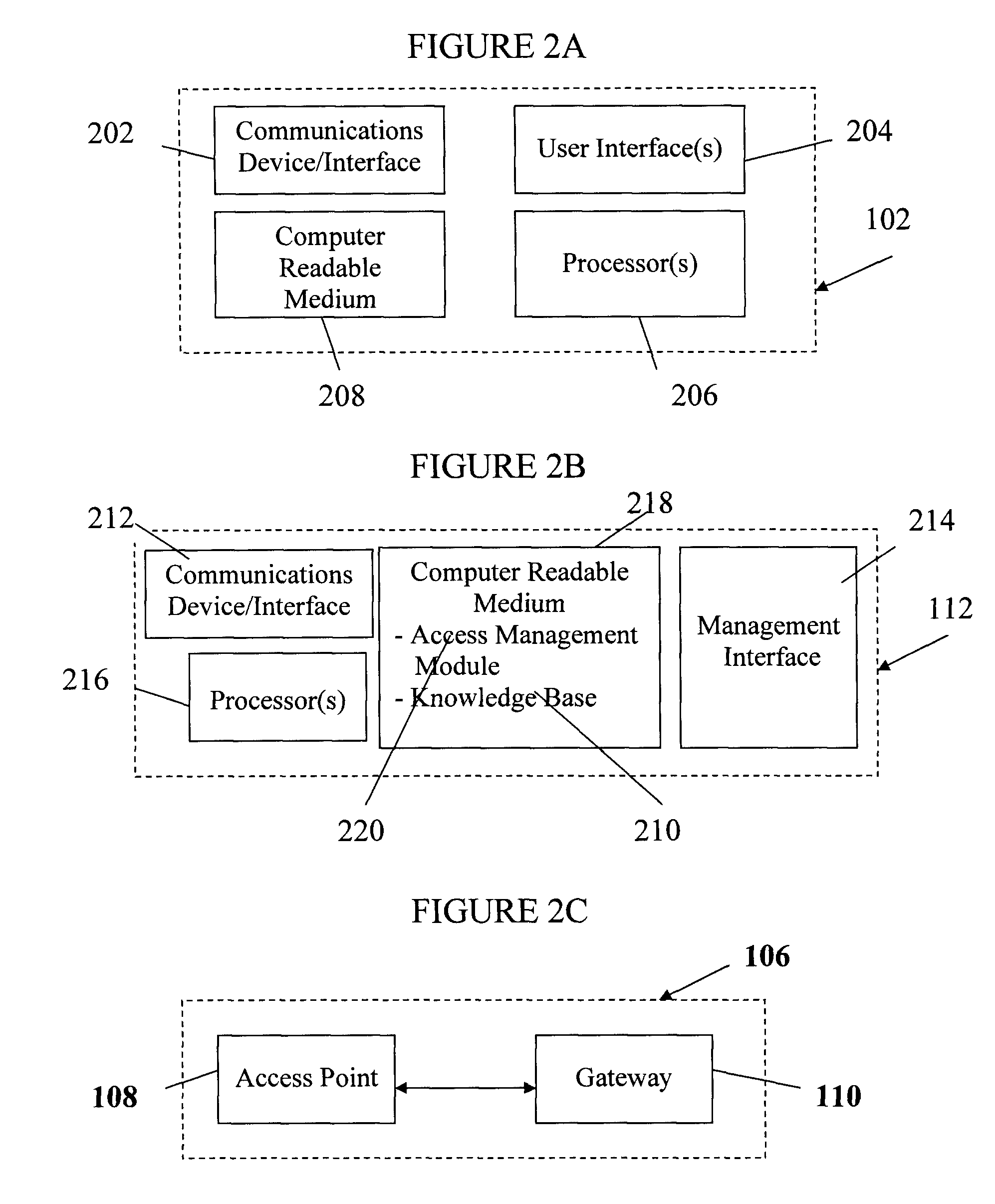
Patents
Literature
713 results about "Data validation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, data validation is the process of ensuring data have undergone data cleansing to ensure they have data quality, that is, that they are both correct and useful. It uses routines, often called "validation rules" "validation constraints" or "check routines", that check for correctness, meaningfulness, and security of data that are input to the system. The rules may be implemented through the automated facilities of a data dictionary, or by the inclusion of explicit application program validation logic.
Multi-dimensional data protection and mirroring method for micro level data
ActiveUS7103824B2Detection errorLow common data sizeCode conversionCyclic codesData validationData integrity
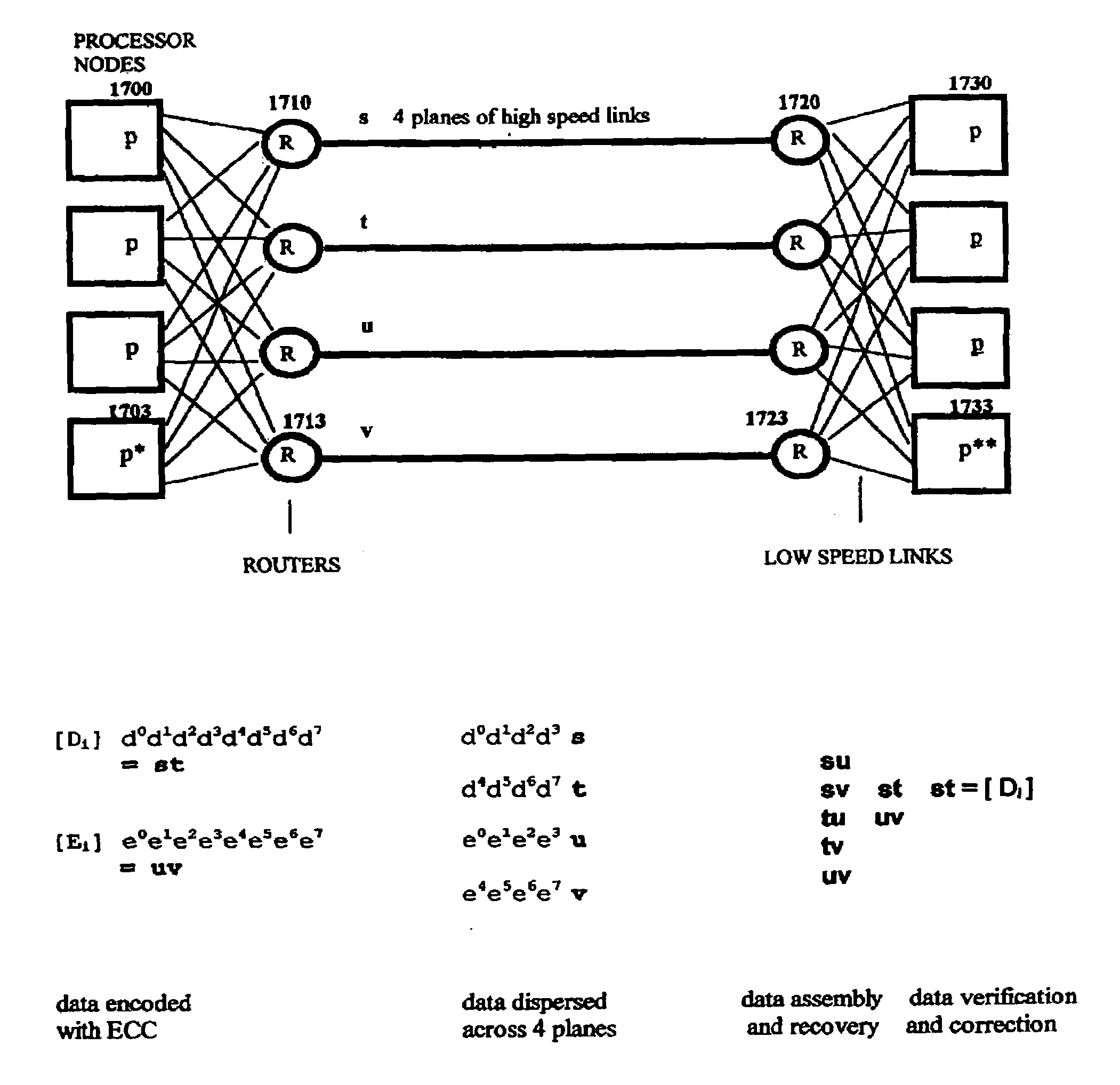
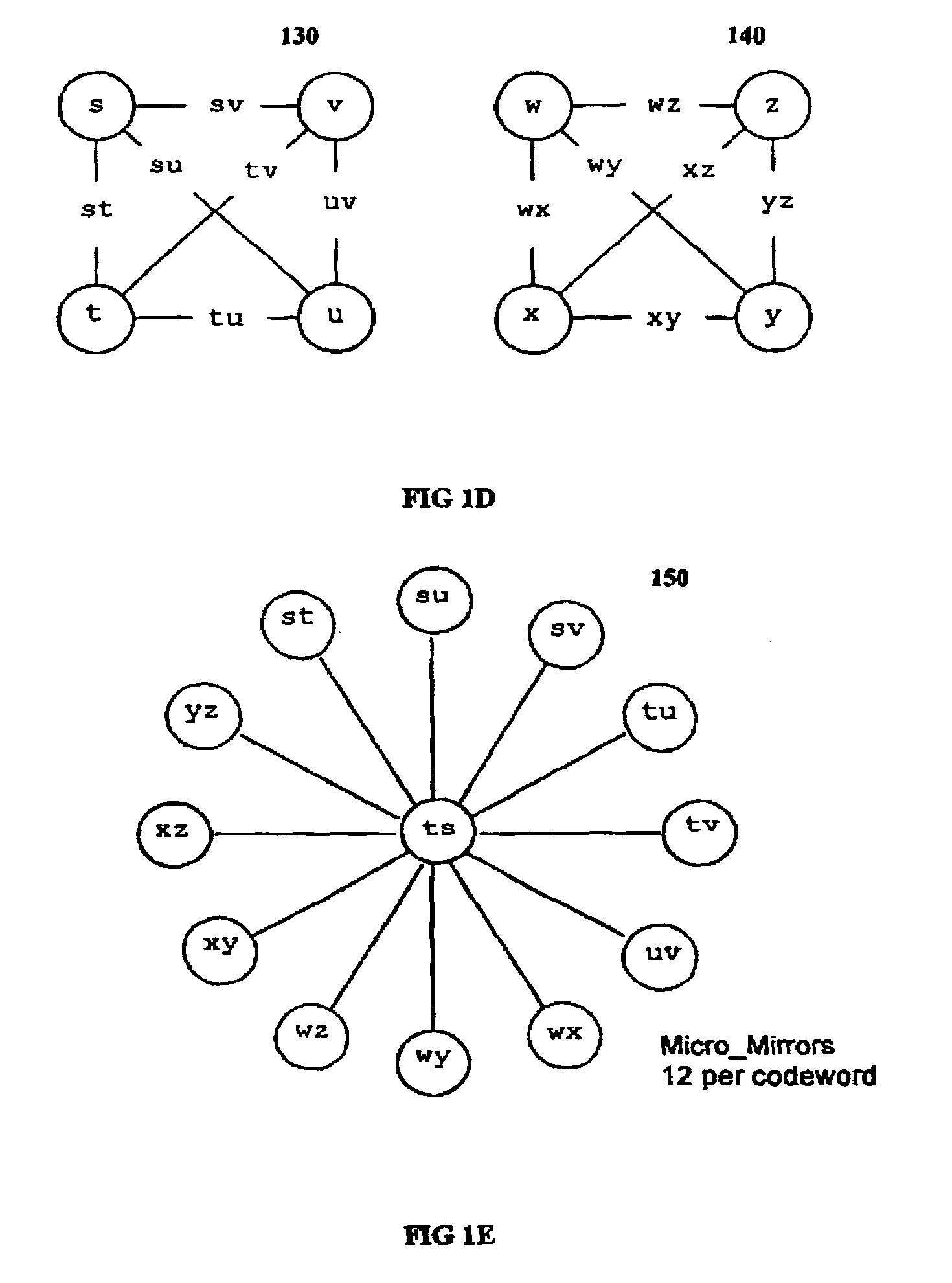
The invention discloses a data validation, mirroring and error / erasure correction method for the dispersal and protection of one and two-dimensional data at the micro level for computer, communication and storage systems. Each of 256 possible 8-bit data bytes are mirrored with a unique 8-bit ECC byte. The ECC enables 8-bit burst and 4-bit random error detection plus 2-bit random error correction for each encoded data byte. With the data byte and ECC byte configured into a 4 bit×4 bit codeword array and dispersed in either row, column or both dimensions the method can perform dual 4-bit row and column erasure recovery. It is shown that for each codeword there are 12 possible combinations of row and column elements called couplets capable of mirroring the data byte. These byte level micro-mirrors outperform conventional mirroring in that each byte and its ECC mirror can self-detect and self-correct random errors and can recover all dual erasure combinations over four elements. Encoding at the byte quanta level maximizes application flexibility. Also disclosed are fast encode, decode and reconstruction methods via boolean logic, processor instructions and software table look-up with the intent to run at line and application speeds. The new error control method can augment ARQ algorithms and bring resiliency to system fabrics including routers and links previously limited to the recovery of transient errors. Image storage and storage over arrays of static devices can benefit from the two-dimensional capabilities. Applications with critical data integrity requirements can utilize the method for end-to-end protection and validation. An extra ECC byte per codeword extends both the resiliency and dimensionality.
Owner:HALFORD ROBERT
Remote service access system and method
InactiveUS20100107225A1Limited accessDigital data processing detailsMultiple digital computer combinationsData validationComputer network
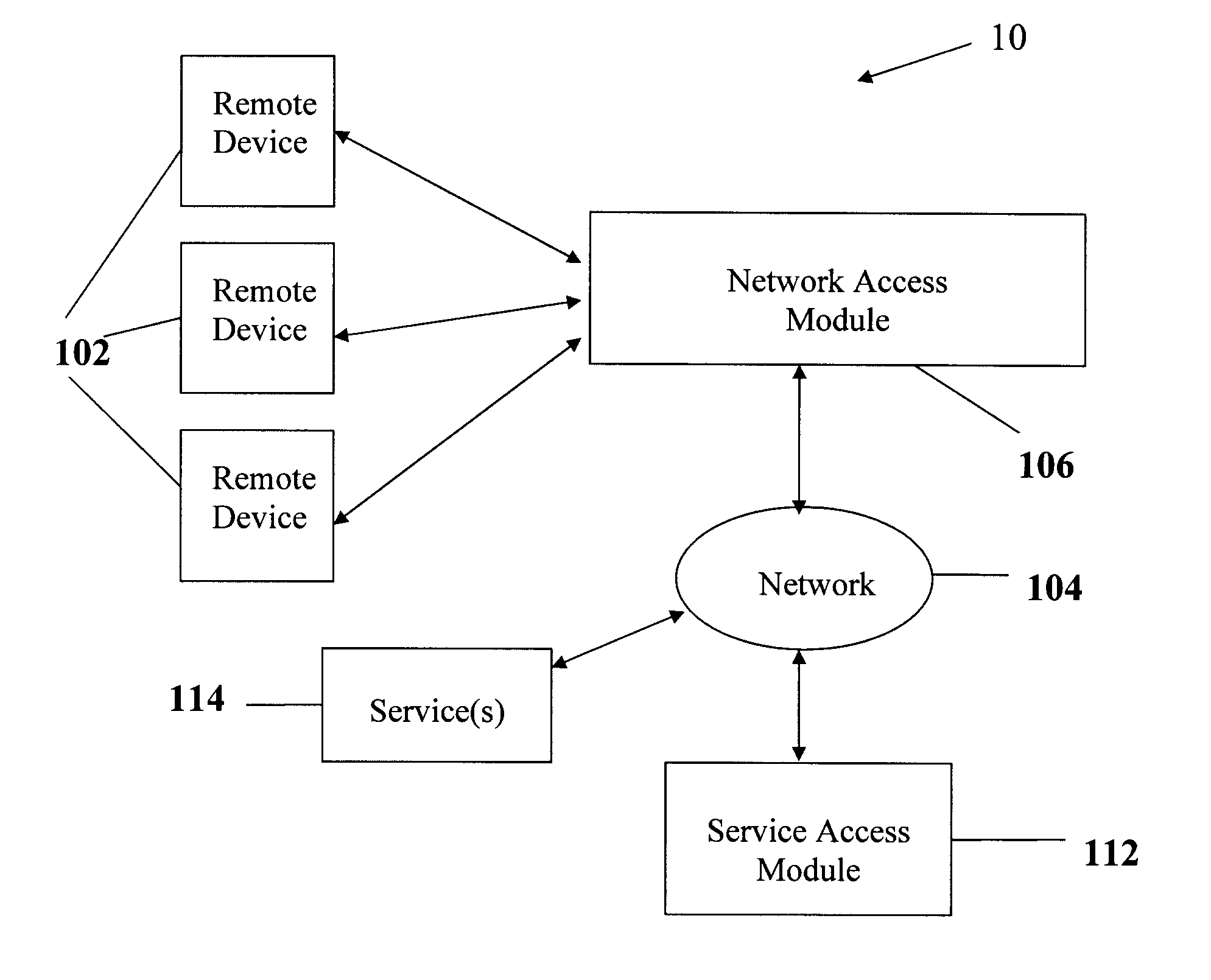
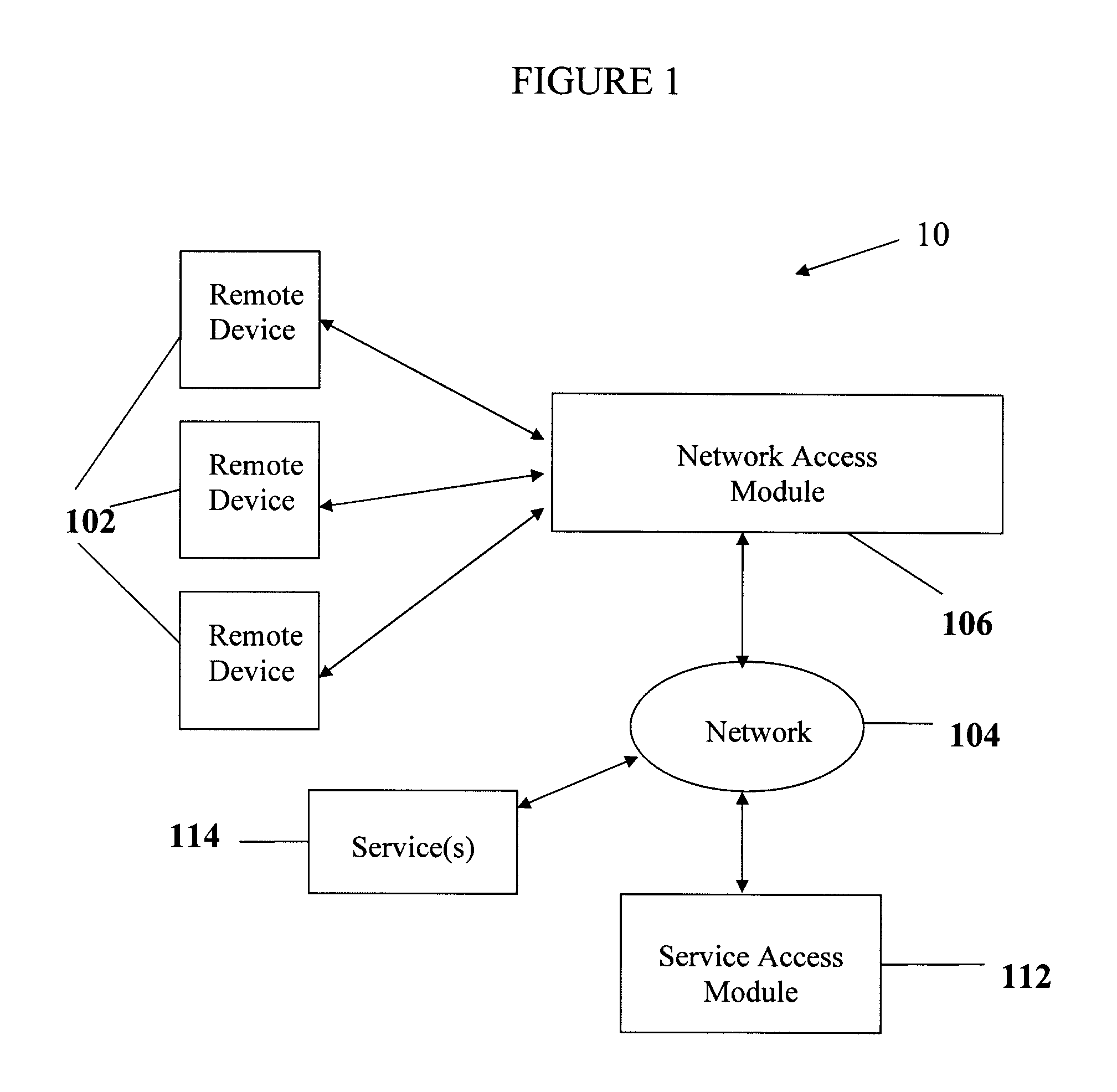
A wireless service access system and method are disclosed. One aspect of the disclosed system provides a remote device wireless access to one or more services over a communication network, the system comprising a network access module adapted for communicating wirelessly with the remote device and for receiving therefrom identifying data; and a service access module, communicatively linked to the network access module, for authenticating the remote device based on the identifying data and authorizing access to the one or more services thereto via the network access module.
Owner:DATAVALET TECH
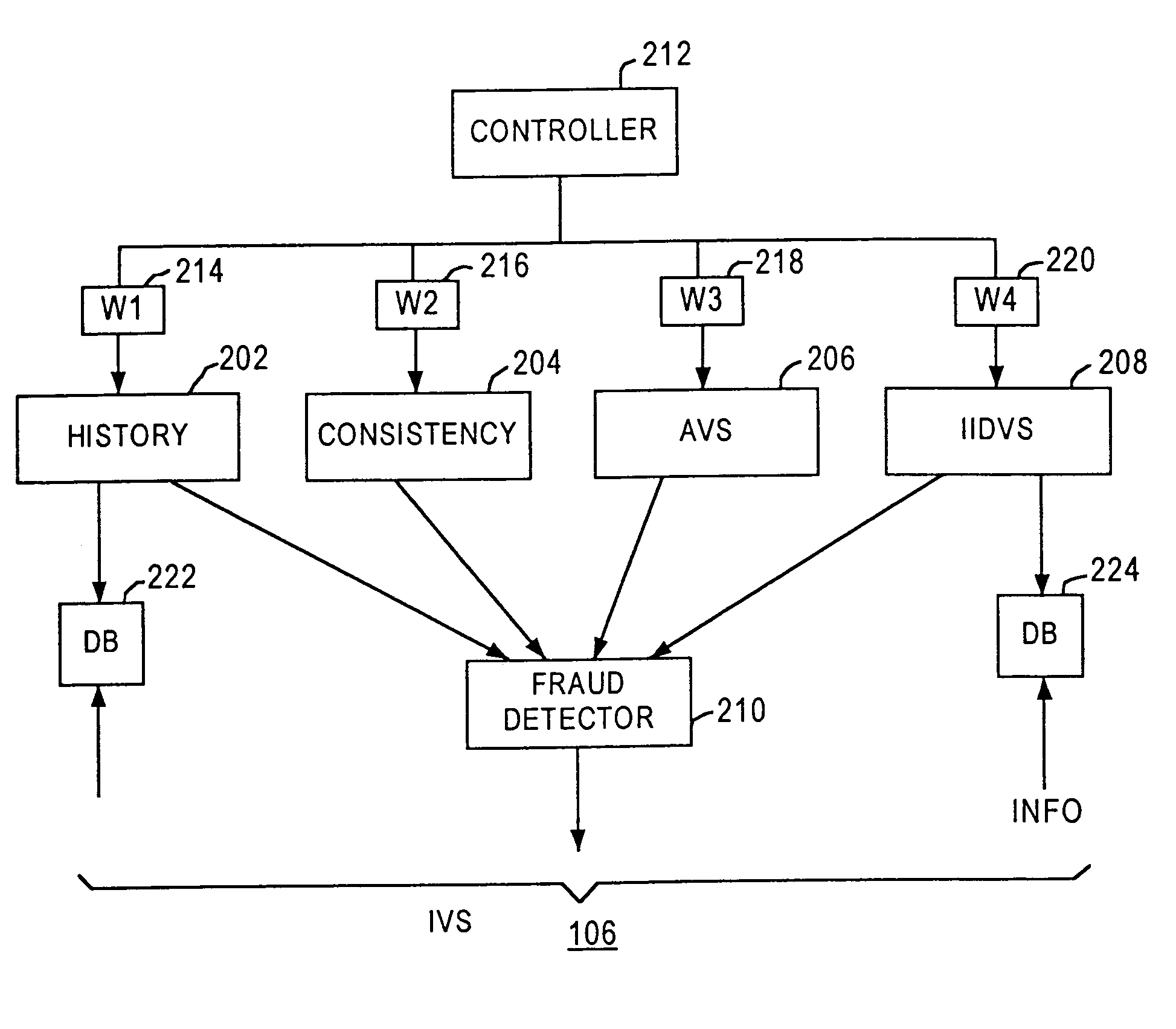
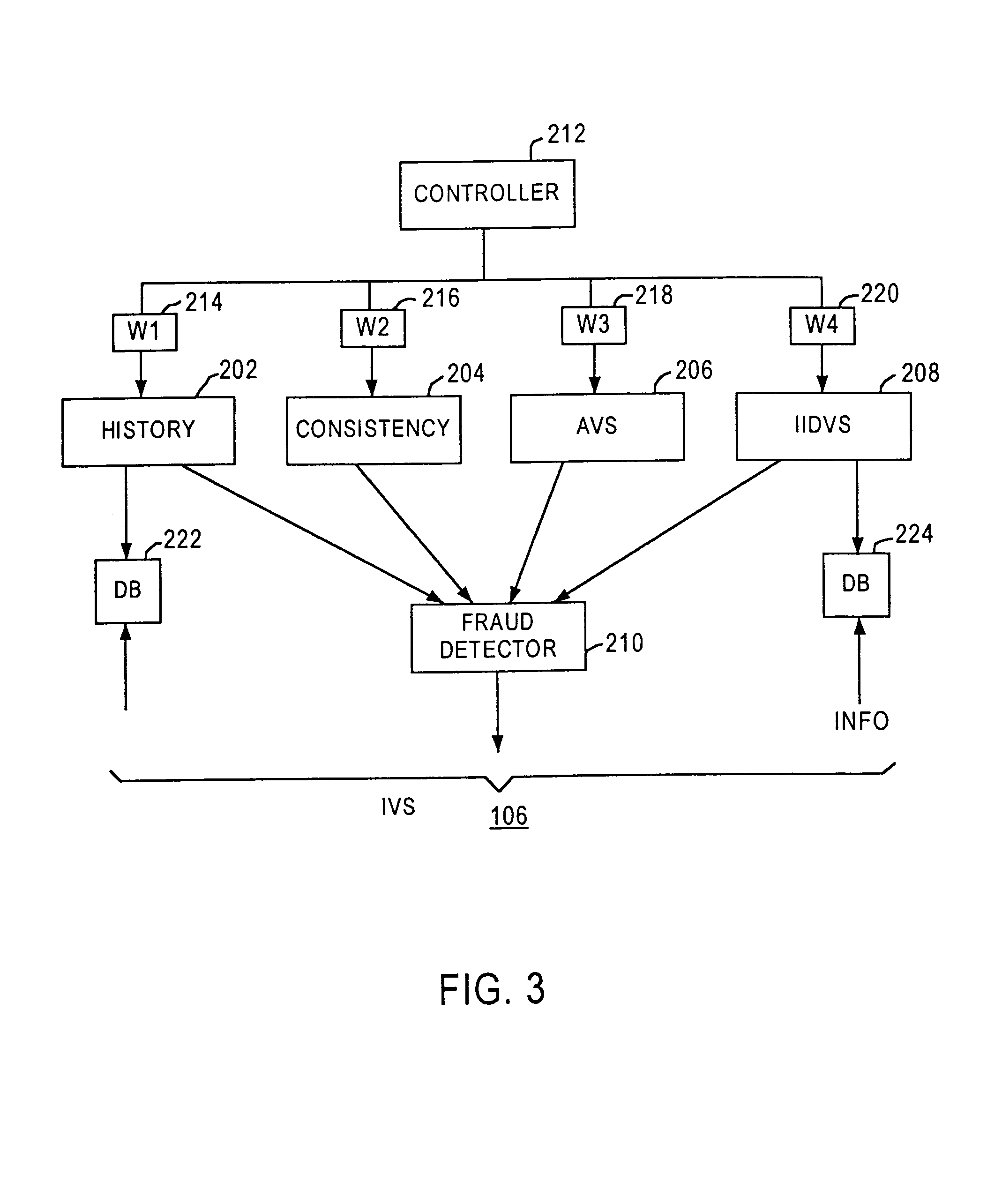
Method and apparatus for evaluating fraud risk in an electronic commerce transaction
A technique for evaluating fraud risk in e-commerce transactions between consumer and a merchant is disclosed. The merchant requests service from the system using a secure, open messaging protocol. An e-commerce transaction or electronic purchase order is received from the merchant, the level of risk associated with each order is measured, and a risk score is returned. In one embodiment, data validation, highly predictive artificial intelligence pattern matching, network data aggregation and negative file checks are used. The system performs analysis including data integrity checks and correlation analyses based on characteristics of the transaction. Other analysis includes comparison of the current transaction against known fraudulent transactions, and a search of a transaction history database to identify abnormal patterns, name and address changes, and defrauders. In one alternative, scoring algorithms are refined through use of a closed-loop risk modeling process enabling the service to adapt to new or changing fraud patterns.
Owner:CYBERSOURCE CORP
Method, system, and computer program product for customer-level data verification
ActiveUS20070284433A1Improve accuracyReduce error rateComplete banking machinesFinanceData validationSource Data Verification
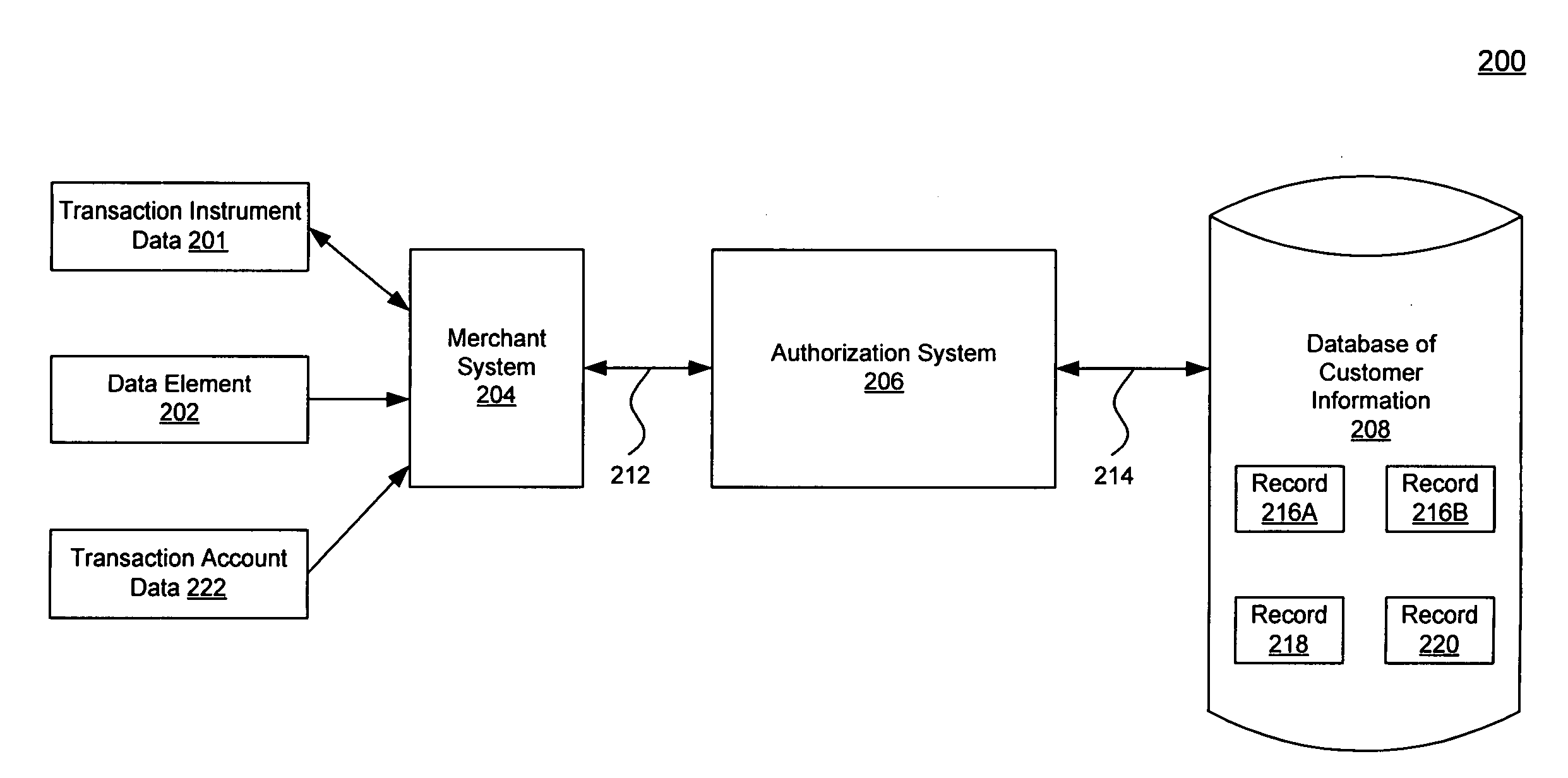
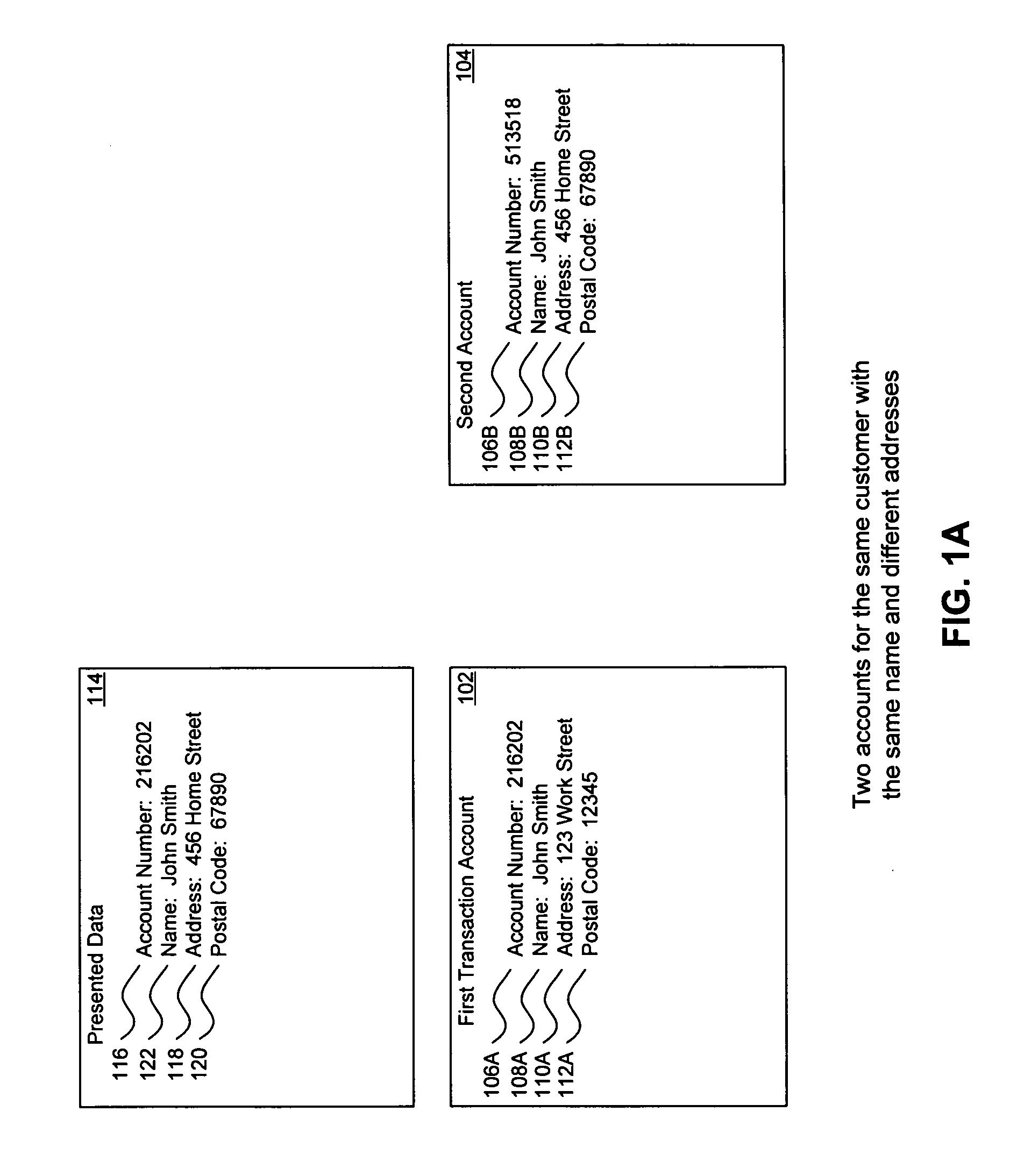
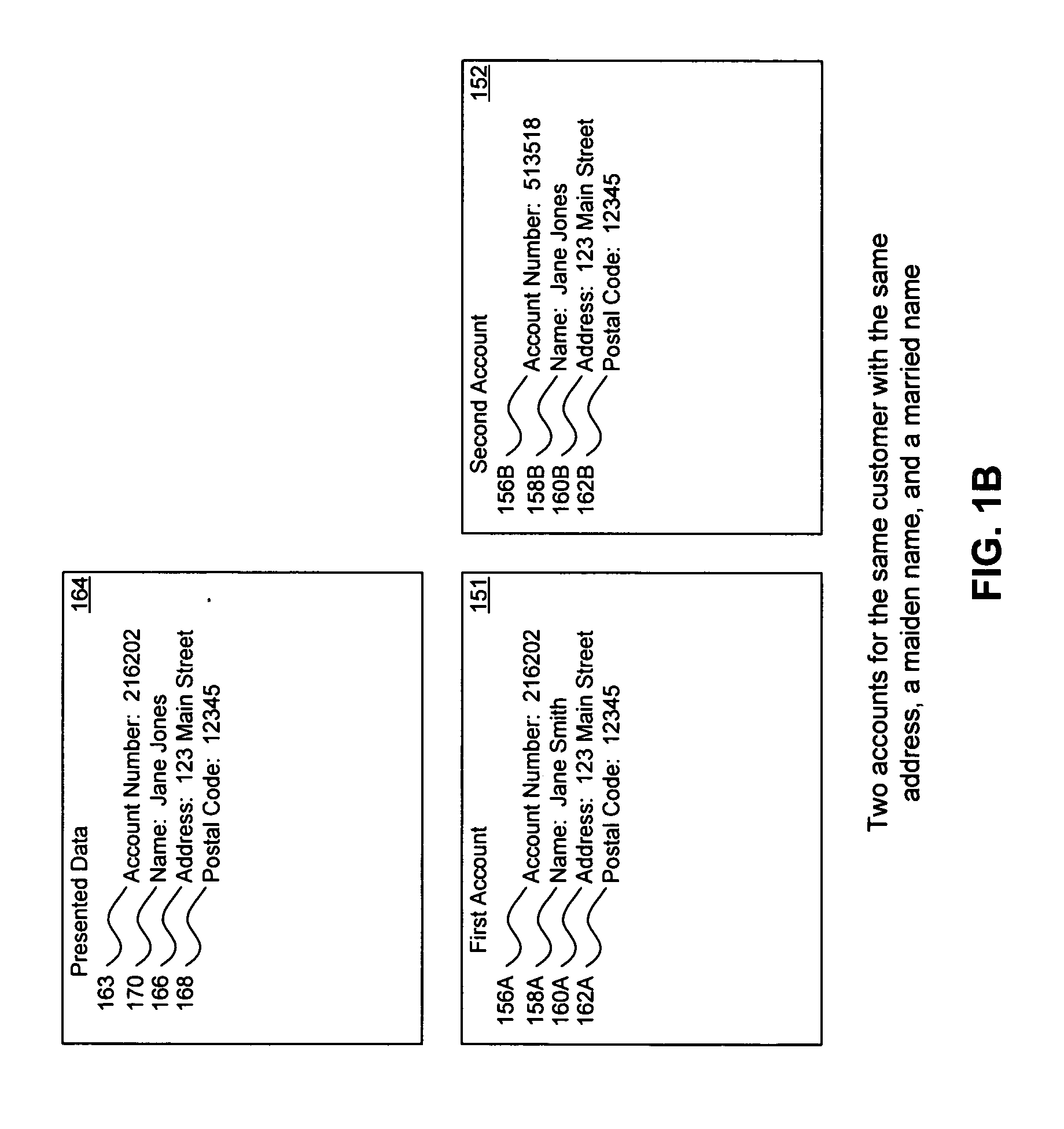
A system, method, and computer program to reduce incorrectly declined transactions and improve risk calculation accuracy by reducing error probability during fraud detection. The tool first receives at least one data element as well as transaction account data and / or financial transaction instrument data. Then a customer is determined from a first record associated with the transaction account data and / or financial transaction instrument data. A record search is performed to identify at least one additional record associated with the customer. Finally, the data element is compared to the information contained in the additional record to create a comparison result that verifies a customer address. The comparison result may be used as an input to transaction risk calculations. The comparison result may also be provided to a merchant system and / or merchant for use in a decision-making process, for example, to verify customer identity.
