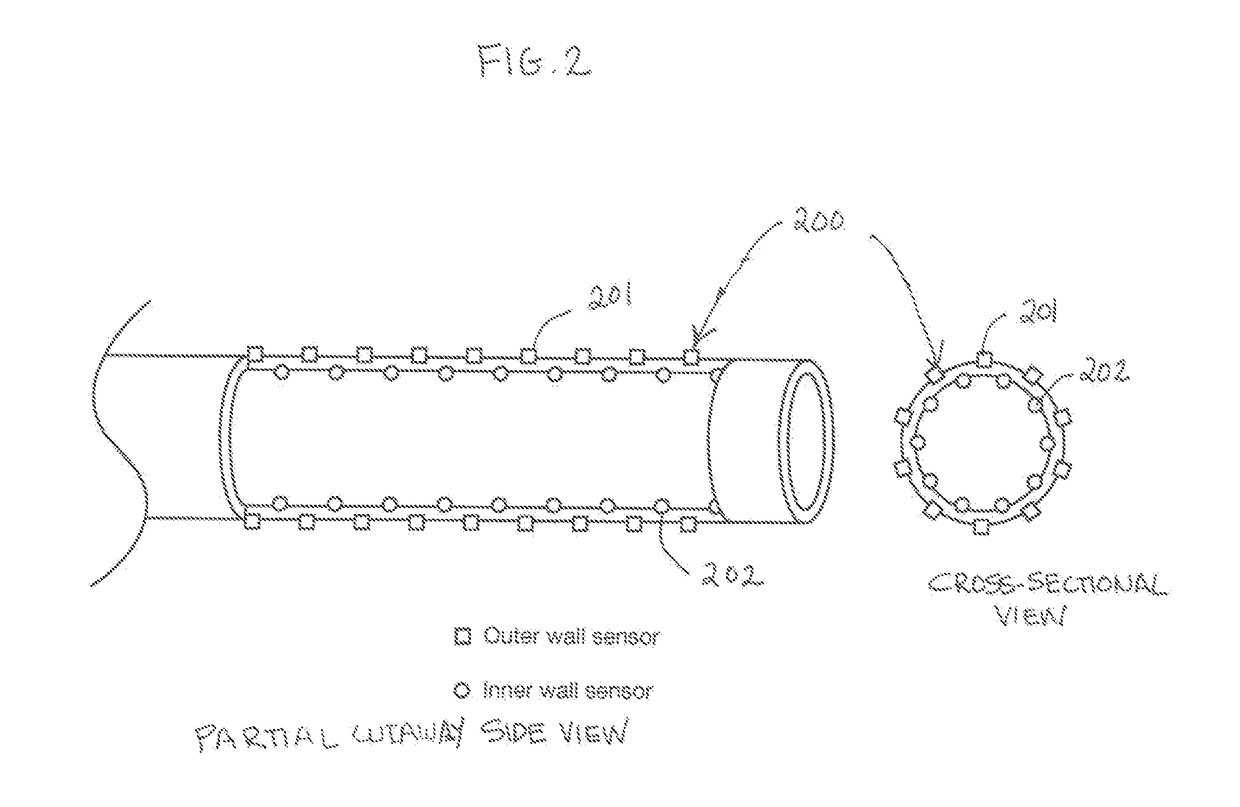
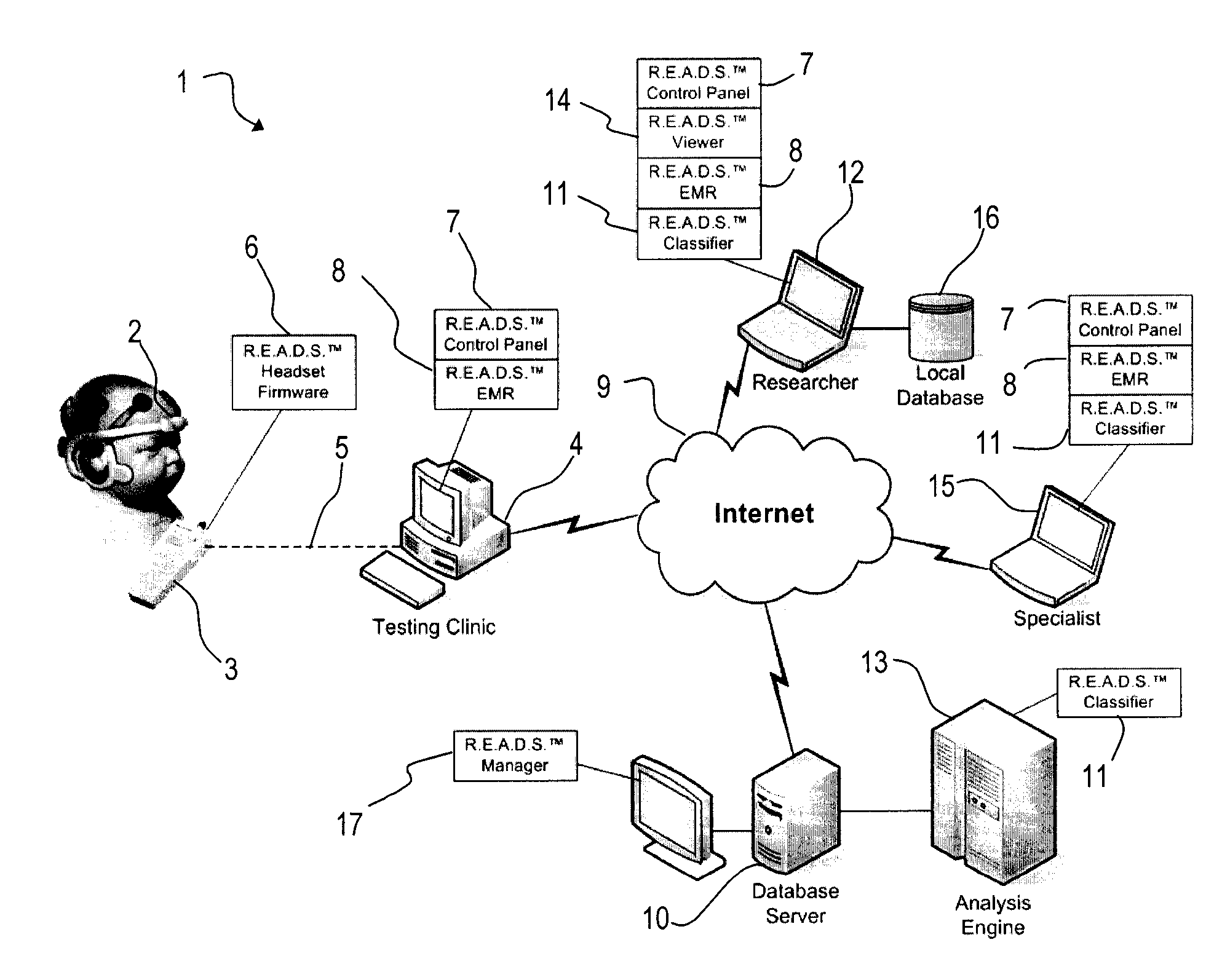
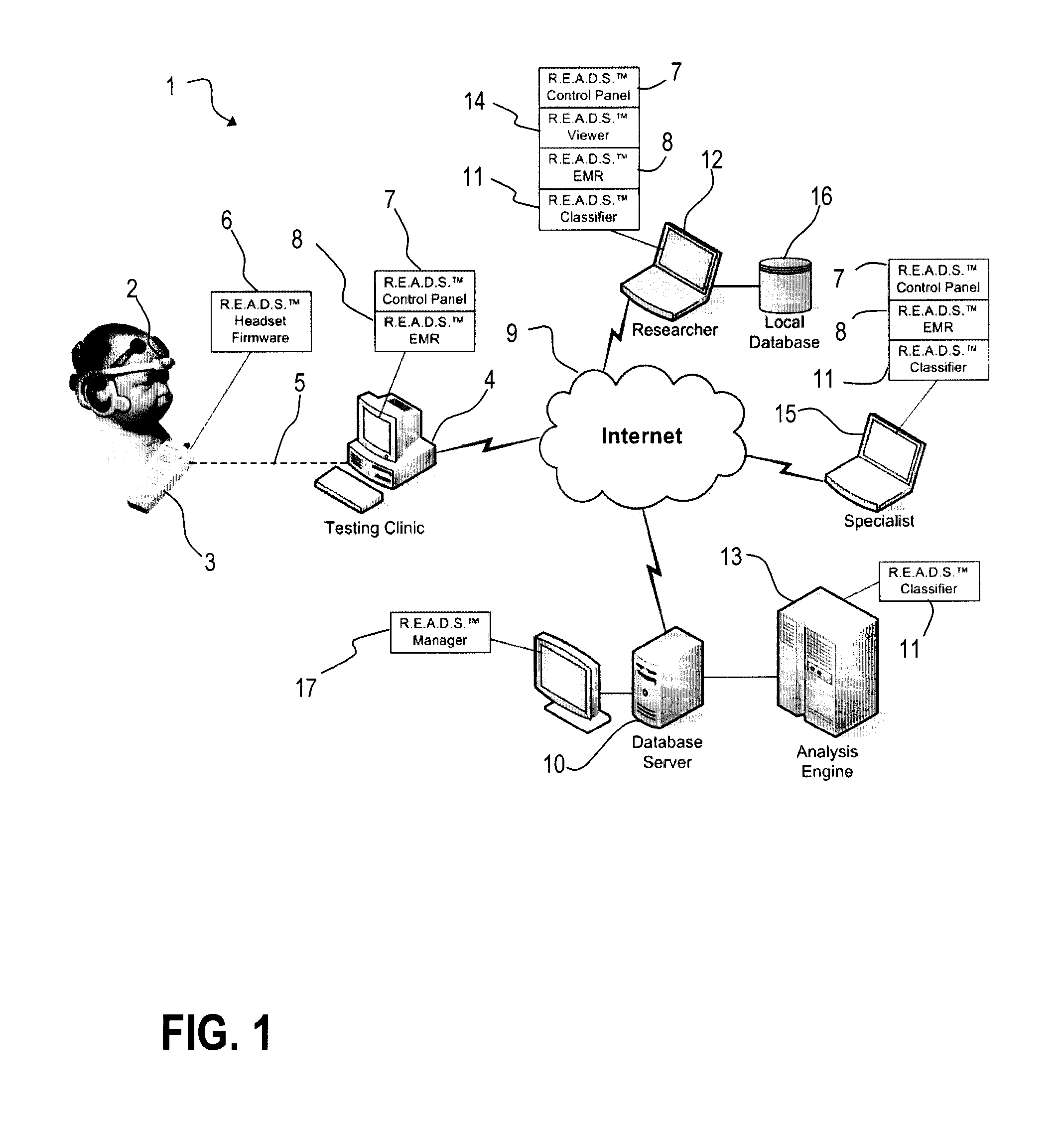
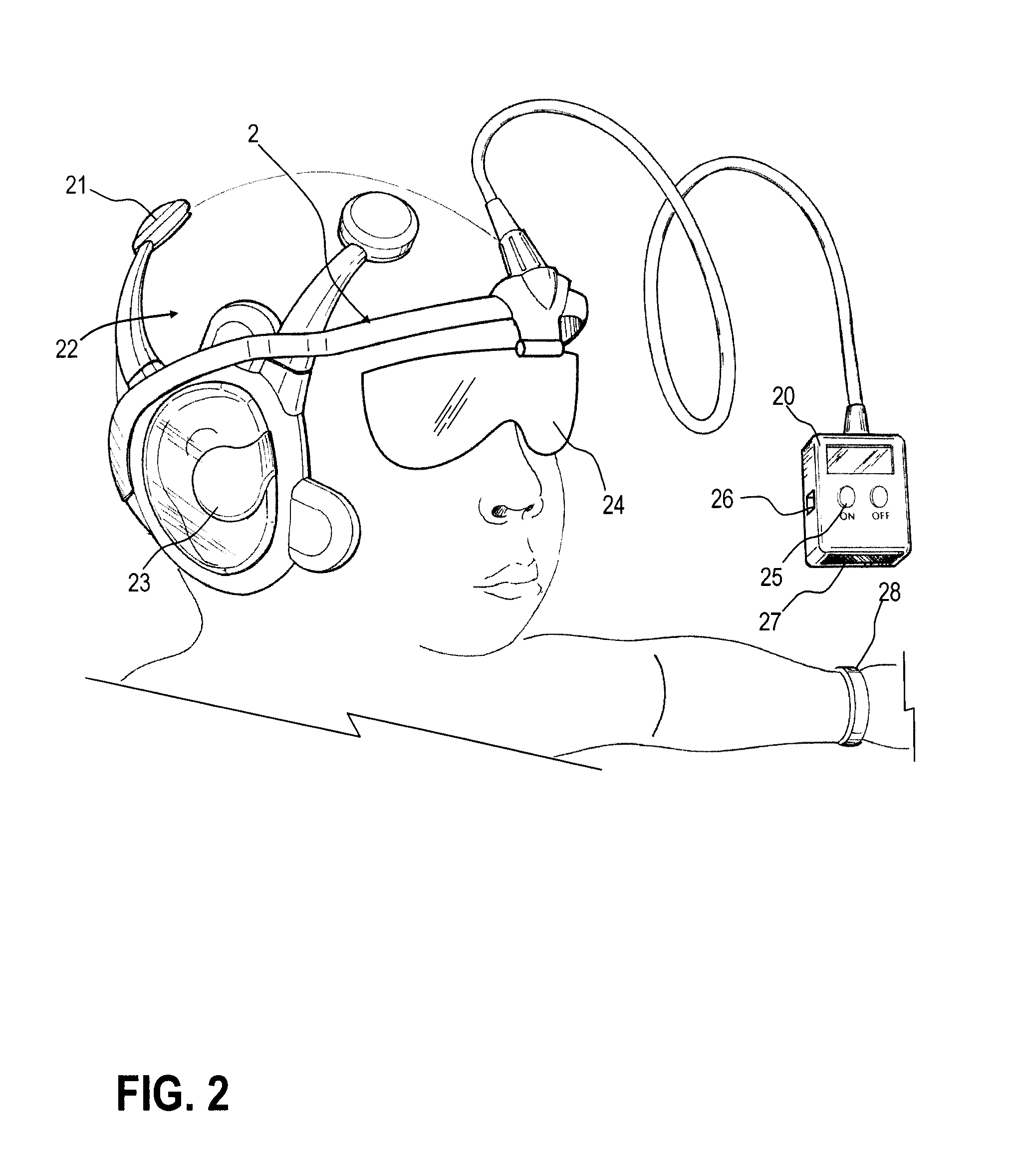
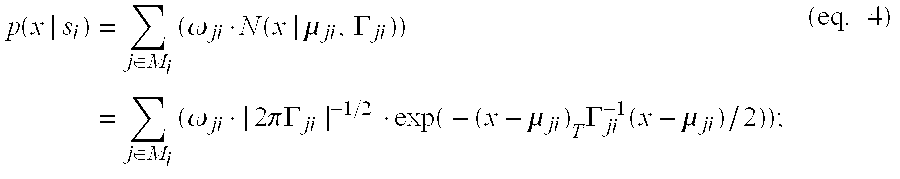Patents
Literature
4108 results about "Decision taking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Decision making is the process of making choices by identifying a decision, gathering information, and assessing alternative resolutions. Using a step-by-step decision-making process can help you make more deliberate, thoughtful decisions by organizing relevant information and defining alternatives.
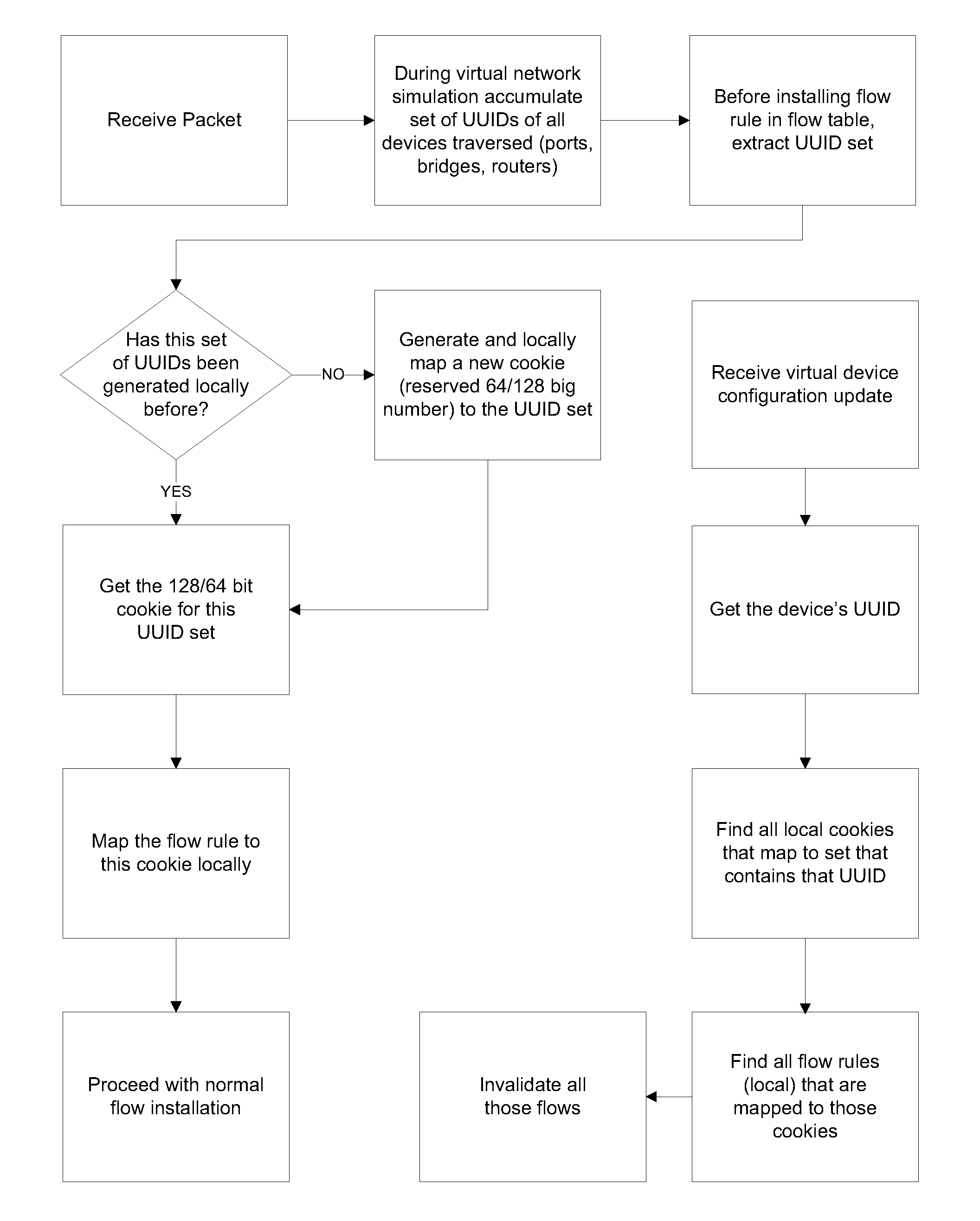
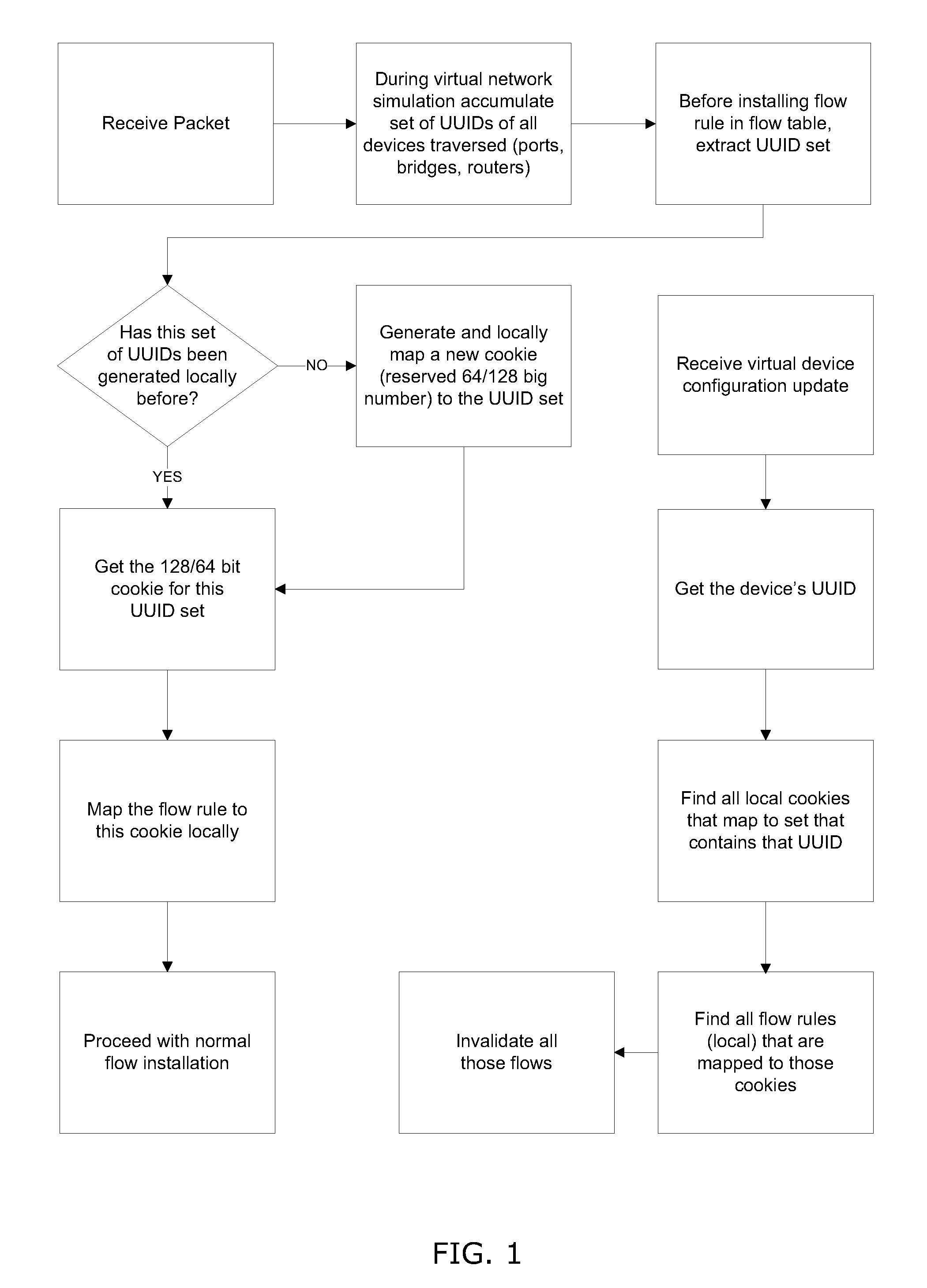
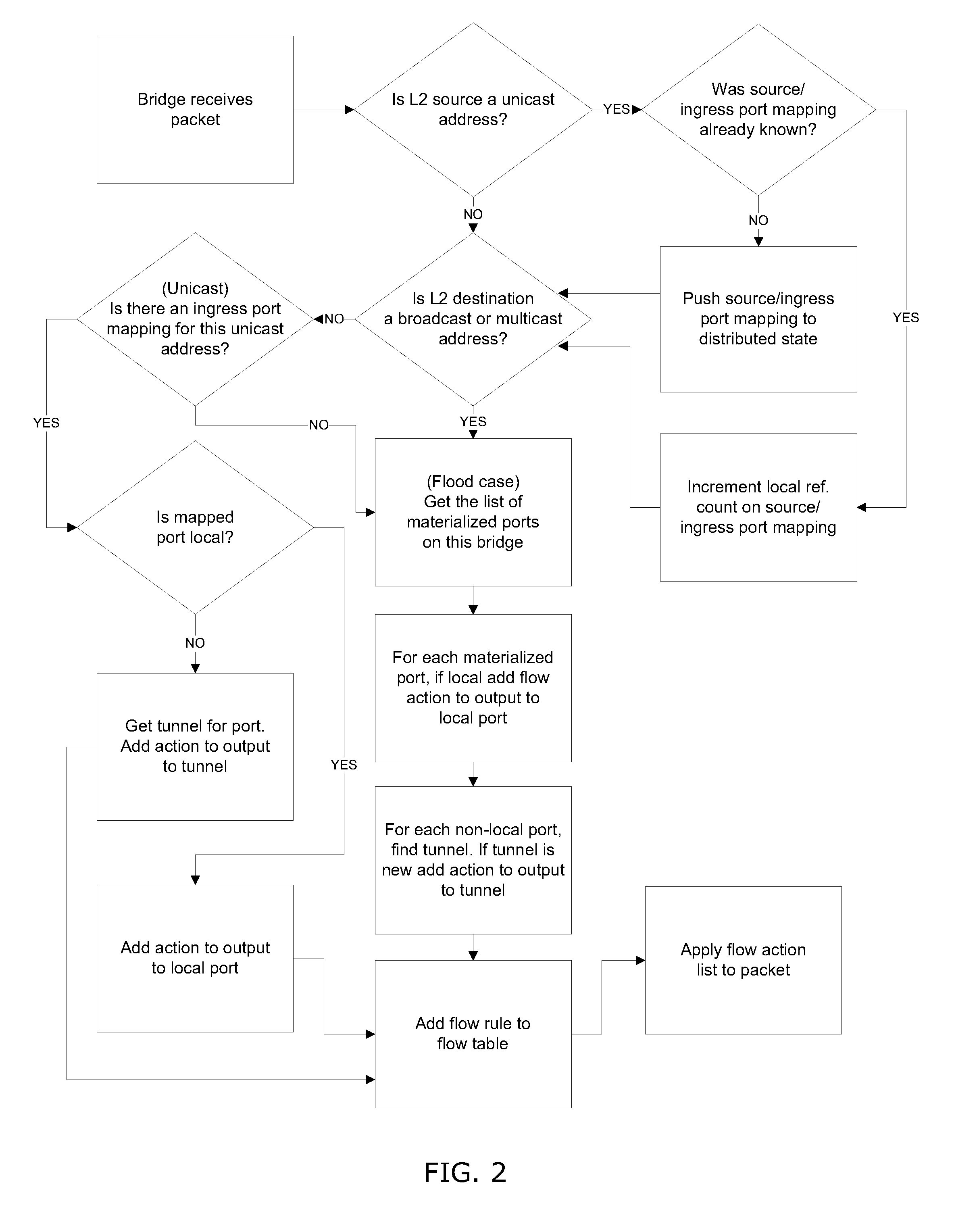
System and method for implementing and managing virtual networks
ActiveUS20140195666A1Digital computer detailsData switching networksVirtual network topologyDecision taking
A system and method for implementing and management virtual networks is disclosed. A method includes receiving a network packet arriving at a first network interface of a first node of an underlying network, communicating at least the packet and an identifier of the first network interface to a decision engine, determining how the packet should be processed based on a simulation by the decision engine of a traversal of a virtual network topology including a plurality of virtual network devices, wherein the decision engine communicates with a shared database accessible from the underlying network that stores the virtual network topology and virtual device configurations for the plurality of virtual network devices; and processing the packet based upon the simulation.
Owner:MIDO HLDG LTD
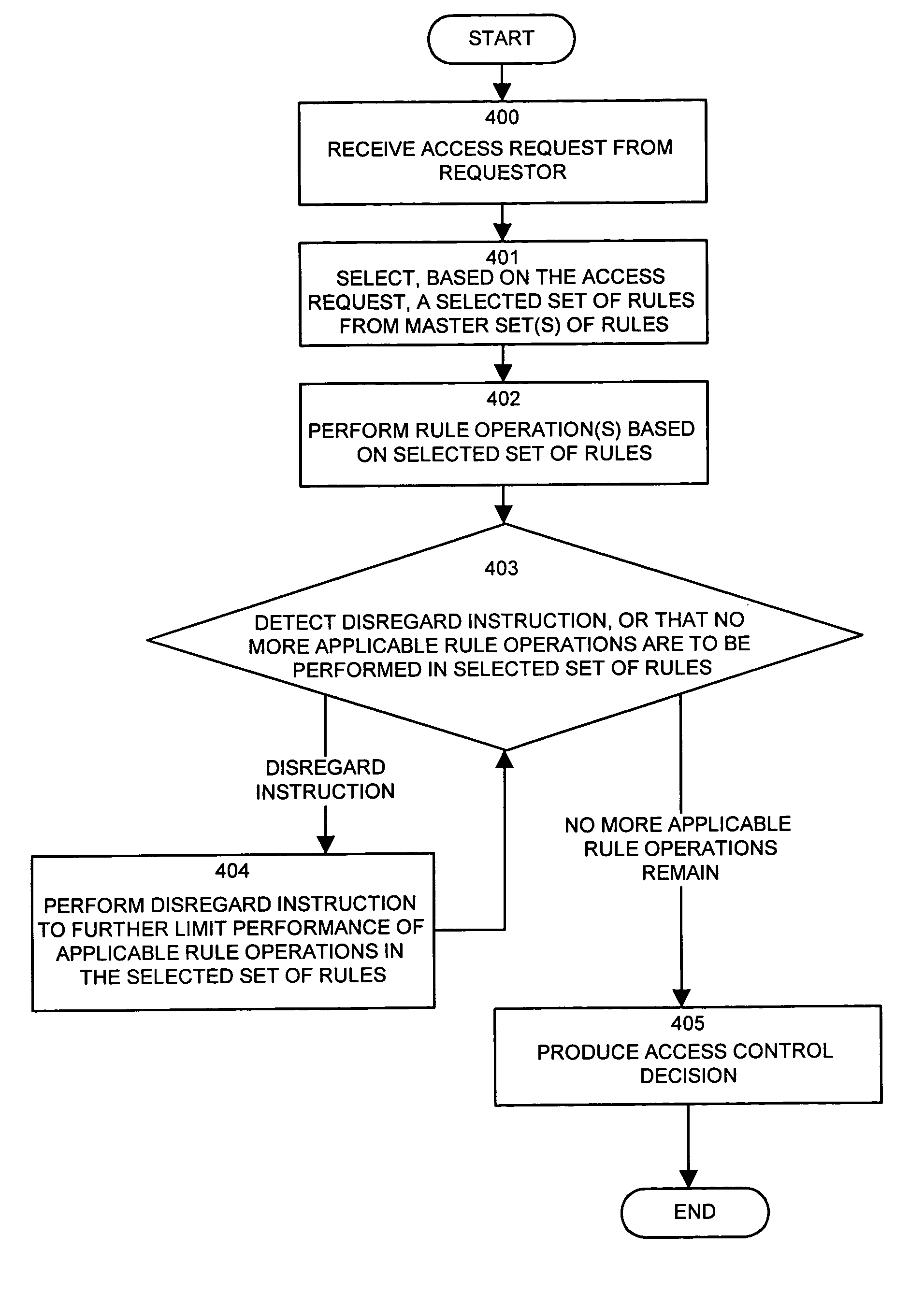
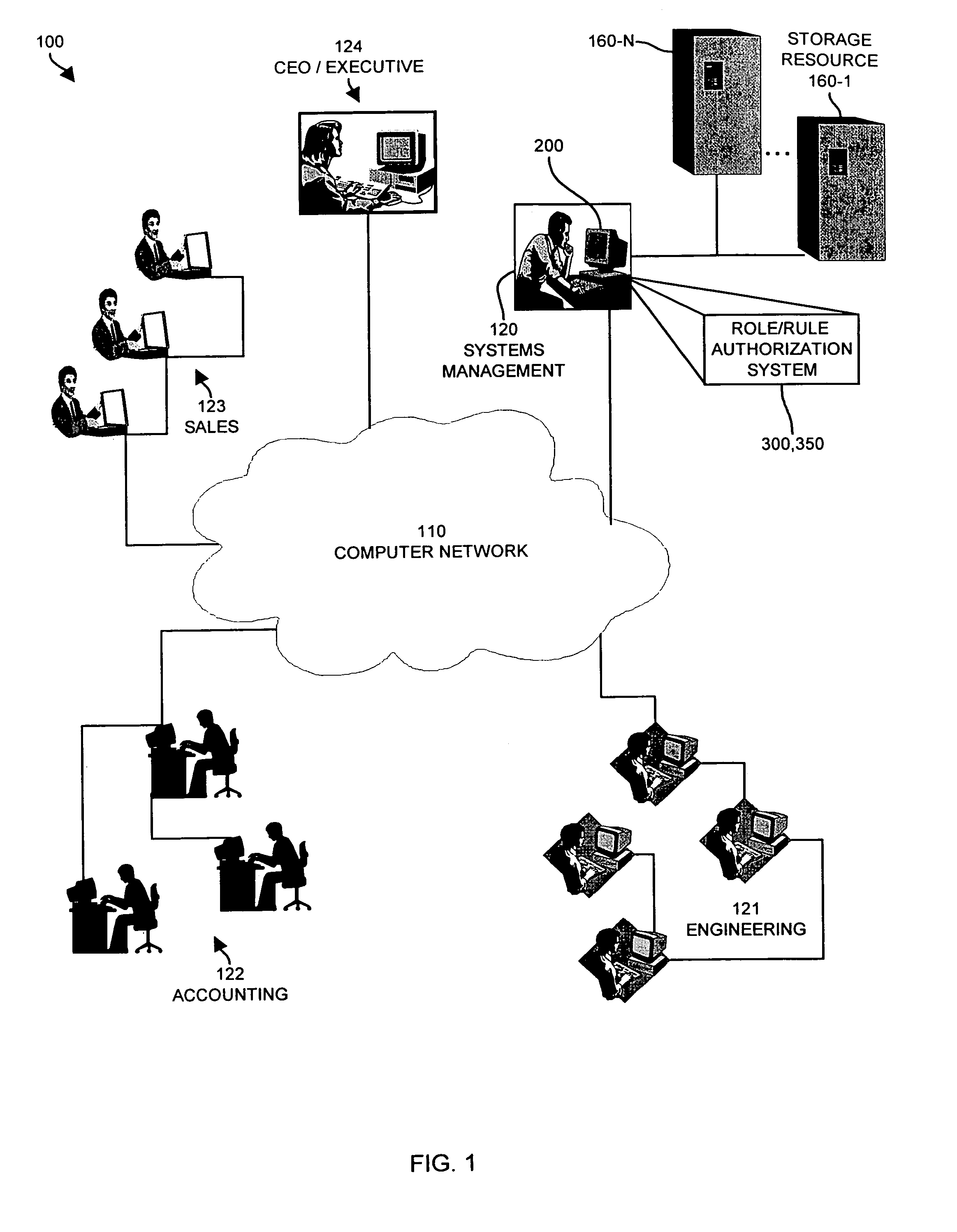
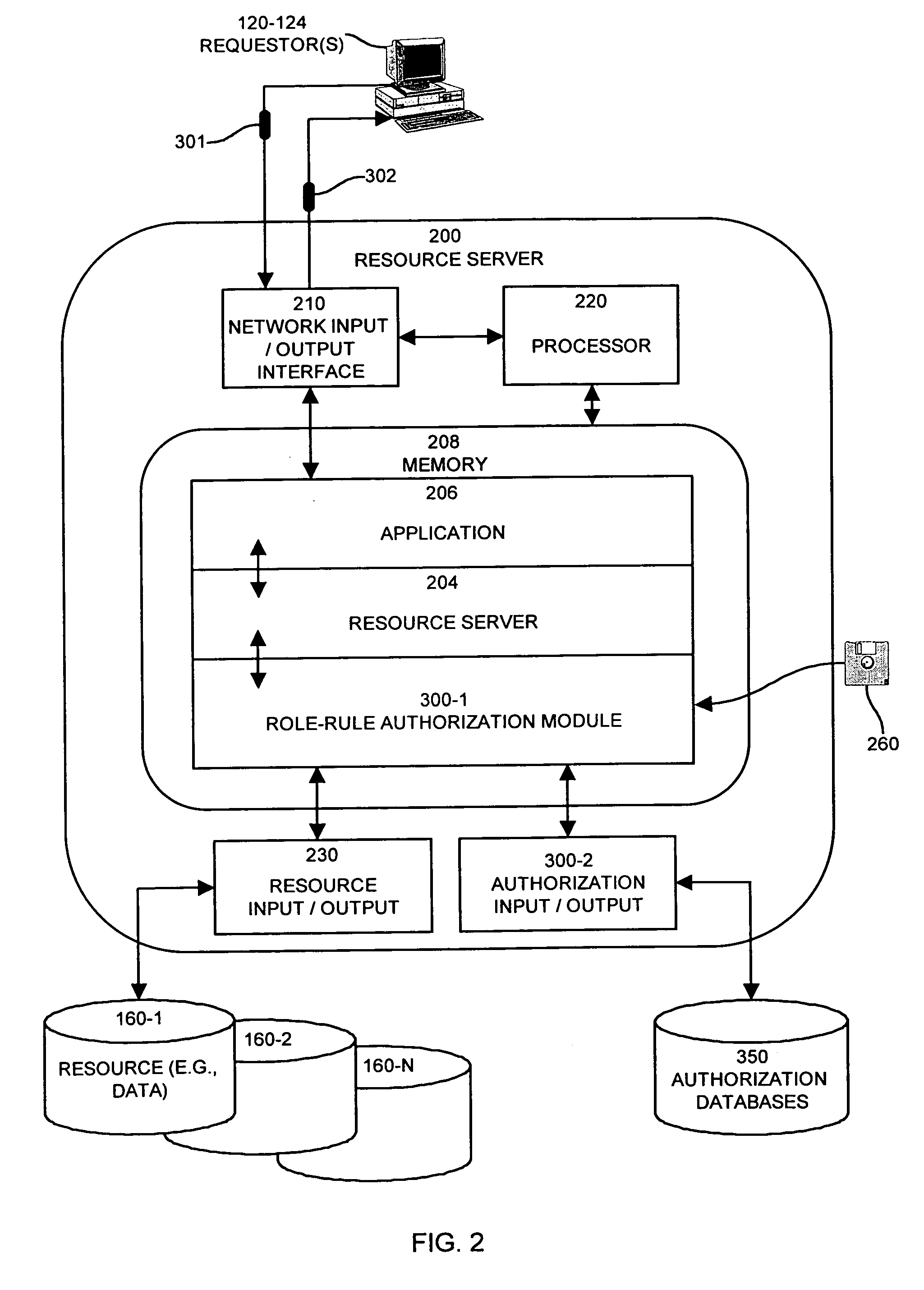
Methods and apparatus for controlling access to a resource
InactiveUS7185192B1Limit staff employee accessVerification of the security policy more straightforwardData processing applicationsDigital data processing detailsProgramming languageDecision taking
An input / output interface receives an access request from a requester. A processor associated with the input / output interface applies a filter operation to select a subset of rules from a master set of rules maintained within an authorization database. Rules can be selected in this manner using filter operations so that all rules in the rule set need not be processed. A rule may include a disregard instruction. The processor further performs at least one rule operation based on the subset of rules to produce an access control decision in the memory system until either a rule operation including a disregard instruction is performed to limit performance of rule operations in the selected set of rules or until all rule operations in the selected set of rules that are applicable to the access control decision are performed.
