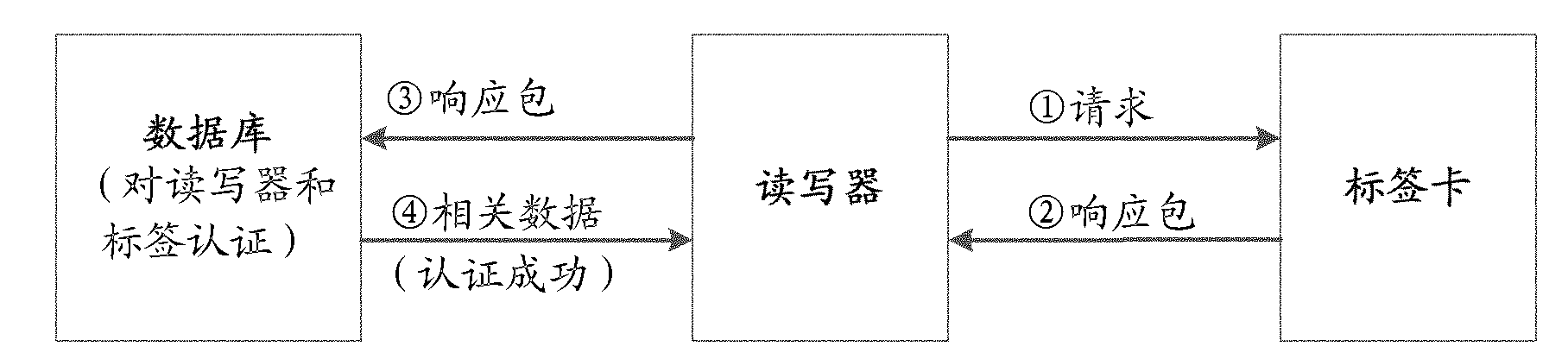
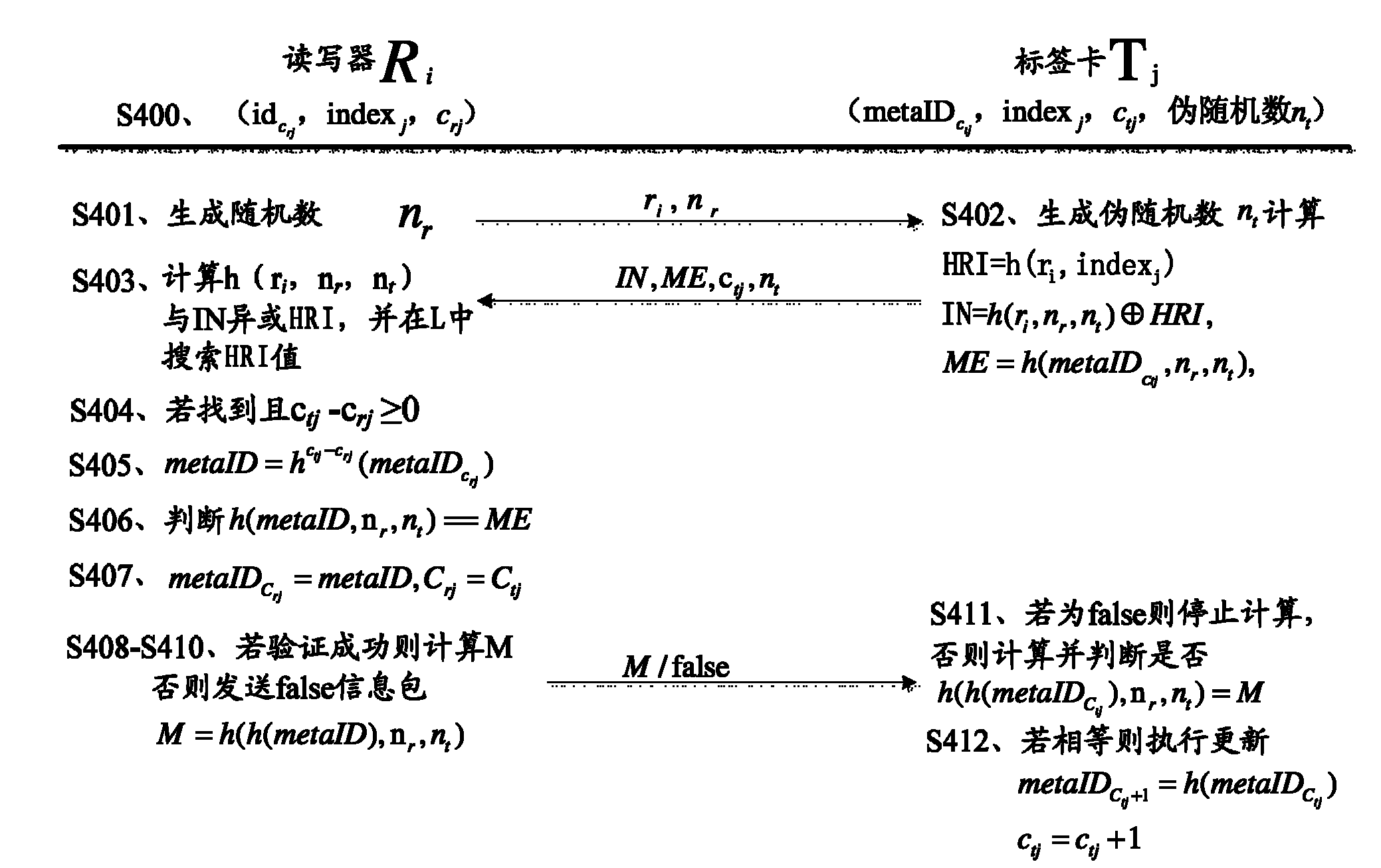
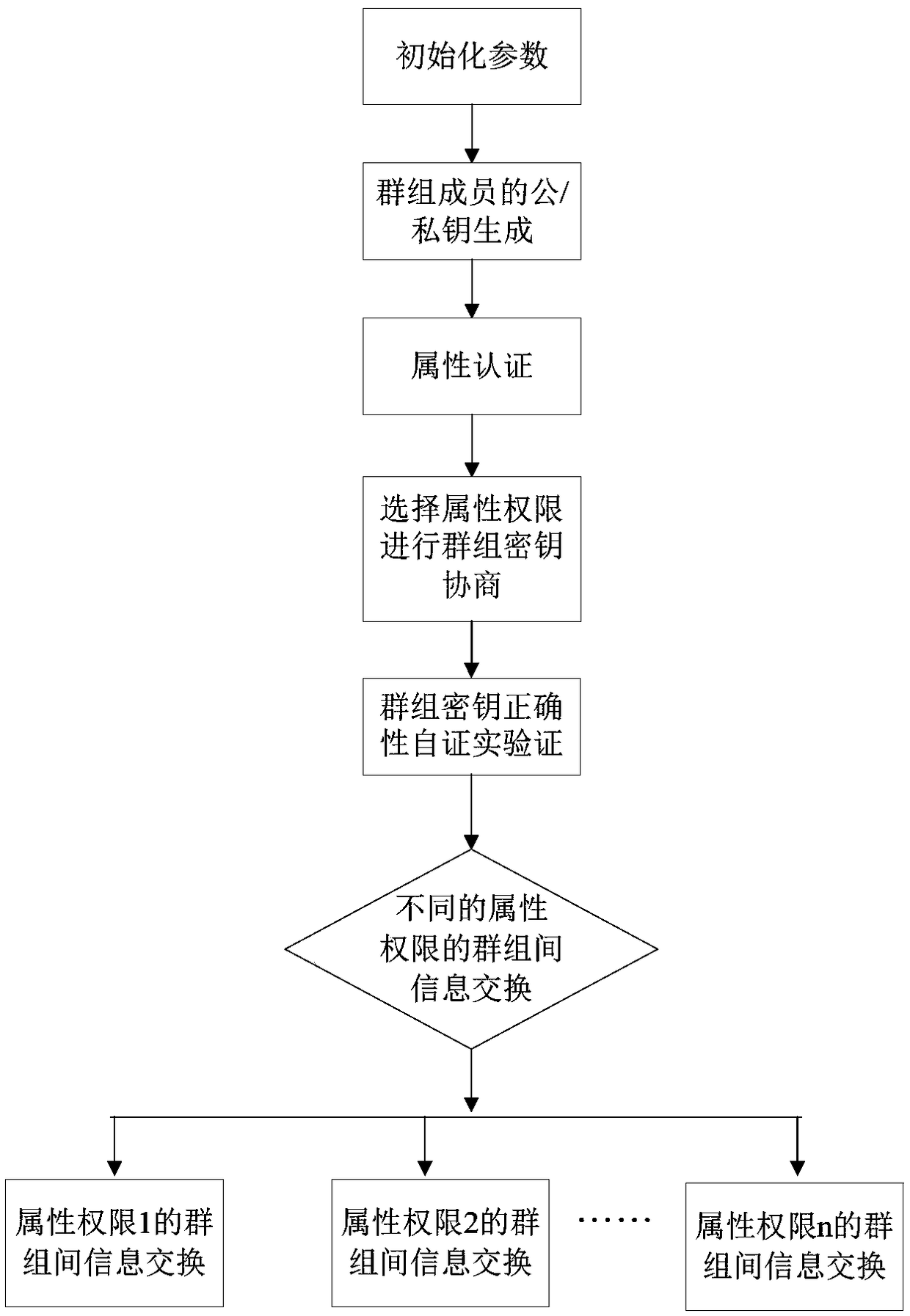
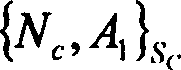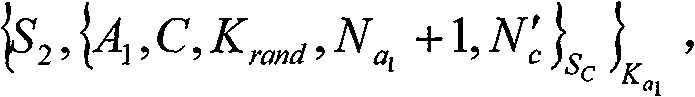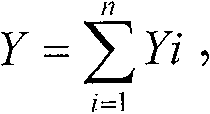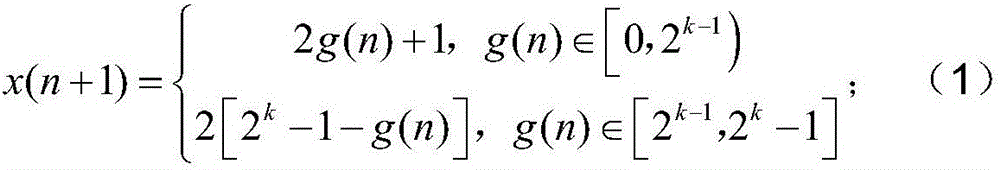Patents
Literature
49results about How to "Prevent impersonation attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
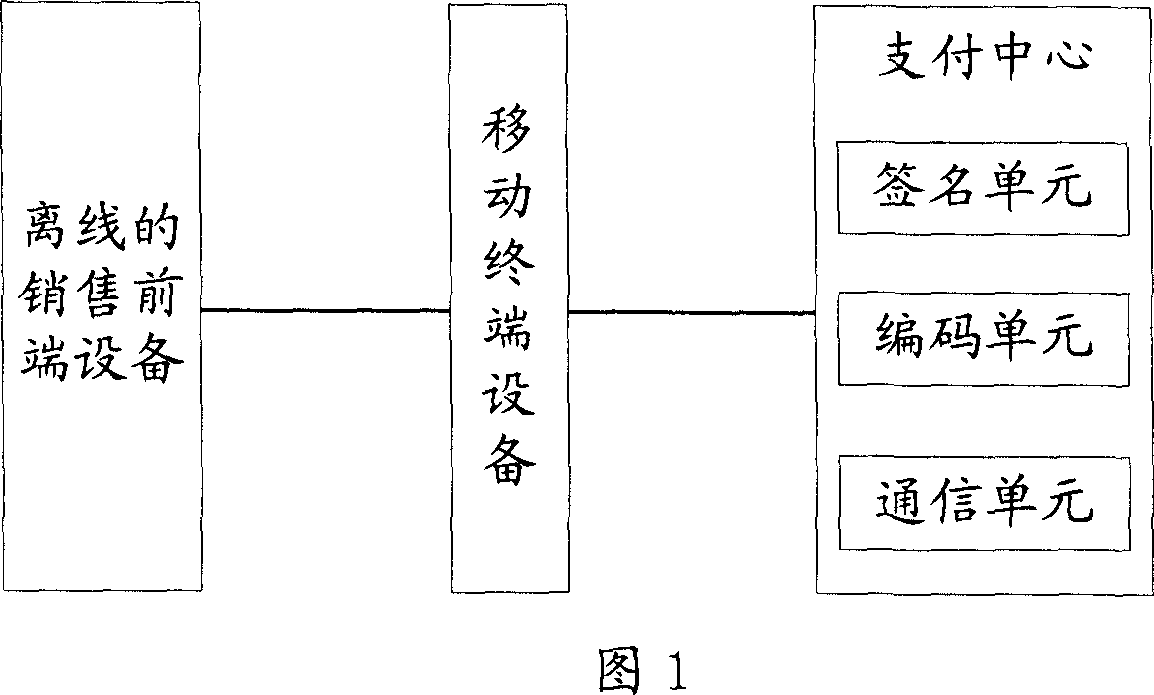
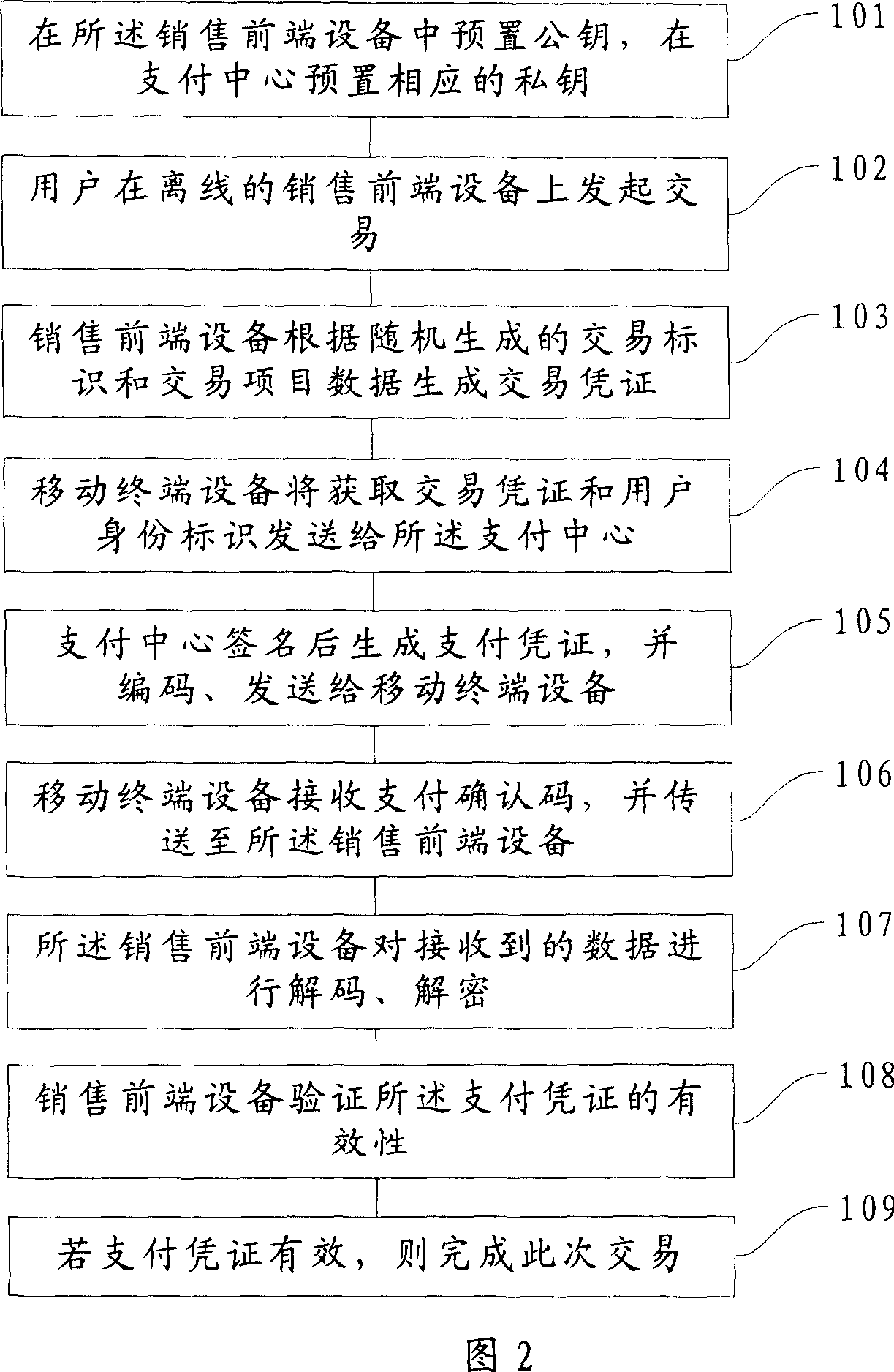
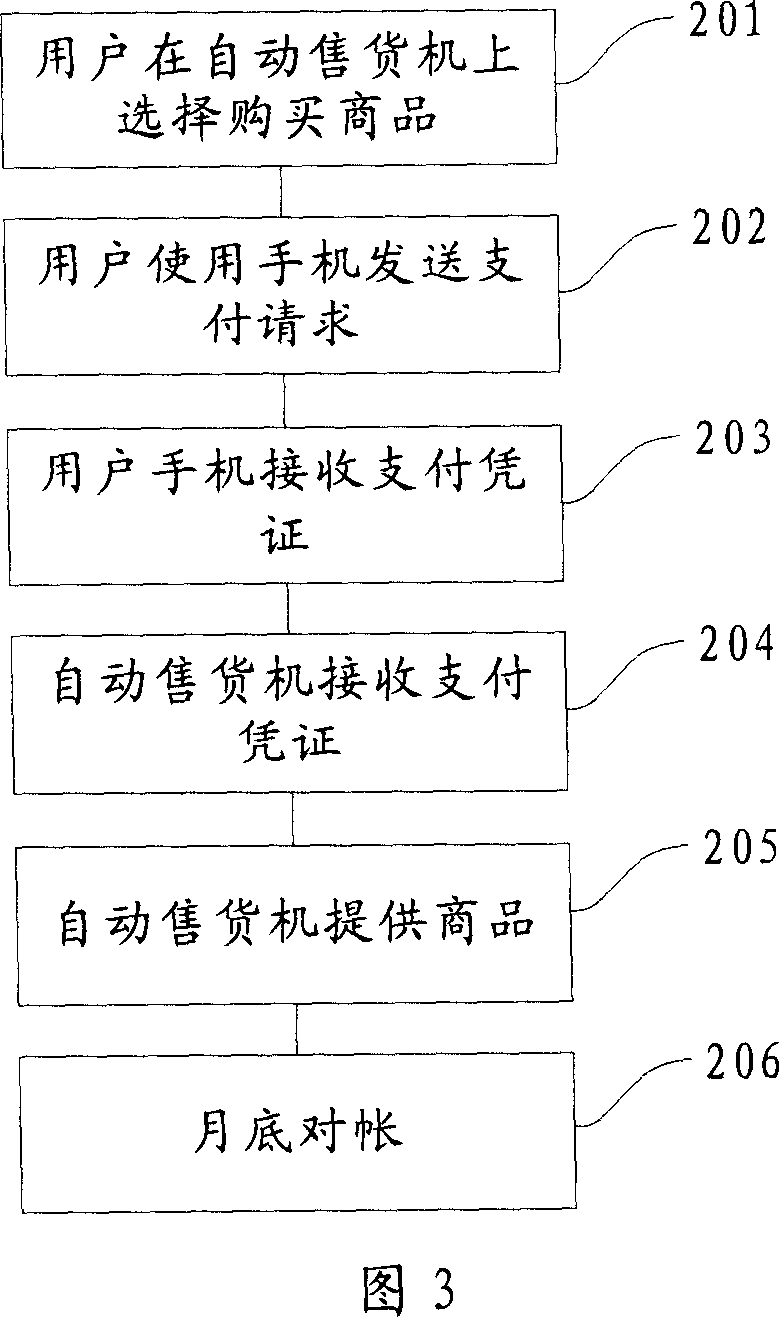
Method, system and device for transaction payment using mobile terminal equipment
The disclosed exchange-paying method by mobile terminal device comprises: the selling device generates exchange receipt included item name and random mark; the mobile terminal acquires the receipt and sends it with user ID to the paying center; the latter signs on the receipt by preset private key and codes to obtain payment ACK code to send to the user terminal; the latter transmits the ACK code to the selling terminal; the latter decodes and deciphers the received data to check up validity and complete the process. This invention is simple and low cost.
