Patents
Literature
636results about How to "Improve execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
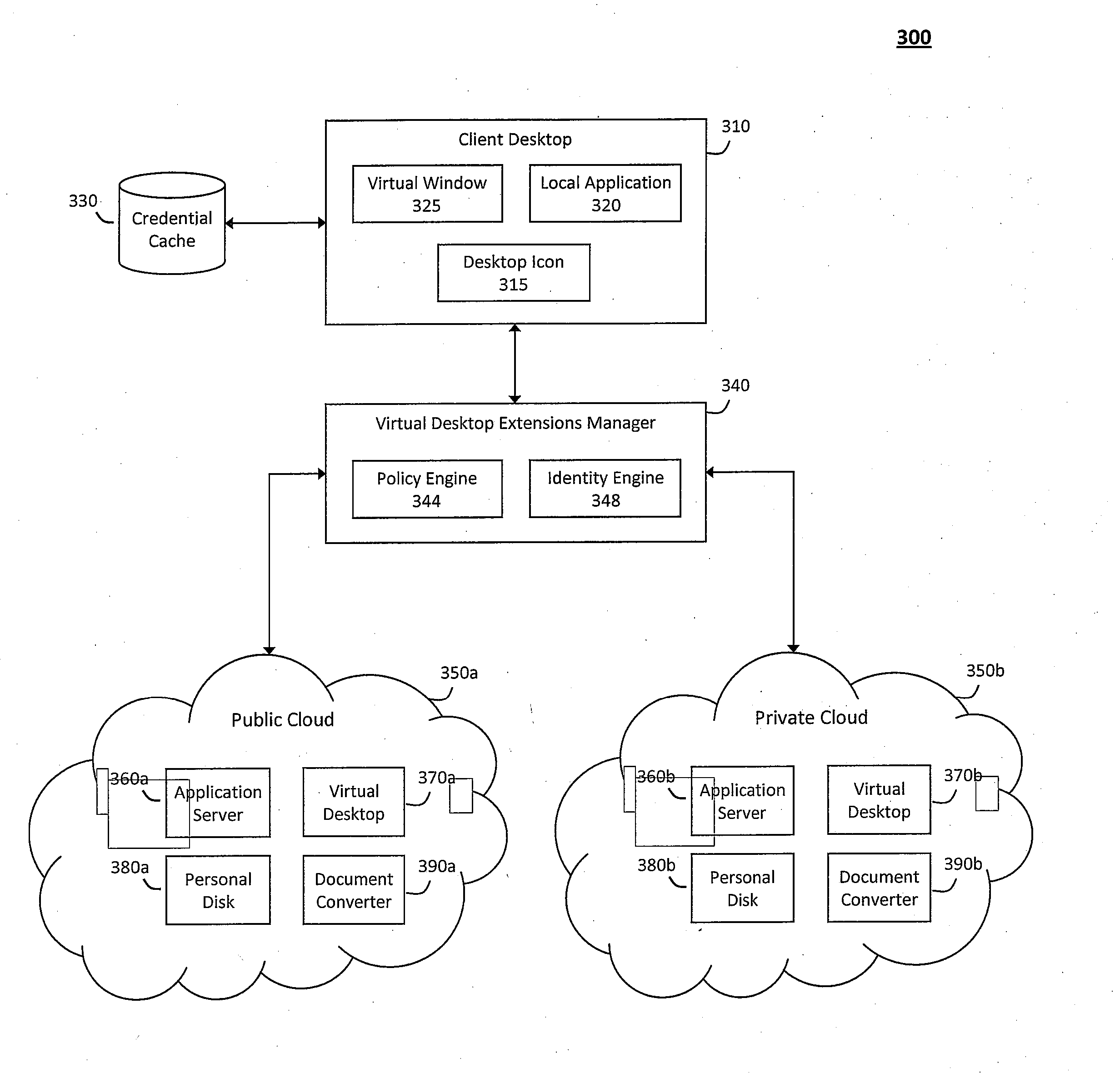
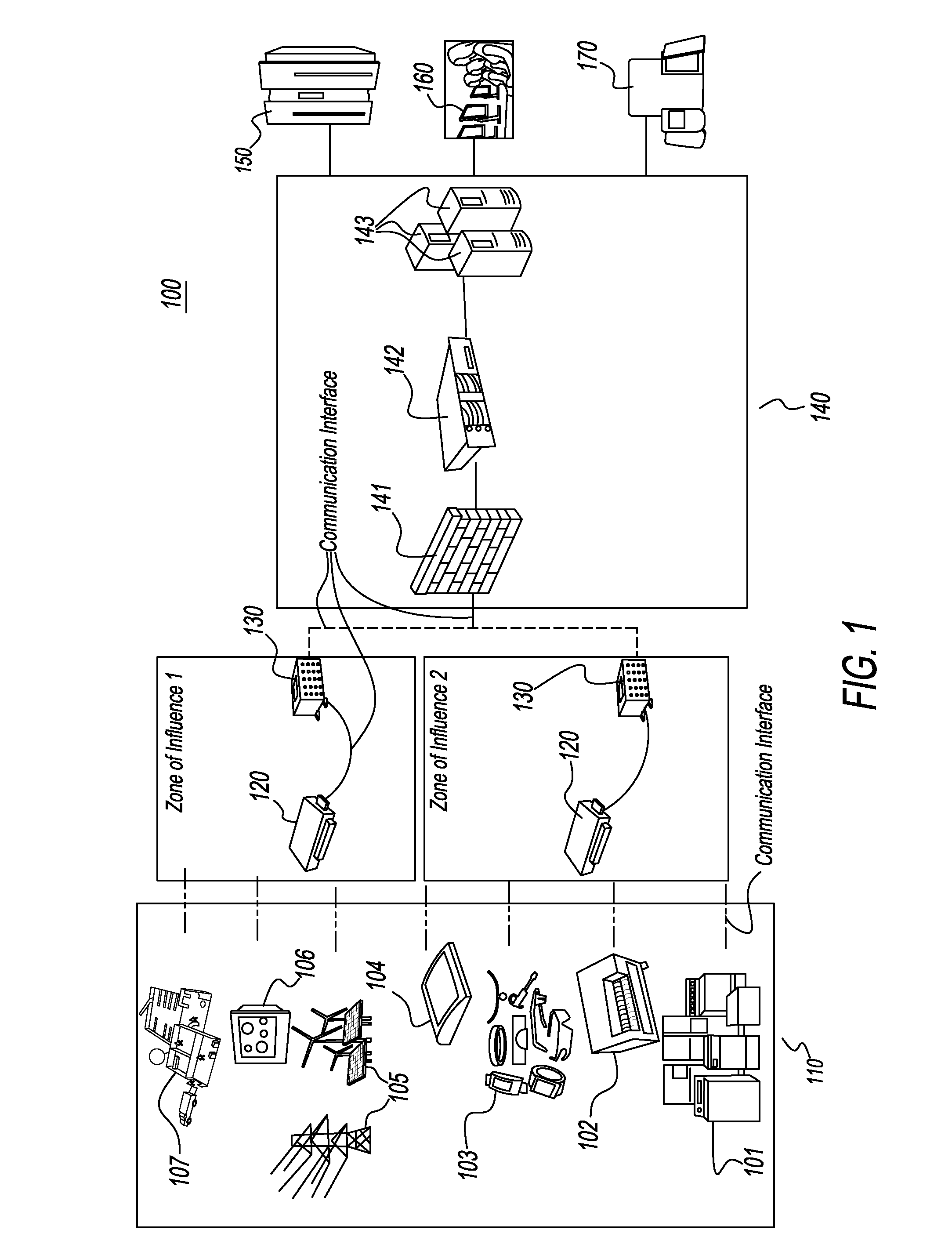
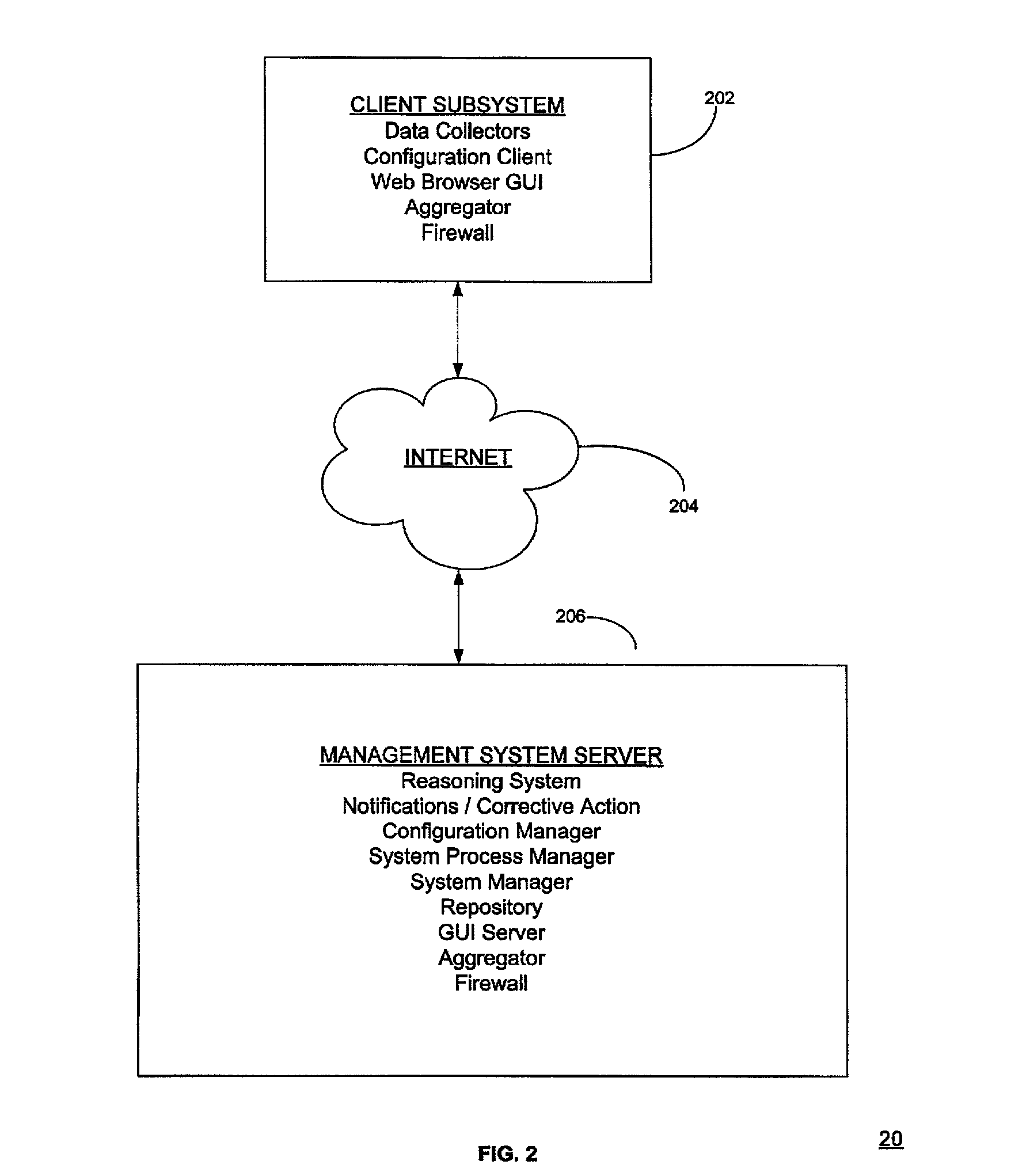
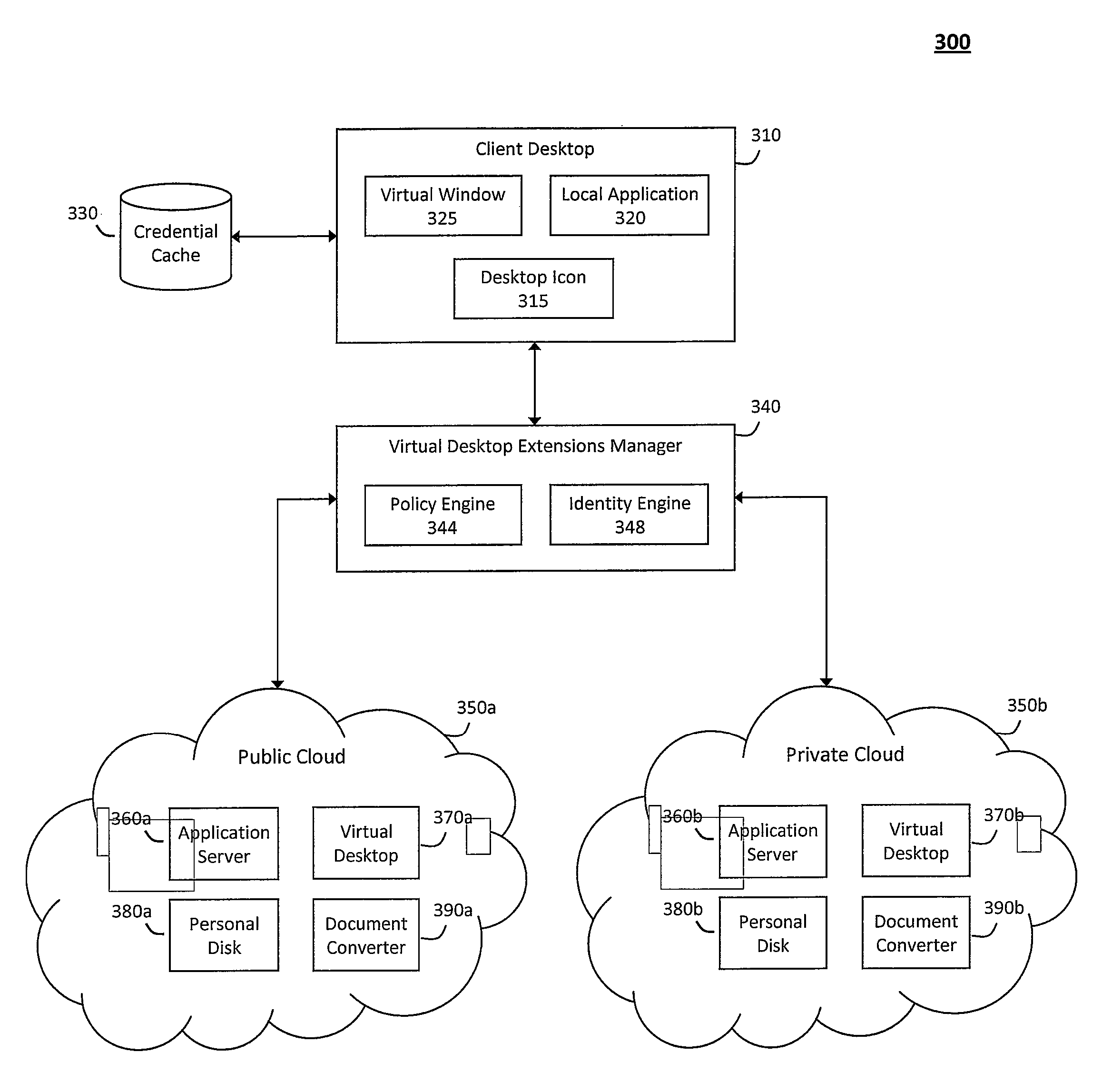
System and method for providing virtual desktop extensions on a client desktop
ActiveUS20110209064A1Simplify complexityProvide capabilityInput/output for user-computer interactionDigital data processing detailsClient-sideCloud computing
The system and method described herein may identify one or more virtual desktop extensions available in a cloud computing environment and launch virtual machine instances to host the available virtual desktop extensions in the cloud. For example, a virtual desktop extension manager may receive a virtual desktop extension request from a client desktop and determine whether authentication credentials for the client desktop indicate that the client desktop has access to the requested virtual desktop extension. In response to authenticating the client desktop, the virtual desktop extension manager may then launch a virtual machine instance to host the virtual desktop extension in the cloud and provide the client desktop with information for locally controlling the virtual desktop extension remotely hosted in the cloud.
Owner:MICRO FOCUS SOFTWARE INC
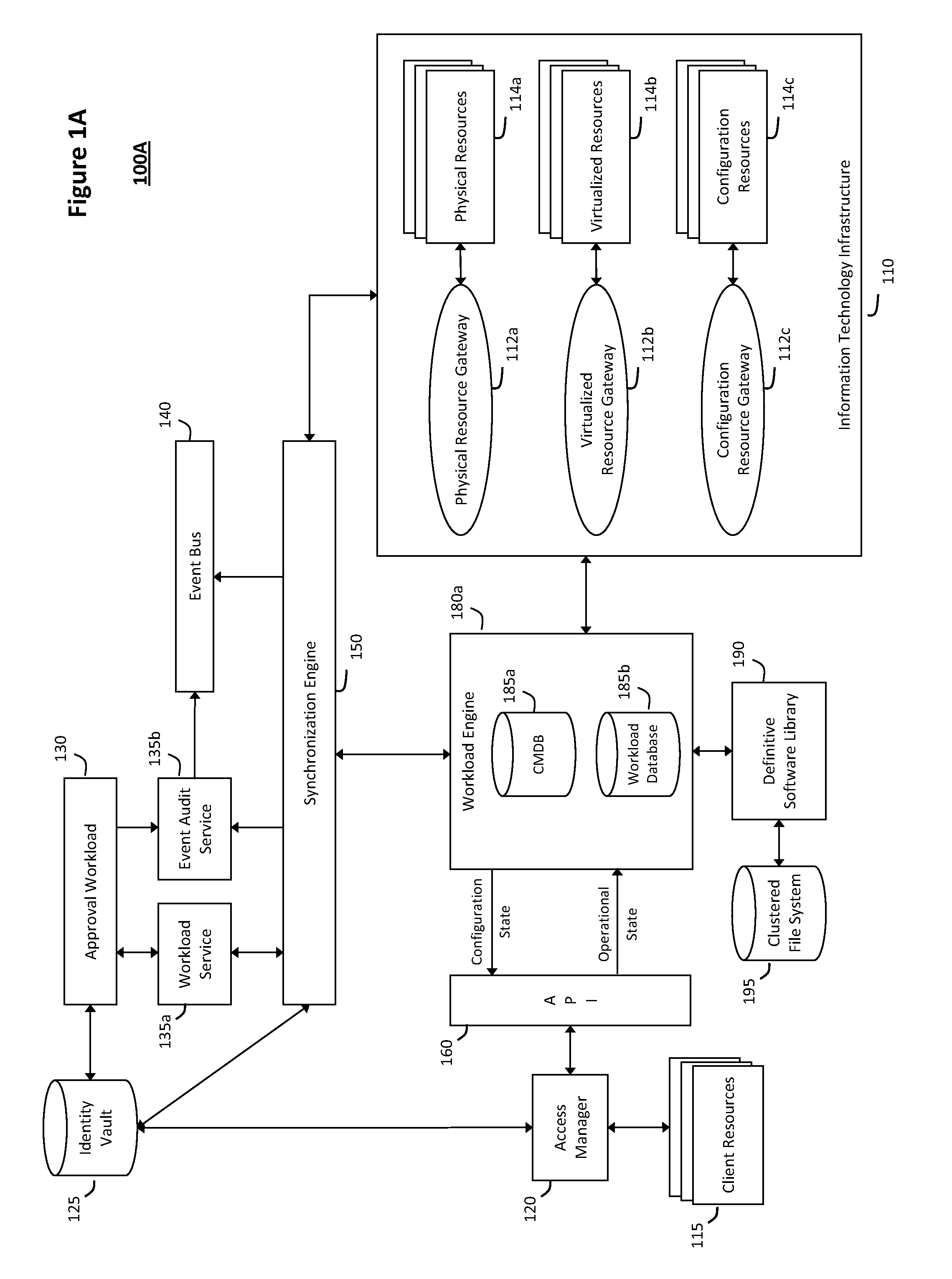
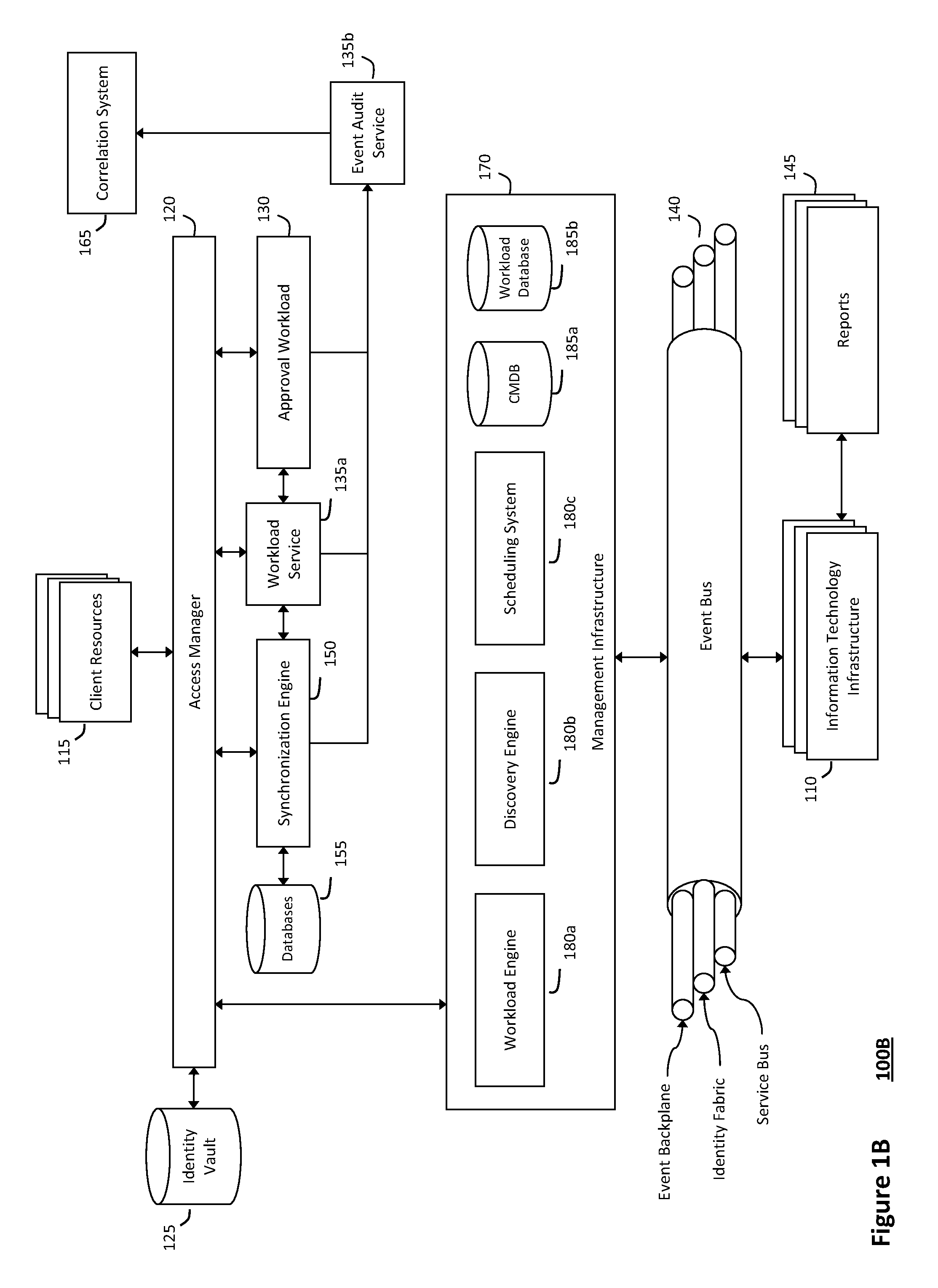
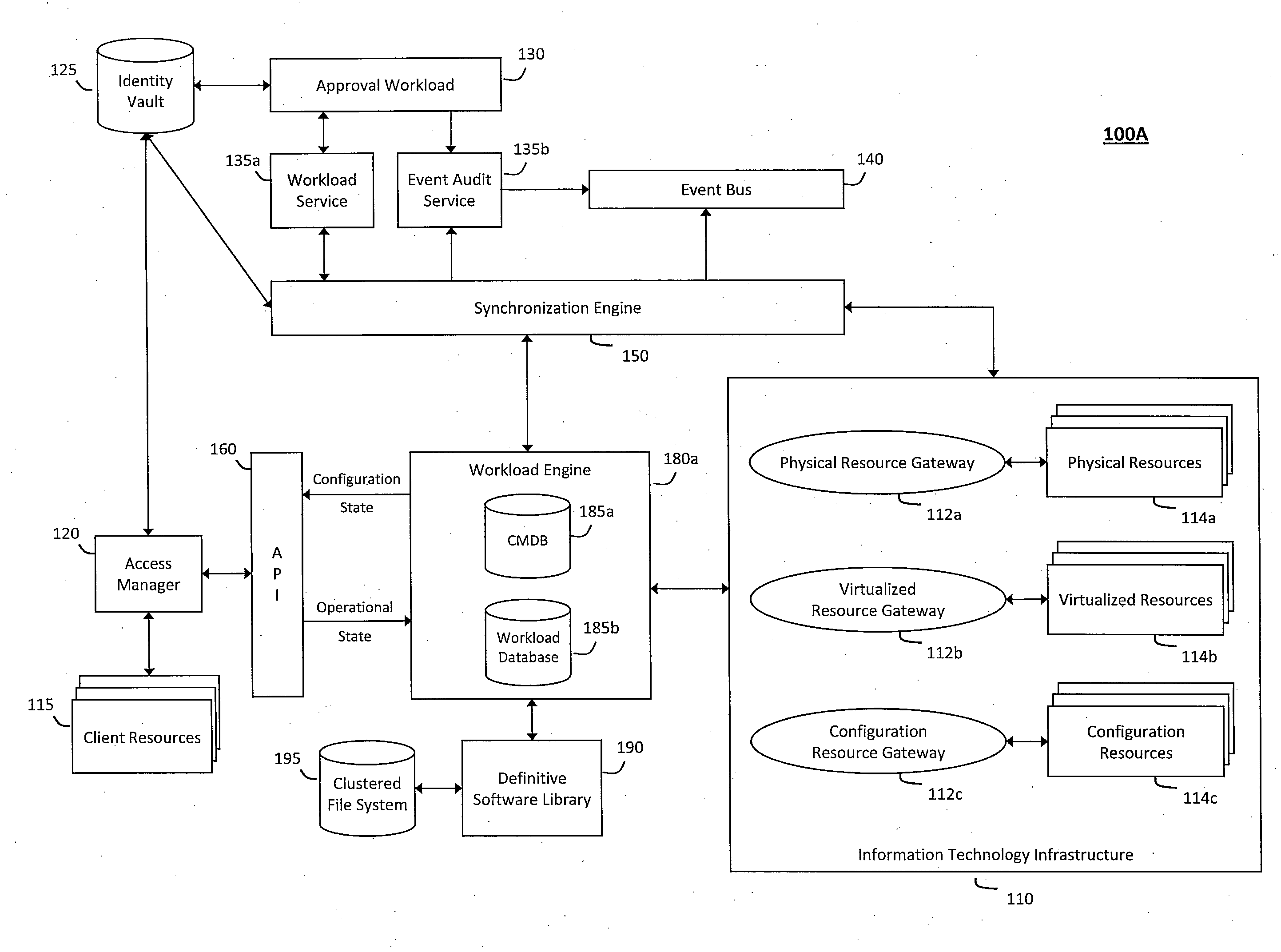
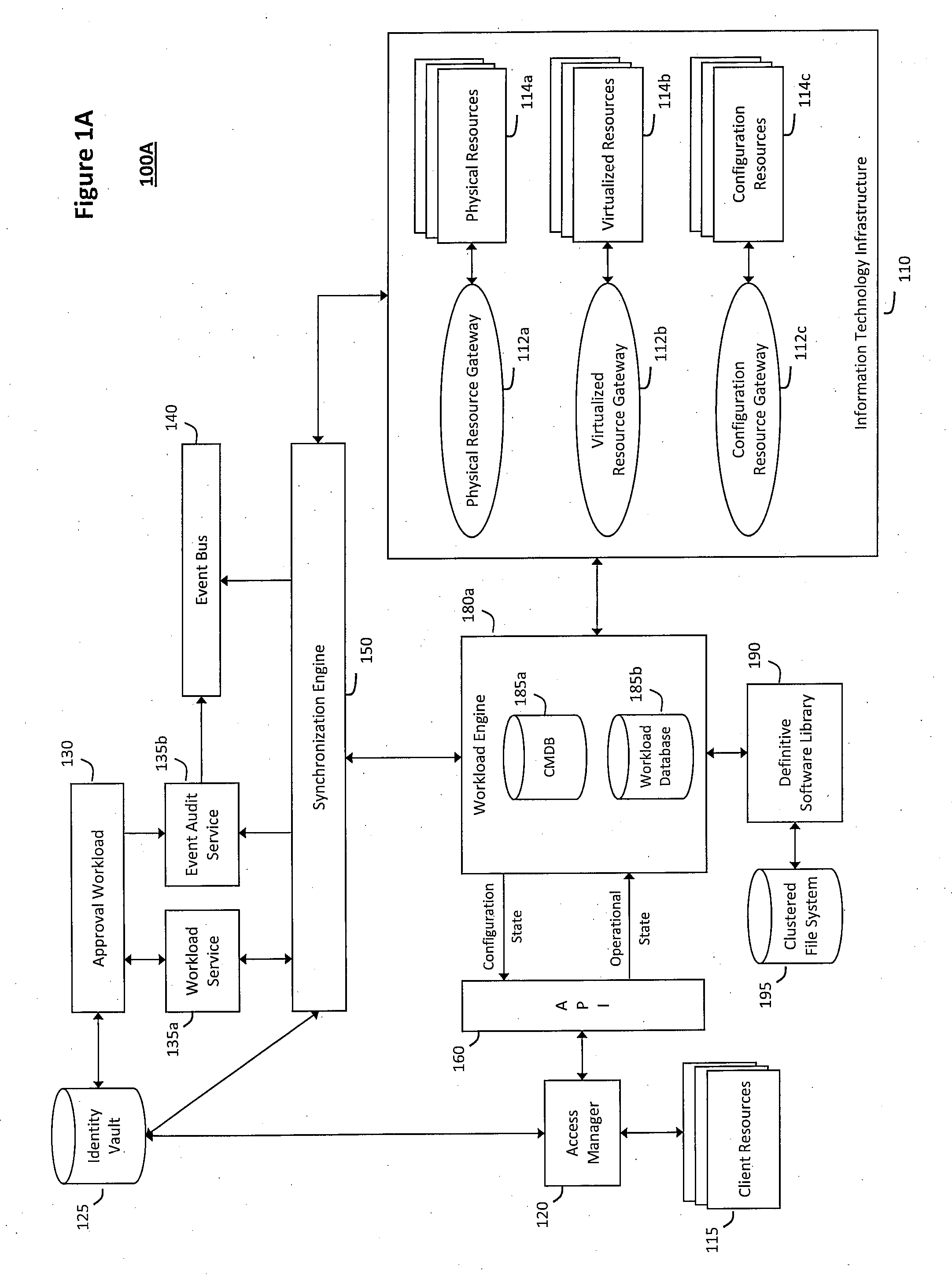
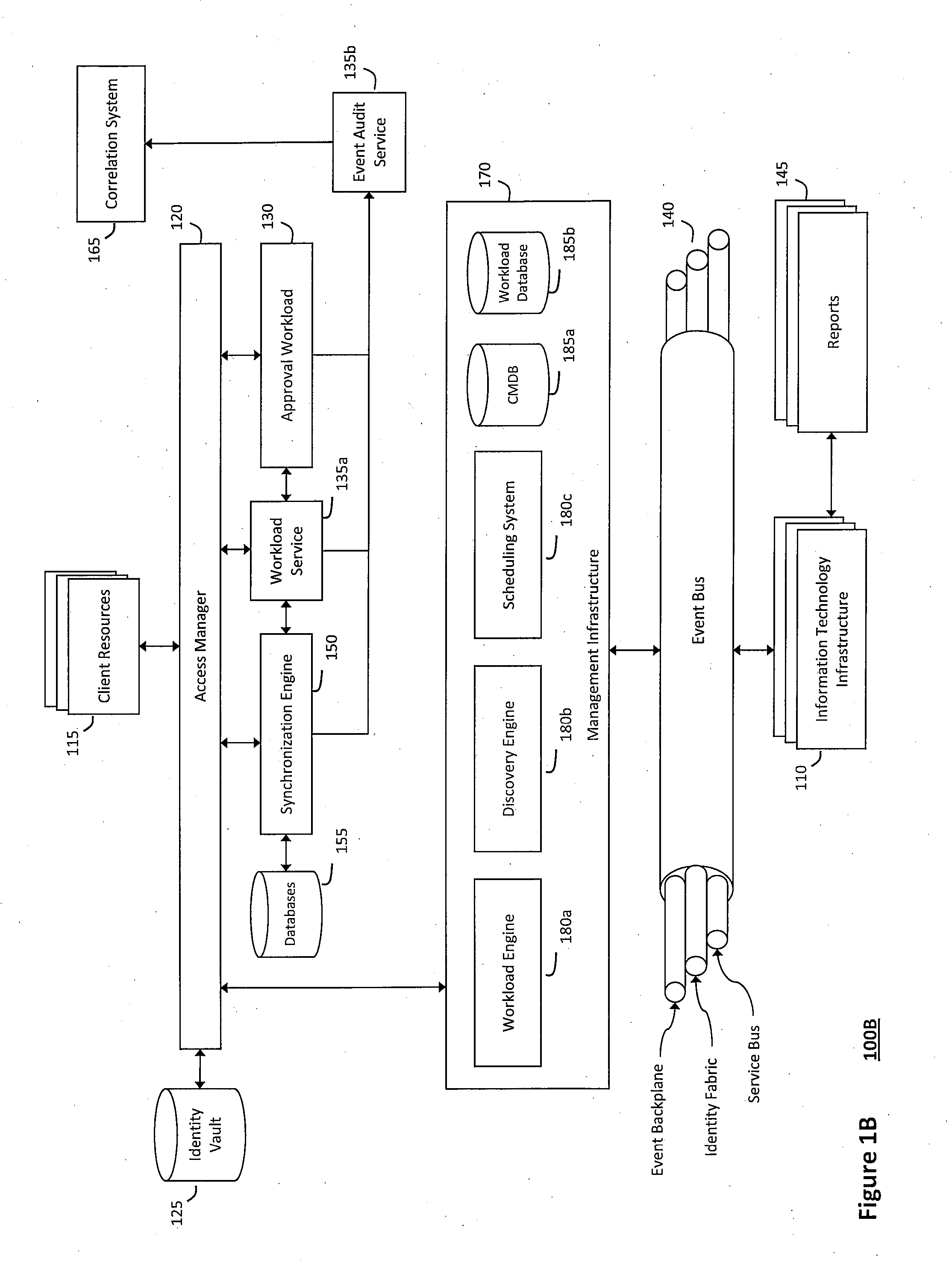
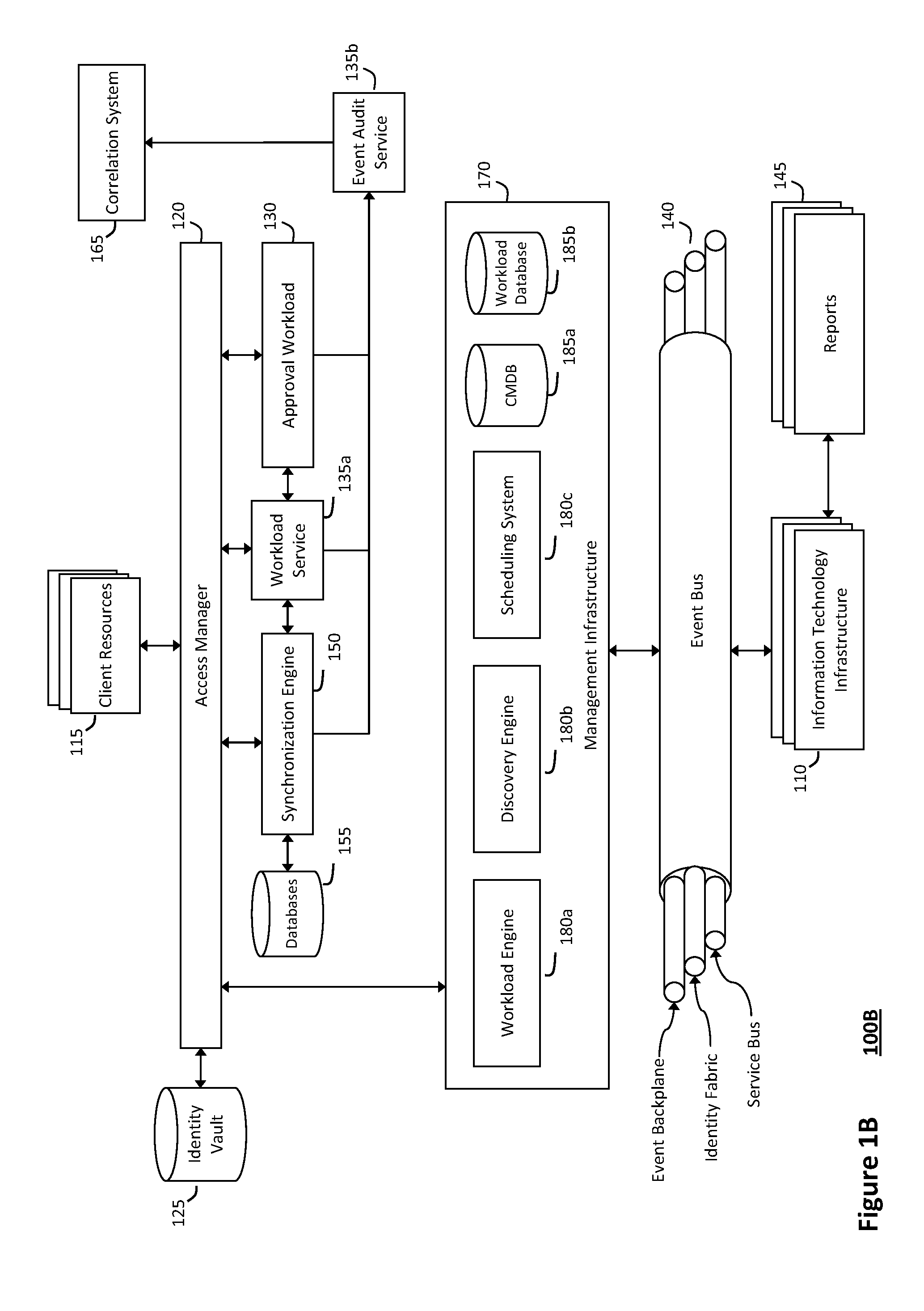
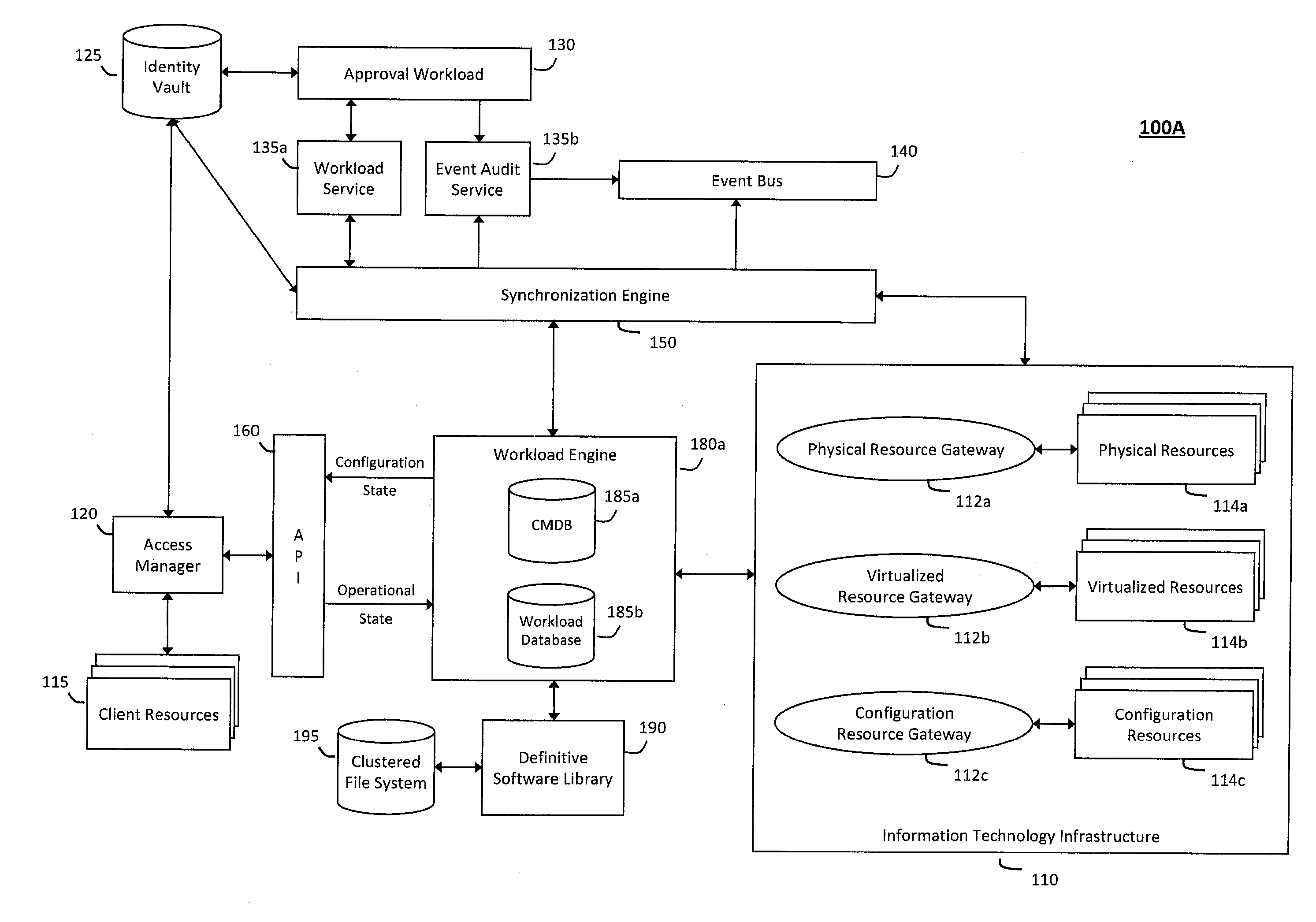
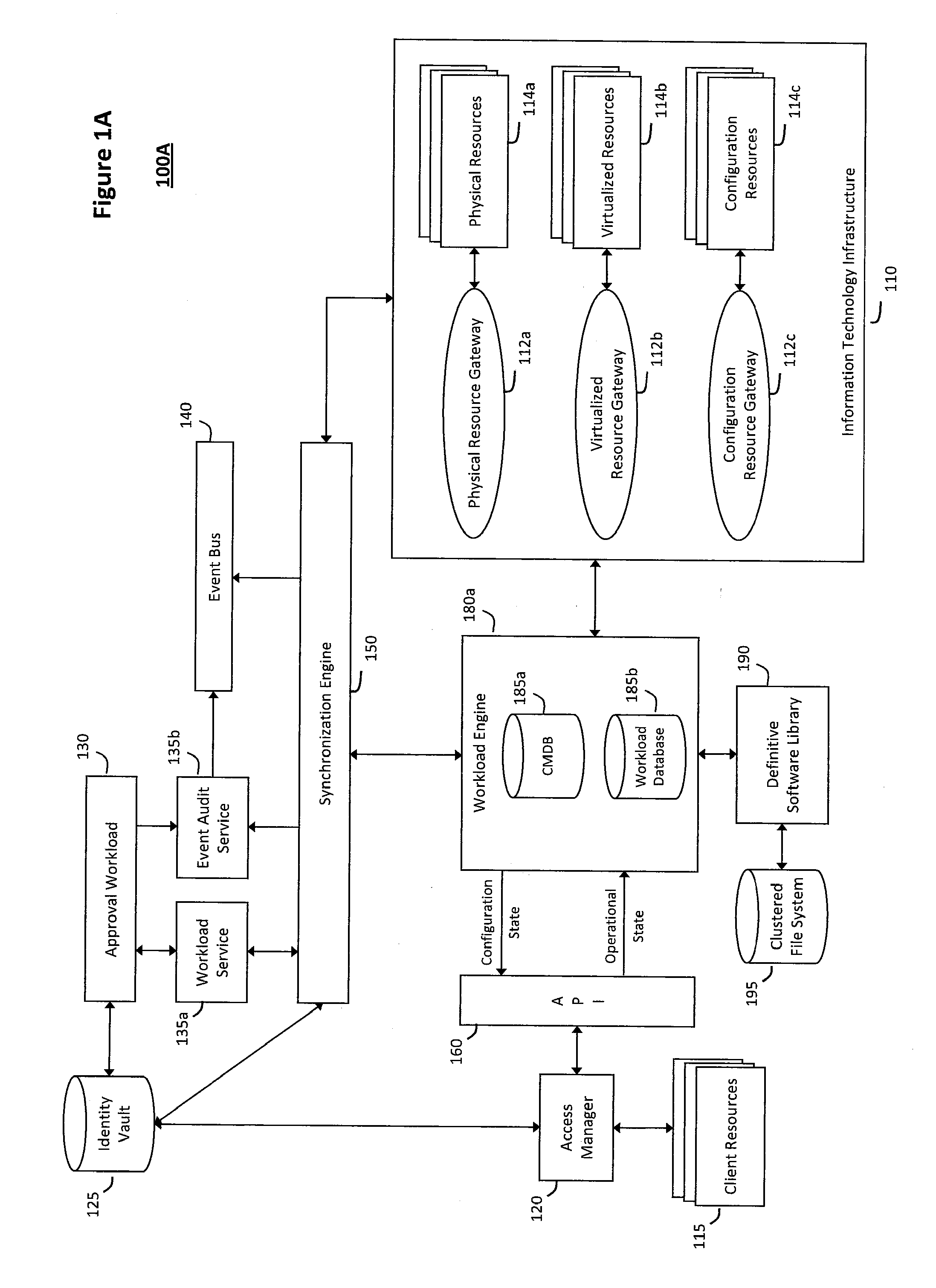
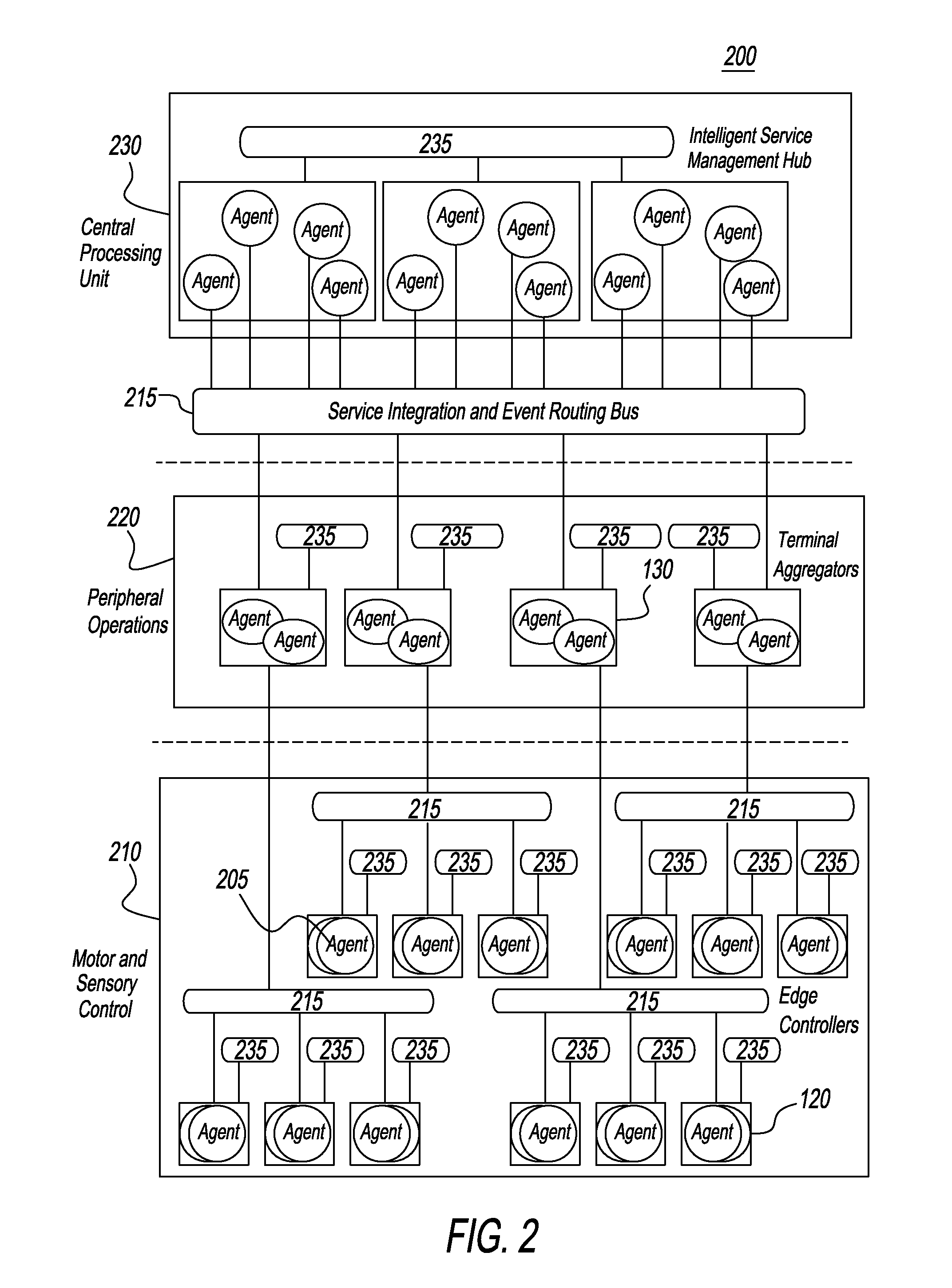
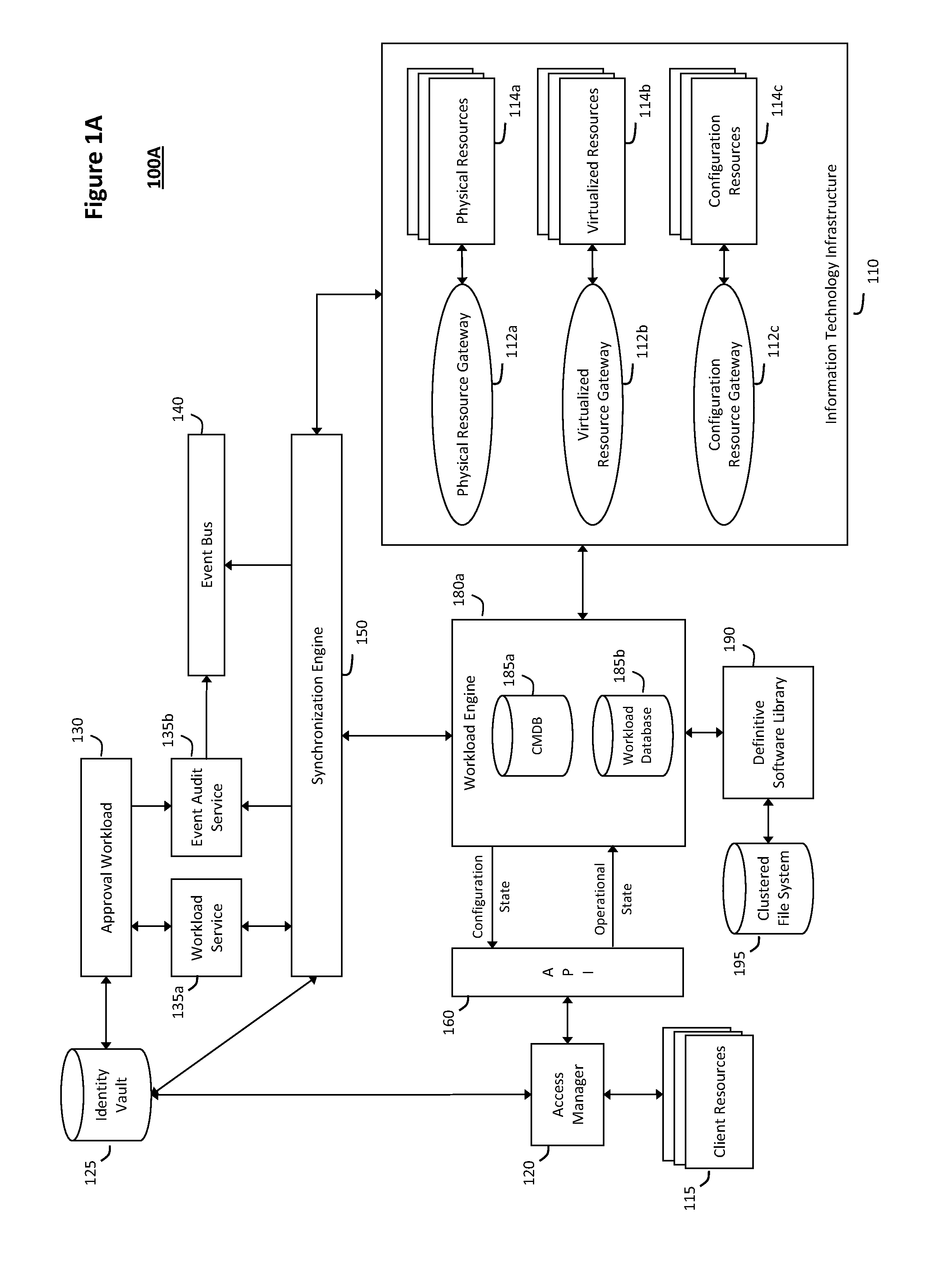
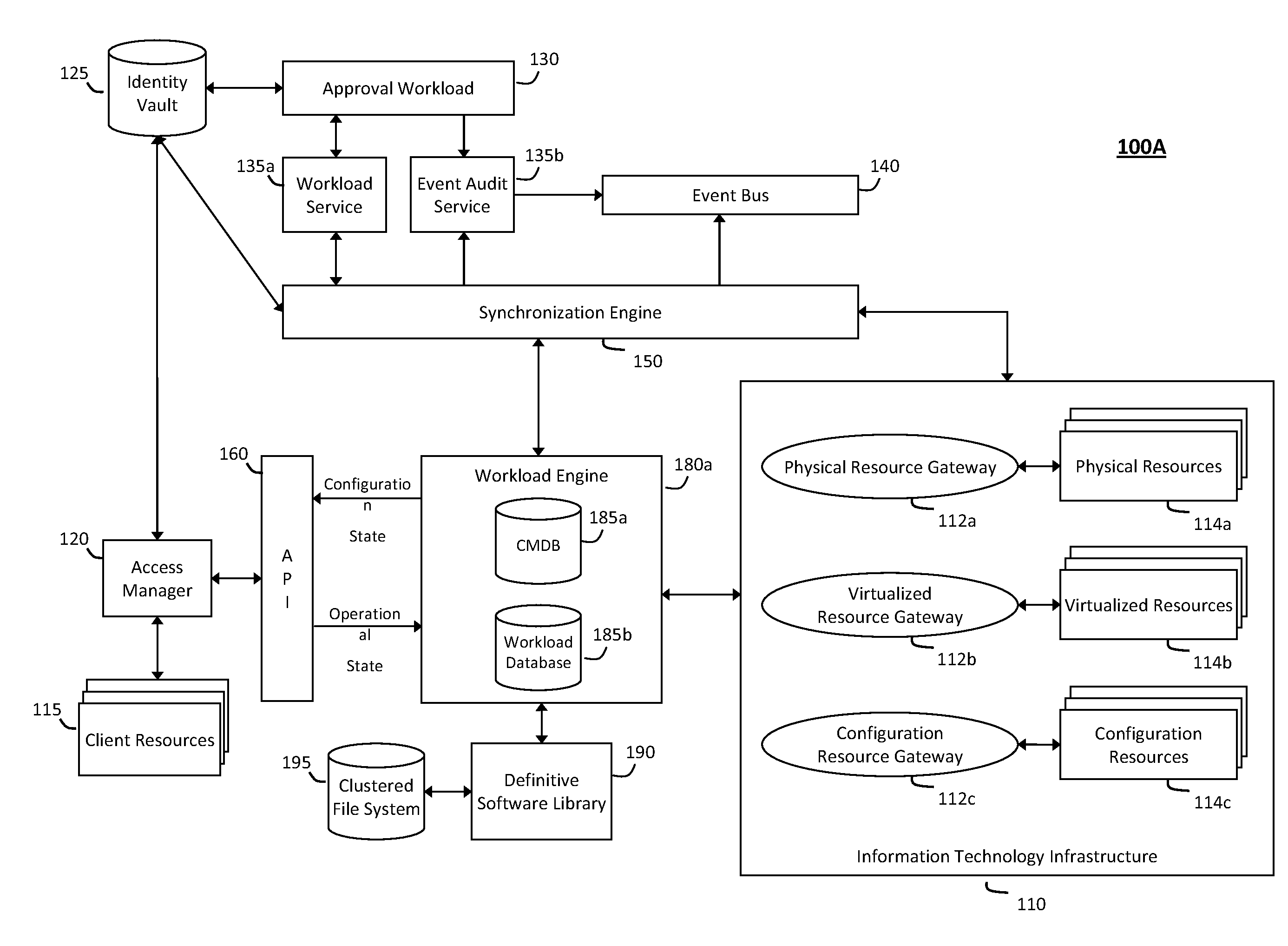
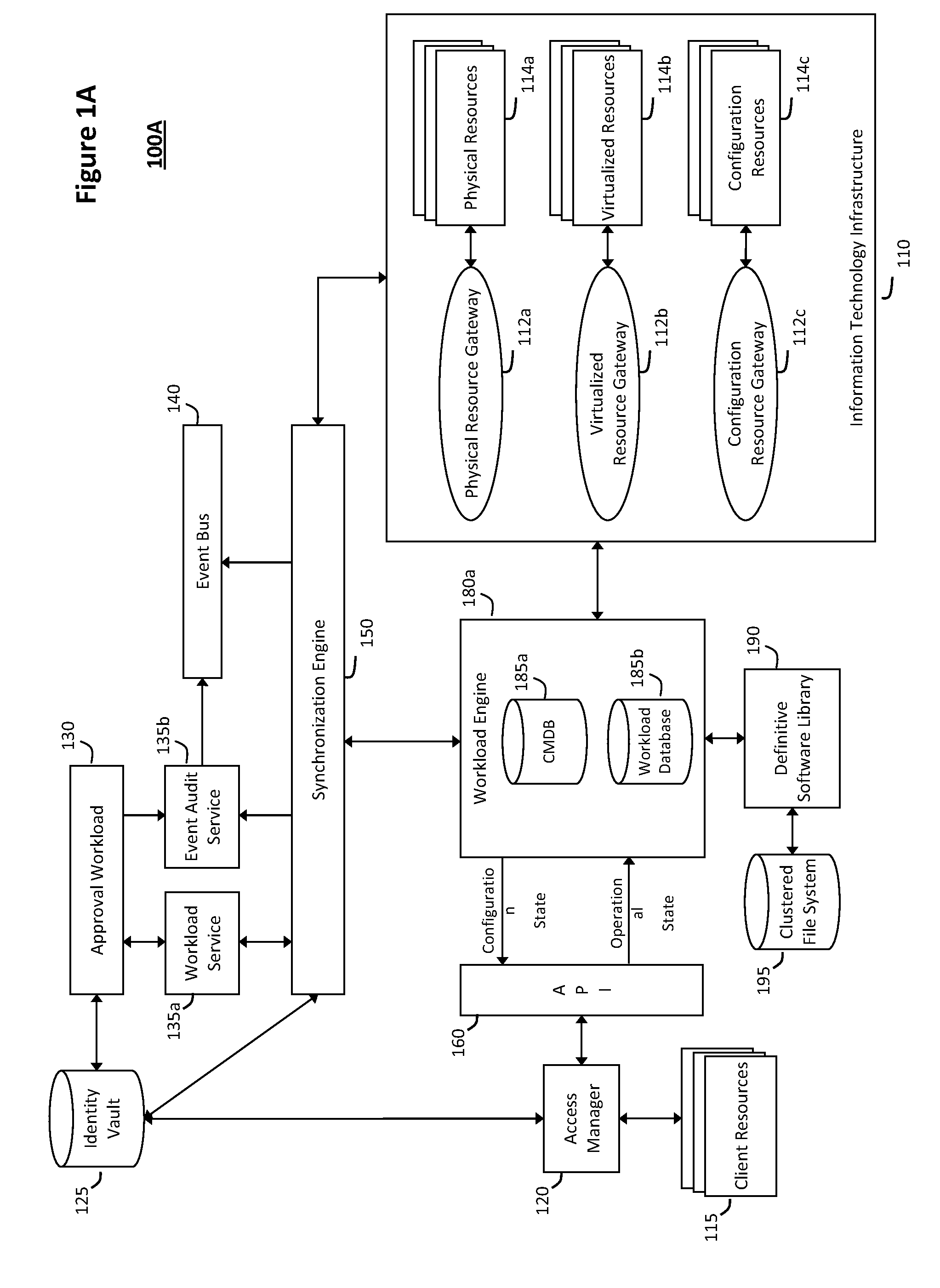
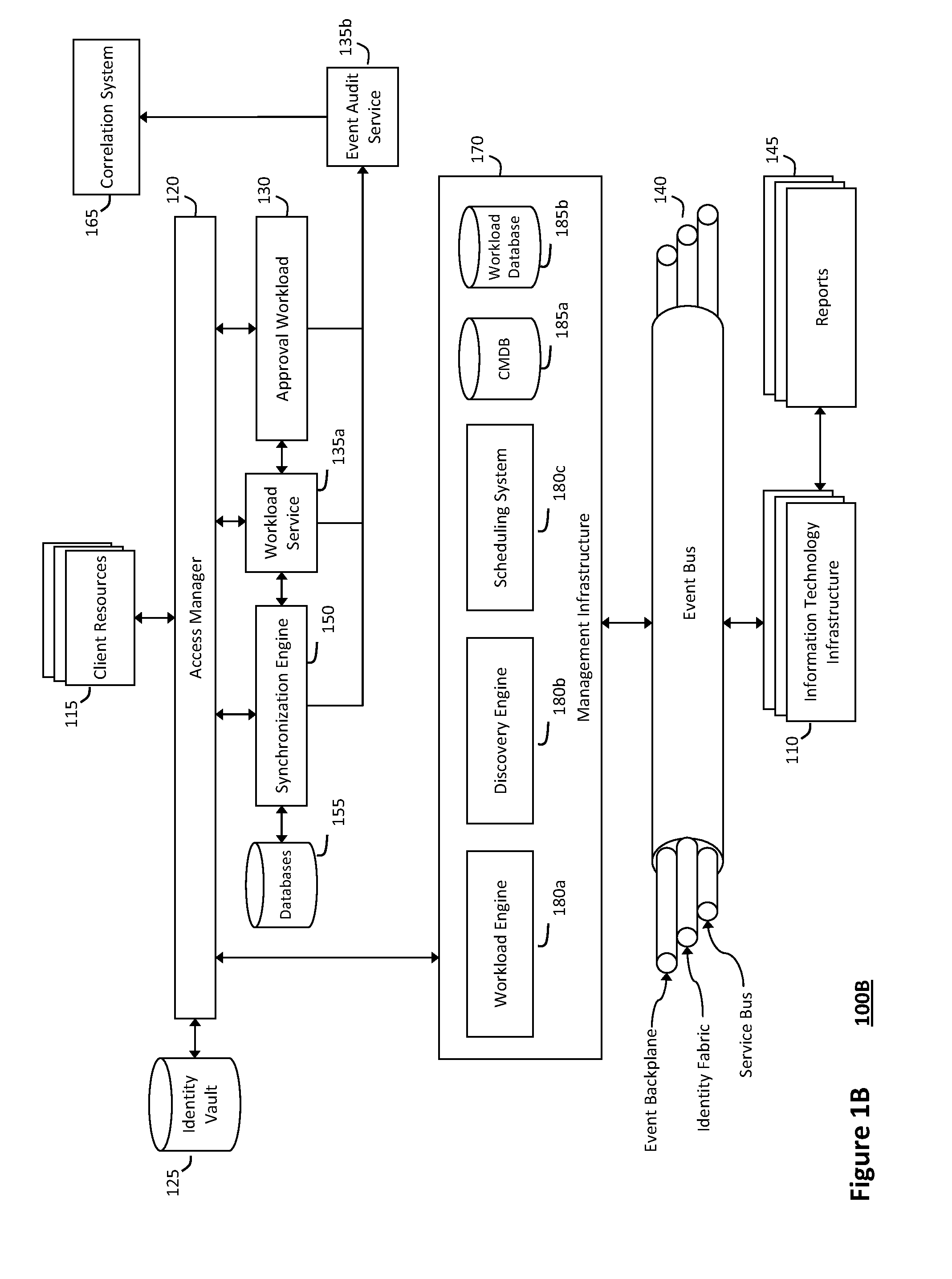
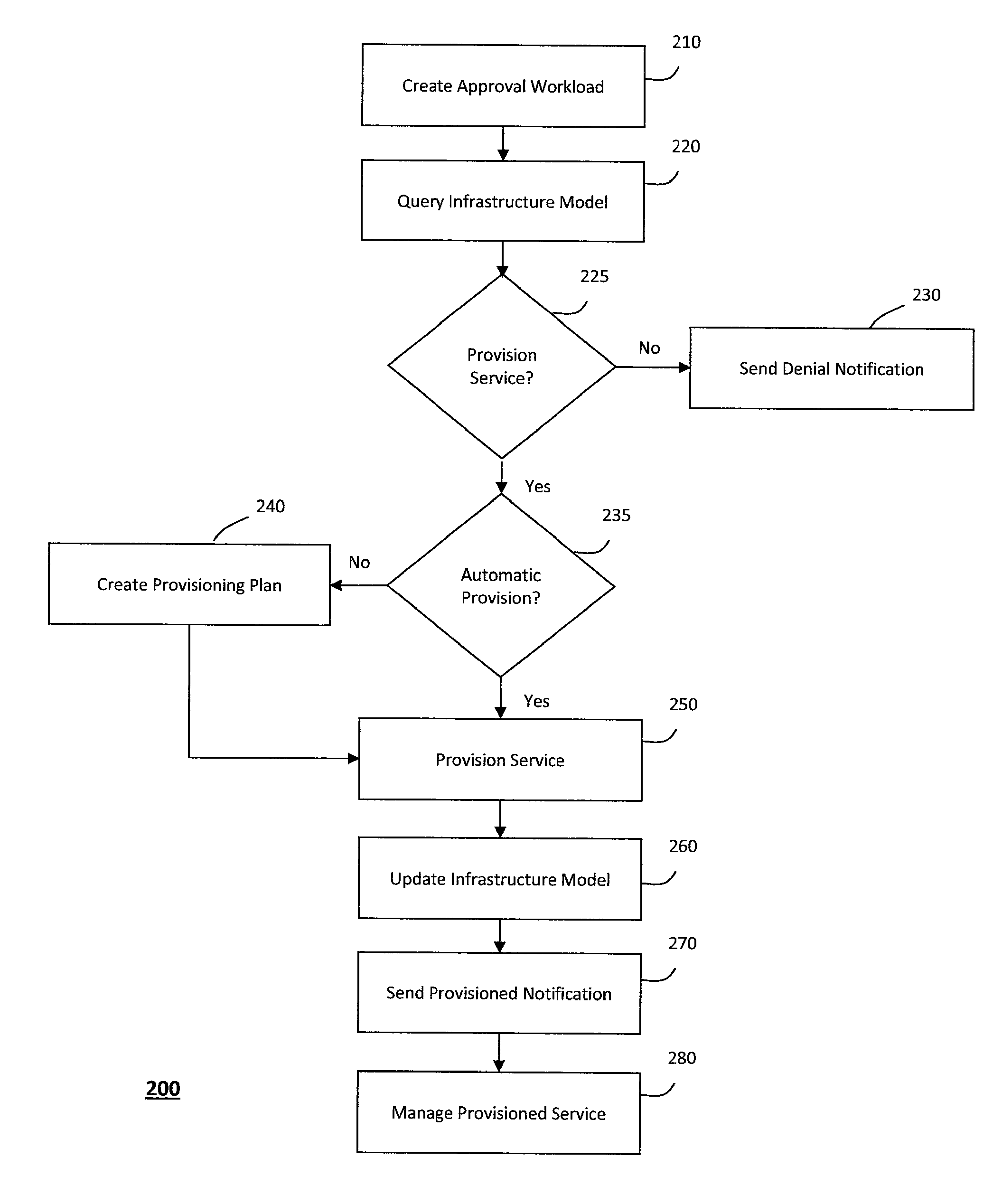
