A block chain-based secure auditing Internet of Things data sharing system and method
A data sharing and blockchain technology, applied in digital data protection, electronic digital data processing, computer security devices, etc., can solve problems such as occupying large communication bandwidth, unsuitable for IoT systems, and unable to realize outsourced decryption functions, etc. To achieve the effect of preventing impersonation attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0135] In order to make the features and advantages of this patent more obvious and easy to understand, the following special examples are described in detail as follows:
[0136] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
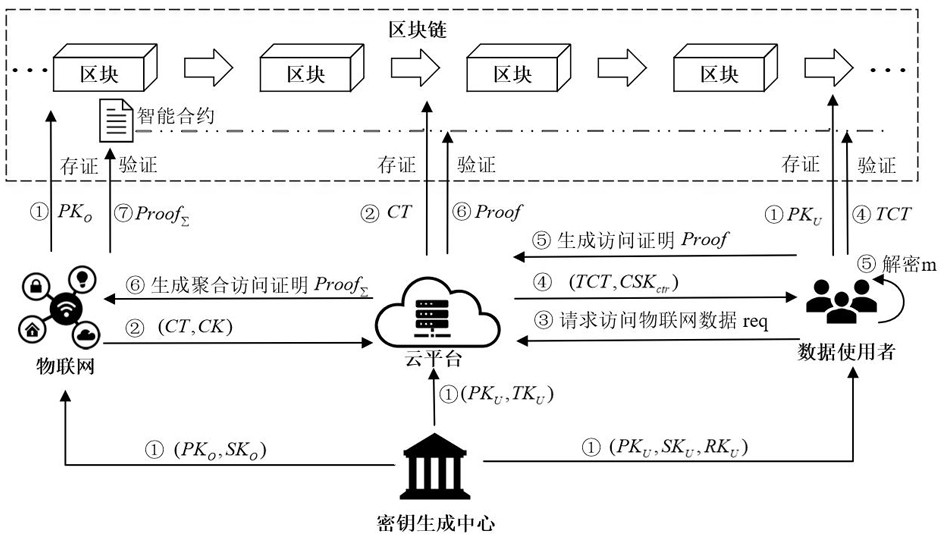
[0137] The system architecture of this embodiment is as follows figure 1 As shown, each role includes key generation center (KGC: key generation center), cloud server, blockchain, Internet of Things and data users. The functions of each entity in the system and the operations performed are outlined below. The definitions of symbols in the system of this embodiment are shown in Table 1.
[0138] Key generation center: responsible for establishing the system and generating public parameters PP, and distributing keys for entities in the system (step ①): distributing public-private key pairs (PK O ,SK O ), distribute public-private key pairs (PK U ,SK U )...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com