Patents
Literature
1626 results about "Mobile Telephone Number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The customer support phone number of Mobile is +1-877-453-1304 / 1-877-413-5903 / 1-888-537-4242 (Click phone number to call). The postal and official address, email address and phone number (helpline) of Mobile Service Center and Mobile customer service phone number is given below.
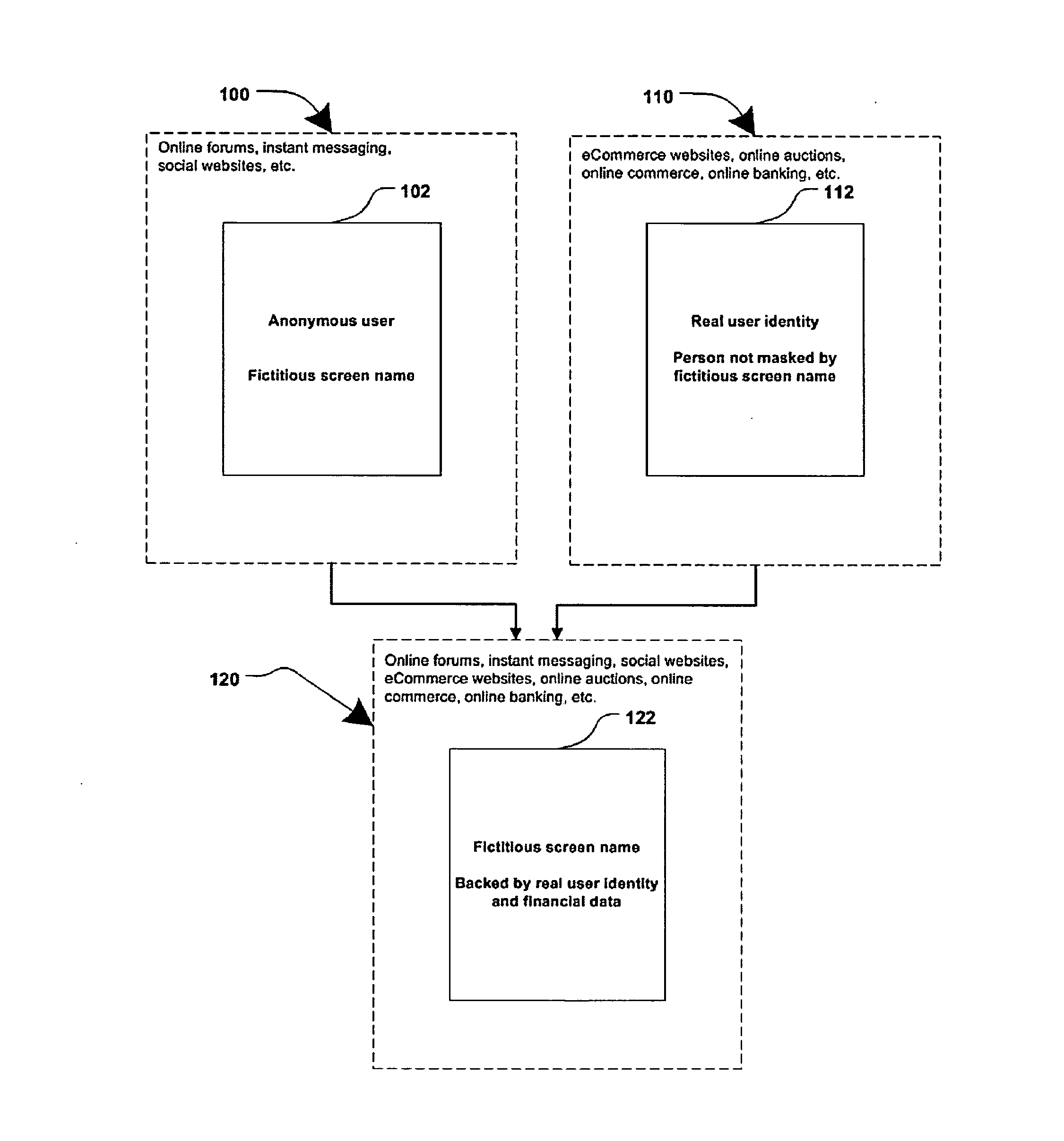
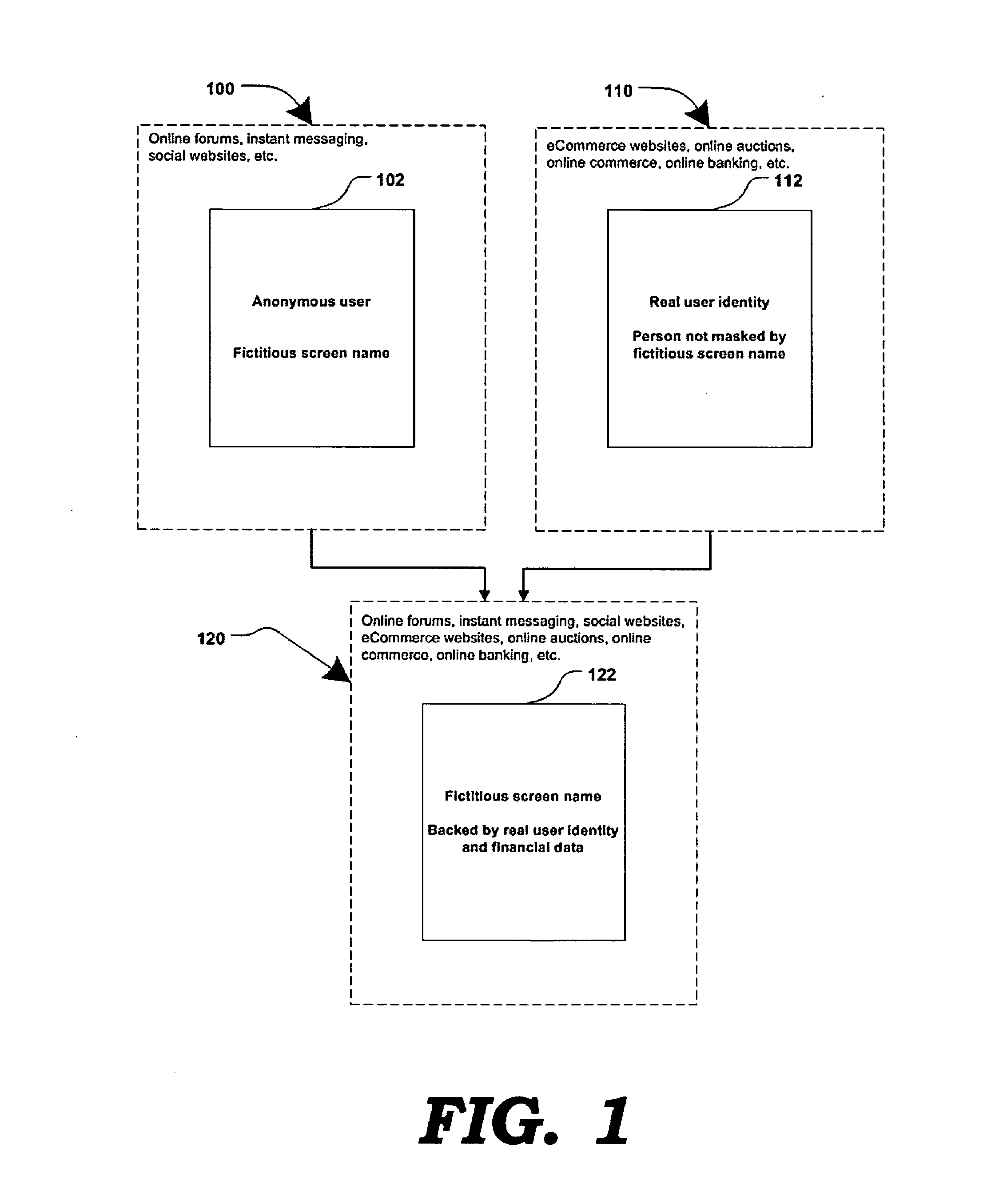
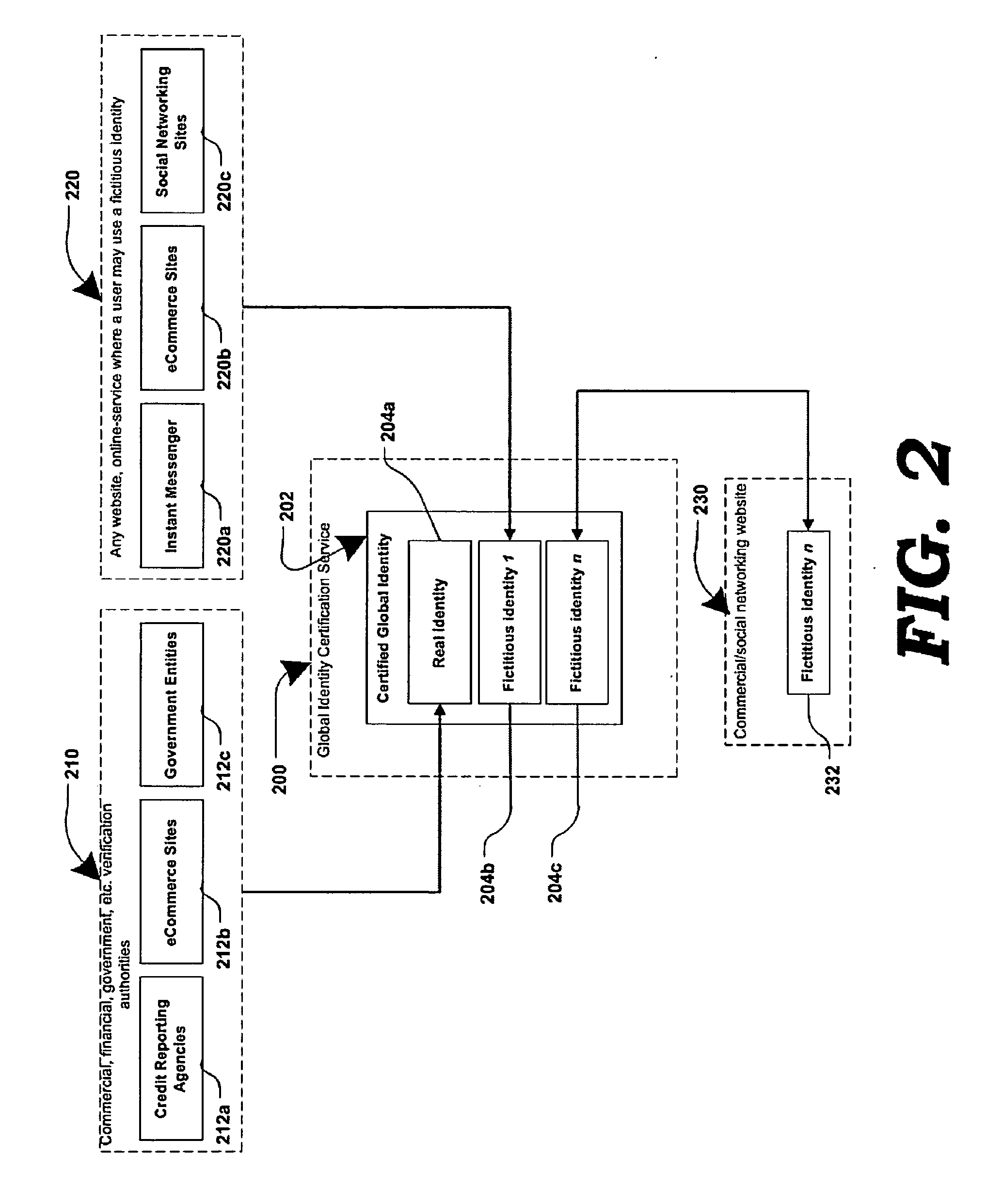
Method and systems for online advertising to users using fictitious user idetities
Various methods, systems and apparatus for associating fictitious user identities (e.g. screen names, user names, email addresses, handles, etc.) used in electronic communications (e.g. over the internet or mobile network via instant messenger, e-mail, social networks, ecommerce, auction websites, etc.) with real personal information (e.g. the true identity of an individual such as their name, address, credit score, driving record, mobile number, etc.) are disclosed. One such method may include discovering, verifying and storing real personal information, associated with fictitious user identities and email addresses. The method may further include allowing a remote user or service to submit a fictitious user identity and a query requesting real-user information associated with the submitted fictitious user identity. In one possible embodiment, a targeted-advertising service may utilize real user information, associated with a fictitious user name, to target advertisements at the user of the fictitious user name.
Owner:JAKOBSON GABRIEL +1
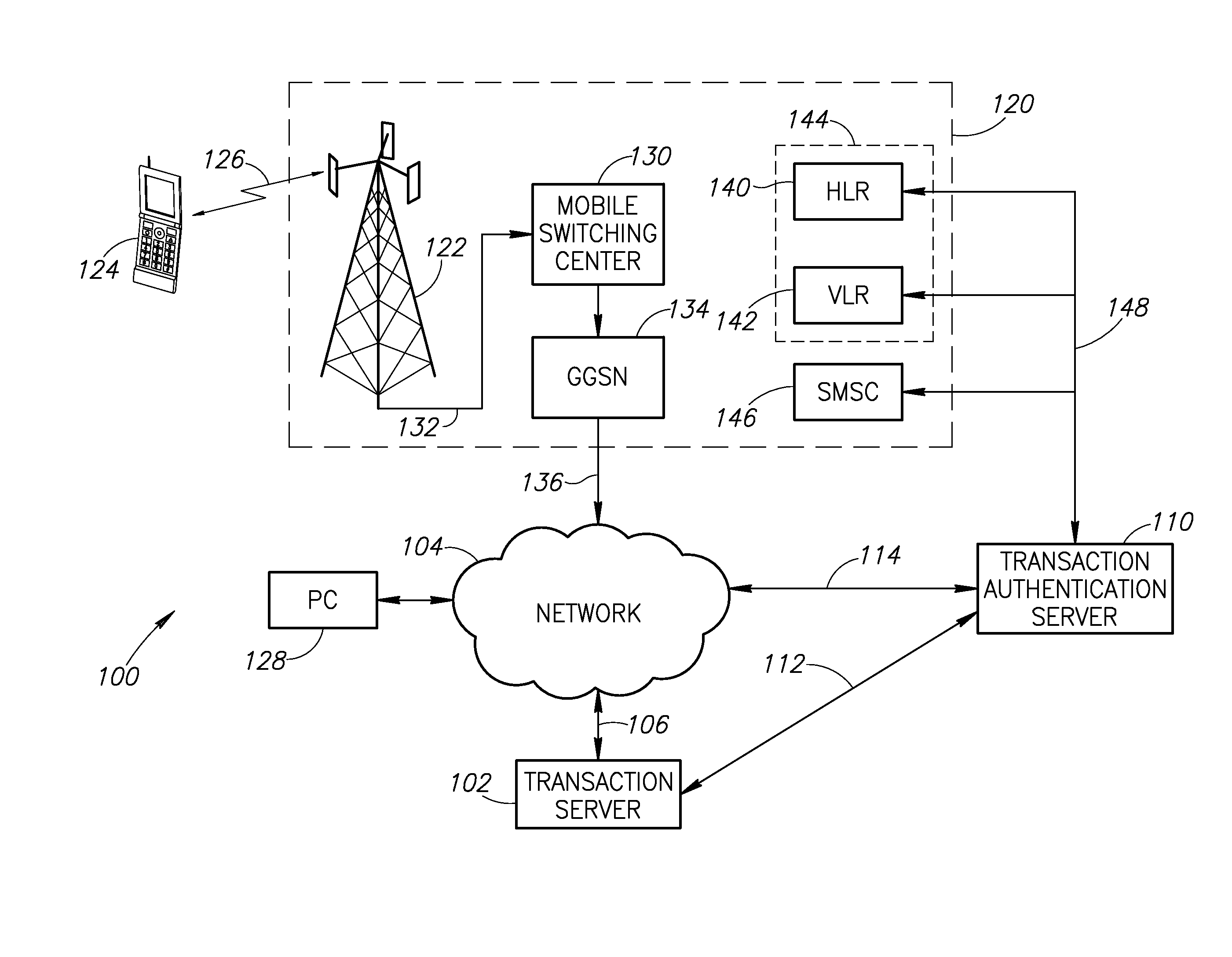
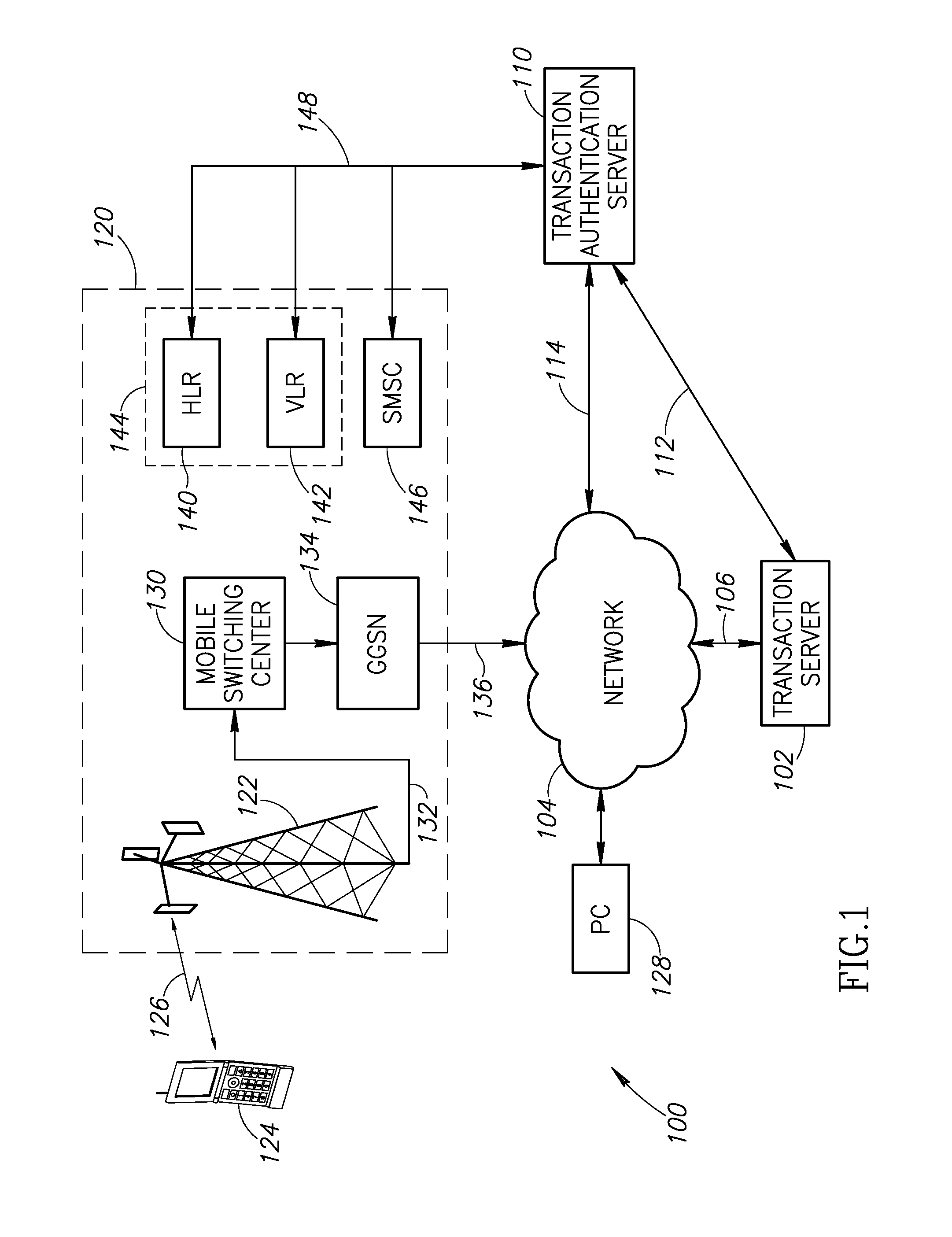
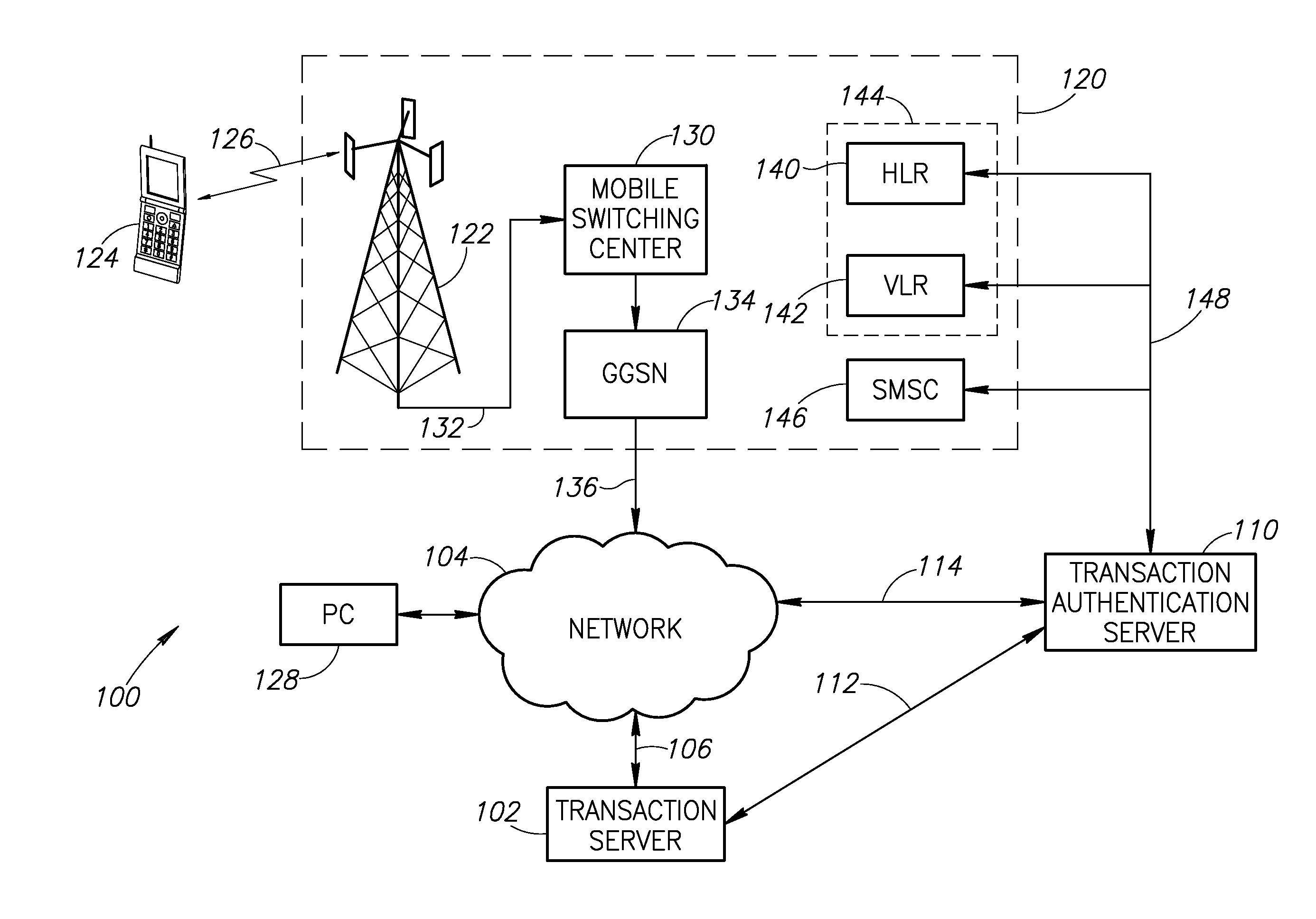
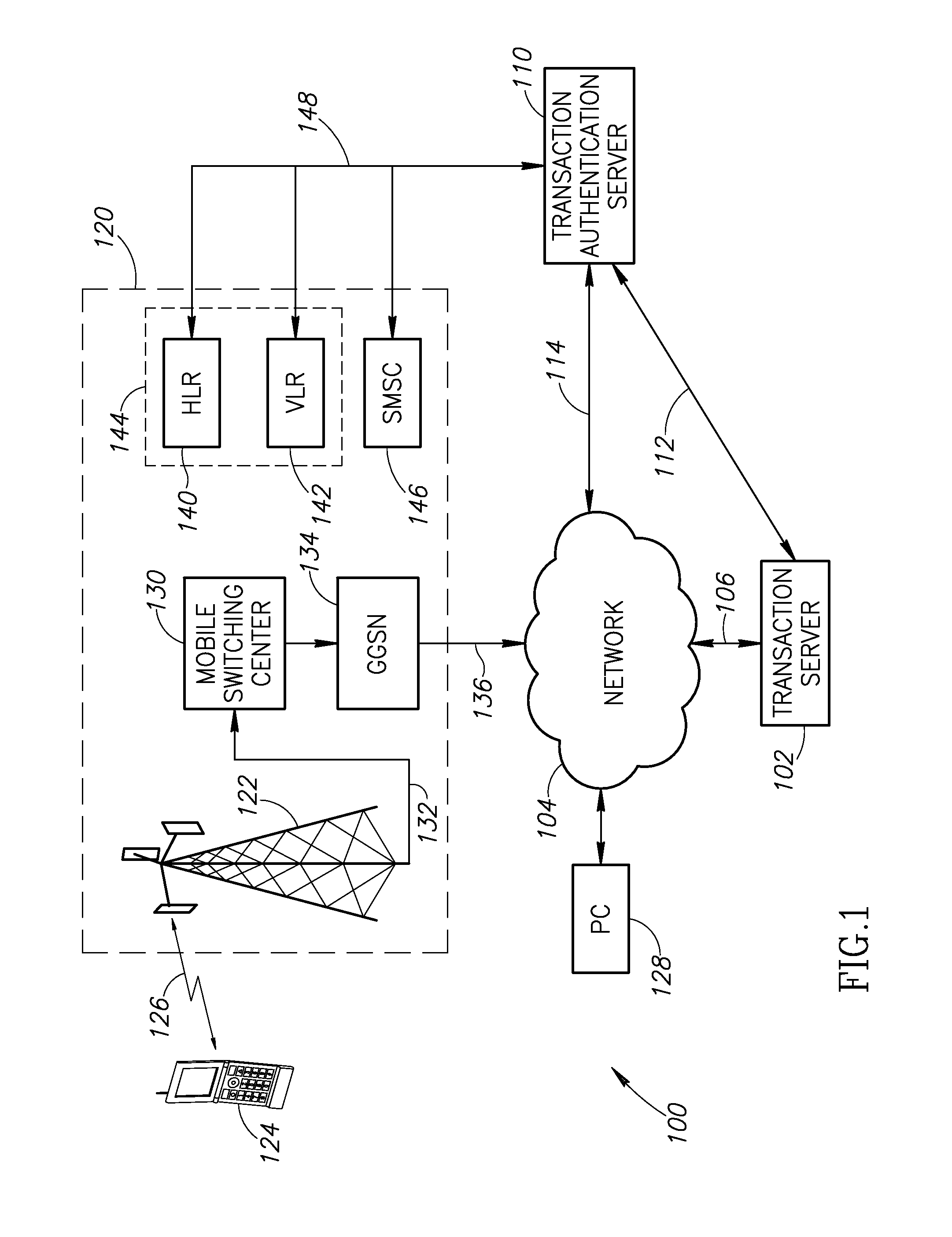
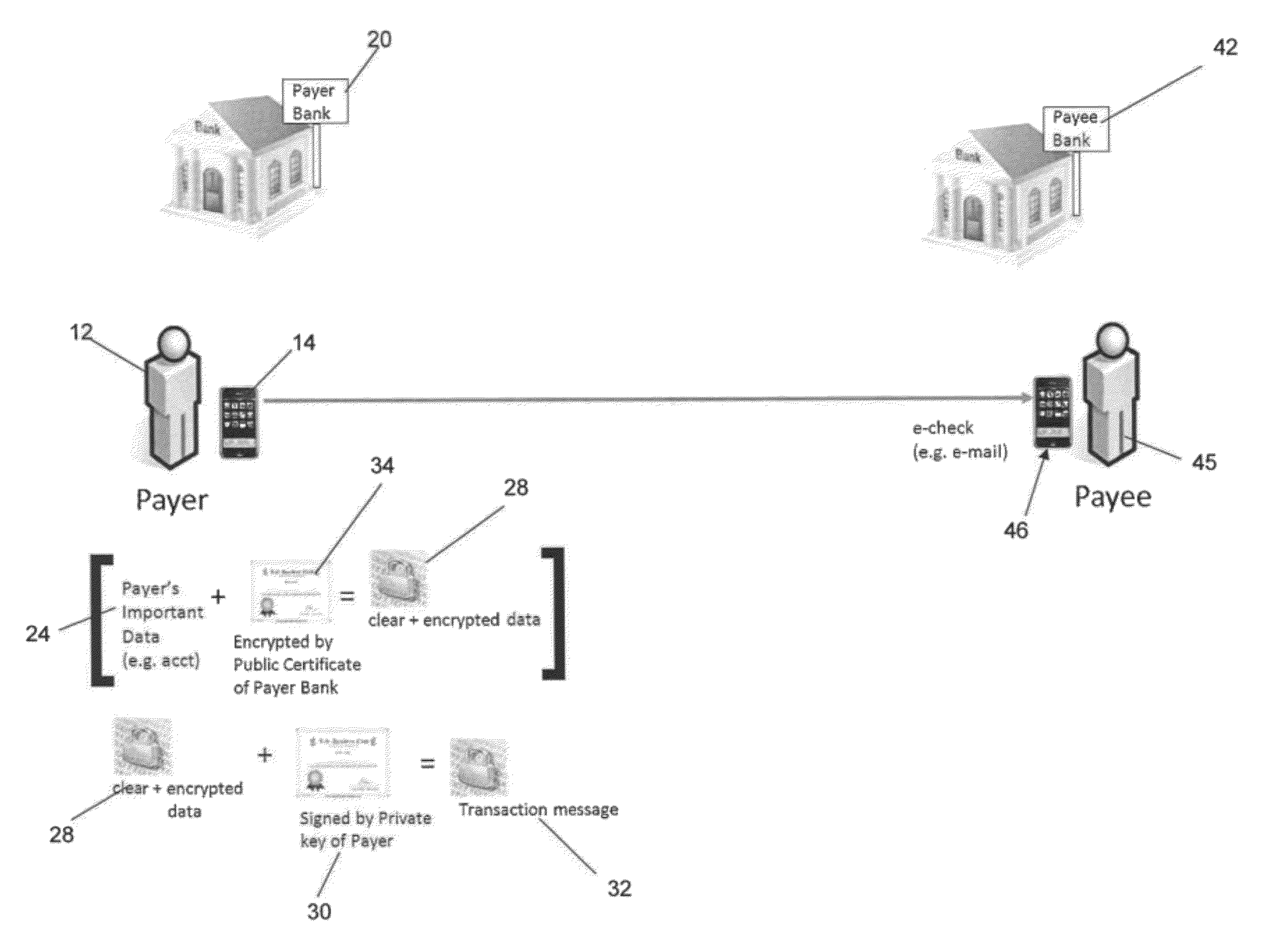
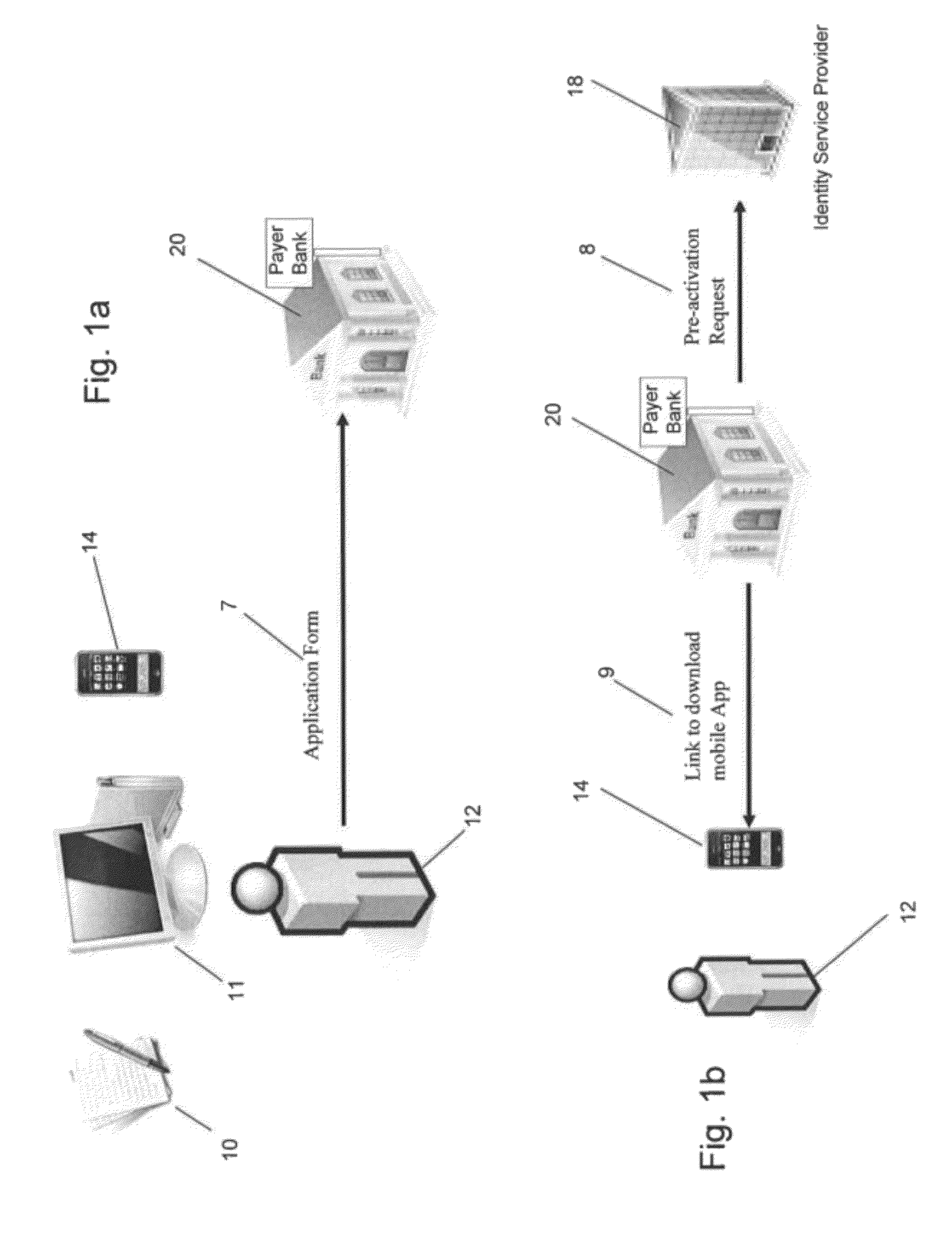
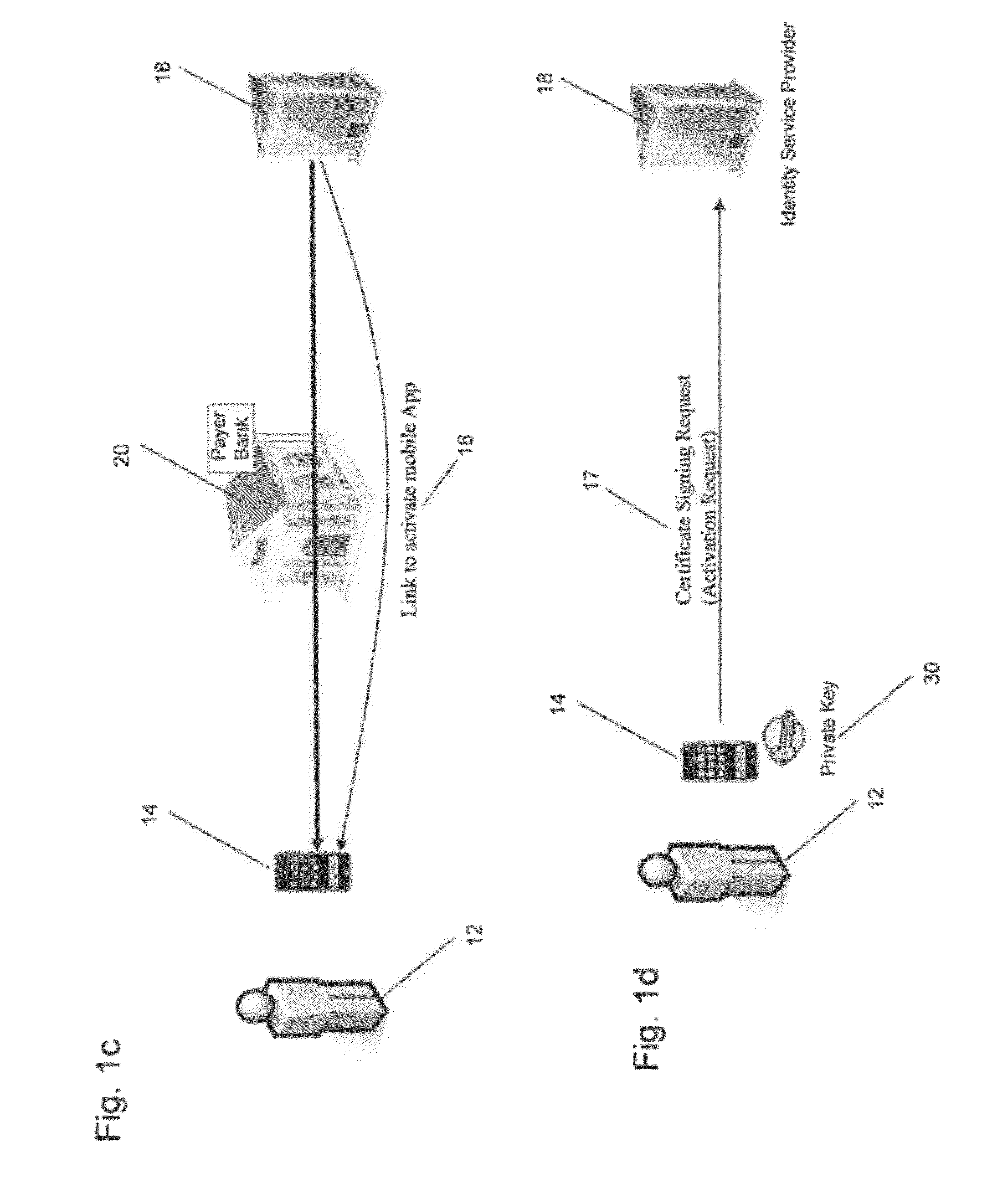
System and method for transaction authentication using a mobile communication device
ActiveUS8577336B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile Telephone NumberAuthentication server
A transaction authentication system uses a computer network and mobile telephone network to authenticate a user. The user initiates a transaction and provides an identity token, such as the mobile telephone number. The identity token is used by an authentication server to initiate the issuance of a new temporary identity for the corresponding mobile device. The new temporary identity is forwarded from the mobile device to the authentication server which issues a security code if there is a match between the new temporary identities. The security code is forwarded to a transaction server which relays it to the authentication server. If the forwarded security code matches the generated security code, the transaction is permitted to continue.
