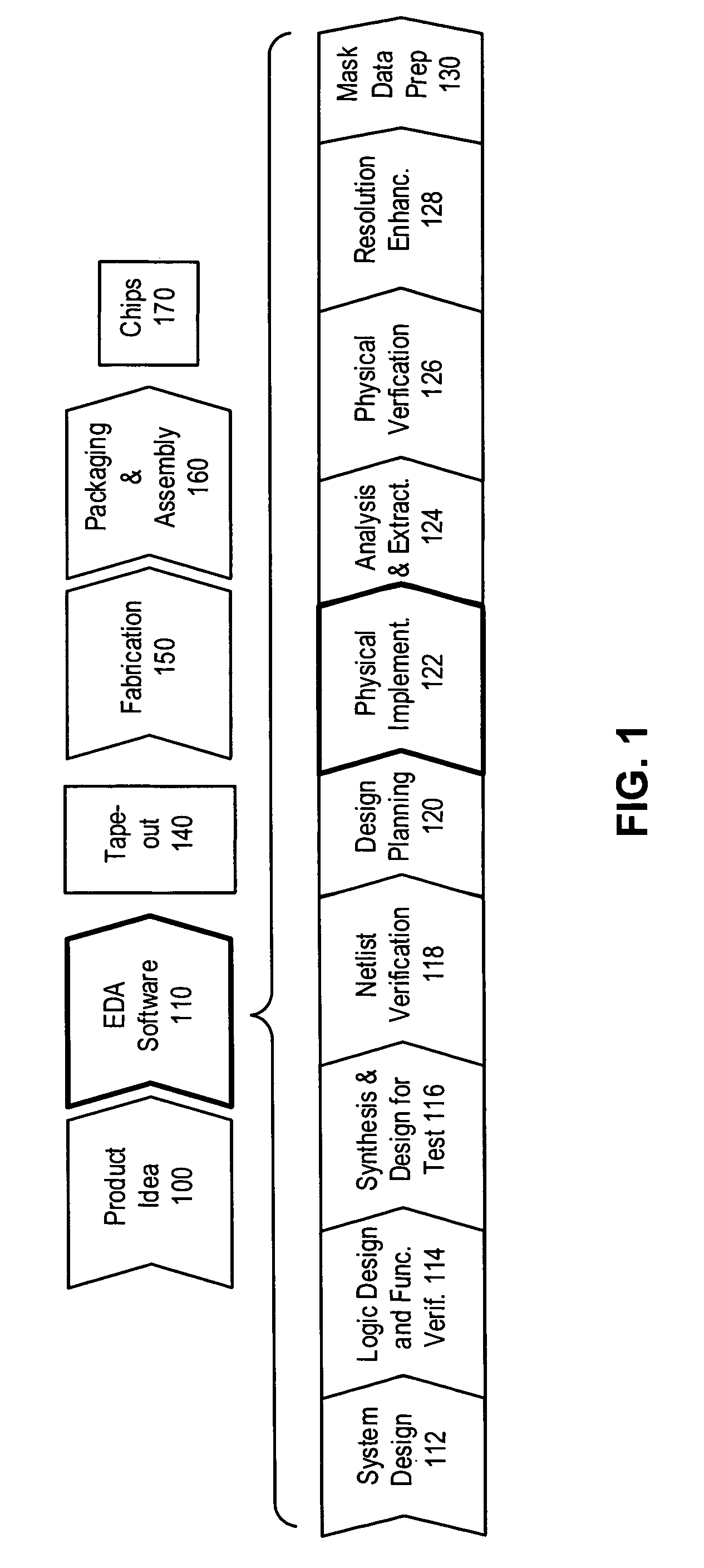
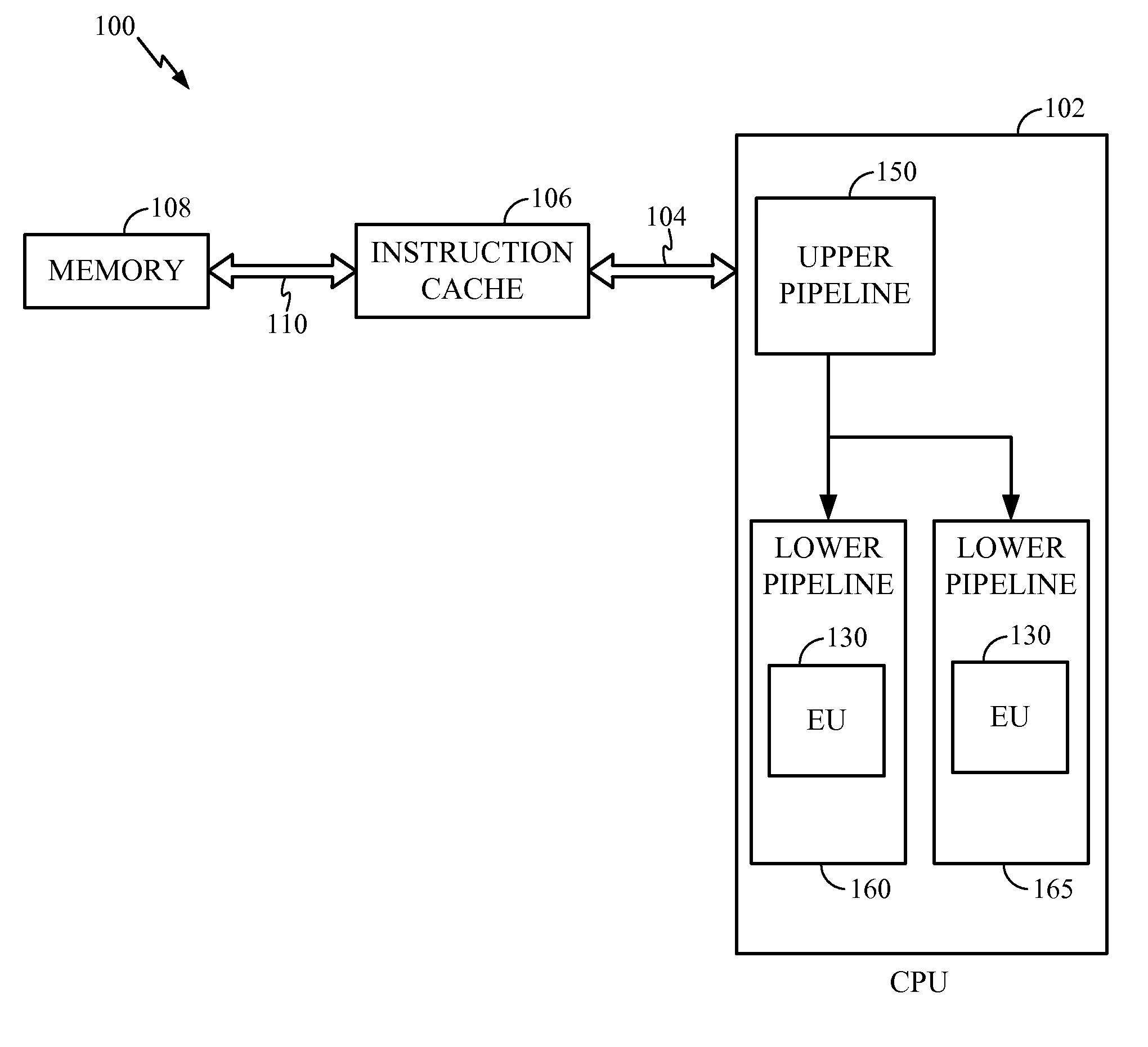
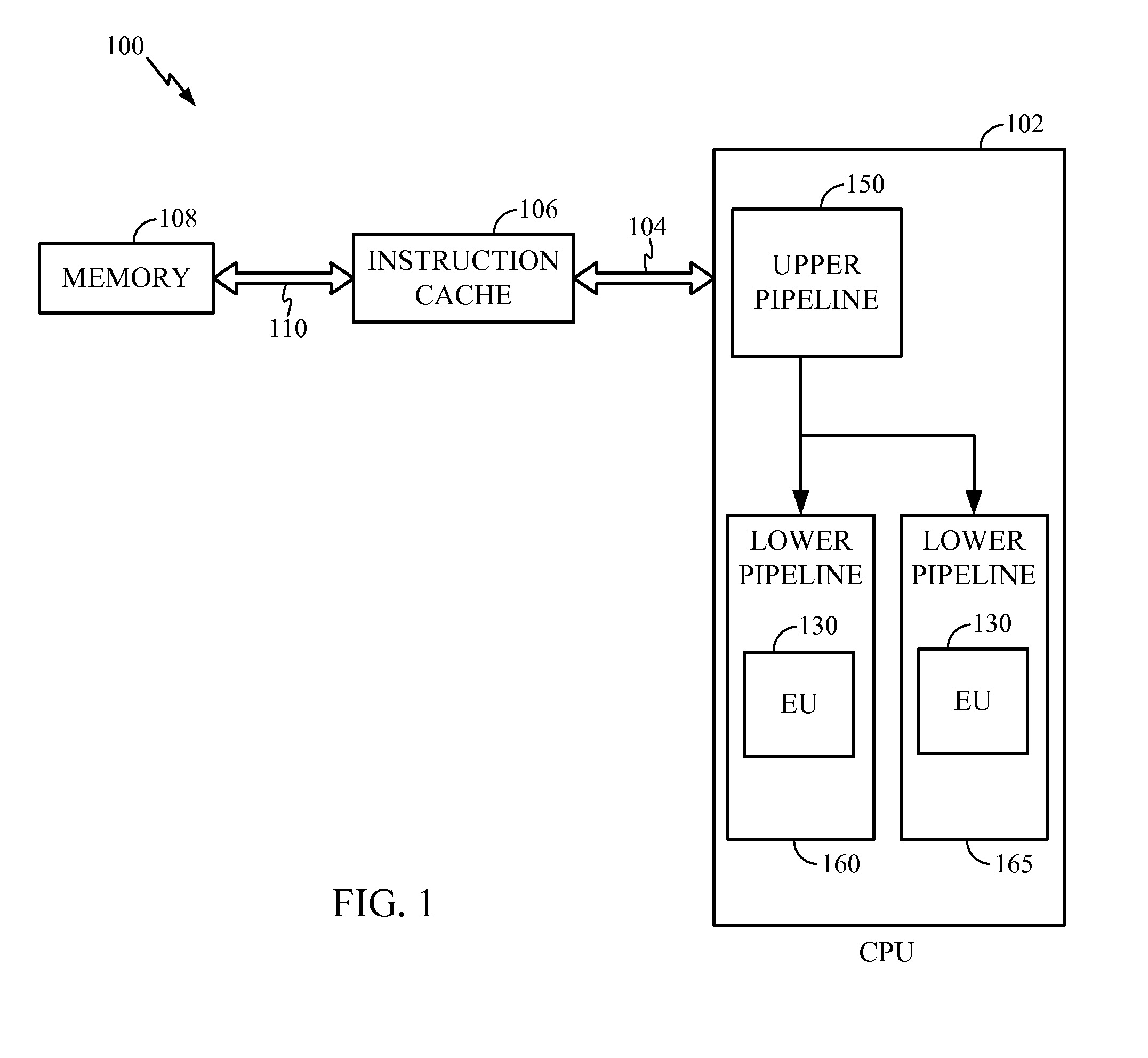
Patents
Literature
200 results about "Register based" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
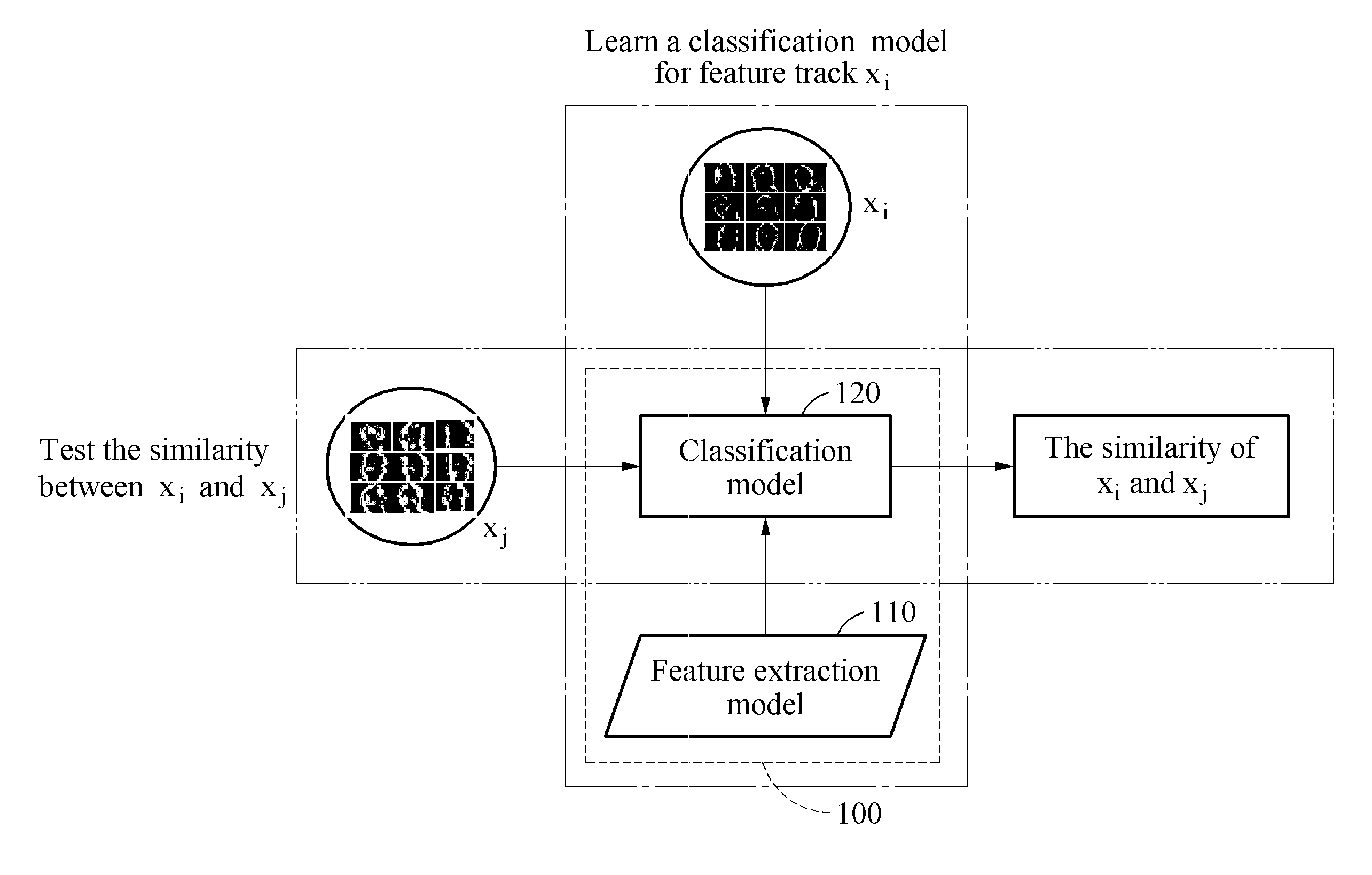
Register-based research is research based on data from records kept by government agencies or other organizations, where the data can be traced back to individuals.
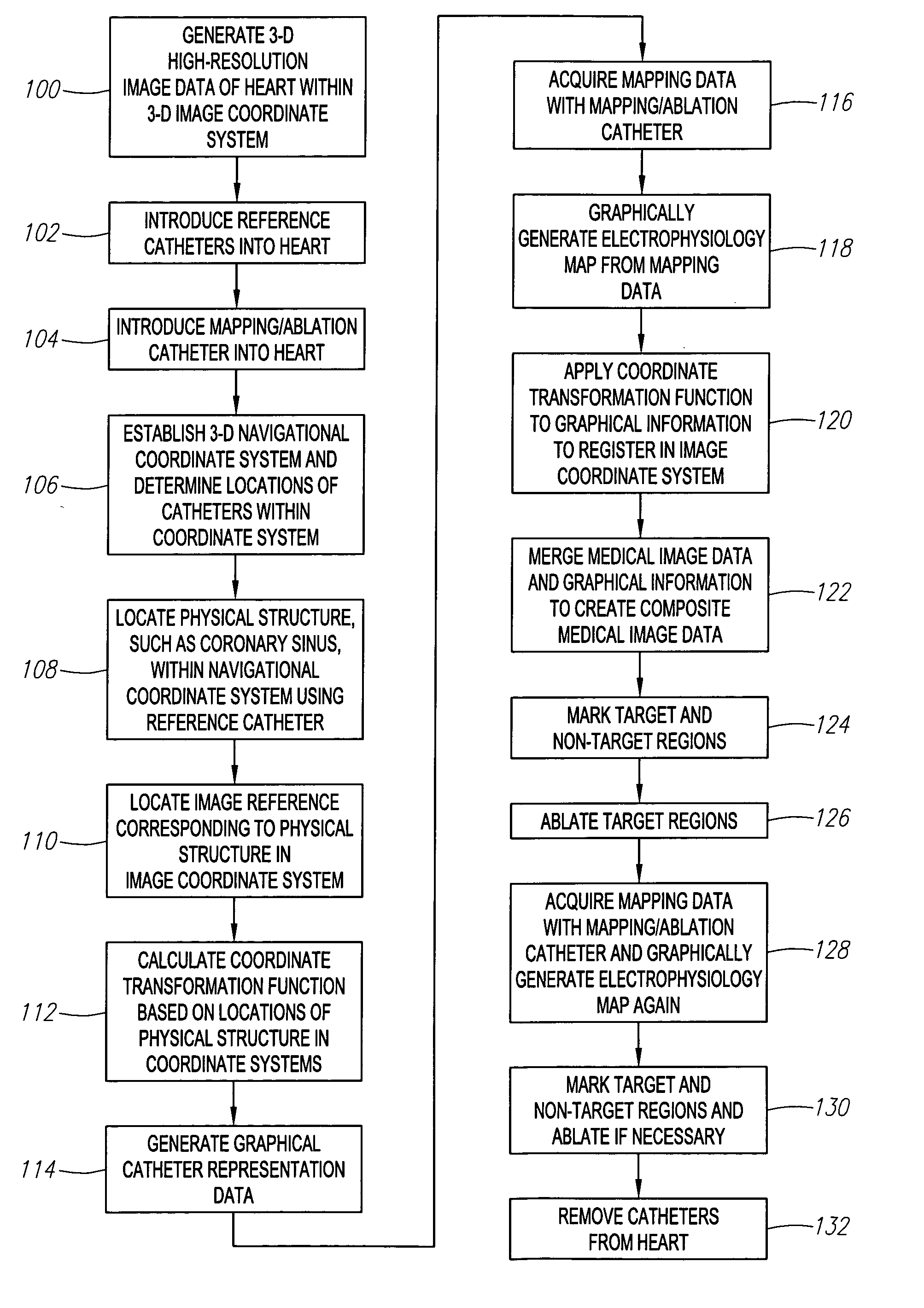
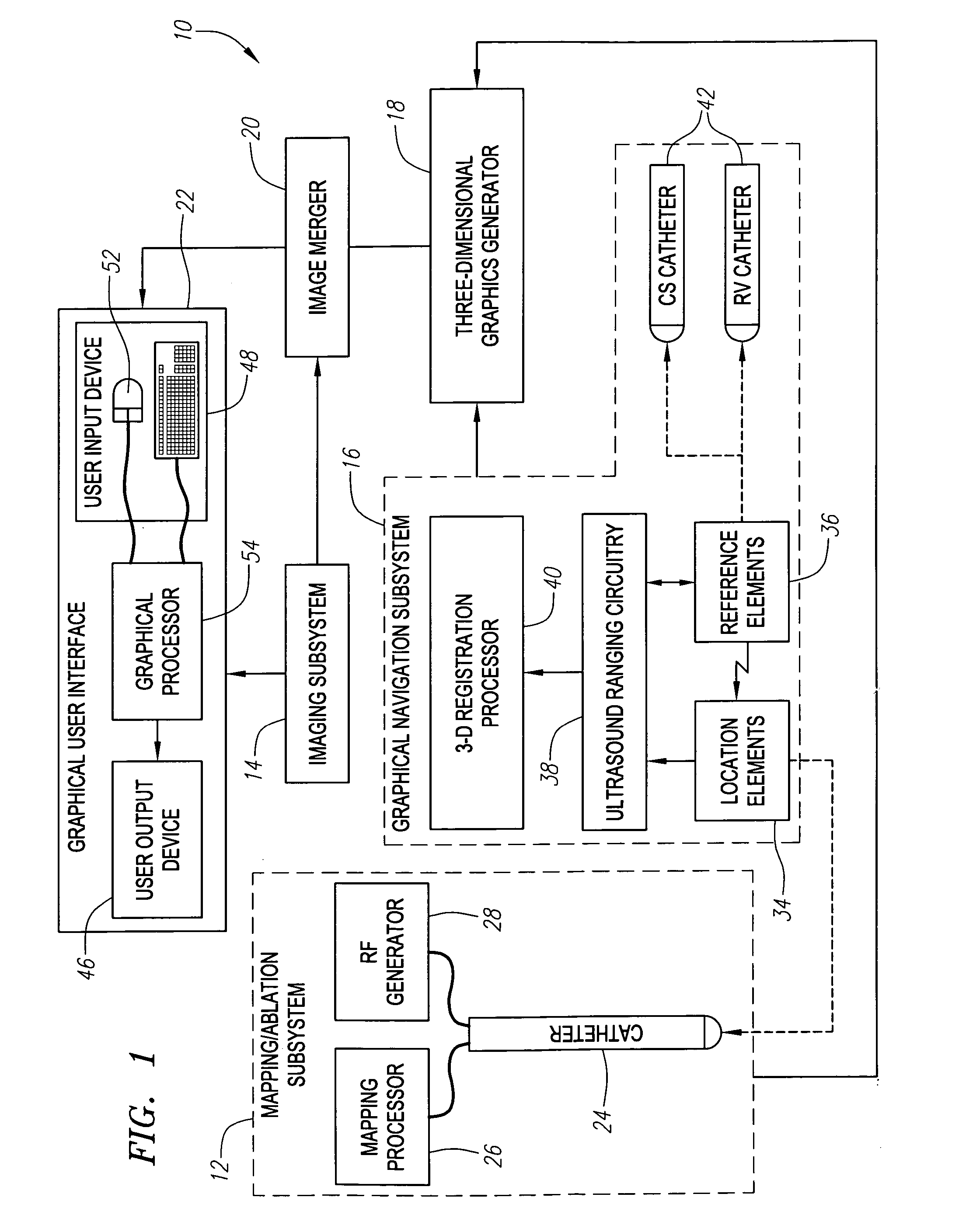
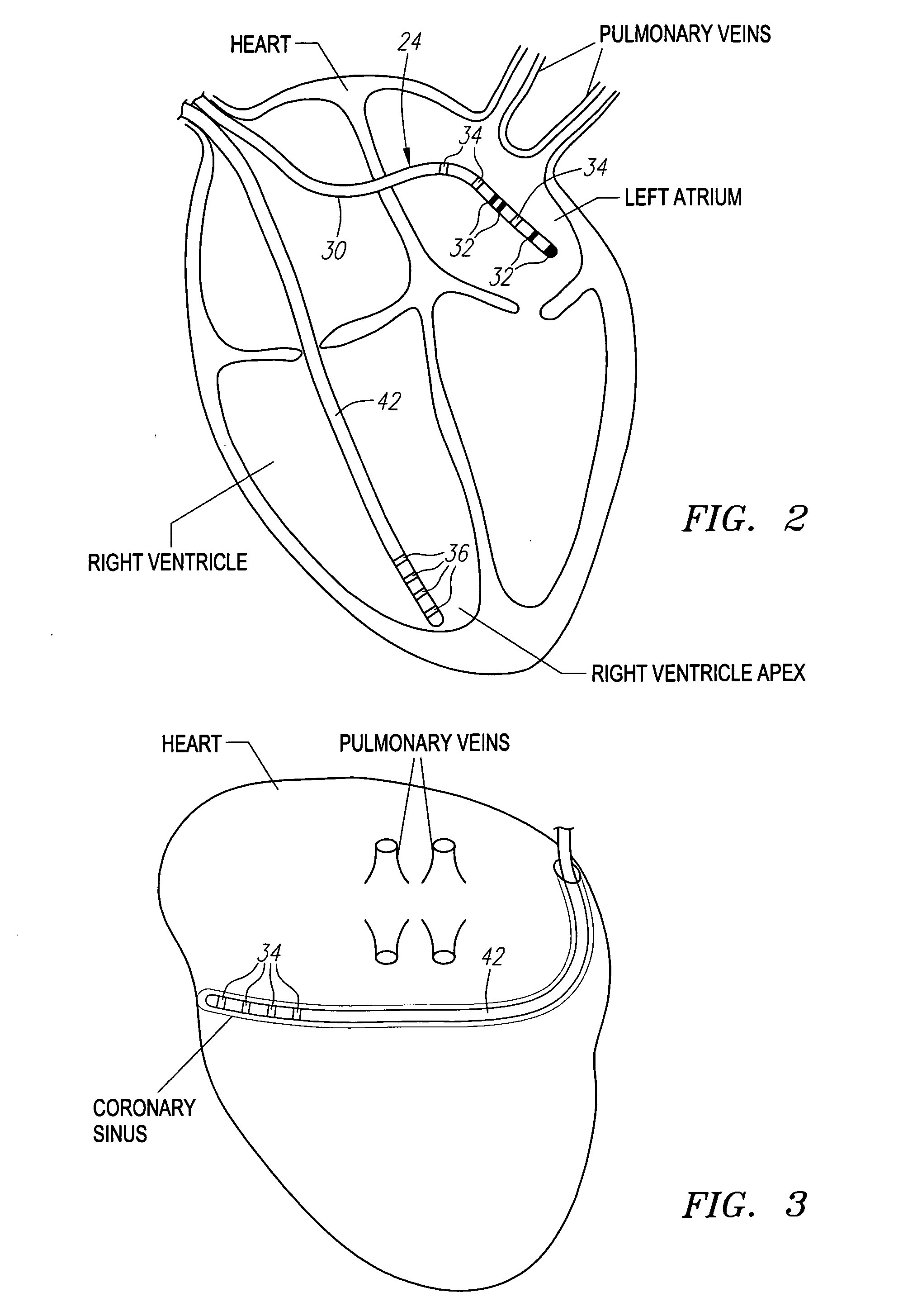
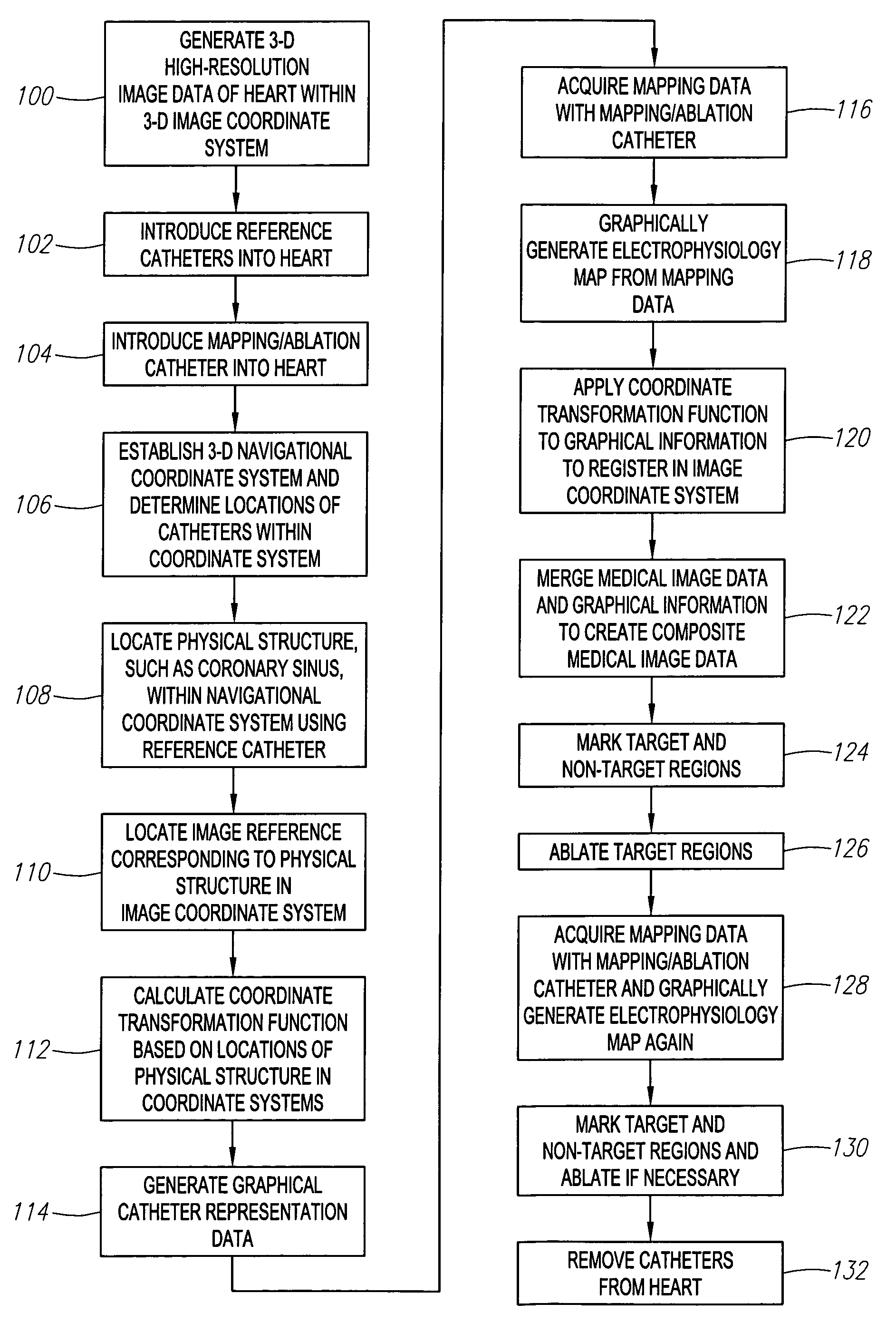
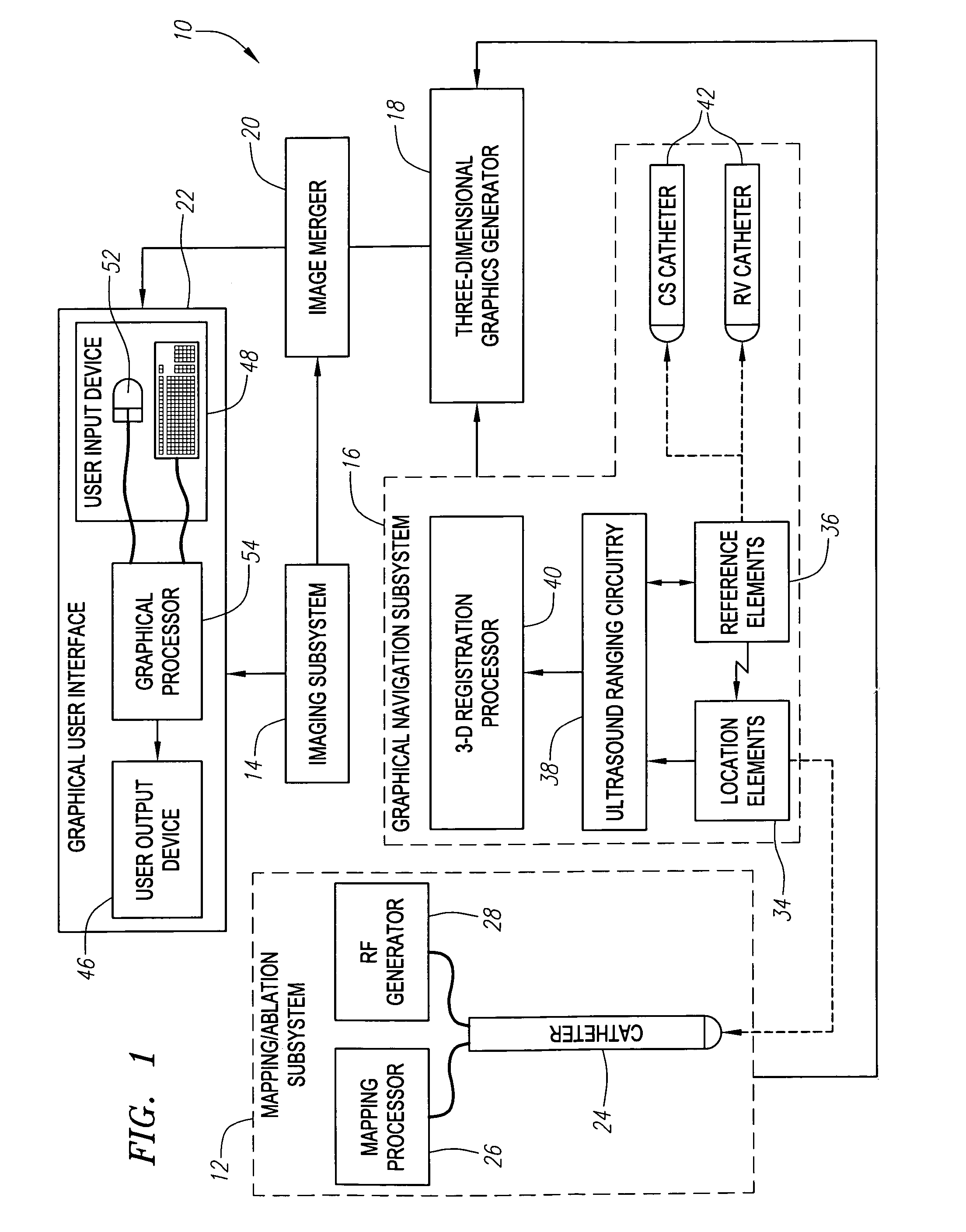
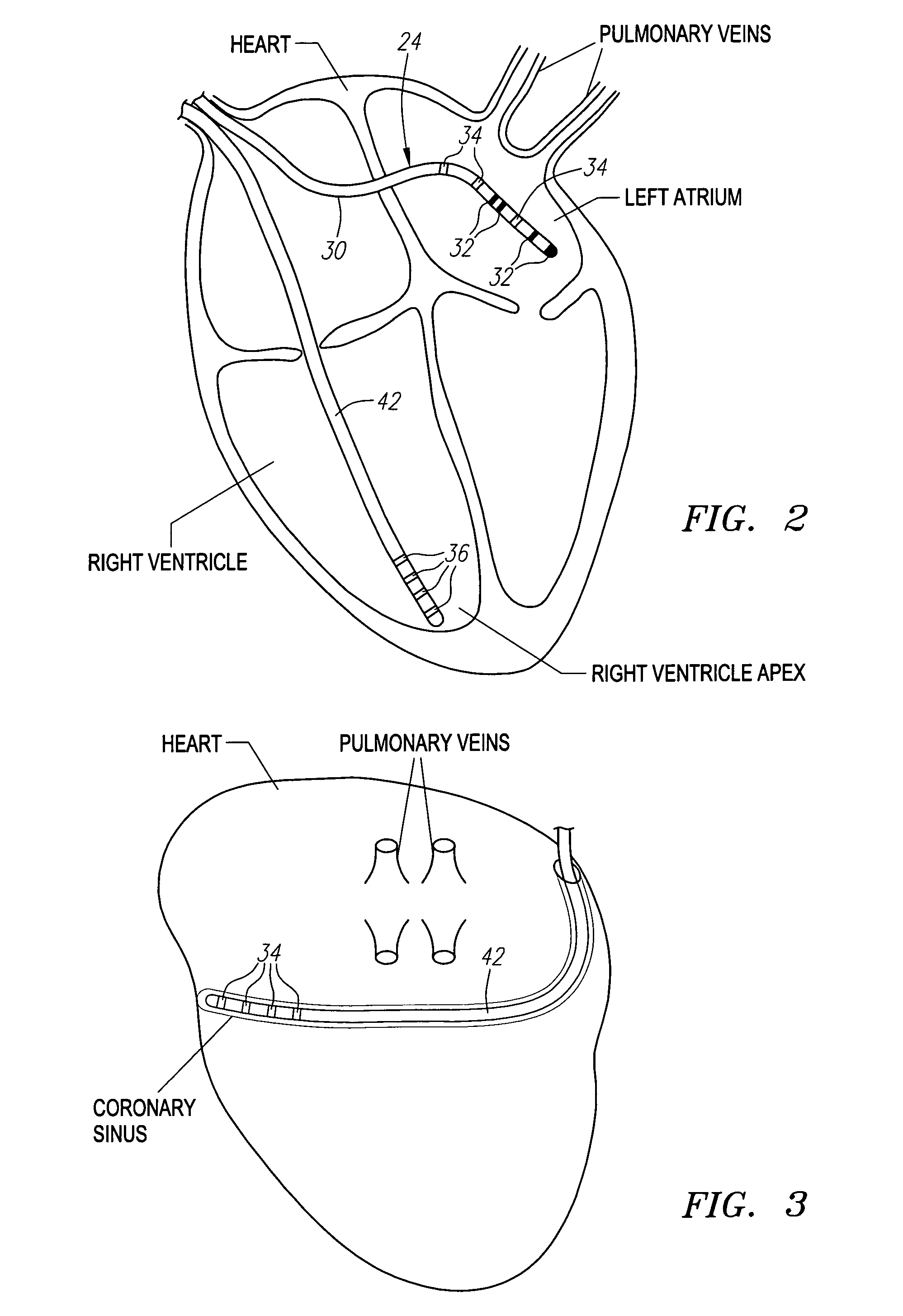
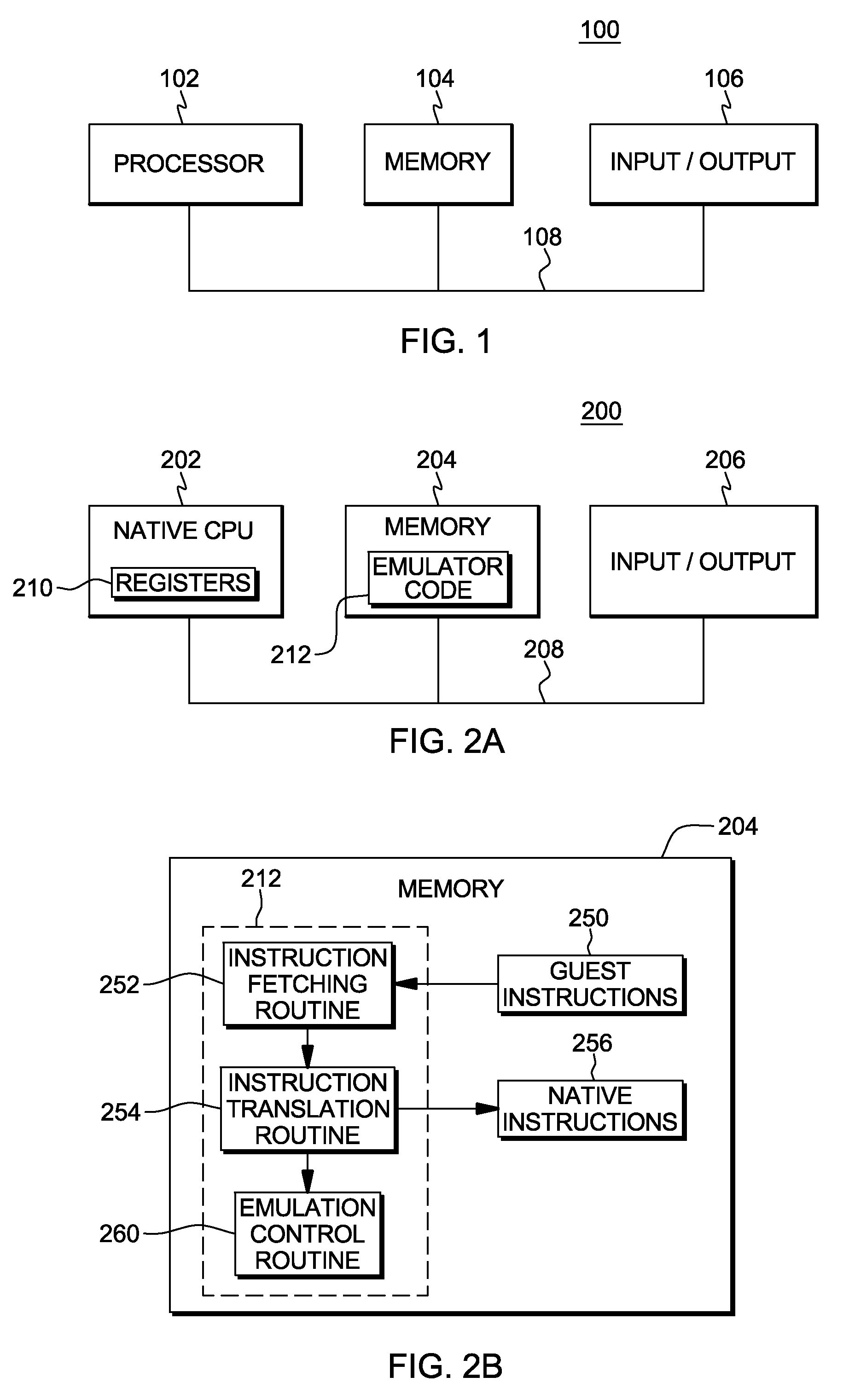
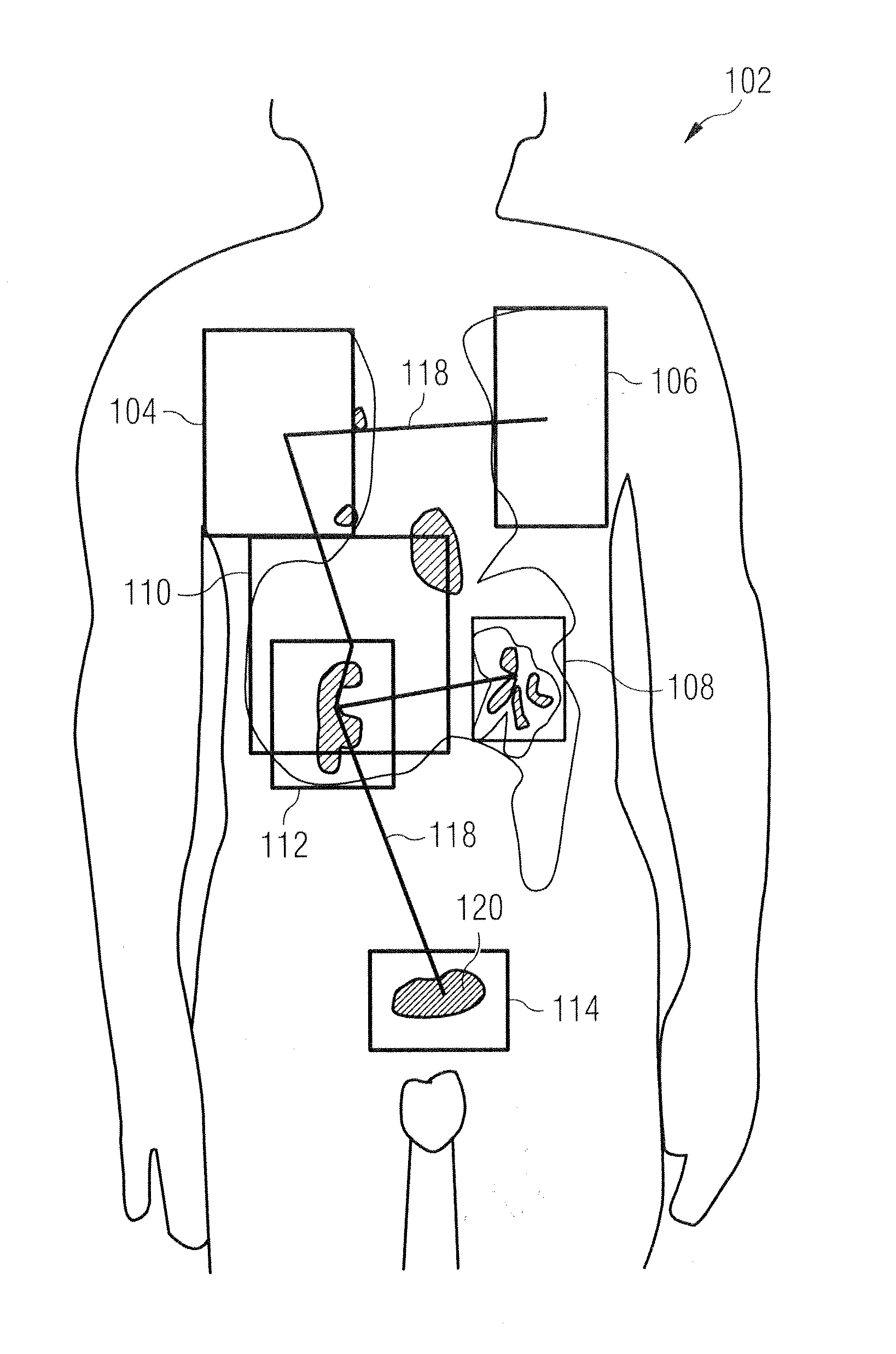
Method and system for registering an image with a navigation reference catheter
ActiveUS20060116575A1Timing errorImage data is accurateUltrasonic/sonic/infrasonic diagnosticsSurgeryGraphicsReference image
Methods and systems for processing and / or superimposing a medical image of an anatomical body (e.g., a heart) with graphical information are provided. Reference elements and / or reference catheter are placed in contact with the anatomical body. A physical structure within a navigational coordinate system is located using the reference elements and / or reference catheter. An image reference within an image coordinate corresponding to the physical structure is located. Location of the image reference can be accomplished, e.g., by displaying the medical image and electronically marking the displayed image reference, or by automatically locating image data corresponding to the image reference. The navigational and image coordinate systems are then registered based on the location of the physical structure within the navigational coordinate system and the location of the image reference within the image coordinate system, which allows graphical information to be accurately merged with the medical image data.
Owner:BOSTON SCI SCIMED INC
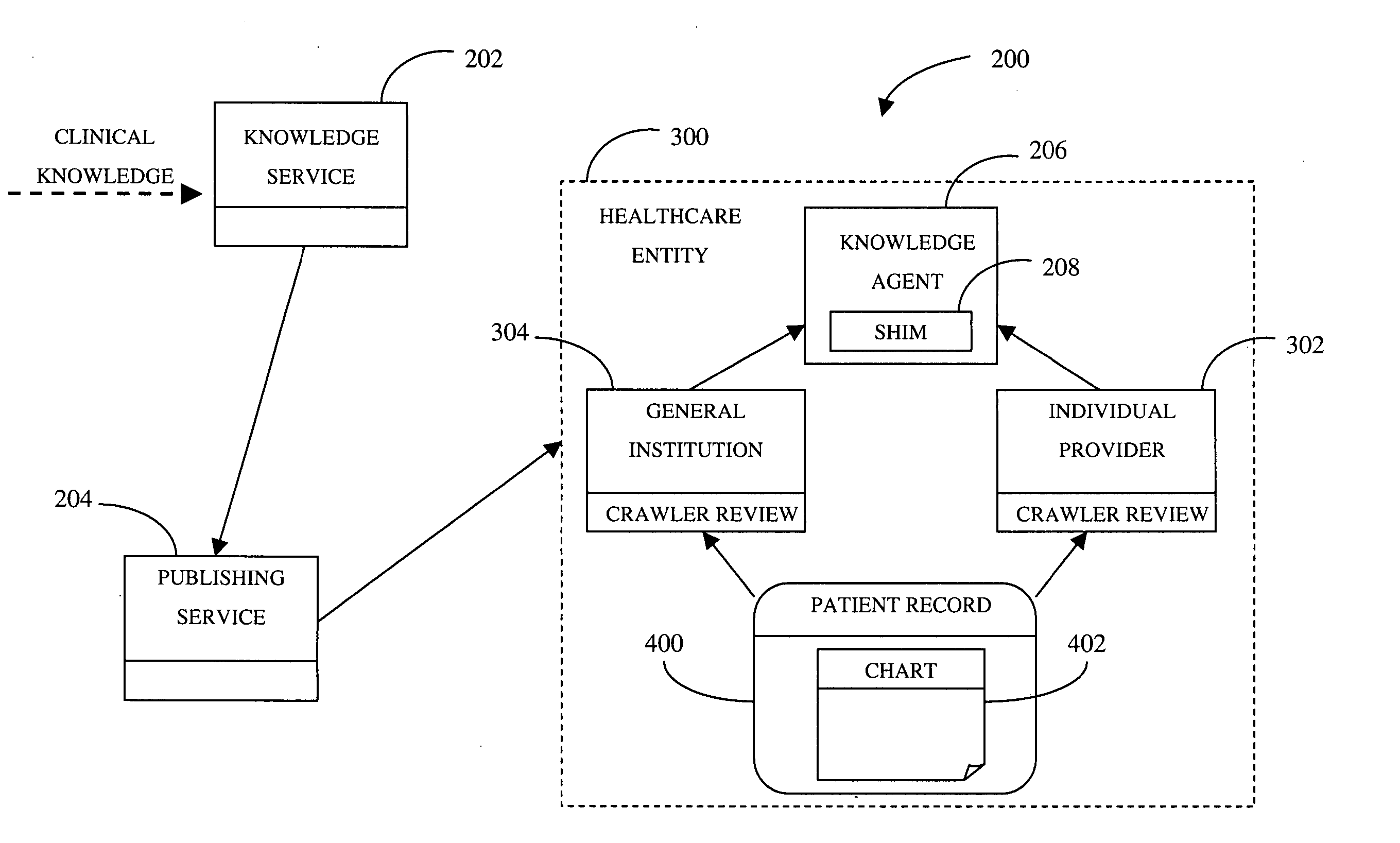
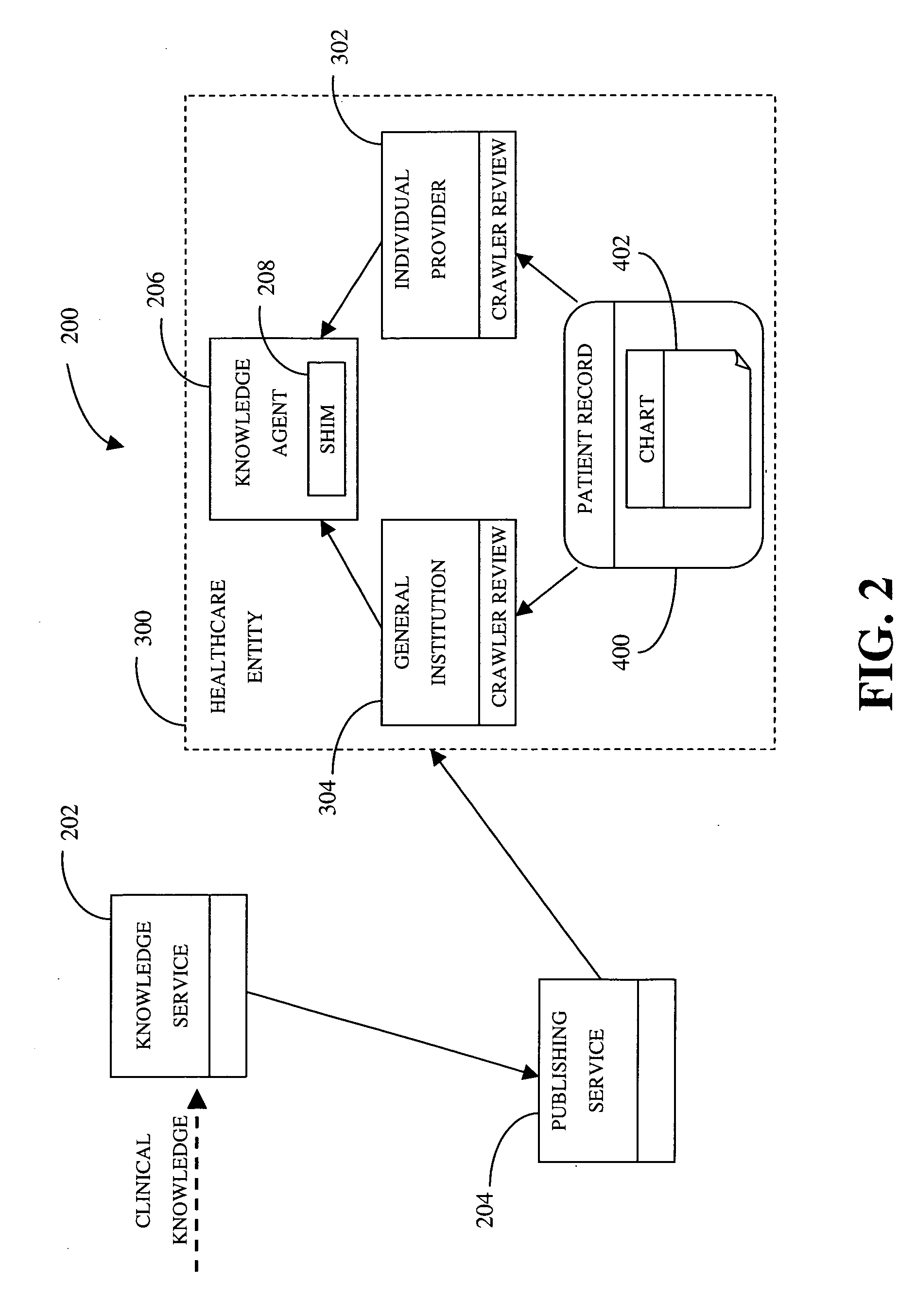
System and methods for distributed analysis of patient records
