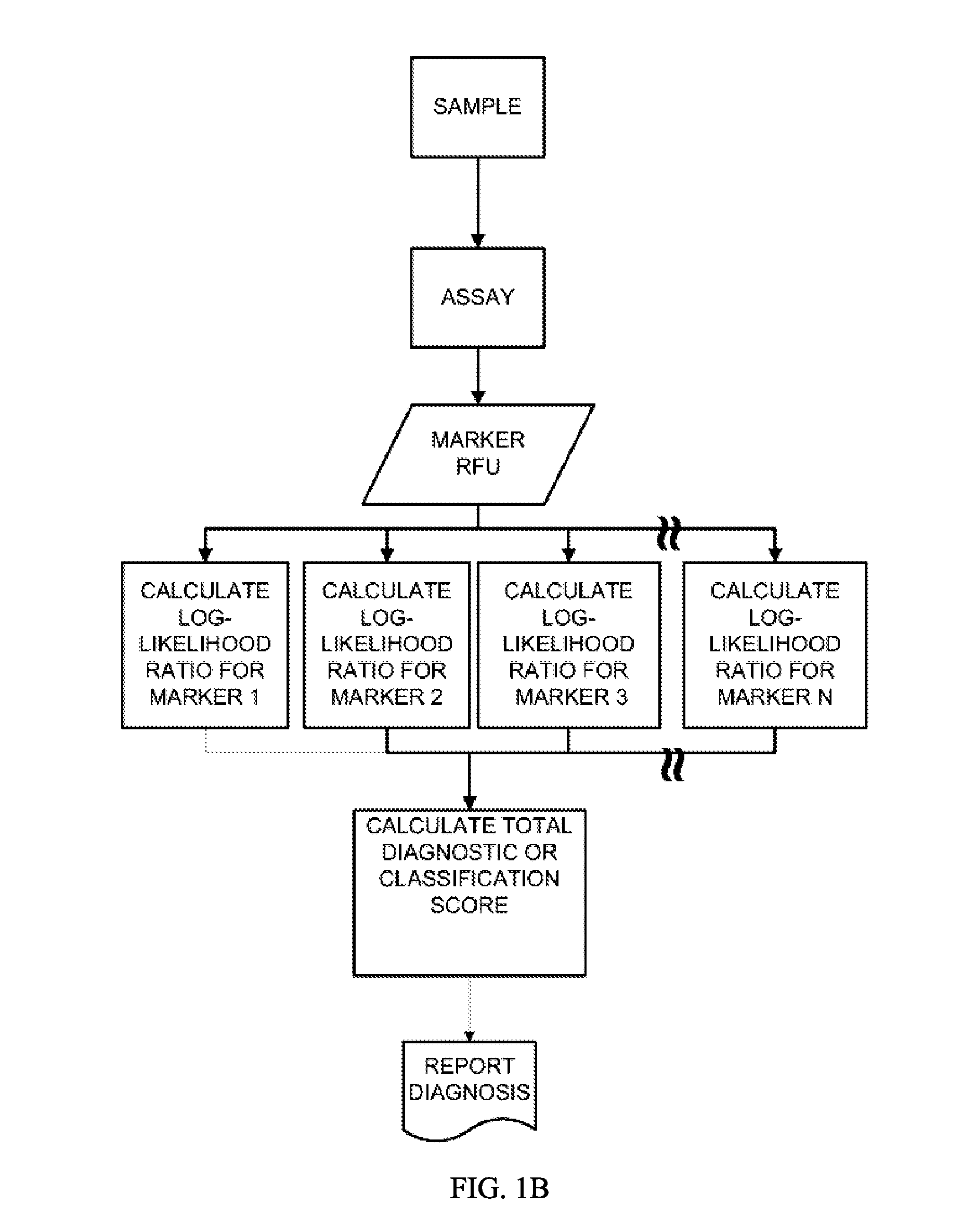
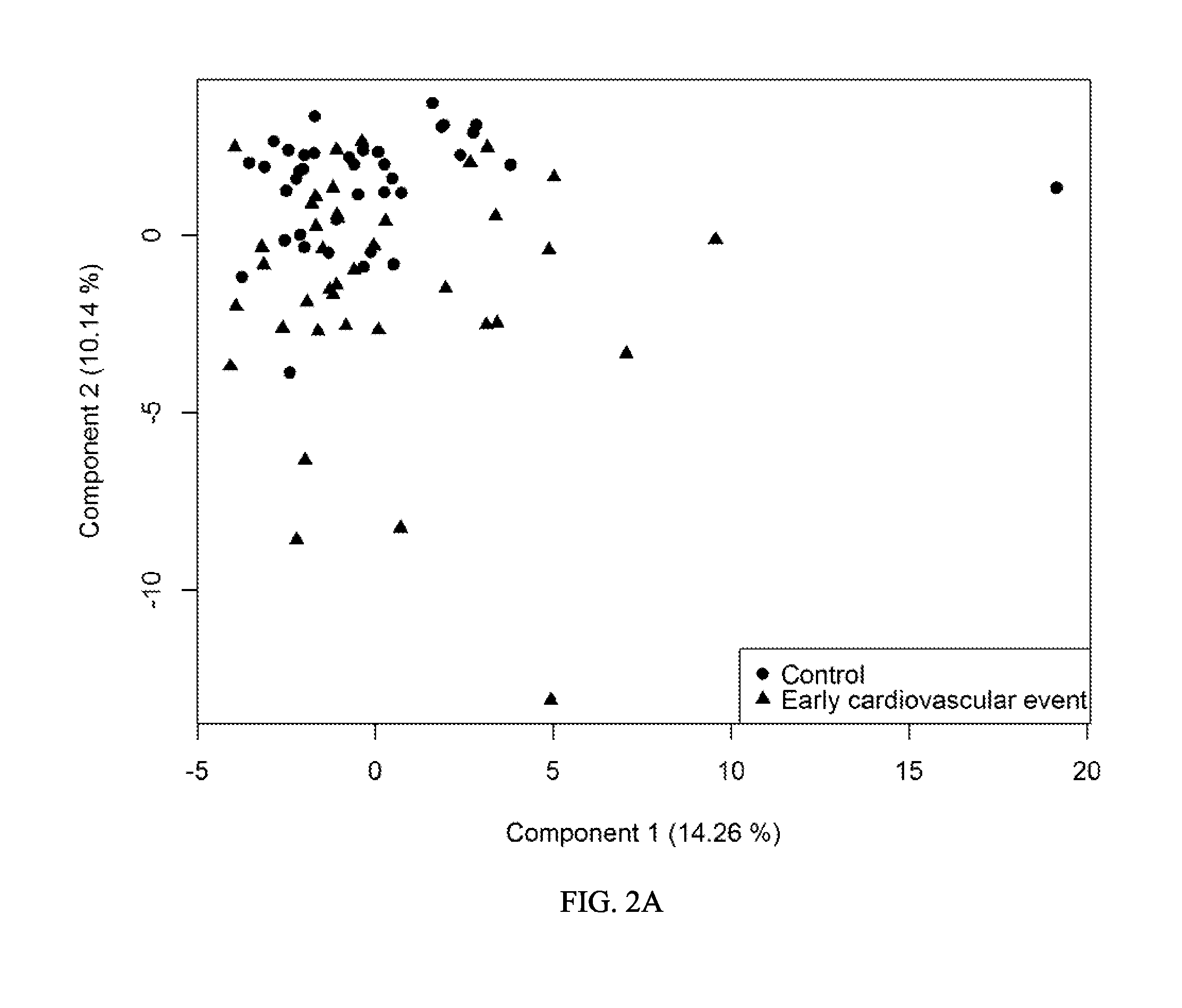
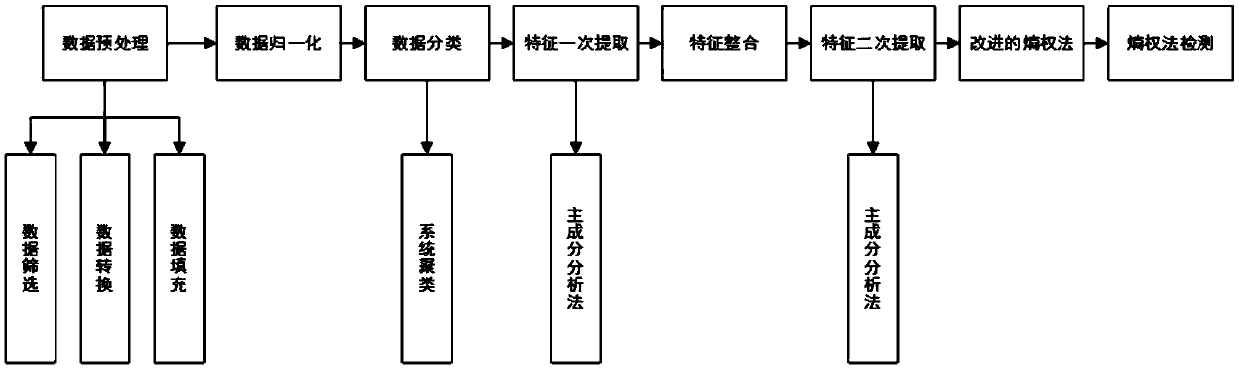
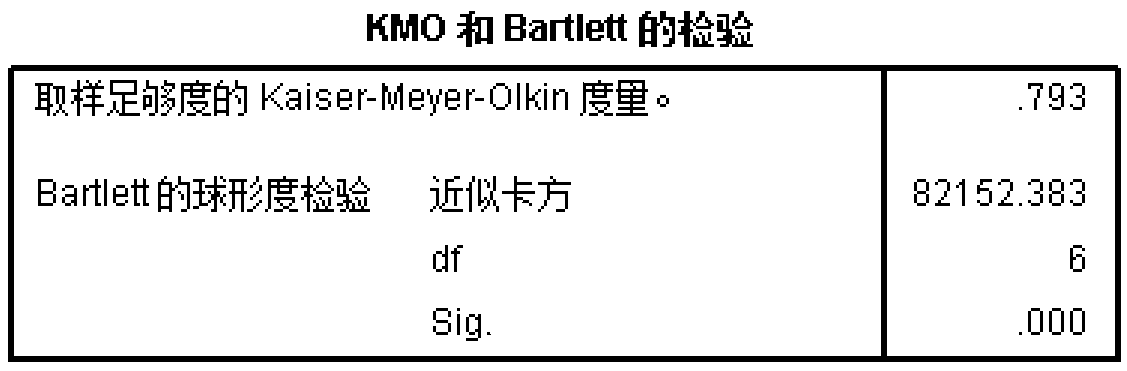
Patents
Literature
84 results about "Event risk" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An event risk is the possibility that an unforeseen event will negatively affect a company, industry or security. 1. ... Event risk can also be defined as the risk associated with a changing portfolio value due to large swings in market prices. It is also referred to as "jump risk."
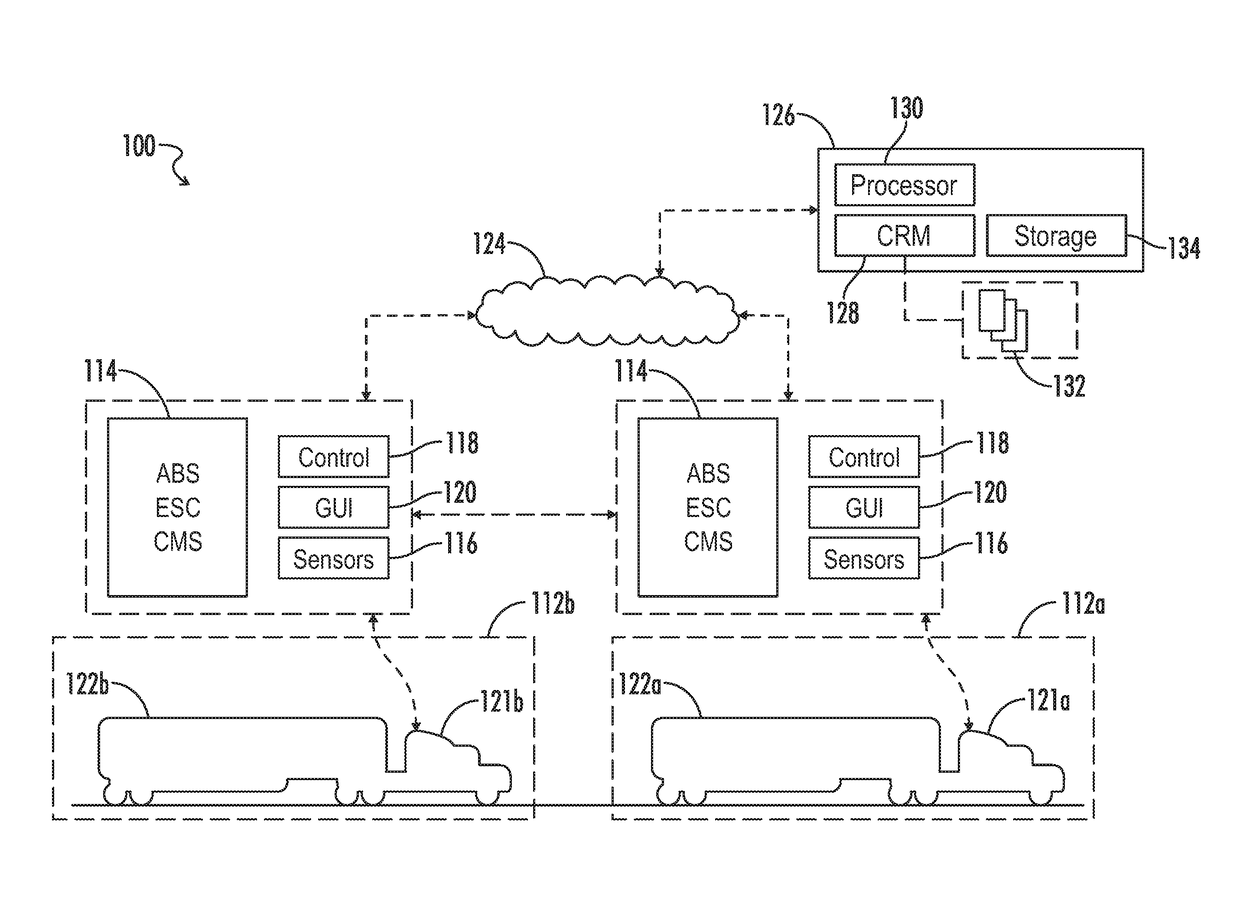
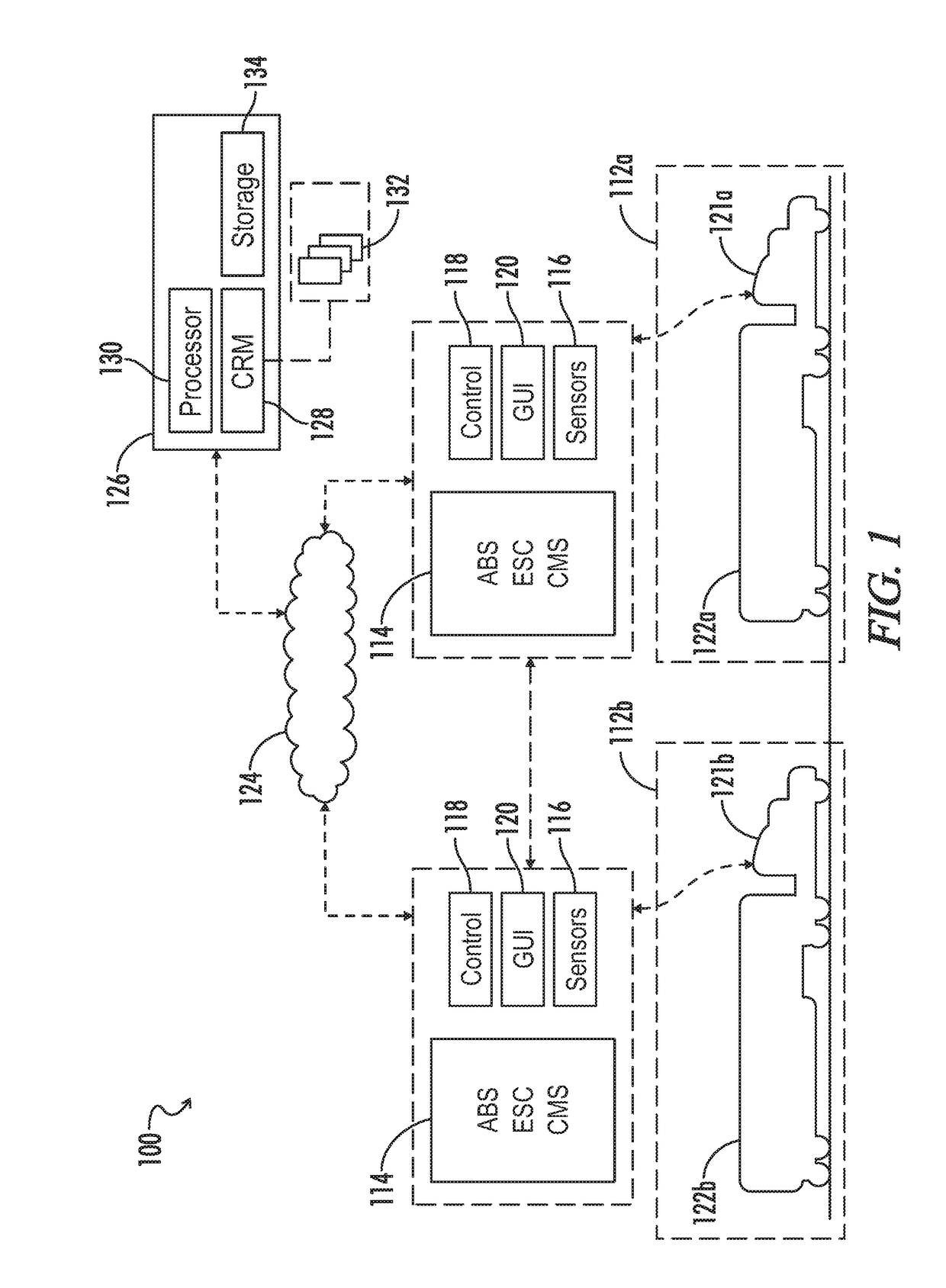
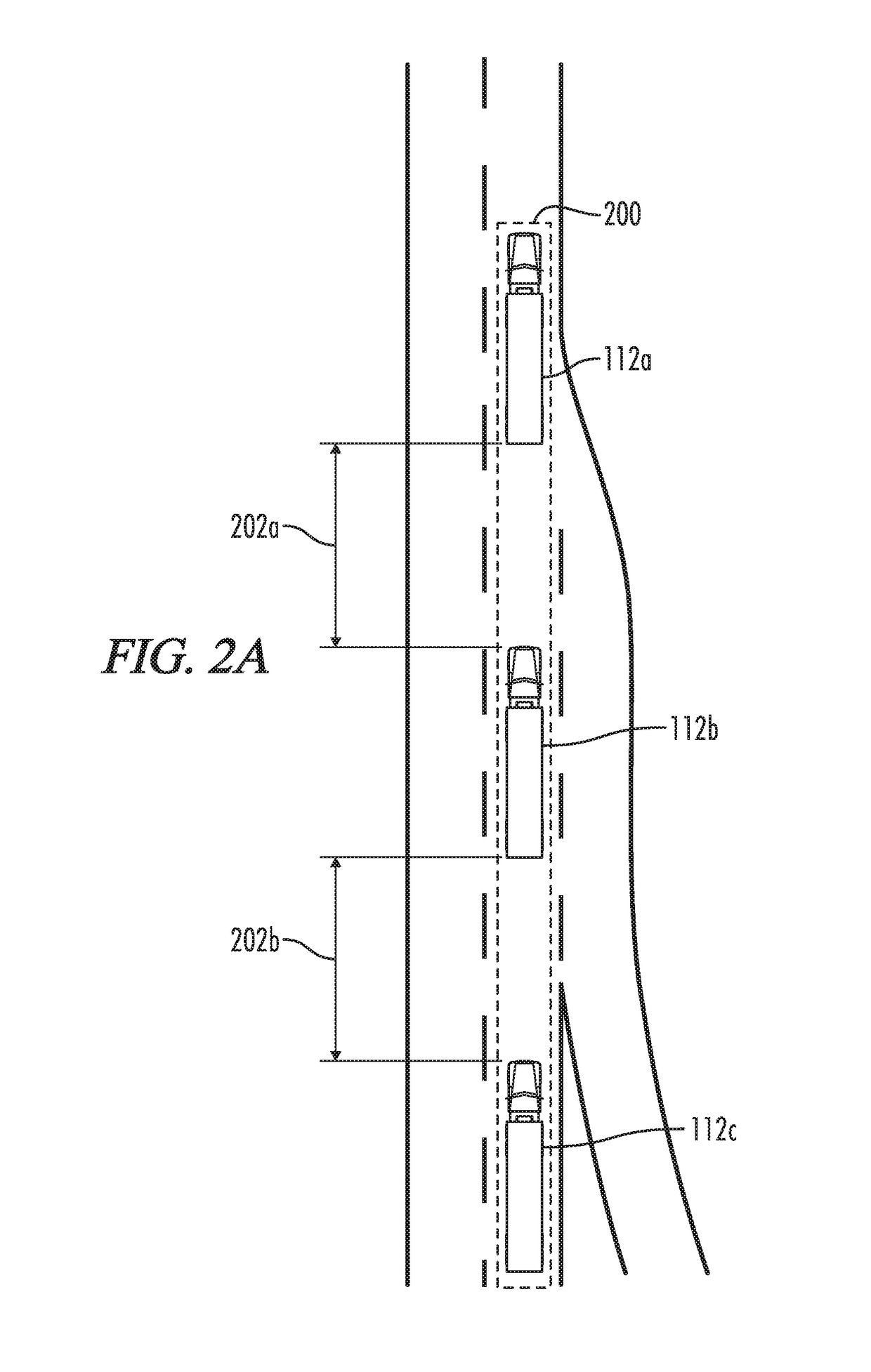
System and method for adjusting vehicle platoon distances based on predicted external perturbations
A control system is provided for platooning a plurality of vehicles, each of which equipped with vehicle braking control systems and V2V communication system components. The system determines nominal following distances for each of said following vehicles relative to an immediately preceding vehicle, based in part on brake performance capabilities. Vehicle sensors throughout the platoon are implemented to monitor target vehicles positioned relative to the platoon, and some or all of the nominal following distances are dynamically adjusted to account for braking event risks associated with the target vehicles. Adjustment to following distances for trailing vehicles may be proactively applied even before braking reaction is determined or applied for a lead vehicle, and control signals are simultaneously generated implementing vehicle movement adjustments based on the following distance adjustments. Adjustments may be based on threshold violations associated with target vehicles in front, laterally merging into, or tailgating behind the platoon.
Owner:WABCO USA LLC
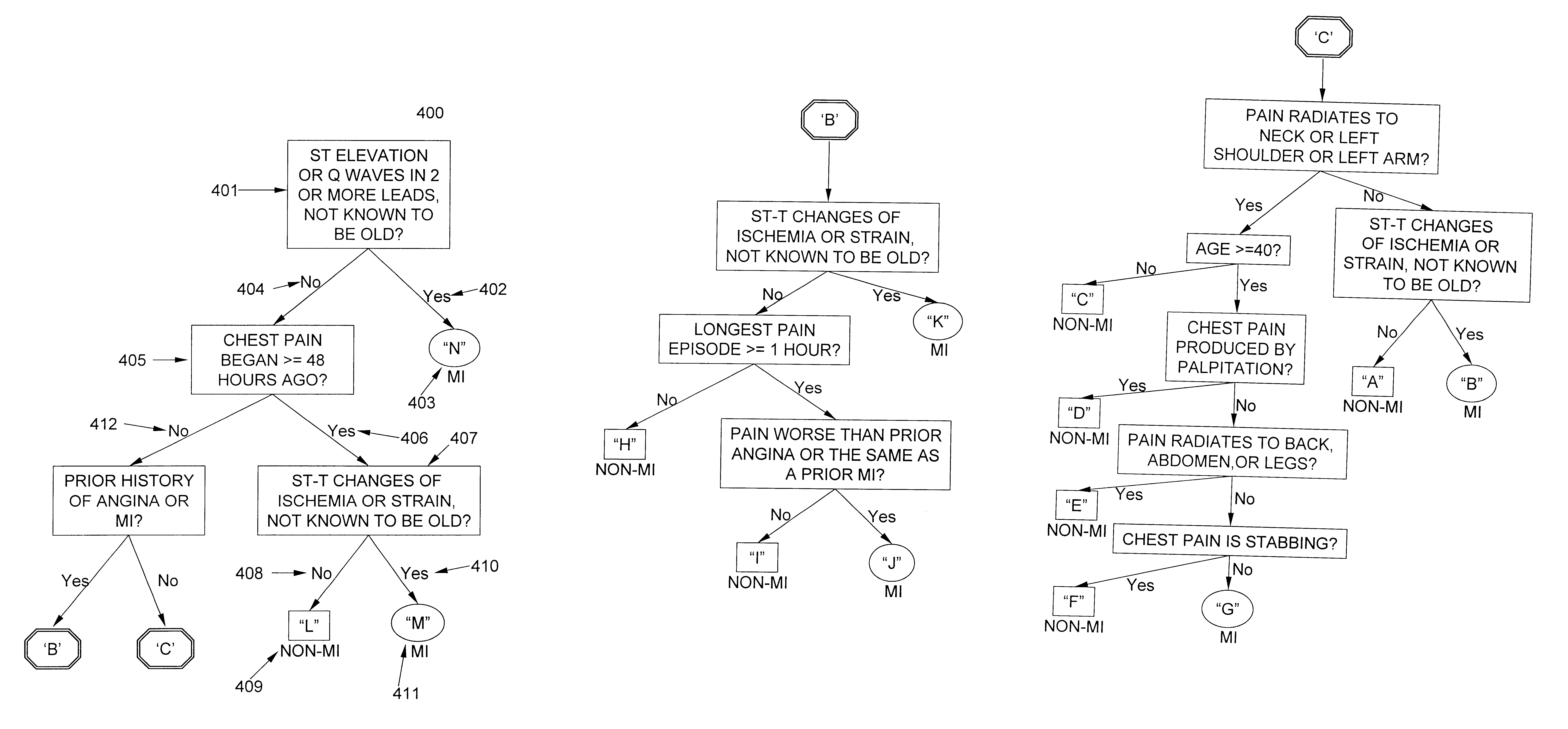
Computer system and method for a self administered risk assessment
InactiveUS6334192B1SurgeryComputer-assisted medical data acquisitionComputer monitorComputerized system
A computer system for performing an interactive assessment of the risk of an event, has a computer monitor to present to a user of the system a series of questions and potential responses, and a keyboard or other device to select a response to the question. The system can administer complex inverted tree type decision algorithms, in which the questions that are presented to the user, depend upon the response to the previous question, and an assessment of the risk of an event is presented to the user whenever they reach the terminus point in the decision tree. The risk assessment algorithm is data driven and a risk assessment is defined by entries in a file, which is available over a network. The system provides options so each user may view the path through the sequence of questions and answers, and interact with the risk assessment, in a manner customized for their own interactive session.
