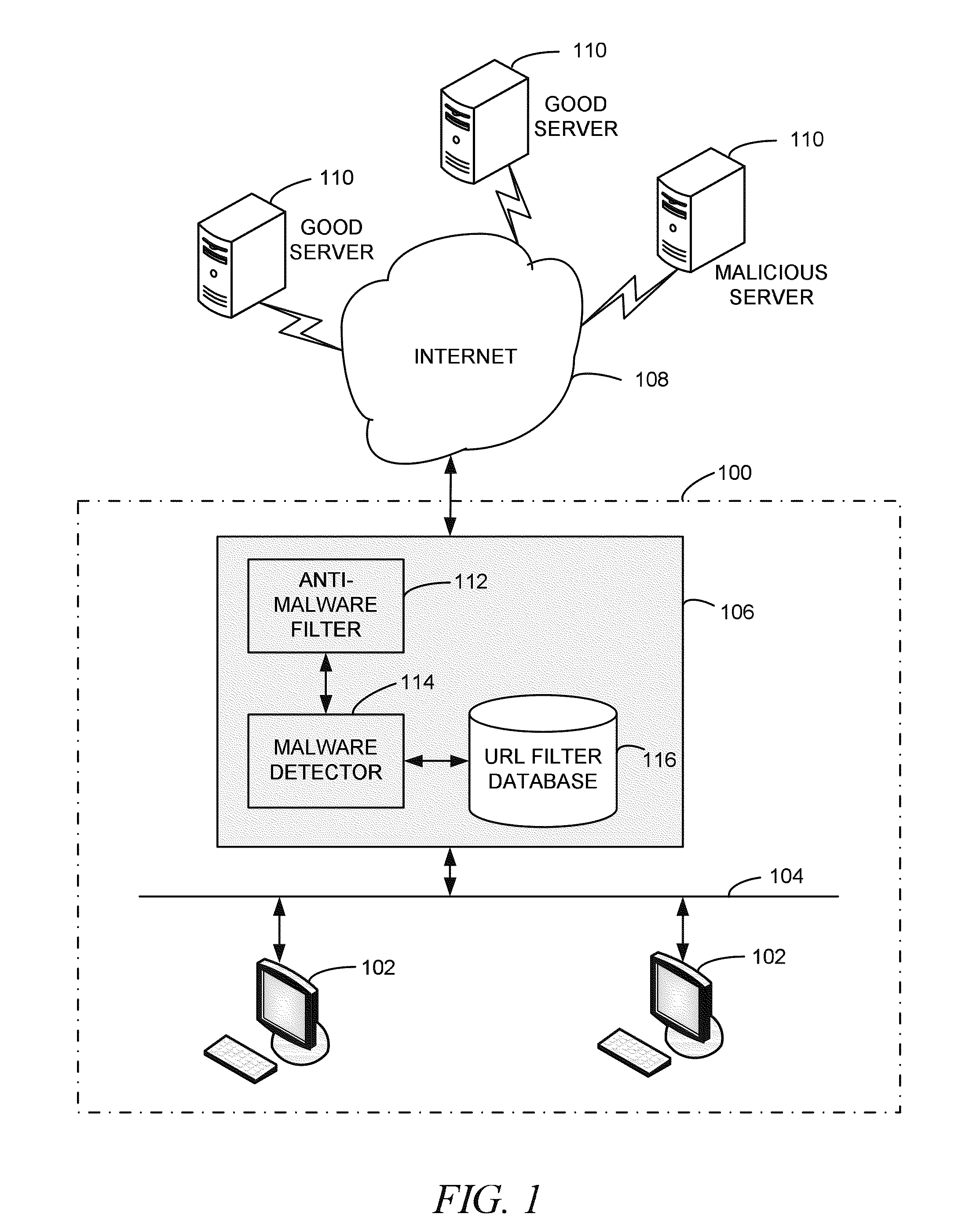
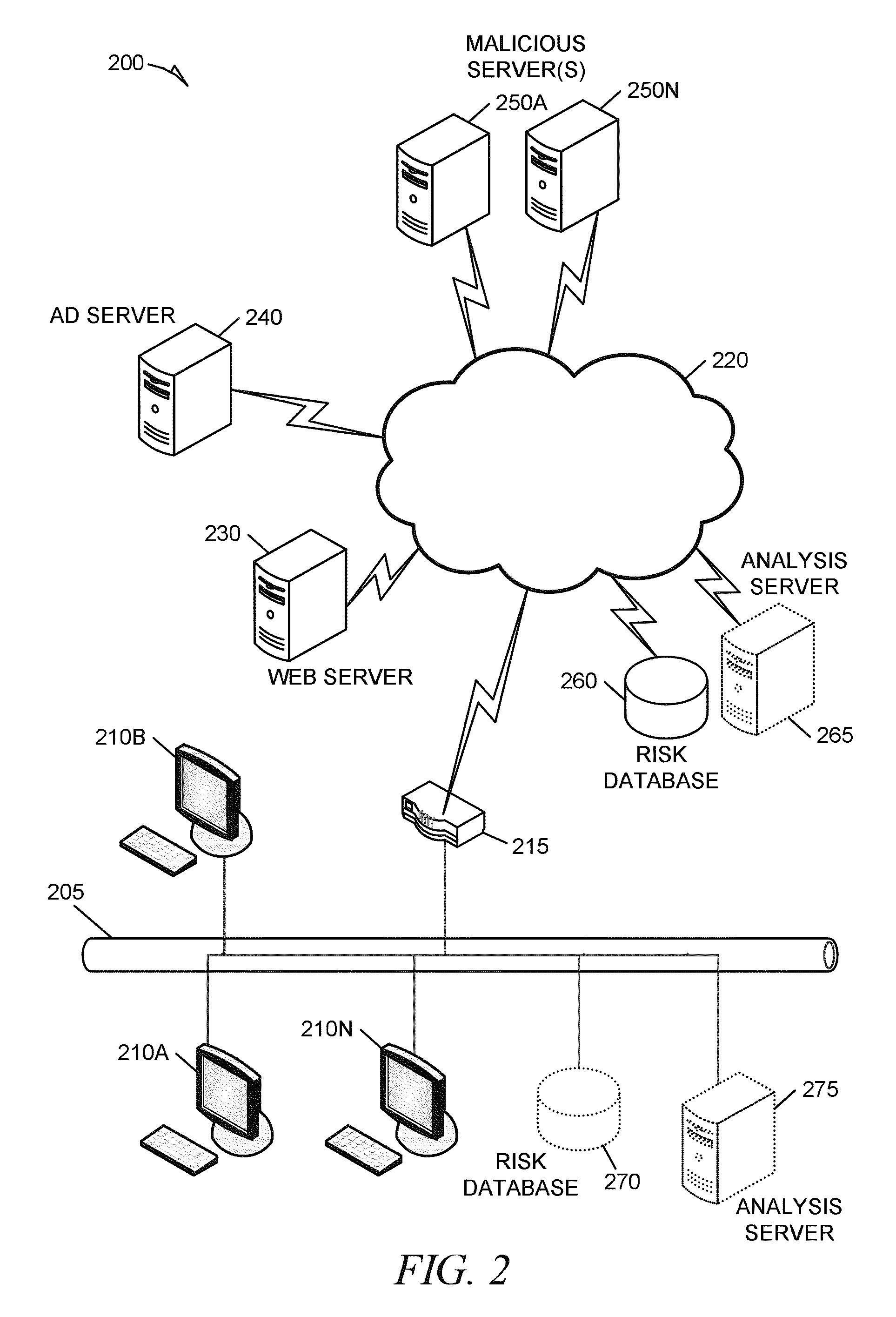
Patents
Literature
760 results about "Risk rating" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
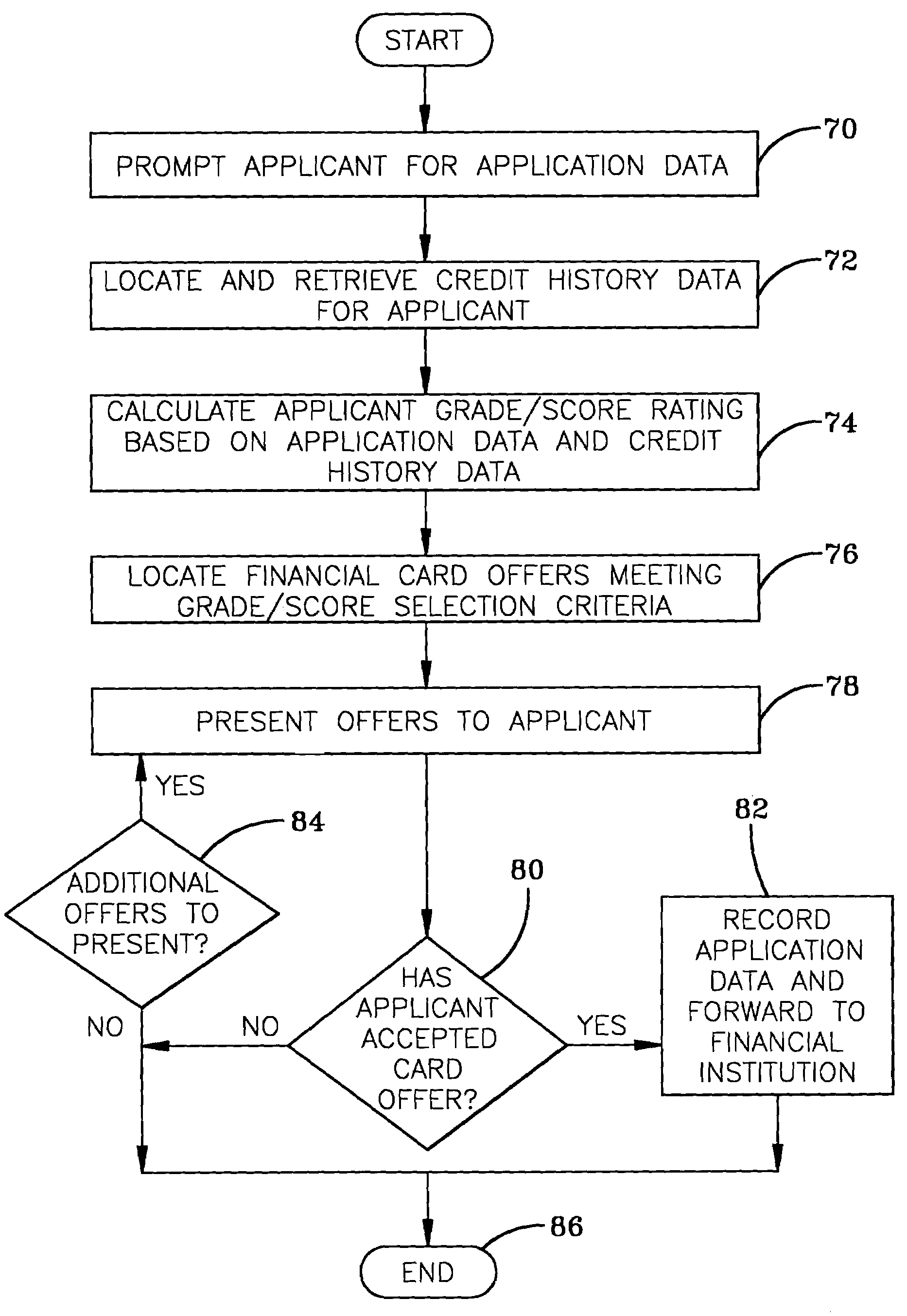
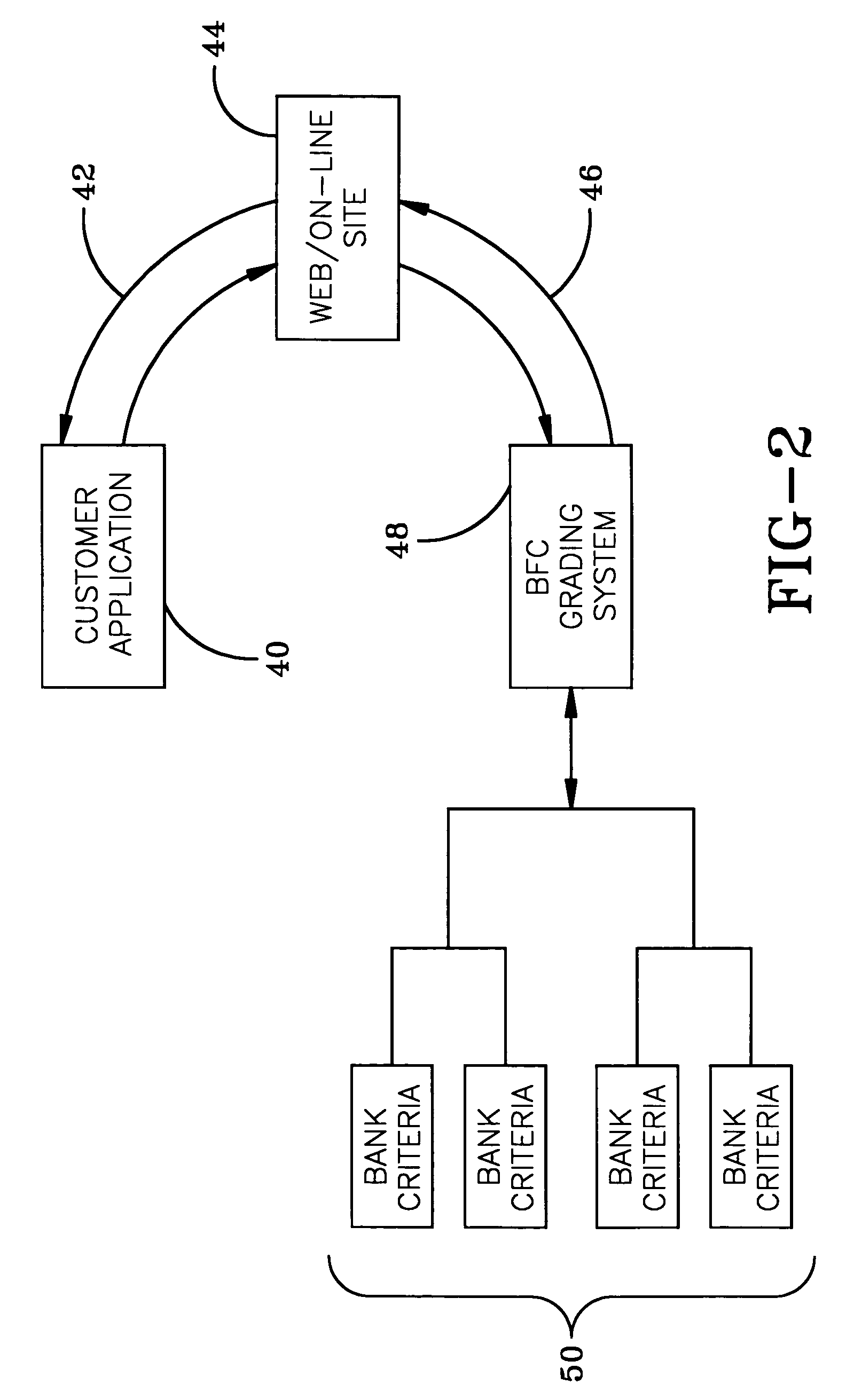
Real-time financial card offer and application system
A system is disclosed for presenting financial card (e.g., credit card, debit card) offers to potential customers. Financial card applicant selection criteria and financial card term data are provided by participating financial institutions. An applicant interested in applying for a new financial card accesses the system via the Internet / World Wide Web. The applicant provides personal and financial data that are then analyzed in conjunction with data from outside sources (such as credit bureaus) to determine a financial risk rating for the applicant. The rating is used to locate financial card offers appropriate for the applicant. The applicant then peruses the offers and chooses one that meets his or her personal selection criteria. The applicant's data is then forwarded for processing to the participating financial institution that made the selected offer.
Owner:BLOCK FINANCIAL
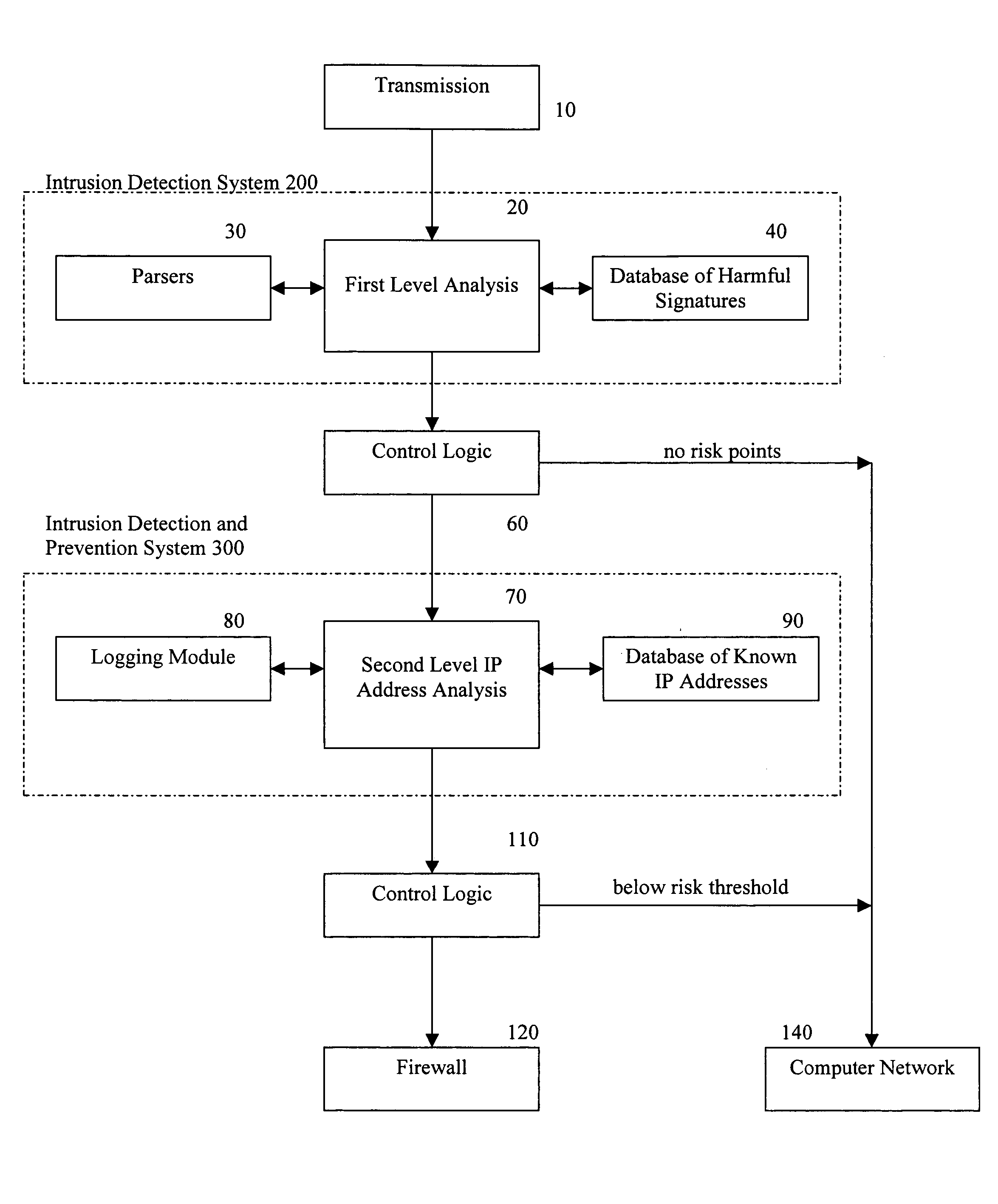
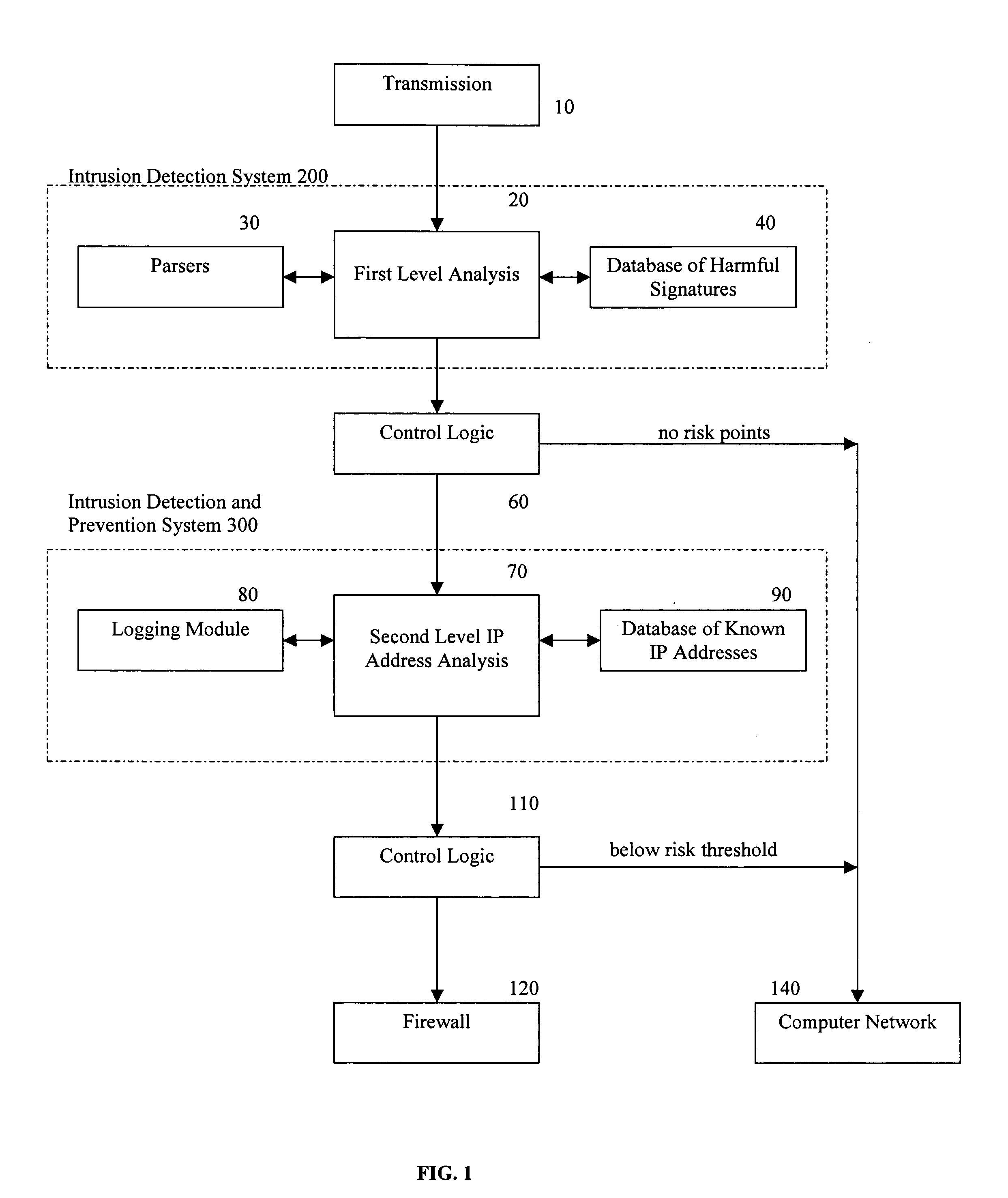
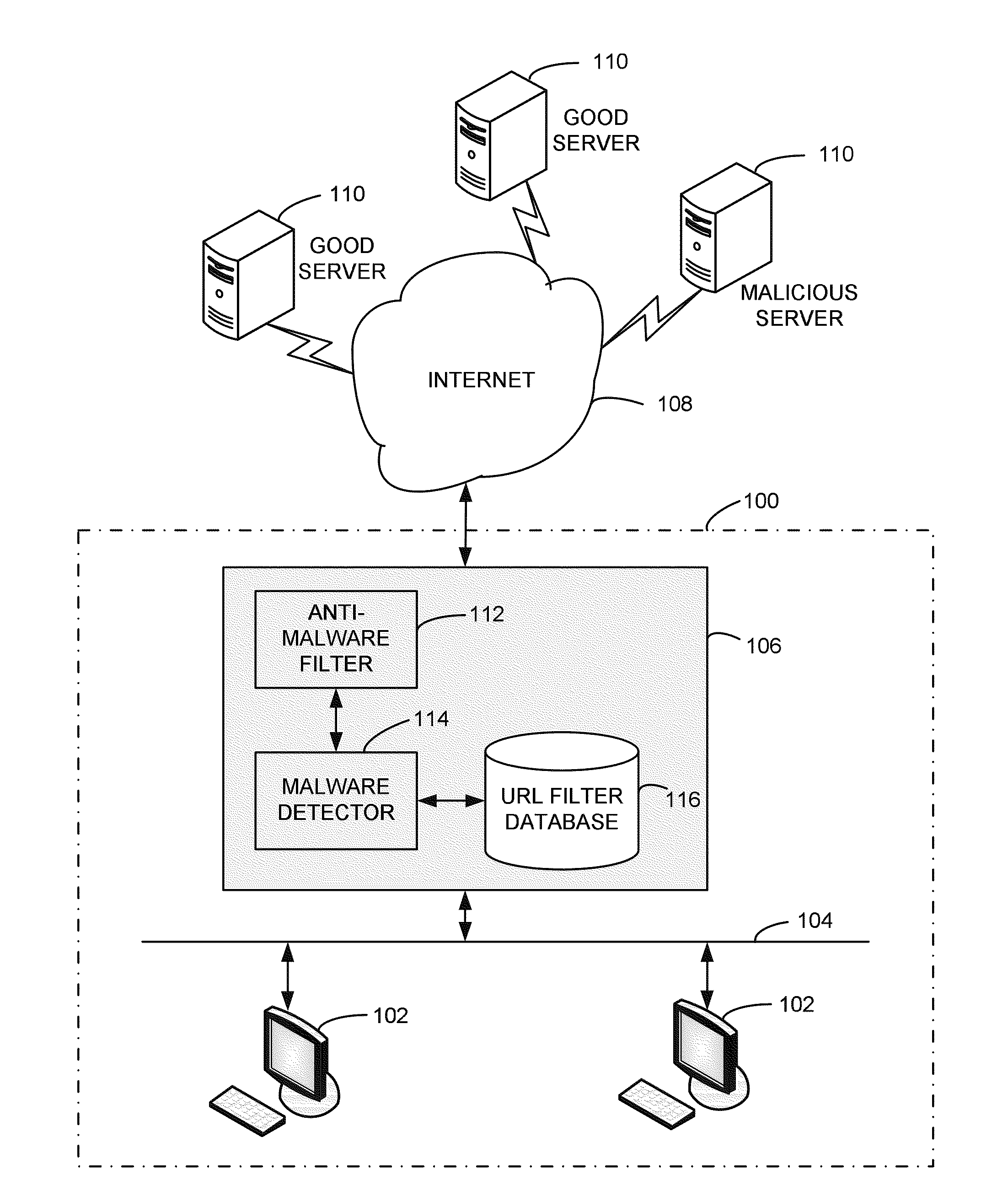
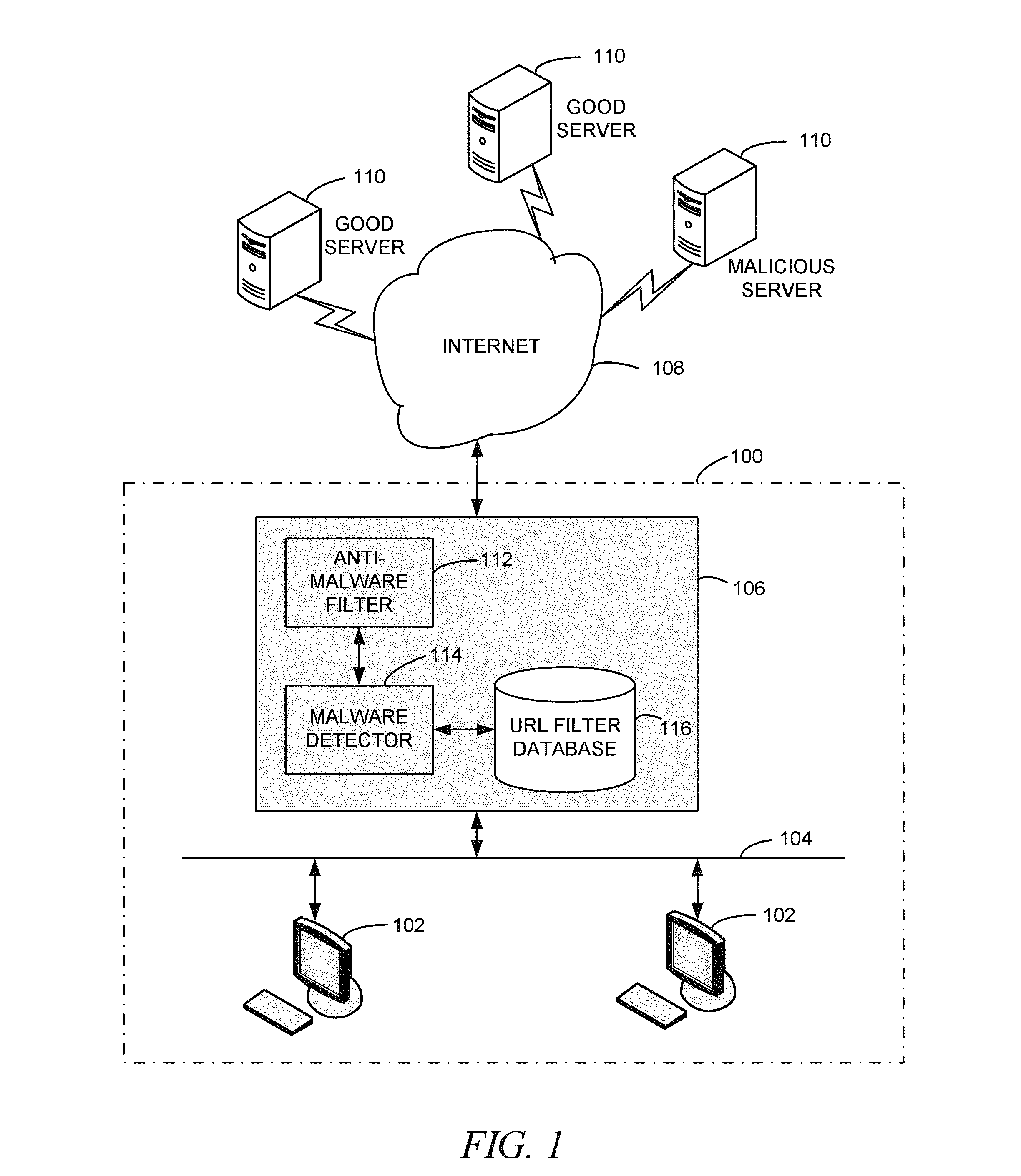
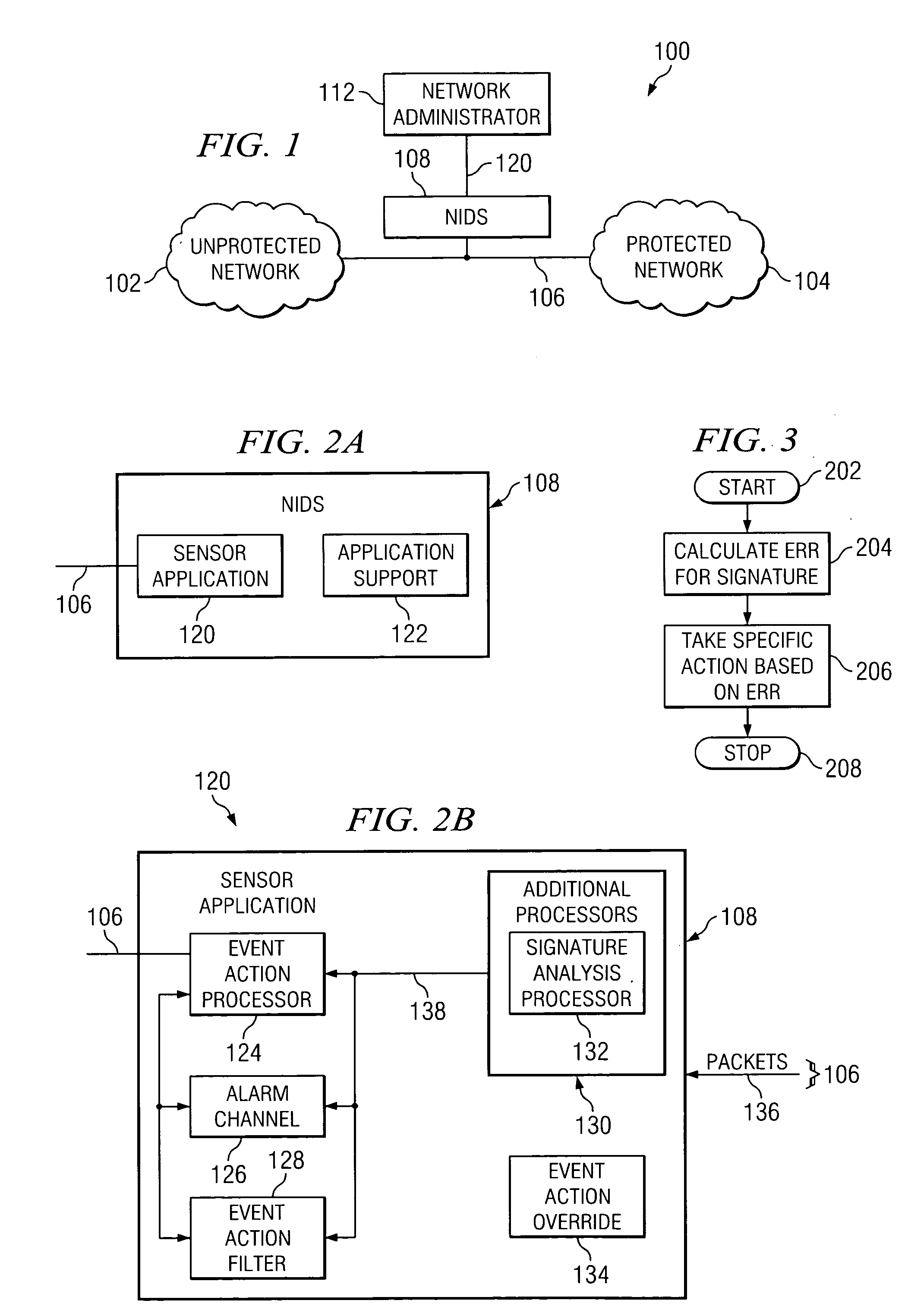
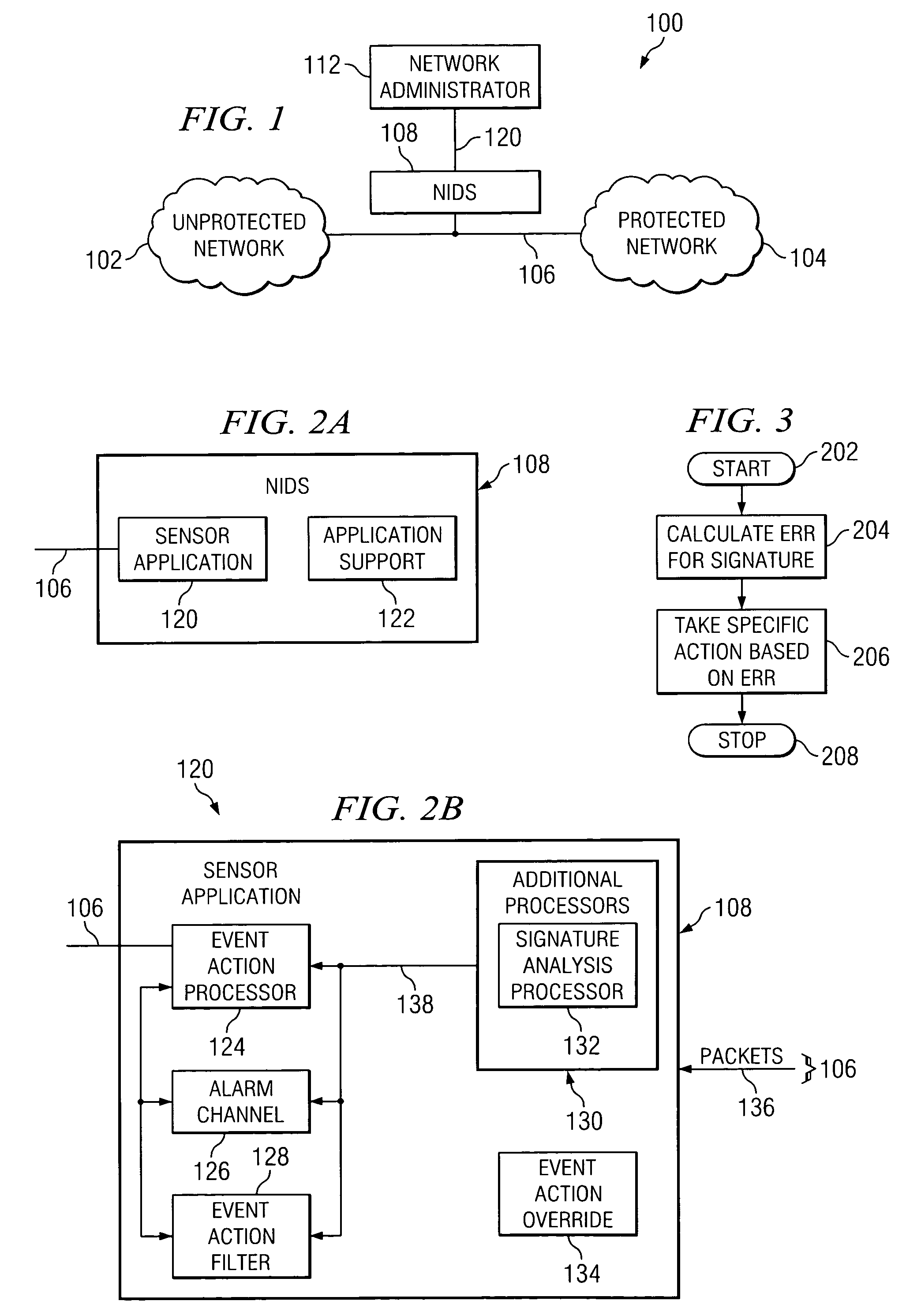
Methods and apparatus for computer network security using intrusion detection and prevention
InactiveUS20050262556A1Overcome disadvantagesMemory loss protectionDigital data processing detailsIp addressIntrusion detection and prevention
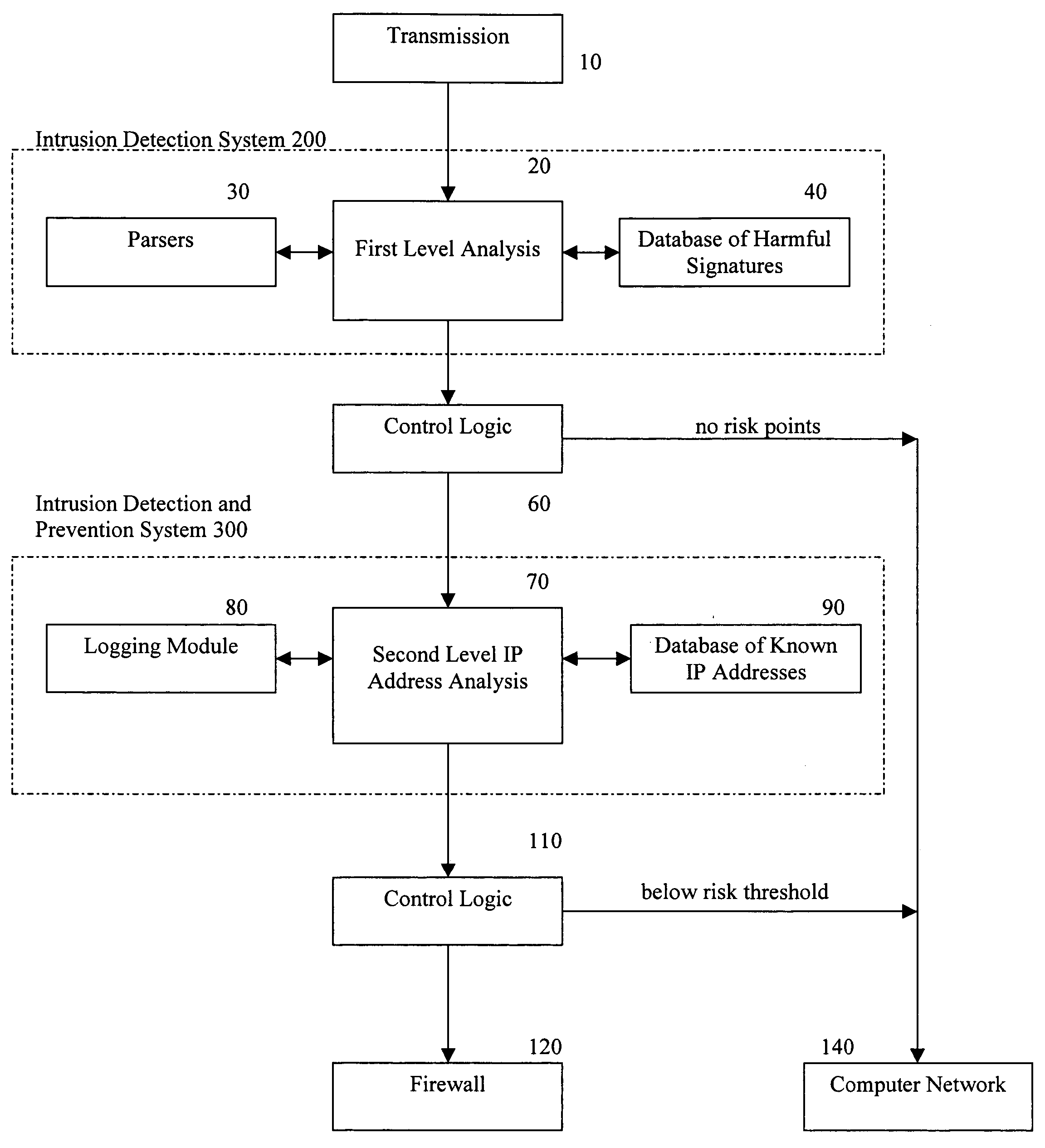
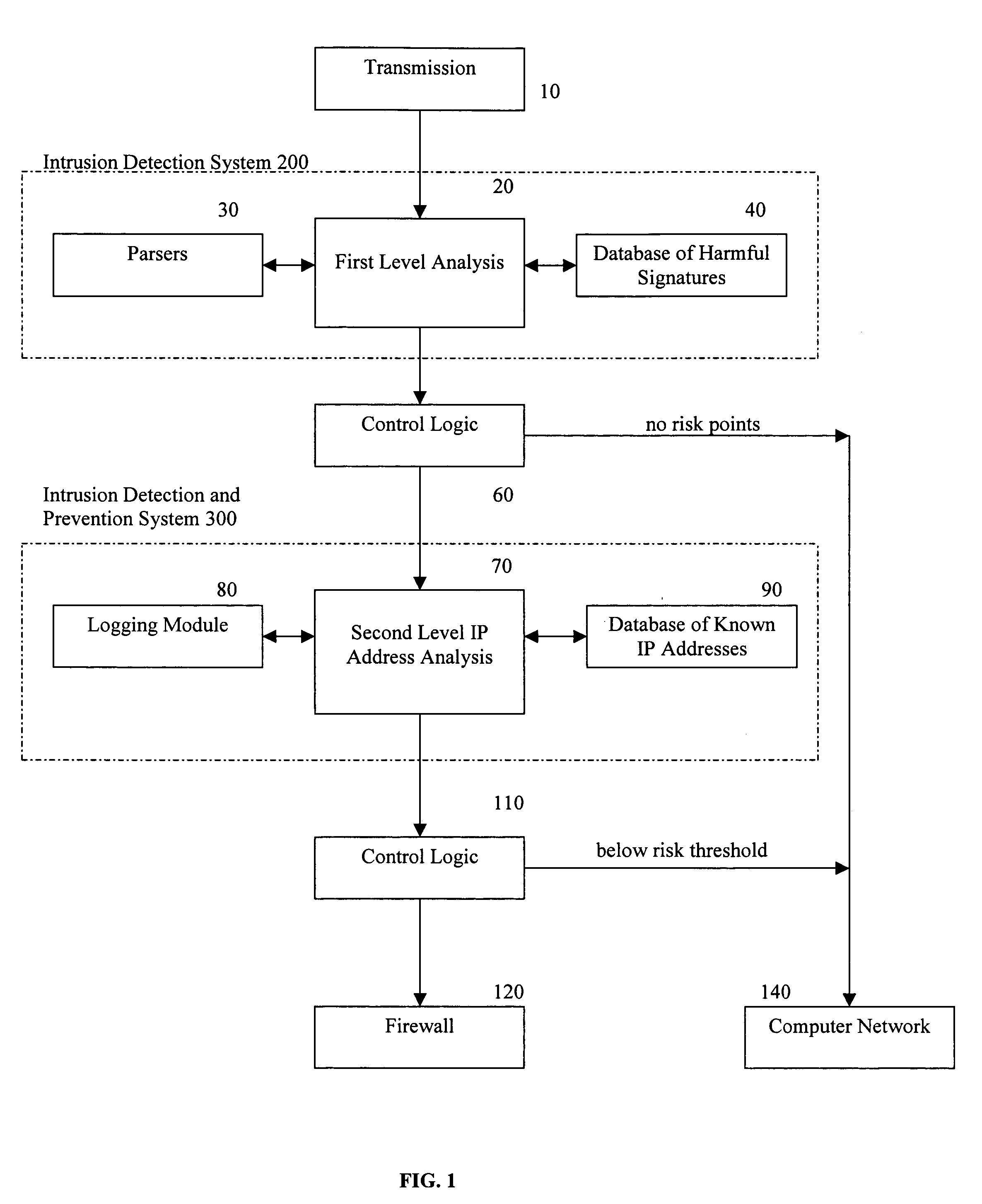
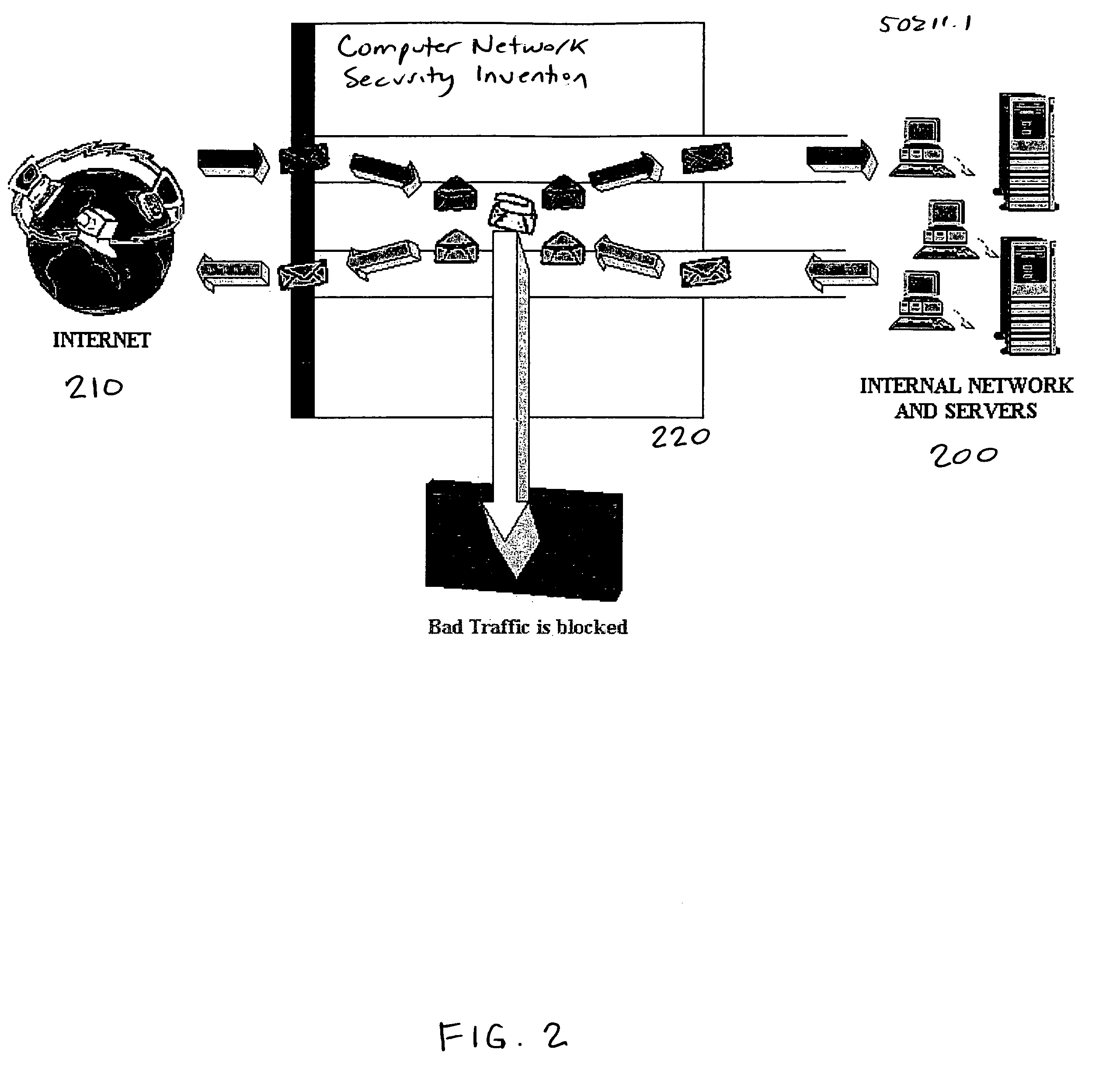
A method for providing security to a computer network by selectively blocking network transmissions from selected IP addresses comprising the steps of: establishing a risk threshold whereby transmissions from IP addresses exceeding said risk threshold are selectively blocked; receiving a network transmission having an originating IP address and payload; analyzing the payload of said transmission and assigning a current risk rating to said IP address on the basis of said analysis; comparing the originating IP address of said transmission to a database of known IP addresses, each of said said previous cumulative assigned risk rating being based on at least one previous transmission from a known IP address; known IP addresses having a previous cumulative assigned risk rating, assigning a new cumulative risk rating to said originating IP address, said new cumulative risk rating being the sum of said current risk rating and said previous cumulative assigned risk rating for said originating IP address, with the proviso that where