A system and associated methods provide healthcare entities with analyzing capabilities for records of a patient population. The analyzing process seeks to find matches between a piece of clinical knowledge introduced to a healthcare entity and data contained in the patient population records. According to one method, a service generates executable code based on the piece of clinical knowledge. Through a communication with the service, the healthcare entity makes a determination as to what extent the clinical knowledge has relevance to a patient population of the healthcare entity. Based on this determination, the healthcare entity receives at least a portion of the executable code. Then, the records of the patient population may be analyzed by the executable code to register matches of the clinical knowledge with data contained within the records. System activity may then be initiated based on the matches registered. Examples of system activity include compiling a contact list of patients and / or healthcare providers associated with specific records where matches occurred, generating a report about the matches registered, and flagging specific records where matches occurred so that care providers may discuss issues surrounding the clinical knowledge with associated patients in a future encounter with the healthcare entity, among others.
Owner:CERNER INNOVATION
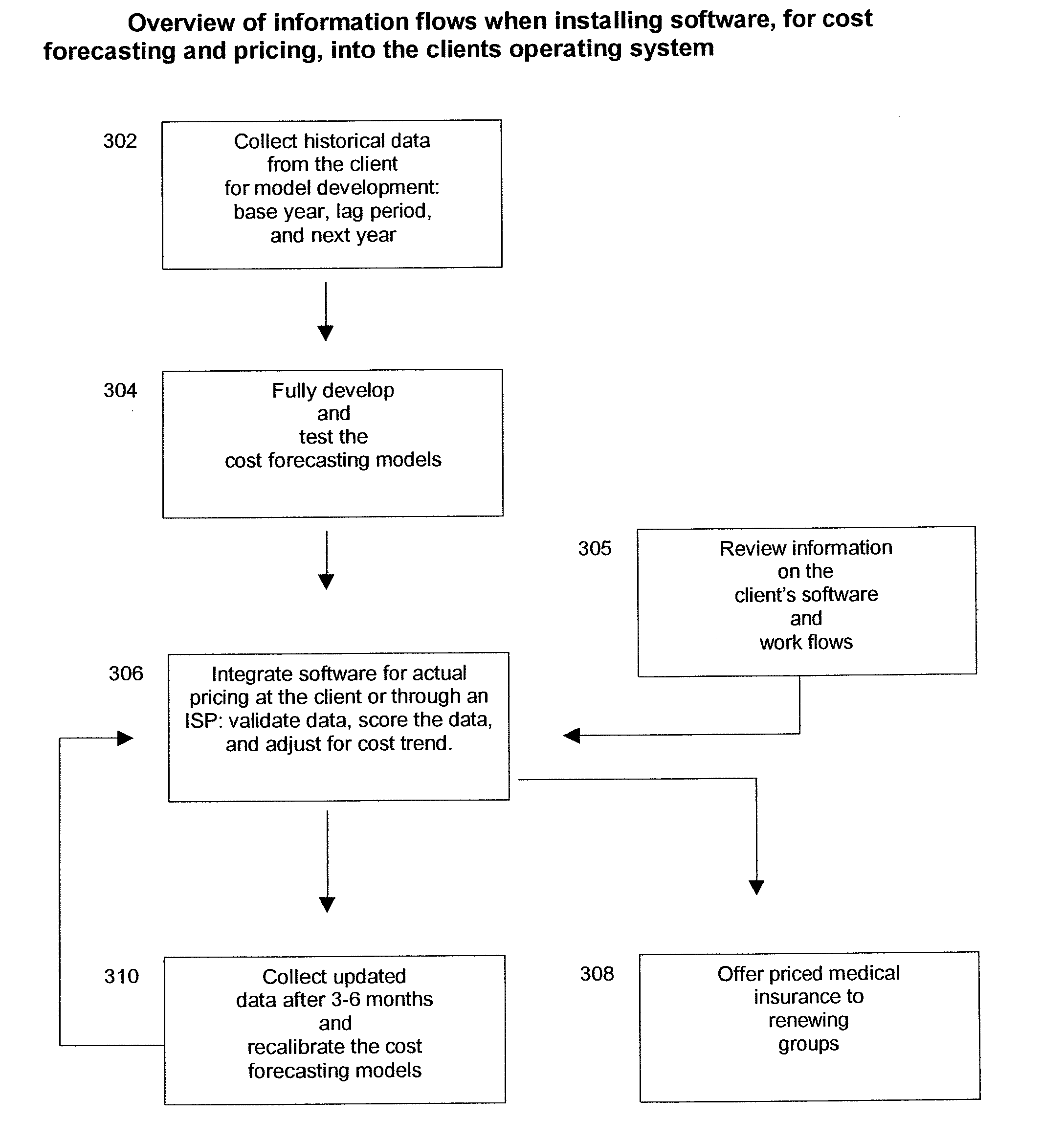
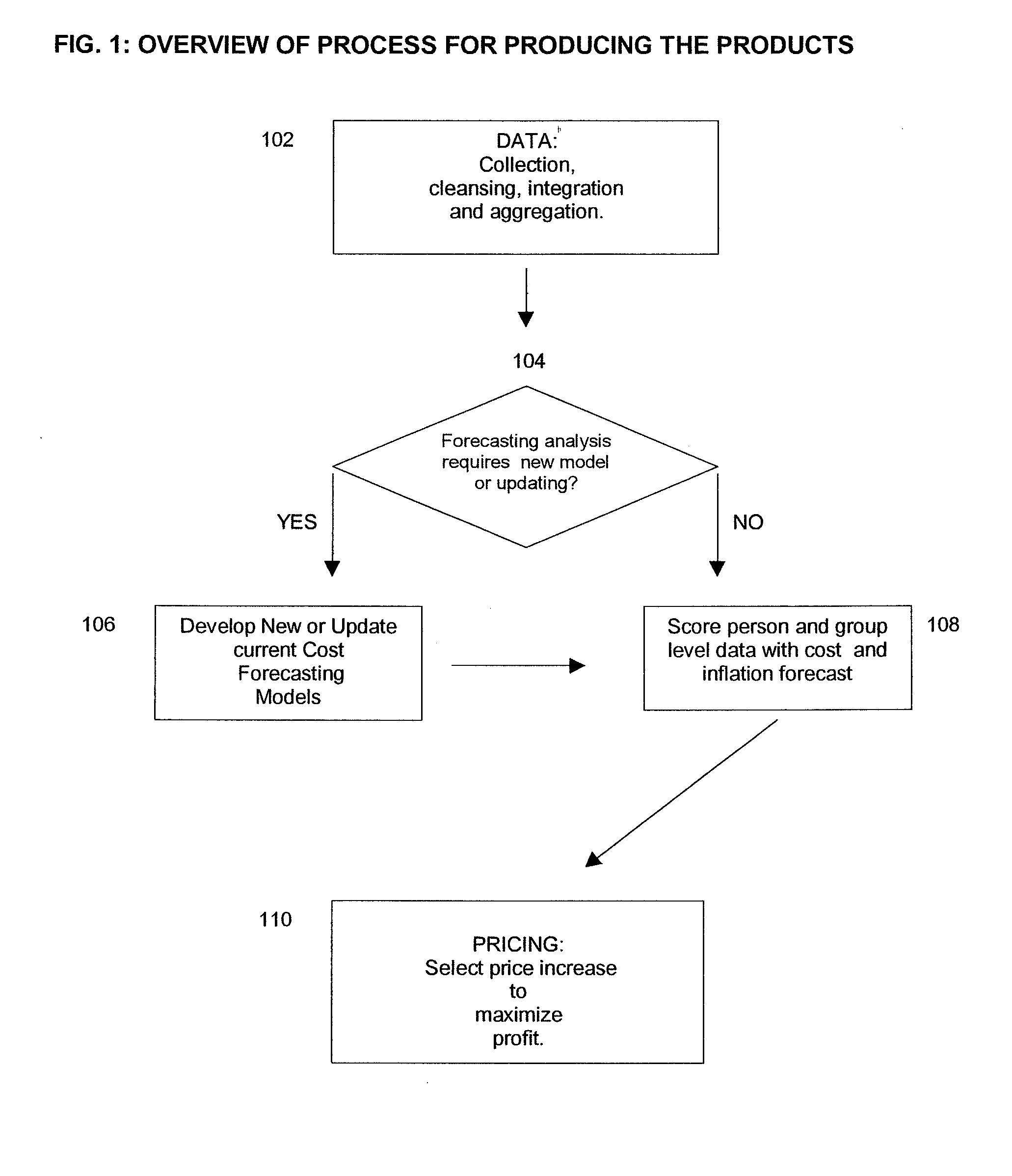
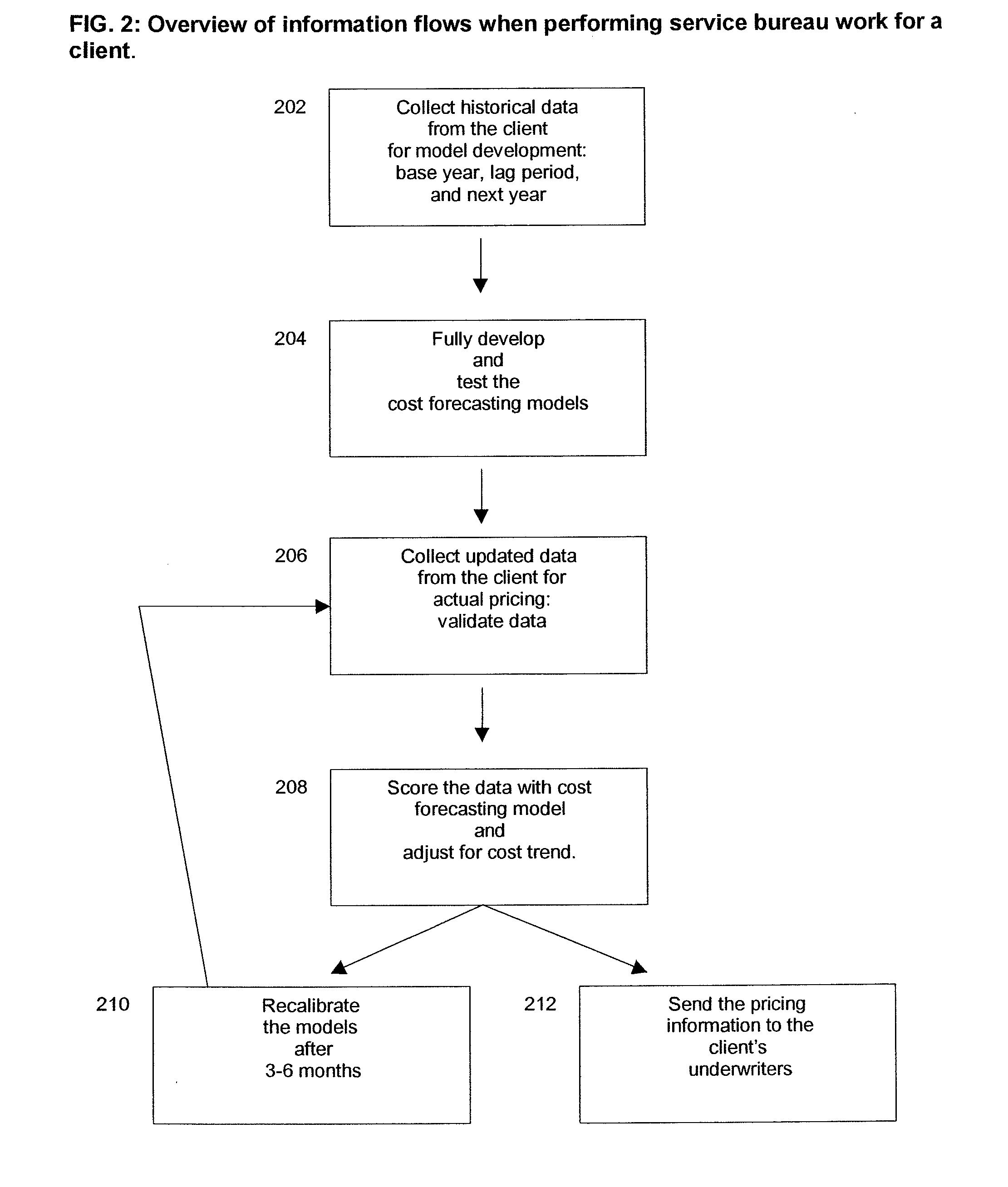
Insurance claim forecasting system
A computer-implemented process of developing a person-level cost model for forecasting future costs attributable to claims from members of a book of business, where person-level data are available for a substantial portion of the members of the book of business for an actual underwriting period, and the forecast of interest is for a policy period is disclosed. The process uses development universe data comprising person-level enrollment data, historical base period health care claims data and historical next period claim amount data for a statistically meaningful number of individuals. The process also provides at least one claim-based risk factor for each historical base period claim based on the claim code associated with the health care claim and provides at least one enrollment-based risk factor based on the enrollment data. The process also develops a cost forecasting model by capturing the predictive ability of the main effects and interactions of claim based risk factors and enrollment-based risk factors, with the development universe data through the application of an interaction capturing technique to the development universe data.
