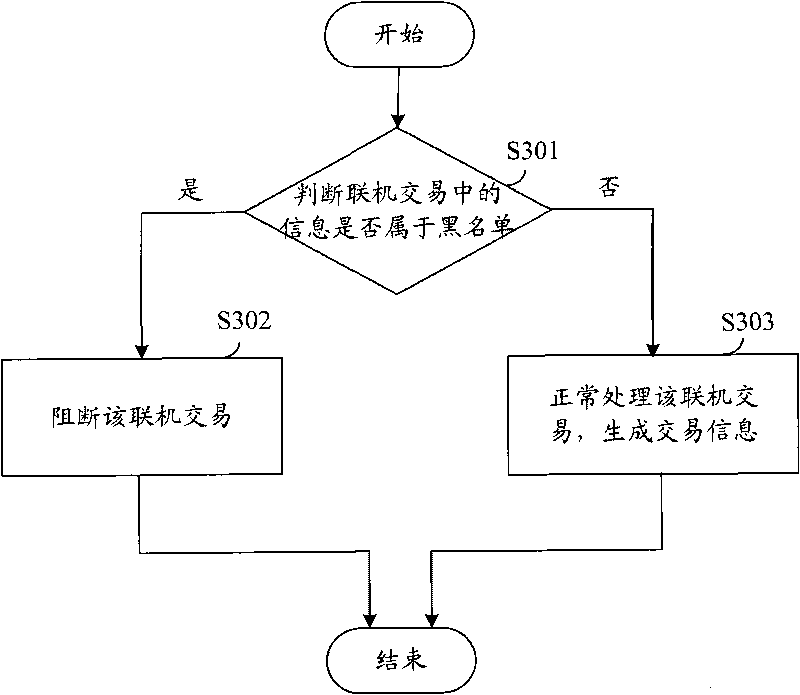
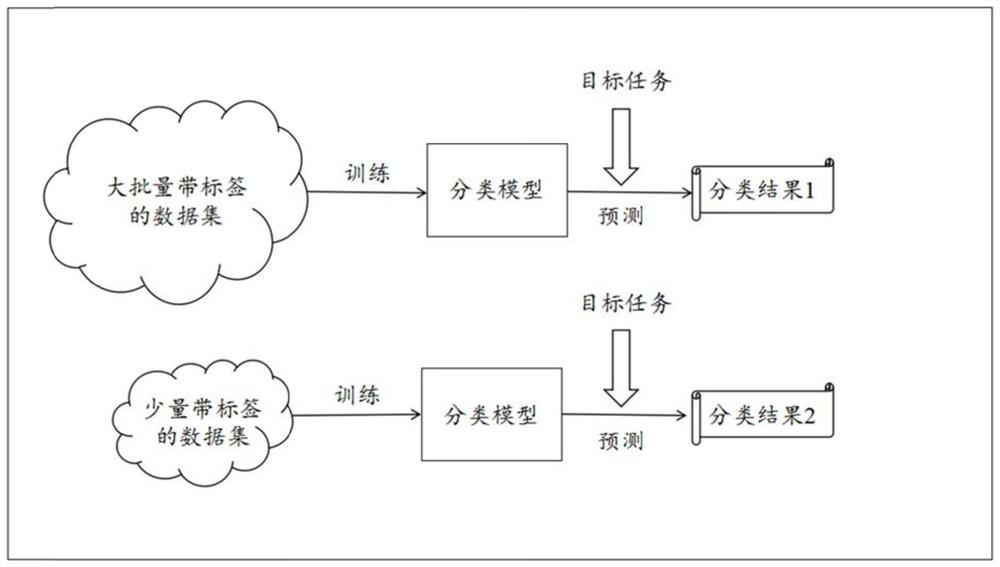
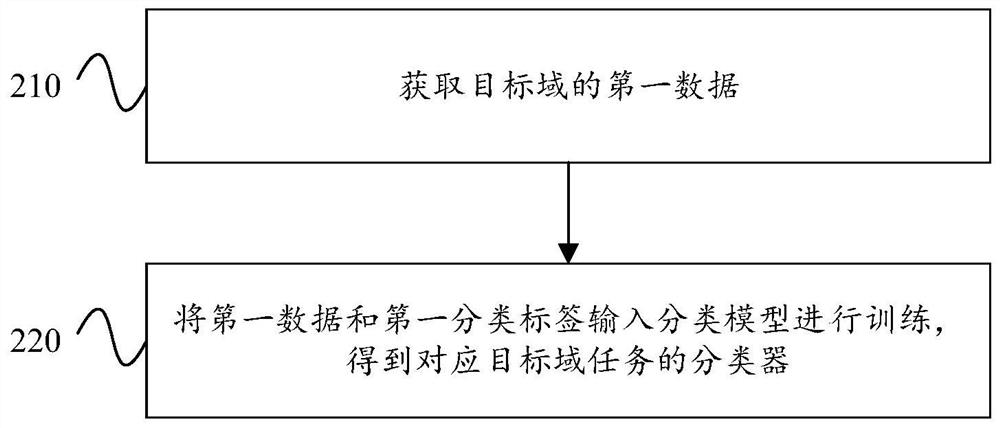
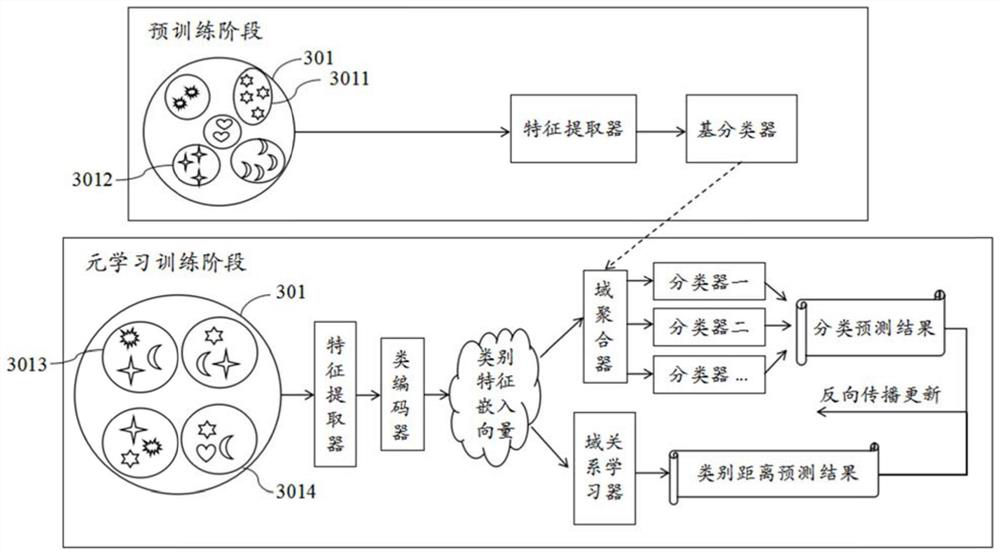
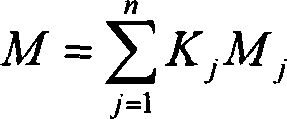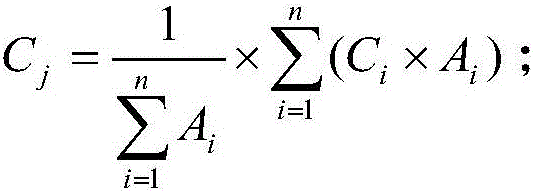Patents
Literature
1332 results about "Risk identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Risk Identification. Definition: Risk identification is the process of determining risks that could potentially prevent the program, enterprise, or investment from achieving its objectives.
Systems and methods for investigation of financial reporting information
InactiveUS20050222929A1FinanceSpecial data processing applicationsCluster algorithmStatistical analysis
Owner:PRICEWATERHOUSECOOPERS LLP
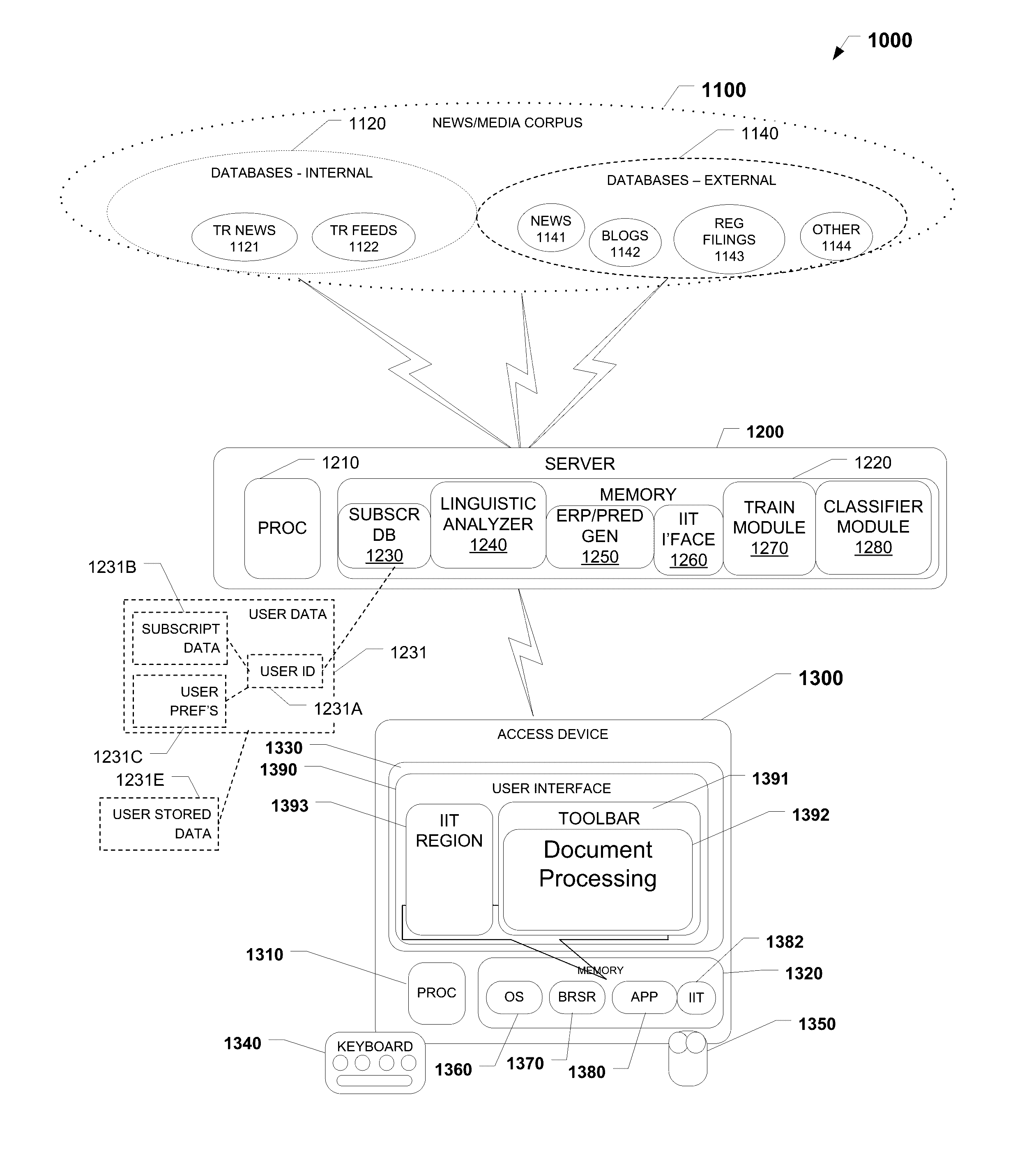
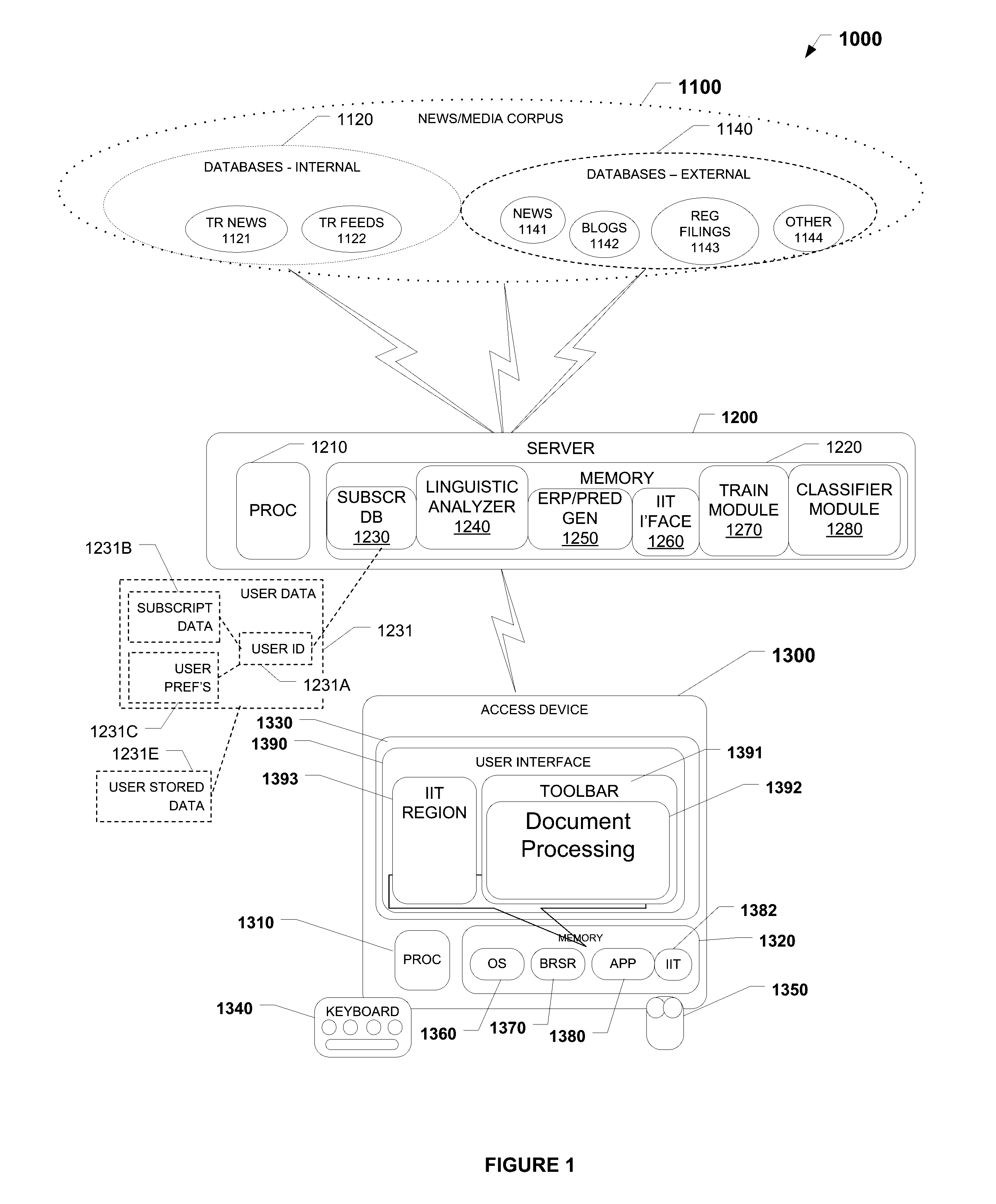
Methods and systems for risk mining and for generating entity risk profiles
A computer implemented method for mining risks includes providing a set of risk-indicating patterns on a computing device; querying a corpus using the computing device to identify a set of potential risks by using a risk-identification-algorithm based, at least in part, on the set of risk-indicating patterns associated with the corpus; comparing the set of potential risks with the risk-indicating patterns to obtain a set of prerequisite risks; generating a signal representative of the set of prerequisite risks; storing the signal representative of the set of prerequisite risks in an electronic memory; and aggregating potential risks linked to an entity to an entity risk profile (ERP). A computing device or system for mining risks includes an electronic memory; and a risk-identification-algorithm based, at least in part, on the set of risk-indicating patterns associated with a corpus stored in the electronic memory.
Owner:REFINITIV US ORG LLC
Processing method and system for risk monitoring and controlling of transaction data
The embodiment of the invention discloses a processing method and a system for risk monitoring and controlling of the transaction data. The method comprises the following steps: receiving the transaction data generated in the business processing information; calling the related transaction data of the transaction data according to the transaction data; calculating the risk monitoring index data threshold value according to the transaction data and the related transaction data; judging that the business processing information generating the transaction data is quasi-risk business processing information when the transaction data is more than the risk monitoring index data threshold value; and setting the quasi-risk business processing information into the risk business processing information. The method and the system of the invention can automatically generate a risk control threshold value, identifies and controls the risk according to the different conditions, can provide a risk monitoring process flow and a rule improvement mechanism, thus saving the economic cost, improving the accuracy and the efficiency of the risk event checking, and greatly improving the monitoring efficiency and effect of the banking business risks.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Methods and systems for risk mining and for generating entity risk profiles and for predicting behavior of security
A computer implemented method for mining risks includes providing a set of risk-indicating patterns on a computing device; querying a corpus using the computing device to identify a set of potential risks by using a risk-identification-algorithm based, at least in part, on the set of risk-indicating patterns associated with the corpus; comparing the set of potential risks with the risk-indicating patterns to obtain a set of prerequisite risks; generating a signal representative of the set of prerequisite risks; storing the signal representative of the set of prerequisite risks in an electronic memory; aggregating potential risks linked to an entity to an entity risk profile (ERP); and predicting a movement in a security associated with an entity.
Owner:REFINITIV US ORG LLC
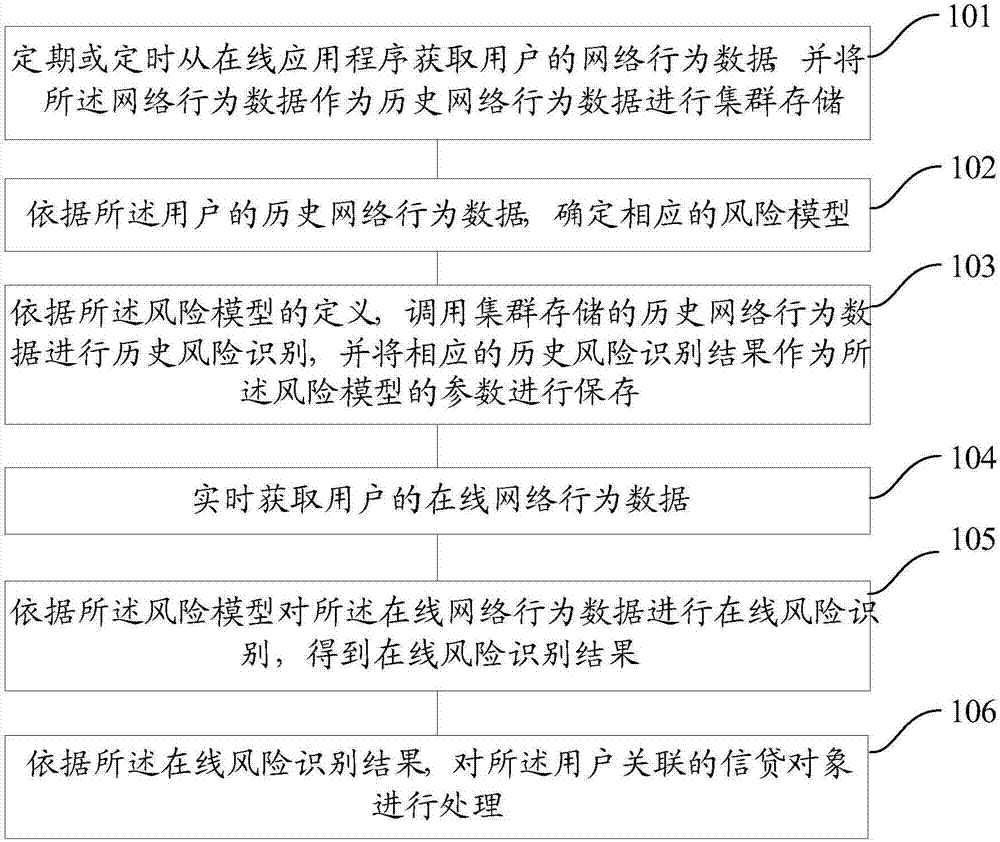
Method and system for monitoring network behavior data
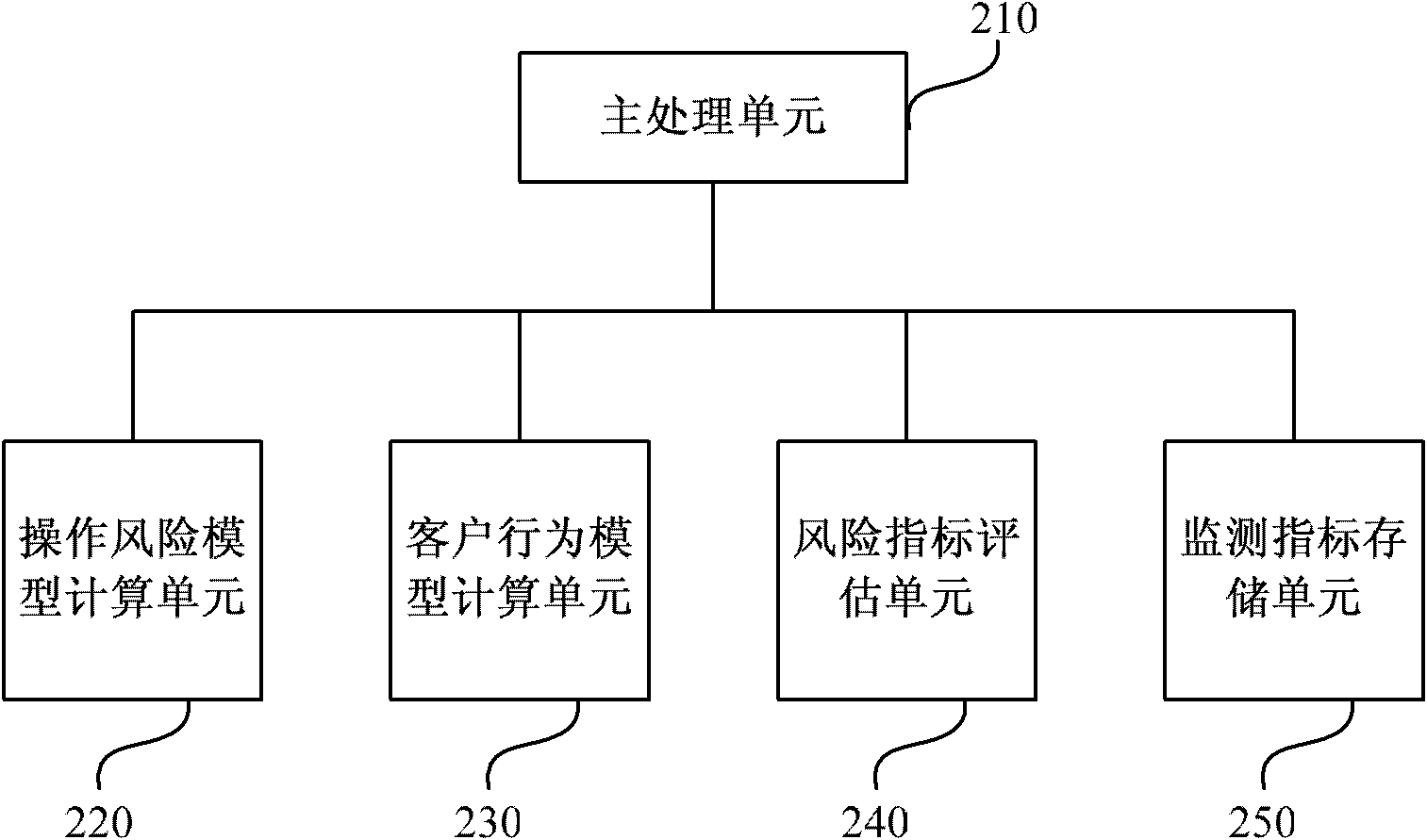
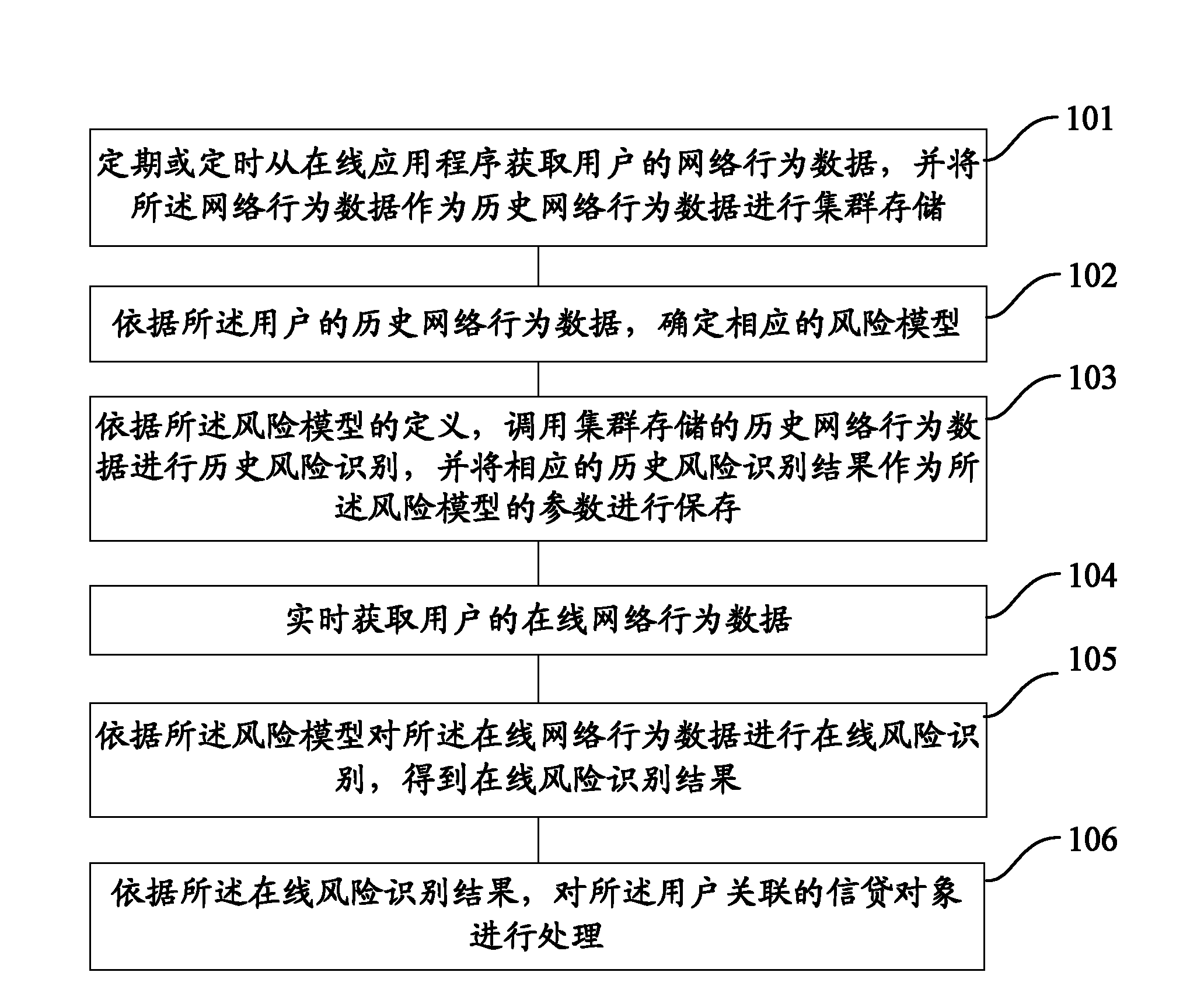
The invention provides a method and system for monitoring network behavior data. The method particularly comprises the steps of: obtaining network behavior data of a user from an online application program periodically or regularly, and regarding the network behavior data as historical network behavior data for collective storage; determining a corresponding risk model based on the historical network behavior data of the user; calling the collectively stored historical network behavior data for historical risk identification based on the definition of the risk model, and regarding a corresponding historical risk identification result as a parameter of the risk model for storage; obtaining the online network behavior data of the user in real time; performing online risk identification on the online network behavior data based on the risk model so as to obtain an online risk identification result; and processing a credit object associated with the user based on the online risk identification result. The method and system for monitoring the network behavior data can improve timeliness and accuracy of credit risk monitoring.
