Patents
Literature
262 results about "Consent Type" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In common speech, consent occurs when one person voluntarily agrees to the proposal or desires of another. The concept of consent has been operationalized in several major contexts, including in law, medicine and sexual relationships. Types of consent include implied consent, expressed consent, informed consent and unanimous consent.
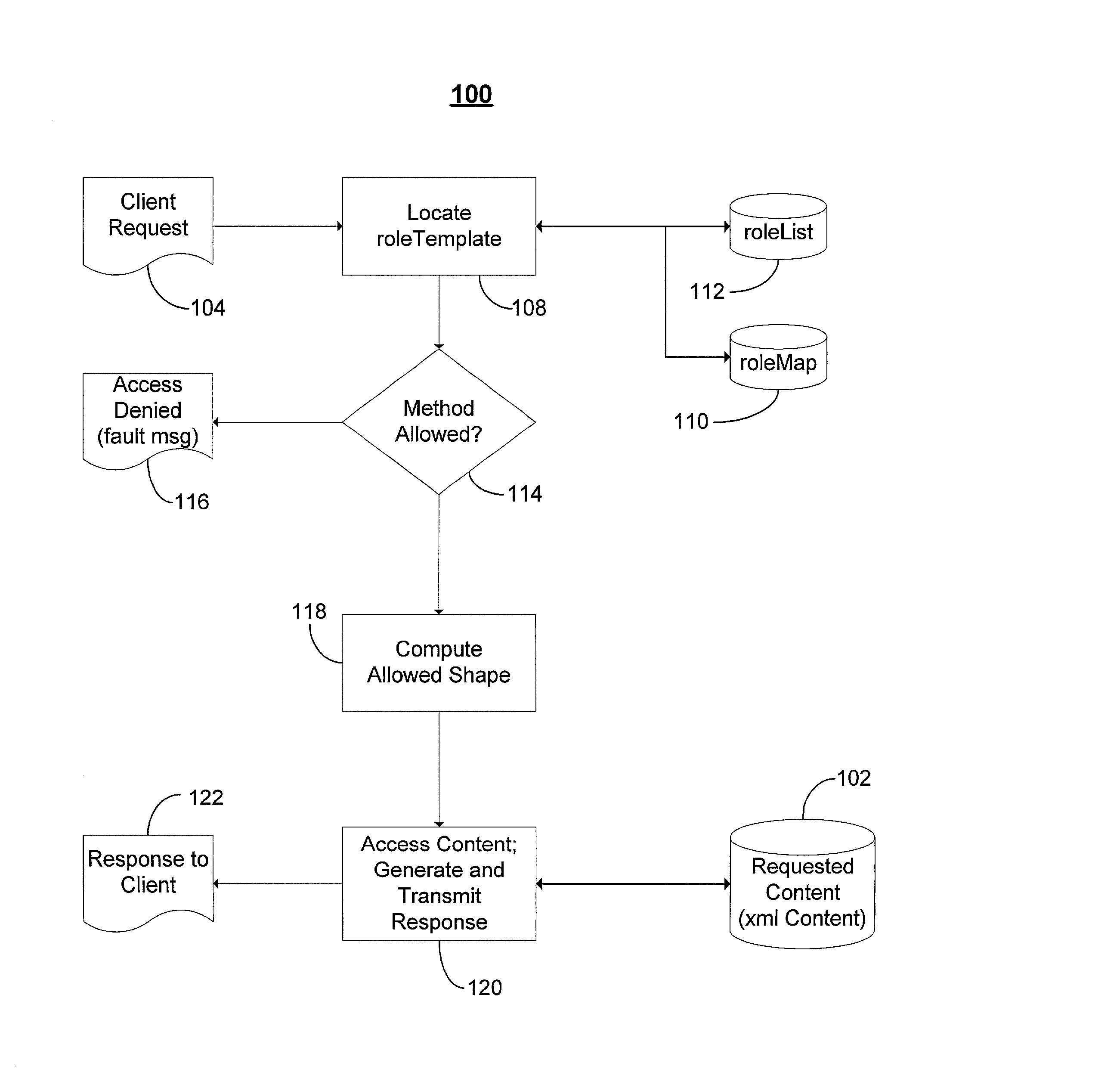
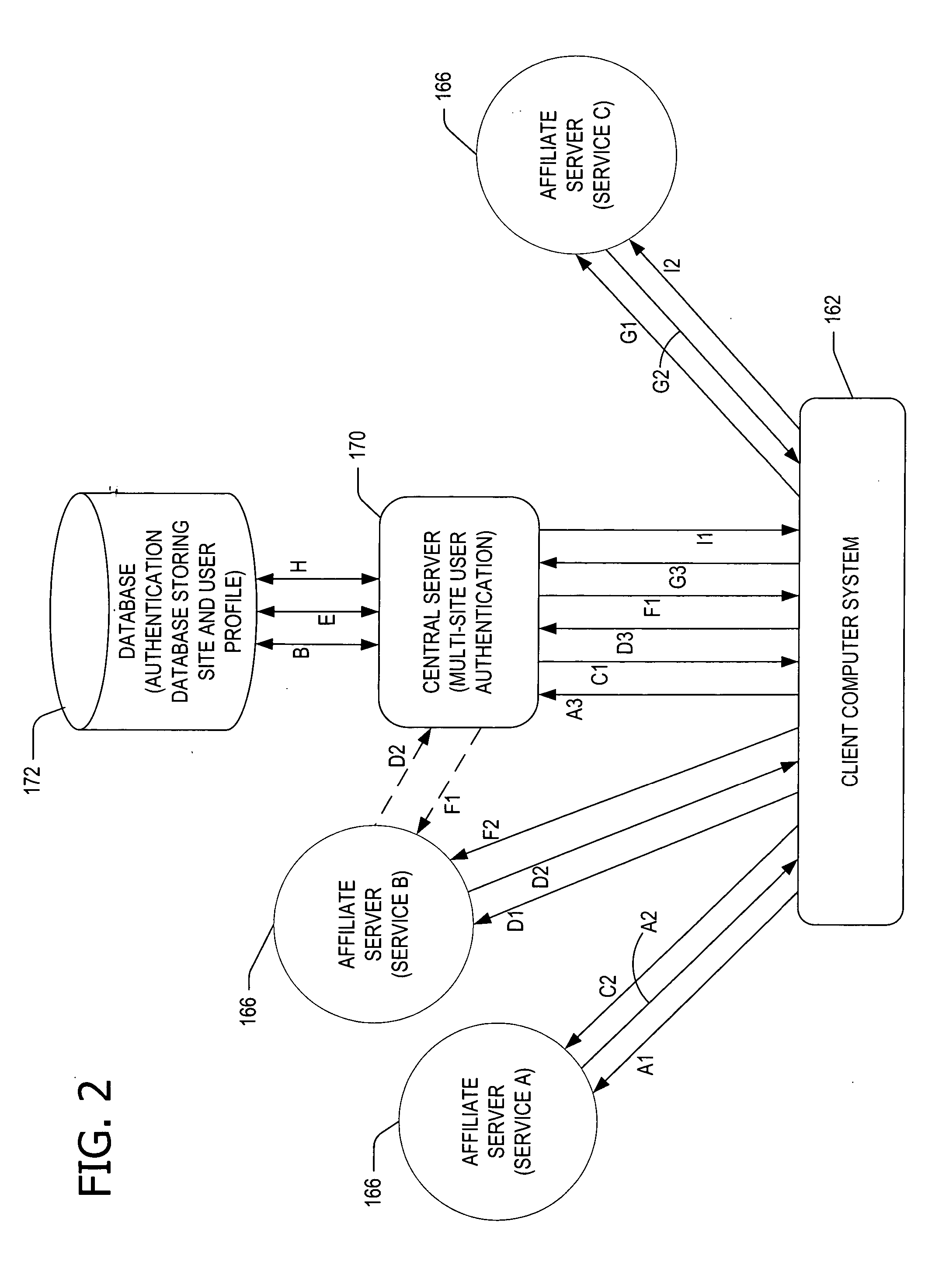
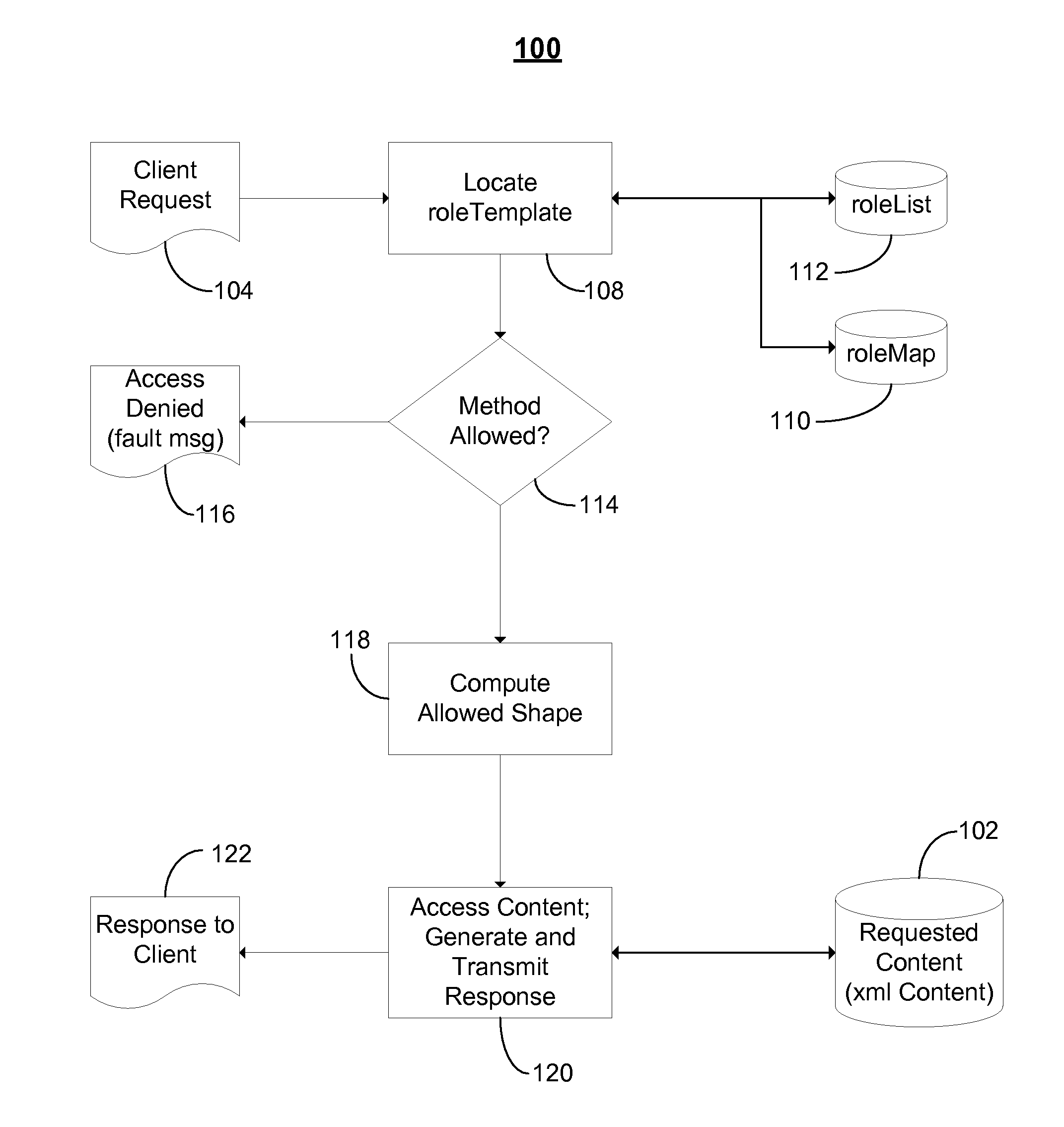
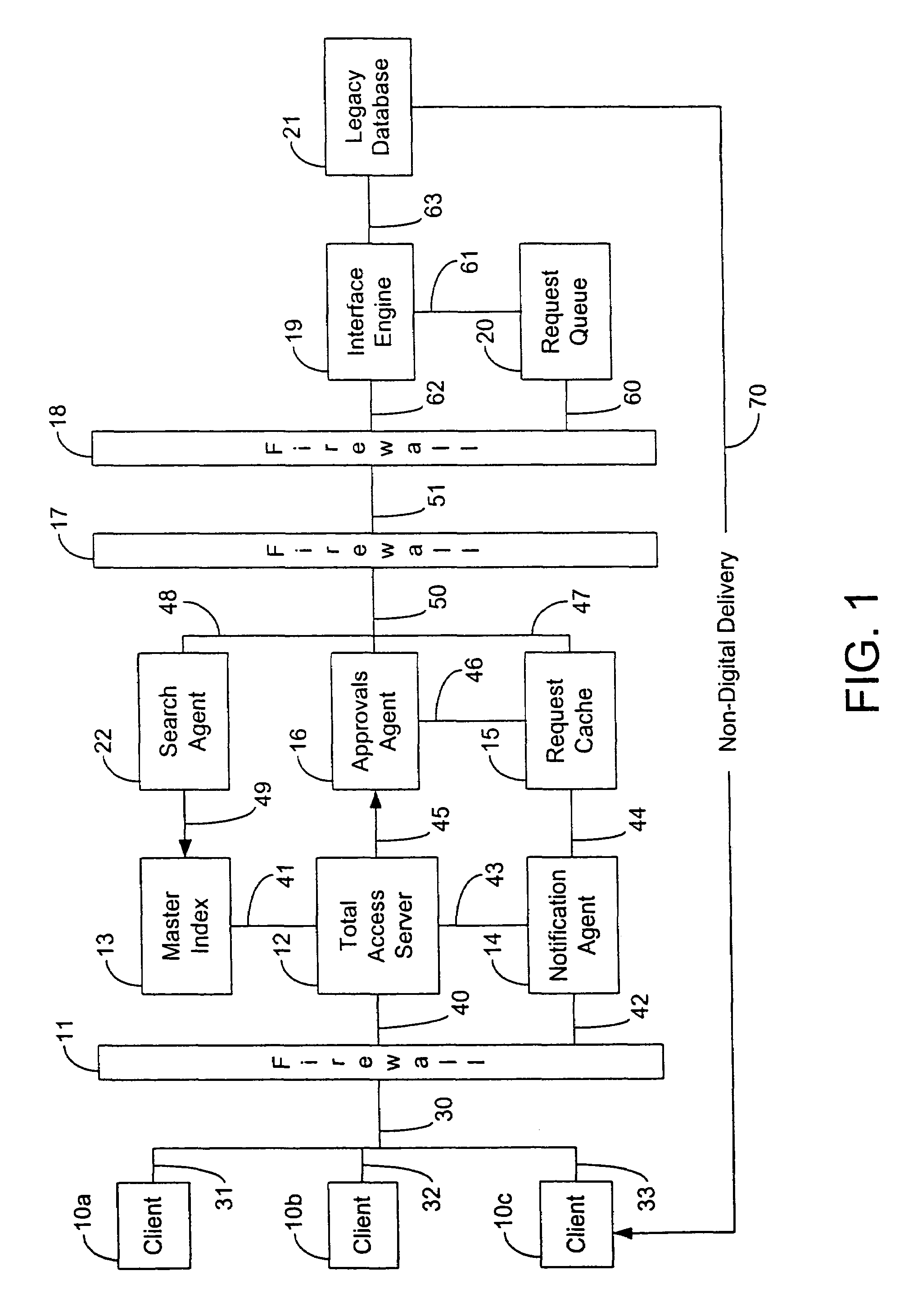
User-centric consent management system and method
ActiveUS7076558B1Access controlDigital data processing detailsAnalogue secracy/subscription systemsWeb serviceClient-side
In a network computing environment, a user-centric system and method for controlling access to user-specific information maintained in association with a web-services service. When a web-services client desires access to the user-specific information, the client sends a request. The request identifies the reasons / intentions for accessing the desired information. The request is compared to the user's existing access permissions. If there is no existing access permission, the request is compared to the user's default preferences. If the default preferences permit the requested access, an access rule is created dynamically and the client's request is filled, without interrupting the user. If the default preferences do not permit the request to be filled, a consent user interface may be invoked. The consent user interface presents one or more consent options to a party with authority to grant consent, thereby permitting the user to control whether the client's access will be filled.
Owner:MICROSOFT TECH LICENSING LLC
Personal choice biometric signature
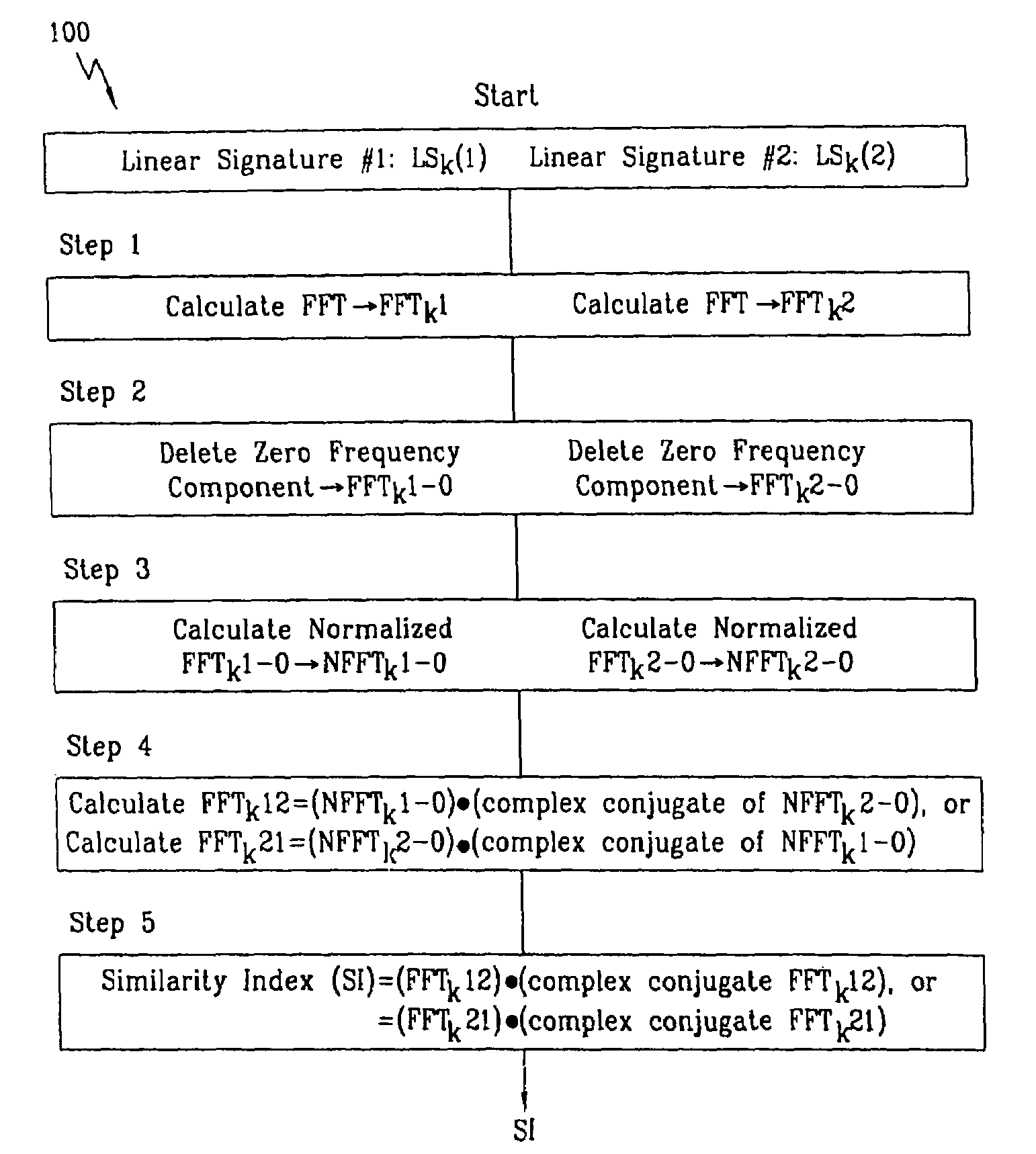
InactiveUS7013030B2Improved high security method and systemEasy to useElectric signal transmission systemsImage analysisCombined useLinearity
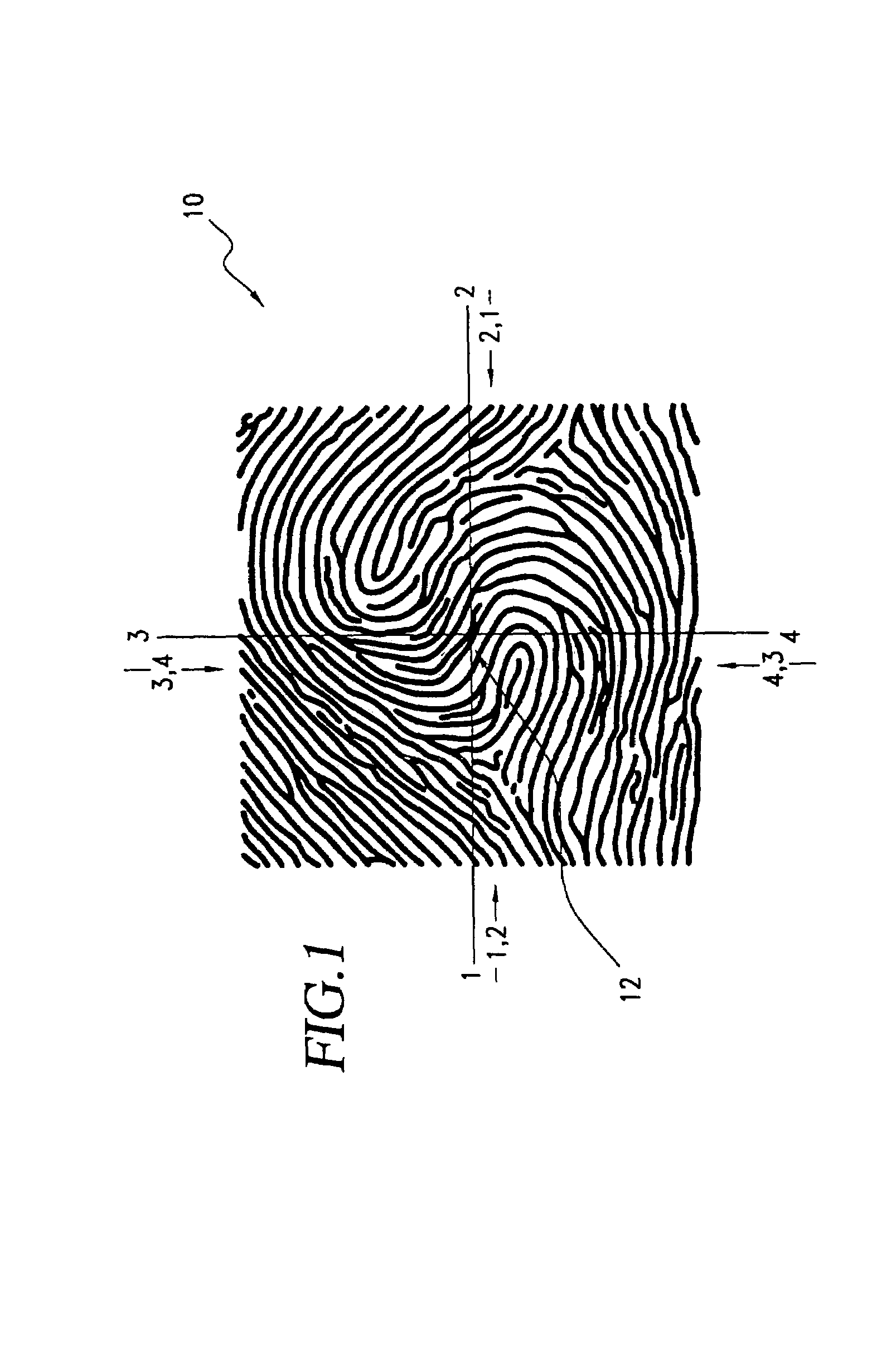
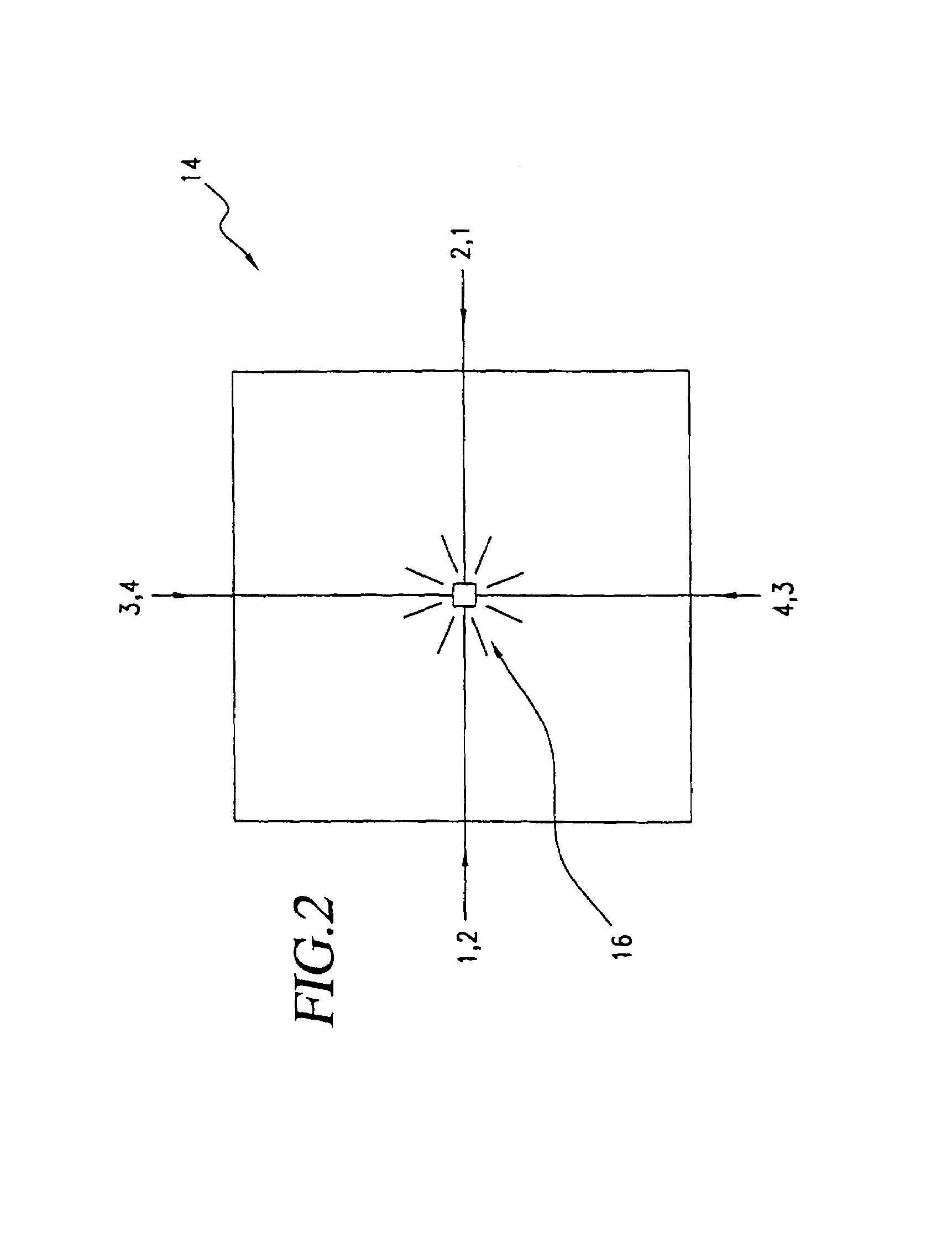
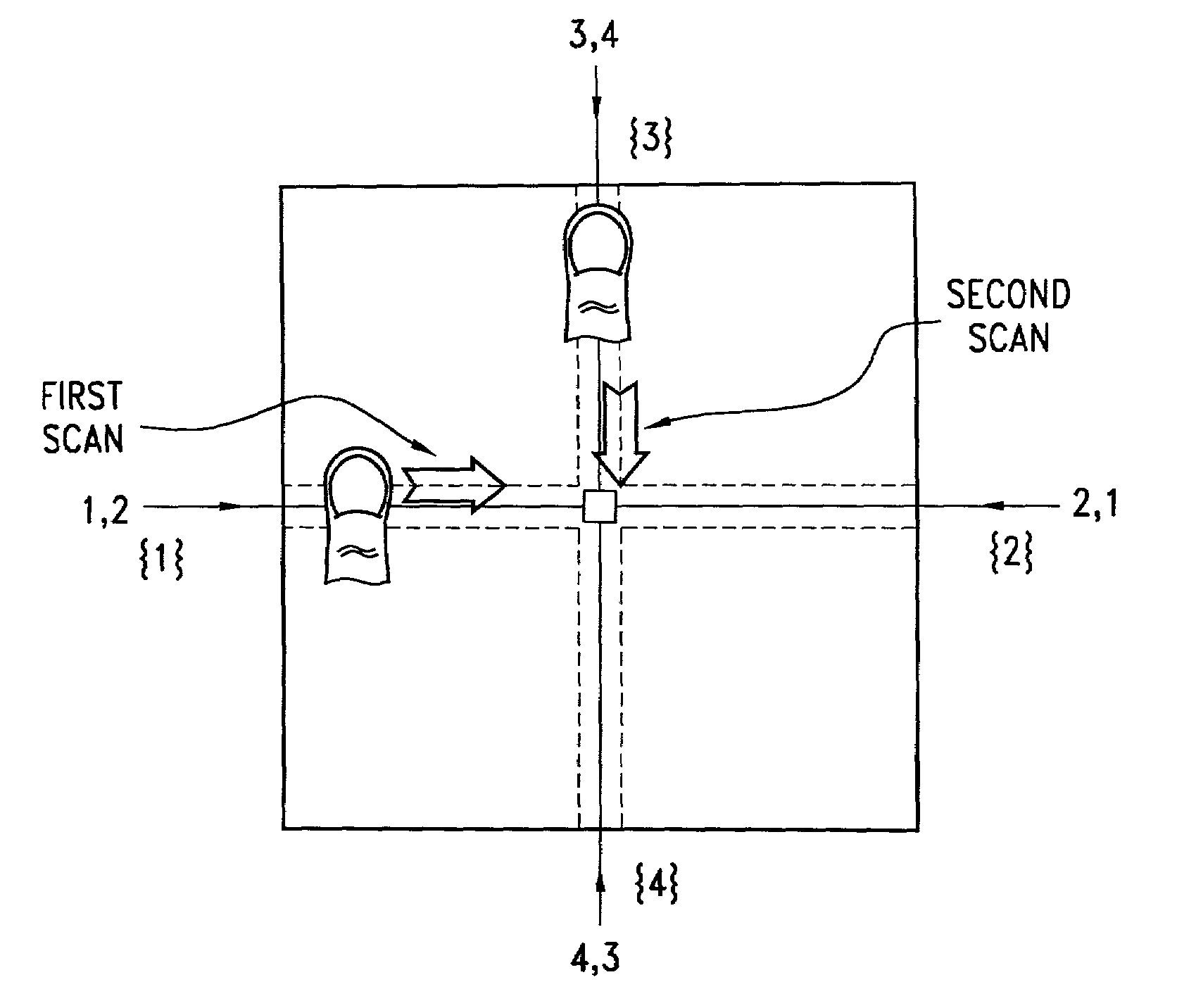
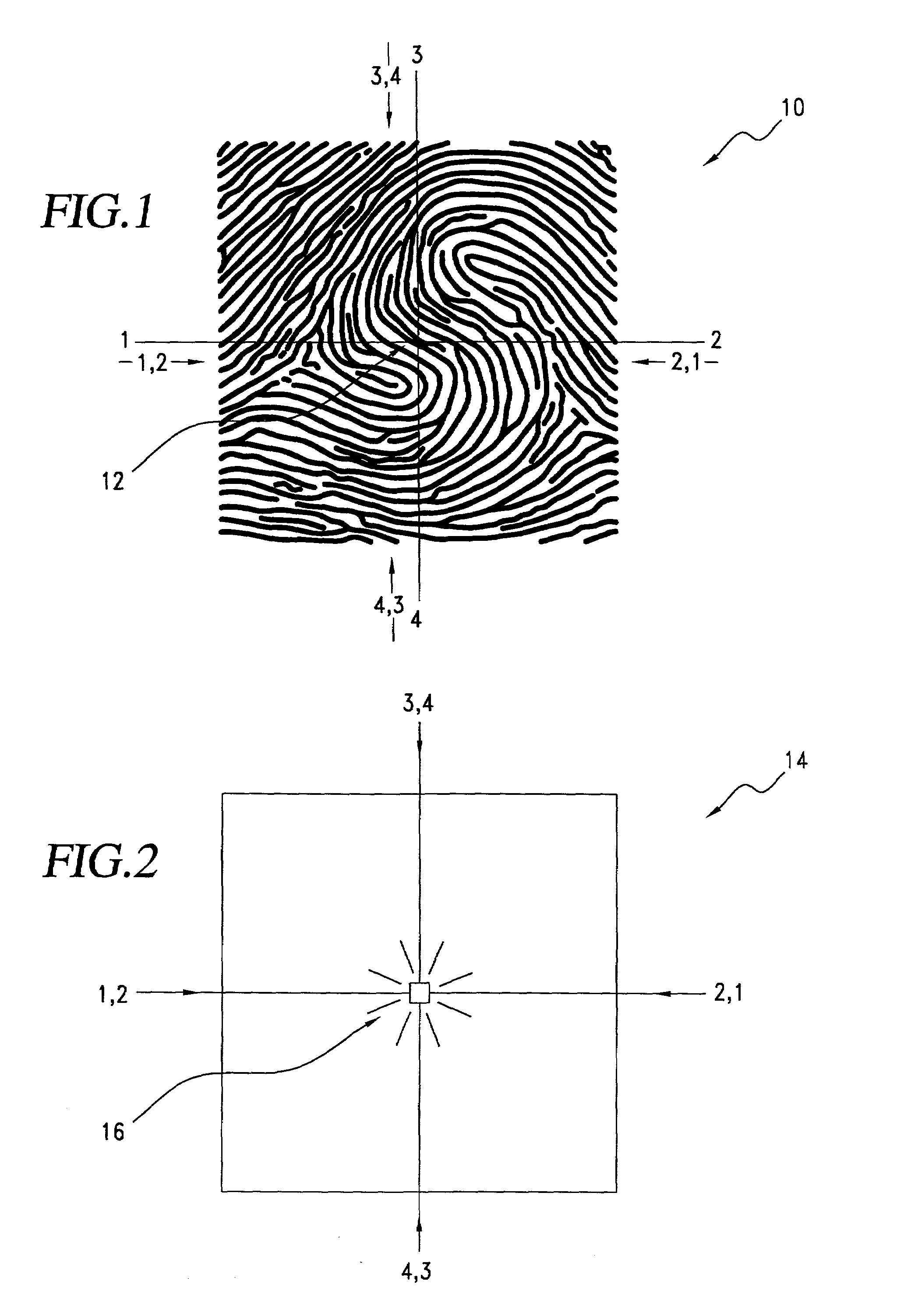
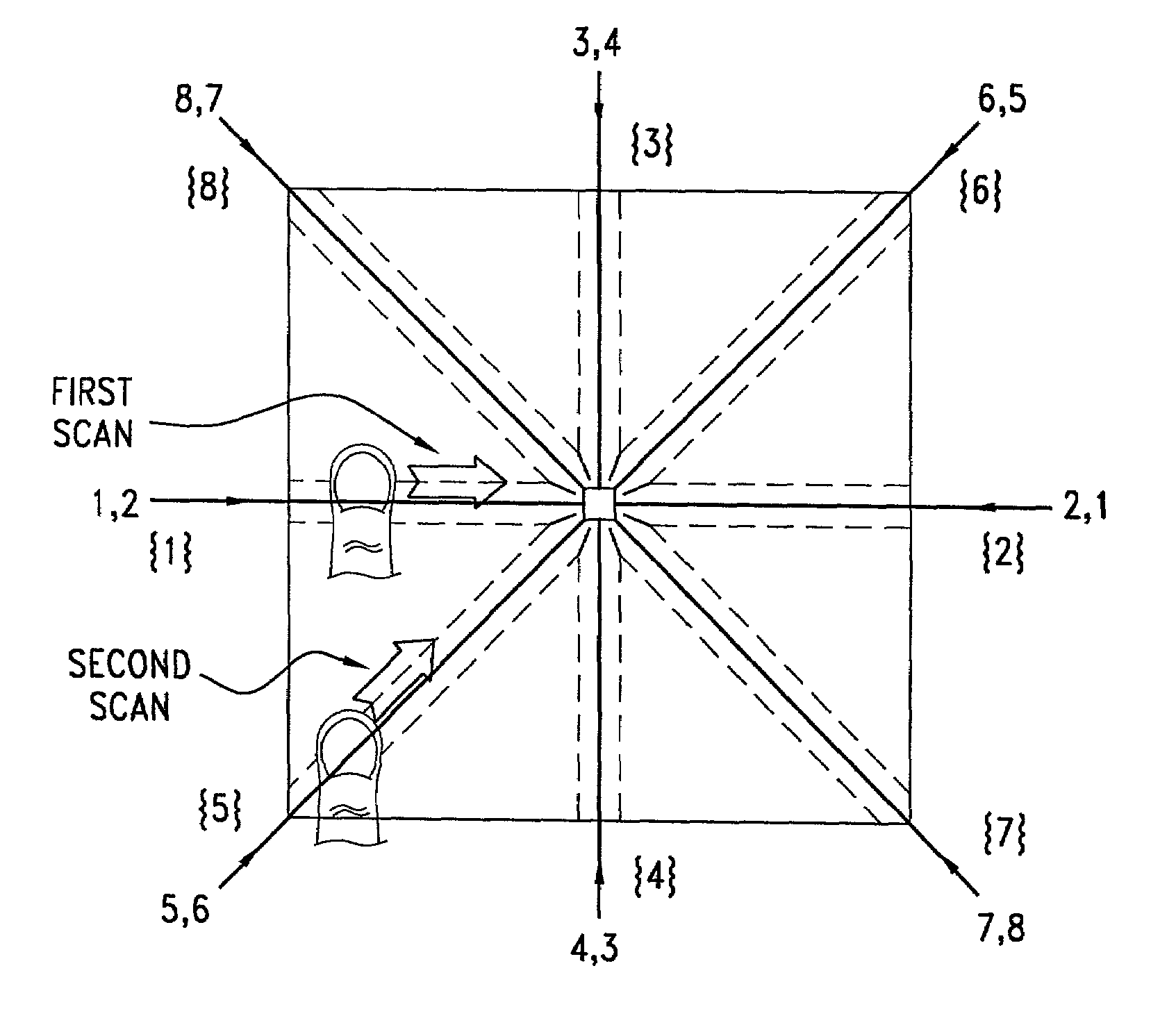
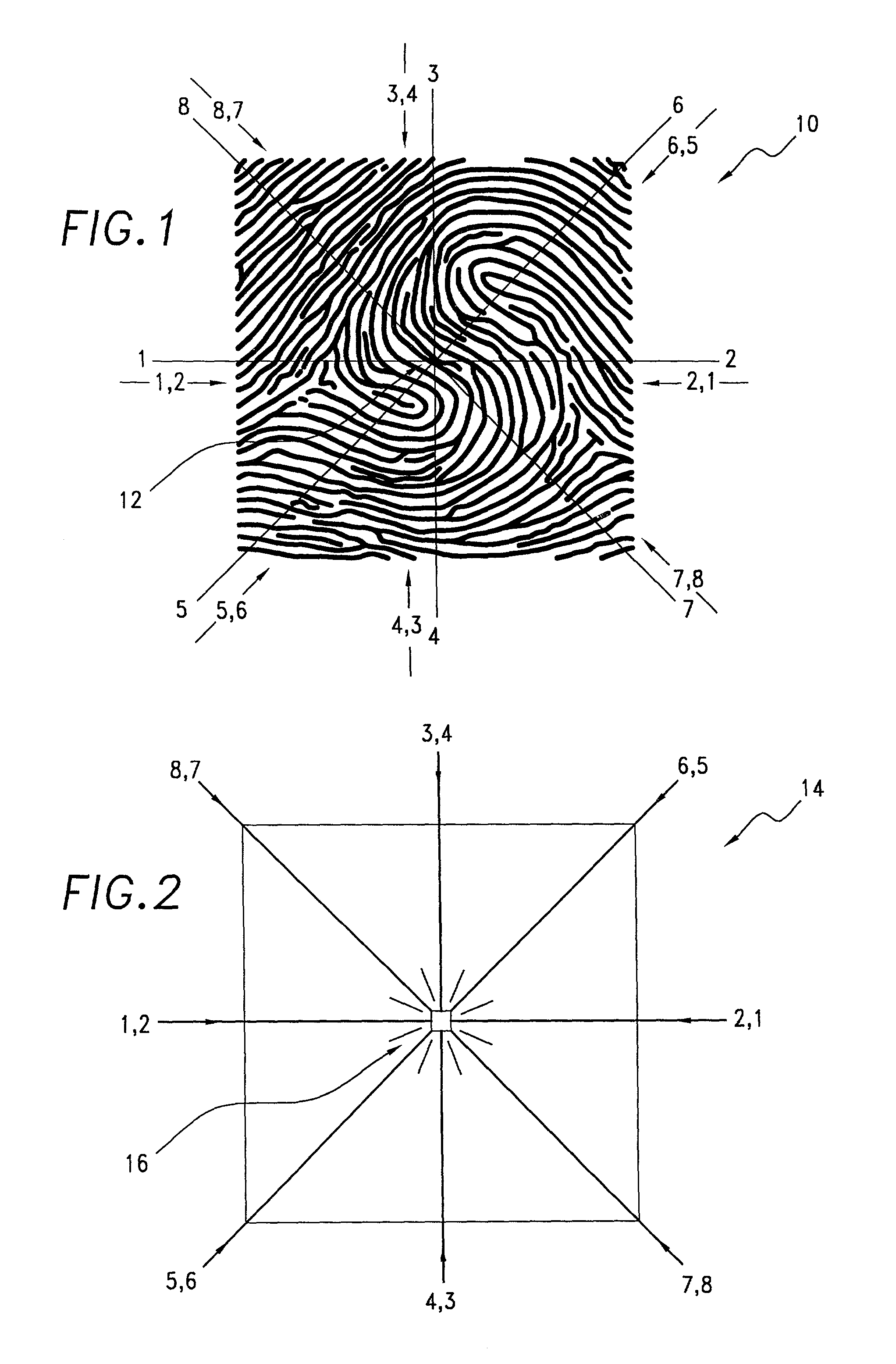
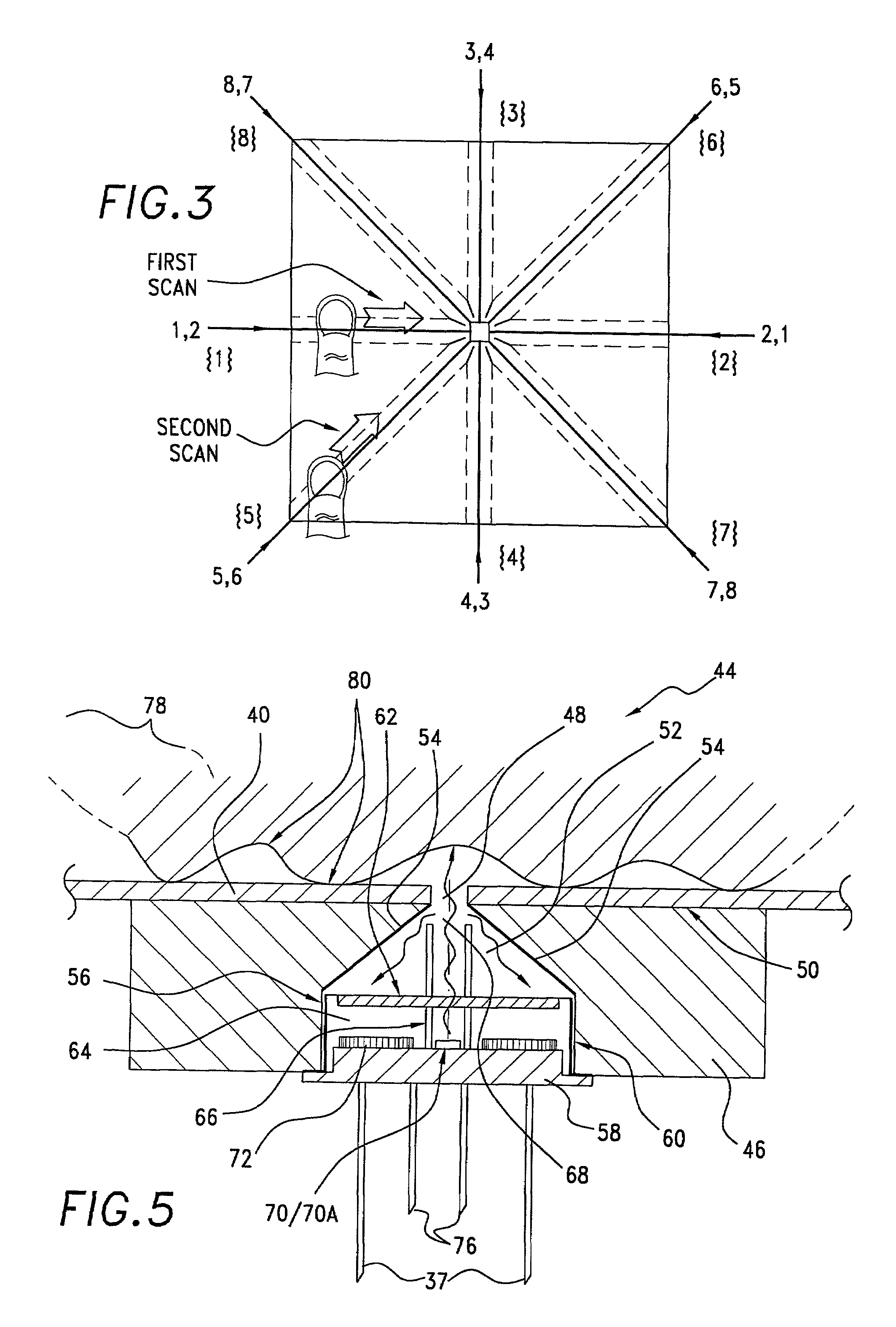
A biometric method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. This approach is further enhanced by employing a frequency domain technique for calculating a Similarity Index of the partial fingerprint signatures. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains four (illustratively) linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. In an advanced embodiment, the same two candidate signatures in the chosen sequence are processed in a unique FFT / DFT process to produce a highly reliable Similarity Index to authenticate or verify the identity of individuals. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y +1
