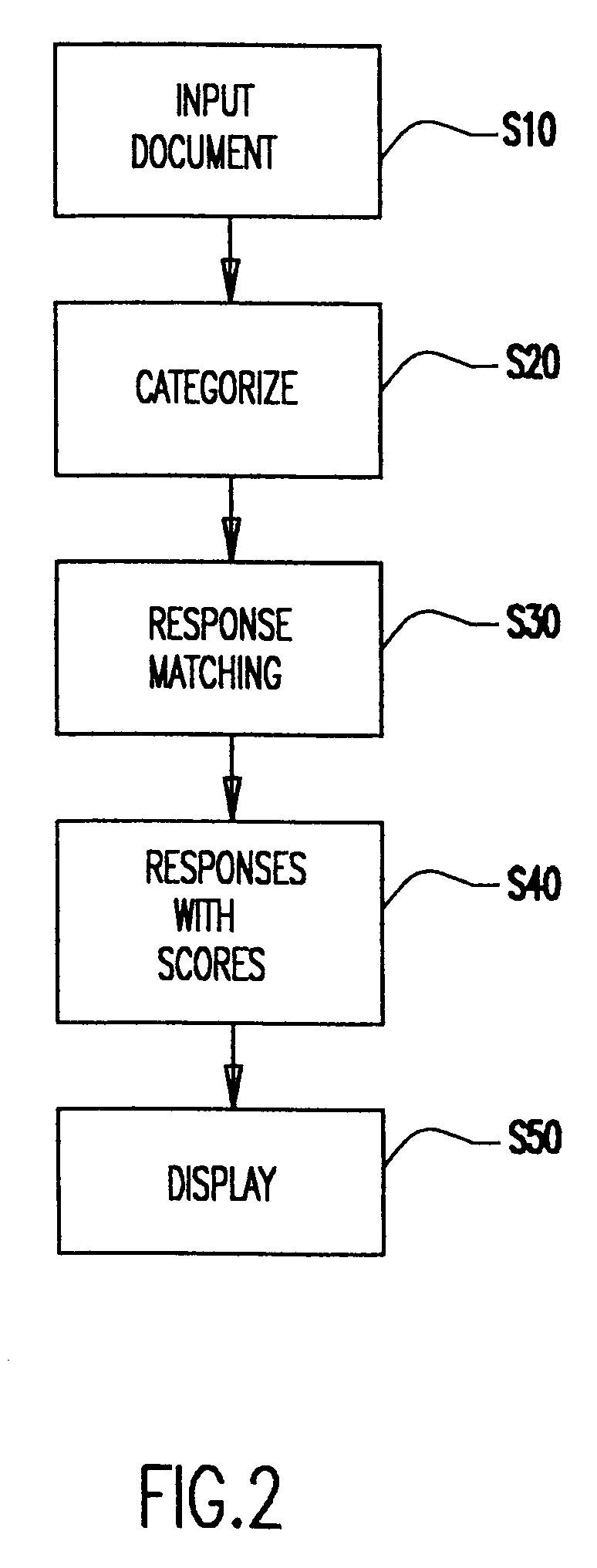
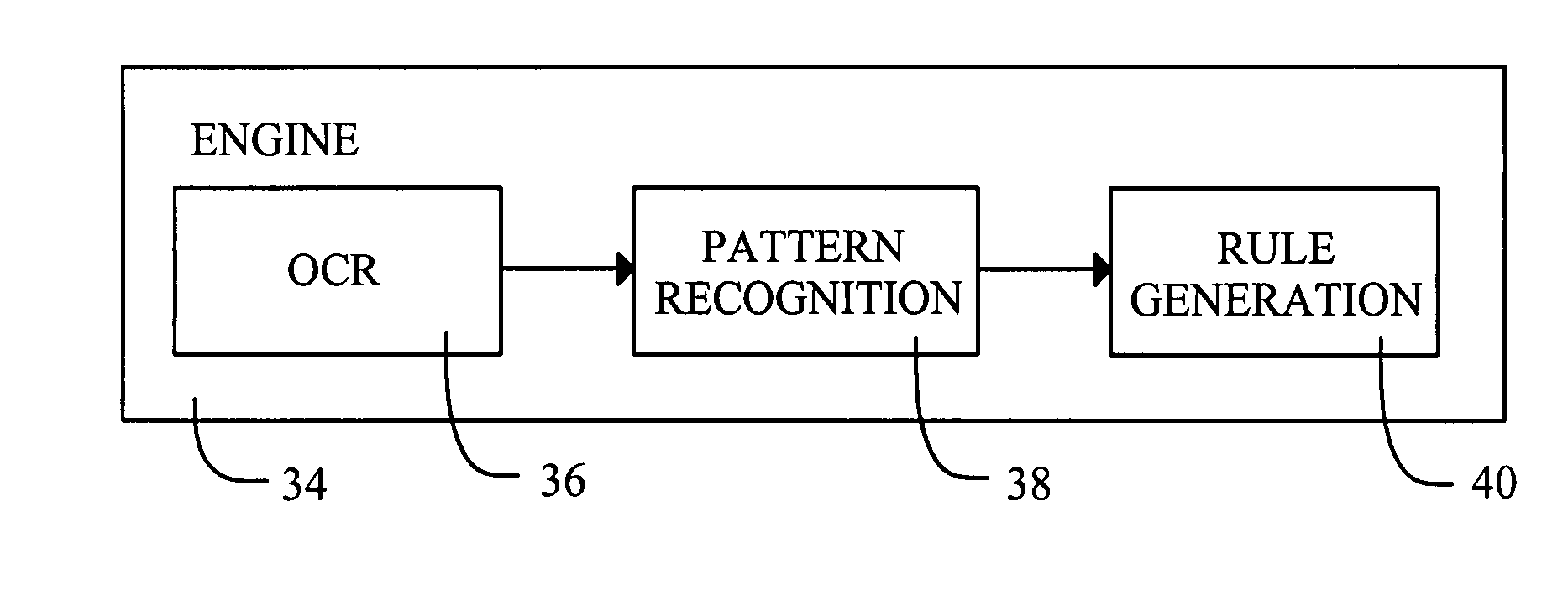
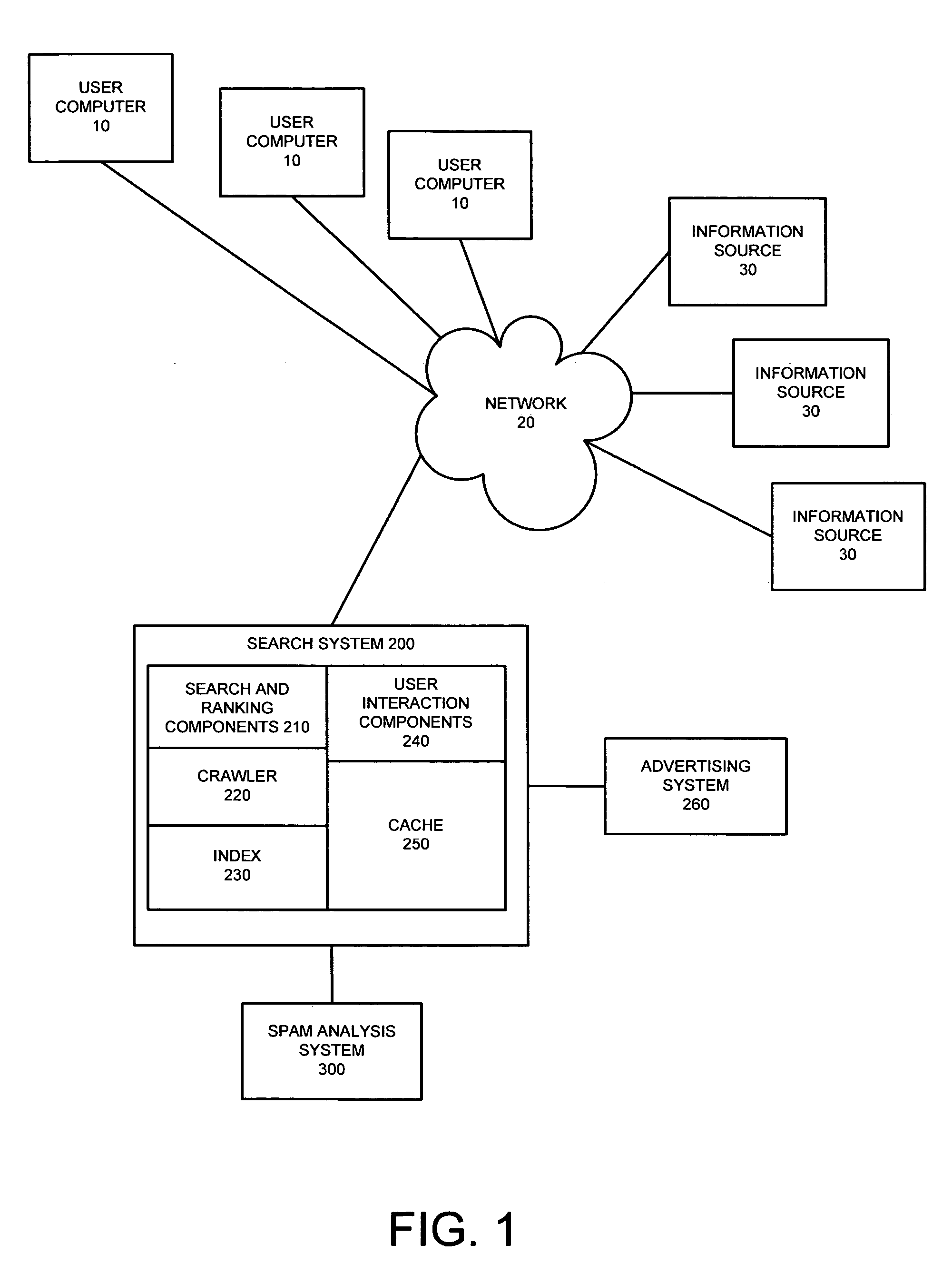
Patents
Literature
319 results about "Automated technique" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
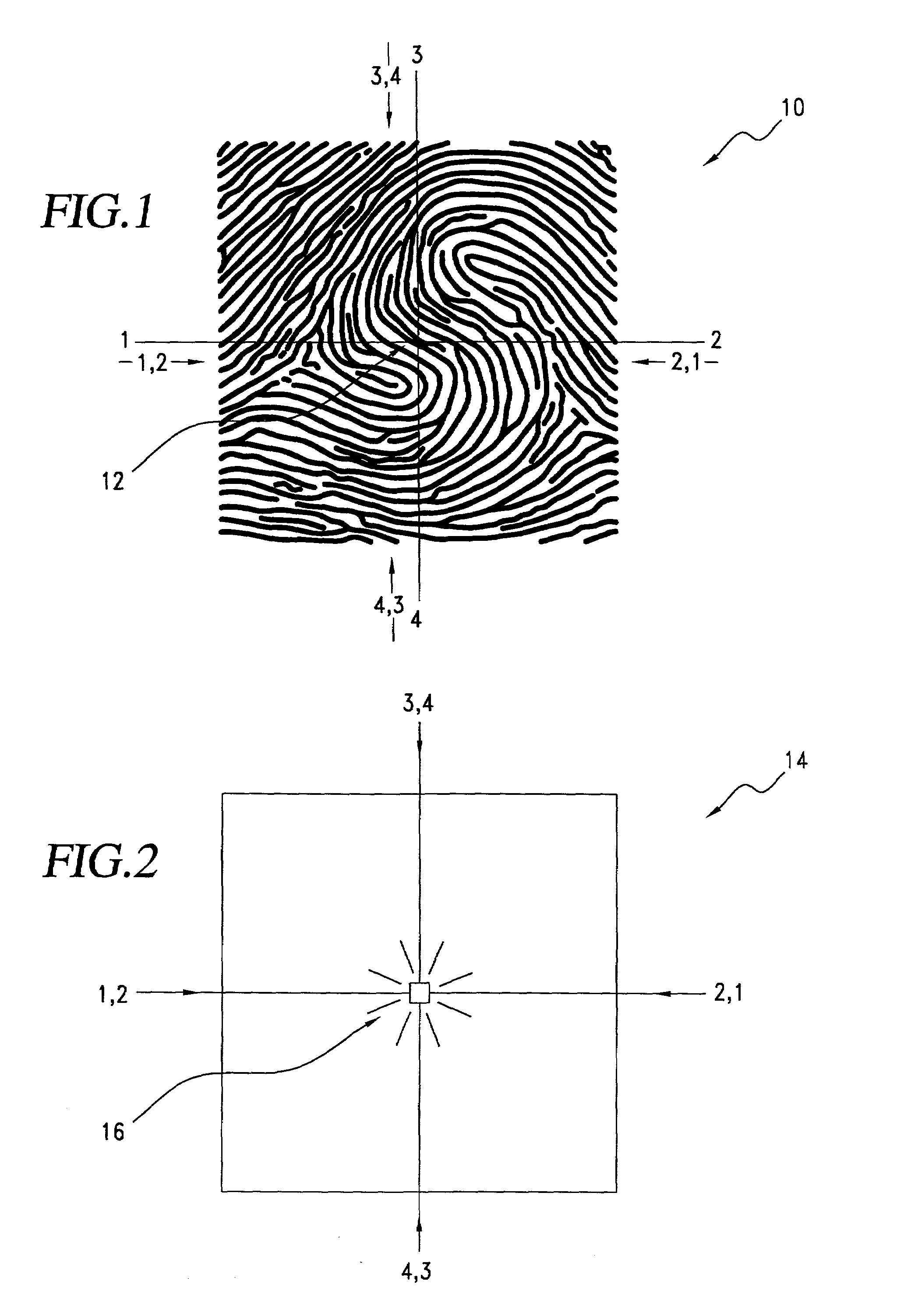
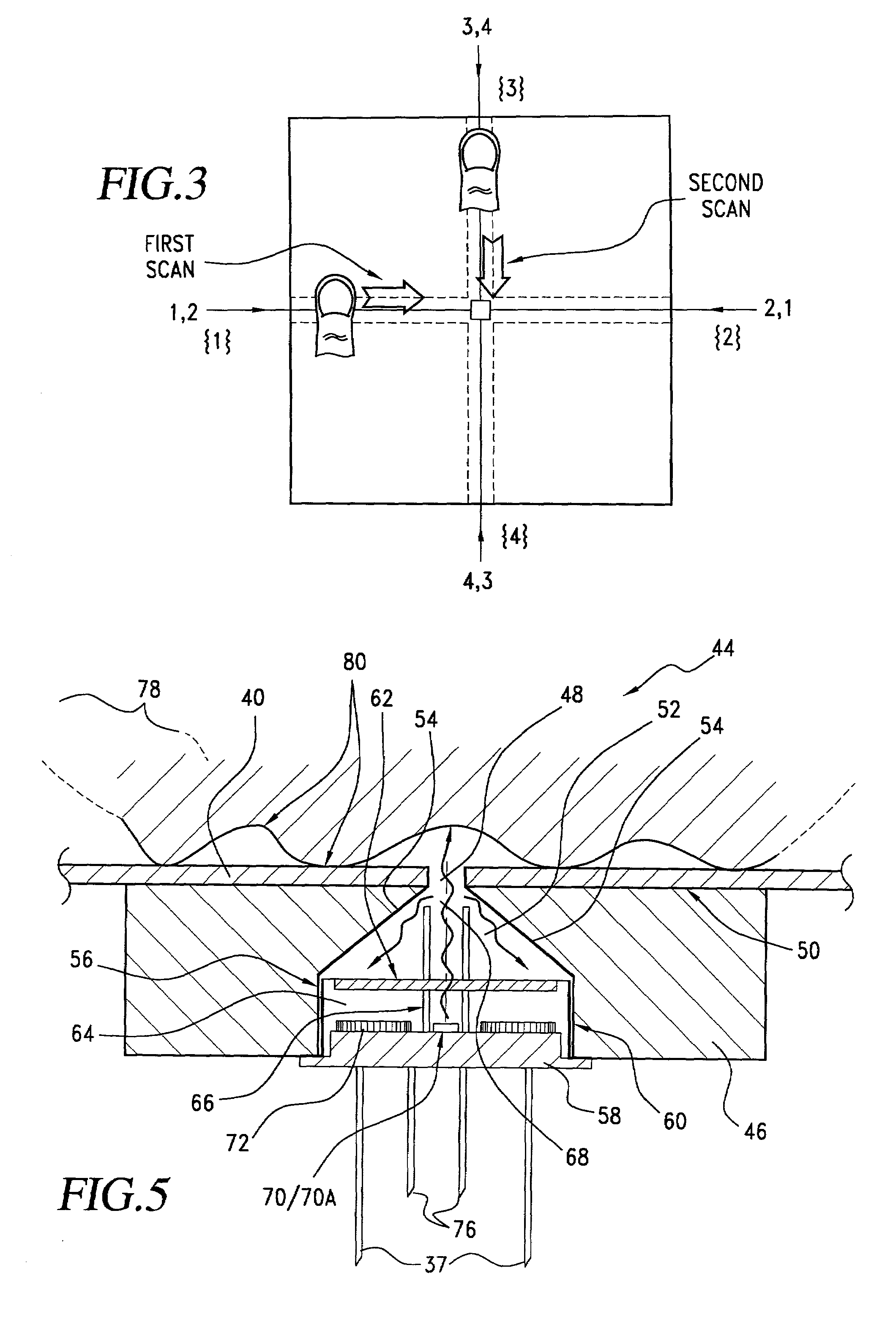
Personal choice biometric signature
InactiveUS7013030B2Improved high security method and systemEasy to useElectric signal transmission systemsImage analysisCombined useLinearity
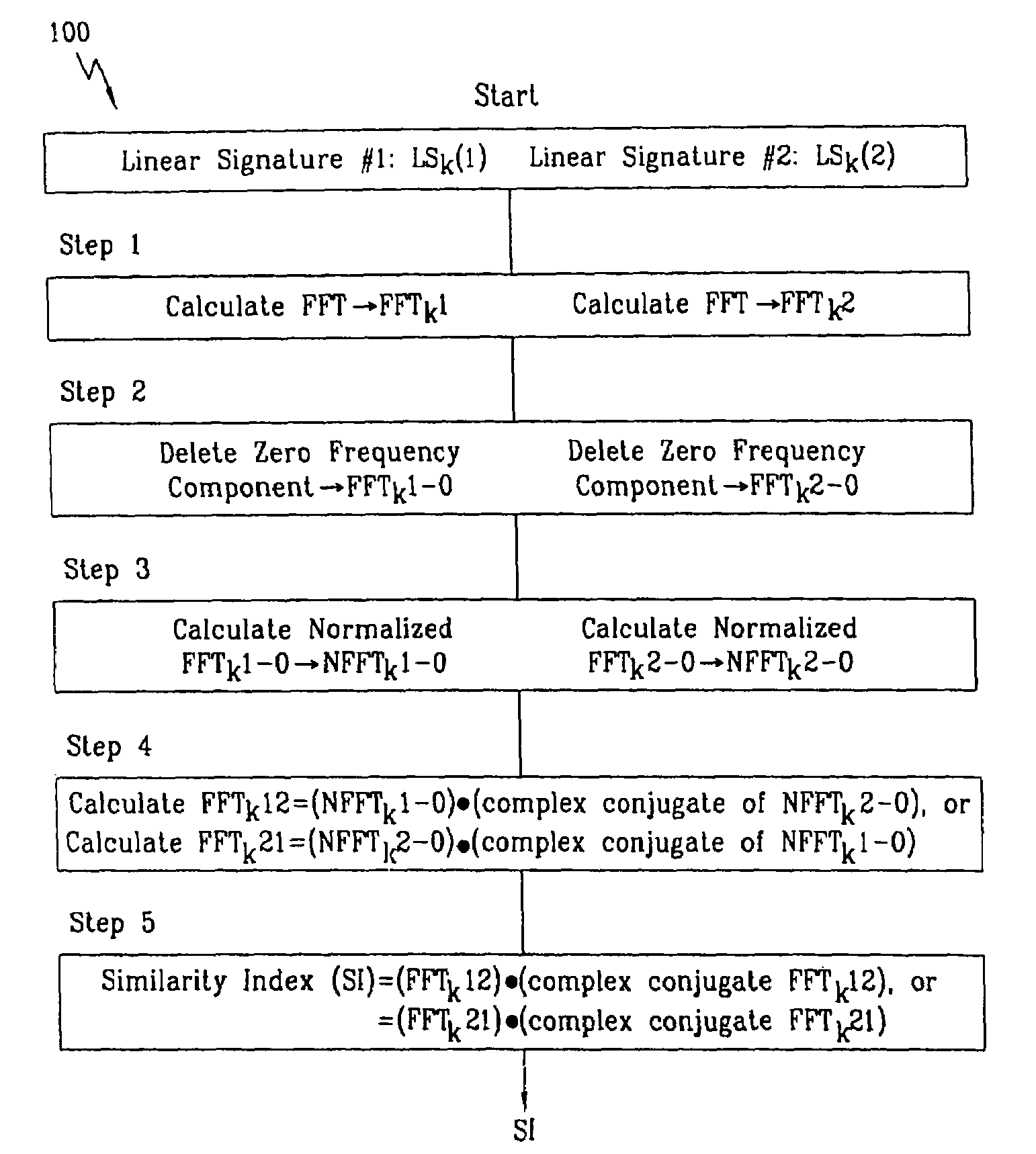
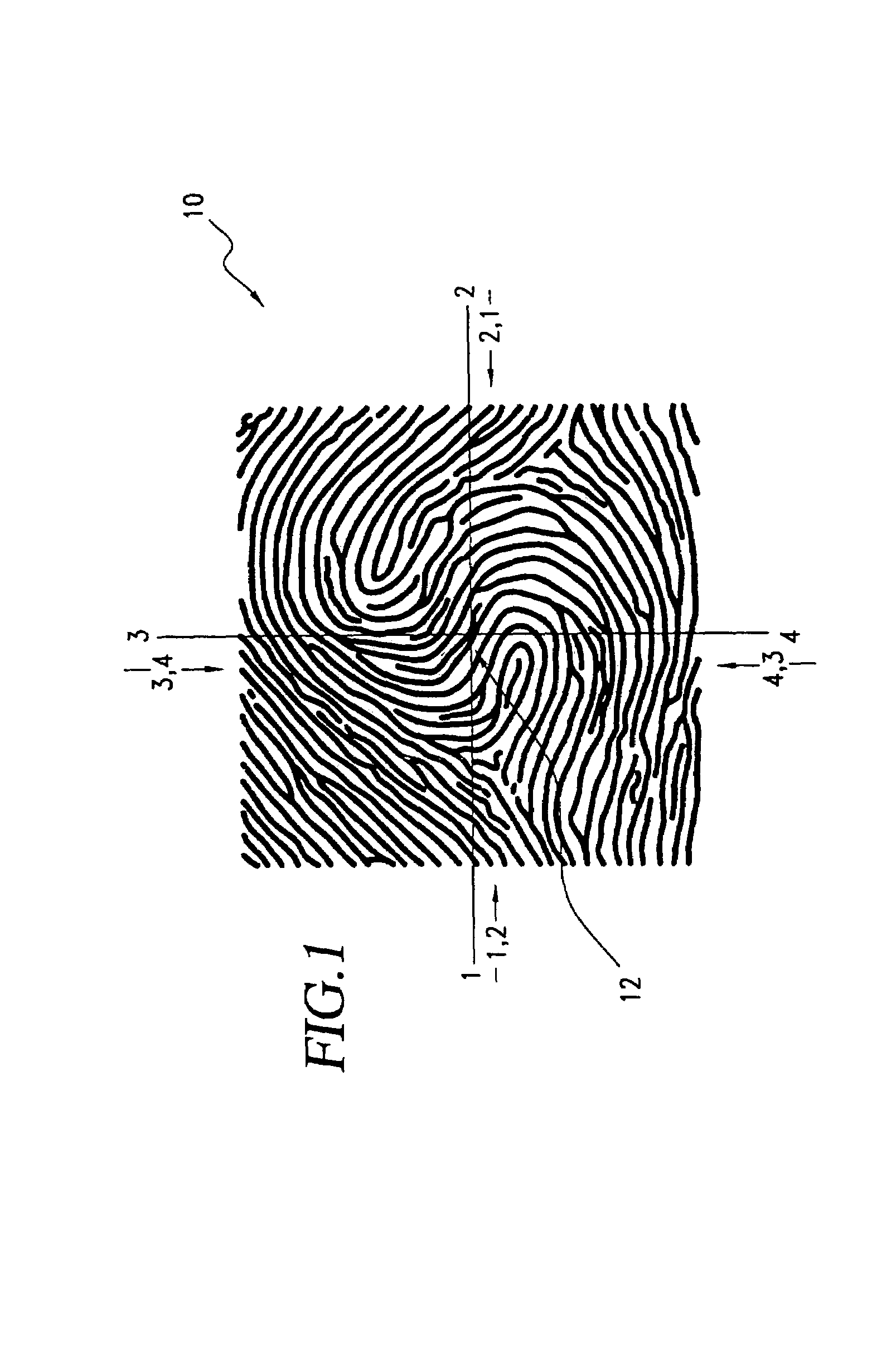
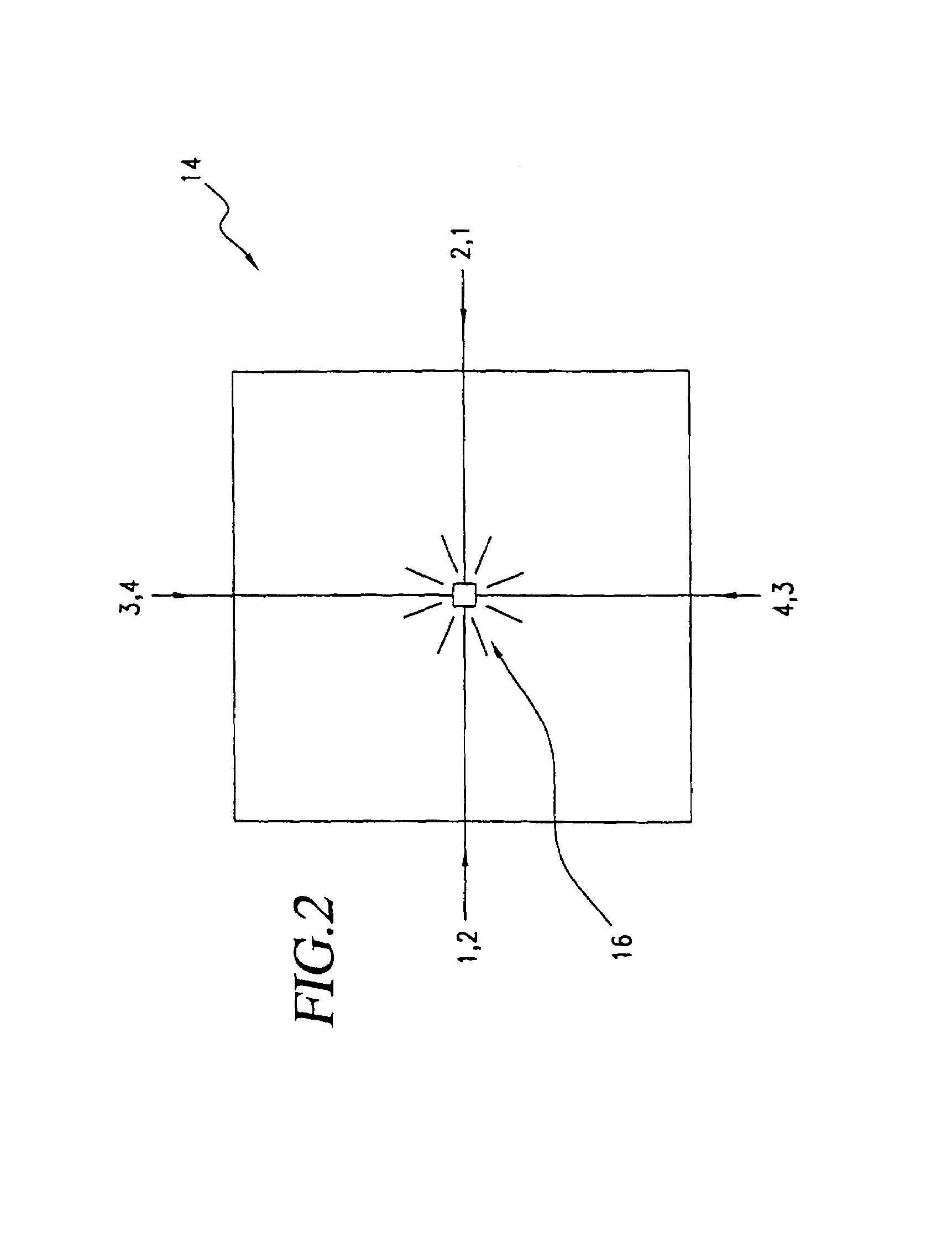
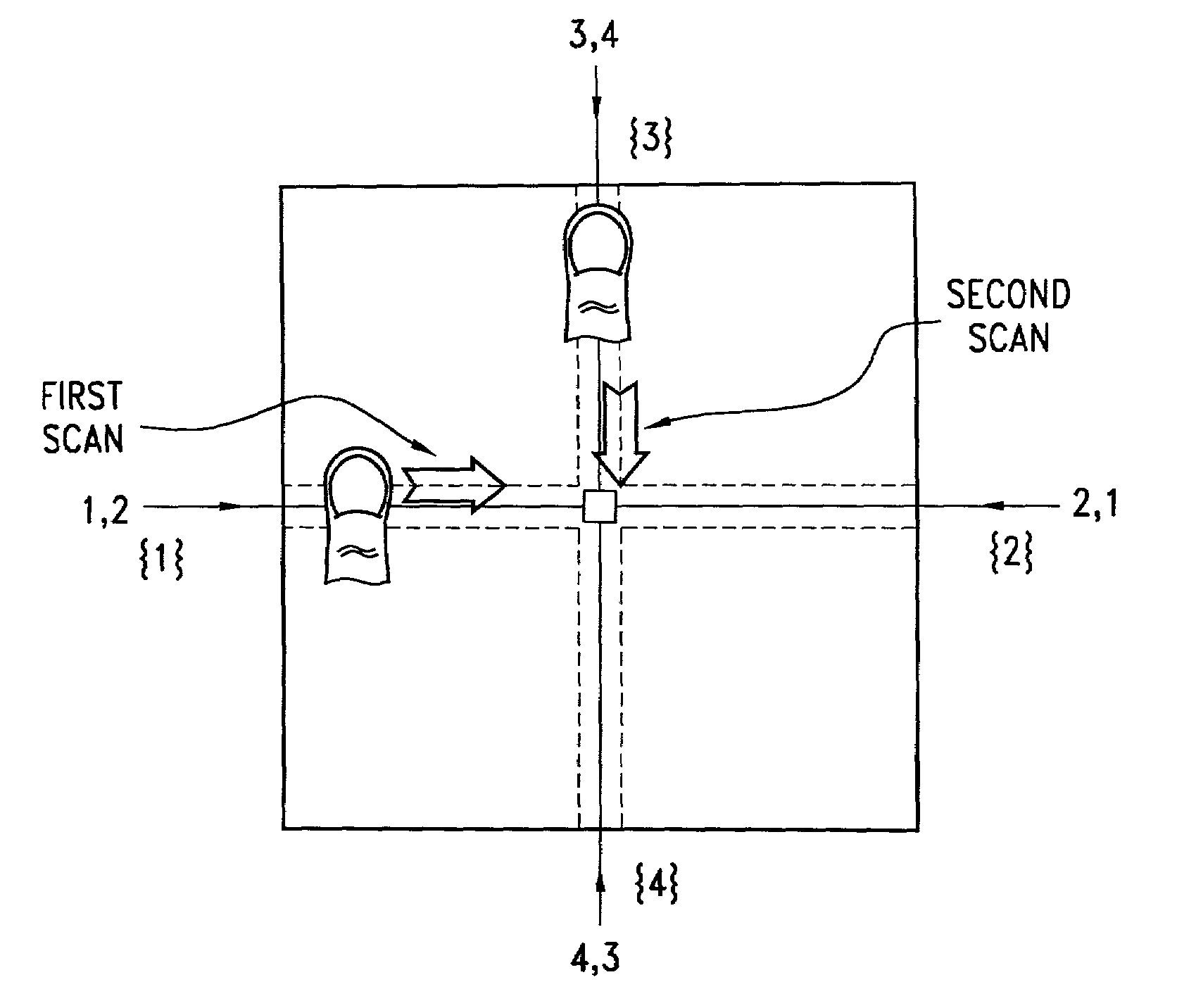
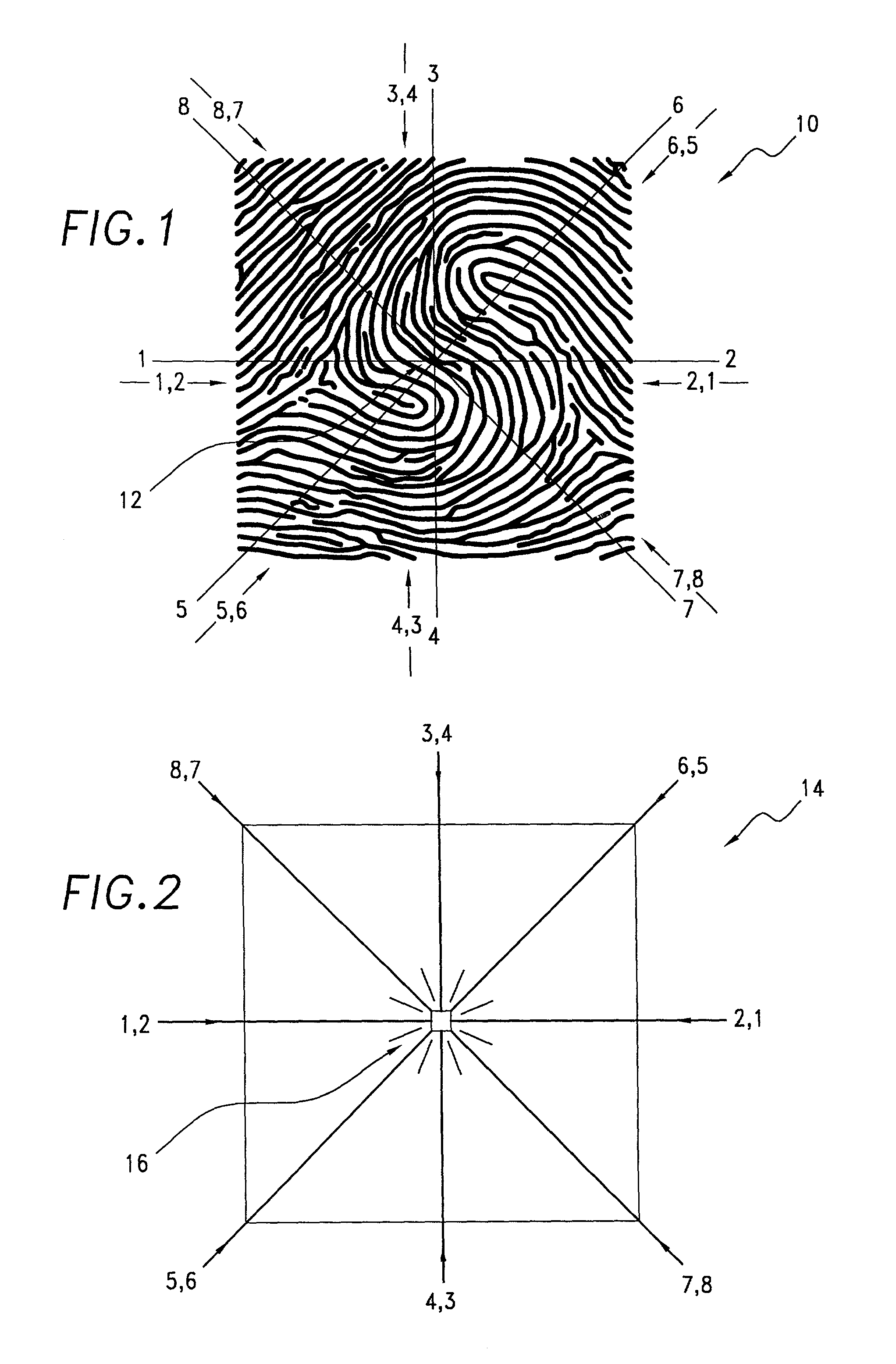
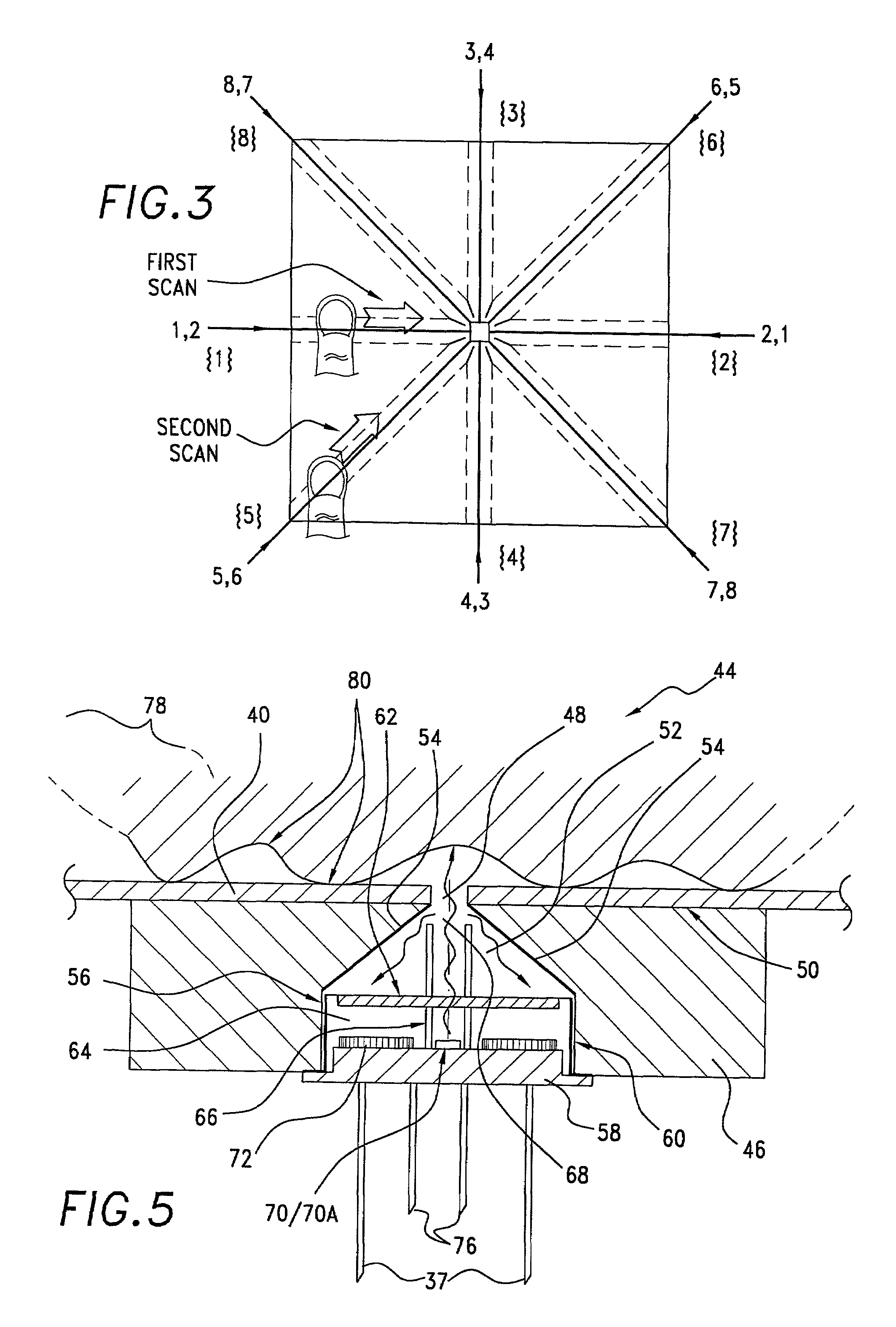
A biometric method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. This approach is further enhanced by employing a frequency domain technique for calculating a Similarity Index of the partial fingerprint signatures. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains four (illustratively) linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. In an advanced embodiment, the same two candidate signatures in the chosen sequence are processed in a unique FFT / DFT process to produce a highly reliable Similarity Index to authenticate or verify the identity of individuals. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y +1
Personal choice biometric signature
InactiveUS7035443B2Complicated processSpatial variation is minimizedElectric signal transmission systemsImage analysisPattern recognitionProximity sensor
A biometric method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. This approach is further enhanced by employing a frequency domain technique for calculating a Similarity Index of the partial fingerprint signatures. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains a reference set of linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. In an advanced embodiment, a pair of proximity sensors located along each of the linear tracks used for developing the linear partial signatures produce finger sensing signals which compensate for finger movement speeds and hence significantly improves the calculated Similarity Index values. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y
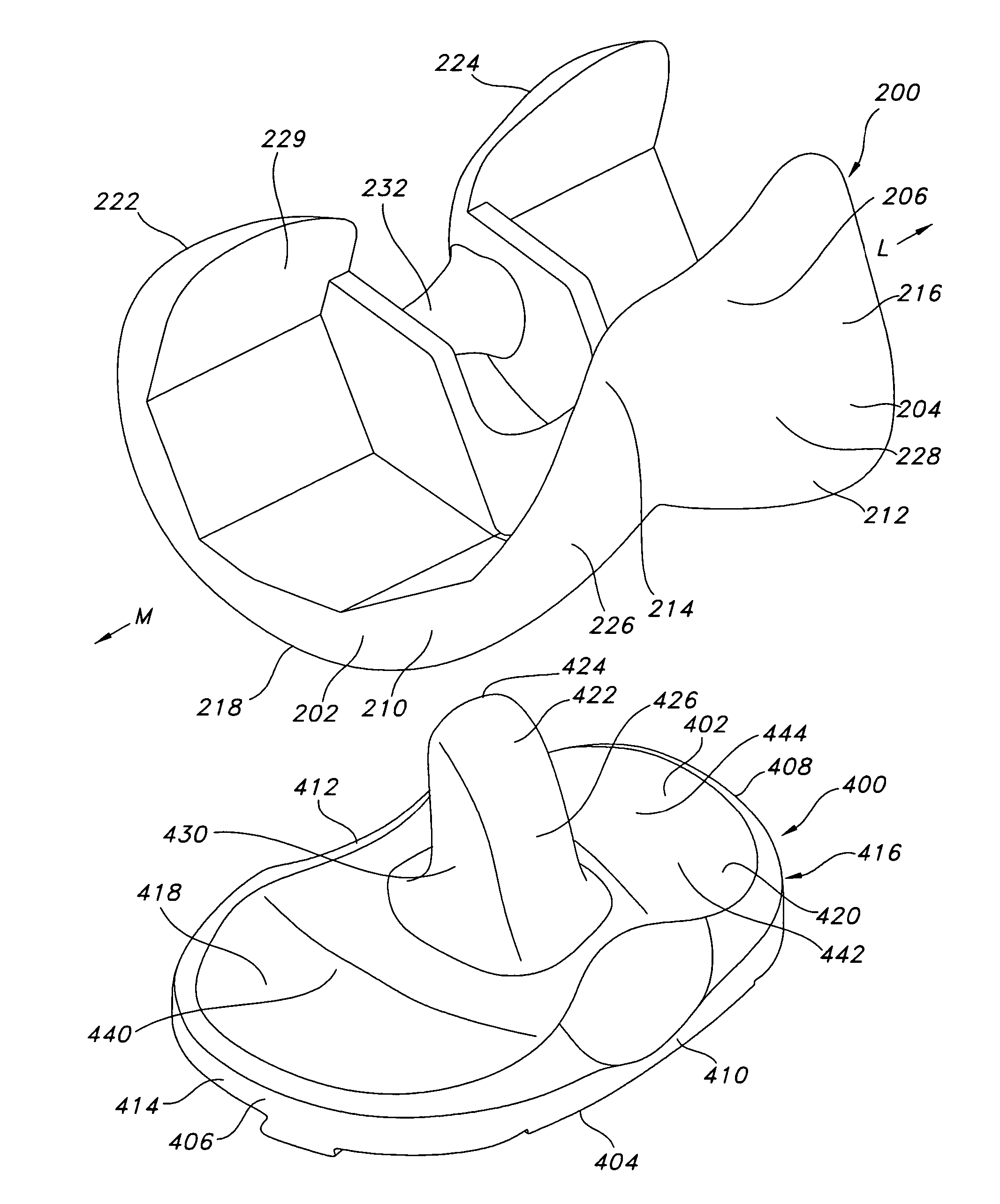
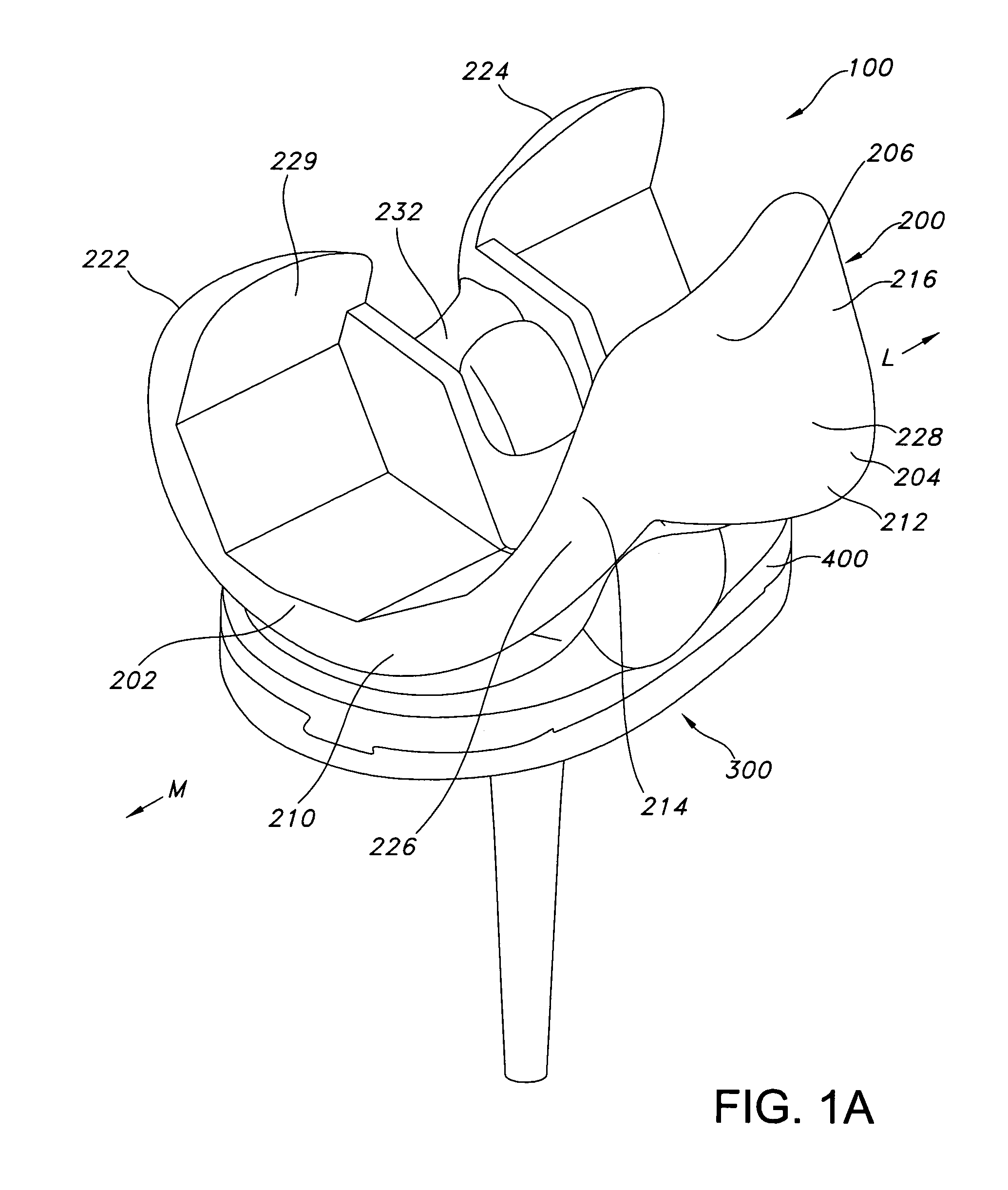