said originating IP address is not contained in said database of known IP addresses, the new cumulative risk rating will equal the current risk rating; logging the new cumulative risk rating for said originating IP address in said database of known IP addresses, with the proviso that where the originating IP address of said transmission is not contained in said database of known IP addresses, a new record is created for the originating IP address and said new cumulative risk rating in said database of known IP addresses; comparing said new cumulative risk rating to said risk threshold; and automatically blocking said transmission if said new cumulative risk rating exceeds said risk threshold.
Owner:DIGITAL SECURITY NETWORK
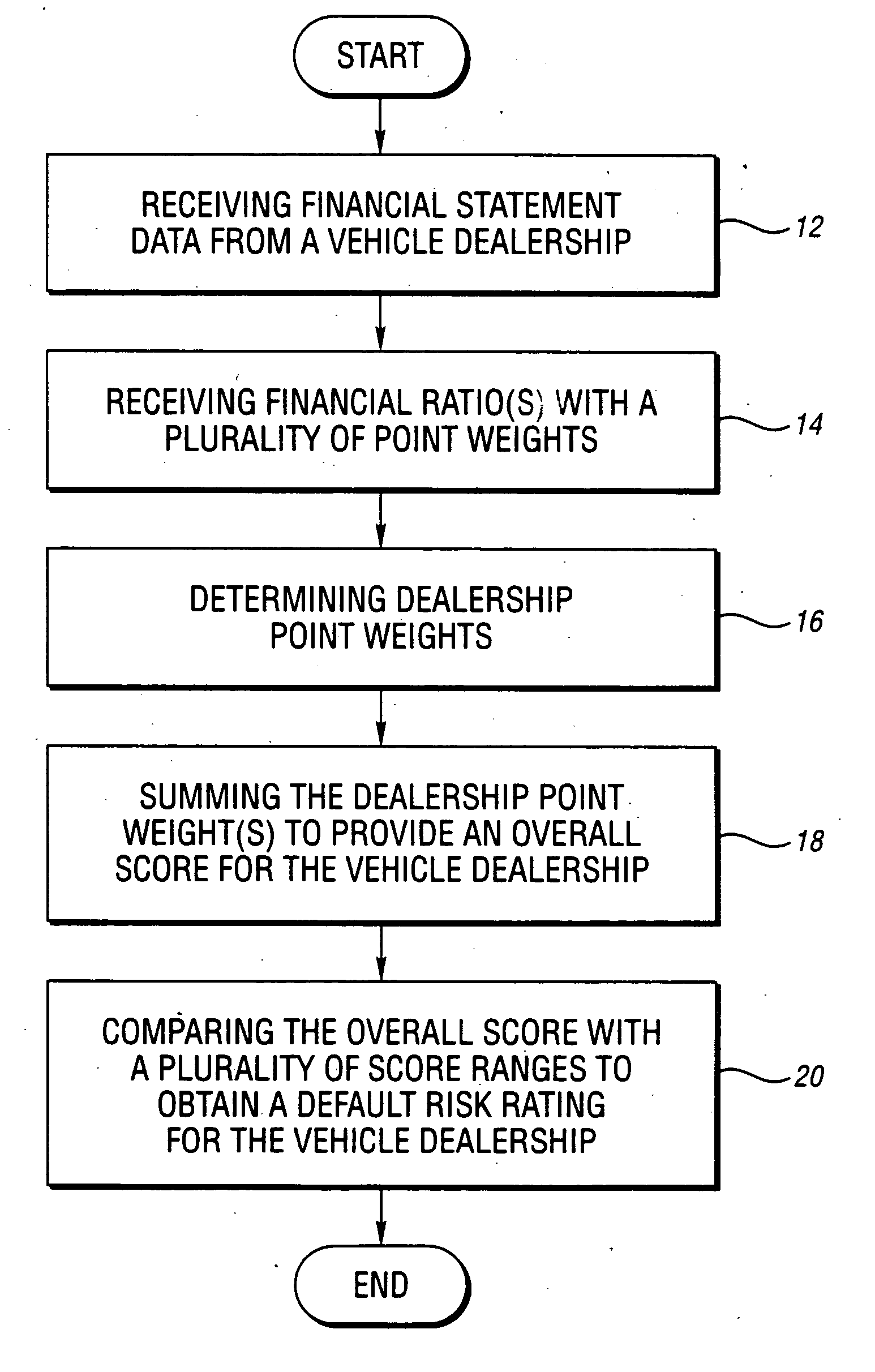
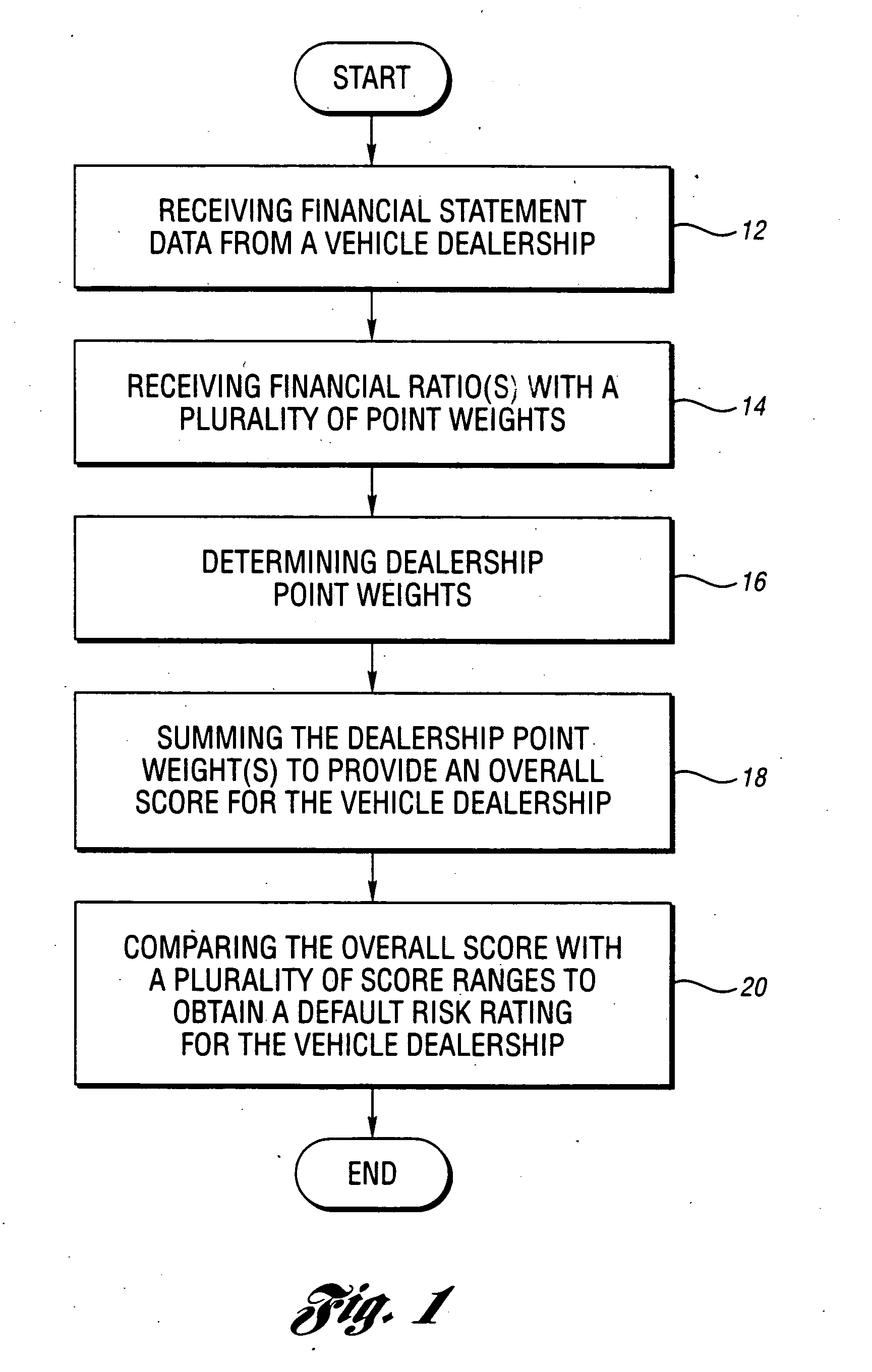
Method and system for assessing the risk of a vehicle dealership defaulting on a financial obligation
The present invention relates to a method and system of assessing the risk of a vehicle dealership defaulting on a financial obligation. A preferred method embodiment of the present invention includes receiving at least one financial factor with a plurality of point weights and vehicle dealership financial statement information and determining a dealership point weight for each financial factor based on the plurality of point weights and the financial statement data to obtain a default risk rating based on the dealership point weight(s).
Owner:FORD MOTOR CO
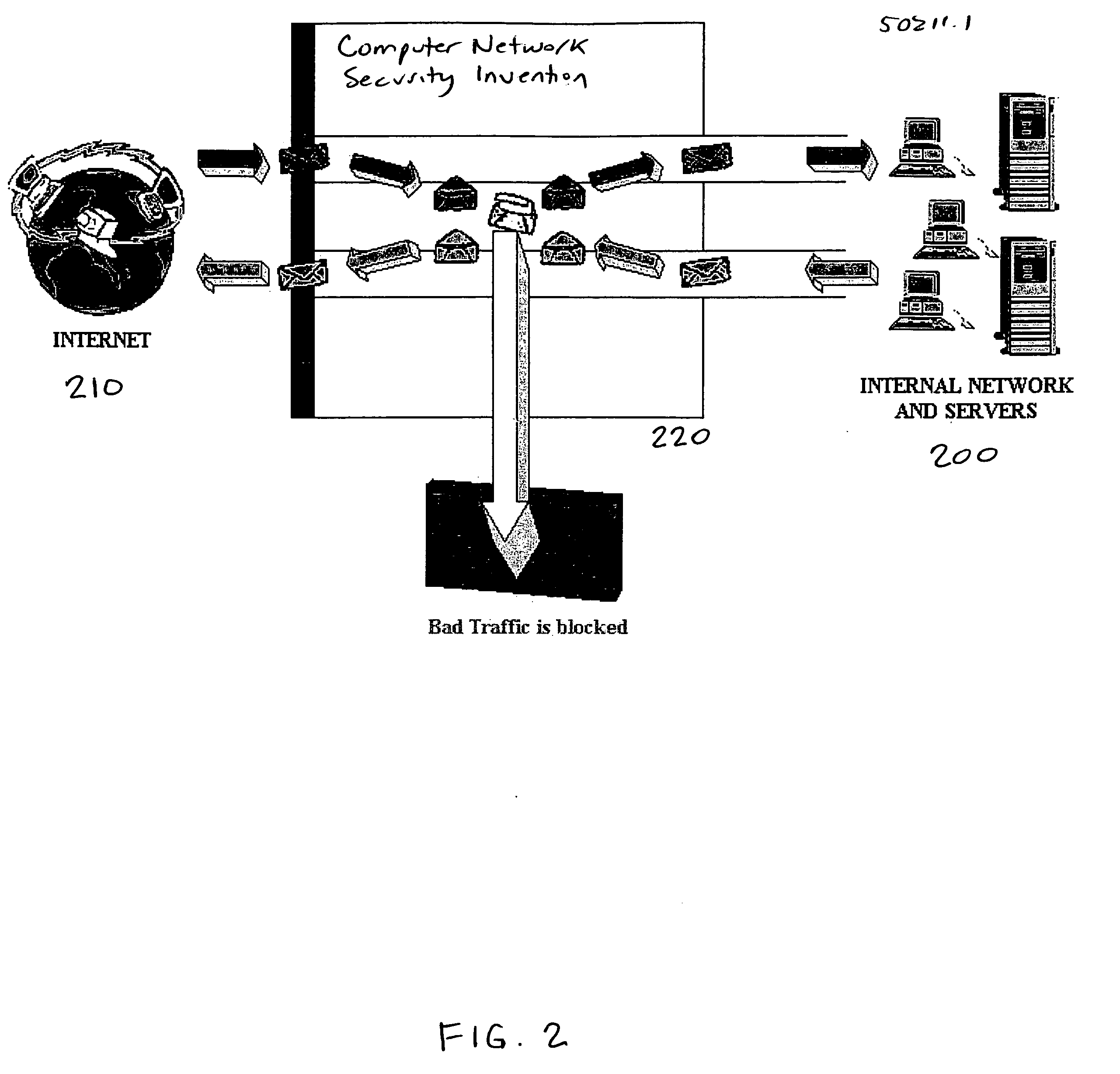
Methods and apparatus for computer network security using intrusion detection and prevention
InactiveUS7225468B2Memory loss protectionDigital data processing detailsIp addressIntrusion detection and prevention
A method provides security to a computer network by selectively blocking network transmissions from selected IP addresses. The method includes the steps of: establishing a risk threshold whereby transmissions from IP addresses exceeding said risk threshold are selectively blocked; receiving a network transmission having an originating IP address and payload; analyzing the payload of said transmission and assigning a current risk rating to said IP address on the basis of said analysis; comparing the originating IP address of said transmission to a database of known IP addresses, each of said known IP addresses having a previous cumulative assigned risk rating, said previous cumulative assigned risk rating being based on at least one previous transmission from a known IP address; assigning a new cumulative risk rating to said originating IP address; logging the new cumulative risk rating for said originating IP address in said database of known IP addresses. The new cumulative risk rating is compared to said risk threshold and the transmission is blocked if said new cumulative risk rating exceeds said risk threshold.