Personal choice biometric signature
InactiveUS7035443B2Complicated processSpatial variation is minimizedElectric signal transmission systemsImage analysisPattern recognitionProximity sensor
A biometric method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. This approach is further enhanced by employing a frequency domain technique for calculating a Similarity Index of the partial fingerprint signatures. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains a reference set of linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. In an advanced embodiment, a pair of proximity sensors located along each of the linear tracks used for developing the linear partial signatures produce finger sensing signals which compensate for finger movement speeds and hence significantly improves the calculated Similarity Index values. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y
Architecture and method for operational privacy in business services
Consent-based application programming interfaces (APIs) are used to provide privacy access controls to operational systems for business services accomplished particularly in an electronic and / or networked environment. An API implementation device or host provides a link between a channel application, configured to provide an interface with a customer, and privacy data as used by operational applications and obtained from databases such as data warehouses. The privacy APIs provide per-customer choice / consent to obtaining and / or retrieval of privacy information / data and per-customer access thereto. In one form, the privacy APIs are used in business initiated self service applications wherein an activity or event triggers business to customer initiation.
Owner:TERADATA US
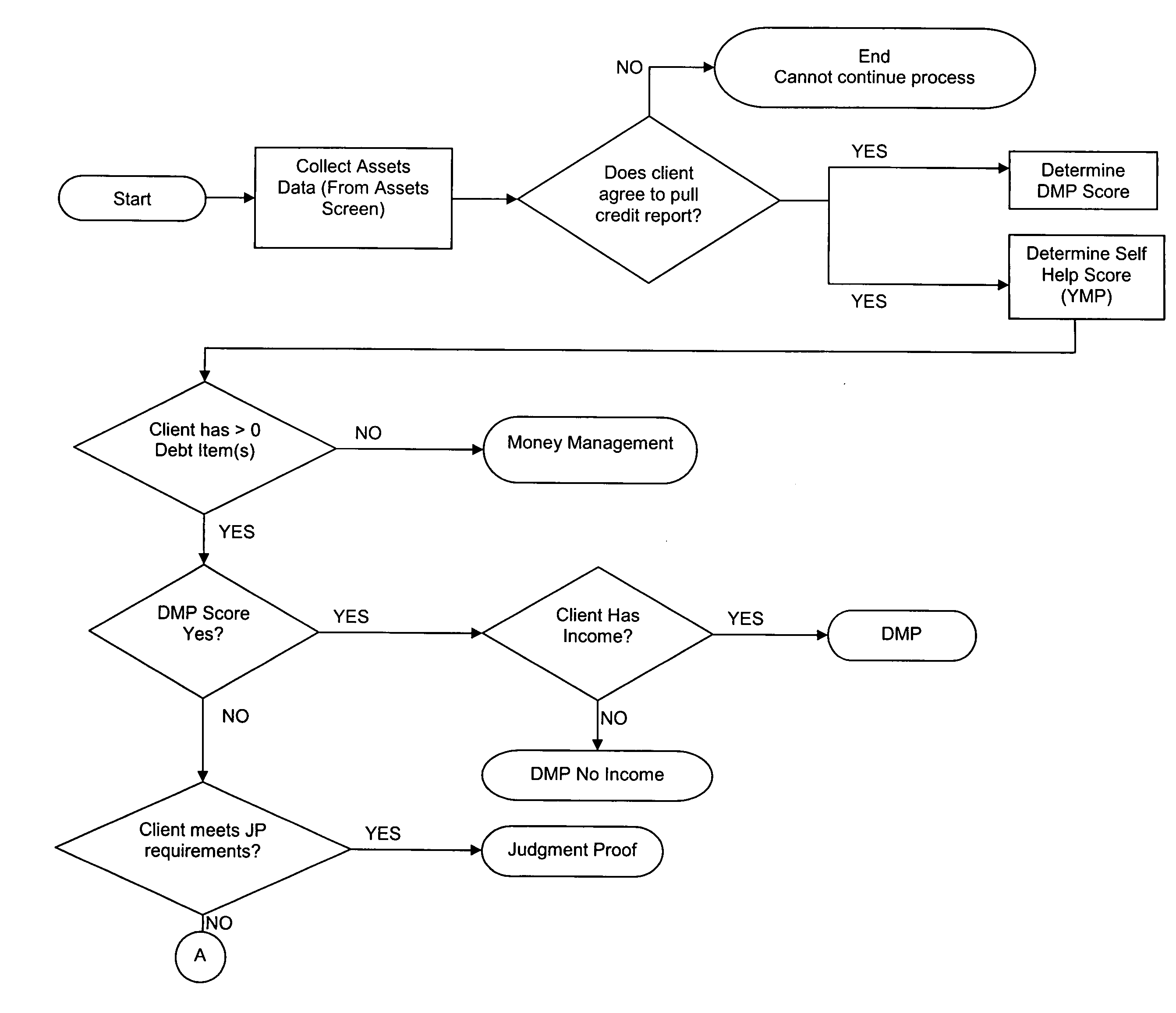
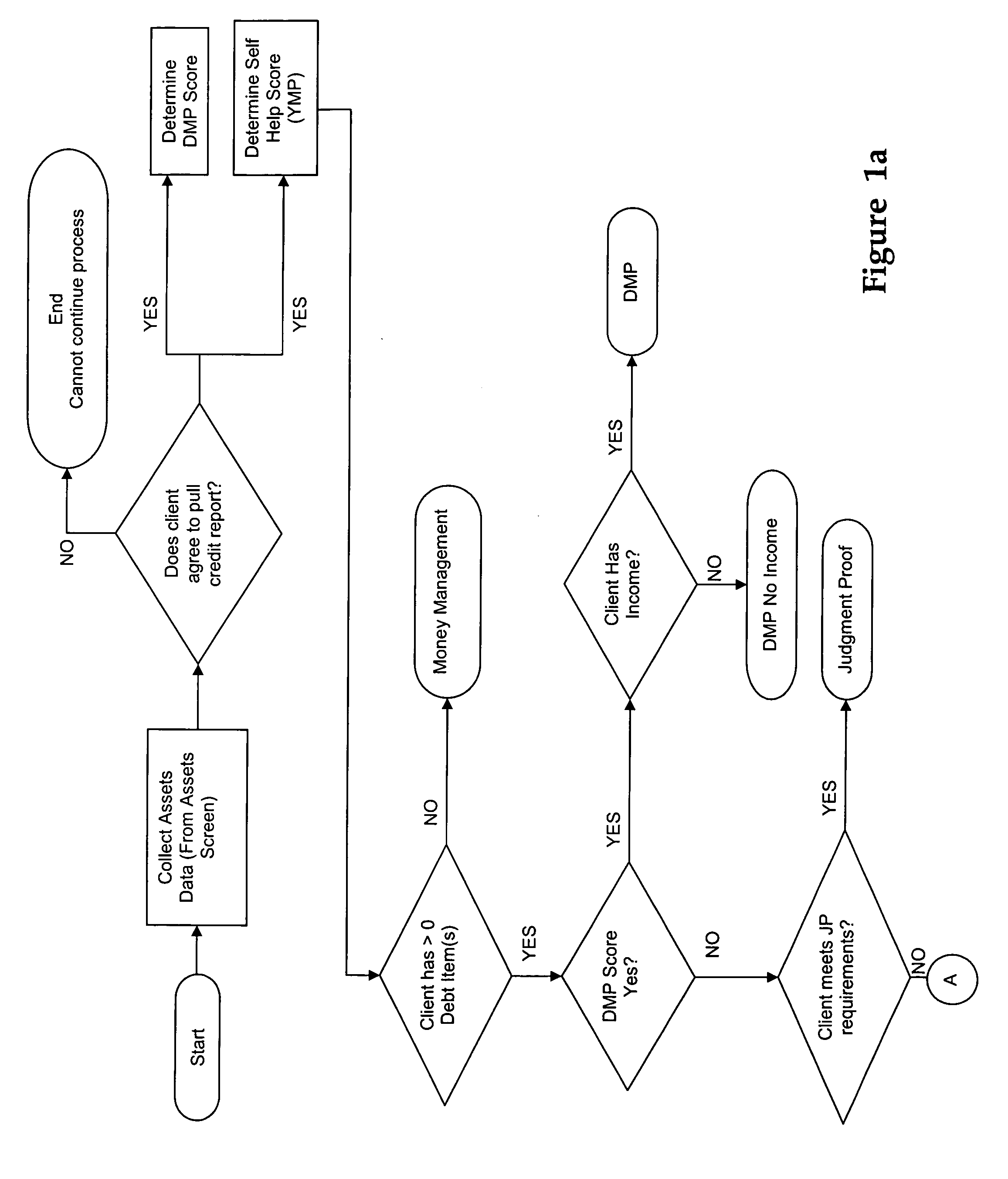
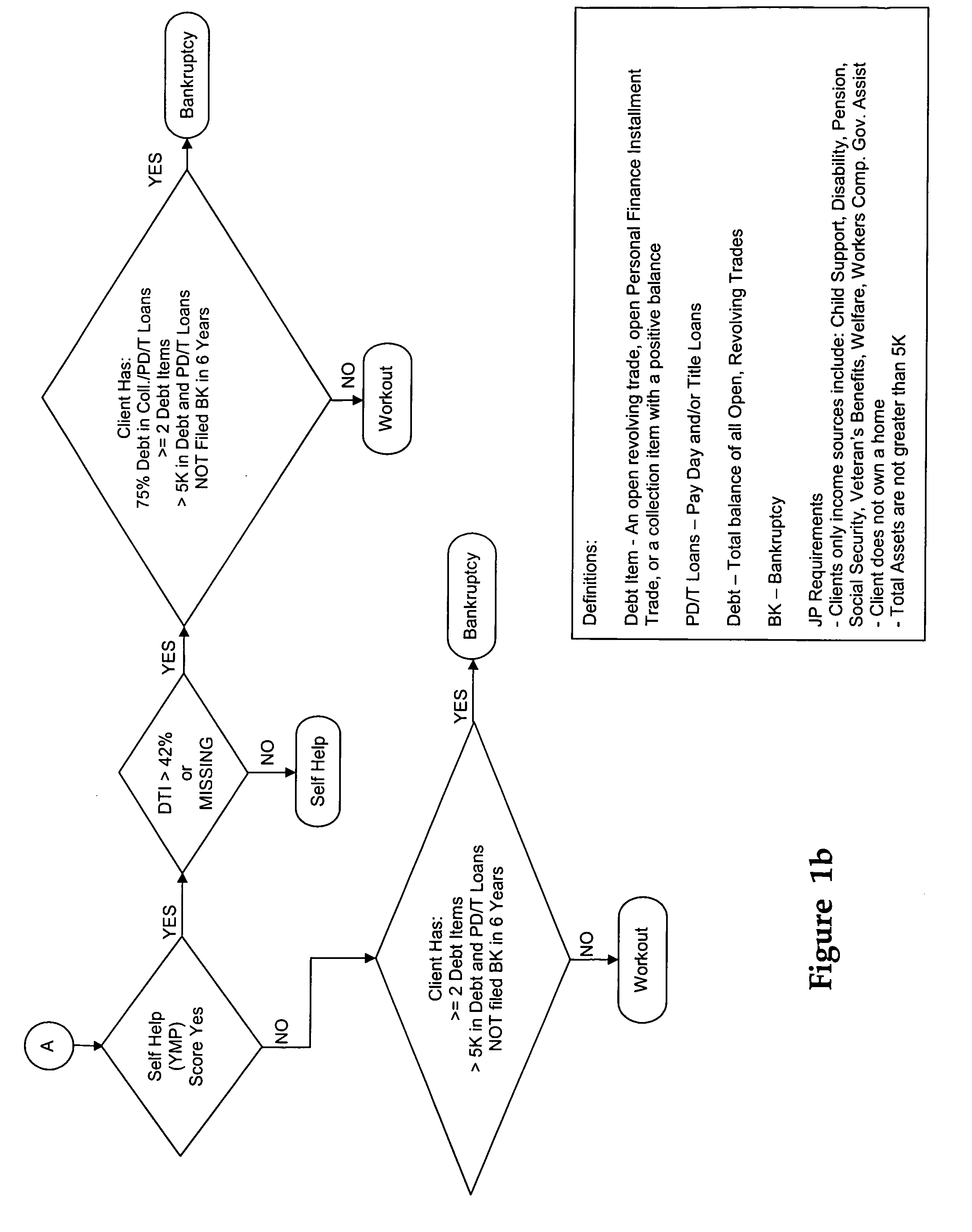
Method and system for financial counseling
Financial institutions providing counseling to costumers have to spend a significant amount of time gathering data from their clients and analyzing that data before offering appropriate financial advice to their customers. Some Debt Management Programs allow costumers to enroll using online systems without appropriate education or counseling. The present invention allows a costumer to obtain financial counseling automatically. A Credit Report Data Integration system, furthermore, streamlines the process by allowing the system to obtain data, with consent of the customer, from the credit bureaus to determine the financial needs of the client. The system allows the counselor to concentrate on counseling the client, instead of dealing with data entry and analysis. Furthermore, the client has the opportunity, if desired, to receive counseling from the system without having to actually meet a counselor.
