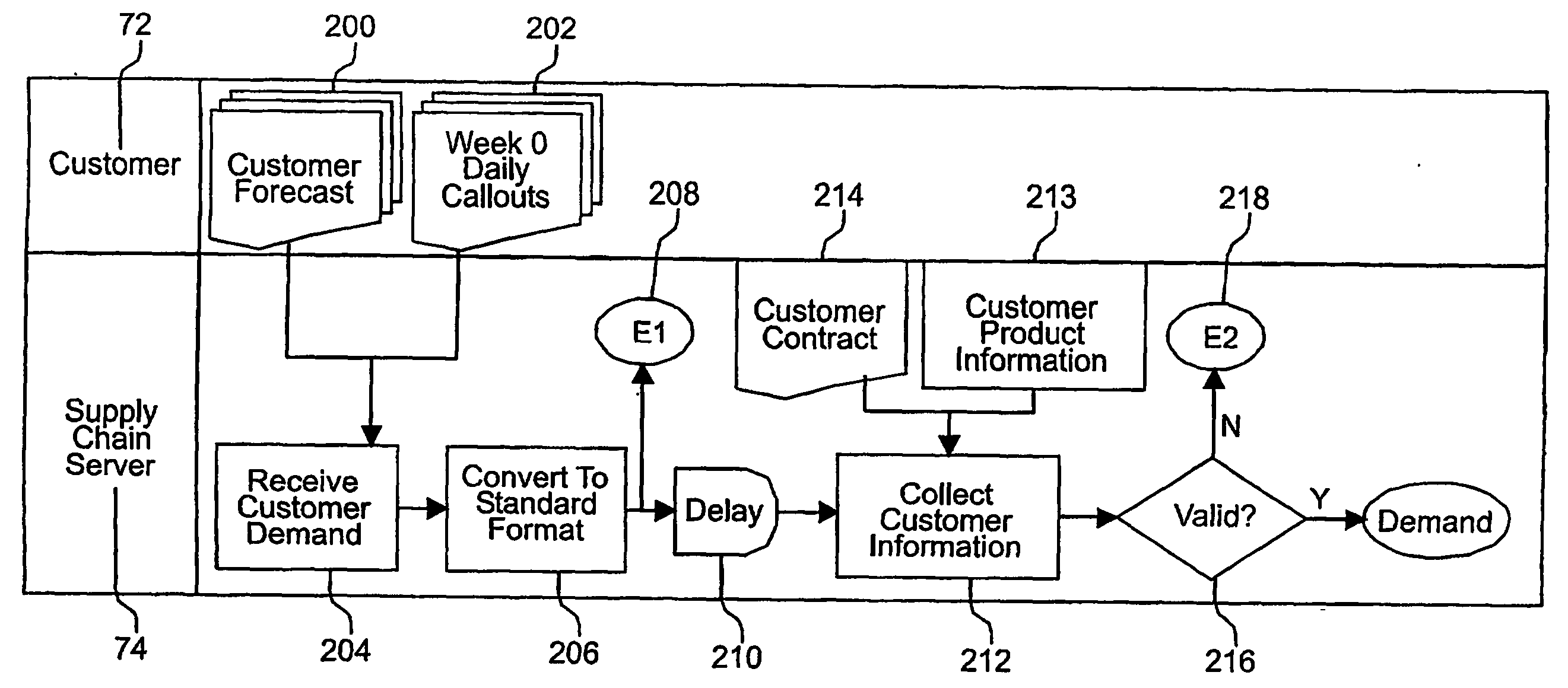
A supply chain network (70) in which customers (72), suppliers (76), logistics providers (78), carriers, and financial institutions are all connected to a centralized supply chain server (74). The supply chain server (74) is central to a many-to-many relationship. Accordingly, the server (74) handles various management activities for each member of the supply chain, such as negotiating prices, terms and conditions, managing supply and demand, and maintaining transaction information. In the process, the supply chain server, (74) gathers significant amounts of relevant data and becomes a central repository for such information. Consequently, the supply chain server (74) is in a unique position to utilize the data for the benefit of the members of the supply chain and others.
Owner:ISUPPLI
Cross-pollination synchronization of data
ActiveUS20060020804A1Duplicative entries can be eliminatedData processing applicationsUser identity/authority verificationPollinationPersonal computer
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for automating the root cause analysis of system failures
InactiveUS20050210331A1Multiple digital computer combinationsNon-redundant fault processingRoot causeRoot cause analysis
A method for analyzing the root cause of system failures on one or more computers. An event is generated when a computer system detects a system failure. The cause of the failure is determined. The event, including the cause is transmitted from the computer system to a central repository. And the system failure is analyzed in the central repository.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
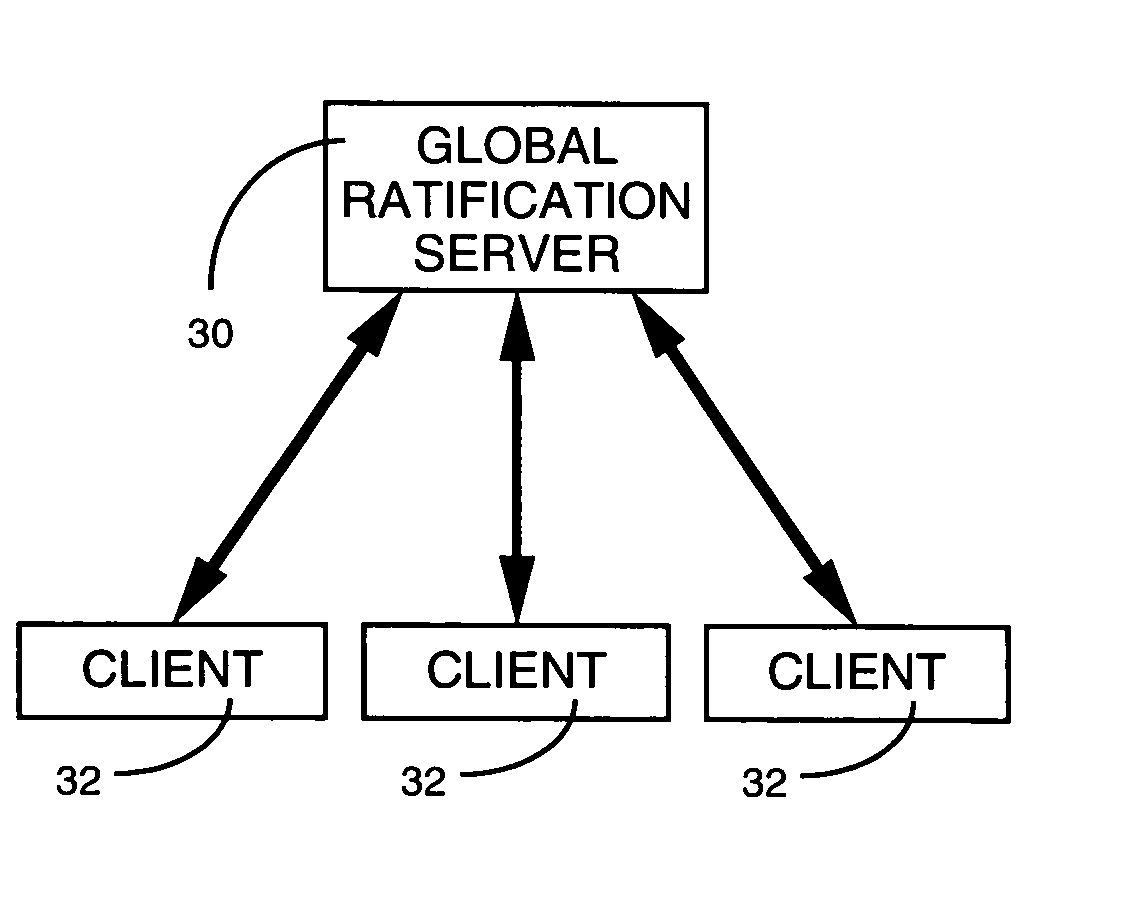
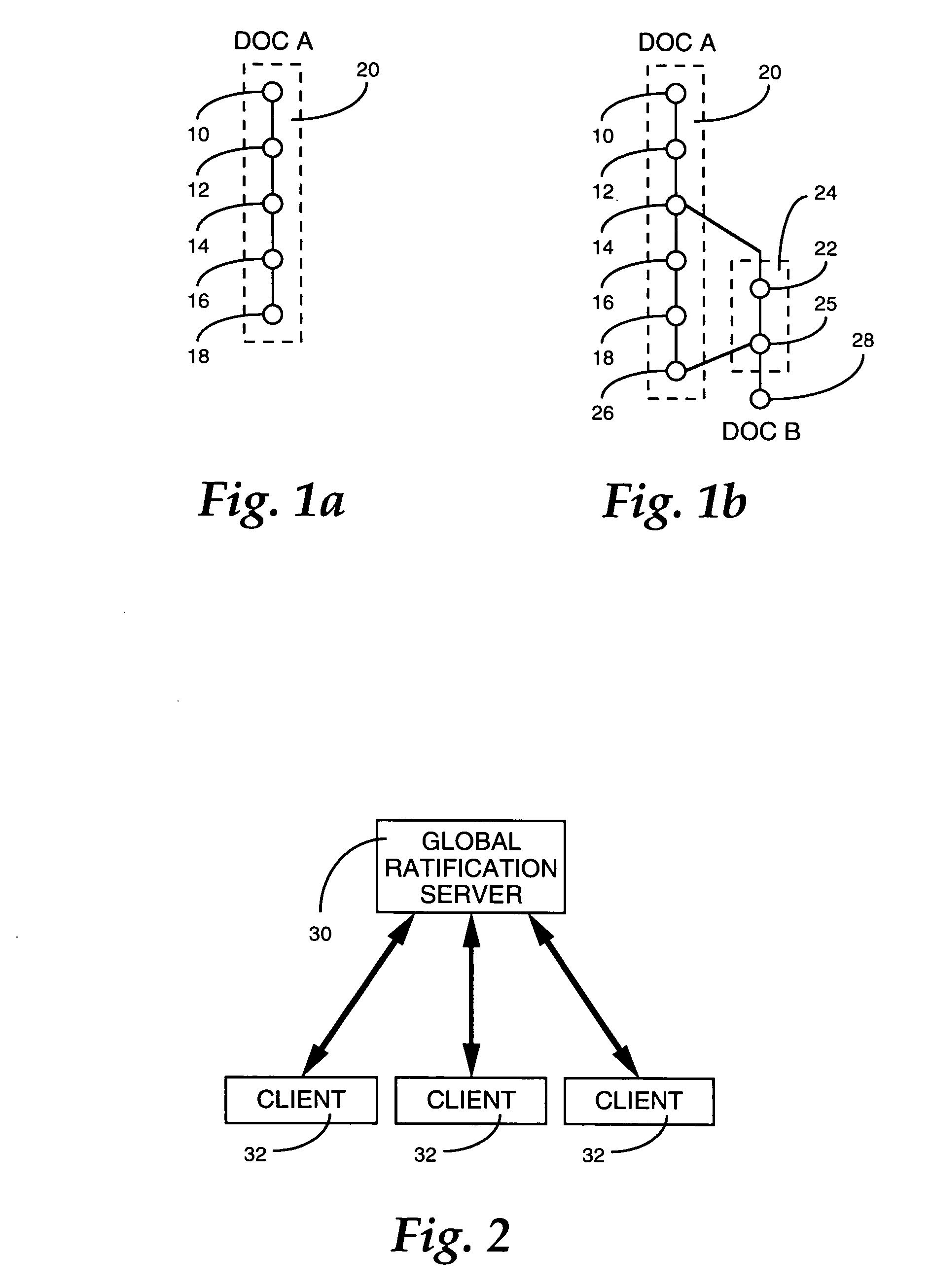
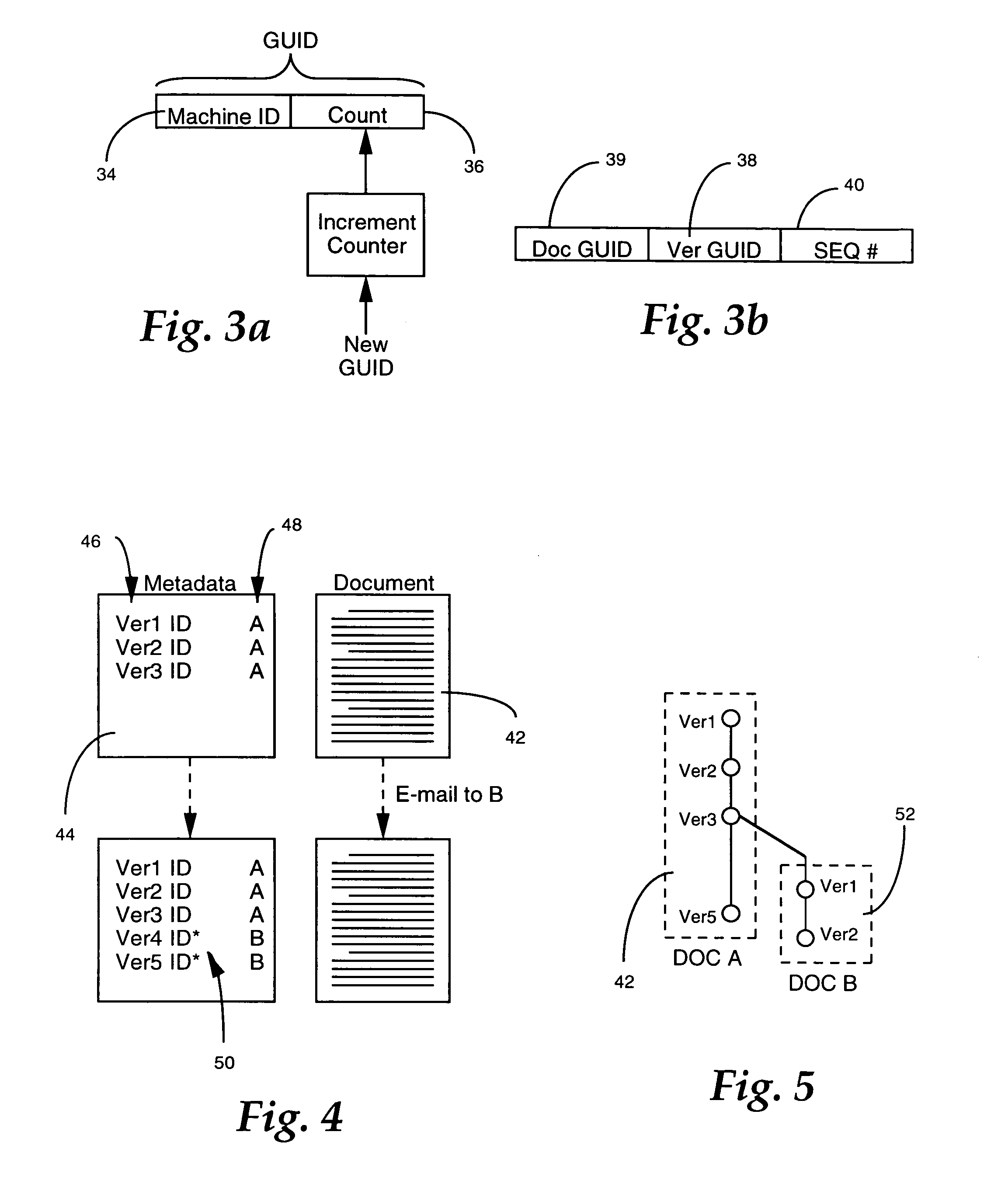
Storage-and transport-independent collaborative document-management system
ActiveUS20060136511A1Digital data processing detailsNatural language data processingUnique identifierPaper document
A document management system enables multiple users to collaboratively contribute to the contents of a document via any suitable medium for transporting and storing documents, including email, shared drives, replicated work spaces and centralized storage systems. A tracking strategy is employed, in lieu of a central repository, that is based upon medium-independent versioning. Each version of a document that is created and saved by a user is given a unique identifier. The versions are submitted to a global service for ratification as the next authoritative version of a document. A submitted version that forms the next step in a linear sequence is ratified as the authoritative version of the document, whereas the version which does not meet this criterion becomes identified as a new document. Support is provided for users who create versions off-line, as well as users who are not subscribers to the system.
