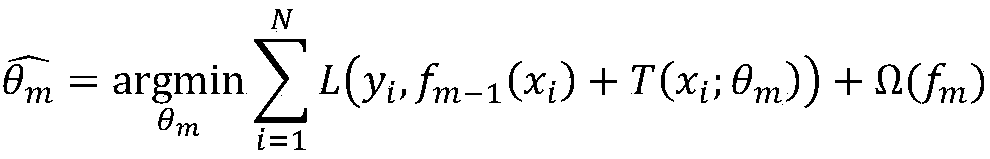Patents
Literature
755 results about "Online machine learning" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, online machine learning is a method of machine learning in which data becomes available in a sequential order and is used to update our best predictor for future data at each step, as opposed to batch learning techniques which generate the best predictor by learning on the entire training data set at once. Online learning is a common technique used in areas of machine learning where it is computationally infeasible to train over the entire dataset, requiring the need of out-of-core algorithms. It is also used in situations where it is necessary for the algorithm to dynamically adapt to new patterns in the data, or when the data itself is generated as a function of time, e.g., stock price prediction. Online learning algorithms may be prone to catastrophic interference, a problem that can be addressed by incremental learning approaches.
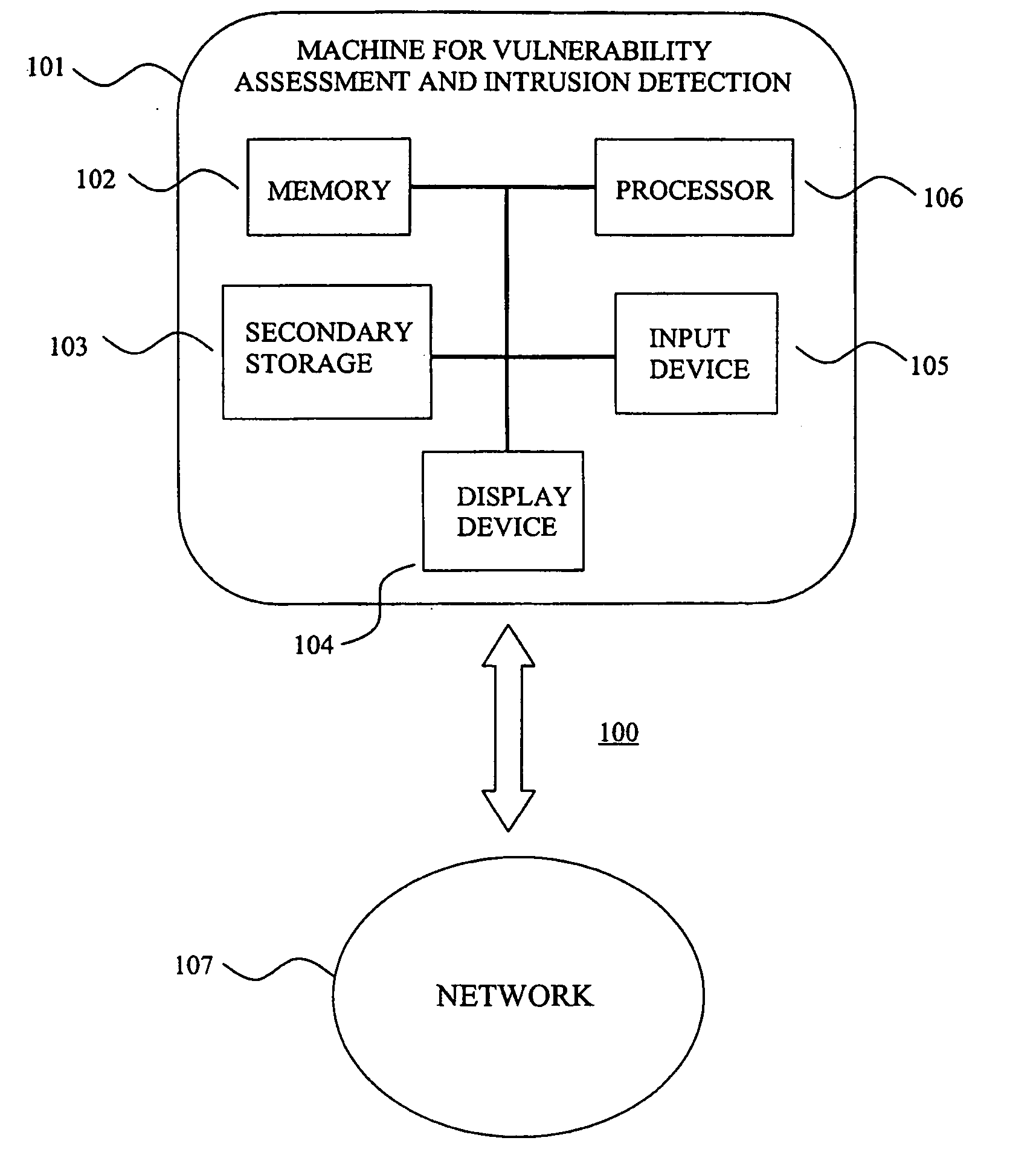
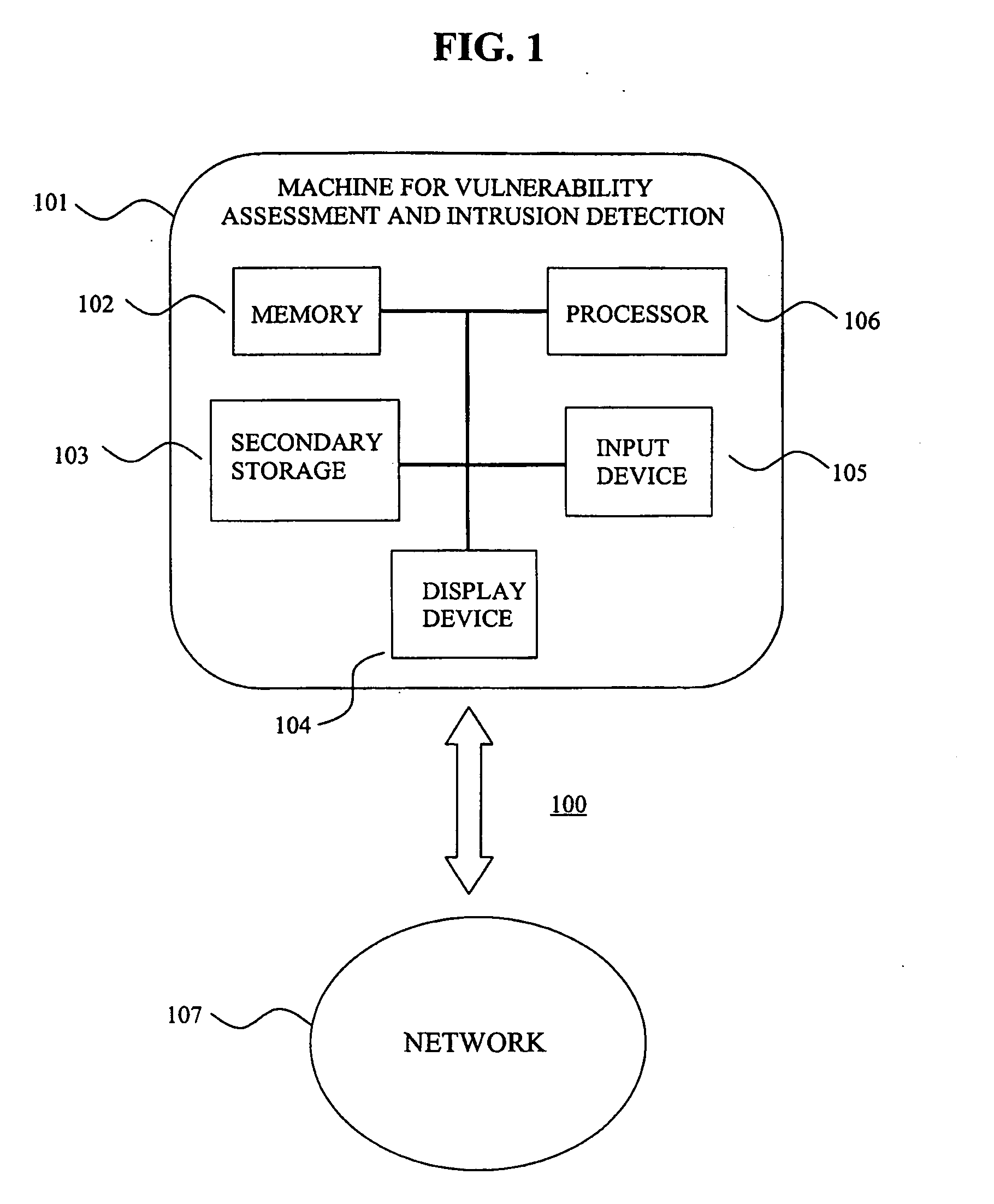
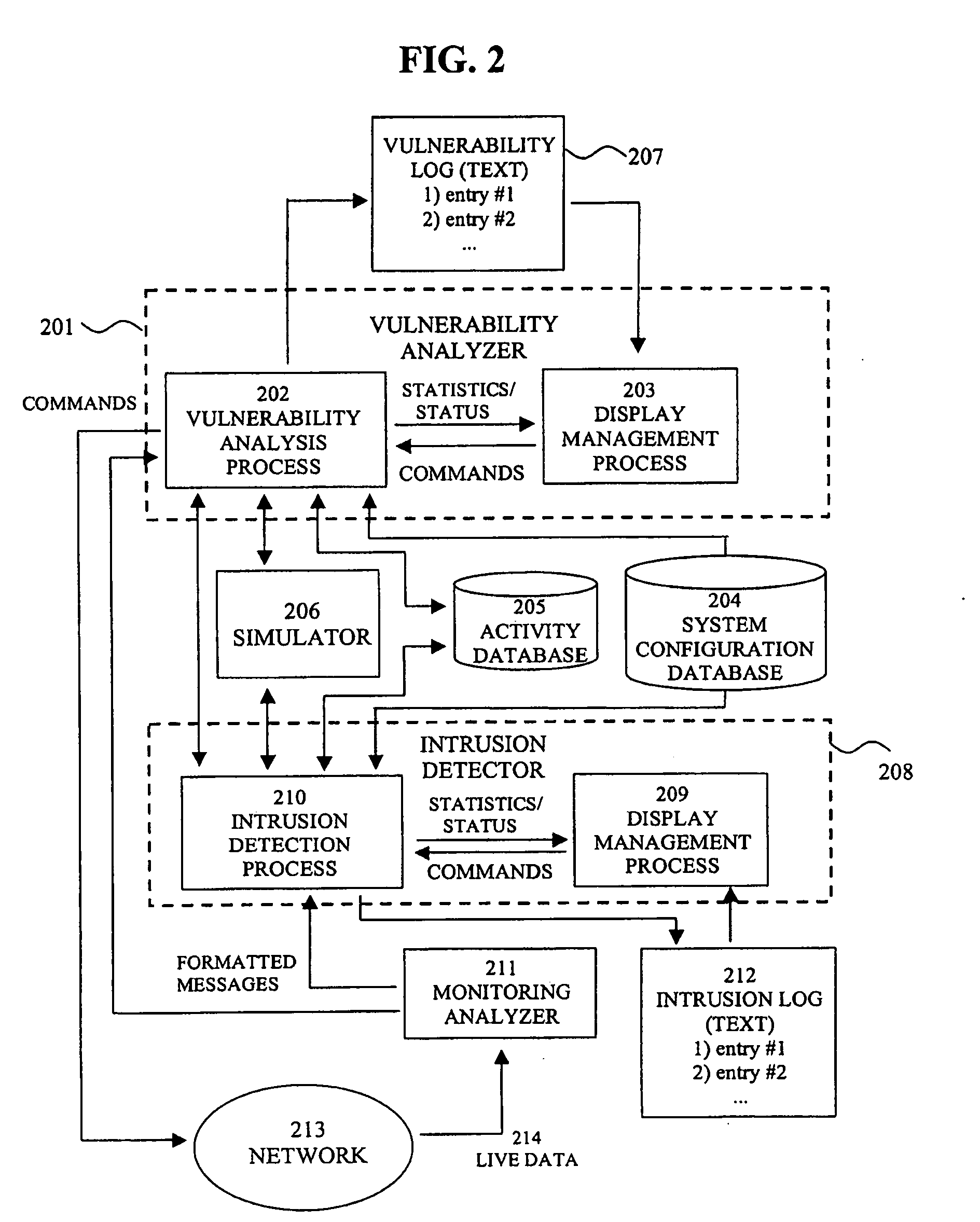
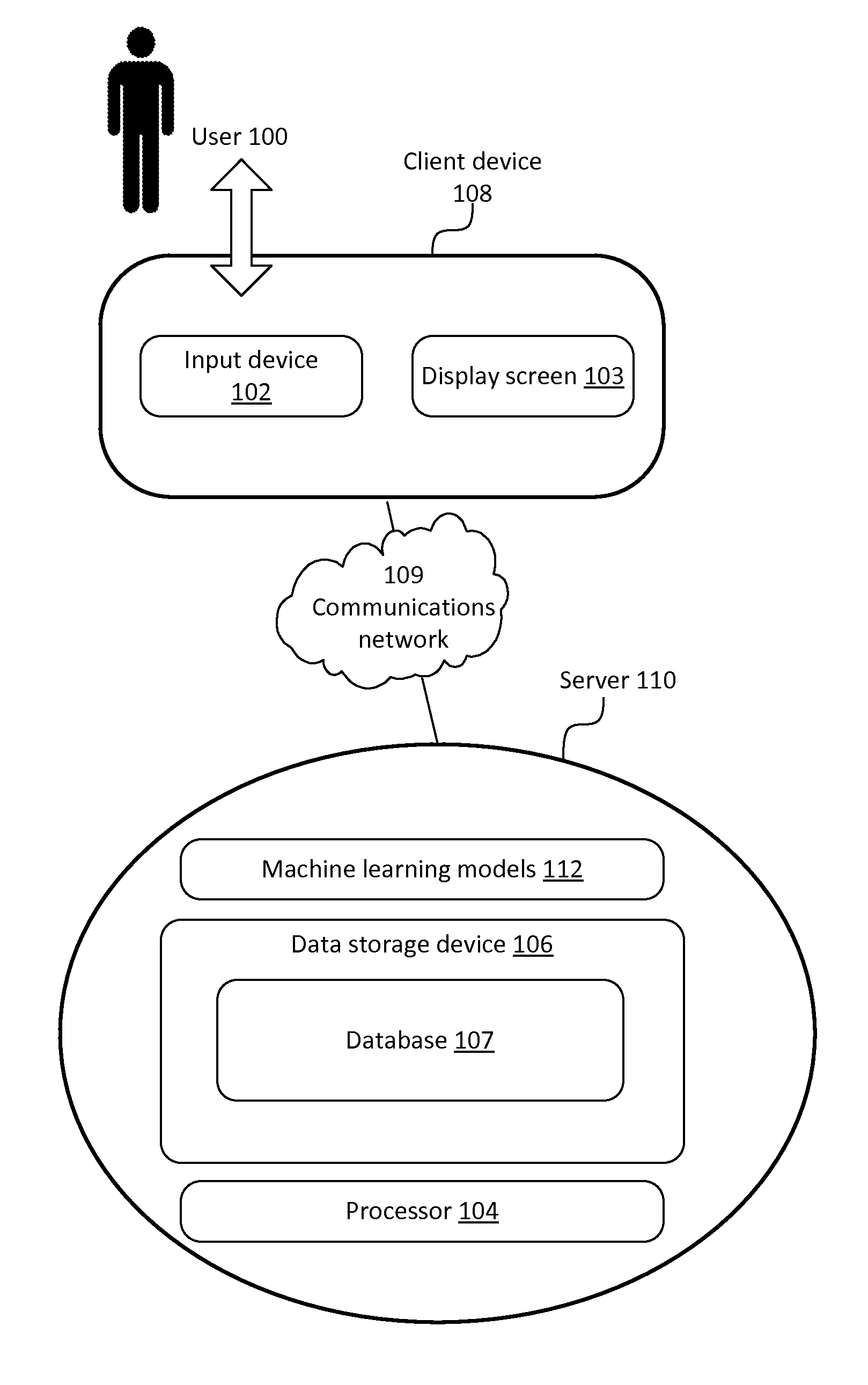
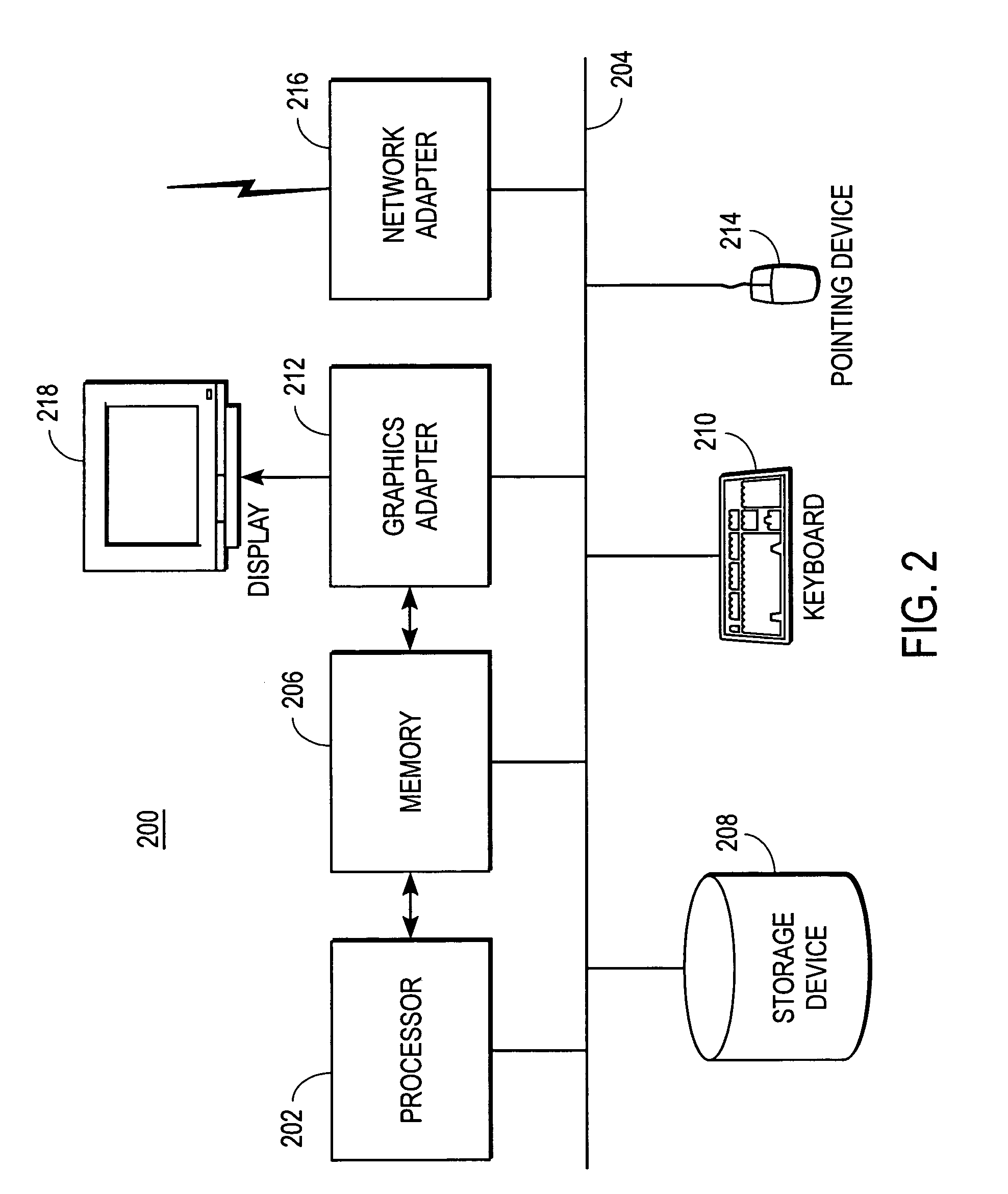
System for intrusion detection and vulnerability assessment in a computer network using simulation and machine learning
InactiveUS20060191010A1Memory loss protectionError detection/correctionComputer configurationData transmission
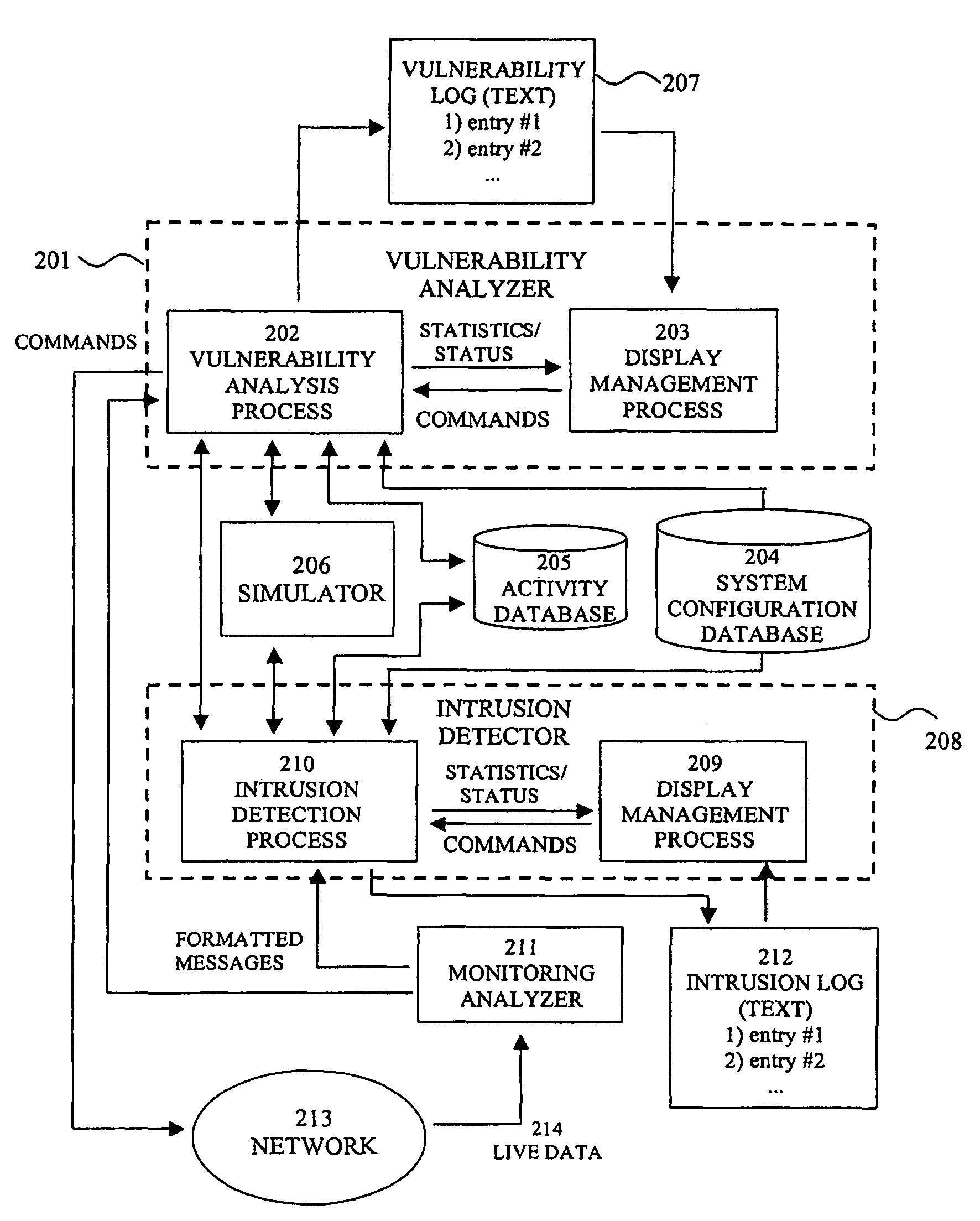
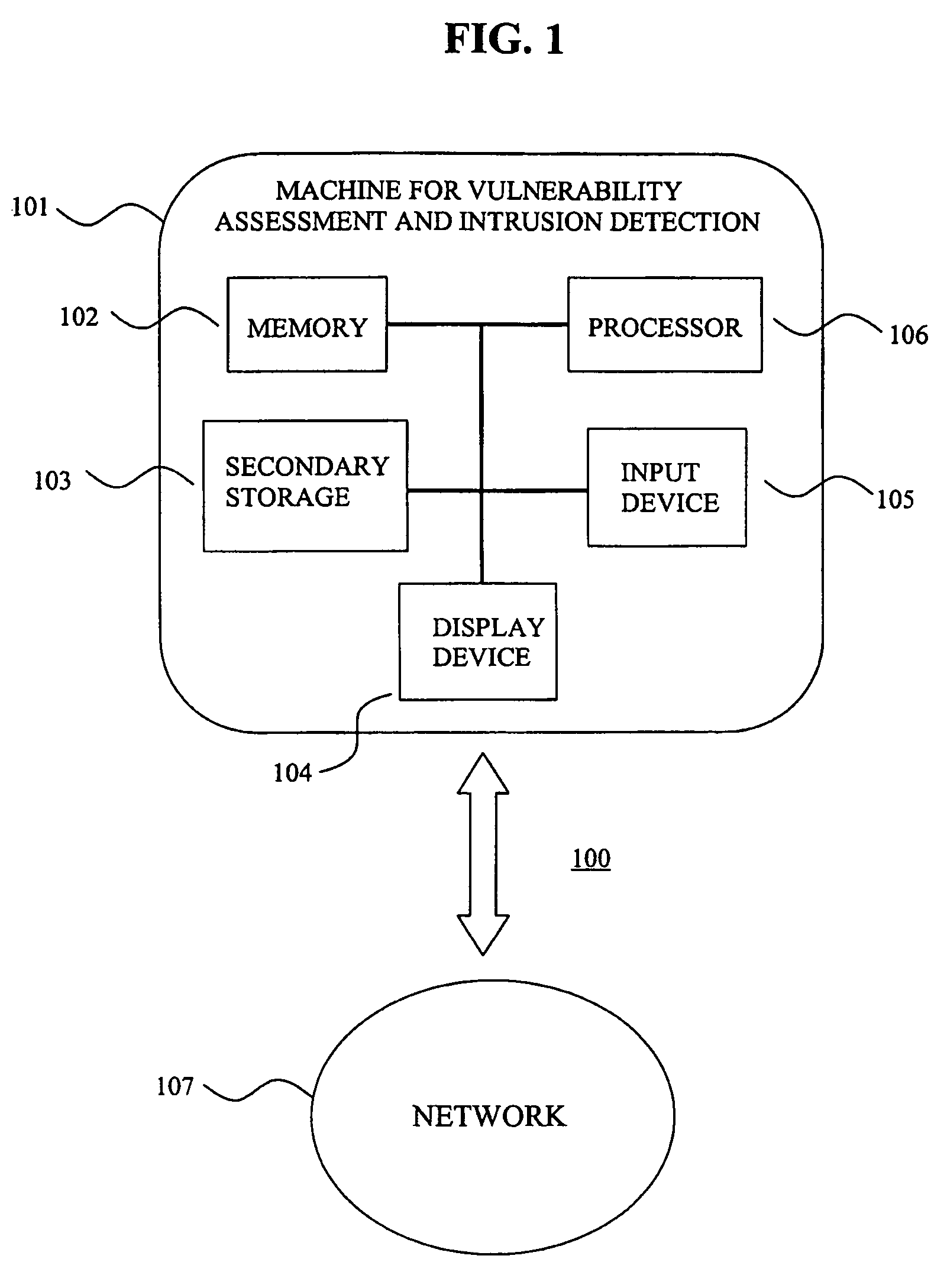
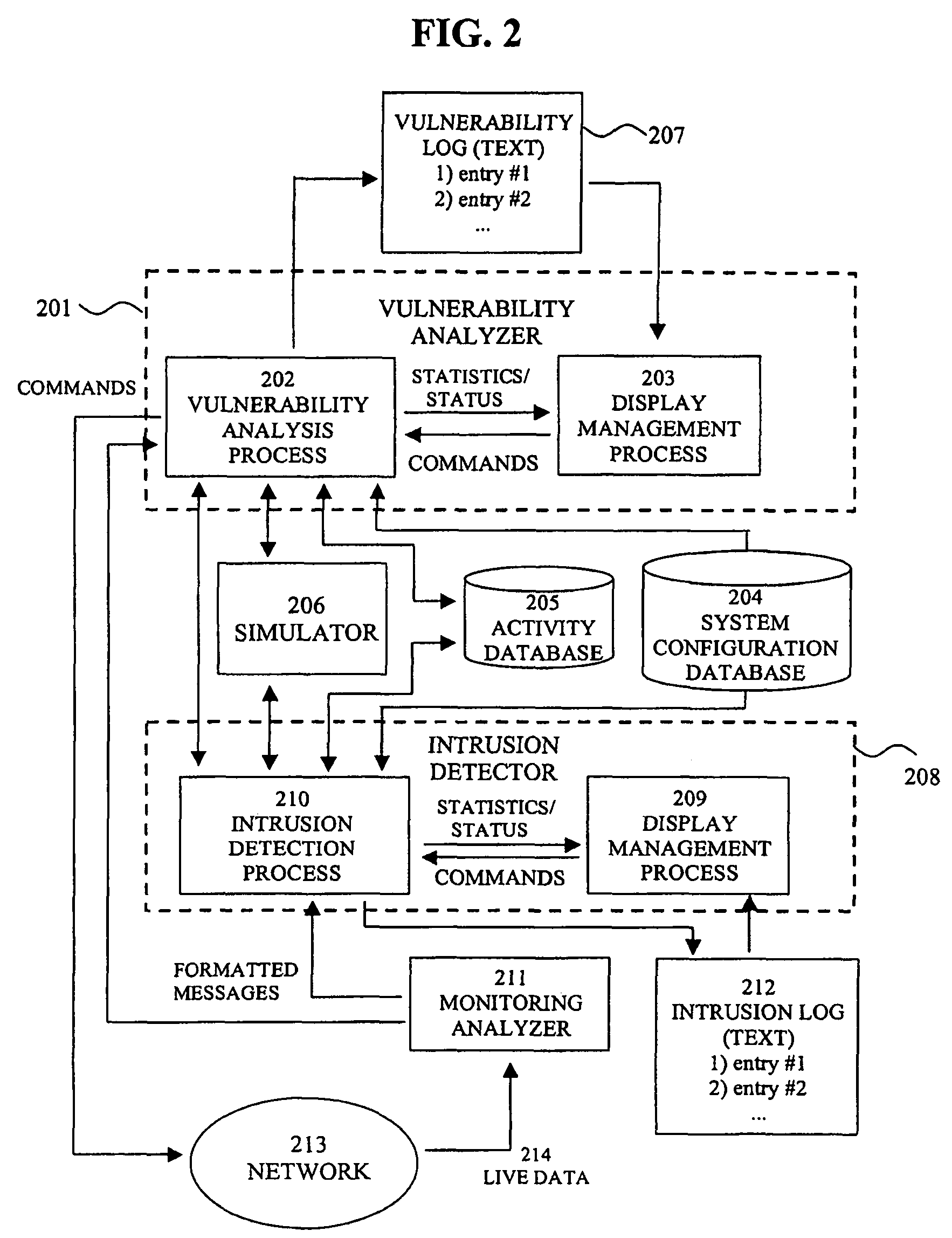
The present invention provides a system and method for predicting and preventing unauthorized intrusion in a computer configuration. Preferably, the invention comprises a communication network to which at least two computing devices connect, wherein at least one of the computing devices is operable to receive data transmitted by the other computing device. The invention further comprises a database that is accessible over the network and operable to store information related to the network. A vulnerability assessment component is provided that is operable to execute a command over the communication network, and a data monitoring utility operates to monitor data transmitted over the communication network as the vulnerability assessment component executes commands. Also, an intrusion detection component is included that is operable to provide a simulated copy of the network, to generate a first data transmission on the simulated copy of the network that represents a second data transmission on the communication network, and to compare the first data transmission with a second data transmission. The vulnerability assessment component preferably interfaces with the intrusion detection component to define rules associated with the first and second data transmissions, to store the rules in the database, and to retrieve the rules from the database in order to predict and prevent unauthorized intrusion in the computer configuration.
