Patents
Literature
85 results about "Mobile equipment identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
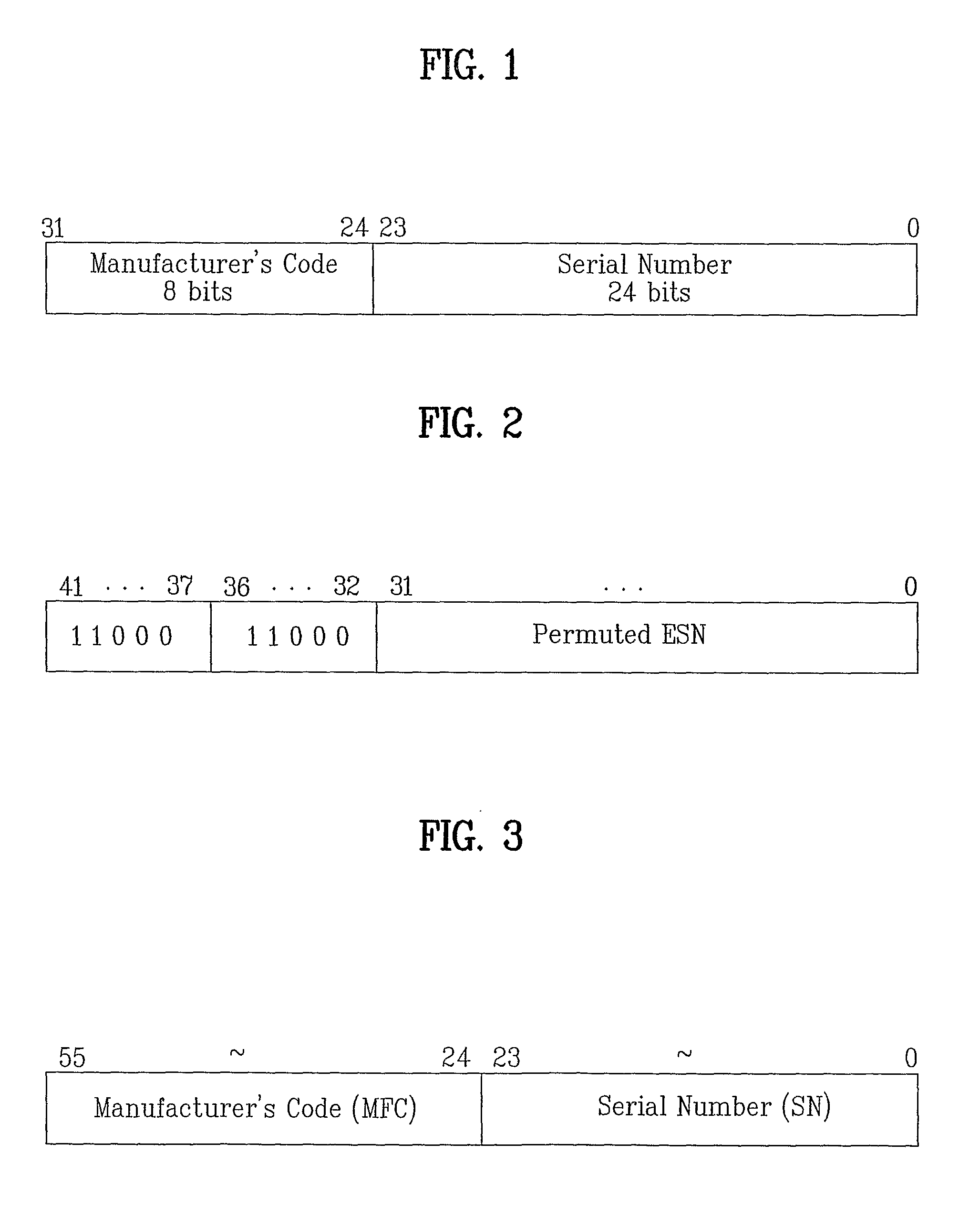
A mobile equipment identifier (MEID) is a globally unique number identifying a physical piece of CDMA2000 mobile station equipment. The number format is defined by the 3GPP2 report S.R0048 but in practical terms, it can be seen as an IMEI but with hexadecimal digits.
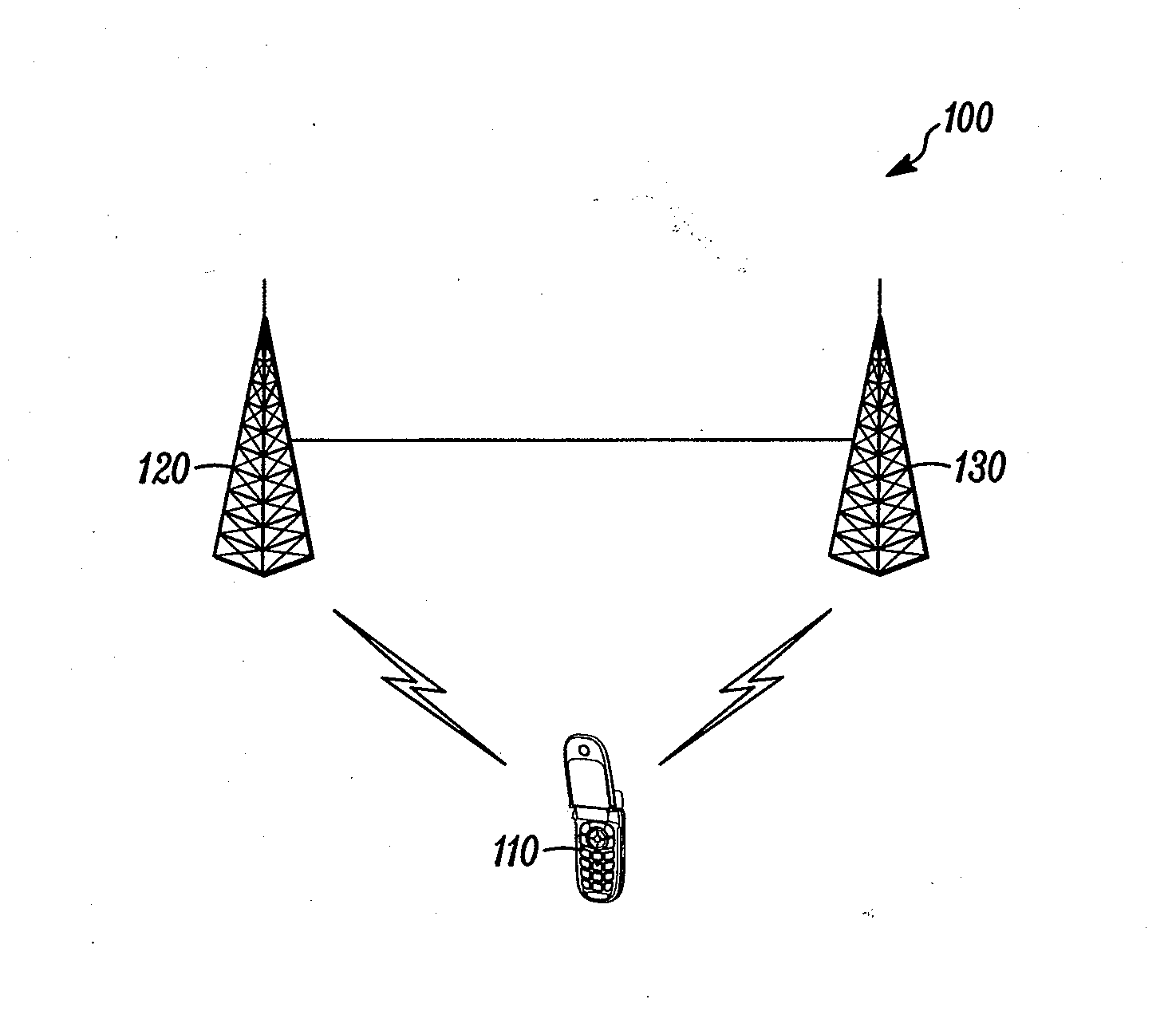
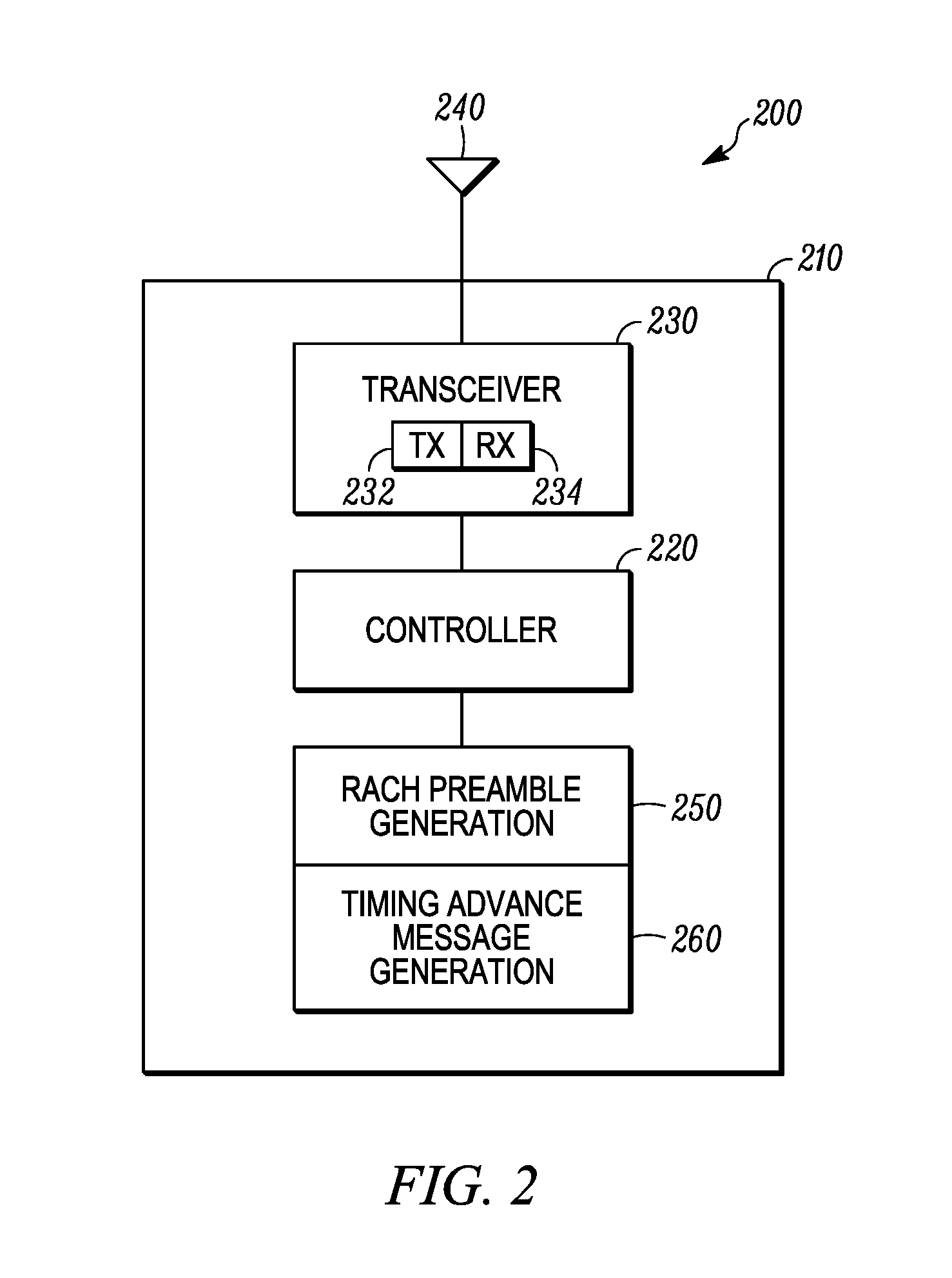
Method and apparatus for handover in a wireless communication system
ActiveUS20080267127A1Effectively contention-freeEliminates and minimizes timeSynchronisation arrangementRadio/inductive link selection arrangementsCommunications systemMobile equipment identifier
A method and apparatus for handover in a wireless communication system. A handover indication can be received from a source base station (120) that is connected with a mobile station (110). The handover indication can include a random access channel preamble. The random access channel preamble can include a temporary mobile equipment identifier. The random access channel preamble can be received from the mobile station. A timing advance message can be sent in response to receiving random access channel preamble. The timing advance message can be addressed by the random access channel preamble and a source base station identifier. The connection with the mobile station can be switched from the source base station to a target base station (130).
Owner:GOOGLE TECH HLDG LLC
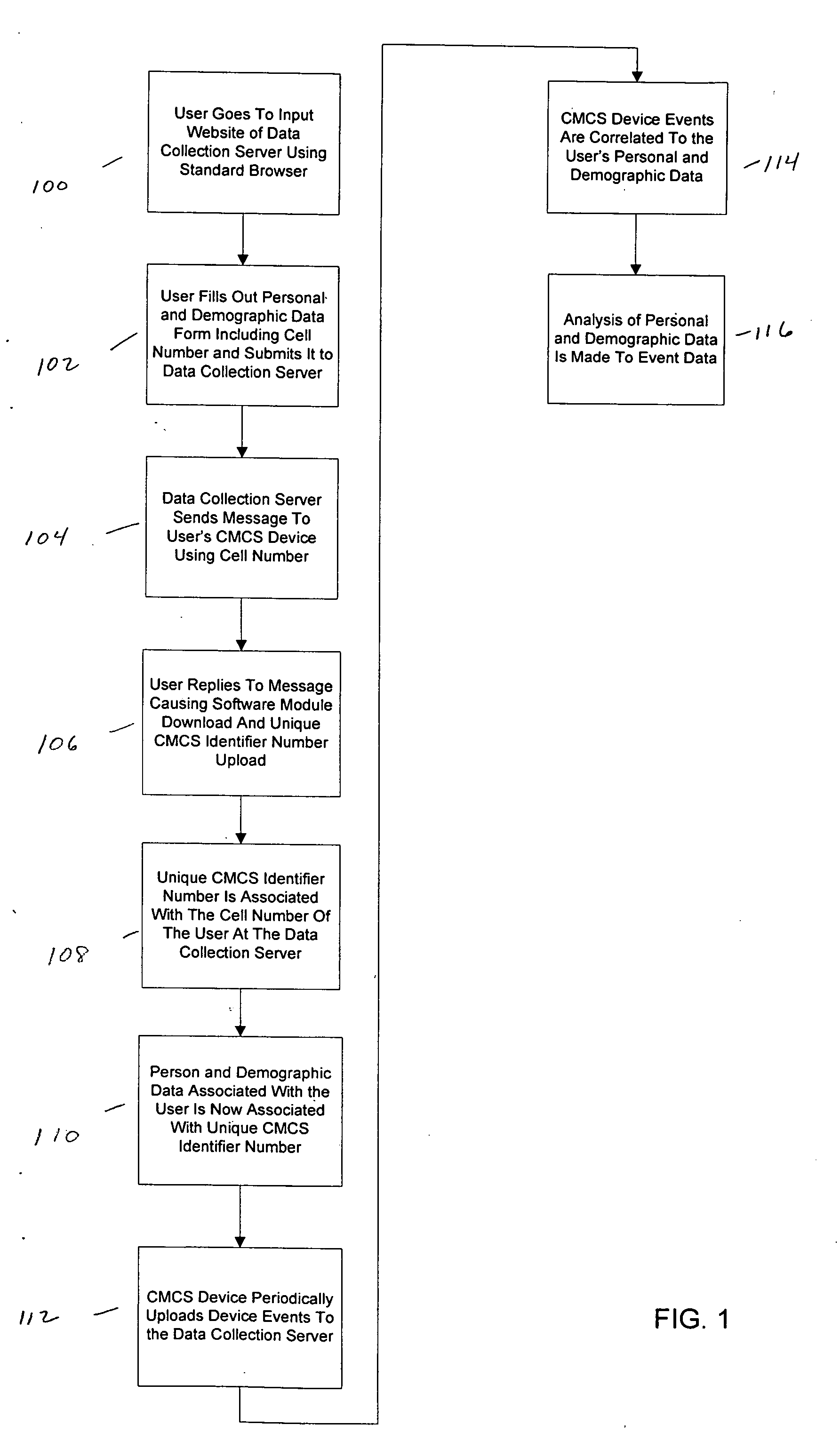
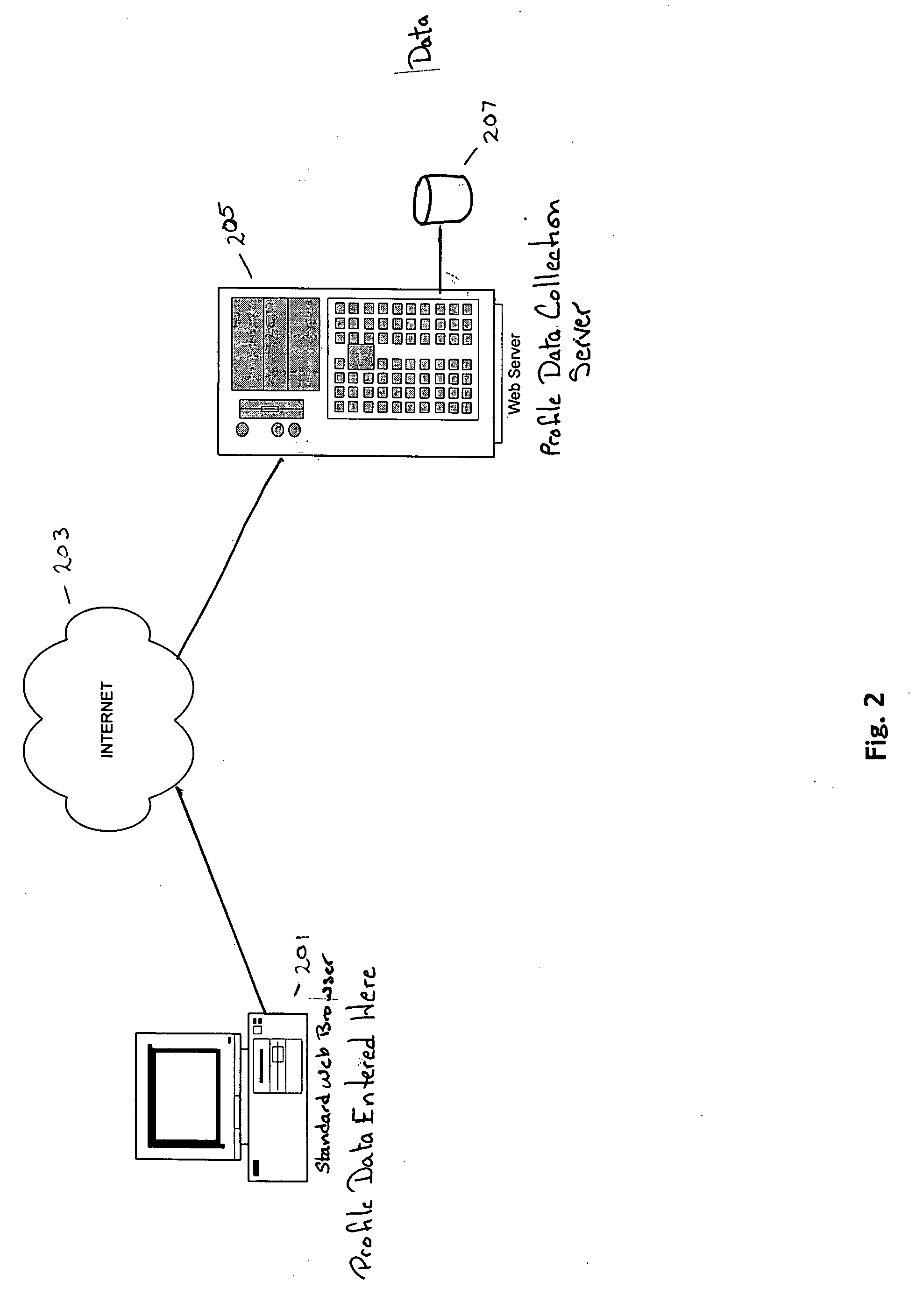