Owner:INCHARGE INST OF AMERICA
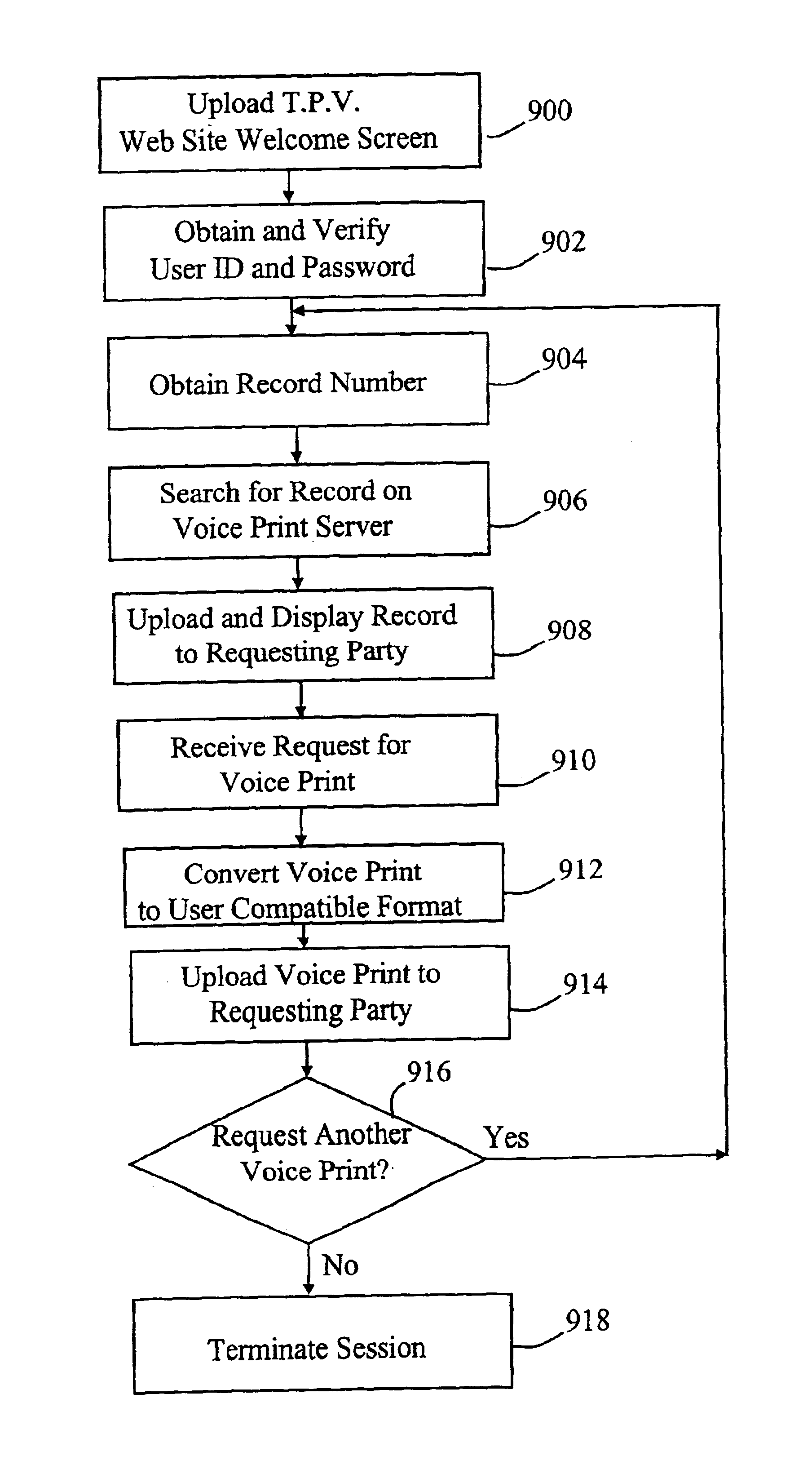
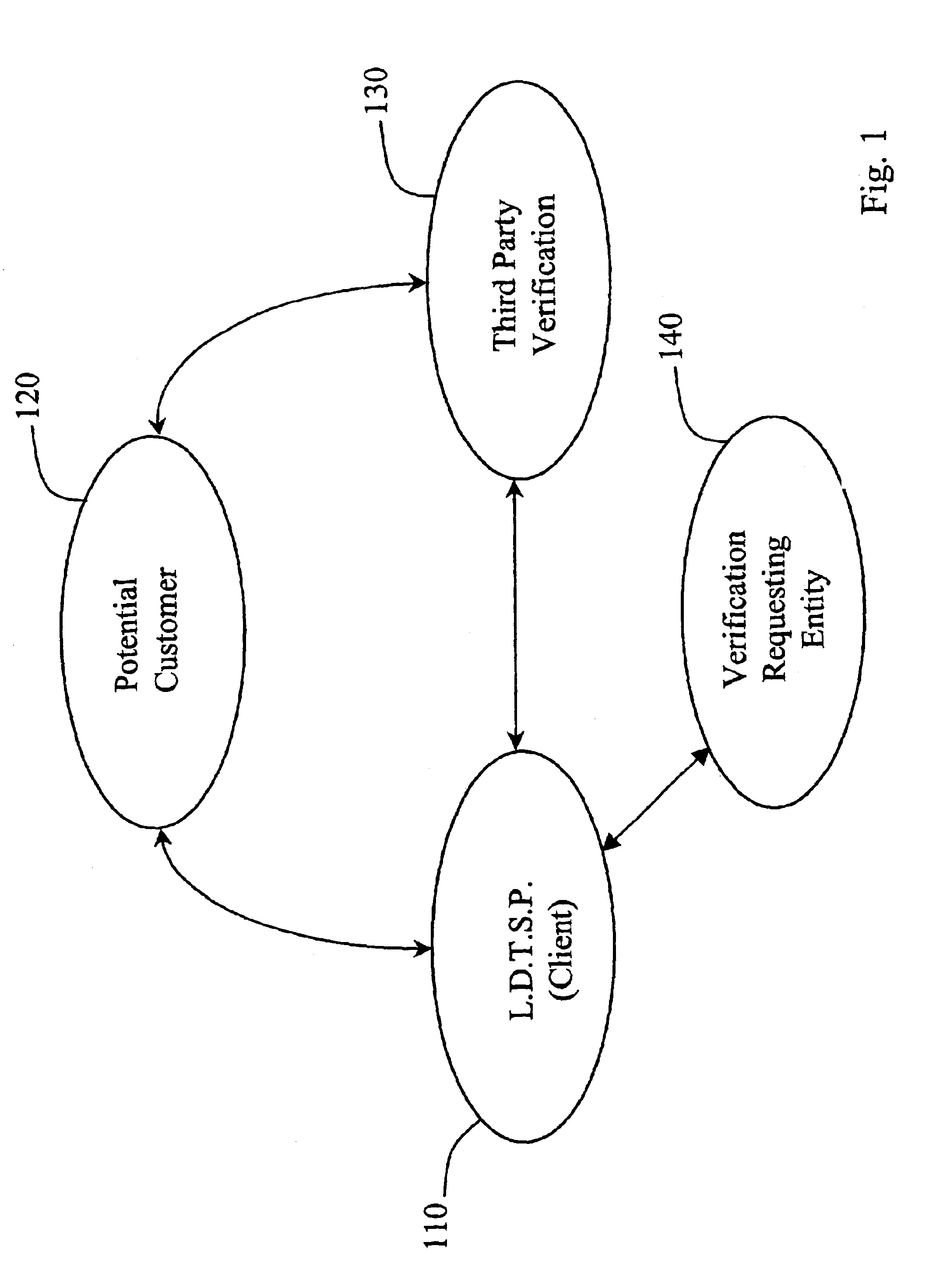
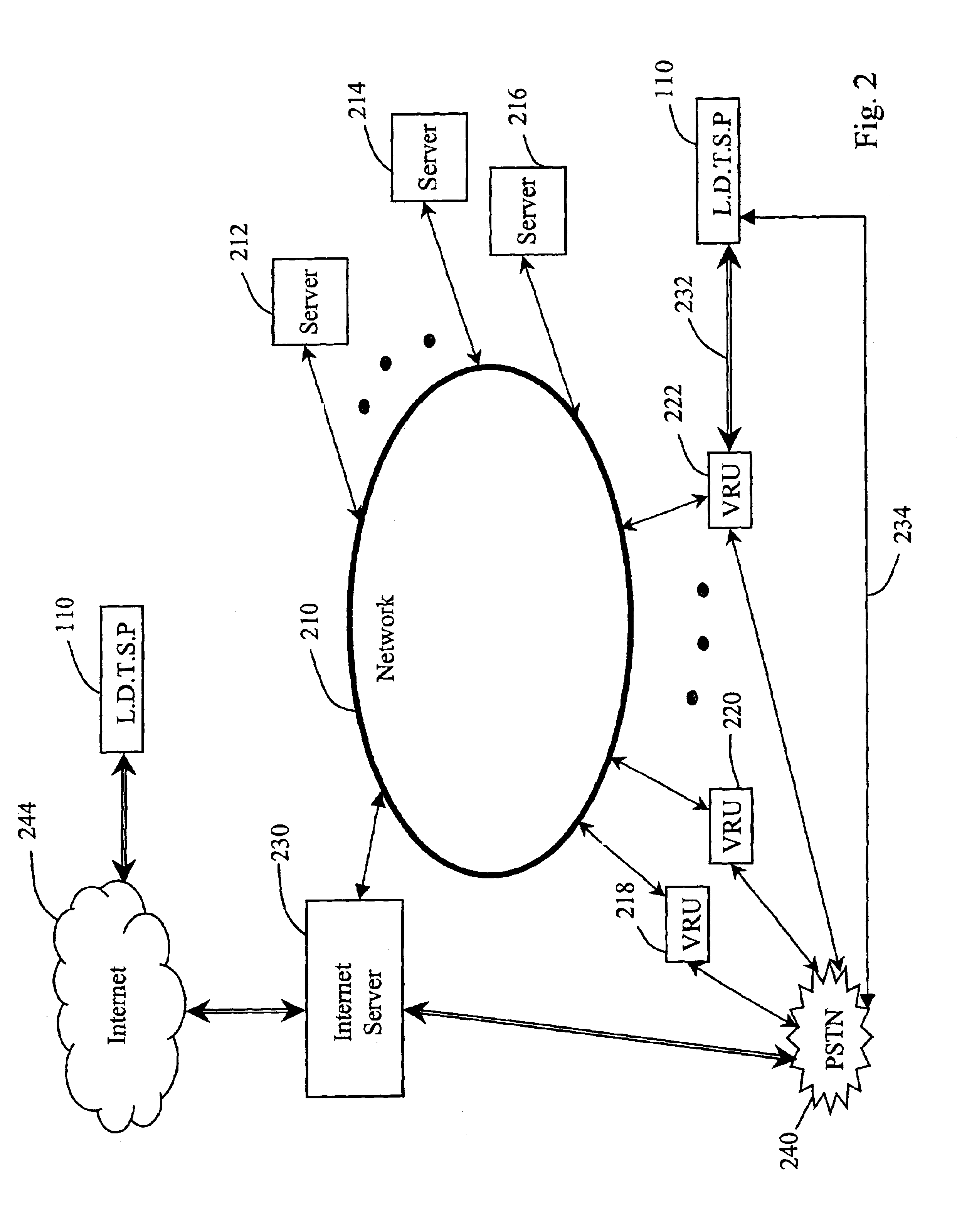
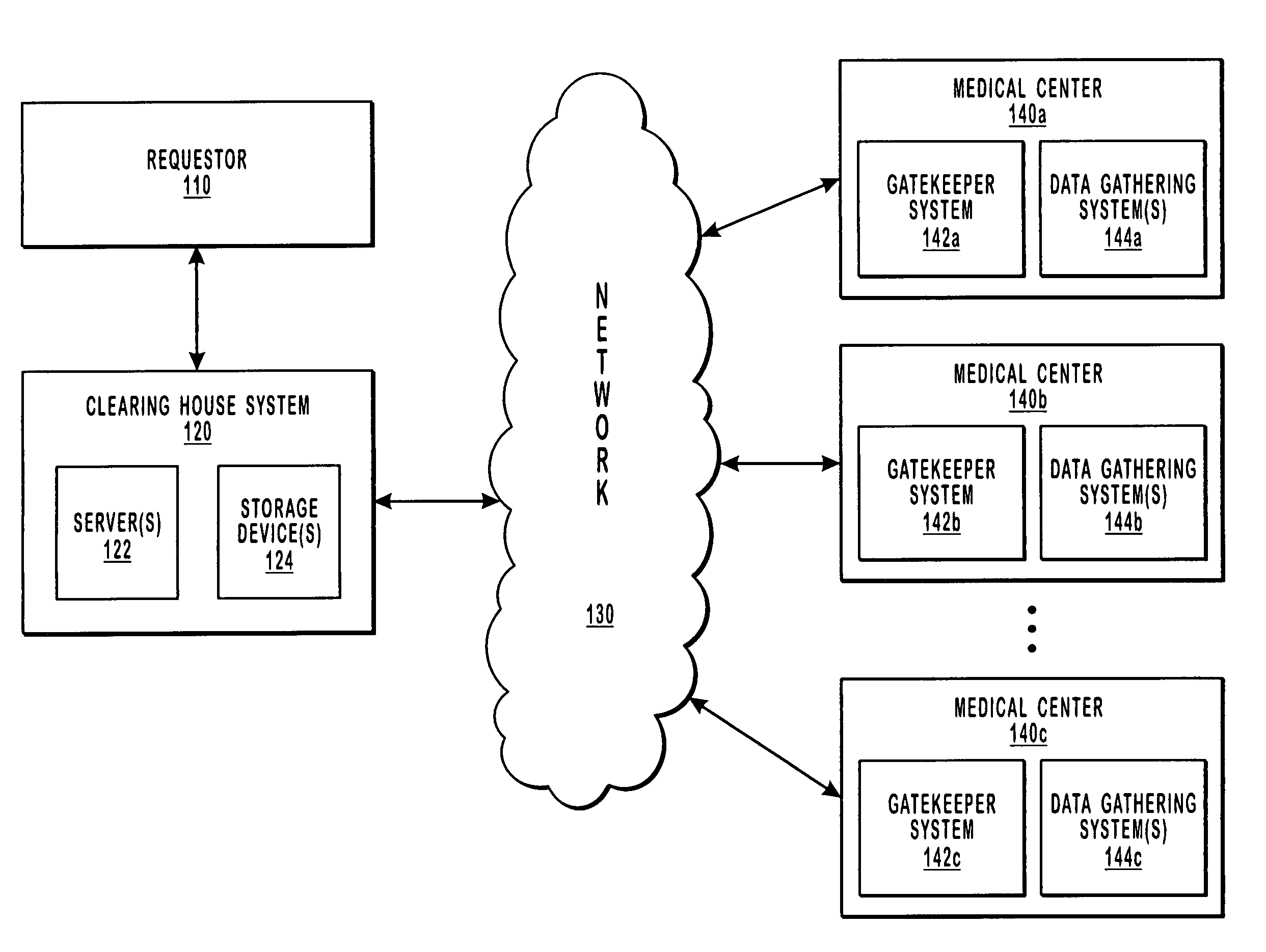
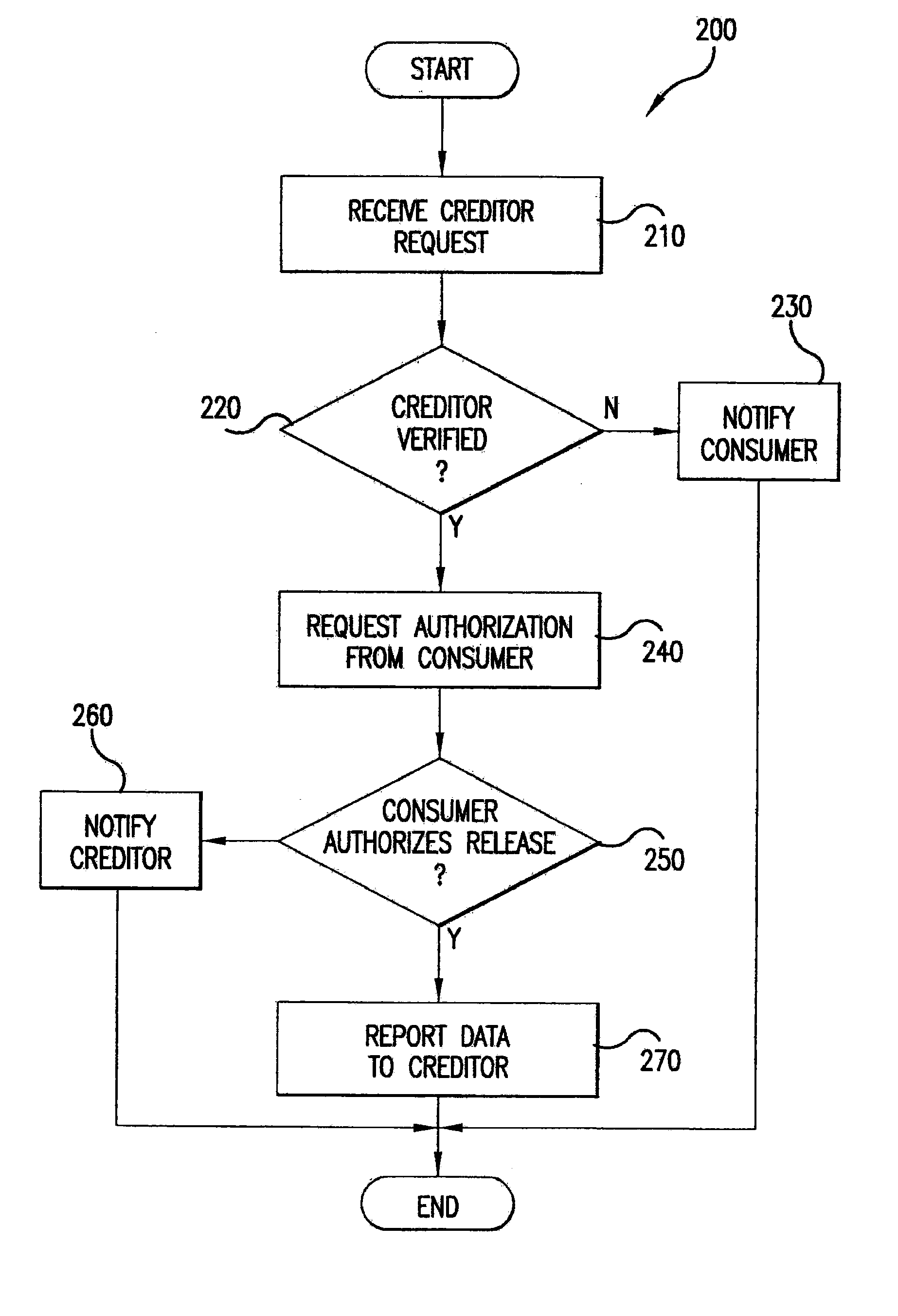
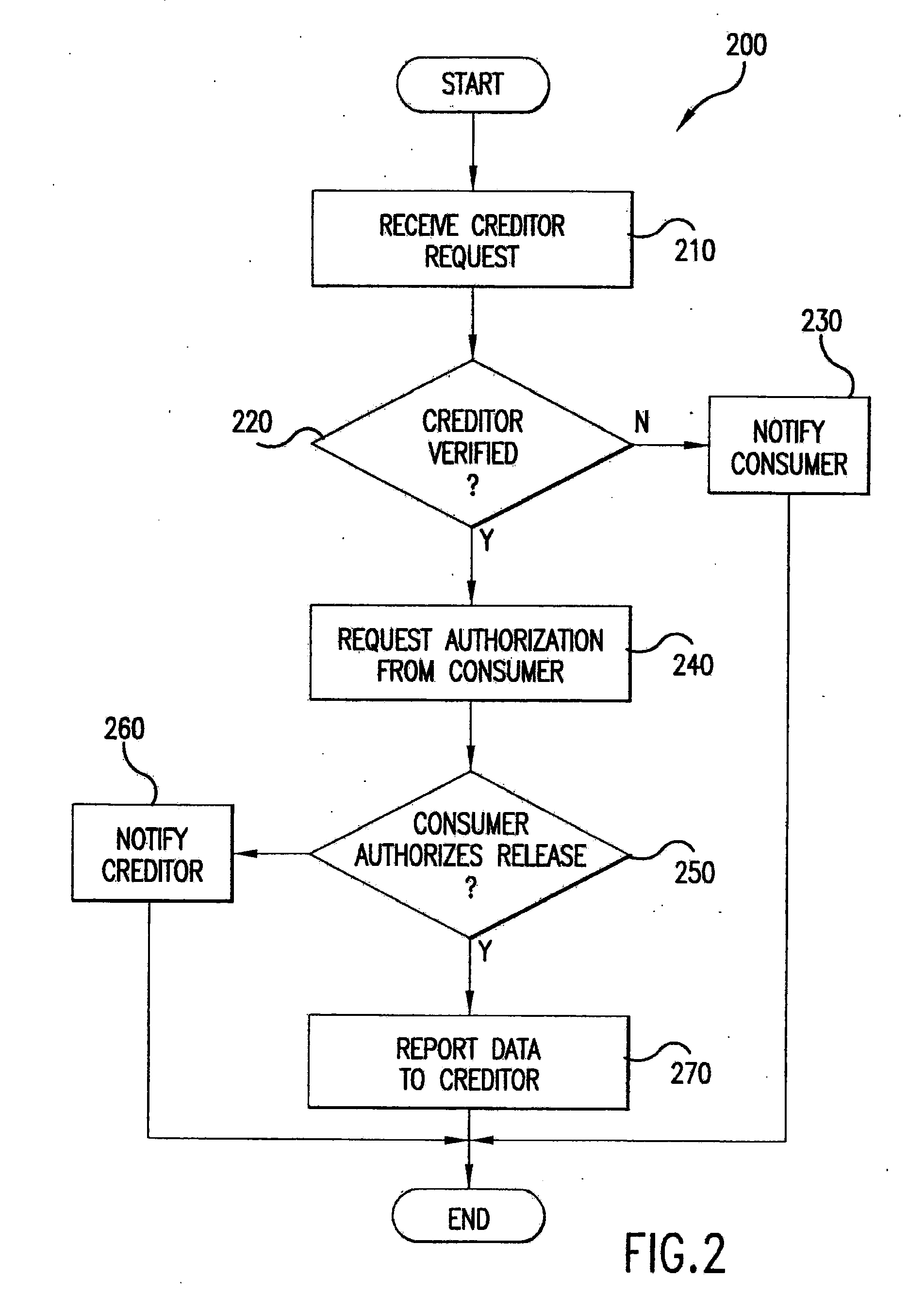
Automated third party verification system
A verification system for obtaining, storing and providing access to information regarding a commitment or position of an individual or entity is provided. In one embodiment the verification system comprises an interactive voice response system or computer program interface capable of obtaining and recording information regarding any of a number of commitments from an individual or entity, such as a commitment to change long distance telephone service providers. The verification system comprises a voice response unit configured to query pertinent information from an individual and record the responses to the queries in a digital format. Upon completion of a successful session, the voice response unit forwards the recorded responses confirming consent, to a storage device, such as a computer server. As desired, the recorded responses can be retrieved from the server by telephone or computer for verification of the consent, commitment, or position of the individual or entity.
Owner:RED HAT
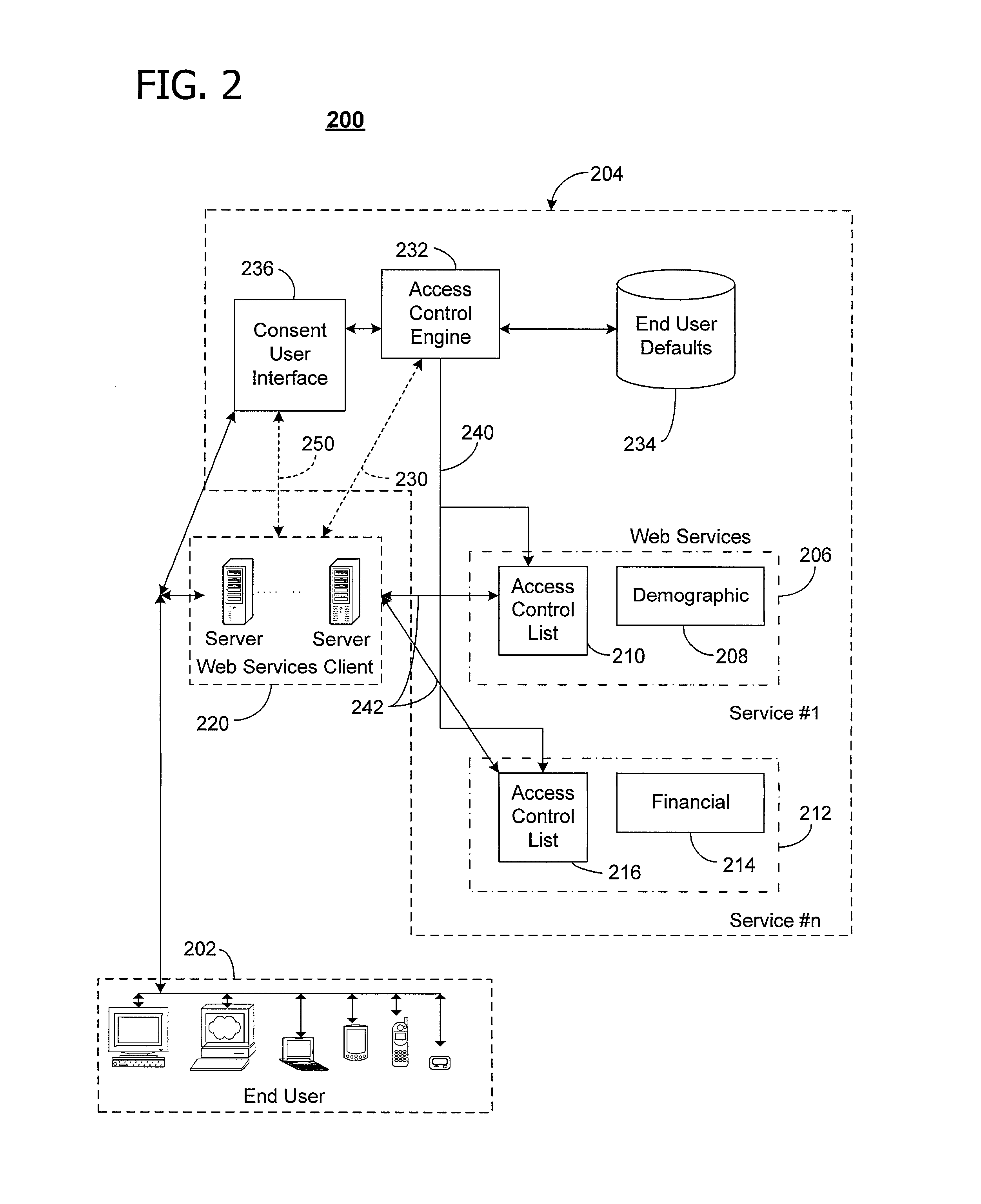
Profile and consent accrual
ActiveUS7590705B2Enhance information sharingLess laborDigital data processing detailsDigital data protectionPersonal detailsClient-side
Consent management between a client and a network server. In response to a request for consent, a central server determines if requested user information is included in a user profile associated with a user and if the user has granted consent to share the requested user information. A user interface is provided to the user via a browser of the client to collect the requested user information that is not included in the user profile and the consent to share the requested user information from the user. After receiving the user information provided by the user via the user interface, the service provided by the network server is allowed access to the received user information, and the central server updates the user profile. Other aspects of the invention are directed to computer-readable media for use with profile and consent accrual.