Owner:LIBERTY PEAK VENTURES LLC
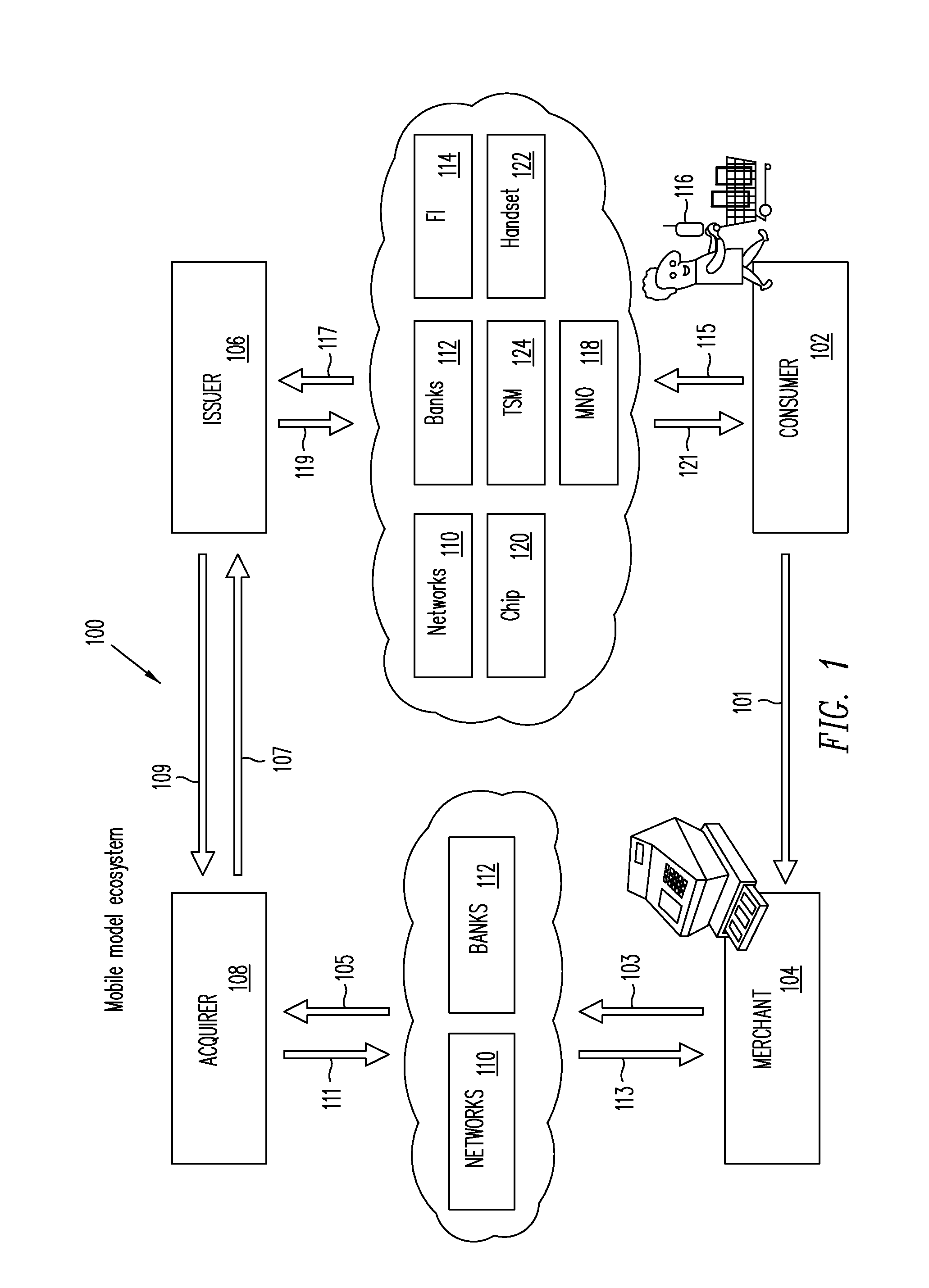
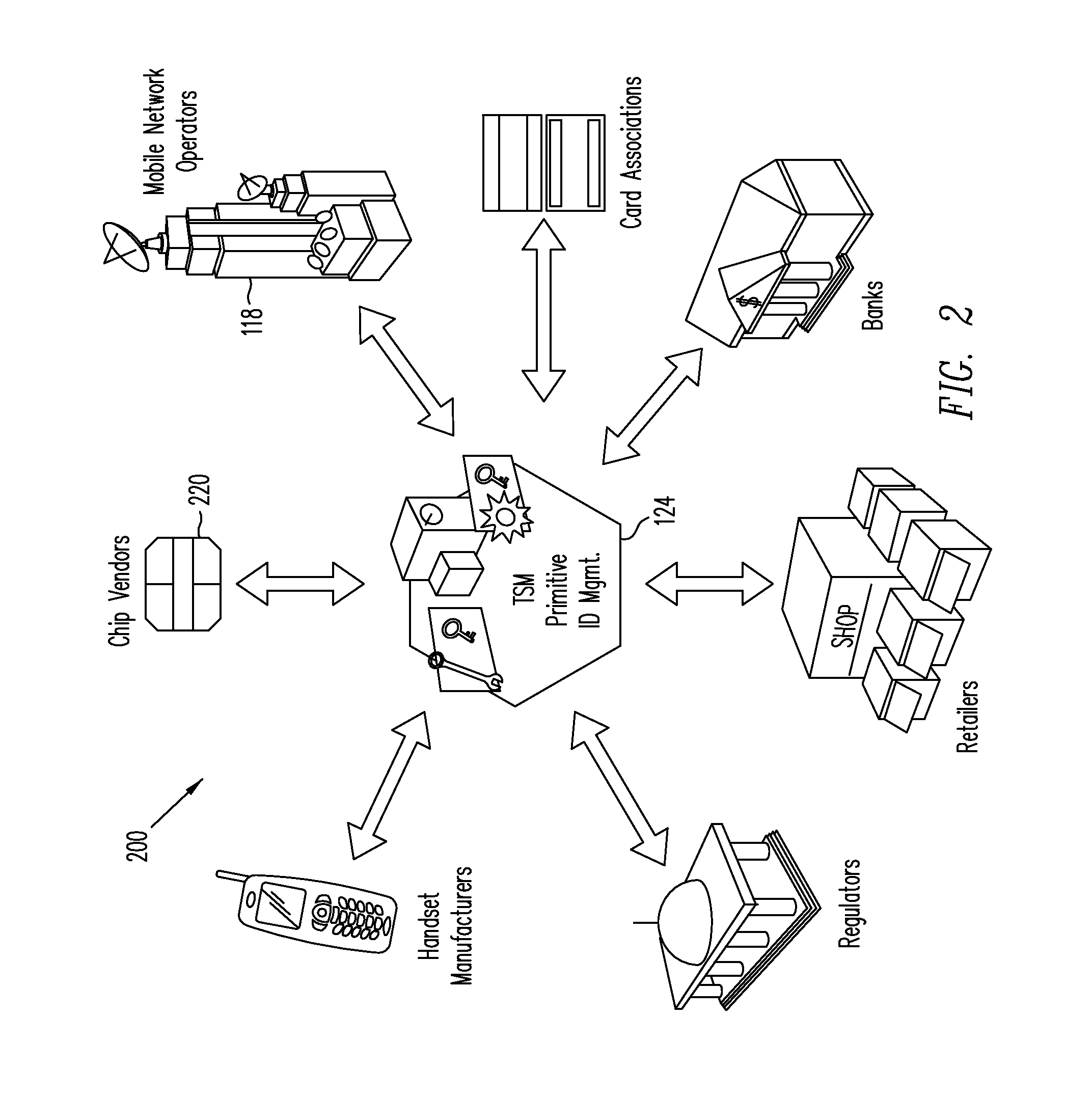
Trusted Integrity Manager (TIM)
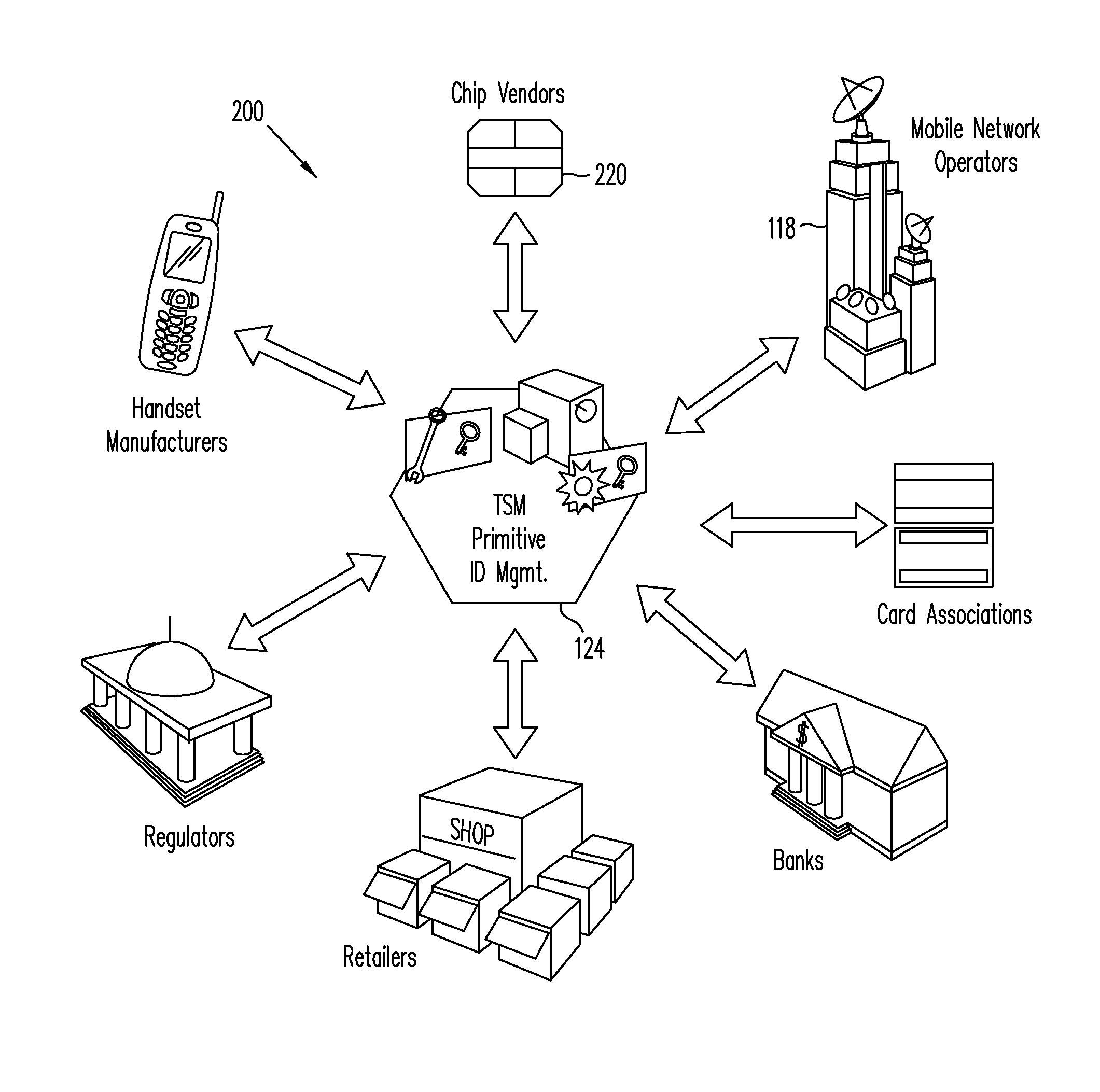
A system for use with a trusted service manager (TSM) and a mobile device having a subscriber unique identifying data, according to one embodiment, includes: a server in which the server validates an application against the unique and identifying data of the mobile device and provides the validated application for the mobile device; and a secure element (SE) acting as a client in which the SE is present in the mobile device as client; the validated application from the server is installed in the SE; and the SE is adapted to execute the validated application to perform a service process. The service process includes enablement of payment functions on the mobile device, in which enablement of payment functions includes: providing secure communication between the mobile device and the server; secure provisioning of a payment instrument on the mobile device, wherein authentication and verification for the payment instrument on the mobile device is provided by the server; and binding the payment instruments and the validated application to the mobile device to provide a strong ID management for enhanced user protection and system security and integrity.
Owner:PAYPAL INC
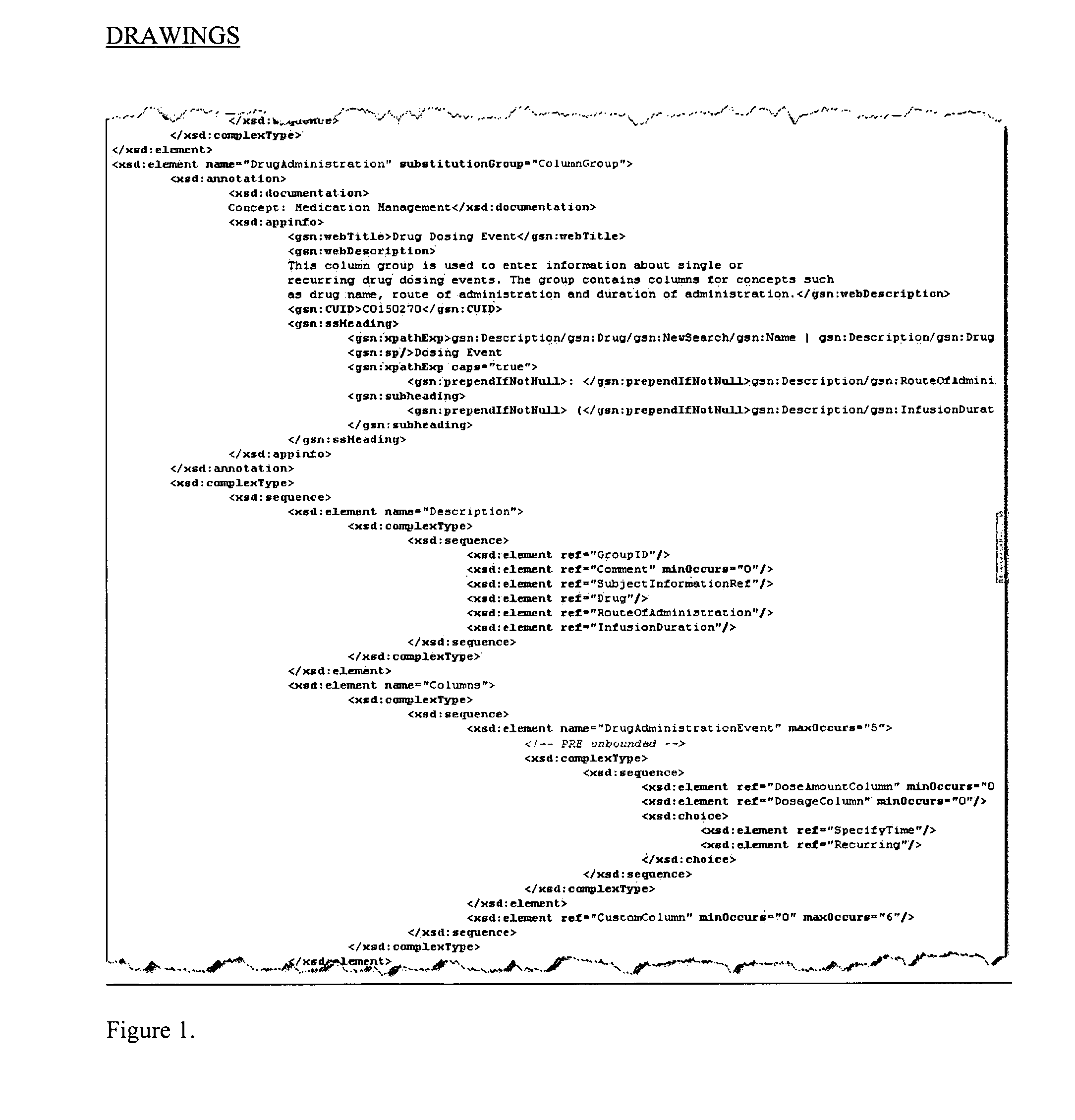
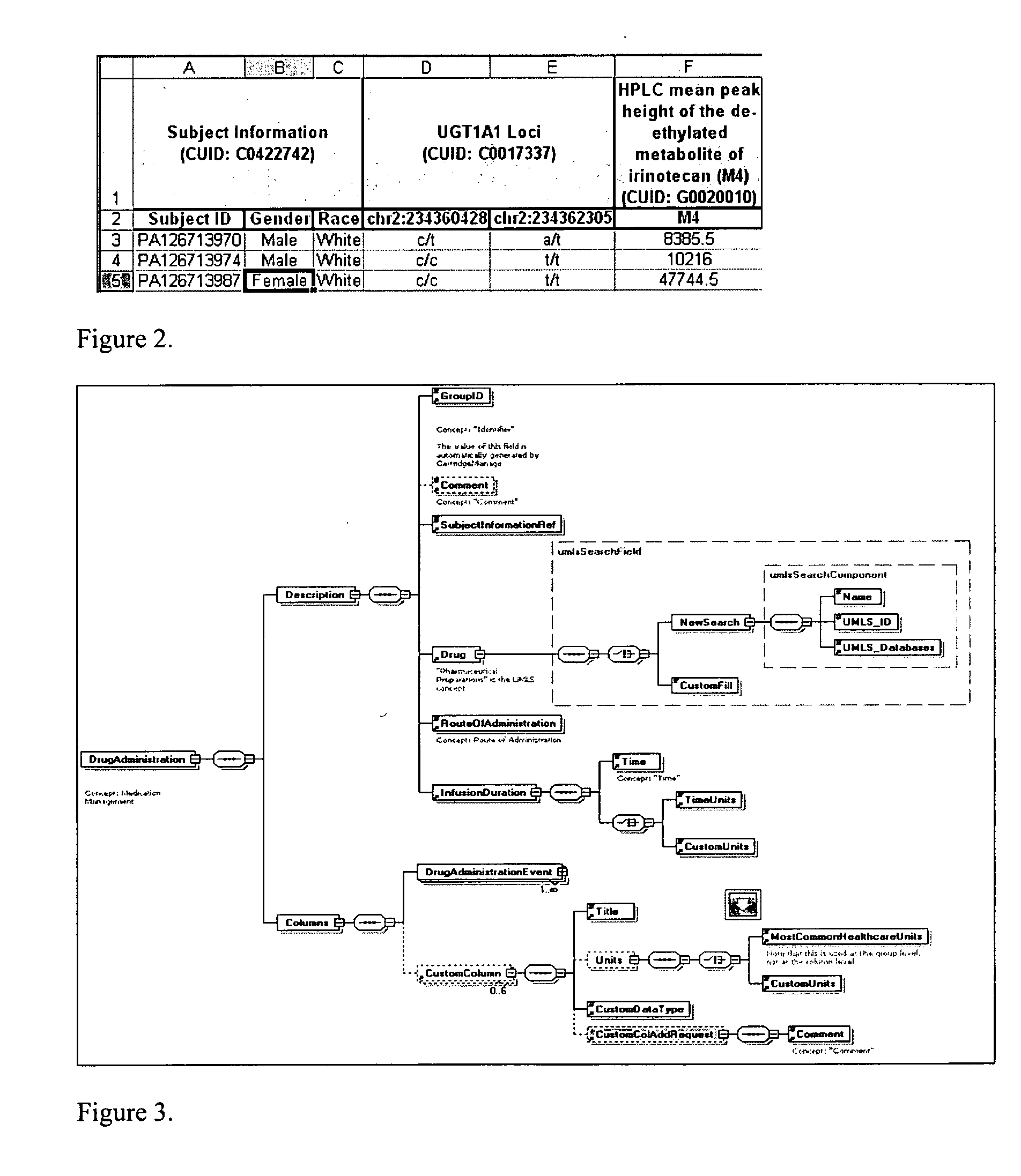
System and method for integrating and validating genotypic, phenotypic and medical information into a database according to a standardized ontology
InactiveUS20070178501A1Safest and most effective treatmentGood decisionData processing applicationsMicrobiological testing/measurementData validationMedical record
The system described herein enables clinicians and researchers to use aggregated genetic and phenotypic data from clinical trials and medical records to make the safest, most effective treatment decisions for each patient. This involves (i) the creation of a standardized ontology for genetic, phenotypic, clinical, pharmacokinetic, pharmacodynamic and other data sets, (ii) the creation of a translation engine to integrate heterogeneous data sets into a database using the standardized ontology, and (iii) the development of statistical methods to perform data validation and outcome prediction with the integrated data. The system is designed to interface with patient electronic medical records (EMRs) in hospitals and laboratories to extract a particular patient's relevant data. The system may also be used in the context of generating phenotypic predictions and enhanced medical laboratory reports for treating clinicians. The system may also be used in the context of leveraging the huge amount of data created in medical and pharmaceutical clinical trials. The ontology and validation rules are designed to be flexible so as to accommodate a disparate set of clients. The system is also designed to be flexible so that it can change to accommodate scientific progress and remain optimally configured.
Owner:NATERA
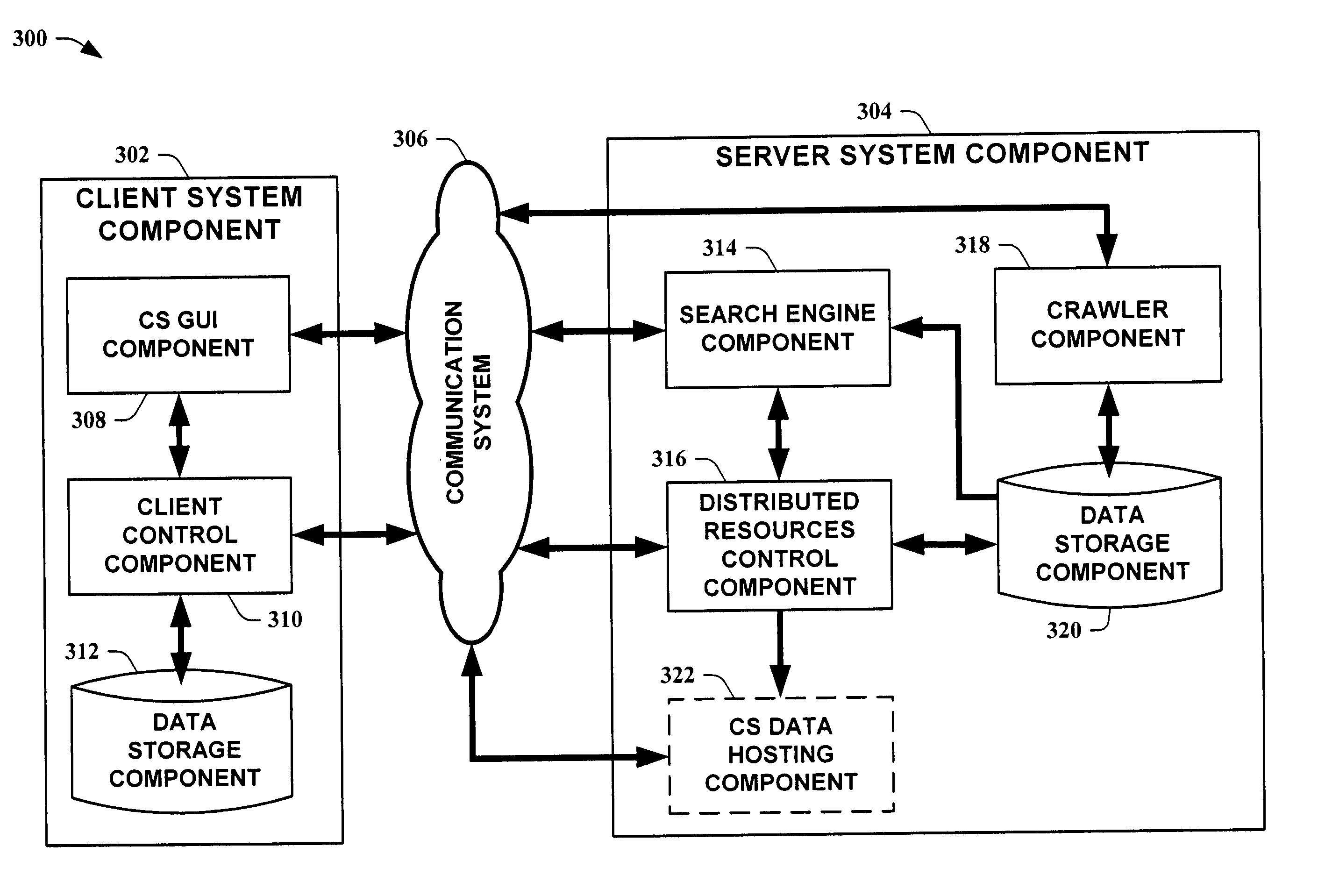
Systems and methods for client-based web crawling
InactiveUS20050071766A1The process is fast and accurateReducing server-client communication trafficData processing applicationsWeb data indexingData validationSource Data Verification
The present invention provides systems and methods for obtaining information from a networked system utilizing a distributed web crawler. The distributed nature of clients of a server is leveraged to provide fast and accurate web crawling data. Information gathered by a server's web crawler is compared to data retrieved by clients of the server to update the crawler's data. In one instance of the present invention, data comparison is achieved by utilizing information disseminated via a search engine results page. In another instance of the present invention, data validation is accomplished by client dictionaries, emanating from a server, that summarize web crawler data. The present invention also facilitates data analysis by providing a means to resist spoofing of a web crawler to increase data accuracy.
Owner:MICROSOFT TECH LICENSING LLC
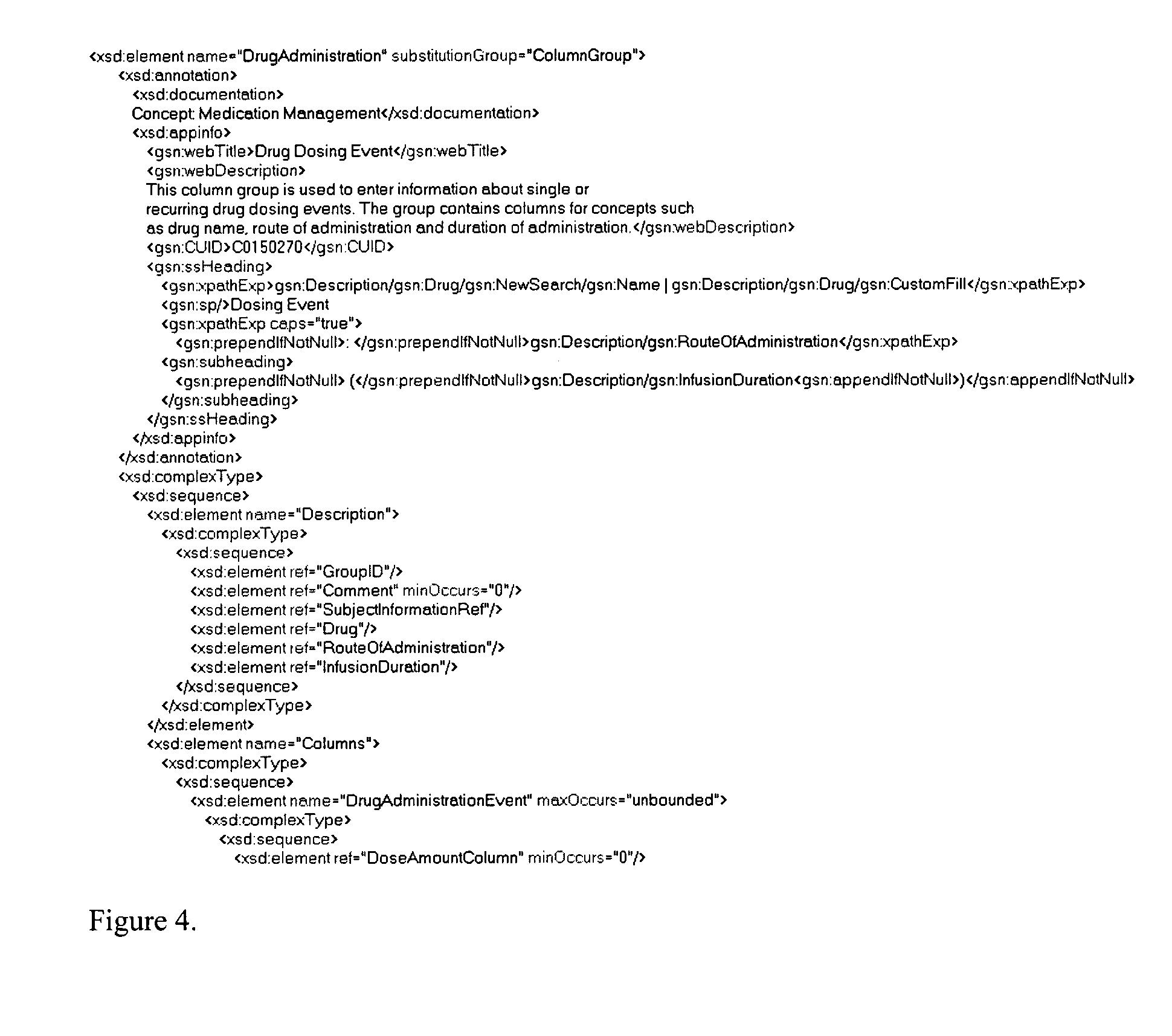
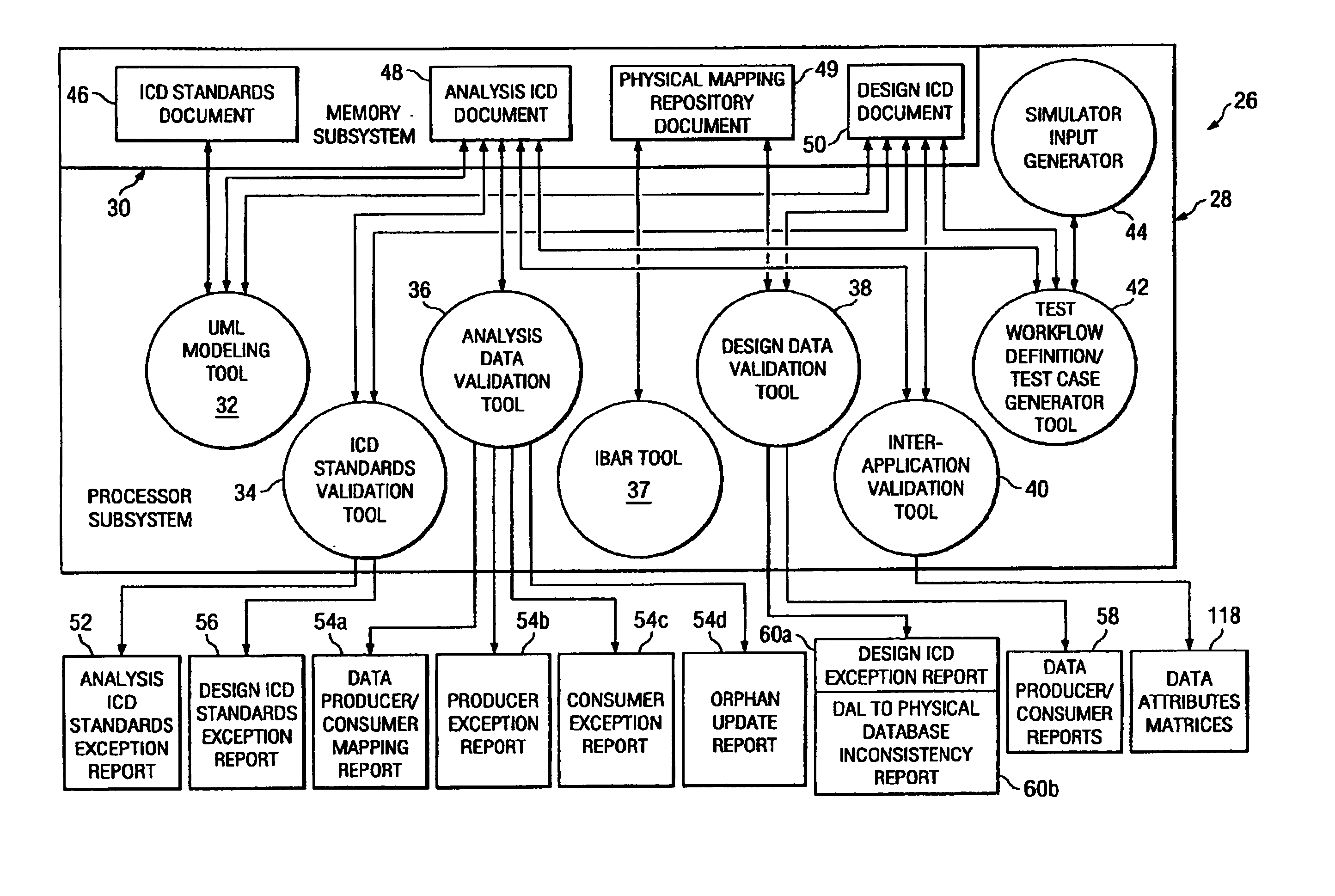
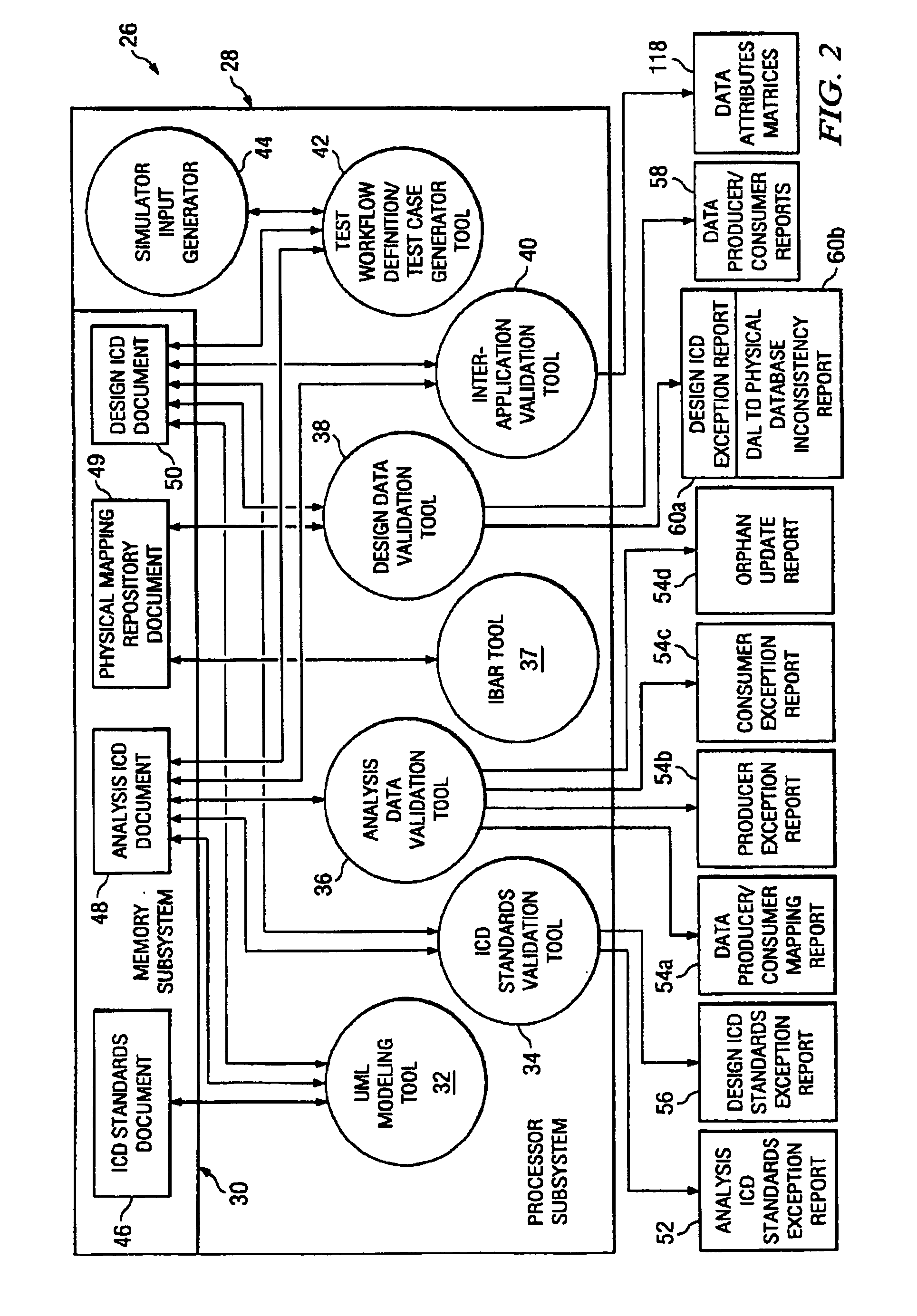
Design data validation tool for use in enterprise architecture modeling
InactiveUS7203929B1Requirement analysisSpecific program execution arrangementsData validationSequence diagram
A selected scenario of a design ICD document for an integrated enterprise is validated by examining each IDL call of each sequence diagram forming part of the selected scenario. A list of data attributes contained in one or more of the IDL calls are generated and each IDL call associated therewith is generated. A physical location to which each such IDL call is mapped is then associated with the IDL call. By analyzing the IDL calls and associated physical locations on a data attribute-by-data attribute basis, inconsistencies in the physical mapping of the data attributes to the databases forming an IIS for the integrated enterprise may be identified and subsequently corrected.