System and method for discovery enrichment in an intelligent workload management system
InactiveUS20110126275A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationVirtualizationService-oriented architecture
The system and method described herein for discovery enrichment in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing identities and access credentials, which may provide information that can enrich discovery of physical and virtual infrastructure resources. For example, a discovery engine may reference federated identity information stored in an identity vault and enrich a discovered infrastructure model with the federated identity information. Thus, the model may generally include information describing physical and virtualized resources in the infrastructure, applications and services running in the infrastructure, and information derived from the federated identity information that describes dependencies between the physical resources, the virtualized resources, the applications, and the services.
Owner:MICRO FOCUS SOFTWARE INC
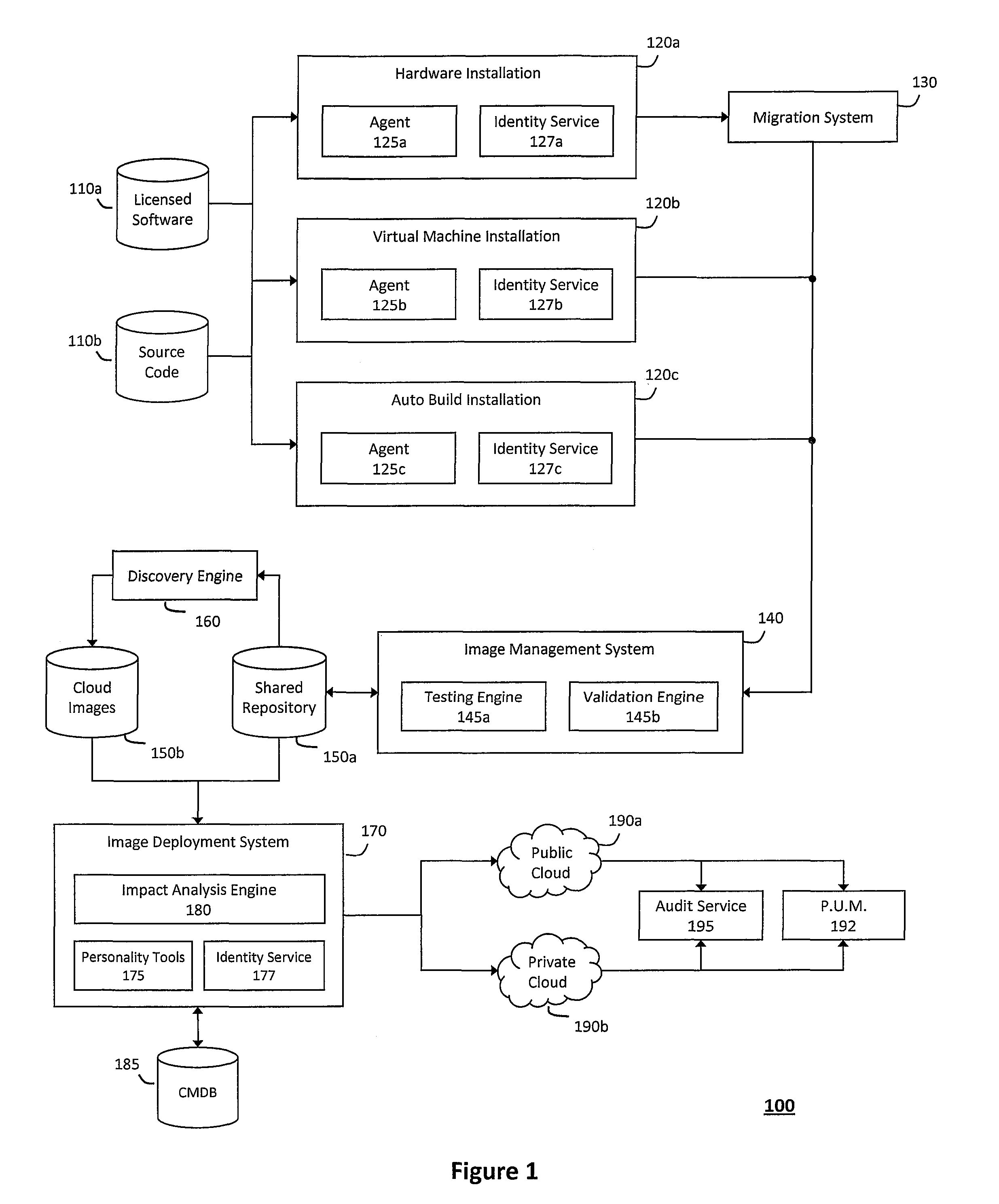
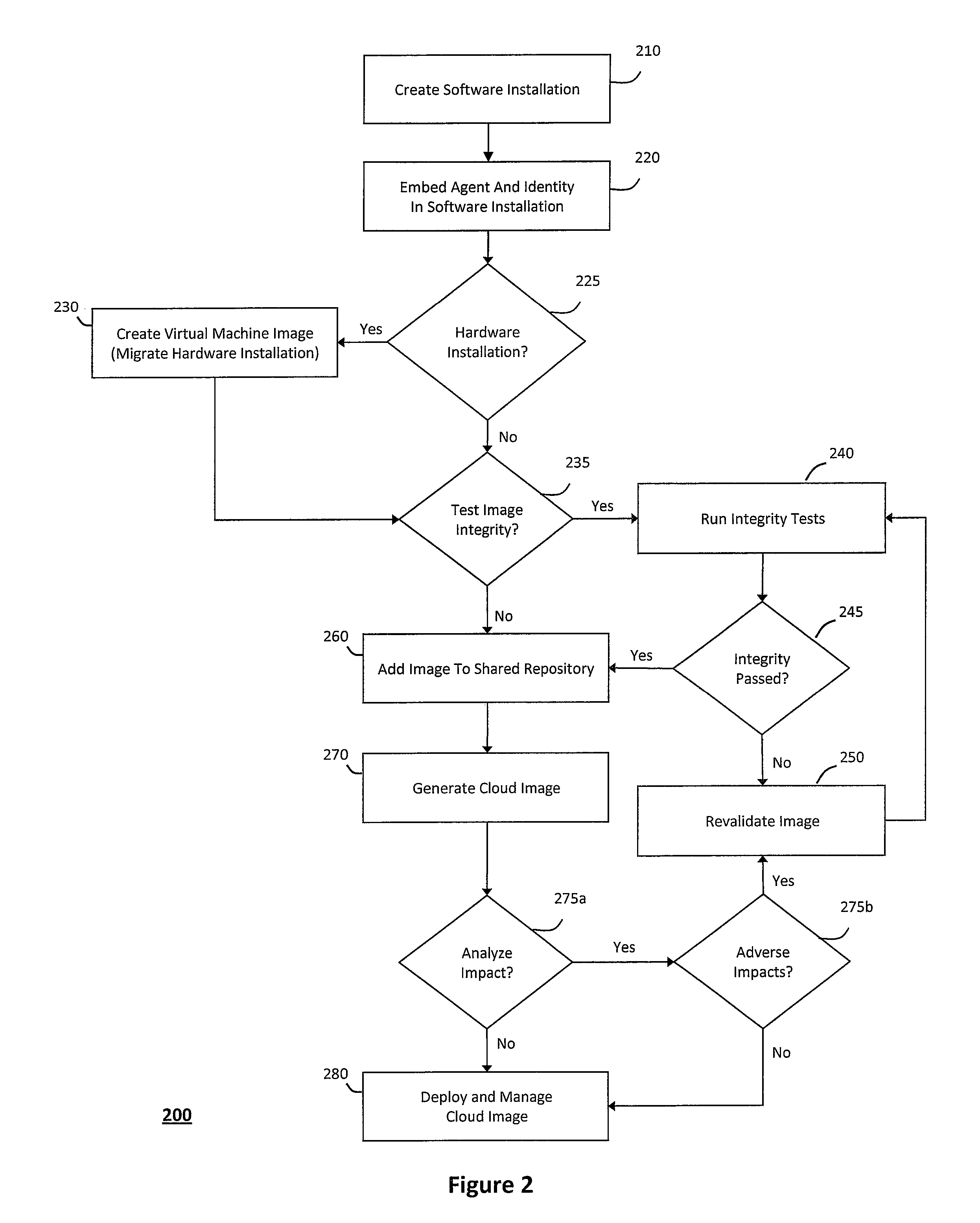
System and method for controlling cloud and virtualized data centers in an intelligent workload management system
InactiveUS20110126197A1Free computational resourceAgile and flexible managementDigital computer detailsDigital data authenticationData centerService-oriented architecture
The system and method for controlling cloud and virtualized data centers described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, and further to creating cloud images having embedded management agents and identity services for validating the cloud images prior to deployment into the cloud and virtualized data centers and controlling, monitoring, and auditing activity associated with the cloud images following deployment into the cloud and virtualized data centers.