Owner:EMC IP HLDG CO LLC
Method of buying or selling items and a user interface to facilitate the same
InactiveUS20060069635A1Easy to useFast and efficient and intuitive and user friendlySpecial service provision for substationFinanceMarket placeFinancial transaction
A method of buying or selling items having at least one market and its associated processes are disclosed. The method includes the steps of, under control of a client system, displaying information identifying at least one item and a bid and / or ask price for the item in the market; and specifying transaction conditions based on a user directed position of a moveable icon, where the transaction conditions are related to the buying or selling of the identified item in the active market. Then, in response to an action of the user sending a user transaction request at the transaction conditions displayed at the time of said action, facilitating financial transactions for the user in accordance with the transaction conditions to complete the transaction. In this manner, the item may be bought or sold by the user at the transaction conditions specified. A user interface to facilitate this method is also disclosed. A quantity recommendation system to facilitate the quantity decision of a financial transaction is further disclosed.
Owner:RAM PRANIL
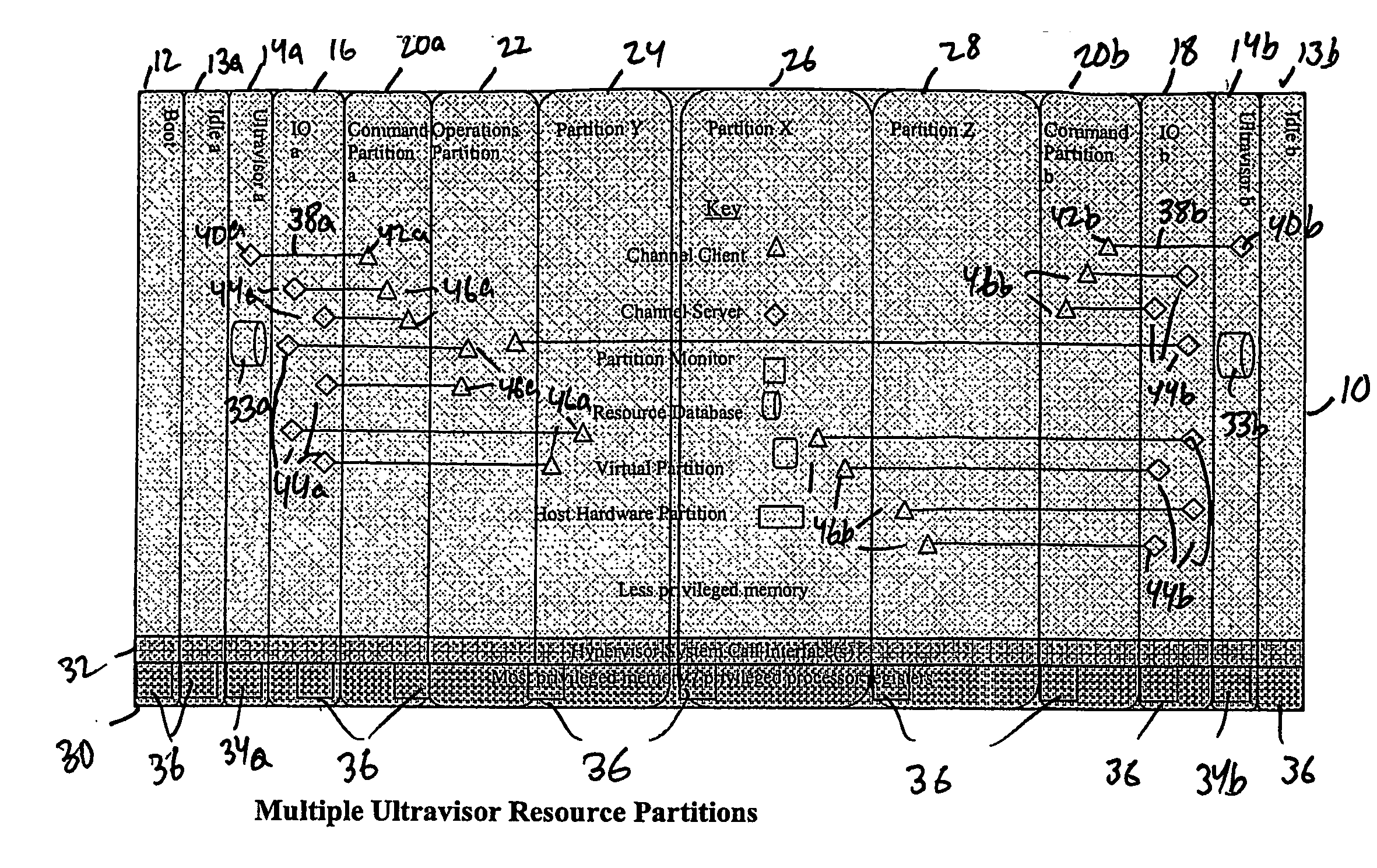
Virtual data center that allocates and manages system resources across multiple nodes
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
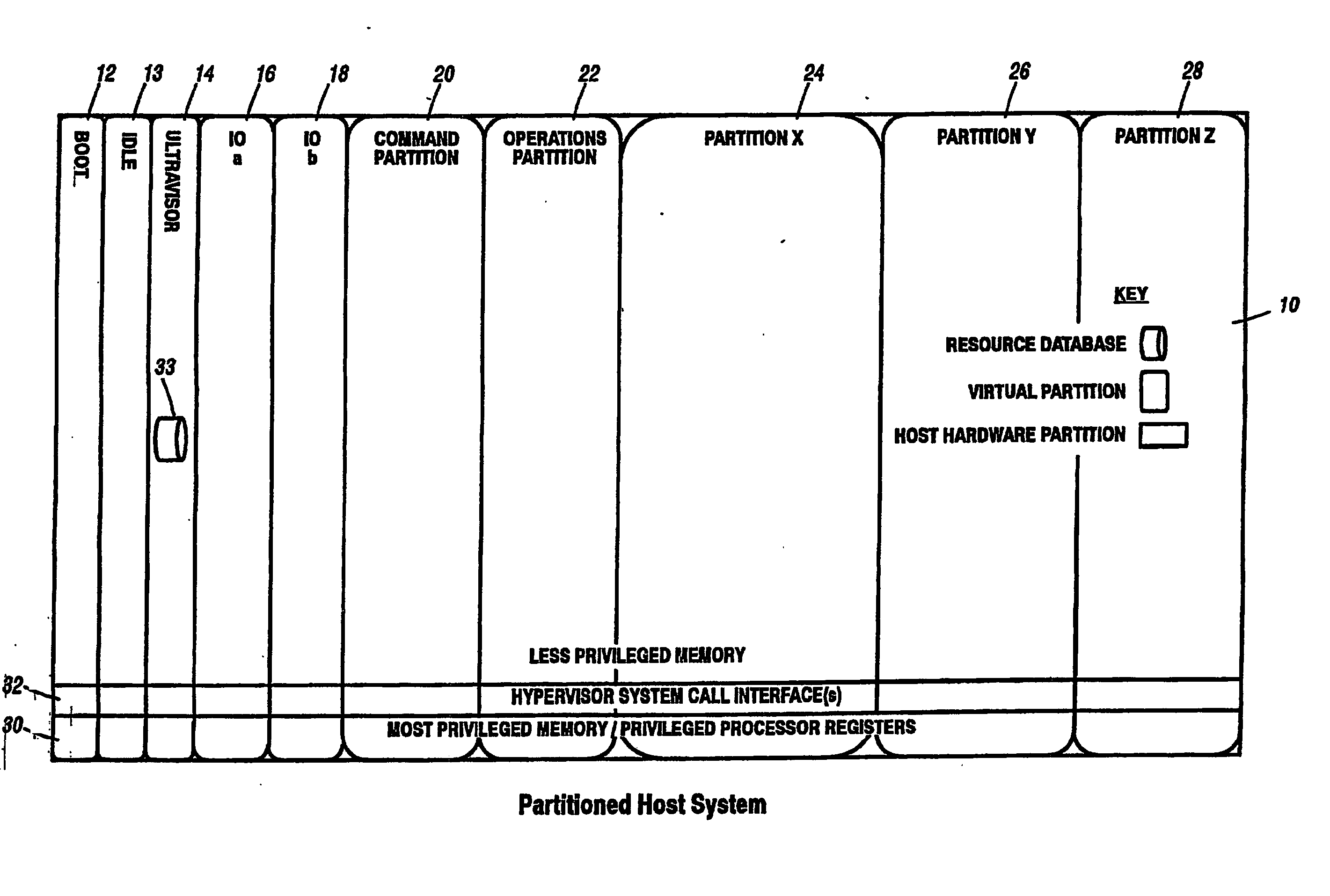
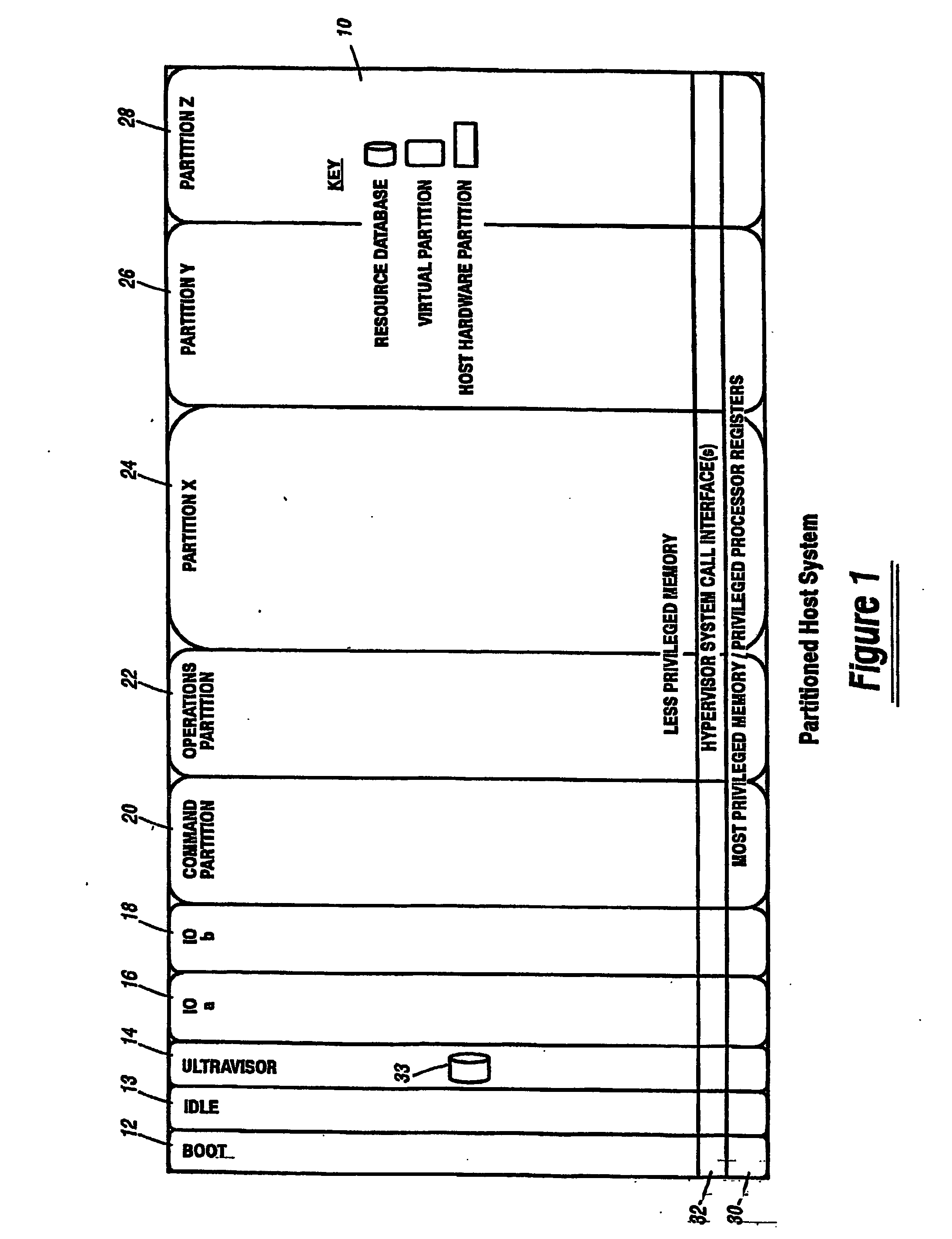
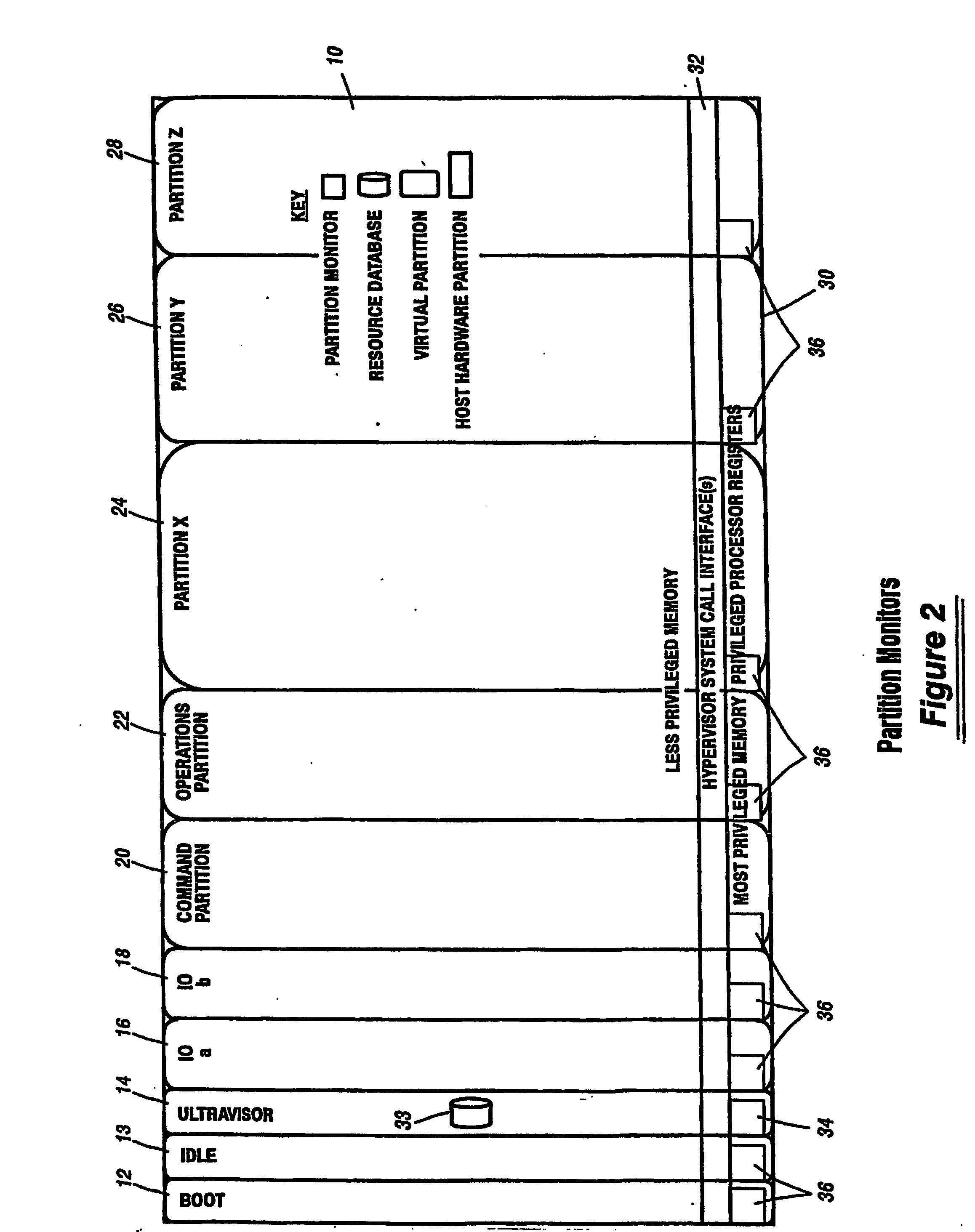
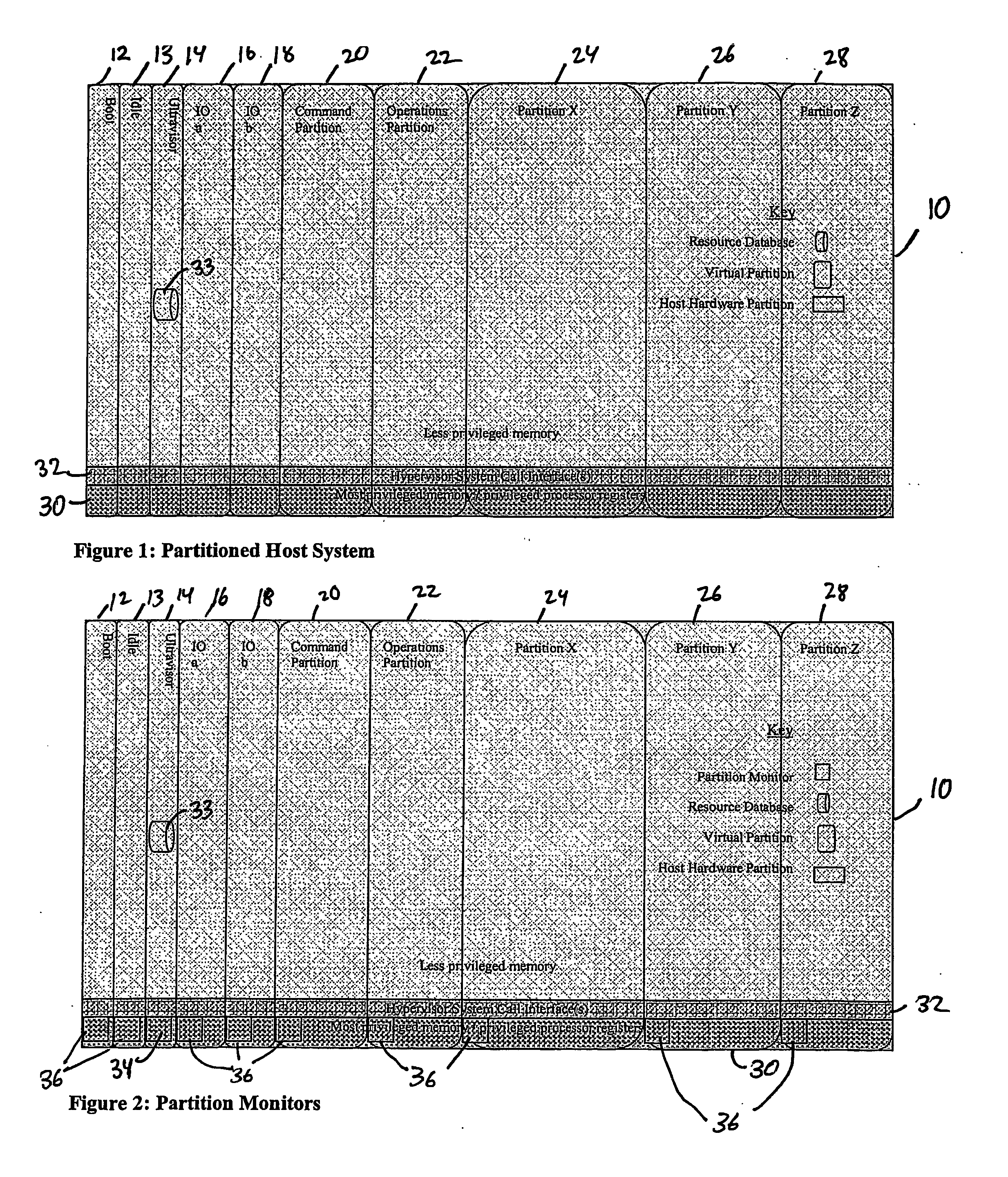
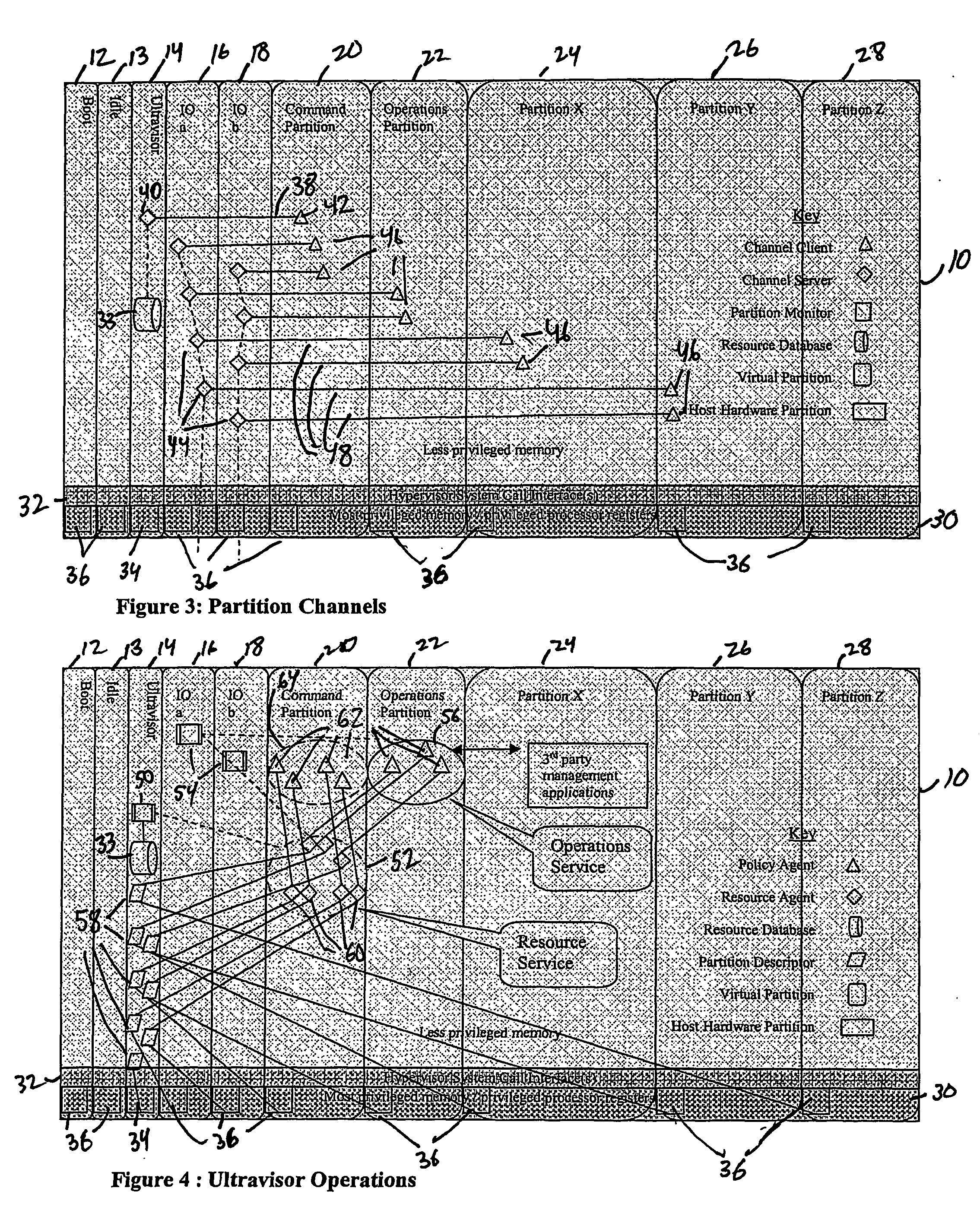
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
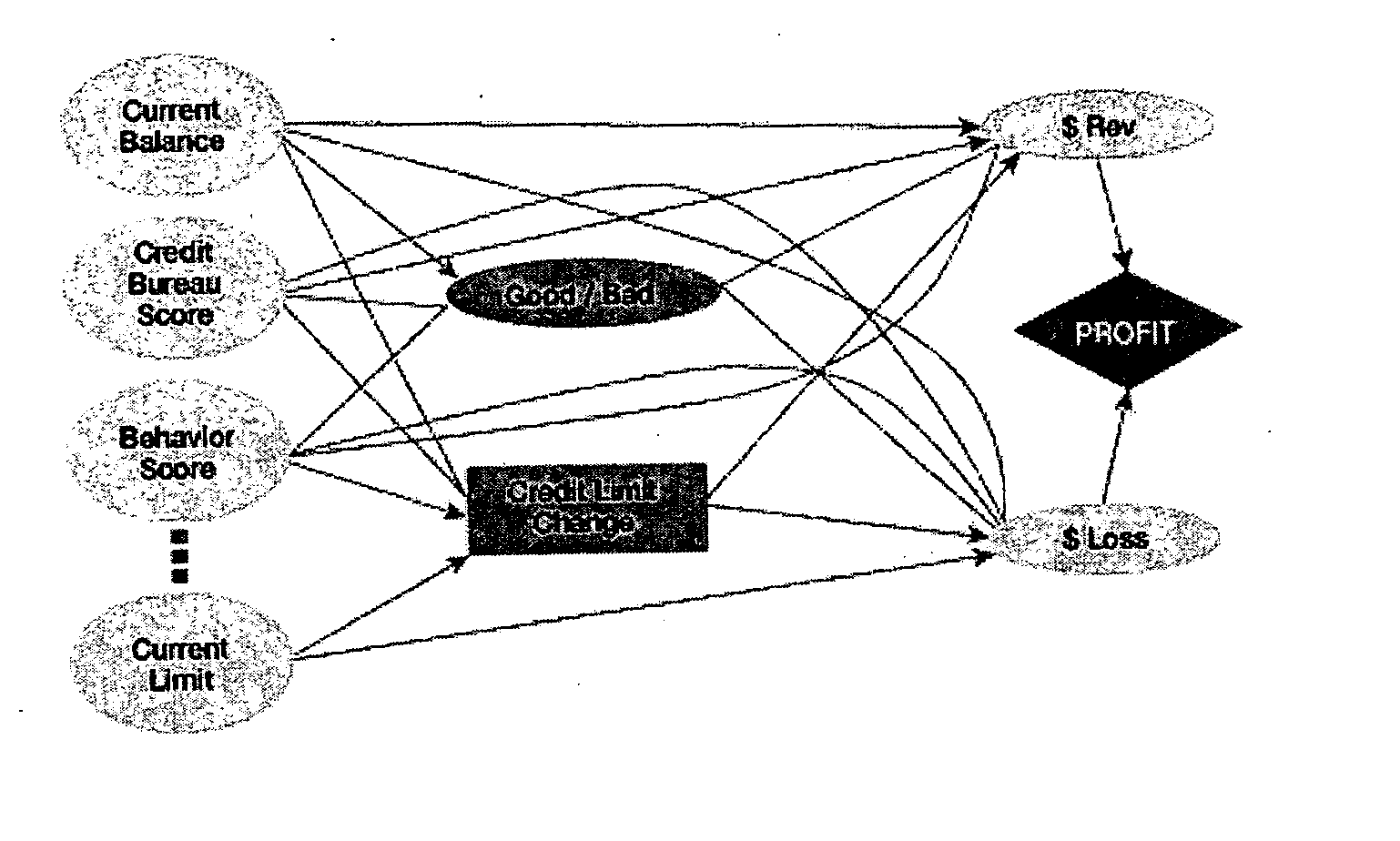
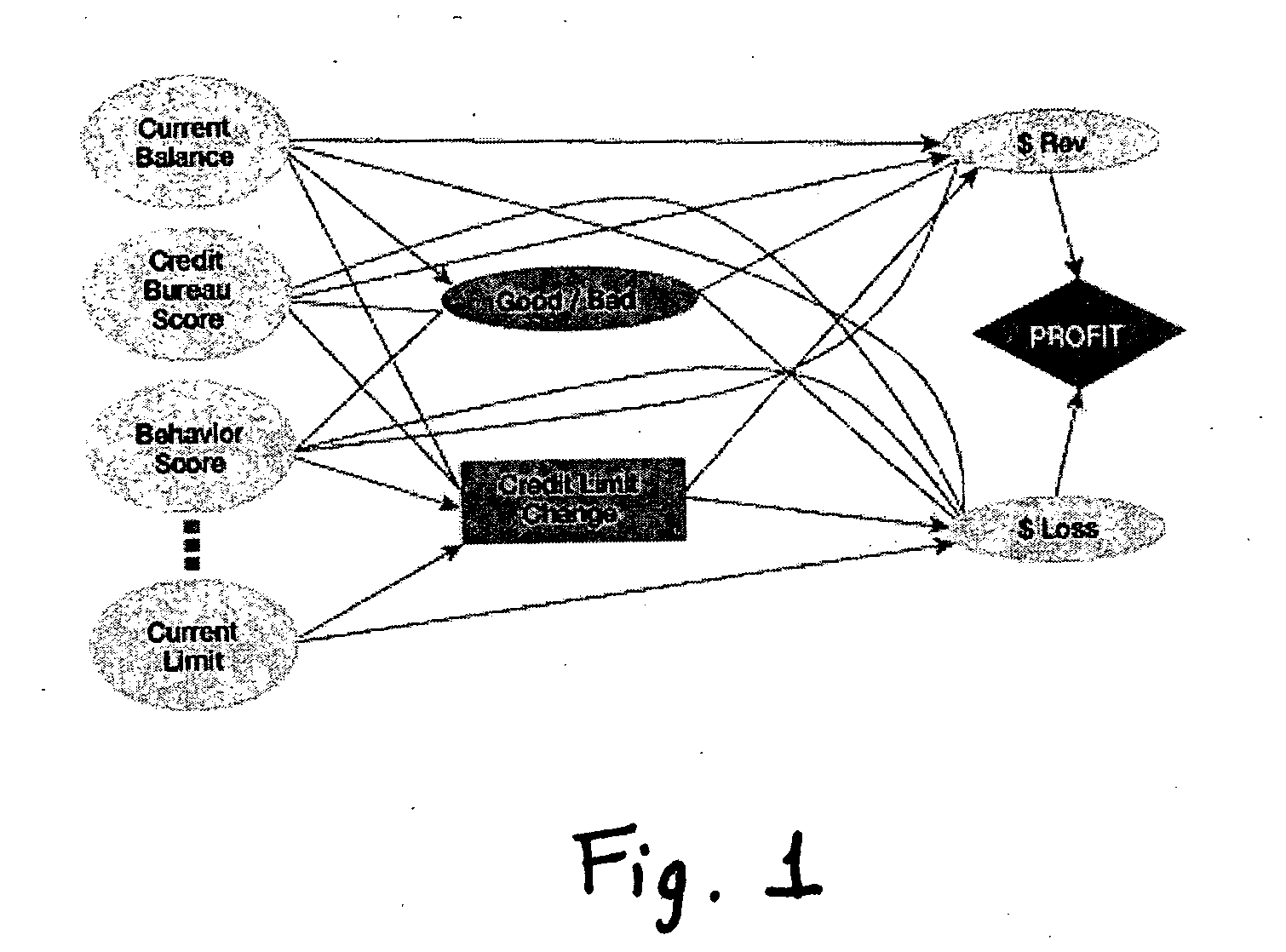
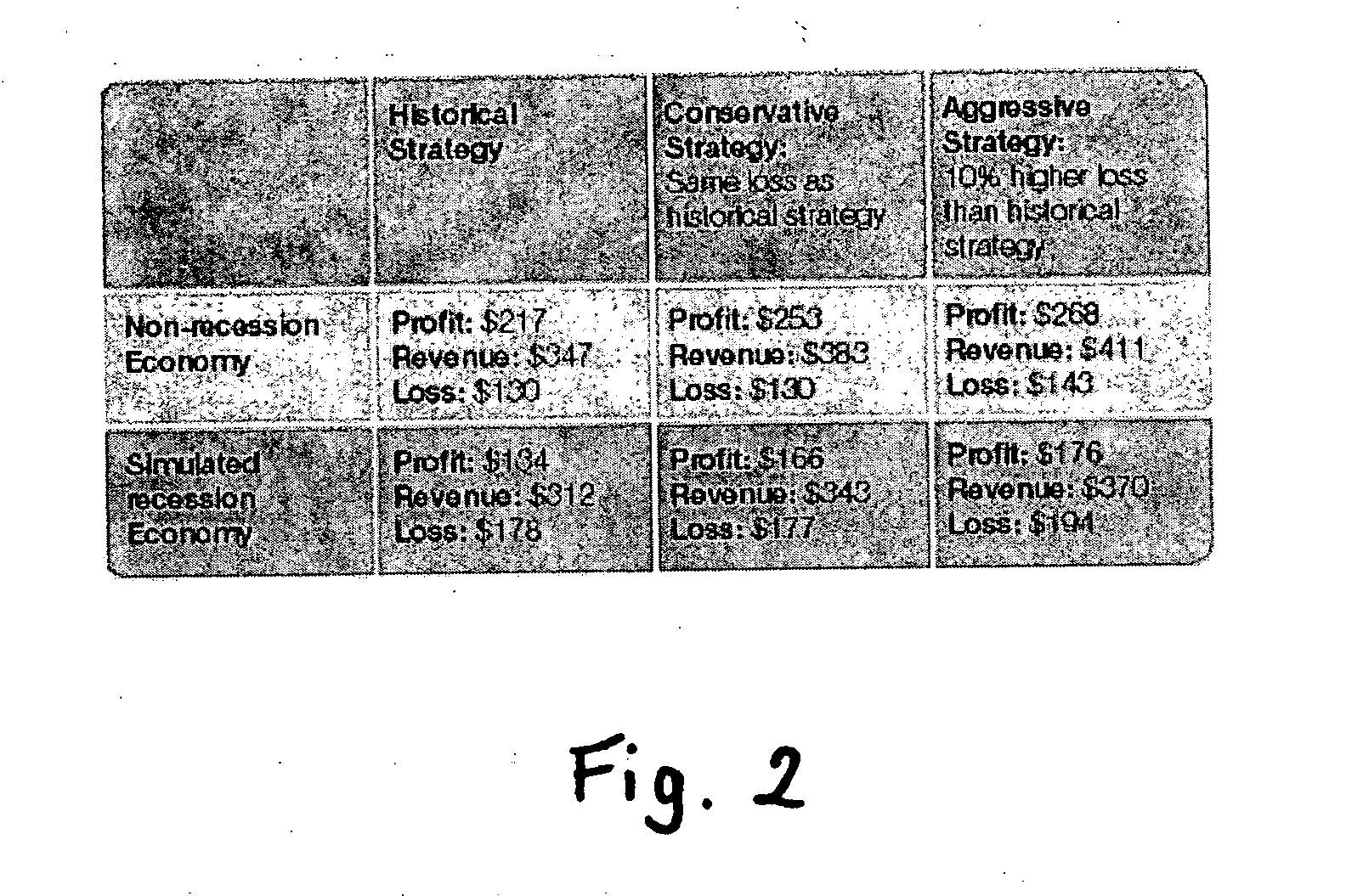
Method and apparatus for creating and evaluating strategies
A method and apparatus for strategy science methodology involving computer implementation is provided. The invention includes a well-defined set of procedures for carrying out a full range of projects to develop strategies for clients. One embodiment of the invention produces custom consulting projects that are found at one end of the full range of projects. At the other end of the range are, for example, projects developing strategies from syndicated models. The strategies developed are for single decisions or for sequences of multiple decisions. Some parts of the preferred embodiment of the invention are categorized into the following areas: Team Development, Strategy Situation Analysis, Quantifying the Objective Function, Data Request and Reception, Data Transformation and Cleansing, Decision Key and Intermediate Variable Creation, Data Exploration, Decision Model Structuring, Decision Model Quantification, An Exemplary Score Tuner, Strategy Creation, An Exemplary Strategy Optimizer, An Exemplary Uncertainty Estimator, and Strategy Testing. Each of the sub-categories are described and discussed in detail under sections of the same headings. The invention uses judgment in addition to data for developing strategies for clients.