Owner:DIGITAL SECURITY NETWORK
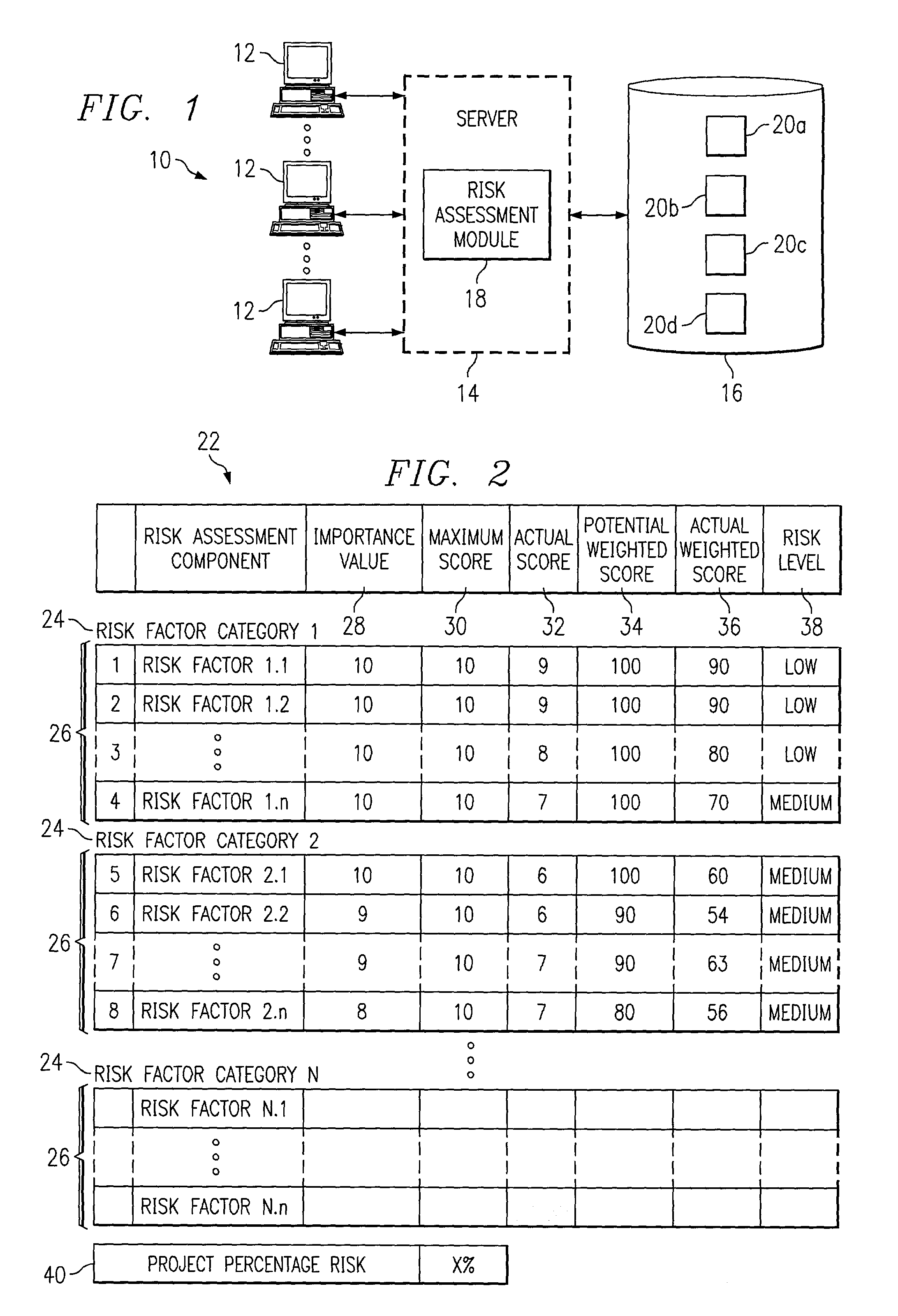
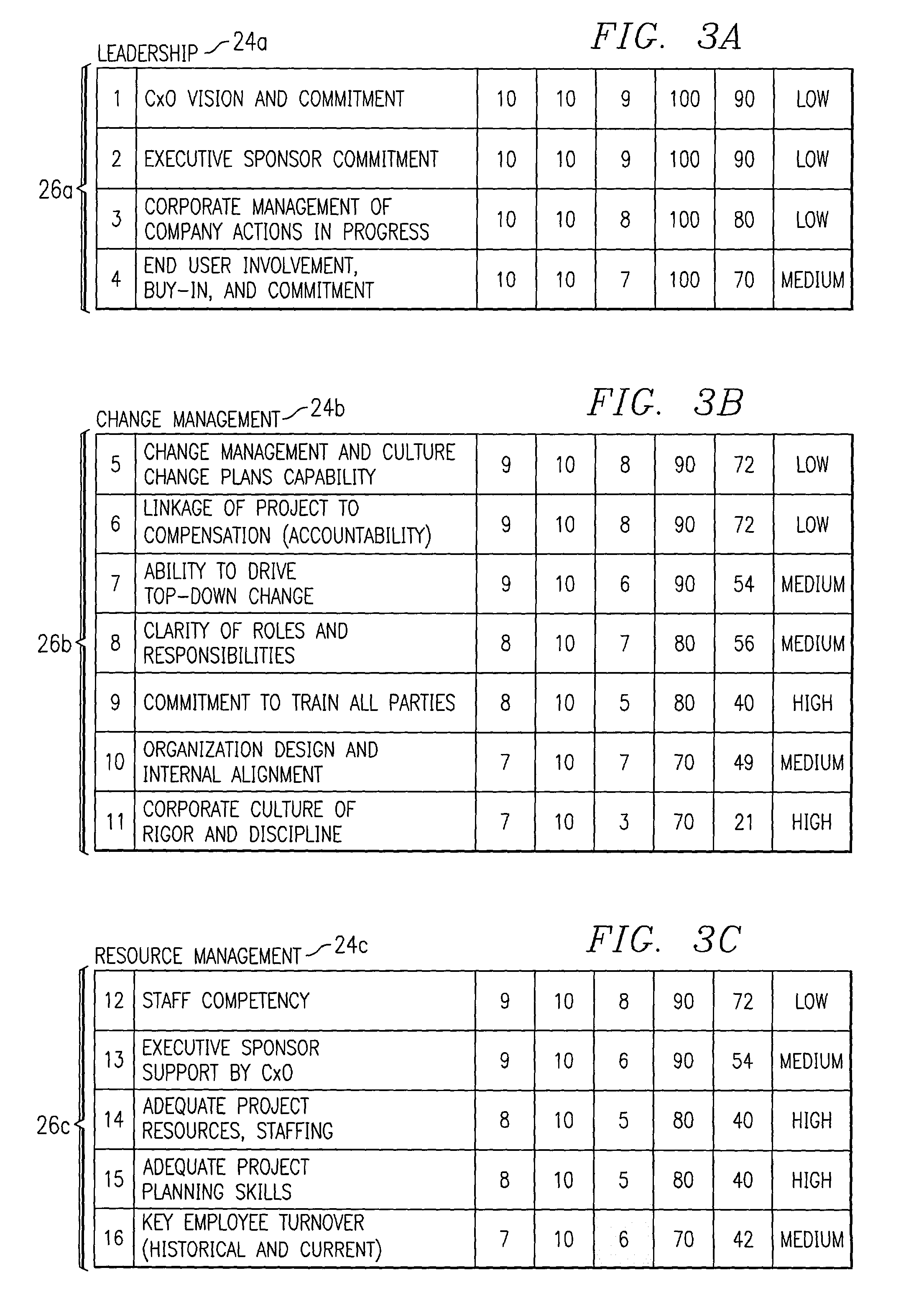
Generating a risk assessment regarding a software implementation project
InactiveUS7359865B1Disadvantages can be reduced eliminatedImplementation be reduced eliminatedFinanceResourcesRisk levelItem generation
A computer-implemented method for generating a risk assessment regarding a software implementation project includes accessing a previously specified importance value and maximum score for each of a multiple of risk factors. The importance value for each risk factor reflects experience of an implementing entity regarding the extent to which the factor may negatively impact a software implementation project if the factor is not adequately addressed, the importance value and maximum score for each factor being multiplied to define a potential weighted score for the factor. An actual score for a particular software implementation project is received for each factor based on an analysis specific to the particular project. An actual weighted score for the particular project is generated for each factor by multiplying the importance value and actual score for the factor, and a relationship between the potential weighted score and actual weighted score for each factor. A risk level for the particular project is assigned to each factor according to the relationship between the potential weighted score and the actual weighted score for the factor. The risk level for each factor represents an assessment regarding the extent to which the factor may negatively impact the particular project if the factor is not adequately addressed. A risk assessment is generated for the particular project including one or more of the assigned risk levels for the particular project for one or more corresponding factors.
Owner:BLUE YONDER GRP INC
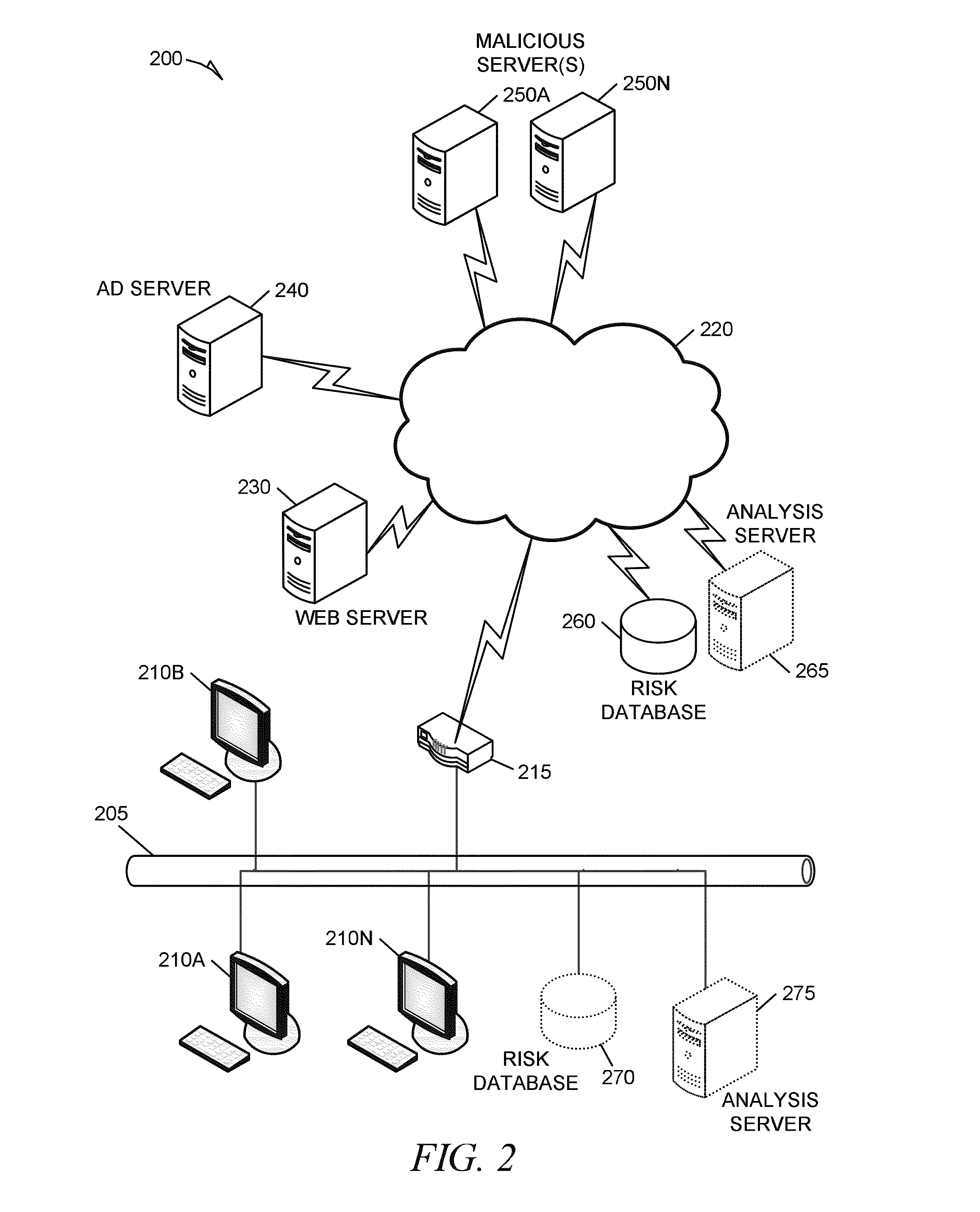
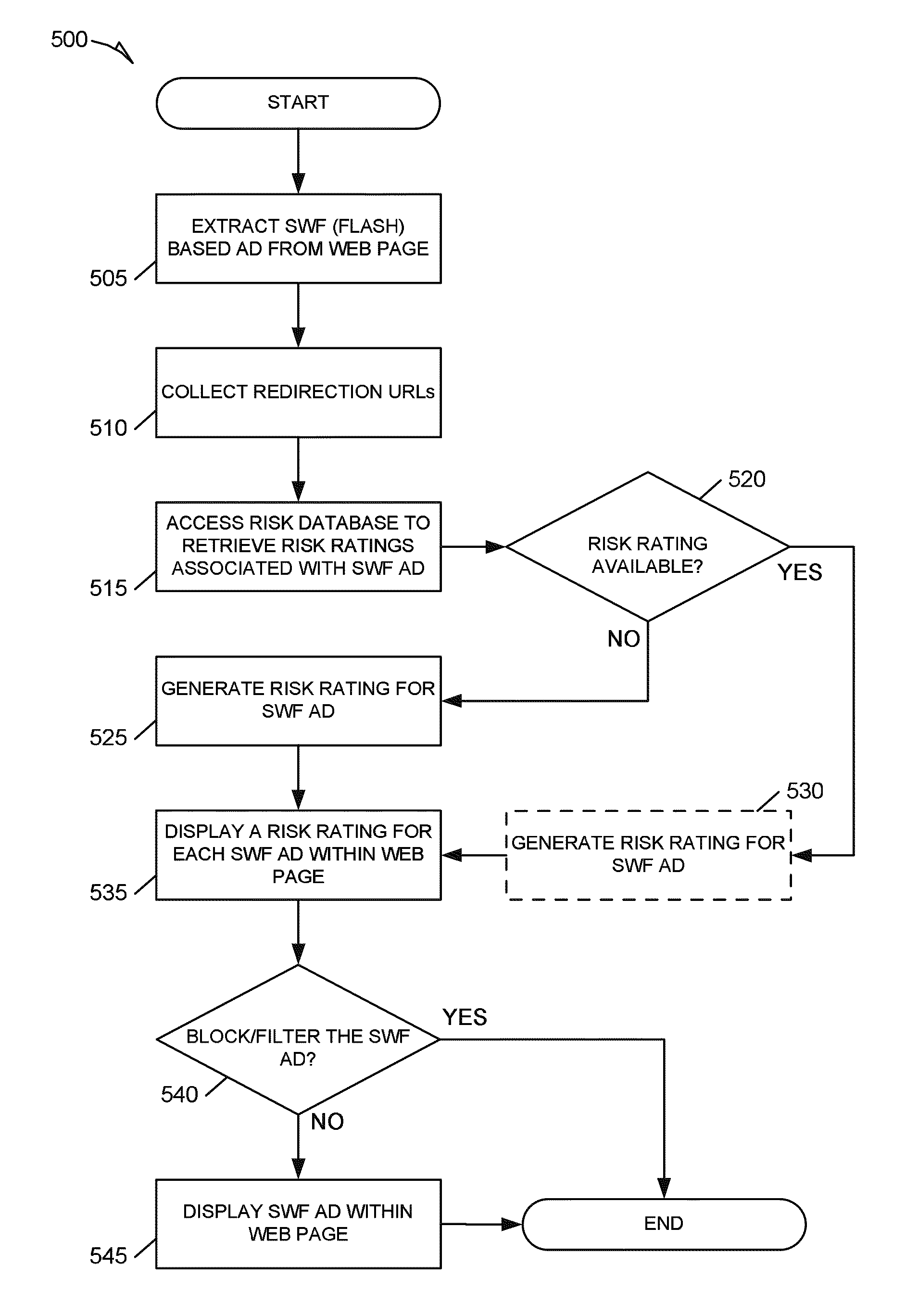
Systems and methods for risk rating and pro-actively detecting malicious online ads
Methods and systems for risk rating and pro-actively detecting malicious online ads are described. In one example embodiment, a system for risk rating and pro-actively detecting malicious online ads includes an extraction module, an analysis engine, and a filter module. The extraction module is configured to extract a SWF file from a web page downloaded by the system. The analysis engine is communicatively coupled to the extraction module. The analysis engine is configured to determine a risk rating for the SWF file and send the risk rating to a web application for display. In an example, determining the risk rating includes locating an embedded redirection URL and determining a risk rating for the embedded redirection URL. The filter module is configured to determine, based on the risk rating, whether to block the SWF file and send a warning to the web application for display.
Owner:MCAFEE LLC
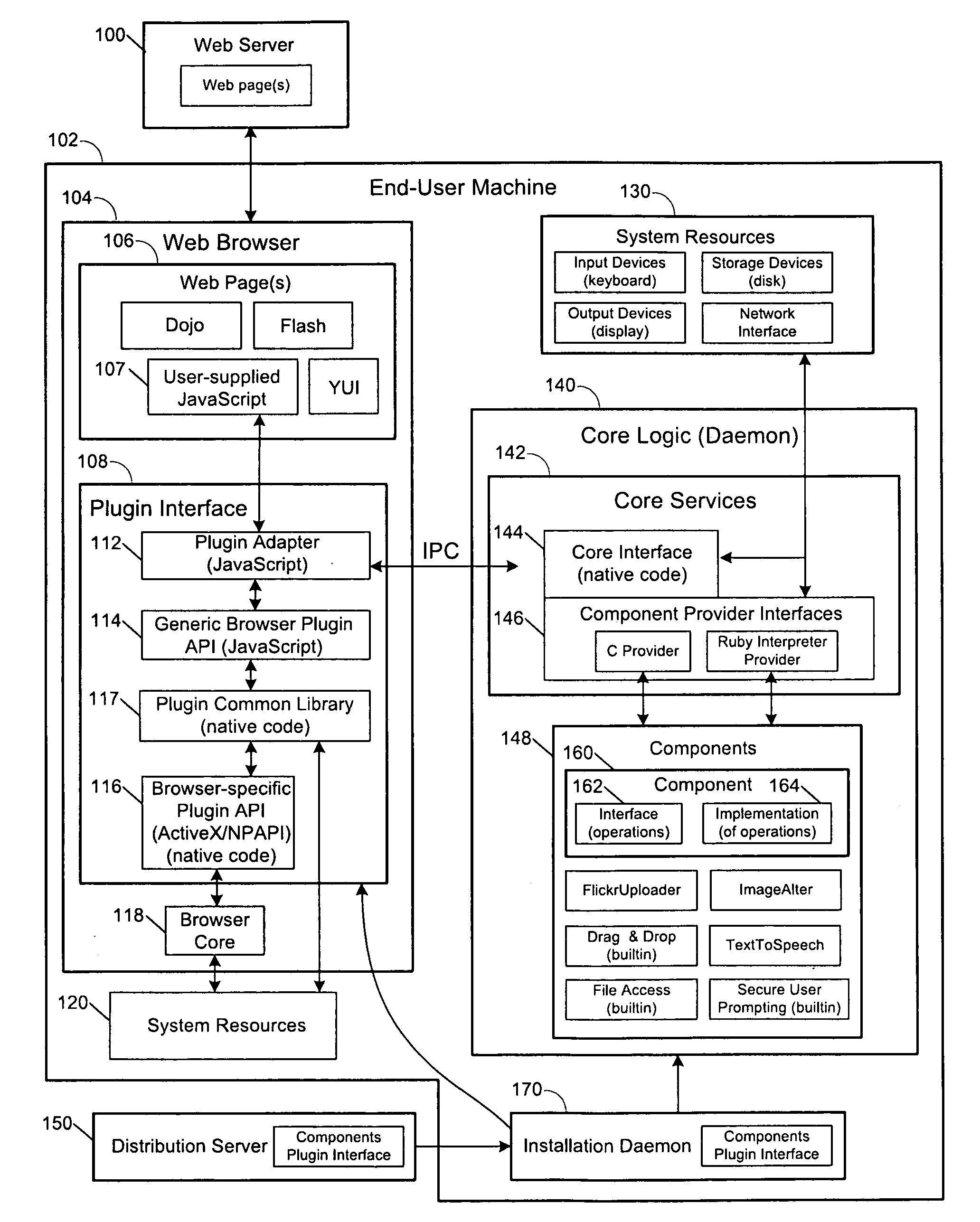
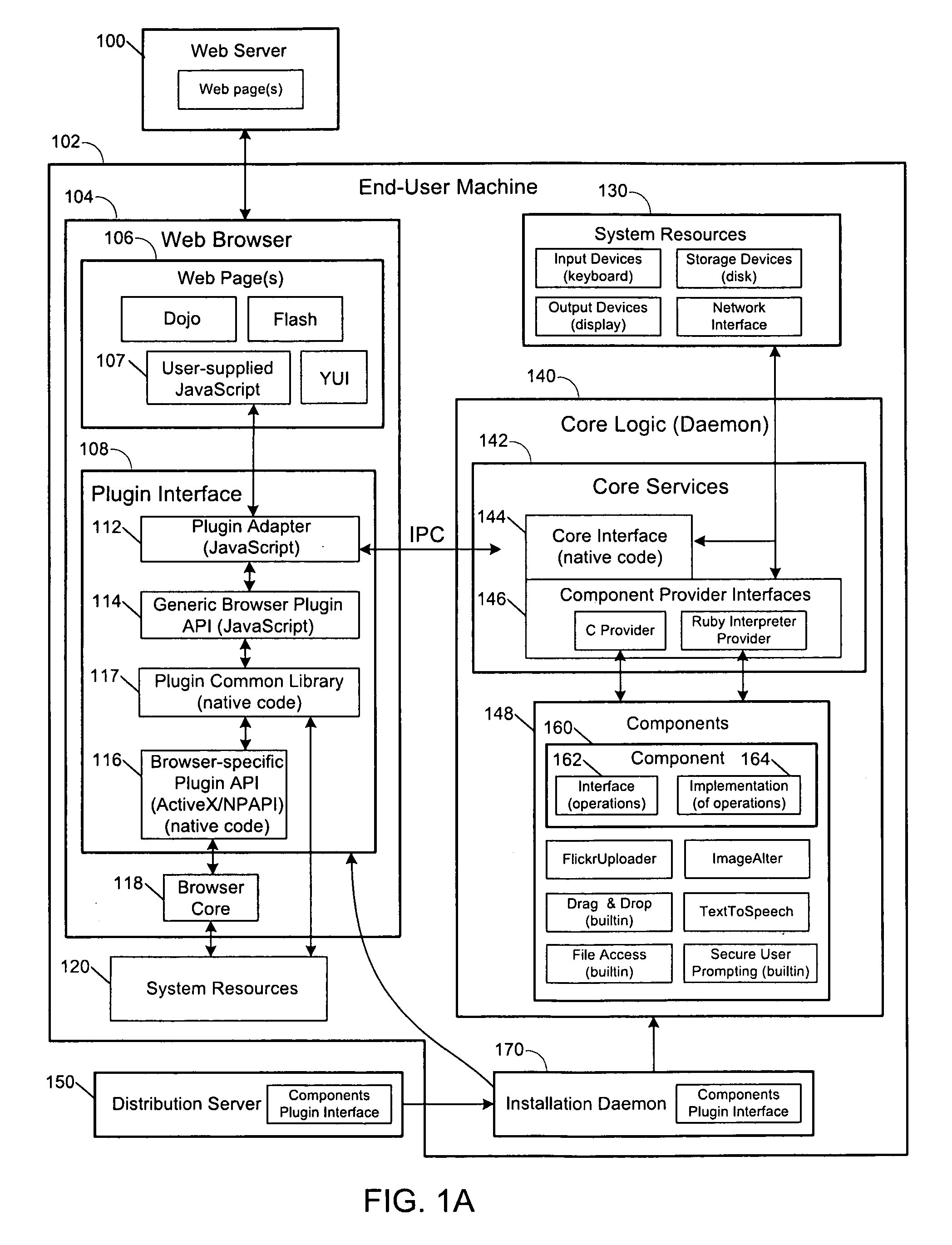
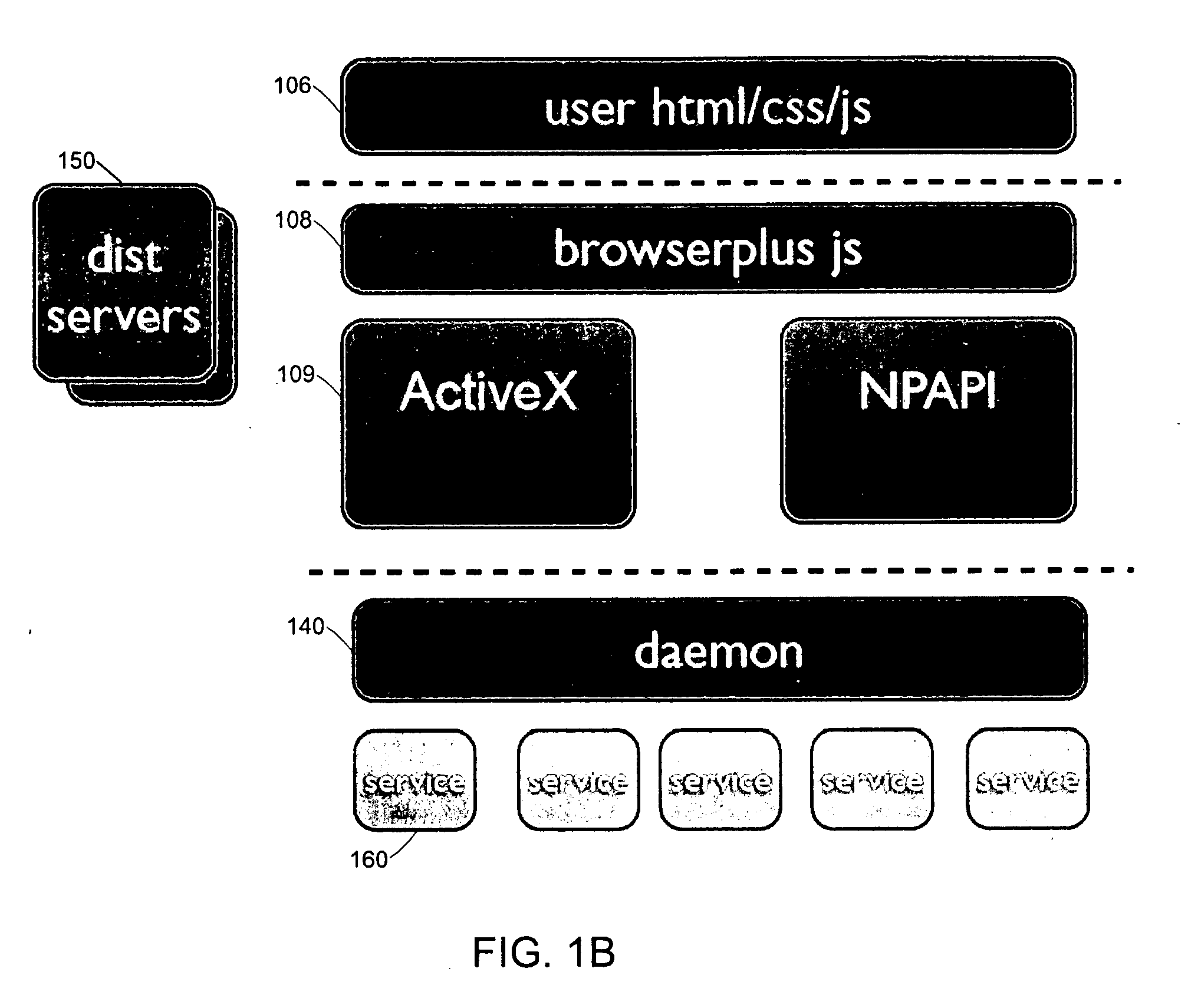
Secure browser-based applications
Techniques are provided for execution of restricted operations by computer program code in web browsers, where the code is permitted to invoke restricted operations if implicit or explicit consent is received. Such techniques may include generating a risk rating for a computer program code component, where the component includes at least one component operation for executing at least one restricted system operation; and prompting a user for permission to execute the restricted system operation, wherein the prompt includes the risk rating and a description of the component operation. The program code may include script code associated with a web page that invokes a web browser plugin, which in turn invokes the restricted system operation. The code may invoke the restricted system operation in response to receiving an input from a user via the web browser, where the input is for causing an action associated with performing the operation, the action implicitly granting consent to perform the operation.
Owner:R2 SOLUTIONS
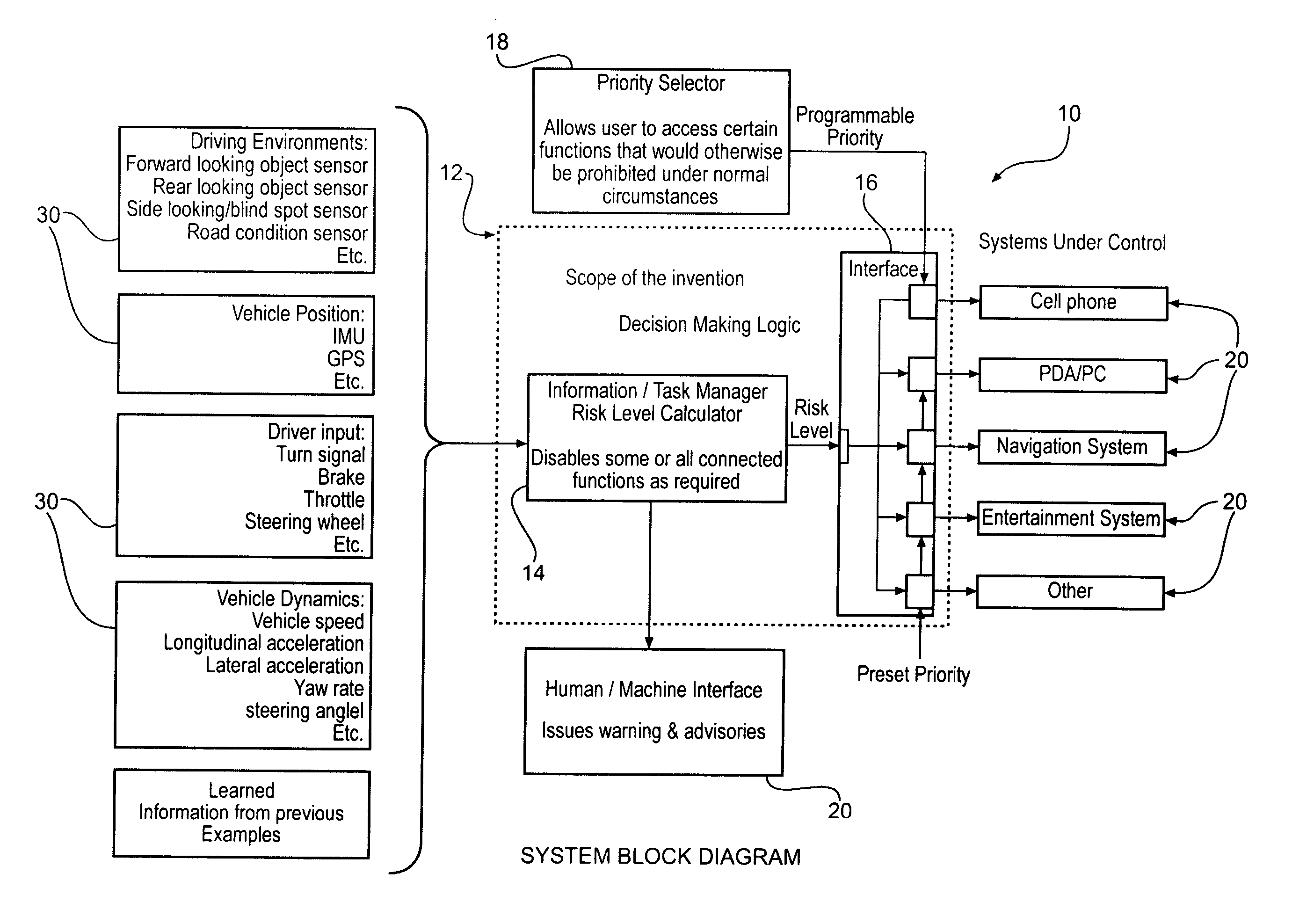
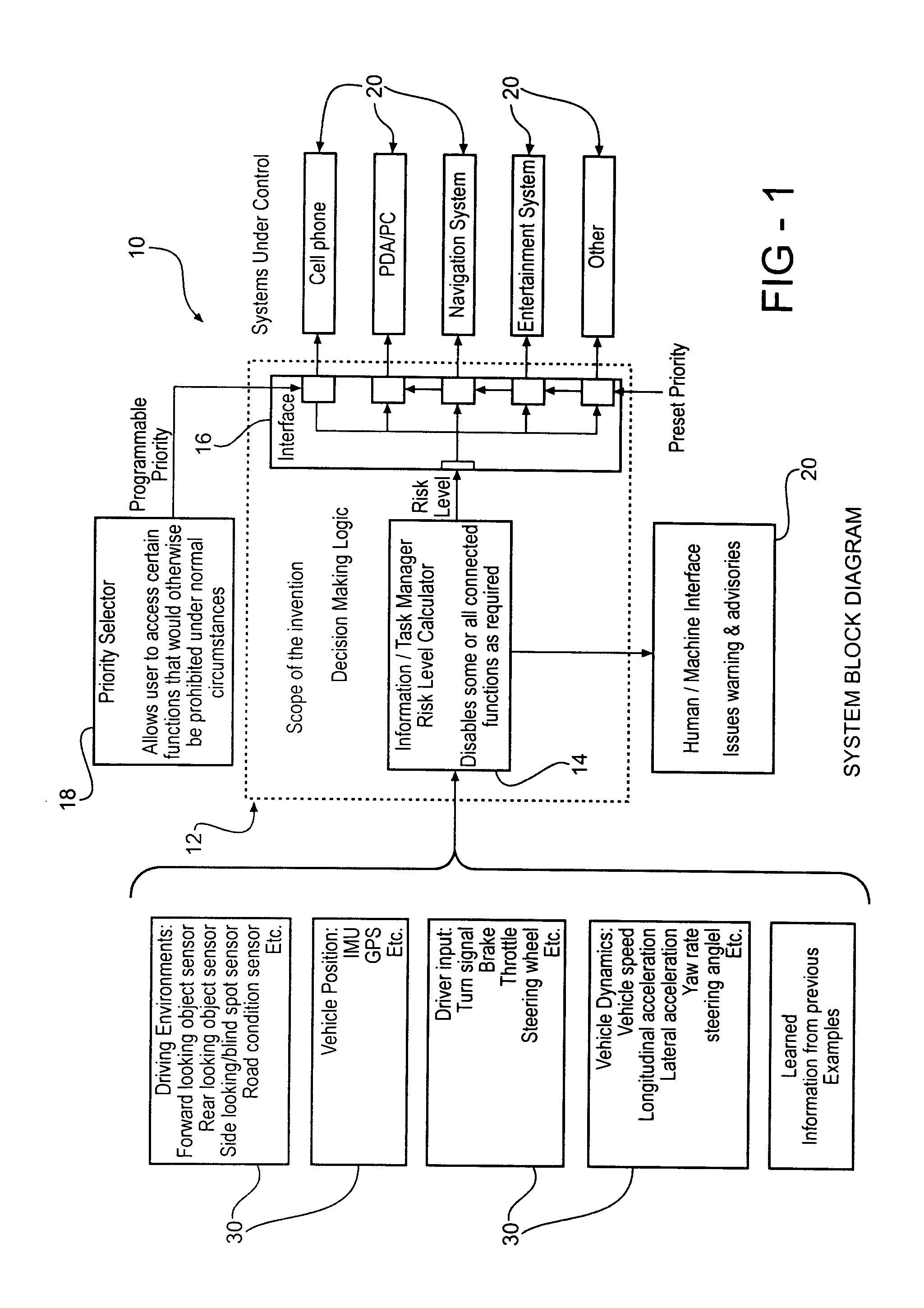
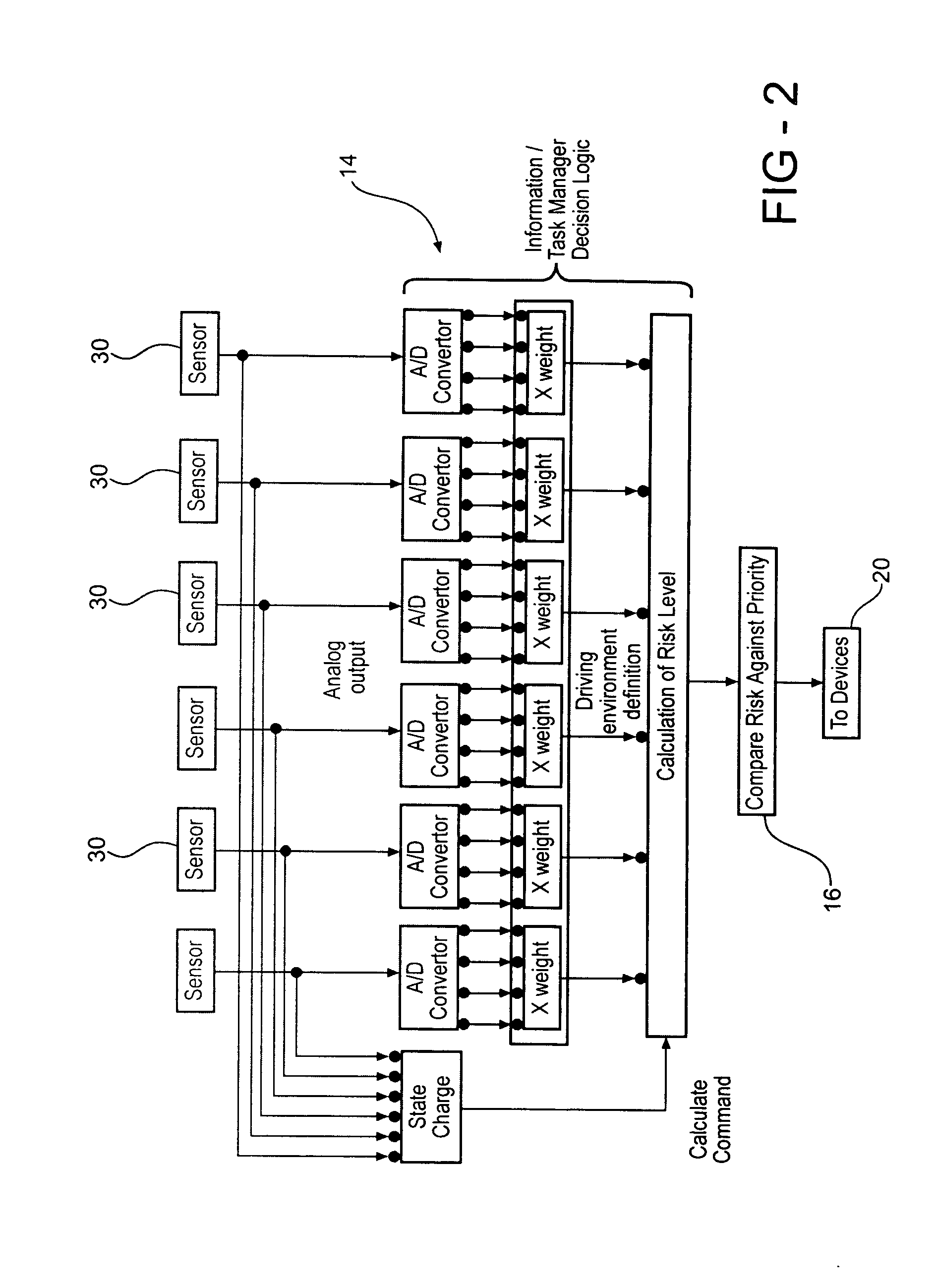
Vehicle information/task manager
InactiveUS20050038573A1Digital data processing detailsInstrument arrangements/adaptationsSystem usageRECREATIONAL EQUIPMENT
The present invention is operative to disable at least one infotainment device under certain conditions relative to the current driving environment of the user. The system uses a weighted matrix to assign risk to certain sensed conditions while driving. A changed condition is assigned a weight and the weighted risks are summed to calculate risk level information. The risk level information is thereafter compared to priority level information associated with at least one infotainment device. When the risk level information exceeds or is equal to the priority level information of the at least one infotainment device the system temporarily disables the infotainment device until the driving environment changes to a condition where it is safe to operate the infotainment device.