Owner:BINNS GREGORY S +1
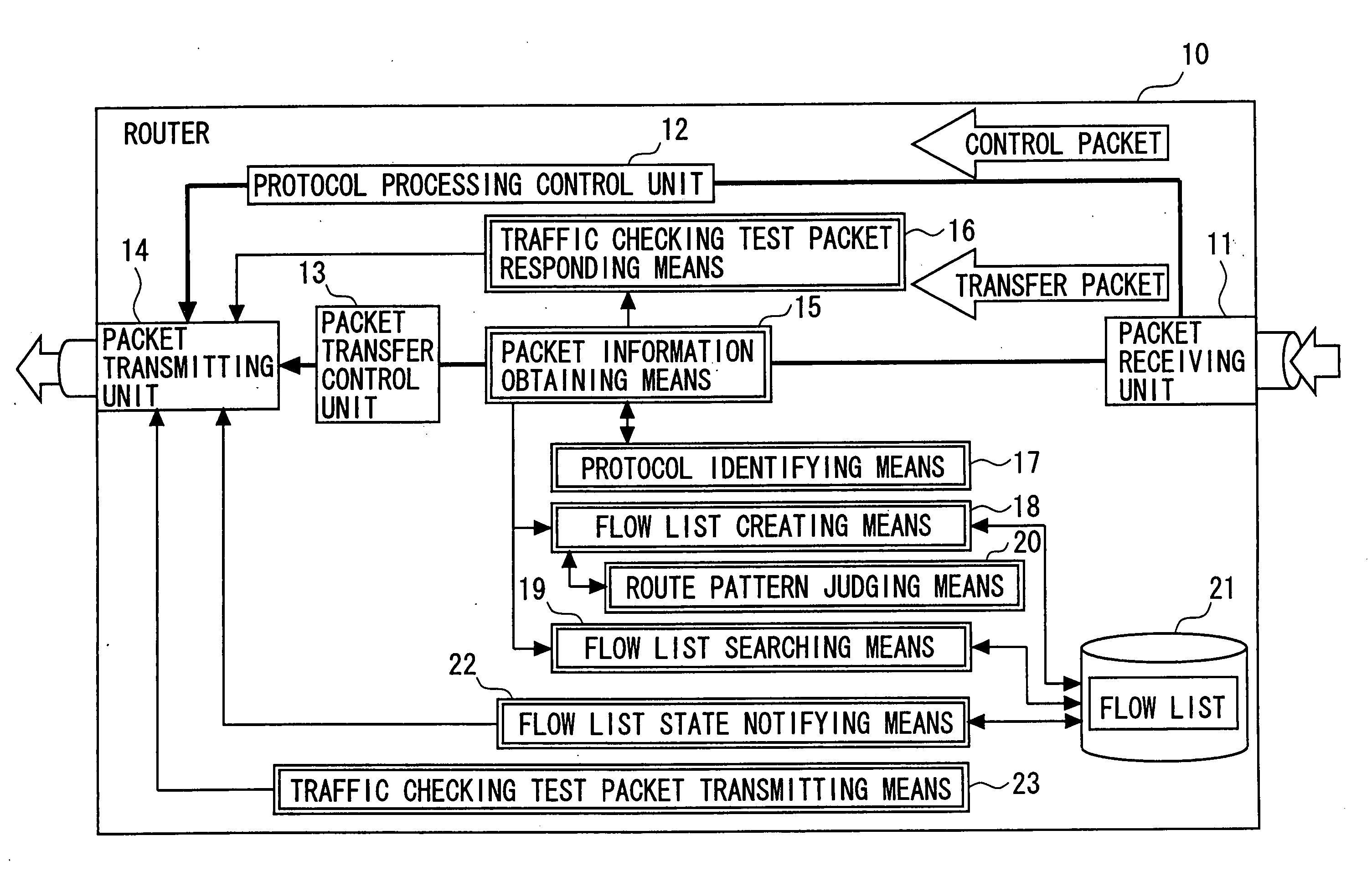
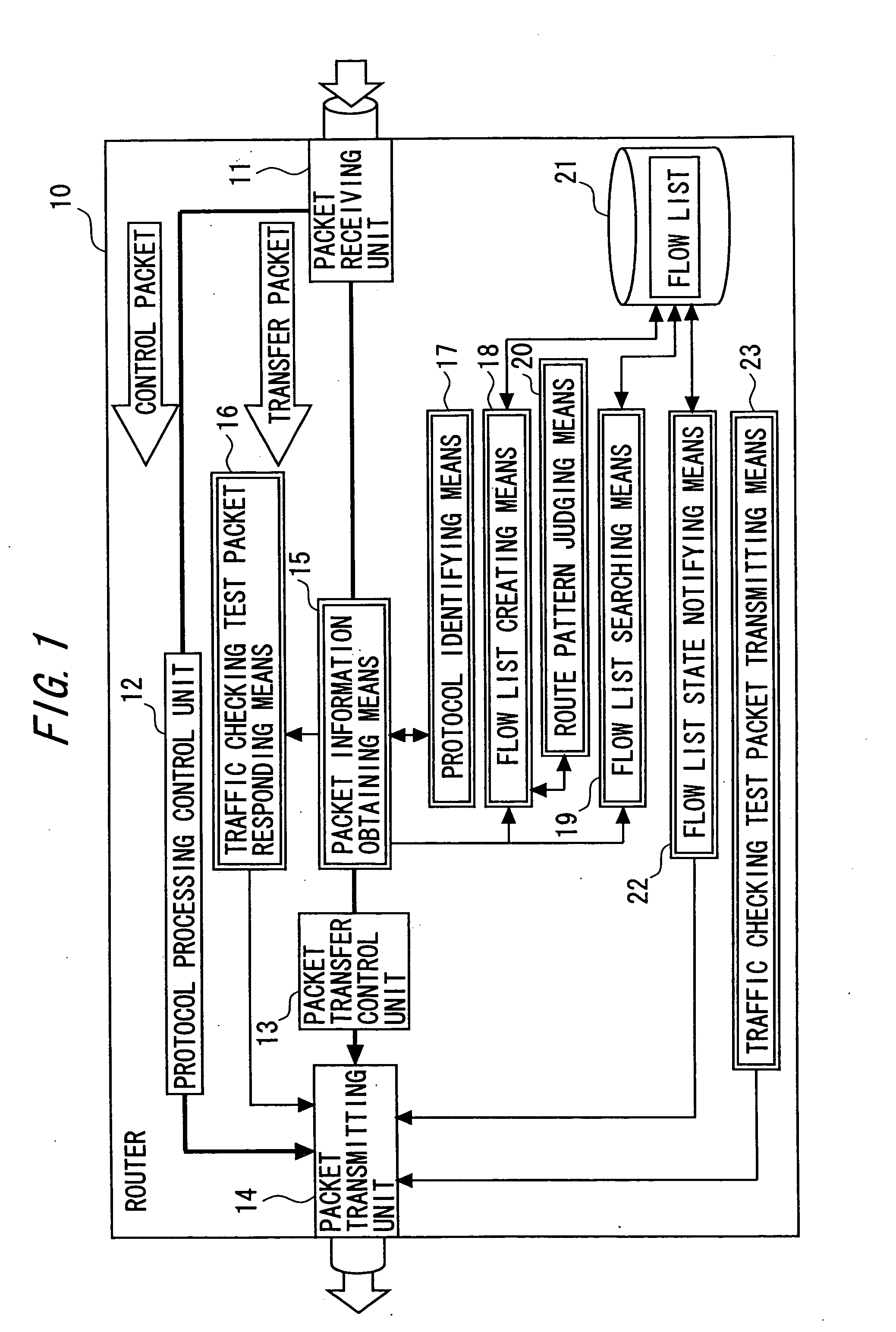
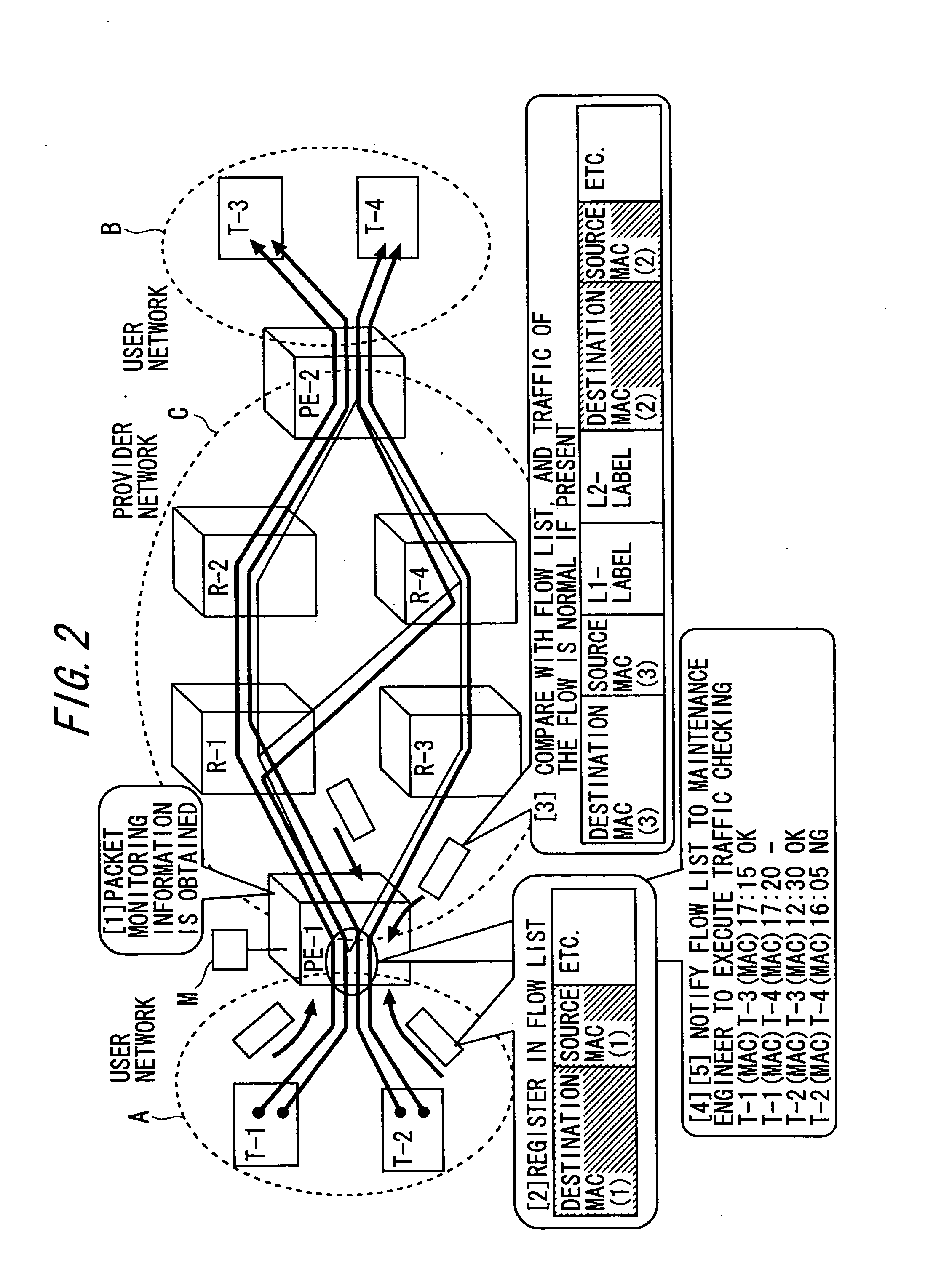
Provider network for providing L-2 VPN services and edge router
The provider network that interconnects user networks includes a plurality of edge routers. At least one of the plurality of edge routers includes an obtaining unit for obtaining information of a packet transferred by the edge router itself, a creating unit for creating a flow list in which flow information of packets transferred from the user network side to the provider network side is registered based on the packet information, a monitoring unit for monitoring a traffic state of a flow of each packet registered in the flow list based on information of packets transferred from the provider network to the user network, and a notifying unit for notifying the traffic state of the flow registered in the flow list to a maintenance engineer.
Owner:FUJITSU LTD
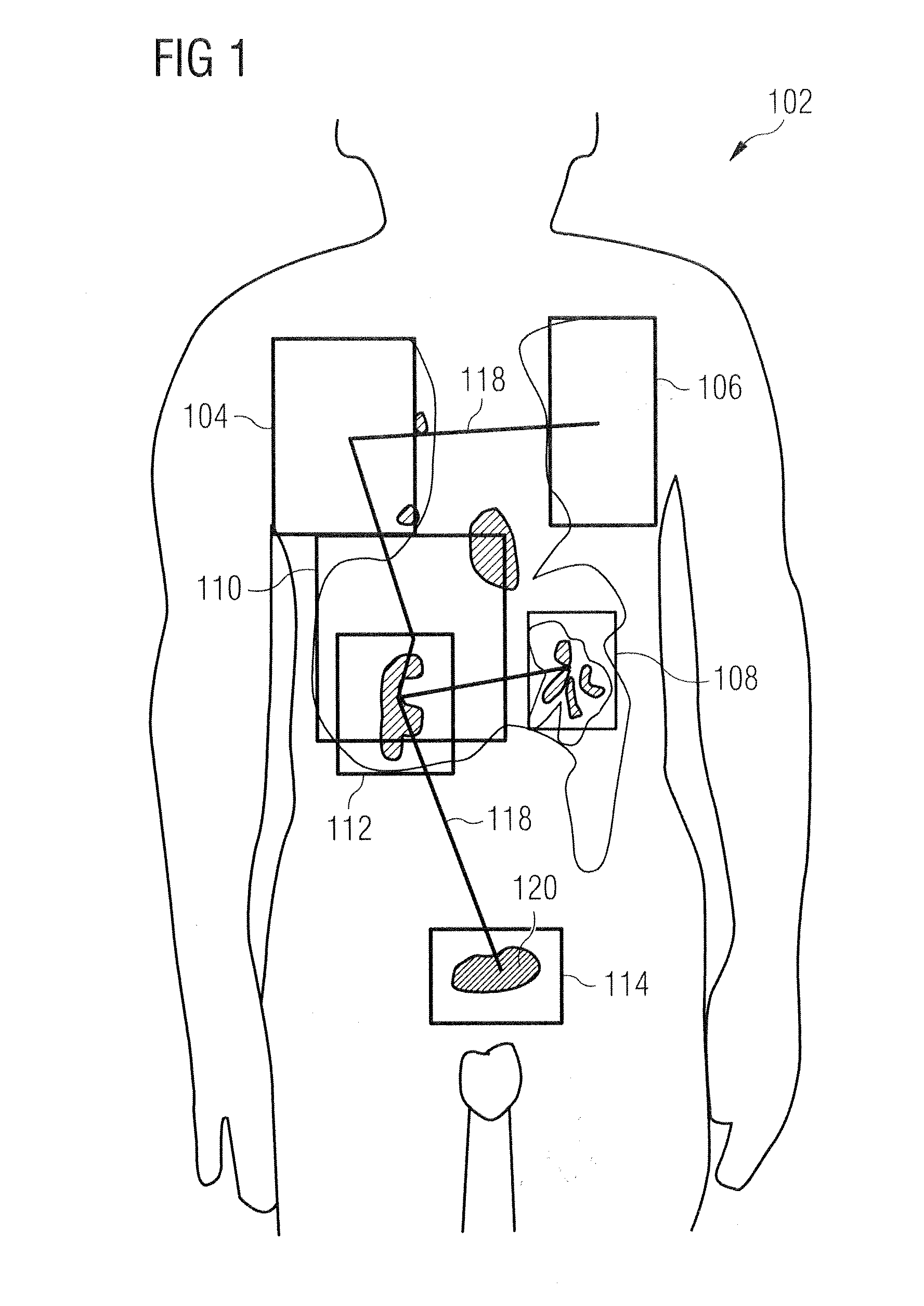
Method and system for registering an image with a navigation reference catheter
ActiveUS7720520B2Image data is accurateTiming errorUltrasonic/sonic/infrasonic diagnosticsSurgeryGraphicsMarine navigation
Methods and systems for processing and / or superimposing a medical image of an anatomical body (e.g., a heart) with graphical information are provided. Reference elements and / or reference catheter are placed in contact with the anatomical body. A physical structure within a navigational coordinate system is located using the reference elements and / or reference catheter. An image reference within an image coordinate corresponding to the physical structure is located. Location of the image reference can be accomplished, e.g., by displaying the medical image and electronically marking the displayed image reference, or by automatically locating image data corresponding to the image reference. The navigational and image coordinate systems are then registered based on the location of the physical structure within the navigational coordinate system and the location of the image reference within the image coordinate system, which allows graphical information to be accurately merged with the medical image data.
Owner:BOSTON SCI SCIMED INC
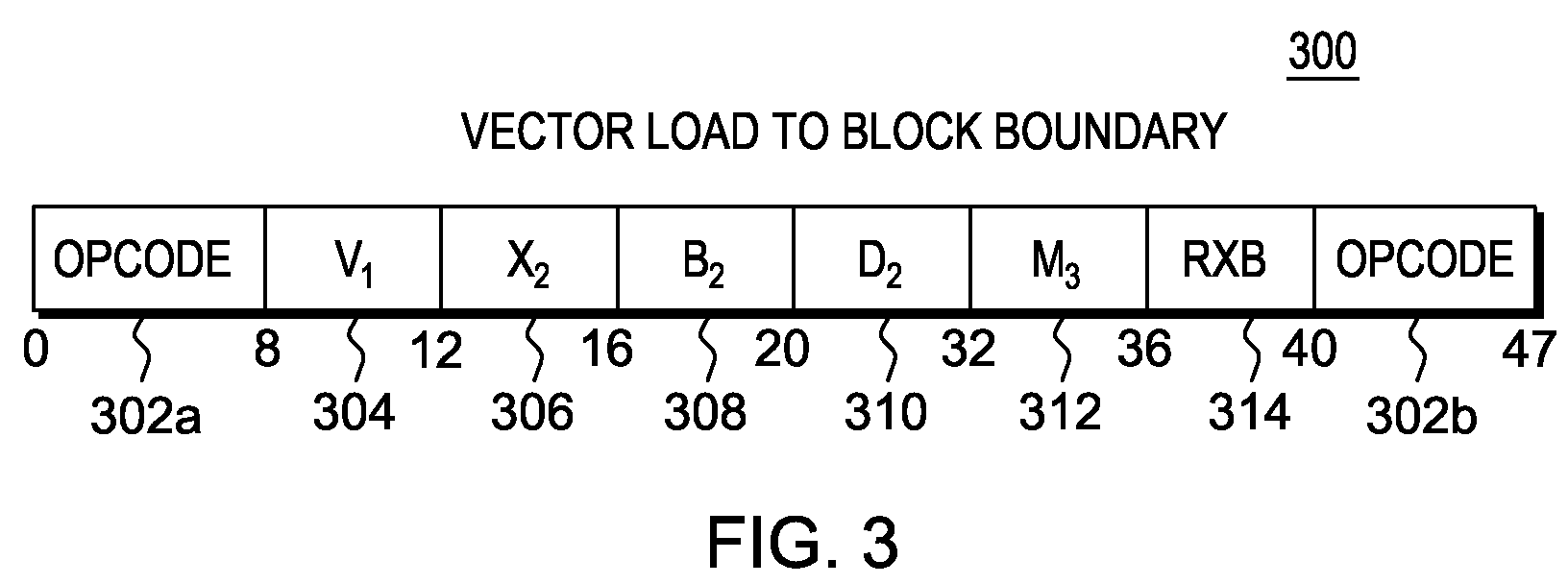
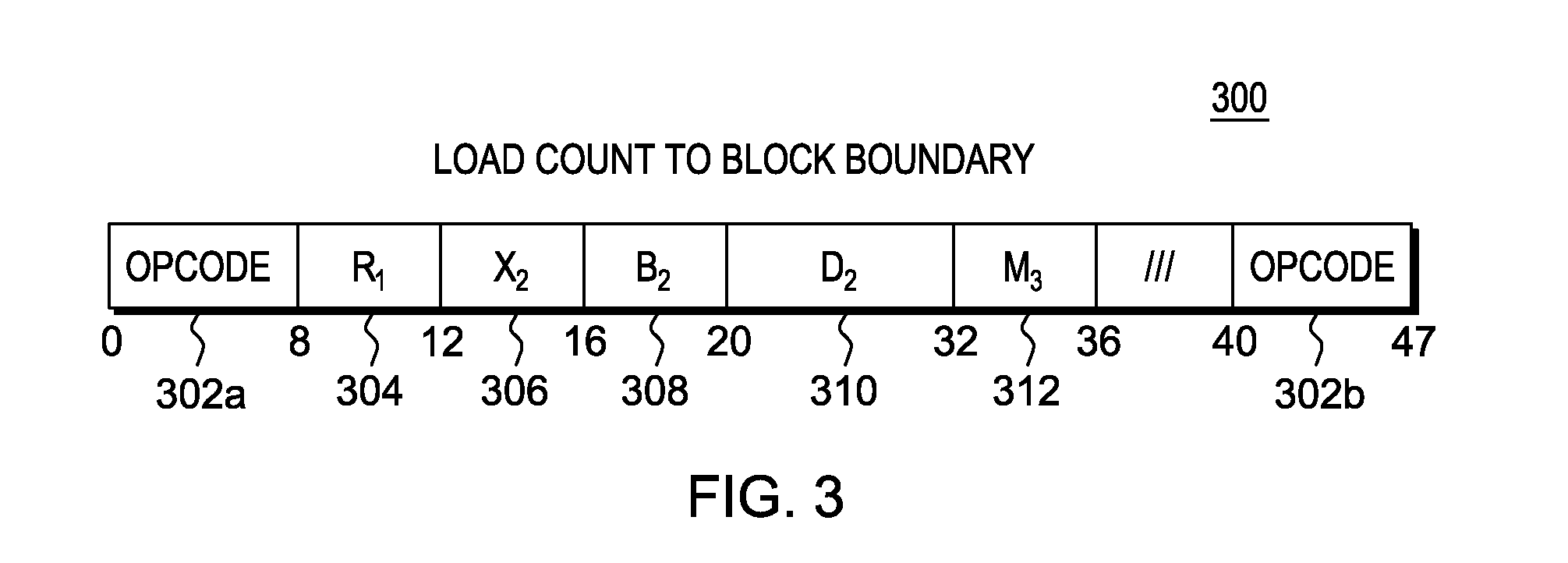
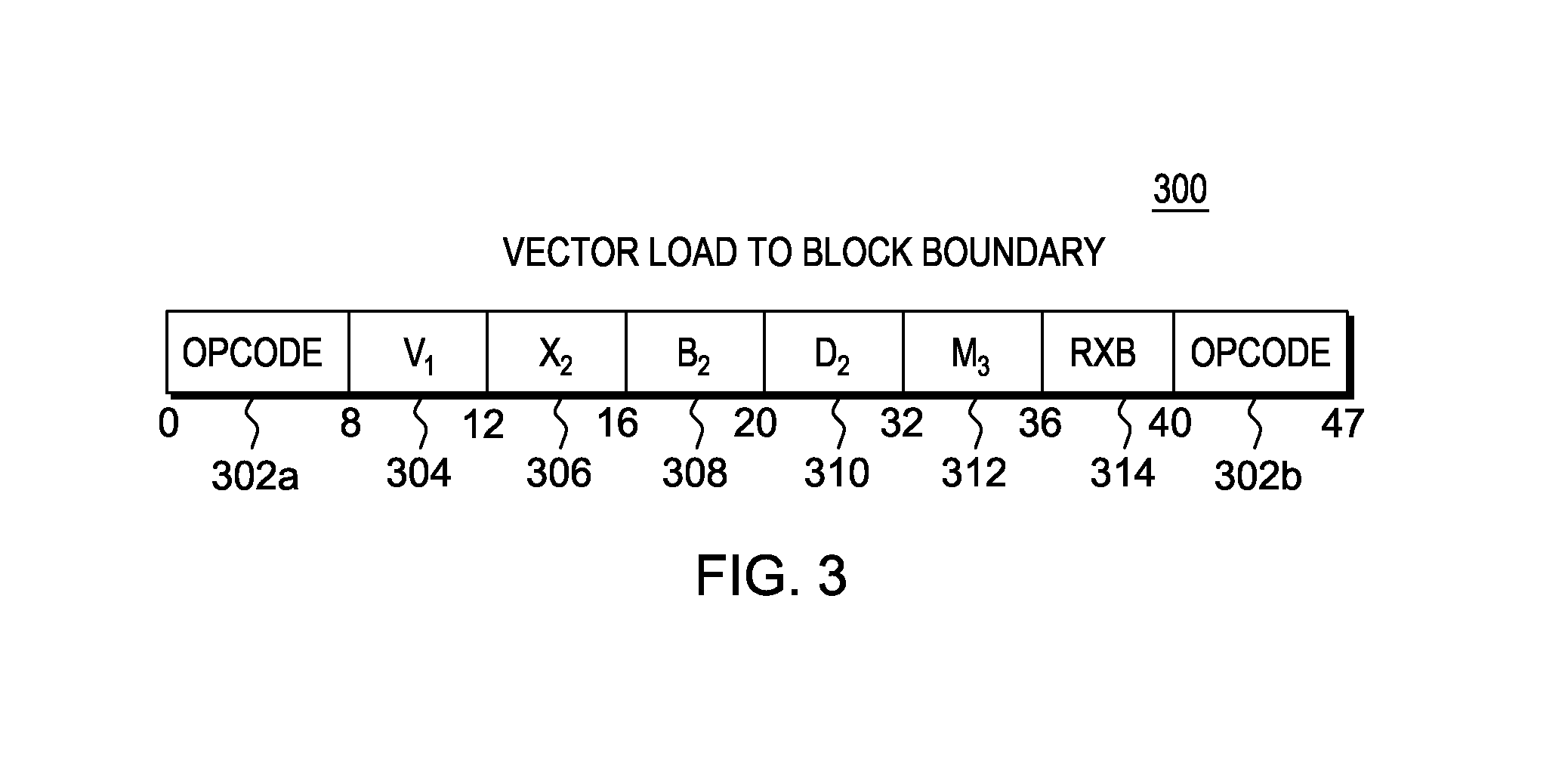
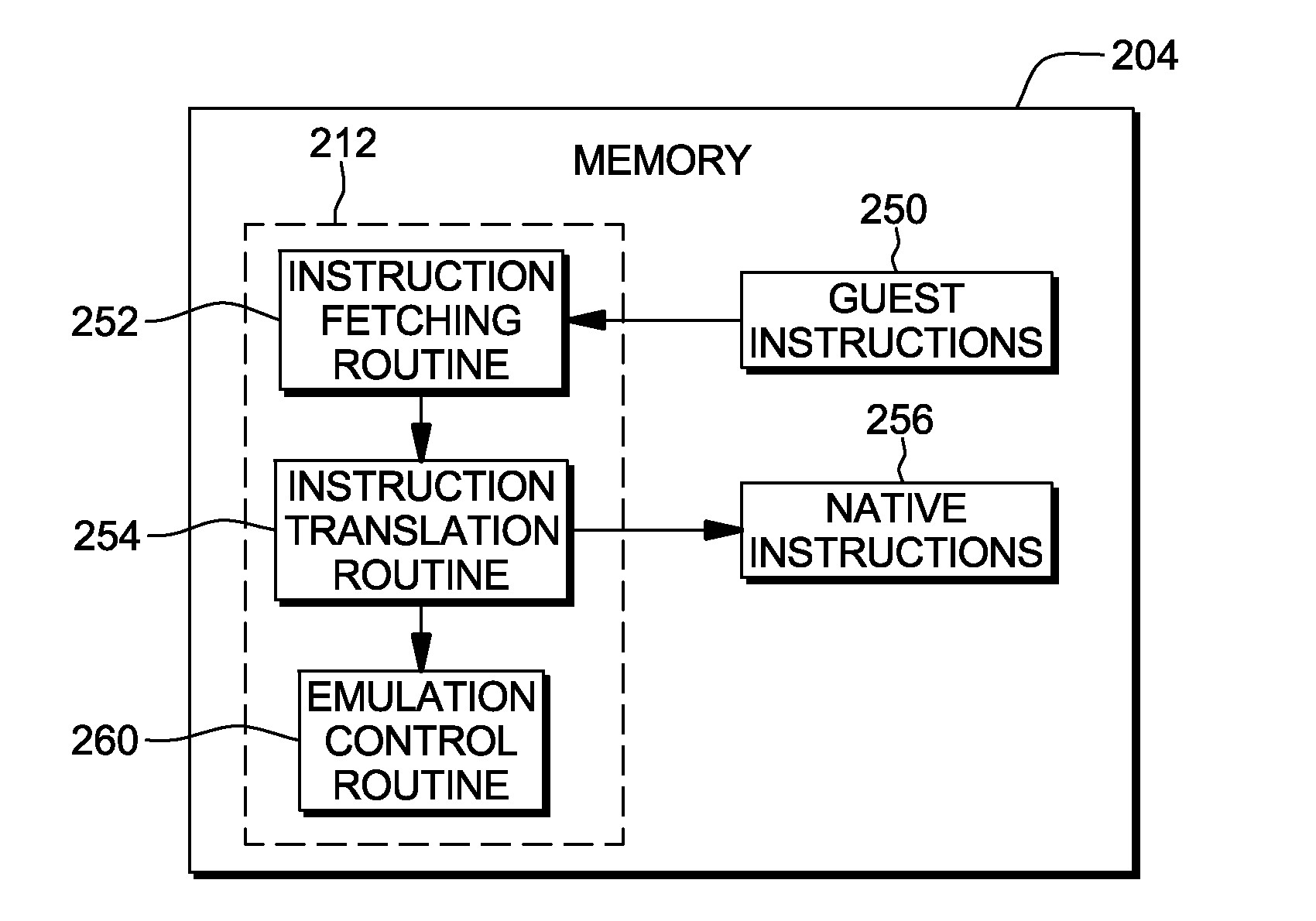
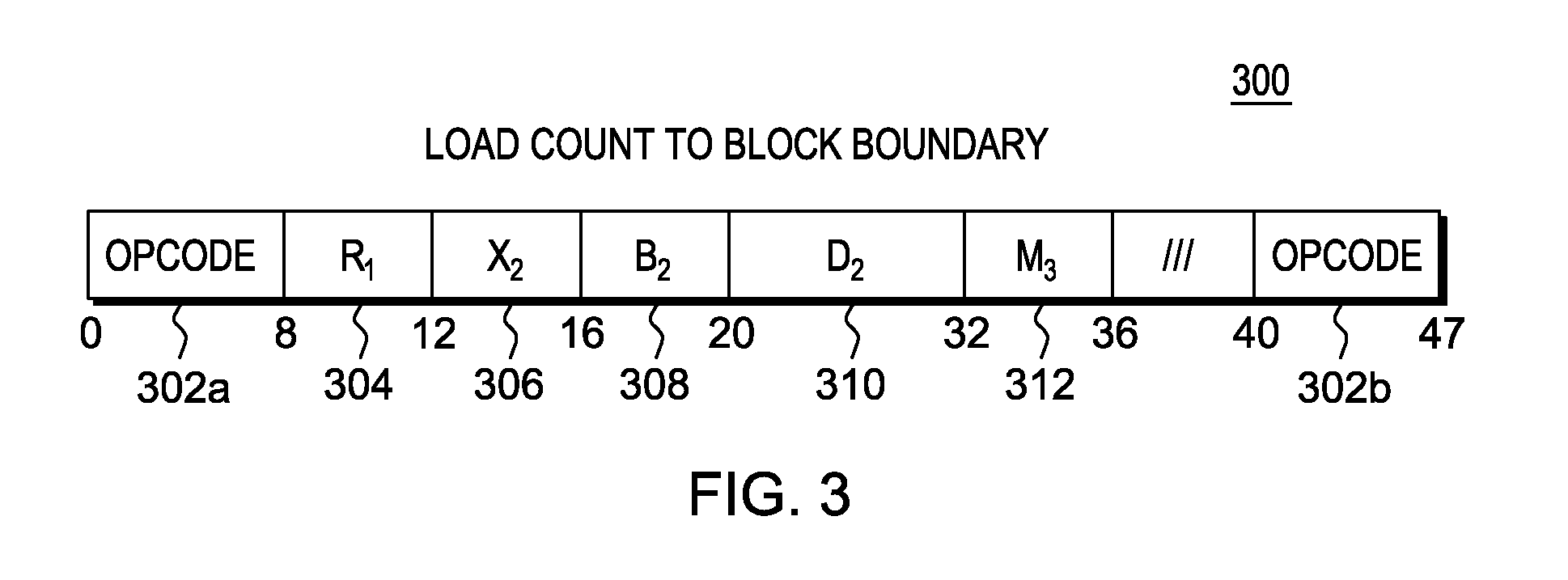
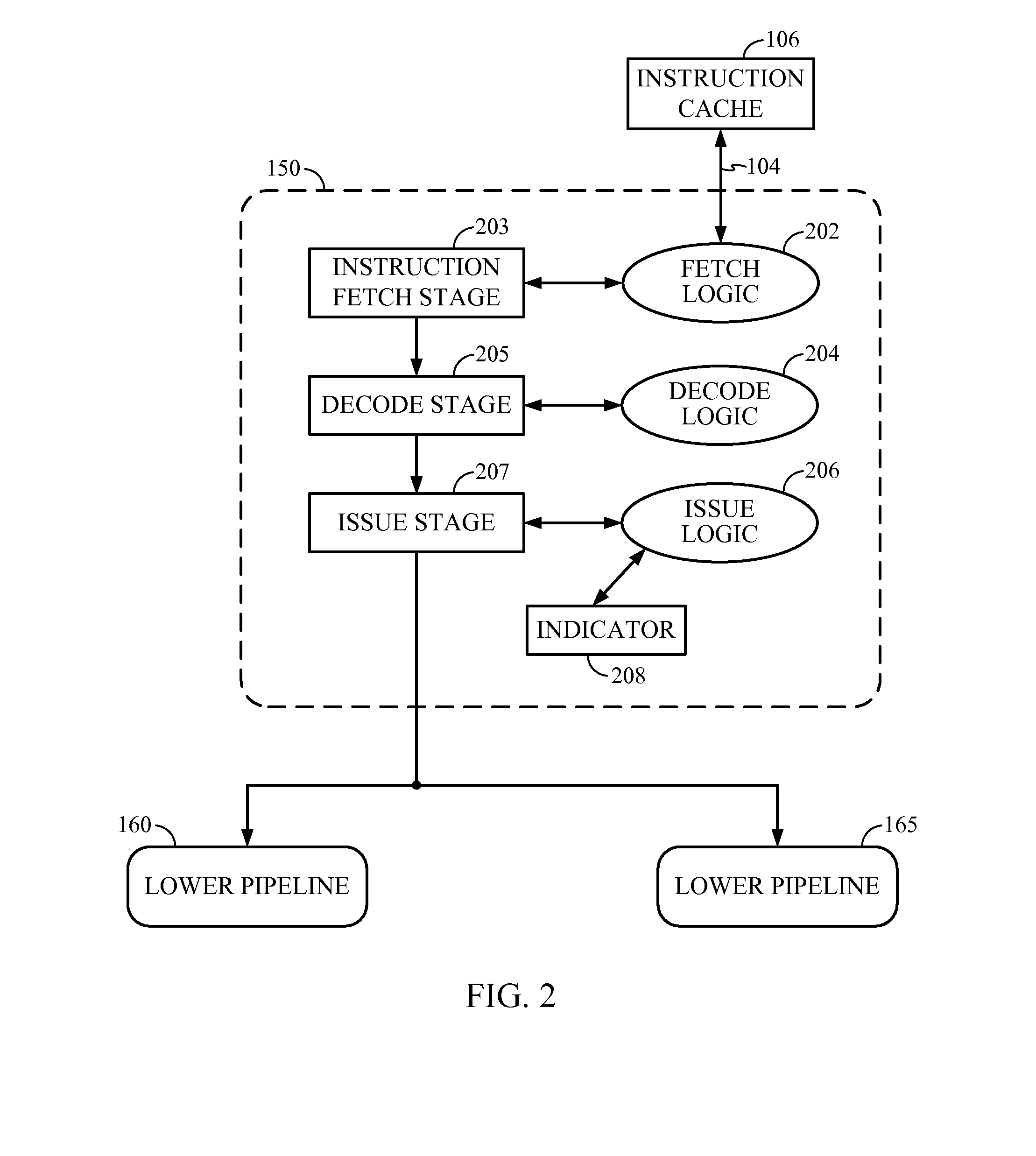
Instruction to load data up to a specified memory boundary indicated by the instruction
ActiveUS20130246764A1Quick conversionAccurate operationRegister arrangementsInstruction analysisProcessor registerParallel computing
A Load to Block Boundary instruction is provided that loads a variable number of bytes of data into a register while ensuring that a specified memory boundary is not crossed. The boundary may be specified a number of ways, including, but not limited to, a variable value in the instruction text, a fixed instruction text value encoded in the opcode, or a register based boundary.