Owner:PROOFPOINT INC
Method and system for detecting restricted content associated with retrieved content
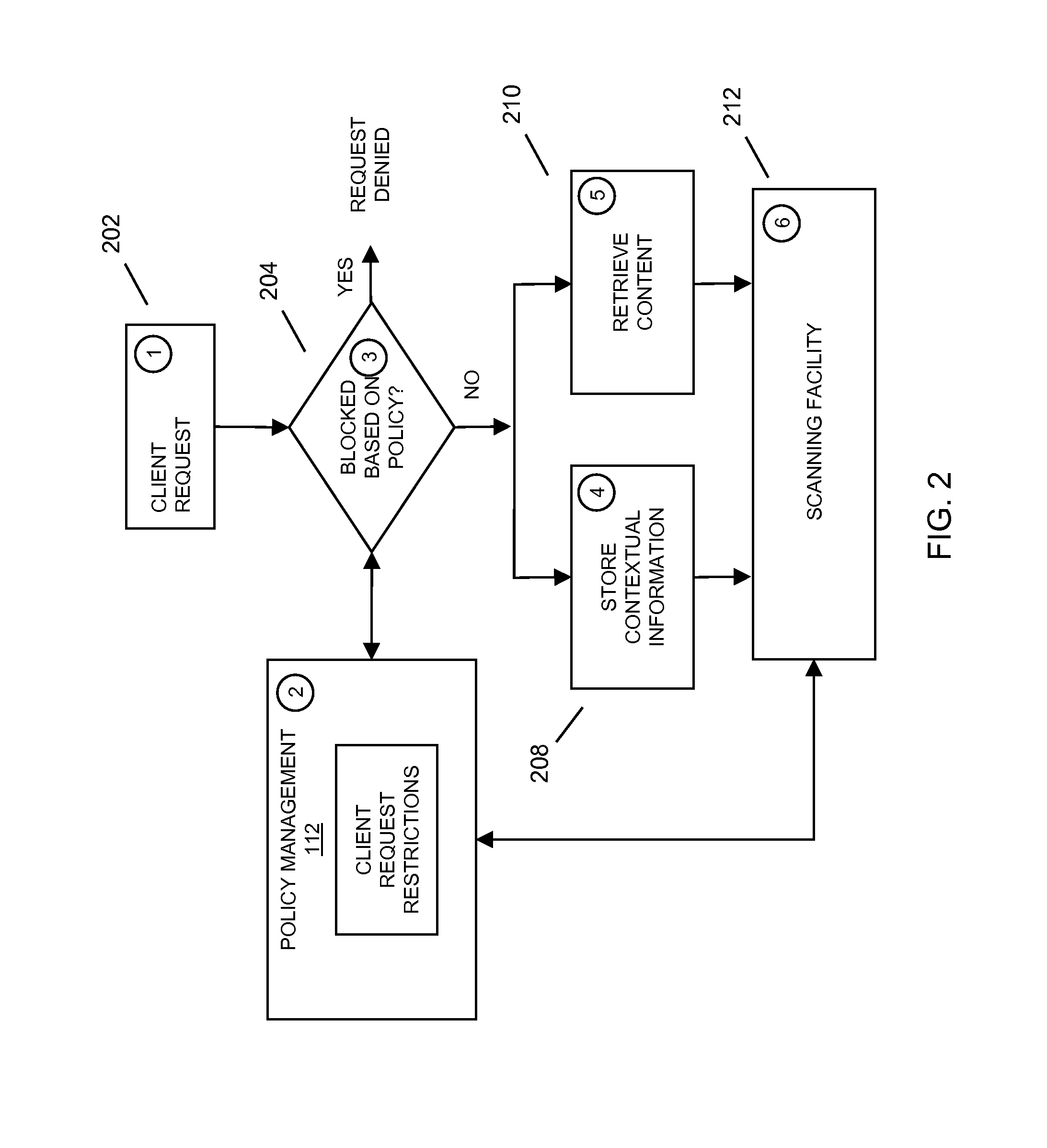
InactiveUS20090248696A1Increase opportunitiesIncrease contentComputer security arrangementsTransmissionInternet privacyClient-side
In embodiments of the present invention improved capabilities are described for receiving contextual information relating to a client request for content, determining that content delivered in response to the client request is restricted content through a scanning facility, and communicating the contextual information to a central repository for use in detection rules generation. Further, the content may be delivered to the central repository along with the contextual information.
Owner:SOPHOS
Intelligent autofill
ActiveUS20050257134A1Minimize effortData augmentationData processing applicationsMetal-working feeding devicesDatabaseCentral repository
The present invention provides a unique system and method that can employ machine learning techniques to automatically fill one or more fields across a diverse array of web forms. In particular, one or more instrumented tools can collect input or entries of form fields. Machine learning can be used to learn what data corresponds to which fields or types of fields. The input can be sent to a central repository where other databases can be aggregated as well. This input can be provided to a machine learning system to learn how to predict the desired outputs. Alternatively or in addition, learning can be performed in part by observing entries and then adapting the autofill component accordingly. Furthermore, a number of features of database fields as well as constraints can be employed to facilitate assignments of database entries to form values—particularly when the web form has never been seen before by the autofill system.
Owner:MICROSOFT TECH LICENSING LLC
Source Classification For Performing Deduplication In A Backup Operation
ActiveUS20100312752A1Digital data processing detailsError detection/correctionData segmentFingerprint
A system, method, and computer program product for backing up data from a backup source to a central repository using deduplication, where the data comprises source data segments is disclosed. A fingerprint cache comprising fingerprints of data segments stored in the central repository is received, where the data segments were previously backed up from the backup source. Source data fingerprints comprising fingerprints (e.g., hash values) of the source data segments are generated. The source data fingerprints are compared to the fingerprints in the fingerprint cache. The source data segments corresponding to fingerprints not in the fingerprint cache may not be currently stored in the central repository. After further queries to the central repository, one or more of the source data segments are sent to the central repository for storage responsive to comparison.
Owner:VERITAS TECH
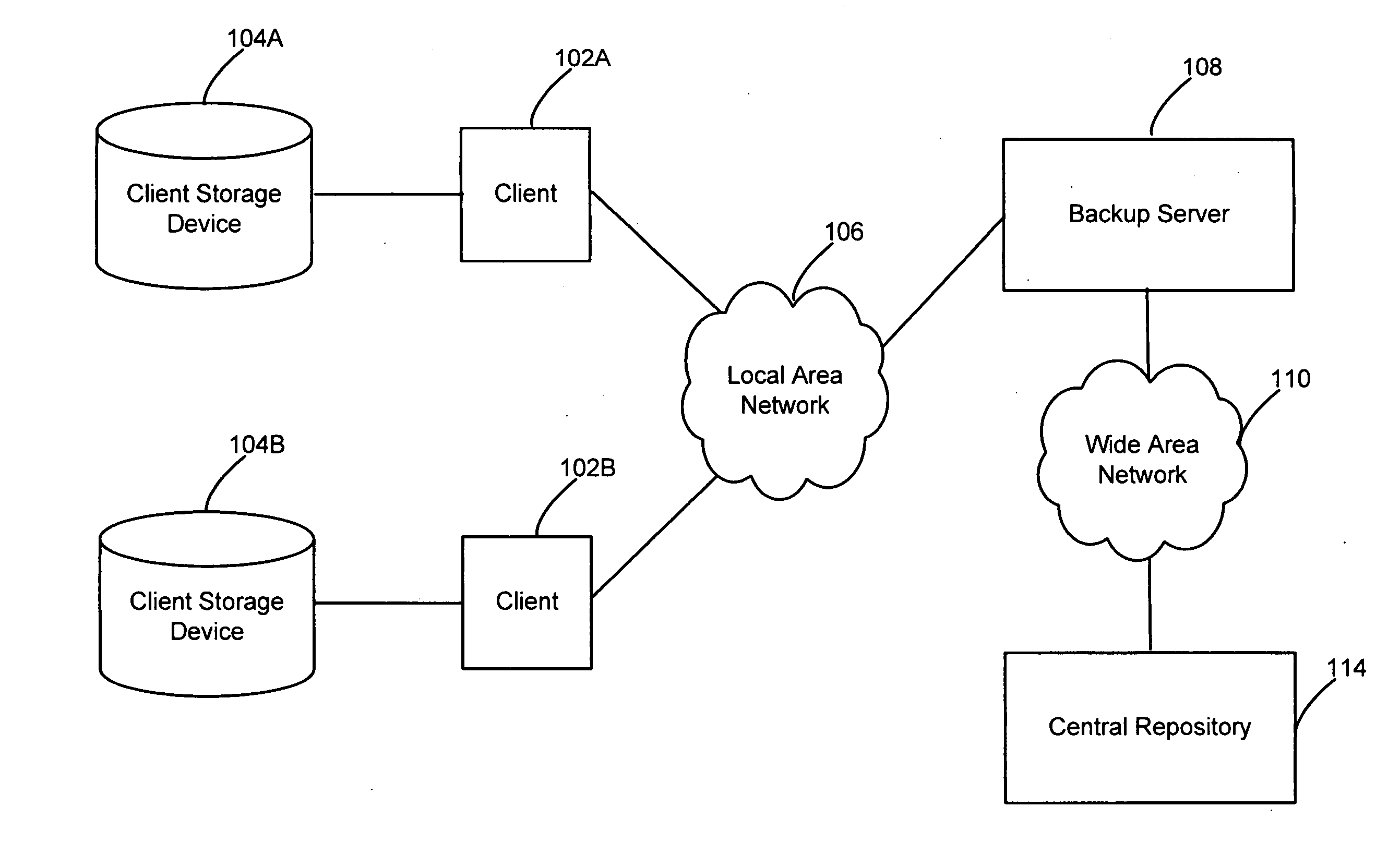
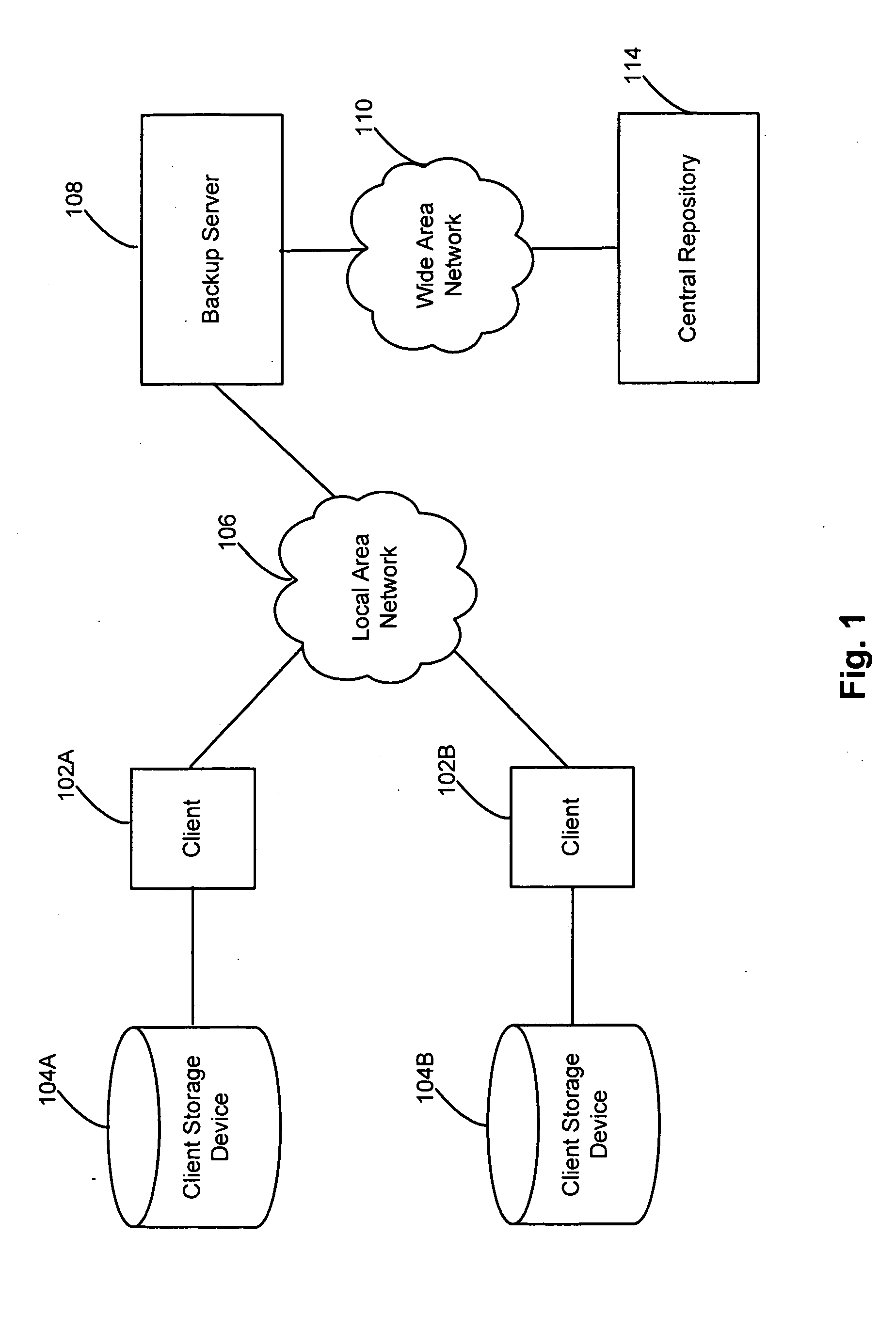
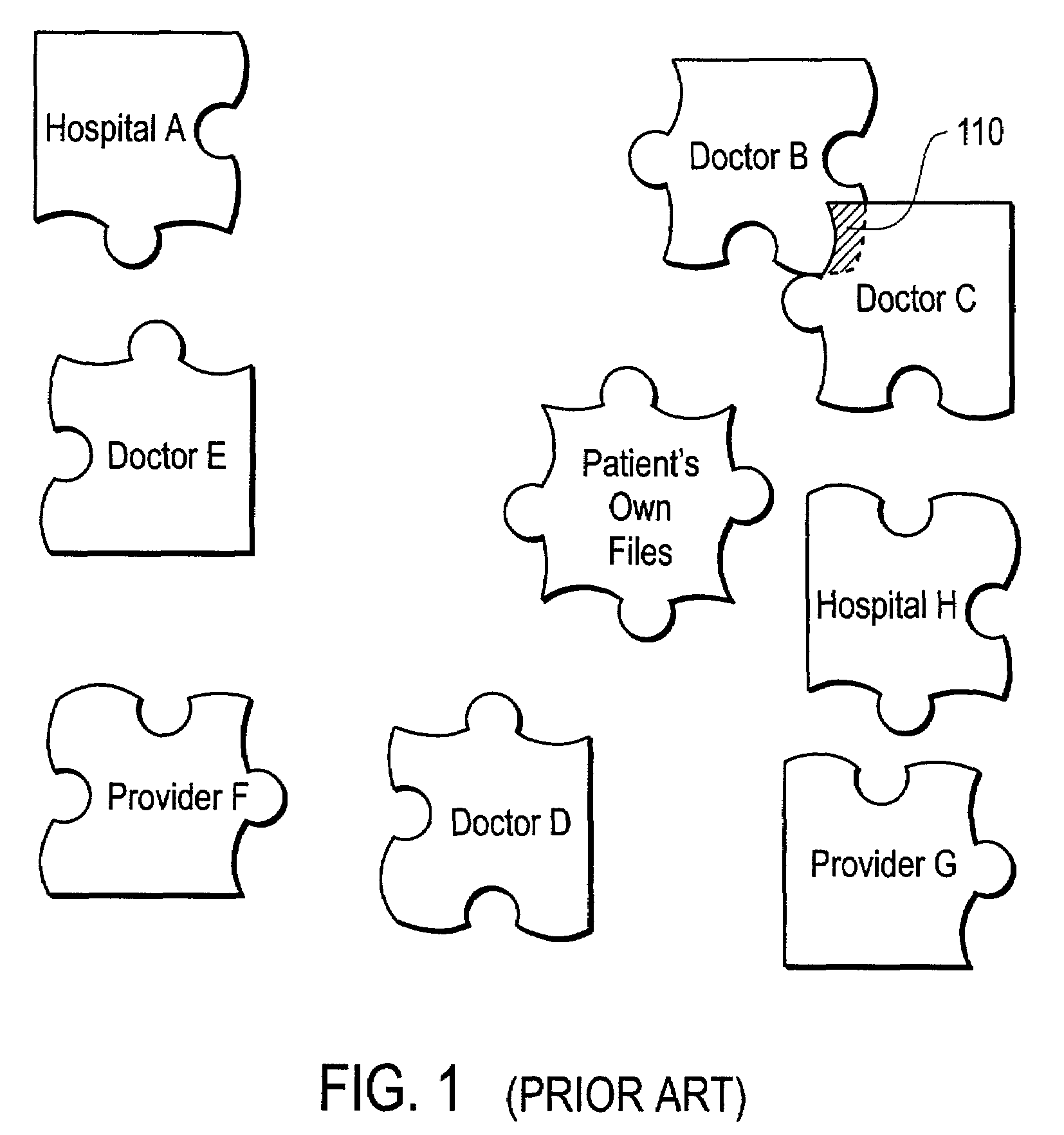
Patient directed system and method for managing medical information
InactiveUS7647320B2Promote generationImprove distributionData processing applicationsDigital data processing detailsThird partyMedical record
A system and method is provided for the management of a patient's medical records by a central data repository under the direction of the patient and enabled by an entity managing records on behalf of the patient. Medical records from a plurality of the patient's healthcare providers, including past and present healthcare providers, are maintained in this central repository in a way that provides a centralized, comprehensive, and accessible medical history of the patient, as well as a comprehensive organizational structure across all records. An embodiment has the patient directed central repository as the hub in a hub-and-spoke arrangement, where each spoke goes to one of the patient's healthcare providers, both past and present. The patient's medical records are collected from all the patient's healthcare providers, then classified, stored, and organized for use by the patient, healthcare providers, and any other authorized individuals. The records in the repository can be sorted and / or selected in several different ways and displayed to the patient or to his designated medical care providers, and to certain patient designated third parties.