Owner:MICRO FOCUS SOFTWARE INC
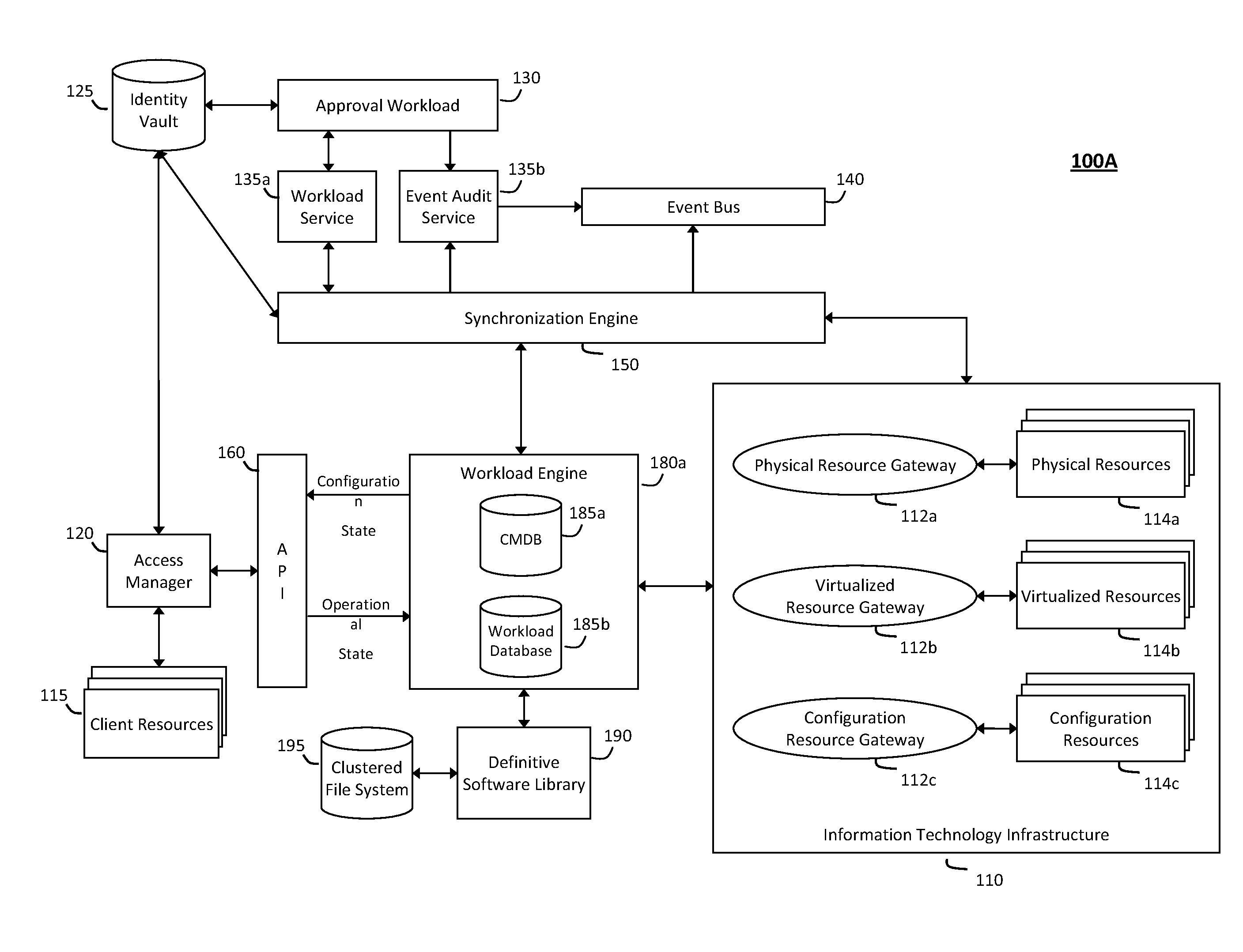
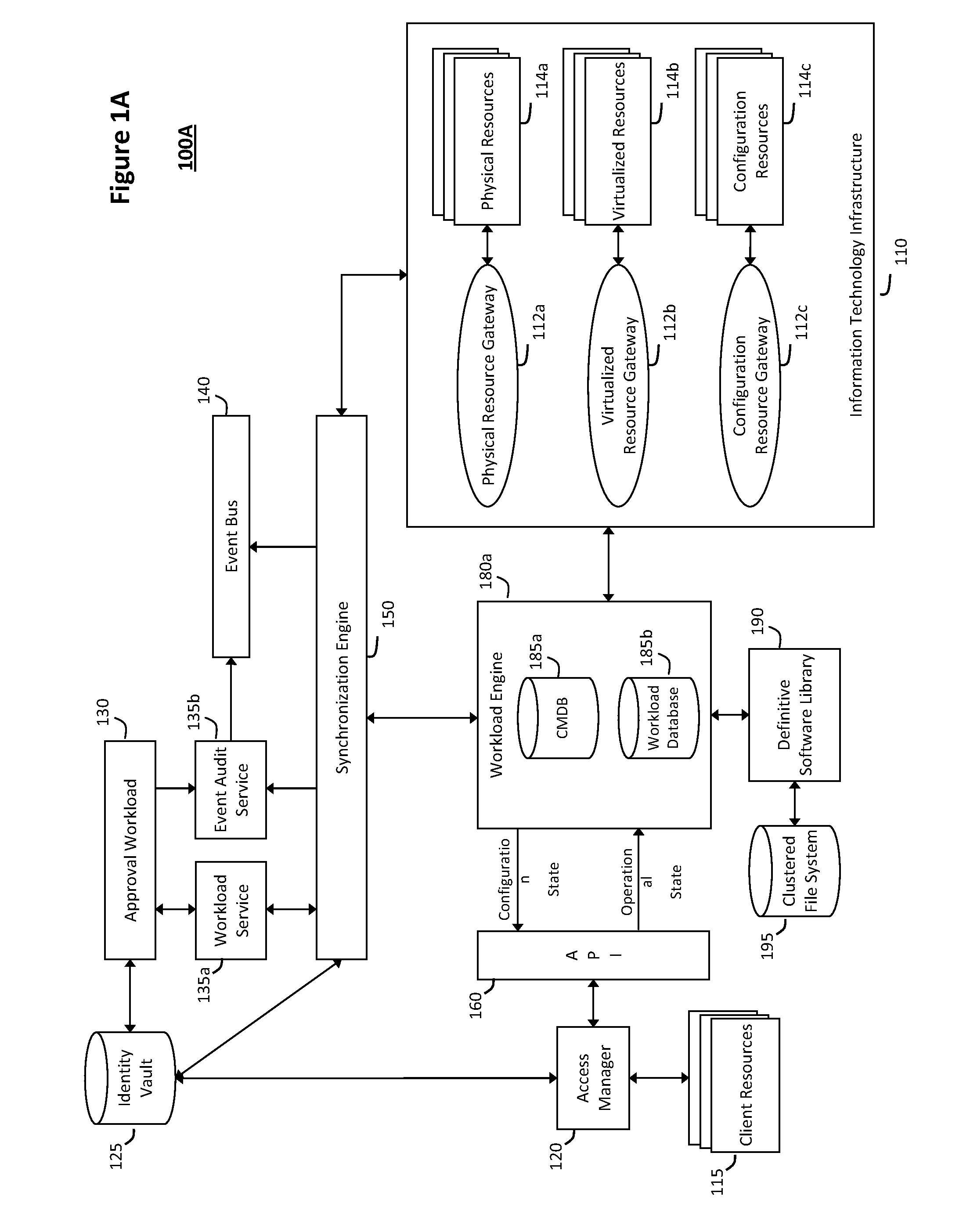
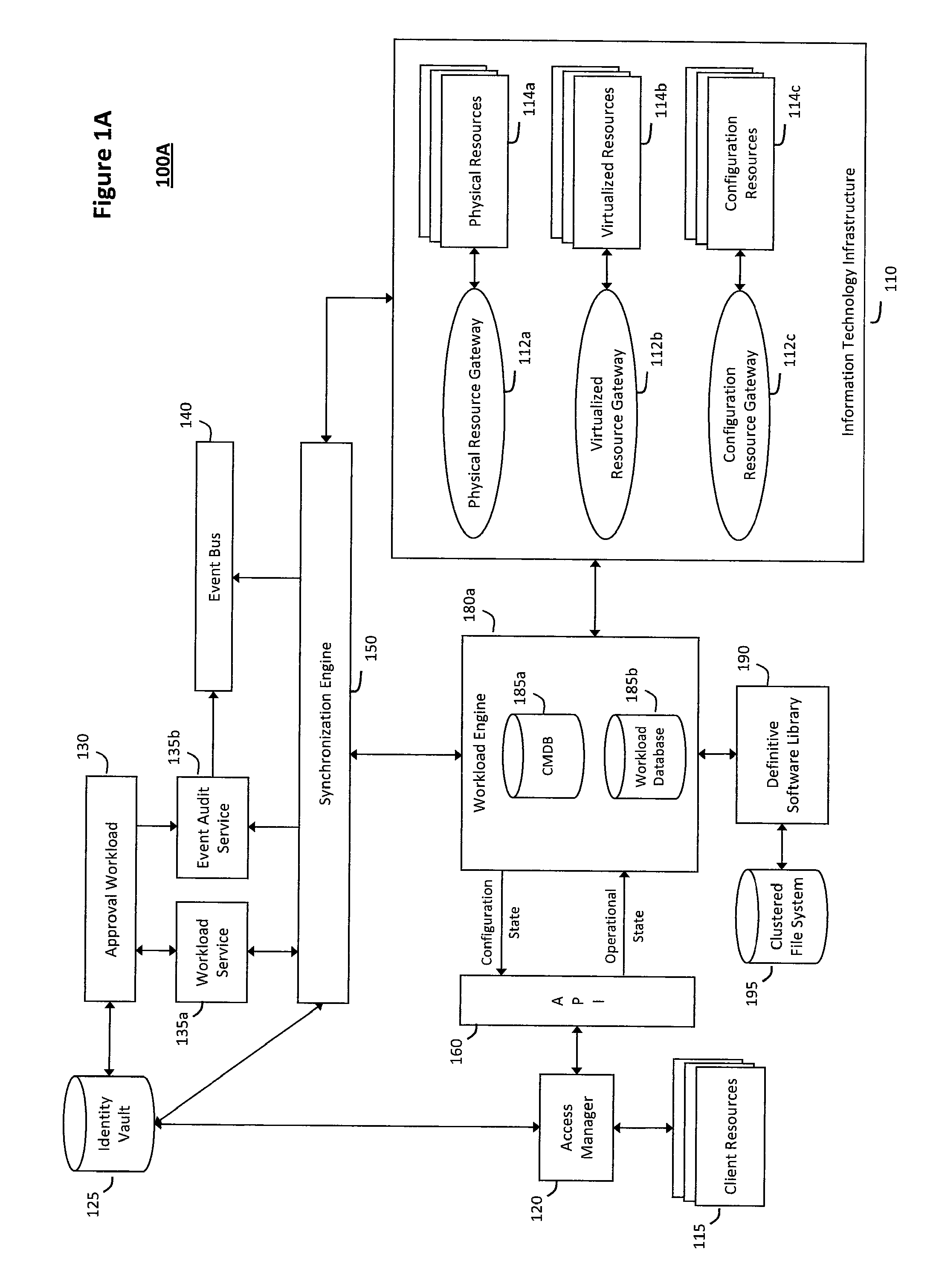
System and method for intelligent workload management
ActiveUS20110125894A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationAuthentication serverService-oriented architecture
The system and method for intelligent workload management described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, wherein the management threads may converge information for managing identities and access credentials, enforcing policies, providing compliance assurances, managing provisioned and requested services, and managing physical and virtual infrastructure resources. In one implementation, an authentication server may generate authentication tokens defining access credentials for managed entities across a plurality of authentication domains, wherein the authentication tokens may control access to resources in an information technology infrastructure. For example, a management infrastructure may create service distributions for the managed entities, which may include virtual machine images hosted on physical resources. Further, the authentication tokens may be embedded in the service distributions, whereby the embedded authentication tokens may control access to the resources in the information technology infrastructure.
Owner:MICRO FOCUS SOFTWARE INC
System and method for providing annotated service blueprints in an intelligent workload management system
InactiveUS20110126207A1Free computational resourceAgile and flexible managementMultiprogramming arrangementsDigital data authenticationService blueprintService-oriented architecture
The system and method described herein for providing annotated service blueprints in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for creating annotated service blueprints to provision and manage tessellated services distributed within an information technology infrastructure. For example, in response to a request to provision a service, a service blueprint describing one or more virtual machines may be created. The service blueprint may then be annotated to apply various parameters to the virtual machines, and the annotated service blueprint may then be instantiated to orchestrate the virtual machines with the one or more parameters and deploy the orchestrated virtual machines on information technology resources allocated to host the requested service, thereby provisioning the requested service.
Owner:MICRO FOCUS SOFTWARE INC
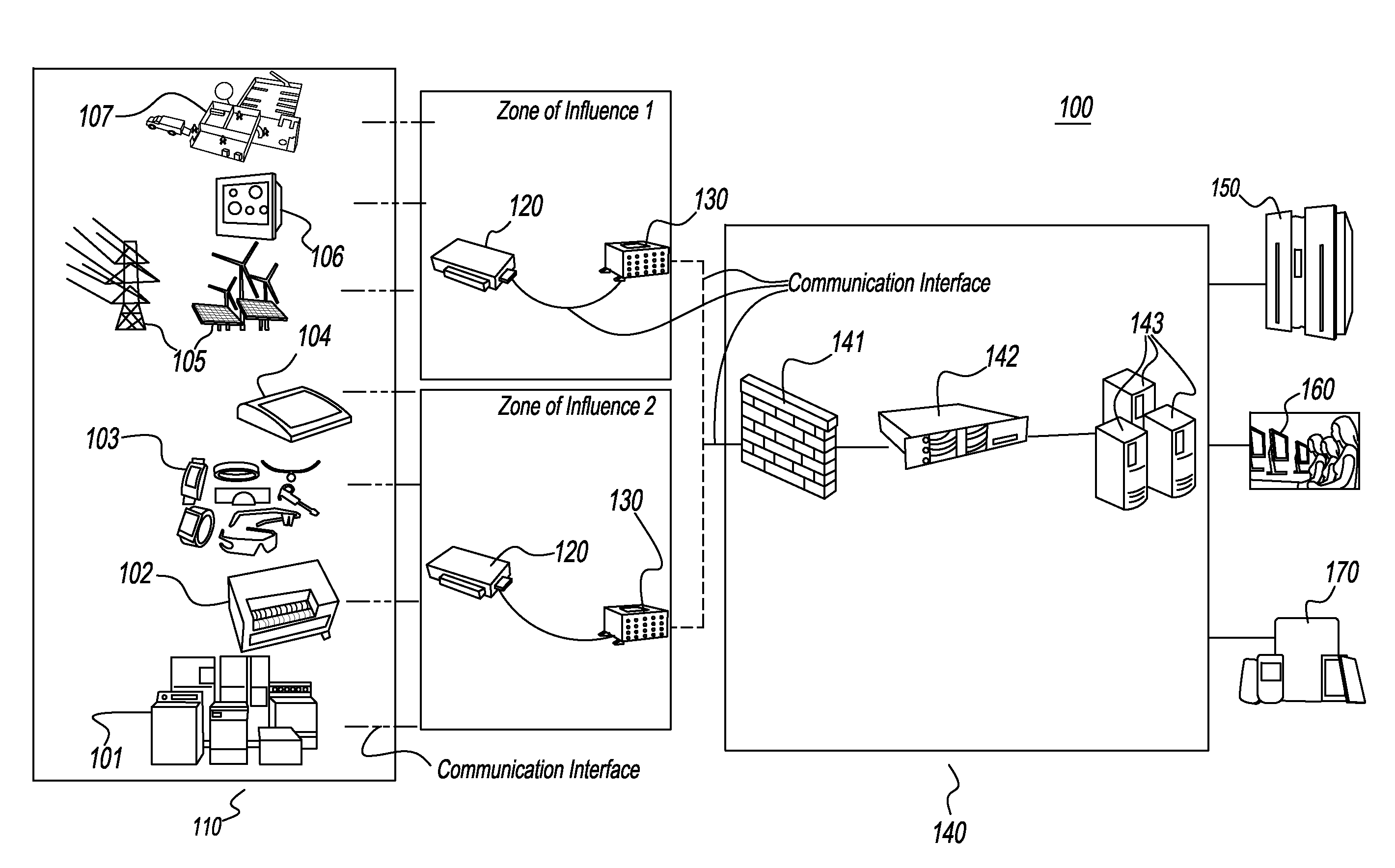
Cognitive Intelligence Platform for Distributed M2M/ IoT Systems
InactiveUS20170006141A1Condition may changeEasy to operateNetwork topologiesTransmissionNervous systemCollective intelligence
Systems and methods to leverage and manage data and knowledge in a M2M or Internet of Things (IoT) network are provided. More particularly, a cognitive intelligence platform for an IoT network that provides autonomic decision support system at or near real-time and executes a dynamic runtime is provided. The hardware, software and communication design of the platform replicates the structural and operational model of the human nervous system to achieve cognitive intelligence through adaptation, collaborative learning, knowledge sharing and self-adjustment. Further, in one embodiment, the cognitive intelligence platform has three logical processing layers of increasing complexity, each of which has agents that use statistical and machine learning techniques and algorithms to resolve situational needs and update knowledge. Furthermore, each processing layer of the platform has a basic level of intelligence and additionally the hierarchy of layers aggregates the learning and intelligence at each layer.
Owner:BHADRA PRASENJIT
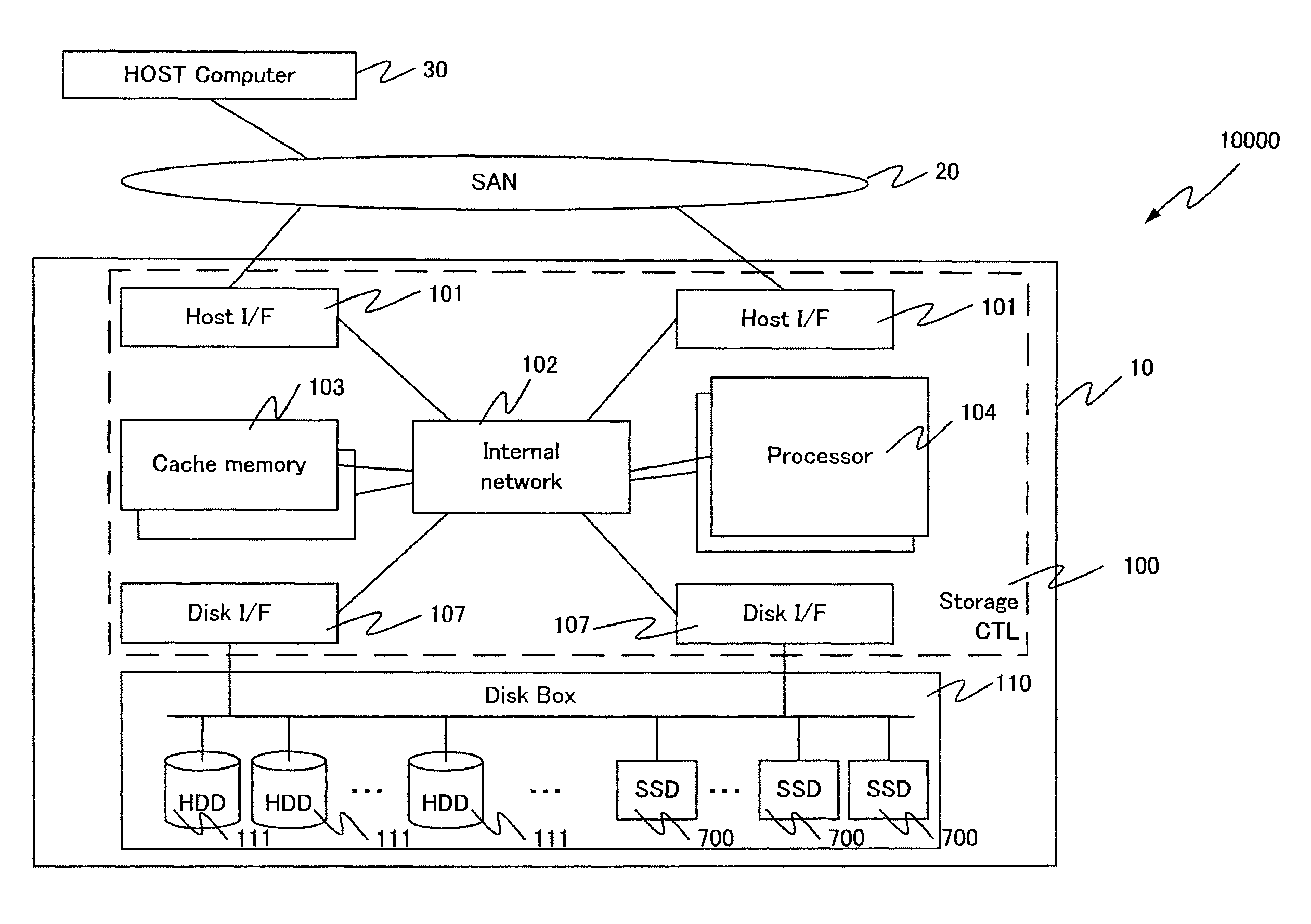
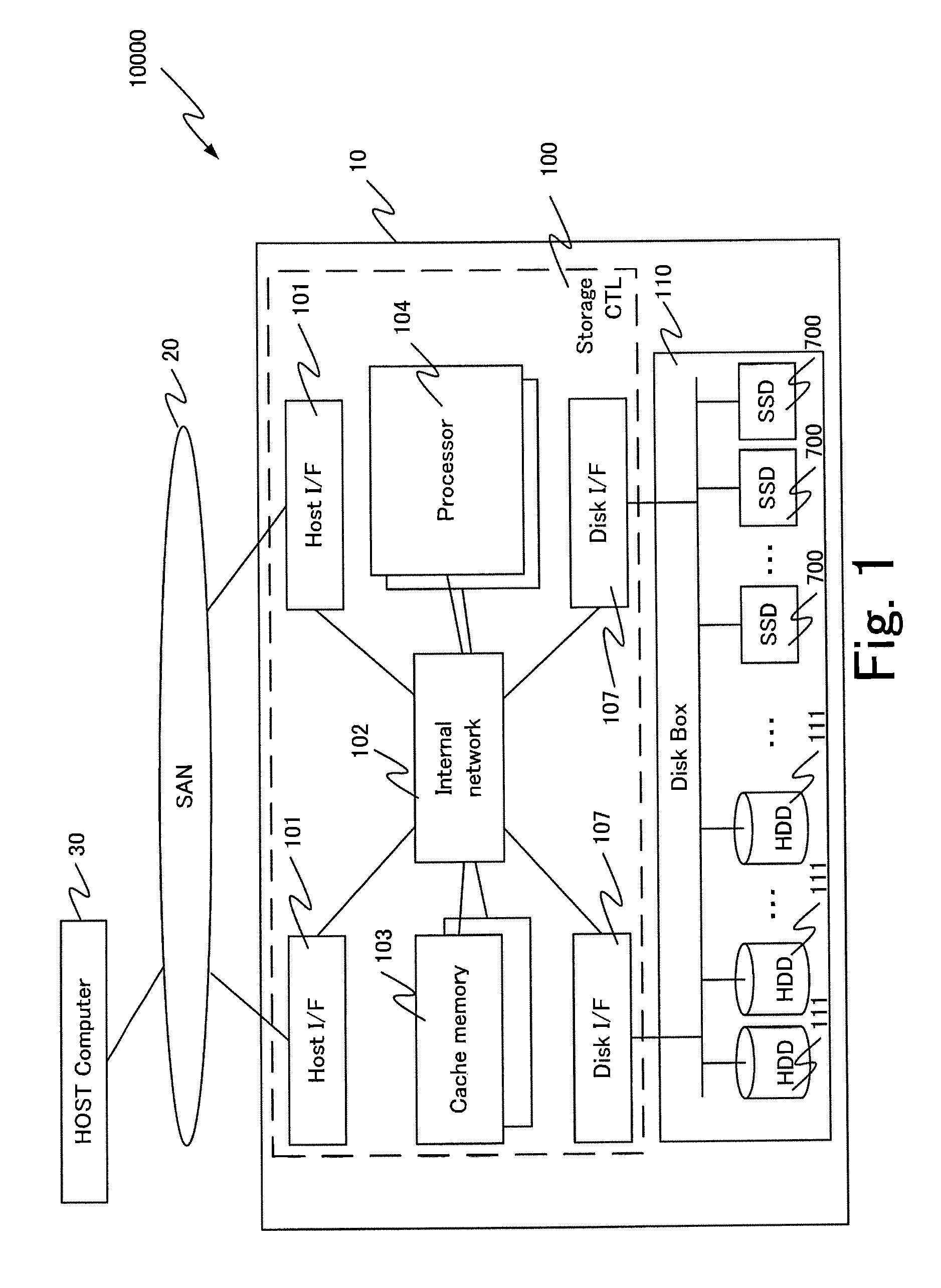
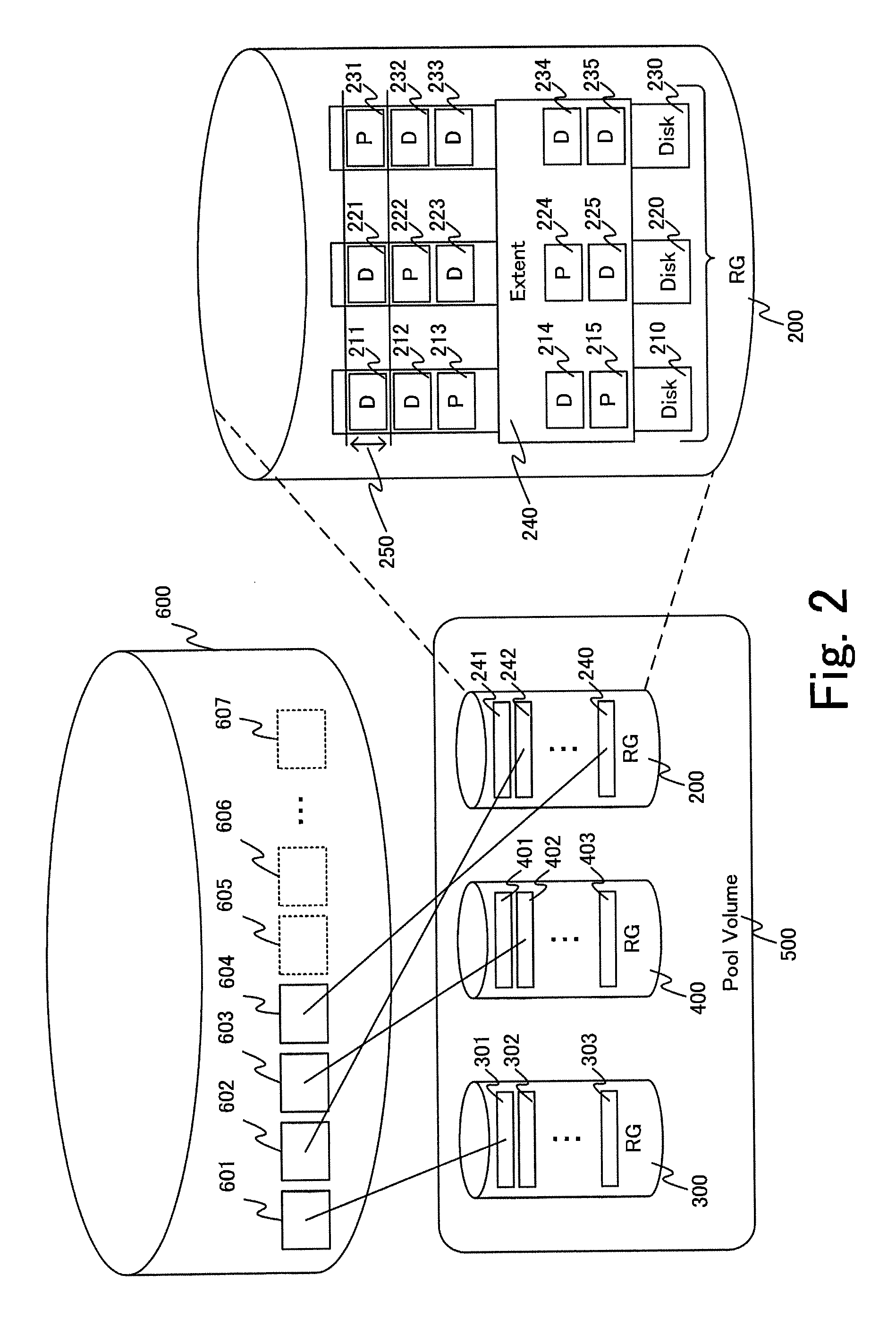
Storage apparatus provided with a plurality of nonvolatile semiconductor storage media and storage control method
ActiveUS9405478B2Increase loadHigh precisionInput/output to record carriersMemory systemsControl storeSemiconductor
A storage apparatus is provided with a plurality of nonvolatile semiconductor storage media and a storage controller that is a controller that is coupled to the plurality of semiconductor storage media. The storage controller identifies a first semiconductor storage unit that is at least one semiconductor storage media and a second semiconductor storage unit that is at least one semiconductor storage media and that is provided with a remaining length of life shorter than that of the first semiconductor storage unit based on the remaining life length information that has been acquired. The storage controller moreover identifies a first logical storage region for the first semiconductor storage unit and a second logical storage region that is provided with a write load higher than that of the first logical storage region for the second semiconductor storage unit based on the statistics information that indicates the statistics that is related to a write for every logical storage region. The storage controller reads data from the first logical storage region and the second logical storage region, and writes data that has been read from the first logical storage region to the second logical storage region and / or writes data that has been read from the second logical storage region to the first logical storage region.
Owner:HITACHI LTD
Data processing method and device
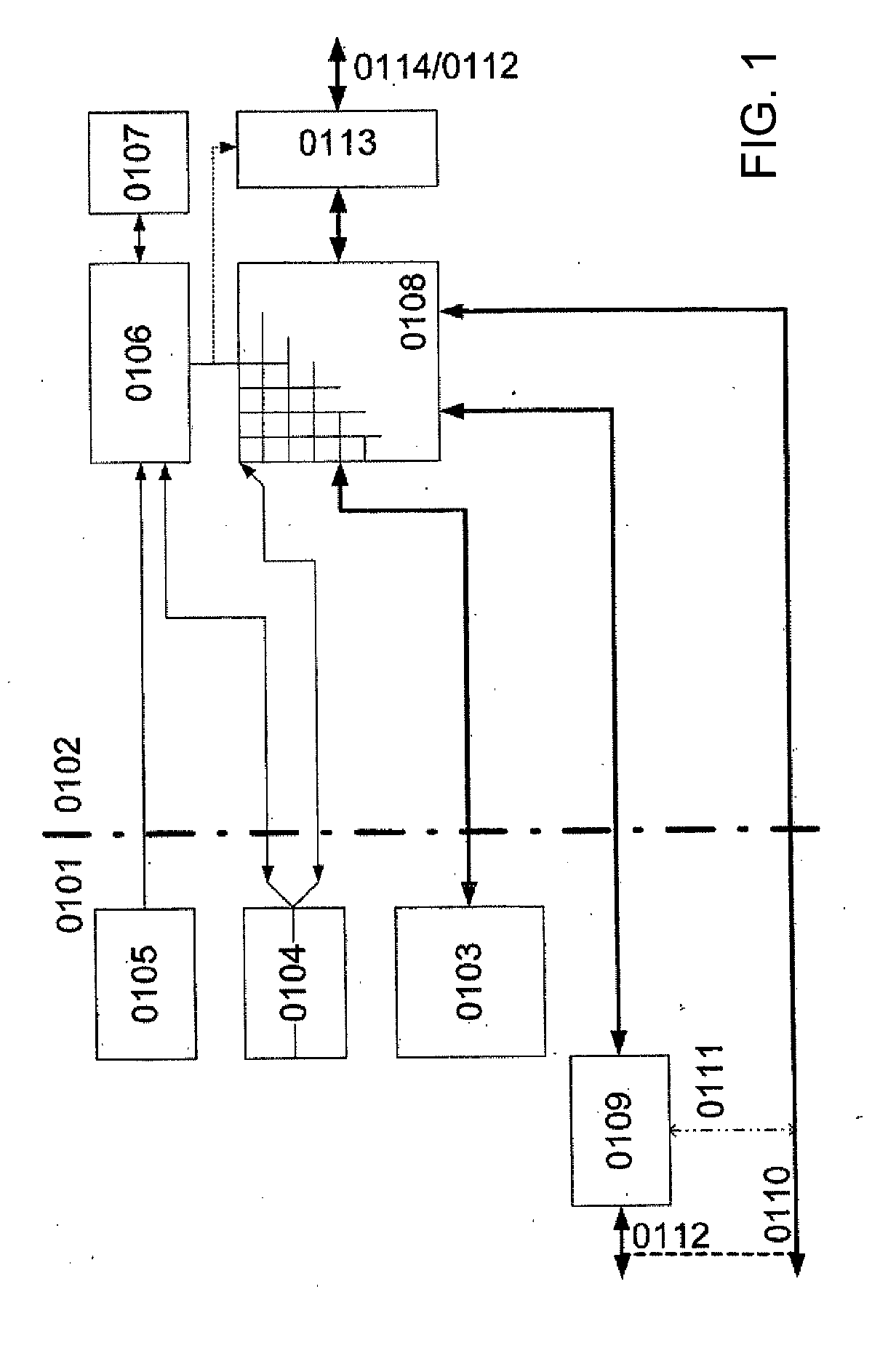
ActiveUS20070050603A1Improve data throughputDelay problemMemory adressing/allocation/relocationConcurrent instruction executionParallel computingData processing
In a data-processing method, first result data may be obtained using a plurality of configurable coarse-granular elements, the first result data may be written into a memory that includes spatially separate first and second memory areas and that is connected via a bus to the plurality of configurable coarse-granular elements, the first result data may be subsequently read out from the memory, and the first result data may be subsequently processed using the plurality of configurable coarse-granular elements. In a first configuration, the first memory area may be configured as a write memory, and the second memory area may be configured as a read memory. Subsequent to writing to and reading from the memory in accordance with the first configuration, the first memory area may be configured as a read memory, and the second memory area may be configured as a write memory.