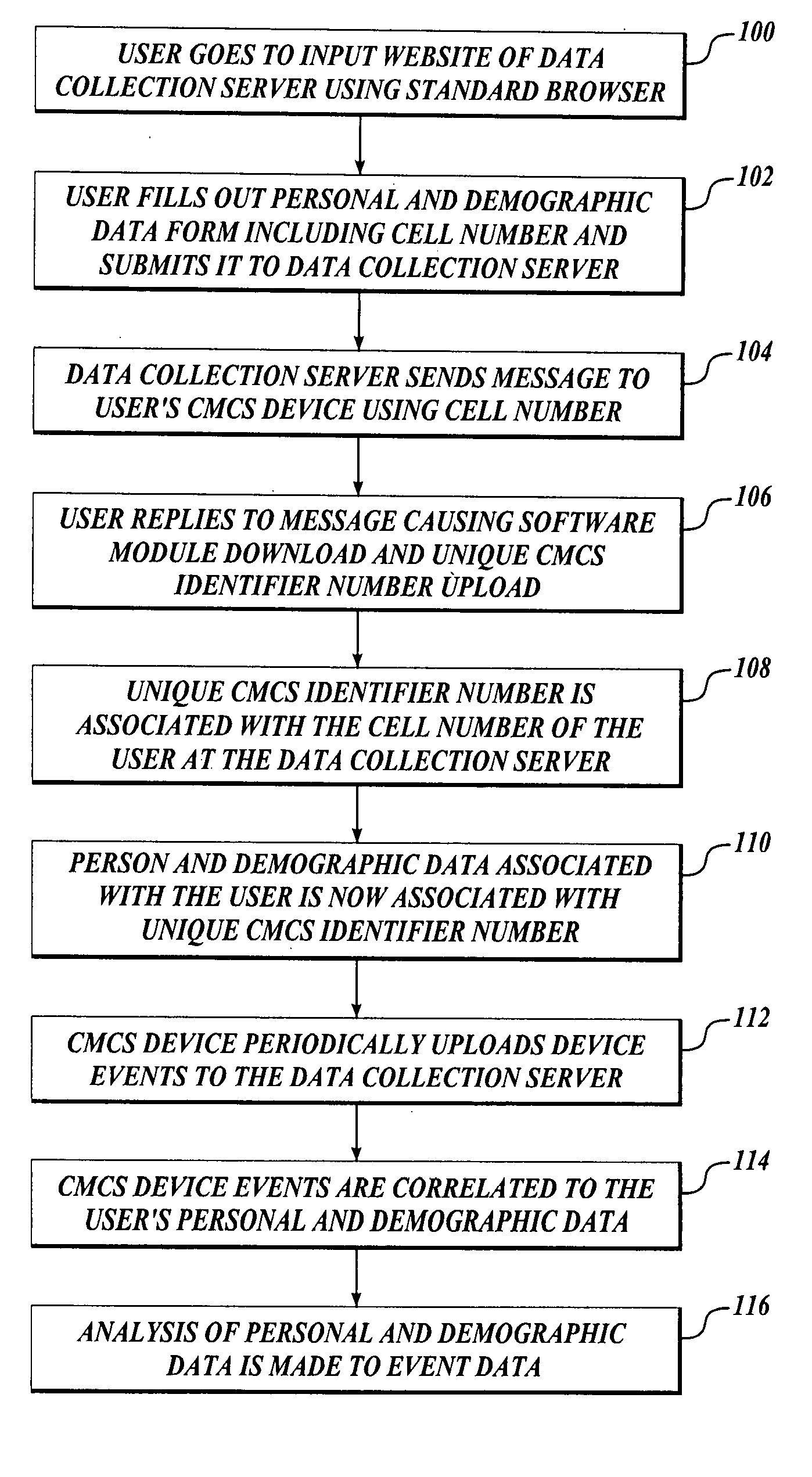
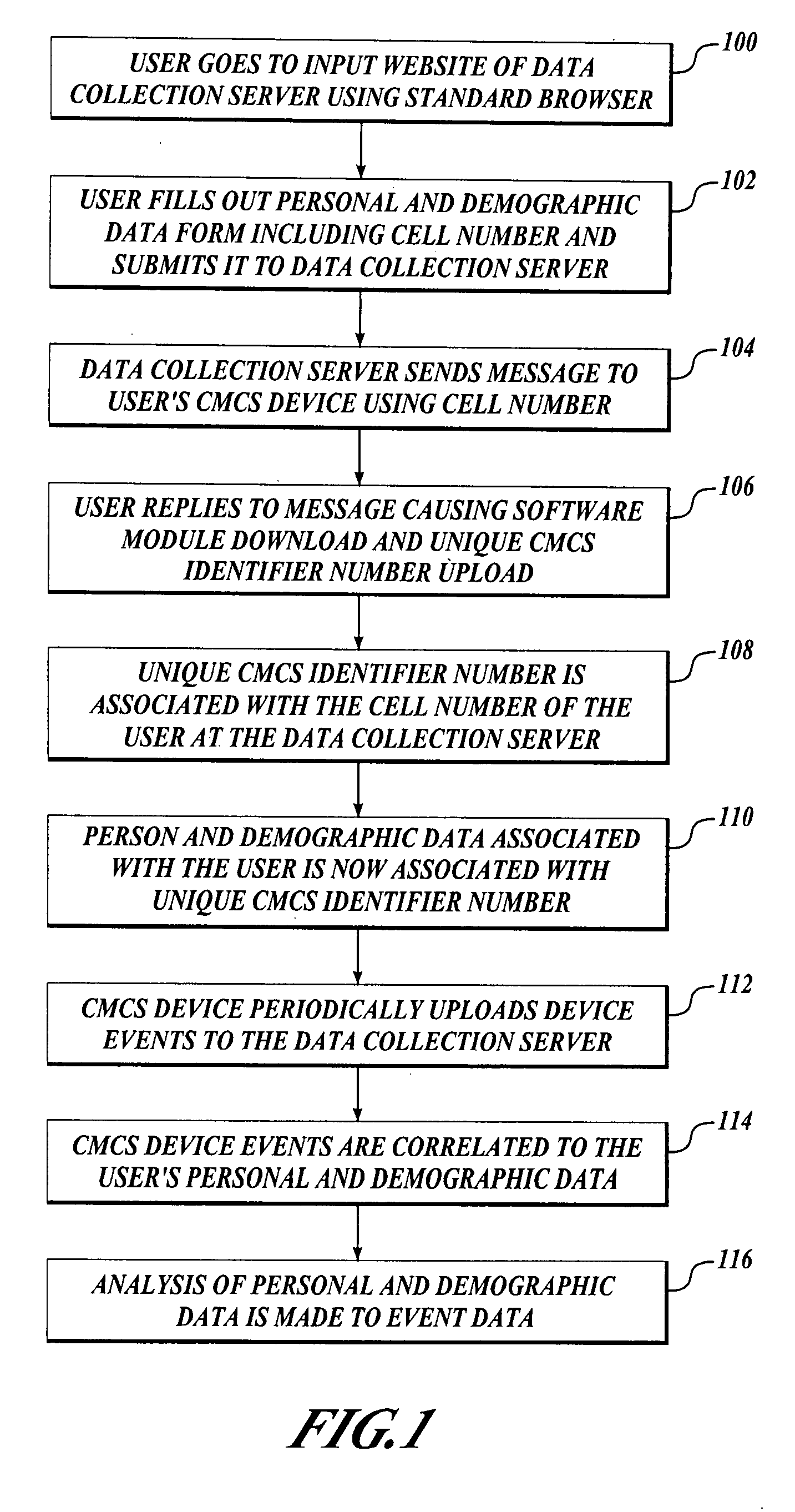
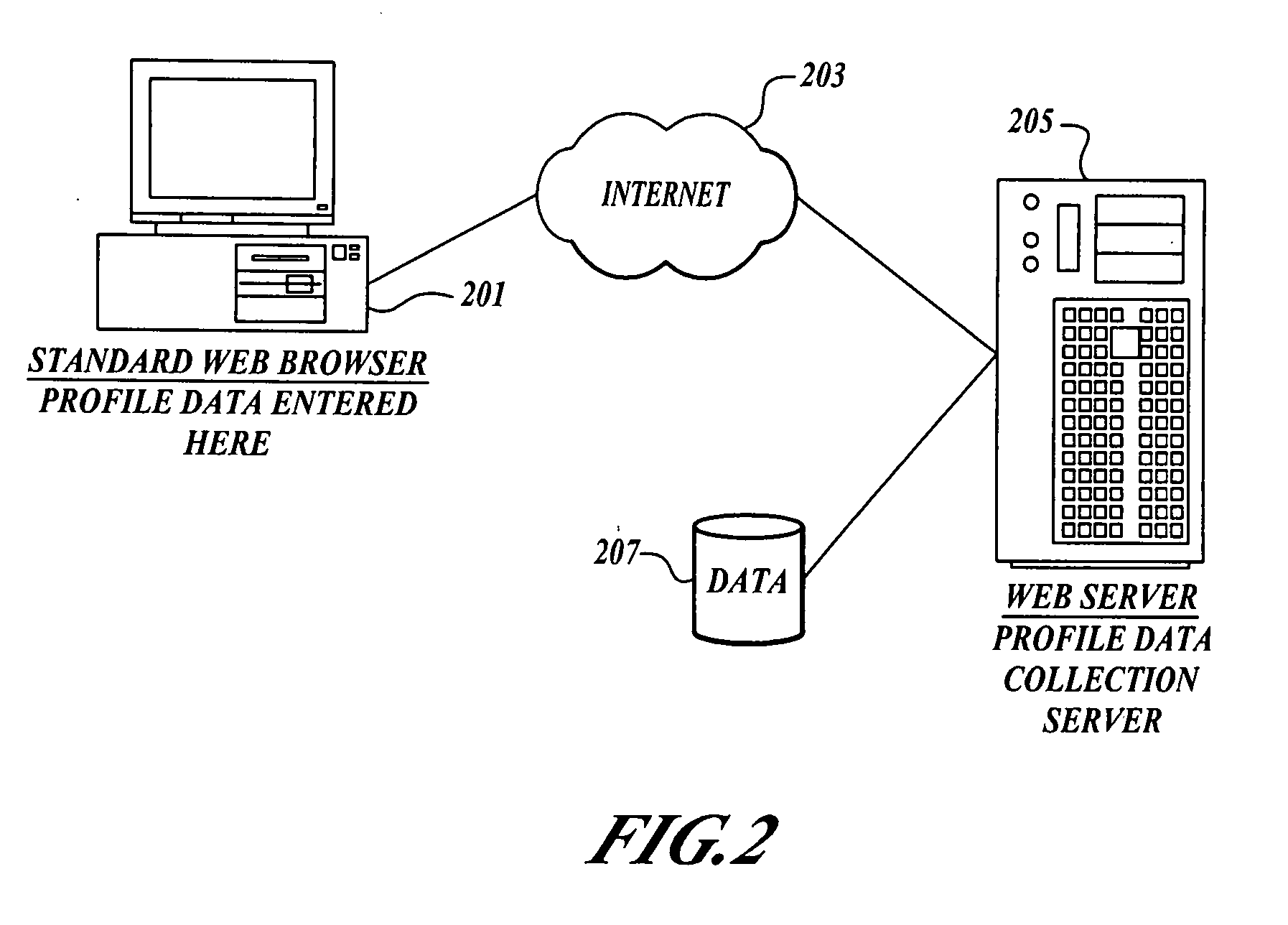
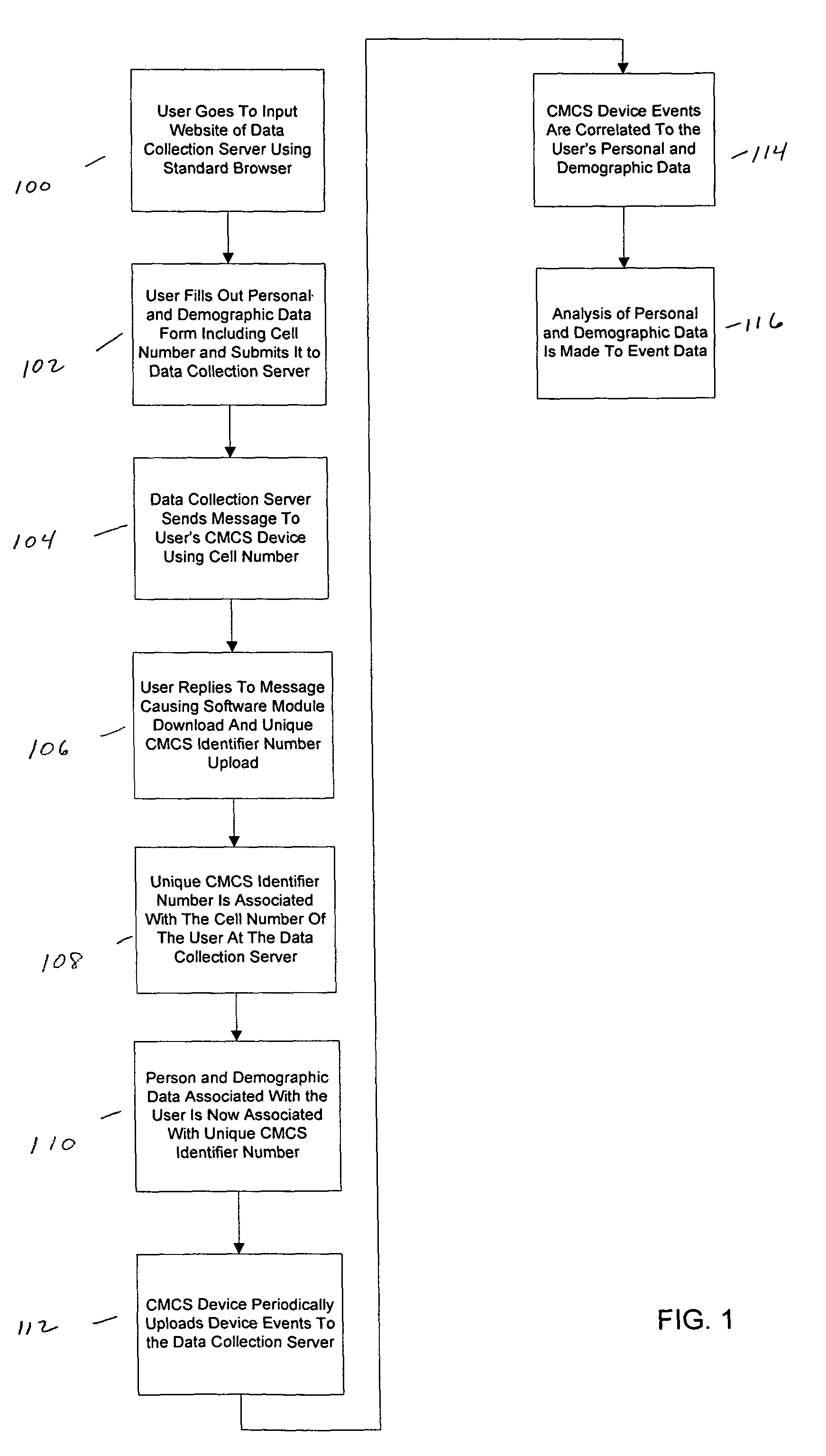
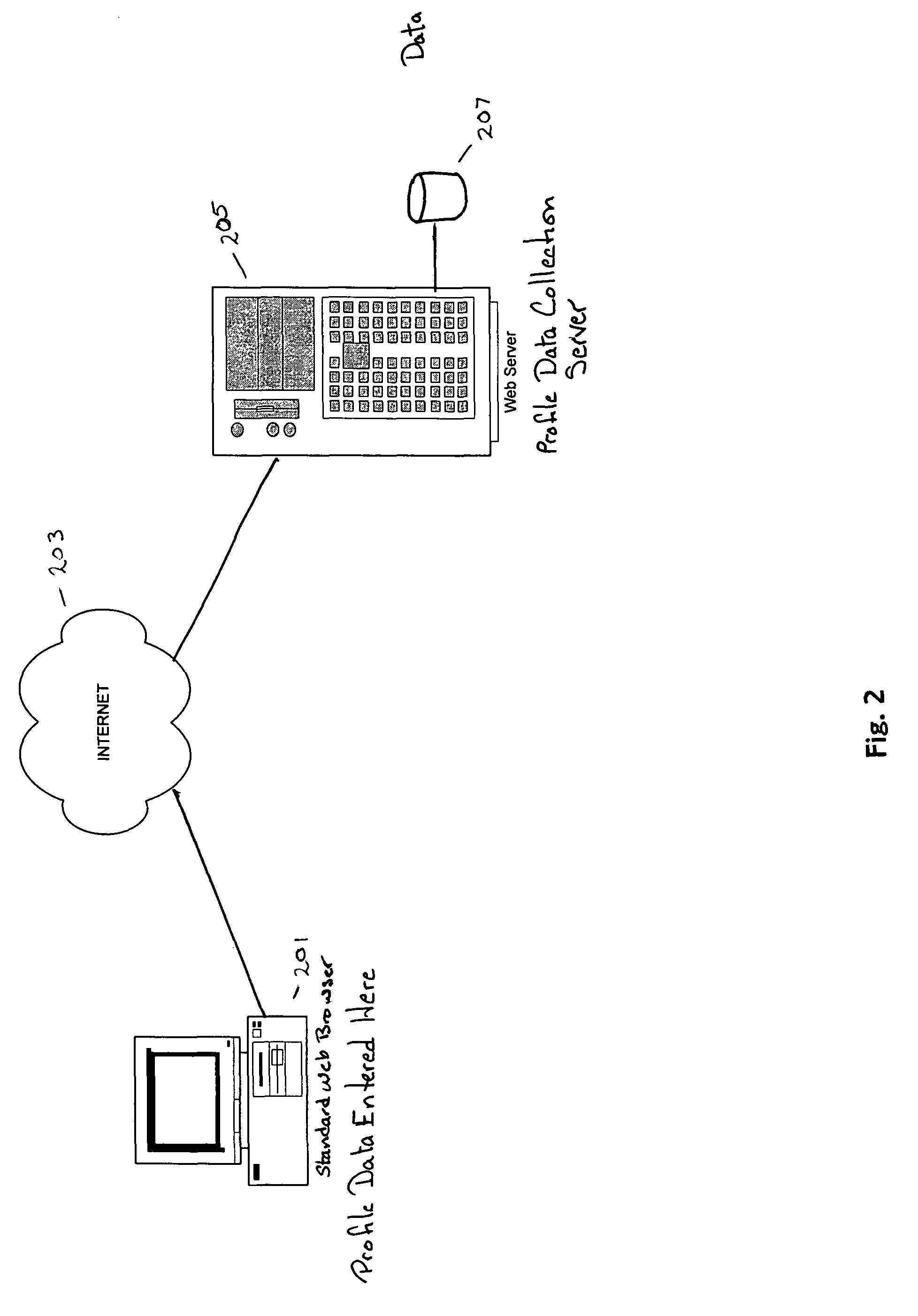
Acquiring, storing, and correlating profile data of cellular mobile communications system's users to events
ActiveUS20060294225A1Telephonic communicationMultiple digital computer combinationsCommunications systemWeb browser
Owner:COMSCORE
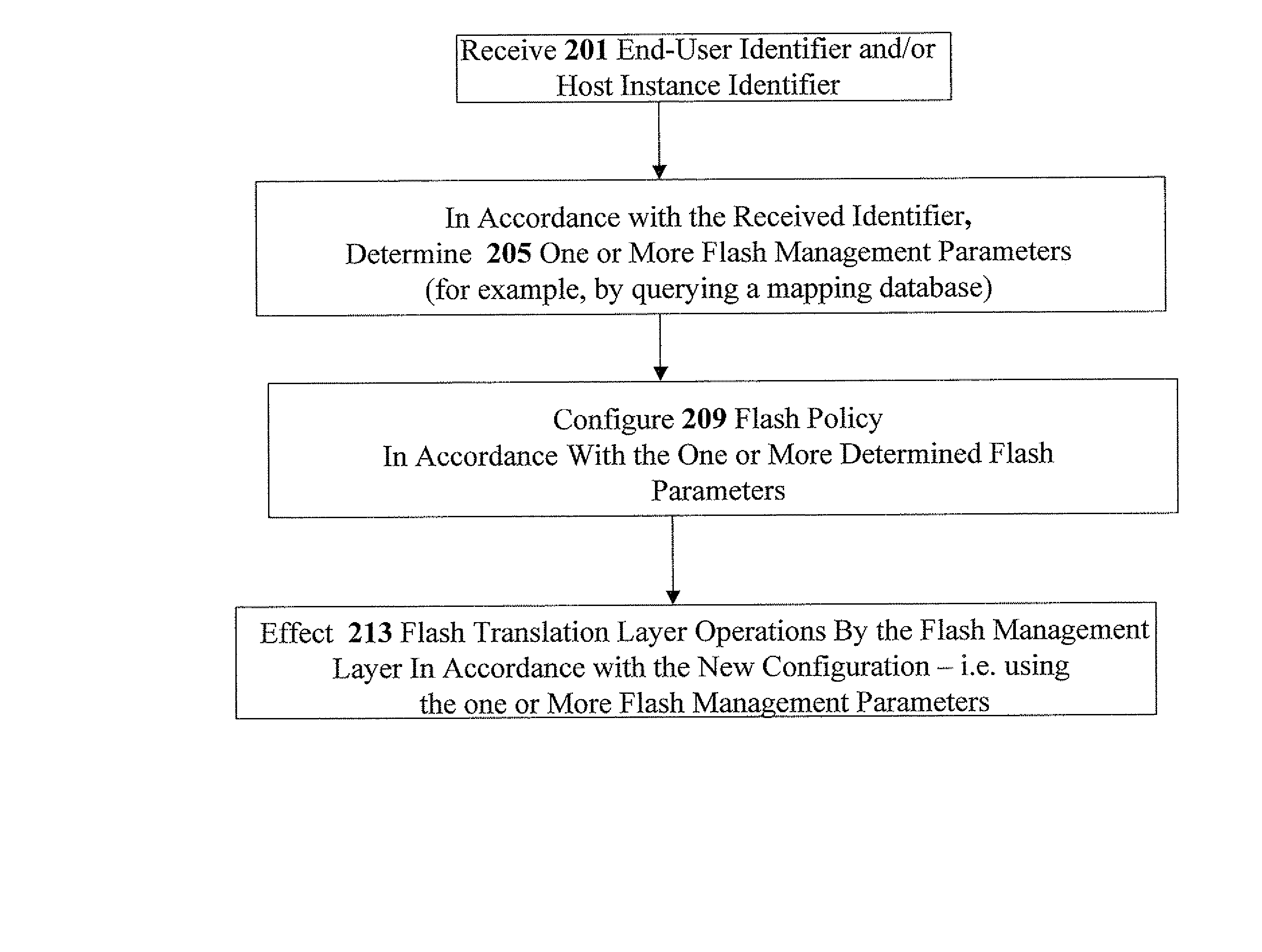
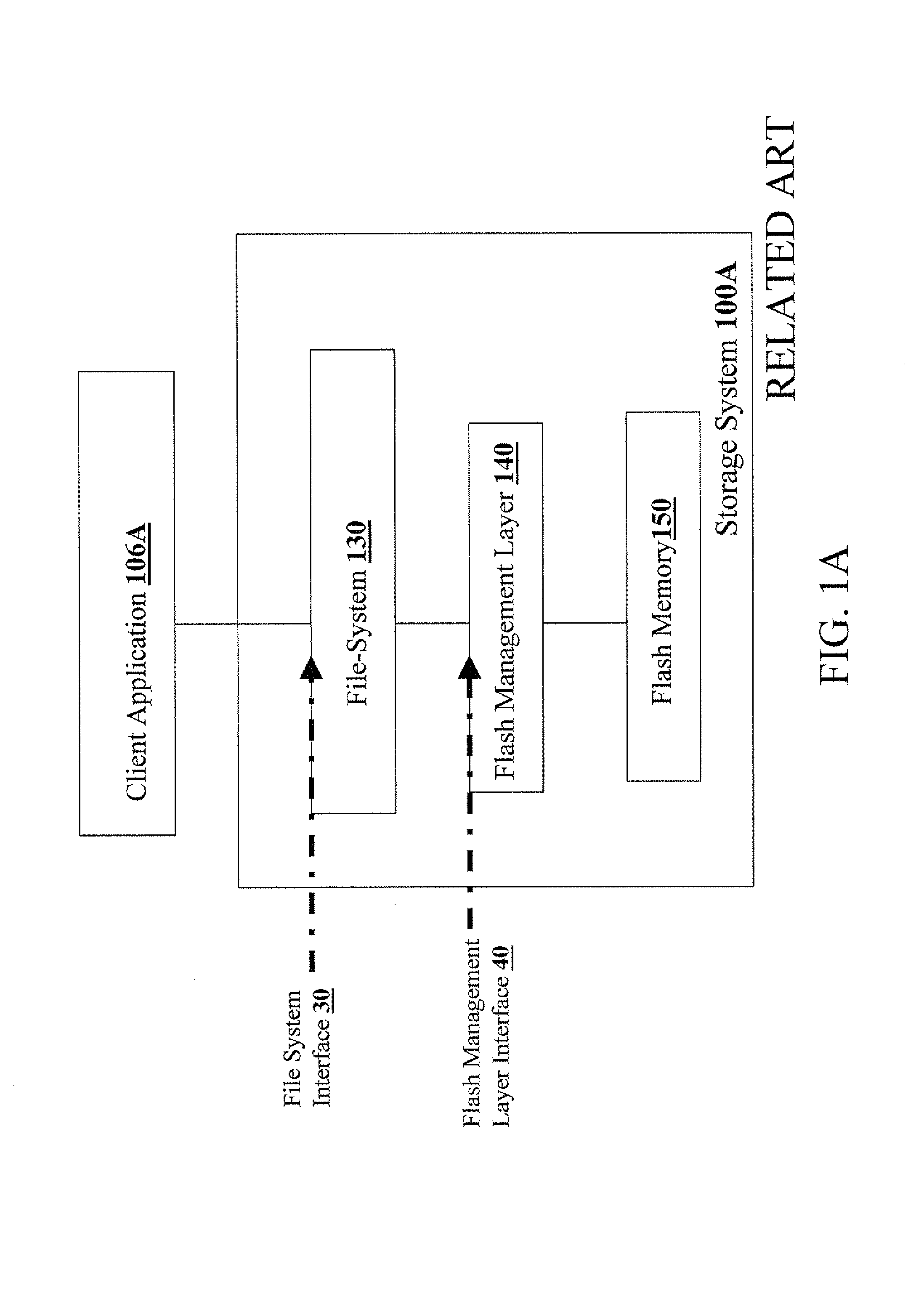
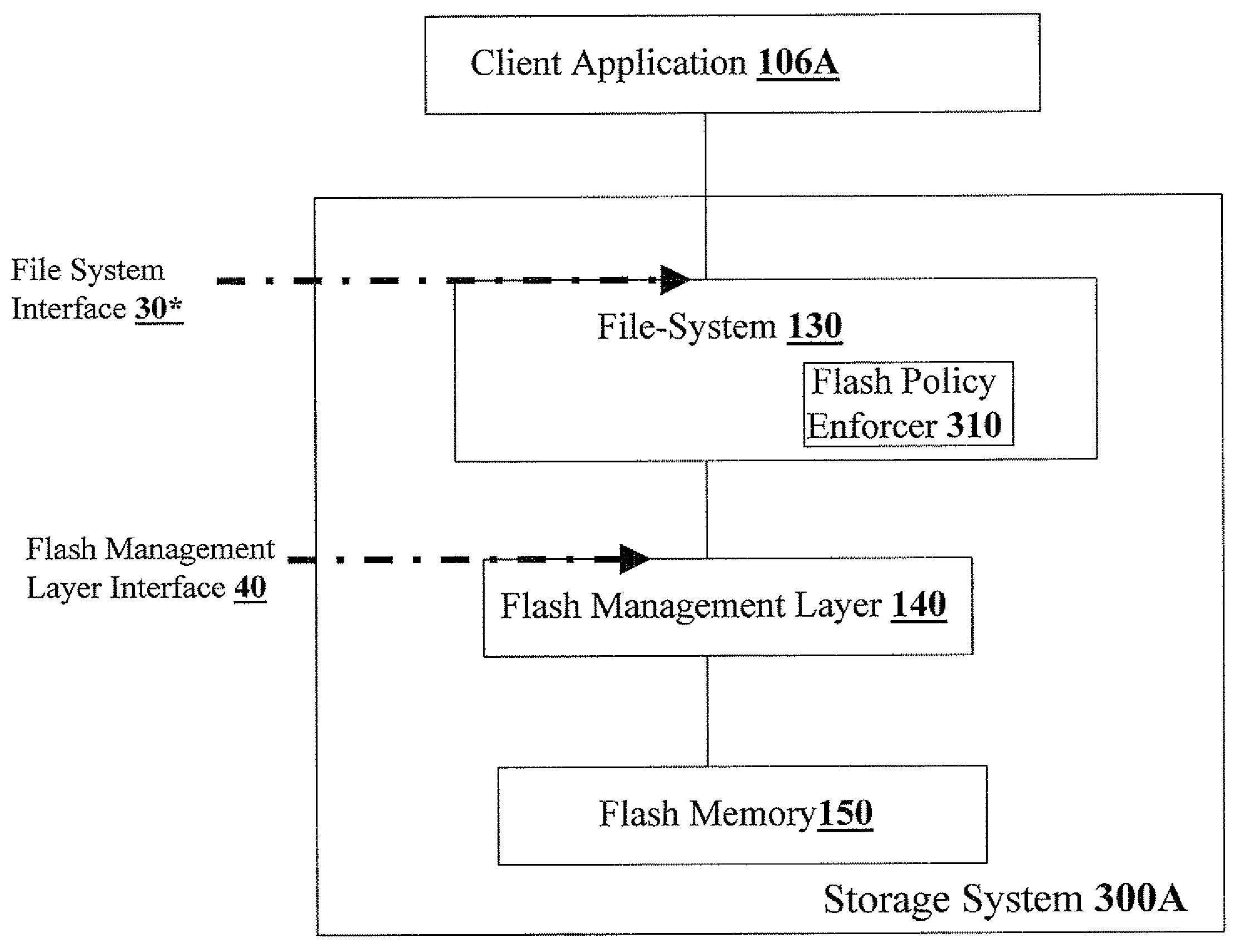
Identity-based flash management
Methods, apparatus, and computer code for effecting flash policy configuration operations in accordance with an end-user identifier and / or a host-instance identifier are disclosed herein. Exemplary flash policy configuration operations include (i) configuring a flash error-correction policy, (ii) configuring a flash-management table storage policy; (iii) configuring a wear-leveling policy; (iv) configuring a bad-block management policy and (v) configuring a flash-programming voltage parameter. Exemplary end-user identifiers include but are not limited to email account identifiers, logon user names, and International Mobile Subscriber Identities (IMSI). Exemplary host-instance identifiers may include but are not limited to International Mobile EQUIPMENT Identifiers (IMEI). Optionally, the flash policy configuration is contingent on authentication context data—for example, strength of the authentication (e.g. login / password vs. smartcard authentication or biometric authentication), date of the authentication, and identity provider information.