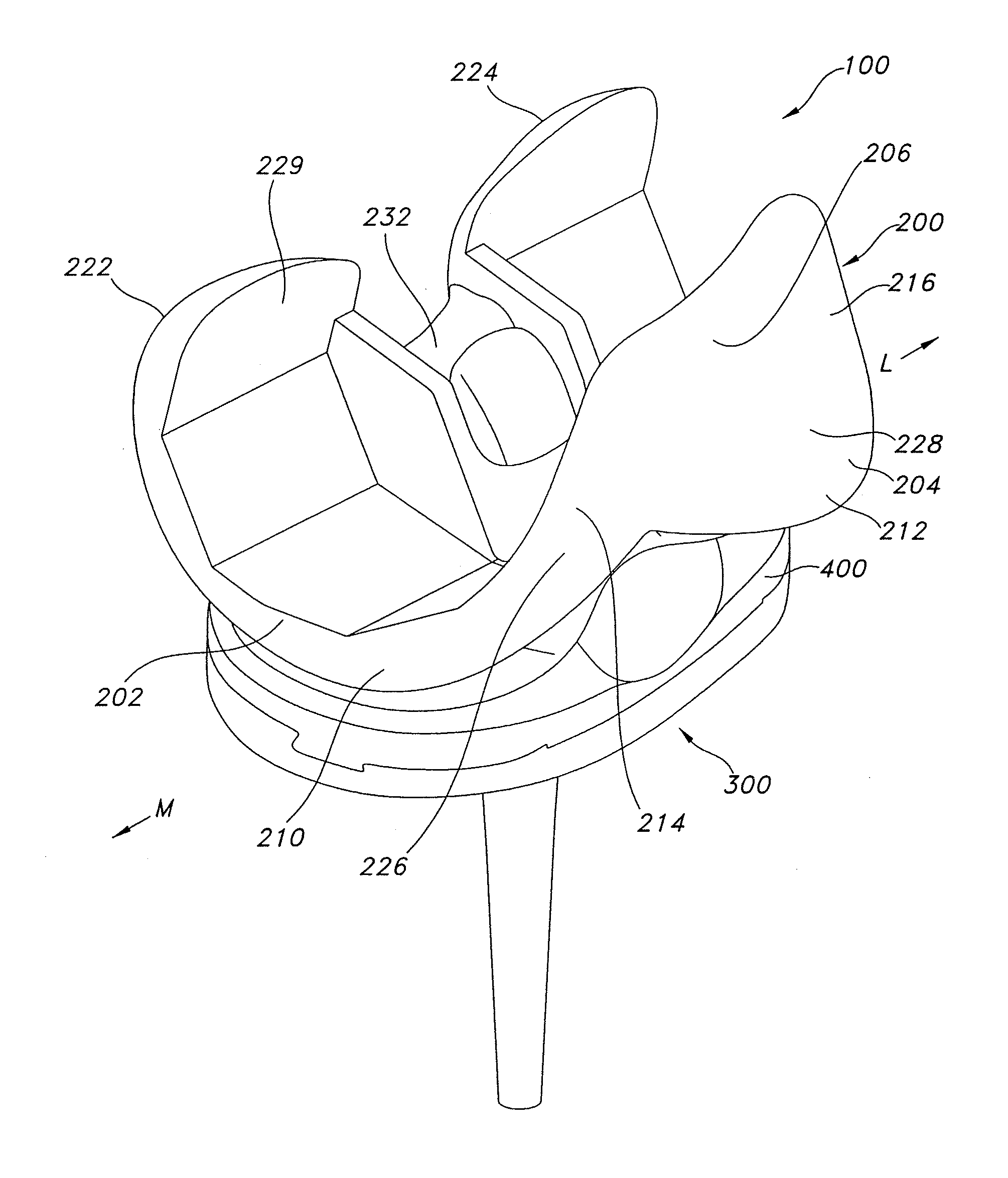
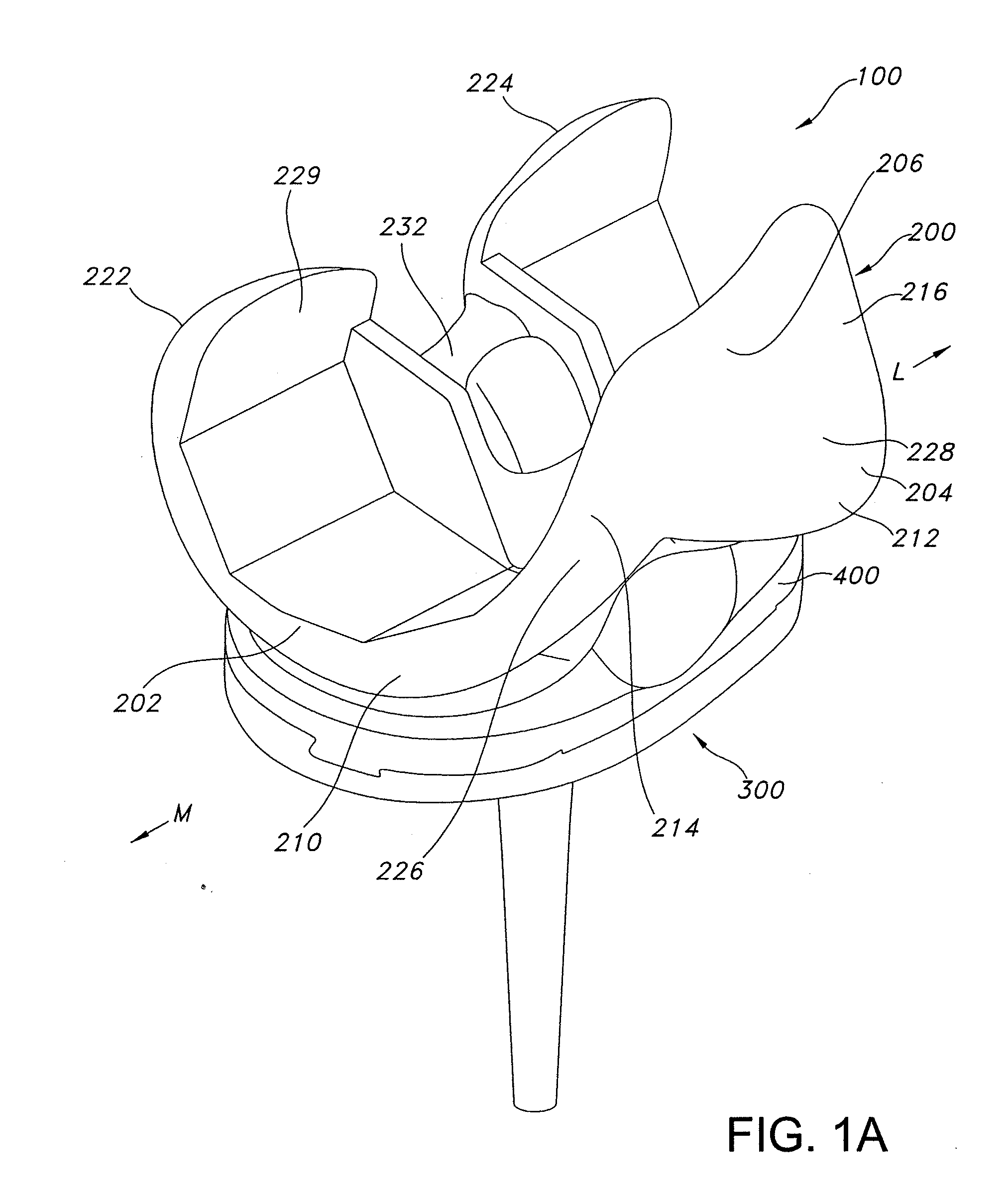
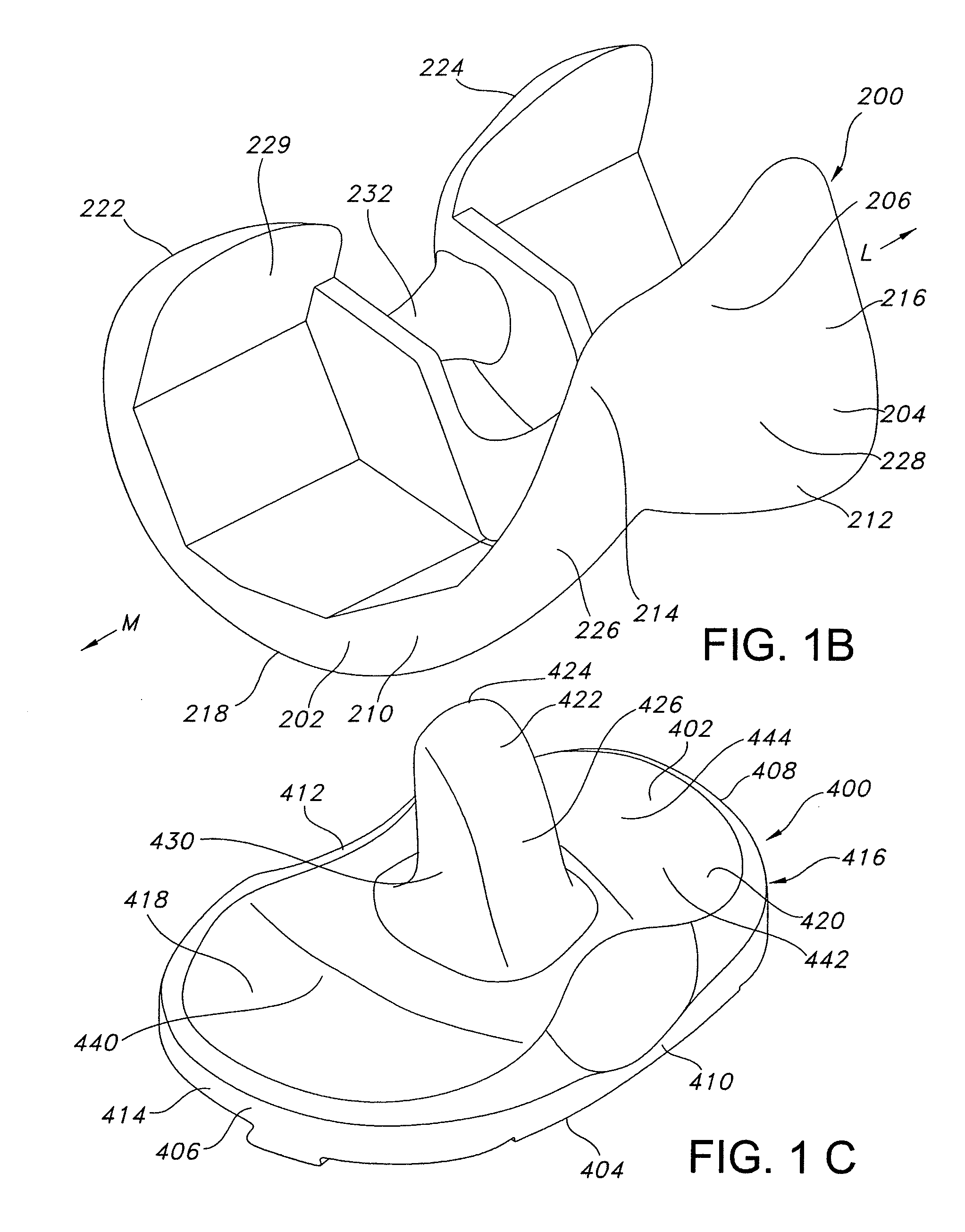
High performance knee prostheses
ActiveUS7326252B2Faithful replicationLittle strengthJoint implantsKnee jointsStructure and functionFemoral component
Knee prostheses featuring components that more faithfully replicate the structure and function of the human knee joint in order to provide, among other benefits: greater flexion of the knee in a more natural way by promoting or at least accommodating internal tibial rotation in a controlled way, replication of the natural screw home mechanism, and controlled articulation of the tibia and femur respective to each other in a more natural way. In a preferred embodiment, such prostheses include an insert component disposed between a femoral component and a tibial component, the insert component preferably featuring among other things a reversely contoured postereolateral bearing surface that helps impart internal rotation to the tibia as the knee flexes. Other surfaces can also be specially shaped to achieve similar results, preferably using iterative automated techniques that allow testing and iterative design taking into account a manageable set of major forces acting on the knee during normal functioning, together with information that is known about natural knee joint kinetics and kinematics.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA +1
Authentication method utilizing a sequence of linear partial fingerprint signatures selected by a personal code
InactiveUS7039223B2Improved high security method and systemEasy to useProgramme controlElectric signal transmission systemsCombined usePersonal computer
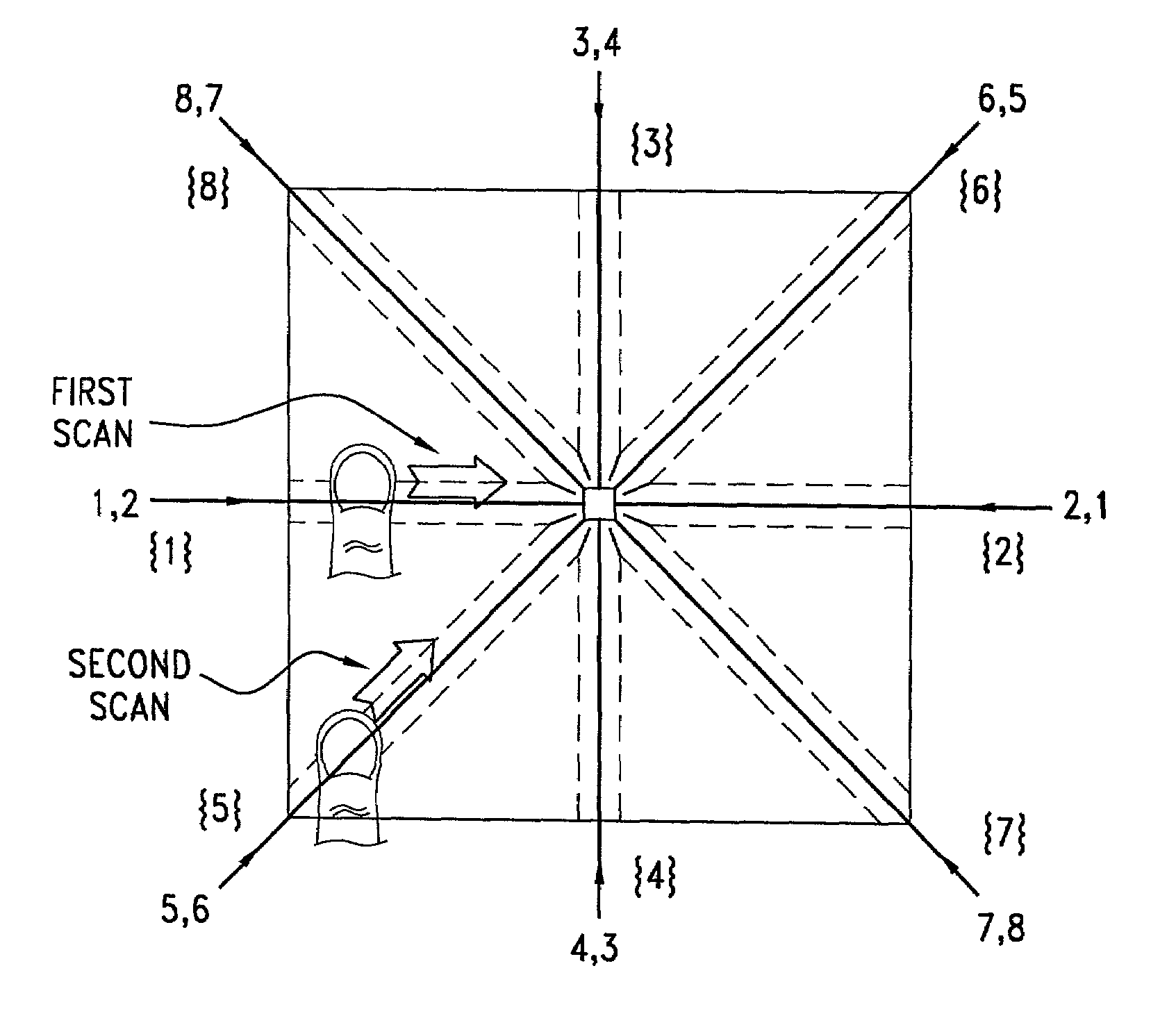
A method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains eight (illustratively) linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y
High performance knee prostheses
ActiveUS20080119940A1Faithful replicationLittle strengthJoint implantsKnee jointsStructure and functionFemoral component