Owner:KARPF RONALD S
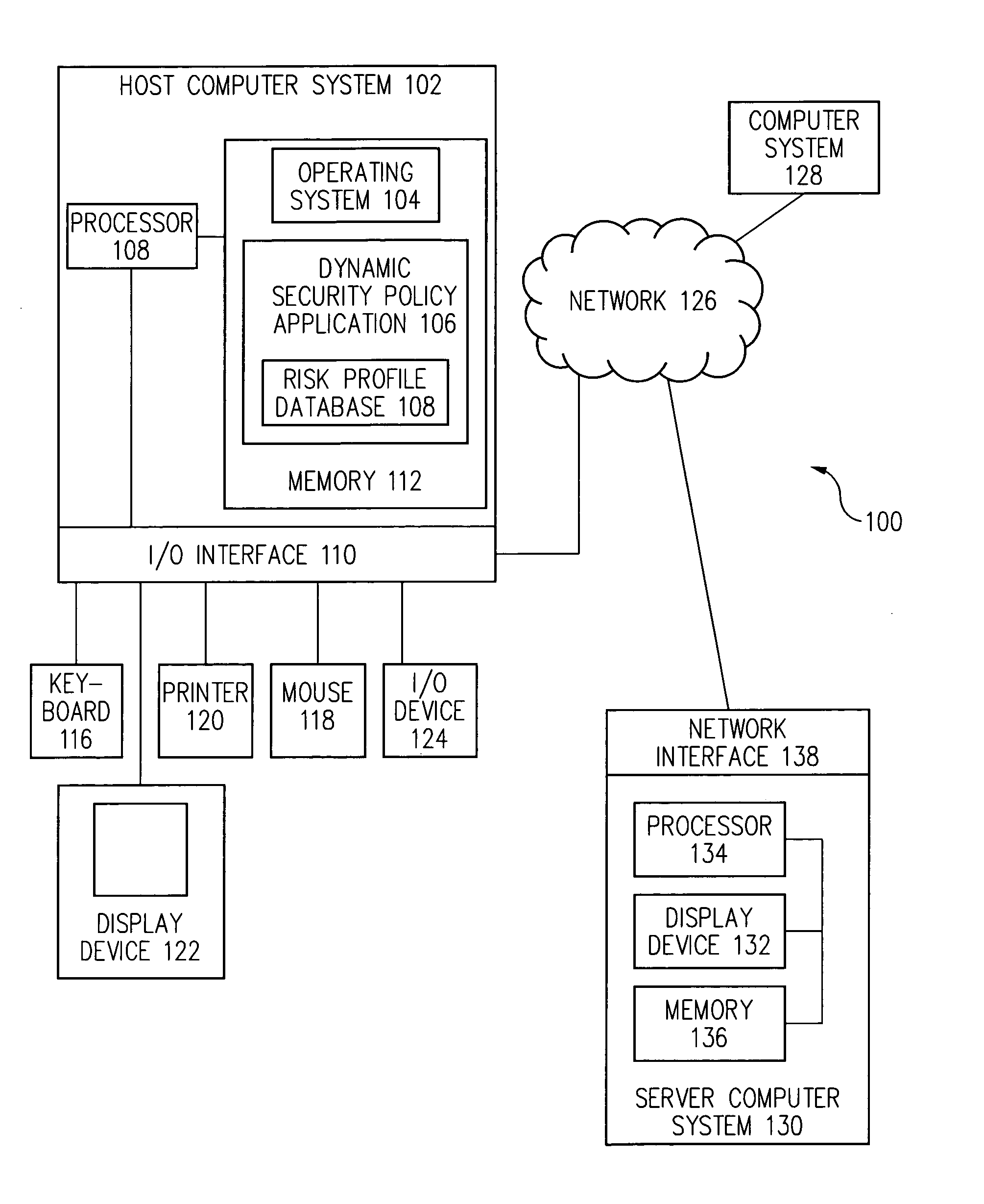
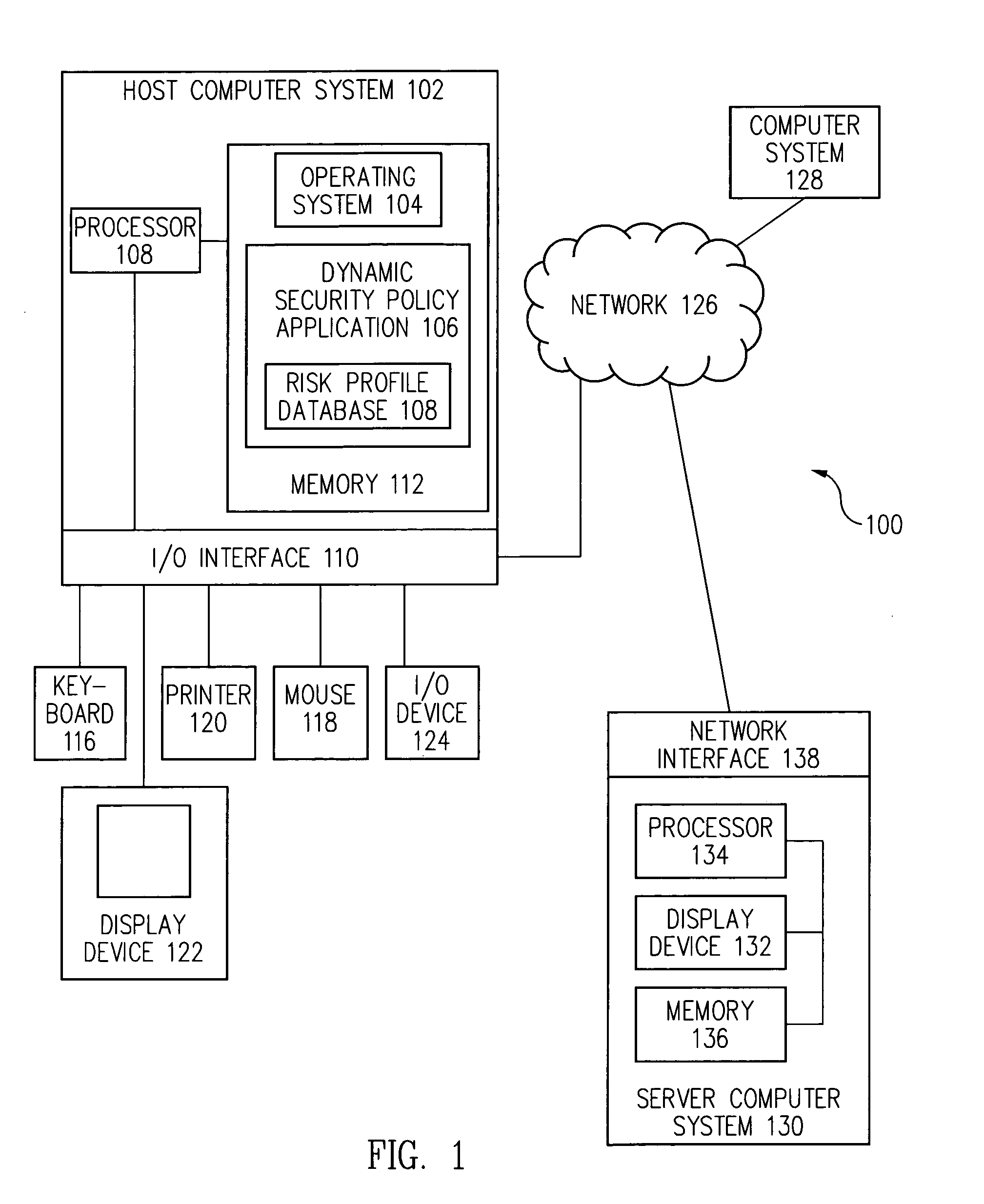
Dynamic security policy through use of empirical security events
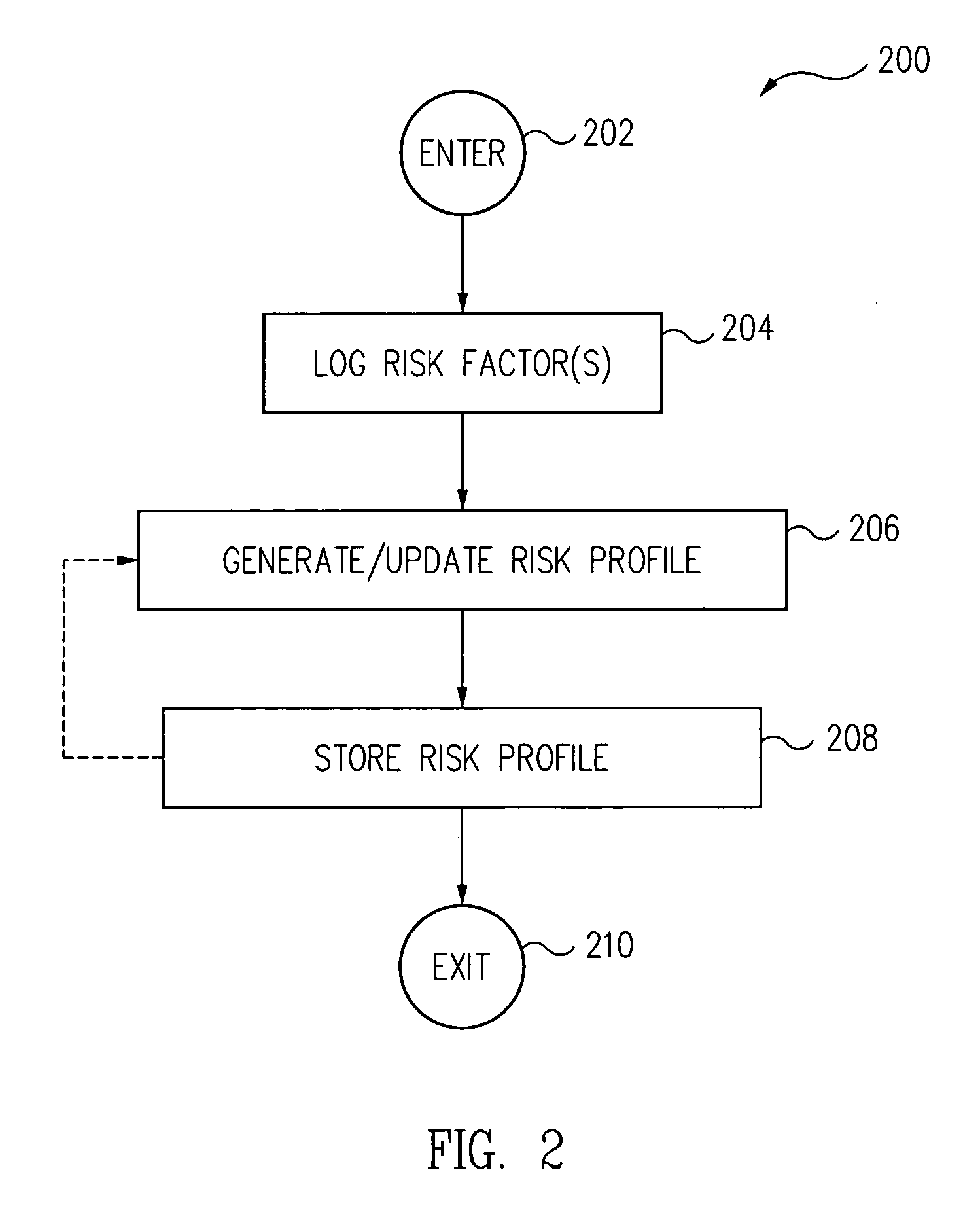
Risk events occurring on a computer system are logged over time and a risk profile is dynamically generated and updated based on the logged risk events. In one embodiment, a security policy is dynamically set and updated based on the risk profile.
Owner:CA TECH INC
Financial products having demand-based, adjustable returns, and trading exchange therefor
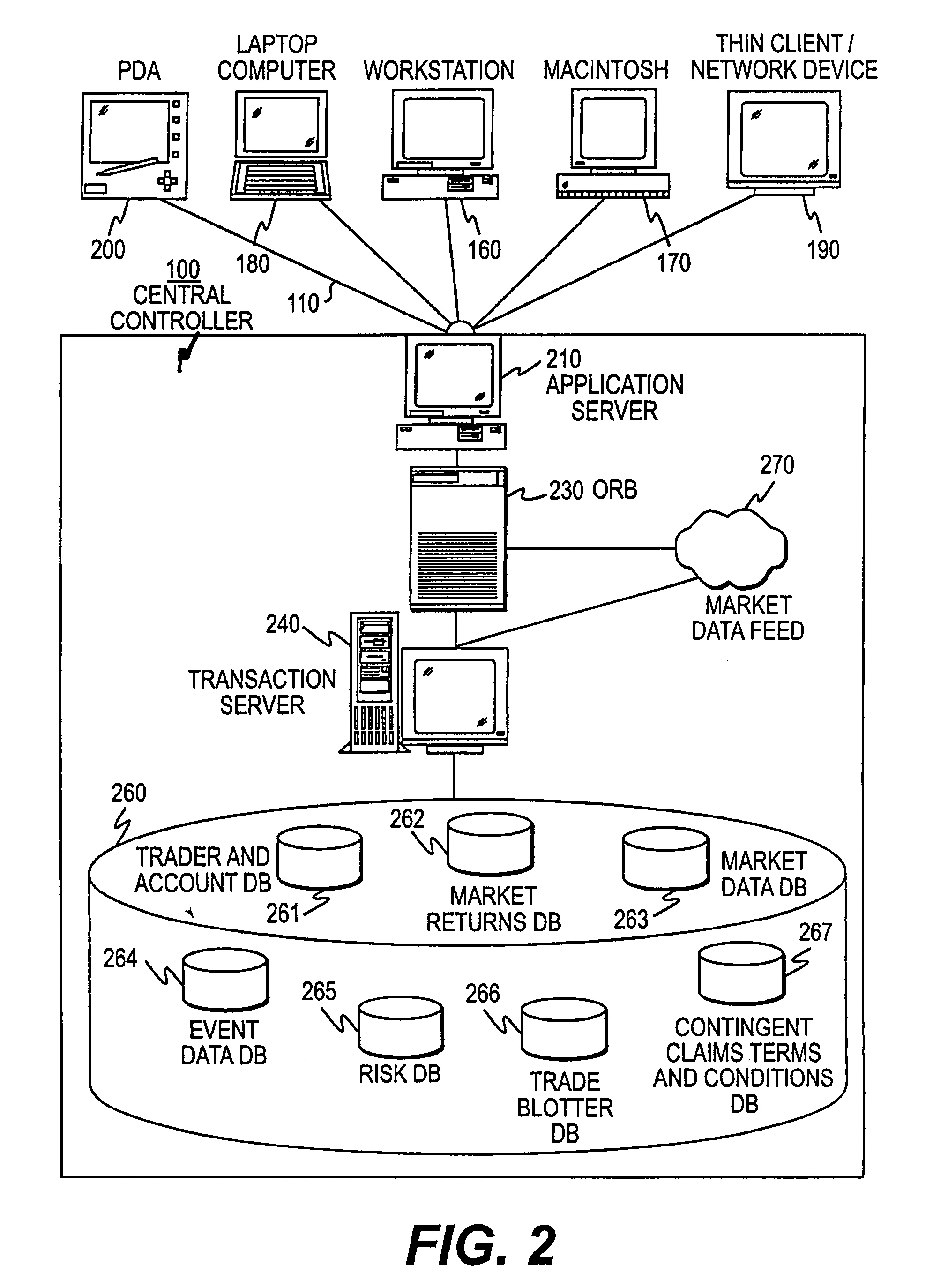
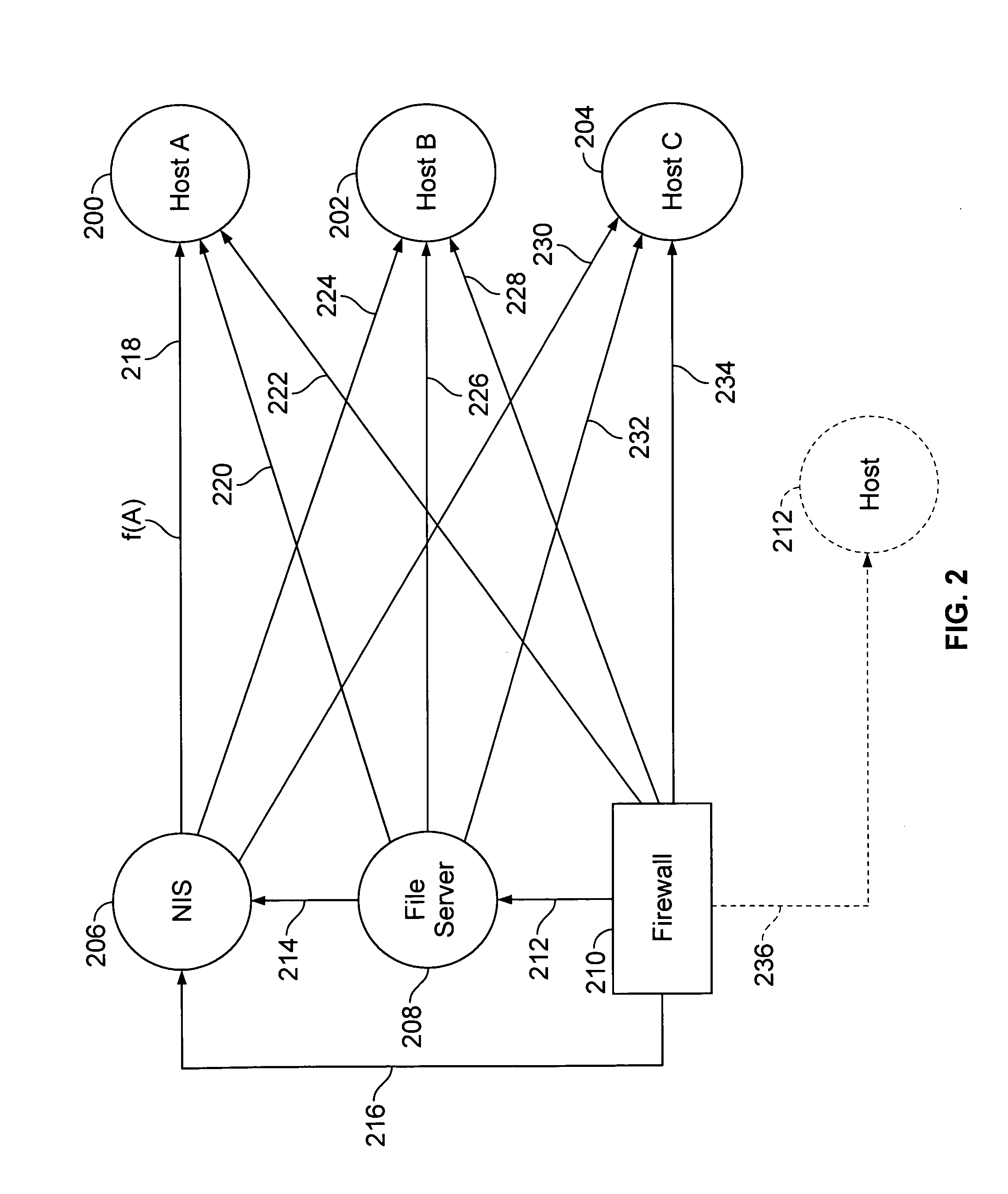
This invention provides methods and systems for trading and investing in groups of demand-based adjustable-return contingent claims, and for establishing markets and exchanges for such claims. (FIG. 2, item 262, 263, 264, 265) The advantages of the present invention, as applied to the derivative securities and similar financial markets, include increased liquidity, reduced credit risk, improved information aggregation, increased price transparency, reduced settlement or clearing costs, reduced hedging costs, reduced model risk, reduced event risk, increased liquidity incentives, improved self-consistency, reduced influence by market makers, and increased ability to generate and replicate arbitrary payout distributions. In addition to the trading of derivative securities, the present invention also facilitates the trading of other financial-related contingent claims; non-financial-related contingent claims such as energy, commodity, and weather derivatives; traditional insurance and reinsurance contracts; and contingent claims relating to events which have generally not been readily insurable or hedgeable such as corporate earnings announcements, future semiconductor demand, and changes in technology.
Owner:LONGITUDE LLC
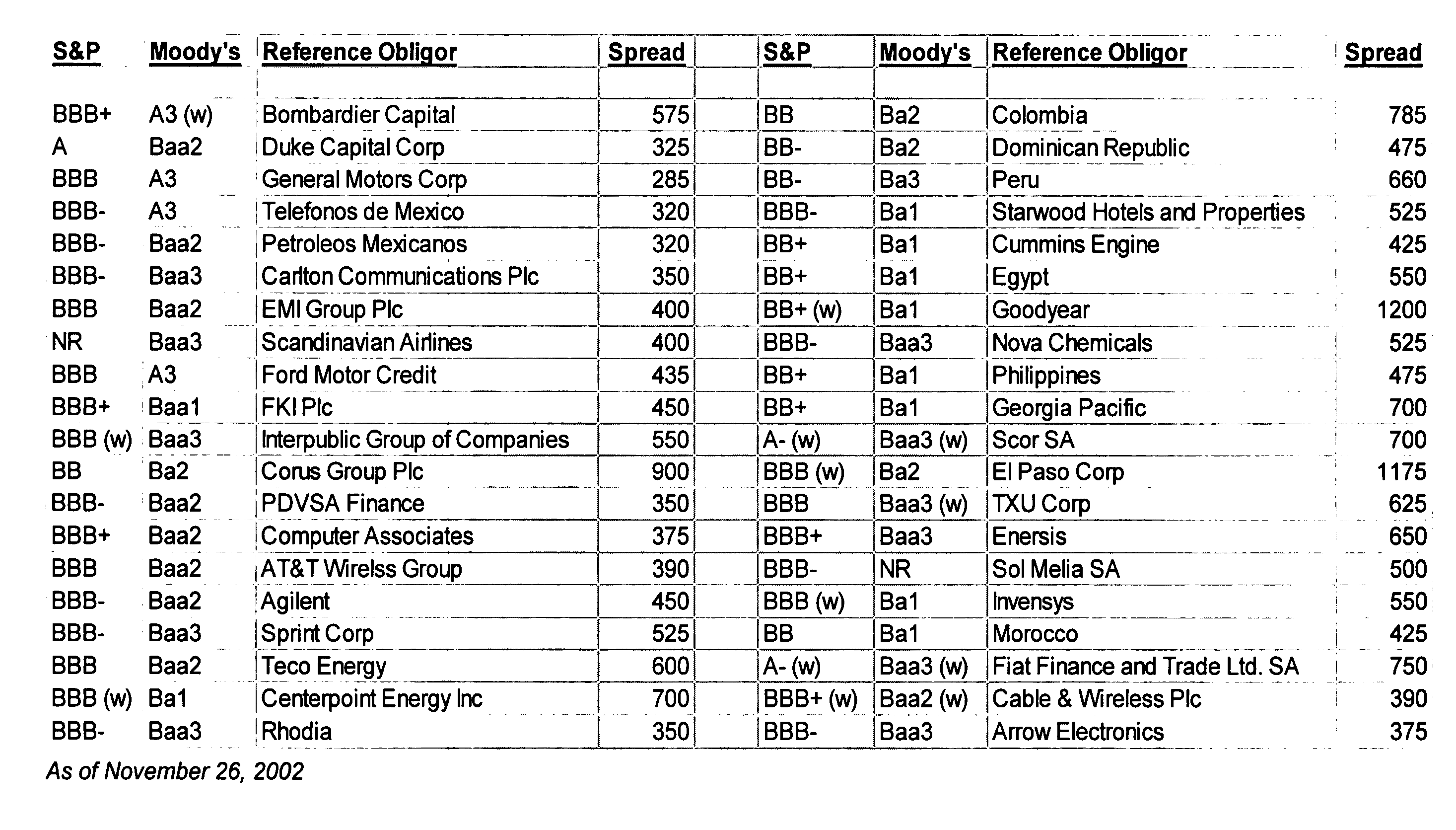
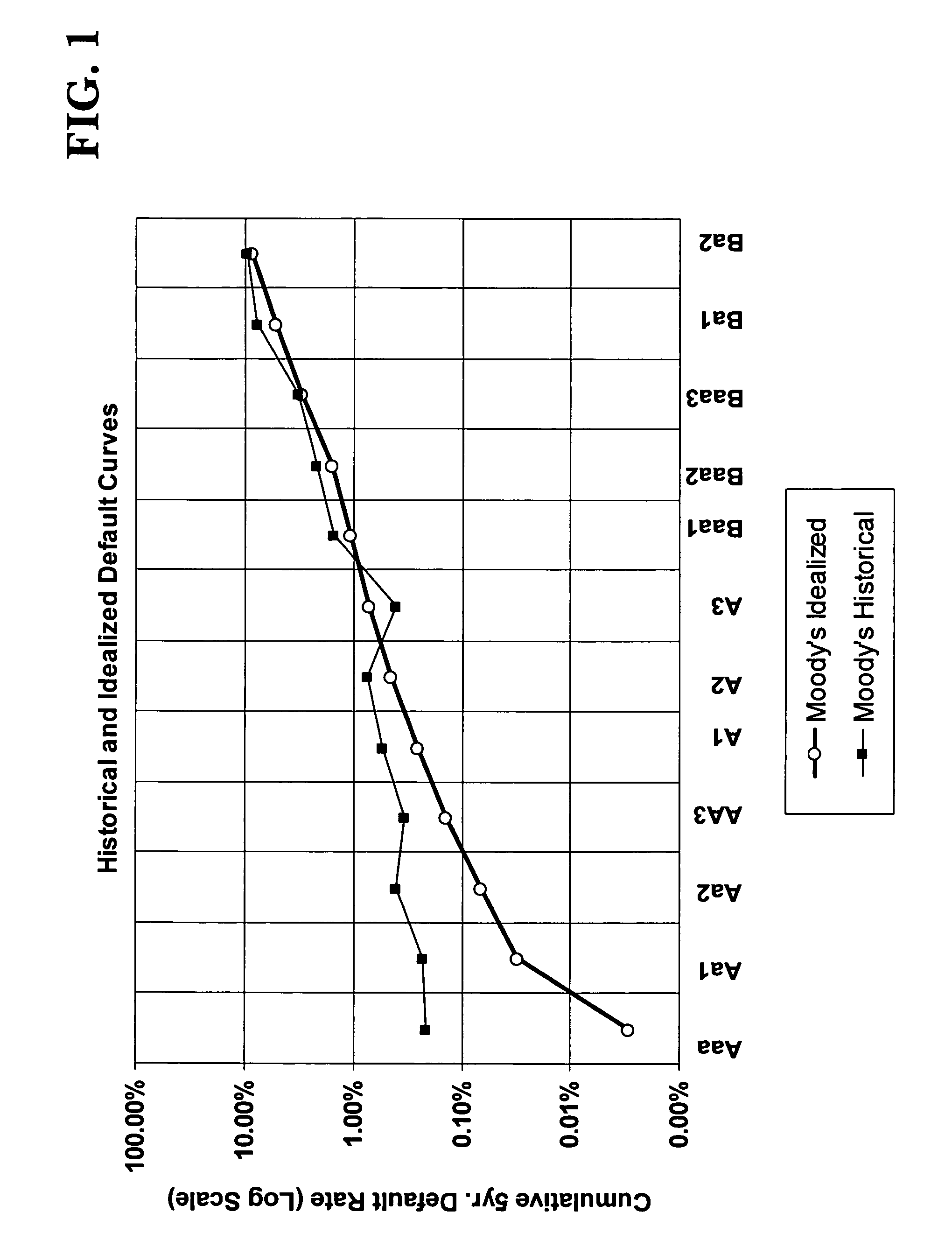
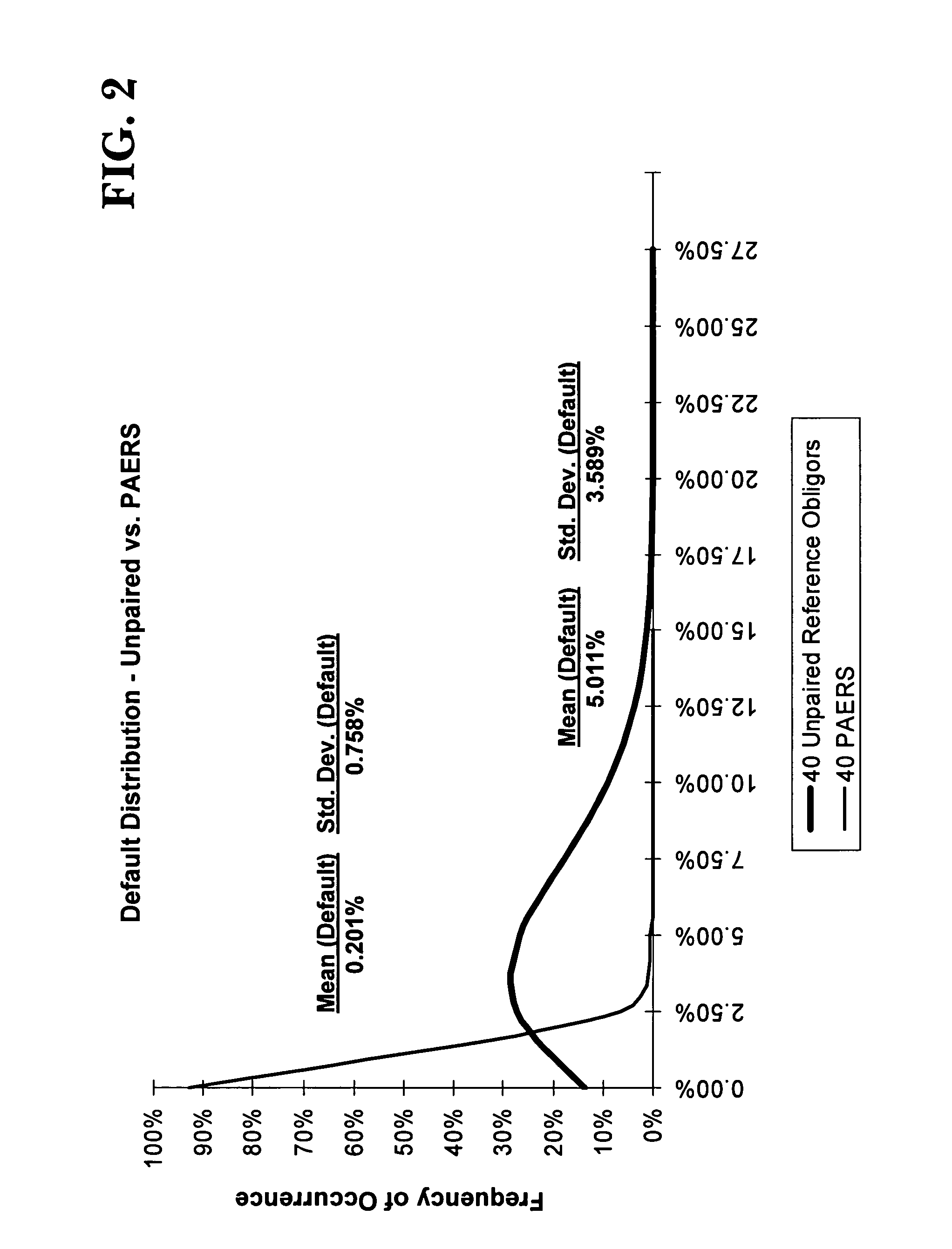
Hybrid securities having protection against event risk using uncorrelated last-to-default baskets
InactiveUS20050044029A1Reduce probabilityObtained inexpensivelyFinanceOffice automationData miningEvent risk
Hybrid securities defined as last-to-default credit default swaps over multiple name baskets and having protection against event risk. In the preferred embodiment, the hybrid security is defined as a second-to-default credit default swap over a two-name basket, wherein the underlying reference obligors in the basket are uncorrelated or substantially uncorrelated. A portfolio of second-to-default swaps over two-name baskets is provided, wherein the portfolio is defined in a manner that further reduces default risk through enhanced diversification achieved by recombining underlying reference obligors in different second-to-default baskets. A structured investment in a portfolio of underlying second-to-default swaps over two-name baskets is provided using a collateralized debt obligation (CDO) structure.