Owner:钟杨 +2
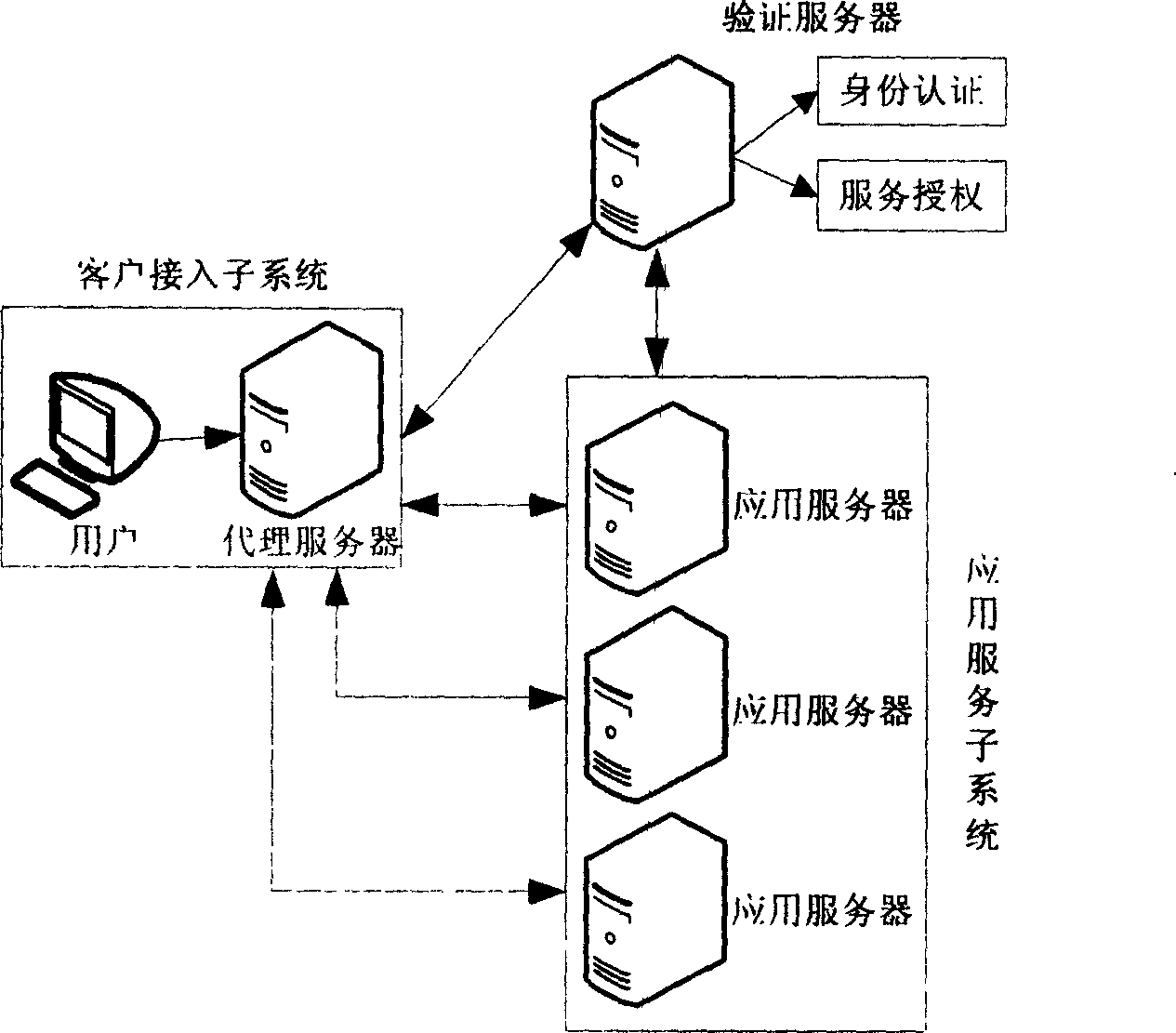
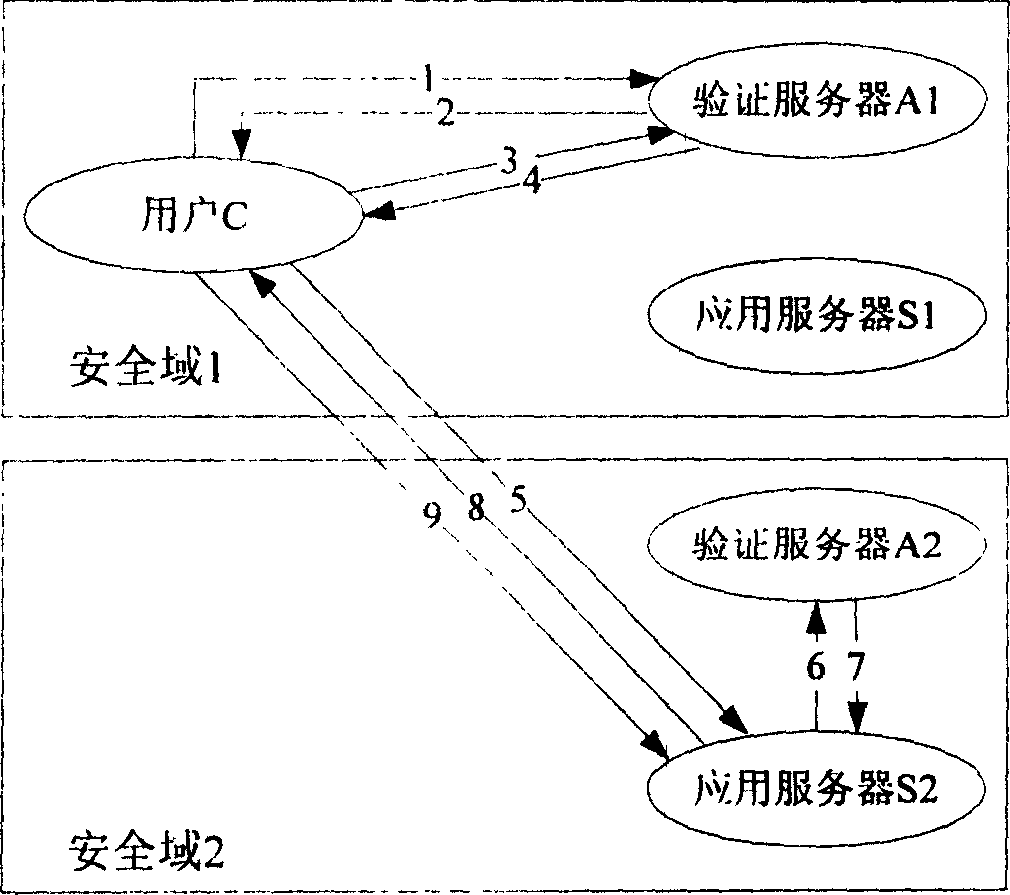
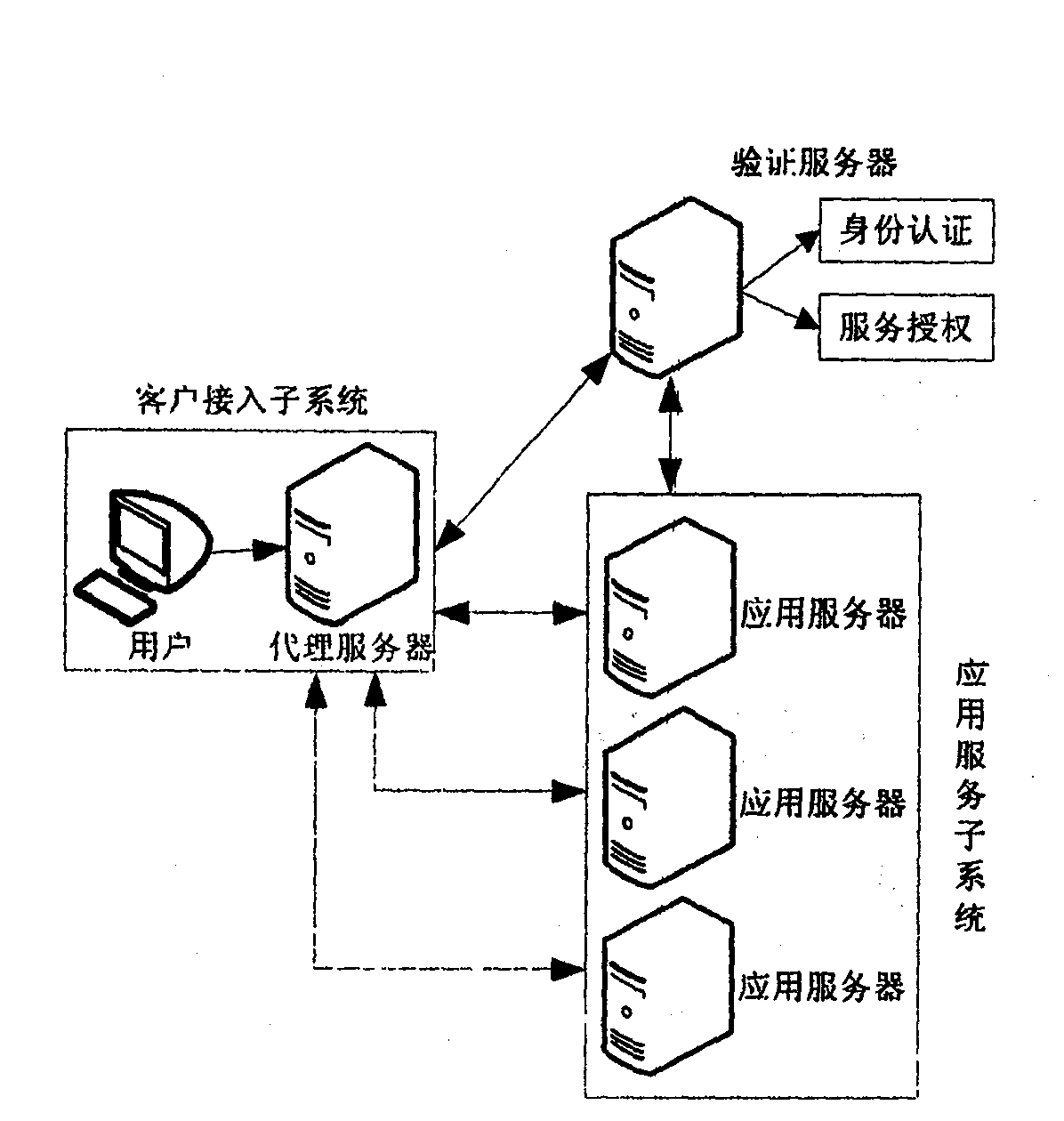
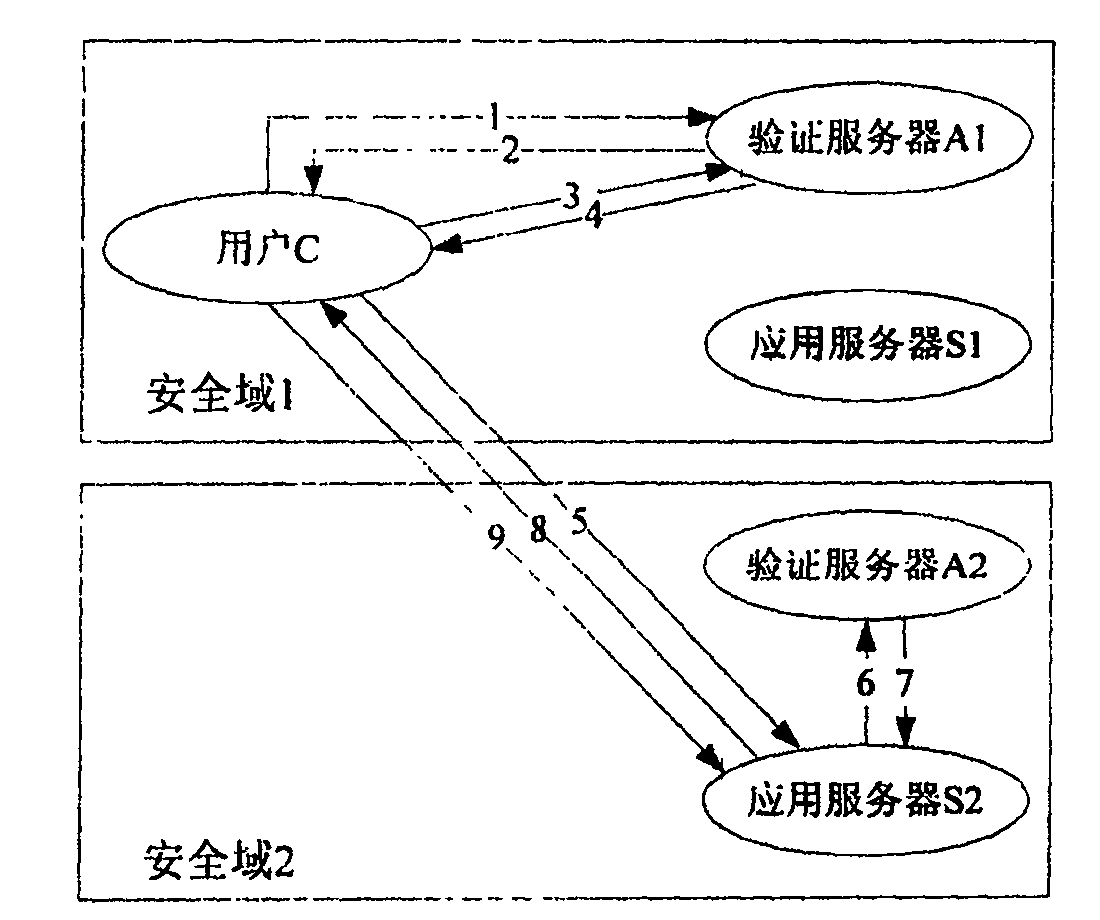
Network authentication and key allocation method across secure domains
InactiveCN1805341AOvercoming the shortcomings of decentralized authenticationEnsure safetyKey distribution for secure communicationUser identity/authority verificationApplication serverWeb authentication
The invention relates to a network authentication and key distribution method. based on the single point log-in, connecting one authentication server and several application servers into each safety field; distributing the authentication and keys according to the demand of application server when the user accesses into different safety fields. First, user processes the identification authentication in said safety field to attain a server card communicating with the application server in another safety field; then the user at the accessed safety field validates the card to attain the service connecting with the application server; at last, the user processes the identification authentication on said application server. The inventive system comprises a client access subsystem, an application service subsystem and a validate server which can complete the user identification authentication and the service authorization. The invention has simple process, with high safety and effect.
Owner:XIDIAN UNIV
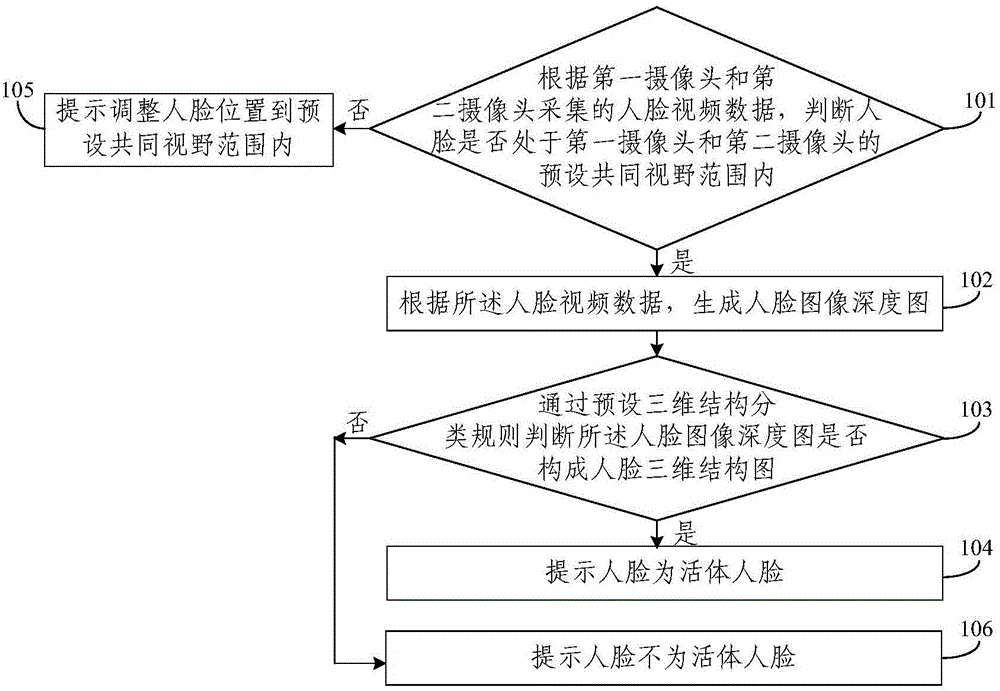
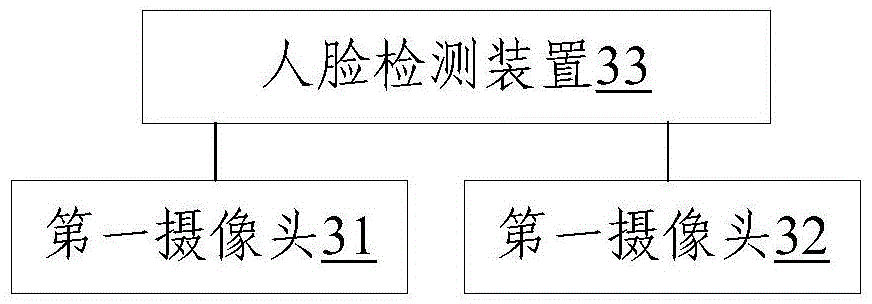
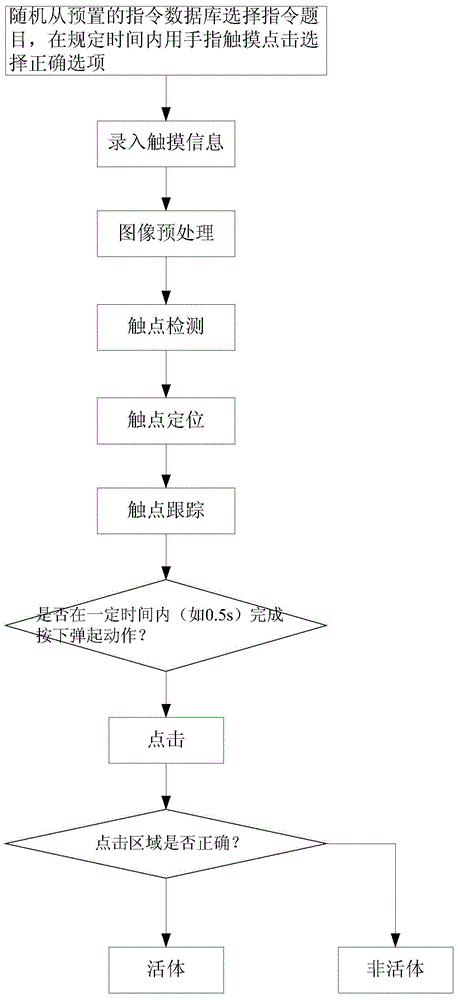
Binocular stereo vision-based human face detection method, device and system
ActiveCN104834901AReliable performanceProtect against video and photo impersonation attacksCharacter and pattern recognitionVision basedClassification rule
The invention discloses a binocular stereo vision-based human face detection method, device and system. The method comprises a step of collecting human face video data according to a first pick-up head and a second pick-up head and determining whether or not a human face is in a preset common visual range of the first pick-up head and the second pick-up head; a step of generating a human face image depth map according to the human face video data if the human face is in the preset common visual range of the first pick-up head and the second pick-up head; a step of determining whether or not the human face image depth map forms a human face three-dimension structure diagram according to a preset three-dimension structure classification rule; and a step of indicating that the human face is a face of a living body if the human face image depth map forms the human face three-dimension structure diagram. With the binocular stereo vision-based human face detection method, device and system, the detection of the human face of the living body can be performed without depending on motion cooperation of a user, and a problem that the user may be not cooperative is solved.
Owner:BEIJING HISIGN TECH
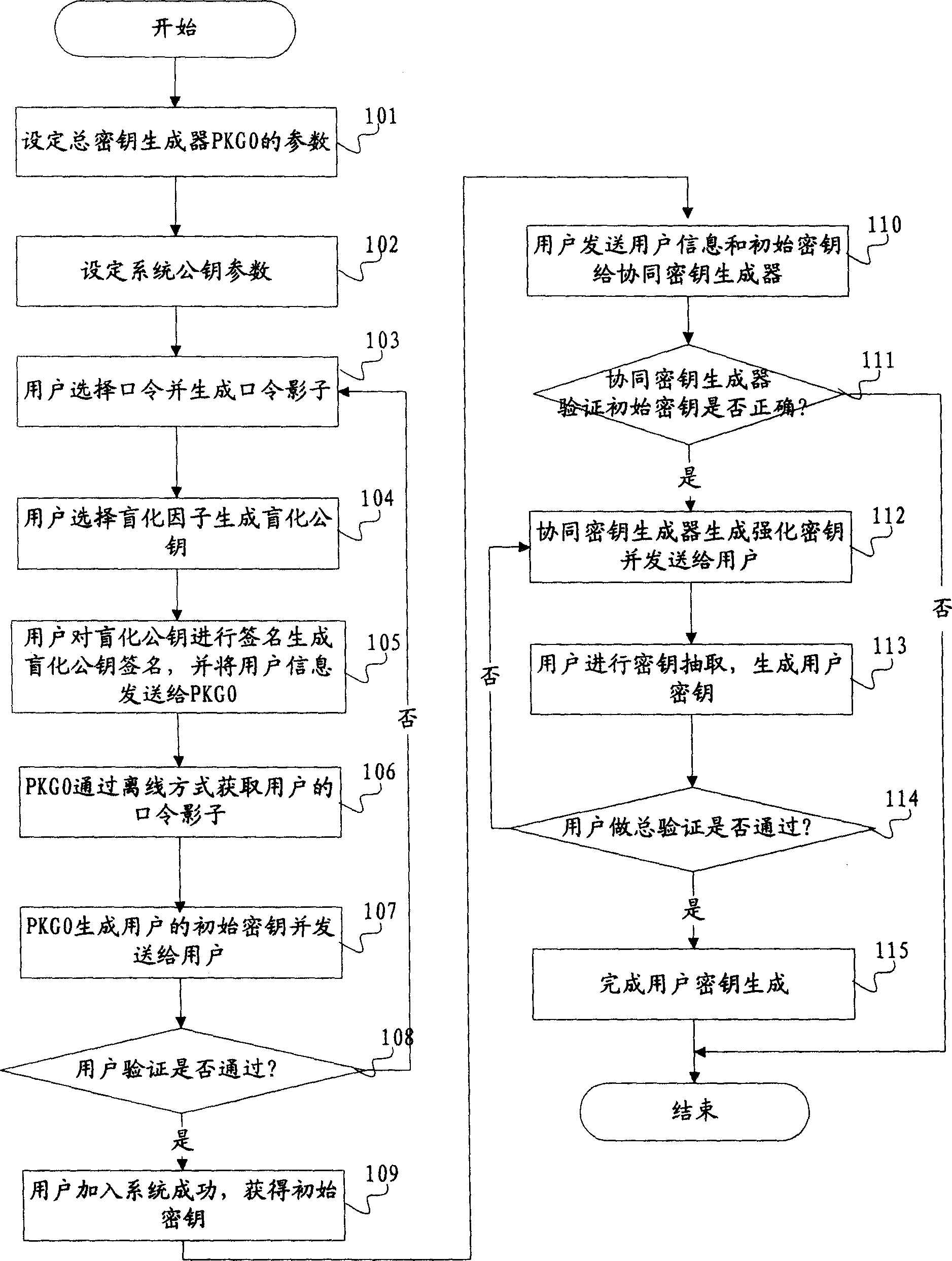
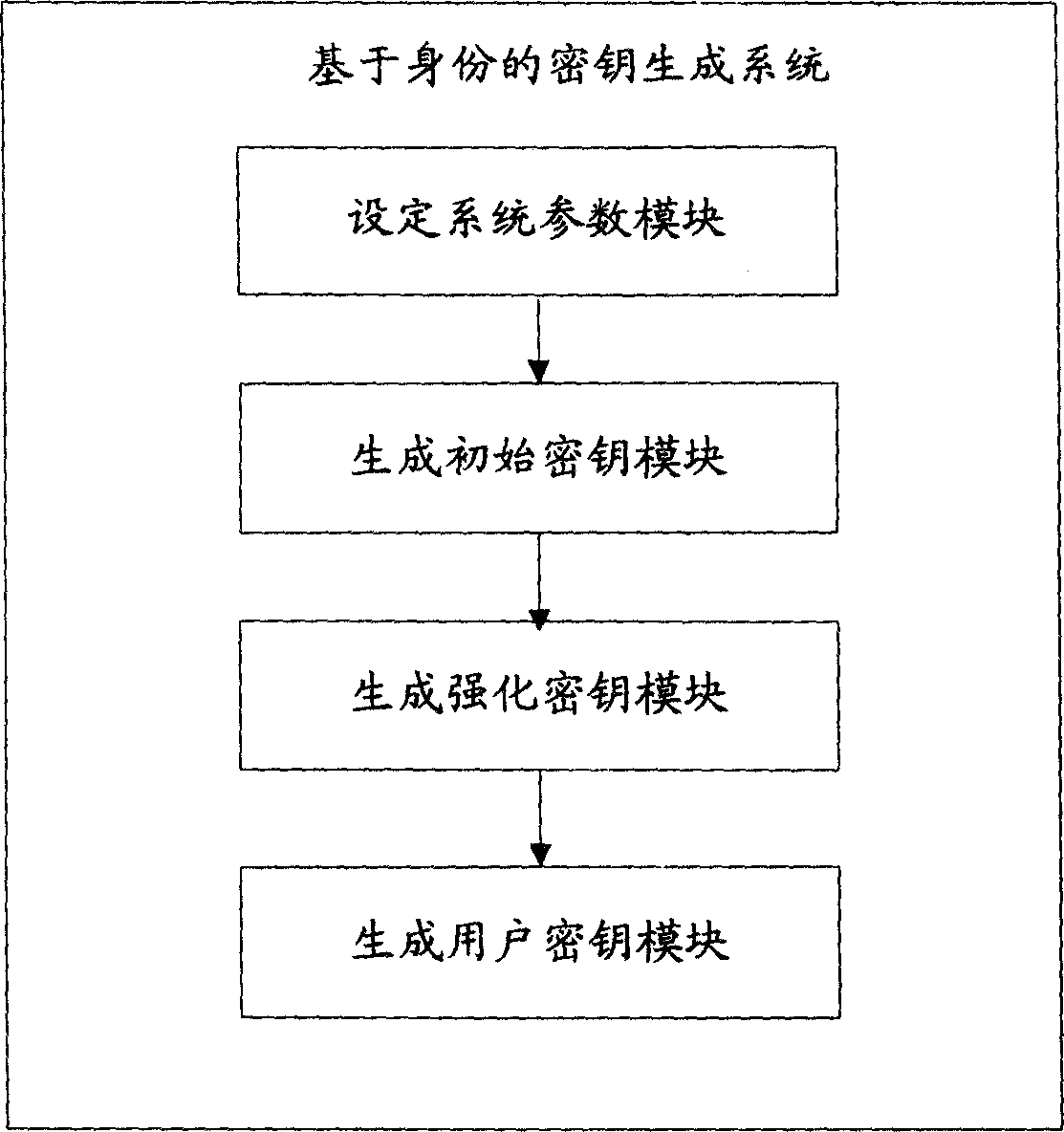
Cryptographic key generation method and system based on identity
InactiveCN1878060AEliminate dependenciesPractical use of cryptographic systemUser identity/authority verificationCryptographic key generationComputer hardware
The invention discloses a key generating method and system based on identity in the computer communication and electronic business applying domain, which comprises the following steps: setting system parameter; generating user information; producing original key; detecting original key; generating reinforced key; producing user key. The system comprises the following parts: system parameter generating mode, user information generating mode, original key generating mode, original key detecting mode, reinforced key generating mode and user key generating mode. The invention solves the problem of reliability for safe channel and key trust, which prevents kinds of jactitation attack.