Owner:MICROSOFT TECH LICENSING LLC
Authentication method utilizing a sequence of linear partial fingerprint signatures selected by a personal code
InactiveUS7039223B2Improved high security method and systemEasy to useProgramme controlElectric signal transmission systemsCombined usePersonal computer
A method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains eight (illustratively) linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y
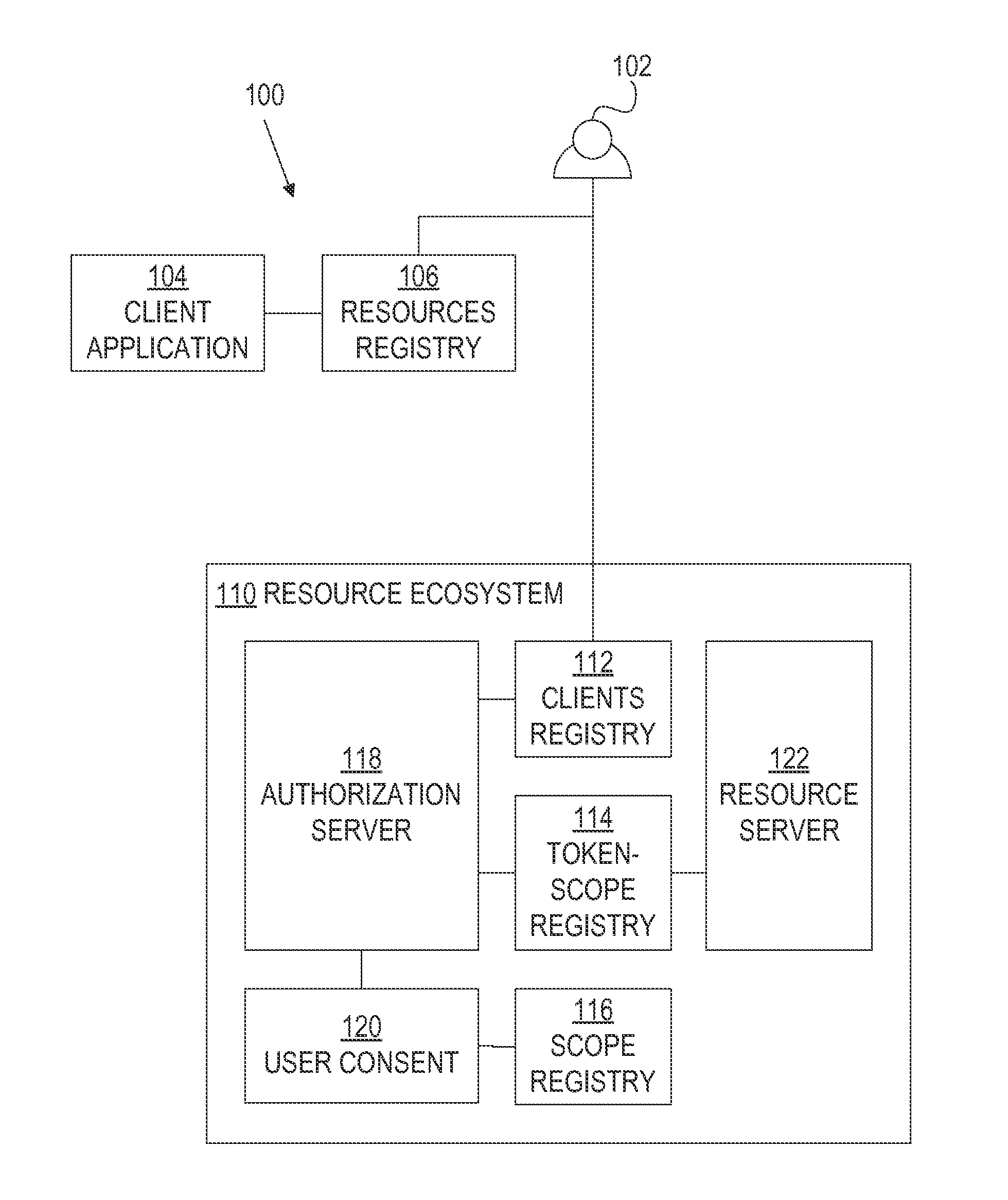
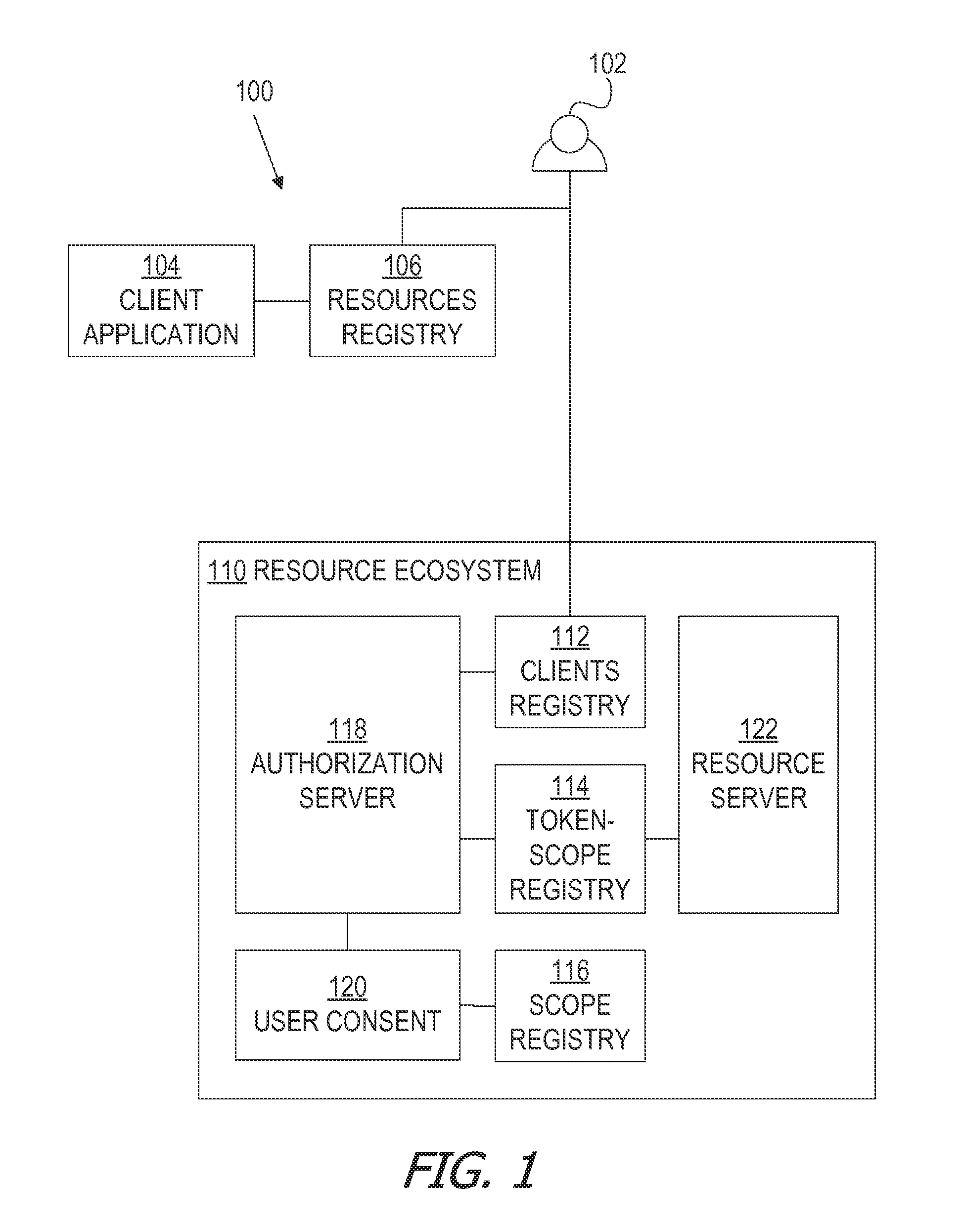
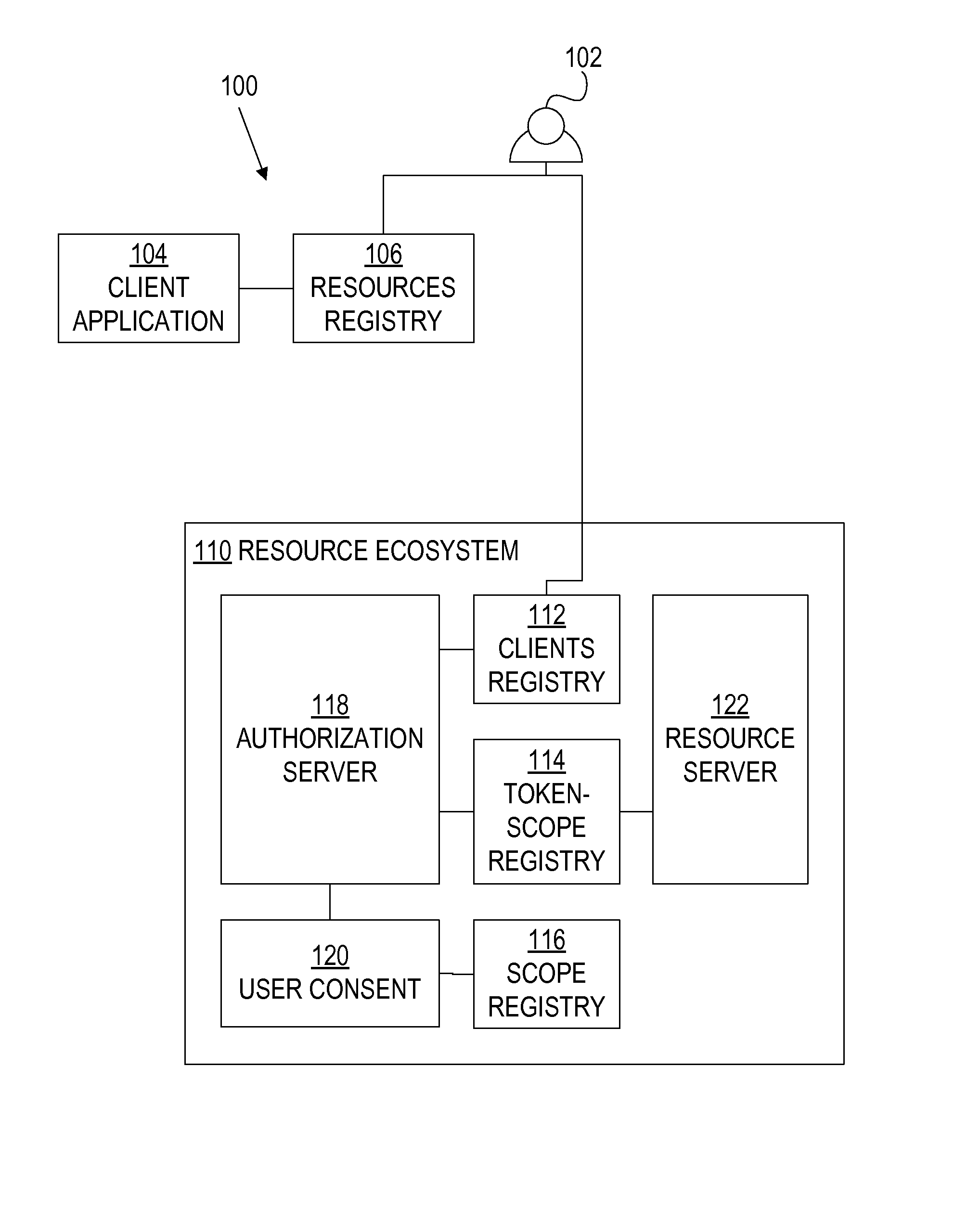
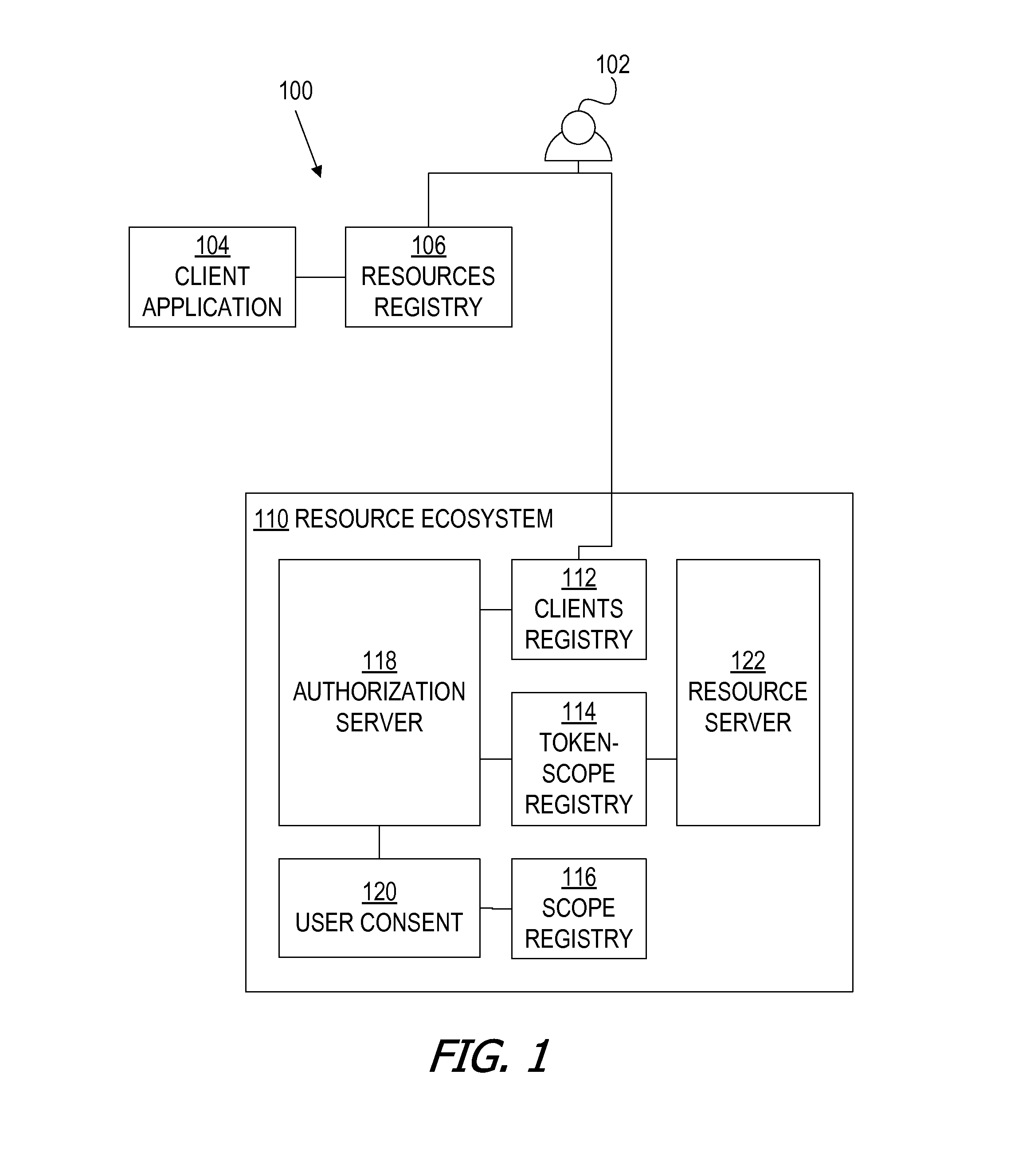
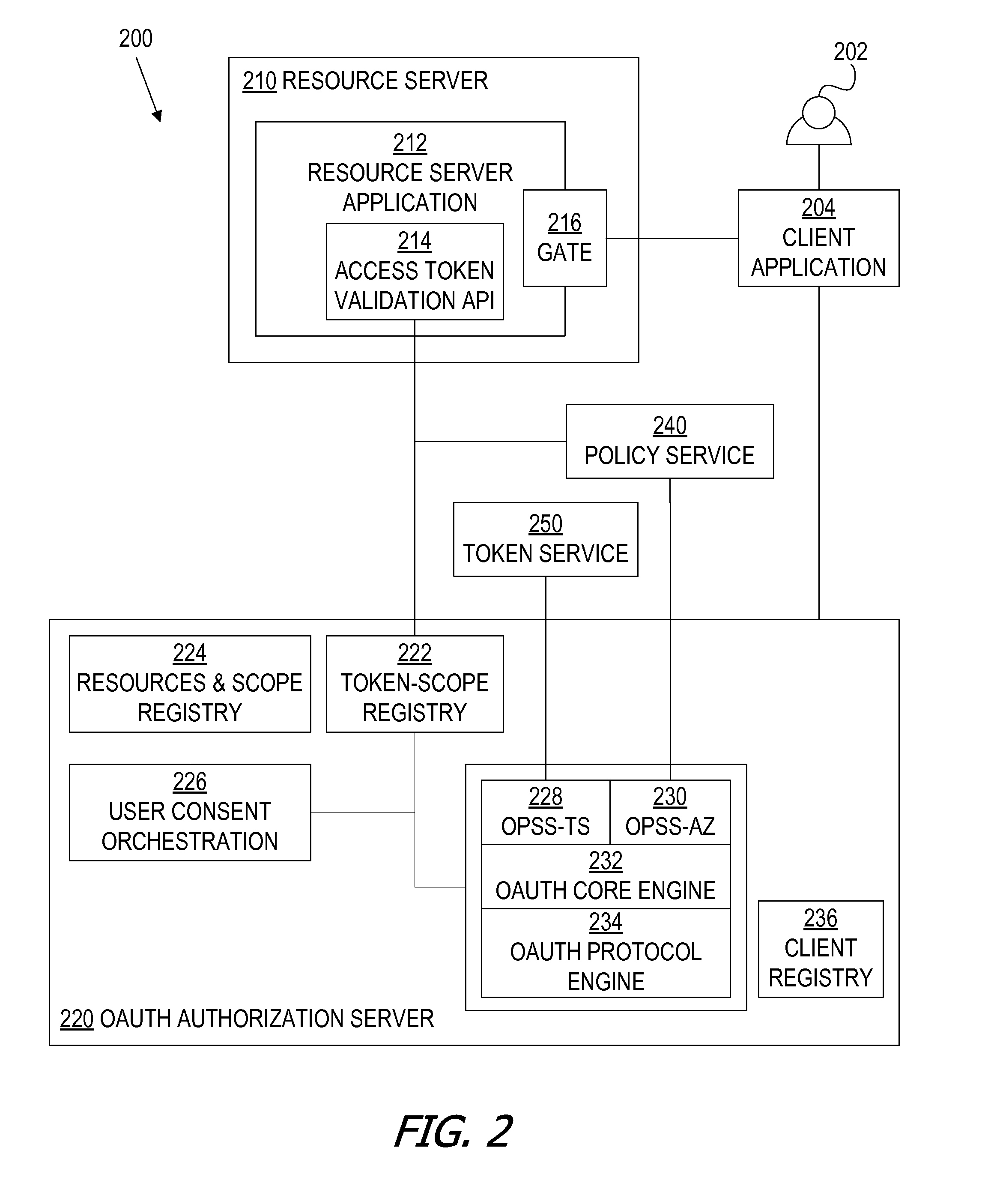
Oauth framework
ActiveUS20130086645A1More customizableEasy to customizeDigital data processing detailsMultiple digital computer combinationsClient-sideAccess token
A framework, which conforms to the OAuth standard, involves a generic OAuth authorization server that can be used by multiple resource servers in order to ensure that access to resources stored on those resource servers is limited to access to which the resource owner consents. Each resource server registers, with the OAuth authorization server, metadata for that resource server, indicating scopes that are recognized by the resource server. The OAuth authorization server refers to this metadata when requesting consent from a resource owner on behalf of a client application, so that the consent will be of an appropriate scope. The OAuth authorization server refers to this metadata when constructing an access token to provide to the client application for use in accessing the resources on the resource server. The OAuth authorization server uses this metadata to map issued access tokens to the scopes to which those access tokens grant access.
Owner:ORACLE INT CORP
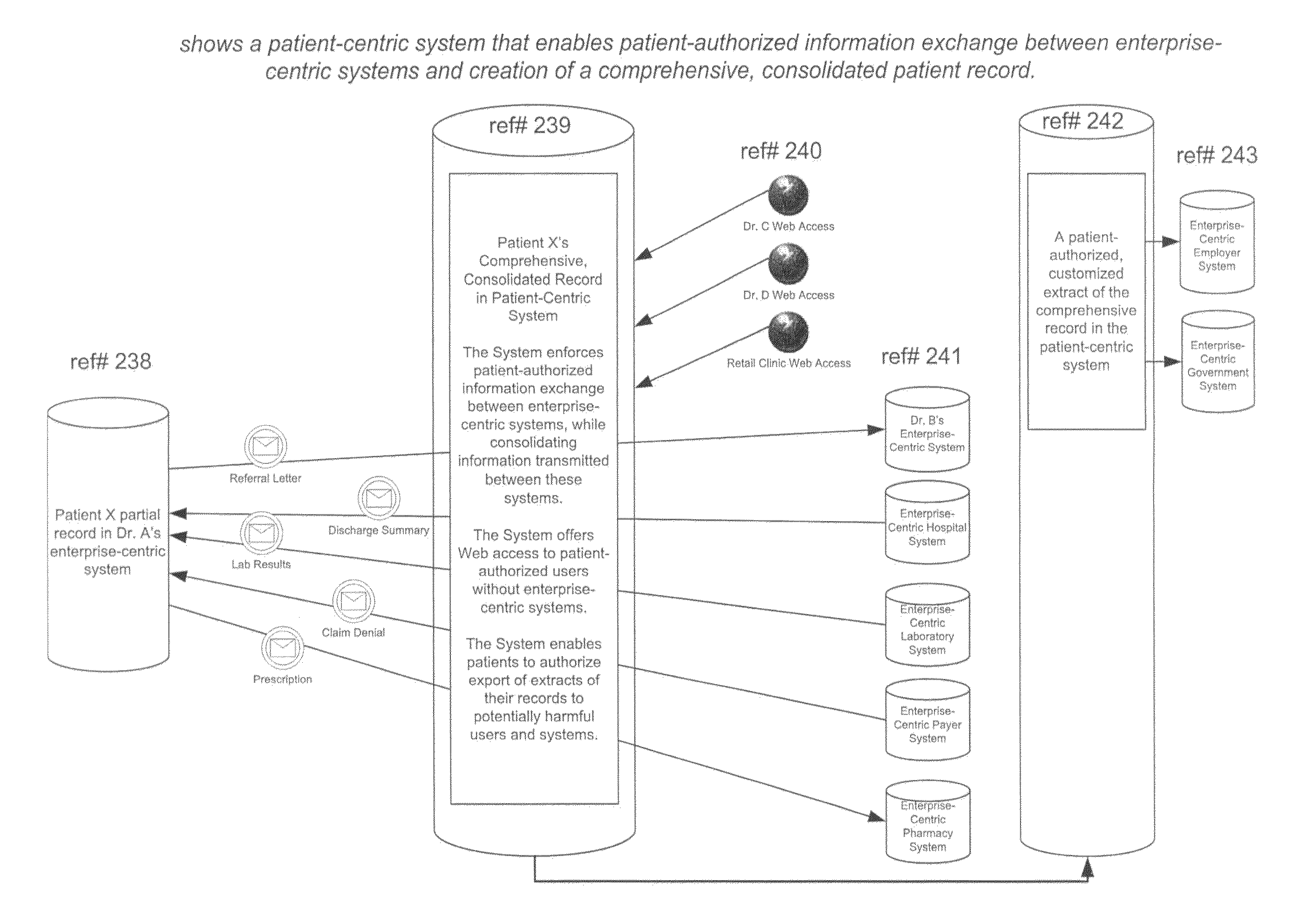
Client-centric e-health system and method with applications to long-term health and community care consumers, insurers, and regulators
InactiveUS20110082794A1Overcomes shortcomingFinanceUser identity/authority verificationRelational databaseWeb service
A patient-centric system and method for accessing personal health records of a patient, stored in relational databases and containing comprehensive records of multiple patients with each patient's records incorporating many different data categories and functions including manual or automated data exchange, consolidation, storage, routing and transmission, consistent with consent directives assigned to authorized users and computer systems of authorized users by the patient or designated representative thereof. The consent directives define privileges of access in each of said data categories and functions within the patients records. The patients records are stored in relational databases hosted by Web servers on a computer network through which the authorized users interact under the control of programming logic consistent with the consent directives assigned by the patient or designated representative thereof.
Owner:PROSOCIAL APPL
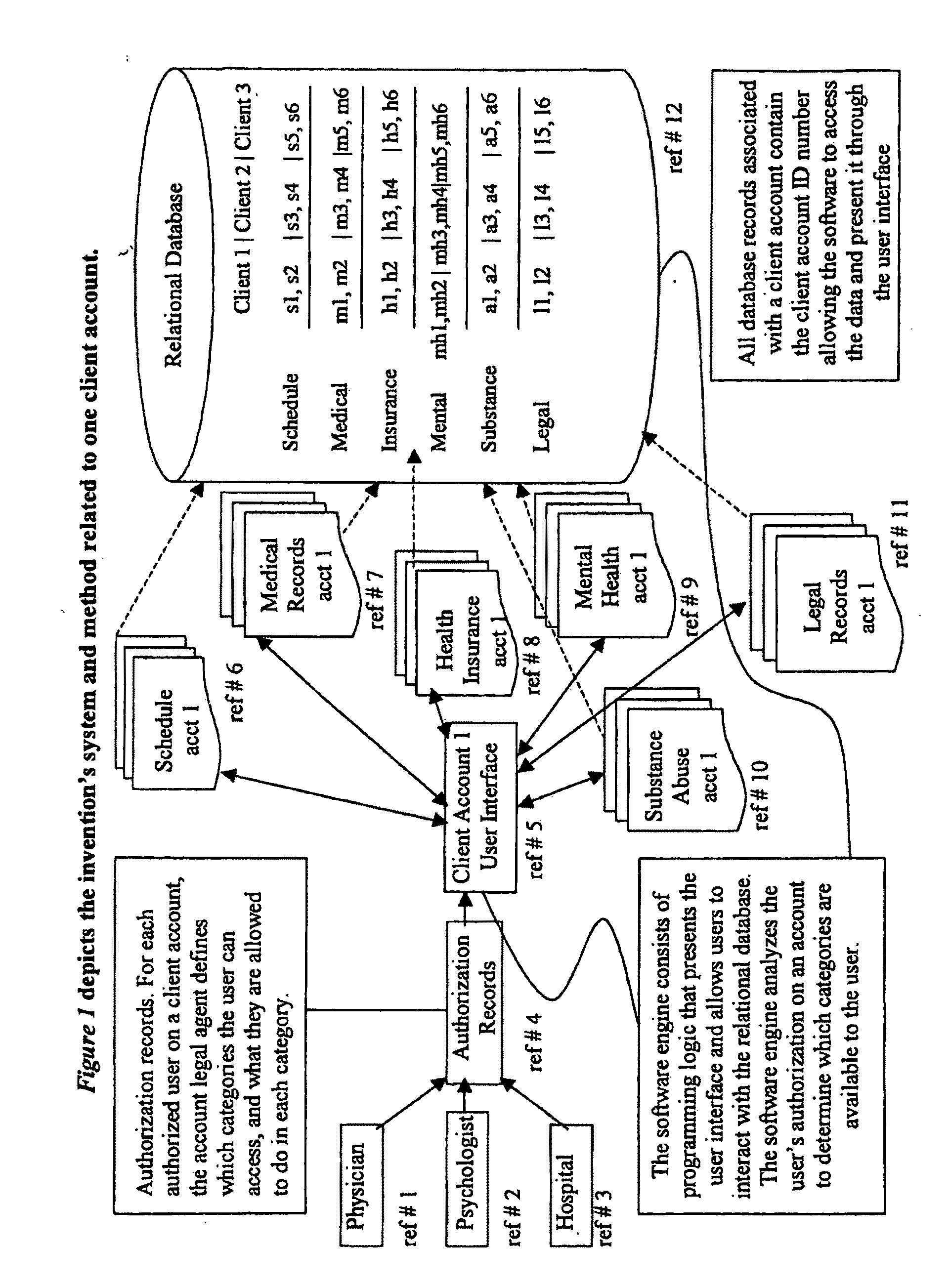
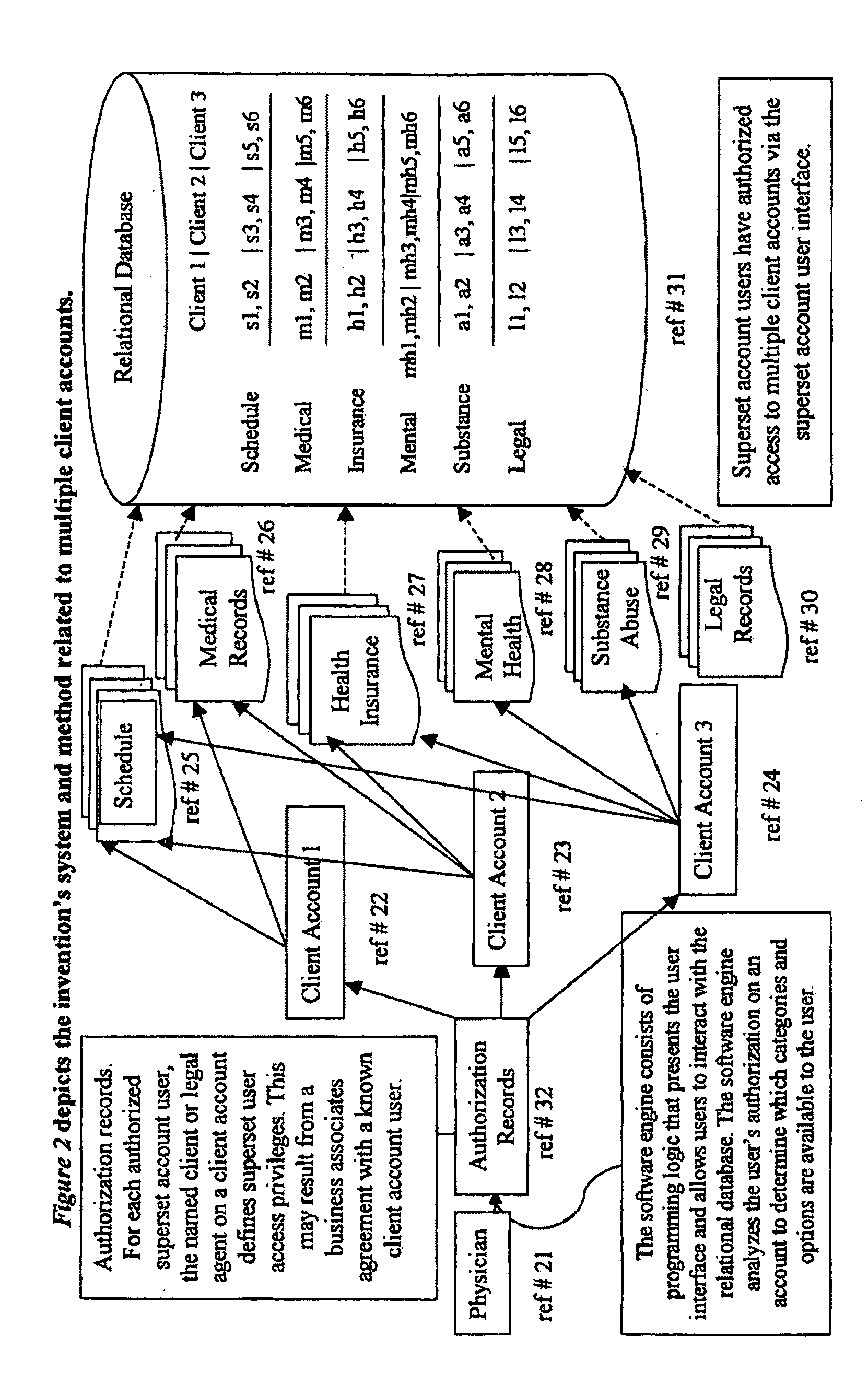
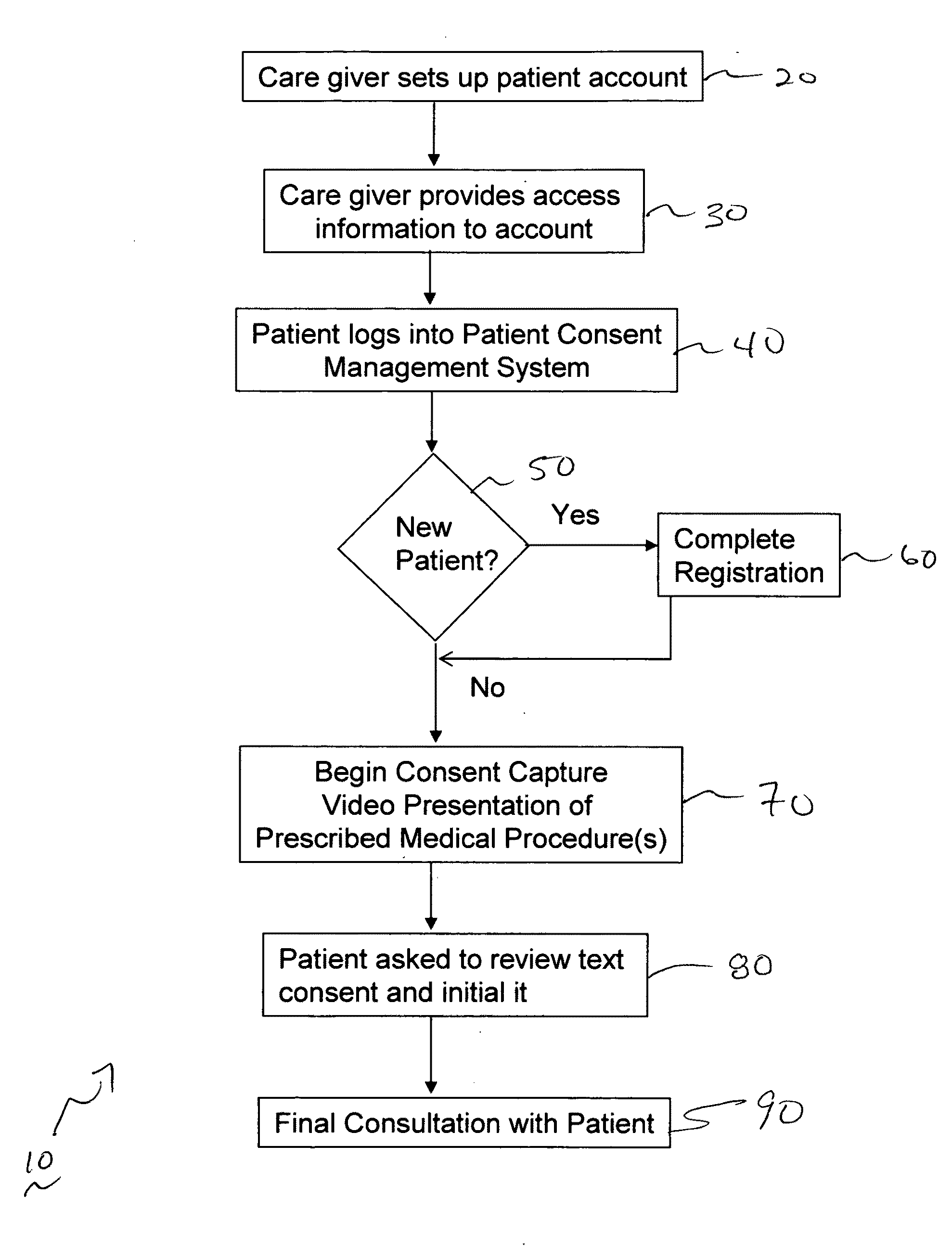
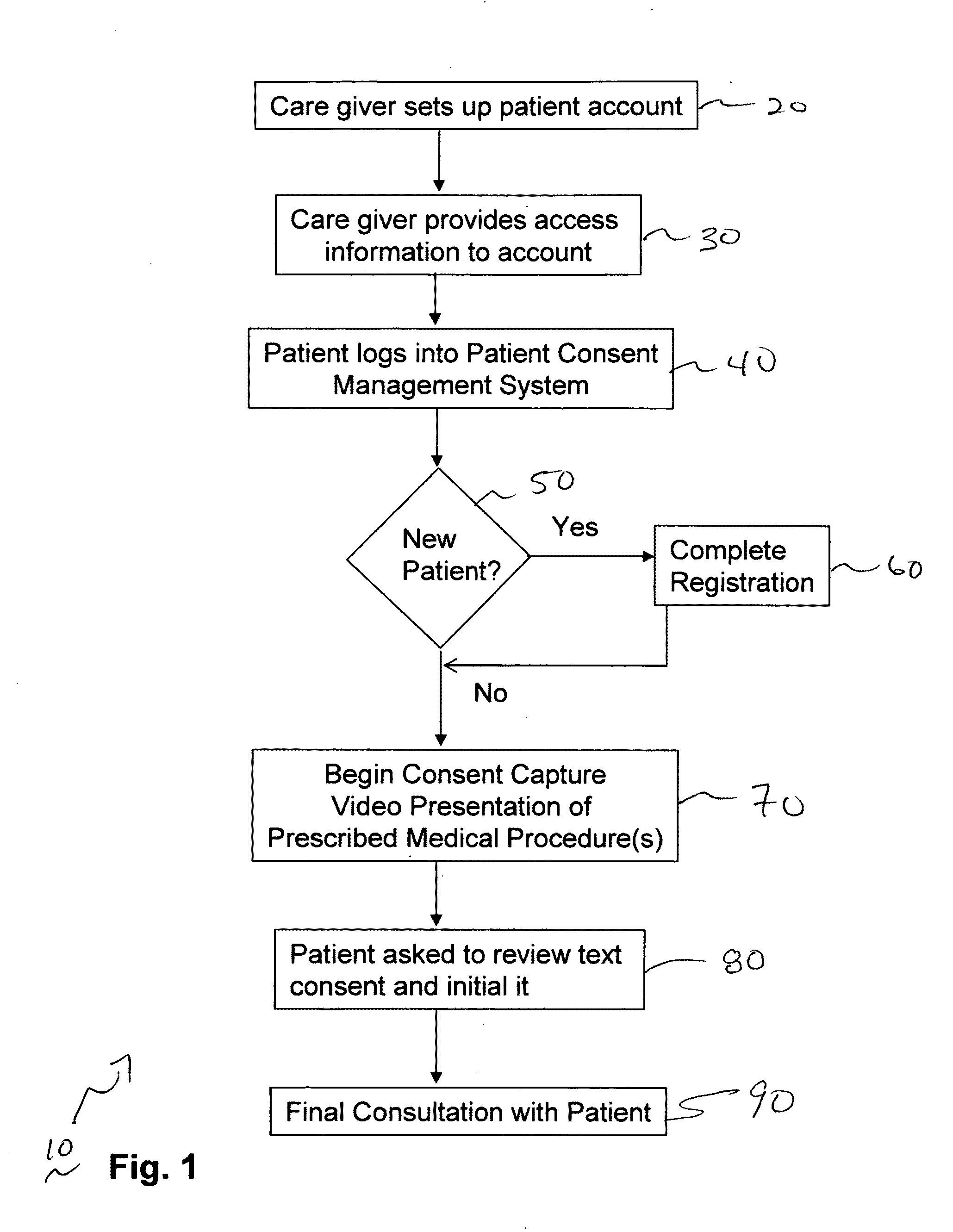
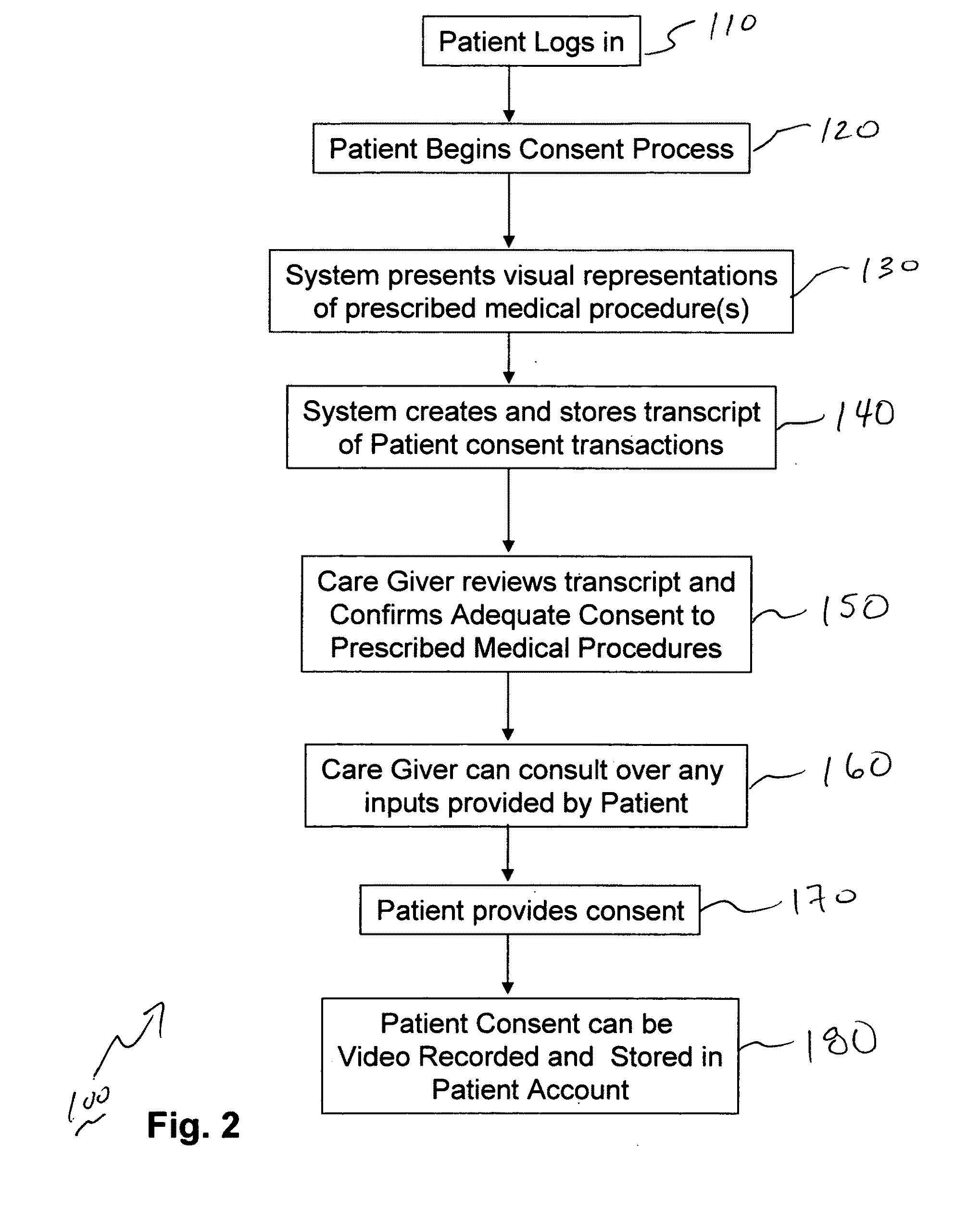
Methods and system for capturing and managing patient consents to prescribed medical procedures
InactiveUS20100094650A1Data processing applicationsComputer-assisted medical data acquisitionCare giverConsent Type
A method of capturing patient consents to a prescribed medical procedures. Patient accounts are created on a computerized patient consent management system. The system authenticates a login attempt by a patient and displays a visual representation of a prescribed medical procedure to the patient. The patient consent management system presents at least one consent request input field for accepting a consent input from the patient and stores the consent input as part of the patient account. The patient consent management system presents the consent input to at least one care giver in order to determine if the patient has given consent to the prescribed medical procedure.