Owner:PACE UNIVERSITY
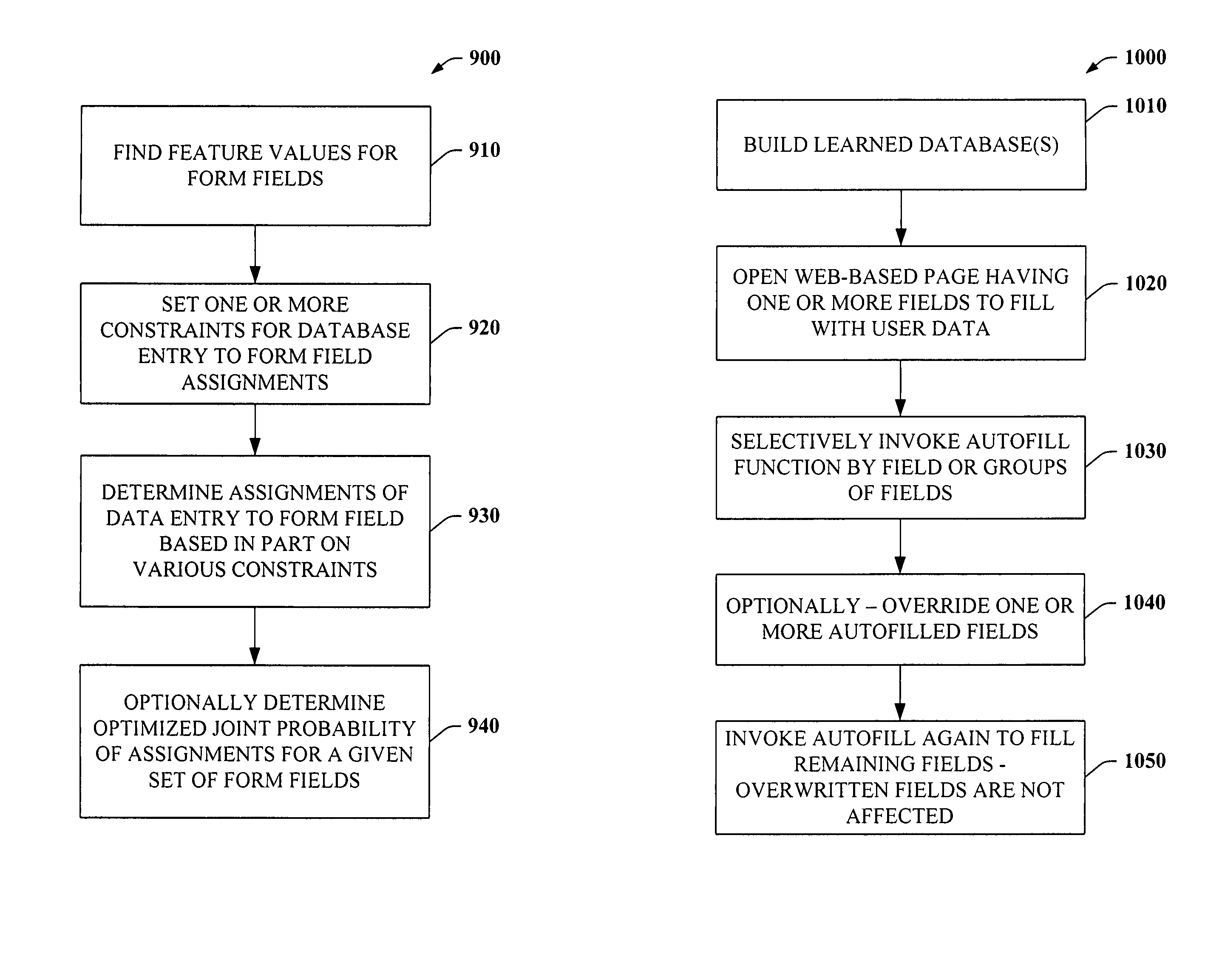
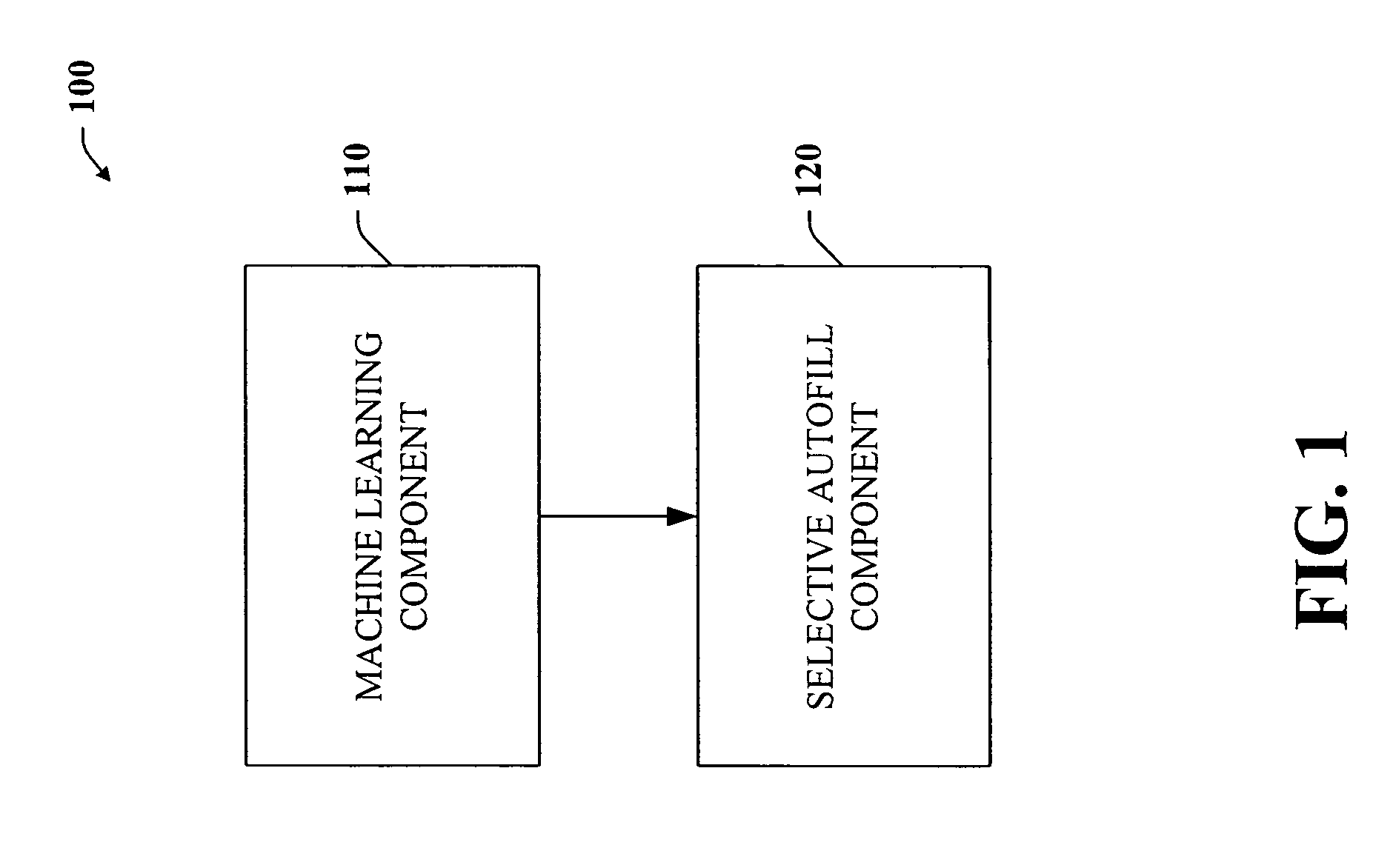
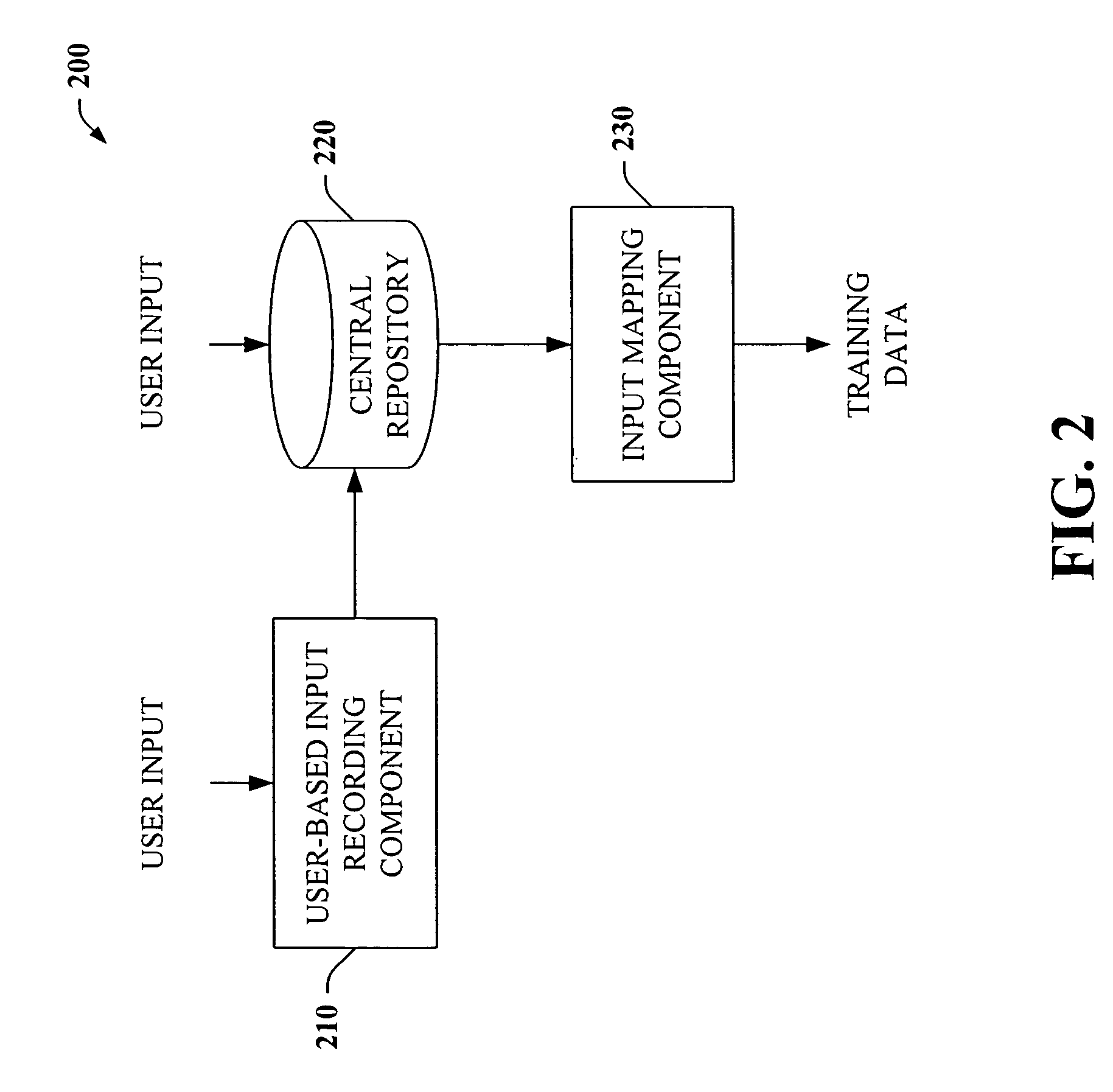
Intelligent autofill
InactiveUS7254569B2Minimize effortData augmentationData processing applicationsMetal-working feeding devicesData miningData entry
The present invention provides a unique system and method that can employ machine learning techniques to automatically fill one or more fields across a diverse array of web forms. In particular, one or more instrumented tools can collect input or entries of form fields. Machine learning can be used to learn what data corresponds to which fields or types of fields. The input can be sent to a central repository where other databases can be aggregated as well. This input can be provided to a machine learning system to learn how to predict the desired outputs. Alternatively or in addition, learning can be performed in part by observing entries and then adapting the autofill component accordingly. Furthermore, a number of features of database fields as well as constraints can be employed to facilitate assignments of database entries to form values—particularly when the web form has never been seen before by the autofill system.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for detecting malicious behavioral patterns in a computer, using machine learning
InactiveUS20080184371A1Memory loss protectionError detection/correctionComputer wormTheoretical computer science
Method for detecting malicious behavioral patterns which are related to malicious software such as a computer worm in computerized systems that include data exchange channels with other systems over a data network. According to the proposed method, hardware and / or software parameters that can characterize known behavioral patterns in the computerized system are determined. Known malicious code samples are learned by a machine learning process, such as decision trees, Naïve Bayes, Bayesian Networks, and artificial neural networks, and the results of the machine learning process are analyzed in respect to these behavioral patterns. Then, known and unknown malicious code samples are identified according to the results of the machine learning process.
Owner:DEUTSCHE TELEKOM AG
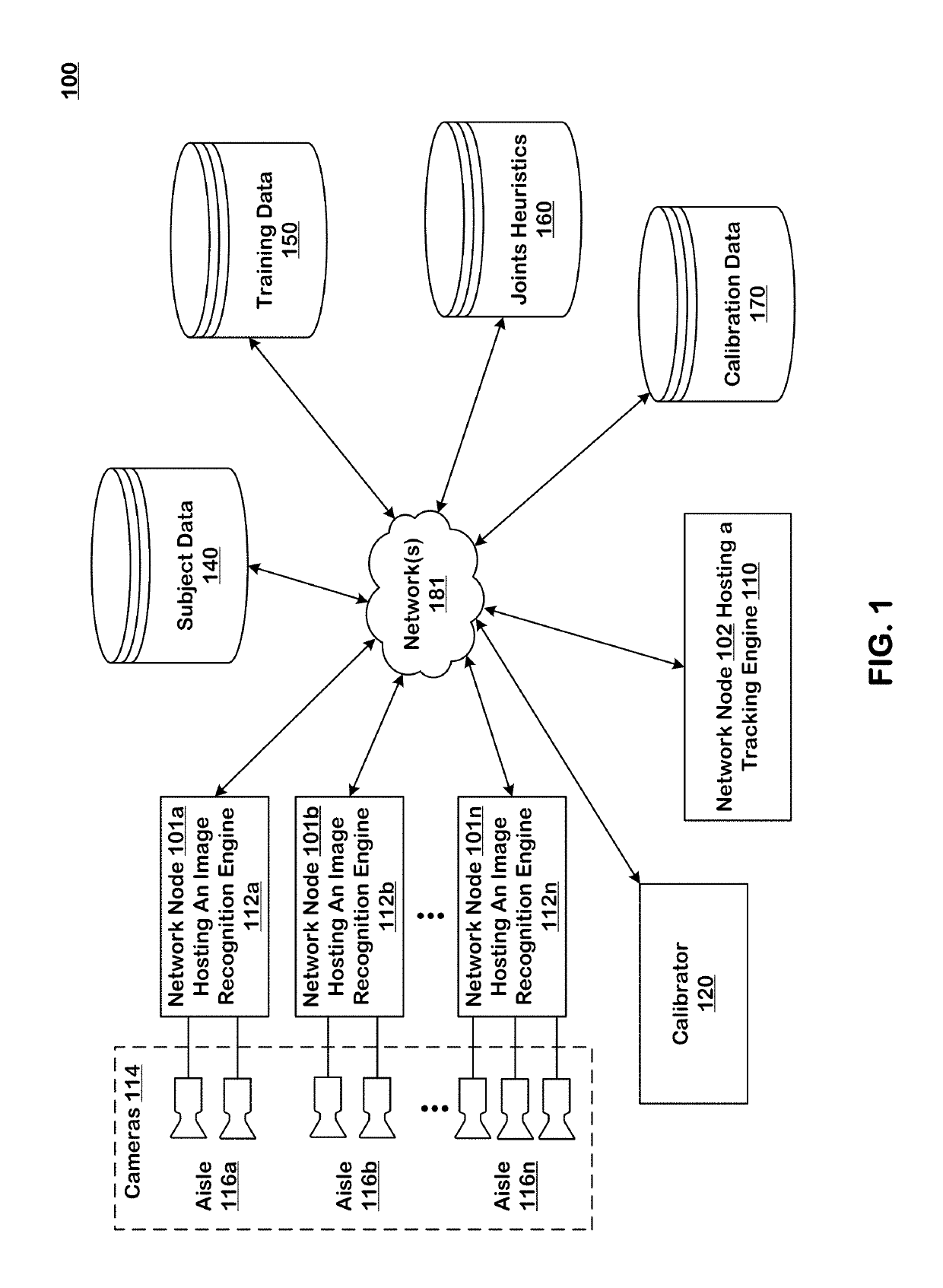
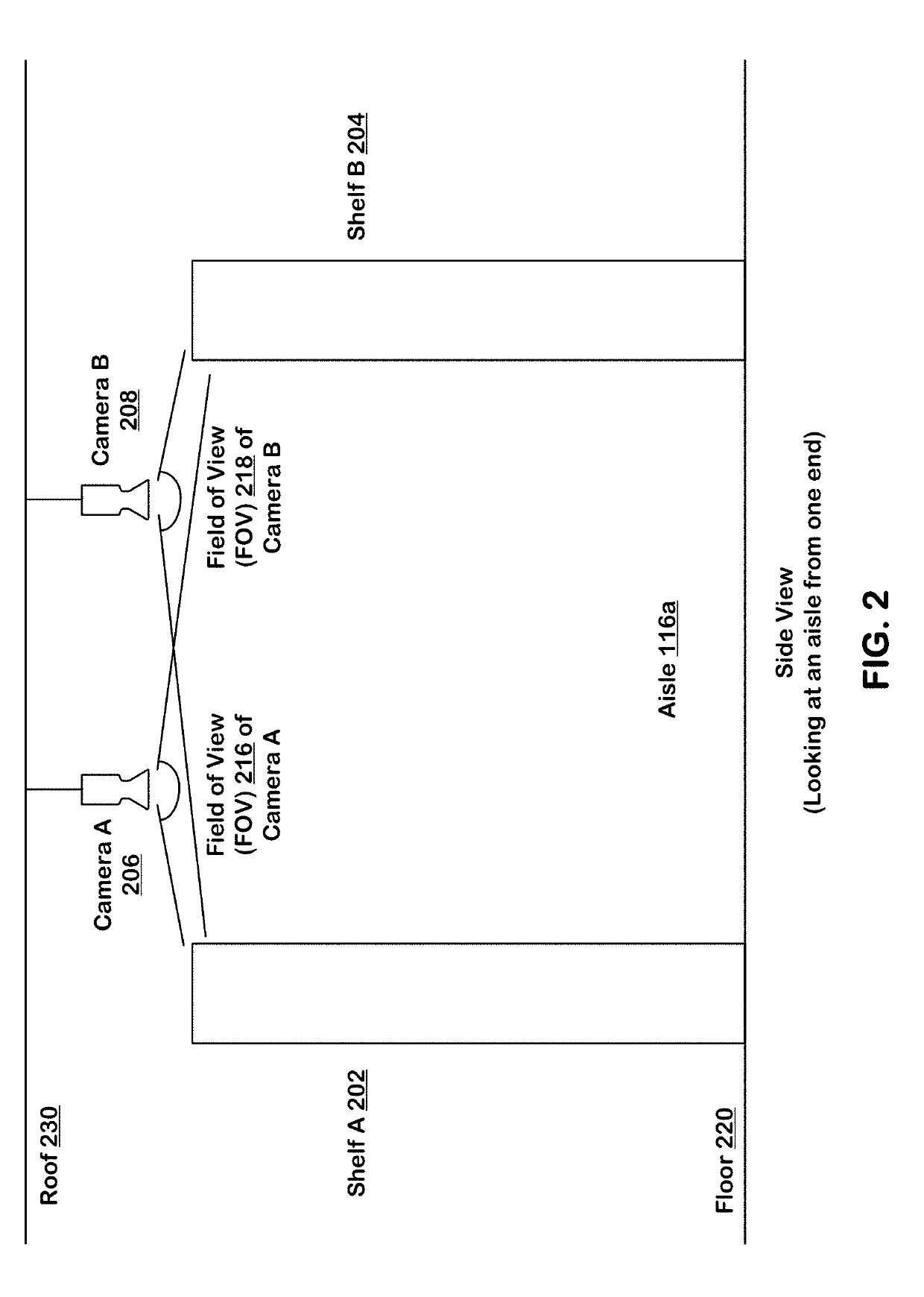
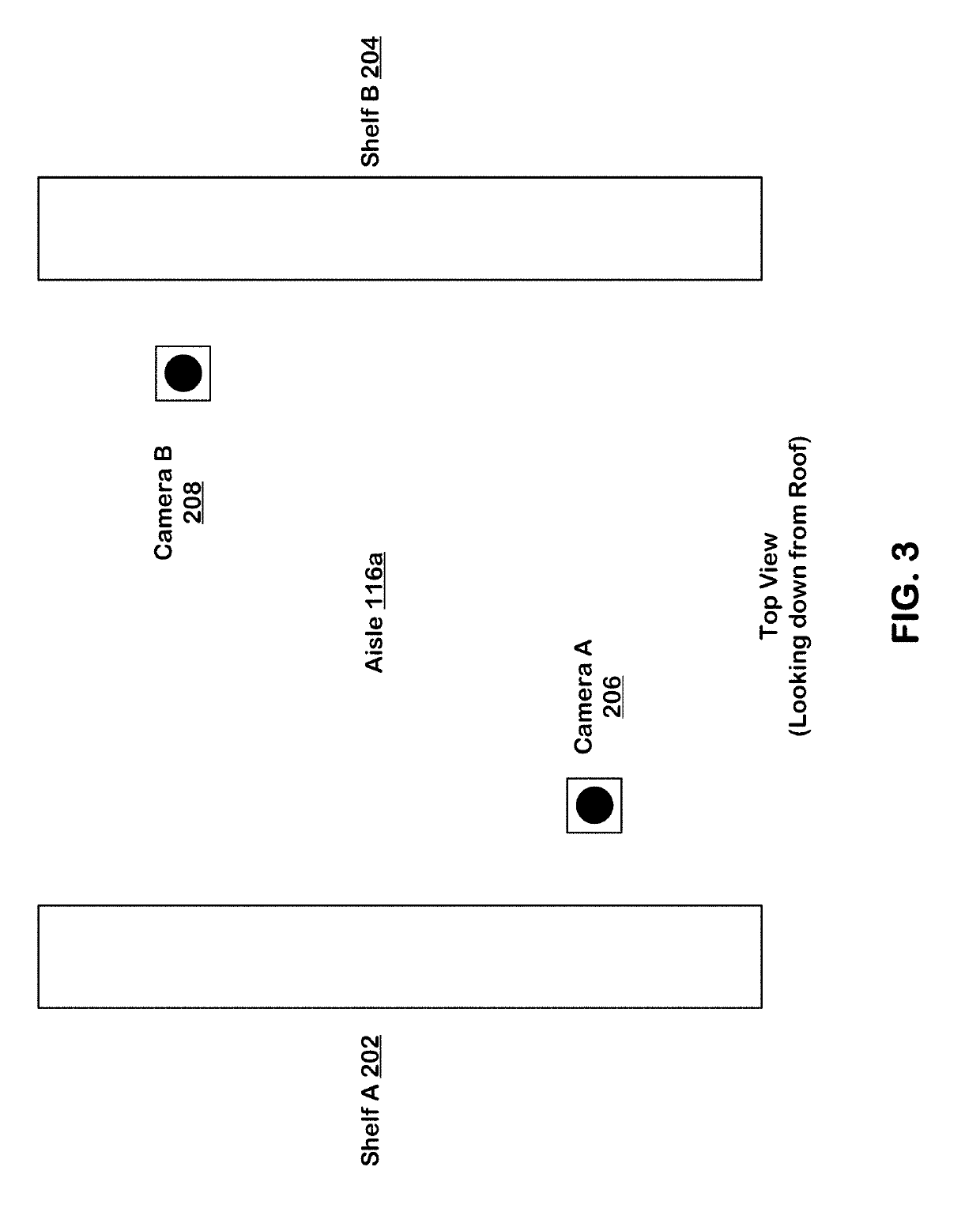
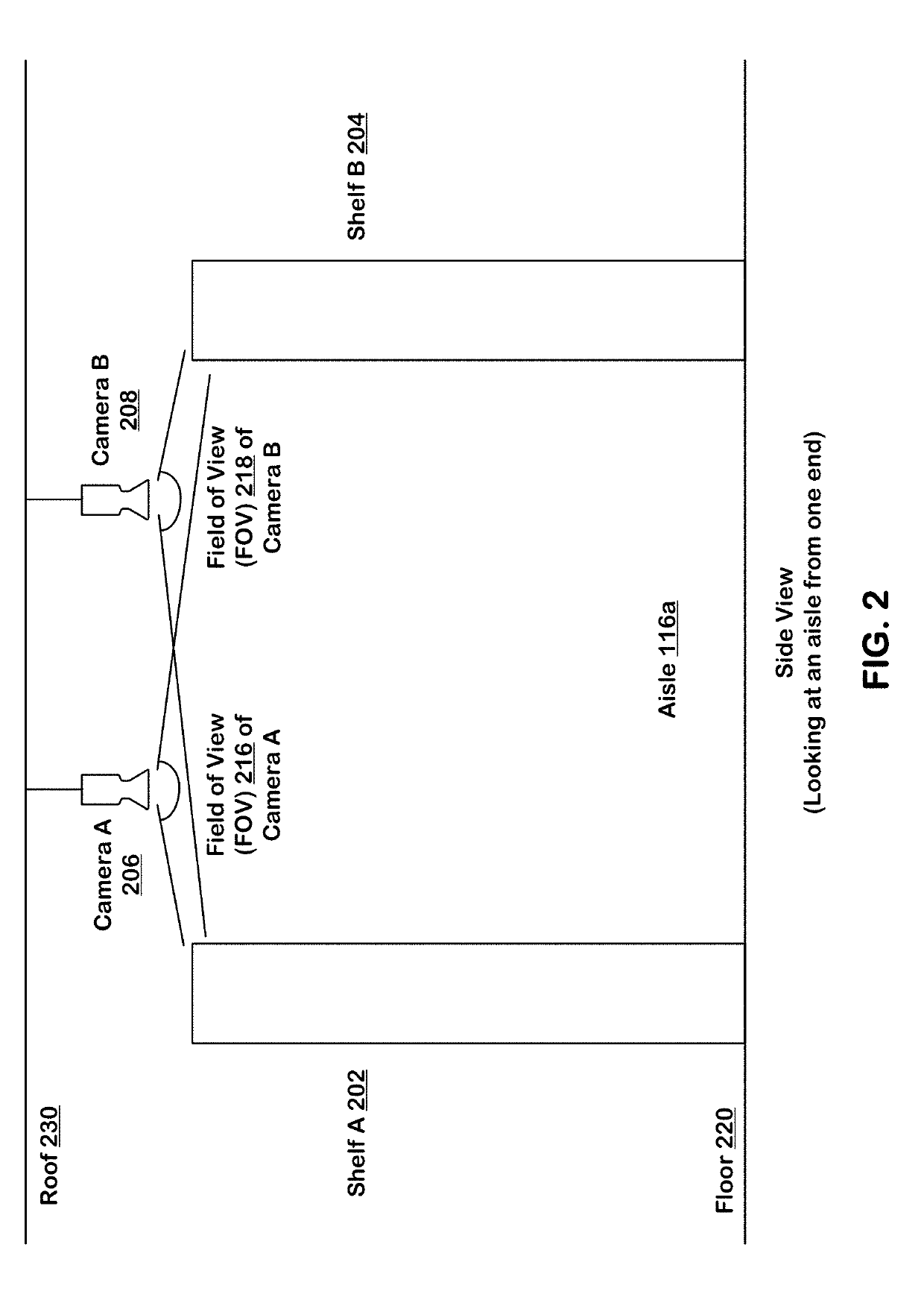
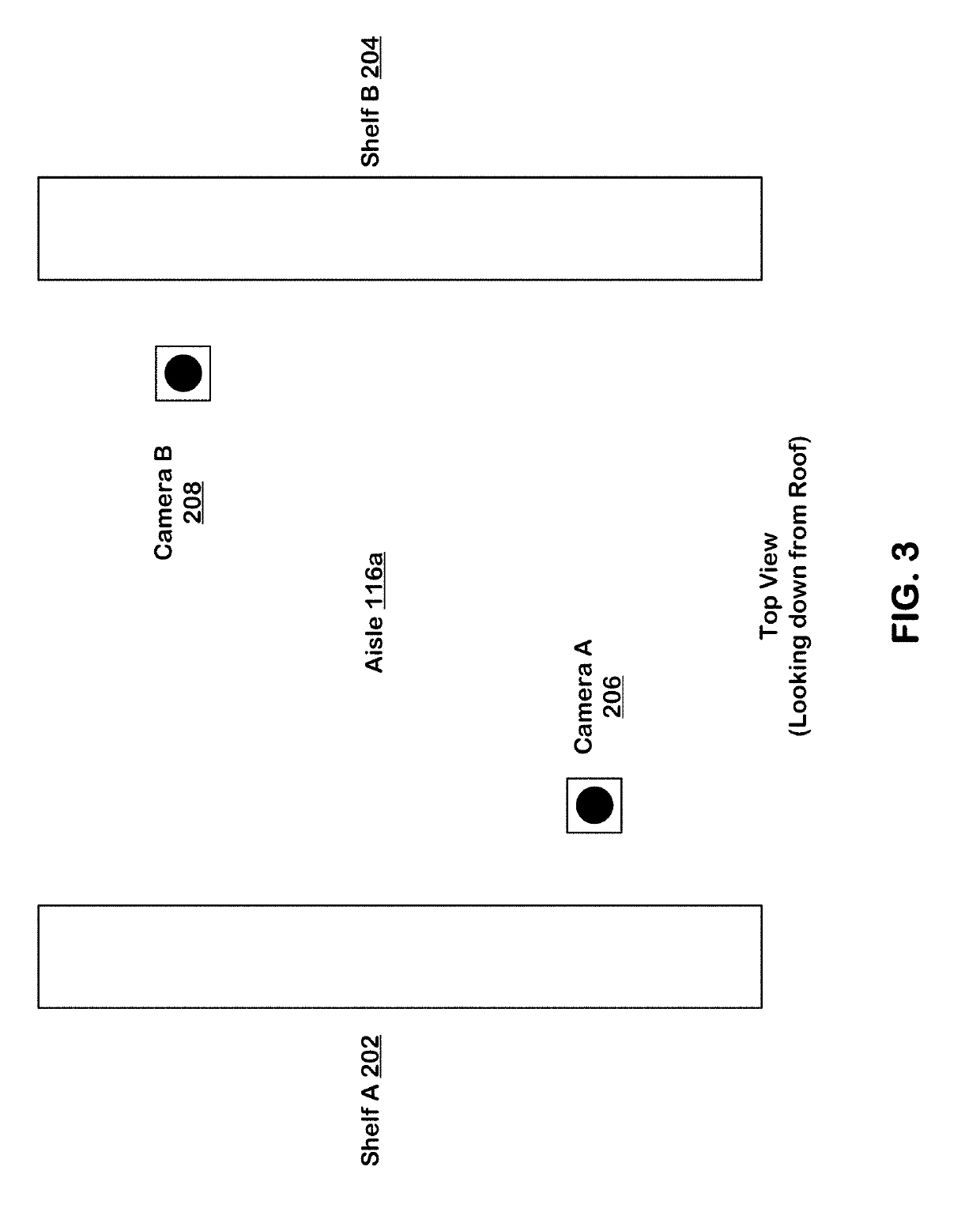
Machine learning-based subject tracking
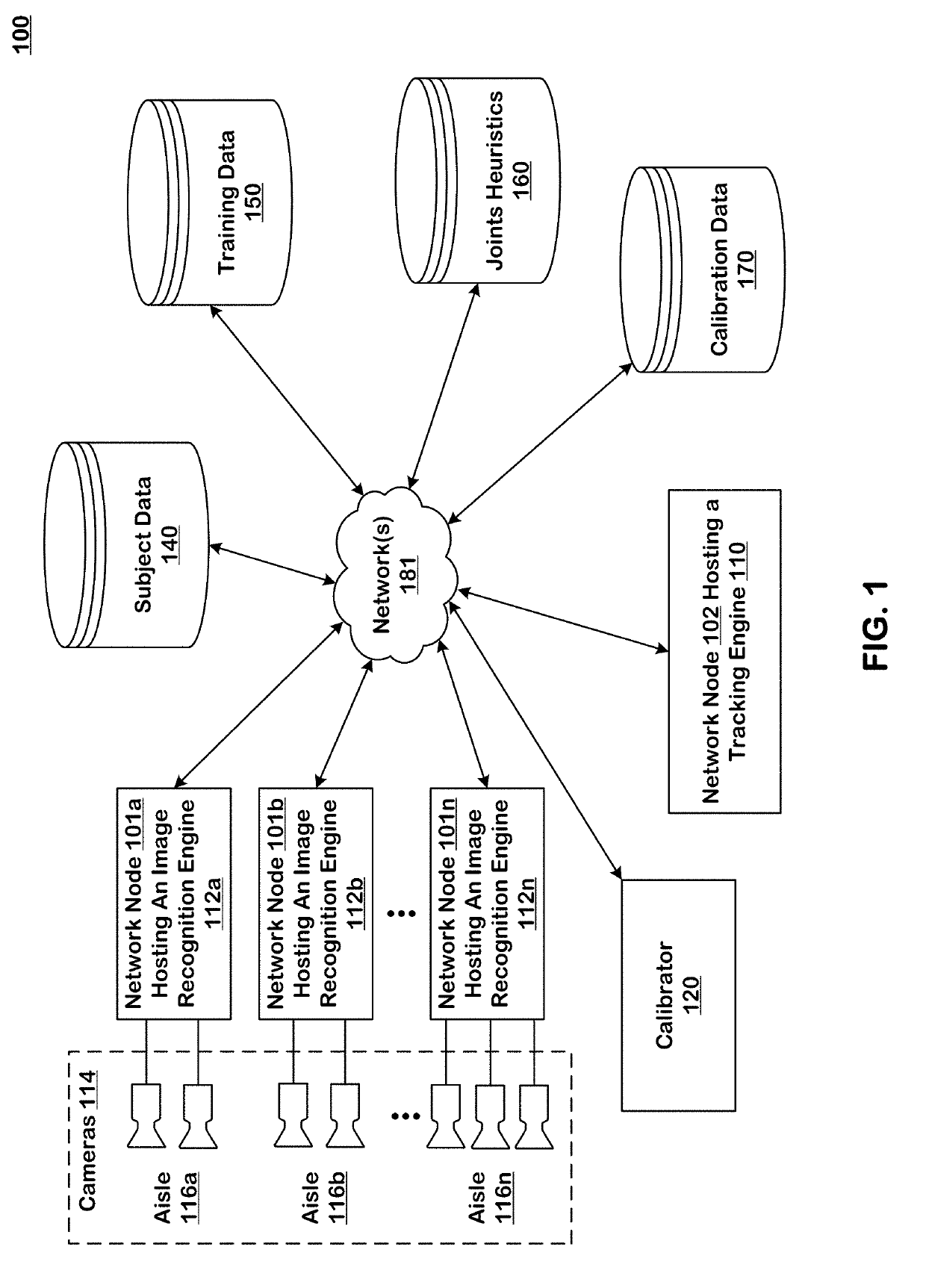
ActiveUS10474992B2ConfidenceImprove accuracyImage enhancementImage analysisLearning basedBackground image
Systems and techniques are provided for tracking puts and takes of inventory items by subjects in an area of real space. A plurality of cameras with overlapping fields of view produce respective sequences of images of corresponding fields of view in the real space. In one embodiment, the system includes first image processors, including subject image recognition engines, receiving corresponding sequences of images from the plurality of cameras. The first image processors process images to identify subjects represented in the images in the corresponding sequences of images. The system includes second image processors, including background image recognition engines, receiving corresponding sequences of images from the plurality of cameras. The second image processors mask the identified subjects to generate masked images. Following this, the second image processors process the masked images to identify and classify background changes represented in the images in the corresponding sequences of images.