Owner:SPRINT CORPORATION
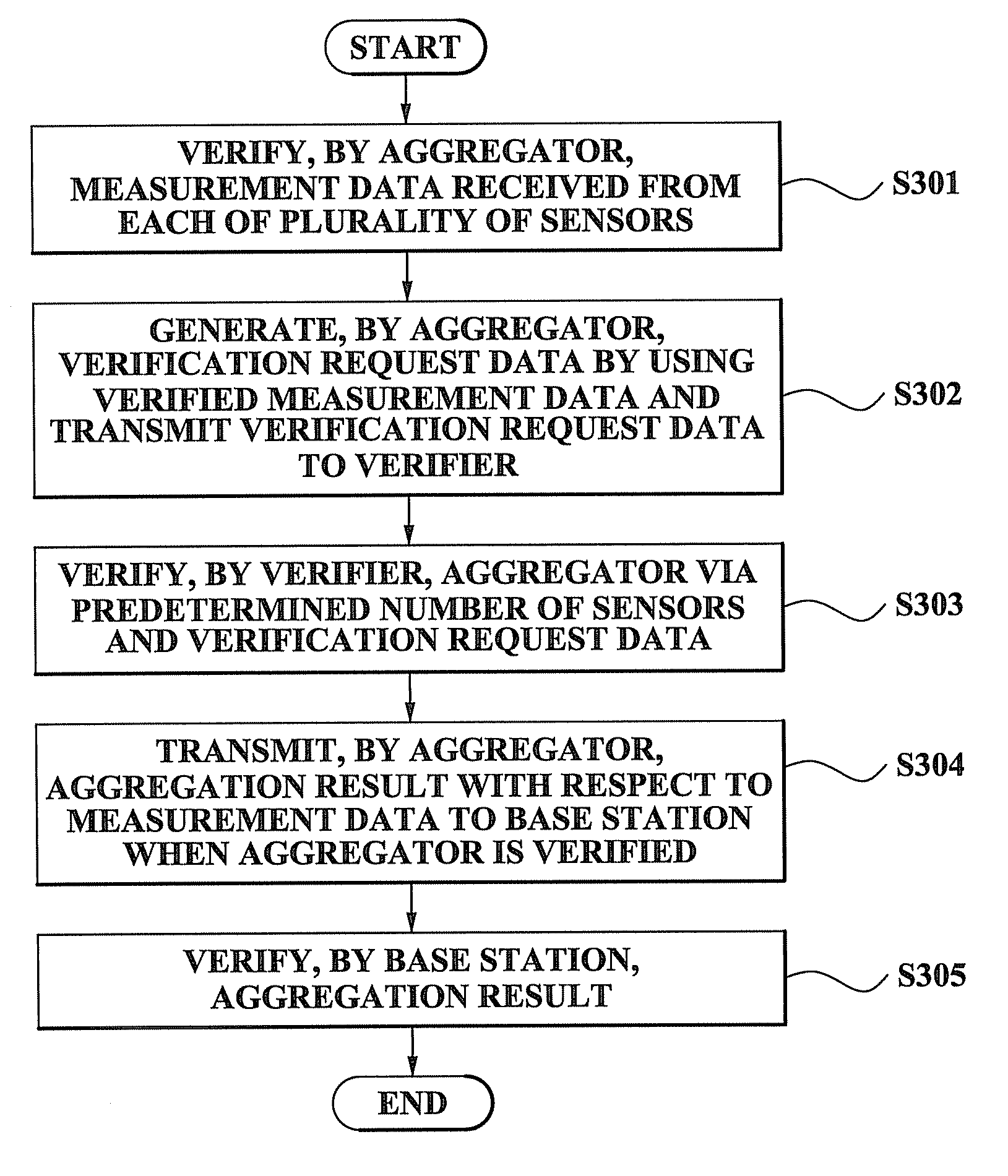
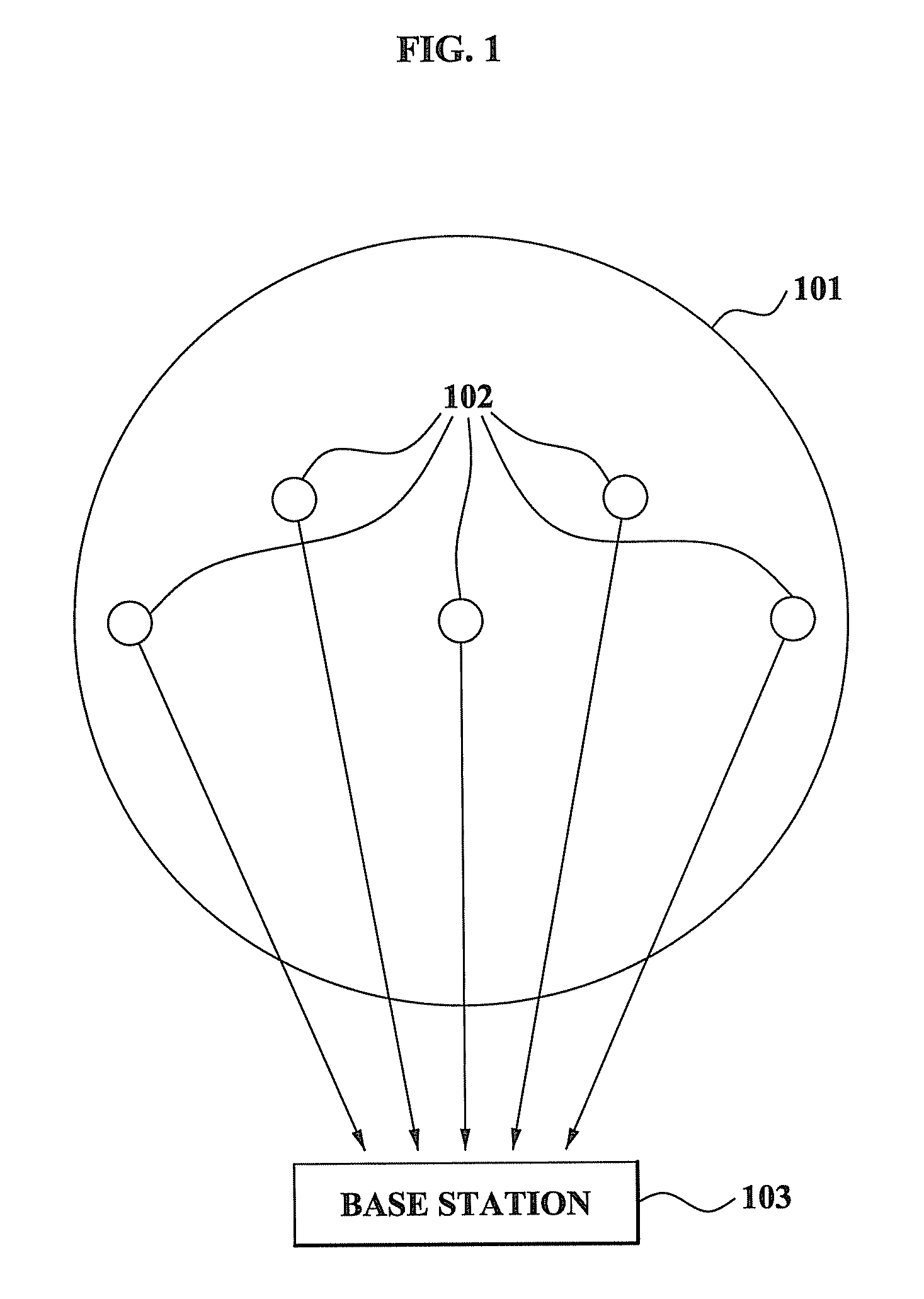
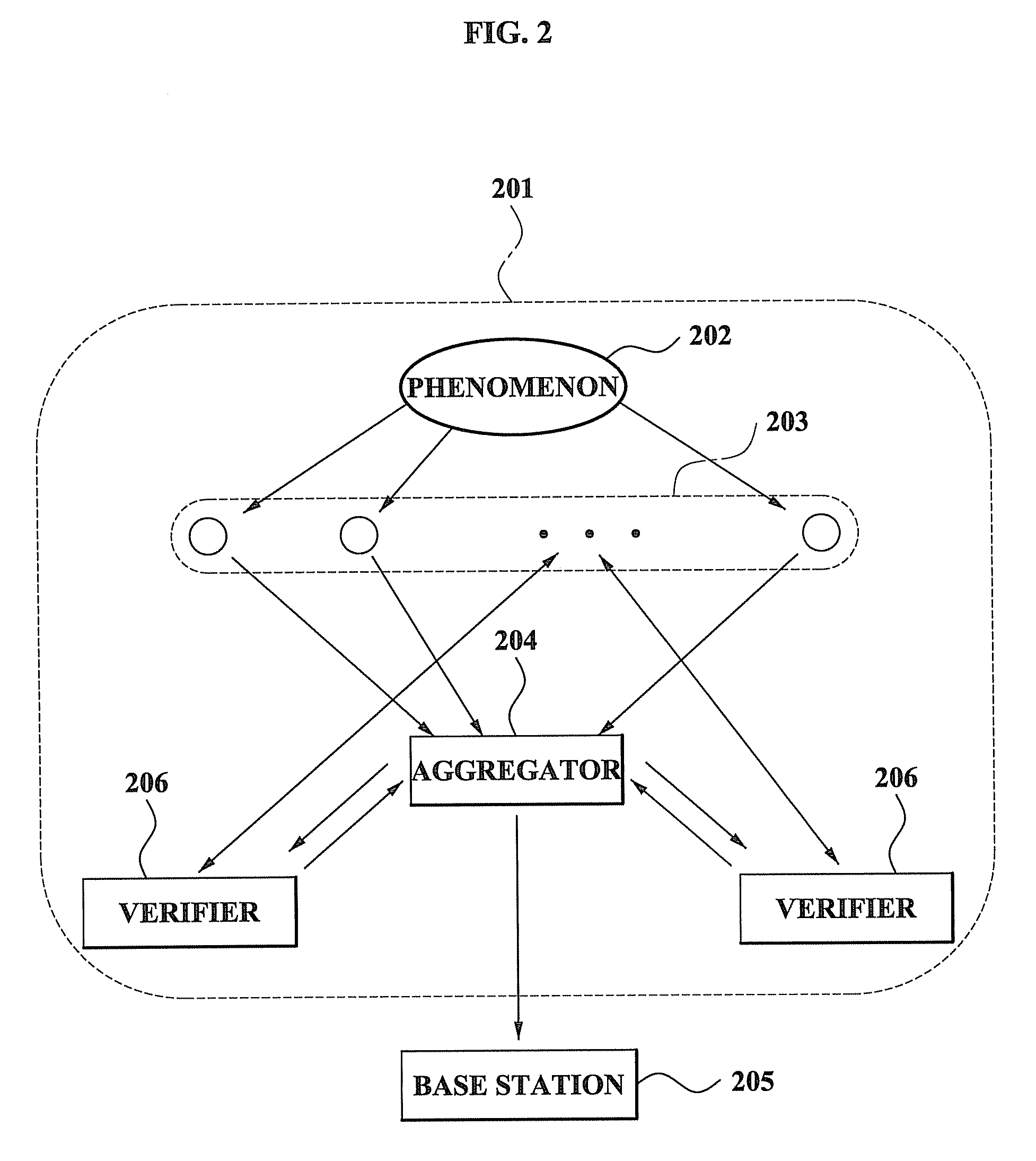
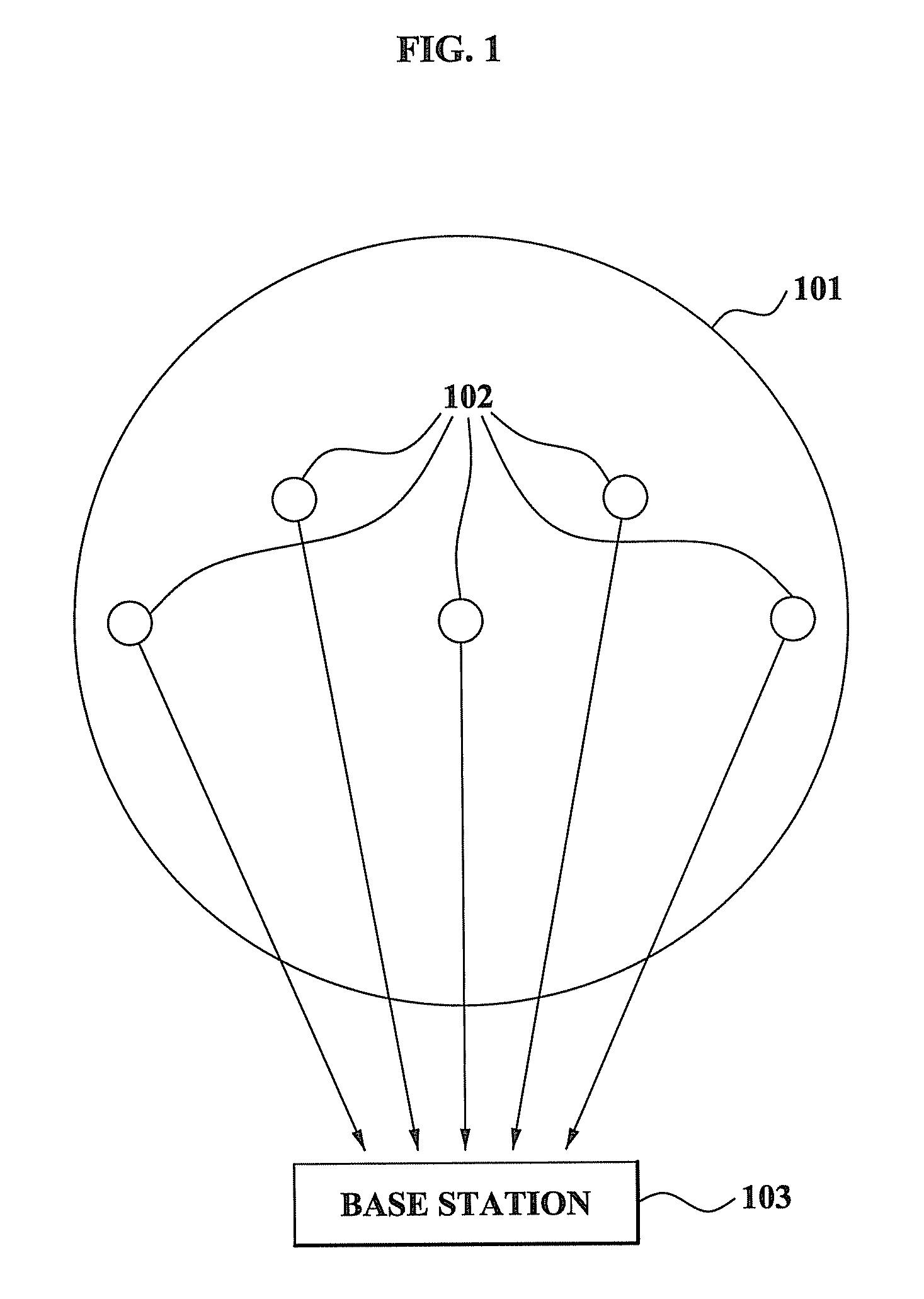
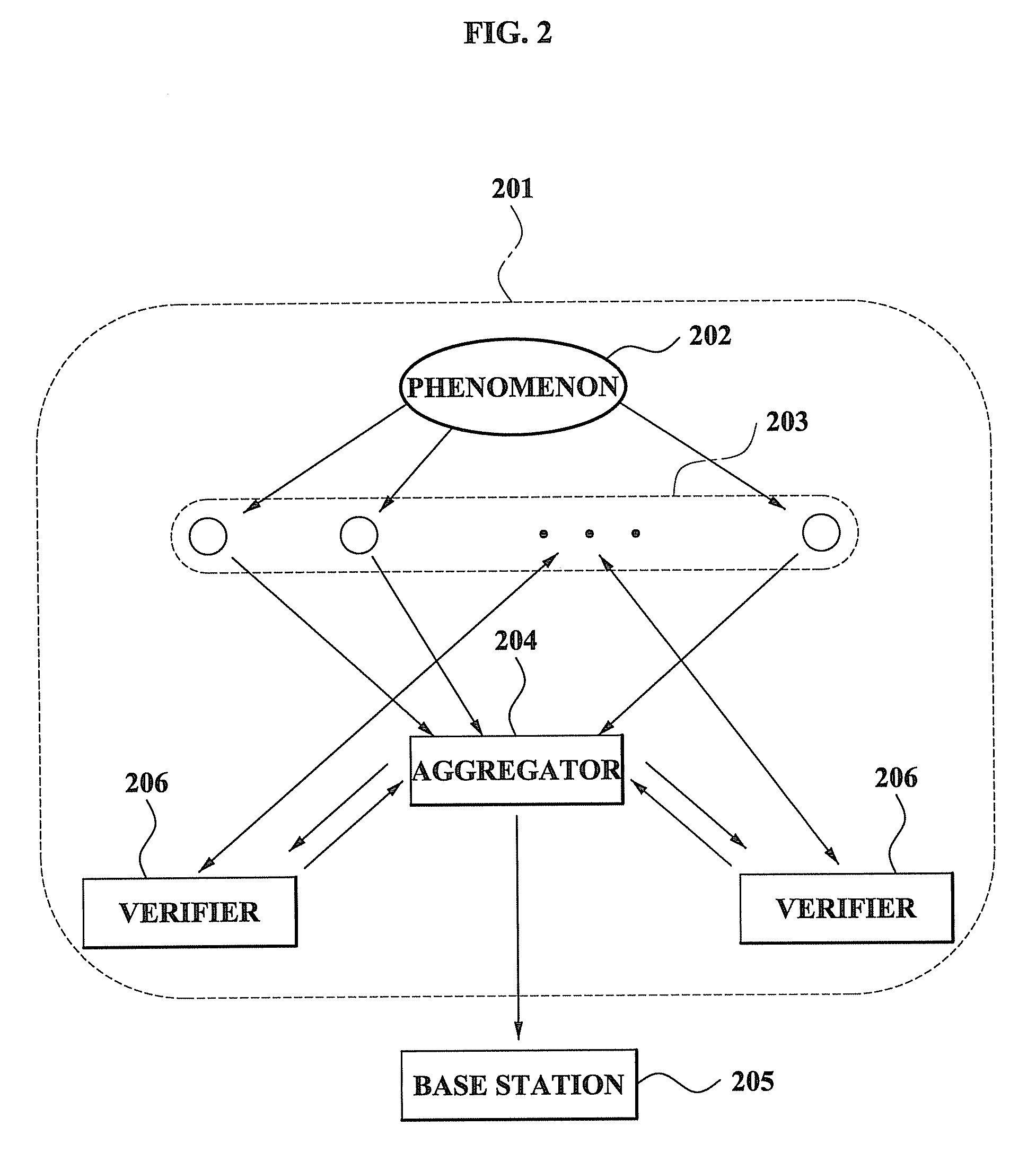
Method and system for performing distributed verification with respect to measurement data in sensor network
ActiveUS20080262798A1Efficient managementImprove securityAmplifier modifications to reduce noise influenceDigital data processing detailsData validationSource Data Verification
A method and system for performing a distributed verification with respect to measurement data in a sensor network. The method of performing the distributed verification with respect to measurement data in a sensor network includes: verifying, by an aggregator, the measurement data received from each of a plurality of sensors; generating, by the aggregator, verification request data by using the verified measurement data; transmitting the verification request data to a verifier; and verifying, by the verifier, the aggregator via a predetermined number of sensors of the plurality of sensors and the verification request data. The method of performing a distributed verification with respect to measurement data in a sensor network further includes transmitting, by the aggregator, an aggregation result with respect to the measurement data to a base station when the aggregator is verified; and verifying, by the base station, the aggregation result.
Owner:SAMSUNG ELECTRONICS CO LTD
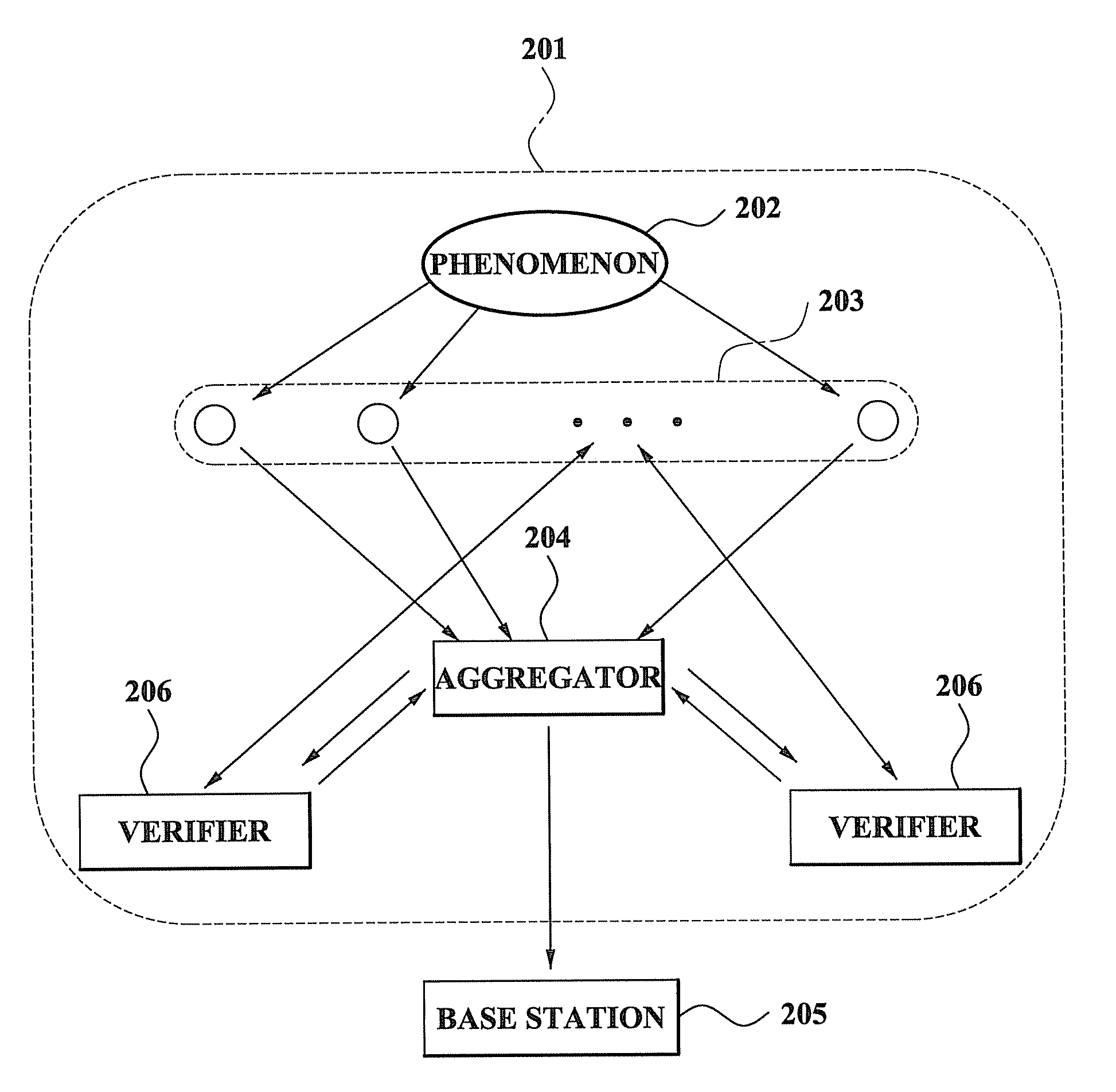
Method and system for performing distributed verification with respect to measurement data in sensor network
ActiveUS8255689B2Efficient managementImprove securityDigital data processing detailsUser identity/authority verificationData validationDistributed computing
A method and system for performing a distributed verification with respect to measurement data in a sensor network. The method of performing the distributed verification with respect to measurement data in a sensor network includes: verifying, by an aggregator, the measurement data received from each of a plurality of sensors; generating, by the aggregator, verification request data by using the verified measurement data; transmitting the verification request data to a verifier; and verifying, by the verifier, the aggregator via a predetermined number of sensors of the plurality of sensors and the verification request data. The method of performing a distributed verification with respect to measurement data in a sensor network further includes transmitting, by the aggregator, an aggregation result with respect to the measurement data to a base station when the aggregator is verified; and verifying, by the base station, the aggregation result.
Owner:SAMSUNG ELECTRONICS CO LTD
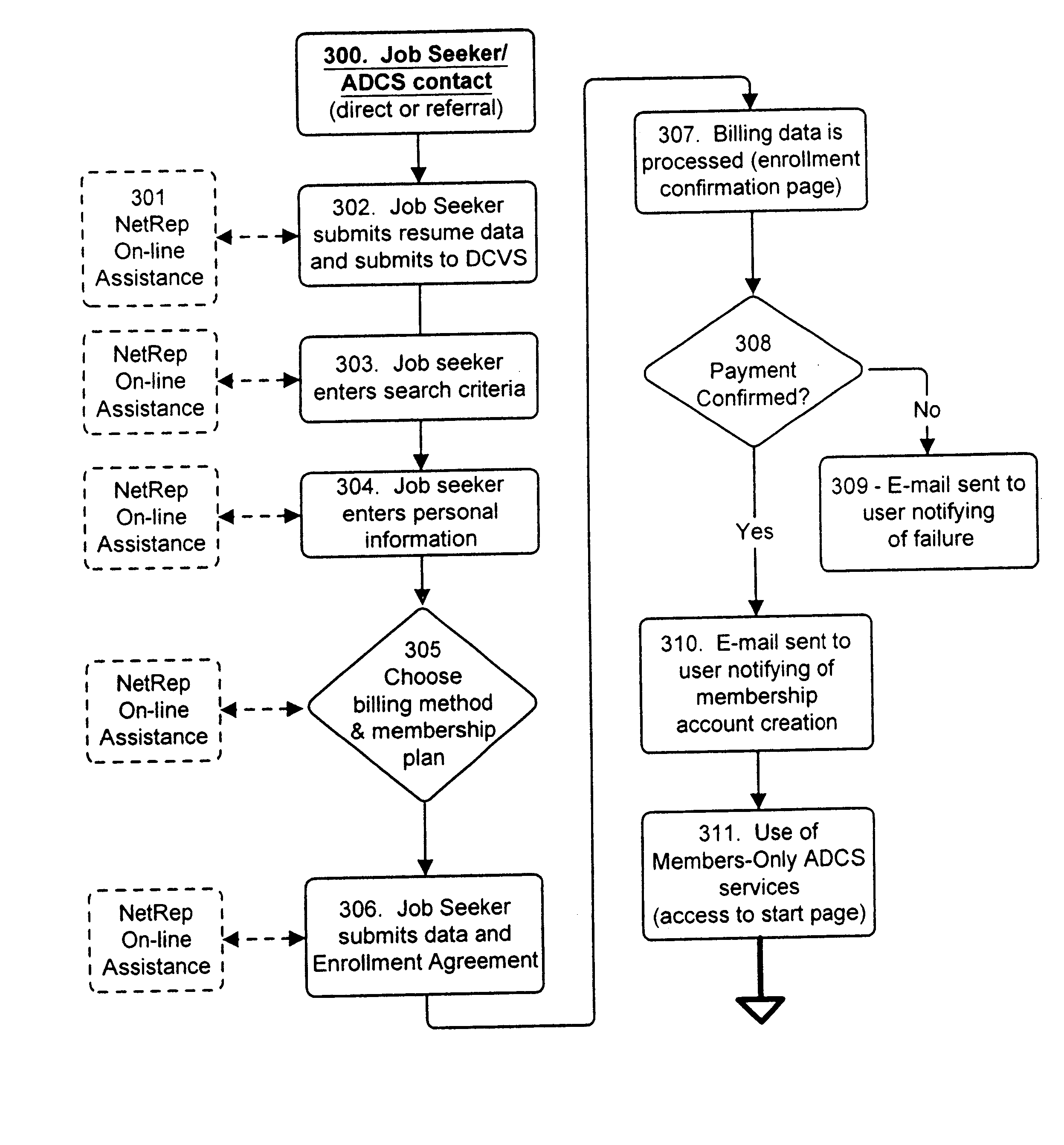
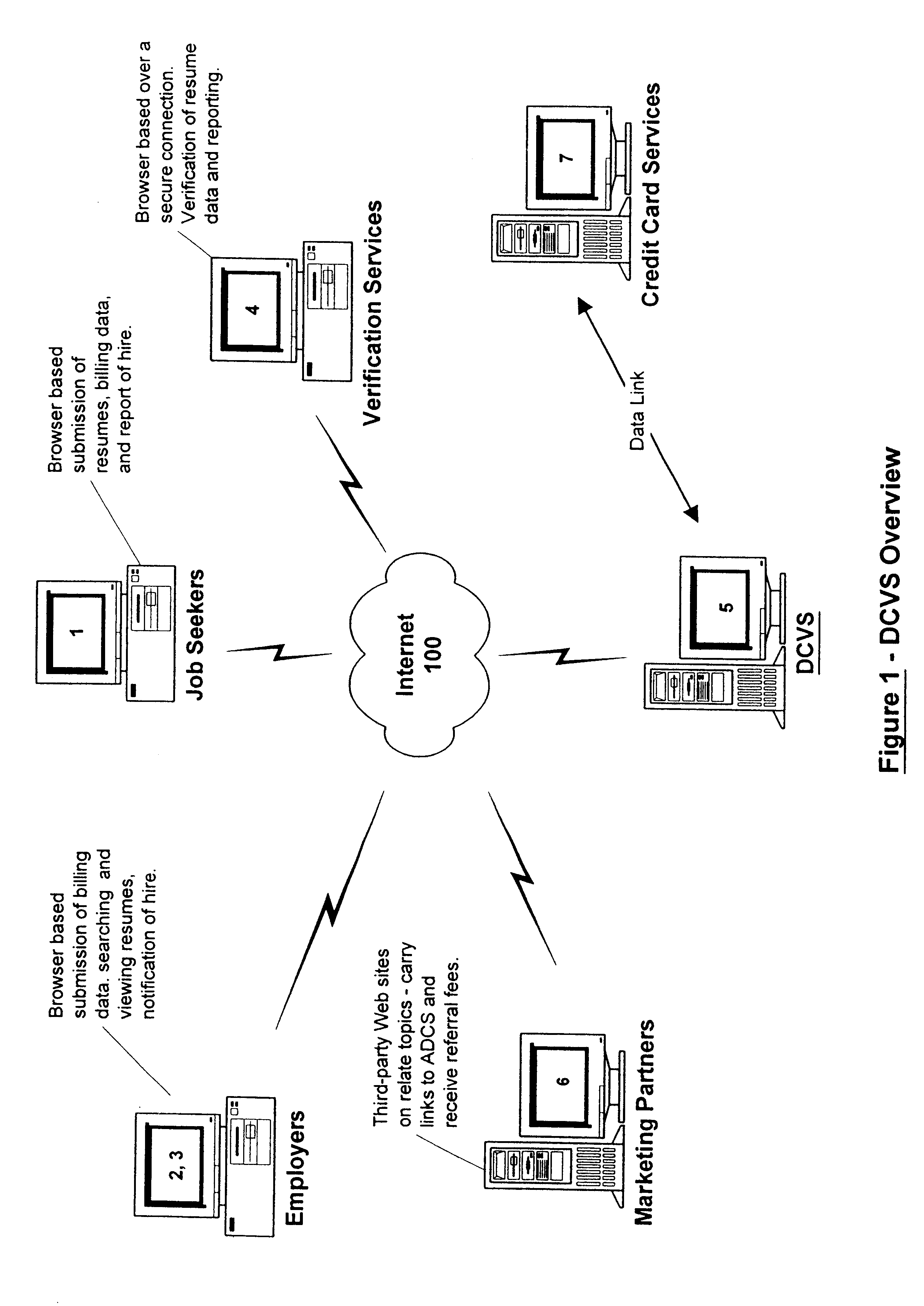
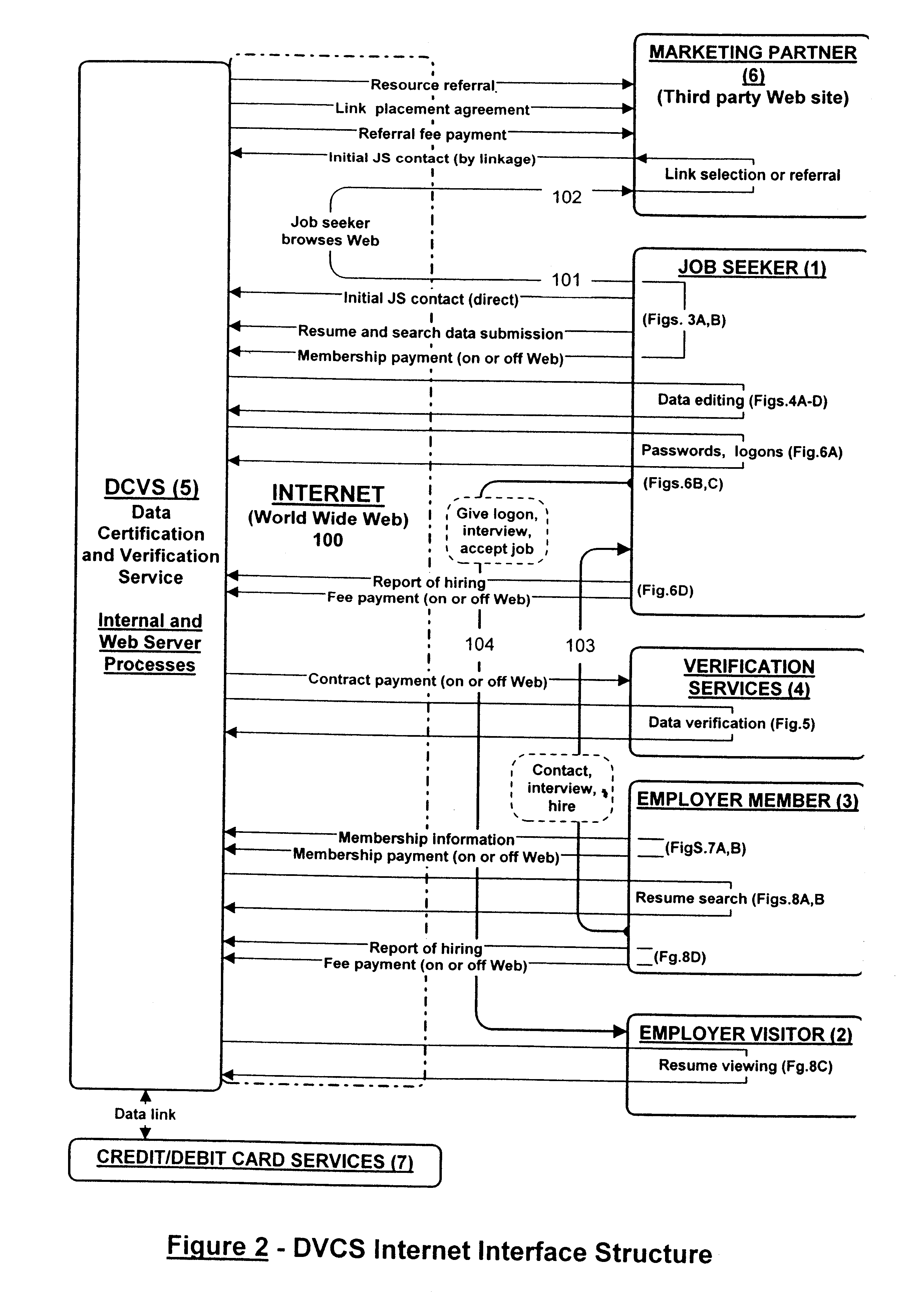
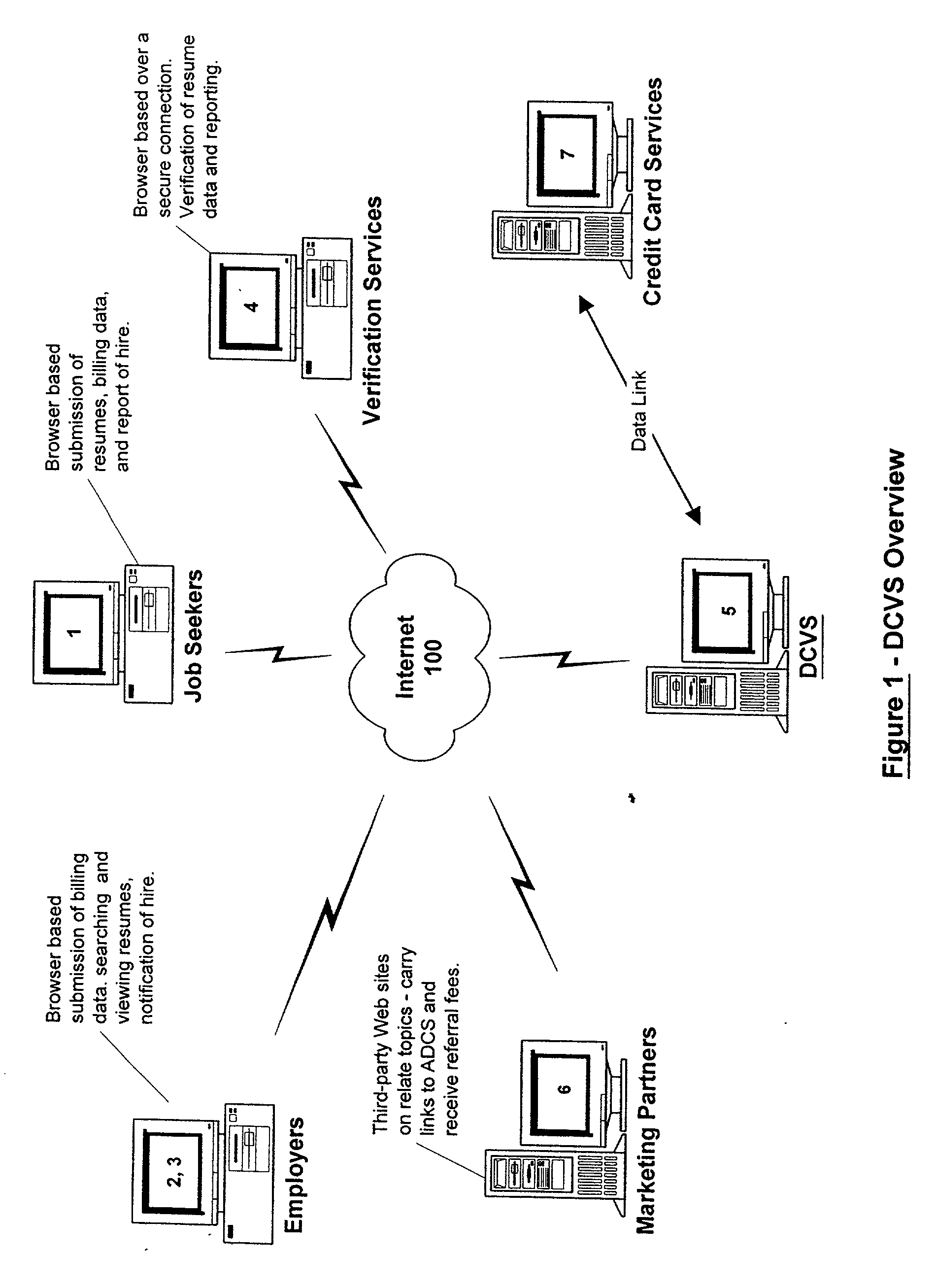
Data certification and verification system having a multiple-user-controlled data interface
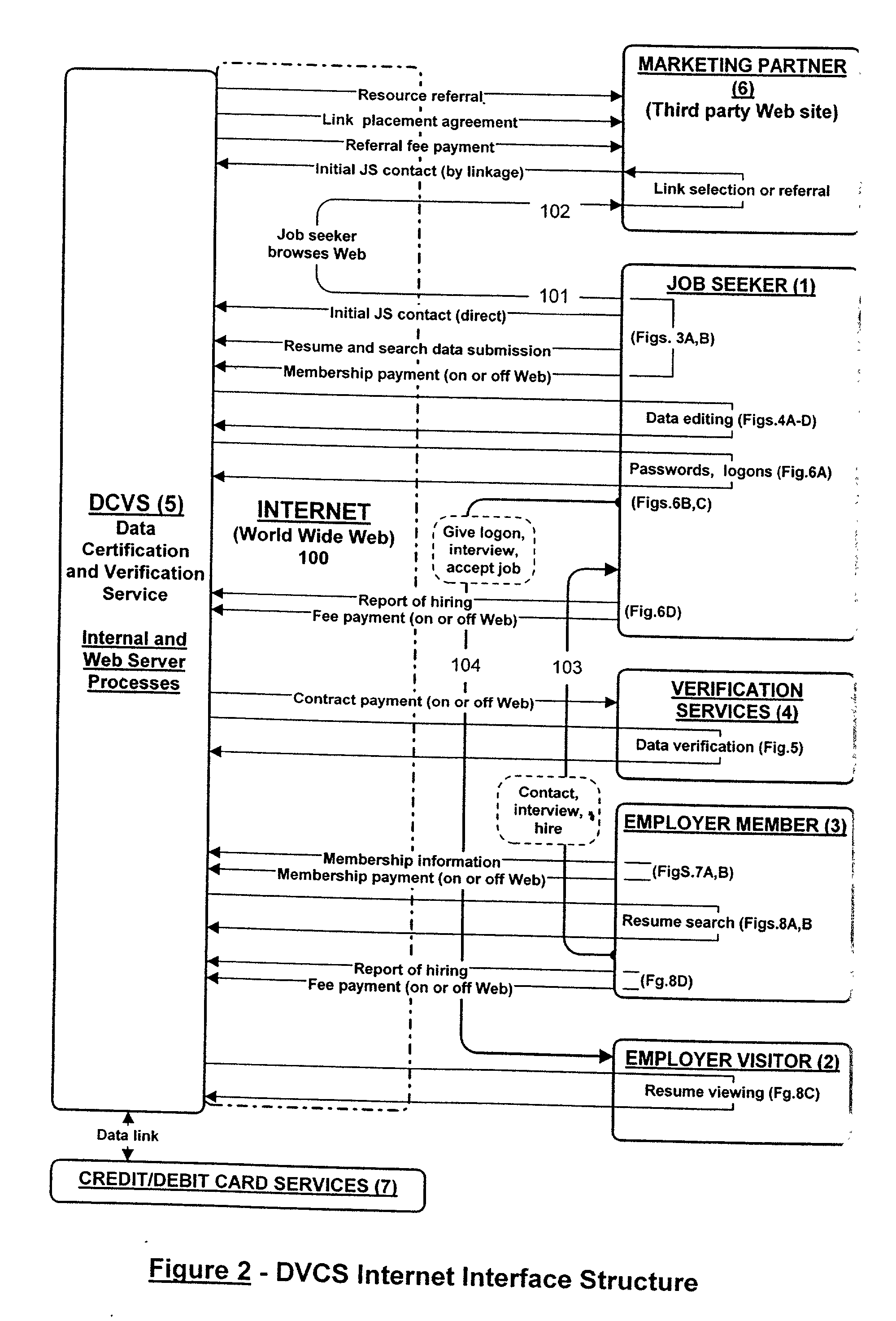
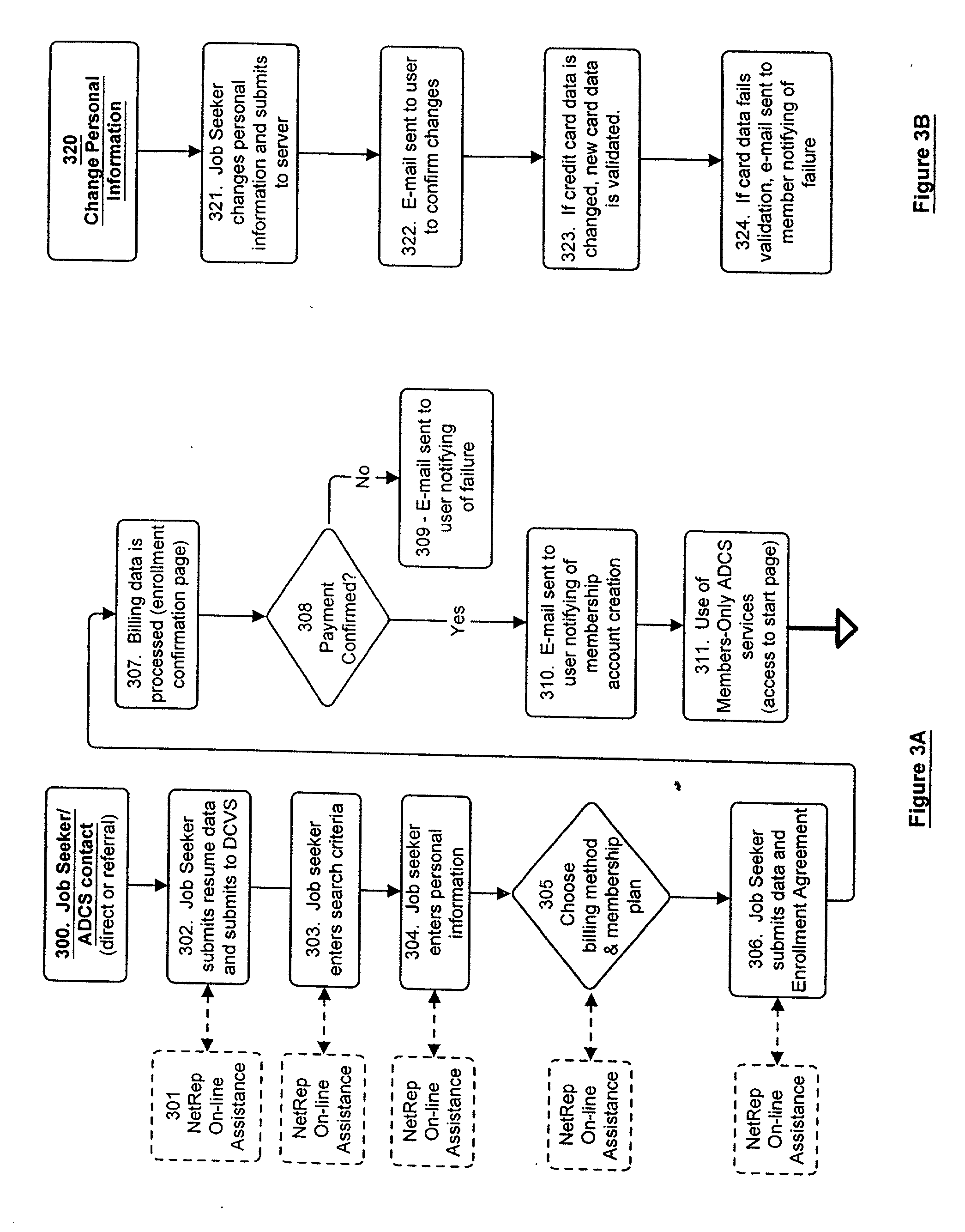
InactiveUS6658400B2Preserve valueFast and cost-effective operationComputer security arrangementsOffice automationData validationSource Data Verification
A method and apparatus is described for multiple-party data attribute management system and interface structure which permits different categories of users to contribute and control different types of source data, while adding informational value to data contributed by other users. The system provides a secure repository for verified and authenticated data, and provides a system of controlled access to the repository. The preferred embodiment of the invention comprises a data verification and certification system which in a principal embodiment is useful to create a data bank to match job seekers with potential employers based on verified resume data and employer specified search criteria. The interface structure The system of the invention preferably includes computer databases and interactive Internet based server systems.