Owner:ALIBABA GRP HLDG LTD
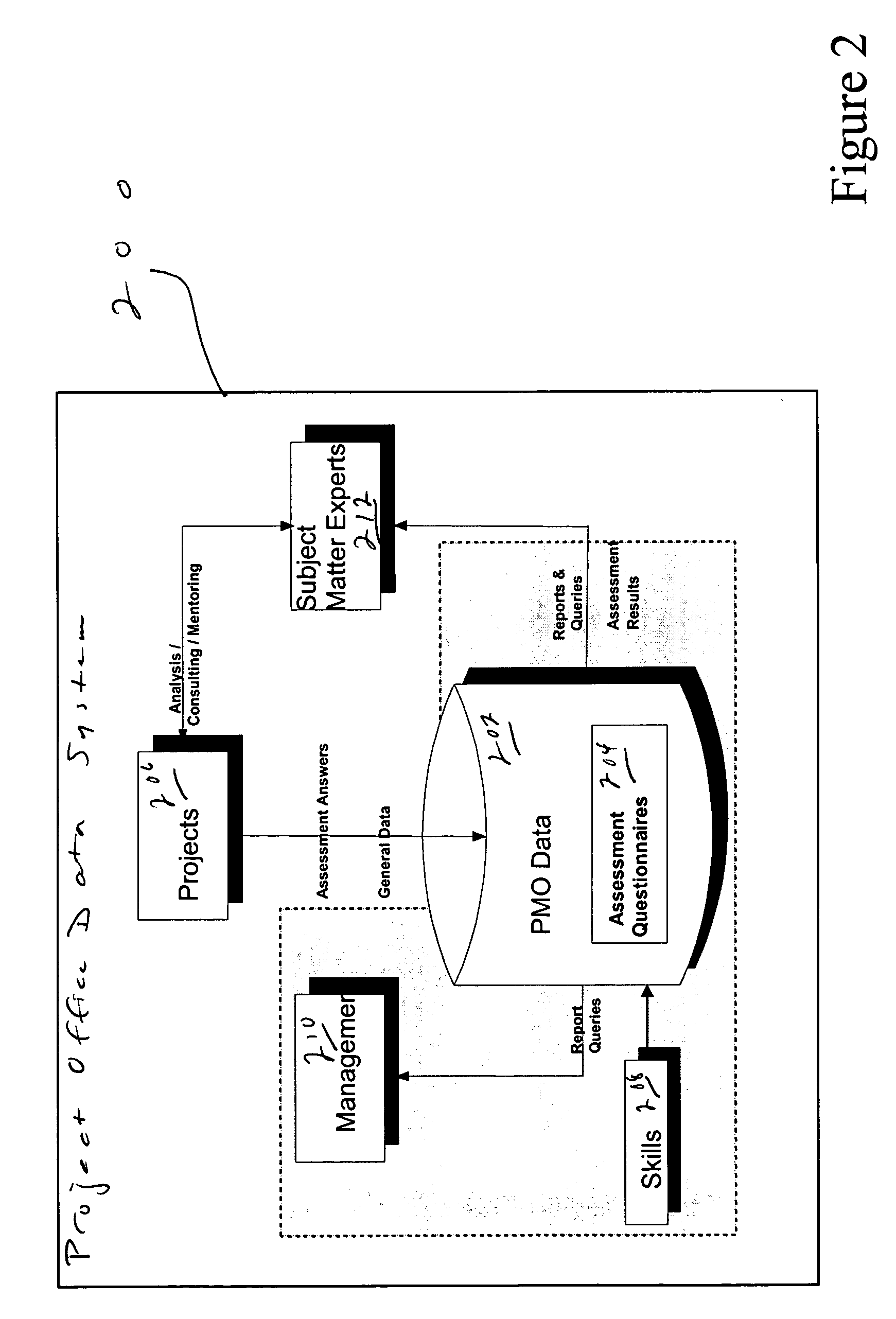
System and method for an automated project office and automatic risk assessment and reporting
ActiveUS20060173762A1Avoid lost organizational productivityImprove abilitiesFinanceResourcesRisk levelRisk identification
In the automation of project risk identification, various qualitative and quantitative measures are combined to report a project's risk level, areas, and mitigation in an automatic and objective manner. The software package includes a risk assessment and report framework and a risk engine, a portfolio analysis, a project plan validator, an integrated project management office toolkit and process asset library, and an integrated skills tracking, locating and availability module with a skills engine.
Owner:COMP AID INC
Risk identification and risk register generation system and engine
PendingUS20160371618A1Improve good performanceImprove consistencyDigital data information retrievalKernel methodsElectronic formRisk identification
The present invention relates to a computer-based system for generating a risk register relating to a named entity. The system comprises a computing device, a risk database accessible by the computing device and having stored therein a set of risk types based on an induced taxonomy of risk types previously derived at least in part upon operation of a machine learning module, an input adapted to receive a set of source data, the set of source data being in electronic form and representing textual content comprising potential risk phrases, a entity-risk relation classifier adapted to identify and extract entity-risk relations from the set of source data, a risk tagger adapted to identify in the set of source data a set of risk candidates (ri) based on the set of risk types, a entity tagger adapted to identify mentions of entity names (ci) in the set of source data, and a risk register aggregator adapted to generate a first risk register based on the set of tuples associated with a first entity.
Owner:REFINITIV US ORG LLC
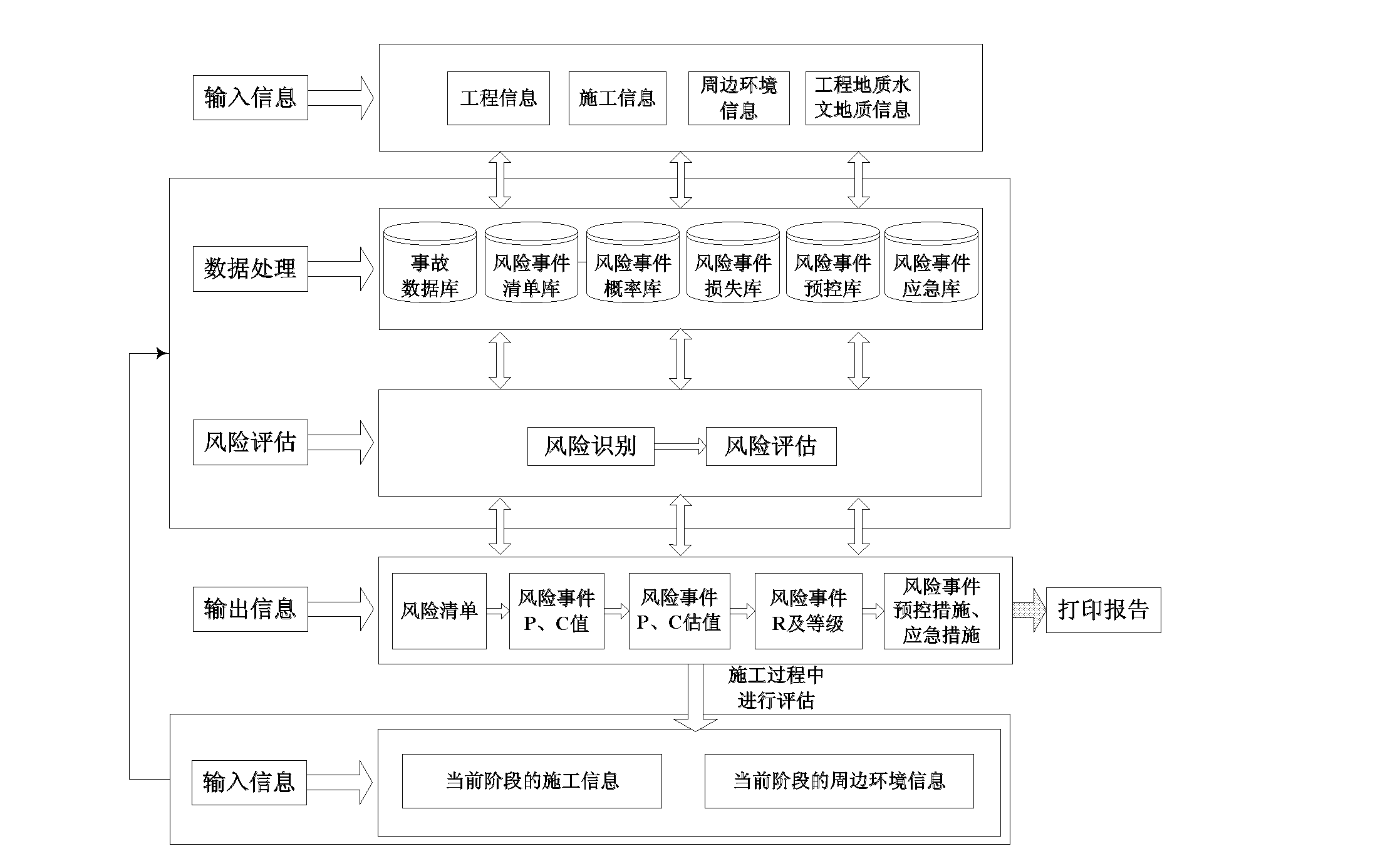
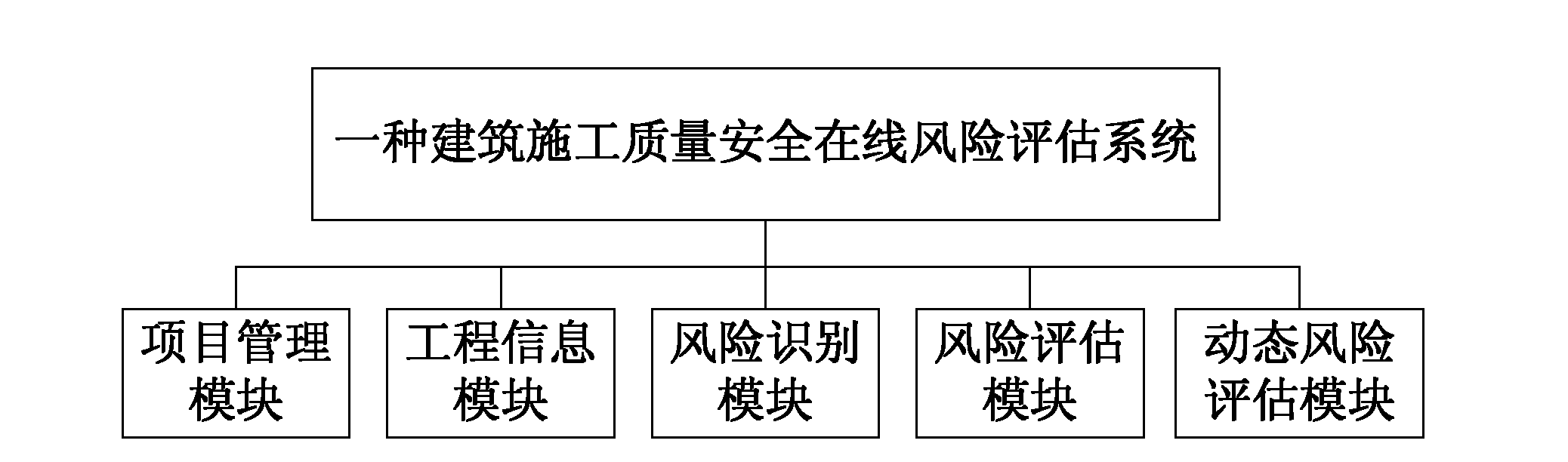
Building construction quality safety online risk assessment system
ActiveCN102521710AWith self-learning functionPromote self-learningResourcesRisk identificationEngineering
The invention provides a building construction quality safety online risk assessment system. The system comprises: a project management module, an engineering information module, a risk identification module, a risk assessment module and a dynamic risk assessment module. The project management module is used for information management of a building construction project and a case library. The engineering information module is used for general situation information management of the building construction project. The risk identification module can automatically identify a risk event and a risk factor according to an engineering general situation information system so as to form a risk list and a risk tree. The risk assessment module carries out data reasoning according to comparison of the project general situation information and the similar project information in a database, estimates a risk event generation probability and losses, determines a risk grade, determines an importance degree of the risk factor through a sensitivity analysis and automatically searches the database so as to obtain a pre-control measure and form a risk assessment report. The dynamic risk assessment module is used for risk tracking, monitoring and situation evaluation during an engineering construction process.
Owner:SHANGHAI JIANKE ENG CONSULTING
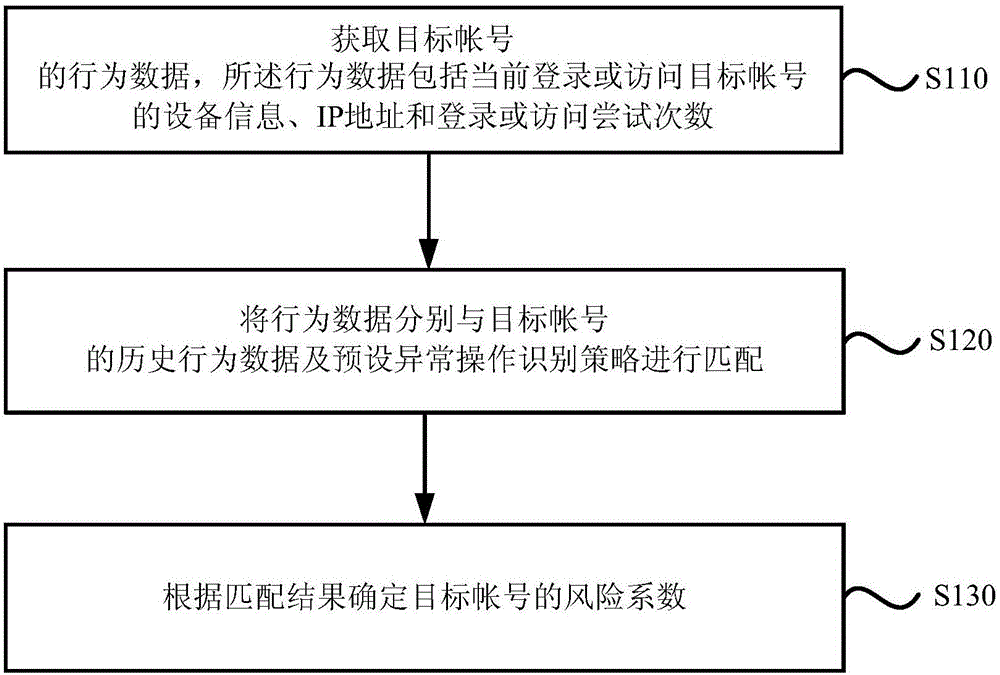
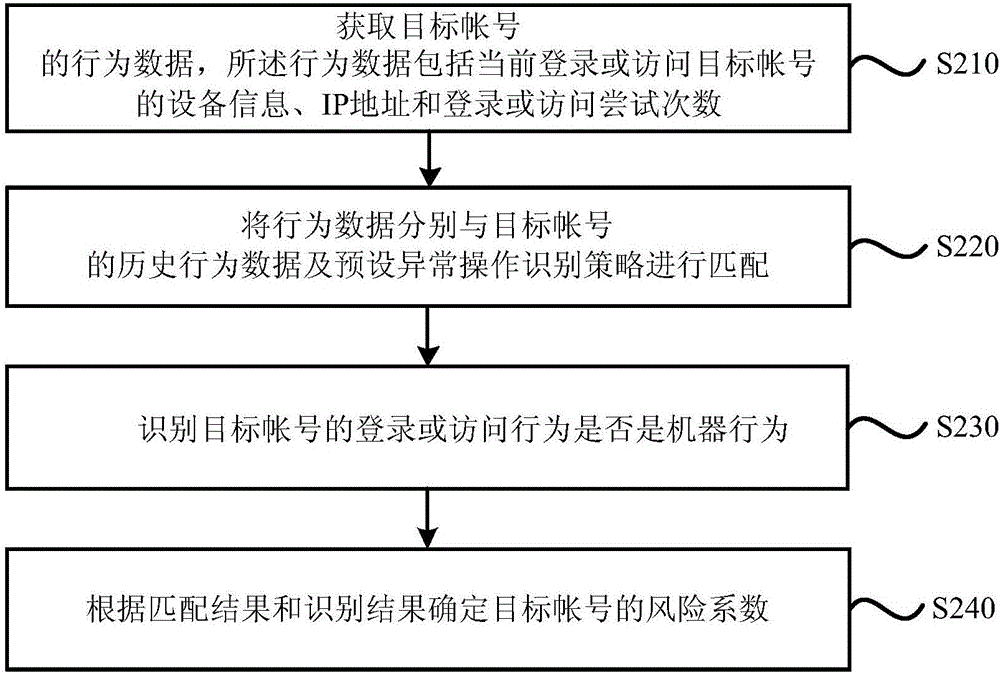
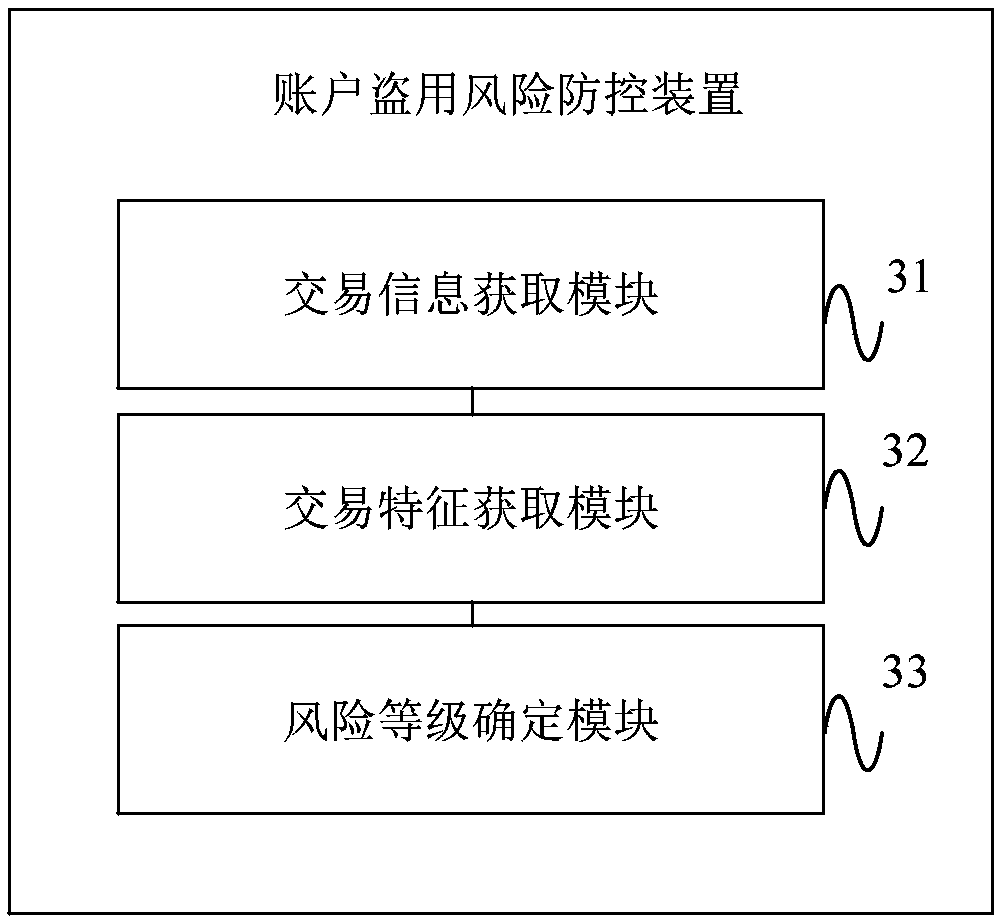
Account risk identification method and device
InactiveCN106529288AEnsure safetyImprove accuracyPlatform integrity maintainanceIp addressRisk identification
The embodiment of the invention discloses an account risk identification method and device. The method comprises the following steps of: obtaining the behavior data of a target account, wherein the behavior data comprises the information, the IP (Internet Protocol) address and the login or access attempting frequency of equipment which logs in or accesses the target account at present; matching the behavior data respectively with the historical behavior data of the target account and a preset abnormal operation identification strategy; and according to a matching result, determining the risk factor of the target account. The above technical scheme can be adopted to improve target account risk identification accuracy so as to guarantee the safety of the target account.