Owner:PEOPLECHART CORP
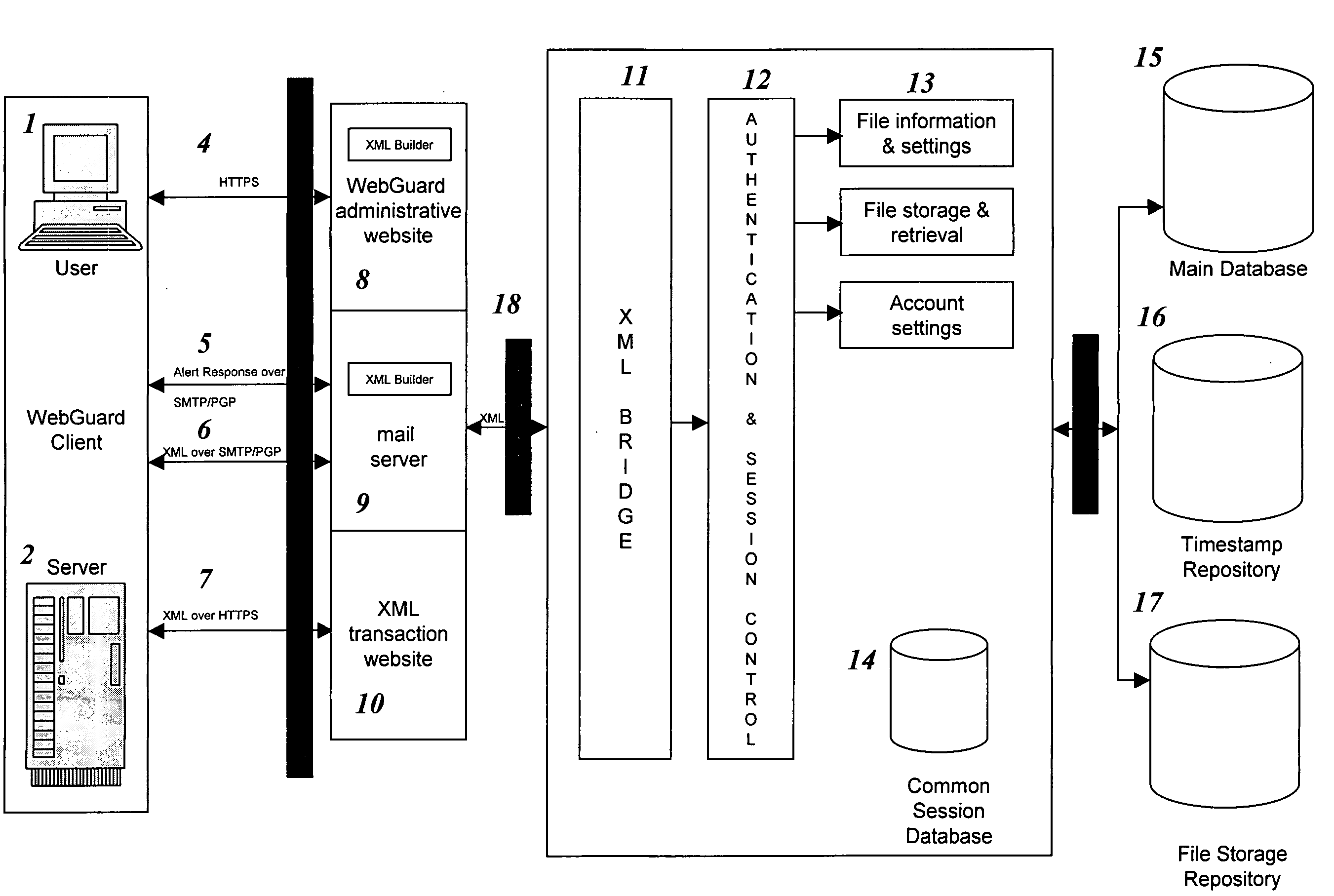
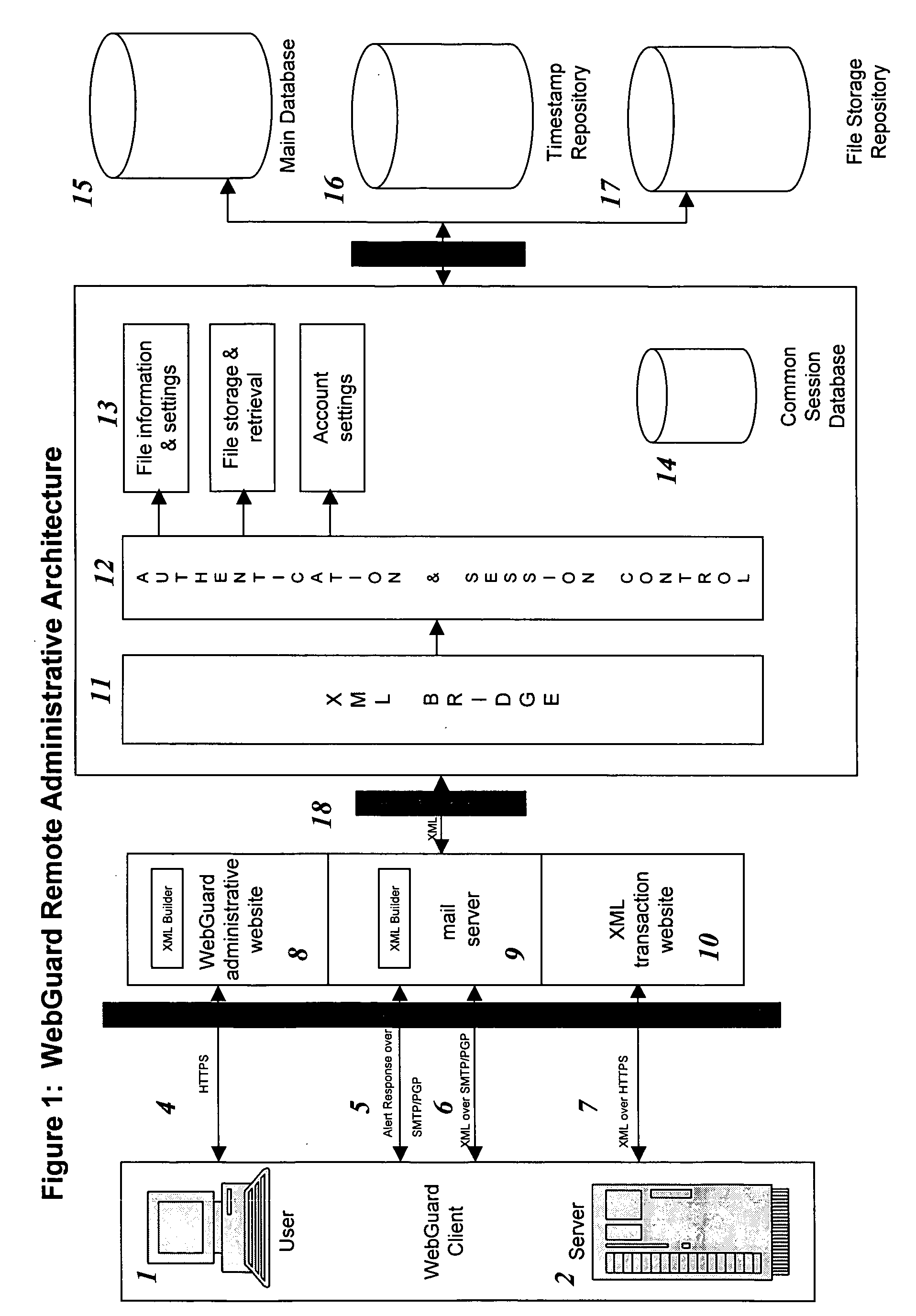
Remote web site security system
InactiveUS20050114658A1Digital data processing detailsUnauthorized memory use protectionWeb siteDatabase
The invention is a method for monitoring a file in a file security system, including providing a first file representation of a file in which the file is disposed at a first location and first processing the first file representation to provide first signals in accordance with the first file representation. The first signals are stored in a central repository disposed at a second location wherein the second location is remote from the first location. A second file representation of the file is provided wherein the file is disposed at a third location remote from the second location. Second processing of the second file representation is performed to provide second signals in accordance with the second file representation. The first signals are accessed from the central repository and the first signals are compared with the second signals. A status of the file is determined in accordance with the comparing.
Owner:SHORE VENTURE GROUP
System for dynamically tracking the location of network devices to enable emergency services
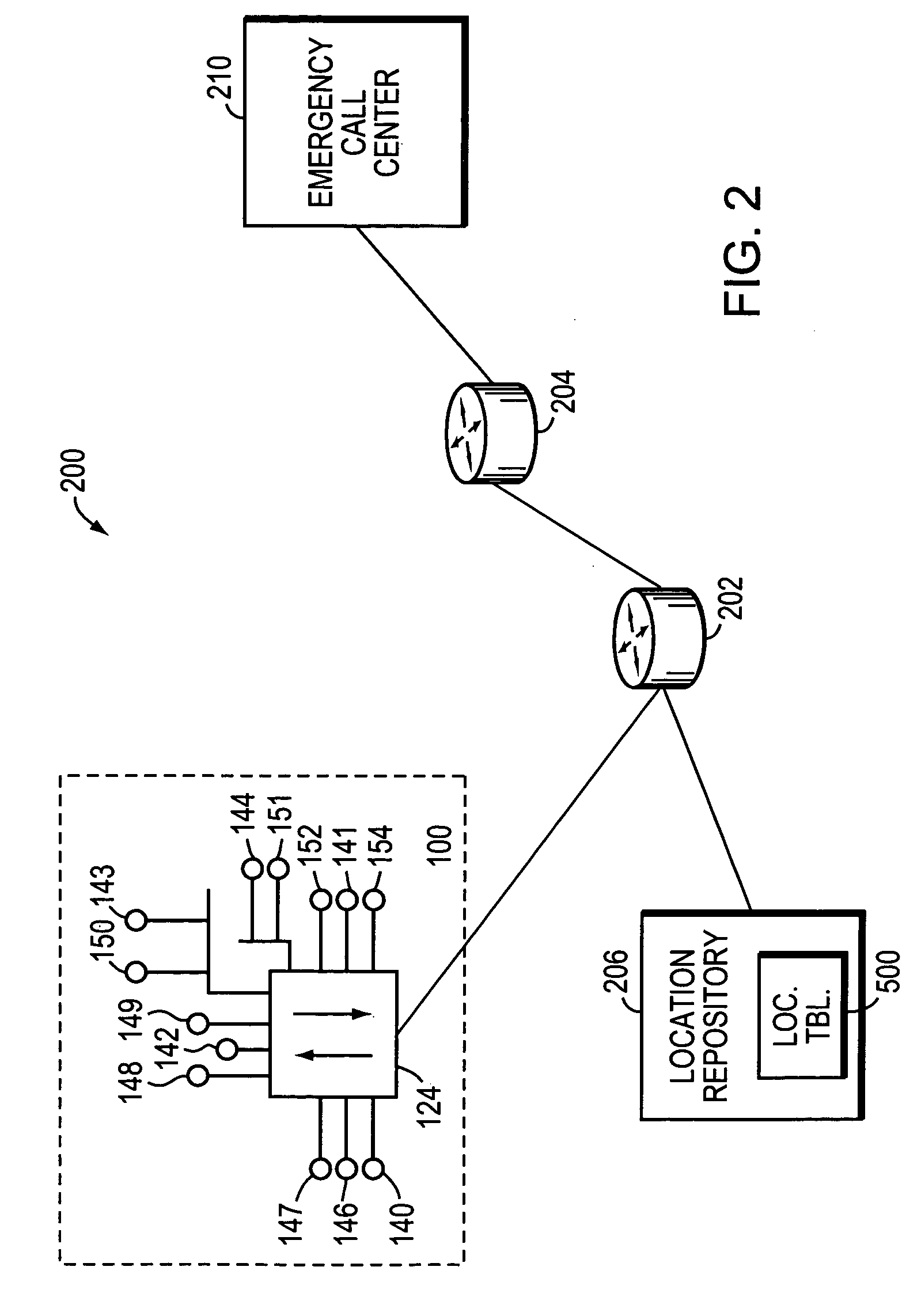
InactiveUS7149499B1The location information is accurateEmergency connection handlingPosition fixationGeolocationRadio frequency
A system dynamically discovers the geographic location of entities of a computer network. A network entity is configured to include a location determination engine and a radio frequency (RF) receiver unit. A plurality of RF base stations are disposed in the area proximate to the network entity. Each RF base station has a beacon for transmitting a radio frequency (RF) signal encoded with the location, e.g., the physical coordinates, of the respective RF base station and the time of transmission. The encoded RF signals are received by the RF receiver unit at the network entity and passed to the location determination engine, which uses the received information to compute its location. The location determination engine then reports its location by loading the computed location into a network message and transmitting that message to a central repository.
Owner:CISCO TECH INC
Multiple personas for mobile devices
InactiveUS7086008B2Good choiceCathode-ray tube indicatorsProgram loading/initiatingGraphicsGraphical user interface
A computer system is disclosed which may adopt one of many personas, depending upon the role that its owner is currently playing. The computer system includes a central repository of extensible personas available to all applications running on the computer system. Each such persona has associated therewith a suite of parameters, or specific values for parameters, which are appropriate for conducting computer implemented transactions under a particular persona. The computer system further includes a graphical user interface which allows the user to switch from persona to persona by selecting a particular persona from a list of available personas displayed on a display screen of the computer system. By selecting such persona, the user causes the computer system to globally change the entire suite of parameter values so that subsequent transactions conducted with the computer system employ the parameter values of the current persona.