Owner:IBM CORP
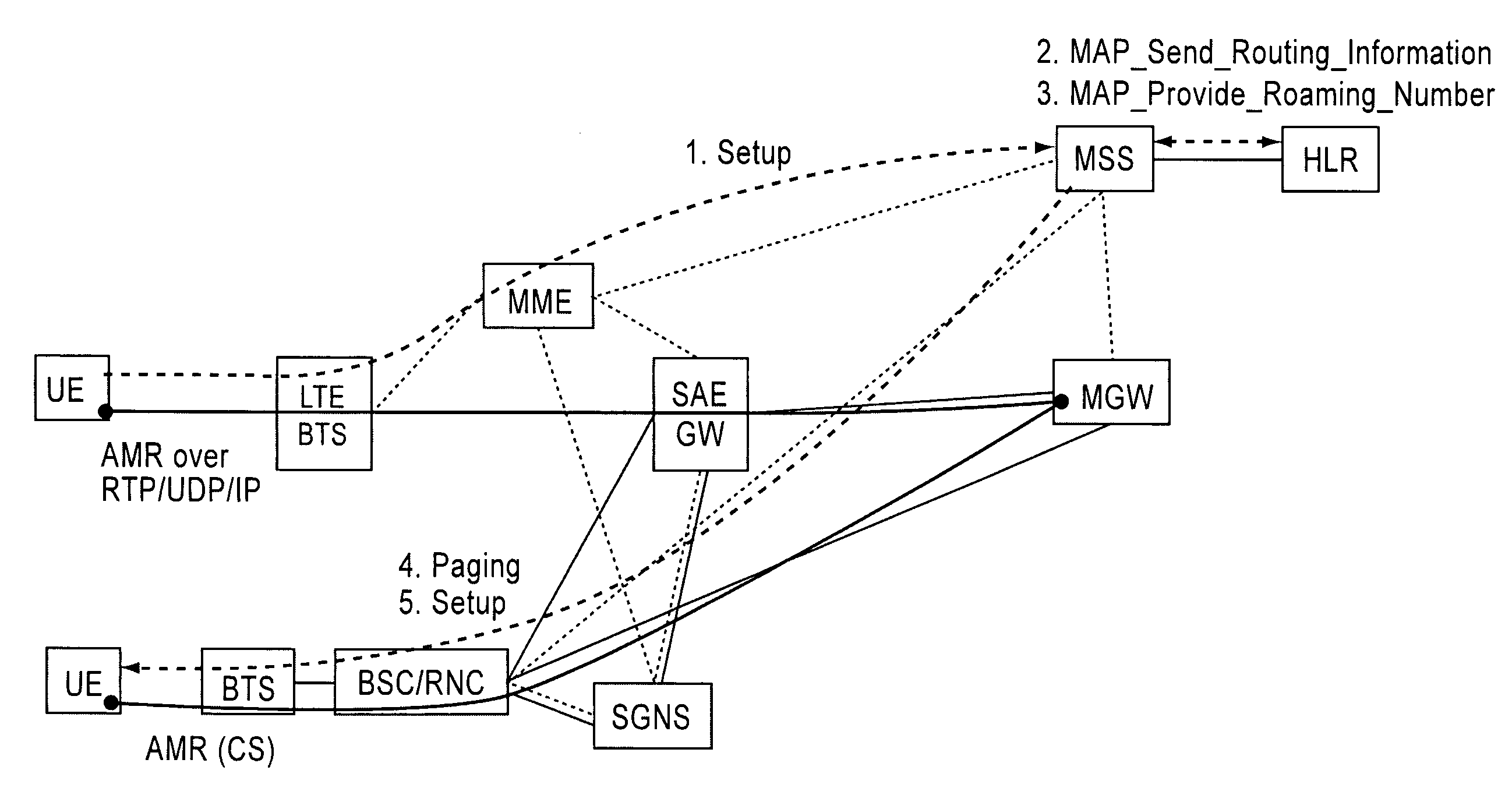
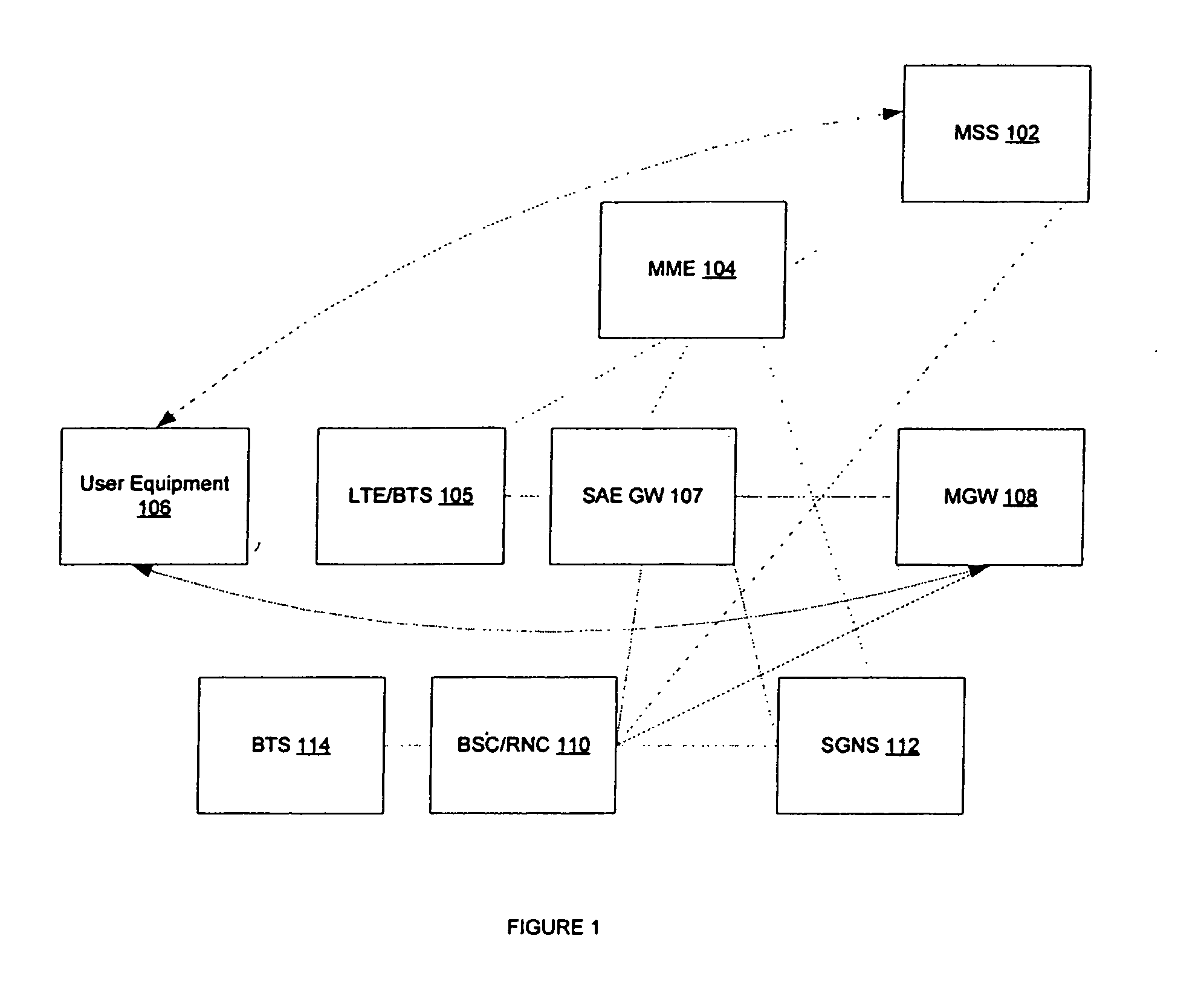
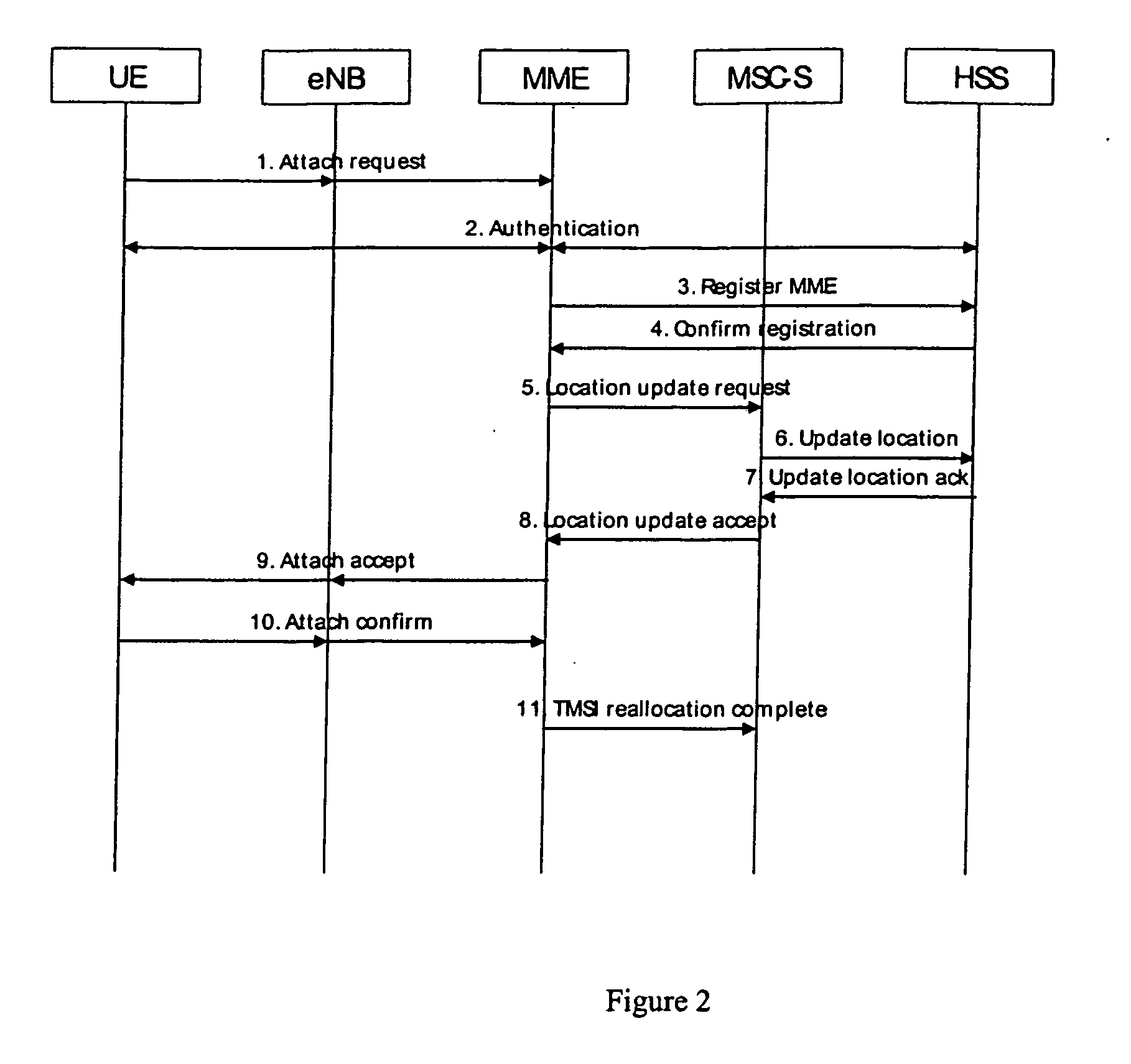
Circuit switched domain services with long term evolution/sytem architecture evolution access
ActiveUS20080214190A1Enhanced call controlCircuit switching systemsRadio/inductive link selection arrangementsSystem Architecture EvolutionMobility management
An apparatus and method including attaching a user equipment to a long term evolution system and simultaneously registering the user equipment attached to the long term evolution system to a circuit switched domain, is disclosed. The user equipment is simultaneously registered based on an interface between a mobility management entity and a mobile switching center server. For a mobile originated call from the user equipment attached to the long term evolution system, an enhanced call control is carried via the mobility management entity to the mobile switching center server. For a mobile terminated call, an enhanced call control is carried via the mobility management entity to the mobile switching center server, after the mobile switching center server pages the user equipment. The user equipment is offered existing circuit switched domain services while connected to the long term evolution system.
Owner:NOKIA TECHNOLOGLES OY
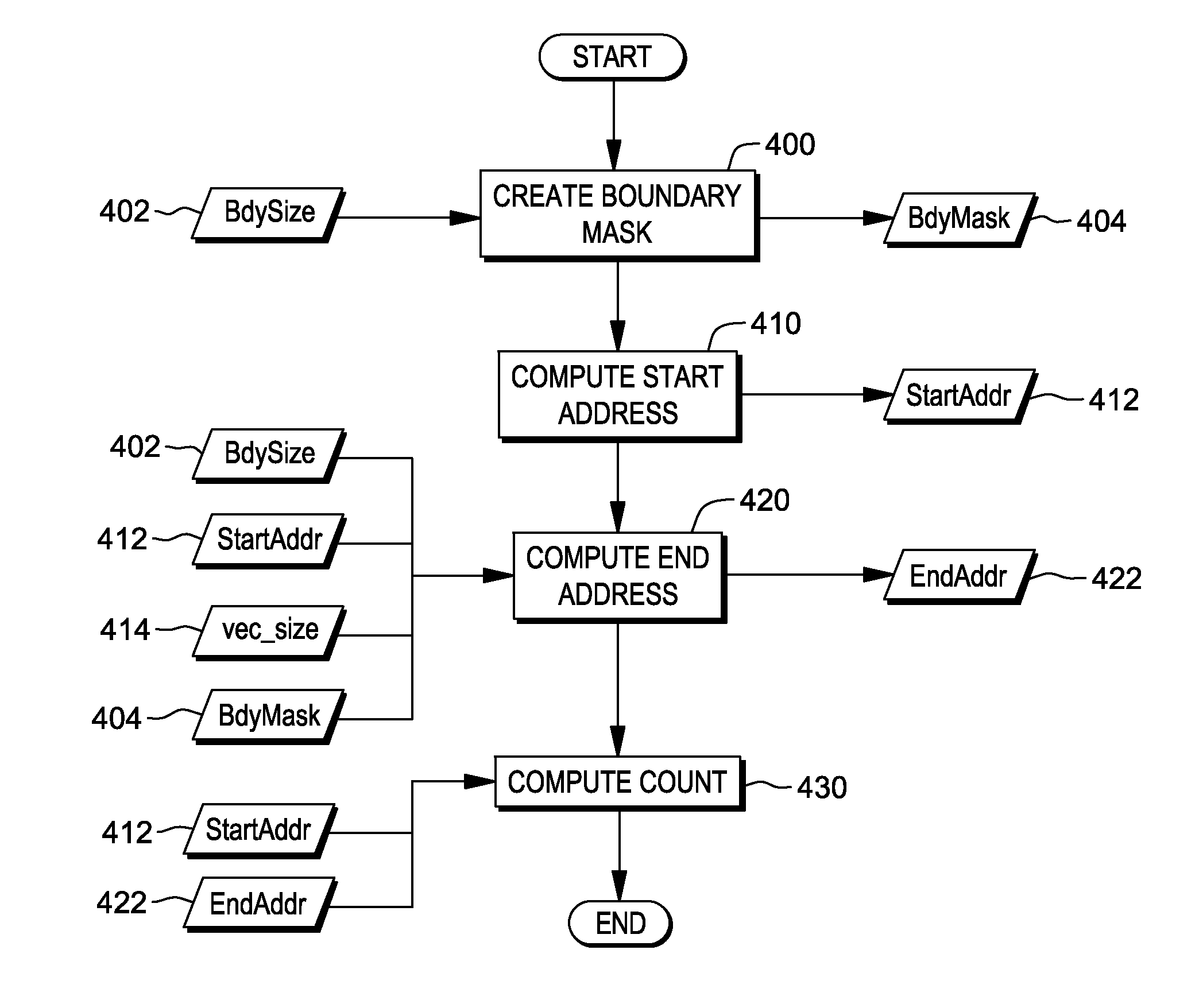
Instruction to compute the distance to a specified memory boundary
ActiveUS20130246767A1Quick conversionAccurate operationInstruction analysisDigital computer detailsMemory addressProcessor register
A Load Count to Block Boundary instruction is provided that provides a distance from a specified memory address to a specified memory boundary. The memory boundary is a boundary that is not to be crossed in loading data. The boundary may be specified a number of ways, including, but not limited to, a variable value in the instruction text, a fixed instruction text value encoded in the opcode, or a register based boundary; or it may be dynamically determined.
Owner:IBM CORP
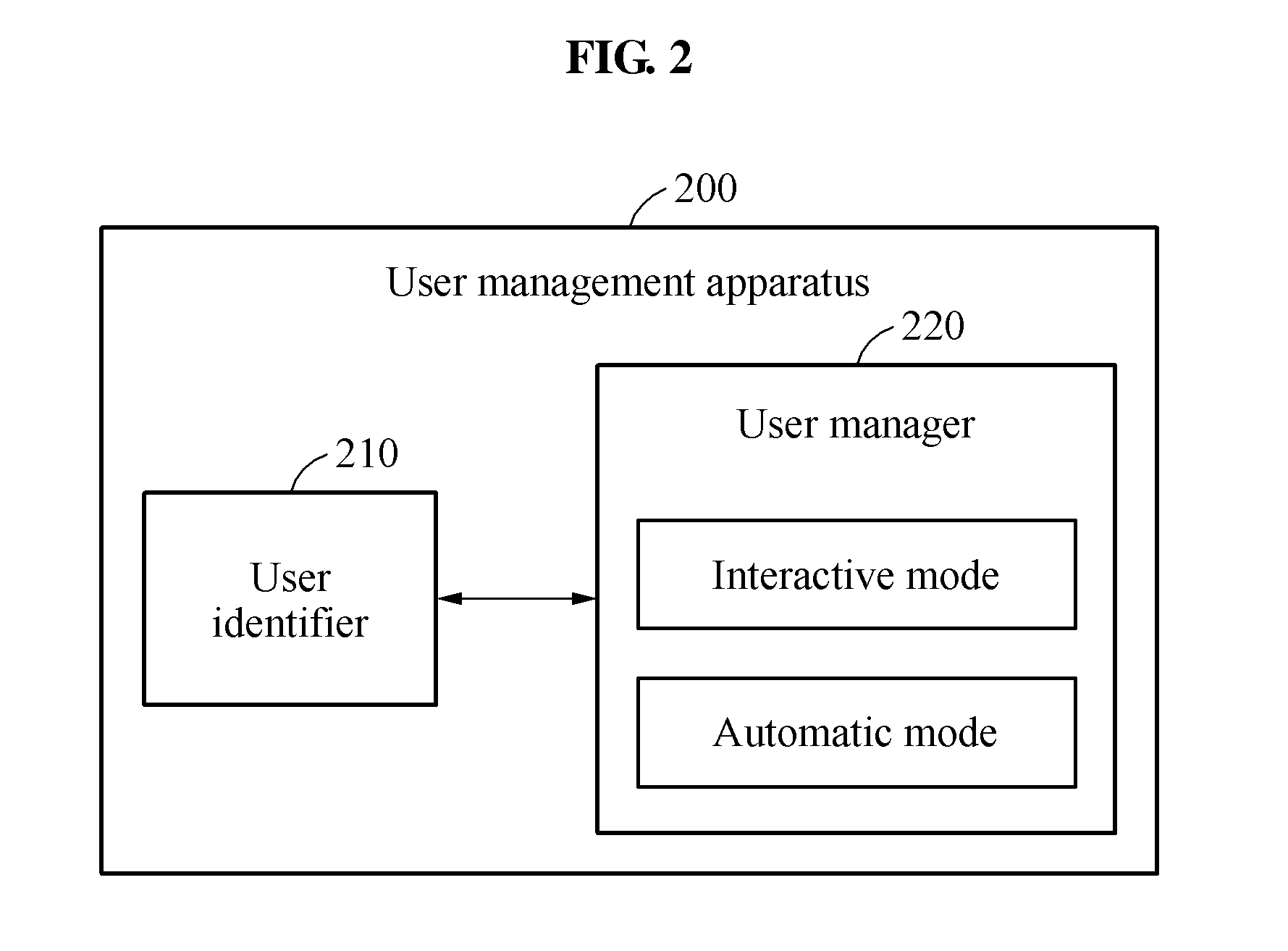
User management method and apparatus
InactiveUS20160217198A1Relational databasesCo-operative working arrangementsApproaches of managementData mining
Owner:SAMSUNG ELECTRONICS CO LTD
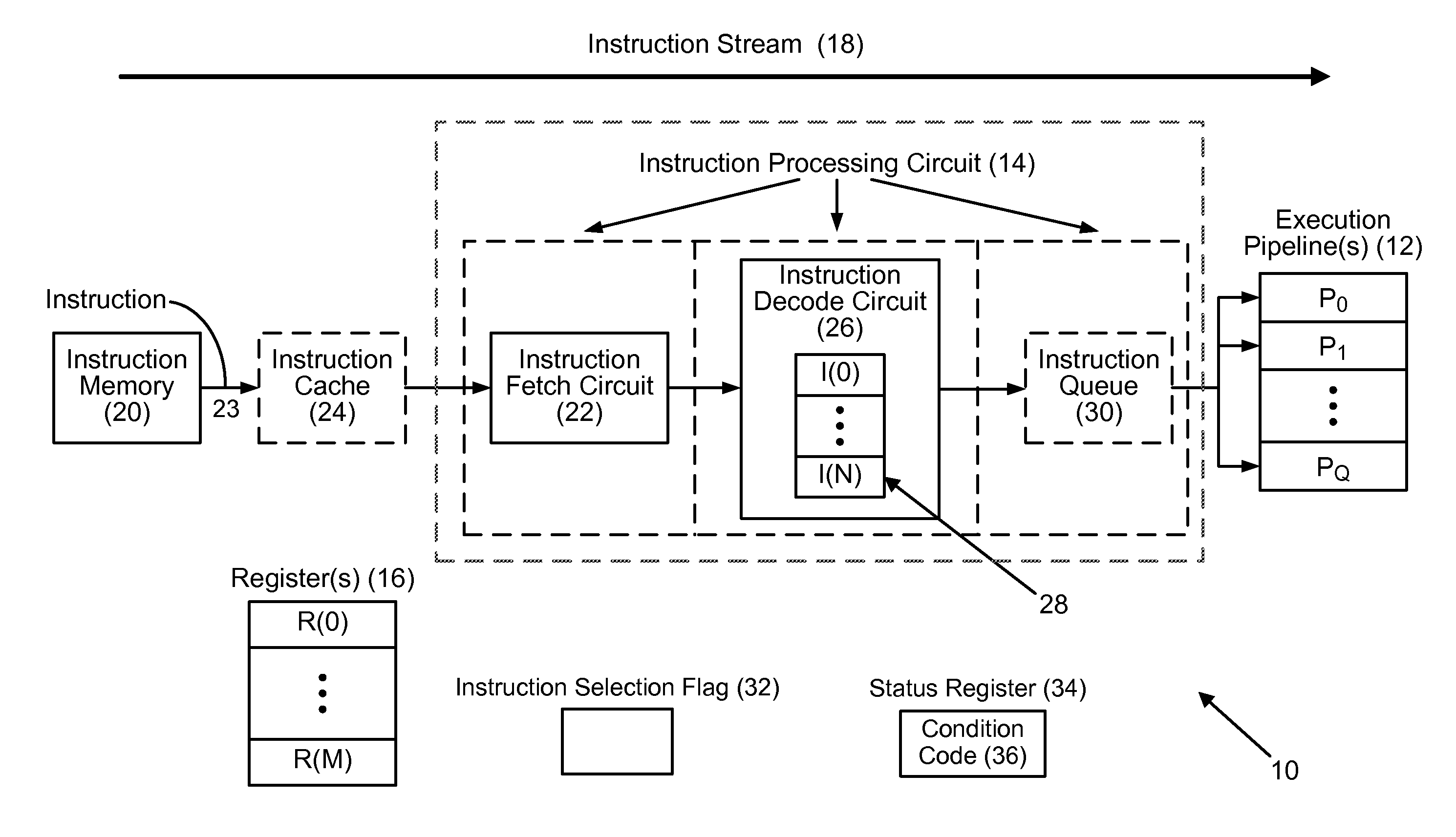
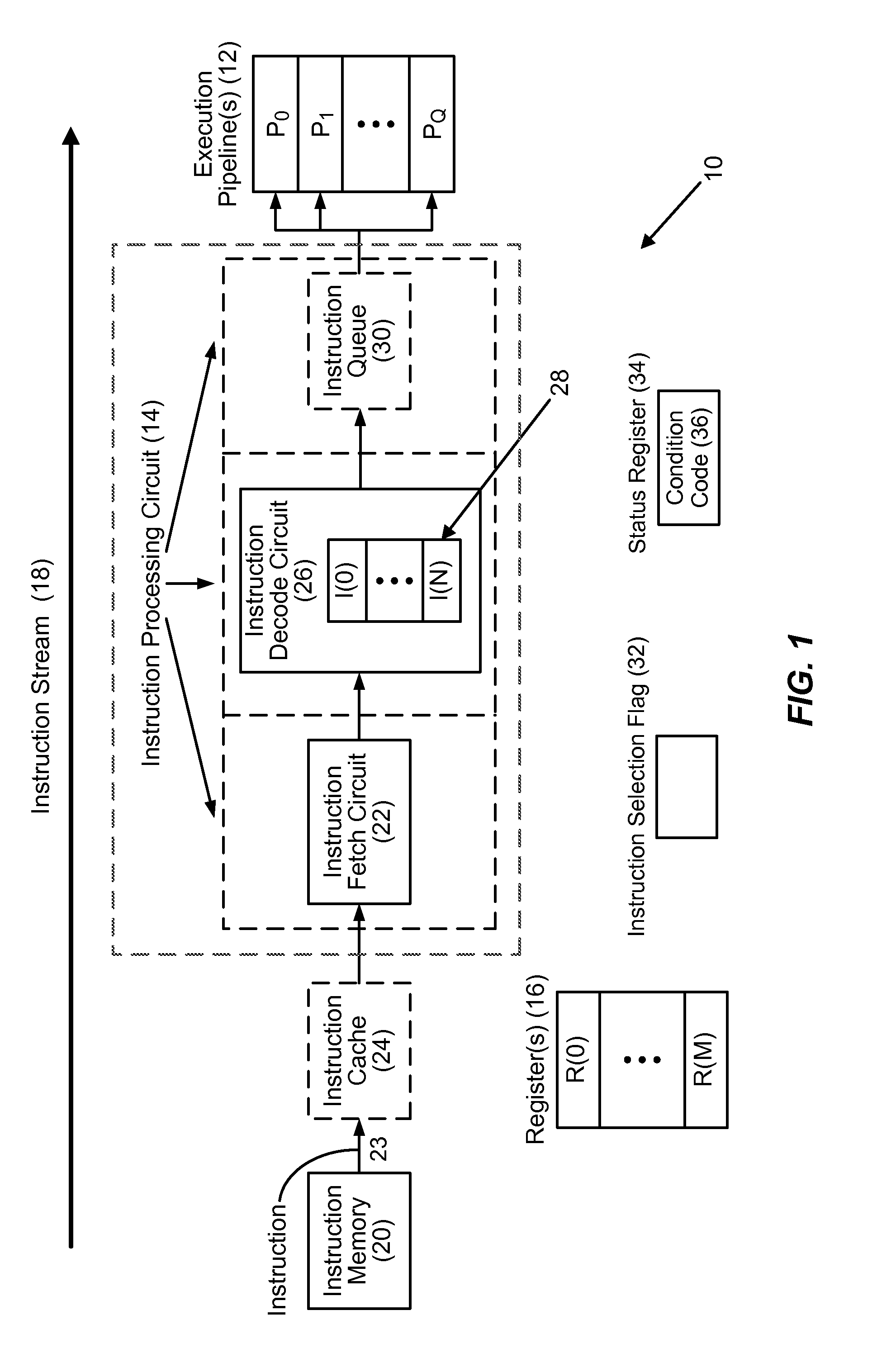
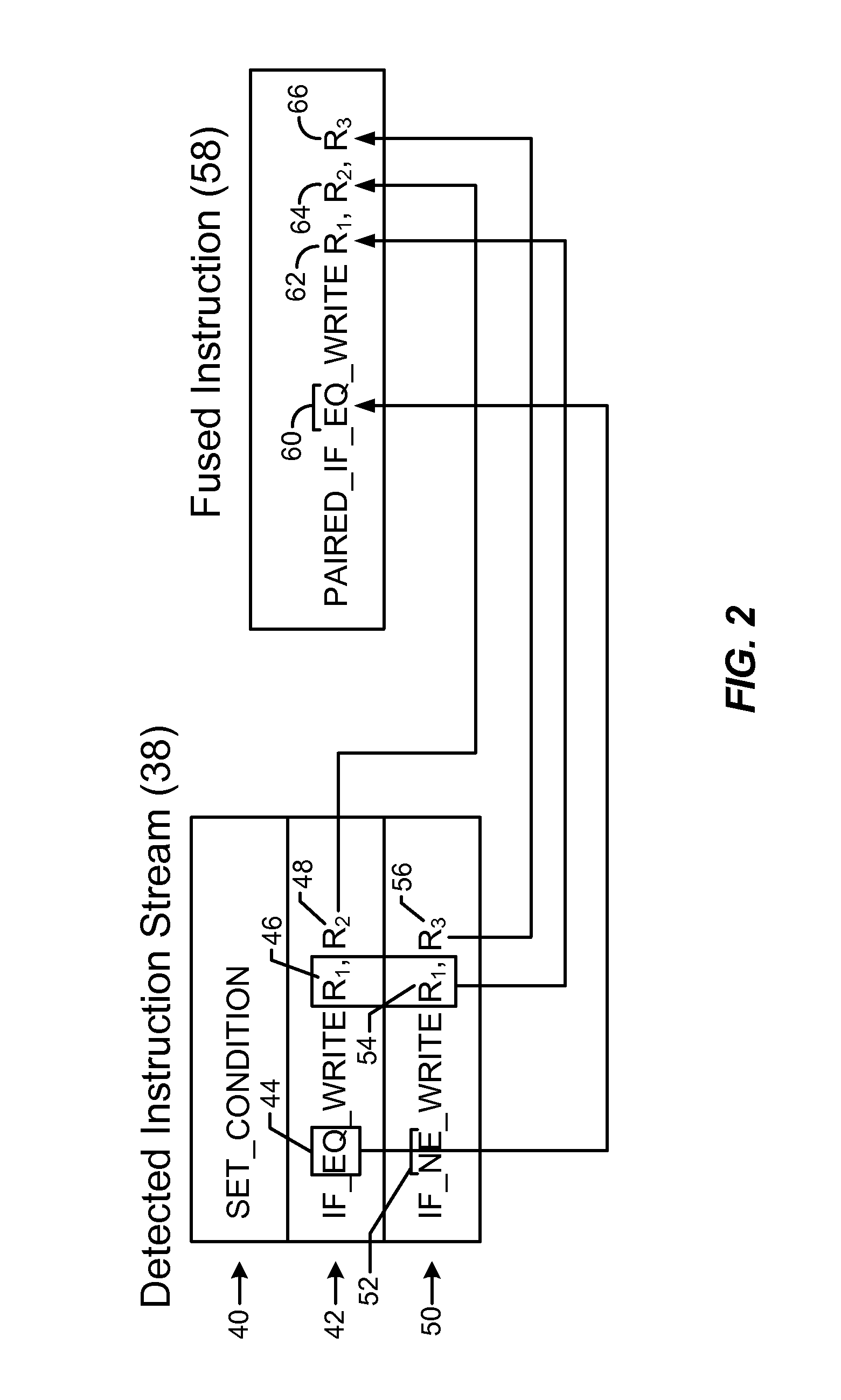
Fusing conditional write instructions having opposite conditions in instruction processing circuits, and related processor systems, methods, and computer-readable media
ActiveUS20130311754A1Increased CPU performanceEliminate hazardsRuntime instruction translationDigital computer detailsParallel computingRegister based
Fusing conditional write instructions having opposite conditions in instruction processing circuits and related processor systems, methods, and computer-readable media are disclosed. In one embodiment, a first conditional write instruction writing a first value to a target register based on evaluating a first condition is detected by an instruction processing circuit. The circuit also detects a second conditional write instruction writing a second value to the target register based on evaluating a second condition that is a logical opposite of the first condition. Either the first condition or the second condition is selected as a fused instruction condition, and corresponding values are selected as if-true and if-false values. A fused instruction is generated for selectively writing the if-true value to the target register if the fused instruction condition evaluates to true, and selectively writing the if-false value to the target register if the fused instruction condition evaluates to false.