Owner:ZHIZHESIHAIBEIJINGTECH CO LTD
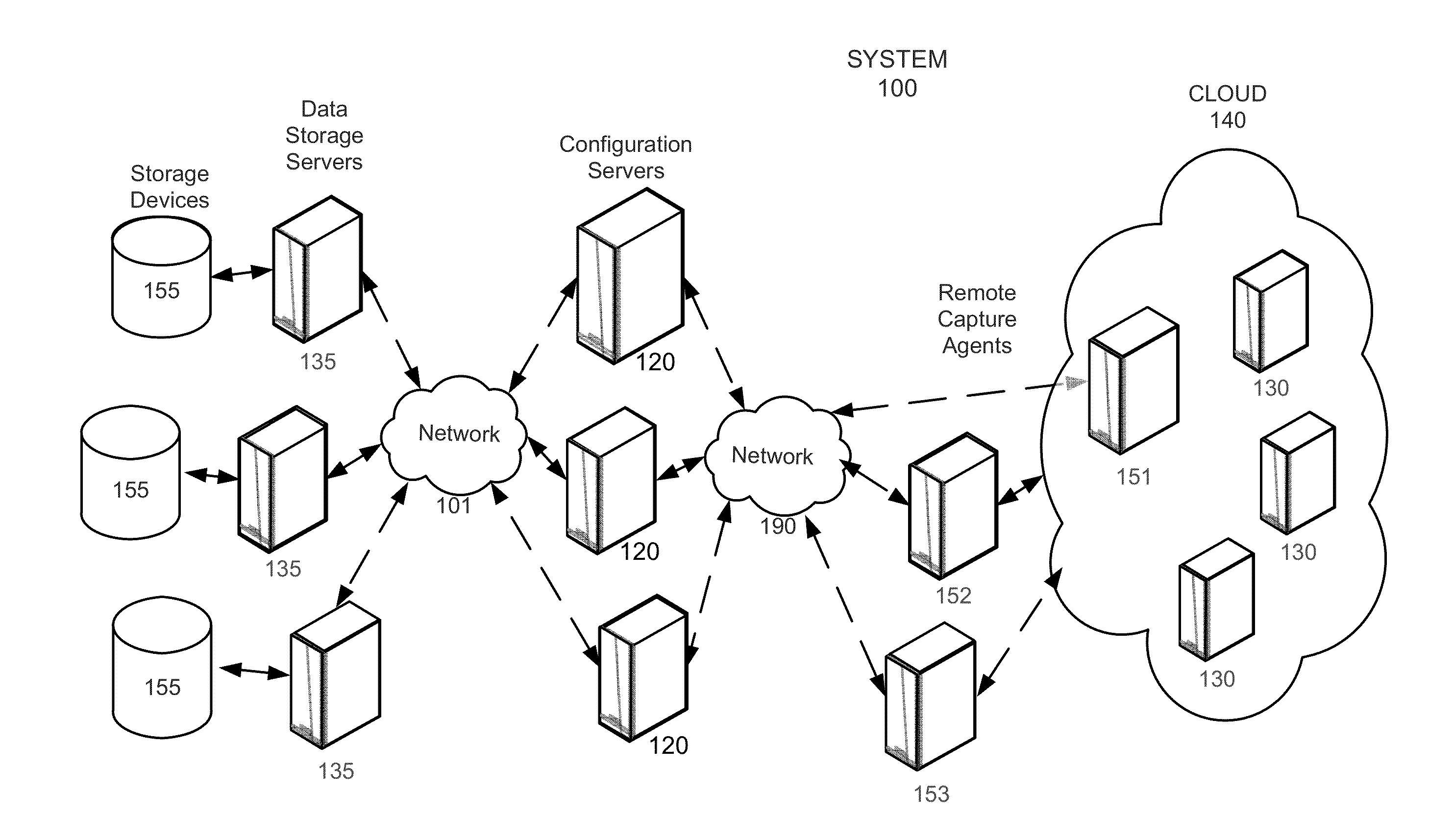
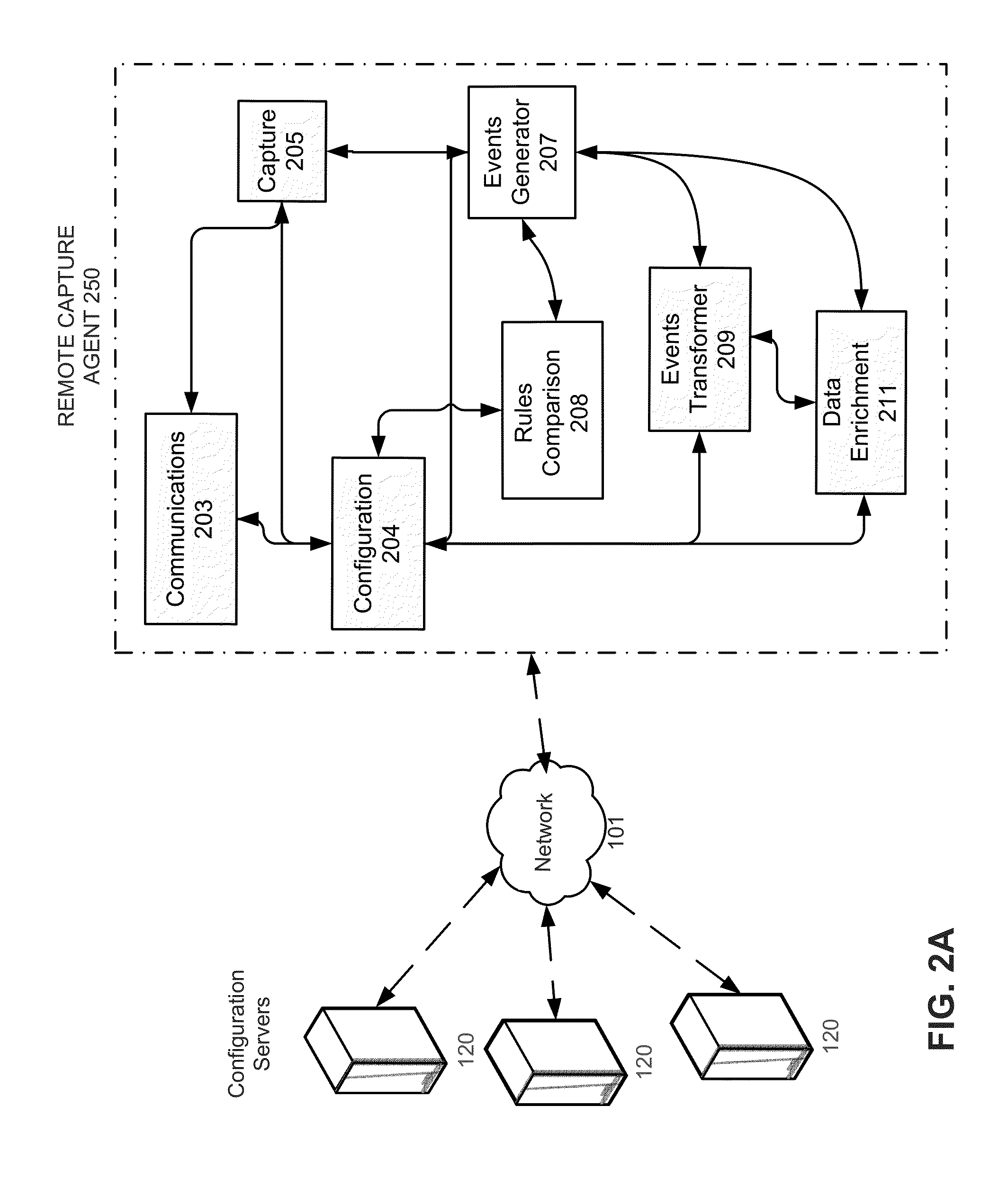
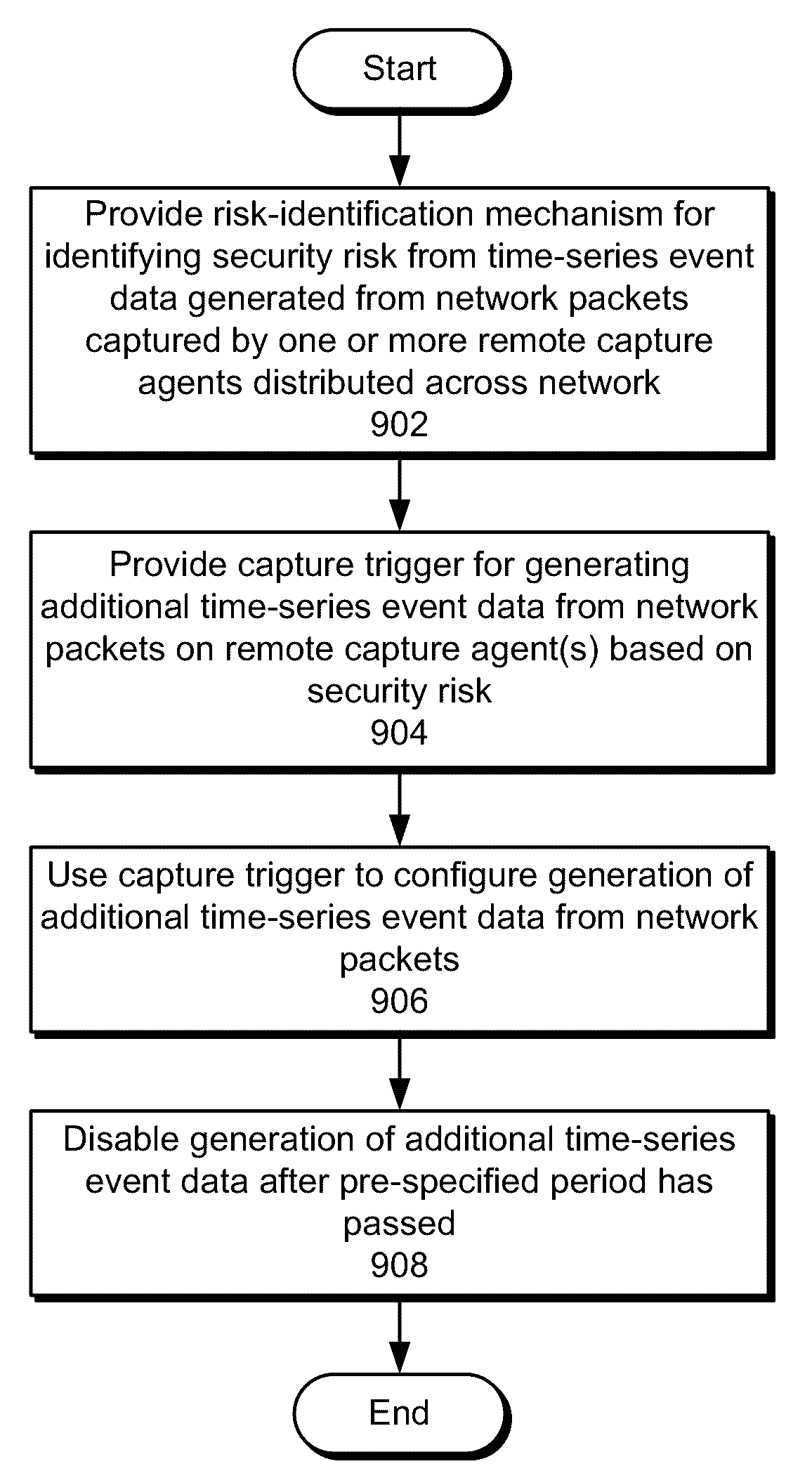
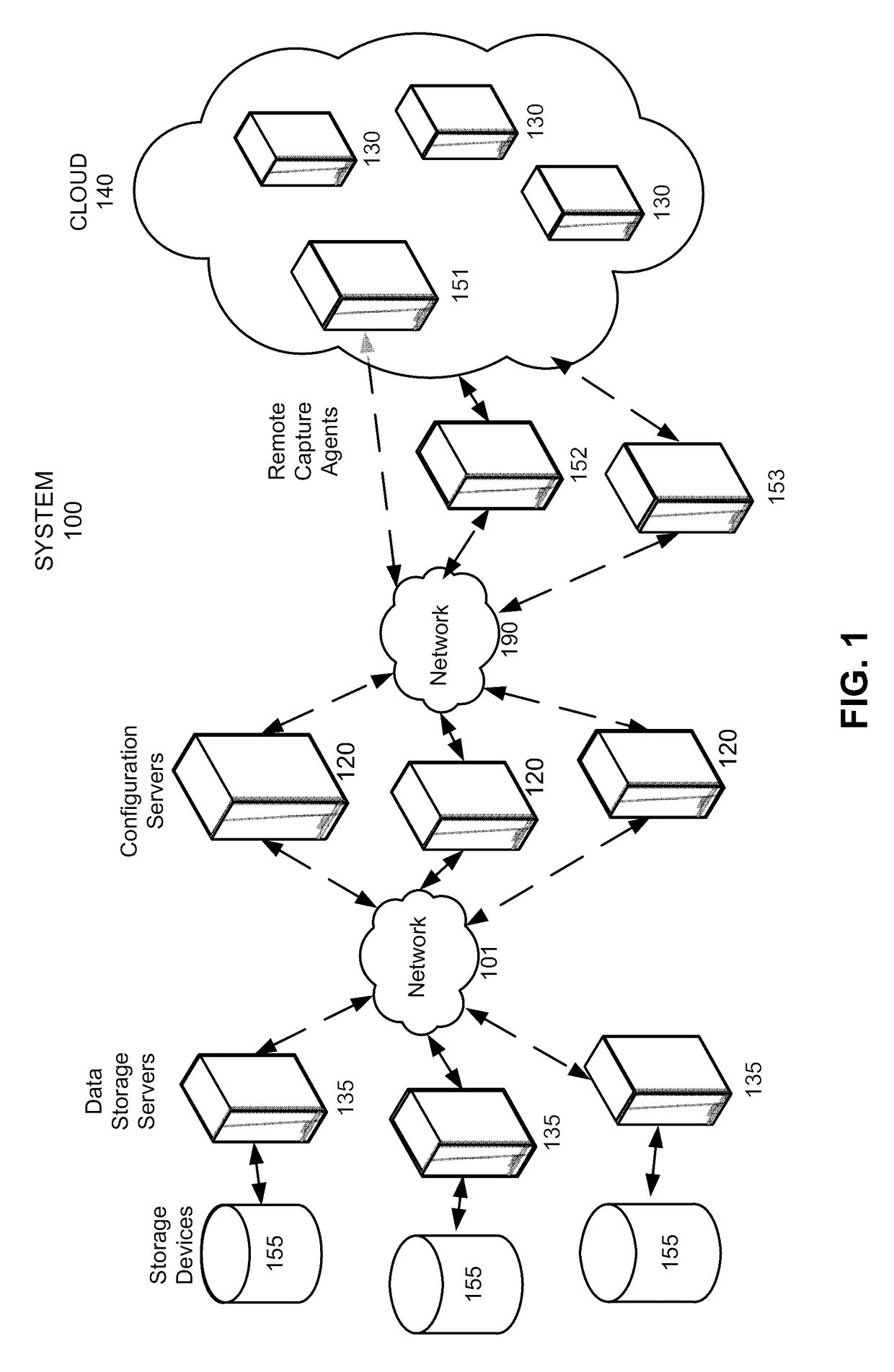
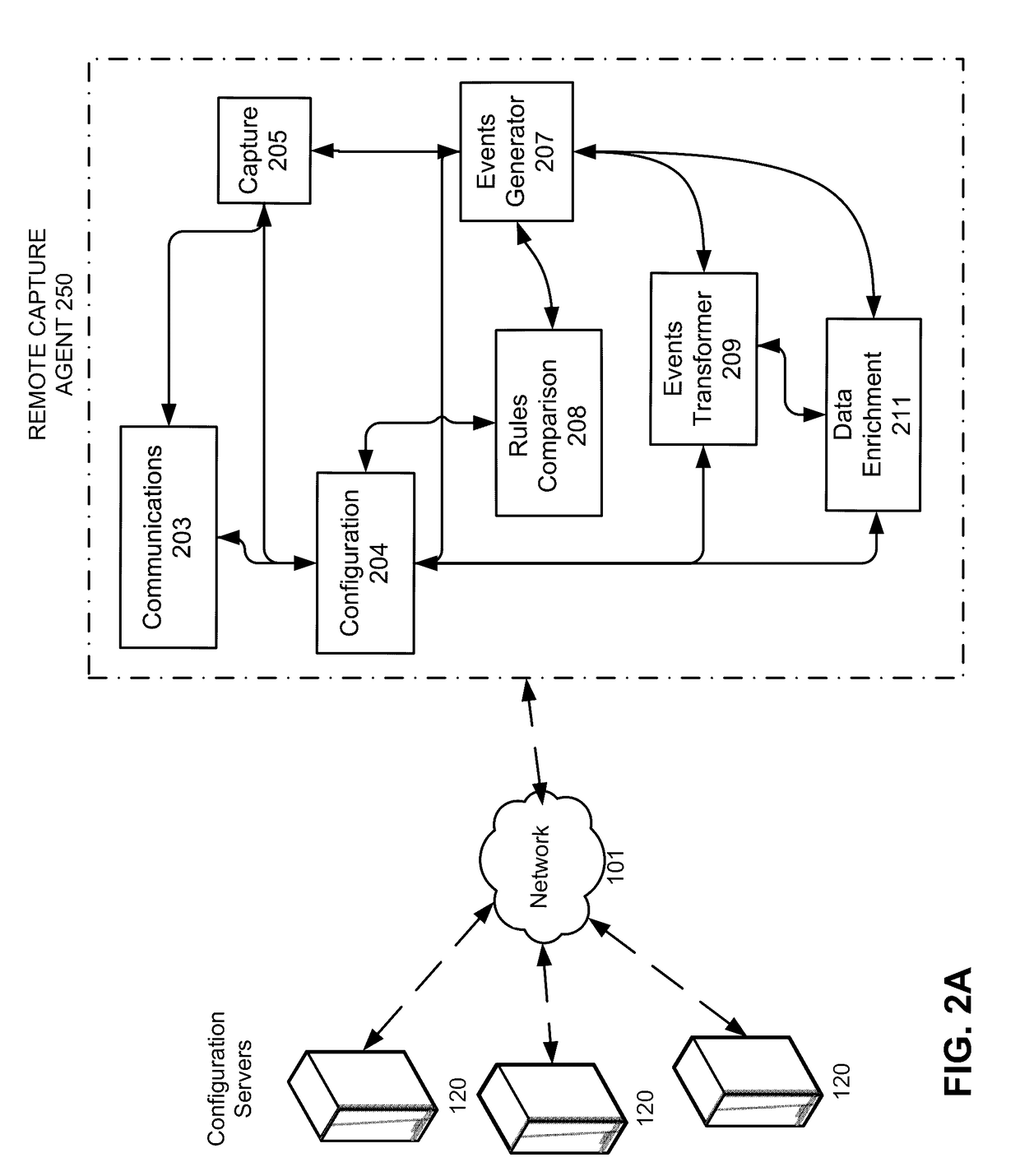
Capture triggers for capturing network data
ActiveUS20160127401A1Easy to analyzeEasy to processMultiple digital computer combinationsProgram controlNetwork packetEvent data
The disclosed embodiments provide a system that facilitates the processing of network data. During operation, the system provides a risk-identification mechanism for identifying a security risk from time-series event data generated from network packets captured by one or more remote capture agents distributed across a network. Next, the system provides a capture trigger for generating additional time-series event data from the network packets on the one or more remote capture agents based on the security risk, wherein the additional time-series event data includes one or more event attributes.
Owner:SPLUNK INC
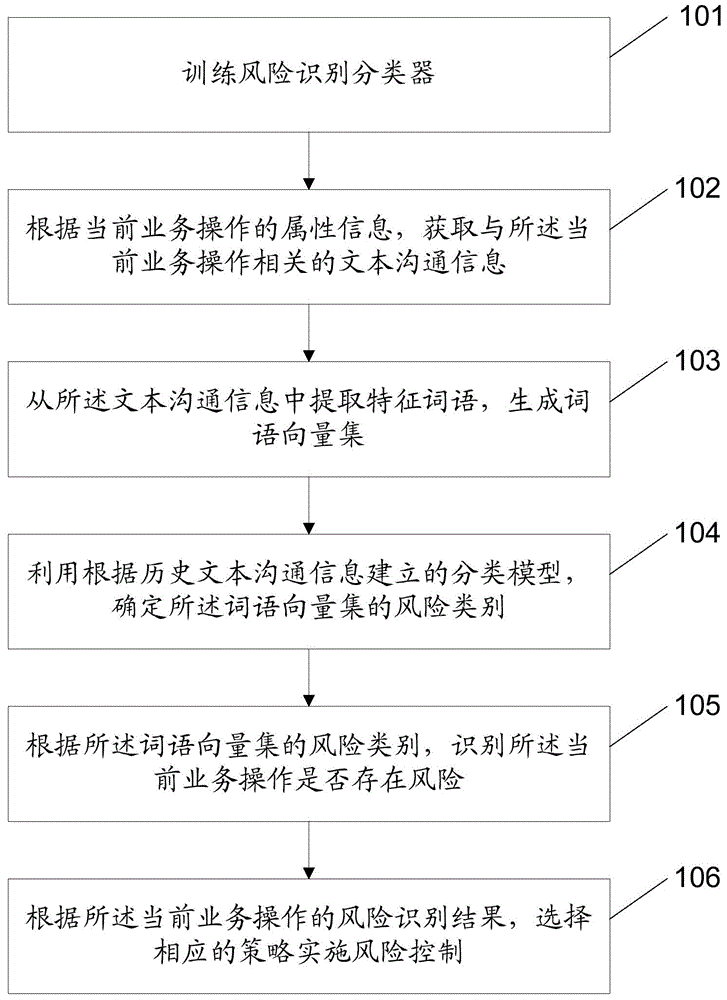
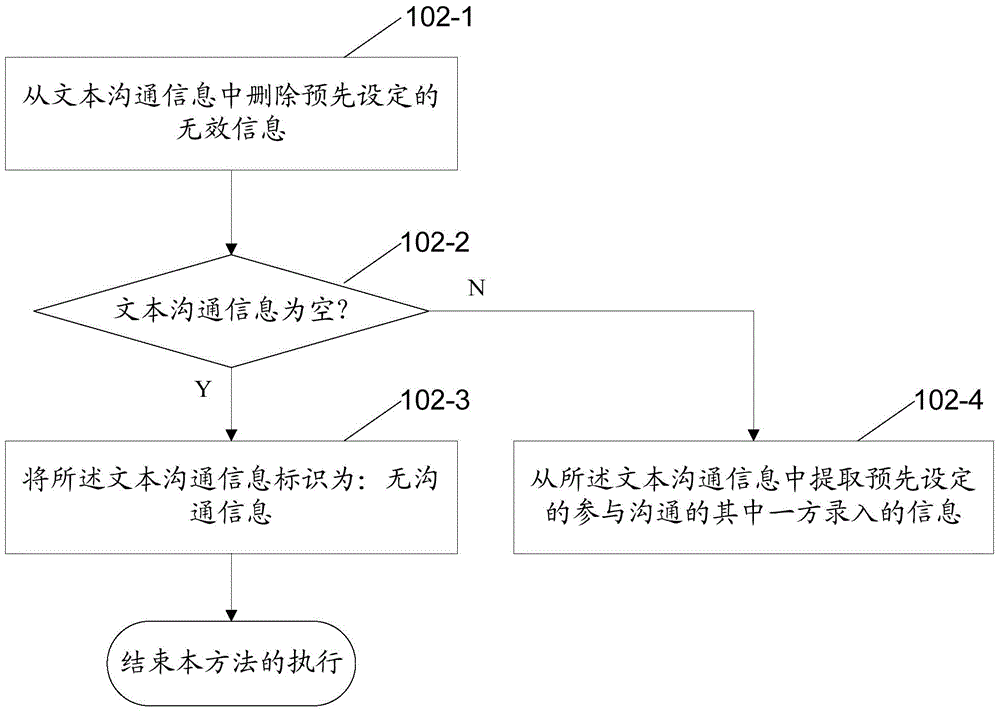
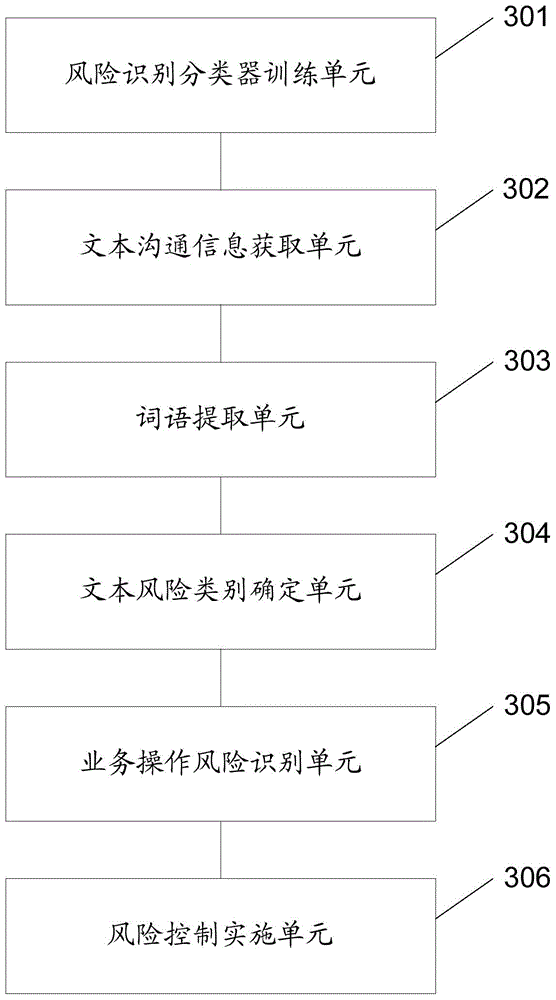
Risk identification method and device
InactiveCN106296195AGuaranteed accuracyEfficient identificationFinanceCharacter and pattern recognitionRisk ControlRisk identification
The application discloses a risk identification method comprising the following steps: acquiring text communication information related to a current service operation according to the attribute information of the current service operation; extracting feature words from the text communication information to generate a word vector set; determining the risk category of the word vector set using a classification model built according to historical text communication information; and identifying whether the current service operation is at risk or not according to the risk category of the word vector set. The application further provides a risk identification device. The method provides a new way of service operation risk identification. Through risk identification according to the text communication information related to the current service operation, a service operation which may be at risk can be identified efficiently, and a powerful reference is provided for the subsequent risk control link.