Owner:TOYOTA TECHN CENT USA
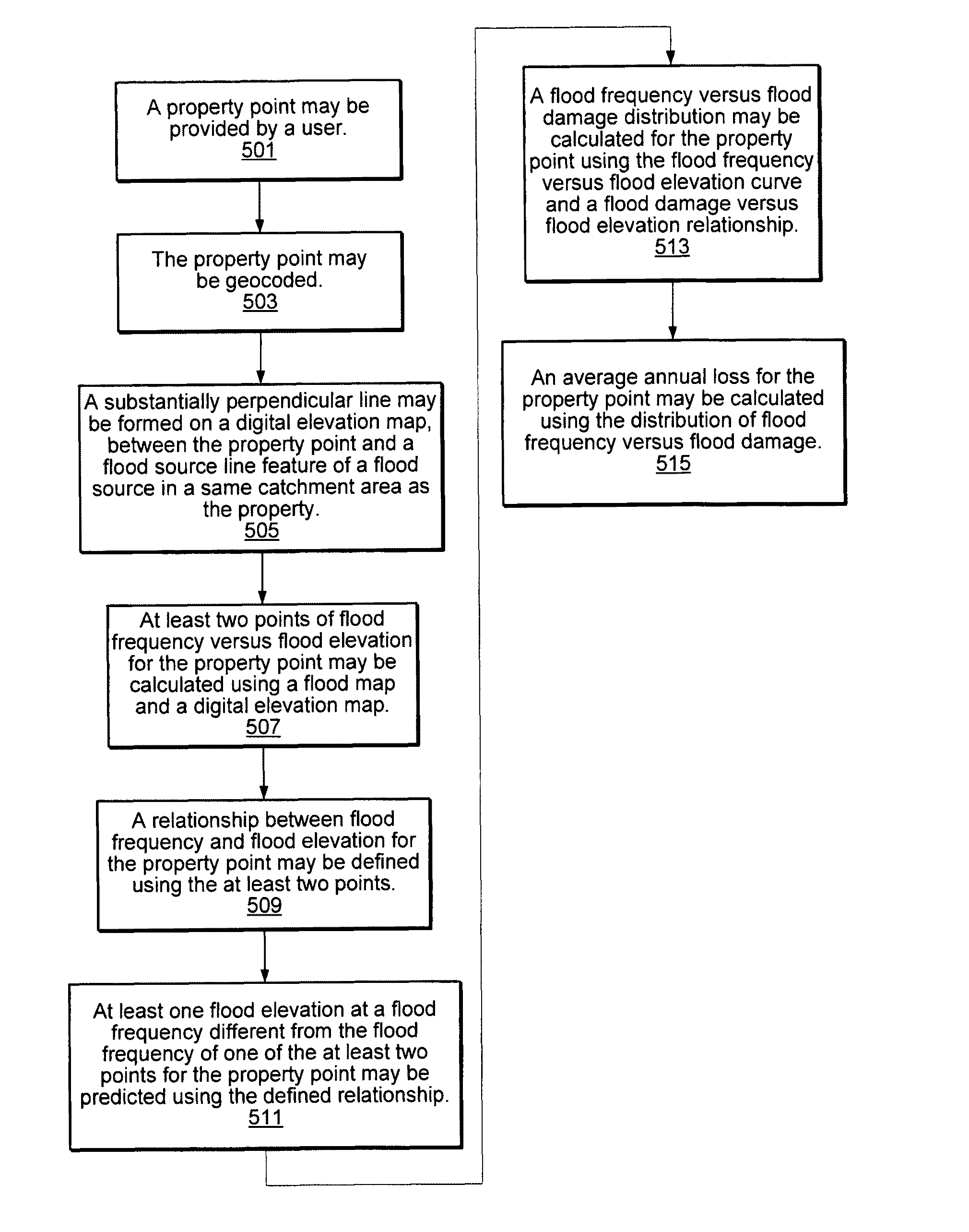
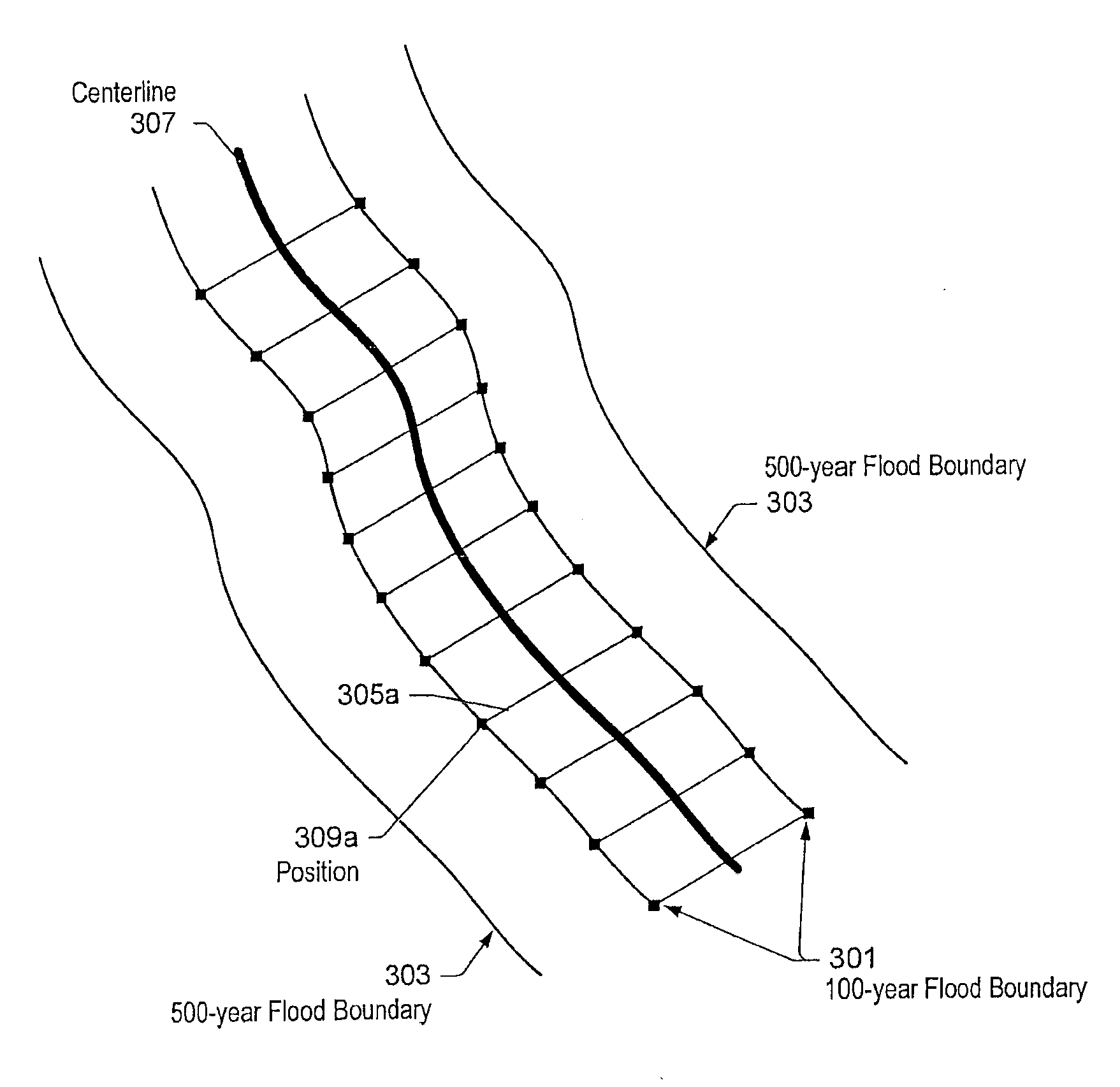
Systems and methods for flood risk assessment
ActiveUS7917292B1Reduce uncertaintyImprove accuracyData processing applicationsClimate change adaptationFlood risk assessmentData set
In various embodiments, points from flood maps (e.g., geospatial flood risk zoning maps) may be used in generating a flood frequency versus flood elevation curve for reducing the uncertainty in the flood risk assessment. In some embodiments, geospatial flood elevation lines for flood elevation lines at different flood frequency levels may be defined based on elevation datasets where there are inconsistencies between the elevation datasets and flood maps that were generated. The flood frequency versus flood loss curve may be derived based on the computed flood frequency versus flood elevation curve, digital elevation datasets, and collected damage curve. In some embodiments, the flood risk rating may also be derived and a flood risk assessment report may be generated.
Owner:CORELOGIC SOLUTIONS
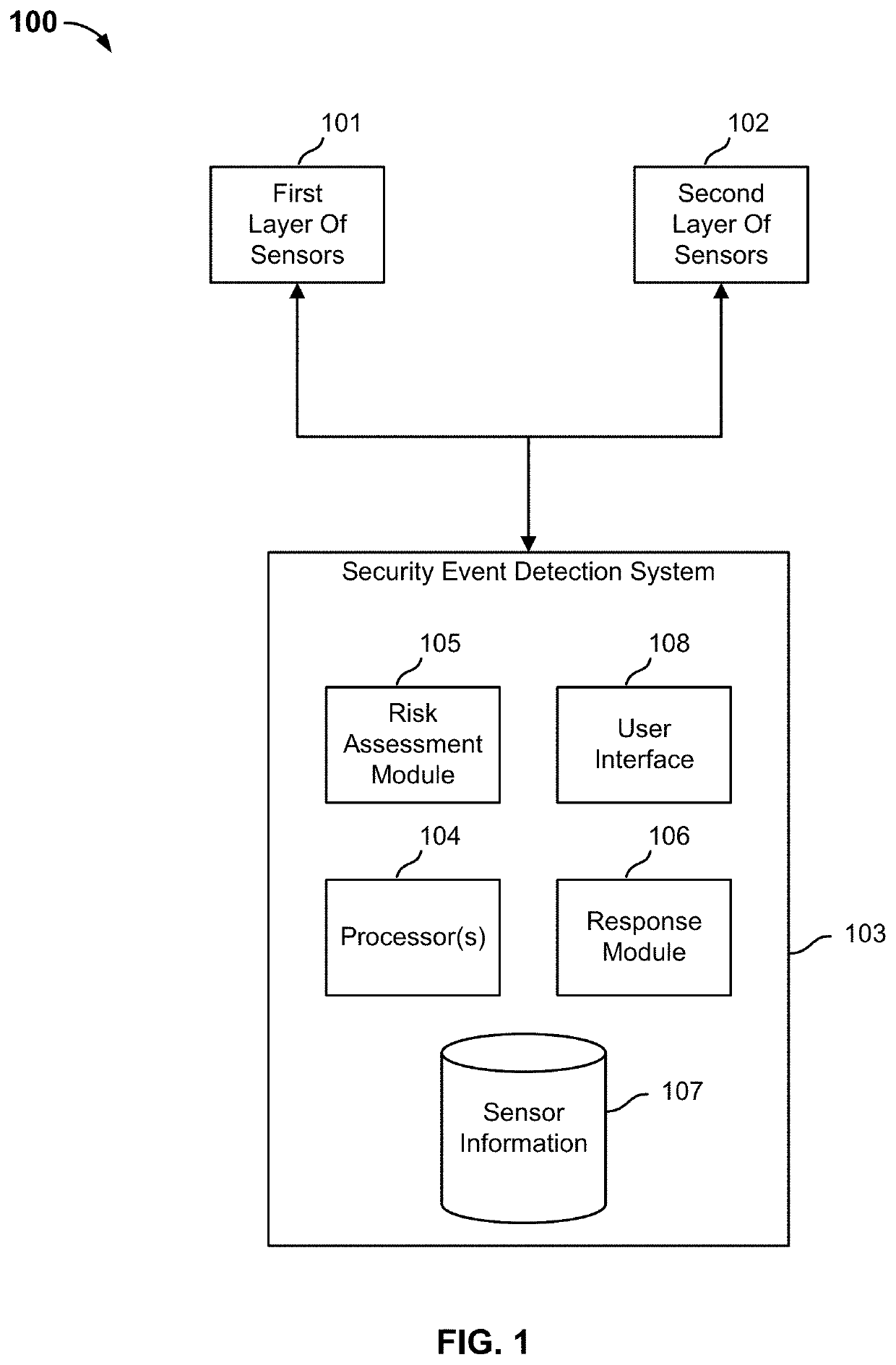
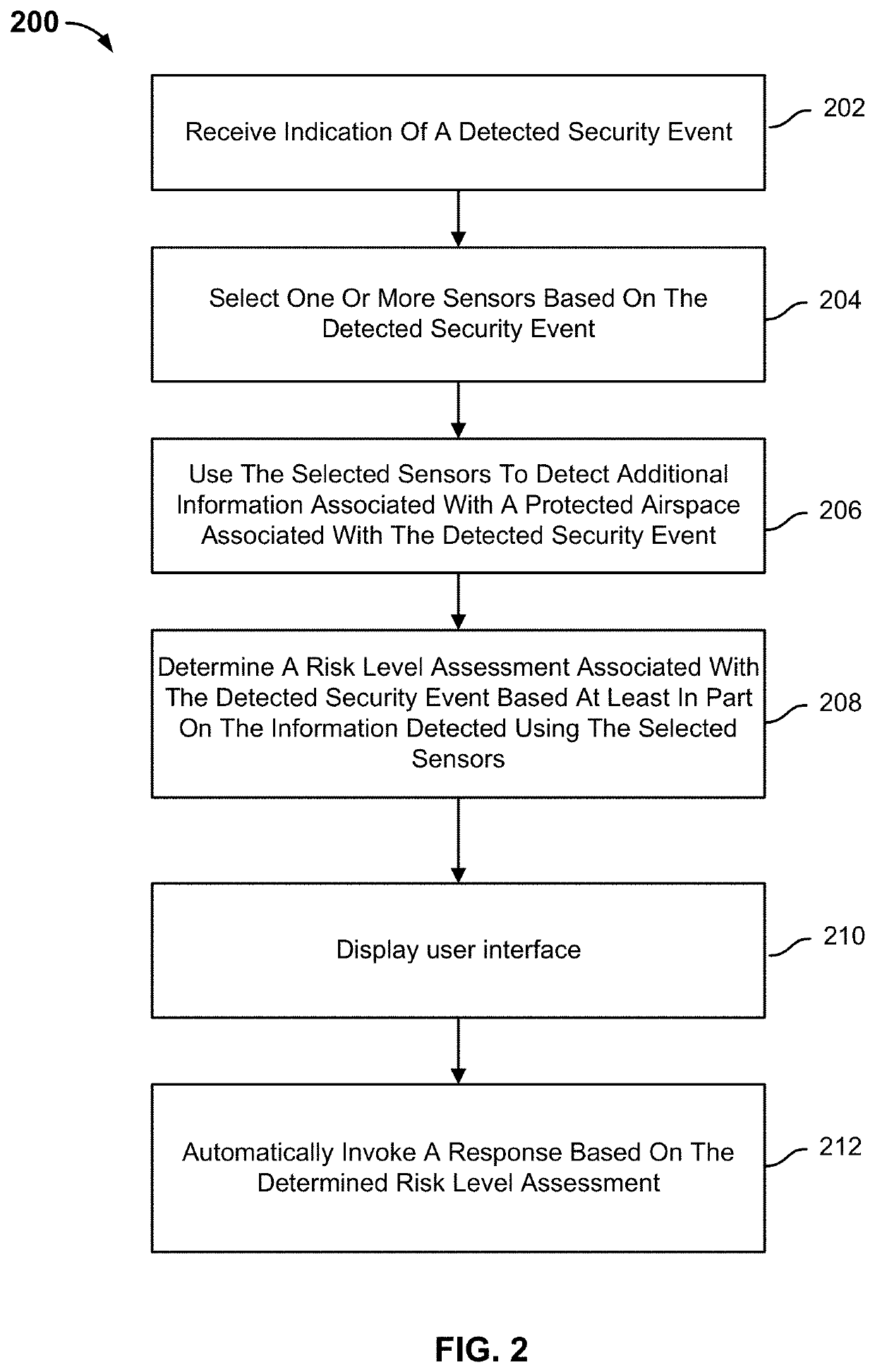
Security event detection and threat assessment
An indication of a detected security event is received. One or more sensors are selected based on the detected security event. The selected sensors are used to detect additional information associated with a protected airspace associated with the detected security event. A risk level assessment associated with the detected security event is determined based at least in part on the additional information detected using the selected sensors. A response is automatically invoked based on the determined risk level assessment.
Owner:AIRSPACE SYST INC
Methods, systems, and media for applying scores and ratings to web pages, web sites, and content for safe and effective online advertising
ActiveUS20120010927A1Safe and effective online advertisingSafe and effectiveAdvertisementsWeb data retrievalOnline advertisingSubject matter
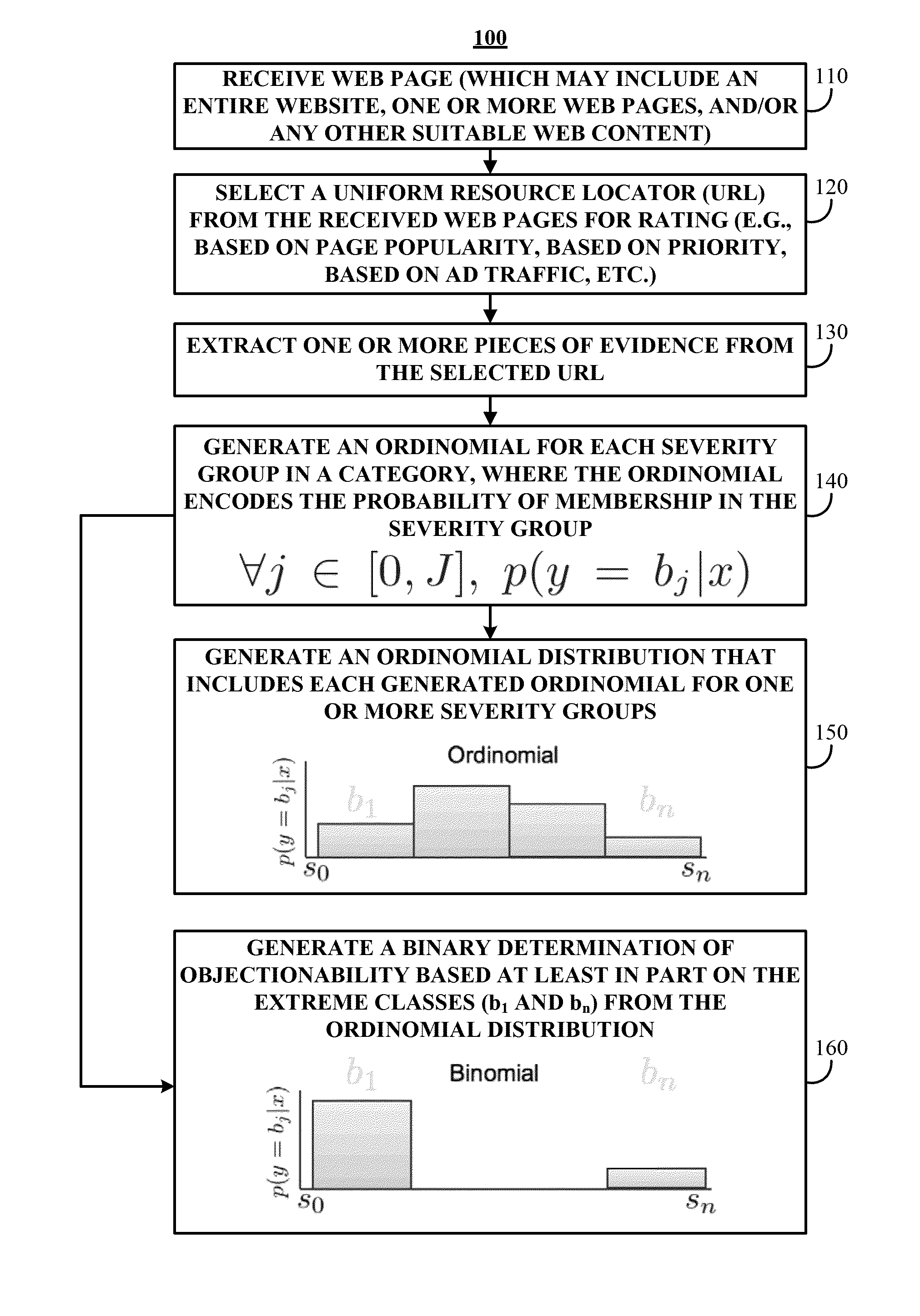
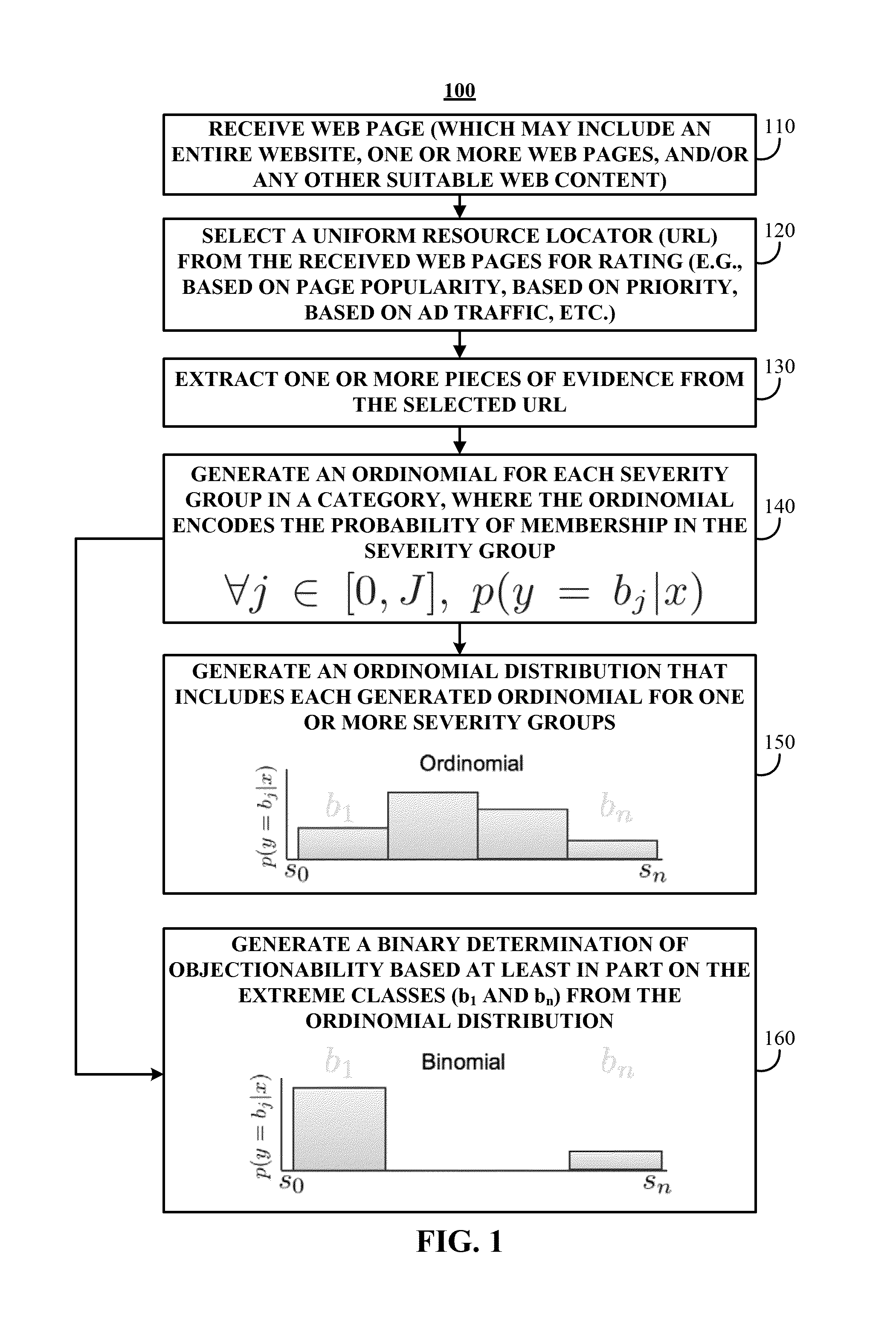
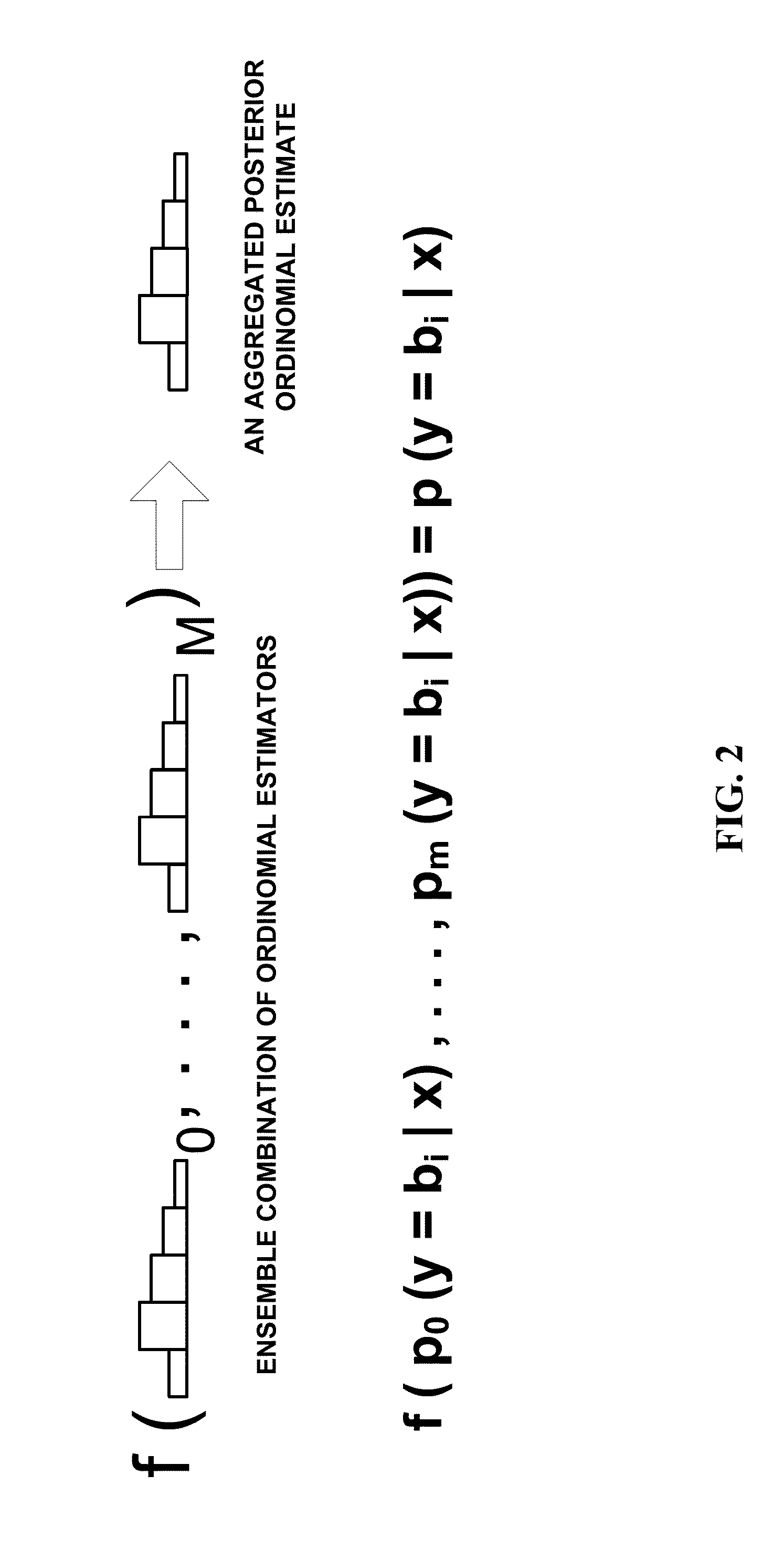
Systems, methods, and media for rating websites for safe advertising are provided. In accordance with some embodiments of the disclosed subject matter, the method comprises: extracting one or more features from a piece of web content; applying a plurality of statistical models to the extracted features to generate a plurality of ordinomial estimates, wherein each ordinomial estimate represents a probability that the web content is a member of one of a plurality of severity groups; determining a posterior ordinomial estimate for the web content by combining the plurality of ordinomial estimates; generating a risk rating that encodes severity and confidence based on the determined posterior ordinomial estimate, wherein the risk rating identifies whether the web content is likely to contain objectionable content of a given category; and providing the risk rating for determining whether an advertisement should be associated with the web content.