Owner:SHANGHAI JIAO TONG UNIV +1
Method for realizing dependable SSH based on dependable computing
InactiveCN101741842AAvoid security threatsProtection against replay attacksKey distribution for secure communicationUser identity/authority verificationKey exchangeMan-in-the-middle attack
The invention provides a method for realizing dependable SSH based on dependable computing. The method integrates remote authentication of the dependable computing with key exchange of an SSH protocol so as to closely combine platform status information verification with session key negotiation; and the method enhances the security of data at a communication end point on the premise that safe transmission of the data is ensured. The method requires that both a server and a client are provided with dependable security chips; and the platform status can be measured by a measurement module and a dependable operating system. The method can not only effectively prevent the security threat that the communication with an unknown end point by using a security channel may undergo various attacks in the SSH protocol, but also effectively protect against replay attack, impersonation attack and man-in-the-middle attack.
Owner:BEIJING JIAOTONG UNIV
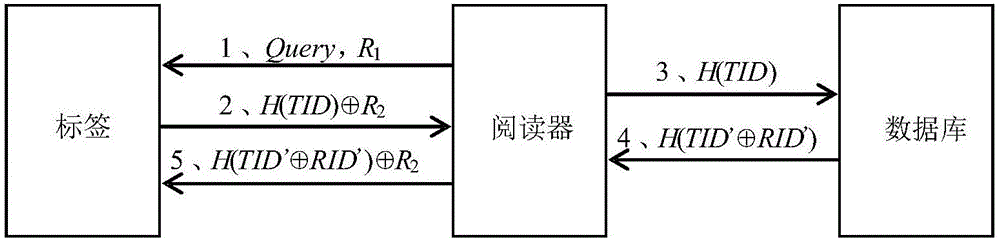
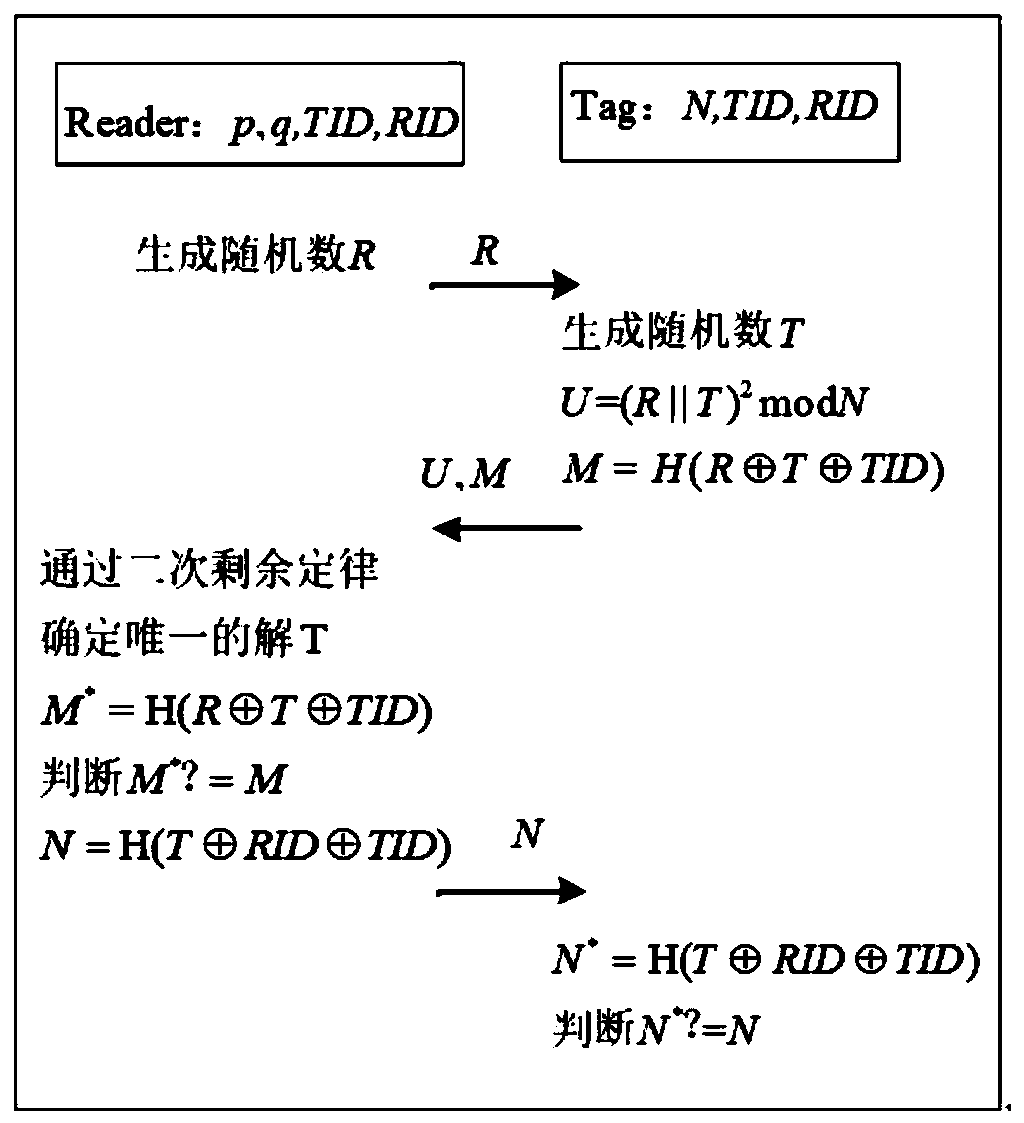
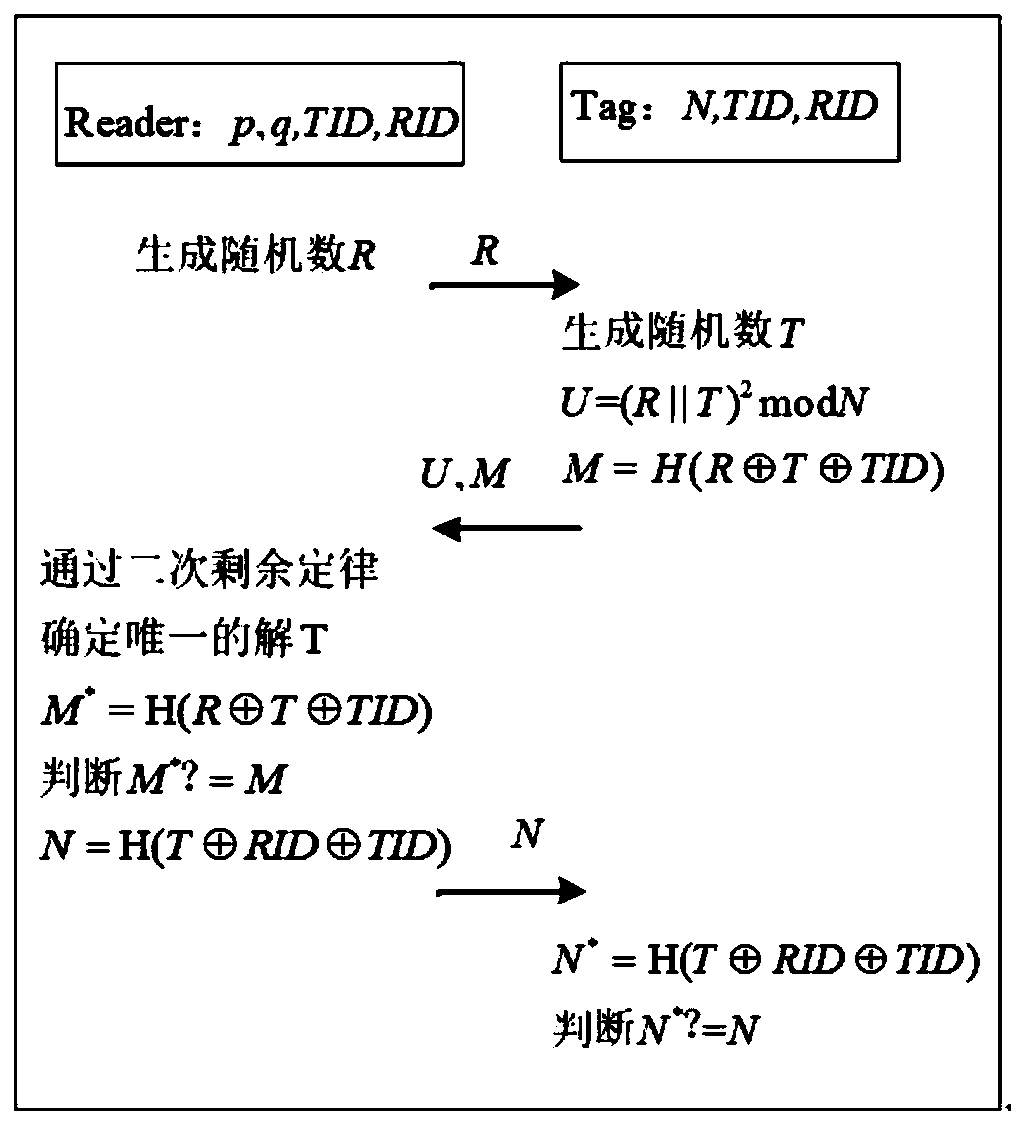
Dynamic authentication method between reader and tag card and implementing device thereof
InactiveCN102136079AEasy to useEffectively hideCo-operative working arrangementsDigital data authenticationComputer hardwareHash table
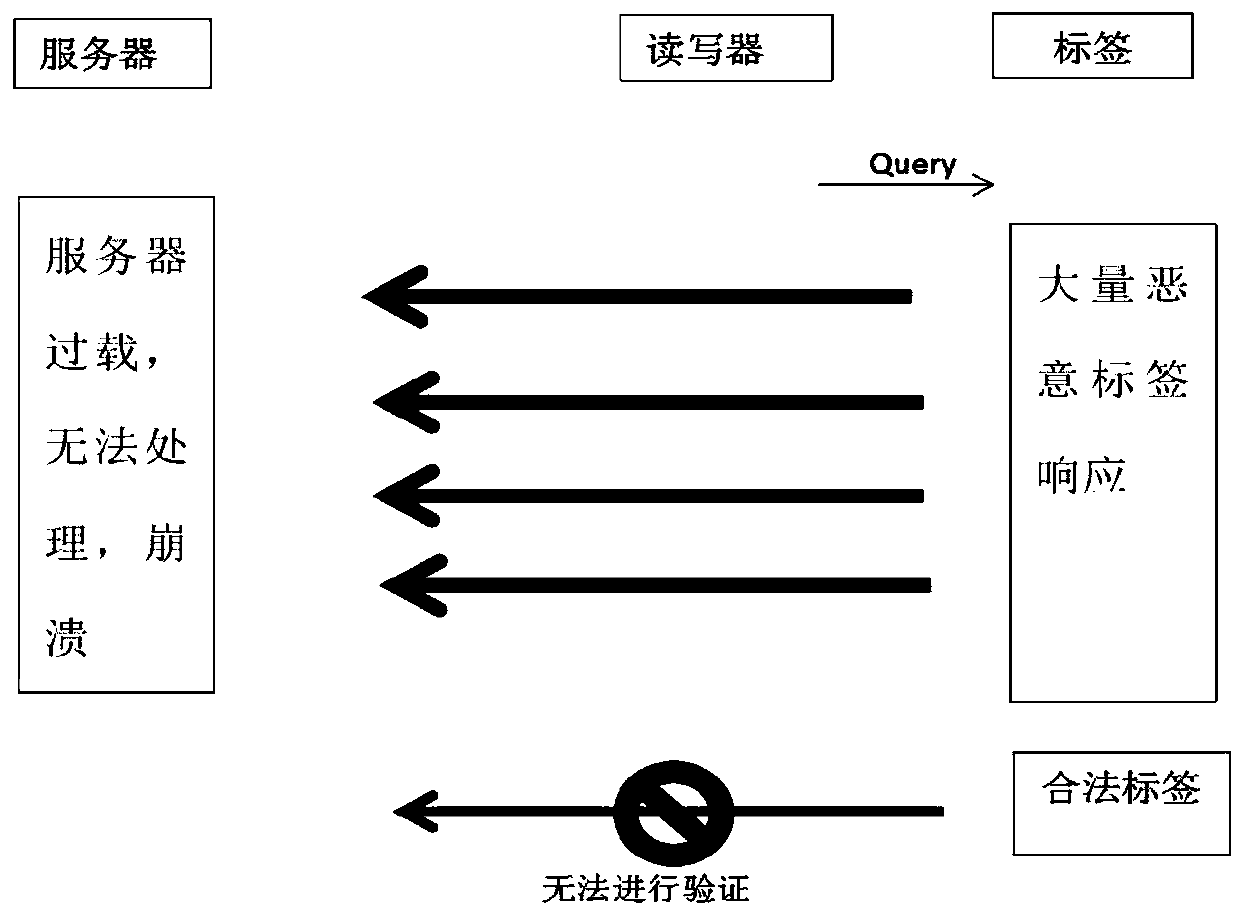
The invention discloses a dynamic authentication method between a reader and a tag card and an implementation device thereof for solving the technical problem that the traditional authentication method must depend on real-time online reliable and safe connection with a backstage database, and cannot authenticate the tag card with the reader autonomously at a high degree. In the method, only a legal reader can acquire corresponding tag authentication information from an authentication database to authenticate or update the state of the corresponding tag; only a legal tag can be processed by the legal reader; a dynamic updating mechanism is applied to the tag identification (ID) in the authenticating process to ensure the forward security, and the reader stores the tag card information by adopting a Hash table, thereby improving the authentication speed; and data synchronization is realized skillfully in an attribute value mode; and the use of random numbers ensures that different data packets can be used in each authentication, so that the position information of the tag is effectively concealed and high security characteristic is provided.
Owner:ZTE CORP
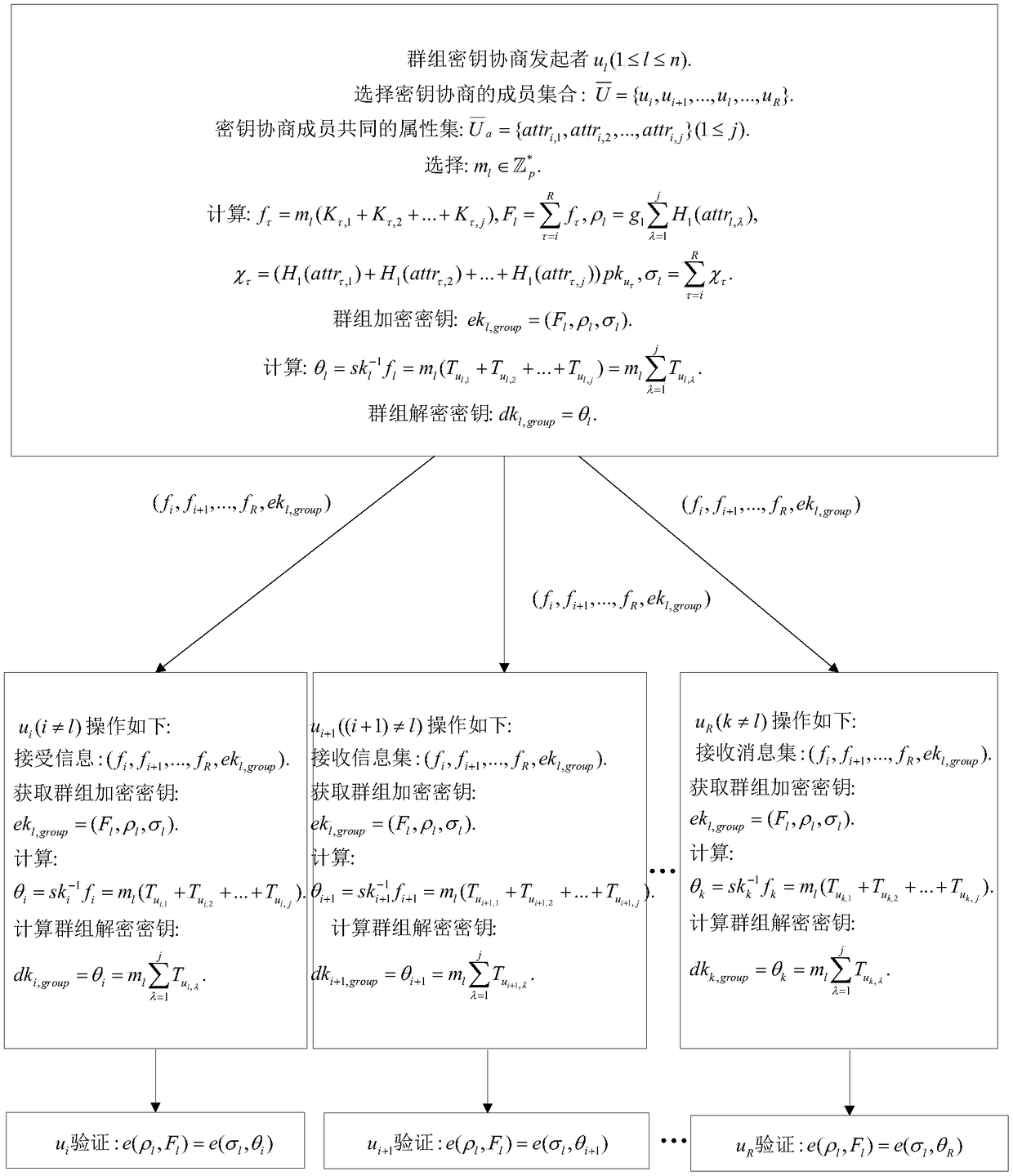
An asymmetric group key negotiation method based on permissioninformation exchange
ActiveCN109257173AIncrease flexibilityPrevent impersonation attacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPlaintextNon symmetric
The invention provides an asymmetric group key negotiation method based on permission information exchange, which takes attributes of terminal members as right parameters, and each terminal member sends its attribute set and hash value signature of the attribute set to a key generation center. The key generation center verifies the signature of the attribute set hash column value of the terminal member. If the authentication is passed, the member obtains the right key parameter corresponding to the attribute; based on the sensitivity of the exchanged information, encrypting and broadcasting the information to be broadcast to the group members with the right key parameter corresponding to the specific attribute and the selected random key factor; a member with the access right of the sensitive information calculates a decryption key of the broadcast ciphertext information by using a key parameter corresponding to the access right, and obtains the corresponding plaintext information by decrypting the broadcast ciphertext through the decryption key, so as to realize the secret information sharing among the group members with the specific right. The invention can prevent unauthorized members from participating in group key negotiation and protect personal privacy.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
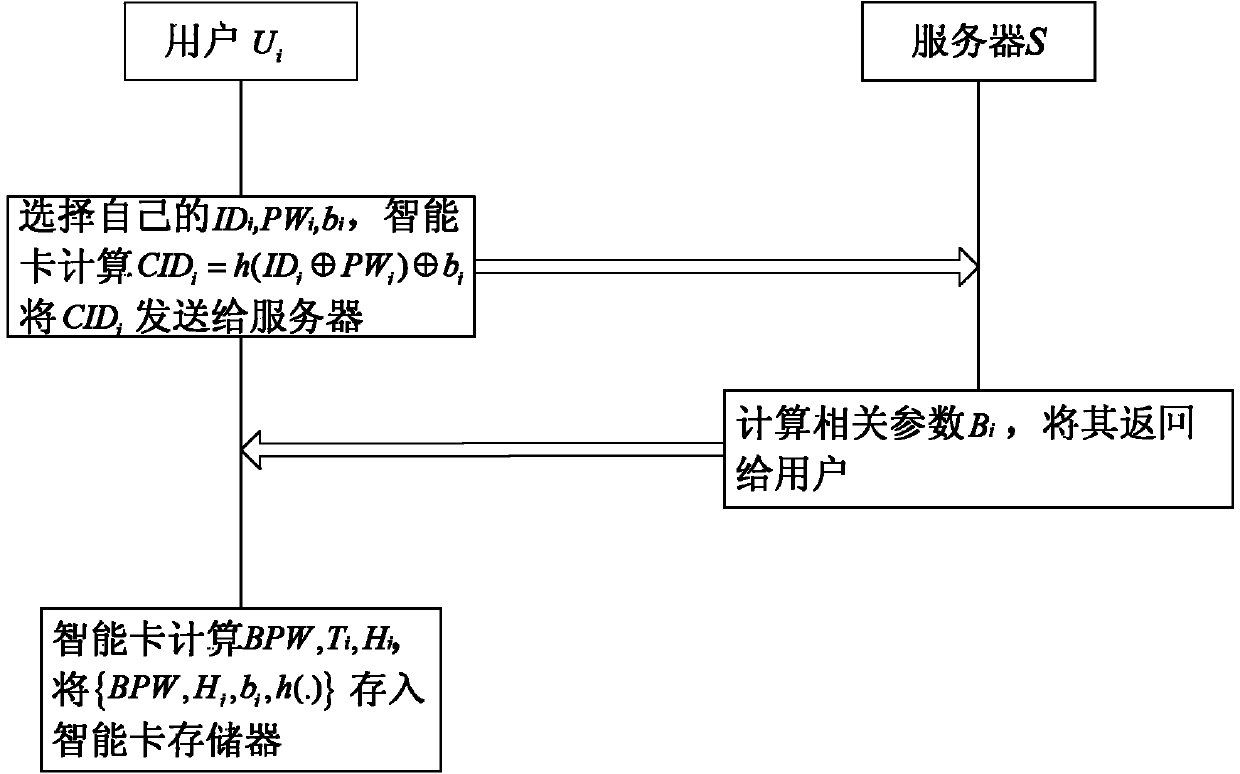
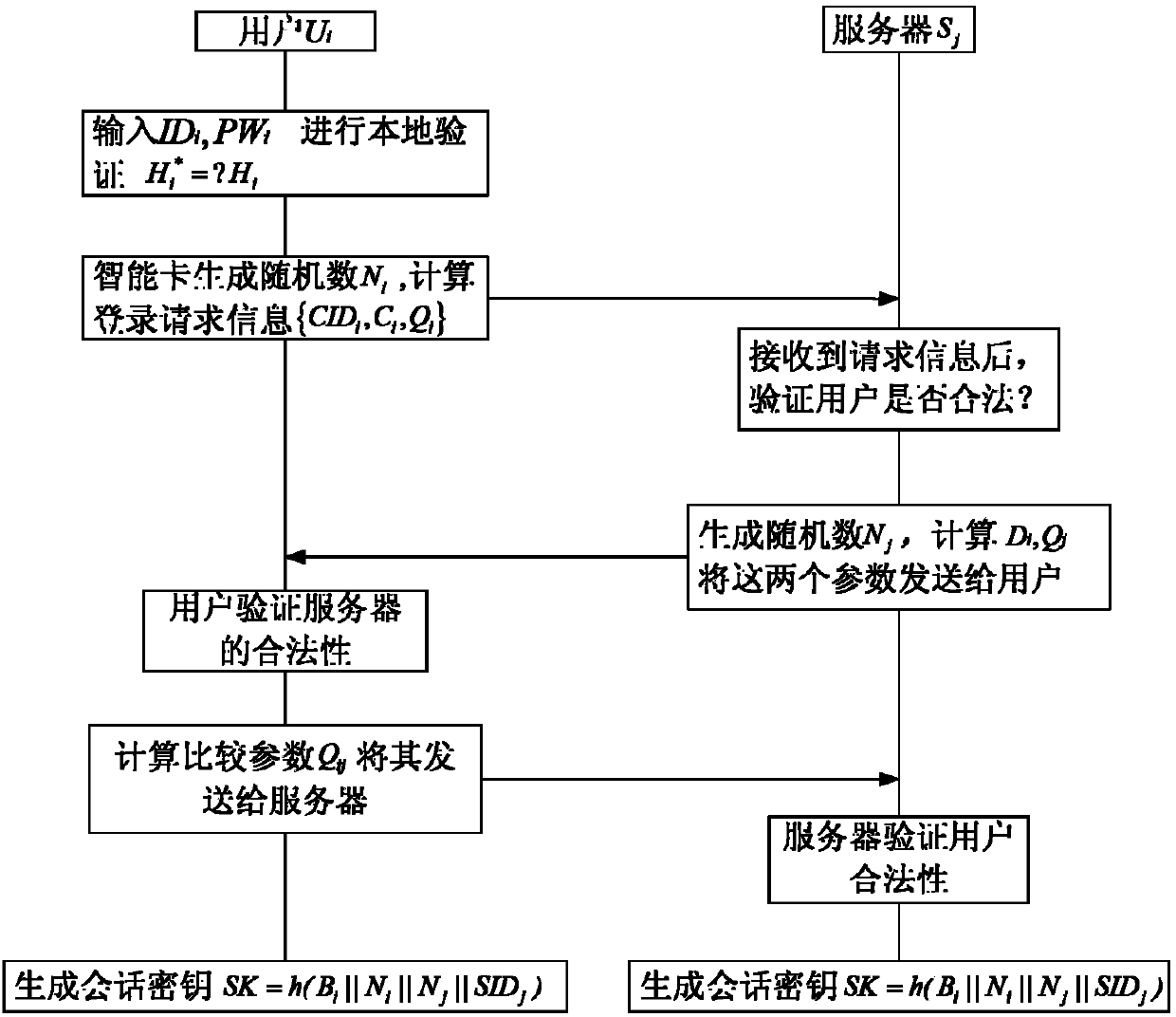
Low-complexity identity authentication method based on intelligent card and under multiserver environment
InactiveCN103346887AAvoid loss attackPrevent impersonation attacksUser identity/authority verificationDigital data authenticationSmart cardImpersonation attack
The invention discloses a low-complexity identity authentication method based on an intelligent card and under a multiserver environment. The low-complexity identity authentication method comprises the steps of registering, logging and authentication, wherein the registering further comprises the steps that registering information of a user is converted by a registration center and the intelligent card and then is stored in the intelligent card; the logging further comprises the steps that the intelligent card carries out local legitimacy verification on the identity of the user, and if the identity of the user is legitimate, a random number is generated, and first verification data are generated and sent to a server; the authentication further comprises the steps that the server carries out the legitimacy verification on the identity of the user, and if the identity of the user is legitimate, second verification data are generated and sent to the intelligent card; the intelligent card carries out the legitimacy verification on the identity of the server, and if the identity of the server is legitimate, third verification data are generated and sent to the server; the server carries out secondary verification on the identity of the user, and if the identity of the user is legitimate, the server and the intelligent card generate the same session key. The low-complexity identity authentication method avoids intelligent card losing attacks and impersonation attacks.