Owner:WESTERN DIGITAL ISRAEL LTD
Method and system of preventing handset from theft by using international id code of mobile facilities
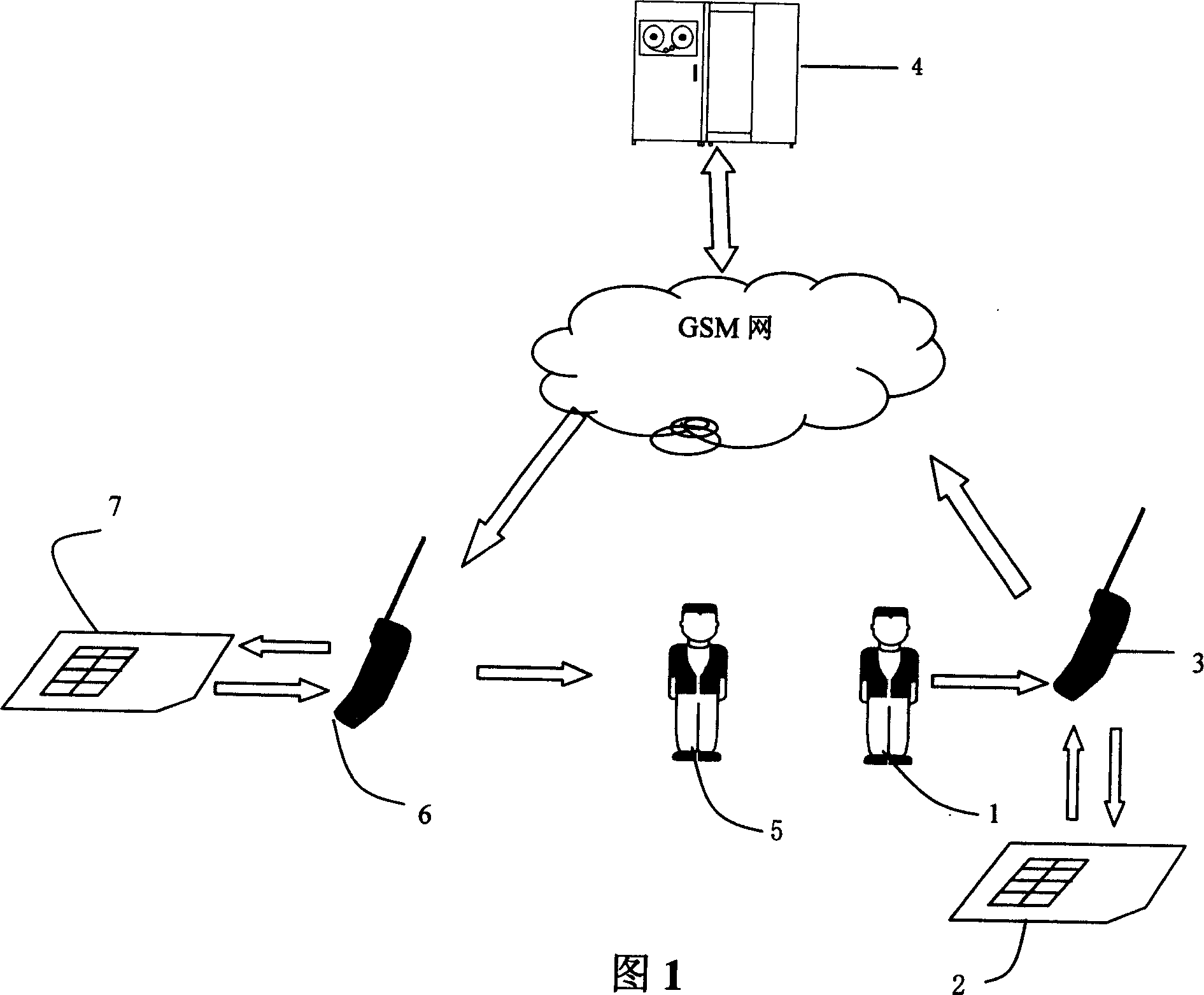
ActiveCN1541015AGood for businessEasy to manageUnauthorised/fraudulent call preventionSpecial service for subscribersMobile Telephone NumberMobile equipment identifier
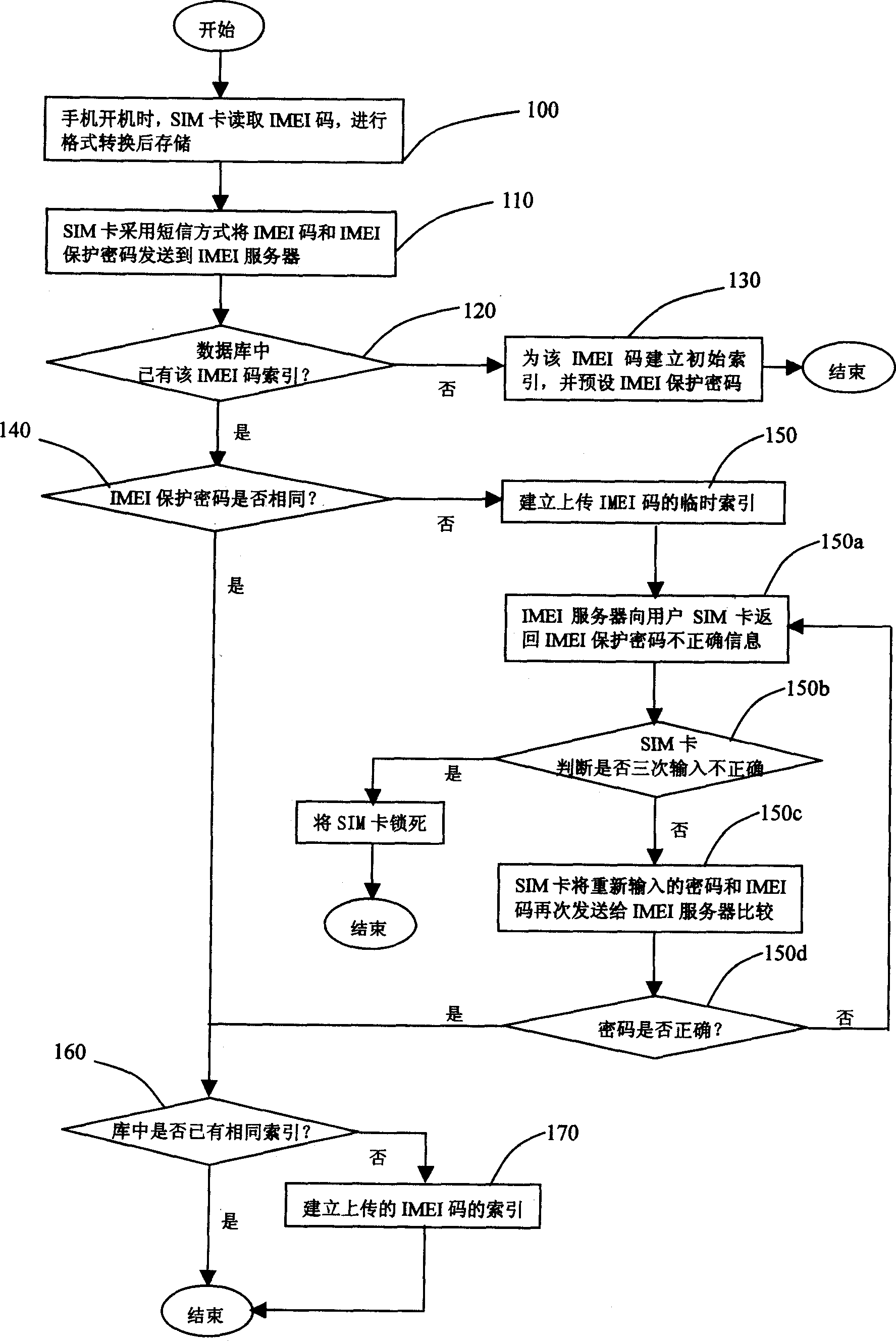
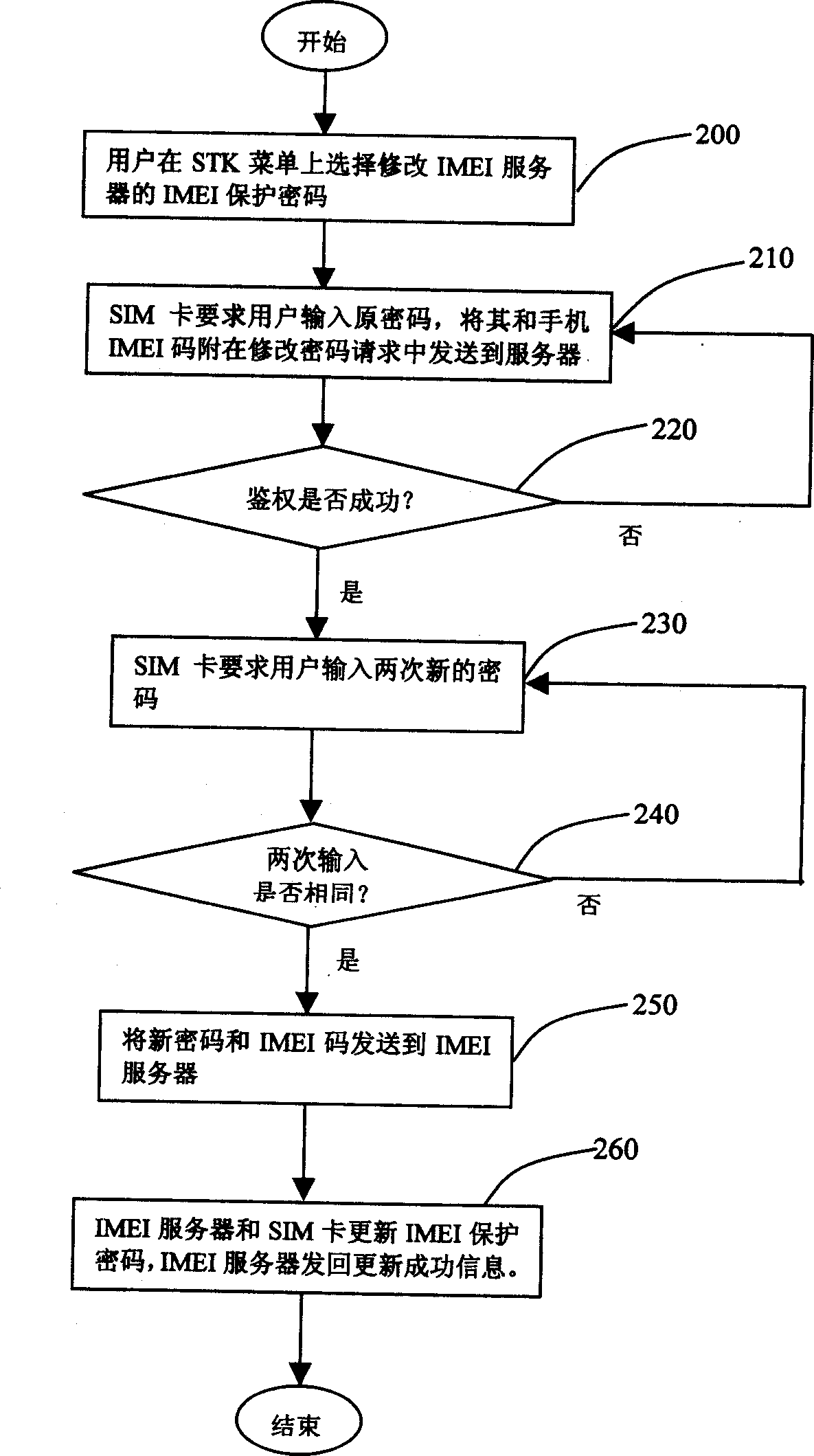
The system is composed of handset, SIM card, network and international mobile equipment identification (IMEI) server. Using the system, handset user logs on network and sends IMEI number automatically. IMEI server receives IMEI code sent by SIM card, and binds IMEI code with user's IMSI code and number of the handset, building corresponding user's index database. Using IMEI protection cipher carries out authentication of handset user's id. Temporary index for illegal user is built. If illegal user logs on network by using stealing handset, id of illegal user can be known from IMEI.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Identity-based flash management
ActiveUS20090100215A1Memory architecture accessing/allocationMemory adressing/allocation/relocationContext dataIdentity provider
Methods, apparatus, and computer code for effecting flash policy configuration operations in accordance with an end-user identifier and / or a host-instance identifier are disclosed herein. Exemplary flash policy configuration operations include (i) configuring a flash error-correction policy, (ii) configuring a flash-management table storage policy; (iii) configuring a wear-leveling policy; (iv) configuring a bad-block management policy and (v) configuring a flash-programming voltage parameter. Exemplary end-user identifiers include but are not limited to email account identifiers, logon user names, and International Mobile Subscriber Identities (IMSI). Exemplary host-instance identifiers may include but are not limited to International Mobile EQUIPMENT Identifiers (IMEI). Optionally, the flash policy configuration is contingent on authentication context data—for example, strength of the authentication (e.g. login / password vs. smartcard authentication or biometric authentication), date of the authentication, and identity provider information.
Owner:WESTERN DIGITAL ISRAEL LTD
Acquiring, storing, and correlating profile data of cellular mobile communications system's users to Events
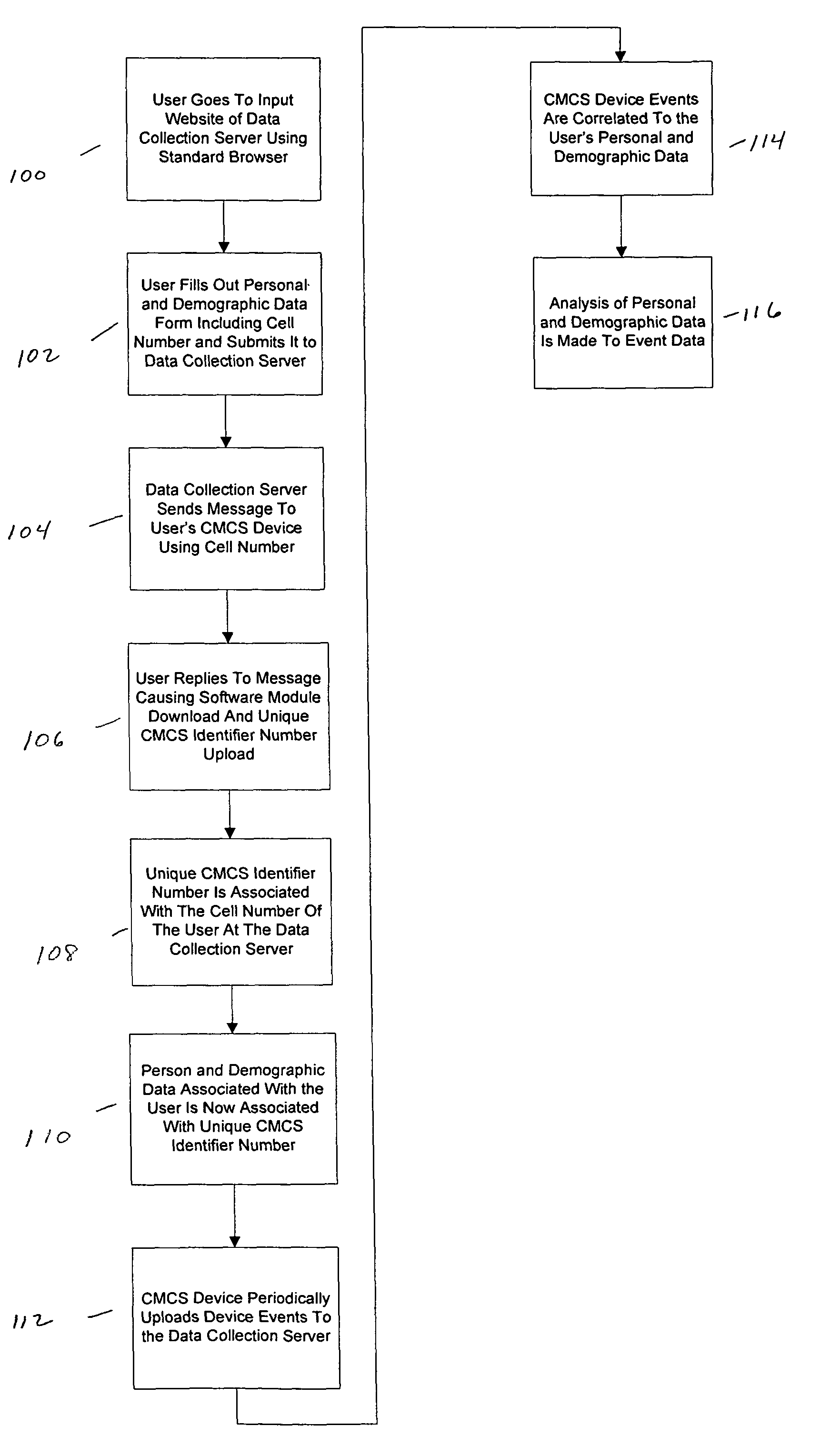
A system to collect personal and demographic data from user's of cellular mobile communications system devices. This system uses a standard web browser to collect the personal and demographic data instead of the device itself because of the limited interactive experience available to cellular mobile communications system device users. After obtaining data from the user including the user's cellular mobile communications system device's cellular phone number, a message is sent to the device. When a link is the message is activated a small event collection data software module is downloaded to the cellular mobile communications system device. The return message to the data collection entity incorporates the cellular mobile communications system device's International Mobile Equipment Identifier (IMEI) number. This number then ties the event data collected by the module to the personal and demographic information collected from the cellular mobile communications system device user.
Owner:M METRICS +1
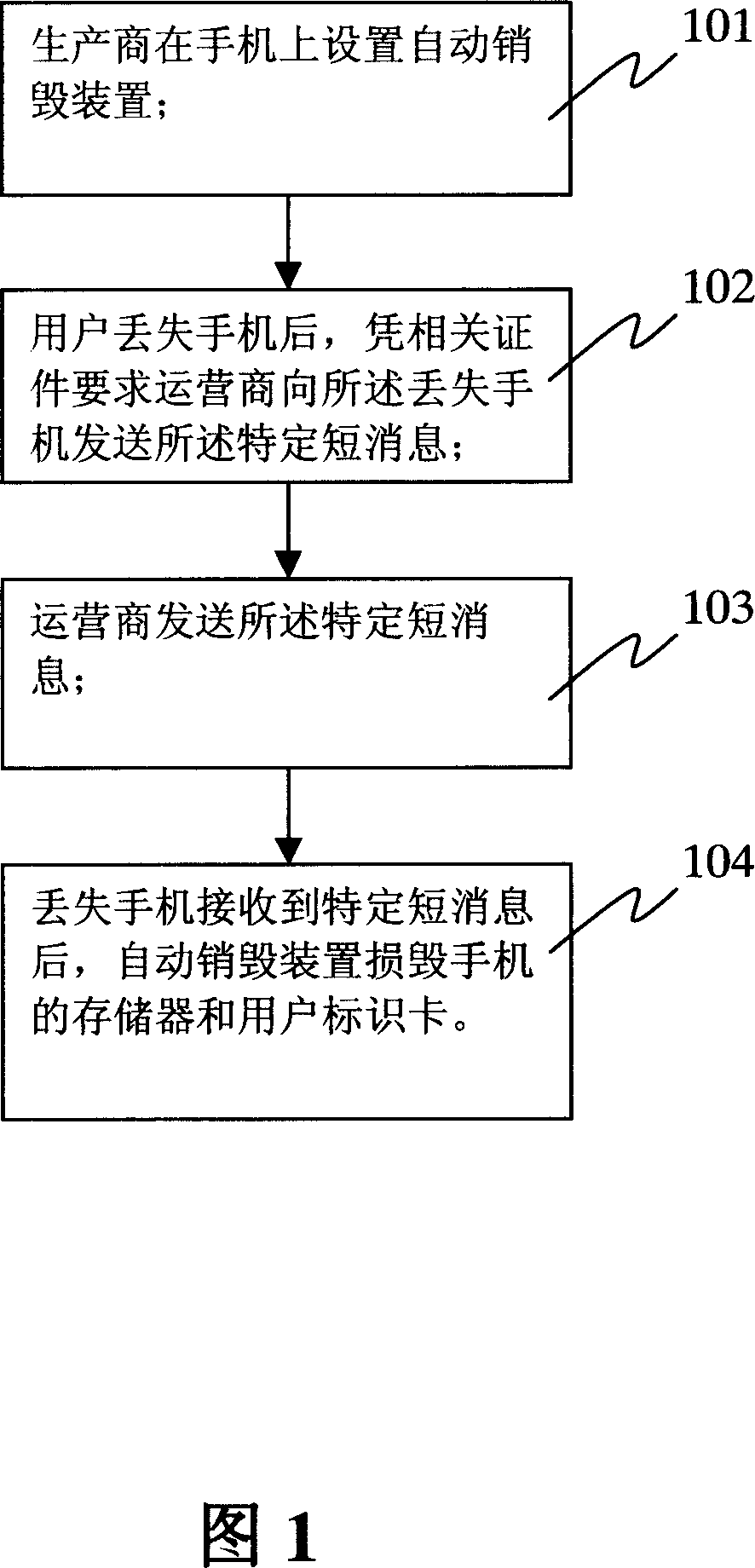
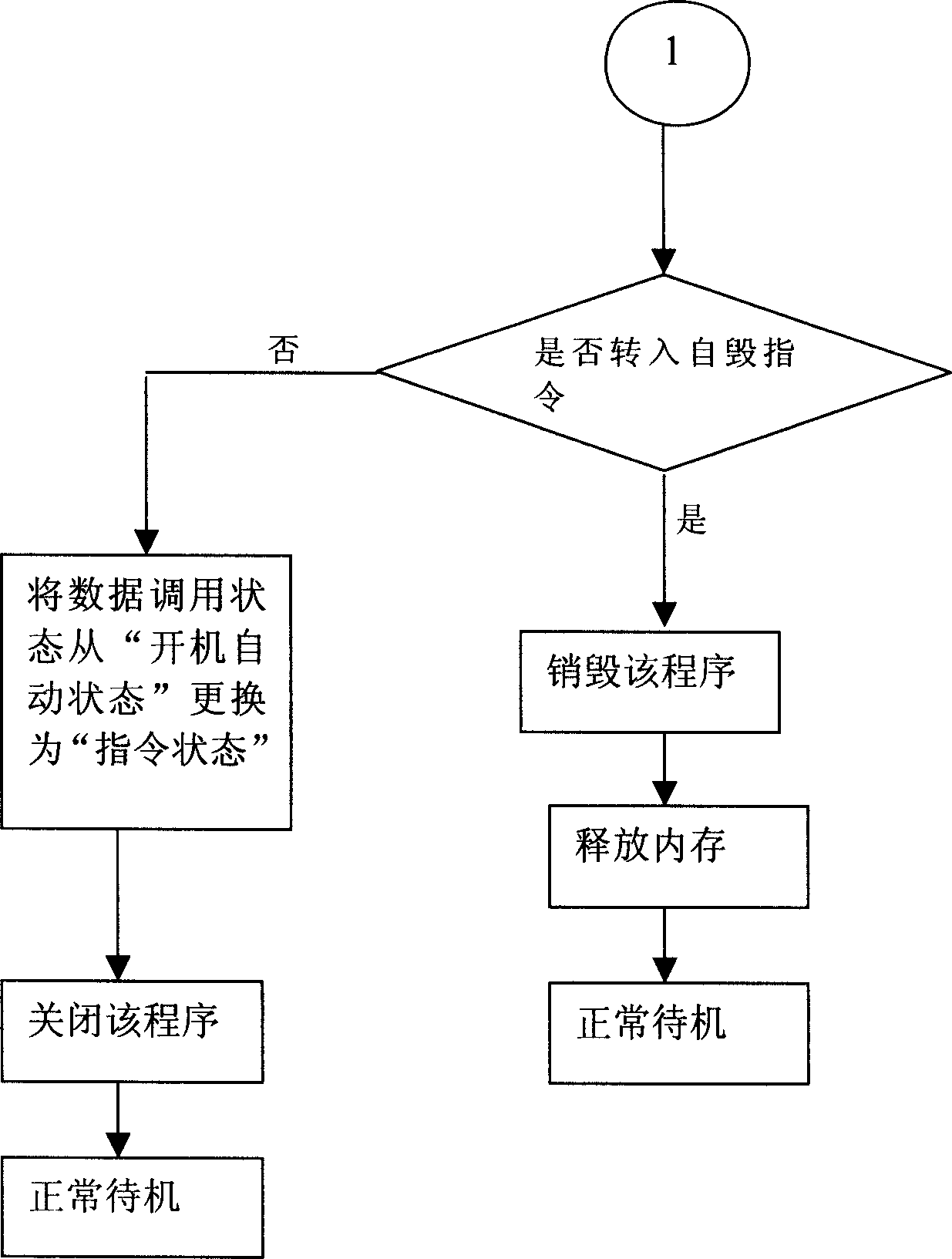
Method for automatically destroying cell phone and cell phone thereof
InactiveCN1941958AReduce leakageSubstation equipmentRadio/inductive link selection arrangementsMobile equipment identifierComputer science
The invention sets an automatically-destroying unit in the mobile phone; after user loses his mobile phone, he can use an IMEI (International Mobile Equipment Identification Number) code as unique identification code of the mobile phone and sends a short message to the mobile phone to trigger the destruction of SIM (subscriber identification module)card and memory card.
Owner:INSPUR LG DIGITAL MOBILE COMMUNICATIONS CO LTD
Mobile device with an obfuscated mobile device user identity
ActiveUS20080293378A1Improve securityEnsuring privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyUnique identifier
A mobile device identifier (such as an MSISDN) that typically accompanies a mobile device request is replaced with an “enriched” identifier that exposes the mobile device user's home operator but obfuscates the mobile device's (and, thus, the device user's) identity. In one embodiment, the identifier comprises a first part, and a second part. The first part comprises a data string that identifies (either directly or through a database lookup) the mobile device user's home operator. The second part, however, is an opaque data string, such as a one-time-use unique identifier (UID) or a value that is otherwise derived as a function of the MSISDN (or the like). The opaque data string encodes the mobile device's identity in a manner that preferably can be recovered only by the user's home operator (or an entity authorized thereby). When the mobile device user roams into a foreign network, that network receives the enriched identifier in lieu of an MSISDN. The foreign network uses the first part to identify the mobile device user's home network, e.g., to determine whether to permit the requested access (or to provide some other value-added service). The foreign network, however, cannot decode the second part; thus, the mobile device's identity (as well as the identity of the mobile device user) remains obscured. This ensures that the user's privacy is maintained, while preventing third parties from building a profile of the device based on the requests that include the MSISDN or similar identifier.
Owner:IBM CORP
Smart card dynamic binding method, device and system
InactiveCN105228125AMeet the security needs of bindingEasy to operateSecurity arrangementMachine-to-machine/machine-type communication servicePersonal identification numberMobile equipment identifier
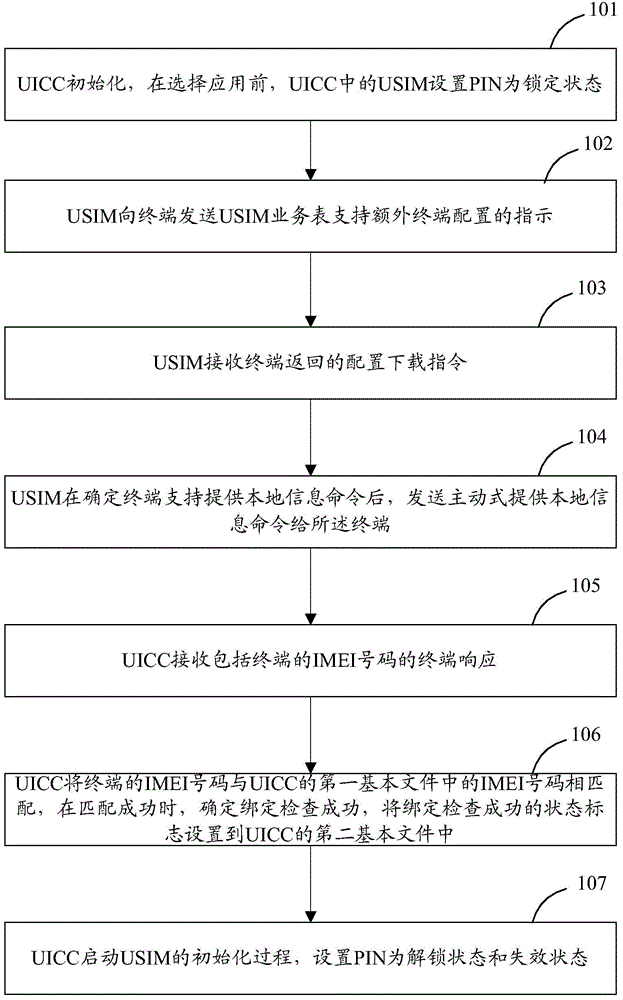
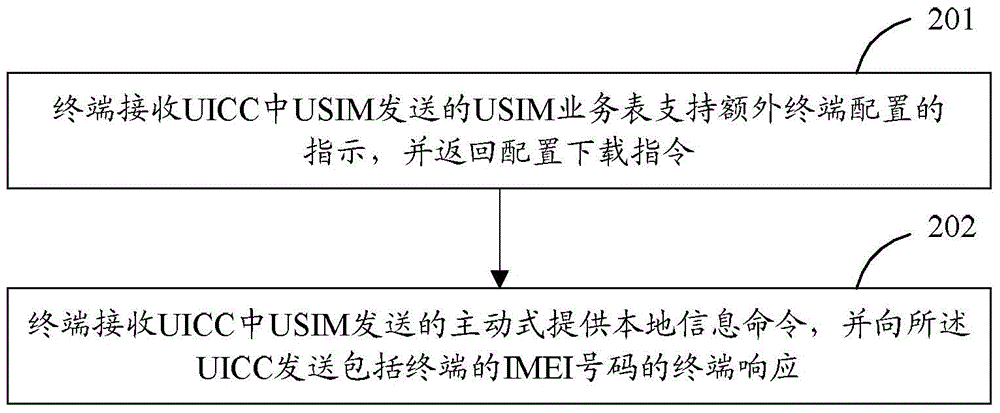
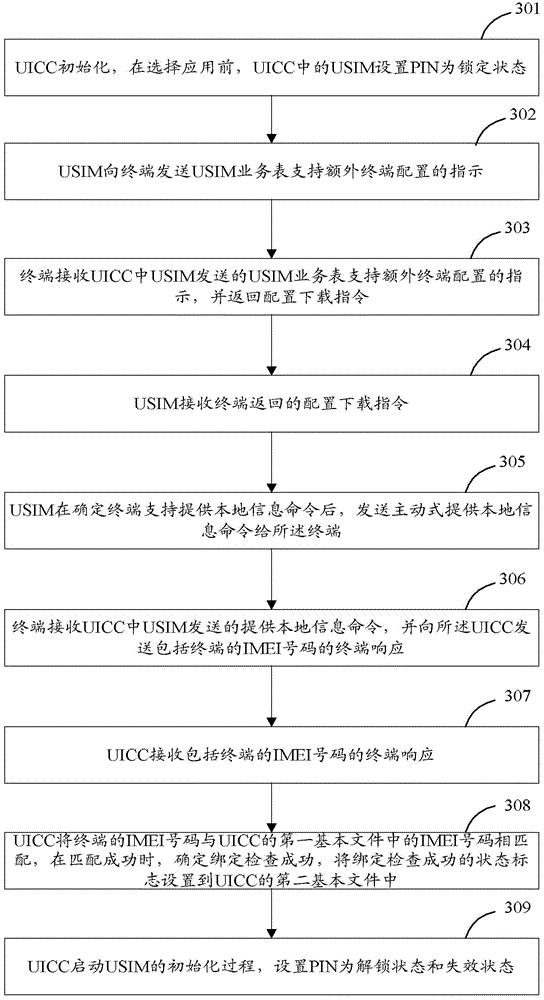
The invention discloses a smart card dynamic binding method. An integrated circuit card (UICC) is provided with a first basic file and a second basic file. Before the application selecting process, a global user identification module (USIM) sets a personal identification code (PIN) in the locked state, indicates a USIM service table to a terminal to enable the additional terminal configuration, and receives a configuration downloading instruction. When the USIM determines that the terminal enables a local information command, the USIM actively sends a local information command to the terminal. The UICC receives a terminal response containing the international mobile equipment identity (IMEI) of the terminal, matches the IMEI with an IMEI in the first basic file, sets a status flag for indicating the successful binding into the second basic file after the matching operation is successfully done, starts the initialization process of the USIM, and sets the PIN in the unlocked and invalid state. The invention also discloses a smart card dynamic binding device and a smart card dynamic binding system.