Owner:FAIR ISAAC & CO INC
Computer system para-virtualization using a hypervisor that is implemented in a partition of the host system
ActiveUS20070028244A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemSystem call
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
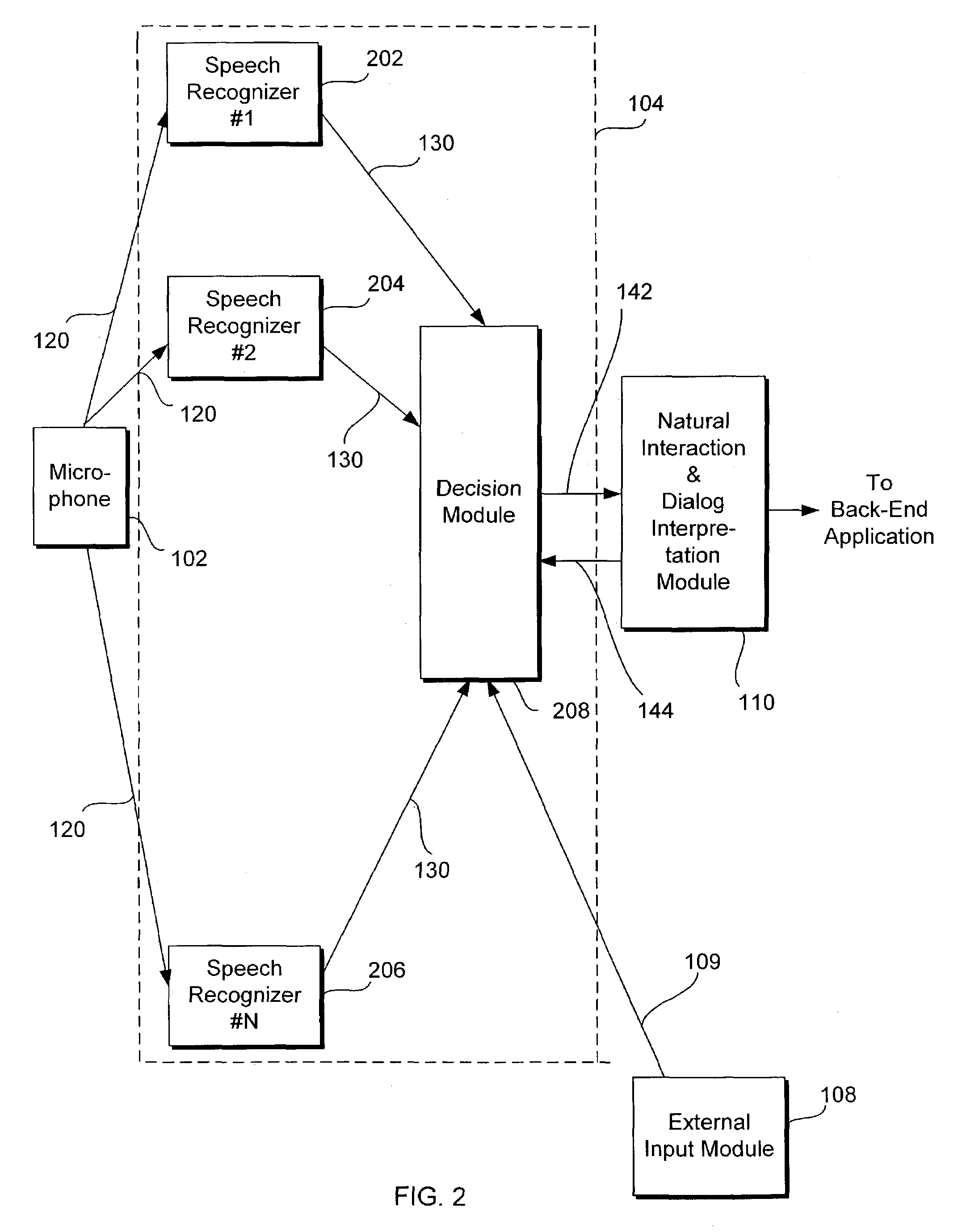
Speech recognition system having multiple speech recognizers
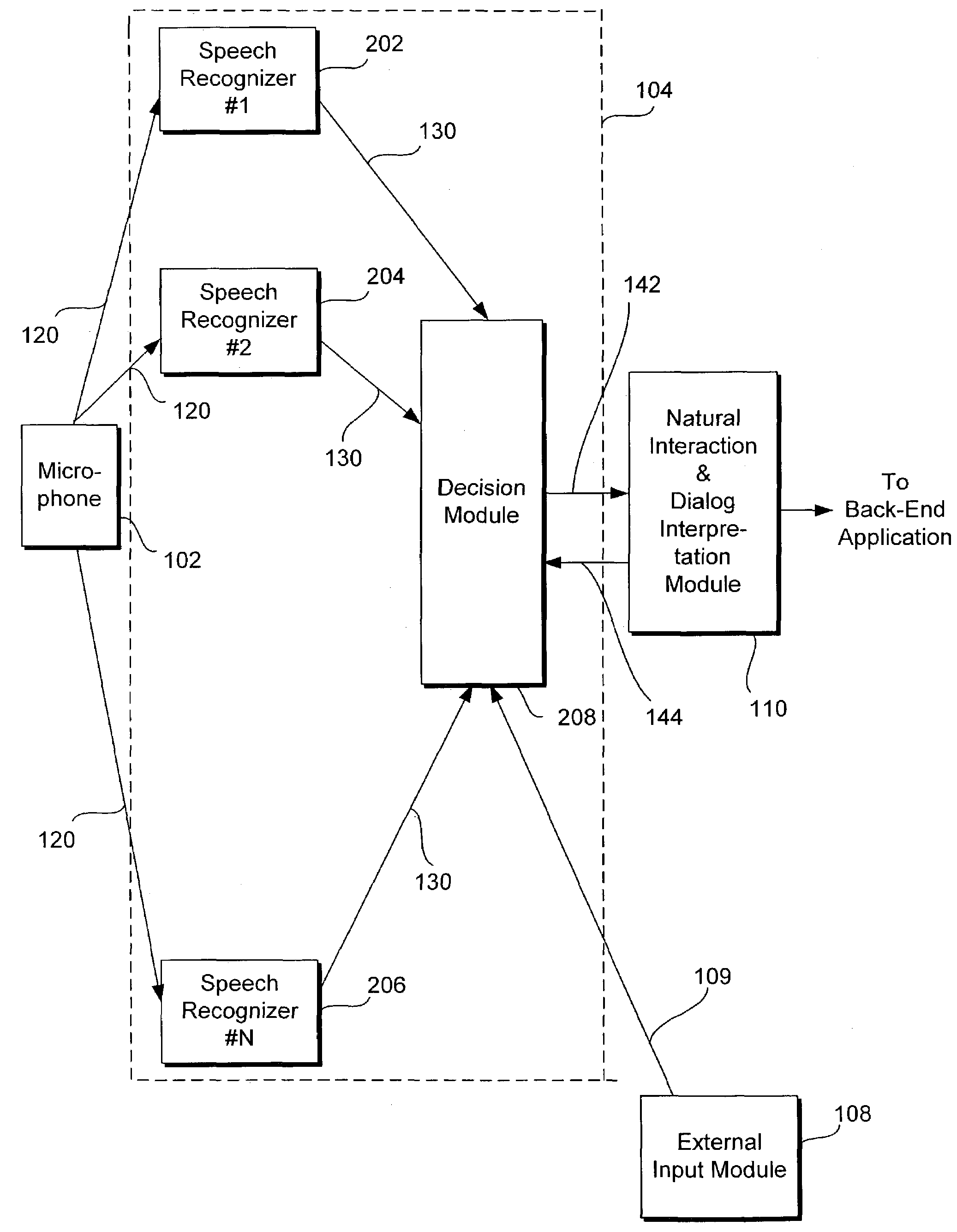
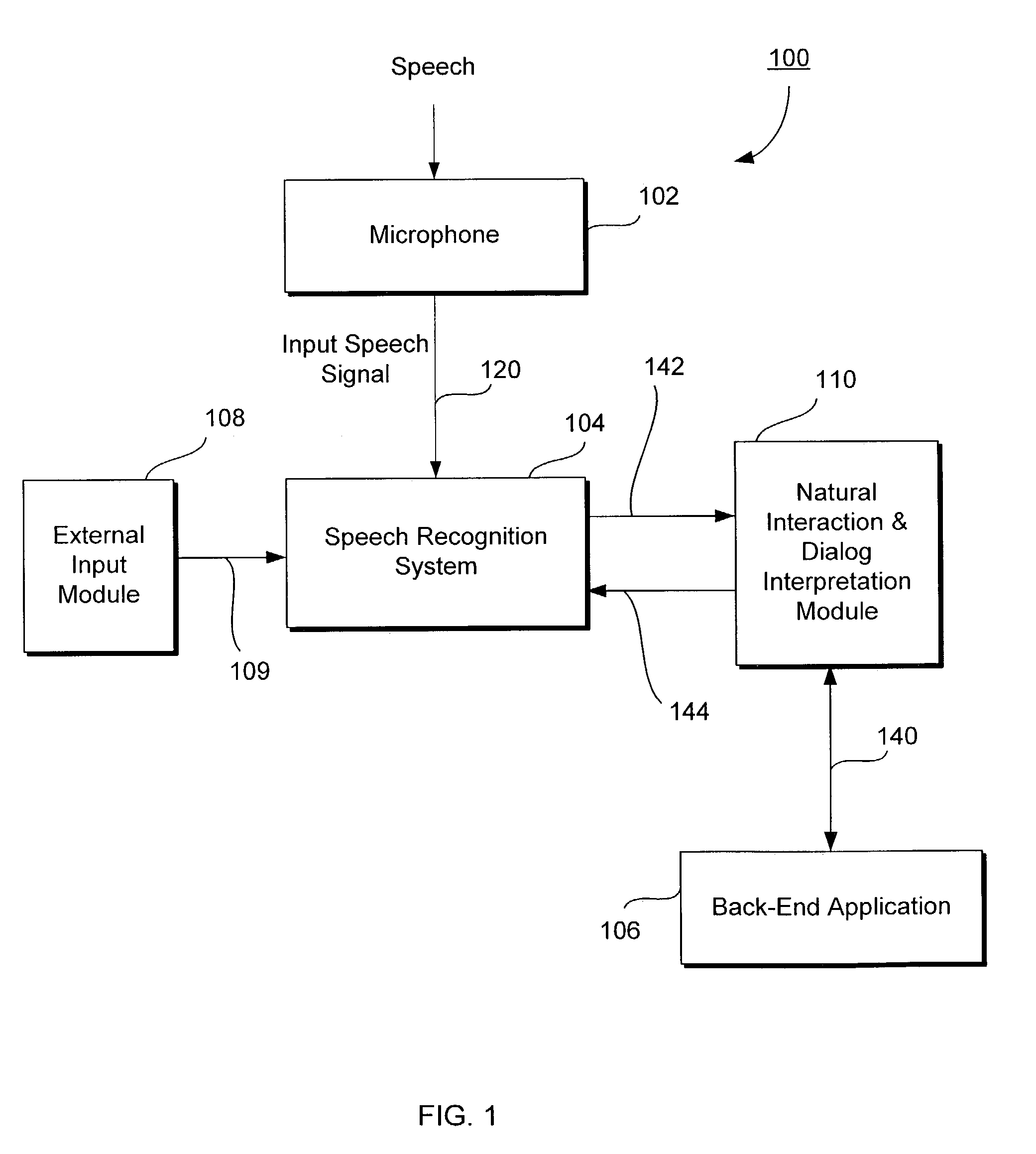
InactiveUS7228275B1Reduce intensityExcessive signalingSpeech recognitionSpeech identificationDecision taking
A speech recognition system recognizes an input speech signal by using a first speech recognizer and a second speech recognizer each coupled to a decision module. Each of the first and second speech recognizers outputs first and second recognized speech texts and first and second associated confidence scores, respectively, and the decision module selects either the first or the second speech text depending upon which of the first or second confidence score is higher. The decision module may also adjust the first and second confidence scores to generate first and second adjusted confidence scores, respectively, and select either the first or second speech text depending upon which of the first or second adjusted confidence scores is higher. The first and second confidence scores may be adjusted based upon the location of a speaker, the identity or accent of the speaker, the context of the speech, and the like.
Owner:TOYOTA INFOTECHNOLOGY CENT CO LTD +1
Evaluating public records of supply transactions for financial investment decisions
ActiveUS20110173093A1Promote generationEasy to shareFinanceBuying/selling/leasing transactionsThird partyDecision taking
Owner:PANJIVA
System, method to generate transliteration and method for generating decision tree to obtain transliteration
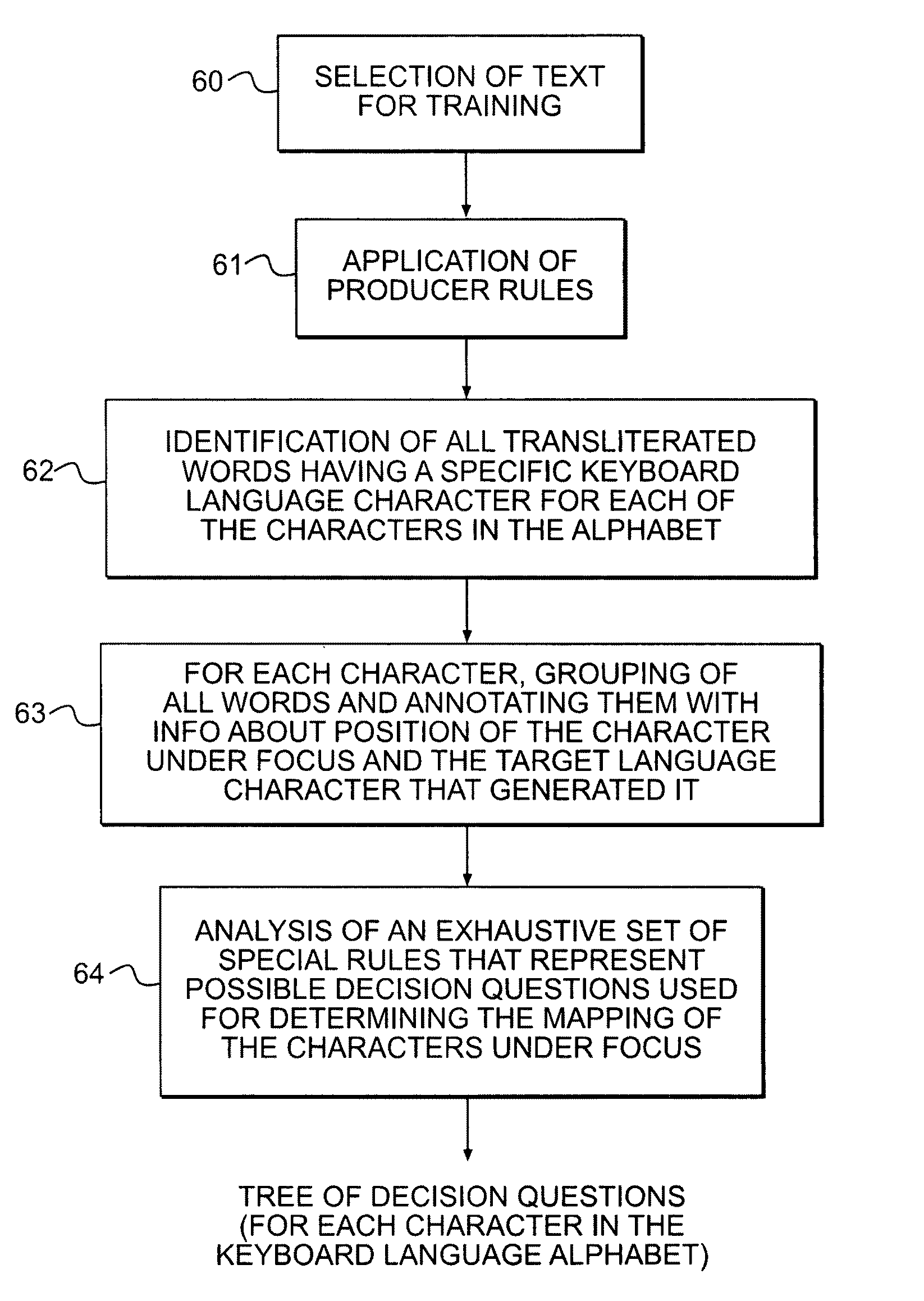
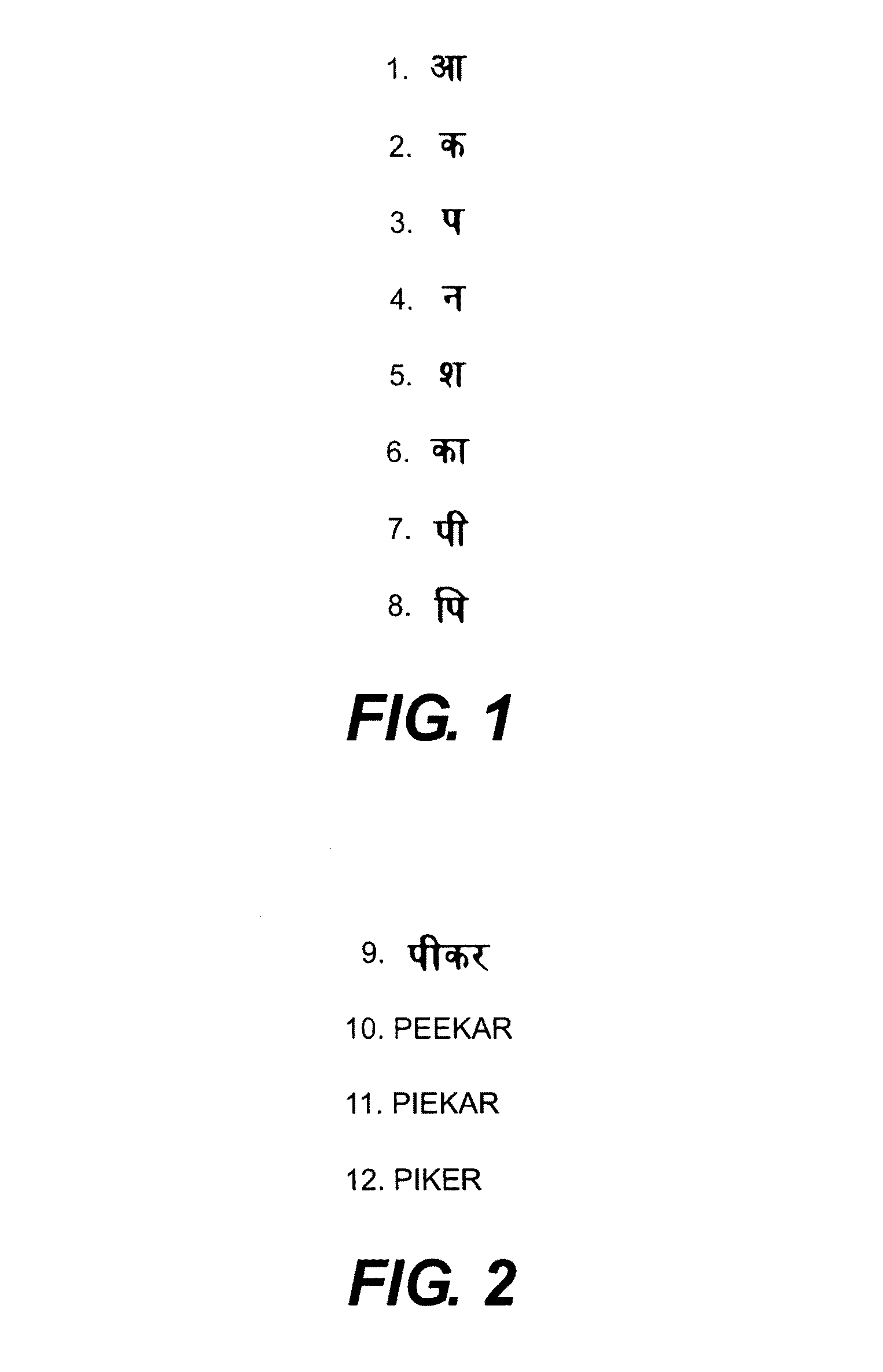
InactiveUS8005664B2Easily transliterateFast and efficient and accurate methodNatural language data processingSpecial data processing applicationsProgramming languageTransliteration
Owner:TACHYON TECH PVT
System and method for integrating and validating genotypic, phenotypic and medical information into a database according to a standardized ontology
InactiveUS20070178501A1Safest and most effective treatmentGood decisionData processing applicationsMicrobiological testing/measurementData validationMedical record
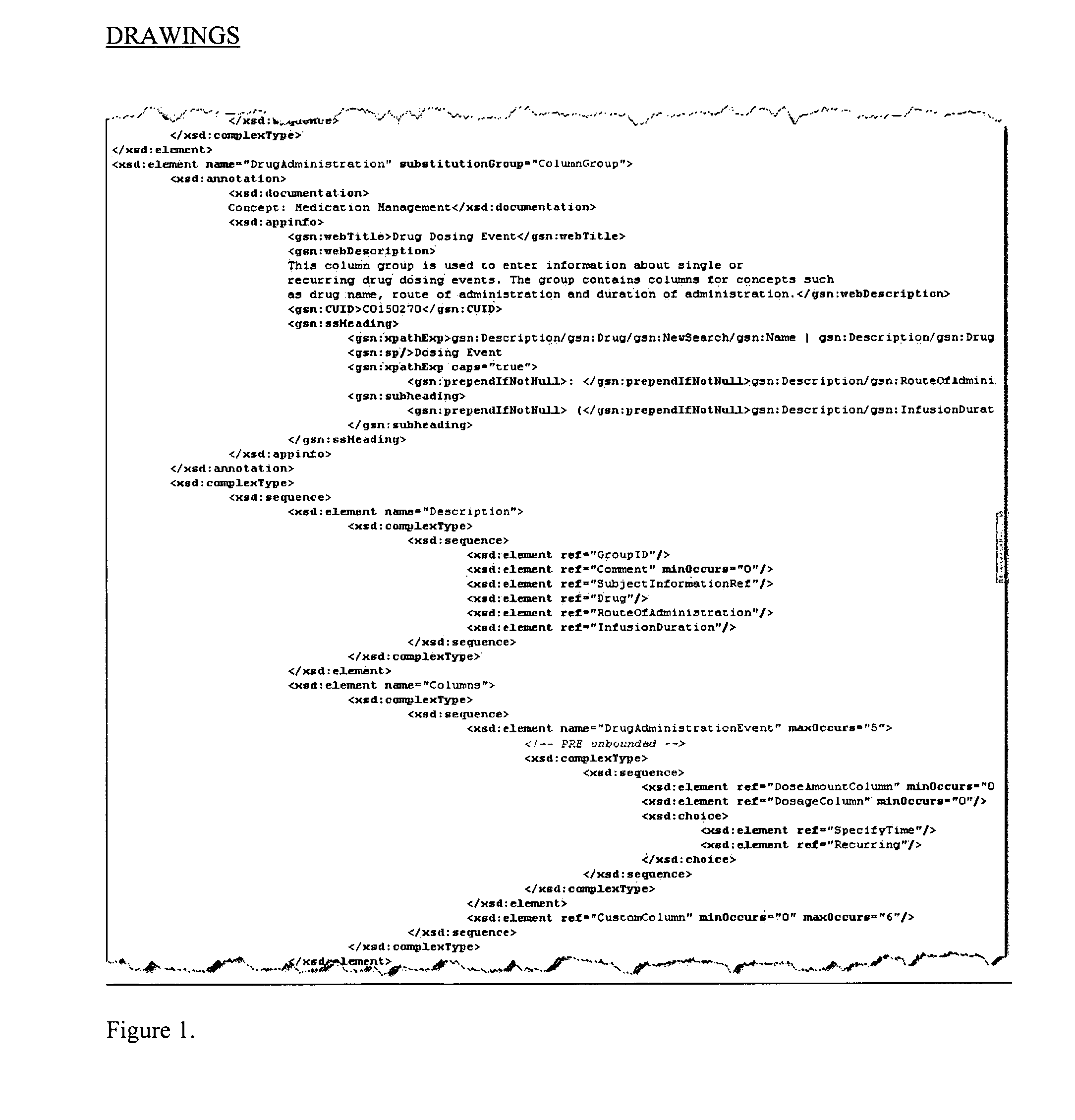
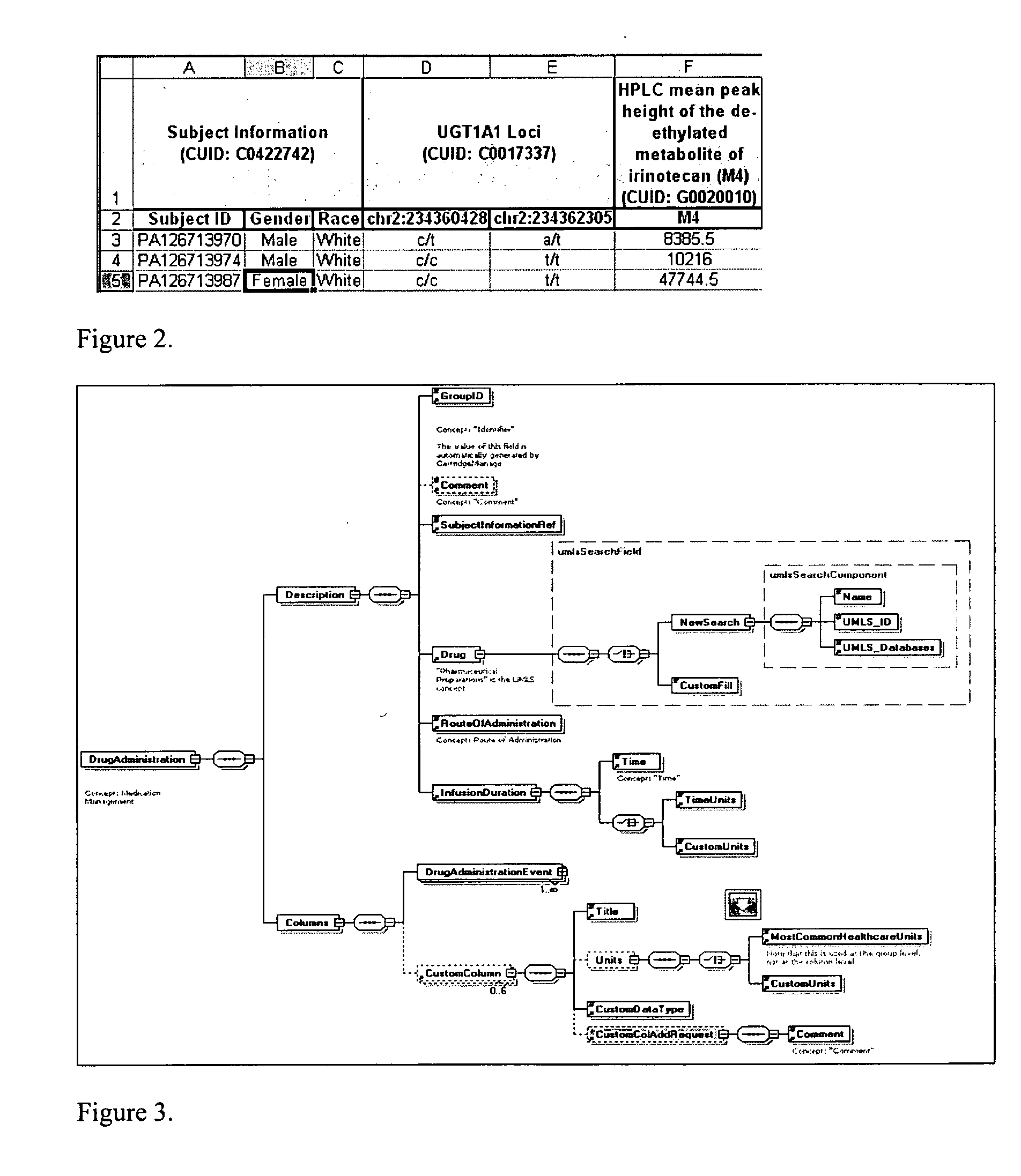
The system described herein enables clinicians and researchers to use aggregated genetic and phenotypic data from clinical trials and medical records to make the safest, most effective treatment decisions for each patient. This involves (i) the creation of a standardized ontology for genetic, phenotypic, clinical, pharmacokinetic, pharmacodynamic and other data sets, (ii) the creation of a translation engine to integrate heterogeneous data sets into a database using the standardized ontology, and (iii) the development of statistical methods to perform data validation and outcome prediction with the integrated data. The system is designed to interface with patient electronic medical records (EMRs) in hospitals and laboratories to extract a particular patient's relevant data. The system may also be used in the context of generating phenotypic predictions and enhanced medical laboratory reports for treating clinicians. The system may also be used in the context of leveraging the huge amount of data created in medical and pharmaceutical clinical trials. The ontology and validation rules are designed to be flexible so as to accommodate a disparate set of clients. The system is also designed to be flexible so that it can change to accommodate scientific progress and remain optimally configured.