Owner:QUALCOMM INC
Instruction to load data up to a specified memory boundary indicated by the instruction
ActiveUS20130246738A1Quick conversionAccurate operationRegister arrangementsInstruction analysisProcessor registerParallel computing
A Load to Block Boundary instruction is provided that loads a variable number of bytes of data into a register while ensuring that a specified memory boundary is not crossed. The boundary may be specified a number of ways, including, but not limited to, a variable value in the instruction text, a fixed instruction text value encoded in the opcode, or a register based boundary.
Owner:IBM CORP
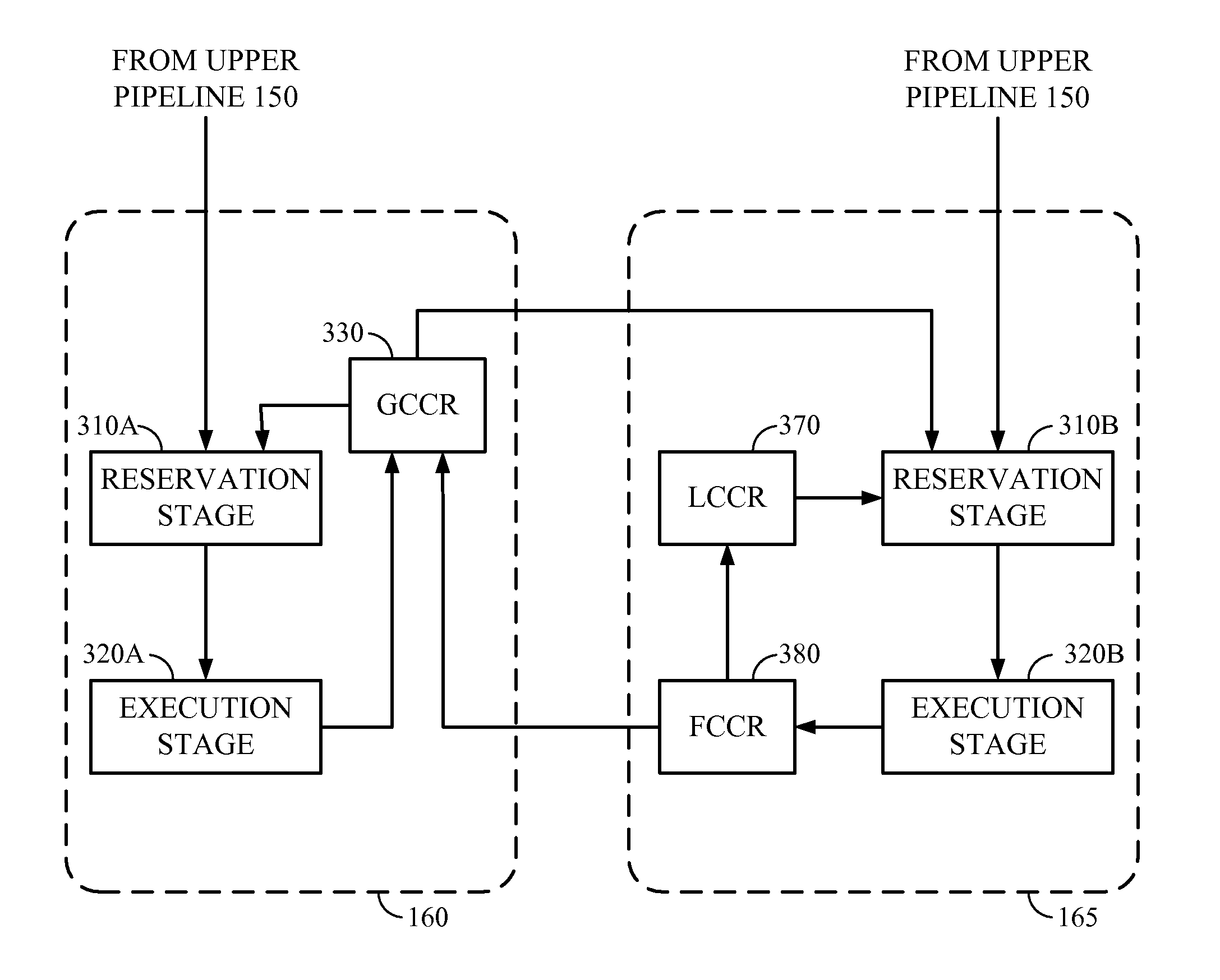
System and method for using a local condition code register for accelerating conditional instruction execution in a pipeline processor
InactiveUS8555039B2Improve executionSpeed up executionConditional code generationDigital computer detailsProcessor registerParallel computing
A method of executing a conditional instruction within a pipeline processor having a plurality of pipelines, the processor having a first condition code register associated with a first pipeline and a second condition code register associated with a second pipeline is disclosed. The method saves a most recent condition code value to either the first condition code register or the second condition code register. The method further sets an indicator indicating whether the second condition code register has the most recent condition code value and retrieves the most recent condition code value from either the first or second condition code register based on the indicator. The method uses the most recent condition code value to determine if the conditional instruction should be executed.
Owner:QUALCOMM INC
Methods and apparatus for registration of medical images
InactiveUS20110019885A1Robust registrationImage enhancementImage analysisAnatomical featureRegister based
In methods and an apparatus for registering two medical images of a subject, a first image is compared with a first anatomical atlas and a second image with a second anatomical atlas, to generate labels for anatomical features in each image. The first anatomical atlas has at least two anatomical features in common with the second, and each label includes a suggested location of the anatomical feature to which it relates. A number of labels are identified for each image, and a value of a similarity function between labels of the respective images is calculated. The two images are registered based on the value of the similarity function.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
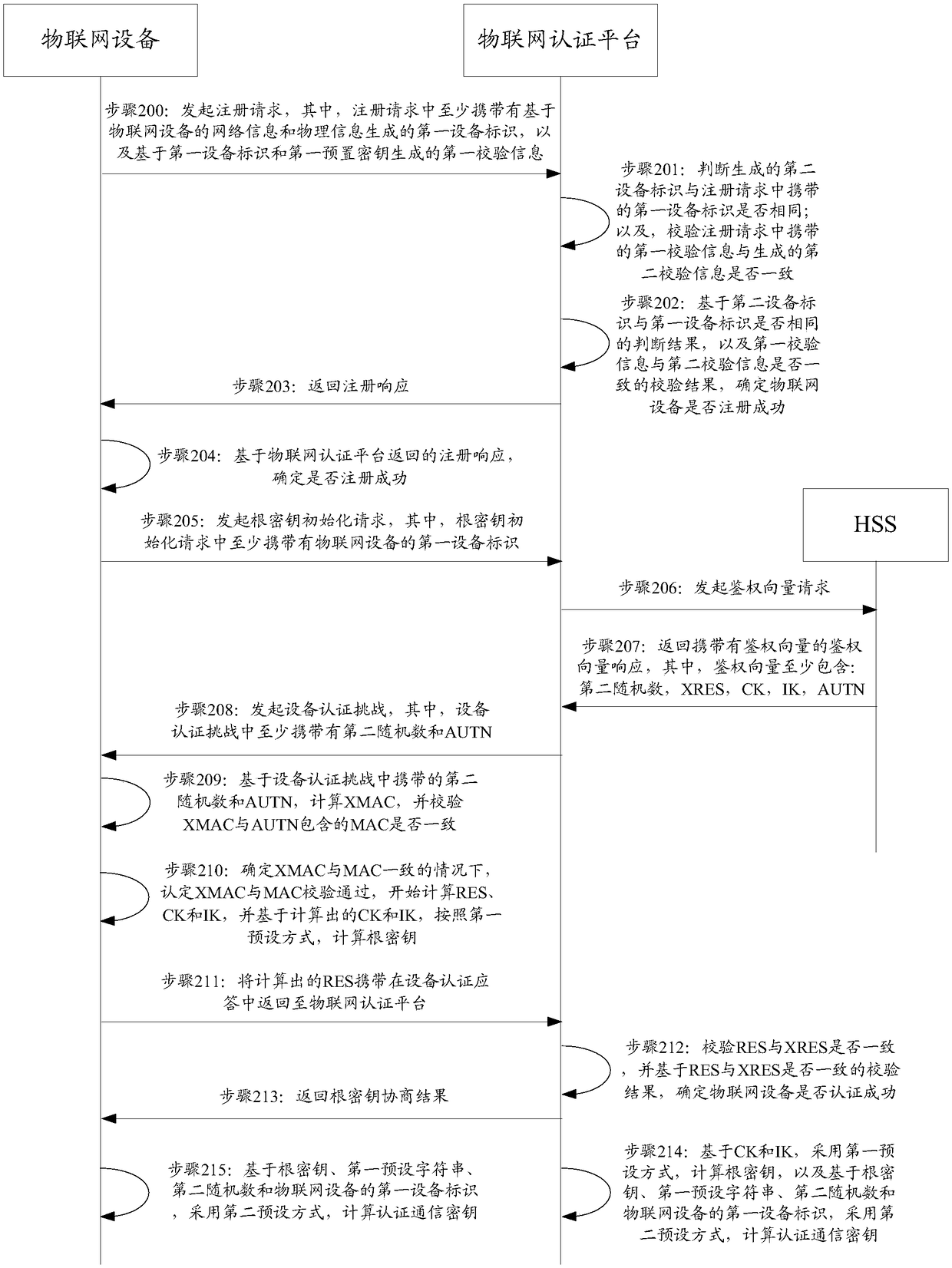
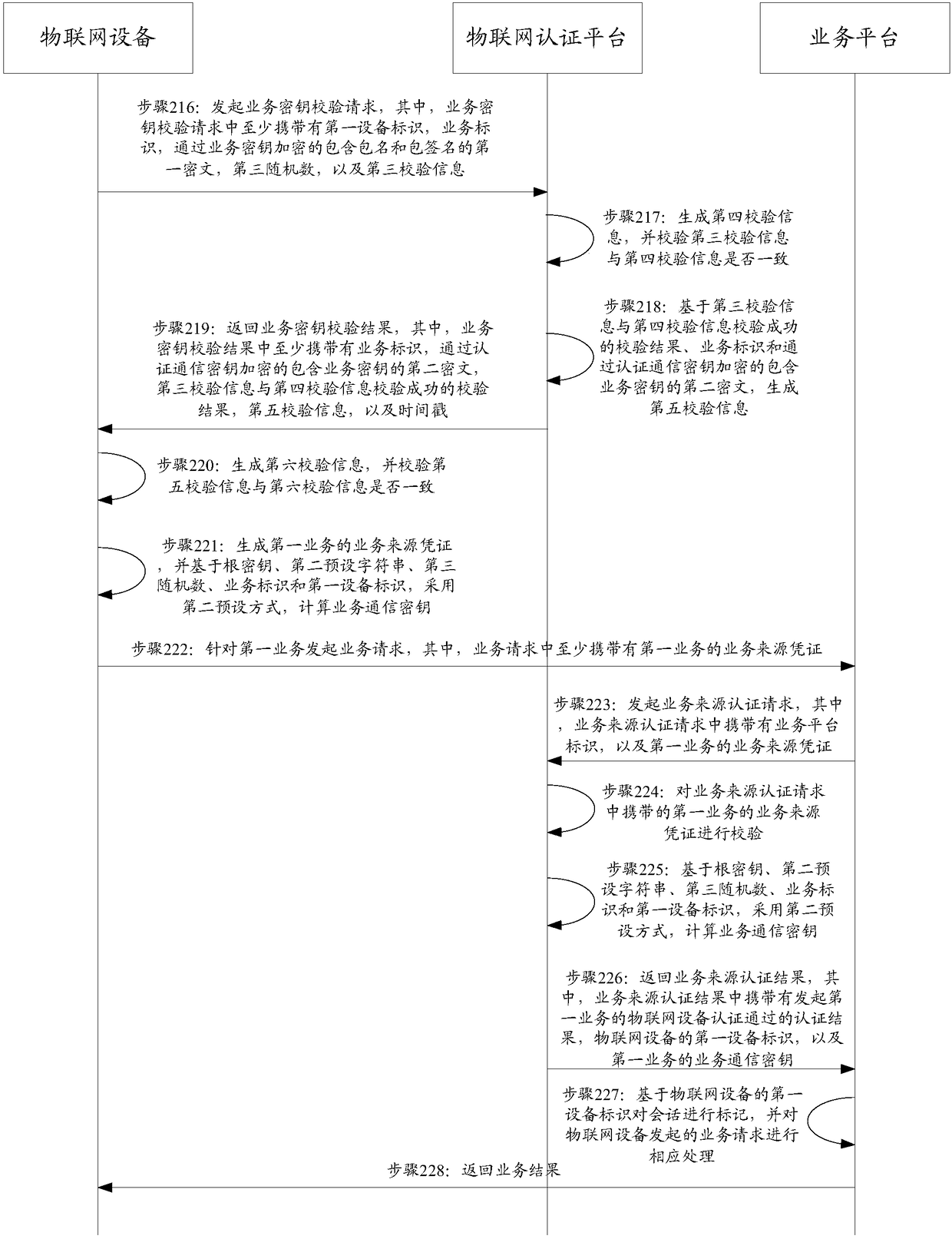
Internet of Things equipment, Internet of Things authentication platform, and authentication method and system
InactiveCN108632231AUniqueness guaranteedRealize physical associationTransmissionThe InternetPhysical information
The invention discloses Internet of Things equipment, an Internet of Things authentication platform, and an authentication method and system, and is used for solving the problem of poor authenticationeffect of the Internet of Things equipment. The method includes steps: the Internet of Things equipment initiates a registration request to the Internet of Things authentication platform, wherein theregistration request carries a first equipment identifier generated based on network information and physical information; and the Internet of Things authentication platform generates a second equipment identifier based on pre-saved network information and physical information, determines whether the Internet of Things equipment is successfully registered based on a determination result that whether the second equipment identifier and the first equipment identifier are the same, and returns a registration response to the Internet of Things equipment. The equipment identifiers are generated through the network information and the physical information of the Internet of Things equipment so that the uniqueness of the equipment identifiers is guaranteed, the equipment identifiers can be boundto each hardware of the Internet of Things equipment, the Internet of Things equipment fails to be forged and replaced, and a good authentication basis is provided for authentication of the Internetof Things equipment in a registration process.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
Instruction to compute the distance to a specified memory boundary
A Load Count to Block Boundary instruction is provided that provides a distance from a specified memory address to a specified memory boundary. The memory boundary is a boundary that is not to be crossed in loading data. The boundary may be specified a number of ways, including, but not limited to, a variable value in the instruction text, a fixed instruction text value encoded in the opcode, or a register based boundary; or it may be dynamically determined.
Owner:IBM CORP
Method and apparatus for generating a variation-tolerant clock-tree for an integrated circuit chip
ActiveUS20080168412A1Raise priorityMaximizes inclusionProbabilistic CADSoftware simulation/interpretation/emulationProcessor registerTime critical
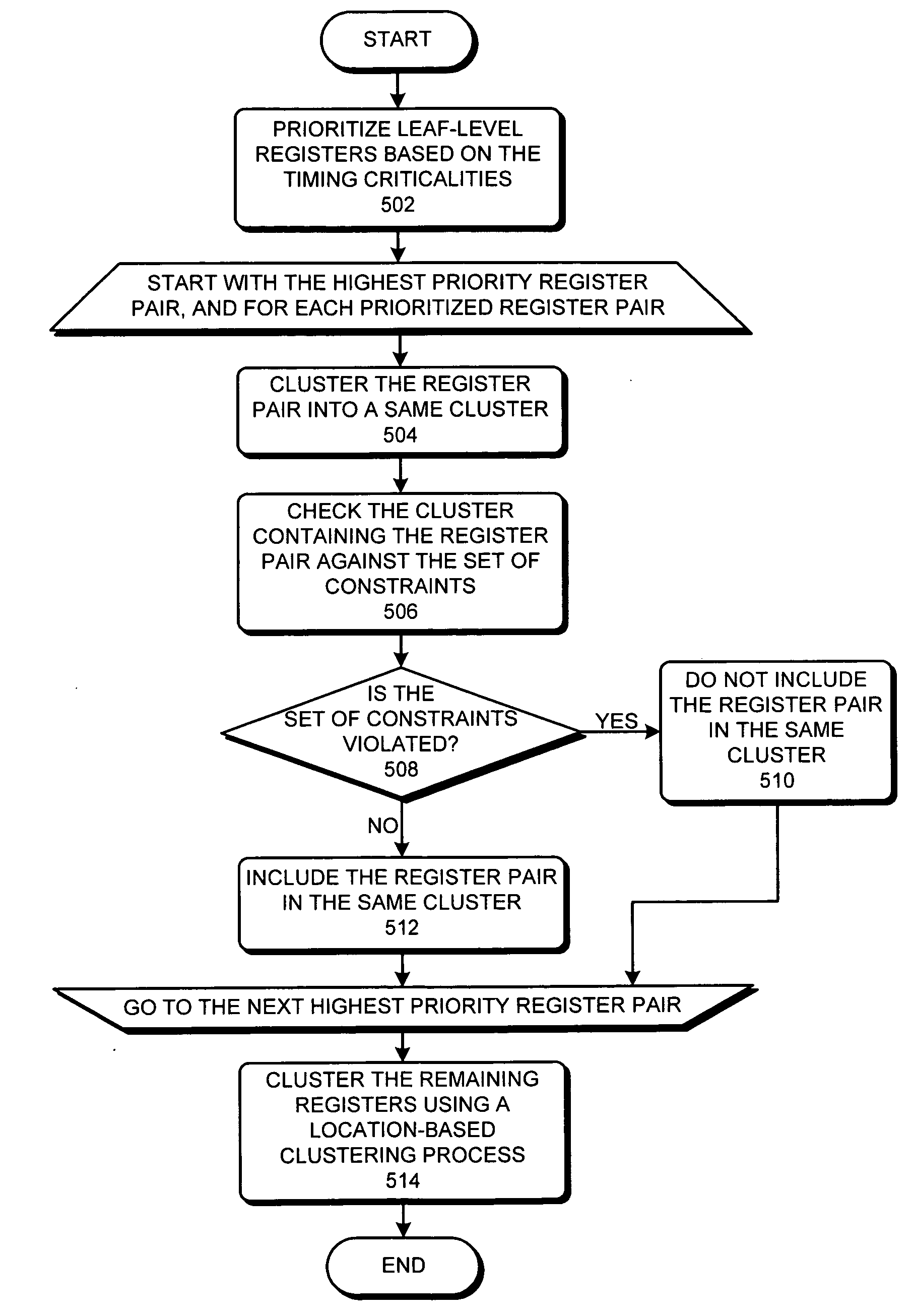
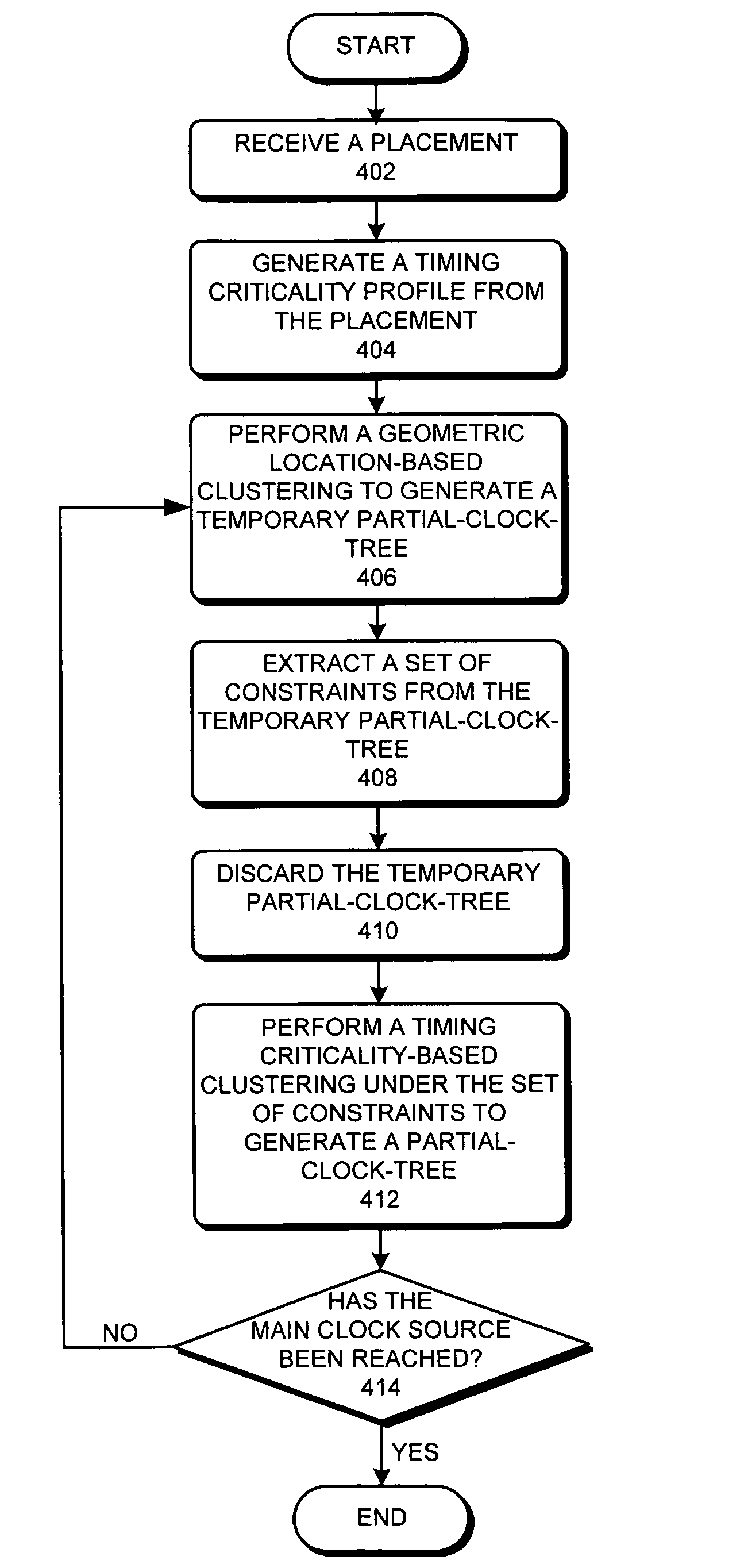
One embodiment of the present invention relates to a process that generates a clock-tree on an integrated circuit (IC) chip. During operation, the process starts by receiving a placement for a chip layout, where the placement includes a set of registers at fixed locations in the chip layout. The process then generates a timing criticality profile for the set of registers, wherein the timing criticality profile specifies timing criticalities between pairs of registers in the set of registers. Next, the process clusters the set of registers based on the timing criticality profile to create a clock-tree for the set of registers. By clustering the registers based on the timing criticality profile, the process facilitates using commonly-shared clock paths in the clock-tree to provide clock signals to timing critical register pairs.
Owner:SYNOPSYS INC
Method and apparatus for generating a variation-tolerant clock-tree for an integrated circuit chip
ActiveUS7546567B2Raise priorityMaximizes inclusionProbabilistic CADSoftware simulation/interpretation/emulationTime criticalConfigfs
One embodiment of the present invention relates to a process that generates a clock-tree on an integrated circuit (IC) chip. During operation, the process starts by receiving a placement for a chip layout, where the placement includes a set of registers at fixed locations in the chip layout. The process then generates a timing criticality profile for the set of registers, wherein the timing criticality profile specifies timing criticalities between pairs of registers in the set of registers. Next, the process clusters the set of registers based on the timing criticality profile to create a clock-tree for the set of registers. By clustering the registers based on the timing criticality profile, the process facilitates using commonly-shared clock paths in the clock-tree to provide clock signals to timing critical register pairs.
Owner:SYNOPSYS INC
System and Method for using a Local Condition Code Register for Accelerating Conditional Instruction Execution in a Pipeline Processor
InactiveUS20080276072A1Speed up executionEfficient use of resourcesConditional code generationDigital computer detailsProcessor registerParallel computing
A method of executing a conditional instruction within a pipeline processor having a plurality of pipelines, the processor having a first condition code register associated with a first pipeline and a second condition code register associated with a second pipeline is disclosed. The method saves a most recent condition code value to either the first condition code register or the second condition code register. The method further sets an indicator indicating whether the second condition code register has the most recent condition code value and retrieves the most recent condition code value from either the first or second condition code register based on the indicator. The method uses the most recent condition code value to determine if the conditional instruction should be executed.