Owner:SCIENTIA SOL MENTIS AG
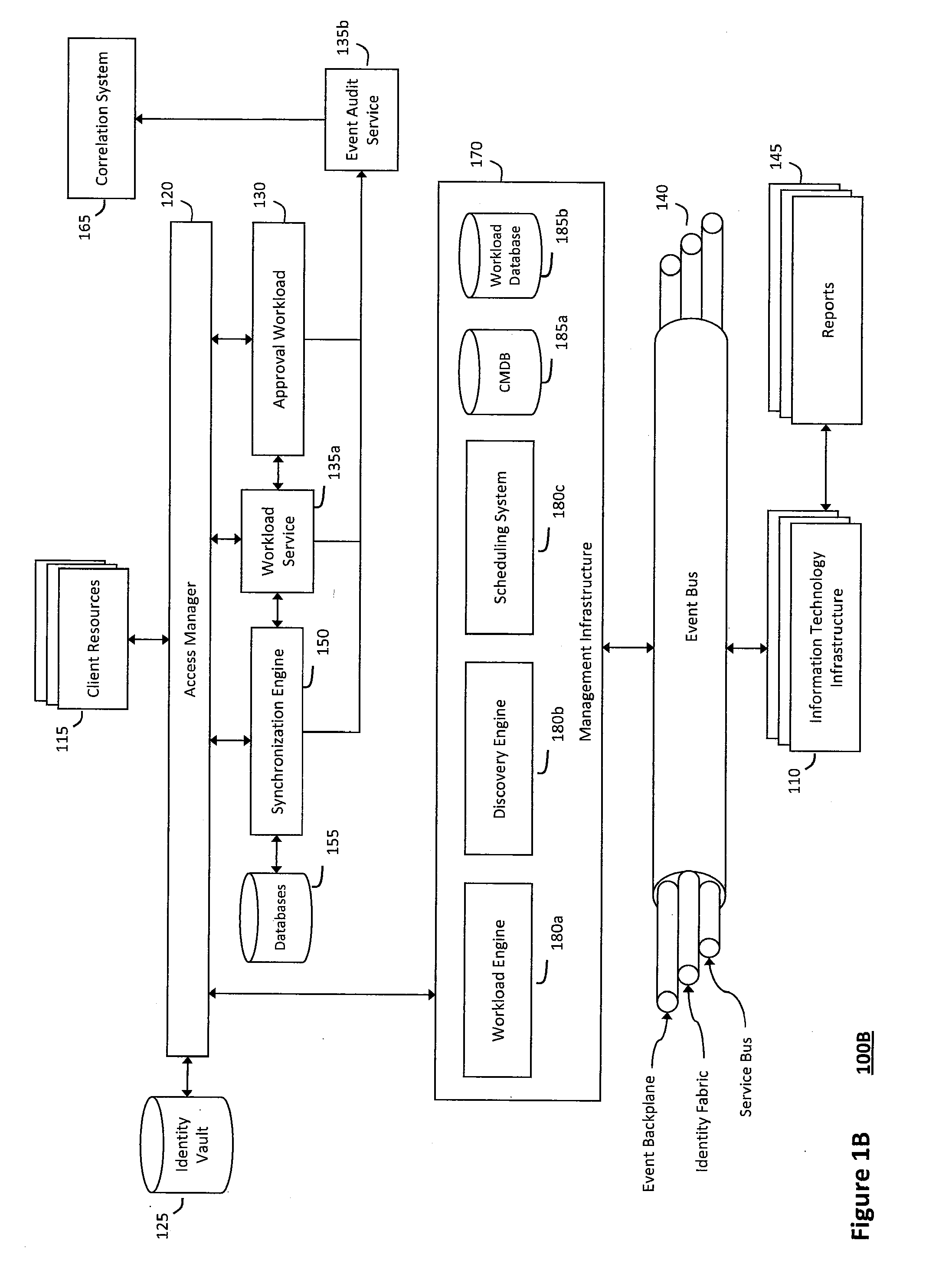
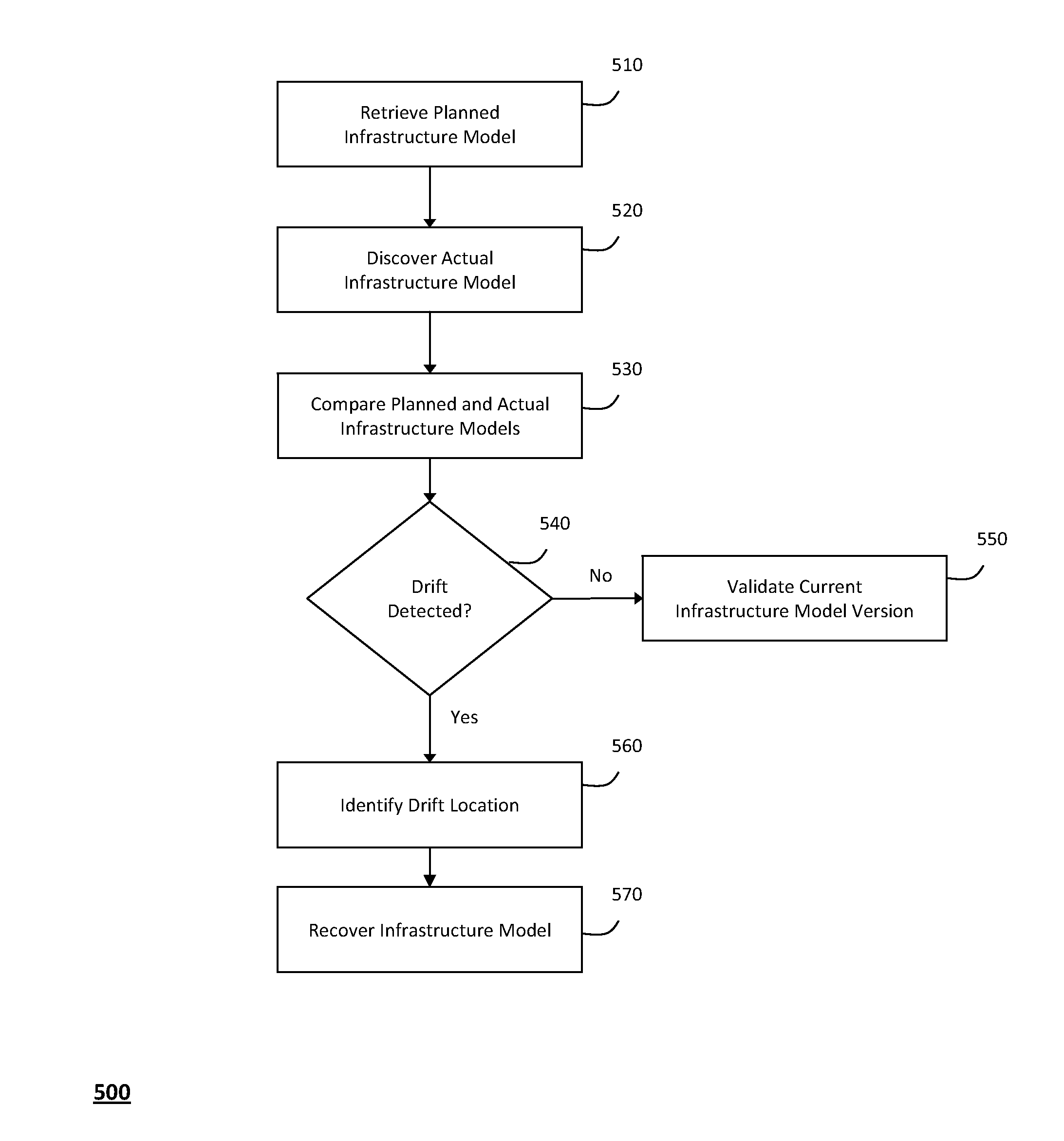
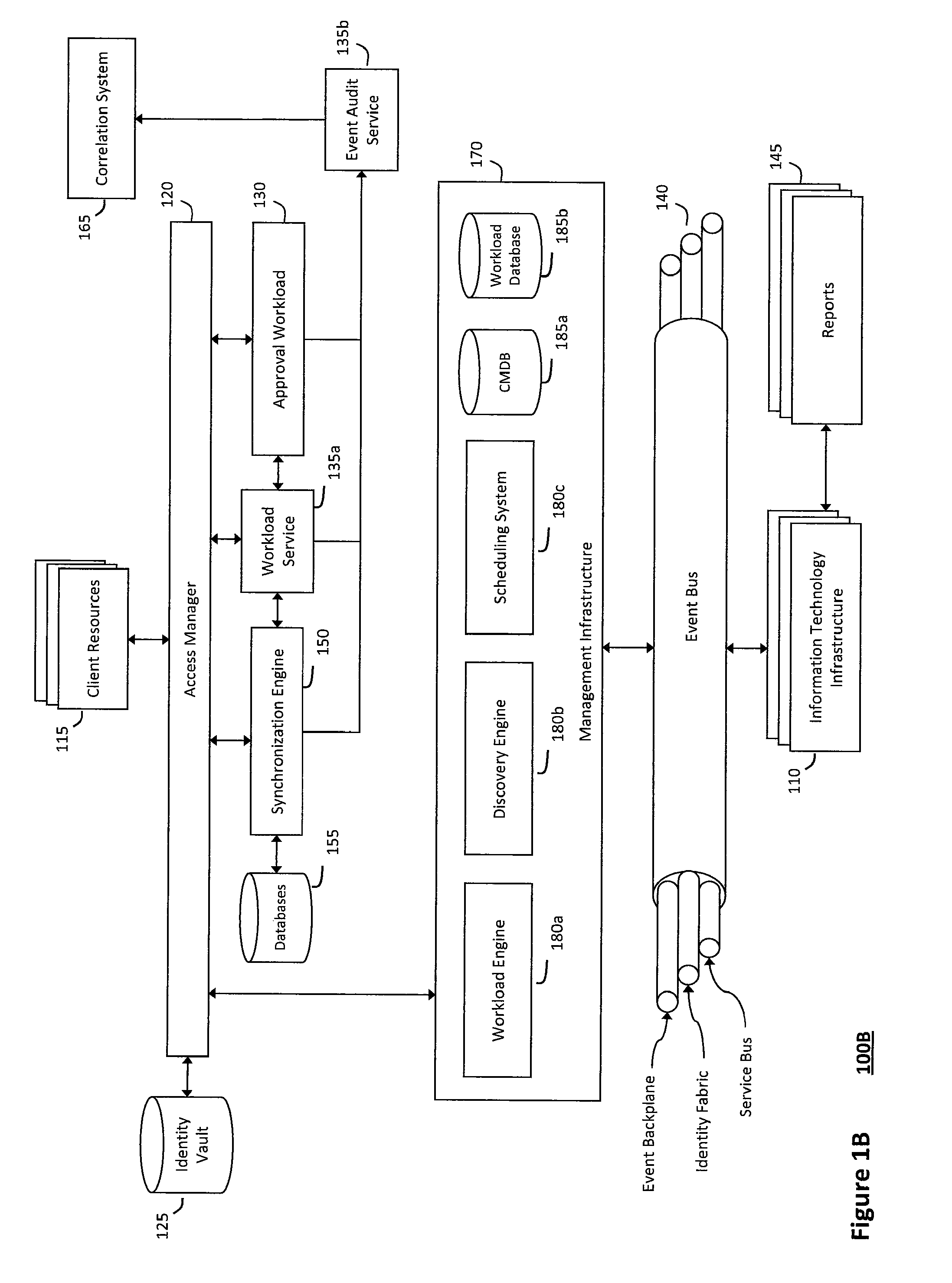
System and method for managing information technology models in an intelligent workload management system
ActiveUS20110126047A1Free computational resourceAgile and flexible managementFault responseDigital computer detailsPlanned changeService-oriented architecture
The system and method described herein for managing information technology models in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing planned changes and recovery processes for version-controlled snapshots of the information technology models. For example, a discovery engine may enrich models of an infrastructure with identity information obtained from an identity vault and the infrastructure itself, and a management infrastructure may then manage planned changes to the infrastructure model. In particular, the management infrastructure may construct implementation plans that coordinate interaction between managed entities to implement the planned changes, and may further detect drifts between operational states and planned states for the infrastructure models.
Owner:MICRO FOCUS SOFTWARE INC
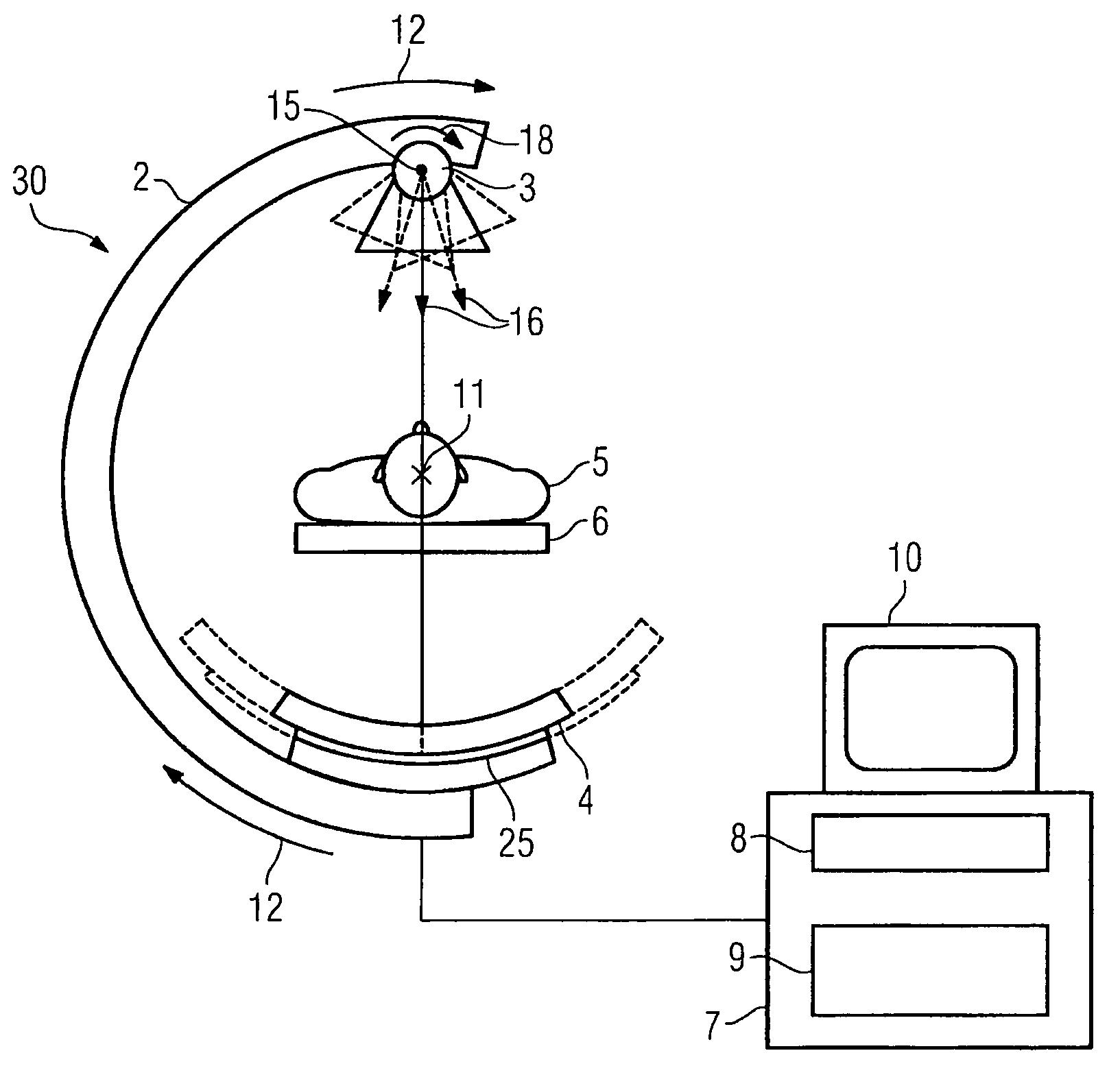
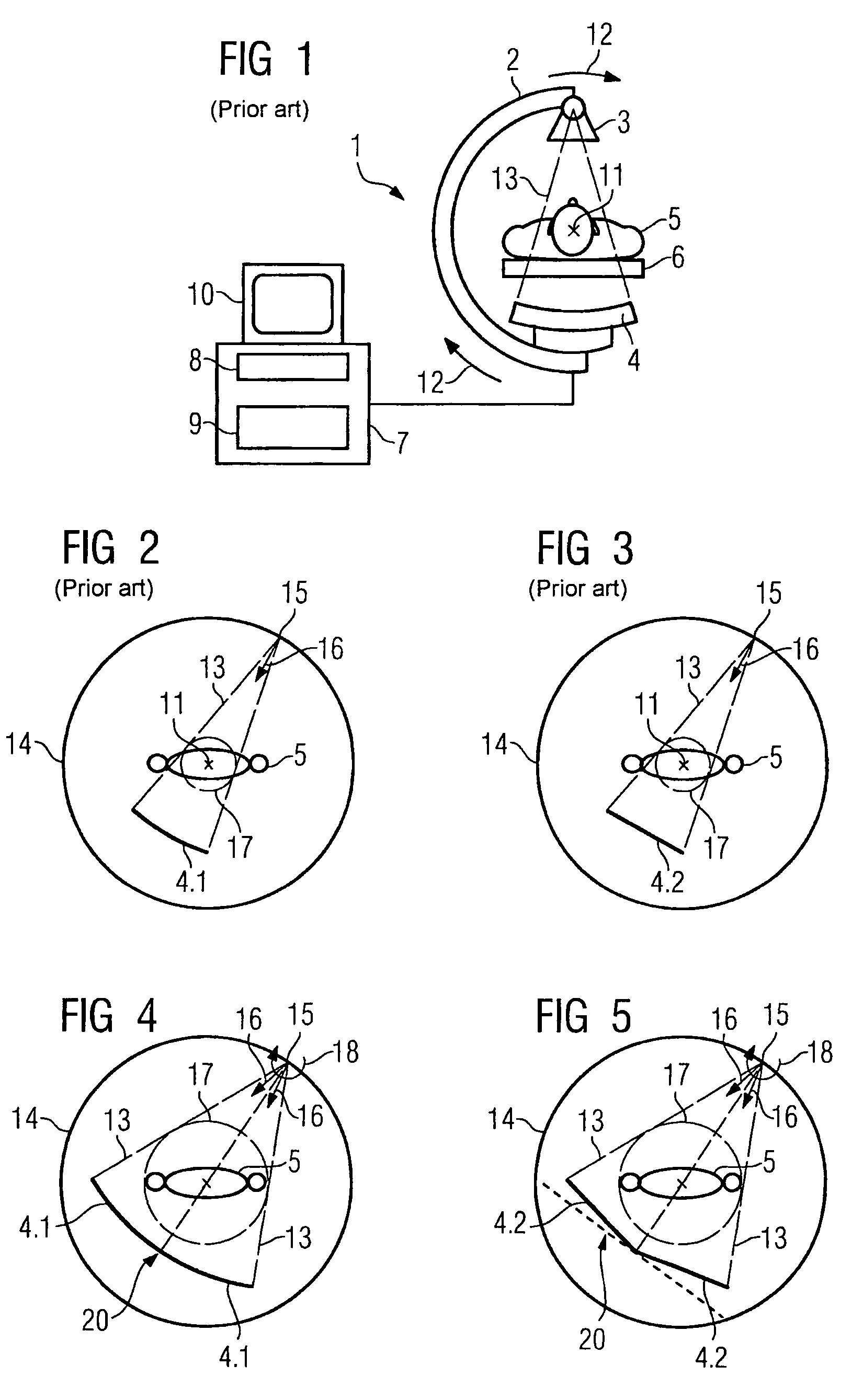
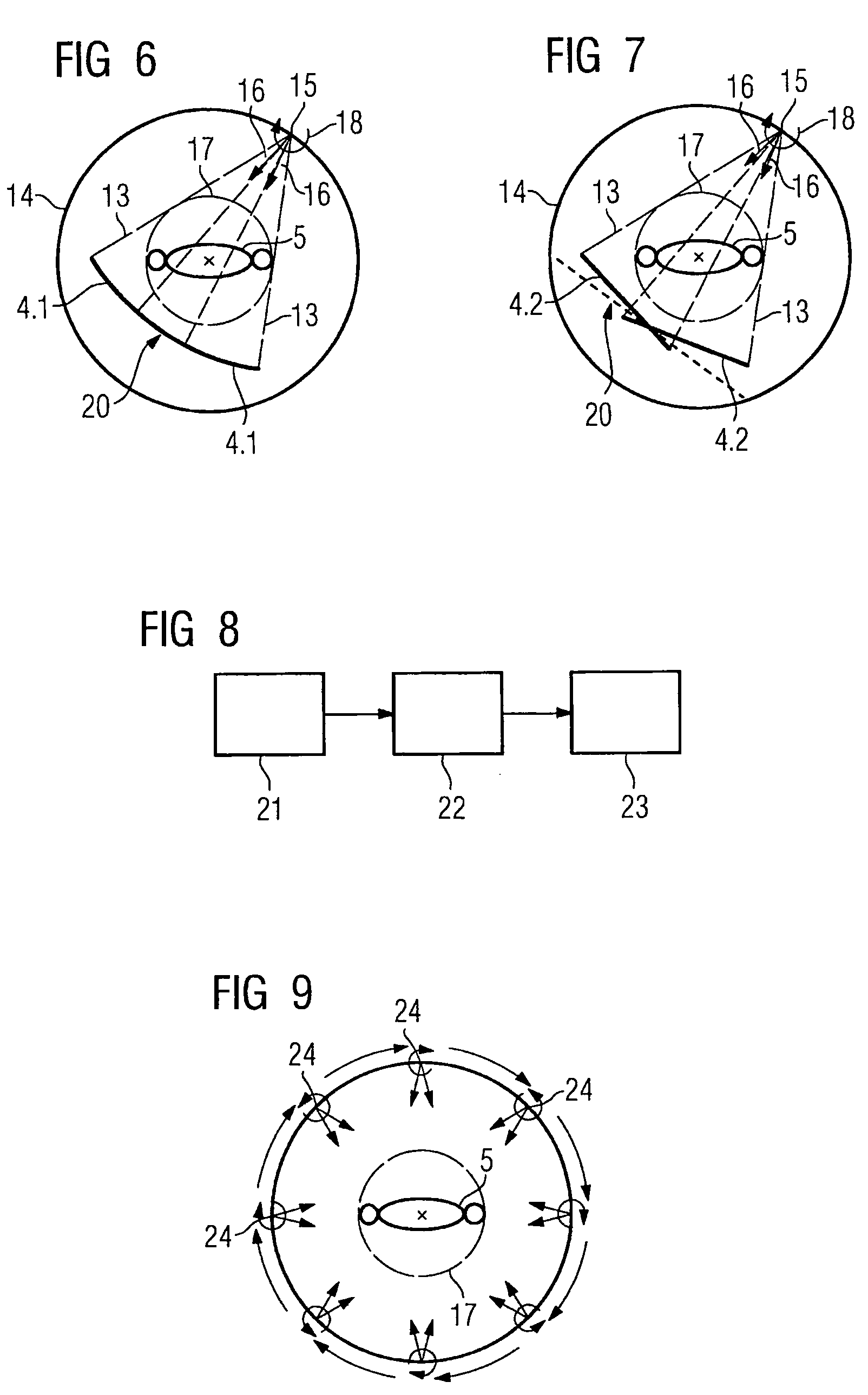
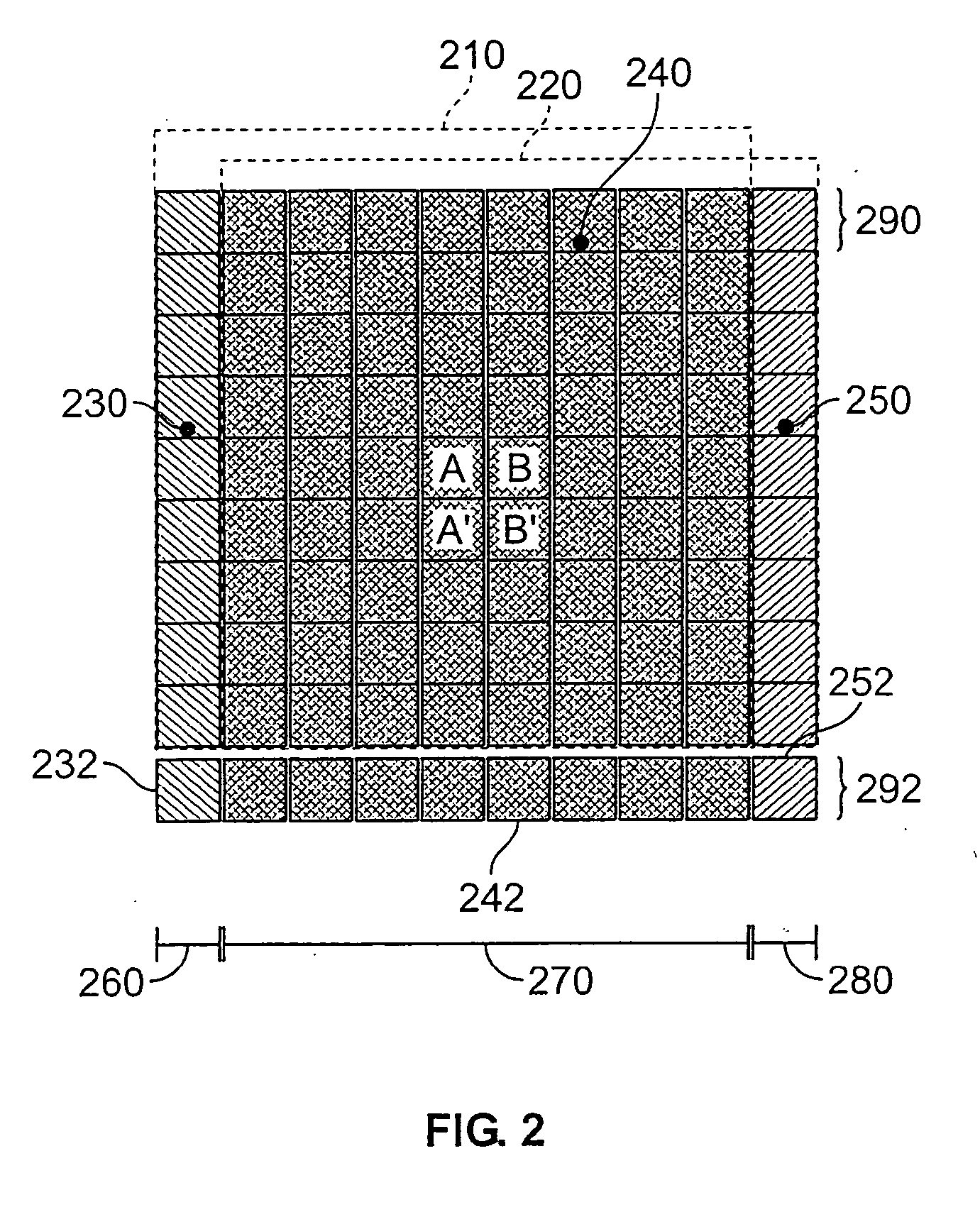
Method for reconstructing a three-dimensional image volume and x-ray devices
InactiveUS7711083B2Improve executionMaterial analysis using wave/particle radiationRadiation/particle handlingVoxelProjection image
Owner:SIEMENS HEALTHCARE GMBH
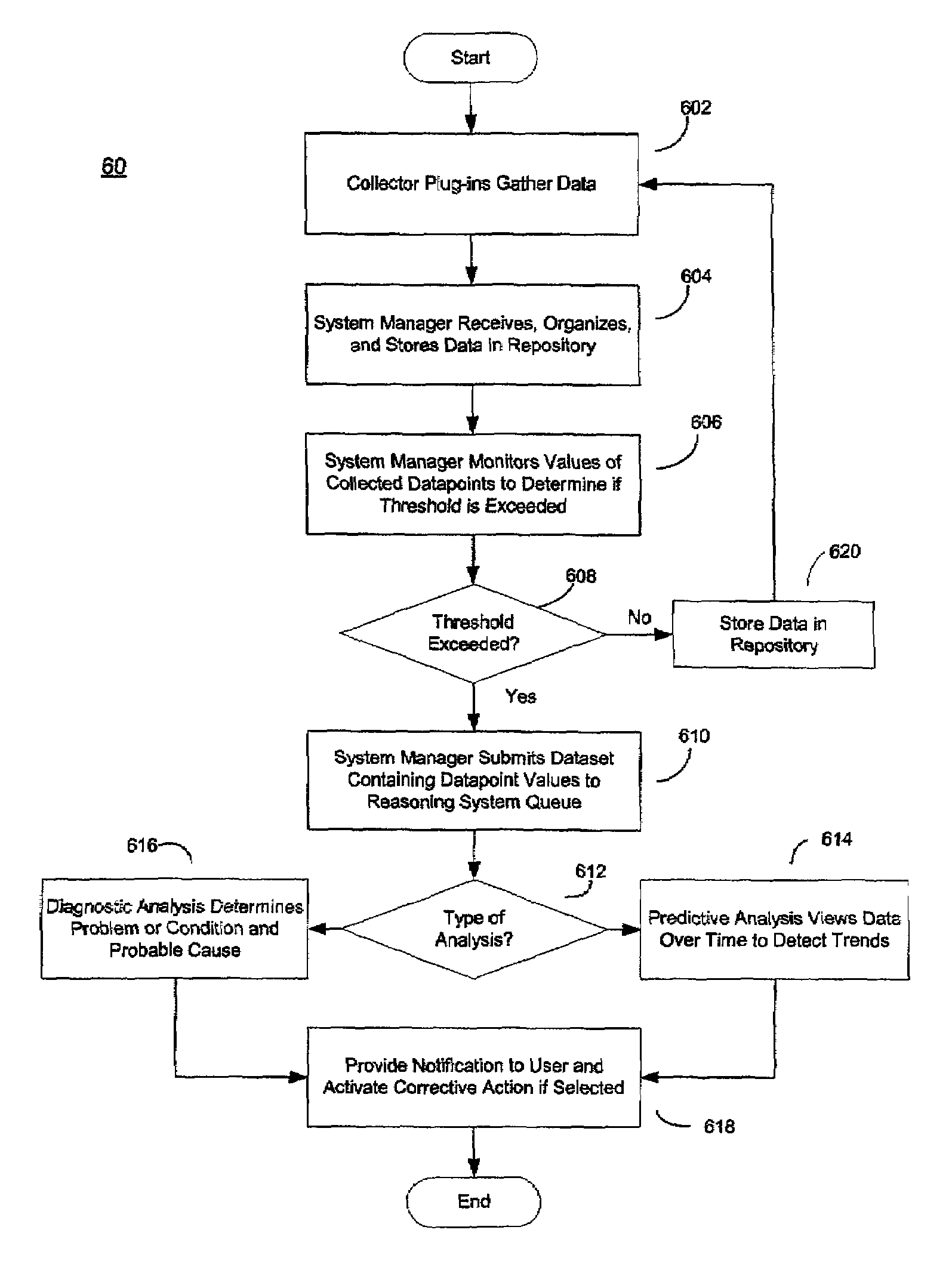
System and method for business systems transactions and infrastructure management
InactiveUS7065566B2Increase costImprove performanceDigital computer detailsBuying/selling/leasing transactionsSecure communicationCollection system
The system and method for business systems transactions and infrastructure management includes a client side collection system and a server side system having the capability to communicate with the other over a secure communication path. The collection system extracts transaction and infrastructure data from a business system and transmits the extracted data to the management server over a secure communication path. The management server receives the extracted data over the secure communication path, compares it to threshold analyzes the data that exceed threshold values, and notifies a user of the results of the analysis. The management server also has the capability to activate corrective scripts in the client business system and to reconfigure the client business system.
Owner:CA TECH INC
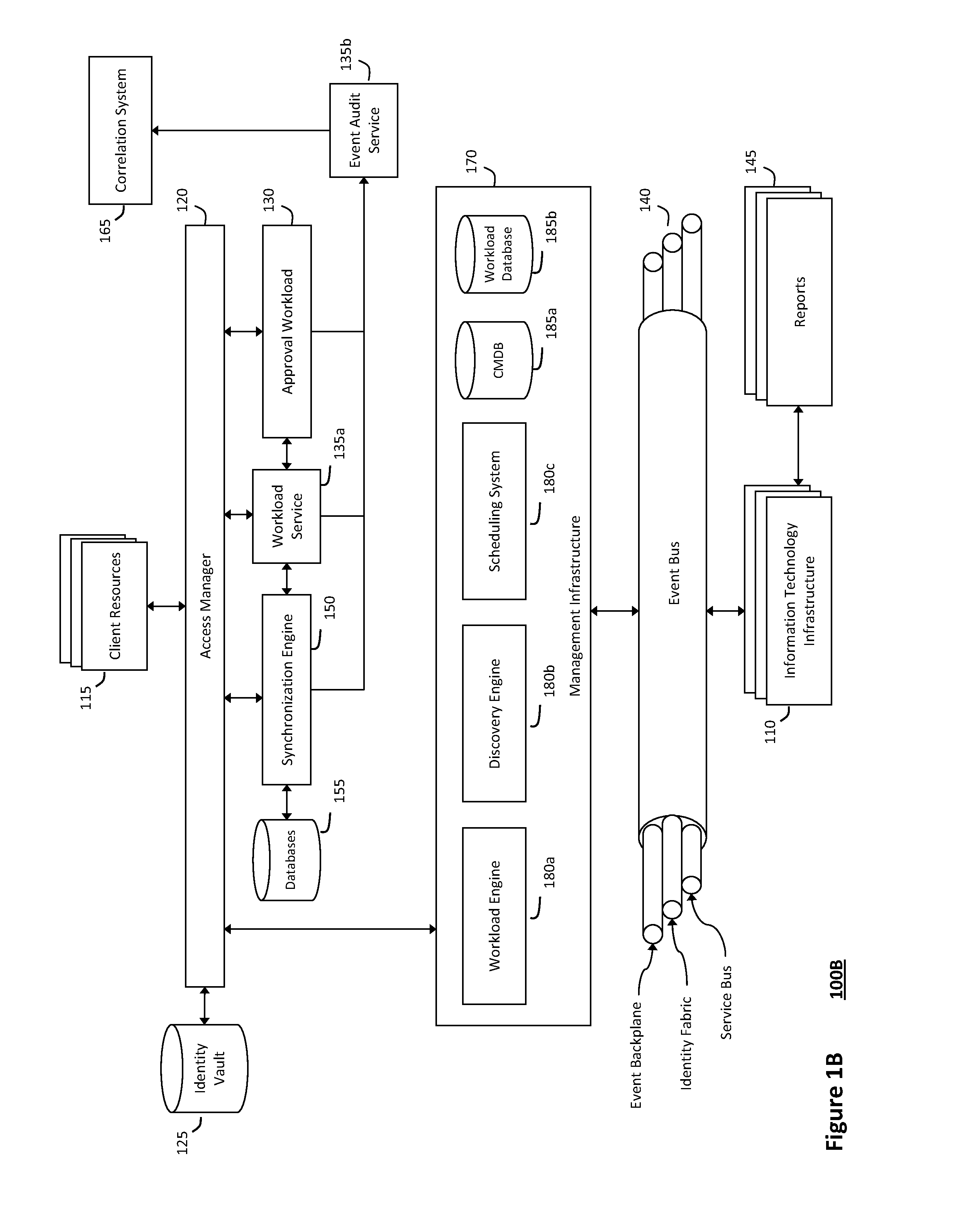
System and method for recording collaborative information technology processes in an intelligent workload management system
InactiveUS20110126099A1Free computational resourceAgile and flexible managementInput/output for user-computer interactionDigital computer detailsService-oriented architectureKnowledge management
The system and method described herein for recording collaborative information technology processes in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may include one or more data structures that converge information describing interaction between managed entities and content that may relate to such interaction in time-ordered series of events. The time-ordered event stream may then be replayed in a real-time stream to remediate, roll back, or otherwise analyze the collaborative information technology processes.
Owner:MICRO FOCUS SOFTWARE INC
System and method for providing annotated service blueprints in an intelligent workload management system
InactiveUS8448170B2Agile and flexible managementMove efficiently through the infrastructureMultiprogramming arrangementsDigital data authenticationService blueprintService-oriented architecture
The system and method described herein for providing annotated service blueprints in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for creating annotated service blueprints to provision and manage tessellated services distributed within an information technology infrastructure. For example, in response to a request to provision a service, a service blueprint describing one or more virtual machines may be created. The service blueprint may then be annotated to apply various parameters to the virtual machines, and the annotated service blueprint may then be instantiated to orchestrate the virtual machines with the one or more parameters and deploy the orchestrated virtual machines on information technology resources allocated to host the requested service, thereby provisioning the requested service.