Owner:NATERA
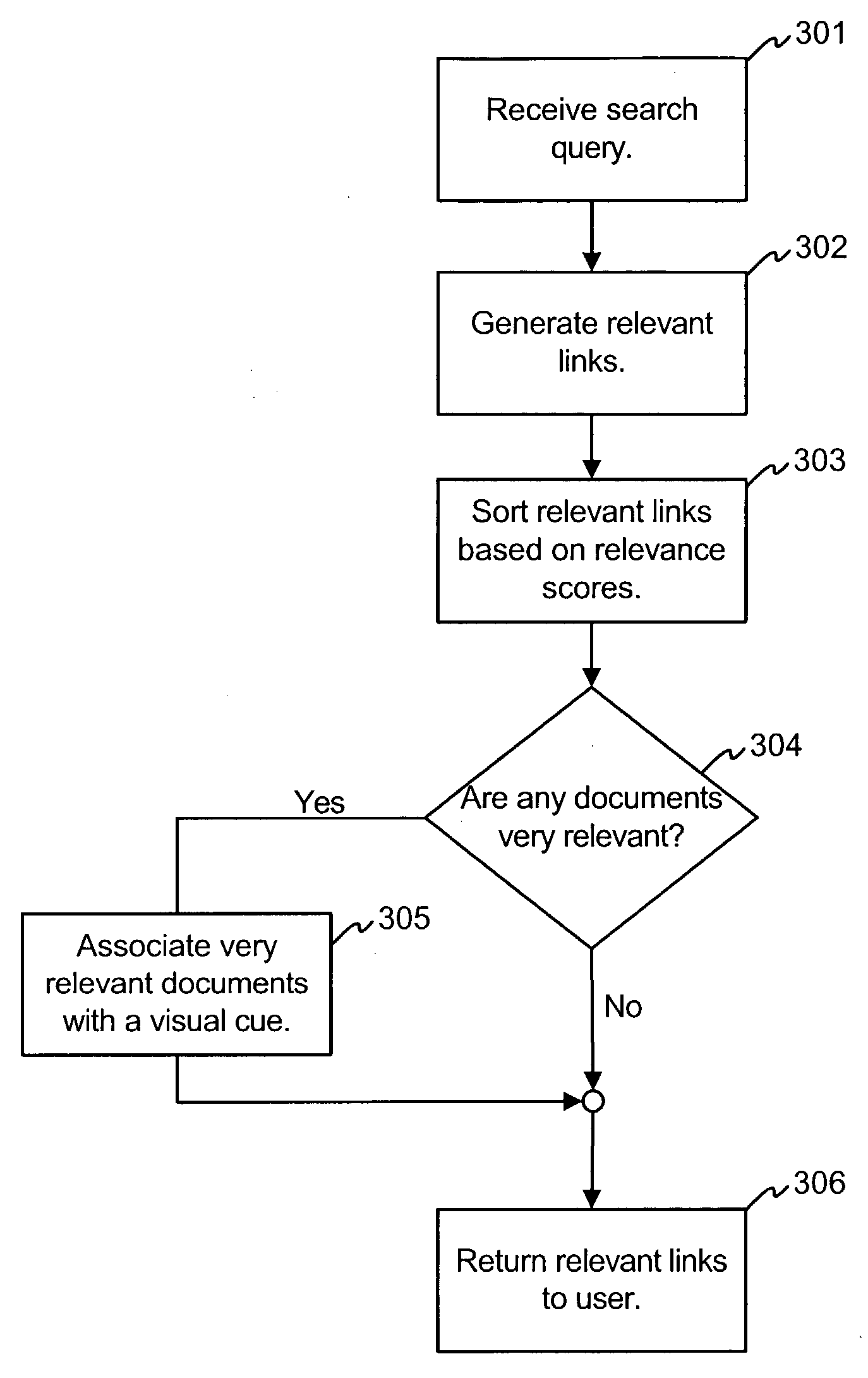
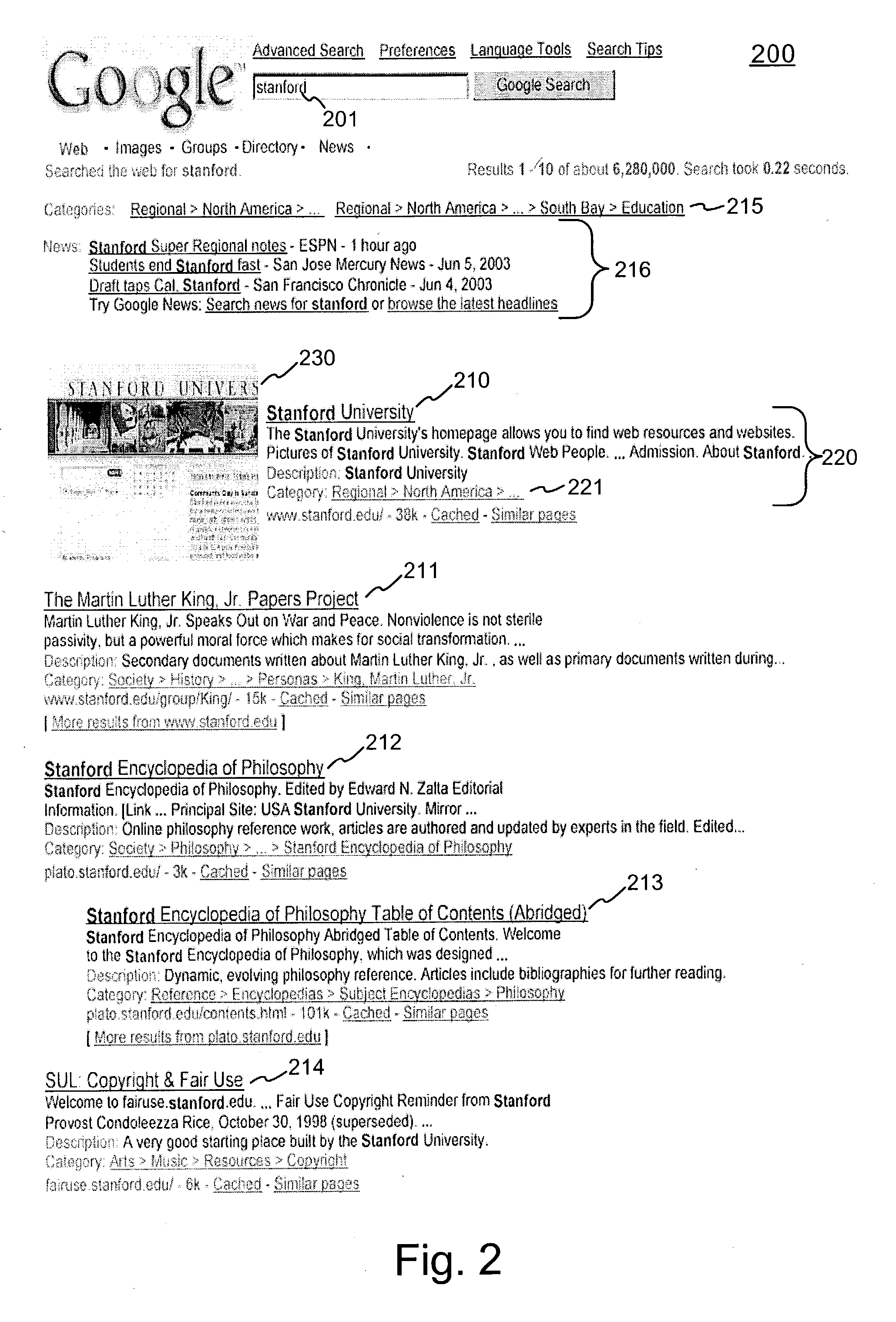
Document search engine including highlighting of confident results
A search engine includes a decision component that determines whether documents that are returned in response to a user search query are likely to be very relevant to the search query. Links that refer to documents that the search engine determines to likely be very relevant may be displayed with visual cues that assist the user in browsing the links. The decision component may base its decision on a number of parameters, including: (1) the position of the document in a ranked list of search results, (2) the click through rate of the document, (3) relevance scores for the document and other documents that are returned as hits in response to the search query, and (4) whether the document is classified as a pornographic document (the search engine may refrain from showing visual cues for potentially pornographic documents).
Owner:GOOGLE LLC
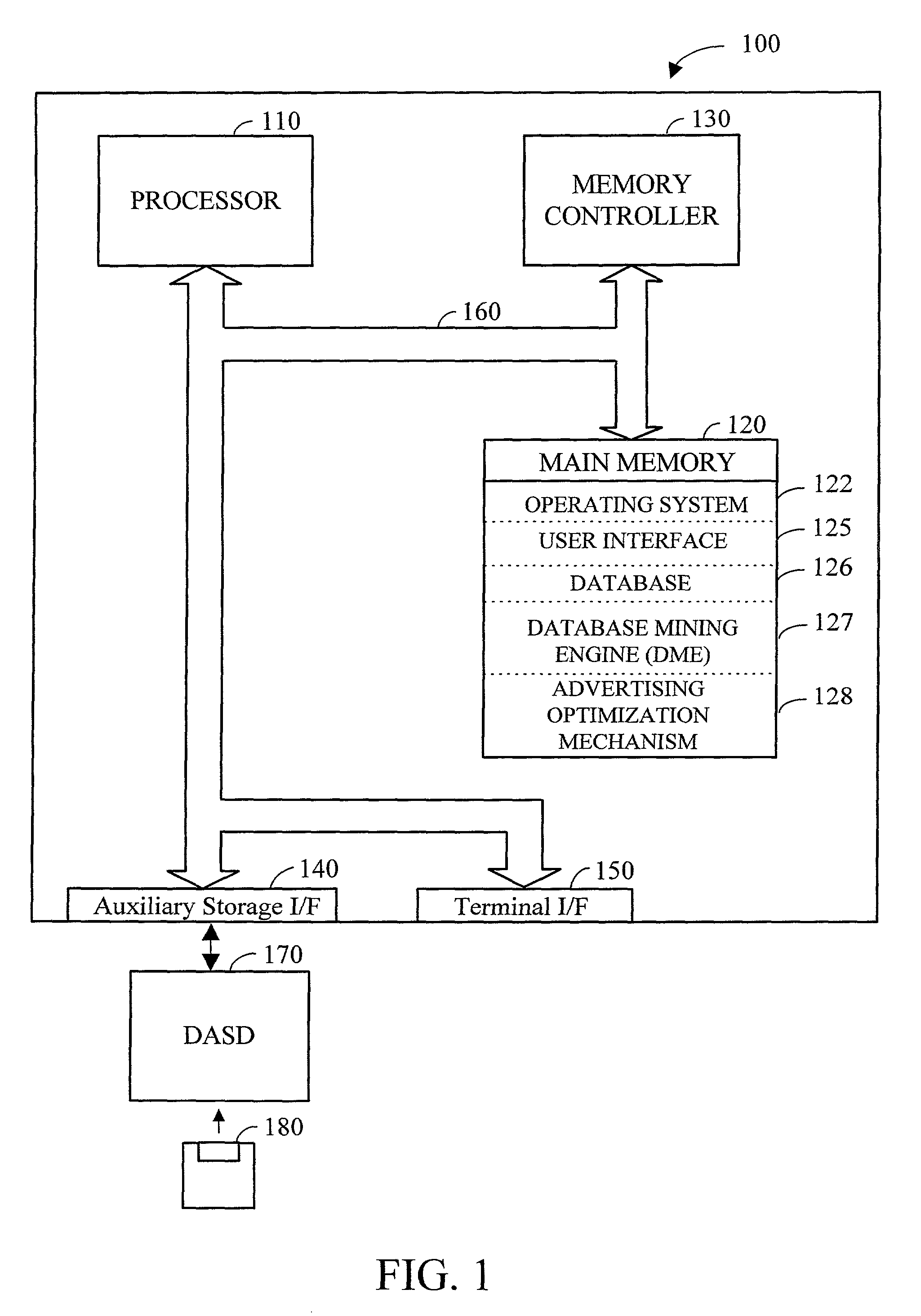
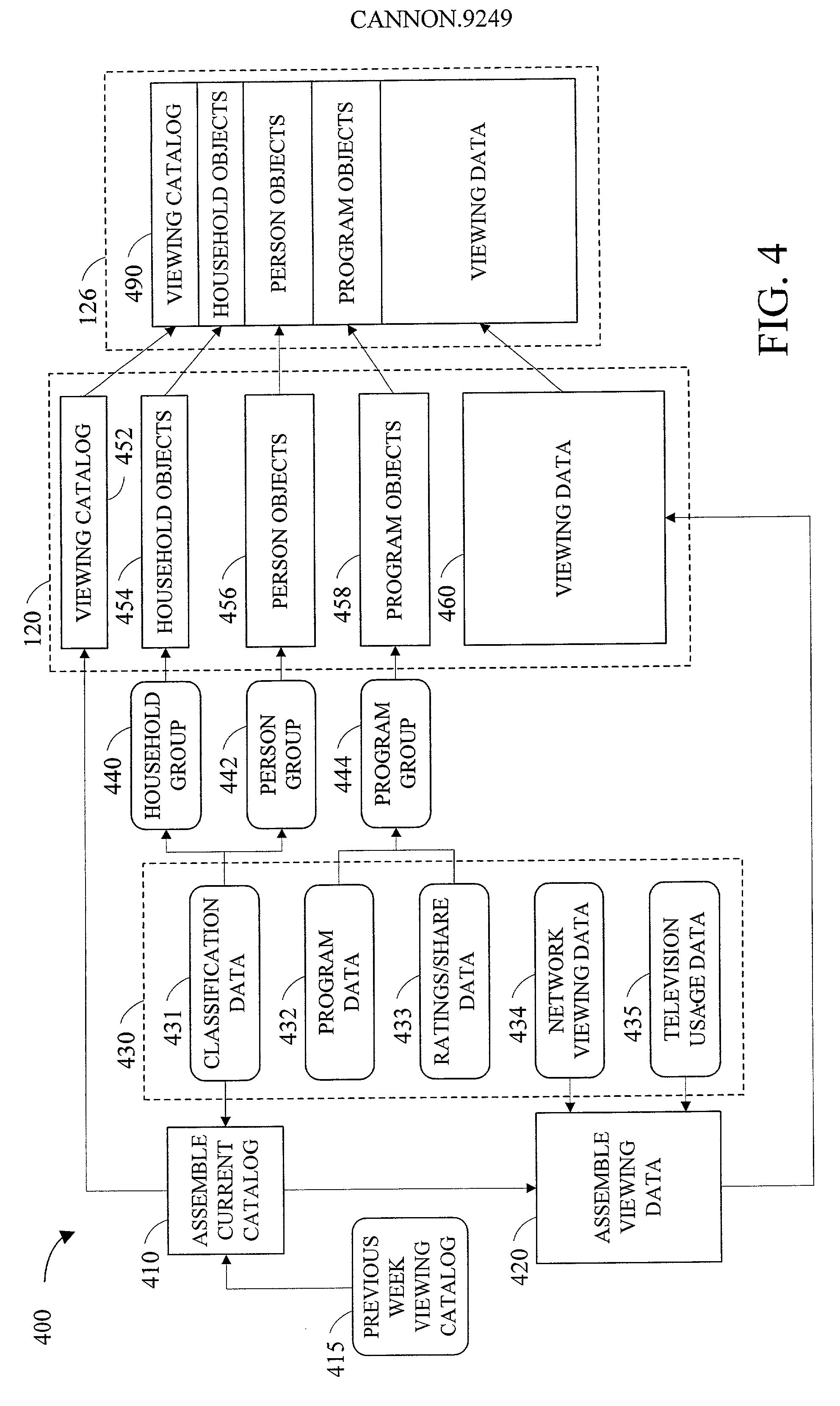
Method and apparatus for analyzing data and advertising optimization
InactiveUS20010020236A1Readily availableGood choiceDigital data processing detailsBroadcast services for monitoring/identification/recognitionAnalysis dataDecision maker
The most preferred embodiment of the present invention is a computer-based decision support system that includes three main components: a database mining engine (DME); an advertising optimization mechanism; and a customized user interface that provides access to the various features of the invention. The user interface, in conjunction with the DME, provides a unique and innovative way to store, retrieve and manipulate data from existing databases containing media-related audience access data, which describe the access habits and preferences of the media audience. By using a database with a simplified storage and retrieval protocol, the data contained therein can be effectively manipulated in real time. This means that previously complex and lengthy information retrieval and analysis activities can be accomplished in very short periods of time (typically seconds instead of minutes or even hours). Further, by utilizing the advertising optimization mechanism of the present invention, businesses, networks, and advertising agencies can interactively create, score, rank and compare various proposed or actual advertising strategies in a simple and efficient manner. This allows the decision-makers to more effectively tailor their marketing efforts and successfully reach the desired target market while conserving scarce advertising capital. Finally, the user interface for the system provides access to both the DME and the optimization mechanism in a simple and straightforward manner, significantly reducing training time.
Owner:CANNON MARK E
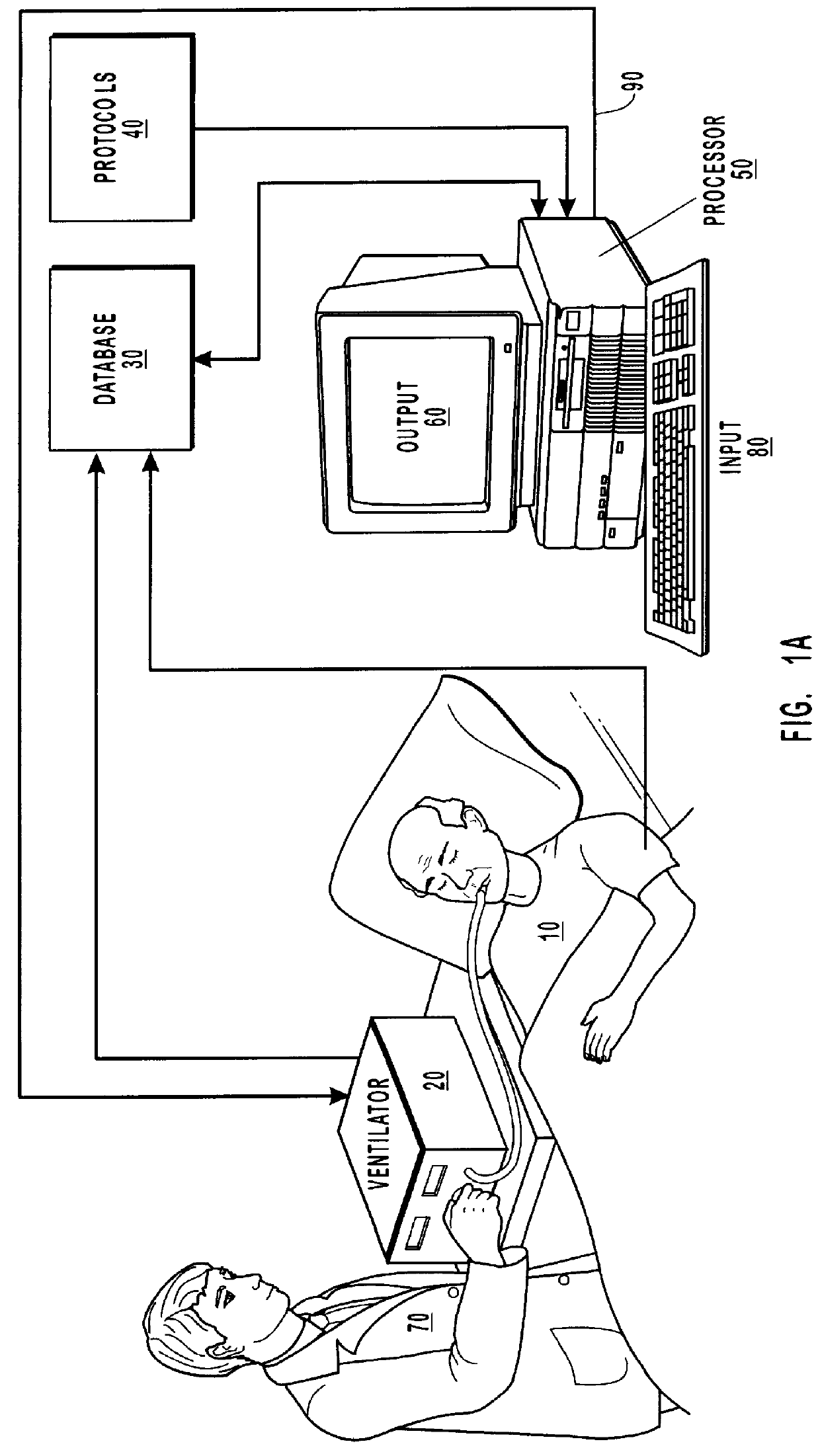
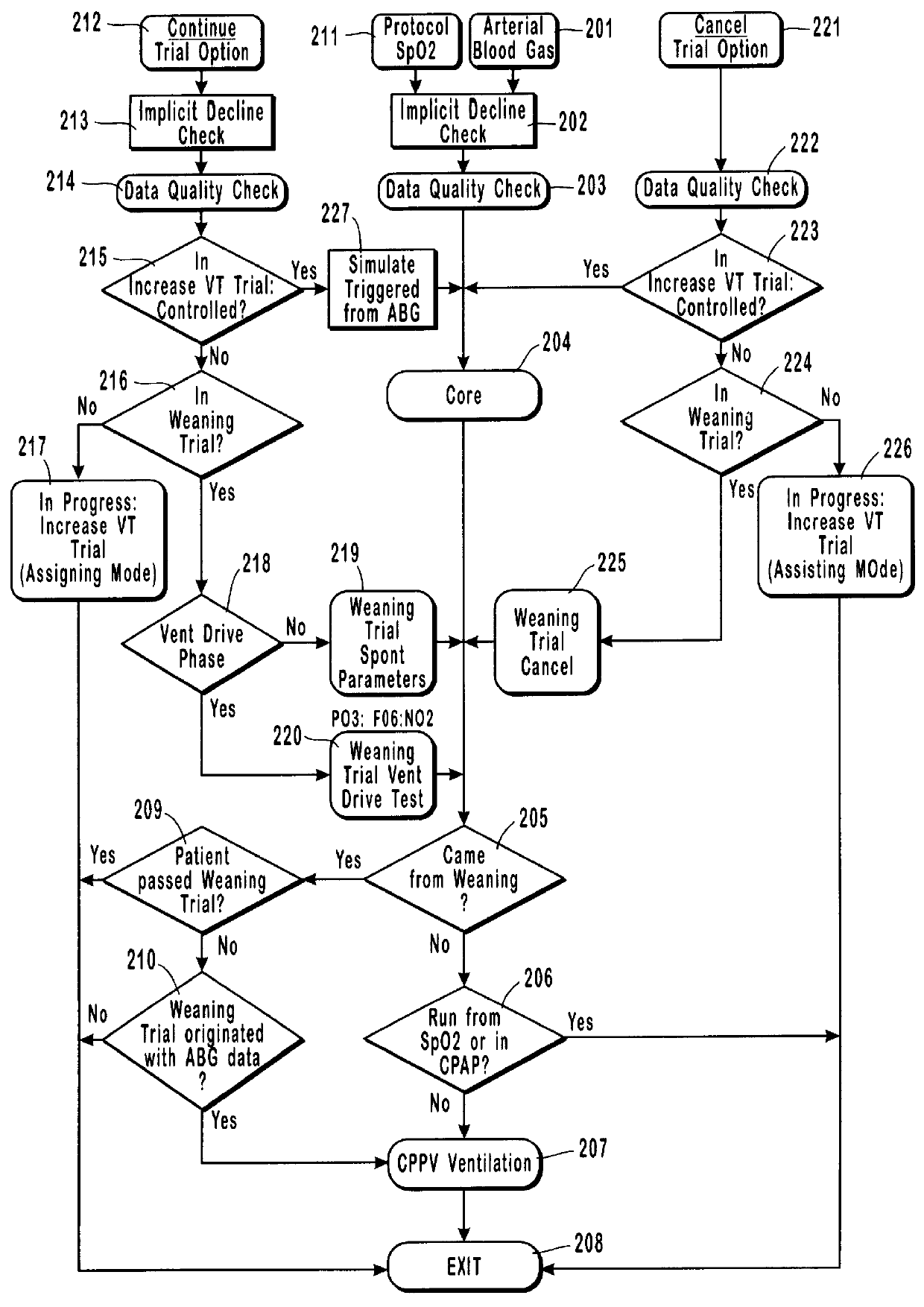
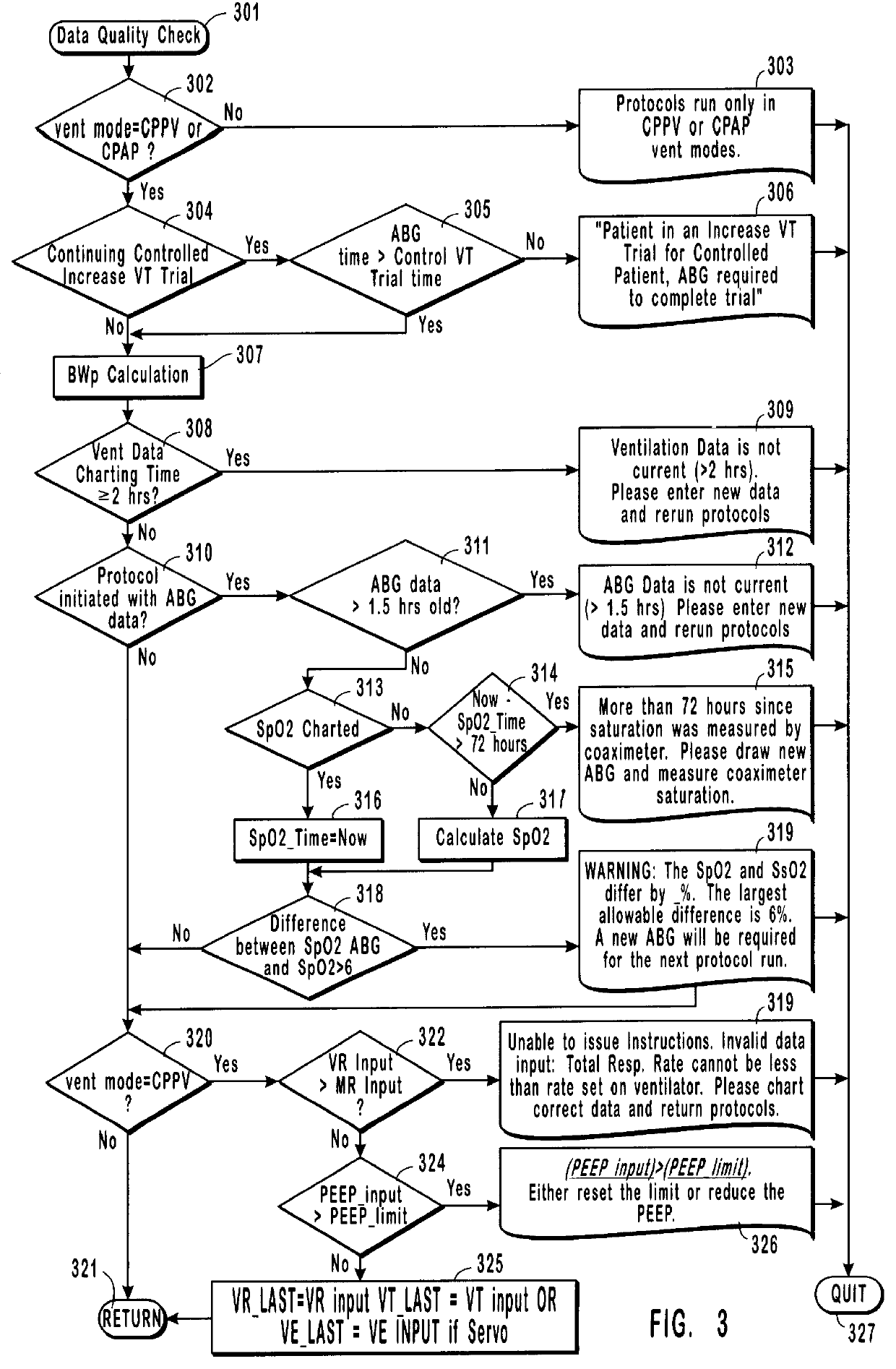
Method and system for patient monitoring and respiratory assistance control through mechanical ventilation by the use of deterministic protocols
InactiveUS6148814AReducing ventilator rateRelieve pressureRespiratorsBreathing masksDiseaseClinical staff
A method and system for managing mechanical ventilation of patients with respiratory disorders is described. The main objective of the system is to generate executable instructions for patient care which take into account a large number of parameters of patient condition and ventilation. Data regarding the state of the patient are stored in a database. Patient data are processed according to a set of protocols which contain rules for patient care decisions arranged in a logical sequence to generate detailed, executable instructions for patient care. Instructions are updated when new data are entered into the database. The data can be acquired in an automated fashion, or the clinician can be instructed to collect and enter new data into the clinical database. Likewise, patient care instructions can be carried out automatically or manually, but it is preferred that instructions are carried out manually as a safety check. The preferred embodiment of the invention includes a computer system, software for processing patient data, and a display device for presenting patient care instructions to the clinician. The system maintains a record of patient data, patient care instructions, whether instructions were followed by the clinical staff, and if not, a reason why.