Owner:SHANDONG UNIV OF SCI & TECH
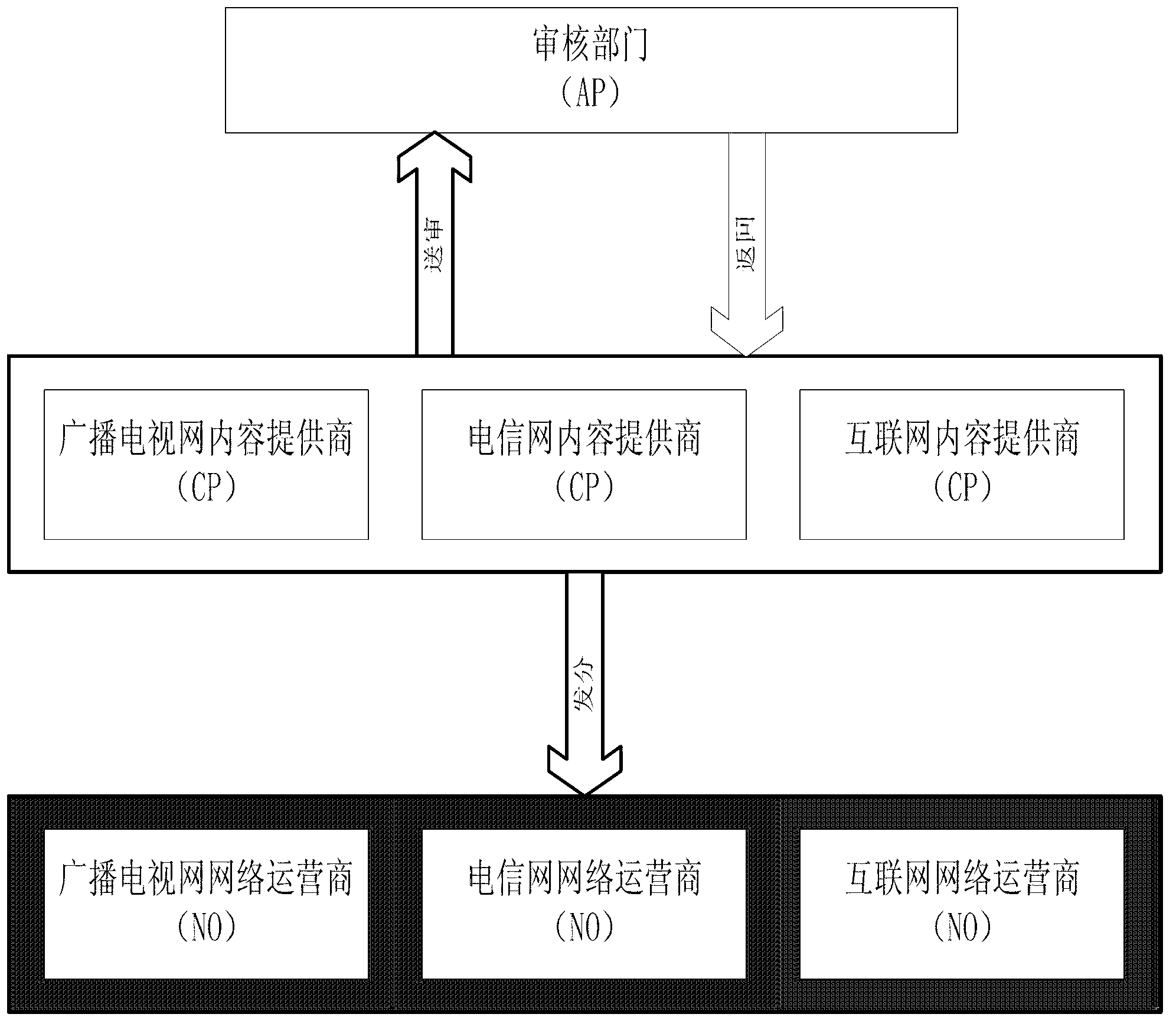
Safety responsibility identifying method of video content for integration of three networks
InactiveCN103313142AQuick fixPrevent impersonation attacksSelective content distributionComputer networkContent security
The invention relates to a safety responsibility identifying method of video content for integration of three networks, and belongs to the field of computer information security. The method is designed by aiming at the problem that the video content is transmitted in an open network and interacts with a plurality of unreliable main bodies, and when illegal video content is transmitted, a responsible party cannot be determined. The method comprises the following steps of selecting a plurality of key frames of a video randomly in time dimension and dividing the frames into a plurality of groups according to numbers of the frames; in space dimension, dividing each key frame into a central area, a fringe area and a corner area and distributing different sampling rates for different areas; after cascading the sampling information of the key frames in the same group, performing bit commitment; in the transmission process, negotiating a confidential correspondence identifier by both parties, wherein the recipient determines whether the video content is falsified or not by verifying the confidential correspondence identifier and the bit commitment value. Once dispute occurs, a confidential comparison protocol is adopted between both parties to confidentially compare the bit commitment result so as to achieve responsibility confirmation.
Owner:COMMUNICATION UNIVERSITY OF CHINA
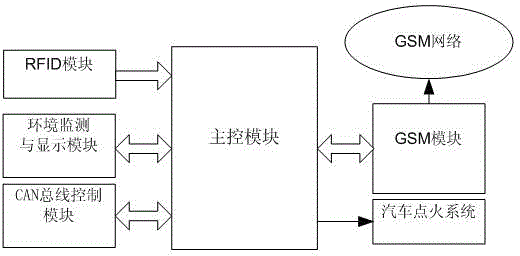
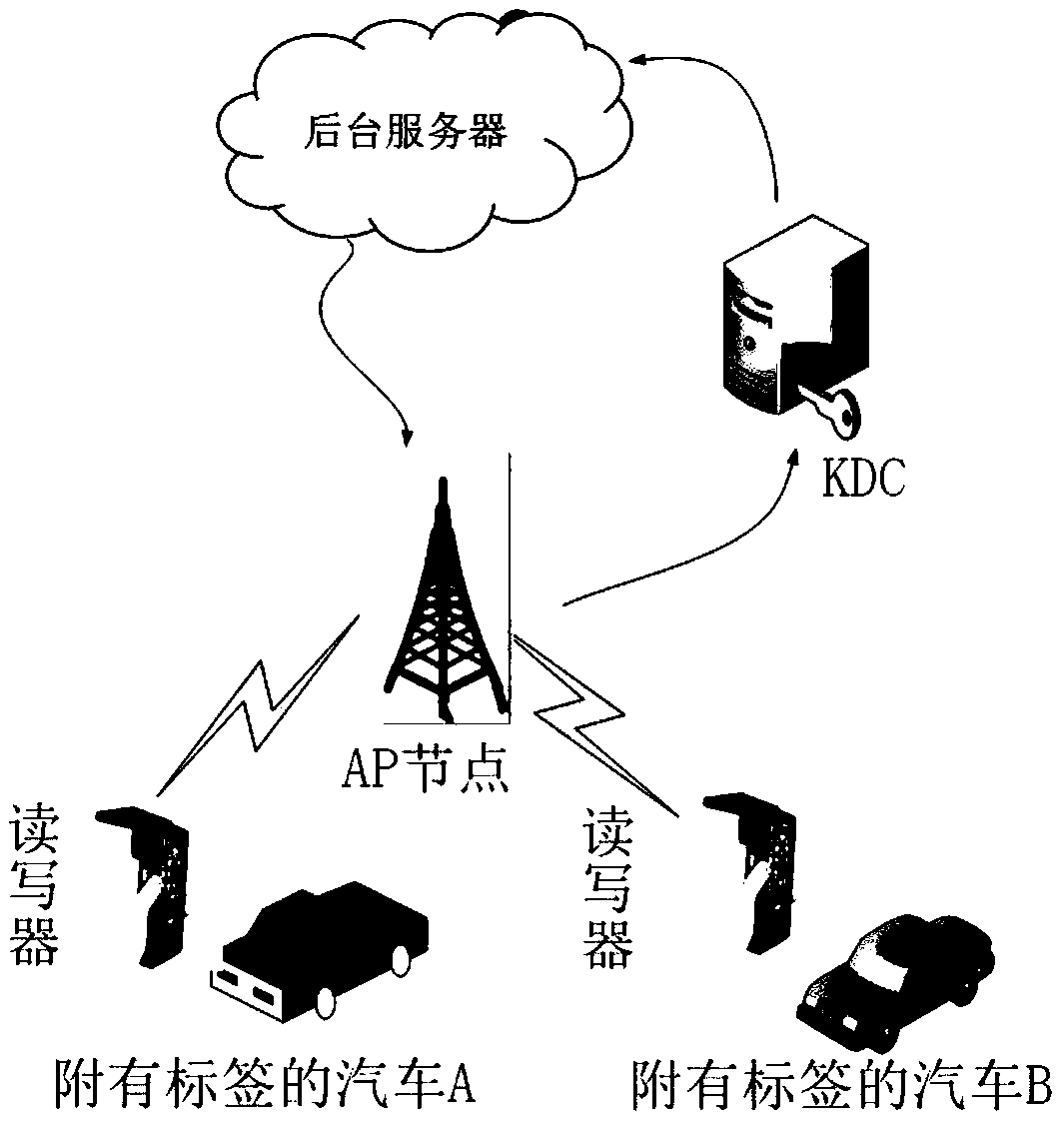
RFID (Radio Frequency Identification Device) safety method based on updating of dynamic ID (Identifier) and key of automobile security system
InactiveCN104486080APrevent impersonation attacksUser identity/authority verificationCo-operative working arrangementsElectronic taggingComputer module
The invention discloses an RFID (Radio Frequency Identification Device) safety method based on updating of a dynamic ID (Identifier) and a key of an automobile security system and relates to the technical fields of network type automobile security systems and wireless communication. A network type automobile security system is mounted in a car; a reader-writer of a radio frequency identifying device is mounted at a door of the car; a user can have communication in a spatial wireless signal channel by holding an electronic label close to the reader-writer; a main control module is used for data processing; information interaction can be implemented by RFID security protocol identification with the dynamic ID and the key updating between the label and the reader-writer; if the label is legal, the label and the ID and the key of a background server are simultaneously updated, the door of the car is opened, and an ignition system of the car can be started; if the label is illegal, the ID and the key are not updated, the door of the car cannot be opened, and the ignition system of the car is in a closed state. The method disclosed by the invention can be used for guaranteeing accuracy and safety of the protocol.
Owner:JILIN UNIV
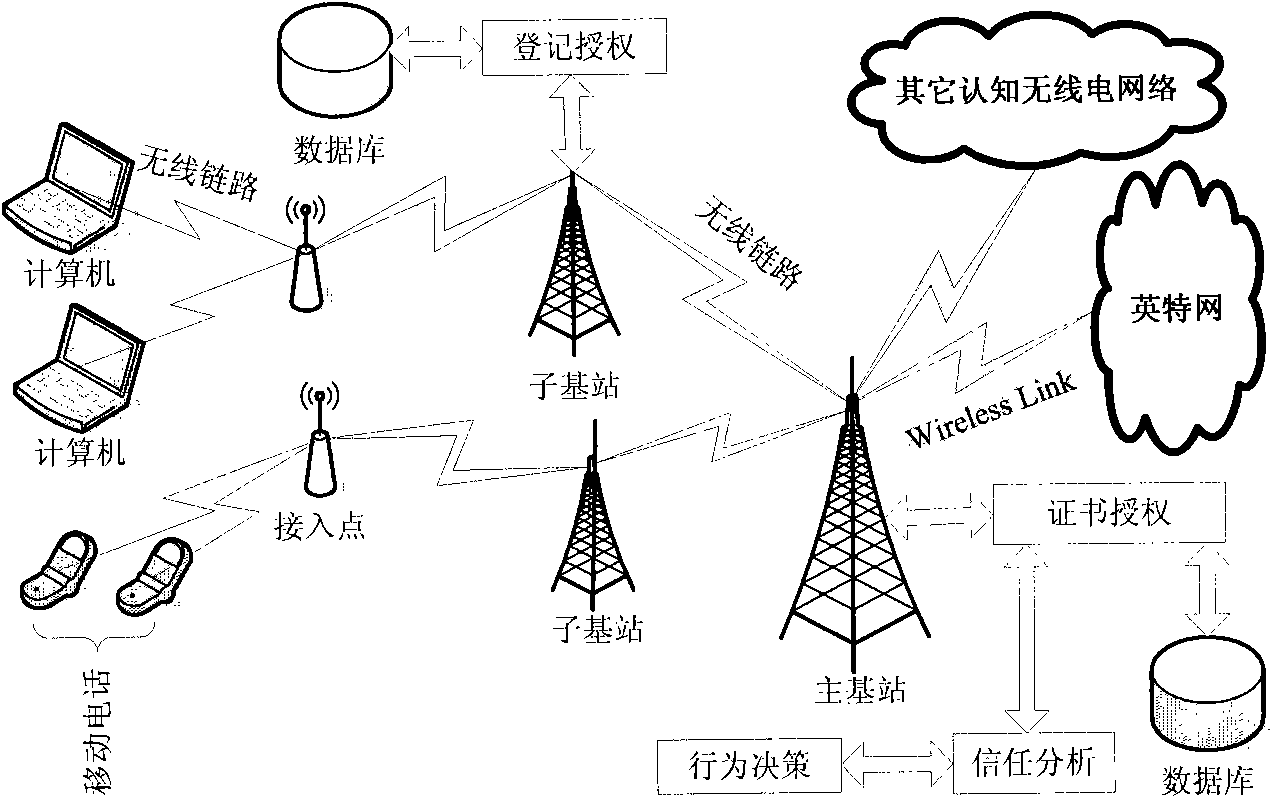
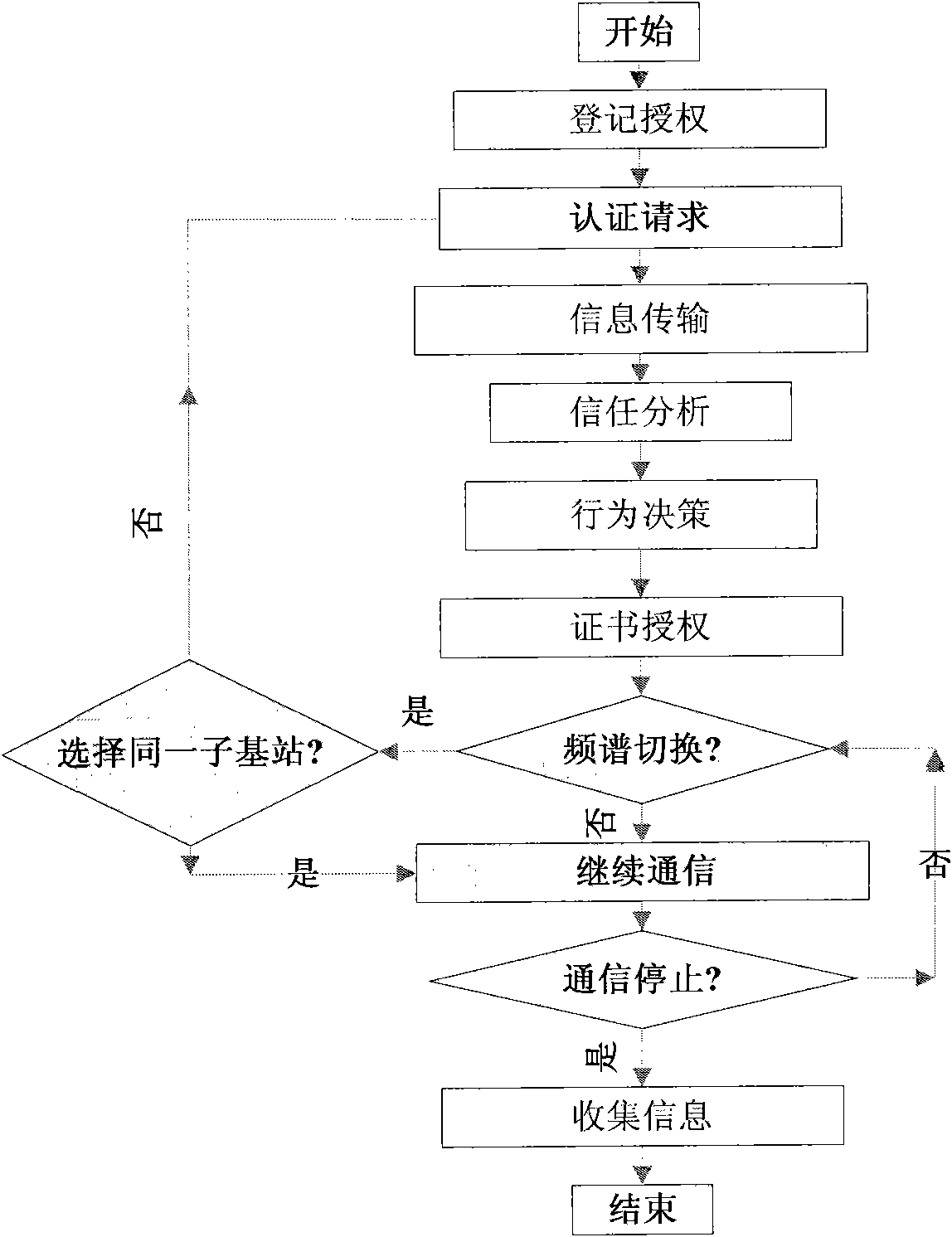
Entity authenticating system and method of cognitive radio network based on hierarchical structure
InactiveCN101860861APrevent impersonation attacksAvoid congestionAssess restrictionSecurity arrangementSecure communicationSecurity question
The invention provides entity authenticating system and method of a cognitive radio network, which relates to the relevant applying field in information safety technology. The entity authenticating system and the method of the cognitive radio network based on a hierarchical structure ensure the safe communication between secondary users by authenticating the identities of the secondary users in the cognitive radio network. In the process of sending the authentication request by the secondary user, the credibility is judged, and the public key verification is allowed to further execute only in the premise that the condition is satisfied. The trusting mechanism can effectively prevent the malignant users from generating multiple attacks in the network. The safety is based on n RSA algorithm, and simultaneously the symmetrical keys and the public key system are combined. In the premise of ensuring that the authenticating safety is not decreased, the authenticating efficiency is greatly enhanced, thereby effectively decreasing the authenticating delay. In addition, the invention has obvious effects on the safety problems of preventing the reproducing attack, controlling network congestion and the like.