Owner:STANDARD COGNITION CORP
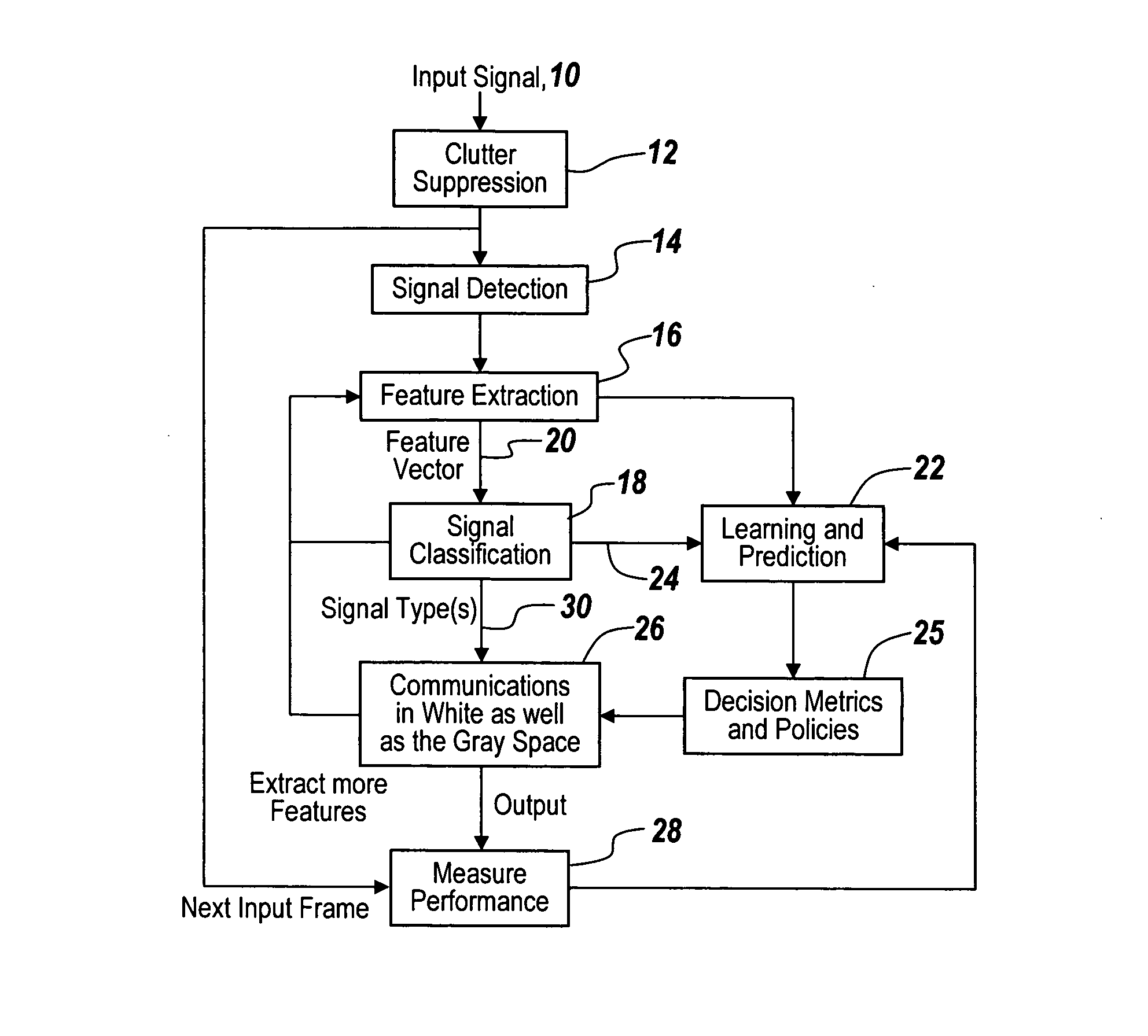
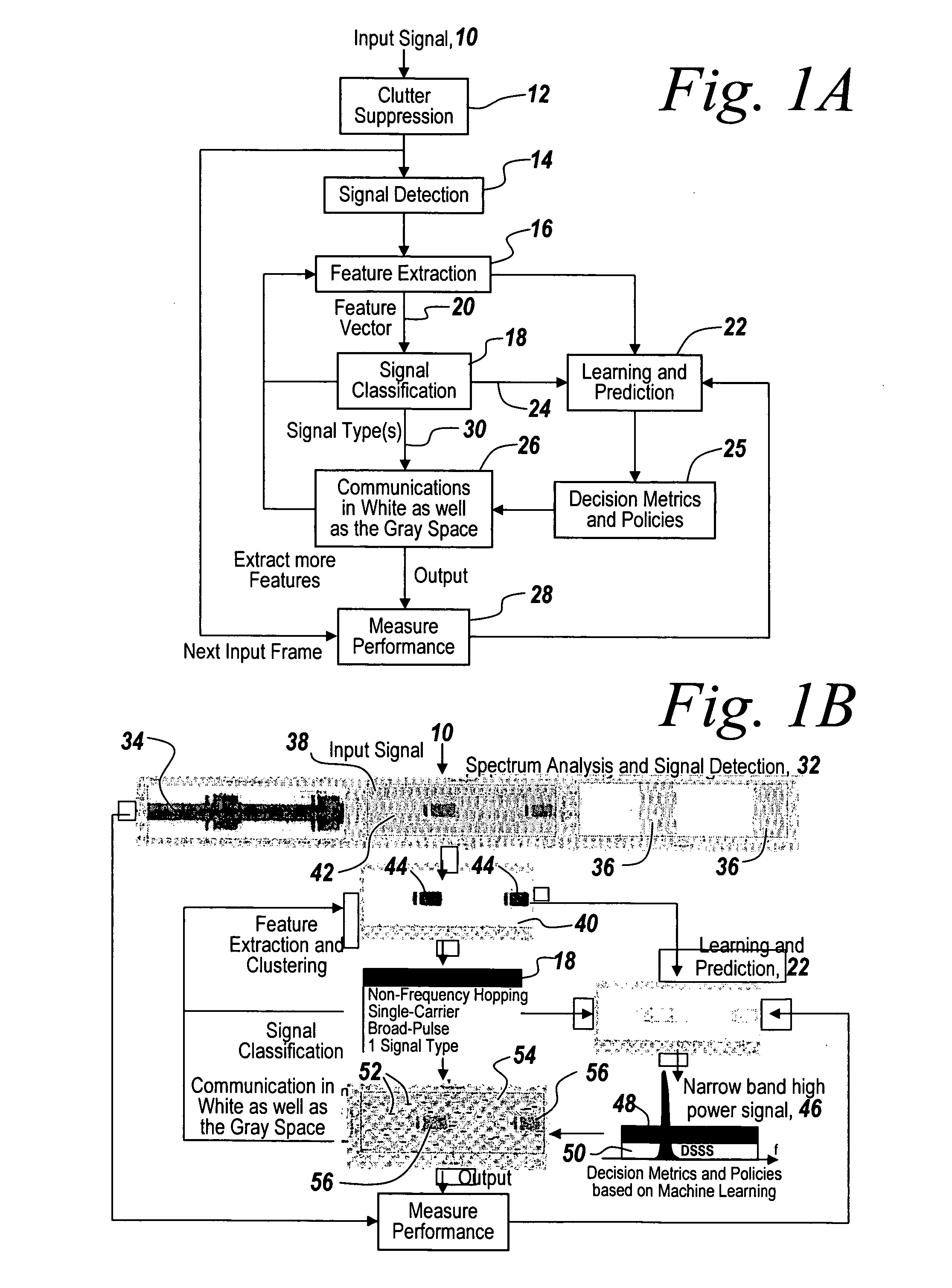
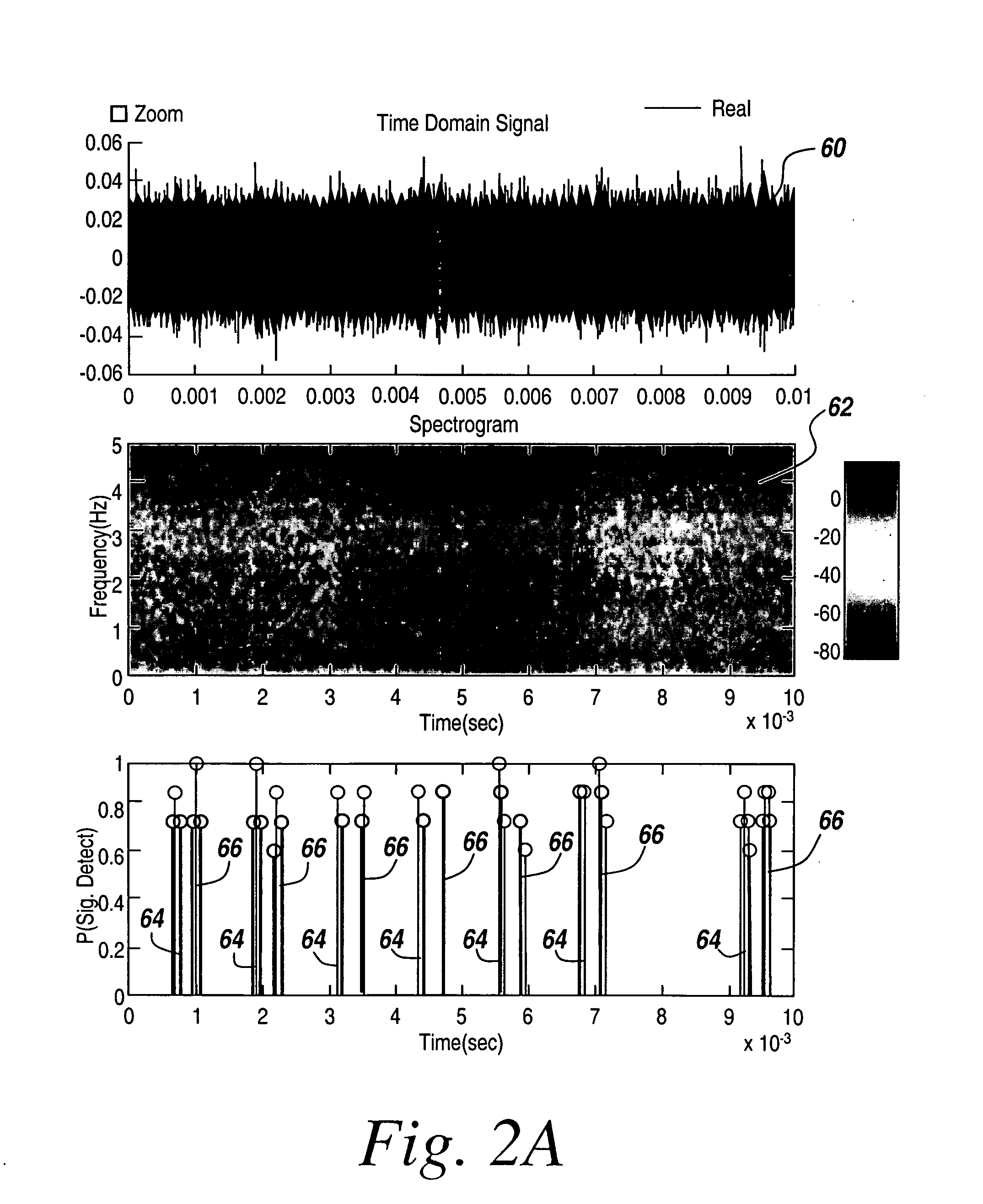
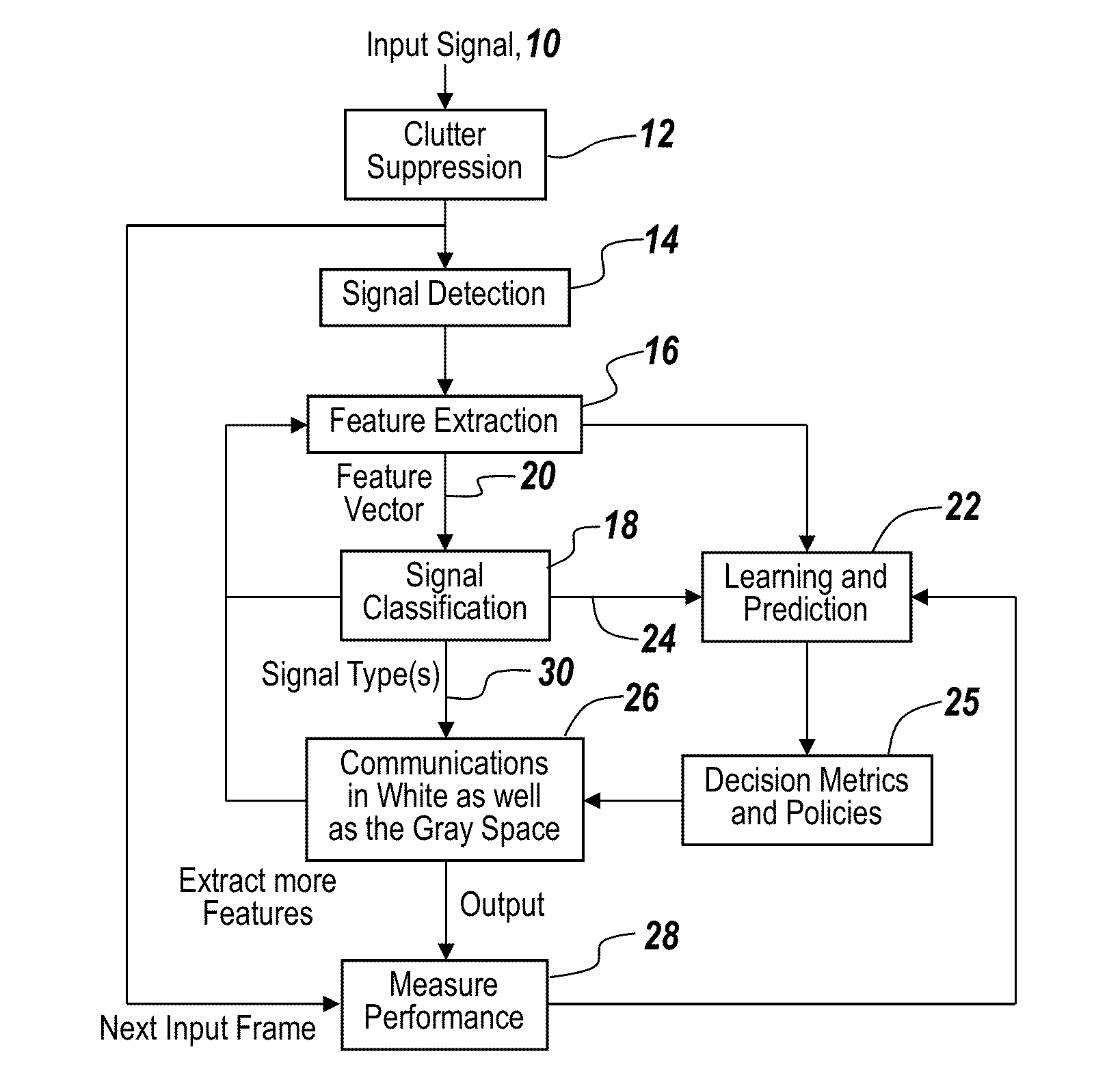
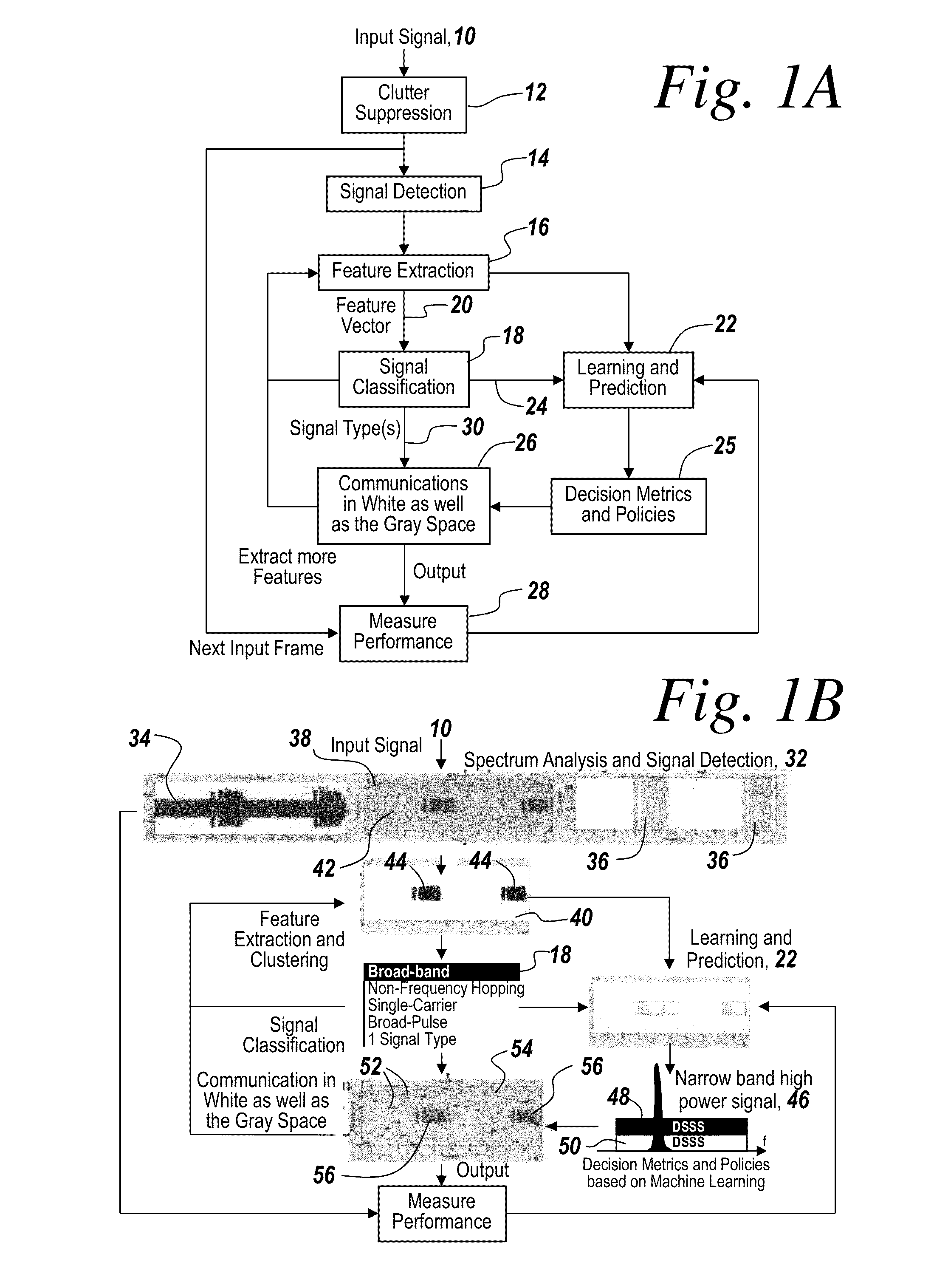
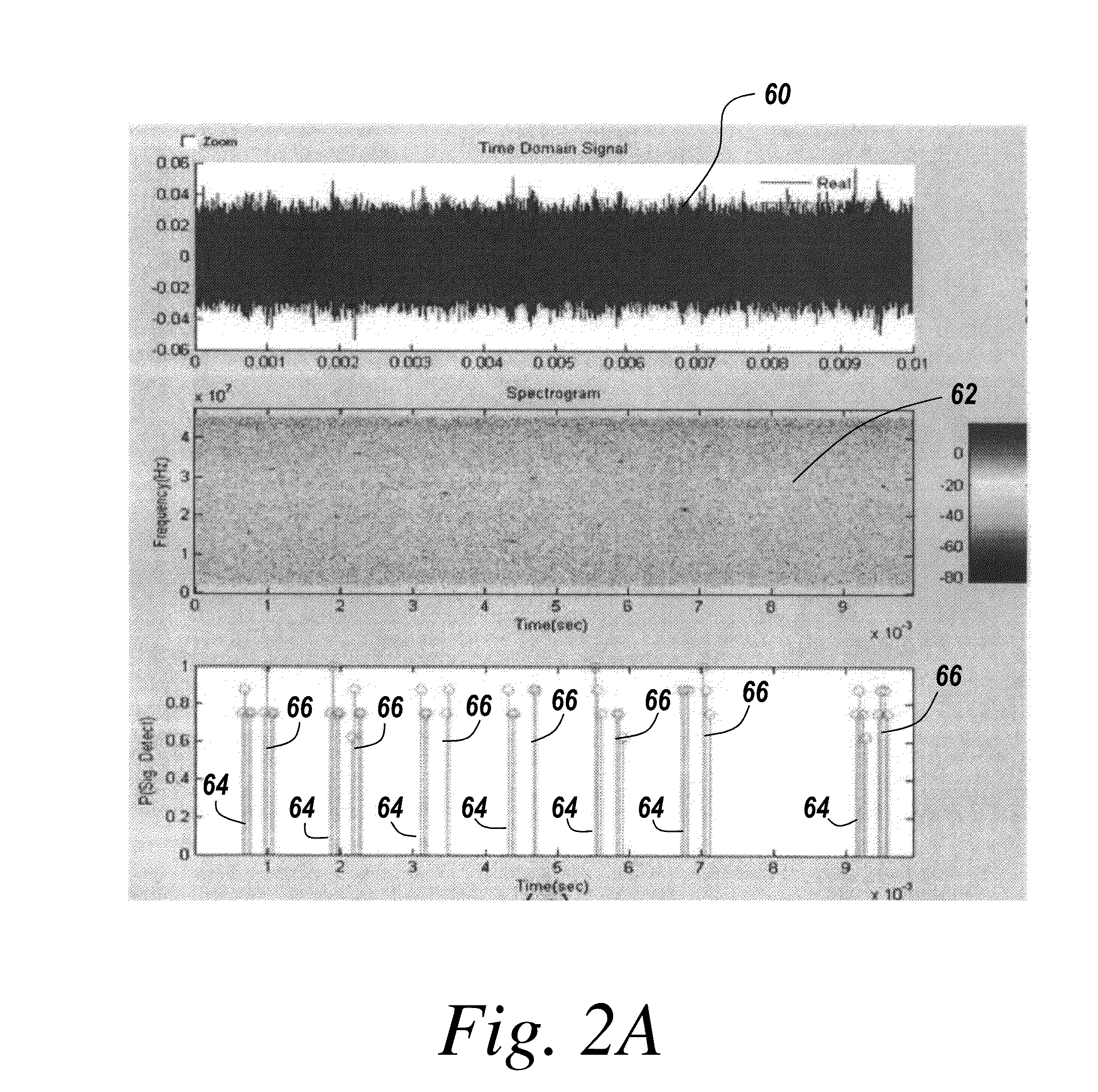
Cognitive radio methodology, physical layer policies and machine learning
ActiveUS8515473B2Easy to adaptEasy to classifyEnergy efficient ICTAssess restrictionFrequency spectrumCognitive communication
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Cognitive radio methodology, physical layer policies and machine learning
ActiveUS20130288734A1Easy to adaptEasy to classifyAssess restrictionRadio transmissionCognitive communicationPhysical layer
In a method of cognitive communication a system for generating non-interfering transmission, includes conducting radio scene analysis to find grey space using external signal parameters for incoming signal analysis without having to decode incoming signals.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTEGRATION INC
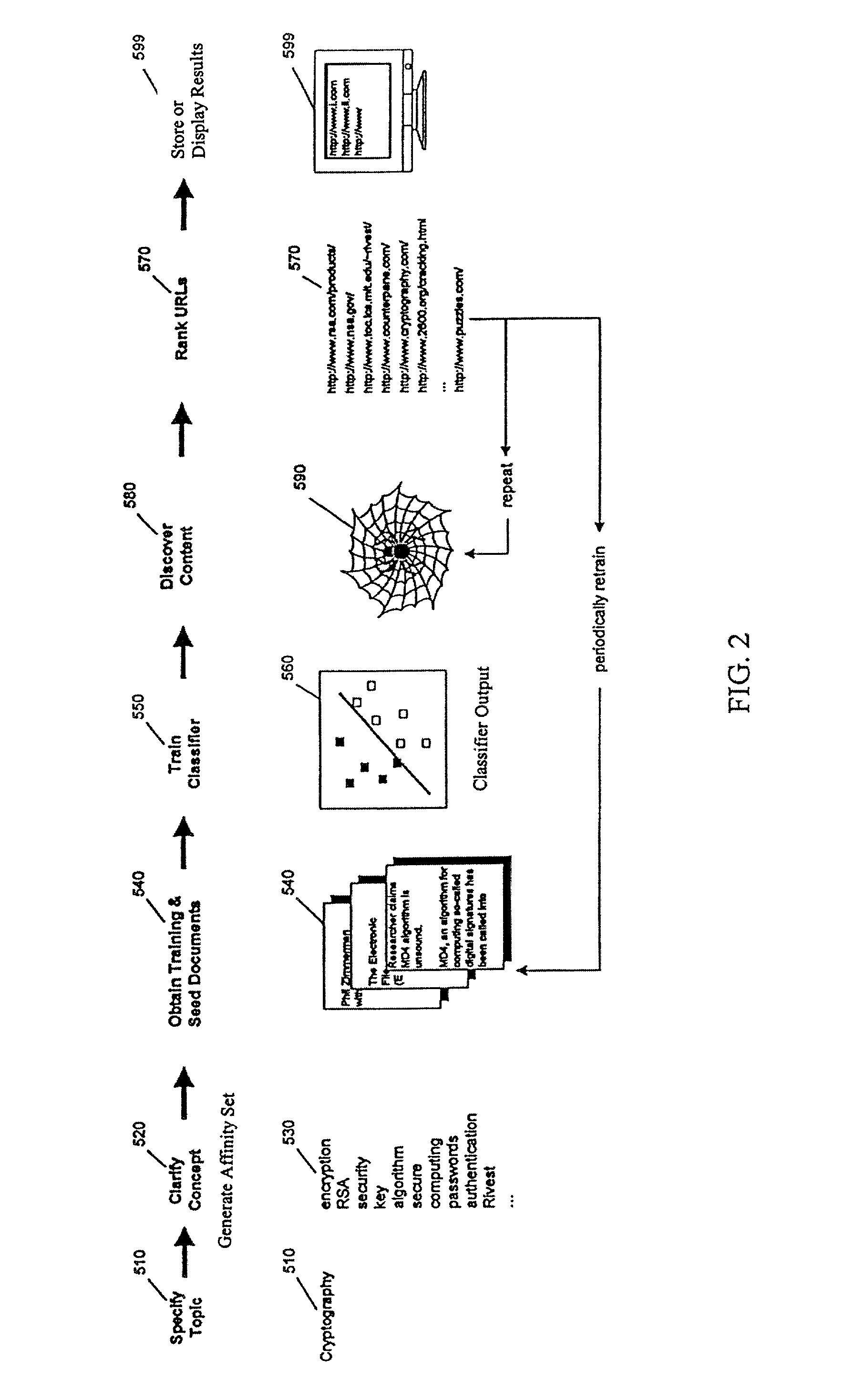
Directed web crawler with machine learning
InactiveUS20020194161A1Web data indexingDigital data processing detailsHuman search engineSubject matter
A web crawler identifies and characterizes an expression of a topic of general interest (such as cryptography) entered and generates an affinity set which comprises a set of related words. This affinity set is related to the expression of a topic of general interest. Using a common search engine, seed documents are found. The seed documents along with the affinity set and other search data will provide training to a classifier to create classifier output for the web crawler to search the web based on multiple criteria, including a content-based rating provided by the trained classifier. The web crawler can perform it's search topic focused, rather than "link" focused. The found relevant content will be ranked and results displayed or saved for a specialty search.