Owner:INTERMOUNTAIN INTELLECTUAL ASSET MANAGEMENT LLC
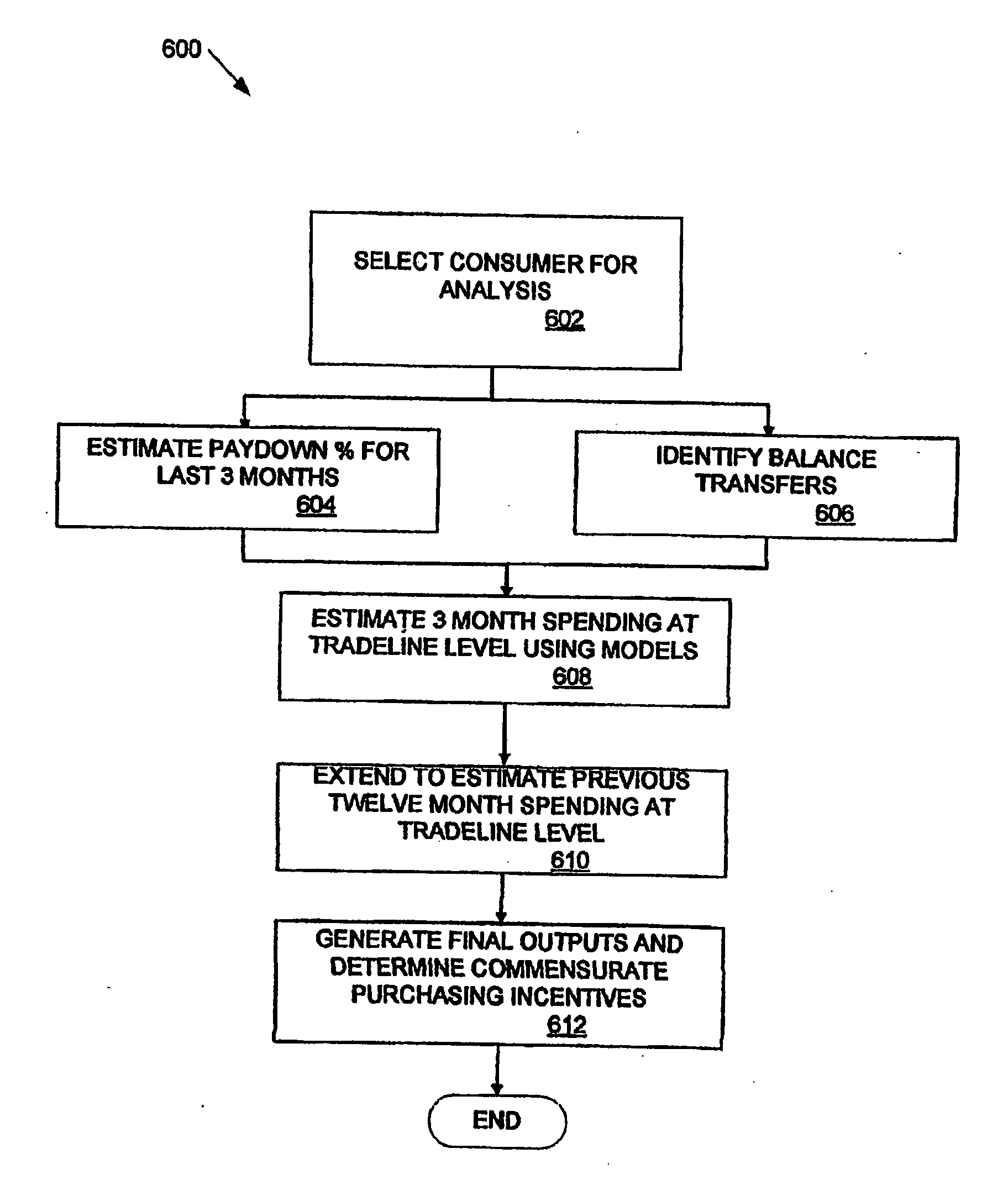
Method and apparatus for consumer interaction based on spend capacity
ActiveUS20060242046A1Efficient use ofEfficient managementFinancePayment architectureBalance transferInsurance life
Share of Wallet (“SoW”) is a modeling approach that utilizes various data sources to provide outputs that describe a consumer's spending capability, tradeline history including balance transfers, and balance information. These outputs can be appended to data profiles of customers and prospects and can be utilized to support decisions involving prospecting, new applicant evaluation, and customer management across the lifecycle. In addition to credit card companies, SoW outputs may be useful to companies issuing, for example: private label cards, life insurance, on-line brokerages, mutual funds, car sales / leases, hospitals, and home equity lines of credit or loans. “Best customer” models can correlate SoW outputs with various customer groups. A SoW score focusing on a consumer's spending capacity can be used in the same manner as a credit bureau score.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
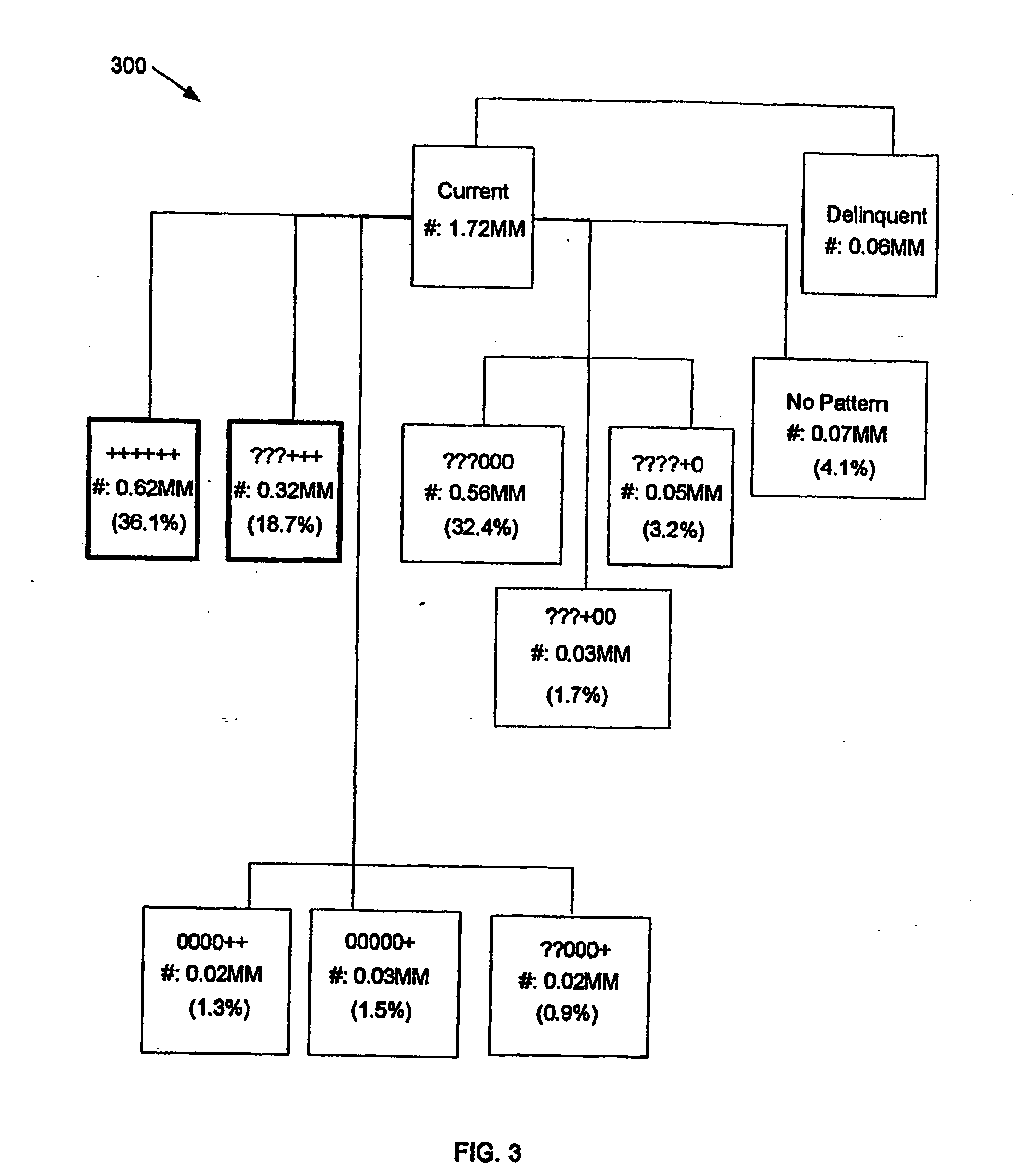
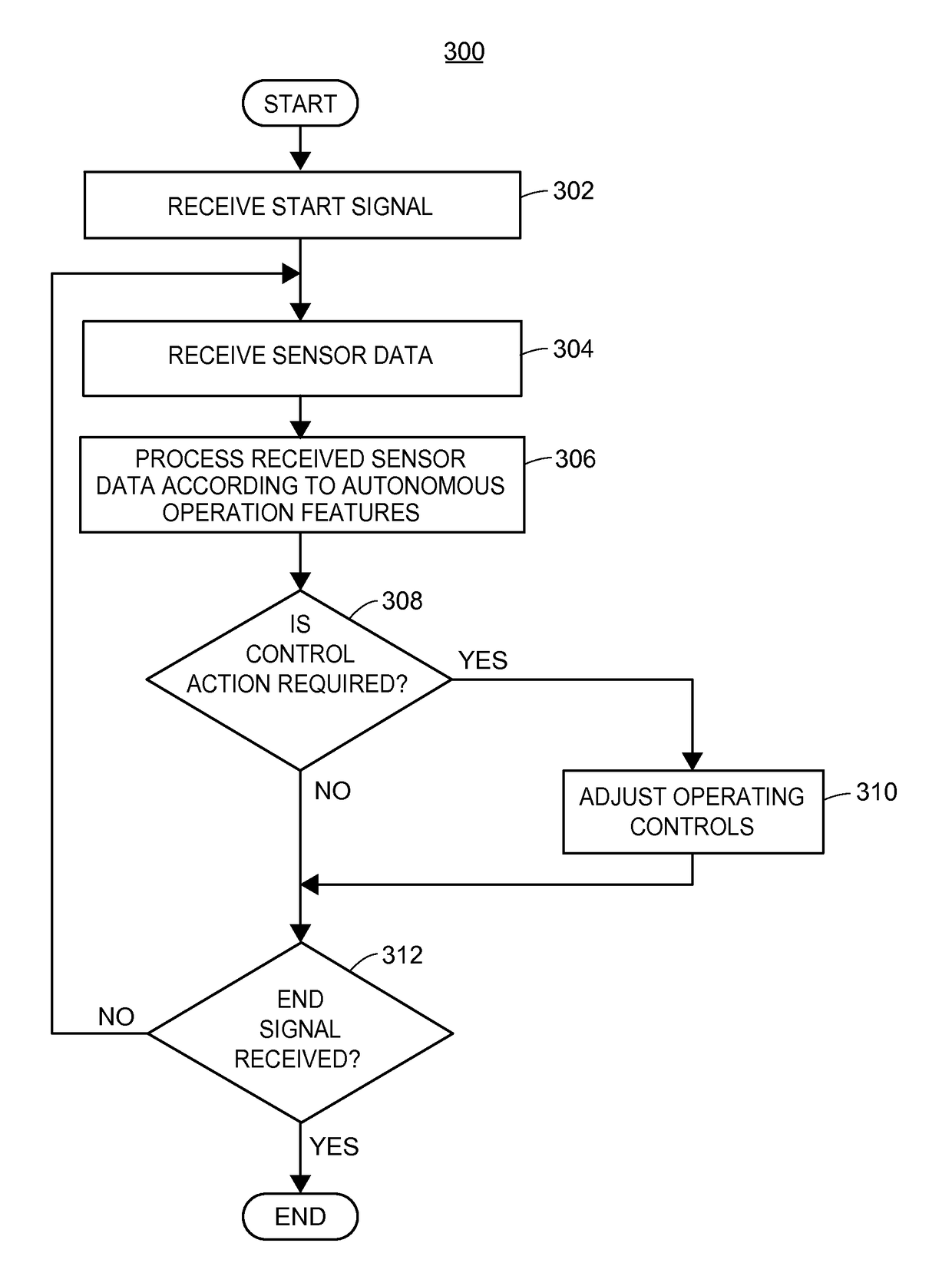
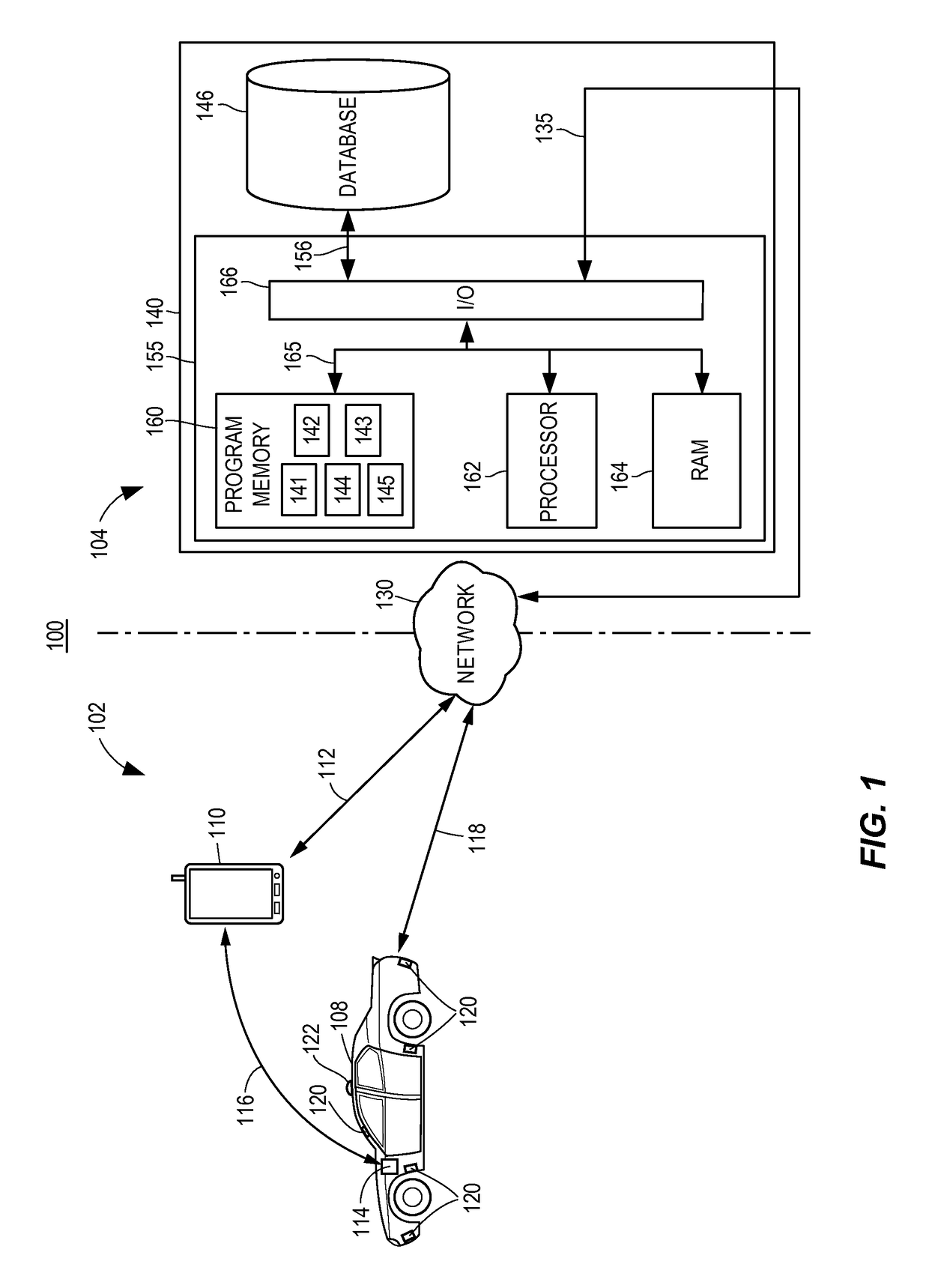
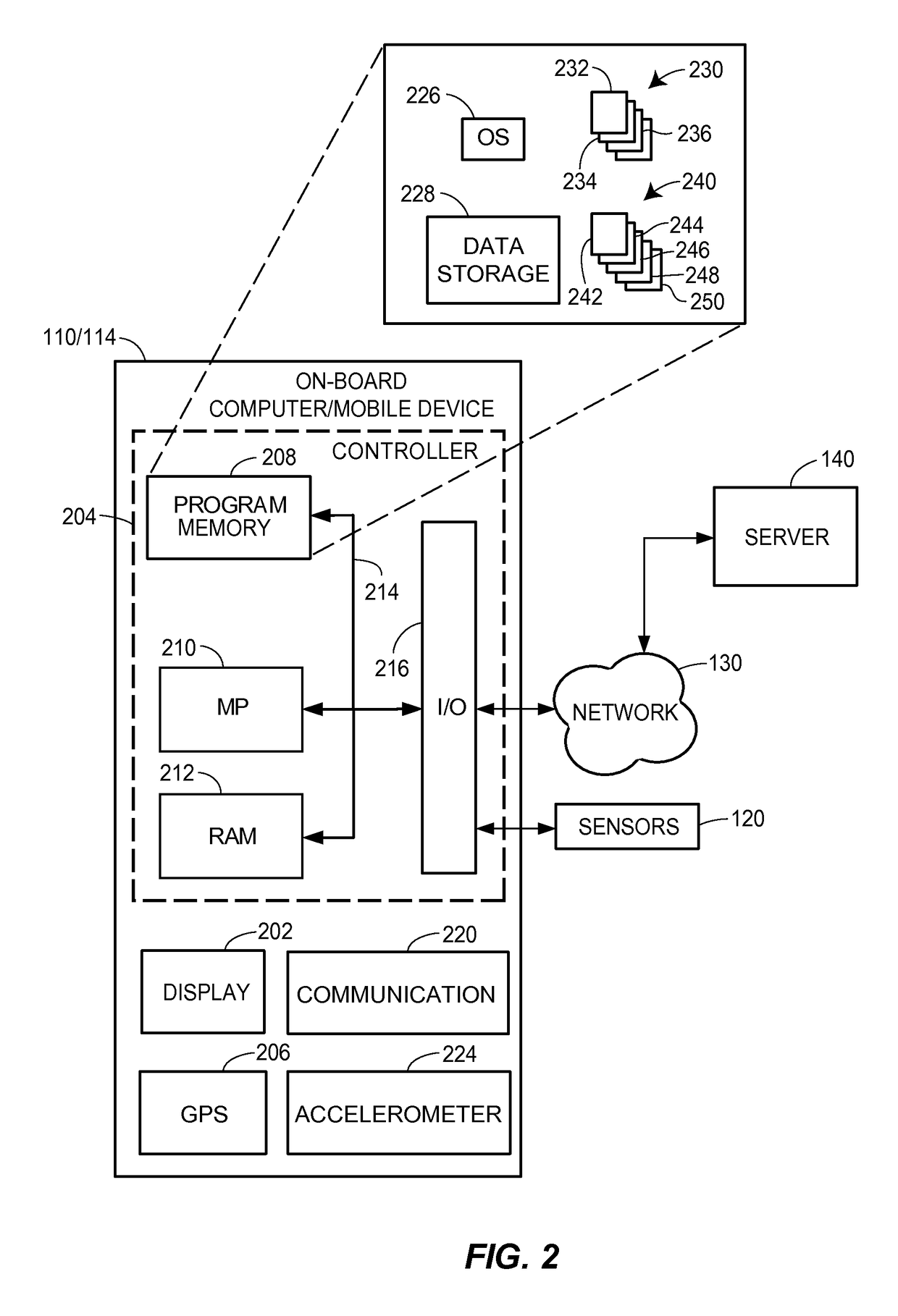
Autonomous vehicle operation feature monitoring and evaluation of effectiveness
ActiveUS9754325B1Operation moreFacilitate risk assessment and premium determinationRegistering/indicating working of vehiclesControl with pedestrian guidance indicatorRisk levelDecision taking
Owner:STATE FARM MUTAL AUTOMOBILE INSURANCE COMPANY
Restriction of program process capabilities
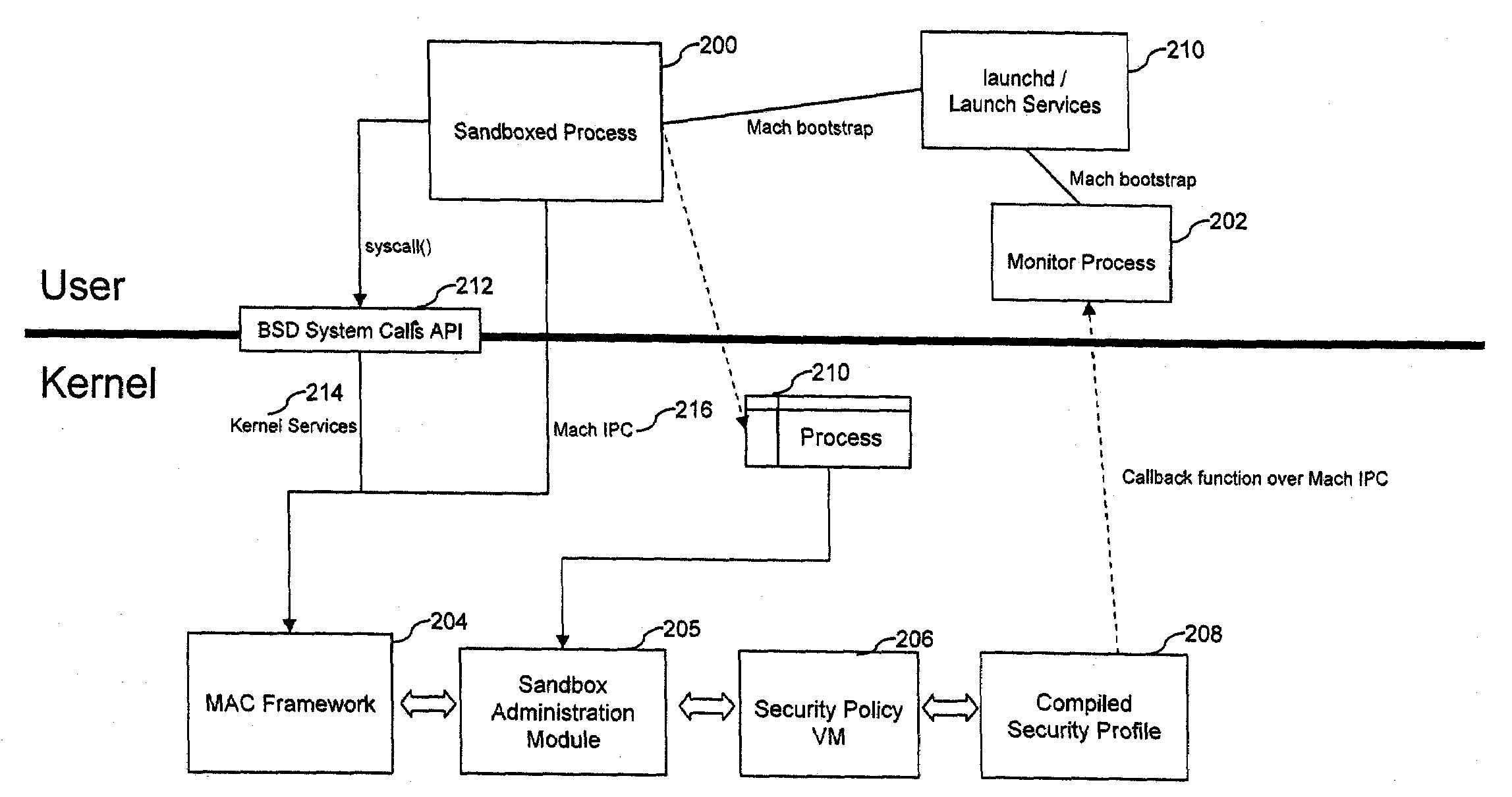
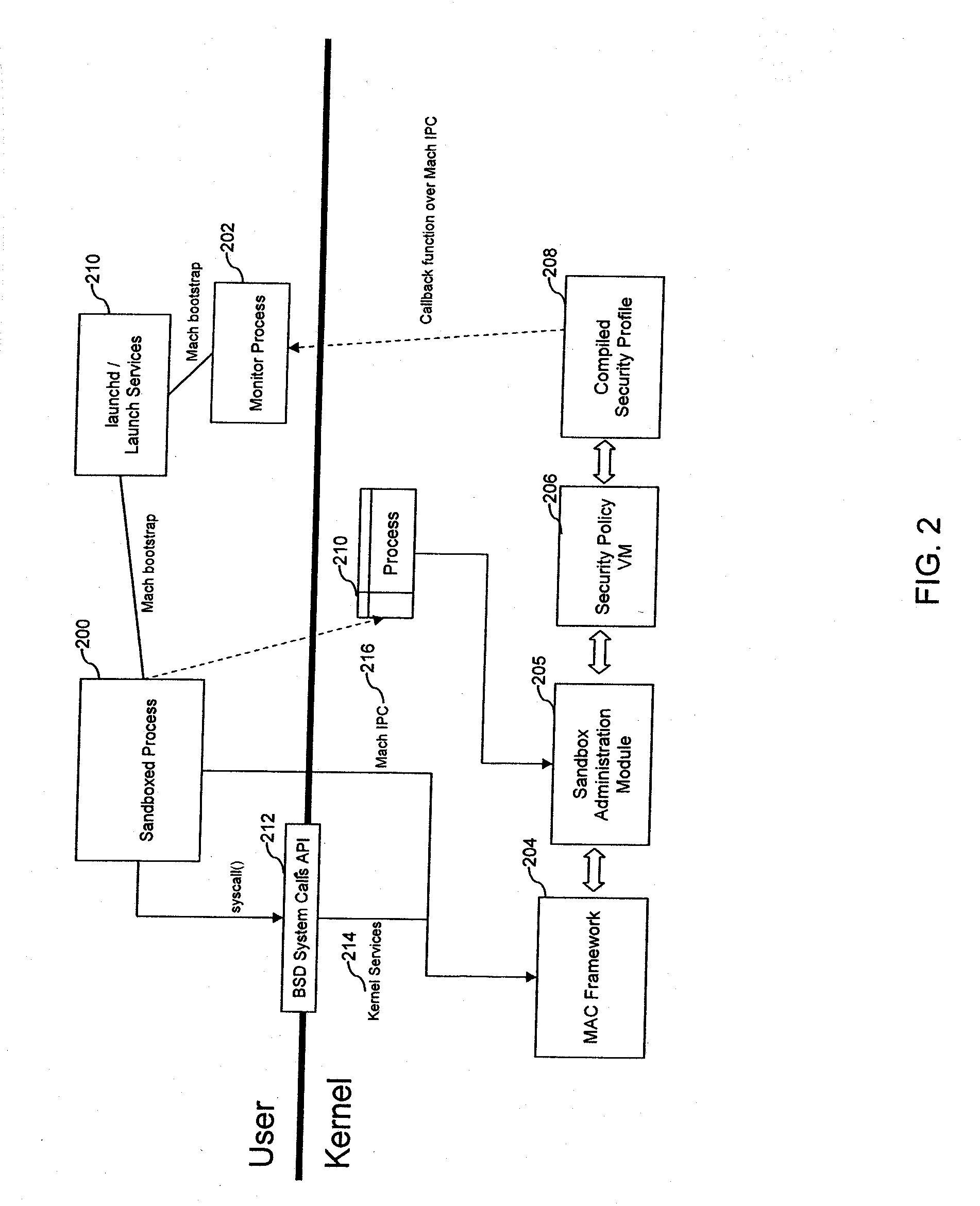
ActiveUS20080127292A1Digital data processing detailsUser identity/authority verificationOperational systemDecision taking
This document describes systems and methods for restricting program process capabilities. In some implementations, the capabilities are restricted by limiting the rights or privileges granted to an application. A plurality of rules may be established for a program, or for a group of programs, denying that program the right to take actions which are outside of the actions needed to implement its intended functionality. A security policy is implemented to test actions initiated in response to an application against the rules to enable decisions restricting the possible actions of the program. Embodiments are disclosed which process the majority of decisions regarding actions against a security profile through use of a virtual machine. In some embodiments, the majority of decisions are resolved within the kernel space of an operating system.
Owner:APPLE INC
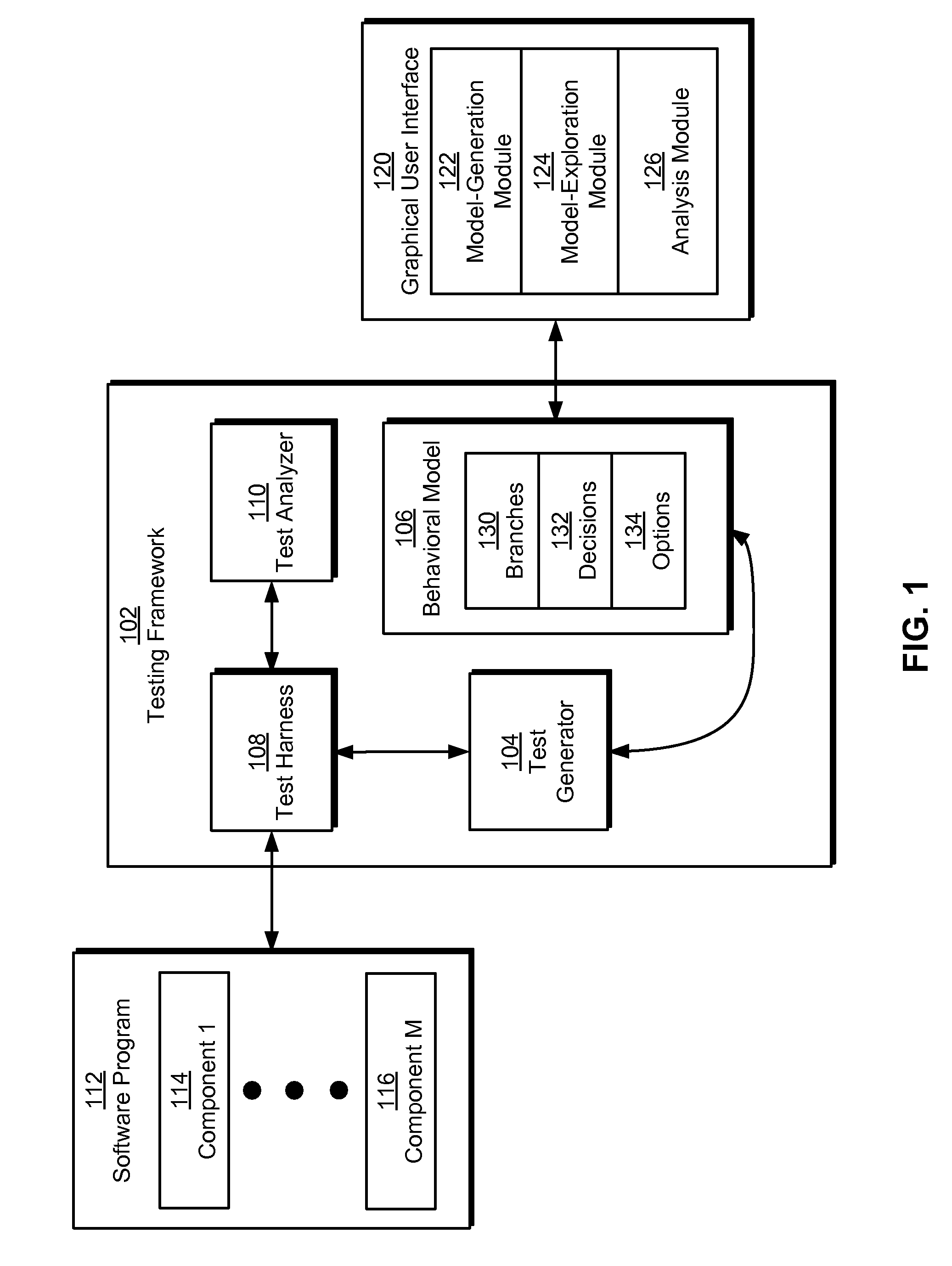
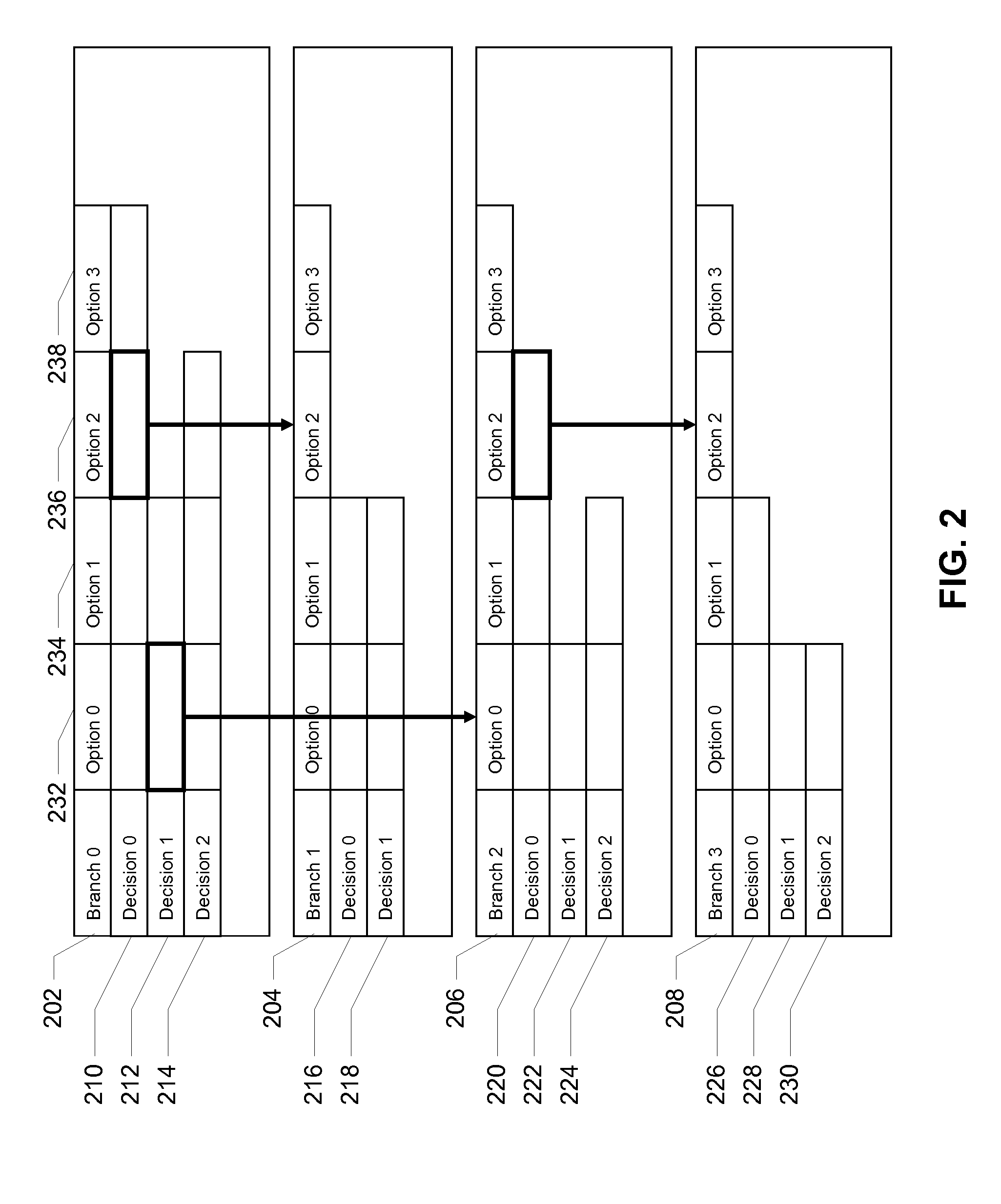
Model-based testing using branches, decisions, and options
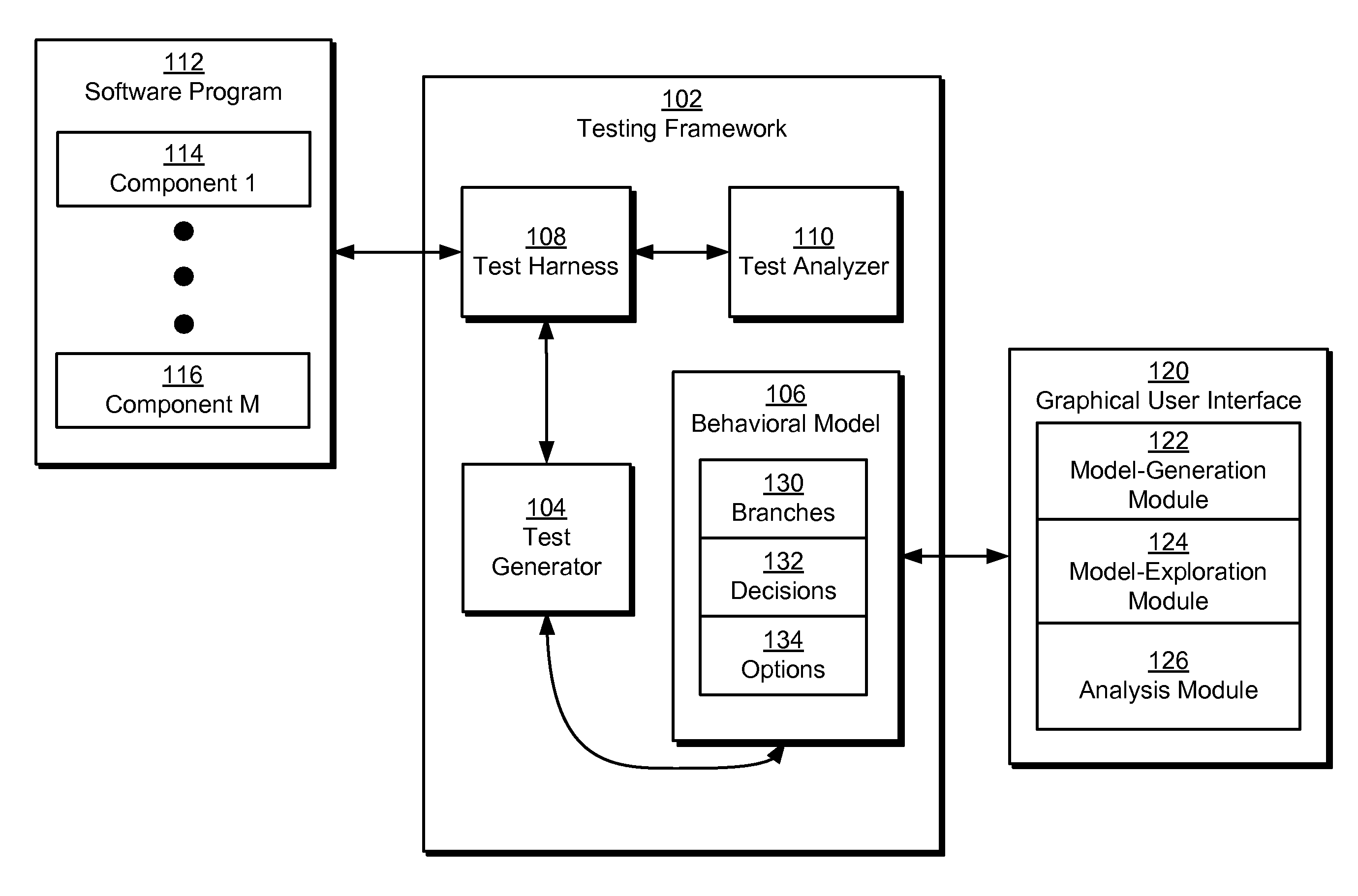
ActiveUS8225288B2Digital data processing detailsError detection/correctionSystems analysisTheoretical computer science
Some embodiments of the present invention provide a system that tests a software program. During operation, the system creates a behavioral model of the software program using branches, decisions, and options. Next, the system generates a test case from the behavioral model and executes the test case on the software program. Finally, the system analyzes an output of the executed test case to determine a validity of the software program.
Owner:INTUIT INC
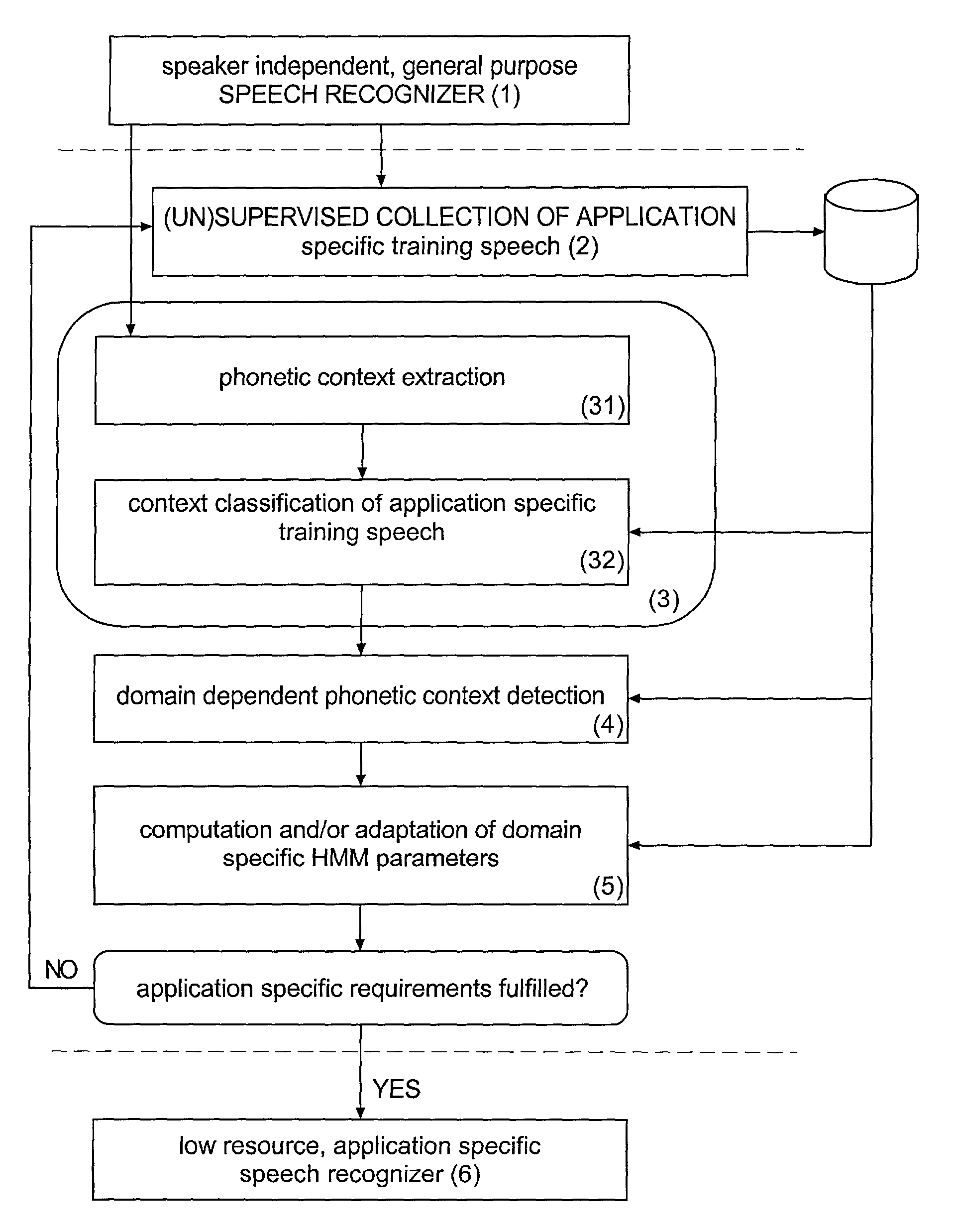
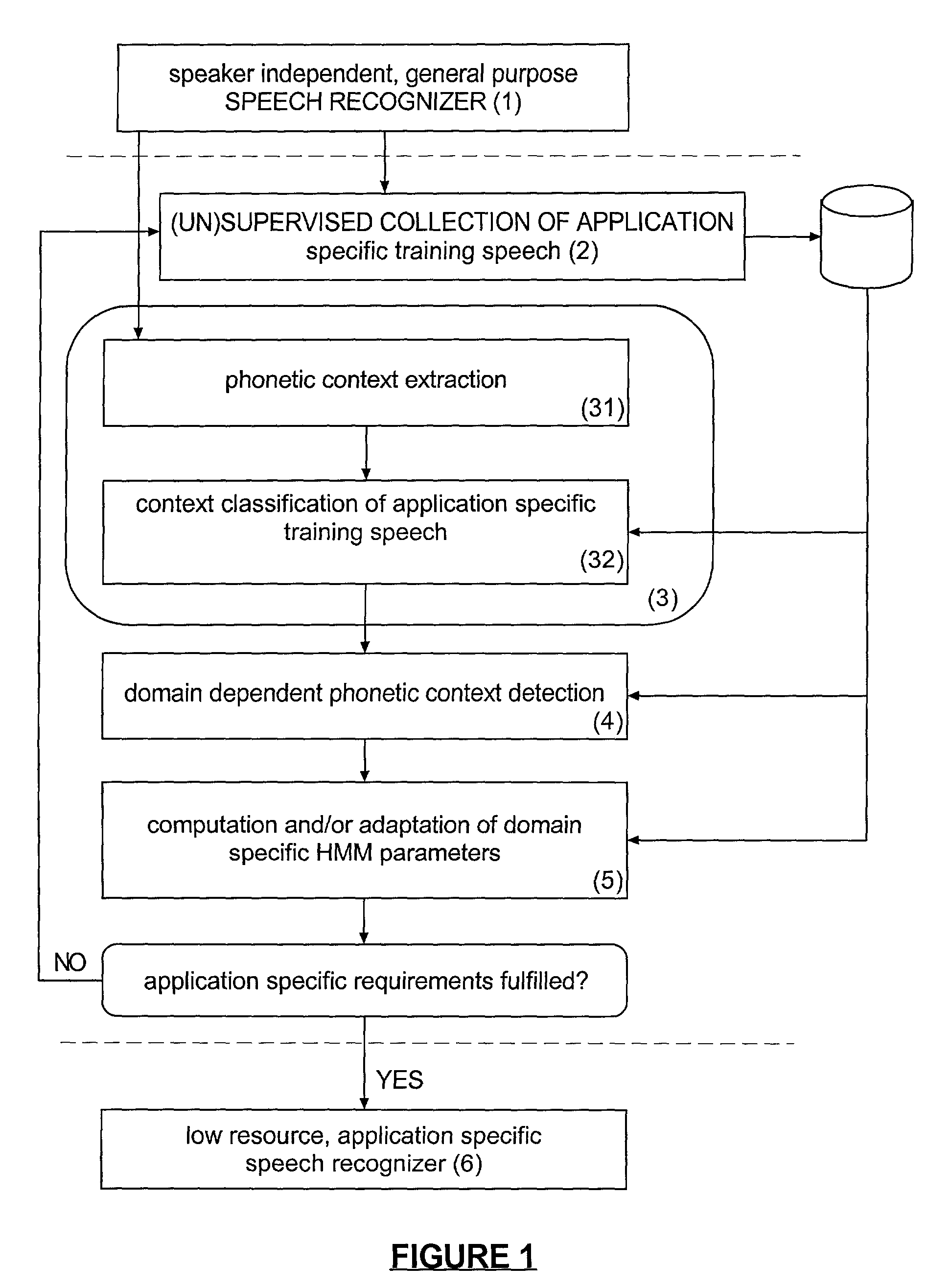
Method and apparatus for phonetic context adaptation for improved speech recognition
The present invention provides a computerized method and apparatus for automatically generating from a first speech recognizer a second speech recognizer which can be adapted to a specific domain. The first speech recognizer can include a first acoustic model with a first decision network and corresponding first phonetic contexts. The first acoustic model can be used as a starting point for the adaptation process. A second acoustic model with a second decision network and corresponding second phonetic contexts for the second speech recognizer can be generated by re-estimating the first decision network and the corresponding first phonetic contexts based on domain-specific training data.