Owner:TRAN SON NAM +2
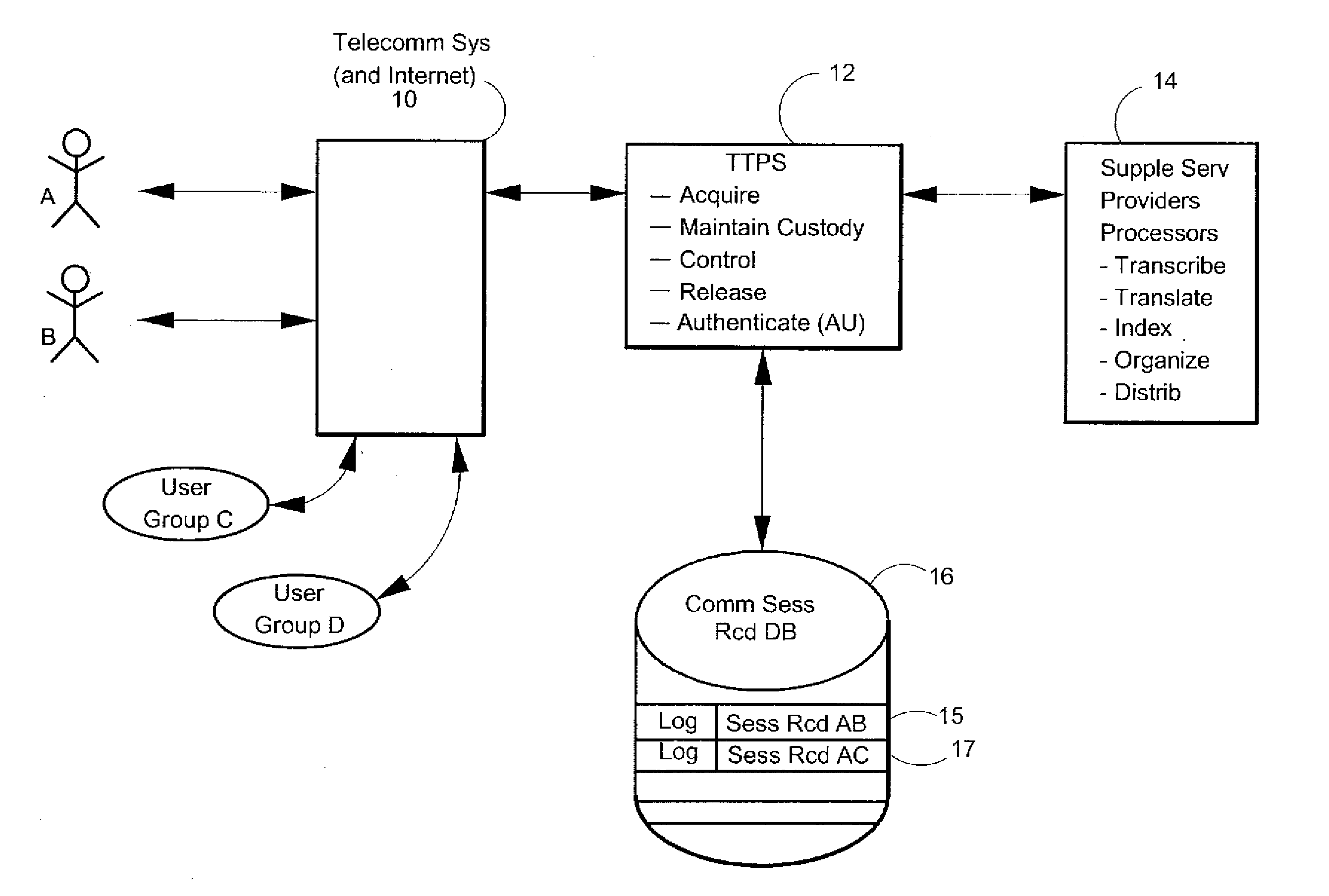
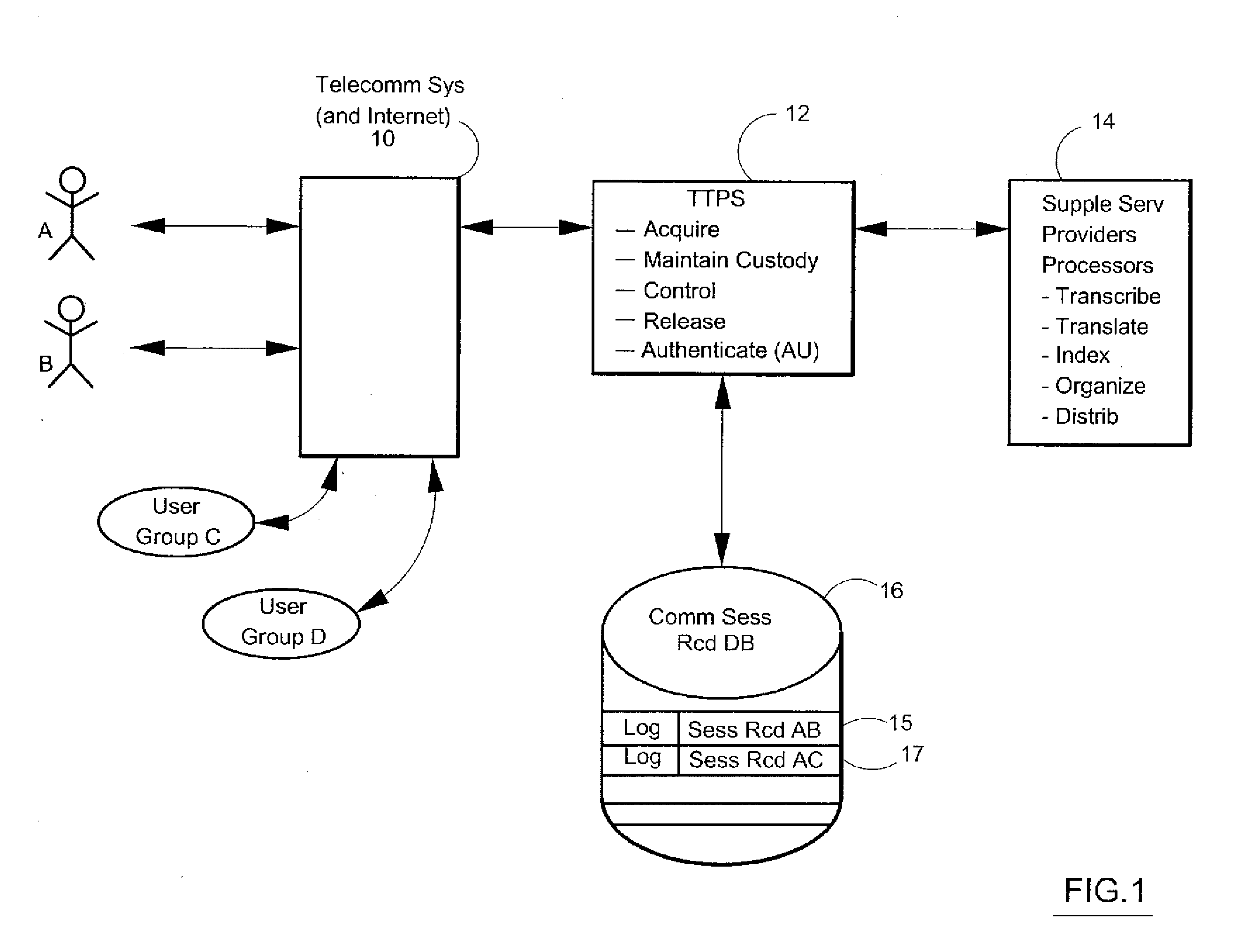
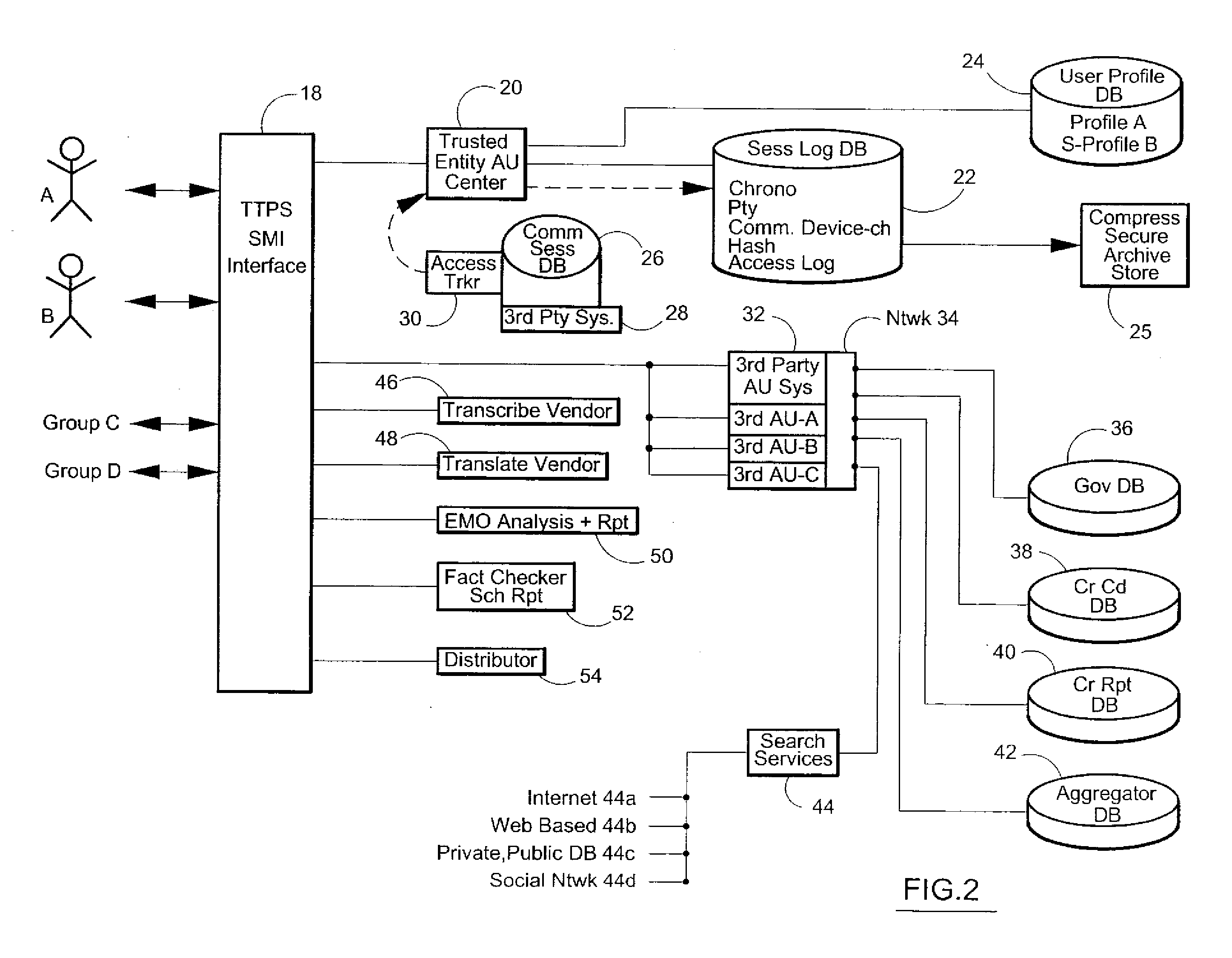
Consent, Signature and Recording Retention in a Certified Communications System
InactiveUS20110287748A1Increase credibilityHigh quality archivalInterconnection arrangementsSpecial service for subscribersComputer hardwareData acquisition
System has consent, signature, recording and retention functions. Near post-sessional data acquisition gathers nominal comm device information from participants. Active online phones are sent a SMS with the recorded event ID, a hyperlink and password for system access. Otherwise, data is acquired for another text message enabled phone or user email. If disconnected, the user is called for additional data. A contractual relationship is established with these functions. With an ACK-consent upon system access, an ACK-consent by the parties, a RECORD ON command, and a recorded intent-to-contract, the system creates an enforceable contract by storing the ACKs and recorded session.
Owner:CERTICALL
Dynamic digital consent
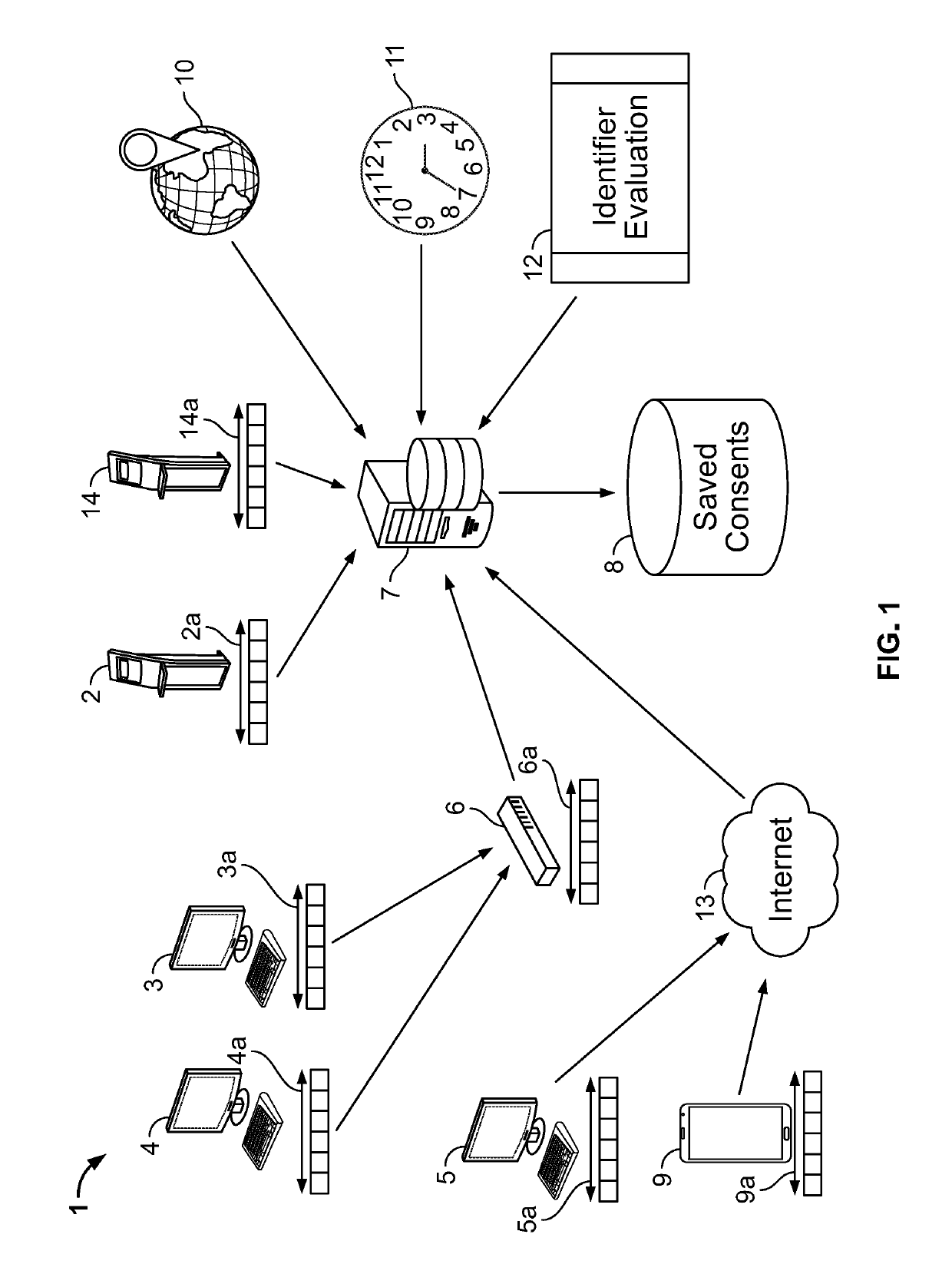
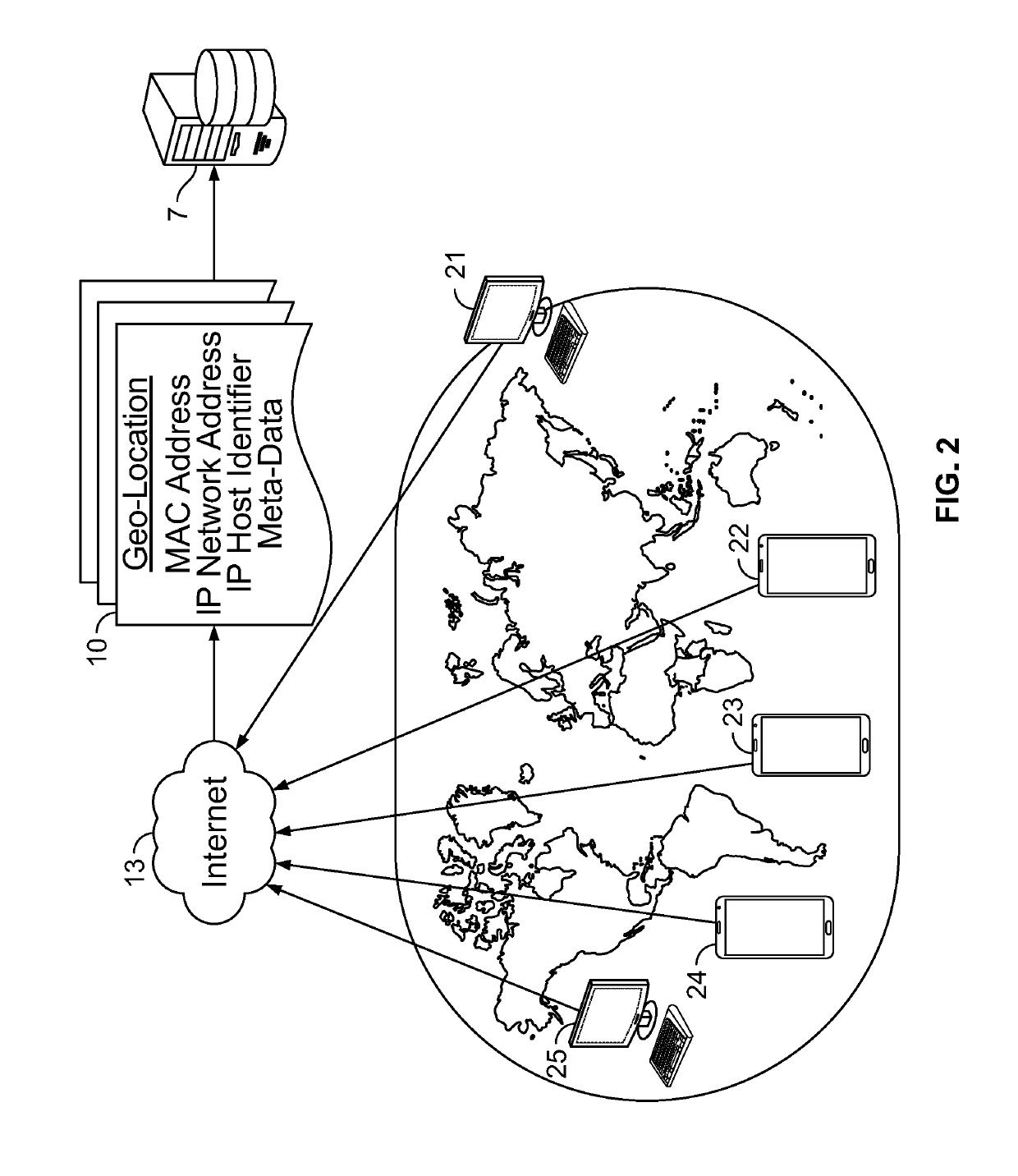
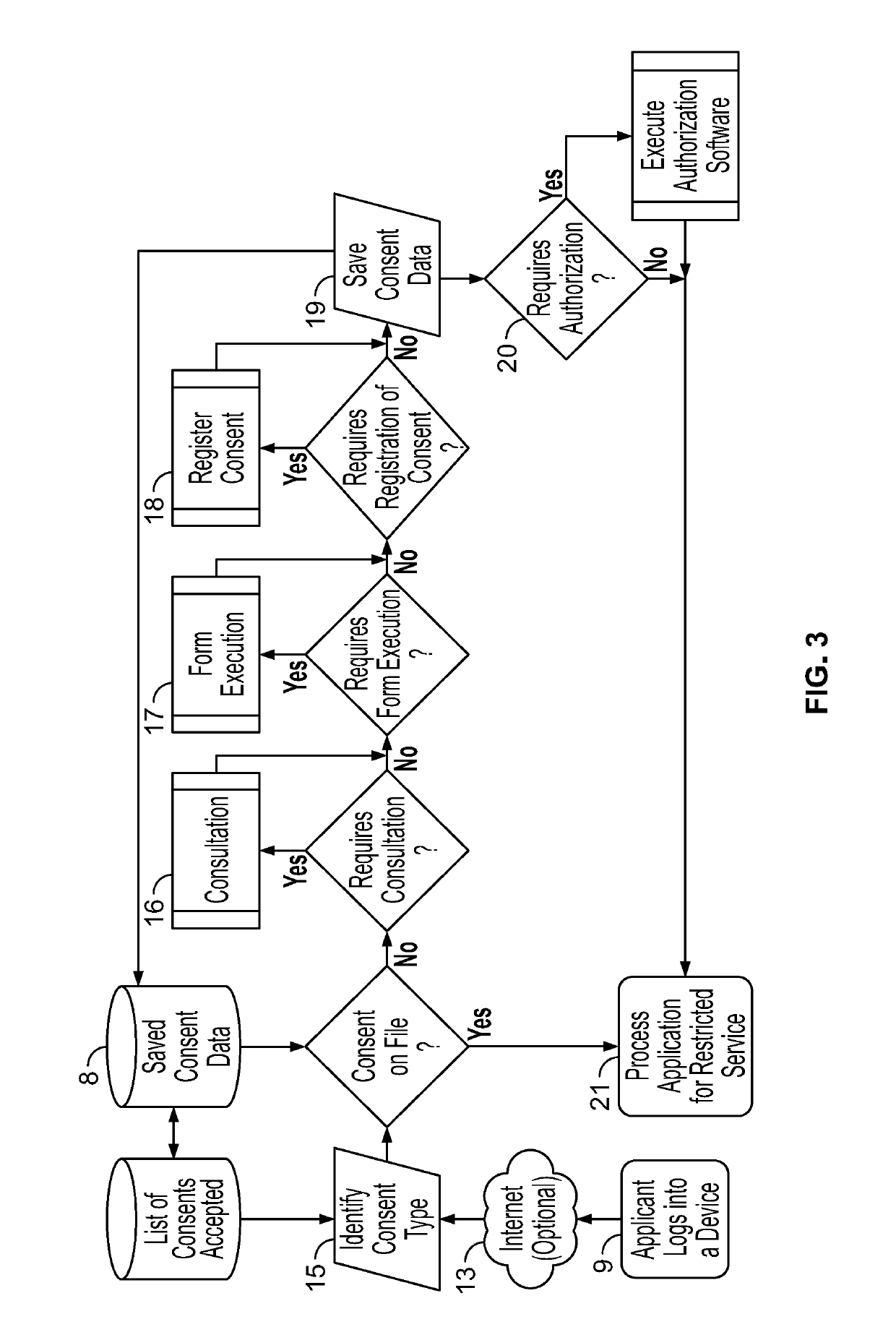
ActiveUS10417401B2Improve performanceDigital data protectionDigital data authenticationIp addressGeolocation
Method and apparatus for a system to harden digital consents. The system uses an evaluation of geographic locations, transaction times, and device identities to control the upload of consent data. Evaluations occur using numerous techniques including MAC address evaluation, IP address evaluation, meta-data evaluation, and physical location of restricted equipment such as ATMs and kiosks. Reliability of consent data entered into the system may be enhanced by strictly evaluating geographic locations, transaction times, and / or device identities.