Owner:ADVANCED NEW TECH CO LTD
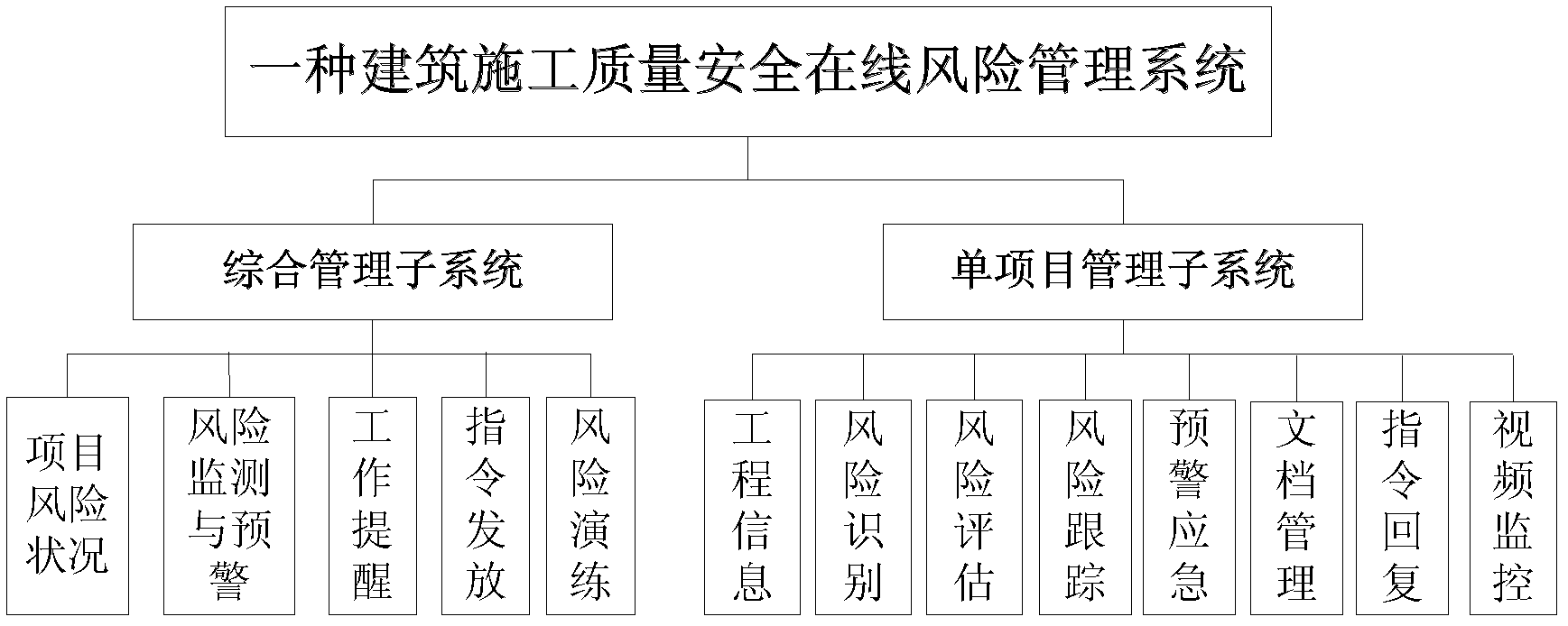
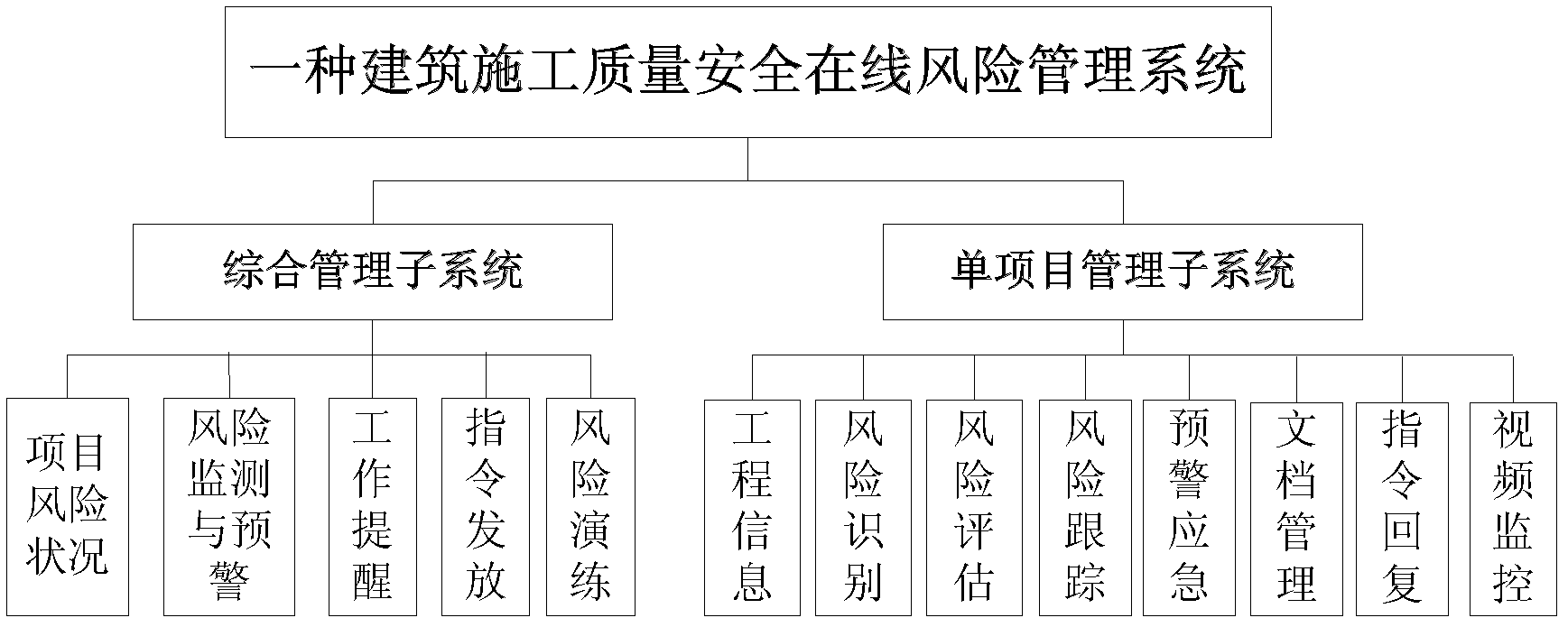
Building construction quality safety online risk management system
ActiveCN102521709APowerful self-learning mechanismPowerful self-learning functionResourcesVideo monitoringProject management
The invention provides a building construction quality safety online risk management system, which relates to the technical field of risk management of building engineering and comprises a general subsystem and a single project management subsystem. The general management subsystem consists of a project risk condition function module, a risk monitoring and early warning function module, a work reminder function module, an instruction issuing function module, an emergency practice function module and the like, and is used for browsing relevant information of all the projects undertaken by a company, transmitting instructions to project departments and checking daily work of the project departments; and the single project management subsystem comprises an engineering information function module, a risk identification function module, a risk assessment function module, a risk tracking function module, an early warning emergency function module, a document management function module, a work reminder function module, an instruction reply function module, a video monitoring function module and the like, and is used for realizing risk identification, assessment and tracking and early warning emergency by the aid of engineering situation information and remotely monitoring an engineering field. An online risk assessment system, a remote monitoring system and a risk management information platform are integrated in the building construction quality safety online risk management system, and real-time management and whole-process management for risks of large-size building construction engineering projects are realized.
Owner:SHANGHAI JIANKE ENG CONSULTING
Method and system for monitoring network behavior data, risk monitoring method and risk monitoring system
The invention provides a method and a system for monitoring network behavior data, a risk monitoring method and a risk monitoring system, wherein the method particularly comprises the steps of regularly acquiring network behavior data of a user from an online application, and using the network behavior data as historical network behavior data for performing cluster storage; determining a corresponding risk model according to the historical network behavior data of the user; according to the definition of the risk model, calling historical network behavior data in cluster storage for performing historical risk identification, and using a corresponding historical risk identification result as a parameter of the risk model for storage; acquiring online network behavior data of the user in real time; performing online risk identification on the online network behavior data according to the risk model, and obtaining an online risk identification result; and according to the online risk identification result, processing a credit object which is related with the user according to the online risk identification result. The method, the system, the risk monitoring method and the risk monitoring system can improve timeliness and accuracy in credit risk monitoring.
Owner:ADVANCED NEW TECH CO LTD
Risk management platform for steel trade financial business and risk management method
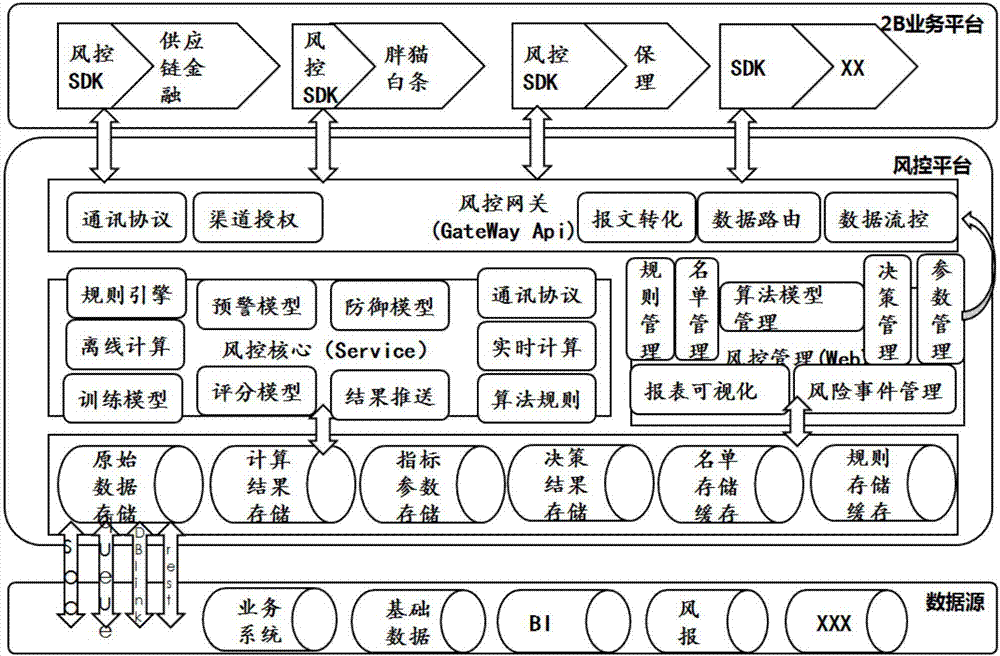
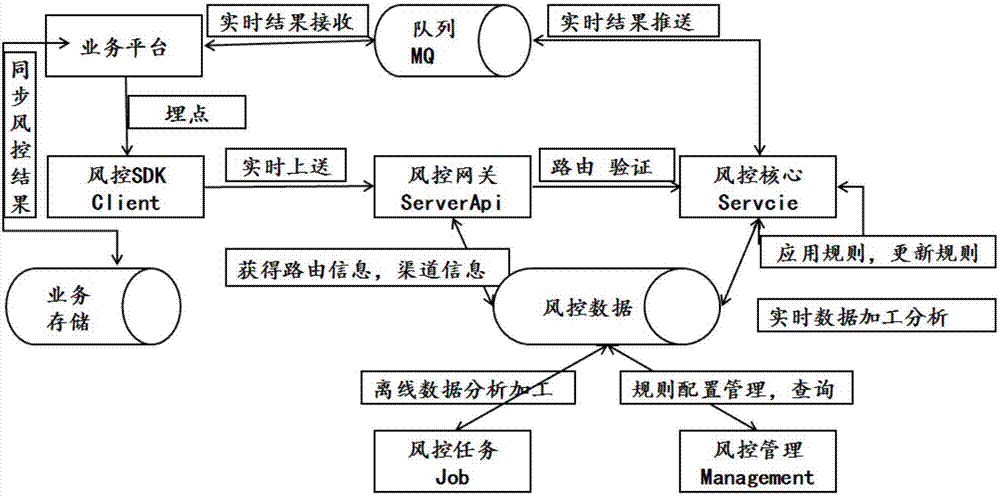
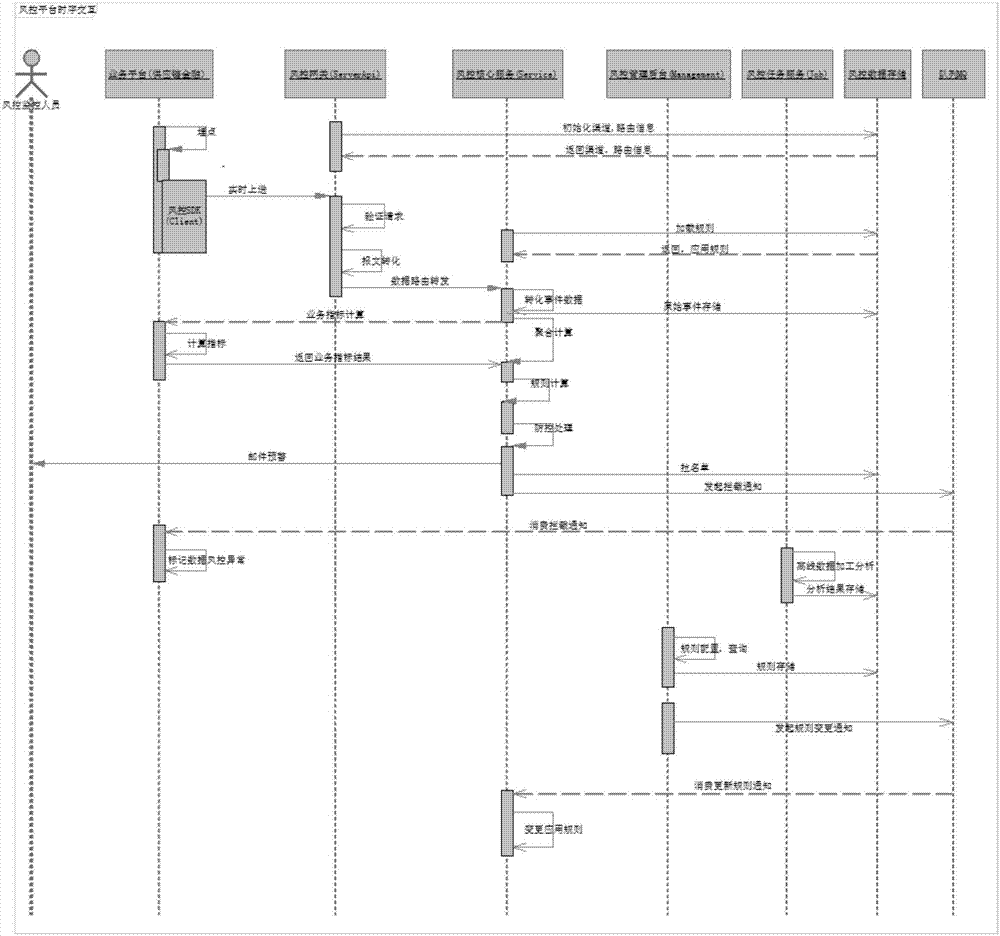
ActiveCN107491885APrevent and Avoid RisksLoss prevention and avoidanceResourcesSpecial data processing applicationsReal time analysisBusiness process
A risk management platform a steel trade financial business is a universal integrated risk management service platform which can automatically perform dynamic identification, real-time analysis, risk result processing and evaluation and quantifying the risk according to the data on the risks that are related in a steel trade financial business process based on a risk identification rule. The risk management platform comprises a risk management client frontend unit, a risk management channel gateway unit, a risk management core real-time service unit, a risk management background management service unit, a risk management offline service unit, a risk management near-line service unit and a risk management data service unit. The risk management platform and the risk management method have advantages of realizing abstract universal data model, integrating a rule engine which can be dynamically managed and changed, separating a real-time processing data according to a scene chronergy characteristic, realizing near-line model processing and offline model processing, finishing full-scene coverage of a risk management business, realizing independence between a client and a gateway architecture, reducing impact of business system change to a risk management back-end core, and flexibly decoupling a risk management logic and a business logic.
Owner:SHANGHAI GANGFU E COMMERCE
Method and system for identifying computer risks based on account clustering
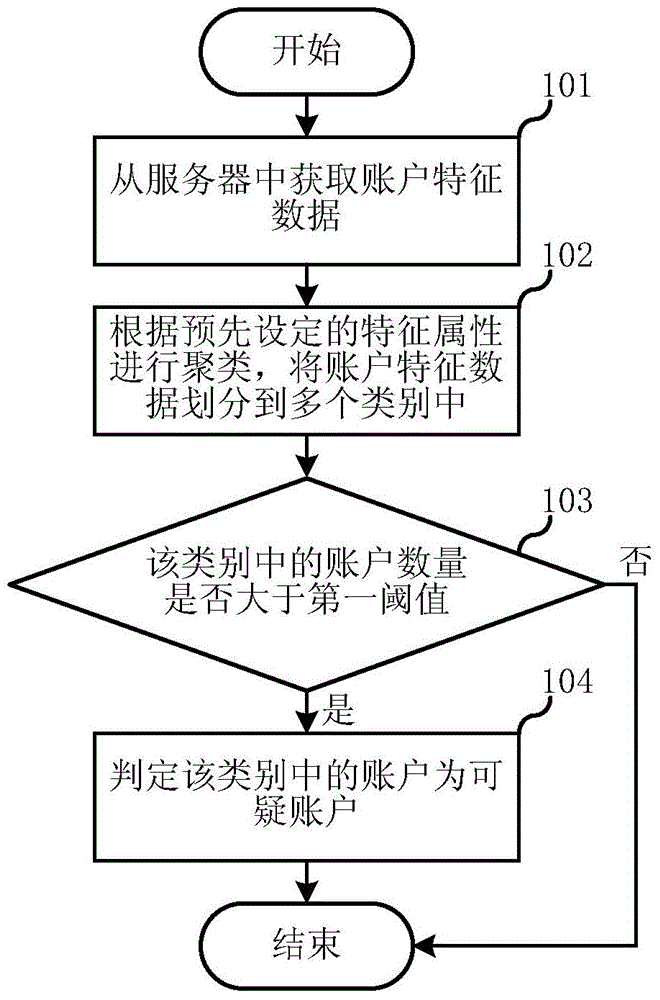
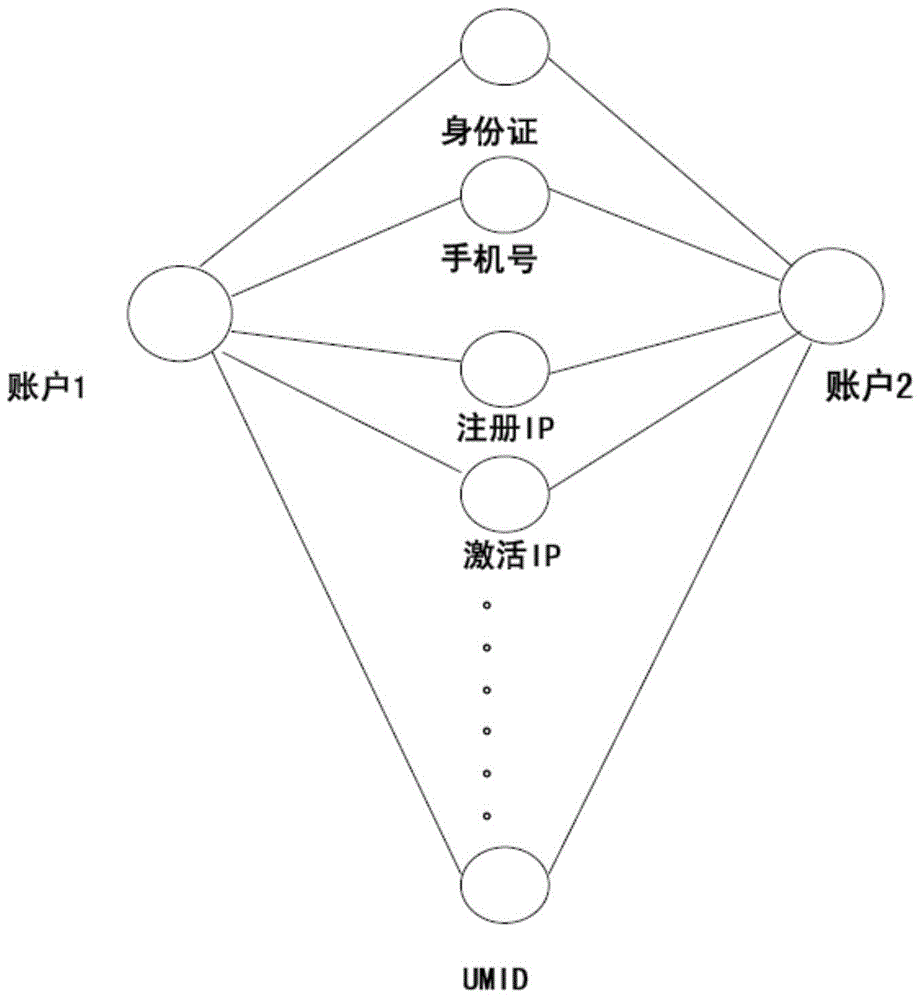
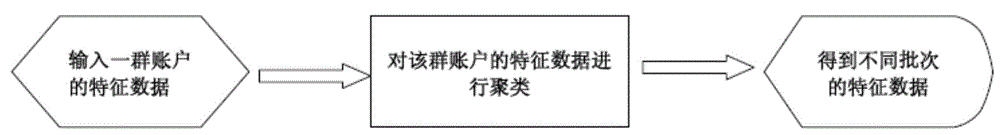
ActiveCN105791255AReduce riskSpeed up online risk identificationTransmissionSpecial data processing applicationsRisk identificationMultiple category
The invention relates to an account security technology, and discloses a method and system for identifying computer risks based on account clustering. In the method disclosed by the invention, clustering is carried out according to a pre-set characteristic attribute; account characteristic data is divided into multiple categories; furthermore, whether the account number in various categories after division is greater than a first threshold value or not is judged, such that a potential batch suspicious account is identified; therefore, risks are avoided effectively; in addition, judgement of the suspicious account is completed through an offline server; furthermore, a service permission table is generated; an online server can find the suspicious account in time according to the service permission table and forbid the suspicious account to use corresponding services; therefore, the online risk identification speed is enhanced; and better services are provided.