Owner:INTEGRAL AD SCI
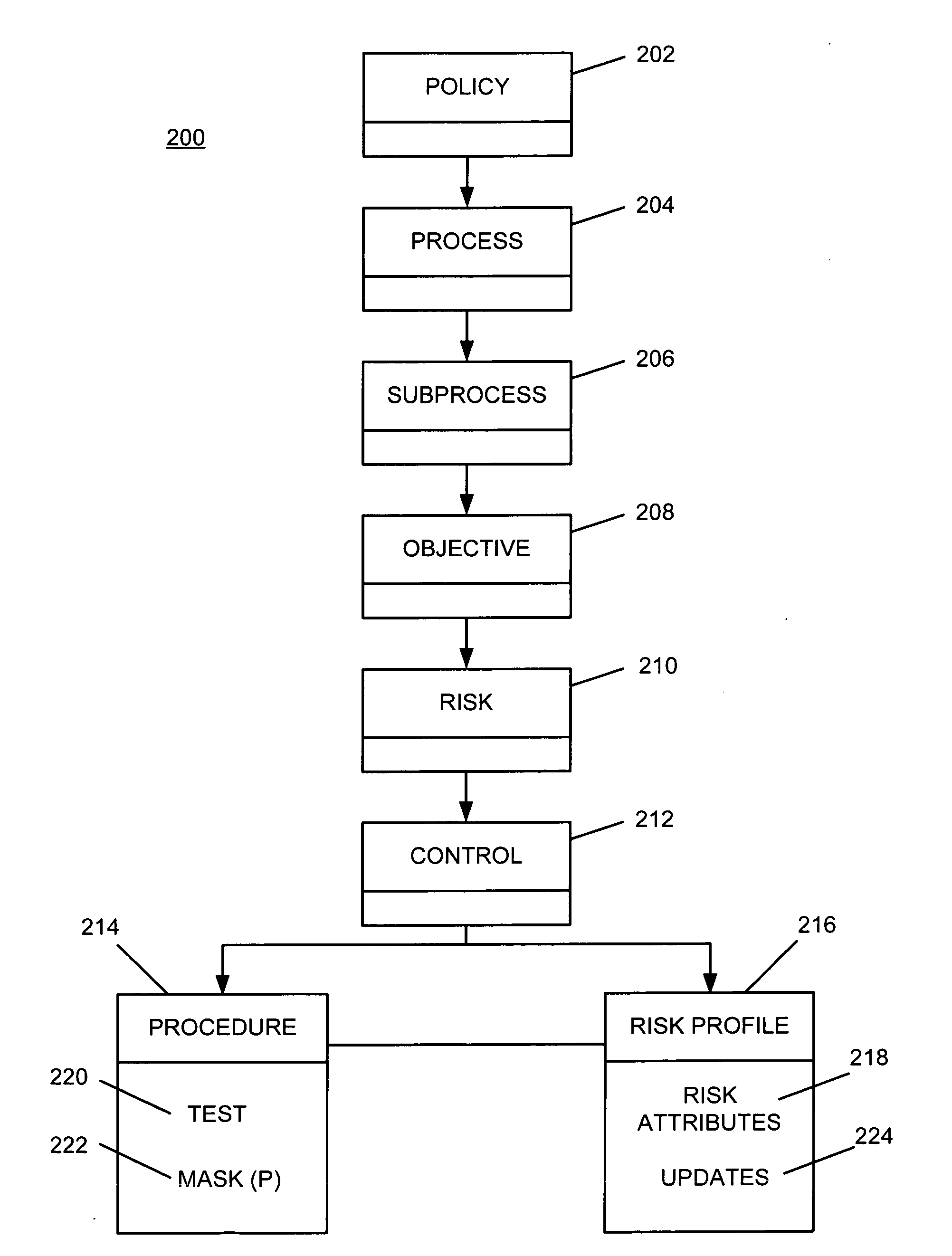
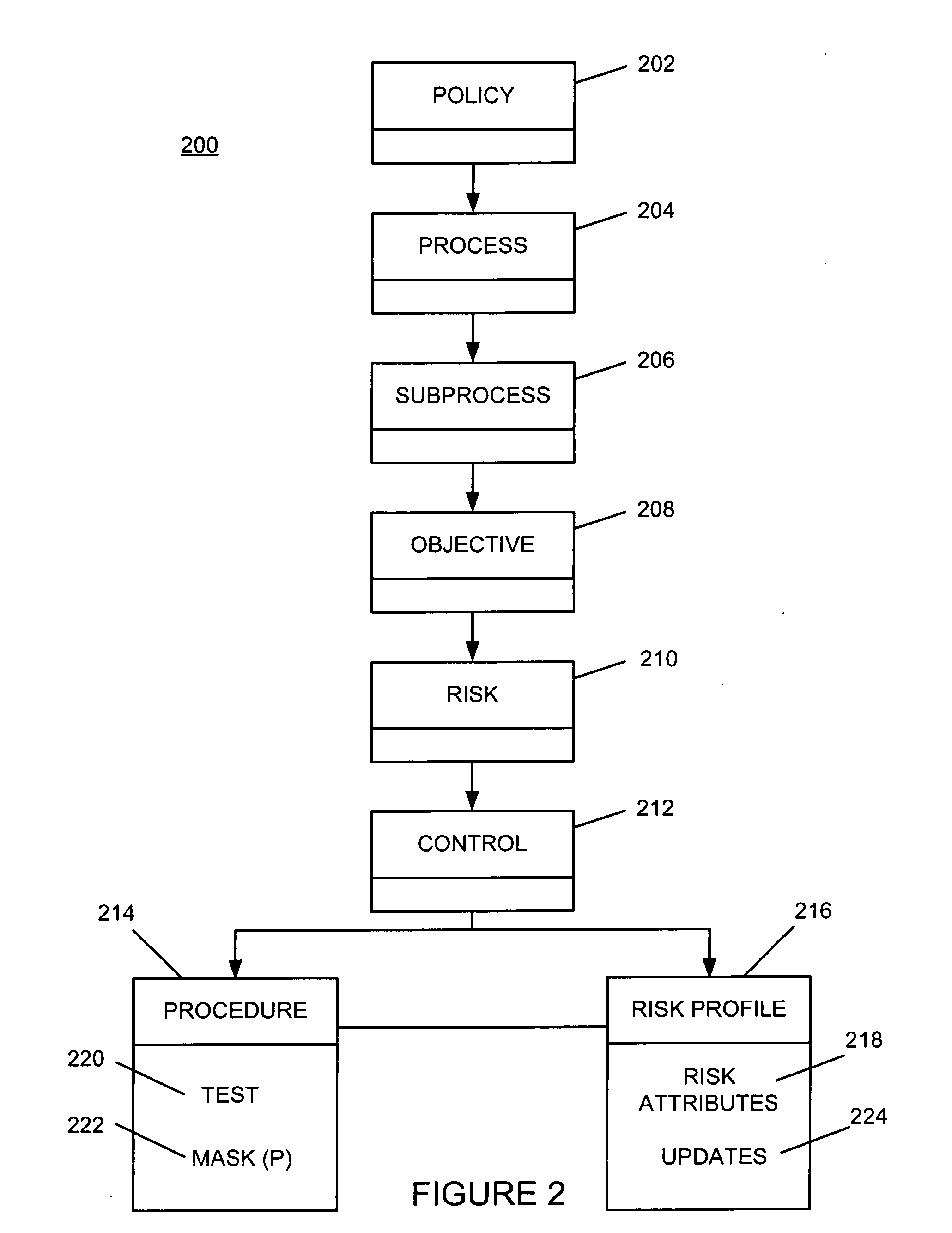
Risk profiling for enterprise risk management
ActiveUS20090228316A1Increased riskImproves risk and opportunity managementFinanceResourcesRisk profilingRisk rating
A risk profile element is created and associated with a control element within a risk hierarchy associated with an organization. A risk attribute is updated automatically within the risk profile element in response to an event associated with the control element. The updated risk attribute is processed to evaluate risk associated with the control element.
Owner:IBM CORP
Systems and methods for risk rating and pro-actively detecting malicious online ads
Methods and systems for risk rating and pro-actively detecting malicious online ads are described. In one example embodiment, a system for risk rating and pro-actively detecting malicious online ads includes an extraction module, an analysis engine, and a filter module. The extraction module is configured to extract a SWF file from a web page downloaded by the system. The analysis engine is communicatively coupled to the extraction module. The analysis engine is configured to determine a risk rating for the SWF file and send the risk rating to a web application for display. In an example, determining the risk rating includes locating an embedded redirection URL and determining a risk rating for the embedded redirection URL. The filter module is configured to determine, based on the risk rating, whether to block the SWF file and send a warning to the web application for display.
Owner:MCAFEE LLC
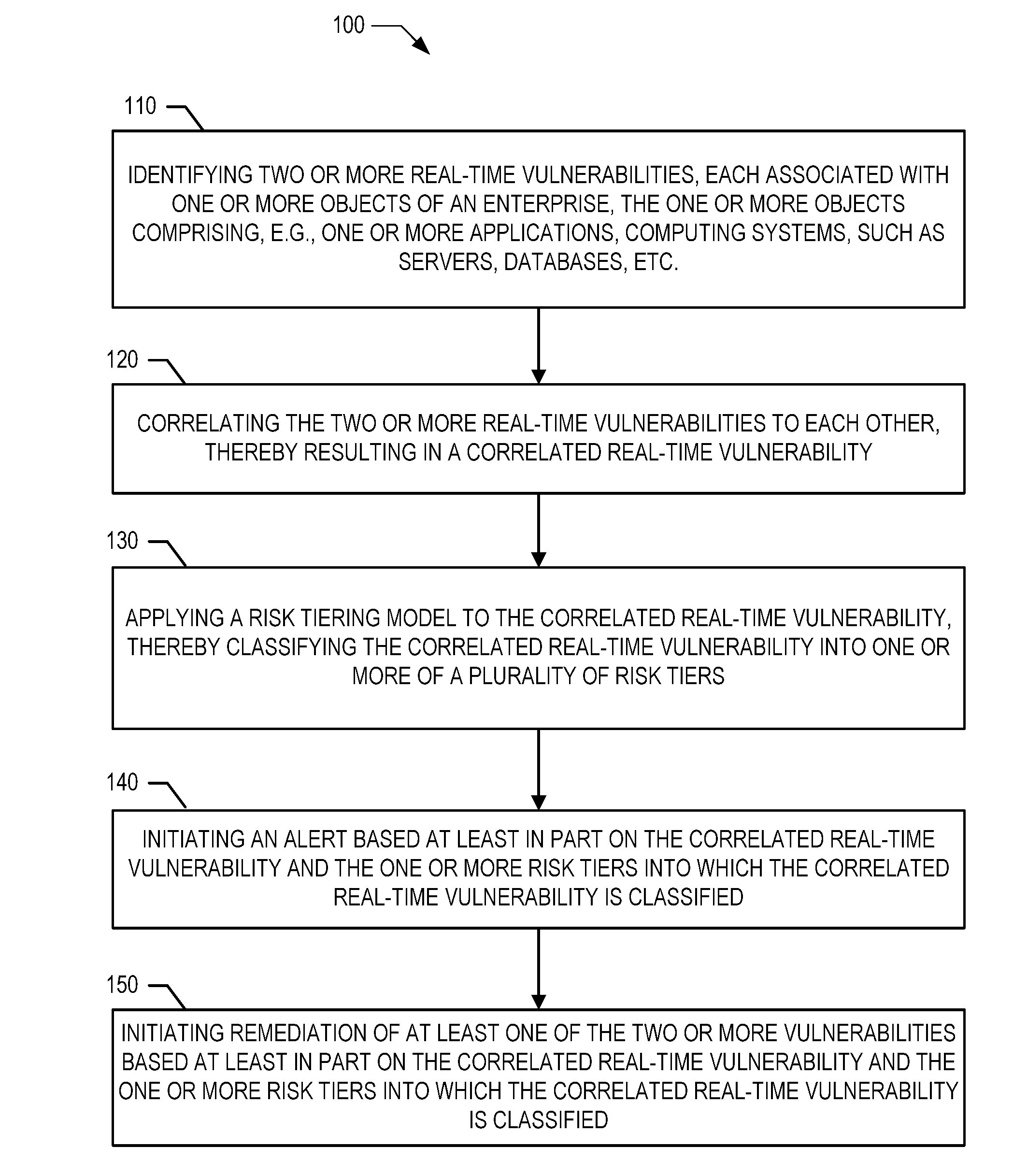
Tiered risk model for event correlation
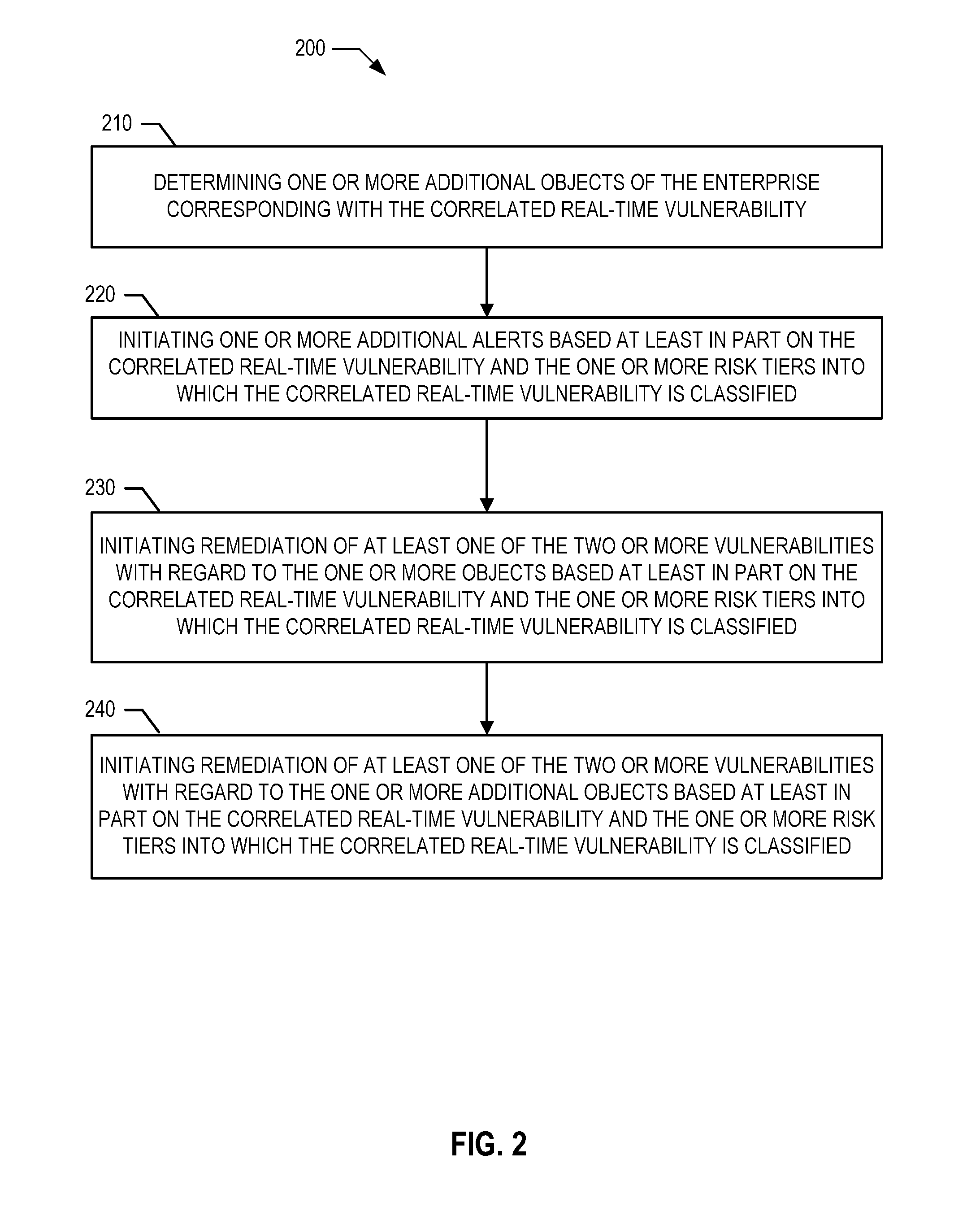
A method for real-time threat monitoring includes identifying two or more real time vulnerabilities, each associated with one or more objects of an enterprise, correlating the two or more real-time vulnerabilities to each other, applying a risk tiering model to the correlated real-time vulnerability, thereby classifying the correlated real-time vulnerability into risk tiers, and initiating an alert based on the correlated real-time vulnerability and the risk tiers into which the correlated real-time vulnerability is classified. According to other embodiments a method includes applying a risk methodology to log data contained in one or more object logs thereby identifying one or more security events, applying a risk tiering model to the one or more security events, thereby classifying the security events into risk tiers, and initiating an alert based on the security events and the risk tiers into which the security events are classified.
Owner:BANK OF AMERICA CORP
Multi-cycle installment decision making method and system
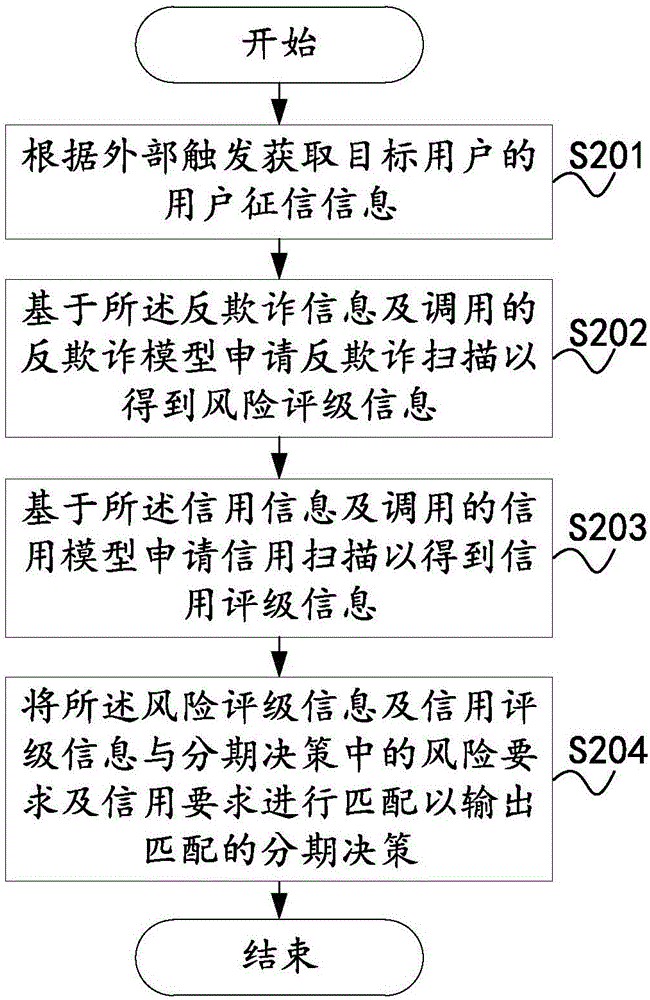
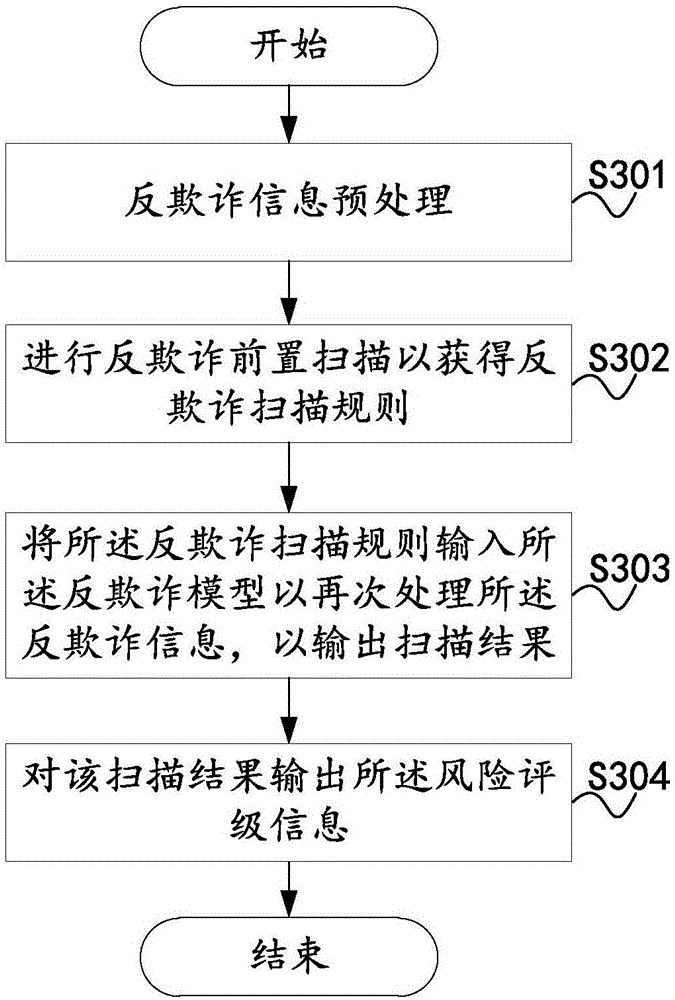
The invention provides a multi-cycle installment decision making method and a multi-cycle installment decision making system. The multi-cycle installment decision making method comprises the steps of: acquiring user credit investigation information of a target user according to an installment request input by a user end or an external trigger, wherein the user credit investigation information comprises anti-fraud information and credit information of the user; applying for anti-fraud scanning based on the anti-fraud information and a called anti-fraud model, so as to obtain risk rating information; applying for credit scanning based on the credit information and a called credit model, so as to obtain credit rating information; and matching the risk rating information with a risk requirement and matching the credit rating information with a credit requirement in installment decision making, so as to output matched installment decisions. The multi-cycle installment decision making method and the multi-cycle installment decision making system can extract effective user information for data processing through classifying and integrating a large amount of user information, and feed back installment decision making schemes timely and accurately.
Owner:快睿登信息科技(上海)有限公司
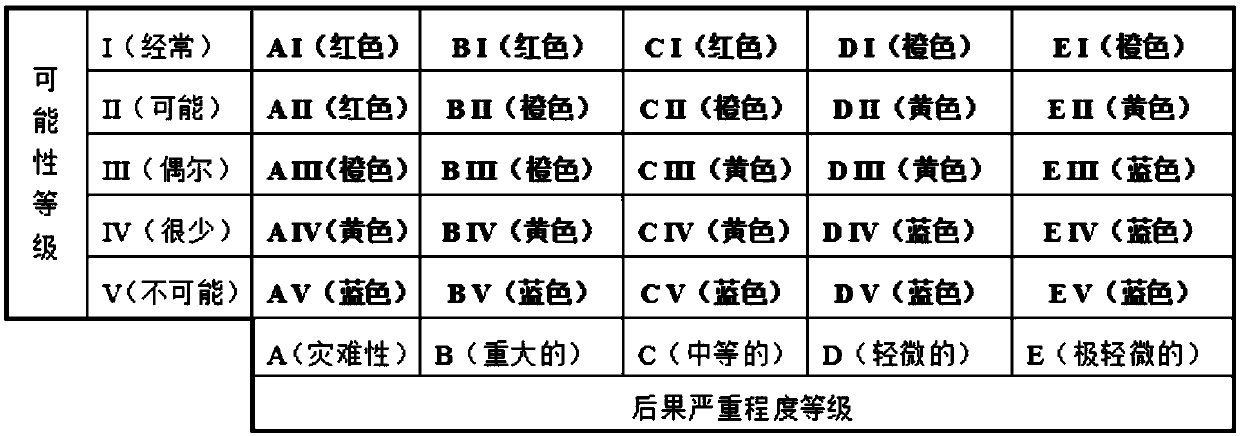
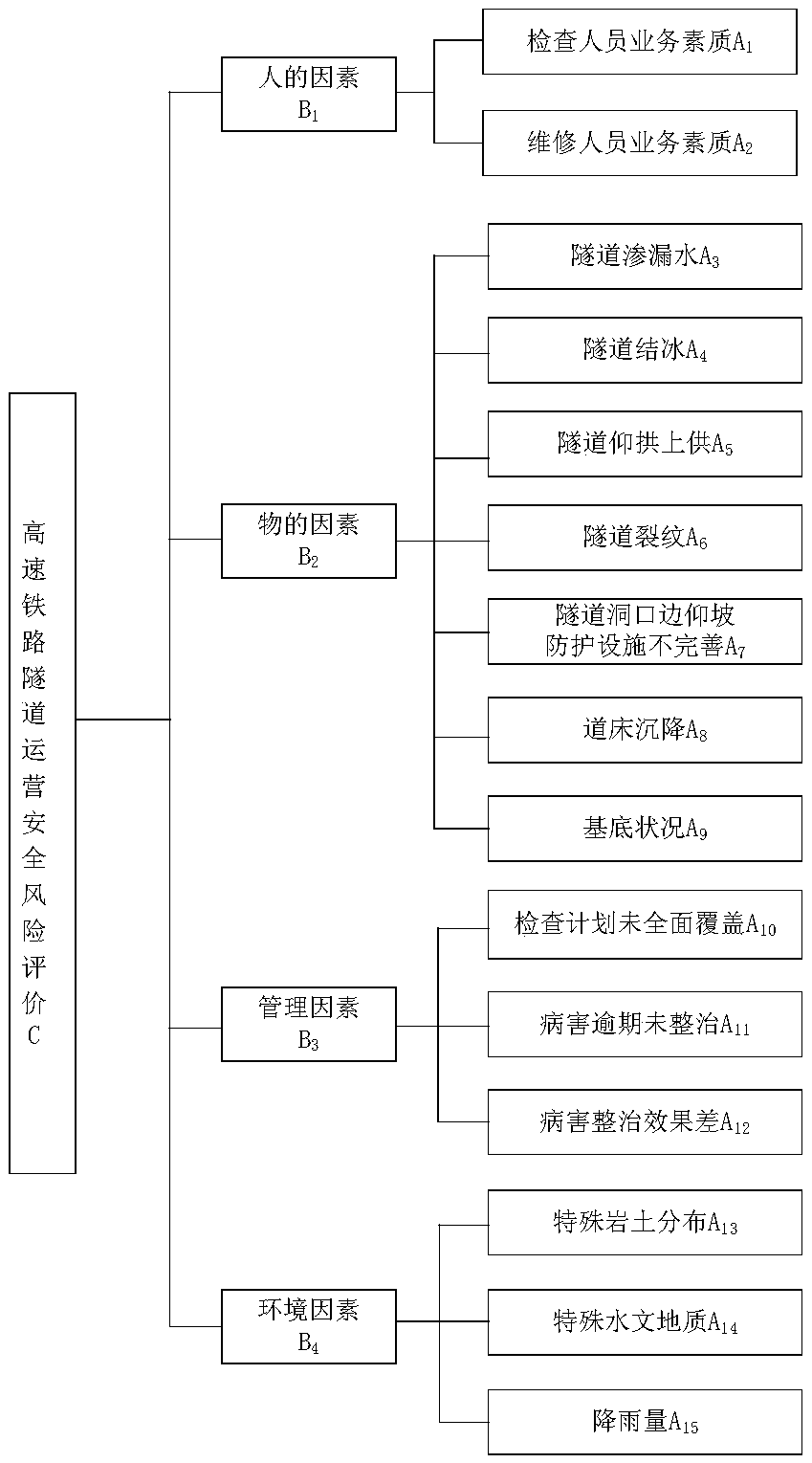
Security risk assessment and early warning method for high-speed railway tunnel during operation period
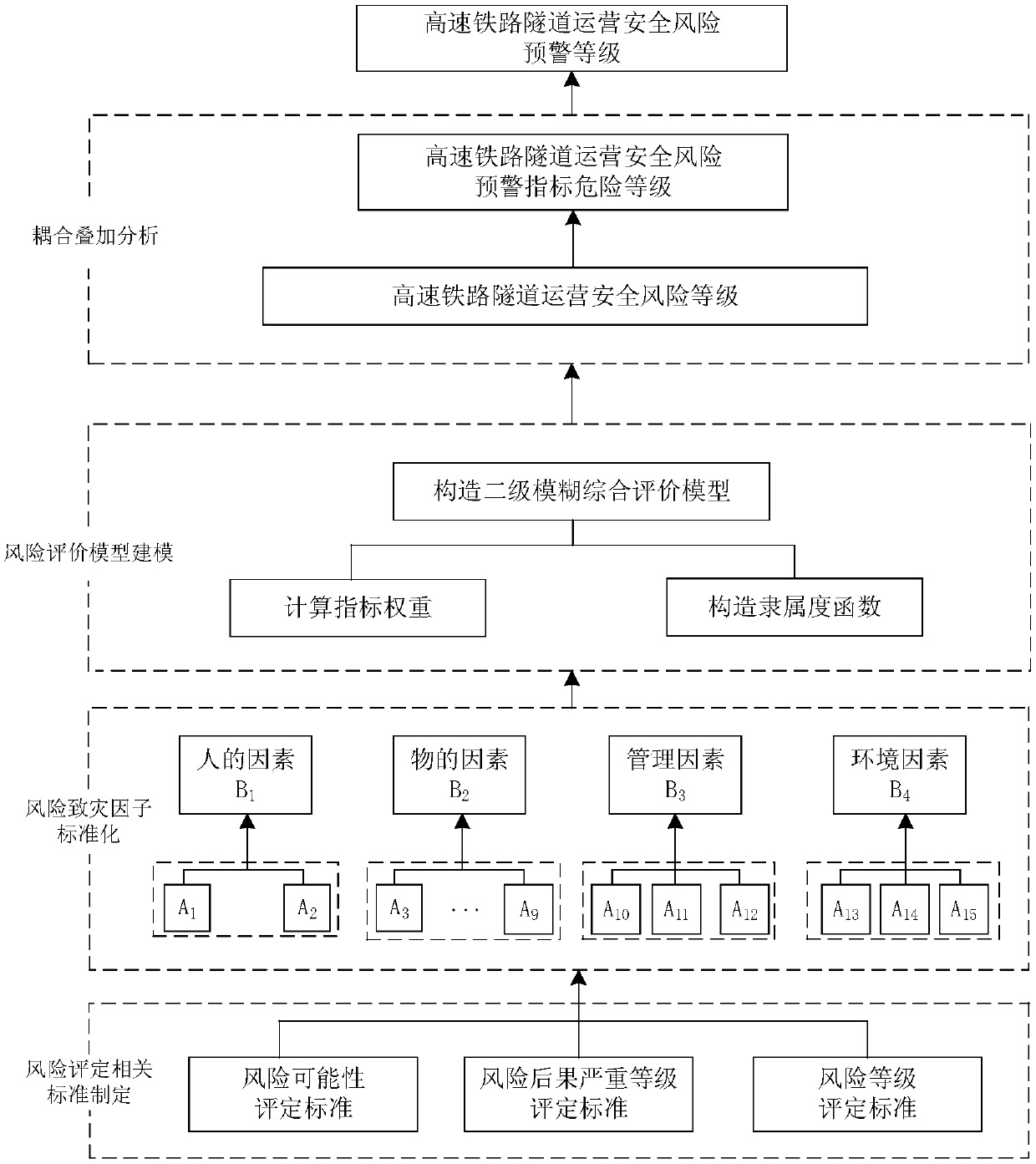
The invention relates to a security risk assessment and early warning method for a high-speed railway tunnel during operation period. The method comprises the first step of constructing an evaluationbasis, including a risk rating assessment standard, an evaluation index system and an early warning mechanism establishment: the risk rating assessment standard includes a risk possibility assessmentstandard and a risk consequence severity rating assessment standard. The risk rating assessment is based on the risk probability rating as the ordinate, and the risk consequence severity rating as theabscissa to construct a risk assessment matrix. The evaluation index system is established by the hazard factors of the four aspects of "human- things-management-environment ", and constructs the risk probability membership function of the hazard factors. The early warning mechanism is established by four-color early warning. The second step of risk rating assessment is quantitatively calculatedbased on the membership function and the second-level fuzzy comprehensive evaluation model, and conducted combining the risk consequence severity rating assessment standard and the risk rating assessment matrix. The third step of determining the early warning rating: obtained by coupling the superposition analysis risk rating and the early warning indicator risk rating. The beneficial effects of the security risk assessment and early warning method for a high-speed railway tunnel during operation period are that the evaluation results are quantified, and the decision is based on science.