Owner:BANK OF AMERICA CORP
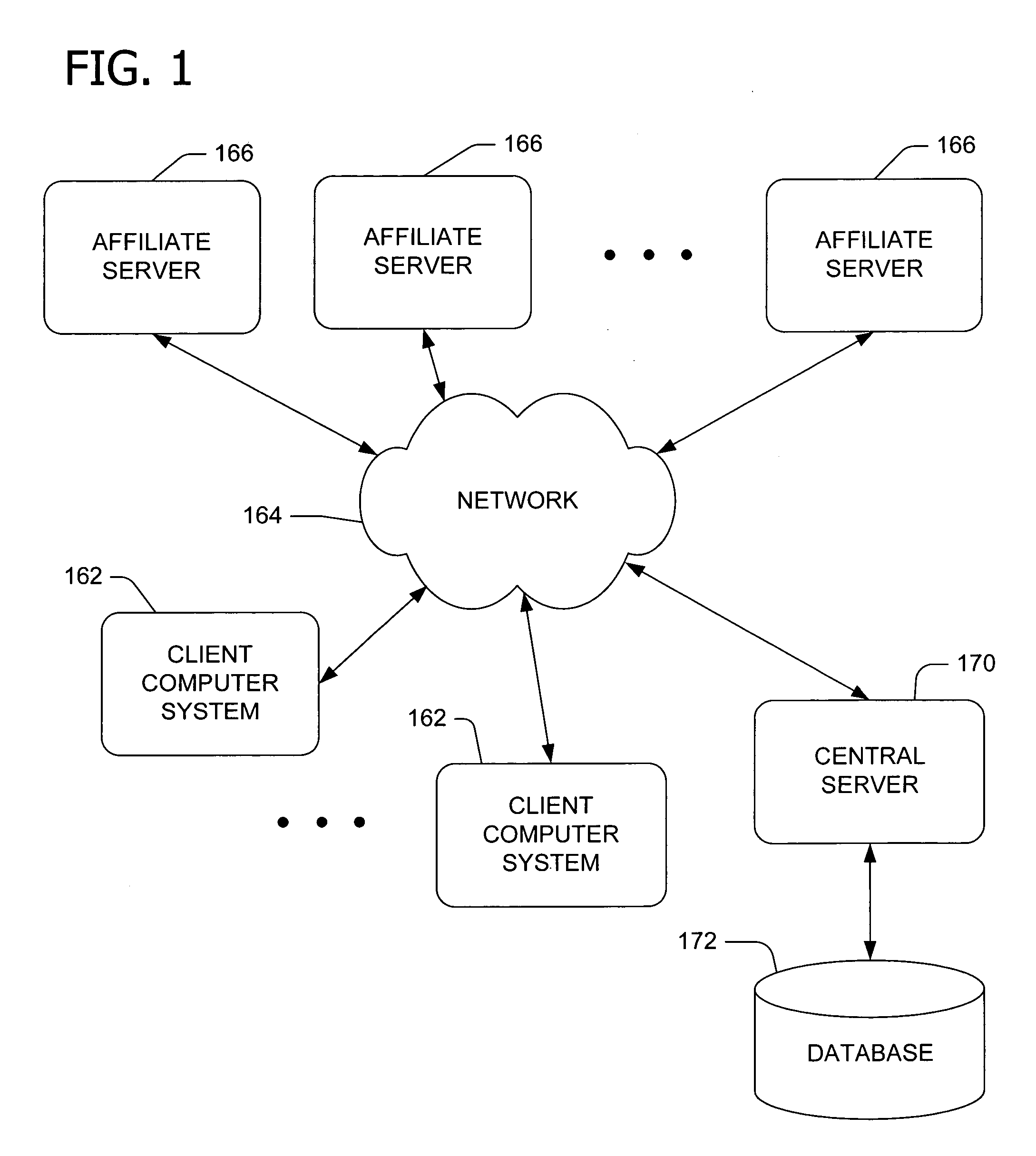
Dynamically and customizably managing data in compliance with privacy and security standards
InactiveUS9049314B2Preserving professional confidencesAvoid identificationDigital data protectionOffice automationDocumentation procedureRecordset
Owner:VERISMA SYST
Profile and consent accrual
ActiveUS20050193093A1Enhance information sharingLess laborDigital data processing detailsDigital data protectionInternet privacyPersonal details
Consent management between a client and a network server. In response to a request for consent, a central server determines if requested user information is included in a user profile associated with a user and if the user has granted consent to share the requested user information. A user interface is provided to the user via a browser of the client to collect the requested user information that is not included in the user profile and the consent to share the requested user information from the user. After receiving the user information provided by the user via the user interface, the service provided by the network server is allowed access to the received user information, and the central server updates the user profile. Other aspects of the invention are directed to computer-readable media for use with profile and consent accrual.
Owner:MICROSOFT TECH LICENSING LLC
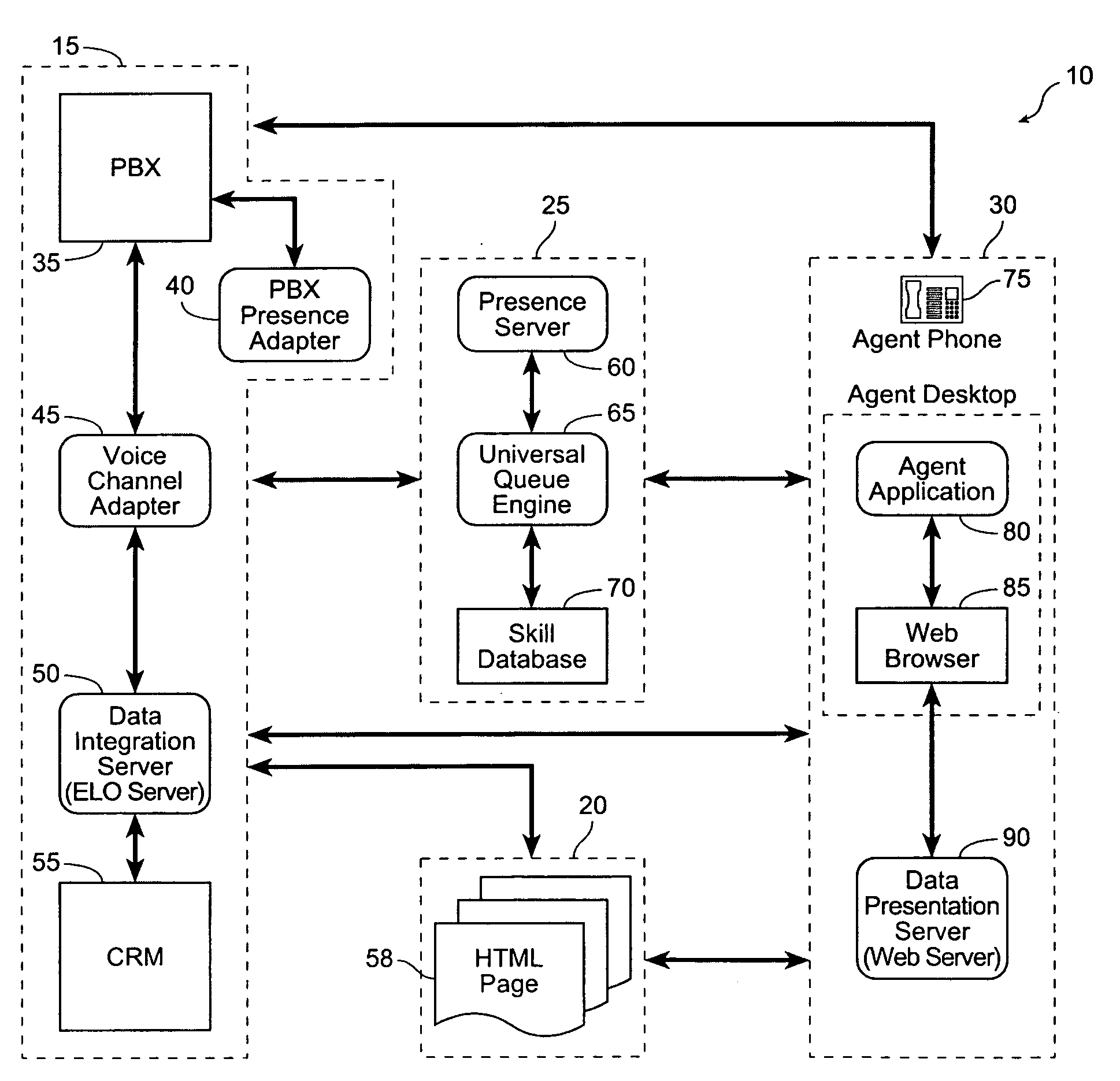
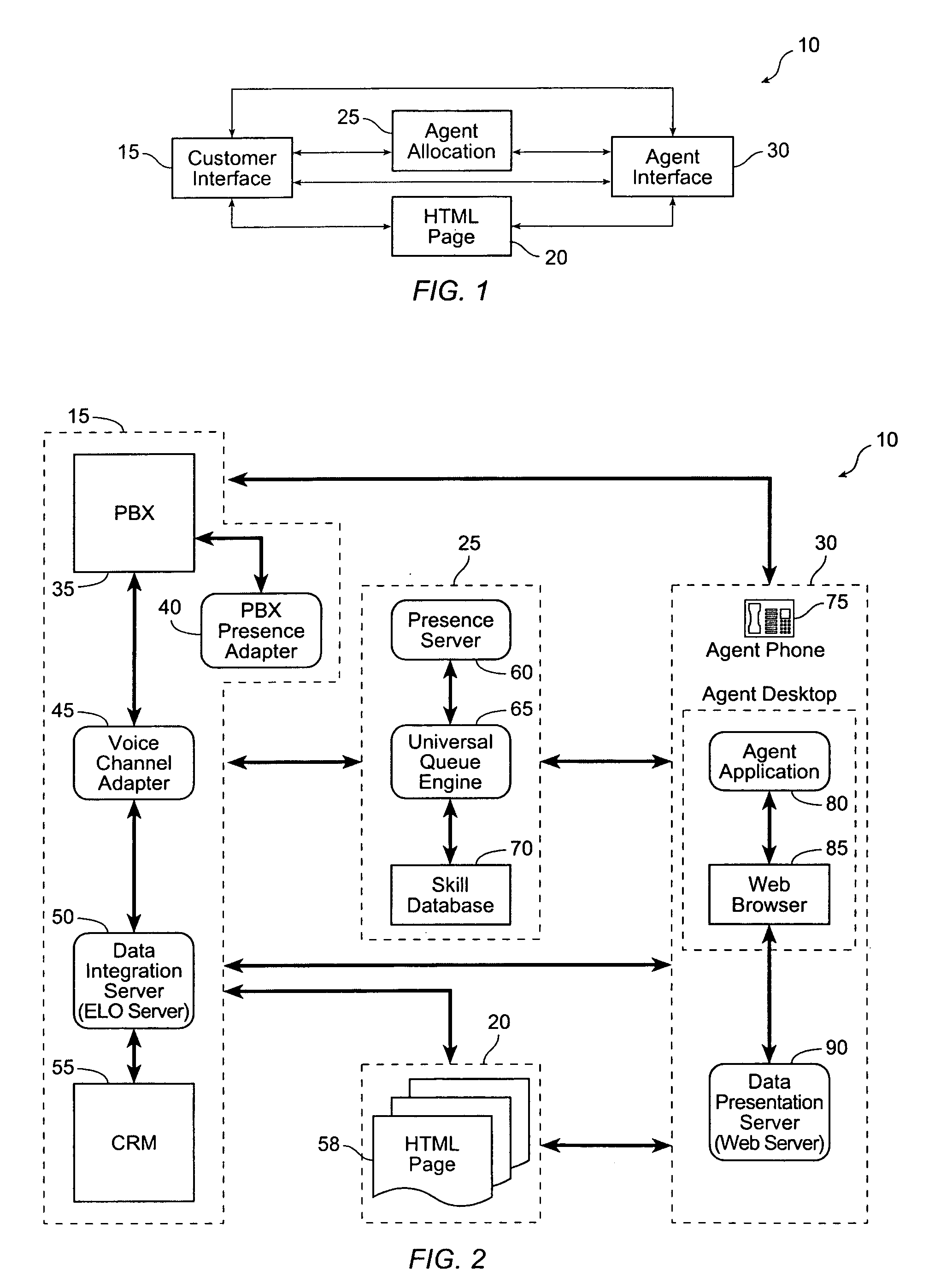
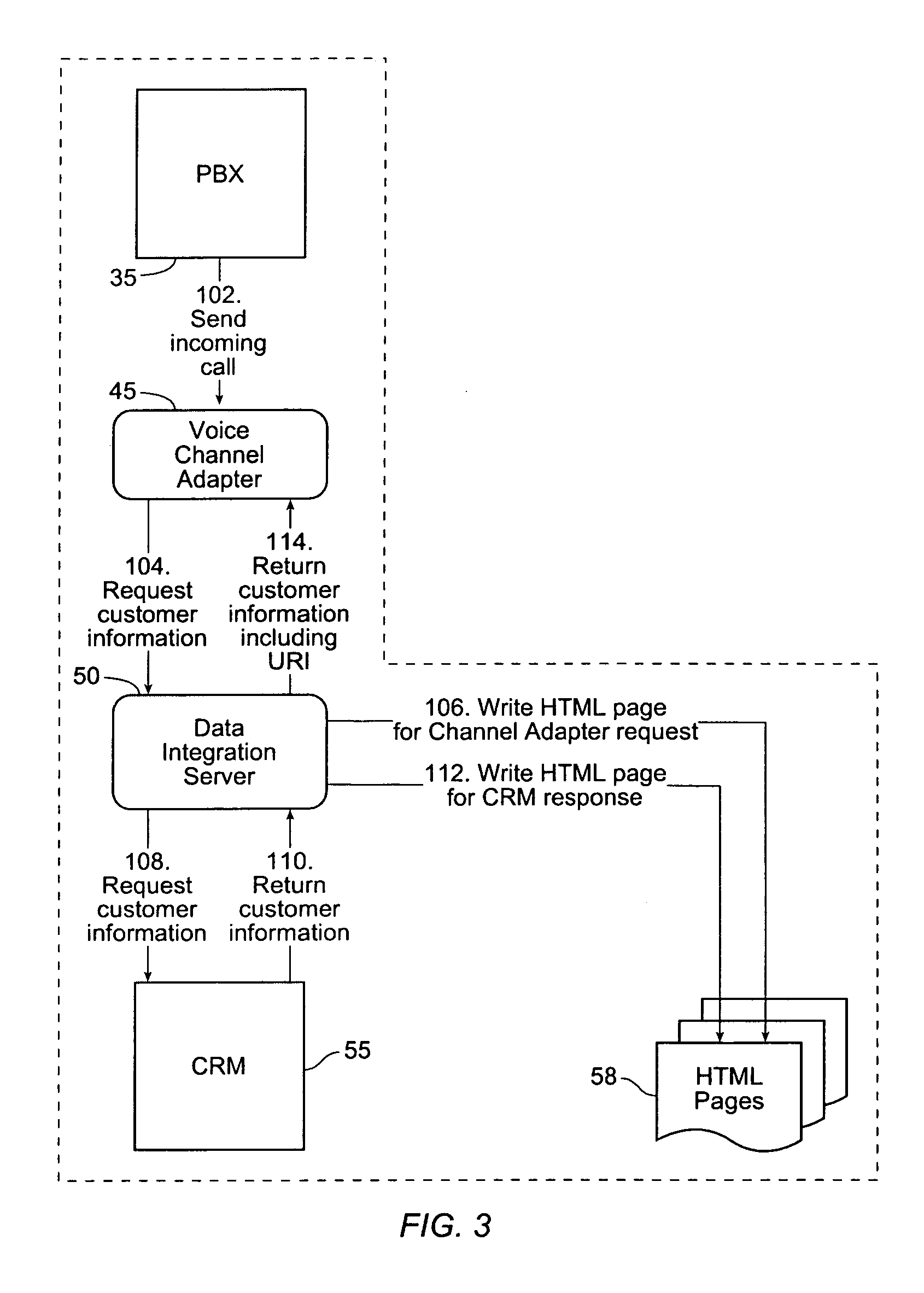
"Pull" architecture contact center
A system and method for processing a user inquiry. The method includes receiving a user inquiry, sending a first request for user information to a first database, providing the user information from the first database, and selecting a first agent. The first agent has a desirable set of skills and is available. Additionally, the method includes sending the user information to the selected first agent with a first web browser and sending the user inquiry to the selected first agent in response to a first signal indicative of a first consent from the selected first agent within a predetermined period of time.
Owner:ACQUEON TECH
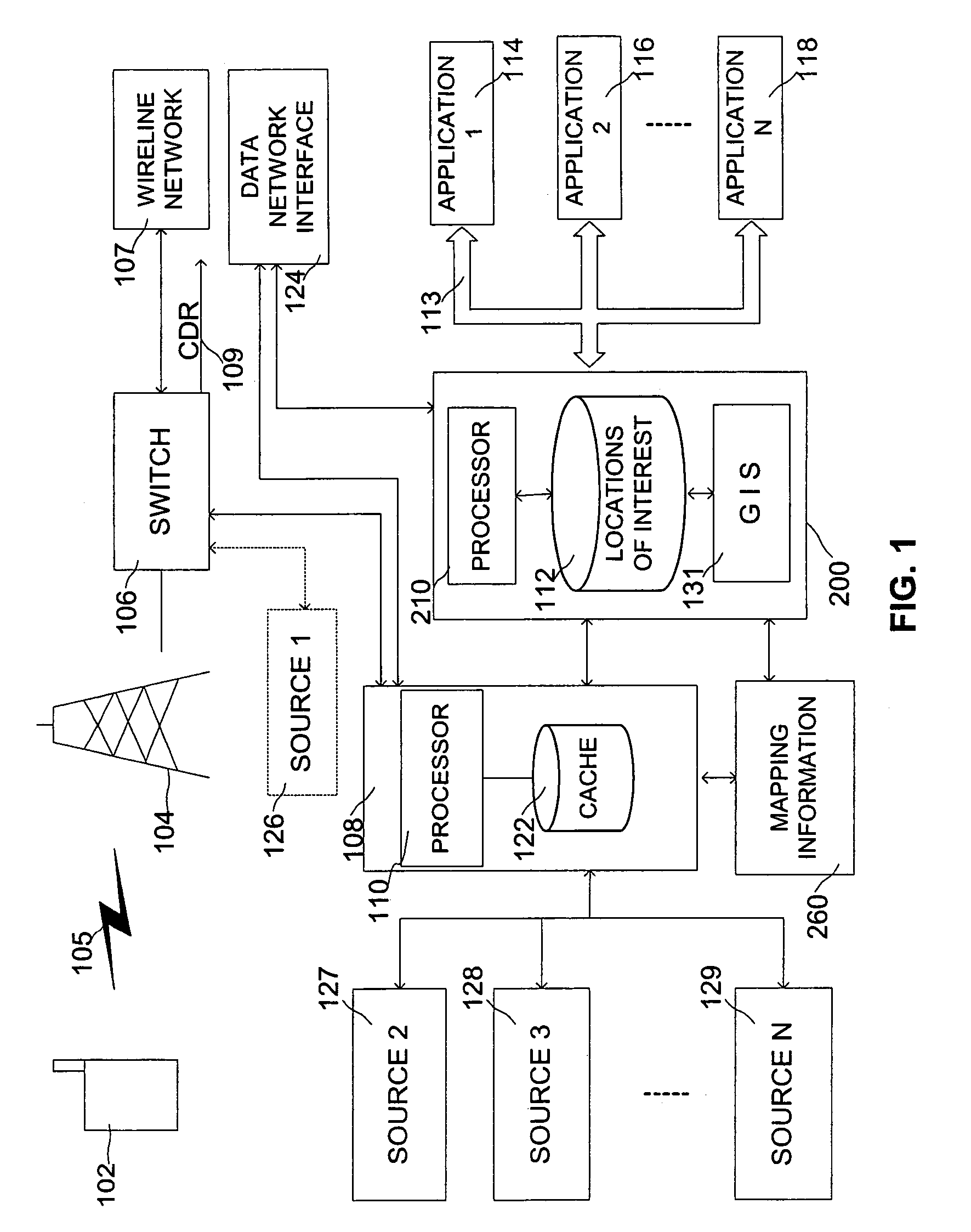
Lawful intercept service
InactiveUS7231218B2Effectively locateEffective monitoringSpecial service for subscribersRadio/inductive link selection arrangementsAuthorizationConsent Type
A system and method is provided for monitoring the activities and / or locations of wireless units in a wireless network independent of location-based service preferences of those wireless units. That is, a system and method is provided that allows an authorized requester override location-based service preferences (e.g., privacy settings) that may be set for a wireless unit. In this regard, an authorized entity may be able to effectively locate and / or monitor the activities of a wireless unit associated with an individual of interest. Furthermore, if proper authorization exists, such monitoring may be done surreptitiously without the wireless unit user's knowledge and / or consent. For example, in some instances, law enforcement agencies may be authorized to monitor call traffic and / or the location of persons utilizing wireless units.
Owner:UNWIRED PLANET
Enhanced authorization
Owner:ASSA ABLOY AB
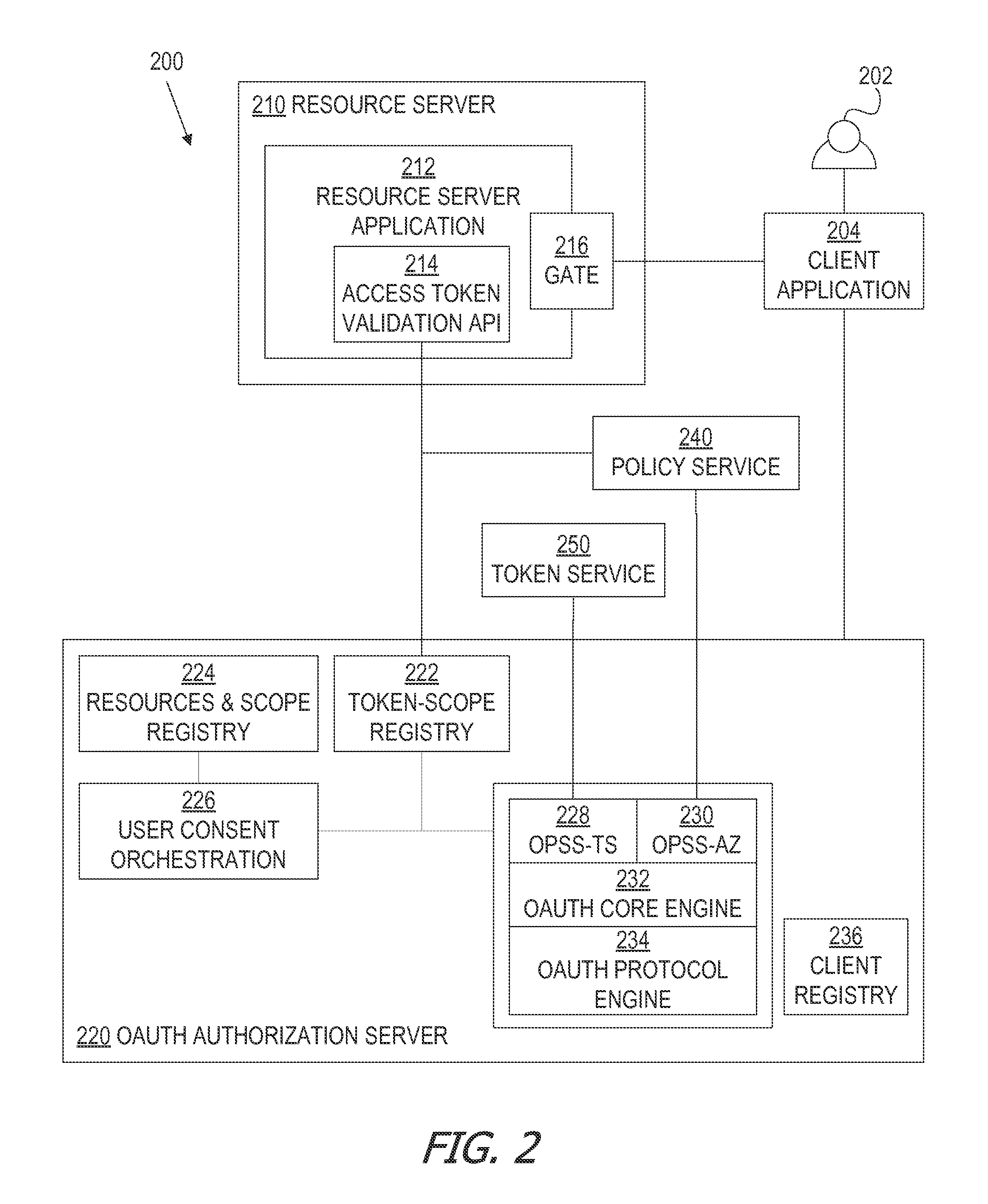
Multiple resource servers interacting with single oauth server
ActiveUS20160028737A1Easy to customizeDigital data processing detailsMultiple digital computer combinationsClient-sideAccess token
A framework, which conforms to the OAuth standard, involves a generic OAuth authorization server that can be used by multiple resource servers in order to ensure that access to resources stored on those resource servers is limited to access to which the resource owner consents. Each resource server registers, with the OAuth authorization server, metadata for that resource server, indicating scopes that are recognized by the resource server. The OAuth authorization server refers to this metadata when requesting consent from a resource owner on behalf of a client application, so that the consent will be of an appropriate scope. The OAuth authorization server refers to this metadata when constructing an access token to provide to the client application for use in accessing the resources on the resource server. The OAuth authorization server uses this metadata to map issued access tokens to the scopes to which those access tokens grant access.
Owner:ORACLE INT CORP
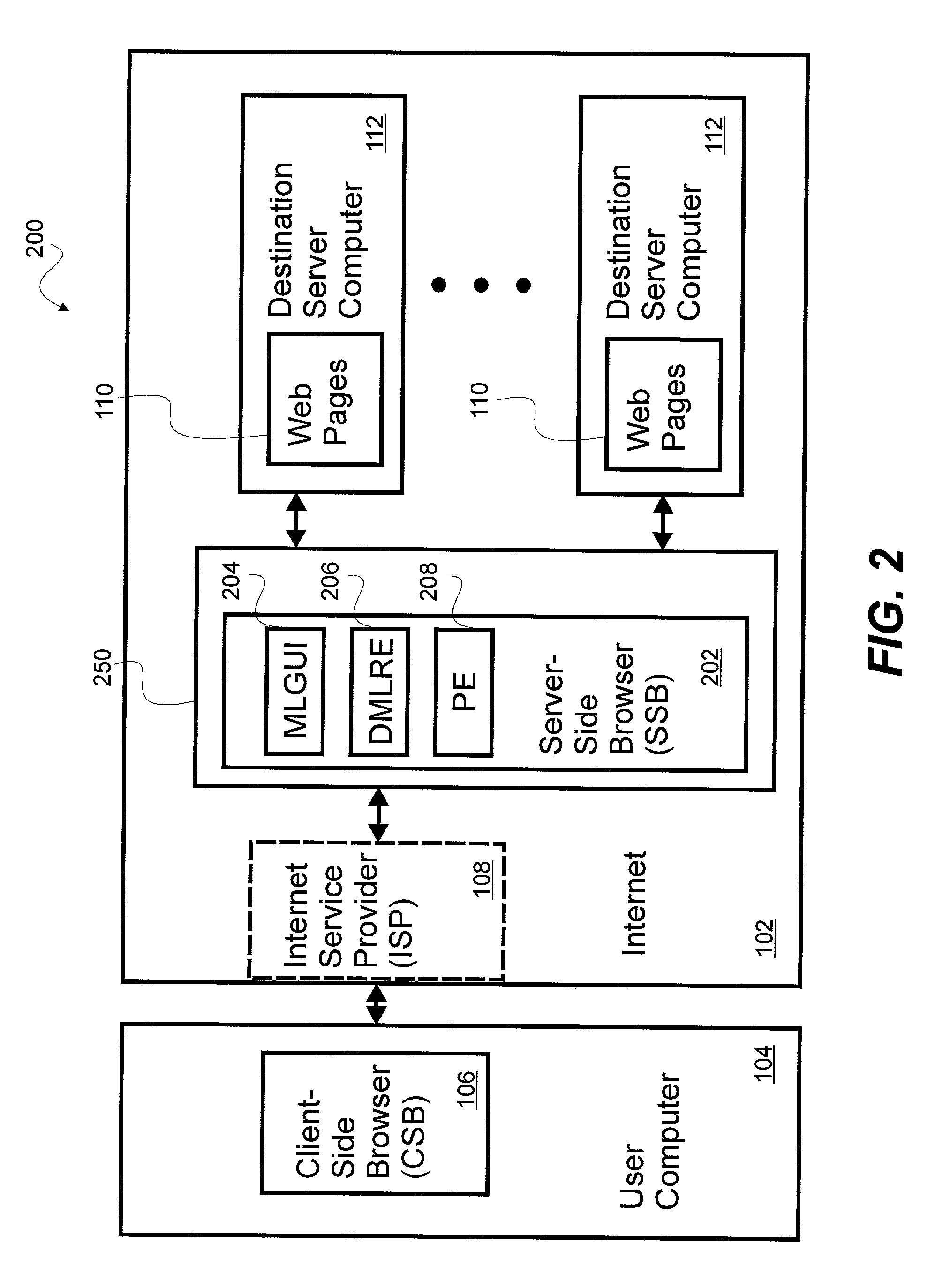
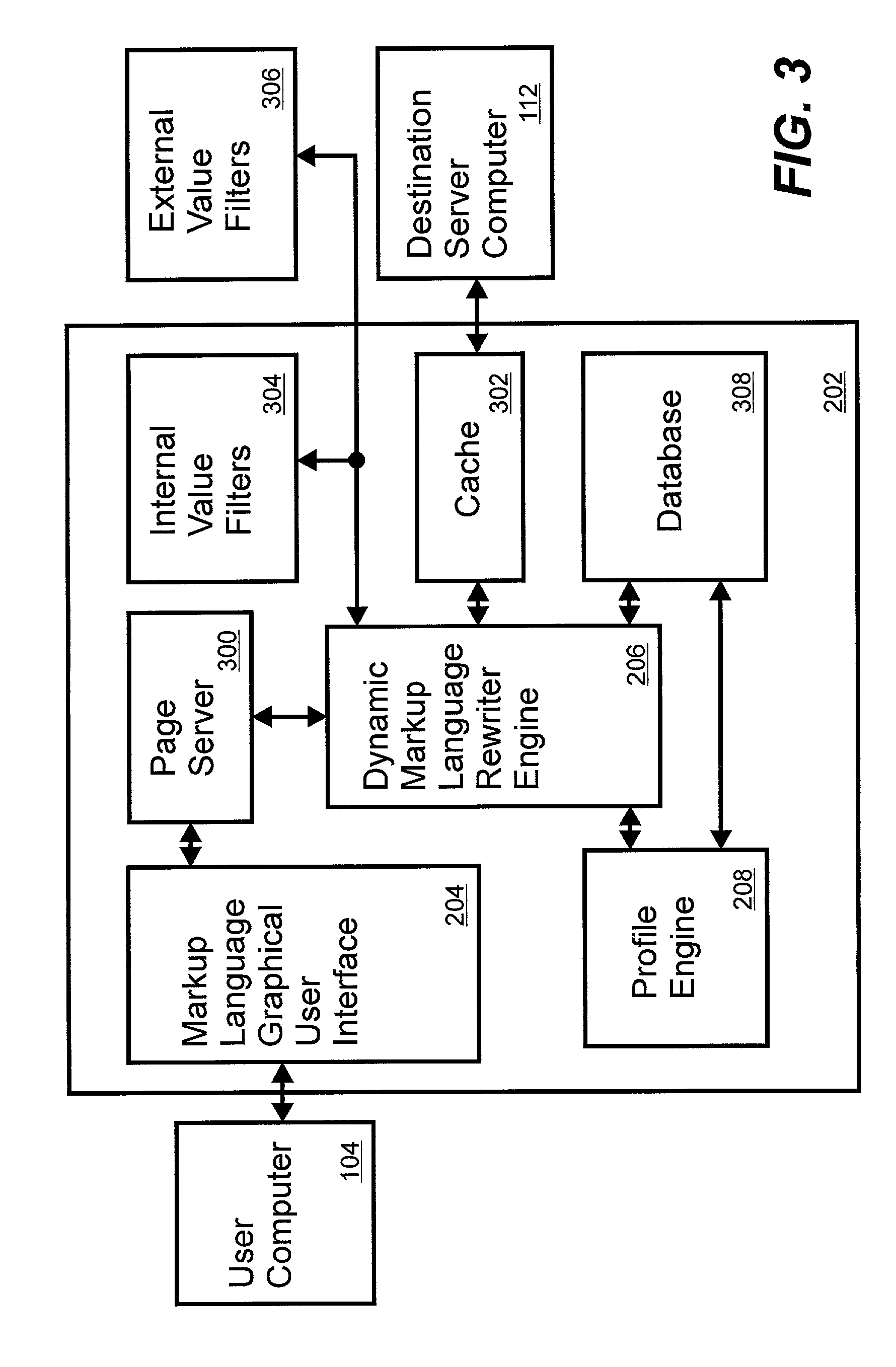
System and method for a server-side browser including markup language graphical user interface, dynamic markup language rewriter engine and profile engine
The invention is a system and method for customizing access and delivery of information distributed in a packet-based network. The system includes a user computer and a destination server computer separated by a server-side browser (SSB) server computer hosting a SSB. The SSB includes a markup language graphical user interface (MLGUI), a dynamic markup language rewriter engine (DMLRE) and a profiling engine (PE). The SSB may be configured as an intermediary infrastructure residing on the Internet providing customized information gathering for a user. The components of the SSB allow for controlling, brokering and distributing information more perfectly by controlling both browser functionality (on the client-side) and server functionality (on the destination site side) within a single point and without the necessity of incremental consents or integration of either side.