Owner:MOBILESPHERE HLDG
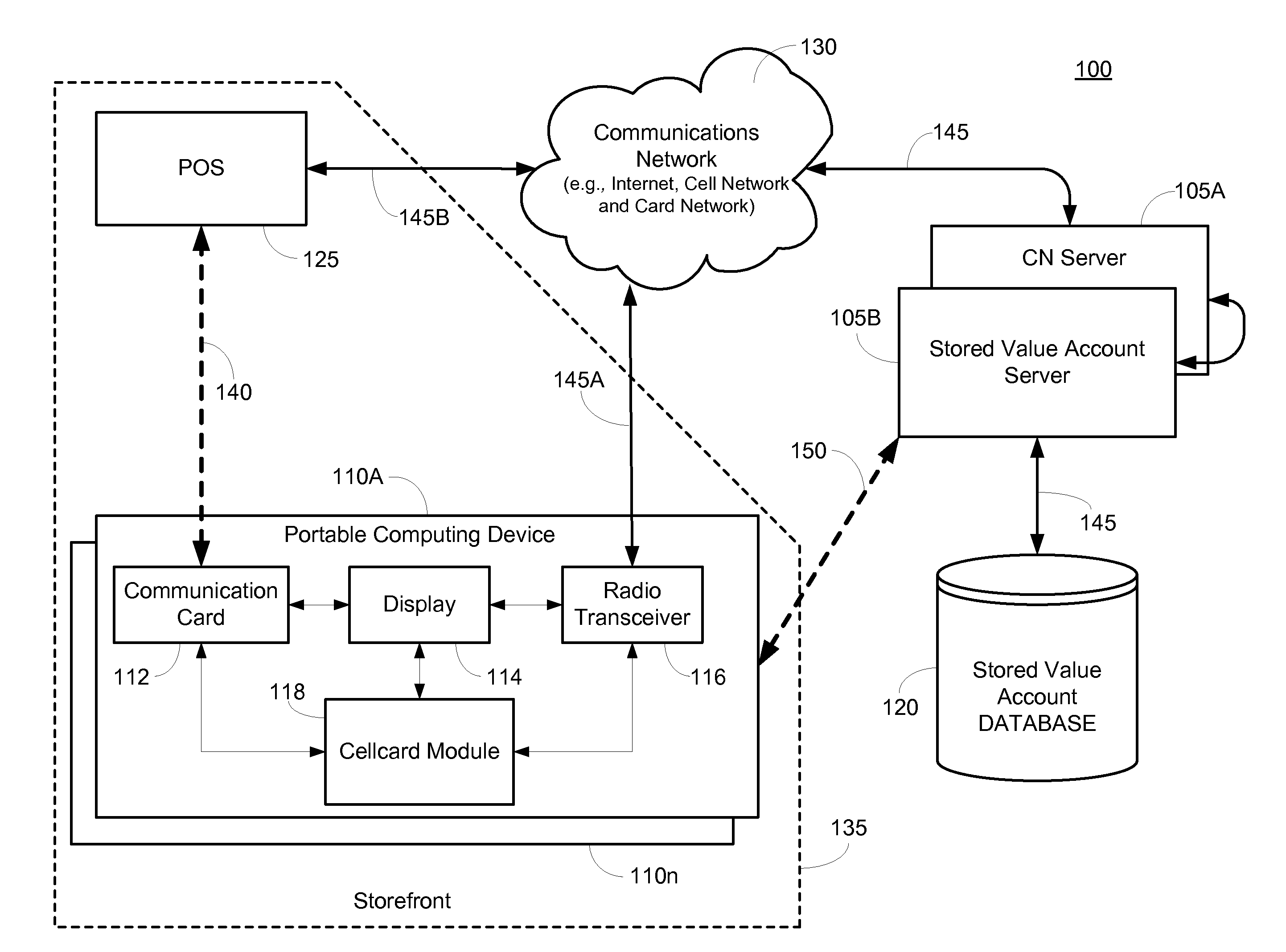
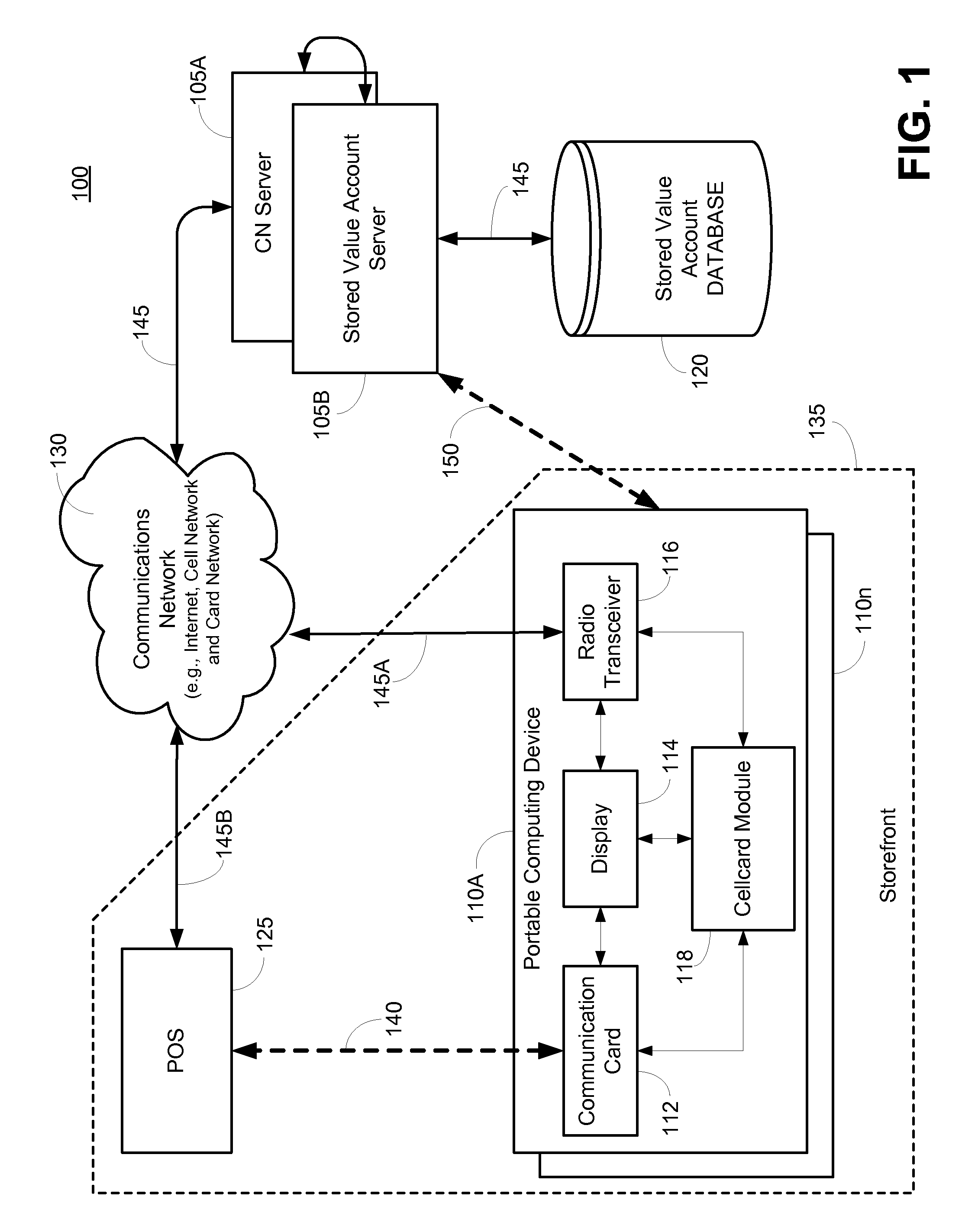
System and method for presentment of nonconfidential transaction token identifier
InactiveUS20120246071A1Easy to rememberEasy to useFinancePayment architecturePaymentMobile Telephone Number
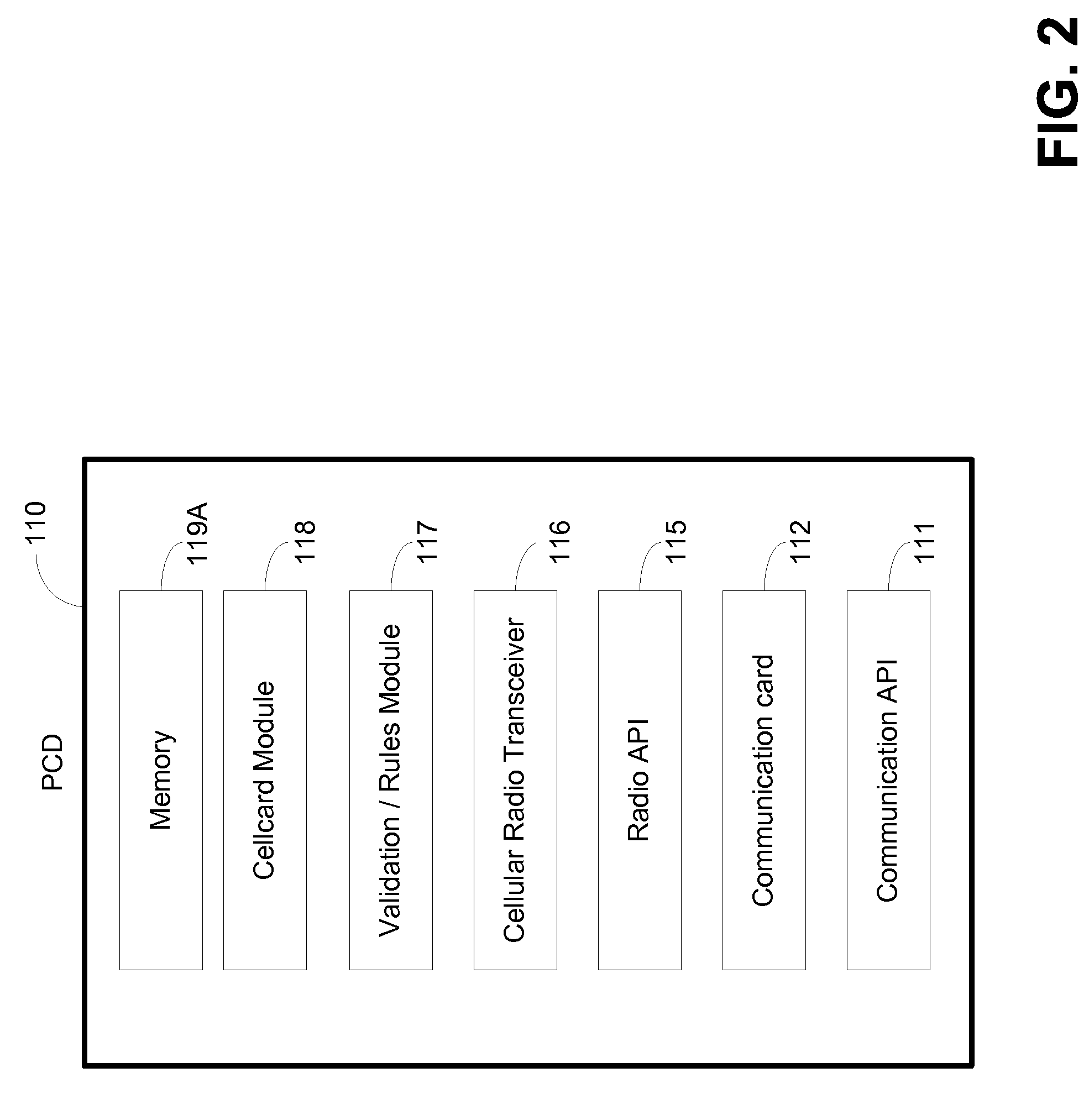
In an exemplary embodiment, a method for leveraging a payment token comprising a non-confidential number (i.e., “cellcard number”), such as a phone number associated with a user's portable computing device (“PCD”), to effect purchase transactions against one of possibly a plurality of value accounts associated with the non-confidential number comprises presenting a cellcard number for purchase of goods, requesting that a value account associated with the cellcard number be debited and, before debiting the value account and completing the purchase transaction, transmitting a request for authorization of the transaction to the user's PCD.
Owner:QUALCOMM INC
Secure payment and billing method using mobile phone number or account
ActiveUS20110295750A1Metering/charging/biilling arrangementsAccounting/billing servicesMobile Telephone NumberAuthorization
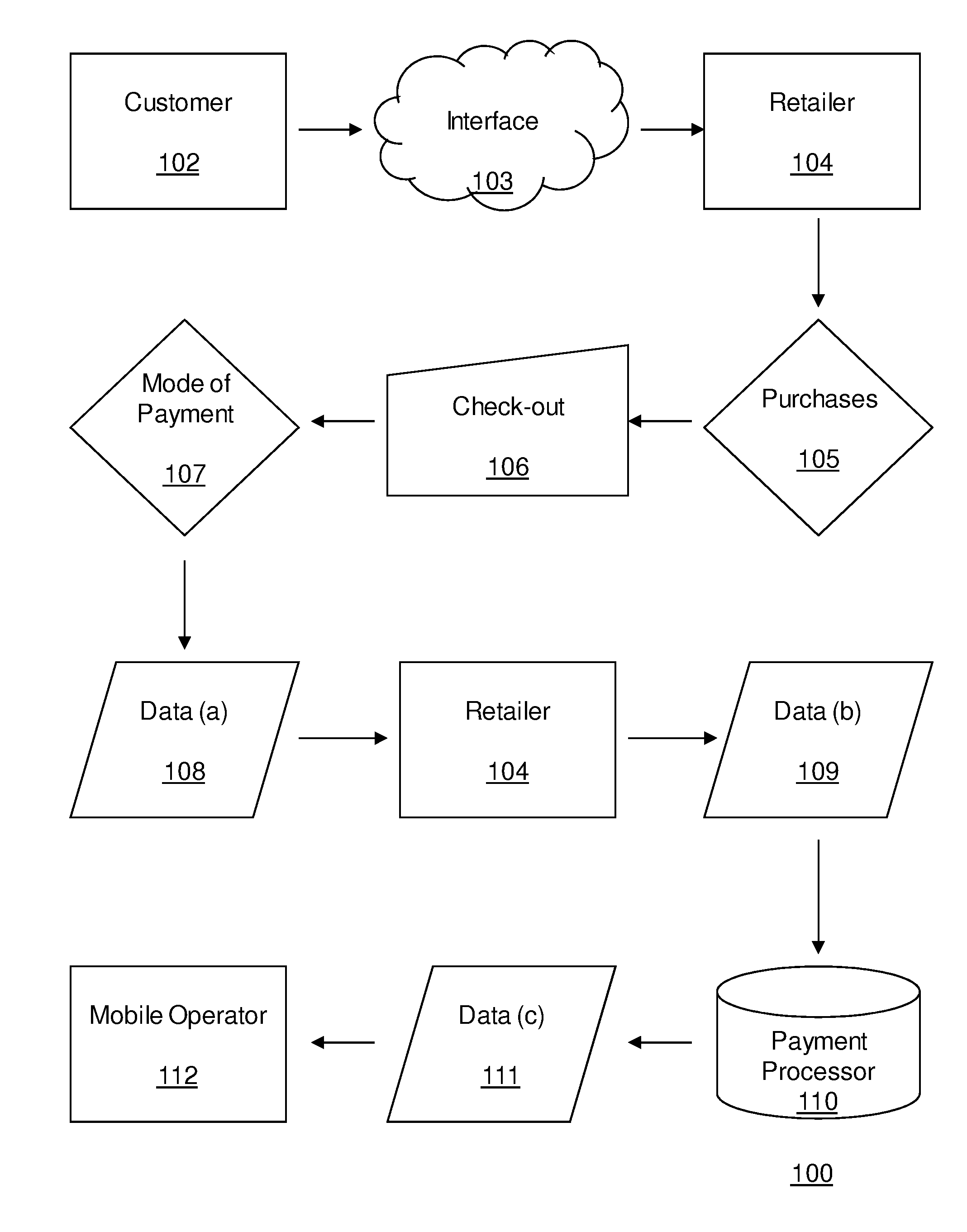
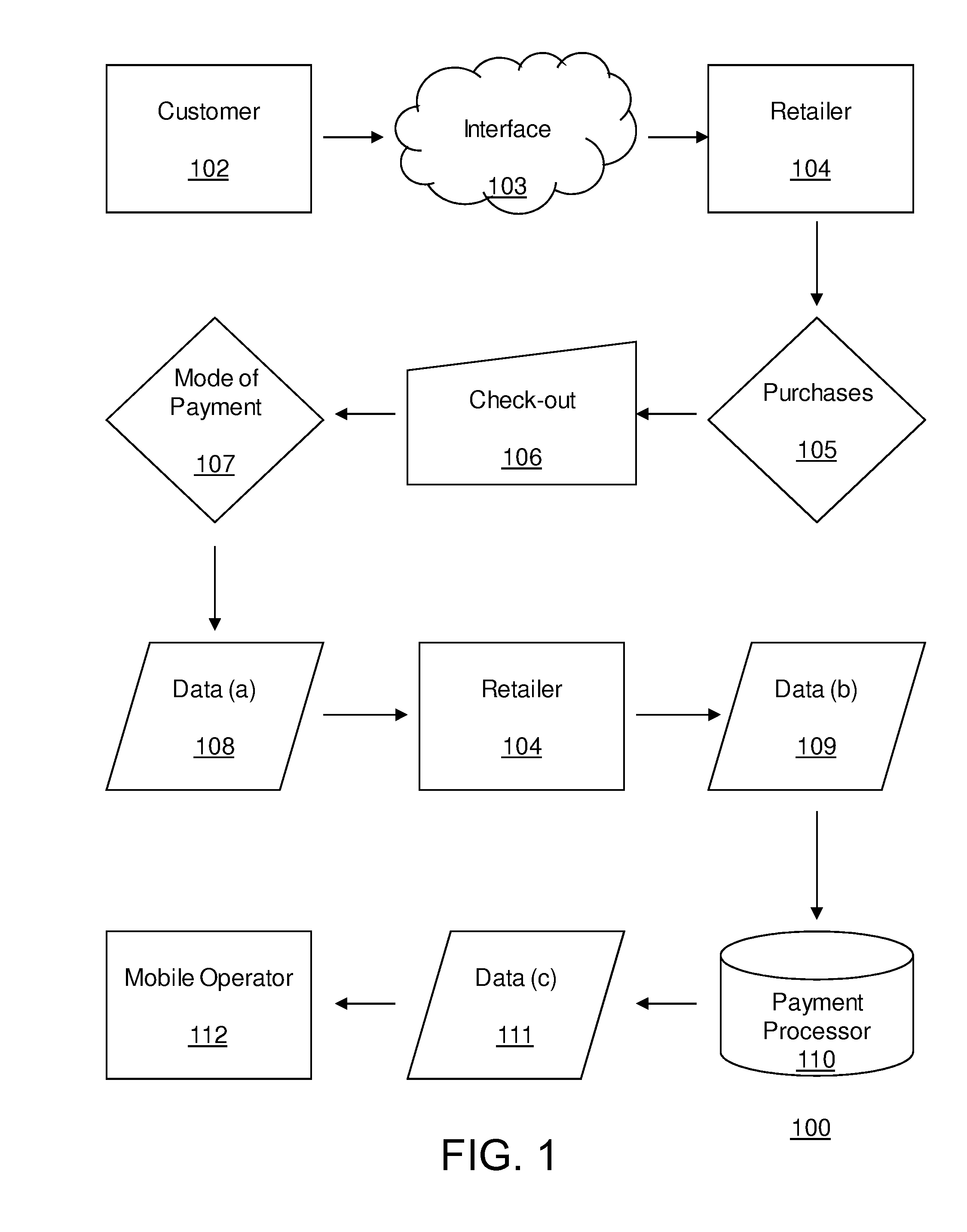
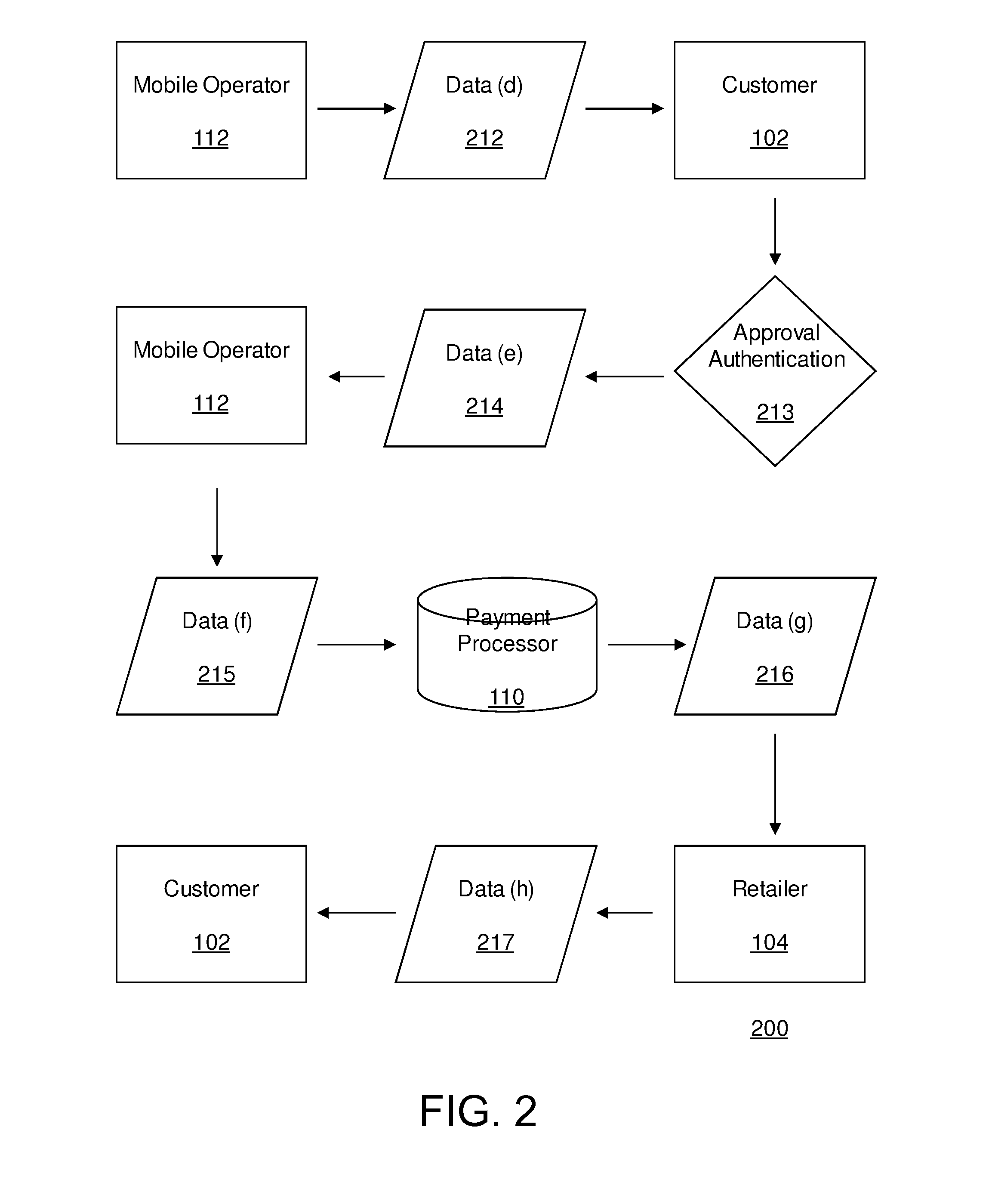
A system, method and computer program product for processing payments for goods or services, including a payment processor that receives a payment request from a merchant for goods or services and that includes a mobile phone number or mobile phone account of a user, sends a payment authorization request text message to the mobile phone requesting payment authorization, and receives a payment authorization text message from the mobile phone authorizing or not authorizing the payment. If the payment is authorized, the payment processor pays the merchant and charges the mobile phone account for the payment. If the payment is not authorized or if the payment is not received within a predetermined period of time, the payment processor declines to pay the merchant for the goods or services.