Owner:ZTE CORP
Acquiring, storing, and correlating profile data of cellular mobile communications system's users to events
ActiveUS7849154B2Telephonic communicationMultiple digital computer combinationsCellular telephoneSoftware modules
A system to collect personal and demographic data from user's of cellular mobile communications system devices. This system uses a standard web browser to collect the personal and demographic data instead of the device itself because of the limited interactive experience available to cellular mobile communications system device users. After obtaining data from the user including the user's cellular mobile communications system device's cellular phone number, a message is sent to the device. When a link is the message is activated a small event collection data software module is downloaded to the cellular mobile communications system device. The return message to the data collection entity incorporates the cellular mobile communications system device's International Mobile Equipment Identifier (IMEI) number. This number then ties the event data collected by the module to the personal and demographic information collected from the cellular mobile communications system device user.
Owner:COMSCORE
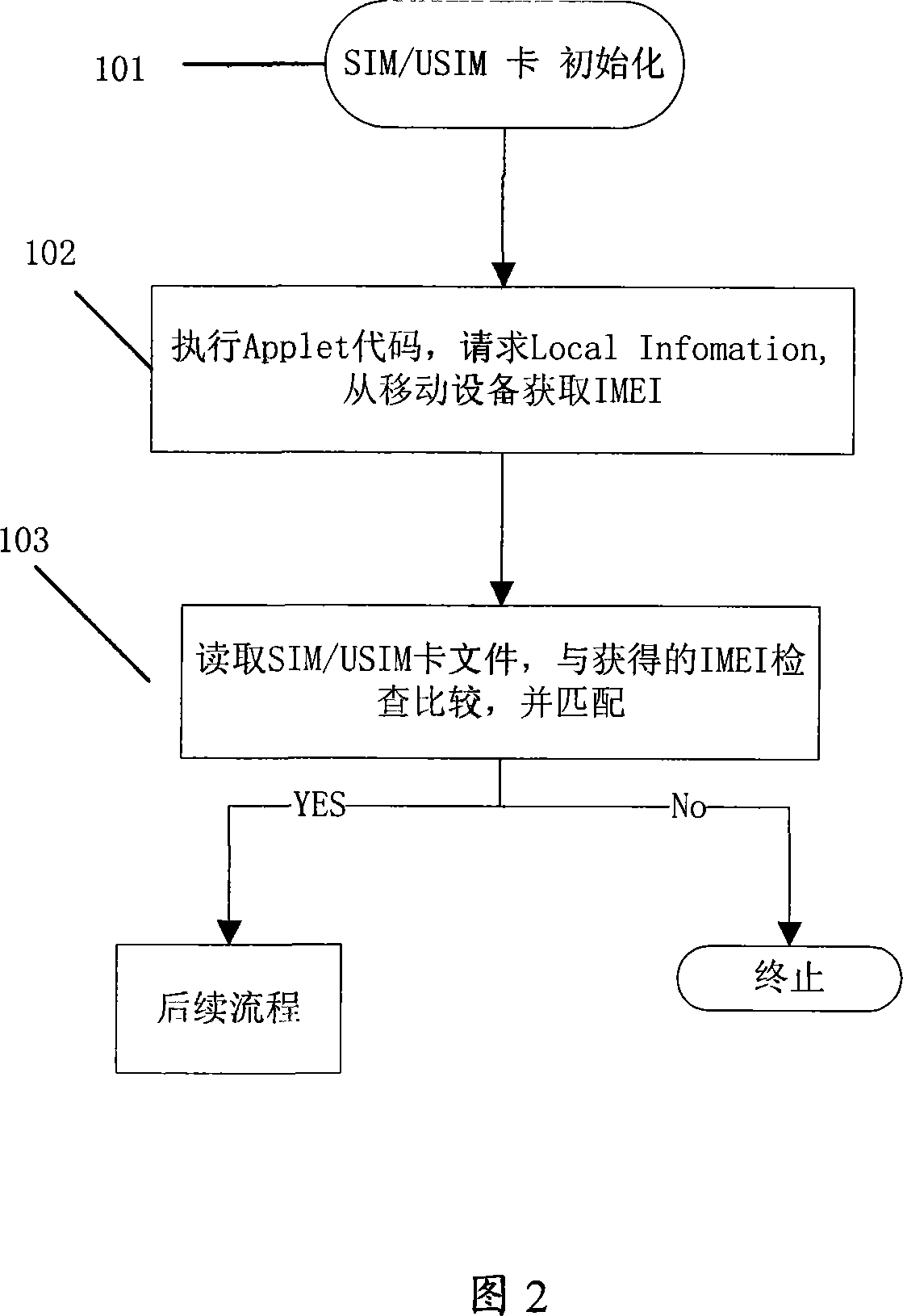
Method for realizing SIM/USIM card locked to special terminal
InactiveCN101072403ACompatible with other SIM/USIM card requirementsOvercoming complexityRadio/inductive link selection arrangementsTelephone set constructionsMobile equipment identifierApplication software
The method includes steps: step 101, initializing SIM / USIM card; step 102, running small application program codes embedded in SIM / USIM card, and obtaining solidified international mobile device ID code from mobile device; step 103, reading script file of small application program embedded in SIM / USIM card, and comparing it with the obtained information of international mobile device ID code; based on matched and checked result to determine whether the subsequent authorization interactive program is gong to be executed or not. Comparing with prior art, the method possesses features of simple operation, easy of implementation, no need of additional equipment. The invention also let mobile device compatible to other SIM / USIM cards.
Owner:ZTE CORP
Method for identifying invalid international mobile equipment identity number and apparatus thereof
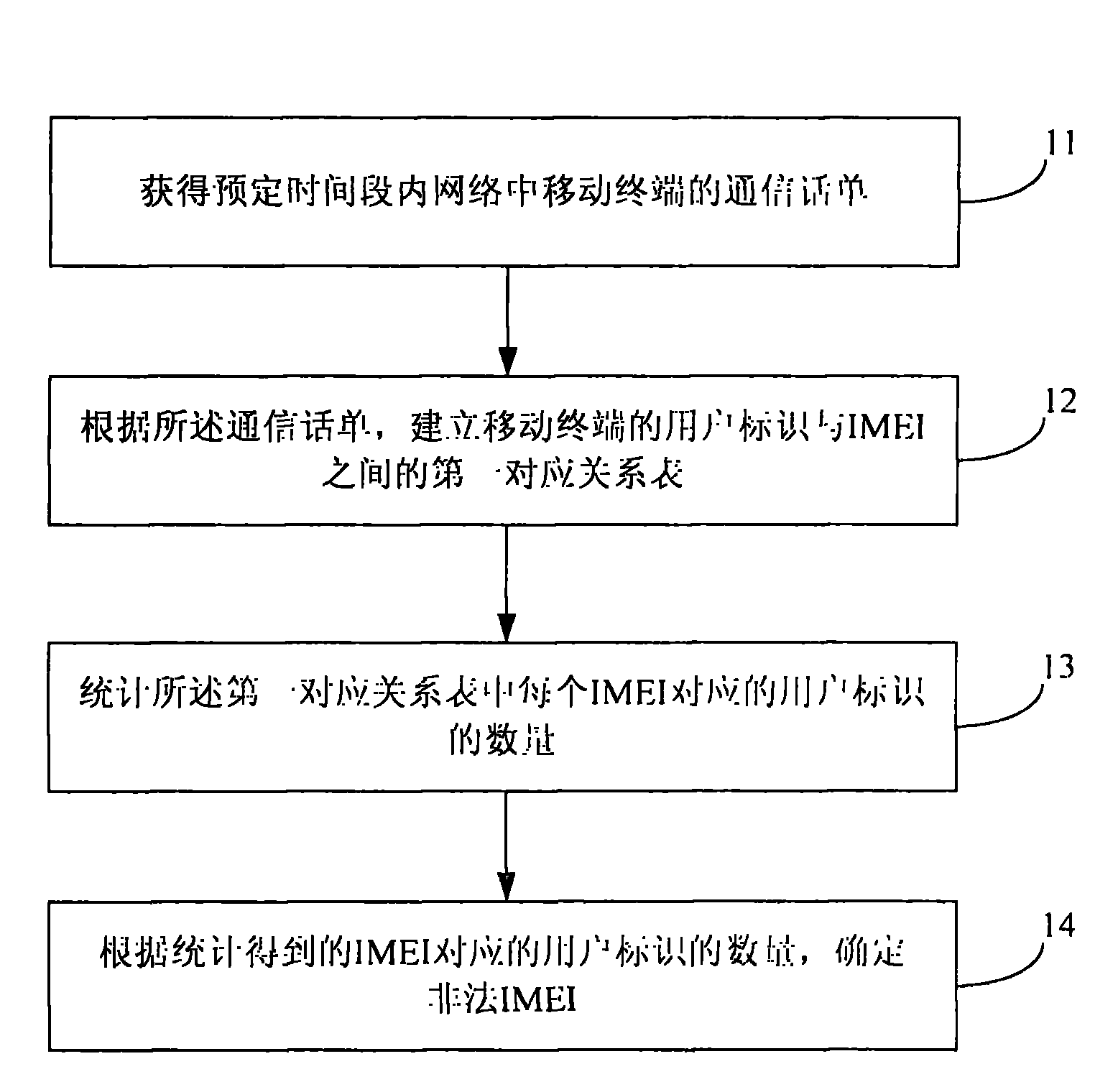
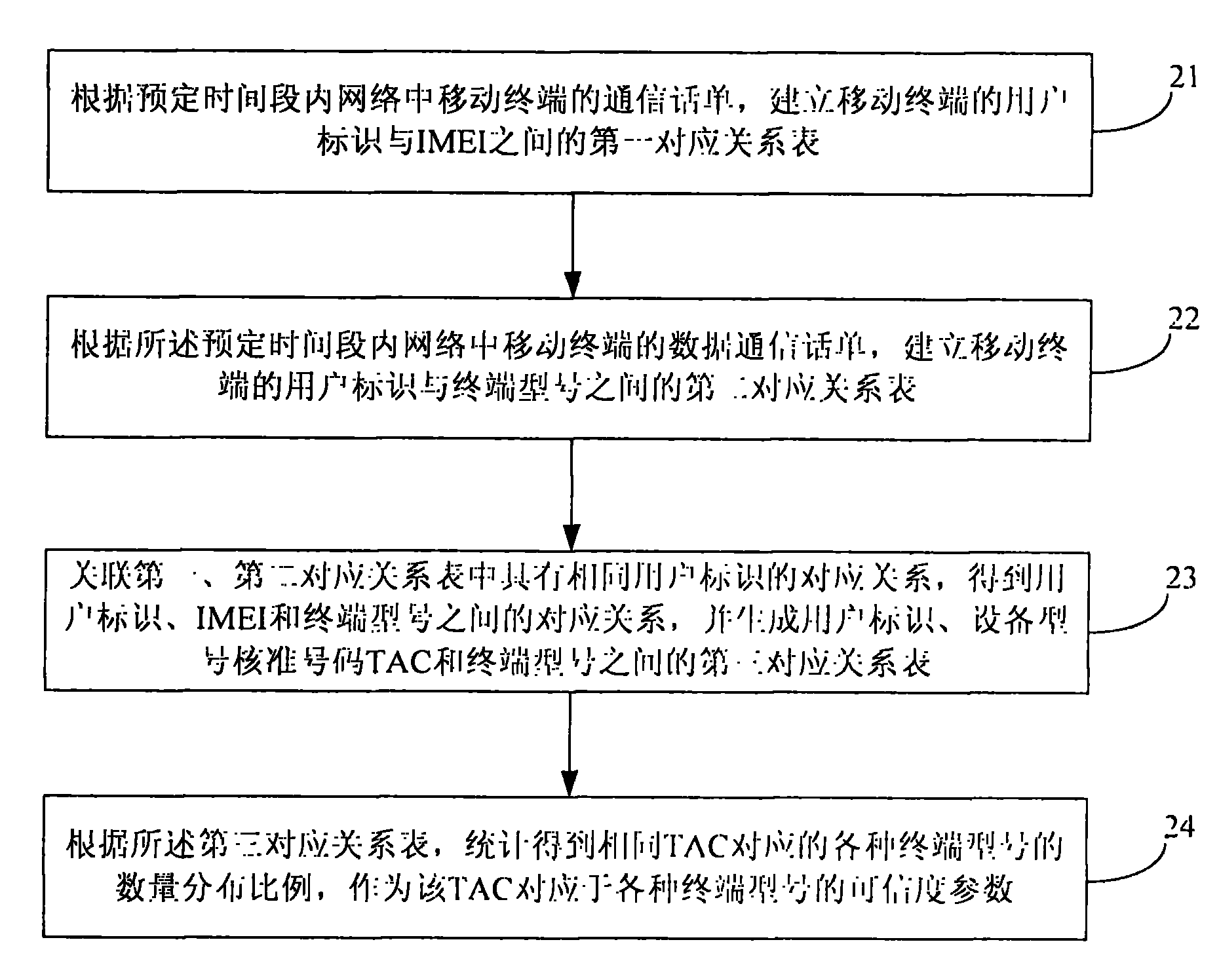
The invention provides a method for identifying an invalid international mobile equipment identity (IMEI) number and an apparatus thereof. The method comprises the following steps: acquiring a communication bill of a mobile terminal in a network in a predetermined time segment; according to the communication bill, establishing a corresponding relation table between subscriber identities and IMEI numbers of the mobile terminal; calculating quantity of the subscriber identities corresponding to each IMEI number in the corresponding relation table; according to the quantity, determining invalid IMEI numbers. According to the method and the apparatus of the invention, the invalid IMEI numbers existed in a mobile network can be identified.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD
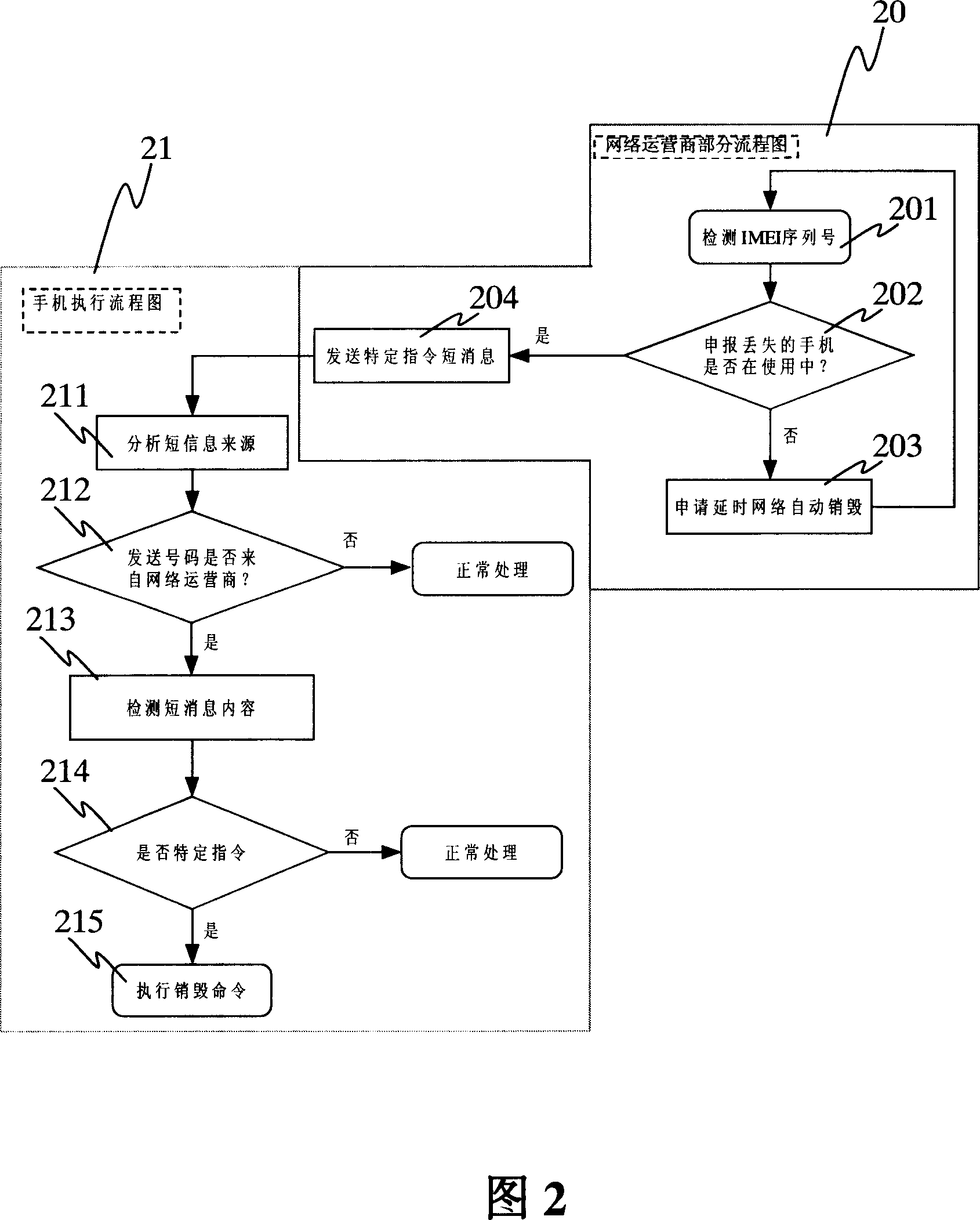
Method for realizing information destroying at network side
InactiveCN1980459AAutomatically initiate an auto-destroy operationRadio/inductive link selection arrangementsSecurity arrangementMobile equipment identifierMobile communication systems
This method applies in the net side of the mobile comm. system. The bonding info of user identification codes (IC) and the international mobile equipment IC is stored in the net side. The corresponding relation between the user IC and the service code of spare operation is also stored in the net side. This method includes the following steps. The net side (a) receives from user the request of destroying the aim mobile terminal (AMT) info; (b) confirms the user right of destroying the info; (c) searches the user IC of AMT and waits for AMT registering; (d) orientates the new user IC of AMT in HLR once finds AMT registering; (e) sends to AMT the related info destroying instruction to destroy the info. After the handset registers on the net server, once the handset is lost, the net side auto destroys all handset info.
Owner:ZTE CORP
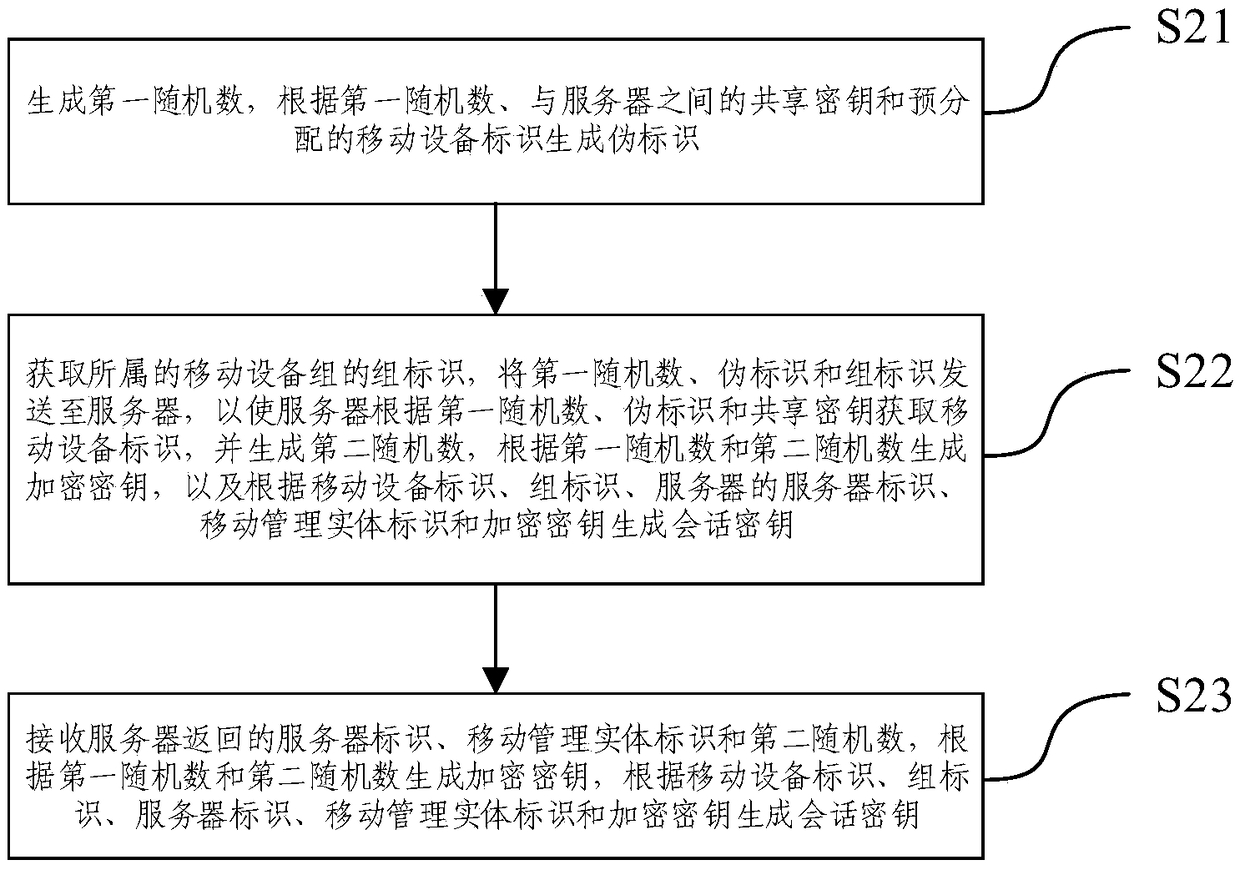
Key negotiation method and equipment in mobile communication
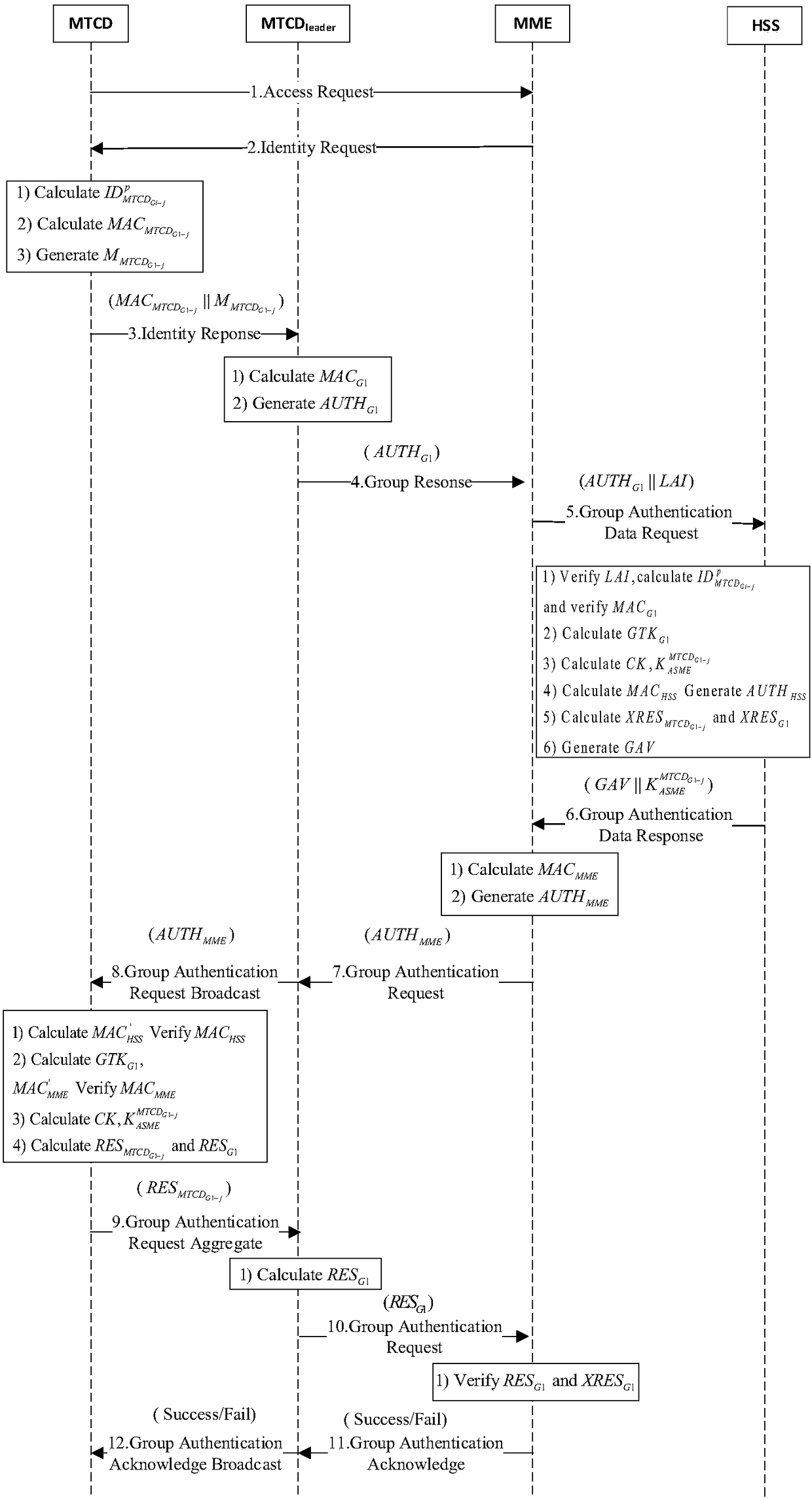
ActiveCN108616354AImprove securityReduce computational overheadKey distribution for secure communicationSignal allocationCryptographic key generationEntity identifier
An embodiment of the invention provides a key negotiation method and key negotiation equipment in mobile communication. The key negotiation method comprises the steps of: generating a pseudo identifier at a mobile equipment side according to a shared password and mobile equipment identifiers in real time, transmitting the pseudo identifier and a group identifier of a mobile equipment group to a server side, acquiring the mobile equipment identifiers by means of the server side according to the pseudo identifier, generating an encrypted key according to random numbers, generating a session keyaccording to the mobile equipment identifiers, the group identifier, a server identifier of the server, an acquired mobile management entity identifier and the encrypted key, returning the server identifier and the mobile management entity identifier to the mobile equipment side, and generating a session key by means of the mobile equipment side through using an algorithm the same as the server side. Through generating the pseudo identifier at the mobile equipment side and using the pseudo identifier for interaction in the signal interaction process, the security of the signal interaction process is improved; and the mobile equipment side and the server side generate the session keys just by adopting the plurality of the identifiers and the random numbers, and save the computational overhead and communication overhead.
Owner:BEIJING INFORMATION SCI & TECH UNIV
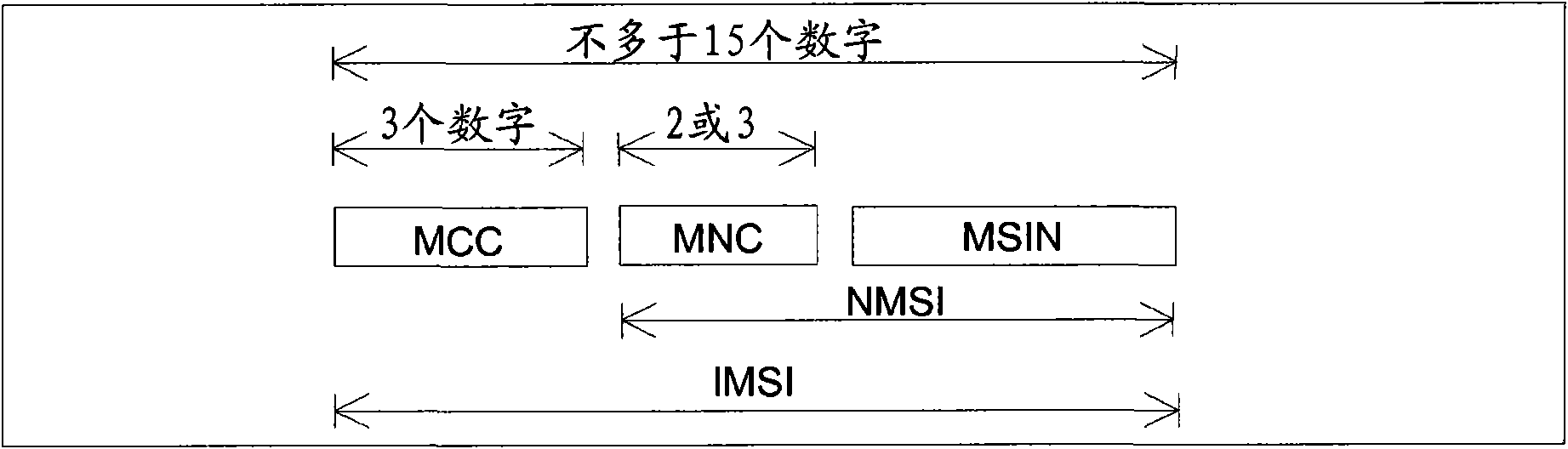
Derivation of user equipment identifiers
Solutions are described that enable a user equipment (UE) for a communication system always to derive required identifiers using an international mobile subscriber identity (IMSI). The Mobile Network Code (MNC) may be two or three digits long. The SIM may not provide information regarding the MNC length. One solution is based on a table, or list, that is maintained in the UE and which is used to retrieve the MNC for a given Mobile Country Code (MCC). Another solution is based on always taking a predetermined number of digits of the IMSI and determining the MNC in a DNS server. Yet another solution is based on try-and-fail signaling with a DNS server. In consequence, the UE does not always need to know how many digits of the IMSI are used to indicate the mobile network code (MNC), which in some situations is impossible to know anyway.