Owner:BABCOCK & BROWN
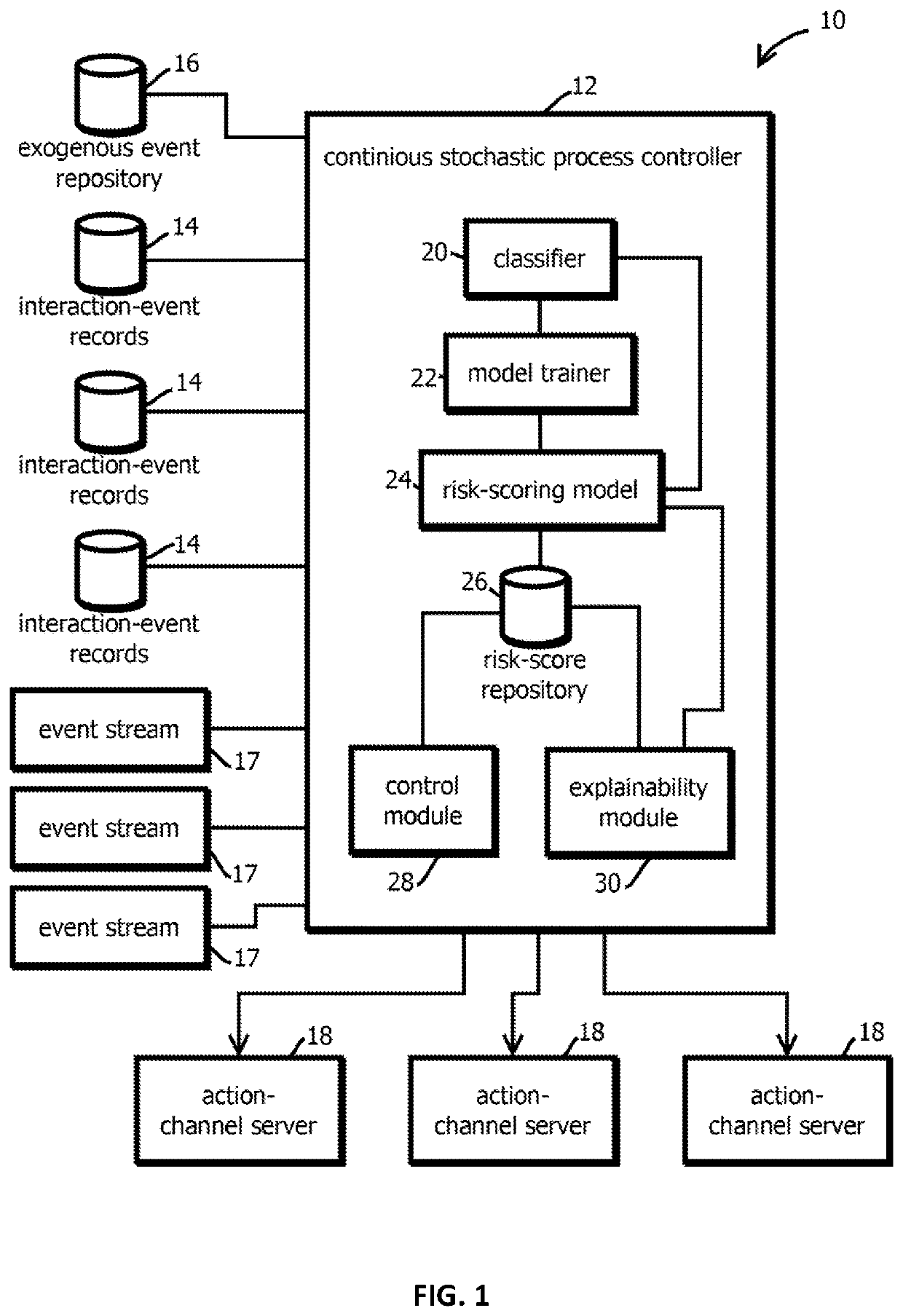
Monitoring and controlling continuous stochastic processes based on events in time series data
Owner:CEREBRI AI INC
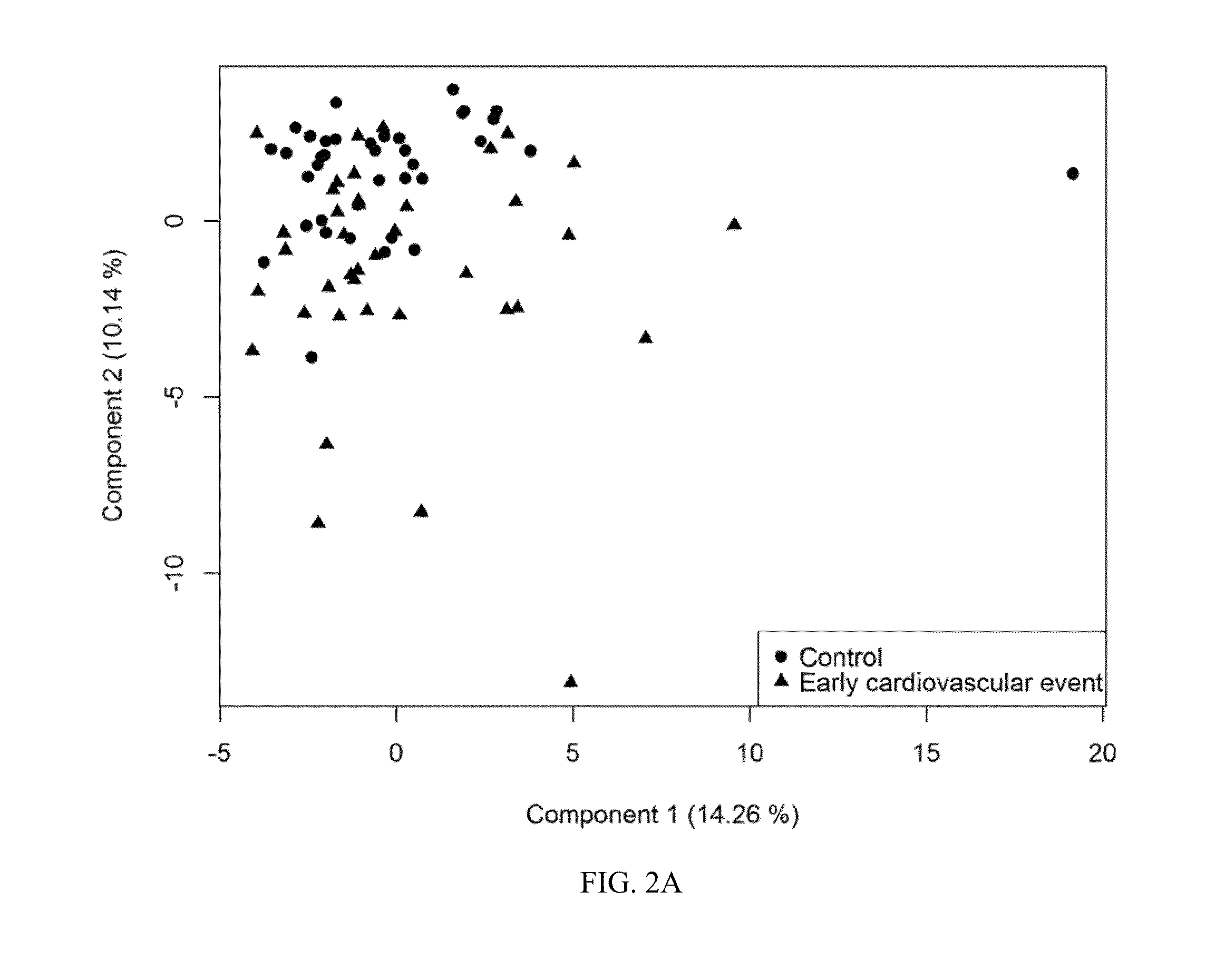
Cardiovascular Risk Event Prediction and Uses Thereof
InactiveUS20130085079A1Improve performanceEasy to usePeptide librariesNucleotide librariesVascular riskCvd risk
Owner:SOMALOGIC INC
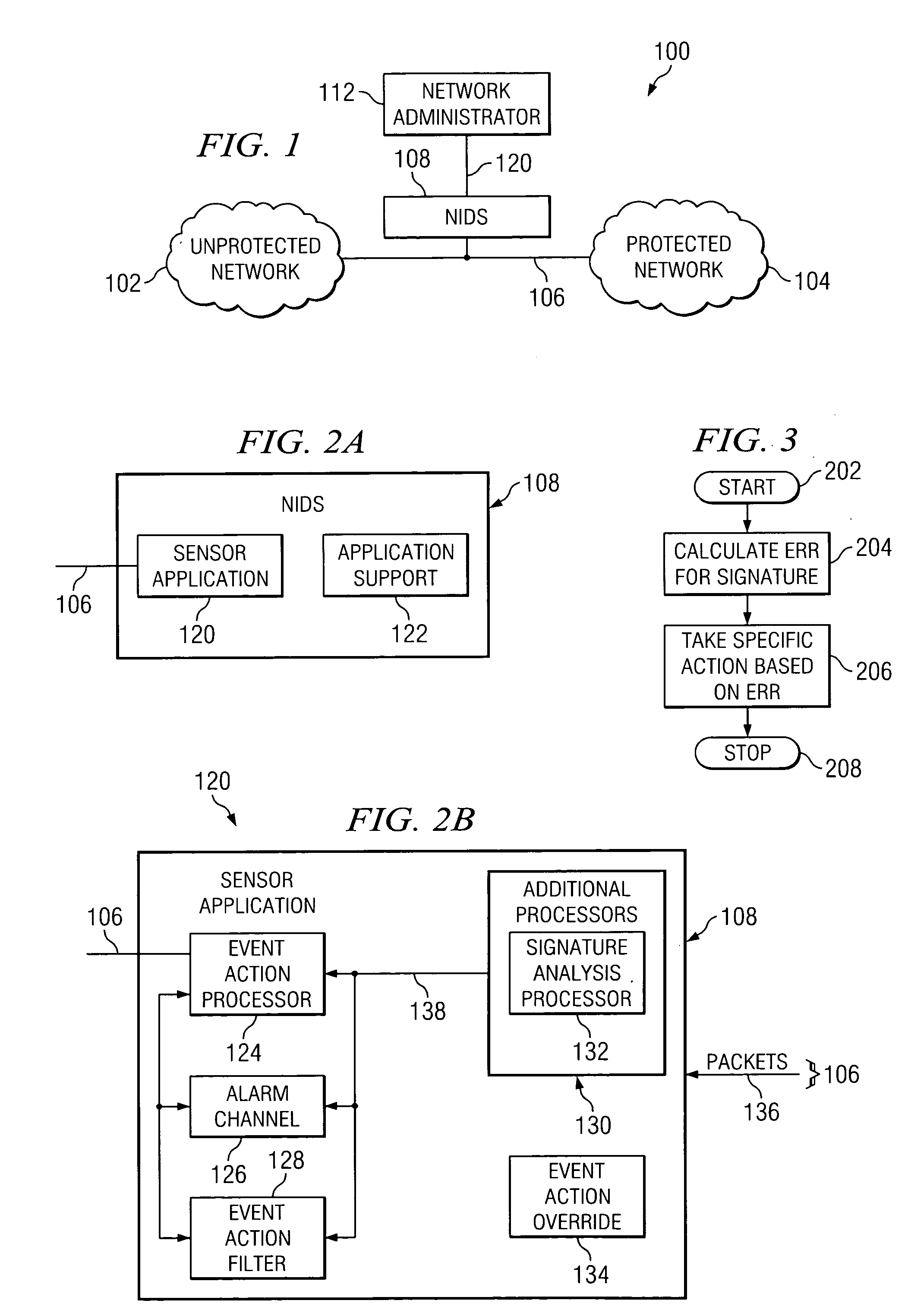
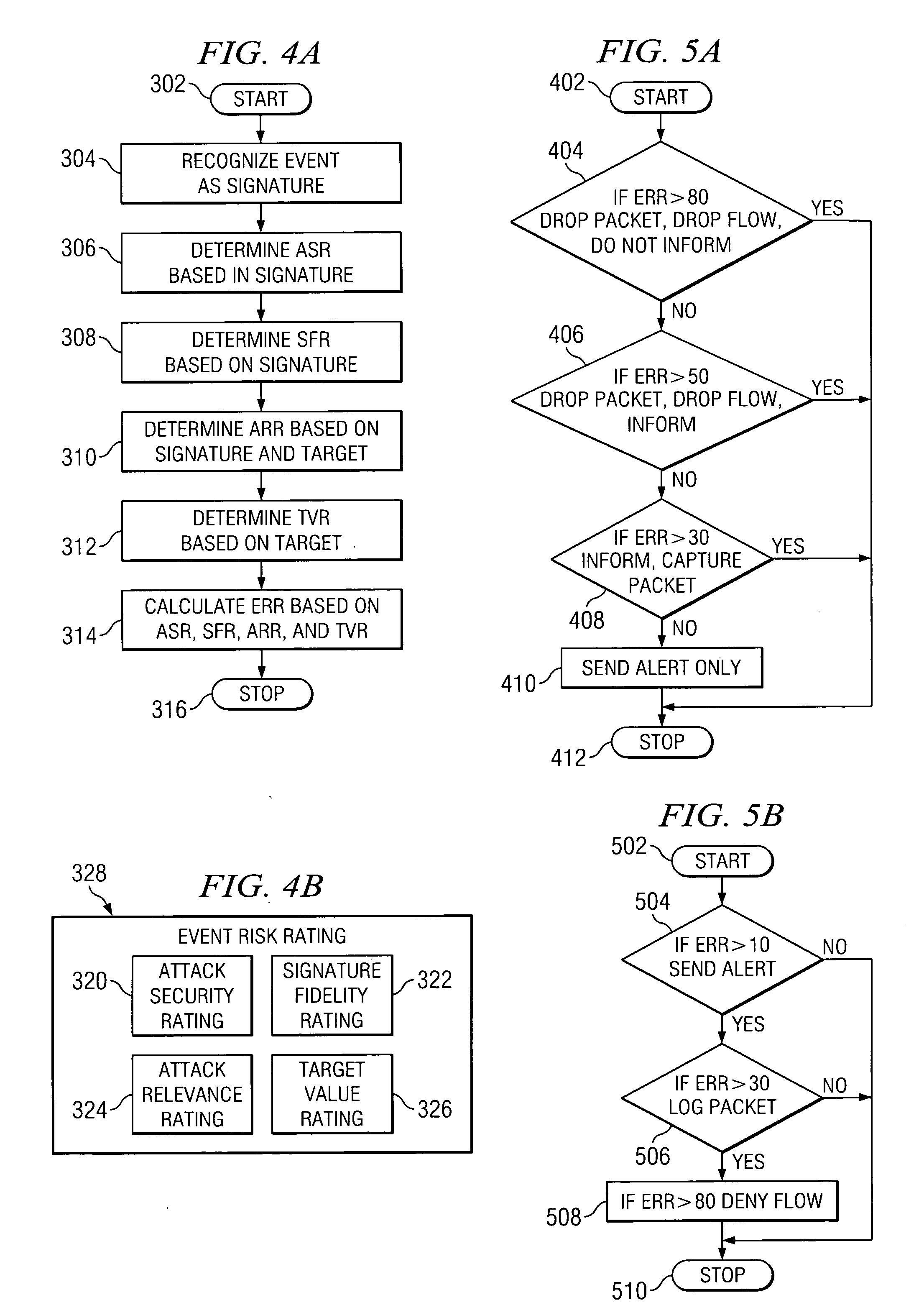
Method and system for addressing intrusion attacks on a computer system
ActiveUS20050097339A1Actual risk of an attack can be more accurately assessedMemory loss protectionUser identity/authority verificationData streamRisk rating
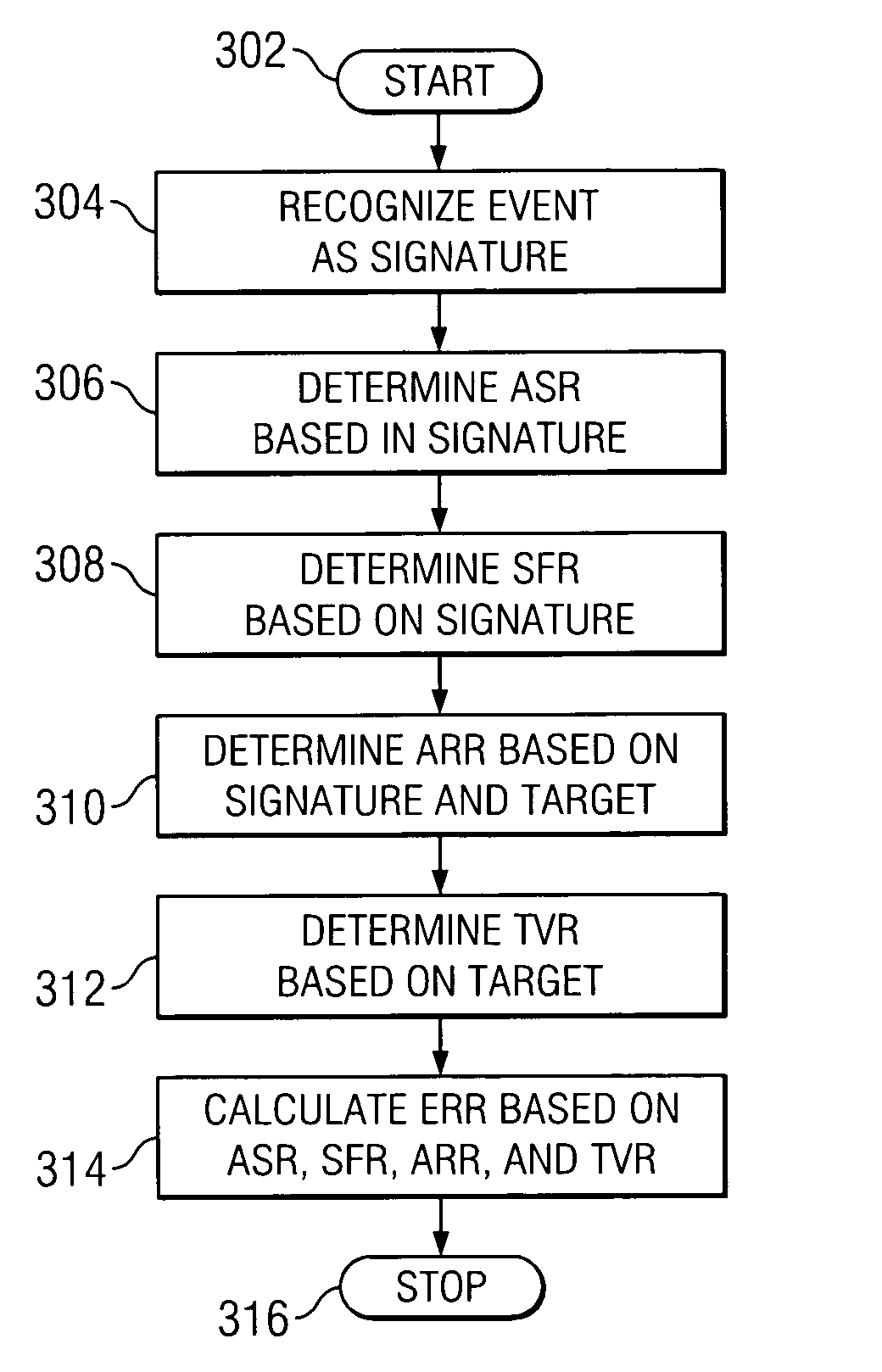
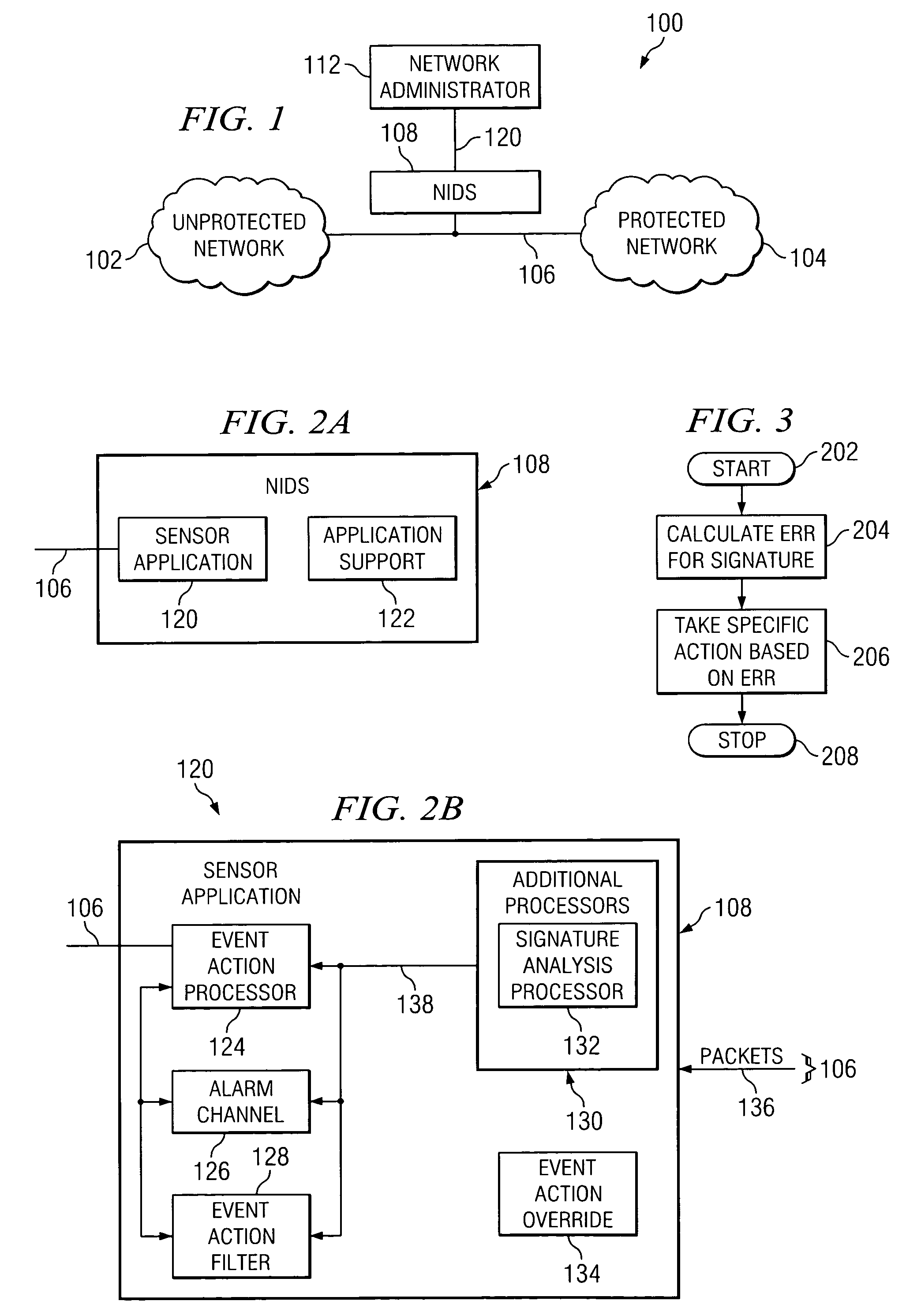
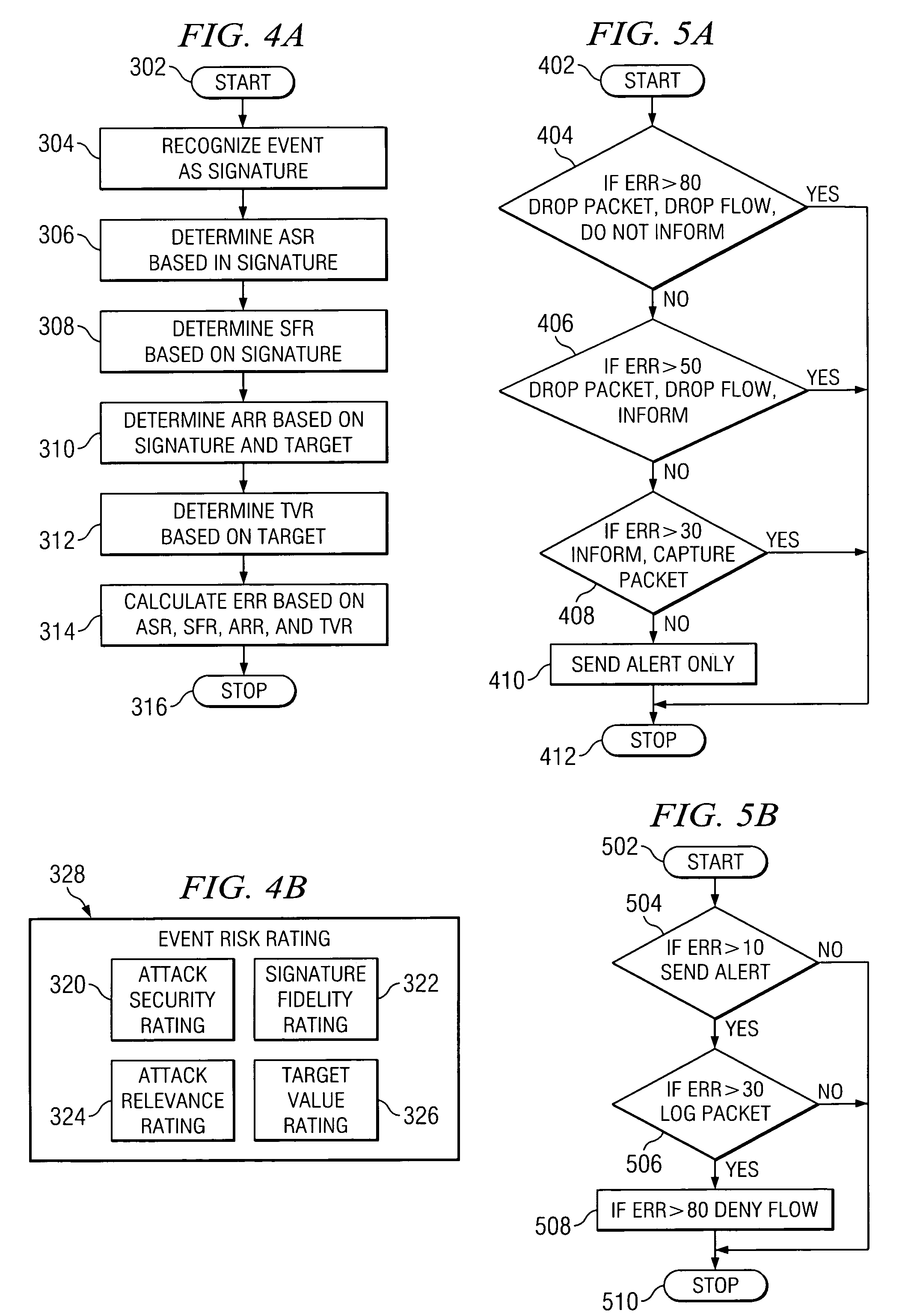
According to one embodiment of the invention, a computerized method for addressing intrusion attacks directed at a computer includes receiving a data stream corresponding to a potential attack on the computer and calculating an event risk rating for the data stream. Calculating the event risk rating includes determining at least one component risk rating. In one embodiment, the component risk ratings are: a signature fidelity rating indicative of the likelihood the potential attack will affect the computer in the absence of knowledge regarding the computer, an attack relevance rating indicative of the relevance of the potential attack to the computer, and a target value rating indicative of the perceived value of the computer. The method also includes responding to the potential attack based on the calculated risk rating.
Owner:CISCO TECH INC
Method and system for addressing intrusion attacks on a computer system
ActiveUS7526806B2Actual risk of an attack can be more accurately assessedMemory loss protectionUser identity/authority verificationData streamComputerized system
According to one embodiment of the invention, a computerized method for addressing intrusion attacks directed at a computer includes receiving a data stream corresponding to a potential attack on the computer and calculating an event risk rating for the data stream. Calculating the event risk rating includes determining at least one component risk rating. In one embodiment, the component risk ratings are: a signature fidelity rating indicative of the likelihood the potential attack will affect the computer in the absence of knowledge regarding the computer, an attack relevance rating indicative of the relevance of the potential attack to the computer, and a target value rating indicative of the perceived value of the computer. The method also includes responding to the potential attack based on the calculated risk rating.