Owner:BOLORO GLOBAL LTD
Systems and Methods for Electronic Gifting
InactiveUS20080172306A1Overcome disadvantagesMarketingProtocol authorisationMobile Telephone NumberInternet privacy
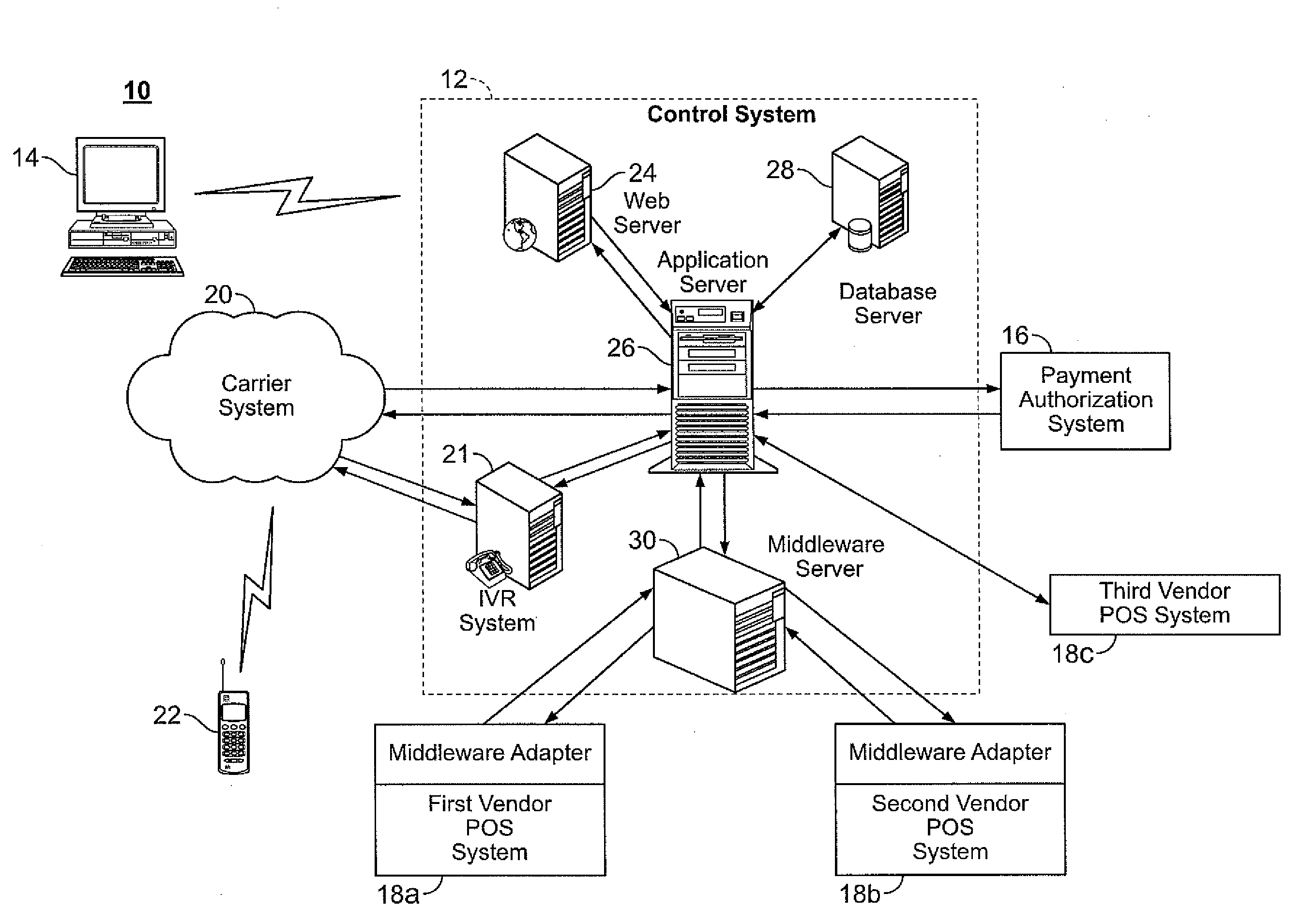
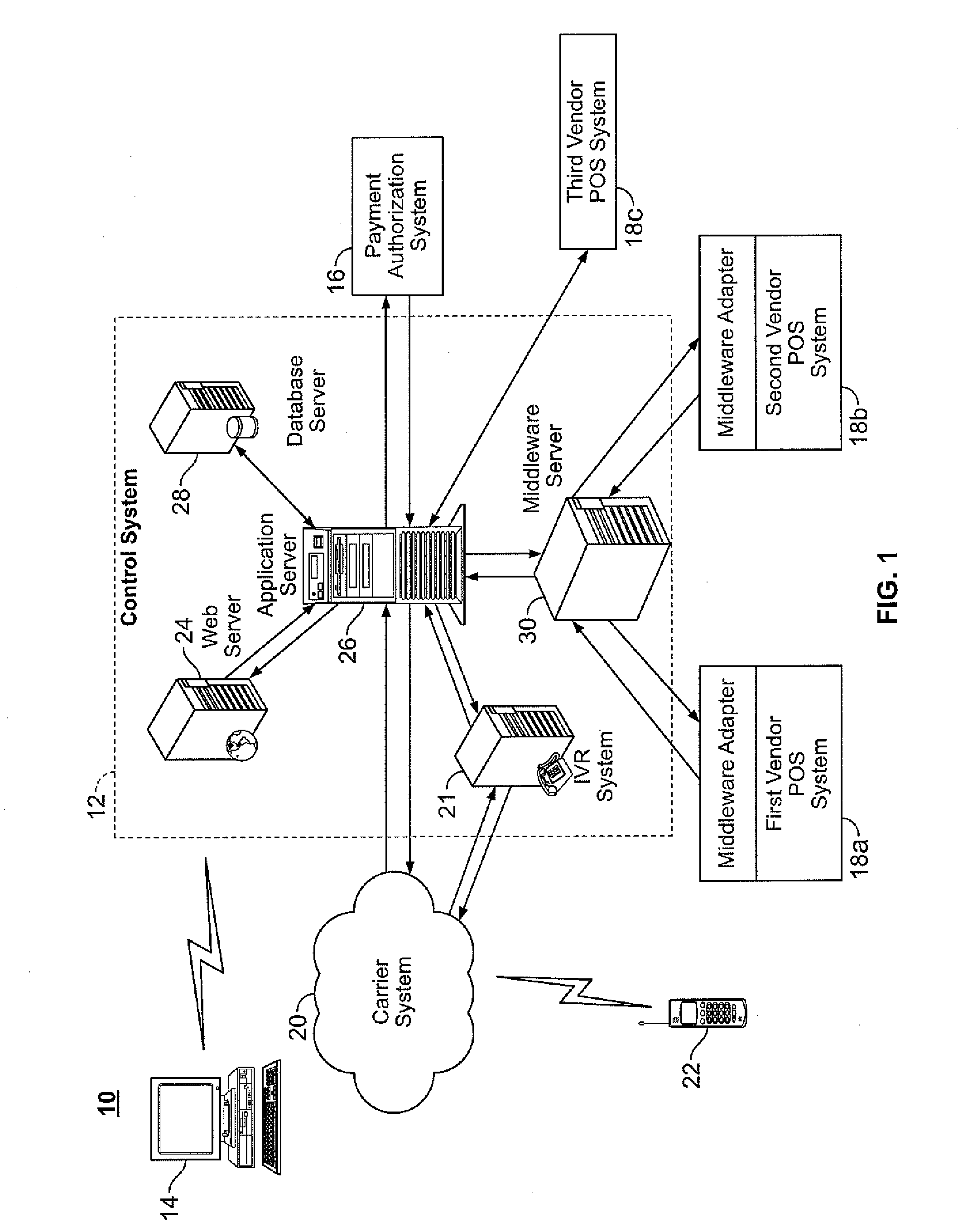
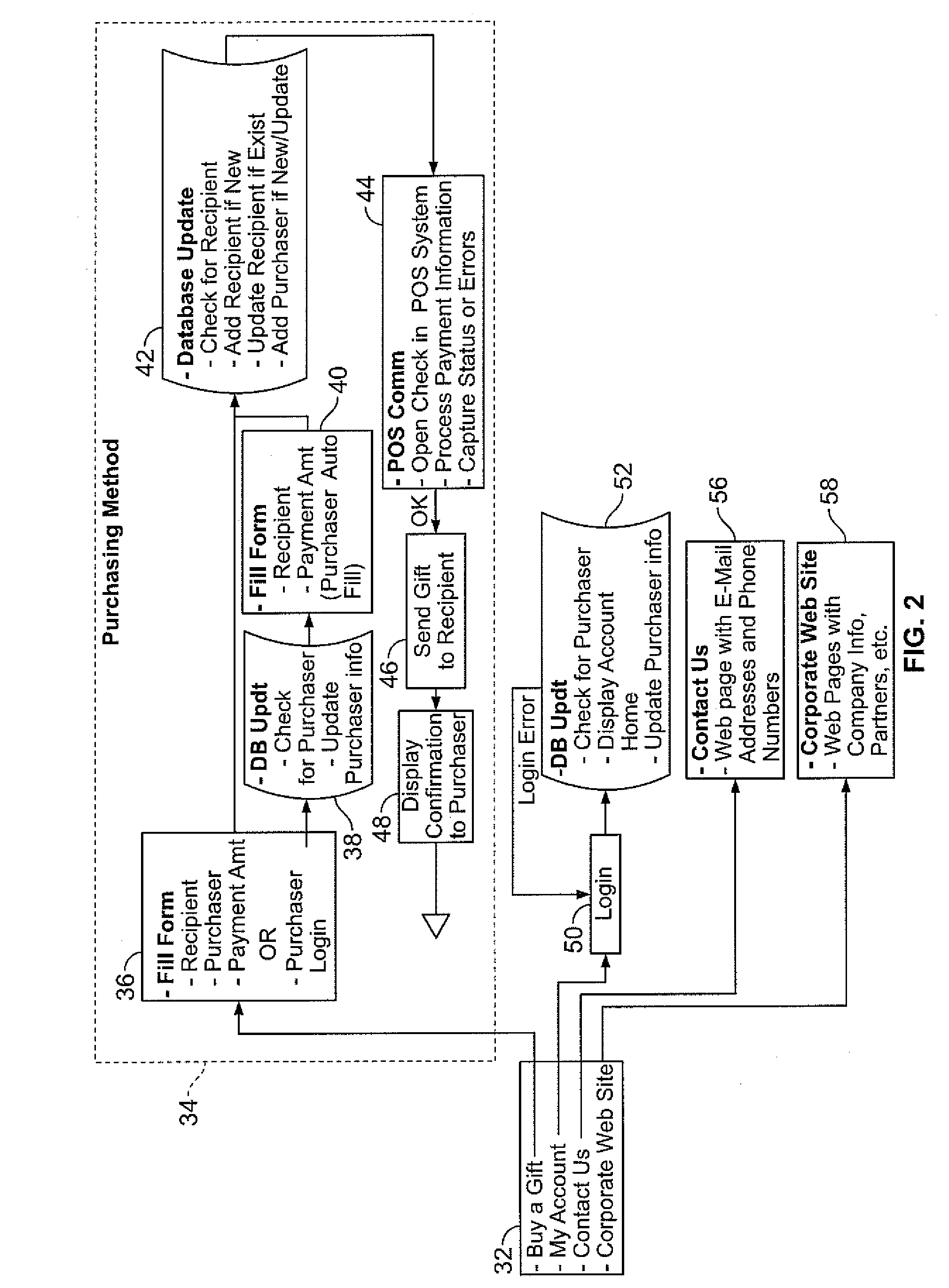
Disclosed herein are systems and methods for electronic gifting. In an exemplary gift purchasing method, a control system receives from a purchasing system a gift purchase request that includes a mobile telephone number (or other unique telephonic identifier) associated with a wireless gift recipient system, sends to a payment authorization system a payment authorization request, receives a payment authorization, and notifies the wireless gift recipient system of an electronic gift certificate. In an exemplary gift redemption method, the control system receives a gift redemption request for goods / services from a point-of-sale (POS) system, sends an authentication request addressed to the wireless gift recipient system by way of text message or other format, receives an authentication confirmation originating from the wireless gift recipient, and sends a redemption authorization to the vendor POS system. The control system has modules for conducting a targeted marketing campaign utilizing purchase and / or redemption information.
Owner:SCHORR RONNI E +1
Communication assistance system and method
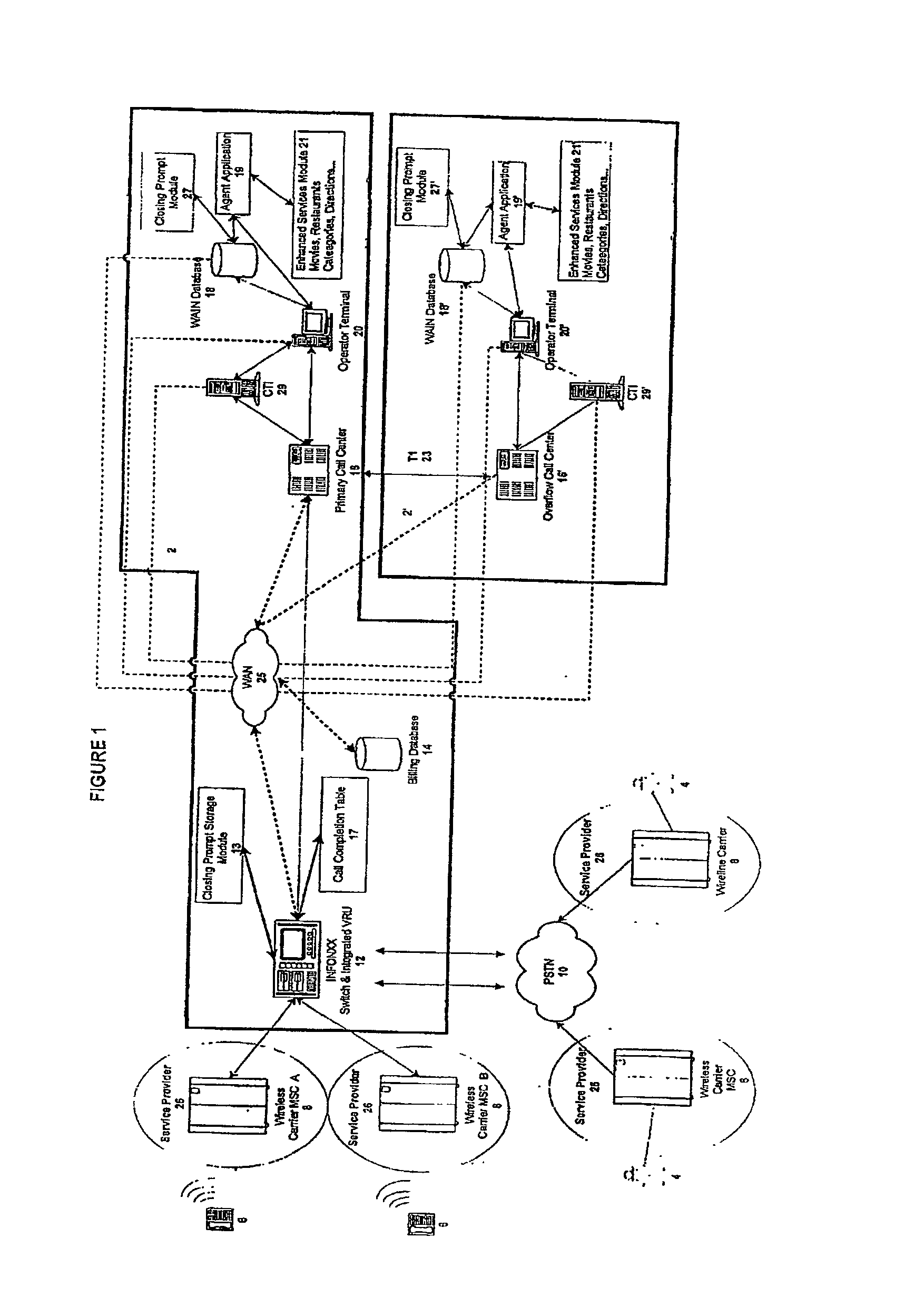
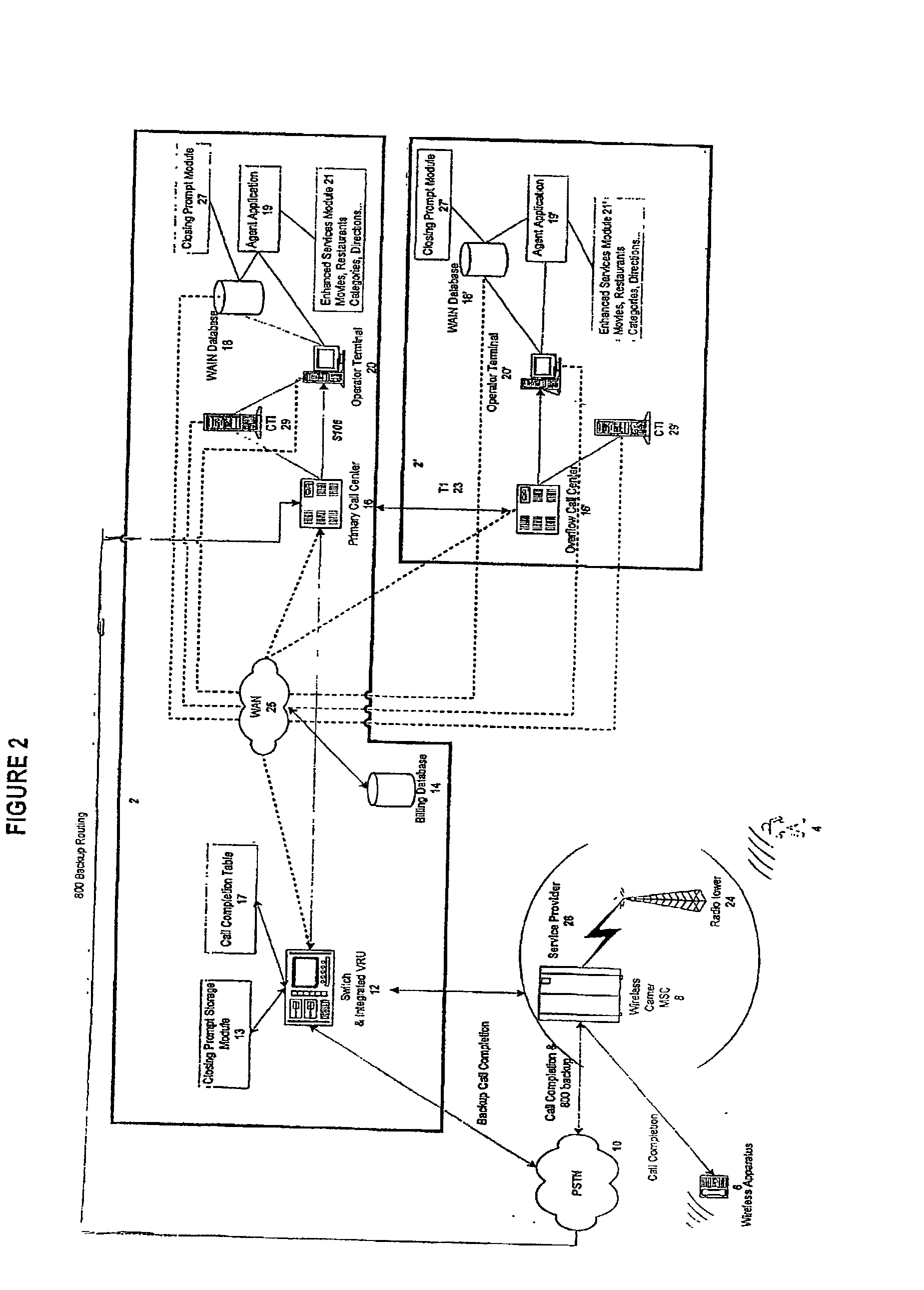
InactiveUS20030007625A1Convenient and efficient accessImprove securitySynchronisation arrangementInterconnection arrangementsMobile Telephone NumberAuxiliary system
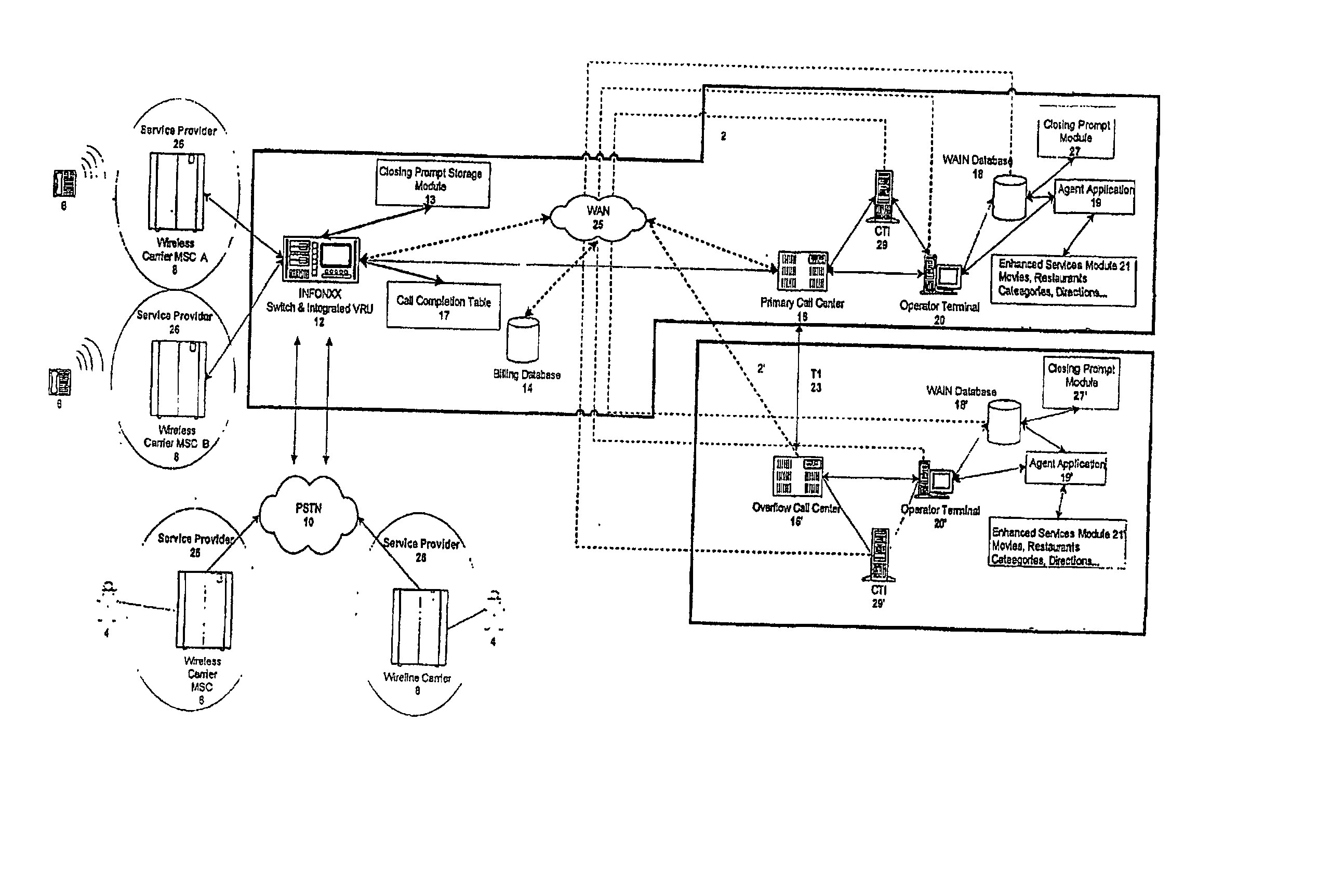
A communication assistance system (2) is provided for accessing information corresponding to a plurality of subscribers (6). This system is comprised of a telephone switch (12) for receiving calls from a plurality of requesters (4), a call center (16) for routing each of said received calls to an operator terminal (20), and a first database (18) configured to store said information corresponding to each of said subscribers (6). The system (2) provides: a dynamically controlled closing prompt; an interface feature allowing subscribers (6) to update their own information; a dial string translator for identifying service provider of the requester (4); a billing database (14) for transferring call charges of the subscriber (6) to the requester (4); a processor to notify subscribers (6) to update their information; the ability to store license plate numbers of the subscribers (6); a masking feature that allows system (32) to connect requester (4) to subscriber (6) without revealing subscriber's (6) mobile telephone number, a searchable database of subscriber (6) information based on particular information found in the subscriber (6) listing.
Owner:GRAPE TECH GROUP
Method and apparatus for improved transaction security using a telephone as a security token
ActiveUS20070174080A1Improve securityIncreased riskFinancePayment architectureMobile Telephone NumberTransaction security
A method and apparatus are disclosed by which customers of an institution, such as a bank, may register one or more of their landline telephone or mobile telephone numbers and associate the telephone numbers with their account and thereafter in conjunction with a remote transaction, use the registered telephone to call into a bank system, or be called by a bank system, for verification, whereby the registered telephone becomes a security token that elevates the security of the transaction.
Owner:OUTWATER CHRISTOPHER SCOTT
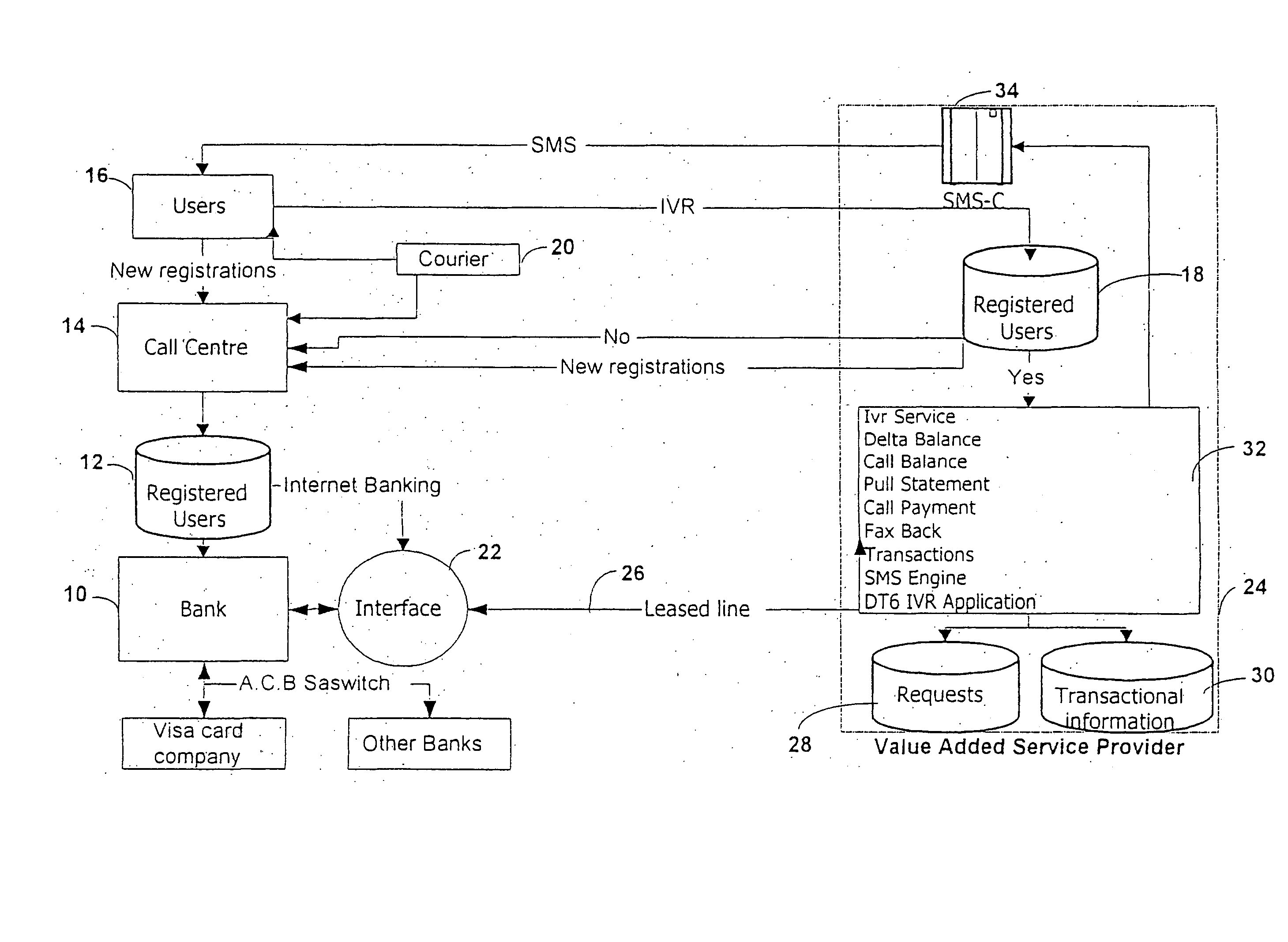
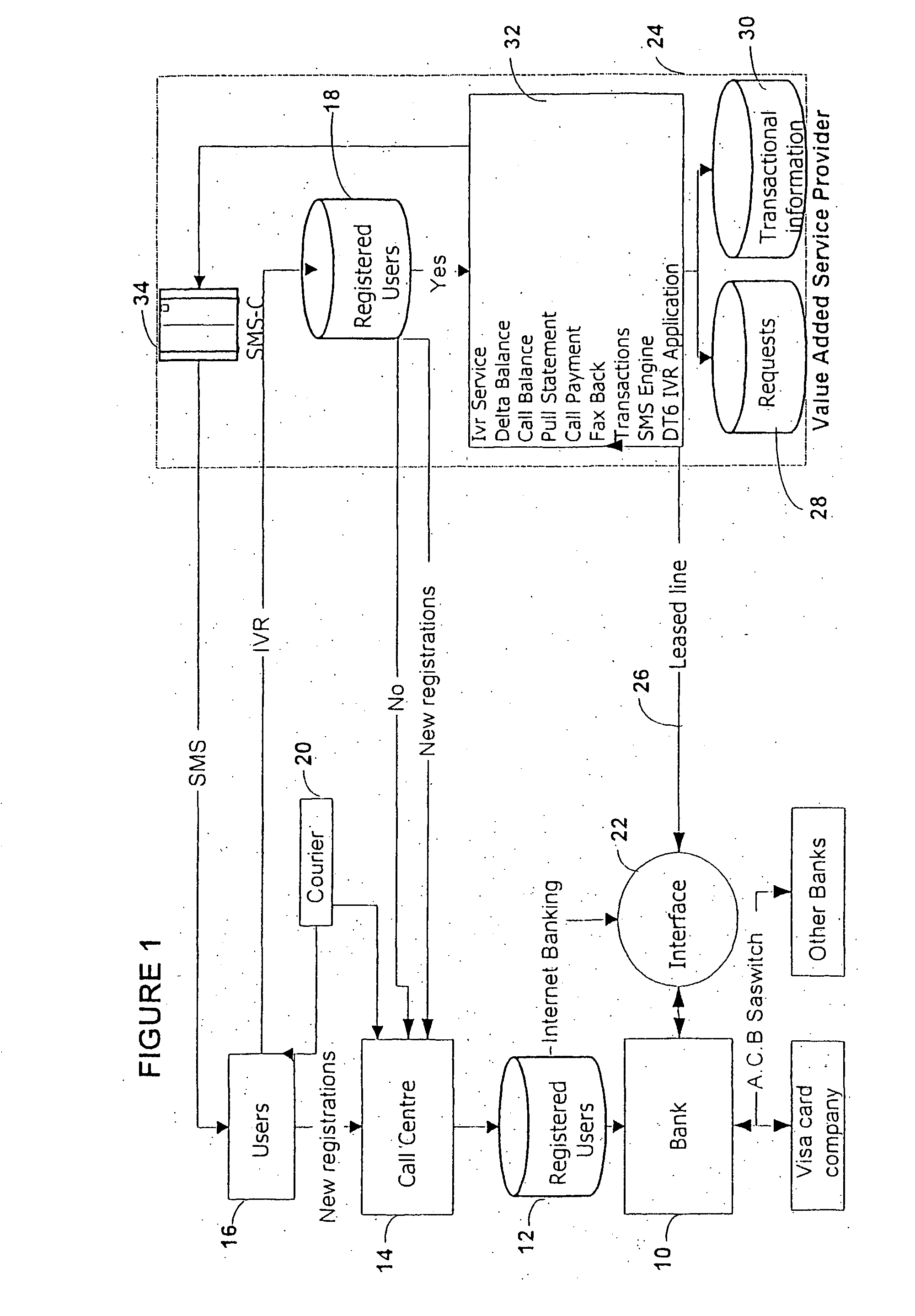
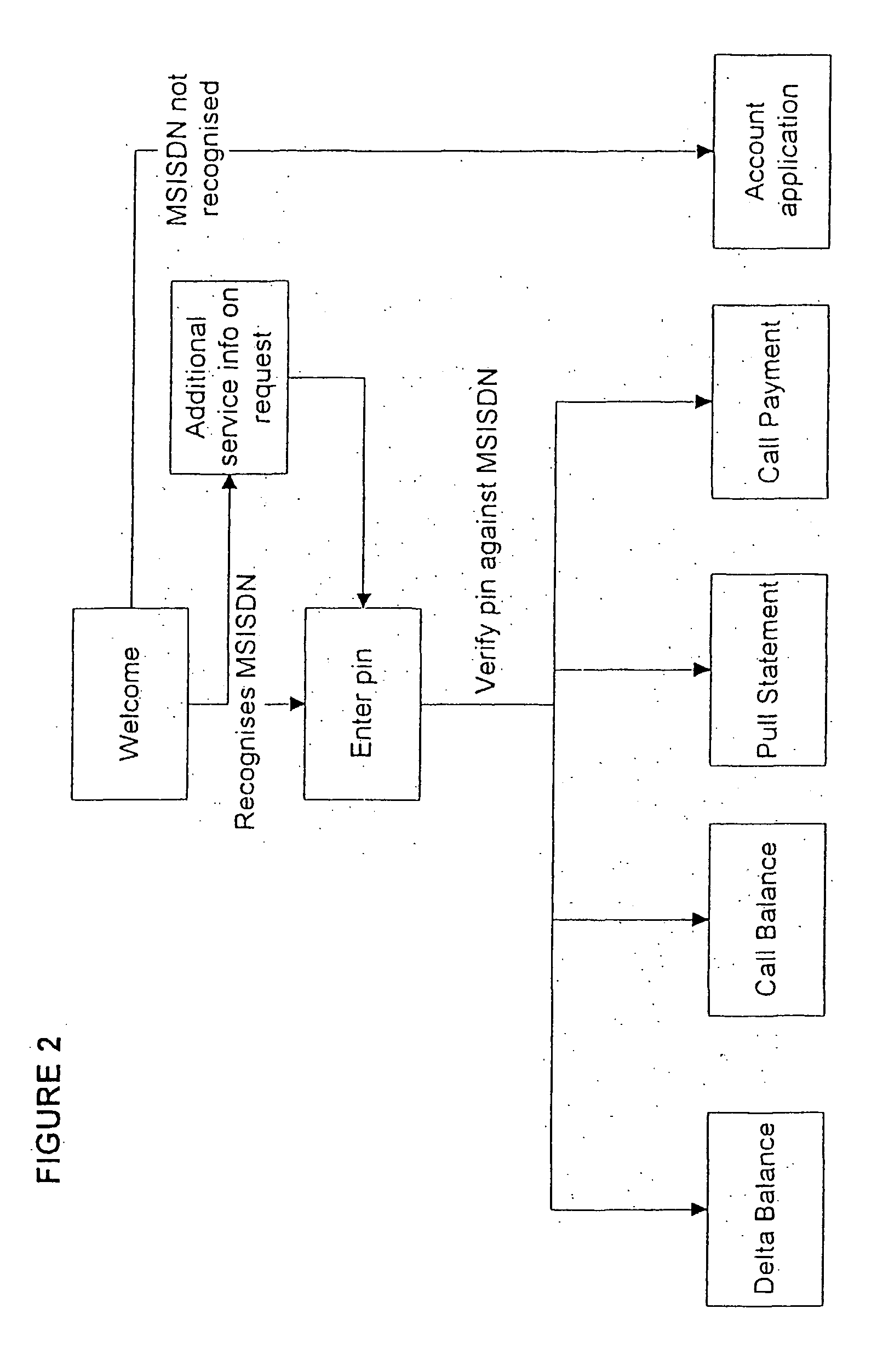
Method and system for operating a banking service
A method and system for operating a banking service are included. The system includes a database (12) for storing client registration data and a unique number, which is preferably the MSISDN or mobile telephone number of the client. This number is used as the client's account number. A call center (14) receives calls from clients and verifies their identity from data transmitted by their mobile telephones. The system allows clients to conduct various banking transactions including balance, statement and payment transactions. A database stores details of balances and / or transactions in each user's account. The system serves for clients to be notified by an SMS transmitted to their mobile telephone of transactions, such as changes to their bank balances or the crediting or debiting of their account. The system can also interface with conventional banking services.