Owner:APPLE INC
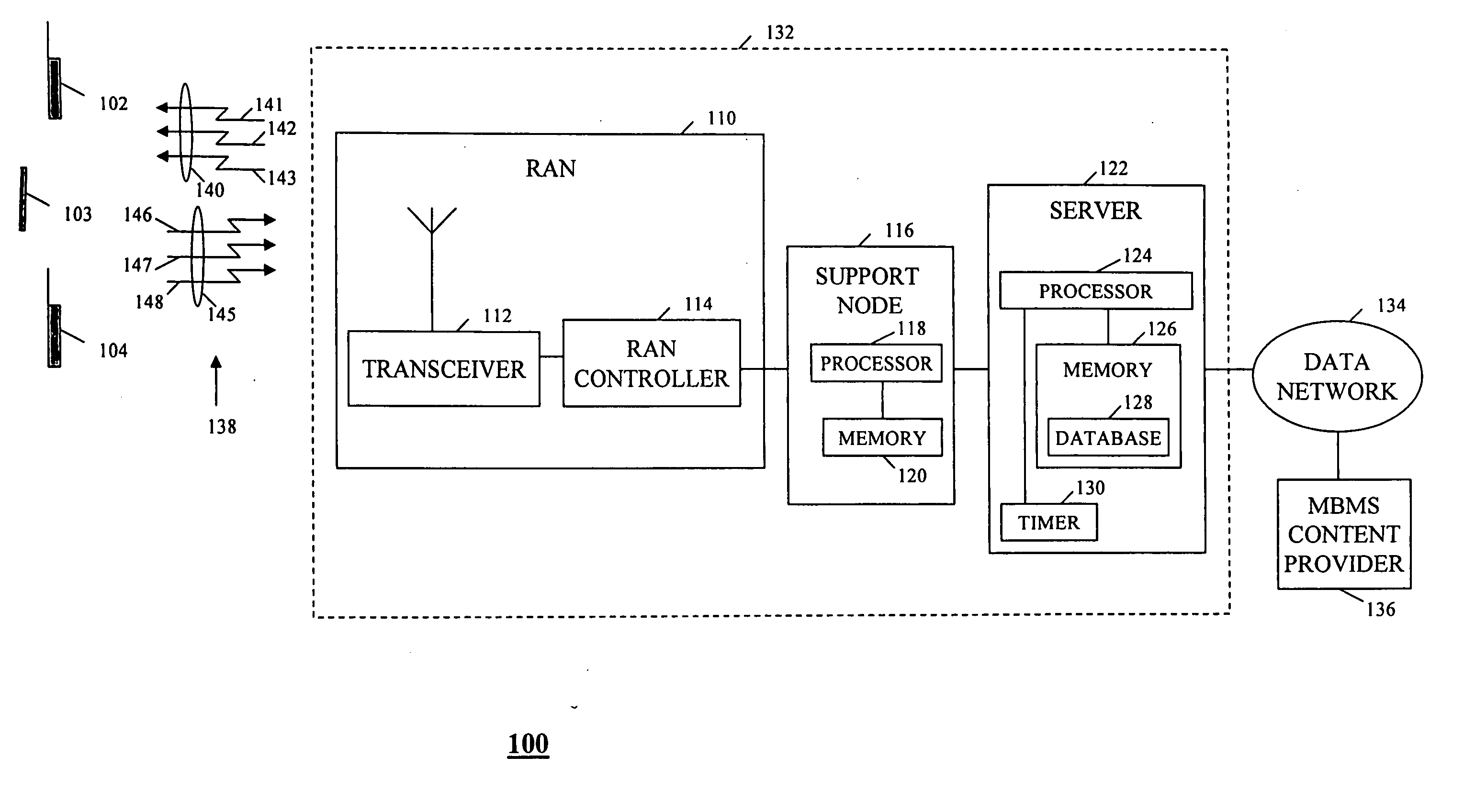
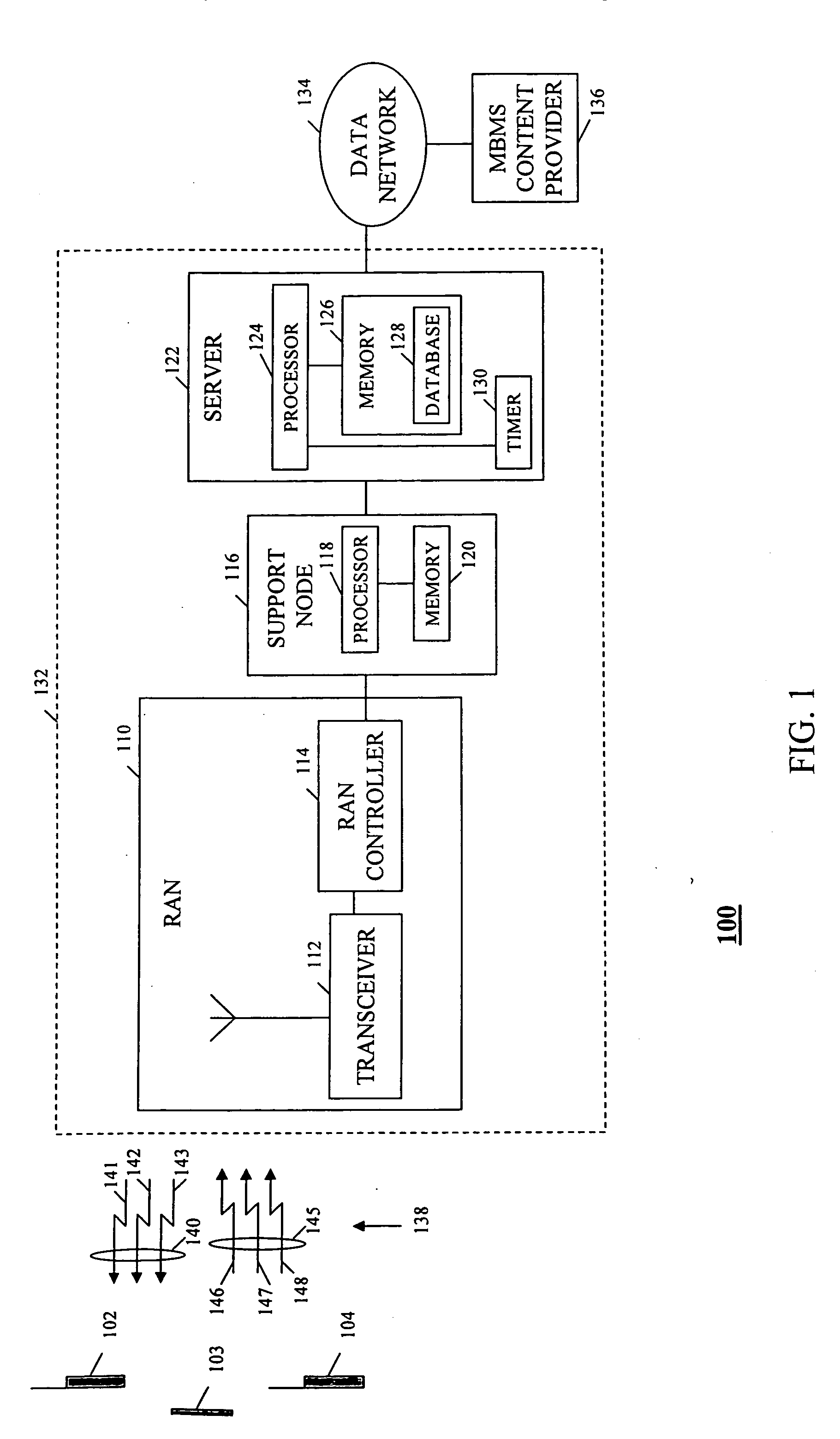
Method and apparatus for assigning temporary mobile group identity in a multimedia broadcast/multicast service
InactiveUS20050076369A1Special service provision for substationBroadcast with distributionCommunications systemMobile station
A Multimedia Broadcast / Multicast Service (MBMS) server in a packet data communication system generates and assigns Temporary Mobile Group Identities (TMGIs) to MBMS services, thereby serving as a central repository for the TMGIs. In response to receiving a request to participate in an MBMS service, the MBMS server generates a TMGI. The MBMS server assigns the TMGI to the MBMS service and stores the TMGI in association with information relating to the MBMS service to produce a stored TMGI. The MBMS server further conveys the TMGI to a source of the received request, thereby providing for a distribution of the TMGI to mobile stations subscribed to the MBMS service. The subscribed mobile stations may then use the TMGI to receive data packets associated with the MBMS service.
Owner:MOTOROLA INC
Collecting, sharing, comparing, and displaying resource usage data
ActiveUS8176095B2Save resourcesConservation usageDigital data processing detailsOffice automationGraphicsInteractive displays
Resource usage data is automatically collected for an individual, household, family, organization, or other entity. The collected data is transmitted to a central repository, where it is stored and compared with real-time and / or historical usage data by that same entity and / or with data from other sources. Graphical, interactive displays and reports of resource usage data are then made available. These displays can include comparisons with data representing any or all of community averages, specific entities, historical use, representative similarly-situated entities, and the like. Resource usage data can be made available within a social networking context, published, and / or selectively shared with other entities.
Owner:ABL IP HLDG
Digital imaging system for evidentiary use
InactiveUS20010033661A1Separate controlImprove securityDigital data processing detailsUser identity/authority verificationComputer hardwareDigital imaging
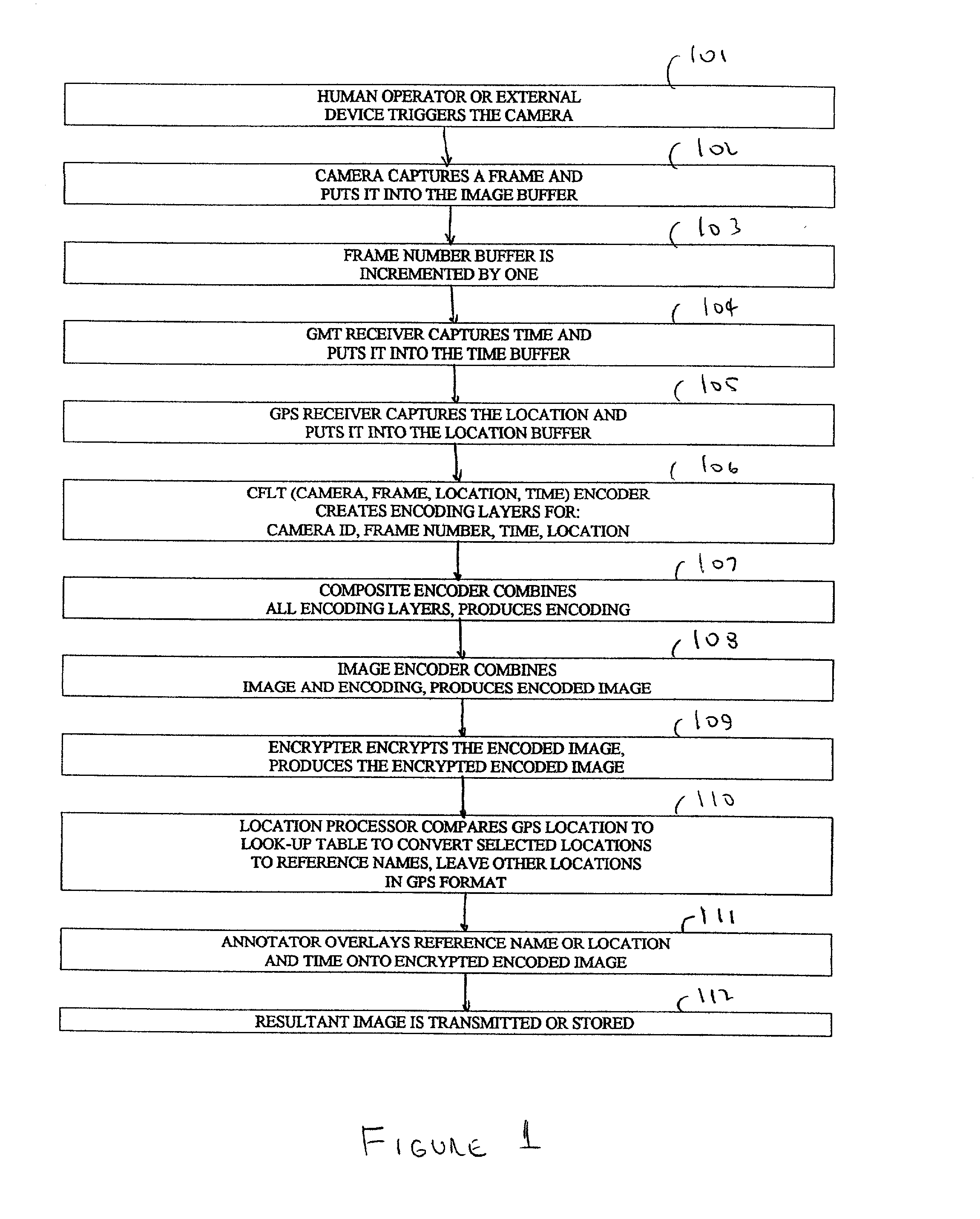
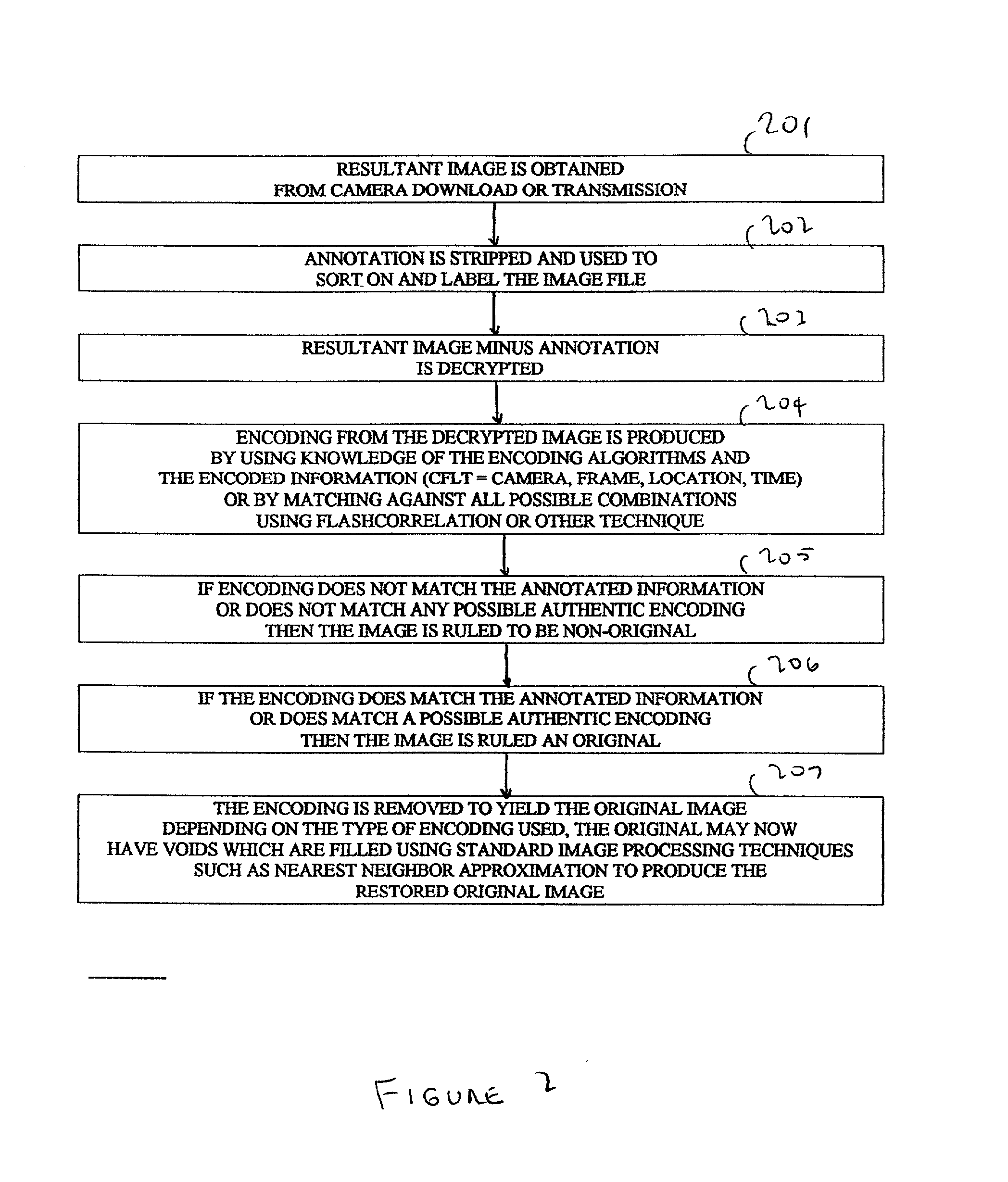
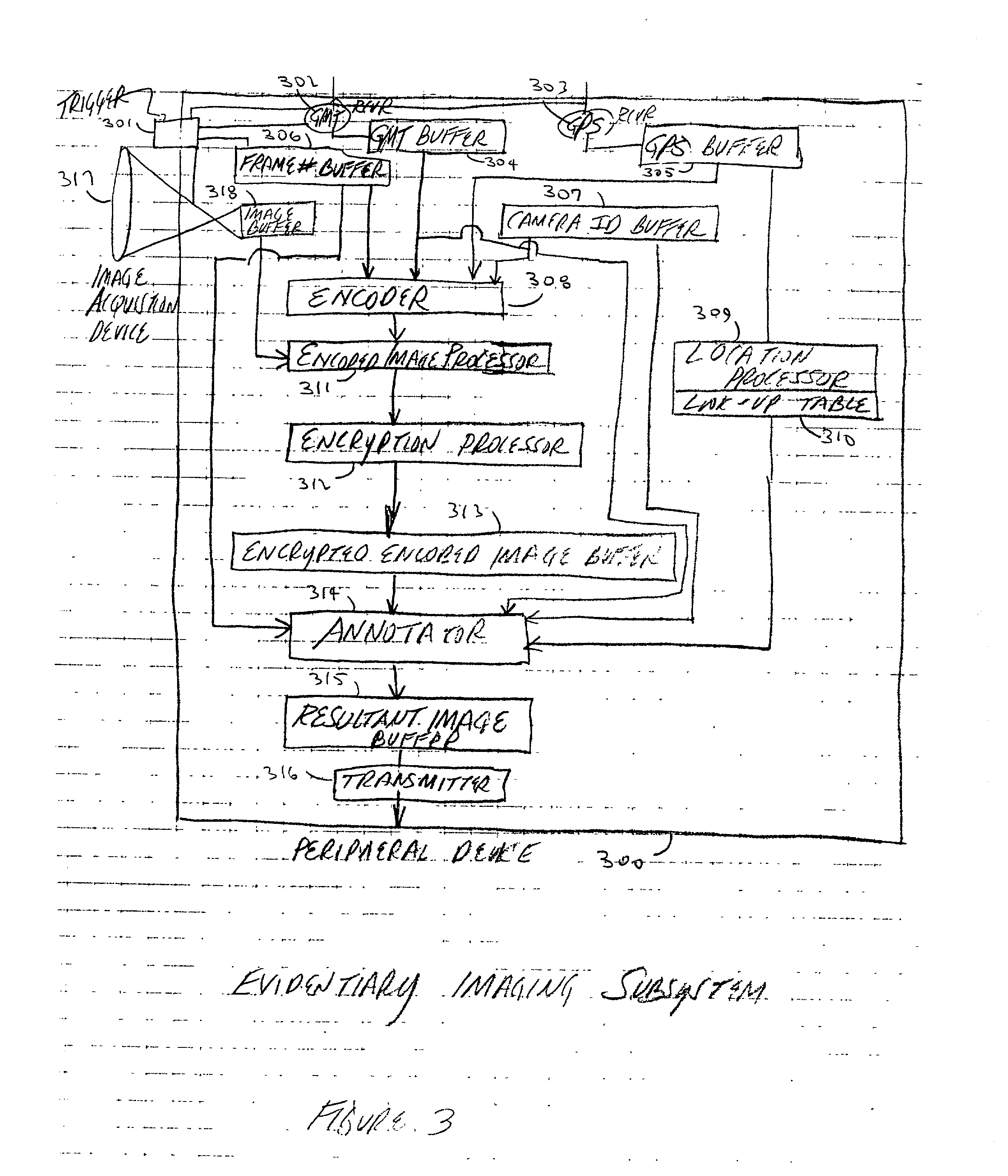
The Evidentiary Imaging System (EIS) provides secure storage or transmission of a digital image into which is encoded the date, time, and location at which the image was taken, along with the camera ID and frame number. The encoding is dispersed throughout the image so that the image cannot be modified without distorting the encoding. The image may be encrypted for additional security. Annotation can be superimposed on the encoded or encoded and encrypted image to classify or identify the image to human or automated scanning systems. The annotation can also be used to key the decoding and decryption tasks. The EIS produces imagery which may be authenticated as to originality, time and location of imaging. The imagery may be stored, duplicated, and transmitted while retaining its authenticity. However, any modifications to the image, including any local changes, are readily detected because the encoding will not decode correctly. The EIS is designed to provide imagery which may be used for evidentiary proof of authenticity, ownership, originality, date and time, and location of imaged events. Certain users of EIS systems, such as police forensics labs, may have a central depository for the decoding and decryption keys used with their cameras. Other users may rely upon authentication services provided by the EIS manufacturer or an independent expert in the EIS technique. While many different schemes for encoding and encryption may be used, FlashCorrelation(R) provides a computationally simple and rapid method for encoding each item of information; allowing for separate or total encoding and readout of encoding layers representing: date, time, location, camera ID, and frame number. As covered in the issued FlashCorrelation(R) U.S. Pat. Nos. 5,583,950 and 5,982,932, readout and authentication can be done by one party authorized to have the decoding and decryption schemes, or readout and authentication may require two or more parties.