Knee prostheses featuring components that more faithfully replicate the structure and function of the human knee joint in order to provide, among other benefits: greater flexion of the knee in a more natural way by promoting or at least accommodating internal tibial rotation in a controlled way, replication of the natural screw home mechanism, and controlled articulation of the tibia and femur respective to each other in a more natural way. In a preferred embodiment, such prostheses include an insert component disposed between a femoral component and a tibial component, the insert component preferably featuring among other things a reversely contoured posterolateral bearing surface that helps impart internal rotation to the tibia as the knee flexes. Other surfaces can also be specially shaped to achieve similar results, preferably using iterative automated techniques that allow testing and iterative design taking into account a manageable set of major forces acting on the knee during normal functioning, together with information that is known about natural knee joint kinetics and kinematics.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA +1
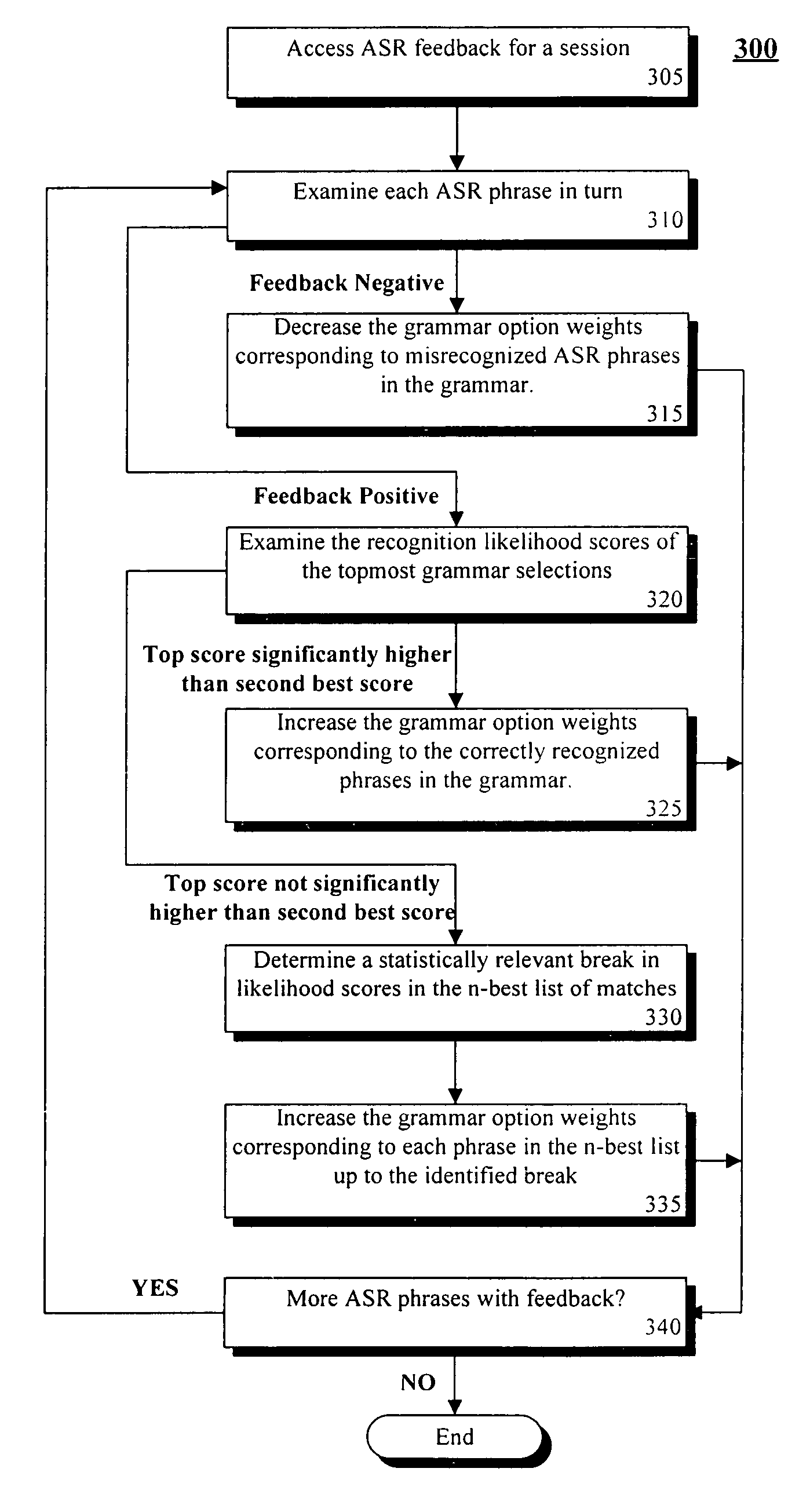
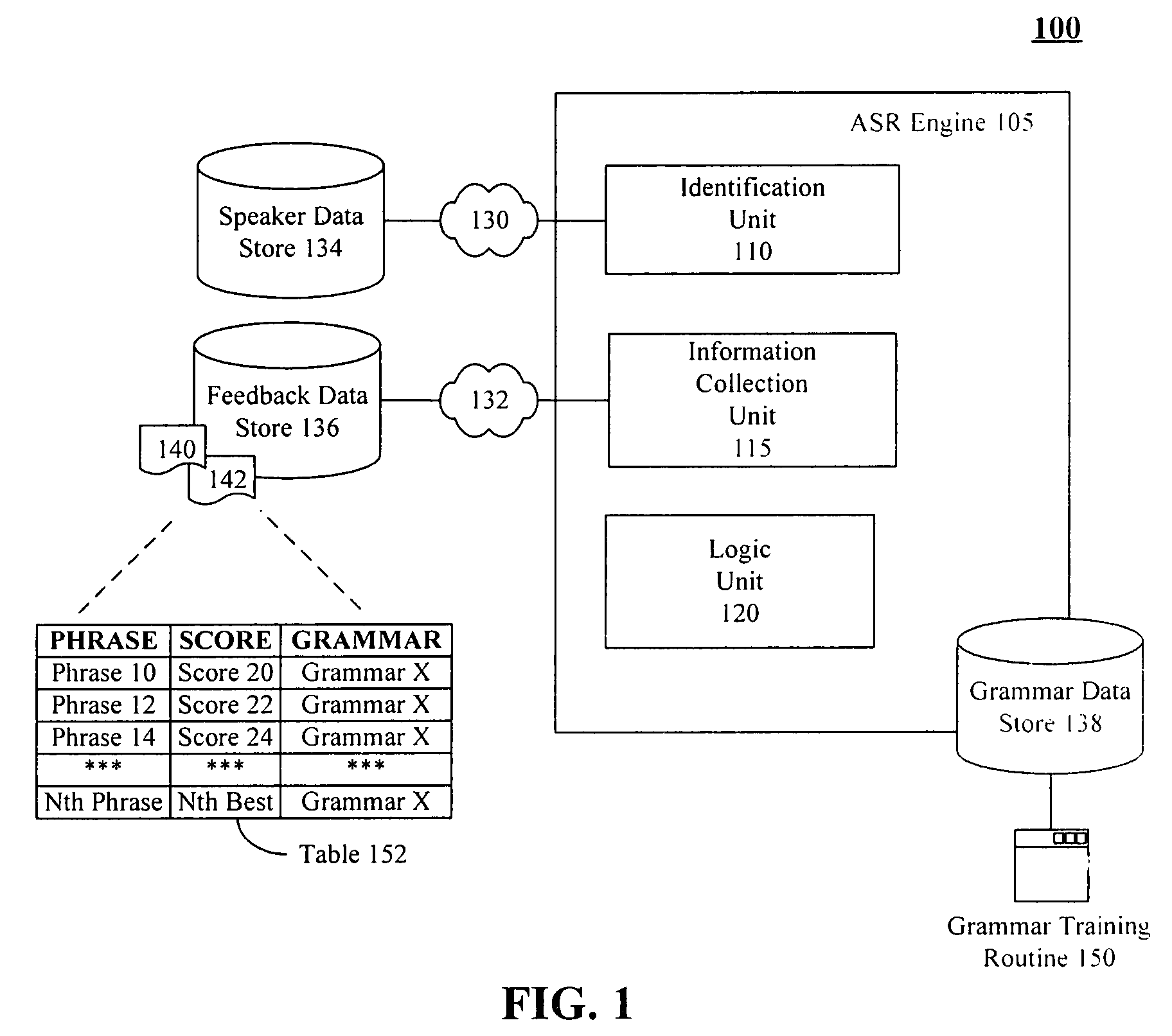
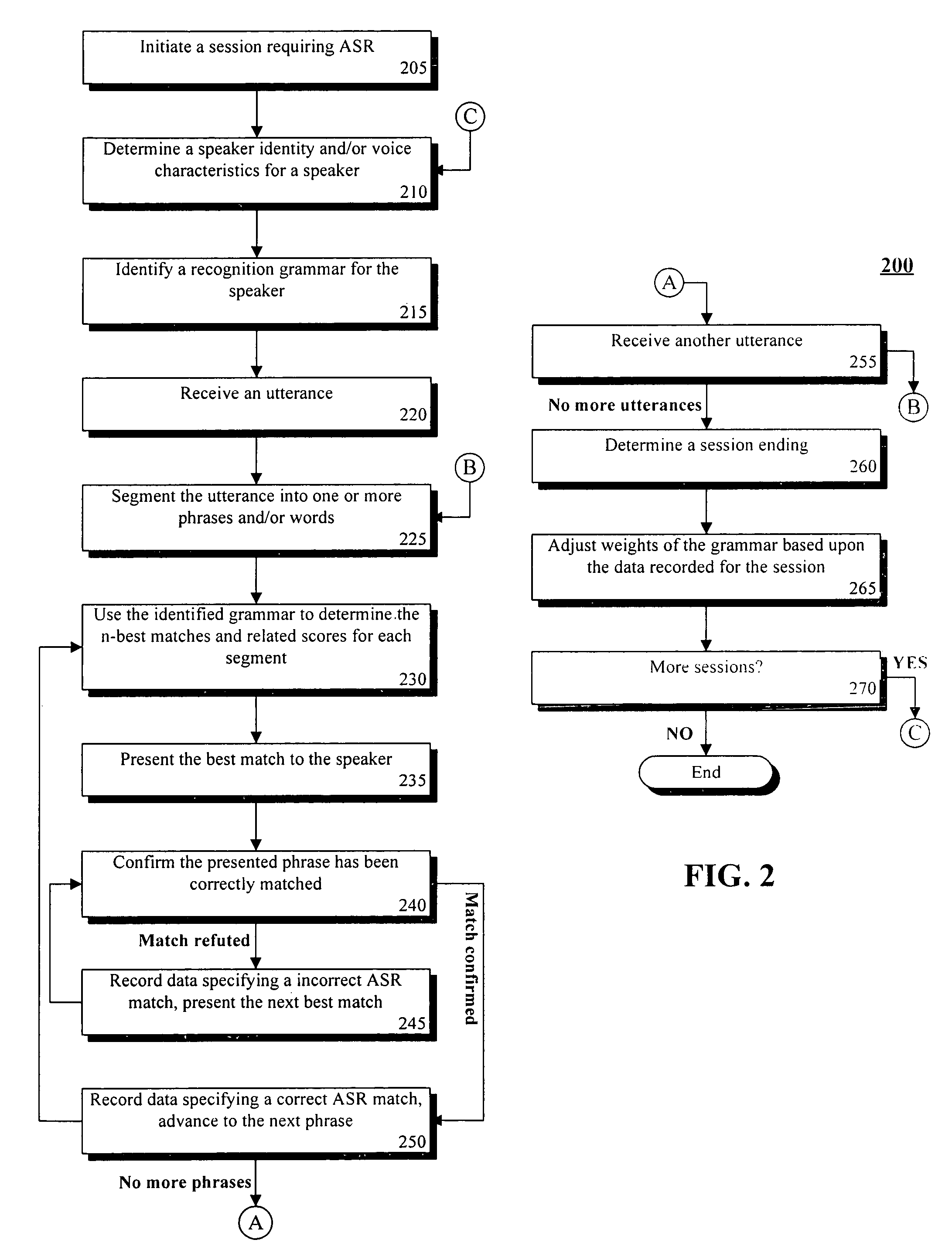
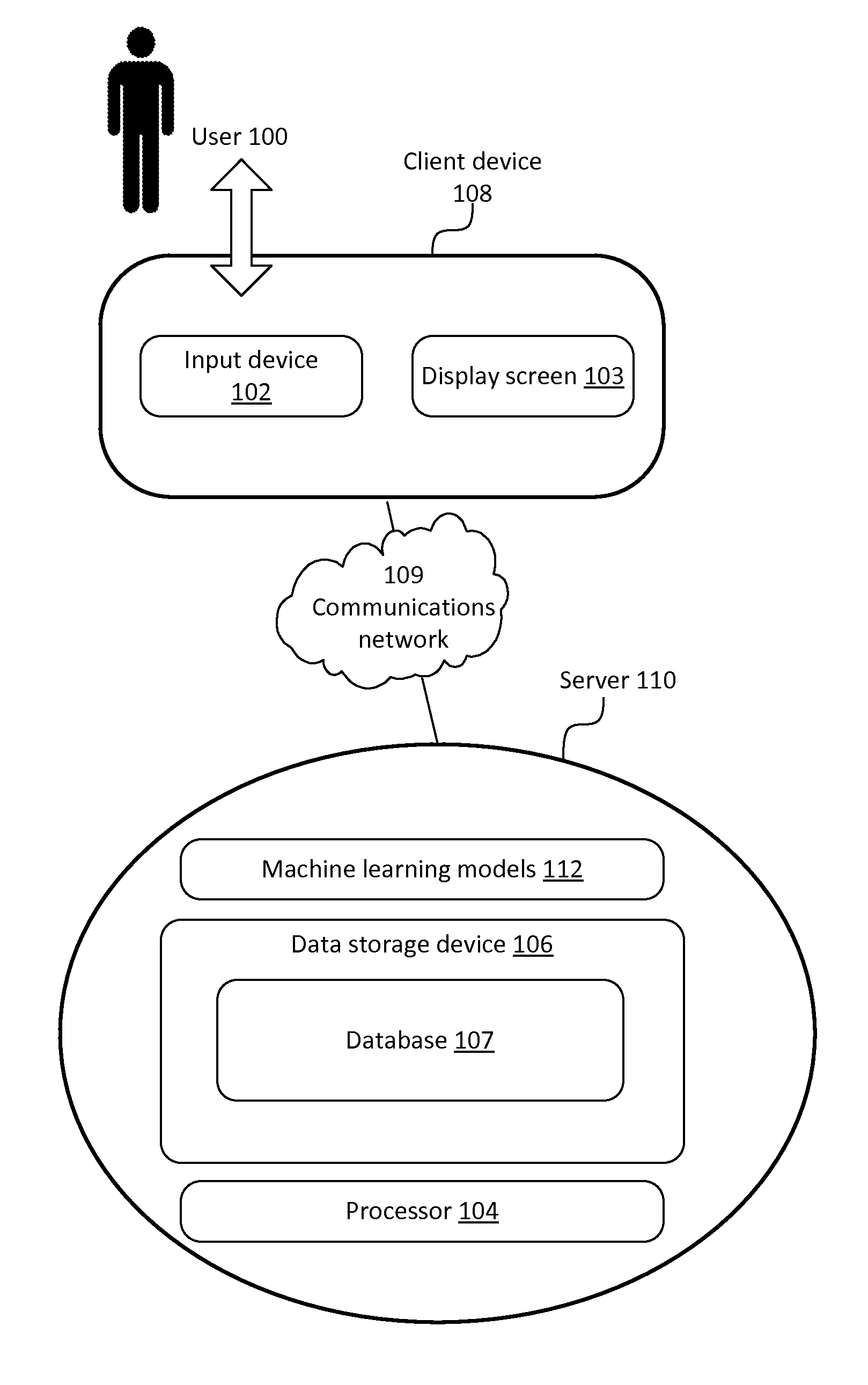
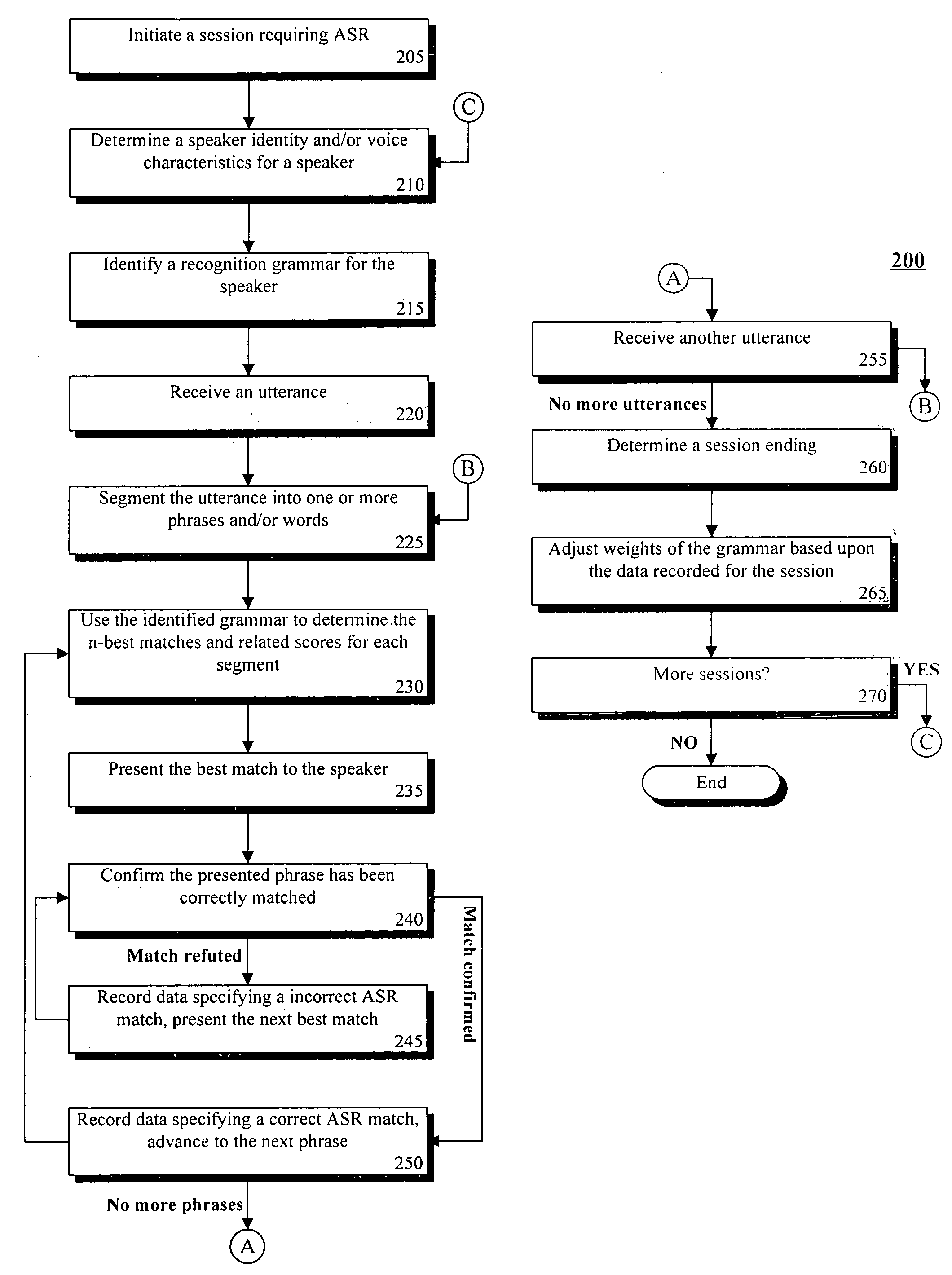
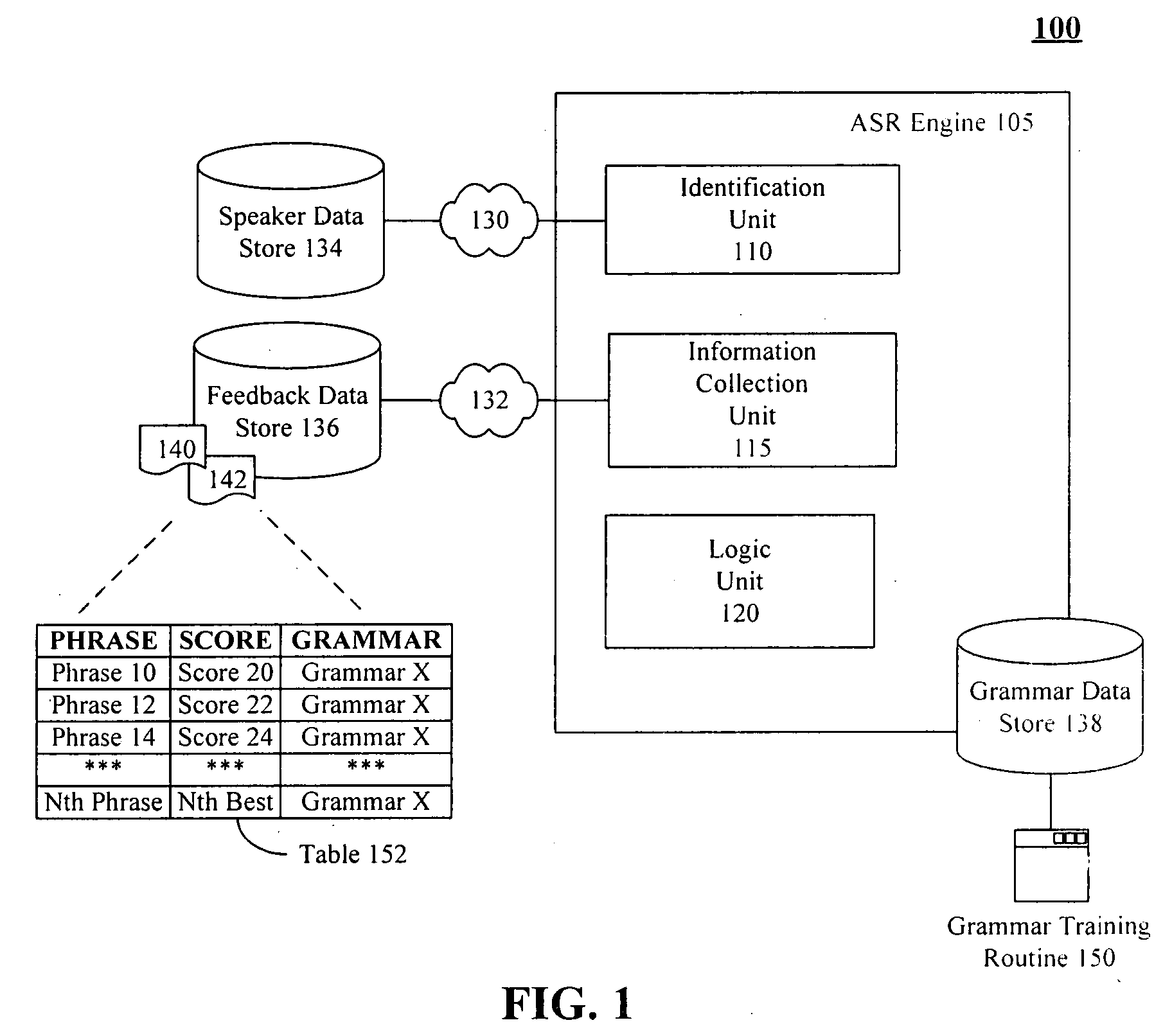
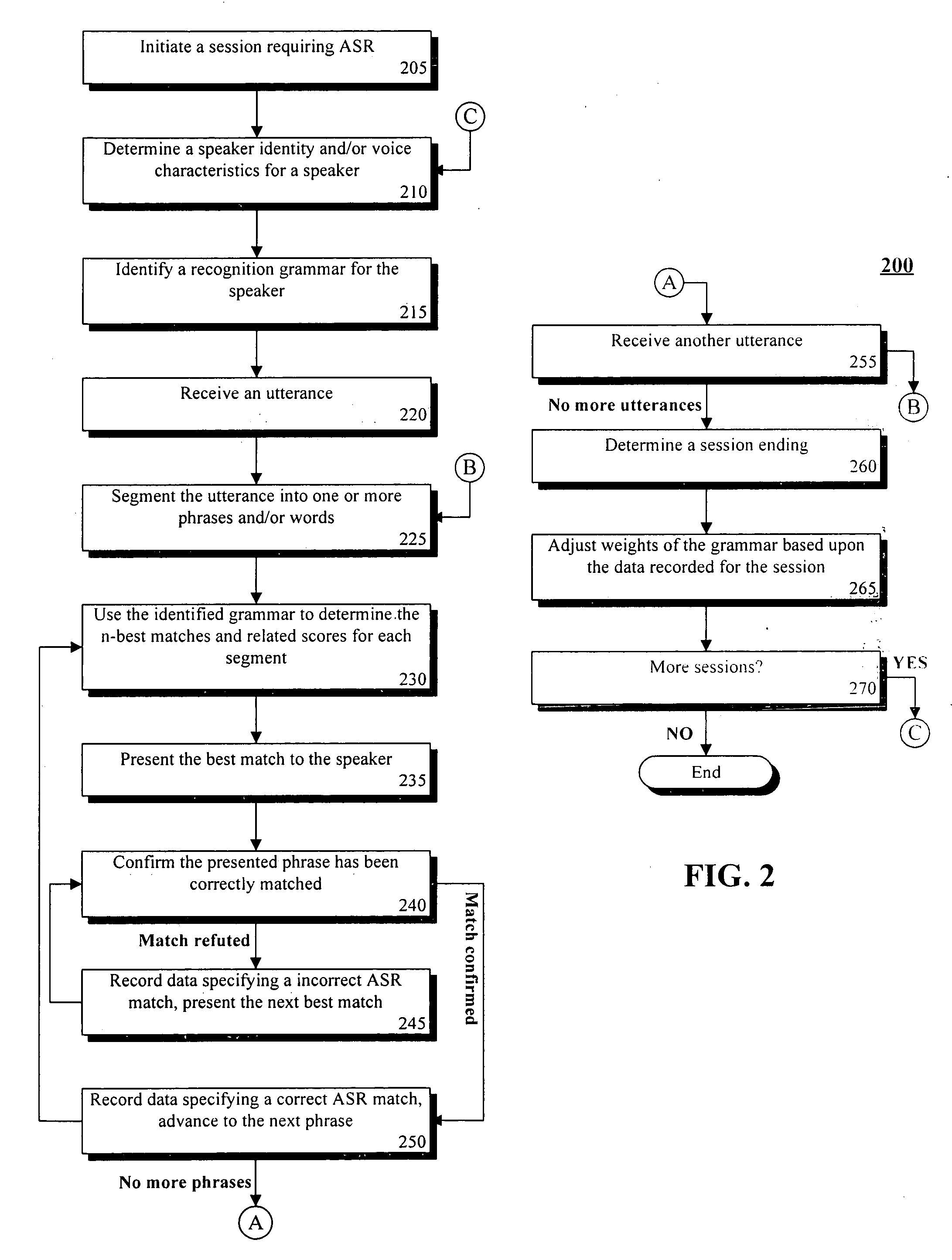
Training speaker-dependent, phrase-based speech grammars using an unsupervised automated technique
InactiveUS7778830B2Improve accuracyLower performance requirementsSpeech recognitionSpecial data processing applicationsAutomatic speechSpeech sound
The present invention can include a method for tuning grammar option weights of a phrase-based, automatic speech recognition (ASR) grammar, where the grammar option weights affect which entries within the grammar are matched to spoken utterances. The tuning can occur in an unsupervised fashion, meaning no special training session or manual transcription of data from an ASR session is needed. The method can include the step of selecting a phrase-based grammar to use in a communication session with a user wherein different phrase-based grammars can be selected for different users. Feedback of ASR phrase processing operations can be recorded during the communication session. Each ASR phrase processing operation can match a spoken utterance against at least one entry within the selected phrase-based grammar. At least one of the grammar option weights can be automatically adjusted based upon the feedback to improve accuracy of the phrase-based grammar.