Owner:VIIJOEN NIEL EBEN
Binding, unbinding and binding updating method for third-party application account and mobile phone number
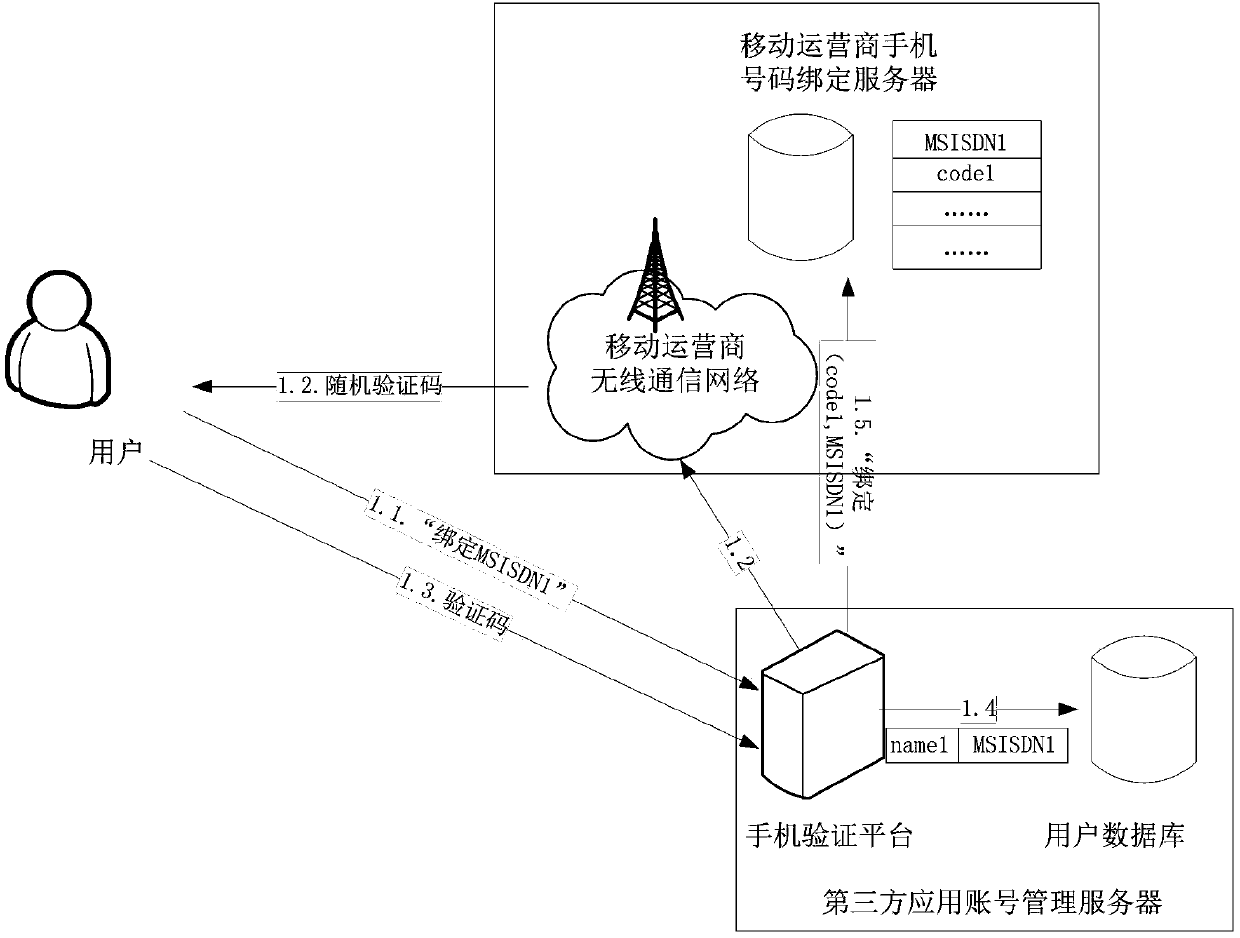
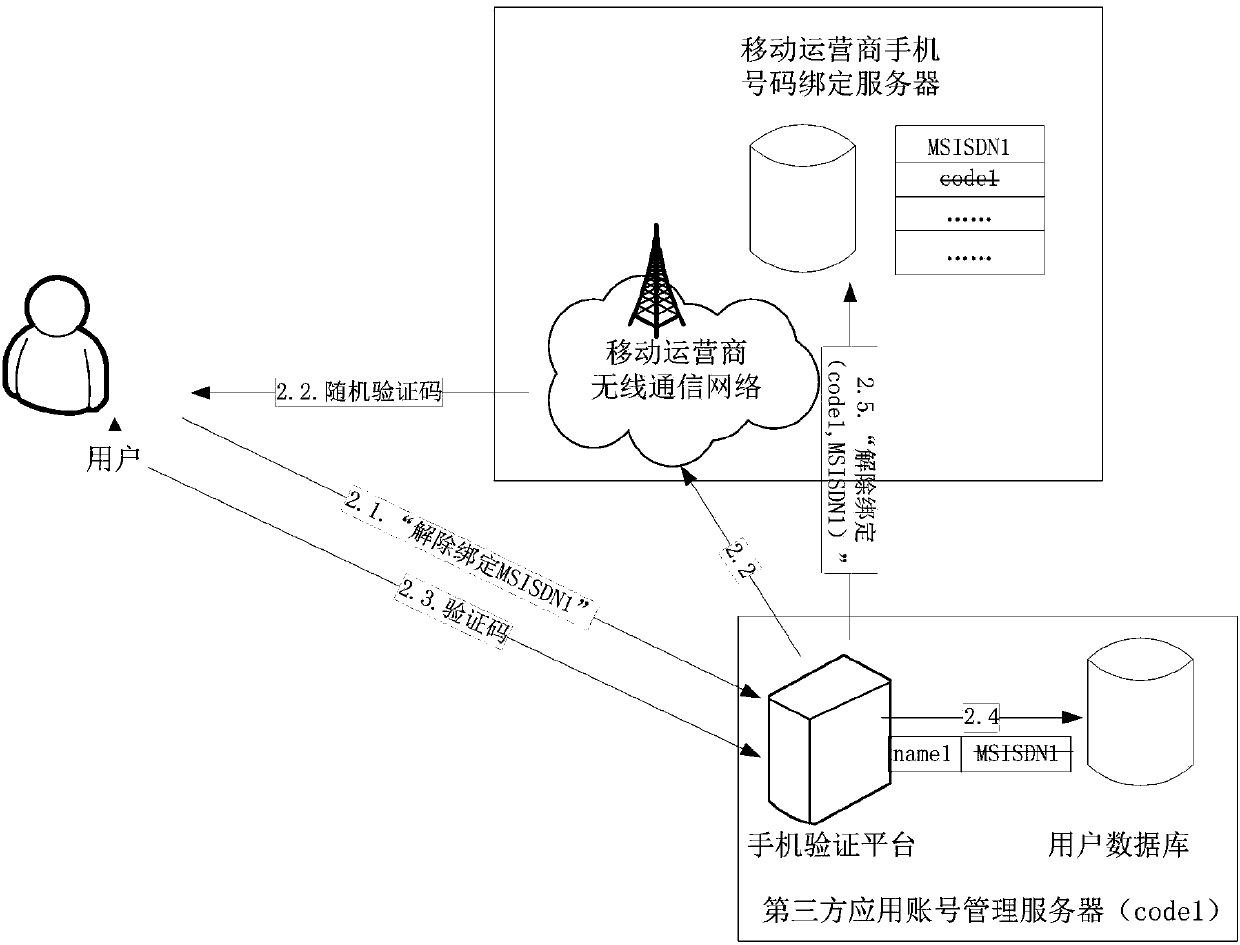
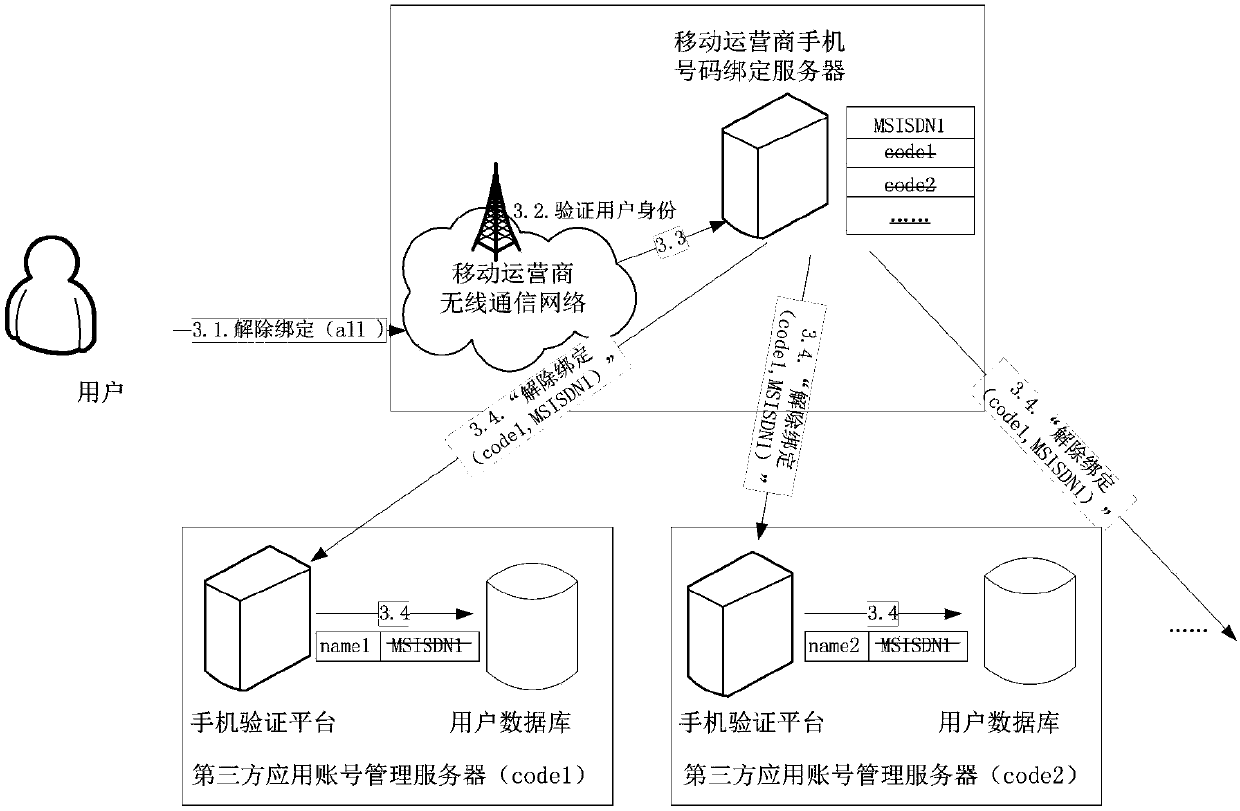
ActiveCN103746792AImprove privacy and securityEasy to moveSpecial data processing applicationsSecuring communicationMobile Telephone NumberThird party
The invention discloses a binding method, an unbinding method and a binding updating method for a third-party application account and a mobile phone number. The binding method comprises the following steps that (1) a user transmits a mobile phone number to be bound to a mobile phone verification platform of a third-party application account management server; (2) the mobile phone verification platform of the third-party application account management server generates a random verification code, and transmits the random verification code to the user of the mobile phone number to be bound through a mobile operator network; (3) the user receives a verification short message, and transmits the verification code back to the mobile phone verification platform of the third-party application account management server; (4) a user database of the third-party application account management server records an association relationship between an account of the user and the mobile phone number; (5) the mobile phone verification platform of the third-party application account management server transmits a service name code and the mobile phone number to a mobile phone binding server of the mobile operator through a binding message, and associates the mobile phone number of the user and the bound third-party application service name code.
Owner:郑盈盈
Method for call forwarding a call from a mobile telephone
InactiveUS6856806B1Special service for subscribersRadio/inductive link selection arrangementsMobile Telephone NumberService provision
A method of call forwarding a call originally placed to a mobile telephone number of a mobile telephone to a landline telephone number of a landline telephone is provided, wherein the call is routed through a telephone network by a service provider. A forwarding location of the mobile telephone is determined using a mobile location technology. The landline telephone number of the landline telephone is provided to the service provider. A current mobile telephone location is determined by a mobile location technology. The mobile location technology is capable of locating the mobile telephone using service provider equipment. The service provider determines that the call is being made to the mobile telephone when the current mobile telephone location is at the forwarding location. The call to the mobile telephone number is forwarded to the landline telephone number when the current mobile telephone location is at the forwarding location.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
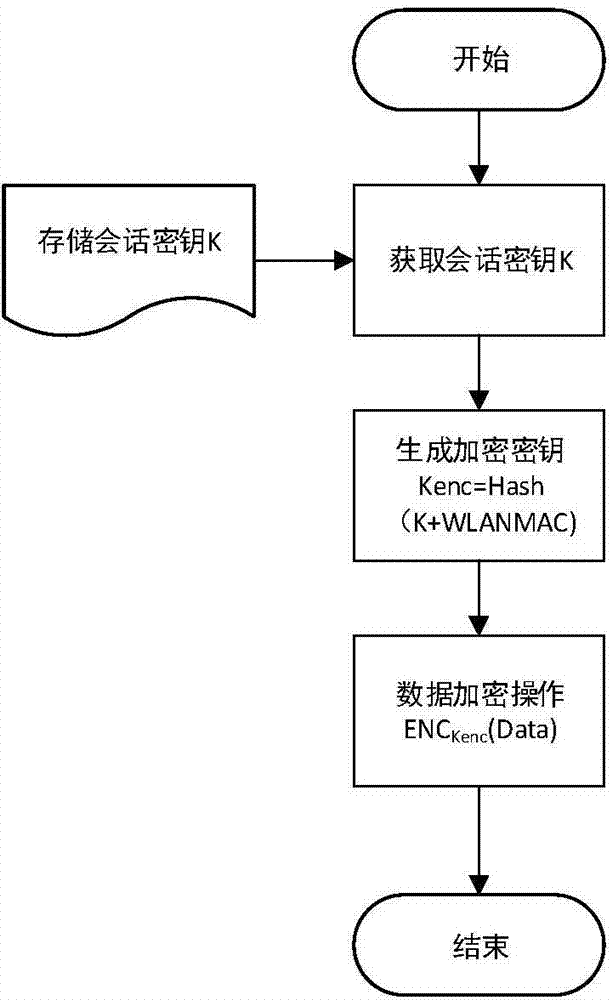
Safety communication secret key negotiation interaction scheme
ActiveCN104506534AGuarantee authenticityEnsure communication securityKey distribution for secure communicationUser identity/authority verificationThe InternetNetwork service
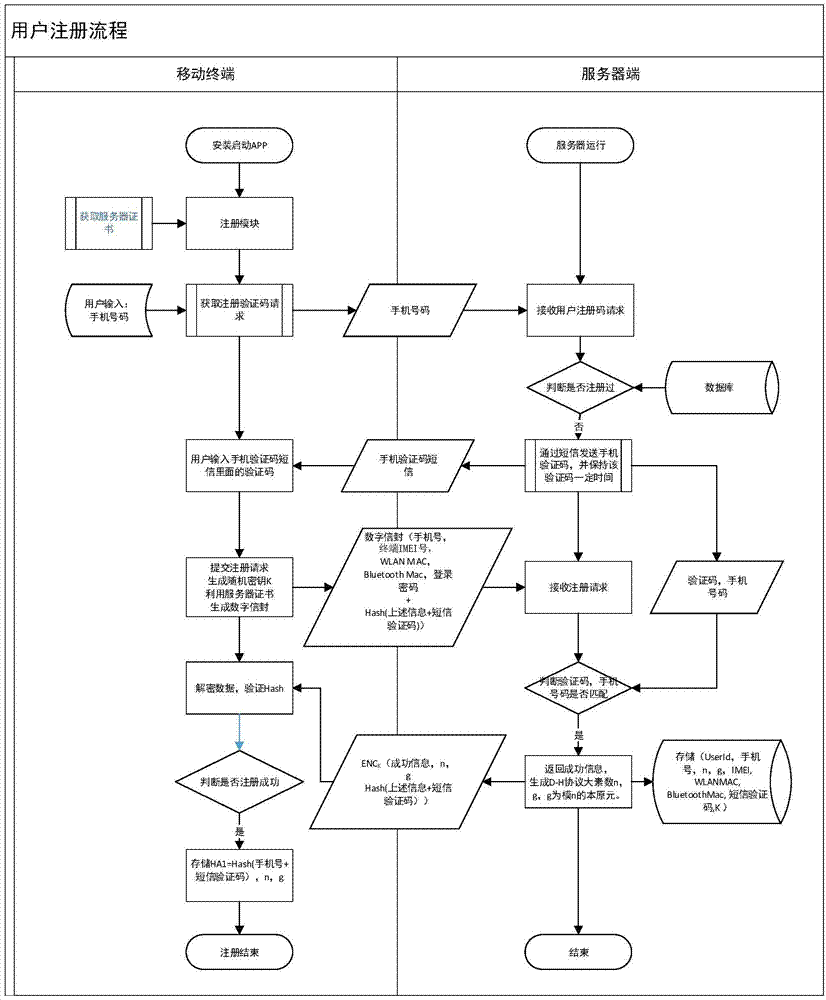
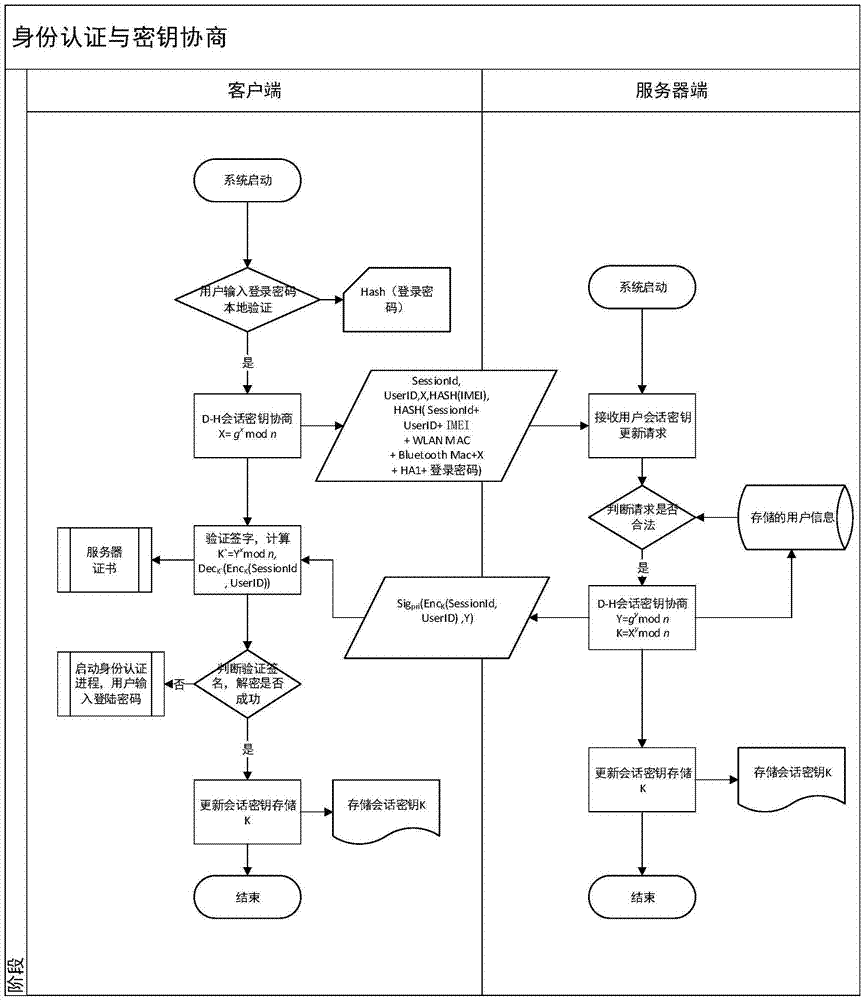
The invention provides a method for safety communication between an application on a mobile terminal and a network server. Shared secrets of a user and a server are overlapped and bound with an identification code of mobile intelligent terminal equipment and a mobile phone number of the user by utilizing a cryptology; then the obtained product is applied to an identity authentication system to implement authentication on a client side; a digital certificate and a digital signature mechanism are utilized to implement authentication on the server; a session key is established with a network server by utilizing a Differ-Hellman secret key negotiation protocol so as to carry out safety data communication. The method is characterized in that the shared secrets are overlapped and bound with identification code of the machine and the mobile phone number of the user and the shared secrets are updated regularly; even though information is stolen by an attacker, a system still cannot be influenced. The user not only needs to provide a login password, but also needs to use the system on designated equipment. The method can ensure that the user carries out safety communication with the server on internet by the mobile equipment.
Owner:QINGDAO WEIZHIHUI INFORMATION
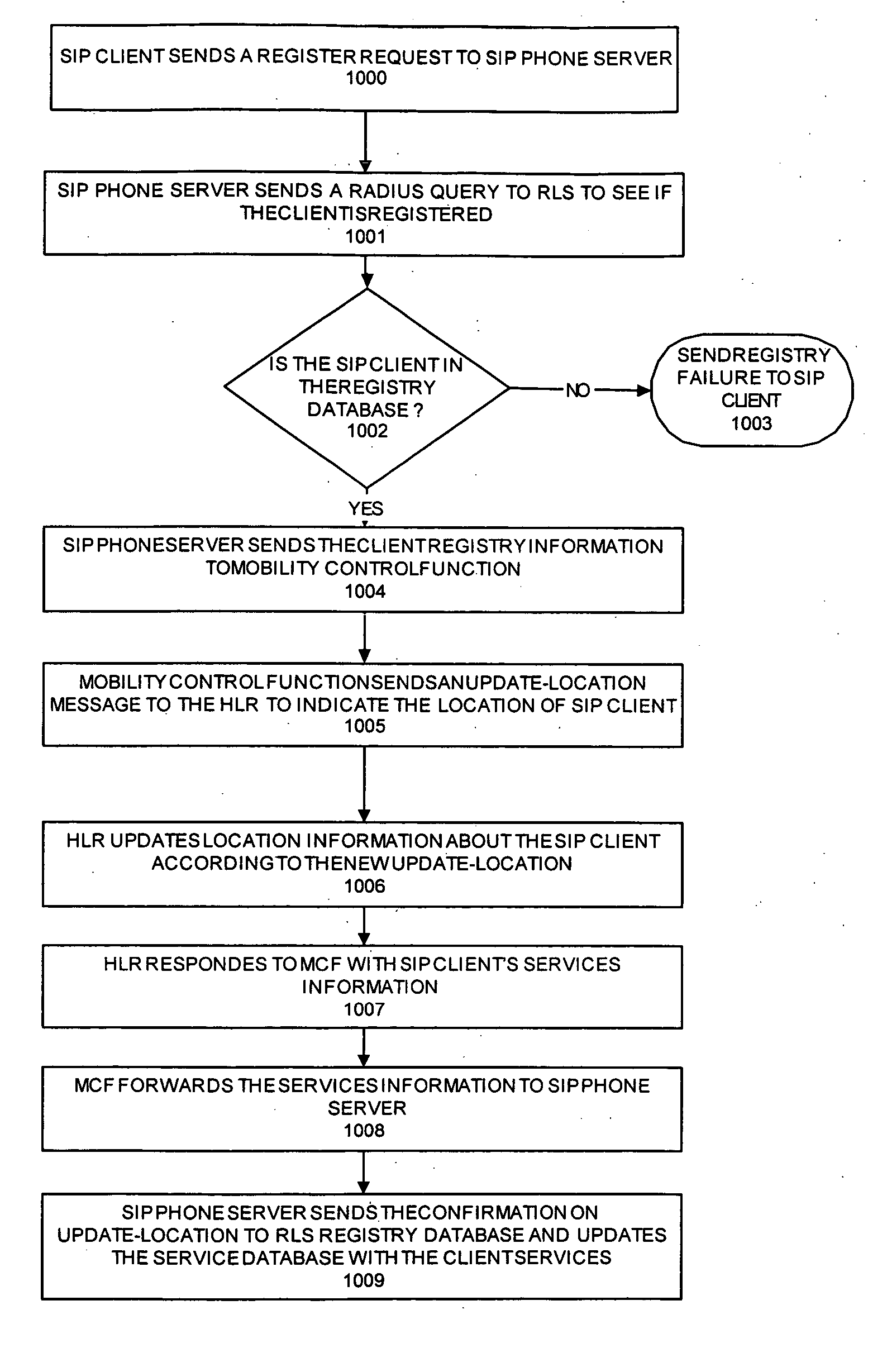
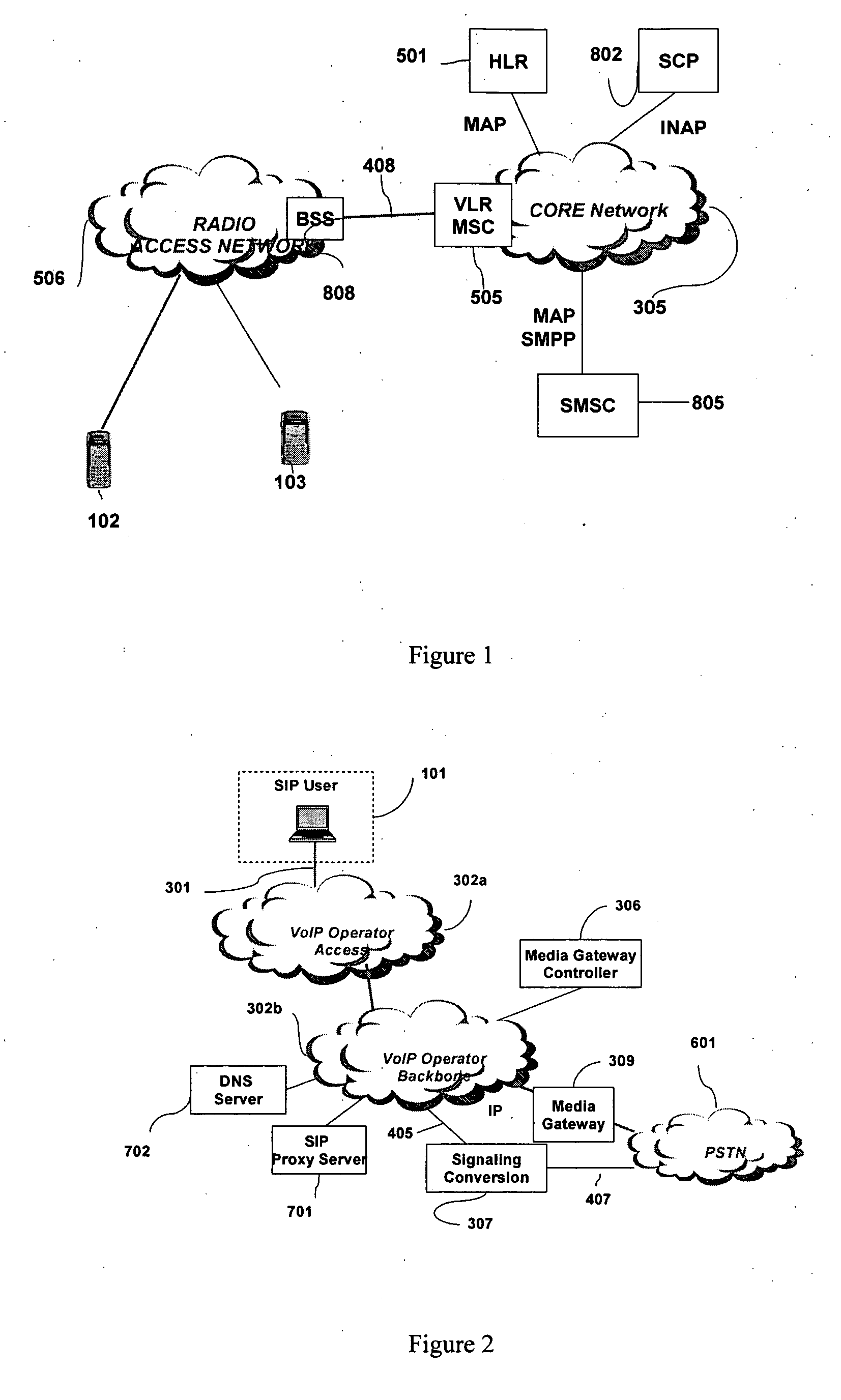
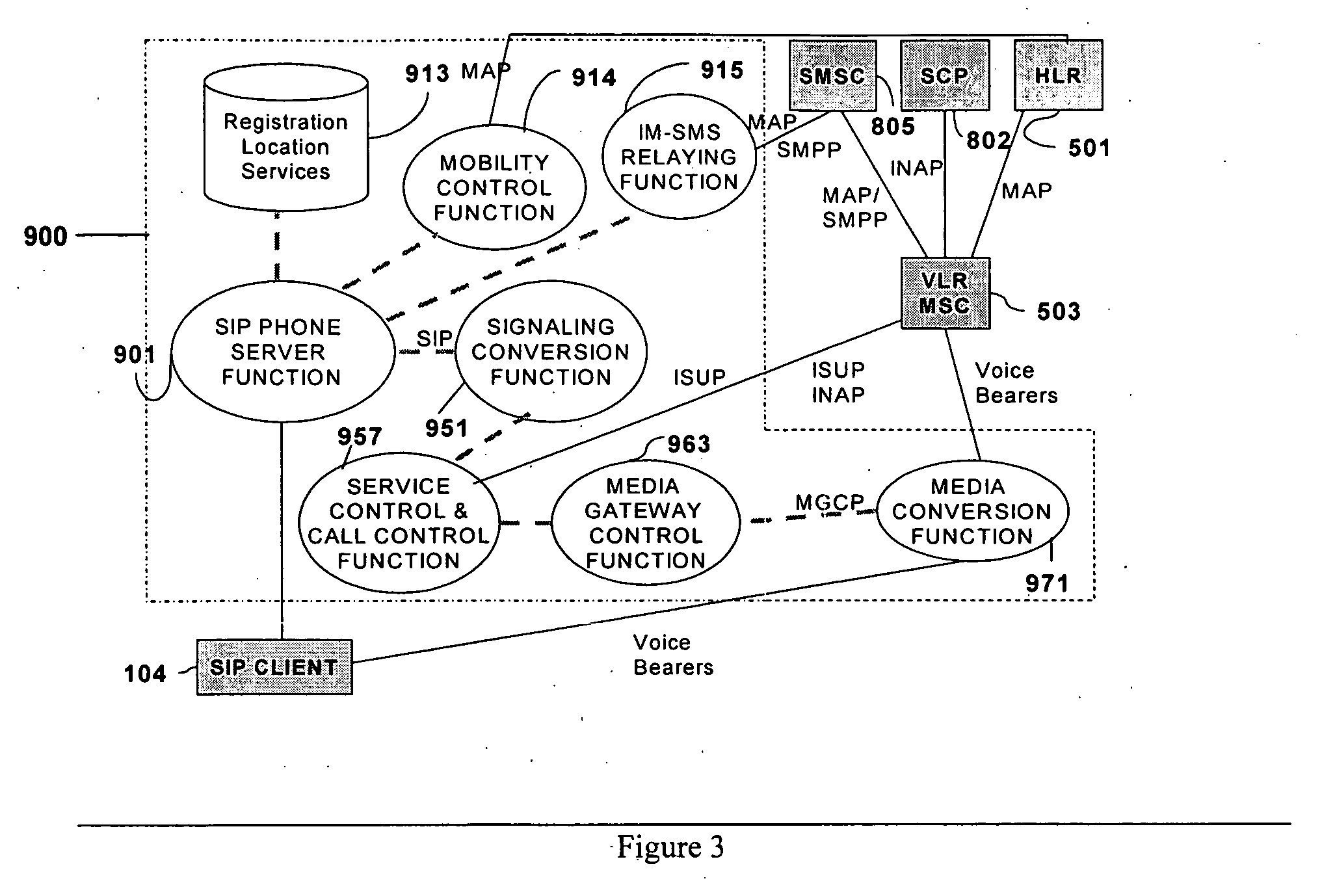
SIP2 mobile gateway
InactiveUS20060198334A1Time-division multiplexConnection managementMobile Telephone NumberRing back tone
A system and method for using an IP client attached to the Public Internet, acting as a virtual mobile terminal such as a cell phone, to have full access to mobile telephony services offered by a mobile operator using a SIP2 Mobile gateway. The services include a mobile telephone number, capabilities of sending and receiving short messages and mobile intelligent services such as prepaid billing, number translation, and ring back tones.
Owner:ARGELA TECH
Method and apparatus for an adaptive target vehicle notification system
InactiveUS20090174572A1Easy to deployRemarkable effectRoad vehicles traffic controlDriver/operatorEngineering
Methods and apparatus are described to improve emergency vehicle deployment by automatically alerting all other nearby vehicles on the road as to the presence and intention of the emergency vehicle. Since the use of audible sirens has somewhat marked effectiveness, in selecting the most practical automated method to notify most drivers a review is given of the various data-links that are available today, including plans for new standards. The invention focuses on the ubiquitous cellular telephone and methods are described to relay an emergency vehicle's siren through the device to help clear the road ahead for the emergency services vehicle. Furthermore, the method uses techniques to determine which cell users are in the path of the vehicle and targets only those cell devices to relay the siren. The relaying is virtual as it may use siren or similar ring-tones that respond to the emergency notification to the user's cell phone number. The invention makes use of calls, broadcasts, SMS messaging, text messaging, Push to Talk (PTT), e mails, and other means of cell phone communication.