Owner:CISCO TECH INC
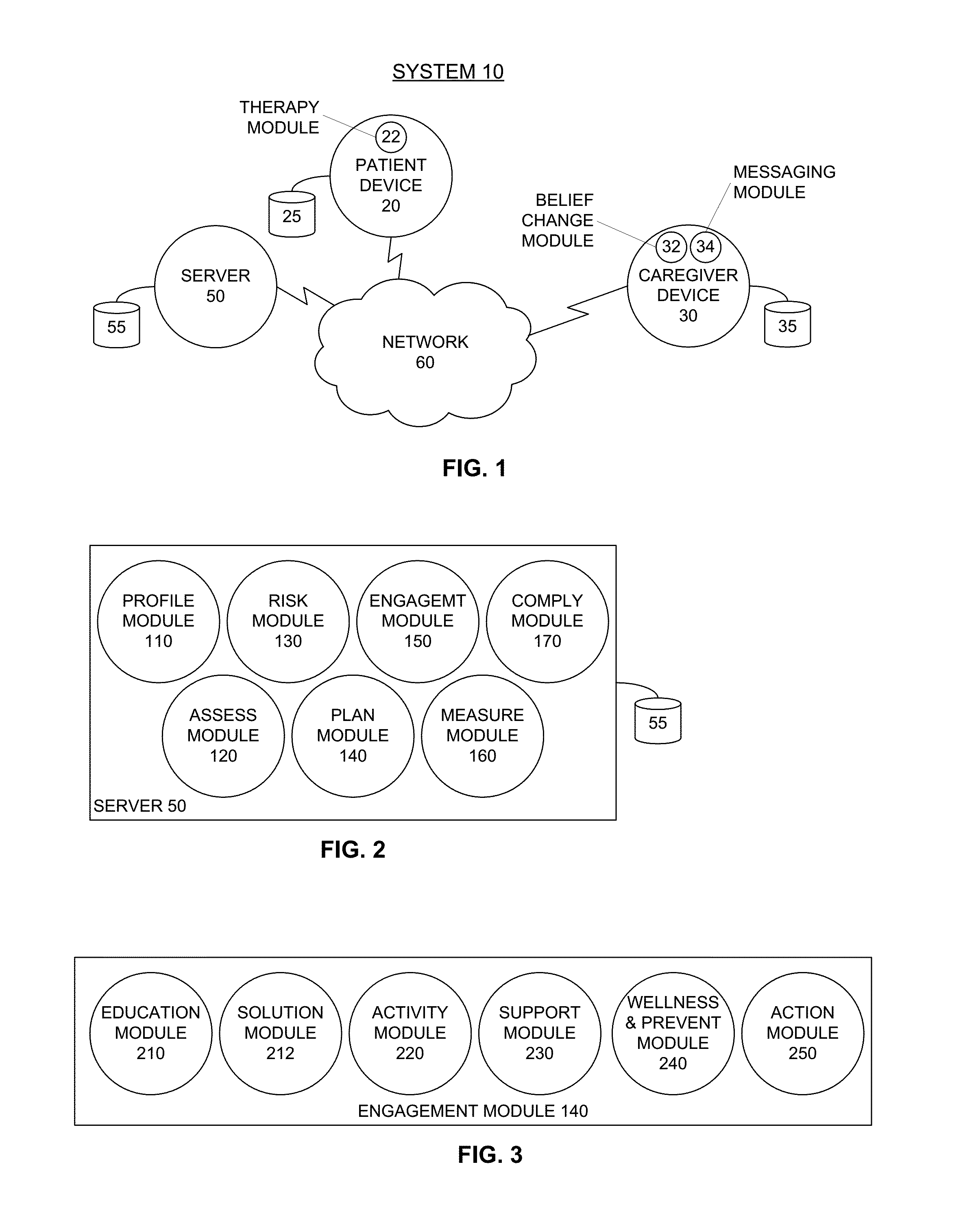
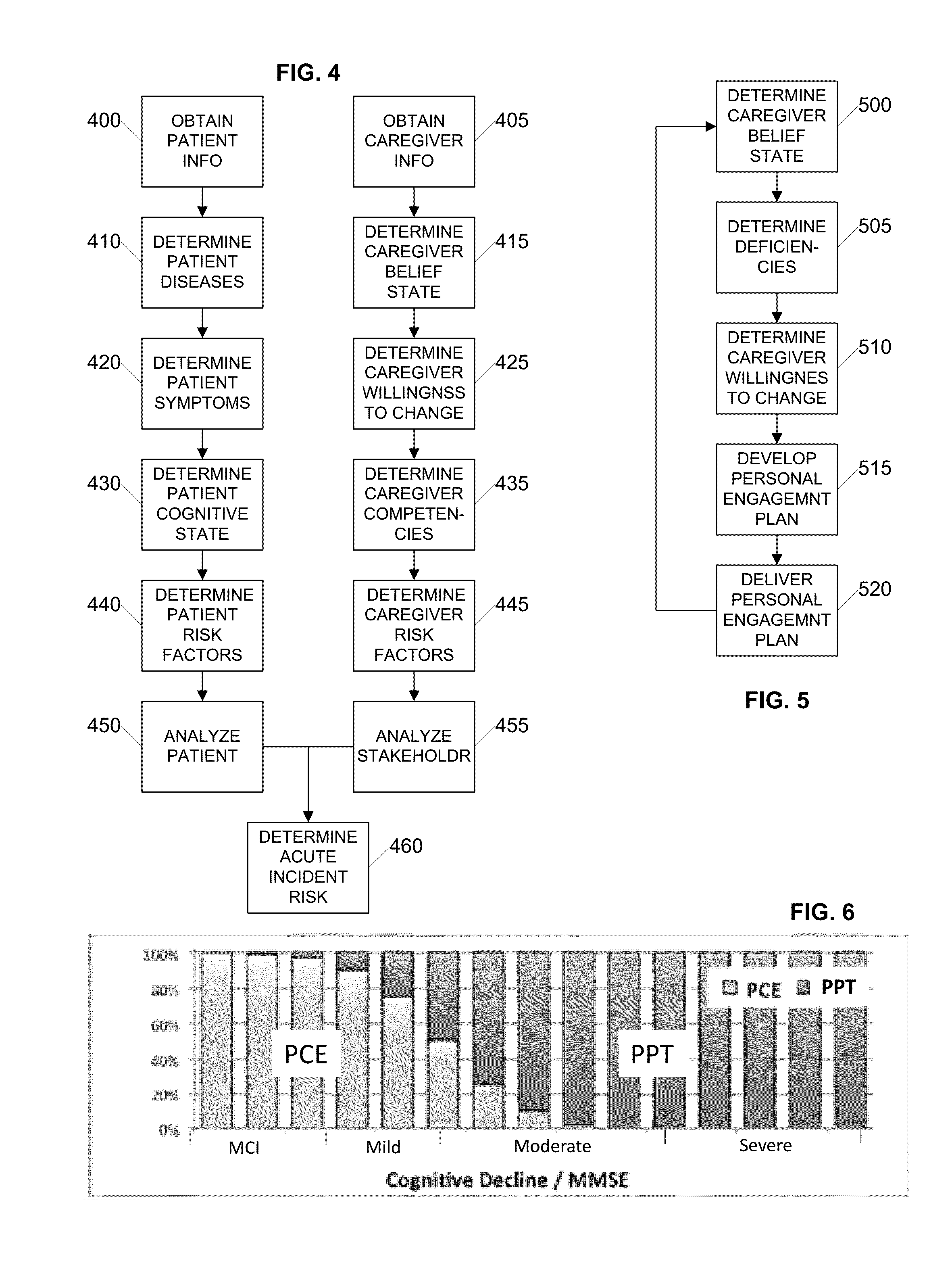
System and method for reducing acute incident risk
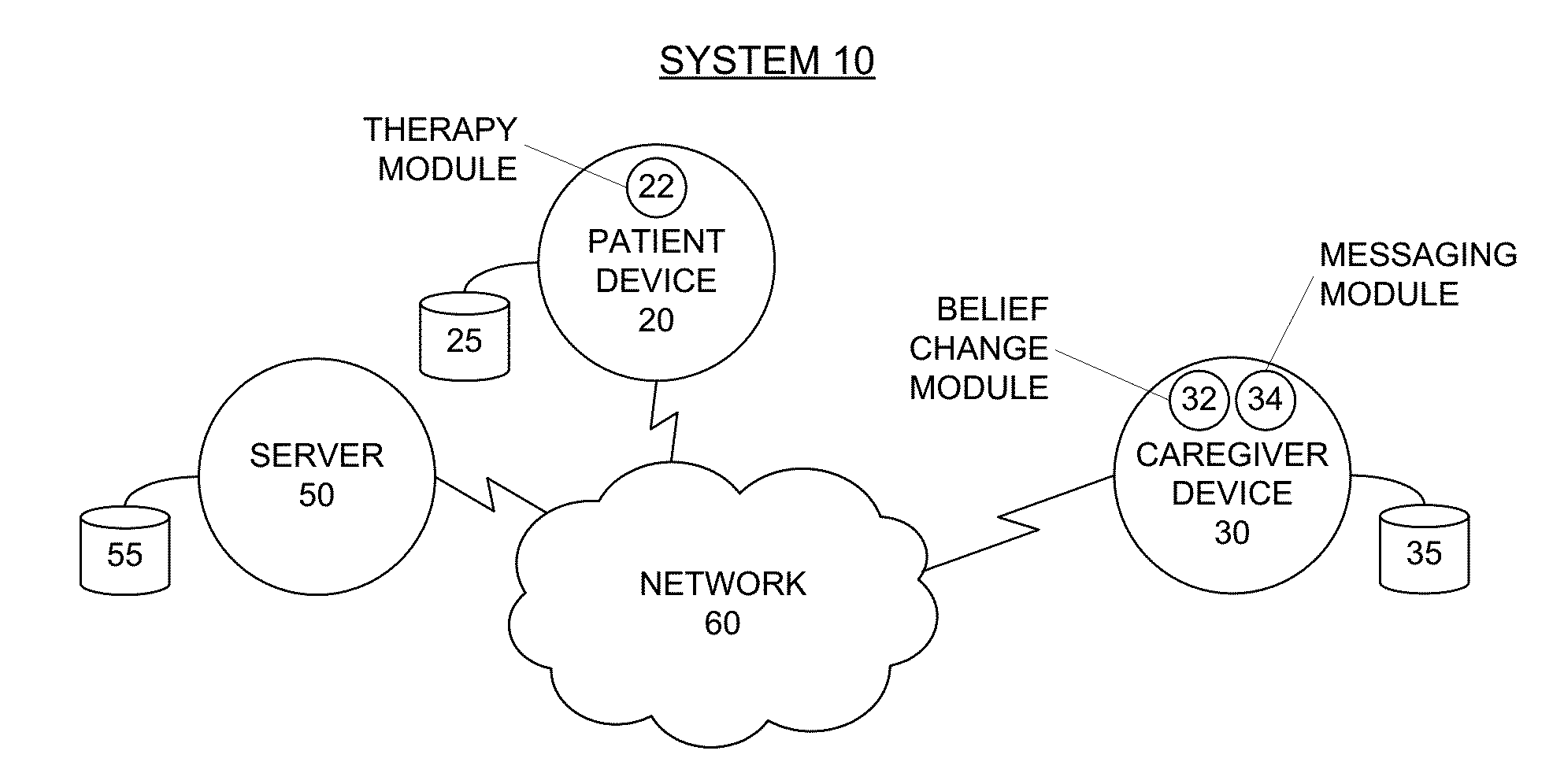
ActiveUS20150154372A1Reducing acute incident riskReduce the burden onData processing applicationsHealth-index calculationCaregiver personCaregiver burden
Systems and methods for reducing acute incident risks for dementia patients are provided. Benefits of the systems and methods include reducing healthcare costs, improving patient and caregiver outcomes and reducing caregiver burden. A server system analyzes data related to a dementia patient and the corresponding caregivers (e.g., family member, paid caregiver, physician) and calculates an acute incident risk. Based on the acute incident risk, the server system determines patient therapies to reduce the acute incident risk and also identifies caregiver education to improve the caregiver belief state, which reduces the acute incident risk. The system periodically re-calculates the acute incident risk and identifies patient therapies and caregiver education and motivation to further reduce or maintain the acute incident risk.
Owner:CERESTI HEALTH
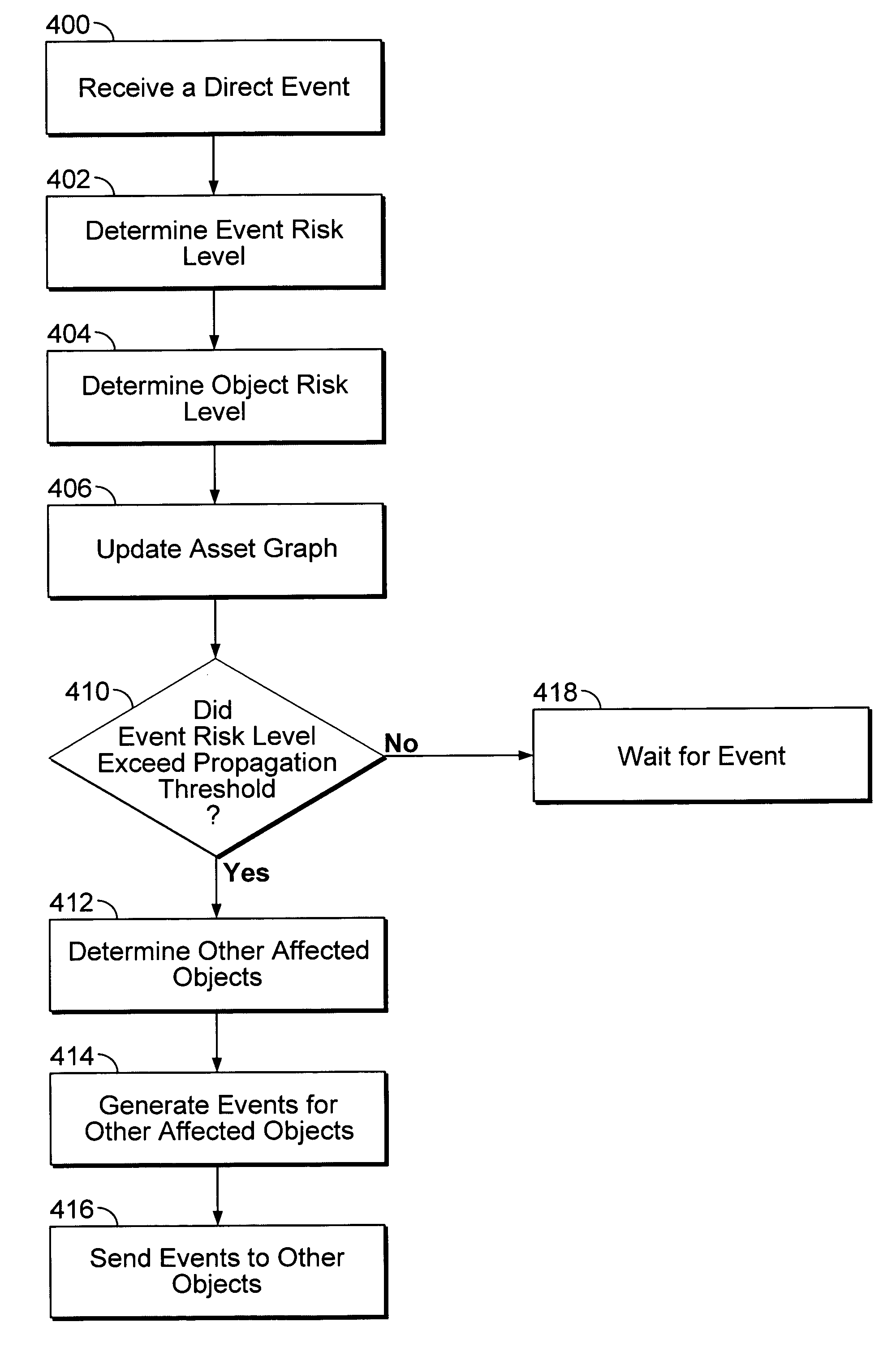
Network risk analysis
A system and method are disclosed for analyzing security risks in a computer network. The system constructs asset relationships among a plurality of objects in the computer network and receives an event associated with a selected object, where the event has an event risk level. The system also propagates the event to objects related to the selected object if the event risk level exceeds a propagation threshold.
Owner:CA TECH INC
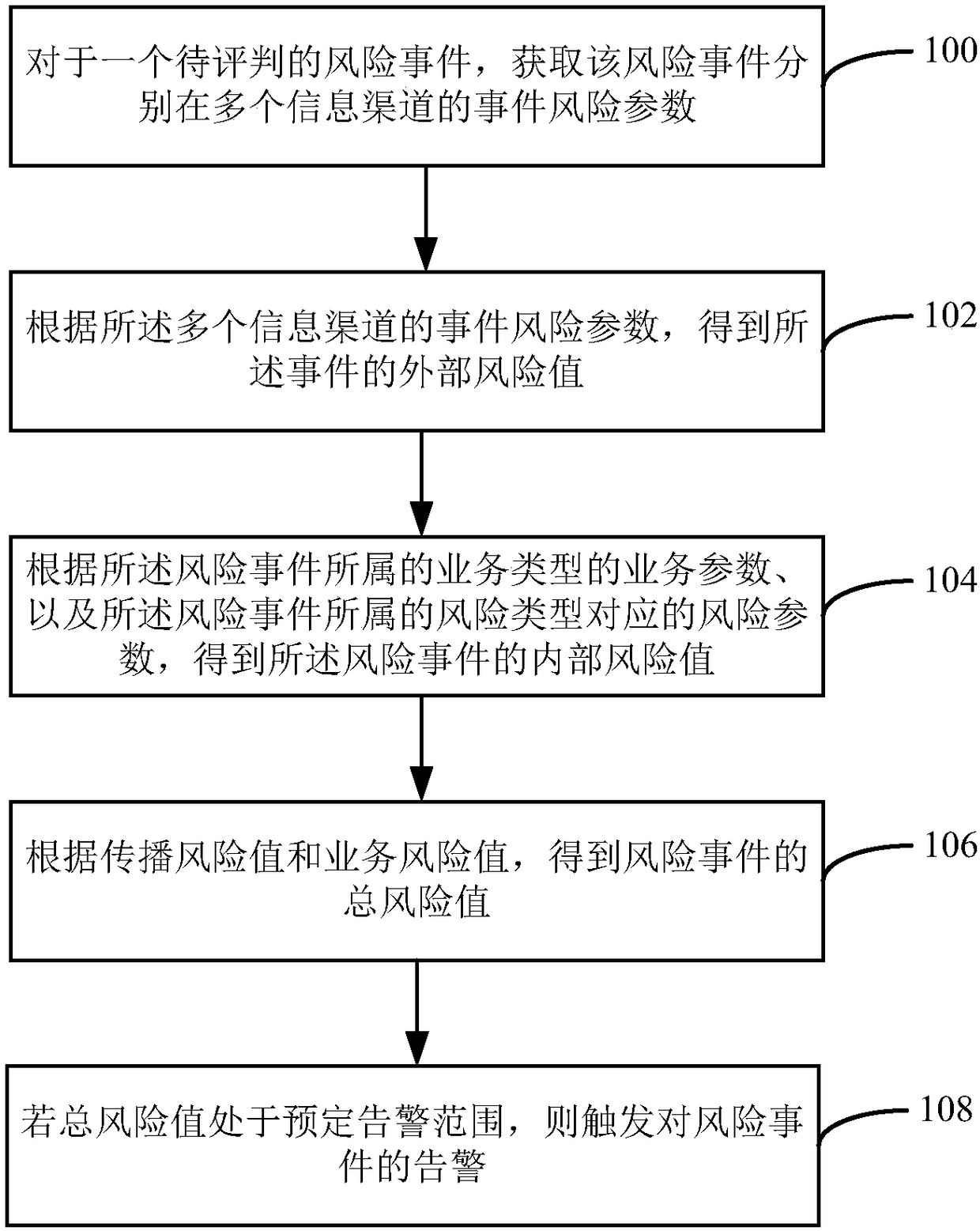
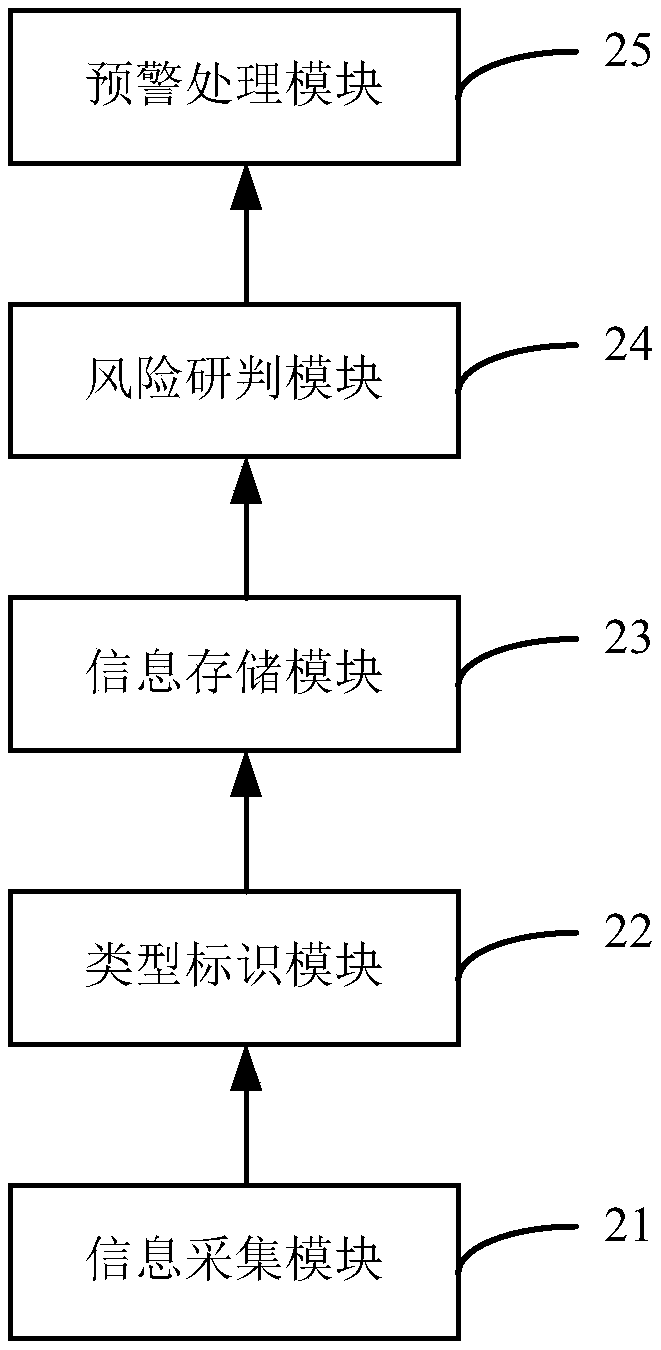
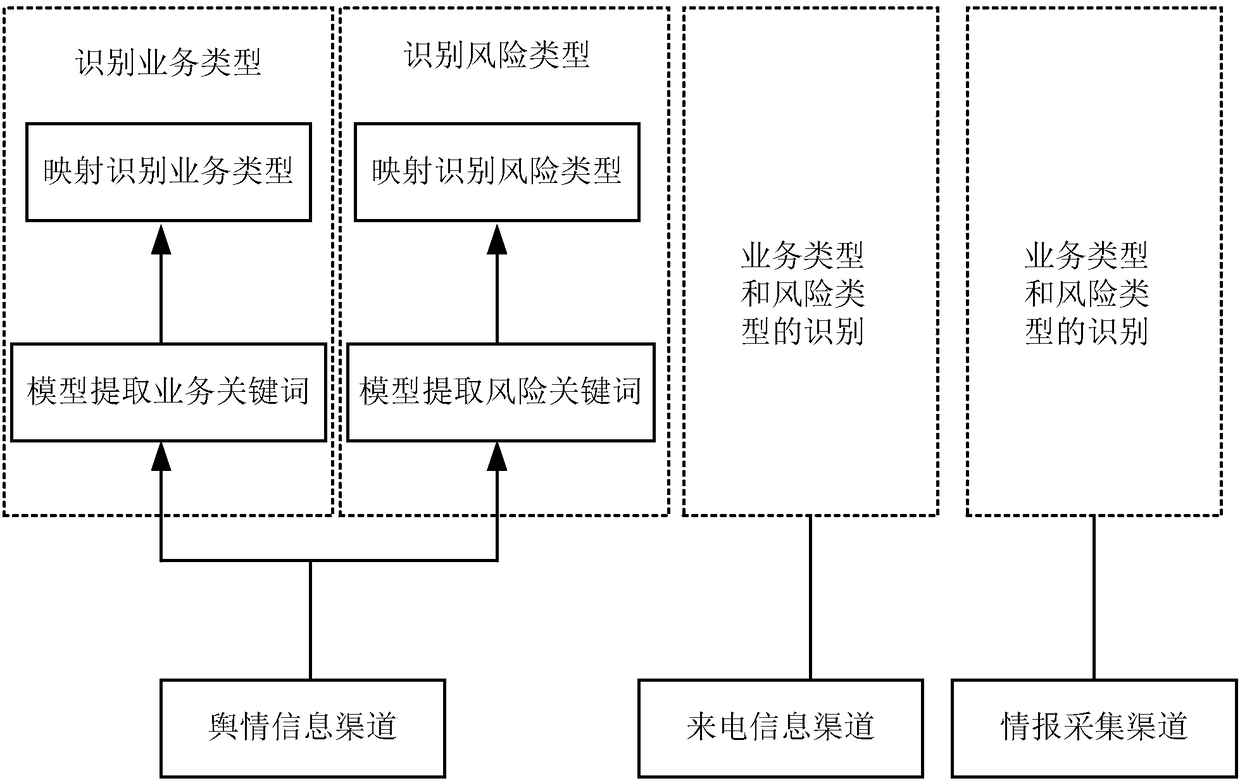
Risk event alarm method and device
The embodiment of the invention provides a risk event alarm method and device. The method comprises the steps of: obtaining event risk parameters of a risk event to be evaluated in a plurality of information channels, and obtaining a propagation risk value of the risk event according to the event risk parameters of the information channels; obtaining a business risk value corresponding to the riskevent according to the business parameter of a business type to which the risk event belongs and risk parameters corresponding to the risk type to which the risk event belongs; and obtaining a totalrisk value of the risk event according to the propagation risk value and the business risk value; and if the total risk value is located in a predetermined alarm range, triggering alarm for the risk event.
Owner:ADVANCED NEW TECH CO LTD
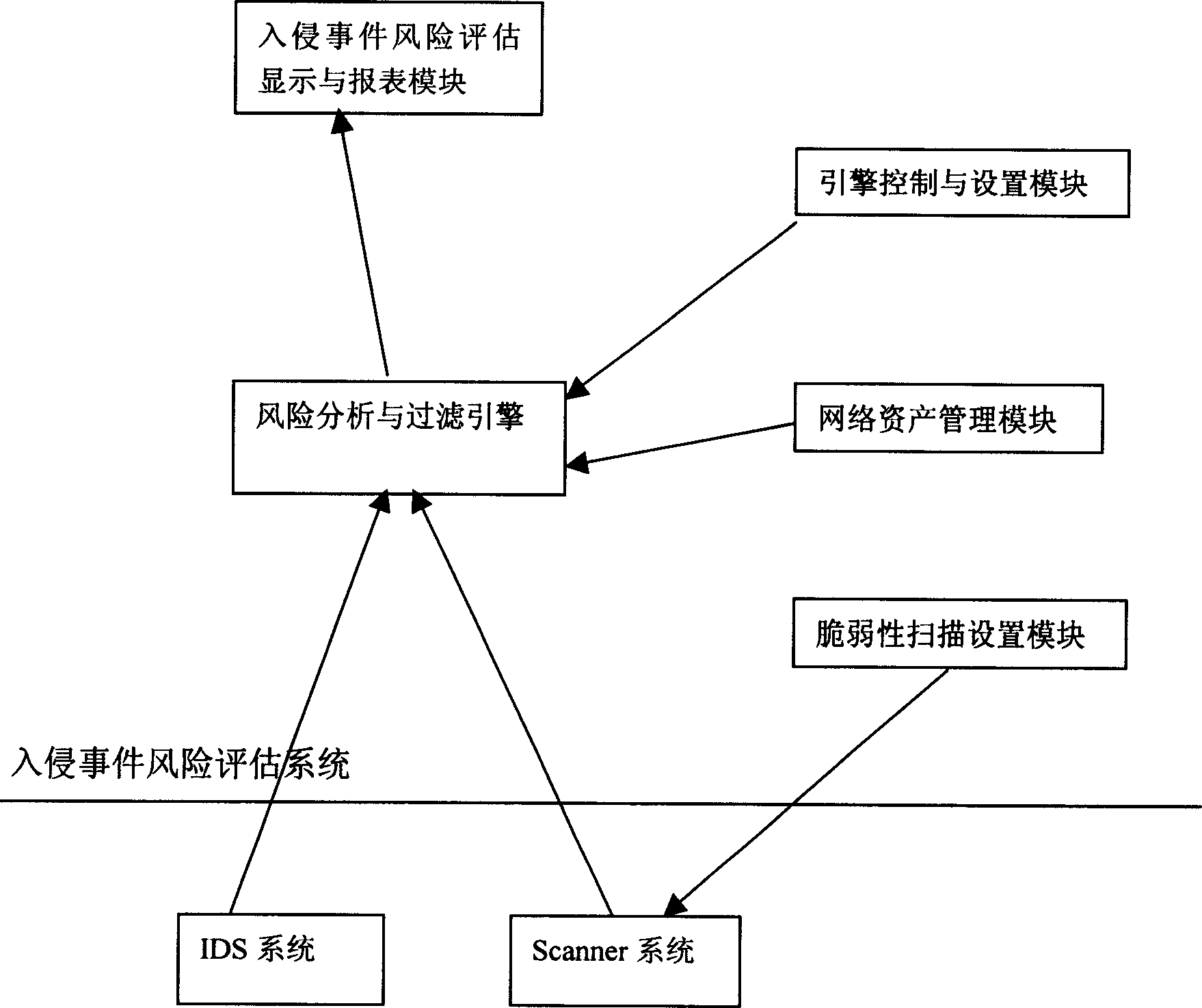
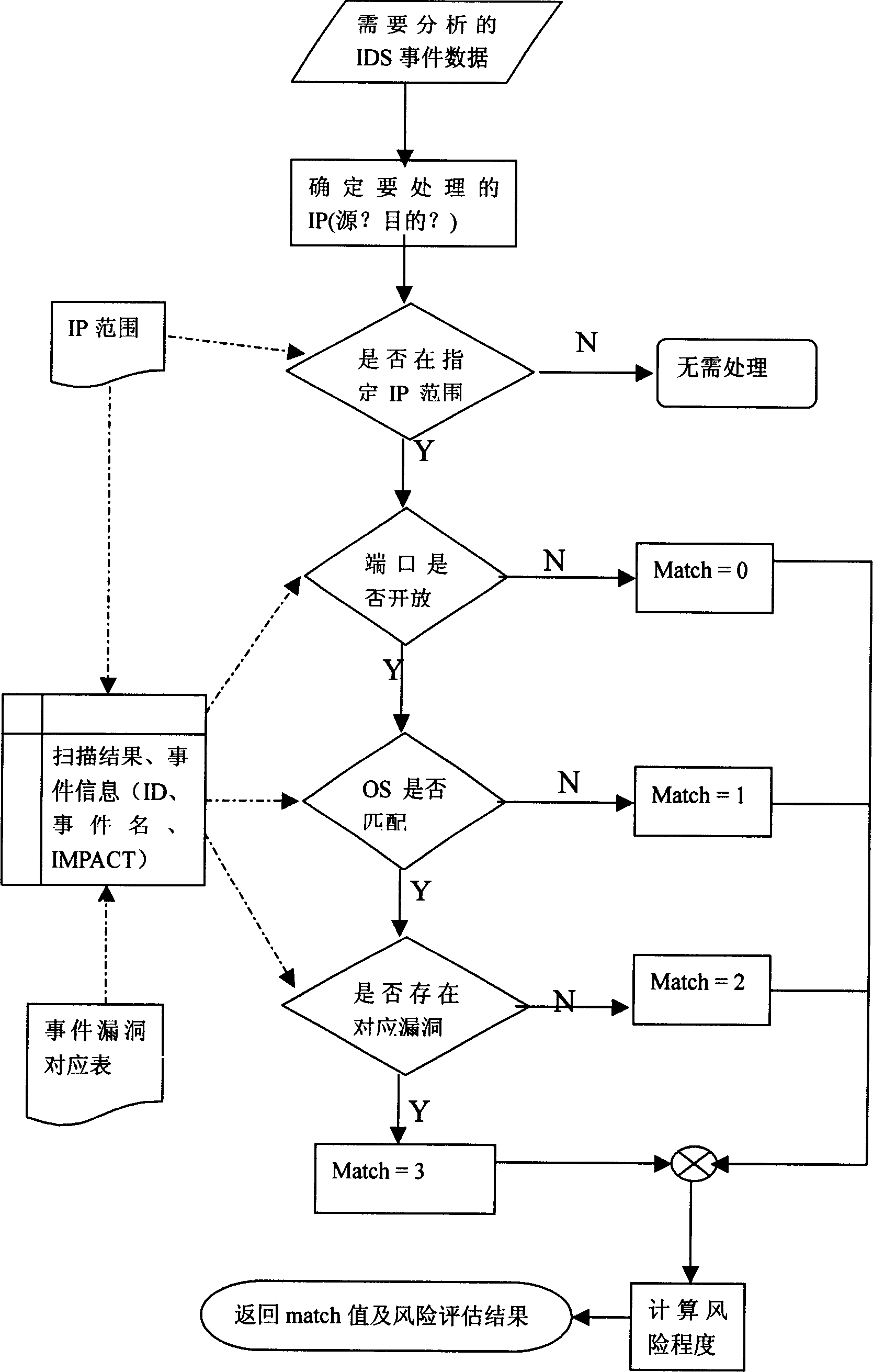
Network invading event risk evaluating method and system
InactiveCN1741472AImprove use valueAccurate analysisData switching networksManagement unitComputer science
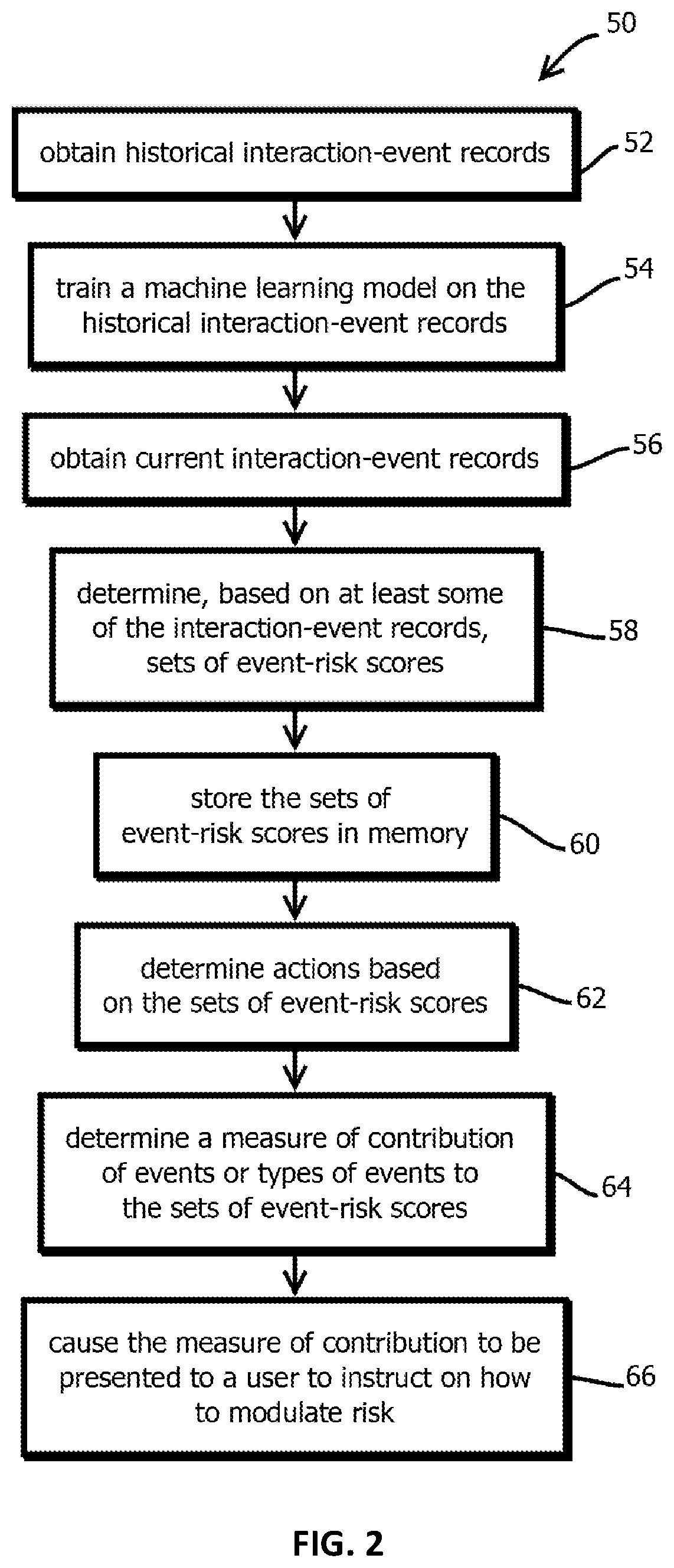
A risk estimating system of network intrusion event comprises engine module for carrying out effectiveness analyzing filter and risk estimating calculation to intrusion event according to set condition , controlling and managing unit of engine module , display and report module of risk estimation result on intrusion event .