Owner:MIKOS
System and method for dynamic distribution of intrusion signatures
ActiveUS20050076245A1Easy to detectMinimize impactMemory loss protectionDigital data processing detailsNetworked systemCentral repository
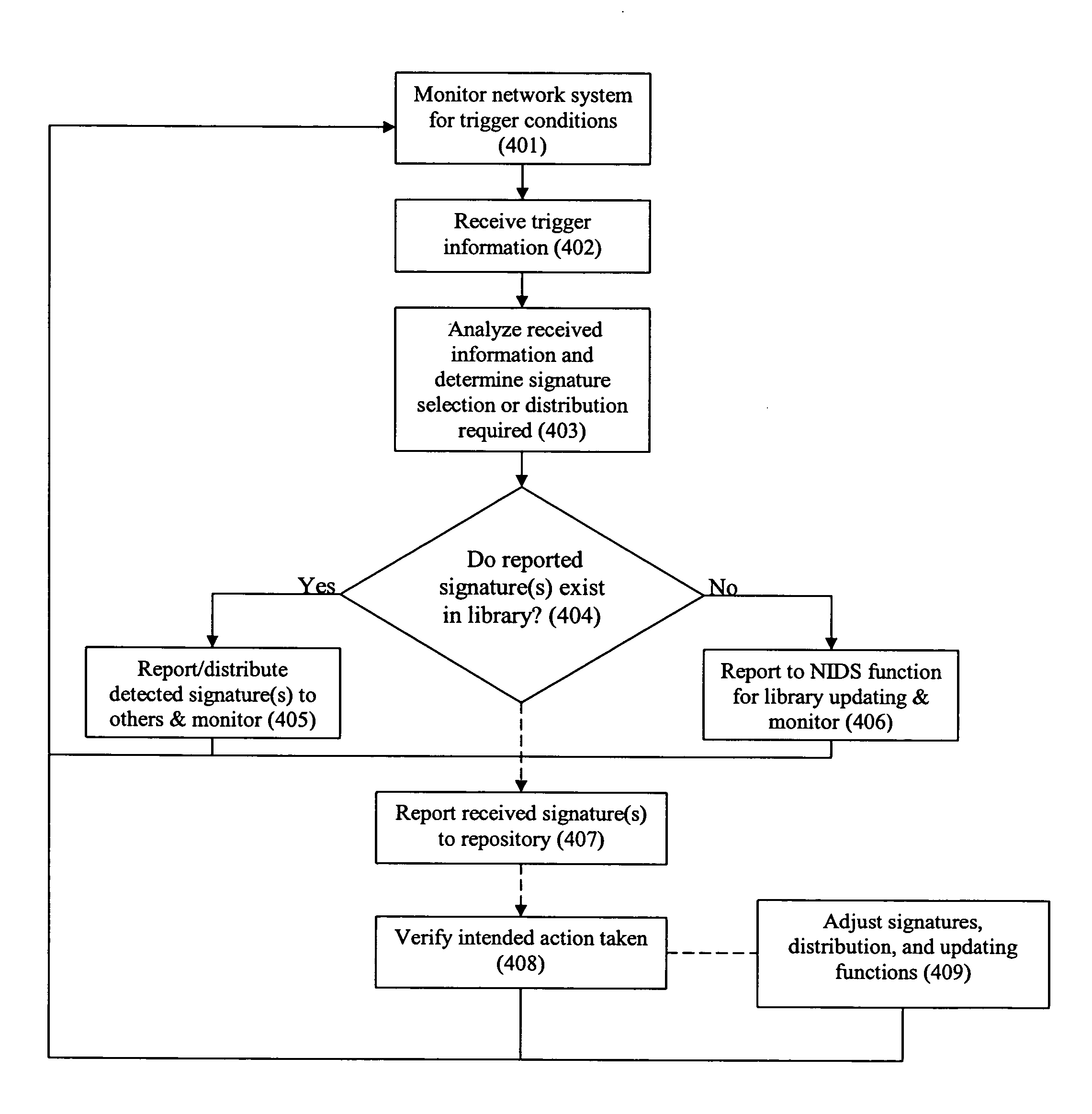
A system and method for the dynamic distribution of intrusion signatures to aid in protecting a network system from harmful activities. An analysis function includes means for identifying one or more intrusion signatures to be dynamically distributed to an intrusion detection function for monitoring. The analysis function and / or the intrusion detection function may be centralized or distributed. Monitoring may be prioritized, localized, and made operational or non-operational. The intrusion detection function may be embodied in either or both of an appliance and a network forwarding device. The analysis function may distribute the intrusion detection function in addition to the intrusion signatures. In one embodiment of the invention, the system includes an intrusion detection function and a dynamic intrusion signatures function. The intrusion detection function monitors for and reports detected intrusion signatures. The dynamic intrusion signatures function determines whether reported intrusion signatures exist in a library of signatures associated with a particular intrusion detection function. If the reported signature does not exist in the library, the library is updated. Detected intrusion signatures are reported to similarly enabled devices for library analysis and updating, if necessary. The related method includes the steps of monitoring for intrusion signatures or other triggering events, analyzing the events and updating IDS signature libraries as necessary. Optional steps of the method include verifying that reported information has been received and acted upon, and recording of the detection, reporting, and updating information in a central repository. The system and method enable dynamic distribution of IDS signatures enabling improved network IDS coverage while limiting the processing and storage requirements of network devices, particularly forwarding devices such as switches and routers that may include the IDS function. That capability enables broader coverage, faster and better tuned responses to harmful activities.
Owner:EXTREME NETWORKS INC