Owner:VERIFIED HIRING
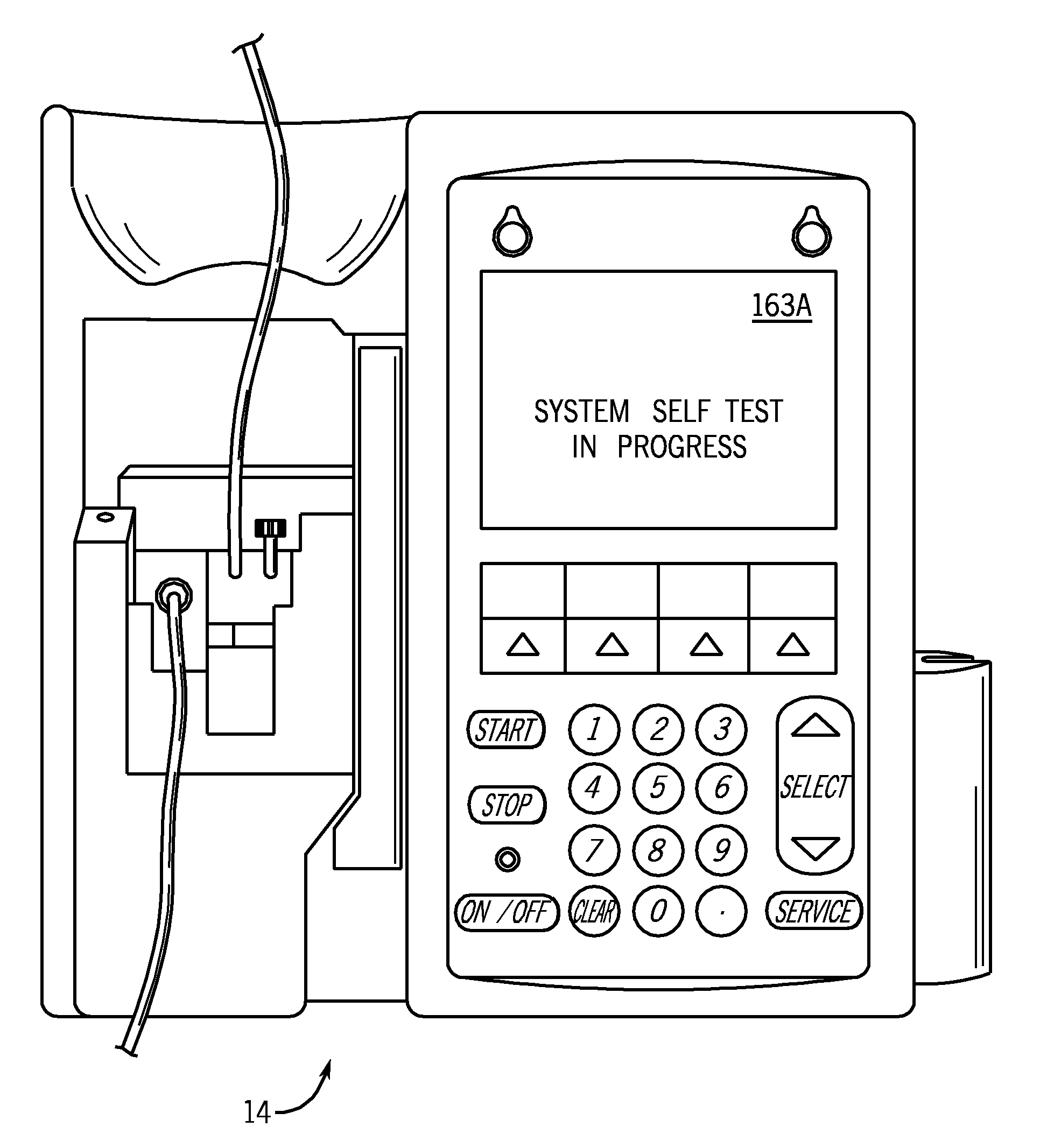
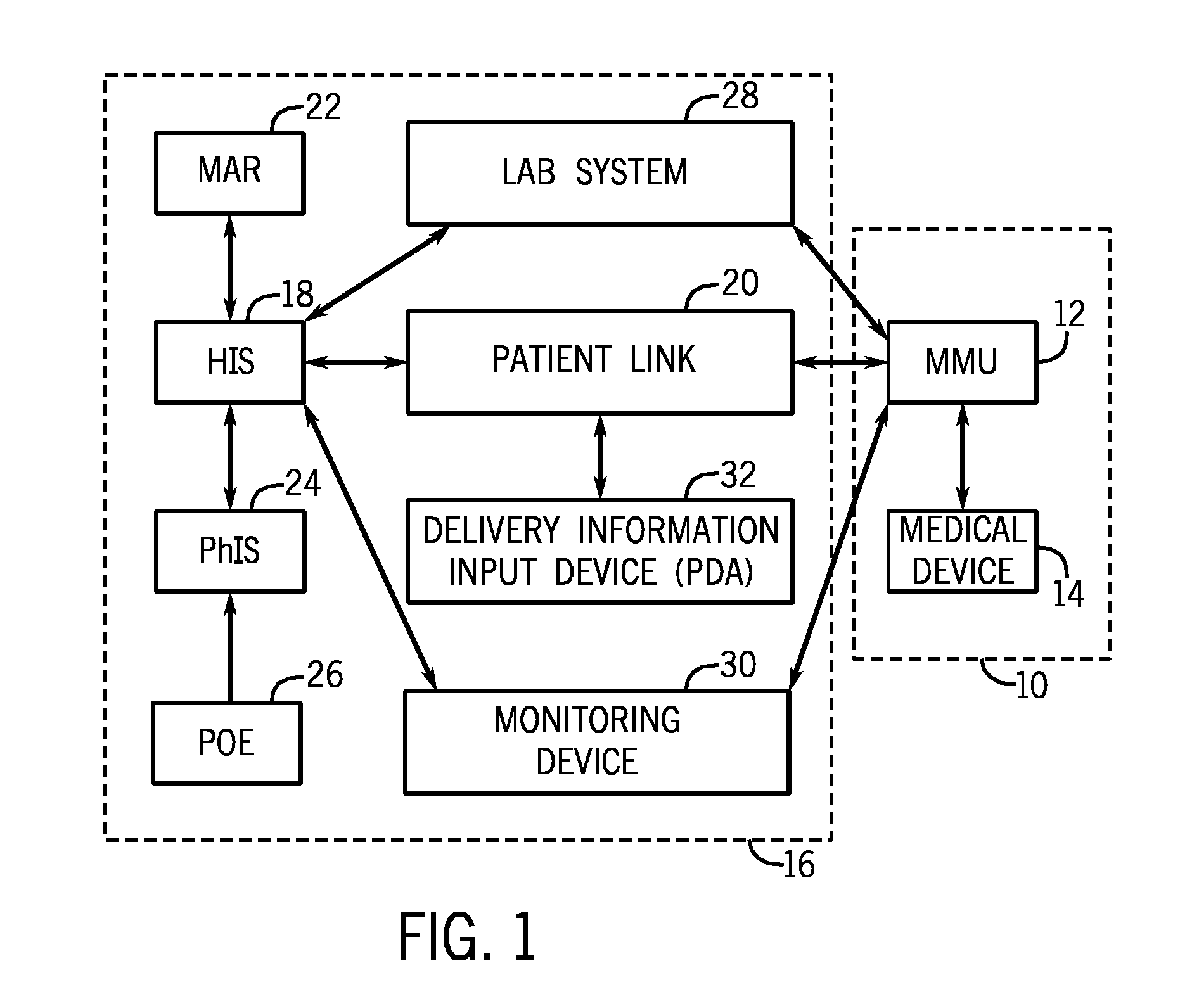
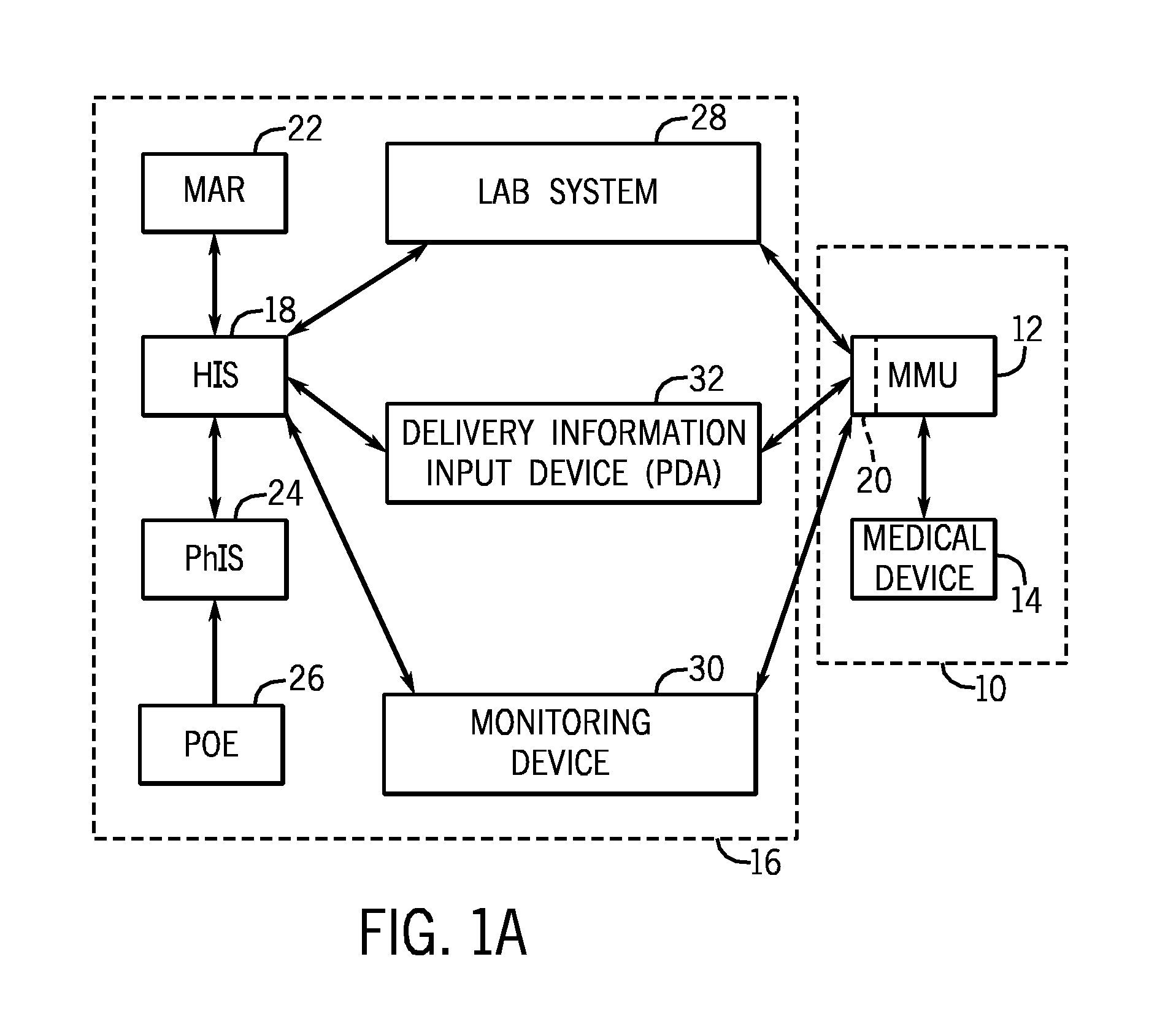
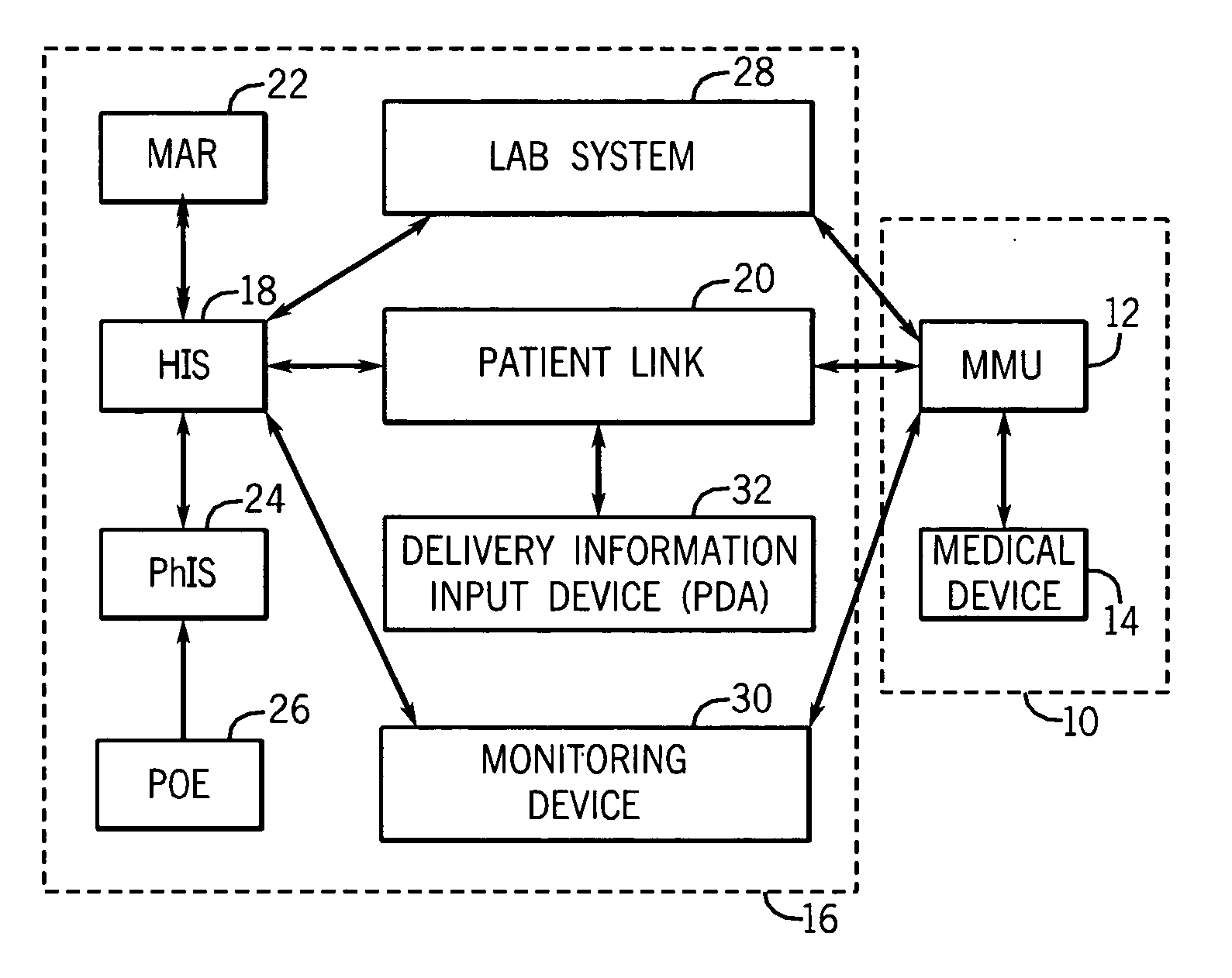
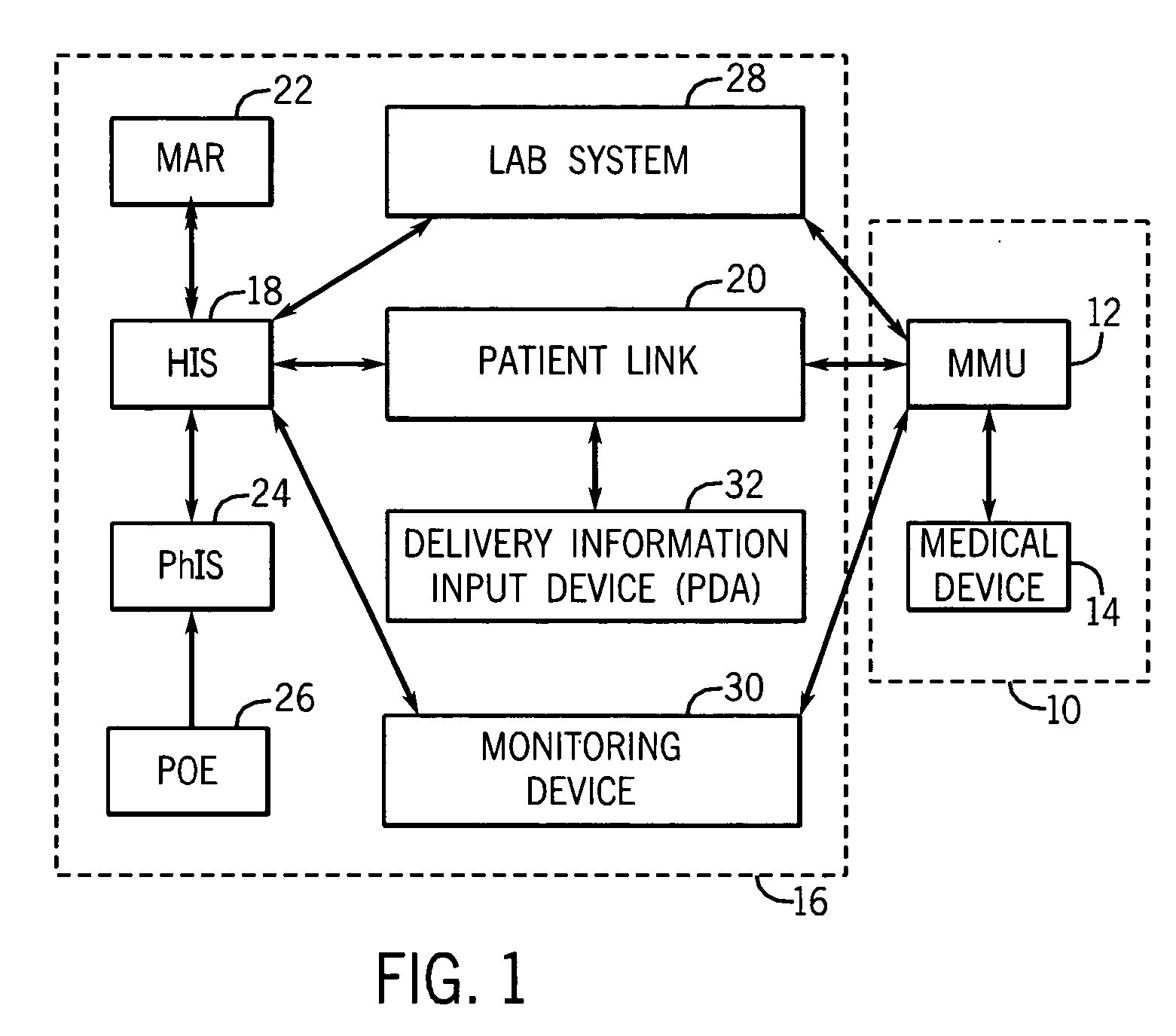
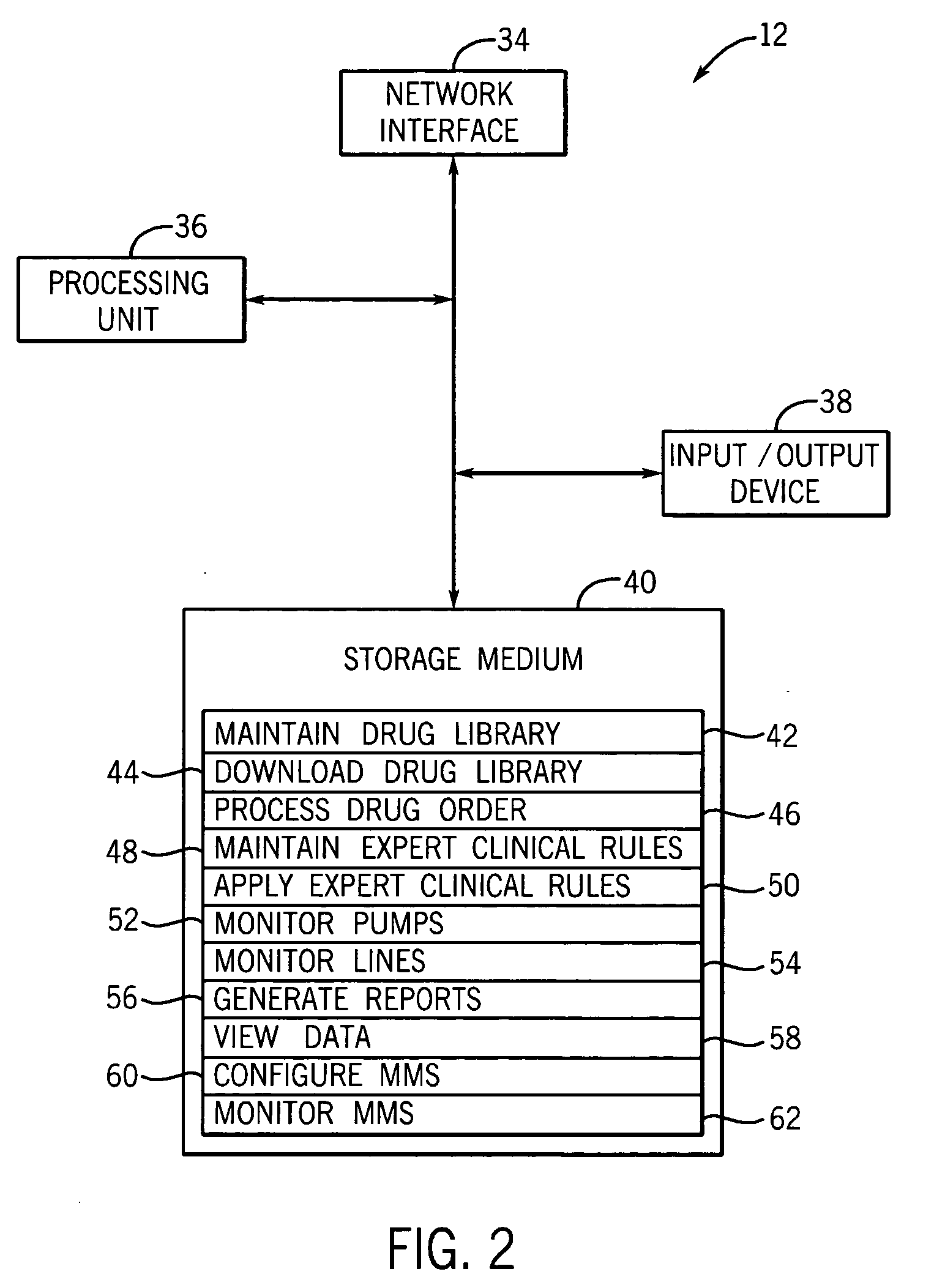
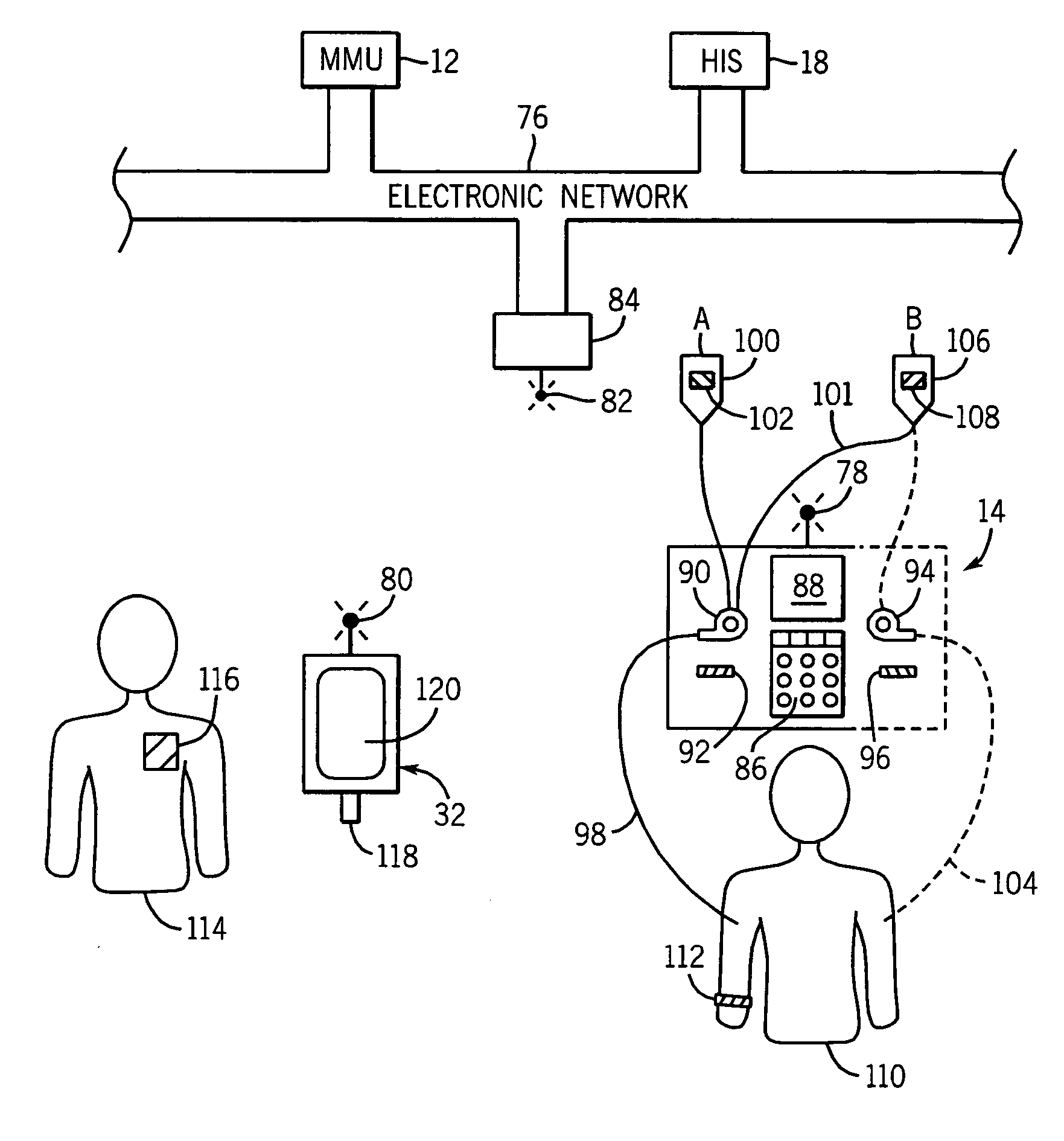
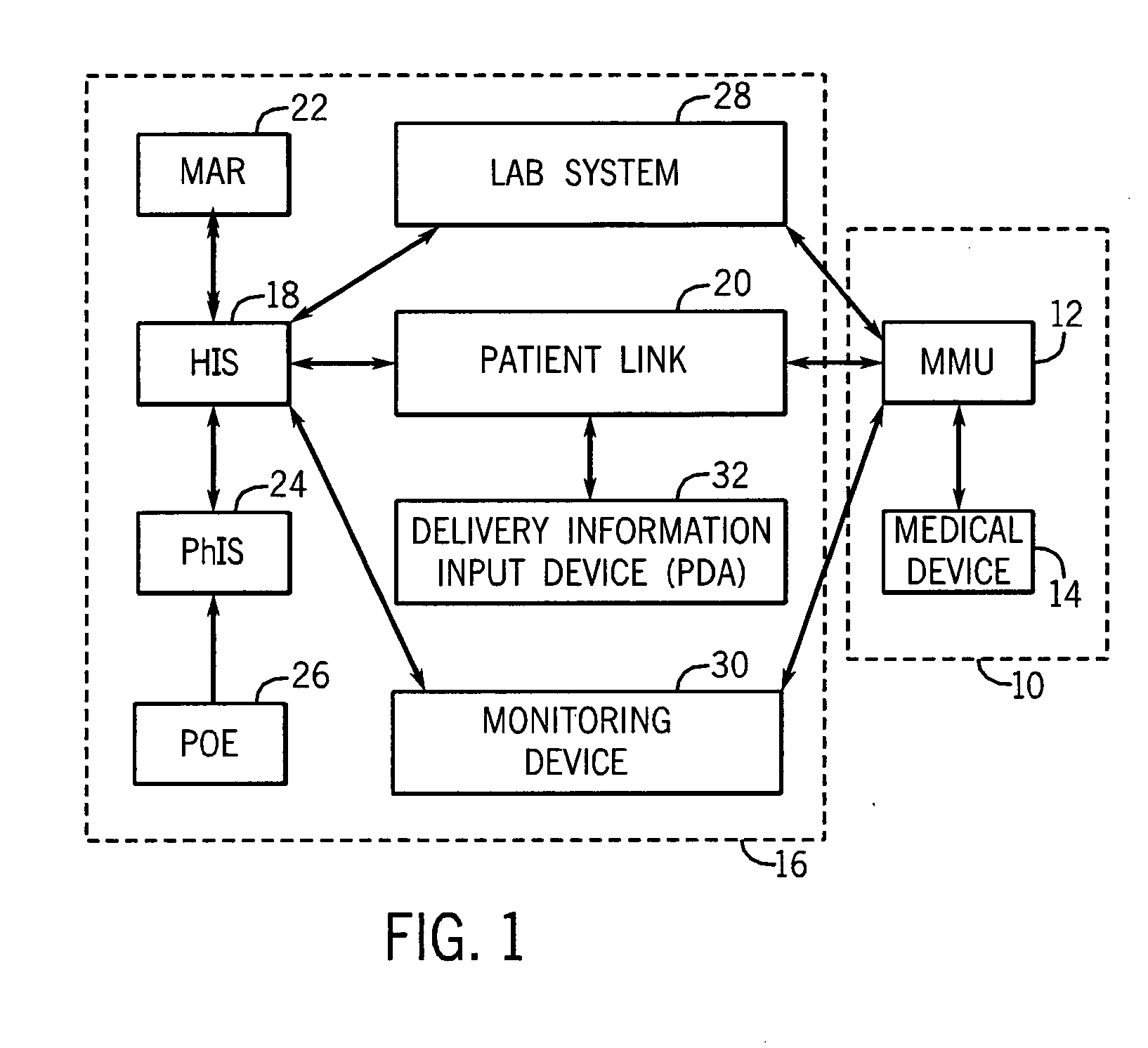
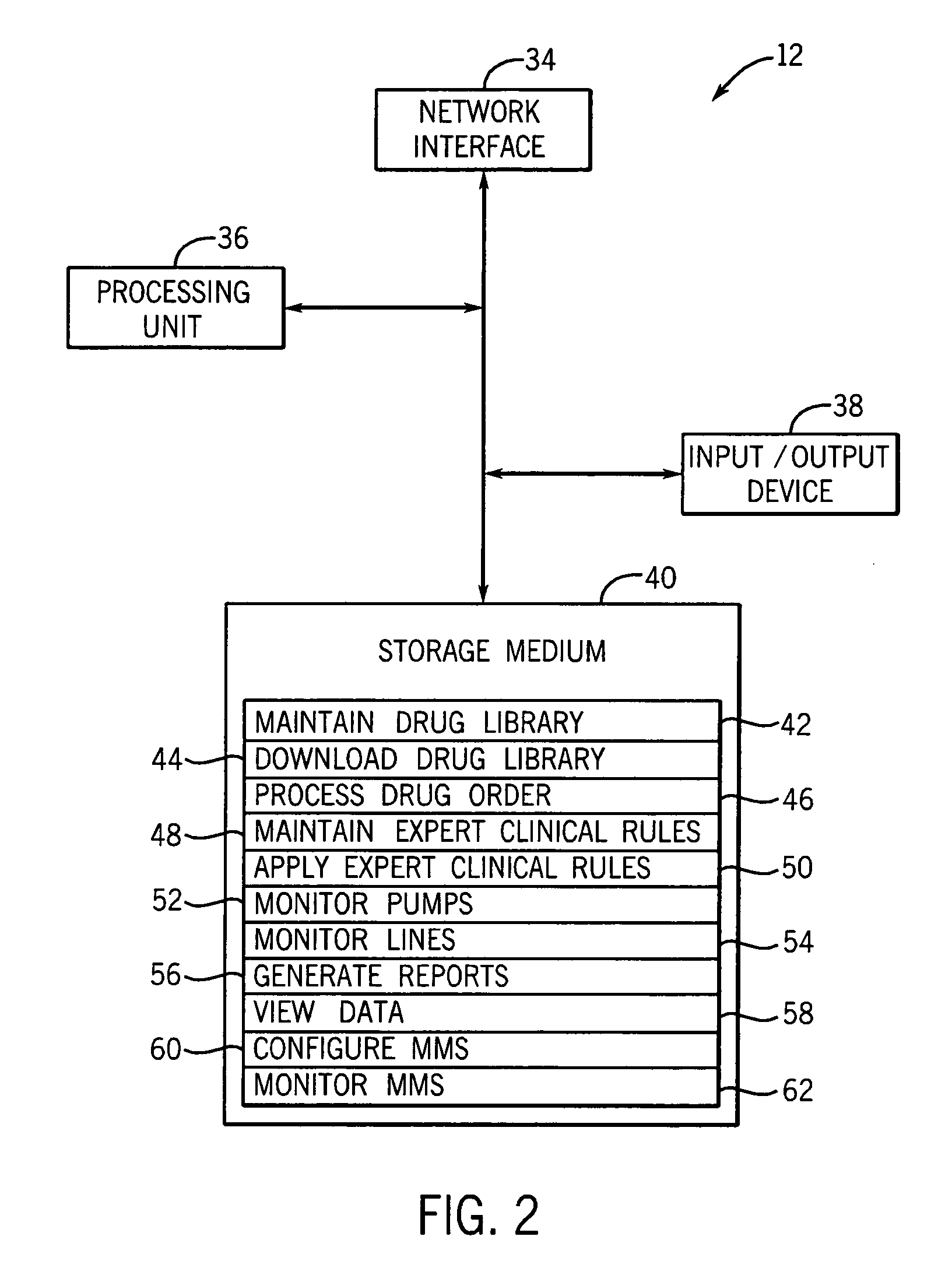
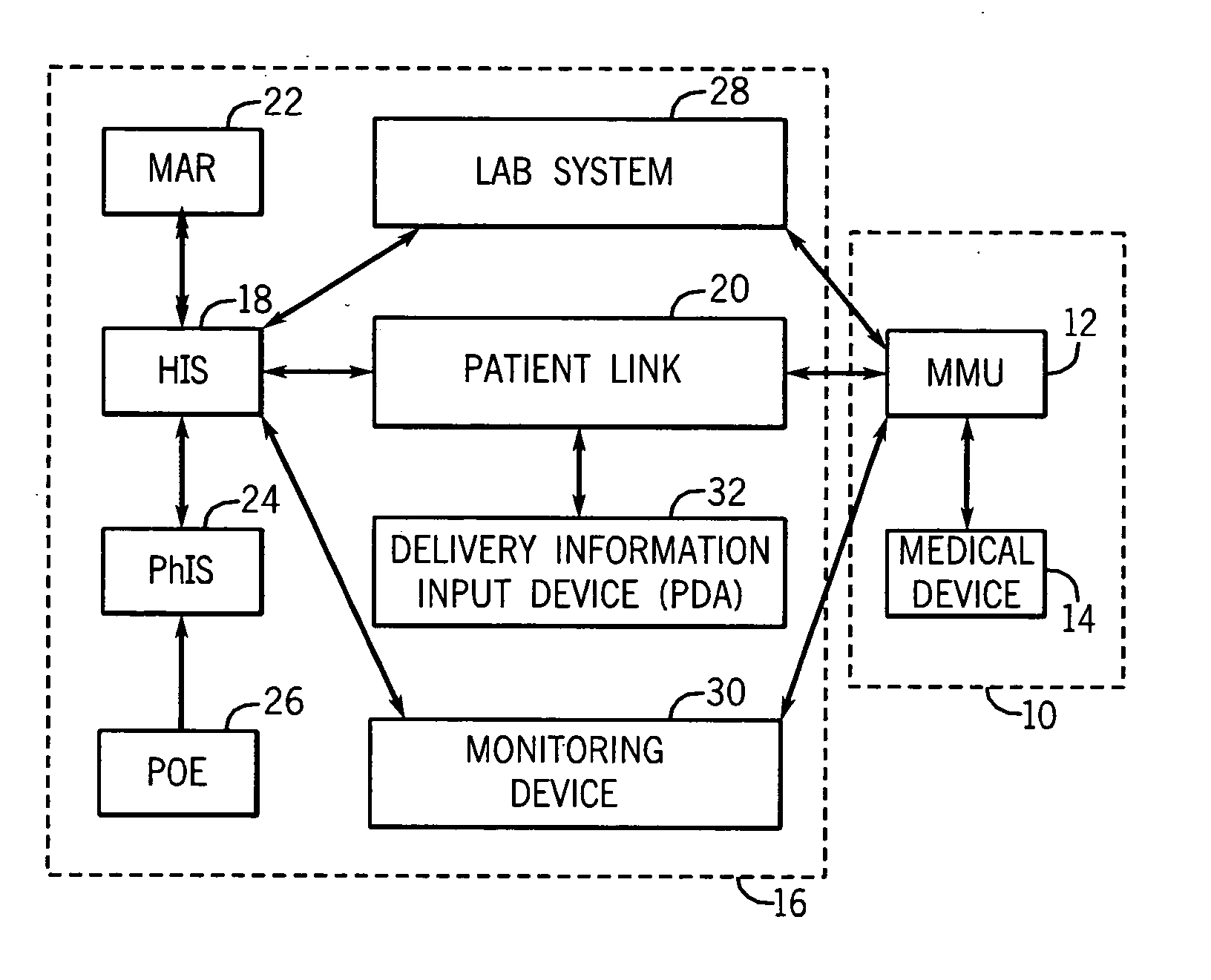
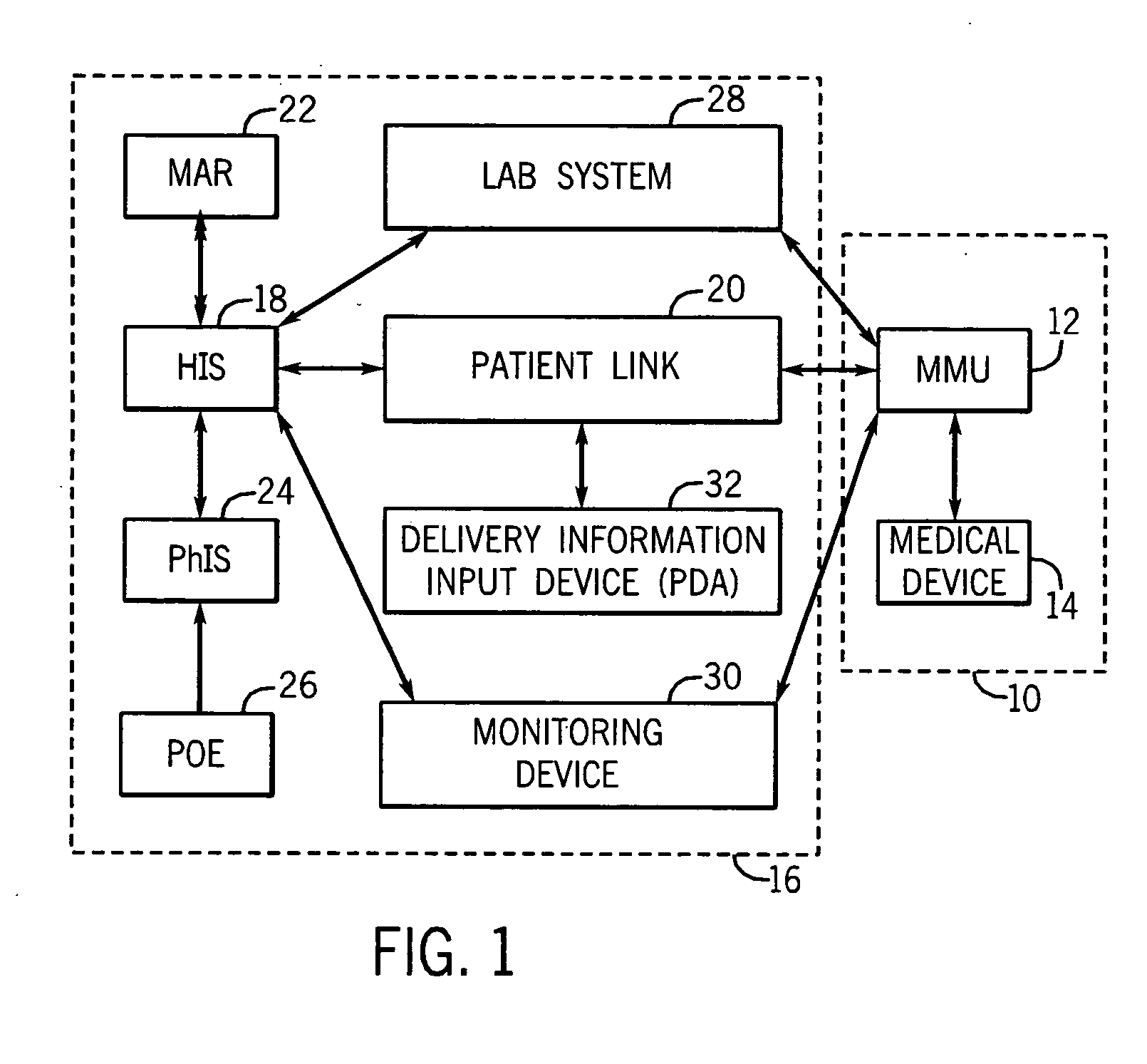
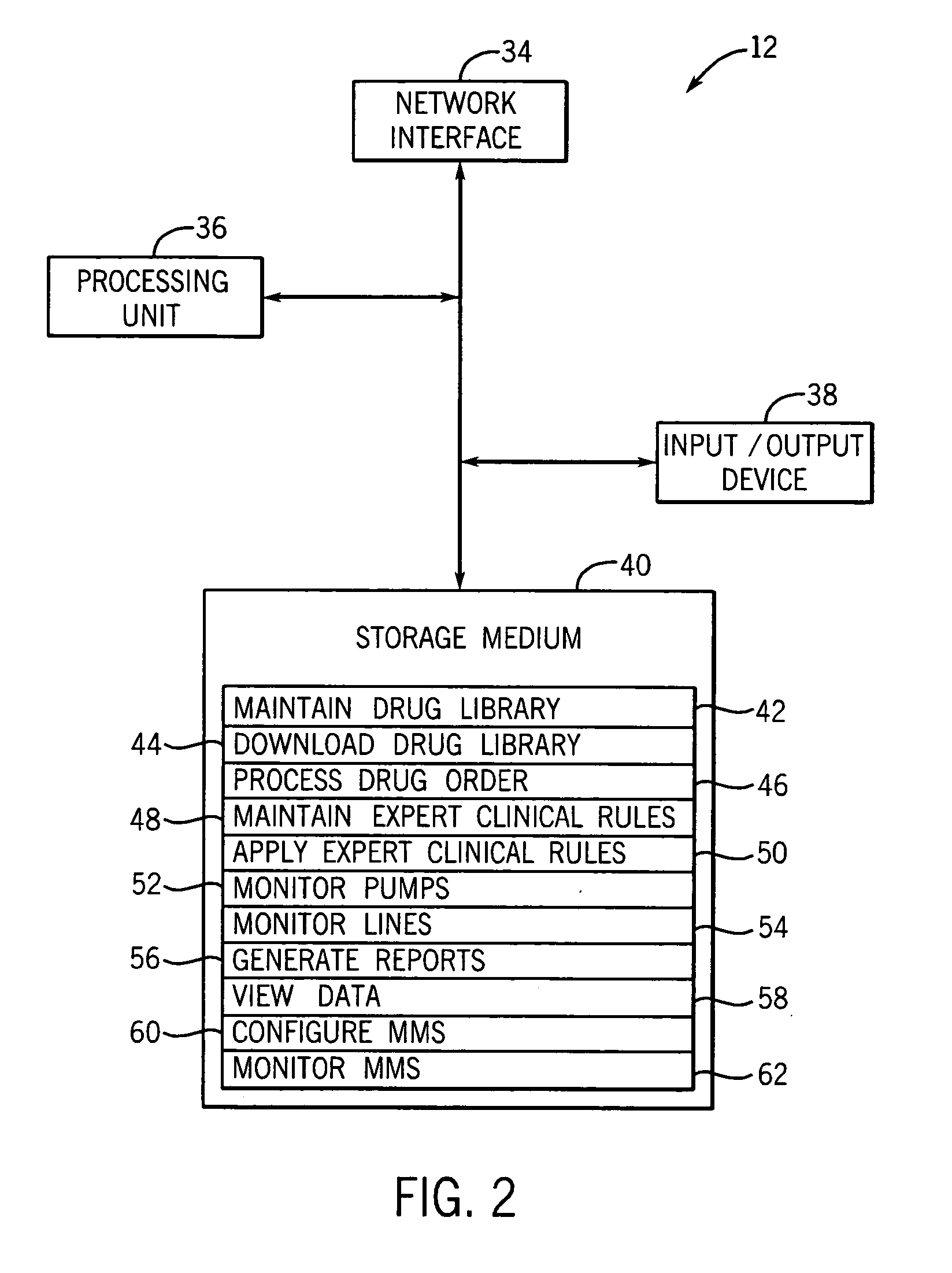
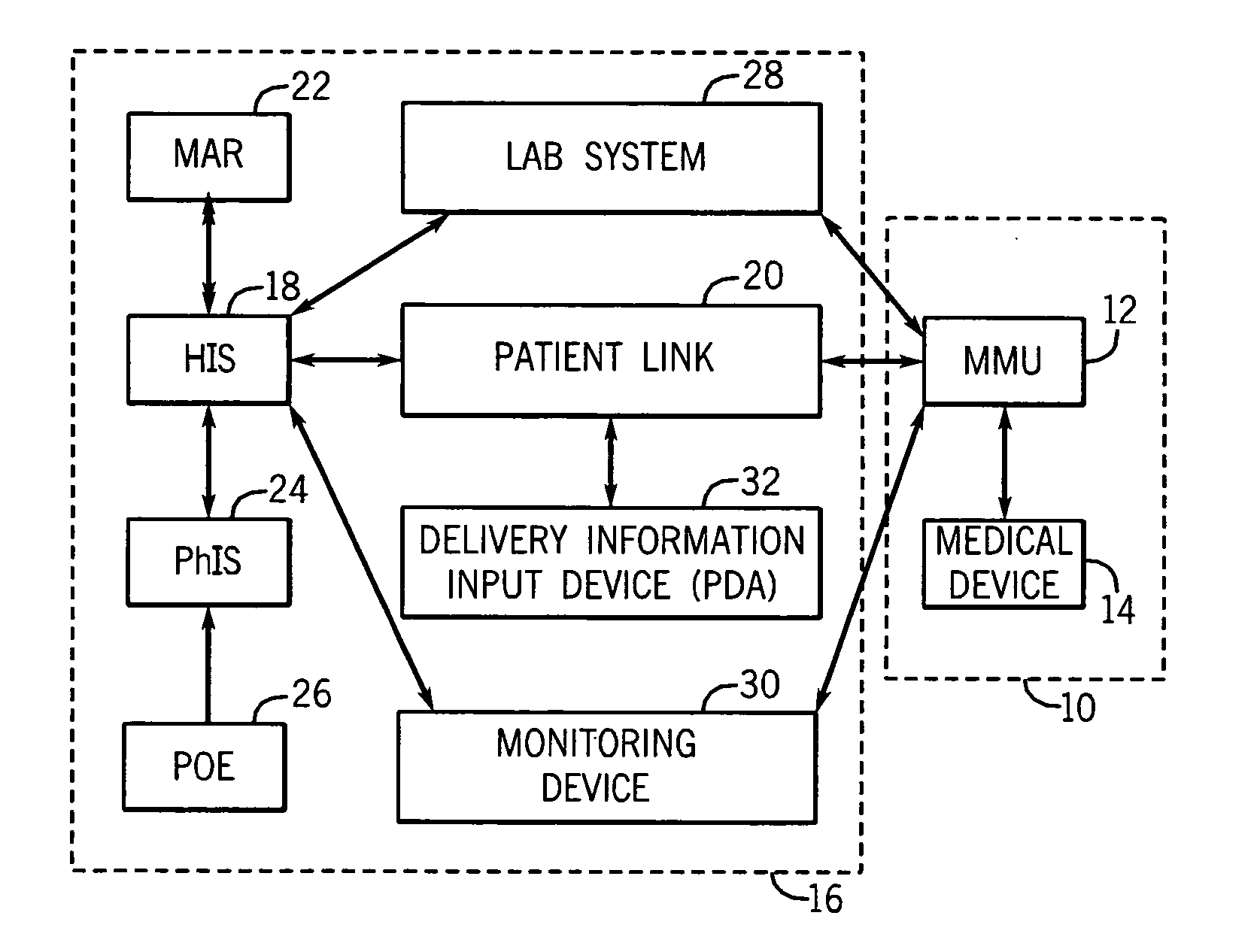
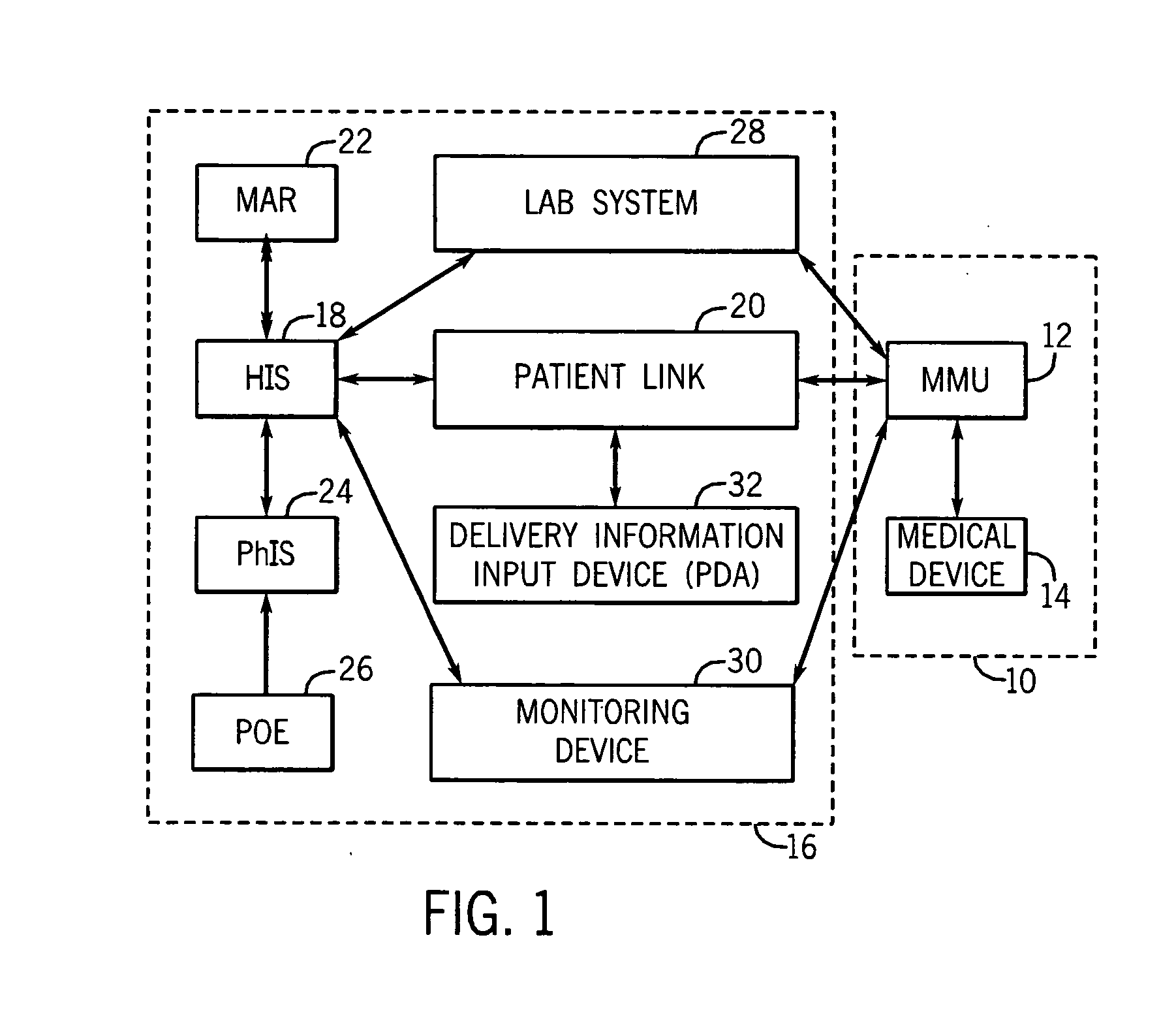
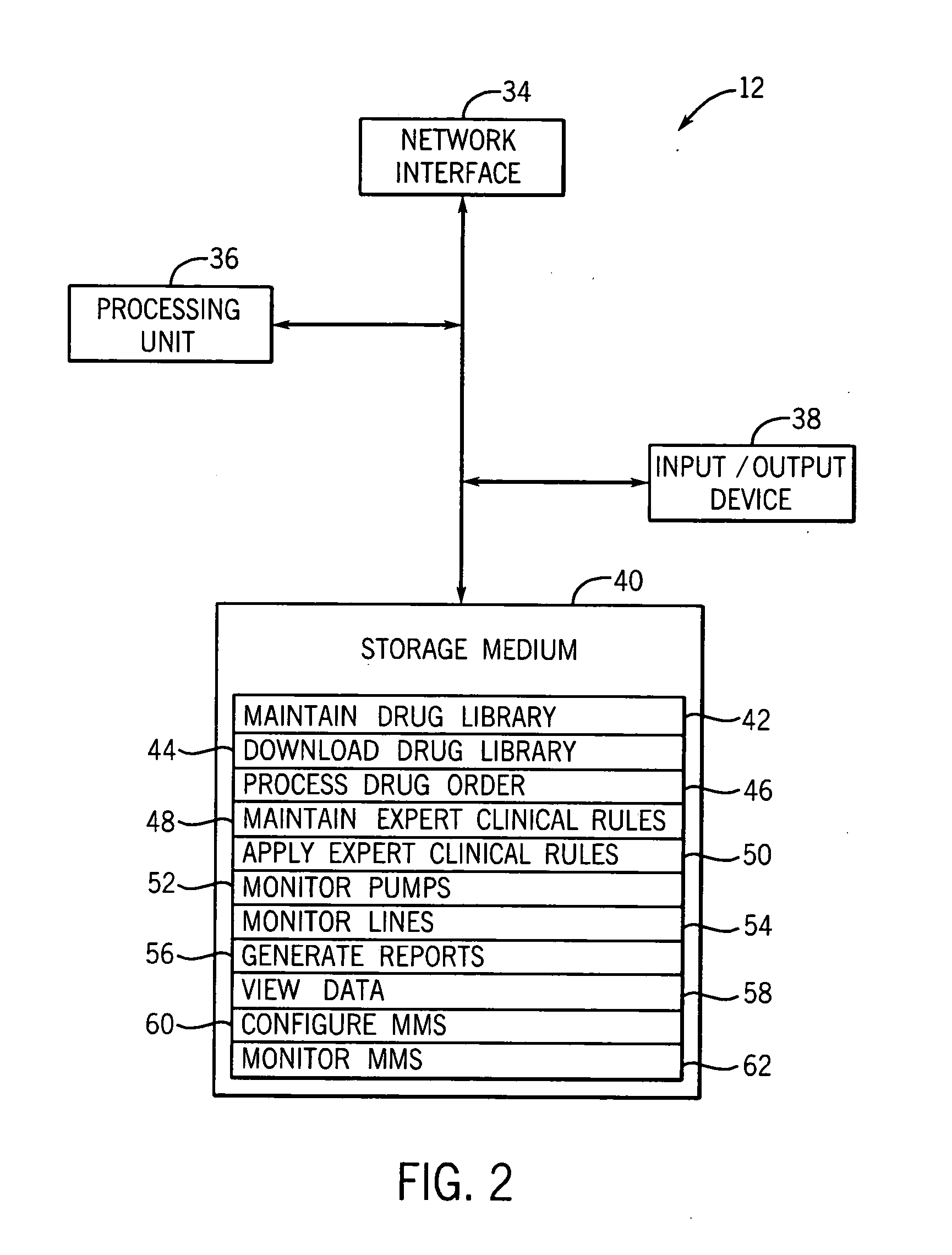
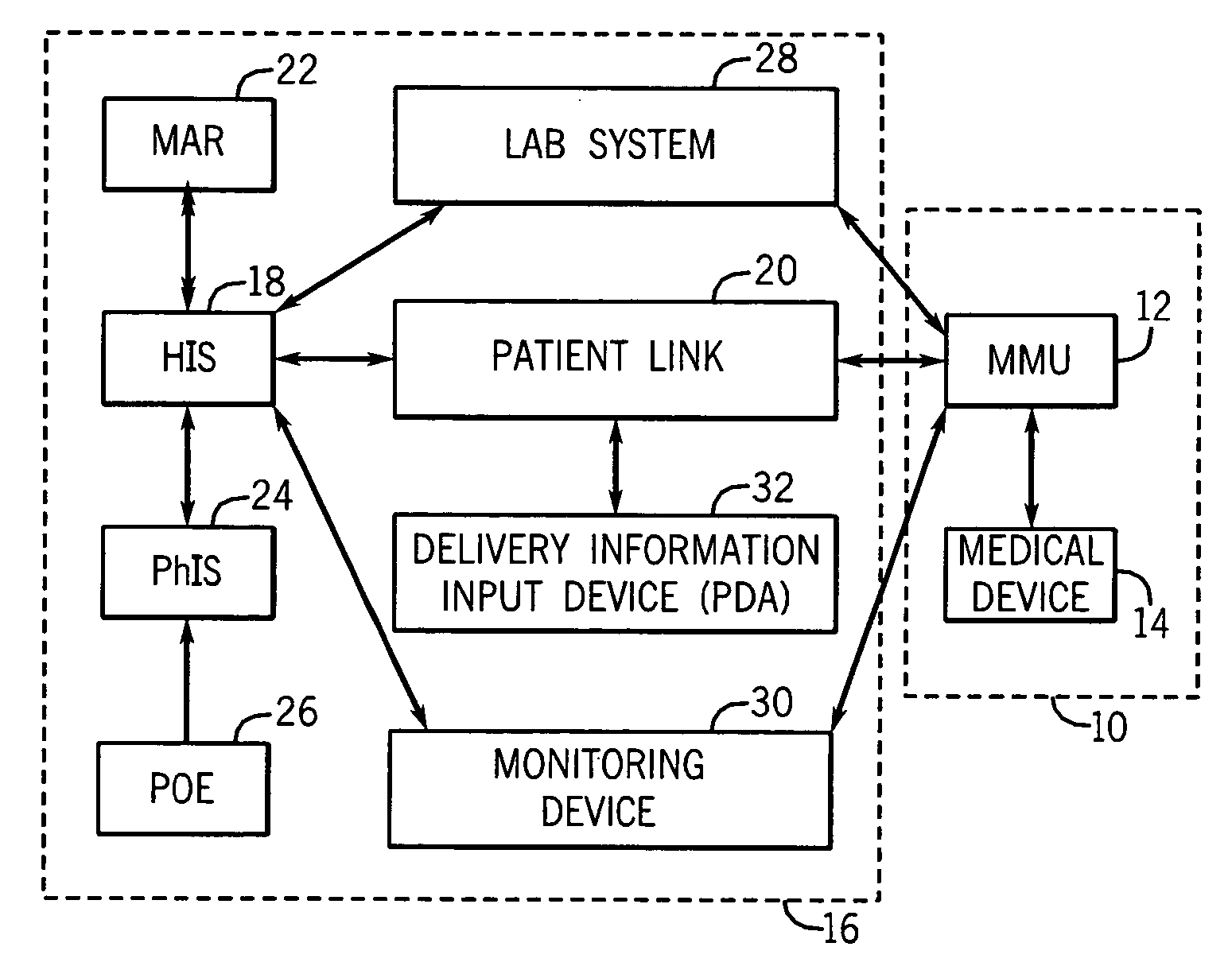
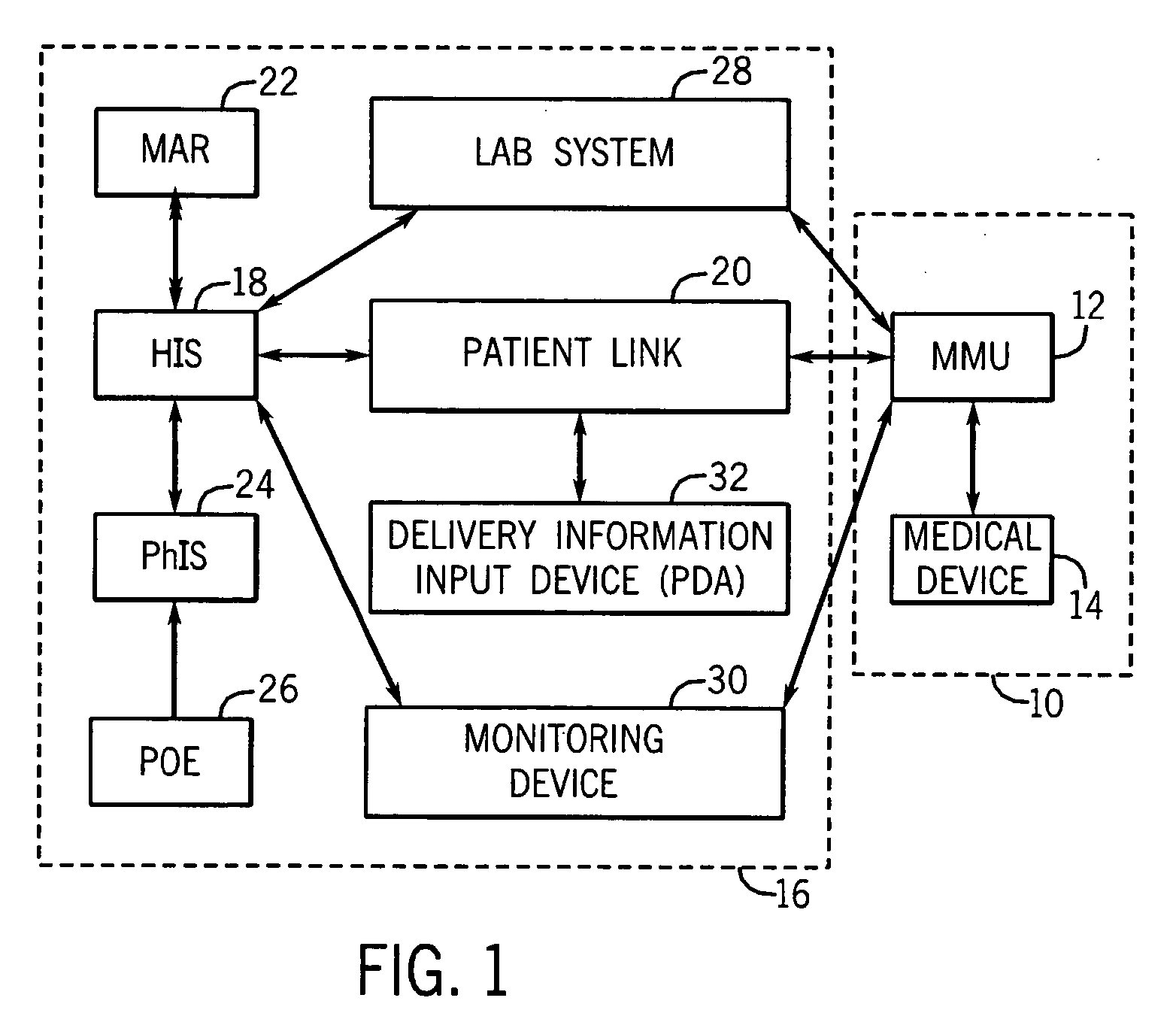
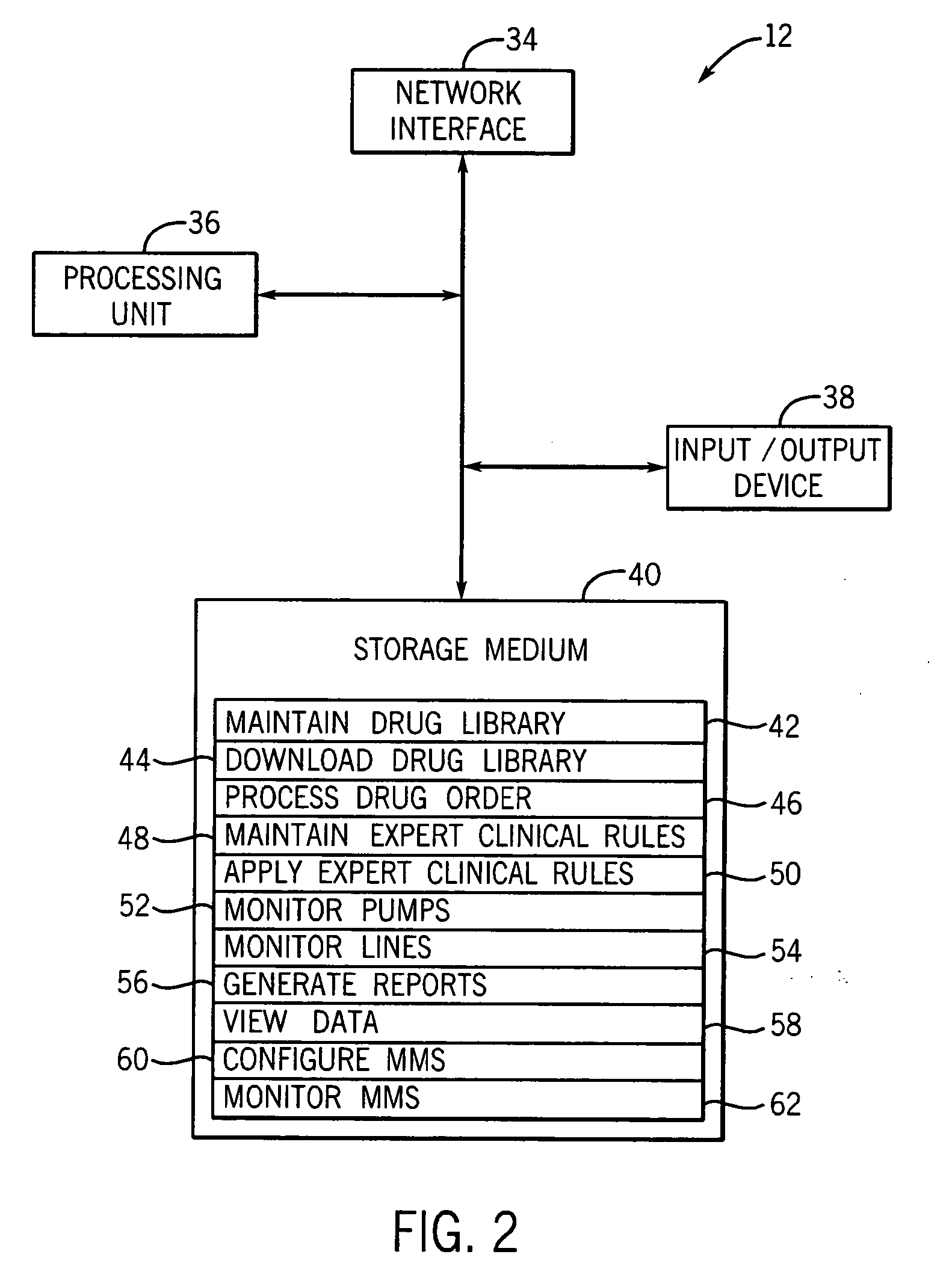
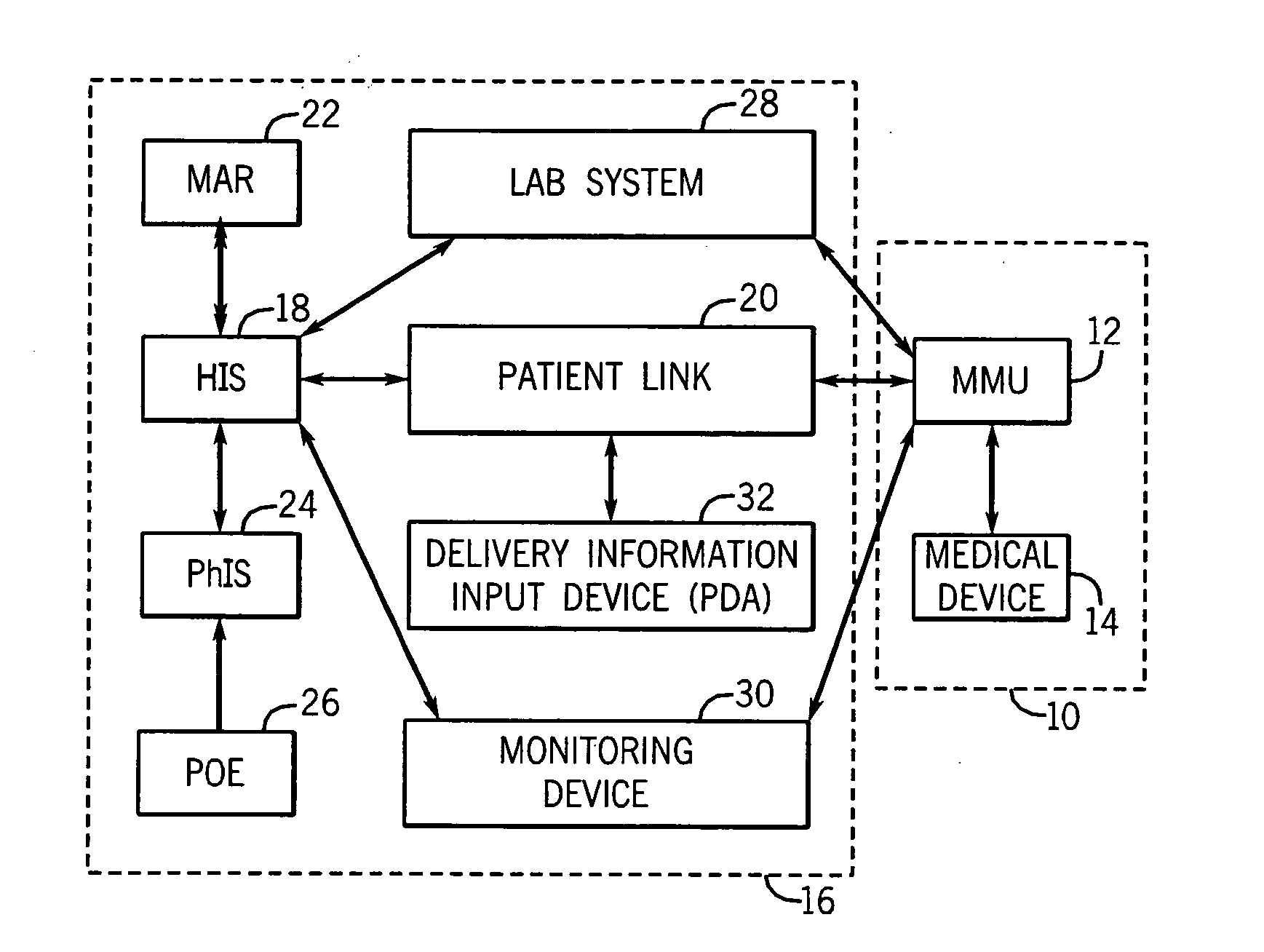
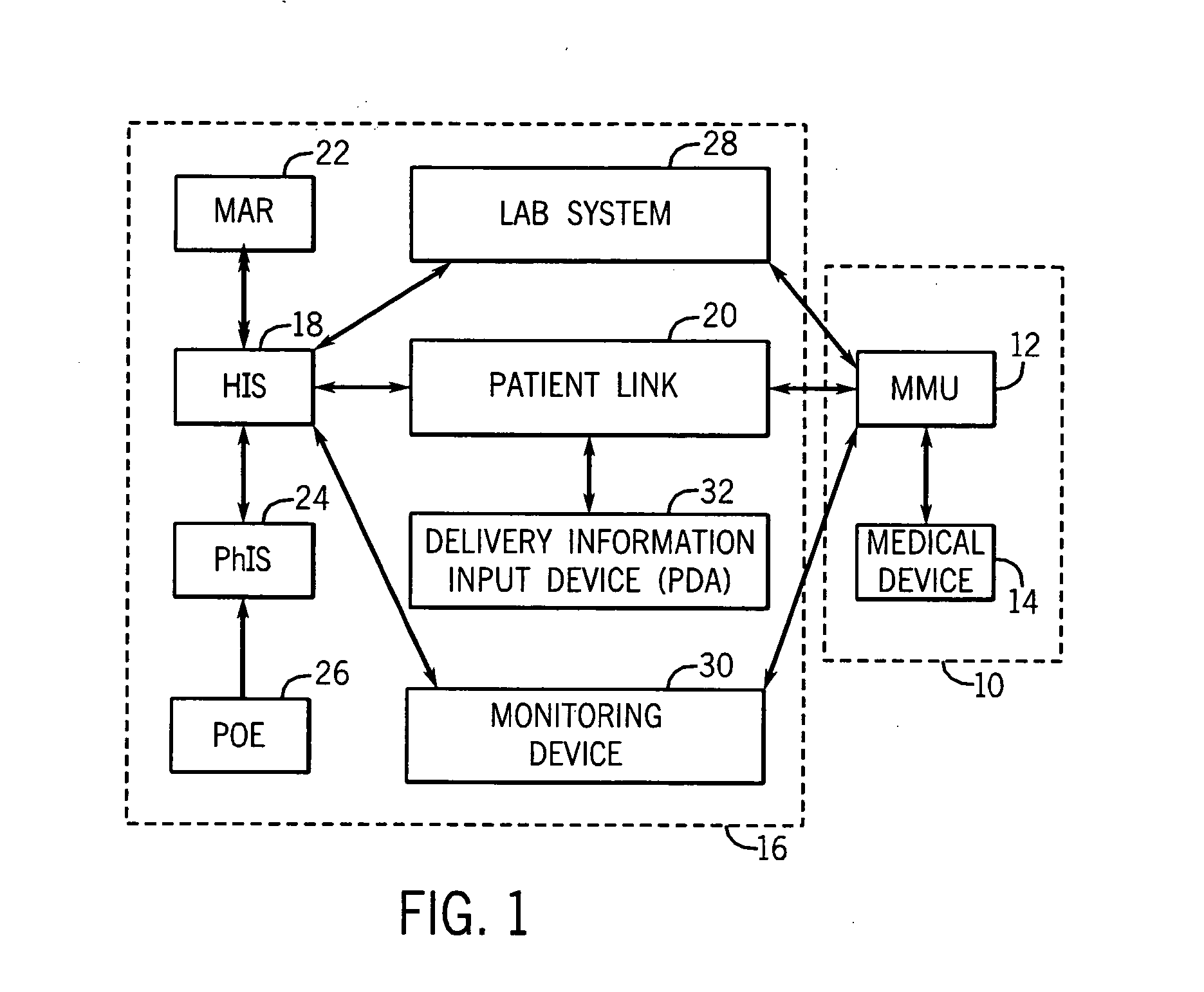