Owner:UNIV OF SCI & TECH BEIJING
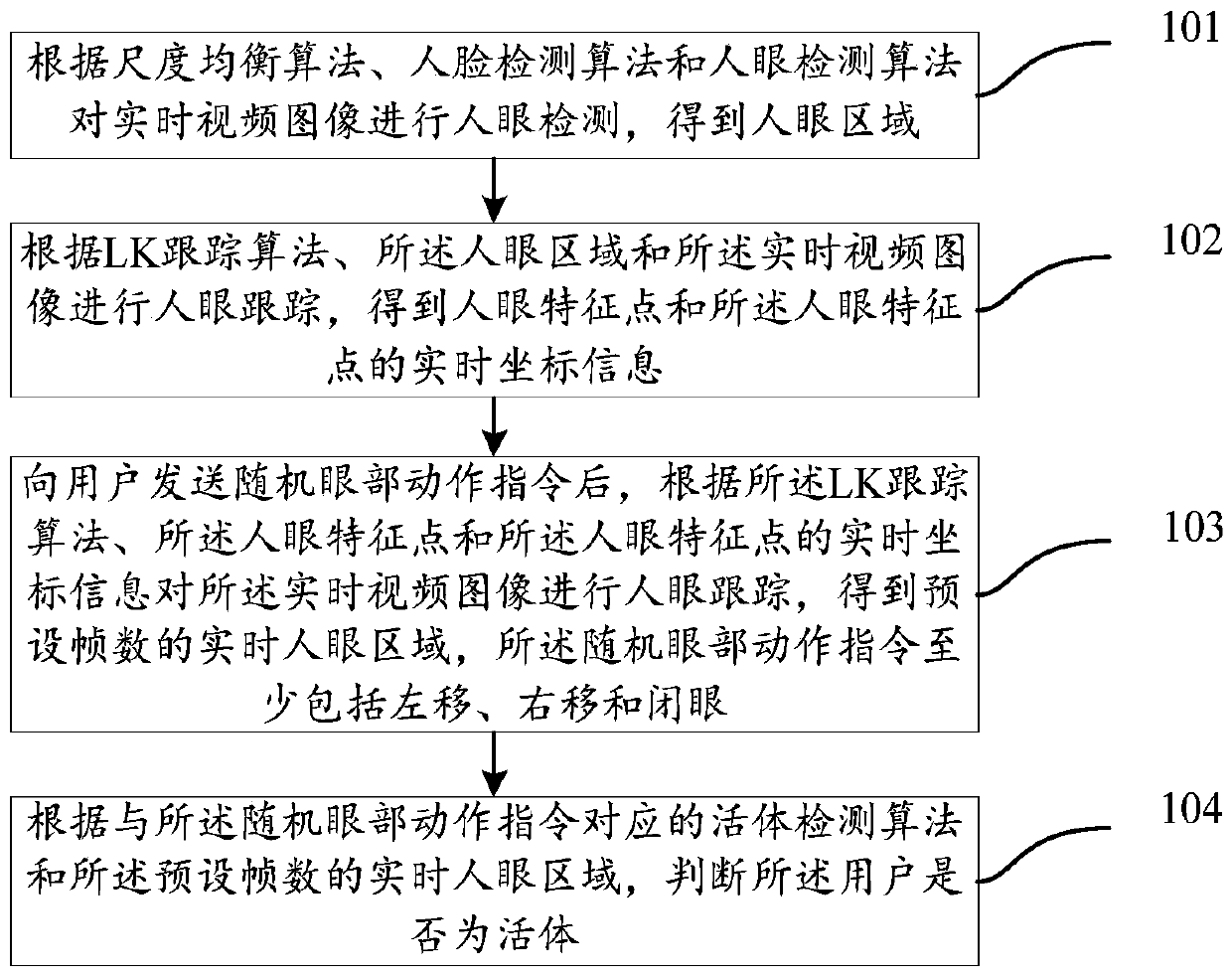
Living body detection method and apparatus based on active state of human eye region
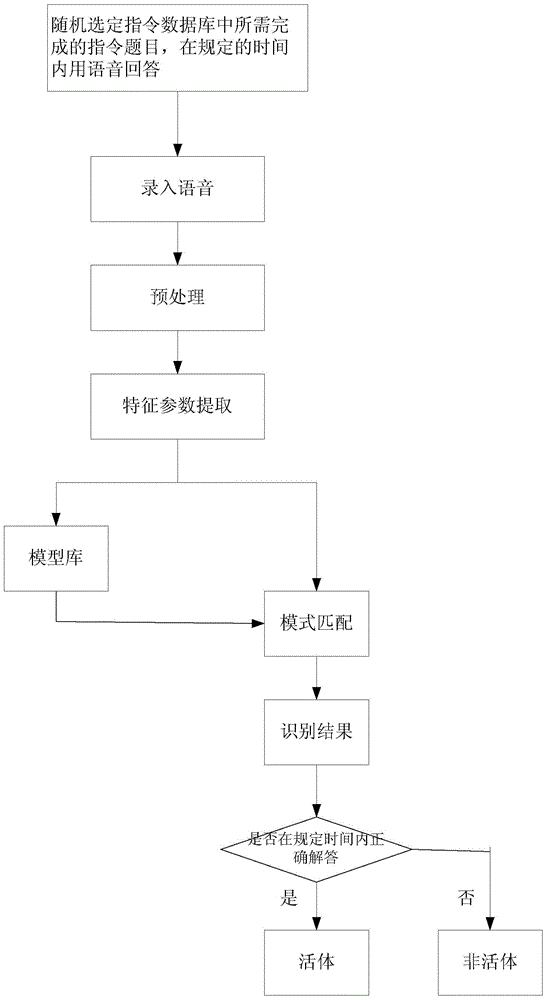
ActiveCN105138967APrevent Video Impersonation AttacksPrevent impersonation attacksCharacter and pattern recognitionLiving bodyCharacteristic point
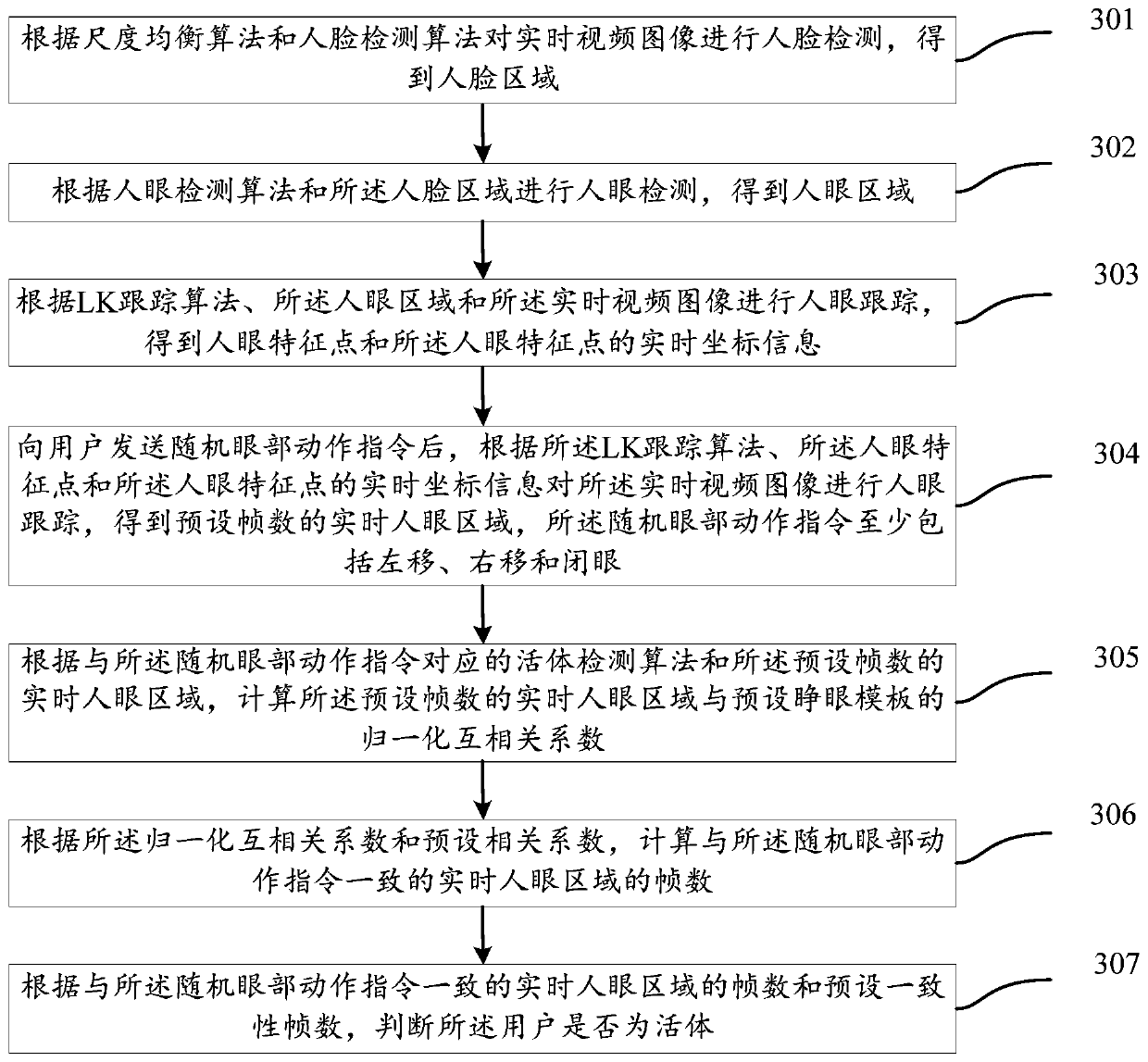
The present invention discloses a living body detection method and apparatus based on an active state of a human eye region, and belongs to the computer application field. The method comprises: carrying out human eye detection on real-time video images according to a scale equalization algorithm, a human face detection algorithm and a human eye detection algorithm to obtain a human eye region; carrying out human eye tracking according to an LK tracking algorithm, the human eye region and the real-time video images to obtain human eye characteristic points and real-time coordinate information of the human eye characteristic points; after sending a random eye action instruction to a user, carrying out human eye tracking on the real-time video images according to the LK tracking algorithm, the human eye characteristic points and the real-time coordinate information of the human eye characteristic points to obtain a preset number of frames of real-time human eye regions; and determining whether the user is alive according to the living body detection method and the preset number of frames of real-time human eye regions. According to the living body detection method and apparatus provided by the present invention, by means of the human eye tracking and the random eye action instruction, the living body detection can be performed effectively, thereby preventing an attack caused by a faking video.
Owner:CHINA THREE GORGES UNIV
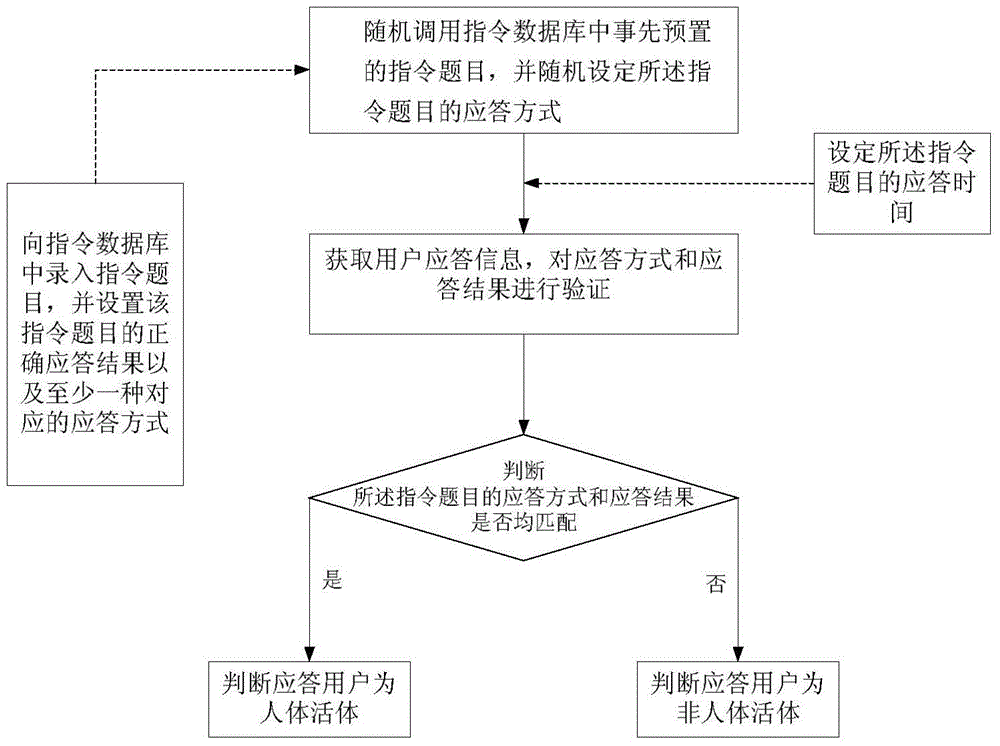
Human living body detection method and device based on human brain intelligence and man-machine interaction
InactiveCN104965589APrevent Fraud AttacksLow costInput/output for user-computer interactionGraph readingHuman bodyHuman–robot interaction
The invention discloses a human living body detection method based on human brain intelligence and man-machine interaction. The human living body detection method comprises the following steps: randomly transferring an instruction subject which is pre-configured in an instruction database in advance, and randomly setting a response mode; acquiring user response information and verifying the response mode and a response result; and if the response mode and the response result of the instruction subject are matched successfully, judging that a response user is a human living body. According to the method, the subject is appointed randomly to enable the user to answer in regulated time by the randomly-appointed response mode, and the transmitted instruction subject can be answered through the brain thinking of the user, so that an impostor can not adopt manners such as pure voice and / or video synthesis or editing and the like to cheat a human living body detection system. According to the human living body detection method, lawless persons can be effectively prevented from carrying out impersonation attacks through various means, so that the human living body detection system becomes more effective and reliable.
Owner:GUANGDONG MICROPATTERN SOFTWARE CO LTD
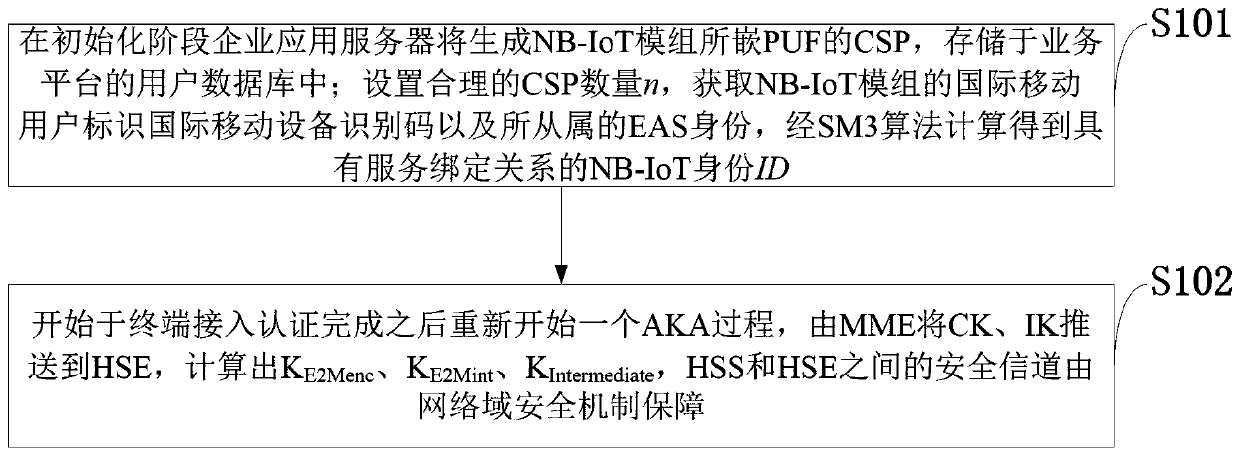
power grid NB-IoT end-to-end data processing method based on a physical unclonable function
ActiveCN109756872AImprove securityPrevent impersonation attacksSecurity arrangementMachine-to-machine/machine-type communication serviceComputer hardwarePower grid
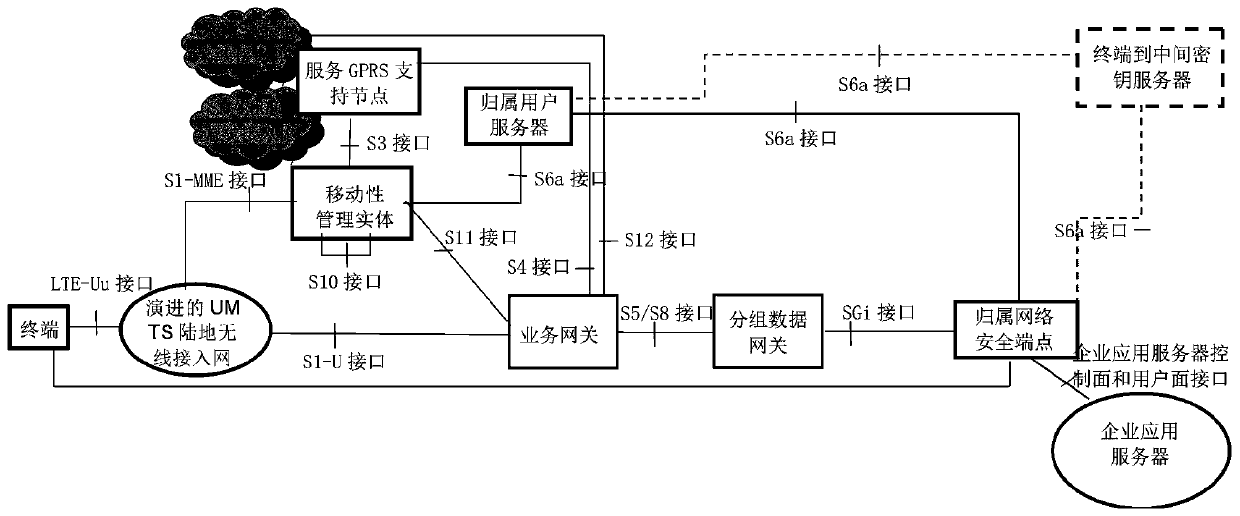
The invention belongs to the technical field of end-to-end communication, and discloses a power grid NB-IoT end-to-end data processing method based on a physical unclonable function. At the initialization stage, the enterprise application server generates a CSP of the PUF embedded in the NB-IoT module and stores the CSP in a user database of the service platform; A reasonable CSP number n is set,an international mobile user identifier, an international mobile device identification code and a subordinated EAS identity of the NB-IoT module are obtained, and an NB-IoT identity ID with a servicebinding relation is obtained through calculation of an SM3 algorithm; And the MME pushes the CK and the IK to the HSE, and a secure channel between the KE2Menc, the KE2Mint, the KIntermediate, the HSSand the HSE is calculated and is guaranteed by a network domain security mechanism. Compared with the prior art, the method has the characteristics of light weight and flexible updating, and the security of the service system is further enhanced.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY
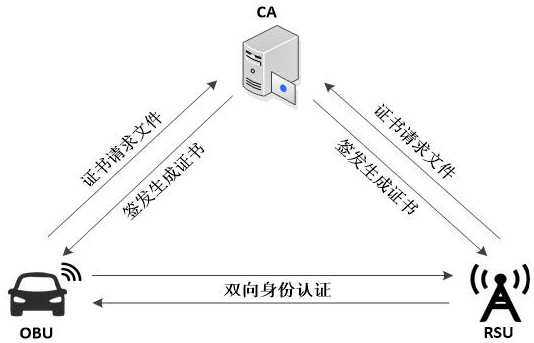
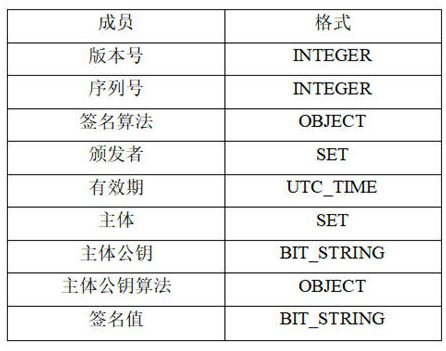
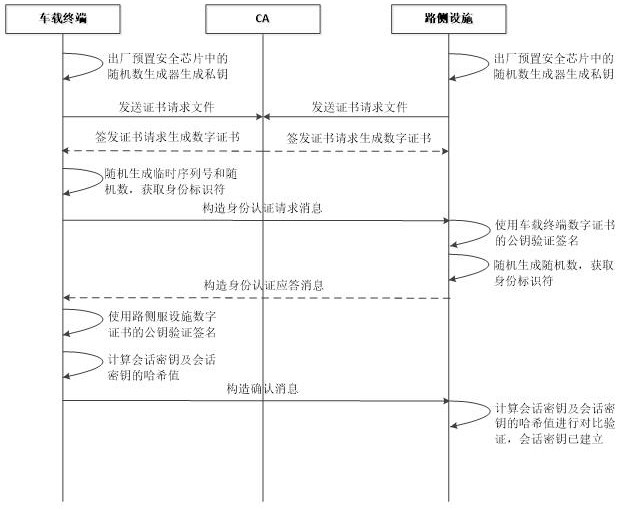
Internet of vehicles communication security authentication method, system and equipment based on national cryptographic algorithm
ActiveCN114154135ASecure transmissionReduce the number of timesRandom number generatorsDigital data protectionCommunications securityAlgorithm
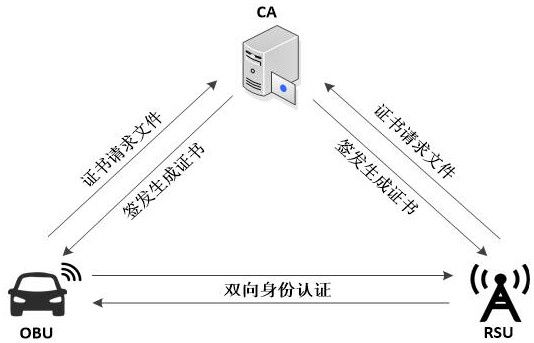
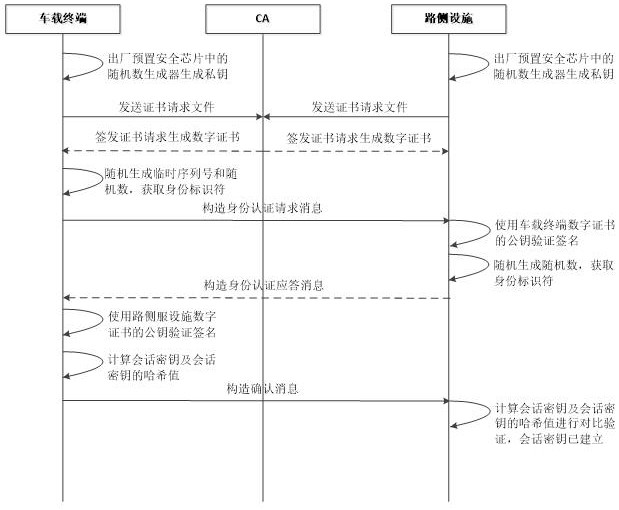
The invention belongs to the technical field of Internet of Vehicles security, and discloses an Internet of Vehicles communication security authentication method, system and device based on a national cryptographic algorithm. The method comprises the following steps: a vehicle-mounted terminal constructs an identity authentication request message and sends the identity authentication request message to a roadside facility; the vehicle-mounted terminal receives the identity authentication response message and verifies the signature; if verification succeeds, the vehicle-mounted terminal calculates a session key and a hash value thereof, constructs a confirmation message and sends the confirmation message to the roadside facility; a session key and a hash value of the session key are calculated by the roadside facility for comparison verification; if the hash values are equal, the security authentication succeeds and a session key is generated, and if not, the security authentication fails. According to the method, the SM2 digital signature algorithm, the SM2 public key encryption algorithm and the SM3 hash algorithm are combined, so that the method can be applied to the communication process of the vehicle-mounted terminal and the roadside facility, and various attacks can be resisted with relatively low total computing resources and relatively low communication bandwidth.