Owner:ADVANCED NEW TECH CO LTD
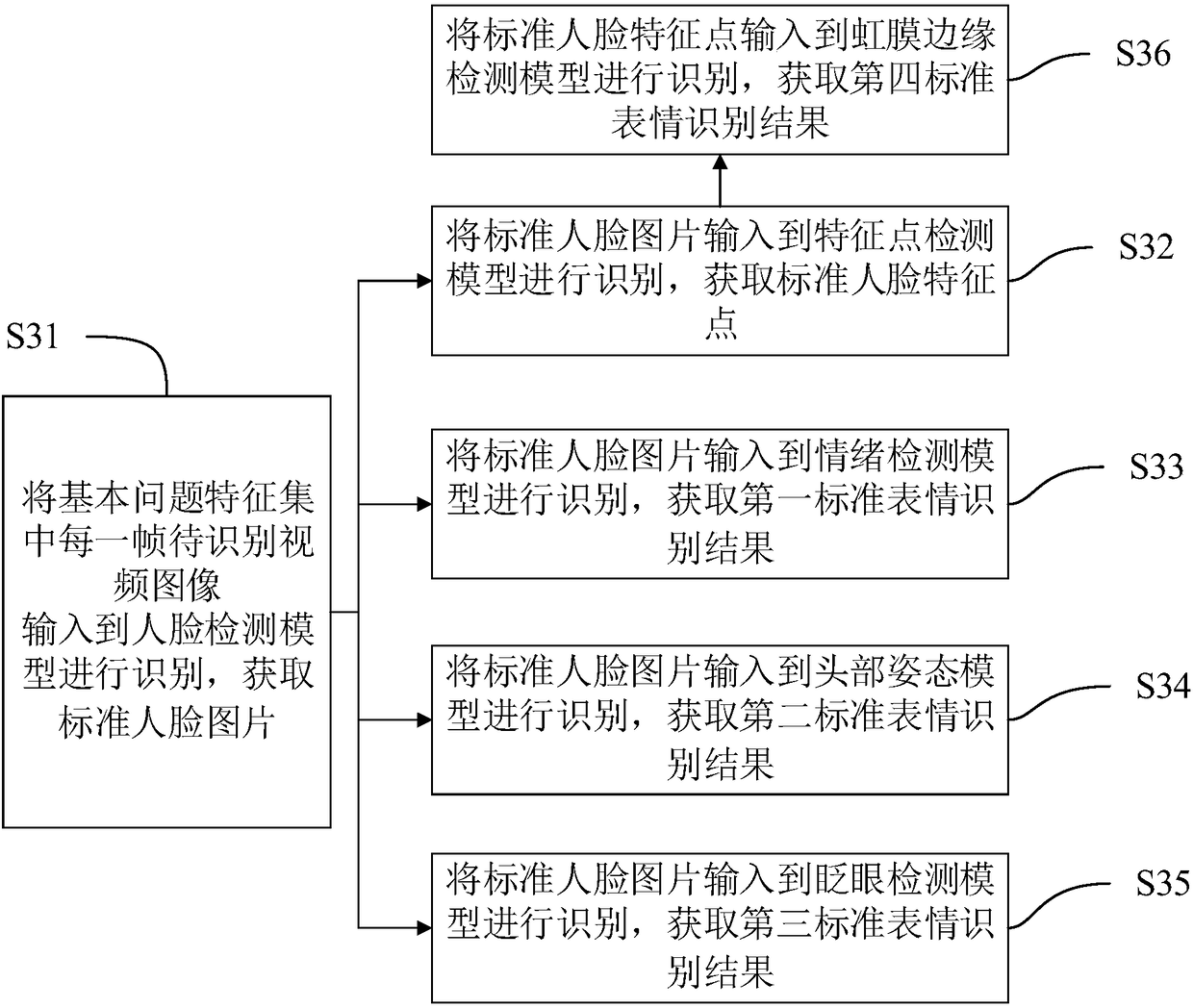
Micro-expression-based risk identification method and device, equipment and medium
PendingCN108537160AImprove accuracyEasy to calculateFinanceEnsemble learningPattern recognitionRisk Control
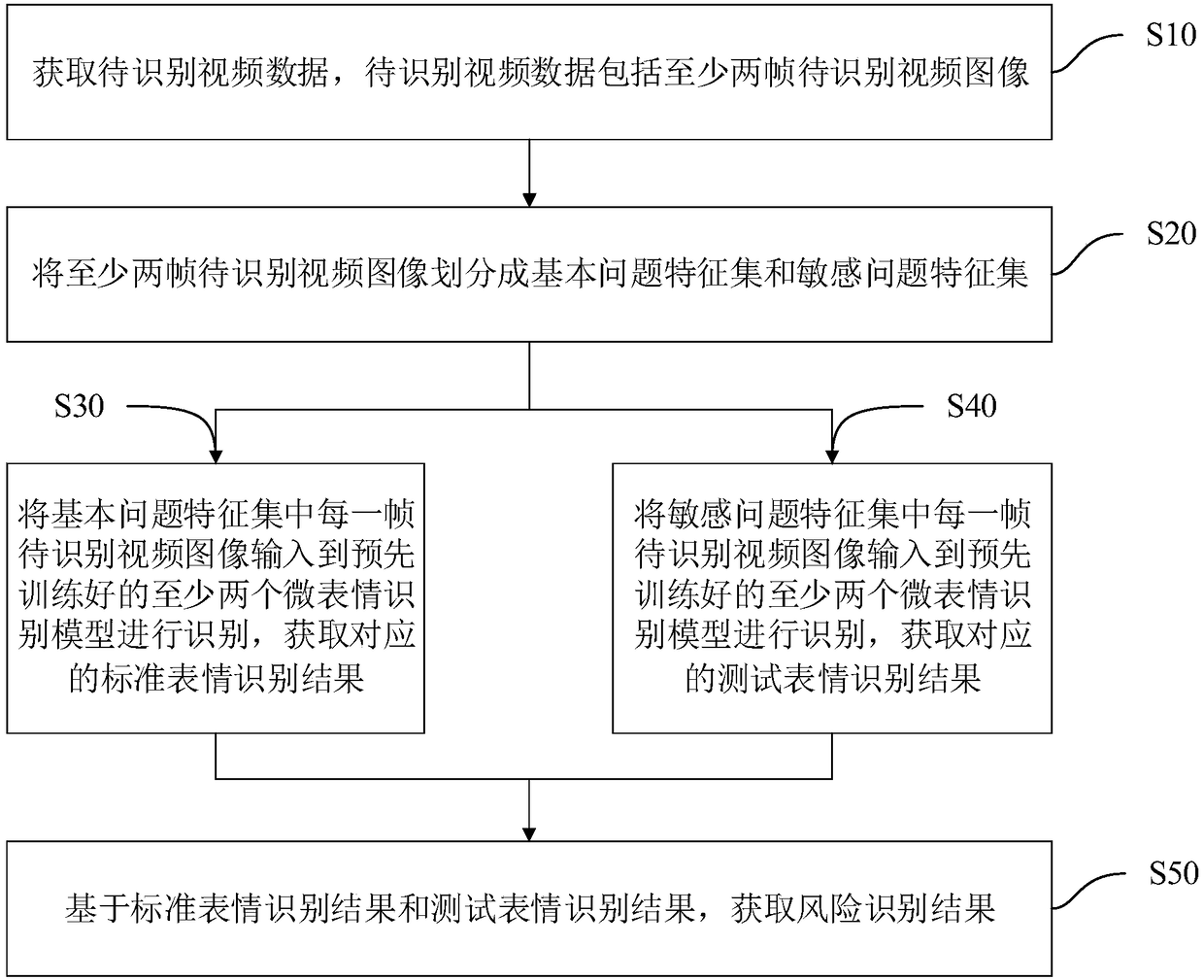
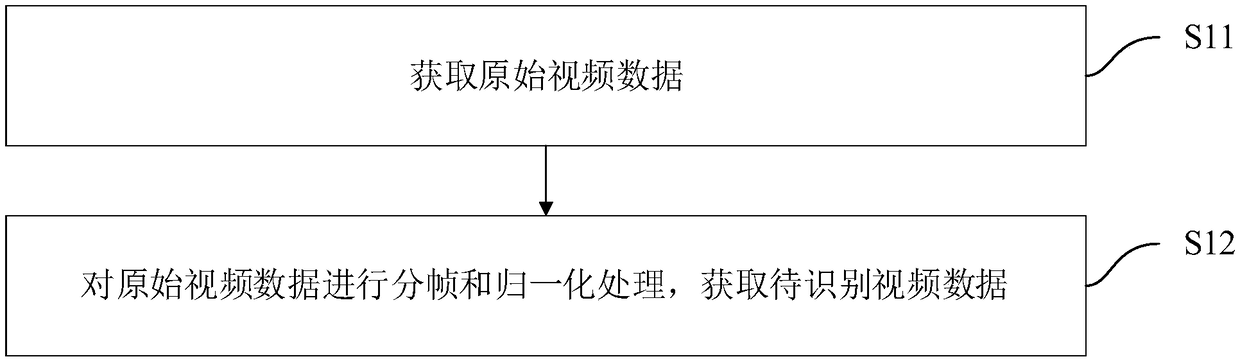
The invention discloses a micro-expression-based risk identification method and device, equipment and a medium. The micro-expression-based risk identification method comprises: to-be-identified videodata are obtained, wherein the to-be-identified video data include at least two frames of to-be-identified video images; the at least two frames of to-be-identified video images are classified into abasic problem feature set and a sensitive question feature set; each frame of to-be-identified video image in the basic problem feature set is inputted into at least two pre-trained micro-expression recognition models for identification and corresponding standard expression recognition results are obtained; each frame of to-be-identified video image in the sensitive question feature set is inputted into at least two pre-trained micro-expression recognition models for identification and thus corresponding testing expression recognition results are obtained; and on the basis of the standard expression recognition results and the testing expression recognition results, a risk identification result is obtained. With the micro-expression-based risk identification method disclosed by the invention, problems of low result trustiness and poor auxiliary effect of the current risk control result can be solved.
Owner:PING AN TECH (SHENZHEN) CO LTD
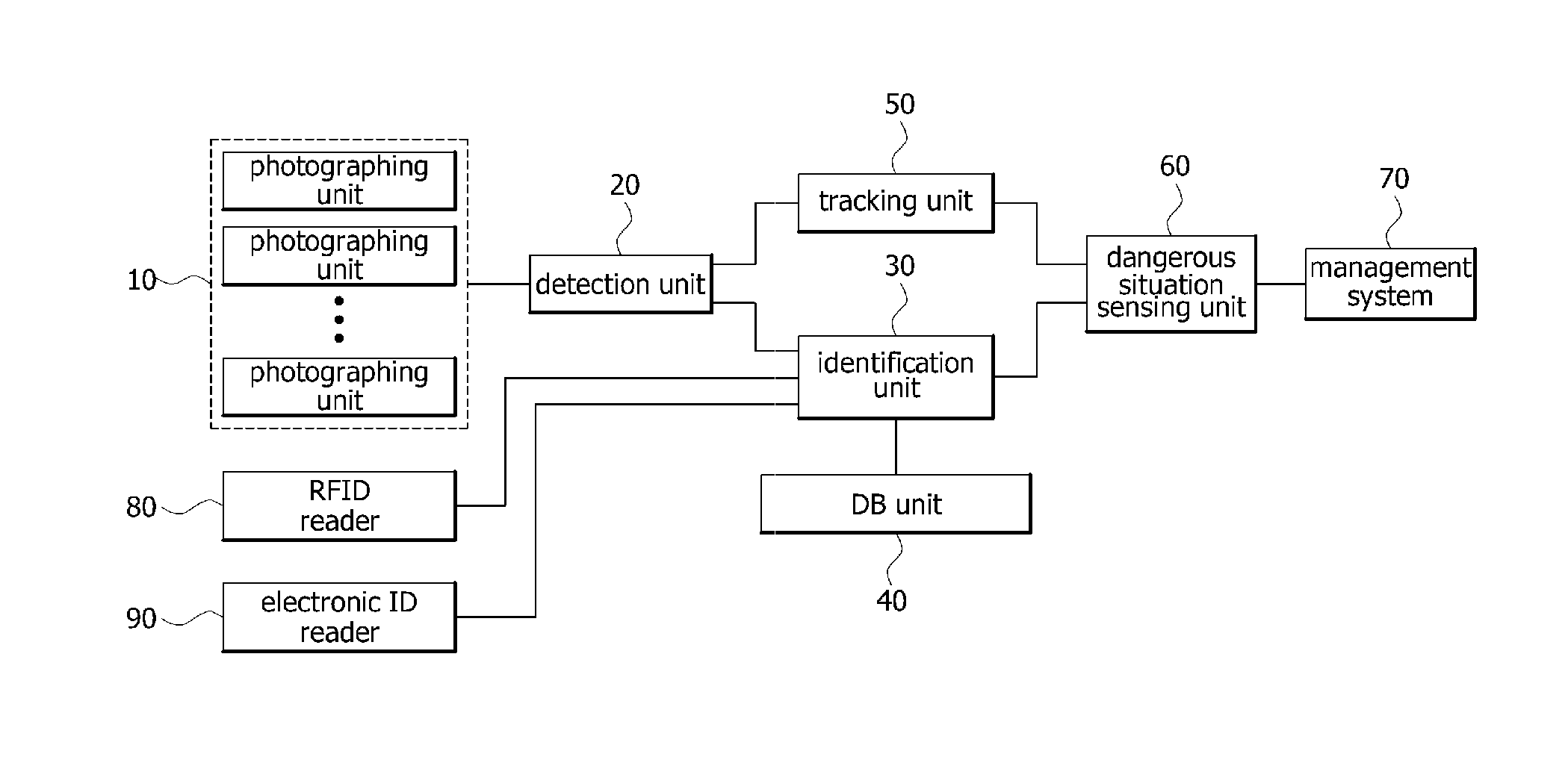
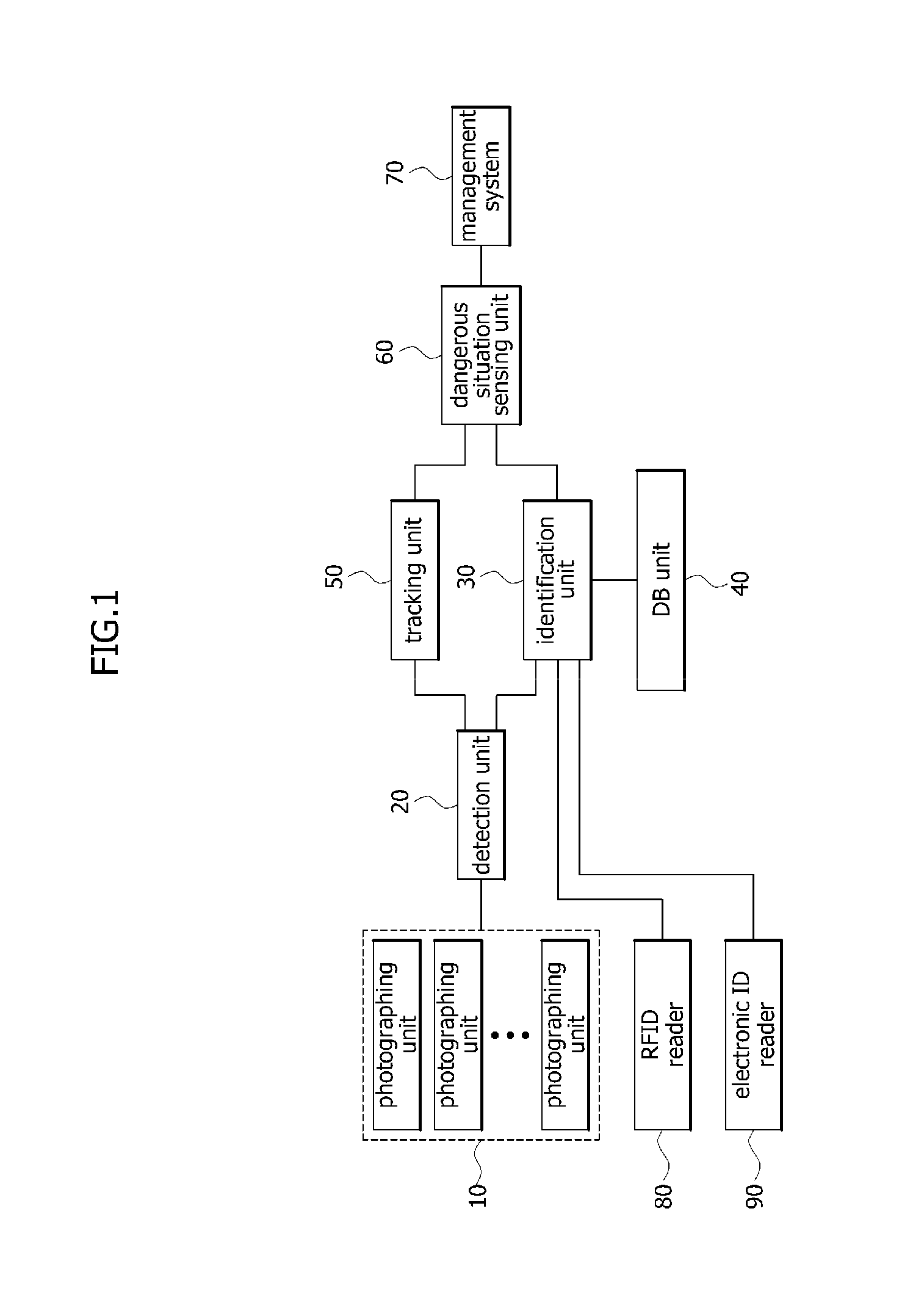
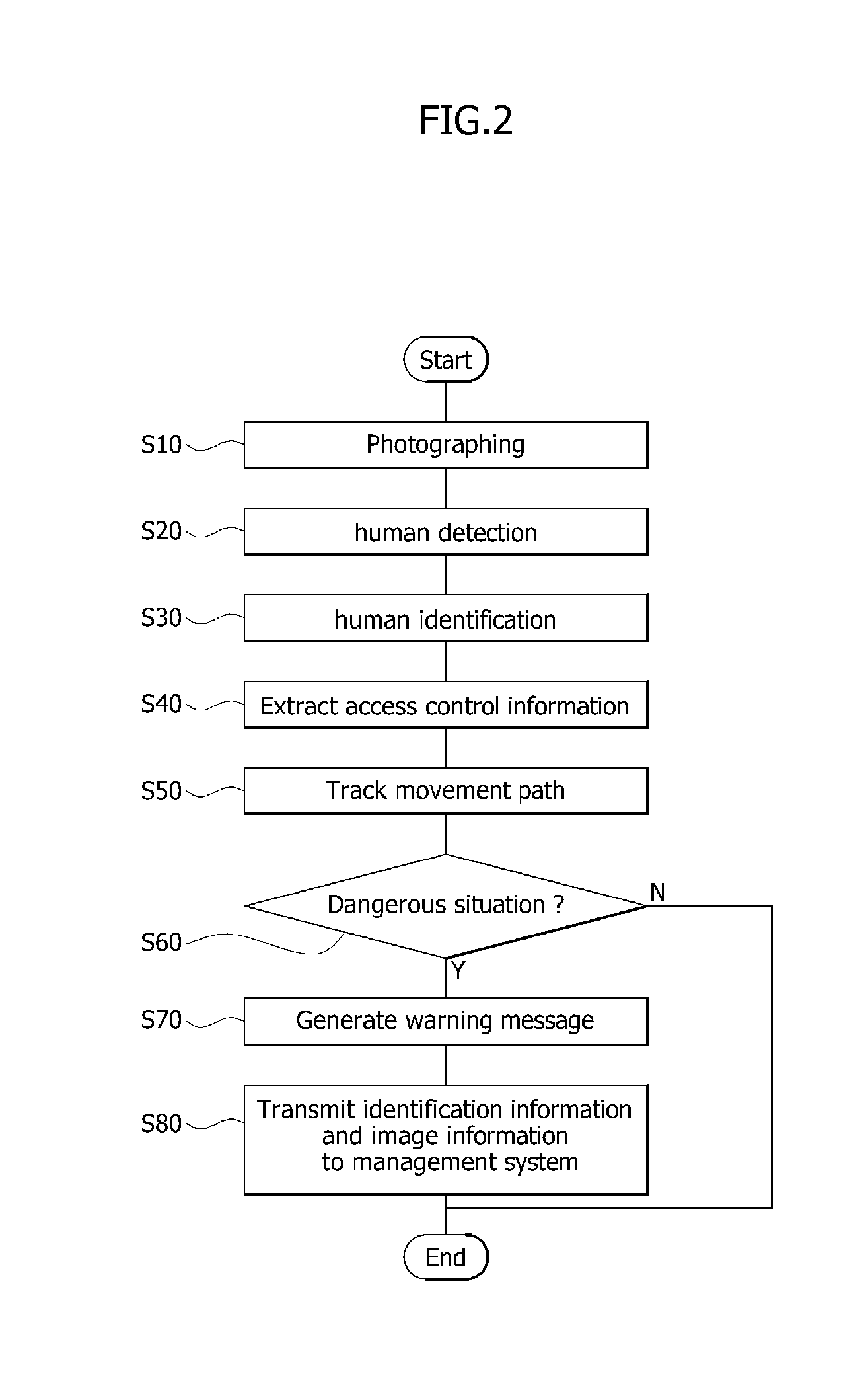
Risk recognition method for use in video surveillance system based on human identification
InactiveUS20130188031A1Character and pattern recognitionColor television detailsVideo monitoringPattern recognition
A risk recognition method based on human identification is disclosed, which identifies a human being from a captured image, such that it can recognize a dangerous situation of each person. The risk recognition method includes detecting a person from photographed image information, and identifying the detected person, thereby generating identification information for each person; extracting access control information for each person using the identification information; analyzing the access control information simultaneously while tracking a movement path for each person, and determining whether a dangerous situation for each person occurs; and if the dangerous situation occurs, selectively warning of the dangerous situation of the person who causes the dangerous situation.
Owner:ELECTRONICS & TELECOMM RES INST
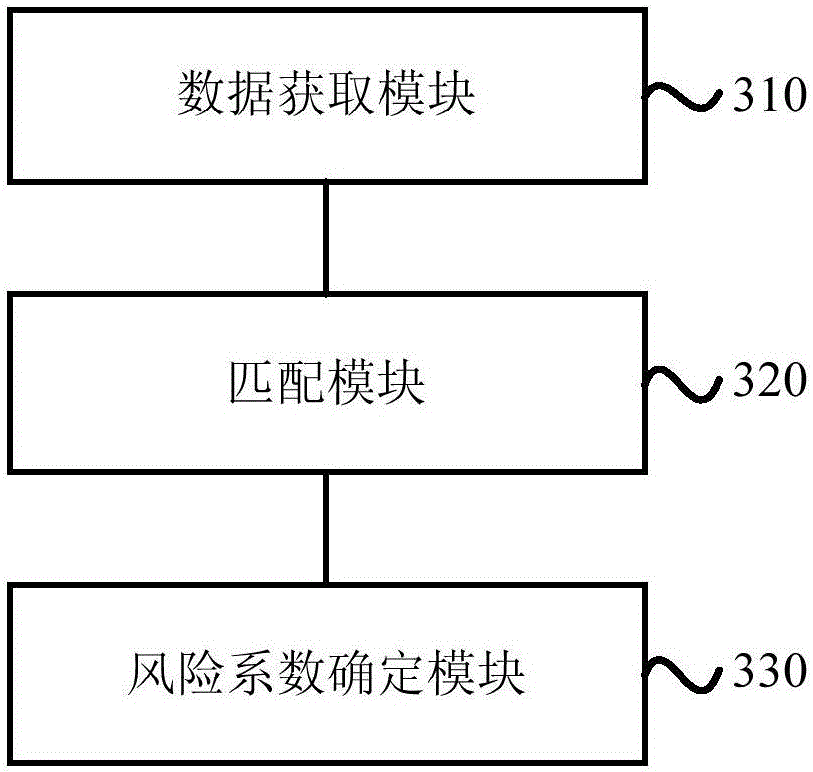
Account risk identification method and device
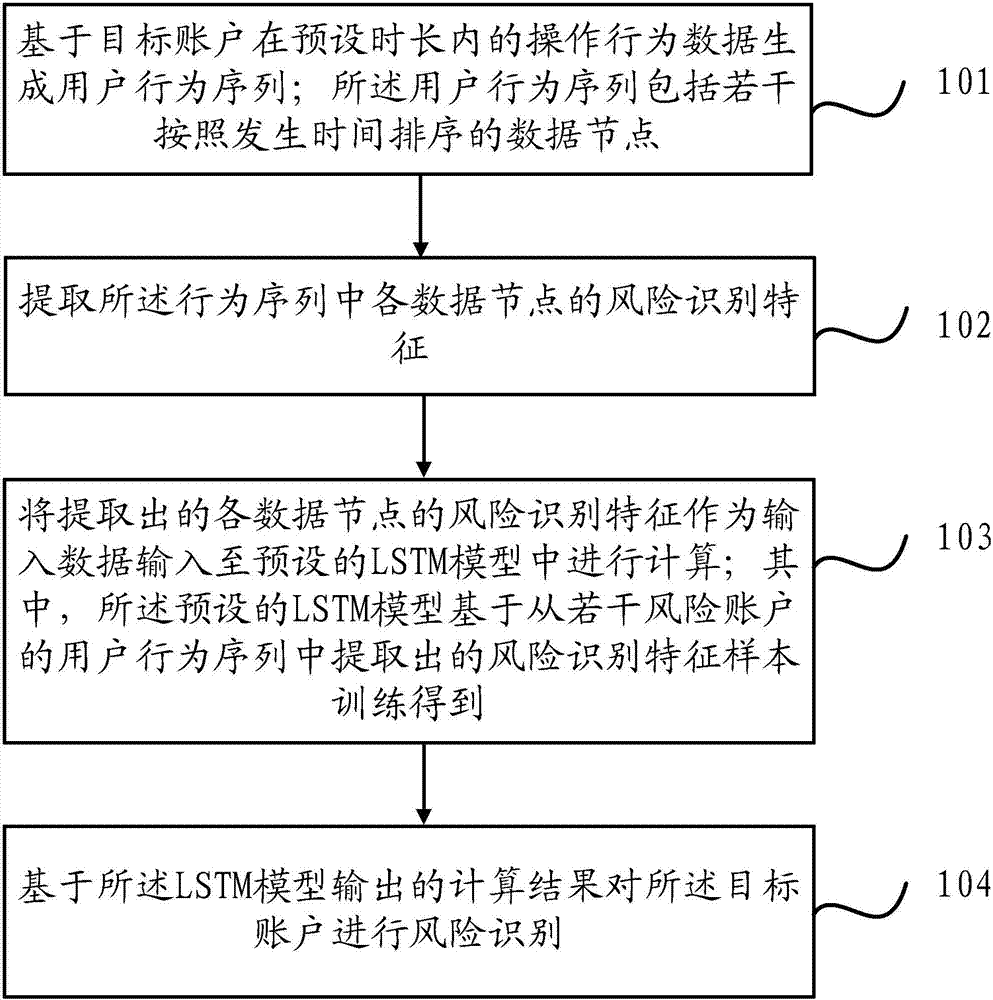
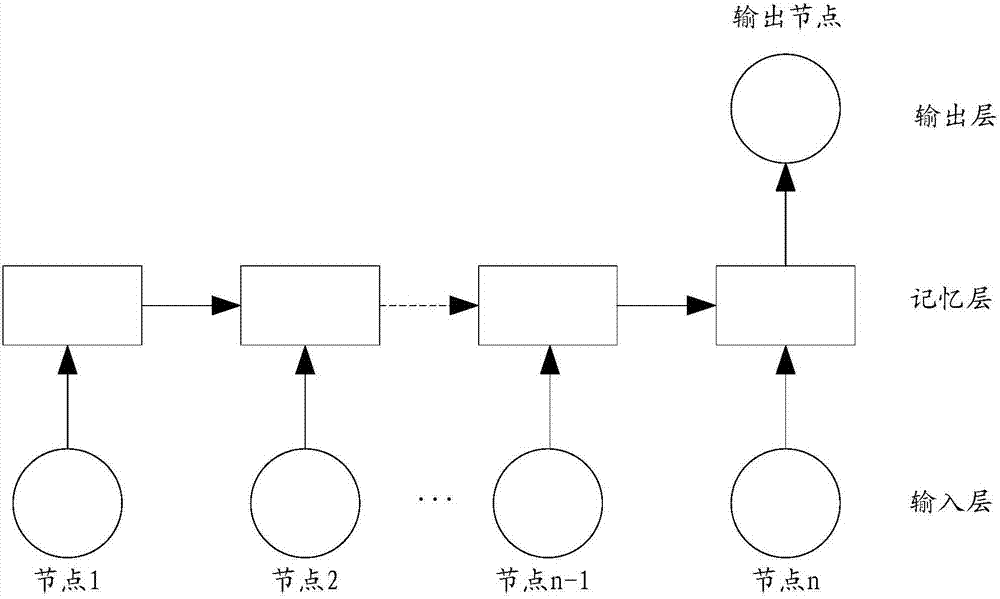
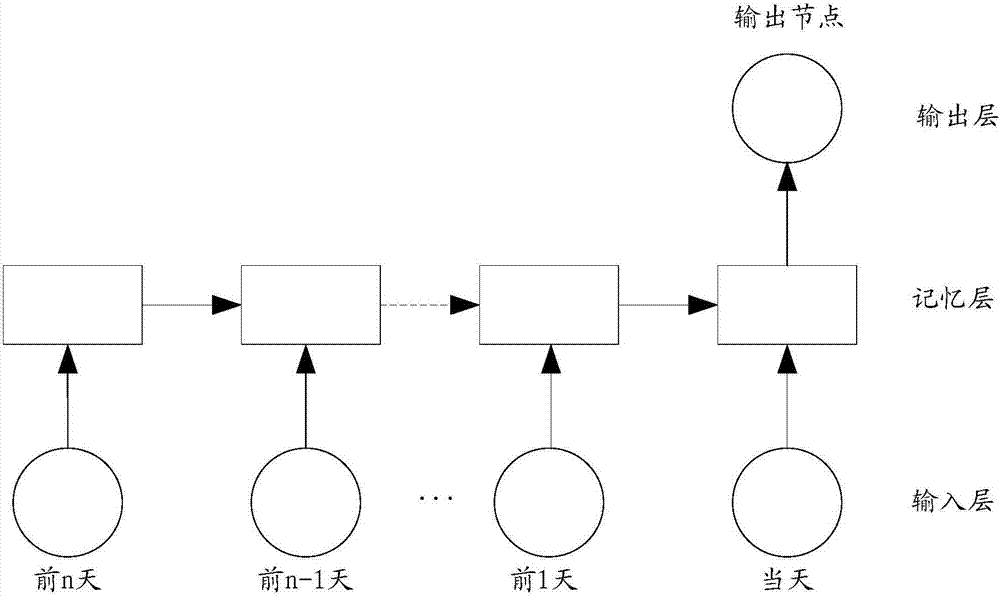
The invention provides an account risk identification method and device. The method comprises the steps that a user behavior sequence is generated based on operation behavior data of a target account within a preset duration; the user behavior sequence comprises a plurality of data nodes ordered according to occurrence time; risk identification features of all the data nodes in the behavior sequence are extracted; the extracted risk identification features of all the data nodes are used as input data, and the input data is input into a preset long and short term memory (LSTM) model for calculation, wherein the preset LSTM model is obtained through sample training based on the risk identification features extracted from the user behavior sequence of a plurality of risk accounts; and risk identification is performed on the target account based on a calculation result output by the LSTM model. Through the account risk identification method and device, the sensitivity and accuracy of performing risk assessment on the target account can be overall improved.