Owner:MCNAMEE J PAUL +4
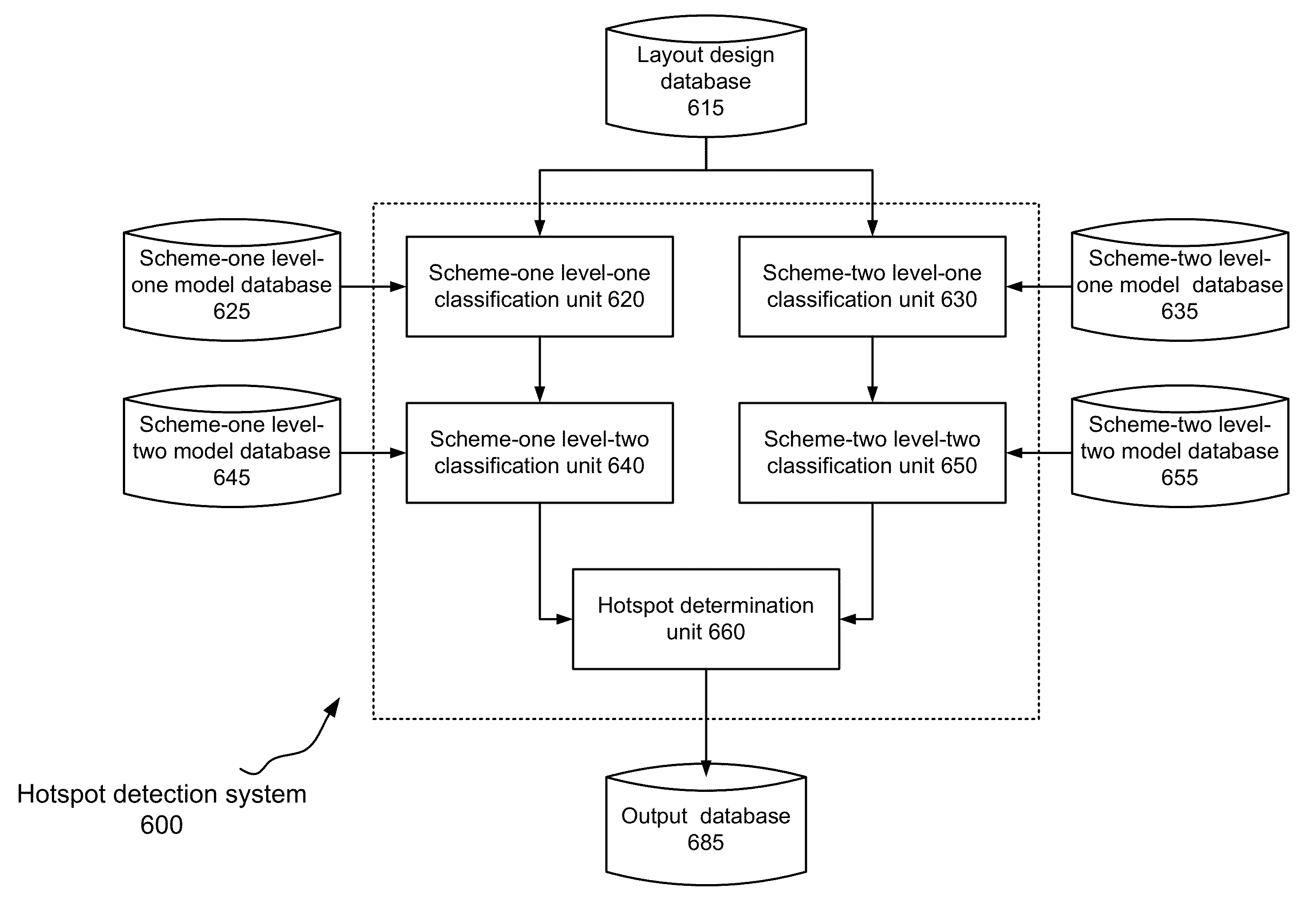
Hotspot detection based on machine learning
ActiveUS8402397B2Originals for photomechanical treatmentComputer aided designLearning basedStudy methods
Aspects of the invention relate to machine-learning-based hotspot detection techniques. These hotspot detection techniques employ machine learning models constructed using two feature encoding schemes. When two-level machine learning methods are also employed, a total four machine learning models are constructed: scheme-one level-one, scheme-one level-two, scheme-two level-one and scheme-two level-two. The four models are applied to test patterns to derive scheme-one hotspot information and scheme-two hotspot information, which are then used to determine final hotspot information.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
Method and system for detecting malicious behavioral patterns in a computer, using machine learning
InactiveUS20070294768A1Memory loss protectionUnauthorized memory use protectionComputer wormComputerized system
Method for detecting malicious behavioral patterns which are related to malicious software such as a computer worm in computerized systems that include data exchange channels with other systems over a data network. Accordingly, hardware and / or software parameters are determined in the computerized system that is can characterize known behavioral patterns thereof. Known malicious code samples are learned by a machine learning process, such as decision trees and artificial neural networks, and the results of the machine learning process are analyzed in respect to the behavioral patterns of the computerized system. Then known and unknown malicious code samples are identified according to the results of the machine learning process.
Owner:DEUTSCHE TELEKOM AG
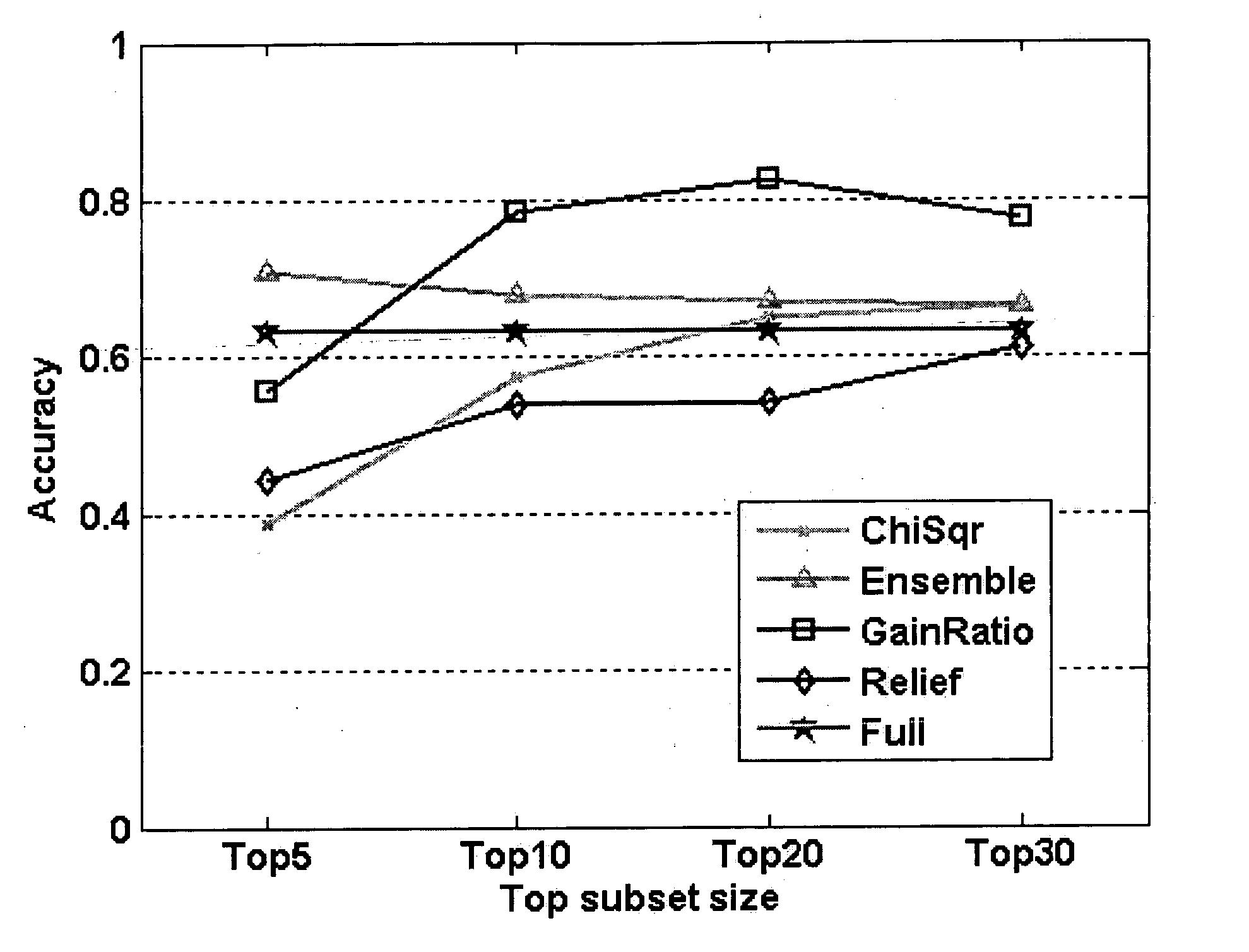
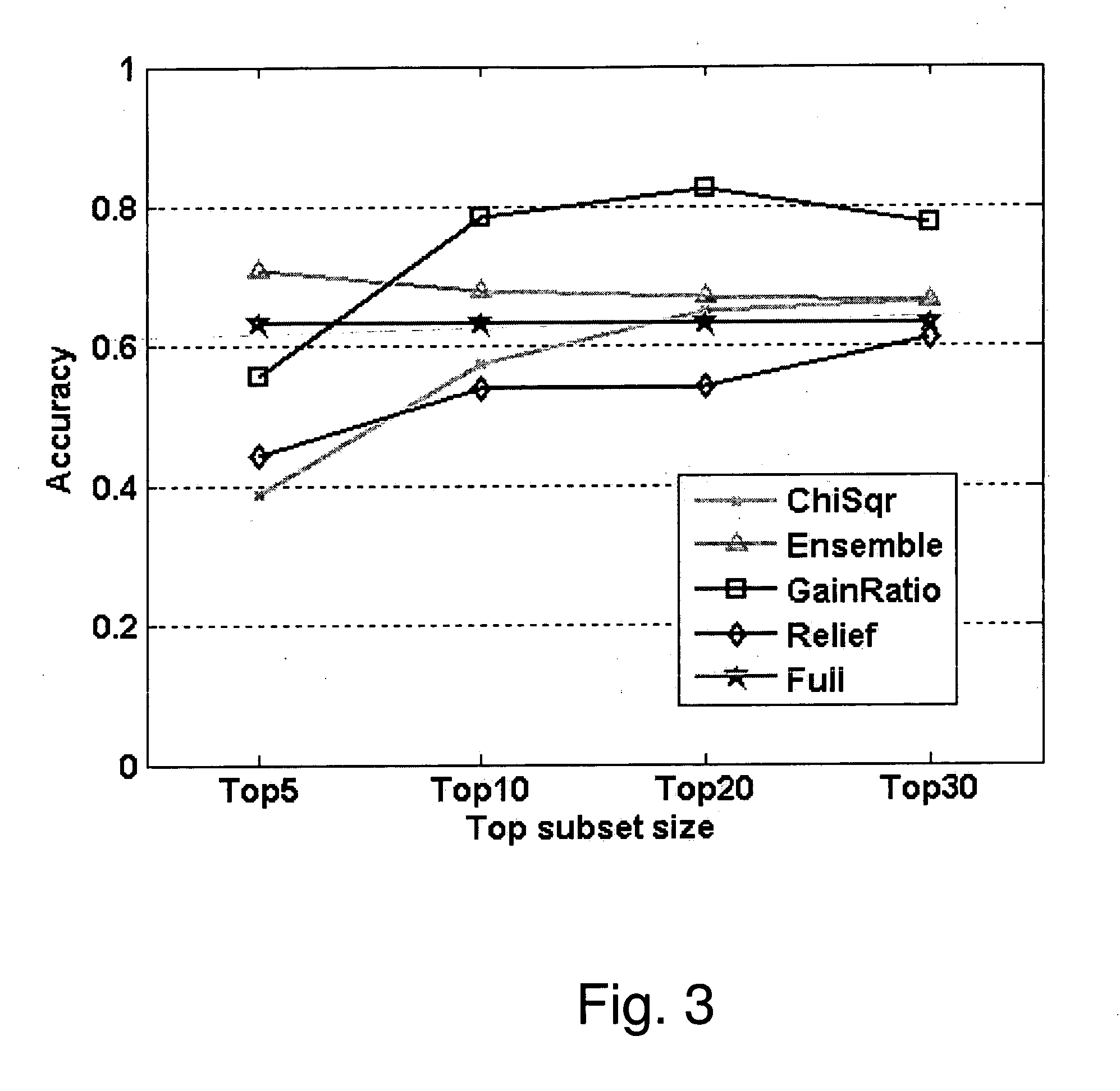
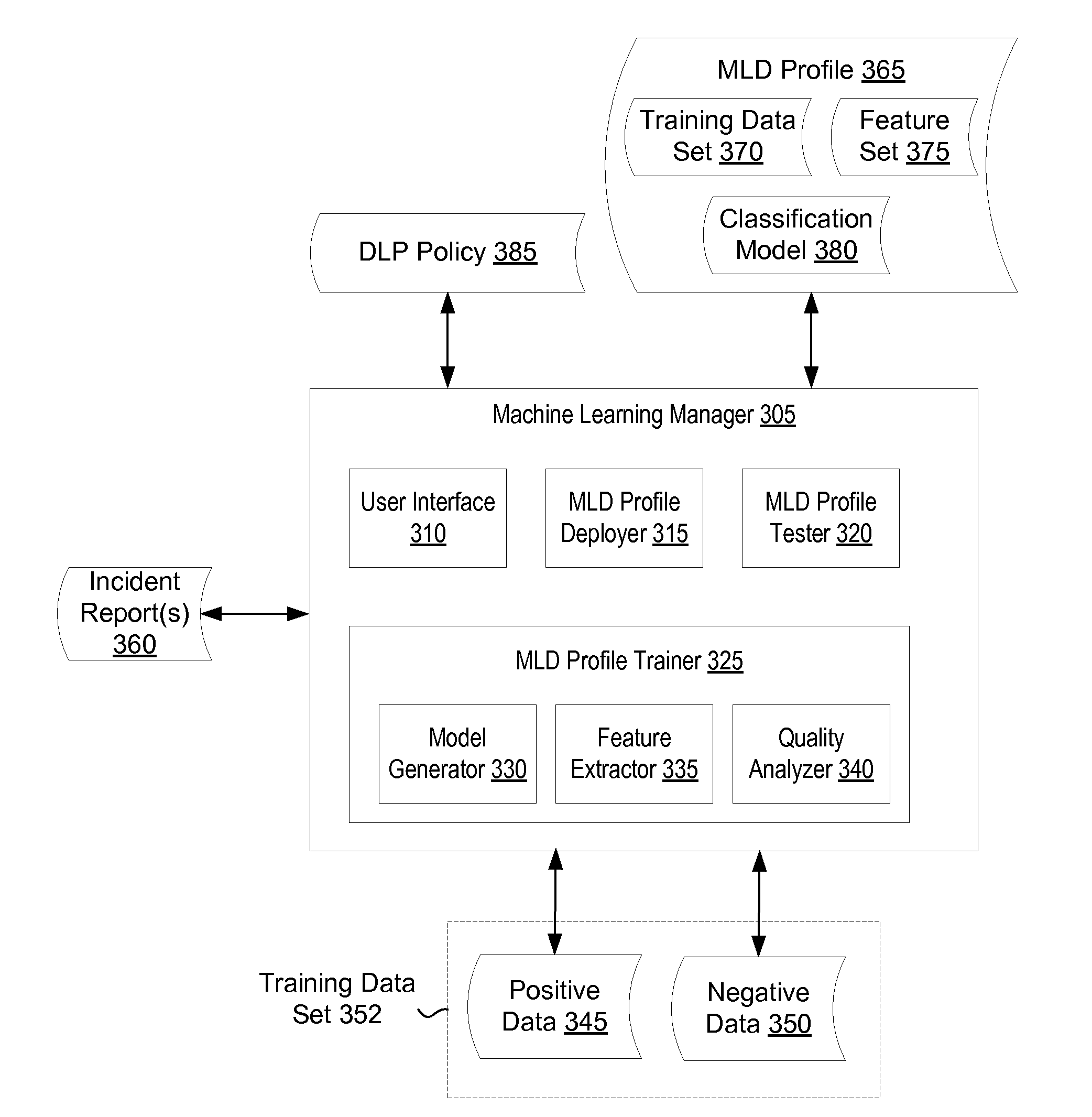
User interface and workflow for performing machine learning
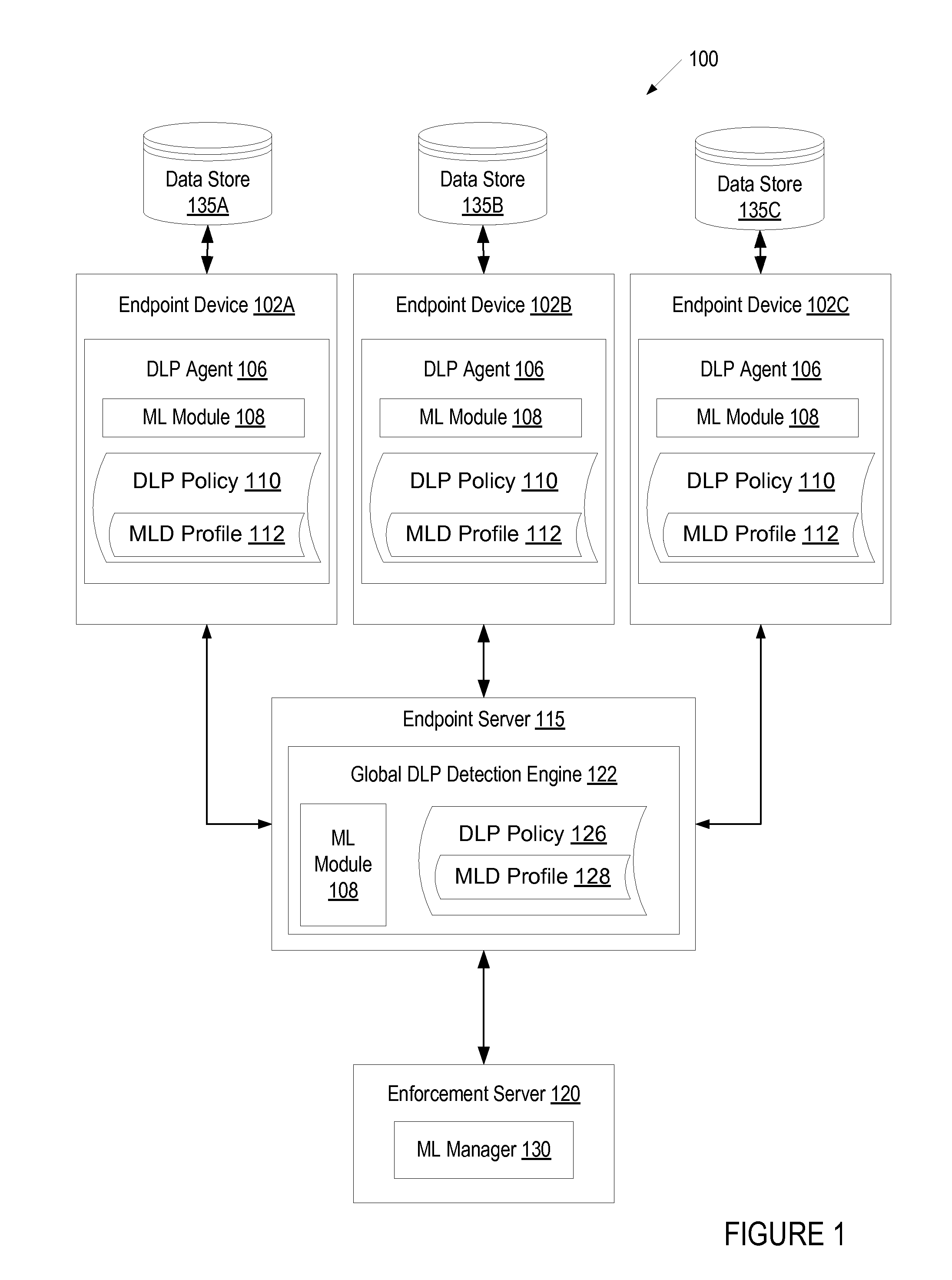
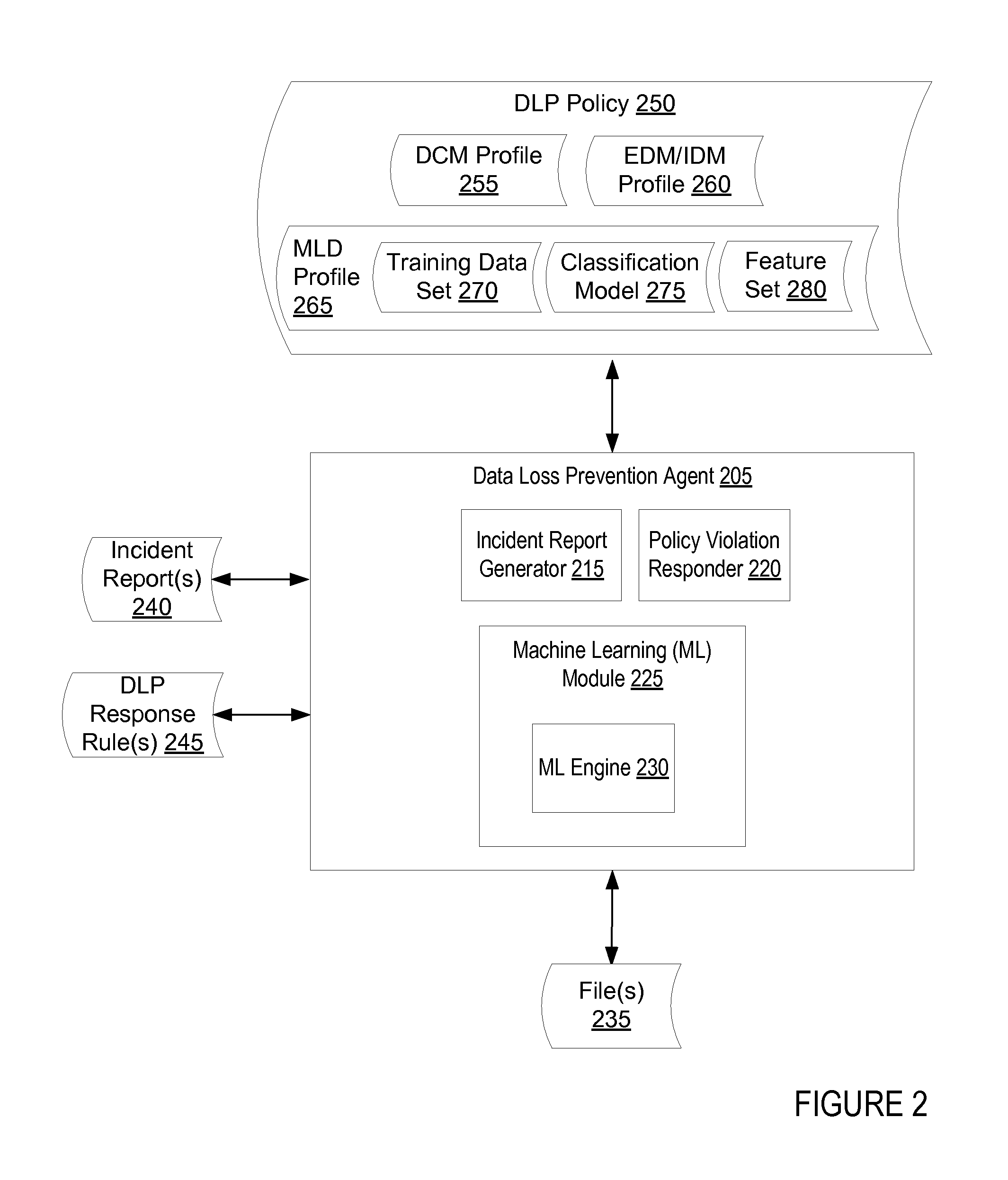
A computing device receives a training data set that includes a plurality of positive examples of sensitive data and a plurality of negative examples of sensitive data via a user interface. The computing device analyzes the training data set using machine learning to generate a machine learning-based detection (MLD) profile that can be used to classify new data as sensitive data or as non-sensitive data. The computing device displays a quality metric for the MLD profile in the user interface.
Owner:CA TECH INC
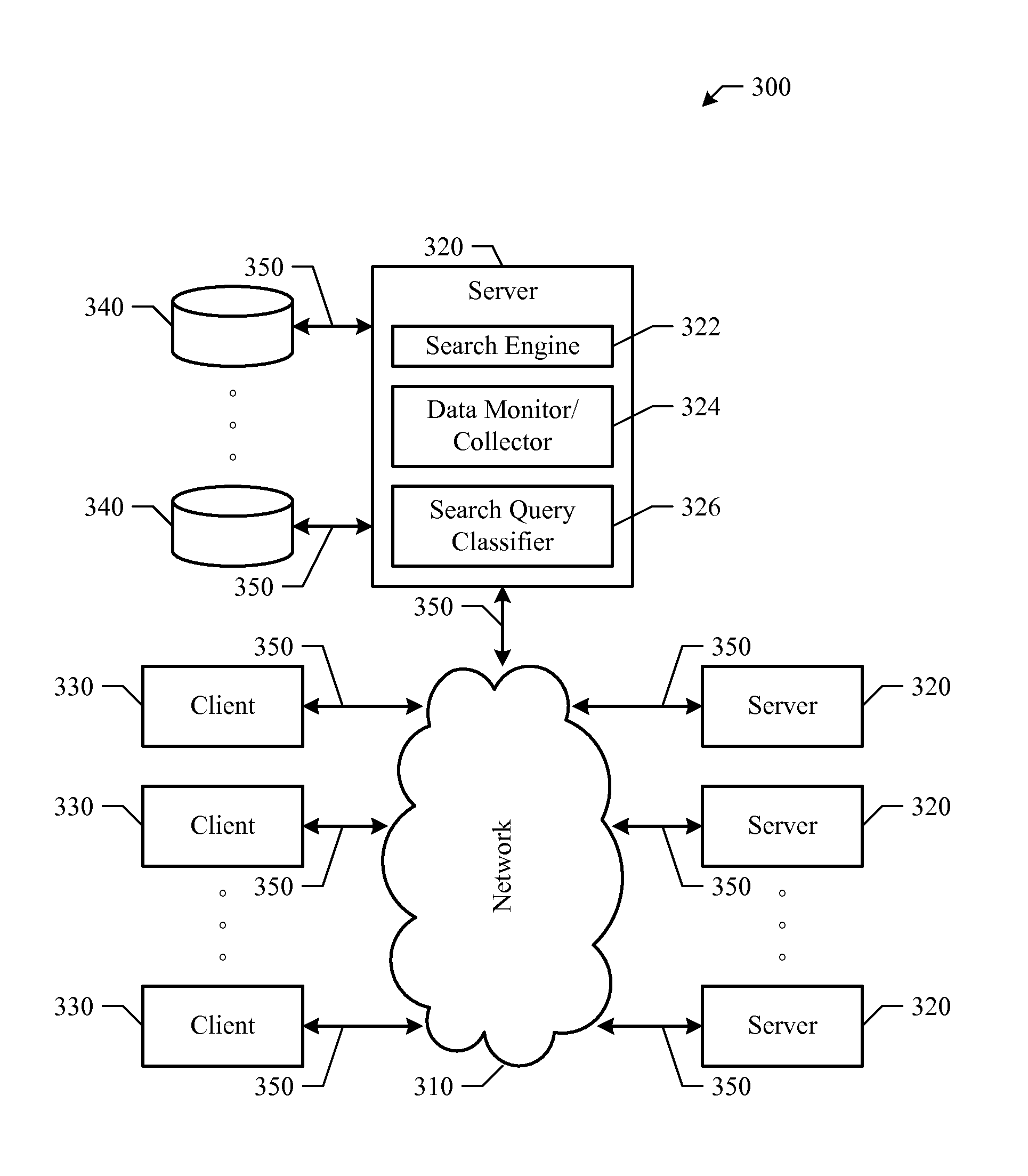
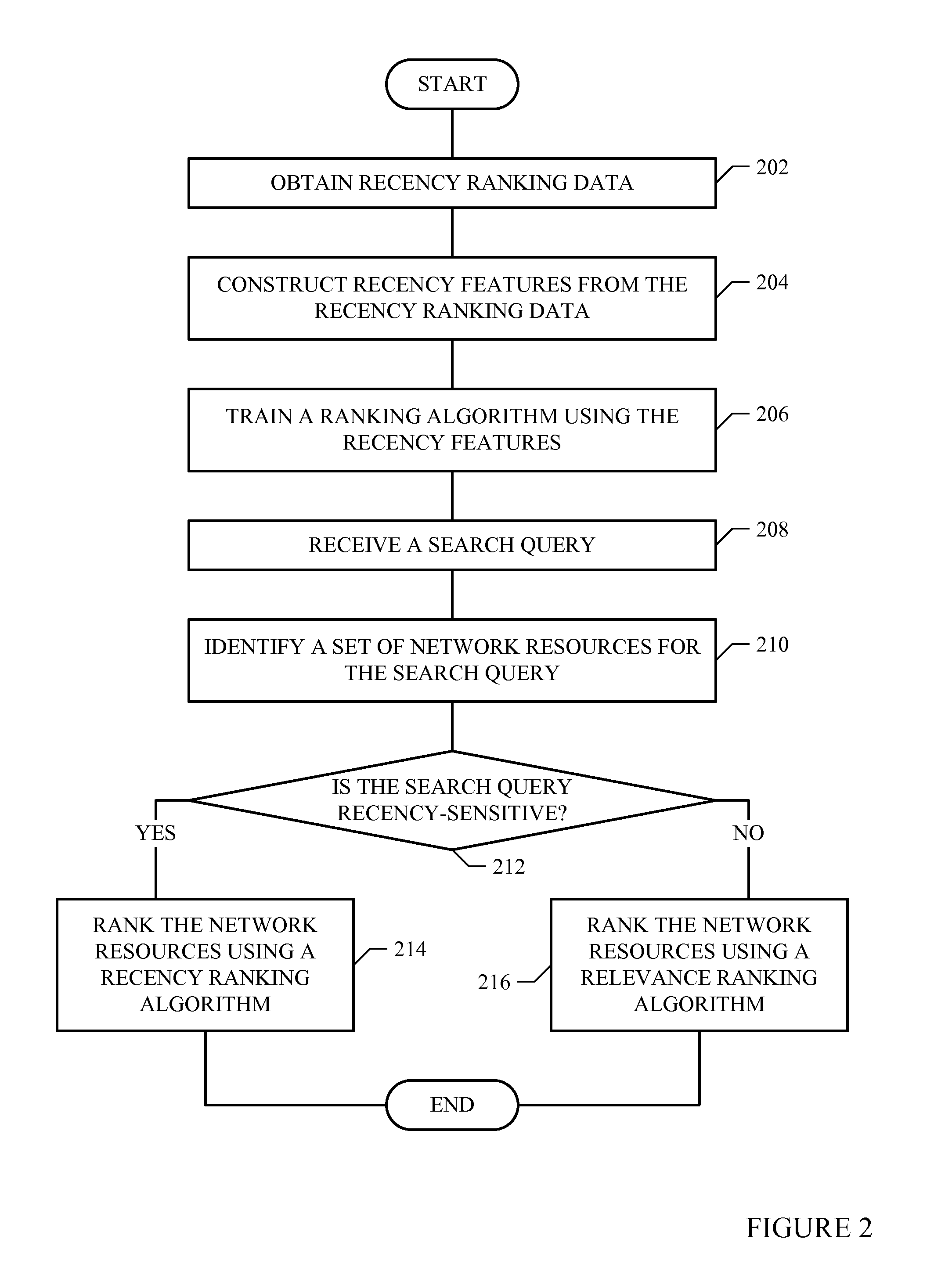
Incorporating Recency in Network Search Using Machine Learning
InactiveUS20110093459A1Quality improvementDigital data information retrievalDigital data processing detailsTimestampData mining
In one embodiment, access a set of recency ranking data comprising one or more recency search queries and one or more recency search results, each of the recency search queries being recency-sensitive with respect to a particular time period and being associated with a query timestamp representing the time at which the recency search query is received at a search engine, each of the recency search results being generated by the search engine for one of the recency search queries and comprising one or more recency network resources. Construct a plurality of recency features from the set of recency ranking data. Train a first ranking model via machine learning using at least the recency features.