Owner:NUANCE COMM INC
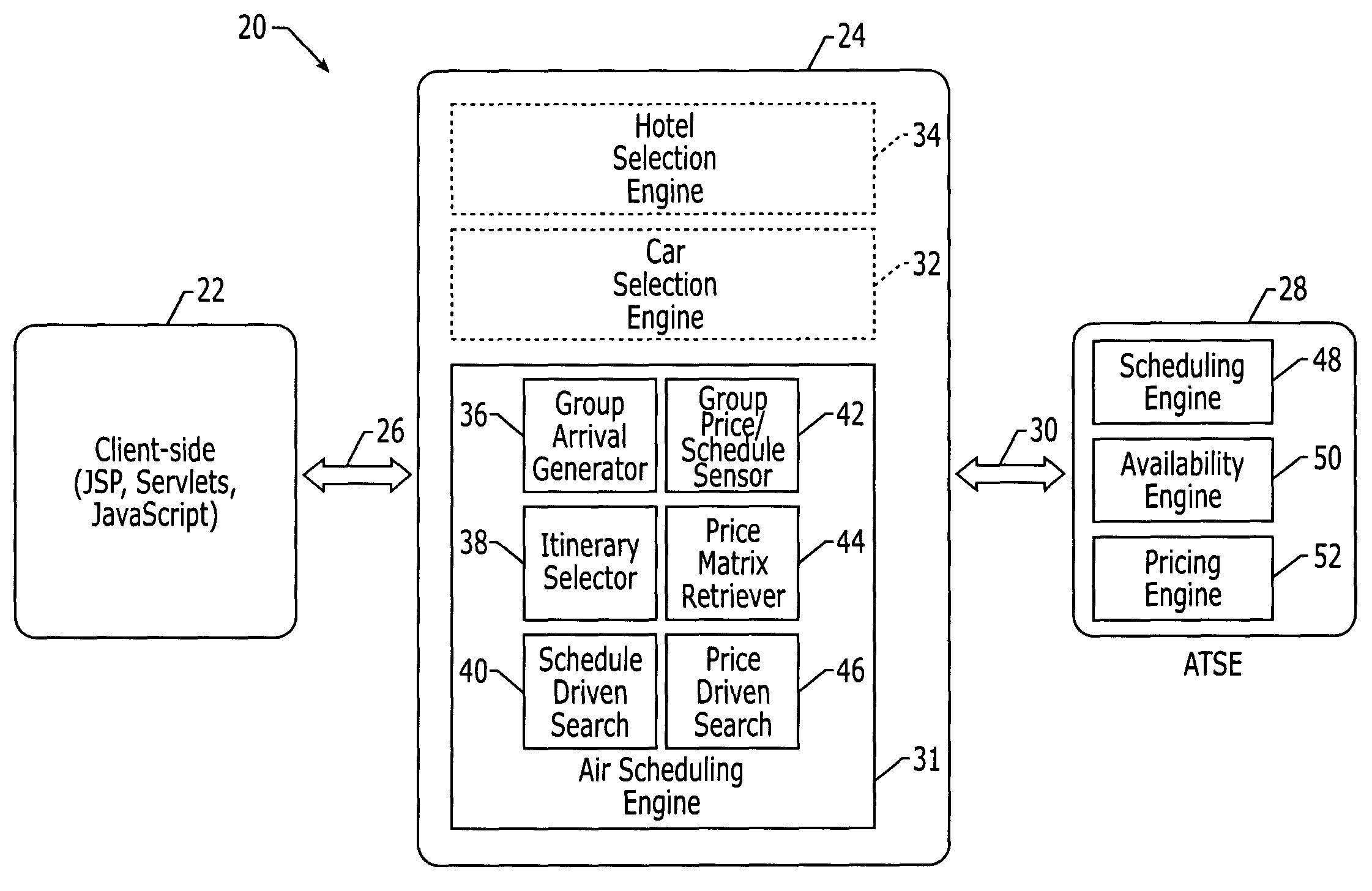
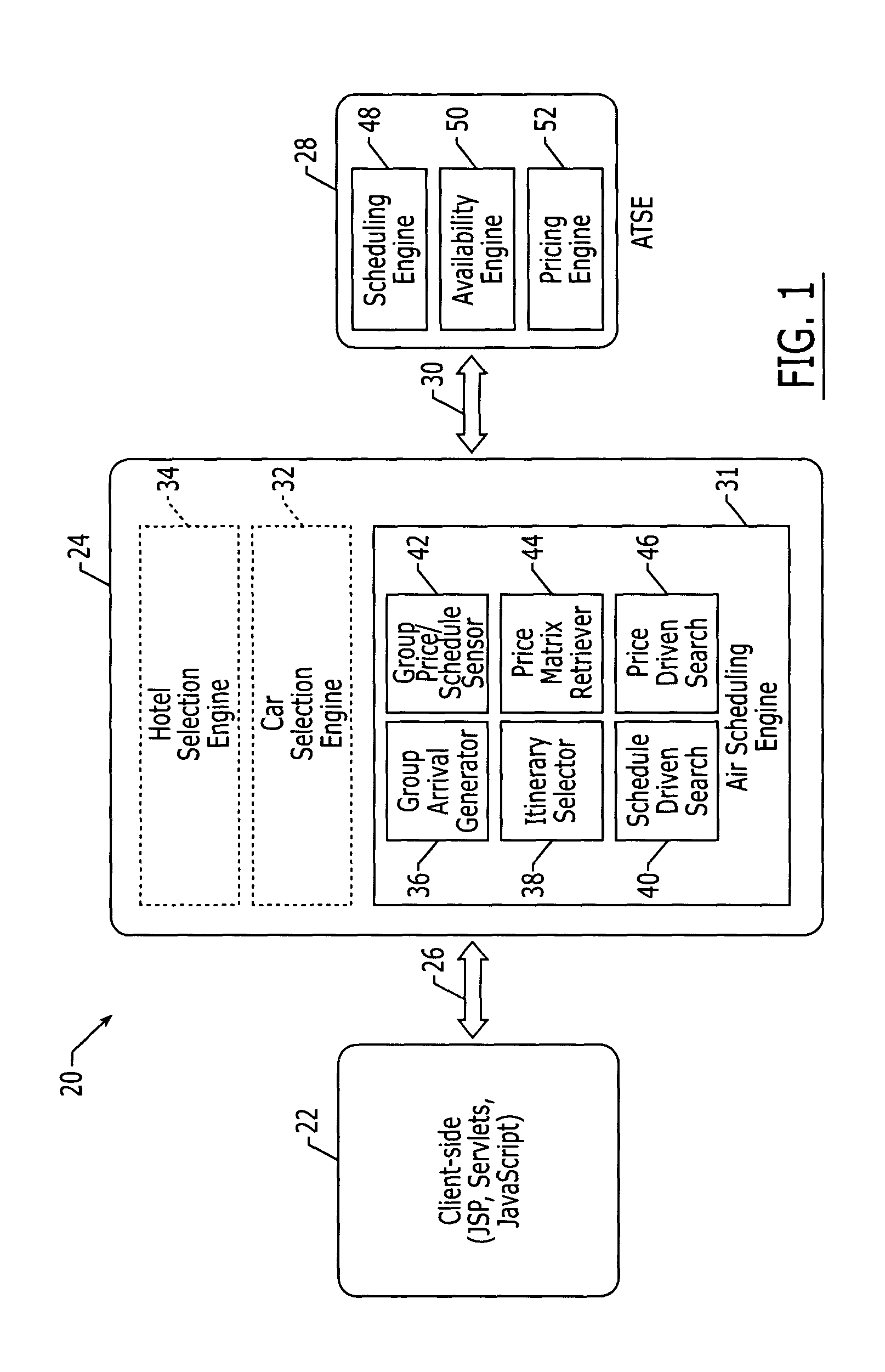
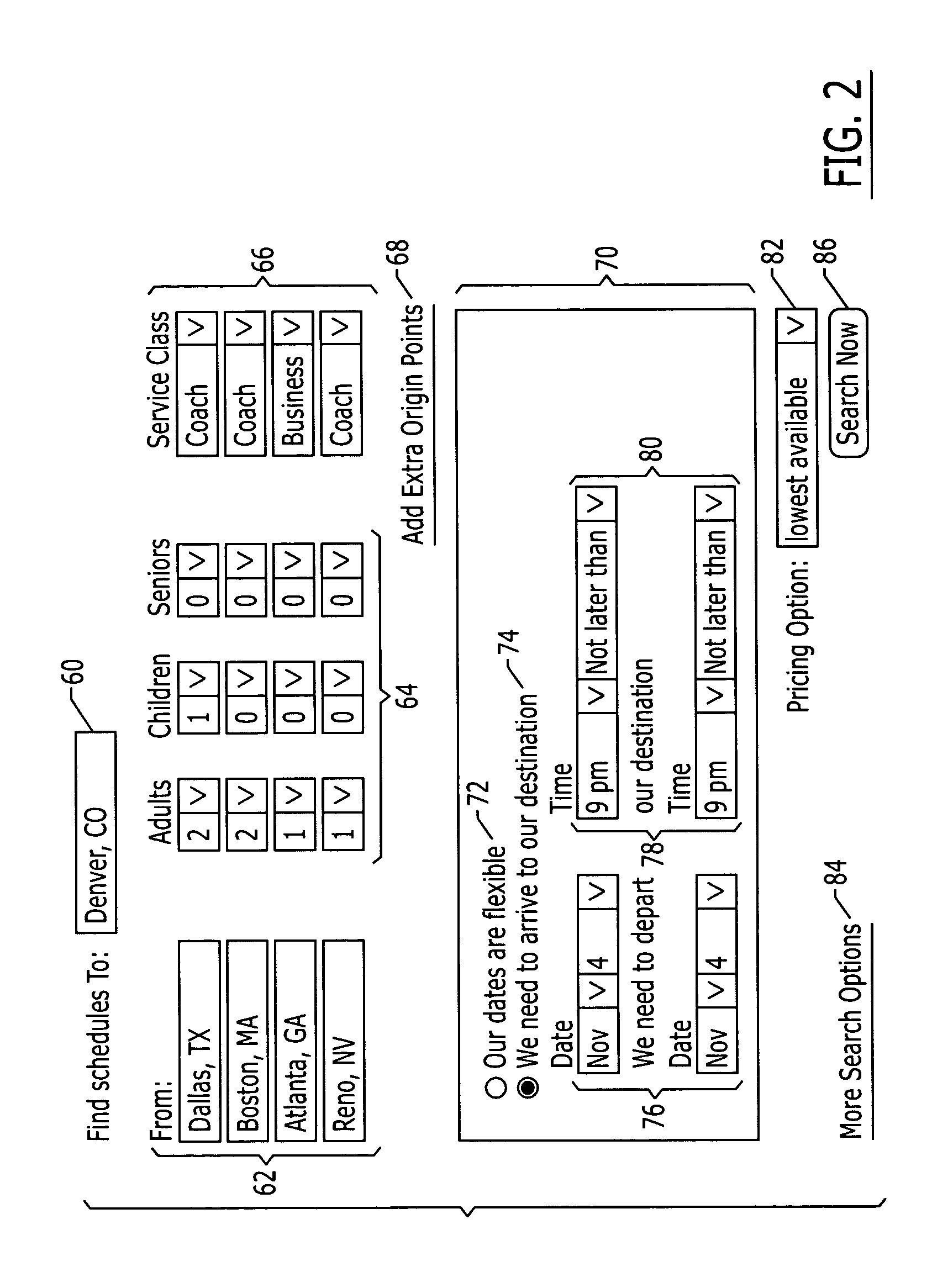
System and method for coordinating travel itineraries
ActiveUS20050033614A1Quickly and accurately determineEasy to changeReservationsNavigation instrumentsTime scheduleComputer science
Owner:TLV CO LTD
Resolving and merging duplicate records using machine learning
InactiveUS20160357790A1Digital data information retrievalProbabilistic networksFeature vectorMachine learning
According to various embodiments of the present invention, an automated technique is implemented for resolving and merging fields accurately and reliably, given a set of duplicated records that represents a same entity. In at least one embodiment, a system is implemented that uses a machine learning (ML) method, to train a model from training data, and to learn from users how to efficiently resolve and merge fields. In at least one embodiment, the method of the present invention builds feature vectors as input for its ML method. In at least one embodiment, the system and method of the present invention apply Hierarchical Based Sequencing (HBS) and / or Multiple Output Relaxation (MOR) models in resolving and merging fields. Training data for the ML method can come from any suitable source or combination of sources.
Owner:XANT INC
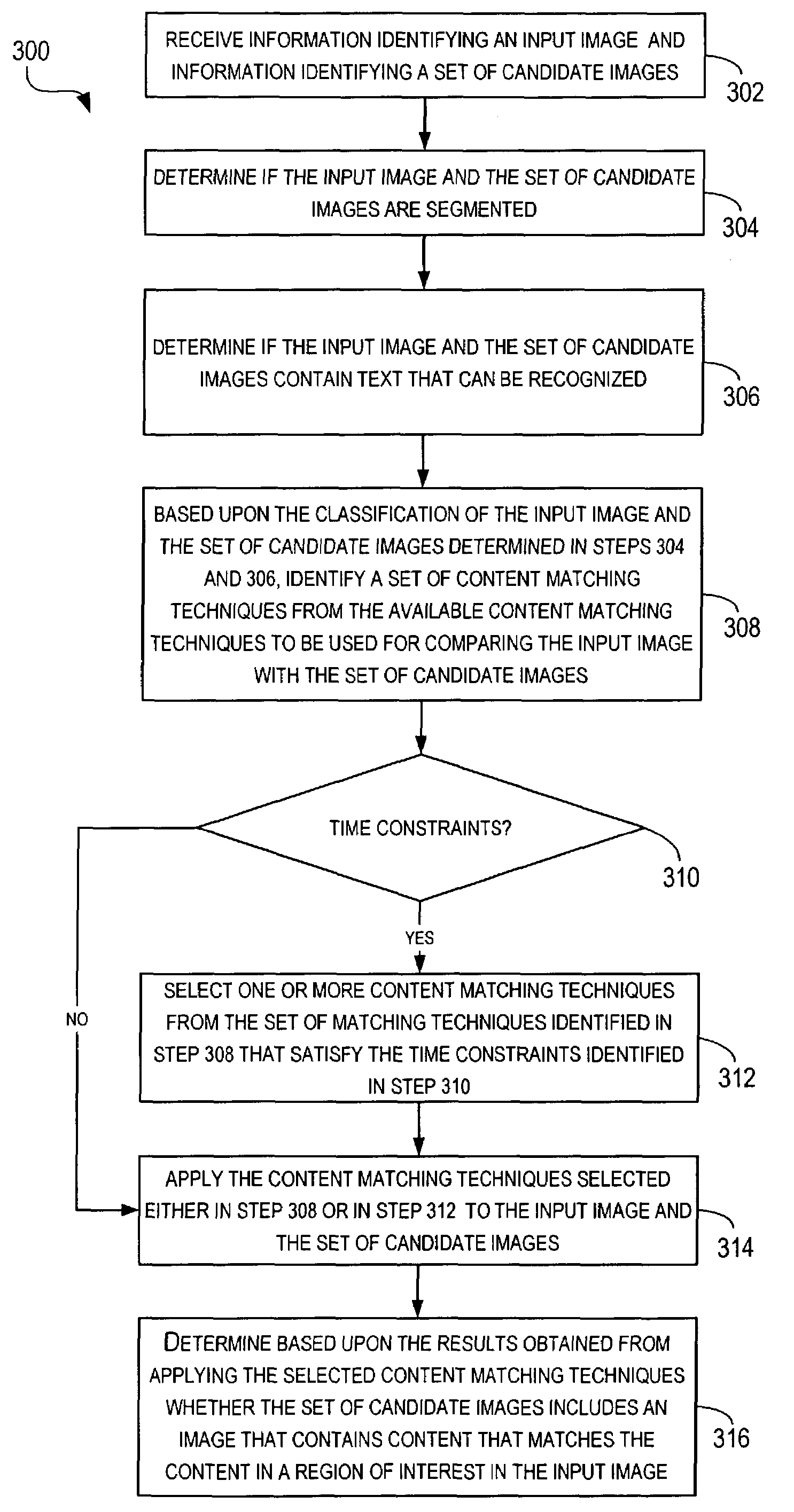
Automated techniques for comparing contents of images
ActiveUS7236632B2High confidence scoreImage analysisDigital data information retrievalRegion of interestCandidate image
Automated techniques for comparing contents of images. For a given image (referred to as an “input image”), a set of images (referred to as “a set of candidate images”) are processed to determine if the set of candidate images comprises an image whose contents or portions thereof match contents included in a region of interest in the input image.
Owner:RICOH KK
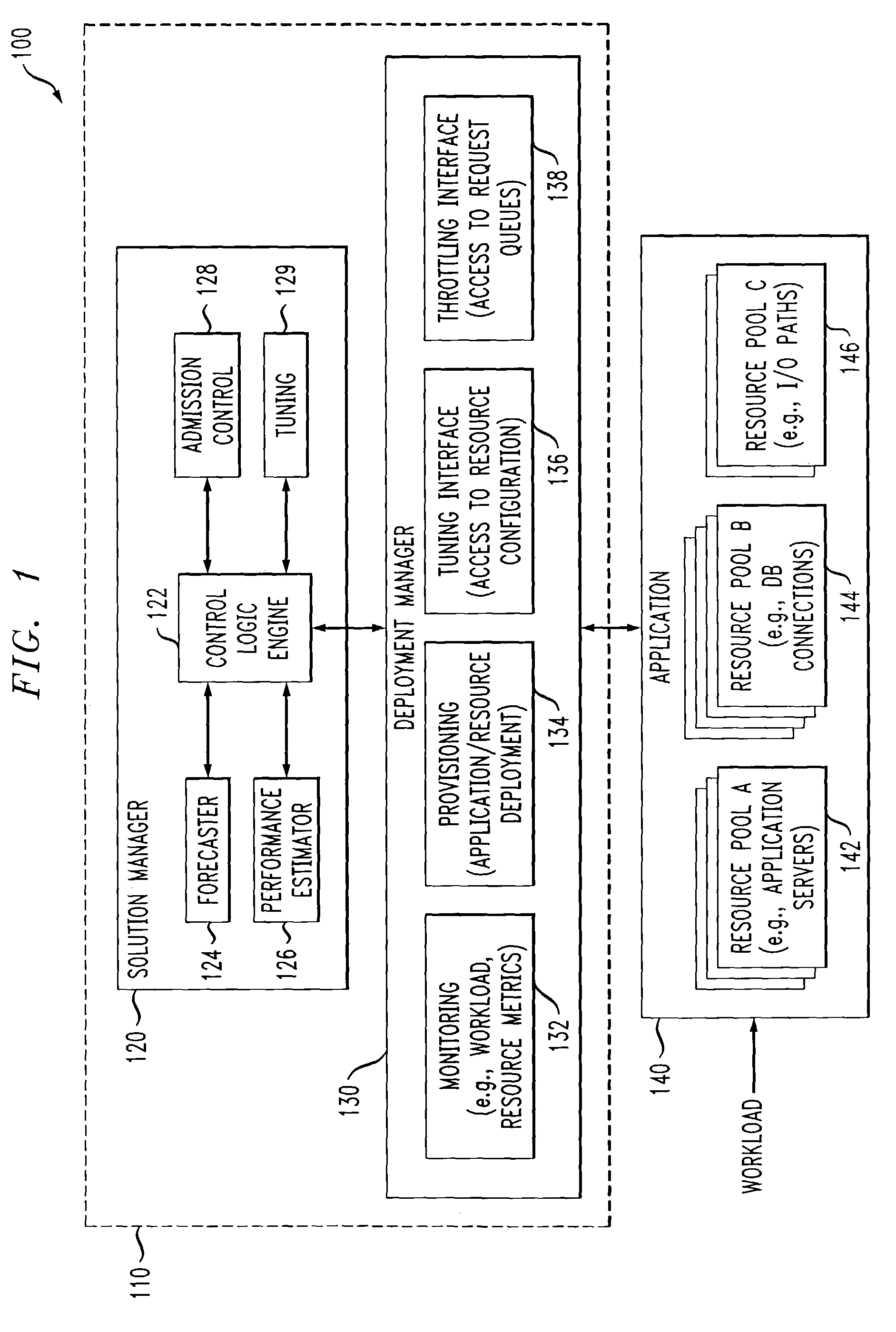
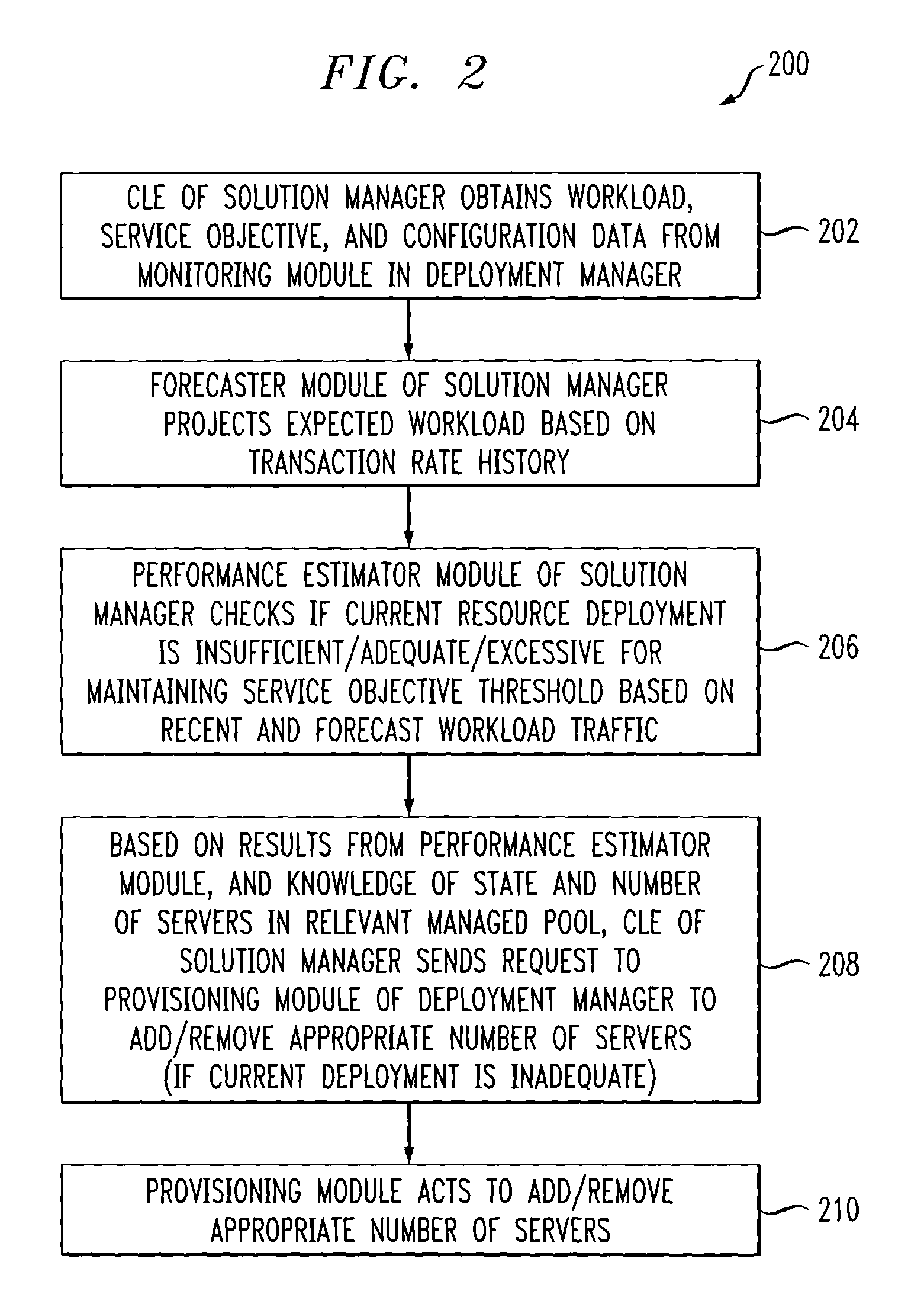
Methods and apparatus for managing computing deployment in presence of variable workload
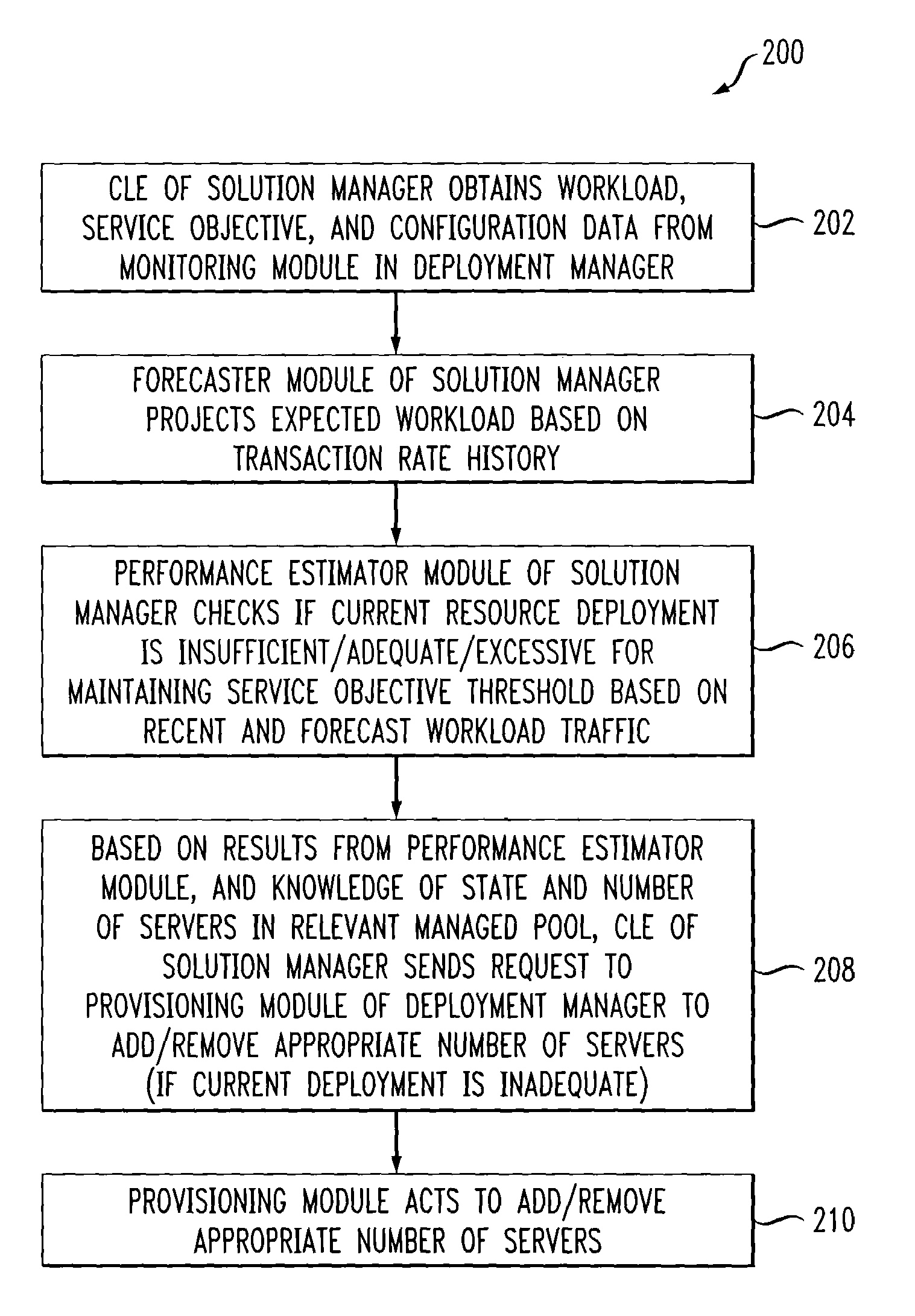
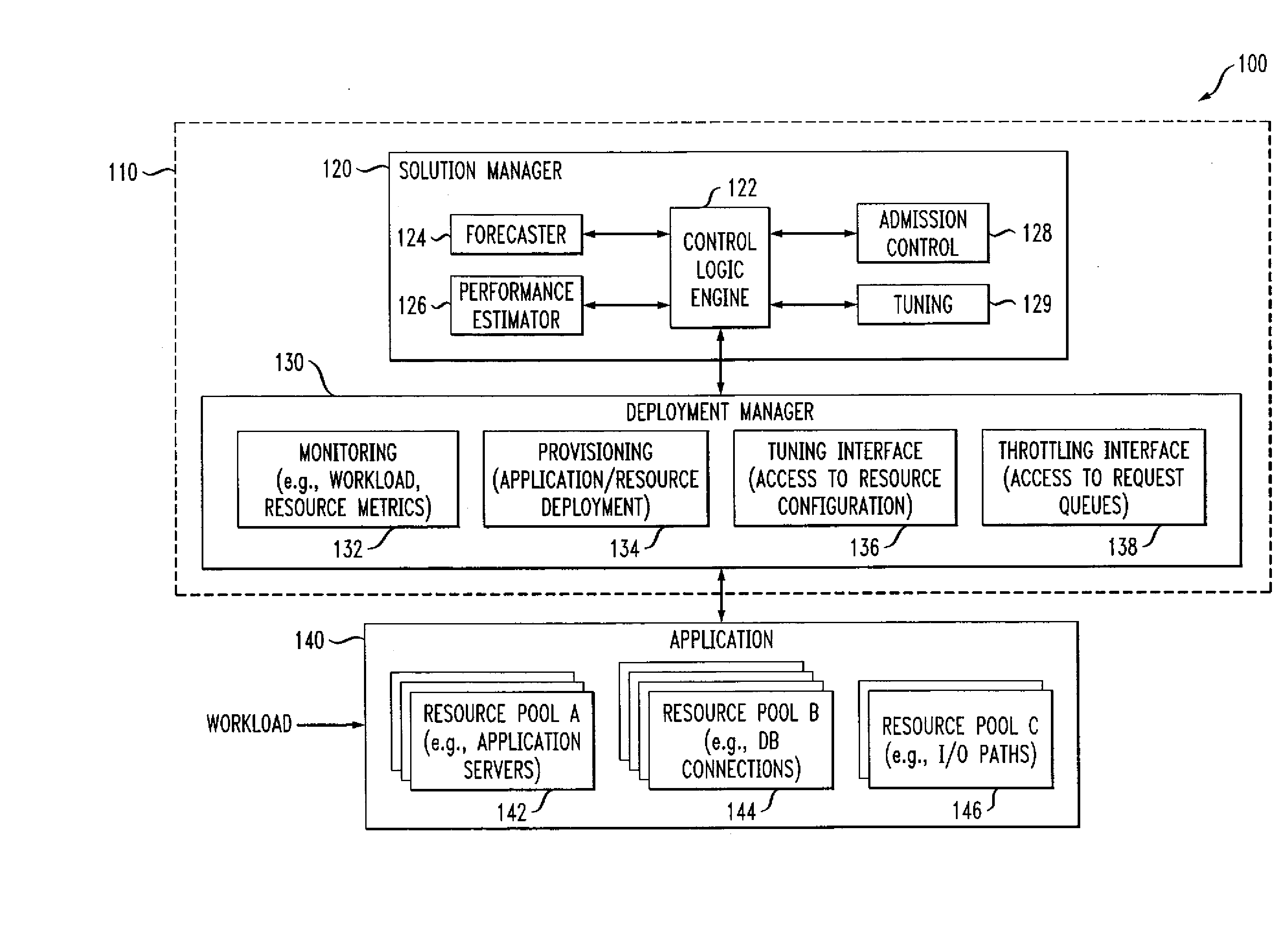
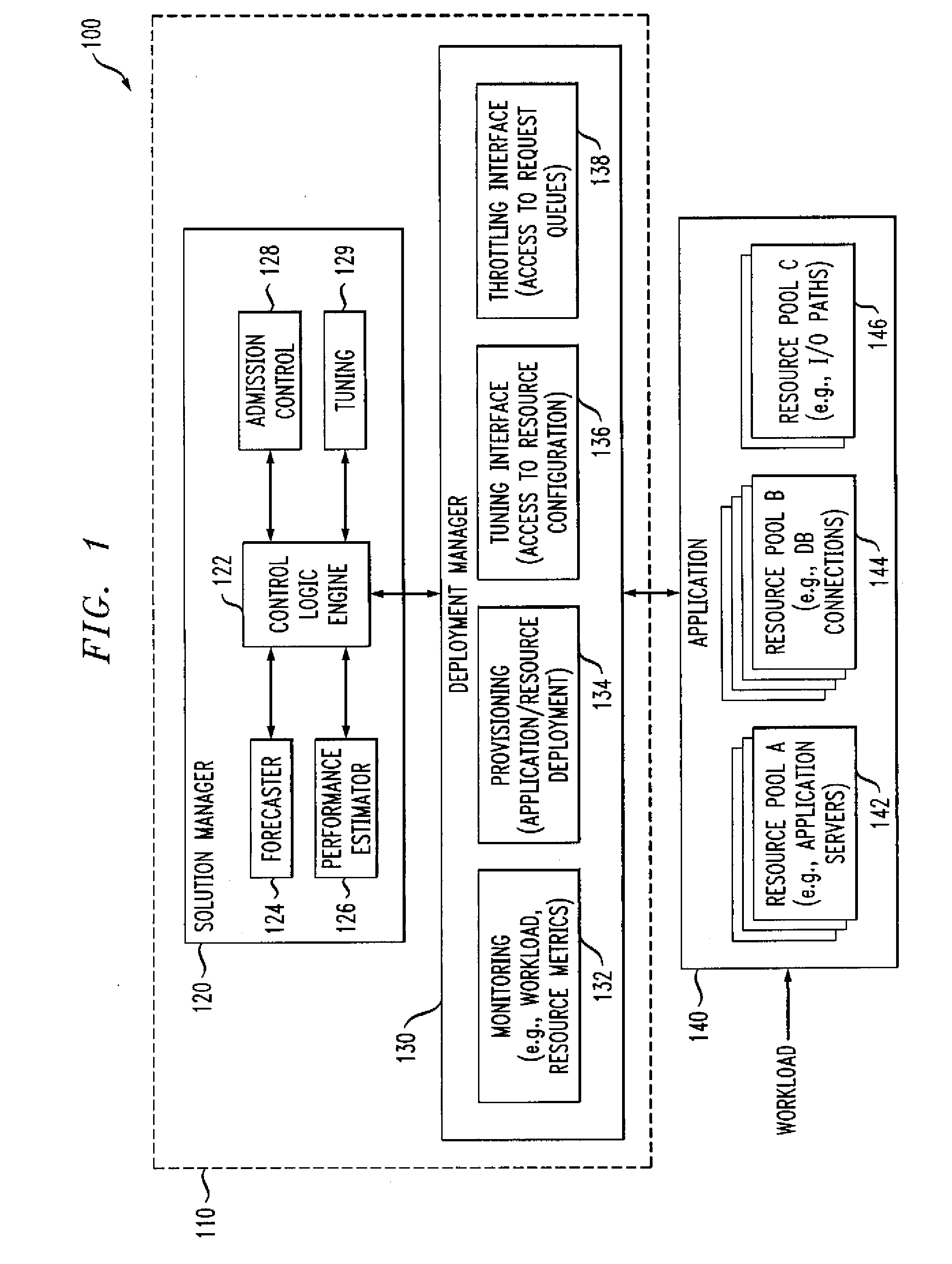
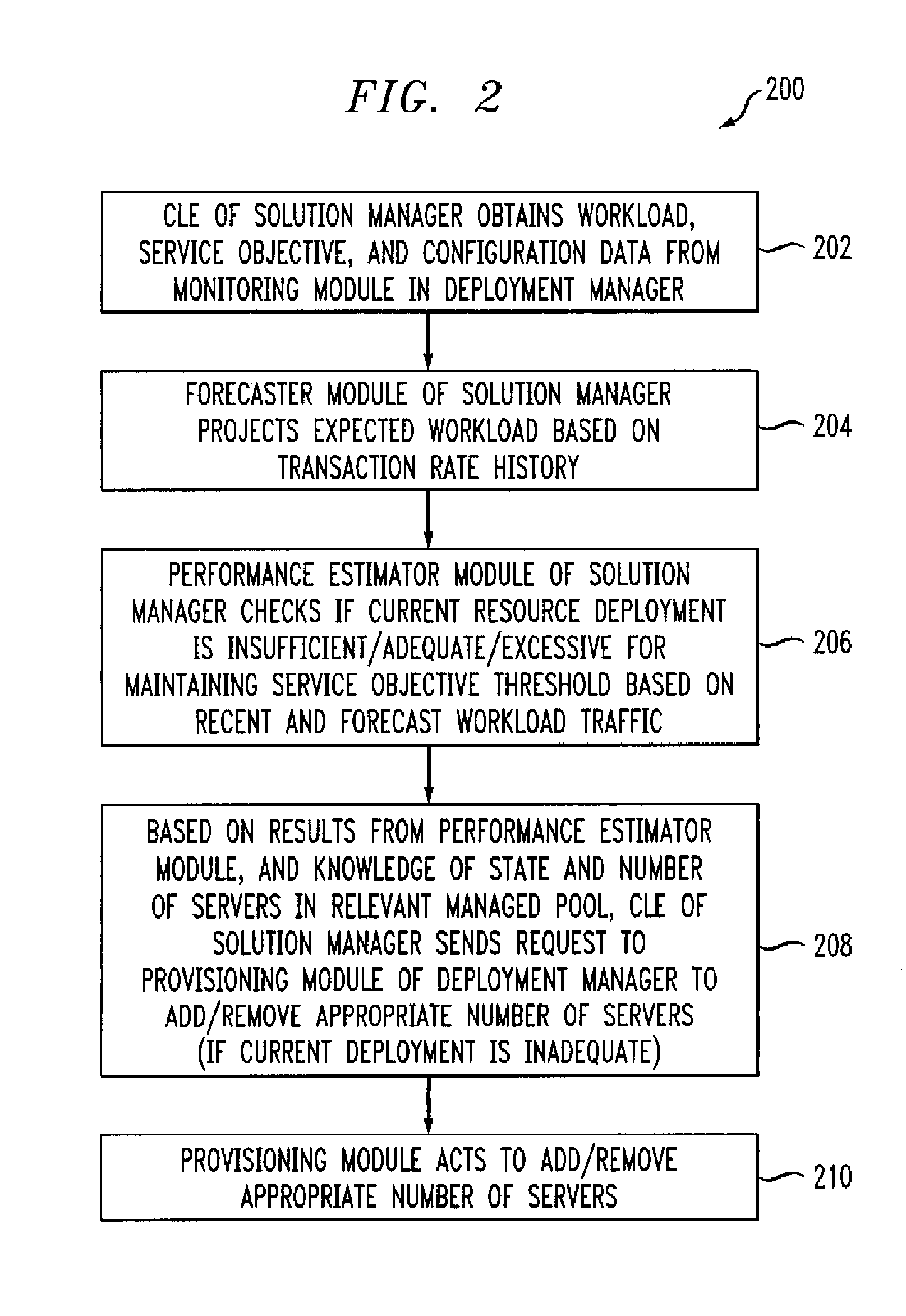
ActiveUS7350186B2Efficient and effectiveAccommodating unanticipated workloadResource allocationReliability/availability analysisWorkloadDistributed computing
Automated or autonomic techniques for managing deployment of one or more resources in a computing environment based on varying workload levels. The automated techniques may comprise predicting a future workload level based on data associated with the computing environment. Then, an estimation is performed to determine whether a current resource deployment is insufficient, sufficient, or overly sufficient to satisfy the future workload level. Then, one or more actions are caused to be taken when the current resource deployment is estimated to be insufficient or overly sufficient to satisfy the future workload level. Actions may comprise resource provisioning, resource tuning and / or admission control.