Owner:CRRC CONSTR ENG CO LTD
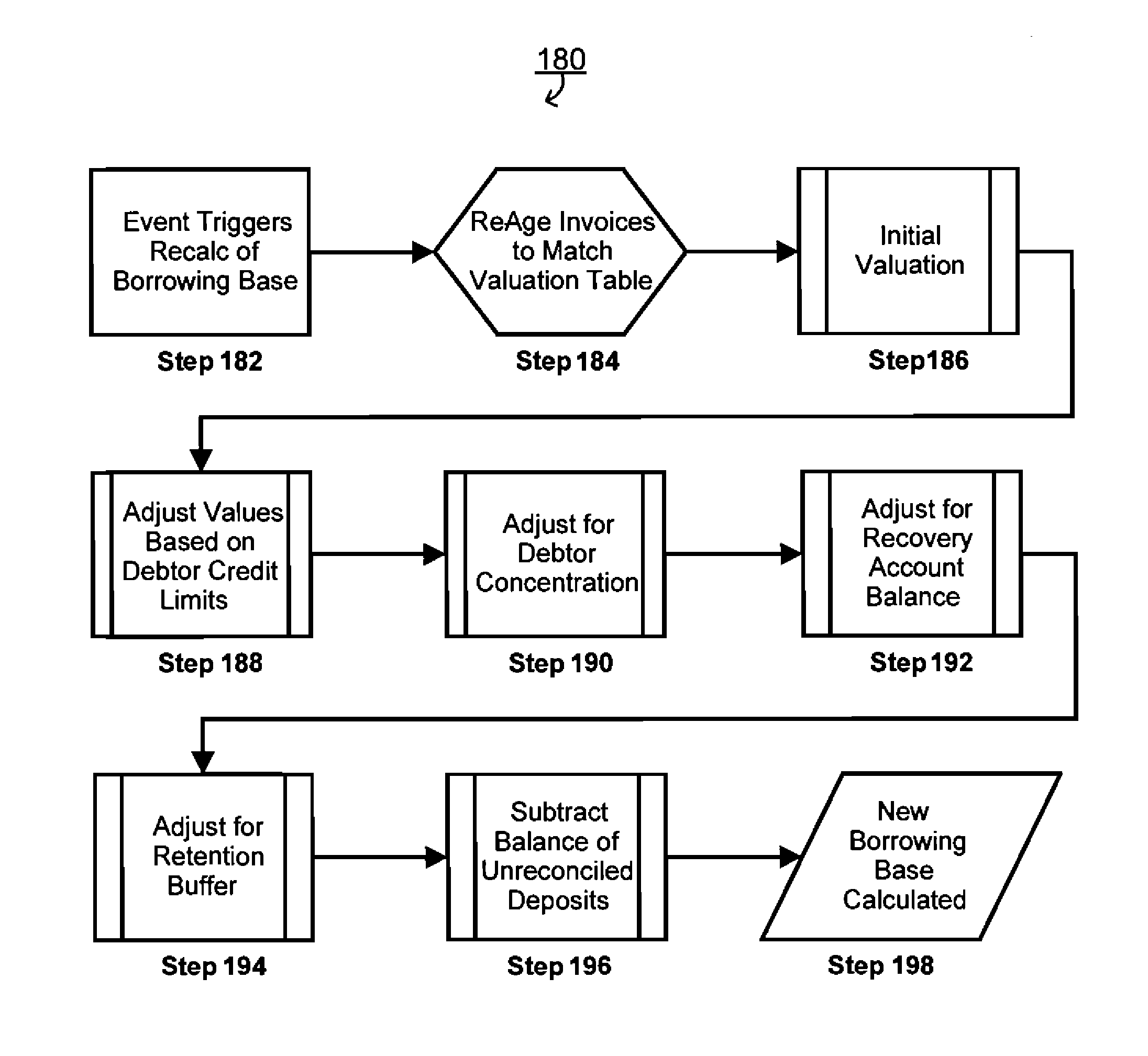
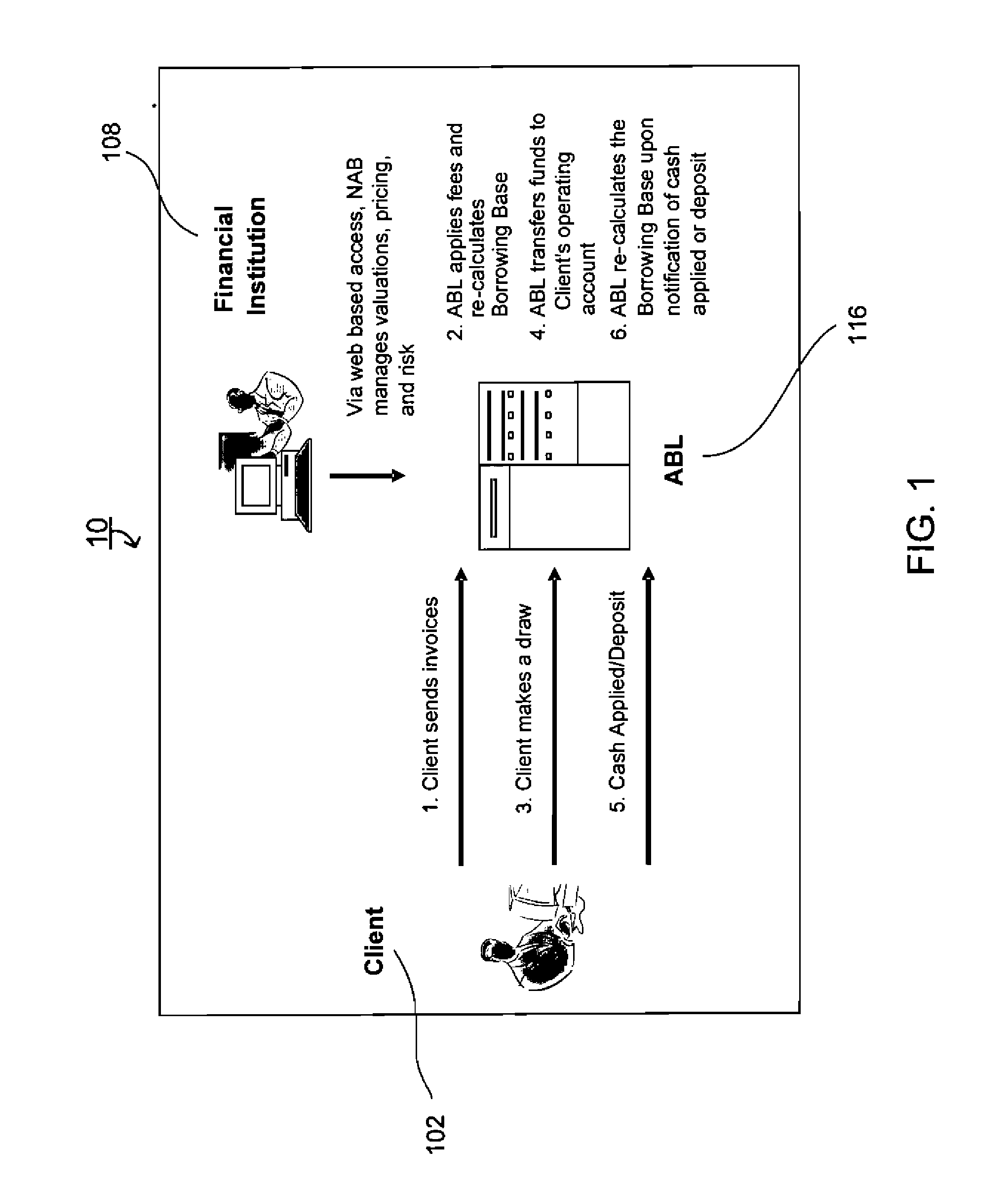
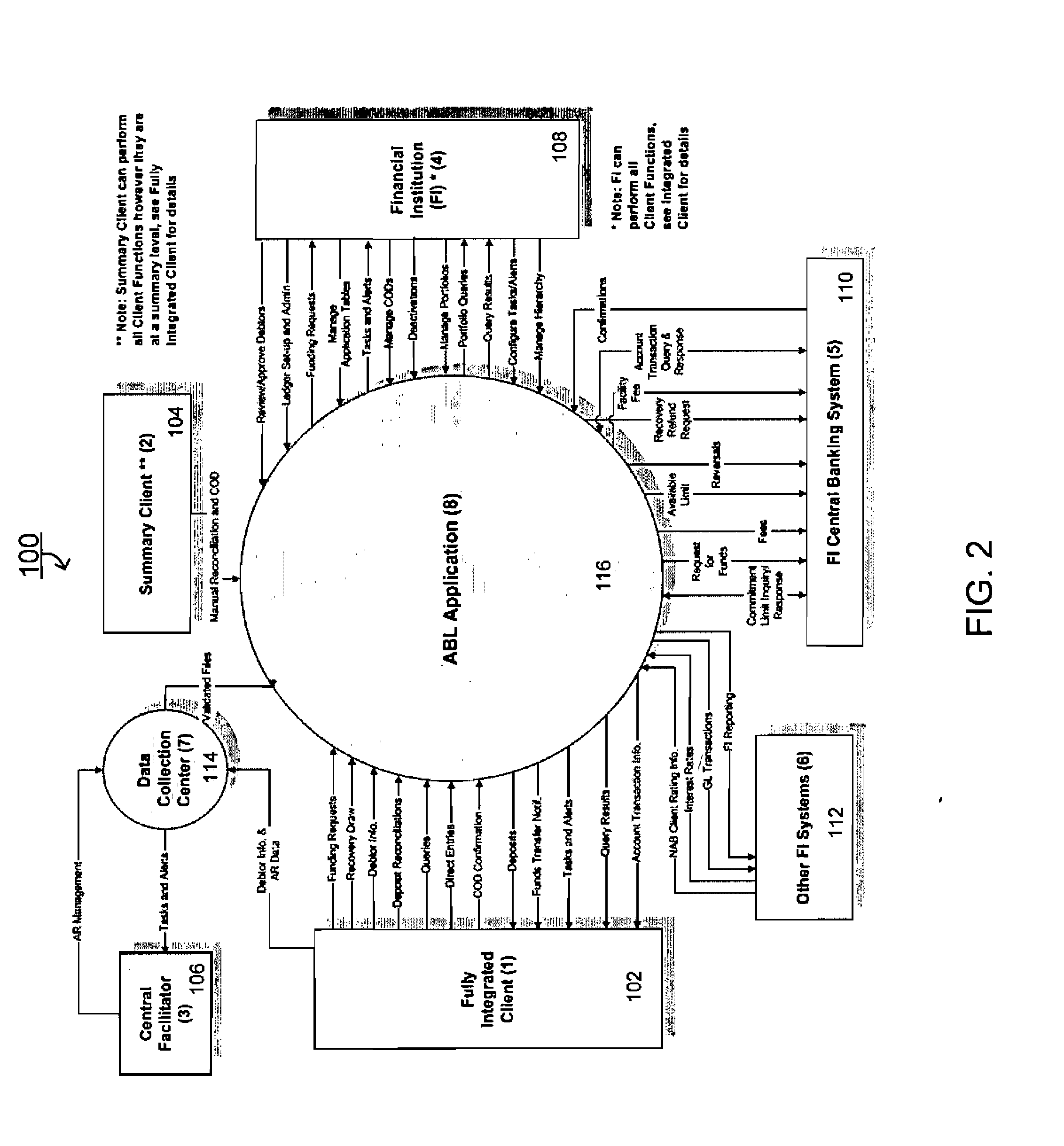
Systems and methods for asset based lending (ABL) valuation and pricing
An automated asset based lending (ABL) system that integrates supplier receivables data, allowing financial institutions optimally to value and price lending against those receivables, thus enabling financial institutions to offer suppliers a maximum borrowing base with minimum risk and highest return to the financial institution, further enabling the financial institution to conduct business in multiple currencies, time zones and countries using a computer based ABL process. In an asset based lending system having a client and at least one financial institution, a method for valuing and pricing client's receivables, the method comprising, downloading accounts receivable information from the client, the accounts receivable information having a specified currency, calculating a borrowing base for the client via utilizing debtor risk ratings, pricing profiles, valuation profiles and pricing tiers, and applying fees and interest as specified in the pricing profile associated with the valuation profile.
Owner:PRIMEREVENUE
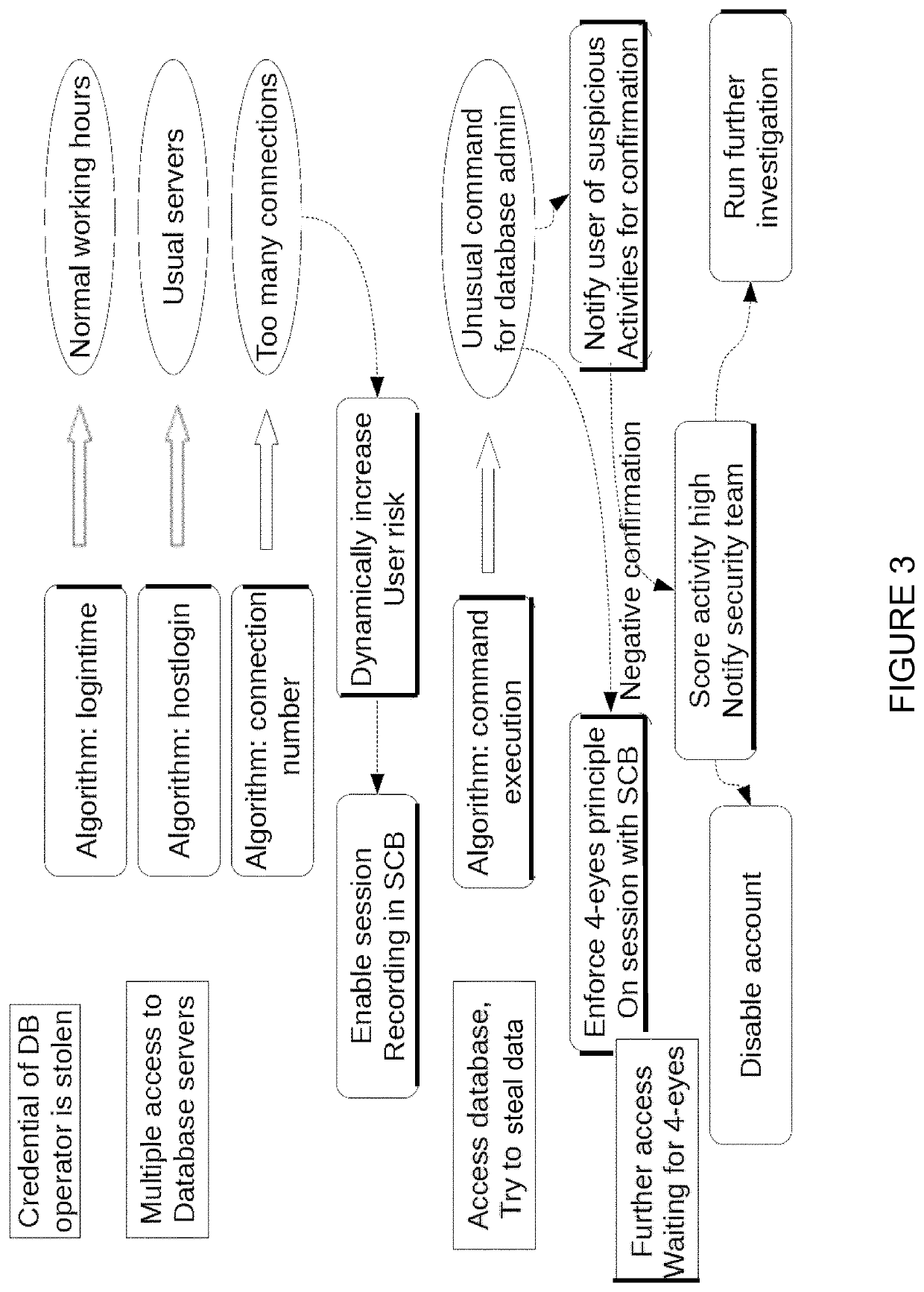
Computer-implemented method for determining computer system security threats, security operations center system and computer program product
ActiveUS10681060B2Improve securityQuick and efficientPlatform integrity maintainanceMachine learningRisk levelSecurity operations center
A computer-implemented method for determining computer system security threats, the computer system including user accounts established on the computer system, the method including the steps of: (i) for a plurality of user accounts, assigning a risk level to each account; (ii) in a time interval, for a plurality of events, wherein each event is linked to a respective user account, assigning an event score relating to deviation from normal behavior of each event with respect to the respective user account; (iii) in the time interval, for the plurality of events, calculating an event importance which is a function of the respective event score and the respective user account risk level; (iv) prioritizing the plurality of events by event importance, and (v) providing a record of the plurality of events, prioritized by event importance.
Owner:BALABIT SA
Systems and methods for flood risk assessment
InactiveUS20120259550A1Reduce uncertaintyImprove accuracyData processing applicationsClimate change adaptationFlood risk assessmentData set
In various embodiments, points from flood maps (e.g., geospatial flood risk zoning maps) may be used in generating a flood frequency versus flood elevation curve for reducing the uncertainty in the flood risk assessment. In some embodiments, geospatial flood elevation lines for flood elevation lines at different flood frequency levels may be defined based on elevation datasets where there are inconsistencies between the elevation datasets and flood maps that were generated. The flood frequency versus flood loss curve may be derived based on the computed flood frequency versus flood elevation curve, digital elevation datasets, and collected damage curve. In some embodiments, the flood risk rating may also be derived and a flood risk assessment report may be generated.
Owner:CORELOGIC SOLUTIONS
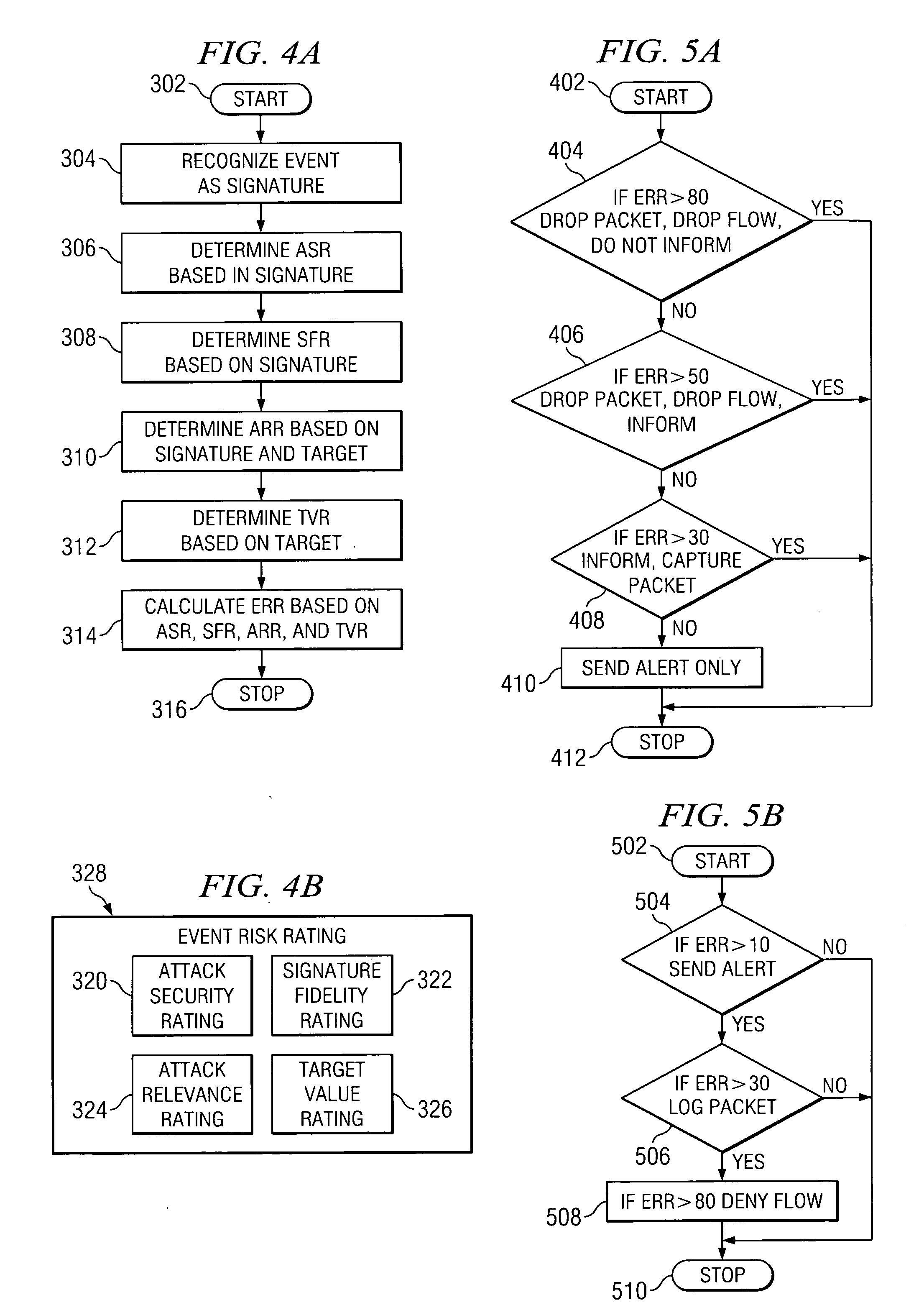
Method and system for addressing intrusion attacks on a computer system
ActiveUS20050097339A1Actual risk of an attack can be more accurately assessedMemory loss protectionUser identity/authority verificationData streamRisk rating
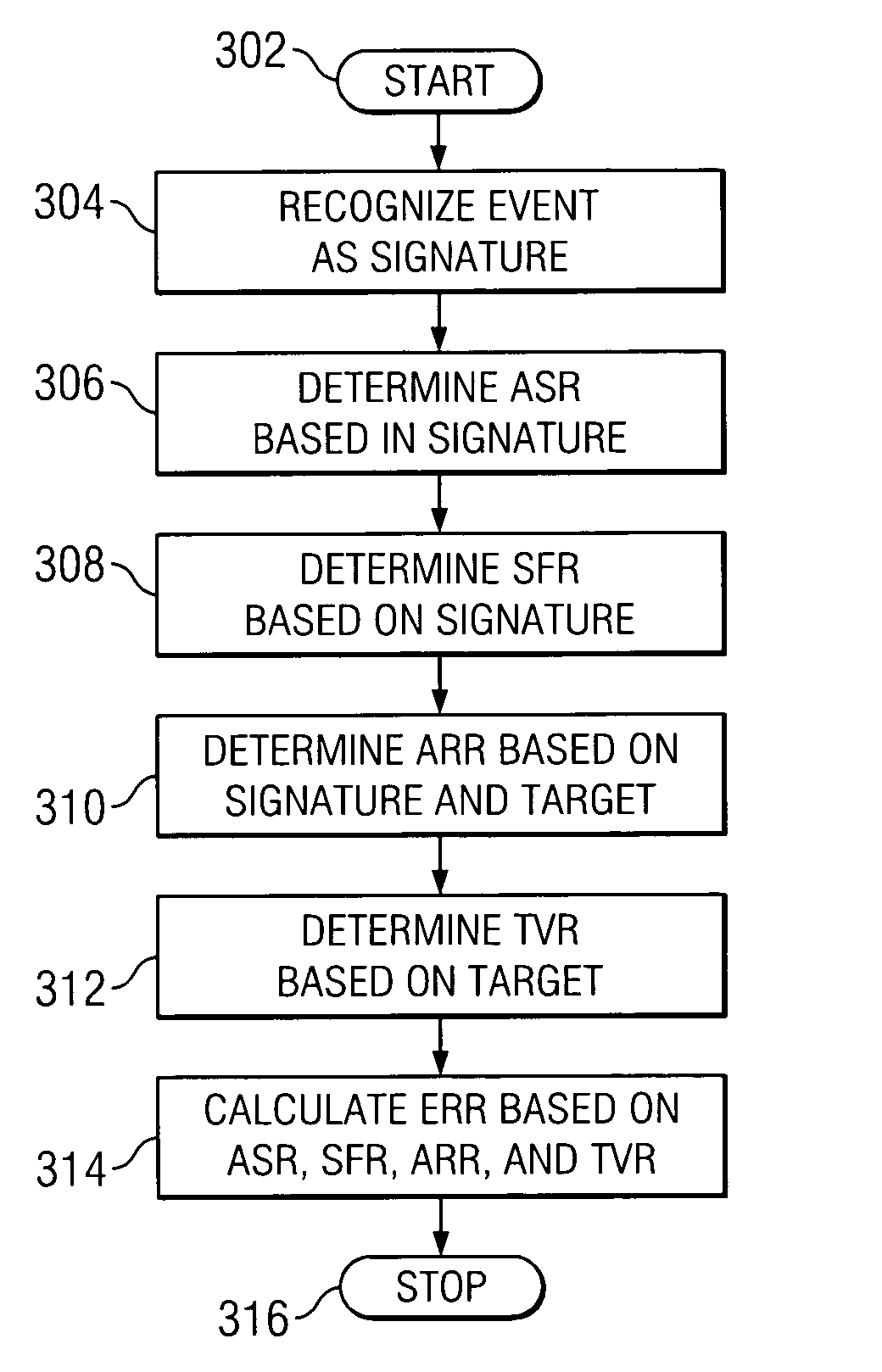
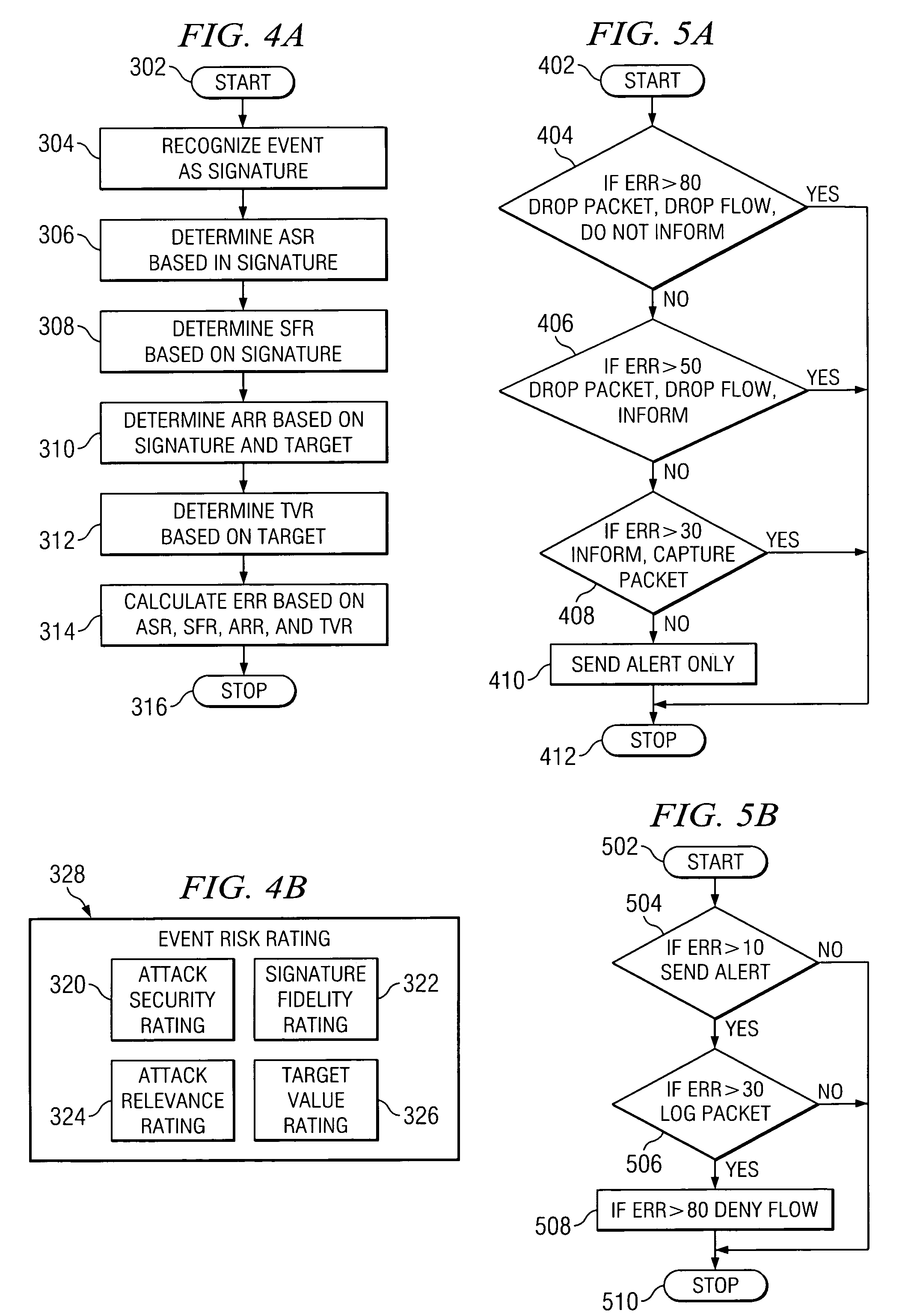
According to one embodiment of the invention, a computerized method for addressing intrusion attacks directed at a computer includes receiving a data stream corresponding to a potential attack on the computer and calculating an event risk rating for the data stream. Calculating the event risk rating includes determining at least one component risk rating. In one embodiment, the component risk ratings are: a signature fidelity rating indicative of the likelihood the potential attack will affect the computer in the absence of knowledge regarding the computer, an attack relevance rating indicative of the relevance of the potential attack to the computer, and a target value rating indicative of the perceived value of the computer. The method also includes responding to the potential attack based on the calculated risk rating.