Owner:R2 SOLUTIONS
Resolving and merging duplicate records using machine learning
According to various embodiments of the present invention, an automated technique is implemented for resolving and merging fields accurately and reliably, given a set of duplicated records that represents a same entity. In at least one embodiment, a system is implemented that uses a machine learning (ML) method, to train a model from training data, and to learn from users how to efficiently resolve and merge fields. In at least one embodiment, the method of the present invention builds feature vectors as input for its ML method. In at least one embodiment, the system and method of the present invention apply Hierarchical Based Sequencing (HBS) and / or Multiple Output Relaxation (MOR) models in resolving and merging fields. Training data for the ML method can come from any suitable source or combination of sources.
Owner:XANT INC
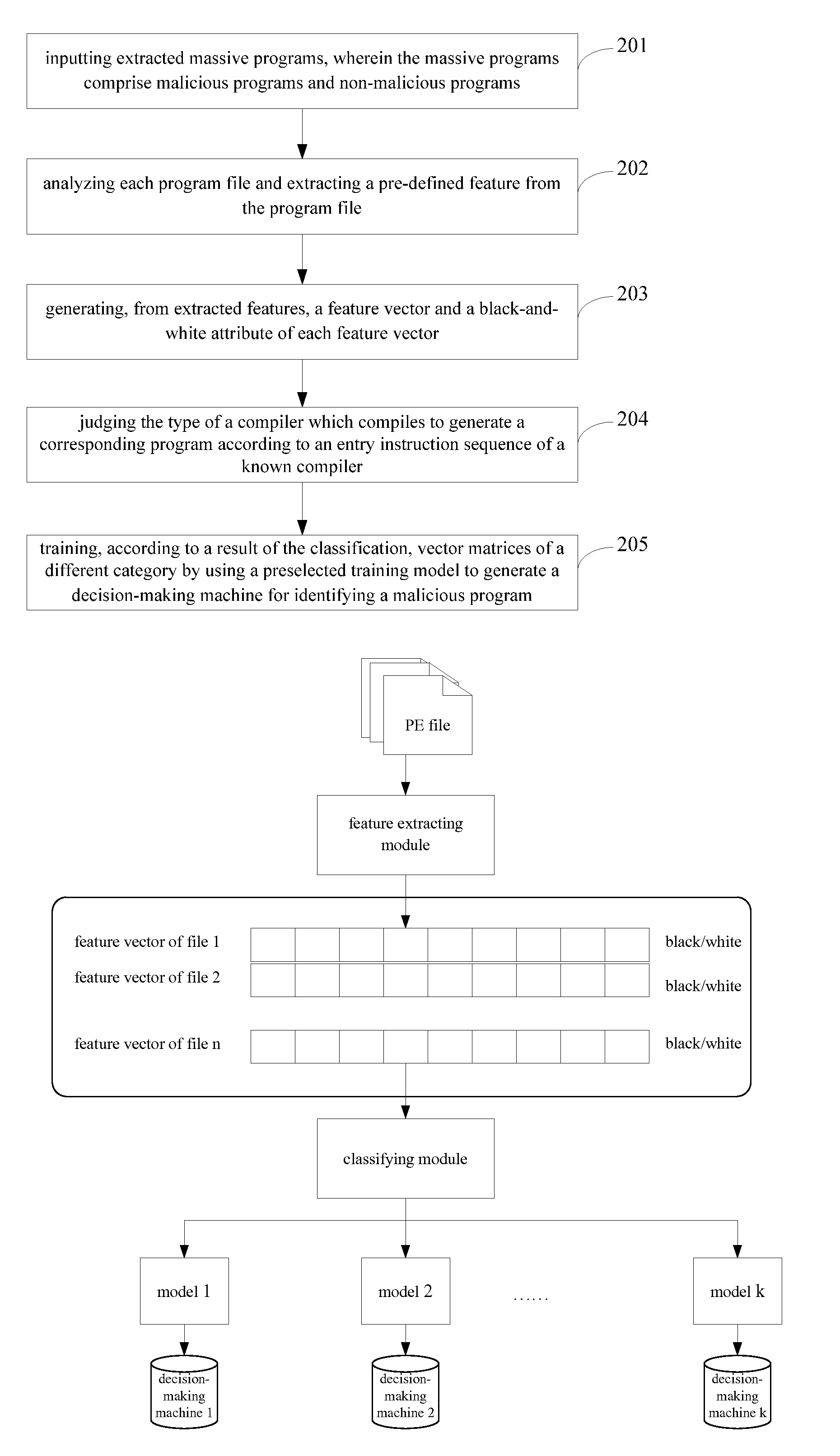
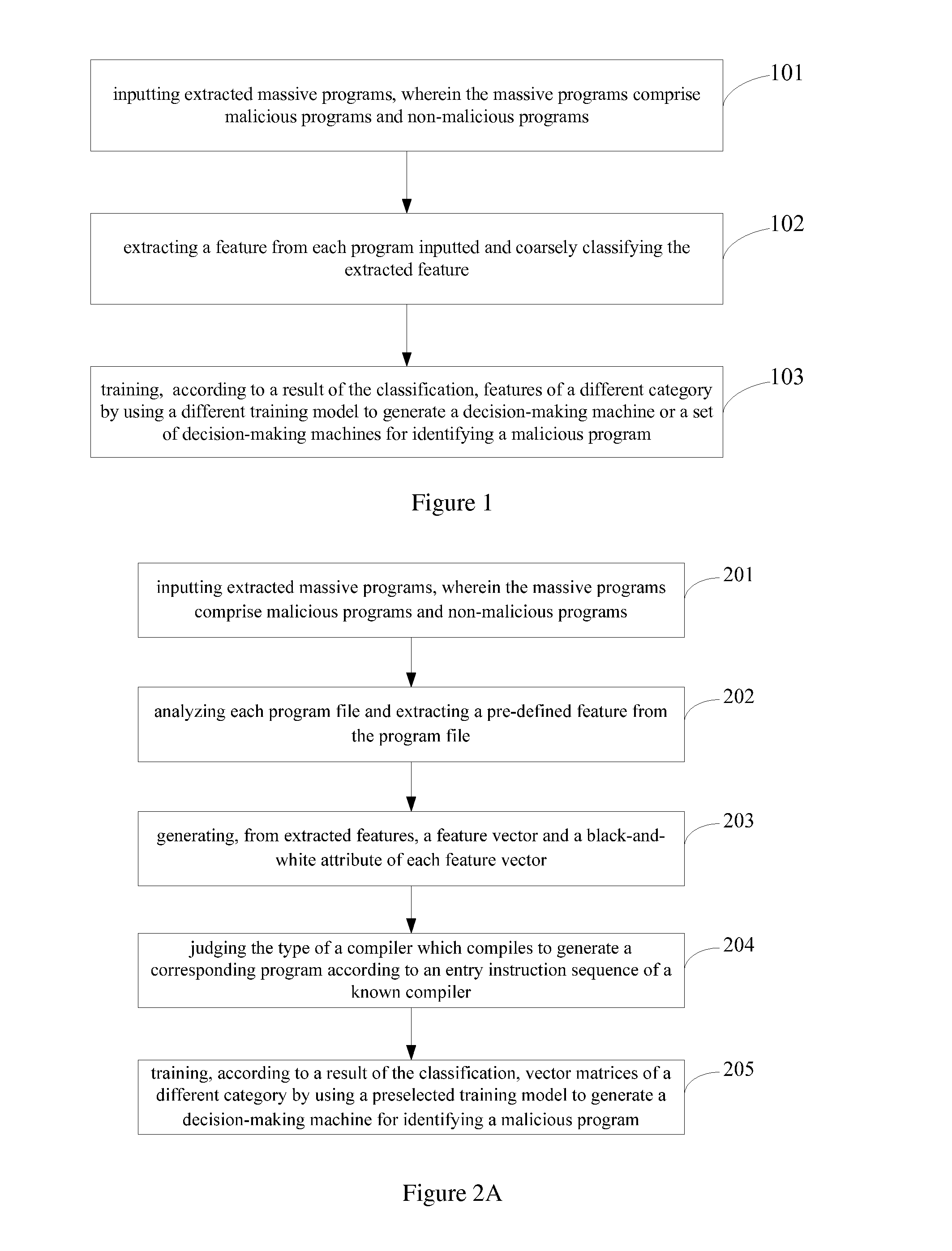
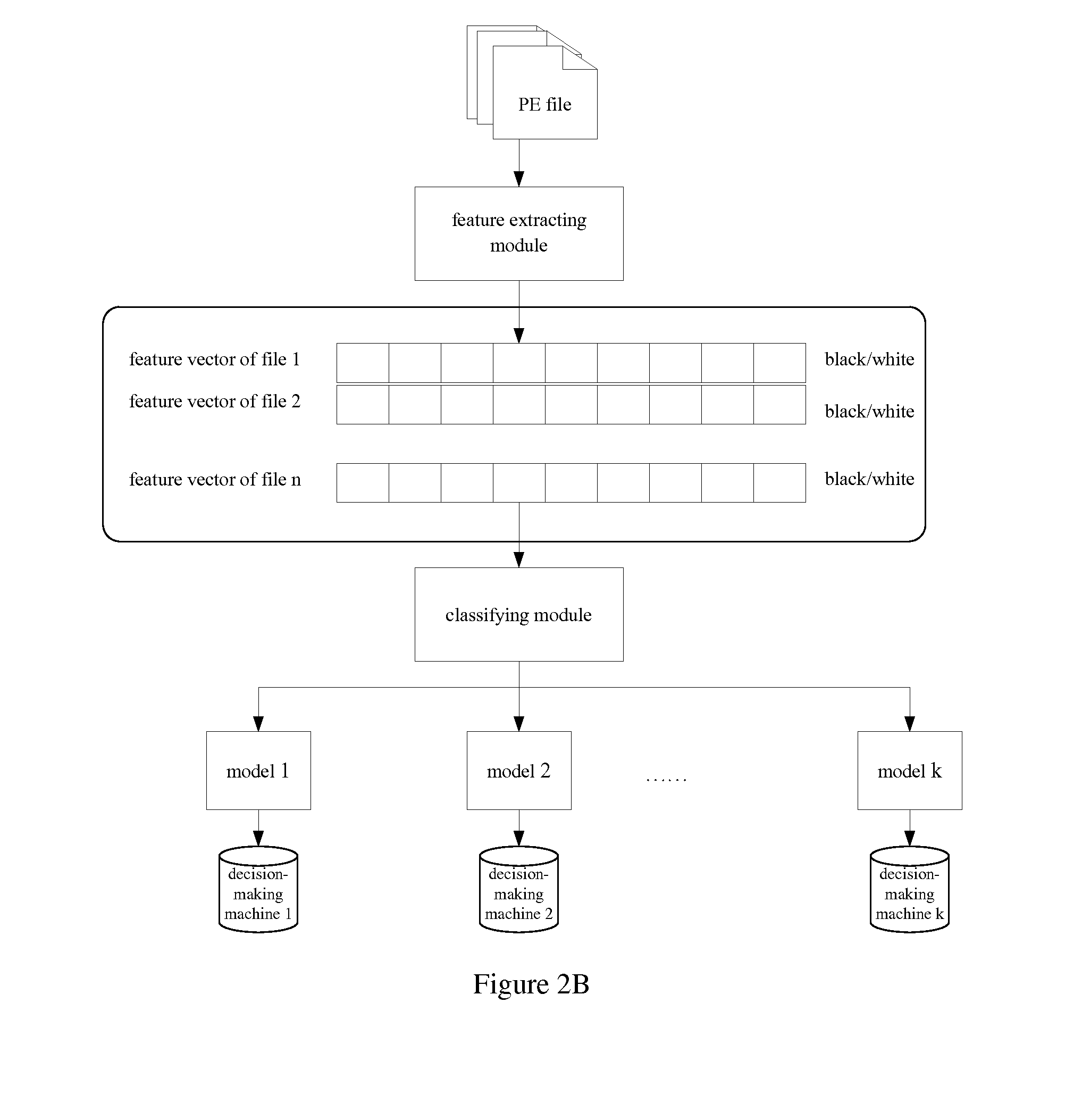
Method and Device for Program Identification Based on Machine Learning
ActiveUS20130291111A1Save a lot of manpowerImprove recognition efficiencyMemory loss protectionError detection/correctionUnknown procedureTheoretical computer science
The invention discloses a method and device for programidentification based on machine learning. The method comprises: analyzing an inputted unknown program, and extracting a feature of the unknown program; coarsely classifying the unknown program according to the extracted feature; judging by inputting the unknown program into a corresponding decision-making machine generated by training according to a result of the coarse classification; and outputting an identification result of the unknown program, wherein the identification result is a malicious program or a non-malicious program. The embodiments of the invention adopt the machine learning technology, achieve the decision-making machine for identifying a malicious program by analyzing a large number of program samples, and can save a lot of manpower and improve the identification efficiency for a malicious program by using the decision-making machine; and furthermore, can find an inherent law of programs based on data mining for massive programs, prevent a malicious program that has not happened and make it difficult for a malicious program to avoid killing.
Owner:BEIJING QIHOO TECH CO LTD
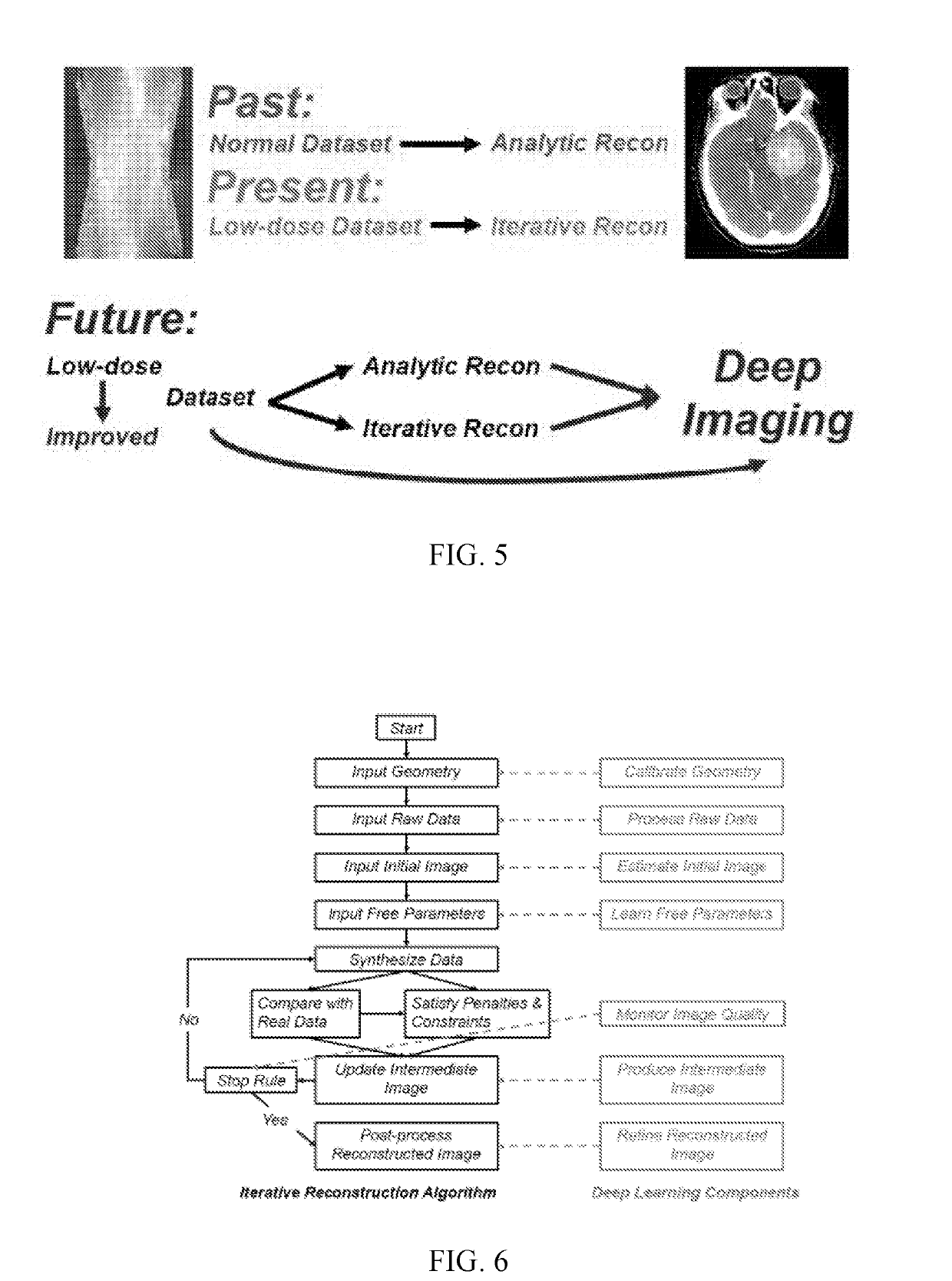
Tomographic image reconstruction via machine learning
ActiveUS20190325621A1Drawback can be addressedReconstruction from projectionDiagnostic recording/measuringPattern recognitionIntermediate image
Tomographic / tomosynthetic image reconstruction systems and methods in the framework of machine learning, such as deep learning, are provided. A machine learning algorithm can be used to obtain an improved tomographic image from raw data, processed data, or a preliminarily reconstructed intermediate image for biomedical imaging or any other imaging purpose. In certain cases, a single, conventional, non-deep-learning algorithm can be used on raw imaging data to obtain an initial image, and then a deep learning algorithm can be used on the initial image to obtain a final reconstructed image. All machine learning methods and systems for tomographic image reconstruction are covered, except for use of a single shallow network (three layers or less) for image reconstruction.
Owner:RENESSELAER POLYTECHNIC INST
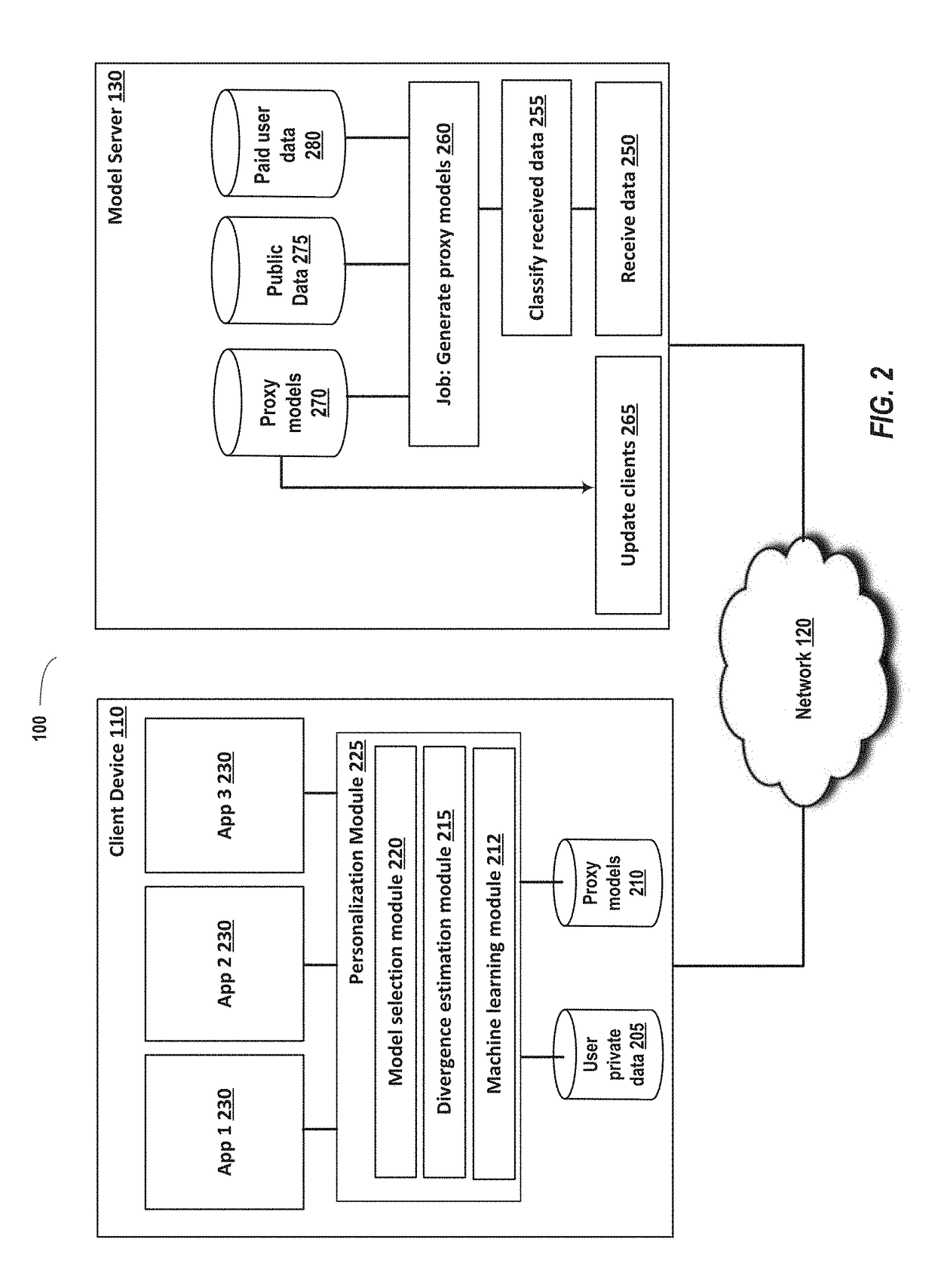
Using proxies to enable on-device machine learning
ActiveUS20180025287A1Improve experienceIncrease speedMachine learningInference methodsApplication softwareClient-side
Systems and methods are disclosed for a server generating a plurality of proxy prediction models for each of a plurality of applications for use by client devices. Providing a prediction model based on a data distribution that more closely matches the user private data of the actual user of the client device, as opposed to a generic model, can improve the accuracy of predictions and improve the benefits to the user of the client device. The plurality of prediction models are generated by a server and provided to a plurality of clients. For a particular application, a client device can use previously collected private user data to select one of the plurality of prediction models for the application as being a closest matching prediction model to use for a particular user.
Owner:APPLE INC
Entity Matching Using Machine Learning
ActiveUS20130185306A1Improve the level ofImprove precision and relevanceDigital data information retrievalDigital data processing detailsBusiness enterpriseData field
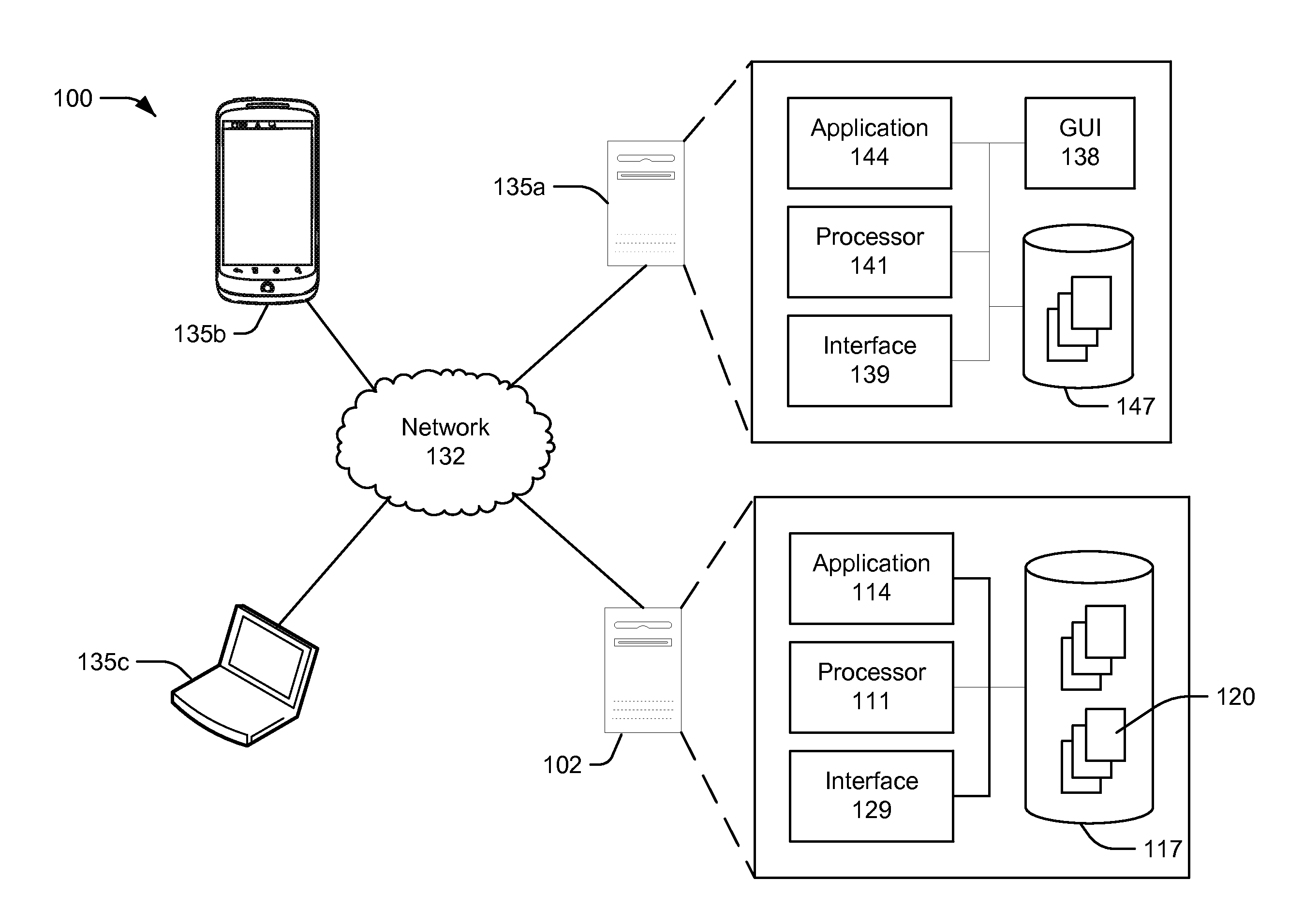
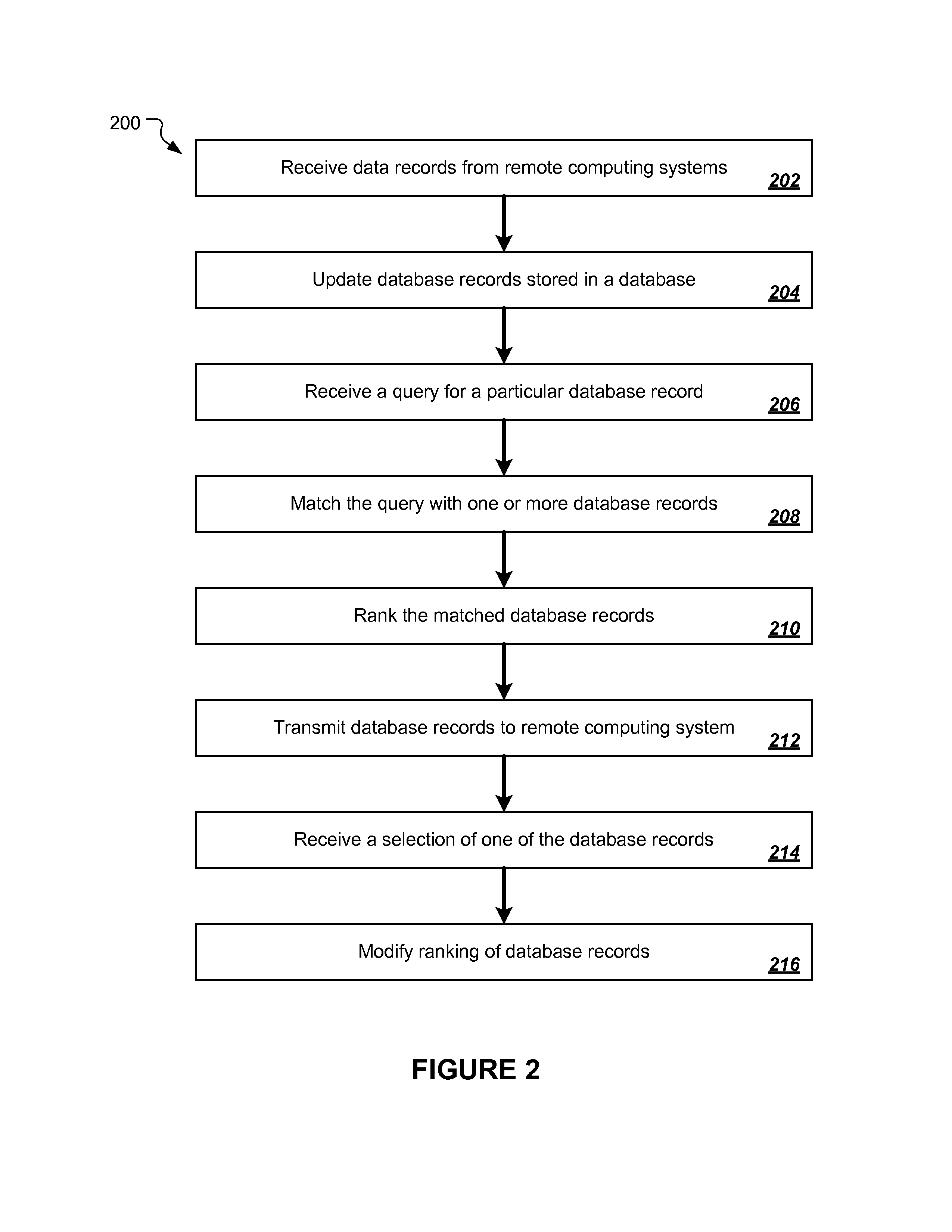
Techniques for information retrieval include receiving a plurality of data records, each data record including data fields associated with a business enterprise, the data fields including a name of the business enterprise; updating a plurality of database records associated with the received plurality of data records stored in a database, each database record including attributes including the name of the business enterprise and an alias associated with the name of the business enterprise; receiving a query for a particular database record, the query including at least one of the name of the business enterprise or the alias associated with the name of the business enterprise; and preparing for display, in response to the query, one or more of the database records based on at least one of the name of the business enterprise or the alias associated with the name of the business enterprise.
Owner:BUSINESS OBJECTS SOFTWARE
Machine learning-based subject tracking
ActiveUS20190156274A1ConfidenceImprove accuracyImage enhancementImage analysisLearning basedBackground image
Systems and techniques are provided for tracking puts and takes of inventory items by subjects in an area of real space. A plurality of cameras with overlapping fields of view produce respective sequences of images of corresponding fields of view in the real space. In one embodiment, the system includes first image processors, including subject image recognition engines, receiving corresponding sequences of images from the plurality of cameras. The first image processors process images to identify subjects represented in the images in the corresponding sequences of images. The system includes second image processors, including background image recognition engines, receiving corresponding sequences of images from the plurality of cameras. The second image processors mask the identified subjects to generate masked images. Following this, the second image processors process the masked images to identify and classify background changes represented in the images in the corresponding sequences of images.