Owner:ADVANCED NEW TECH CO LTD
Risk identification method and device
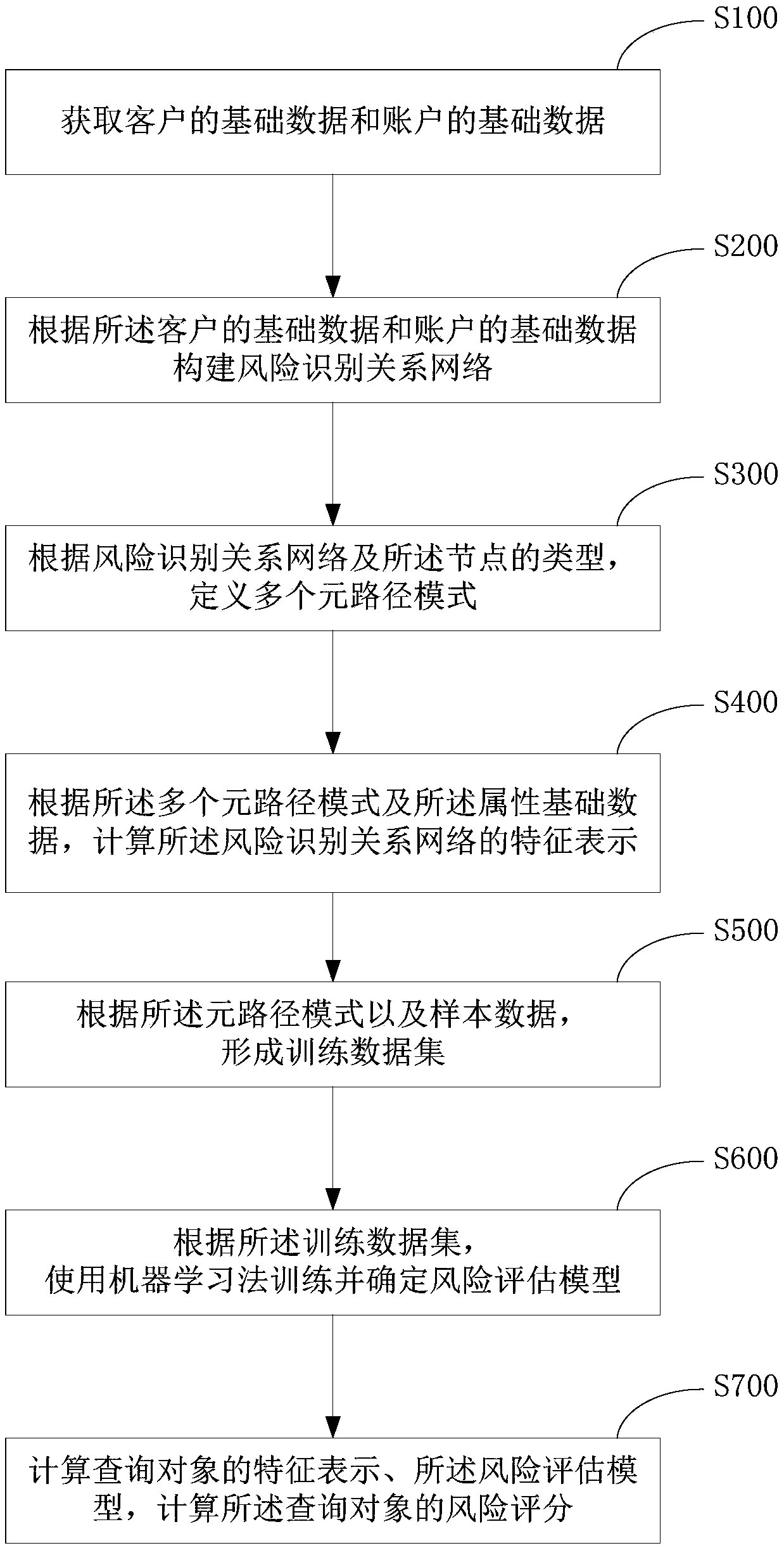
ActiveCN109003089AEasy to identifyImprove the accuracy of prevention and control identificationFinanceResourcesFeature vectorData set
The embodiment of the invention provides a risk identification method and a device. The method comprises the following steps: acquiring the basic data of a customer and the basic data of an account; constructing a financial transaction relationship network according to customer basic data and account basic data; defining multiple meta-path patterns according to the types of financial transaction relationship networks and nodes; according to the multiple meta-path patterns and attribute basic data, calculating the feature representation of the target entity in the financial transaction relationship network; forming a training data set according to the relationship network eigenvector and the sample data; according to the training data set, training and determining the risk assessment modelby a machine learning method; calculating the feature representation and risk assessment model of the query object, and calculating the risk score of the query object.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Method and device for preventing and controlling account take-over fraud risk
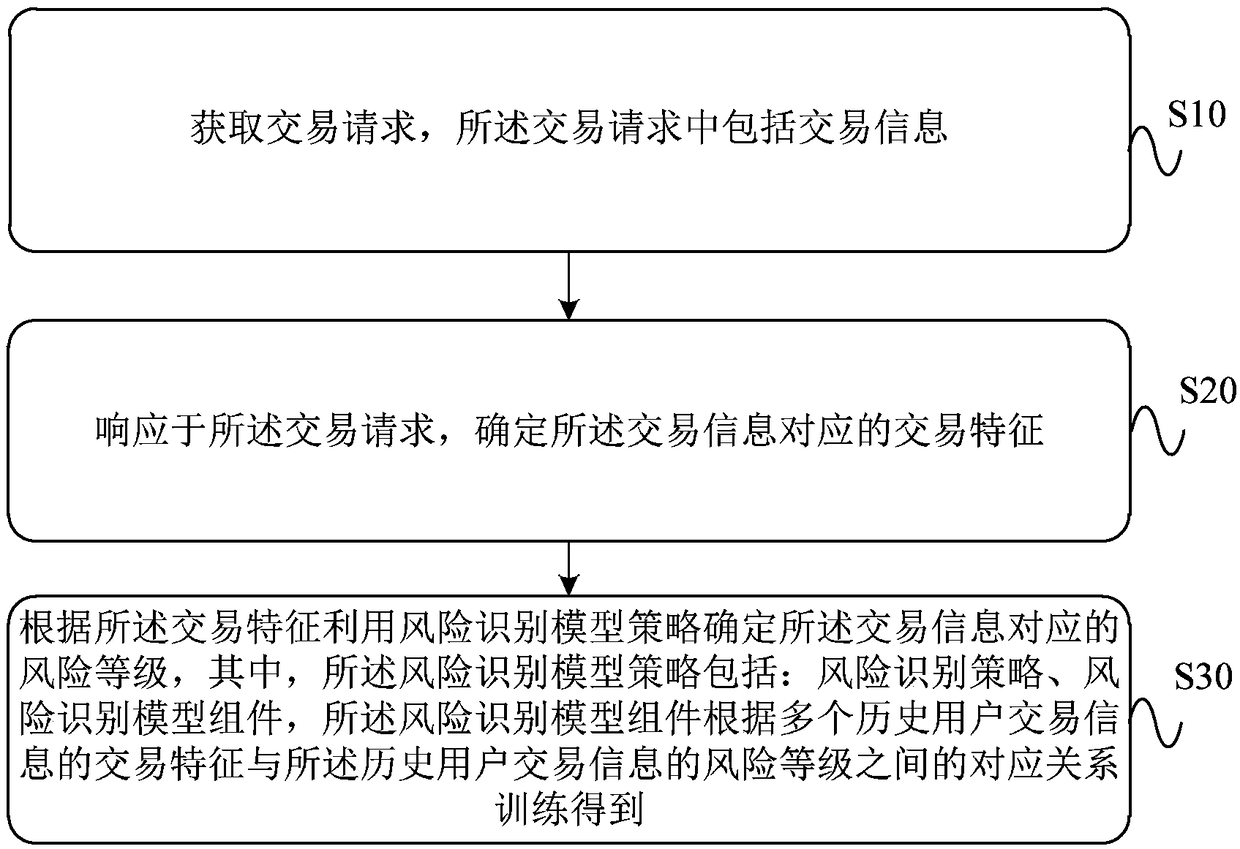
ActiveCN109064175ARealize intelligent risk prevention and control functionRealization of risk prevention and controlFinanceProtocol authorisationRisk preventionRisk level
The application provides a method and device for preventing and controlling an account take-over fraud risk. The method comprises: a transaction request is obtained, wherein the transaction request includes transaction information; a transaction feature corresponding to the transaction information is determined by responding to the transaction request; according to the transaction feature, a risklevel corresponding to the transaction information is determined by using a risk identification model policy, wherein the risk identification model policy includes a risk identification policy and a risk identification model assembly and the risk identification model assembly is obtained by training based on a corresponding relationship between transaction features of a plurality of pieces of historical user transaction information and risk levels of the historical user transaction information. Therefore, the intelligent risk prevention and control function of the account take-over fraud is realized; and thus the risk prevention and control of the transaction account take-over fraud in the payment field is realized.
Owner:ADVANCED NEW TECH CO LTD
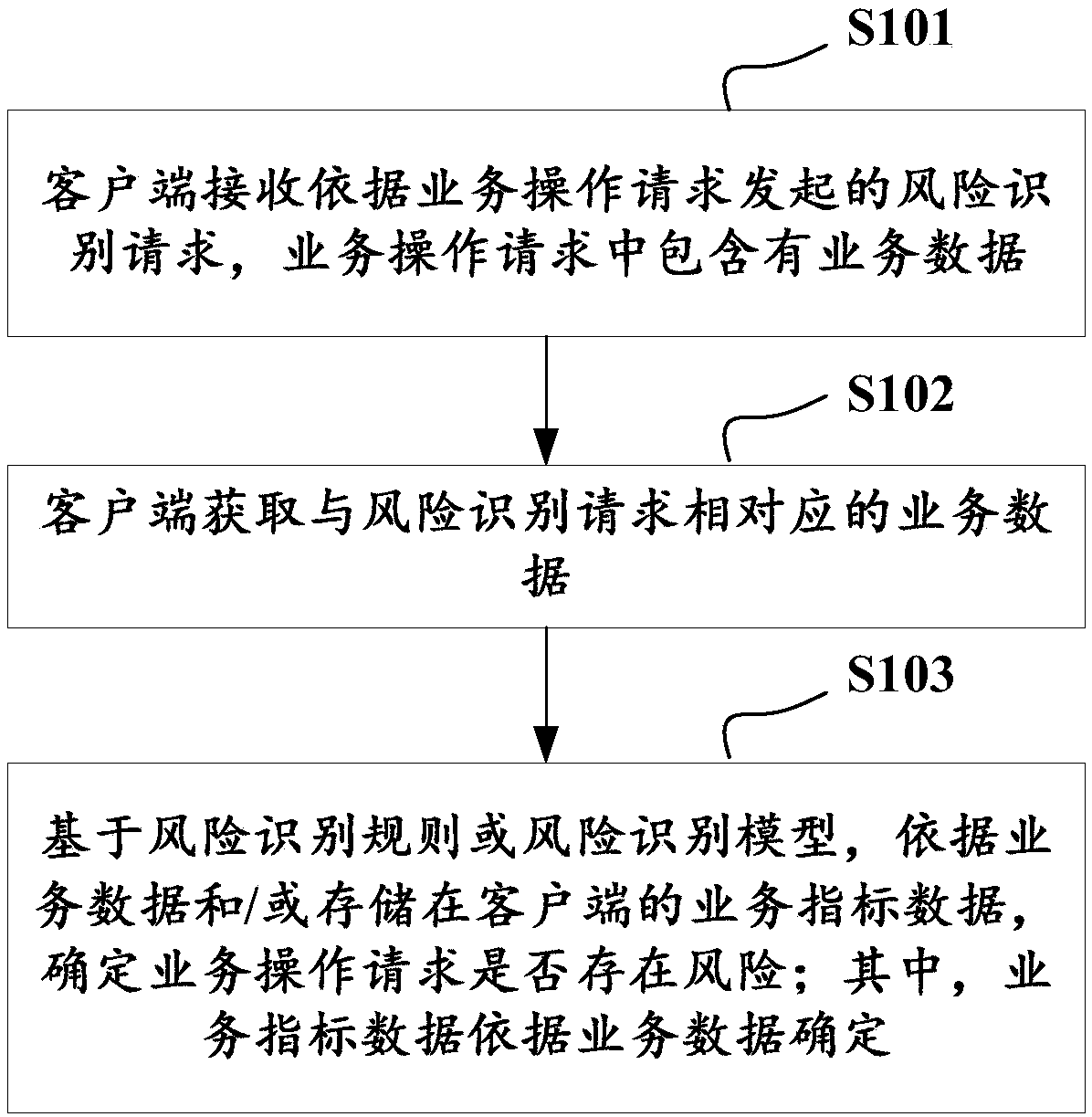
Risk identification method, client device and risk identification system
InactiveCN107644340AReduce storage costsLow storage costTransmissionCommerceRisk identificationClient-side
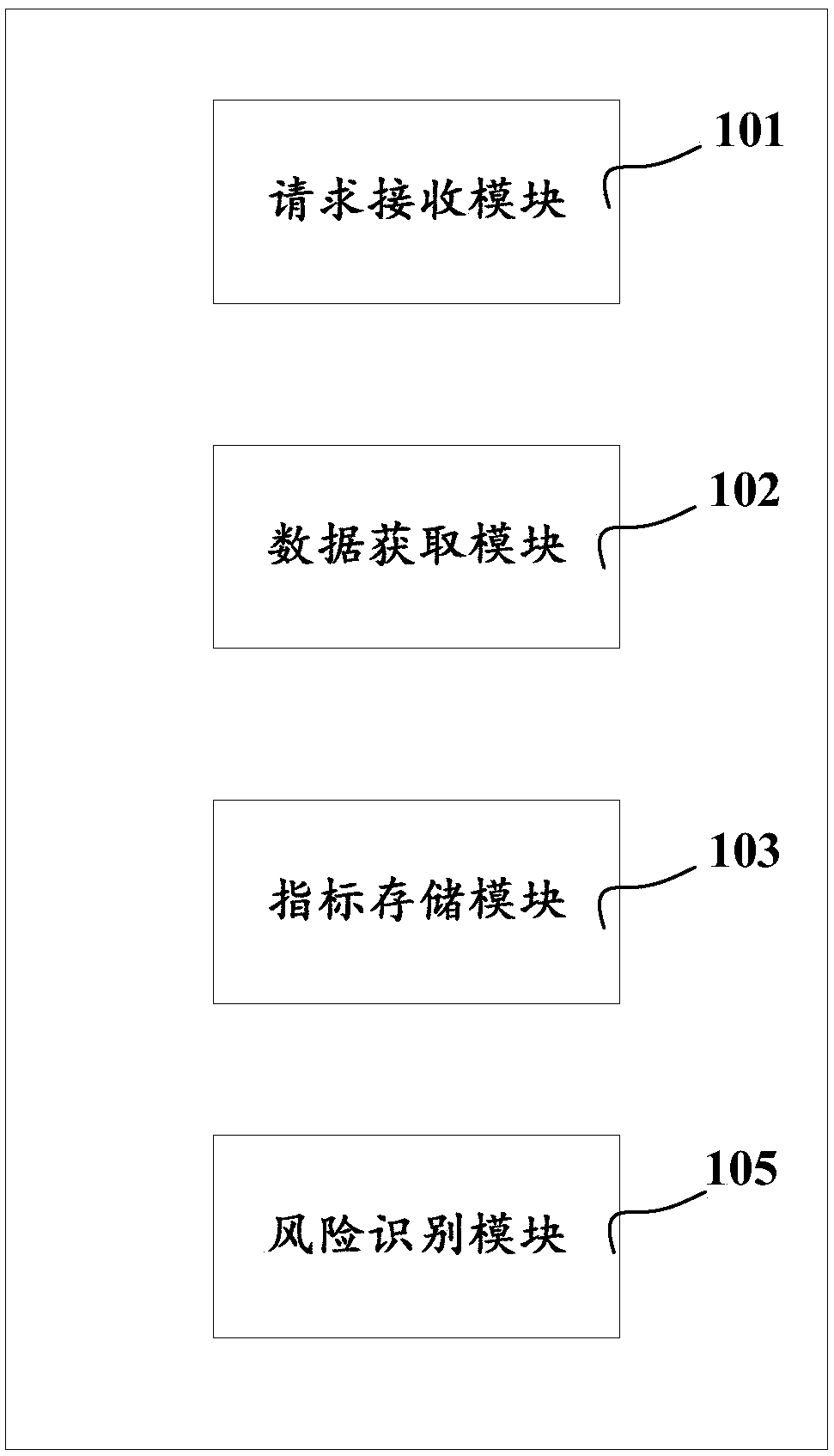
The present invention discloses a risk identification method. The method comprises: receiving a risk identification request initiated according to a service operation request through a client, whereinthe service operation request comprises service data; obtaining service data corresponding to the risk identification request by the client; and based on a risk identification rule or a risk identification model, determining whether the service operation request has risks or not according to the service data and / or service index data stored in the client, wherein the service index data is determined according to the service data. The present invention further discloses a risk identification device. The risk identification device comprises a data obtaining module, an index storage module and arisk identification module. The present invention further discloses a risk identification system. The system comprises a client device and a server device, or a client device, a server device and a cloud risk identification device. The problem is solved that the cost of a server is too high in the prior art, consumption for the server is reduced, and storage cost of risk identification and control is reduced.
Owner:ADVANCED NEW TECH CO LTD
Industrial park surroundings risks recognizing method
InactiveCN101136090ASolve the problem of poor authenticity and credibilityAvoid accidentsForecastingVery low riskLower risk
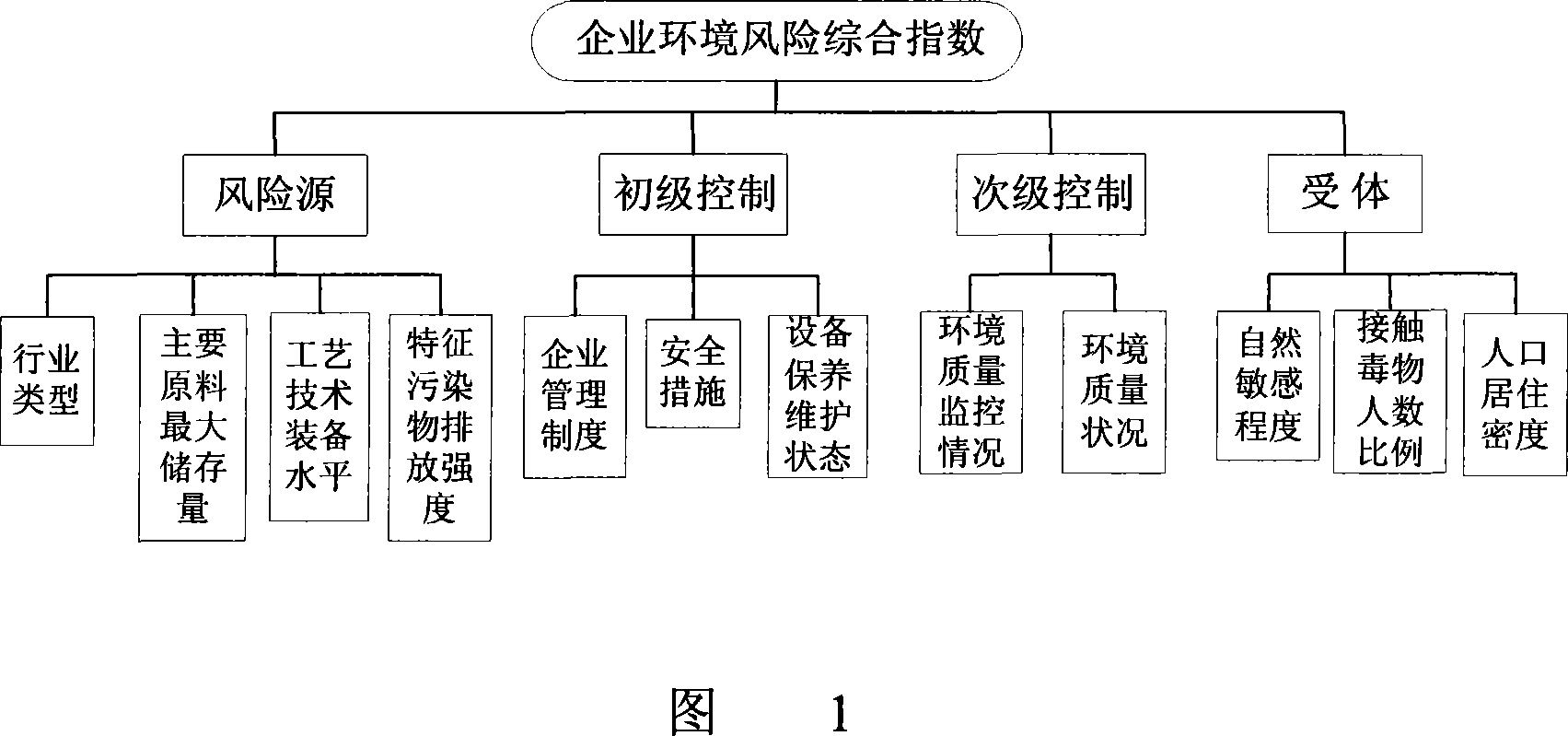
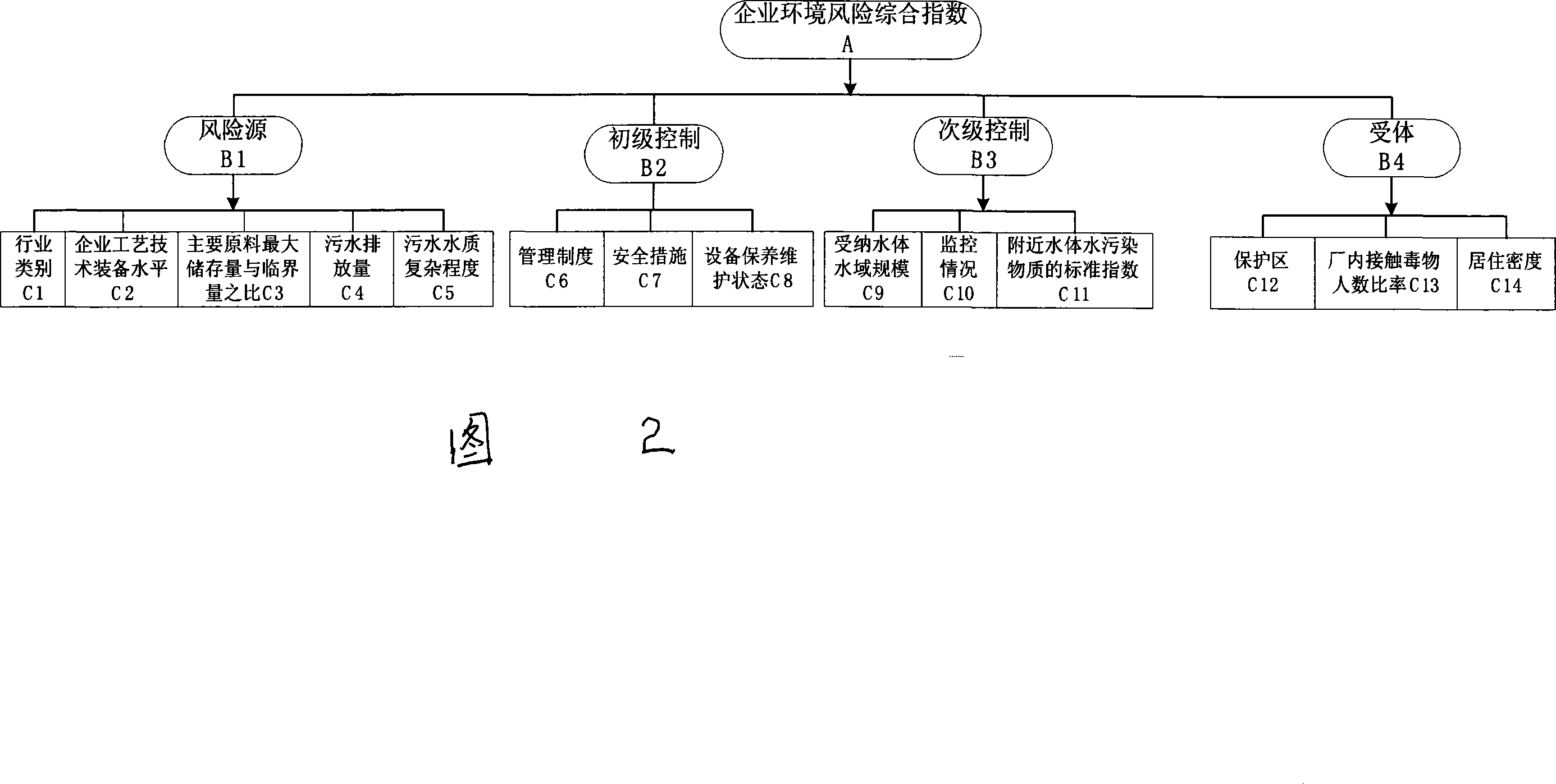
The method comprises: 1) establishing an environment risk recognizing index system and its sorting terms; 2) calculating the enterprise environment risk hybrid index; based on the grading score of each factor, using directly summation or weight summation to get the enterprise environment risk hybrid index; 3) making a grading for the industrial park enterprises environment risk to form 4 areas which are high risk, middle risk, low risk, and very low risk area; 4) confirming the main factor of industrial park enterprises environment risks.