Owner:CISCO TECH INC
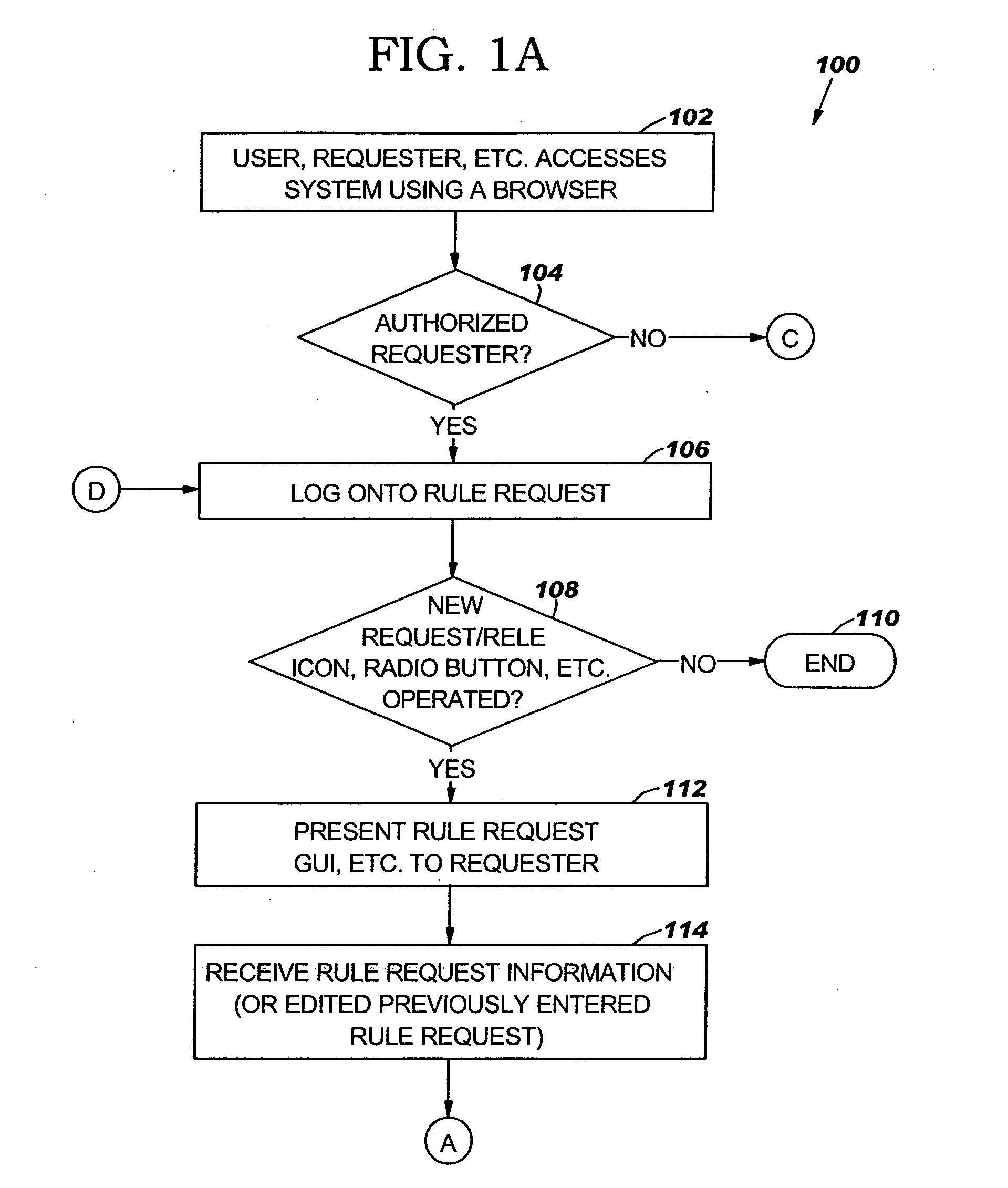
Method and system for automated risk management of rule-based security
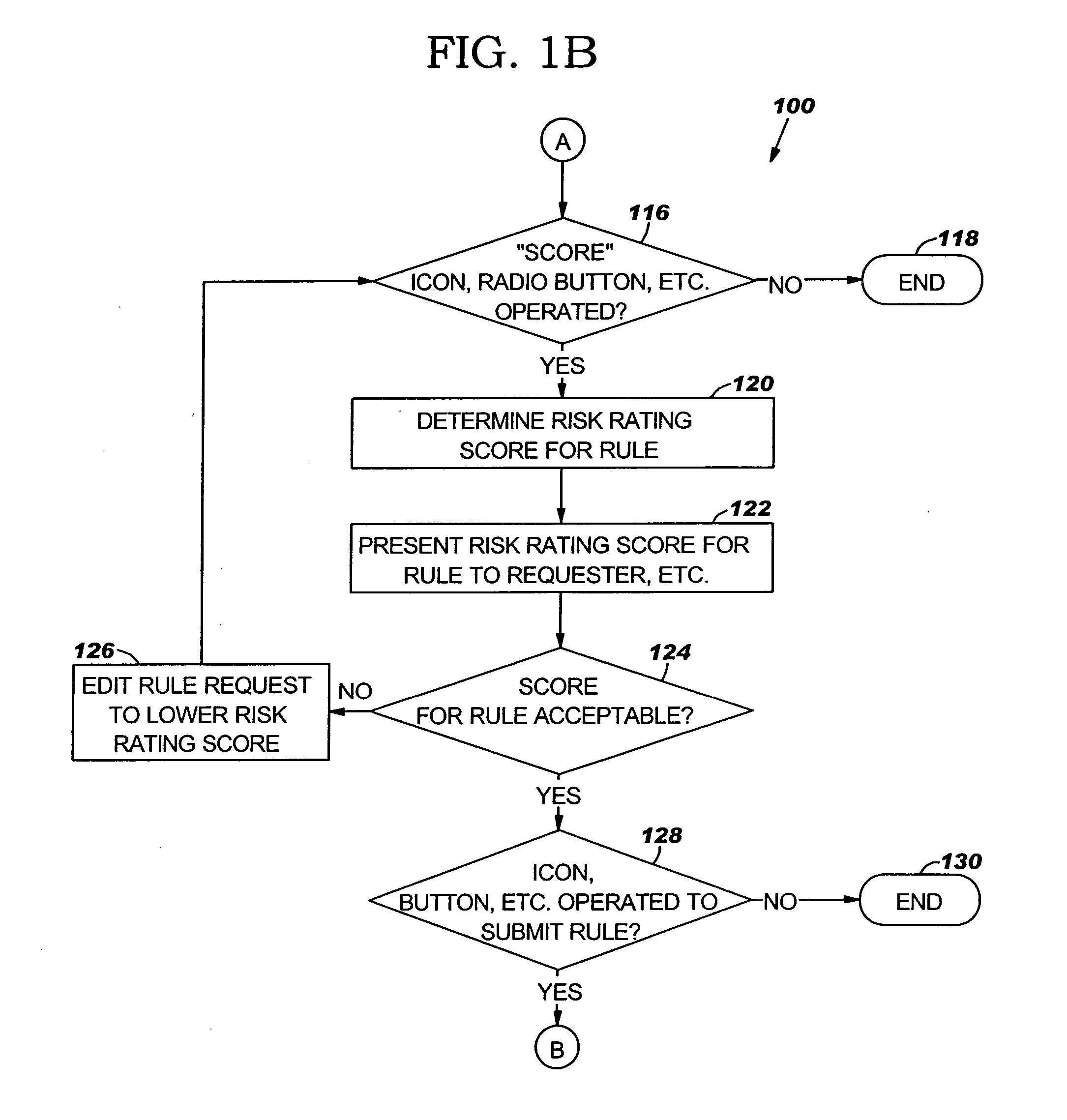
A method for automated risk management may include presenting a rule request graphical user interface (GUI) for a requester to enter information related to a rule request for a rule. The method may also include determining a risk rating score for the rule based on information entered in the rule request GUI. The information may include at least one of source information, destination information, service information and port information.
Owner:BANK OF AMERICA CORP
Method and system for addressing intrusion attacks on a computer system
ActiveUS7526806B2Actual risk of an attack can be more accurately assessedMemory loss protectionUser identity/authority verificationData streamComputerized system
According to one embodiment of the invention, a computerized method for addressing intrusion attacks directed at a computer includes receiving a data stream corresponding to a potential attack on the computer and calculating an event risk rating for the data stream. Calculating the event risk rating includes determining at least one component risk rating. In one embodiment, the component risk ratings are: a signature fidelity rating indicative of the likelihood the potential attack will affect the computer in the absence of knowledge regarding the computer, an attack relevance rating indicative of the relevance of the potential attack to the computer, and a target value rating indicative of the perceived value of the computer. The method also includes responding to the potential attack based on the calculated risk rating.
Owner:CISCO TECH INC
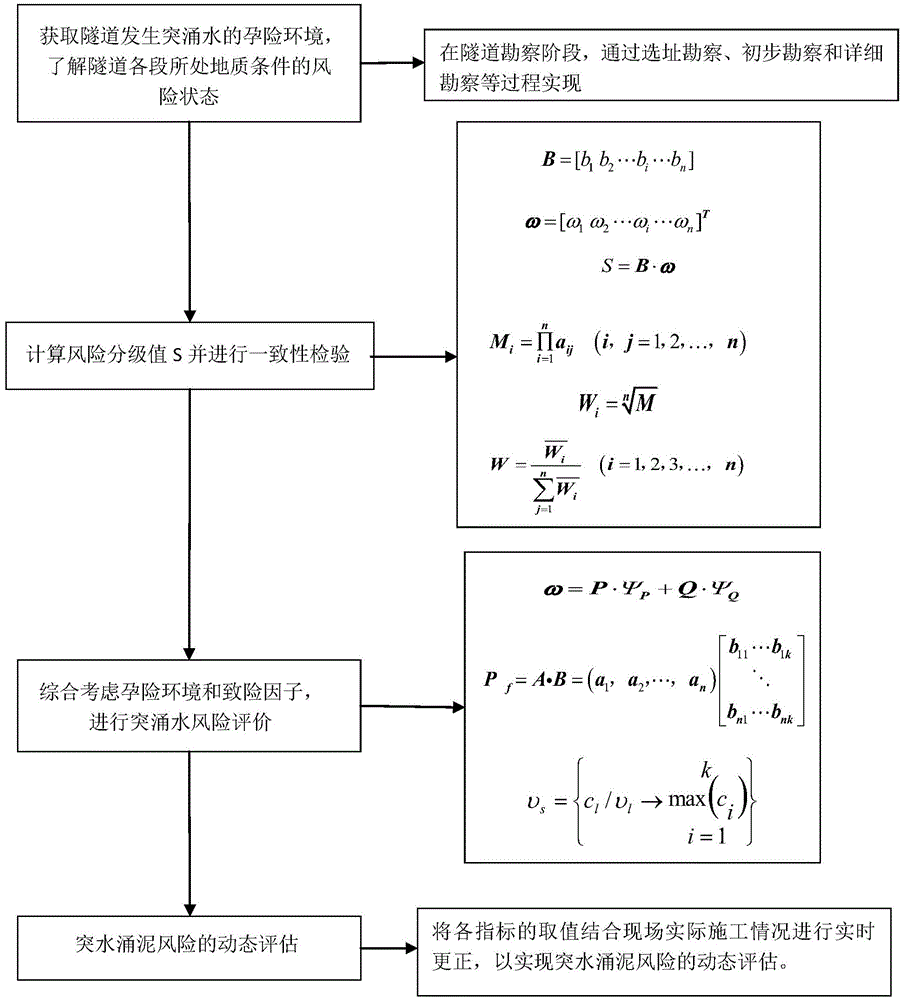
Karst tunnel water outburst and mud outburst overall process gradual dynamic risk assessment method
InactiveCN104636612AEnables dynamic evaluationSpecial data processing applicationsEnvironmental resource managementCvd risk
The invention discloses a karst tunnel water outburst and mud outburst overall process gradual dynamic risk assessment method. The method includes the steps that 1, in the tunnel investigation stage, the tunnel address and the hydrogeological information of the surrounding rock near the tunnel are obtained, that is, the hidden danger environment for water outburst of the tunnel is obtained, and the risk states of the geological conditions of all segments of the tunnel are known; 2, the risk rating value is worked out according to an expert evaluation vector and a factor weight vector, and consistency check is conducted; 3, danger factors are introduced to influence factors of risk evaluation, the hidden danger environment and the danger factors are considered comprehensively, water outburst risk evaluation is conducted, and the segment distribution feature with the tunnel water outburst risk is divided; 4. The values of all indexes are corrected in real time in combination with actual field construction so as to achieve dynamic evaluation of the water outburst and mud outburst risks. The purposes of optimizing construction organization design and avoiding medium and large water outburst geological disasters are achieved through dynamic construction risk evaluation and control, and important data are provided for later-period tunnel operation risks, and the method has very wide application prospects.
Owner:SHANDONG UNIV
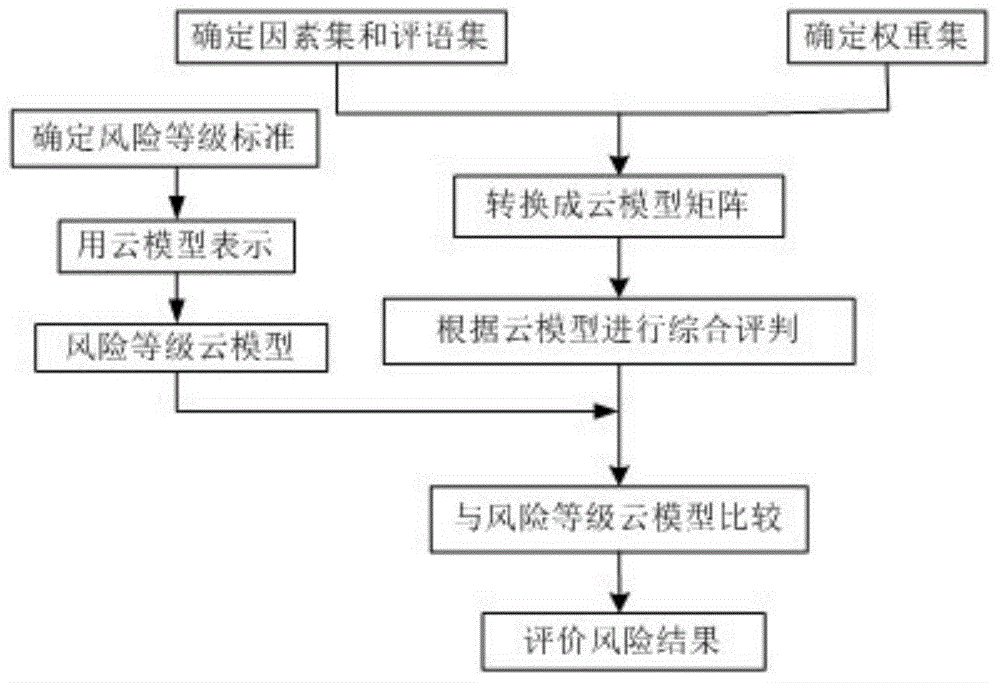
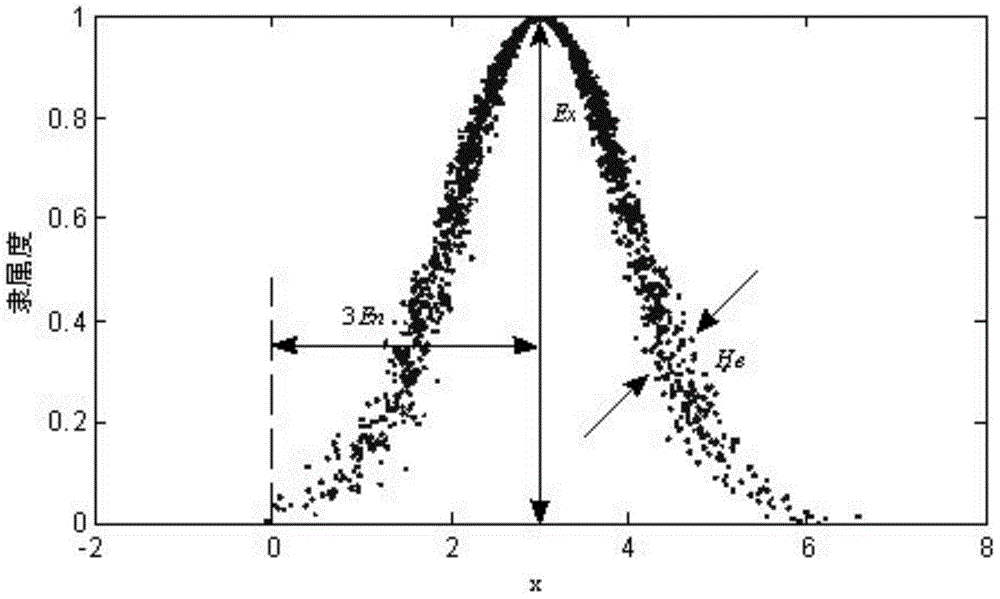
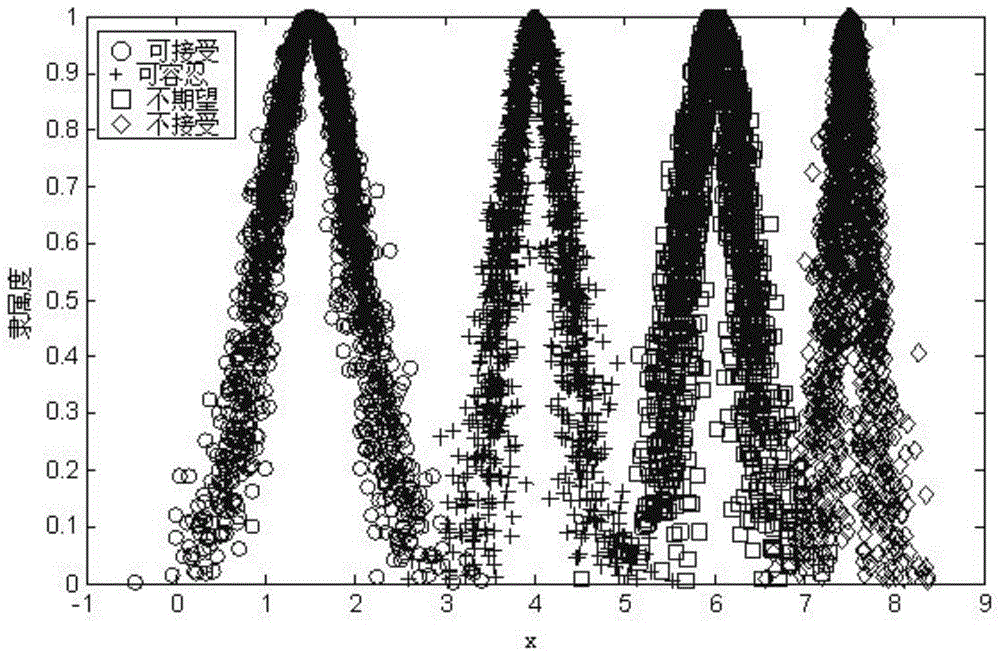
Application of cloud model fuzzy analytical hierarchy process in risk analysis of railway signal system
InactiveCN104102762AThe risk assessment results are objectiveThe risk assessment results are accurateSpecial data processing applicationsWeight coefficientRisk evaluation
The invention discloses an evaluation method applied to the field of risk analysis of a railway signal system. The method comprises the steps of firstly, formulating the levels of risk of the railway system, expressing a cloud model for evaluating the levels of risk by a forward cloud generator of a MATLAB simulation software, and generating a standard risk grade evaluation set cloud model figure; marking the failure mode of a function by an expert according to the formulated levels of risk to obtain a risk factor set, and converting the risk factor set into a comprehensive evaluation matrix R; utilizing an analytic hierarchy process to obtain risk factor set weight coefficients corresponding to all parameters in the risk factor set by the expert, and calculating a comprehensive evaluation result cloud model figure by fuzzy synthetic operator; comparing the comprehensive evaluation result cloud model figure with the standard risk grade evaluation set cloud model figure to obtain the level of risk of the comprehensive evaluation result. After the method is adopted, the risk evaluation result is more objective and accurate.
Owner:LANZHOU JIAOTONG UNIV
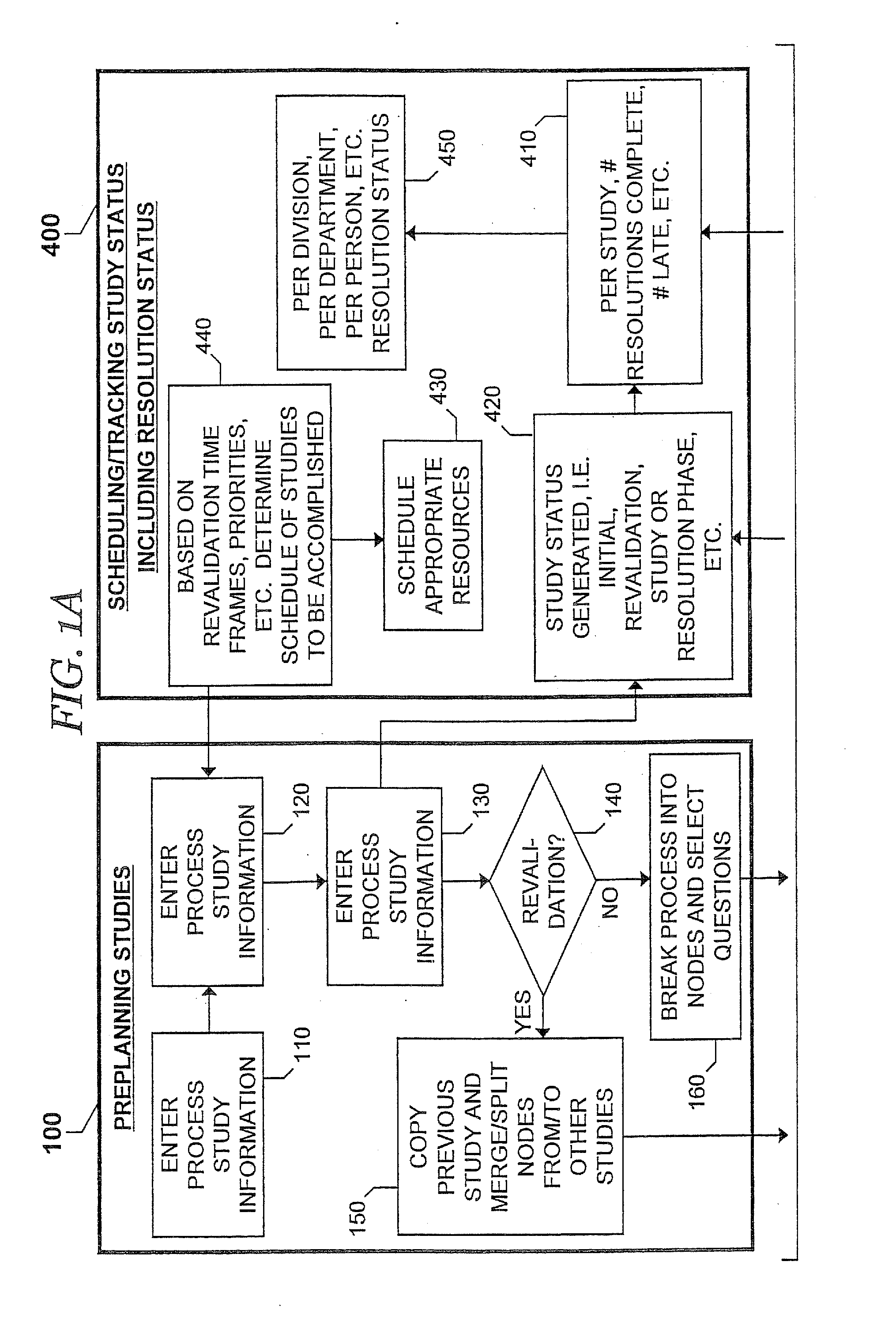
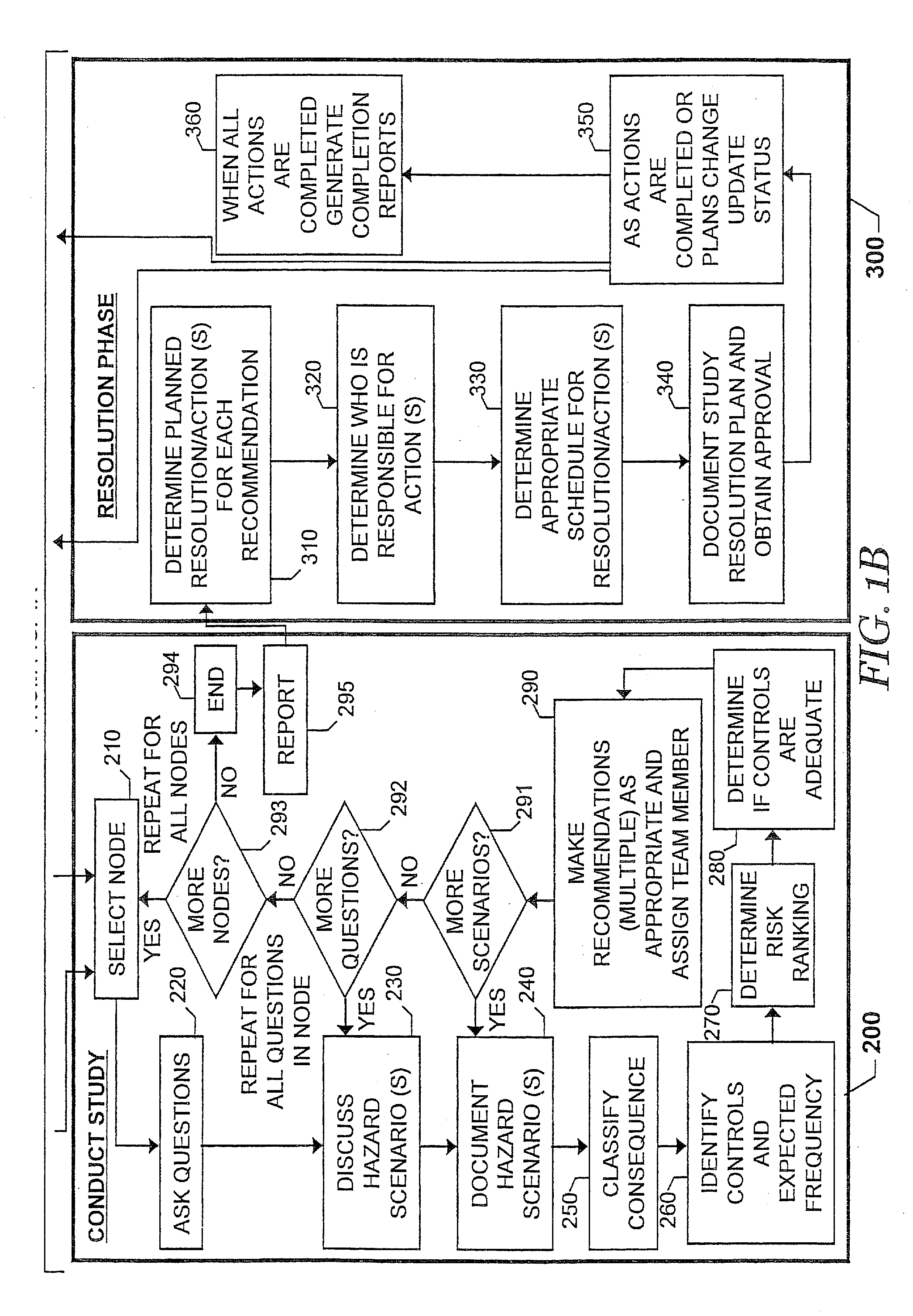
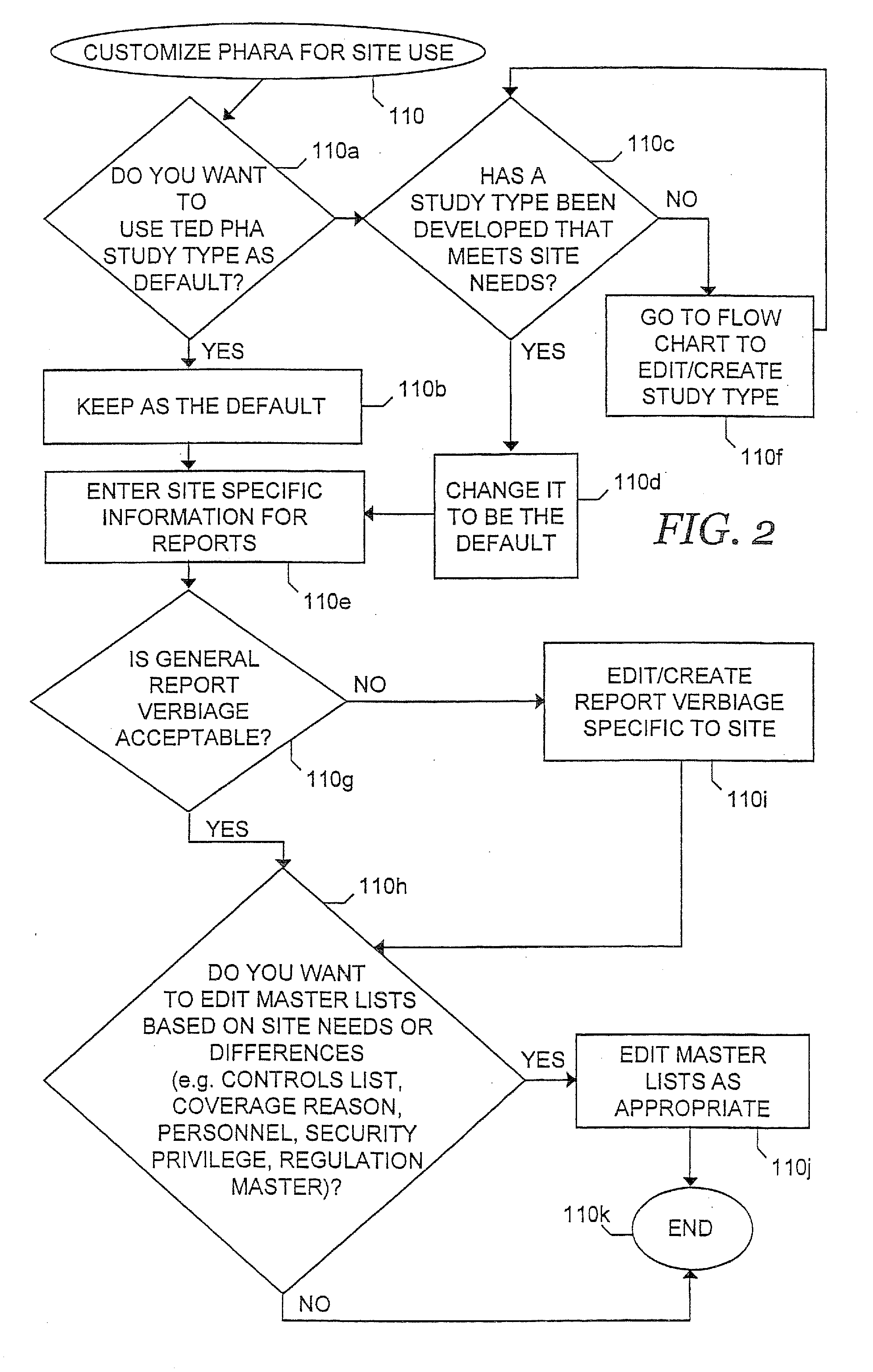
Systems, Methods and Computer Program Products for Preparing, Documenting and Reporting Chemical Process Hazard Analyses
InactiveUS20070122911A1Efficiently meetFacilitate complianceData processing applicationsBiological testingStudy TypeSolution analysis
A process hazard analysis (PHA) is performed in a data processing system. A chemical process to be evaluated is selected, after which a study type to be performed on the chemical process is also selected. The study type is conducted to evaluate the chemical process for the presence of hazard scenarios and any associated deficiencies requiring recommendations. After conducting the study, resolution plans to address the recommendations are generated. The study type used in the analysis may be customized or may be a known study type. The study type may use a risk matrix to generate a risk ranking for the hazard scenario. The risk matrix used may be created by the user, or may be a known risk matrix from another study type. After a resolution plan is generated, a resolution database may also be generated.