Owner:STANDARD COGNITION CORP
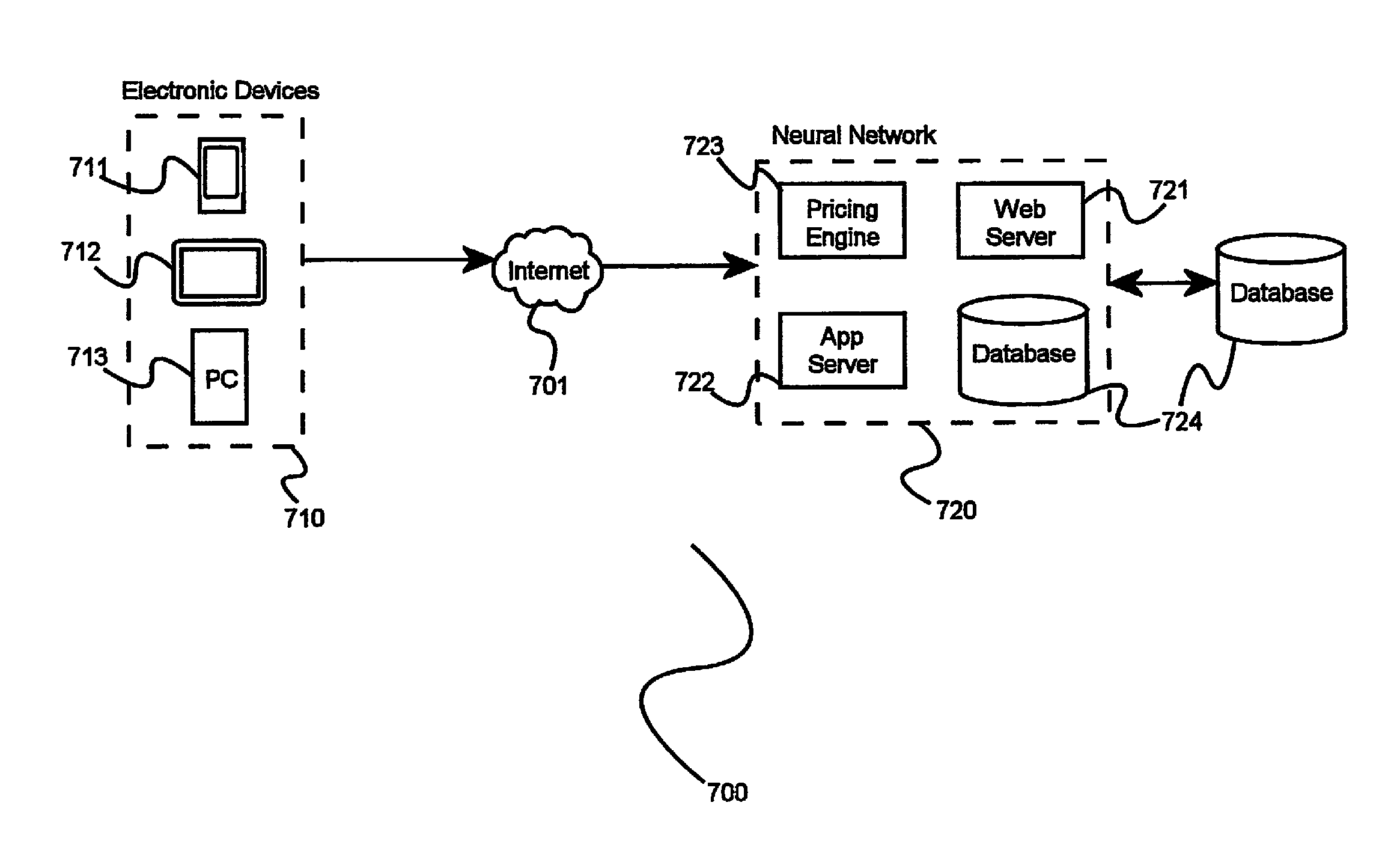
Optimization utilizing machine learning
A system for providing adaptive price optimization, comprising an adaptive neural network, the neural network further comprising a plurality of static and adaptive data, and a method for providing adaptive data learning behavior comprising the steps of making predictions based on data sources, comparing observed results to predicted results, and updating adaptive data sources.
Owner:GTH SOLUTIONS SP Z O O
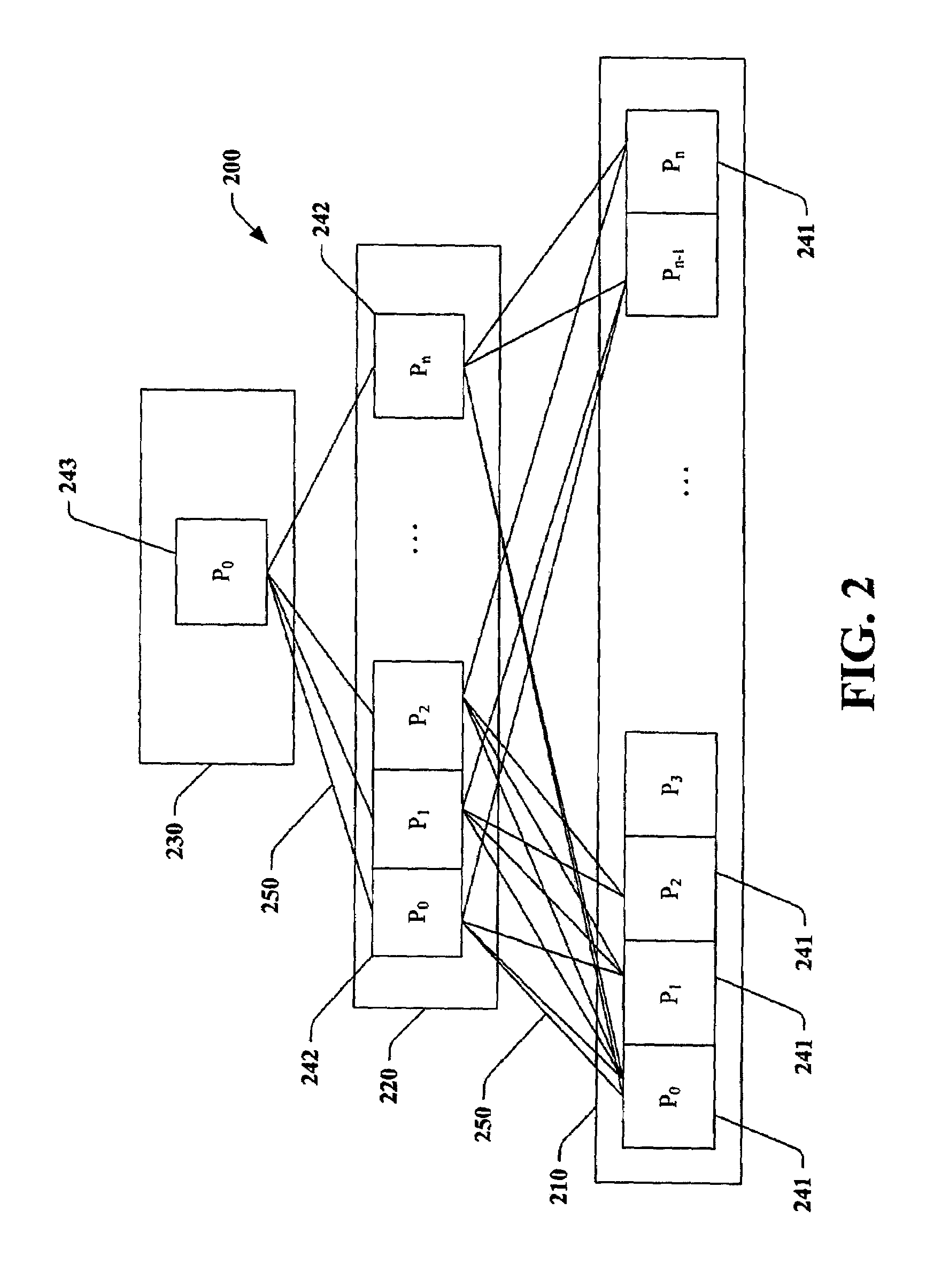
Asynchronous parameter aggregation for machine learning
ActiveUS20190311298A1Character and pattern recognitionNavigation instrumentsData setMachine learning
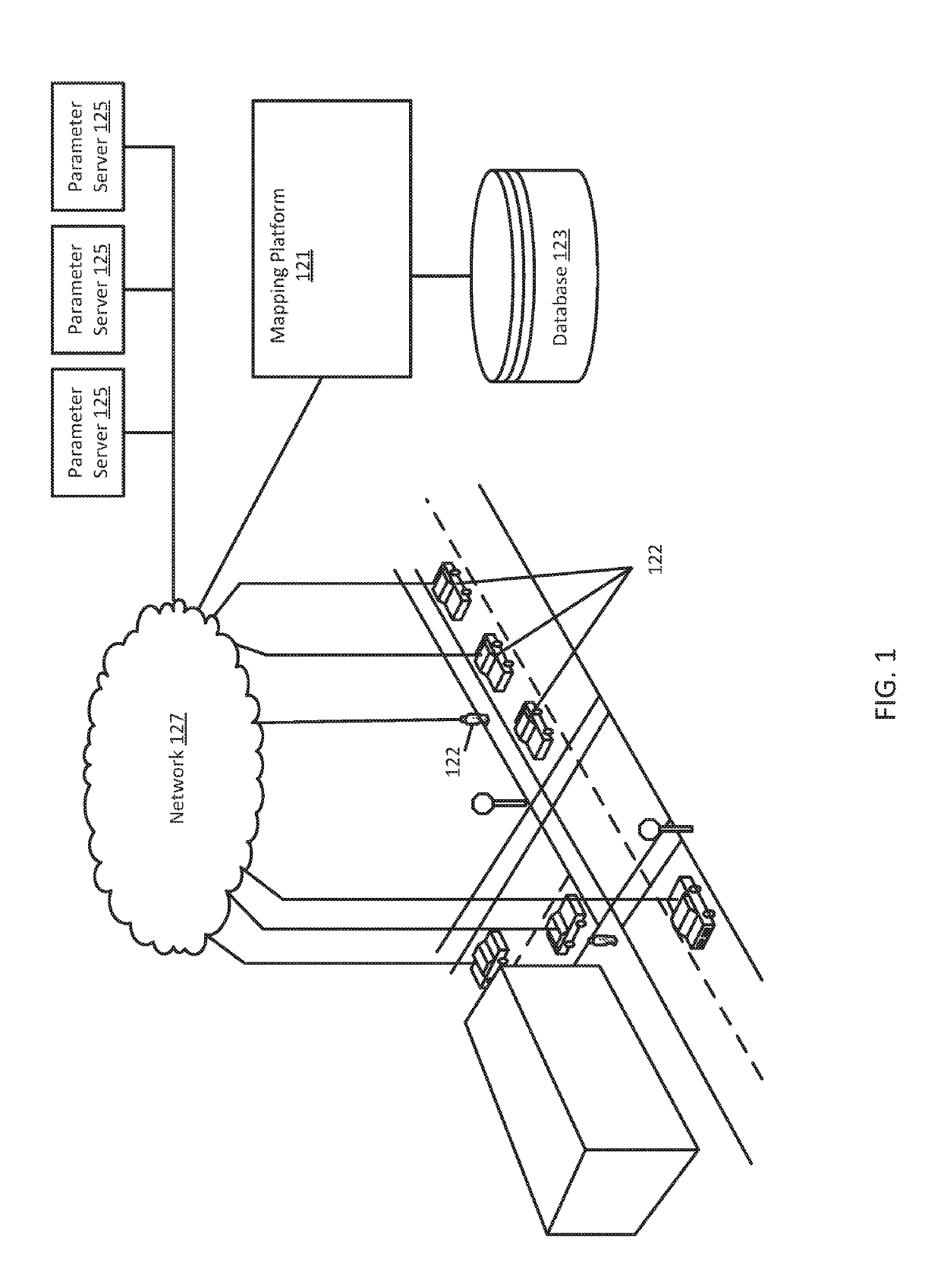
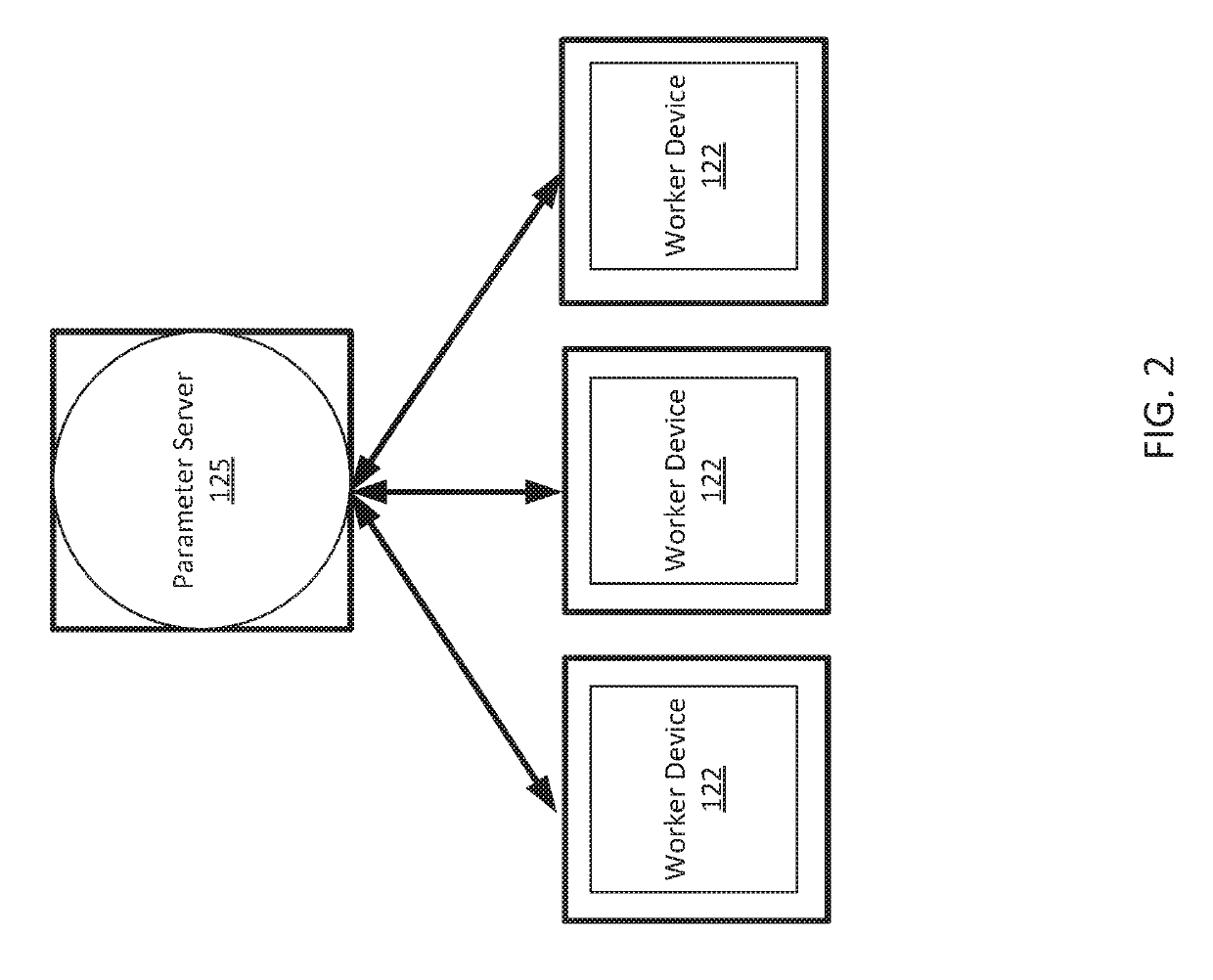
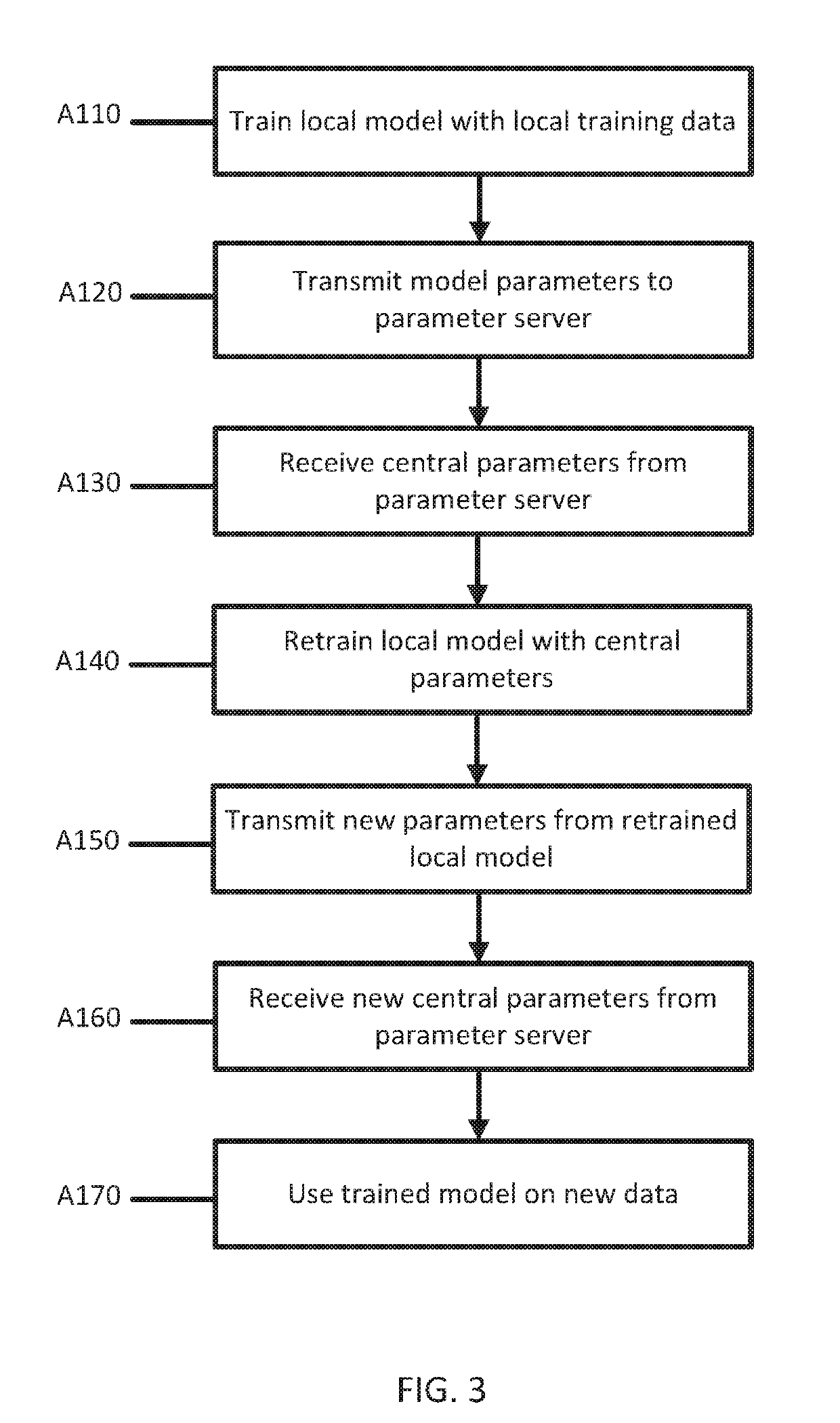
Systems and methods are provided for training a machine learned model on a large number of devices, each device acquiring a local set of training data without sharing data sets across devices. The devices train the model on the respective device's set of training data. The devices communicate a parameter vector from the trained model asynchronously with a parameter server. The parameter server updates a master parameter vector and transmits the master parameter vector to the respective device.
Owner:HERE GLOBAL BV
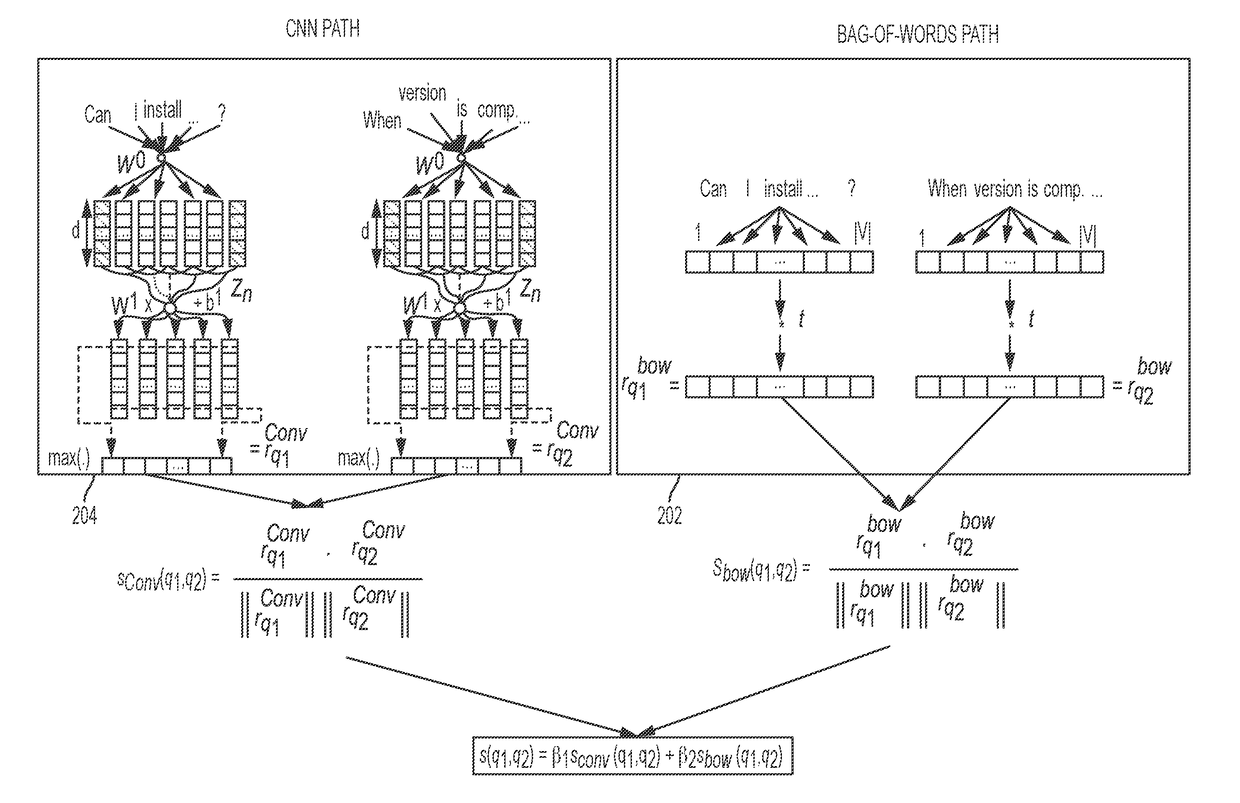
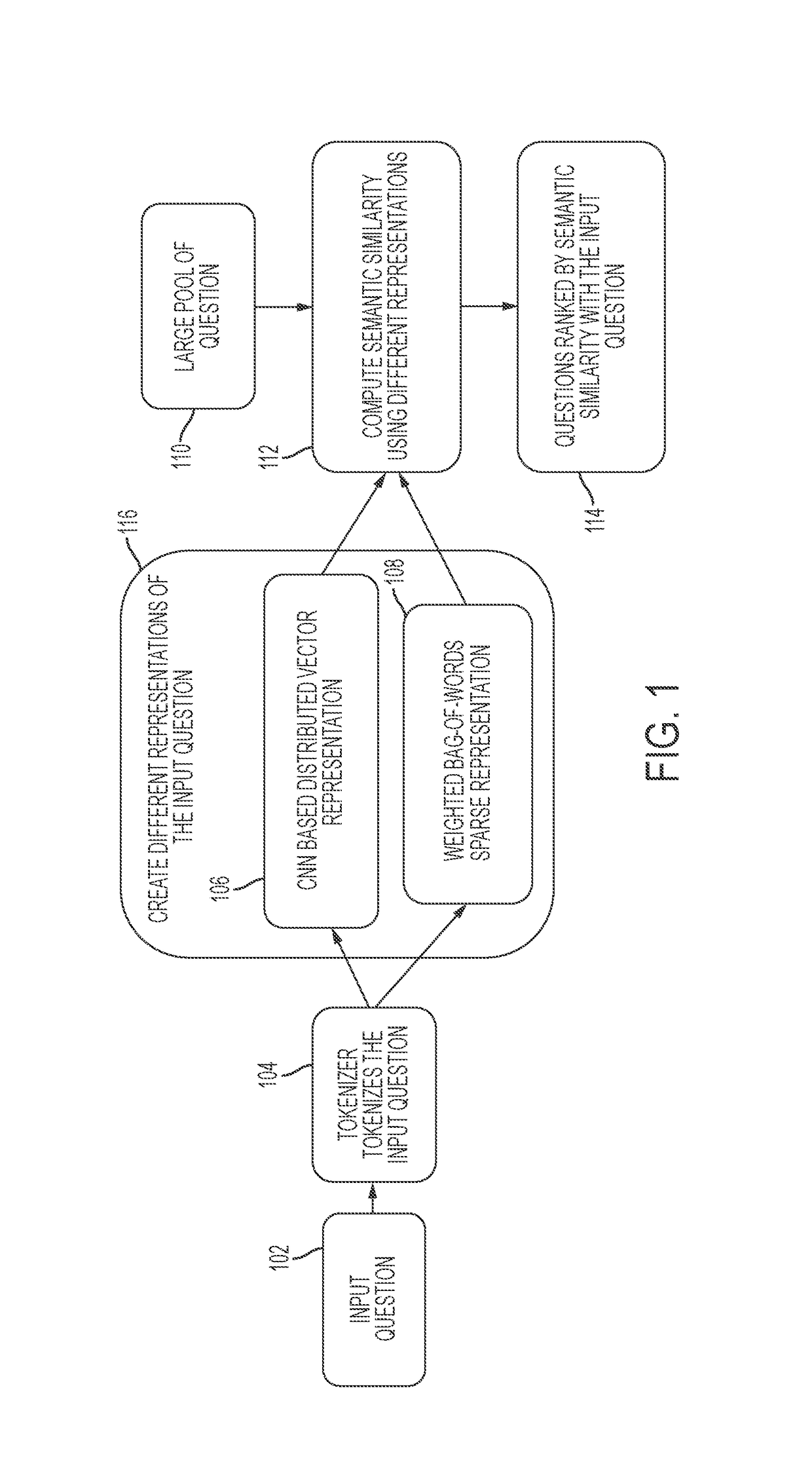
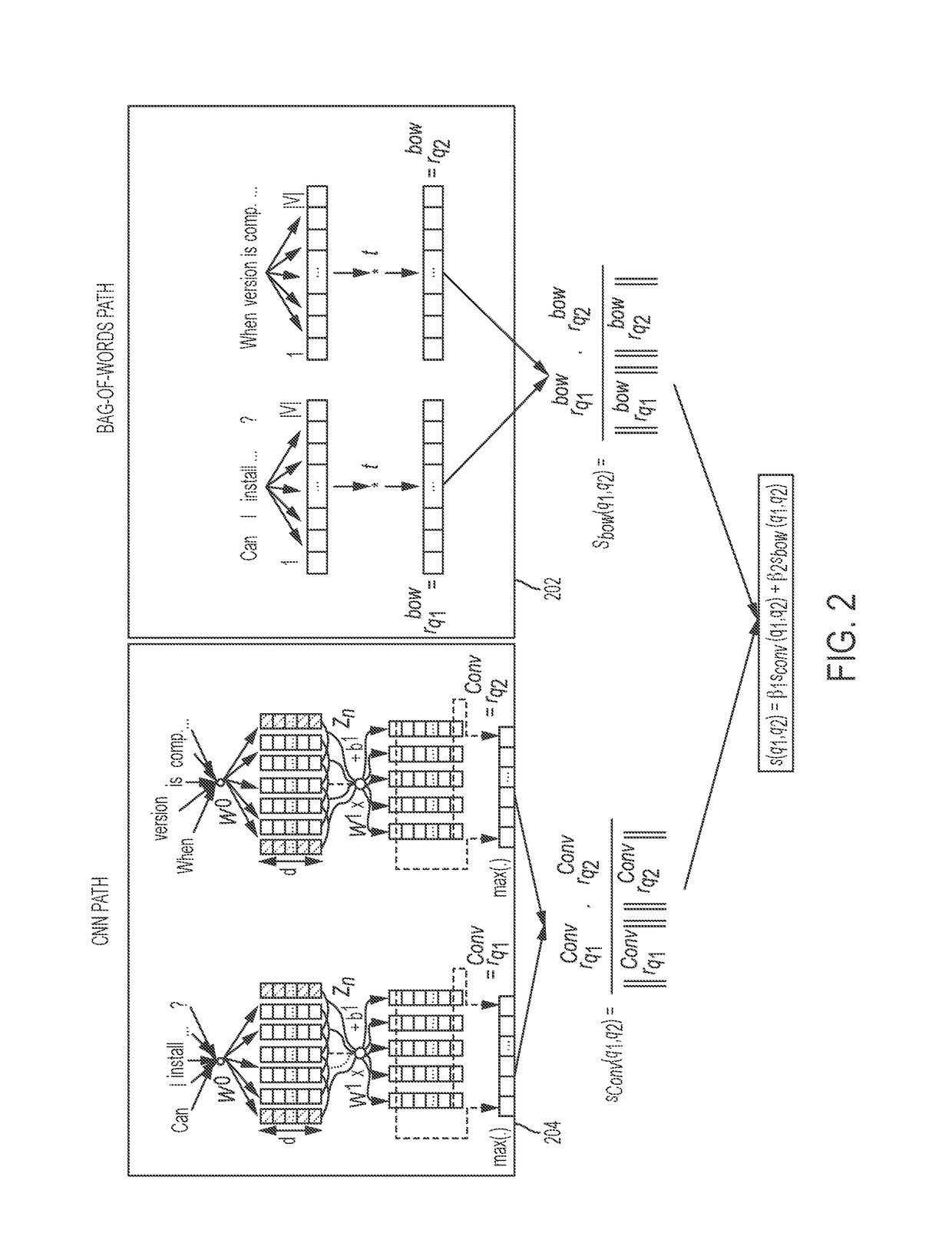
Machine learning and training a computer-implemented neural network to retrieve semantically equivalent questions using hybrid in-memory representations
ActiveUS9659248B1Natural language translationSemantic analysisStochastic gradient descentComputational semantics
Determining semantically equivalent text or questions using hybrid representations based on neural network learning. Weighted bag-of-words and convolutional neural networks (CNN) based distributed vector representations of questions or text may be generated to compute the semantic similarity between questions or text. Weighted bag-of-words and CNN based distributed vector representations may be jointly used to compute the semantic similarity. A pair-wise ranking loss function trains neural network. In one embodiment, the parameters of the system are trained by minimizing a pair-wise ranking loss function over a training set using stochastic gradient descent (SGD).