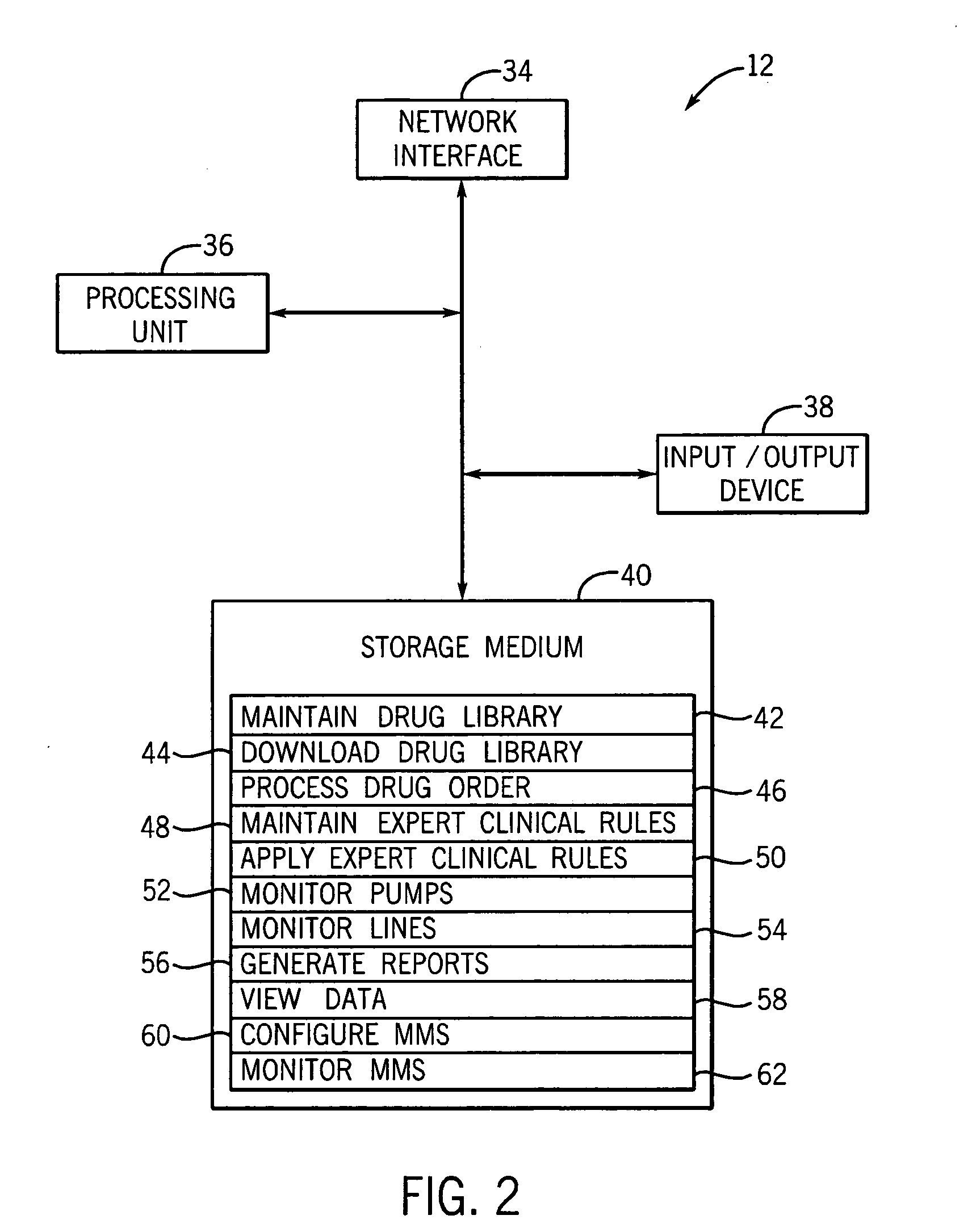
Medication managment system
InactiveUS20100130933A1Prevent wrong actionSave nursing timeData processing applicationsDrug and medicationsData validationManagement unit
A medication management system (MMS) includes a medication management unit (MMU) associated with a medical device. The MMU downloads medication delivery code based on a medication delivery order to the medical device only if information from a first input matches information from a second input. The medical device receives delivery information electronically only from the MMU. The medication order is performed only after delivery data validation. The MMU also determines drug-drug incompatibility. The MMU can modulate (start, stop, sequence and dynamically adjust) medication order performance.