Owner:BEIJING VENUS INFORMATION TECH
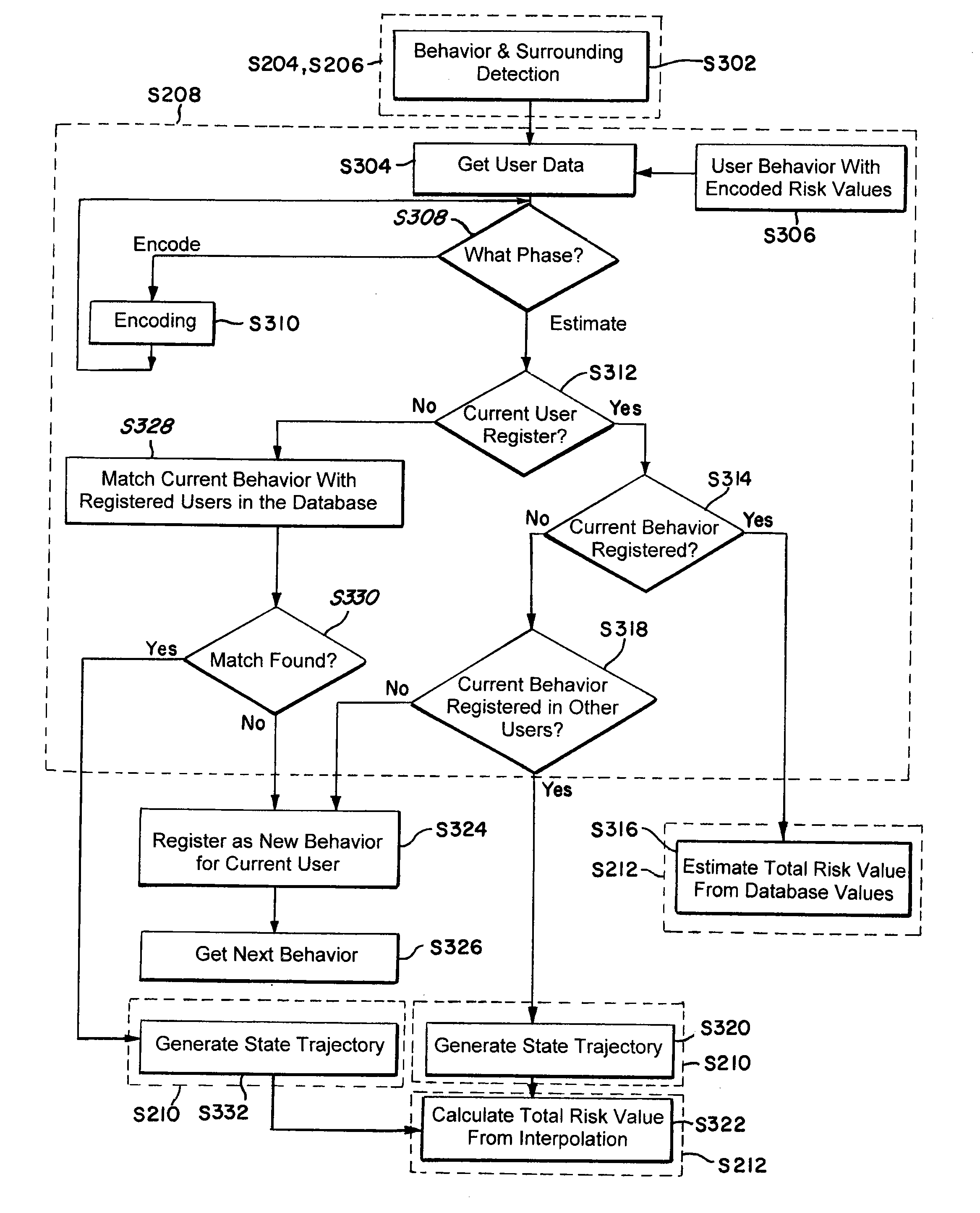
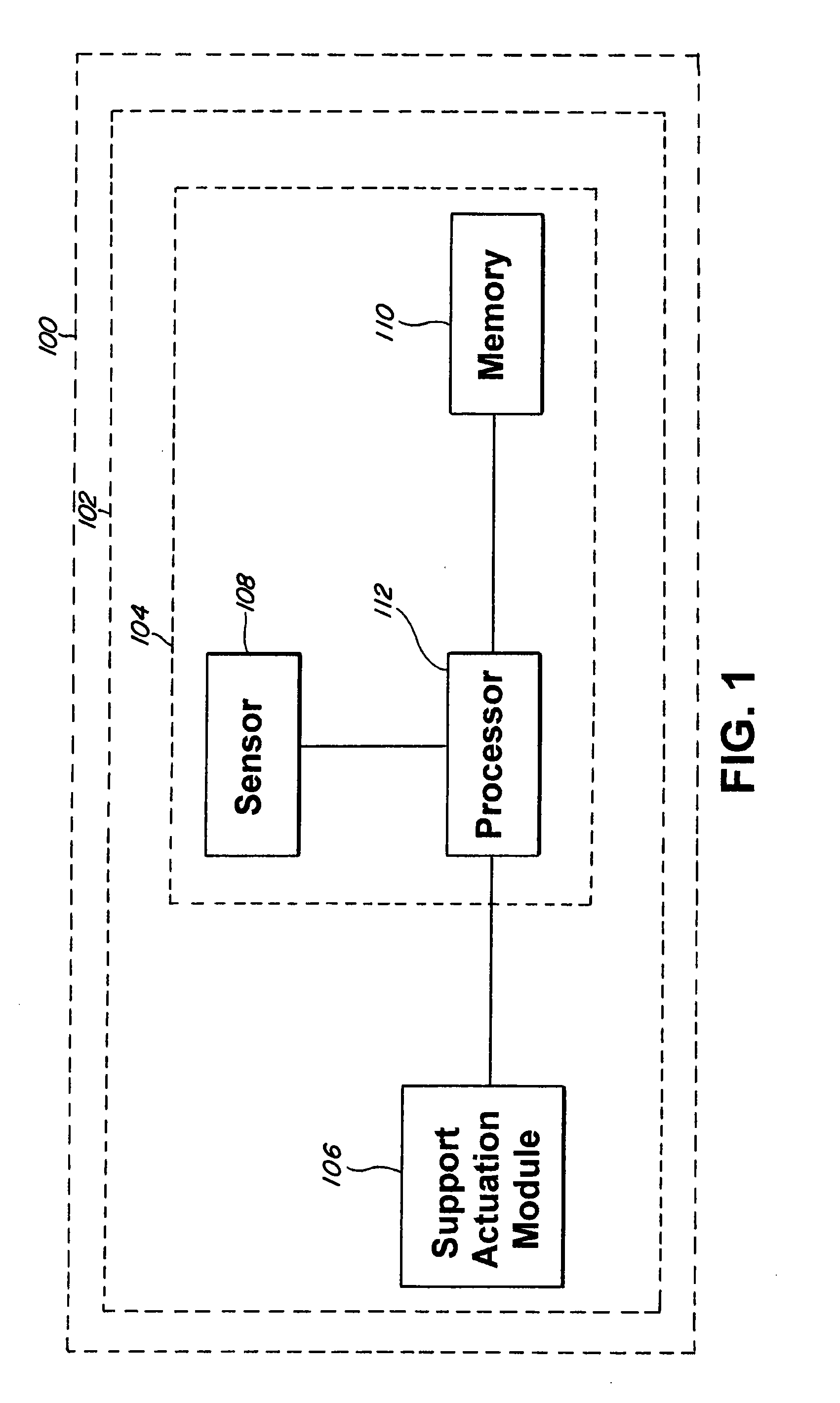
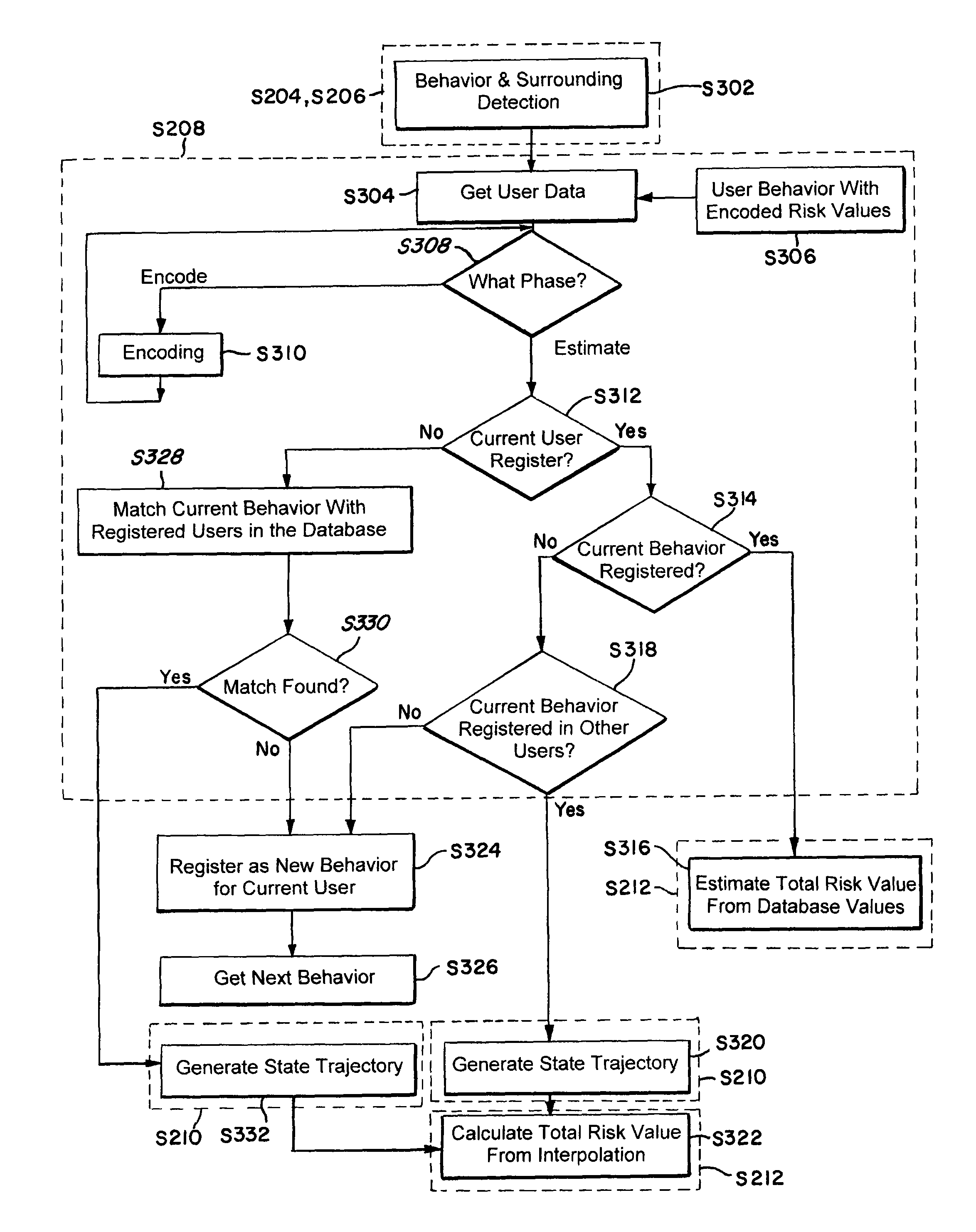
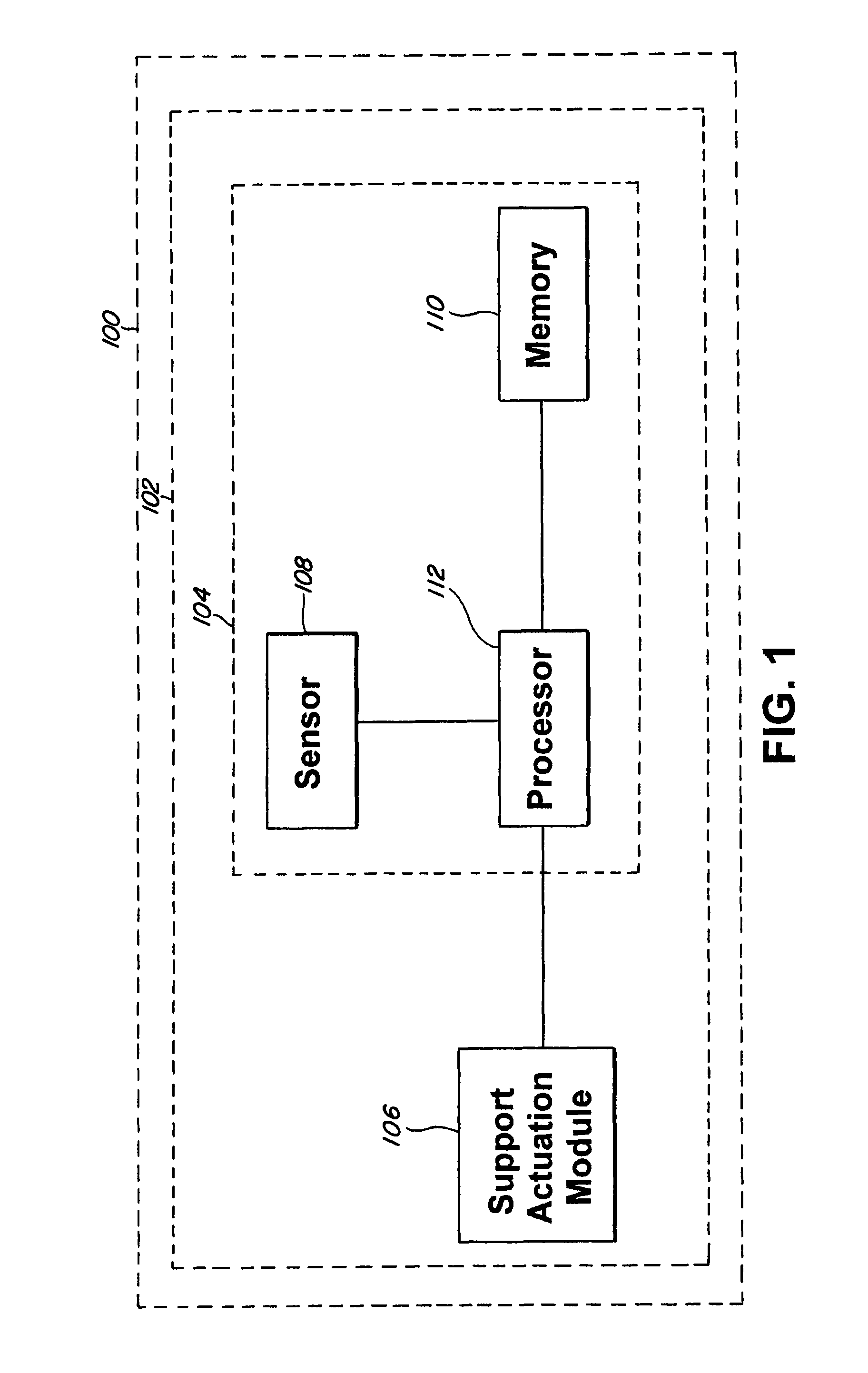
Method and system for risk prediction for a support actuation system
ActiveUS20120083942A1Accurate risk assessmentComputation using non-denominational number representationExternal condition input parametersTotal riskAmbient data
The present invention relates to a method and system for risk prediction for a support actuation system. The present invention includes a support actuation system for an automobile having a support actuation module and / or a risk prediction system. The risk prediction system includes a sensor, a processor, and / or a memory. The sensor detects images corresponding to identity data, environment data, event data, and / or behavior data, which are stored in the memory. The memory also stores a database including identities of users, environment risk values, event risk values, and / or behavior risk values. Using the identity data, the environment data, the event data, and / or the behavior data, the processor determines the environment risk value, the event risk value, the behavior risk value, and / or the total risk value for a user. When the total risk value is above a predetermined risk threshold, the support actuation module performs support actuation.
Owner:TOYOTA JIDOSHA KK
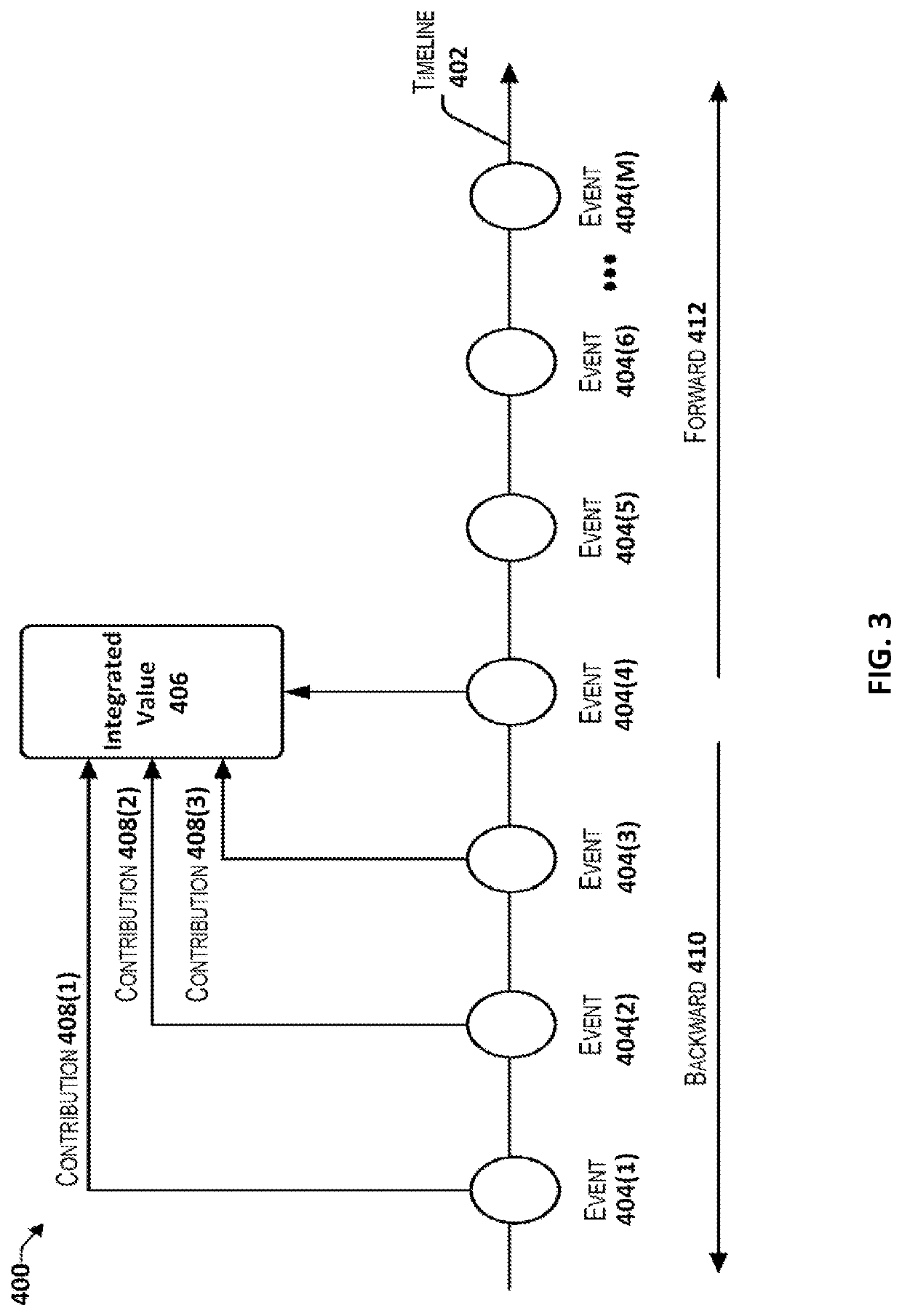
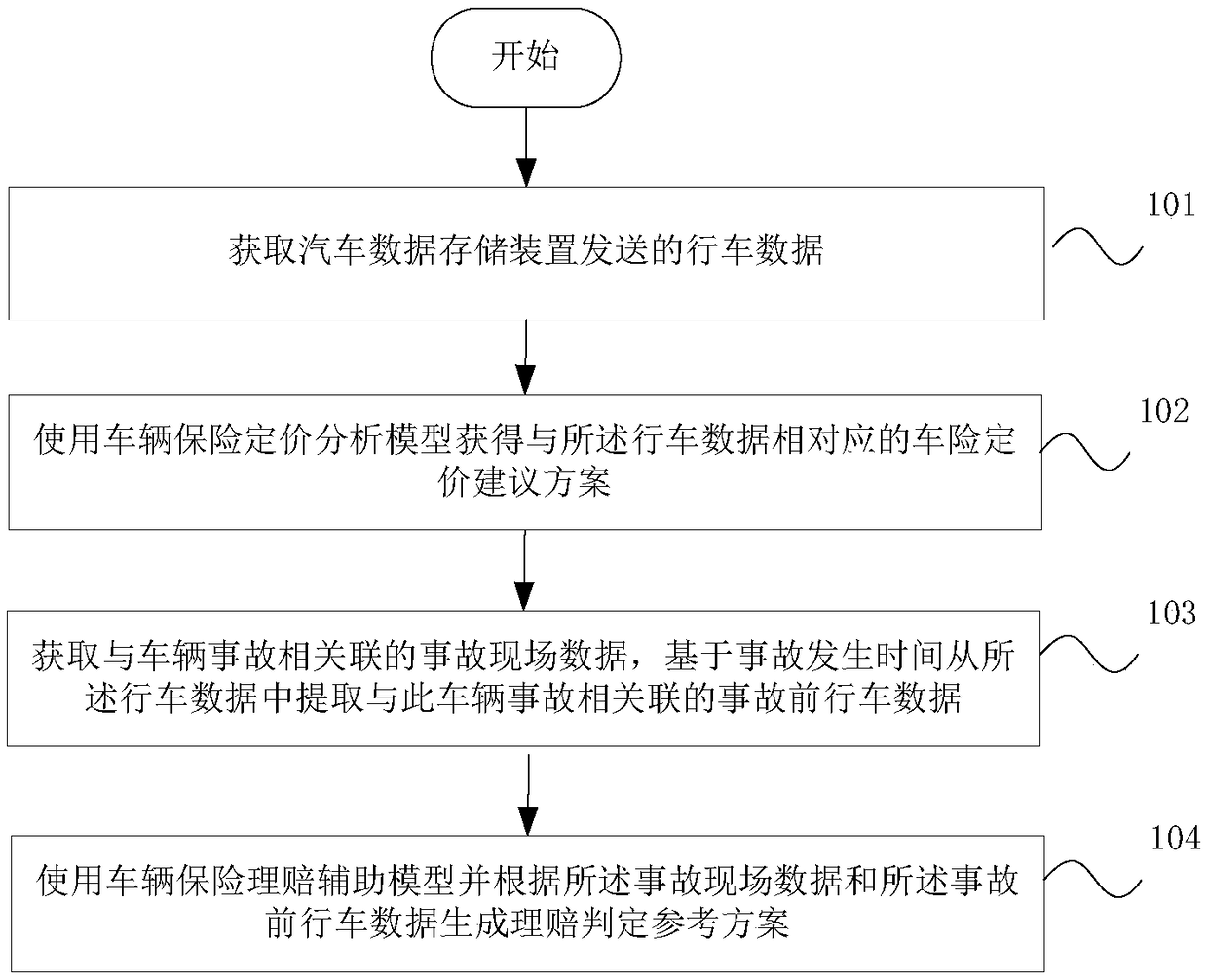
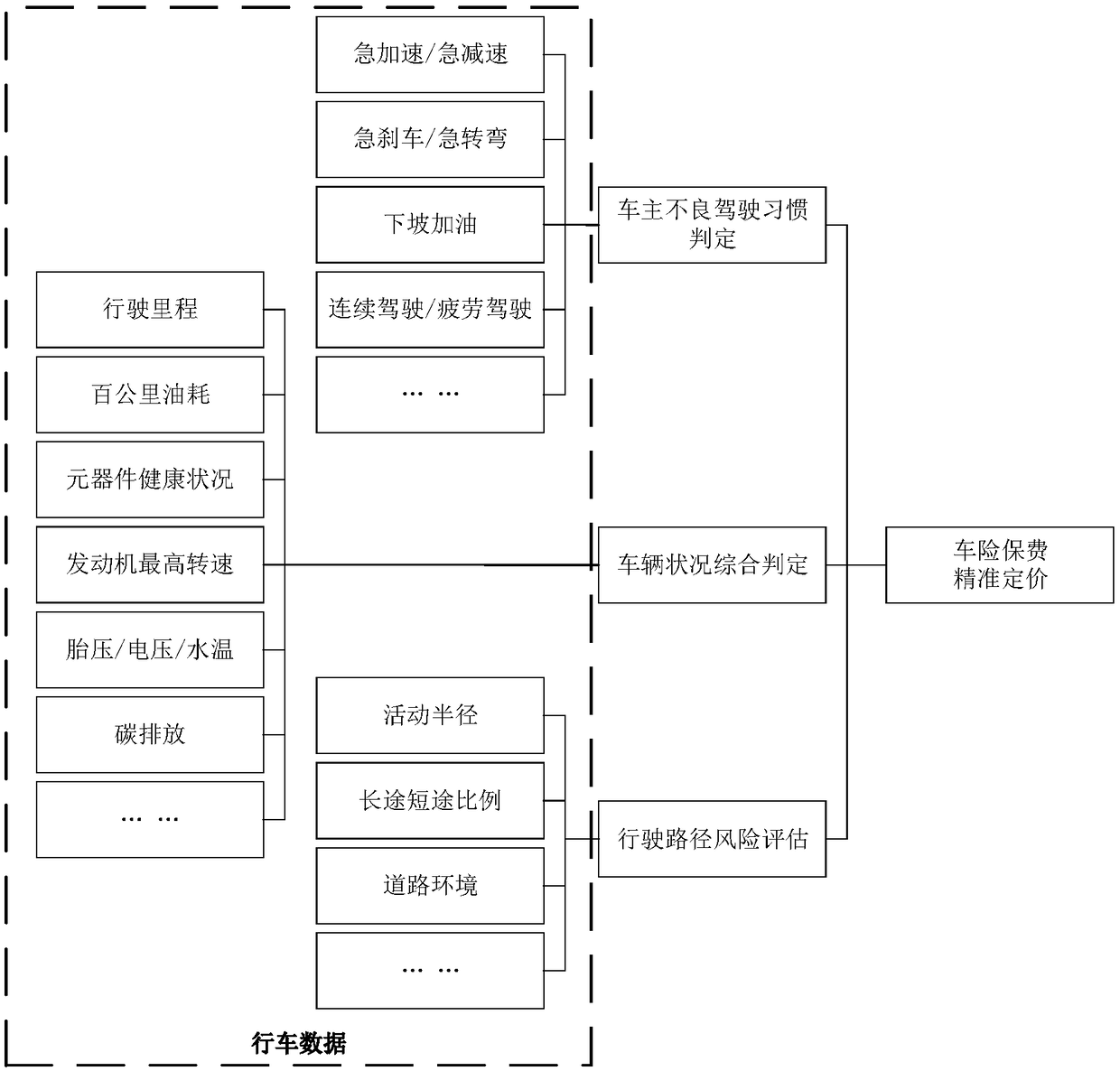
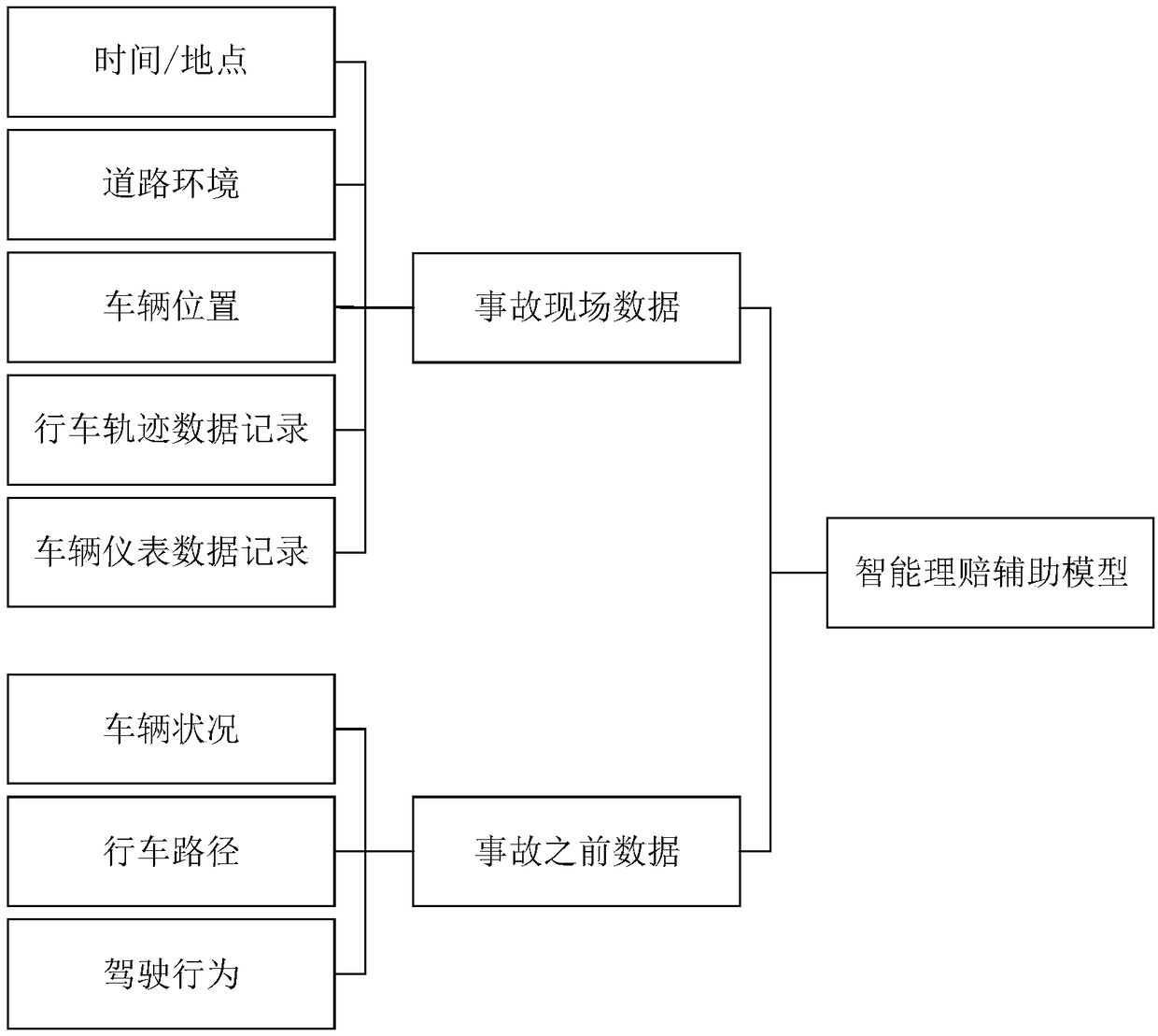
Vehicle insurance service data analysis method and system
InactiveCN108734592AGuaranteed reliabilityAvoid dishonest nodesFinanceInterconnectionAnalysis method
The embodiment of the invention discloses a vehicle insurance service data analysis method and system. The method comprises the steps of obtaining a vehicle pricing suggestion scheme corresponding todriving data through utilization of a vehicle insurance pricing analysis module; obtaining accident site data associated with a vehicle accident, and extracting before-accident driving data associatedwith the vehicle accident from the driving data based on accident occurring time; and generating a claim settlement decision reference scheme according to the accident site data and the before-accident driving data through utilization of a vehicle insurance claims settlement auxiliary model. According to the method and the system provided by the invention, the smart car information interconnection industry-oriented vehicle insurance data analysis method based on a safety multiparty computing system is provided; the reference for vehicle insurance precise pricing can be provided; a vehicle before-event risk threshold is computed; an accident process and an after-event site are analyzed; the reference for precise claim settlement decision can be provided; and the data is stored and verifiedthrough adoption of a blockchain technology, so the data is prevented from being tampered or disturbed.