Owner:NANJING UNIV OF SCI & TECH
RFID multi-tag joint authentication system and method based on Internet-of-Things application
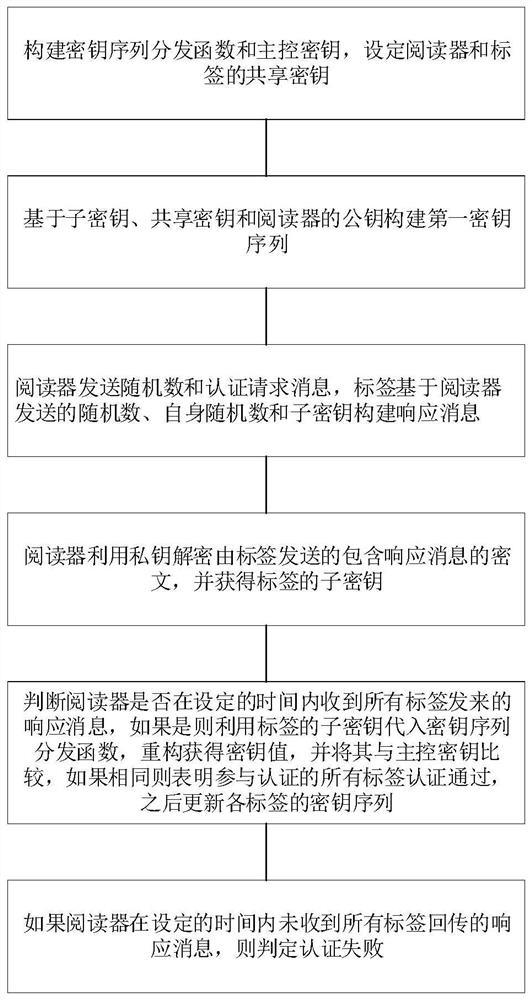
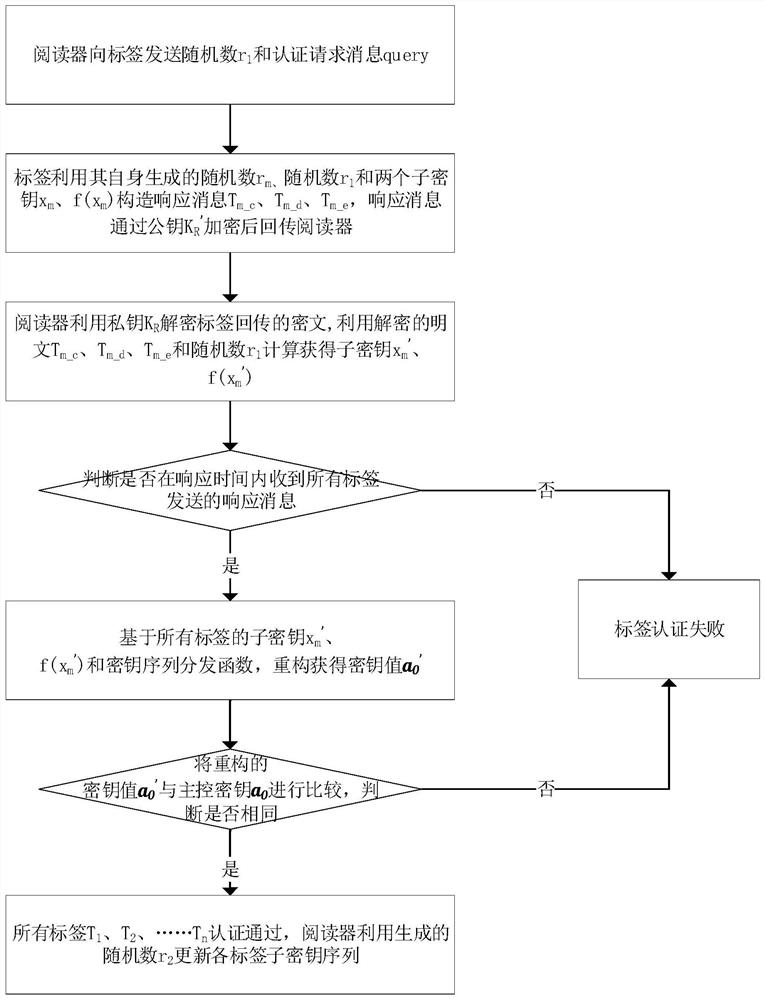
ActiveCN113365270ARealize the authentication functionRealize practical needsSecurity arrangementInternet privacyCiphertext
The invention provides an RFID multi-label joint authentication system and method based on Internet-of-Things application. The method comprises the following steps: constructing a key sequence distribution function and a main control key, and setting a shared key of a reader and a label; constructing a first key sequence based on the sub-key, the shared key and a public key of the reader, and sending the first key sequence to the tag; enabling the reader to send a random number and an authentication request message, enabling the tag to construct a response message based on the random number sent by the reader, the random number of the tag and the sub-key, and encrypting and then returning the response message through the public key to the reader; enabling the reader to decrypt the ciphertext by using the private key and obtain the sub-key of the tag; judging whether the reader receives response messages sent by all the tags within a set time, if so, substituting the sub-keys of the tags into a key sequence distribution function, reconstructing to obtain a key value, and comparing the key value with a main control key, if the sub-keys of the tags are the same, indicating that all the tags participating in authentication pass the authentication, and otherwise, judging that the authentication fails; and therefore, achieving a multi-label joint authentication function.
Owner:深圳市科易博软件有限公司
A block chain-based secure auditing Internet of Things data sharing system and method
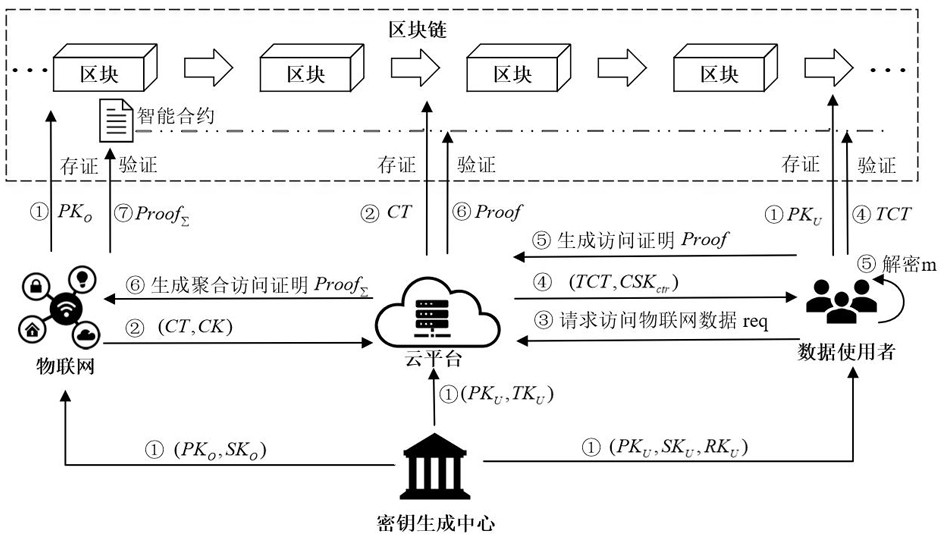
PendingCN114036539AReduce decryption overheadReduce computational overheadDigital data protectionPaymentCore function
The invention provides a block chain-based secure auditing Internet of Things data sharing system and method. The security of Internet of Things secure data sharing is improved by using a block chain technology. Fine-grained control over the data access authority of the Internet of Things is achieved in an attribute-based encryption mode, and the computing overhead of a user side is reduced through an outsourcing decryption technology. One core function of the system is to control the number of access times of the user, and manage each access of the user by using algorithms such as synchronous aggregation signature and verifiable random function. And in the payment use model, the system distributes limited number of Internet of Things data access permissions according to the payment condition of the user to the data. Meanwhile, the intelligent contract function of the block chain provides user management, signature verification and access auditing functions for the system.
Owner:STATE GRID CORP OF CHINA +2
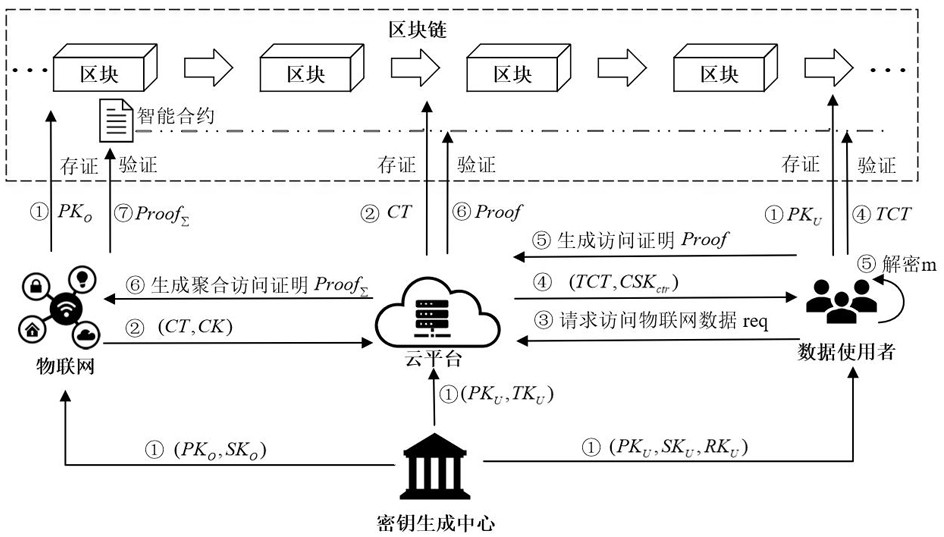
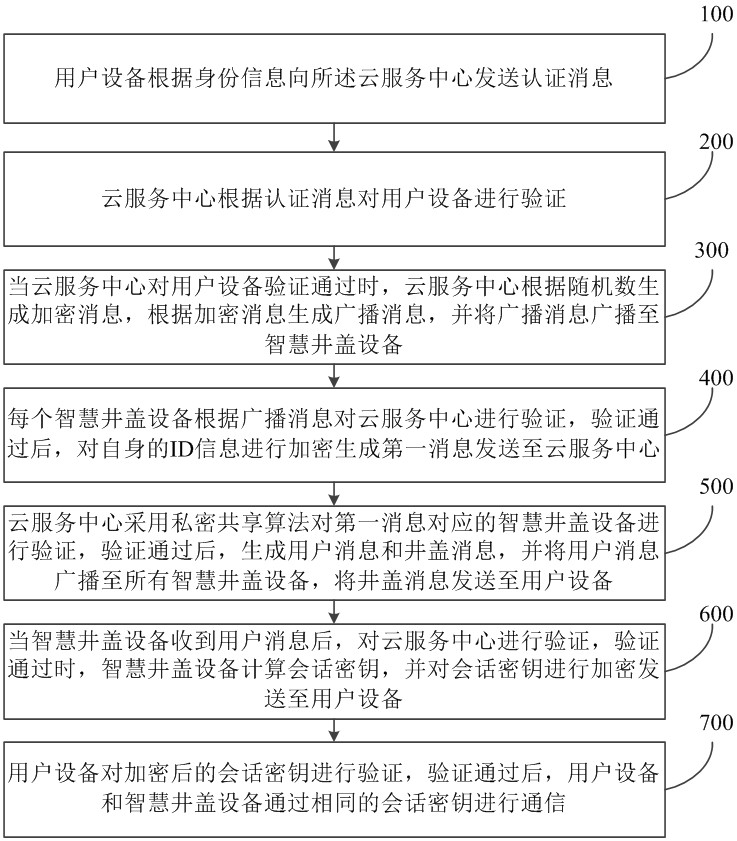
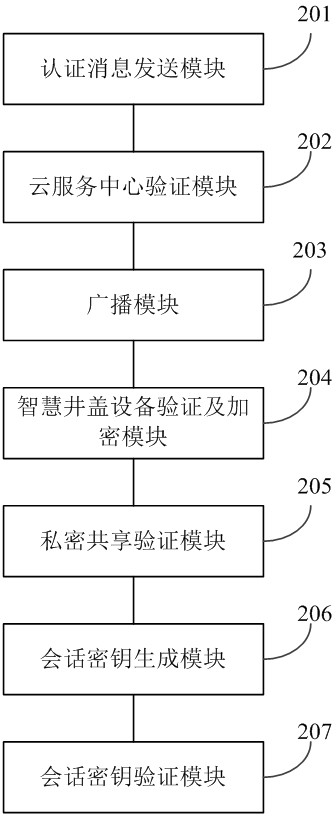
Authentication method and system of intelligent well lid equipment
ActiveCN114401153AImprove securityEnsure safetyKey distribution for secure communicationPublic key for secure communicationPasswordAttack
The invention relates to an authentication method and system for intelligent well lid equipment, and belongs to the technical field of information security. According to the method, an authorized user is supported to remotely access a group of intelligent well lid equipment, the user is identified in an intelligent well lid environment by adopting a password, biological characteristic identification and an intelligent card technology, and a secure session key is constructed among the legal group of intelligent well lid equipment by utilizing a secret sharing technology and the Chinese remainder theorem. According to the method, the intelligent well lid data can be safely accessed through the session key, common attacks can be resisted, and the communication safety is ensured.
Owner:HKUST TIANGONG INTELLIGENT EQUIP TECH (TIANJIN) CO LTD
High-security radio frequency identification method, device and system based on bidirectional authentication
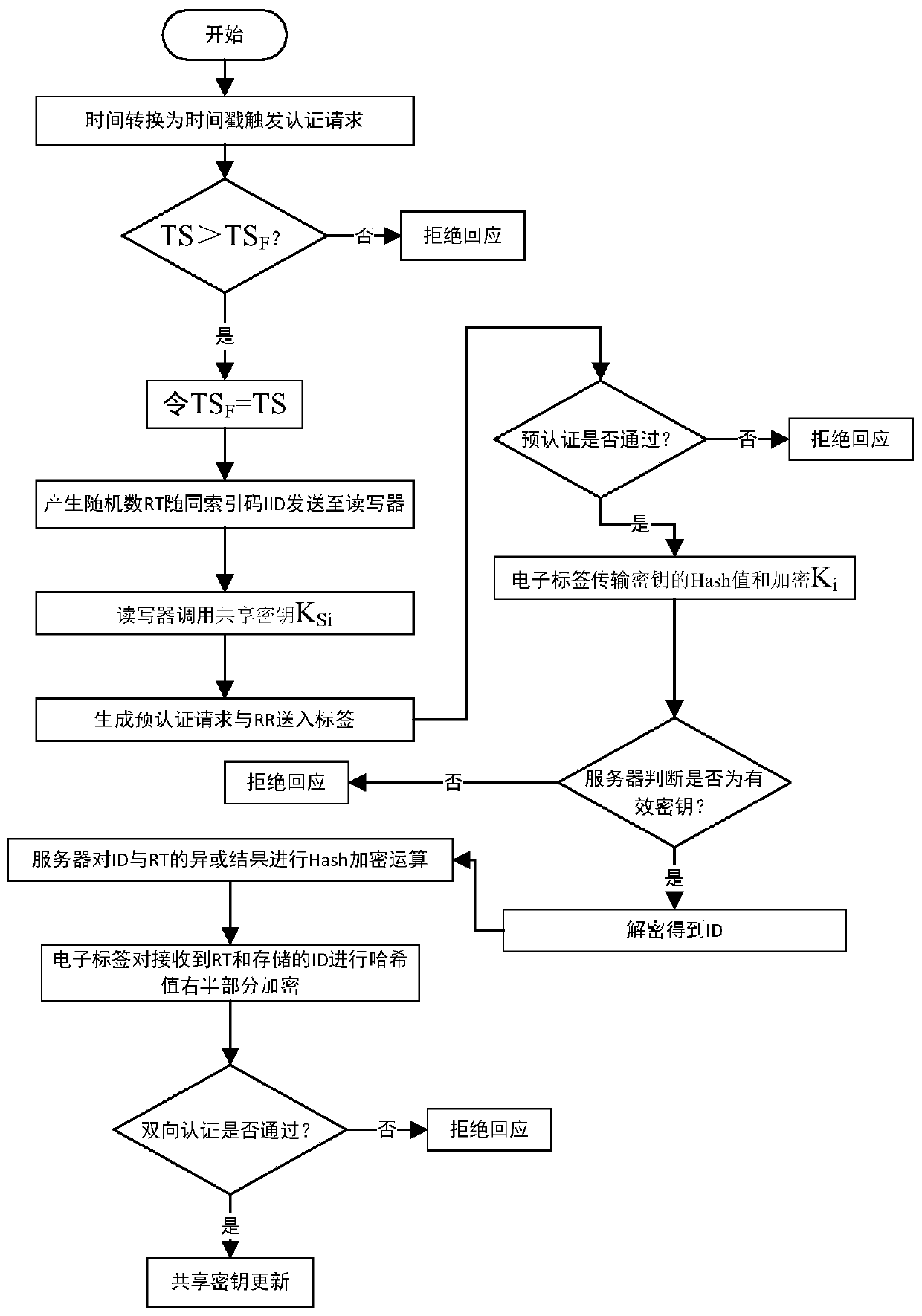
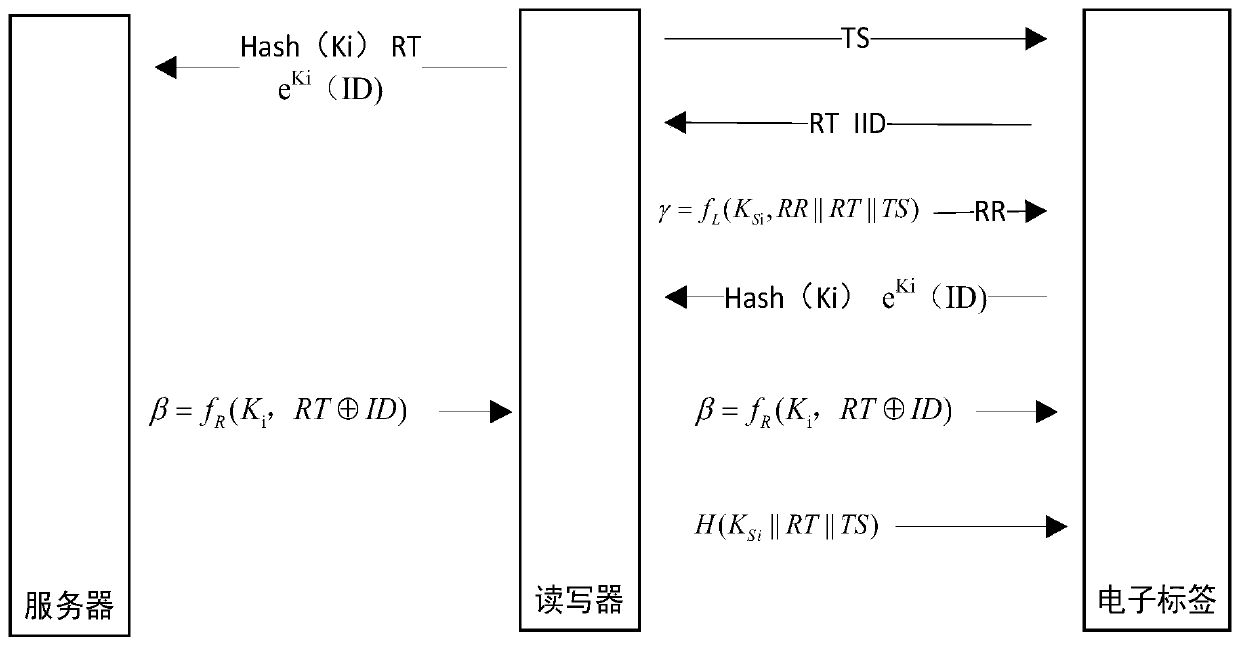
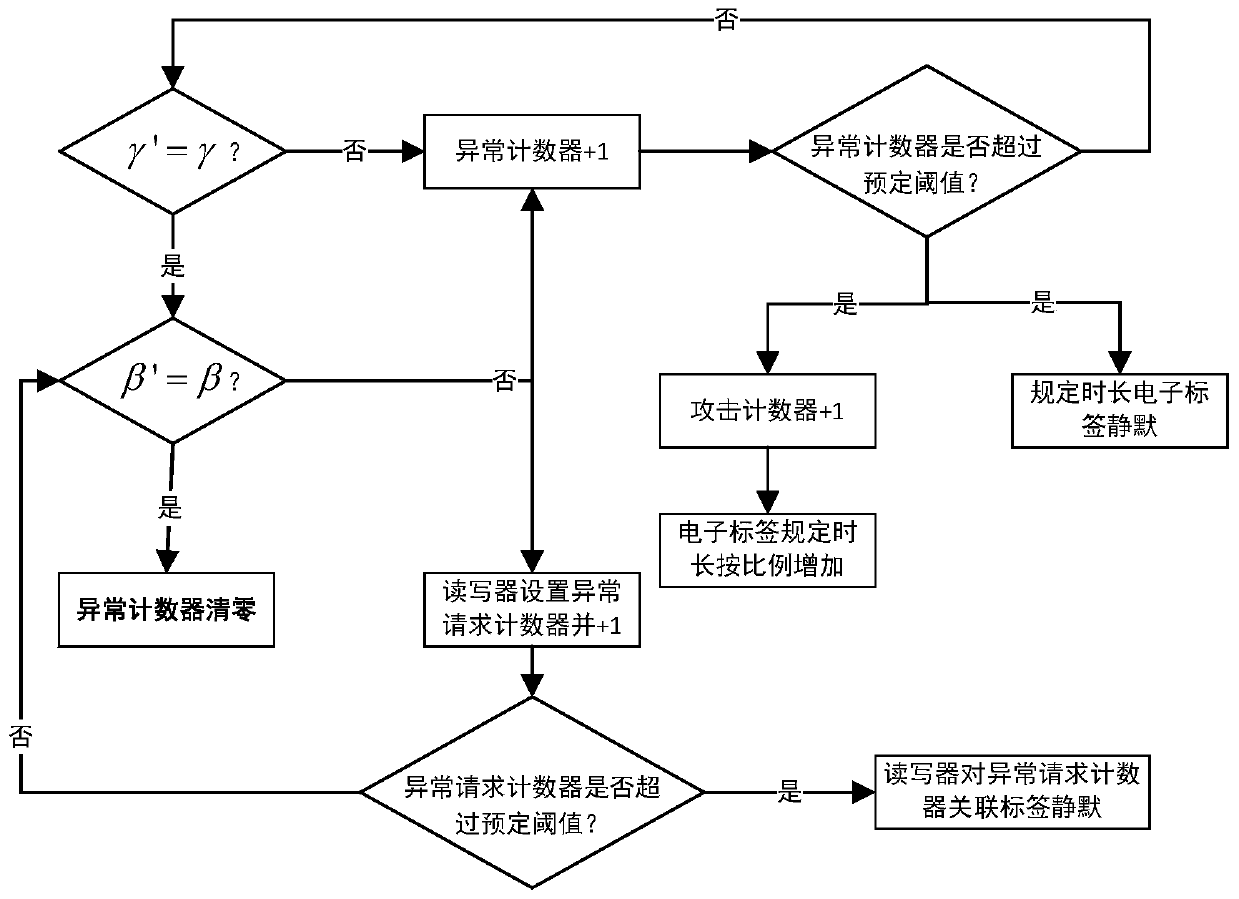
PendingCN110245534ASolve the security and privacy issues of authentication and identificationImprove security levelSecurity arrangementSensing by electromagnetic radiationTimestampPrivacy protection
The invention relates to the technical field of radio frequency identification, and discloses a high-security radio frequency identification method, device and system based on bidirectional authentication. The method comprises the following steps of: carrying out pre-authentication by using an index code and a shared key according to an authentication request in the form of a timestamp, carrying out ID confirmation by using a random number and a multi-key public key algorithm, and carrying out bidirectional final authentication by using the random number, the key and the ID. The device comprises a server, a radio frequency reader-writer and an electronic tag; the system comprises a processor, a storage device and a high-security radio frequency identification device based on bidirectional authentication. Bidirectional authentication of the tag and the reader-writer is realized, the device has good security and privacy protection characteristics, and the security and risk resistance of communication are ensured.