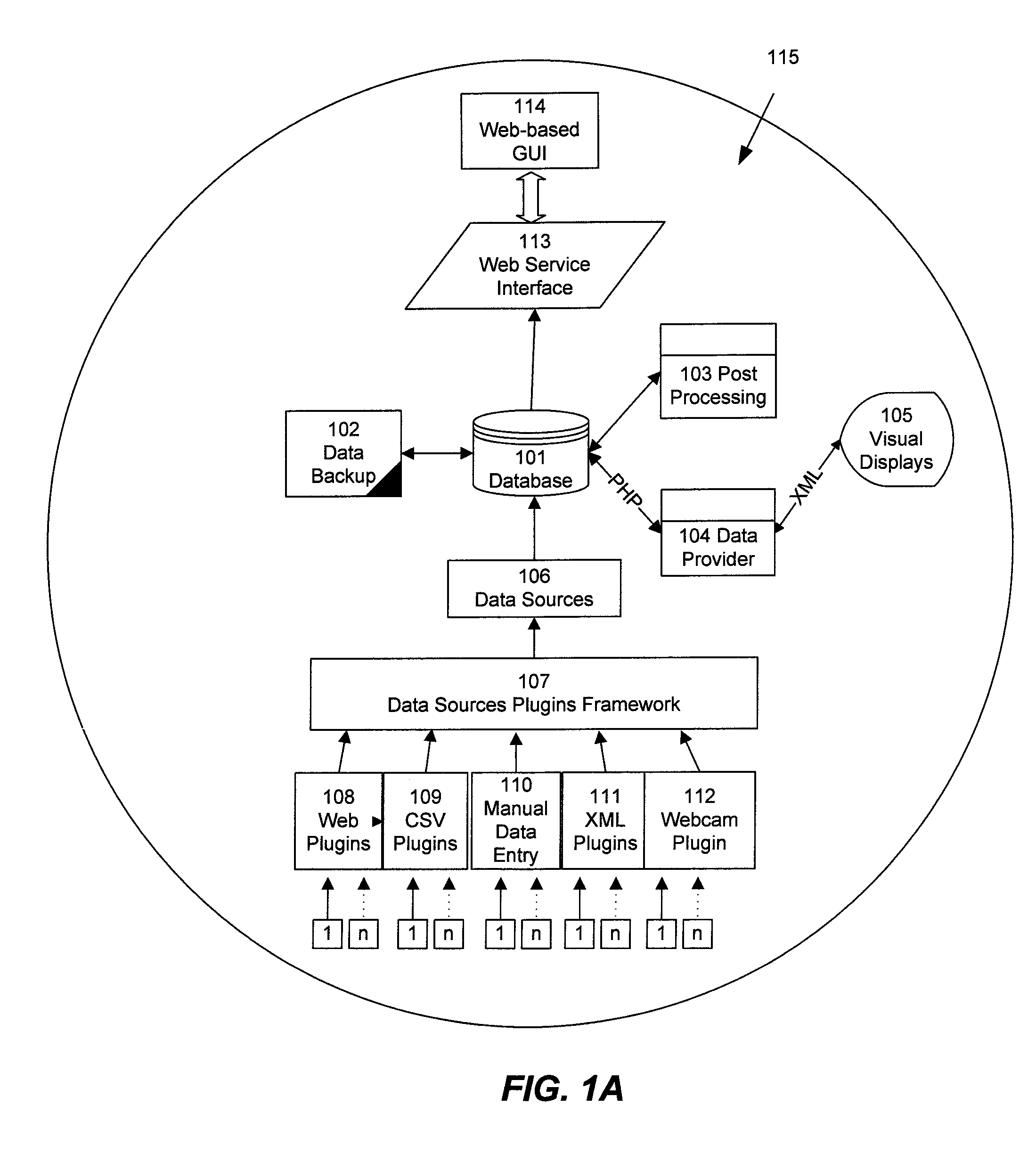
Method and system for on-line content acquisition and distribution
InactiveUS20090044235A1Two-way working systemsBuying/selling/leasing transactionsThird partyMobile telephony
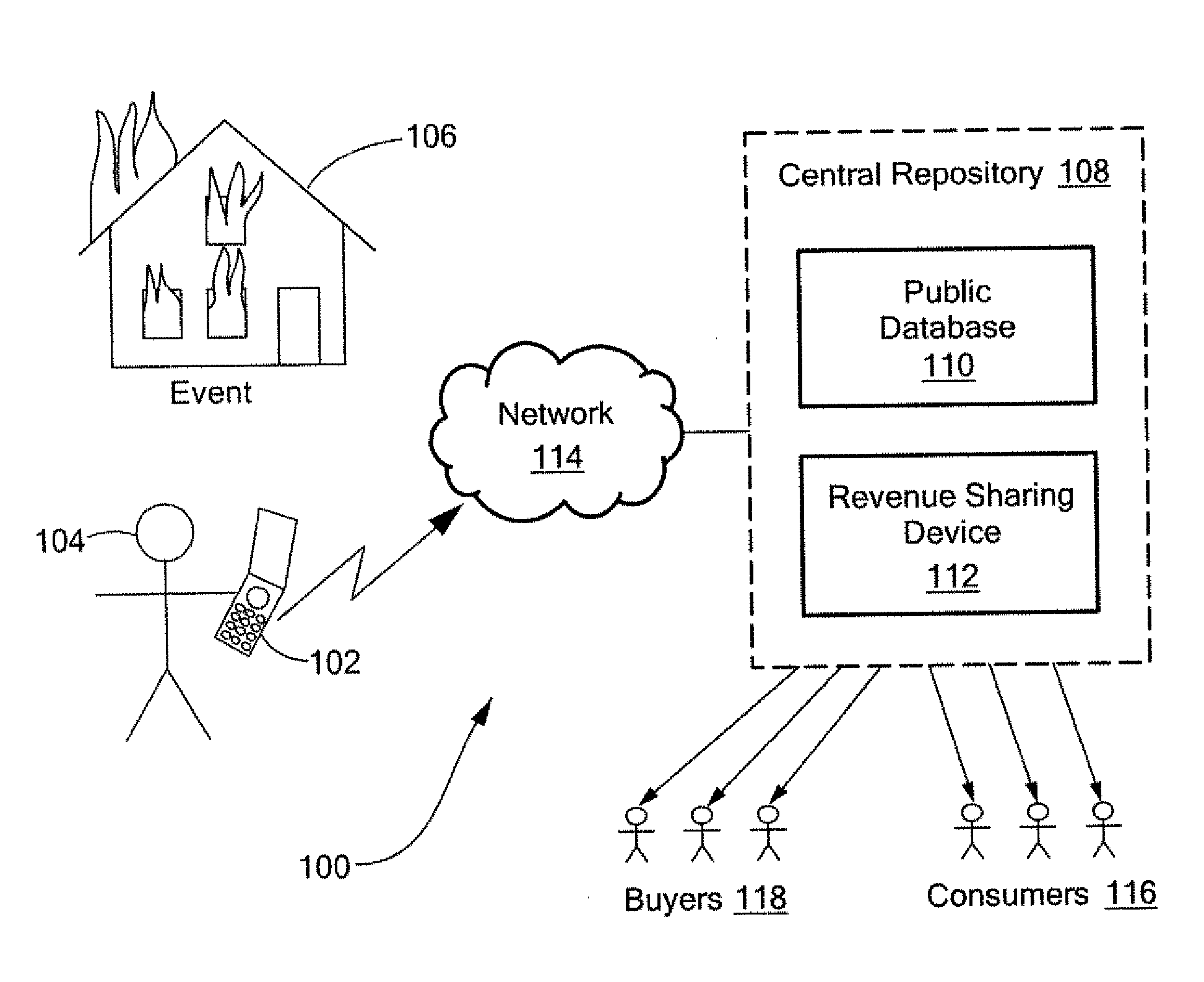
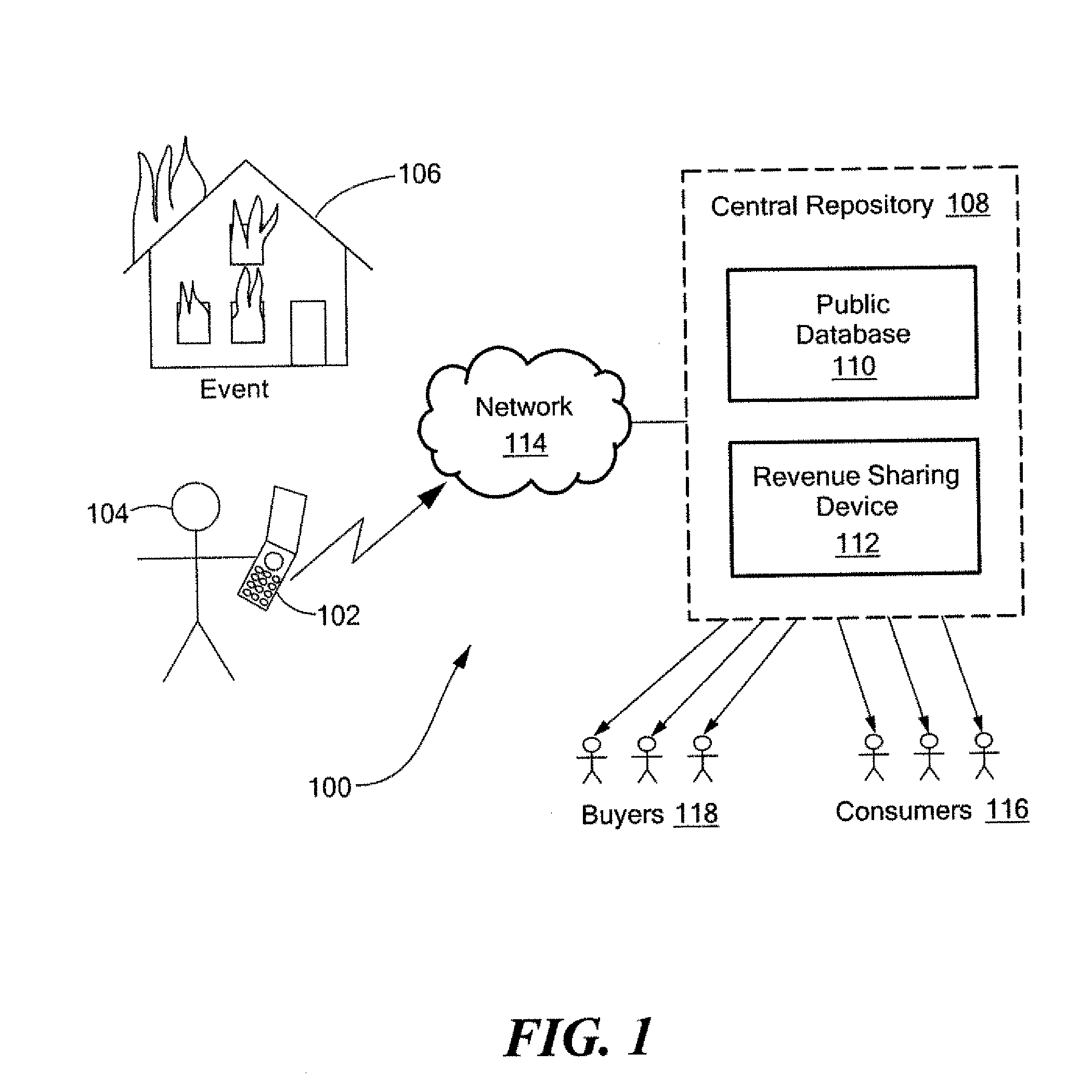
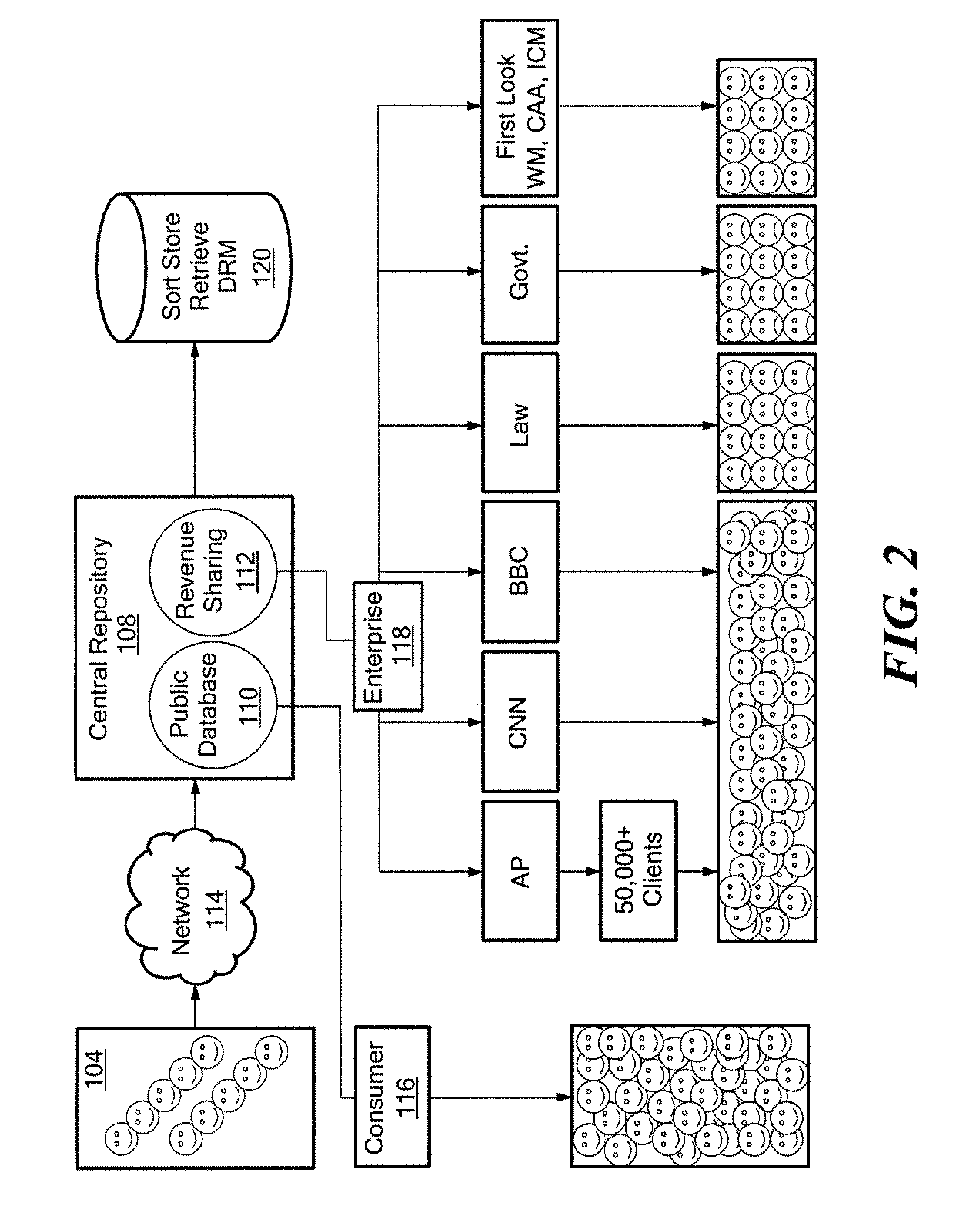
A method and system for capturing and distributing electronic media content over a communications network. One or more subscribers capture media about a specific event with the use of a media capture device such as the camera of a mobile phone. The subscriber contacts a central repository and transmits the media content to the repository where the content can be stored, indexed and categorized. The content can be made available to one or more interested third party subscribers such as, for example, news agencies seeking information about the event. A bidding system can be implemented to allow the agency with the highest bid to receive access to the desired content. In return, the subscriber that submitted the content can receive compensation for the submitted content.
Owner:ENGAGEMENT MEDIA TECH
Intelligent auto-archiving
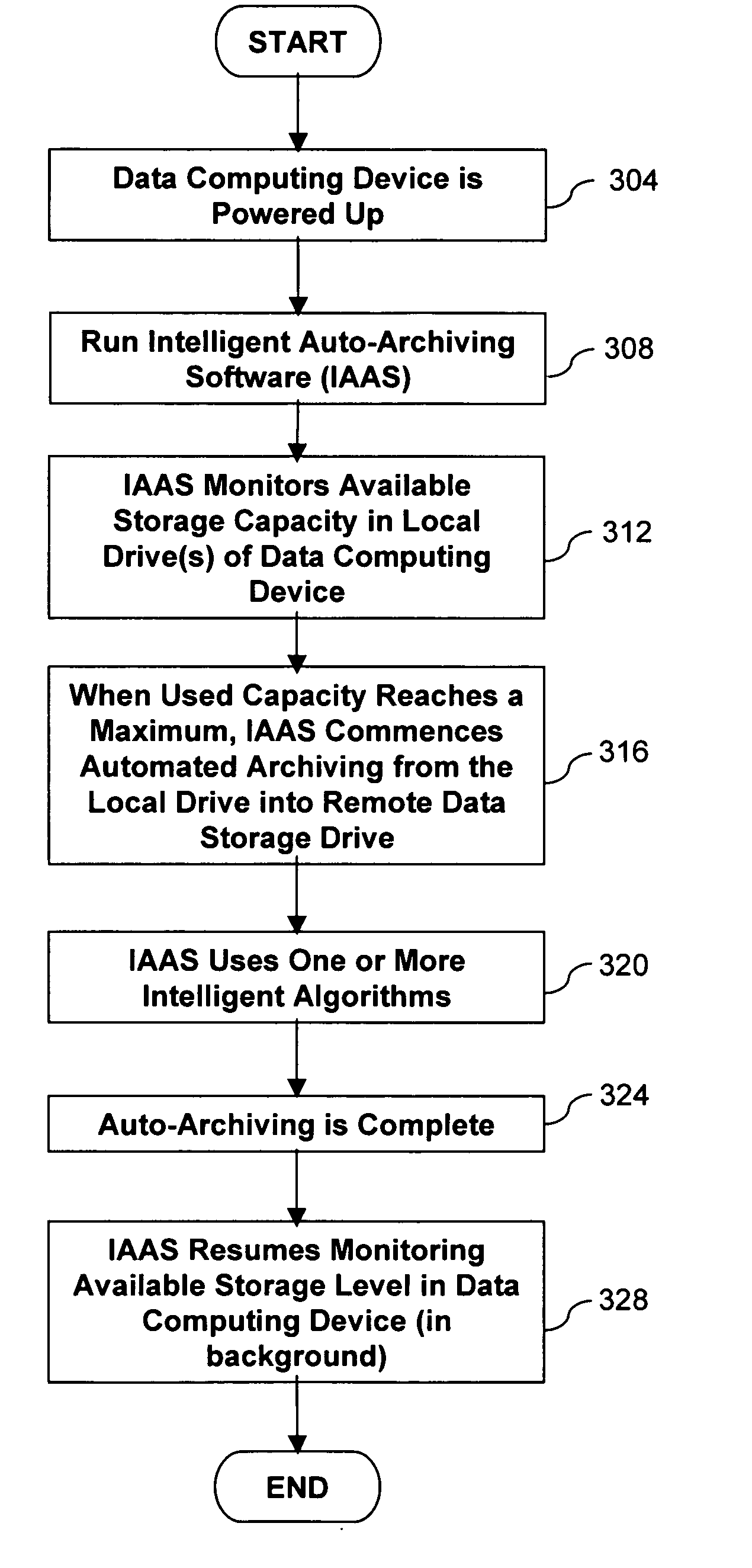
InactiveUS20060230136A1Digital data information retrievalDigital computer detailsData fileData store
Herein described is a method and system for archiving data files into a data storage device. The data storage device acts as a central depository where the data files may be archived by one or more data computing devices. The data storage device may be communicatively coupled to the one or more data computing devices in a network. The method may utilize one or more intelligent algorithms to prioritize which data files in a data computing device are archived into the data storage device. Further, a method and system for swapping data files between a data computing device and a data storage device is presented. An embodiment of a system comprises a first processor in a data computing device, a first software resident in said data computing device, a data storage device, a second processor in said data storage device, and a second software resident in said data storage device.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
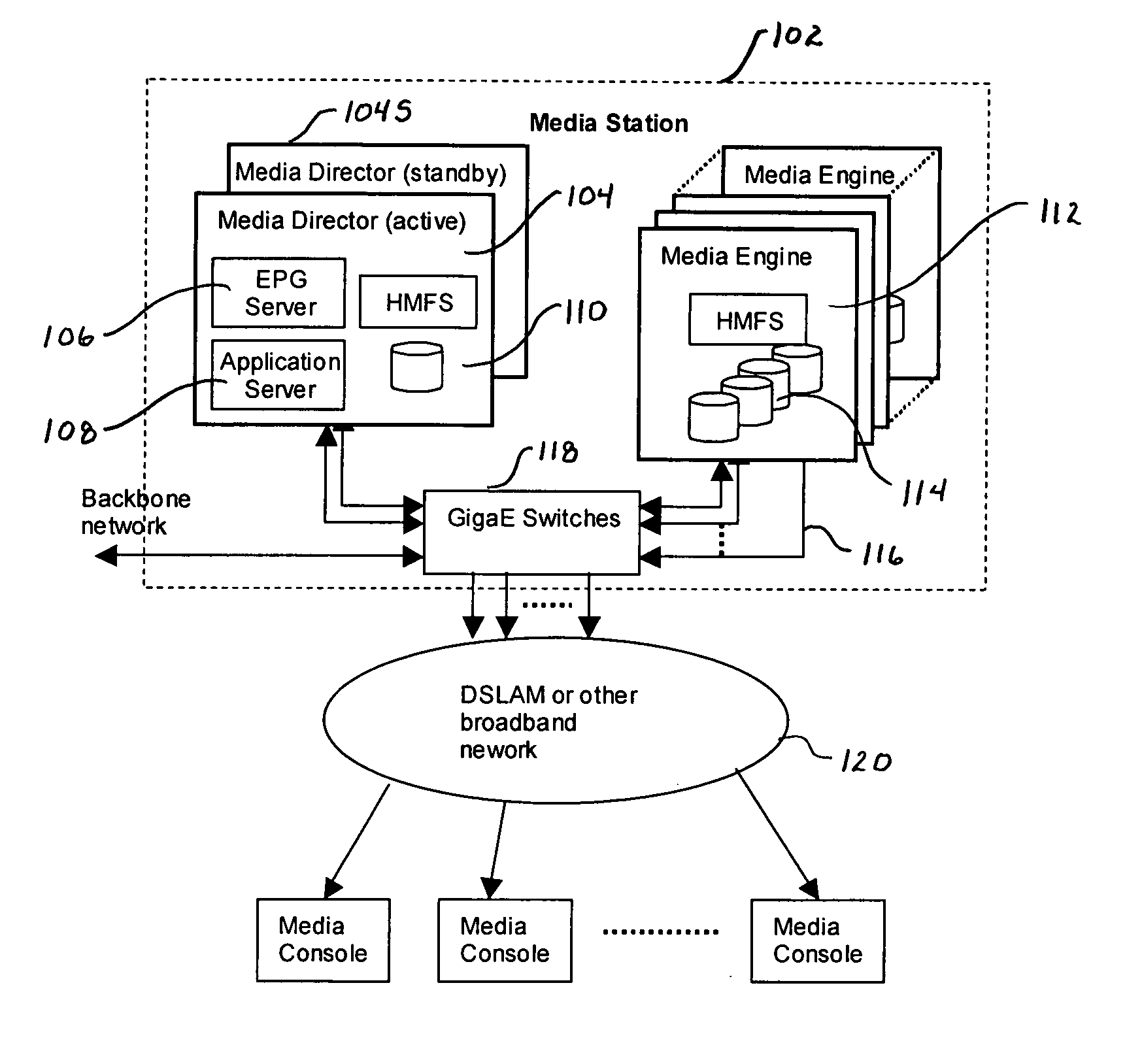
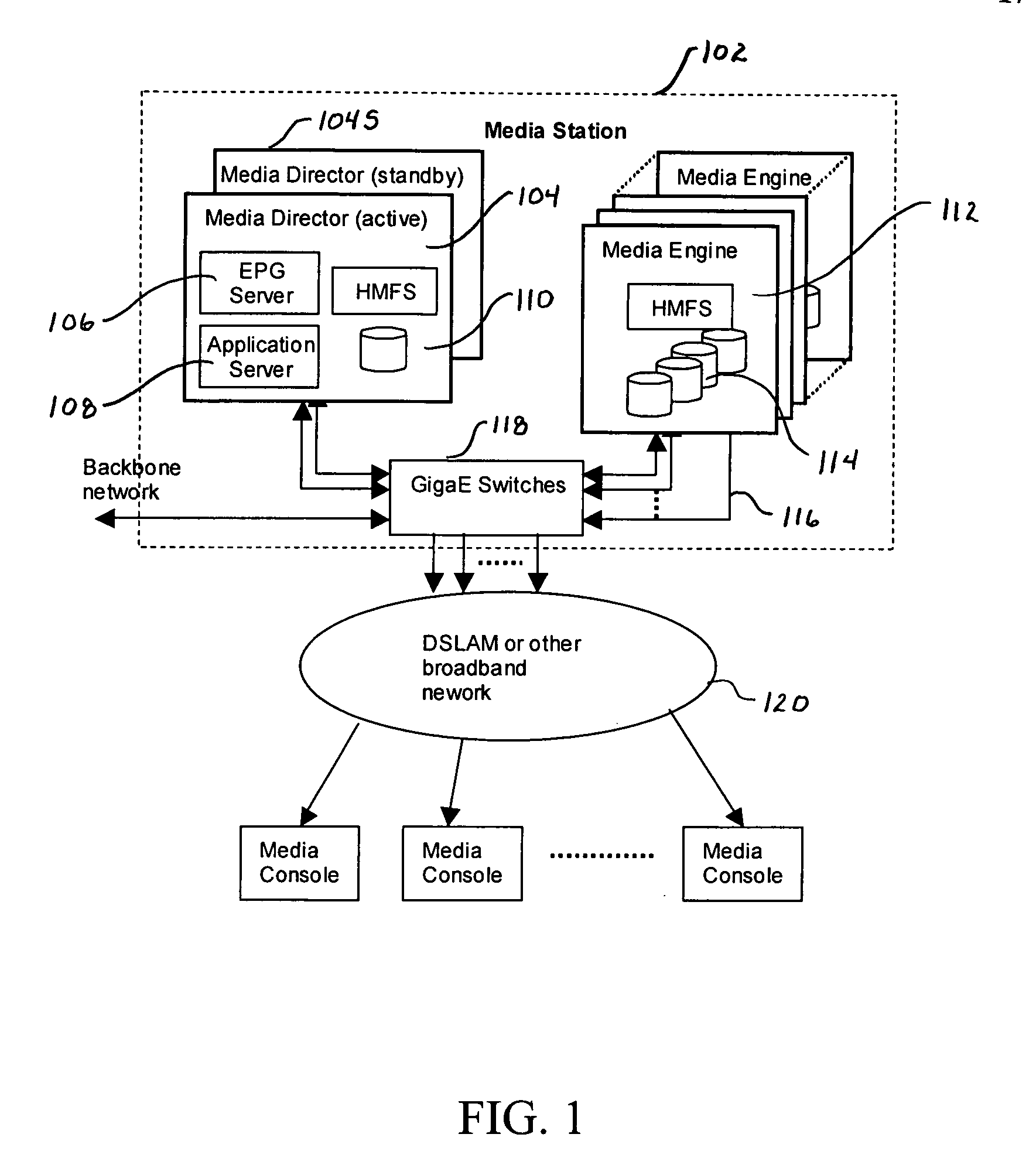
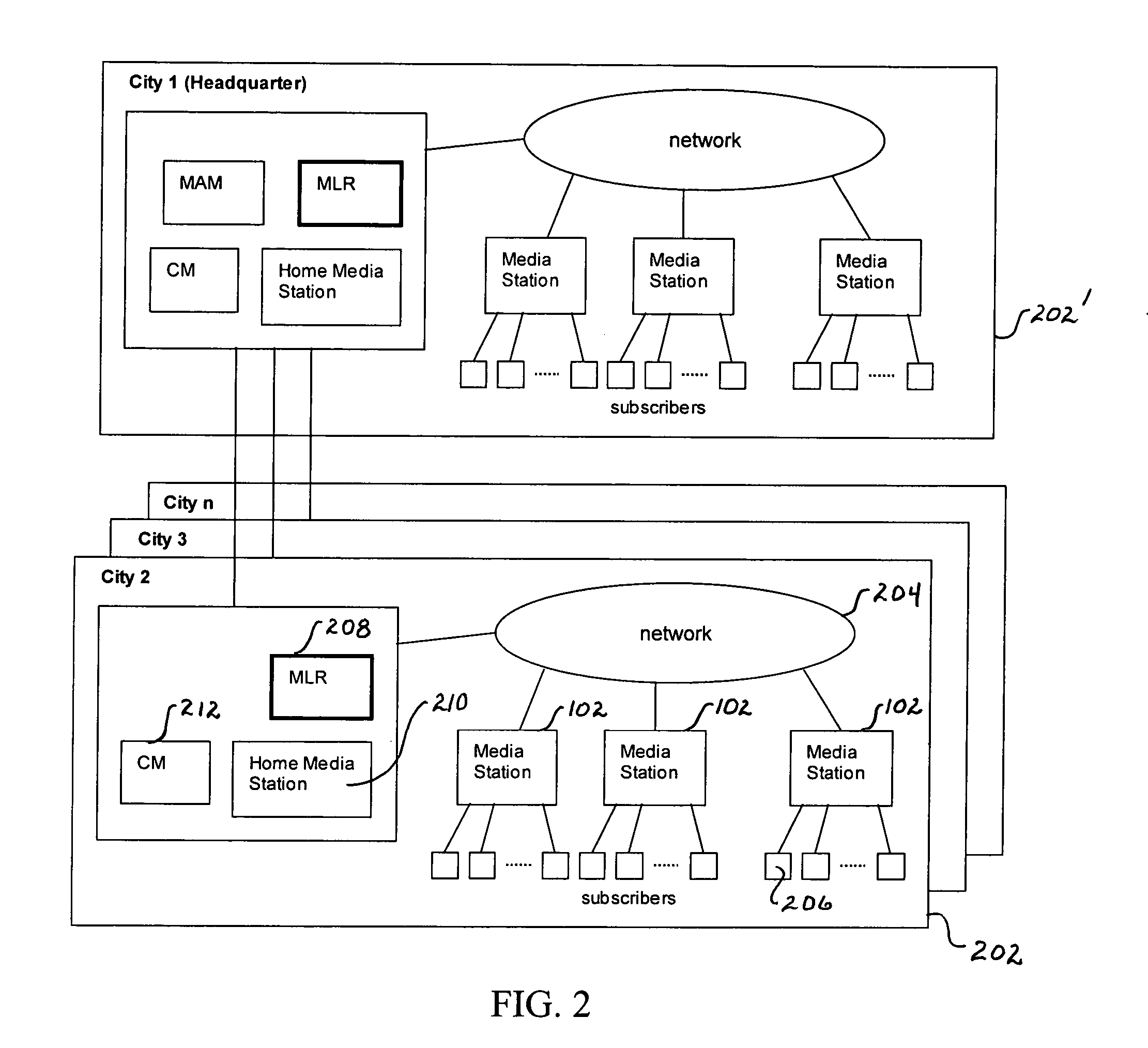