Owner:深圳市图灵奇点智能科技有限公司 +1
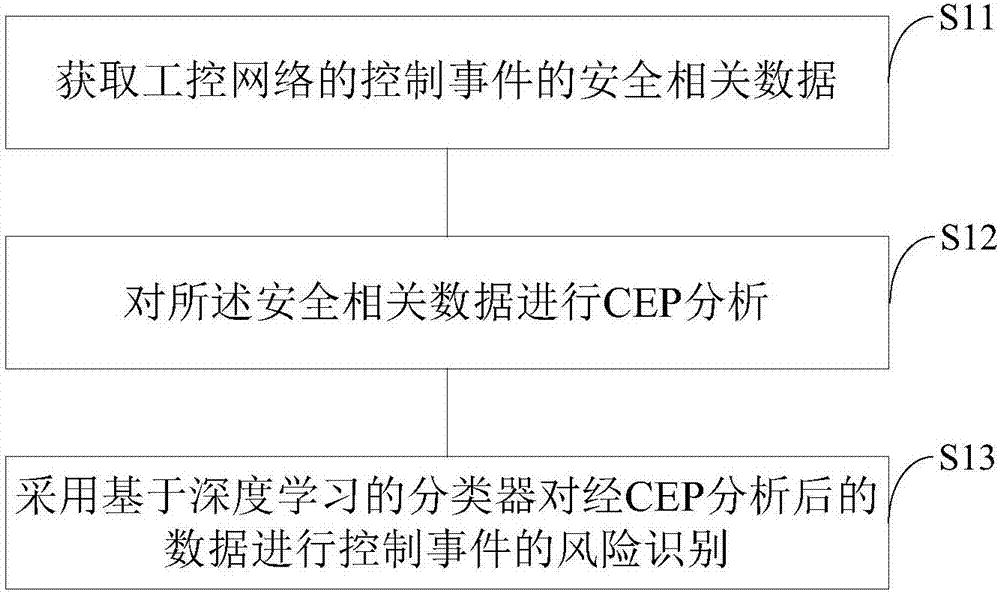
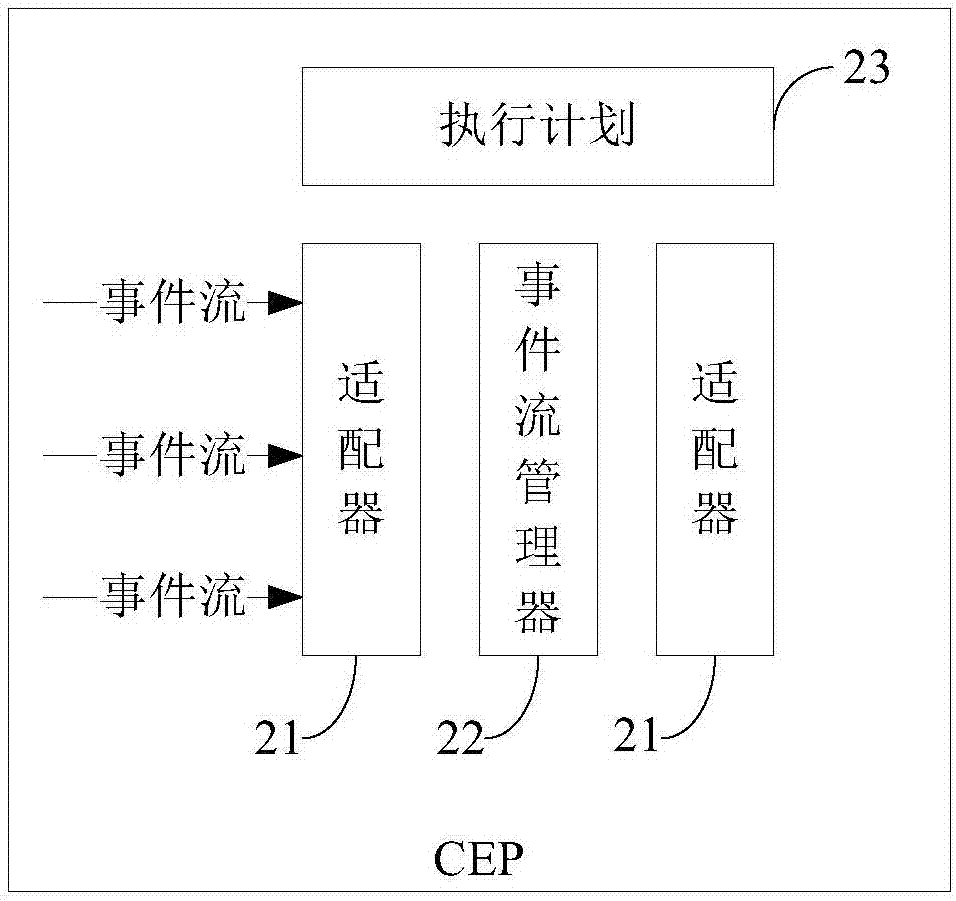
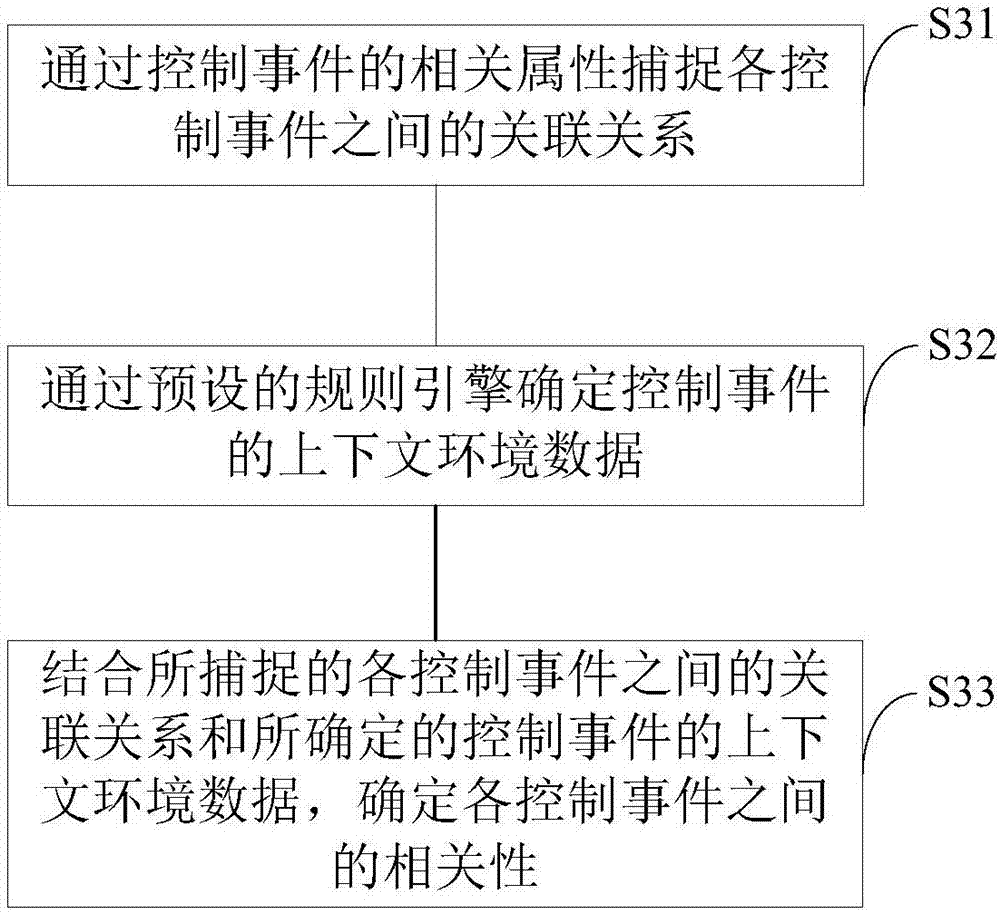
Safety pre-warning method and system for industrial control network
PendingCN107203199ALower latencyFast response timeElectric testing/monitoringReal-time dataComplex event processing
The invention relates to a safety pre-warning method and system for an industrial control network. The safety pre-warning method for the industrial control network comprises steps as follows: acquiring safety related data of a control event of the industrial control network; performing CEP (complex event processing) analysis on the safety related data; adopting a deep learning based classifier to perform control event risk identification on the data subjected to CEP analysis. The safety pre-warning method and system for the industrial control network can be deployed in the resource-constrained industrial control field and are applicable to a single-node or multi-node deployment environment, and the deployment way is more flexible. Furthermore, according to the method deployed in the industrial control field, network delay is reduced, processing response speed of real-time data is increased, and risk pre-warning capacity is improved. Besides, the deep learning based classifier is adopted for risk identification, accuracy rate of identification is higher, and efficiency of risk identification is substantially improved through combination of CEP analysis and deep learning scheme.
Owner:BEIJING KUANGEN NETWORK TECH
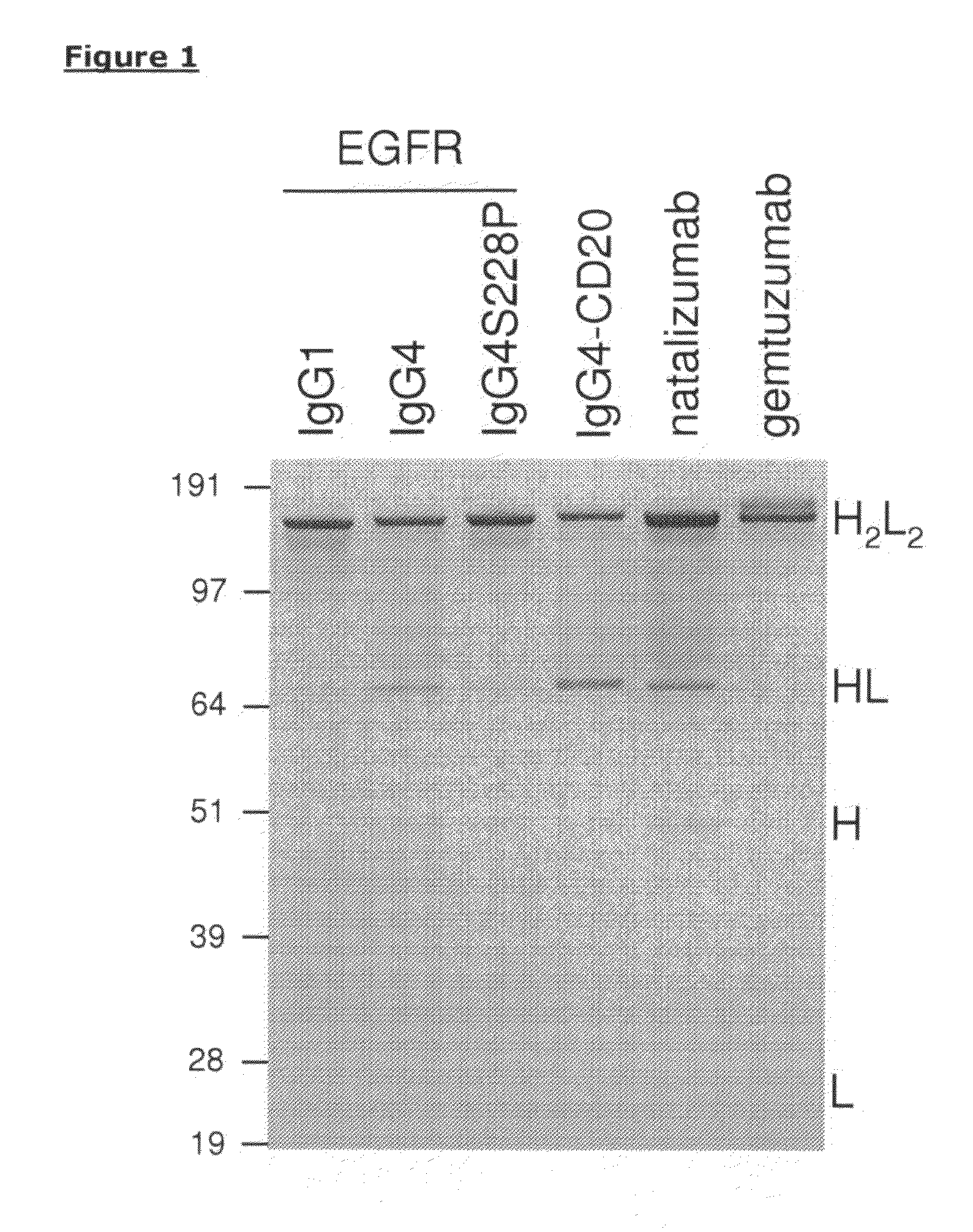
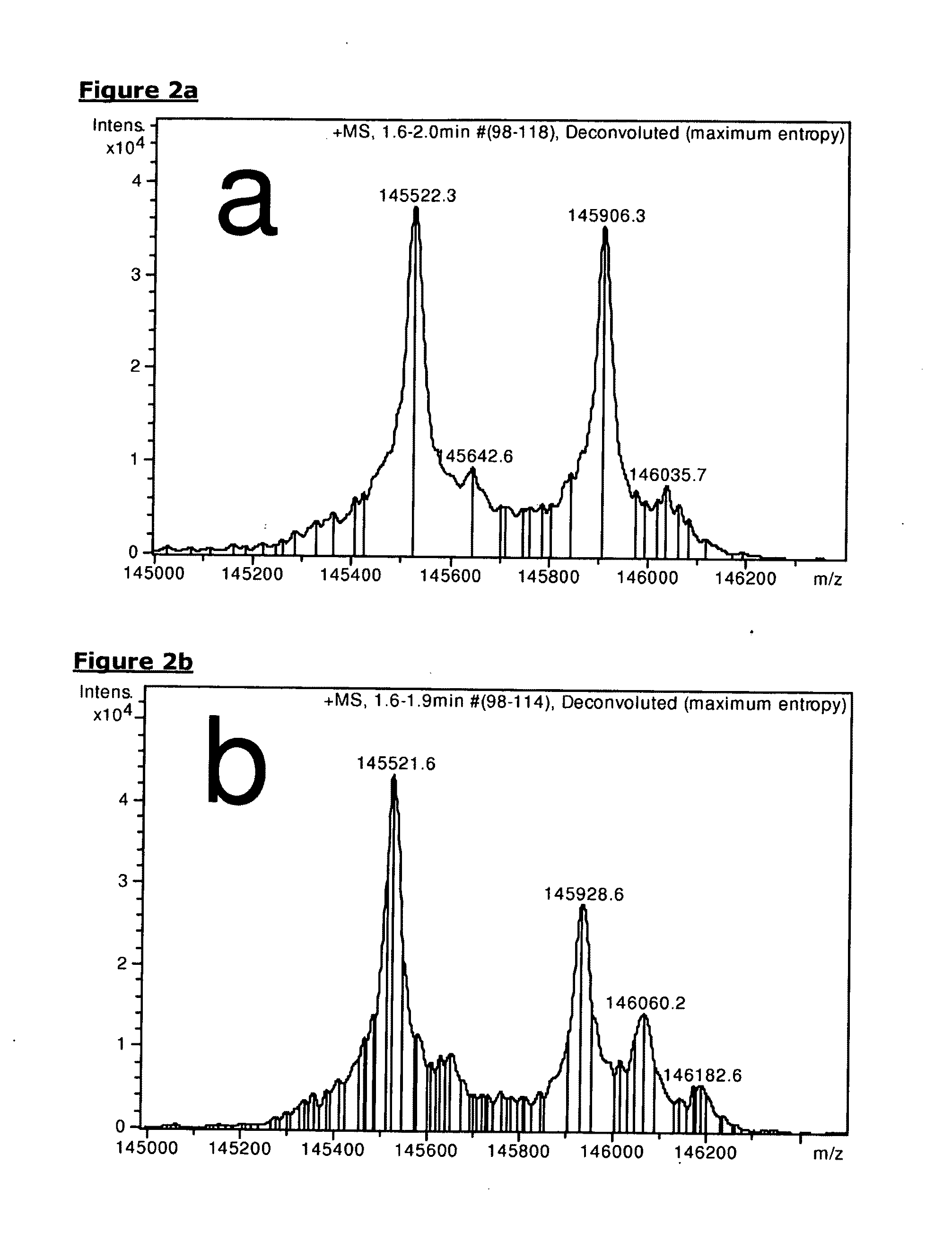
Methods for assessing the risk of adverse events upon treatment with igg4 antibodies
InactiveUS20110086366A1Significant populationHigh infection rateDisease diagnosisBiological testingAntigenTherapeutic antibody
The invention relates to methods and kits for assessing the risk, for an individual, of developing an adverse event upon treatment with a therapeutic antibody which is capable of Fab-arm exchange, said method comprising the steps of: a) providing a sample from an individual who is a candidate for treatment with said therapeutic antibody, b) assaying said sample for the presence of circulating IgG4 antibodies that binds an antigen known or suspected to be associated with a causative agent of said adverse event, and c) assessing, on the basis of the outcome of the assay of step b), the risk that the individual will develop said adverse event upon treatment with the therapeutic antibody, wherein the risk of development of said adverse event increases with increased level of said circulating IgG4 antibodies.
Owner:GENMAB AS
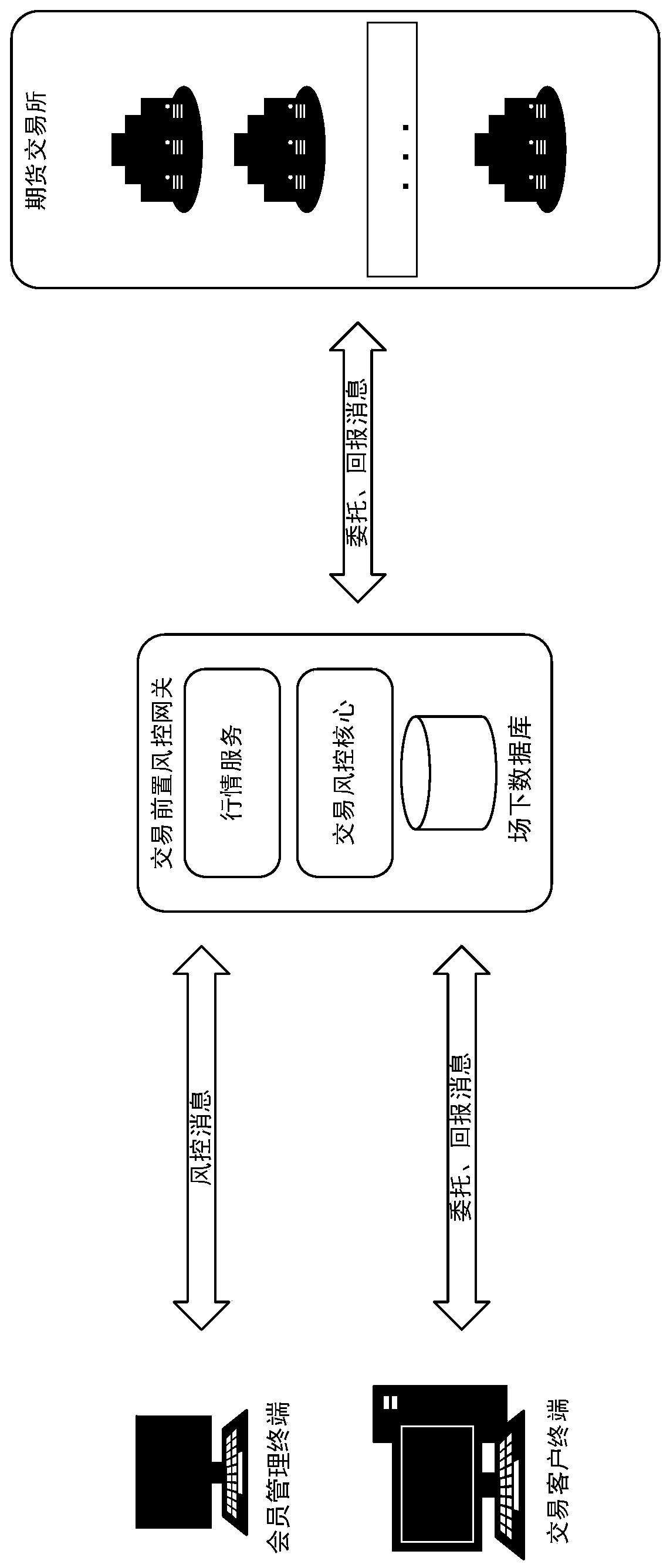
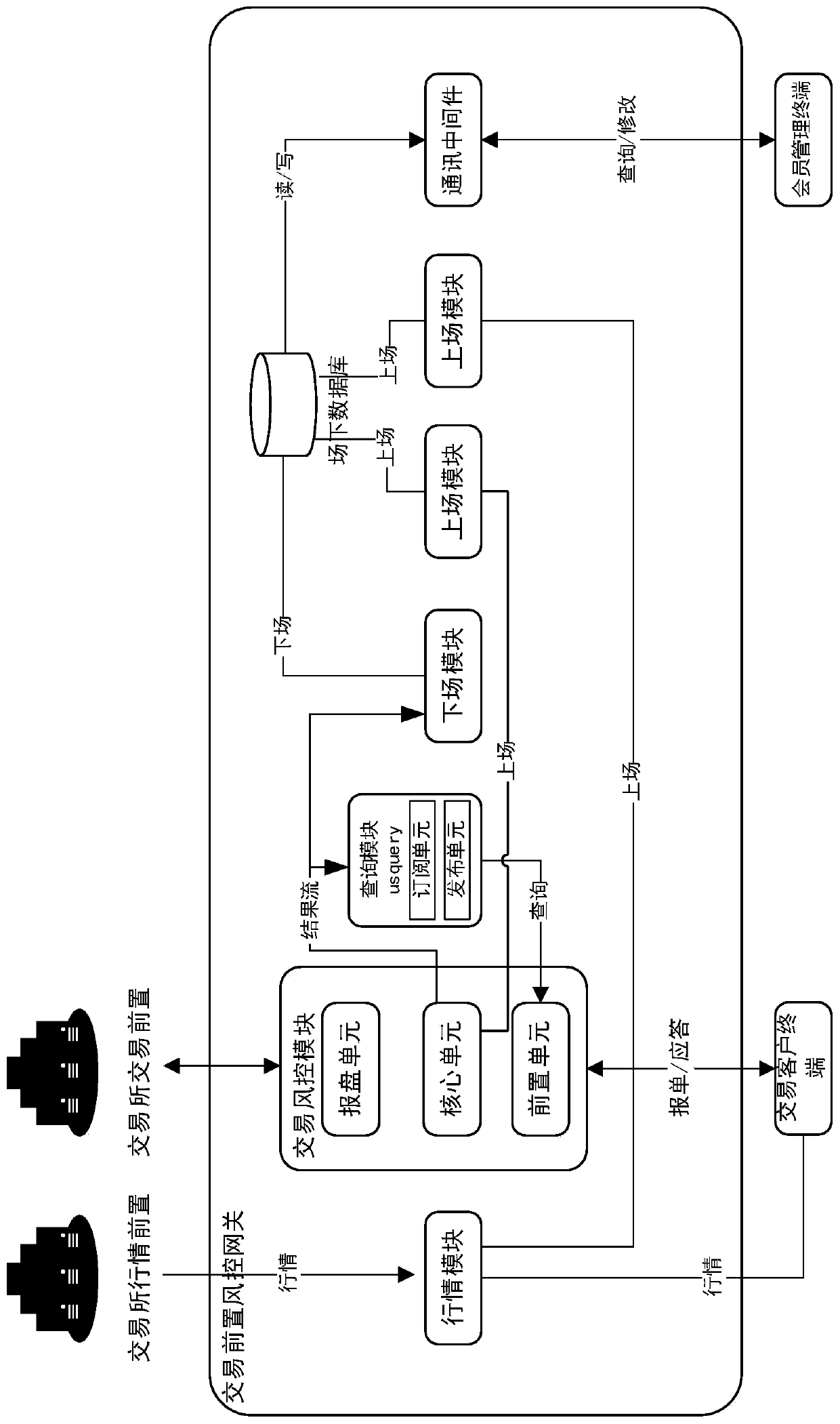
Financial futures trading system
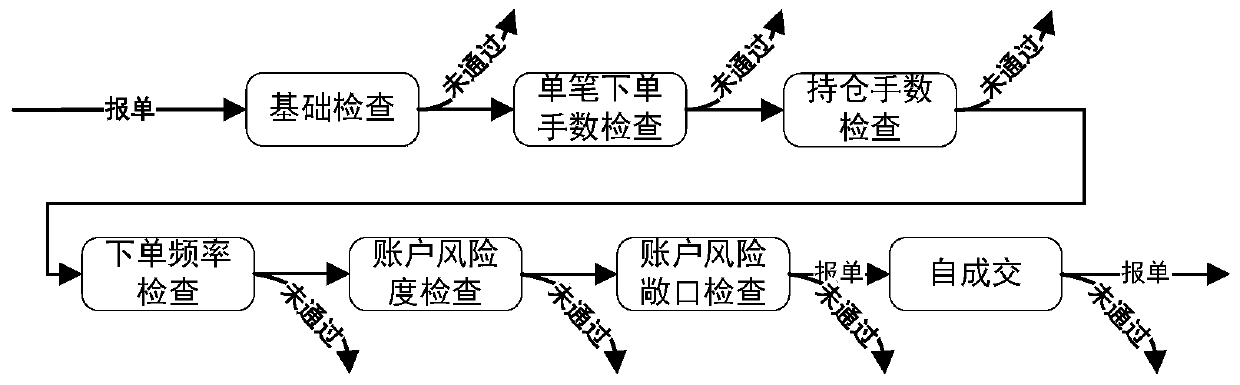
ActiveCN110390596AImprove transaction speedTaking into account compliance and risk controlFinanceResourcesRisk ControlIn-memory database
The invention discloses a financial futures trading system, which improves the trading speed, gives consideration to compliance risk control, provides rich pre-event and post-event risk control indexes for futures companies, and quickly controls risks. According to the technical scheme, the system comprises a member management terminal which is a client used by a broker company and is used for managing system and client information, checking real-time transaction data, displaying real-time data in a disk and setting risk control parameters; a transaction client terminal which is an order placing terminal for investors, and is used for reporting orders, withdrawing orders and querying funds and positions, and receiving market information of transaction products; and a preposed transaction risk control gateway which is deployed in a transaction channel and risk control preposed channel of the broker company, wherein the preposed transaction risk control gateway adopts a memory database for real-time calculation and quick serach, thus achieving quick data transmission between the transcation client terminakl and a transcation dealing system of an exchange. The connection between the preposed transaction risk control gateway and a physical database enables the broker company to control transcation risk and manage data in a real-time manner with the client management terminal.