Owner:MICRO FOCUS SOFTWARE INC
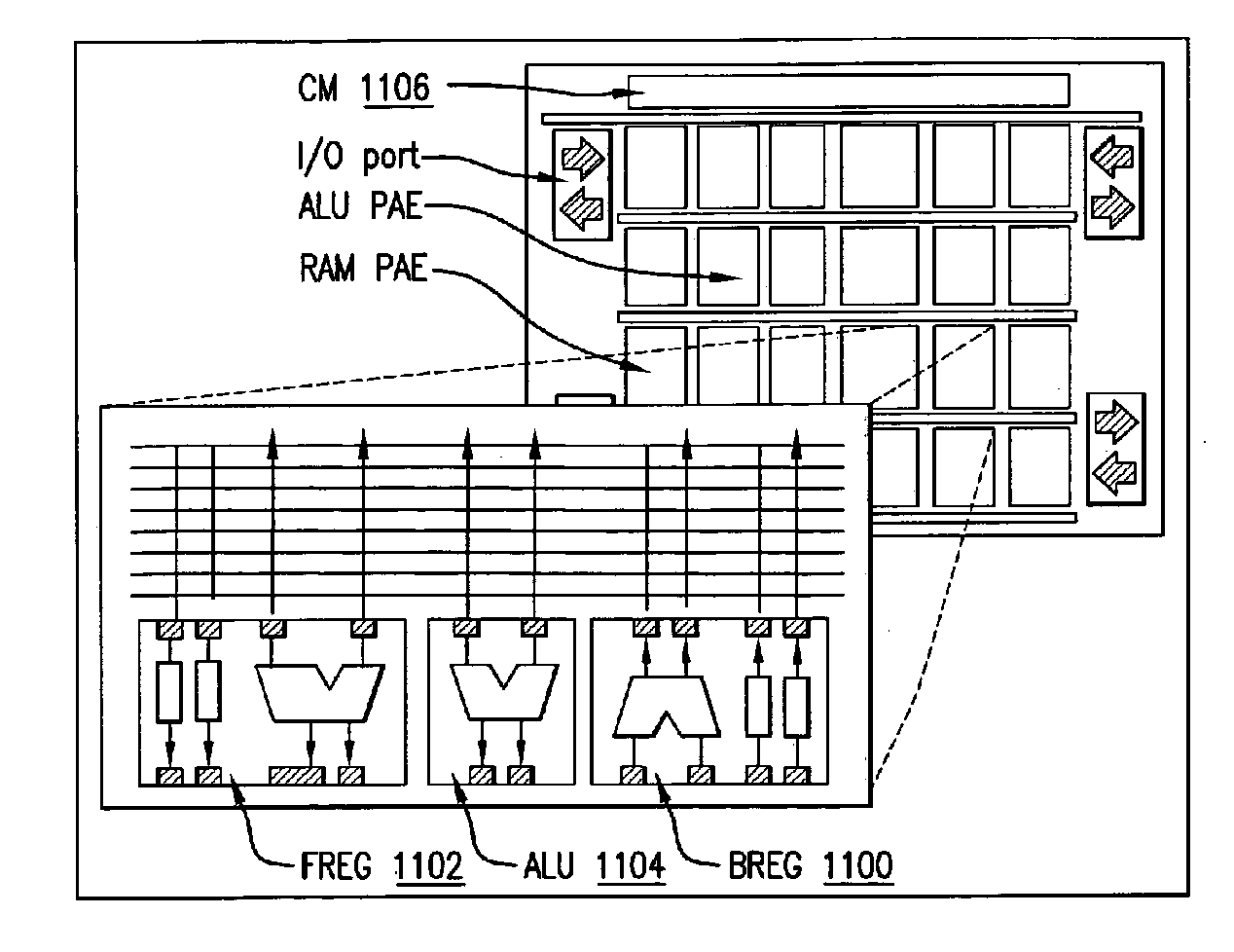
Data Processing System Having Integrated Pipelined Array Data Processor
InactiveUS20150106596A1Improve executionImprove performanceMemory architecture accessing/allocationInstruction analysisData processing systemParallel computing
A data processing system having a data processing core and integrated pipelined array data processor and a buffer for storing list of algorithms for processing by the pipelined array data processor.
Owner:SCIENTIA SOL MENTIS AG
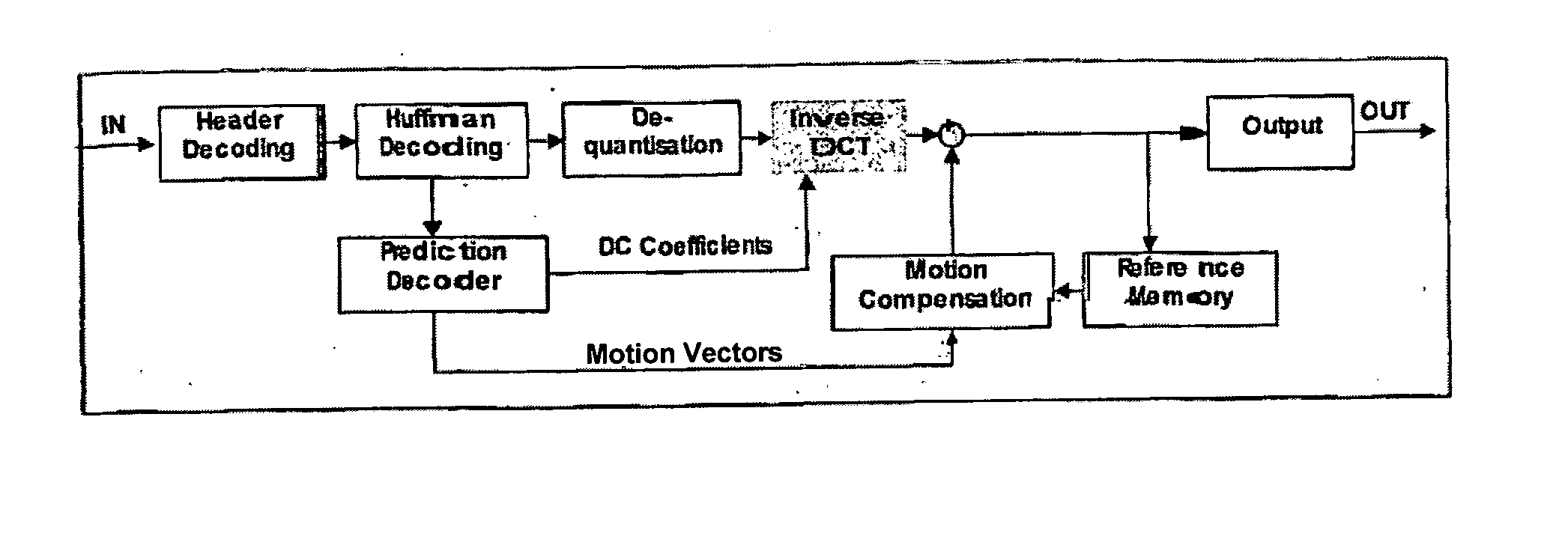
Method and apparatus for processing image data
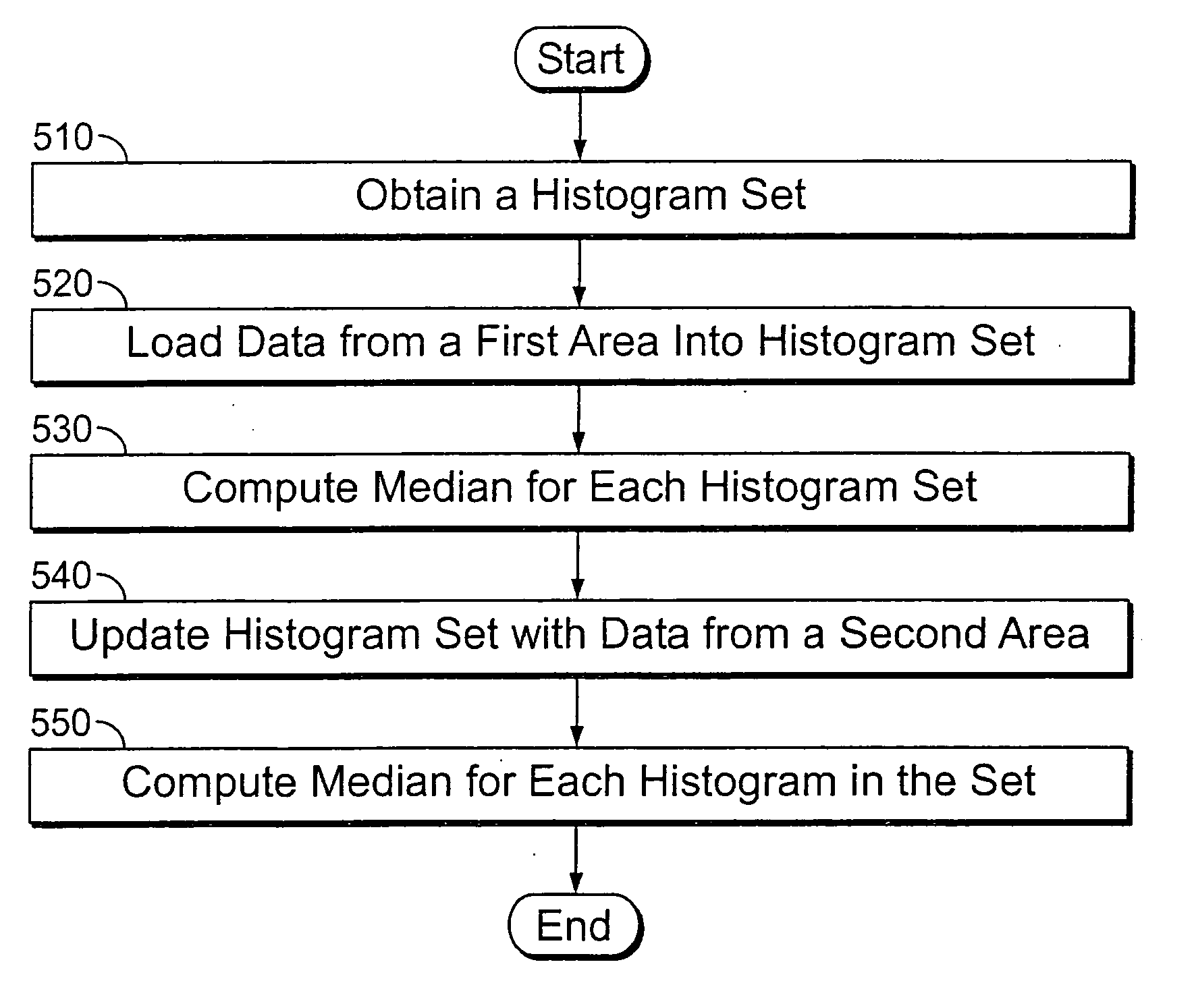
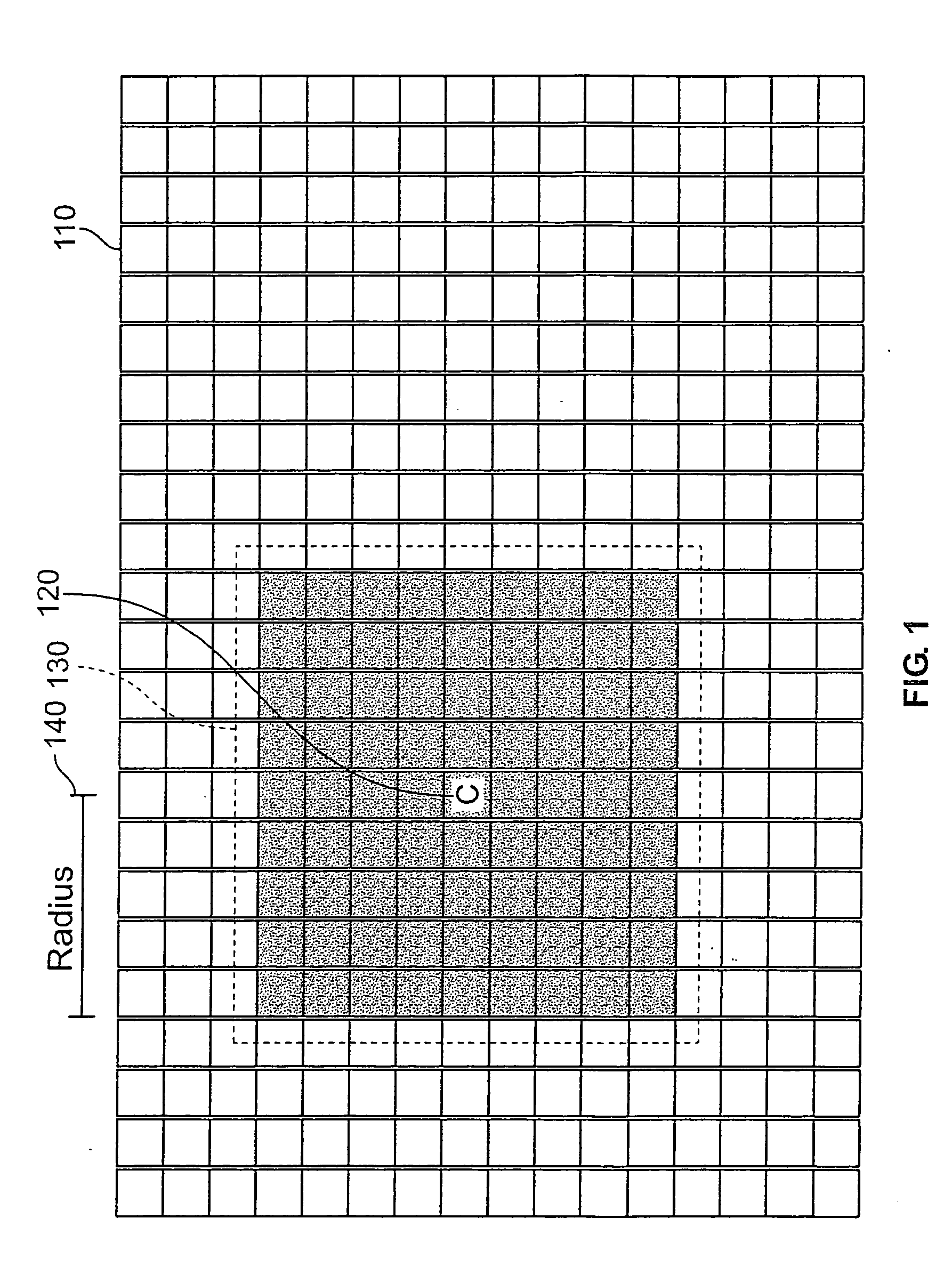
InactiveUS20060110063A1Improve executionIncrease speedImage enhancementTelevision system detailsImaging processingImage resolution
The invention is a method and apparatus for improving image-processing applications. Embodiments of the invention provide methods for preserving computation results and offer intermediary computation steps to allow the processing of images at any location to take advantage of previously processed image areas. The preferred embodiment offers a method for building a median filter that significantly improves the processing speed over basic techniques. By building a histogram hierarchy, image data statistics are added and subtracted using a multiplicity of histograms from the histogram hierarchy, where each histogram describes an image area. Furthermore, a histogram hierarchy is built using multiple layers, each layer defining a level of statistical resolution.
Owner:SHELL & SLATE SOFTWARE
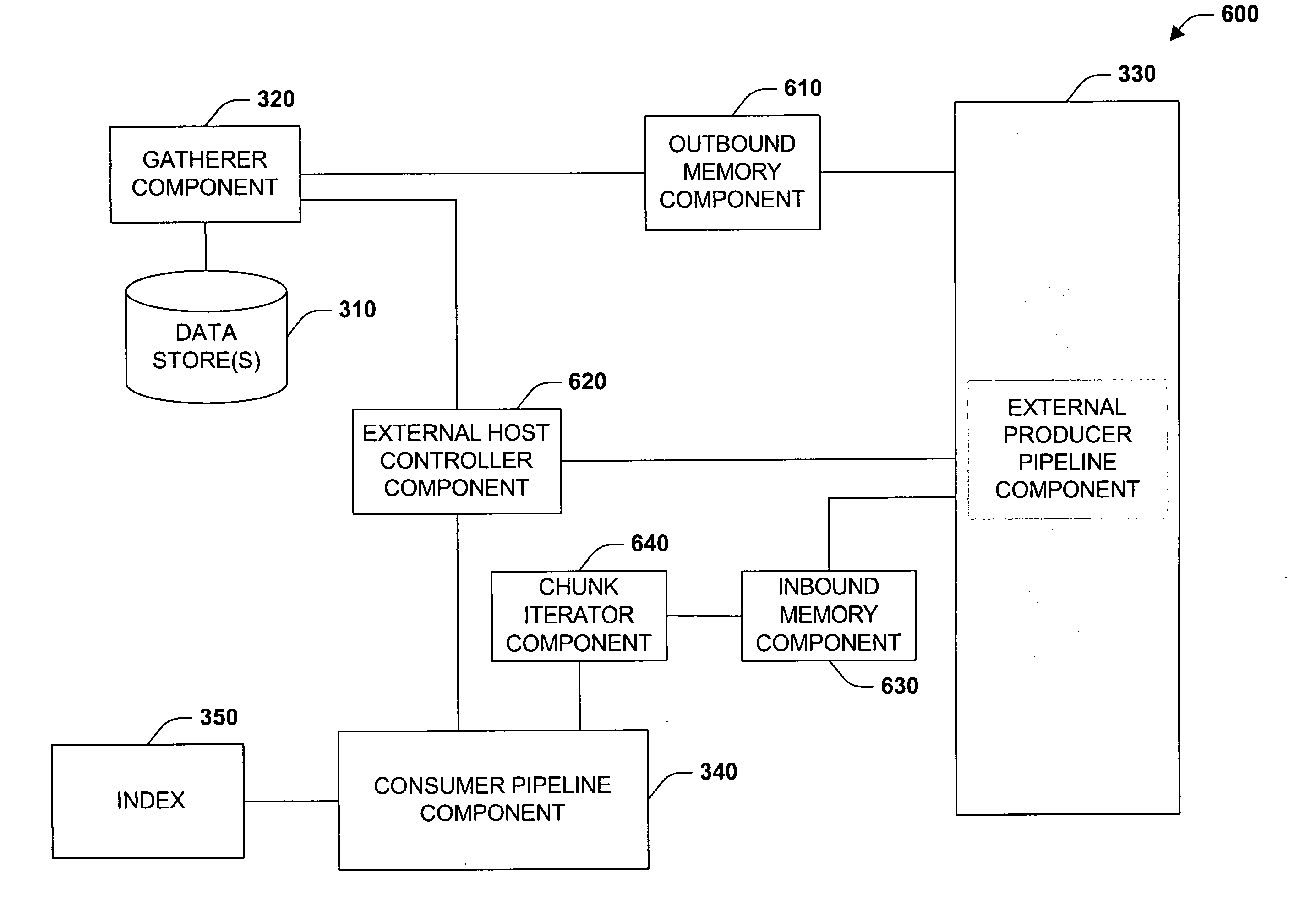
Integrated full text search system and method
ActiveUS20050222975A1Improve execution of queryEnhance manageabilityData processing applicationsWeb data indexingFull text searchMetadata
The present invention relates to an integrated full-text search architecture that integrates full text search with database server applications in a tight manner so that it becomes part of the server in all aspects including storage, metadata, query processing, back / up restore and resource management. This provides improved performance with respect to queries as well as improved manageability. Furthermore, the subject architecture is open and schema directed unlike other conventional full-text search architectures. Accordingly, the full-text search architecture enables expert users (e.g., search providers) to define their own index structures as well as ranking algorithms.
Owner:MICROSOFT TECH LICENSING LLC
System and method for providing virtual desktop extensions on a client desktop
ActiveUS8468455B2Simplify complexityProvide capabilityDigital data processing detailsInterprogram communicationClient-sideCloud computing
The system and method described herein may identify one or more virtual desktop extensions available in a cloud computing environment and launch virtual machine instances to host the available virtual desktop extensions in the cloud. For example, a virtual desktop extension manager may receive a virtual desktop extension request from a client desktop and determine whether authentication credentials for the client desktop indicate that the client desktop has access to the requested virtual desktop extension. In response to authenticating the client desktop, the virtual desktop extension manager may then launch a virtual machine instance to host the virtual desktop extension in the cloud and provide the client desktop with information for locally controlling the virtual desktop extension remotely hosted in the cloud.
Owner:MICRO FOCUS SOFTWARE INC
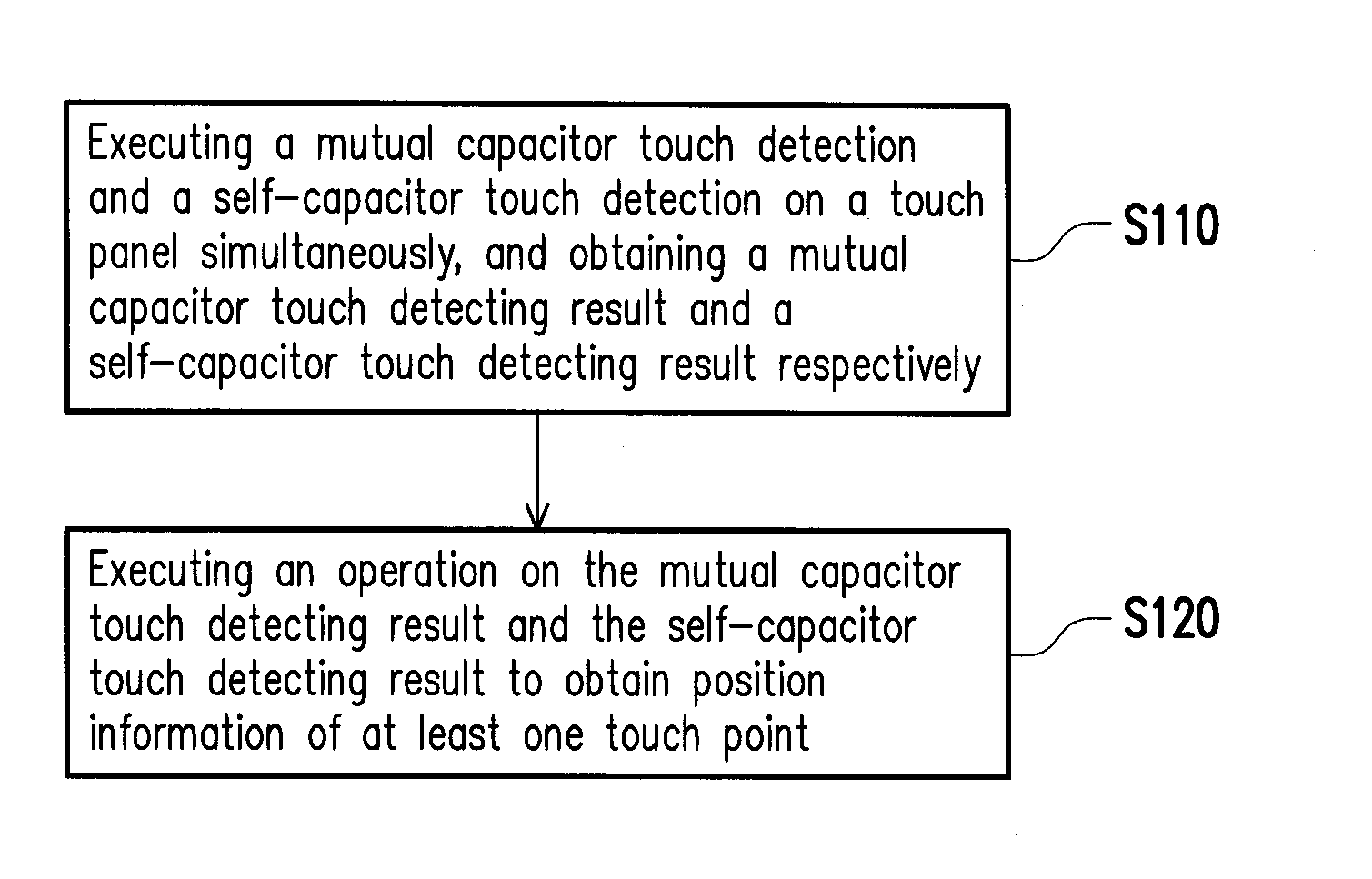
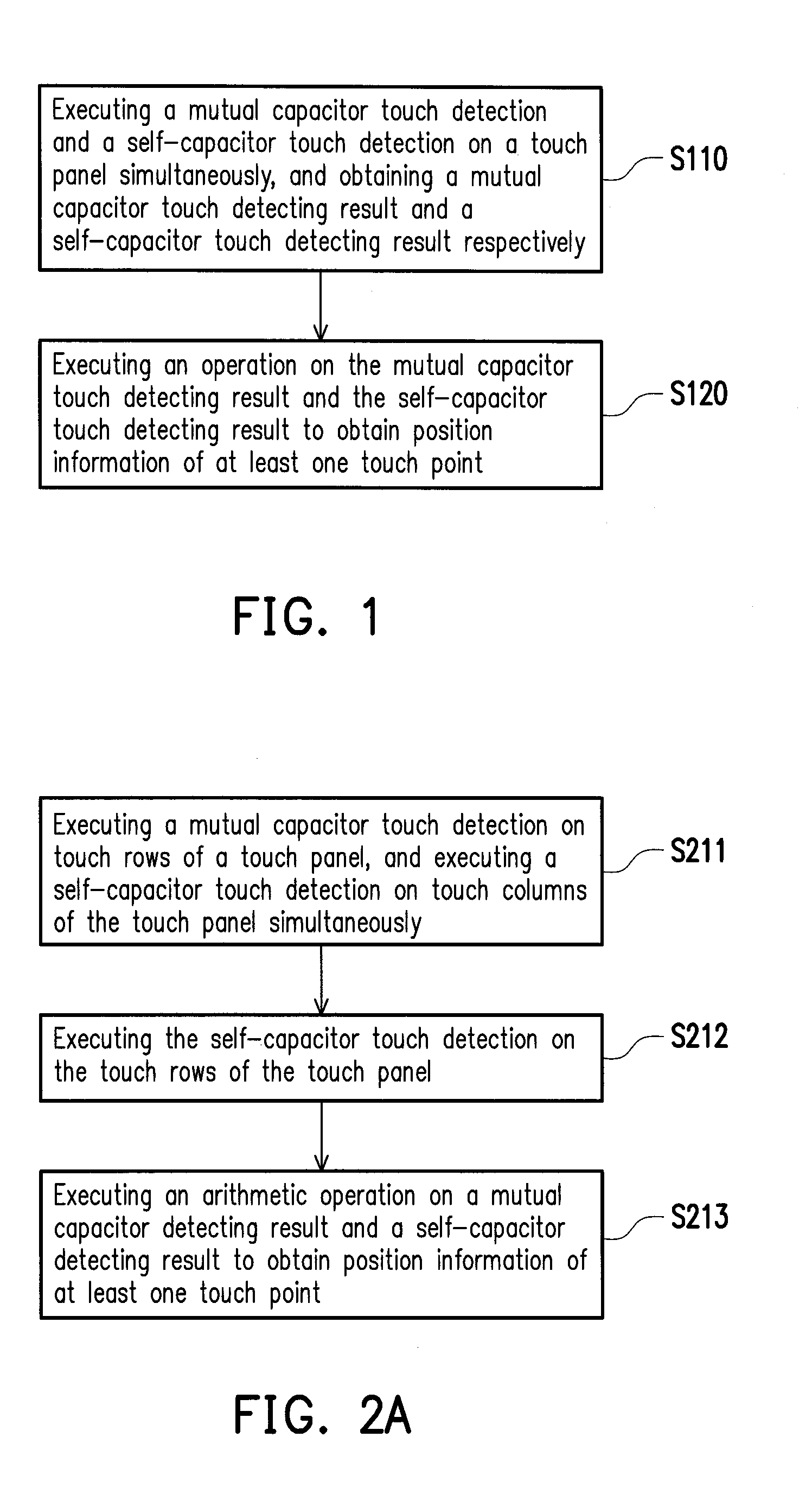
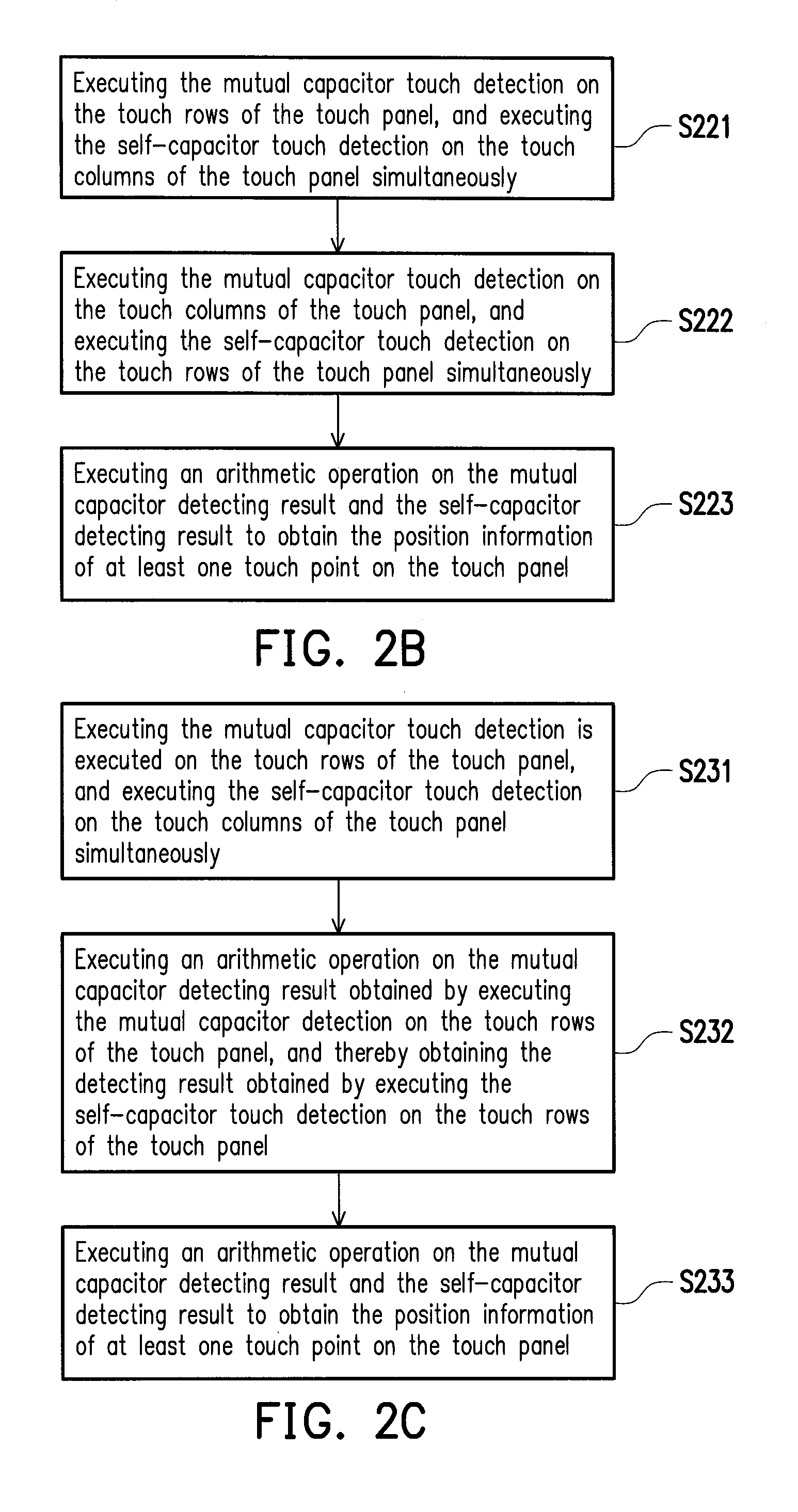
Touch control detecting apparatus and method thereof
InactiveUS20150091847A1Improve efficiencyImprove executionInput/output processes for data processingCapacitanceTouchscreen
A touch control detecting apparatus and method are provided. The touch control detecting method is adapted for a touch panel which has a plurality of touch rows and touch columns. The touch control detecting method includes: executing a mutual capacitor touch detection and a self-capacitor touch detection on the touch panel simultaneously, and obtaining a mutual capacitor touch detecting result and a self-capacitor touch detecting result respectively; and then executing an operation on the mutual capacitor touch detecting result and the self-capacitor touch detecting result to obtain position information of at least one touch point on the touch panel.
Owner:NOVATEK MICROELECTRONICS CORP
Data processing method and device
ActiveUS8156284B2Improve executionImprove performanceMemory adressing/allocation/relocationConcurrent instruction executionParallel computingRead-write memory
In a data-processing method, first result data may be obtained using a plurality of configurable coarse-granular elements, the first result data may be written into a memory that includes spatially separate first and second memory areas and that is connected via a bus to the plurality of configurable coarse-granular elements, the first result data may be subsequently read out from the memory, and the first result data may be subsequently processed using the plurality of configurable coarse-granular elements. In a first configuration, the first memory area may be configured as a write memory, and the second memory area may be configured as a read memory. Subsequent to writing to and reading from the memory in accordance with the first configuration, the first memory area may be configured as a read memory, and the second memory area may be configured as a write memory.