Owner:GOOGLE LLC
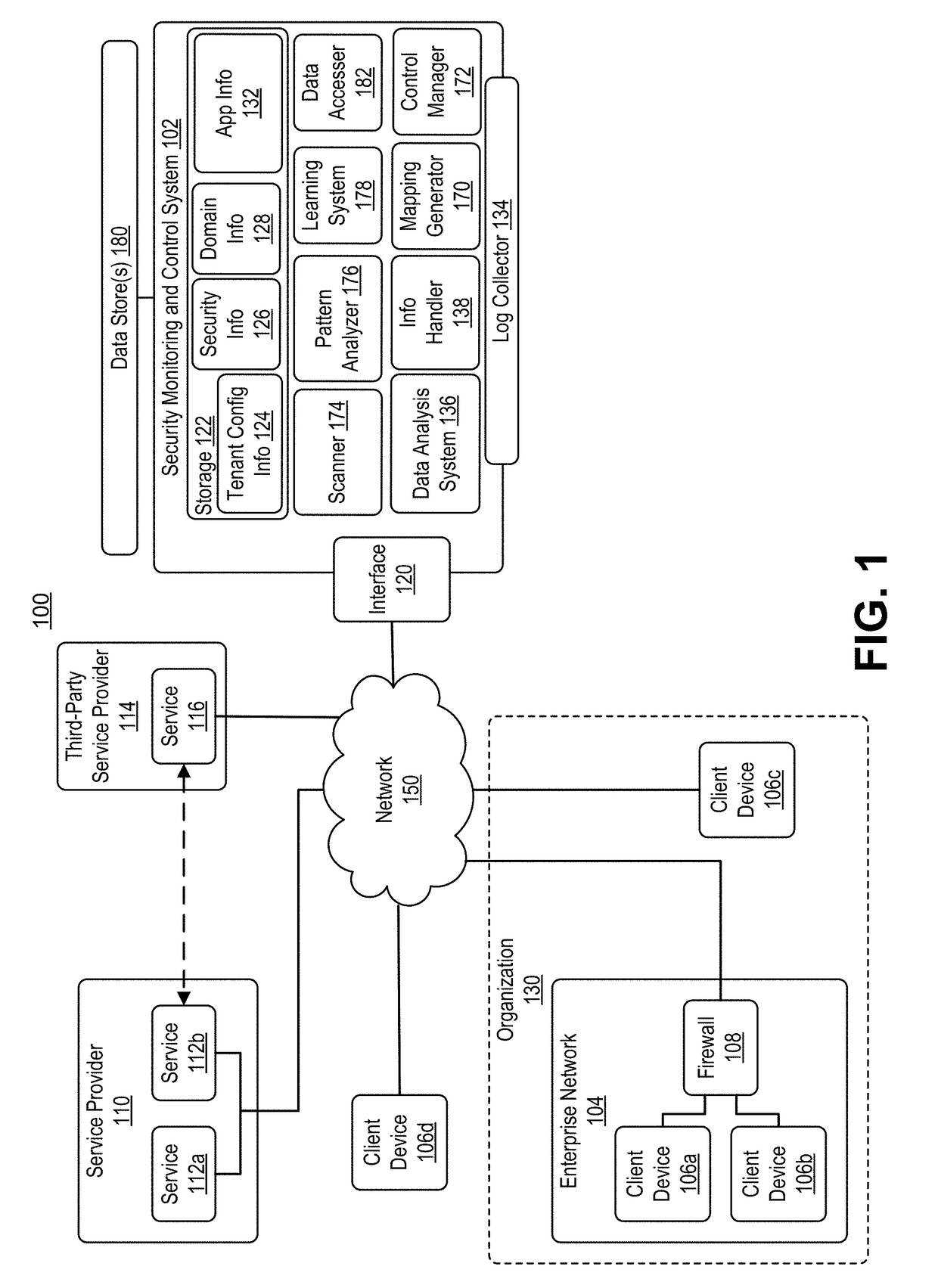
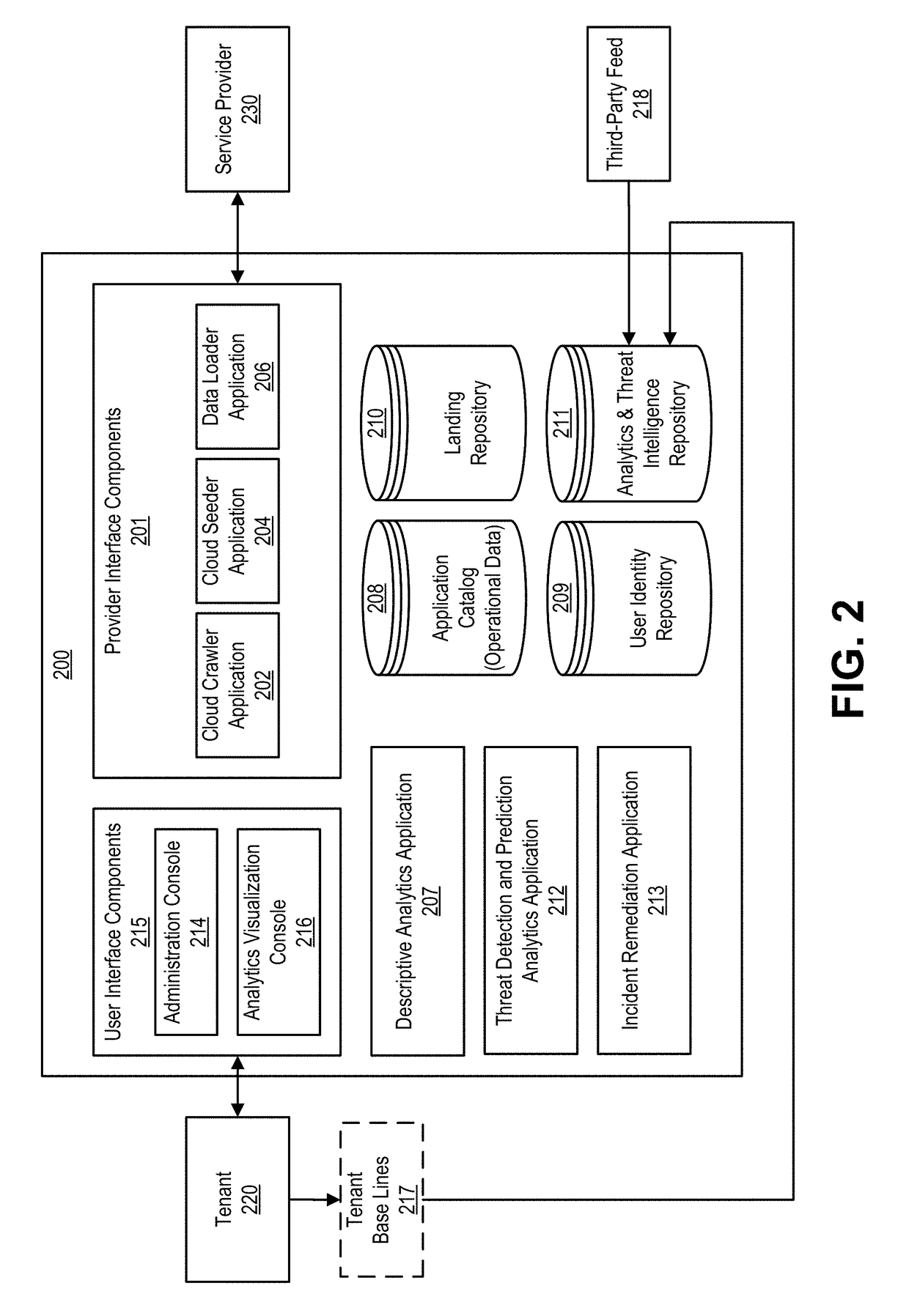
Techniques for monitoring privileged users and detecting anomalous activities in a computing environment
ActiveUS20180375886A1High degreeQuick fixData switching networksSecurity arrangementControl systemSecurity management
In various implementations, a security management and control system for monitoring and management of security for cloud services can include automated techniques for identifying the privileged users of a given cloud service. In various examples, the security management and control system can obtain activity logs from the cloud service, where the activity logs record actions performed by users of an organization in using the cloud service. In various examples, the security management and control system can identify actions in the activity logs that are privileged with respect to the cloud service. In these and other examples, the security management and control system can use the actions in the activity log to identify privileged users. Once the privileged users are identified, the security management and control system can monitor the privileged users with a higher degree of scrutiny.
Owner:ORACLE INT CORP
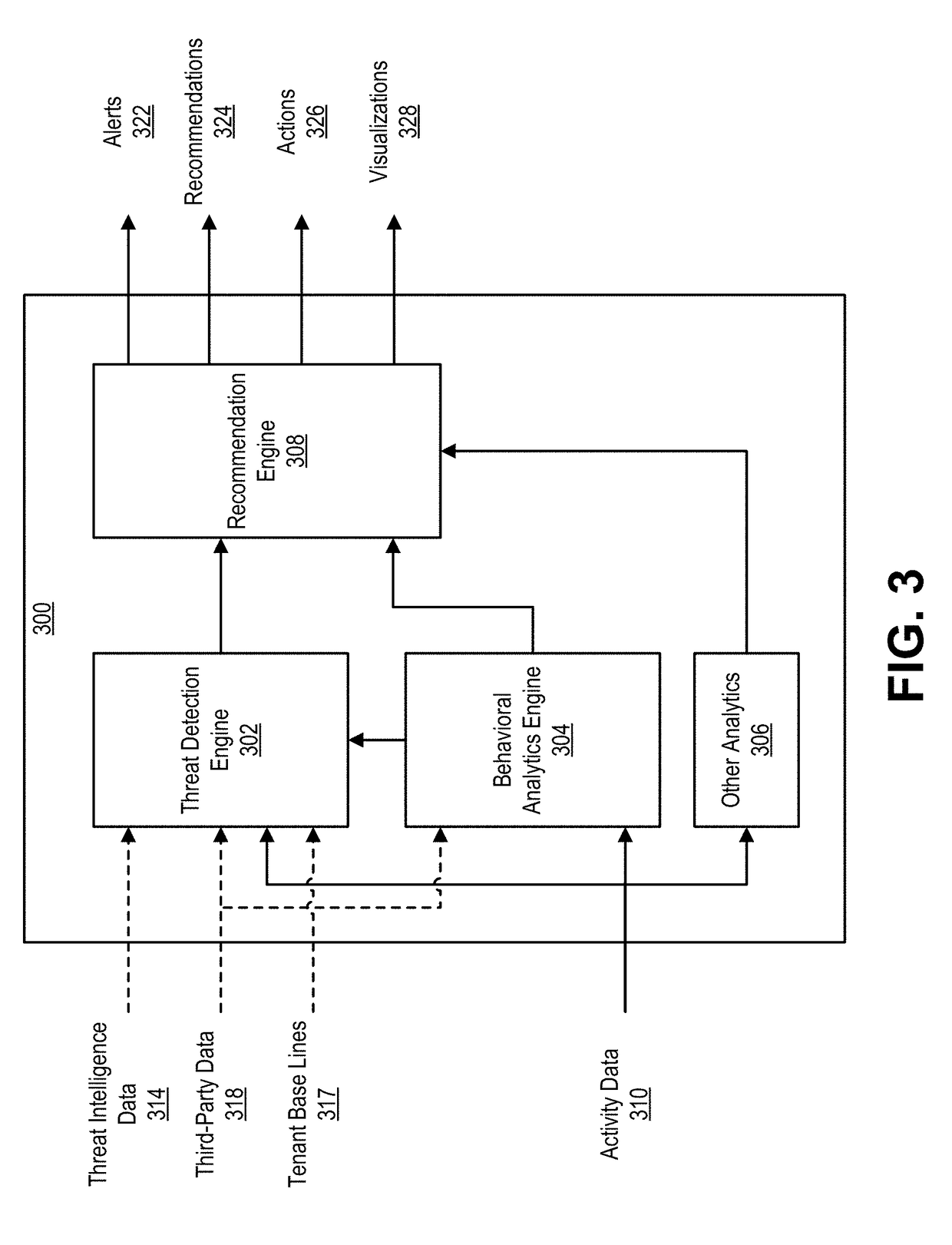
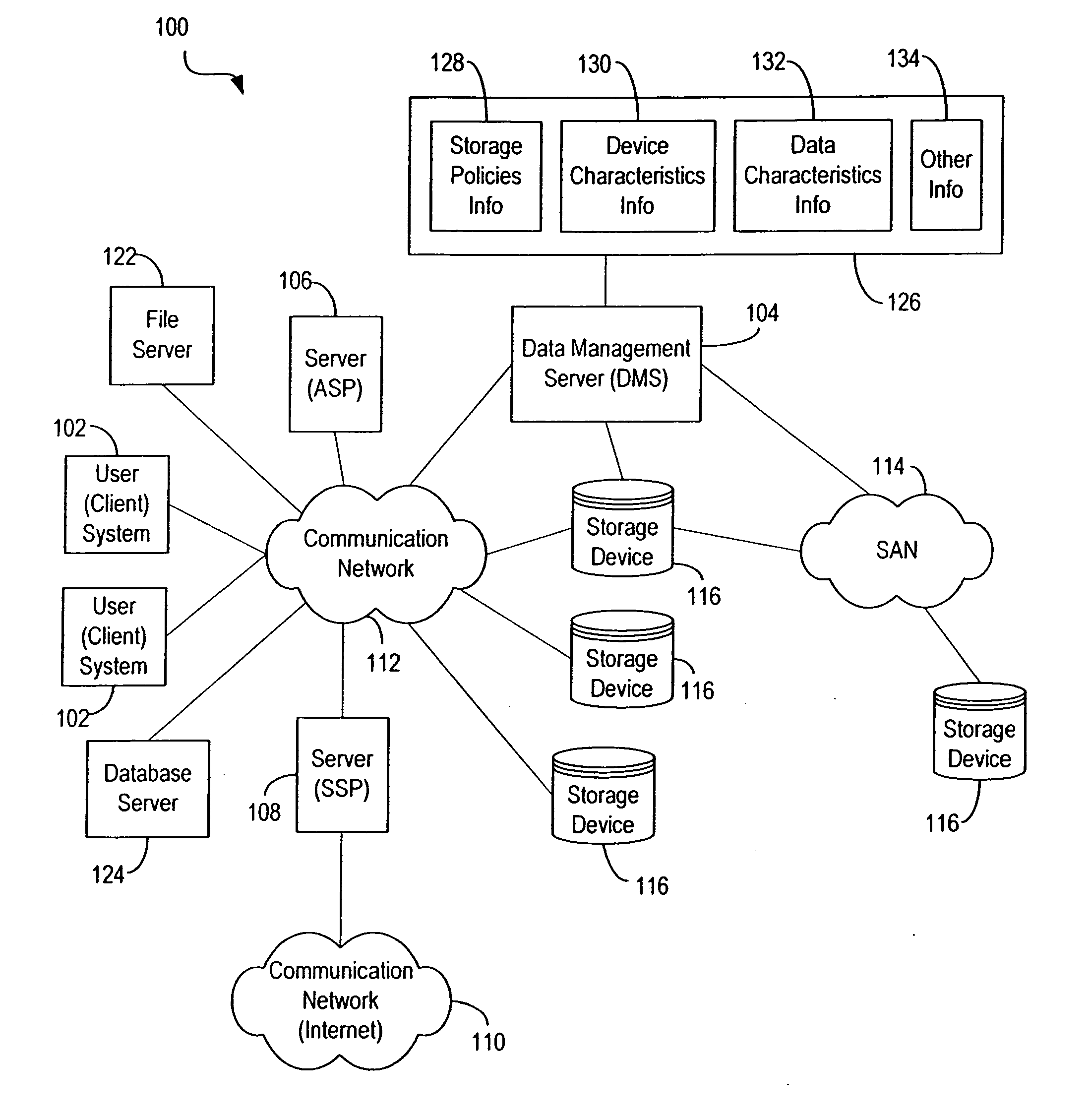
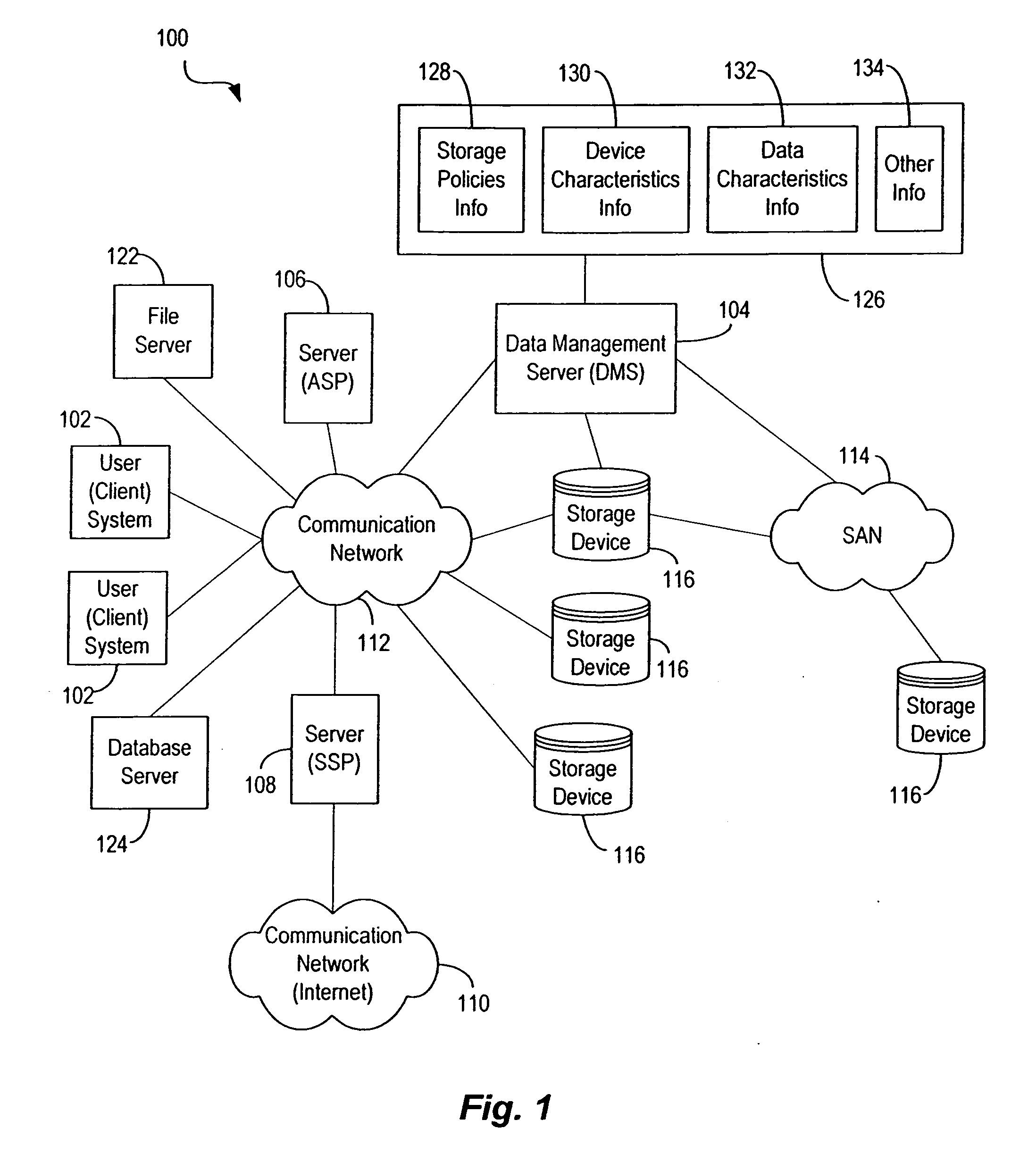
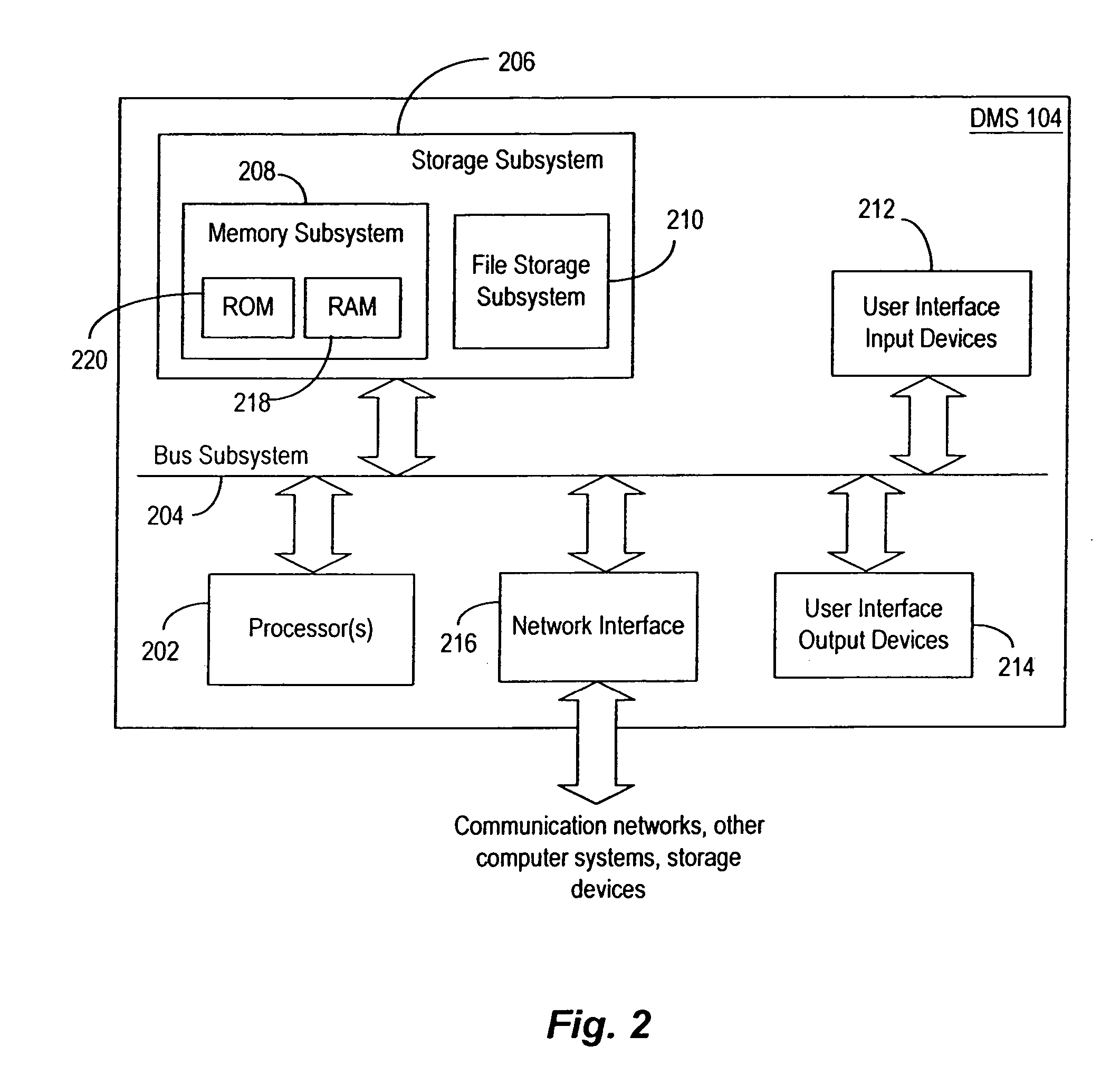
Techniques for storing data based upon storage policies
InactiveUS20070083575A1Data processing applicationsDigital data information retrievalData accessData store
Automated techniques for storing data in a data storage environment. Techniques are provided for determining storage locations for data in a heterogeneous storage environment based upon storage policies configured for the storage environment. The data is stored in storage locations that enable efficient data access while optimizing the use of available storage resources with minimum human intervention.
Owner:ROCKET SOFTWARE
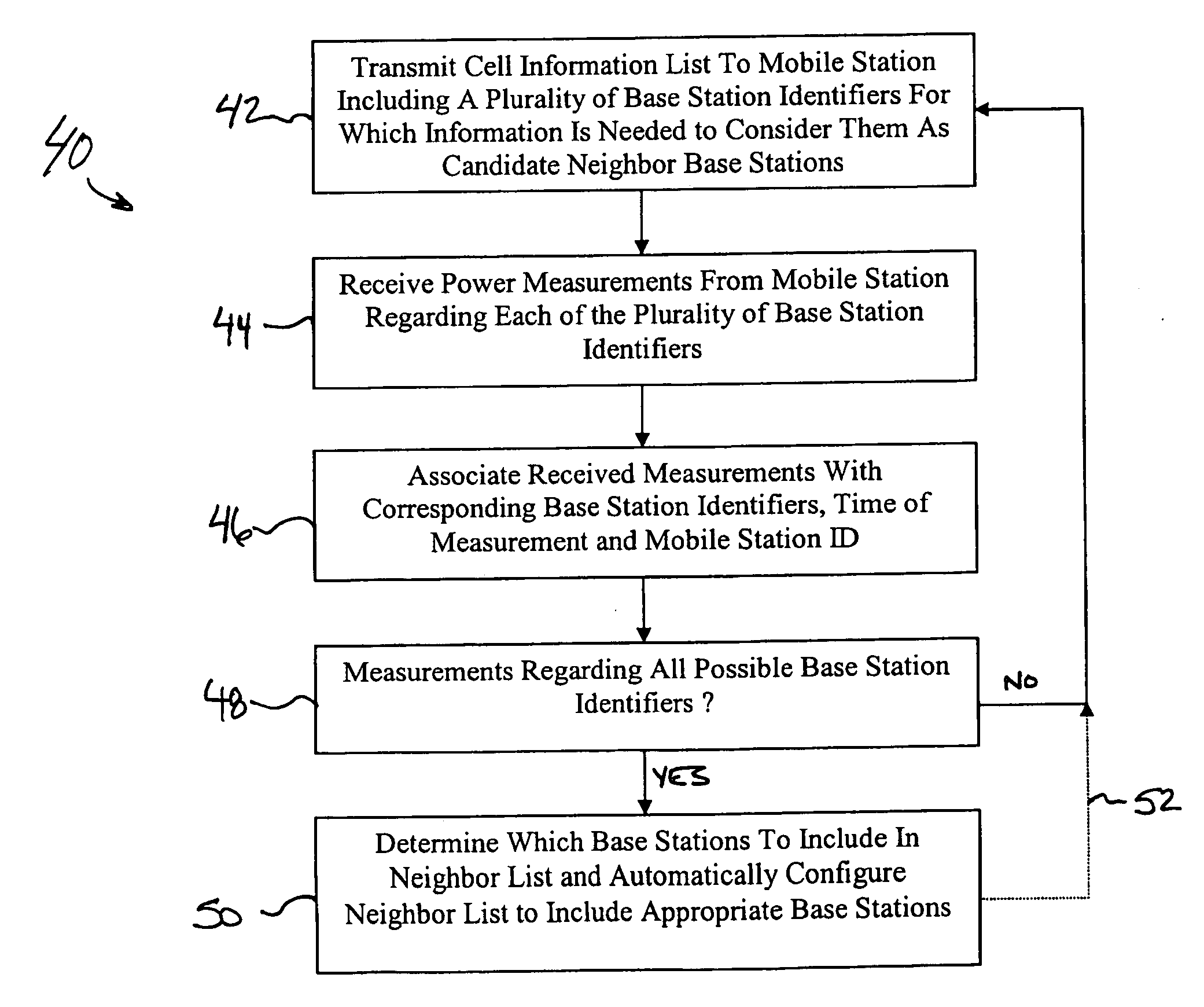
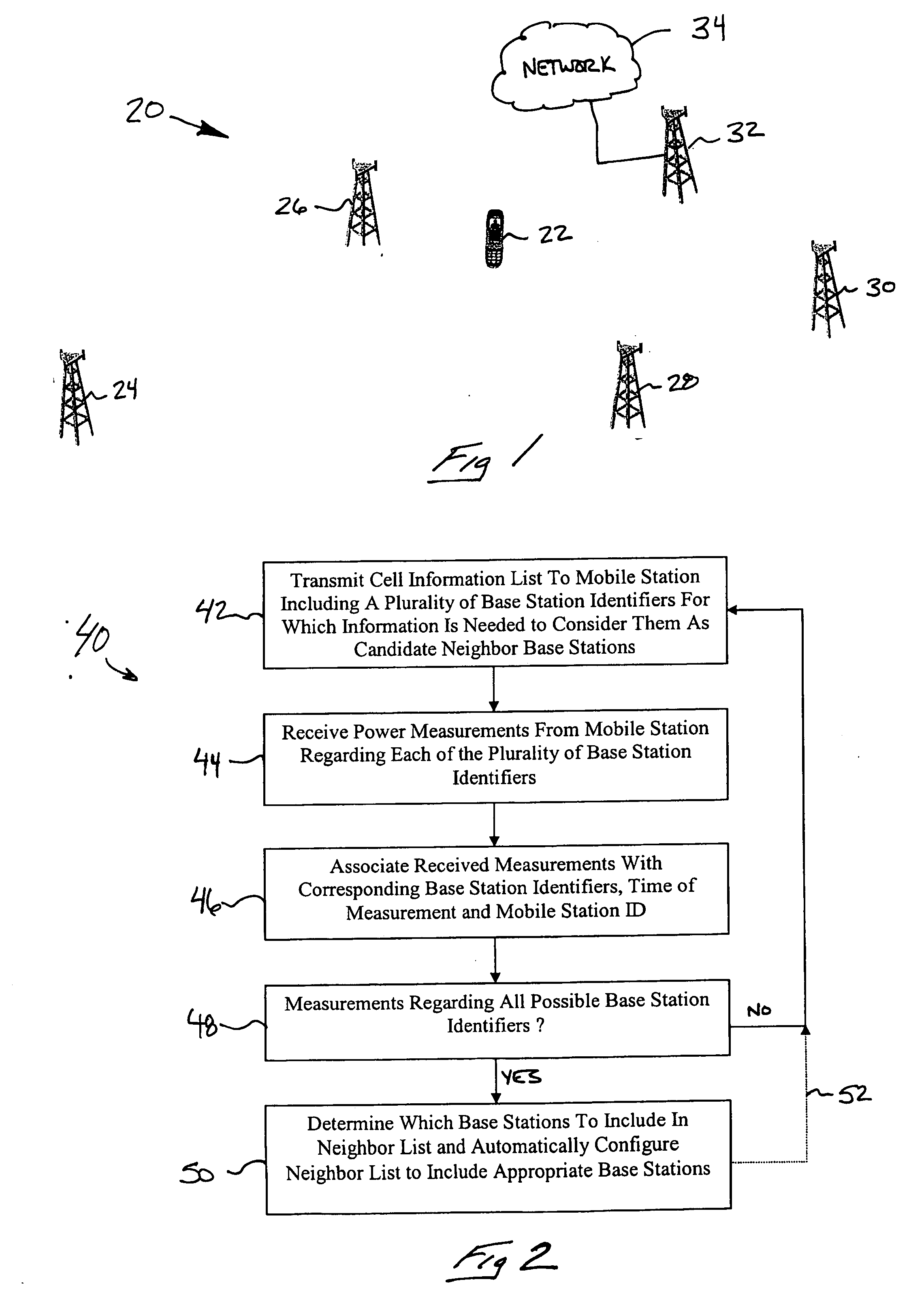
Automatically configuring a neighbor set for a base station
An automated technique for configuring a neighbor set for a base station (32) includes initializing the neighbor set based upon reported measurements from a mobile station (22). In a disclosed example, a newly installed base station (32) transmits a cell information list to a mobile station (22) requesting measurement reports regarding a plurality of candidate base station identifiers. Based upon the reported measurements, a determination is made regarding which of the base stations should be included in the neighbor set for the base station (32). A disclosed example includes the capability of automatically initializing the neighbor set and automatically updating the set. Disclosed examples include utilizing information from a plurality of mobile stations.