Owner:NUANCE COMM INC
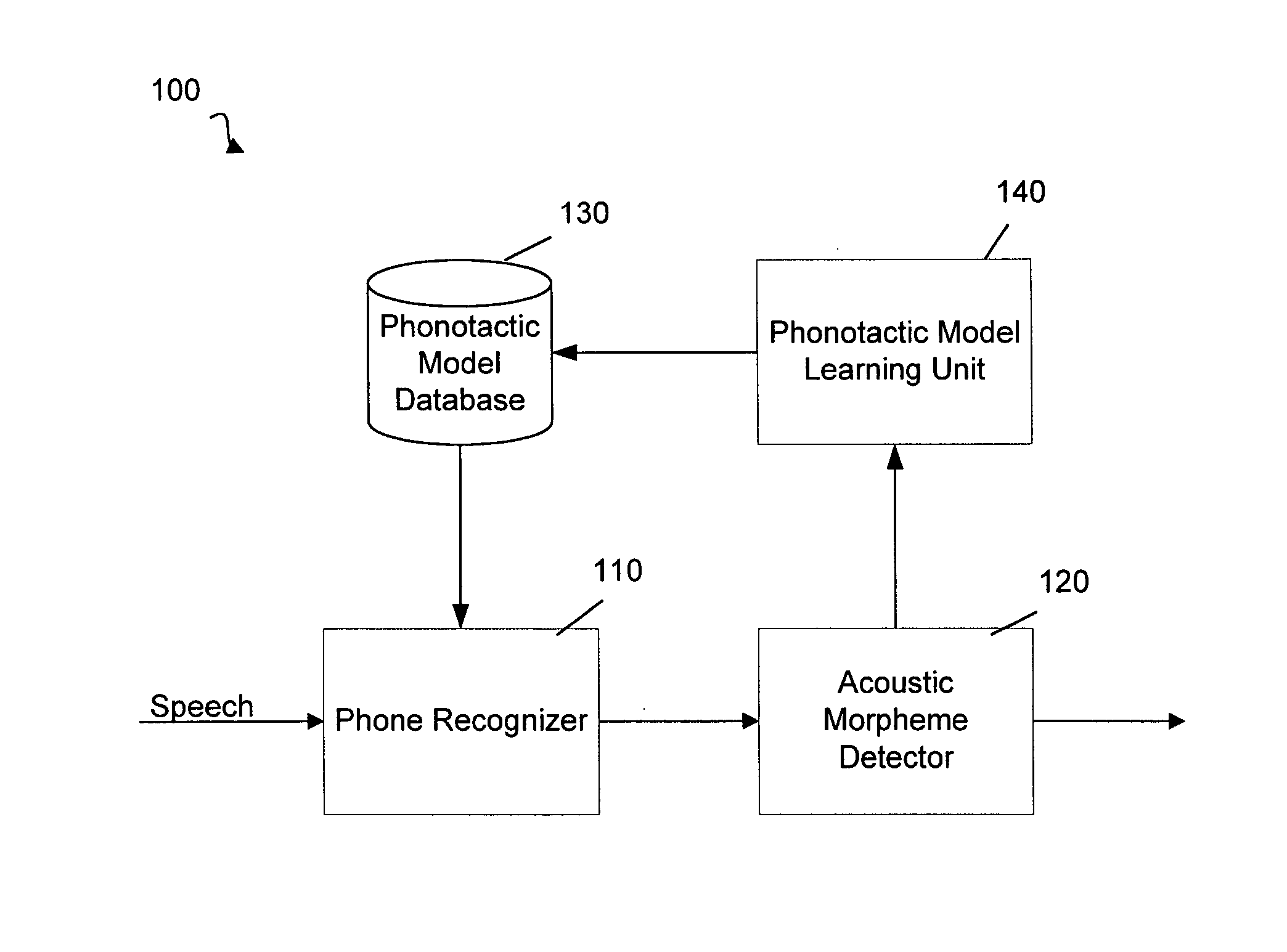
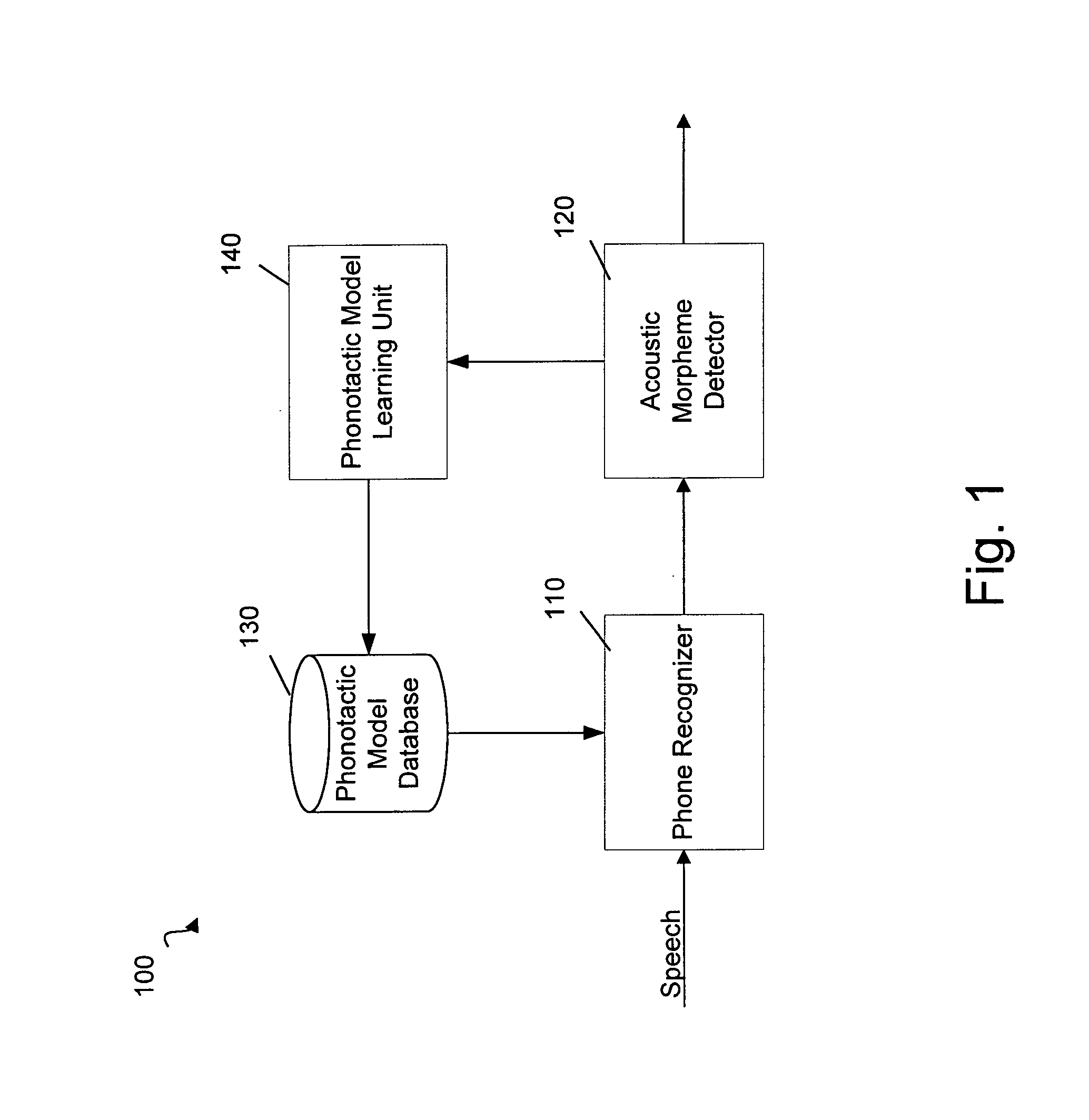
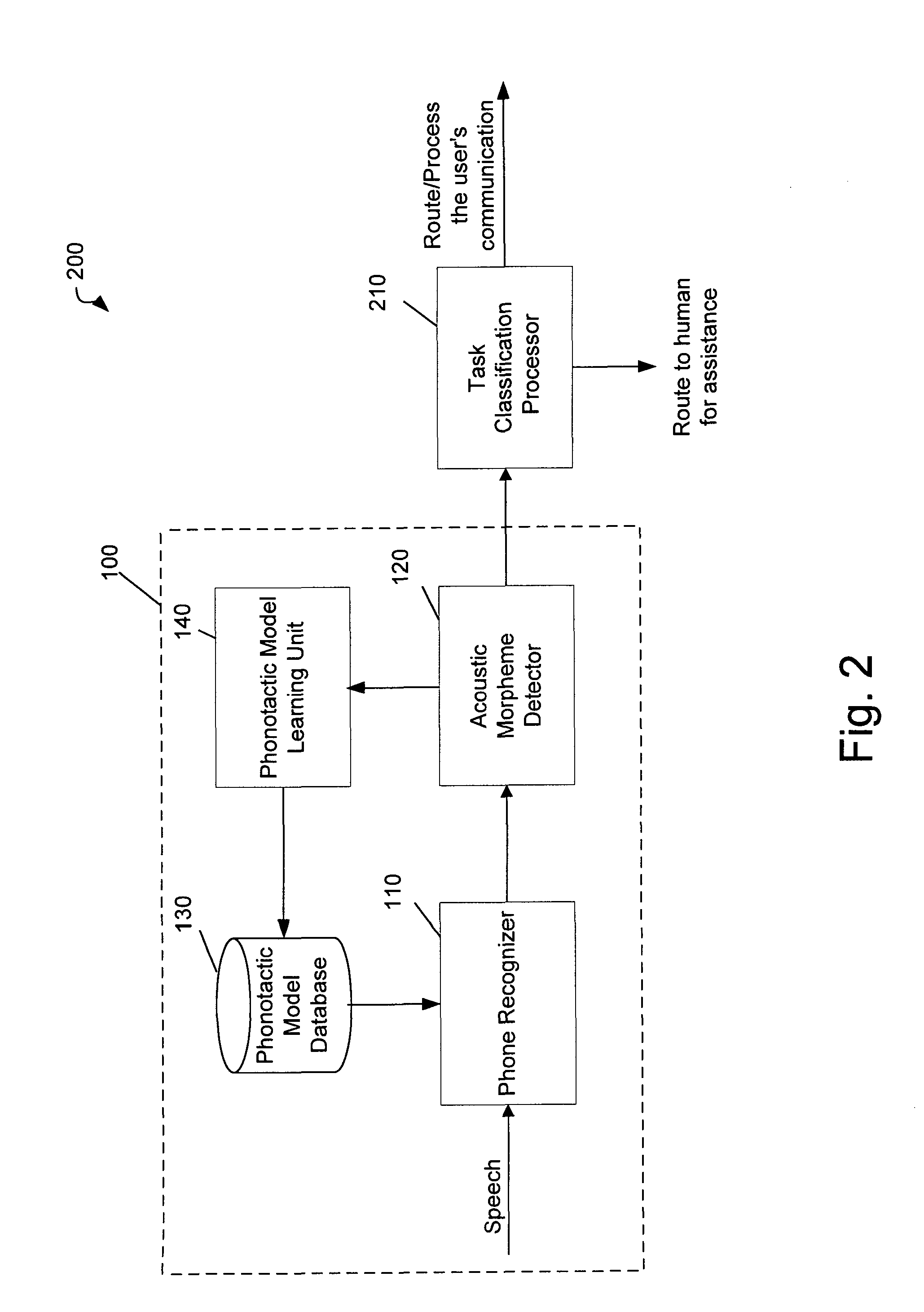
Method and System for Automatically Detecting Morphemes in a Task Classification System Using Lattices
The invention concerns a method and corresponding system for building a phonotactic model for domain independent speech recognition. The method may include recognizing phones from a user's input communication using a current phonotactic model, detecting morphemes (acoustic and / or non-acoustic) from the recognized phones, and outputting the detected morphemes for processing. The method also updates the phonotactic model with the detected morphemes and stores the new model in a database for use by the system during the next user interaction. The method may also include making task-type classification decisions based on the detected morphemes from the user's input communication.
Owner:NUANCE COMM INC
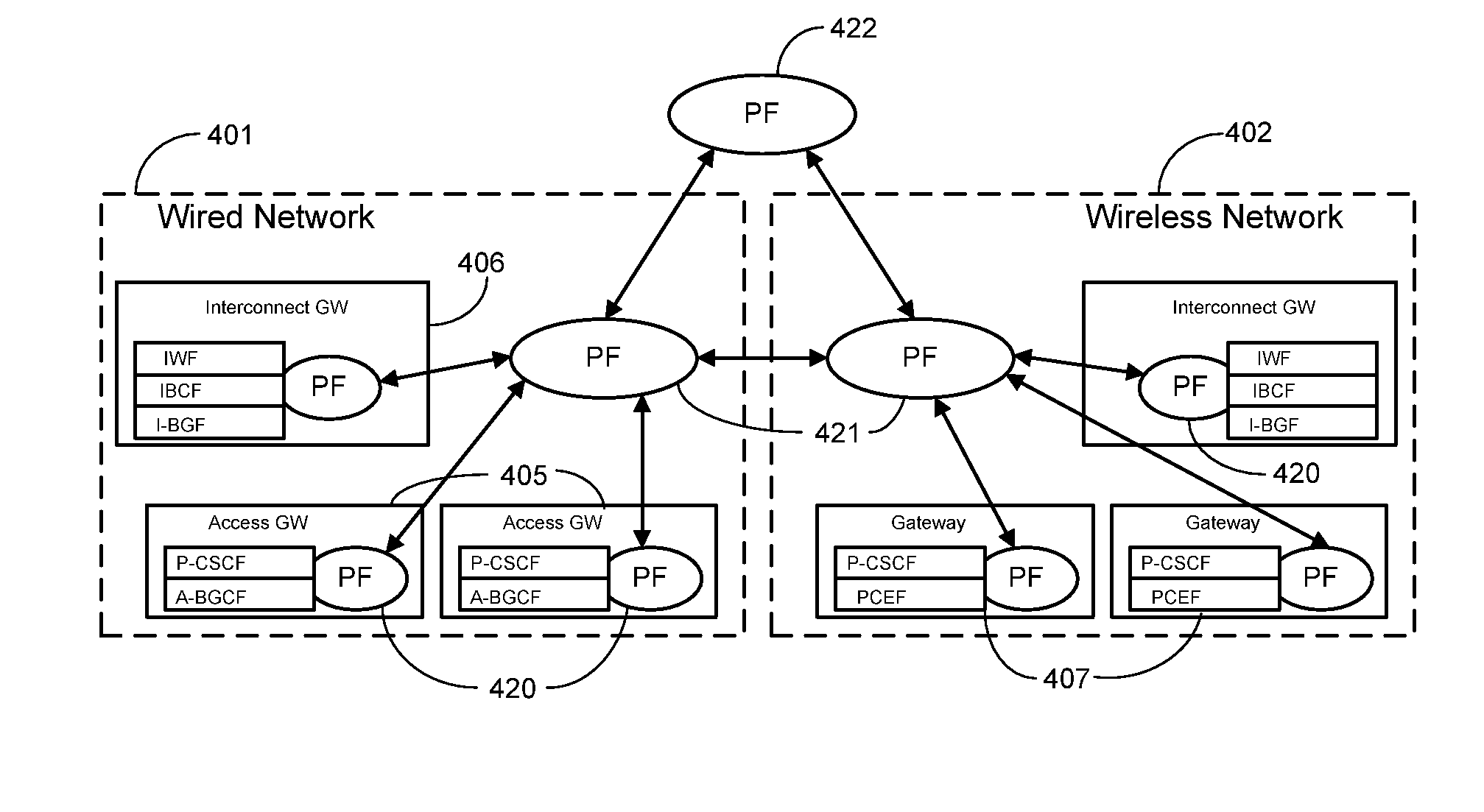
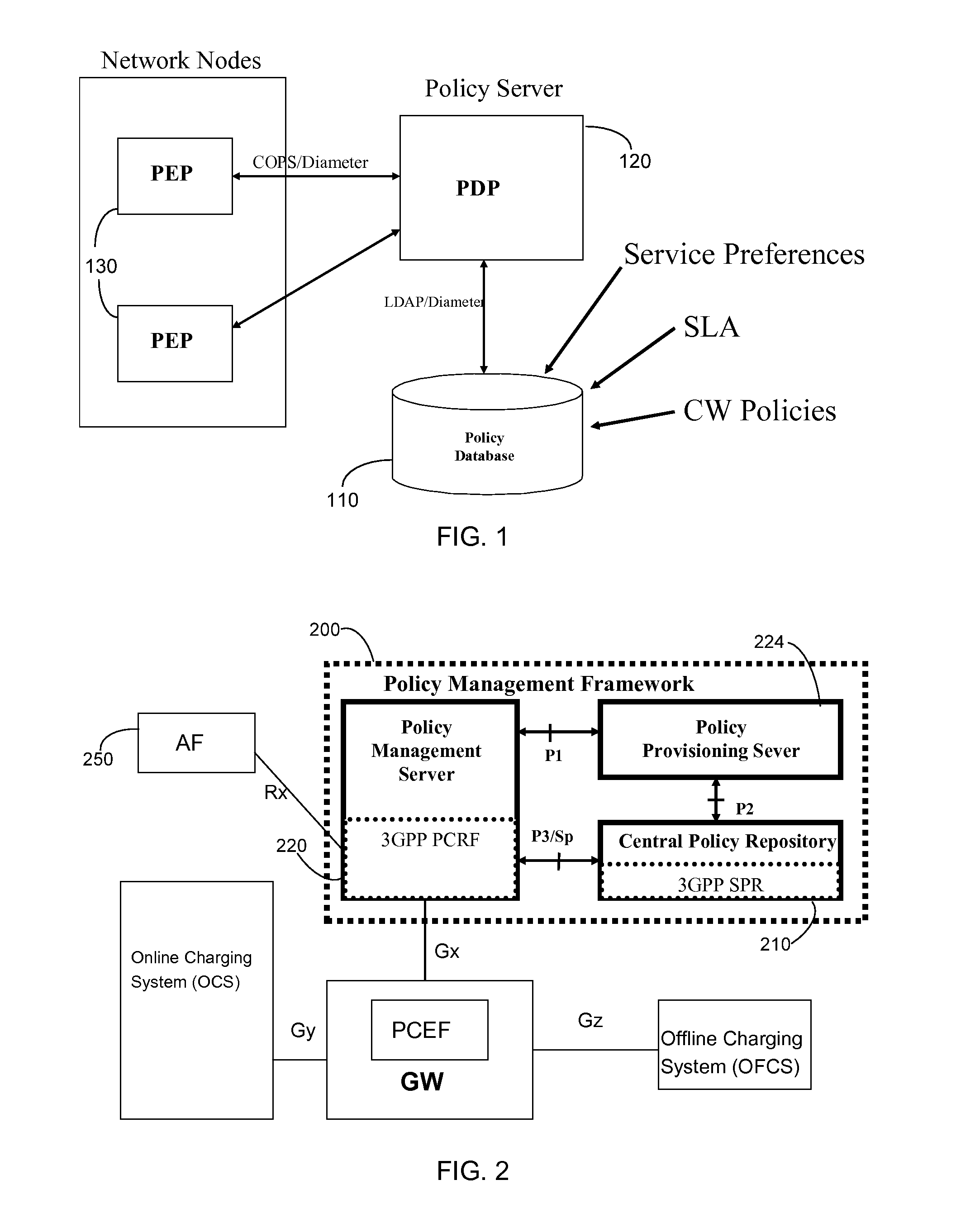
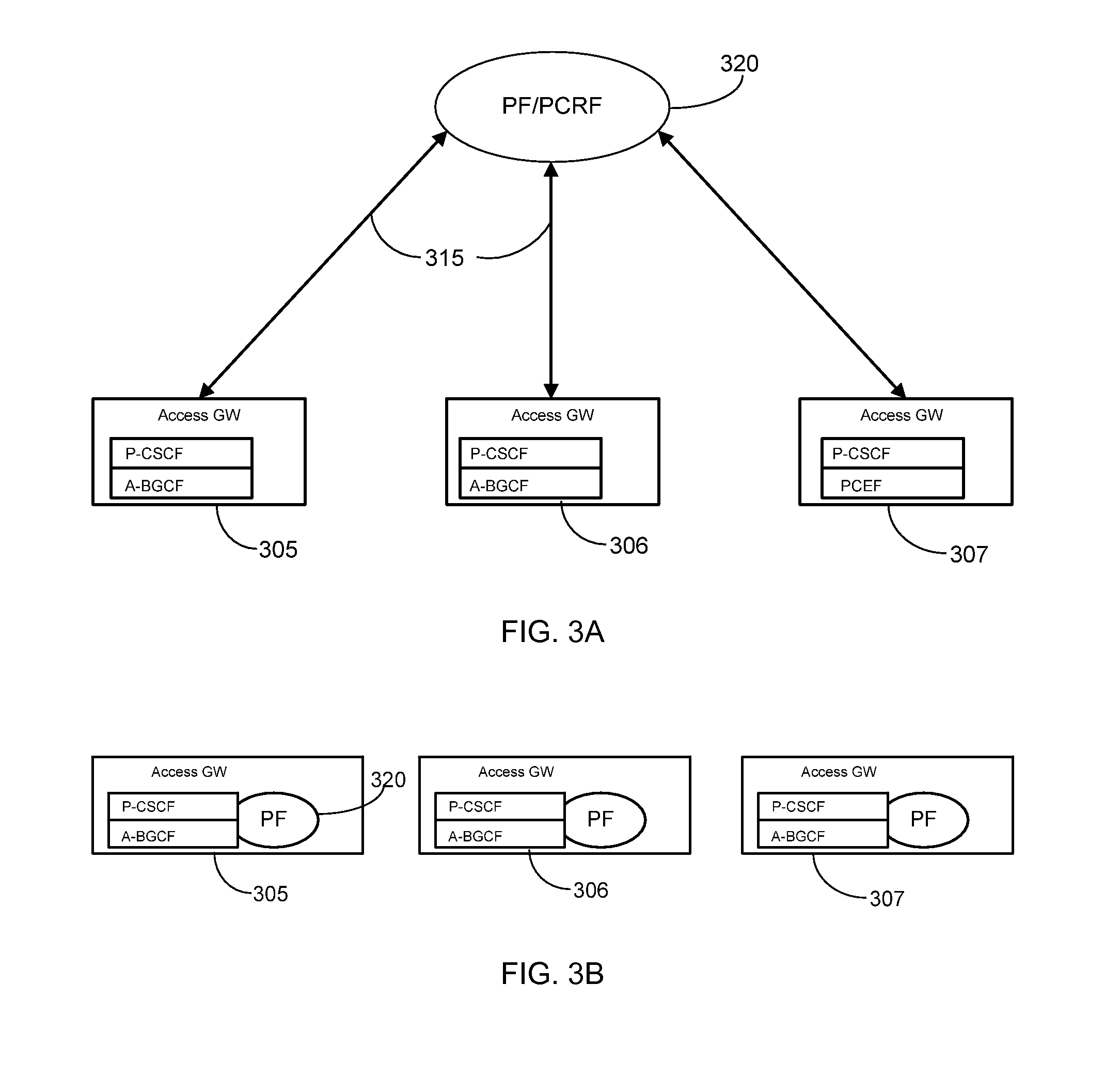
Cascading Policy Management Deployment Architecture
InactiveUS20090113514A1Improve performanceLimitation is enforcedError preventionTransmission systemsPolicy decisionWireless mesh network
Systems and methods are provided to implement a dynamic and efficient cascading policy management framework architecture for both wired and wireless networks. A plurality of Policy Functions (PFs) are assigned to a plurality of Policy Enforcement Points (PEP). The PFs make decisions regarding local policy control at the specific PEP. The PFs then delegate the policy requests or IP flows to a separate PEP that is more conducive to enforcing that policy request. Thus, policy decisions are made at the point where the most information is available, leading to fewer policy requests traversing back and forth across a network. Additionally, this cascading Policy Management Framework Architecture allows for unified policy management across multiple types of networks, including wired (Internet) and wireless (UMTS).
Owner:AT&T MOBILITY II LLC
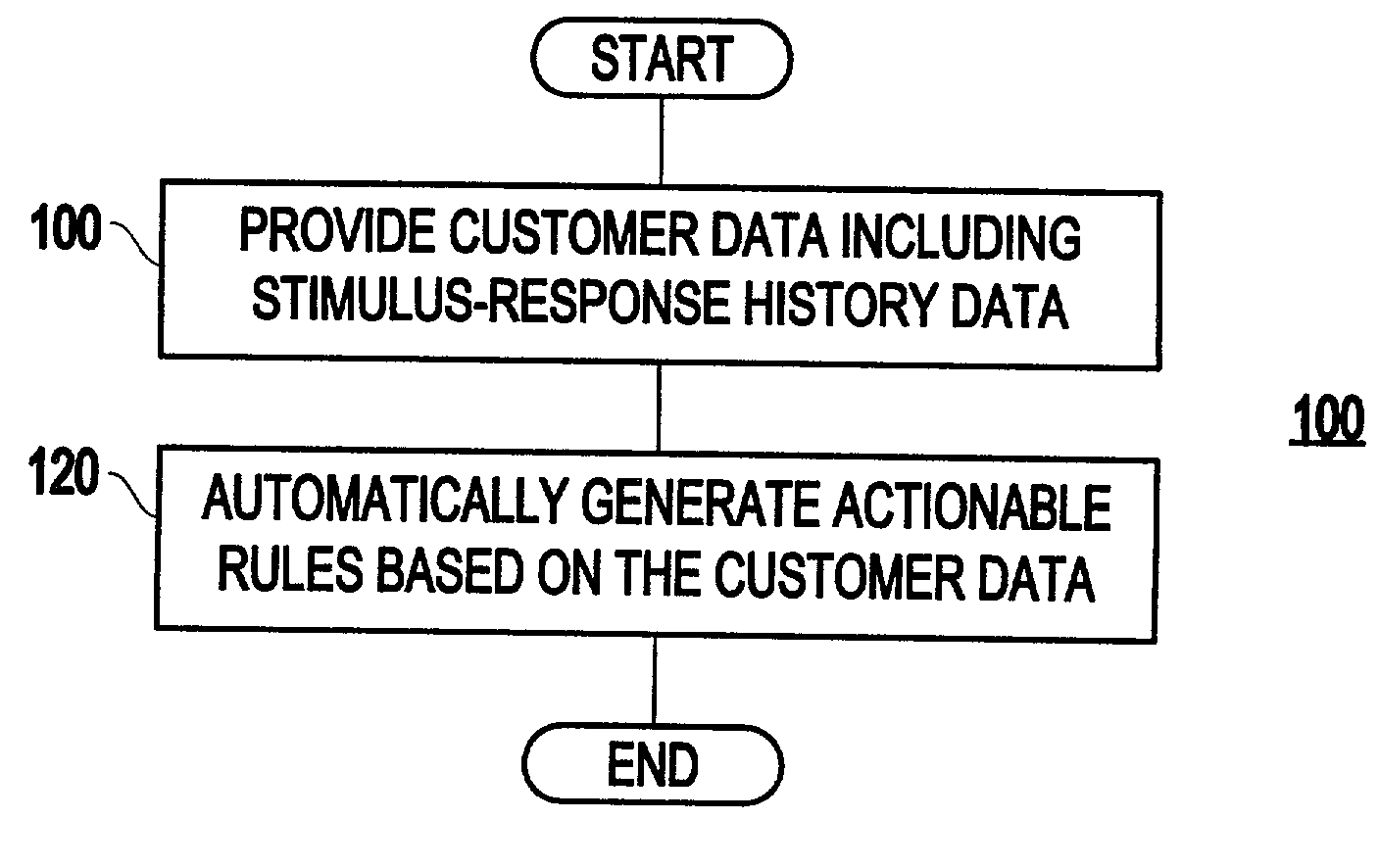
System and method for sequential decision making for customer relationship management
InactiveUS20040015386A1Market predictionsDigital computer detailsCustomer relationship managementData mining
A system and method for sequential decision-making for customer relationship management includes providing customer data including stimulus-response history data, and automatically generating actionable rules based on the customer data. Further, automatically generating actionable rules may include estimating a value function using reinforcement learning.