Owner:ORANGATANGO
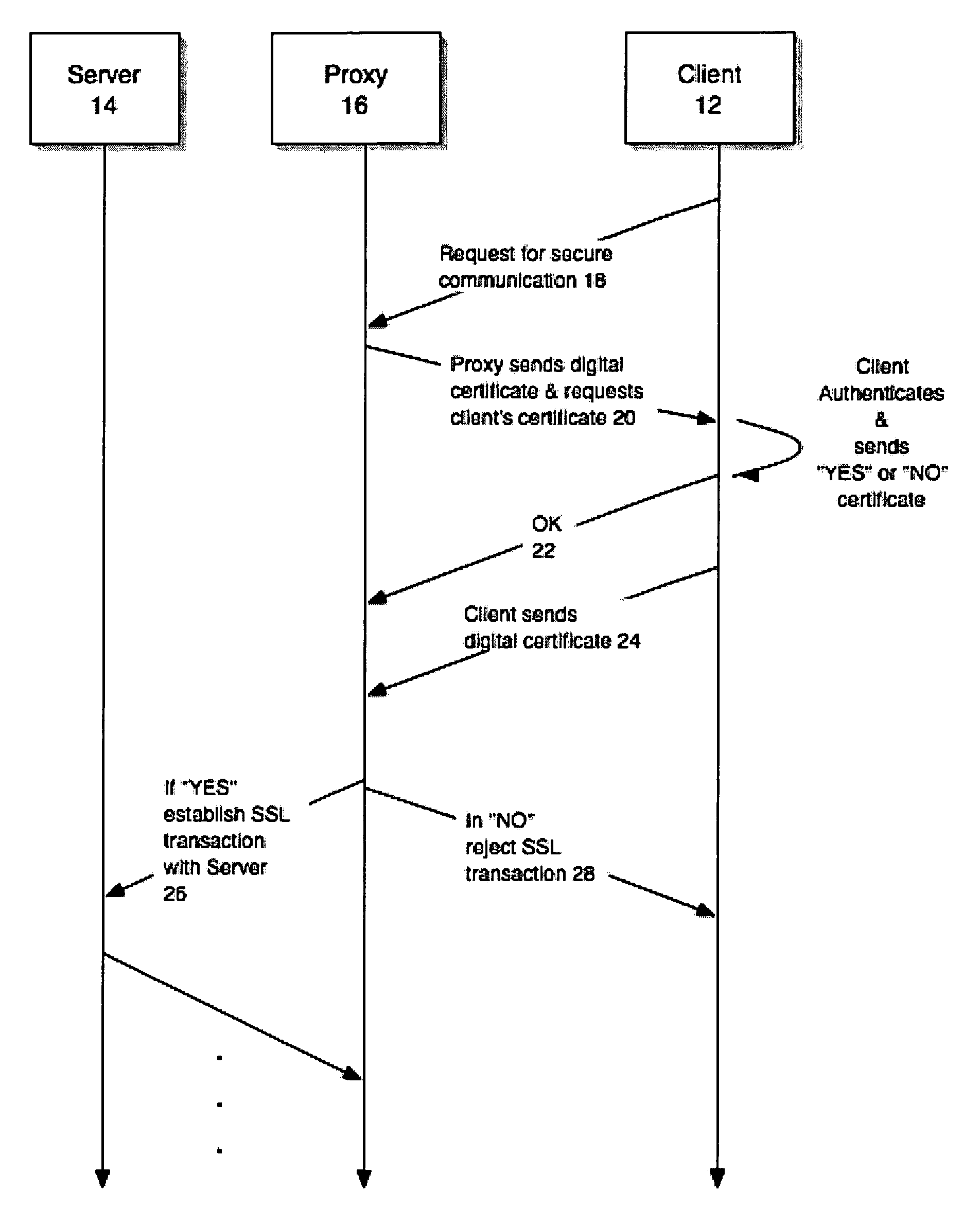
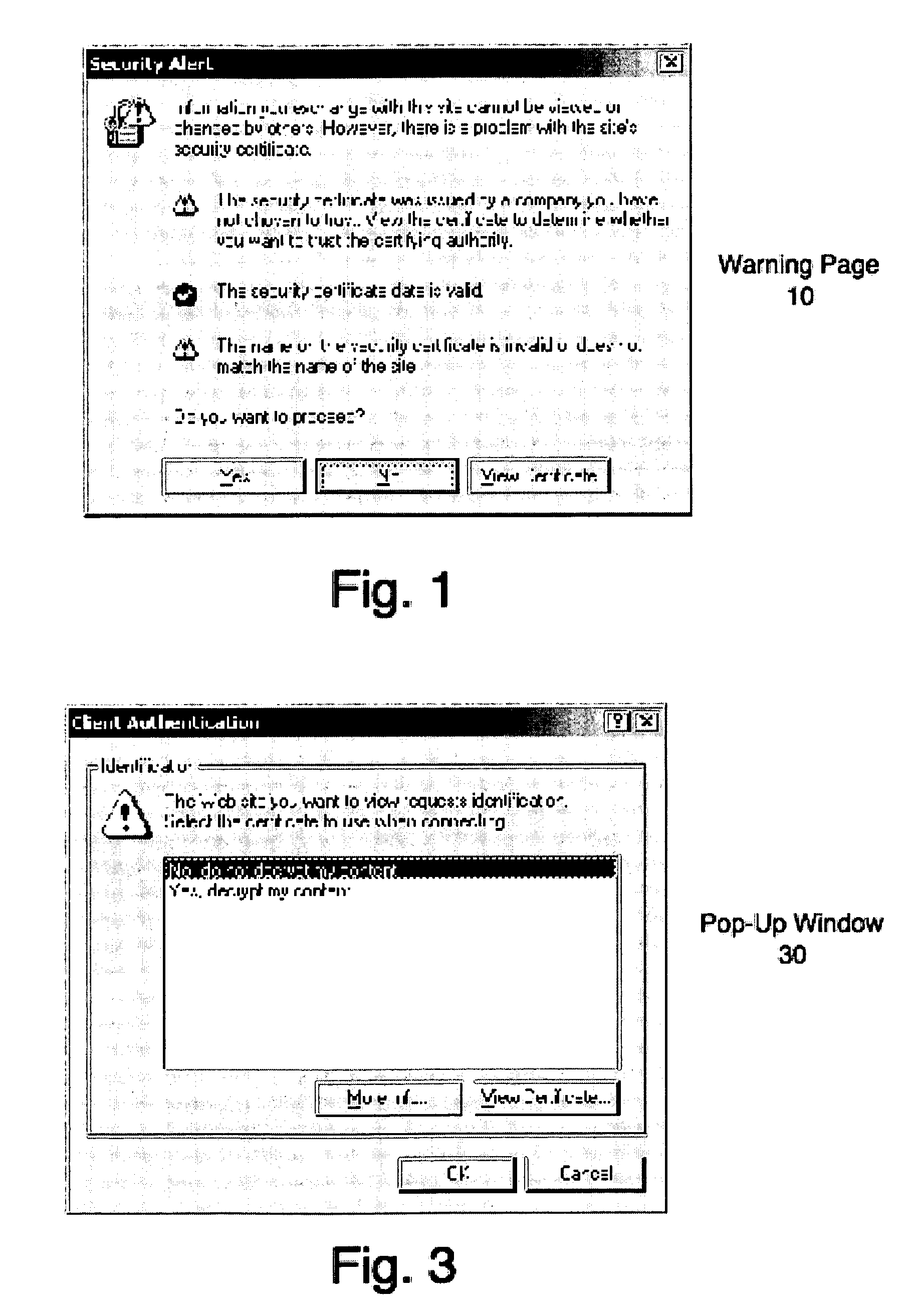
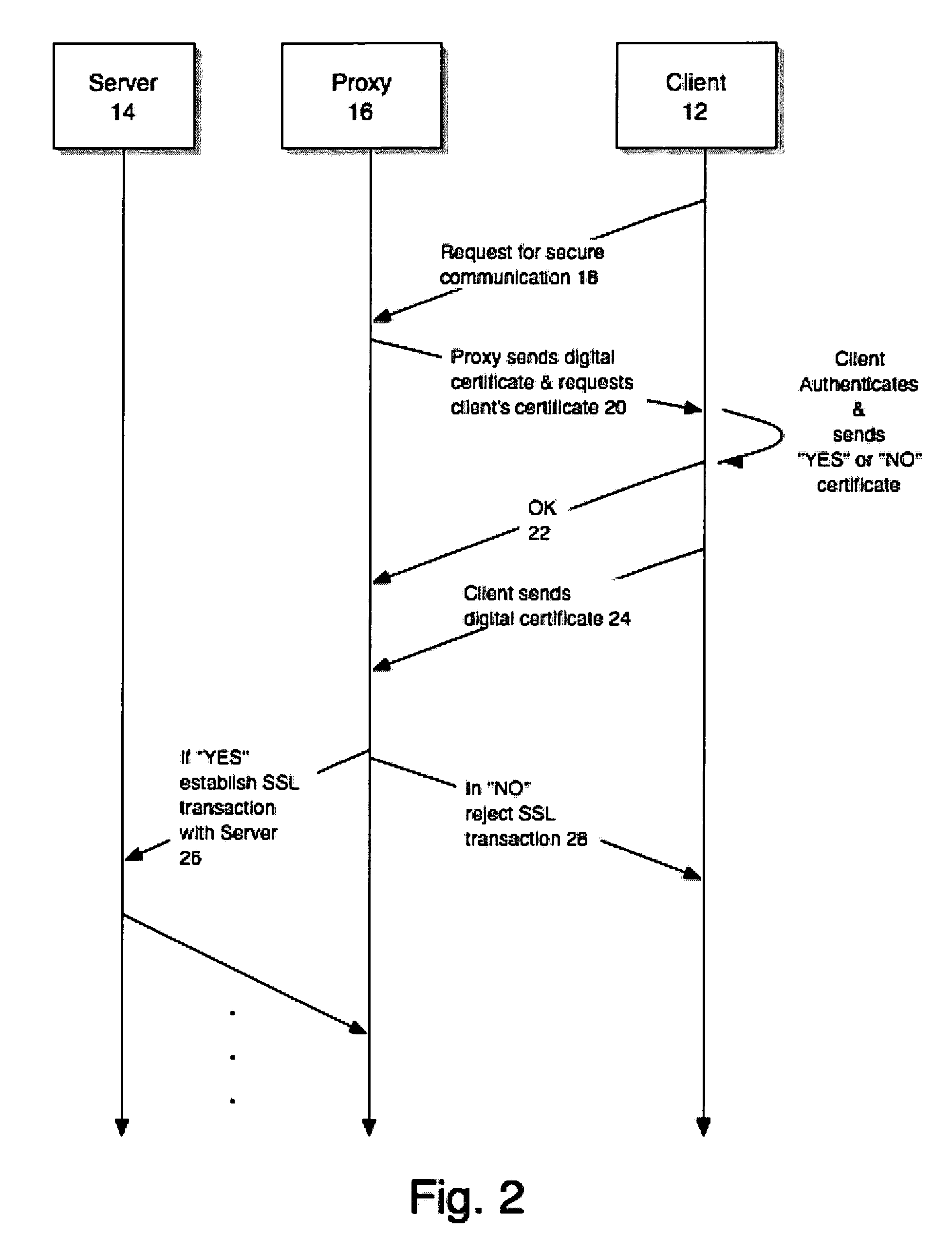
Using digital certificates to request client consent prior to decrypting SSL communications
ActiveUS7543146B1User identity/authority verificationDigital data authenticationComputer resourcesSecure communication
In response to an indication of a desire to initiate a secure communication session (e.g., a session utilizing a the SSL communication protocol) with a computer resource, a digital certificate indicative of whether or not a user consents to monitoring of the secure communication session is requested. The response to this request will permit or deny such monitoring, allowing the session to proceed or be cancelled, accordingly.
Owner:CA TECH INC
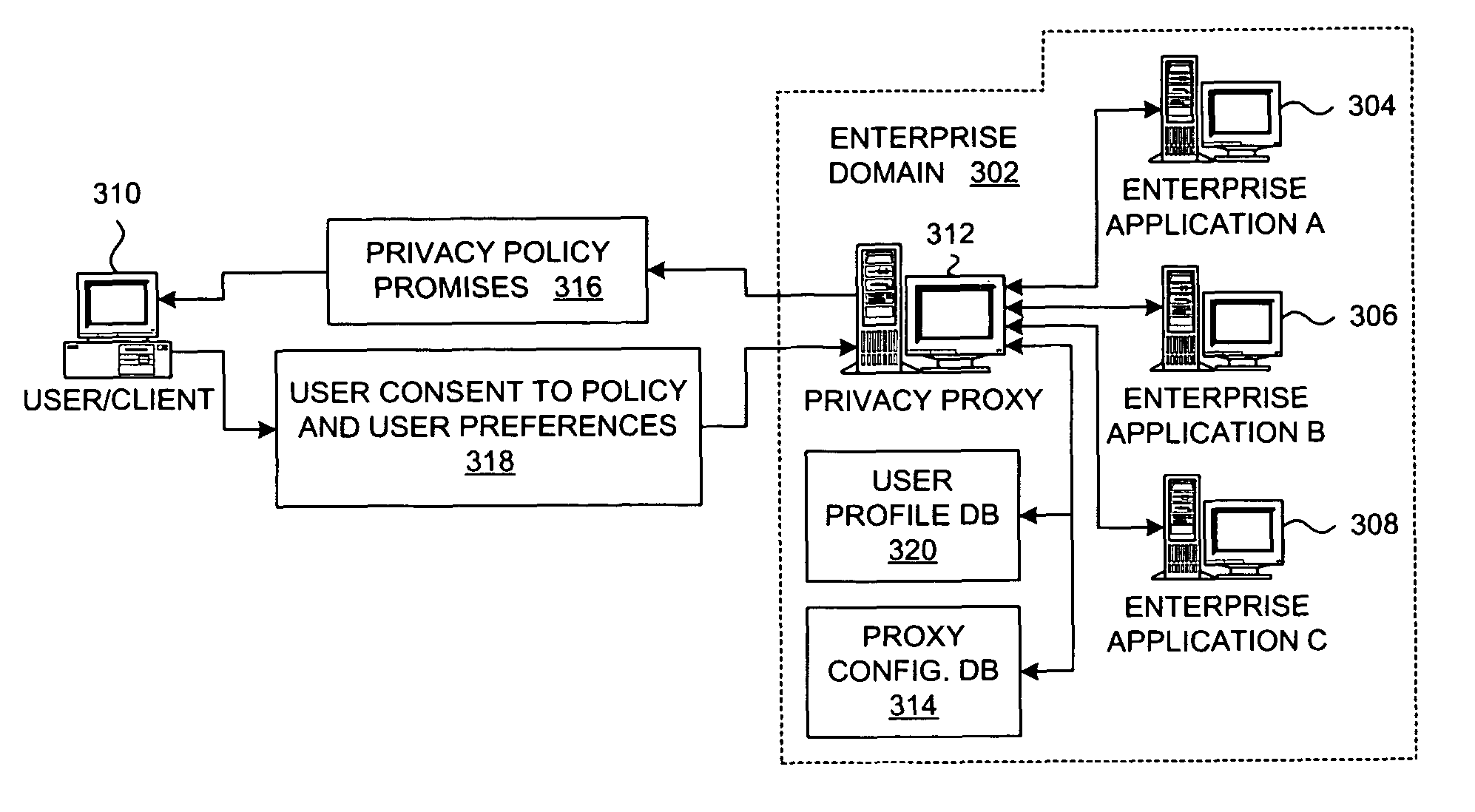
Method and system for implementing privacy notice, consent, and preference with a privacy proxy
ActiveUS8464311B2Digital data processing detailsUser identity/authority verificationData processing systemInternet privacy
A method is presented for processing data for a privacy policy concerning management of personally identifiable information. A proxy intercepts a first message from a server to a client and determines that the first message initiates collection of personally identifiable information from a user of the client. The proxy then sends a second message to the client that requests consent from the user to the privacy policy. If the user provides consent within a third message that is received by the proxy from the client, then the proxy sends the intercepted first message to the client. If the user does not provide consent, then the proxy sends a fourth message to the server that fails the collection of personally identifiable information from the client by the server. The proxy may also obtain user preferences for options concerning management of the personally identifiable information by a data processing system.
Owner:IBM CORP
Systems and methods providing interactions between multiple servers and an end use device
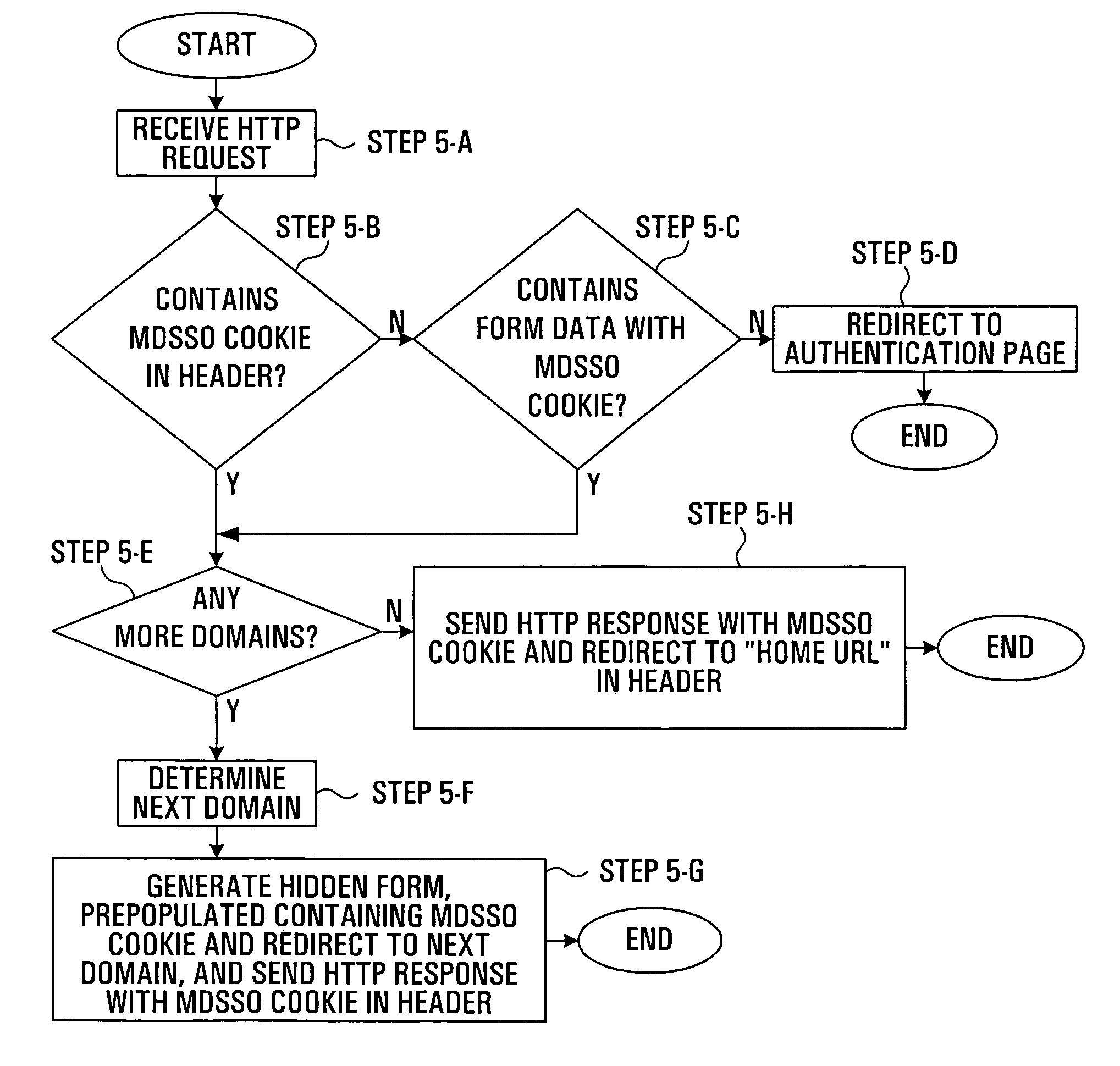
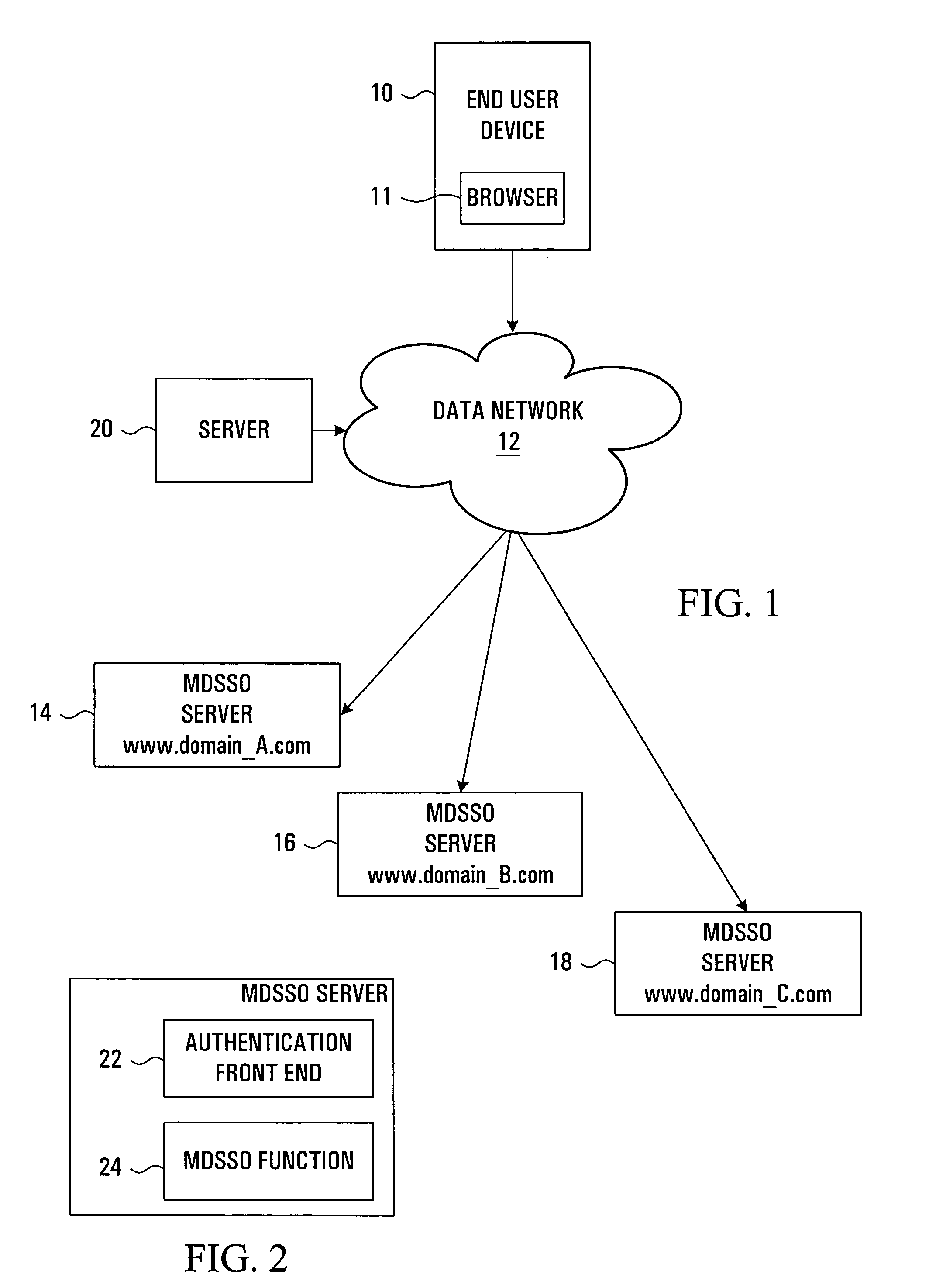
Methods and systems are provided which convey access control information from a first server to a second server through an end user device, for example in a system in which these servers and devices are all connected to the Internet. The method starts after the first server receives a message from the end user device. The first server in response to this message from the end user device sends a response message to the end user device containing the access control information to be conveyed to the second server, optionally after performing authentication. The response message also contains an instruction for the end user device to post a second message to the second server containing the information. The information is preferably contained in a content portion of the message. A hidden form may be used in the response message to contain the information. Optionally, the end user may be presented with an option to post the second message or not. This may allow conformance with data privacy laws requiring end user consent of data transfer. The instruction to post to the second server may consist of active content within the response message's content portion. This can be used to cause an end user device to store a cookie in association with a number of servers in different domains thereby implementing a multiple domain single sign-on function.
Owner:ENTRUST
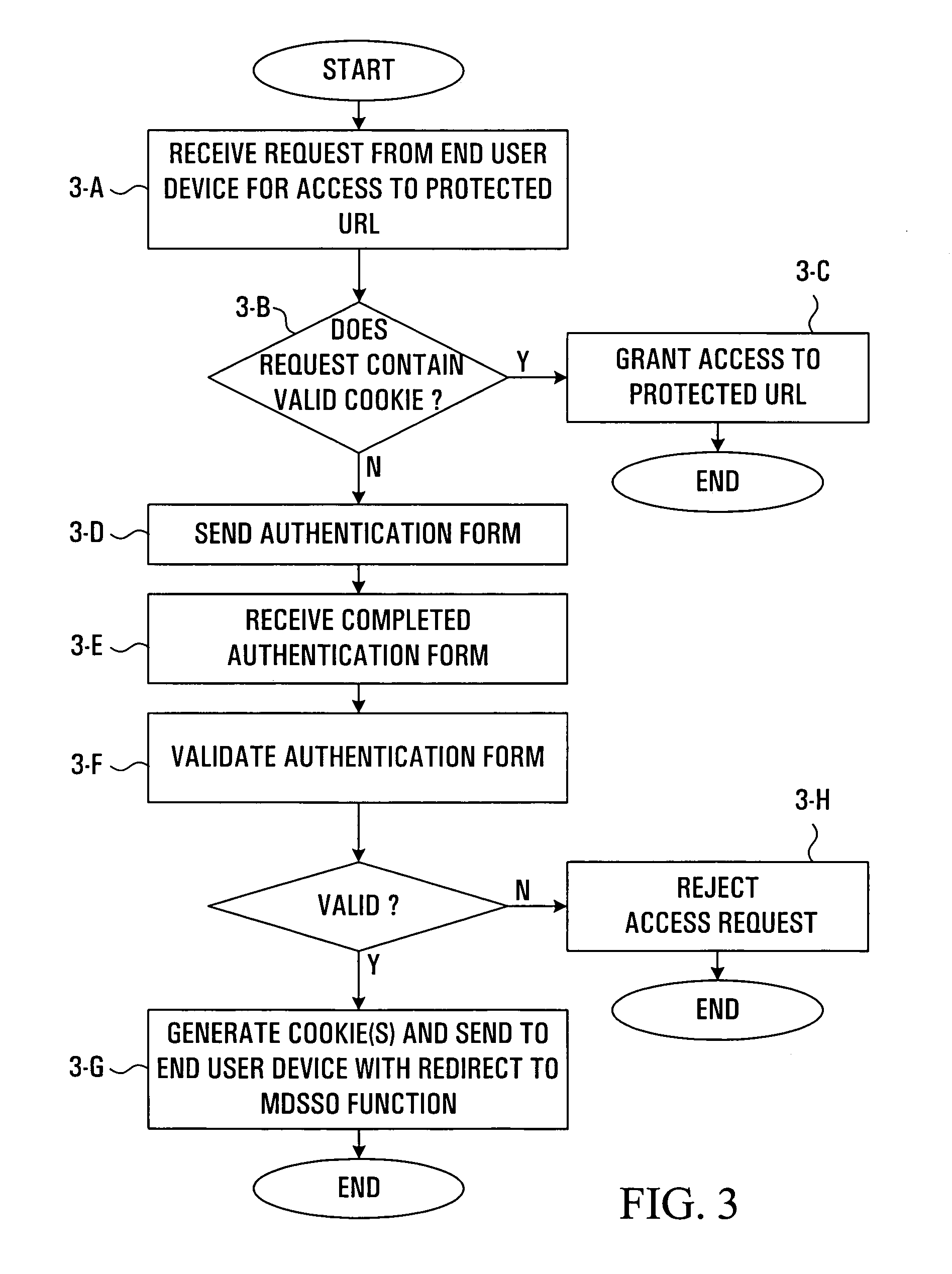
Computer accessible methods for establishing certifiable informed consent for a procedure
InactiveUS6516300B1Easy to learnMonitor stateData processing applicationsMedical practises/guidelinesAccess methodComputer science
A method for establishing certifiable patient informed consent for a medical procedure, where, in one embodiment, the patient interacts with a video training system until mastery of all required information is successfully achieved. Training techniques which permit elicitation of measurable behaviors from a patient as a guide to discerning the level of knowledge of the patient are utilized. Certification is only granted when the measurable behavior approximately coincide with the legal and medical standards for establishing informed consent. The system is capable of adapting to various medical procedures, as well as various patient attitudes and knowledge bases, while still maintaining a level of consistency throughout. In one embodiment, a minimum probability of understanding may be preset, and the training procedure will continue until the actual statistical probability of understanding is at least equal to the preset minimum. An interactive nature of the system is present in the present system for facilitating the training process and continuously monitoring the patient's knowledge.