Owner:TELEFON AB LM ERICSSON (PUBL)
Internet of Things terminal card binding, network access authentication and service authentication method and device
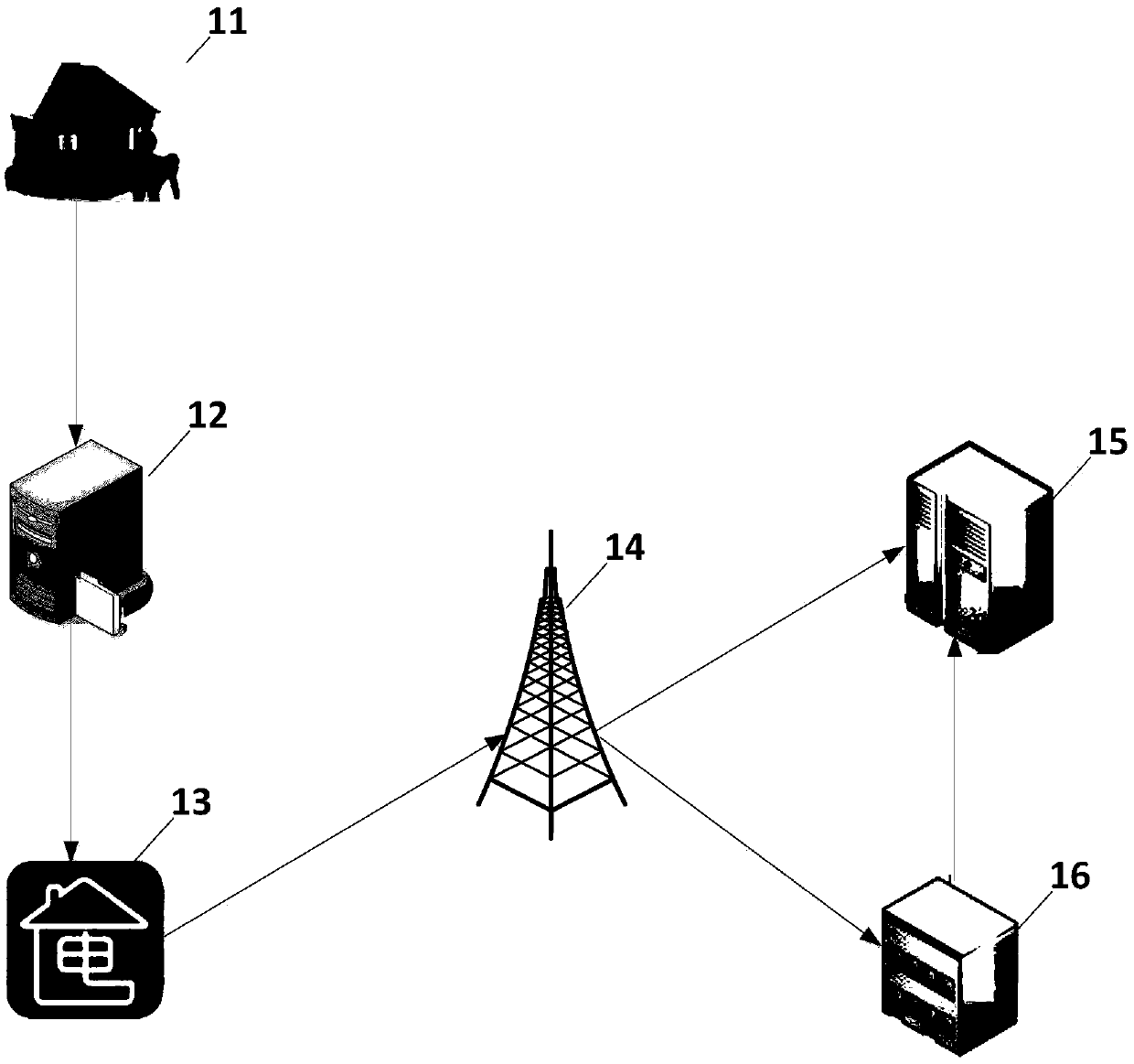
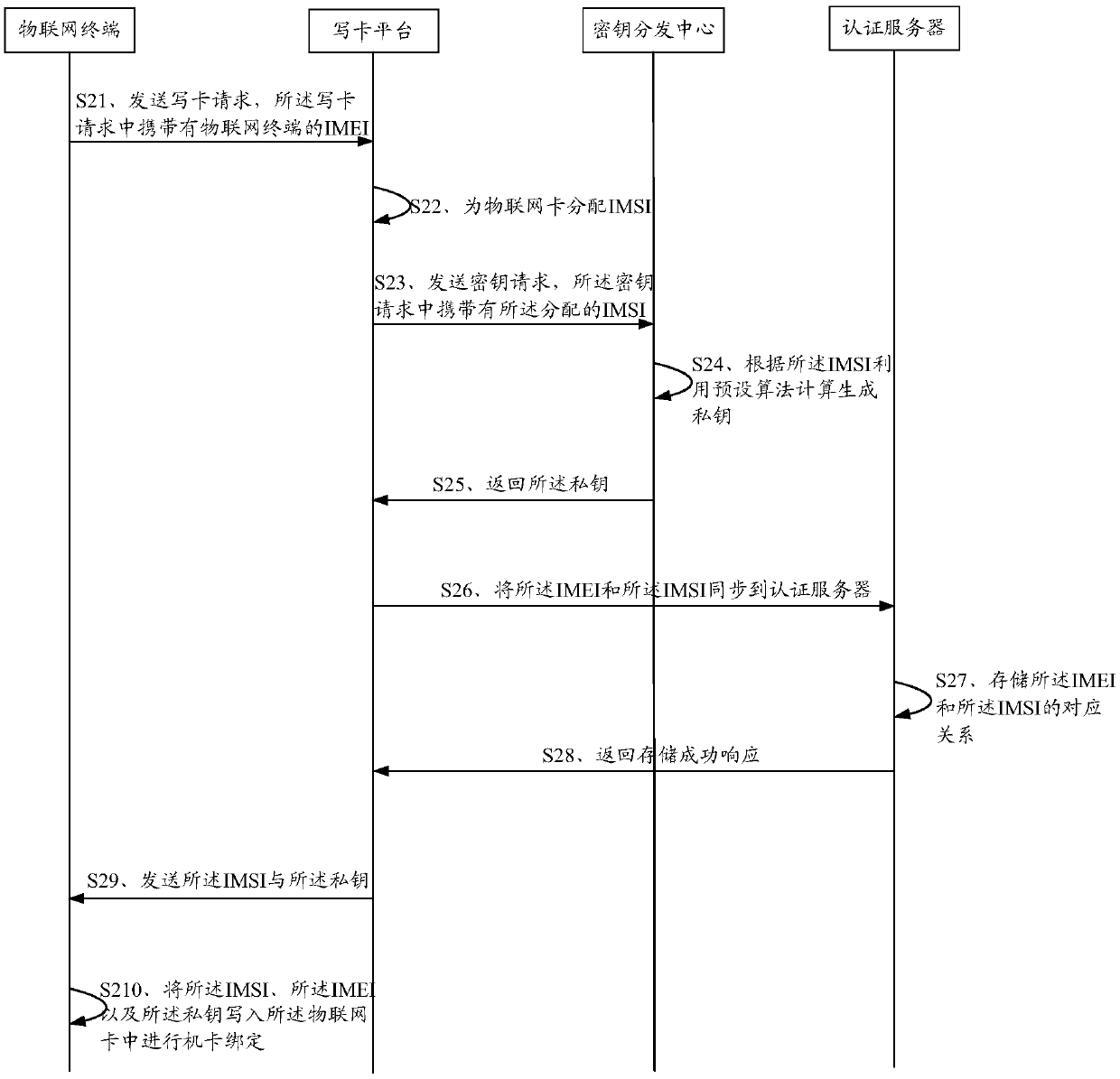
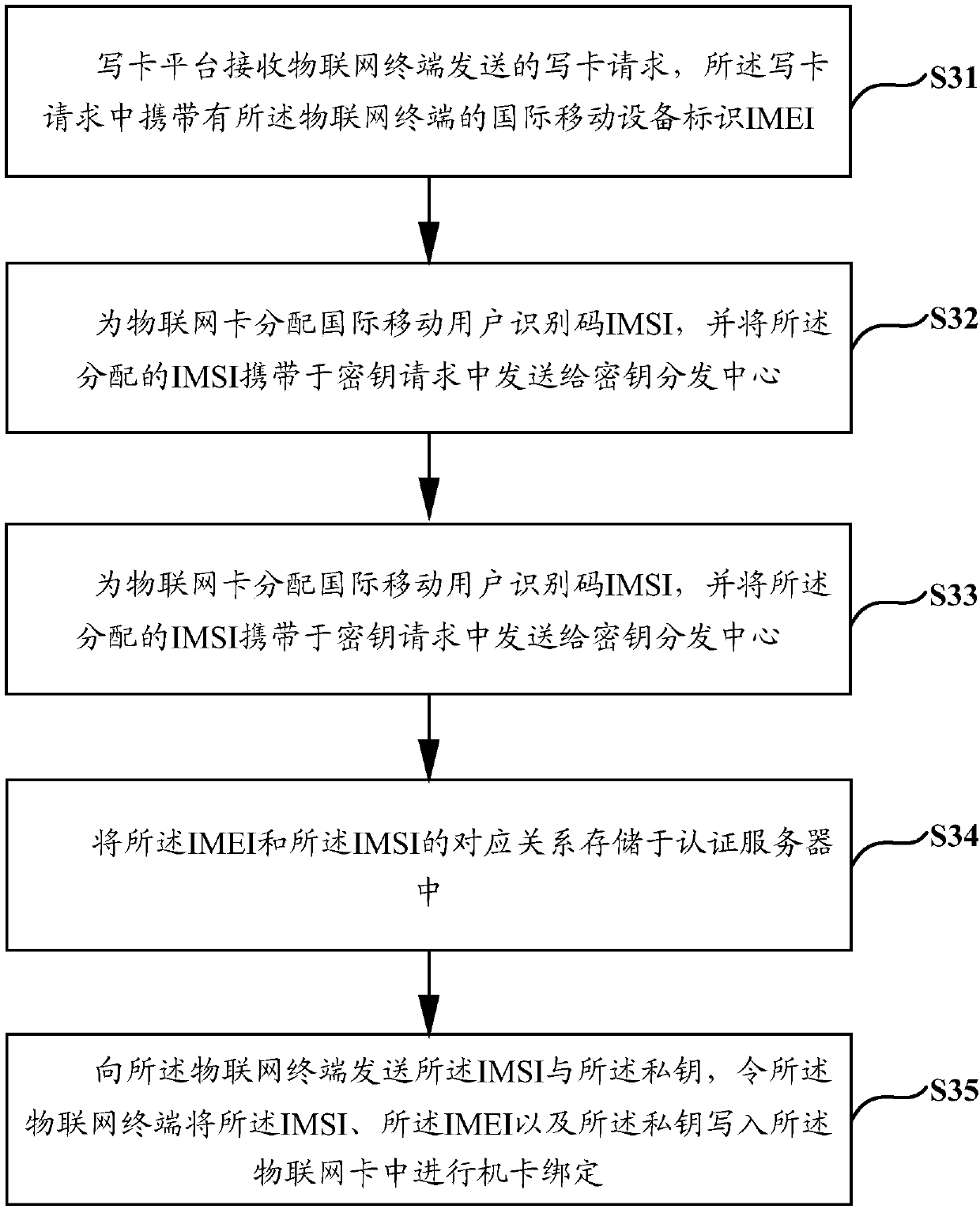
ActiveCN111182521AImprove versatilityReduce transmissionNetwork topologiesSecurity arrangementInternet privacyMobile equipment identifier
The invention discloses an Internet of Things terminal card binding, network access authentication and service authentication method and device, which are used for solving the problems of a complex authentication process and a high cost of Internet of Things equipment in the prior art. The Internet of Things terminal card binding method comprises the following steps: receiving a card writing request sent by an Internet of Things terminal, wherein the card writing request carries an international mobile equipment identifier (IMEI) of the Internet of Things terminal, distributing the IMSI for the Internet of Things card, carrying the distributed IMSI in a key request, sending the key request to a key distribution center, receiving a private key which is sent by the key distribution center and is calculated and generated by utilizing a preset algorithm according to the IMSI, storing the corresponding relationship between the IMEI and the IMSI in an authentication server, sending the IMSIand the private key to the Internet of Things terminal, and enabling the Internet of Things terminal to write the IMSI, the IMEI and the private key into the Internet of Things card for machine-card binding.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
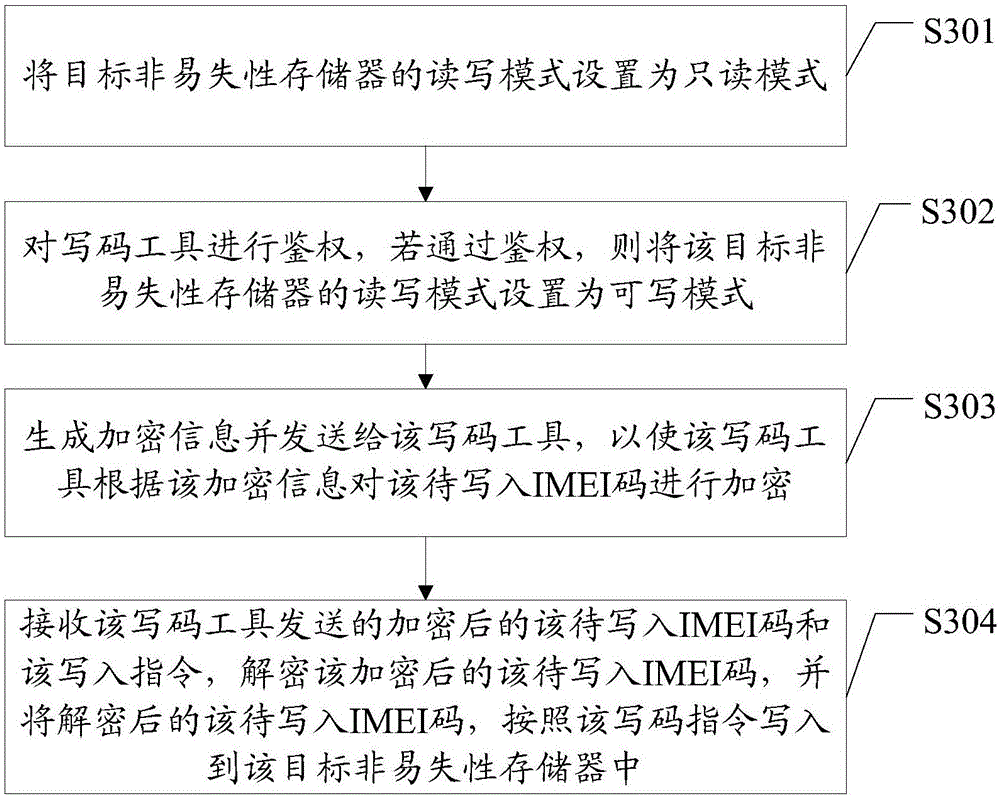
Method and device for writing IMEI (International Mobile Equipment Identity) and mobile terminal
ActiveCN106792637APrevent tamperingAvoid confictSecurity arrangementNetwork data managementThird partyMobile equipment identifier
The embodiment of the invention discloses a method and device for writing an IMEI (International Mobile Equipment Identity) and a mobile terminal, and is applied to the technical field of communications. The method comprises the steps of: setting a read-write mode of a target nonvolatile memory as a read-only mode; carrying out authentication on a coding tool; if passing the authentication, setting the read-write mode of the target nonvolatile memory as a writable mode; receiving an IMEI to be written and a coding instruction which are sent by the coding tool; and according to the coding instruction, writing the IMEI to be written into the target nonvolatile memory. Therefore, by setting the read-write mode of the target nonvolatile memory as the read-only mode and carrying out authentication on the third-party coding tool, a case that the IMEI is randomly tampered by an unauthorized third-party tool can be effectively prevented, so that a conflict caused if different mobile phones have the same IMEI is avoided, and the mobile phones can normally access the network of an operator to achieve a normal call function.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
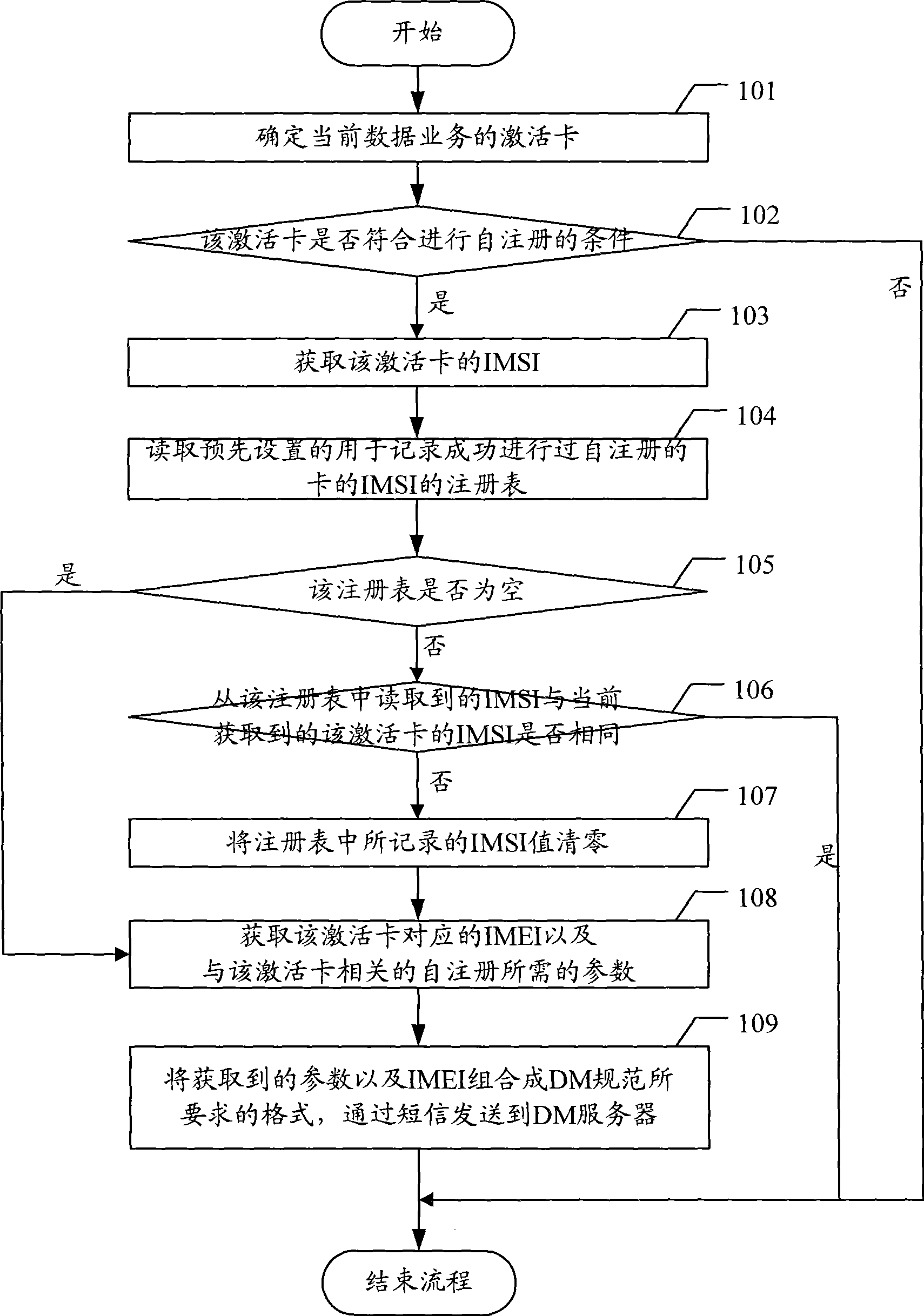
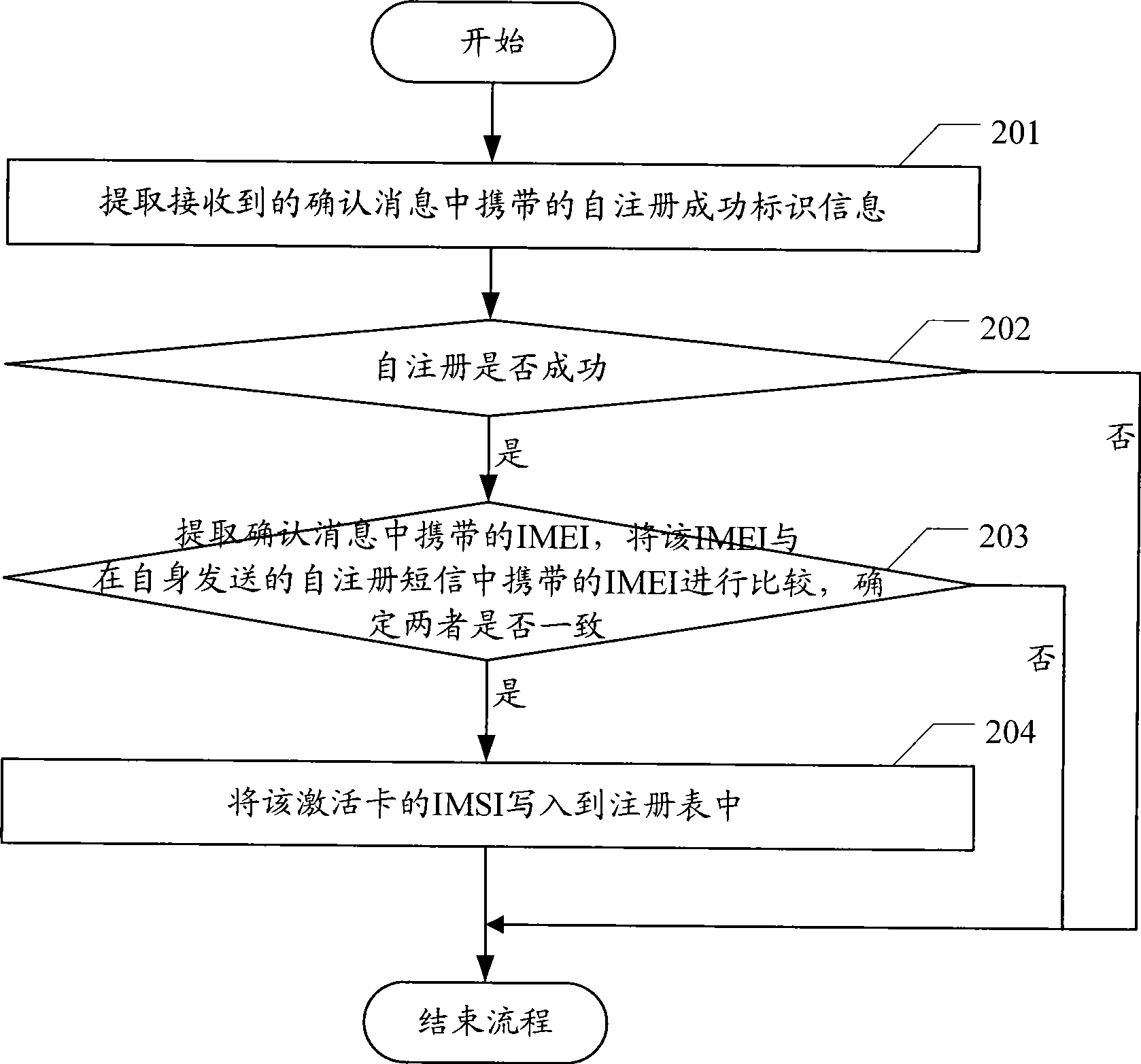
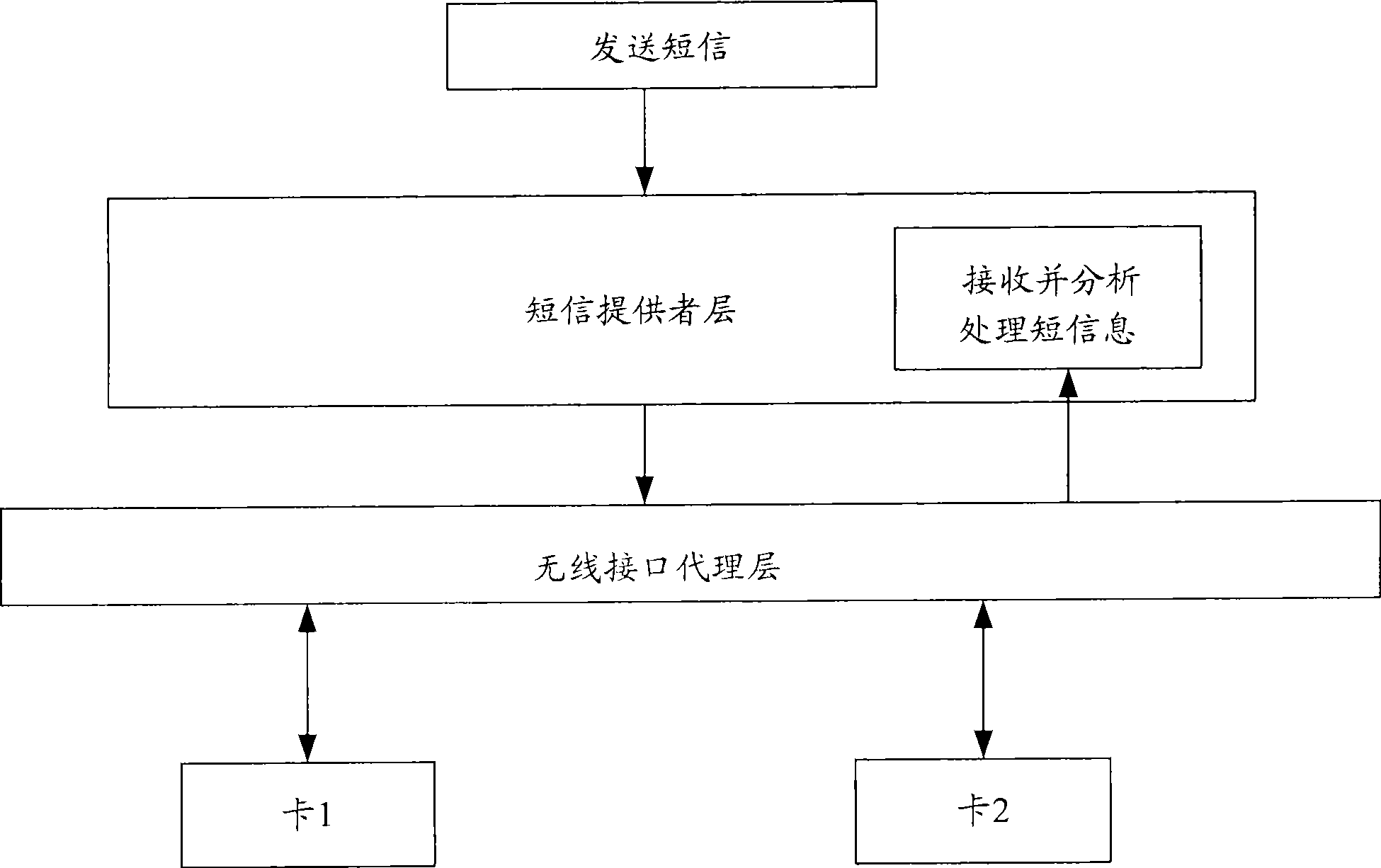
Self log-on method and system for device management terminal and device management terminal thereof
The present invention discloses a terminal management (DM) terminal self-registration method and system in a dual-network dual-standby structure of Windows Mobile platform, including: the DM terminal determining the activated card of the current data service, and acquiring the international mobile equipment identification identifier (IMEI) corresponding to the activated card and parameters required by self-registration related to the activated card; combining the acquired parameters and IMEI into a format required by the DM criterion, and transmitting to the DM server through SMS; and receiving the self-registration success confirmation message returned from the DM server. At the same time, the present invention discloses an DM terminal in a dual-network dual-standby structure of Windows Mobile platform. Application of the inventive method, system and DM terminals, the invention resolves the problem of DM terminal self-registration in a dual-network dual-standby structure based on Windows Mobile platform, thereby facilitating the use of users.