Owner:IBM CORP
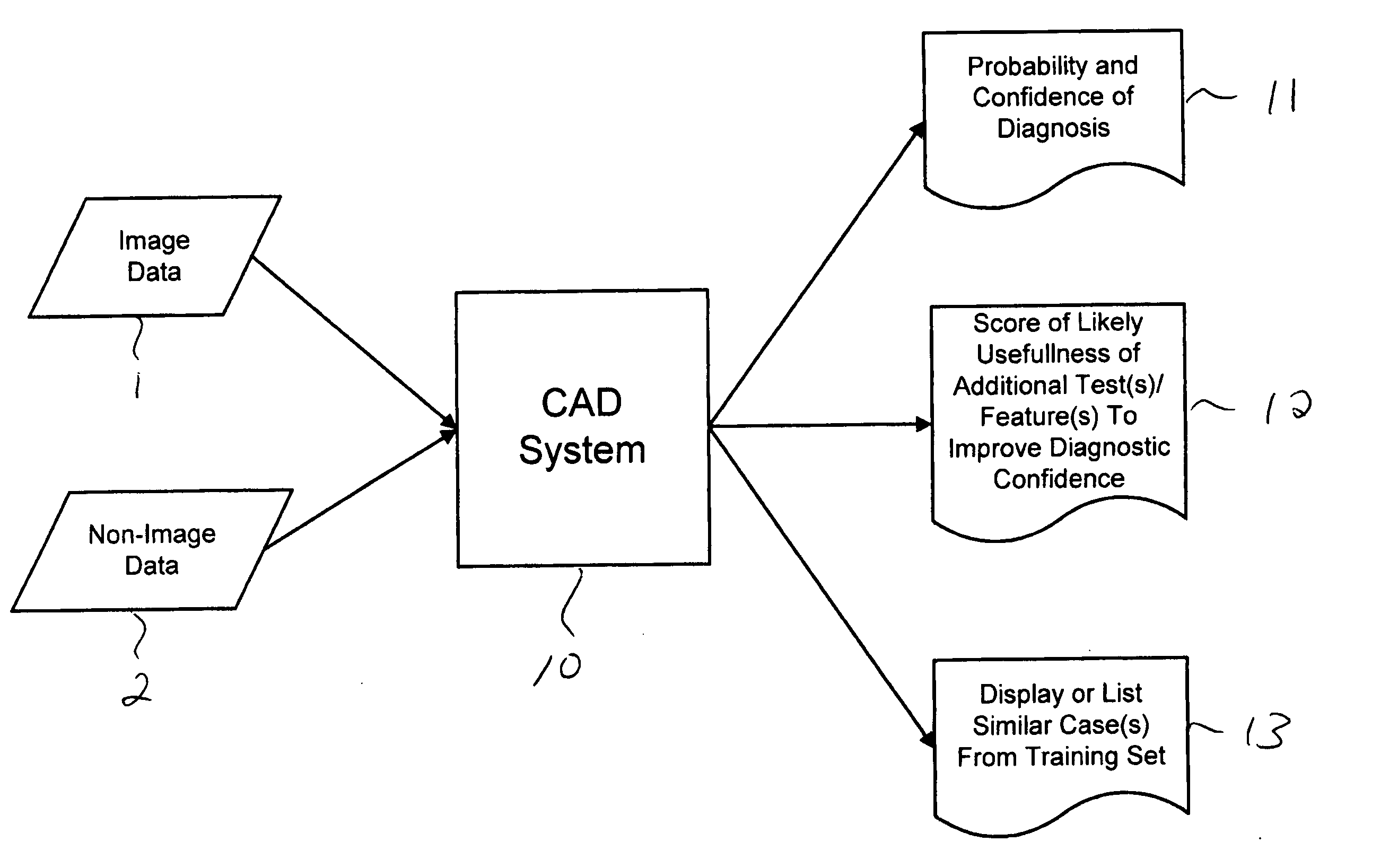
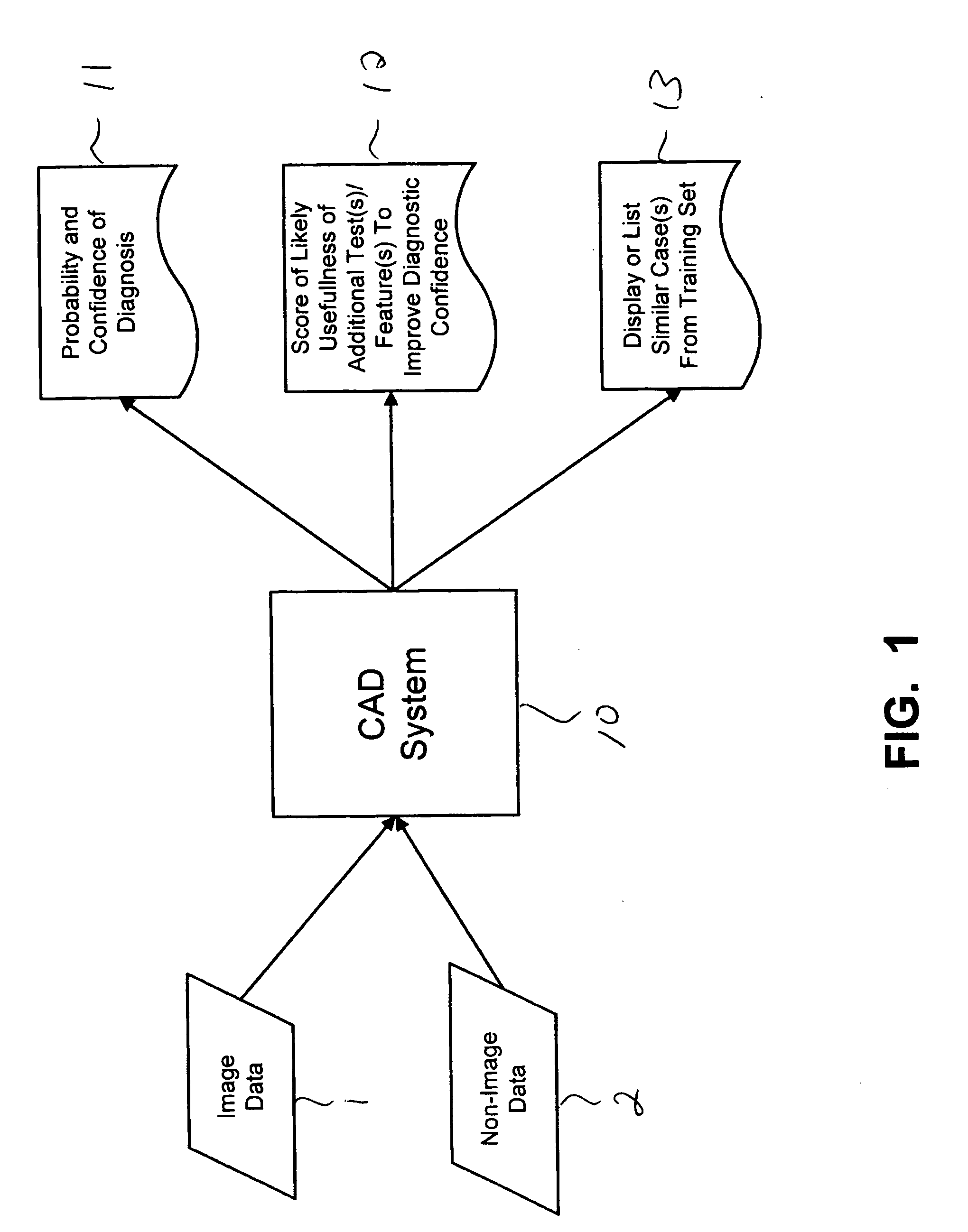
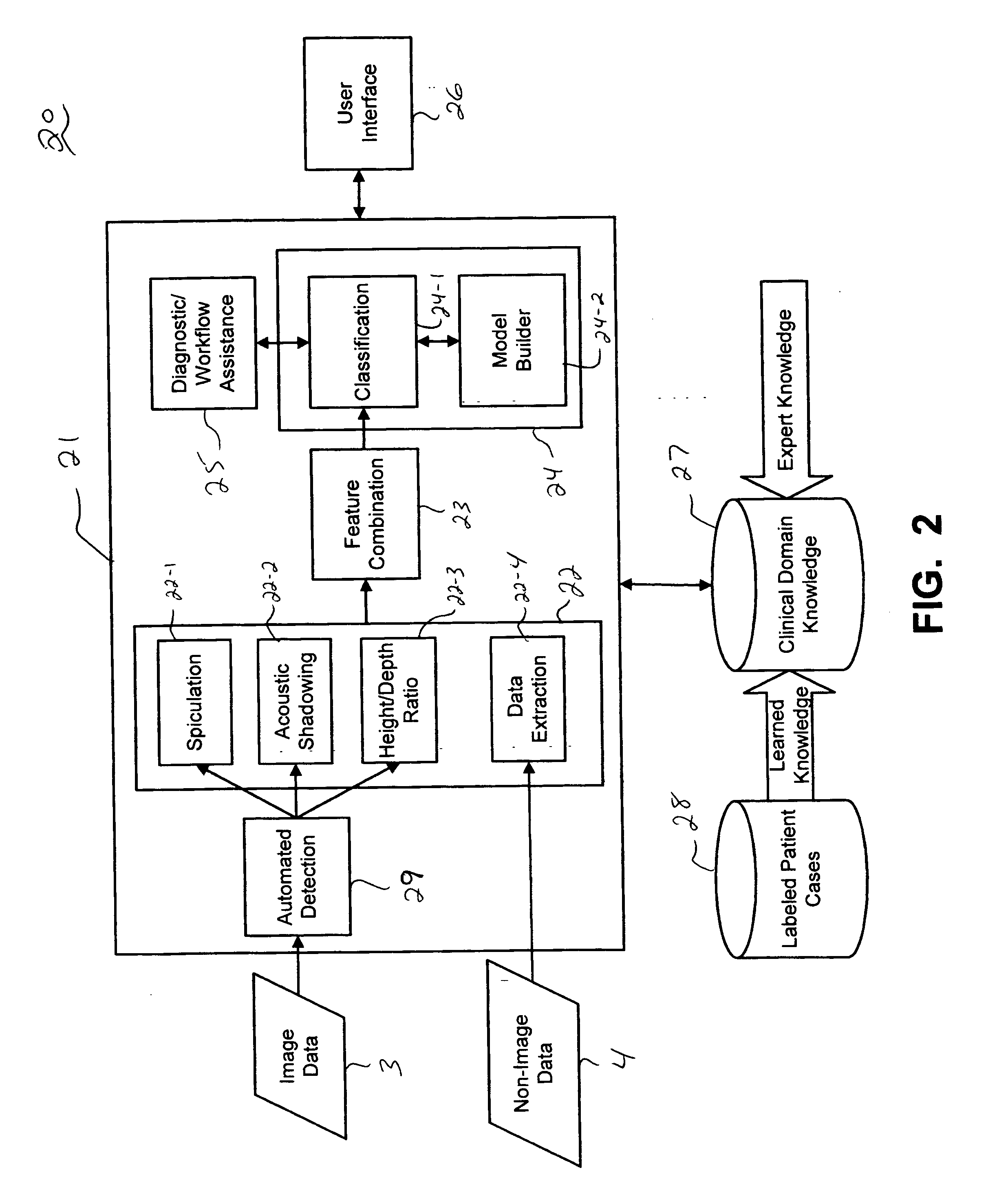
Systems and methods for automated diagnosis and decision support for breast imaging
ActiveUS20050049497A1Ultrasonic/sonic/infrasonic diagnosticsImage enhancementPatient dataDecision taking
CAD (computer-aided diagnosis) systems and applications for breast imaging are provided, which implement methods to automatically extract and analyze features from a collection of patient information (including image data and / or non-image data) of a subject patient, to provide decision support for various aspects of physician workflow including, for example, automated diagnosis of breast cancer other automated decision support functions that enable decision support for, e.g., screening and staging for breast cancer. The CAD systems implement machine-learning techniques that use a set of training data obtained (learned) from a database of labeled patient cases in one or more relevant clinical domains and / or expert interpretations of such data to enable the CAD systems to “learn” to analyze patient data and make proper diagnostic assessments and decisions for assisting physician workflow.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
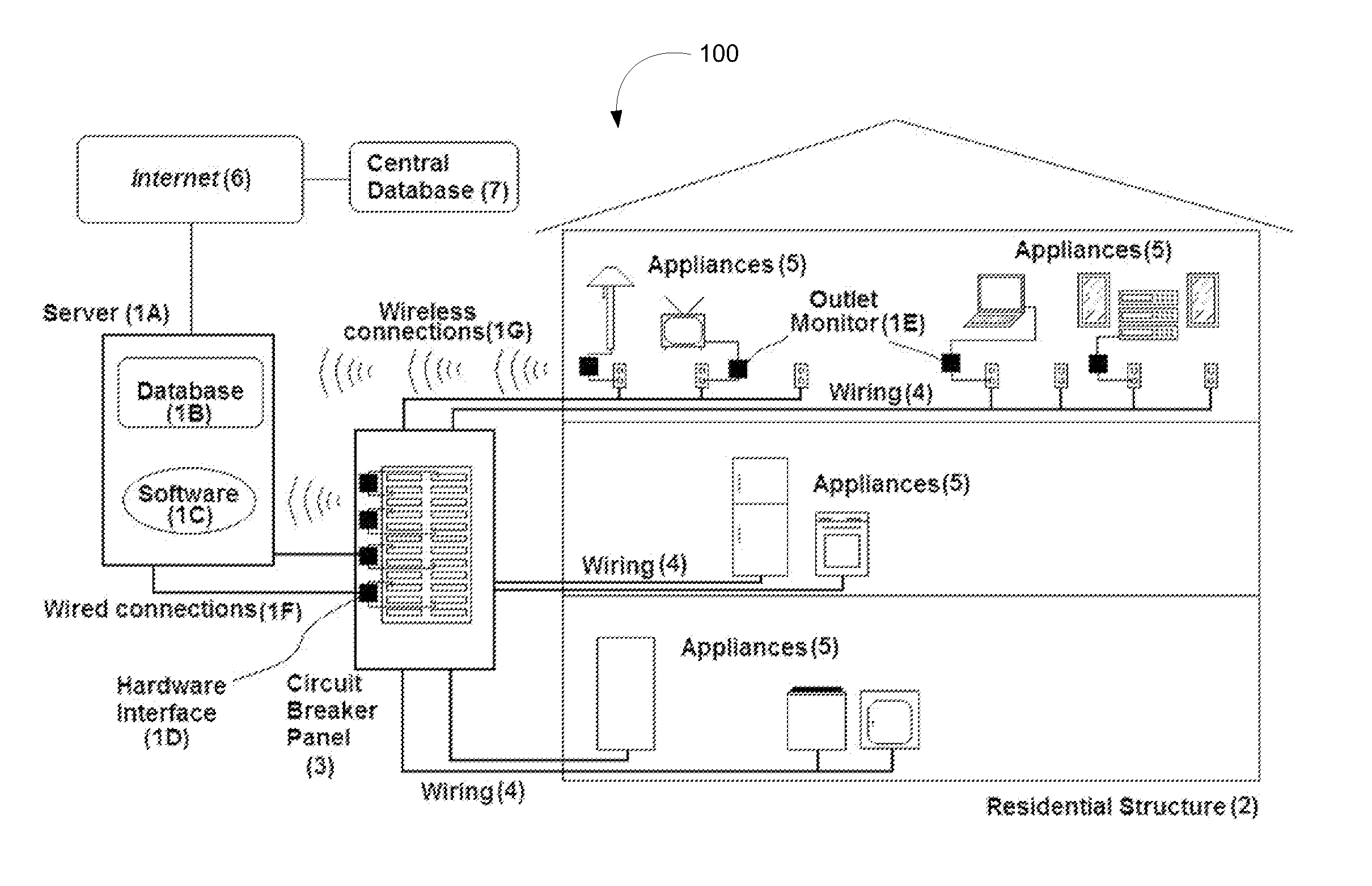
System and method to monitor and manage performance of appliances
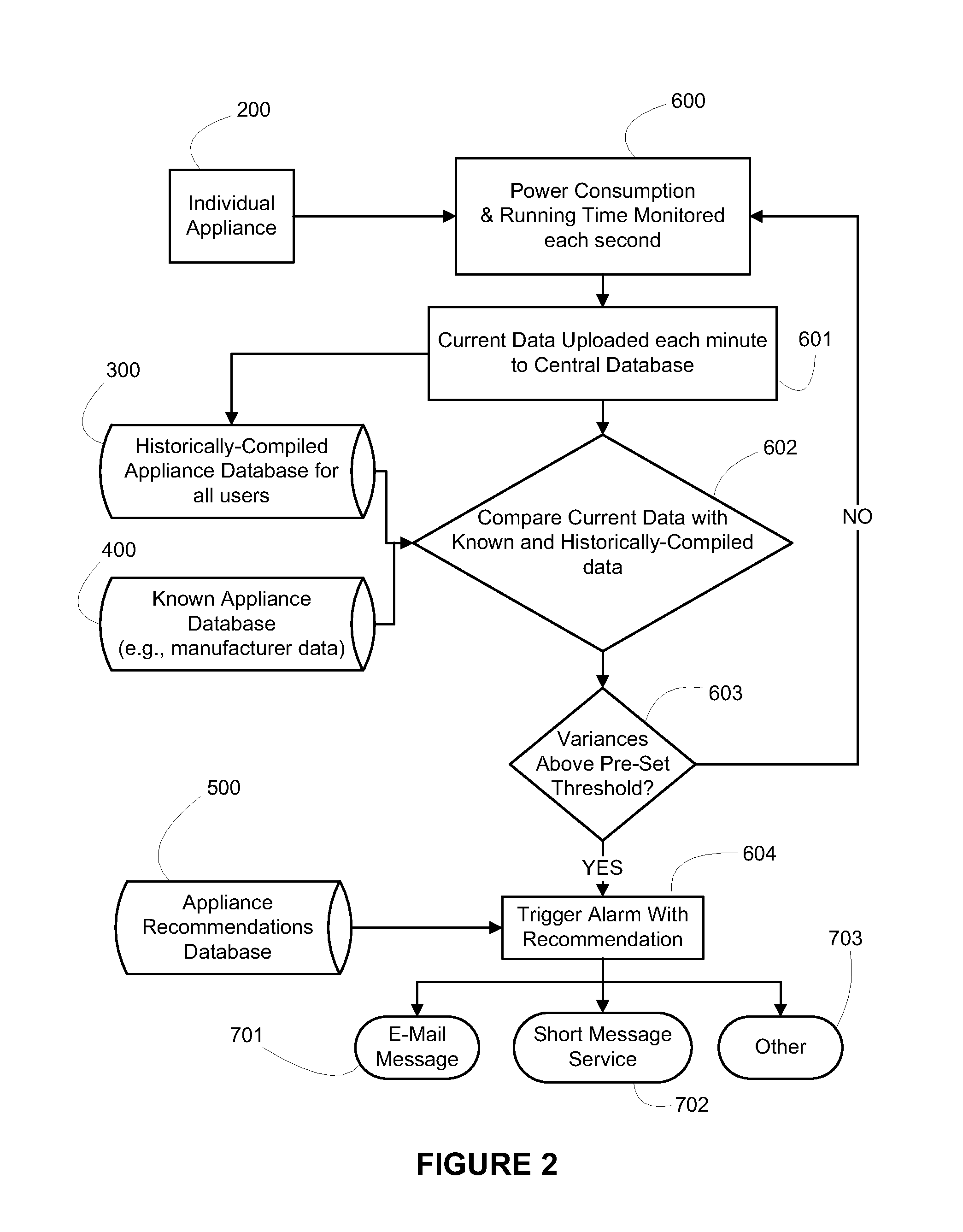
ActiveUS20110040785A1Reduce energy consumptionSimple addressingDigital data processing detailsTesting/monitoring control systemsDecision takingComputer software
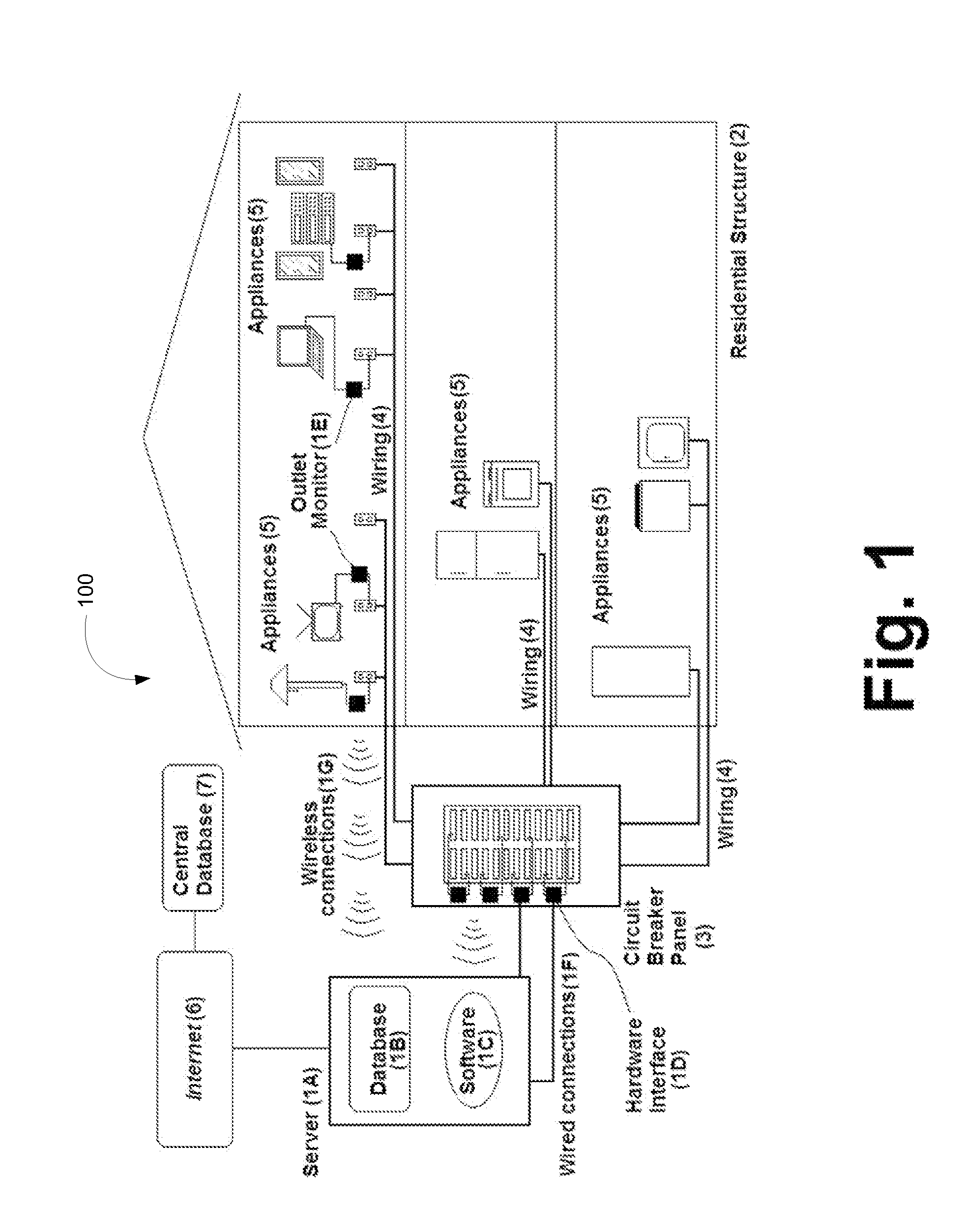
A system and method providing home and small business owners to monitor and manage one or more appliances. This enables a use to understand in detail their electrical consumption, to make informed decisions based on factual data about energy-saving upgrades to their current systems / appliances, and to provide Internet-based surveillance and control of systems for prevention of freezing, breakdown, or possible fire-related losses, including possible loss-of-life. The system and method includes through the use of Internet based computer software and databases, a hardware interface with electrical circuit panel(s) or fuse boxes in communication with the software and databases and optional wireless outlet monitoring units in communication with the software and databases. The databases being formed and created by the system and method for determining performance of appliances.
Owner:POWERHOUSE DYNAMICS
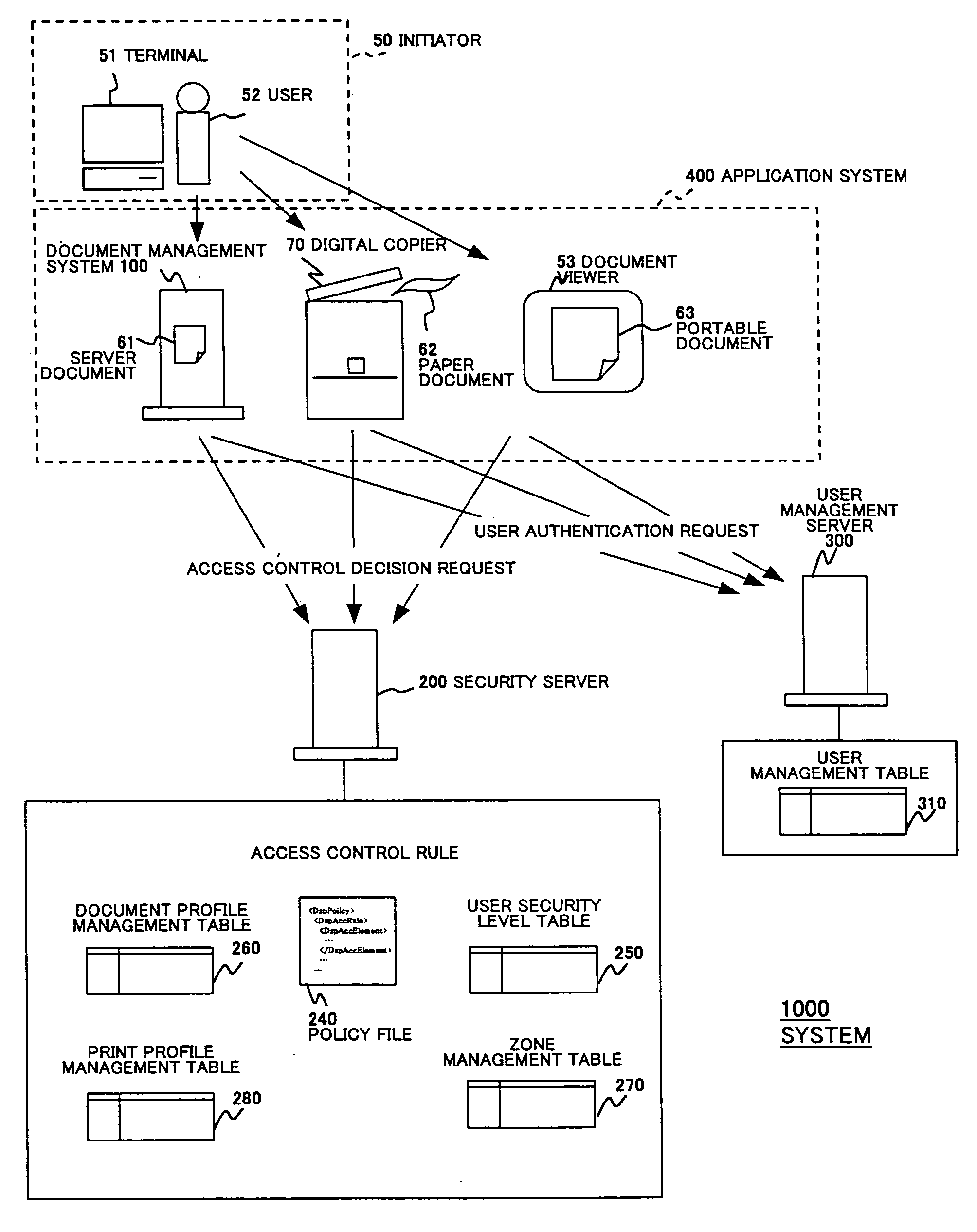
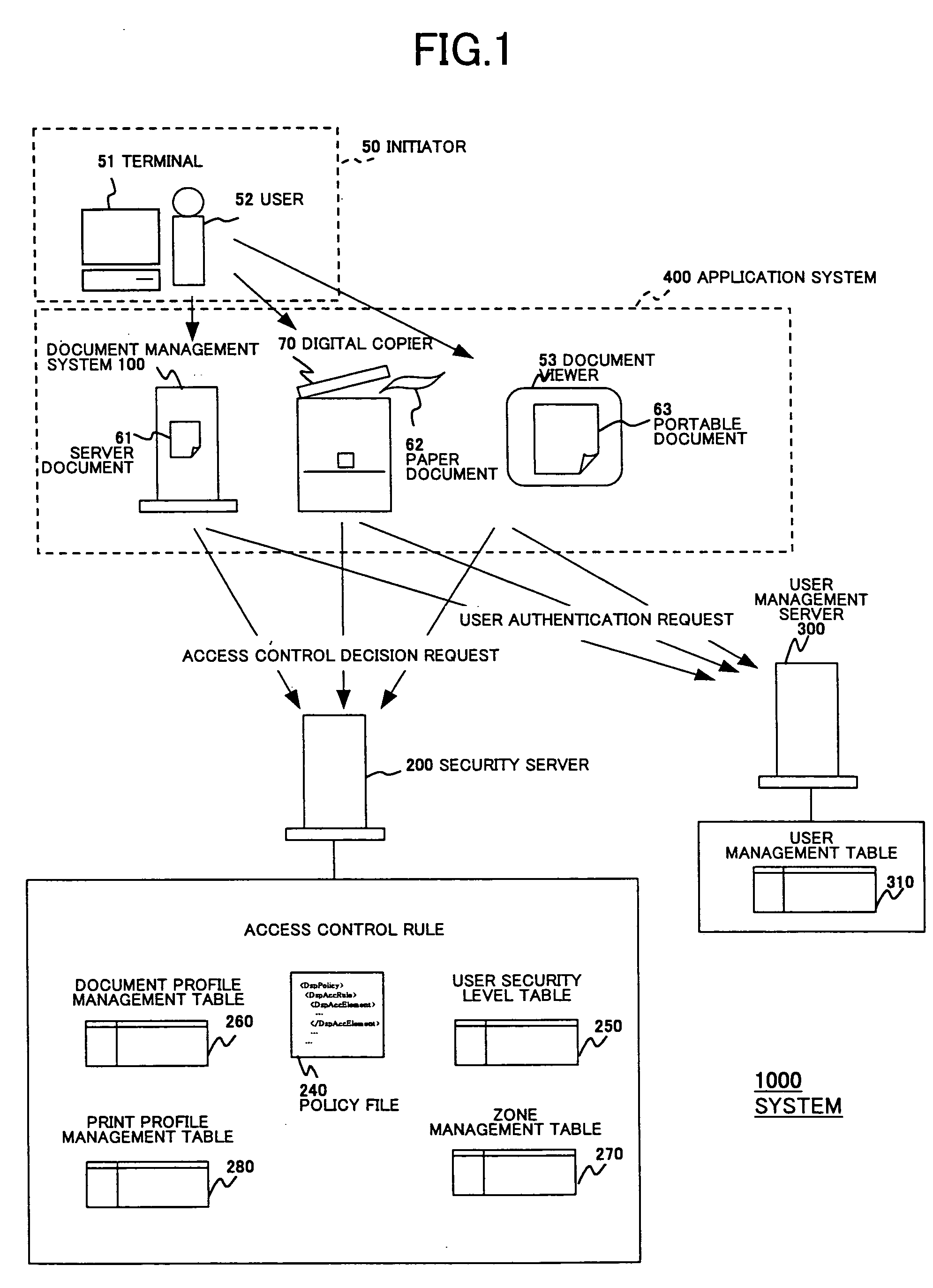
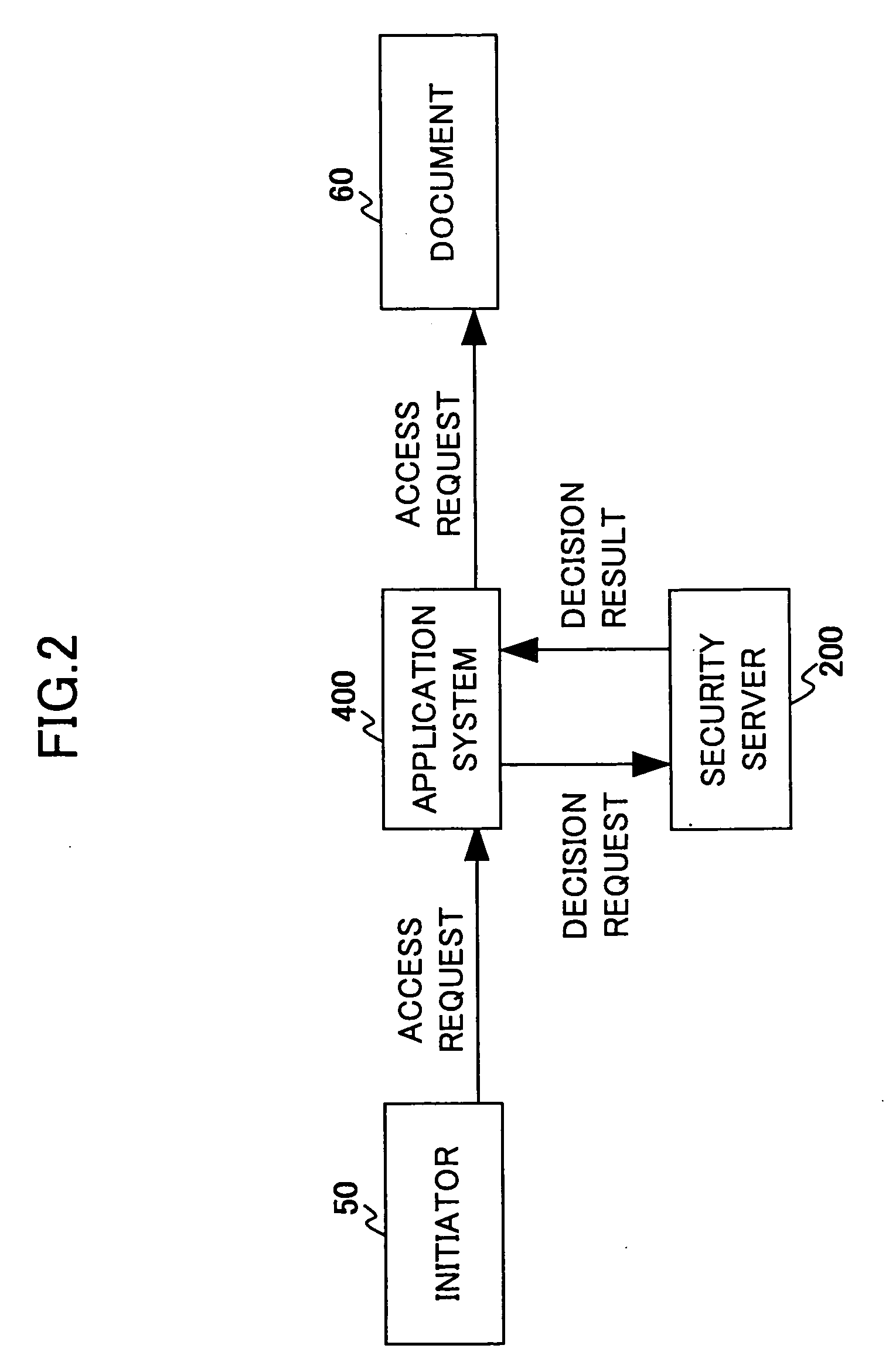
Access control decision system, access control enforcing system, and security policy
In an access control decision system, first information indicated by an access decision request is converted into second information being higher abstract when the access decision request is received. Next, the access control for the subject information is determined by referring a security policy being abstractly regulated based on the second information and a decision result showing the access control for the subject information is sent to a request originator that sent the access decision request.