Owner:ALCATEL-LUCENT USA INC
Techniques for storing data based upon storage policies
InactiveUS7092977B2Data processing applicationsDatabase distribution/replicationData accessData store
Automated techniques for storing data in a data storage environment. Techniques are provided for determining storage locations for data in a heterogeneous storage environment based upon storage policies configured for the storage environment. The data is stored in storage locations that enable efficient data access while optimizing the use of available storage resources with minimum human intervention.
Owner:ROCKET SOFTWARE
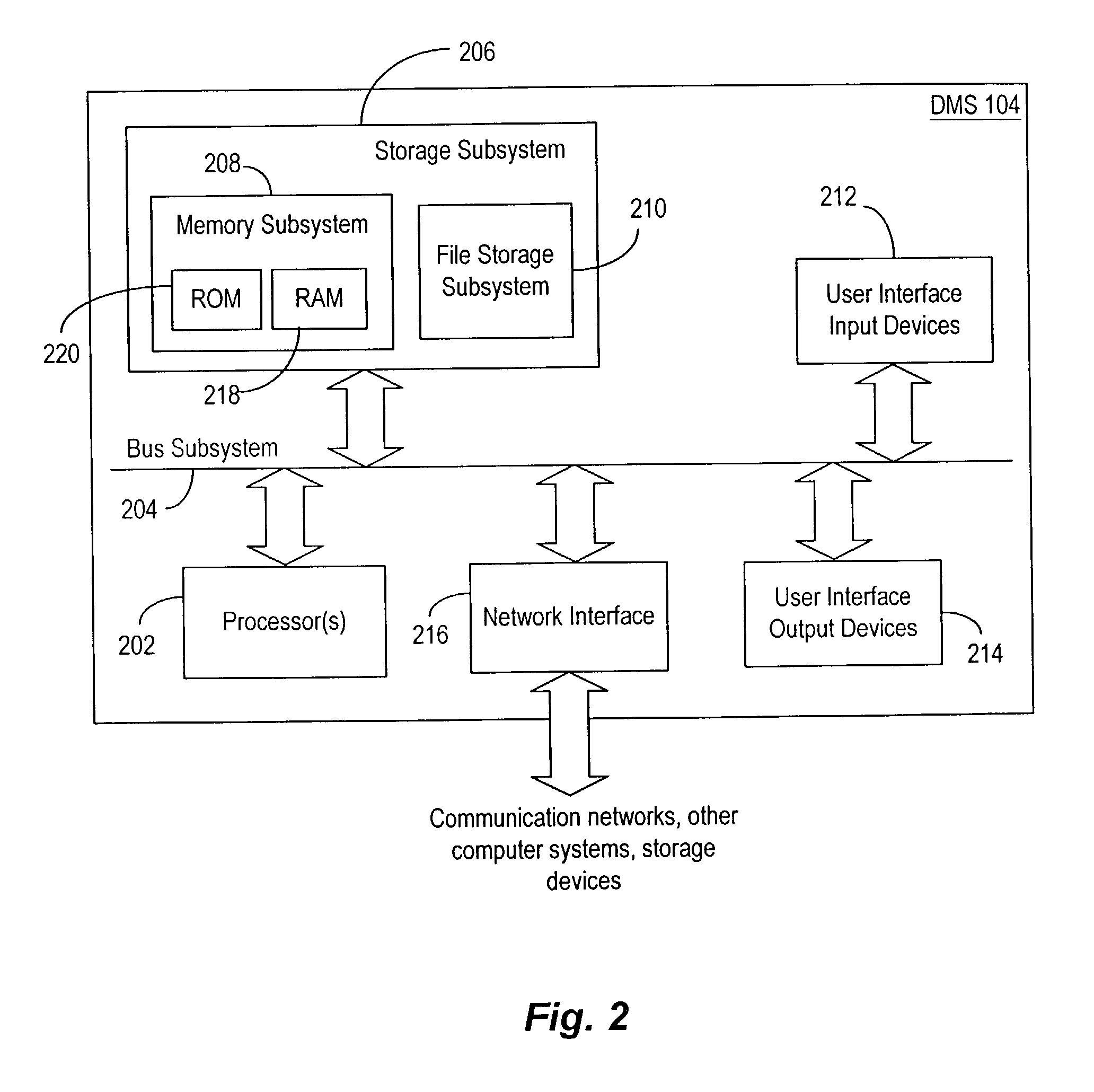
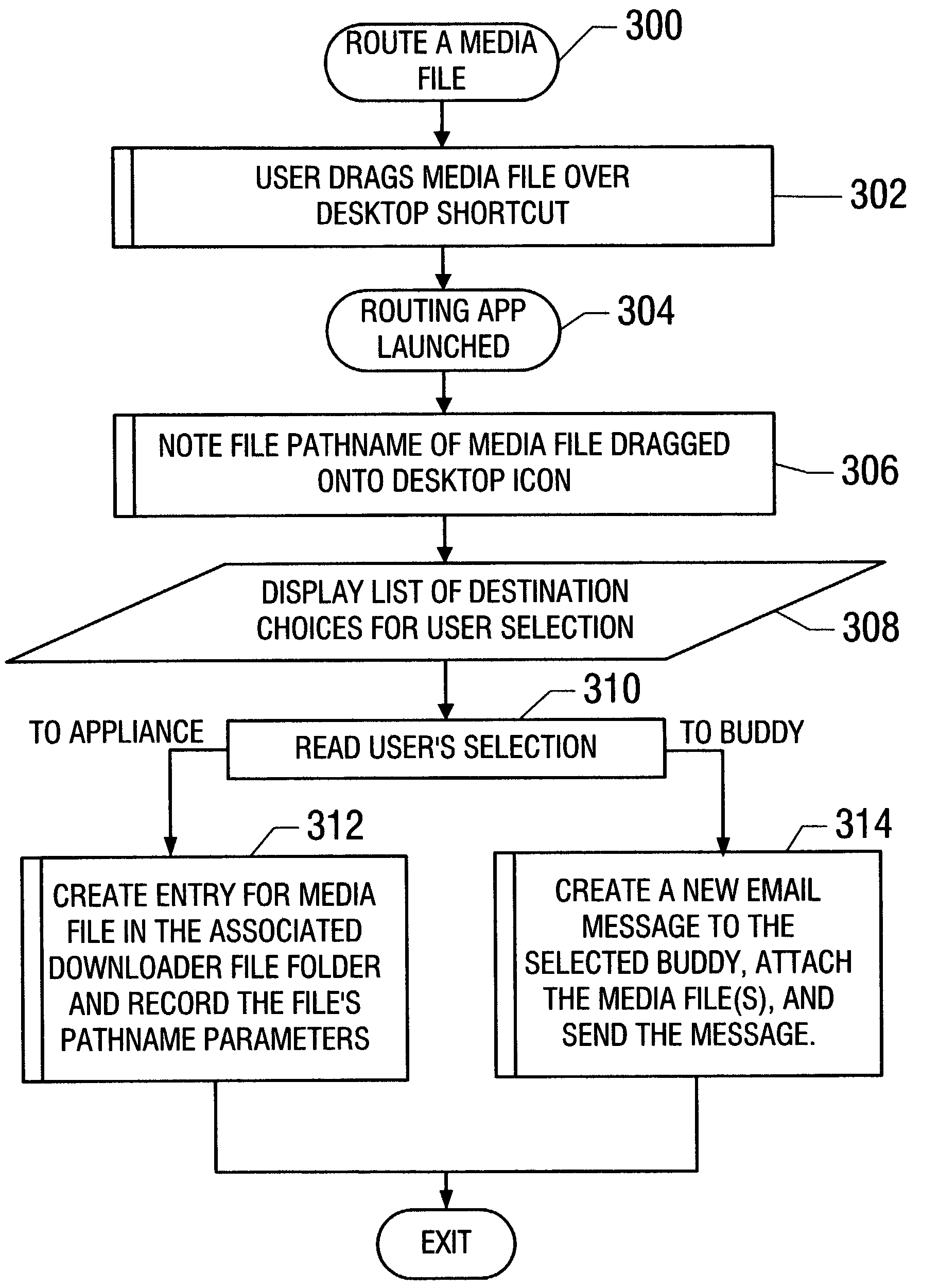
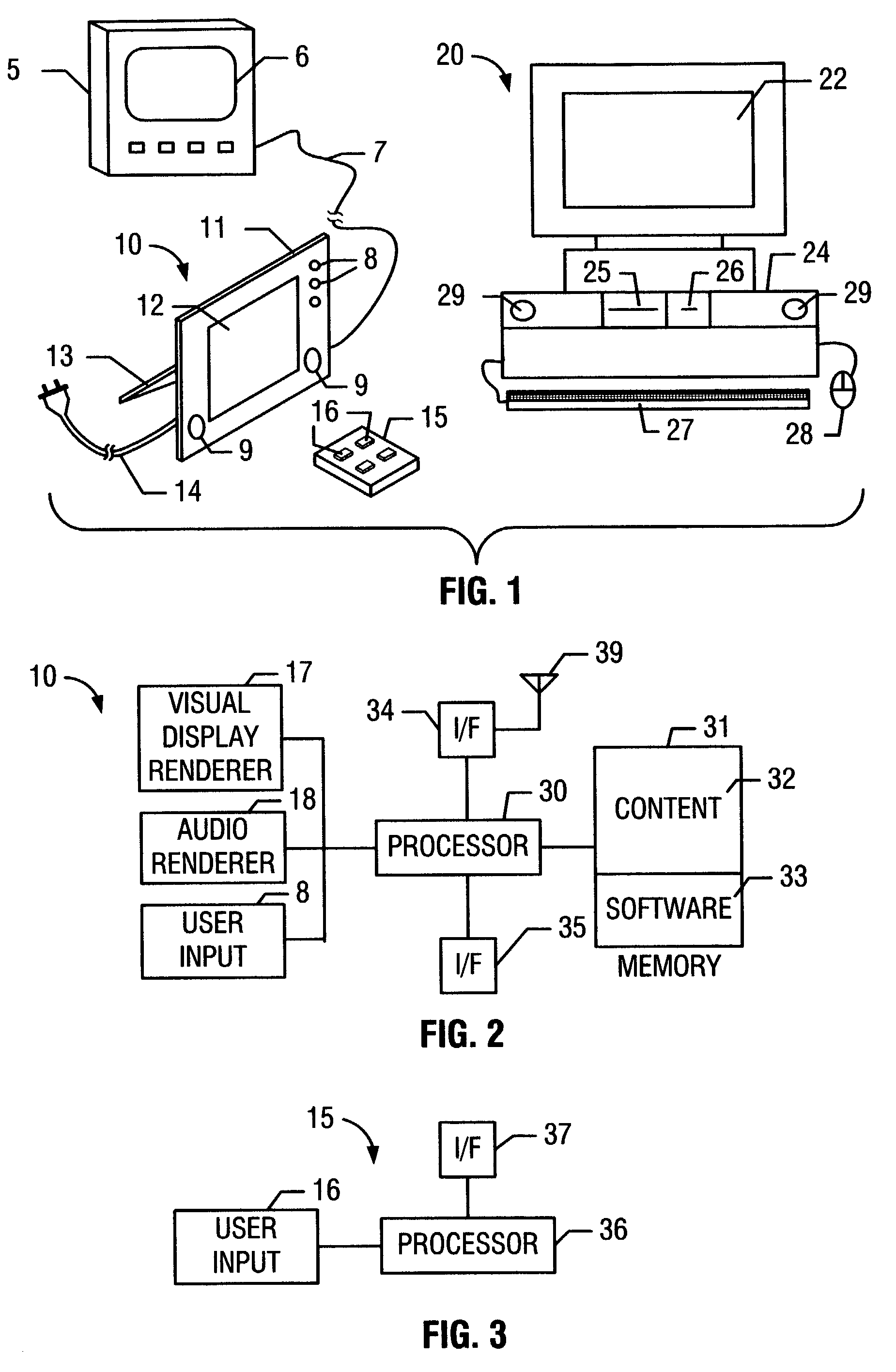
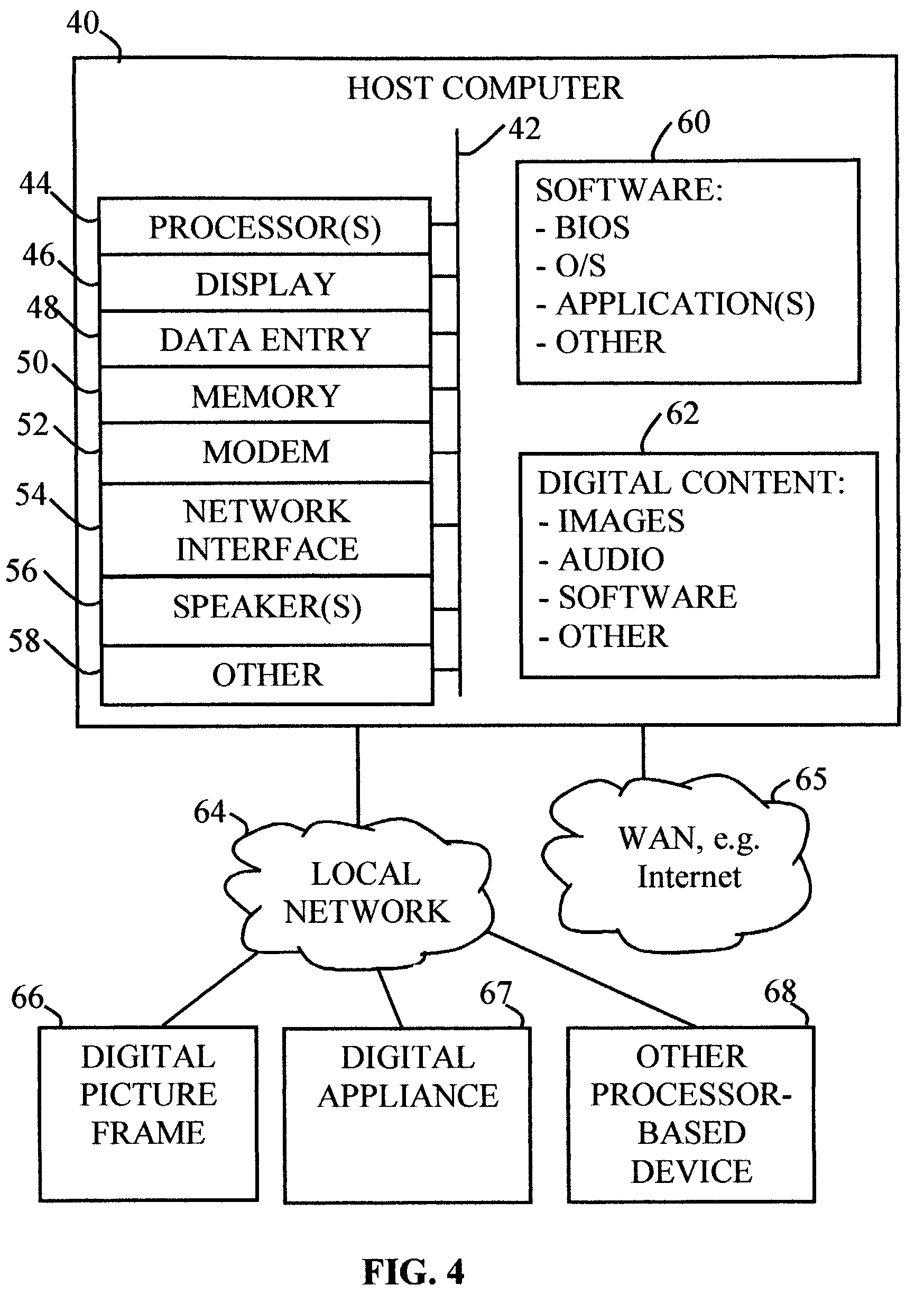
User interface to facilitate exchanging files among processor-based devices
InactiveUS7376696B2Multiple digital computer combinationsSpecial data processing applicationsGraphicsGraphical user interface
A first processor-based device (PBD), such as a personal computer functioning as a host and containing digital media files, may share a selected file with a second PBD. Media file-sharing may be facilitated by an automated technique including graphical user interfaces (GUIs). In one embodiment, when a device user wishes to transfer a file to another device, the user hovers the file over a particular desktop icon and drops it, causing it to be automatically transmitted to a corresponding destination. Optionally, in response to hovering, a software program automatically generates a GUI indicating potential destinations. The user then selects a destination, and the system automatically transfers the file to that destination. In another embodiment, media sharing can be initiated from a digital appliance, such as a digital picture frame, and a file can be sent to another PBD, such as another digital picture frame via an intermediary PBD.
Owner:INTEL CORP
Resolving and merging duplicate records using machine learning
According to various embodiments of the present invention, an automated technique is implemented for resolving and merging fields accurately and reliably, given a set of duplicated records that represents a same entity. In at least one embodiment, a system is implemented that uses a machine learning (ML) method, to train a model from training data, and to learn from users how to efficiently resolve and merge fields. In at least one embodiment, the method of the present invention builds feature vectors as input for its ML method. In at least one embodiment, the system and method of the present invention apply Hierarchical Based Sequencing (HBS) and / or Multiple Output Relaxation (MOR) models in resolving and merging fields. Training data for the ML method can come from any suitable source or combination of sources.
Owner:XANT INC
Training speaker-dependent, phrase-based speech grammars using an unsupervised automated technique
InactiveUS20050261901A1Improve accuracyImprove recognition accuracySpeech recognitionSpecial data processing applicationsAutomatic speechSpeech sound
The present invention can include a method for tuning grammar option weights of a phrase-based, automatic speech recognition (ASR) grammar, where the grammar option weights affect which entries within the grammar are matched to spoken utterances. The tuning can occur in an unsupervised fashion, meaning no special training session or manual transcription of data from an ASR session is needed. The method can include the step of selecting a phrase-based grammar to use in a communication session with a user wherein different phrase-based grammars can be selected for different users. Feedback of ASR phrase processing operations can be recorded during the communication session. Each ASR phrase processing operation can match a spoken utterance against at least one entry within the selected phrase-based grammar. At least one of the grammar option weights can be automatically adjusted based upon the feedback to improve accuracy of the phrase-based grammar.
Owner:NUANCE COMM INC
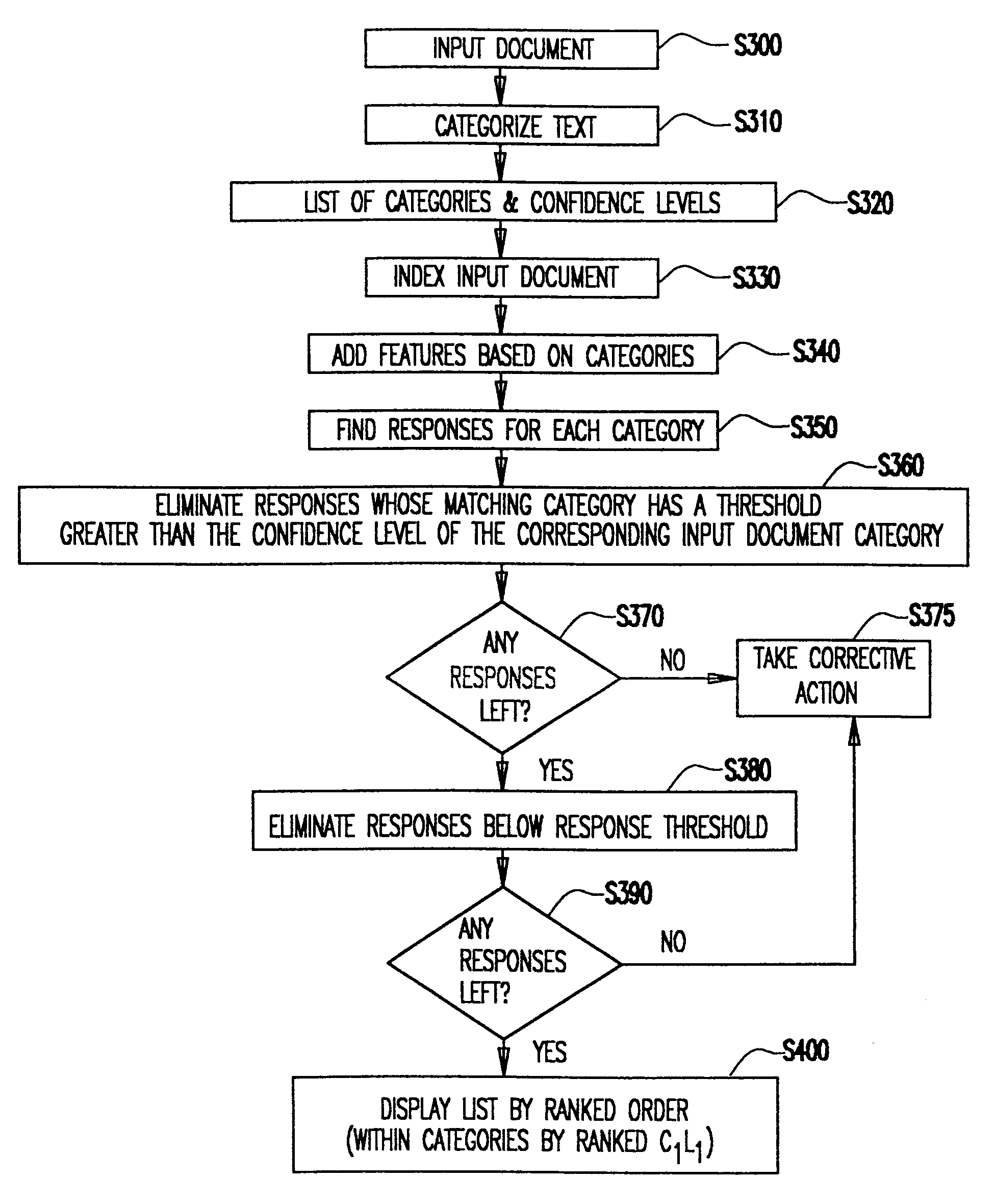
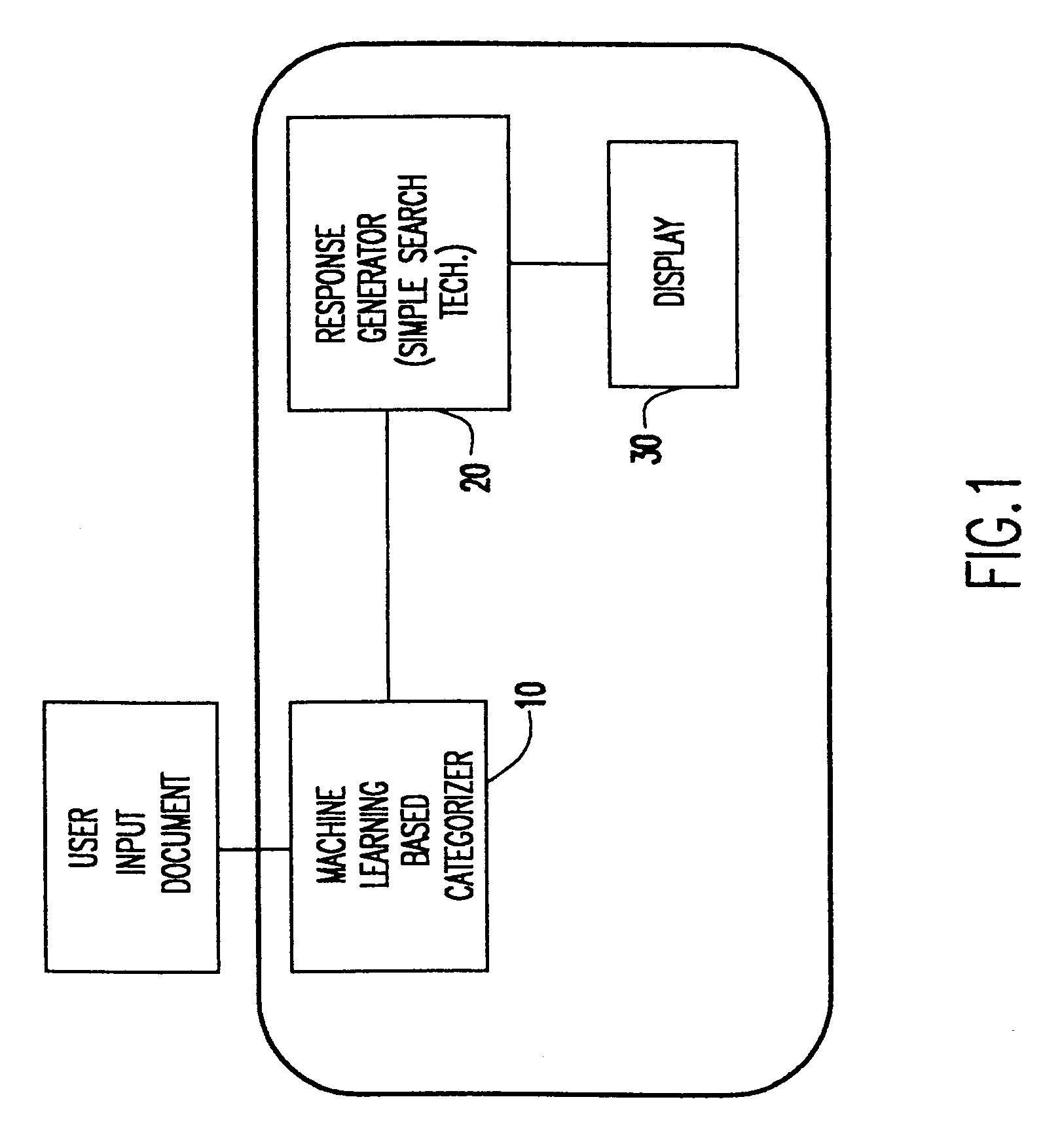
Two stage automated electronic messaging system
InactiveUS6418434B1Accurate informationImproved oddsData processing applicationsDigital data information retrievalWeb siteCustomer representative
A two stage electronic messaging system and method of use that automatically and accurately responds to user queries (e.g., input documents) using a two stage searching and retrieval system. The two stages system includes fast document-matching techniques (e.g., "weak" search techniques) in combination with more advanced categorization and text-search techniques (e.g., machine learning and other semi-automated techniques). The two stage searching and retrieval system may be used via the Internet, an intranet, LAN or other similar system, and may be used for providing requested information to a user (e.g., customer, employee, customer representative and the like) via a content rich web site, a propriety database or any computer related help system.
Owner:IBM CORP
Automated generation of spam-detection rules using optical character recognition and identifications of common features
InactiveUS20090077617A1Efficient managementComputer security arrangementsData switching networksElectronic communicationText string
In a spam detection method and system, optical character recognition (OCR) techniques are applied to a set of images that have been identified as being spam. The images may be provided as the initial training of the spam detection system, but the preferred embodiment is one in which the images are provided for the purpose of updating the spam-detection rules of currently running systems at different locations. The OCR generates text strings representative of content of the individual images. Automated techniques are applied to the text strings to identify common features or patterns, such as misspellings which are either intentionally included in order to avoid detection or introduced through OCR errors due to the text being obscured. Spam-detection rules are automatically generated on the basis of identifications of the common features. Then, the spam-detection rules are applied to electronic communications, such as electronic mail, so as to detect occurrences of spam within the electronic communications.