Owner:TECHFAITH WIRELESS TECH BEIJING
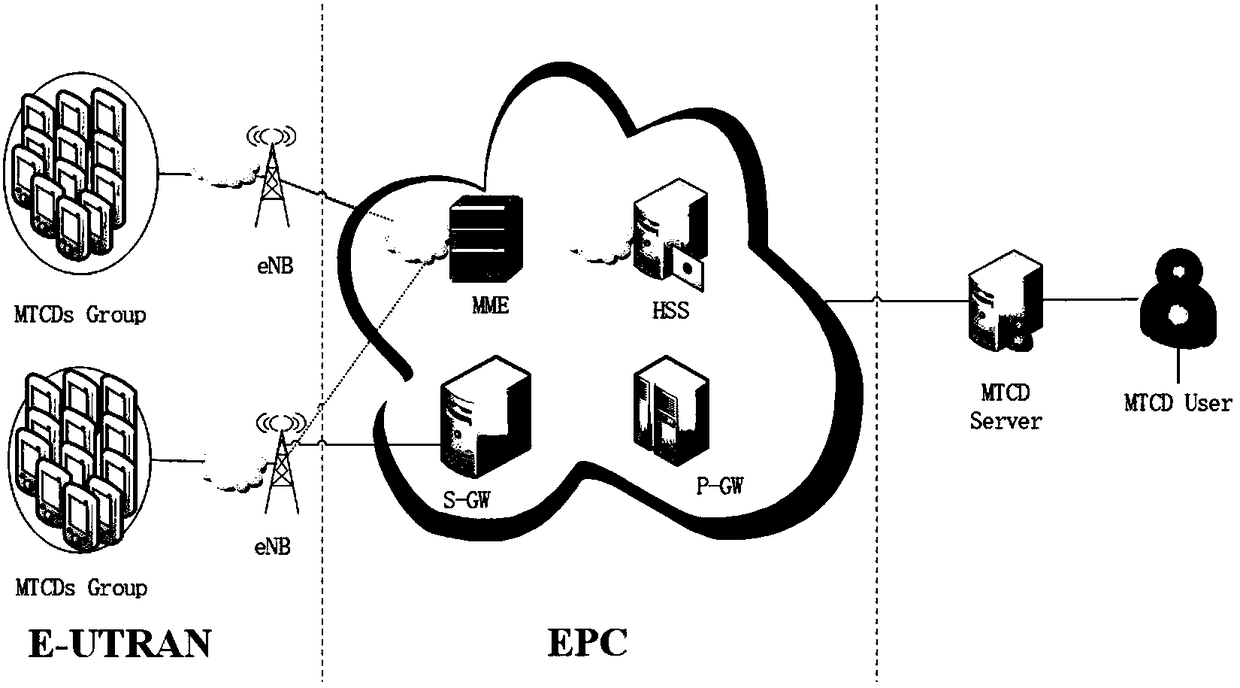
power grid NB-IoT end-to-end data processing method based on a physical unclonable function
ActiveCN109756872AImprove securityPrevent impersonation attacksSecurity arrangementMachine-to-machine/machine-type communication serviceComputer hardwarePower grid
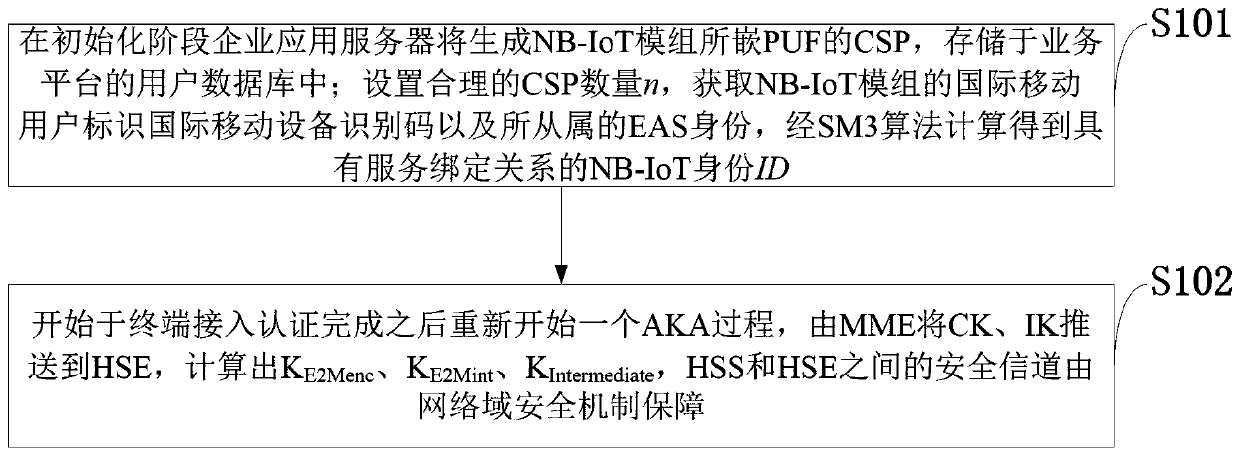
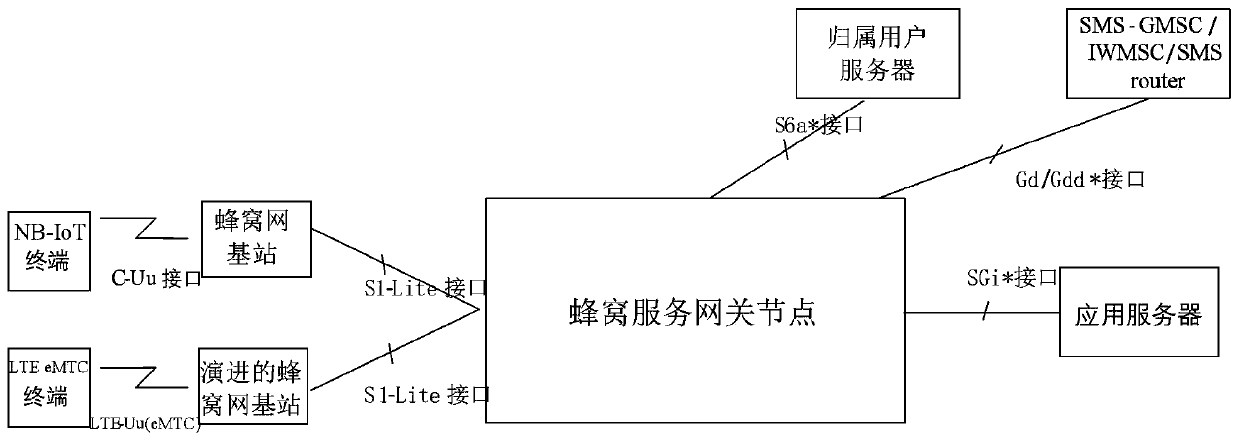
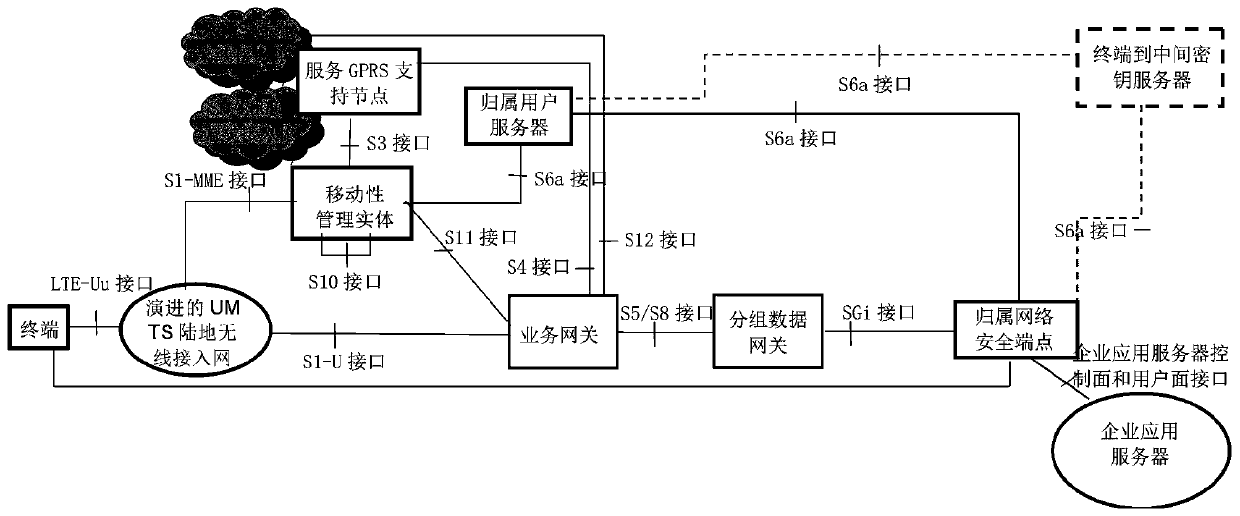
The invention belongs to the technical field of end-to-end communication, and discloses a power grid NB-IoT end-to-end data processing method based on a physical unclonable function. At the initialization stage, the enterprise application server generates a CSP of the PUF embedded in the NB-IoT module and stores the CSP in a user database of the service platform; A reasonable CSP number n is set,an international mobile user identifier, an international mobile device identification code and a subordinated EAS identity of the NB-IoT module are obtained, and an NB-IoT identity ID with a servicebinding relation is obtained through calculation of an SM3 algorithm; And the MME pushes the CK and the IK to the HSE, and a secure channel between the KE2Menc, the KE2Mint, the KIntermediate, the HSSand the HSE is calculated and is guaranteed by a network domain security mechanism. Compared with the prior art, the method has the characteristics of light weight and flexible updating, and the security of the service system is further enhanced.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY
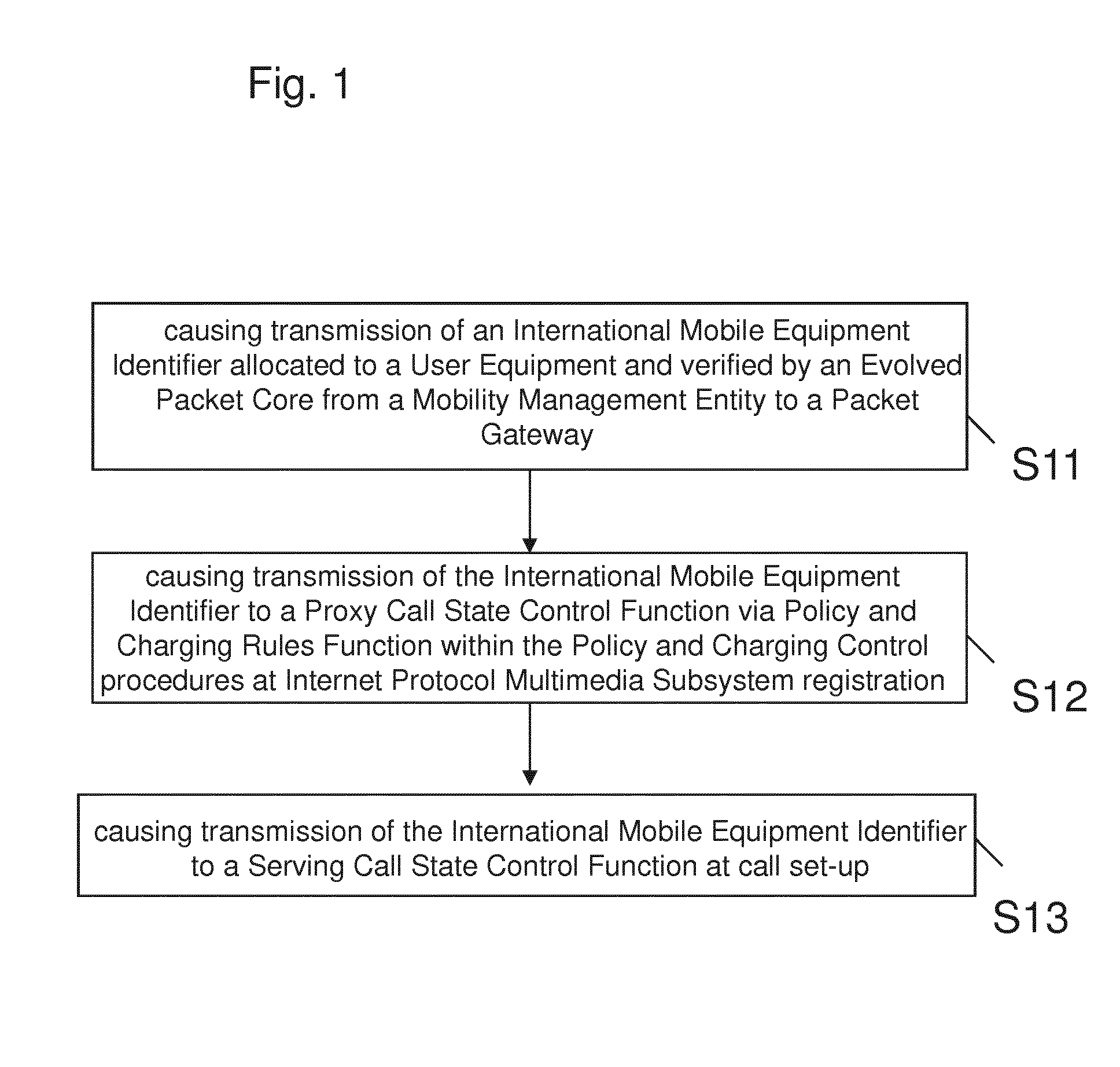
Imei based lawful interception for IP multimedia subsystem
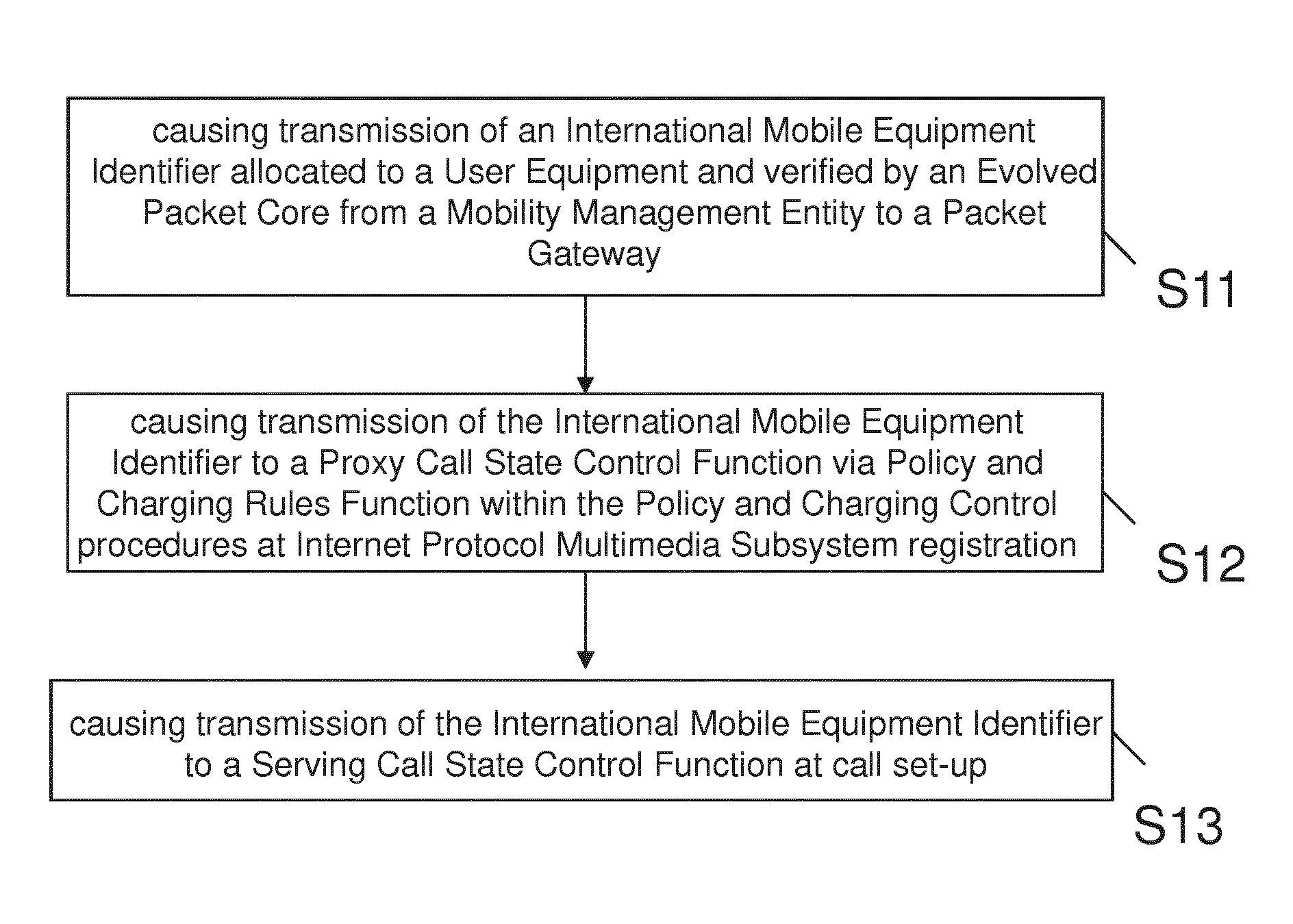
The present invention addresses method, apparatus and computer program product for enabling International Mobile Equipment Identifier based Lawful Interception for Internet Protocol IP Multimedia Subsystem, VoLTE and beyond systems. Thereby, an International Mobile Equipment Identifier allocated to a User Equipment and verified by an Evolved Packet Core is transmitted from a Mobility Management Entity to a Packet Gateway, the International Mobile Equipment Identifier is transmitted to a Proxy Call State Control Function via Policy and Charging Rules Function within the Policy and Charging Control procedures at Internet Protocol Multimedia Subsystem registration, and the International Mobile Equipment Identifier is transmitted to a Serving Call State Control Function at call set-up.
Owner:NOKIA SOLUTIONS & NETWORKS OY
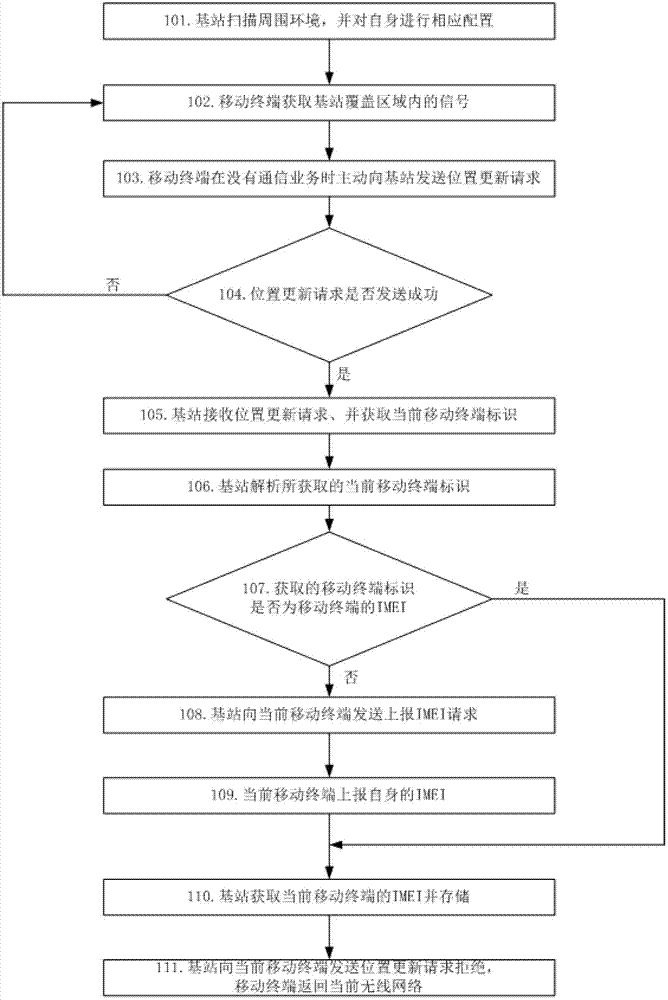
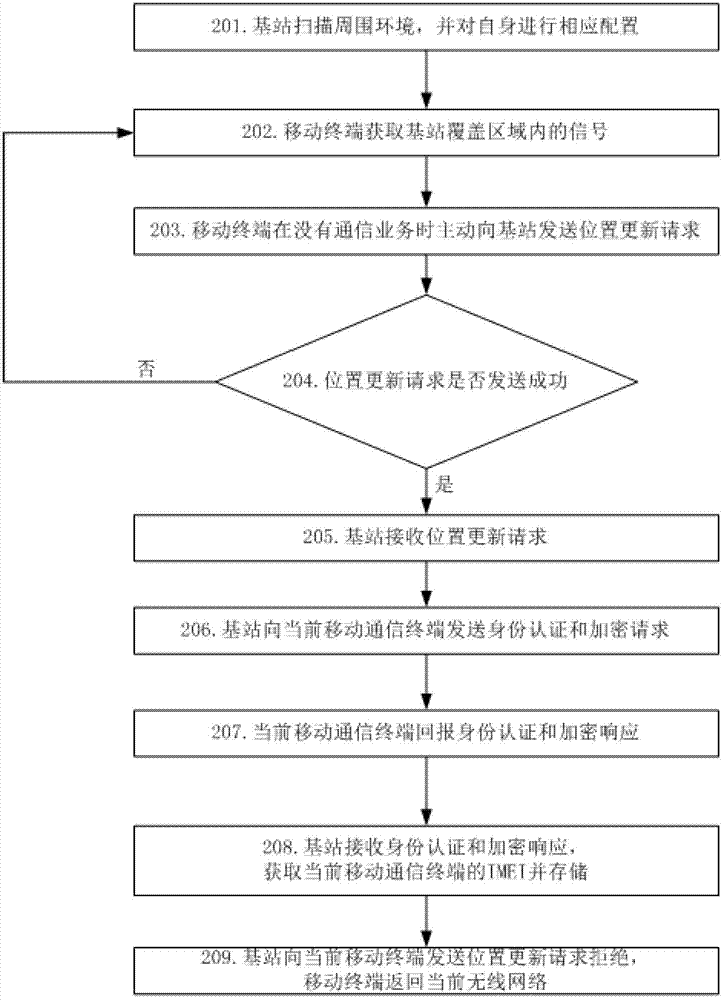
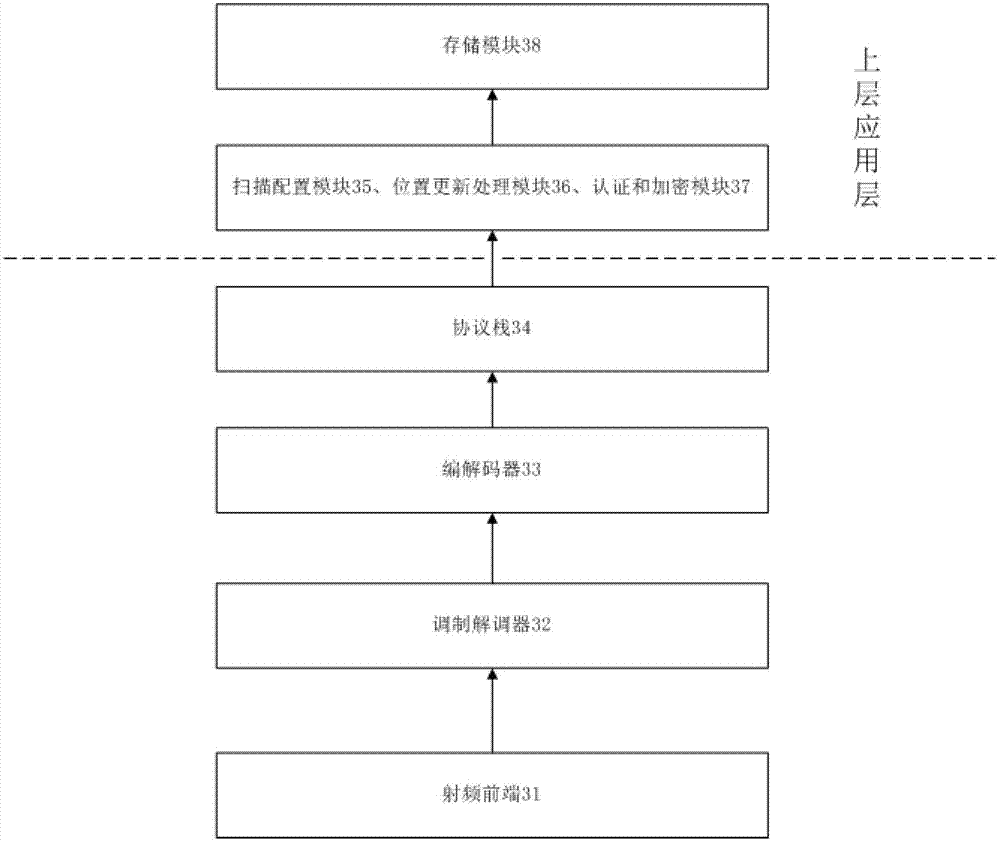
Device and method for obtaining international mobile equipment identifier of mobile communication terminal by base station
InactiveCN102740225AWill not affect normal communicationWill not affect normal operationLocation information based serviceSecurity arrangementModem deviceRadio frequency signal
The invention discloses a device and method for obtaining an international mobile equipment identifier of a mobile communication terminal by a base station. The device comprises a radio frequency front end, a modulator-demodulator, a coder-decoder, a protocol stack, a scanning configuration module, a position updating and processing module, an authentication and encryption module and a storage module, wherein the radio frequency front end is used for transmitting and receiving a radio frequency signal of a global system for mobile communications, receiving a signal from the modulator-demodulator to be transmitted in a free space, and receiving a signal from the free signal to be processed by the modulator-demodulator; and the modulator-demodulator is used for modulating and demodulating the radio frequency signal of the global system for mobile communications, demodulating the signal coded by the coder to be transmitted by the radio frequency front end, and demodulating the signal of the global system for mobile communications, which is received by the radio frequency front end and is decoded by the decoder. By adopting the device and the method, an identifier of a mobile communication terminal in a coverage range of the base station can be immediately obtained.
Owner:SOUTHEAST UNIV
Method and apparatus for handover in a wireless communication system
ActiveUS20160309370A1Effectively contention-freeEliminates and minimizes timeSynchronisation arrangementCommunications systemMobile equipment identifier
A method and apparatus for handover in a wireless communication system. A handover indication can be received from a source base station (120) that is connected with a mobile station (110). The handover indication can include a random access channel preamble. The random access channel preamble can include a temporary mobile equipment identifier. The random access channel preamble can be received from the mobile station. A timing advance message can be sent in response to receiving random access channel preamble. The timing advance message can be addressed by the random access channel preamble and a source base station identifier. The connection with the mobile station can be switched from the source base station to a target base station (130).