Owner:ICU MEDICAL INC
Data certification and verification system having a multiple- user-controlled data interface
InactiveUS20010047347A1Fast and cost-effective operationAvoid effortComputer security arrangementsMultiple digital computer combinationsData validationSource Data Verification
Owner:VERIFIED HIRING
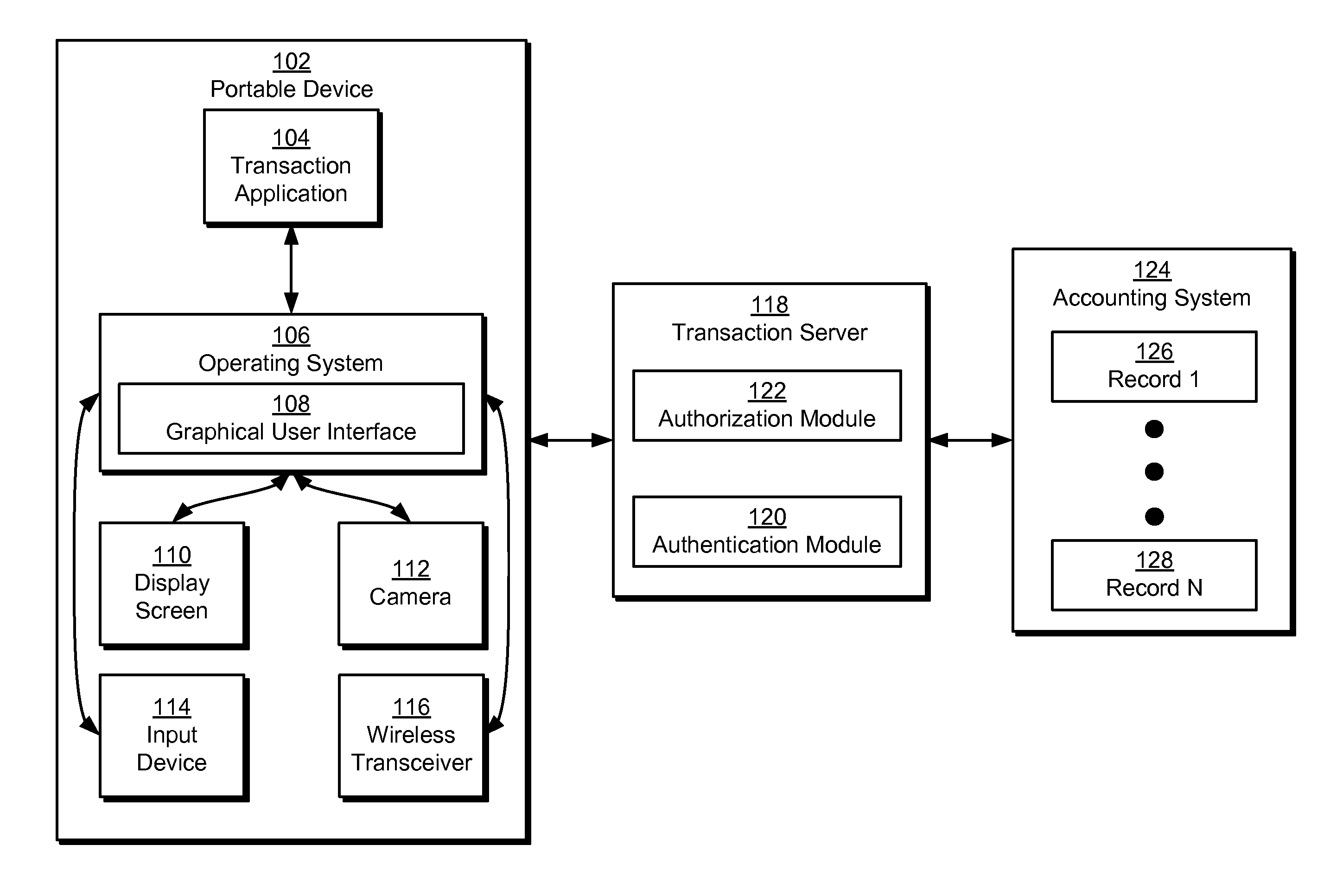
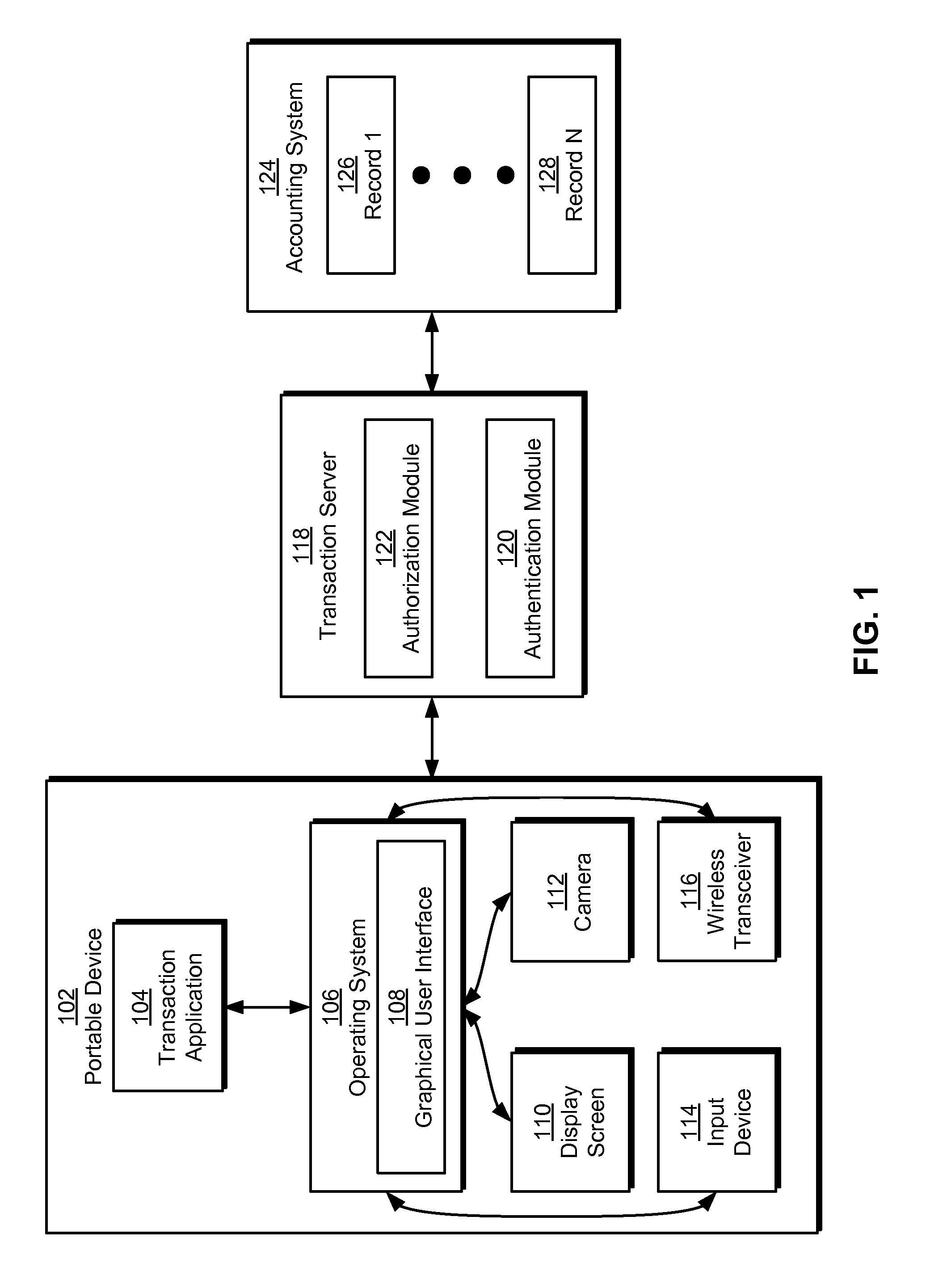
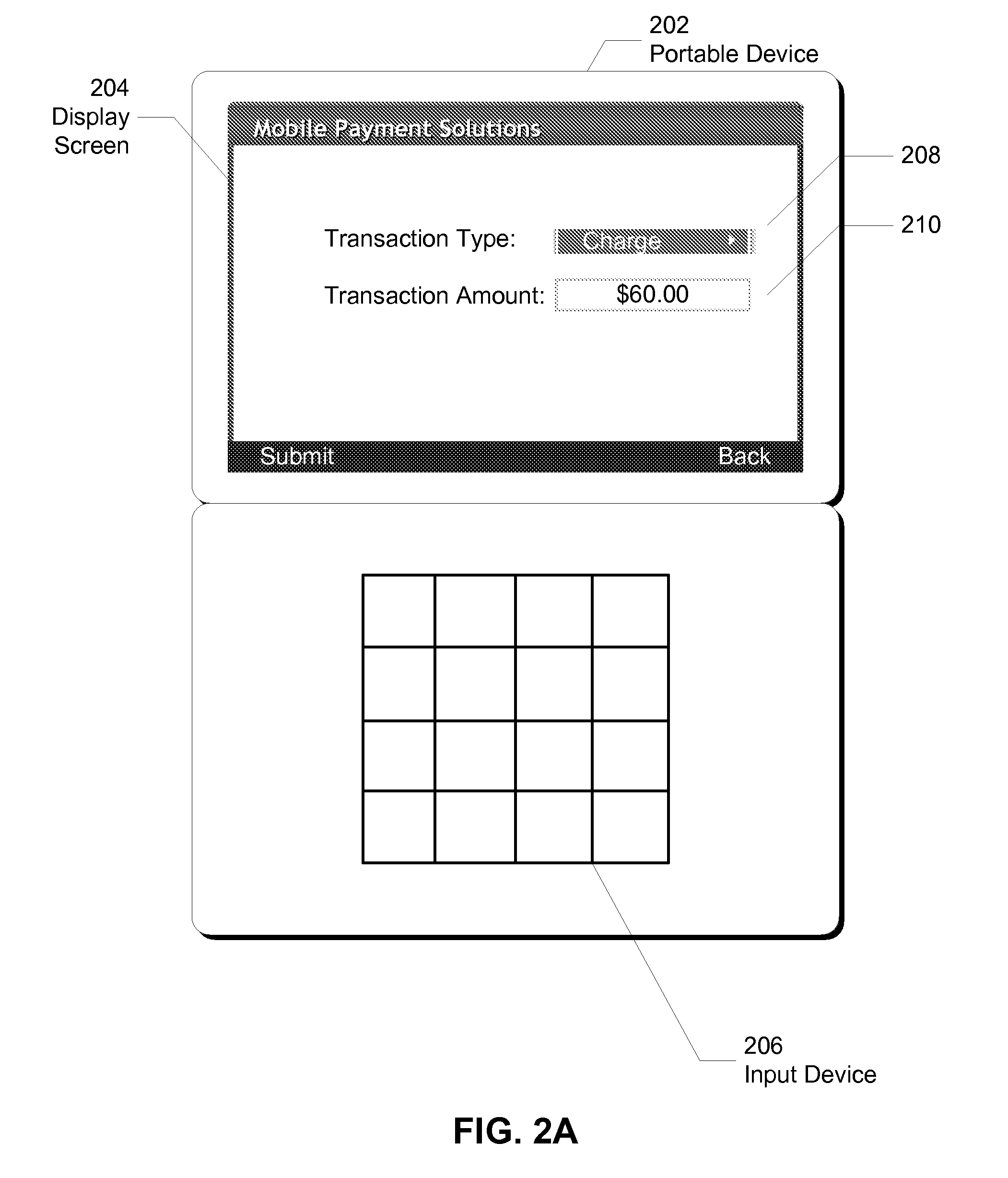
Method and system for performing a card-present transaction using image capture on a portable device
Some embodiments of the present invention provide a system that processes a financial transaction involving a portable device and a transaction server. During operation, the system obtains transaction data associated with the financial transaction that includes a transaction amount, credit card information, and an image of a credit card. The system then sends the transaction data to the transaction server using the portable device. Next, the system verifies a card-present transaction using the transaction data and determines a validity of the transaction data. If the transaction data is valid, the transaction server processes the financial transaction and sends an authorization code confirming the financial transaction to the portable device.
Owner:INTUIT INC
Medication management system
InactiveUS20060100907A1Improve accuracyLabor-intensive taskData processing applicationsDrug and medicationsData validationCaregiver person
A medication management system (MMS) includes a medication management unit (MMU) associated with a medical device. The MMU downloads a medication order to the medical device only if information from a first input matches information from a second input. The medical device receives delivery information only from the MMU. The medication order is performed only after delivery data validation. The MMU also determines drug-drug incompatibility. The MMU can modulate (start, stop, and dynamically adjust) medication order performance. The medical device wirelessly receives a patient ID to automatically associate with the patient. During delivery, the medical device caches an updated drug library to replace an existing one. The medical device displays a patient picture for validation. The MMU evaluates the performance of medical devices and caregivers based medical device feedback. The MMU adjusts the output of medical device information conveyed to a caregiver.
Owner:ICU MEDICAL INC
Medication management system
ActiveUS20060265186A1Prevent wrong actionDrug and medicationsNuclear monitoringCaregiver personData validation
A medication management system (MMS) includes a medication management unit (MMU) associated with a medical device. The MMU downloads a medication order to the medical device only if information from a first input matches information from a second input. The medical device receives delivery information only from the MMU. The medication order is performed only after delivery data validation. The MMU also determines drug-drug incompatibility. The MMU can modulate (start, stop, and dynamically adjust) medication order performance. The medical device wirelessly receives a patient ID to automatically associate with the patient. During delivery, the medical device caches an updated drug library to replace an existing one. The medical device displays a patient picture for validation. The MMU evaluates the performance of medical devices and caregivers based medical device feedback. The MMU adjusts the output of medical device information conveyed to a caregiver.
Owner:FUJIFILM HEALTHCARE CORP +1
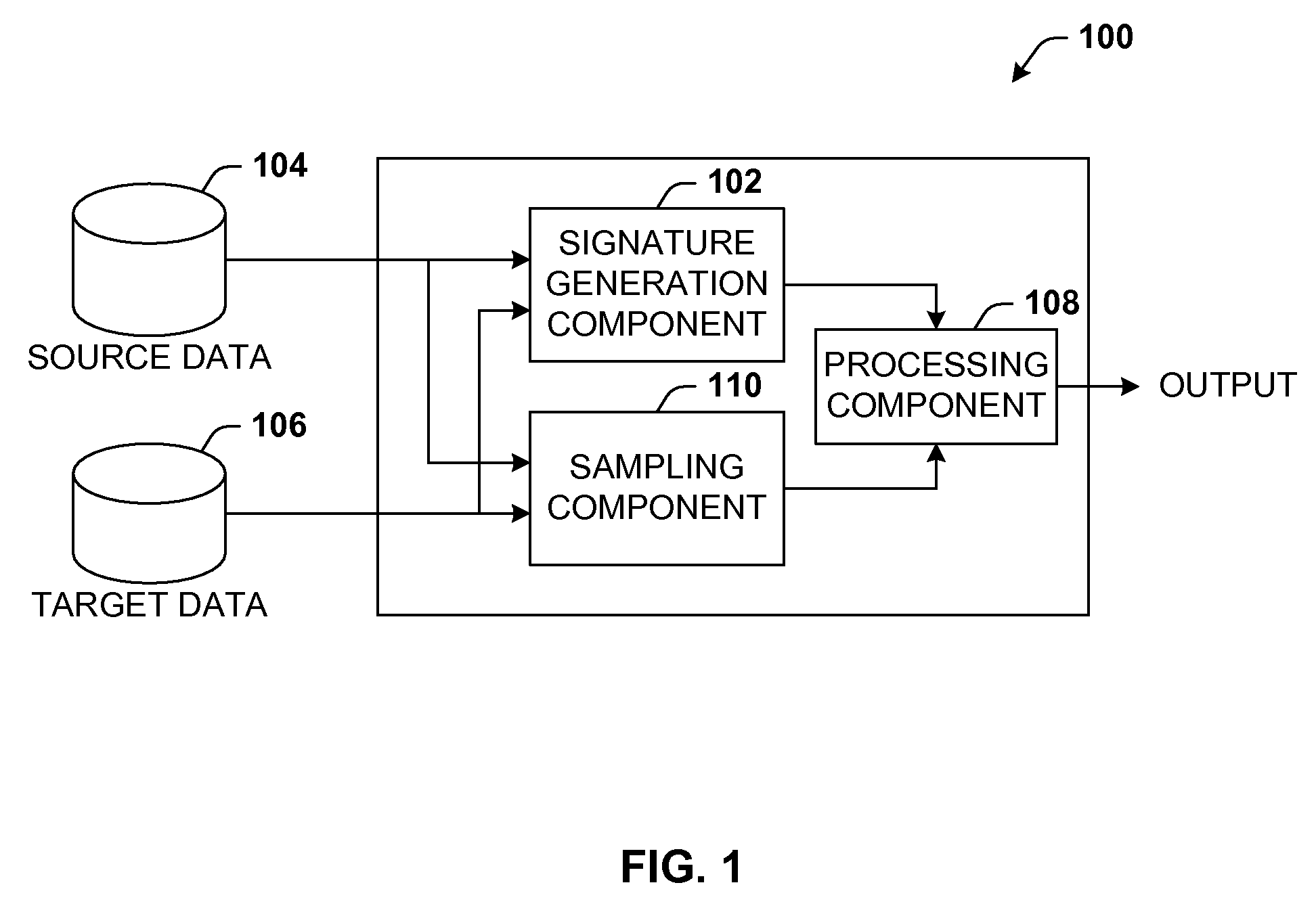
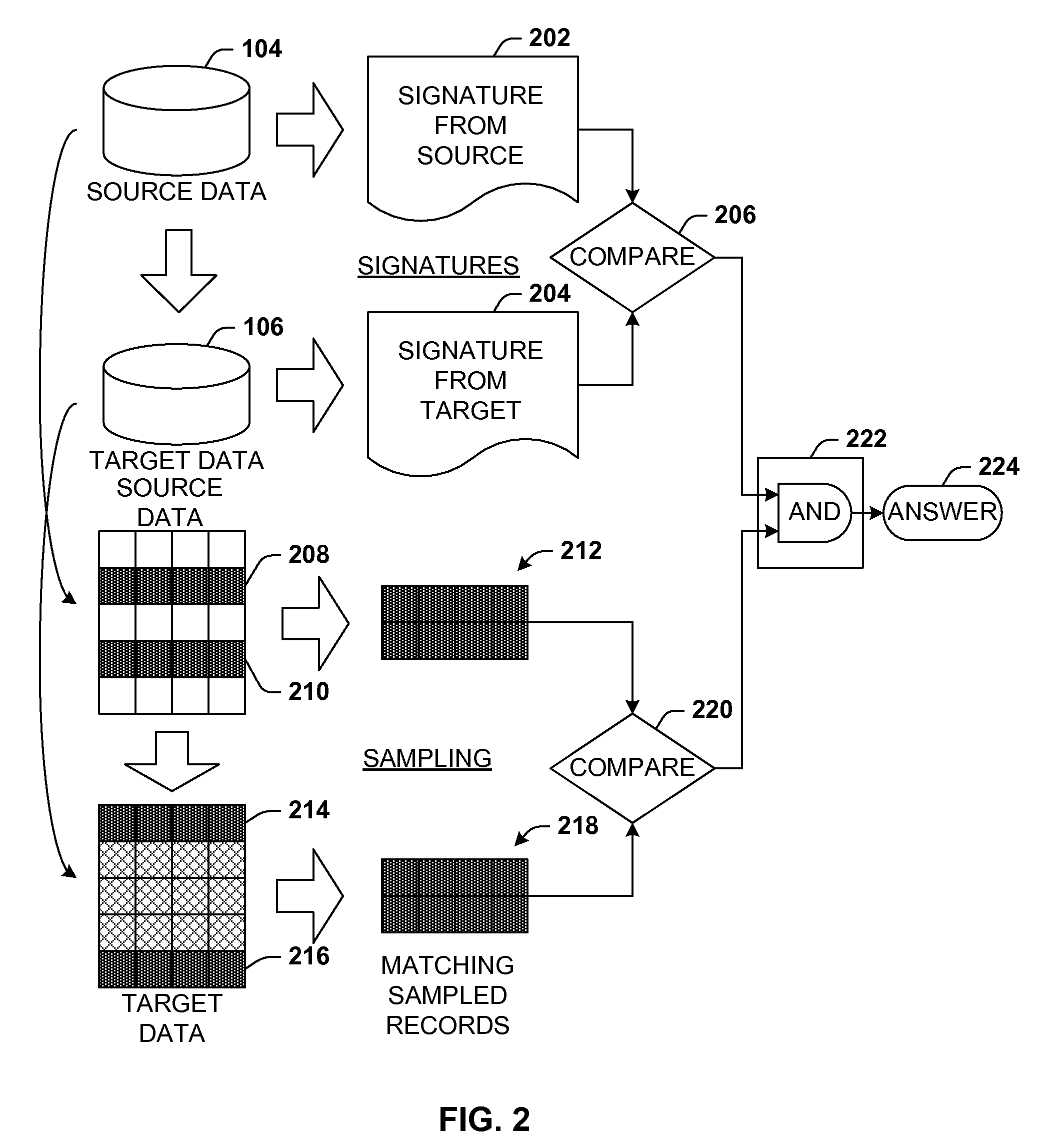
Data validation using signatures and sampling
InactiveUS20090132955A1User identity/authority verificationCharacter and pattern recognitionData validationSource Data Verification
Architecture that facilitates validation of a data mapping of data from a data source to a data target. There is included a signature generation component that generates a source signature of all or a portion of the data source and a target signature of all or a corresponding portion of the data target, and a sampling component that obtains a sample of the source data a corresponding sample of the target data. The data signatures and data samples are compared respectively and processed with a processing component to determine the status of the validation process.
Owner:MICROSOFT TECH LICENSING LLC
Medication management system
InactiveUS20070214003A1Improve accuracyLabor-intensive taskData processing applicationsDrug and medicationsData validationManagement unit
A medication management system (MMS) includes a medication management unit (MMU) associated with a medical device. The MMU downloads a medication order to the medical device only if information from a first input matches information from a second input. The medical,device receives delivery information only from the MMU. The medication order is performed only after delivery data validation. The MMU also determines drug-drug incompatibility. The MMU can modulate (start, stop, and dynamically adjust) medication order performance. The medical device wirelessly receives a patient ID to automatically associate with the patient. During delivery, the medical device caches an updated drug library to replace an existing one. The medical device displays a patient picture for validation. The MMU evaluates the performance of medical devices and caregivers based medical device feedback. The MMU adjusts the output of medical device information conveyed to a caregiver.
Owner:ICU MEDICAL INC
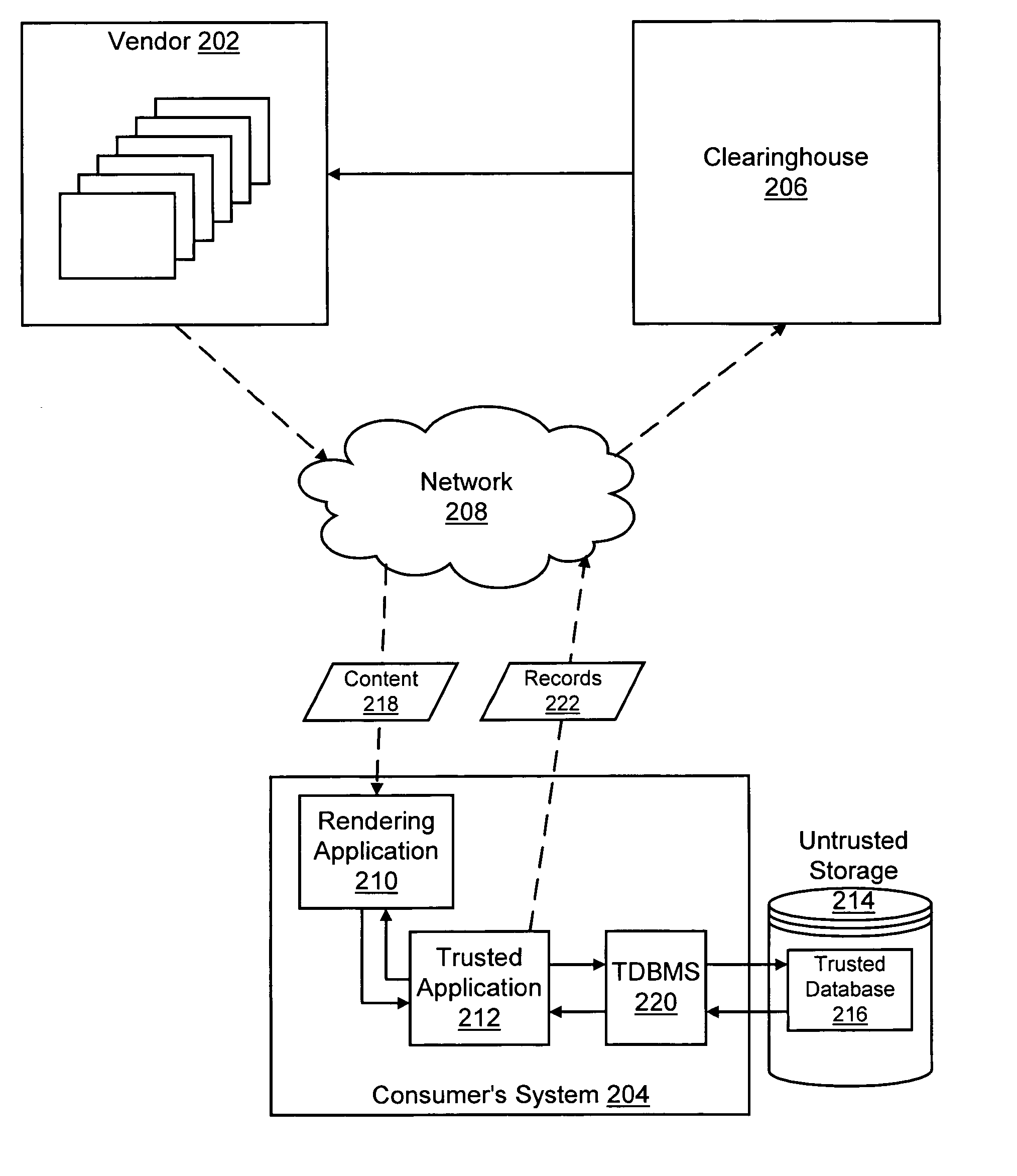
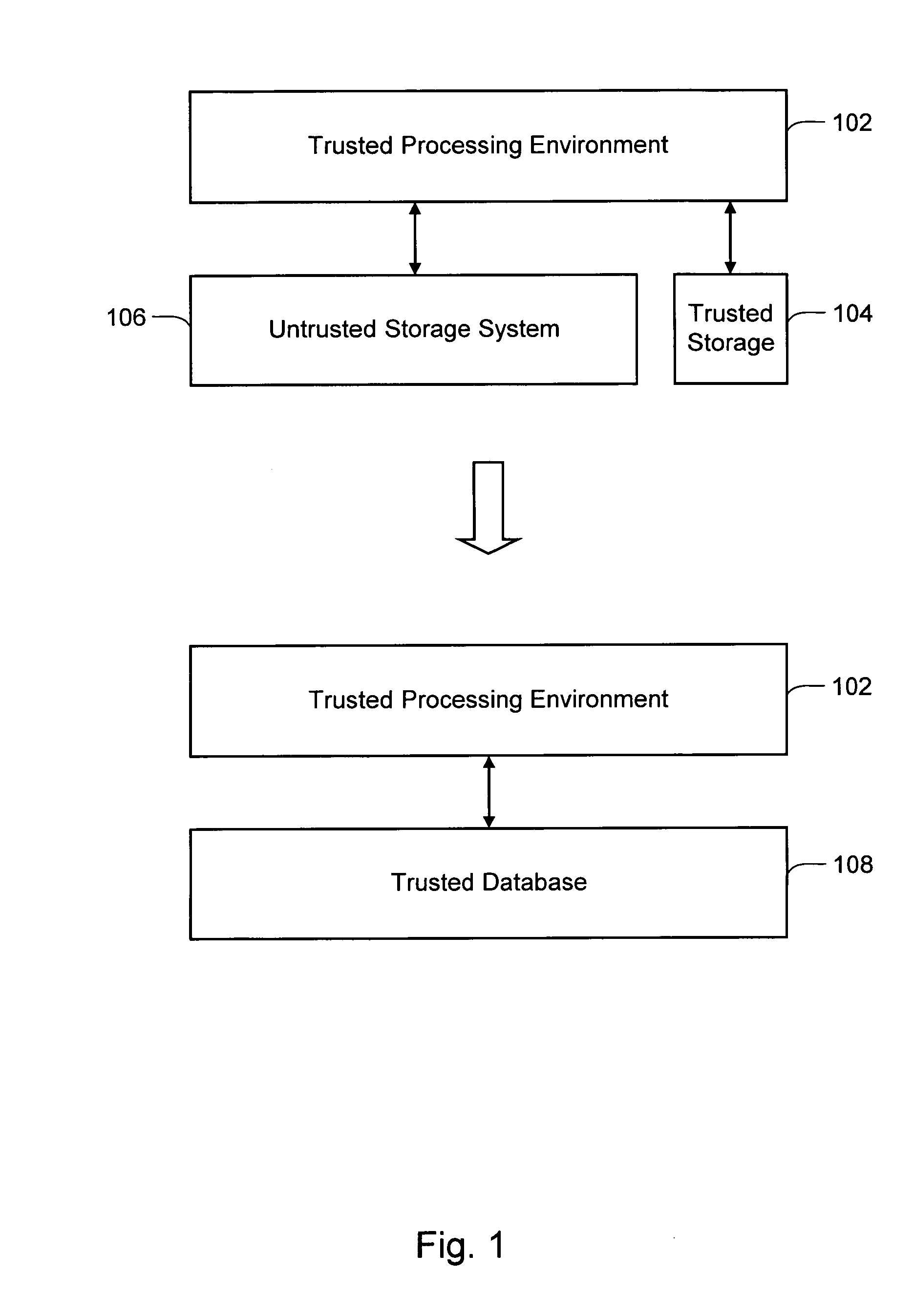
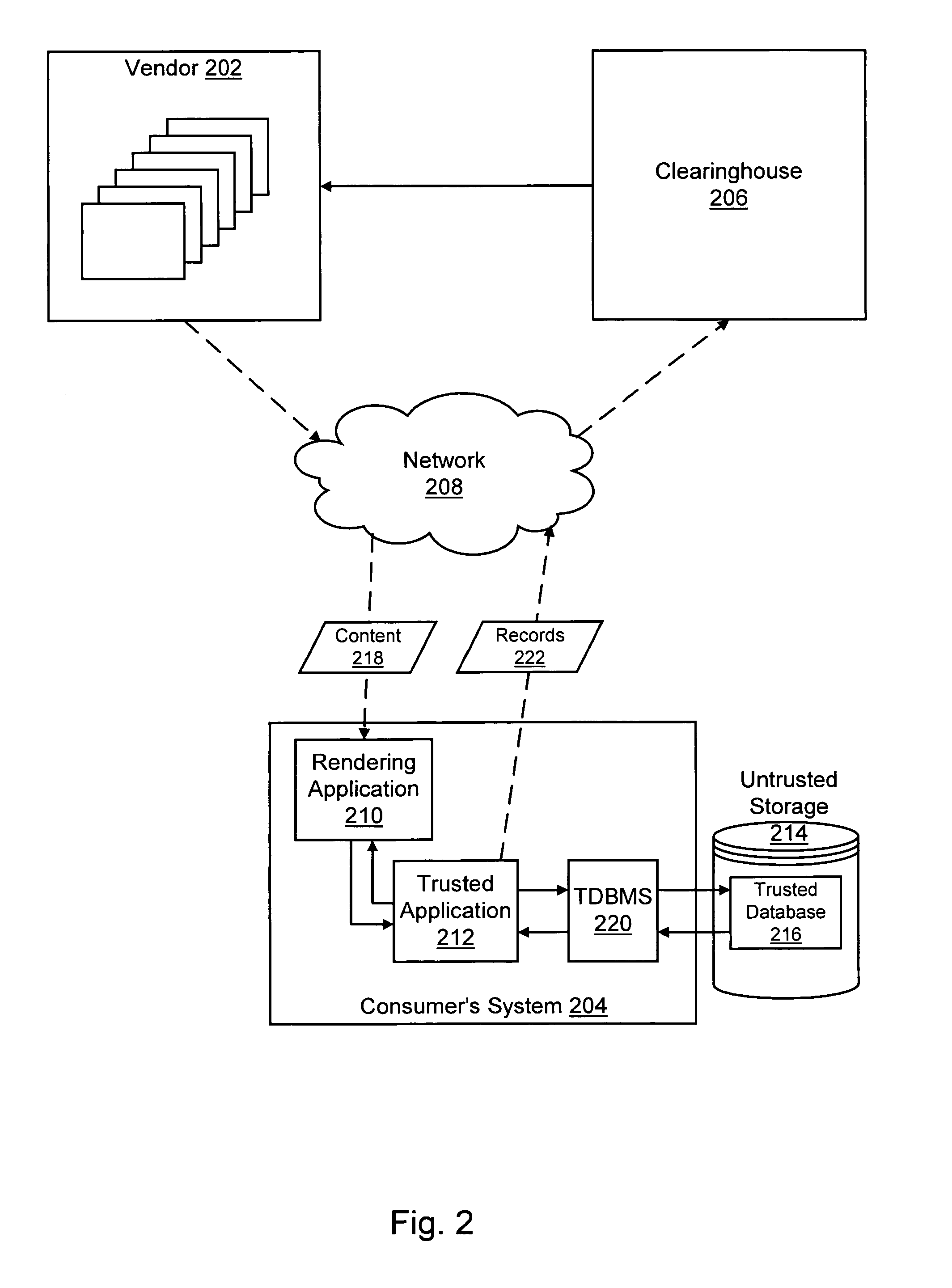
Trusted storage systems and methods
InactiveUS7152165B1Reduces predictabilityEasy to implementDigital data processing detailsUser identity/authority verificationData validationSource Data Verification
Systems and methods are disclosed for providing a trusted database system that leverages a small amount of trusted storage to secure a larger amount of untrusted storage. Data are encrypted and validated to prevent unauthorized modification or access. Encryption and hashing are integrated with a low-level data model in which data and meta-data are secured uniformly. Synergies between data validation and log-structured storage are exploited.