Owner:SCIENTIA SOL MENTIS AG
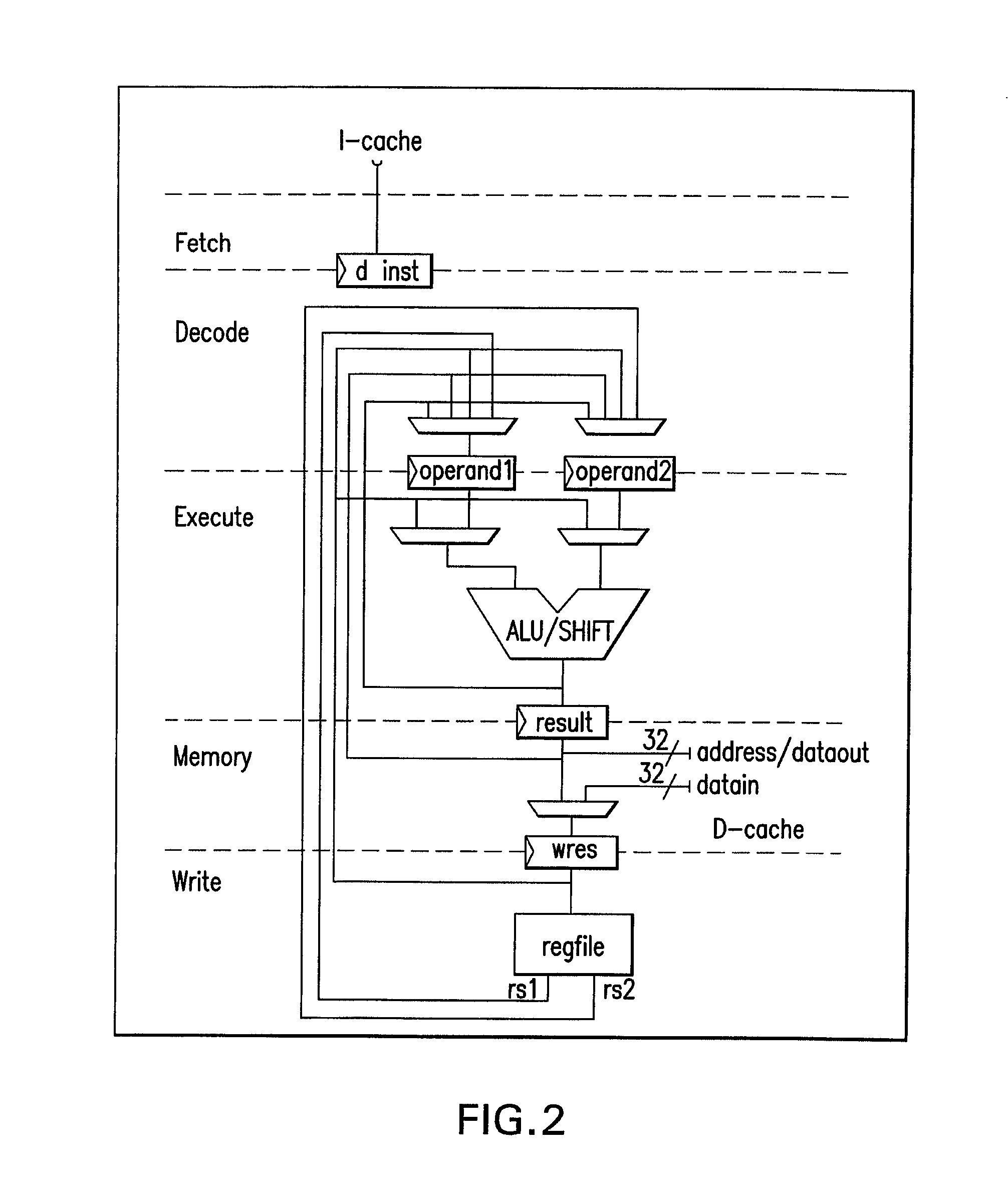
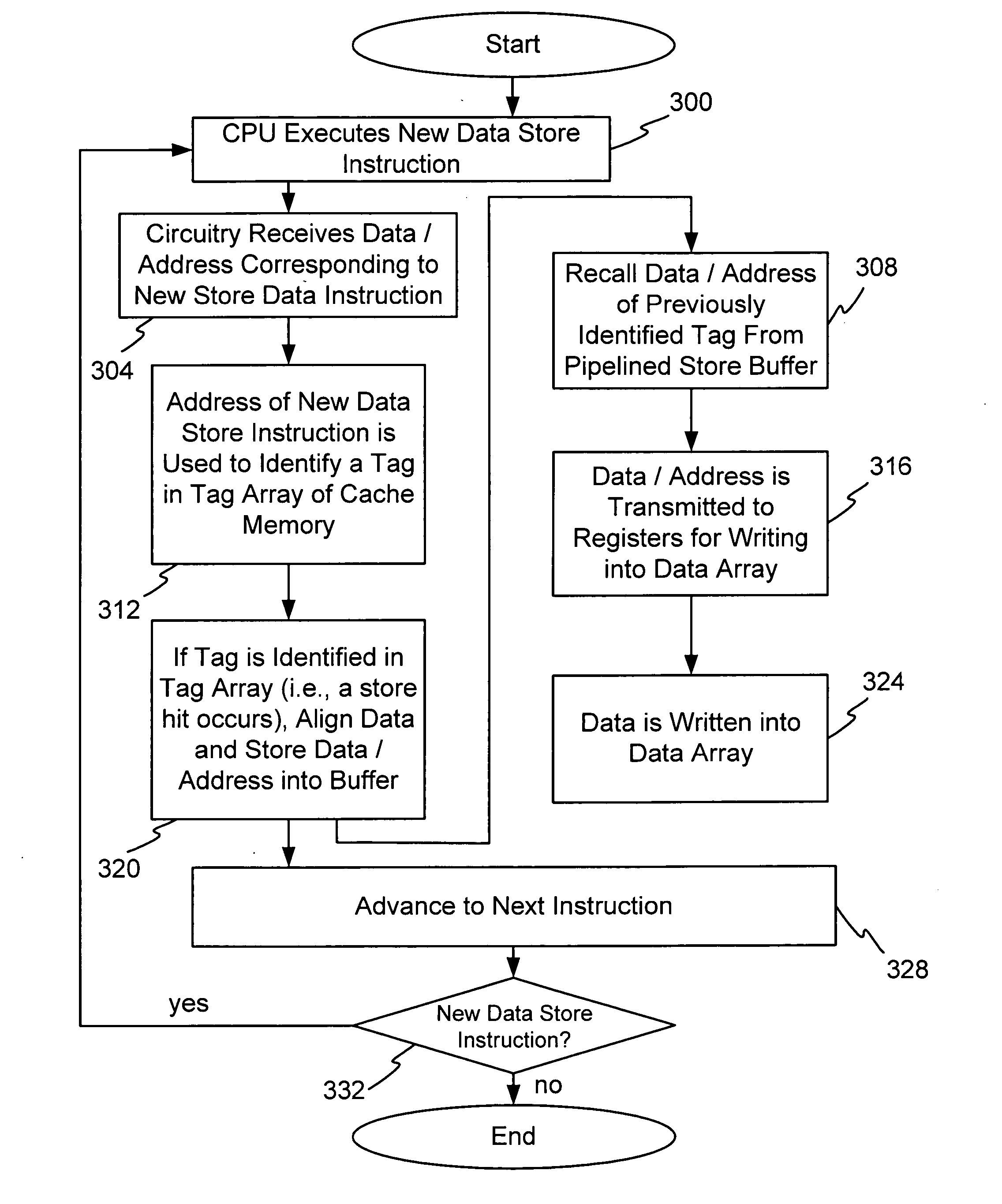
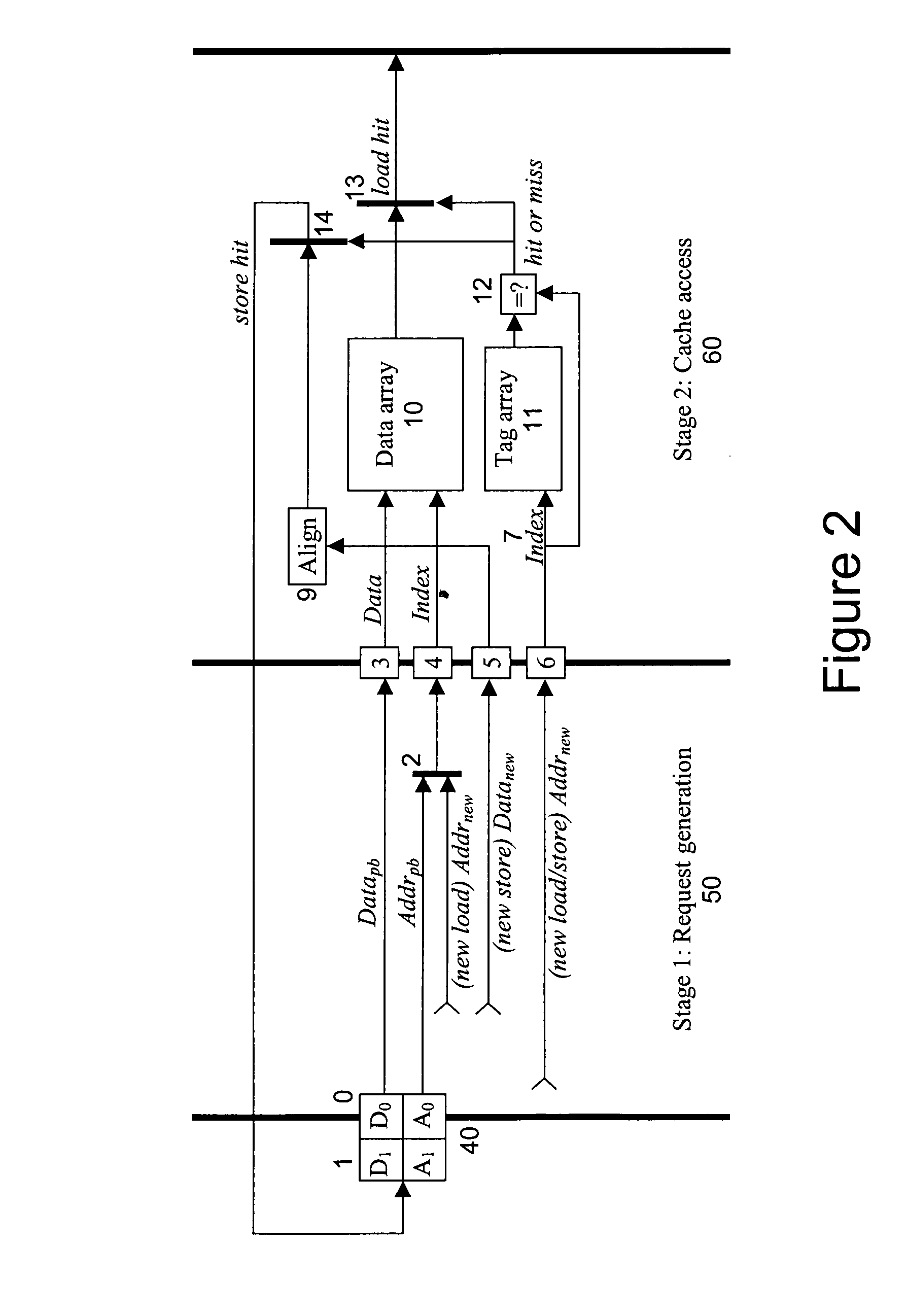
System for supporting unlimited consecutive data stores into a cache memory
InactiveUS20050015552A1Improve executionEfficient processingMemory adressing/allocation/relocationDigital computer detailsParallel computingData storing
One or more methods and systems of improving the performance of consecutive data stores into a cache memory are presented. In one embodiment, the method comprises writing data into a data array associated with at least a first store instruction while accessing a tag in a tag array associated with at least a second store instruction. In one embodiment, the method of processing consecutive data stores into a cache memory comprises updating a first data in a cache memory while concurrently looking up or identifying a second data in the cache memory. In one embodiment, a system for improving the execution of data store instructions of a CPU comprises a pipelined buffer using a minimal number of data entries, a data array used for updating data associated with a first store instruction, and a tag array used for looking up data associated with a second store instruction.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
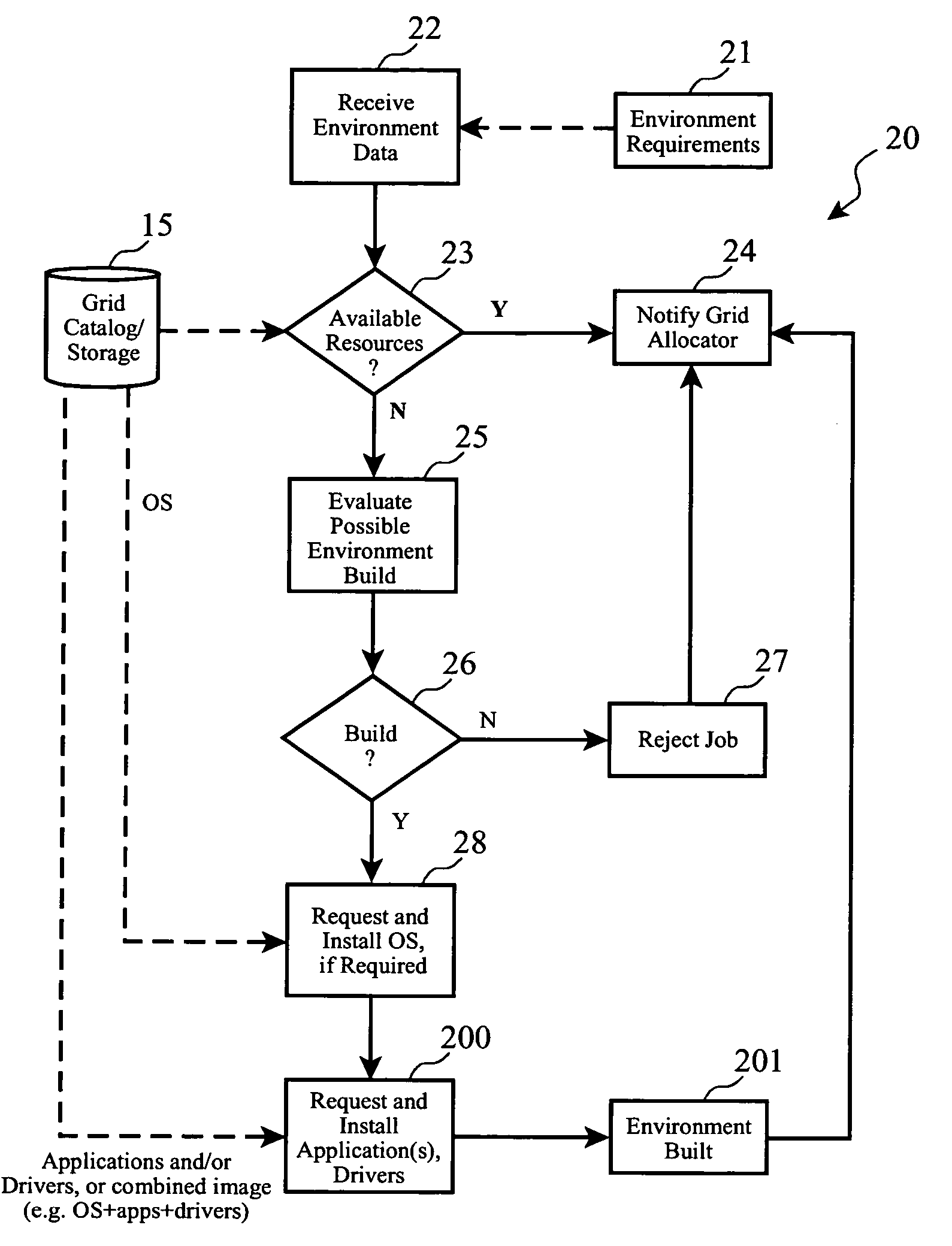
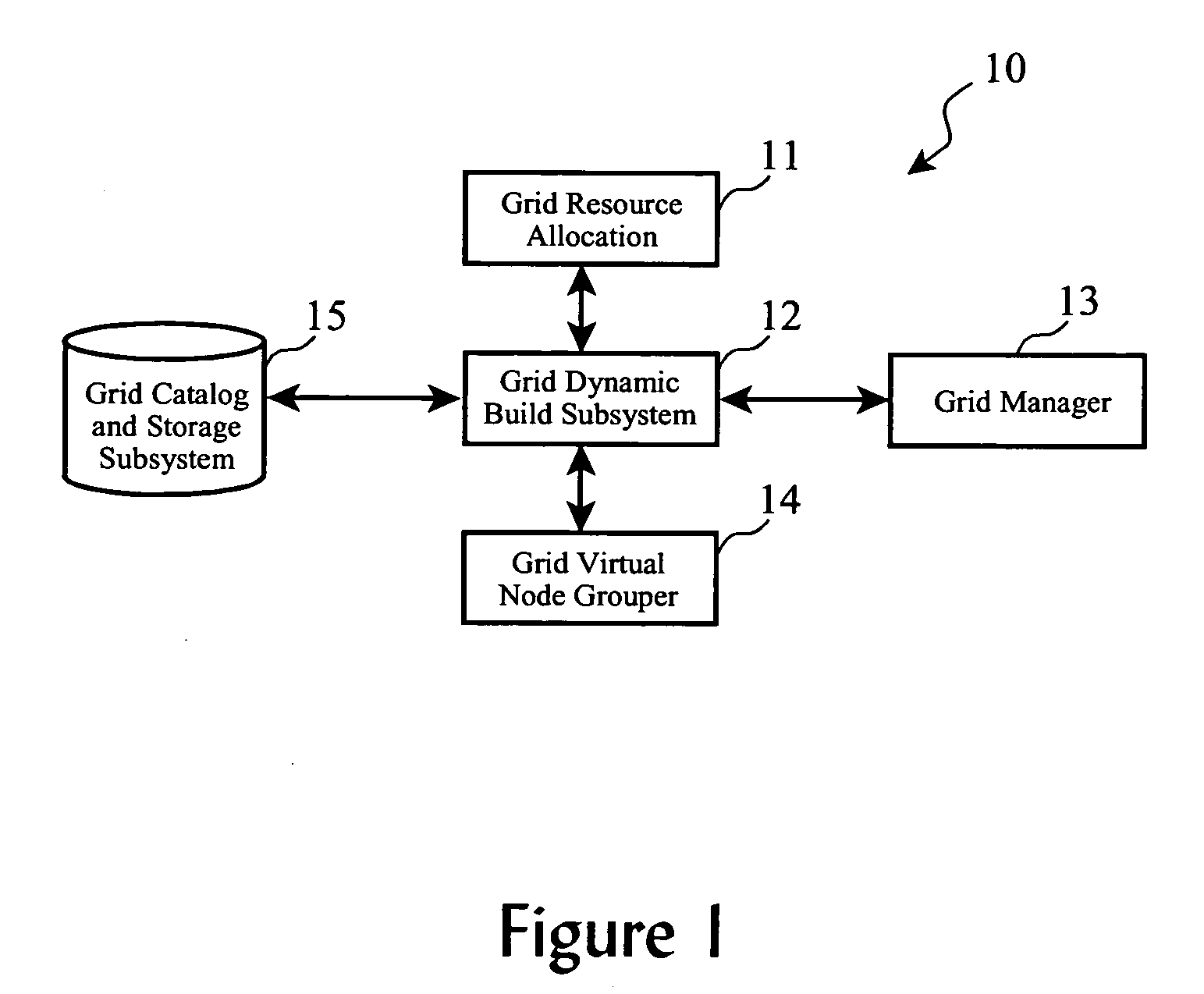
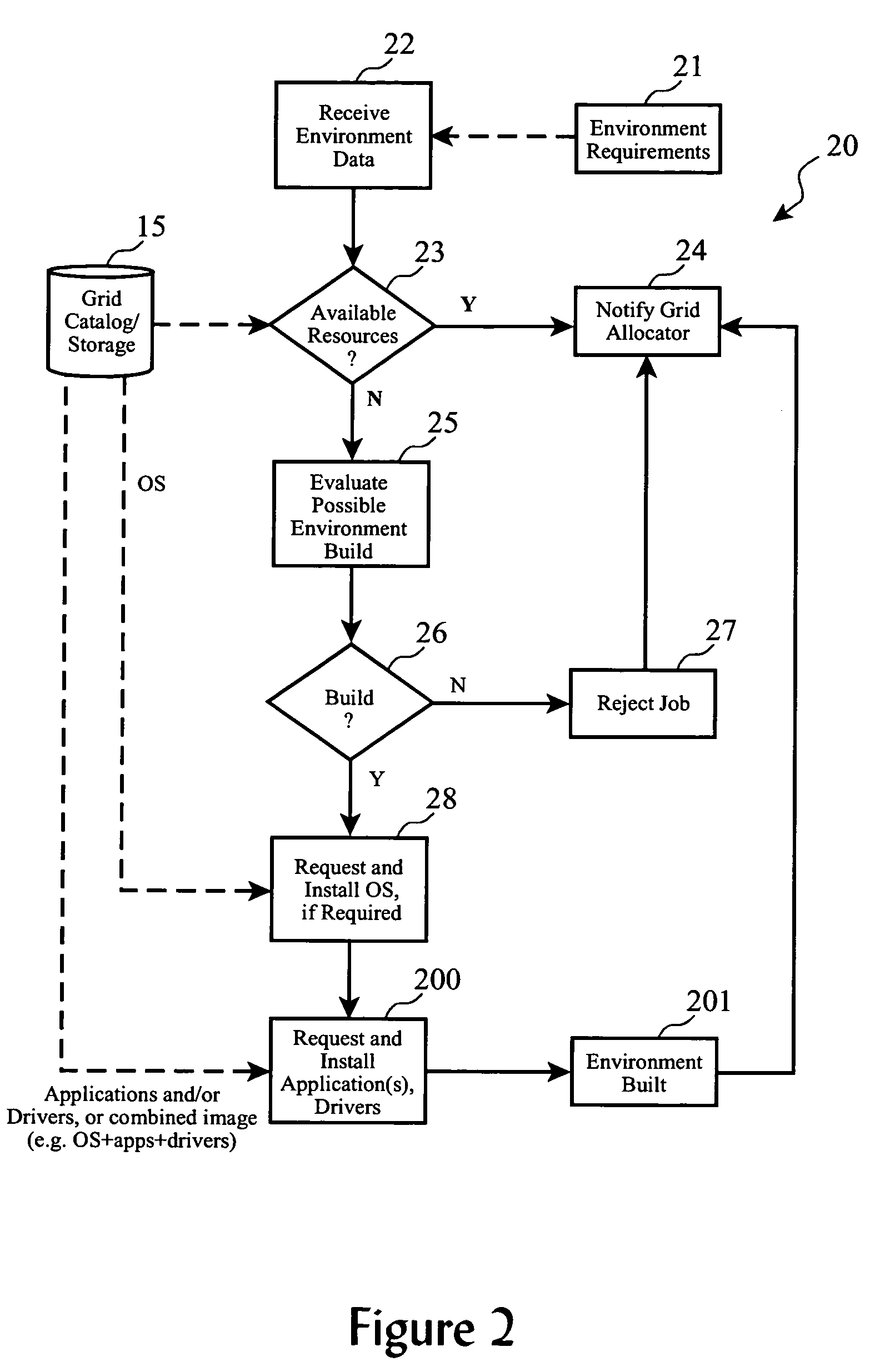
System and method for dynamically building application environments in a computational grid
InactiveUS20060005181A1Advanced resource load balancingExcellent infrastructure for brokering resourcesResource allocationDigital computer detailsOperational systemGrid resource allocation
Computing environments within a grid computing system are dynamically built in response to specific job resource requirements from a grid resource allocator, including activating needed hardware, provisioning operating systems, application programs, and software drivers. Optimally, prior to building a computing environment for a particular job, cost / revenue analysis is performed, and if operational objectives would not be met by building the environment and executing the job, a job sell-off process is initiated.
Owner:IBM CORP
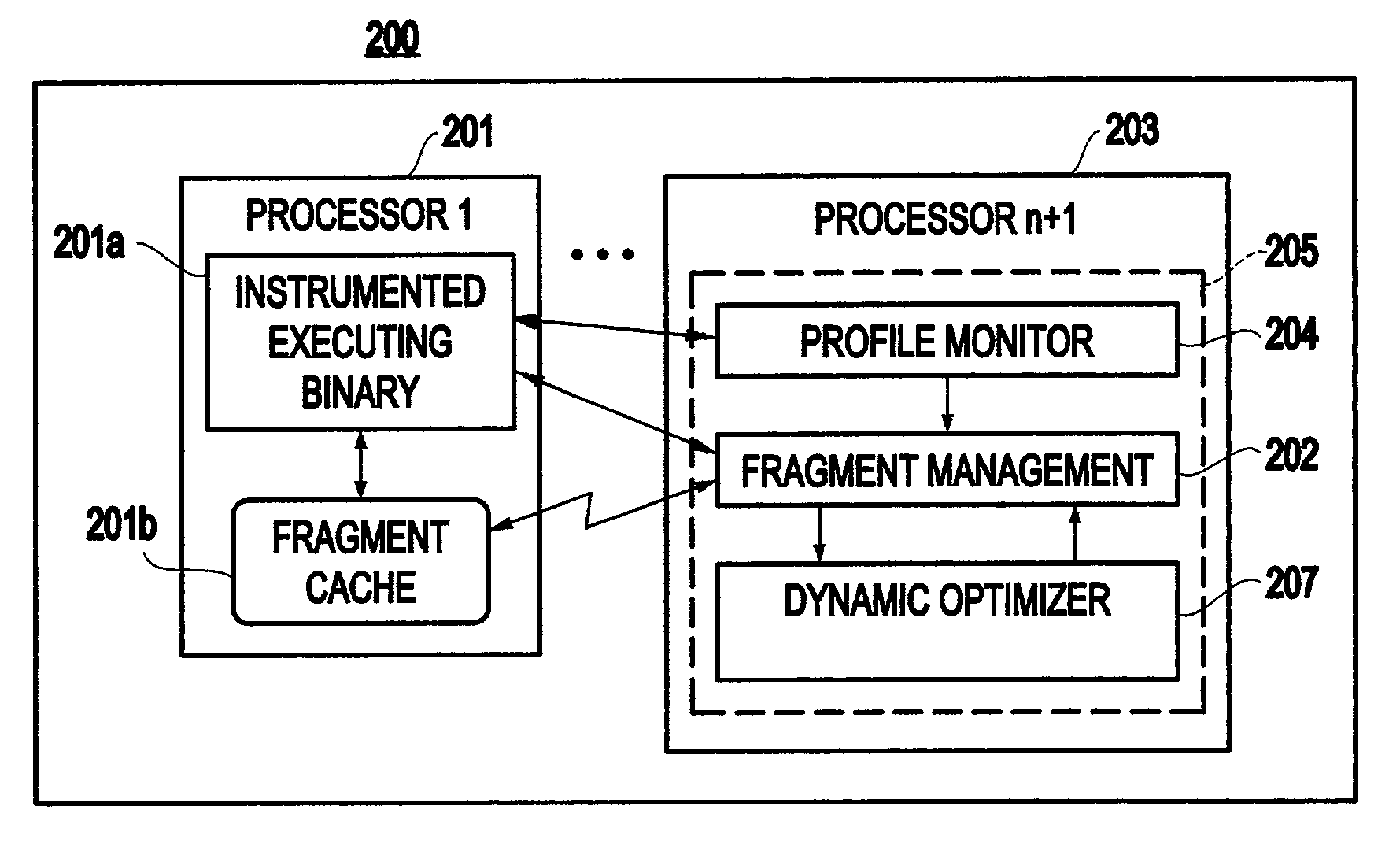
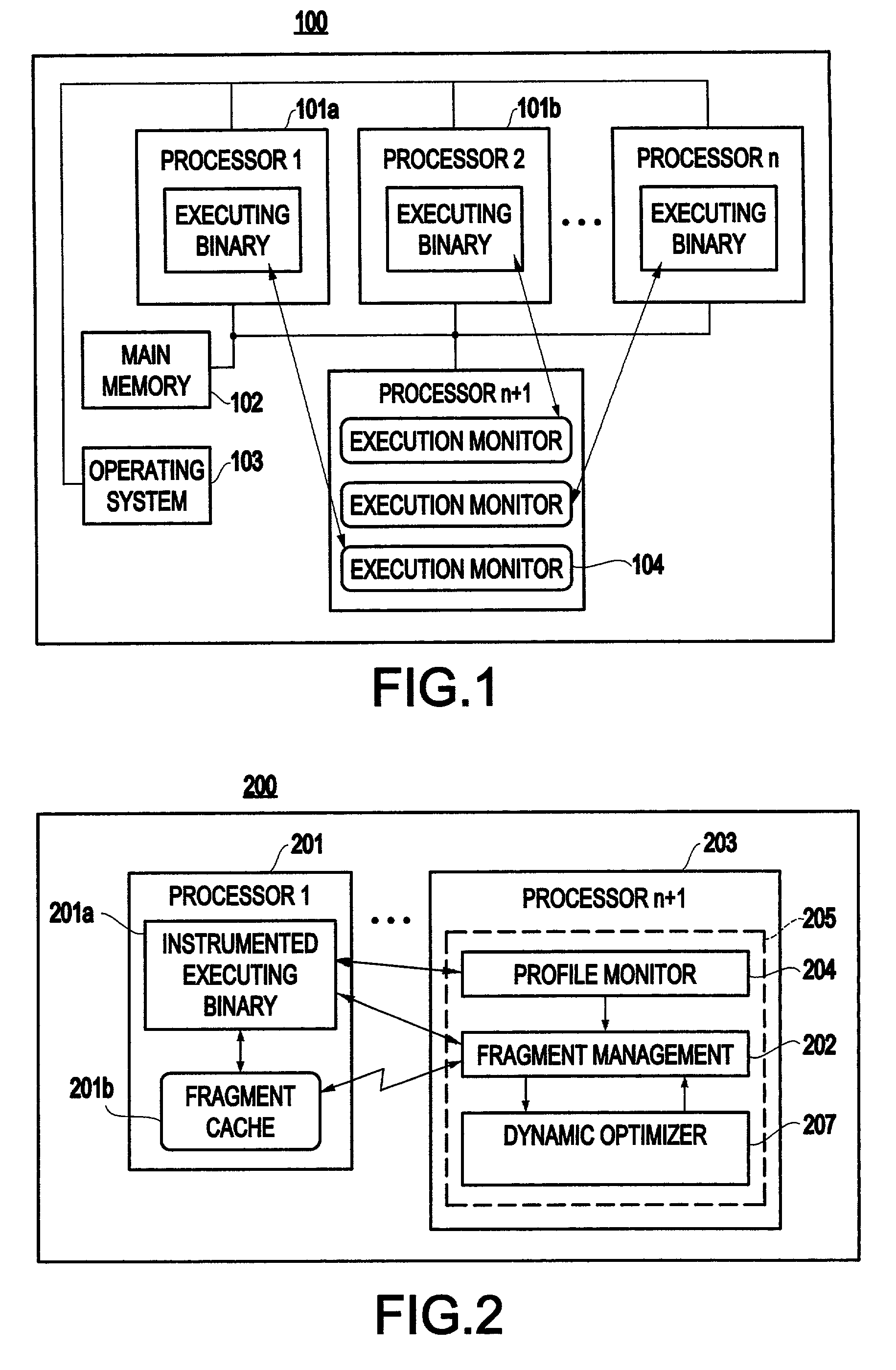
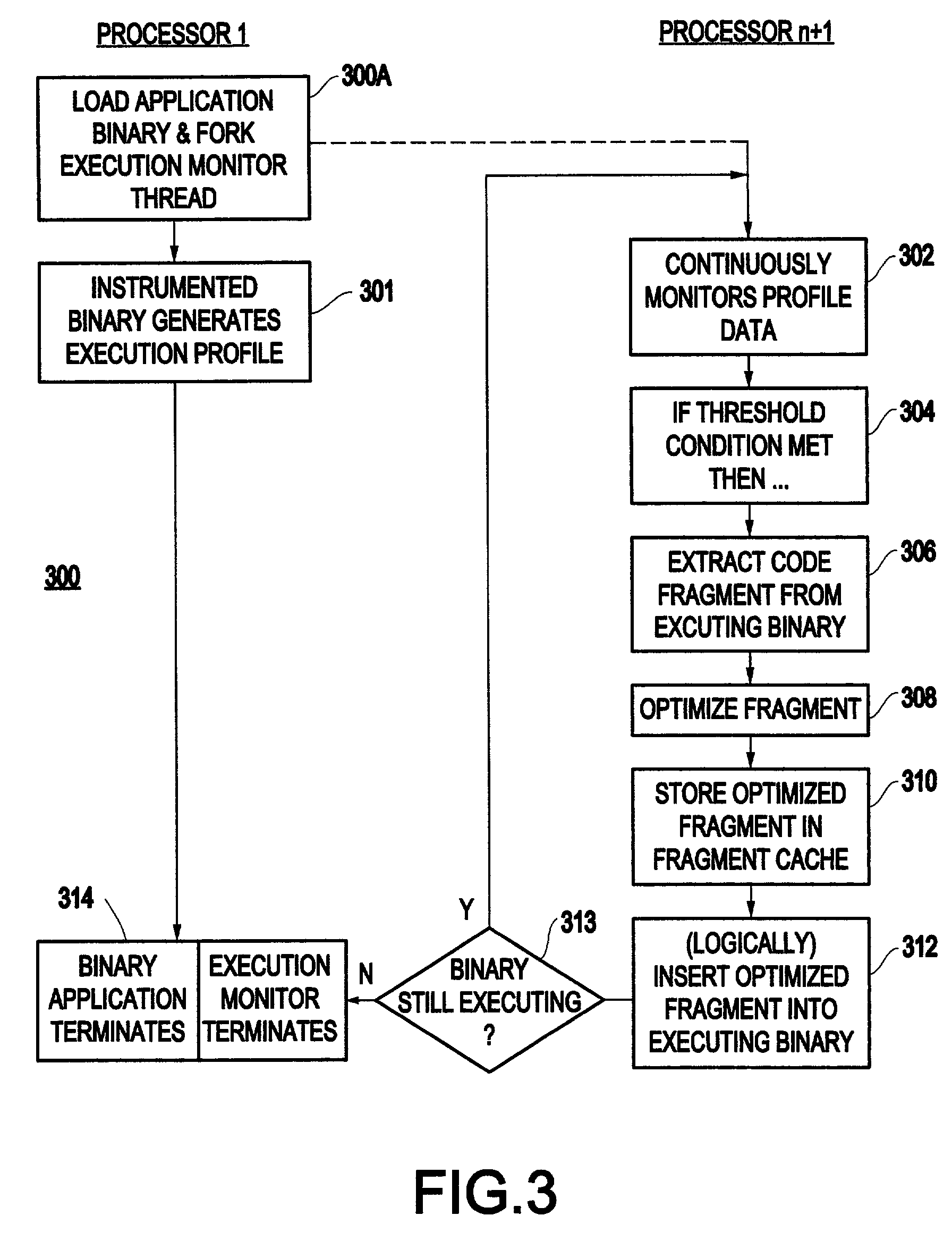
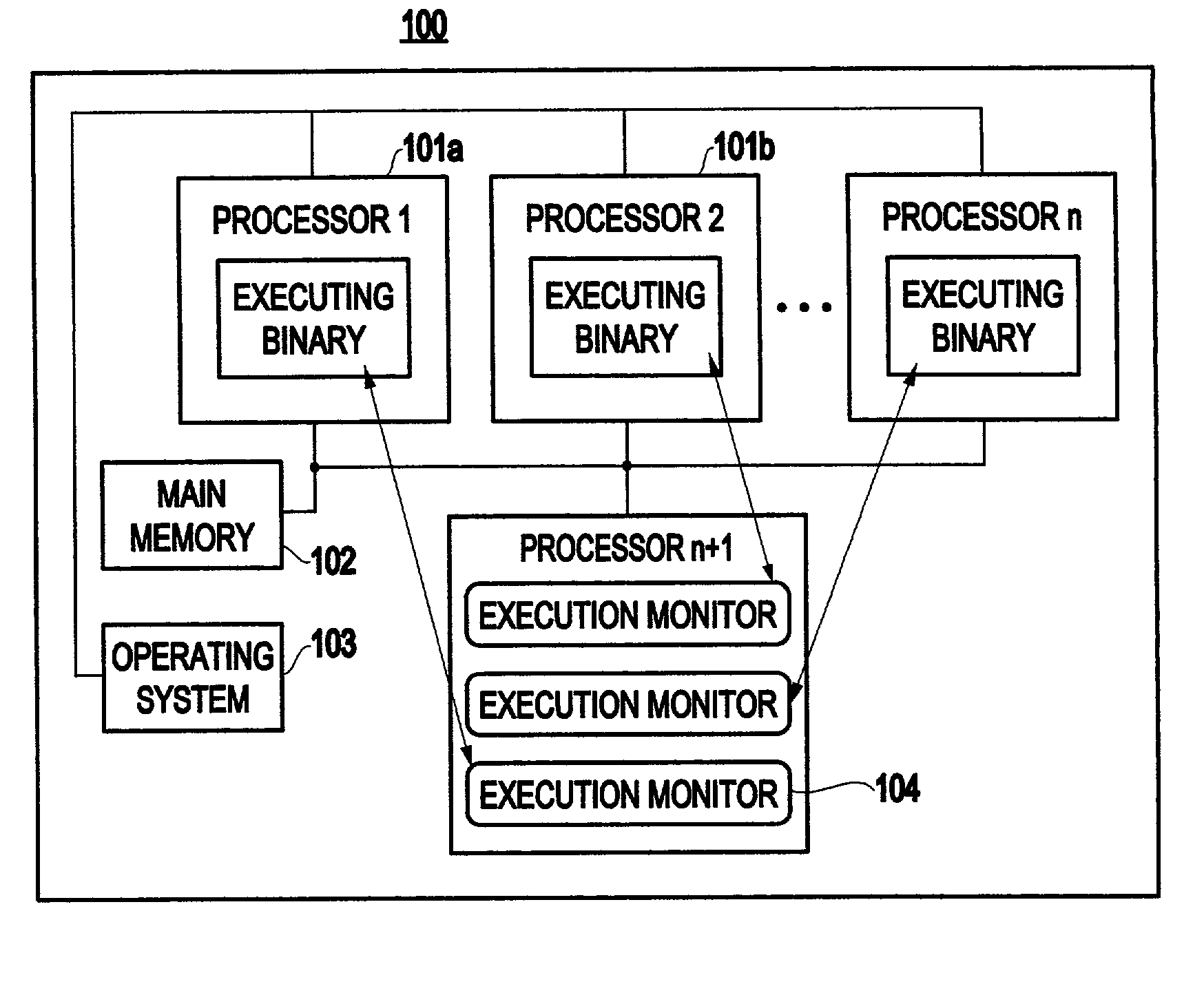
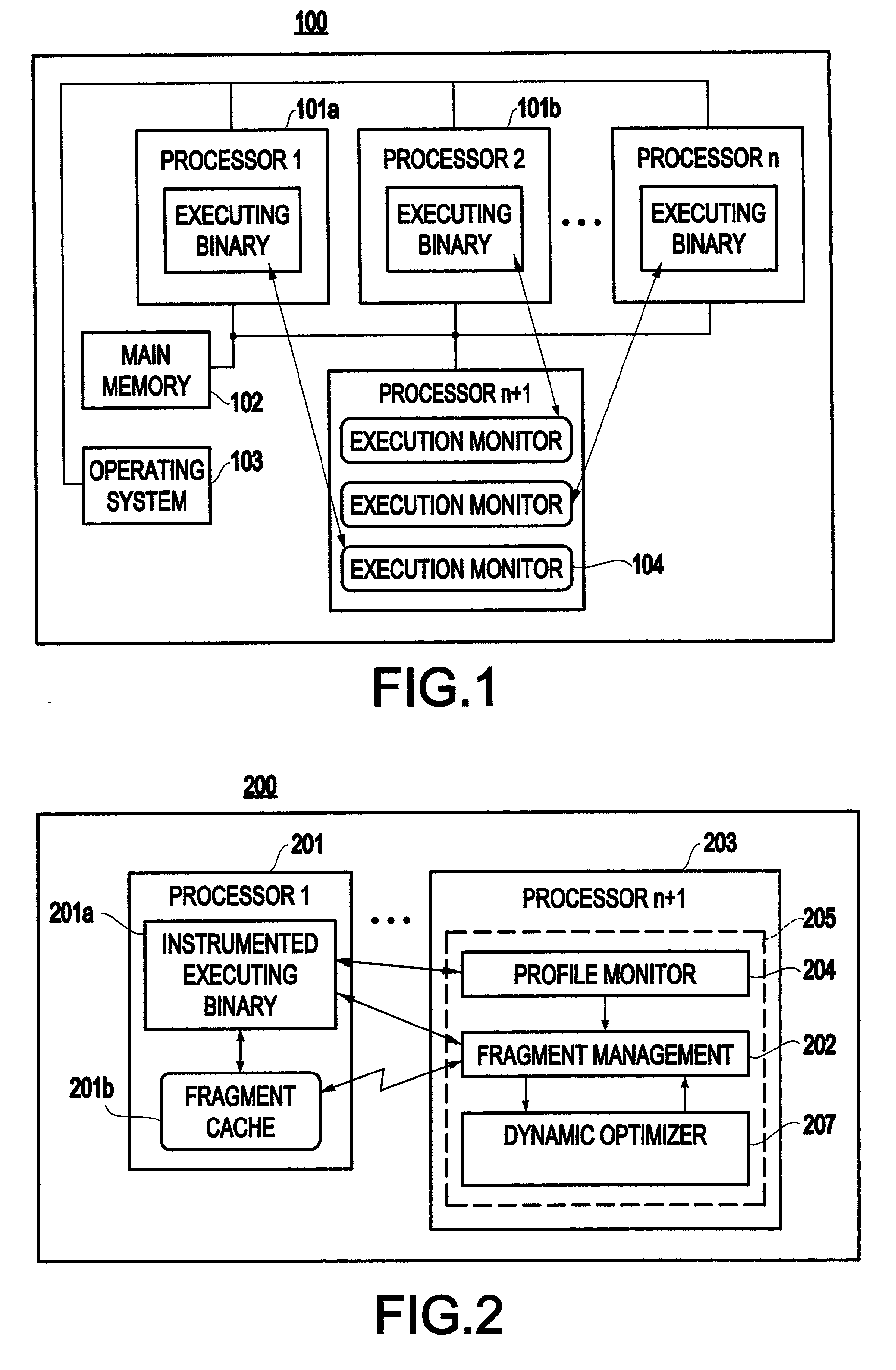
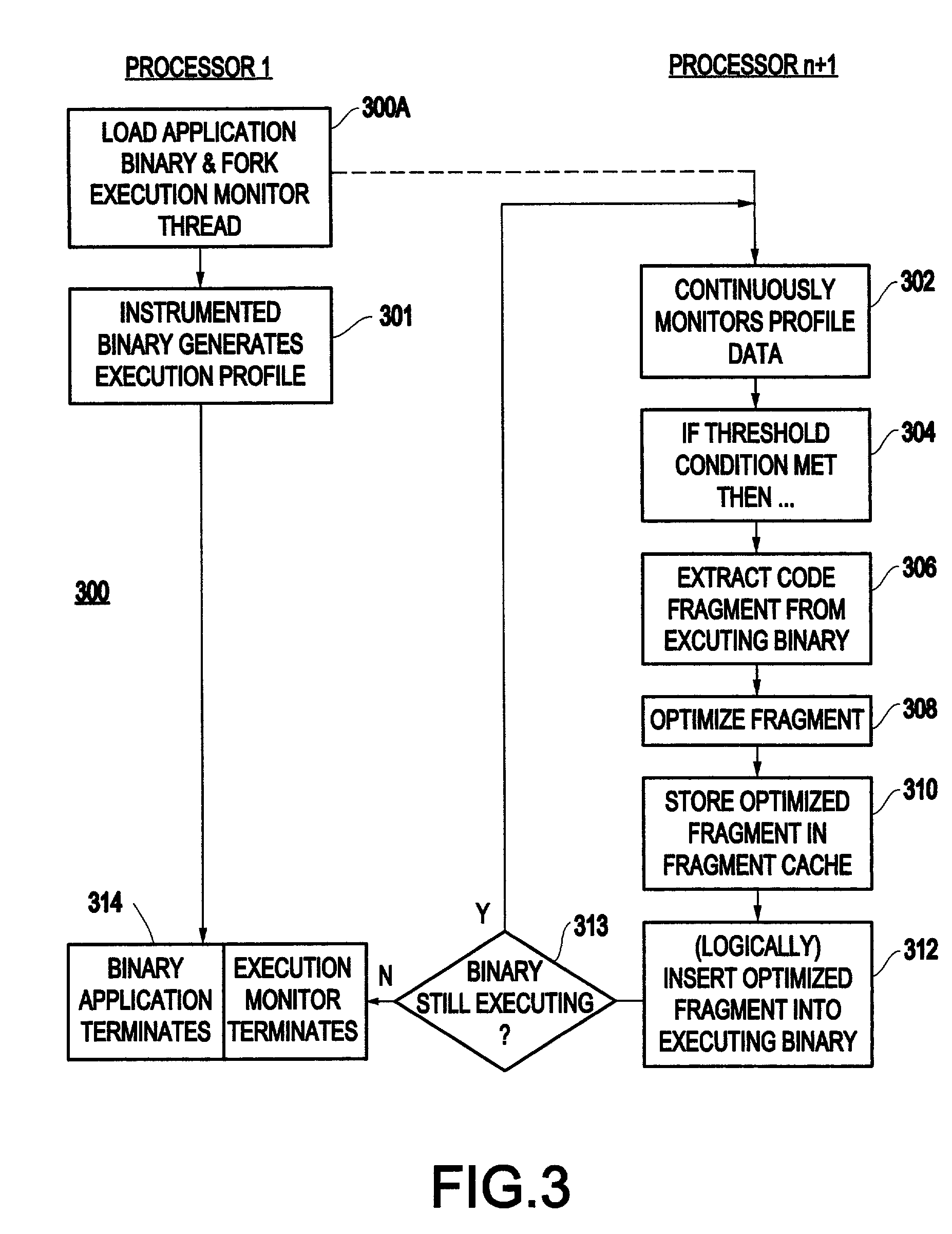
Method and system for transparent dynamic optimization in a multiprocessing environment
InactiveUS7146607B2Improved program execution efficiencyImprove performanceSoftware engineeringDigital computer detailsApplication softwareMultiprocessing
A method (and system) of transparent dynamic optimization in a multiprocessing environment, includes monitoring execution of an application on a first processor with an execution monitor running on another processor of the system, and transparently optimizing one or more segments of the original application with a runtime optimizer executing on the another processor of the system.