Owner:SMITH ALEXANDER E
Citizen communication center
InactiveUS7301450B2Quickly and reliably warn and alertEasy to changeDigital data information retrievalTelephonic communicationTime informationEmail address
Owner:C THREE HLDG LIMITED LIABILITY
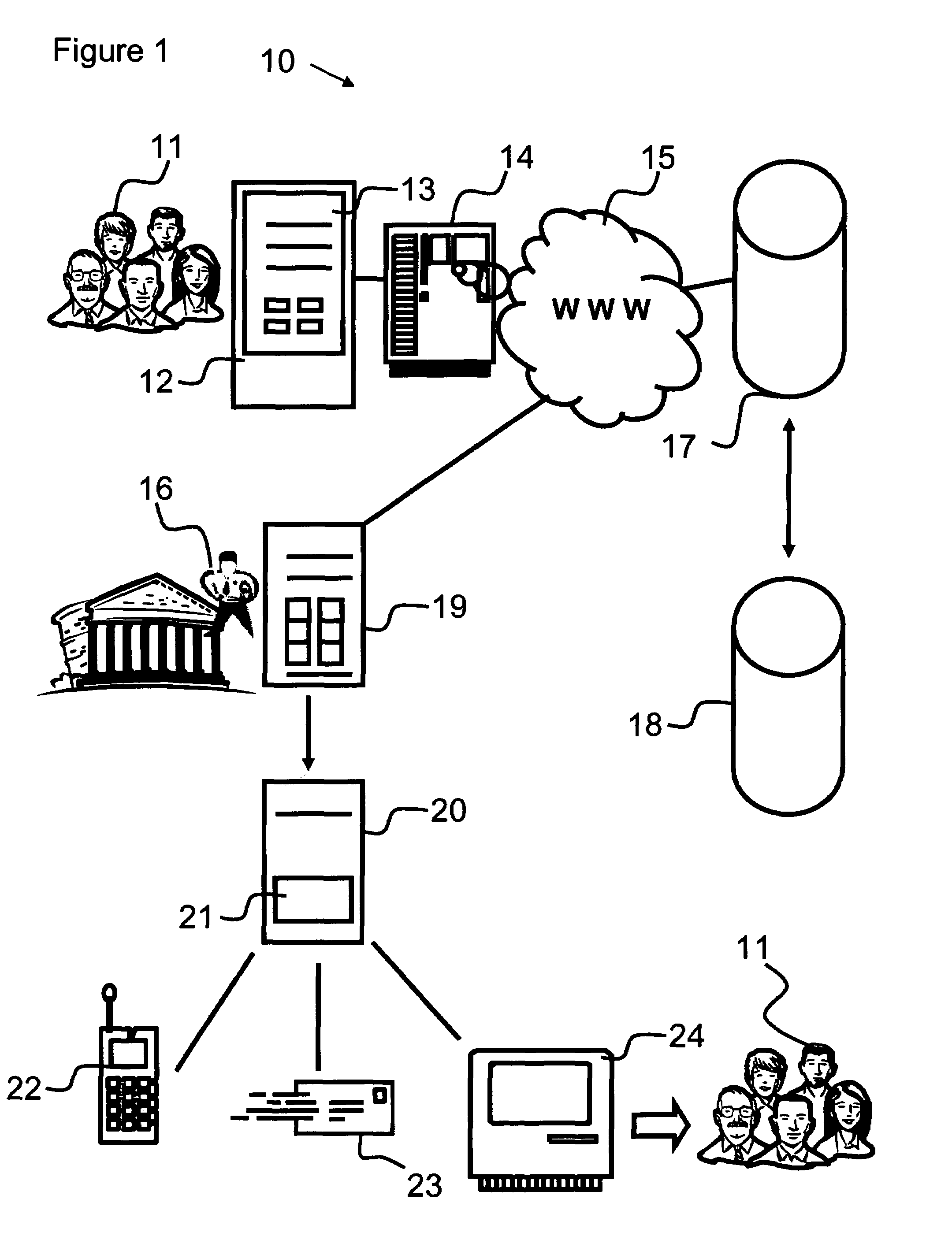
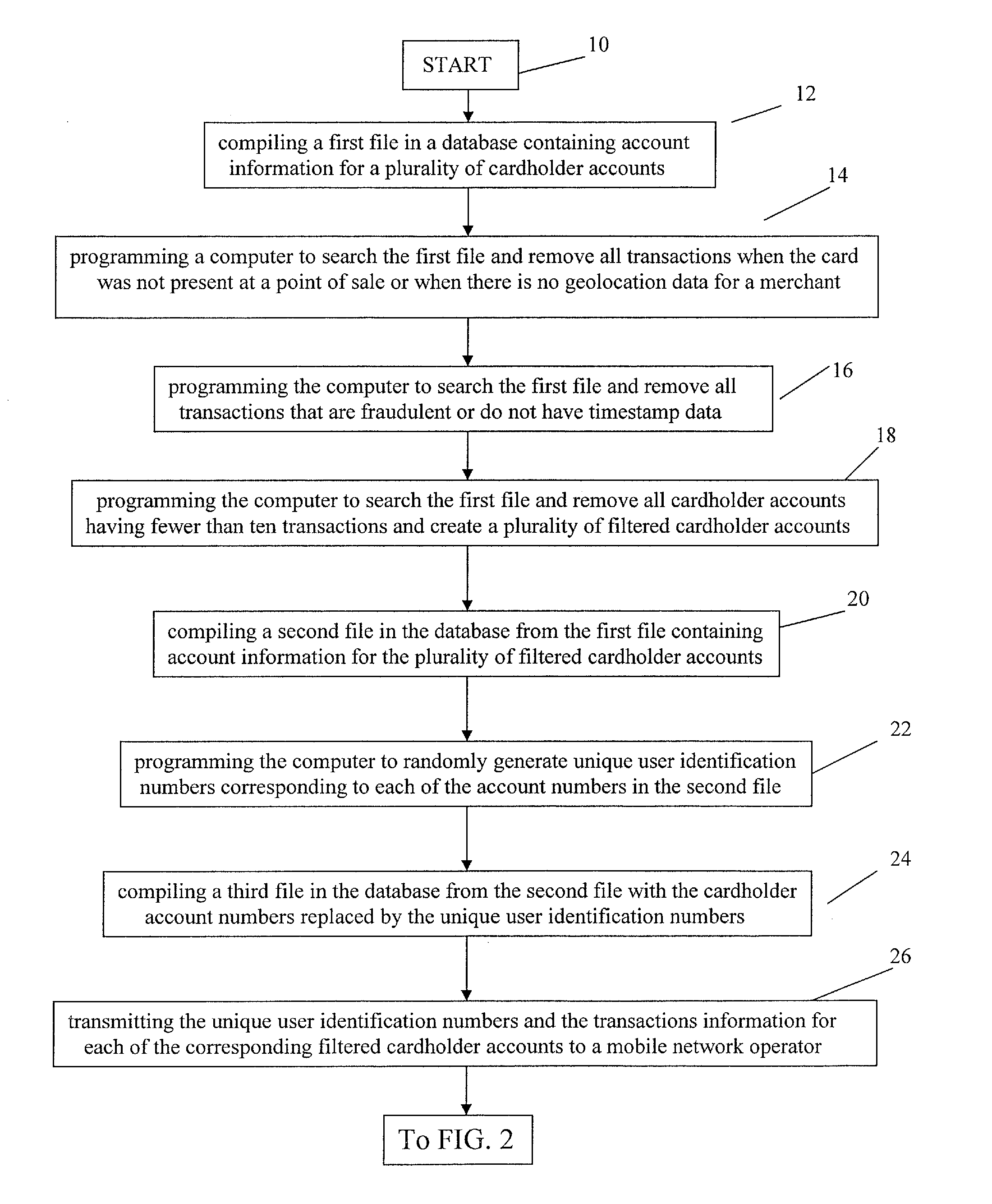
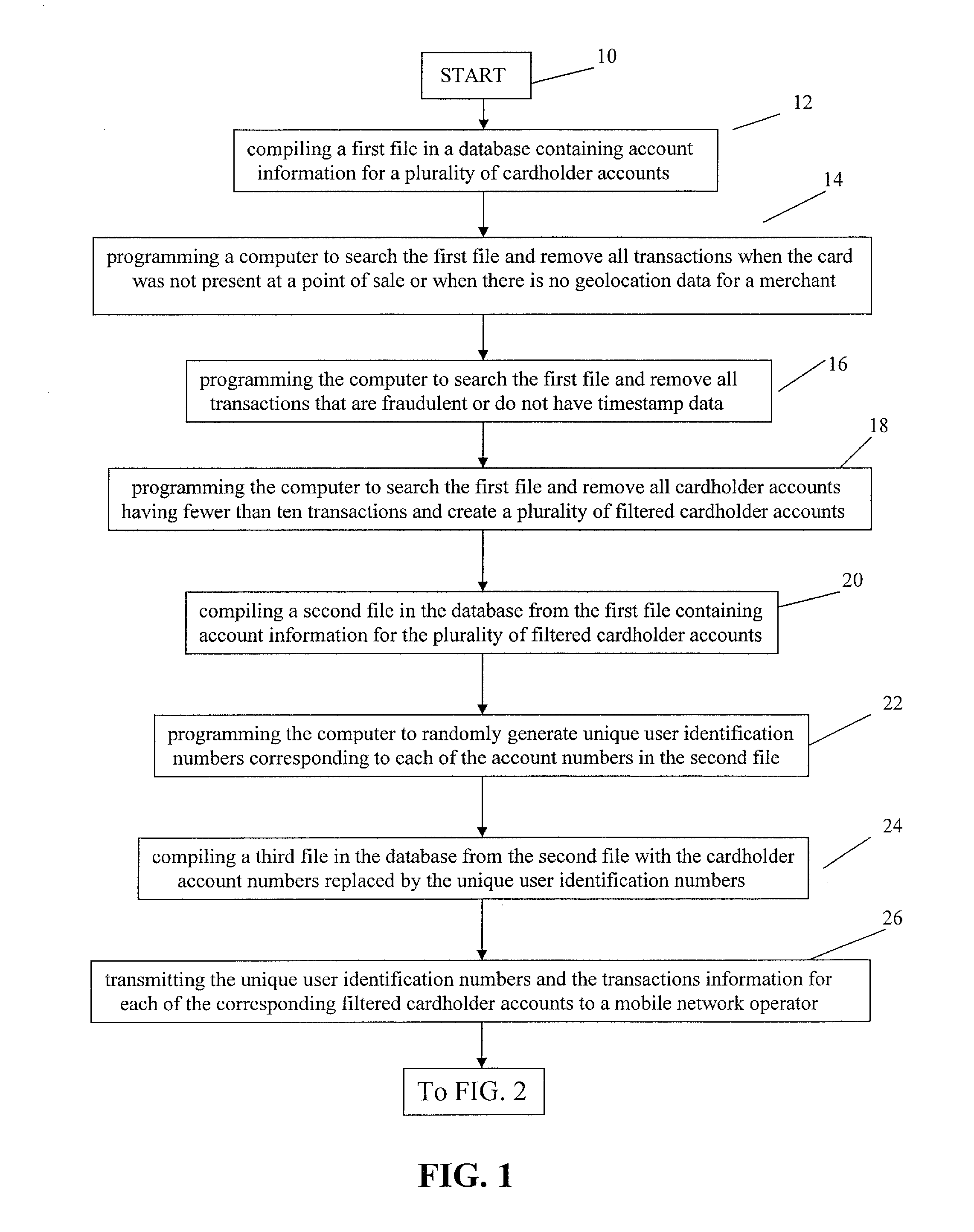
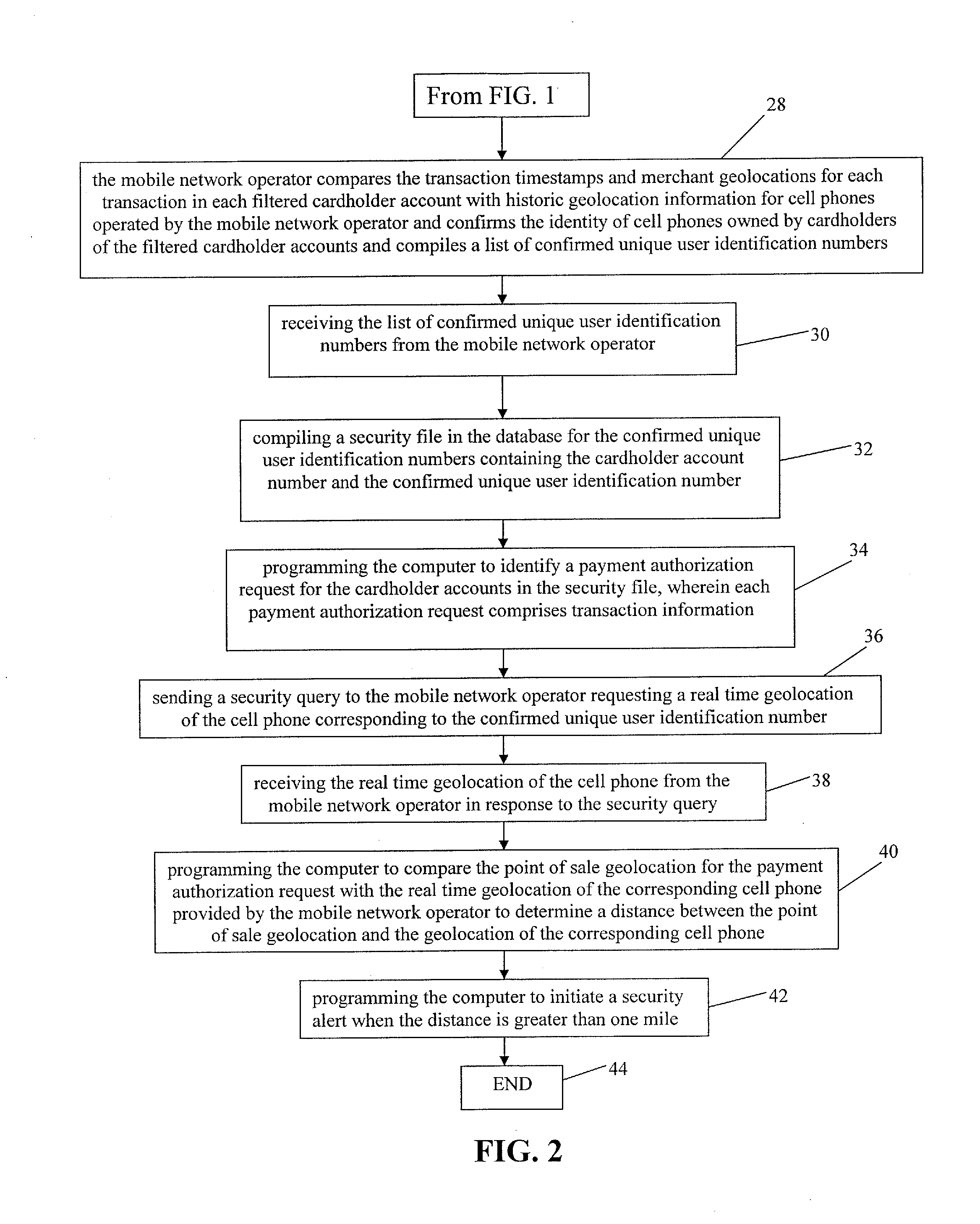
Method for Providing Payment Card Security Using Registrationless Telecom Geolocation Capture
InactiveUS20130290119A1Point-of-sale network systemsProtocol authorisationMobile Telephone NumberGeolocation
A method for providing registrationless payment card security for a payment network that includes maintaining a list of anonymous mobile telephone numbers, which correspond to personal payment card account numbers (PAN). When a card-present authorization for a listed PAN is received, the payment network requests the geolocation of the cell phone of the card holder in real time from the mobile network operator. The mobile network operator determines the geolocation of the cell phone and transmits it to the payment network. The payment network compares the geolocation of the cell phone with the geolocation of the merchant to confirm that the card holder is present at the location of the transaction.
Owner:MASTERCARD INT INC
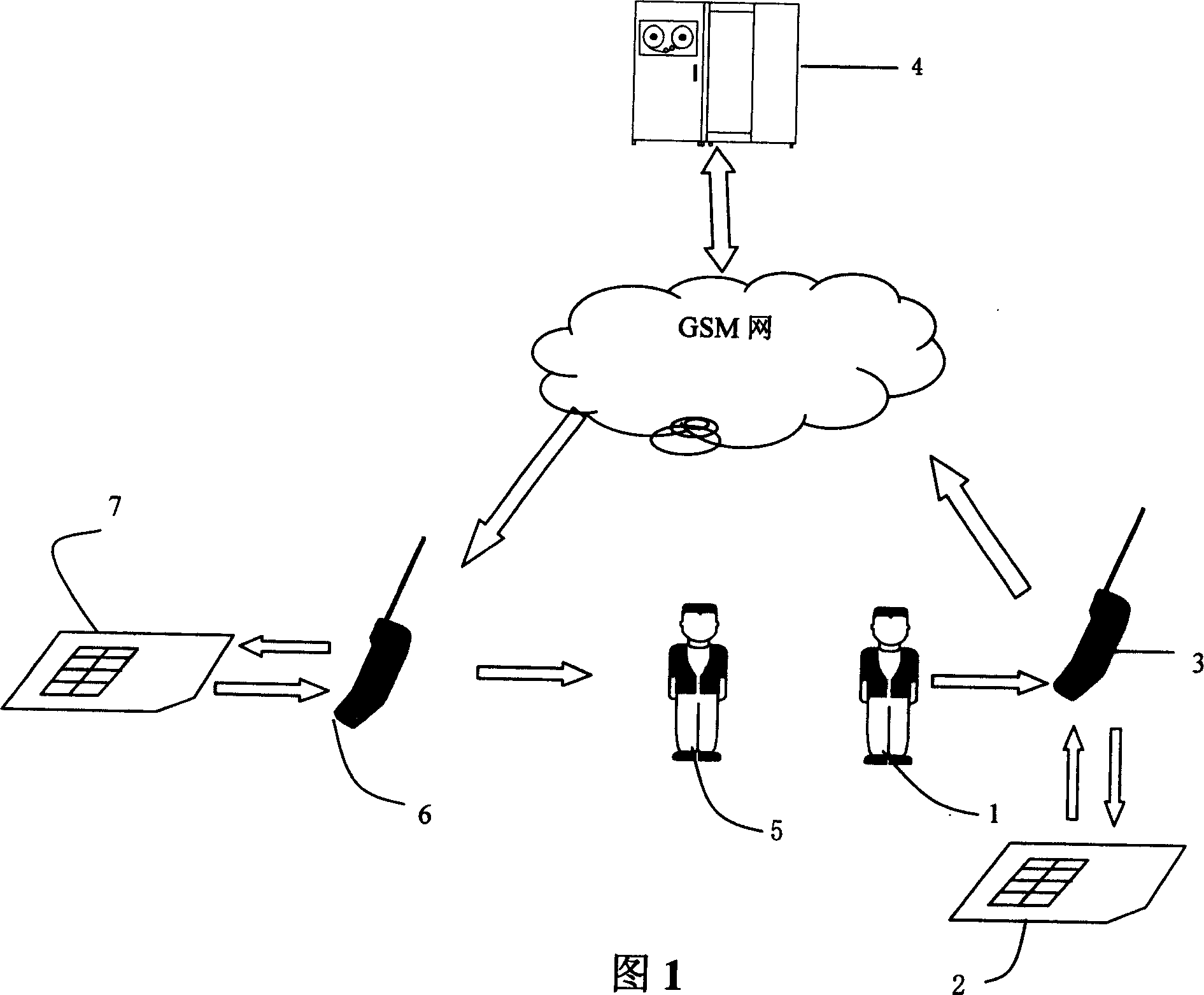
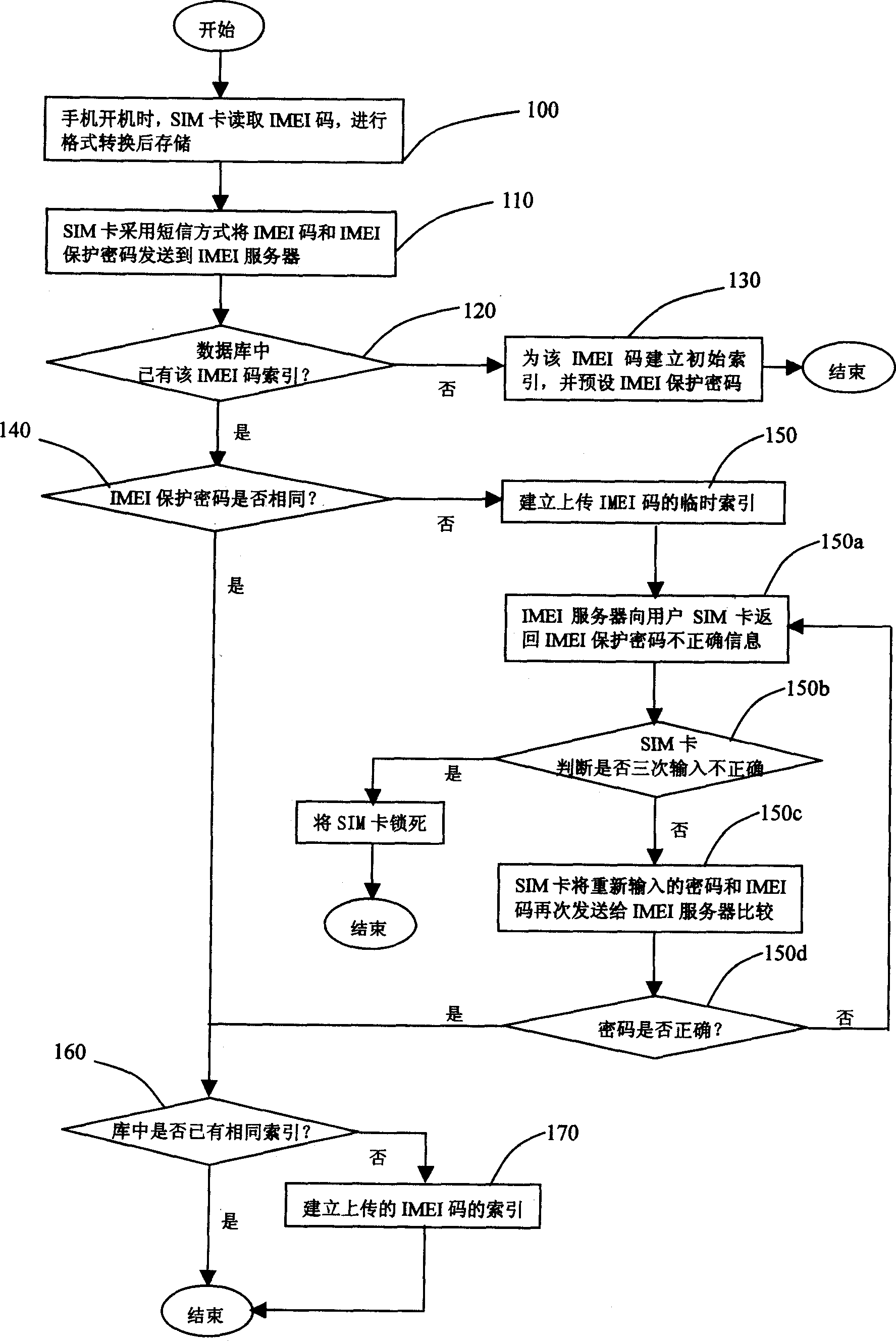
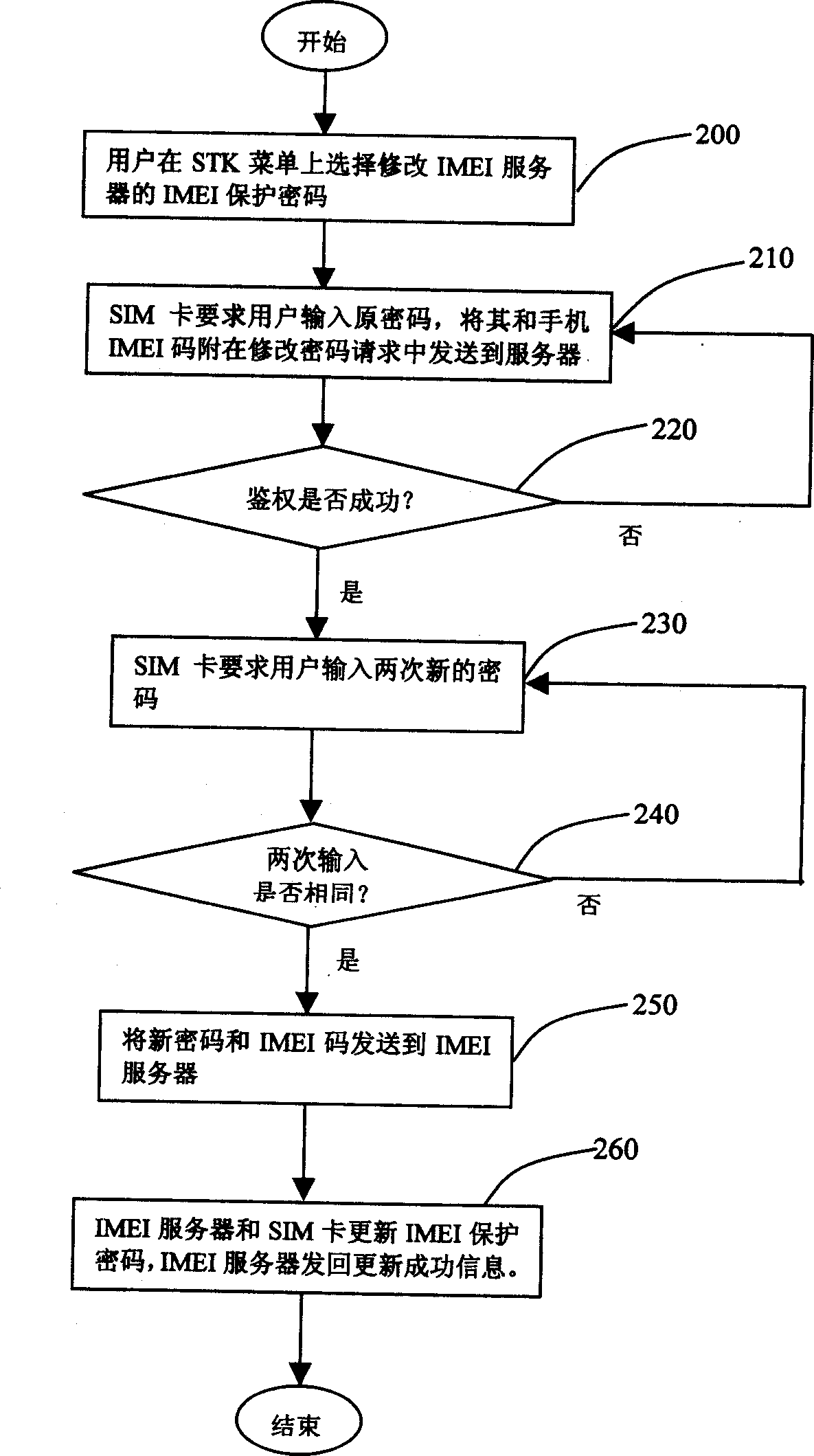
Method and system of preventing handset from theft by using international id code of mobile facilities
ActiveCN1541015AGood for businessEasy to manageUnauthorised/fraudulent call preventionSpecial service for subscribersMobile Telephone NumberMobile equipment identifier
The system is composed of handset, SIM card, network and international mobile equipment identification (IMEI) server. Using the system, handset user logs on network and sends IMEI number automatically. IMEI server receives IMEI code sent by SIM card, and binds IMEI code with user's IMSI code and number of the handset, building corresponding user's index database. Using IMEI protection cipher carries out authentication of handset user's id. Temporary index for illegal user is built. If illegal user logs on network by using stealing handset, id of illegal user can be known from IMEI.
Owner:DATANG MICROELECTRONICS TECH CO LTD
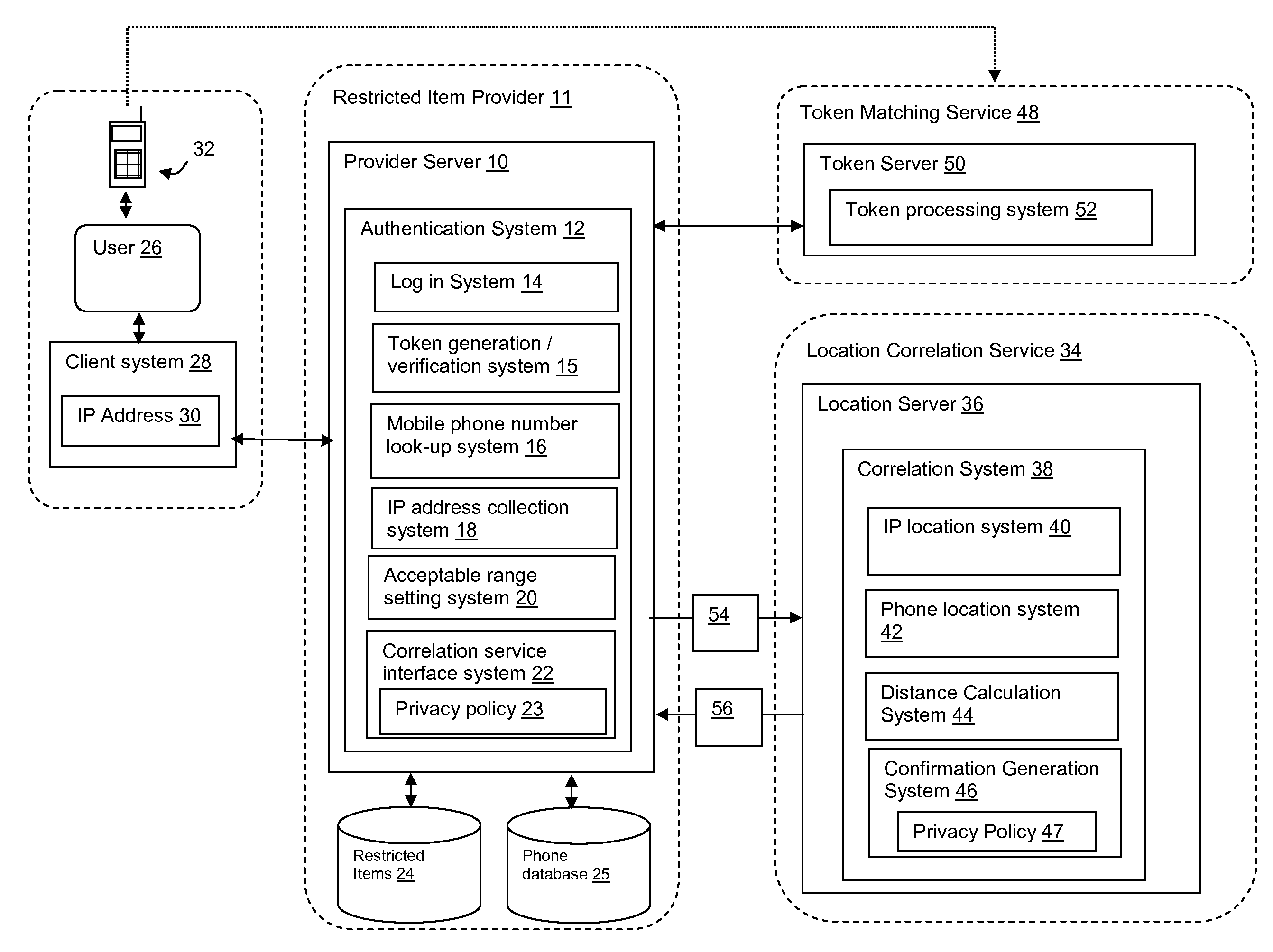
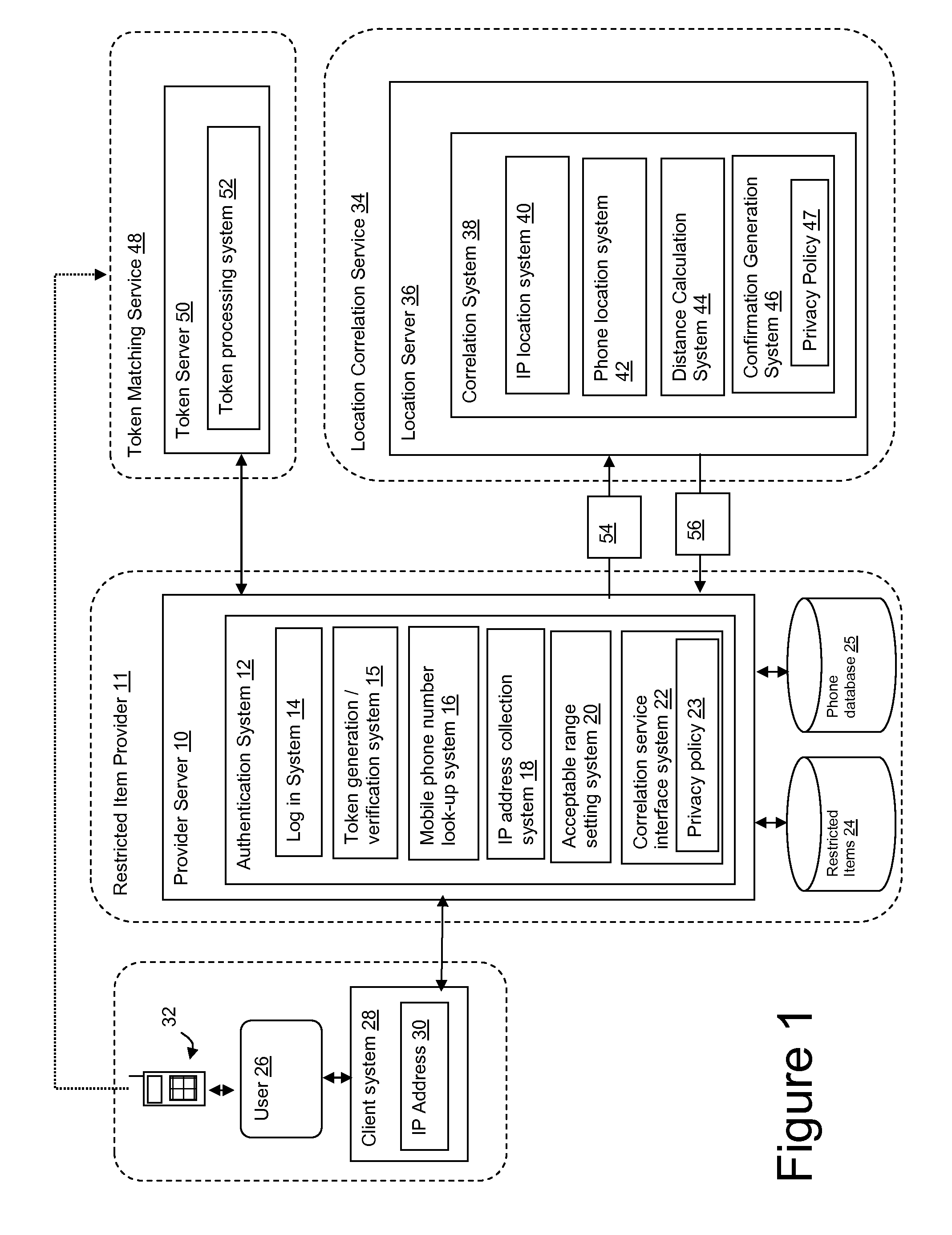
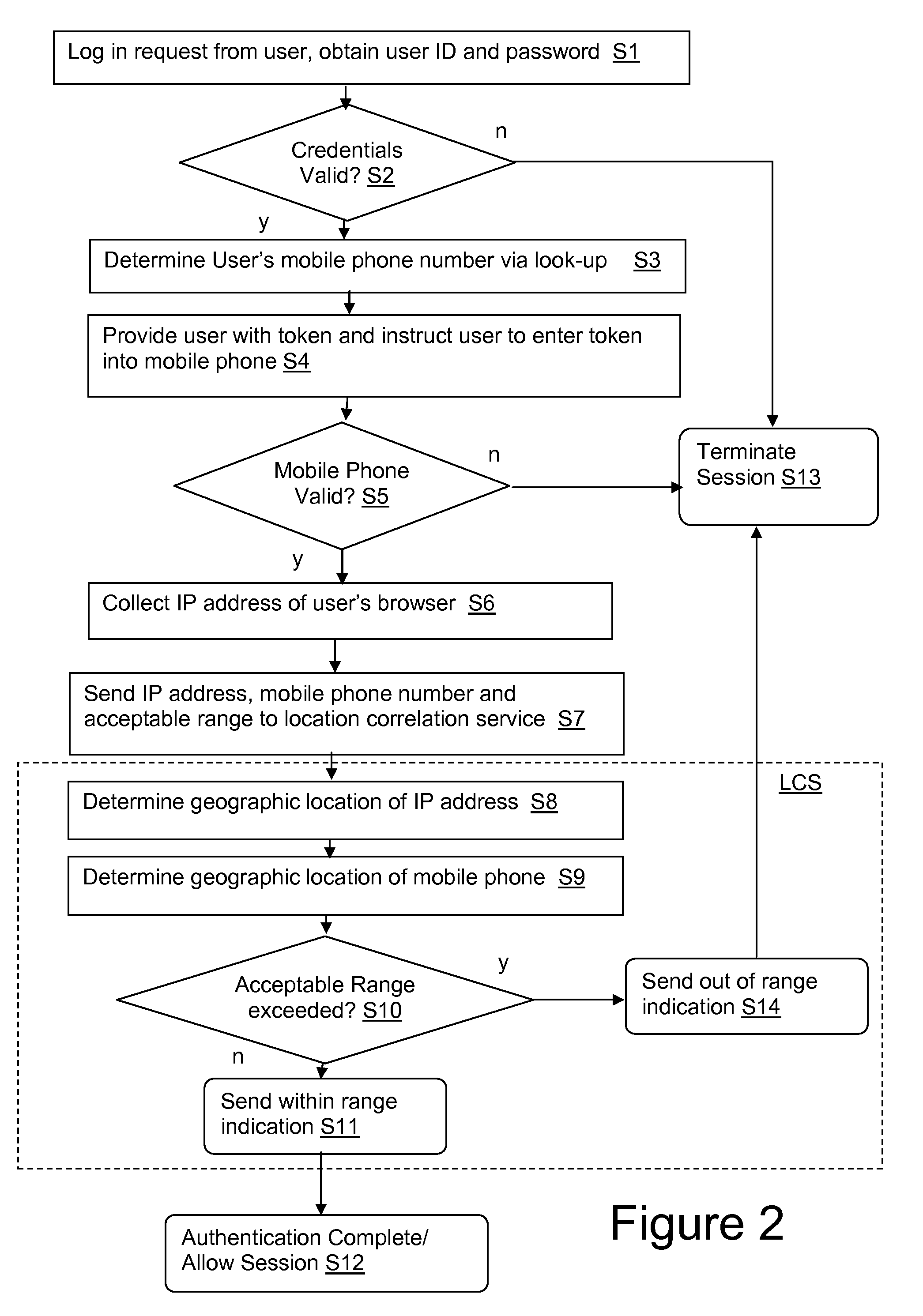
Mobile phone and IP address correlation service
InactiveUS20110138483A1Ensuring privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile Telephone NumberThird party
A system, method and program product for controlling access to a restricted item. A method is provided that includes: receiving a request for access to a restricted item at a computer system associated with a provider, said request originating from a client system; determining an IP address of the client system; determining a mobile phone number of a mobile phone associated with the requester; transmitting to a third party service provider the IP address and mobile phone number; and receiving back from the third party service provider a confirmation message indicating whether or not the IP address and mobile phone are located within an acceptable range of each other.