Owner:上海金融期货信息技术有限公司
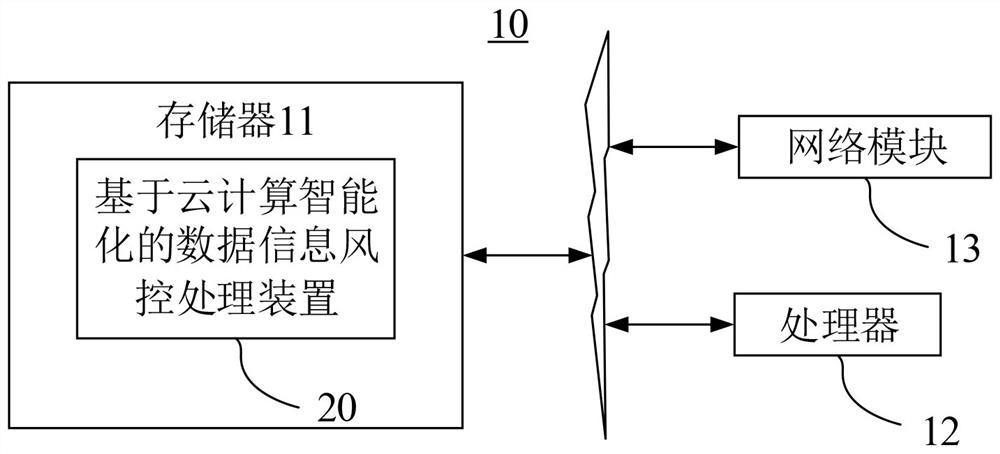
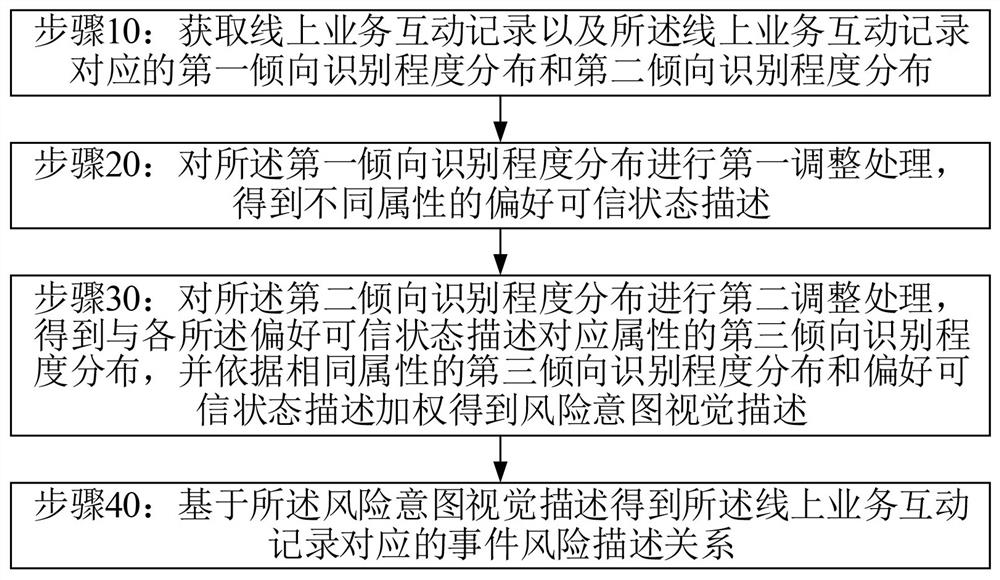
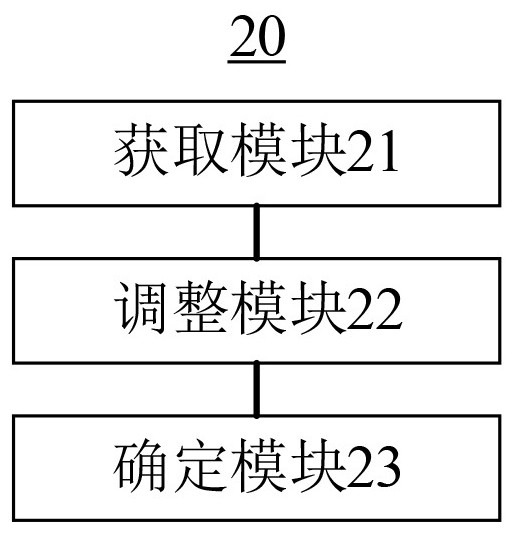
Data information risk control processing method and system based on cloud computing intelligence
InactiveCN113535825AImprove trust indexAccurate and reliable risk control processingForecastingData miningData informationNetwork address
By applying a data information risk control processing method and system based on cloud computing intelligence, an event risk description relation which covers more comprehensive and more accurate information can be obtained; and then event detection and analysis on a risk prediction level are carried out on related information such as business behavior operation intentions and business equipment network addresses of business participants in the obtained online business interaction records, and meanwhile, information covered by the event risk description relationship is more comprehensive and more accurate. When event detection and analysis at a risk prediction level are carried out, deep mining and analysis of various risk factors can be carried out from a global level through an event risk description relationship, so accurate and reliable risk control processing for online business interaction records is ensured, and thus, the risk control efficiency is improved. According to the embodiment of the invention, complete and reliable raw material information (event risk description relation) can be provided for risk control processing, so the trust index of business risk control processing is improved.
Owner:东莞市道滘钒一电子软件技术服务部
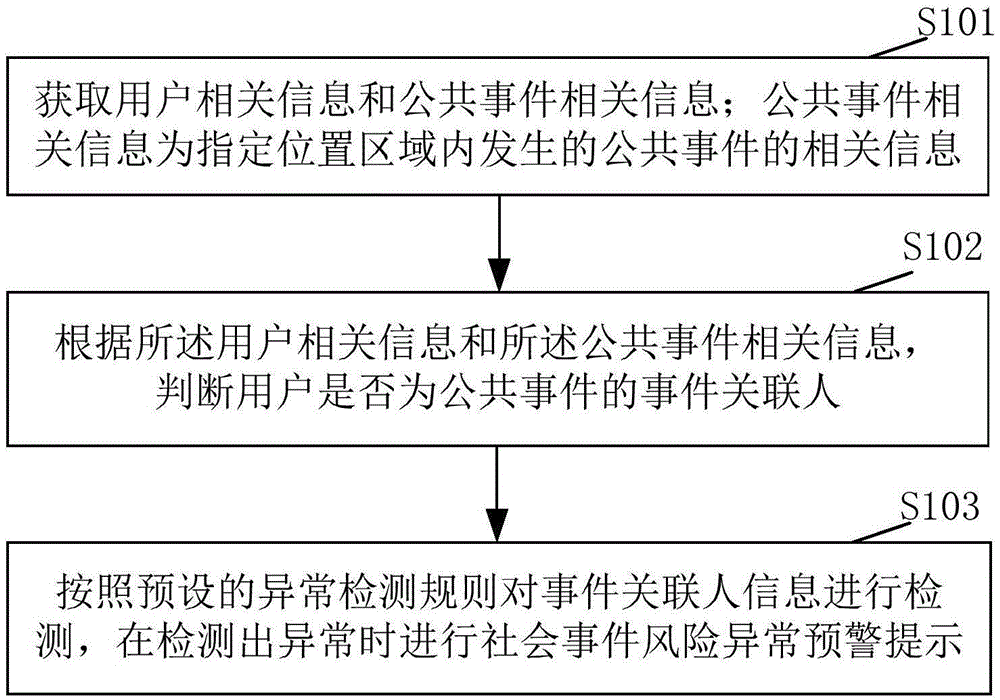
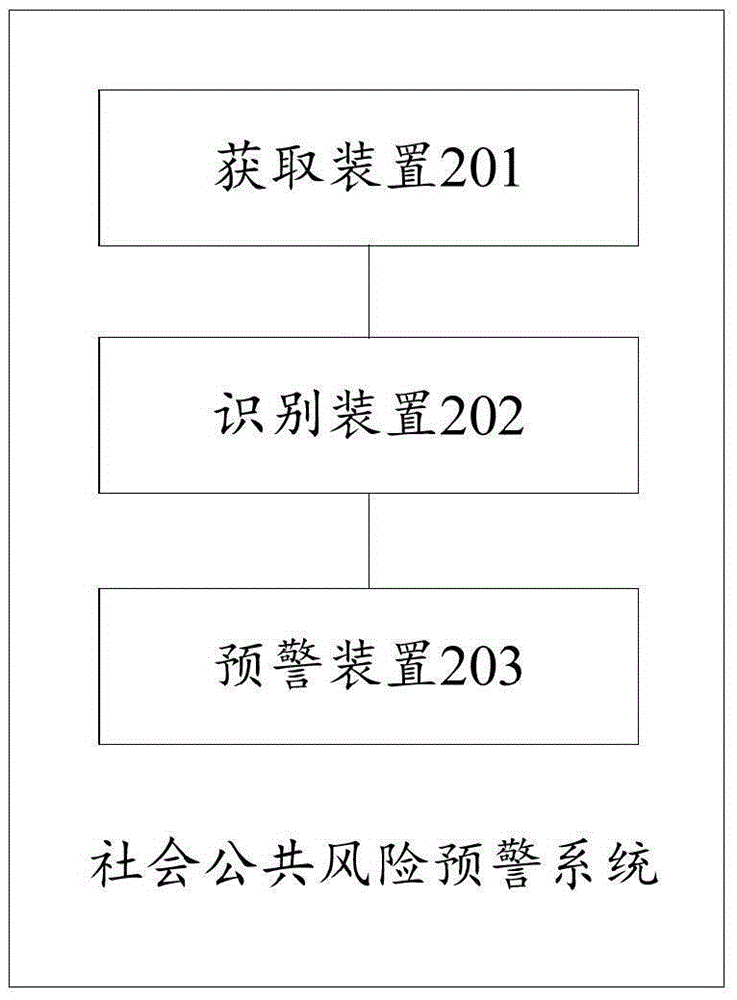
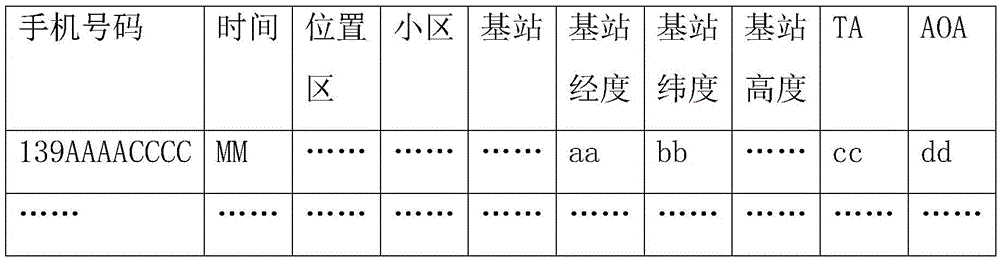
Risk early-warning method and system for social public event
The invention discloses a risk early-warning method and system for a social public event, and the method comprises the steps: obtaining related information of telecommunication behaviors of a user and the related information of the public event; judging whether the user is an event affiliated person of the public event or not according to the related information of telecommunication behaviors of the user and the related information of the public event; carrying out the detection of the event affiliated person according to a preset abnormality detection rule, and carrying out the risk abnormality early-warning prompt of the social public event when an abnormality is detected. The method can maintain the social stability.
Owner:BOCO INTER TELECOM
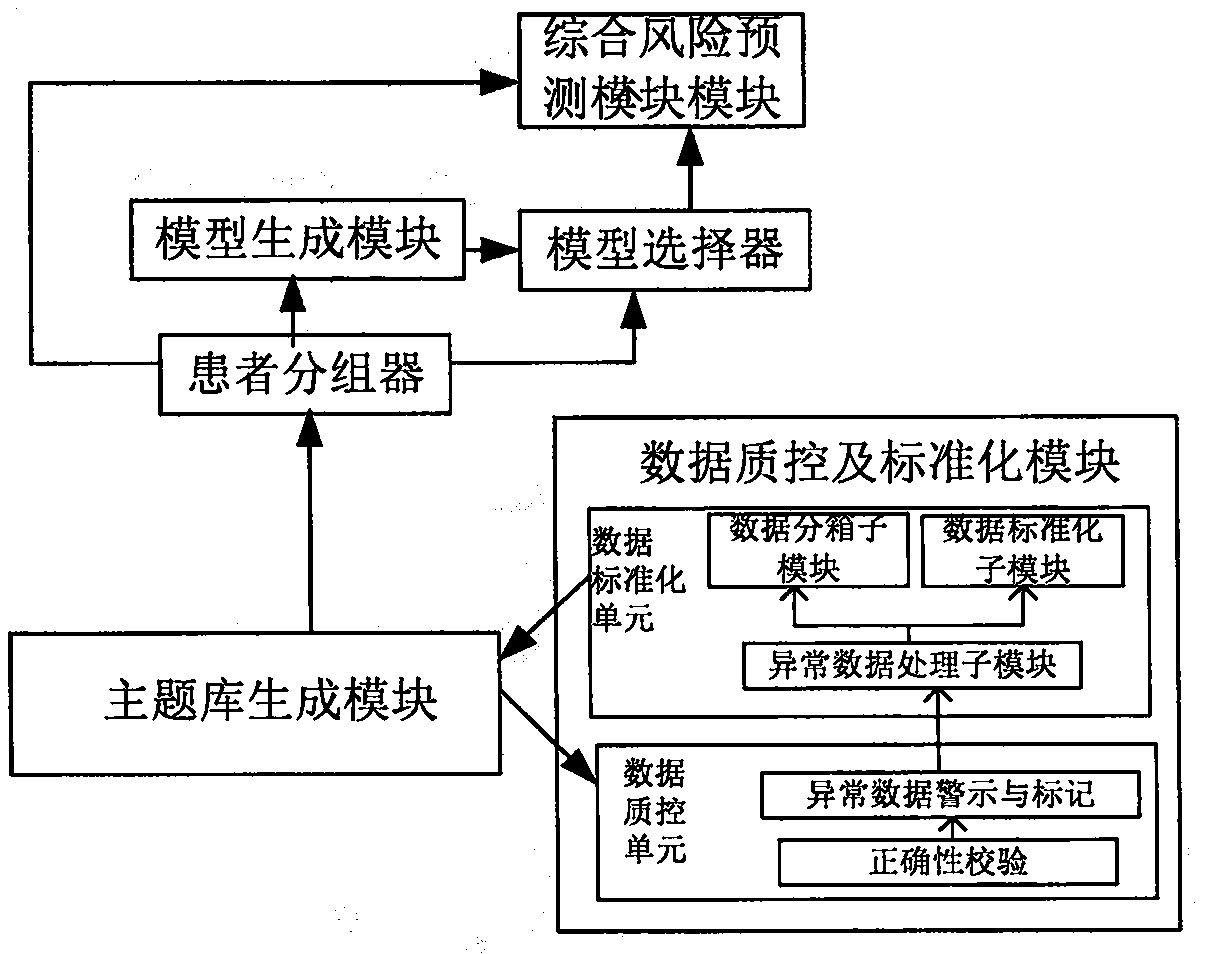
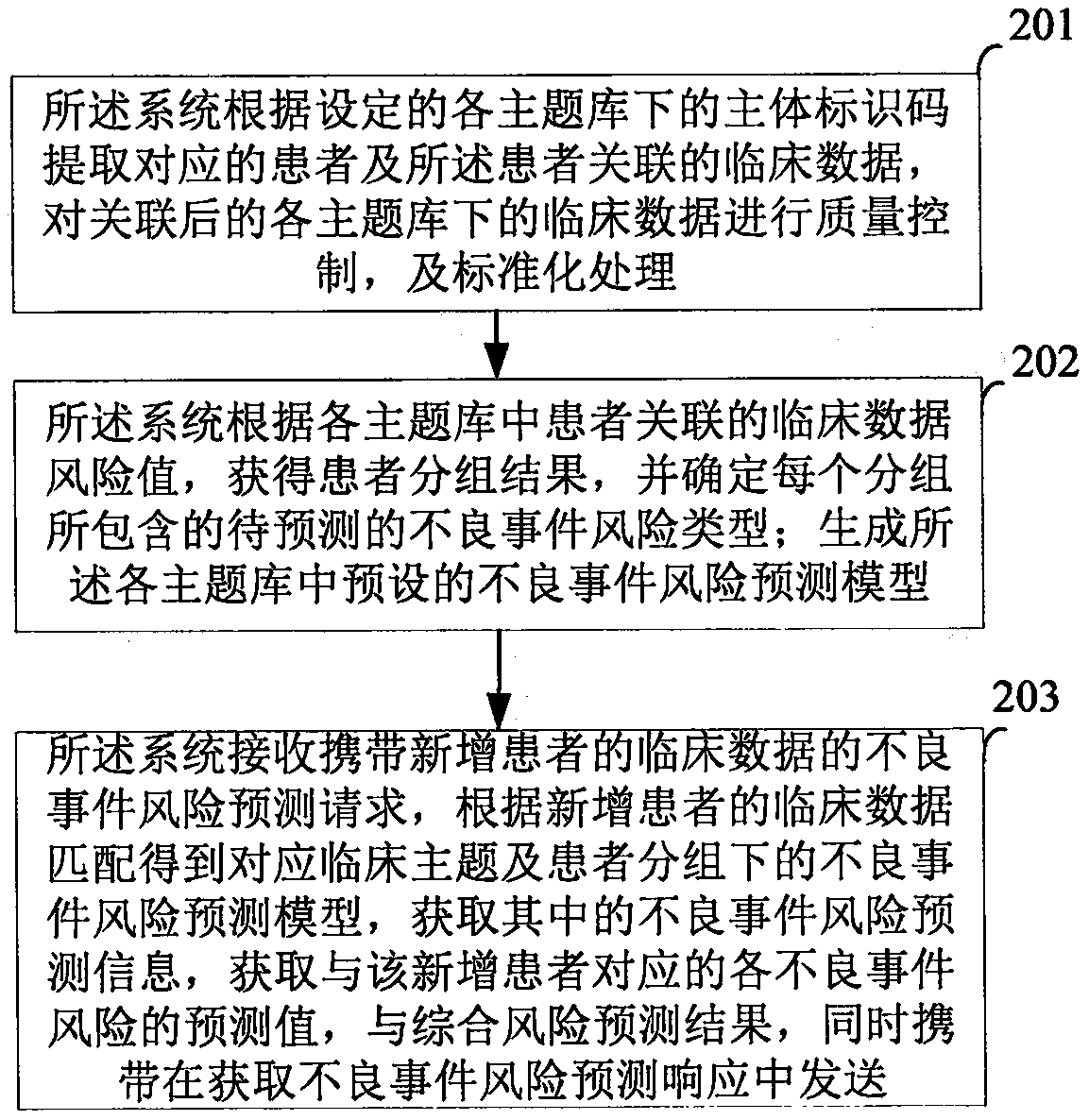
Bad event risk prediction system and method
ActiveCN110175697ARealize unified managementForecastingHealthcare resources and facilitiesQuality controlPrediction system
The embodiment of the invention discloses a bad event risk prediction system and method, and the method comprises the steps: building a bad event risk prediction system at the network side of a medical system, enabling the system to obtain clinical data, and building a bad event risk prediction model of each clinical theme according to the quality control, standardization and grouping processing of the clinical data; when the system receives a bad event risk prediction request carrying clinical data of a patient, obtaining the adverse event risk prediction information therein, and obtaining the risk prediction value, performing comprehensive evaluation according to the adverse event risk prediction information to obtain a prediction result, and carrying the prediction result in the acquisition adverse event risk prediction response. Therefore, the embodiment of the invention realizes the unified management of the clinical data, and provides the risk prediction information of the adverse event of the patient according to the clinical data.