Owner:INT BUSINESS MASCH CORP
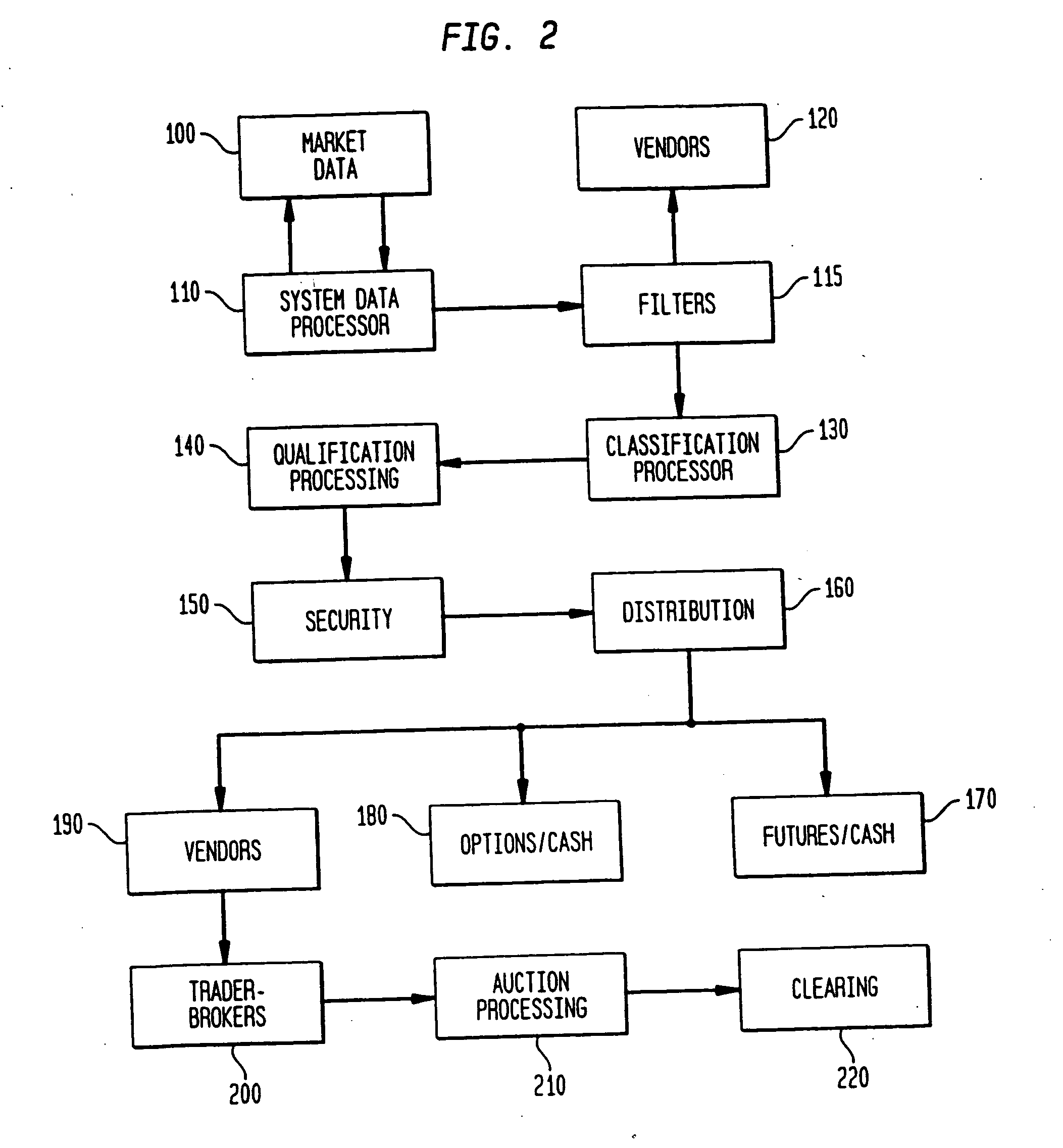
Automated price improvement protocol processor
InactiveUS20050160032A1Avoid excessive errorLow costFinanceBuying/selling/leasing transactionsData processing systemProtocol processing
Owner:CFPH LLC +1
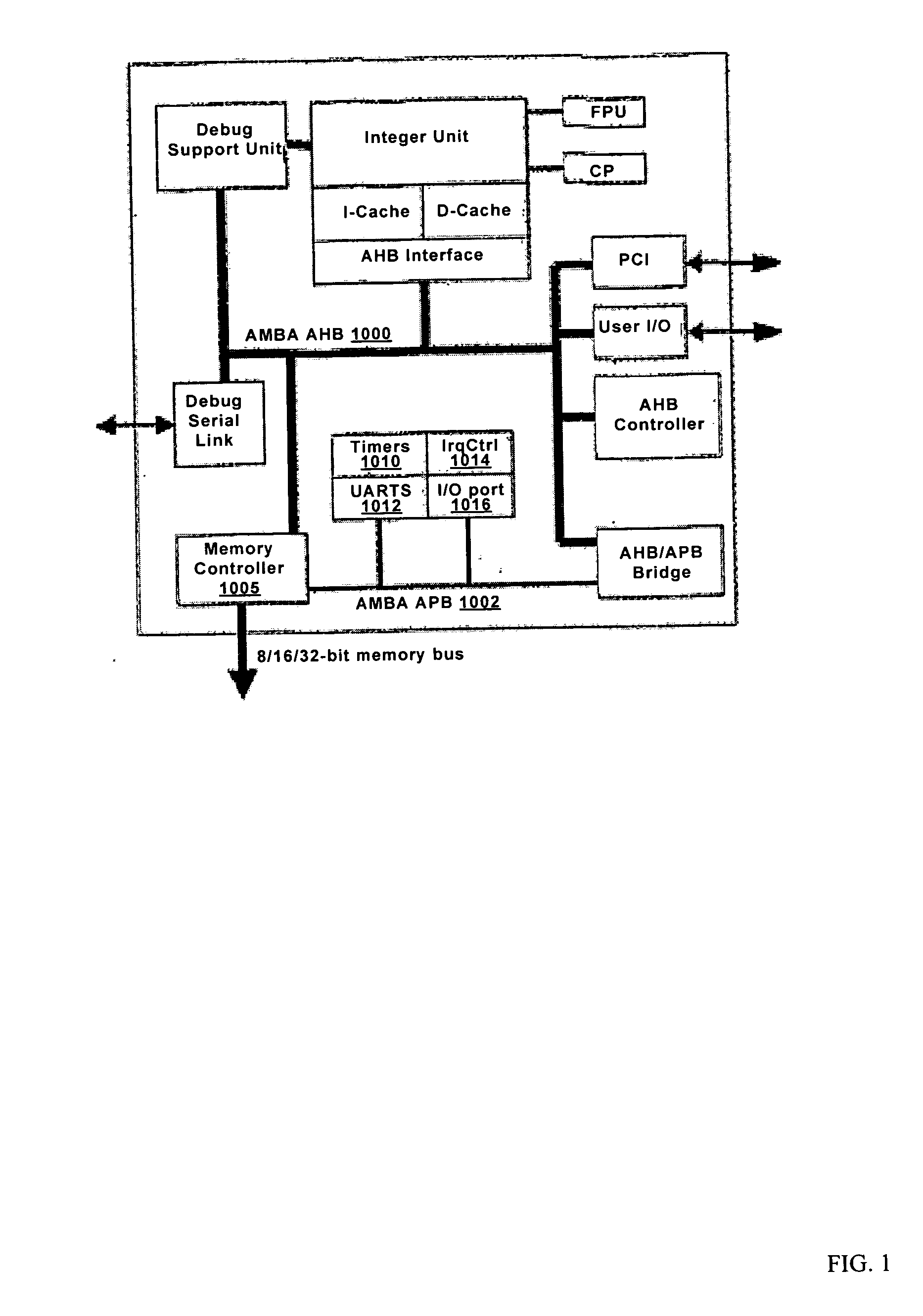
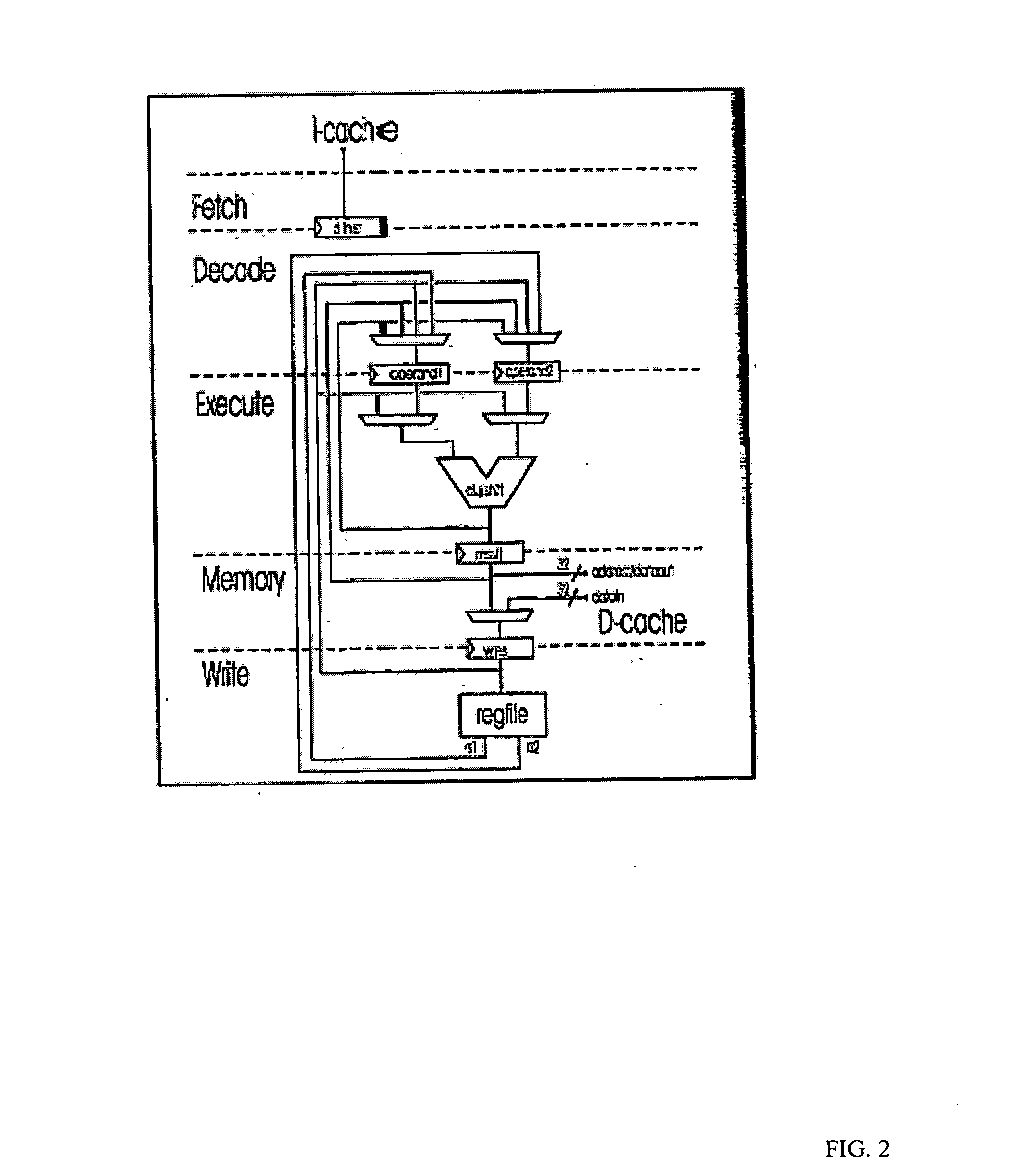
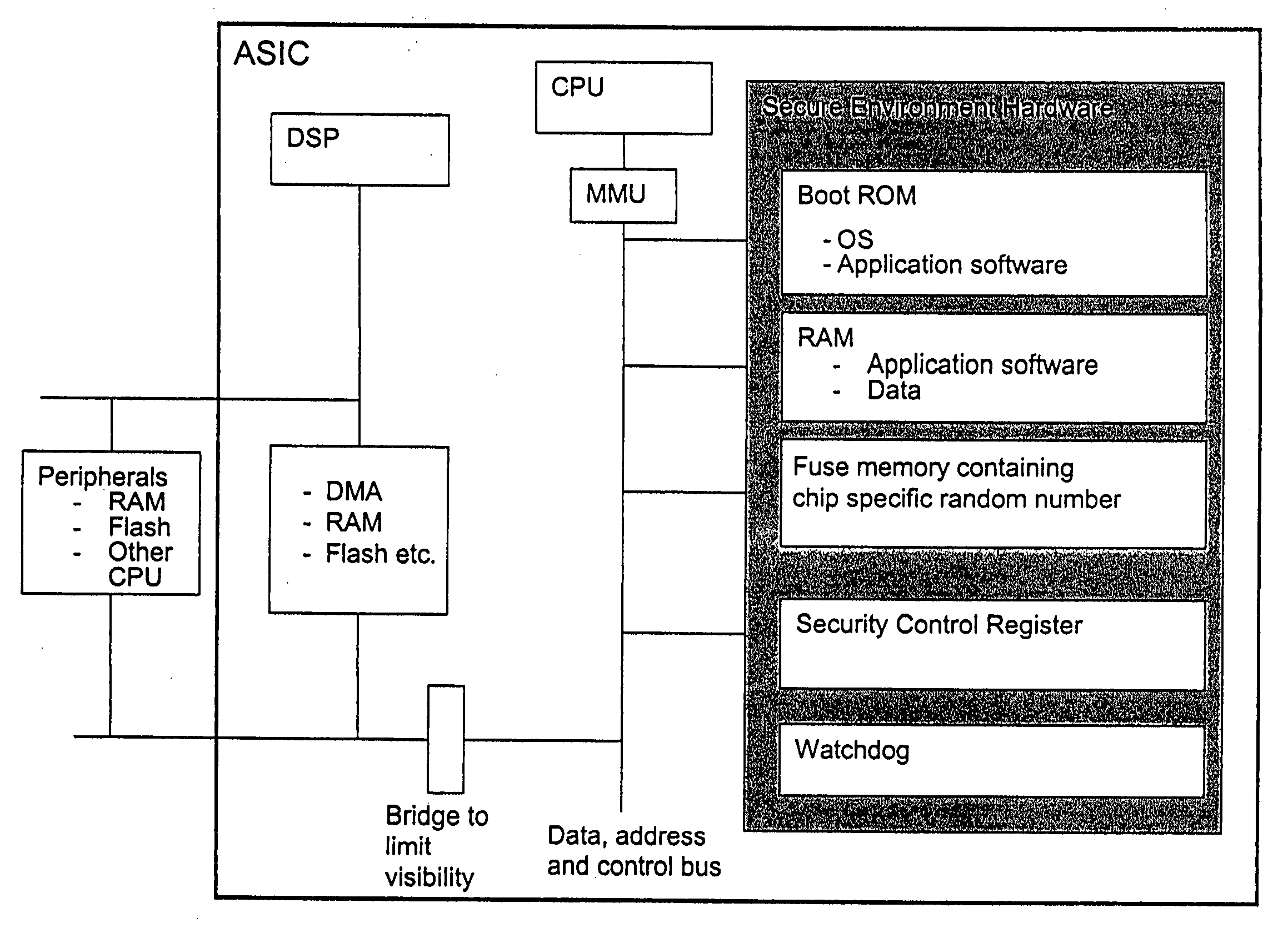
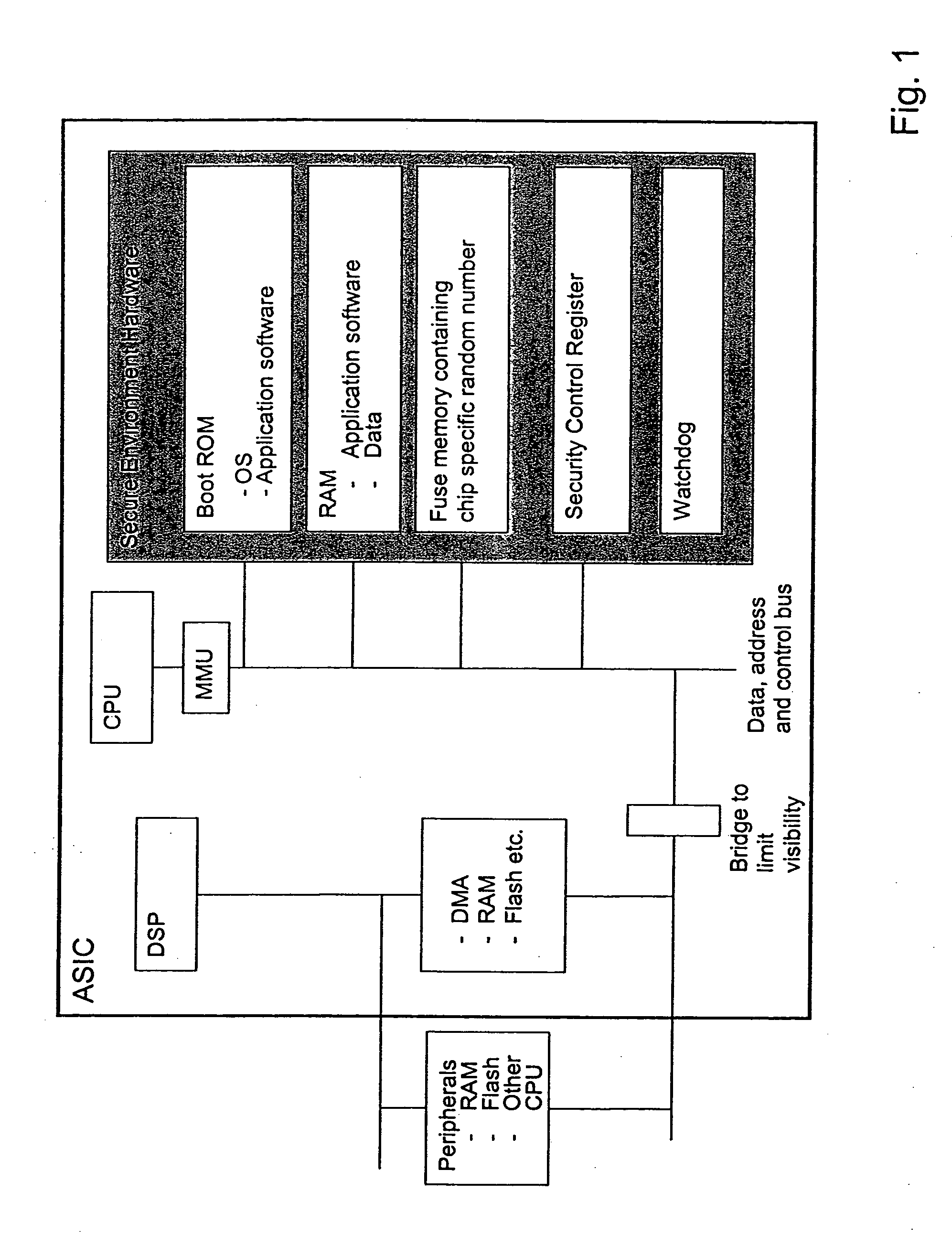
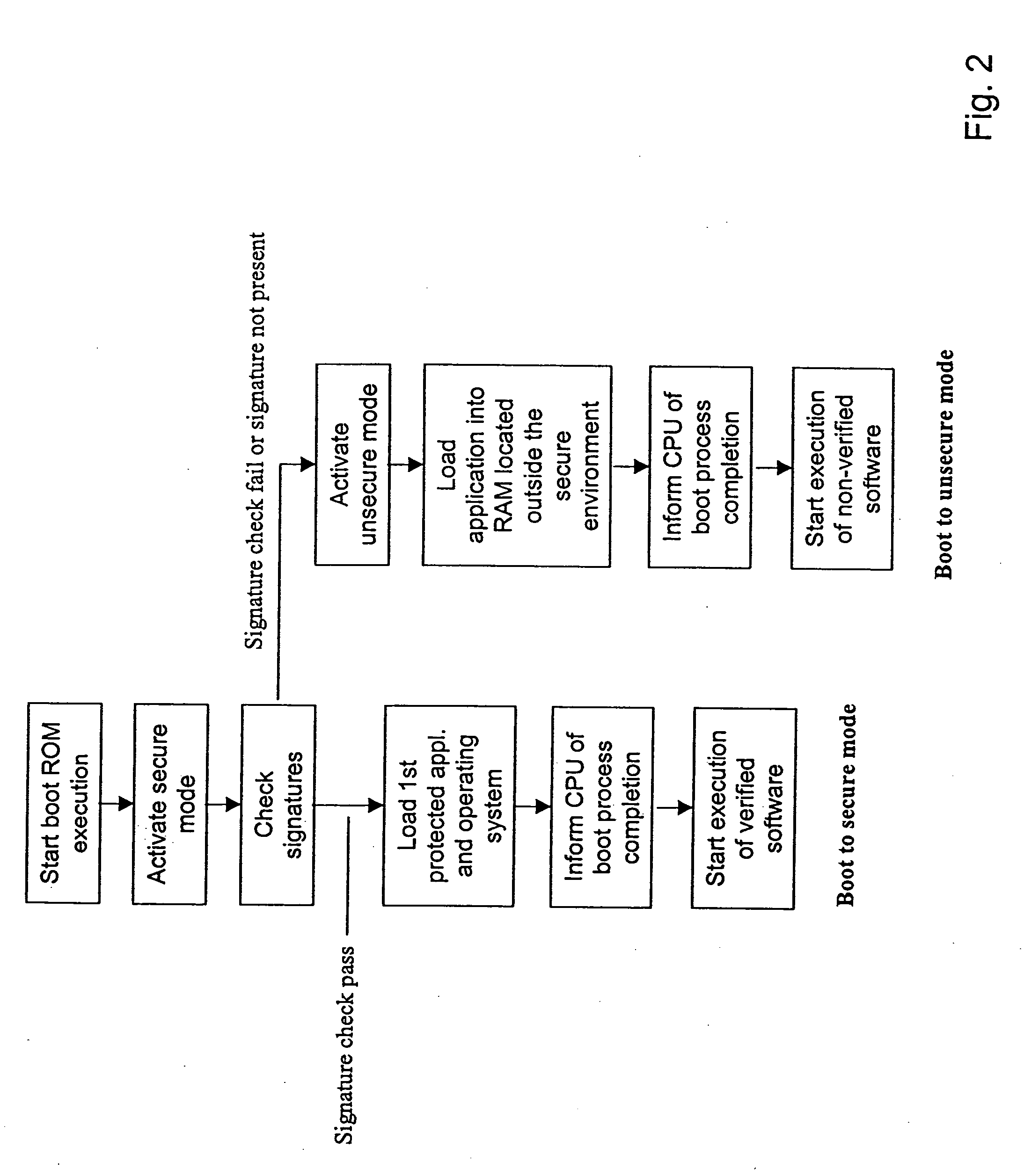
Secure execution architecture
ActiveUS20050033969A1Mode is changingExecuted easy and fastDigital data processing detailsUnauthorized memory use protectionOperation modeSchema for Object-Oriented XML
The present invention relates to circuitry and a method for providing data security, which circuitry contains at least one processor and at least one storage circuit. The invention is based on the idea that circuitry is provided in which a processor is operable in at least two different modes, one first secure operating mode and one second unsecure operating mode. In the secure mode, the processor has access to security related data located in various memories located within the circuitry. The access to these security data and the processing of them need to be restricted, since an intruder with access to security data could manipulate the circuitry. When testing and / or debugging the circuitry, access to security information is not allowed. For this reason, the processor is placed in the unsecure operating mode, in which mode it is no longer given access to the protected data.
Owner:NOKIA TECHNOLOGLES OY
Method and system for transparent dynamic optimization in a multiprocessing environment
InactiveUS20040054992A1Improve performanceImprove executionSoftware engineeringDigital computer detailsApplication softwareMultiprocessing
A method (and system) of transparent dynamic optimization in a multiprocessing environment, includes monitoring execution of an application on a first processor with an execution monitor running on another processor of the system, and transparently optimizing one or more segments of the original application with a runtime optimizer executing on the another processor of the system.
Owner:IBM CORP
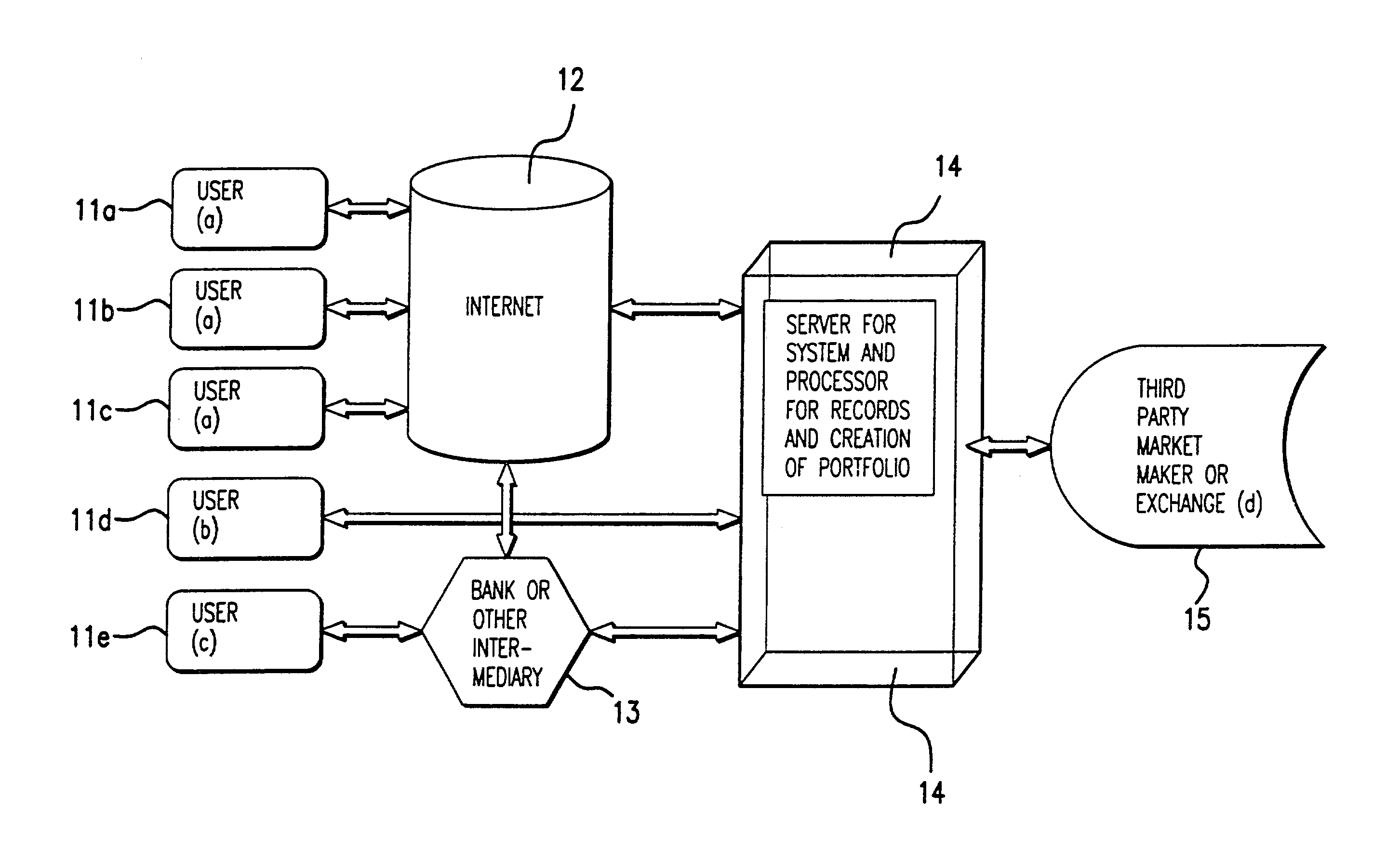
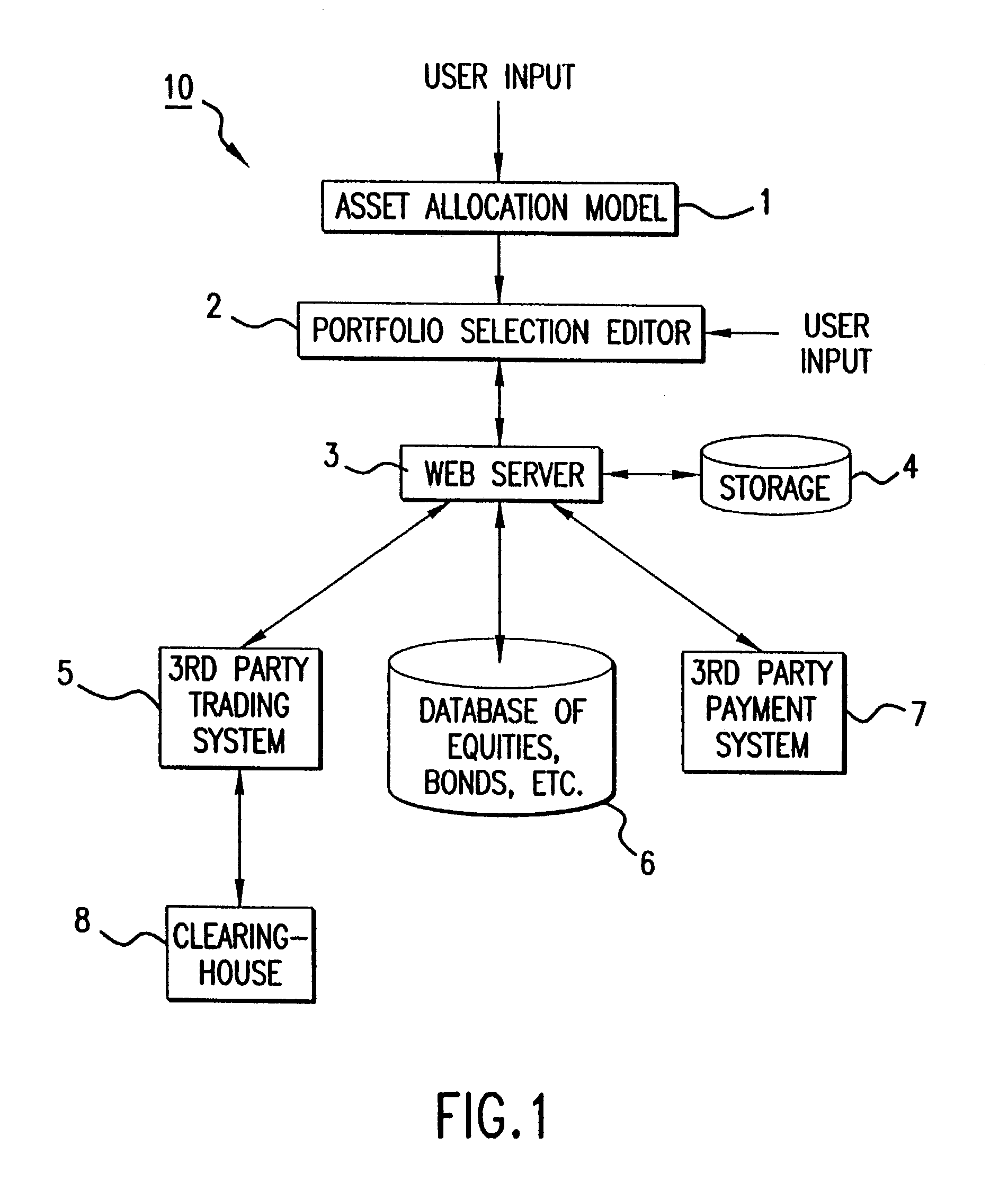
Method and apparatus for enabling individual or smaller investors or others to create and manage a portfolio of securities or other assets or liabilities on a cost effective basis
InactiveUS7110971B2Improve executionLow costFinanceDigital data processing detailsCost effectivenessDecision taking
Smaller investors can create and manage on a cost-effective basis a complex portfolio of securities using a mechanism that enables the investor to provide to the system the investor's preferences regarding his portfolio, to generate a portfolio, including fractional shares, that reflects the investor's preferences. The system then permits aggregation of the orders, and netting of orders, generated by multiple investors at various times during the day for execution. In addition, the structure of the computer-based system of the present invention allows its cost to be based on access to or usage of the system (such as a monthly fee) as opposed to by securities orders entered into the system as per common brokerage. The result is that the investor can create a portfolio of directly owned securities with attributes, such as diversification, similar to a mutual fund. As compared with the problems with existing systems, the computer-based system of the present invention provides complete control for the investor over what securities can be selected, and in what weights and amounts, as well as control over the tax effects of purchases or sales of the securities comprising the portfolio, preventing the investor from being presented with unwanted taxable effects due to discretionary sales transactions of fund managers. In addition, the computer-based system of the present invention provides all the information necessary to monitor and manage tax effects and capability to sell or buy the individual securities in his portfolio to obtain desired tax benefits, all shareholder rights with respect to each security in the portfolio to the investor and full ownership and control over all investment, voting and other decisions regarding such securities. The computer-based system of the present invention also allows for parameters to be set with respect to a portfolio to ensure that it stays within certain diversification or risk limits. Furthermore, the computer-based system of the present invention provides direct control over the charges and expenses that will be incurred, and the possibility of making multiple intra-day investment decisions by the investor, if he wishes. Moreover, the computer-based system of the present invention provides control over all factors in the portfolio and modification of them as the investor sees fit.