Owner:BARRACUDA NETWORKS
Methods and apparatus for pre-filtered access control in computing systems
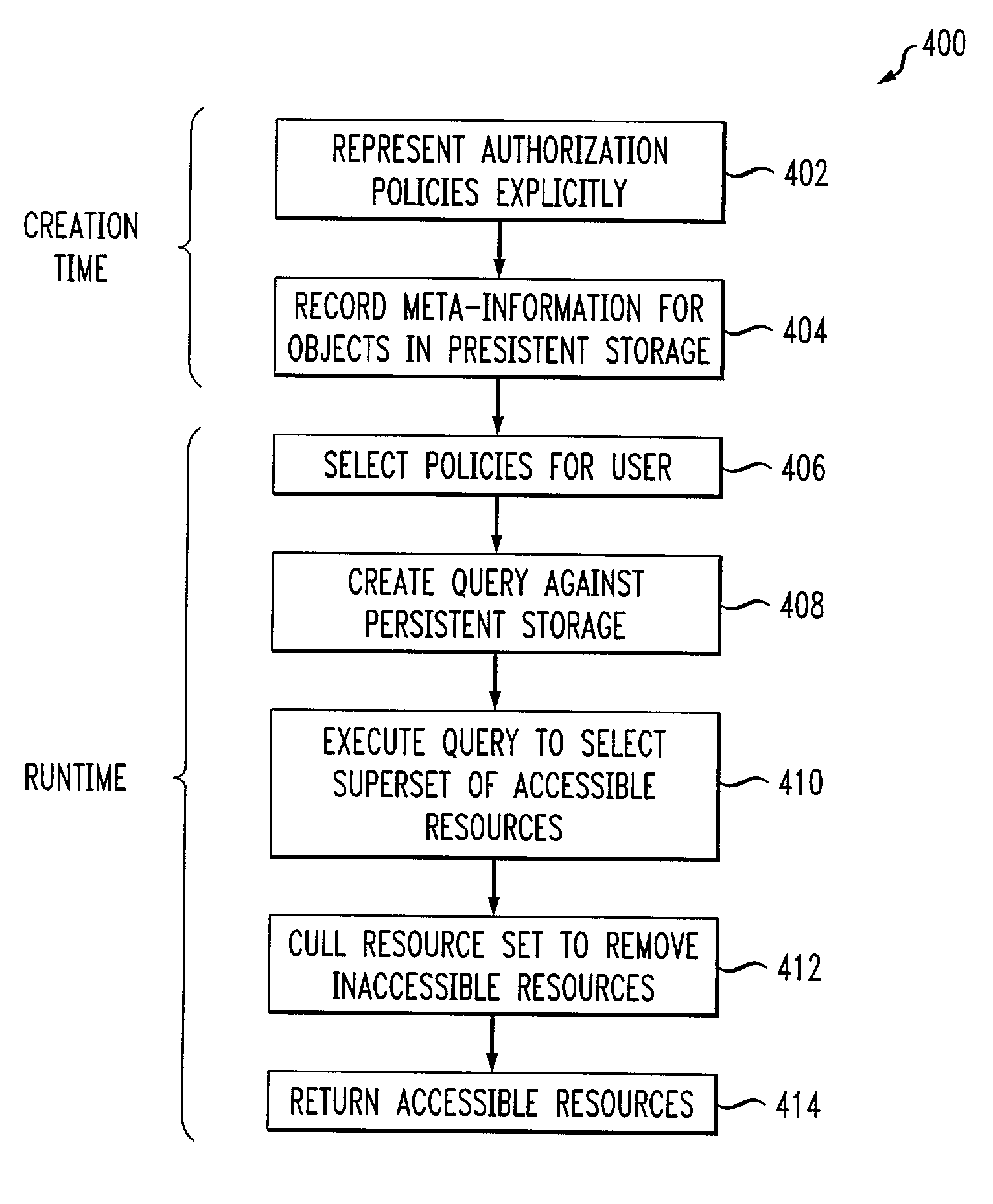
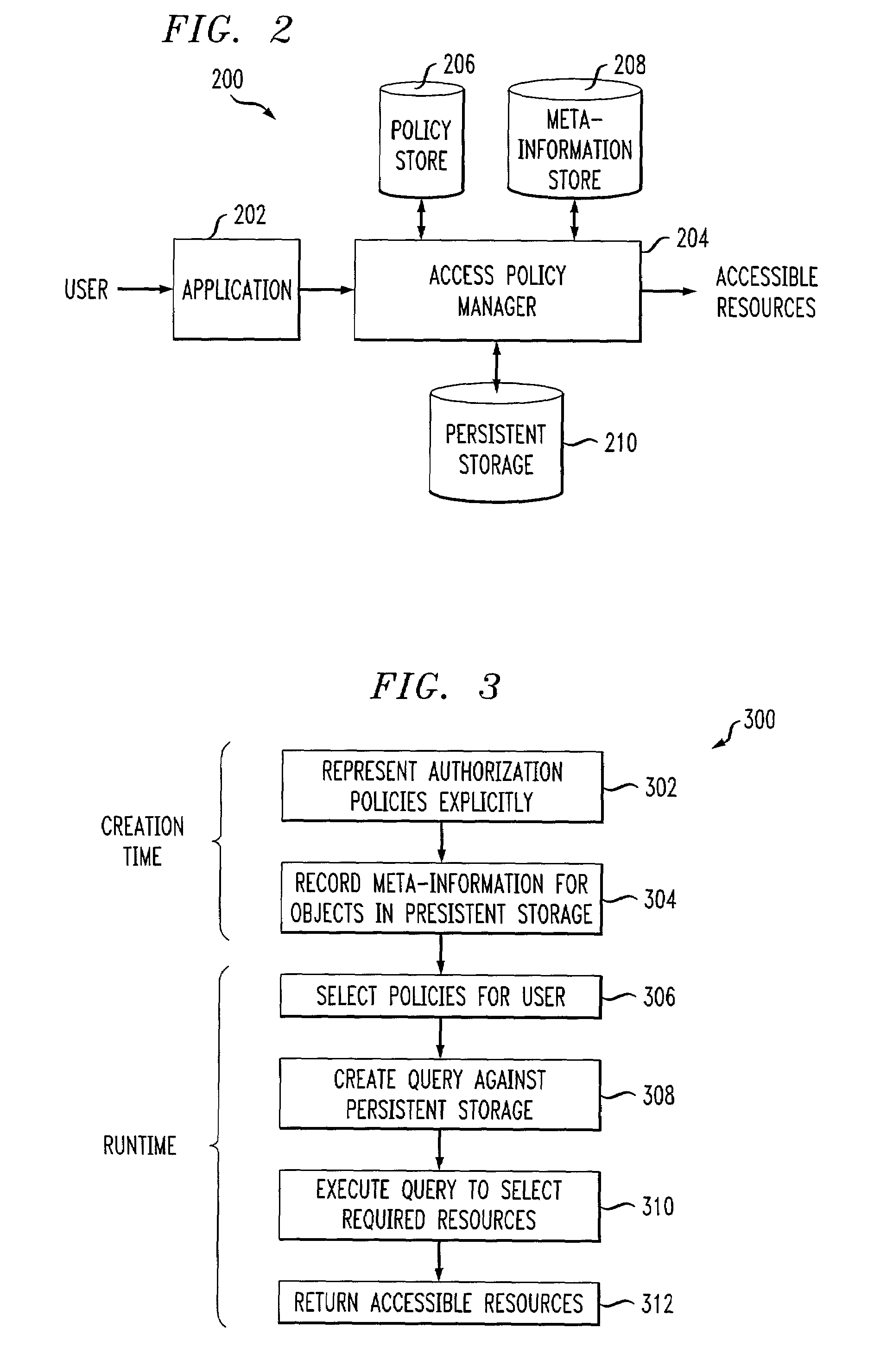
ActiveUS7216125B2Generate efficientlyProvide goodData processing applicationsDigital data processing detailsEngineeringComputing systems
An automated technique implemented in a computer system for selecting one or more resources on which a principal is authorized to perform at least one action comprises the following steps / operations. First, one or more authorization policies that apply to a given principal are selected. Then, the one or more authorization policies are transformed based on meta-information associated with the one or more resources so as to form a query against a resource store that selects the one or more resources on which the one or more authorization policies allow the given principal to perform the at least one action. The query may then be executed to select the one or more resources from the resource store. In another automated technique, the query may be formed without use of the one or more authorization policies, but where the policies are used to remove unauthorized resources from the superset of resources returned as a result of query execution. The techniques may return no resources on which the user is allowed to perform an action, if, for example, no such resources are stored in the resource store. Also, it may also be that no authorization policy applies to the user.
Owner:IBM CORP
Automated tagging of documents
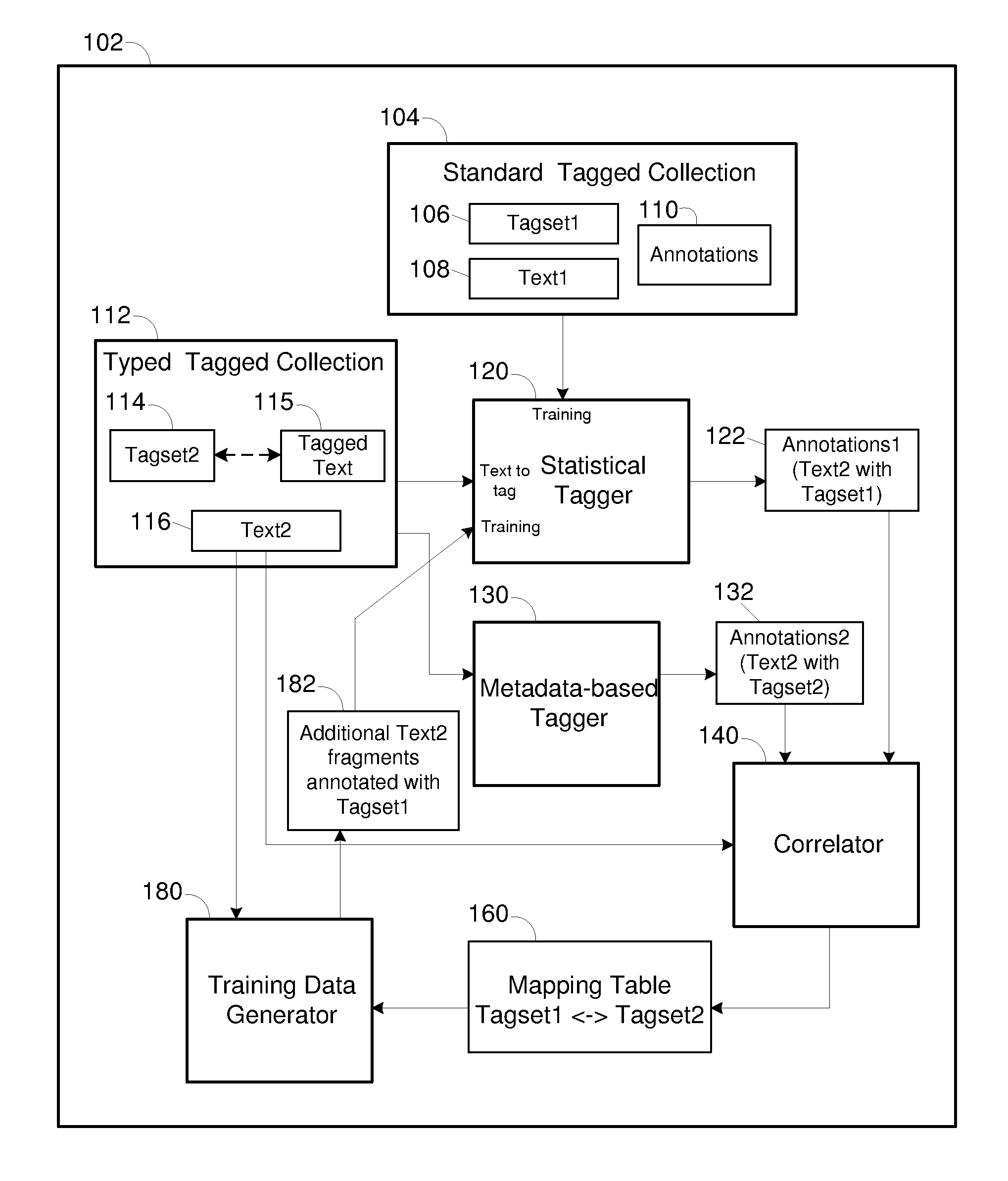
ActiveUS20090281970A1Improve accuracySemantic analysisDigital computer detailsDocument preparationDocumentation
An automated technique for tagging documents includes using a semantic tagger to generate an annotation that associates a standard tag with a first text fragment of the user-defined document, wherein the tagger is trained on a standard document annotated with a standard tag, associating the first user-defined tag with a second text fragment of the user-defined document in response to the second text fragment matching a value associated with the first user-defined tag, and establishing a mapping between the standard tag and the first user-defined tag in response to existence of a requisite correlation between the standard tag and the user-defined tag. The technique may further include selecting from the user-defined document a tagged text fragment that is associated with a second user-defined tag, and providing the tagged text fragment and a standard tag associated by the mapping with the second user-defined tag to the tagger as additional training input.
Owner:R2 SOLUTIONS
Method and system for dynamically arranging multiple product images in a preconfigured panel on an electronic display
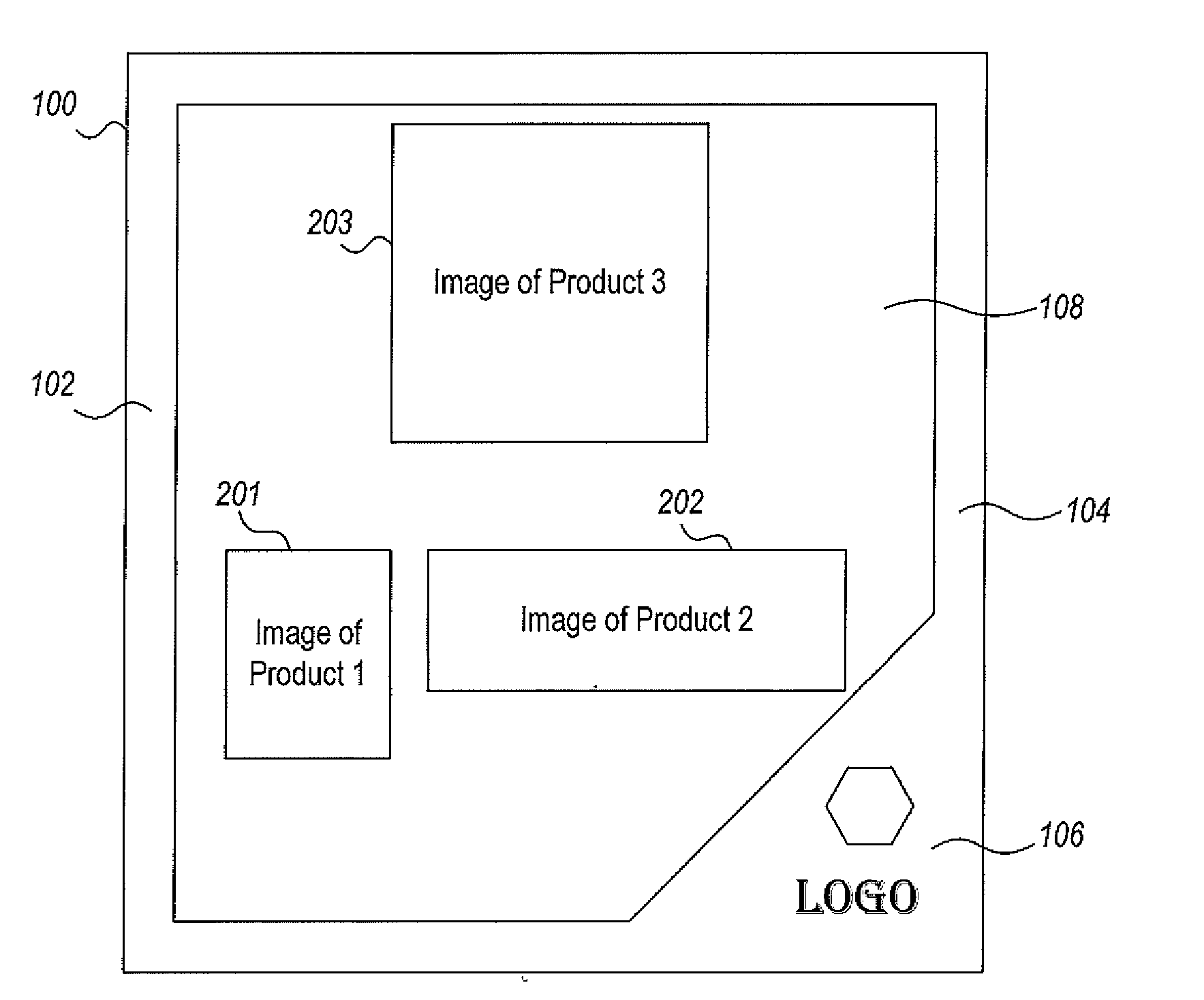
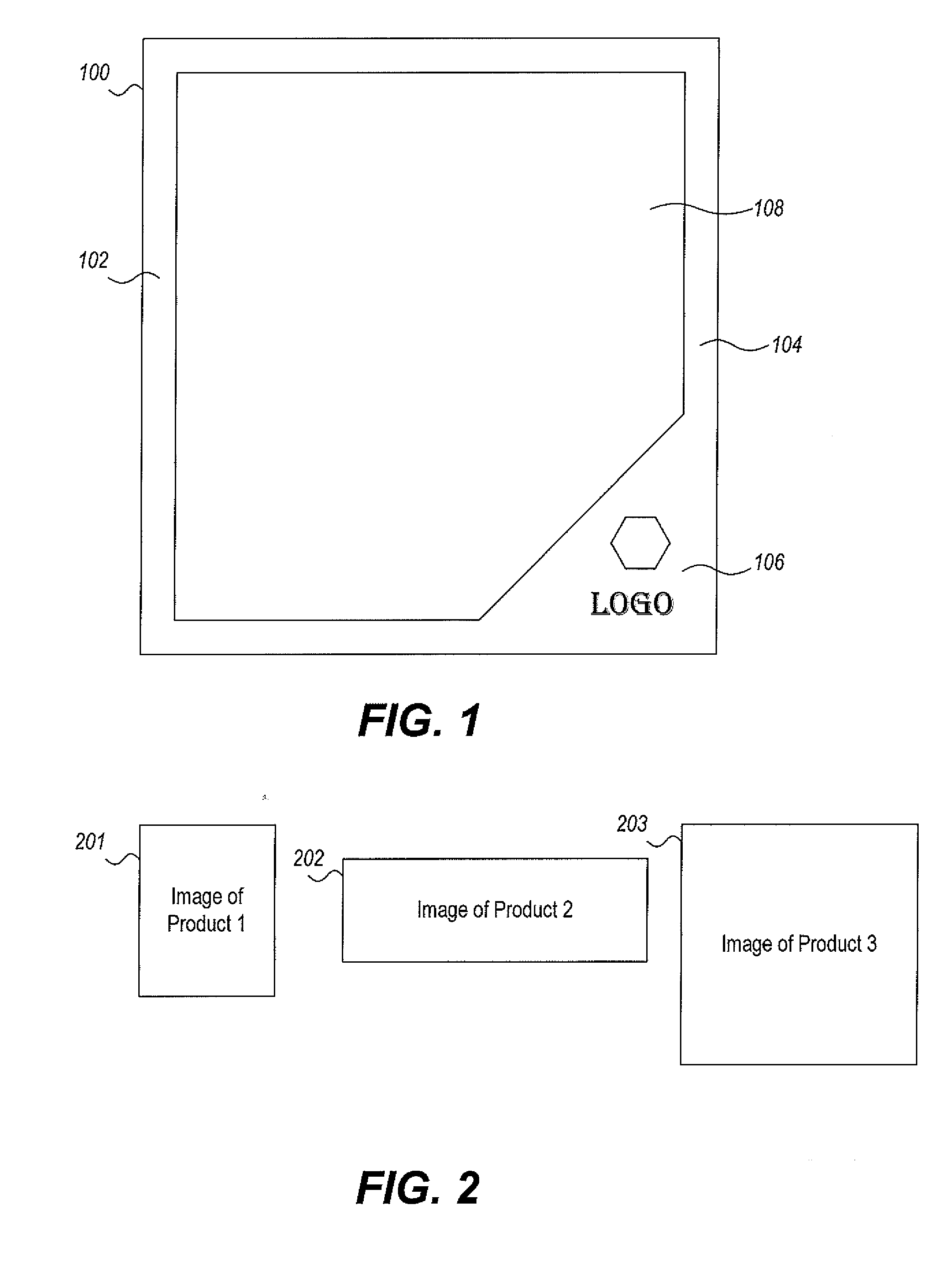
InactiveUS20100321405A1Reduce arrangementReduce workloadGeometric image transformationCathode-ray tube indicatorsComputer visionProduct image
Owner:VISTAPRINT SCHWEIZ
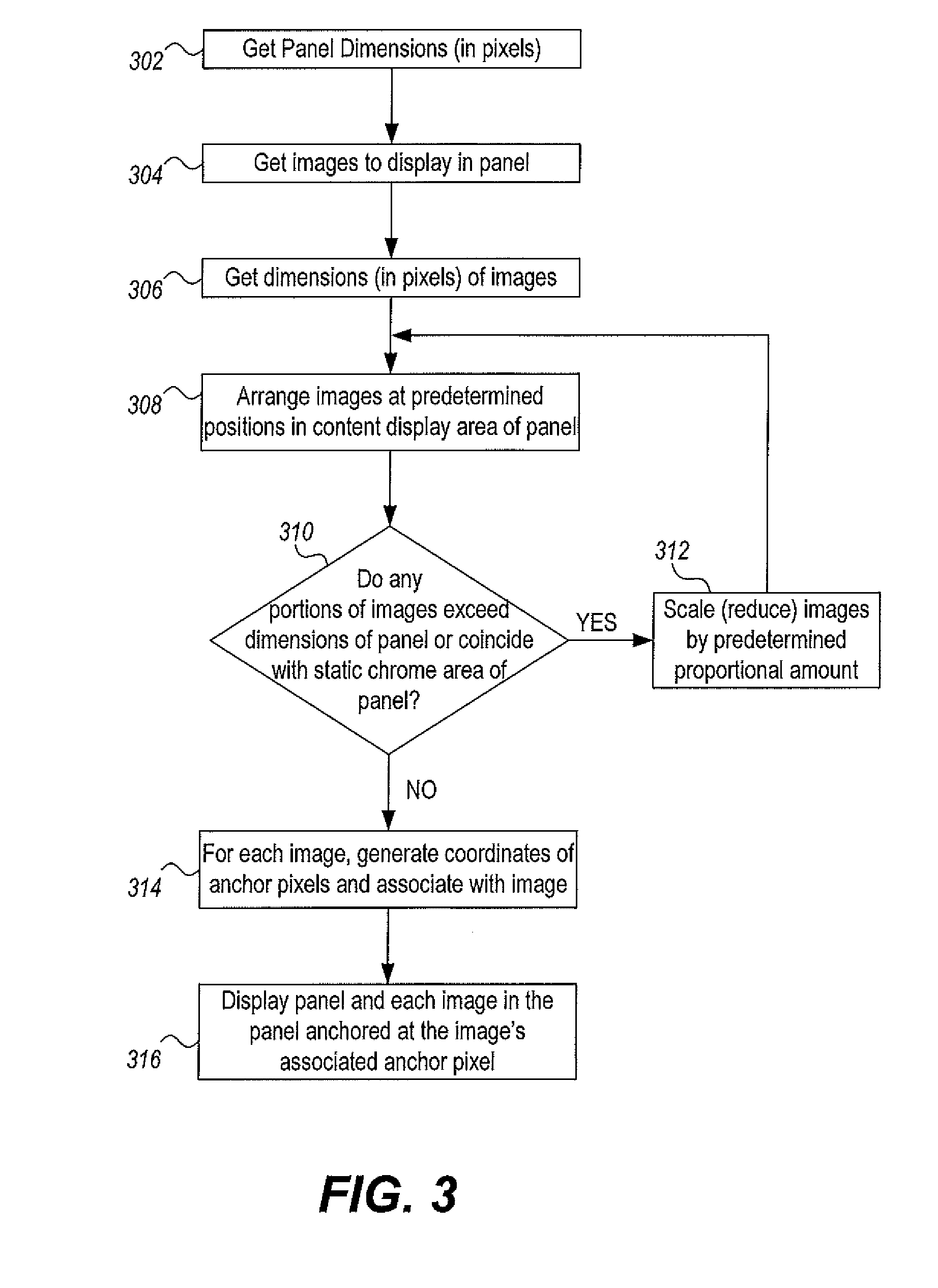
Automated and customizable generation of efficient test programs for multiple electrical test equipment platforms
InactiveUS20050273685A1Electronic circuit testingError detection/correctionDevice materialTest algorithm
Automating techniques provide a way to create efficient test programs for characterizing semiconductor devices, such as those on a silicon die sample. Typically, test program creation is a drawn out process involving data entry for every test to be run as part of the test program. The described techniques improve test algorithm selection and automatically populate the test algorithm data in creating the test program. The automatic population may occur by accessing test structure, header, and test algorithm catalogs. The test structure catalog contains physical data for the test program, while the header catalog contains global parameter values. The test algorithm catalog has all of the various test algorithms that may be run in a given test, where these test algorithms may be in a template form and specific to any number of different test language abstractions. After test program creation, a validation process is executed to determine if the test program data is valid. Invalid data may be flagged, in an example. Once validated, techniques are described for converting the validated test program into an executable form, by formatting the various test algorithm data in the test program into a form compatible with the applicable test language abstraction selected by the user or the tester.
Owner:INTEL CORP
Methods and Apparatus for Managing Computing Deployment in Presence of Variable Workload
ActiveUS20070240162A1Efficient and effectiveAccommodating unanticipated workloadResource allocationReliability/availability analysisWorkloadAdmission control
Automated or autonomic techniques for managing deployment of one or more resources in a computing environment based on varying workload levels. The automated techniques may comprise predicting a future workload level based on data associated with the computing environment. Then, an estimation is performed to determine whether a current resource deployment is insufficient, sufficient, or overly sufficient to satisfy the future workload level. Then, one or more actions are caused to be taken when the current resource deployment is estimated to be insufficient or overly sufficient to satisfy the future workload level. Actions may comprise resource provisioning, resource tuning and / or admission control.
Owner:GOOGLE LLC
System and method for spam identification
InactiveUS20060248072A1Improve the search experienceMemory loss protectionDigital data processing detailsSpammingResult set
A system and method are provided for improving a user search experience by identifying spam results in a result set produced in response to a query. The system may include a user interface spam feedback mechanism for allowing a user to indicate that a given result is spam. The system may additionally include an automated spam identification mechanism for implementing automated techniques on the given result to determine whether the given result is spam. The system may further include a merging component for merging the determinations of the user interface spam feedback mechanism and the automated spam identification mechanism for deriving an indicator of the likelihood that a given result is spam.