Owner:QUALCOMM INC
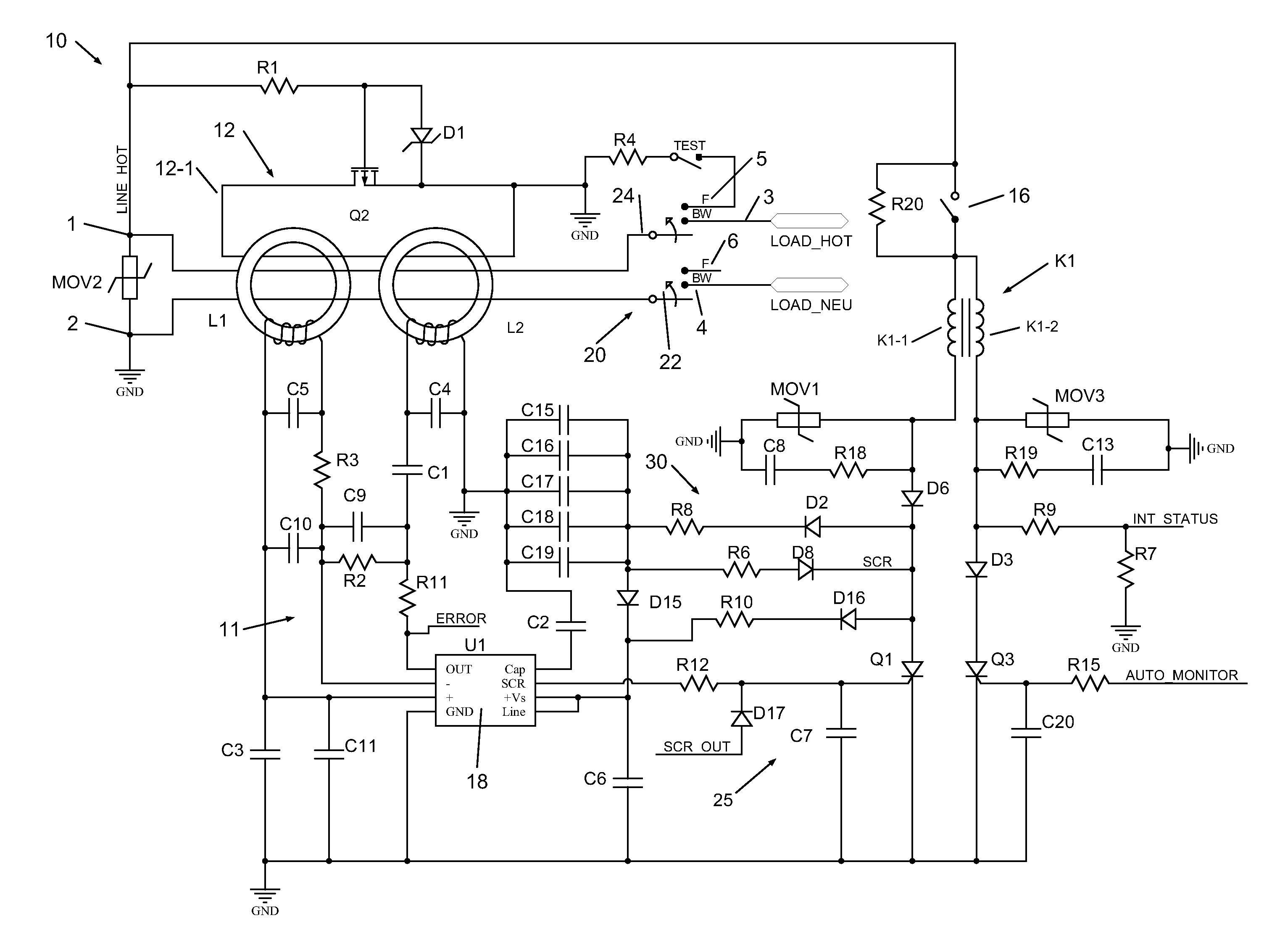
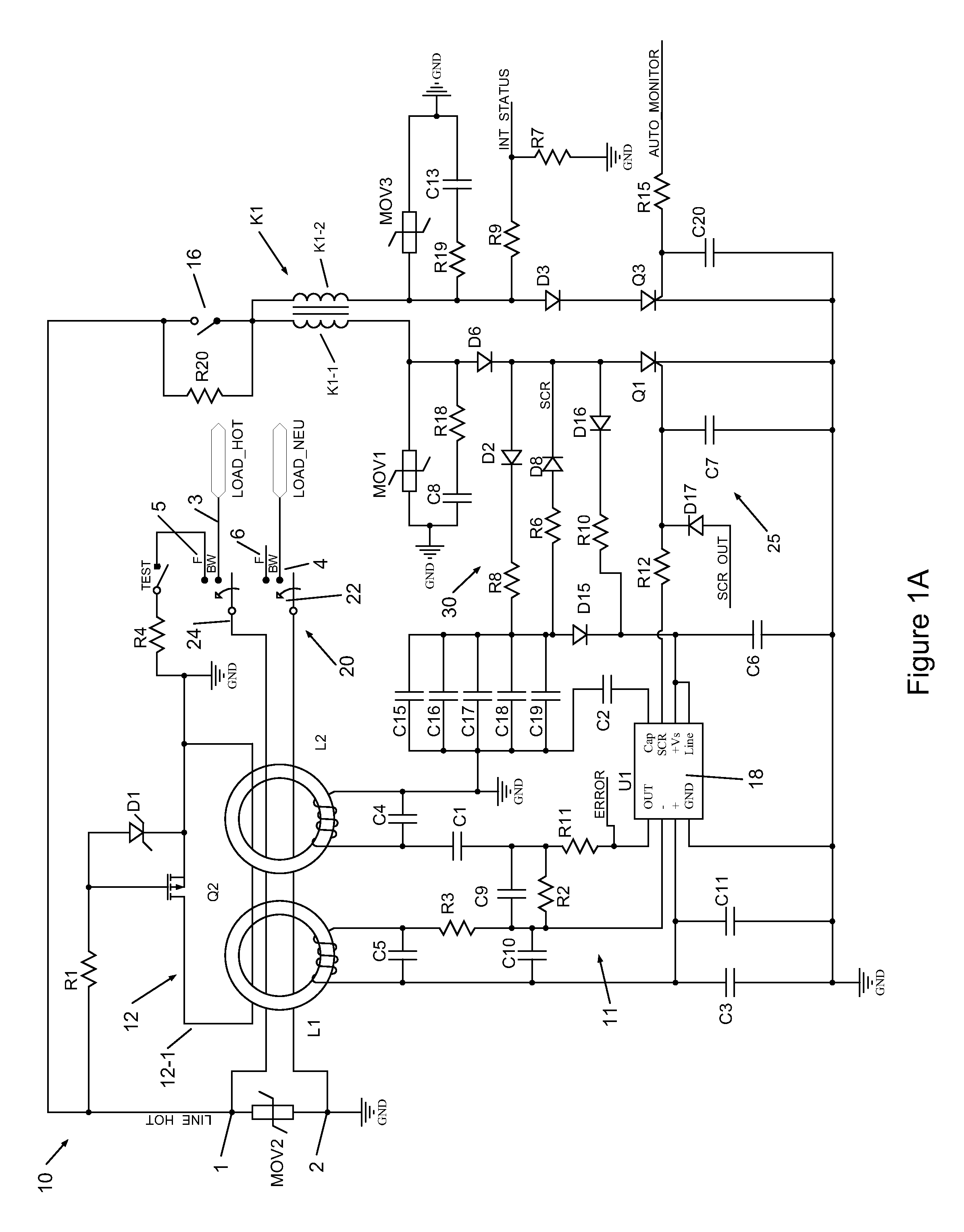
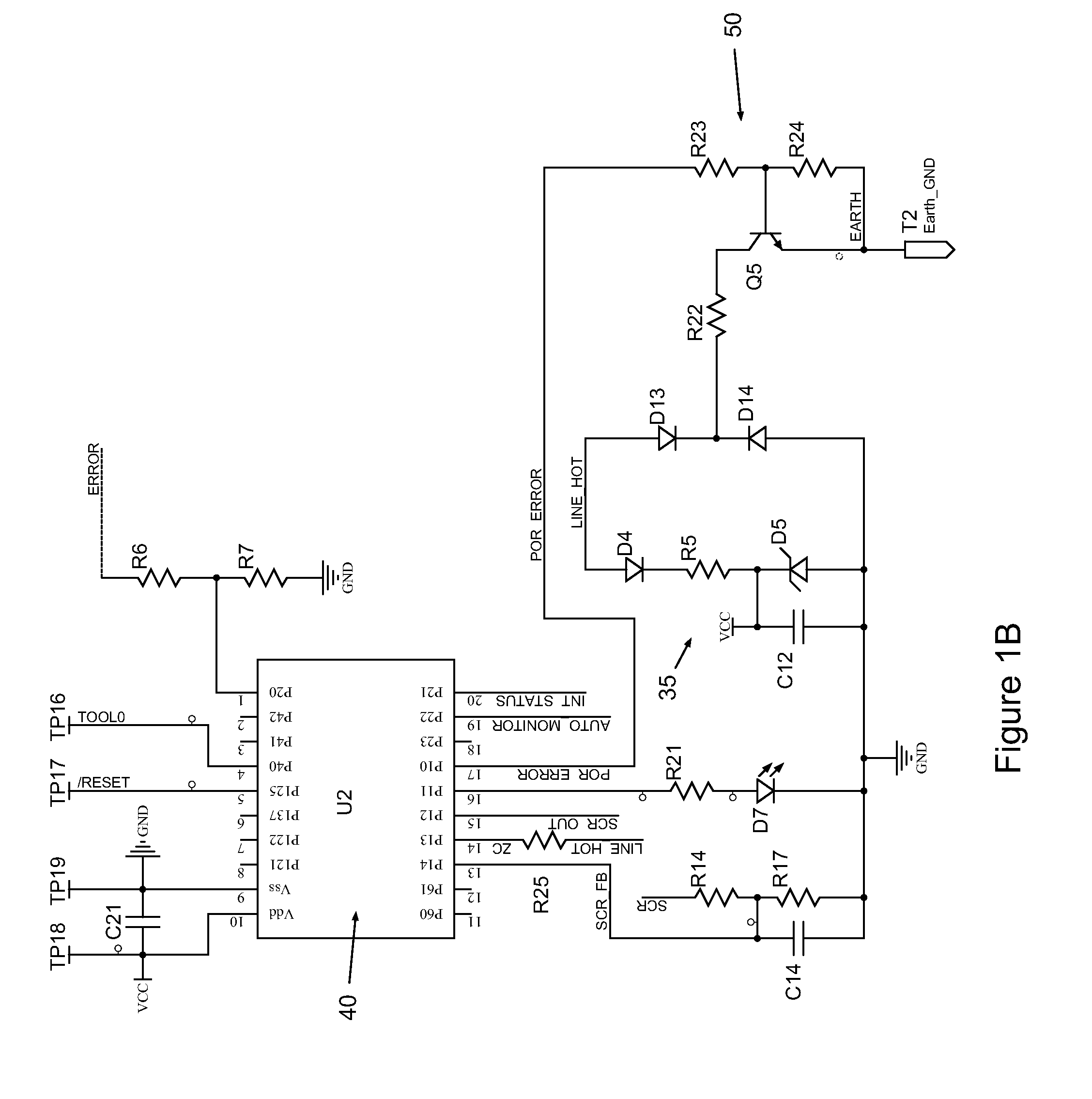
Protective Device With Non-Volatile Memory Miswire Circuit
ActiveUS20140268436A1Emergency protective arrangements for limiting excess voltage/currentArrangements resposive to fault currentProcessor registerState parameter
The present invention is directed to an electrical wiring device that includes a processing circuit is configured to determine the wiring state based on detecting a wiring state parameter at the plurality of line terminals during a predetermined period after the tripped state has been established. The processing circuit is configured to store a wiring state indicator in a wiring state register based on a wiring state determination. The wiring state register being preset to trip the circuit interrupter when the AC power source is applied by an installer to the plurality of line terminals or the plurality of load terminals for the first time.
Owner:PASS SEYMOUR
Immediate communication system and method based on WAP
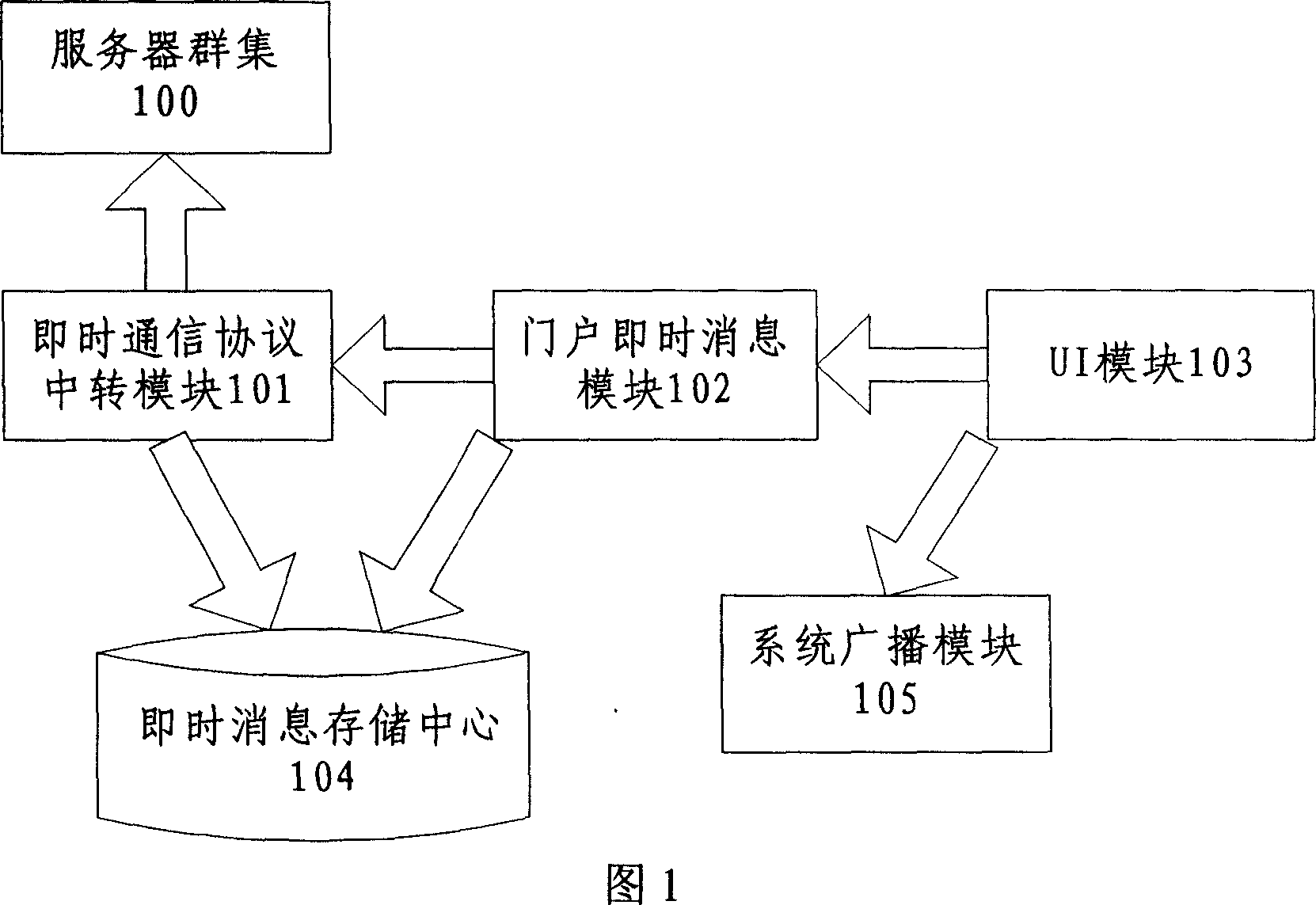
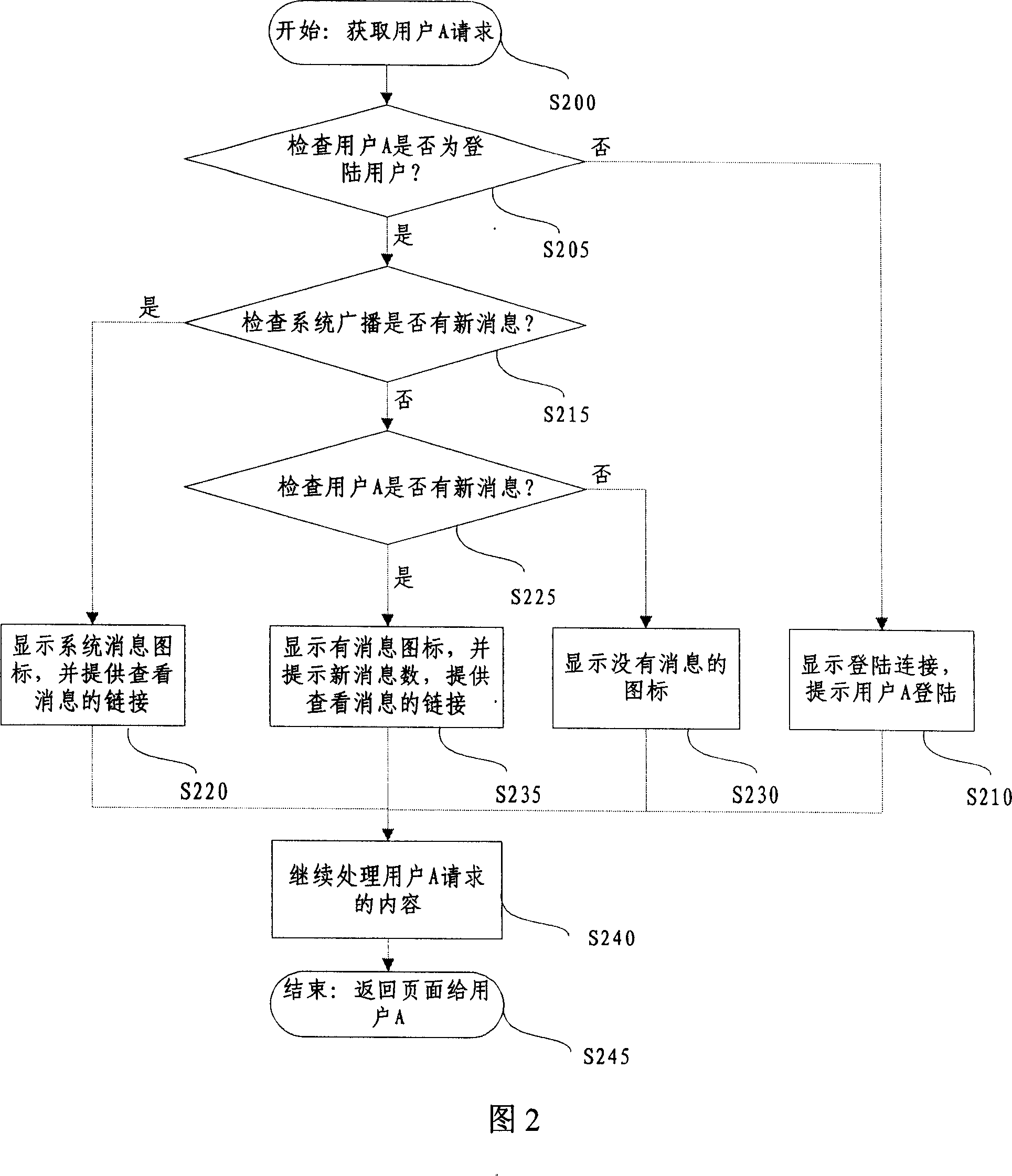
ActiveCN101047654ARealization of instant messagingData switching networksCommunications systemCommunications software
This invention relates to a prompt communication method based on WAP including: 1, obtaining WAP web request of a user, 2, checking if the user has registered based on the request, if so, step 3 is executed, otherwise, it shows the log-on links and prompts the user to log on, 3, checking if said user has new information, if so, it displays it on the web and provides link for examining the new information. This invention also discloses a prompt communication system based on the WAP.
Owner:TENCENT TECH (SHENZHEN) CO LTD
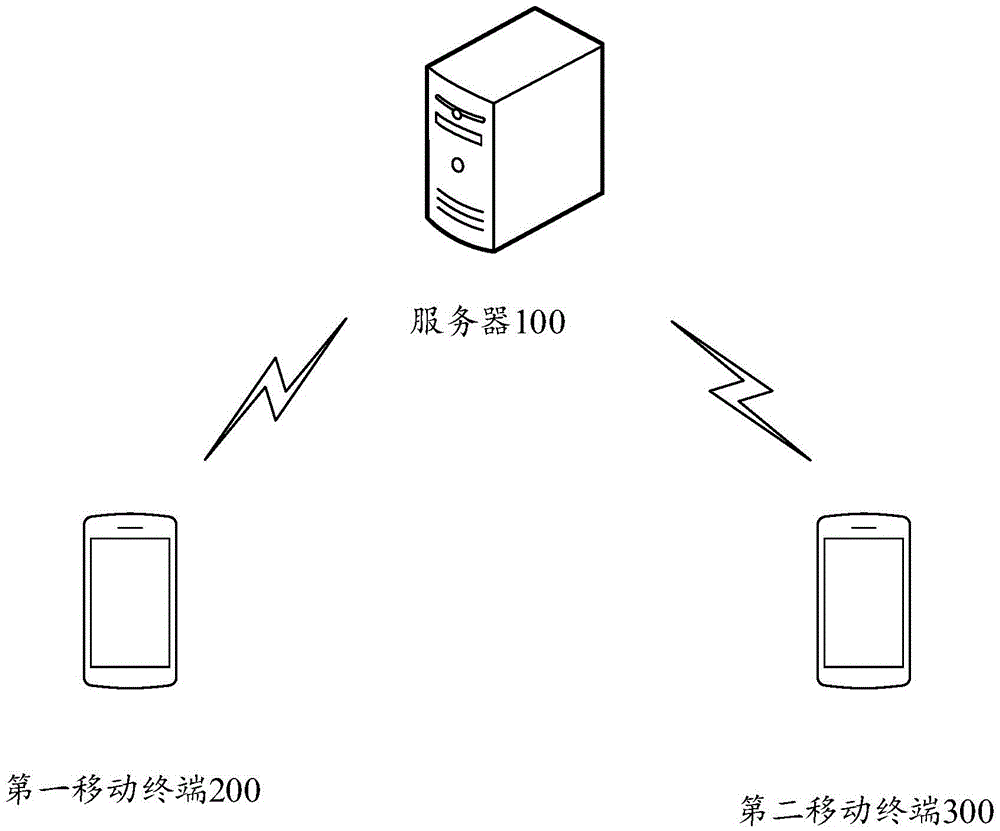
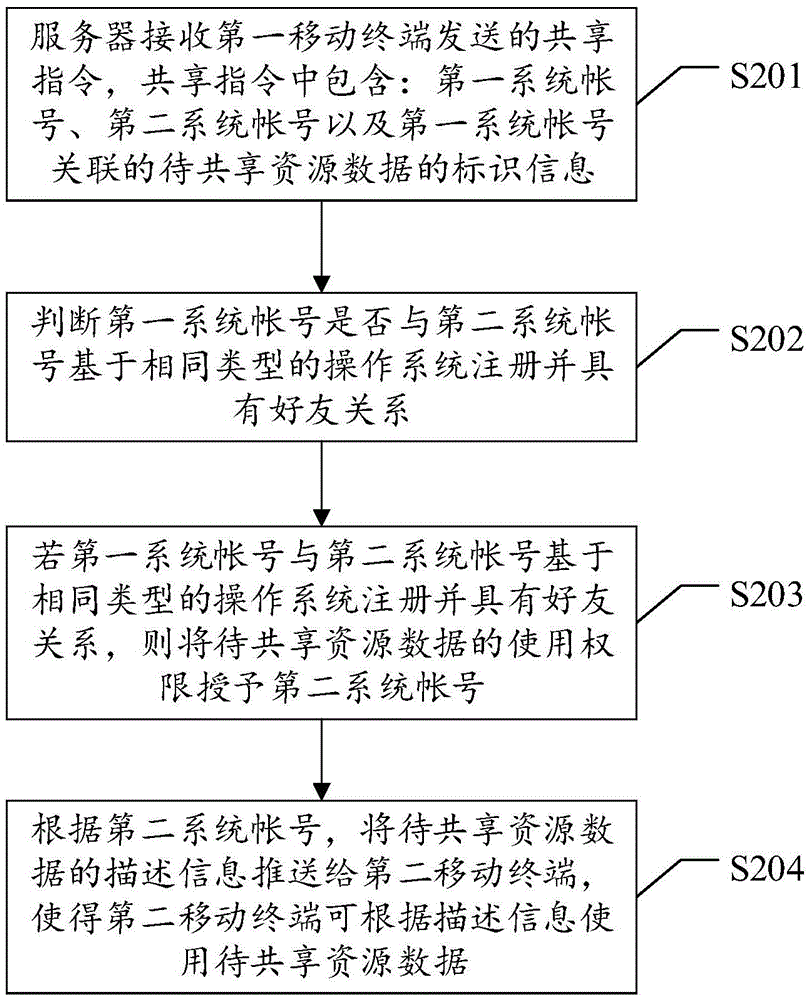
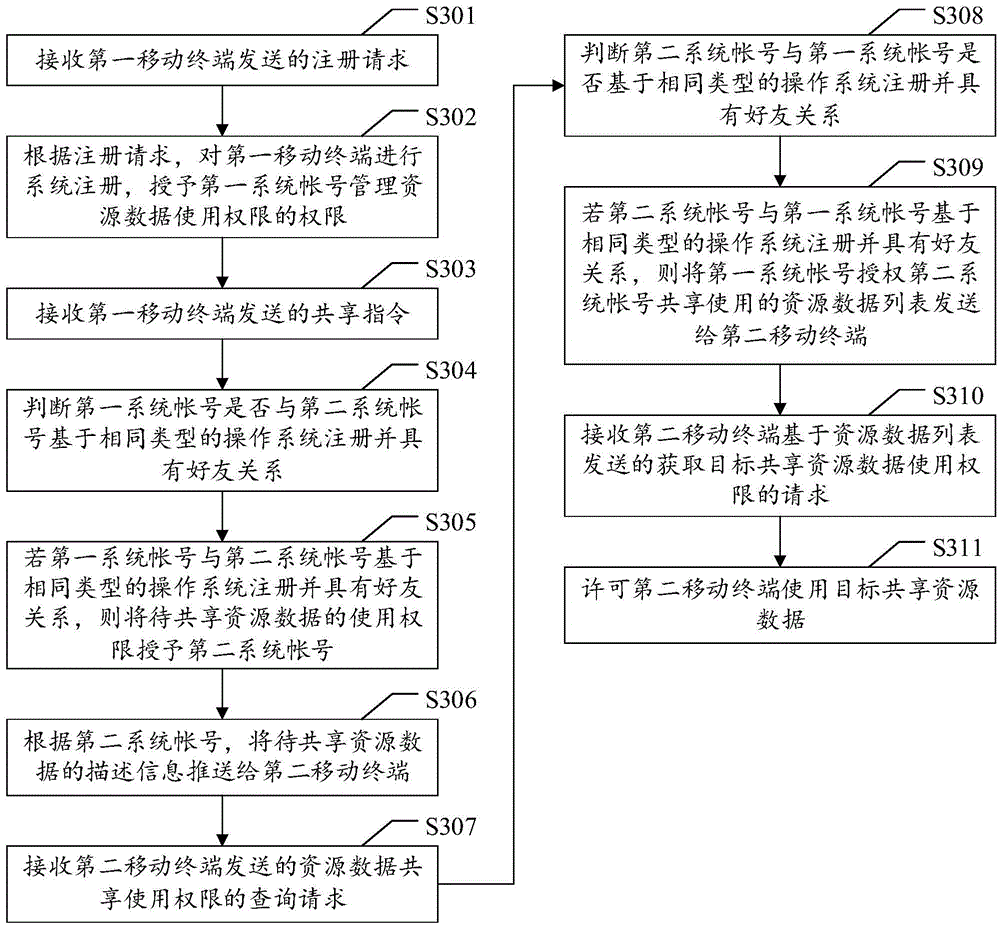
Method, device and system for sharing resource data permission
This invention discloses a method, a device and a system for sharing resource data permission. The method comprises the following steps: a server receives a sharing command sent by a first mobile terminal, wherein the sharing command comprises a first system account, a second system account and identification information of to-be-shared resource data relevant to the first system account; judge whether the first system account and the second system account are registered based on the same type of operating system and have a friend relationship or not; if the first system account and the second system account are registered based on the same type of operating system and have the friend relationship, grant the permission of the to-be-shared resource data to the second system account; and according to the second system account, push descriptors of the to-be-shared resource data to a second mobile terminal so that the second mobile terminal can use the to-be-shared resource data according to the descriptors. By means of this invention, the realizing range for sharing the data is enlarged through sharing the permission of the resource data.
Owner:TENCENT TECH (SHENZHEN) CO LTD
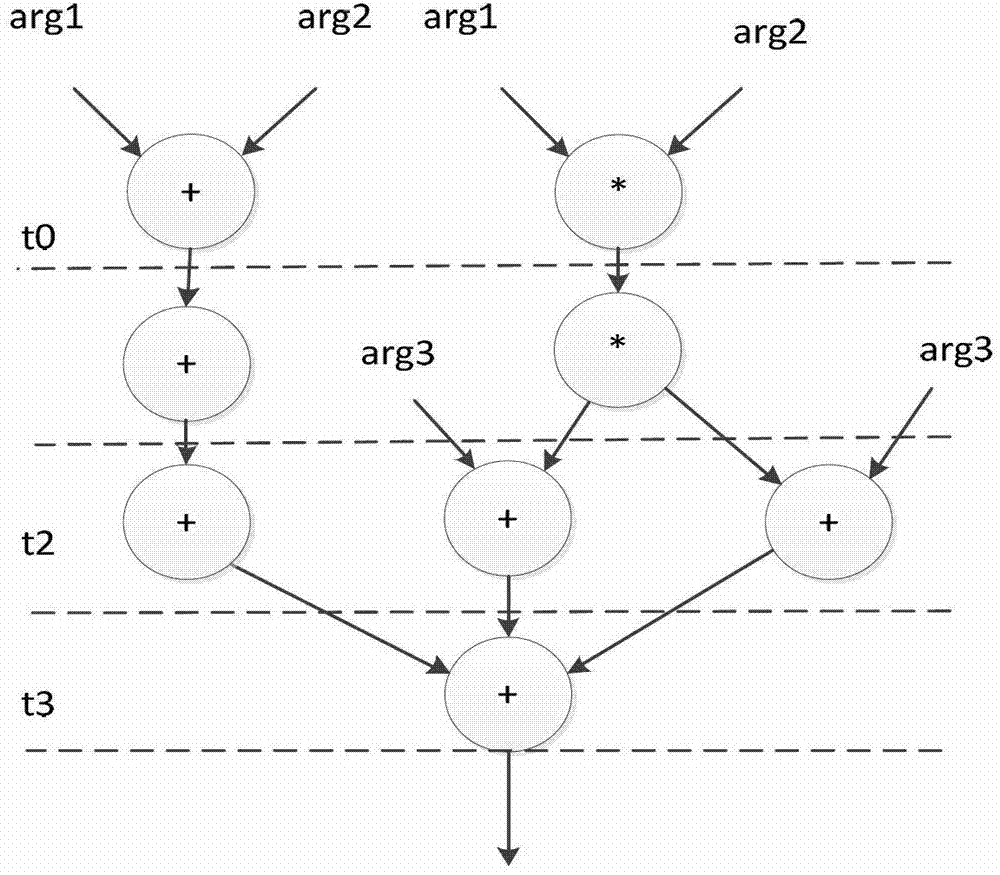
Method of generating optimised stack code
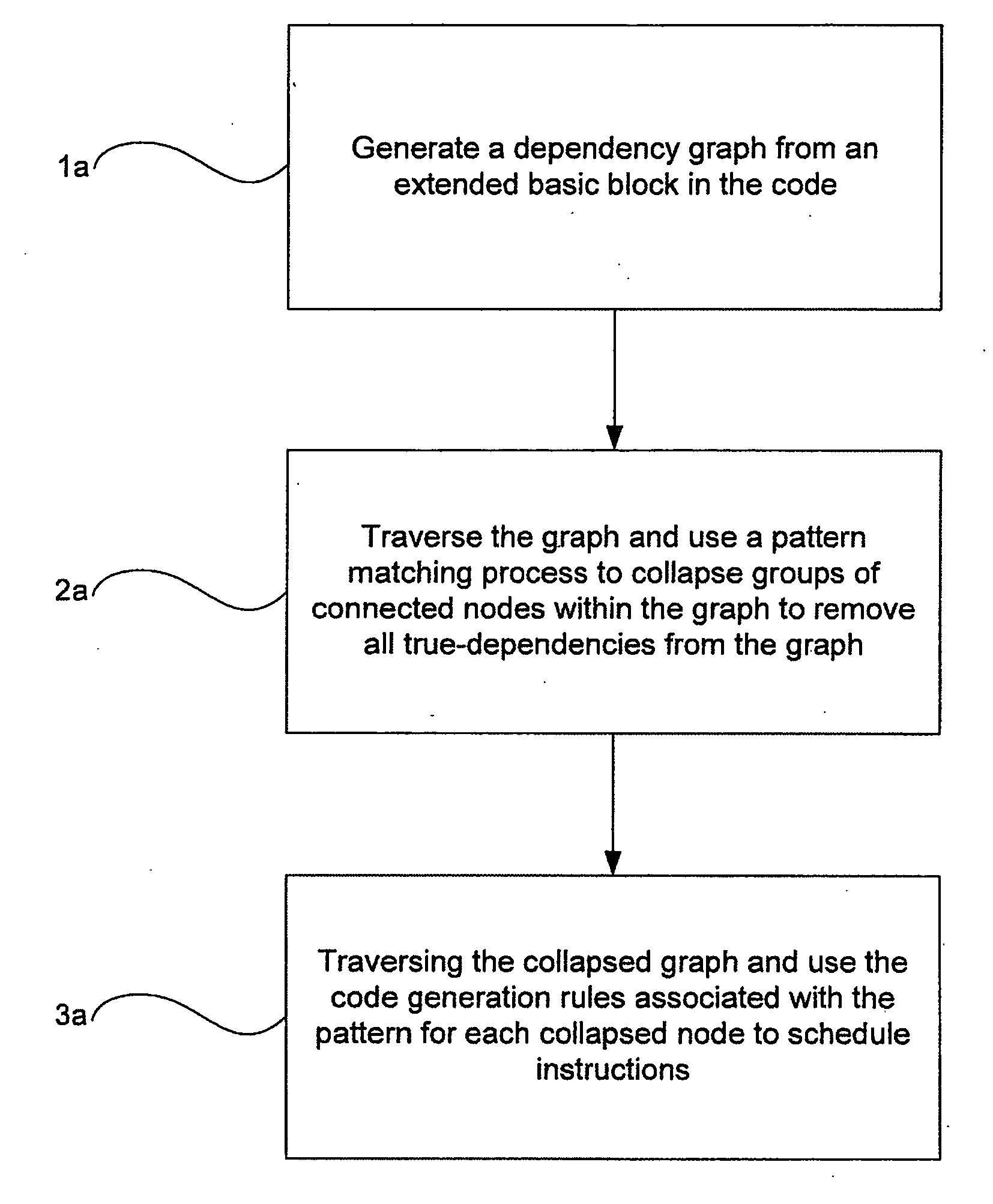
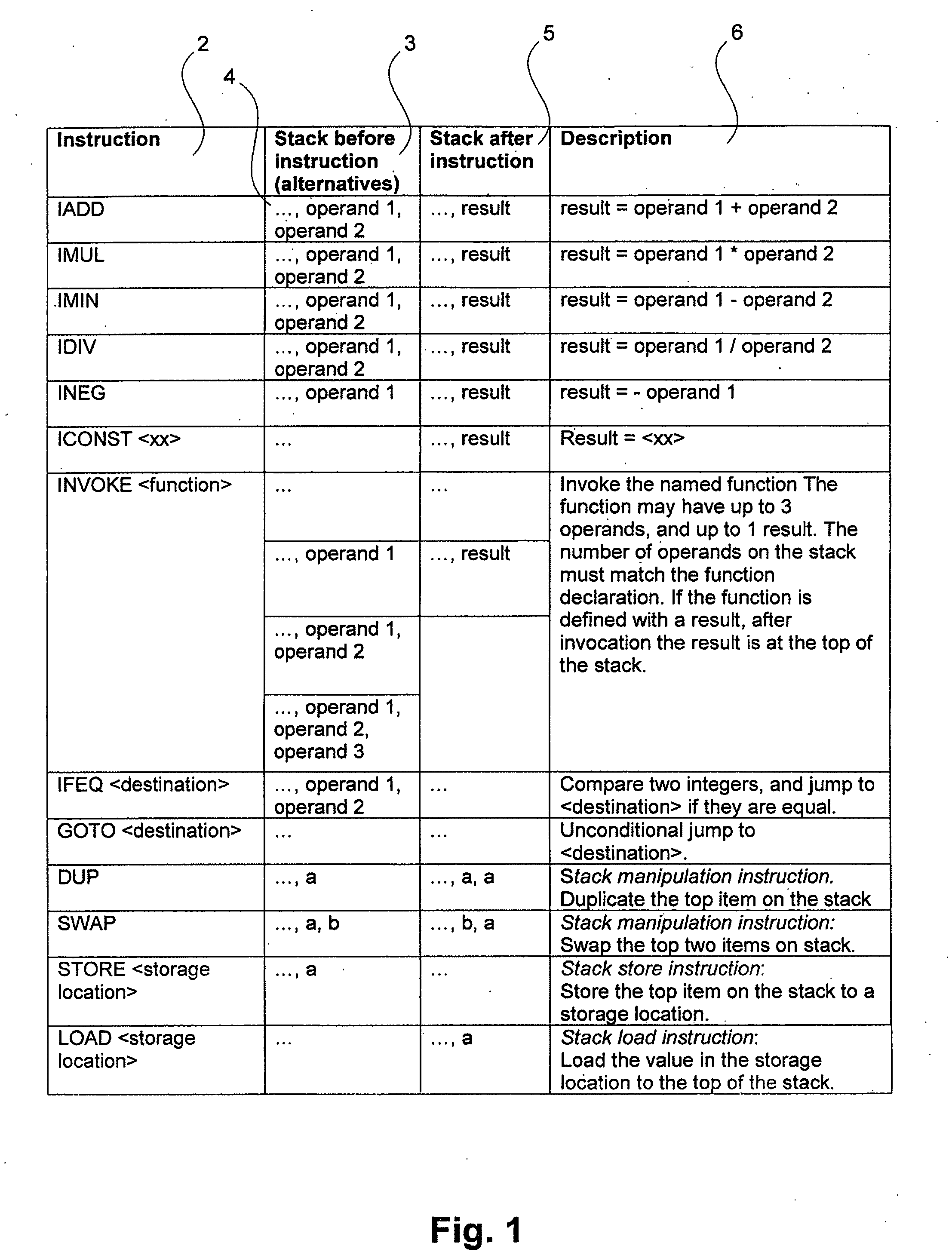
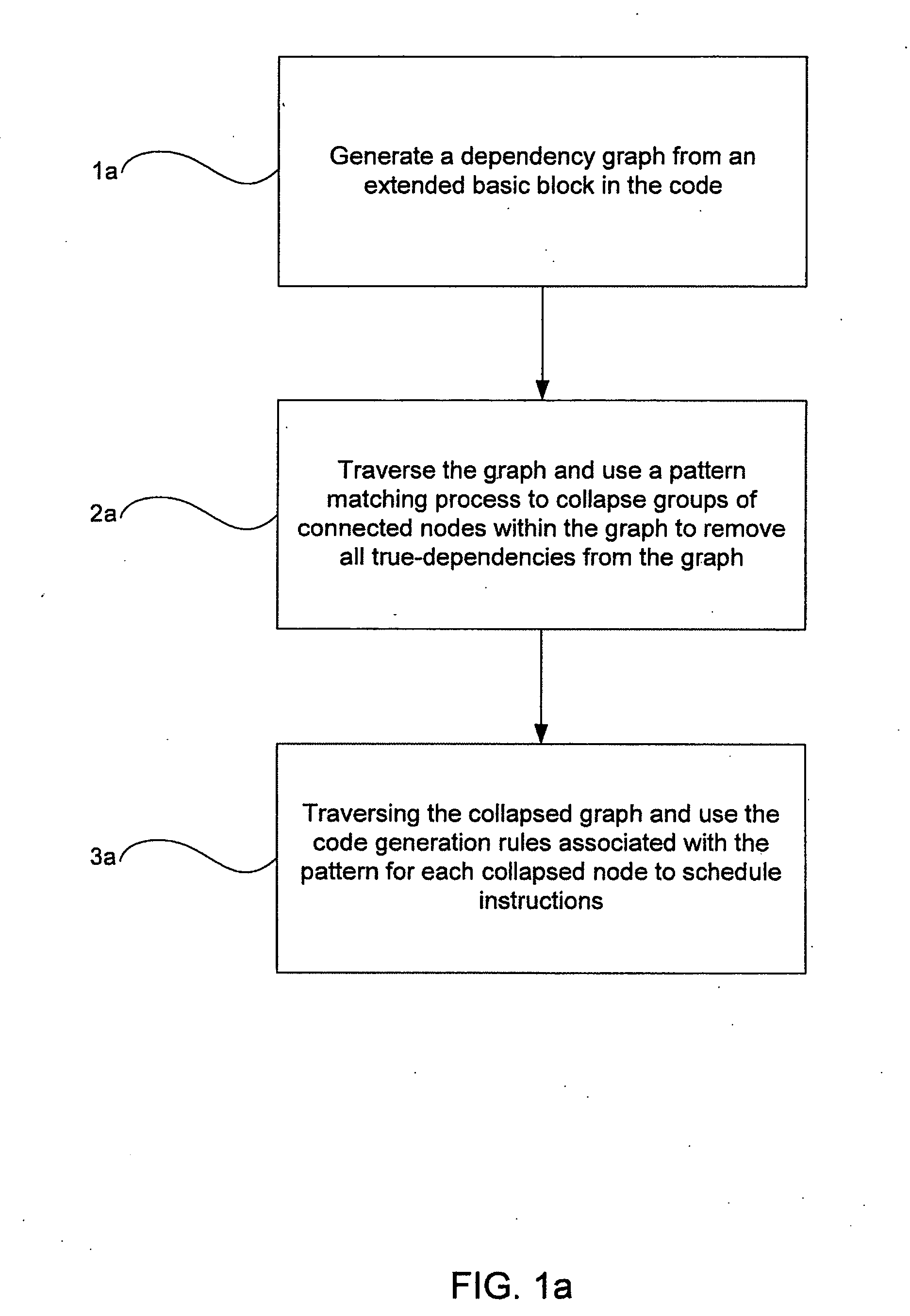
The present invention relates to a method for generating optimised stack code for a stack-based machine from a register-based representation of the original code. The method includes the steps of: creating a dependence graph from the representation; removing true dependencies from the dependence graph by matching portions of the dependence graph with a set of patterns; and defining stack code corresponding to the dependence graph using code generation rules associated with each pattern.