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
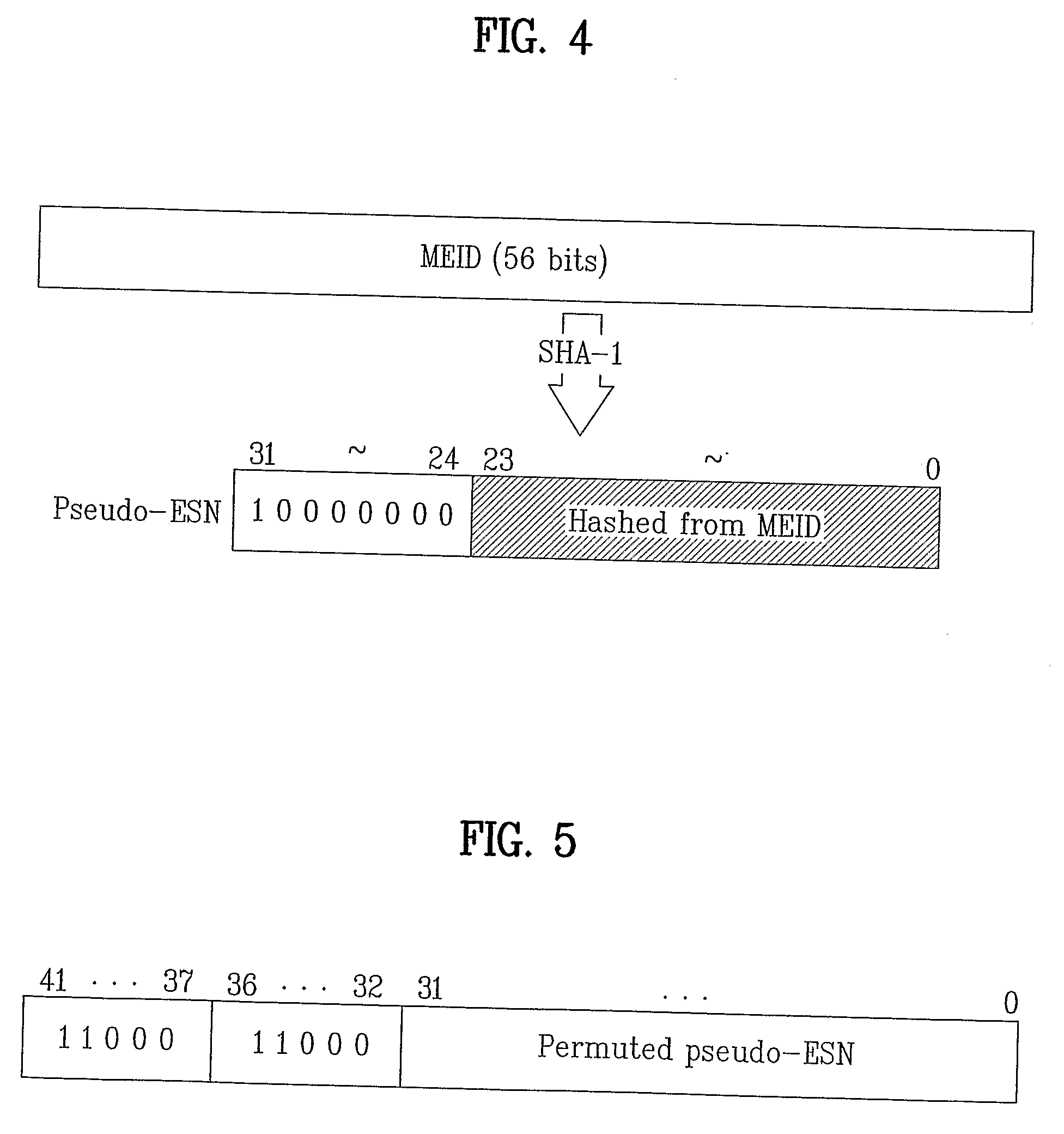
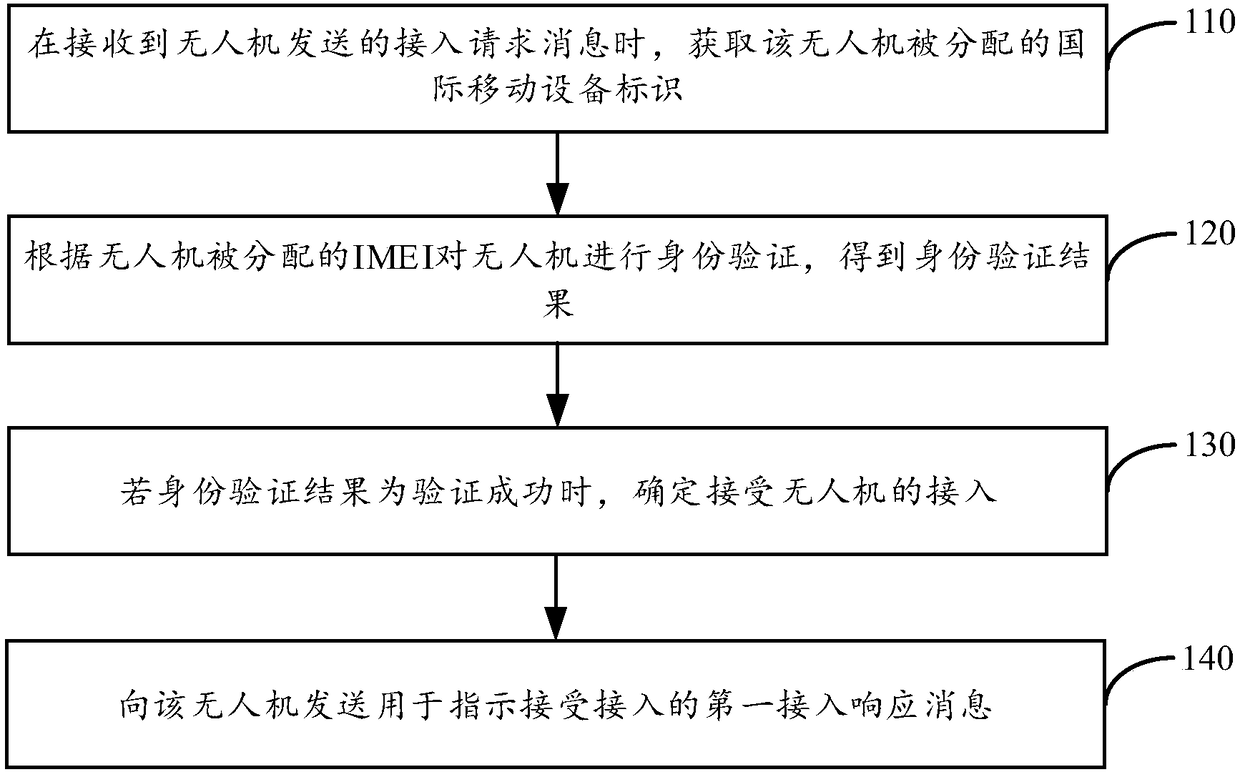
Method for Generating a Pseudo-Esn in Mobile Communication
InactiveUS20080287101A1Network traffic/resource managementUnauthorised/fraudulent call preventionComputer hardwareLeast significant bit
In generating a pseudo terminal identifier (pseudo-ESN; pseudo-Electronic Serial Number), a pseudo terminal identifier generating method includes the steps of generating a first configuration code by hashing a mobile equipment identifier (MEID), selecting a second configuration code from codes not used as an electronic serial number (ESN), and generating the pseudo terminal identifier by setting MSB (most significant bit) to the first configuration code and by setting LSB (least significant bit) to the second configuration code. Accordingly, the present invention provides a pseudo terminal identifier after a related art ESN is exhausted.
Owner:LG ELECTRONICS INC
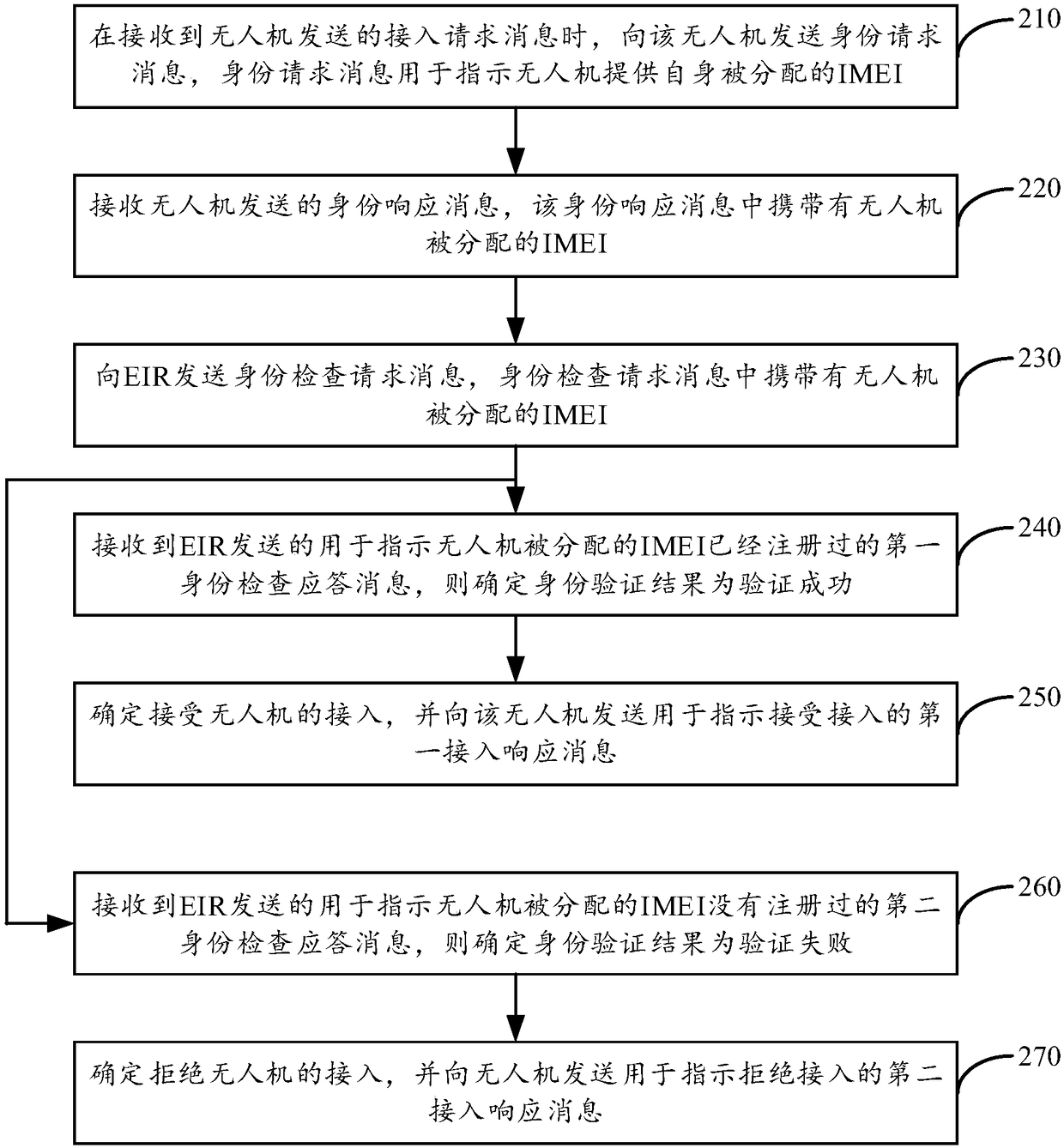
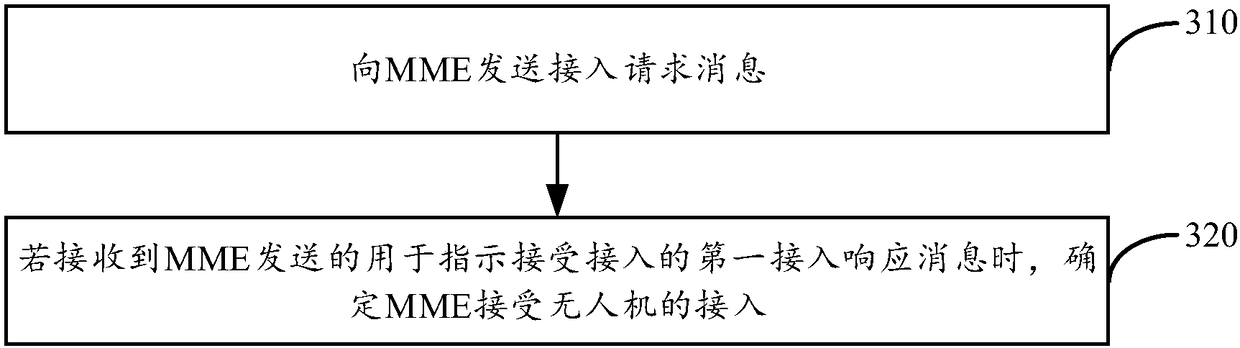
Unmanned aerial vehicle access method and device
ActiveCN109451817AAvoid accessImprove reliabilityAssess restrictionRadio transmissionAccess methodMobile equipment identifier
The present disclosure provides an unmanned aerial vehicle access method and device, the method being used for an MME. Said method comprises: when an access request message sent by an unmanned aerialvehicle is received, acquiring an international mobile equipment identifier (IMEI) of the unmanned aerial vehicle; performing identity authentication on the unmanned aerial vehicle according to the IMEI of the unmanned aerial vehicle, so as to obtain an identity authentication result; if the identity authentication result is authentication success, determining to accept the access of the unmannedaerial vehicle; and sending, to the unmanned aerial vehicle, a first access response message for indicating that the access is accepted. Therefore, the present disclosure can prevent an unmanned aerial vehicle, which does not pass the identity authentication, from accessing a cellular network, thereby reducing interference to the cellular network, improving the reliability of the access of the unmanned aerial vehicle.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
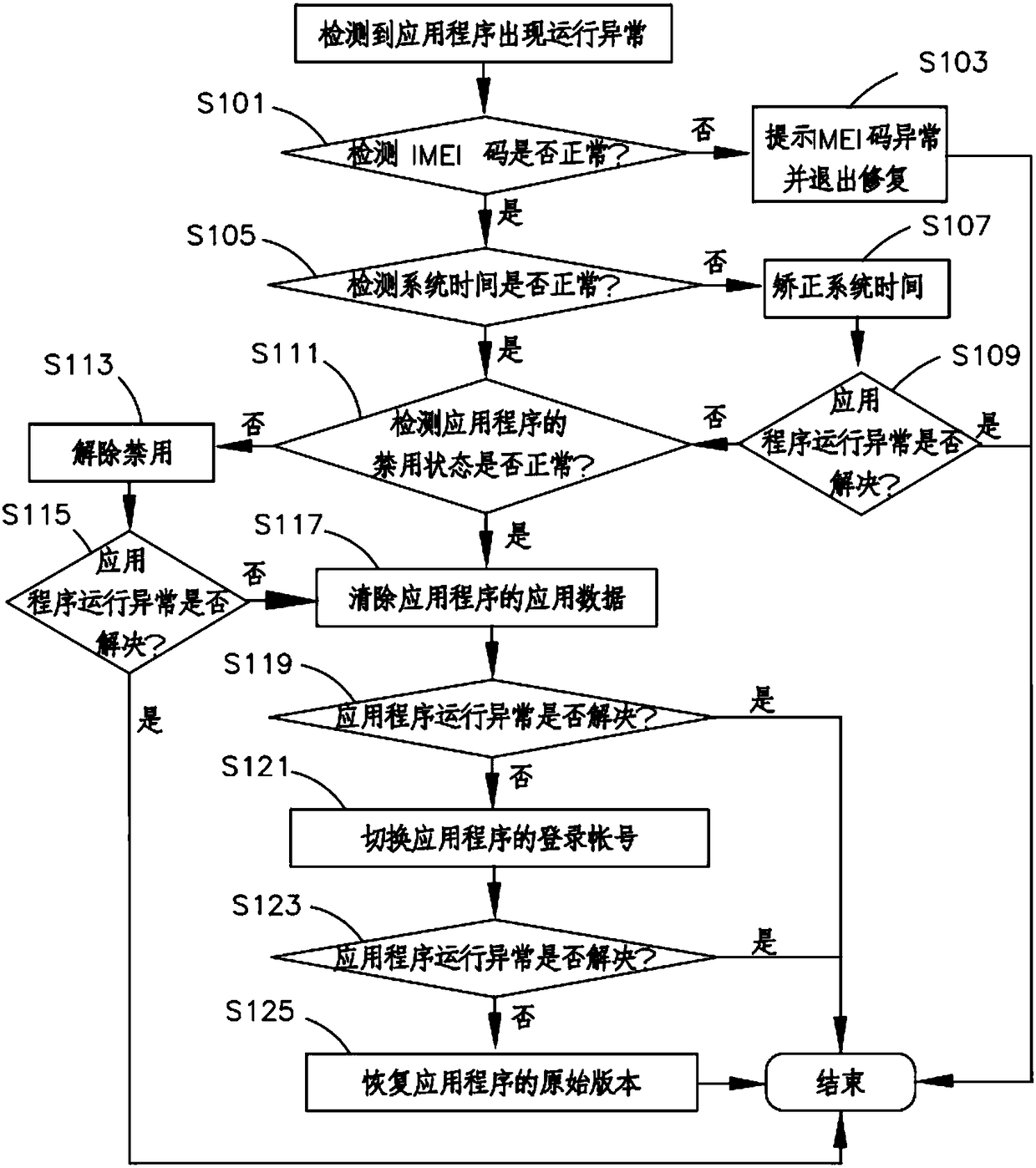
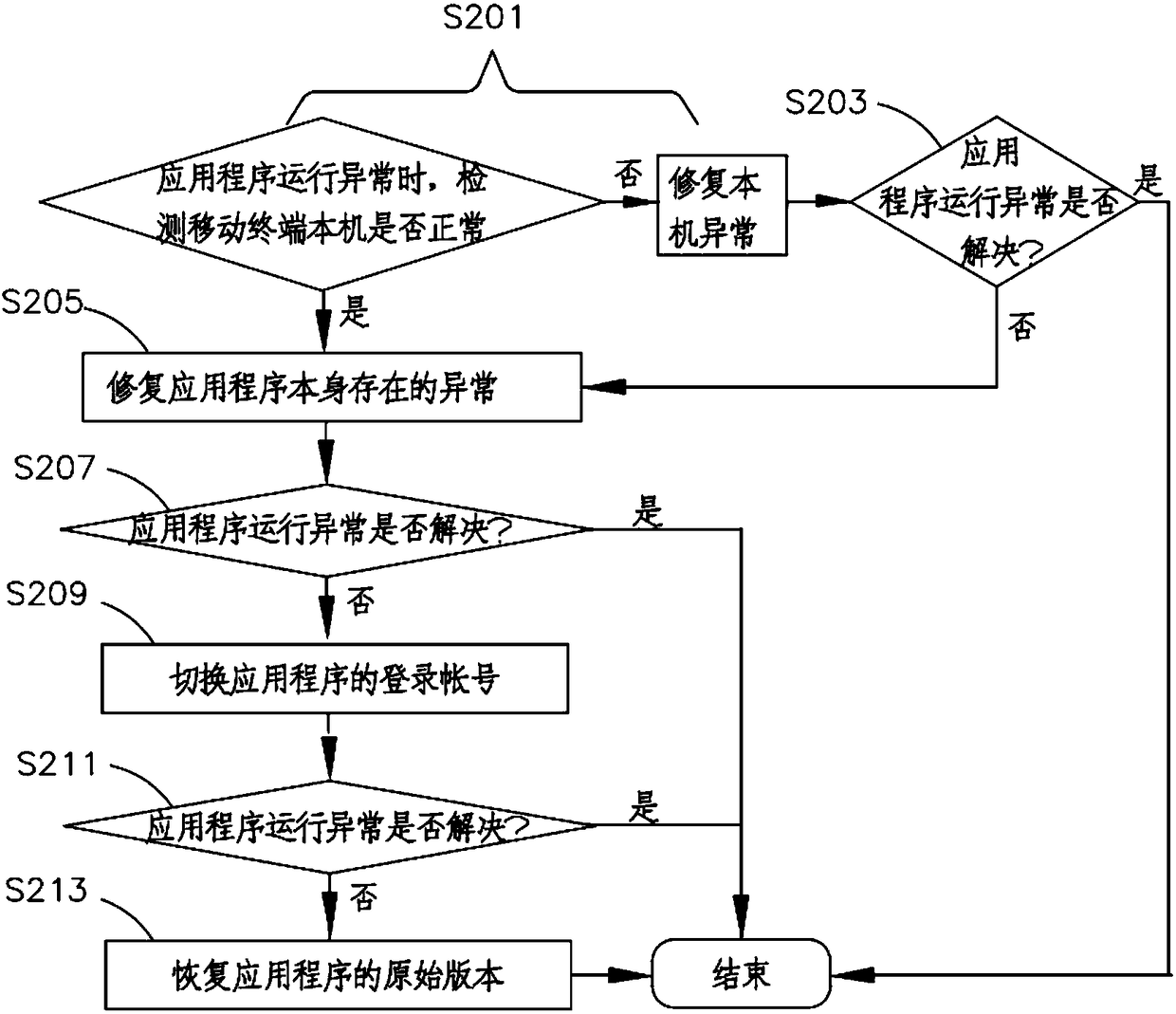
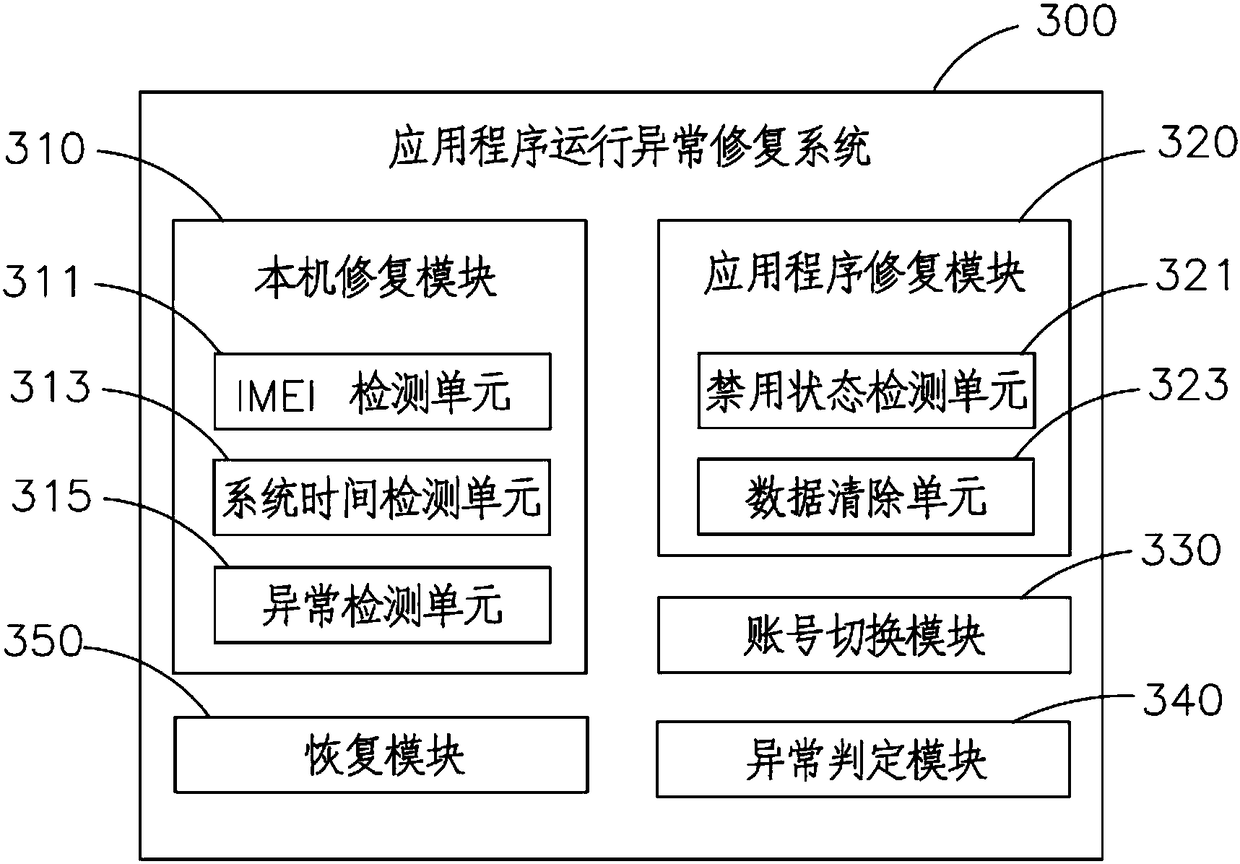
Application running exception restoration method and system, and mobile terminal
ActiveCN108509291AEasy to operateImprove user experienceFault responseRestoration methodMobile equipment identifier
The invention relates to a terminal with an application running exception restoration function, and an application running exception restoration method and system. The application running exception restoration method comprises the steps of detecting whether an international mobile device identification code of the mobile terminal is normal or not; if yes, obtaining system time of the mobile terminal and local time of the mobile terminal; comparing whether the local time is consistent with the system time or not; if yes, detecting whether an application has an exception or not; if not, switching a login account of the application; detecting whether application running exception exists or not; and if yes, restoring an original version of the application. According to the application runningexception restoration method, reasons for the application running exception can be conveniently and automatically checked to assist a user to restore the application running exception.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
A communication module detection method and system based on NB-IOT Internet of Things
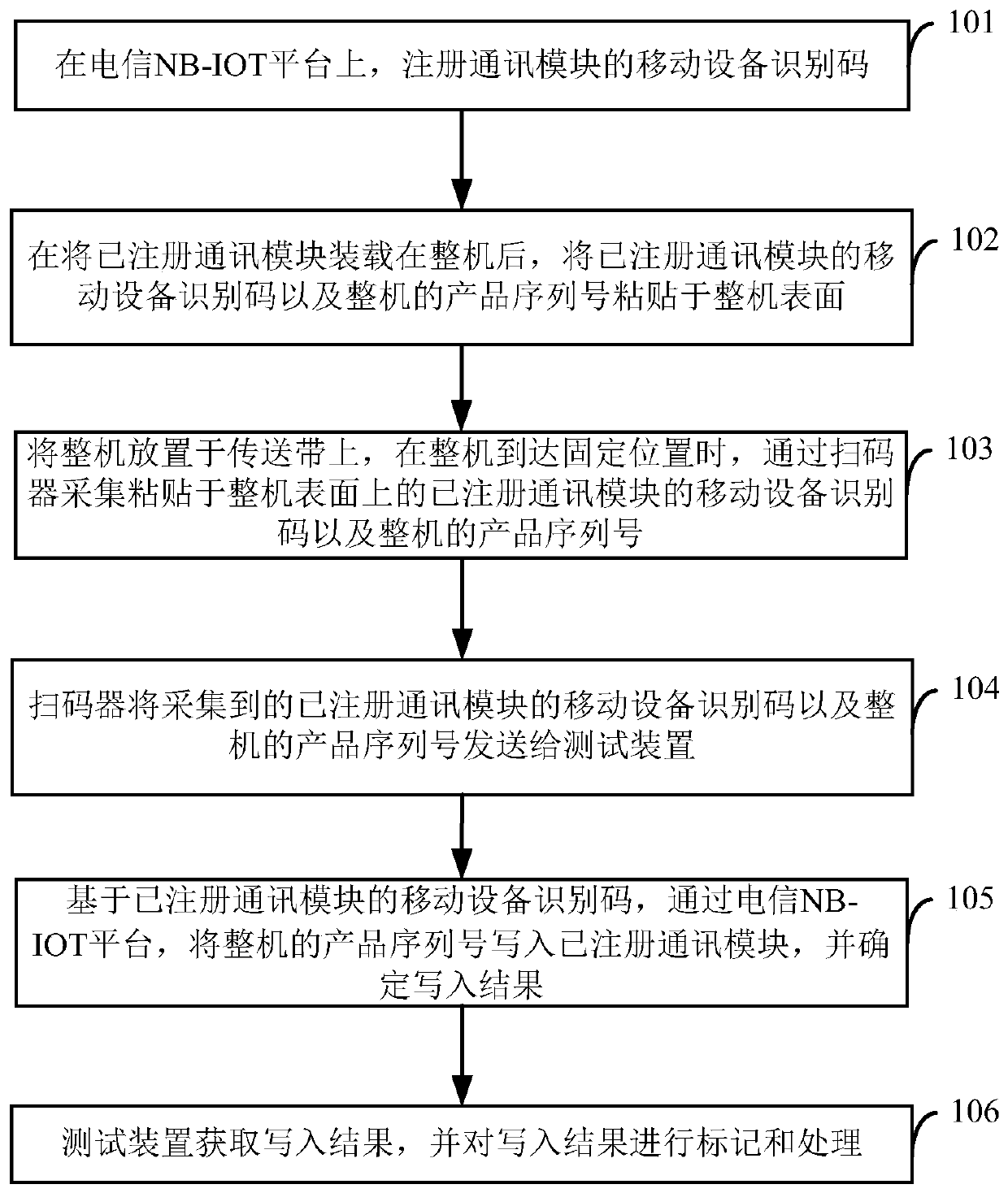
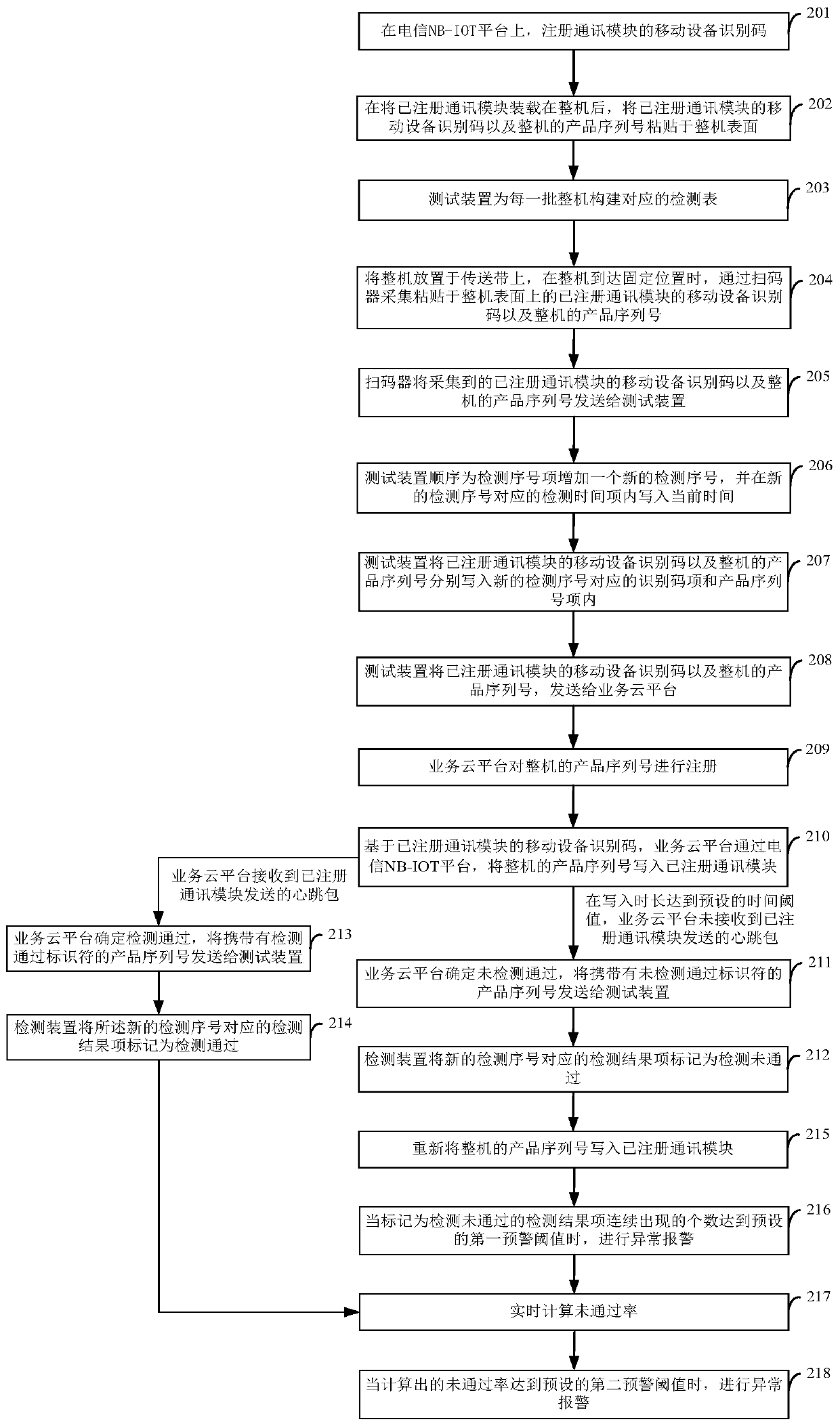
InactiveCN109818827AWire connection avoidanceImprove test efficiencyData switching networksTest efficiencyMobile equipment identifier
The invention provides a communication module detection method and system based on NB-IOT Internet of Things.. The method comprises the following steps of: at a telecommunication NB-IOT platform, a mobile device identification code of the communication module is registered, and after the registered communication module is loaded on the whole machine, the mobile device identification code of the registered communication module and the product serial number of the whole machine are pasted on the surface of the whole machine; A complete machine is placed on a conveyor belt, when the complete machine reaches a fixed position, a code scanner collects a mobile device identification code of a registered communication module and a product serial number of the complete machine, and sends the mobiledevice identification code of the registered communication module and the product serial number of the complete machine to a testing device; the Telecommunications NB-IOT platform writes the productserial number of the whole machine into a registered communication module and determines a writing result; And the test device marks and processes the writing result. According to the scheme providedby the invention, the whole machine production project is tested, and meanwhile, the test efficiency can be effectively improved.