Owner:MICROSOFT TECH LICENSING LLC
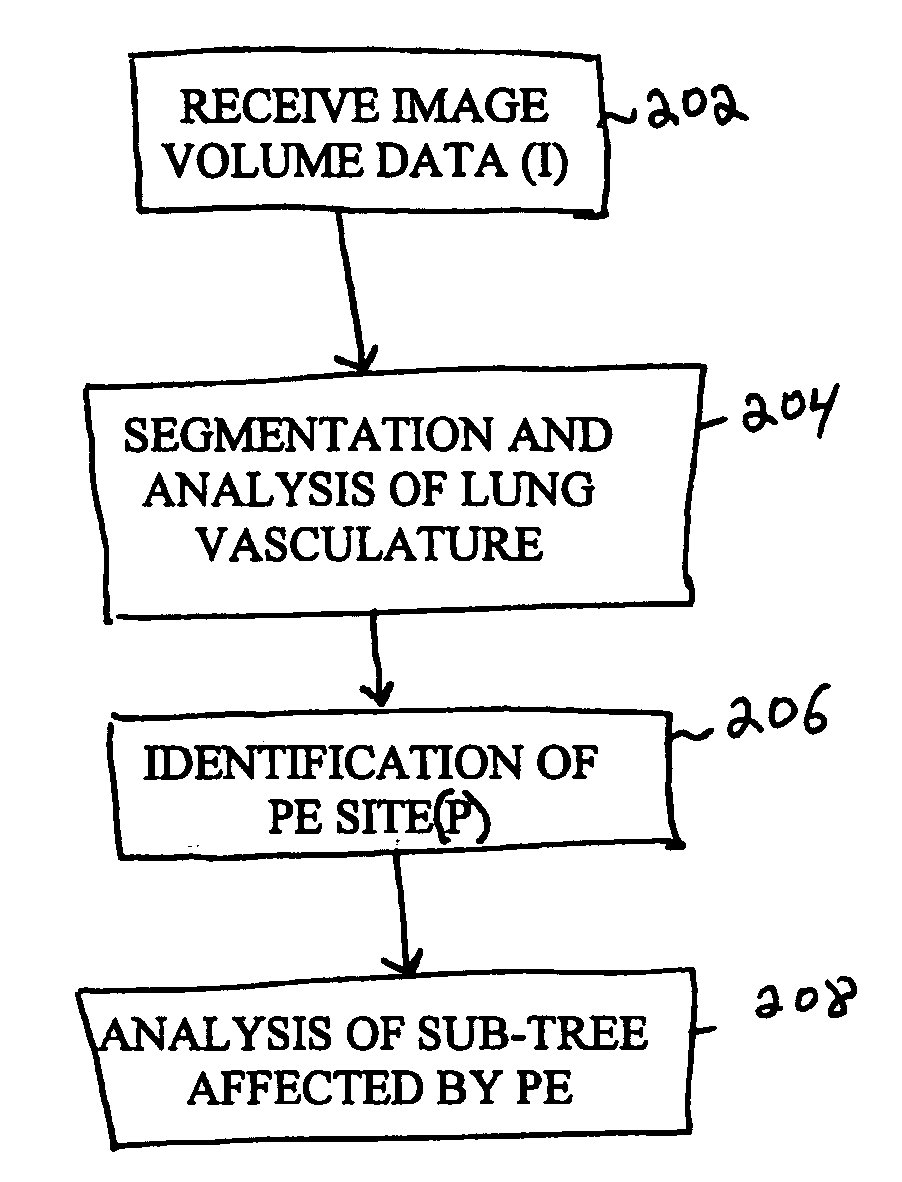
Method and apparatus for embolism analysis
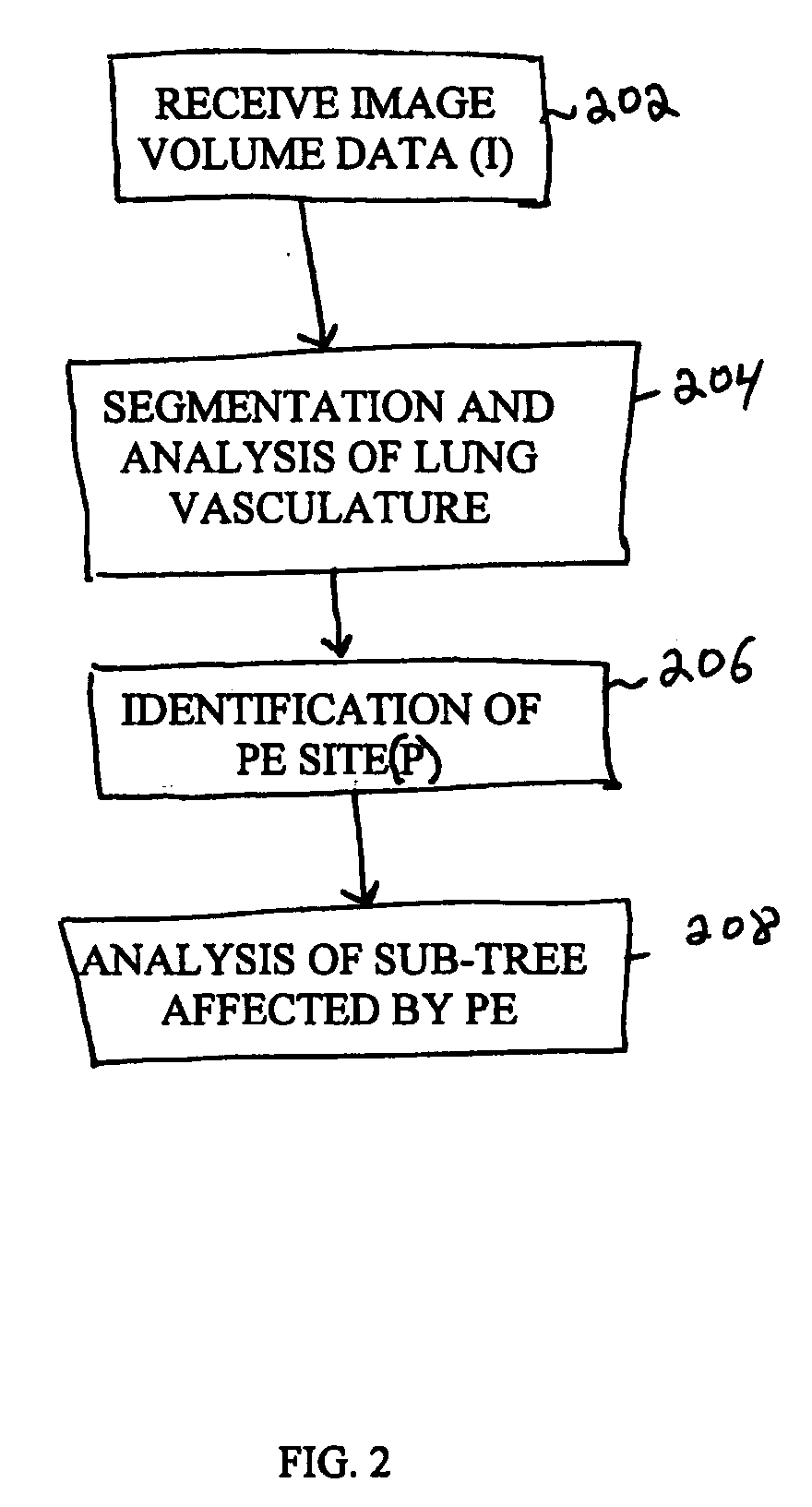
Disclosed is an automated technique for analyzing the affected region due to an embolism in an organ. A segmented image of the organ vasculature is generated using image volume data received, for example, from a Computed Tomography (CT) machine. An embolus is then identified (either manually or automatically) within the segmented image, and the volume of the organ affected by the embolism is automatically determined. The volume of the organ affected by the embolism may be determined by computing a sub-tree within the segmented image, where the sub-tree comprises vessels that are distal to the identified embolus point. In one embodiment, the sub-tree is generated by determining a plane perpendicular to a vessel at the embolus point such that the sub-tree comprises a distal portion of the vasculature with respect to the plane. Unwanted overlapping trees are identified (e.g., by analyzing branch angles) and removed from the sub-tree. The volume of the organ affected by the embolism is determined by calculating a volume of the organ that is perfused by the sub-tree. The affected volume may be adjusted by scaling the volume based on the percentage occlusion of the partial embolus.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC +1
Data processing system and method for detecting mandatory relations violation in a relational database
InactiveUSRE40235E1Increase speedEasily expandableData processing applicationsDigital data processing detailsRelational systemRelational database
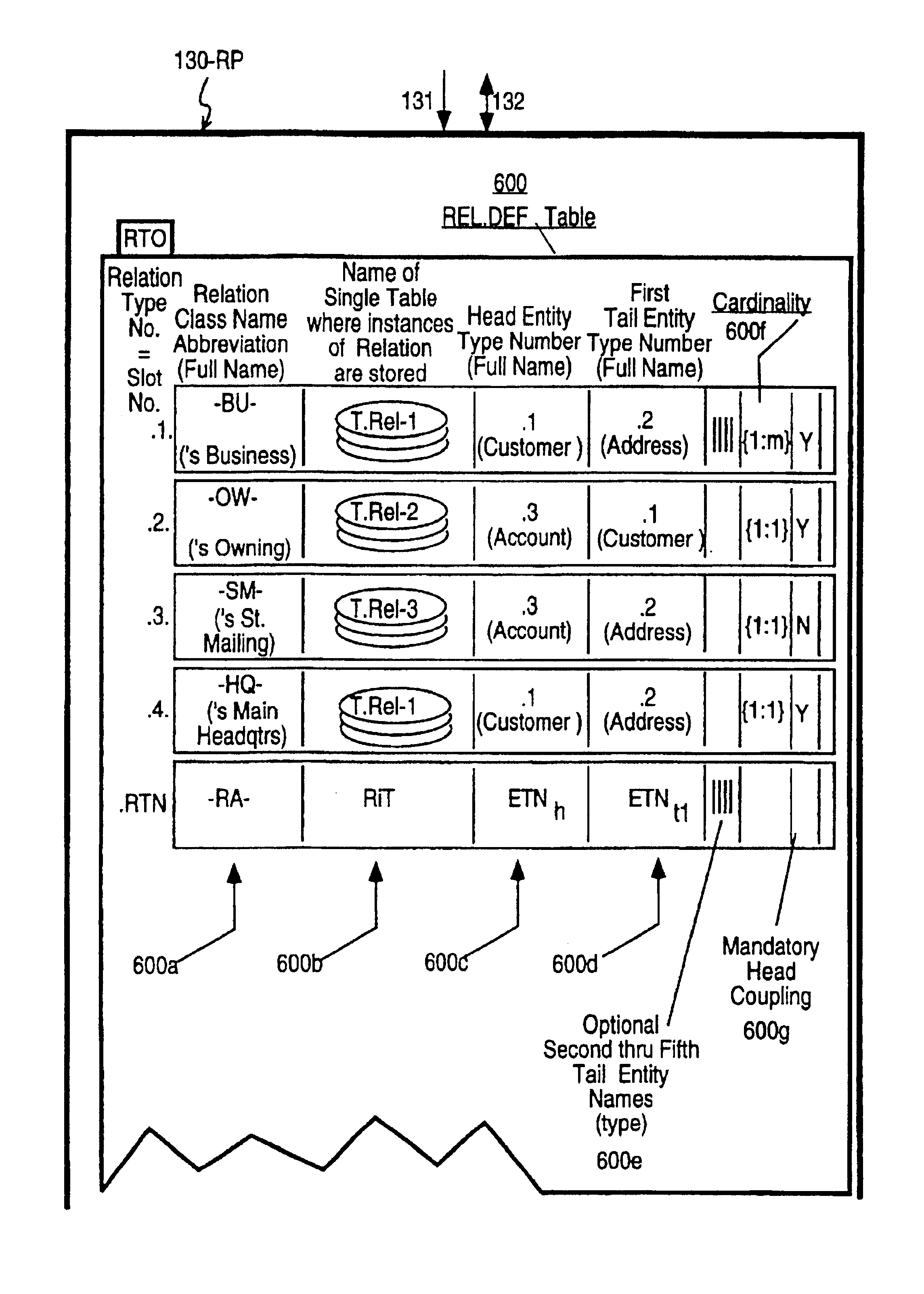
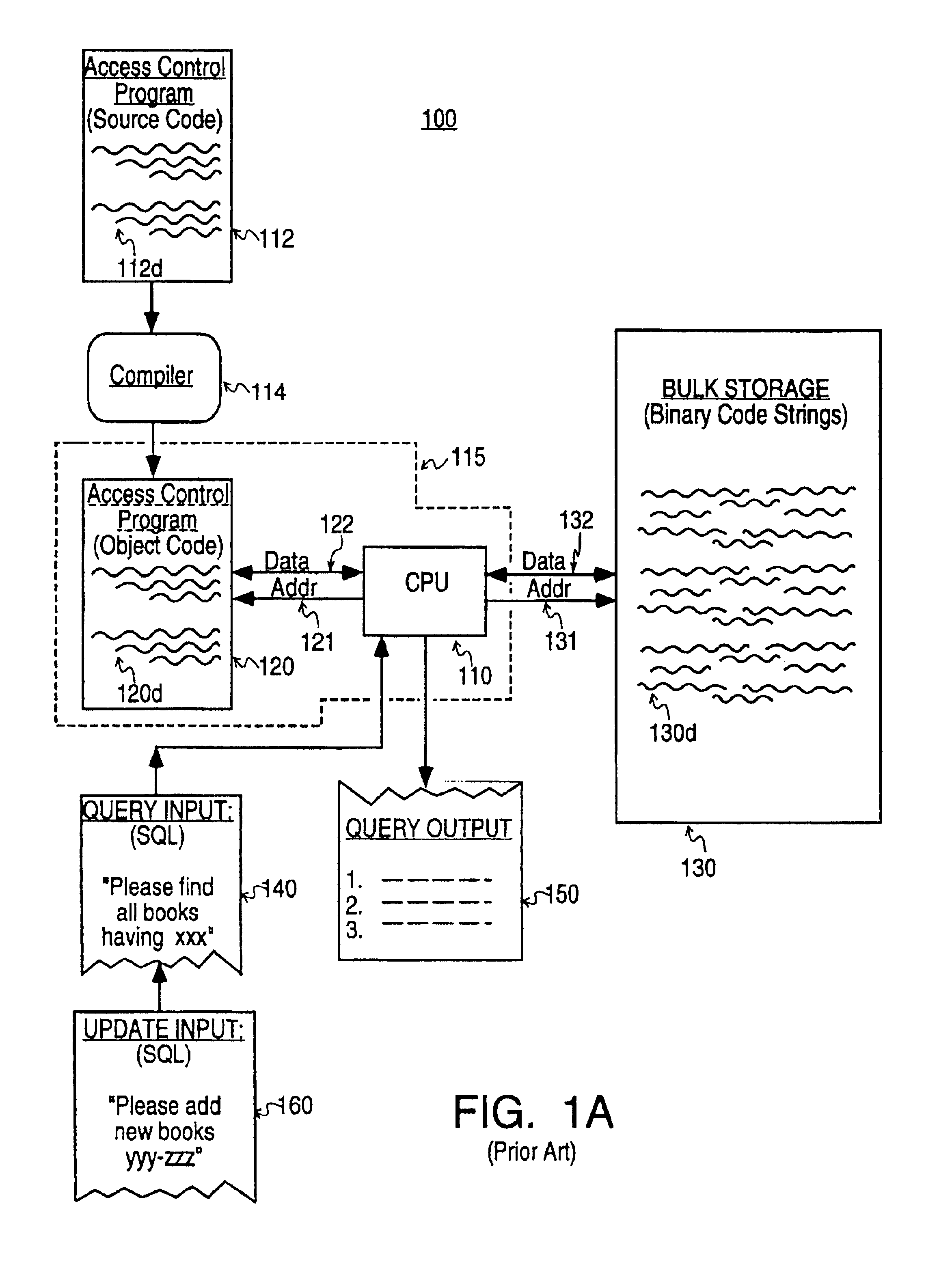
Machine automated techniques are described for a method of data processing called Relationships Processing. A computing system is disclosed which provides for the high speed recording and extraction of data objects (entities) and for the development of data representing a queried relationship between the entities. Furthermore, methods and systems are disclosed to detect mandatory relations violation between entities by examining whether certain relations exist. The system is expandable to handle the relatively voluminous data bases of large commercial data repositories. A user defines a set of entities and allowed relationships between the entities. The user can expand this set of allowed entities and relationships at any time during the life of the system without reprogramming or compiling of computer program code or disrupting concurrent operational use of the system. Large systems can now be built that are no longer limited to the scope of design requirements known during initial system development. For a given set of defined relationships the system allows the user to perform complex inquiries (again without programming at the code level) that would normally require multiple nested inquiries to be coded programmatically and would not achieve the performance levels of the Relationships Processor.
Owner:FINANCIAL SYST TECH
Method of finishing a blade
ActiveUS20140373503A1Improve aerodynamic performanceFlat surfacePump componentsMetal-working apparatusEngineeringGas turbines
An automated technique for finishing gas turbine engine blades or vanes by generating a bespoke tooling path for each blade or vane. The bespoke tooling path is generated by scanning the aerofoil surface to generate a 3-D electronic representation of the surface. The 3-D electronic surface is then analysed to identify imperfections or defects, and then a machining path a generated through which the imperfections can be removed. The machining path is determined so as to smoothly blend the surface back to the underlying surface where the imperfections had been present. In this way, the resulting aerofoil, once machined, has optimized aerodynamic performance.
Owner:ROLLS ROYCE PLC
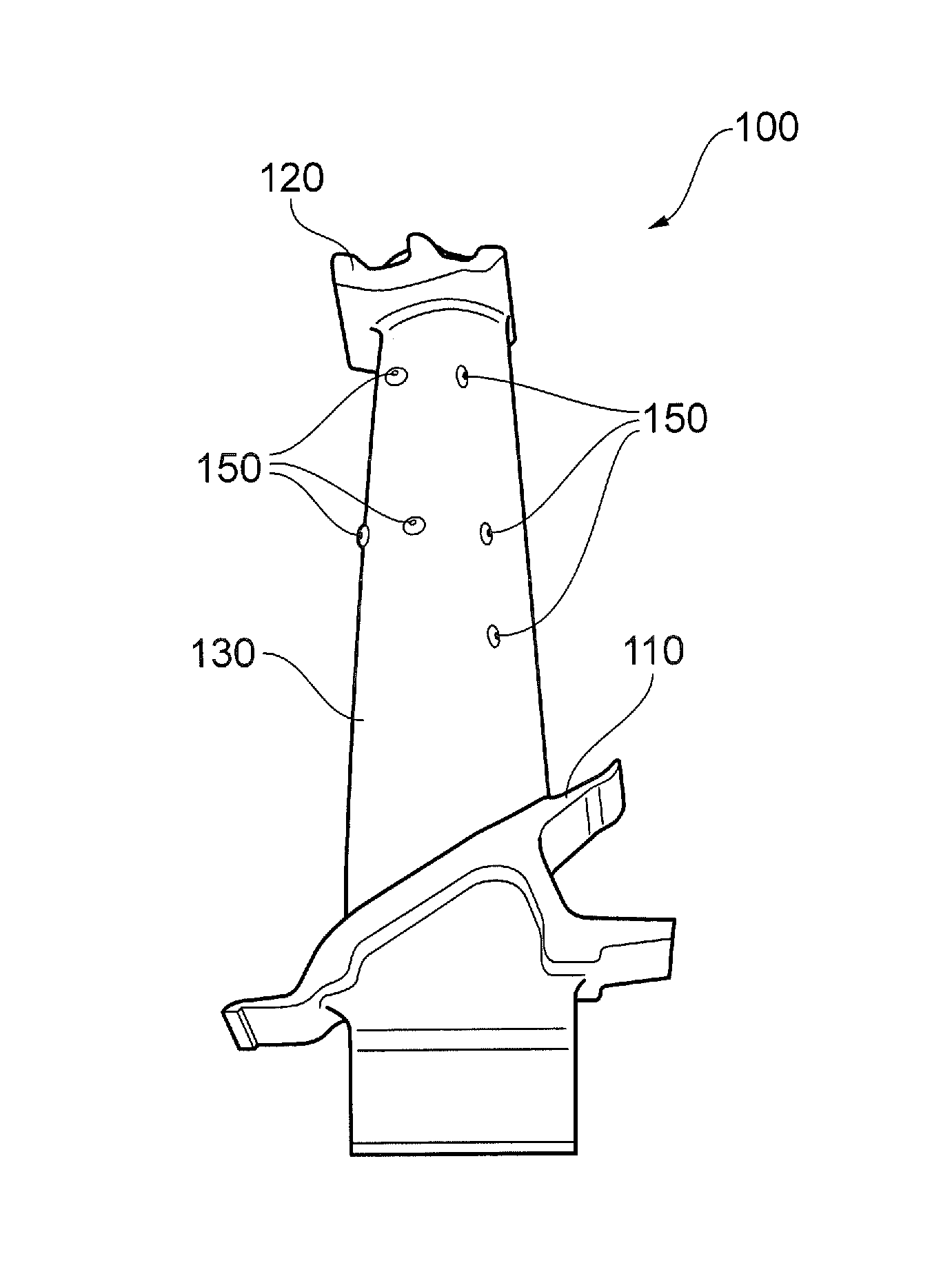
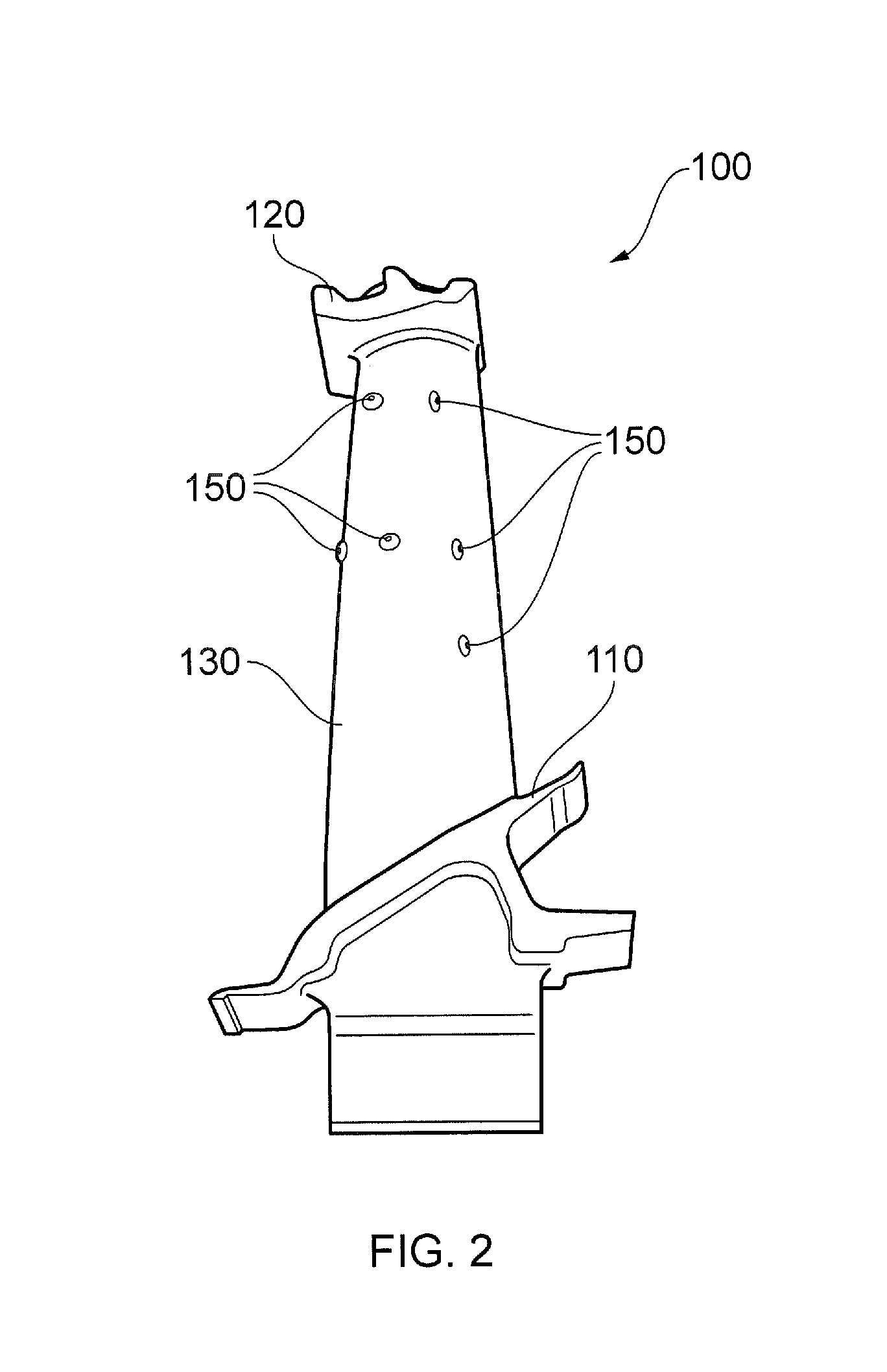
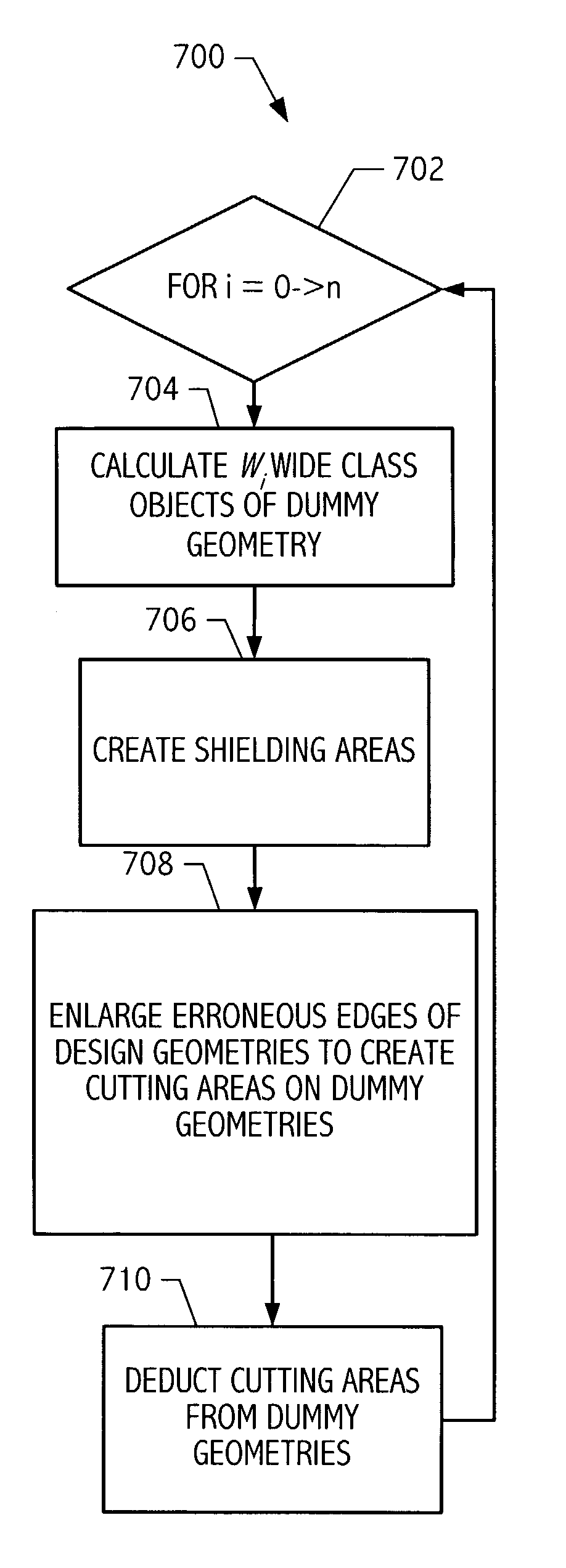
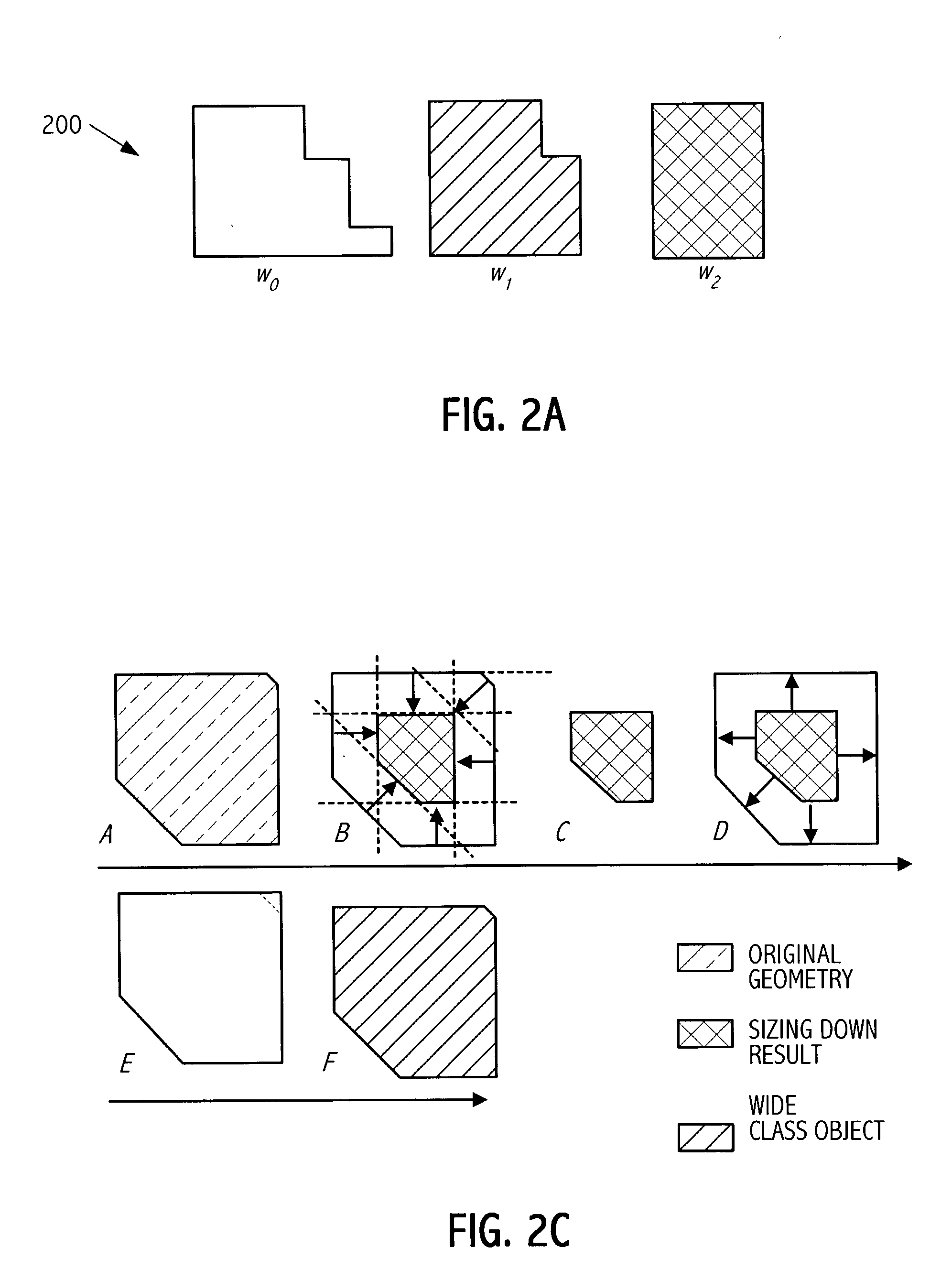
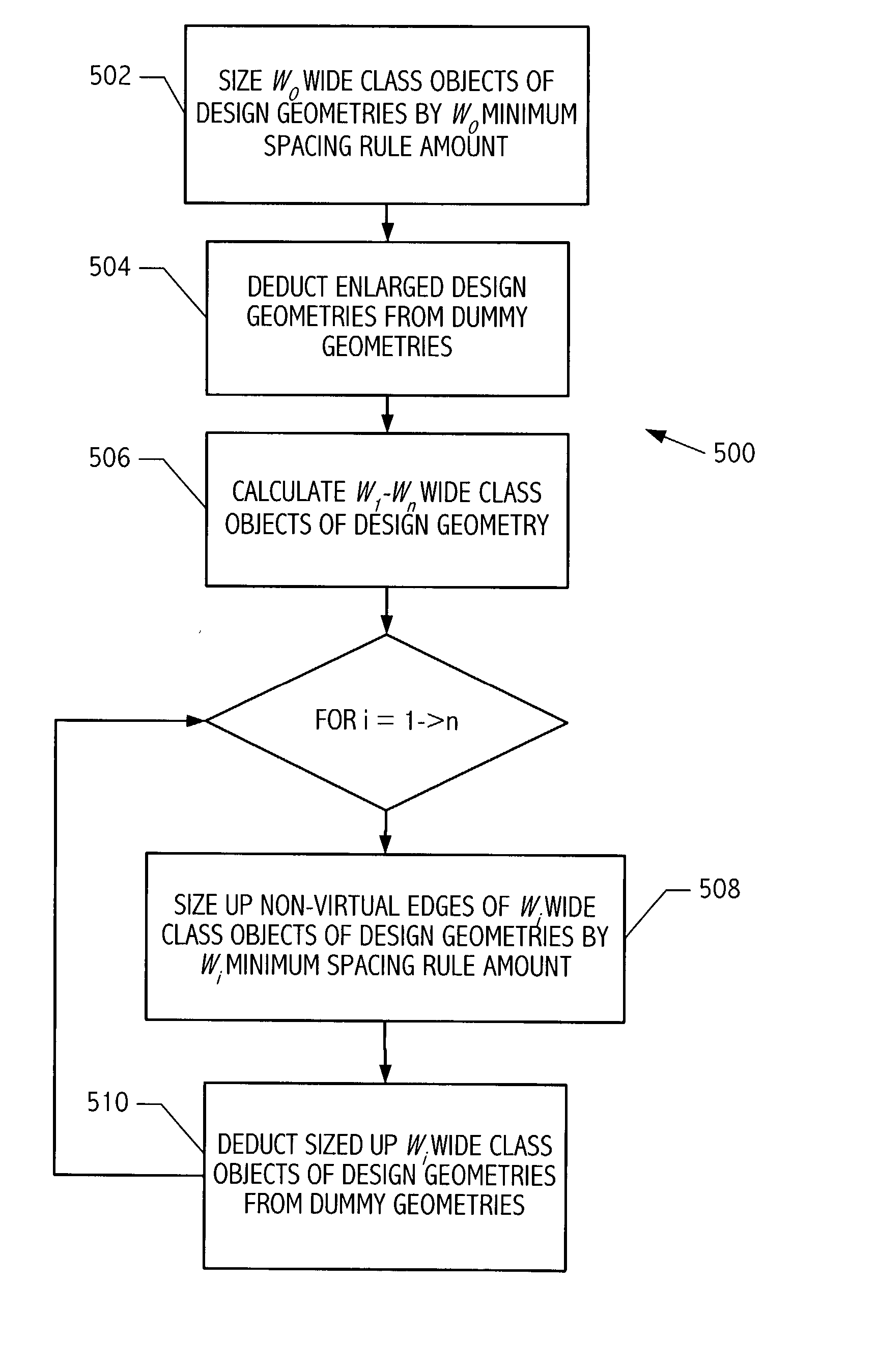
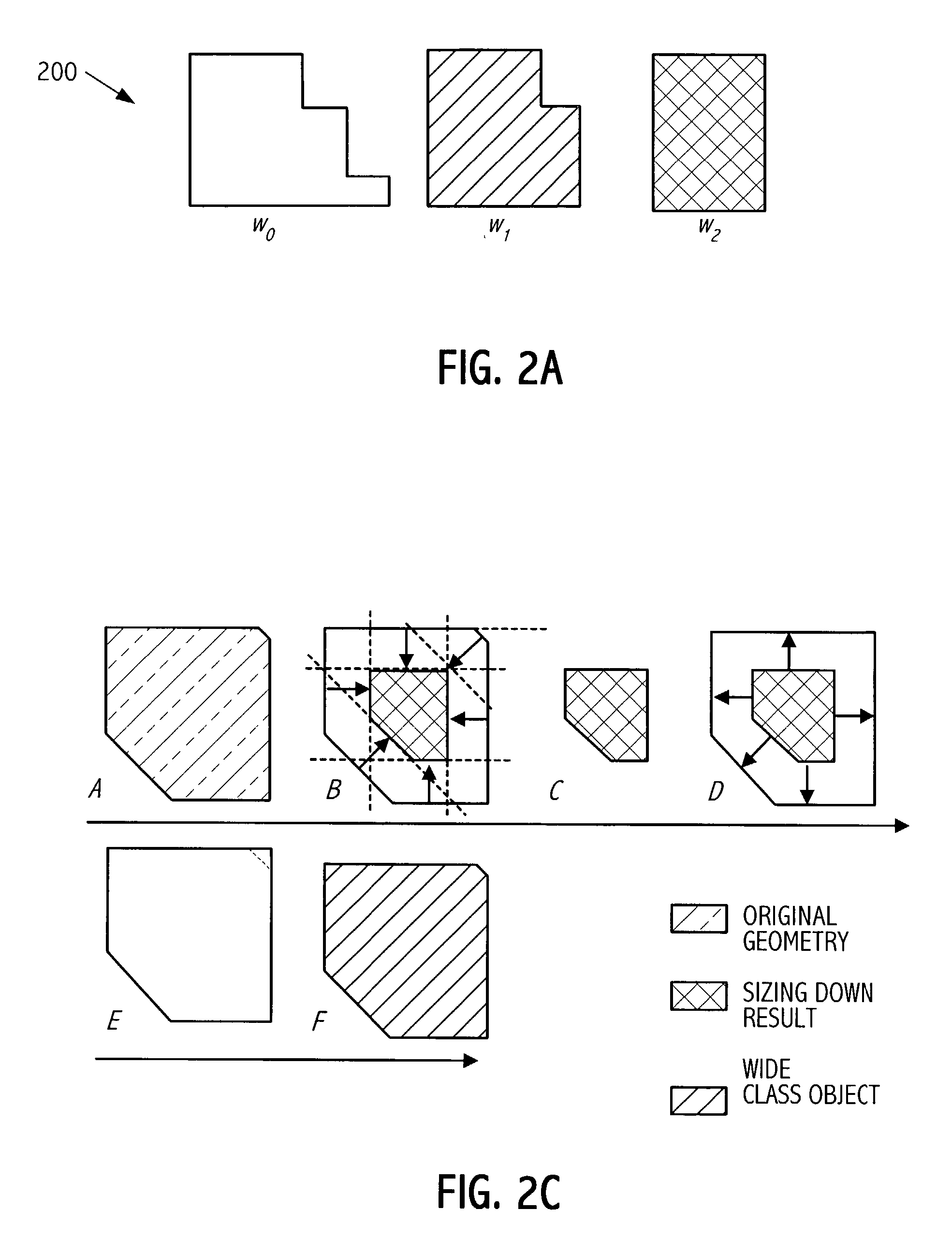
Correction of spacing violations between design geometries and wide class objects of dummy geometries
InactiveUS20040025125A1CAD circuit designSoftware simulation/interpretation/emulationEngineeringAutomated technique
Automated techniques to correct certain rule violations with respect to non-design geometries are used, simplifying and automating the design layout of an electronic circuit, whether embodied as a design encoding or as a fabricated electronic circuit. Correcting minimum spacing rule violations is accomplished by enlarging a design geometry at erroneous boundaries toward one or more non-virtual boundaries of a wide class object of a non-design geometry avoiding one or more shielding areas around one or more virtual edges of the wide class object of the non-design geometry creating an enlarged design geometry; and deducting the enlarged design geometry from the non-design geometry.
Owner:ORACLE INT CORP
Correction of width violations of dummy geometries
Automated techniques to correct certain rule violations with respect to non-design geometries are used, simplifying and automating the design layout of an electronic circuit, whether embodied as a design encoding or as a fabricated electronic circuit. Correcting minimum width rule violations of non-design geometries is accomplished by forming one or more cutting areas adjoining one or more erroneous edges of a non-design geometry, and deducting the cutting areas form the non-design geometry, splitting the non-design geometry into two or more remaining non-design geometries. Any slivers of remaining non-design geometries, i.e., any pieces that are smaller than a minimum size amount, are removed. Cutting areas are formed by stretching ends of erroneous edge segments by a minimum width rule amount and sizing the stretched edge segments which are inside the non-design geometry outward by a minimum spacing rule amount.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com