Owner:COGNIZANT TRIZETTO SOFTWARE GRP INC
User-centric consent management system and method
InactiveUS20070038765A1Digital data processing detailsComputer security arrangementsWeb serviceClient-side
Owner:MICROSOFT TECH LICENSING LLC
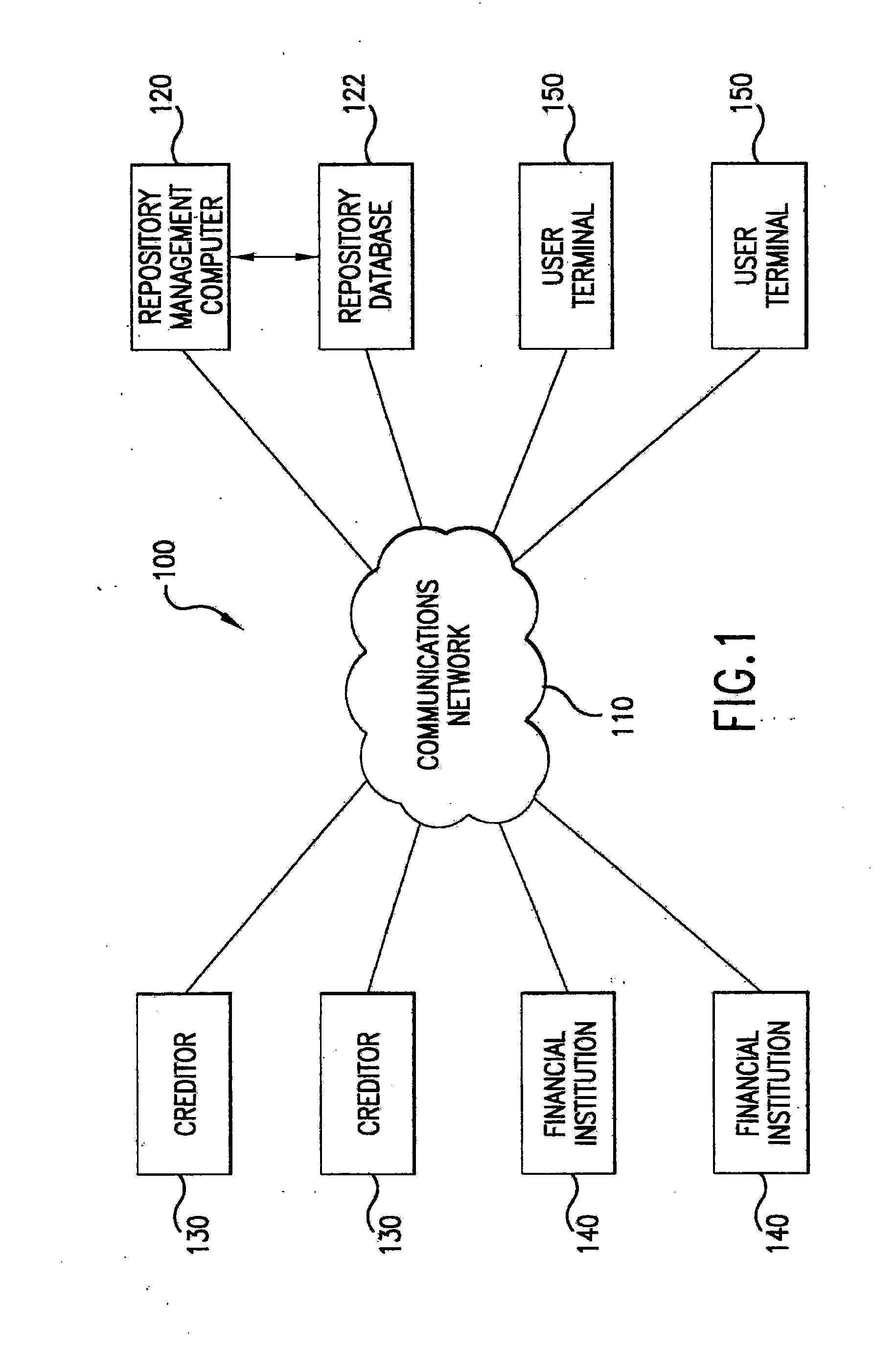
Standing order database search system and method for internet and internet application
InactiveUS7028049B1Improve confidentialityData processing applicationsWeb data indexingMedical recordCost effectiveness
An internet and / or intranet based database search system and method for conducting searches of highly confidential records such as individual patient medical records and to automate the process of securing required approvals to make such records available to a properly authorized and authenticated requesting party. The system's central premise is that the patient has a fundamental right to the confidentiality of their personal medical records and should control that right through specific, informed consent each time that a party requests to receive them. It reinforces the widely held conception of privacy in general as well as of the sanctity of the doctor / patient relationship by granting the doctor the right, subject to the patient's express permission, to initiate a search request. At the same time, it provides an expedited and cost-efficient means for transfer of such records as demanded by many healthcare reform proposals and gives the repositories where these records are held the right to stipulate the specific terms and conditions that must be fulfilled before they will release documents entrusted to their care, thereby substantially reducing the risk of litigation alleging breaches of patient confidentiality. And it carries out all of these legitimate interests in a way that is fast, simple to use and easy to audit. The system optionally includes a billing mechanism to pay for any added cost associated with providing this additional protection; and in its preferred embodiment, is applicable to both digital as well as non-digital records.
Owner:PRIVATE ACCESS +1
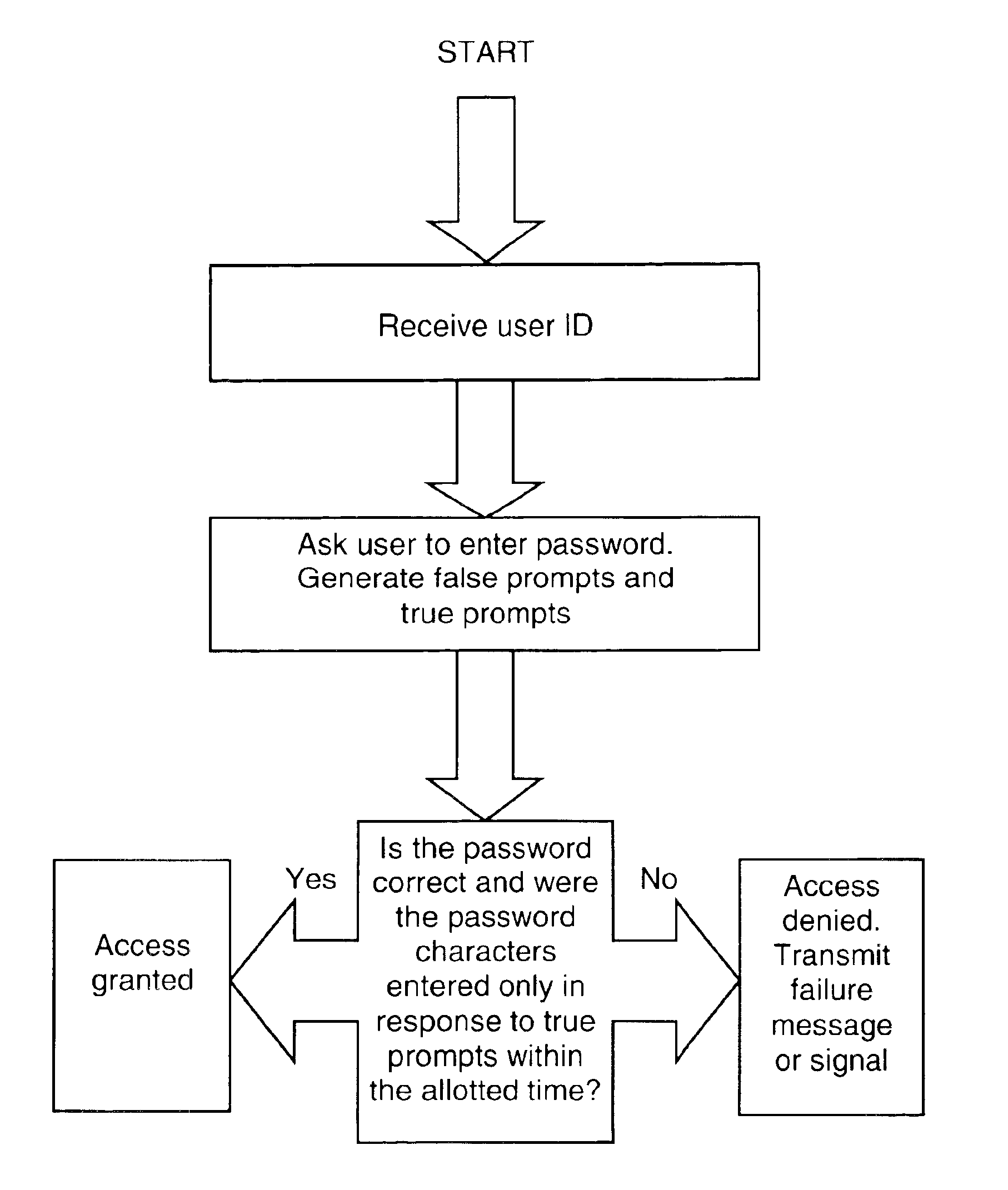
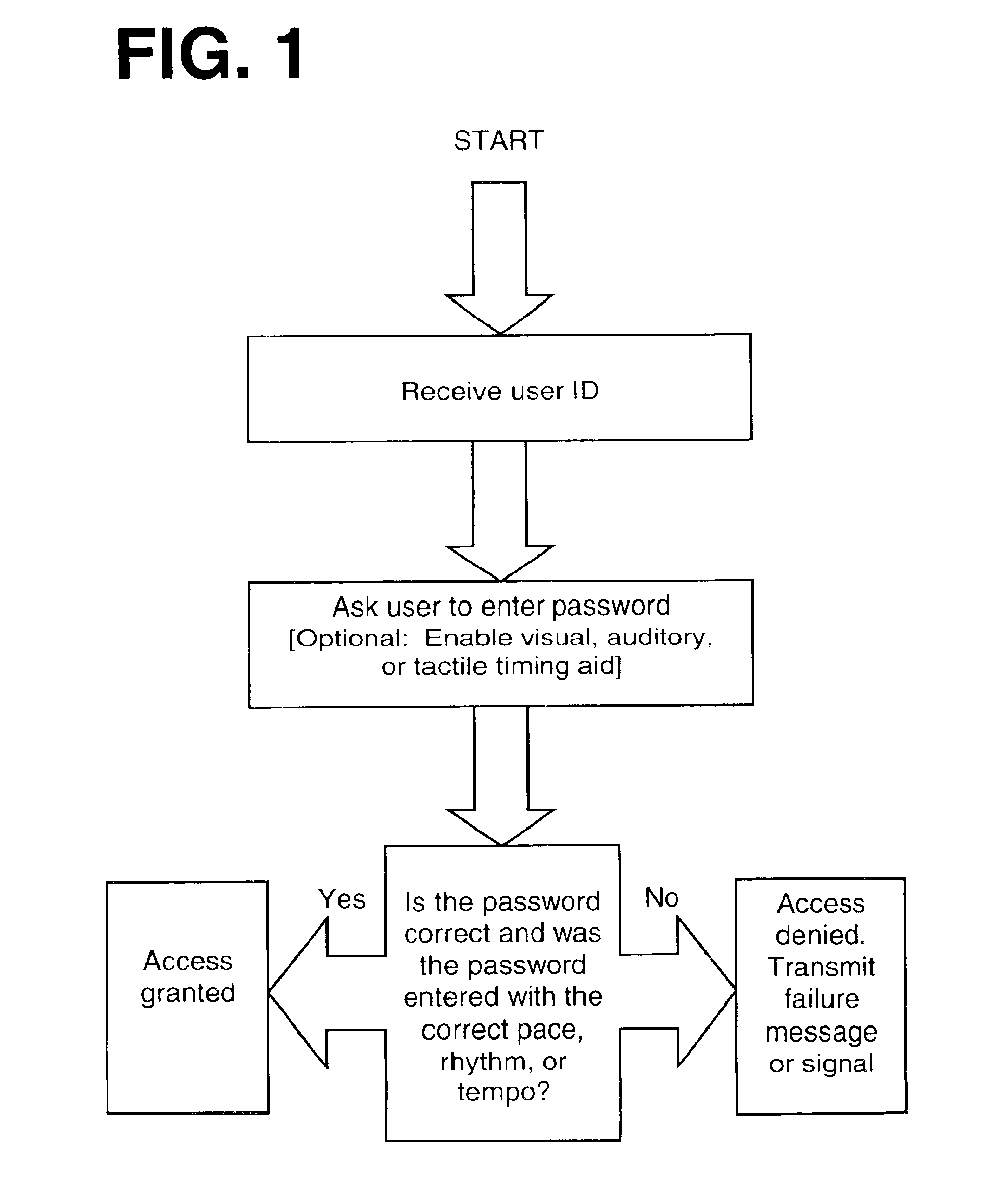
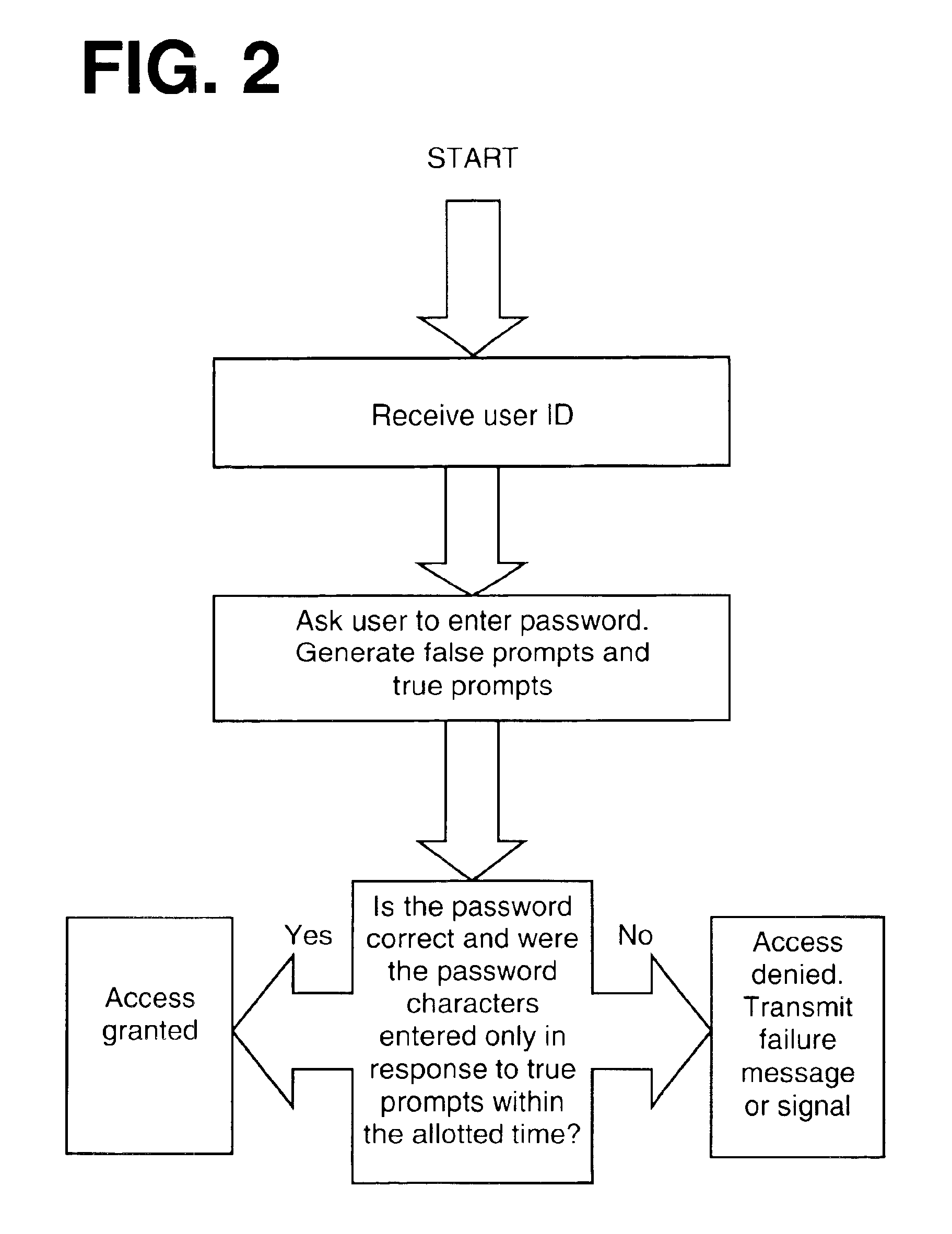
System and method for user authentication with enhanced passwords
InactiveUS6954862B2Less taxingImprove securityDigital data processing detailsUser identity/authority verificationPersonal identification numberTouch Perception
A system and method for enhancing passwords, access codes, and personal identification numbers by making them pace, rhythm, or tempo sensitive. The password includes a sequence of characters and an associated timing element. To access a restricted device or function a user enters the correct character sequence according to the correct pace, rhythm, or tempo. The entered sequence and timing element are compared with stored values and access is granted only if the entered and stored values match. In an alternative embodiment the stored timing element is set, and periodically altered, by a computer or program without consent from the user and visual, auditory, and / or tactile prompts indicate the correct timing element to the user during the authentication process. The meaning of the prompts are provided to the user in advance.
Owner:S AQUA SEMICONDUCTOR LLC
Preferred credit information data collection method
InactiveUS20080027859A1Lower the barrierLower barrierFinanceData acquisition and loggingPaymentCollection methods
A consumer pays their bills using a bill payment service that reports actual payment information to a consumer reporting agency repository. The consumer requests the bill payment service to send their payment information to the CRA repository each month on their behalf to show they pay their bills on time when applying for credit. The bill payment service reports actual bill payment to the CRA reports on behalf of its customers requesting the reporting service. All bill payment data maintained in the CRA repository is maintained securely and will not be released without the consent of the consumer. The bill payment data maintained in the repository is used to report a credit score in addition to the payment data being reported, which occurs only when the consumer authorizes the release of the data.
Owner:PAY RENT BUILD CREDIT
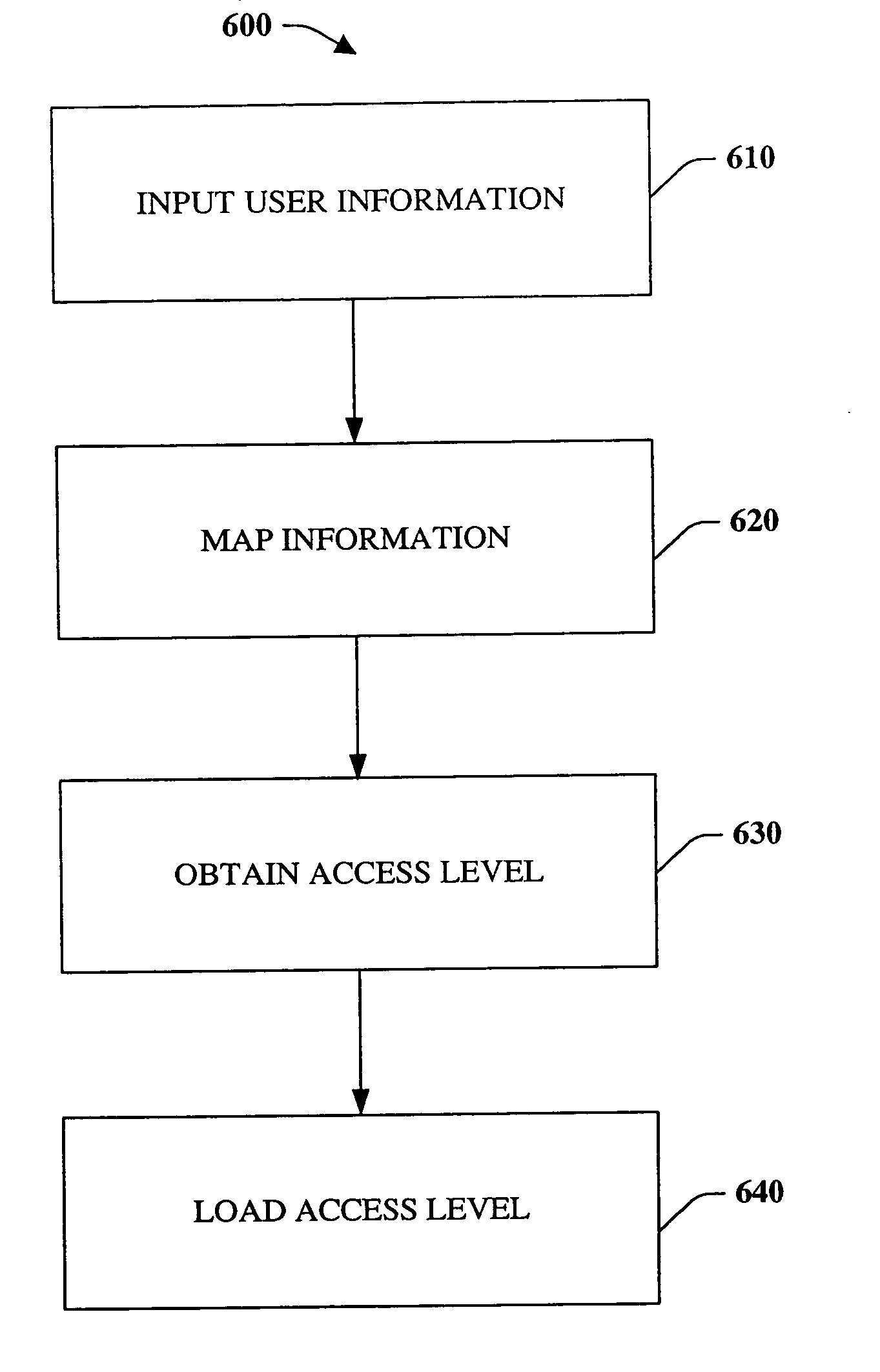
Systems and methods that provide modes of access for a phone
InactiveUS20050070276A1Easy accessReduce utilizationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareCombined use
The present invention relates to systems and methods that provide a user the ability to selectively setup a device with limited functionality for another user. The systems and methods can be employed in connection with devices such as a cell phone, a personal computer and the like, wherein the owner can generate and activate various modes of functionality associated with one or more guest users. The foregoing allows the owner to selectively lock out features such as RF transmission in order to mitigate activation of billable services without the owner's consent. The modes of functionality can be configured such that the owner can activate a particular mode at any given time for a particular or any user, or a mode can be activated based on information related to the current user. The foregoing provides for increased device flexibility, efficiency, security and shareability, while mitigating undesired user activity.
Owner:NOKIA CORP
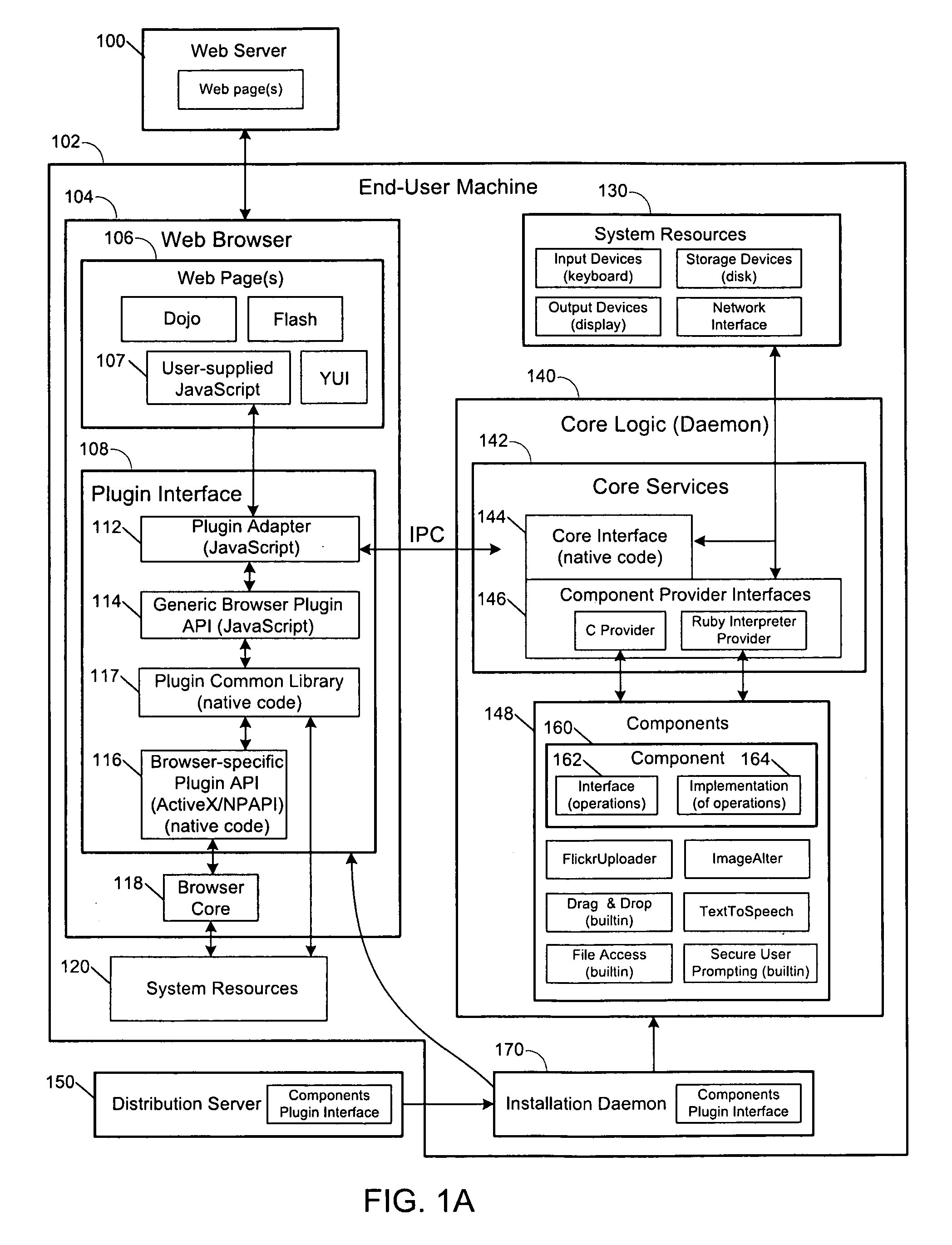
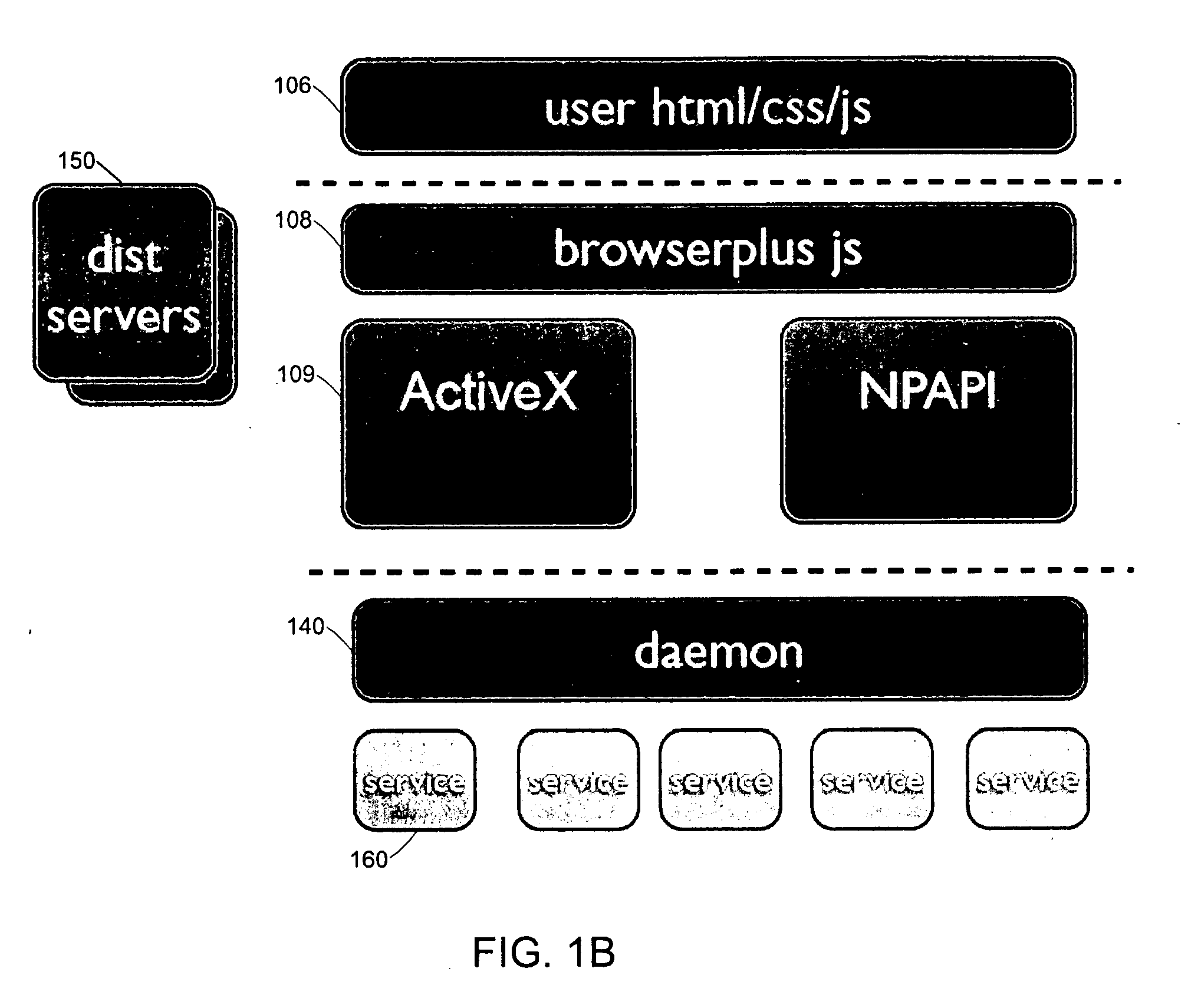
Secure browser-based applications
Techniques are provided for execution of restricted operations by computer program code in web browsers, where the code is permitted to invoke restricted operations if implicit or explicit consent is received. Such techniques may include generating a risk rating for a computer program code component, where the component includes at least one component operation for executing at least one restricted system operation; and prompting a user for permission to execute the restricted system operation, wherein the prompt includes the risk rating and a description of the component operation. The program code may include script code associated with a web page that invokes a web browser plugin, which in turn invokes the restricted system operation. The code may invoke the restricted system operation in response to receiving an input from a user via the web browser, where the input is for causing an action associated with performing the operation, the action implicitly granting consent to perform the operation.
Owner:R2 SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com