Owner:SICHUAN HONGMEI INTELLIGENT TECH CO LTD
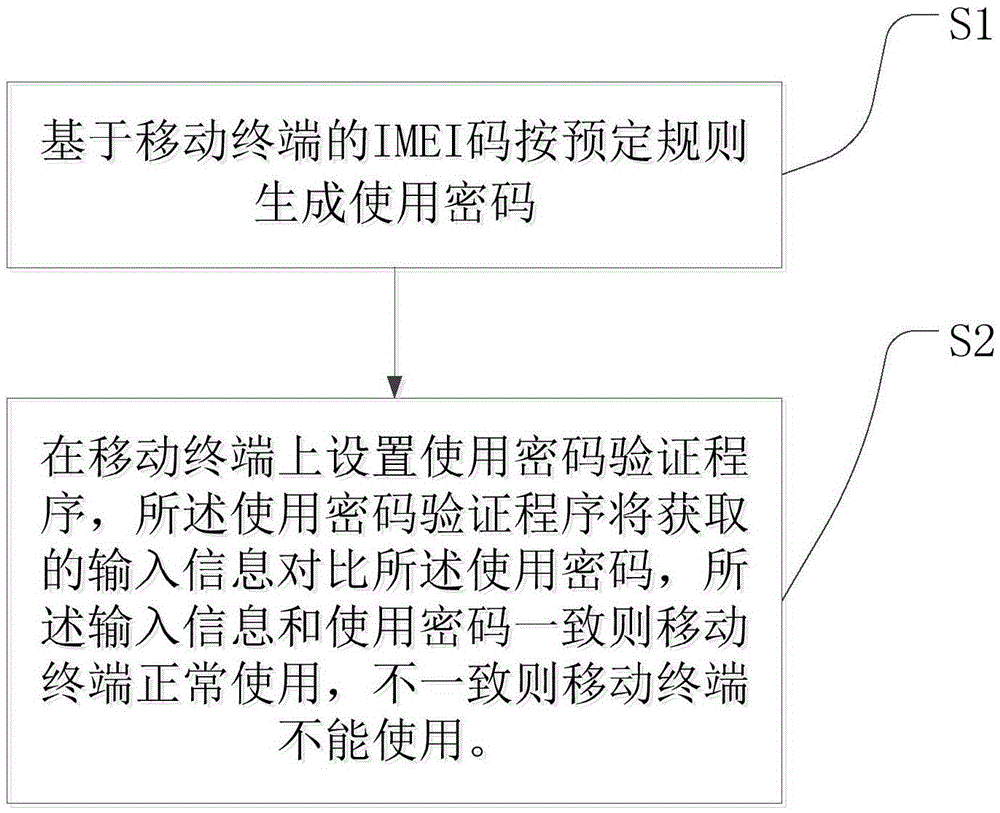
International mobile equipment identifier (IMEI) code based anti-theft method
The invention discloses an international mobile equipment identifier (IMEI) code based anti-theft method. The method comprises the steps of generating a use passcode based on an IMEI code of a mobile terminal according to a preset rule; and setting a use passcode verification procedure on the mobile terminal, and comparing, by the use password verification procedure, acquired input information with the use password, wherein if the input information and the use password are identical, the mobile terminal can be used normally, if the input information and the use password are not identical, the mobile terminal cannot be used. Through adoption of the method, the cellphone can be prevented from being stolen in the inventory period after shipment of the producer and before sale of the merchant, and cannot be used normally, so that mobile terminals in the inventory period are less likely to be stolen, and circulation of the stolen mobile terminals is prevented.
Owner:深圳市水世界信息有限公司
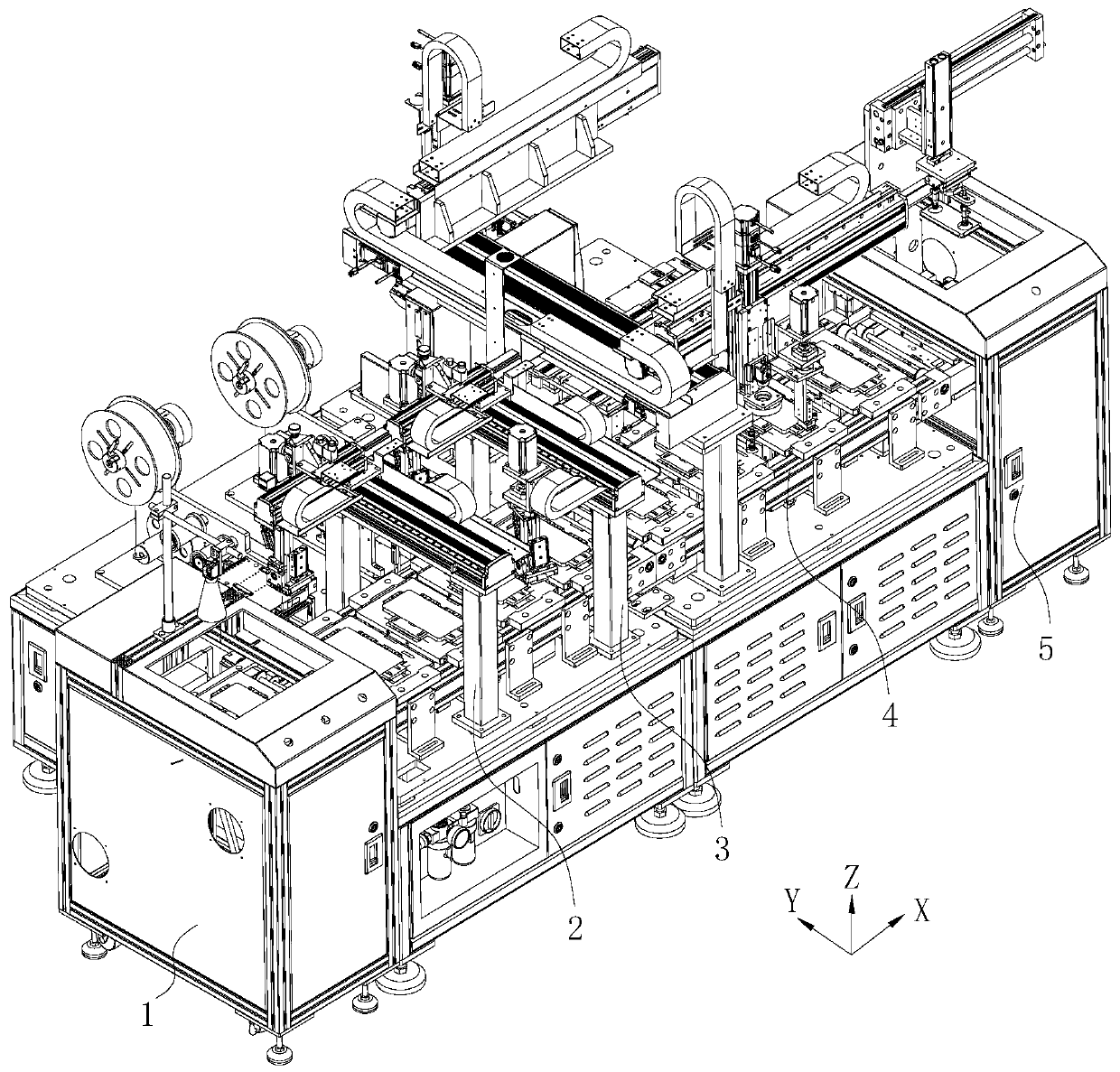
Automatic labeling equipment and labeling method
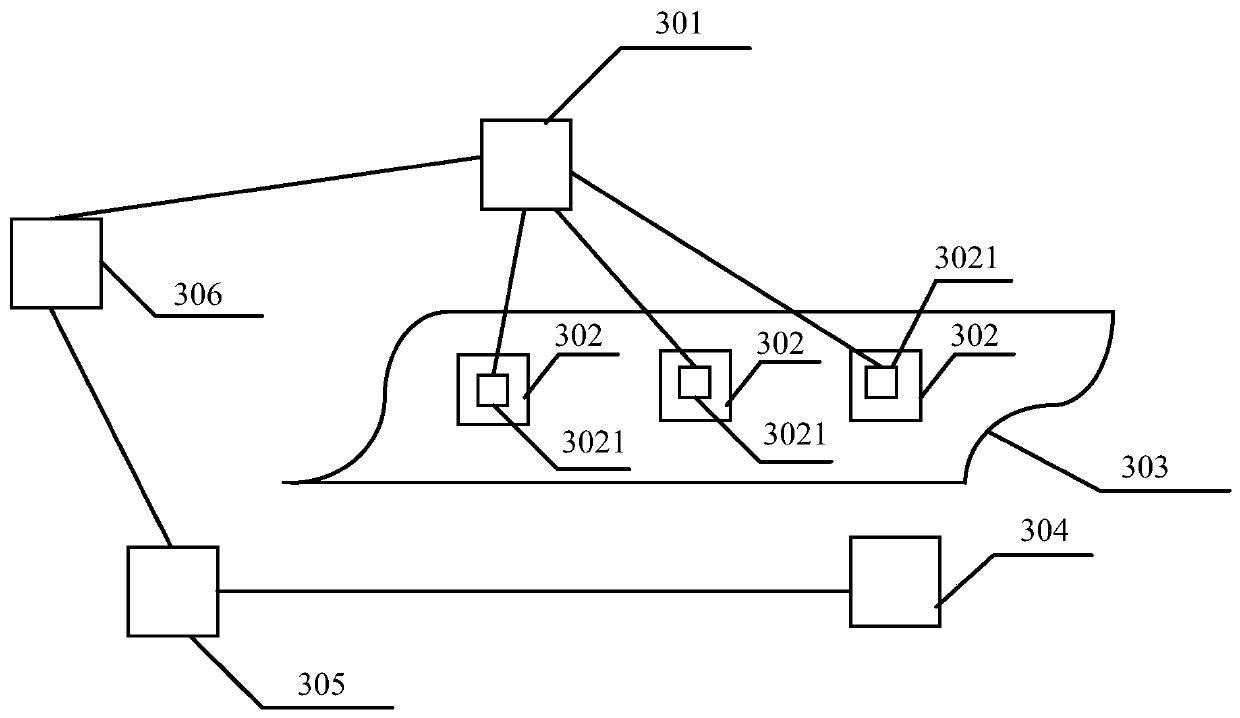
PendingCN109835564AShorten production timeReduce labor costsLabelling machinesAutomatic test equipmentMobile equipment identifier
The invention provides automatic labeling equipment and a labeling method. The automatic labeling equipment comprises a conveying mechanism, a first labeling mechanism and a second labeling mechanism,wherein terminals are placed on the conveying mechanism, the conveying mechanism is used for moving the terminals, the first labeling mechanism comprises a stripping assembly used for stripping firstlabels from a coiled material, and a first labeling assembly used for attaching the first labels to the terminals, the second labeling mechanism comprises a printer used for printing second labels, and a second labeling assembly used for attaching the second labels to the terminals, the second labels are provided with mobile equipment identification codes, and the first labeling mechanism and thesecond labeling mechanism are sequentially arranged in the conveying direction of the conveying mechanism. According to the automatic labeling equipment and the labeling method, the first labeling mechanism and the second labeling mechanism work at the same time, so that the production time is greatly saved; and the automatic labeling equipment conveys the terminals through the conveying mechanism without manually transferring the terminal, so that the labor cost is reduced.
Owner:深圳市鑫信腾科技股份有限公司
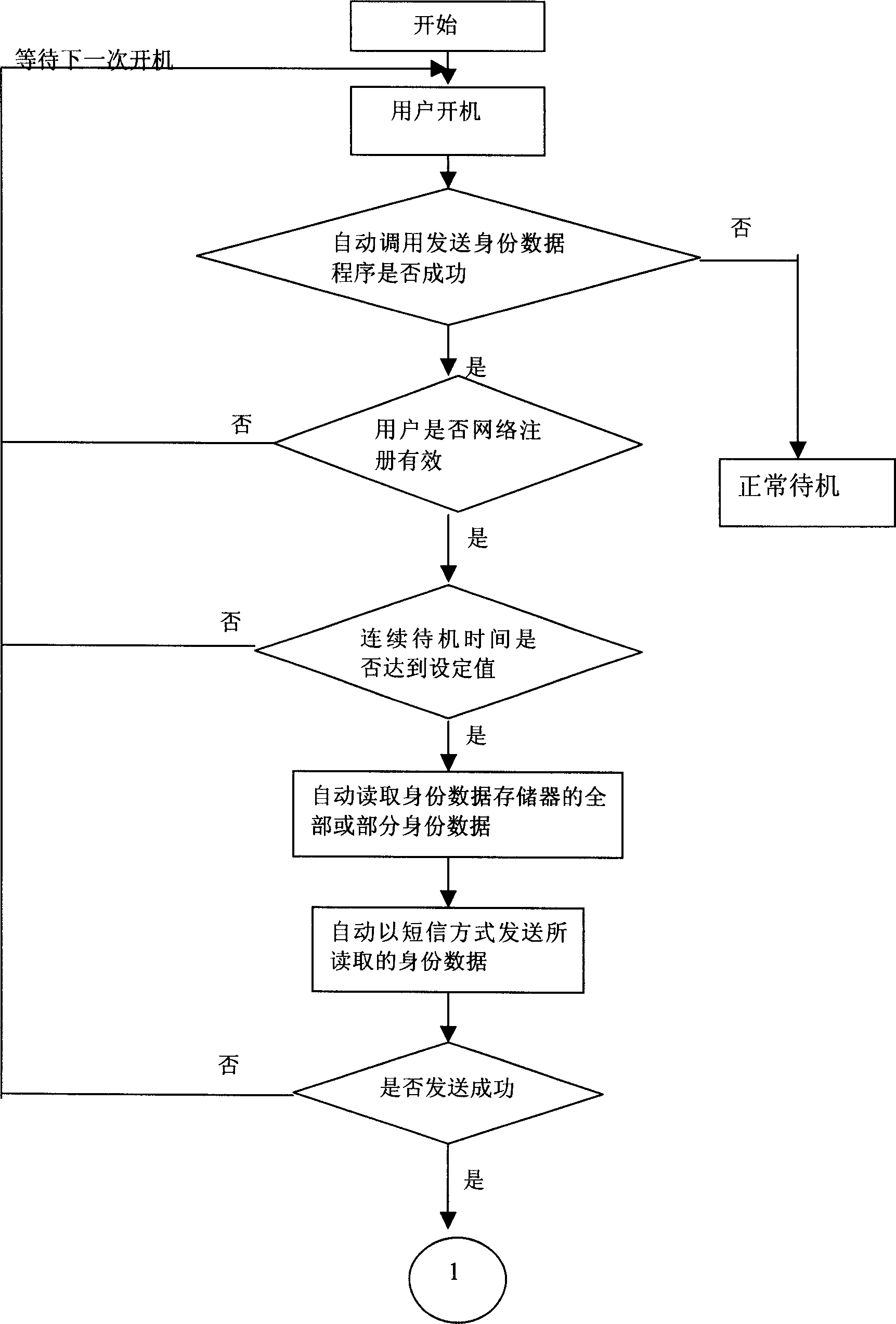
Mobile communication terminal with automatic transmitting identity data function
InactiveCN1756396AAccurate feedbackReal-time releaseRadio/inductive link selection arrangementsMessaging/mailboxes/announcementsLicense numberOperational costs
The mobile communication terminal with collecting identity data function comprises: a network communication unit; and a main control unit, composed of a single-chip microprocessor composed of a timing automatic send SMM device to send identity data with SMM-type to SMM server, and a memory with the first identity data memory to store written with standard international mobile device identification code when manufacture, the second identity data memory to store join-network license number and corporation information when manufacture, the third identity data memory to store sale information, and the fourth identity data memory to store user information. This product needs not manual registration to precise feedback data with low cost.
Owner:杭州波导软件有限公司
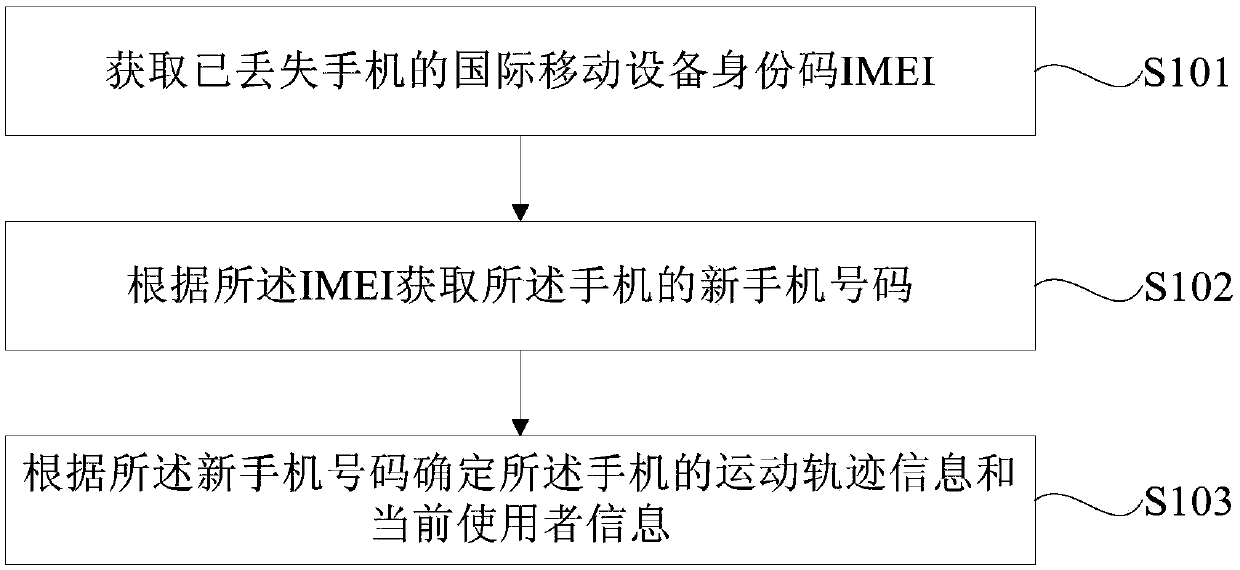
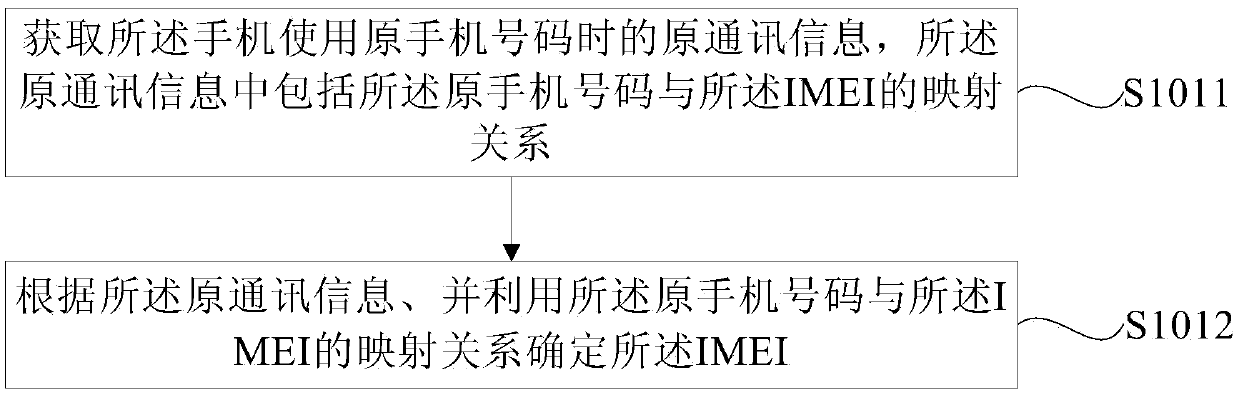
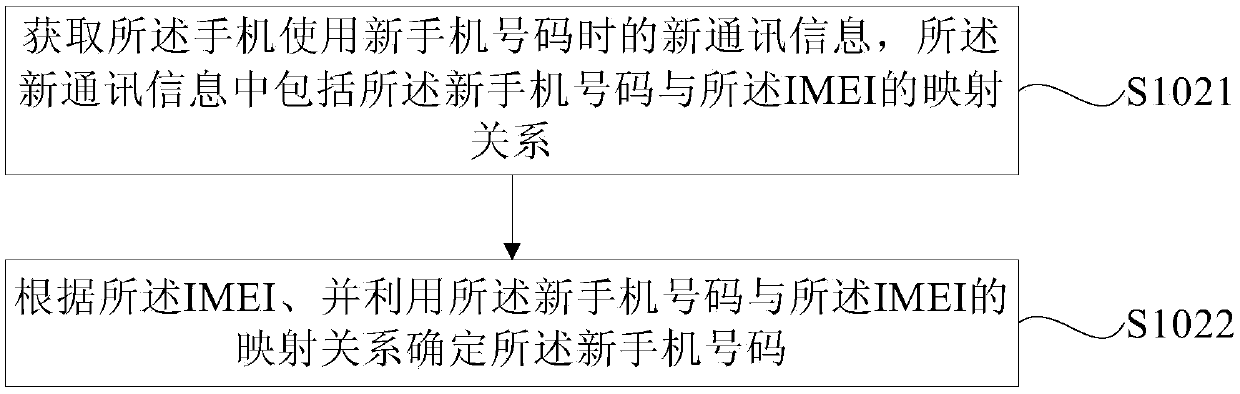
Method, device and terminal for finding mobile phone, and computer readable storage medium
InactiveCN108684035AIncrease the probability of recoveryGuaranteed practicalityLocation information based serviceNetwork data managementMobile equipment identifierComputer terminal
The embodiment of the present invention provides a method, device and terminal for finding a mobile phone, and a computer readable storage medium, wherein the method includes: acquiring the international mobile equipment identifier (IMEI) of a lost mobile phone; acquiring a new number of the mobile phone according to the IMEI; and determining, according to the new mobile phone number, the motion track information and the current user information of the mobile phone. The method, device and terminal for finding a mobile phone and the computer readable storage medium provided by the invention, according to the acquired IMEI and the new mobile phone number of the mobile phone, further obtain the motion track information and the current user information of the mobile phone by using the new mobile phone number, effectively achieve the acquisition of the motion track of the current user and the current user information of the mobile phone by means of the uniqueness of the IMEI of the mobile phone, namely can find out the identity information of the current user, thereby improving the probability of retrieving the mobile phone, ensuring the practicality of the method, and being conducive to market promotion and application.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com