Owner:RICOH KK
Method and apparatus to provide centralized call admission control and load balancing for a voice-over-IP network
InactiveUS6904017B1Improve service qualityBandwidth sharingInterconnection arrangementsError preventionExtensibilityBalancing network
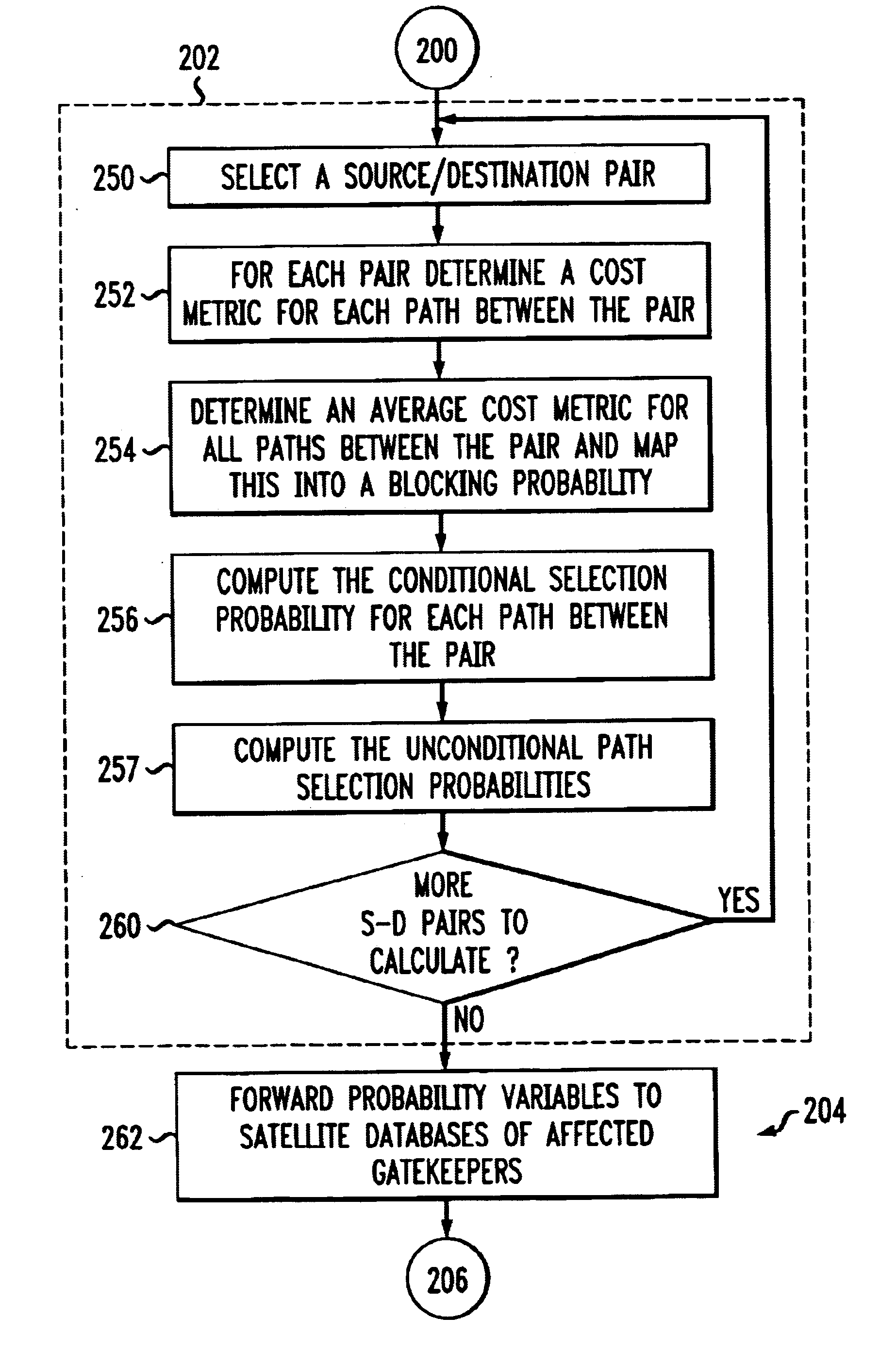
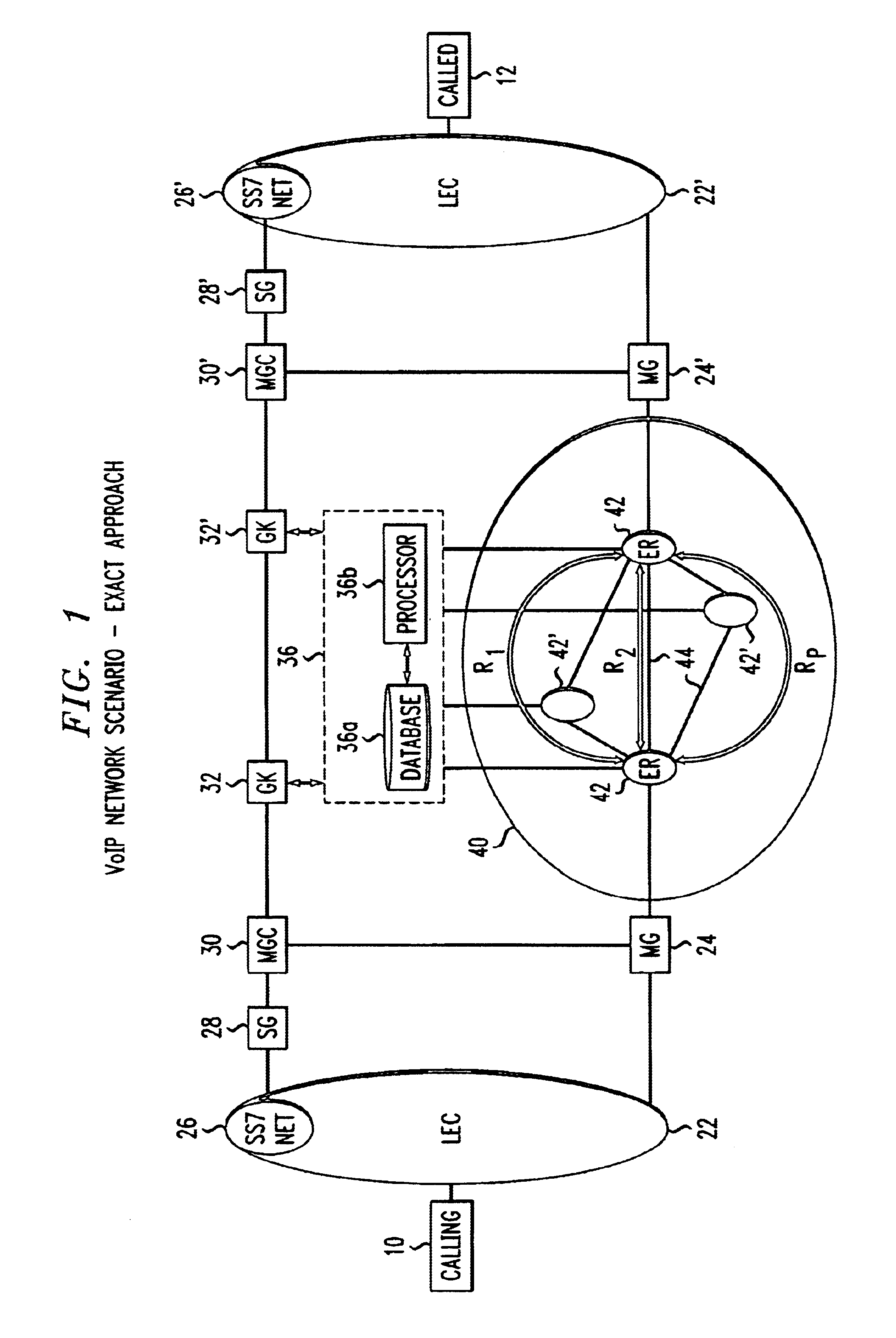
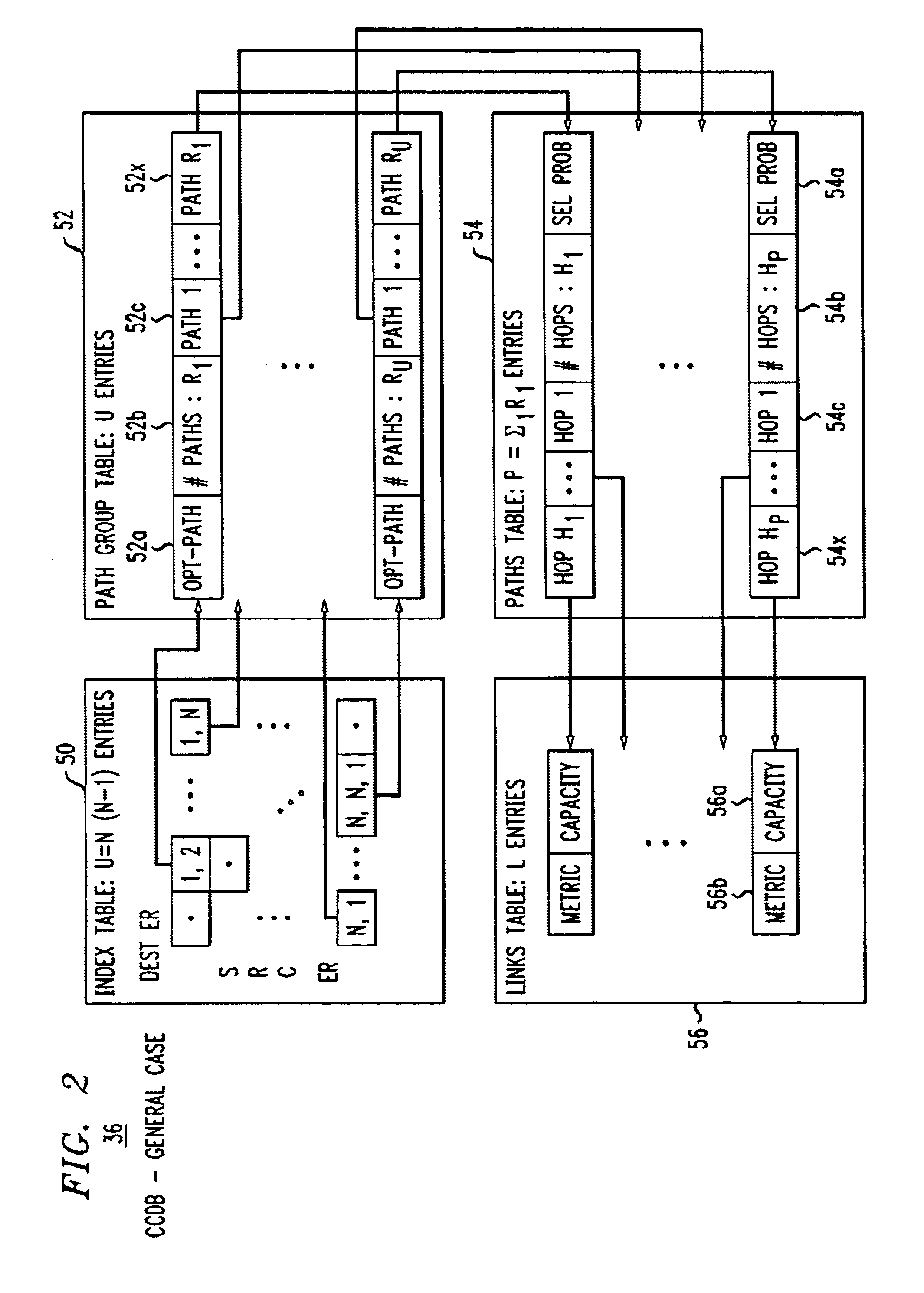
An admission control and load balancing system controls admission of packet streams or calls to a network and balances the packet traffic across the network, improving quality of service. The system includes a central database which stores information including cost data associated with individual paths and links across the network. A processor, in communication with the database, coordinates the admission control and load balancing decisions, and updates of the database cost data to reflect the dynamic network conditions, based on input from appropriate data sources. In one embodiment, referred to as the exact algorithm, the database is consulted by the admission control points or gatekeepers prior to admitting each arriving packet stream, and the database contents are updated call-by-call to reflect the allocation of resources to each admitted stream. In another embodiment, referred to as the inexact algorithm, control decision as well as database updates occur on a periodic rather than on a call-by-call basis to promote better scalability. In this embodiment, the processor periodically calculates admission decisions based on cost data in the central database. These admission decisions are then periodically forwarded to a satellite database associated with each gatekeeper, for storage and use in admission decisions until the next update epoch.
Owner:LUCENT TECH INC
Predictive Analytics for Semi-Structured Case Oriented Processes
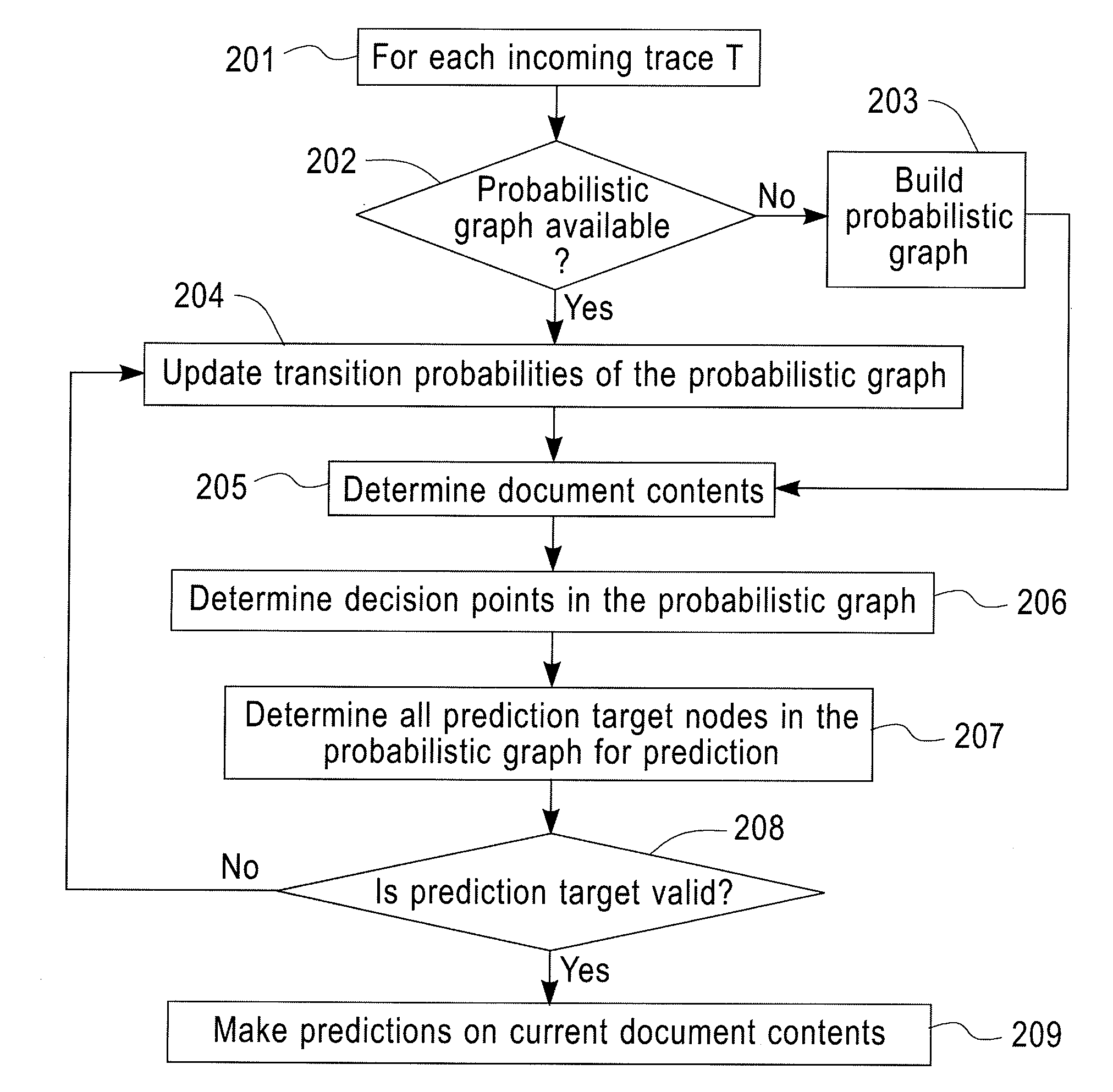
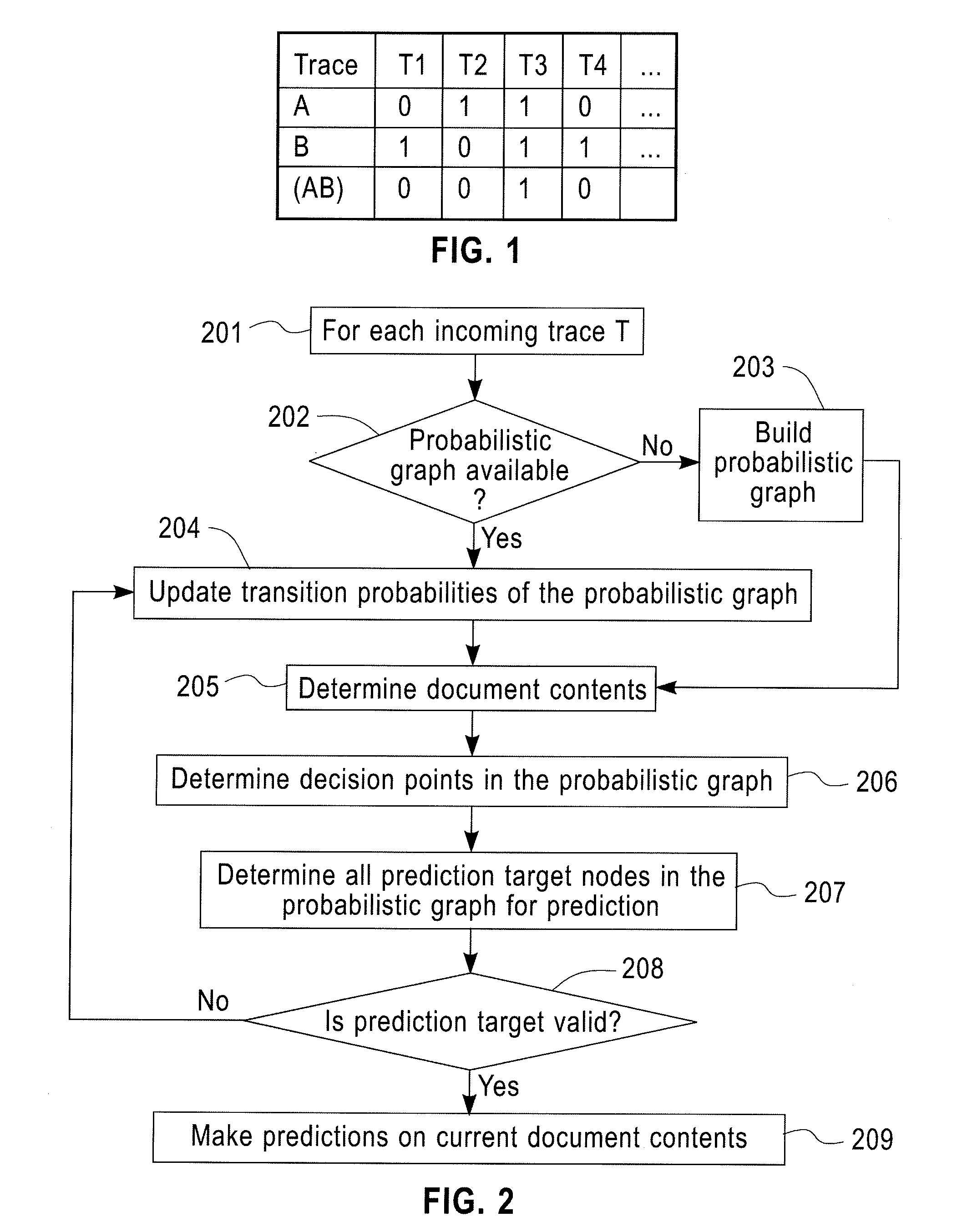
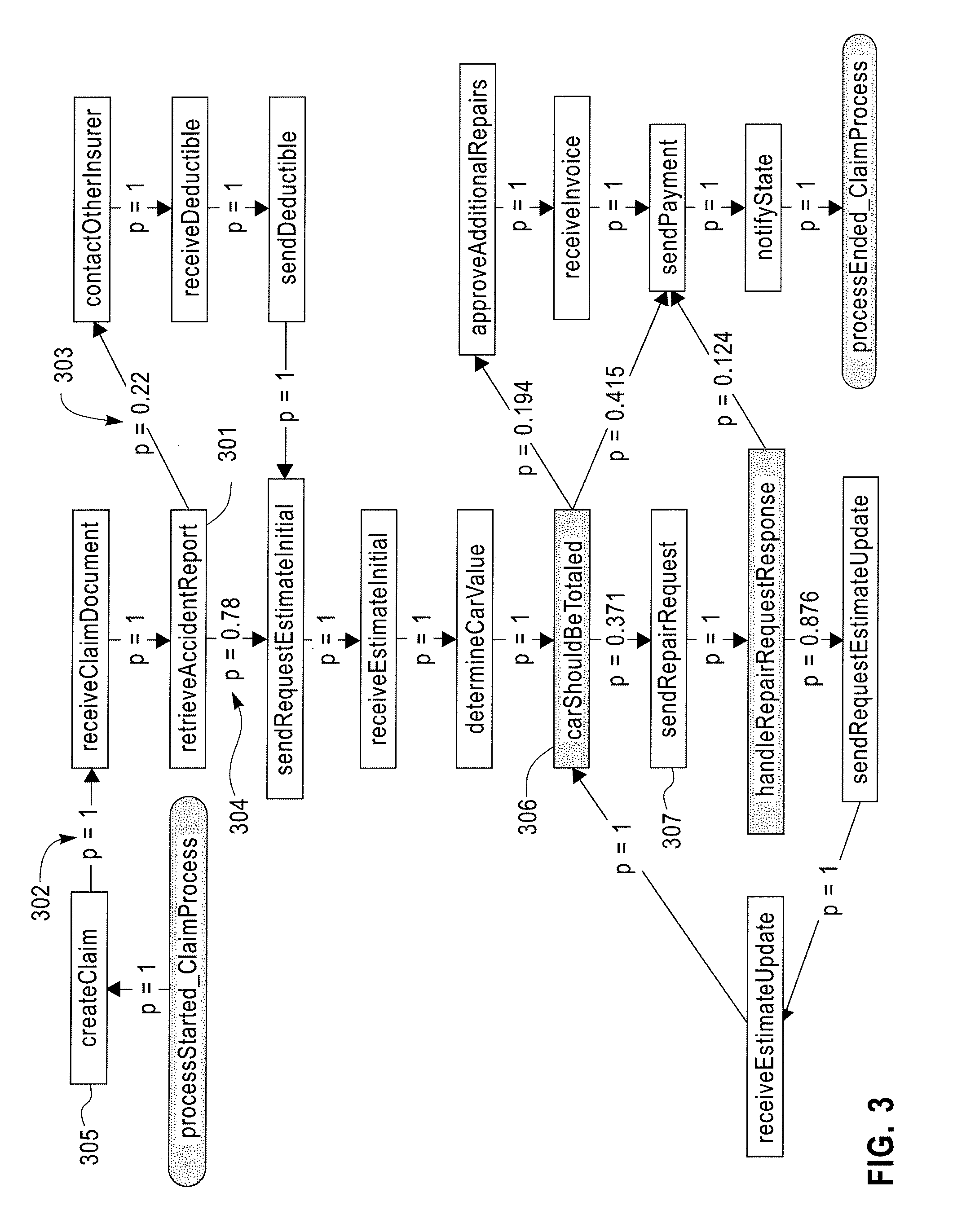
InactiveUS20120066166A1Probabilistic networksFuzzy logic based systemsNODALTheoretical computer science
A method for predictive analytics for a process includes receiving at least one trace of the process, building a probabilistic graph modeling the at least one trace, determining content at each node of the probabilistic graph, wherein a node represents an activity of the process and at least one node is a decision node, modeling each decision node as a respective decision tree, and predicting, for an execution of the process, a path in the probabilistic graph from any decision node to a prediction target node of a plurality of prediction target nodes given the content.
Owner:IBM CORP
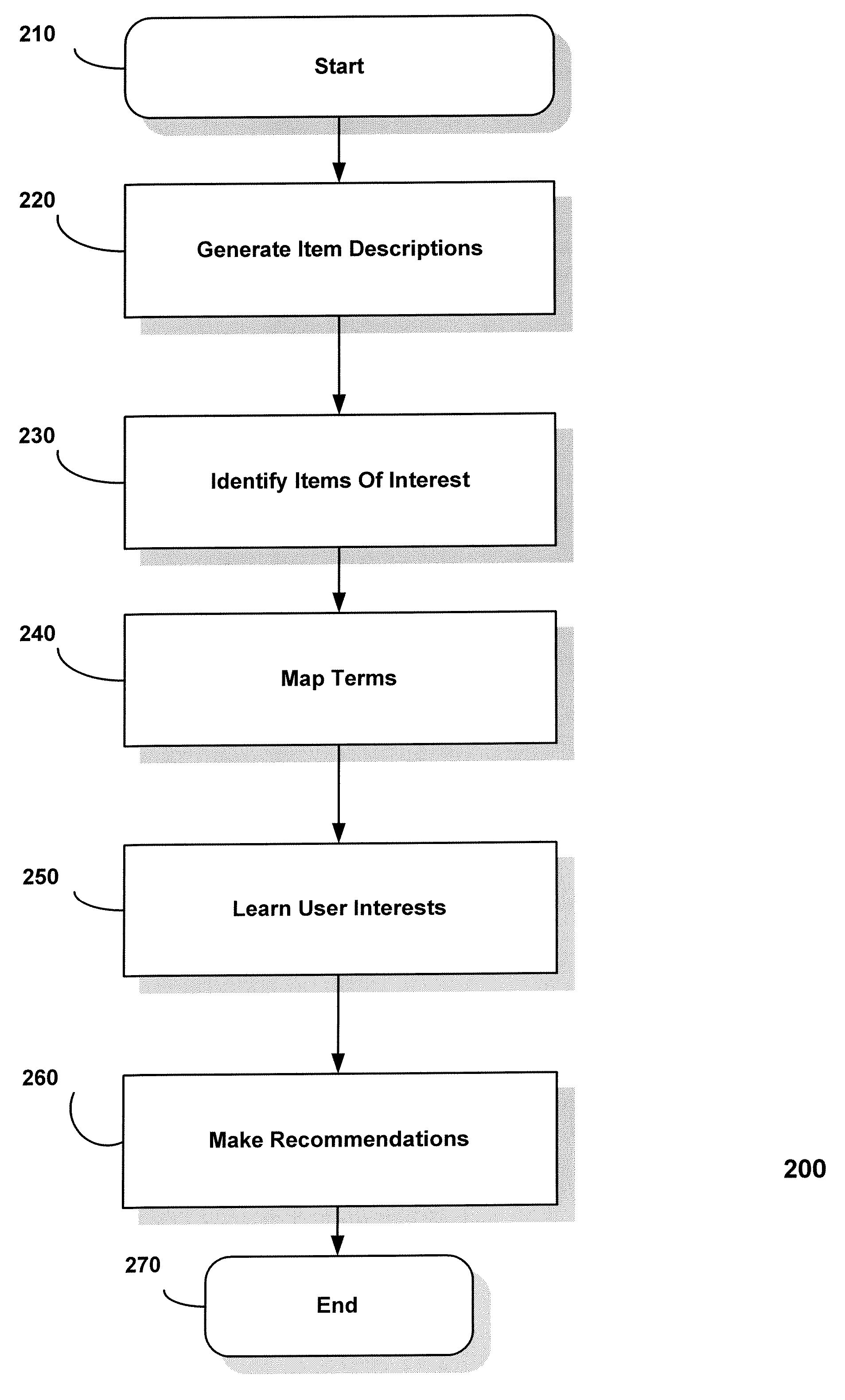
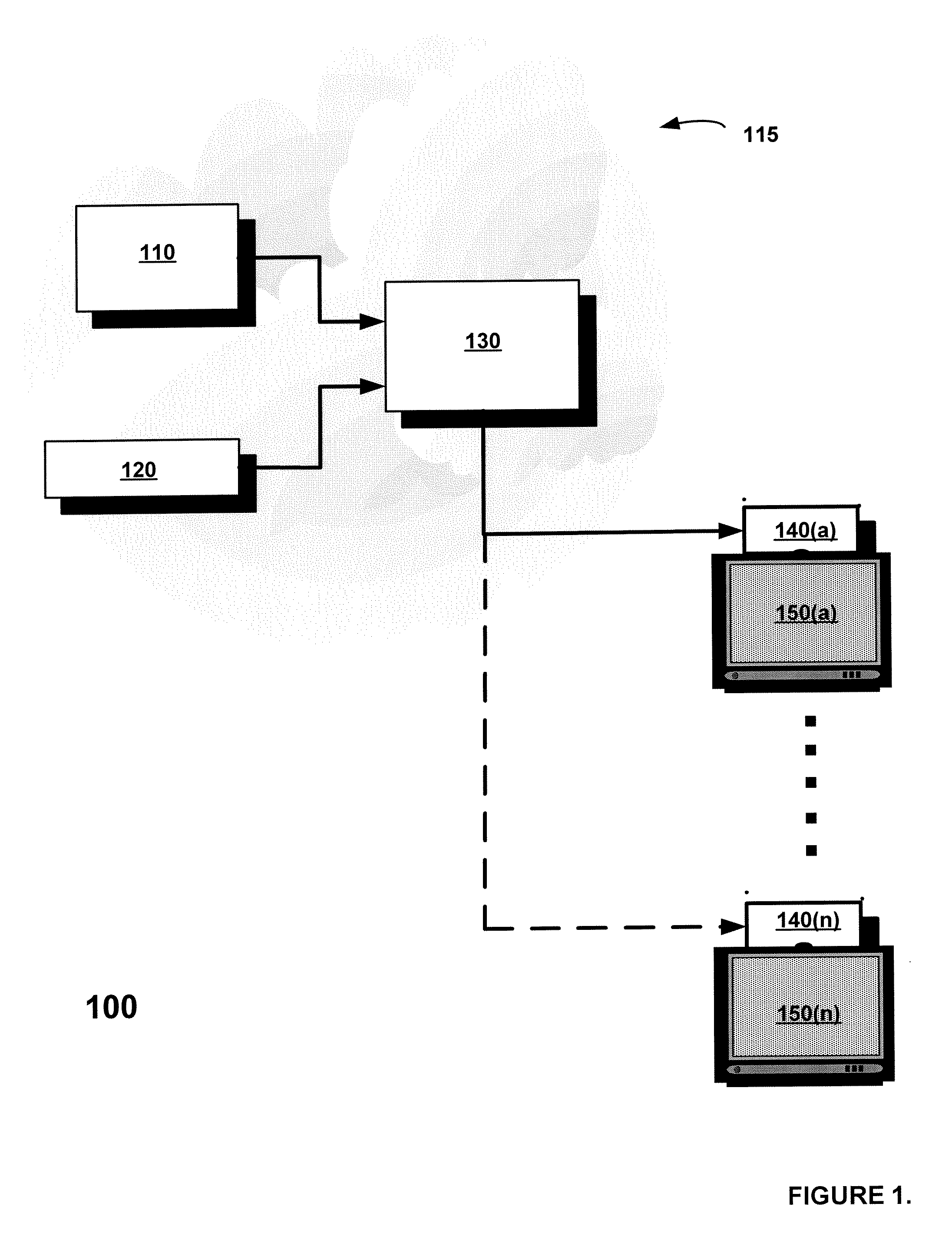
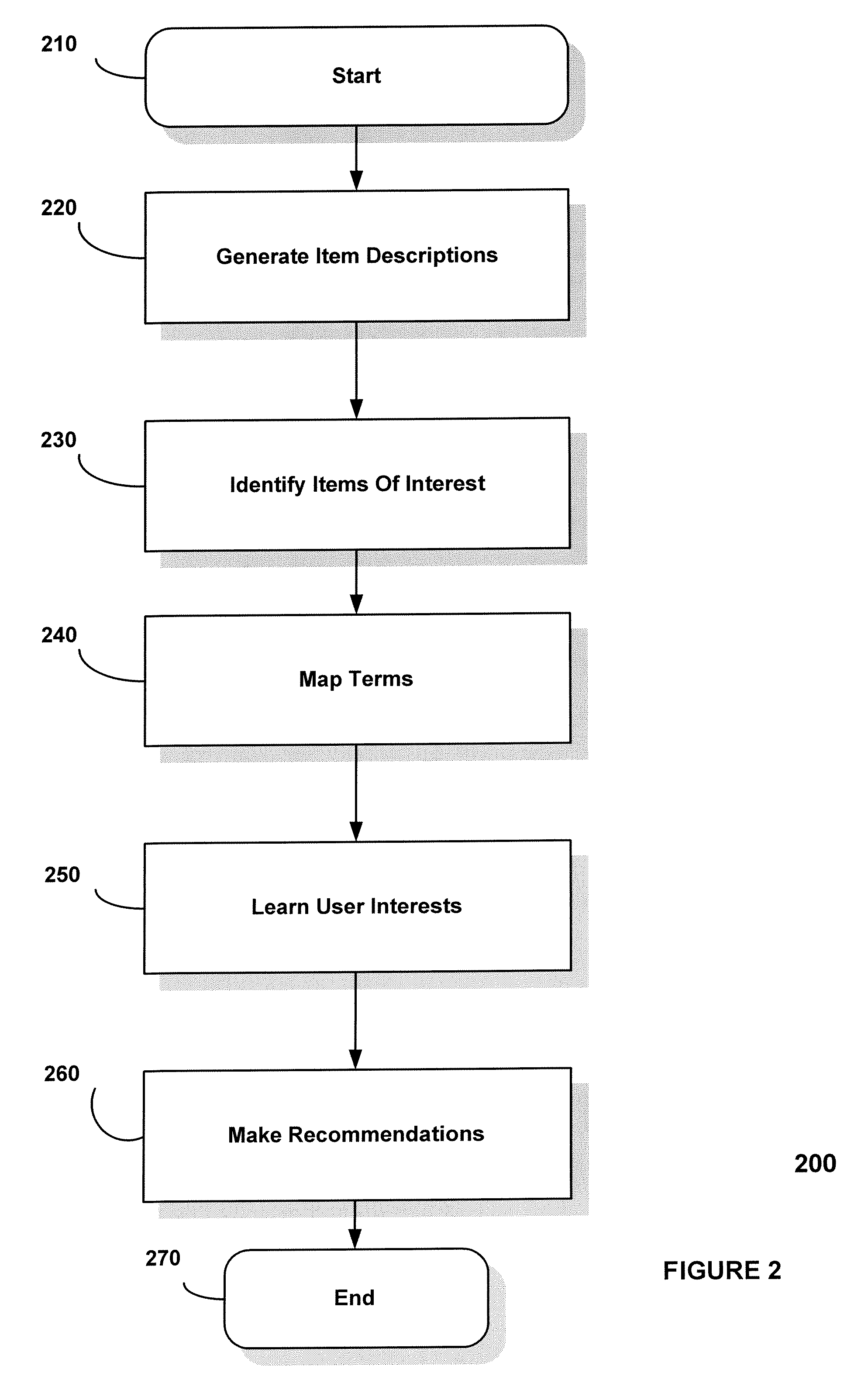
System and method for recommending items of interest to a user
ActiveUS20070078849A1Improve privacyDigital data information retrievalSelective content distributionPersonalizationDecision taking
A system and method is disclosed for recommending items to individual users using a combination of clustering decision trees and frequency-based term mapping. The system and method of the present invention is configured to receive data based on user action, such as television remote control activity, or computer keyboard entry, and when a new item data is made available from sources such as television program guides, movie databases, deliverers of advertising data, on-line auction web sites, and electronic mail servers, the system and method analytically breaks down the new item data, compares it to ascertained attributes of item data that a user liked in the past, and produces numeric ranking of the new item data dynamically, and without subsequent user input, or data manipulation by item data deliverers, and is tailored to each individual user. A embodiment is disclosed for learning user interests based on user actions and then applying the learned knowledge to rank, recommend, and / or filter items, such as e-mail spam, based on the level of interest to a user. The embodiment may be used for automated personalized information learning, recommendation, and / or filtering systems in applications such as television programming, web-based auctions, targeted advertising, and electronic mail filtering. The embodiment may be structured to generate item descriptions, learn items of interest, learn terms that effectively describe the items, cluster similar items in a compact data structure, and then use the structure to rank new offerings. Embodiments of the present invention include, by way of non-limiting example: allowing the assignment of rank scores to candidate items so one can be recommended over another, building decision trees incrementally using unsupervised learning to cluster examples into categories automatically, consistency with “edge” (thick client) computing whereby certain data structures and most of the processing are localized to the set-top box or local PC, the ability to learn content attributes automatically on-the-fly, and the ability to store user preferences in opaque local data structures and are not easily traceable to individual users.
Owner:FOURTHWALL MEDIA
System and method for medical device security, data tracking and outcomes analysis
InactiveUS20170068792A1Easy to createImprove equipment qualitySurgical needlesVaccination/ovulation diagnosticsPersonalizationGuideline
The present invention creates an objective methodology of quantitative accountability for medical device manufacturers, vendors, clinical providers, patients, and payers. In one embodiment, the standardized data received and stored in the medical device database can in turn be used for a variety of applications related to decision support (e.g., medical device selection), education and training (e.g., procedural performance), cost efficacy, evidence based medicine and best practice guidelines, personalized medicine, and comparative performance / safety analytics.
Owner:REINER BRUCE
Biopotential Waveform Data Fusion Analysis and Classification Method
InactiveUS20080208072A1Improve classification accuracyElectroencephalographyMedical data miningTraining phaseData source
Biopotential waveforms such as ERPs, EEGs, ECGs, or EMGs are classified accurately by dynamically fusing classification information from multiple electrodes, tests, or other data sources. These different data sources or “channels” are ranked at different time instants according to their respective univariate classification accuracies. Channel rankings are determined during training phase in which classification accuracy of each channel at each time-instant is determined. Classifiers are simple univariate classifiers which only require univariate parameter estimation. Using classification information, a rule is formulated to dynamically select different channels at different time-instants during the testing phase. Independent decisions of selected channels at different time instants are fused into a decision fusion vector. The resulting decision fusion vector is optimally classified using a discrete Bayes classifier. Finally, the dynamic decision fusion system provides high classification accuracies, is quite flexible in operation, and overcomes major limitations of classifiers applied currently in biopotential waveform studies and clinical applications.
Owner:NEURONETRIX SOLUTIONS
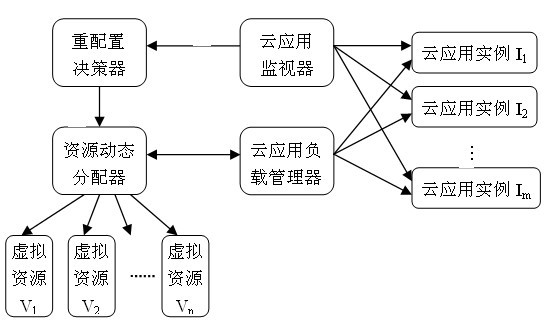
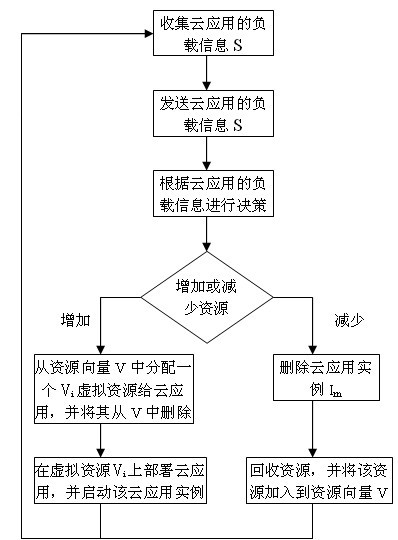
Cloud computing resource scheduling method based on dynamic reconfiguration virtual resources
InactiveCN101938416ADynamic Allocation OptimizationMeeting the Need for Dynamic ScalabilityData switching networksCurrent loadDecision taking
The invention relates to a cloud computing resource scheduling method based on dynamic reconfiguration virtual resources. The method comprises the steps of: using cloud application load information collected by a cloud application monitor as a basis; making a dynamic decision based on the load capacity of the virtual resources for running cloud application and the current load of the cloud application; and dynamically reconfiguring virtual resources for cloud application based on the decision result. Dynamic adjustment of resources is realized by a method for reconfiguring virtual resources for cloud application, without needing dynamic redistribution of physical resources or stopping executing cloud application. The method can dynamically reconfigure the virtual resources according to the load variation of the cloud application, optimize allocation of the cloud computing resources, realize effective use of the cloud computing resources, and meet the requirements on dynamic scalability of cloud application. In addition, the method can avoid waste of the cloud computing resources, and save the cost for using resources for cloud application users.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com