Owner:EASTMAN CHEM CO
Power consumer screening method and system based on multi-dimensional risk evaluate index
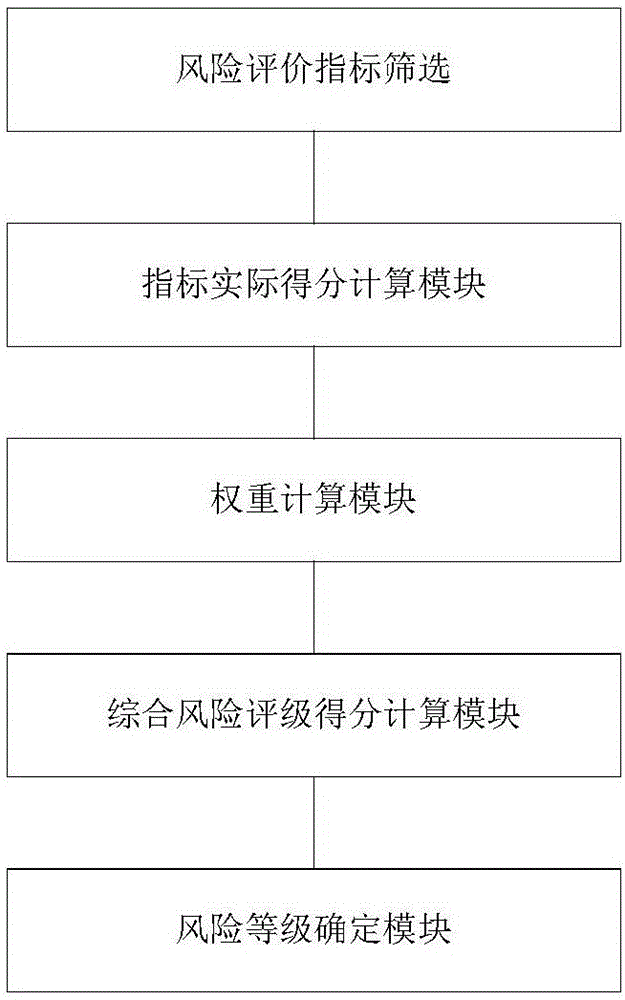
InactiveCN106557882AReduce riskConvenient and intuitive monitoringResourcesScreening methodRisk rating
The invention discloses a power consumer screening method and system based on multi-dimensional risk evaluate indexes; the method comprises the following steps: obtaining power consumer information; screening to obtain a power consumption credit type risk evaluate index and a law credit type risk evaluate index, thus obtaining the basic credit type risk evaluate index; obtaining real scores of various risk evaluate indexes of each power consumer; using a hierarchy analysis method to respectively solve the weight of the basic credit type risk evaluate index and the power consumption credit type risk evaluate index in a two-two comparison mode according to the real score values of the basic credit type risk evaluate index and the power consumption credit type risk evaluate index of the power consumer; obtaining a power consumer integral risk rating score value; presetting risk grades of the power consumer and power consumer integral risk rating score value sections corresponding to each risk grade; finally determining the power consumer risk grade according to the power consumer integral risk rating score value.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
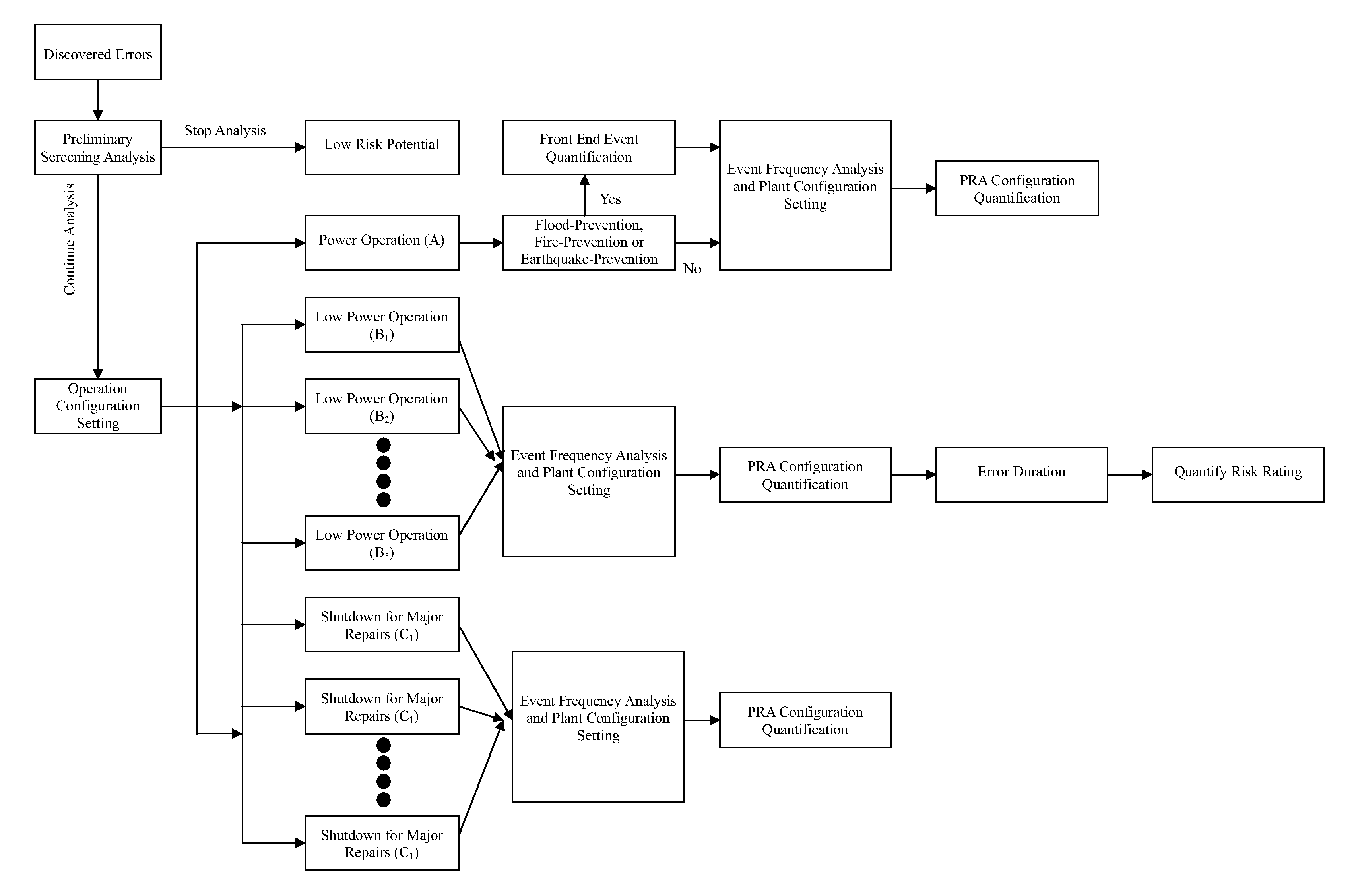
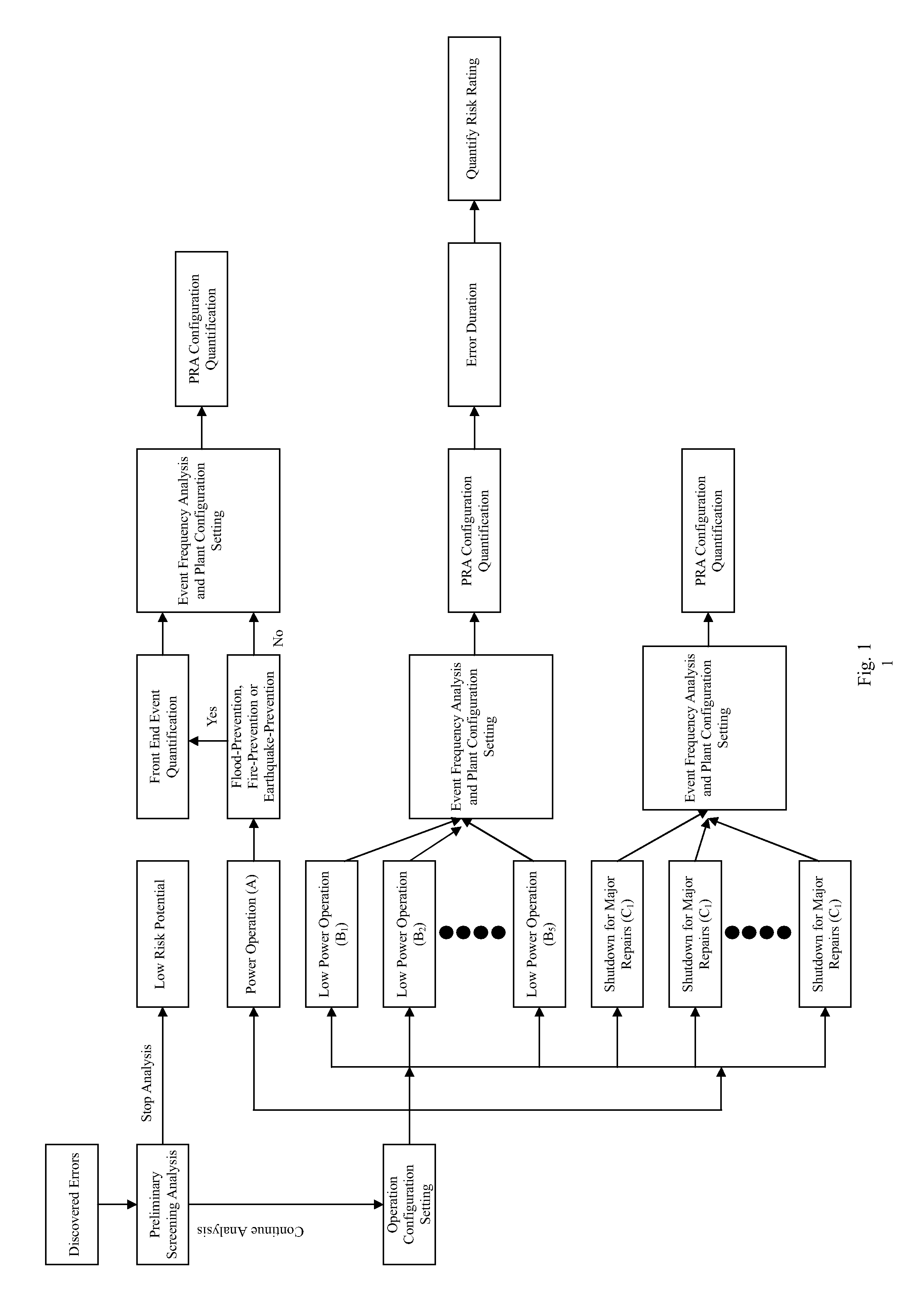
All aspect quantification system for the risk rating of operating errors for an advanced boiling water reactor
InactiveUS20100138253A1Improve consistencyFail to accuratelyFinanceClimate change adaptationProbabilistic risk assessmentRisk effect
Based on the discovered operating errors under all basic operating mode s for advanced boiling water reactor, a suitable quantification analytical model is employed to fast assess the risk situation for the discovered operating errors and quantified results are used to differentiate the risk rating for the operating errors. This is used to determine the necessity and urgency for the corrective measures to respond to the errors. The adopted quantification analytical model is the safety assessment (Probabilistic Risk Assessment, PRA) model for all basic operating mode s for advanced boiling water reactor, including power operation, low power operation and shutdown for major repairs. For the discovered operating error during power operation period, the invention uses the specifically developed safety assessment model for plant event, earthquake, flood and fire to determine risk effect for the discovered operating error on different event to manifest the risk characteristics for the discovered operating error and match the quantification results to existing plant design, operation and maintenance conditions.
Owner:CHAO CHUN CHANG +1
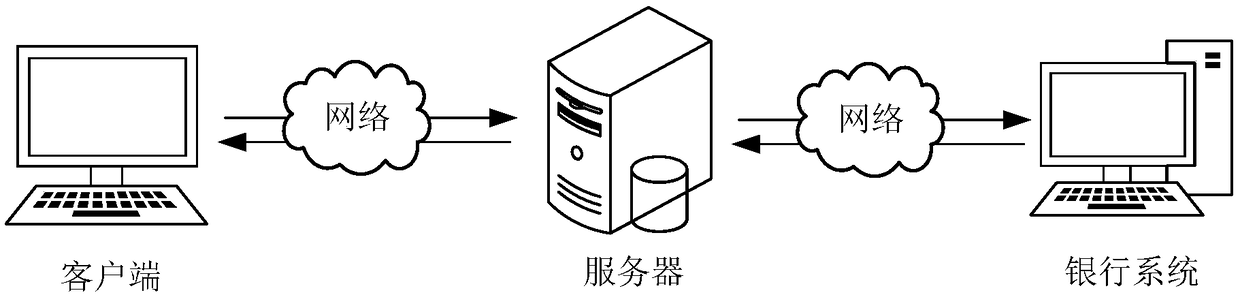
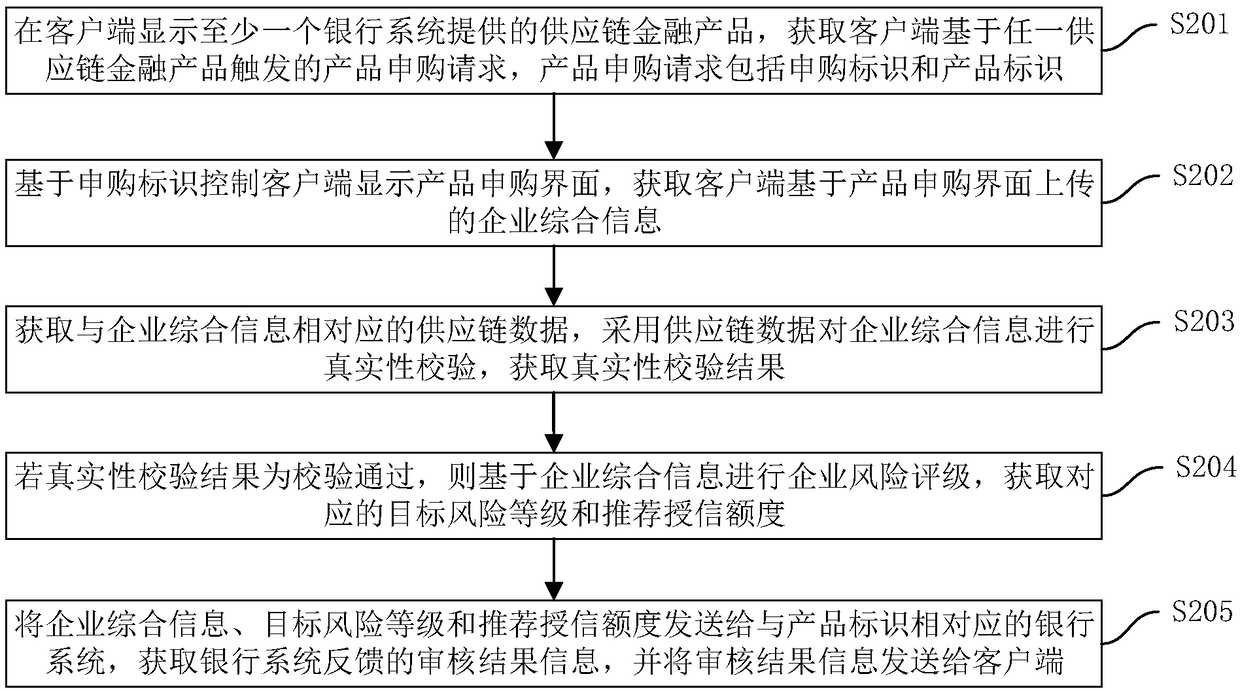
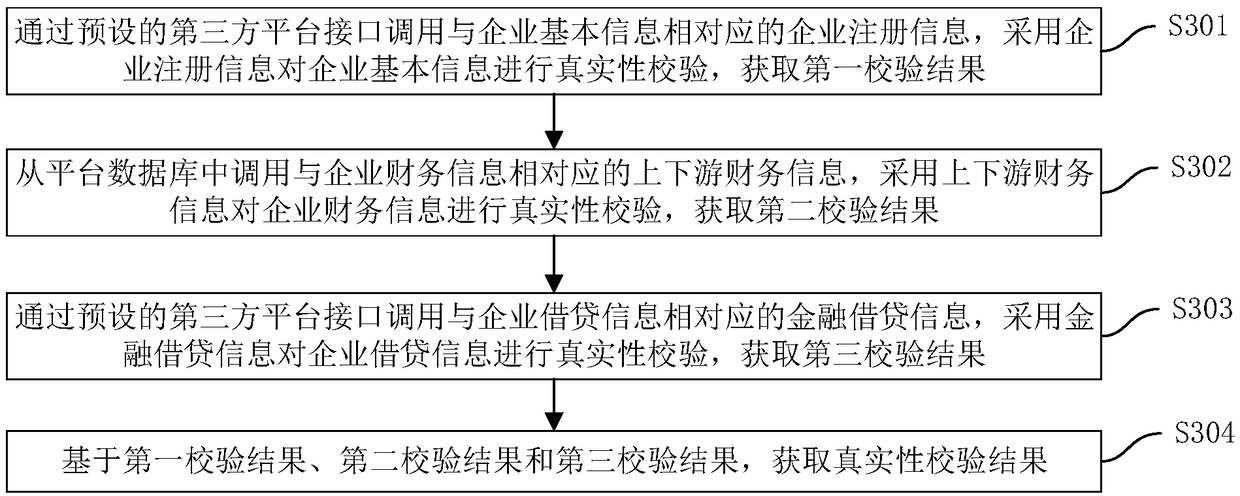
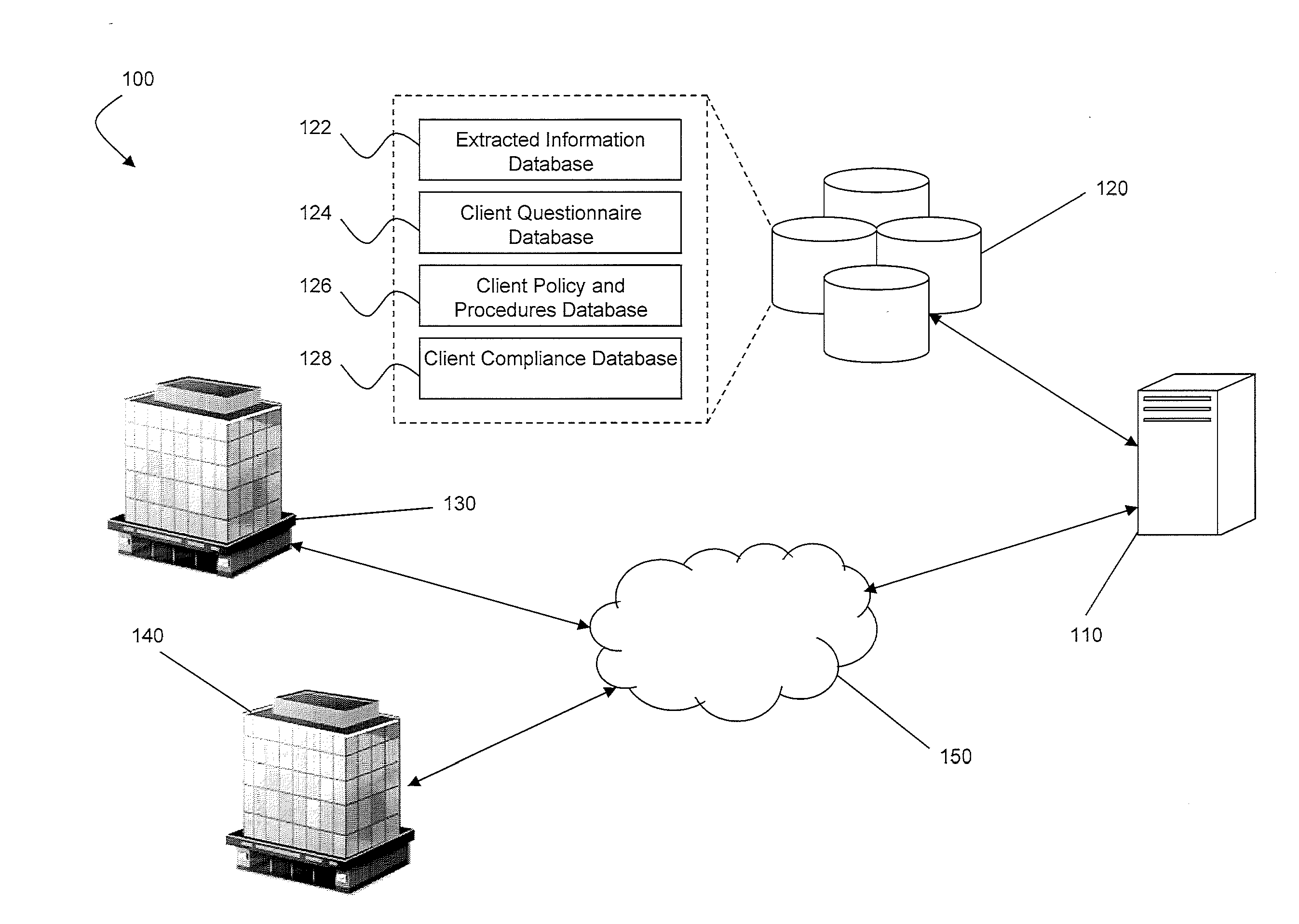
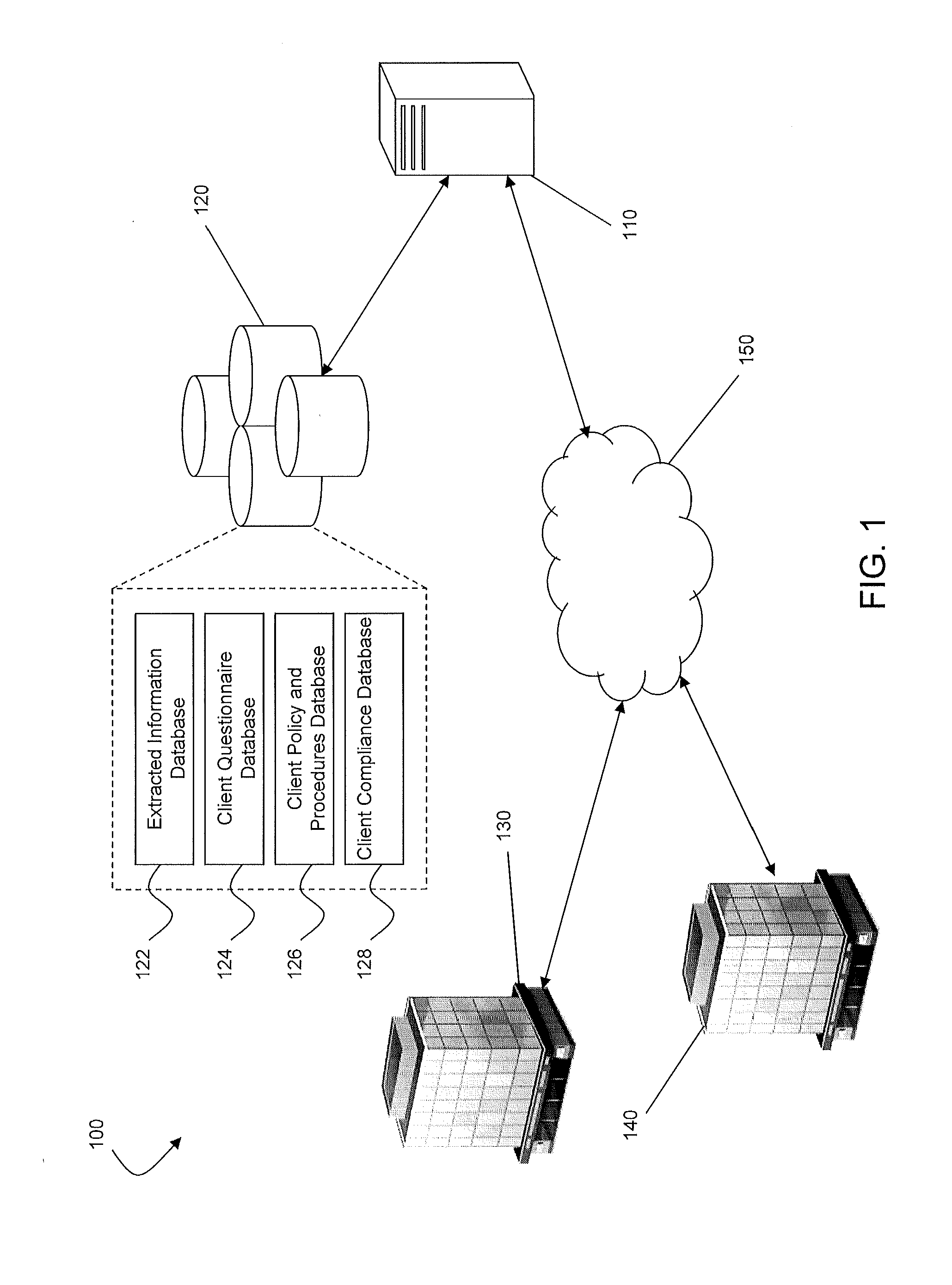
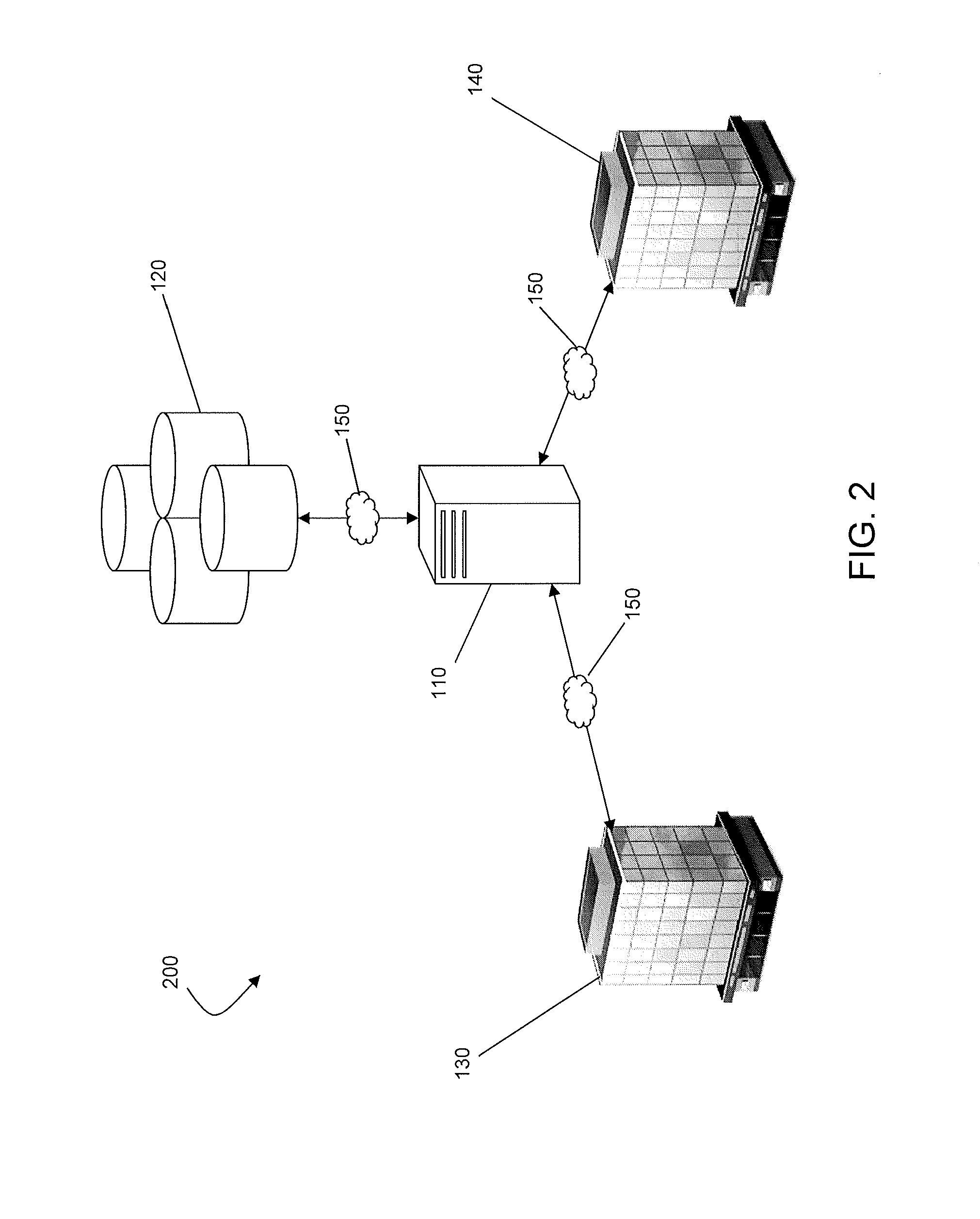
Supply chain financial service processing method, device, computer device and storage medium
The invention discloses a supply chain financial service processing method, a device, a computer device and a storage medium. The method comprises the following steps: displaying at least one supply chain financial product provided by a banking system on a client end, and obtaining a product purchase request triggered by the client end based on any supply chain financial product; Obtaining the comprehensive enterprise information uploaded by the client based on the product requisition interface; Acquiring the supply chain data corresponding to the comprehensive information of the enterprise, verifying the authenticity of the comprehensive information of the enterprise by using the supply chain data, and obtaining the authenticity verification results; If the authenticity verification result is passed, carrying out the enterprise risk rating based on the comprehensive information of the enterprise, and the target risk grade and the recommended credit line are obtained. The comprehensive information of the enterprise, the target risk grade and the recommended credit line are sent to the corresponding bank system of the product identification, and the review result information fed back by the bank system is sent to the client. This method can realize the information integration and enterprise qualification examination of supply chain financial products.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Method and system for assessing compliance risk of regulated institutions
A method for distributing requests for artifacts to a regulated institution for risk assessment includes: storing a client profile including a risk rating value corresponding to a risk that the related regulated institution will not be compliant with a set of regulations; identifying a plurality of artifacts to be provided by the regulated institution, each artifact including a frequency, a weight, one of a plurality of waves, and one of a plurality of categories; assigning a priority value to each of the categories; grouping each artifact into a plurality of buckets, each bucket including artifacts that include a common wave and a common category, and wherein the artifacts are evenly distributed into the buckets; and generating a request schedule, wherein the request schedule is a schedule for the distribution of requests for artifacts included in each bucket over a predetermined period of time.
Owner:AFFIRMX
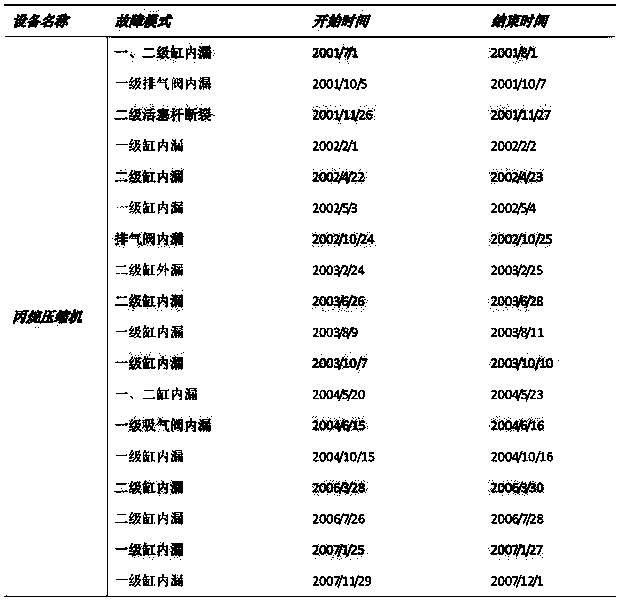
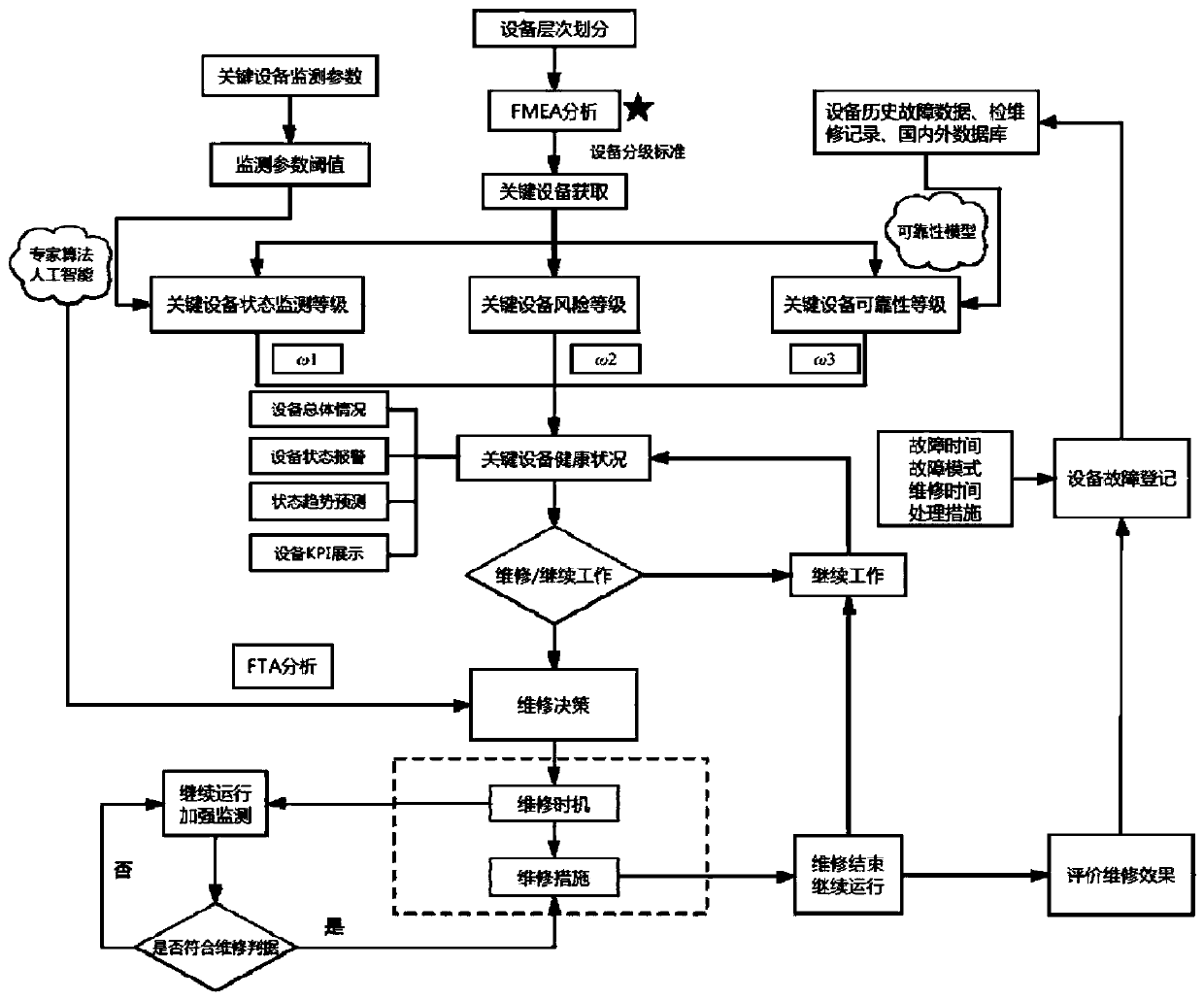
Maintenance decision-making method based on equipment comprehensive health condition analysis and management
InactiveCN111160685ARealize closed-loop processingRealize automatic registrationResourcesRisk levelMaintenance strategy
The invention relates to a maintenance decision-making method based on equipment comprehensive health condition analysis and management. The maintenance decision-making method comprises the followingsteps: collecting data; carrying out equipment hierarchical division; acquiring key equipment; evaluating the risk level of key equipment; evaluating the state monitoring grade of the key equipment; evaluating the reliability level of key equipment; key equipment health conditions; maintenance decision making; device fault management. According to the method, the health condition of the equipmentis comprehensively evaluated from three aspects, namely the reliability level, the risk level and the state monitoring level of the equipment, and the situation that the health condition of one part of equipment is obtained from one side to be overhauled or lost is avoided. A corresponding maintenance strategy is given in combination with the health condition of the equipment, the service life ofthe equipment is prolonged to the maximum extent, and maintenance cost is saved. The fault tree is combined with the state monitoring relation variable of the equipment, and the fault type of the equipment is automatically judged by utilizing the change condition of the relation variable so as to give a reasonable maintenance strategy. The equipment fault, the maintenance record and the operationof the equipment form a closed-loop influence, and the newly added equipment fault record is used as basic data of reliability calculation to re-optimize the reliability model so as to reflect the reliability state of the equipment more accurately and discover the fault of the equipment in time.
Owner:上海安恪企业管理股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com