Owner:INNAWORKS DEV
Method and device for counting messages of output/input port of exchange equipment
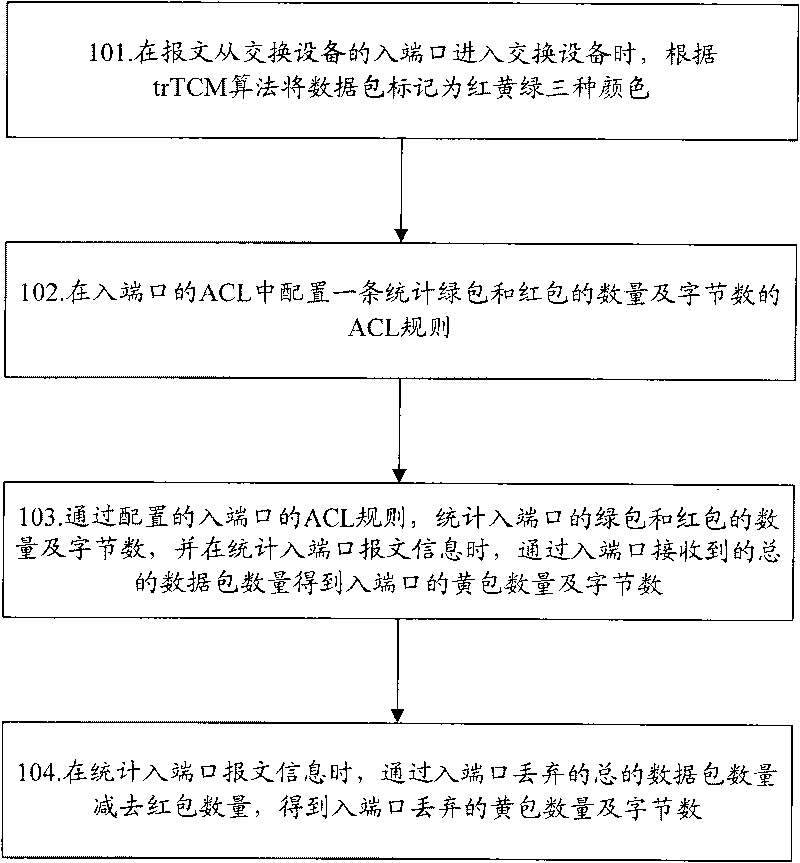
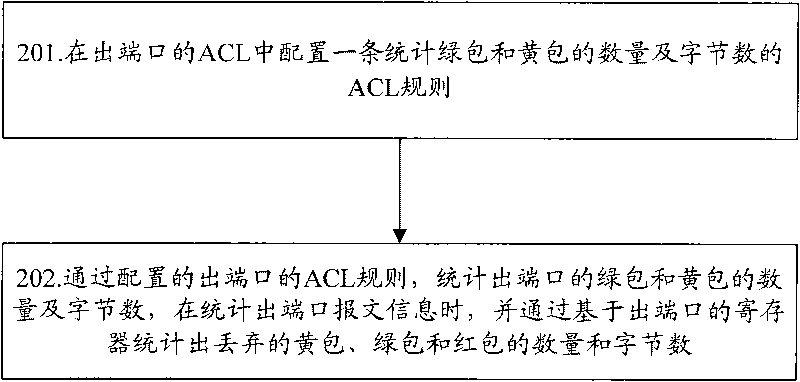
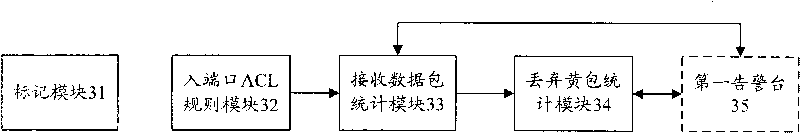
ActiveCN101741739AConvenient statisticsFlexible statisticsData switching networksNetwork packetColor marker
The invention discloses a method for counting messages of output / input port of exchange equipment, which comprises the following steps: marking data packets by three colors including red, yellow and green by dual-rate three-color marker algorithm when the message enters the exchange equipment from the input port of the exchange equipment; in the input port, counting the numbers of the red and green data packets and the number of bytes by a configured access control list (ACL) rule, obtaining the number of the yellow data packet of the input port and the number of bytes by the total number of the data packet received by the input port, and obtaining the number of the yellow data packet discarded by the input port and the number of bytes by the total number of the data packet discarded by the input port; and in the output port, counting the numbers of the green and yellow data packets and the number of bytes by the configured access control list (ACL) rule, and counting the numbers of the yellow, red and green data packets discarded by the output port by a register based on the output port; The invention also discloses a device for counting the messages of output / input port of the exchange equipment; thus, the message information can be counted conveniently and flexibly, and the counting method is also quite simple.
Owner:ZTE CORP
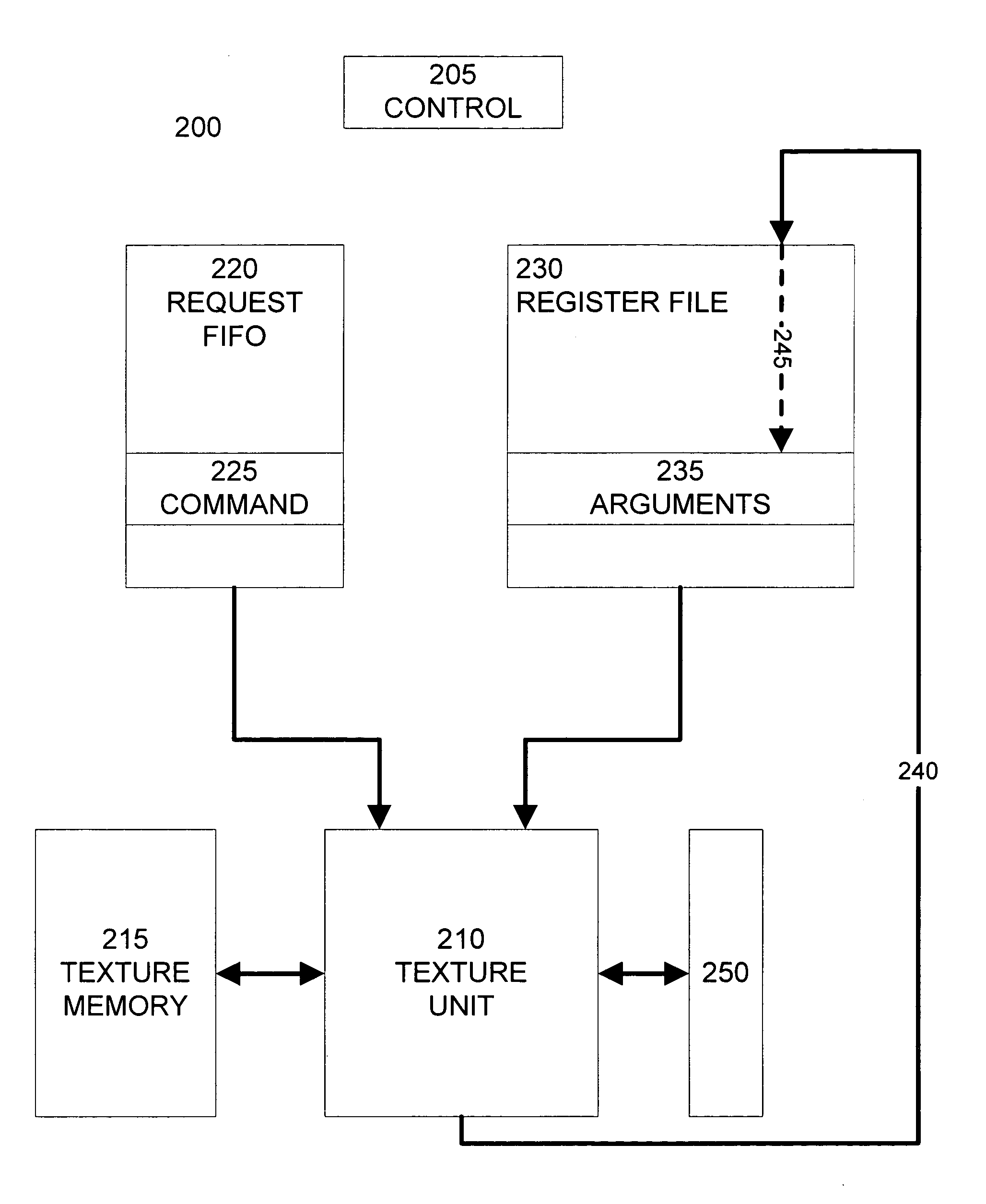
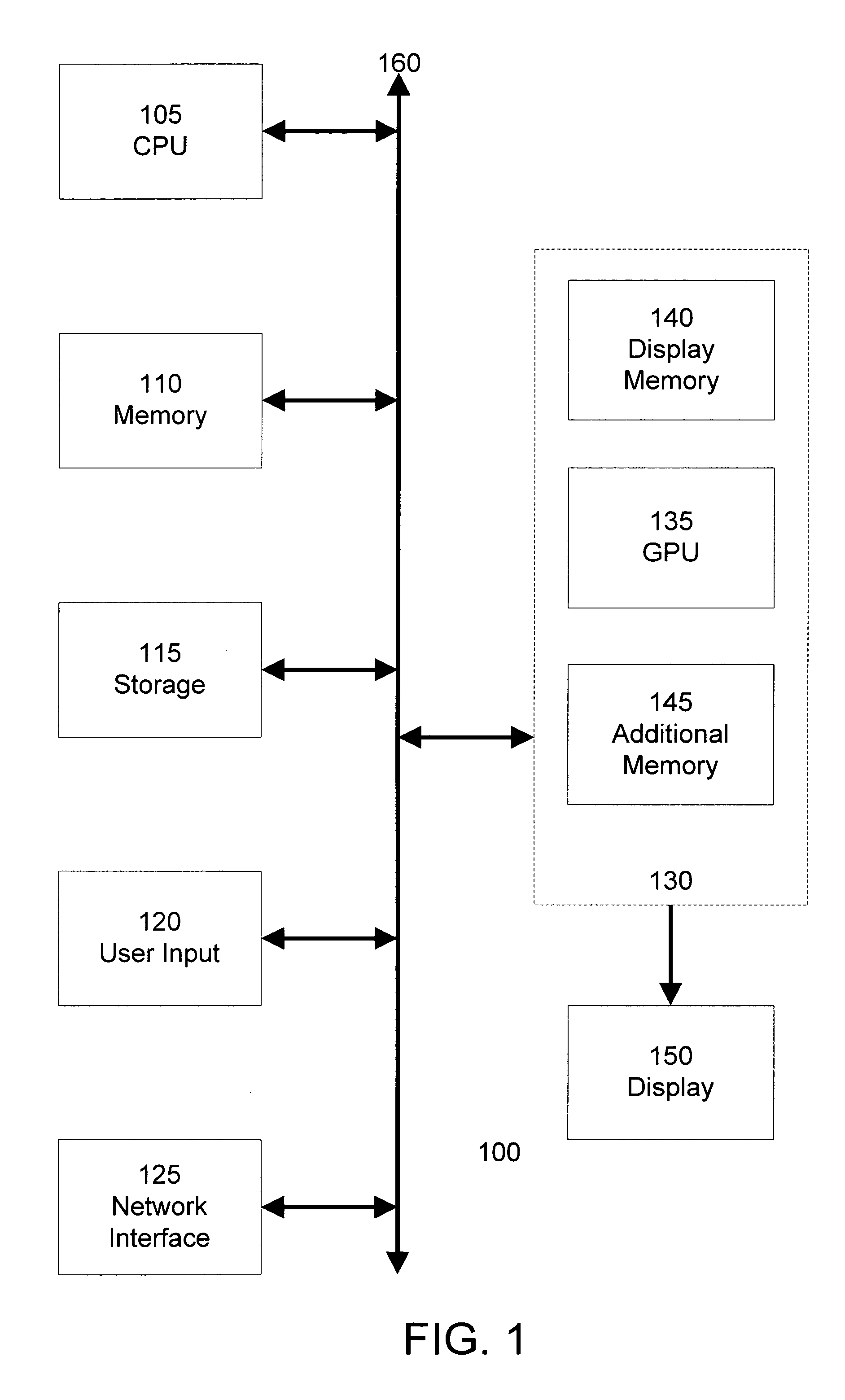
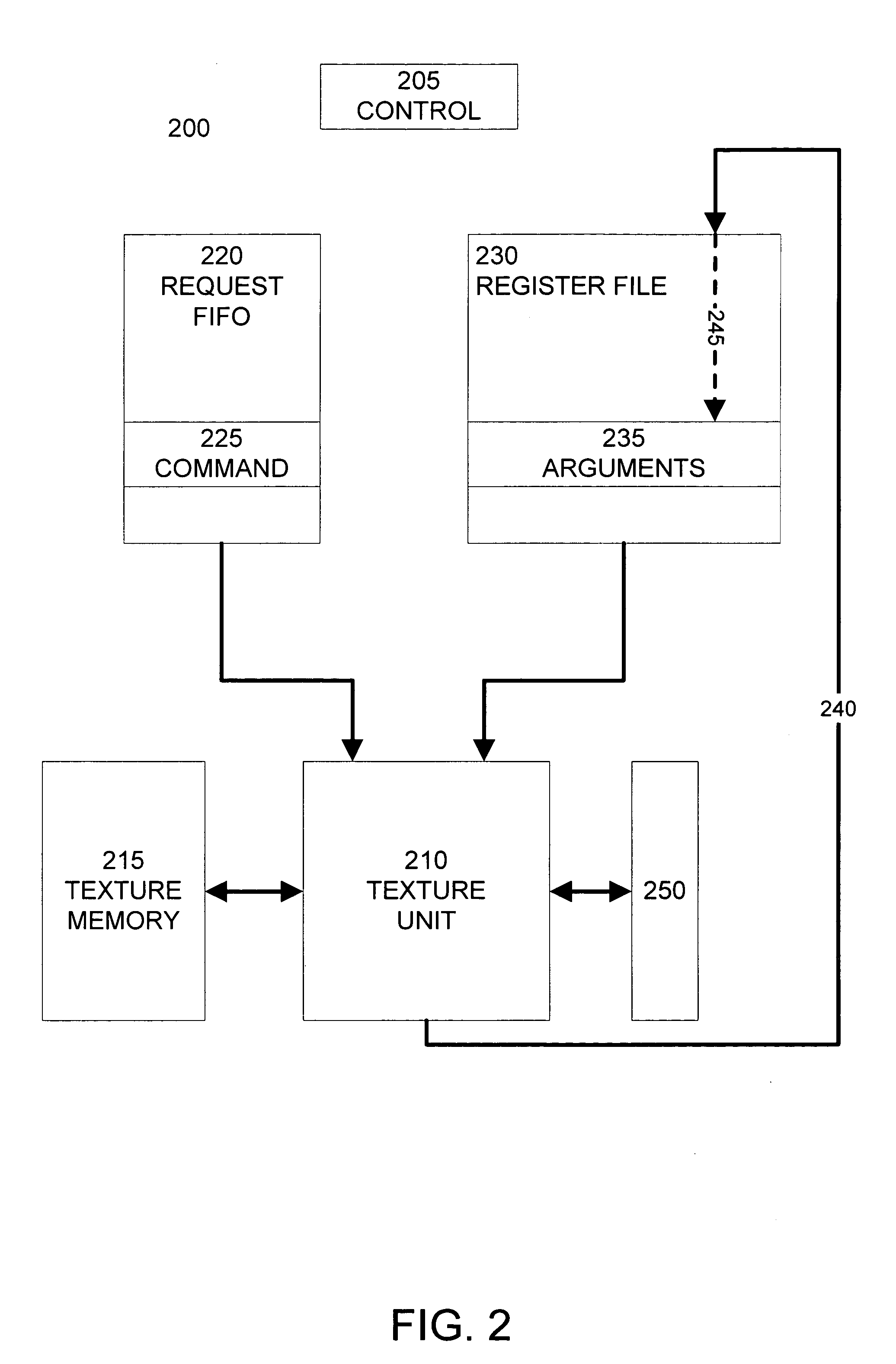
Register based queuing for texture requests
ActiveUS7027062B2Cathode-ray tube indicatorsFilling planer surface with attributesGeneral purposeGraphics
A graphics processing unit can queue a large number of texture requests to balance out the variability of texture requests without the need for a large texture request buffer. A dedicated texture request buffer queues the relatively small texture commands and parameters. Additionally, for each queued texture command, an associated set of texture arguments, which are typically much larger than the texture command, are stored in a general purpose register. The texture unit retrieves texture commands from the texture request buffer and then fetches the associated texture arguments from the appropriate general purpose register. The texture arguments may be stored in the general purpose register designated as the destination of the final texture value computed by the texture unit. Because the destination register must be allocated for the final texture value as texture commands are queued, storing the texture arguments in this register does not consume any additional registers.
Owner:NVIDIA CORP
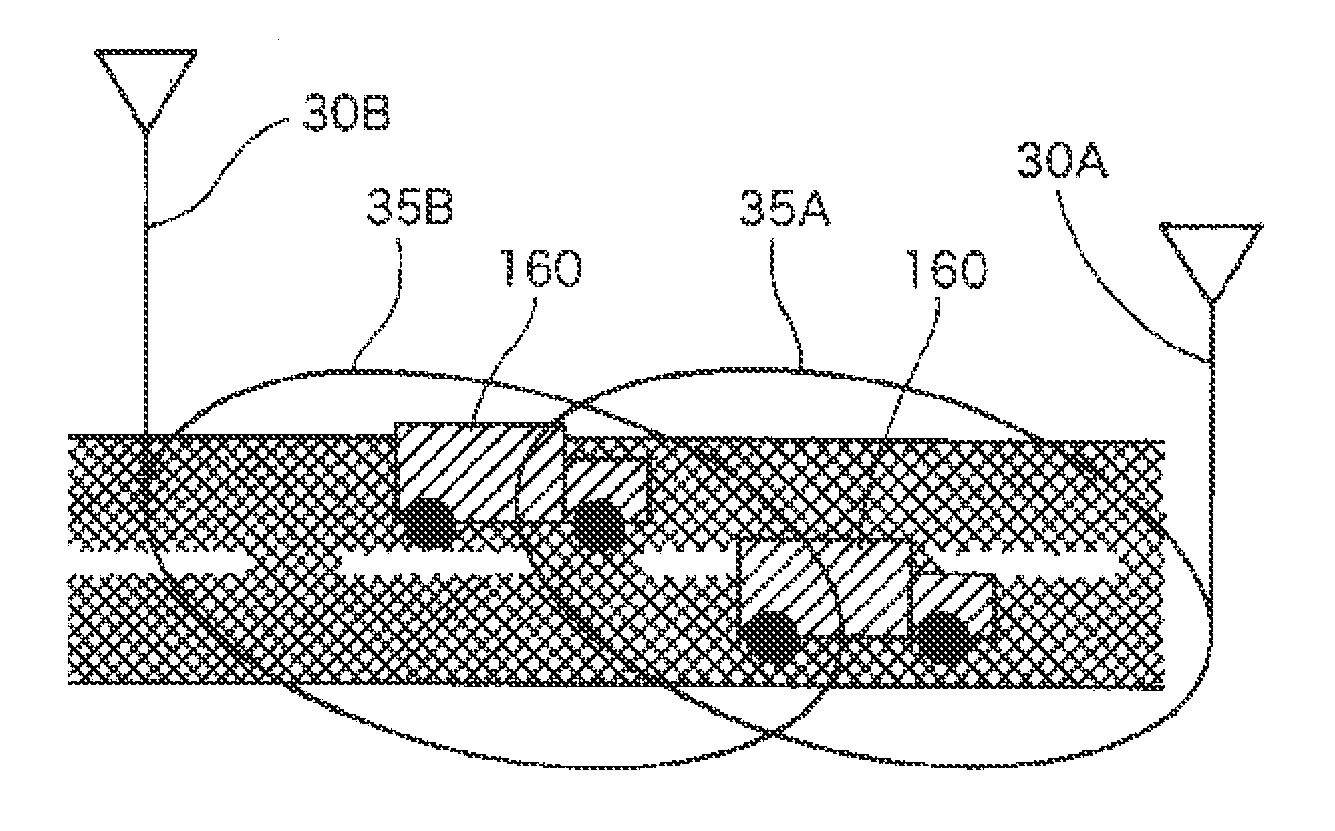
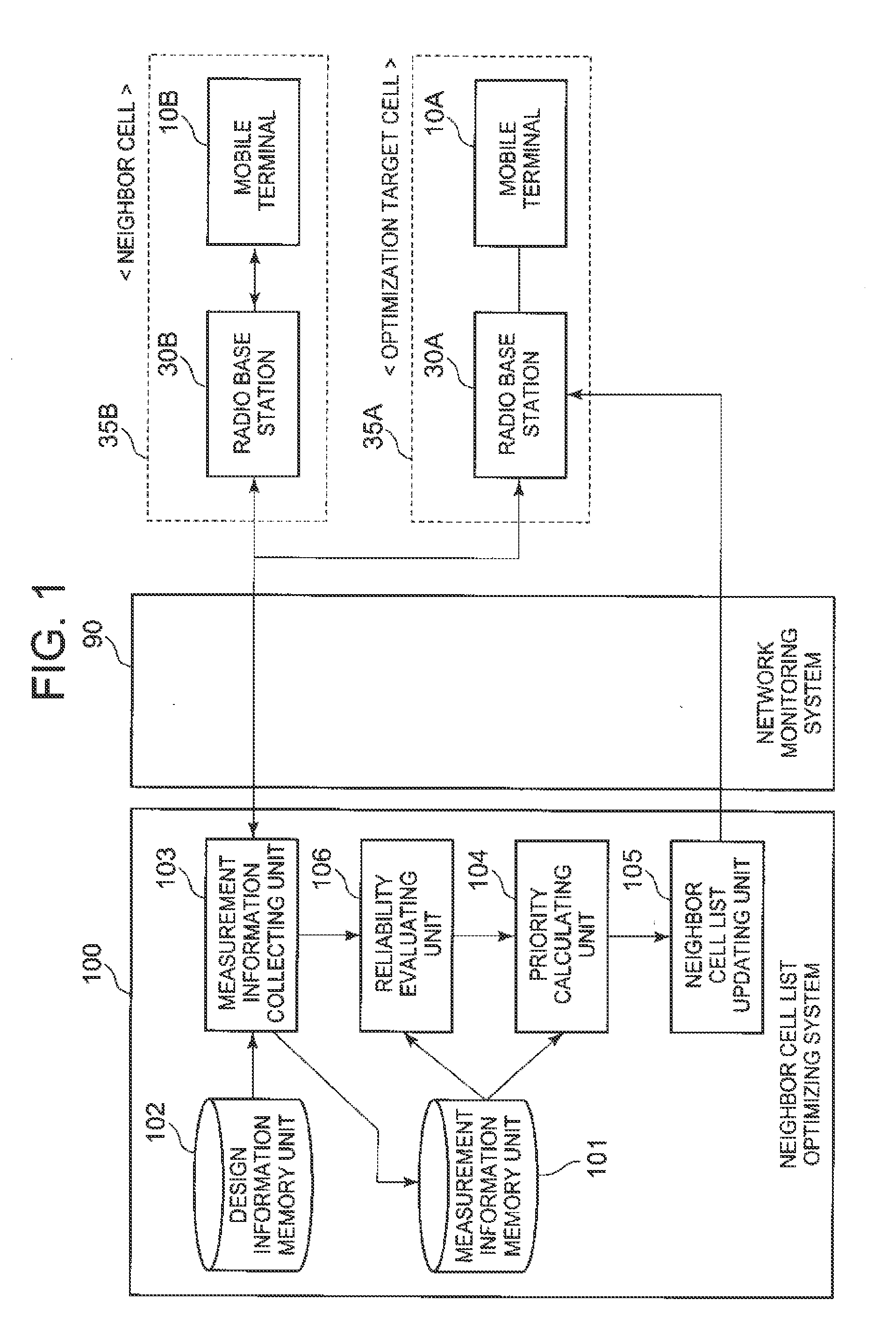
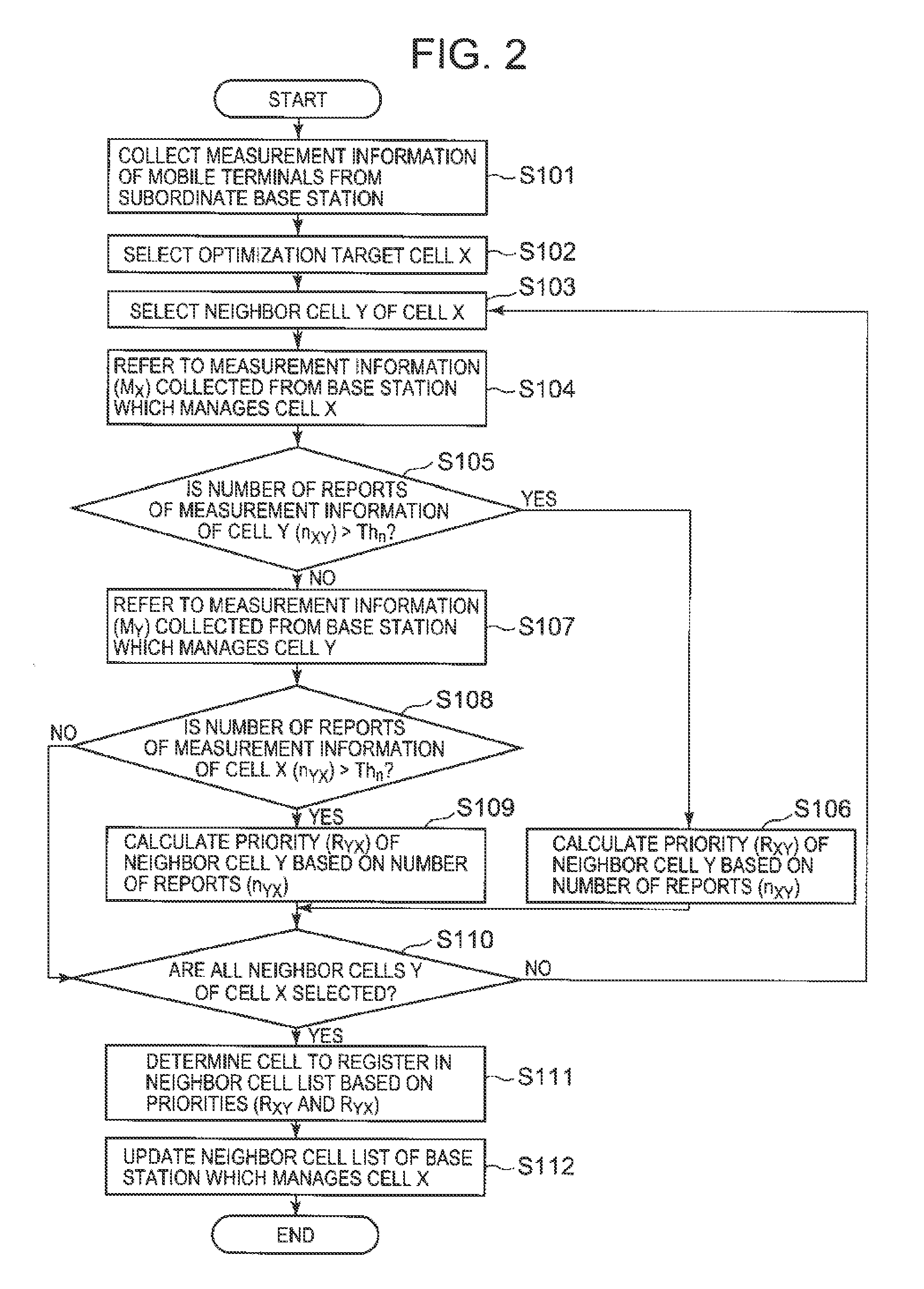
Wireless communication system, neighbor cell list optimizing system, base station, neighbor cell list updating method, and program
ActiveUS20130079005A1Additional flawWireless commuication servicesCommunications systemComputer terminal
A first mobile terminal group has a first measurement information transmitting means which measures radio quality of a second cell, and transmits measurement information to a first base station, a second mobile terminal group has a second measurement information transmitting means which measures radio quality of a first cell, and transmits measurement information to a second base station, and a neighbor cell list optimizing system has: a measurement information collecting means which collects the measurement information of the first and second cells; a reliability evaluating means which performs processing of evaluating reliability of the measurement information of the second cell; a priority calculating means which, when the reliability is a predetermined threshold or less, calculates a priority for registering the second cell in the neighbor cell list of the first cell based on the measurement information of the first cell; and a neighbor cell list updating means which performs control of determining a neighbor cell to be registered based on the priority, and updating the neighbor cell list.