Owner:NANJING UNIV
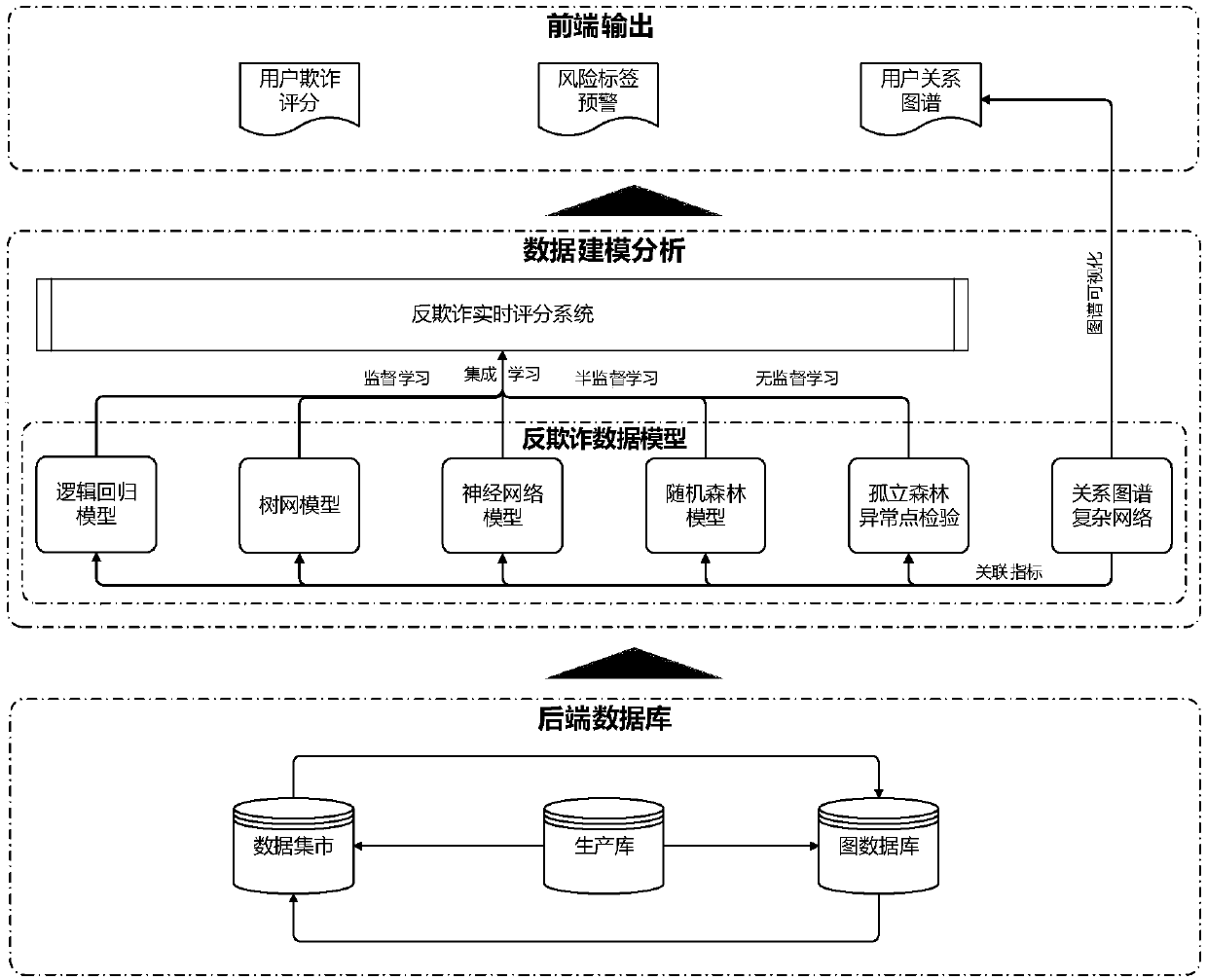
Anti-fraud data analysis method and system
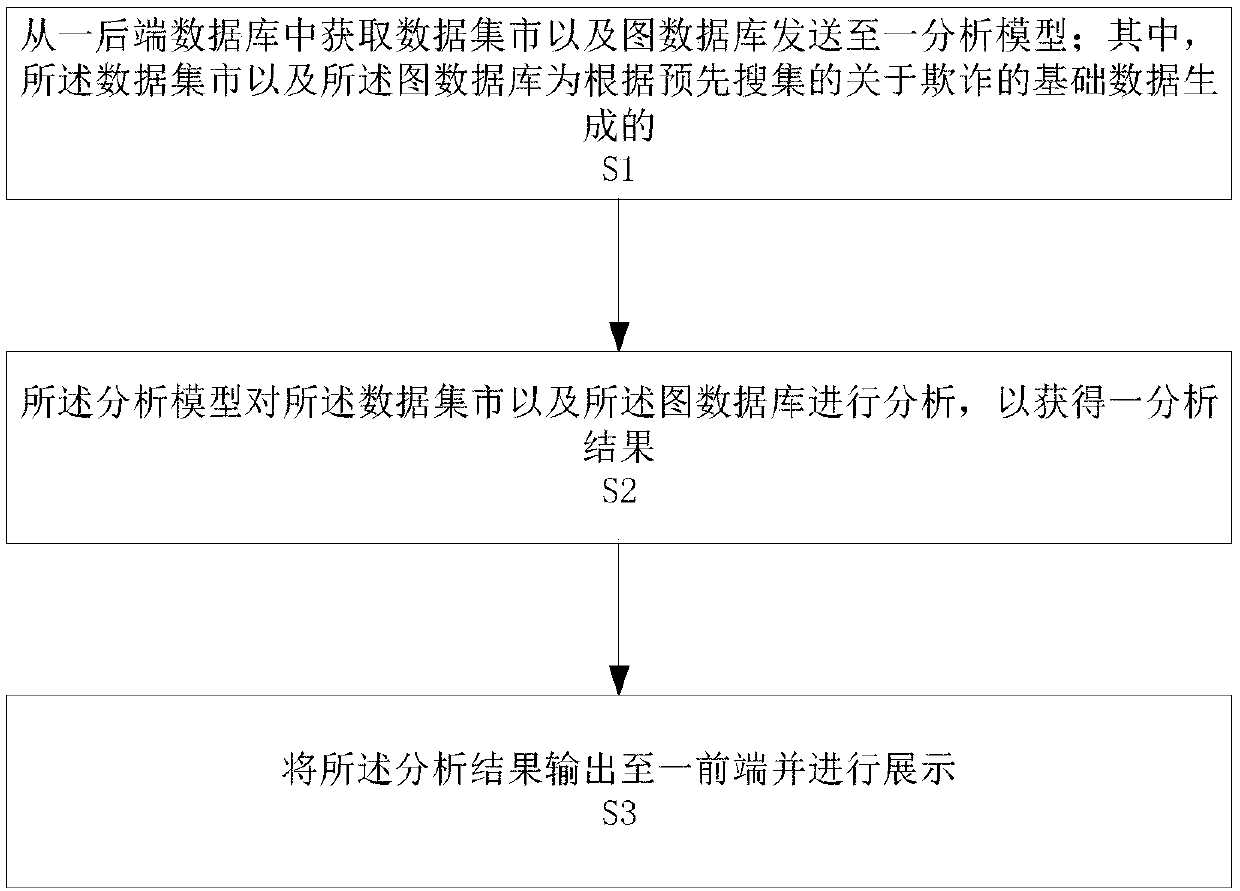
InactiveCN108038700AFast updateObserve intuitivelyCharacter and pattern recognitionBuying/selling/leasing transactionsRisk identificationSupervised learning
The invention provides an anti-fraud data analysis method and system. The method comprises the steps of obtaining a data mart and a graph database from a back-end database, and sending the data mart and the graph database to an analysis model, wherein the data mart and the graph database are generated according to pre-collected basic data on fraud; analyzing the data mart and the graph database bythe analysis model to obtain an analysis result; and outputting the analysis result to a front end and performing display. An individual fraud risk identification model is combined with a group fraudrisk identification model; and an anti-fraud system is completer. Supervised learning, semi-supervised learning and unsupervised learning are integrated; the data is processed; the identification accuracy is improved; and the model is higher in updating speed and higher in adaptability. Meanwhile, an anti-fraud real-time scoring system is established; the scoring calculation is more accurate; andan anti-fraud analysis result is more intuitive to observe. A visual user relationship map also can intuitively display the analysis result, so that the user experience is good.
Owner:SHANGHAI QIANLONG INFORMATION TECH CO LTD
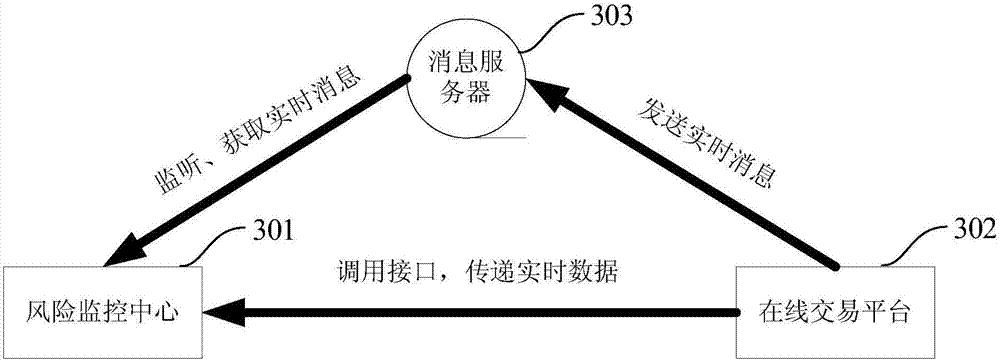
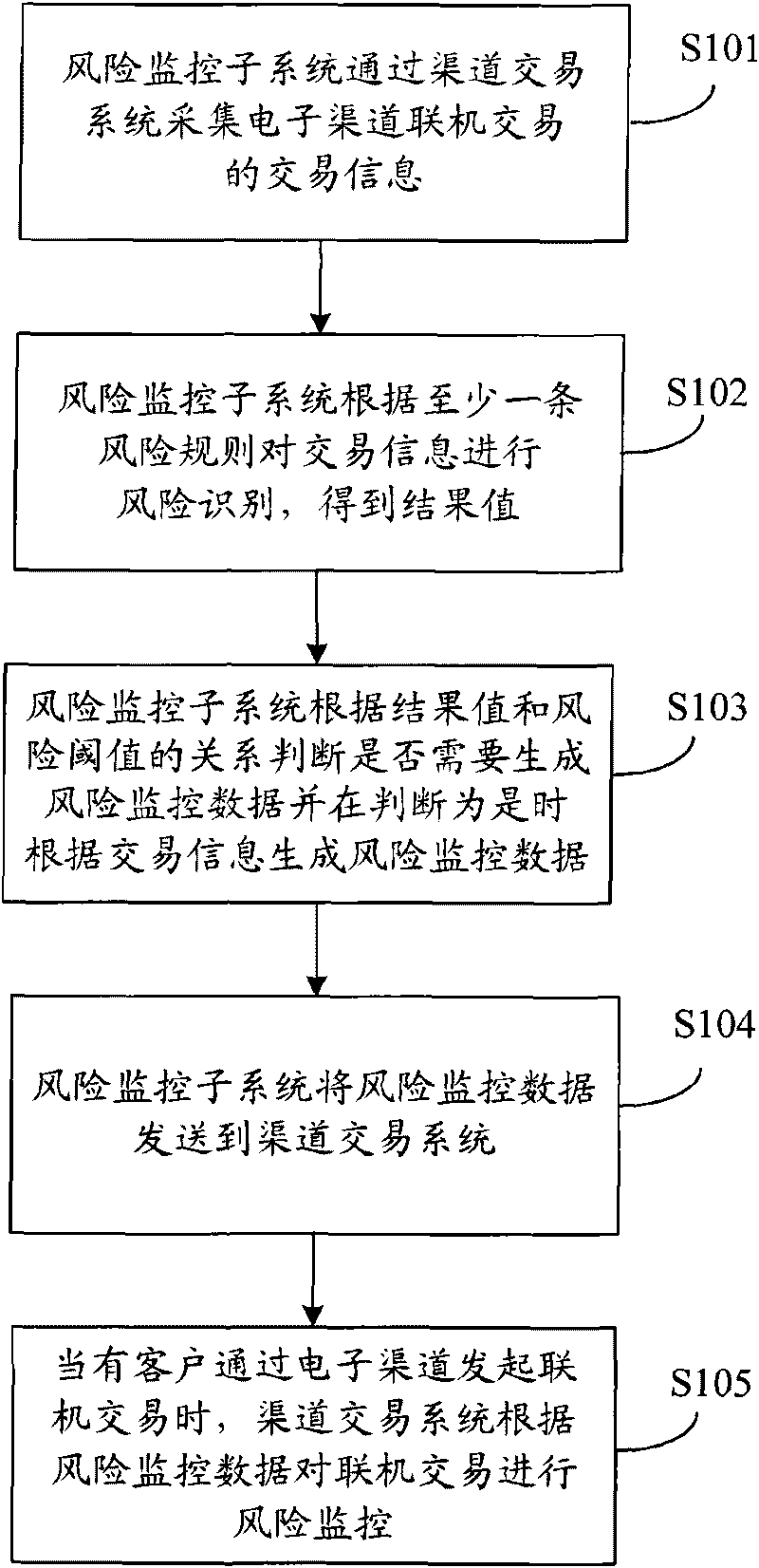
Method and system for monitoring electronic bank risks
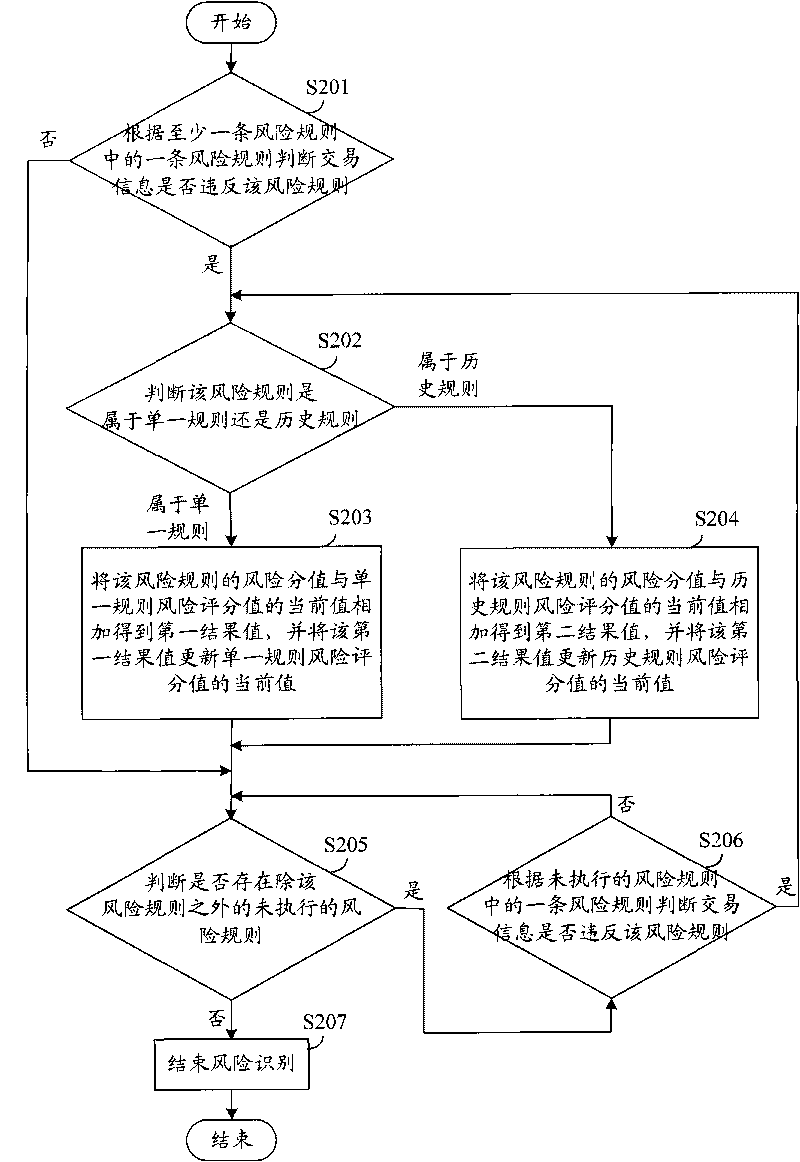
InactiveCN101706937AReduce transaction riskImprove securityFinancePlatform integrity maintainanceRisk identificationData needs
The invention discloses a method and a system for monitoring electronic bank risks, wherein the method comprises the following steps of: collecting trading information on-line traded by an electronic channel through a channel trading system by a risk monitoring subsystem, identifying risks for the trading information according to at least a risk rule, obtaining a result value, judging whether risk monitoring data need to be generated according to the relation between the result value and a risk threshold value, and if so, generating the risk monitoring data according to the trading information and sending the risk monitoring data to the channel trading system; and when a customer initiates on-line trading through the electronic channel, the channel trading system monitors the risks of the on-line trading according to the risk monitoring data. The risk identification of the trading information for electronic banks is carried out through the risk monitoring subsystem, and real-time risk monitoring for the on-line trading is carried out through the channel trading system according to the result of risk identification, thereby reducing the trading risks of each channel of the electronic banks and enhancing the security of customer trading.