Owner:IBM CORP
Privacy-preserving machine learning
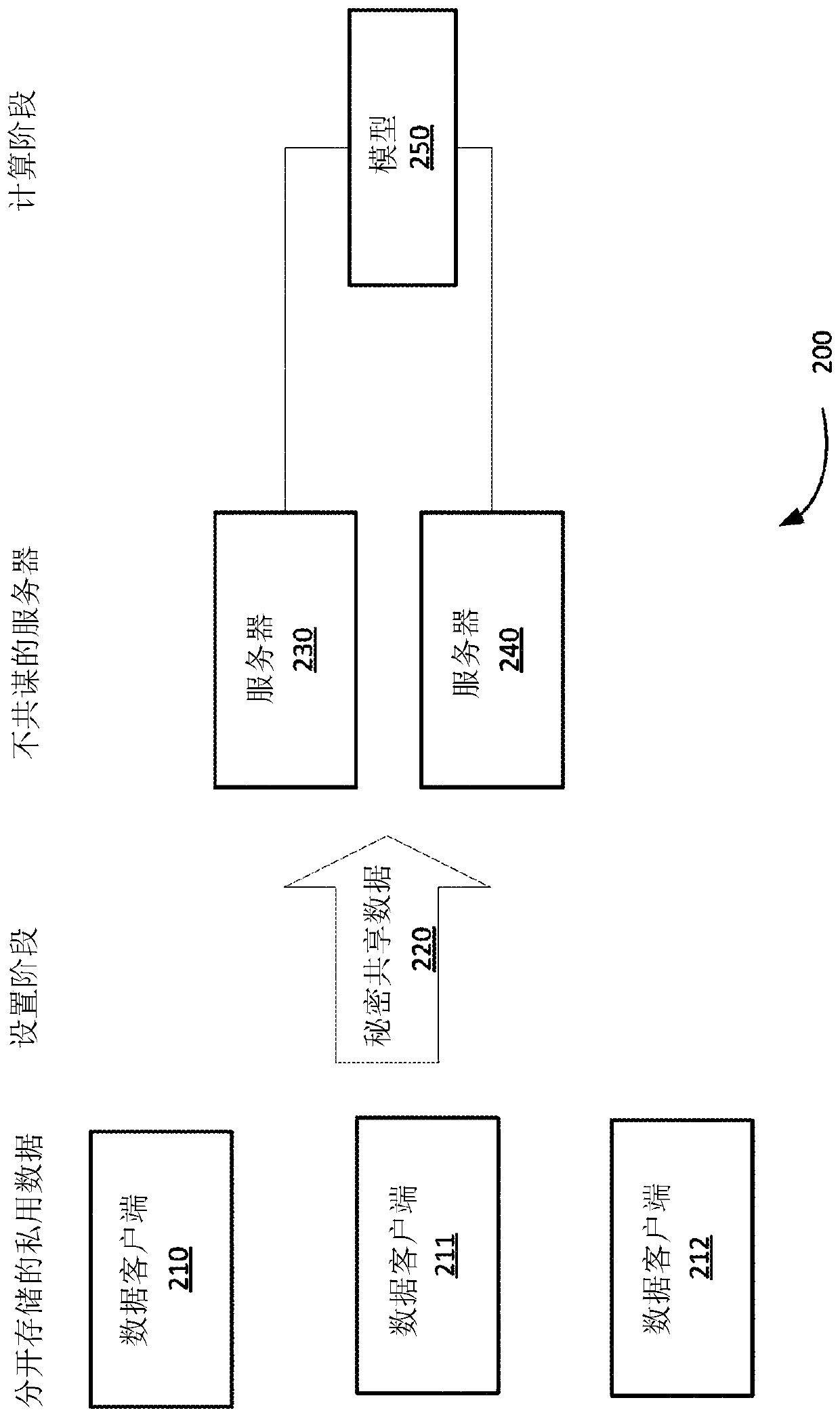
InactiveCN110537191ADigital data protectionNeural architecturesStochastic gradient descentNerve network
Owner:VISA INT SERVICE ASSOC
NRIET fog forecasting method based on machine learning
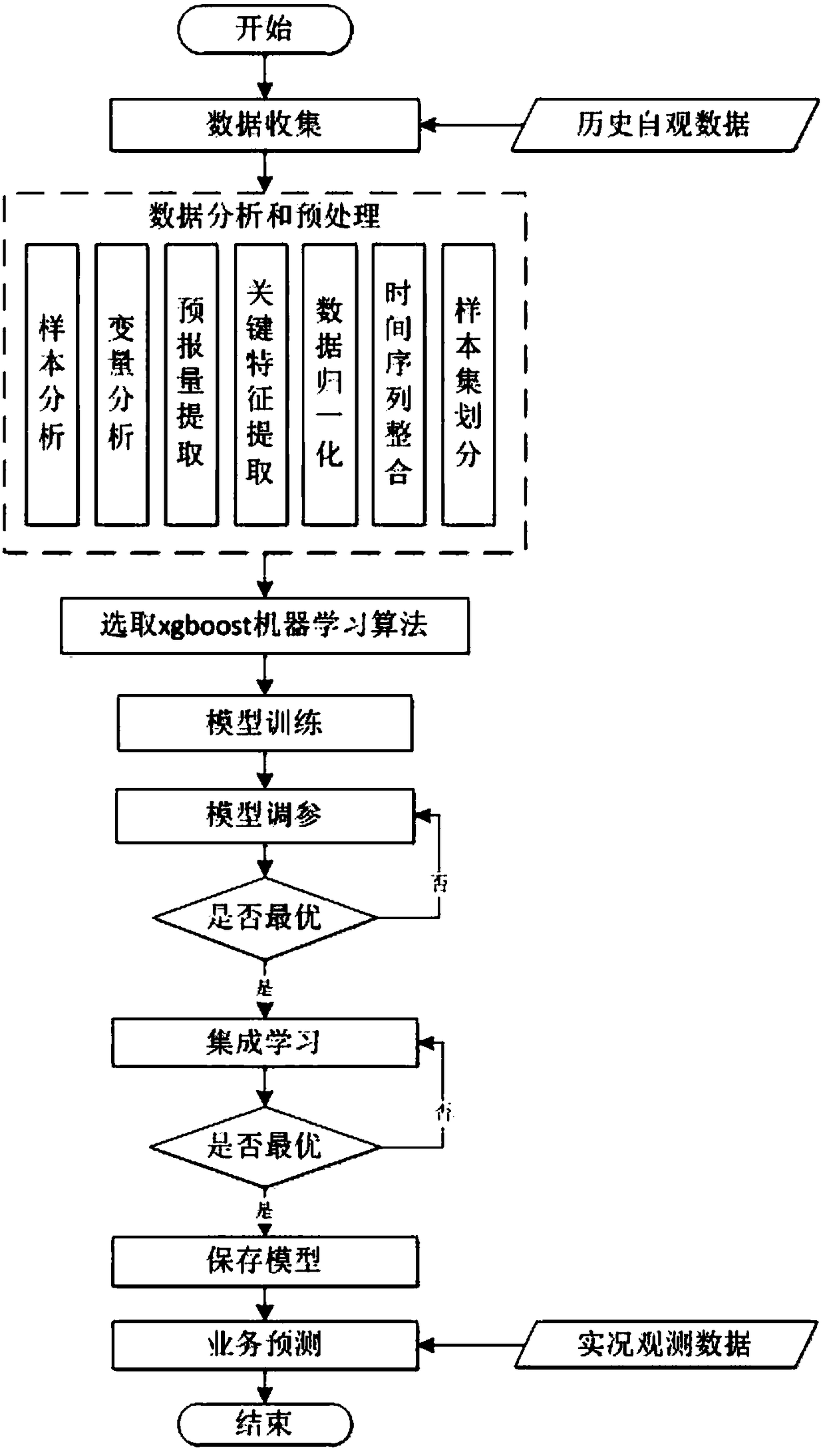
InactiveCN108375808AEnsure traffic safetyTimely and effective fog forecast serviceWeather condition predictionICT adaptationEntity–relationship modelRelational model
The invention discloses an NRIET fog forecasting method based on machine learning. The method comprises steps that historical and forecast data for model training and operational forecasting in and around the forecast area is collected; the collected data is analyzed and processed to be a sample set for training a machine learning model; for problems, an xgboost model algorithm based on a decisiontree is selected, key influence factors generated by the airport fog are screened, and a relationship model between the fog and the influence factors is established; a training set and a verificationset are trained; according to the parameter adjusting sequence, model parameters are repeatedly adjusted till a forecasting model with optimal performance is acquired; an integrated learning method is utilized, and intersect verification and iteration training are carried out for the model to further improve model forecasting performance; observed real-time data is inputted to the forecasting model to acquire the fog forecasting result.
Owner:NANJING NRIET IND CORP
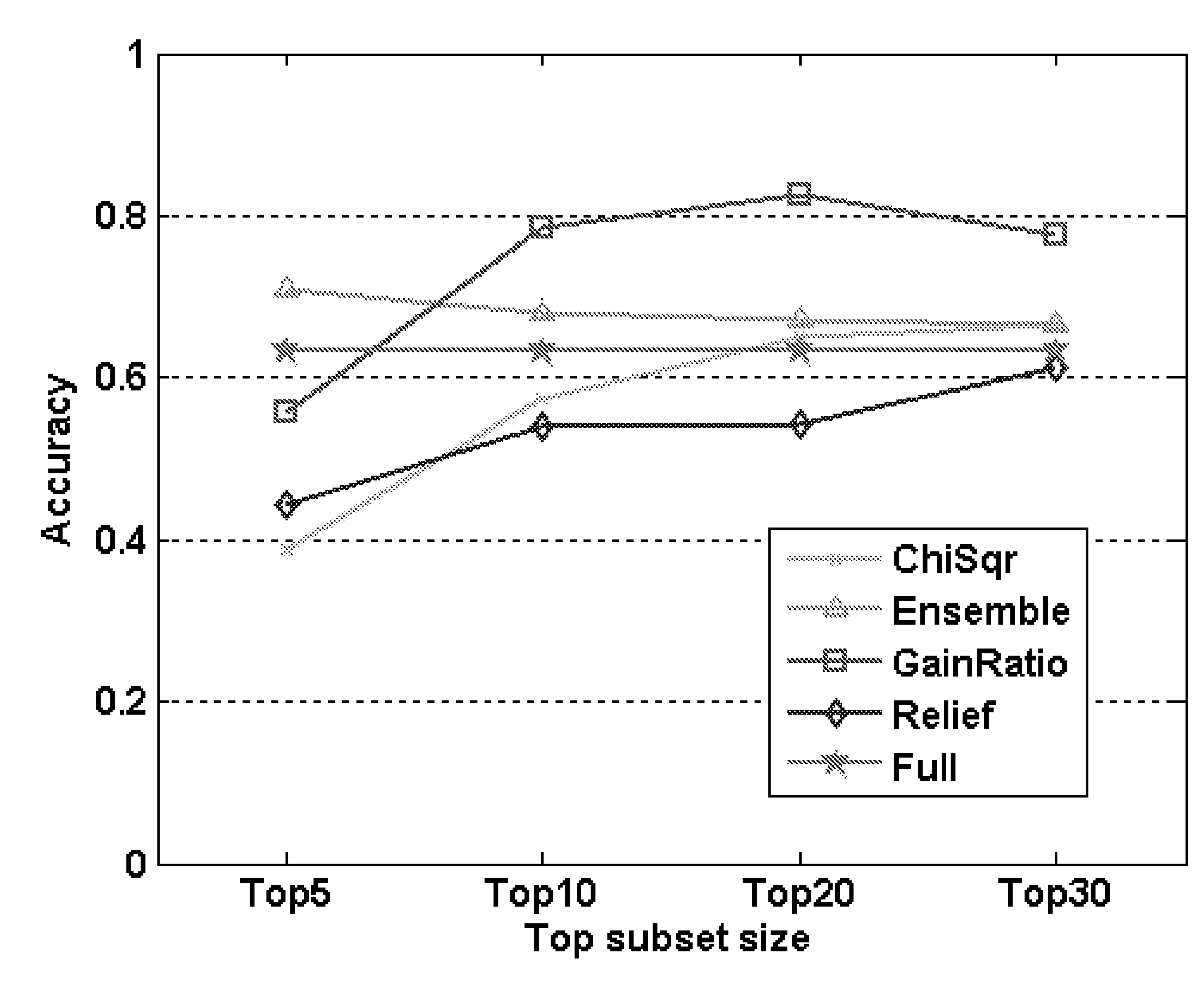
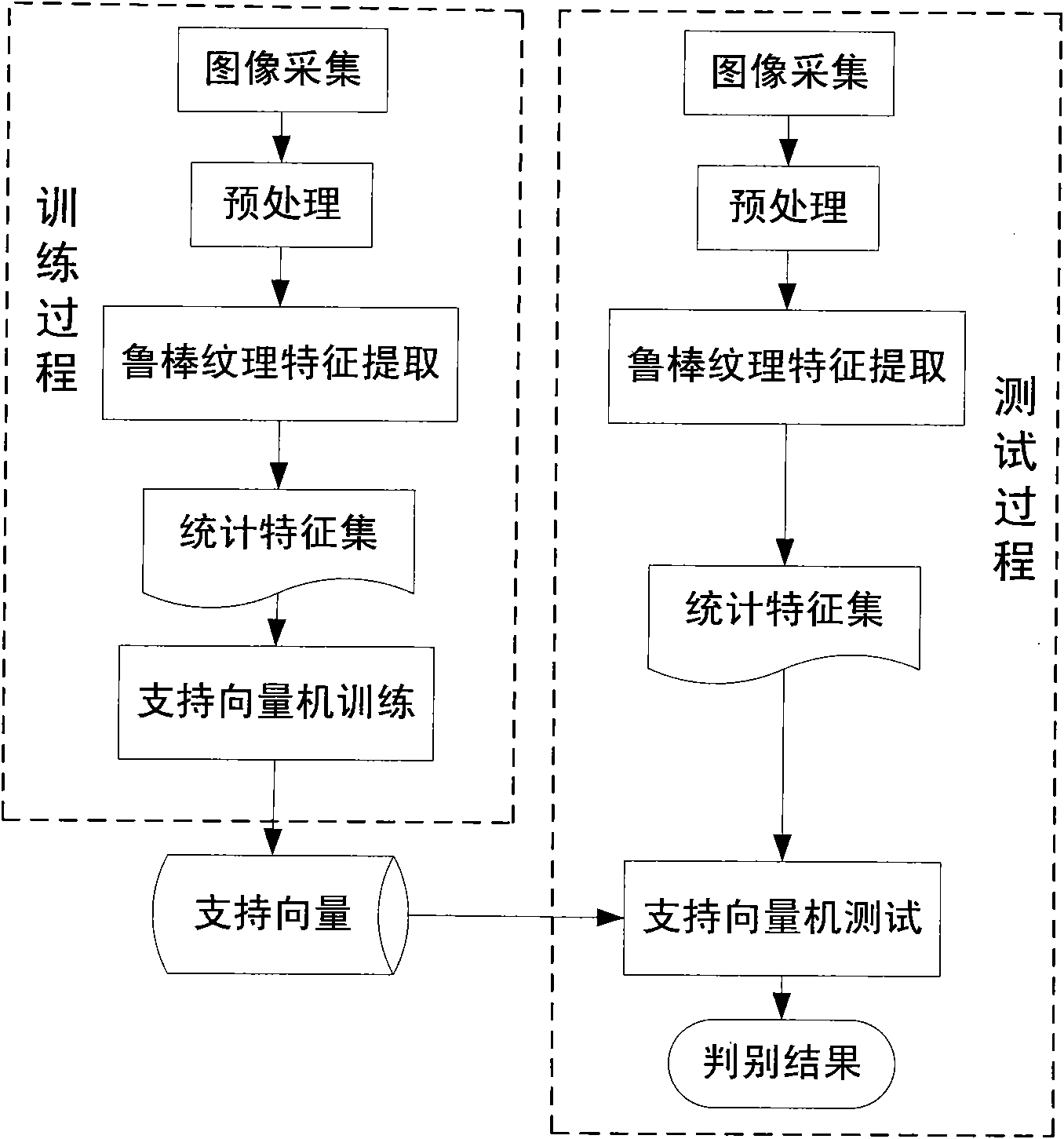
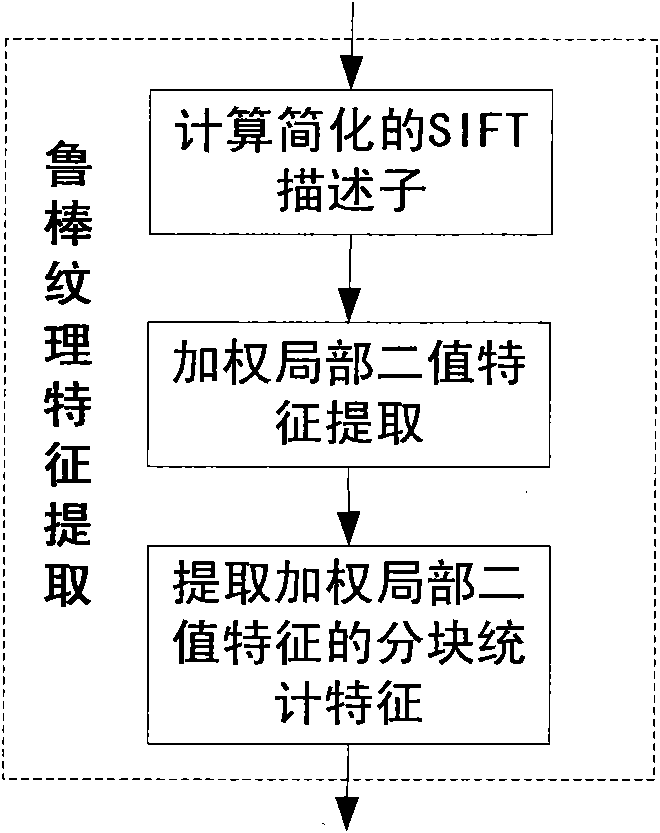
Method for distinguishing false iris images based on robust texture features and machine learning
ActiveCN101923640AImprove stabilityRobustCharacter and pattern recognitionSupport vector machineColor printing
The invention relates to a method for distinguishing false iris images based on robust texture features and machine learning, which comprises the following steps: preprocessing true iris images or false iris images; extracting the partitioned statistical features of a robust weighted partial binary pattern; and carrying out training and sorting of a support vector machine, and judging whether thetest images are false iris images or not according to the output result of a sorter. The method of the invention combines SIFT descriptors and partial binary pattern features to extract the robust texture features, the description of textures is more stable because of the robustness of the SIFT to brightness, translation, rotation and scale change, and the support vector machine enables the method to have better universality. The invention can be used for effectively distinguishing the false iris images, has the advantages of high precision, high robustness and high reliability, can be used for distinguishing false irises such as paper printing irises, color printing contact lenses, synthetic eyes and the like, and can improve the safety of the system when being applied to the applicationsystem in which iris recognition is used for carrying out identification.
Owner:BEIJING IRISKING
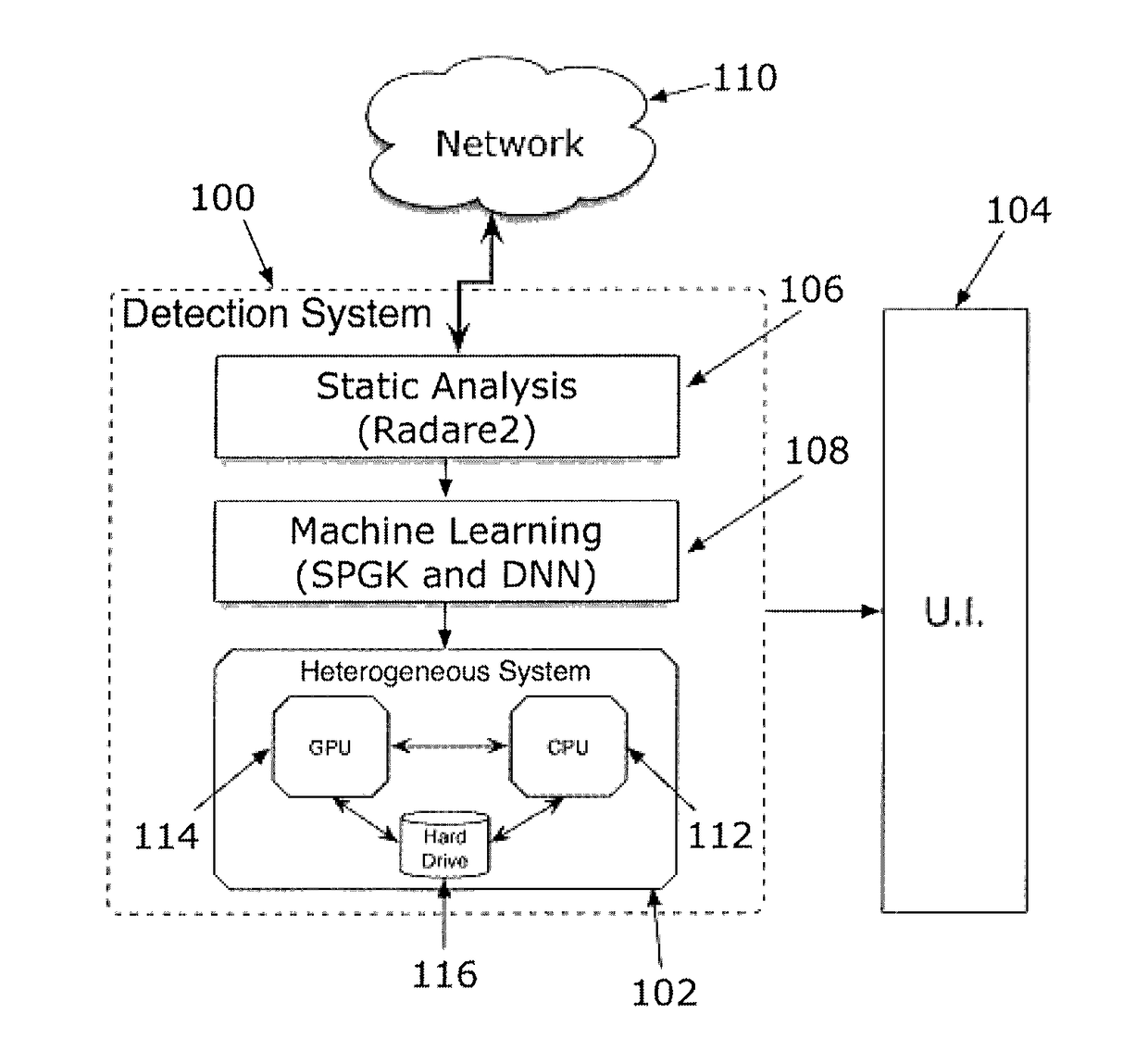
Malware analysis and detection using graph-based characterization and machine learning
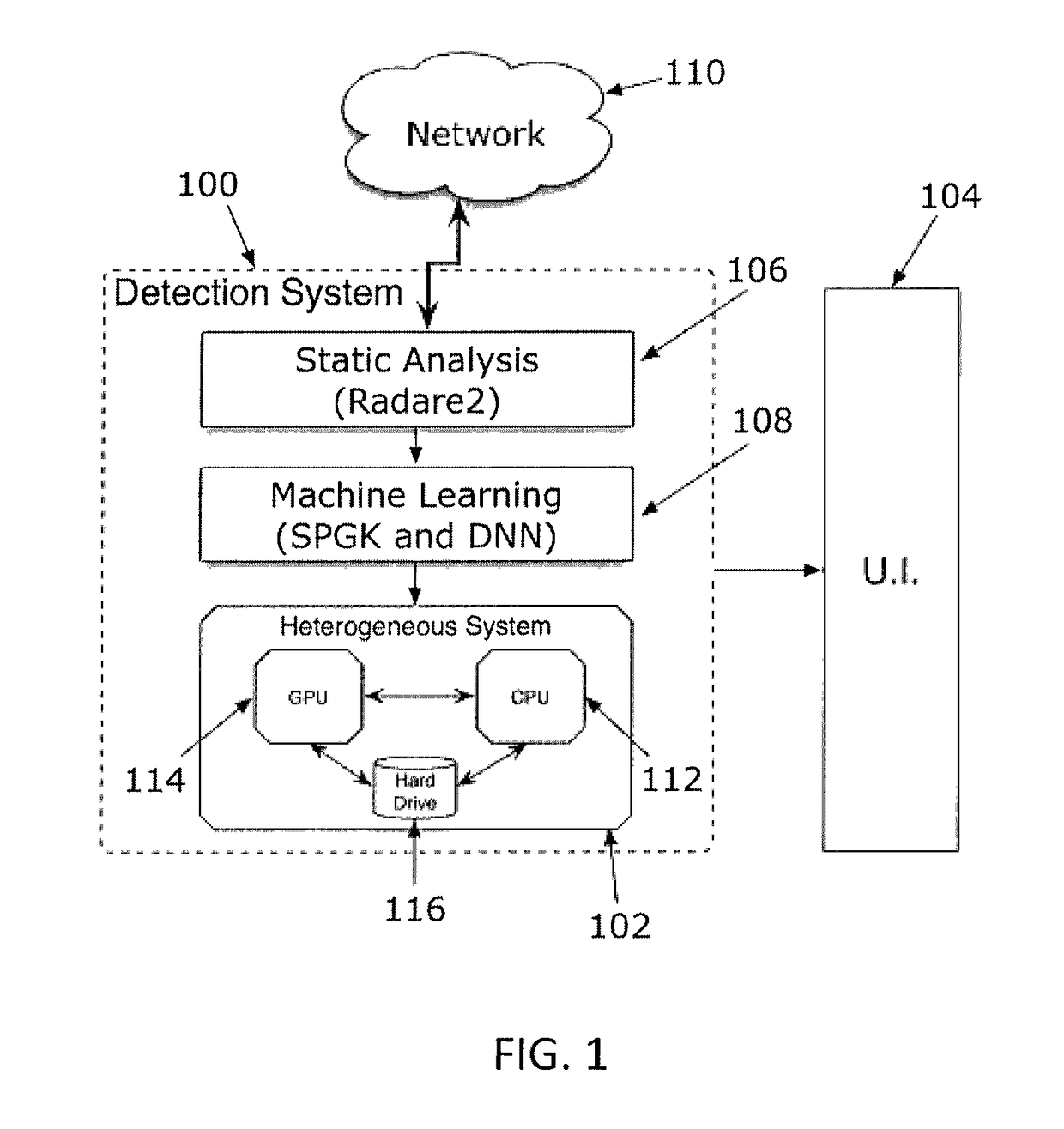
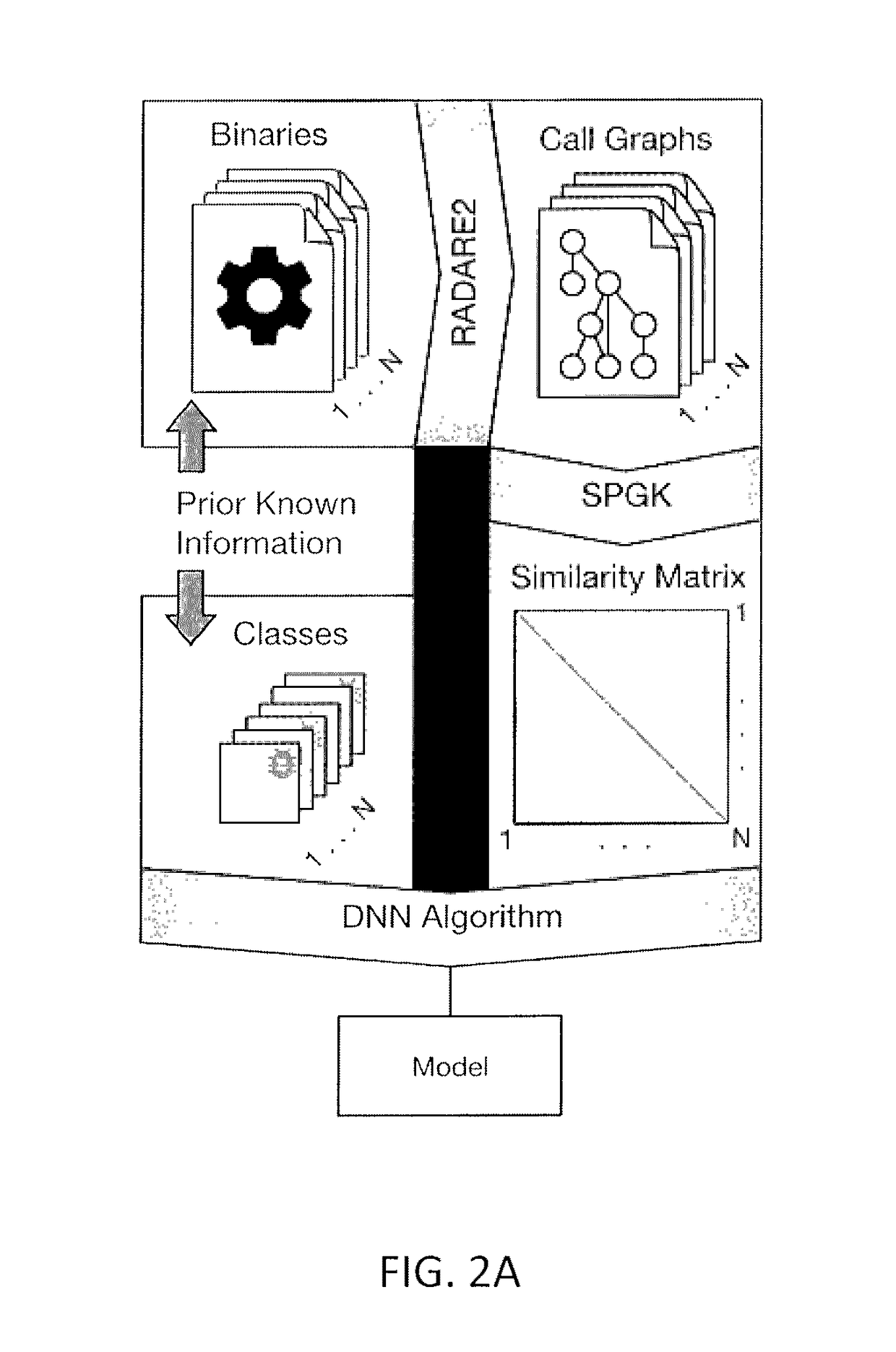
Malware detection methods systems, and apparatus are described. Malware may be detected by obtaining a plurality of malware binary executables and a plurality of goodware binary executables, decompiling the plurality of malware binary executables and the plurality of goodware binary executable to extract corresponding assembly code for each of the plurality of malware binary executables and the plurality of goodware binary executable, constructing call graphs for each of the plurality of malware binary executables and the plurality of goodware binary executables from the corresponding assembly code, determining similarities between the call graphs using graph kernels applied to the call graphs for each of the plurality of malware binary executables and the plurality of goodware binary executables, building a malware detection model from the determined similarities between call graphs by applying a machine learning algorithm such as a deep neural network (DNN) algorithm to the determined similarities, and identifying whether a subject executable is malware by applying the built malware detection model to the subject executable.
Owner:UNIVERSITY OF DELAWARE
Filtering training data for machine learning
InactiveUS7690037B1Improve performanceMachine learningMemory loss protectionError detection/correctionData centerMachine learning
Data center activity traces form a corpus used for machine learning. The data in the corpus are putatively normal but may be tainted with latent anomalies. There is a statistical likelihood that the corpus represents predominately legitimate activity, and this likelihood is exploited to allow for a targeted examination of only the data representing possible anomalous activity. The corpus is separated into clusters having members with like features. The clusters having the fewest members are identified, as these clusters represent potential anomalous activities. These clusters are evaluated to determine whether they represent actual anomalous activities. The data from the clusters representing actual anomalous activities are excluded from the corpus. As a result, the machine learning is more effective and the trained system provides better performance, since latent anomalies are not mistaken for normal activity.