Method and apparatus for a loosely coupled, scalable distributed multimedia streaming system
InactiveUS20050262253A1Multiple digital computer combinationsDigital data authenticationComputer networkScalable distributed
A scalable distributed multimedia streaming system employs at least one media station having a media director and a plurality of media engines. Each media engine incorporates media content storage, communications channels for retrieving and streaming media content over a network. The media director has a controller adapted for directing retrieval over the network of media content by a selected media engine, tracking content stored on the media engines and redirecting a content request from a media console connected to the one media station over the network to a selected one of the media engines storing content corresponding to the request for streaming. Multiple media stations are employed to expand the network using a media location registry as a central repository for storing the location of all media content in the media stations. Intercommunication between the media stations for transfer of content is accomplished through the network.
Owner:UTSTARCOM INC
Method and apparatus for deploying service modules among service nodes distributed in an intelligent network
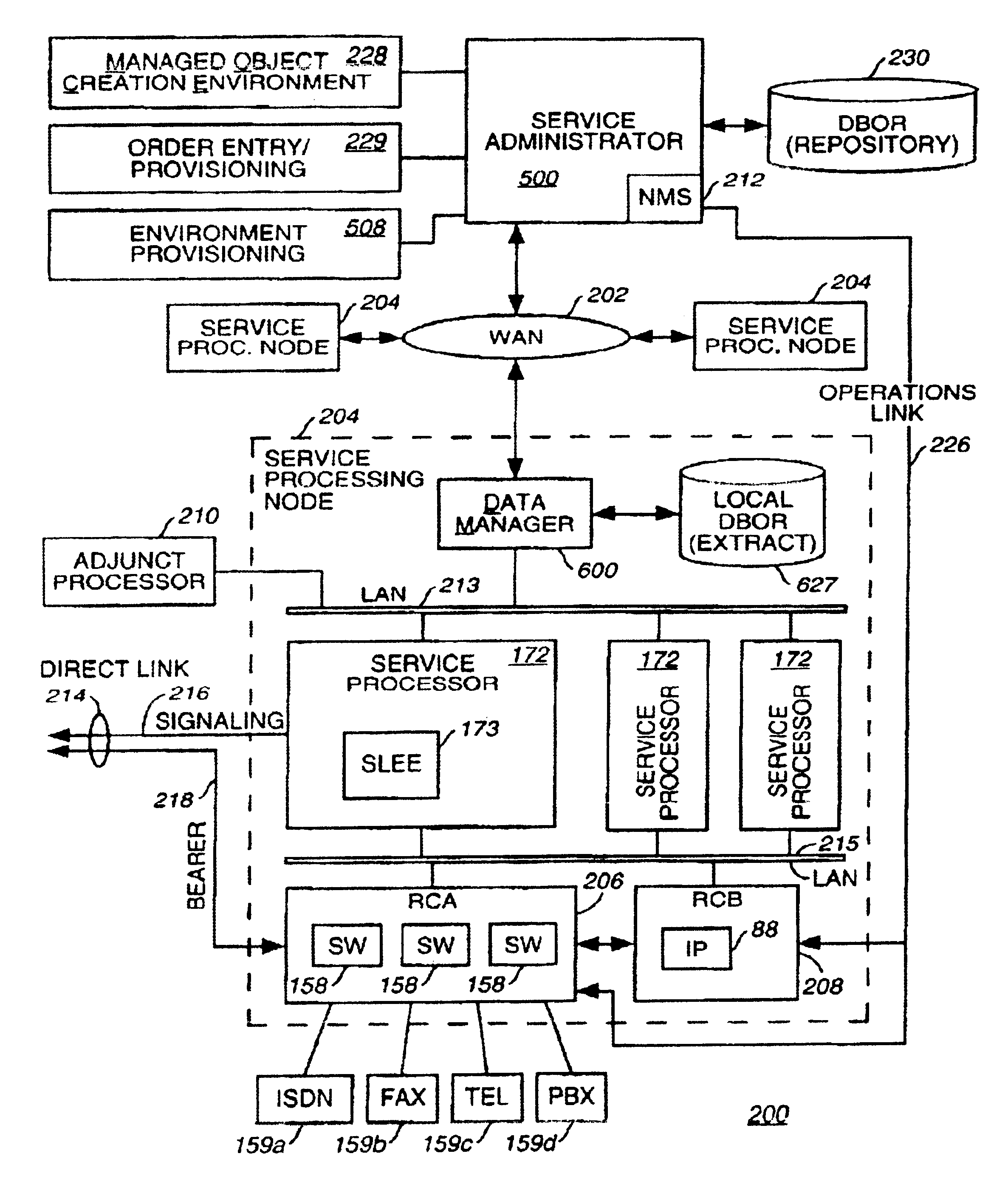
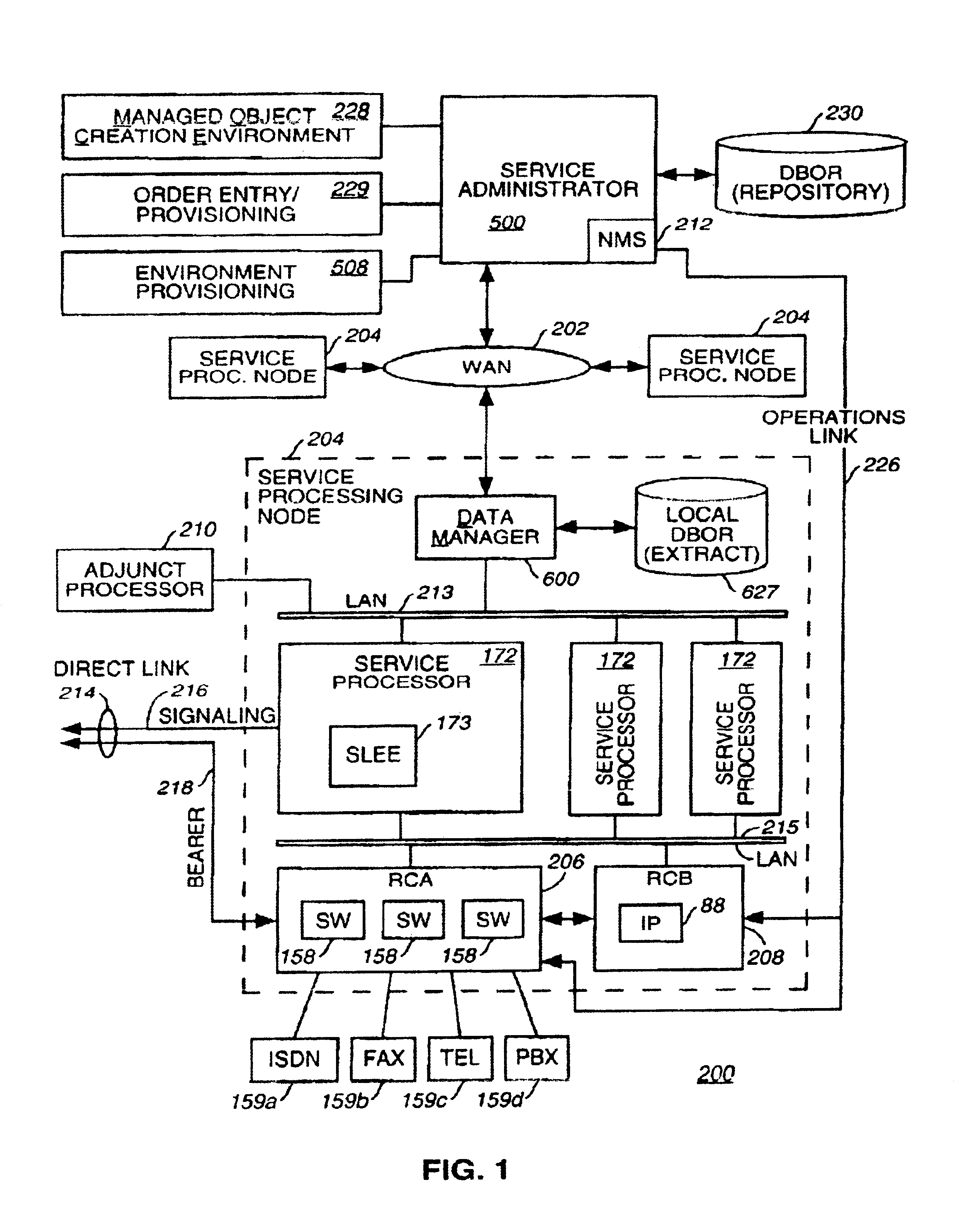
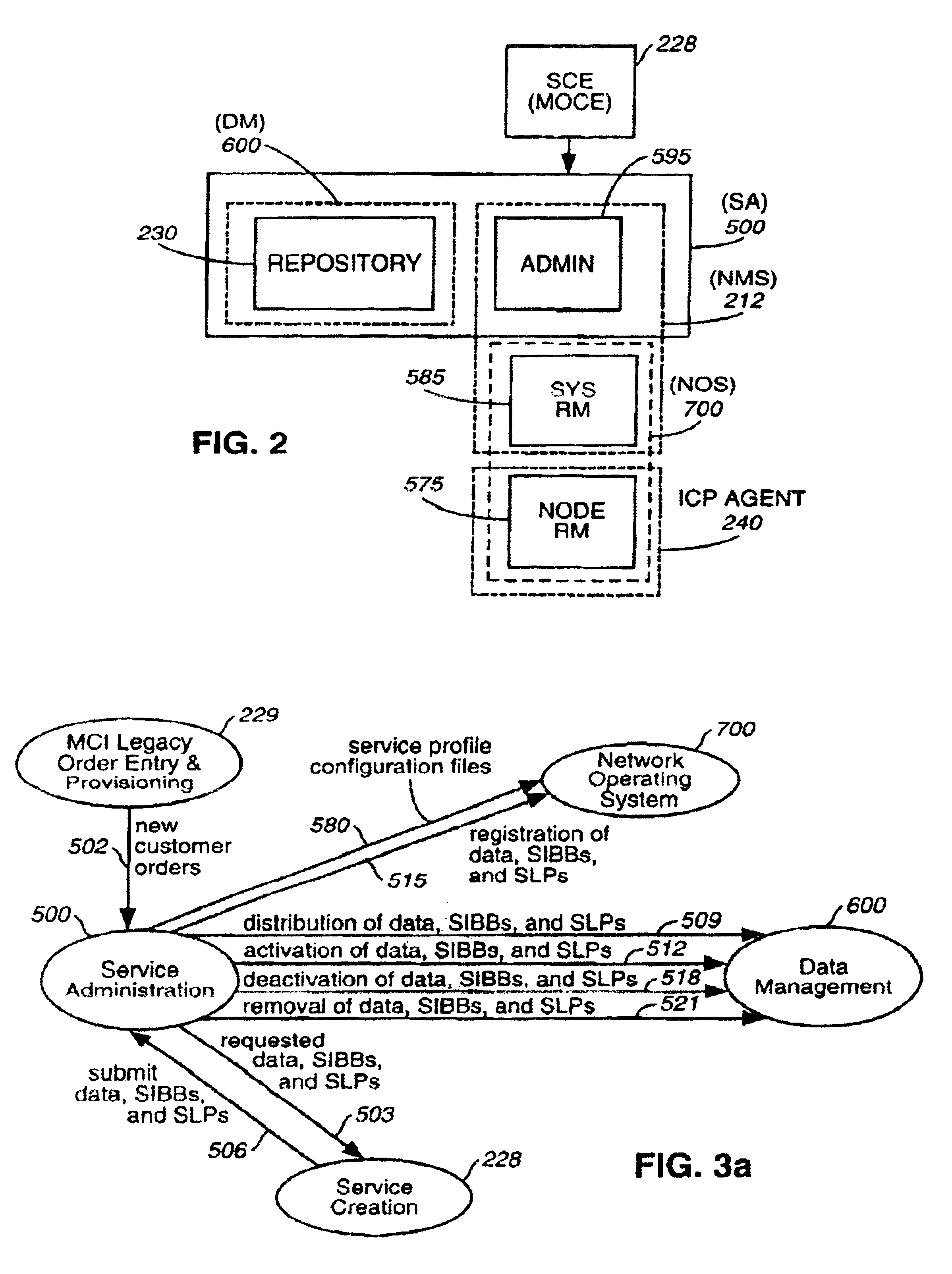
InactiveUS7024450B1Promote recoveryAvoid redundancySpecial service for subscribersMultiple digital computer combinationsIntelligent NetworkManagement object
Owner:VERIZON PATENT & LICENSING INC
Peer-to-Peer Interactive Media-on-Demand
ActiveUS20080037527A1High probability of packet lossImproved scaling characteristicSelective content distributionNetwork connectionsThe InternetClient-side
A scalable Media-on-Demand (MoD) method to a large group of users in the Internet. This method makes use of peer buffering capabilities to collaborate in the distribution and downloading of media, facilitated by a central repository for the search of optimal peers as parent nodes to connect to and for the support of advanced features such as fast forward and backward plays. The method relieves the server load by shifting the media streaming functionality to the client side with high media receiving continuity and quality, leading to well-balanced and low network loads.