Owner:IBM CORP
System and method for transaction authentication using a mobile communication device
ActiveUS20120129492A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile Telephone NumberAuthentication server
A transaction authentication system uses a computer network and mobile telephone network to authenticate a user. The user initiates a transaction and provides an identity token, such as the mobile telephone number. The identity token is used by an authentication server to initiate the issuance of a new temporary identity for the corresponding mobile device. The new temporary identity is forwarded from the mobile device to the authentication server which issues a security code if there is a match between the new temporary identities. The security code is forwarded to a transaction server which relays it to the authentication server. If the forwarded security code matches the generated security code, the transaction is permitted to continue.
Owner:MOBILESPHERE HLDG
Method of implementing mobile phone terminal access authority authentication
InactiveCN101163336AEffective controlEasy to controlAssess restrictionUser identity/authority verificationMobile Telephone NumberData synchronization
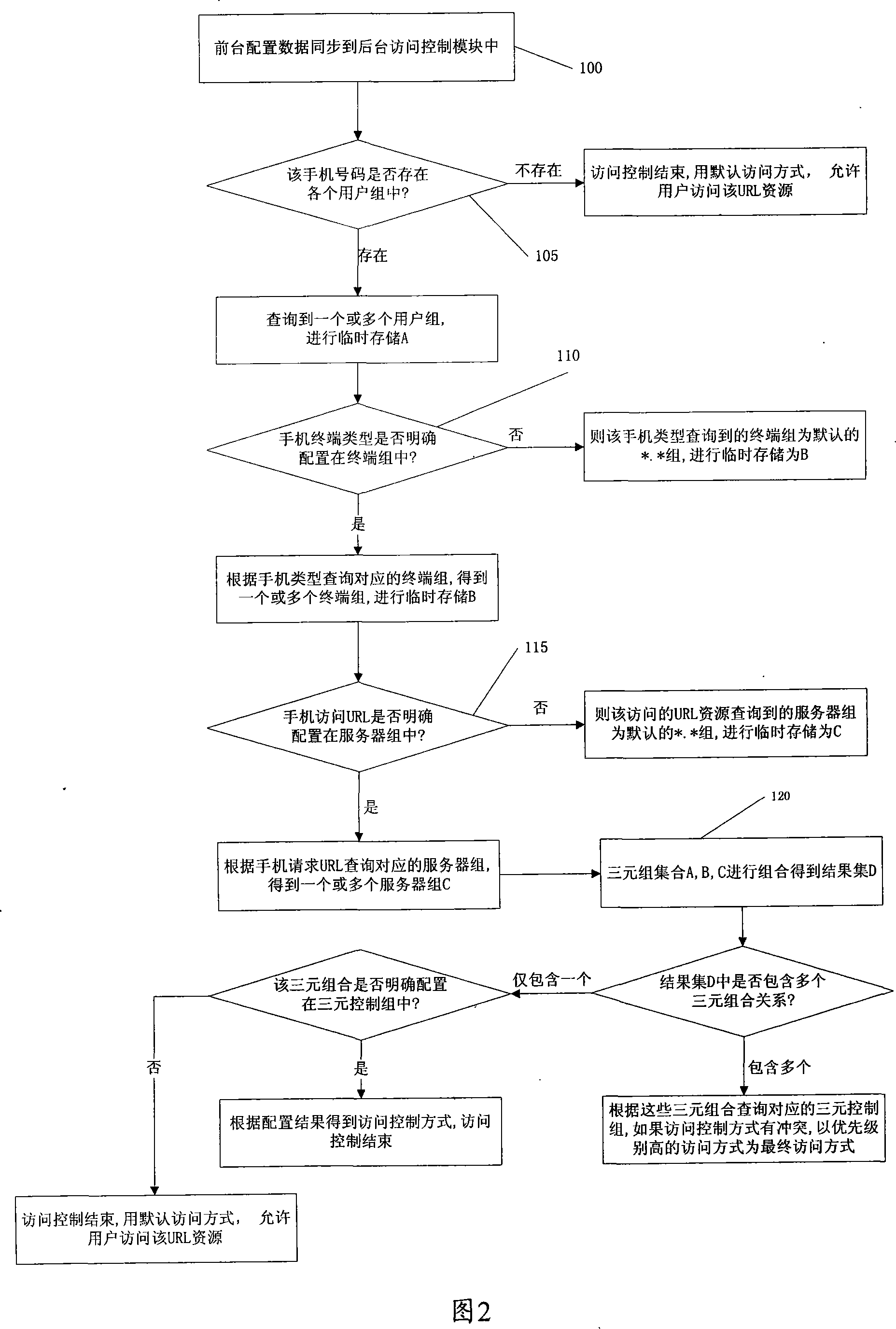
The invention discloses an implementation method of mobile terminal access; the method comprises the following steps that a triplet is collocated on a foreground interface; the collocated data is synchronized to a control module of visit of a background operation processor; a gateway main module gets the mobile terminal type and URL of the required visit with the requirement sent by the mobile terminal and the main module inquires about the corresponding mobile number with the user information; the control module of visit inquires about the triplet collocation data and obtains the control pattern of visit with the obtained mobile number, mobile terminal type and the URL of the required visit. The invention of the WAP gateway integrates the fuzzy matching of regular expression to control the visit to the mobile terminal flexibly through the strategy of triplet control of visit; in this way, various combinations of terminal type, number or number segment and object URL can be controlled and the visit to the mobile terminal is effectively controlled.
Owner:ZTE CORP
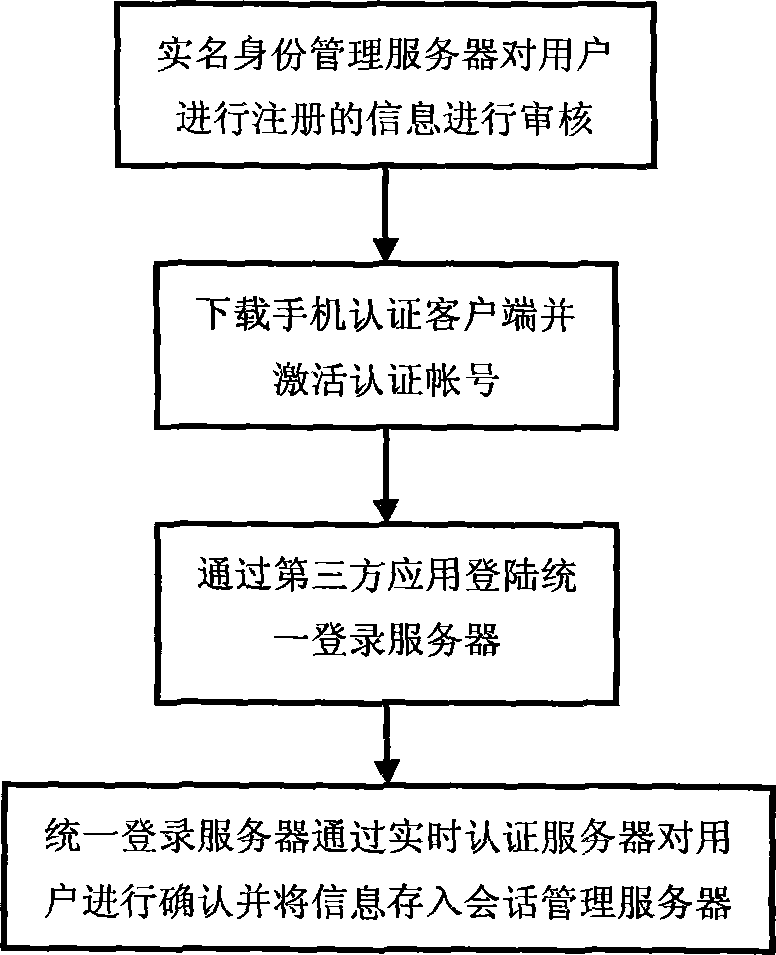
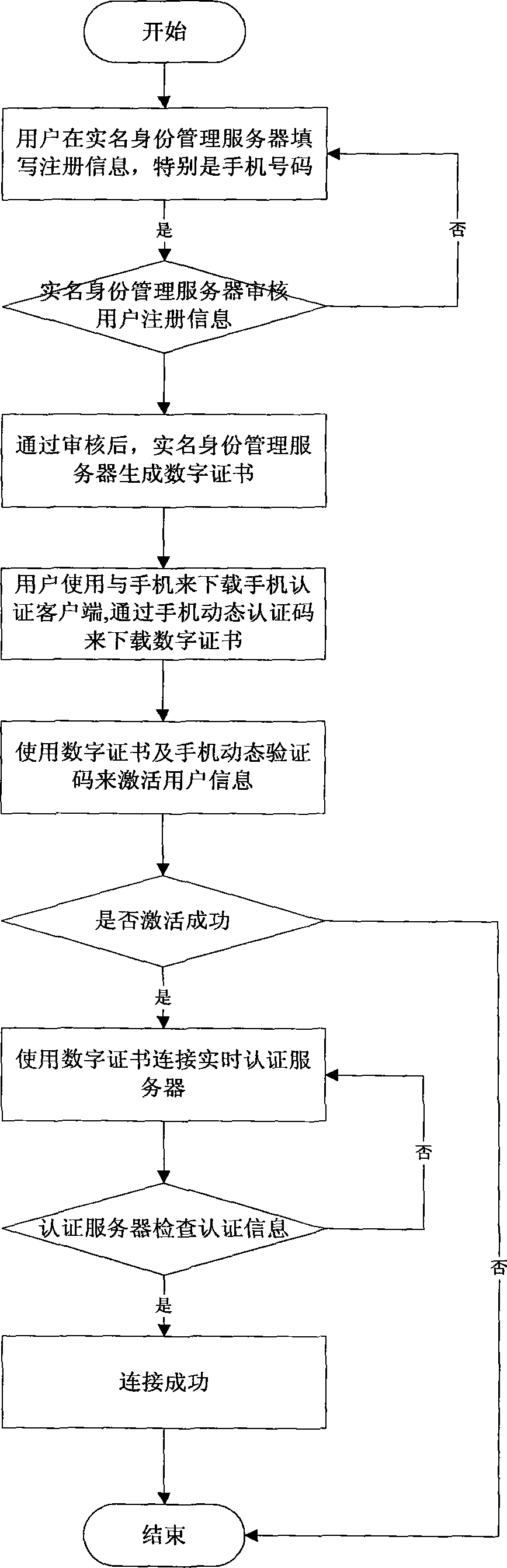
Real-name authentication safe login method and system based on cell phone number
InactiveCN103269270AImprove securityEasy to manageUser identity/authority verificationSecurity arrangementMobile Telephone NumberSession management
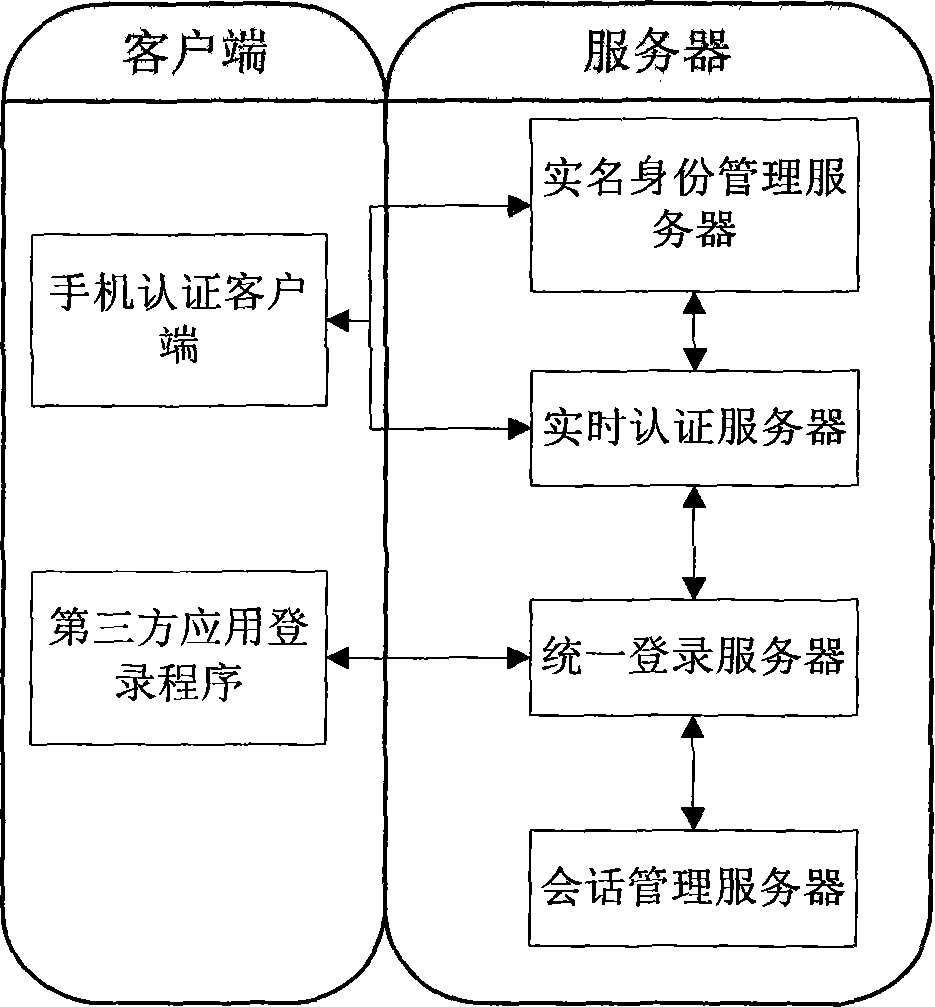
The invention discloses a real-name authentication safe login method and system based on a cell phone number, and relates to the field of internet real-name authentication. The method includes the steps that a real-name identity management server carries out verification and registration according to identity information provided by a user; the user activates an account number through cell phone dynamic verification codes and a digital certificate after passing the verification; a third-party application applies for a login service, a request is sent to a unified login server and transmitted to a real-time authentication server, the real-time authentication server sends the request to the user for validation, the unified login server adjusts whether the third-party application is allowed to log in according to a result returned to the unified login server, and the unified login server saves session information in a session management server and returns the information to the third-party application if the third-party application is allowed to log in. The real-name authentication safe login method and system based on the cell phone number solve the problem that the user relies on user information in different applications, can guarantee safety of the information through cell phone authentication and brings convenience to management for network management departments, the user does not need to maintain personal information again in all the applications, convenience is brought to the user, and worry about privacy disclosure of the user is reduced.
Owner:安徽杨凌科技有限公司
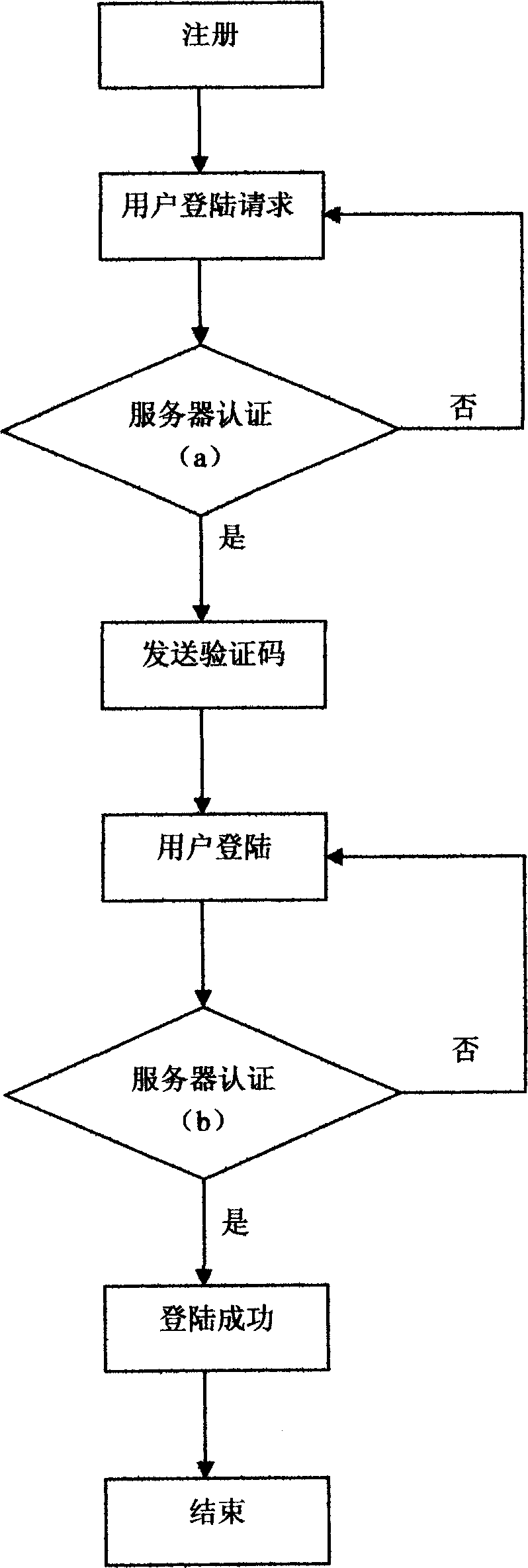
Method for protecting safety of account number cipher
InactiveCN1832401AImprove authentication strengthResistance to attacksMultiple keys/algorithms usageUser identity/authority verificationMobile Telephone NumberAuthentication server
This invention relates to a method for protecting safety of codes of account numbers including the following steps: a user should submit the account number name and its cell phone number to a registration certification server system, which binds the name and the number, logs on the request, then the server certifies and sends it the verification code, the user logs on then the server certifies it.
Owner:陈珂
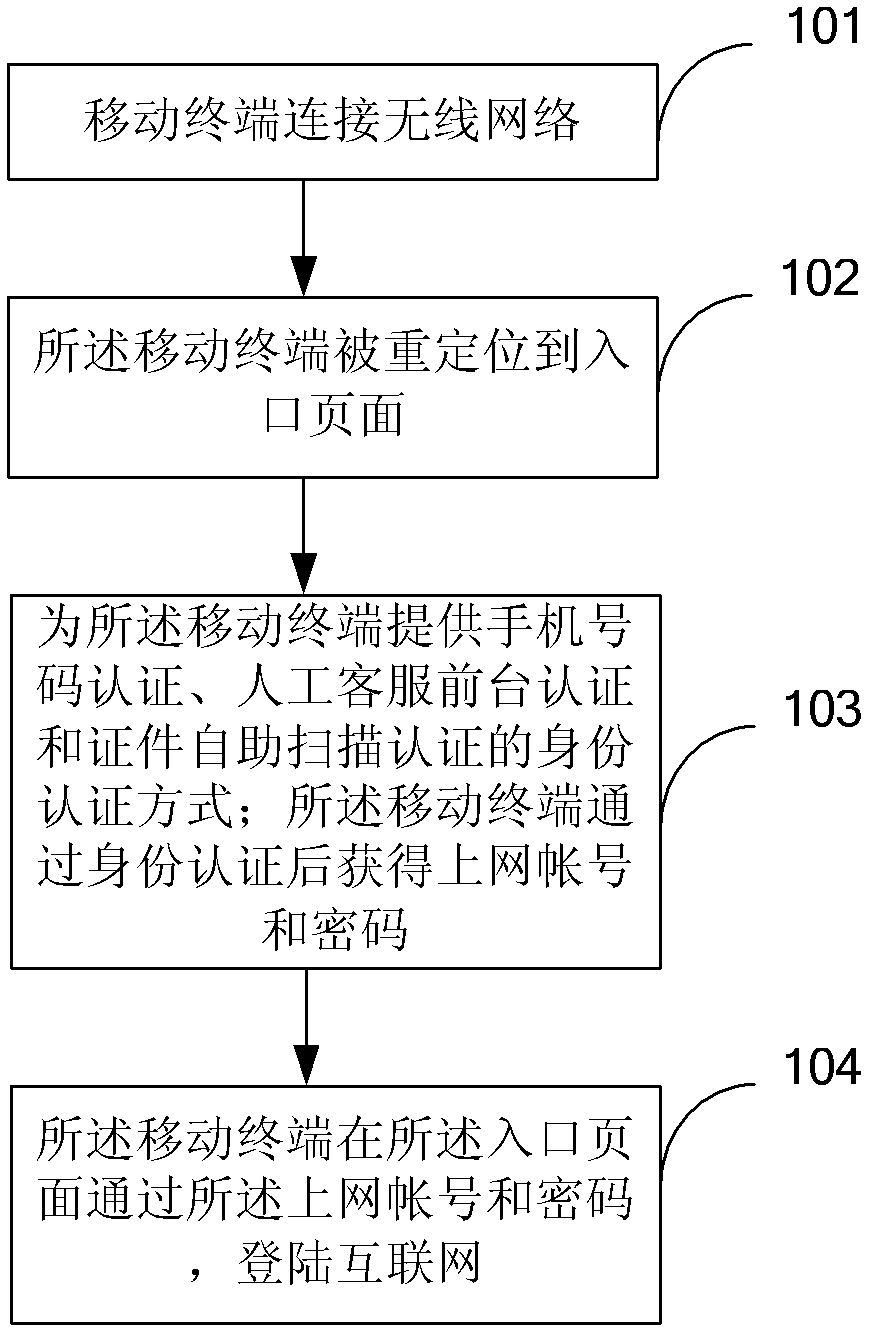
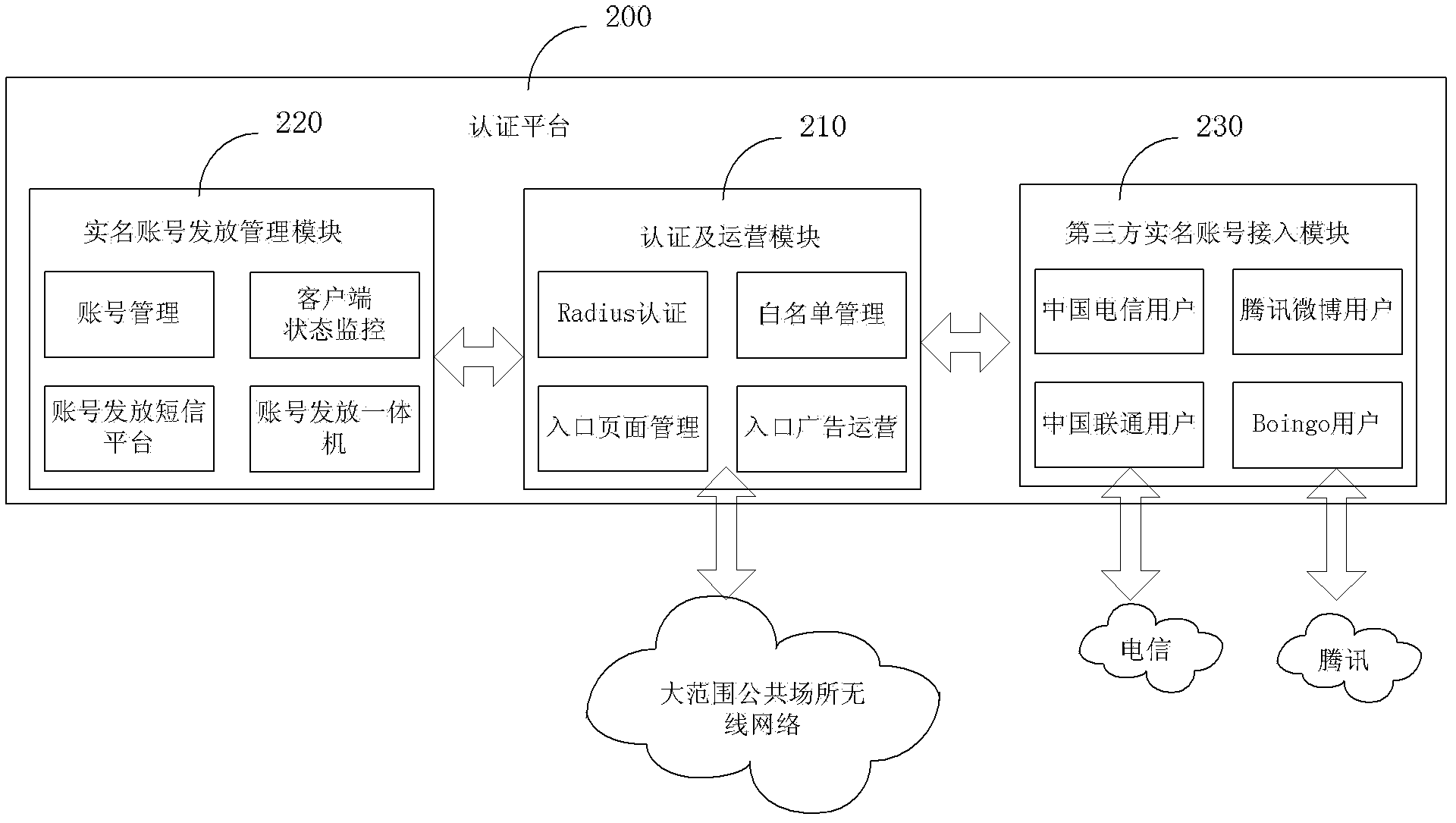
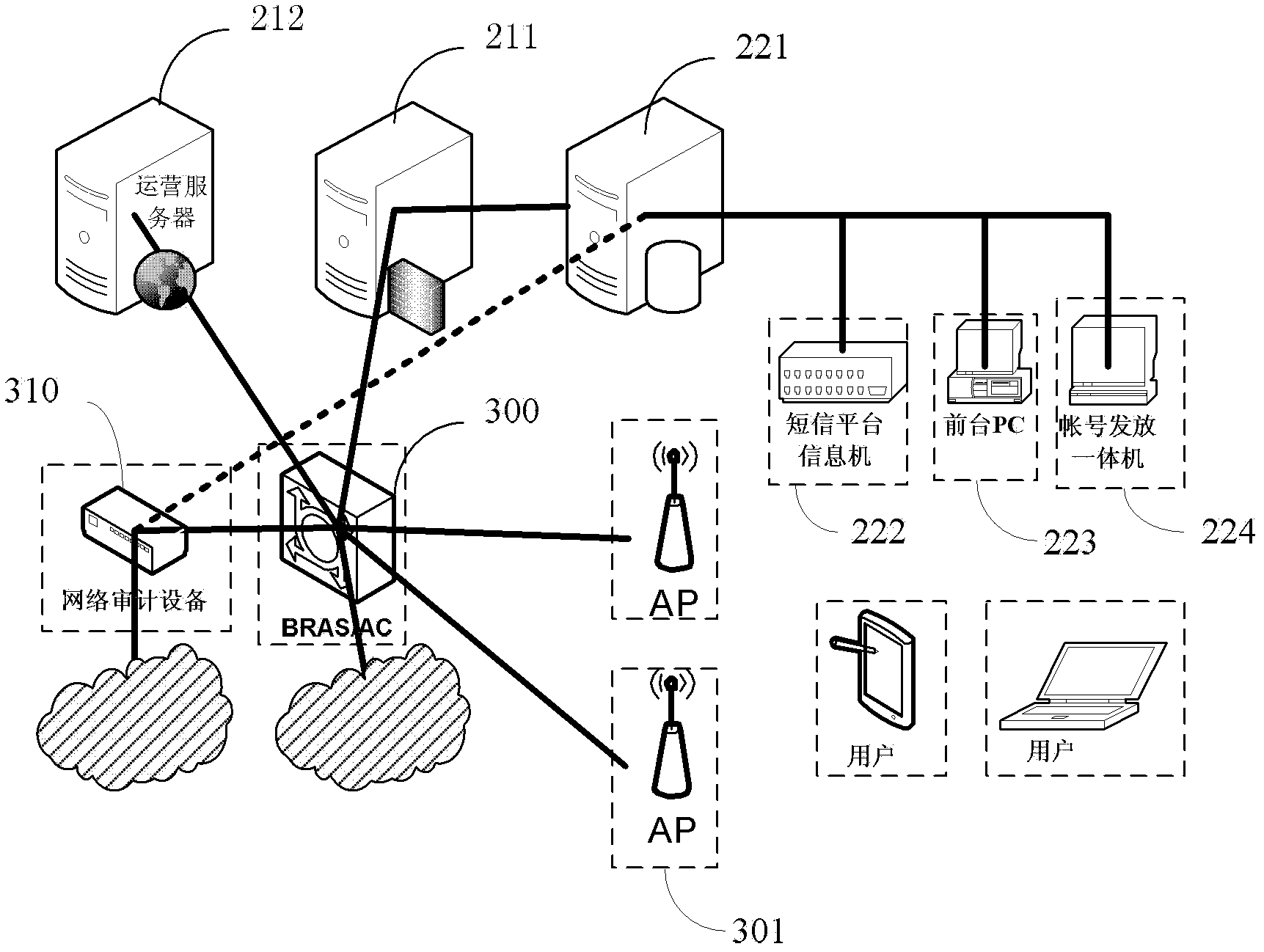
Real name authentication method and authentication platform of wireless networks in a wide range of public places
InactiveCN102594835AConvenient real-name Internet access needsPrompt processing of release requestsSubstation equipmentTransmissionMobile Telephone NumberWireless mesh network
The invention discloses a real name authentication method and an authentication platform of wireless networks in a wide range of public places. The authentication method includes that a mobile terminal is connected with a wireless network; the mobile terminal is relocated to an entry page, provides the mobile terminal with identity authentication modes of mobile phone number authentication, artificial customer service foreground authentication and certificate self-help scanning authentication; obtains an internet account and a password after the identity is authenticated; and logs on the internet in the entry page through the internet account and the password. The real name authentication method and the authentication platform of wireless networks in a wide range of public places can provide quick and convenient identity authentication for wireless network users in a wide range of public places, and solve the problem that wireless networks in large wide range of public places cannot provide large number of users with quick and convenient real name internet service.