Owner:FUWAI HOSPITAL CHINESE ACAD OF MEDICAL SCI & PEKING UNION MEDICAL COLLEGE
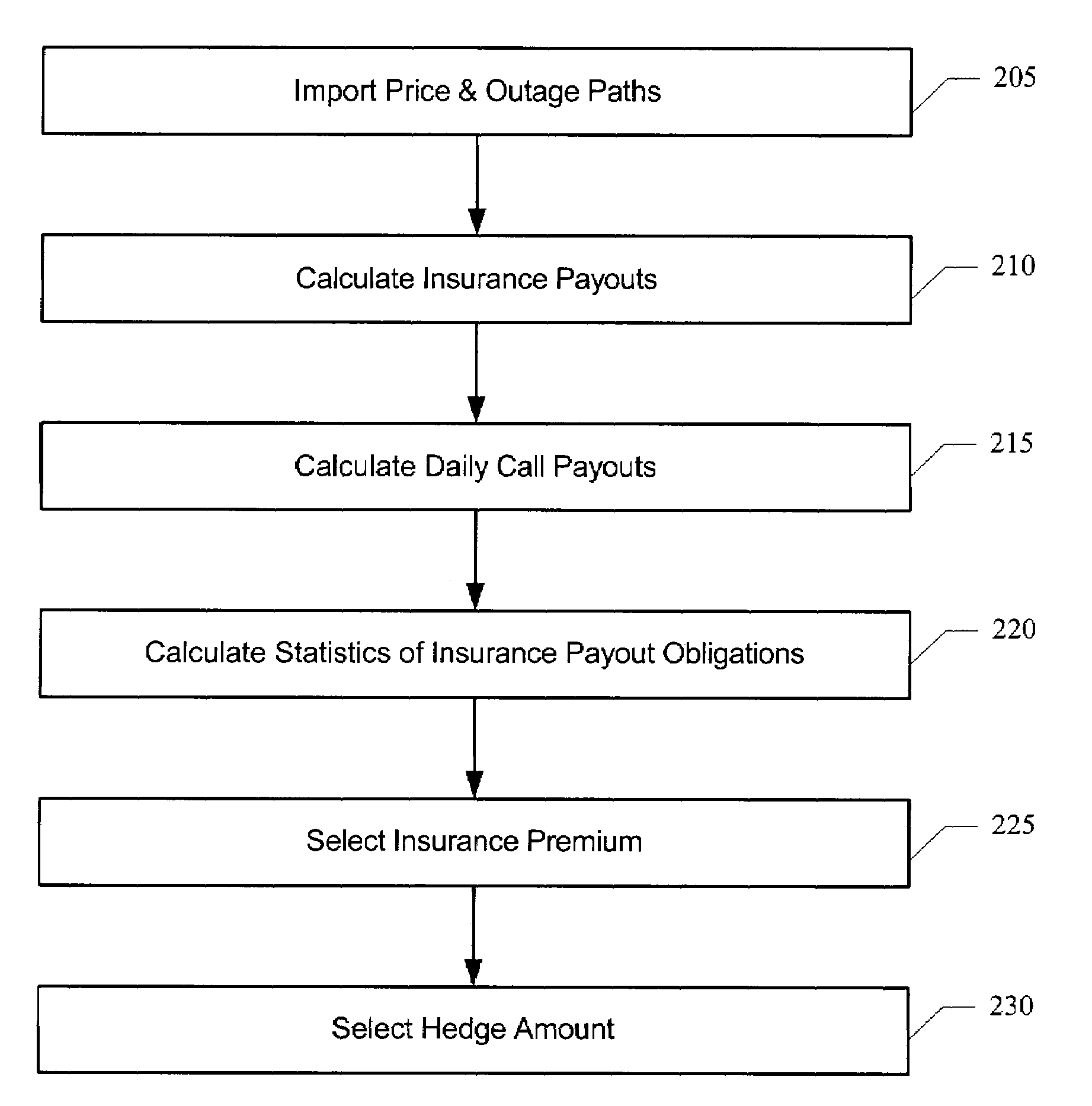
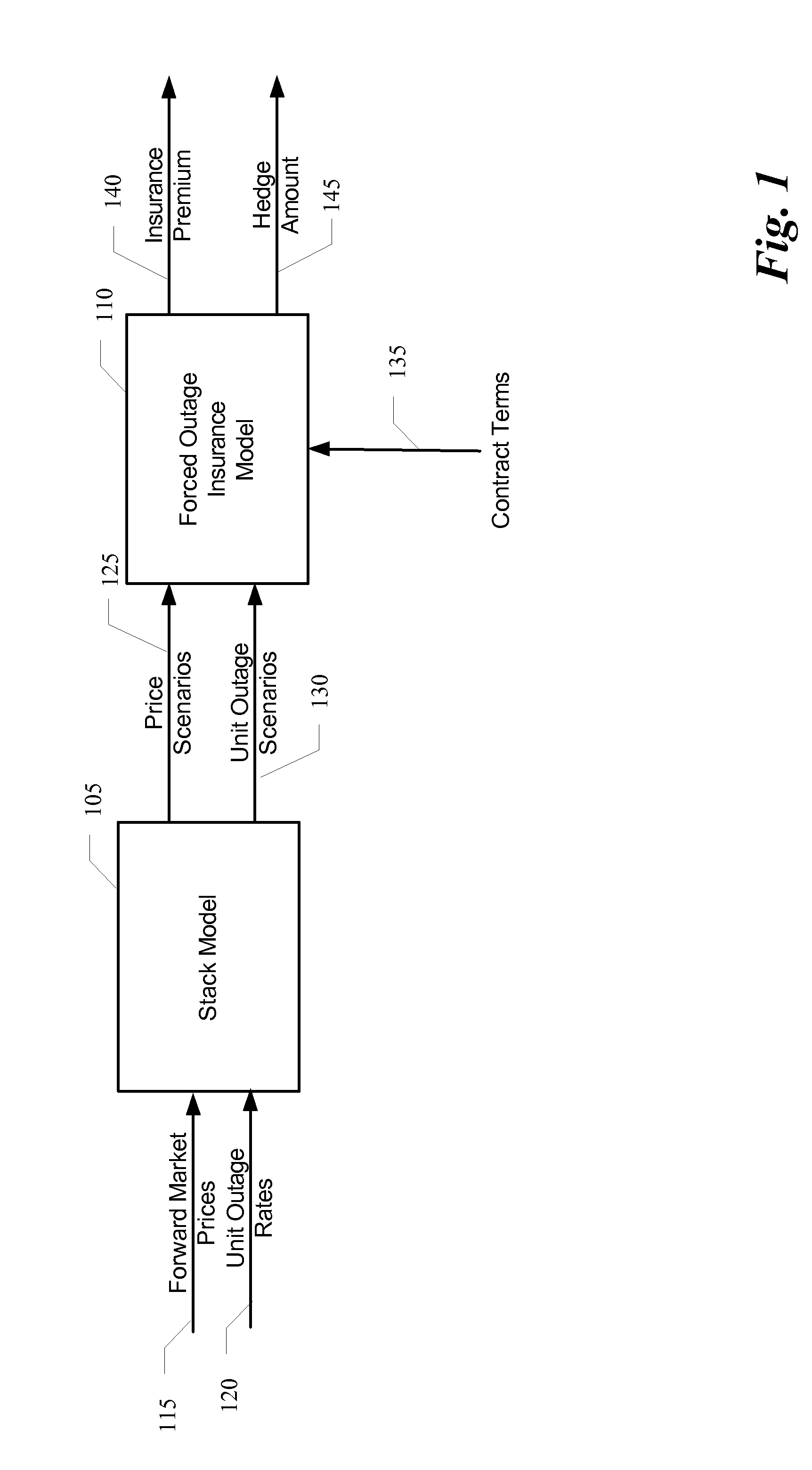
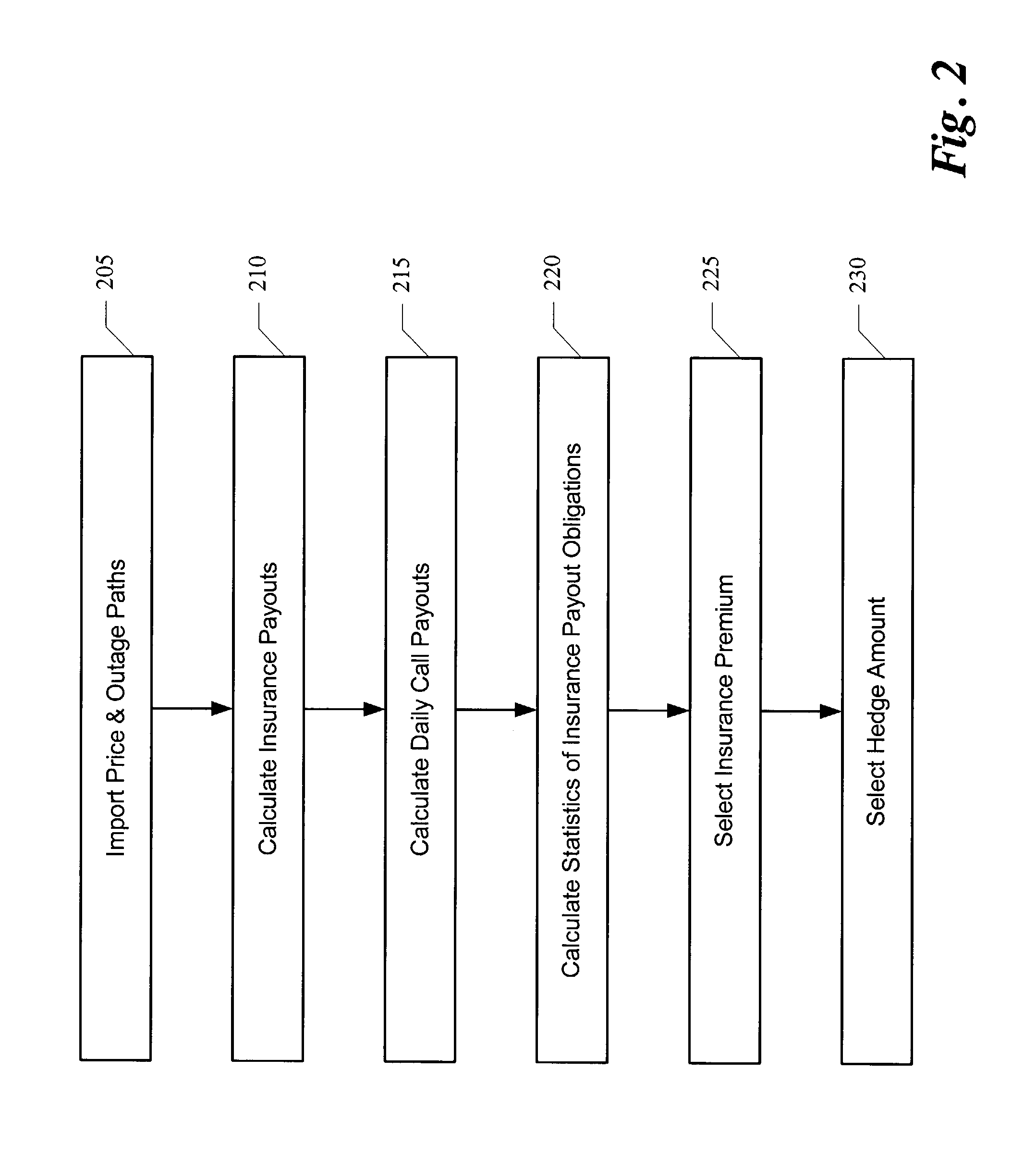
Method for producing a superior insurance model for commodity event risk
Owner:MIRANT INTELLECTUAL ASSET MANAGEMENT & MARKETING
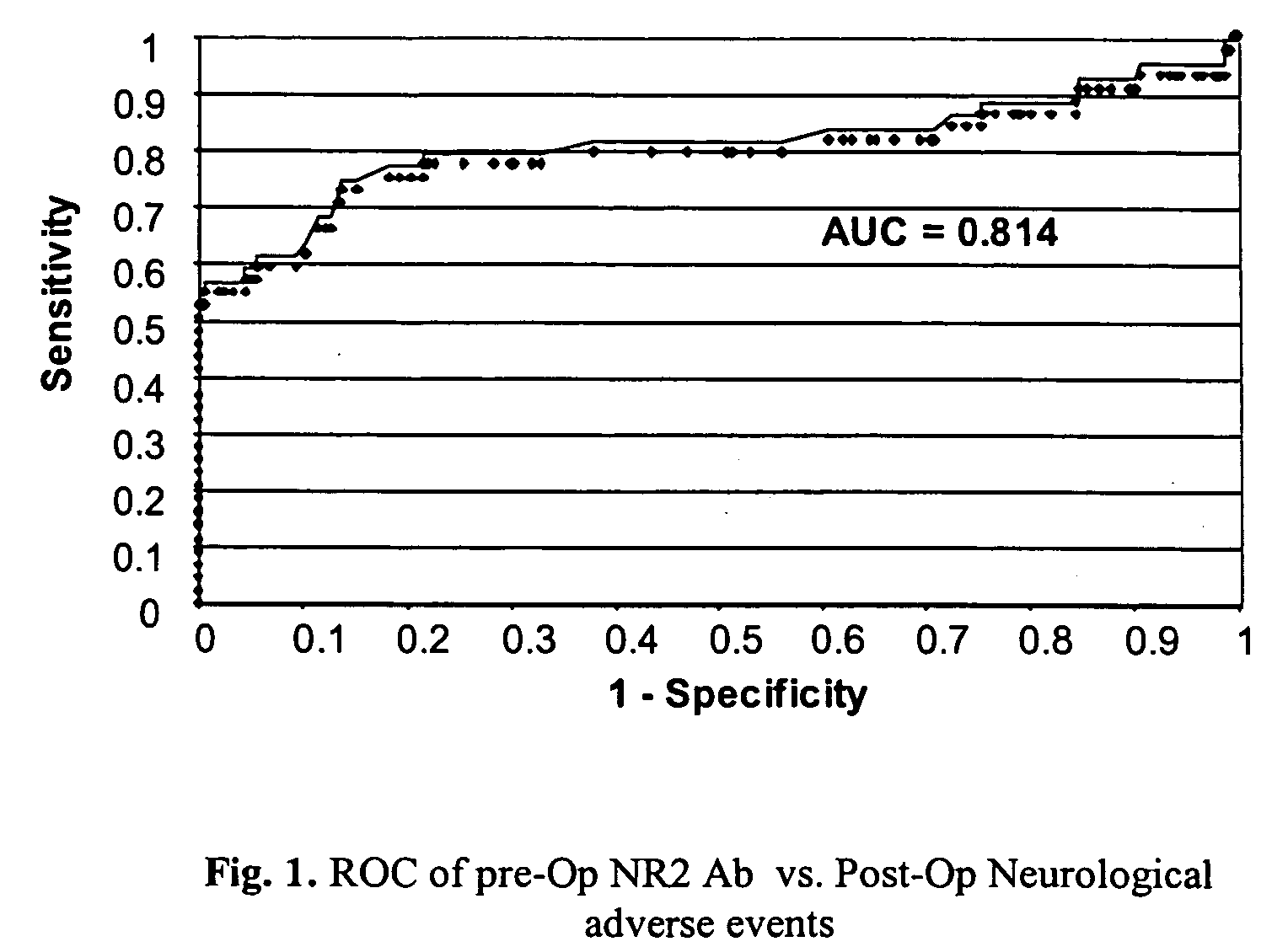
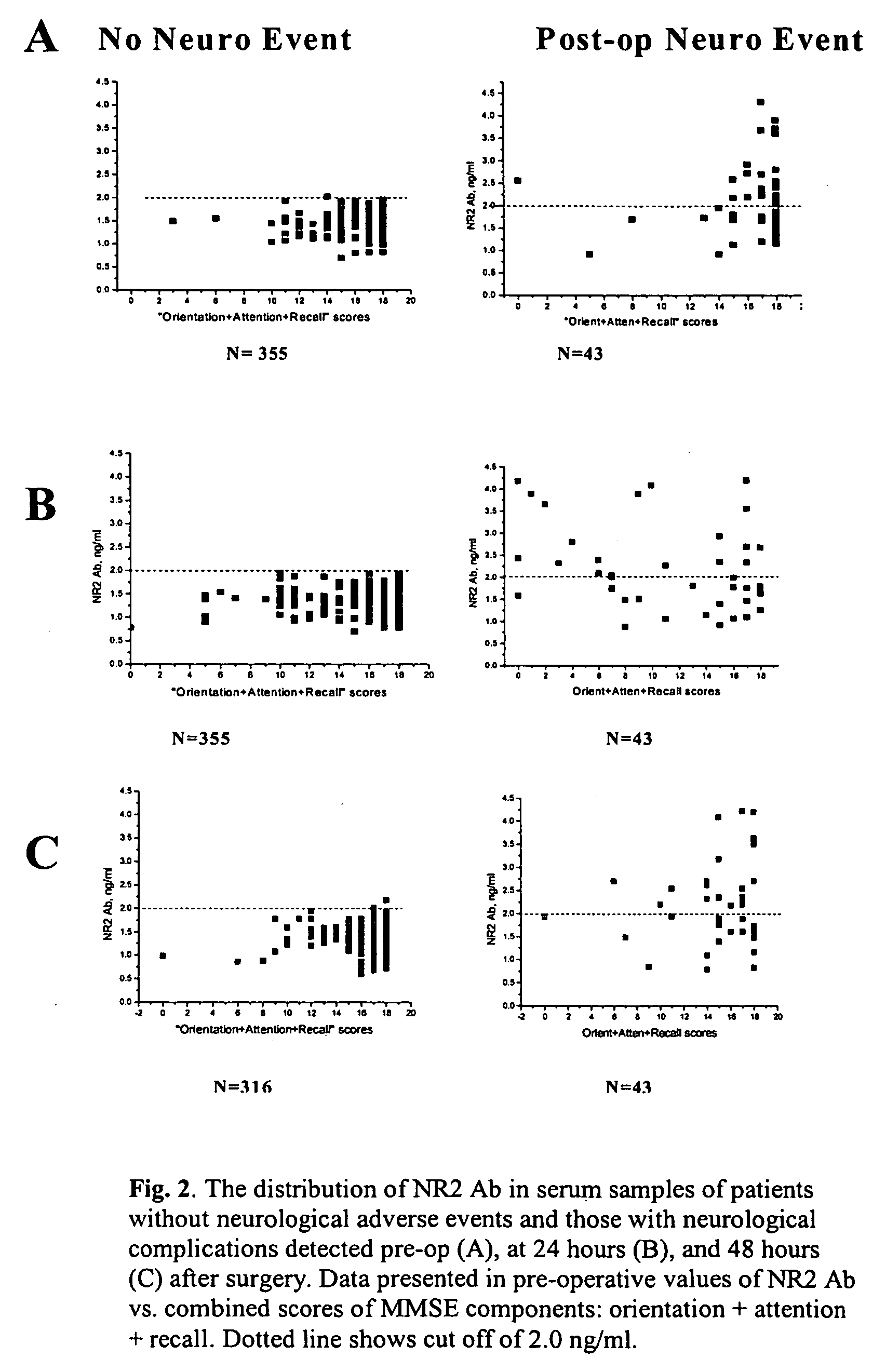
Ischemic biomarkers and their use to predict adverse neurological events from surgery
InactiveUS20060257943A1Accurate predictionValid choiceDisease diagnosisBiological testingNR1 NMDA receptorPredictive methods
Methods are provided for predicting the occurrence of adverse neurological events from surgery. Such adverse events include, for example, stroke, delirium and transient ischemic attack (TIA). The methods are based on the discovery that levels of circulating cerebral NMDA receptor peptides and antibodies can be used to identify patients who are likely to suffer from an adverse neurological event. Also provided are diagnostic procedures for practicing the predictive methods of the current invention, and interventional strategies for reducing the risk of adverse neurological events from surgery.
Owner:CIS BIOTECH
Method and system for risk prediction for a support actuation system
Owner:TOYOTA JIDOSHA KK
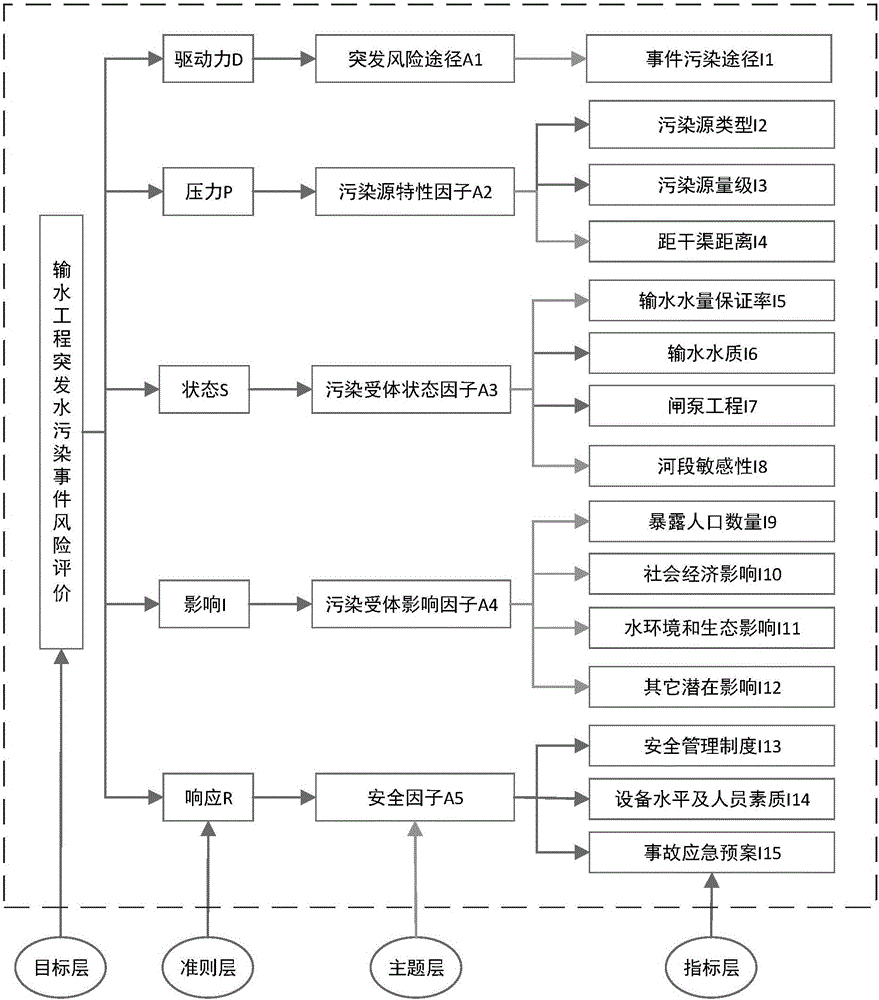
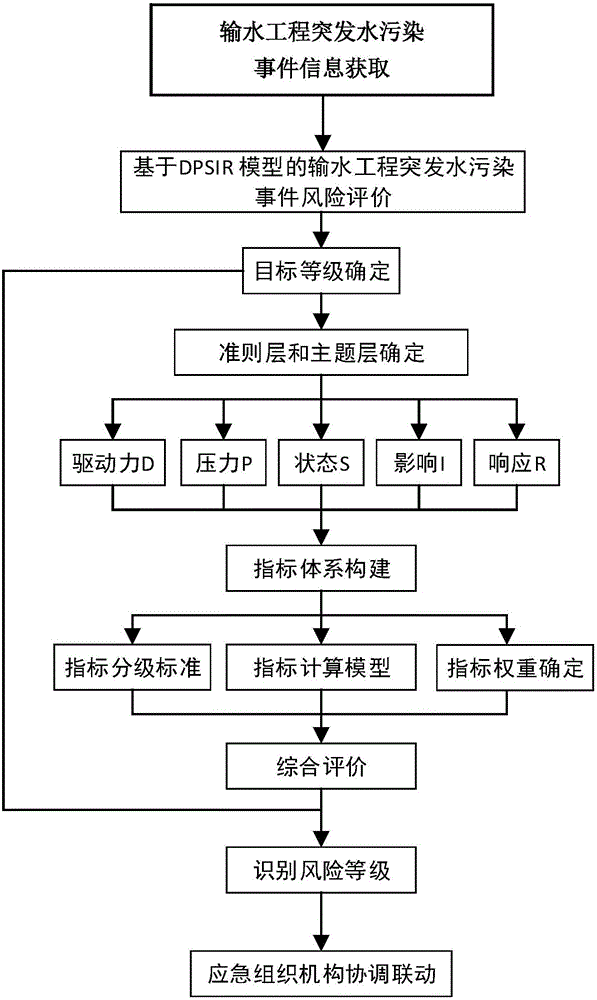
Sudden water pollution event risk evaluation method for water conveyance project
InactiveCN105930975AAccurate risk assessmentTimely and effective emergency measuresGeneral water supply conservationResourcesInformation supportComputational model
The invention discloses a sudden water pollution event risk evaluation method for a water conveyance project. The method comprises the following steps: to begin with, with characteristics of the water conveyance project and characteristics of sudden water pollution events and influence thereof being taken into comprehensive consideration, and based on a DPSIR module, an index system is established, and risk evaluation indexes covering driving force, pressure, state, influence and response five aspects, index grading standard and an index calculation model are provided; a risk evaluation index weight determination method based on an analytic hierarchy process is provided; and finally, overall influence of the sudden water pollution event on the water conveyance project and risk grade are determined through a comprehensive evaluation method. The method and the risk grade evaluation result can effectively judge the influence degree of the sudden water pollution events on the water conveyance project; a more accurate risk evaluation system is established; and the method can provide decision information support for making scientific and effective early warning and preplanning of management personnel of the water conveyance project, and has wide practical prospect.
Owner:TIANJIN UNIV
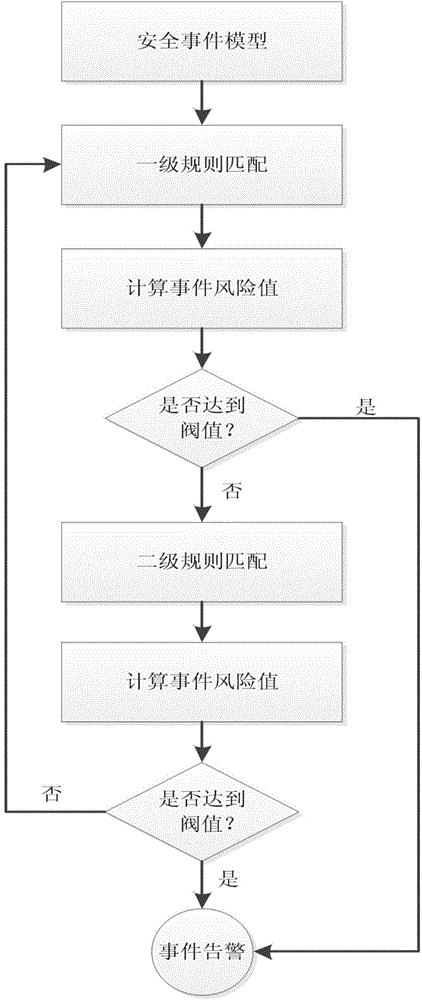
Network security correlation analysis method based on complex event processing
InactiveCN104468545AUseful for detecting potential threatsTransmissionComplex event processingCorrelation analysis
The invention belongs to the field of network security technologies, and particularly relates to a network security correlation analysis method based on complex event processing. Different events from different network even sources are correlated and analyzed. According to the network security correlation analysis method, threatening influences on a whole network by security events and considerations given to importance of directly attacked equipment or software are taken into account, multi-level analysis is performed on security events generated by serial operation on the same object through a multi-level rule, and all security event risk values can be accumulated to achieve the purpose of integrally analyzing the object. The multi-level correlation matching mode is adopted, on one hand, the network security correlation analysis method meets the requirement of the logic mode that an attacker generally needs multiple steps when initiating attacks, on the other hand, risk accumulation summation is performed on the multiple events, and complex relations between the events are comprehensively considered. In this way, potential threats in the network are easily detected so that early warning and processing can be performed to protect the network.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND +1
Risk registering method of petrochemical device
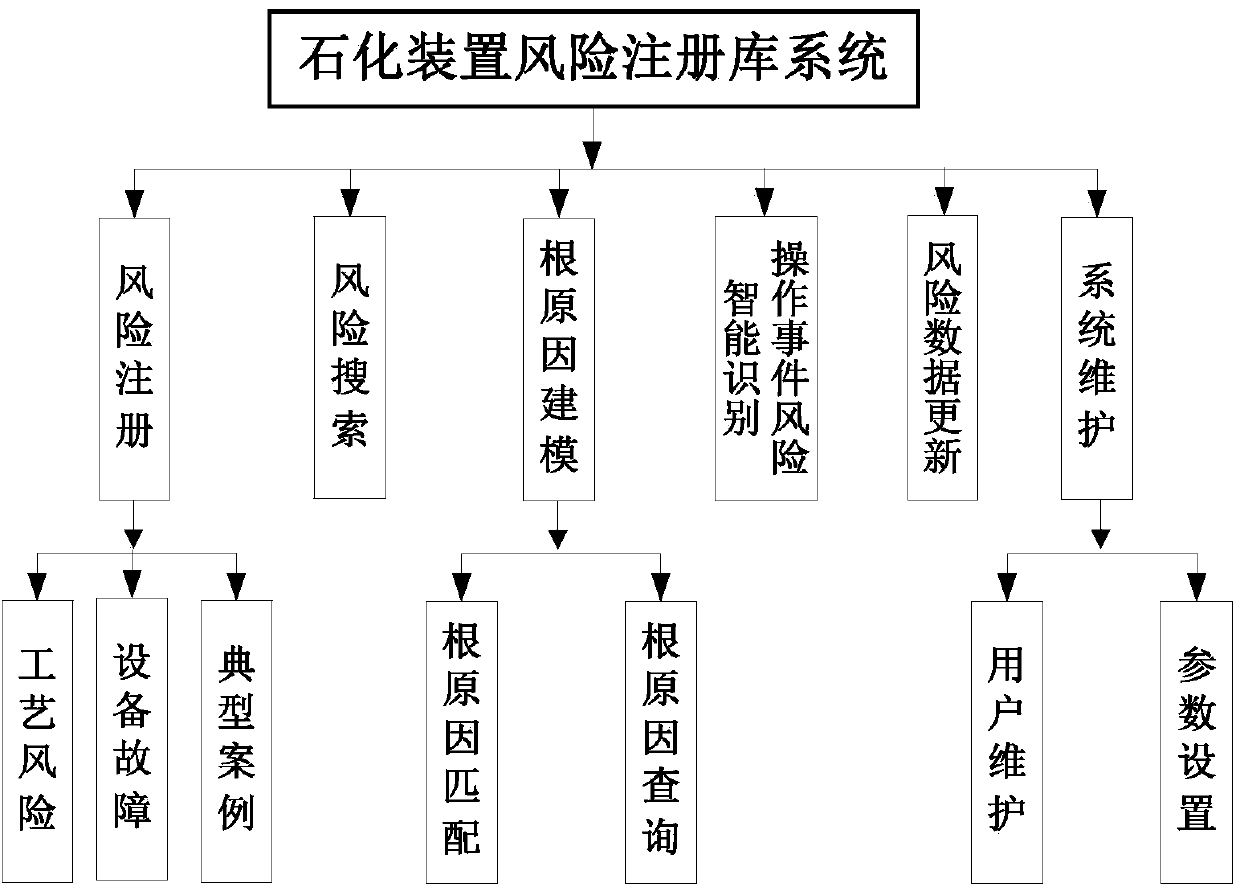
ActiveCN104199854AImprove applicabilitySatisfy operabilityInformaticsSpecial data processing applicationsRisk levelPetrochemical
The invention relates to a risk registering method of a petrochemical device. The risk registering method of the petrochemical device mainly solves the problems that in the prior art, the occurrence probability of the events, caused by people, such as non-planned parking is high and the stability of device operation is low. According to the technical scheme, in the risk registering method of the petrochemical device, qualitative analysis and a quantitative risk matrix are combined for conducting risk assessment, potential risks existing in the production process of the petrochemical device are recognized and assessed, analysis evaluation is conducted on the various risks, classifying, grading and sorting are conducted on the risks, a risk registering database system of the petrochemical device is established by using the database software technology, matching and querying of root causes are realized according to the analysis result, an intelligent operation event risk recognizing function is designed, intelligent correlation of MES (Manufacturing Evaluation System) operation events and a risk registering database is realized, and risk levels, classes, causes and operation recommendation of the operation events are provided timely. The risk registering method of the petrochemical device well solves the problems and can be used in risk registering of the petrochemical device.
Owner:CHINA PETROLEUM & CHEM CORP +1
System and method used for fault diagnosis and recovery of network device and server
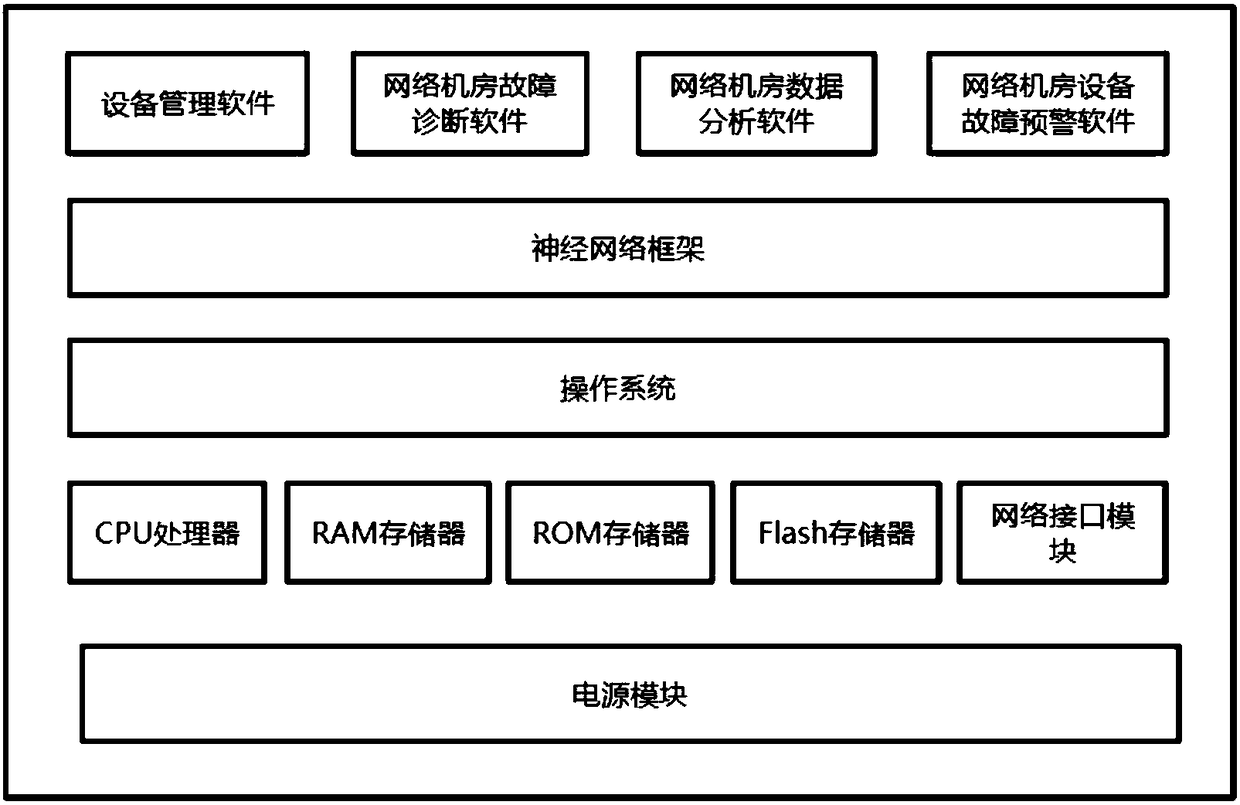
ActiveCN108199922AReduce unmanned managementReduce work intensityNeural architecturesData switching networksVia deviceDevice failure
The invention discloses a system and a method used for fault diagnosis and recovery of a network device and a server. The system comprises a device body, a device state big data storage array and a device log bi data storage array. The method comprises the steps of collecting hardware running information; judging whether a fault or a hidden danger appears through a neutral network model; performing data analysis on the appeared fault and hidden danger through the device log big data array and the device log big data storage array; judging whether the fault or the hidden danger is caused by hardware or software; analyzing a reason which arouses the software fault and solving the problem. The system and the method used for fault diagnosis and recovery of the network device and the server have the advantages as follows: risk identification, trend study and judgment, potential safety hazards, safety pre-warning, device software fault solution and device hardware fault estimation are realized through fault and safety event risk estimation made by a big data and neural network technology and a trend study and judgment platform; the work difficulty of the operator on duty can be lightened; network computer room fault and safety risk are reduced; and the economic loss is decreased.
Owner:承德北网通信工程有限公司
Cardiovascular Risk Event Prediction and Uses Thereof
InactiveUS20150168423A1Cardiovascular events may be avoidedPropensity for such events can be accurately determinedHealth-index calculationMicrobiological testing/measurementVascular riskBiomarker (petroleum)
Owner:SOMALOGIC INC
Event risk early warning method based on data mining, electronic equipment and medium
InactiveCN109685321AImprove availabilityImprove accuracyCharacter and pattern recognitionResourcesData dredgingCluster algorithm
The invention discloses an event risk early warning method based on data mining, electronic equipment and a medium. The event risk early warning method comprises the following steps: acquiring recorddata of a historical terrorist attack event and a to-be-tested event; Preprocessing the record numbers of the historical terrorist attack events and the to-be-tested events; Classifying the data obtained after data preprocessing by adopting a clustering algorithm, and dividing the data into a plurality of types of data; Extracting a plurality of features from each type of data by adopting a principal component analysis algorithm; Performing feature integration on all features extracted from all classes of data to obtain a feature set; Extracting a plurality of index features from the feature set by adopting a principal component analysis algorithm; Calculating the weight of each index feature by adopting an improved entropy weight method; And for the characteristic value of each index characteristic of each event, carrying out weighted calculation by adopting a corresponding weight, sorting calculation results from large to small, outputting a sorting sequence number of the to-be-tested event in all sorts as a result, and if the sorting sequence number is smaller than a set threshold value, sending out an early warning signal.
Owner:SHANDONG NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com