Owner:THE HONG KONG UNIV OF SCI & TECH
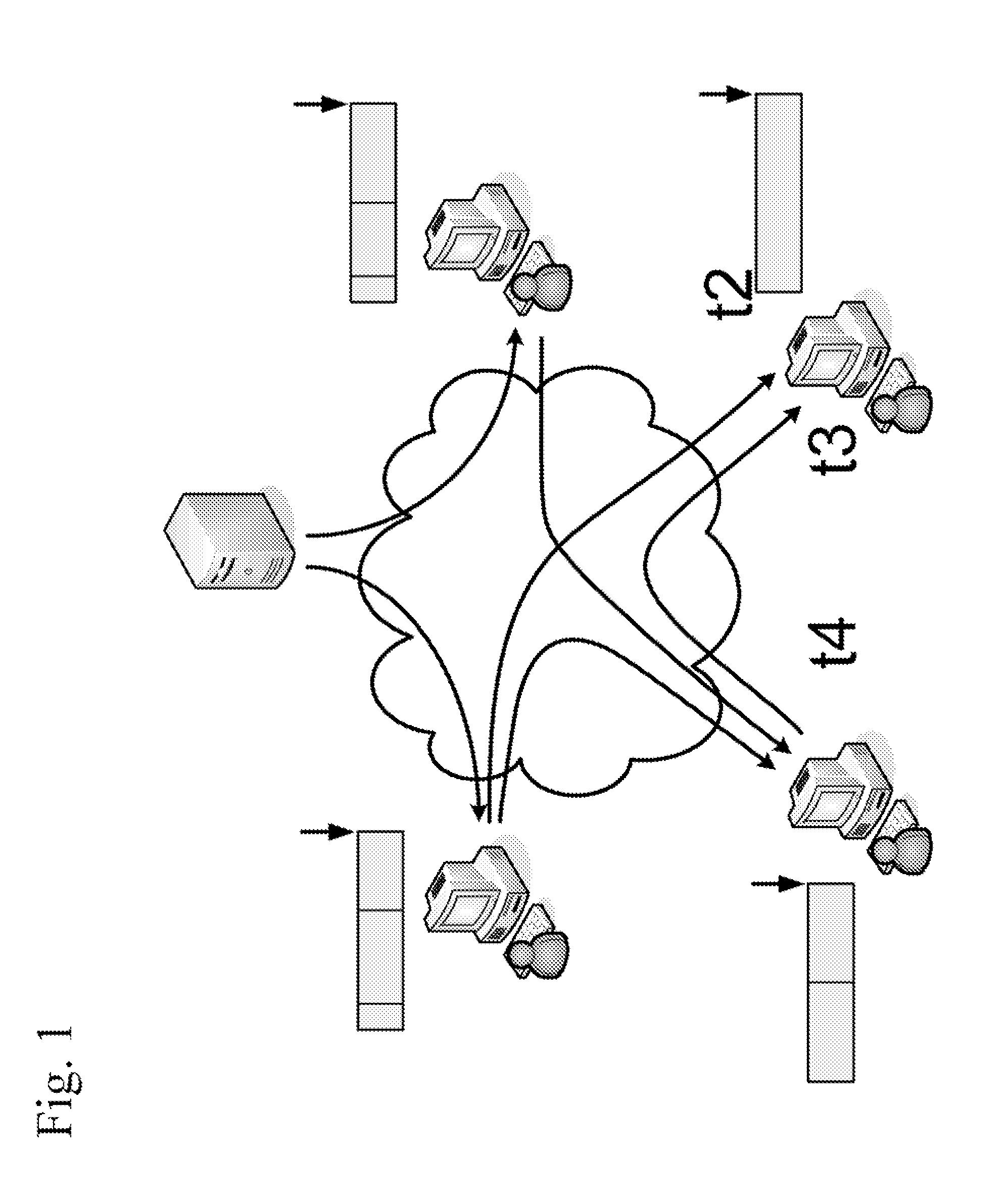
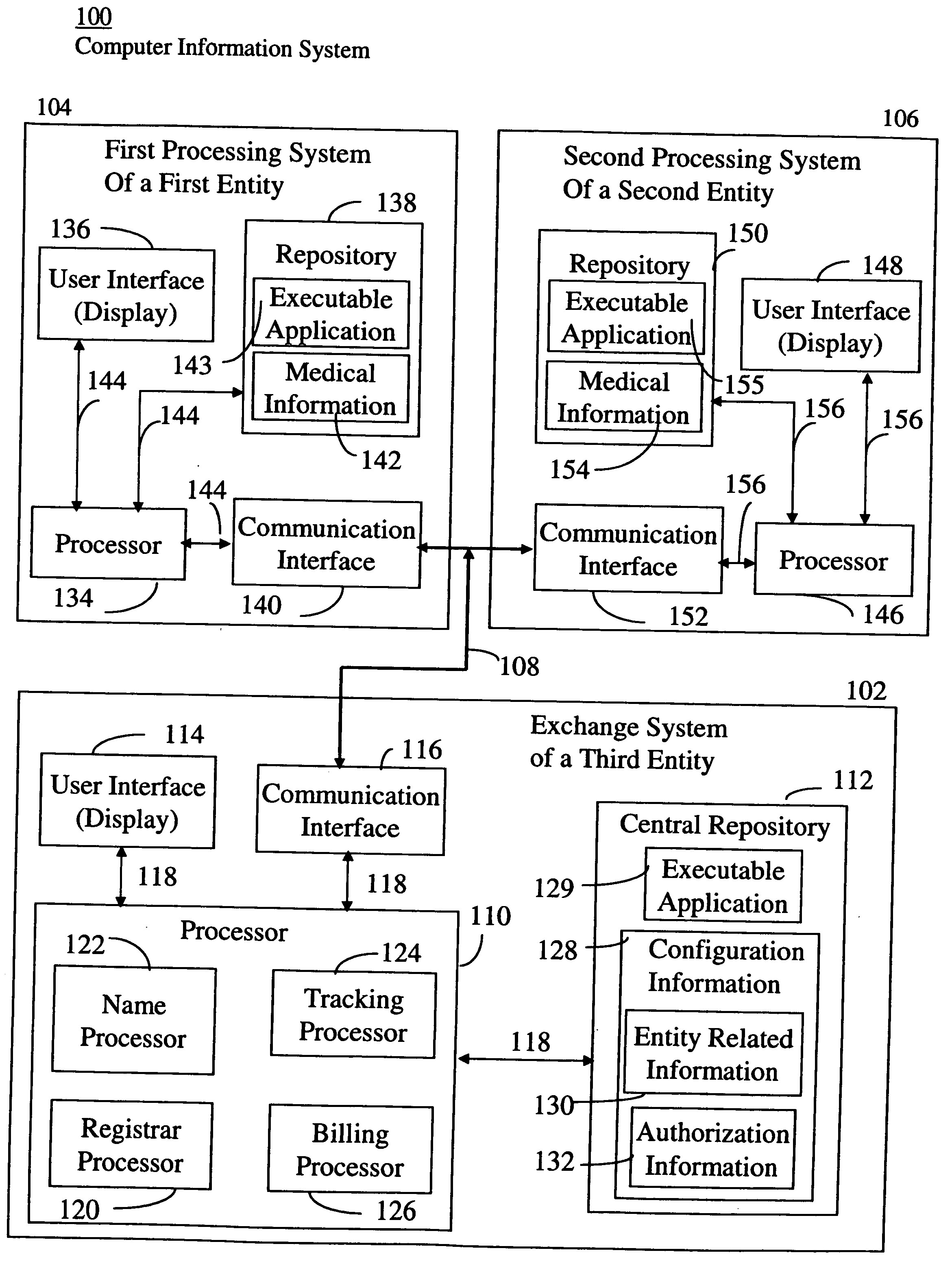
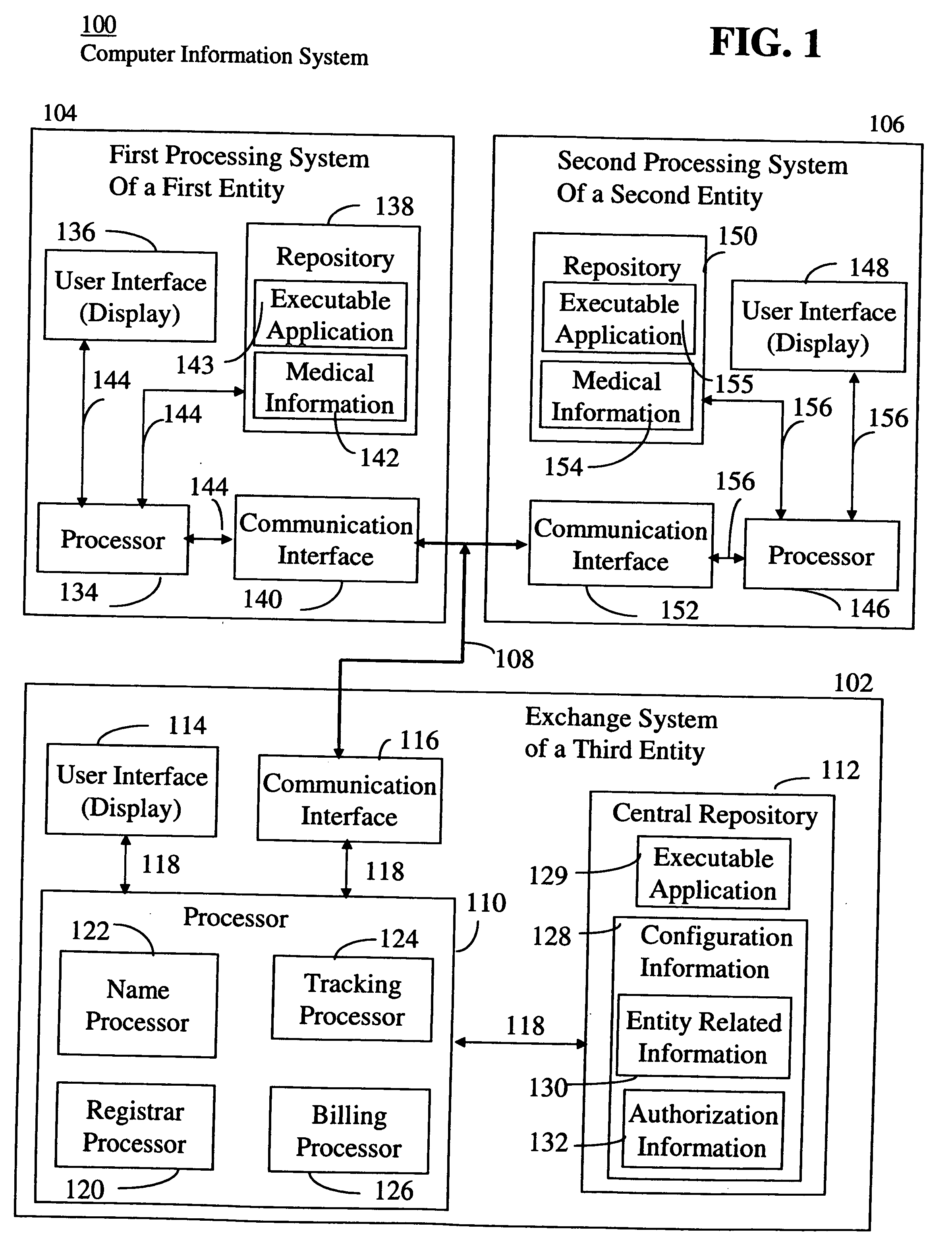
System supporting exchange of medical data and images between different executable applications
InactiveUS20050216314A1Patient personal data managementOffice automationMedical recordApplication procedure
A system, for exchanging medical image data between different processing systems, includes a central repository and an interface. The central repository stores configuration information including entity related information and authorization information. The authorization information associates a user with an indicator of authorization to access particular patient medical records. Multiple different processing systems of corresponding different entities use the configuration information to access medical image data repositories of the corresponding different entities and to enable exchange of medical image data between the different entities. The interface receives, from a first processing system of a first entity, a user initiated request to access a medical image repository of a second processing system of a second entity. The interface accesses the central repository in retrieving configuration information. The interface communicates the retrieved configuration information to the first processing system.
Owner:SIEMENS MEDICAL SOLUTIONS HEALTH SERVICES CORPORAT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com