Owner:北京掌慧纵盈科技股份有限公司
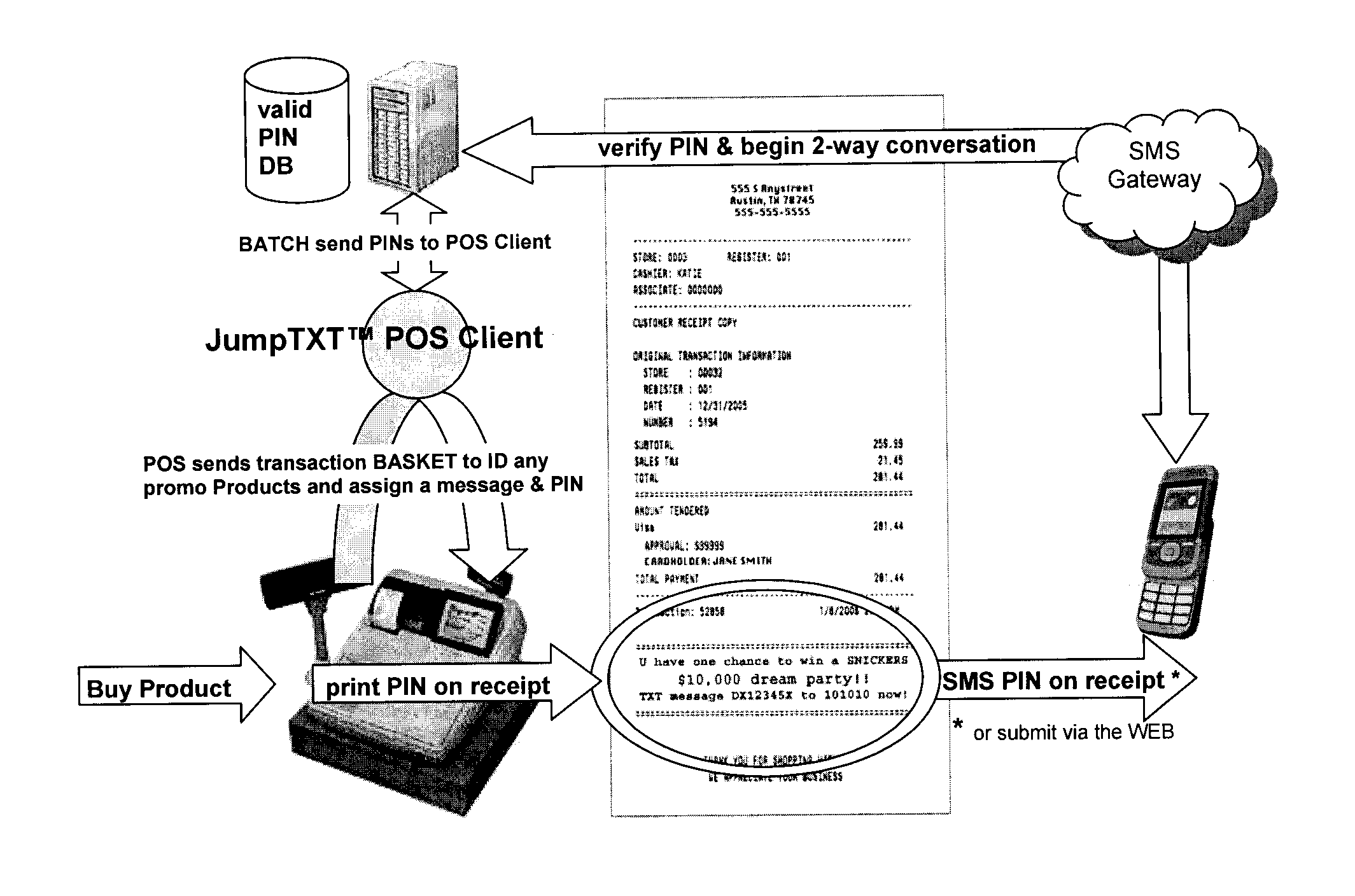
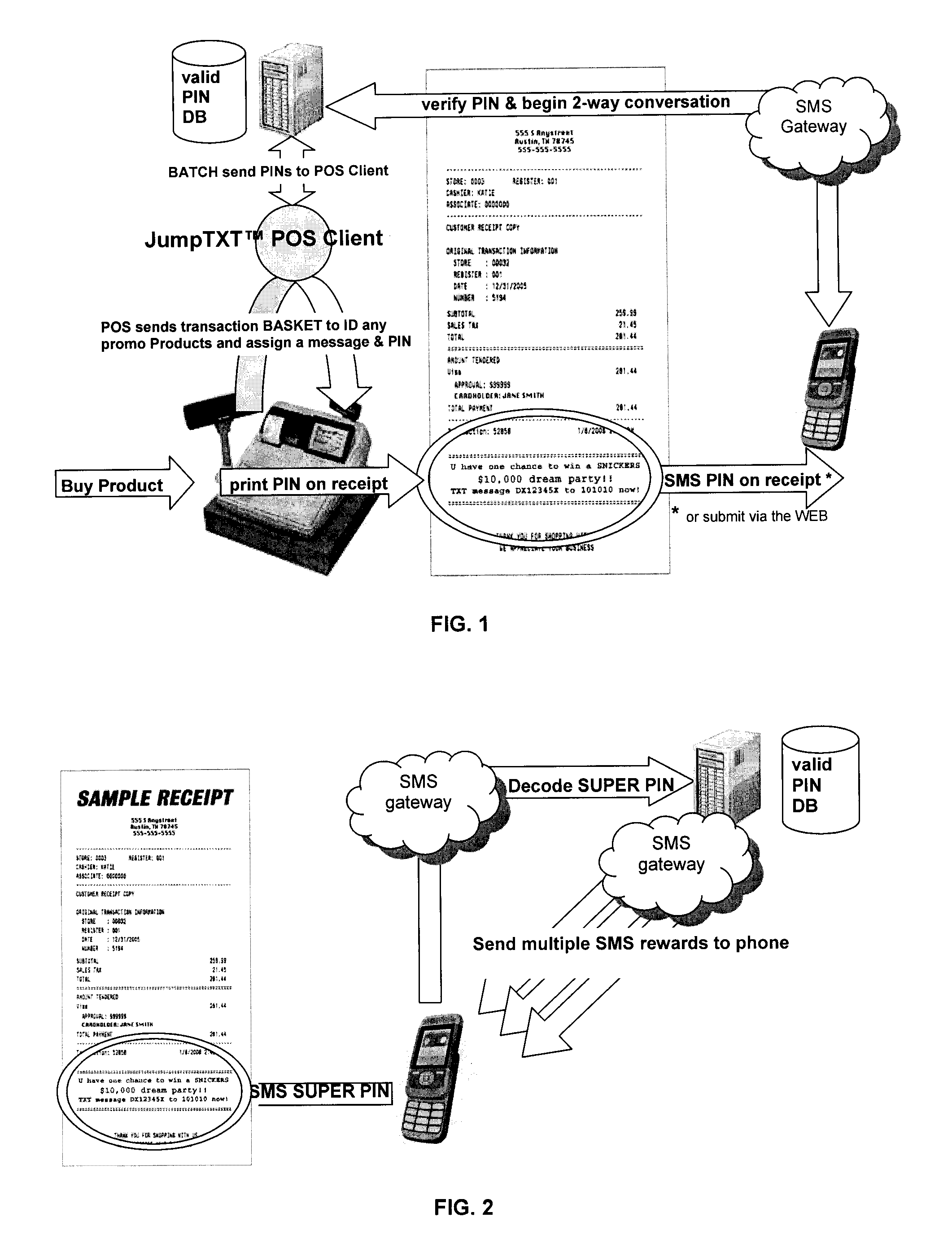
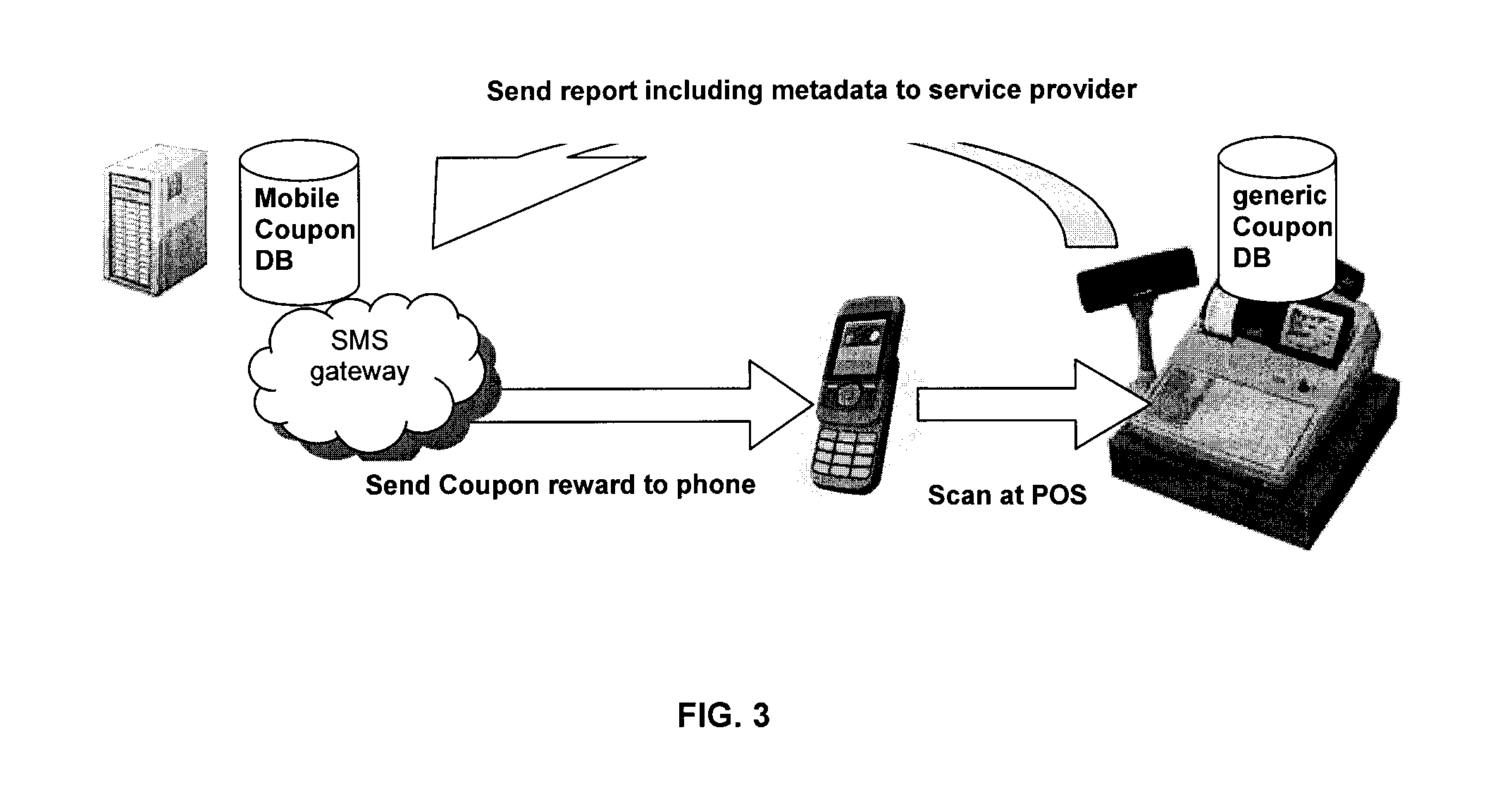
Assigning a mobile-redeemable personal identification number to a consumer as a mobile reward or following a purchase of a promotional item
InactiveUS20110191152A1Enable enhance effectivenessCost-effectively distributedDiscounts/incentivesPayment architectureMobile Telephone NumberPersonal identification number
An unique personal identification number (PIN) is issued when a promotional product is purchased. The consumer receives a receipt with information on how to redeem the PIN with a mobile communication device and qualify for a reward. An MSP (mobile service provider) is able to track the consumer's redemption actions to the consumer's mobile telephone number when the consumer redeems the PIN. In another example, the consumer is able to redeem a generic coupon at a point of sale (POS), redeem a PIN by electronically scanning a mobile phone at the POS, and then use the PIN to obtain rewards. A method, system and software product for issuing and redeeming PINs are described.
Owner:IMPACT MOBILE
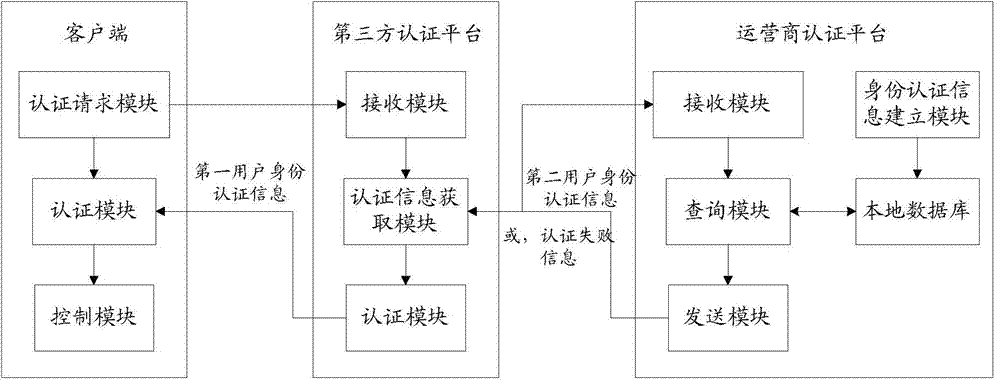
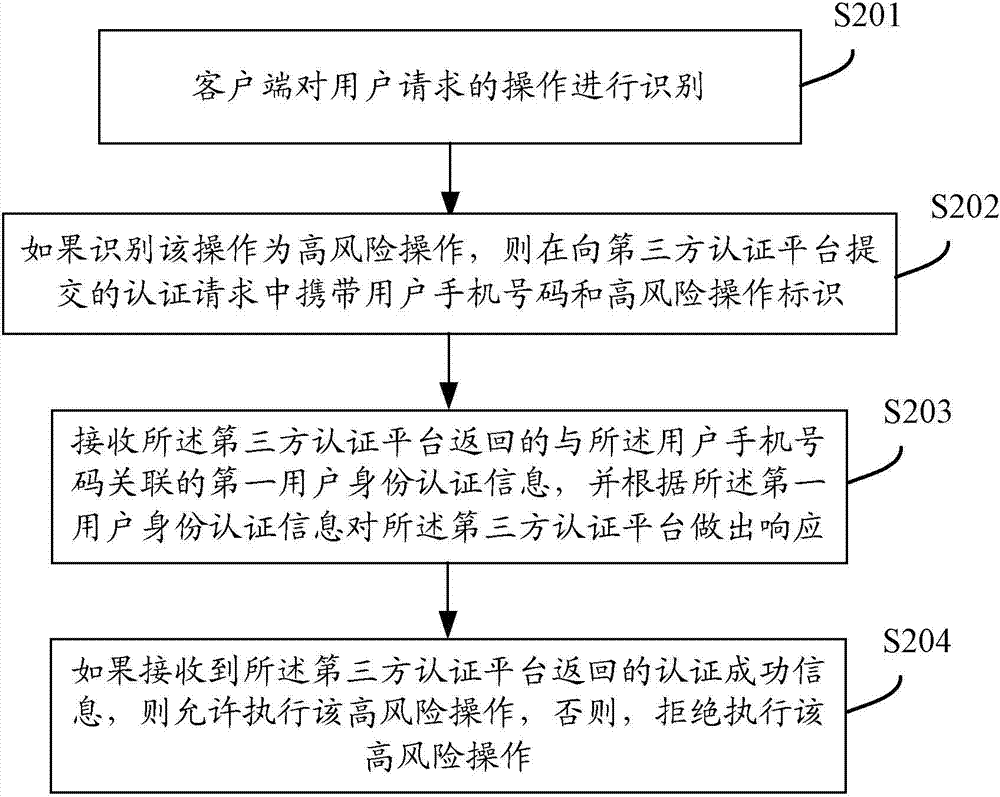
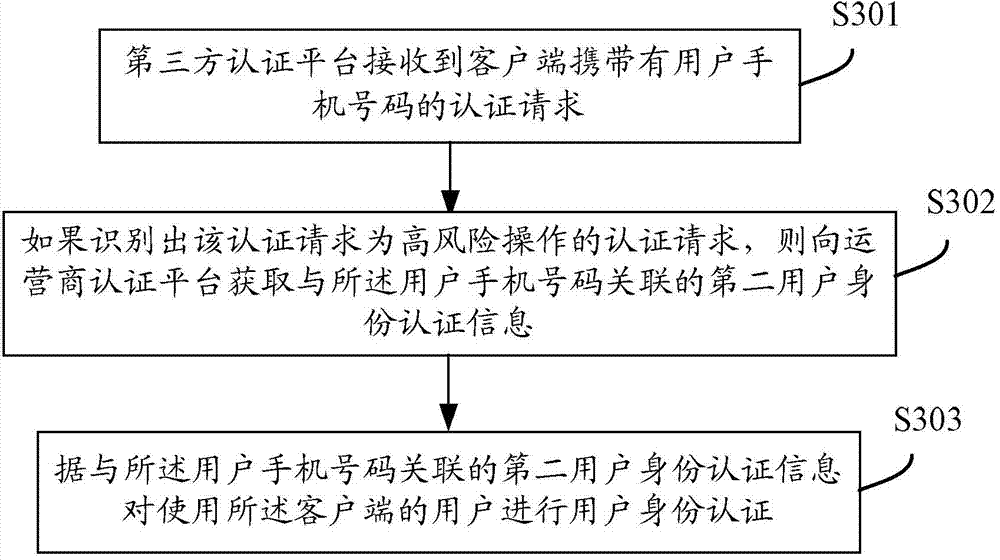
User identity authentication method, third-party authentication platform and operator authentication platform
ActiveCN103944737AEnsure safetyEnhanced Authentication ServicesUser identity/authority verificationInternet Authentication ServiceMobile Telephone Number
The invention discloses a user identity authentication method, a third-party authentication platform and an operator authentication platform all oriented to mobile applications. The system comprises a client, the third-party authentication platform and the operator authentication platform; the third-party authentication platform receives a high-risk operation authentication request carrying a user mobile phone number from the client, and then obtains user identity authentication information associated with the user mobile phone number from the operator authentication platform; the operator authentication platform sends the user identity authentication information which is associated with the user mobile phone number and found in a local database to the third-party authentication platform; the third-party authentication platform authenticates the identity of a user using the client according to the user identity authentication information associated with the user mobile phone number. The user information of the operator is fused with the authentication technology of the third-party applications, so that the authentication services with the mobile user identity as the core can be further enhanced, the authentication level can be increased and the security of the user and the third-party can be guaranteed.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
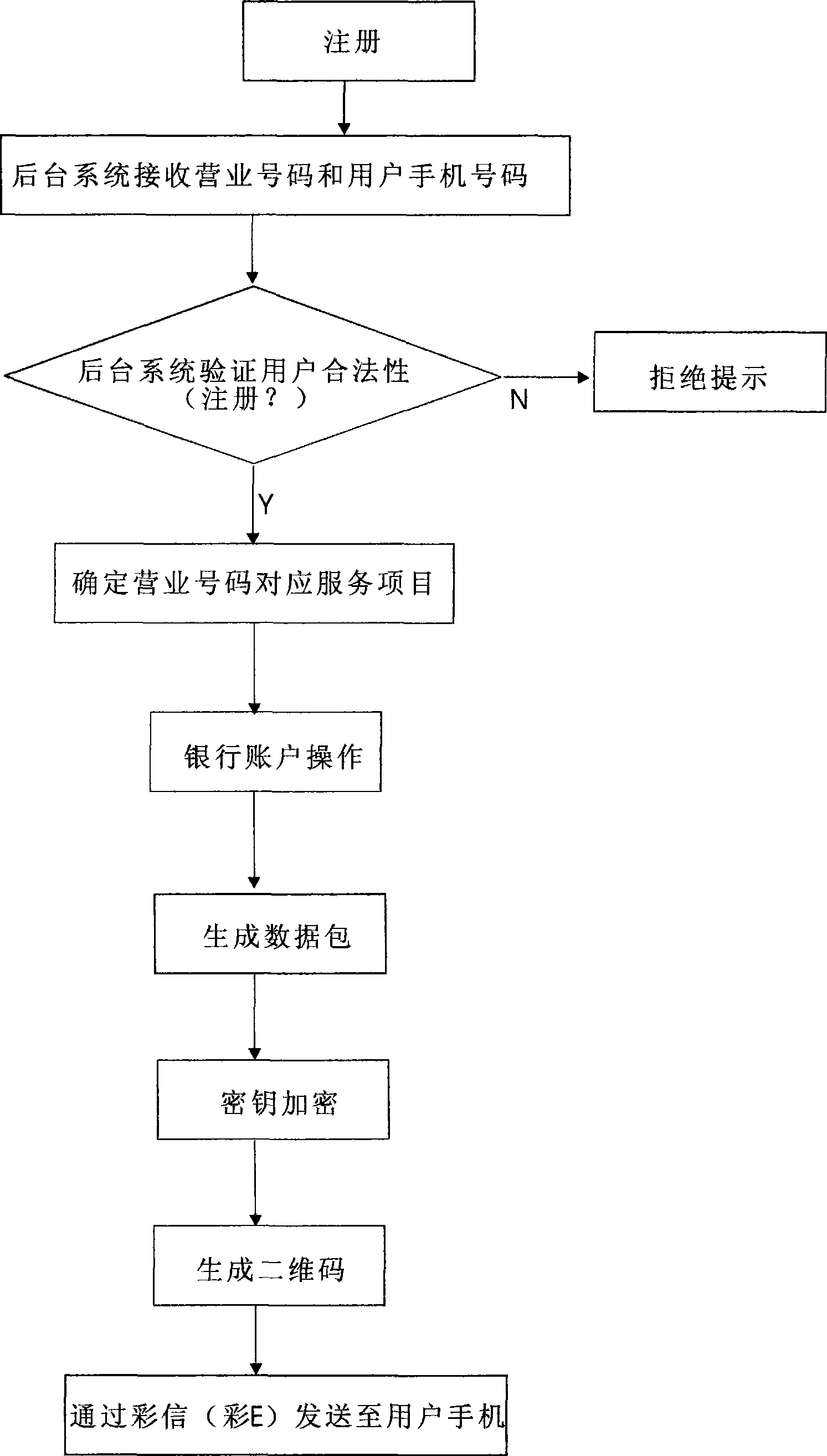
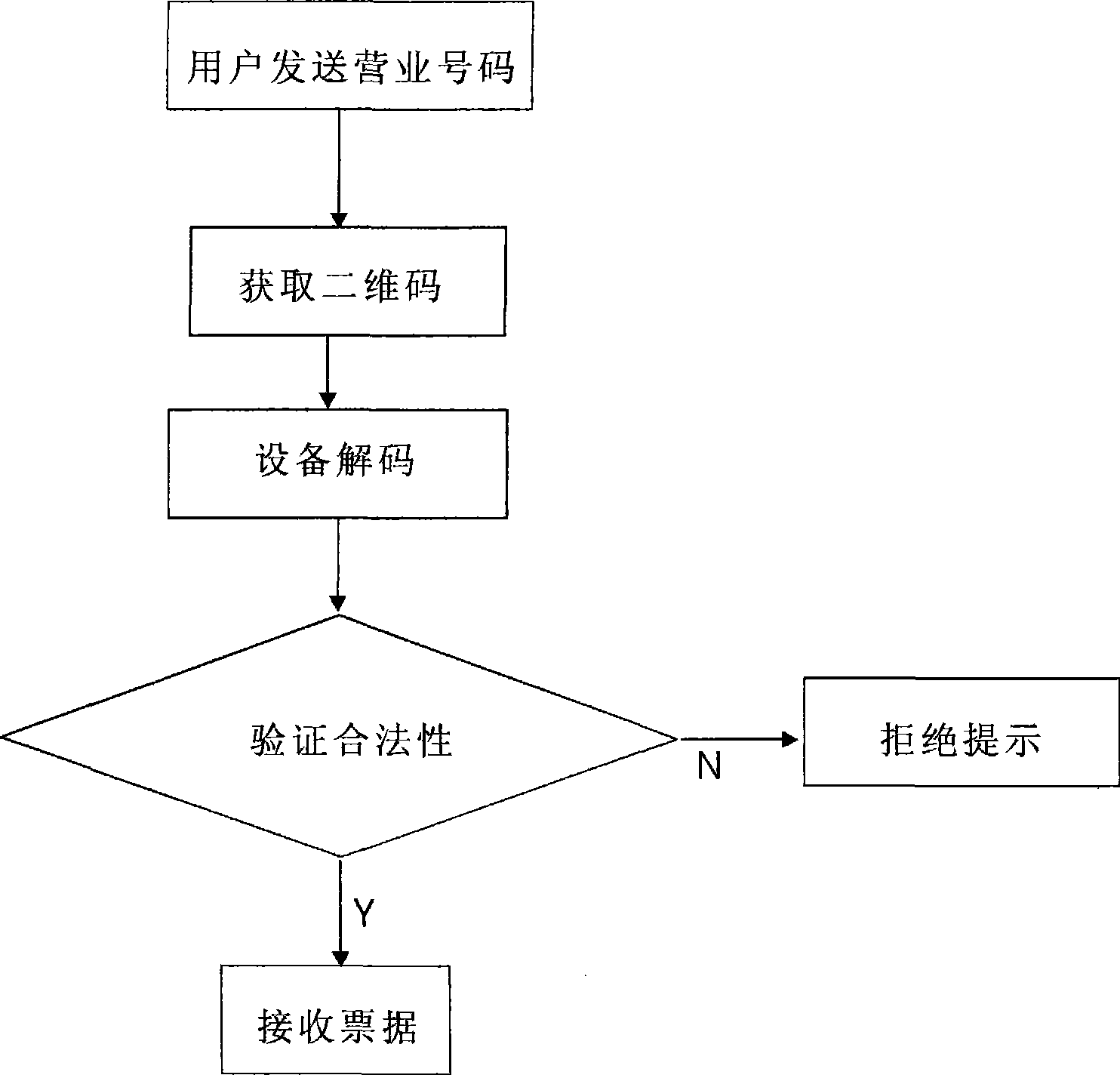
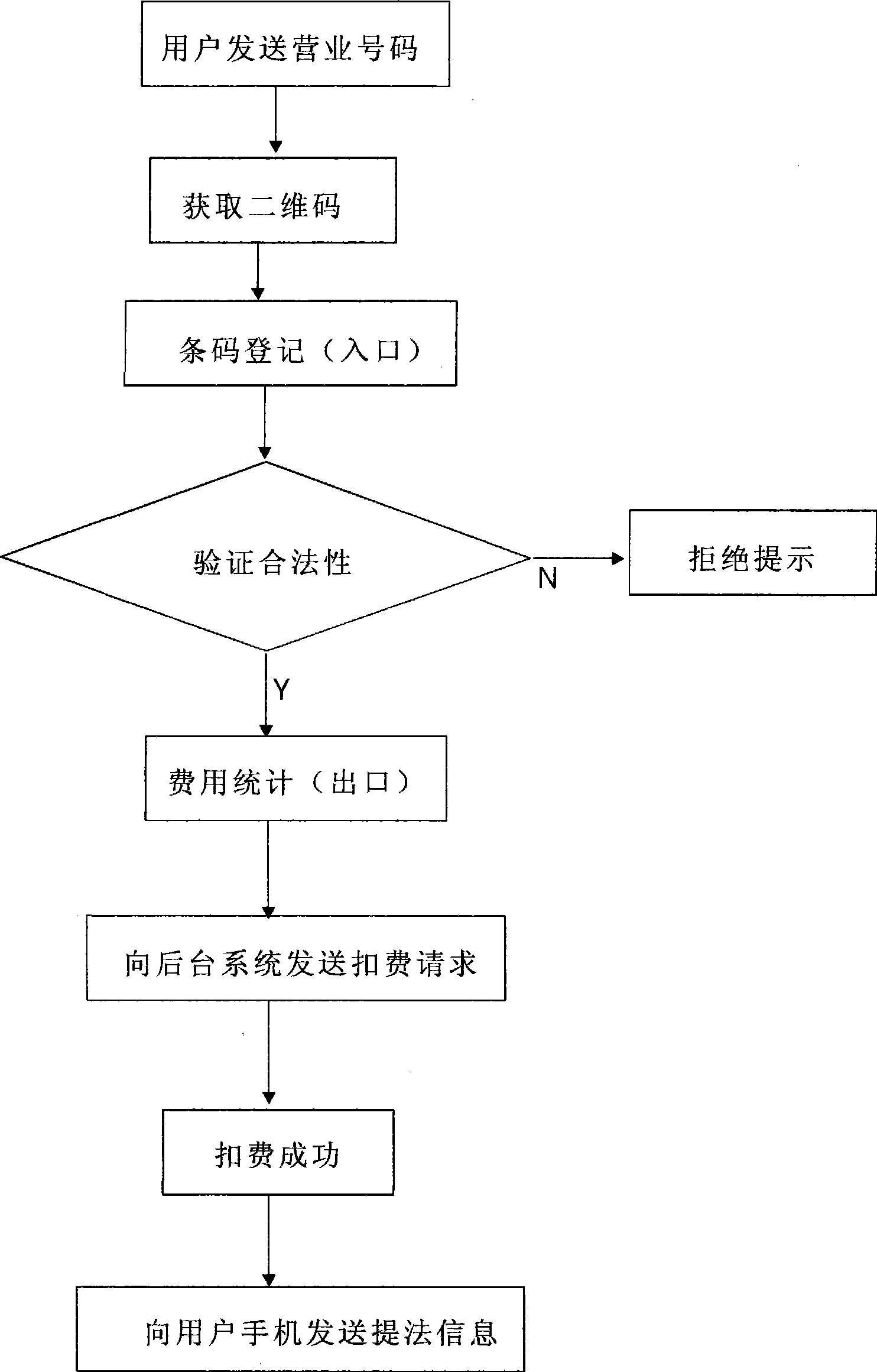
Method for implementing mobile phone payment based on two-dimensional code
InactiveCN101482948AEasy to manageEasy to useUser identity/authority verificationPayment architectureMobile Telephone NumberDimensional modeling
The invention relates to a method for realizing mobile telephone payment based on two-dimension codes, comprising steps of integrally managing complex application types by way of corresponding different business numbers with different services, and organically combining main bodies related with the mobile telephone payment, such as users, businessmen, banks, communication management parts and the like. When the method is applied, users only need to record and upload business numbers with mobile telephones, then a system generates corresponding information by judging the mobile telephone numbers and the business numbers; the information is processed, encoded into two-dimension codes and then sent to the mobile telephones; users apply the mobile telephones to reading and decoding devices corresponding to the business numbers to finish corresponding applications so as to realize mobile telephone payment.