Owner:INTERTRUST TECH CORP
Medication management system
ActiveUS20080133265A1Improve accuracyLabor-intensive taskData processing applicationsDrug and medicationsData validationManagement unit
A medication management system (MMS) includes a medication management unit (MMU) associated with a medical device. The MMU downloads a medication order to the medical device only if information from a first input matches information from a second input. The medical device receives delivery information only from the MMU. The medication order is performed only after delivery data validation. The MMU also determines drug-drug incompatibility. The MMU can modulate (start, stop, and dynamically adjust) medication order performance. The medical device wirelessly receives a patient ID to automatically associate with the patient. During delivery, the medical device caches an updated drug library to replace an existing one. The medical device displays a patient picture for validation. The MMU evaluates the performance of medical devices and caregivers based medical device feedback. The MMU adjusts the output of medical device information conveyed to a caregiver.
Owner:ICU MEDICAL INC
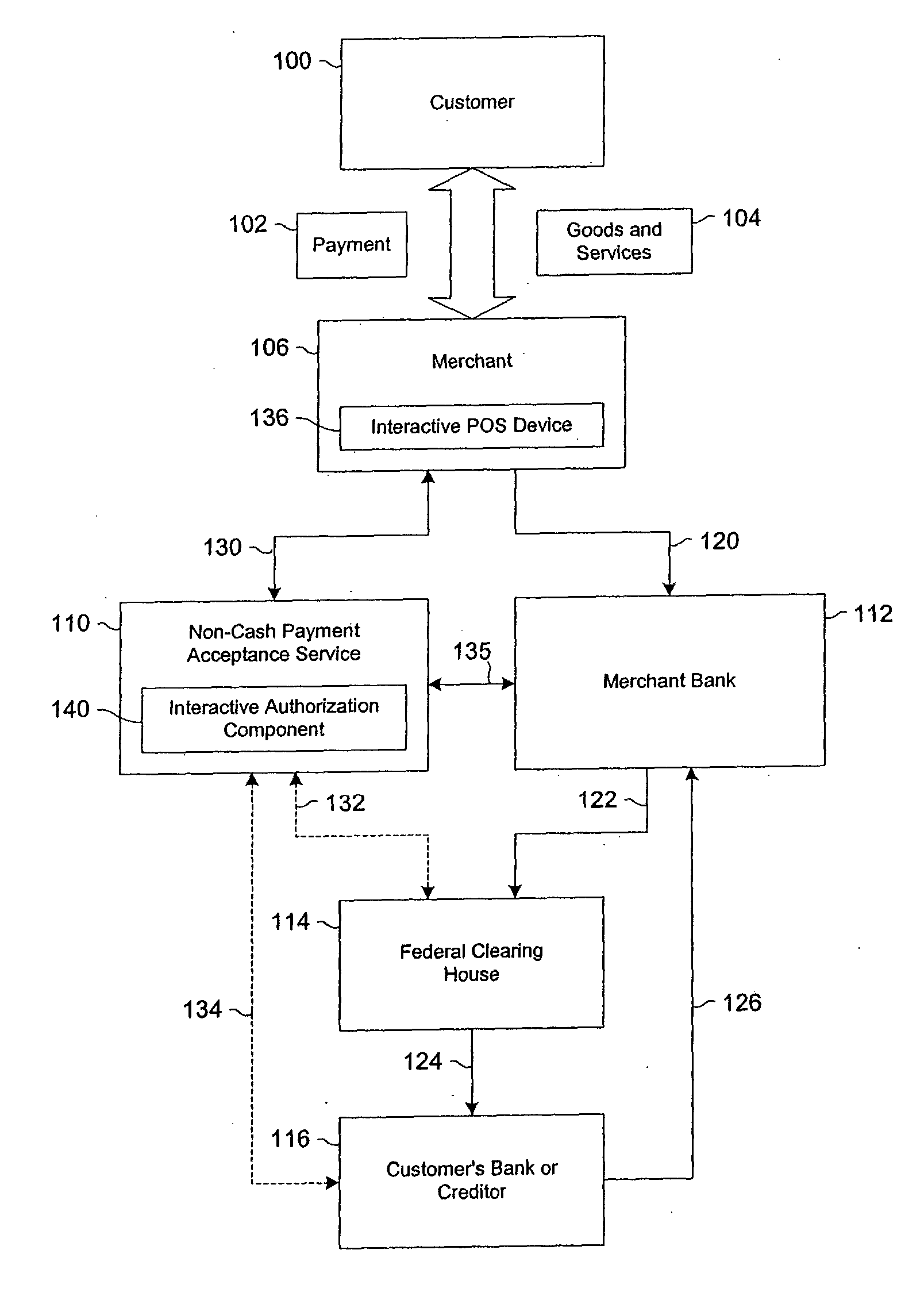
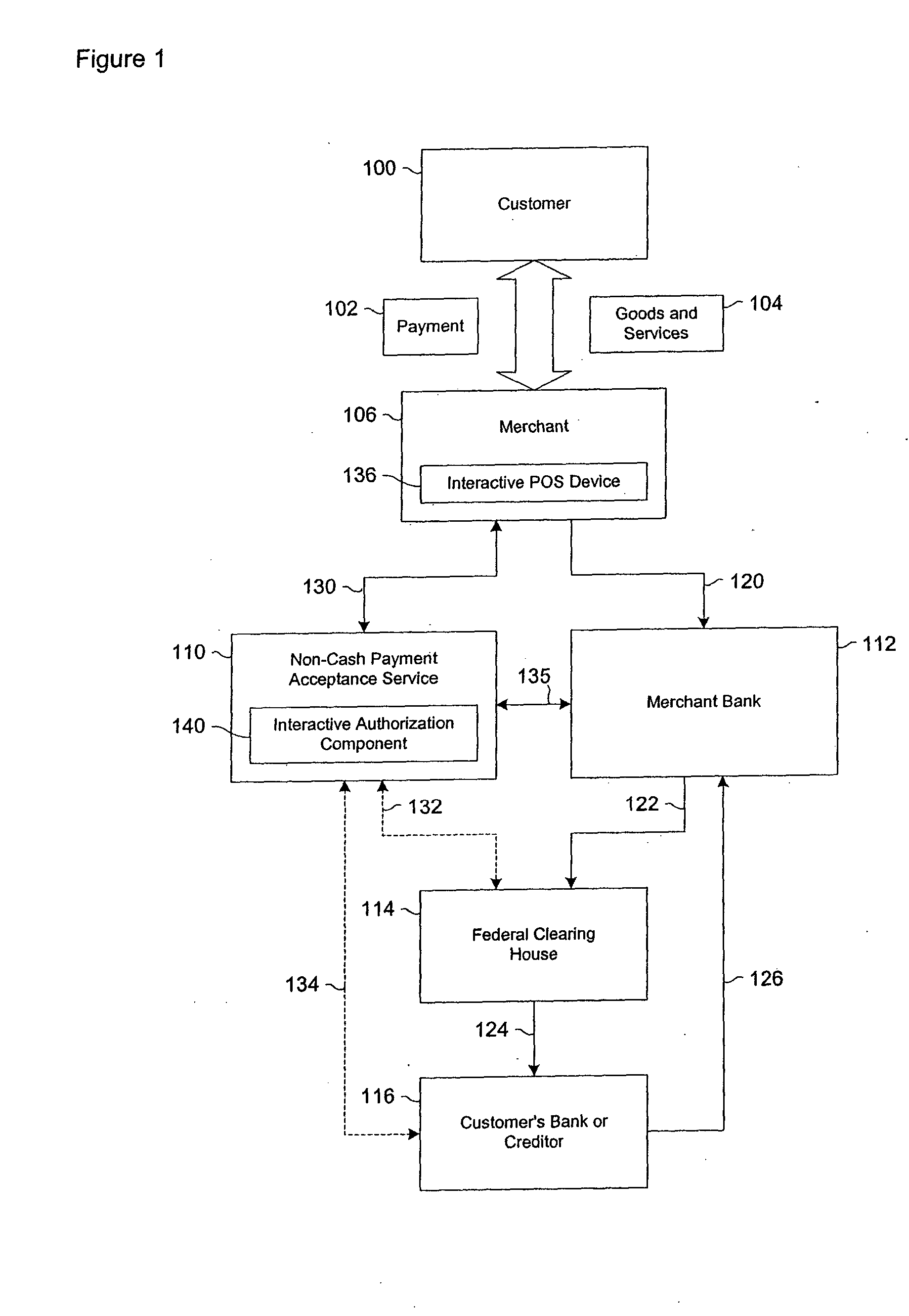
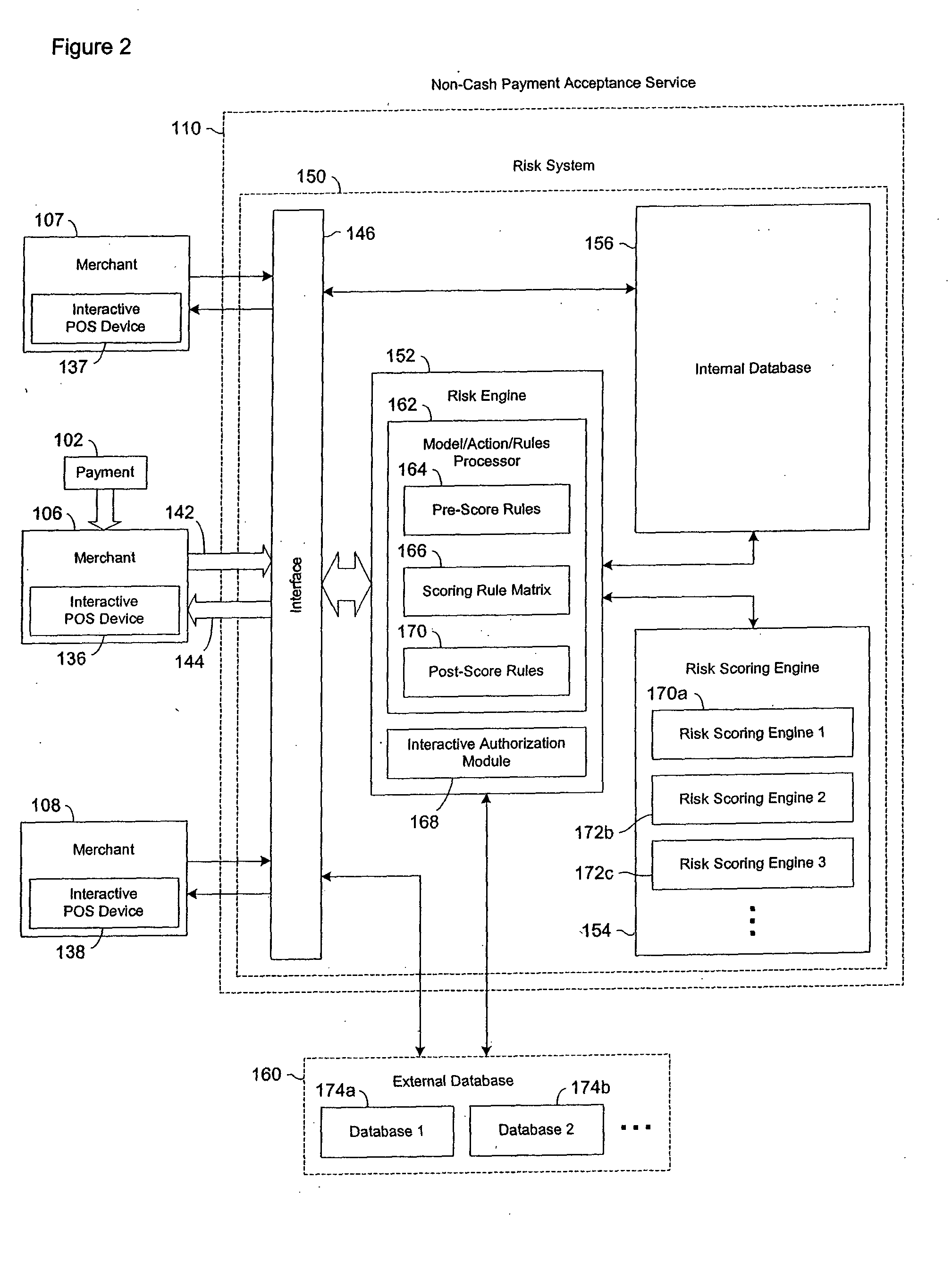
Data validation systems and methods for use in financial transactions
A risk system that performs a risk assessment of a financial transaction to obtain a risk score. Based on the risk score, the risk system may request additional transaction information from a customer and / or a merchant. The request is based at least in part on financial transactions that are of moderate risk to thereby provide a non-cash payment acceptance service with more information to further evaluate the financial transaction risks. Thus, moderately risky financial transactions, that are likely to benefit the non-cash payment acceptance service and the merchant that subscribes to the non-cash payment acceptance service, are authorized for increased profitability and customer satisfaction. Furthermore, the risk system may approve or authorize financial transactions that generally fail standard risk assessments that use a cut-off risk score to divide the financial transactions into either approved or declined groups. As a result, the risk system is capable of re-evaluating some of the moderate risk cases for the purpose of securing beneficial financial transactions.
Owner:FIRST DATA
Medication management system
InactiveUS20050278194A1Improve accuracyLabor-intensive taskElectrotherapyLocal control/monitoringData validationCaregiver person
A medication management system (MMS) includes a medication management unit (MMU) associated with a medical device. The MMU downloads a medication order to the medical device only if information from a first input matches information from a second input. The medical device receives delivery information only from the MMU. The medication order is performed only after delivery data validation. The MMU also determines drug-drug incompatibility. The MMU can modulate (start, stop, and dynamically adjust) medication order performance. The medical device wirelessly receives a patient ID to automatically associate with the patient. During delivery, the medical device caches an updated drug library to replace an existing one. The medical device displays a patient picture for validation. The MMU evaluates the performance of medical devices and caregivers based medical device feedback. The MMU adjusts the output of medical device information conveyed to a caregiver.
Owner:ICU MEDICAL INC
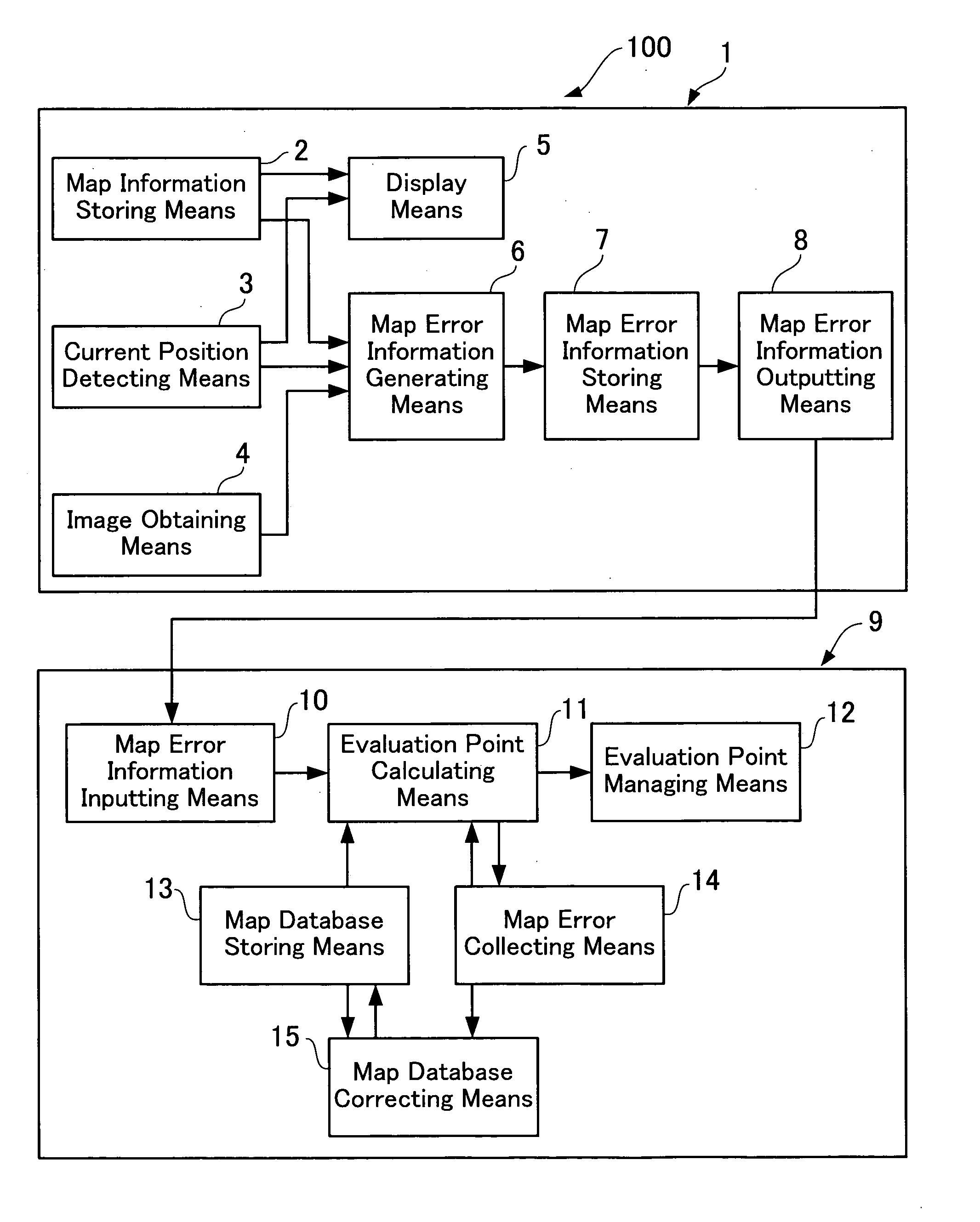
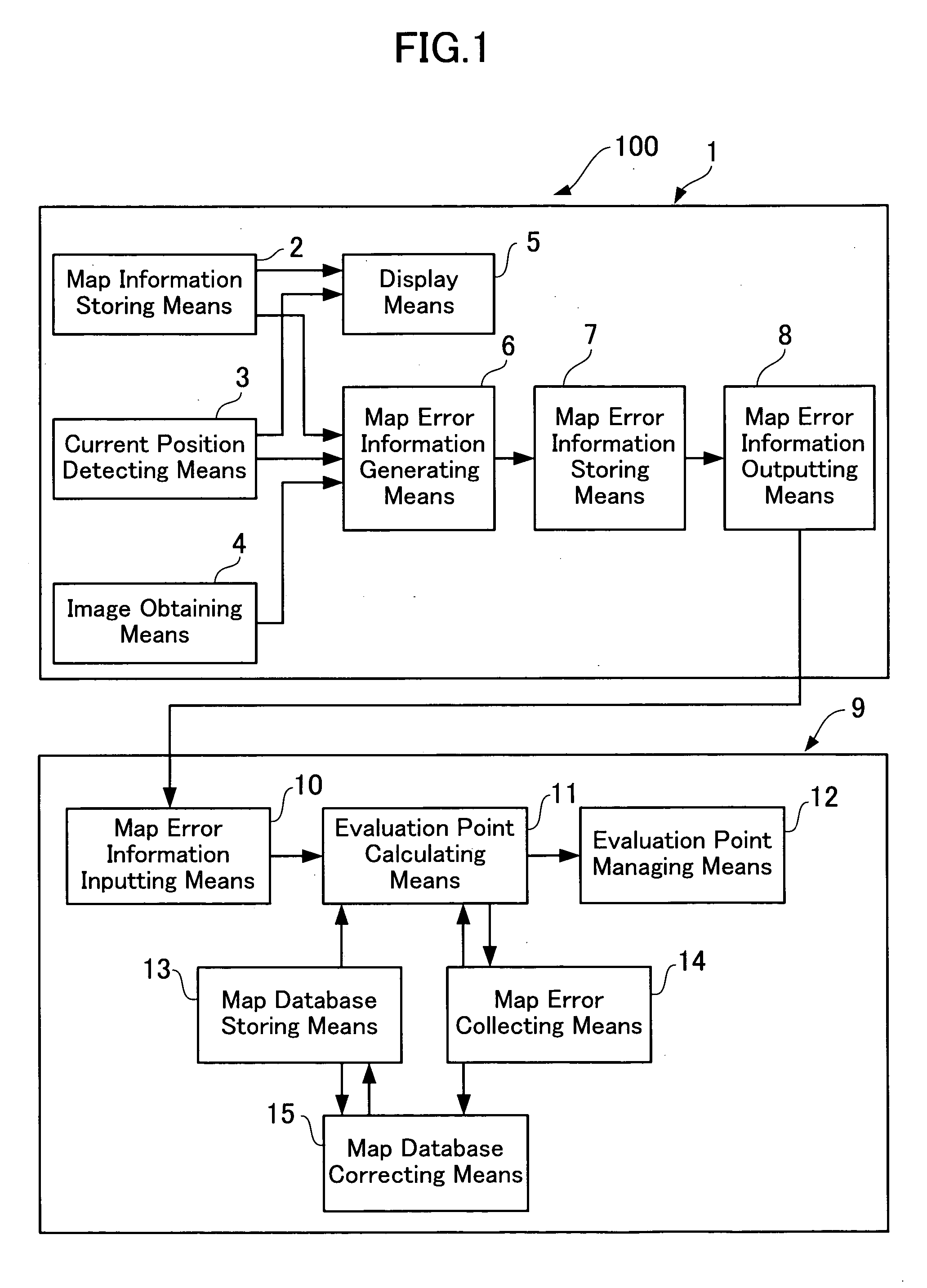
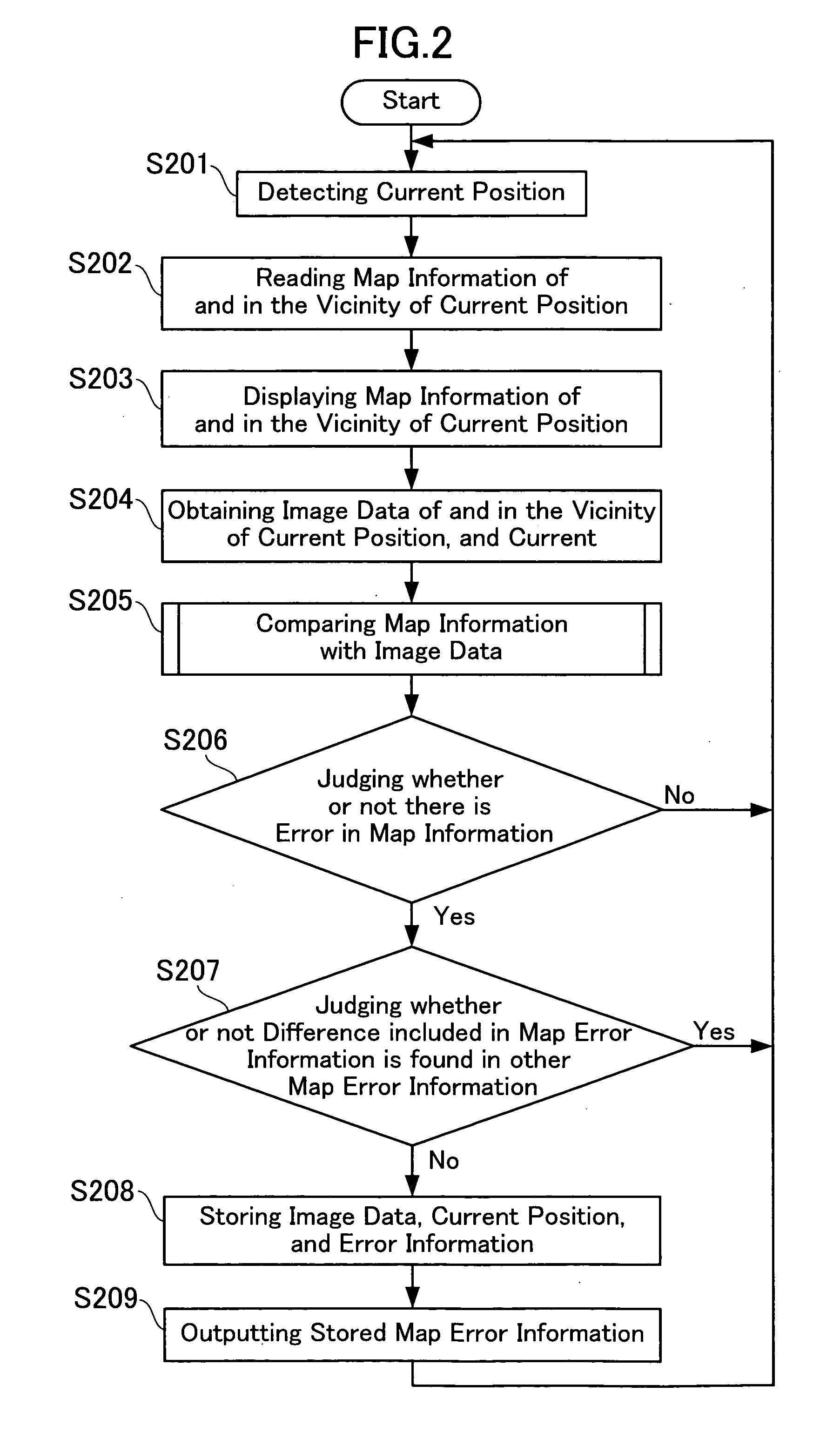
Map error information obtaining system and map error information obtaining method
ActiveUS20050283699A1Easy to collectInstruments for road network navigationError preventionData validationLocation detection
The present invention provides a map error information obtaining system which can promote the collection of the map error information as well as reduce the number of man-hours required for researching the site and verifying whether or not the collected map error information is accurate. The map error information obtaining system herein disclosed comprises a position detecting apparatus including image obtaining means for obtaining image data indicative of an actual condition of and in the vicinity of a current position, and a center apparatus, the position detecting apparatus being operative to transmit map error information including a position of the map information and image data where it is judged that there is a difference, to the center apparatus. The center apparatus is operative to correct the map information after verifying whether or not the difference in the map information is accurate using the image data. Furthermore, the center apparatus is operative to calculate an evaluation point for each of the position detecting apparatuses which have transmitted the map error information so that operators operating the position detecting apparatuses can be rewarded in accordance with their evaluation points.
Owner:PANASONIC CORP
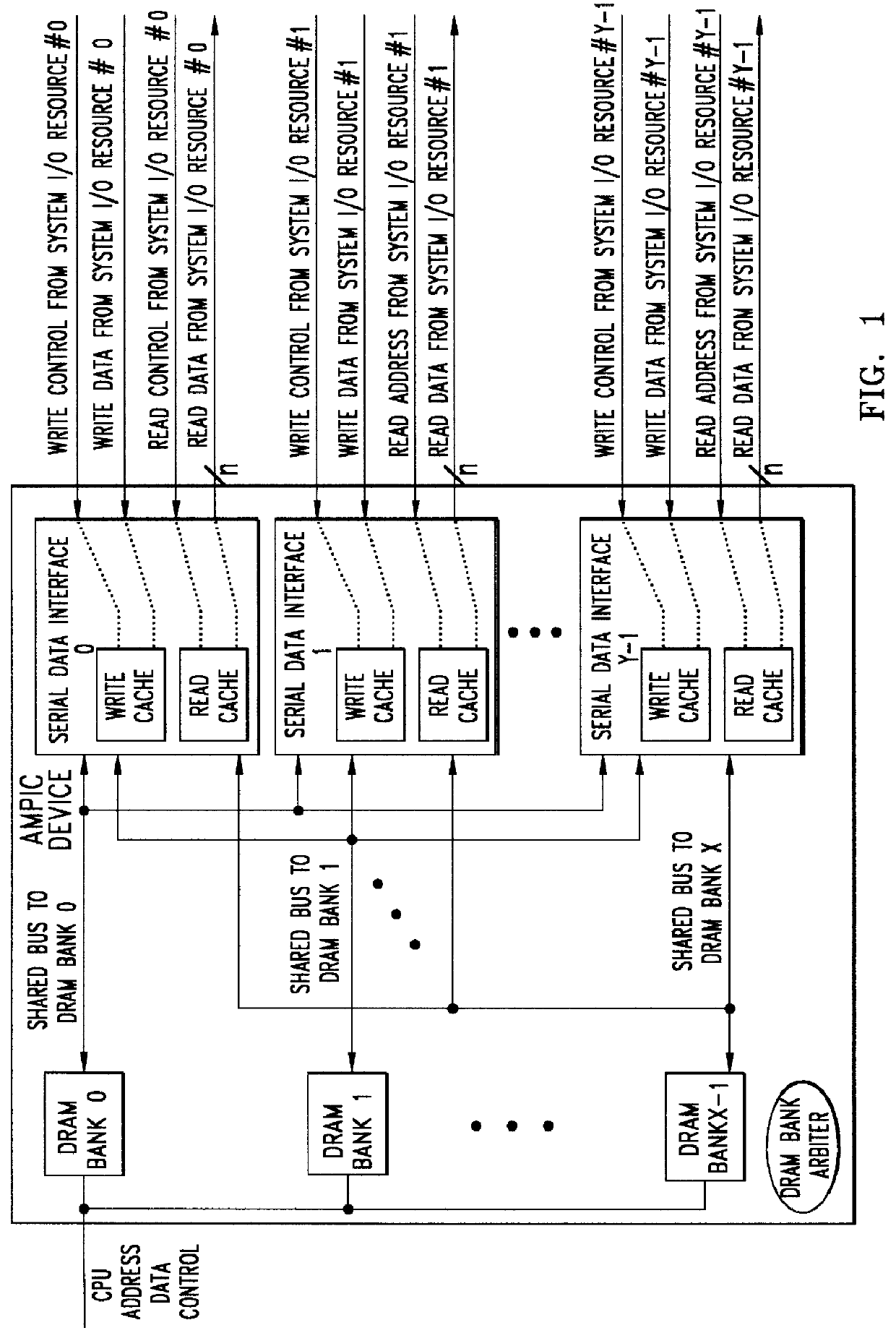
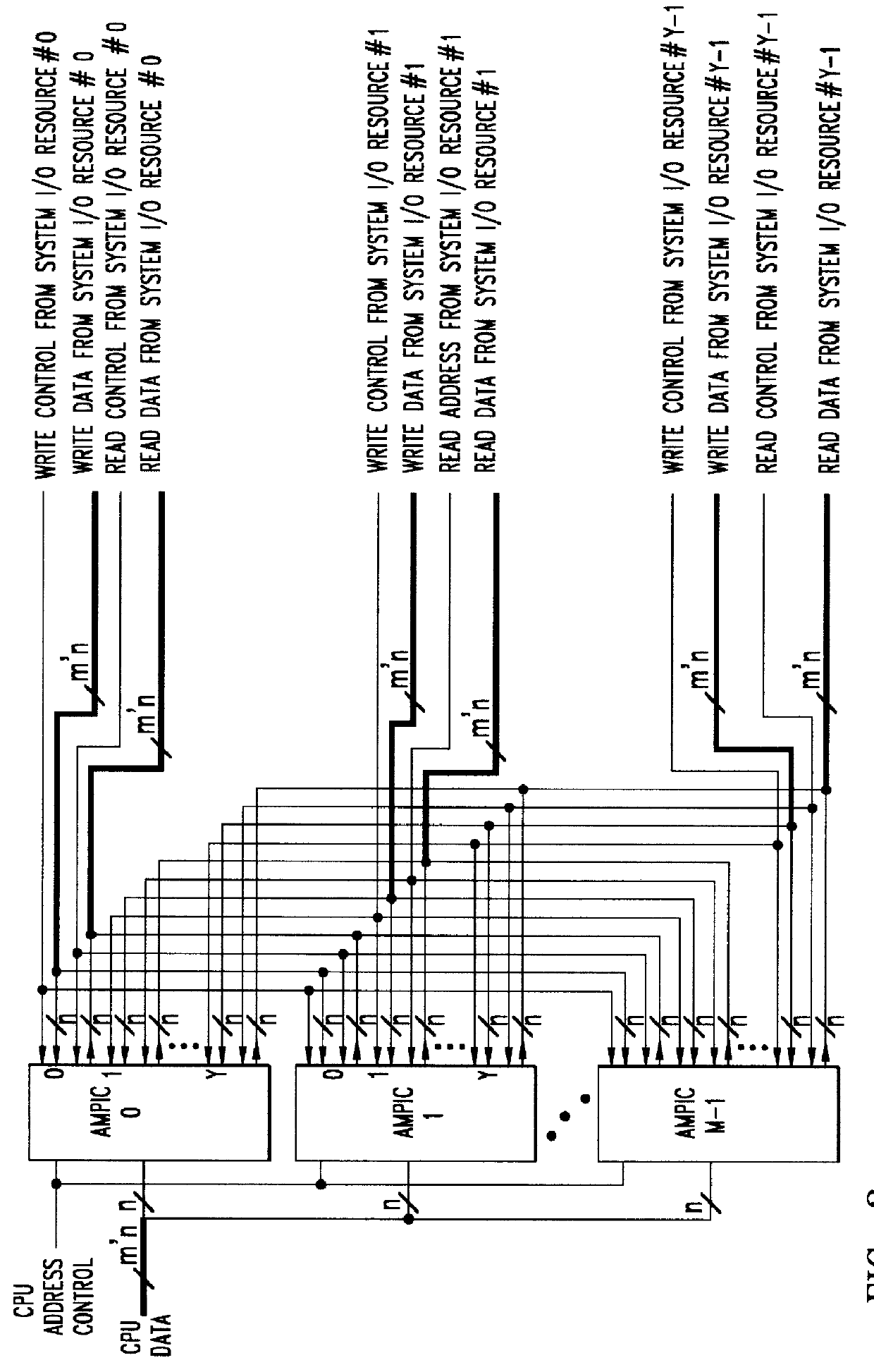
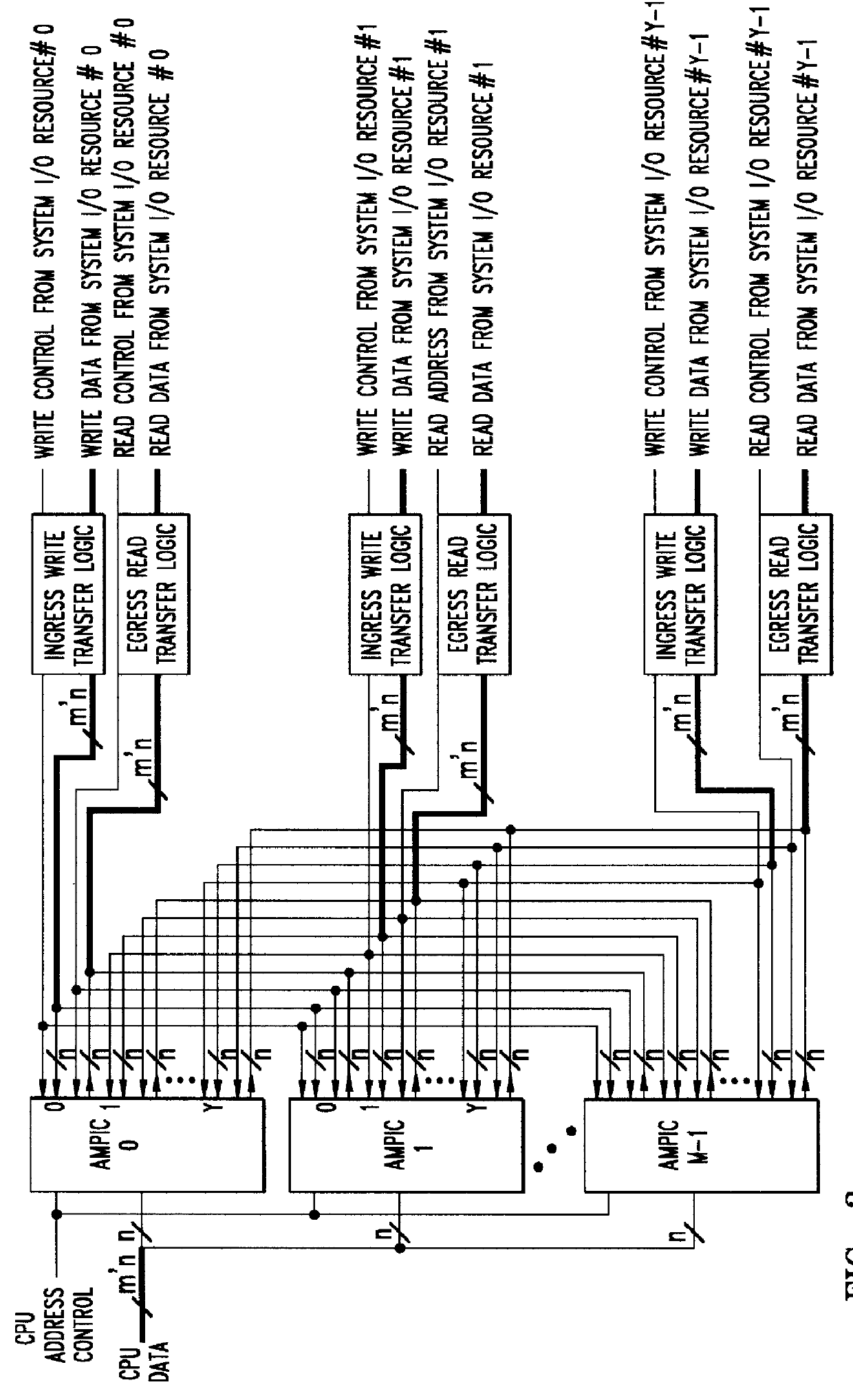
Method of and apparatus for validating data read out of a multi port internally cached dynamic random access memory (AMPIC DRAM)
InactiveUS6085290AEliminates race conditionMemory architecture accessing/allocationMemory adressing/allocation/relocationData validationStatic random-access memory
An apparatus for and method of enhancing the performance of a multi-port internal cached DRAM (AMPIC DRAM) by providing an internal method of data validation within the AMPIC memories themselves to guarantee that only valid requested data is returned from them, or properly marked invalid data. A modified technique for identifying bad data that has been read out of AMPIC memory devices in the system.