Owner:吴新胜
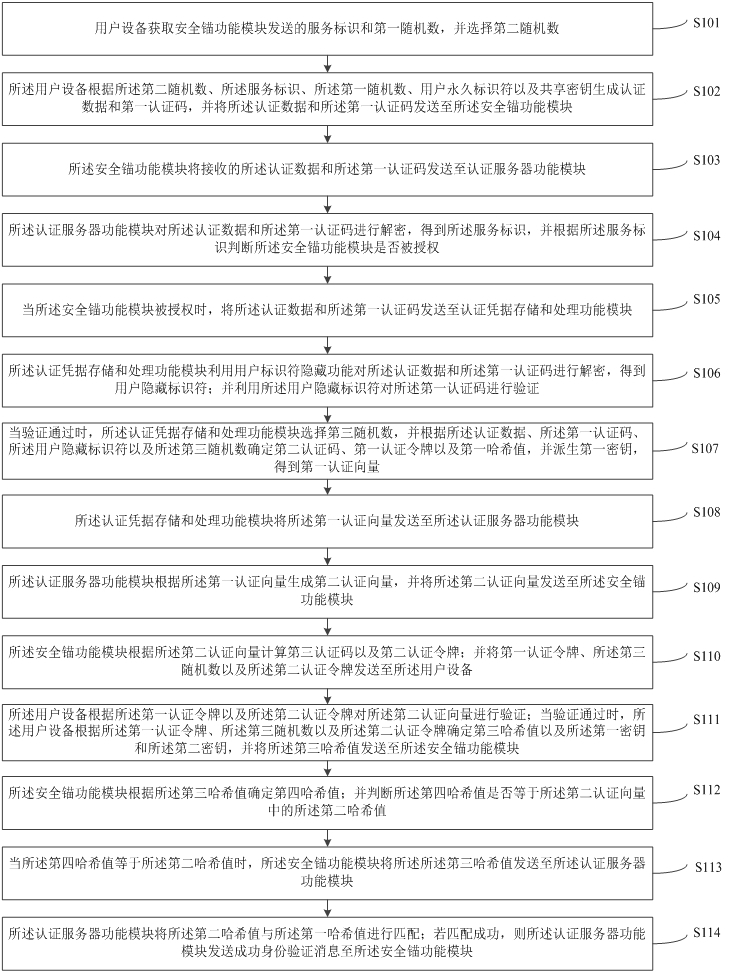
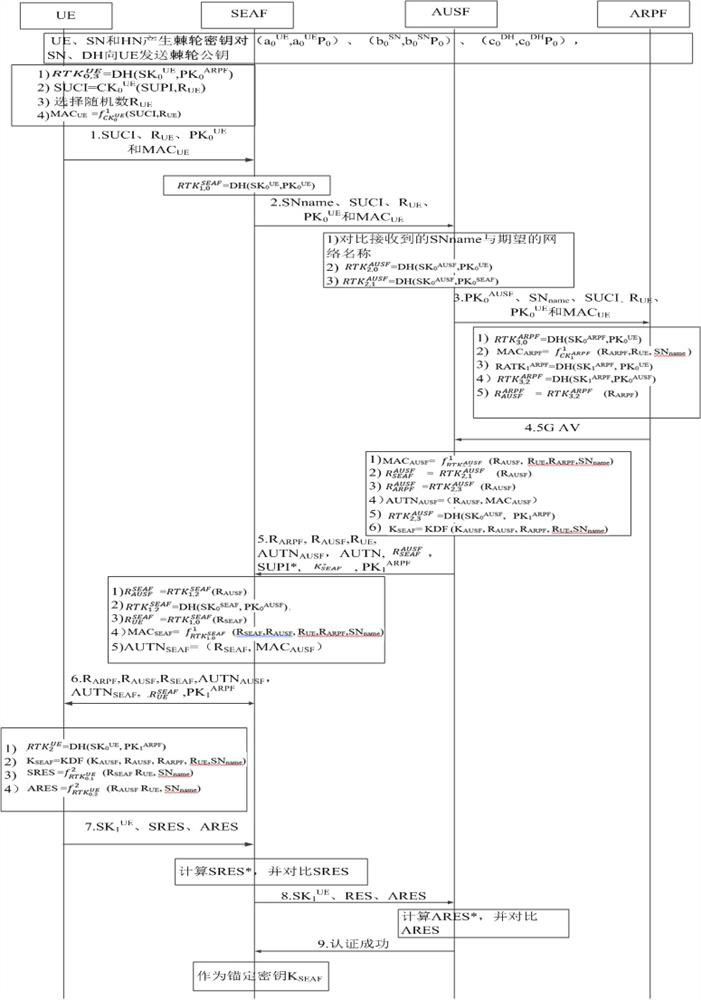
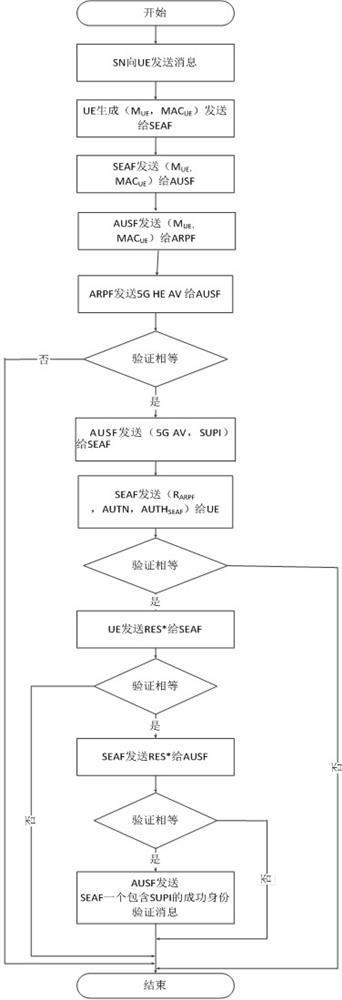
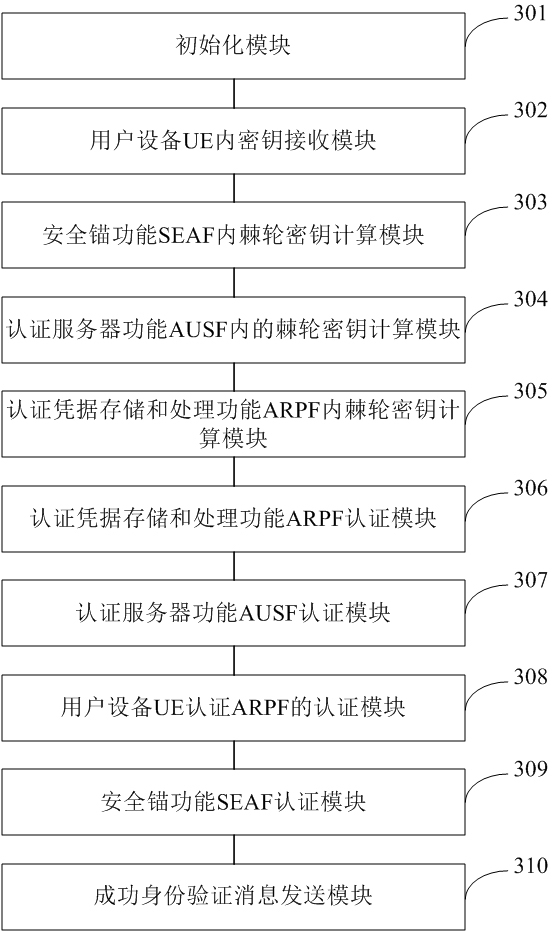
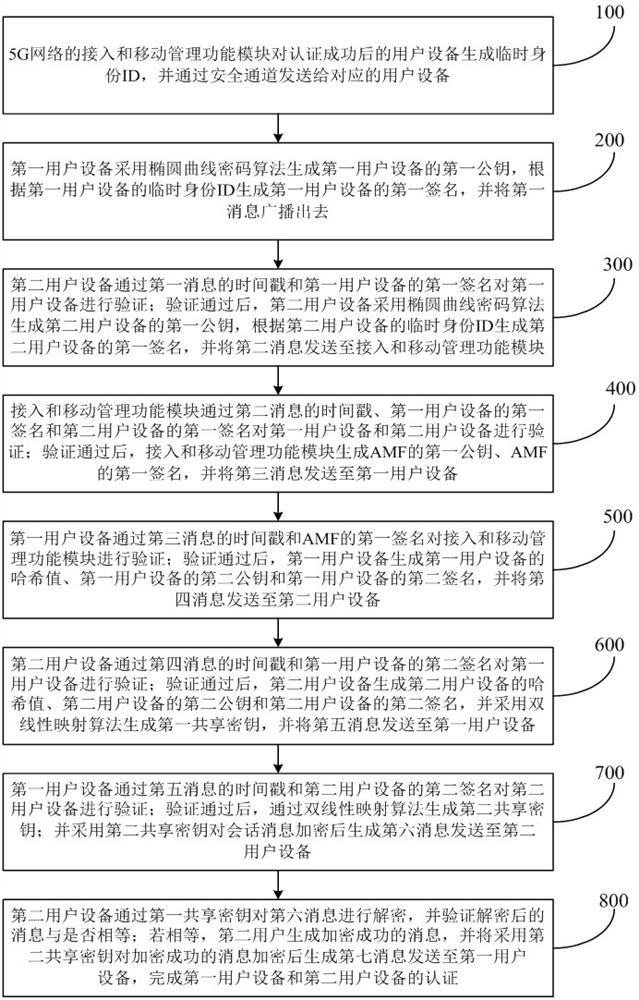
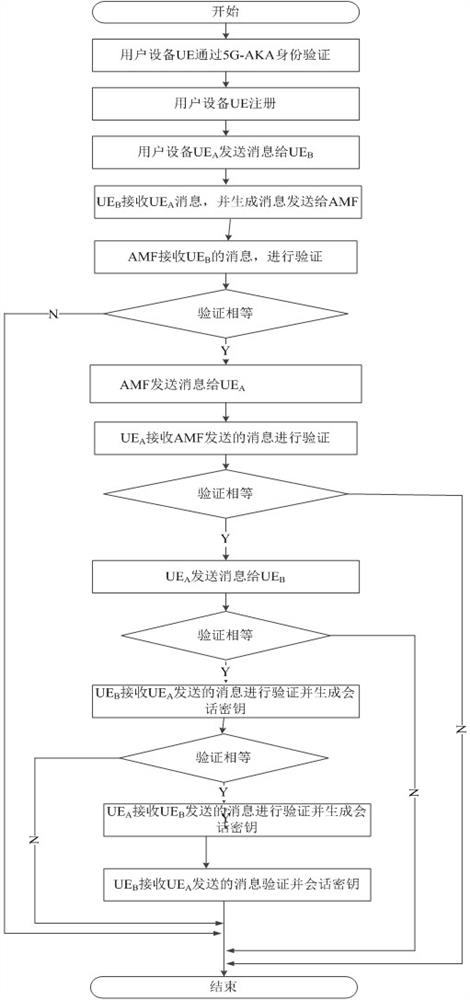
Identity authentication method and system for 5G communication network
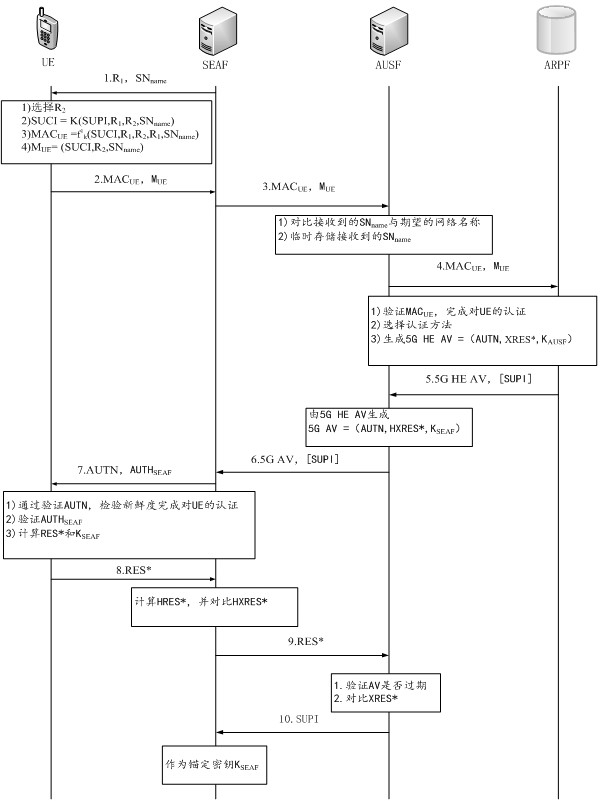
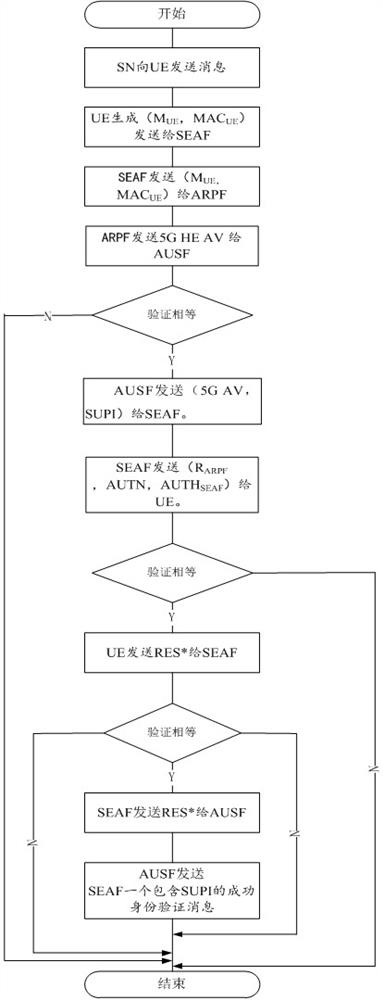
ActiveCN112333705AEnsure safetyGuaranteed freshnessUser identity/authority verificationSecurity arrangementCommunications securityAttack
The invention relates to an identity authentication method and system for a 5G communication network. A security anchor function sends a first random number and a service identifier to the user equipment, the user equipment and the authentication credential storage and processing function module respectively select a second random number and a third random number, the freshness of the message is ensured by replacing a serial number (SQN) with the random numbers, and for synchronization failure, different failure messages do not need to be sent. Therefore, the possibility of tracking is avoided; when the user equipment encrypts the permanent identifier of the user, the shared key is directly used for encryption, so that some problems of computation overhead and public key infrastructure (PKI) are directly avoided; when the authentication credential storage and processing function module authenticates the user equipment, if the identity authentication information comes from an attacker,resource consumption can be avoided; and entities participating in authentication are mutually authenticated, so that counterfeit attacks are avoided, and the communication security is ensured. According to the invention, a user can carry out identity authentication safely and efficiently.
Owner:北京电信易通信息技术股份有限公司
Internet-of-vehicles RFID safety certificating method based on key distribution center
ActiveCN108833097APrevent impersonation attacksPrevent retransmission attacksKey distribution for secure communicationMemory record carrier reading problemsKey distribution centerThe Internet
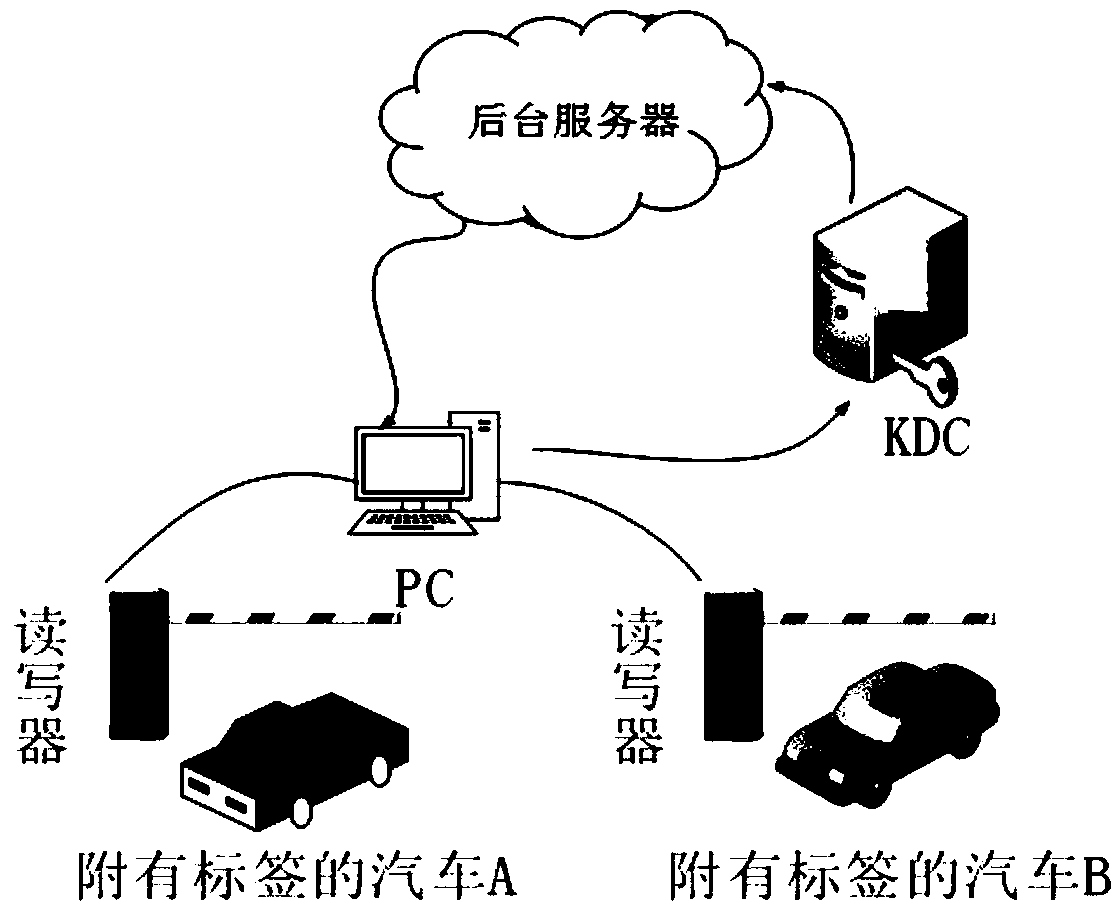
The invention provides an Internet-of-vehicles RFID safety certificating method based on a key distribution center. The method comprises the steps of a protocol process period, transmitting a generated rr to a label by a reader-and-writer, and transmitting the rr to a KDC; generating an rt by the label after receiving the rr, performing calculation according to formulae which are shown in the description, and transmitting a, rt and b to the reader-and-writer; transmitting a, rt and b to the KDC by the reader-and-writer; after the KDC receives a, rt and b, searching a value which matches a, ifthe value exists, authorizing legal of the label, generating an R by the KDC, and transmitting R, b, rr and rt to a background server; and if the value does not exist, authorizing illegal of the labeland stopping communication; after a background server receives the R, b, rr and rt, searching an ID value, after the legal label is authorized, performing calculation according to formulae which arerepresented in the description, and transmitting c and d to the reader-and-writer; after the illegal label is authorized, stopping communication; forwarding the c and the d to the label by the reader-and-writer, after the legal reader-and-writer is authorized, synchronously updating the key by the label according to a formula which is represented in the description, and otherwise, after the illegal reader-and-writer is authorized, stopping communication. The Internet-of-vehicles RFID safety certificating method can effectively prevent counterfeit attack, retransmission attack, tracking attackand DoS attack.
Owner:CHANGAN UNIV
Network authentication and key allocation method across secure domains
InactiveCN100546245COvercoming the shortcomings of decentralized authenticationEnsure safetyKey distribution for secure communicationUser identity/authority verificationService domainWeb authentication
Owner:XIDIAN UNIV
5G network authentication method and system based on DH ratchet algorithm
ActiveCN112399407AGuaranteed confidentialityThe transmission process is safe and reliableEncryption apparatus with shift registers/memoriesSecurity arrangementWeb authenticationAlgorithm
The invention relates to a 5G network authentication method and system based on a DH ratchet algorithm. The method comprises the steps that user equipment encrypts identity information through a ratchet wheel secret key and sends the identity information to a server for verification, and the confidentiality of the identity information is guaranteed; ratchet key pairs are generated for each entityin a 5G network, so that each entity encrypts transmission information through a ratchet key of the entity when transmitting information, information safety is guaranteed, mutual verification betweenthe entities is guaranteed by generating respective identity tokens of the entities, and counterfeit attacks are avoided. Through ratchet wheel stepping, each entity generates different ratchet wheelsecret keys in the session process, so that each session is encrypted by using different ratchet wheel secret keys, and the message transmission process is safer; the session key in 5G is generated through the ratchet wheel key instead of the shared key K, so that the security problem caused by leakage of the shared key K is solved.
Owner:北京电信易通信息技术股份有限公司
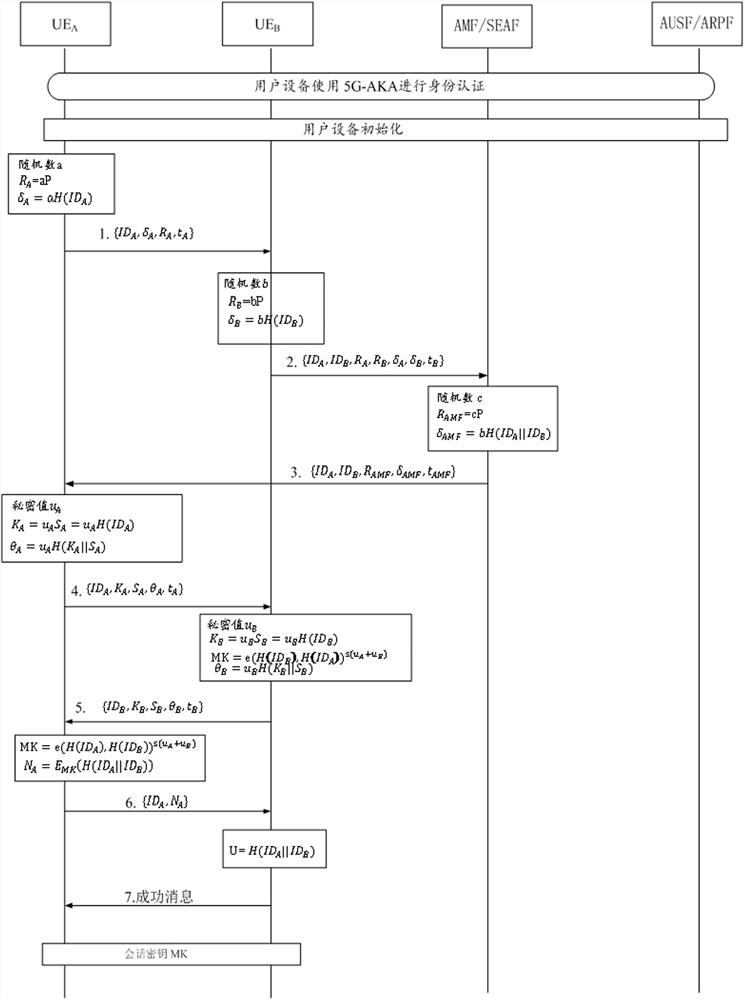
Mobile equipment security authentication method and system based on bilinear pairing
ActiveCN112822018AEnsure safetyGuaranteed freshnessKey distribution for secure communicationPublic key for secure communicationKey-agreement protocolAKA
The invention relates to a mobile equipment security authentication method and system based on bilinear pairings. Aiming at one-to-one mobile equipment communication, user equipment carries out user identity authentication through a 5G authentication and key agreement protocol in a 5G network, and if the authentication is passed, a security channel is established between the user equipment and the 5G network, and the user equipment is initialized through the security channel. When the user equipment prepares to communicate with each other, the user equipment verifies the identity between the equipment through a signature and performs key negotiation by using a bilinear pairing algorithm, so that the equipment can establish connection and communicate with each other through the negotiated key. According to the method, common attacks such as eavesdropping and counterfeiting are effectively resisted, and the forward and backward security of a key is also improved. According to the invention, the mobile devices can communicate with one another safely and efficiently.