Owner:NEC CORP
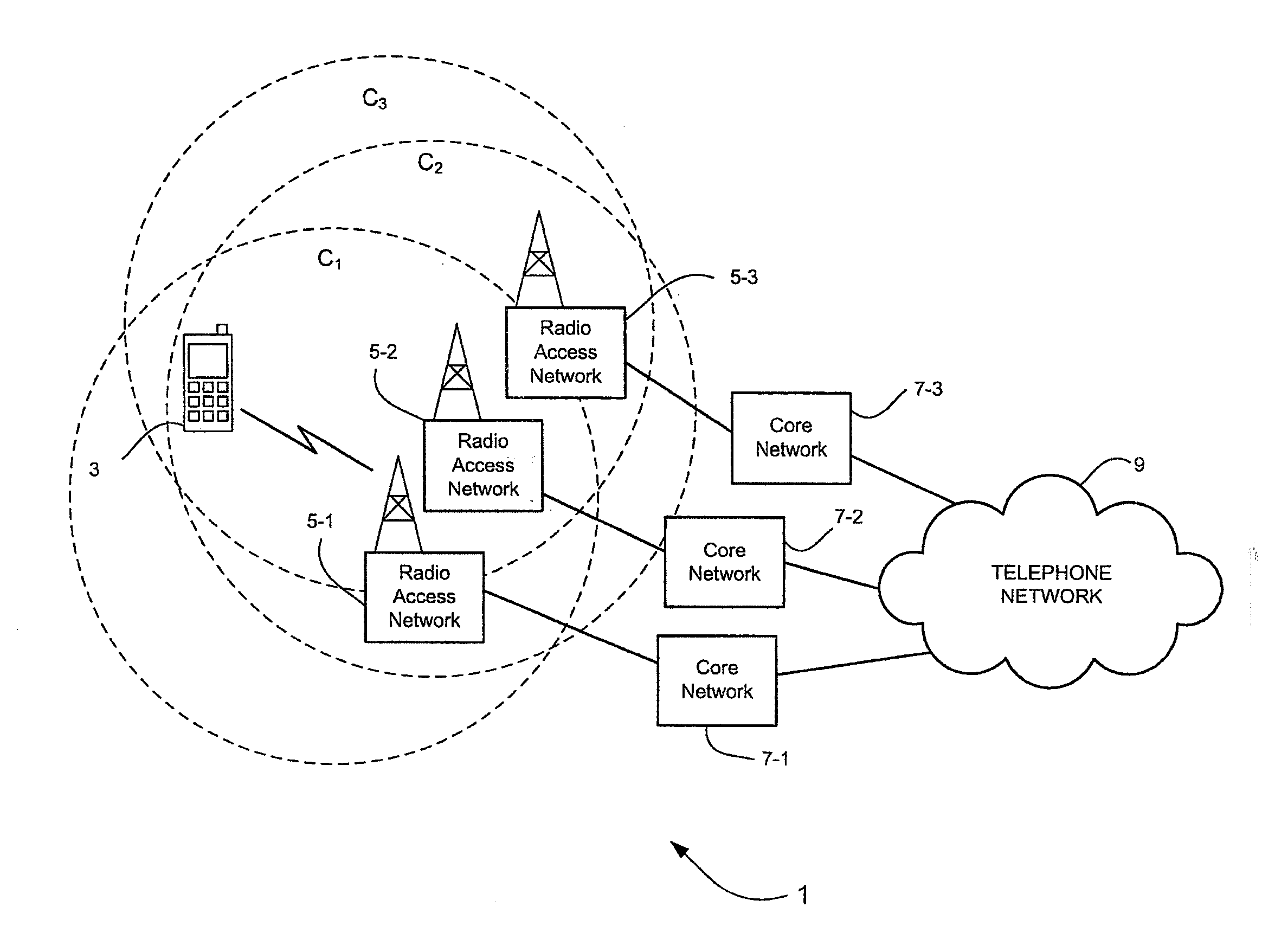
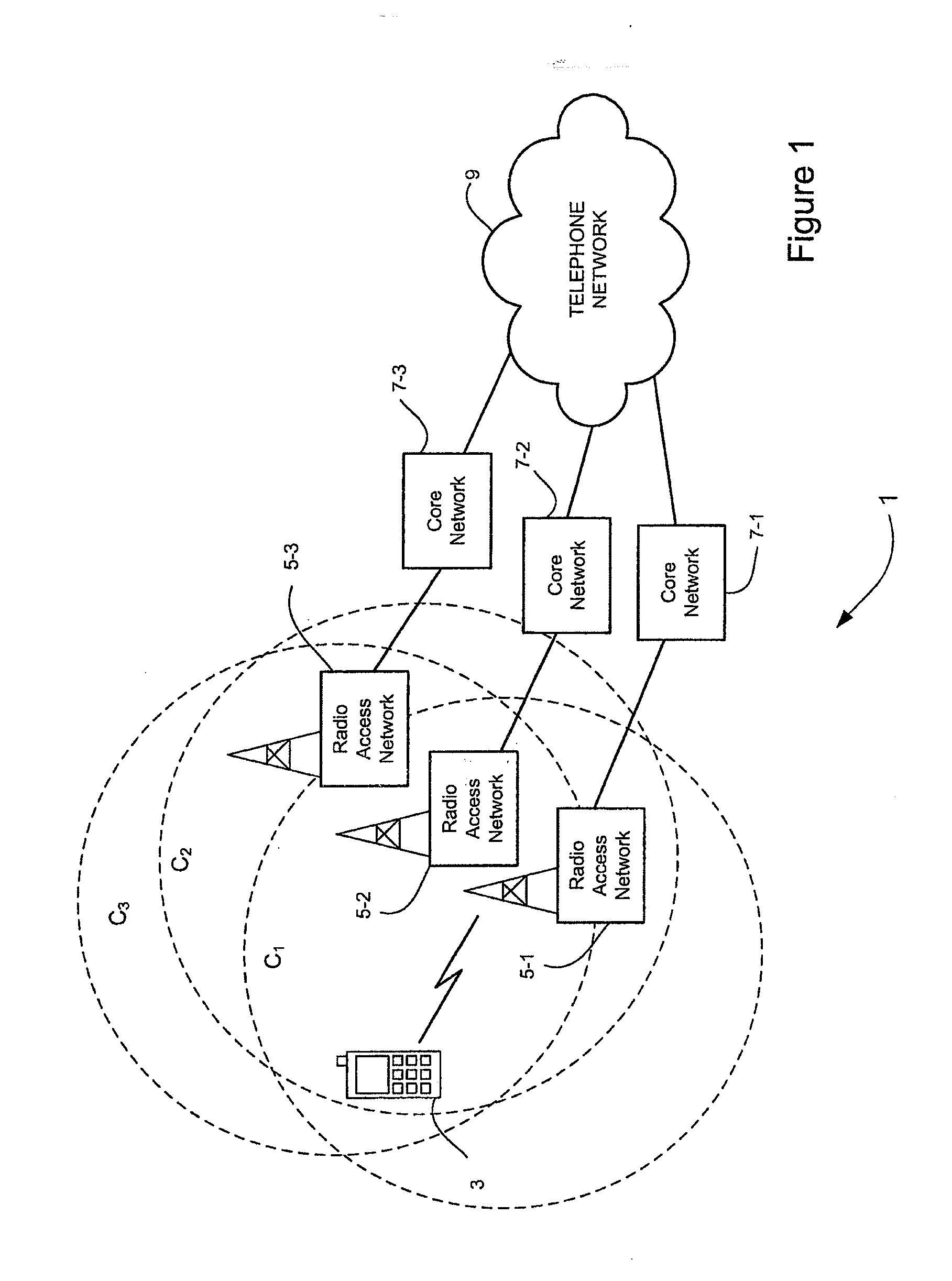
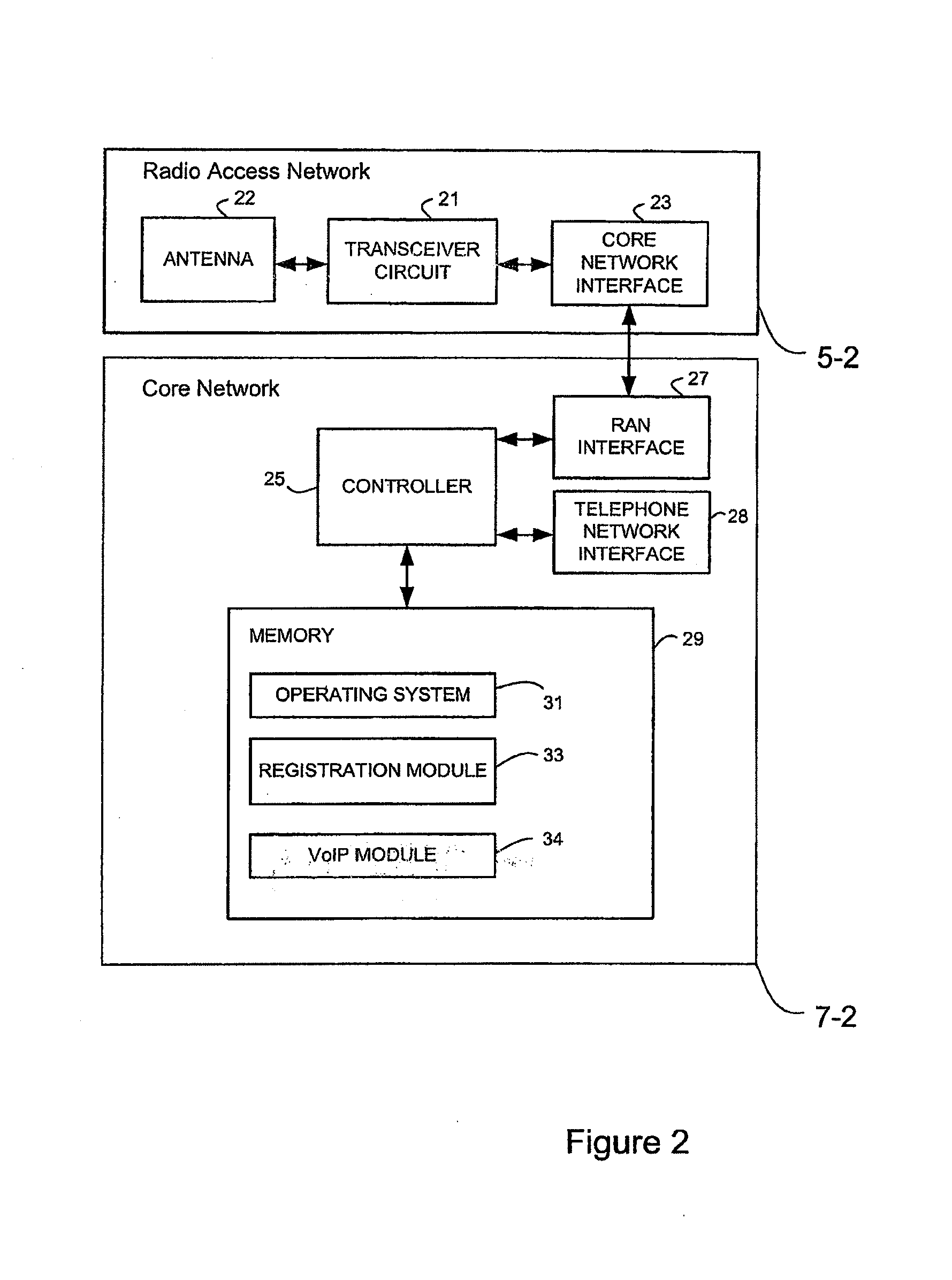
Communications system
ActiveUS20110141910A1Providing serviceError preventionFrequency-division multiplex detailsRadio access technologyCommunications system
A cellular communications system is provided in which a user device selects a cell with which to register based on whether or not a candidate cell can provide an emergency call service. This determination is preferably determined having reference to a radio access technology associated with the candidate cell and, where the cell is an E-UTRA cell, having reference to information provided in system information output by the cell.
Owner:LENOVO INNOVATIONS LTD HONG KONG
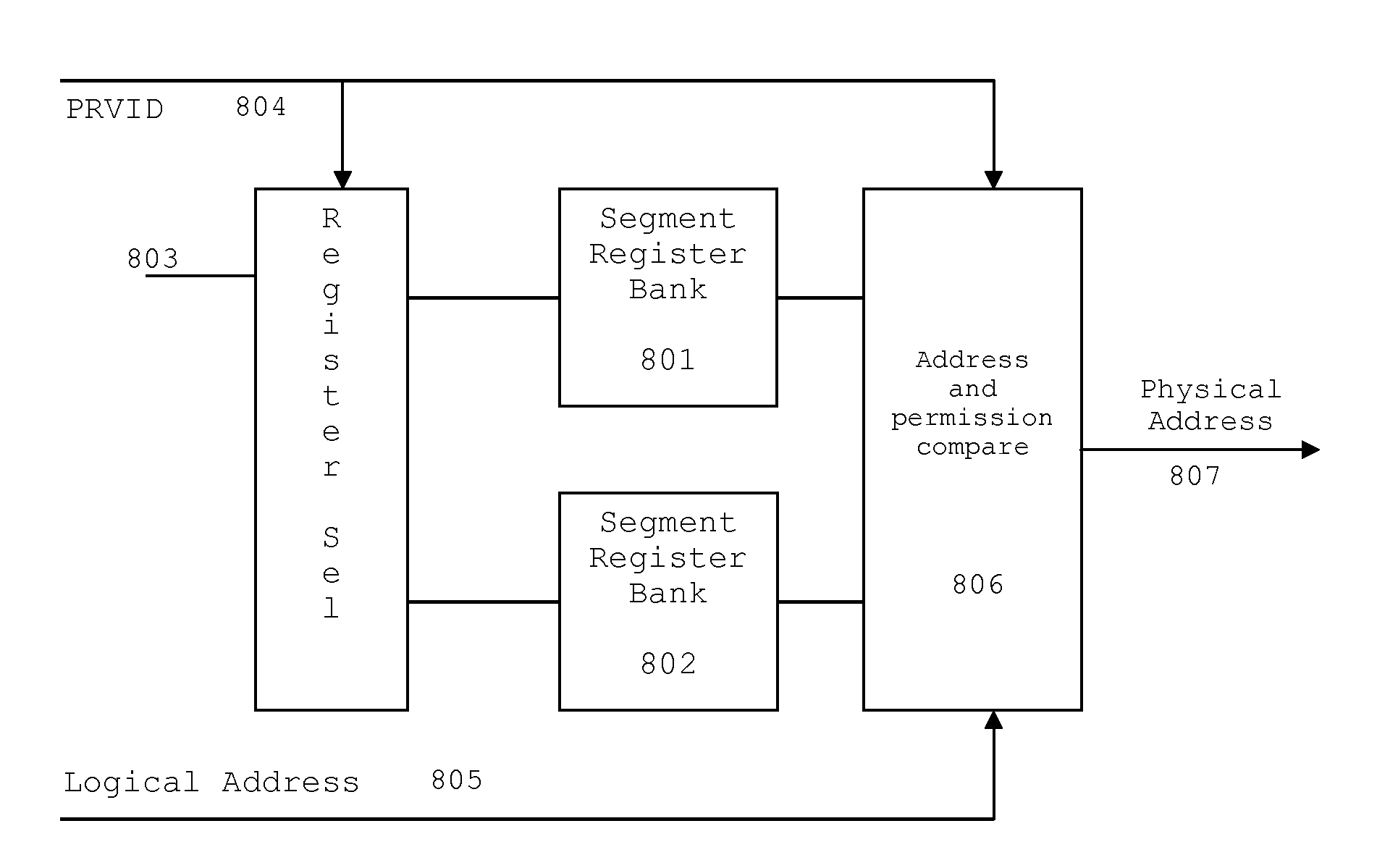
Flexible Memory Protection and Translation Unit
ActiveUS20120191899A1Memory architecture accessing/allocationEnergy efficient ICTProcessor registerProtection system
A memory management and protection system that manages memory access requests from a number of requestors. Memory accesses are allowed or disallowed based on the privilege level of the requestor, based on a Privilege Identifier that accompanies each memory access request. An extended memory controller selects the appropriate set of segment registers based on the Privilege Identifier to insure that the request is compared to and translated by the segment register associated with the requestor originating the request. A set of mapping registers allow flexible mapping of each Privilege Identifier to the appropriate access permission. The segment registers translate the logical address from the requestor to a physical address within a larger address space.
Owner:TEXAS INSTR INC
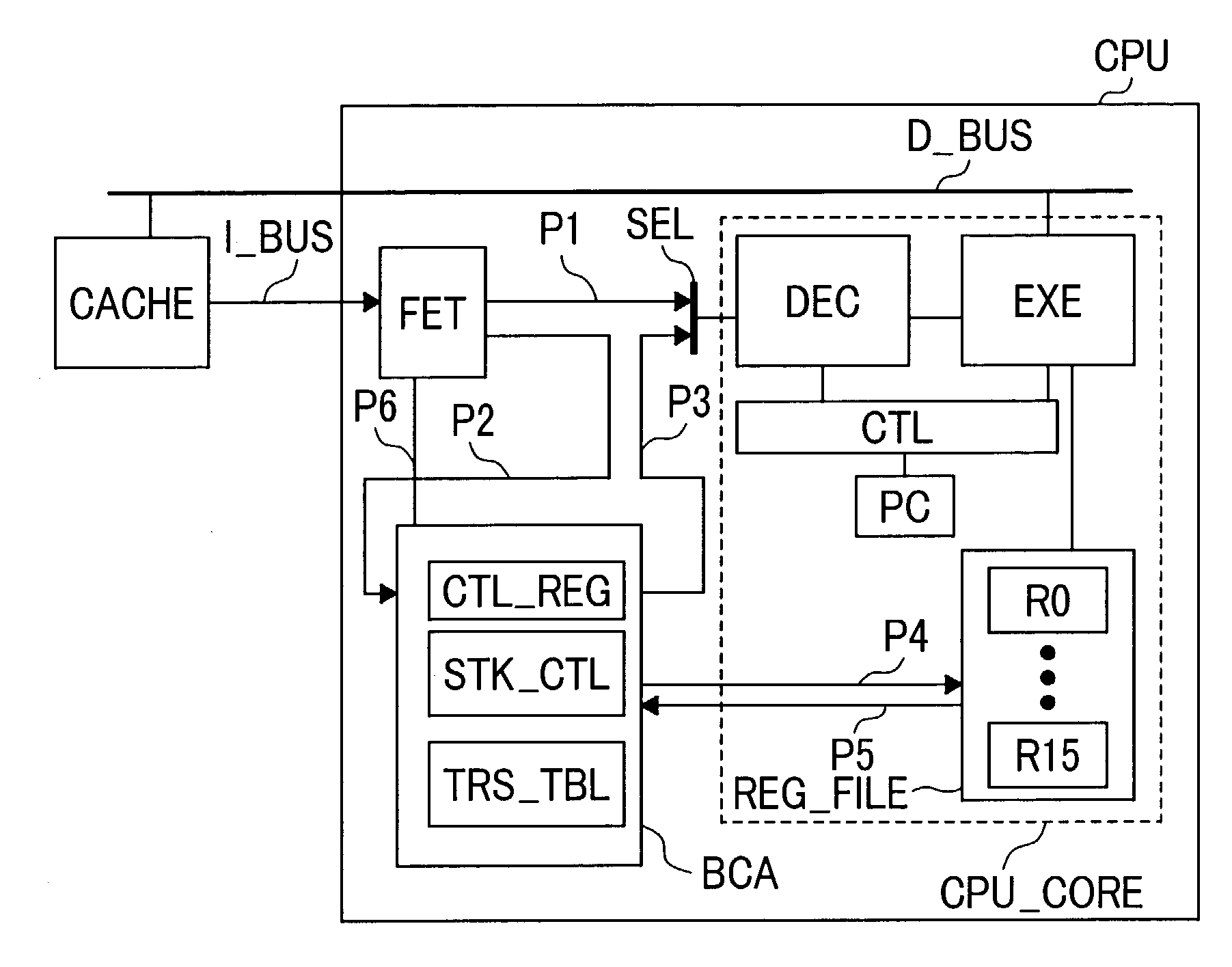
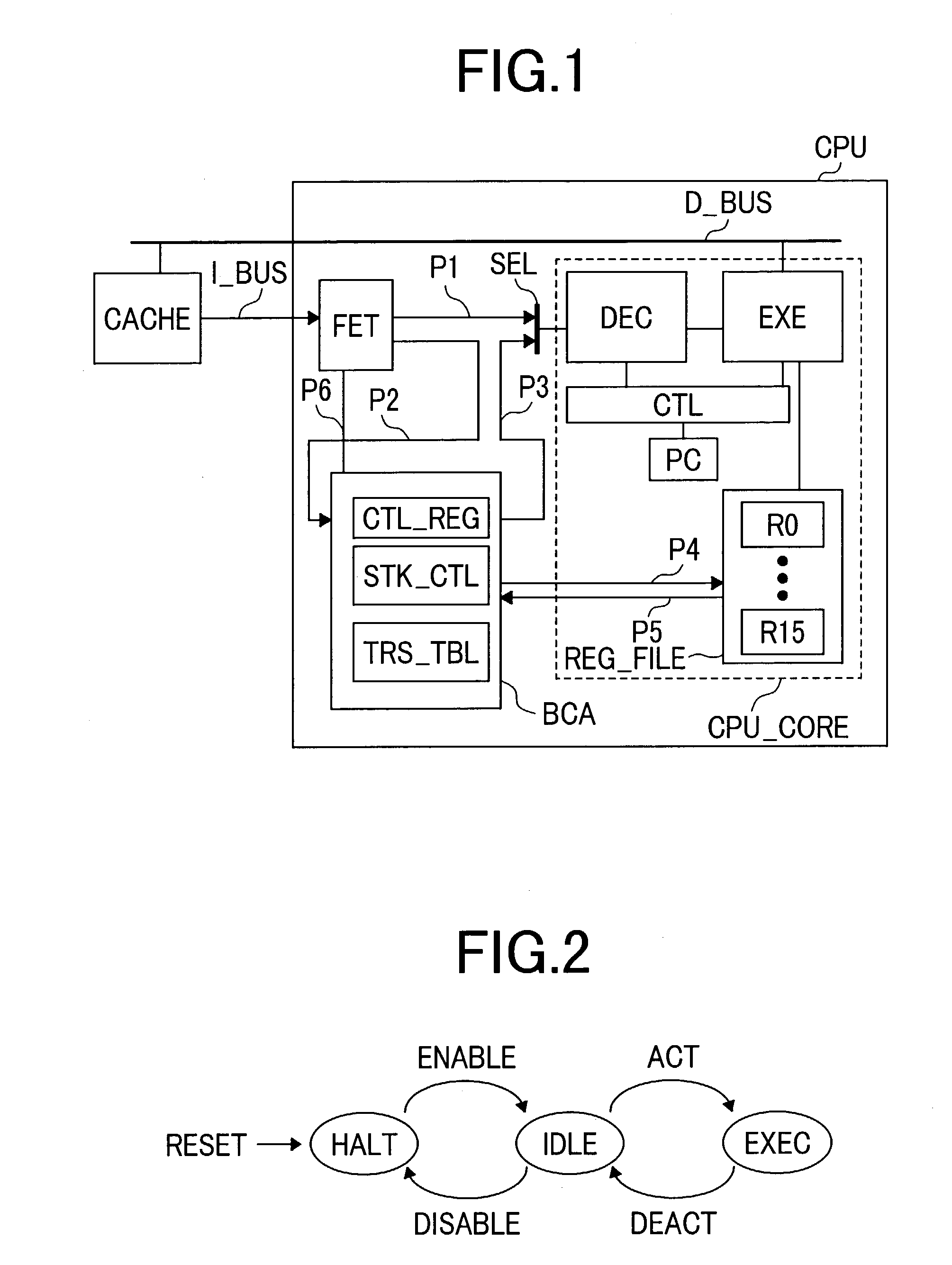
Hardware accelerator for a platform-independent code
ActiveUS7124283B2Speed up the switching processDigital computer detailsConcurrent instruction executionInformation processingByte
The present invention provides a hardware accelerator, which allows faster switching between processing modes. In an information processing device with a bytecode accelerator BCA for translating a stack-based intermediate code (bytecode) into register-based instructions, a selector SEL for switching between BCA and soft VM is posed between an instruction part FET and a decode part DEC and data transfer paths P4 and P5 are formed between BCA and the register file REG_FILE. When bytecode accelerator BCA is activated, the P3 side is selected by the selector SEL and the translated CPU instructions are transferred to the decode part DEC. If the intermediate language code cannot be translated by the BCA, the processing mode is switched to software processing. During switching between the modes, internal information of BCA can be transferred between BCA and REG_FILE in parallel, achieving faster mode switching.
Owner:RENESAS ELECTRONICS CORP
Compiling method for optimizing allocation of register based on C*core processor and compiler
ActiveCN102831005AReduce the number of popsImprove efficiencyProgram controlMemory systemsPush and pullProcessor register
The invention discloses a compiling method for optimizing allocation of a register based on a C*core processor, wherein the method comprises the steps of further processing a medium code which is generated by a front end; and optimizing the allocation of a register according to the type, the quantity and the life cycle characteristic of a variable in a function. Furthermore, the invention discloses a compiler for the method. With the adoption of the technical scheme, the throwing action is reduced to the greatest extent while the register is allocated in the compiling process, the times of pushing and pulling the processor are reduced, and the efficiency of the processor to execute the code is improved.
Owner:天津国芯科技有限公司
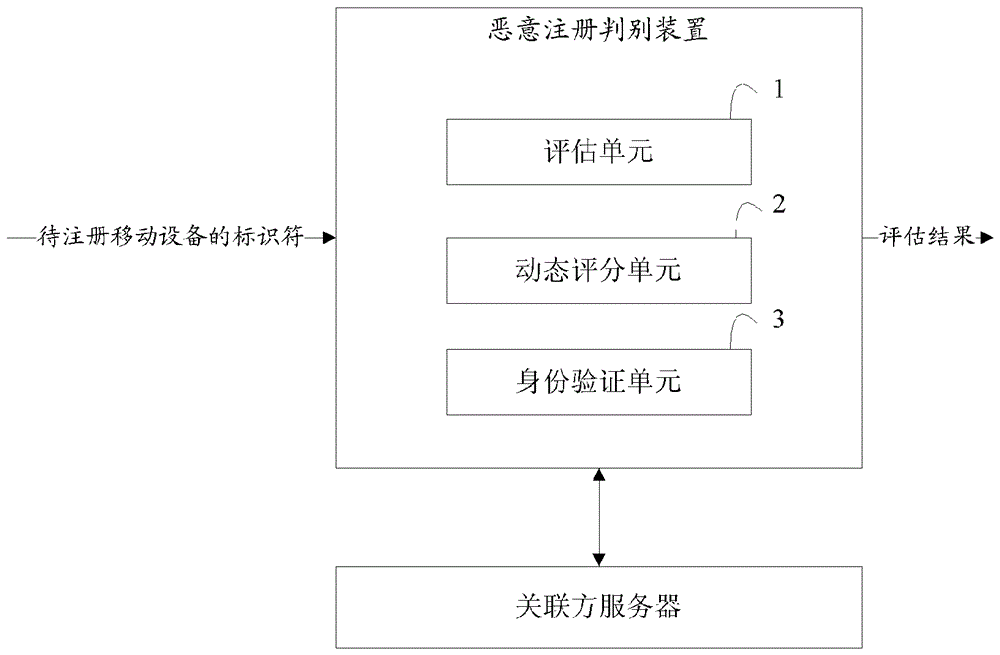
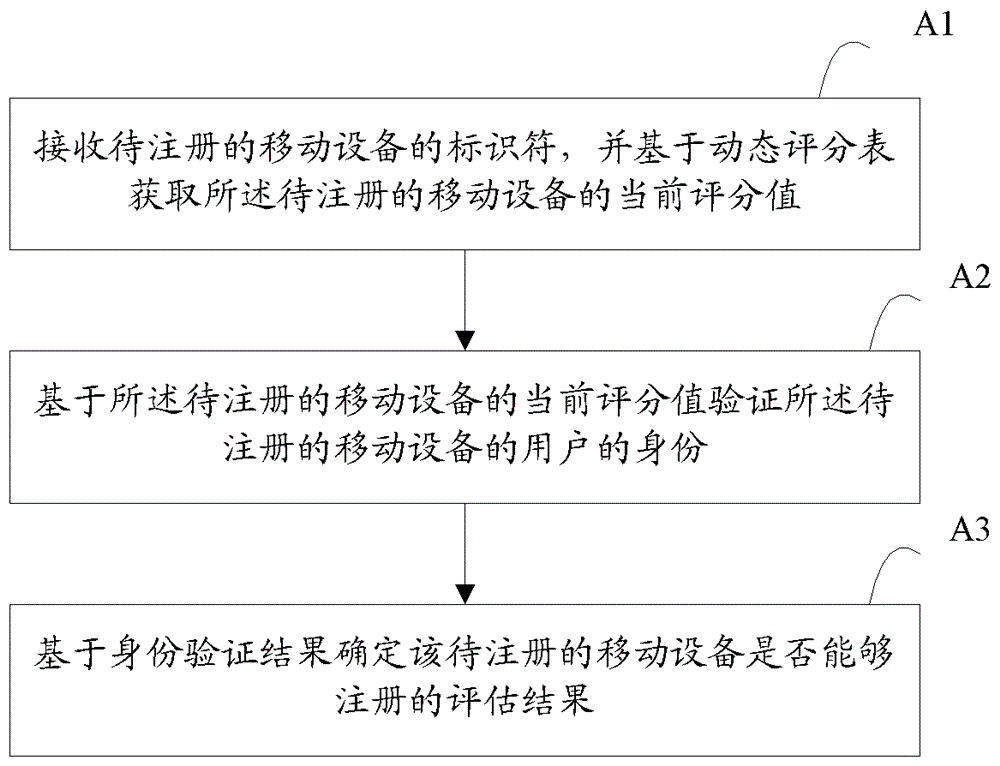
Method and device for preventing malicious registration of mobile device
ActiveCN106507354APrevent Malicious RegistrationCalculate and assess complianceSecurity arrangementMobile deviceRegister based
The invention provides a method and a device for preventing malicious registration of a mobile device. The method comprises the following steps of receiving an identifier of a to-be-registered mobile device and obtaining a current score value of the to-be-registered mobile device based on a dynamic score sheet; verifying identity of a user of the to-be-registered mobile device based on the current score value of the to-be-registered mobile device; and obtaining an assessment result for determining whether the to-be-registered mobile device can be registered based on an authentication result. The method and the device for preventing malicious registration of the mobile device, which are disclosed by the invention, have high judgment accuracy.
Owner:CHINA UNIONPAY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com