Owner:CA TECH INC
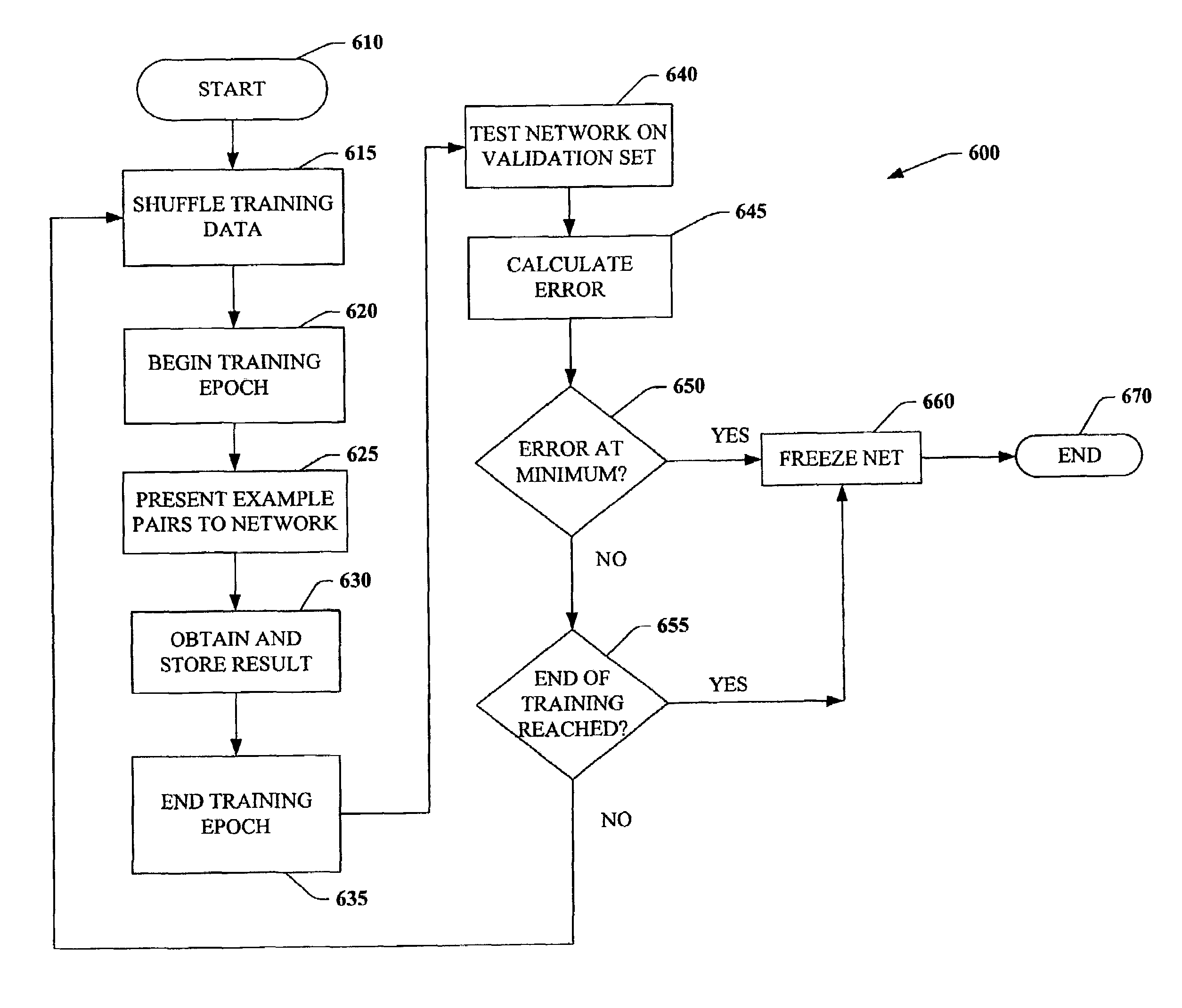
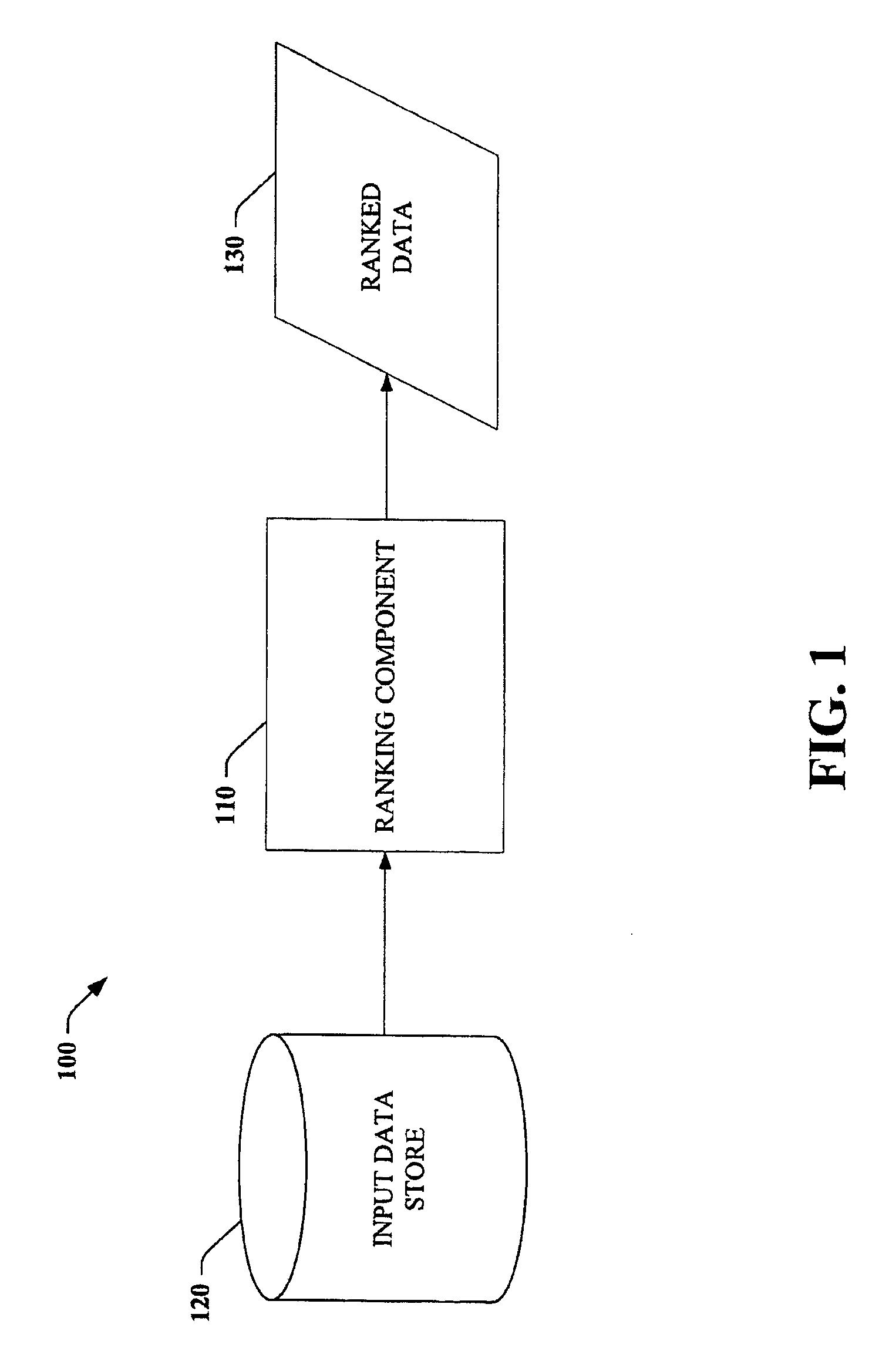
Machine learning system and method for ranking sets of data using a pairing cost function
InactiveUS7689520B2Reduce and ideally eliminate error madeFunction increaseWeb data indexingDigital computer detailsData setCost calculation
A machine learning system to rank data within sets is disclosed. The system comprises a ranking module that has differentiable parameters. The system further comprises a cost calculation module that uses a cost function that depends on pairs of examples and which describes an output of the ranking module. Methods of using the disclosed system are also provided.
Owner:MICROSOFT TECH LICENSING LLC
Bimodal man-man conversation sentiment analysis system and method thereof based on machine learning
ActiveCN106503805AFeatures are comprehensive and thoughtfulImprove accuracySemantic analysisMachine learningSpeech segmentationSingle sentence
The invention comprises a bimodal man-man conversation sentiment analysis system and a bimodal man-man conversation sentiment analysis method based on machine learning. The bimodal man-man conversation sentiment analysis system is characterized by comprising a speech recognition module, a text deep-layer feature extraction module, a speech segmentation module, an acoustic feature extraction module, a feature fusion module and an sentiment analysis module, wherein the speech recognition module is used for recognizing speech content and a time label; the text deep-layer feature extraction module is used for completing the extraction of text deep-layer word level features and text deep-layer sentence level features; the speech segmentation module is used for segmenting single sentence speech from entire speech; the acoustic feature extraction module is used for completing the extraction of acoustic features of the speech; the feature fusion module is used for fusing the obtained text deep-layer features with the acoustic features; and the sentiment analysis module is used for acquiring sentiment polarities of the speech to be subjected to sentiment analysis. The bimodal man-man conversation sentiment analysis method can integrate the text and audio modals for recognizing conversation sentiment, and fully utilizes features of word vectors and sentence vectors, thereby improving the precision of recognition.
Owner:山东心法科技有限公司
Machine learning-based wireless sensing motion identification method
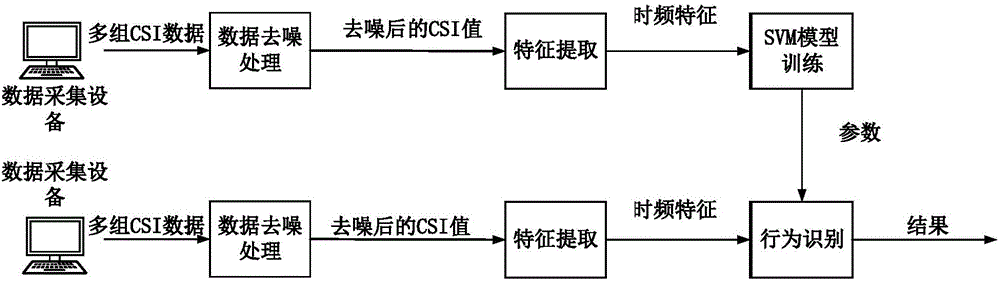
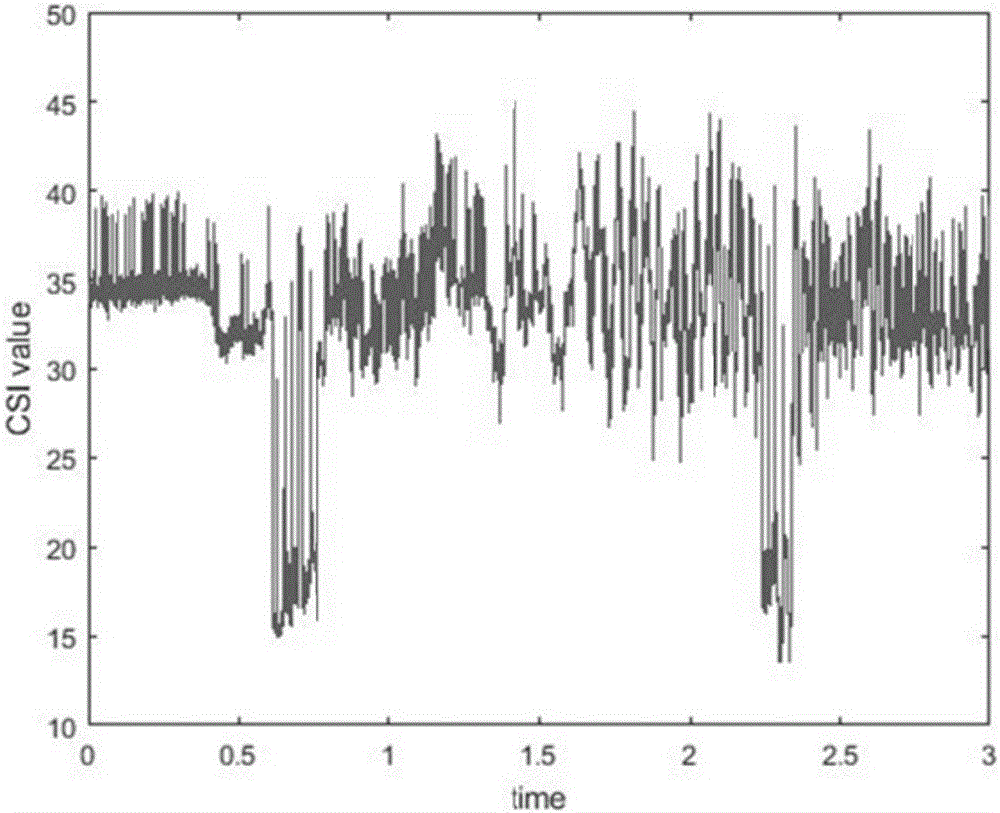
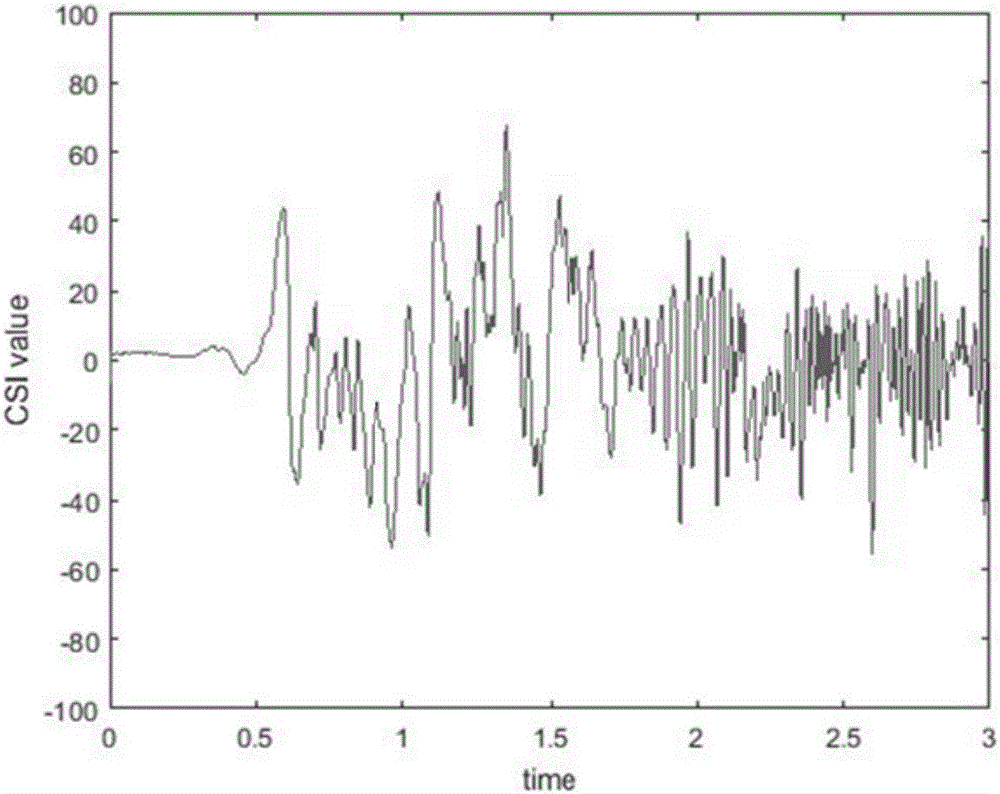
InactiveCN106407905AImprove recognition accuracyRobustCharacter and pattern recognitionData acquisitionColumn vector
The invention discloses a machine learning-based wireless sensing motion identification method which comprises the following steps: a step of data collection, a step of data denoising operation, a step of feature extraction and a step of SVM model training and identifying operation. During data collection operation, absolute value of a group of CSI data collected on each sampling point is obtained and is read into a 30*Nr*Nt matrix form. A PCA mode is mainly adopted for the data denoising operation. Feature extraction operation can be conducted based on discrete wavelet transformation. To make SVM model training convenient, training samples are subjected to Kmeans clustering operation via the machine learning-based wireless sensing motion identification method, n clustering centers can be used as word bags, and voting operation is performed based on feature vectors and best matching items of all the word bags; when the matrix form feature vectors are converted into column vectors, SVM model training can be realized conveniently. The machine learning-based wireless sensing motion identification method is a human body behavior identification method which is high in identification accuracy and high in robustness for environment change.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
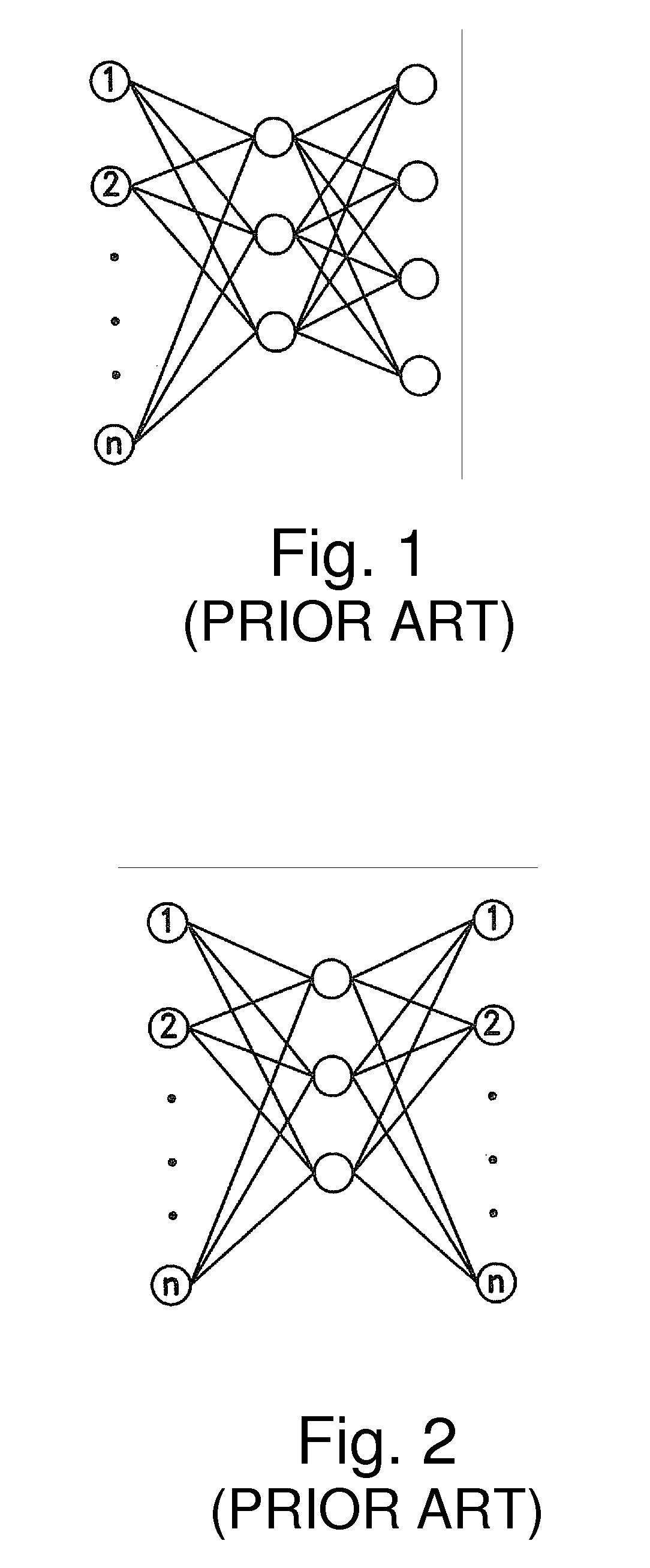
Method and apparatus for performing extraction using machine learning
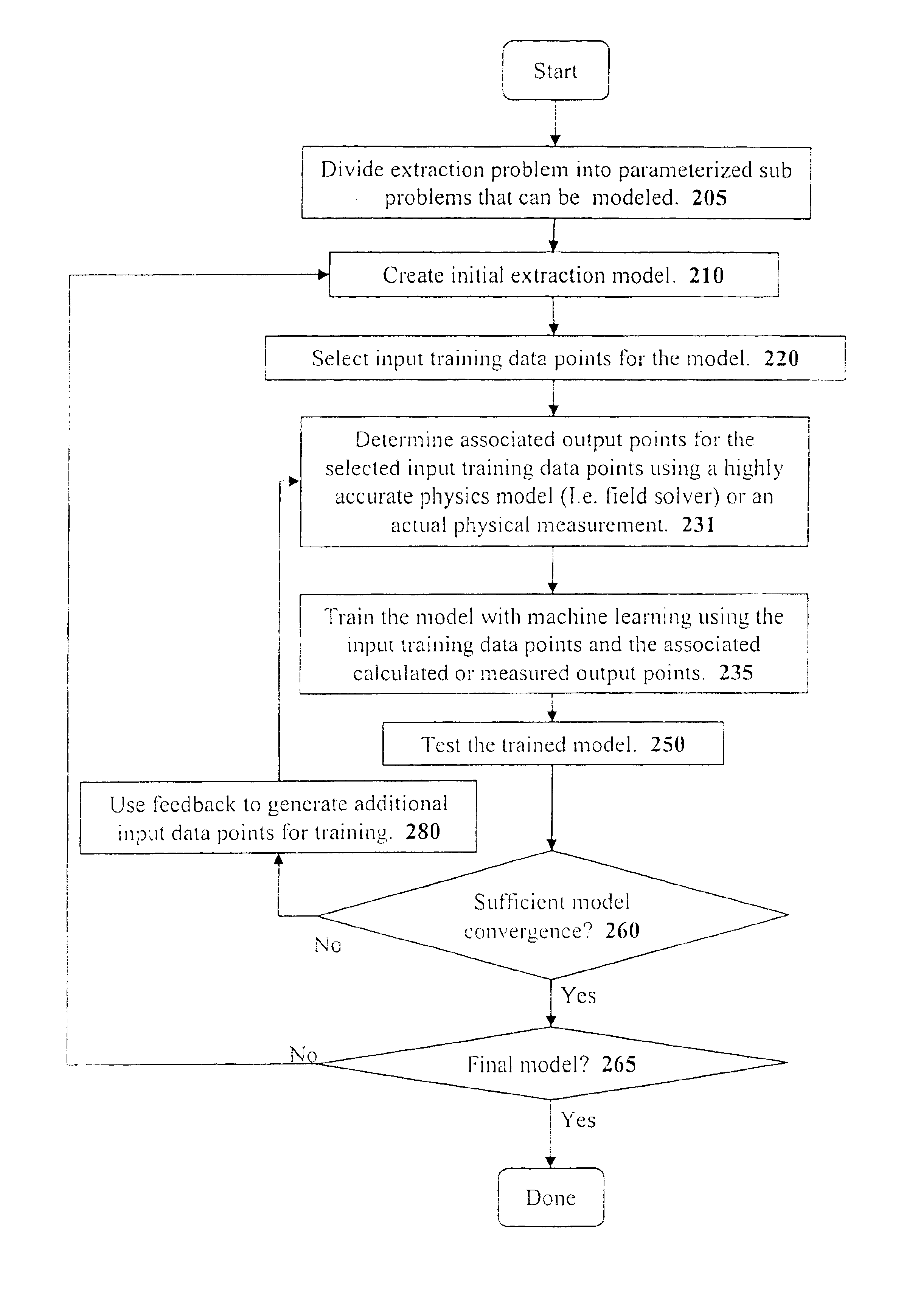
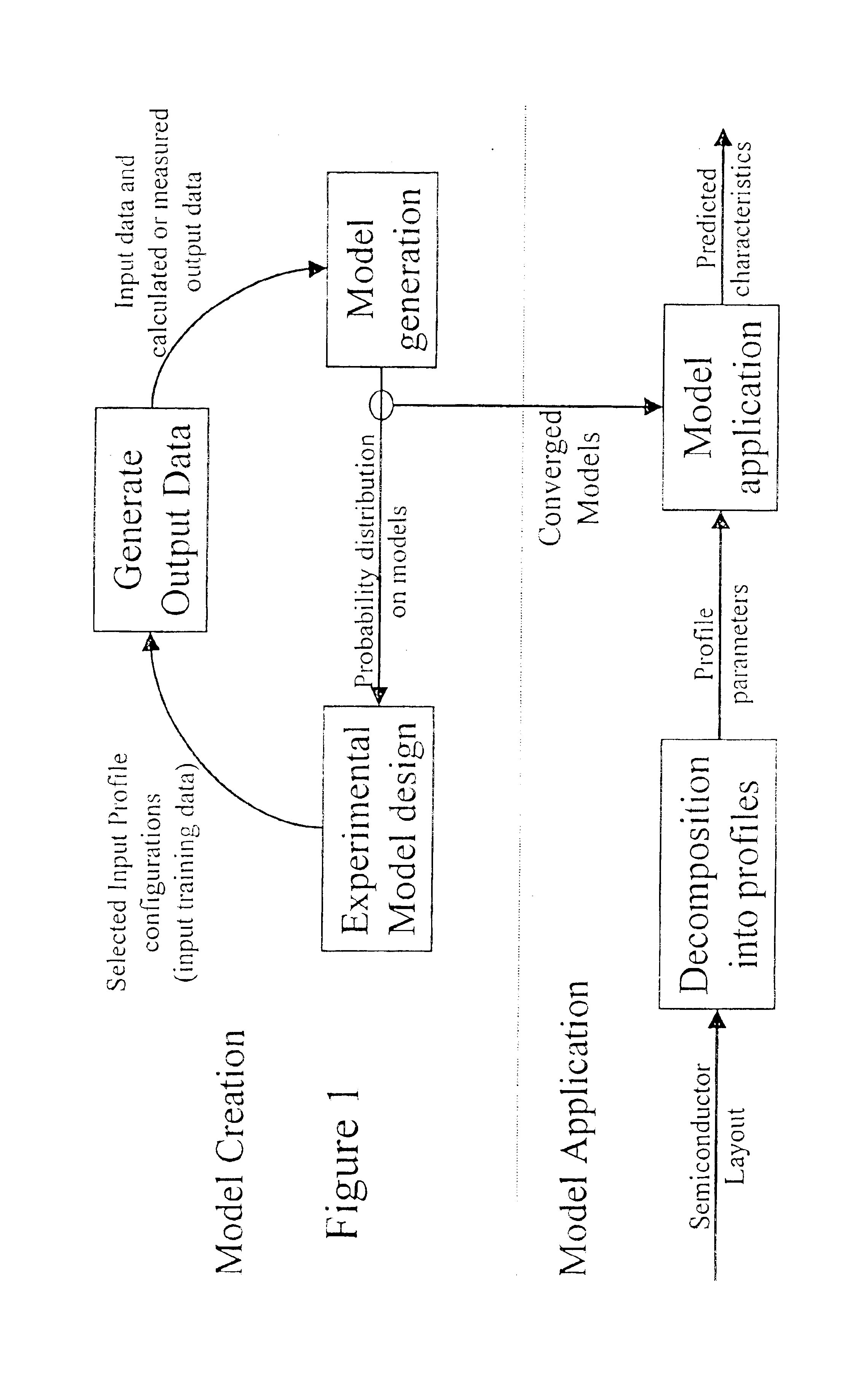
InactiveUS6857112B1Improve accuracyComputer aided designSpecial data processing applicationsData setIntegrated circuit layout
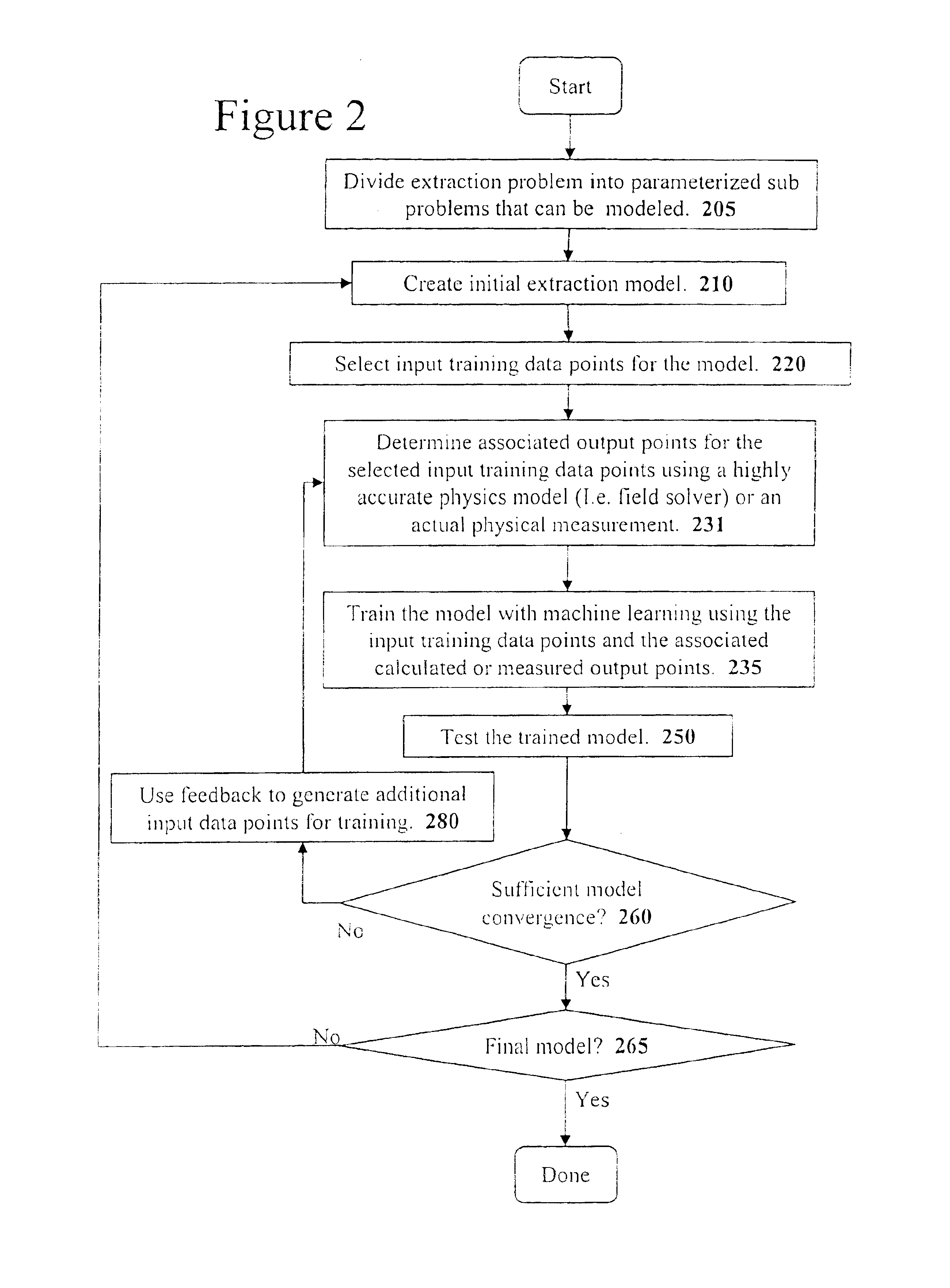
A system for using machine-learning to create a model for performing integrated circuit layout extraction is disclosed. The system of the present invention has two main phases: model creation and model application. The model creation phase comprises creating one or more extraction models using machine-learning techniques. First, a complex extraction problem is decomposed into smaller simpler extraction problems. Then, each smaller extraction problem is then analyzed to identify a set of physical parameters that fully define the smaller extraction problem. Next, models are created using machine learning techniques for all of the smaller simpler extraction problems. The machine learning is performed by first creating training data sets composed of the identified parameters from typical examples of the smaller extraction problem and the answers to those example extraction problems as solved using a highly accurate physics-based field solver. The training sets are then used to train the models. In one embodiment, neural networks are used to model the extraction problems. Bayesian inference is employed by one embodiment in order to train the neural network models. Bayesian inference may be implemented with normal Monte Carlo techniques or Hybrid Monte Carlo techniques. After the creation of a set of models for each of the smaller simpler extraction problems, the machine-learning based models may be used for extraction.
Owner:CADENCE DESIGN SYST INC
System for intrusion detection and vulnerability assessment in a computer network using simulation and machine learning
InactiveUS7784099B2Memory loss protectionError detection/correctionComputer configurationData transmission
The present invention provides a system and method for predicting and preventing unauthorized intrusion in a computer configuration. Preferably, the invention comprises a communication network to which at least two computing devices connect, wherein at least one of the computing devices is operable to receive data transmitted by the other computing device. The invention further comprises a database that is accessible over the network and operable to store information related to the network. A vulnerability assessment component is provided that is operable to execute a command over the communication network, and a data monitoring utility operates to monitor data transmitted over the communication network as the vulnerability assessment component executes commands. Also, an intrusion detection component is included that is operable to provide a simulated copy of the network, to generate a first data transmission on the simulated copy of the network that represents a second data transmission on the communication network, and to compare the first data transmission with a second data transmission. The vulnerability assessment component preferably interfaces with the intrusion detection component to define rules associated with the first and second data transmissions, to store the rules in the database, and to retrieve the rules from the database in order to predict and prevent unauthorized intrusion in the computer configuration.
Owner:PACE UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com