Owner:北京电信易通信息技术股份有限公司
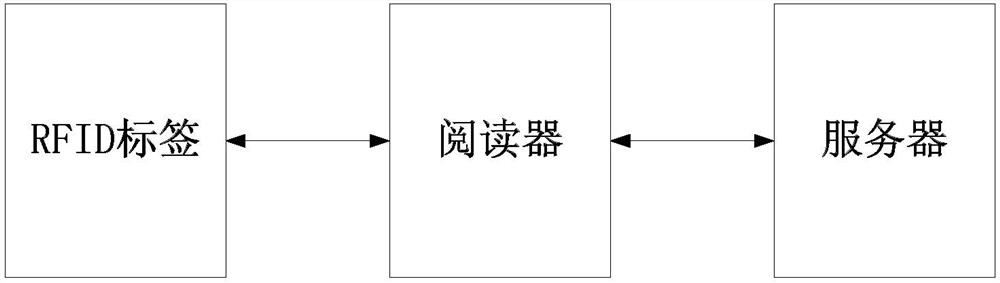
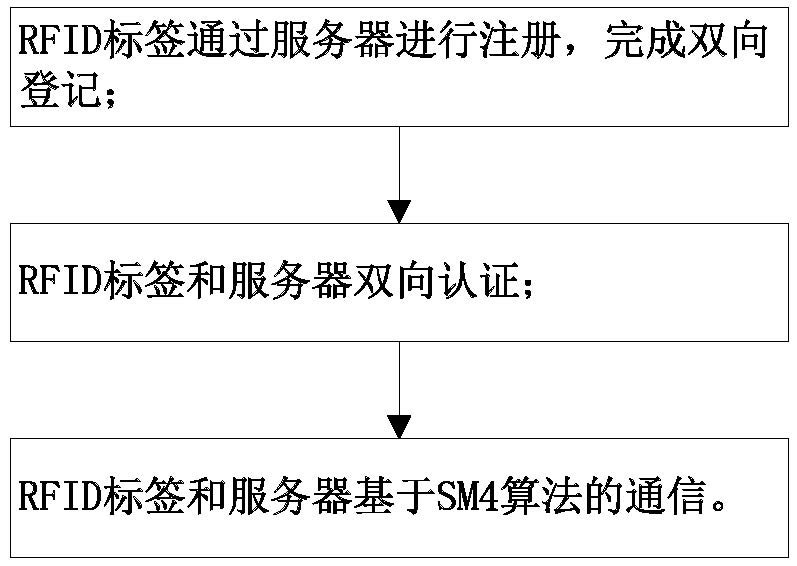
Industrial RFID safety communication method
PendingCN114745123AAvoid Tracking AttacksAvoid impersonation attacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesImpersonation attackMan-in-the-middle attack
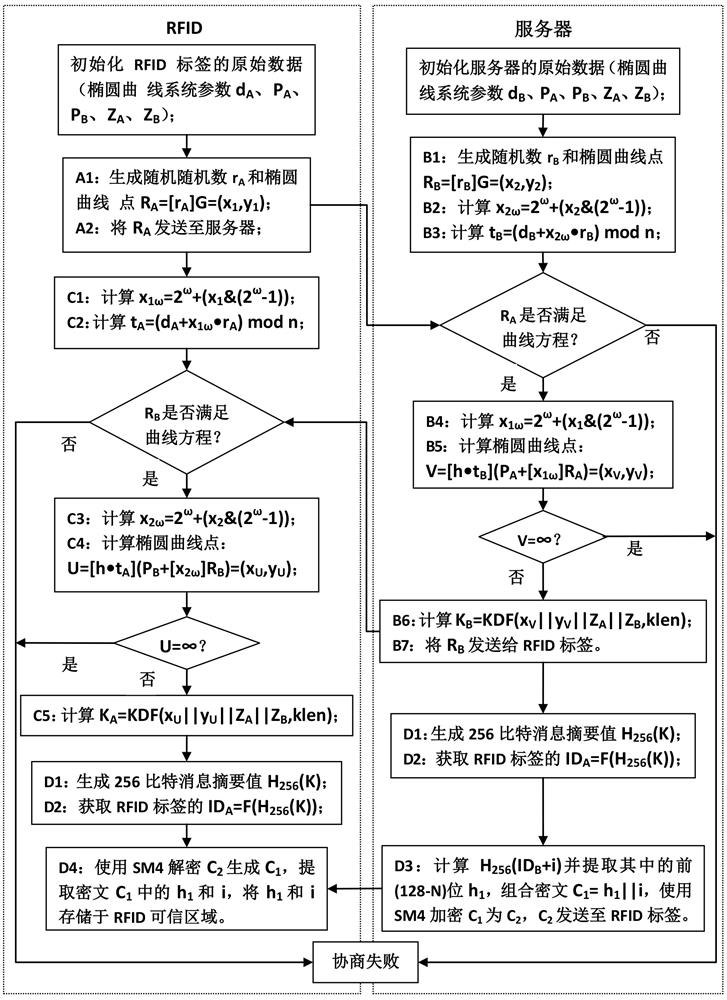
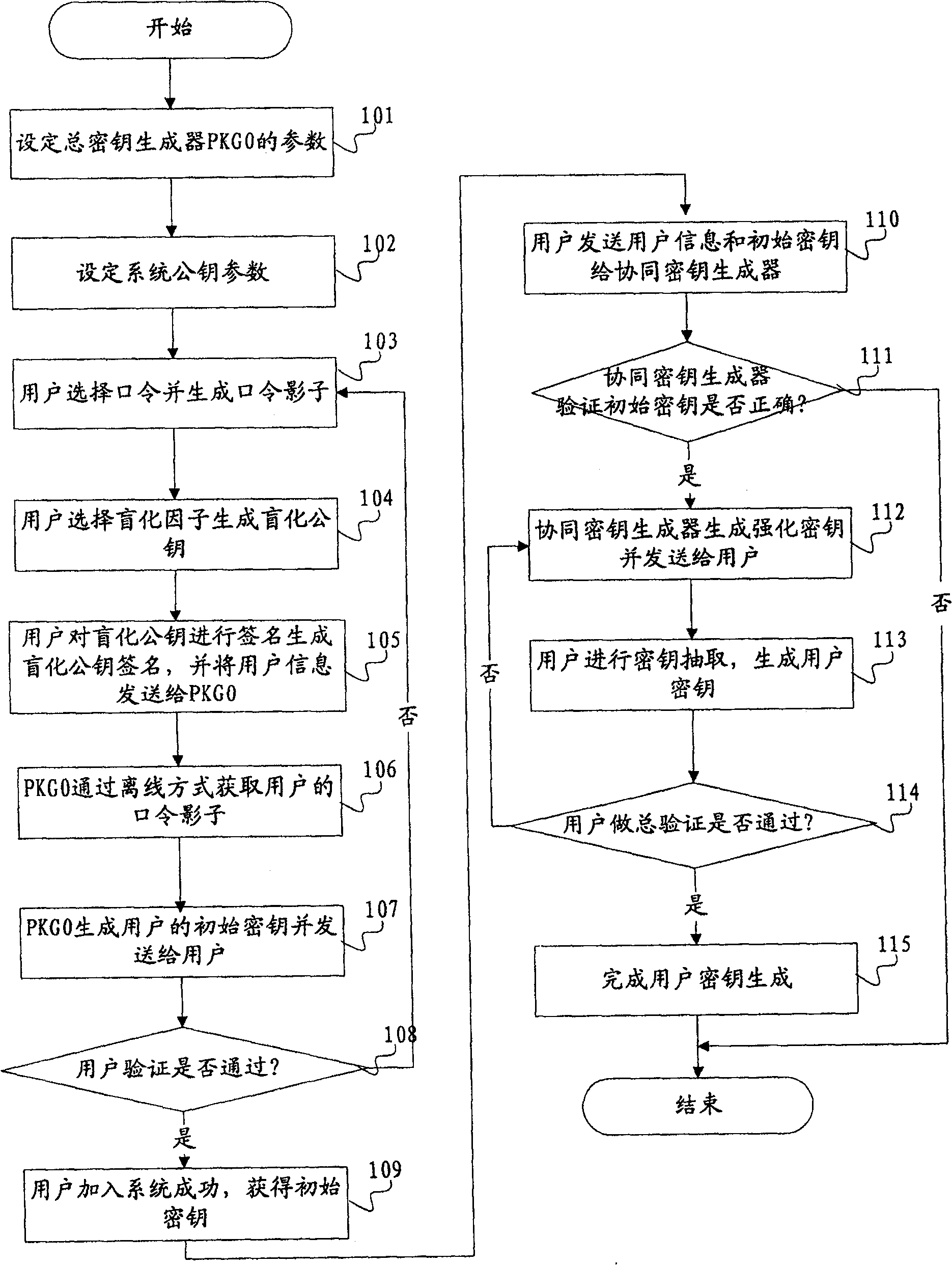
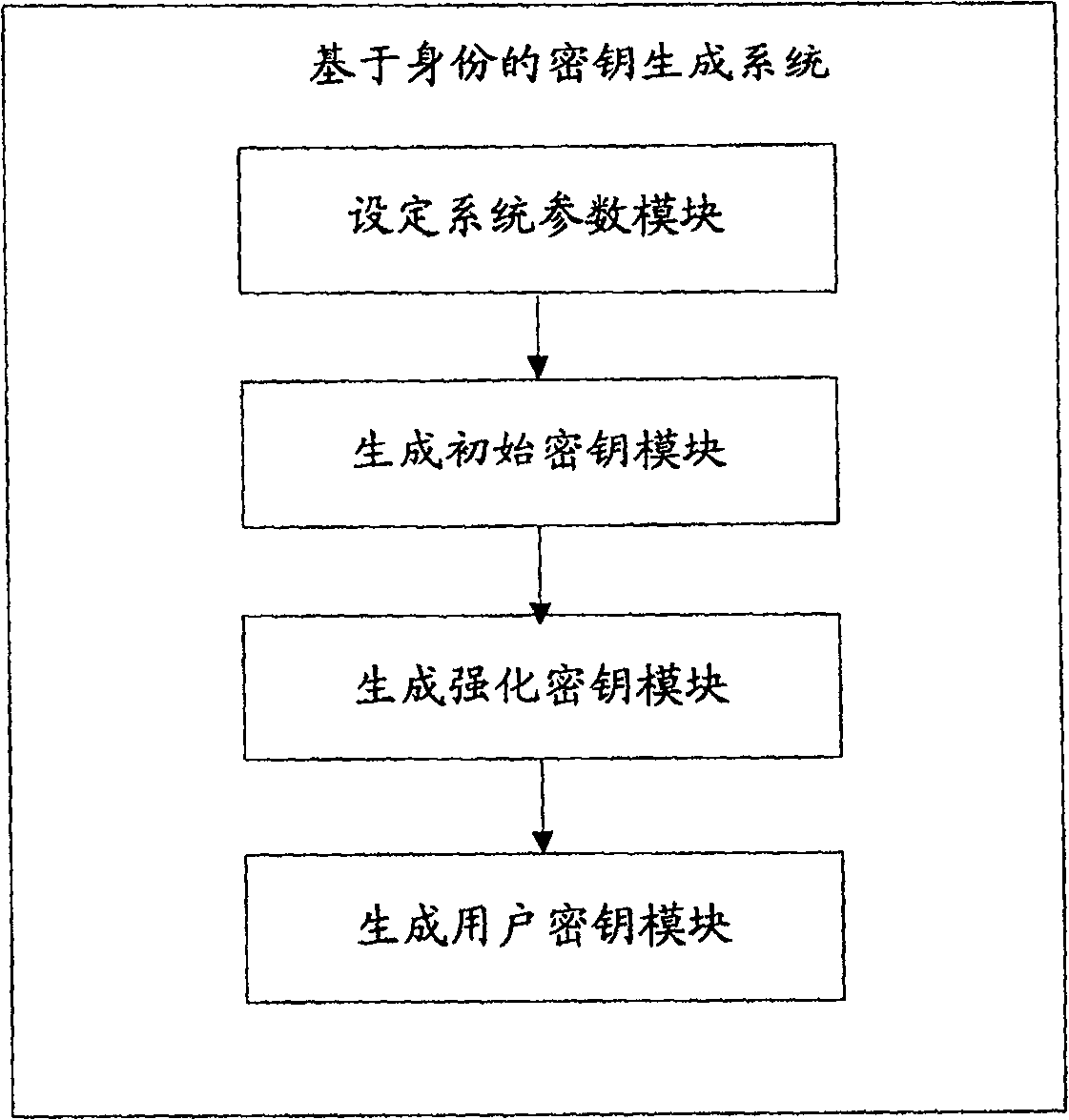
According to the industrial RFID security communication method provided by the invention, the whole-process encryption of tag registration, identity authentication and communication interaction is realized, and the problems that the password technology is immature and the autonomous controllable degree is low in industrial application of the RFID technology are solved. In the registration stage, the RFID tag and the server generate a symmetric key by adopting an SM2 key exchange protocol and generate a tag ID based on the key, the server ID is transmitted to the tag through a variable hash value, and the IDs of the two parties can be shared without direct transmission, so that tracking attacks are avoided; in the authentication stage, real ID transmission is replaced by bidirectional authentication and a variable hash value to avoid impersonation attack and man-in-the-middle attack; aiming at the characteristics of frequent authentication and less information amount in industrial application, an efficient SM4 symmetric encryption and decryption algorithm is used, and information to be encrypted is processed in registration and authentication stages to enable the length of the information to be encrypted not to exceed 128 bits, so that SM4 can be grouped in one time to complete work, and the encryption and decryption efficiency is improved; the symmetric key is updated in each authentication, so that the cracking difficulty is improved.
Owner:JINAN VOCATIONAL COLLEGE
Cryptographic key generation method and system based on identity
InactiveCN100542091CEliminate dependenciesPractical use of cryptographic systemUser identity/authority verificationCryptographic key generationE-commerce
The invention provides an identity-based key generation method and system. It involves computer communication and e-commerce application fields. In order to solve the problems of key escrow and unreliable security channels in the prior art, the present invention provides an identity-based key generation method, which includes setting system parameters, generating user information, and generating initial keys , steps to verify initial key, generate hardened key, and generate user key. The present invention also provides an identity-based key generation system, which includes a module for setting system parameters, a module for generating user information, a module for generating an initial key, a module for verifying an initial key, a module for generating a strengthened key, and a module for generating user information. key module. The technical scheme of the invention solves the problem of dependence on the safe channel and key trusteeship, and effectively prevents various impersonation attacks.
Owner:SHANGHAI JIAO TONG UNIV +1
Lightweight RFID authentication method based on integer chaos
ActiveCN106487495APrevent eavesdroppingPrevent replay attacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesRfid authenticationHash function
The invention discloses a lightweight RFID authentication method based on integer chaos. According to the invention, by use of pseudo random numbers, freshness of labels and communication contents of readers are ensured; and by use of the Hash function, confidentiality of the communication contents is ensured. Thus, common attack means such as counterfeiting attacking, replay attacking and eavesdropping can be resisted.
Owner:BEIJING INSTITUTE OF PETROCHEMICAL TECHNOLOGY
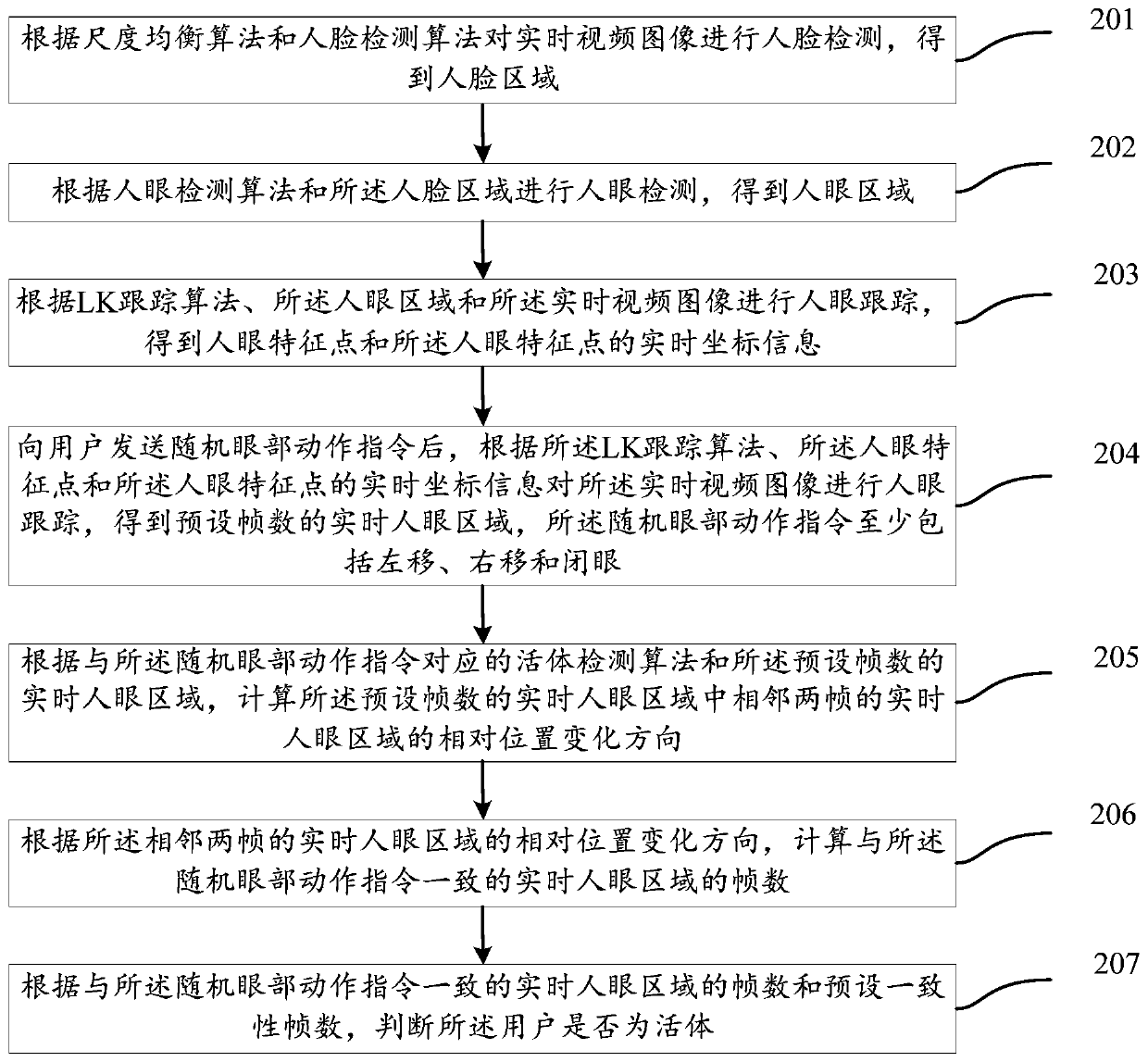
Liveness detection method and device based on activity state of human eye area
ActiveCN105138967BPrevent impersonation attacksLiveness detection worksCharacter and pattern recognitionFace detectionIn vivo
The invention discloses a living body detection method and device based on the activity state of human eye regions, belonging to the field of computer applications. The method includes: performing human eye detection on real-time video images according to a scale equalization algorithm, a human face detection algorithm, and a human eye detection algorithm to obtain a human eye area; Human eye tracking to obtain the real-time coordinate information of the human eye feature points and the human eye feature points; after sending random eye movement instructions to the user, according to the LK tracking algorithm, the human eye feature points and the human eye feature The real-time coordinate information of the point is used to track the human eye of the real-time video image to obtain the real-time human eye area of the preset frame number; according to the living body detection algorithm and the real-time human eye area of the preset frame number, it is judged whether the user is living body. The present invention can effectively perform living body detection through human eye tracking and random eye movement instructions, and prevent video counterfeiting attacks.
Owner:湖北九感科技有限公司
Method, system and device for security authentication of Internet of Vehicles communication based on national secret algorithm
ActiveCN114154135BSecure transmissionReduce the number of timesRandom number generatorsDigital data protectionCommunications securityAlgorithm
The invention belongs to the technical field of vehicle network security, and discloses a vehicle network communication security authentication method, system and equipment based on a national secret algorithm. The method of the present invention includes: the vehicle-mounted terminal constructs an identity authentication request message and sends it to the roadside facility; the vehicle-mounted terminal receives the identity authentication response message and verifies the signature; if the verification is successful, the vehicle-mounted terminal calculates the session key and its hash value and constructs a confirmation message to send To the roadside facility; it is used by the roadside facility to calculate the session key and its hash value for comparison and verification; if the hash values are equal, the security authentication succeeds and a session key is generated; if they are not equal, the security authentication fails. The present invention combines SM2 digital signature algorithm, SM2 public key encryption algorithm and SM3 hash algorithm to ensure that the method can be applied to the communication process between vehicle-mounted terminals and roadside facilities, and can resist Various attacks.
Owner:NANJING UNIV OF SCI & TECH
A radio frequency identification security authentication method and system
ActiveCN109714763APrevent impersonation attacksReduce difficultySecurity arrangementShort range communication serviceRadio frequencyKey storage
The invention discloses a radio frequency identification security authentication method. The method comprises the following steps: initializing parameters of a tag, a reader and a server; Wherein authentication is started after parameter initialization is completed, and the method further comprises the steps that the reader sends an authentication request message to the tag; The tag generates a tag authentication signal after receiving the request message; And when the tag judges that the reader is a legal reader, the authentication is completed. The method has the advantages that security threats such as counterfeit attacks, replay attacks, tracking attacks and denial of service can be prevented, it can be guaranteed that strong forward privacy is not leaked under the enemy enhancement capacity, in addition, a public key encryption mechanism is adopted, the difficulty of secret key storage and management of the system is lowered, and scale expansion of the radio frequency identification system is facilitated.
Owner:JIANGNAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com