Owner:FOLIOFN
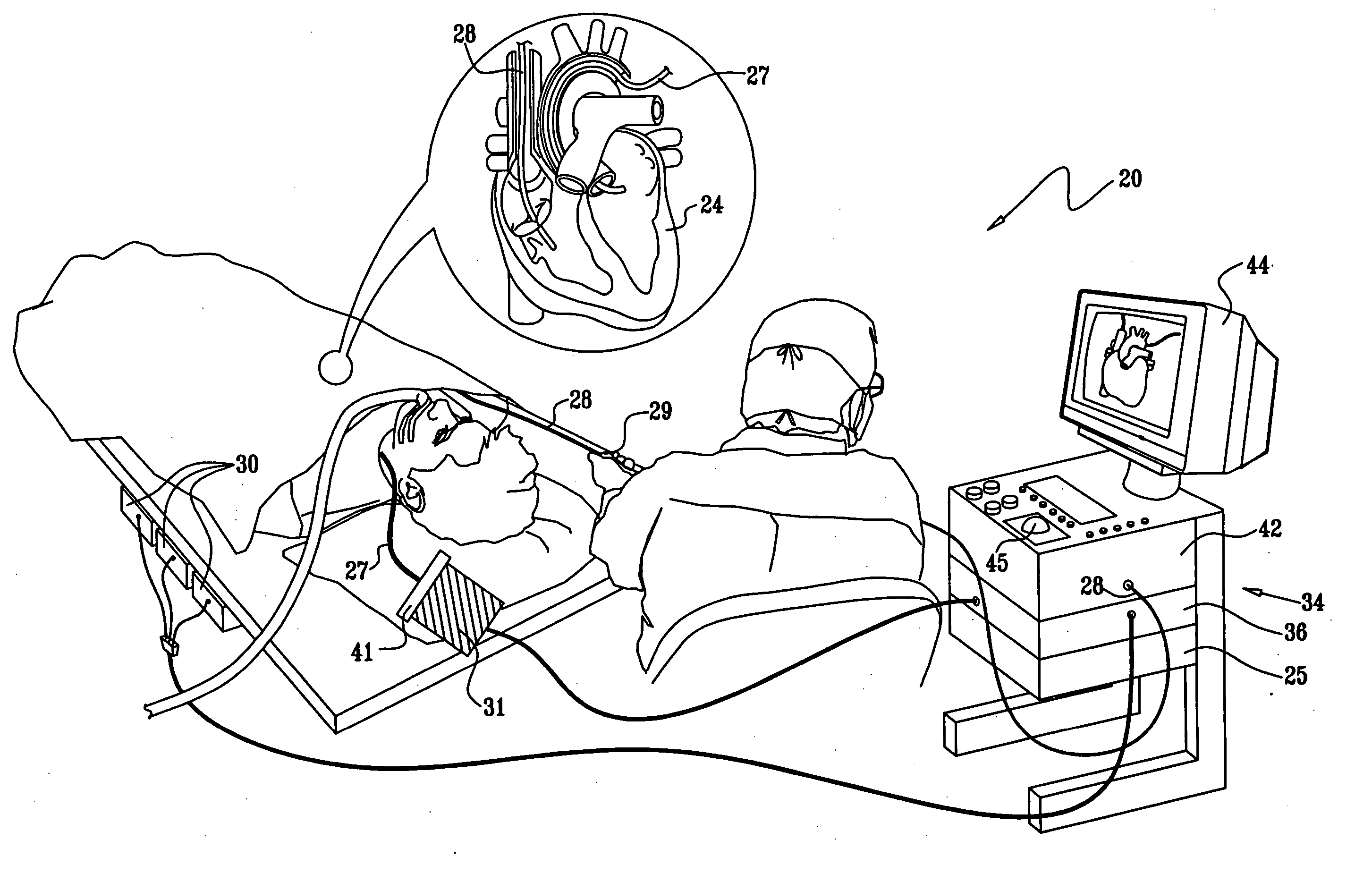
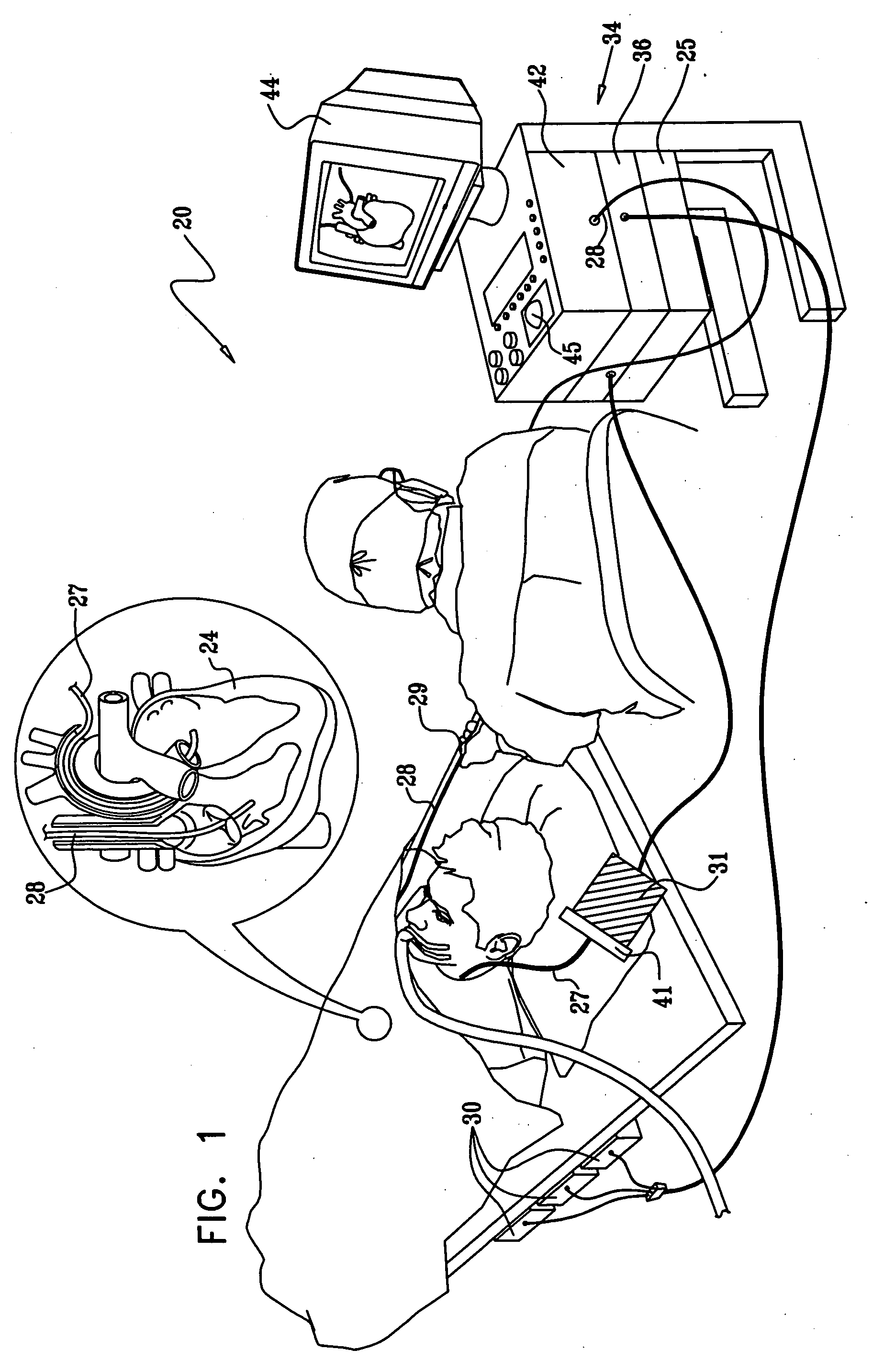
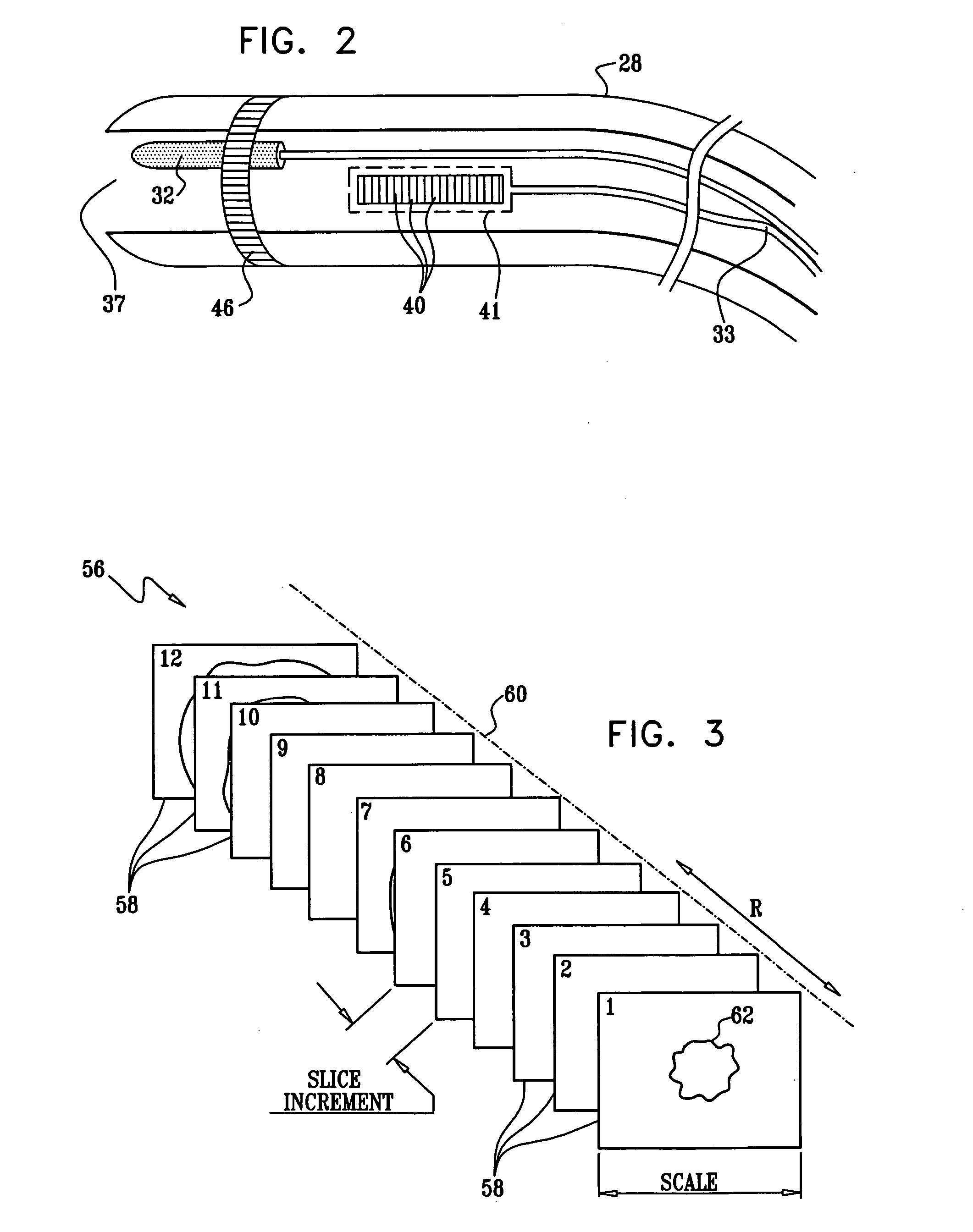
Controlling direction of ultrasound imaging catheter
InactiveUS20070106147A1Structure be loseImprove executionUltrasonic/sonic/infrasonic diagnosticsSurgical navigation systemsUltrasound imagingControl ultrasound
The position of an imaging catheter in a body structure such as the heart is automatically controlled by a robotic manipulator such that its field of view at all times includes the distal end of a second catheter that is employed to effect a medical procedure. A processor receives signals from position sensors in the catheters. The processor utilizes the information received from the sensors and continually determines any deviation of the second catheter from the required field of view of the imaging catheter. The processor transmits compensation instructions to the robotic manipulator, which when executed assure that the imaging catheter tracks the second catheter.
Owner:BIOSENSE WEBSTER INC
Trading tool to enhance stock and commodity index execution
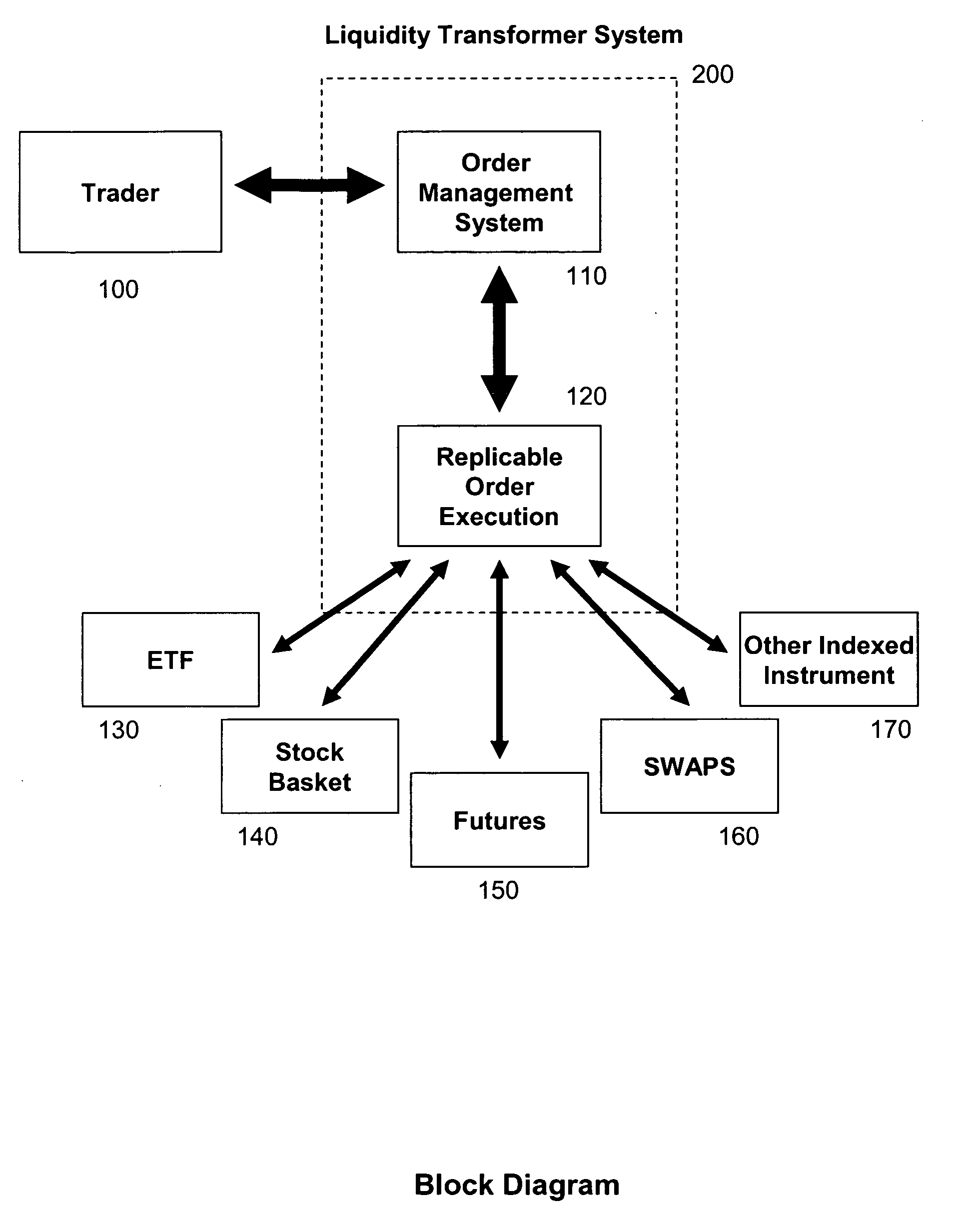
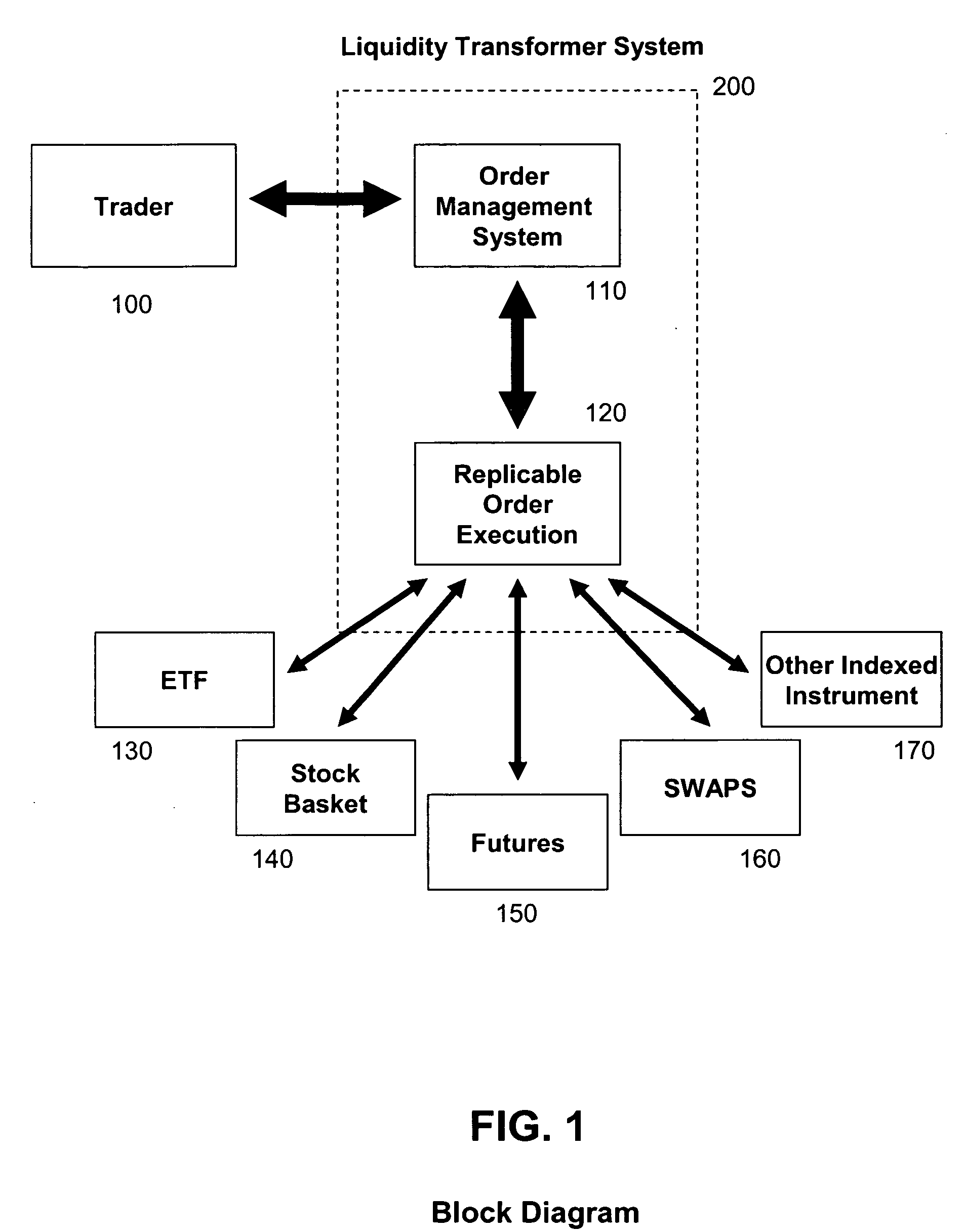
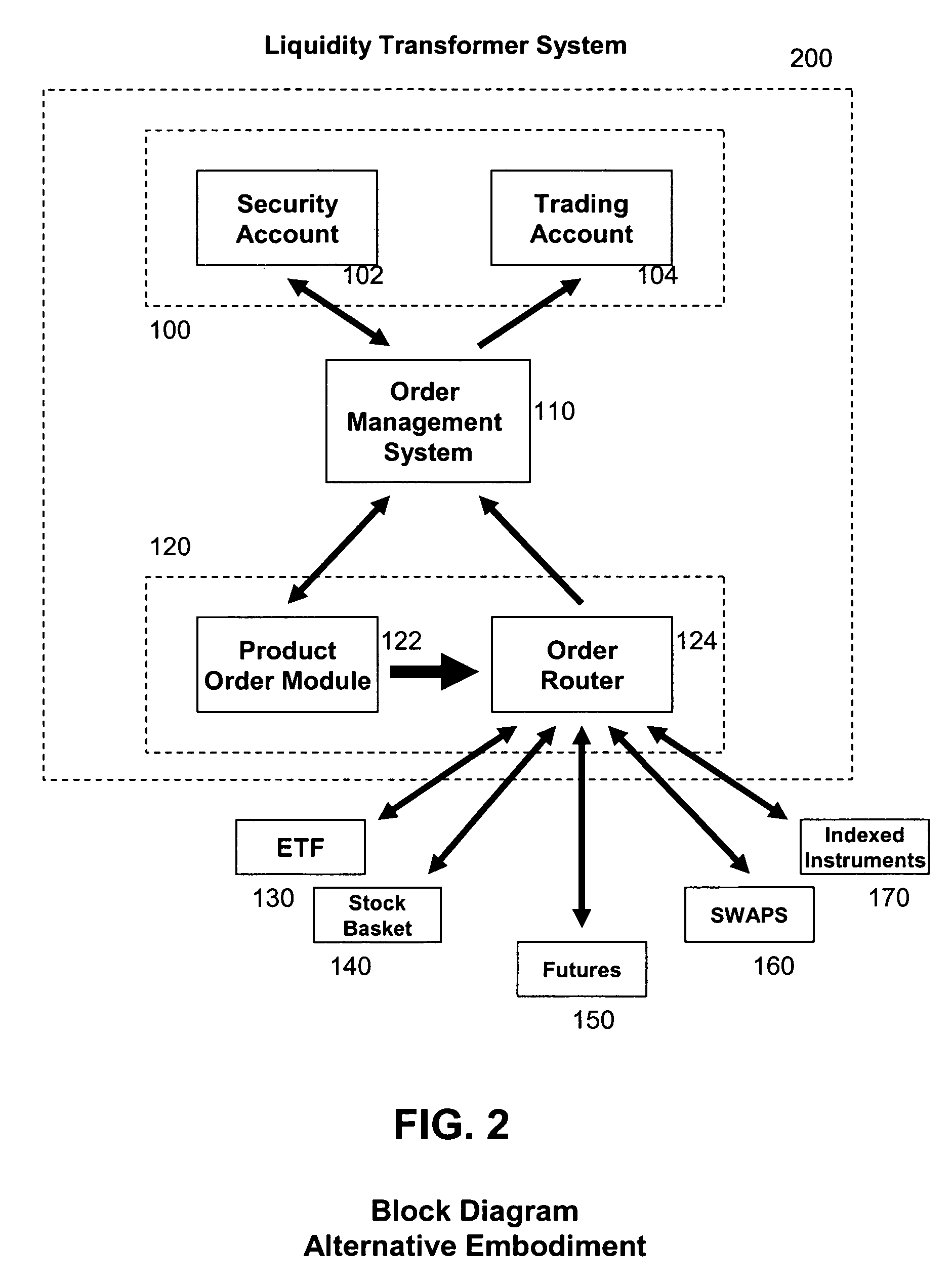
InactiveUS20060184444A1Good priceAdvantageous execution efficiencyFinanceCommerceMultiple formsComputer science
The invention provides systems and methods for providing replicable financial instrument orders, and establishing a fill price that is better than the theoretical upper limit of the industries' best order execution. The system has the capability of transforming a client's index order into a replicable product, such as index futures and / or baskets of the underlying stocks. The system selects whichever method and combination of securities that will achieve the best expected execution for the particular market. The system achieves the best price and execution efficiency by utilizing dynamic market information across all possible liquidity formats, liquidity pools, and high performance trading systems, delivering a product that has multiple forms at the best possible price. The result is a better final execution price that outperforms current industry practices for best order execution. The system delivers the fill order in the original liquidity format at the price, or equivalent price, of the replicable product.
Owner:CREDIT SUISSE FIRST BOSTON
Apparatus and method for processing service interactions
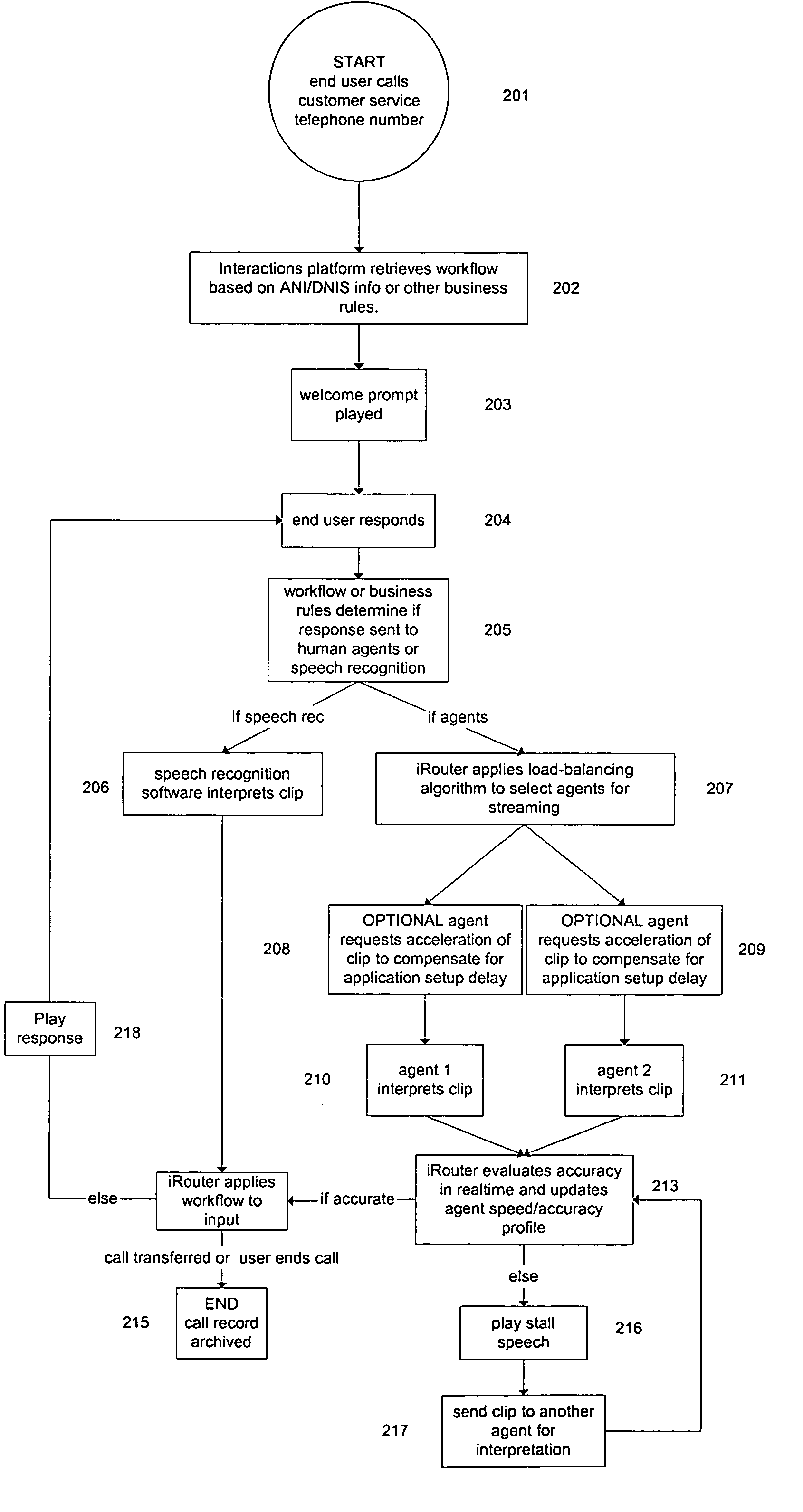
ActiveUS7606718B2Accurately determineImprove accuracyCredit schemesSupervisory/monitoring/testing arrangementsError checkingHuman agent
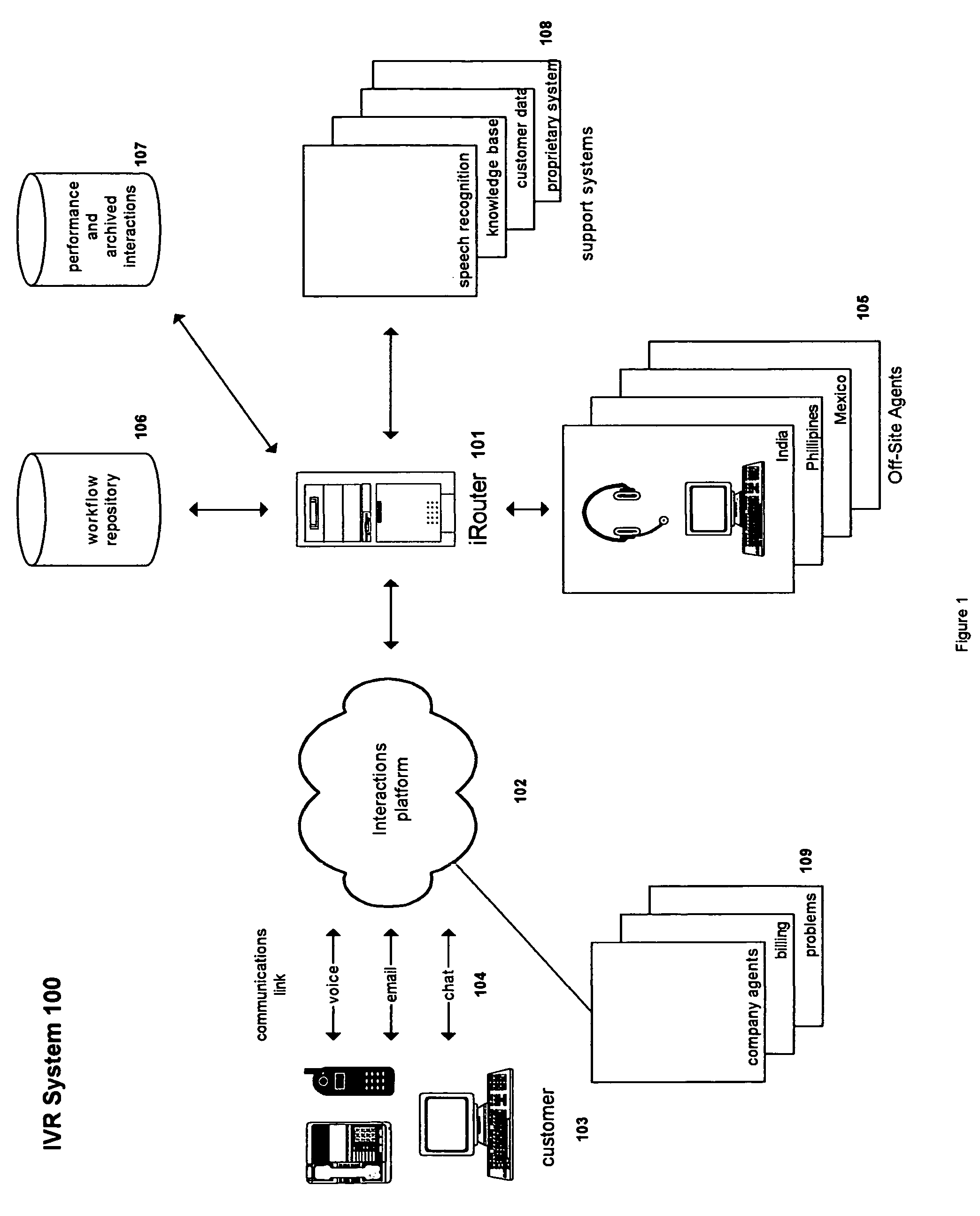
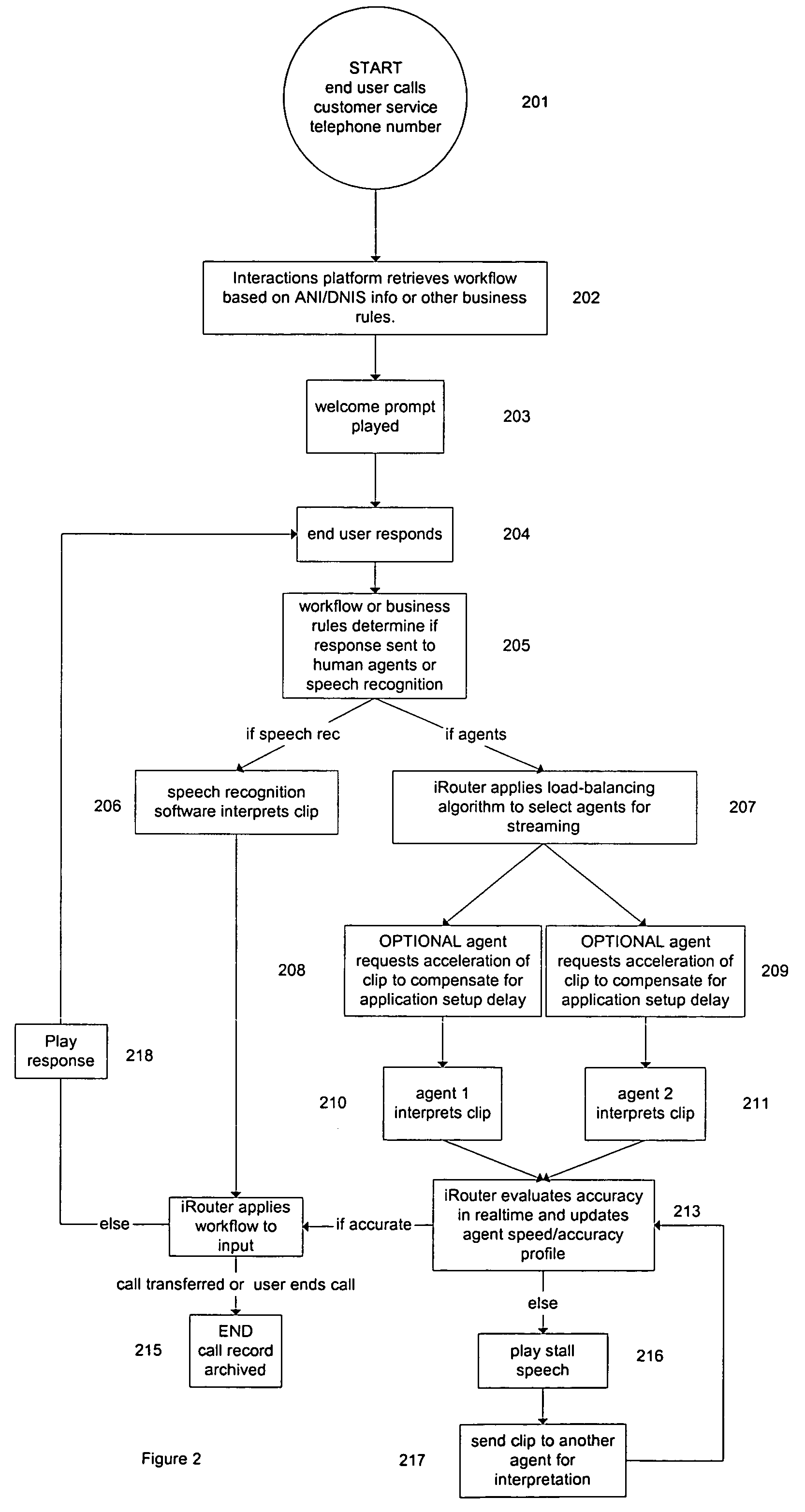
An interactive voice and data response system that directs input to a voice, text, and web-capable software-based router, which is able to intelligently respond to the input by drawing on a combination of human agents, advanced speech recognition and expert systems, connected to the router via a TCP / IP network. The digitized input is broken down into components so that the customer interaction is managed as a series of small tasks rather than one ongoing conversation. The router manages the interactions and keeps pace with a real-time conversation. The system utilizes both speech recognition and human intelligence for purposes of interpreting customer utterance or customer text. The system may use more than one human agent, or both human agents and speech recognition software, to interpret simultaneously the same component for error-checking and interpretation accuracy.
Owner:ARES VENTURE FINANCE
Data processing method and device
ActiveUS20100153654A1Ease memory access problemIncrease data throughputMemory adressing/allocation/relocationDigital computer detailsData processingRead-write memory
In a data-processing method, first result data may be obtained using a plurality of configurable coarse-granular elements, the first result data may be written into a memory that includes spatially separate first and second memory areas and that is connected via a bus to the plurality of configurable coarse-granular elements, the first result data may be subsequently read out from the memory, and the first result data may be subsequently processed using the plurality of configurable coarse-granular elements. In a first configuration, the first memory area may be configured as a write memory, and the second memory area may be configured as a read memory. Subsequent to writing to and reading from the memory in accordance with the first configuration, the first memory area may be configured as a read memory, and the second memory area may be configured as a write memory.
Owner:SCIENTIA SOL MENTIS AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com