Owner:CHINA CONSTRUCTION BANK
Training method and device for financial risk identification model, computer equipment and medium
PendingCN111724083AImprove generalization abilityEfficient training processFinanceCharacter and pattern recognitionEngineeringRisk identification
The invention discloses a training method and device for a financial risk identification model, computer equipment and a medium, and the method comprises the steps: obtaining first user data, with a first credit risk label, of a target domain financial project, inputting the first user data into a meta-learning device for training, and obtaining a classifier corresponding to the target domain financial project for risk identification. According to the method, the classifier corresponding to the target domain financial project is trained in a meta-learning mode, priori knowledge in a source domain task can be effectively migrated, so that the data volume of labeled samples required by model training is small, the generalization performance of the recognition model is improved, and the training process of the model is faster and more efficient. Besides, in the training process of the meta-learner, the source domain correlation among the categories of the task sets is learned, so that prior knowledge can be effectively migrated from tasks closer to the current target domain task during migration learning, and the accuracy of model recognition can be improved. The method can be widelyapplied to the technical field of machine learning.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and device for building equipment risk recognition model
InactiveCN107862468AImprove accuracyCharacter and pattern recognitionResourcesIot gatewayThe Internet
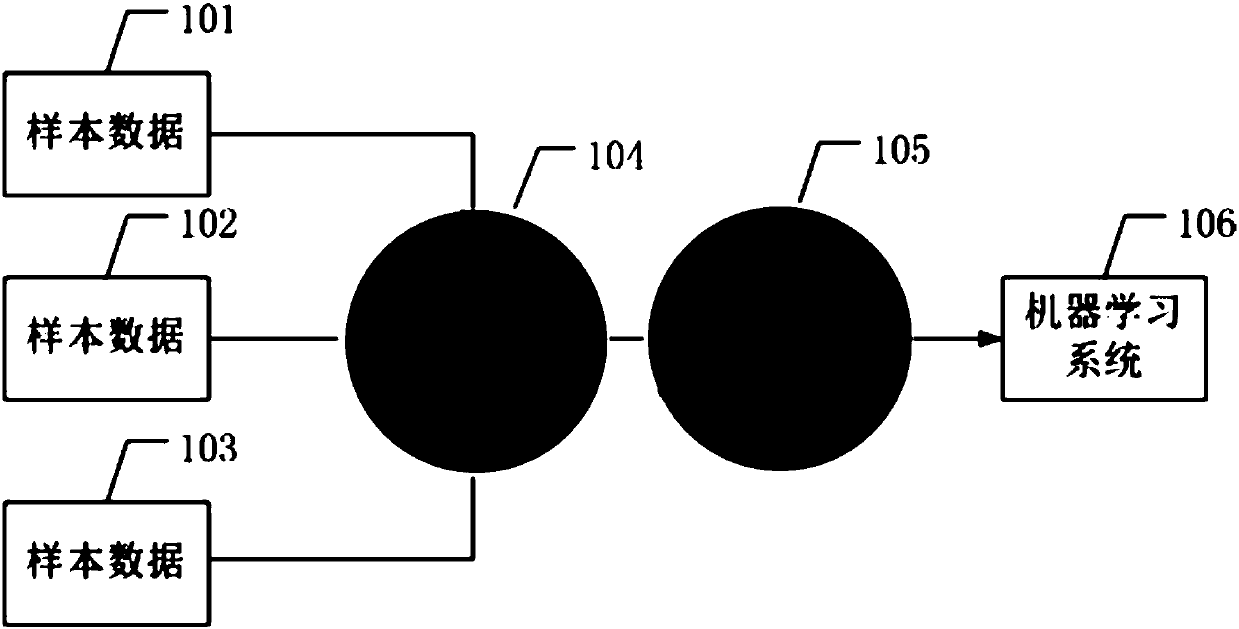
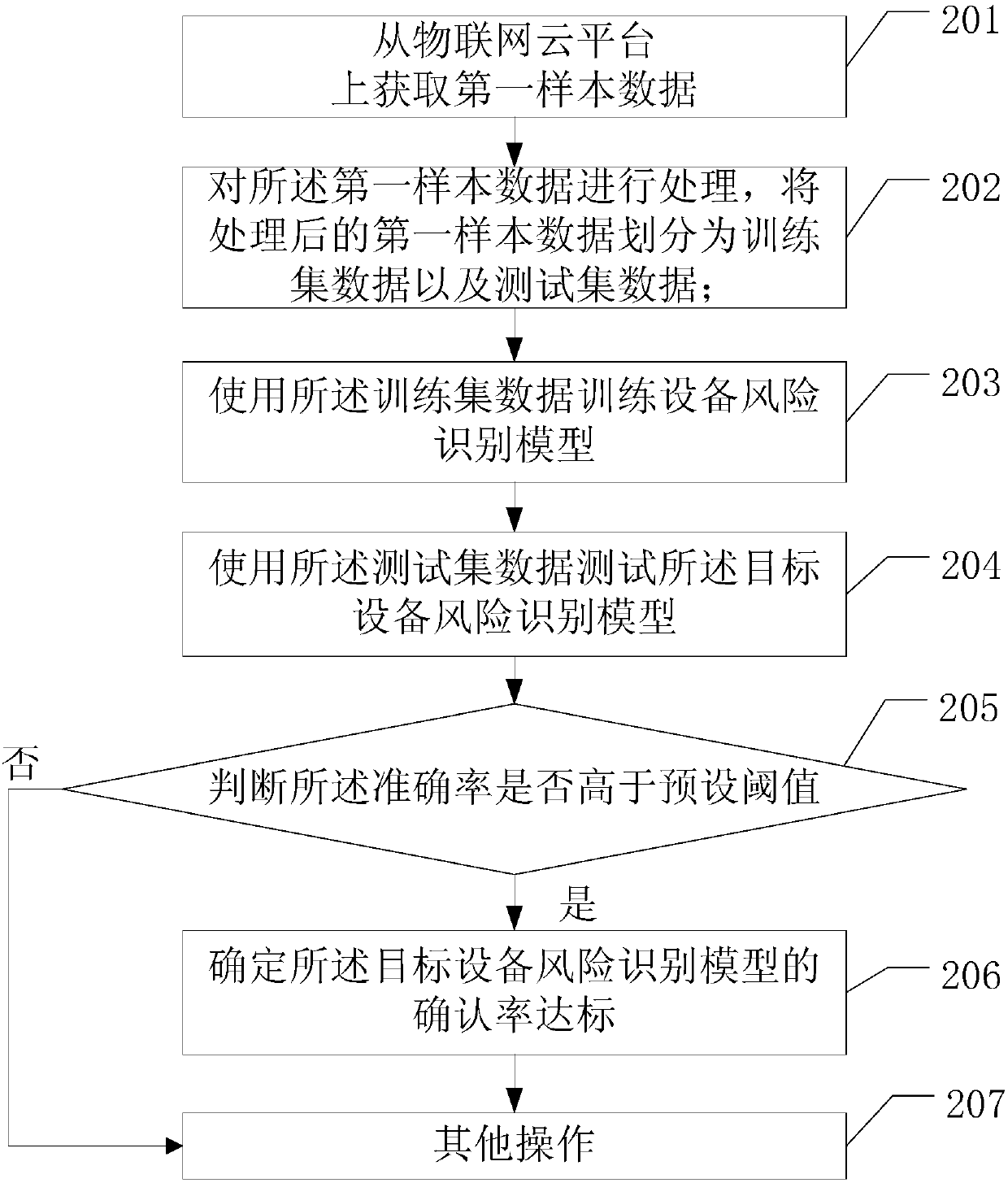
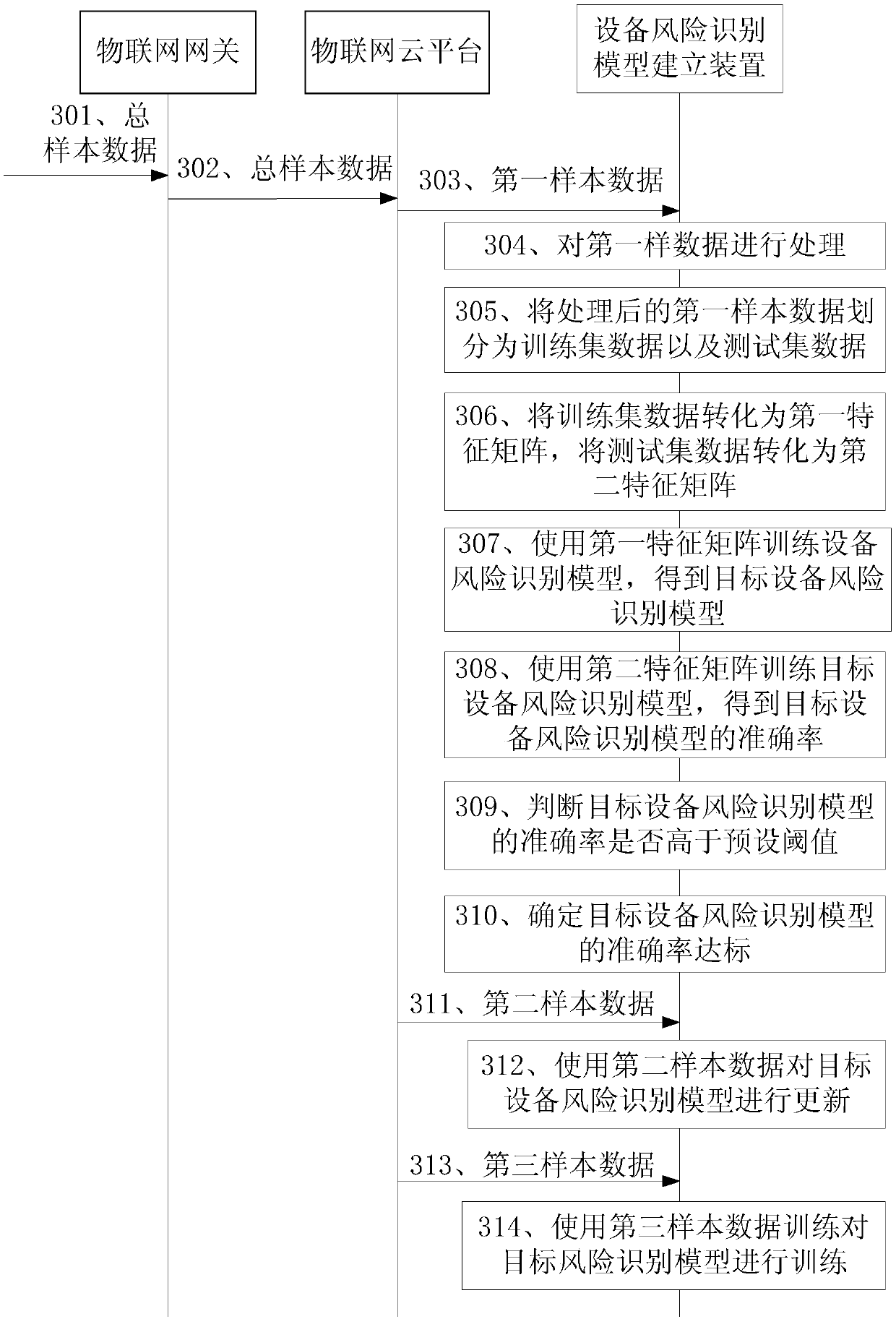
An embodiment of the invention discloses a method and a device for building an equipment risk recognition model. The method includes the steps: acquiring first sample data from an internet of things cloud platform; processing the first sample data, and dividing the processed first sample data into training set data and testing set data; training the equipment risk recognition model by the aid of the training set data to obtain a target equipment risk recognition model; testing the target equipment risk recognition model by the aid of the testing set data to obtain accuracy rate of the target equipment risk recognition model; judging whether the accuracy rate is higher than a preset threshold value or not; determining a fact that identification rate of the target equipment risk recognitionmodel reaches a standard if the accuracy rate is higher than the preset threshold value. Total sample data contain the first sample data and are uploaded to the internet of things cloud platform, andthe equipment risk recognition model is a pre-built equipment risk recognition model to be trained.
Owner:MIXLINKER NETWORKS INC
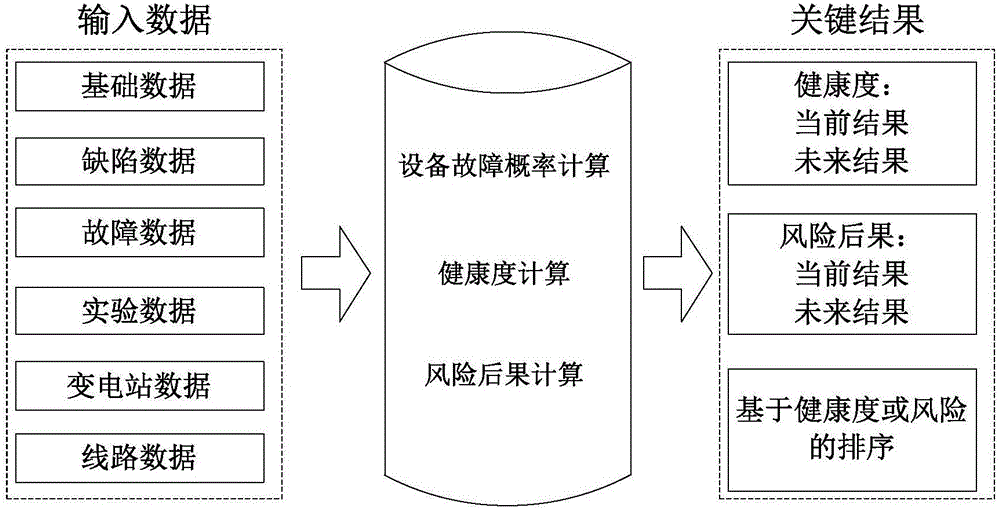
Quantitative risk evaluation method for power equipment based on state evaluation
InactiveCN105956789AImprove securityImprove effectivenessResourcesInformation technology support systemRelational modelRisk identification
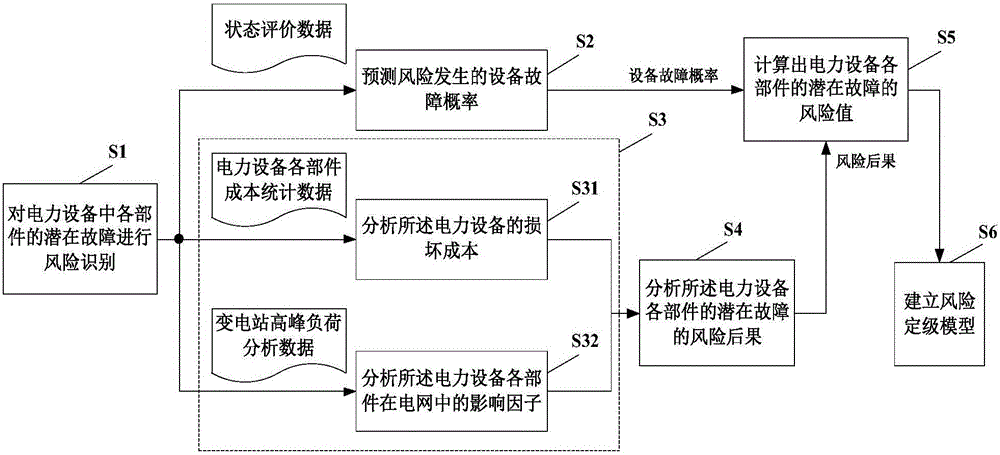
The invention discloses a quantitative risk evaluation method for power equipment based on state evaluation. The method comprises that according to statistic data of power equipment, risks of potential faults of different parts in the power equipment are identified by utilizing an influence analysis method; the fault probability of equipment when the risk occurs is predicted, and the health degree of the equipment is obtained via reference state analysis; a relation model between the fault probability and the healthy degree of the equipment is established, and a risk consequence of potential faults of the parts of the power equipment is analyzed; the influential degree of each part on the equipment function is determined; according to the equipment fault probability and risk consequence, a risk value of the potential fault of each part of the power equipment is calculated; and a risk grading model is established, and according to the risk values, risk grades of the potential faults of the parts of the power equipment are determined. According to technical schemes of the invention, accurate technical basis is provide for operation and maintenance of the power equipment.
Owner:STATE GRID SICHUAN ELECTRIC POWER +2
Capture triggers for capturing network data
Owner:SPLUNK INC
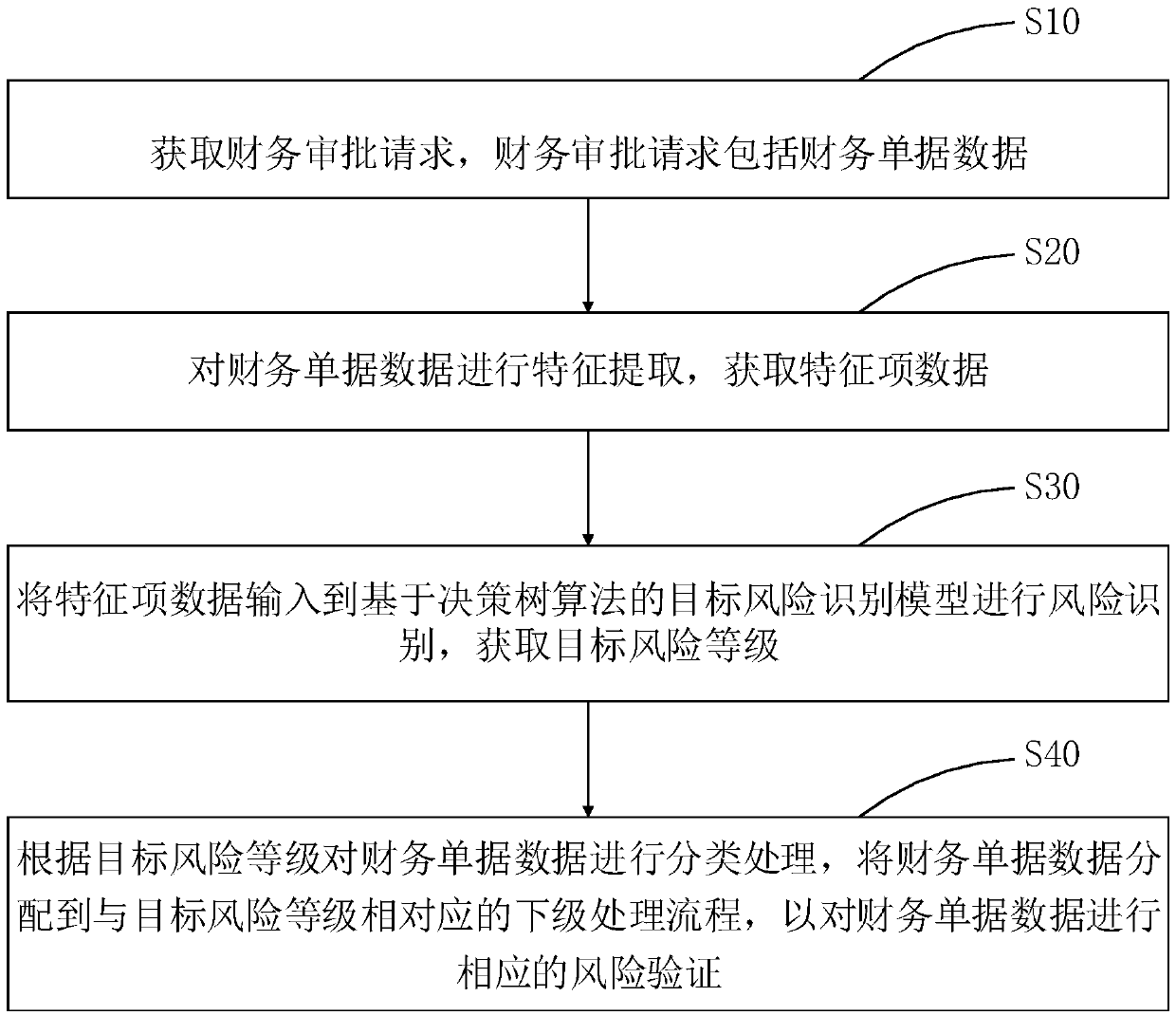
Financial risk verification processing method and device, computer equipment and storage medium
PendingCN108876166AImplement classification processingImprove approval efficiencyFinanceResourcesRisk levelFeature extraction
The invention discloses a financial risks verification processing method and device, computer equipment and a storage medium. The financial risk verification processing method comprises the steps of:obtaining a financial approval request, wherein the financial approval request comprises financial document data; carrying out feature extraction on the financial document data to obtain feature itemdata; inputting the feature item data into a target risk identification model based on a decision tree algorithm to carry out risk identification, and obtaining a target risk level; and classifying the financial document data according to the target risk level, distributing the financial document data to a subordinate processing flow corresponding to the target risk level so as to perform corresponding risk verification on the financial document data. According to the financial risk verification processing method, risk identification is carried out based on the target risk identification model, classification processing is carried out according to the risk level, the approval efficiency of the financial document data is improved, the workload of financial document data approval is saved, and the cost of manual approval is reduced.
Owner:PING AN TECH (SHENZHEN) CO LTD
Account theft risk identification method and device and prevention and control system
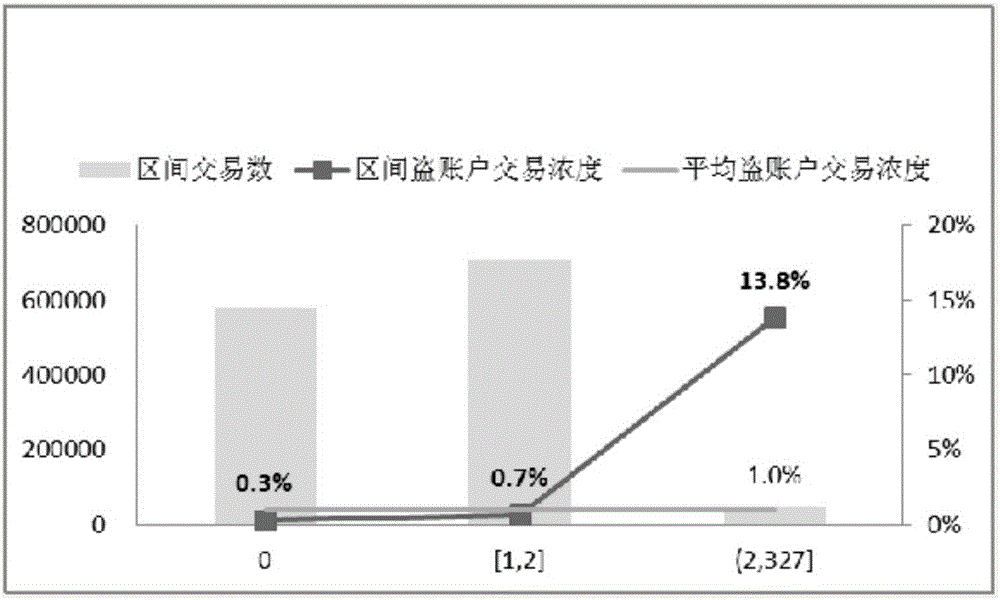
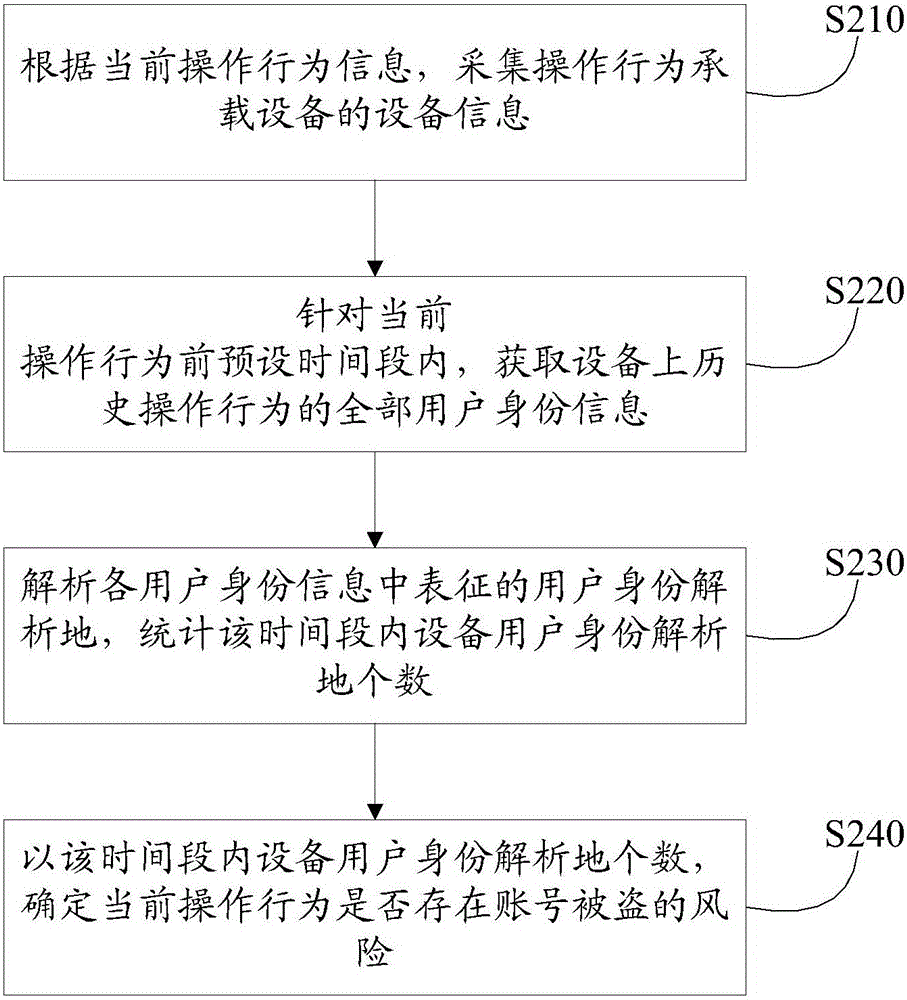
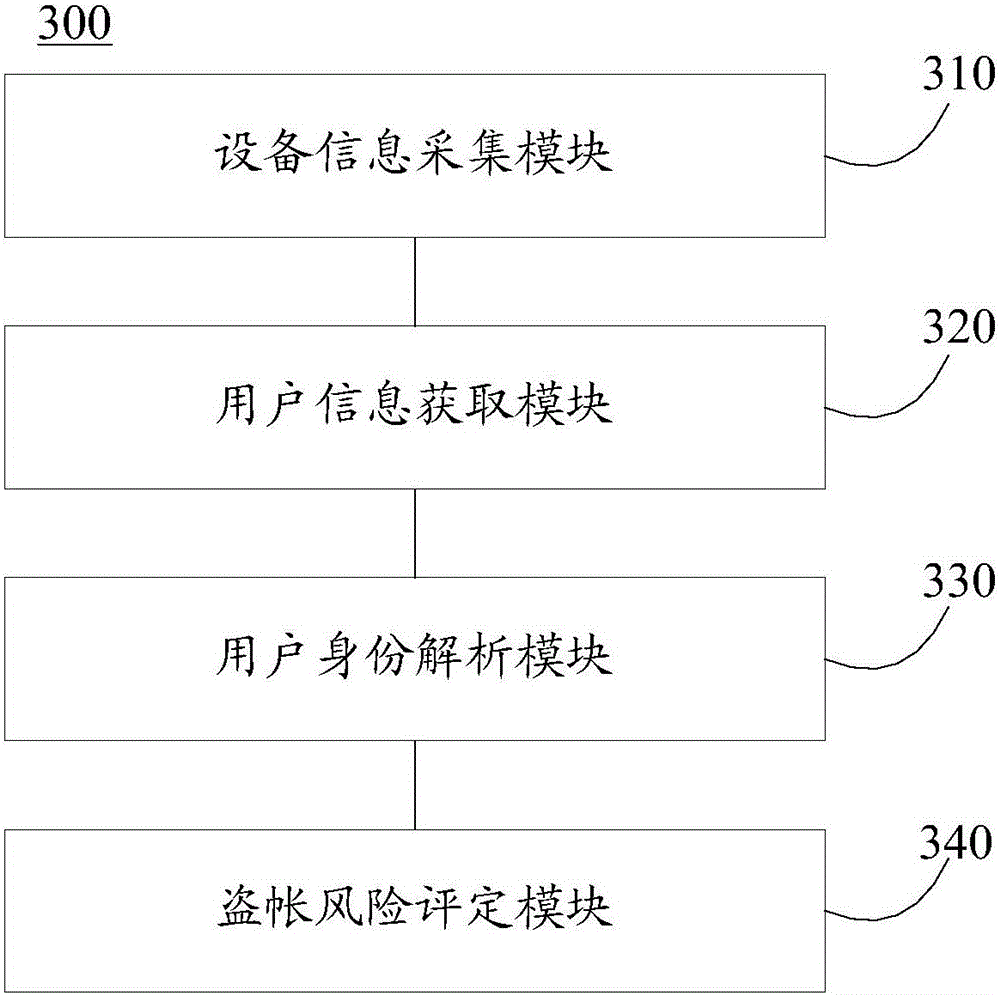
ActiveCN106295349AAccurate removalImprove the ability to distinguish the risk of theftDigital data authenticationPlatform integrity maintainanceControl systemComputer module
The invention provides an account theft risk identification method and device and a prevention and control system. The method comprises the steps that information of a device on which an operation is conducted is collected; identity information of all users of history operations on the device within a preset time period before the operation is obtained; all user identity analysis sites are analyzed, the number of the device user identity analysis sites within the time period is counted, and whether the operation has an account theft risk or not is determined accordingly. The device is provided with a device information collecting module, a user information obtaining module, a user identity analyzing module and an account theft risk evaluation module, and whether a current operation has the account theft risk or not can be determined according to the number of the device user identity analysis sites within the preset time period before the current operation. According to the system, the device which evaluates the risk grade through the number of the user identity analysis sites is adopted, the account theft risk can be identified and processed more efficiently, and a safe network environment can be provided for users.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com