Owner:NEXABIT NETWORKS +1
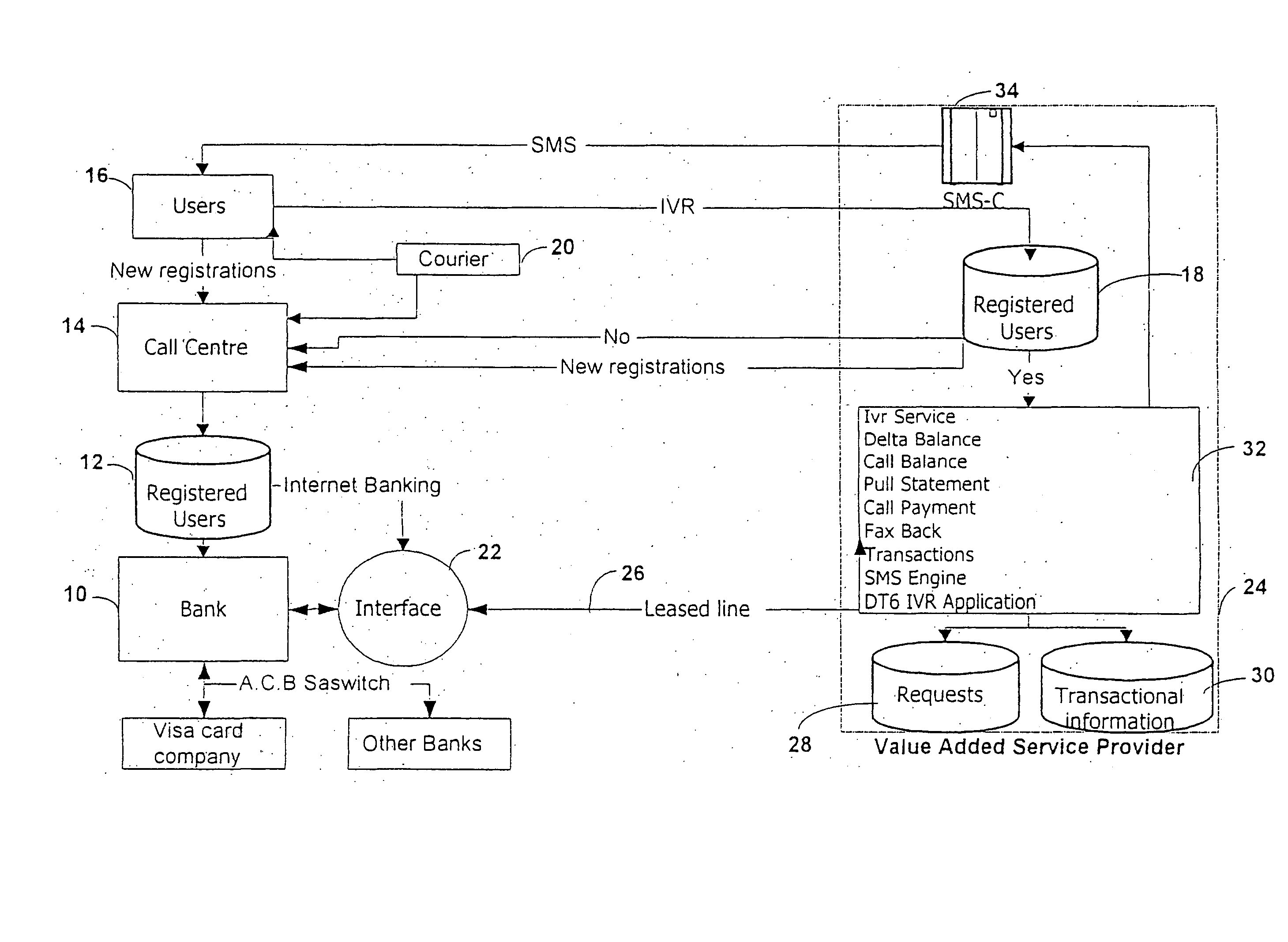
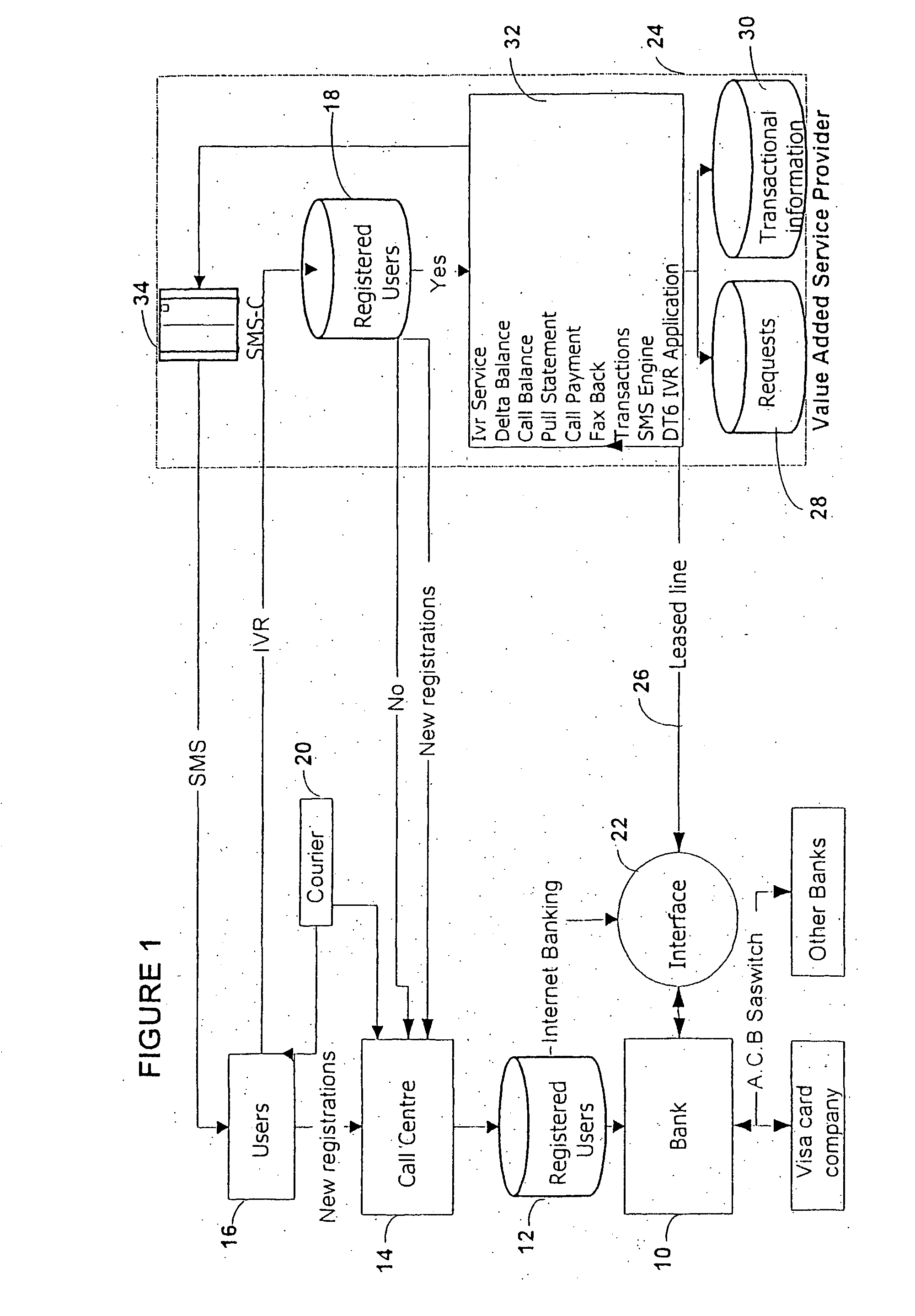
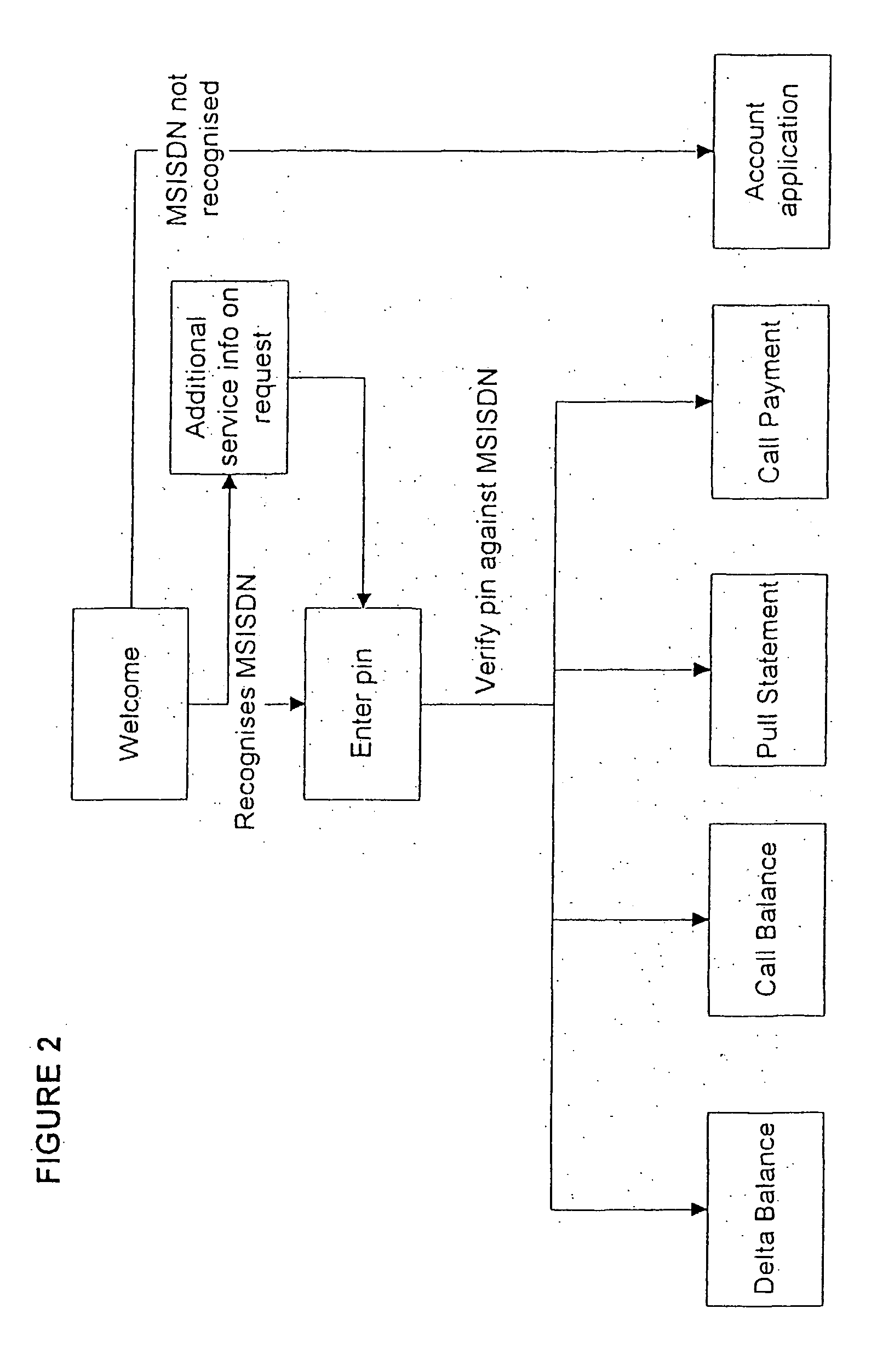
Method and system for operating a banking service
A method and system for operating a banking service are included. The system includes a database (12) for storing client registration data and a unique number, which is preferably the MSISDN or mobile telephone number of the client. This number is used as the client's account number. A call center (14) receives calls from clients and verifies their identity from data transmitted by their mobile telephones. The system allows clients to conduct various banking transactions including balance, statement and payment transactions. A database stores details of balances and / or transactions in each user's account. The system serves for clients to be notified by an SMS transmitted to their mobile telephone of transactions, such as changes to their bank balances or the crediting or debiting of their account. The system can also interface with conventional banking services.
Owner:VIIJOEN NIEL EBEN
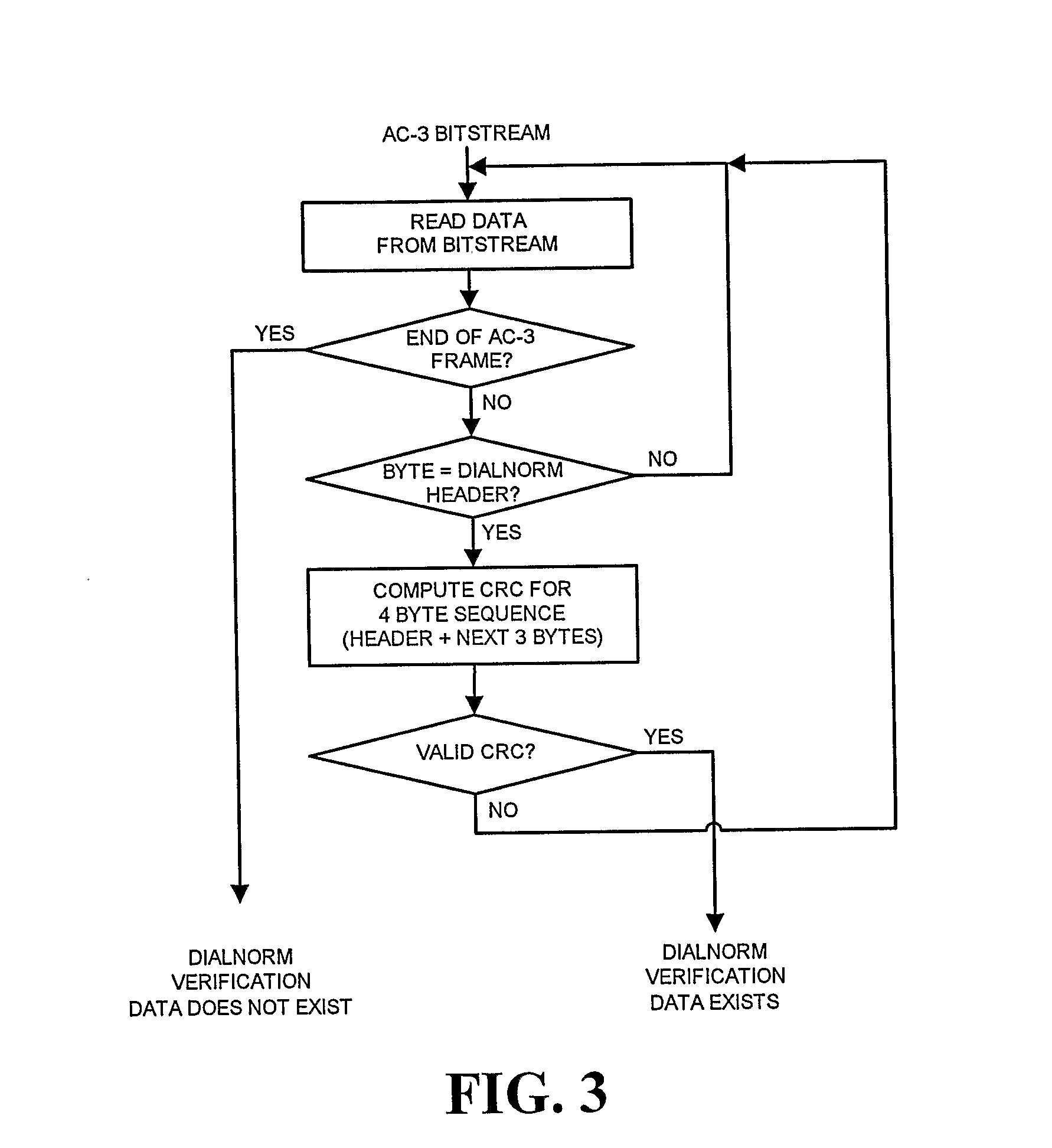
Audio Metadata Verification
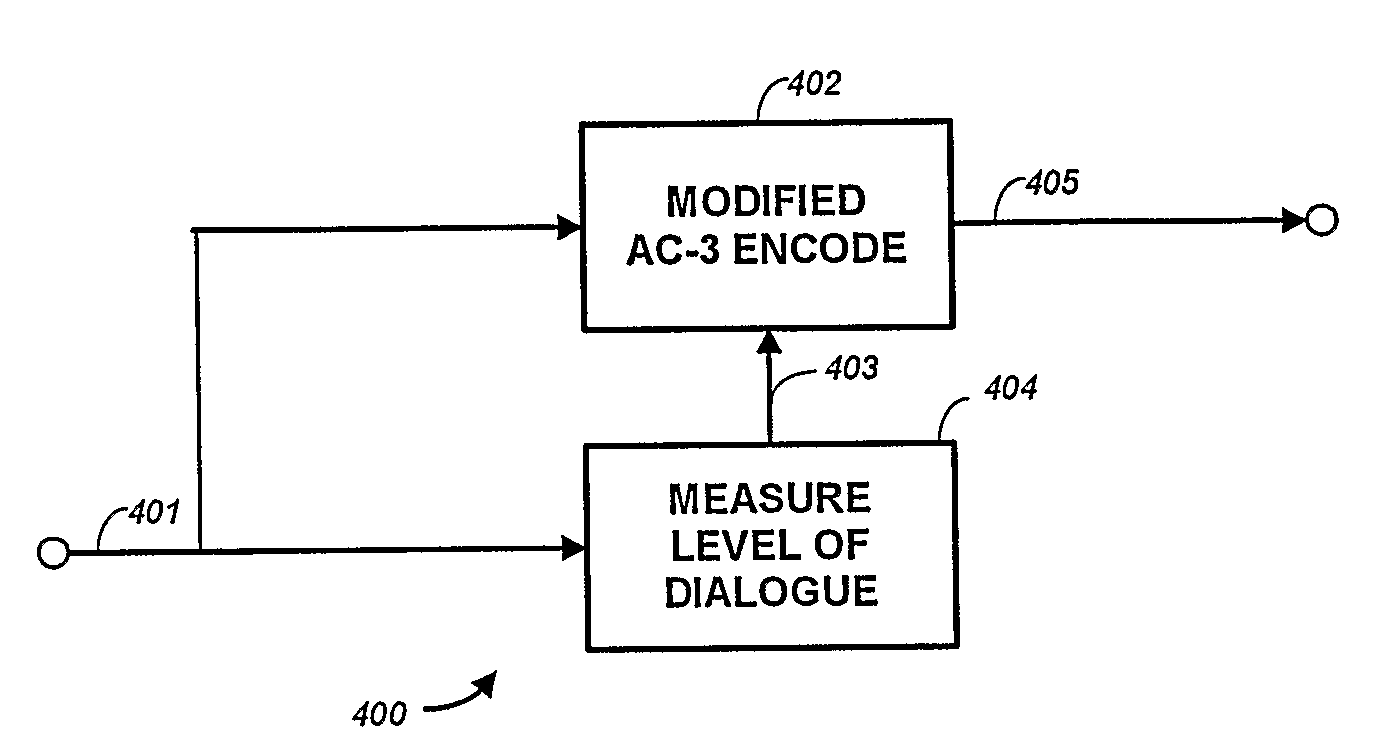
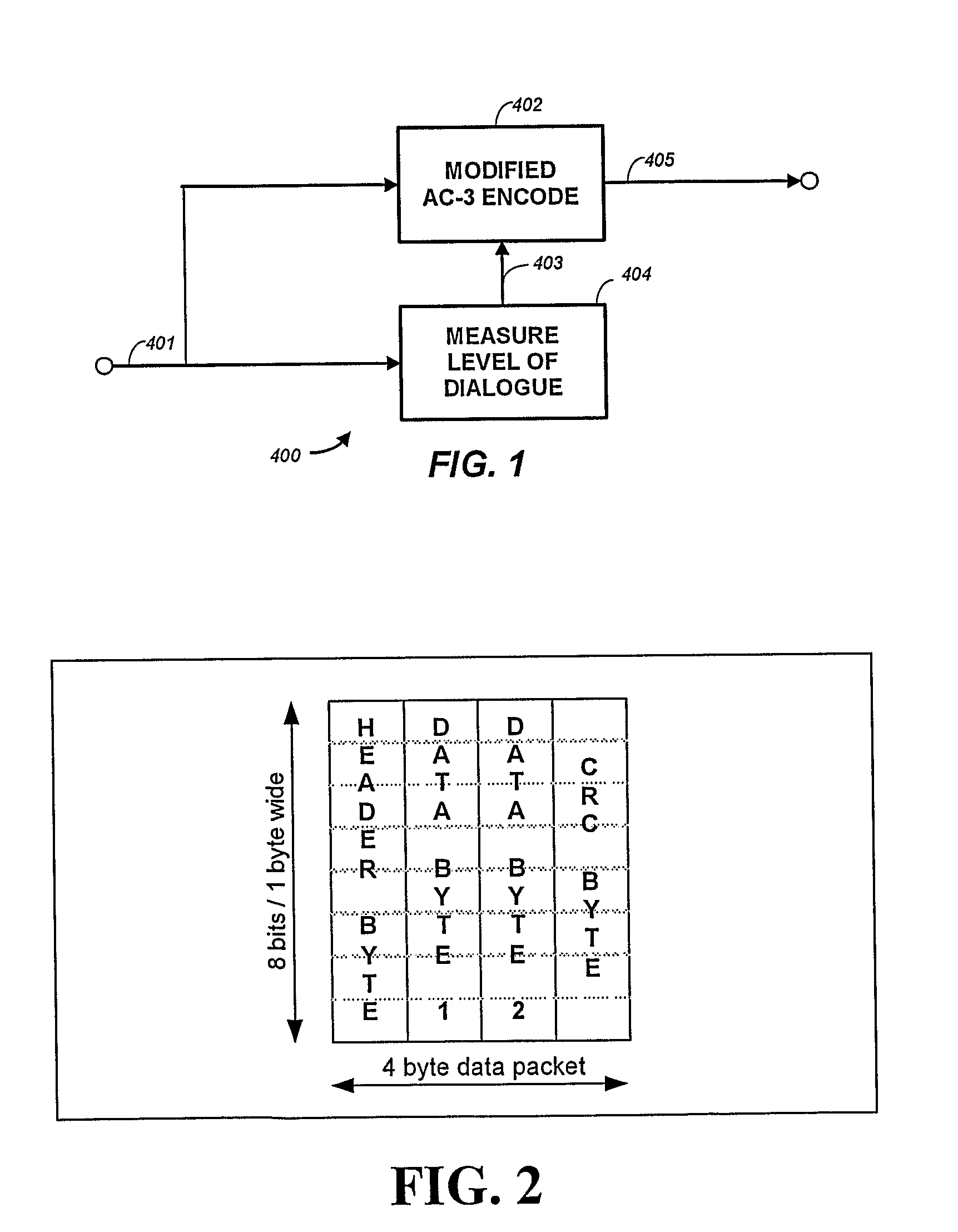
InactiveUS20090063159A1Preserve backward compatibilityData bit may become shortenedElectronic editing digitised analogue information signalsSpeech analysisData validationData compression
A digital bitstream, comprising data bits representing audio, metadata intended to be correct for the audio, and metadata verification information, wherein all or part of the metadata may not be correct for the audio. The metadata verification information is usable to detect whether or not metadata is correct for the audio and, if not correct, to change it so that it is correct. The metadata verification information usable to detect and change metadata may include a copy, or a data-compressed copy, of a correct version of the metadata.
Owner:DOLBY LAB LICENSING CORP
Method and apparatus and program storage device including an integrated well planning workflow control system with process dependencies
A method of well planning in an automatic well planning system comprises the steps of: selecting one or more tasks in a task manager; verifying by a task dependency a proper order of the one or more tasks; retrieving by the task manager from a task base one or more sets of instructions associated with the one or more tasks selected in the task manager and verified by the task dependency; retrieving by the task manager from an access manager one or more sets of input data associated with the one or more sets of instructions retrieved by the task manager from the task base; verifying that each set of input data of the one or more sets of input data retrieved by the task manager from the access manager is received by a corresponding one of the one or more sets of instructions retrieved by the task manager from the task base; executing, by the task manager, the one or more sets of instructions and using, by the task manager, the one or more sets of input data during the executing step thereby generating a set of results; and recording or displaying, by a task view base, the set of results on a recorder or display device.
Owner:SCHLUMBERGER TECH CORP
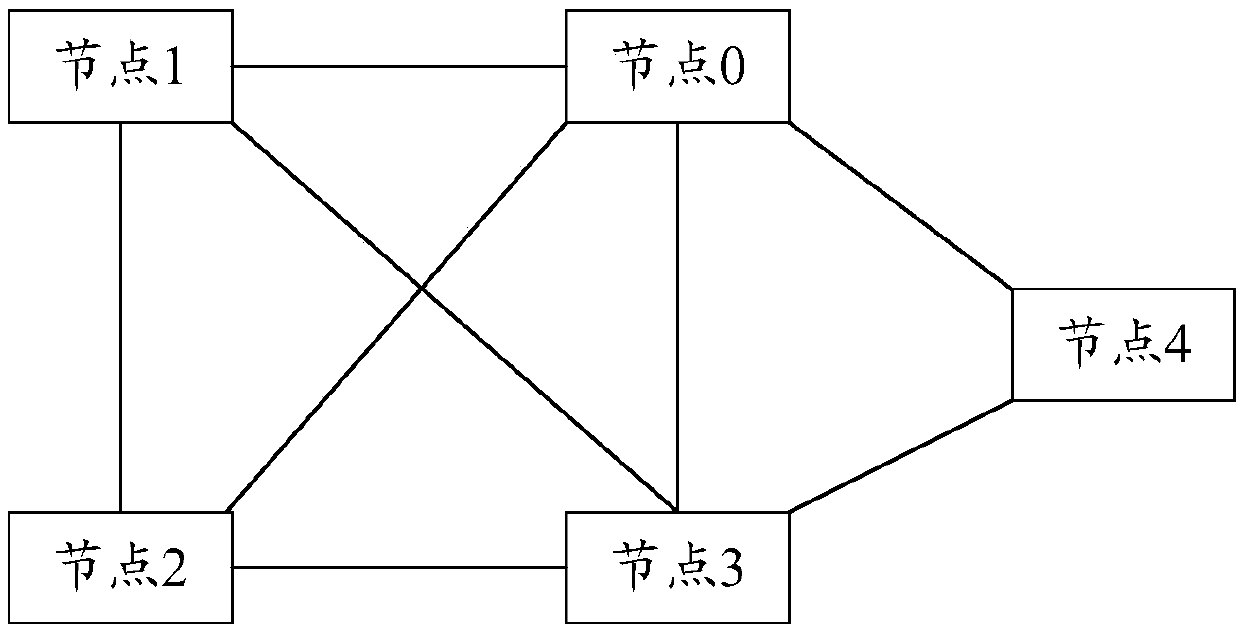
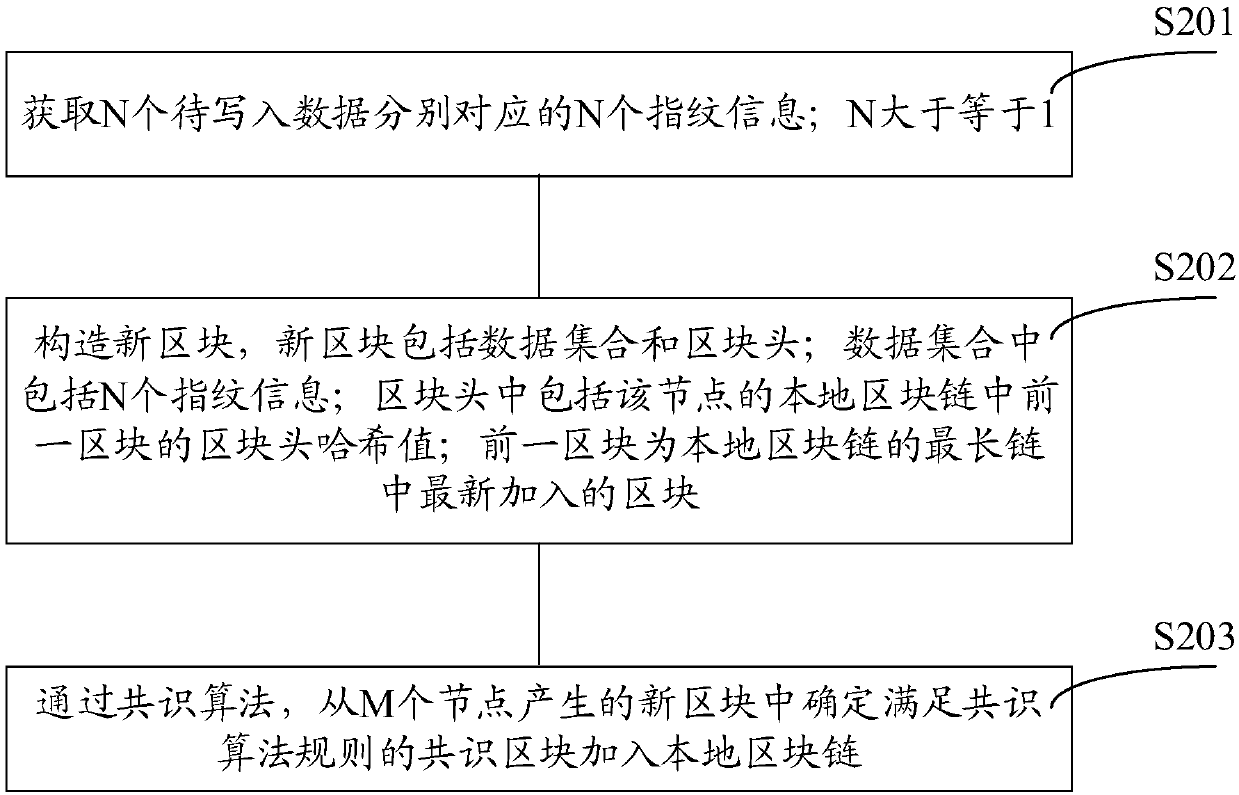
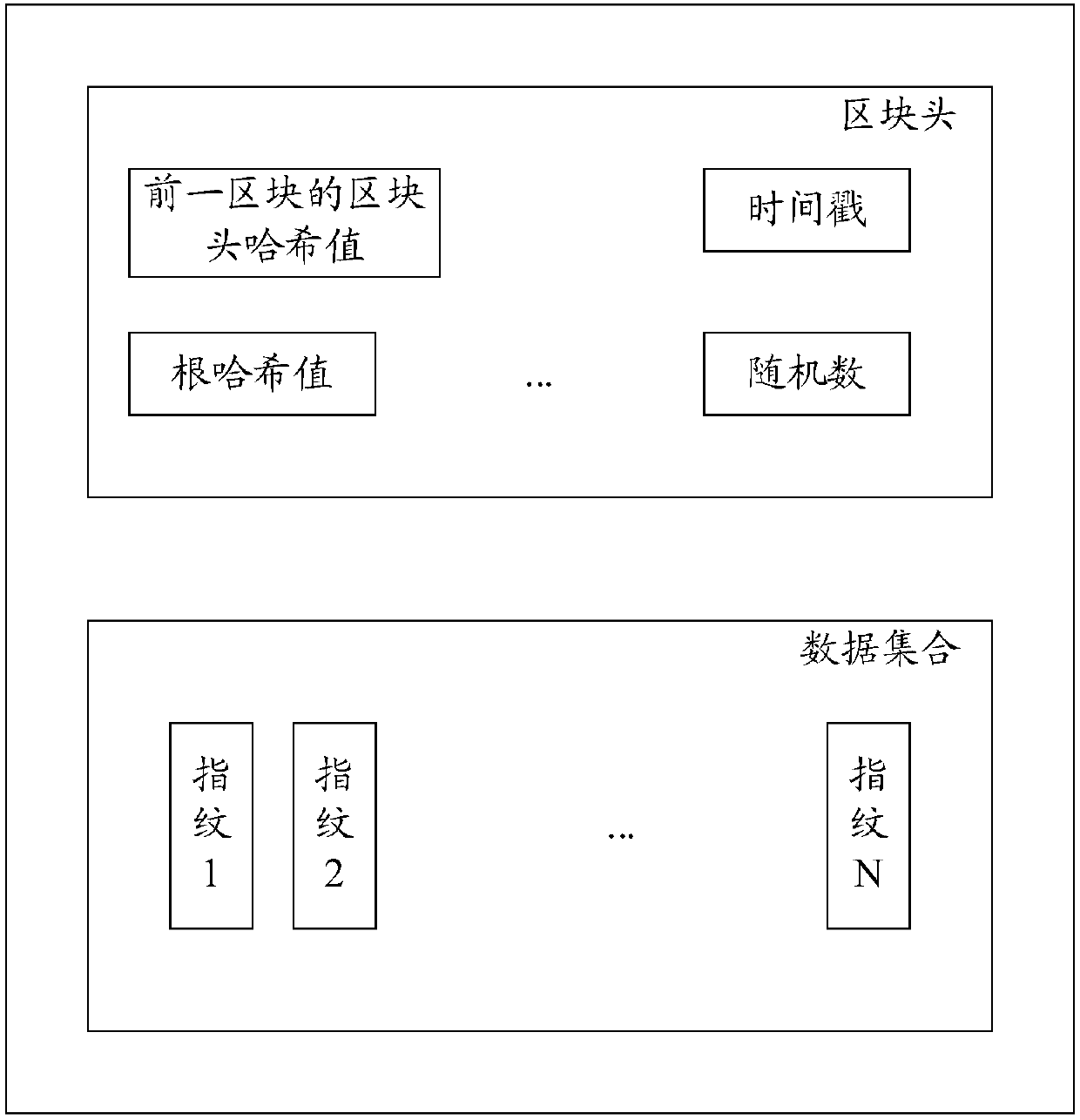
Block chain generation method, data verification method, nodes and system
ActiveCN107807951AReduce occupancyIncrease profitUser identity/authority verificationDigital data protectionData validationData set
The invention discloses a block chain generation method, a data verification method, nodes and a system. The block chain generation method is used for increasing the utilization rate of a storage space and is applied to a block chain system containing M nodes. According to each of the M nodes, the block chain generation method comprises the steps that N pieces of fingerprint information corresponding to N pieces of to-be-written data are acquired, wherein N is greater than or equal to 1; a new block is constructed, wherein the new block comprises a data set and a block head; the data set comprises N pieces of fingerprint information; the block head comprises a Hash value of a block head of a previous block in a local block chain of the node, wherein the previous block is a newly added block in a longest chain of the local block chain; and through a consensus algorithm, a consensus block is determined from new blocks generated by M nodes and is added into the local block chain. In thisway, the storage space occupied by other information of non-to-be-written data in transaction information is saved, and therefore the utilization rate of the storage space and is increased.
Owner:UNION MOBILE PAY
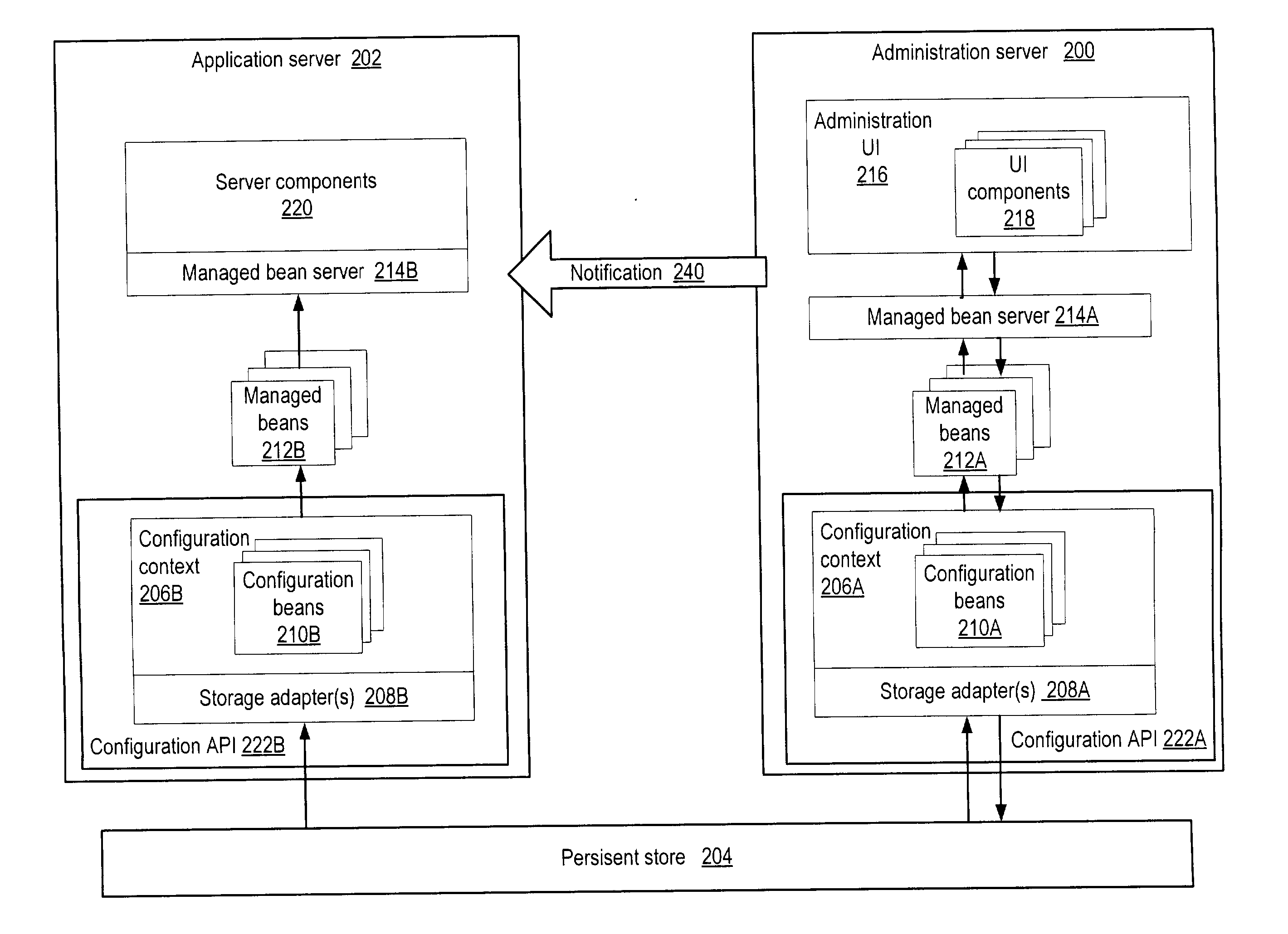
Pluggable semantic verification and validation of configuration data
ActiveUS20040019670A1Digital computer detailsData switching networksData validationSource Data Verification
A pluggable semantic verification and syntactic validation mechanism for server configuration information. In one embodiment, the data verification and validation mechanism may be implemented as modules that may be plugged into a framework. In one embodiment, the mechanism may include a generic test case framework that may call test cases to verify and validate changes to configuration information. In one embodiment, each test case may implement an interface through which the framework calls a test case. The test case may return results, e.g. whether the test passed or failed, and may return additional information, e.g. why the test failed. If the change is valid, then the change may be made to the configuration information. If the change is not valid, the change is not made or alternatively is made with a warning. If the change is made, one or more other servers may be notified of the change.
Owner:ORACLE INT CORP
Medication management system
InactiveUS20060089855A1Improve accuracyLabor-intensive taskLocal control/monitoringDrug and medicationsData validationCaregiver person
A medication management system (MMS) includes a medication management unit (MMU) associated with a medical device. The MMU downloads a medication order to the medical device only if information from a first input matches information from a second input. The medical device receives delivery information only from the MMU. The medication order is performed only after delivery data validation. The MMU also determines drug-drug incompatibility. The MMU can modulate (start, stop, and dynamically adjust) medication order performance. The medical device wirelessly receives a patient ID to automatically associate with the patient. During delivery, the medical device caches an updated drug library to replace an existing one. The medical device displays a patient picture for validation. The MMU evaluates the performance of medical devices and caregivers based medical device feedback. The MMU adjusts the output of medical device information conveyed to a caregiver.
Owner:ICU MEDICAL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com