Owner:唐红波
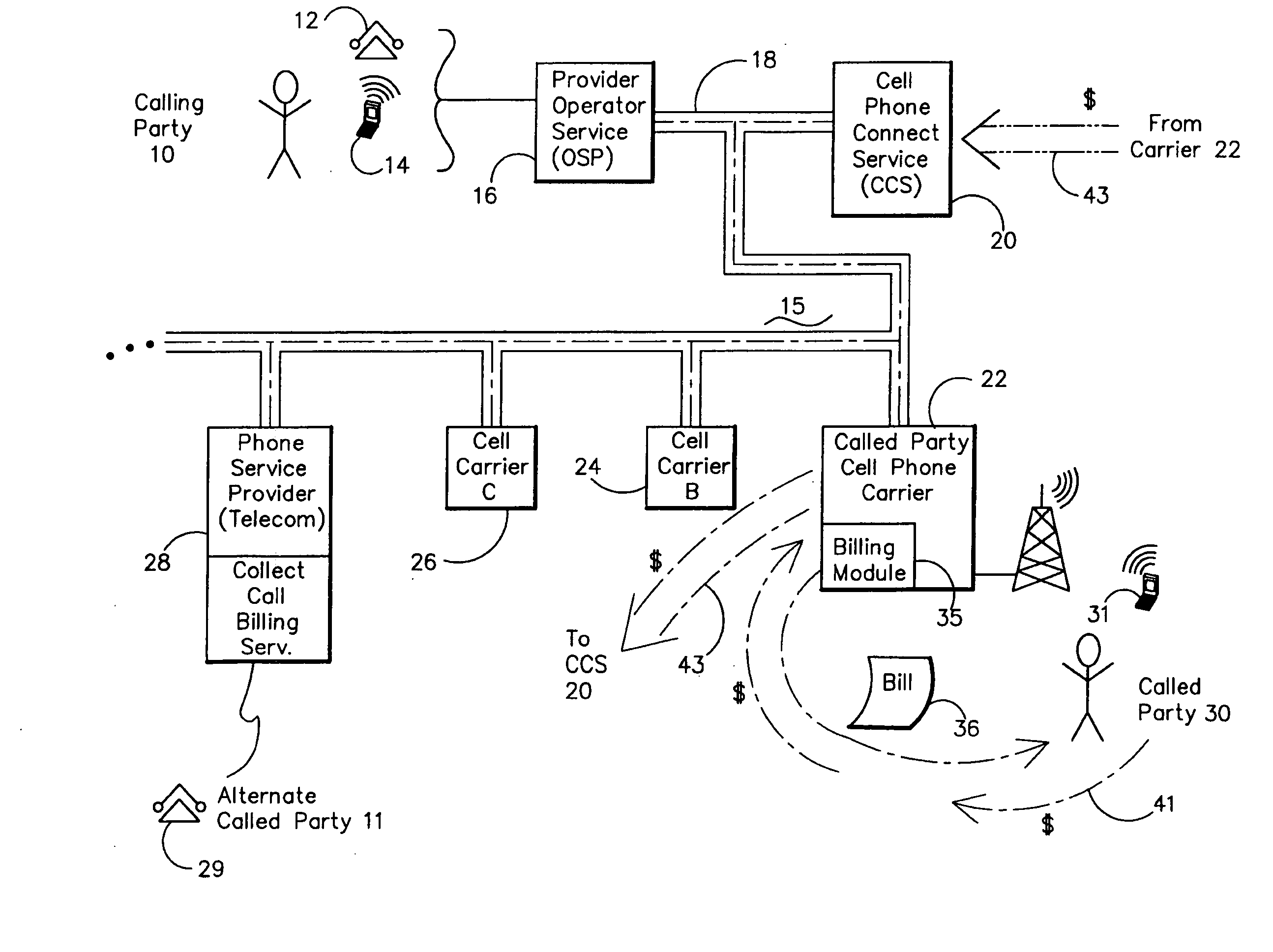
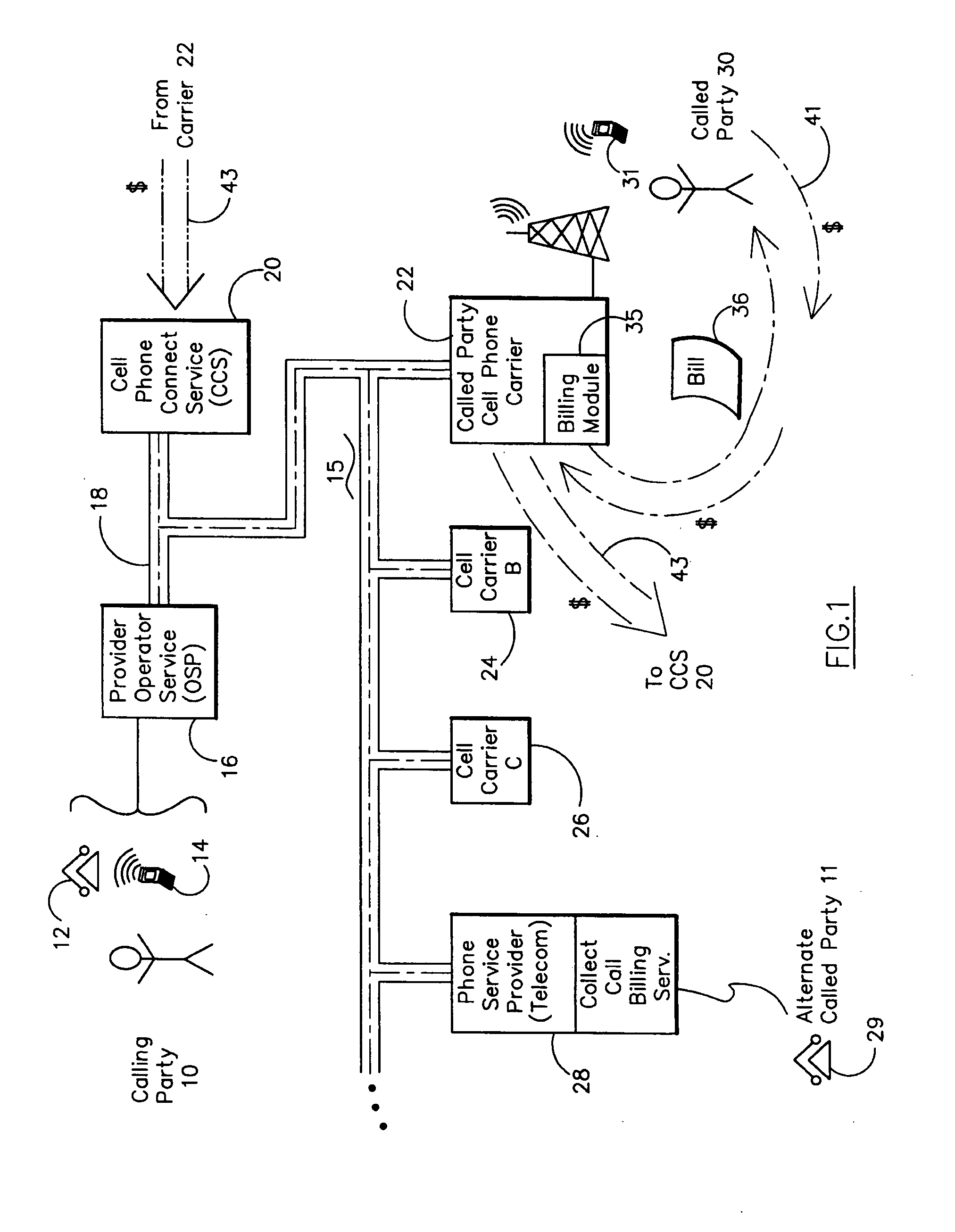
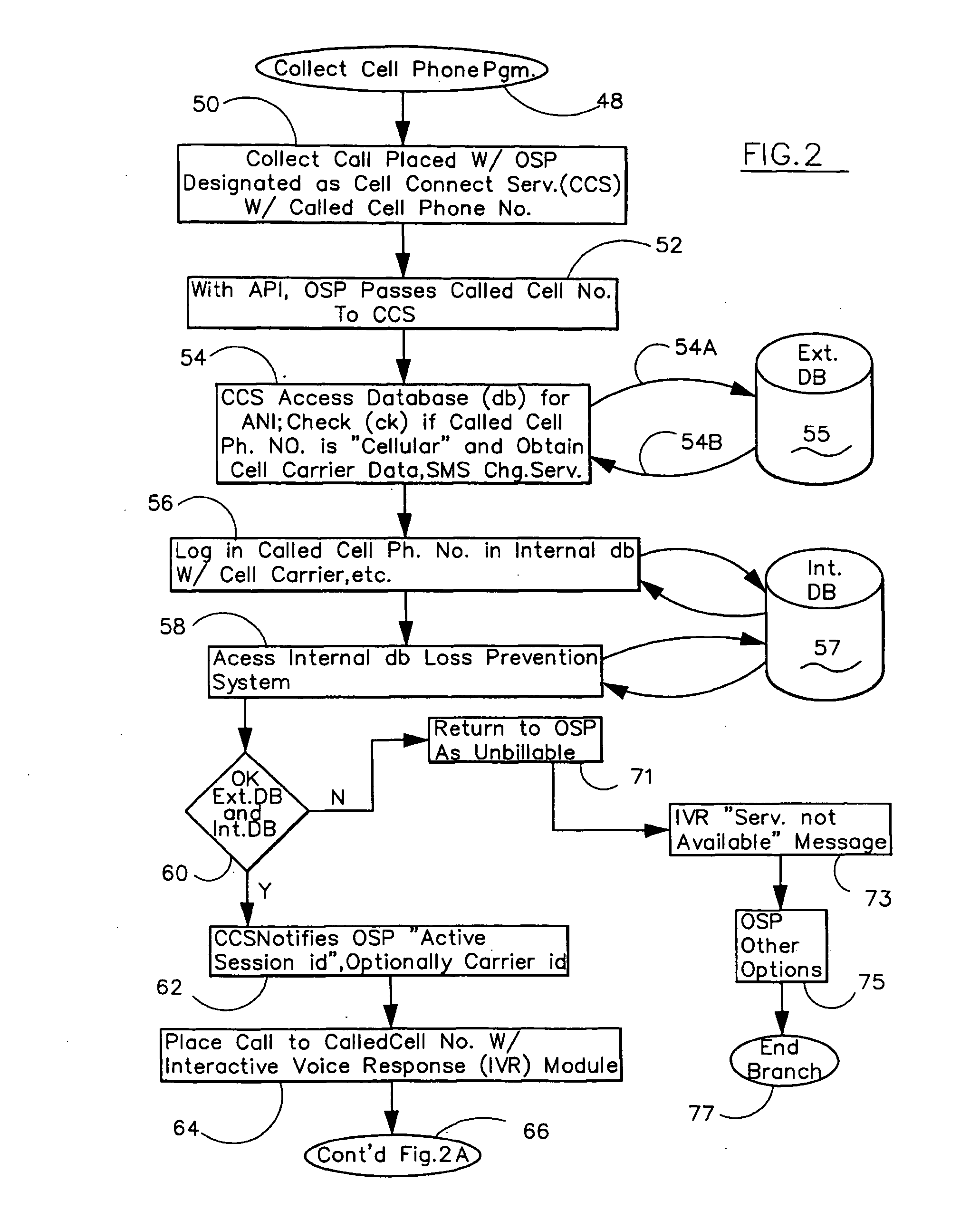
System and Method for Authorizing and Monetizing Collect Cellular Telephone Calls
ActiveUS20090054031A1Facilitate connectionFacilitate completionAccounting/billing servicesTelephonic communicationAuthorizationMessage service
The collect cellular call identifies the cellular telephone carrier and called party cell phone. After determining whether the carrier and phone accept message service charges (SMS), a voice response module seeks positive authorization from the called party with the telephone. If positive, the system facilitates a connection between the calling party and the called party and initiates a predetermined billing charge assigned to the cellular telephone number. If the carrier or the cell phone is not enabled or if no authorization is obtained from the called party, the system facilitates a denial of completion signal. A timer monitors the length a the collect cellular call. Databases are accessed to locate the carrier and called cell phone number approved list of numbers and deny-service list of numbers.
Owner:SECURUS TECH LLC
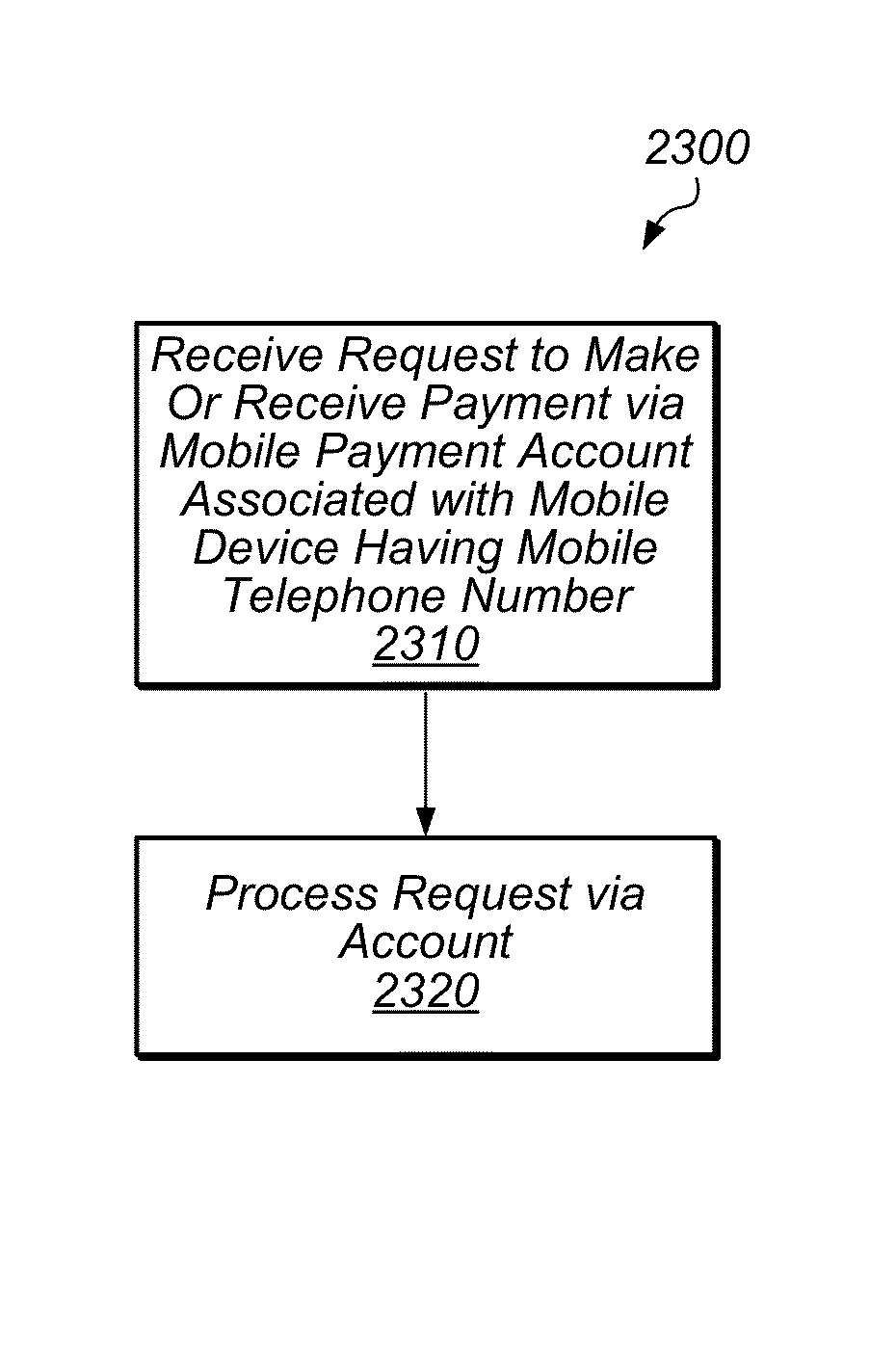
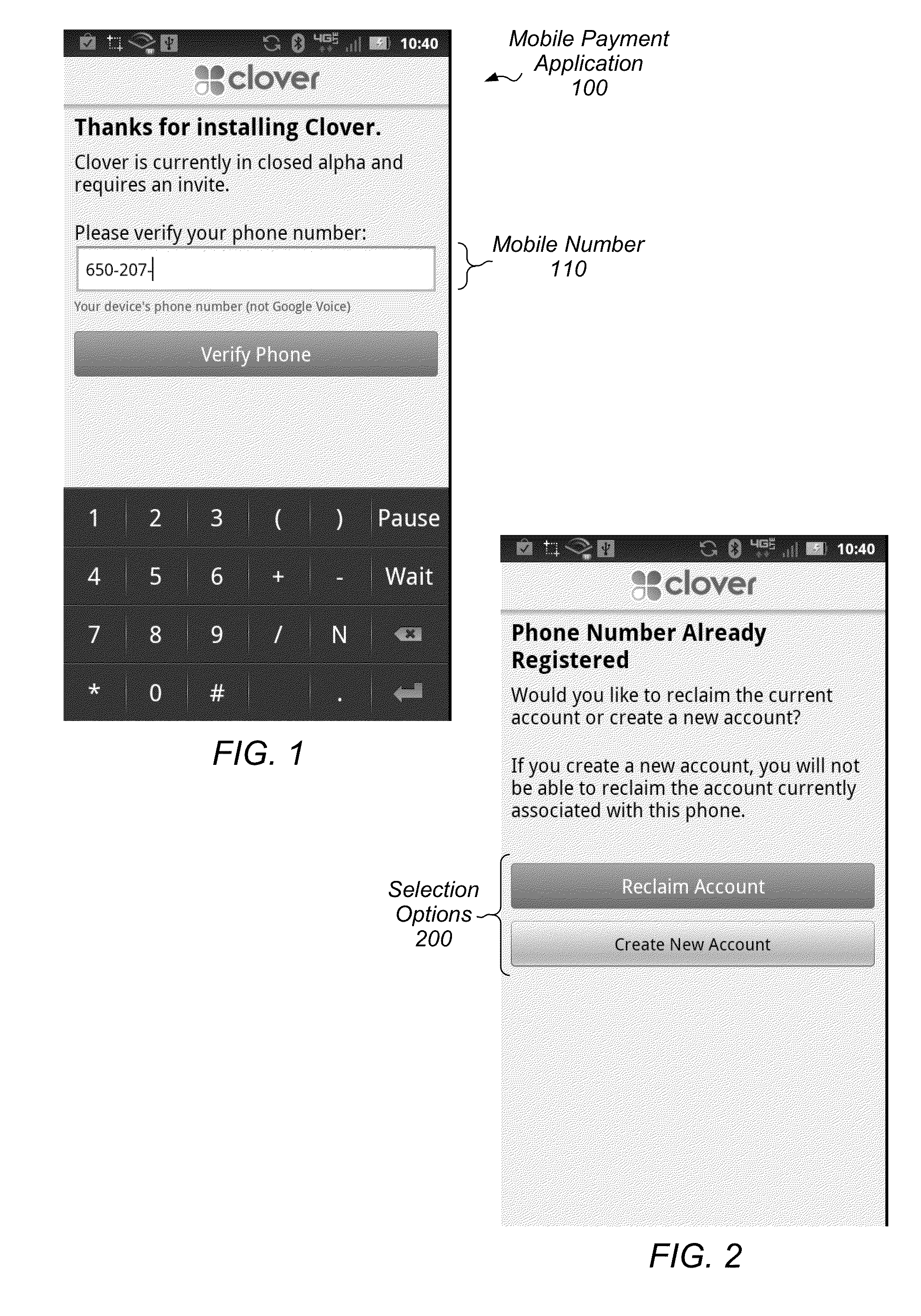
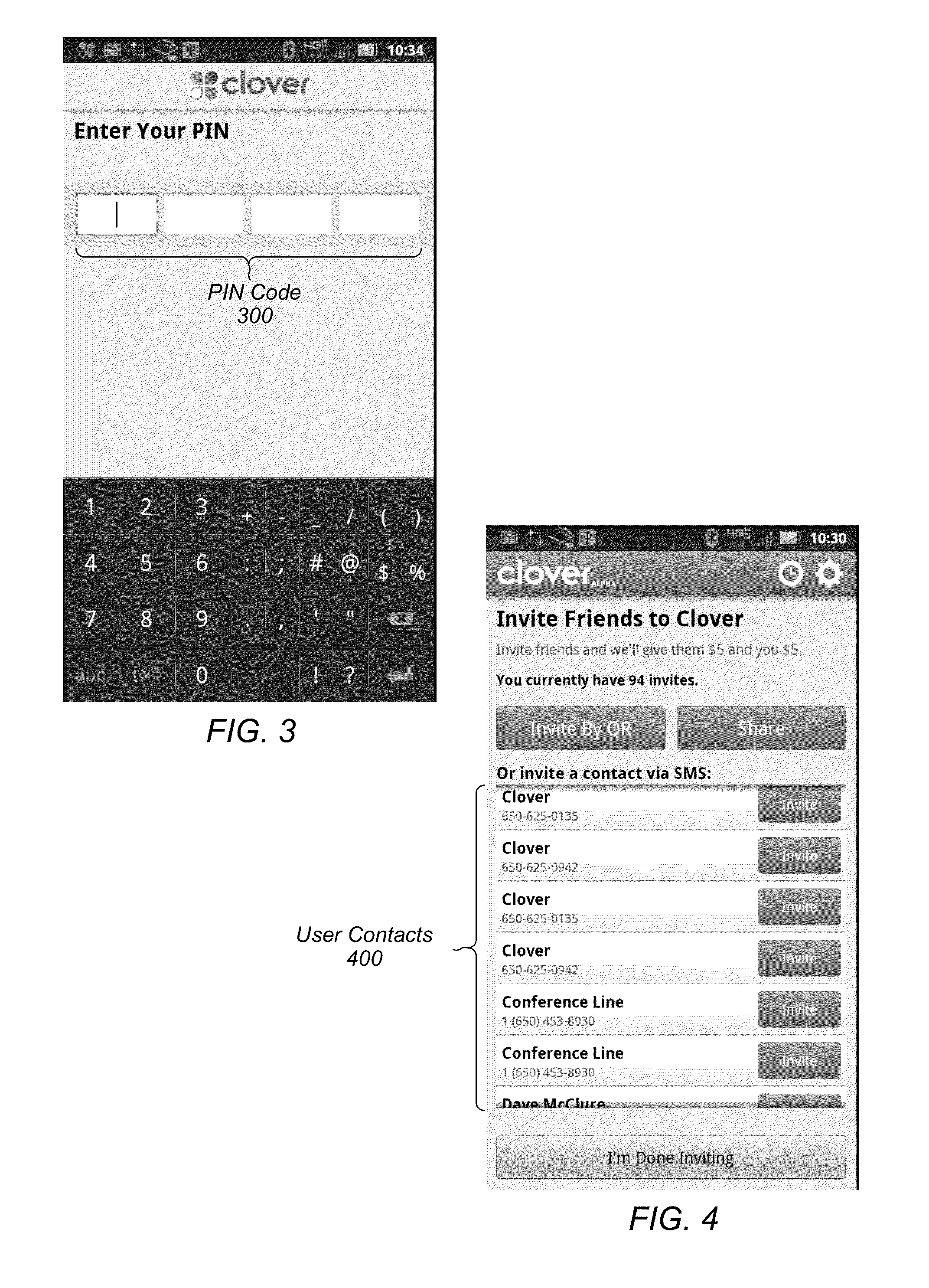
Mobile payment and identity verification system
ActiveUS8774781B1Convenient transactionElegantAccounting/billing servicesFinanceMobile Telephone NumberUser input
Techniques are disclosed relating to facilitating transactions via mobile devices. In one embodiment, an account that is linked to a mobile telephone number of a mobile device is established at a computer system. In such an embodiment, the account permits a user to make and receive payments, and is not accessible without using the mobile device. In some embodiments, the account is established without setting up a username and password. In one embodiment, a request is sent from a payment application of the mobile device to the computer system. In some embodiments, the payment application is made active on the mobile device in response to a user input within a different application running on the mobile device. After the payment application is active, a purchase is confirmed within the payment application such that the request is sent responsive to the confirming and without authenticating the user within the payment application.
Owner:CLOVER NETWORK INC
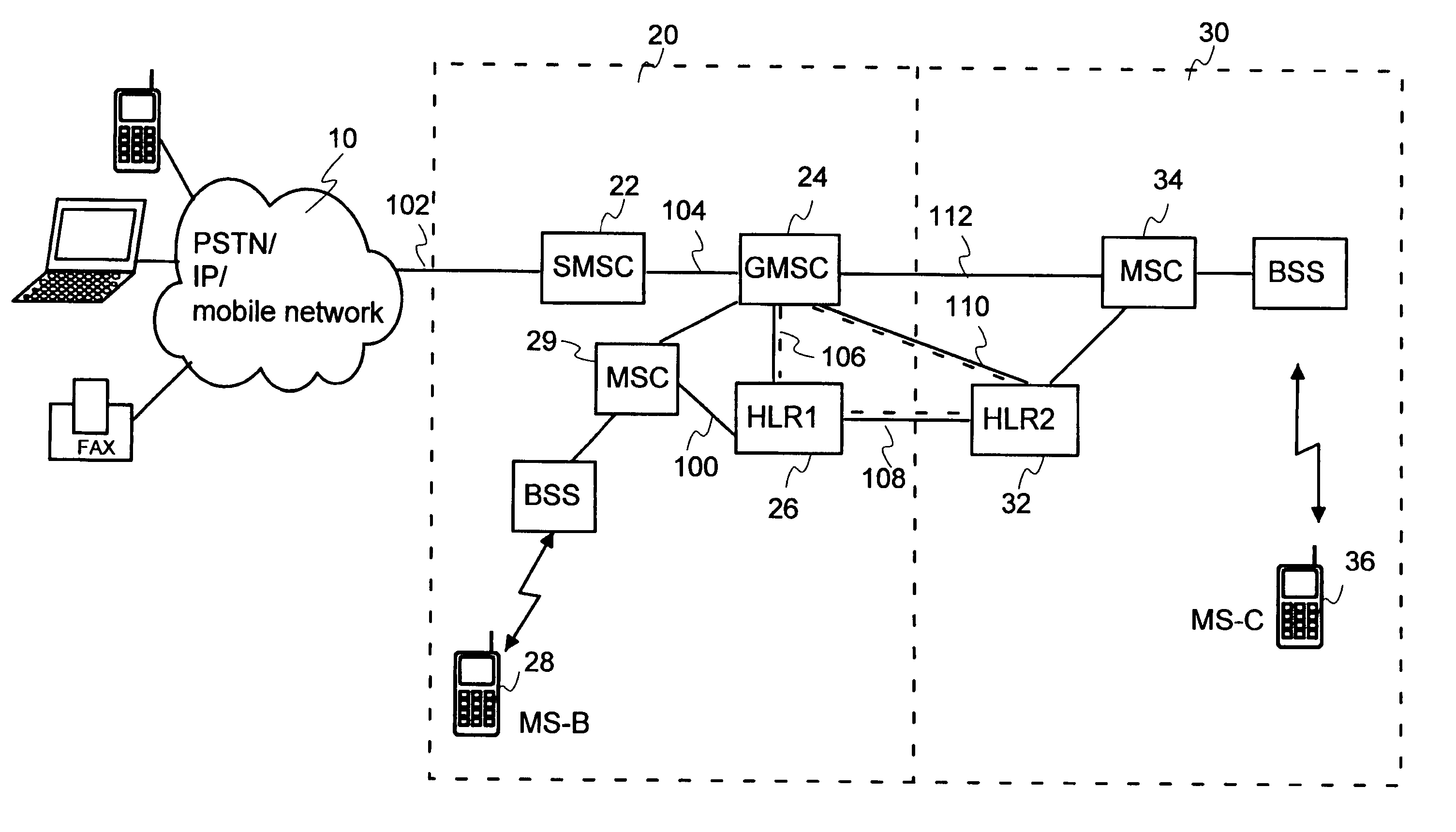
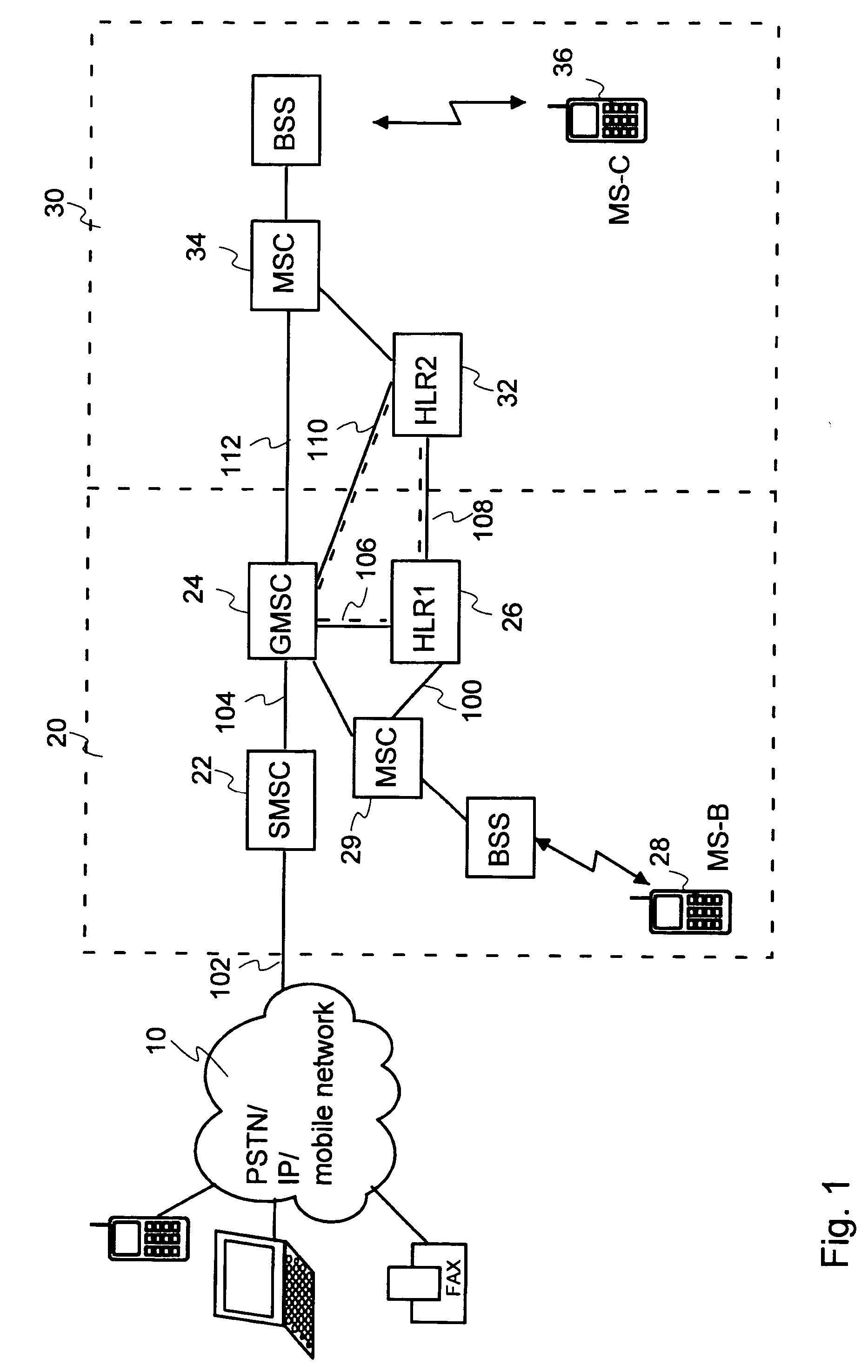
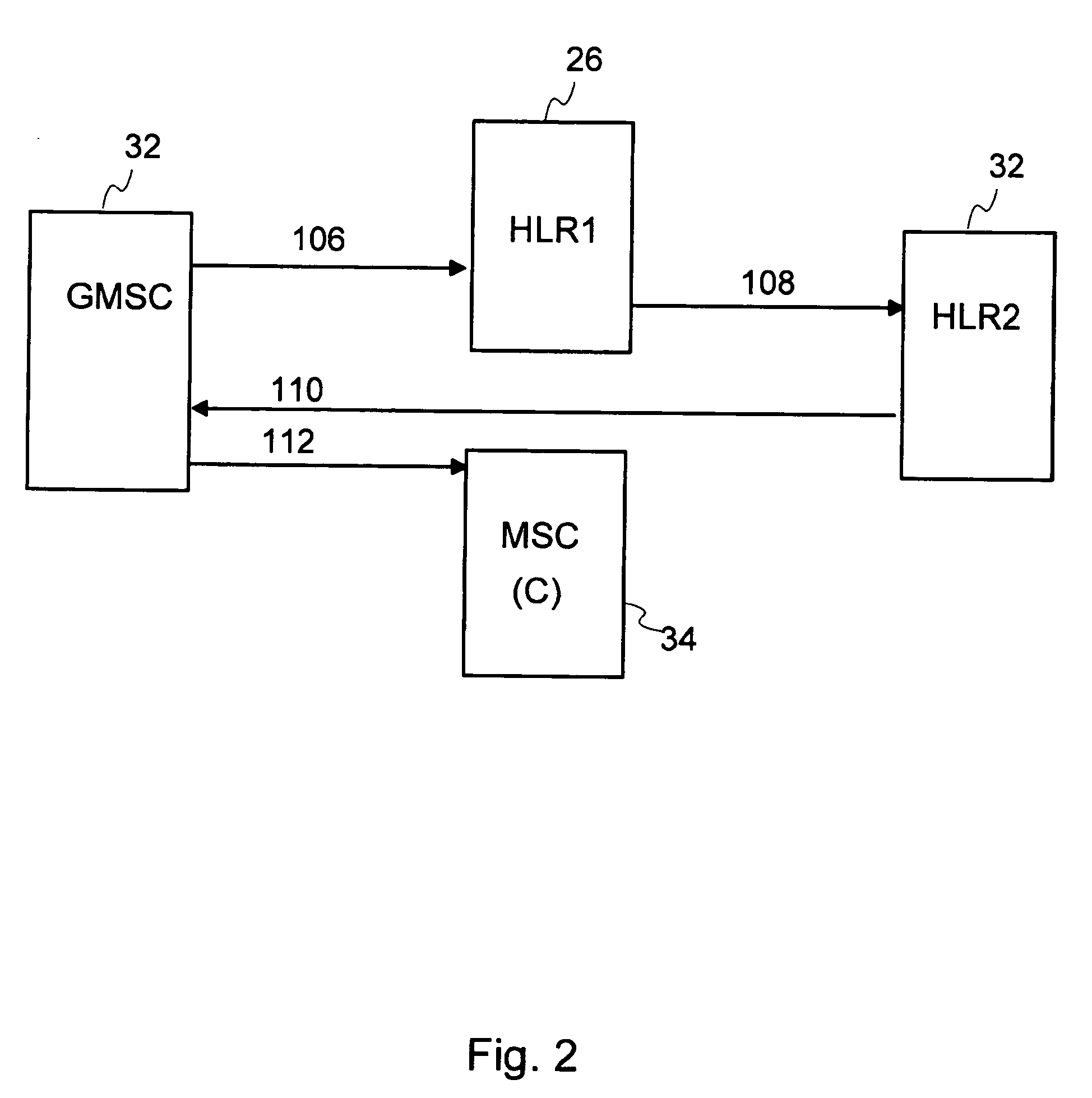
Messaging services offered in mobile communication systems
InactiveUS20050036457A1Commmunication supplementary servicesRadio/inductive link selection arrangementsMobile Telephone NumberCommunications system
A method for rerouting messages in a mobile communications system allowing rerouting between different networks is described. The method—includes a step of setting in a first register node associated with a primary mobile number a request for forwarding messages addressed to the primary mobile number to a second mobile number. The method sends a message addressed to the primary mobile number from a messaging center to a gateway node and sends a request for routing information for the message from the gateway node to a first register node associated with the primary mobile number. Based on the request for forwarding messages, the method sends a request for routing information for the message from the first register node to a second register node associated with the second mobile number. The method sends a response including the routing information for the message to the gateway node.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Method and System for Secure Financial Transactions Using Mobile Communications Devices
InactiveUS20120101951A1Improve protectionImprove securityPayment architectureMobile Telephone NumberEmail address
The present invention employs public key infrastructure to electronically sign and encrypt important personal information on a mobile communications device (MCD), without disclosing private, personal information to the transaction counterparts and middleman, thus preserving highly elevated and enhanced security and fraud protection. In one embodiment, the present invention can use a mobile device identifier, such as a cell phone number or email address, for example, as an index / reference during the entire transaction, so that only the account holder and the account issuer know the underlying account number and other private information.
Owner:S W I F T SCRL
New method for using the mobile number bond with account for identity identification
InactiveCN101087193AUser identity/authority verificationData switching by path configurationMobile Telephone NumberRemote control
The invention relates to the information security field of computer and network, relates to ID attestation system and method, and it can prevent the user account from stolen. The method uses the mobile phone to do network ID attestation, distinguish the computer by the affirmed strings, and the user account and mobile phone can correspond with client computer one by one to identify the validity of user ID. The method can be used in various account affirmations of network services (web management, e-mail, e-business, network game, chatting tool, network bank and the field of remote control), and it also can be used other service relative with network (the operation of ATM). It is a efficient method to prevent the network form being stolen.
Owner:马骏
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com